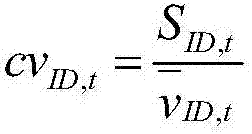Patents
Literature
365 results about "Network key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A wireless network key is used to secure a wireless network with a specified password. These passwords are required to gain access to the Internet connection and files on the network. Network keys are commonly encrypted with Wired Equivalent Privacy (WEP) or Wi-Fi Protected Access (WPA) types of security.
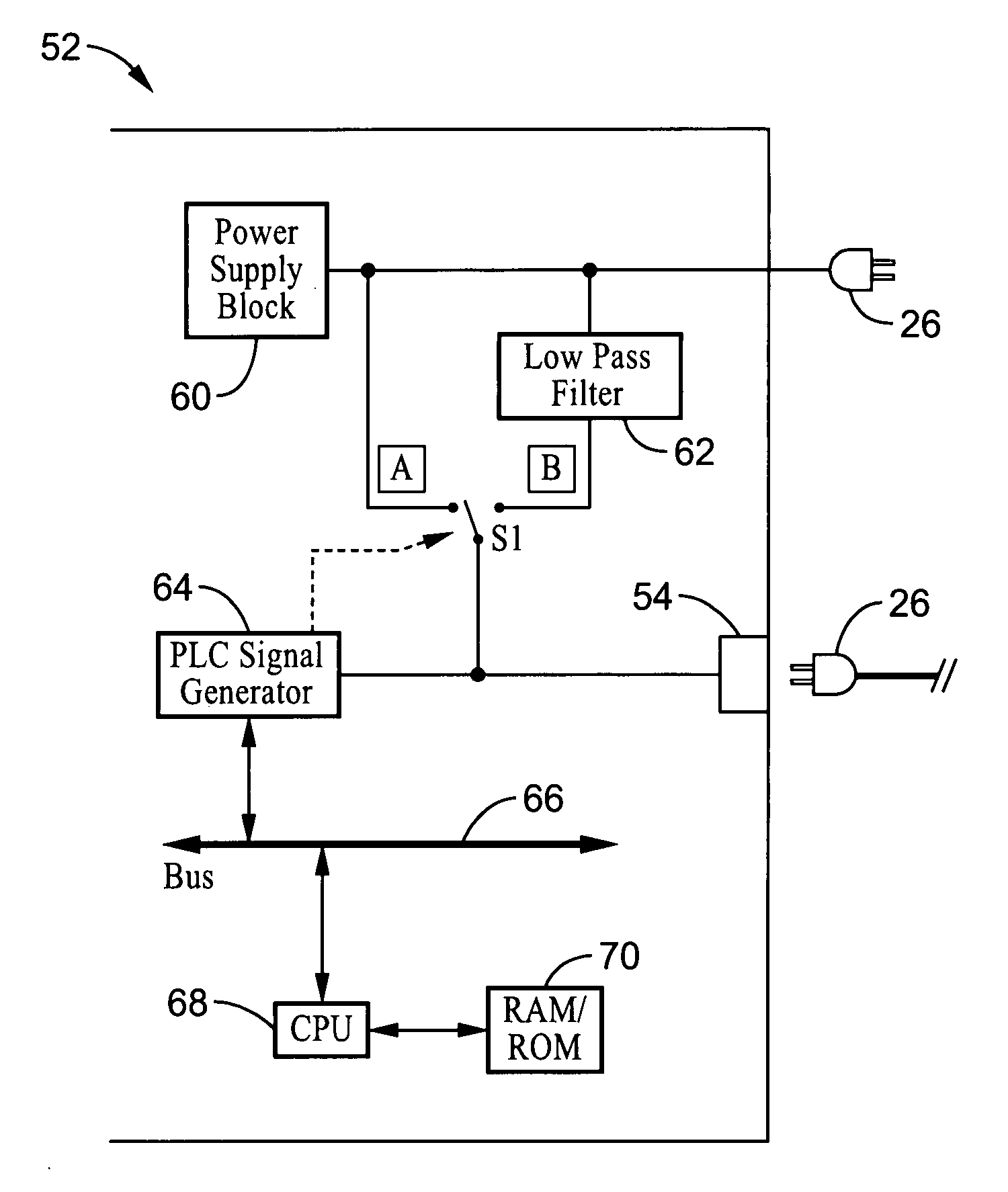
System and method for authenticating/registering network device in power line communication (PLC)
ActiveUS20060038660A1Avoid sharingProvide securitySystems using filtering and bypassingPower distribution line transmissionNetwork keyElectric power
A method and apparatus for protecting privacy in power line communication (PLC) networks. Data transmitted on a PLC network is encrypted according to a network key and can be properly received only by registered devices that have the proper network ID and network key value so that proper decryption can be performed. According to the invention a streaming media device is provided with a compatible network ID and network key during a registration process facilitated by coupling the device (applicant) to a direct power line connection associated with another device (administrator). The network key, and optionally network ID, are then shared over the direct connection without being distributed over the PLC network at large. By way of example, the data is prevented from being distributed across the PLC network in response to using selectable filtering of PLC data, and preferably a secure data communication mechanism, such as public-private key encoding.
Owner:SONY CORP +1
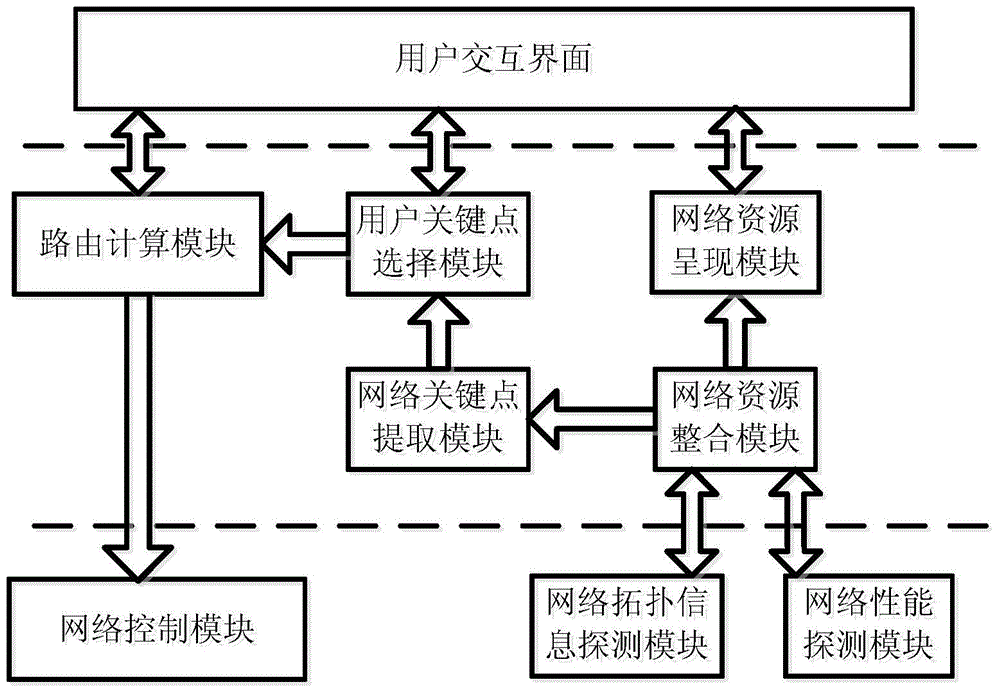
User autonomous routing customization system based on software-defined network
ActiveCN104104718AEfficient collectionRealize intelligenceData switching networksPersonalizationInteraction interface
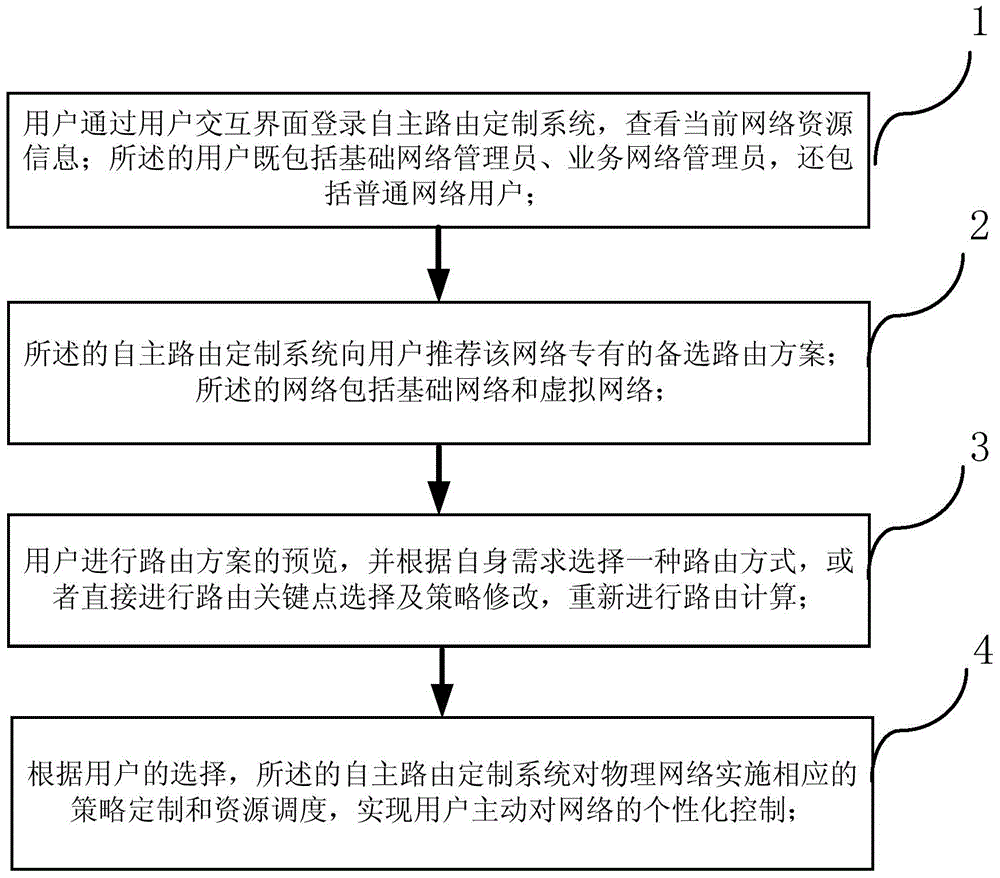
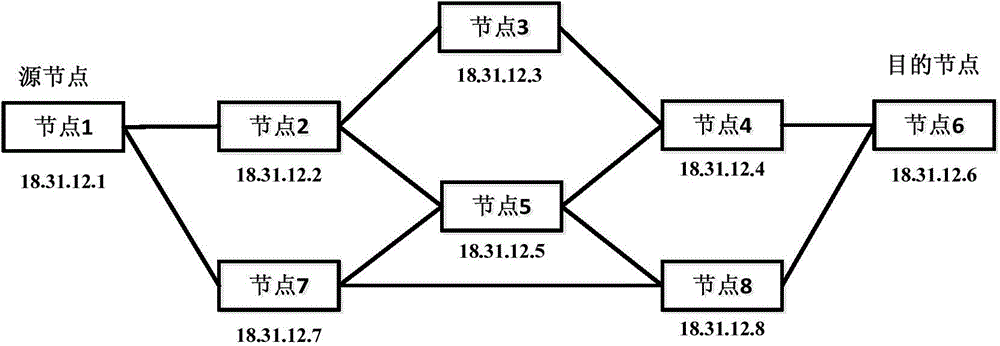
Provided is a user autonomous routing customization system based on a software-defined network. The system comprises a network topology information detection module, a network performance detection module, a network resource integration module, a network resource presenting module, a network key point extraction module, a user key point selection module, a route computation module and a user interaction interface module. Also provided is a user autonomous routing customization method based on the software-defined network. The method comprises the following operation steps that (2) a user logs in a system and views current network resource information; (2) the system recommends candidate routing schemes to the user; (3) the user selects one routing; and (4) strategy customization and resource scheduling are performed on a physical network by the system so that customized control of the network is actively performed by the user. An objective that the user autonomously selects the customized routing schemes is realized by the system and method.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Systems, Methods and Computer Readable Medium To Implement Secured Computational Infrastructure for Cloud and Data Center Environments
InactiveUS20170005990A1Implement securityInput/output to record carriersMultiple keys/algorithms usageData centerNetwork key
Systems, methods, and non-transitory computer-readable medium are provided to secure data centers and cloud computing. A method receives network identifiers for functions, requests a network key for each function, allocates network interfaces, requests a virtual network interface controller allocation, requests a network key for each cloud function, receives storage identifiers for functions, requests a storage key for each cloud function, allocates virtual storage disks, requests a storage interface controller allocation, requests a storage key for each cloud function. Methods secure migration of a virtual machine from a source to a target server. A server includes multiple cores where each core is dedicated to a compute function and a unique key encrypts data of each compute function. A non-transitory computer-readable medium encodes programs that execute the above methods.
Owner:BIRGER ARI
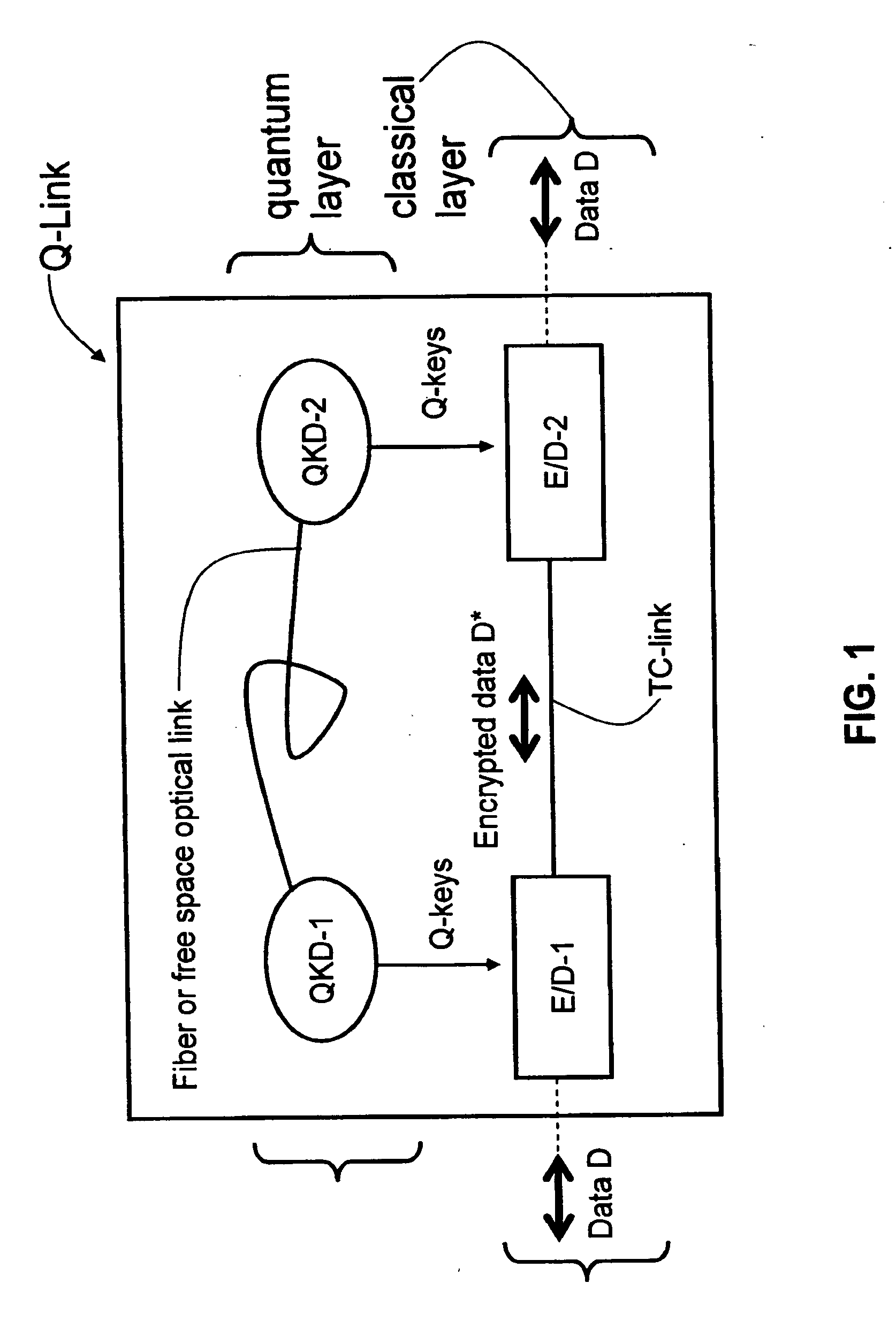
Key manager for QKD networks
ActiveUS20060062392A1Key distribution for secure communicationUser identity/authority verificationNetwork keyKey storage
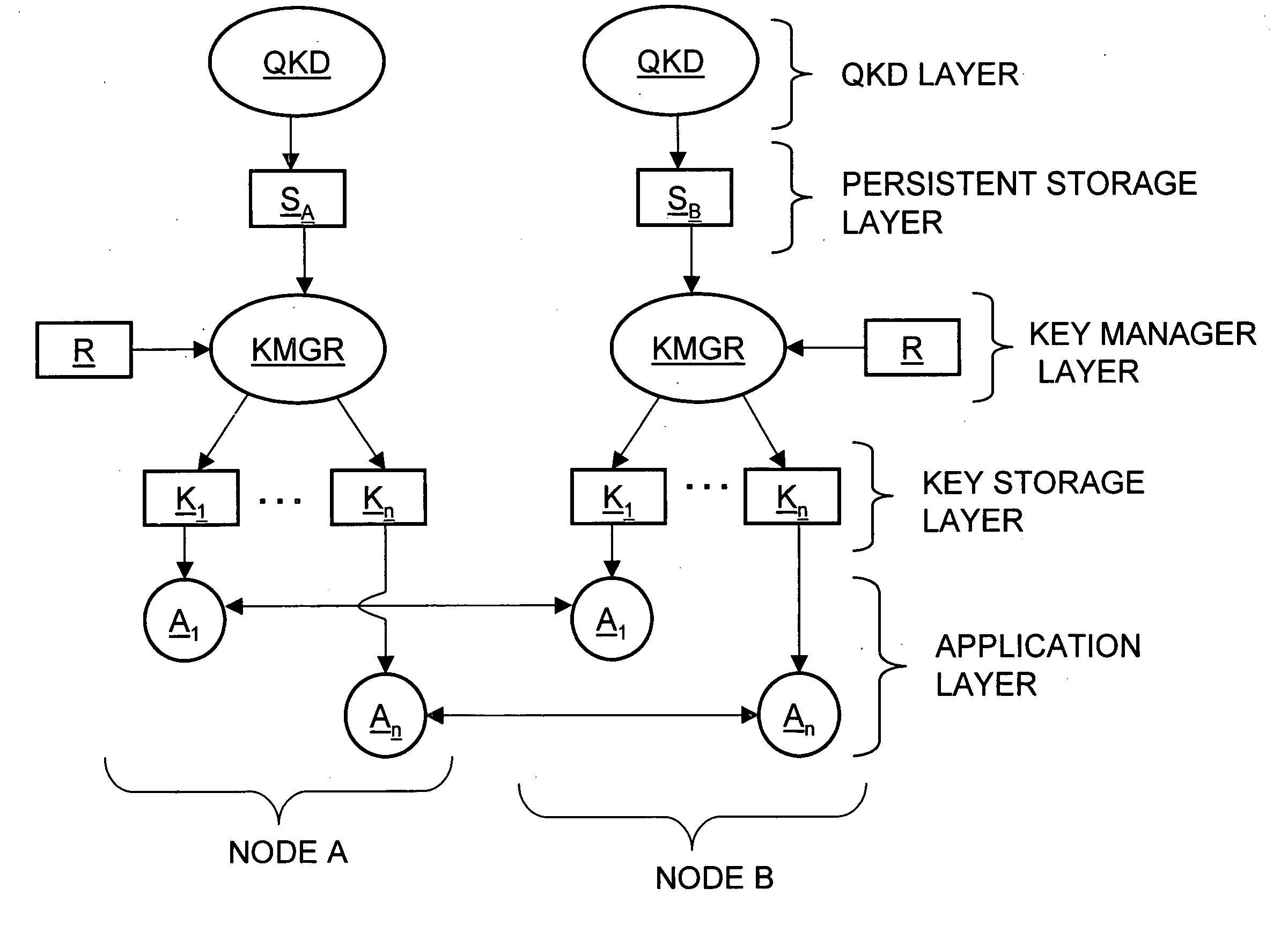
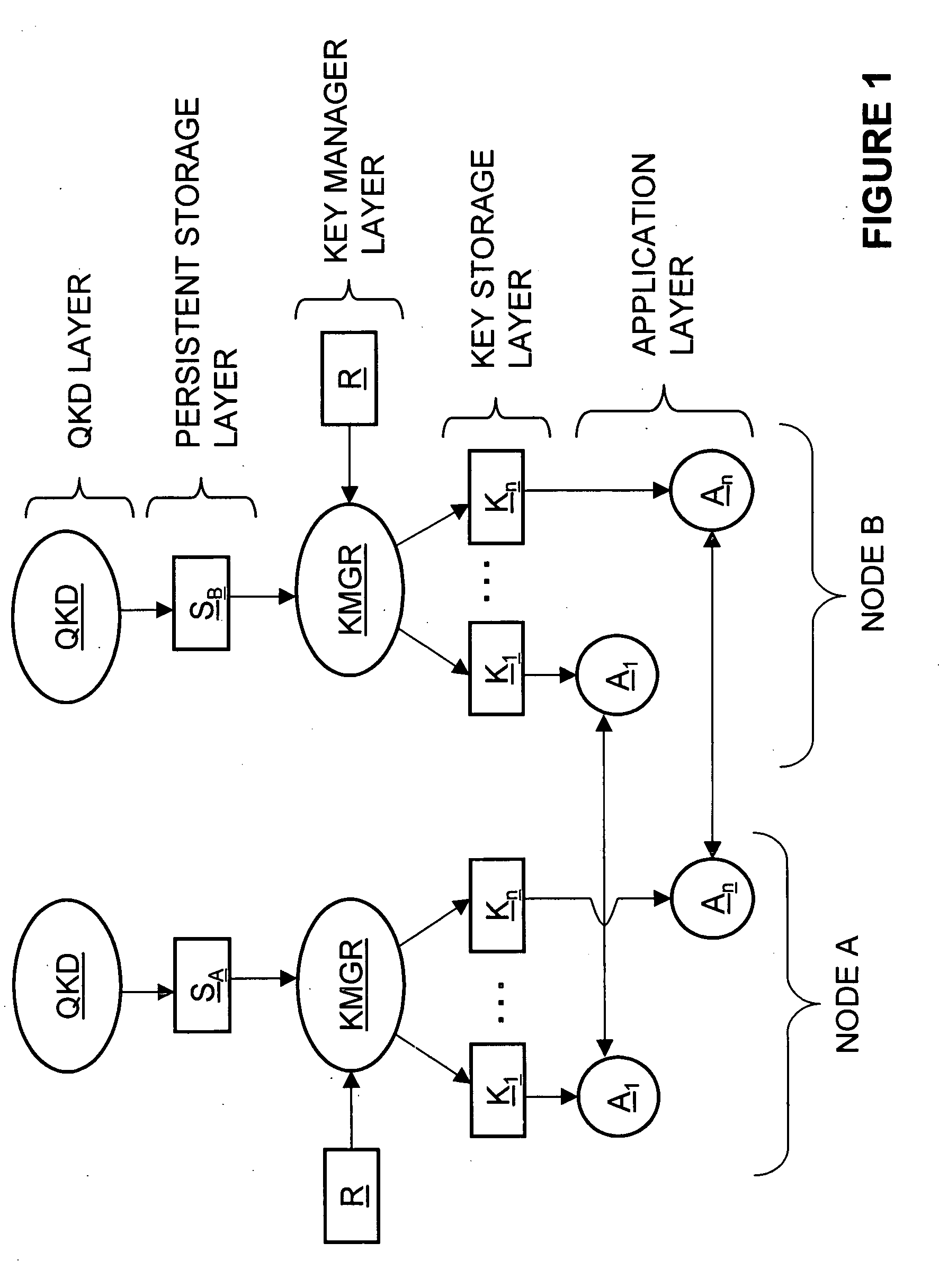
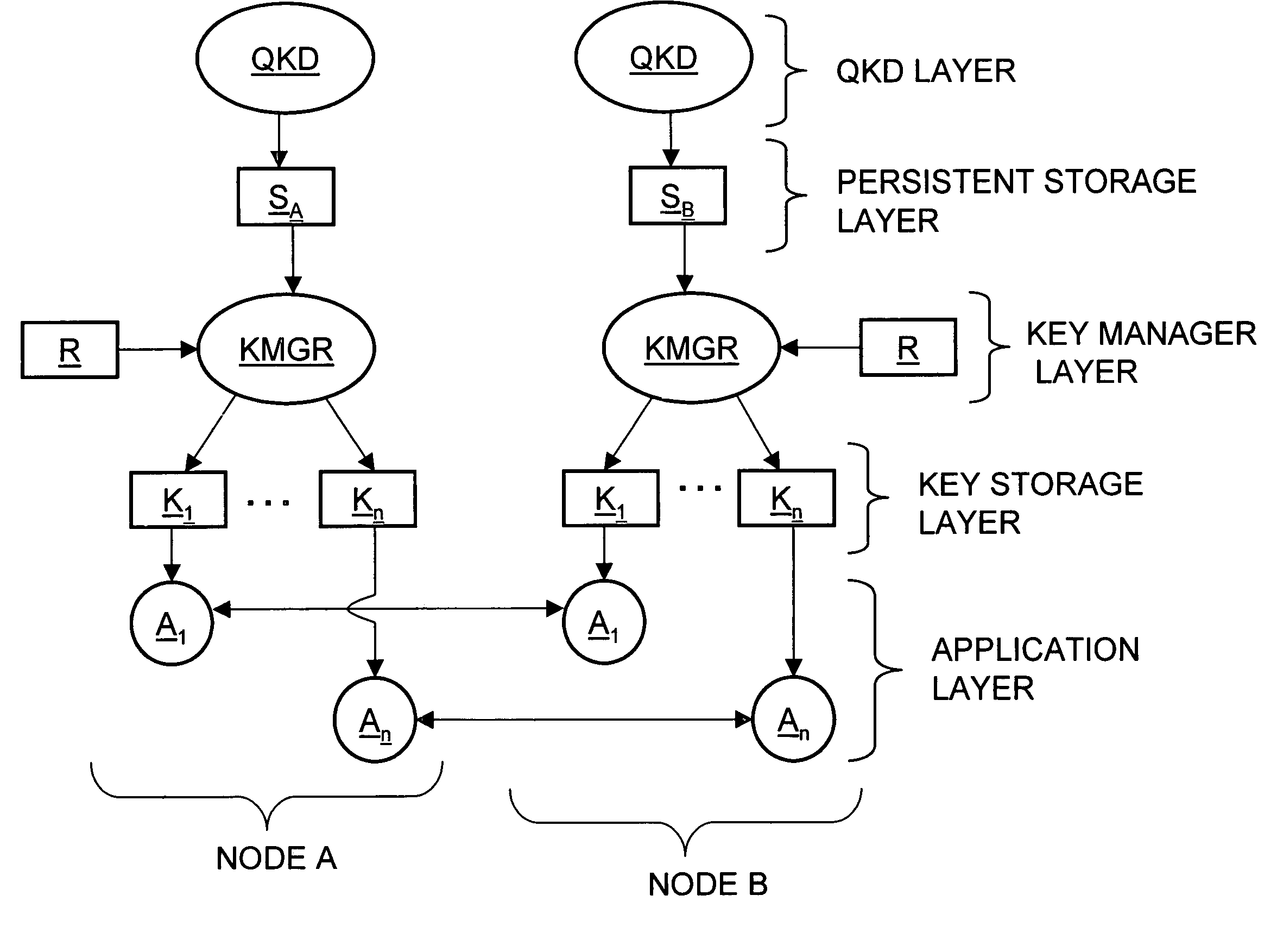
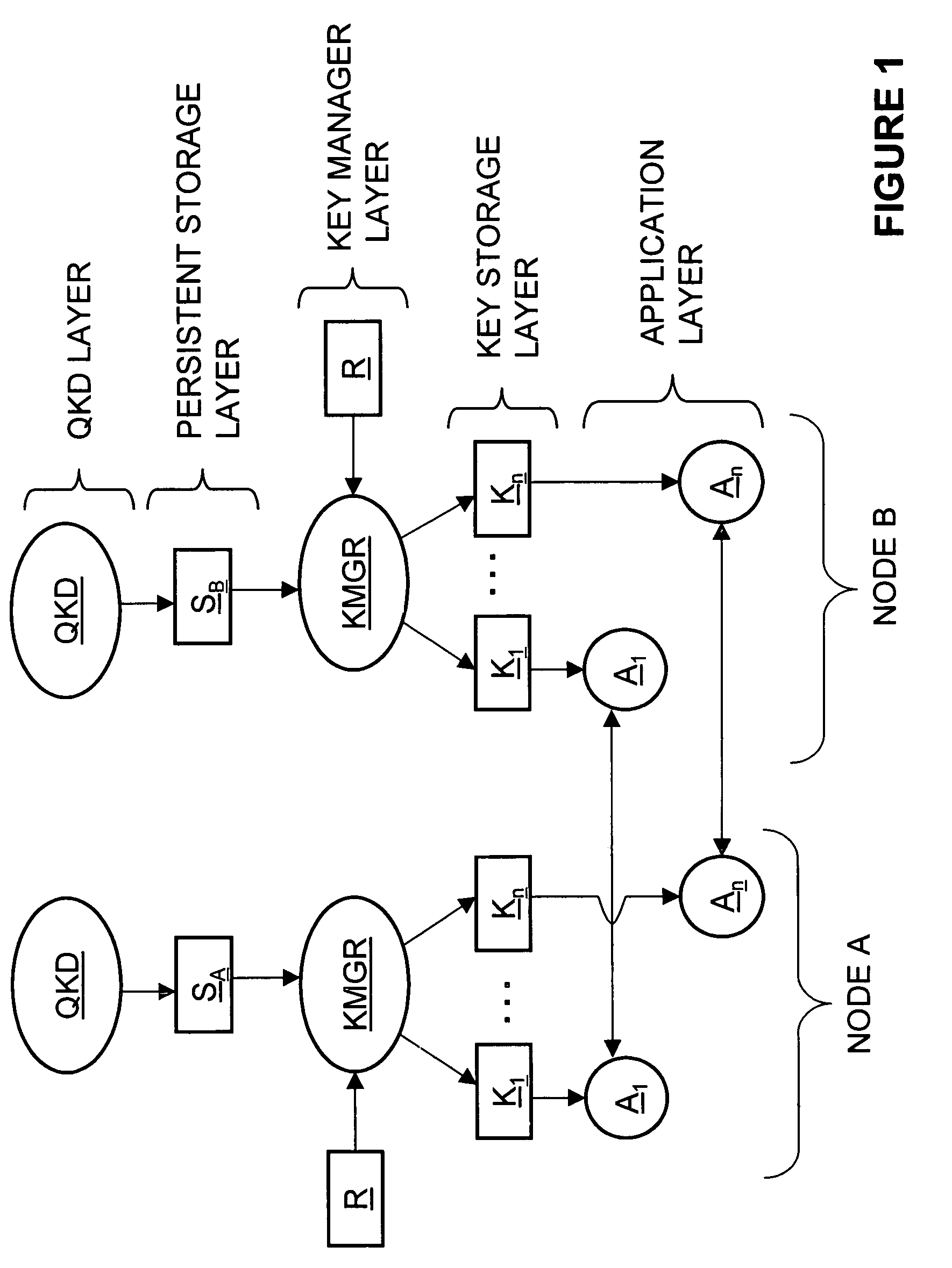
Key manager systems and methods for a QKD-based network are disclosed. The system includes a QKD layer that generates quantum encryption keys, a persistent storage layer that stores the quantum encryption keys, and a key management layer. The key management layer generates an application registration record that includes a list of multiple applications that use the quantum encryption keys. The key management layer also generates a corresponding key storage layer. The multiple applications reside in an applications layer. The applications in each node remove keys from the key storage layer so that each node can encrypt / decrypt data using quantum encryption keys. The methods also include secure QKD system boot-up and authentication that facilitate implementing a commercial QKD system in real-world environments.
Owner:MAGIQ TECH INC
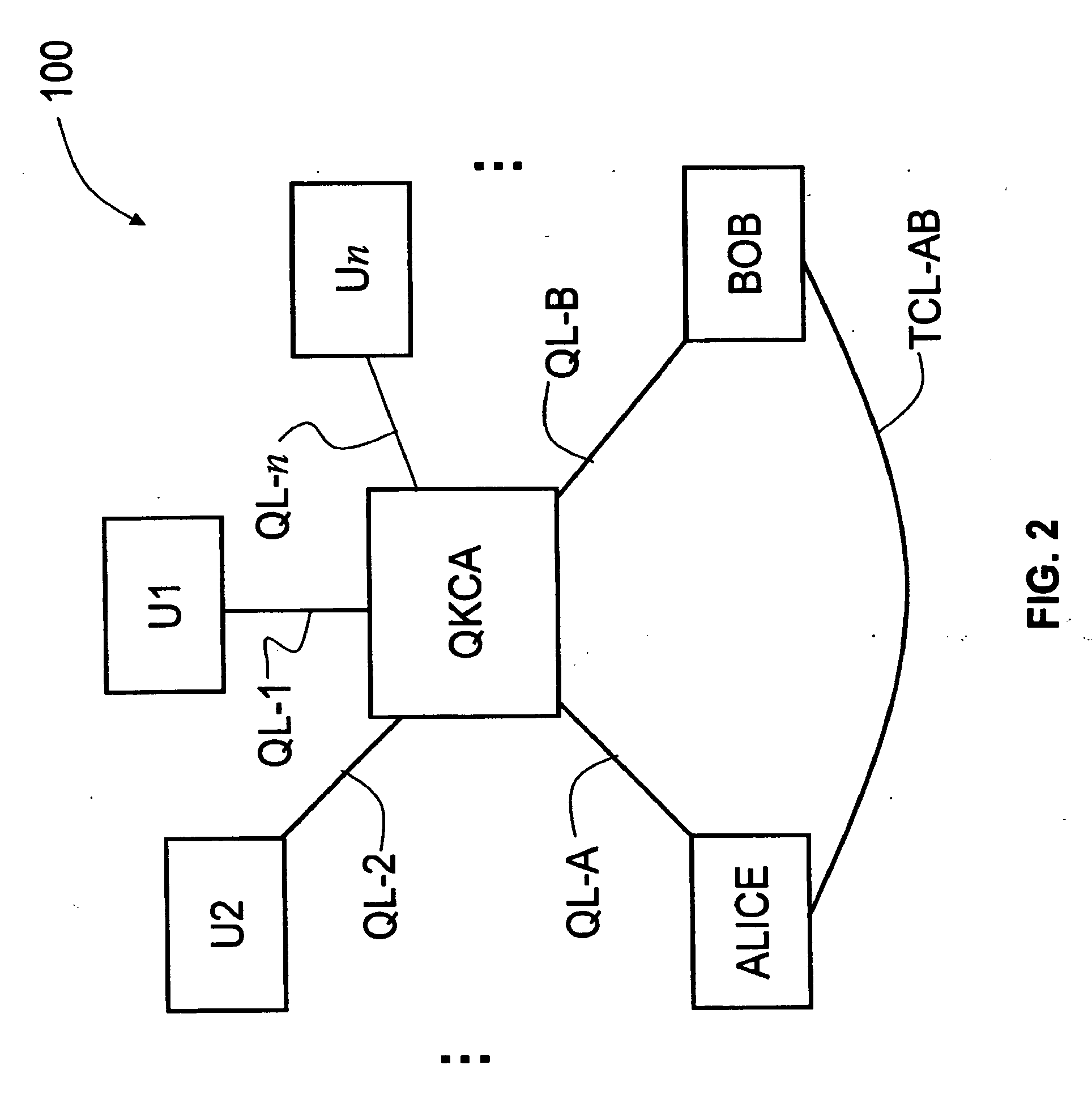
Key Management and User Authentication for Quantum Cryptography Networks
ActiveUS20090175452A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesAlice and BobTelecommunications link
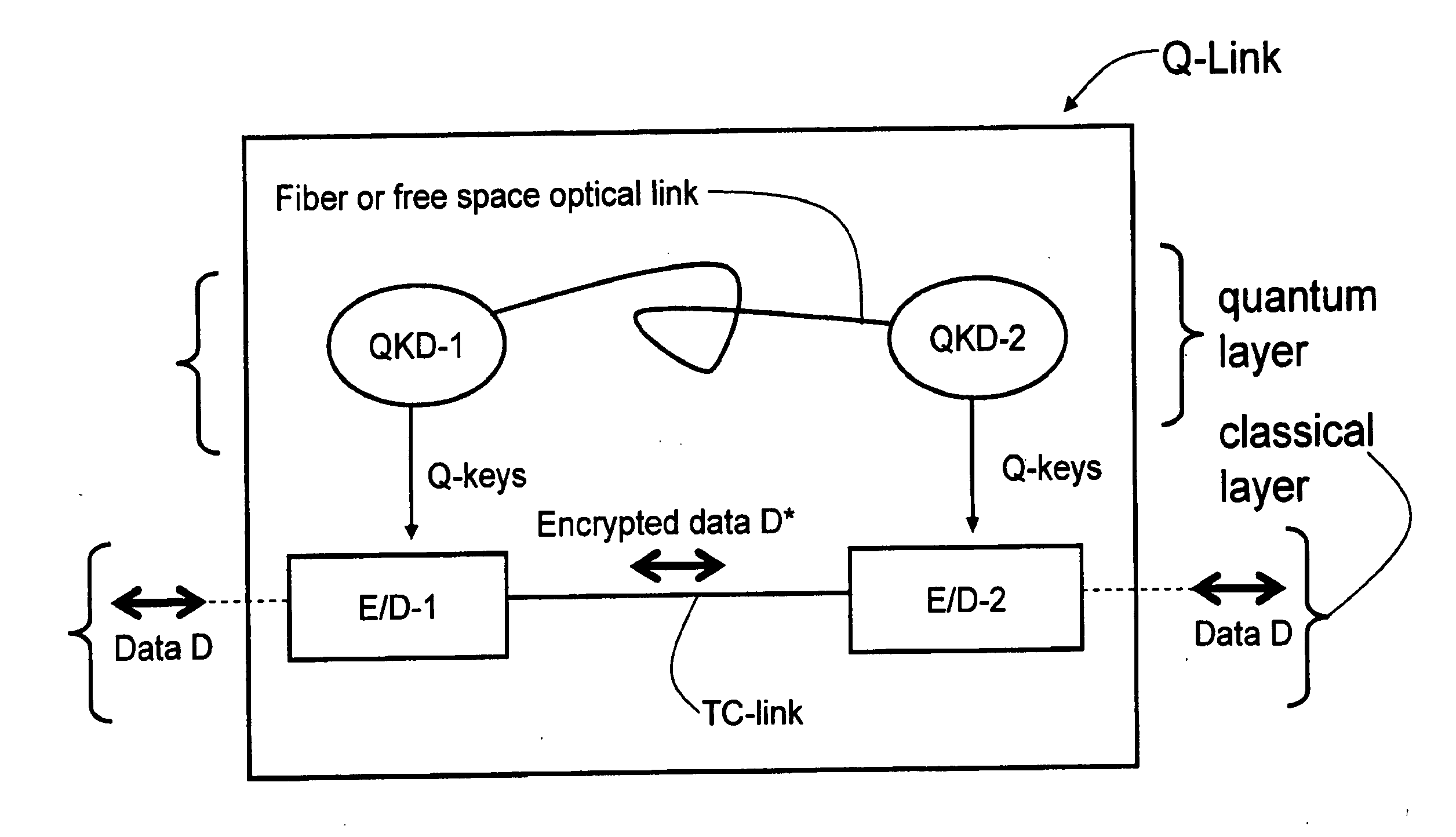
Key management and user authentication systems and methods for quantum cryptography networks that allow for users securely communicate over a traditional communication link (TC-link). The method includes securely linking a centralized quantum key certificate authority (QKCA) to each network user via respective secure quantum links or “Q-links” that encrypt and decrypt data based on quantum keys (“Q-keys”). When two users (Alice and Bob) wish to communicate, the QKCA sends a set of true random bits (R) to each user over the respective Q-links. They then use R as a key to encode and decode data they send to each other over the TC-link.
Owner:MAGIQ TECH INC
Method for transmitting digital data in a local network
ActiveUS20060136718A1Inhibit transferPrevent improper copyingPulse modulation television signal transmissionDigital data protectionDigital dataDigital video
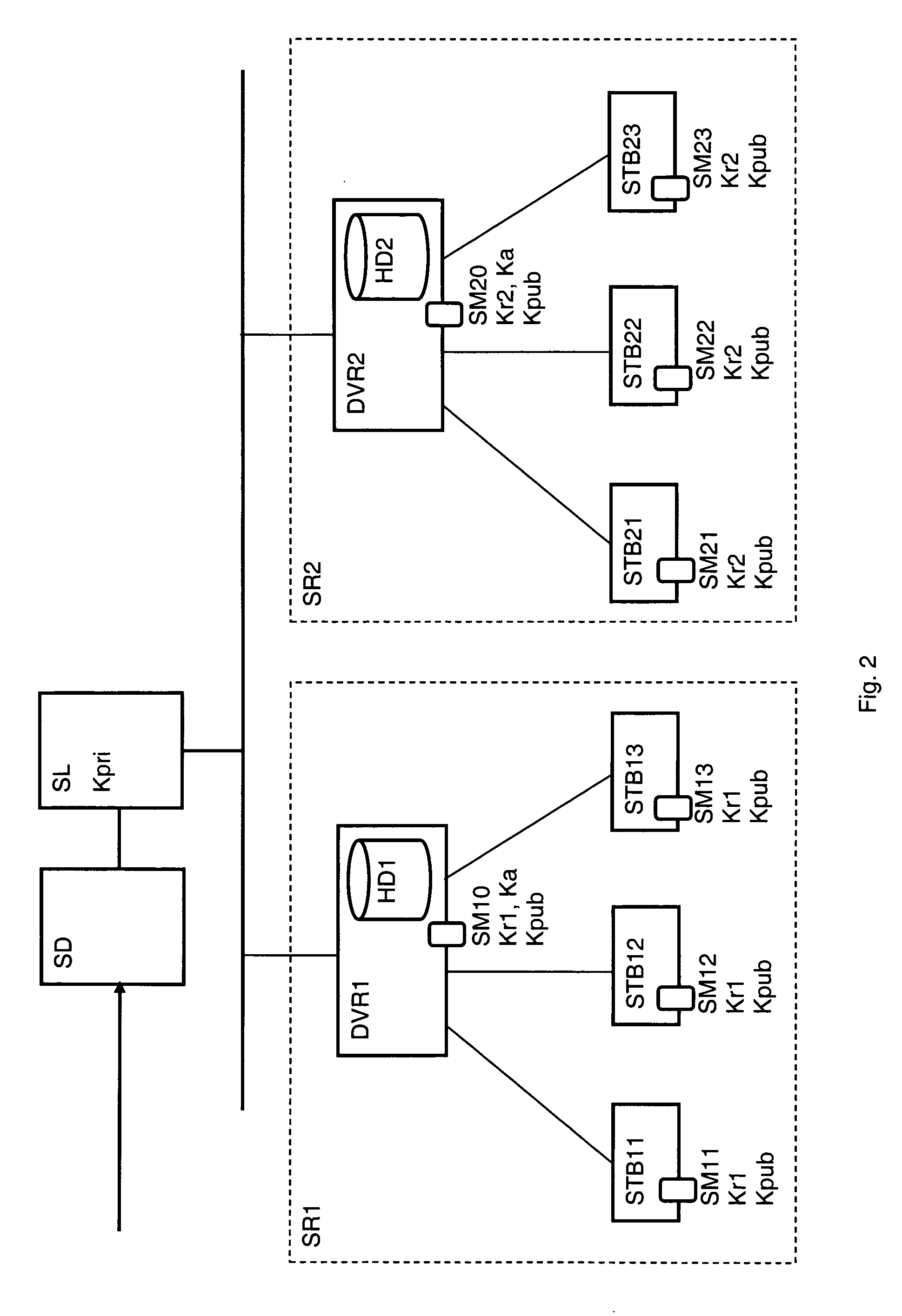
An aim to reach may be on one hand, to allow the reading of a content stored by a digital video recorder from a decoder of the local network regardless of the time elapsed between storage and reading, and on the other hand to prevent the transfer or improper copying of the content stored from one network to another. An aim may be achieved by a method of an embodiment, for transmitting digital data in a local network including members constituted by at least one first multimedia unit having a content storage device and at least one second multimedia unit intended to restore the content. The first multimedia unit may be connected, on one hand, to a broadcasting server of encrypted digital audio / video data and on the other hand to the second multimedia unit, each member possessing a security module including a network key. The first multimedia unit receives and decrypts the encrypted data forming a content broadcasted by the broadcasting server and re-encrypts the content previously decrypted. The method of an embodiment may include steps wherein the content is re-encrypted with a random key and transmitted to the second multimedia unit accompanied by an authorization block including the random key encrypted with the network key, the second multimedia unit decrypts the authorization block, and extracts the random key to be used for decrypting the content.
Owner:NAGRAVISION SA
Remote secure authorization
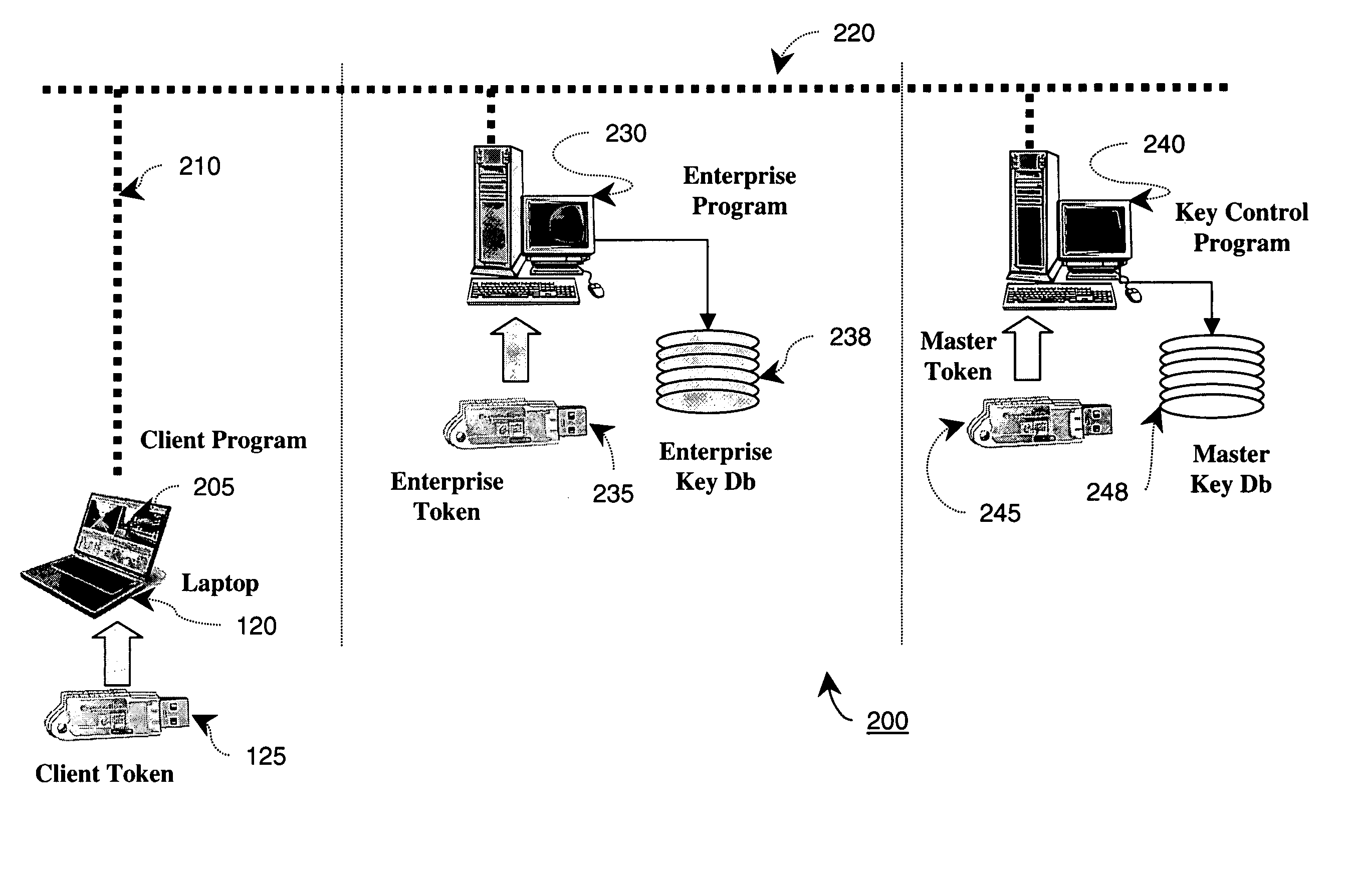
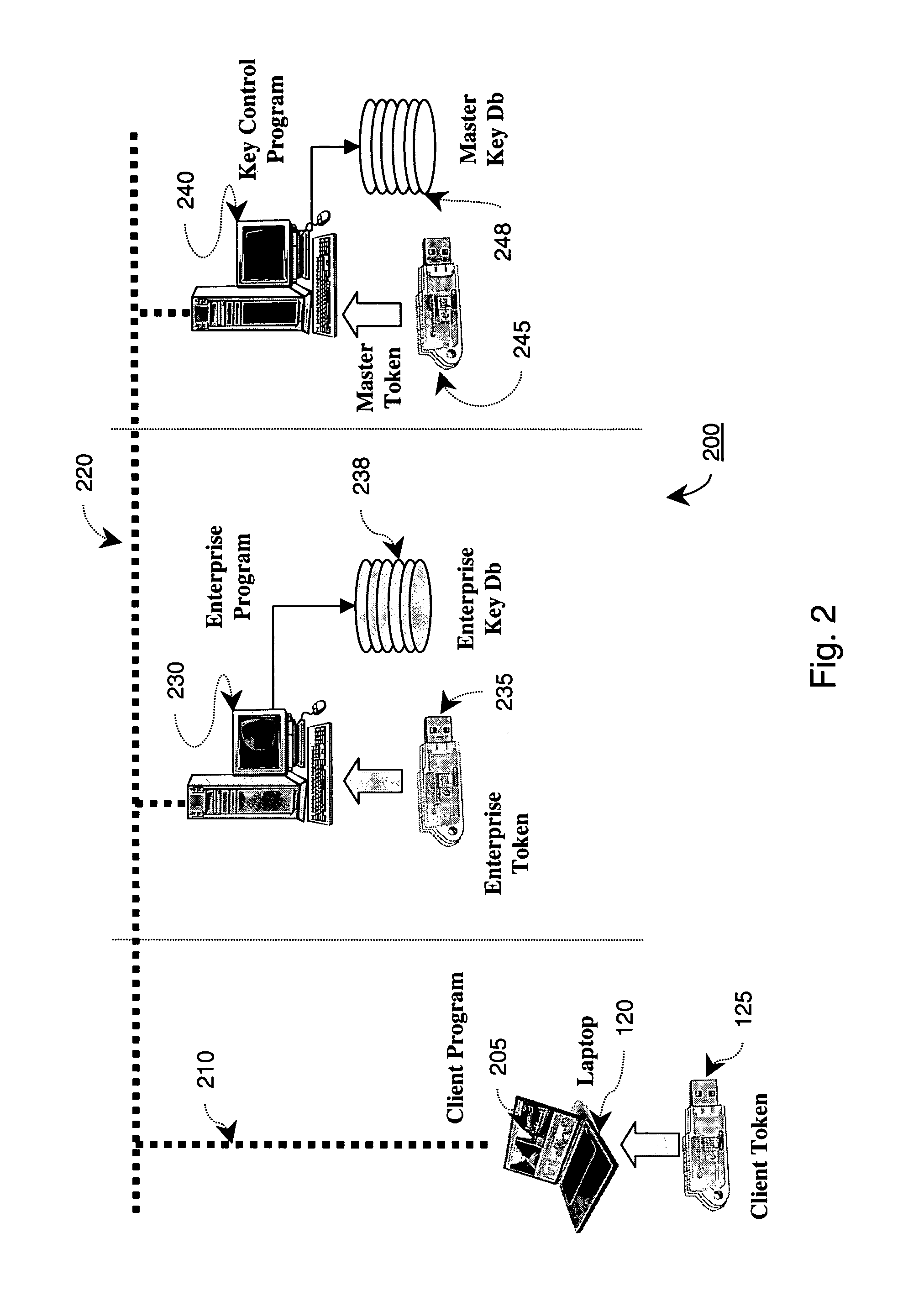
The present invention discloses a technique provisioning network cryptographic keys to a client when direct physical transfer is not feasible. In an embodiment of the invention, a client token generates a temporary key encrypted with a first secret key known only in a master token database and passes this on to an enterprise network token of a network to which service is requested. The enterprise network token then further encrypts the encrypted temporary key with a second secret key and passes that on to the master token database. Since the second secret key is also known by the master token database, the originally encrypted temporary key can be securely decoded only by a master token coupled to the master token database. The decrypted temporary key can then be re-encrypted with a key known only by the enterprise network token and the master token, and returned to the enterprise network token. This allows the enterprise network token to gain secure access to the temporary key of the client token, thereby allowing the enterprise network token to securely provision the remote client token with the appropriate enterprise Network Keys.
Owner:KOOLSPAN
Mass subscriber management
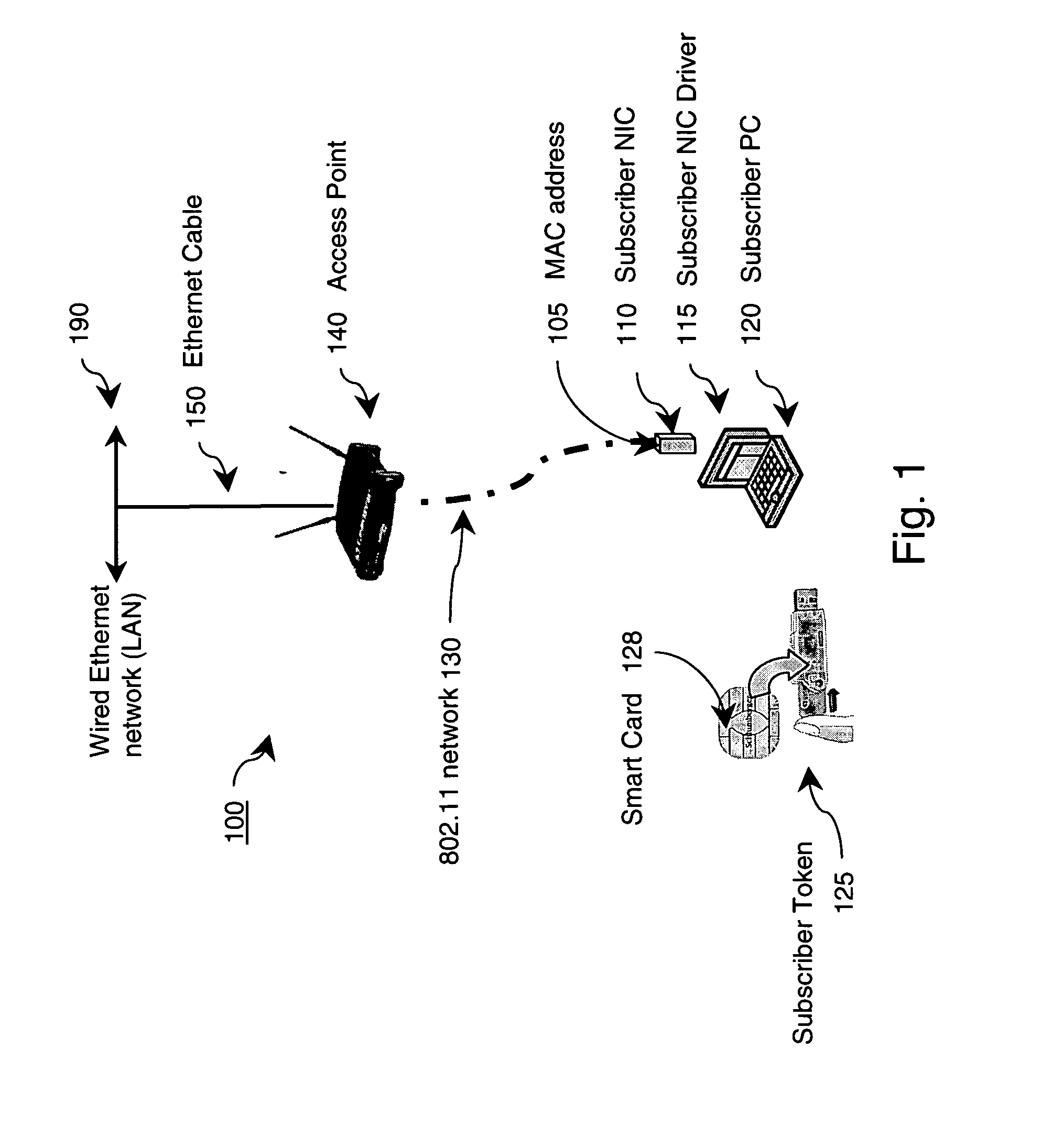
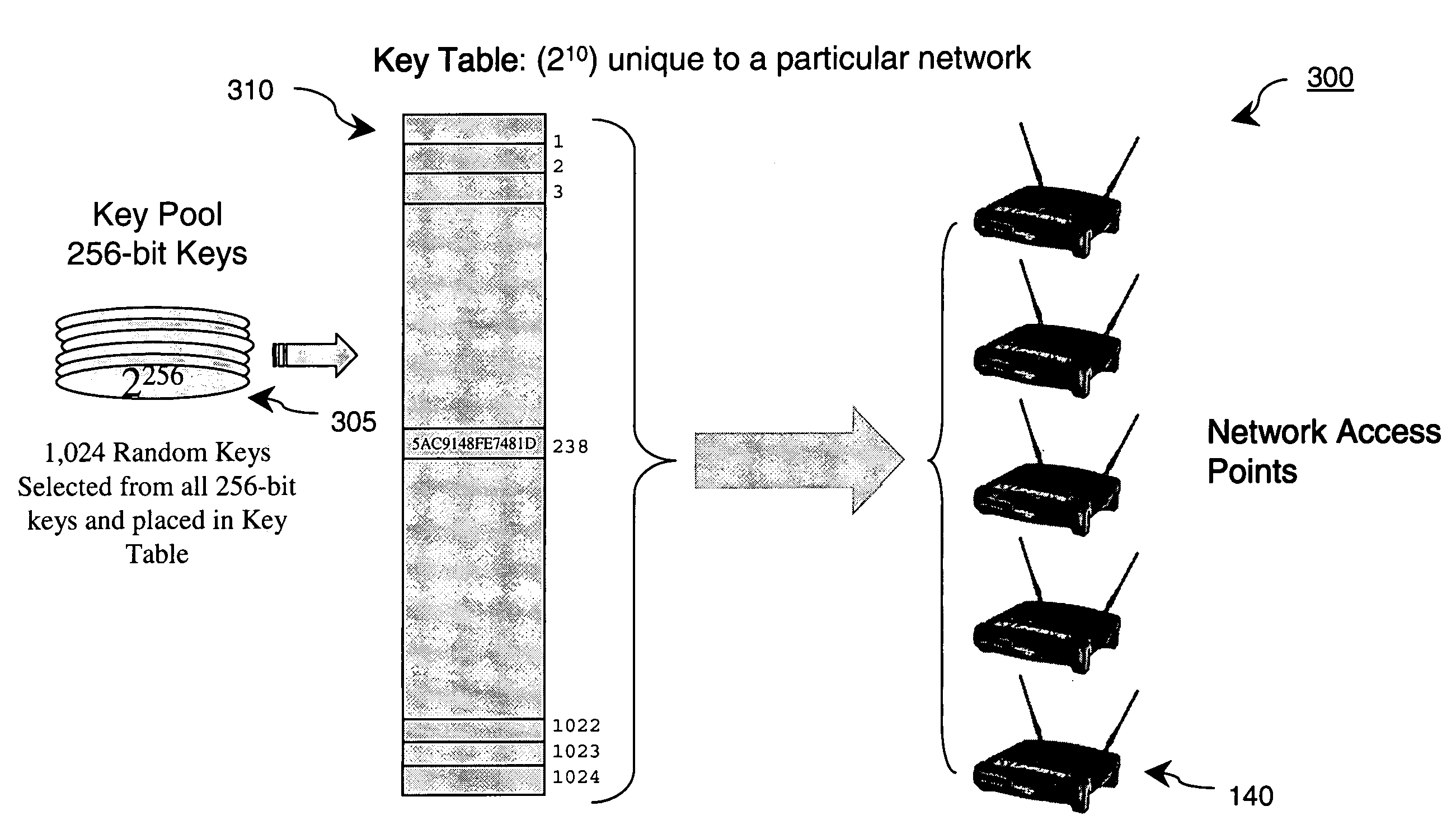
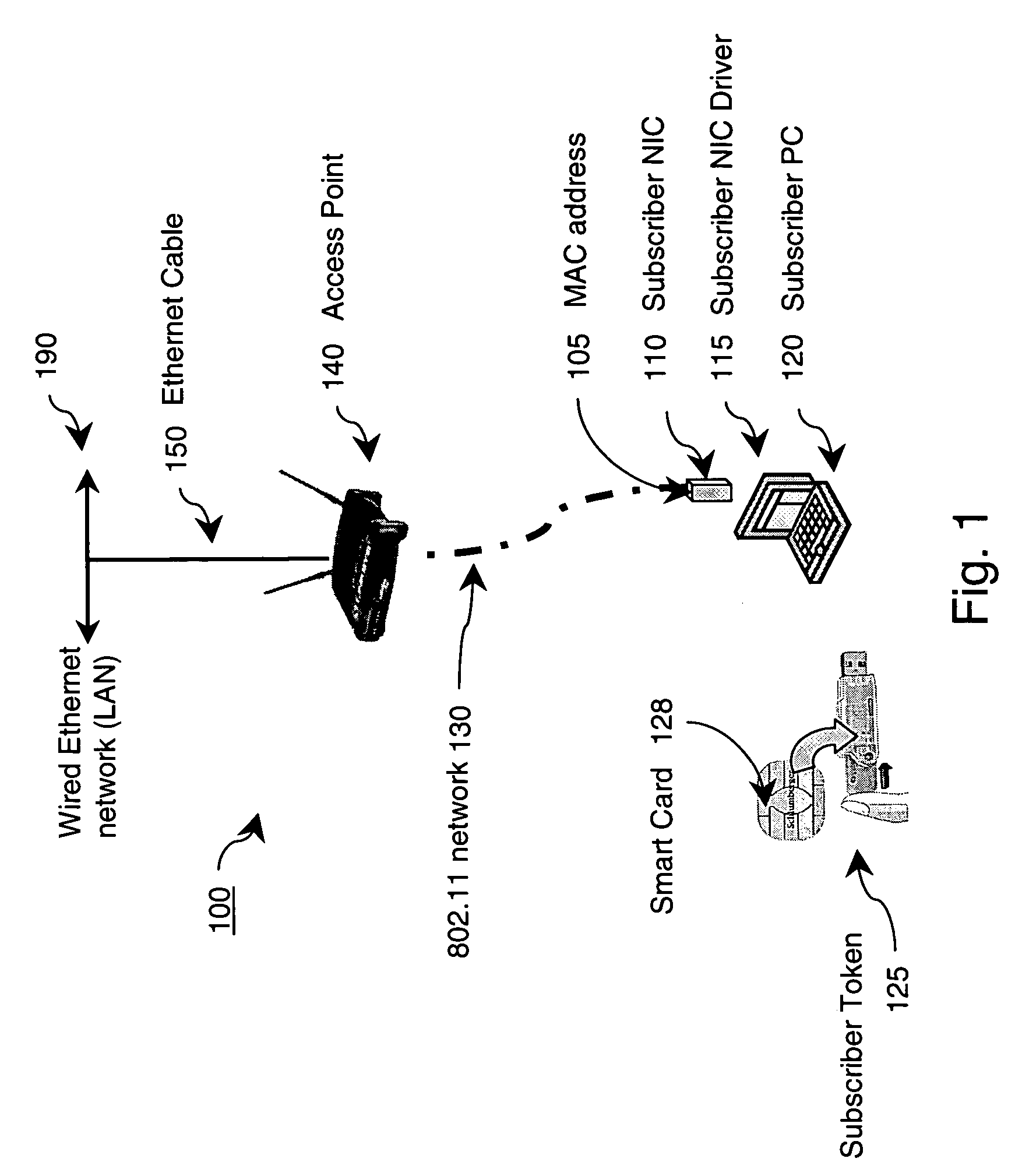
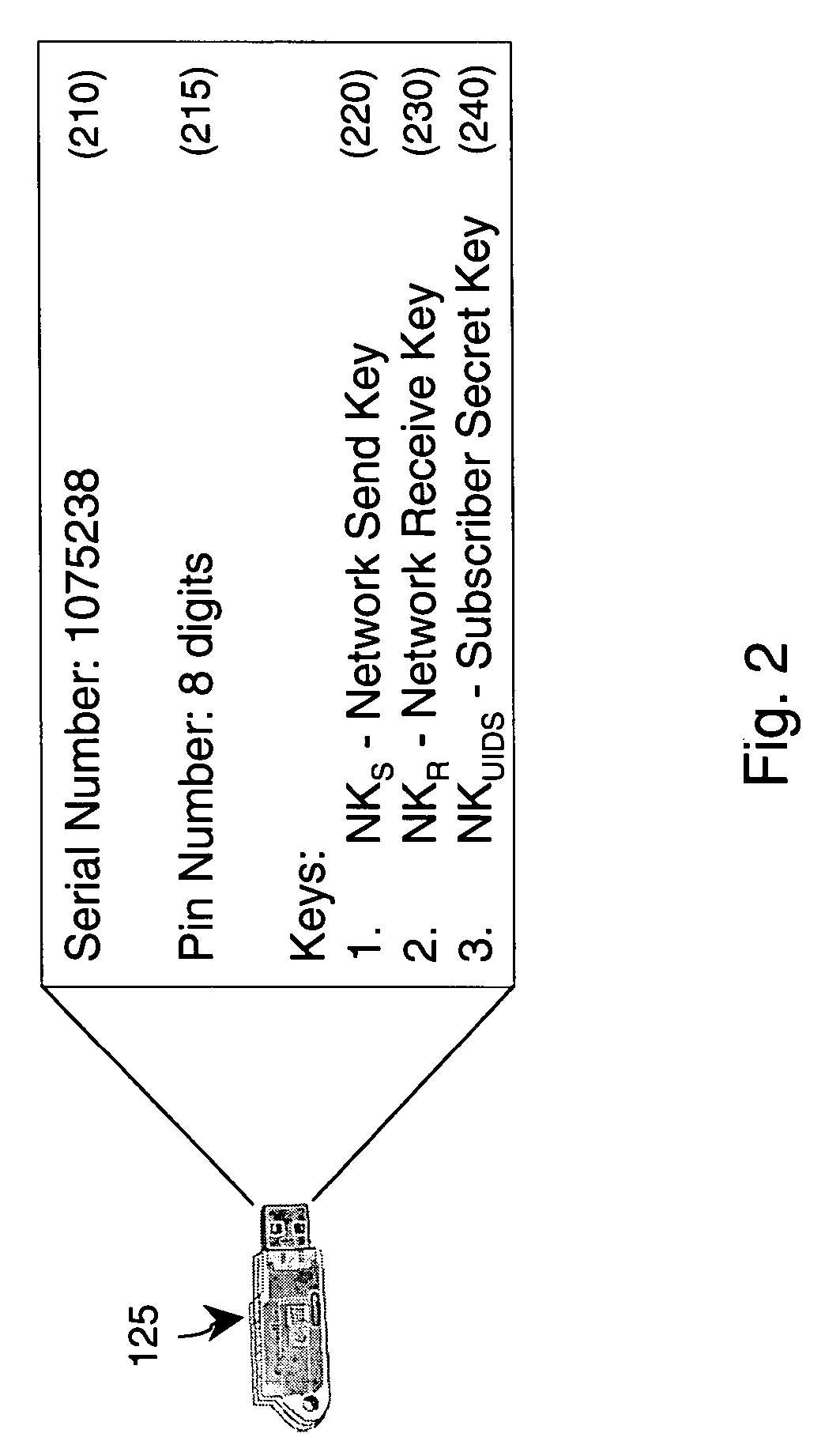
ActiveUS20050074122A1Key distribution for secure communicationDigital data processing detailsNetwork connectionNetwork key
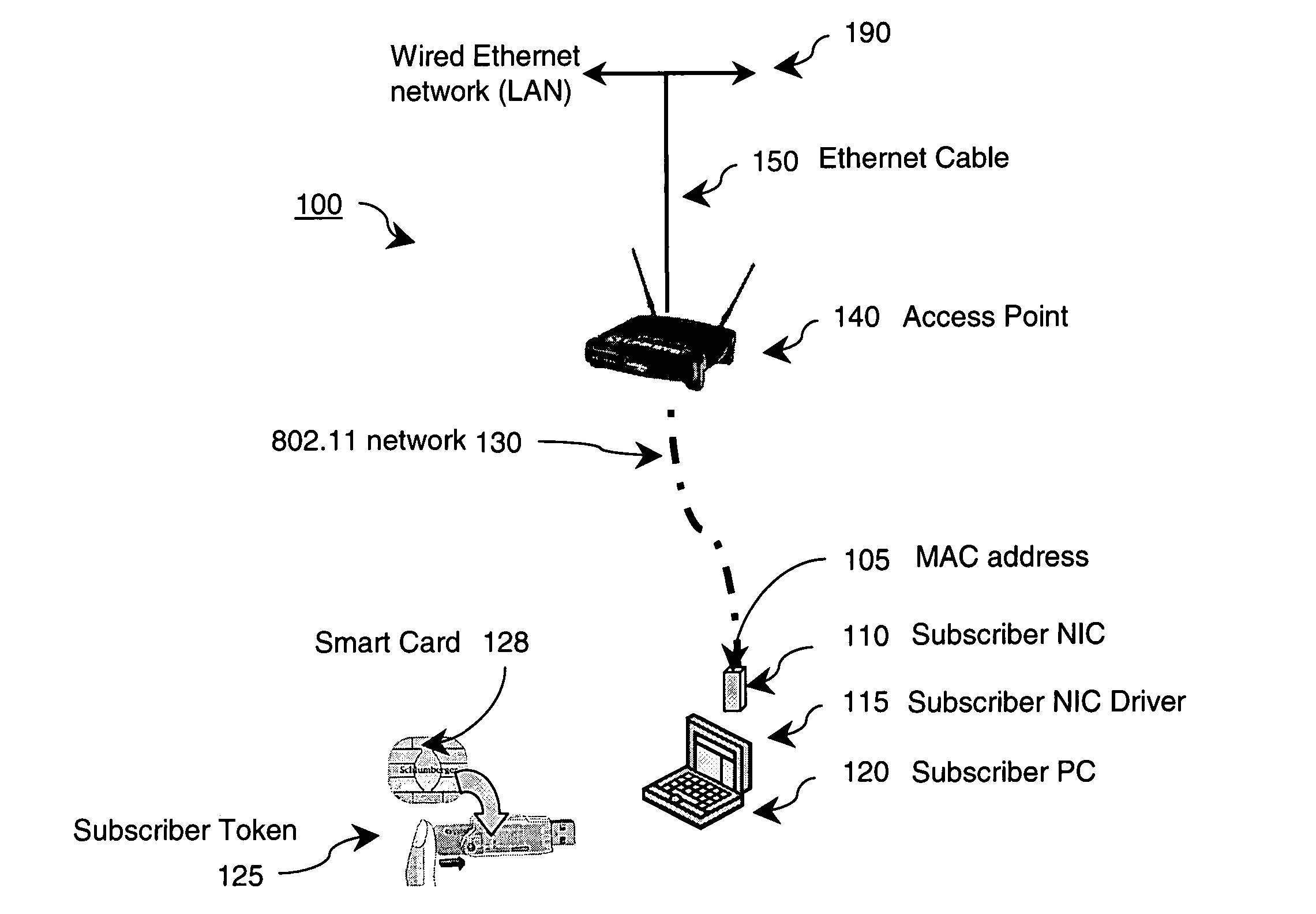
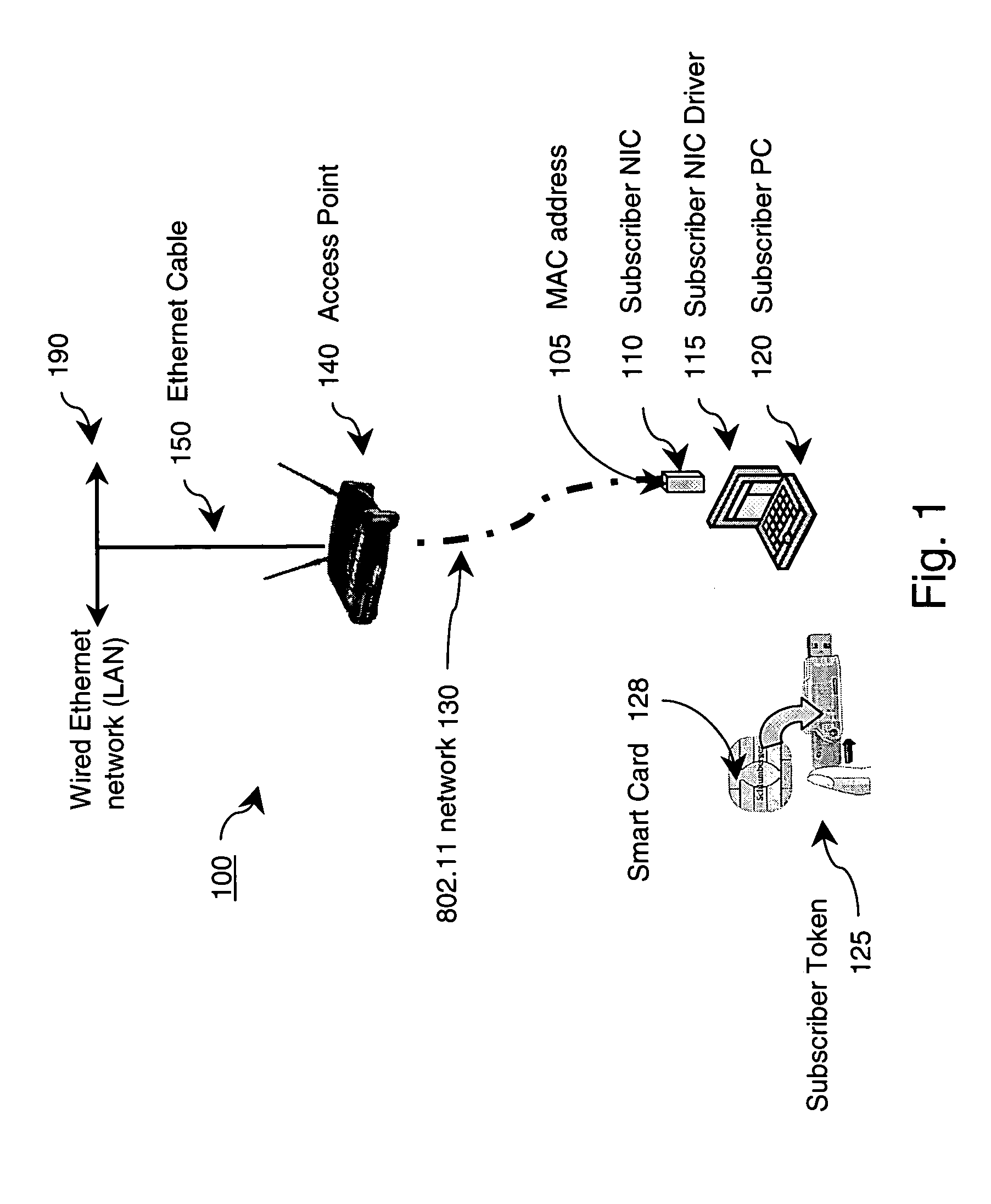
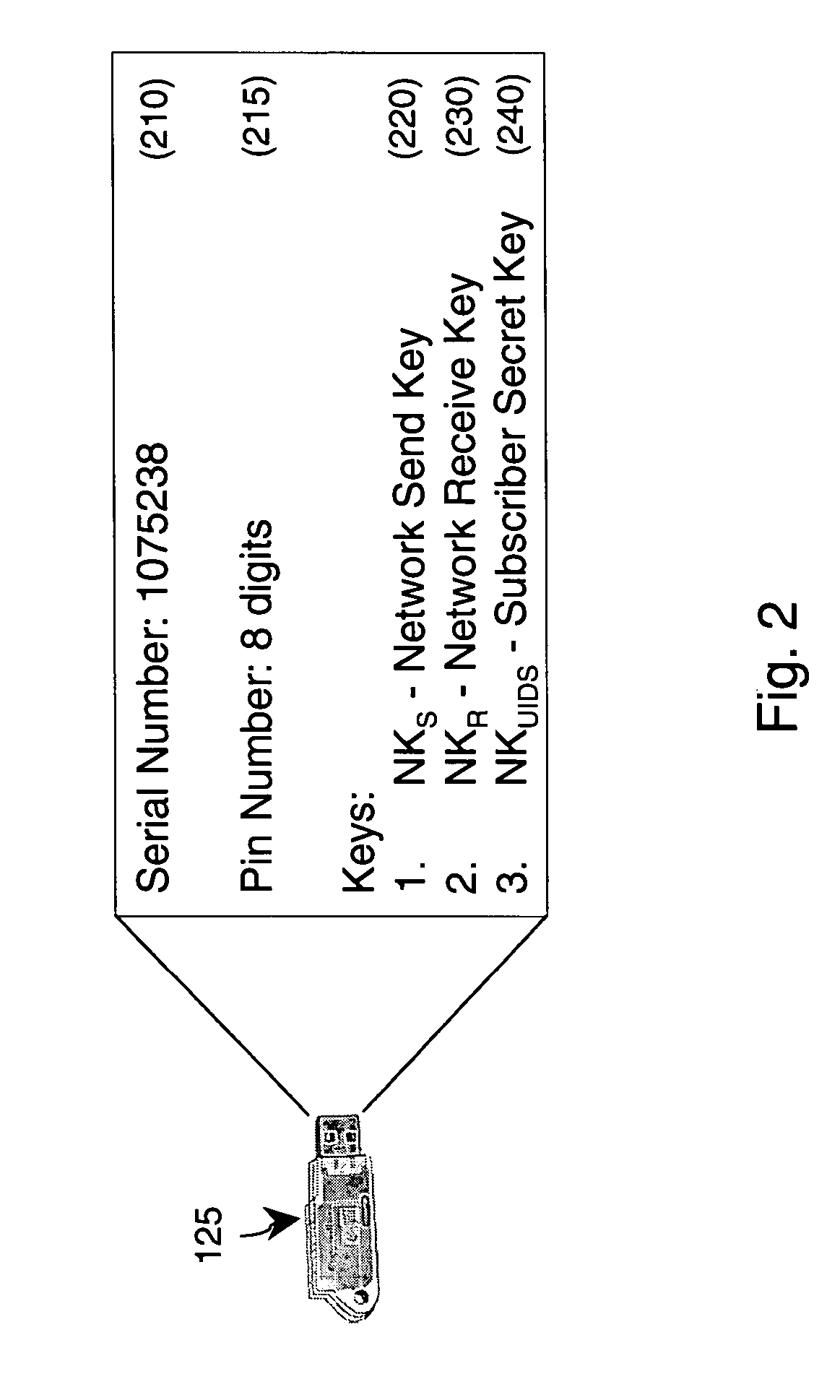
An authentication and mass subscriber management technique is provided by employing a key table derived as a subset of a larger key pool, a network edge device, and authentication tokens attached on both the network edge device and on a subscriber's computing device. The network edge device and subscriber's computing device are provided with secure, tamper-resistant network keys for encrypting all transactions across the wired / wireless segment between supplicant (subscriber) and authenticator (network edge device). In an embodiment of the invention, a secure, secret user key is shared between a number of subscribers based upon commonalities between serial numbers of those subscribers' tokens. In another embodiment of the invention, a unique session key is generated for each subscriber even though multiple subscribers connected to the same network connection point might have identical pre-stored secret keys.
Owner:KOOLSPAN
Mobile terminal network key negotiation method based on bock chain
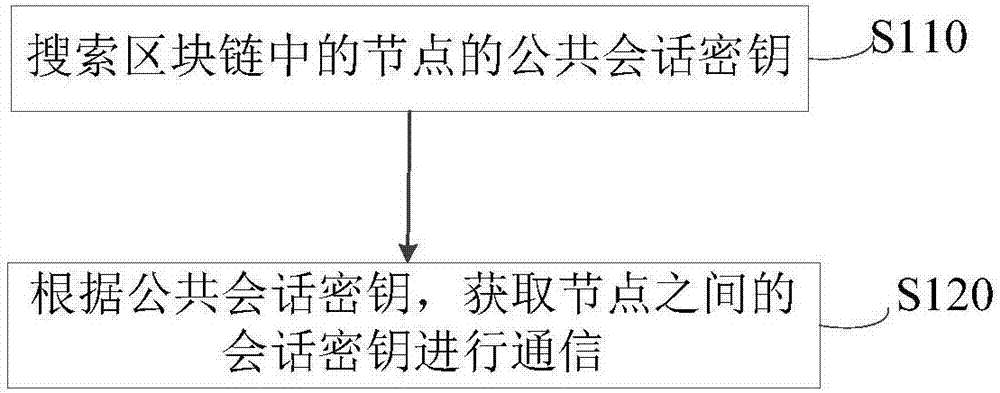
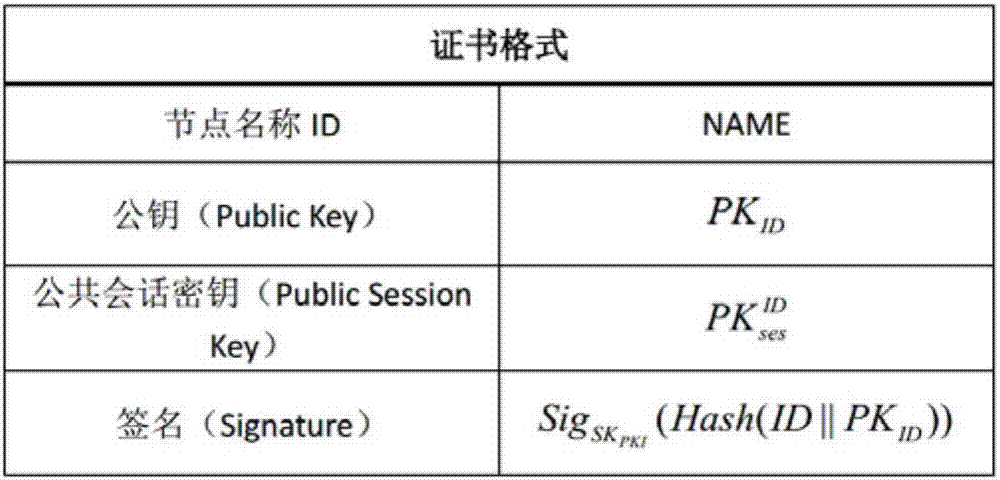
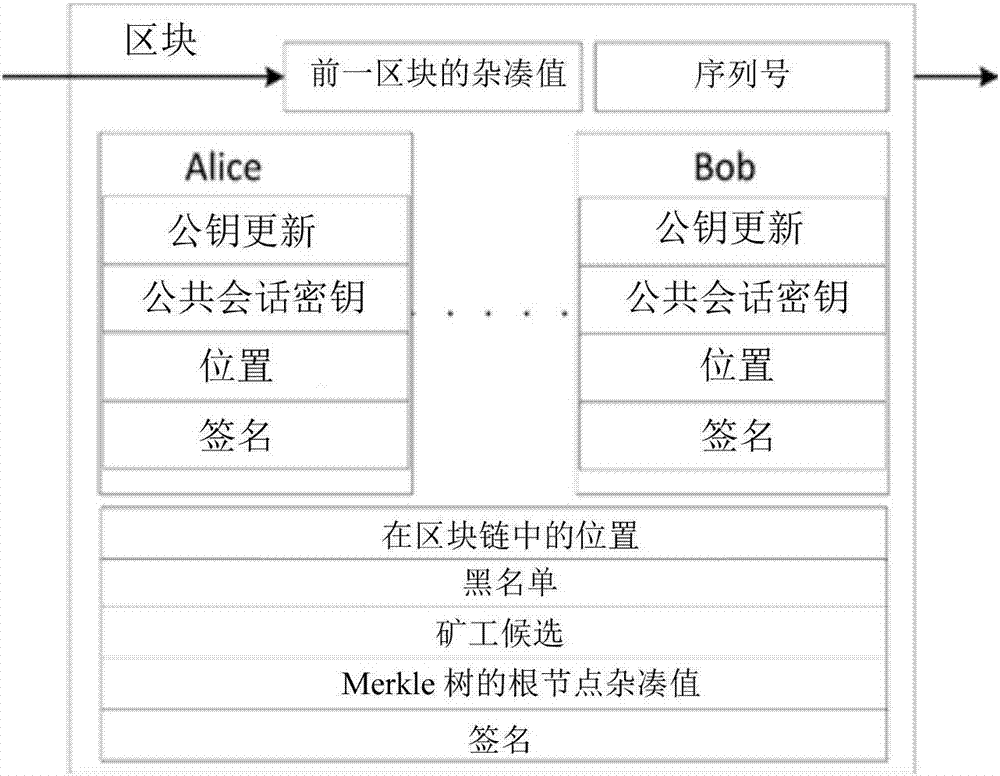
ActiveCN107171806ASolve technical problemsKey distribution for secure communicationPublic key for secure communicationThird partyNetwork key
The invention discloses a mobile terminal network key negotiation method based on a bock chain. The mobile terminal network comprises a plurality of nodes, the node information of the nodes is stored in the form of blocks, a plurality of blocks form a bock chain, the block data in the bock chain are the node information of the nodes, and the node information at least comprises a public session key. The method comprises the following steps: searching the public session keys of the nodes in the bock chain; and obtaining session keys among the nodes according to the public session keys to perform communication. According to the mobile terminal network key negotiation method disclosed by the invention, the bock chain can be regarded as a credible node of a consensus mechanism, and the user in the mobile terminal network participates in the key negotiation according to the features of the bock chain without depending on a credible third party.
Owner:BEIHANG UNIV
Bidirectional authentication method, system and network terminal
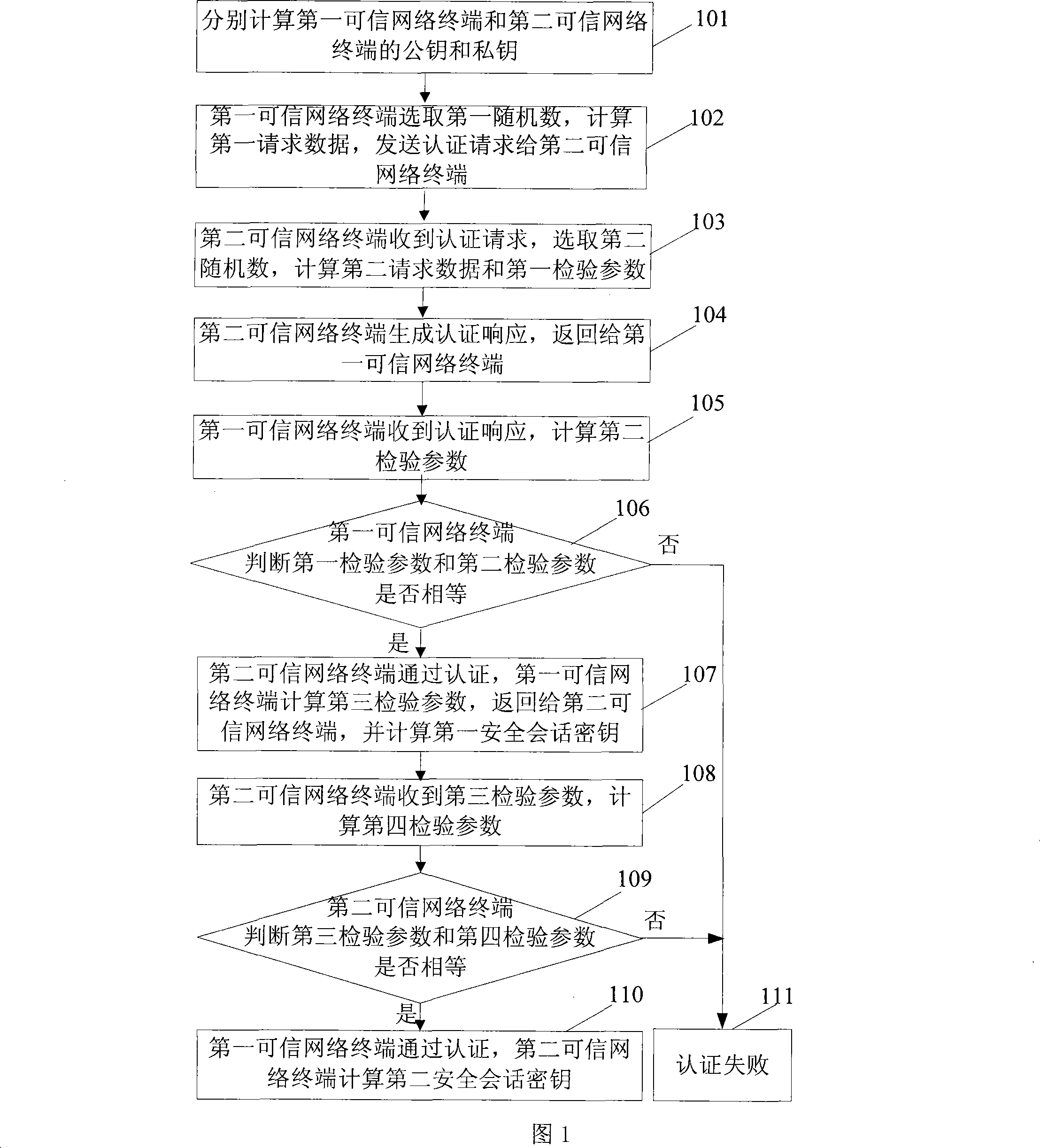
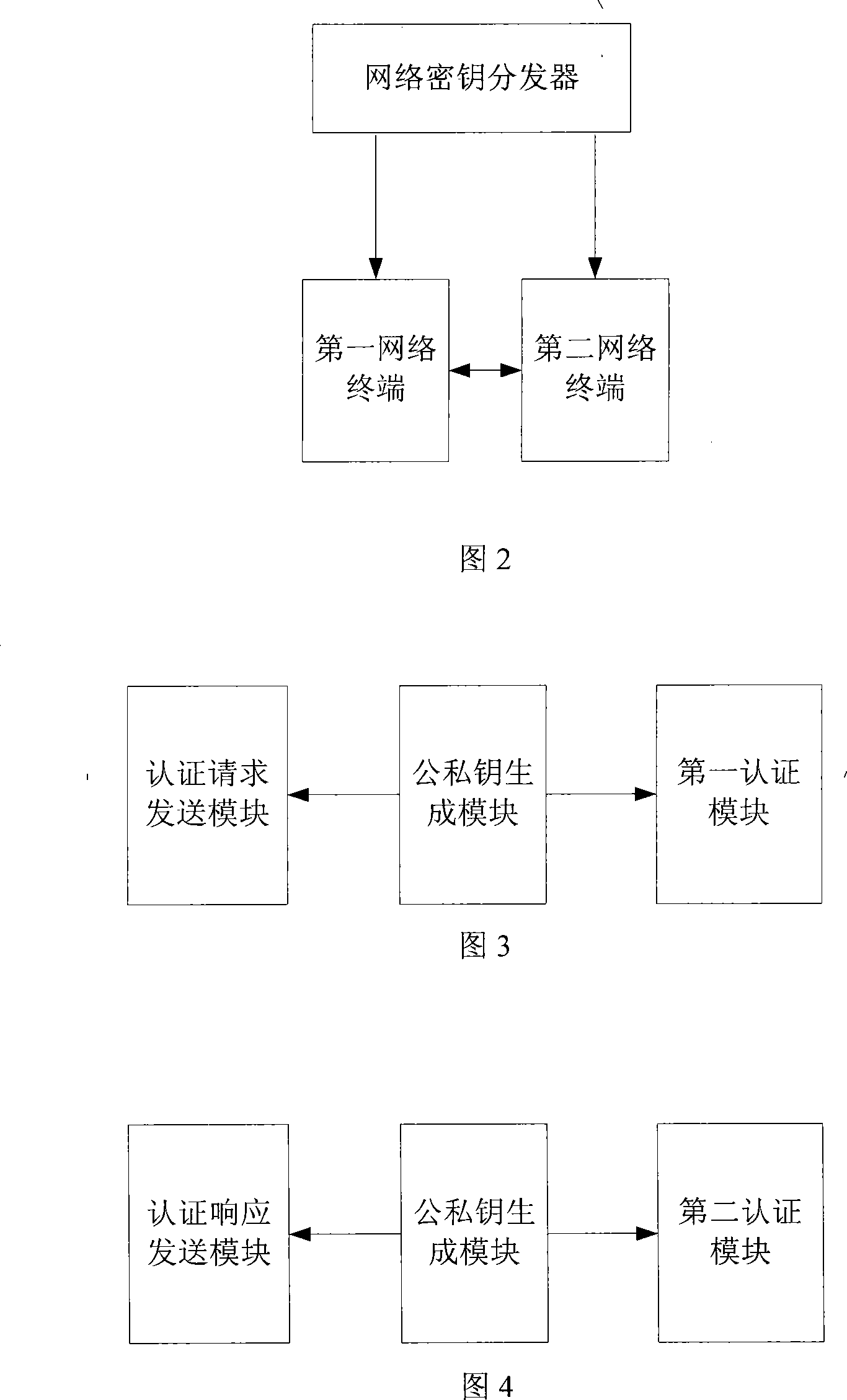
InactiveCN101179380AAvoid computationPublic key for secure communicationUser identity/authority verificationNetwork terminationNetwork key
The present invention discloses a bidirectional authentication method, a system, and a network device, and relates to network information security. The method may include: a network device generates an inspection parameter according to a public key of the peer network device and a private key of the network device, the public key and the private key of the network device being generated according to an identifier of the network device; and the network device performs reciprocal authentication according to the inspection parameter generated by the network device and an inspection parameter sent by the peer network device. A system and a network device for bidirectional authentication are also provided herein. As such, extra calculation caused by certificate authentication is cut down, the system is more secure and reliable, and the key management is simplified.
Owner:SHANGHAI JIAO TONG UNIV +1
Key manager for QKD networks
Key manager systems and methods for a QKD-based network are disclosed. The system includes a QKD layer that generates quantum encryption keys, a persistent storage layer that stores the quantum encryption keys, and a key management layer. The key management layer generates an application registration record that includes a list of multiple applications that use the quantum encryption keys. The key management layer also generates a corresponding key storage layer. The multiple applications reside in an applications layer. The applications in each node remove keys from the key storage layer so that each node can encrypt / decrypt data using quantum encryption keys. The methods also include secure QKD system boot-up and authentication that facilitate implementing a commercial QKD system in real-world environments.
Owner:MAGIQ TECH INC
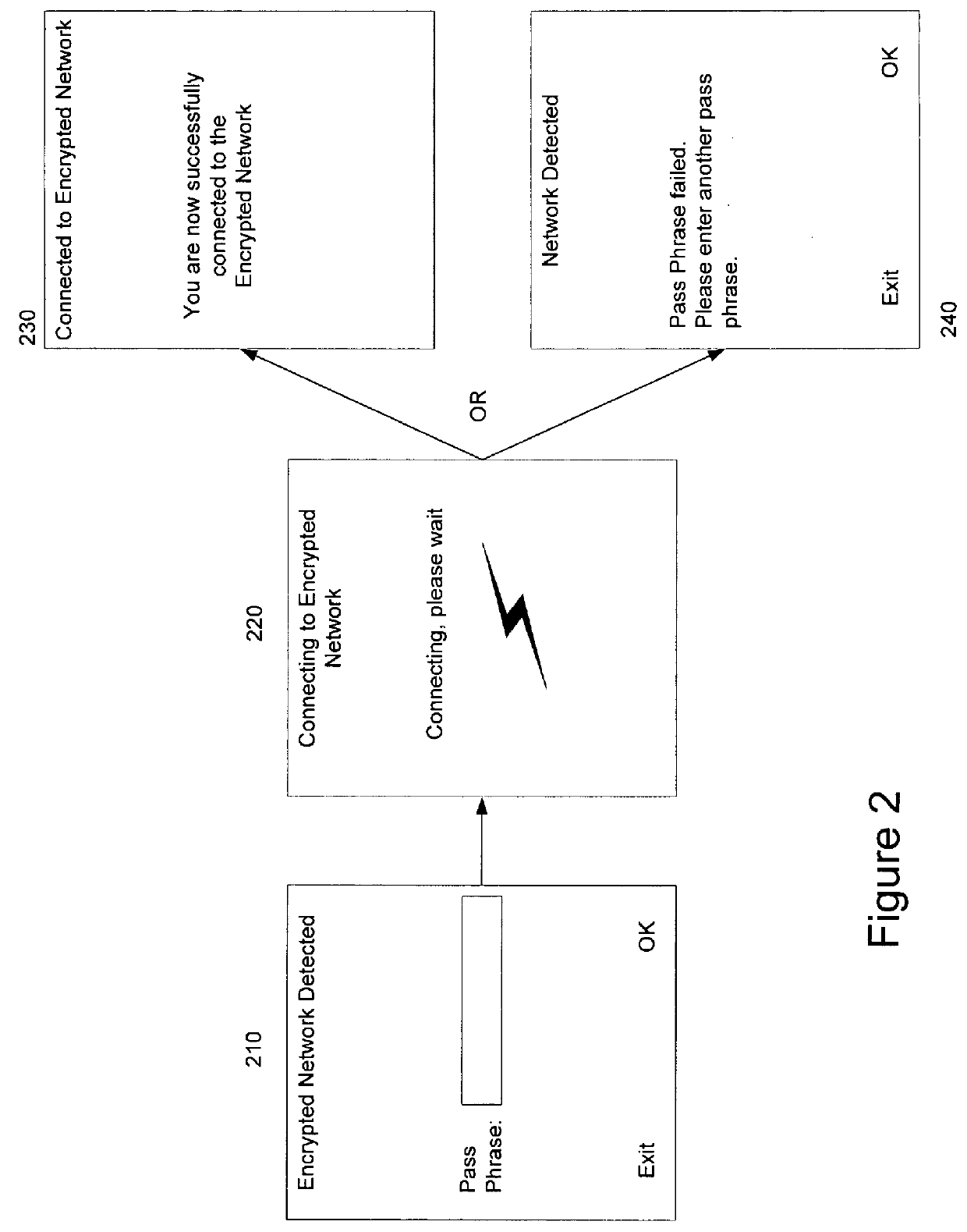
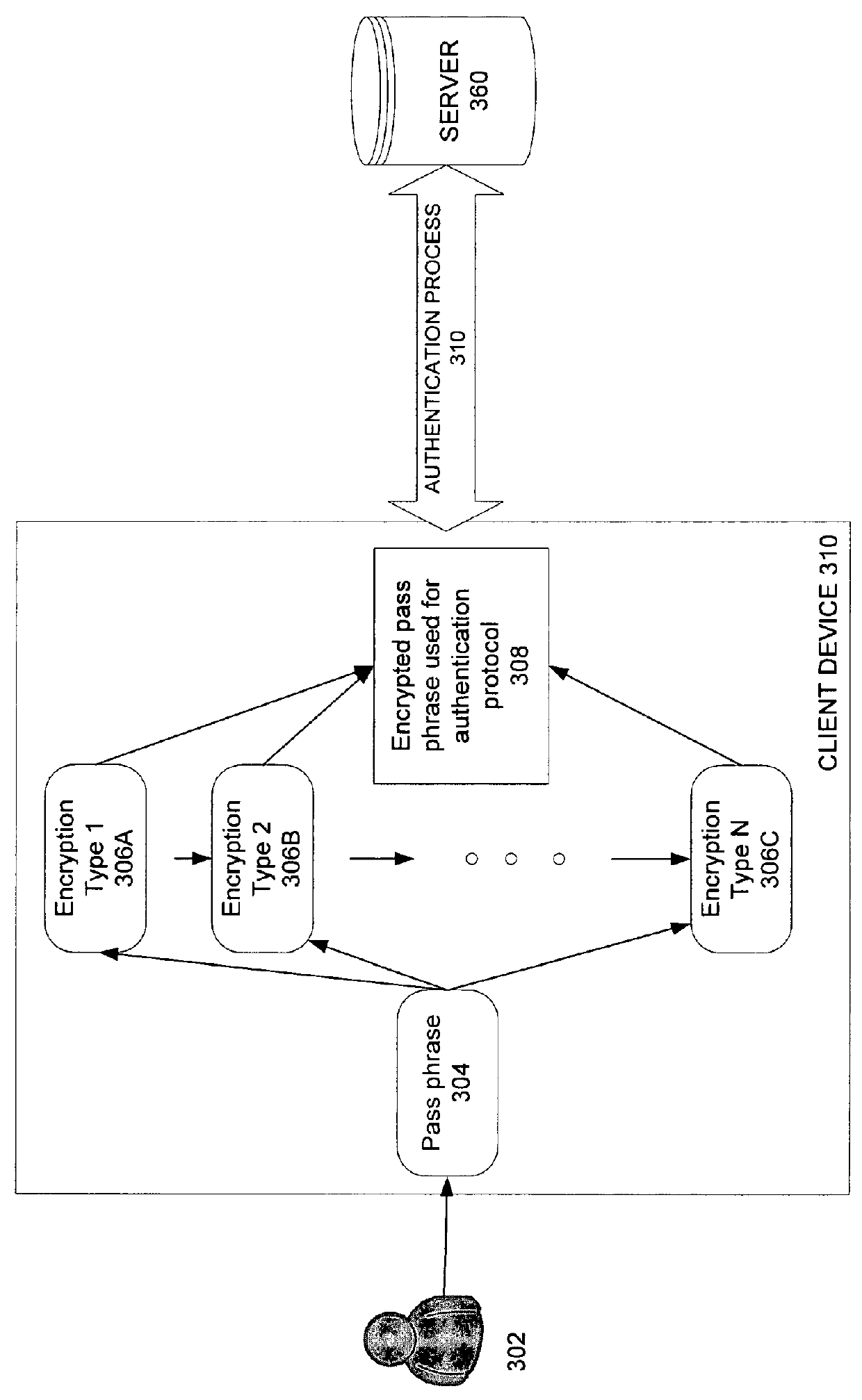
Automatic detection of required network key type
ActiveUS9378343B1User identity/authority verificationDigital data authenticationPassphraseUser input
Methods and apparatuses in automatic detection of a required network key type are described. In one embodiment, a client device prompts a user for a pass phrase, receives a pass phrase and automatically determines the encryption type for the pass phrase to connect to a network. The client device then communicates with a server to authenticate the client device.
Owner:QT +1
Information processing apparatus, content information management method and computer program
InactiveUS20050071279A1Reduce processing loadChange performanceMultiple keys/algorithms usageUnauthorized memory use protectionInformation processingNetwork connection
A content providing server connected to a home network or the like is configured in such a way as to store a content key, which is encrypted by a network key shared by network-connected devices and appropriately updated, in a storage together with encrypted content, and as to hold a network key table in which all network keys including all pre-update network keys, which are being applied to encrypted content keys, are registered and stored. This server performs a key changing operation of changing a content key, which is encrypted by a pre-update network key, to an encrypted key, to which an updated network key is applied, only when needed, for example, at an occurrence of utilization of the content. Consequently, this configuration prevents key changing operations from being wastefully performed. Thus, the processing load on the server is alleviated.
Owner:SONY CORP
Cipher key replacing method, system and device
InactiveCN101483865AImprove communication qualityAvoid lossSecurity arrangementComputer hardwareCommunication quality
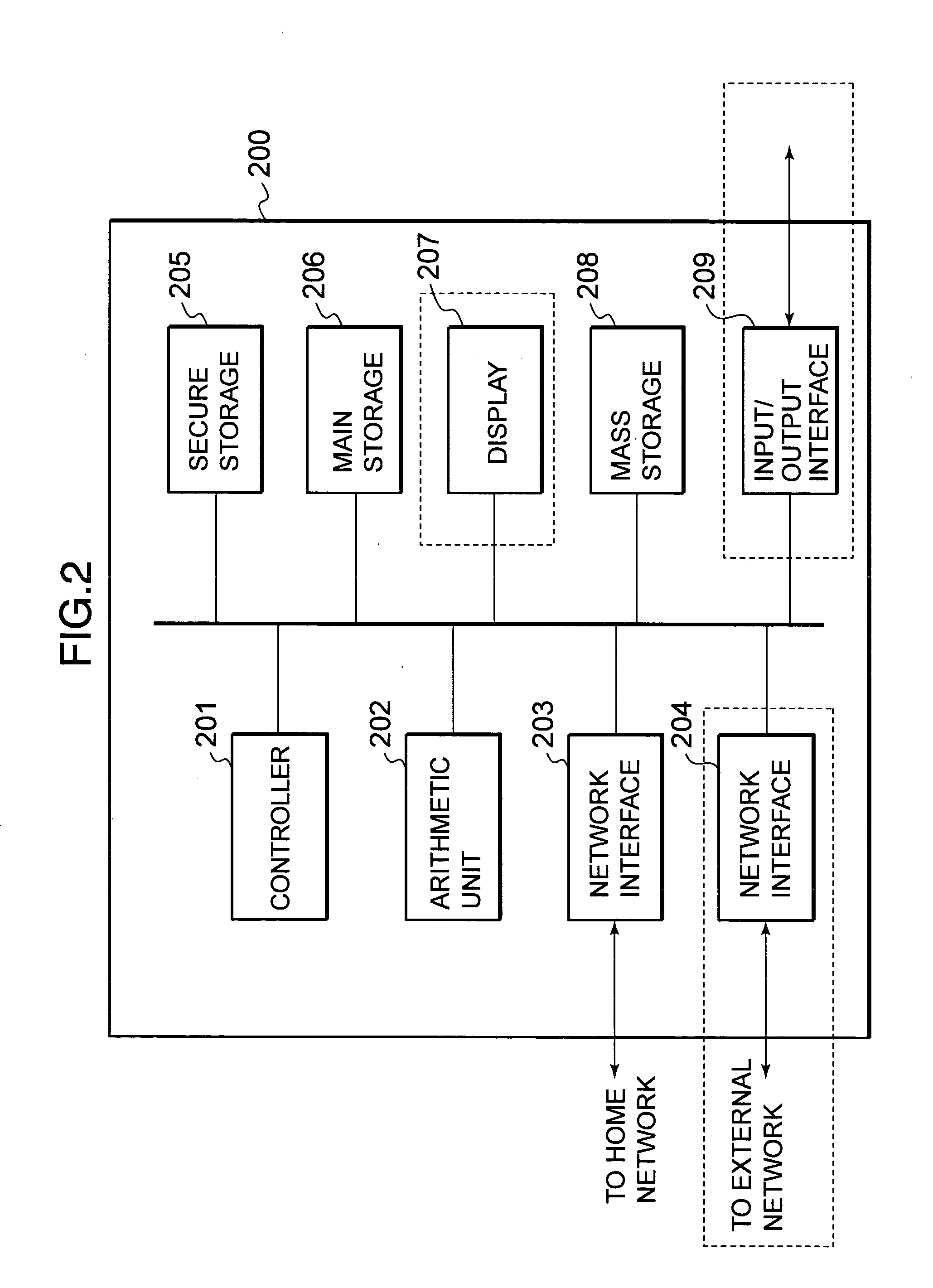
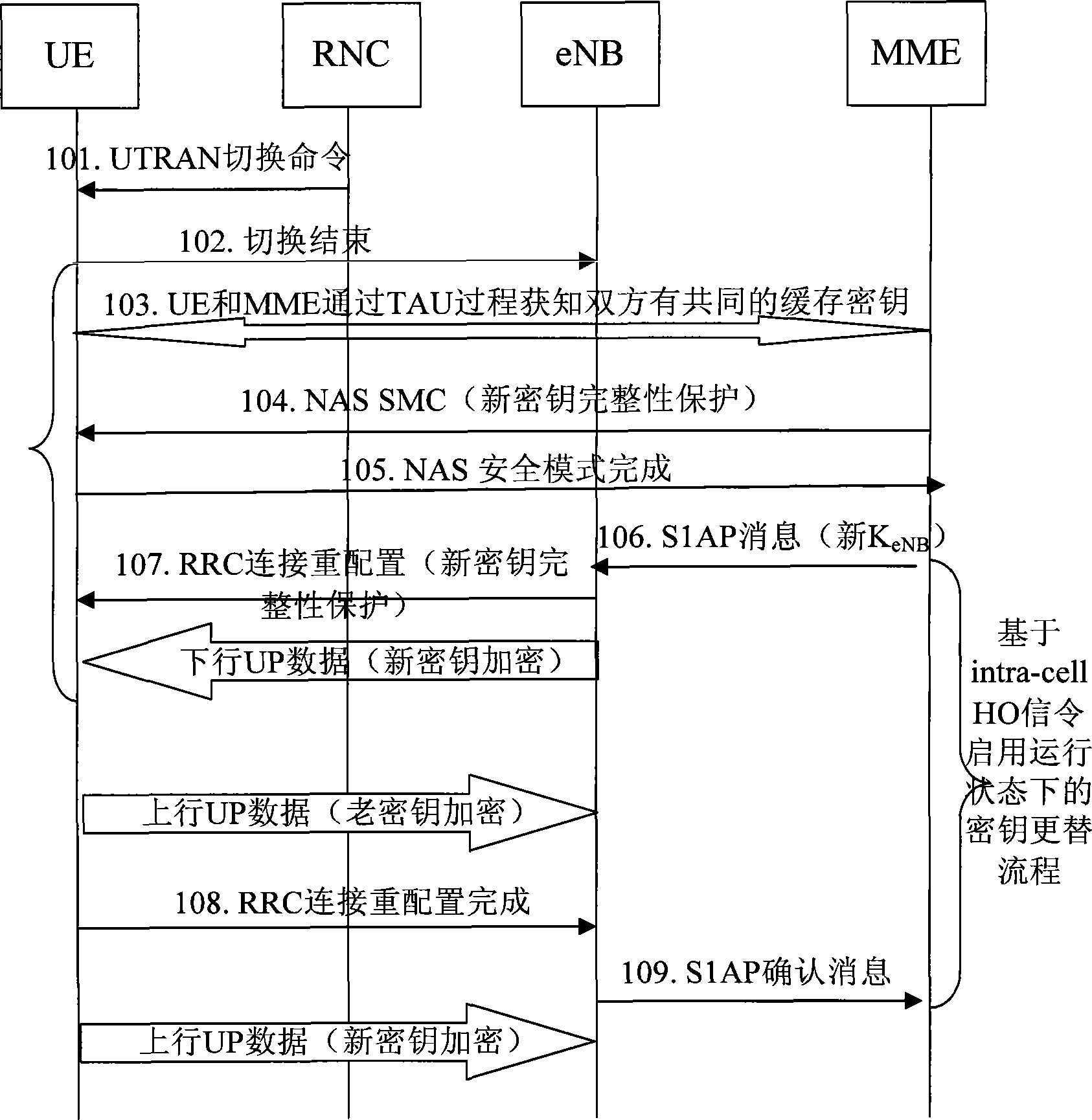
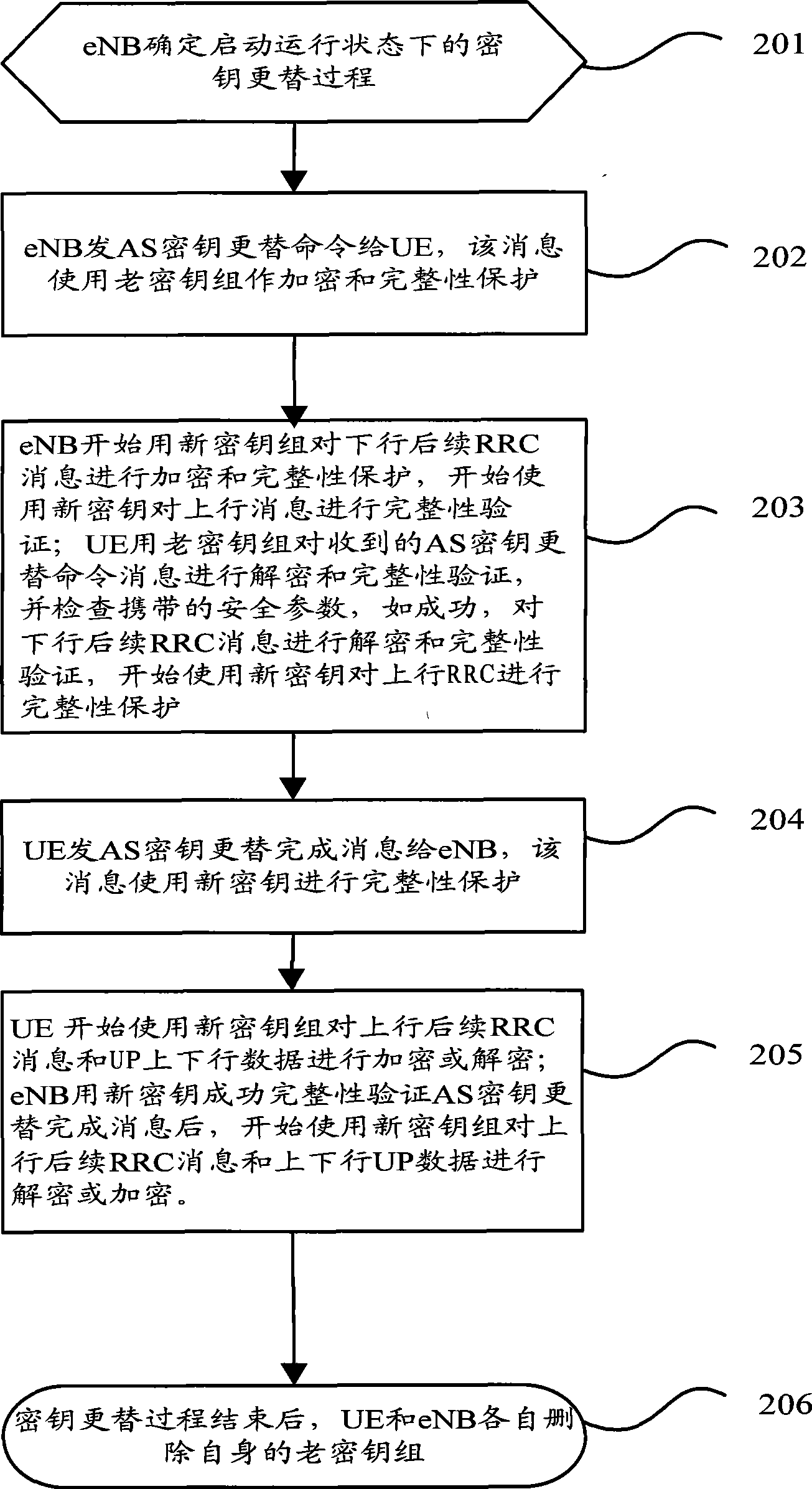
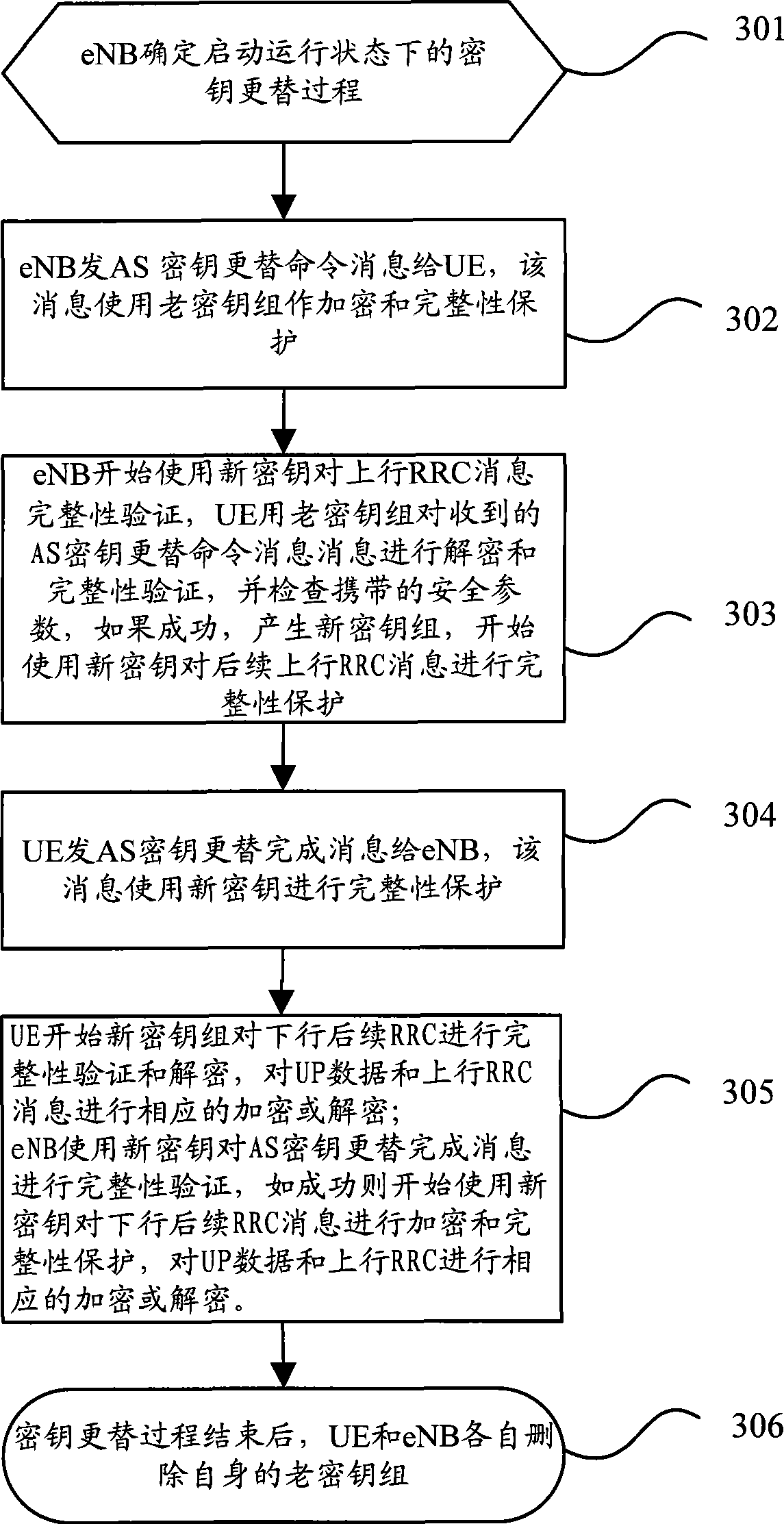
The invention discloses a key replacement method, which comprises: an evolution node point (eNB) sends an AS key replacement command message with the encryption and integration protected by the old key group to the user equipment (UE); the UE processes the AS key replacement command message with the old key group and sends an AS key replacement completion message with the integration protected by the new key to the eNB; then the UE encrypts or decrypts the user plane (UP) data with a new key; the eNB processes the AS key replacement completion message with a new key group and encrypts or decrypts the UP data with the new key. The invention further discloses a key replacement system and the combination equipment thereof. The adoption of the invention can ensure that the key used by the UE and the network user message is synchronous when the key is replaced, thus avoiding user communication data loss caused by asynchronous UE and network key and improving the communication quality of the user.
Owner:ZTE CORP
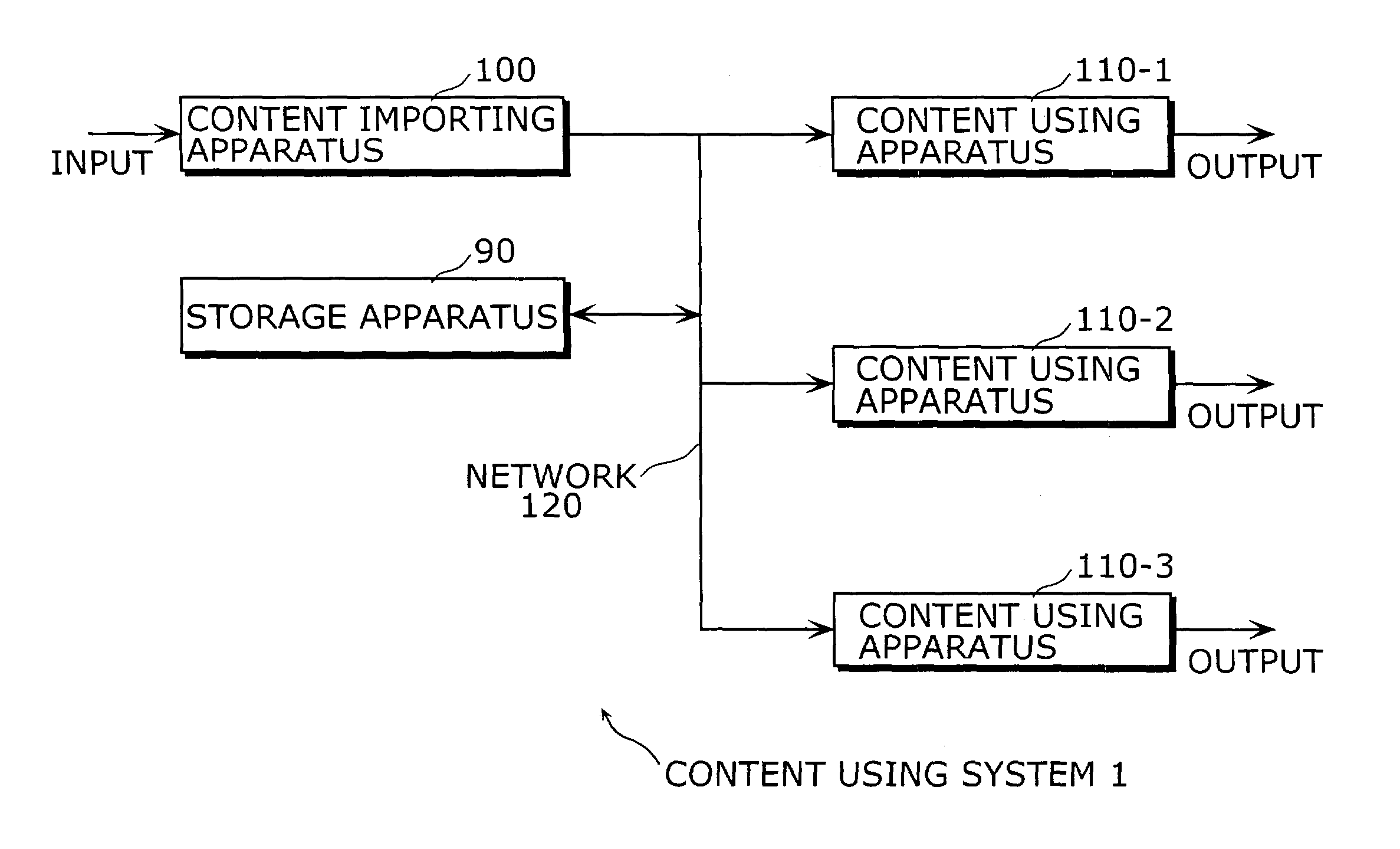
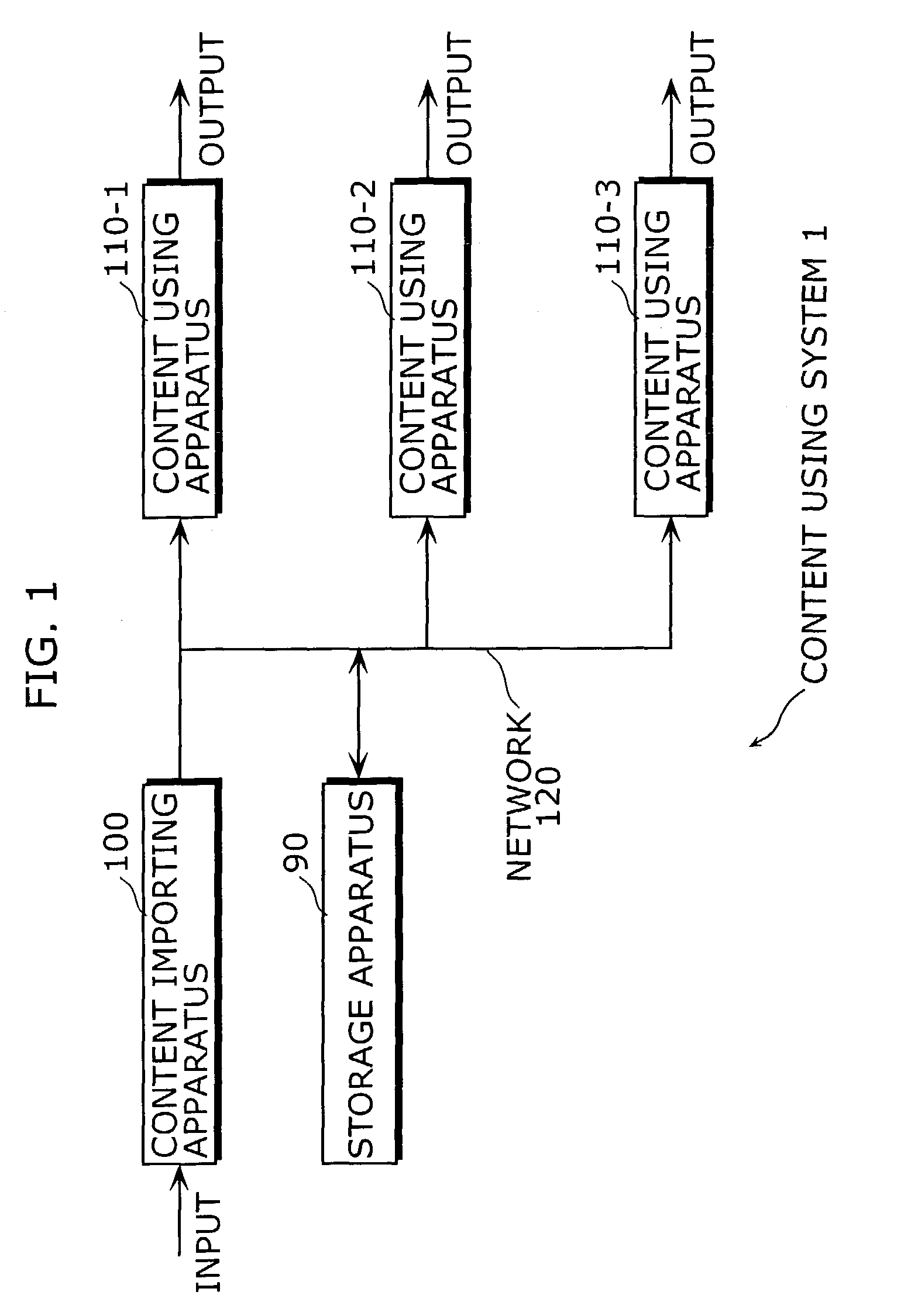
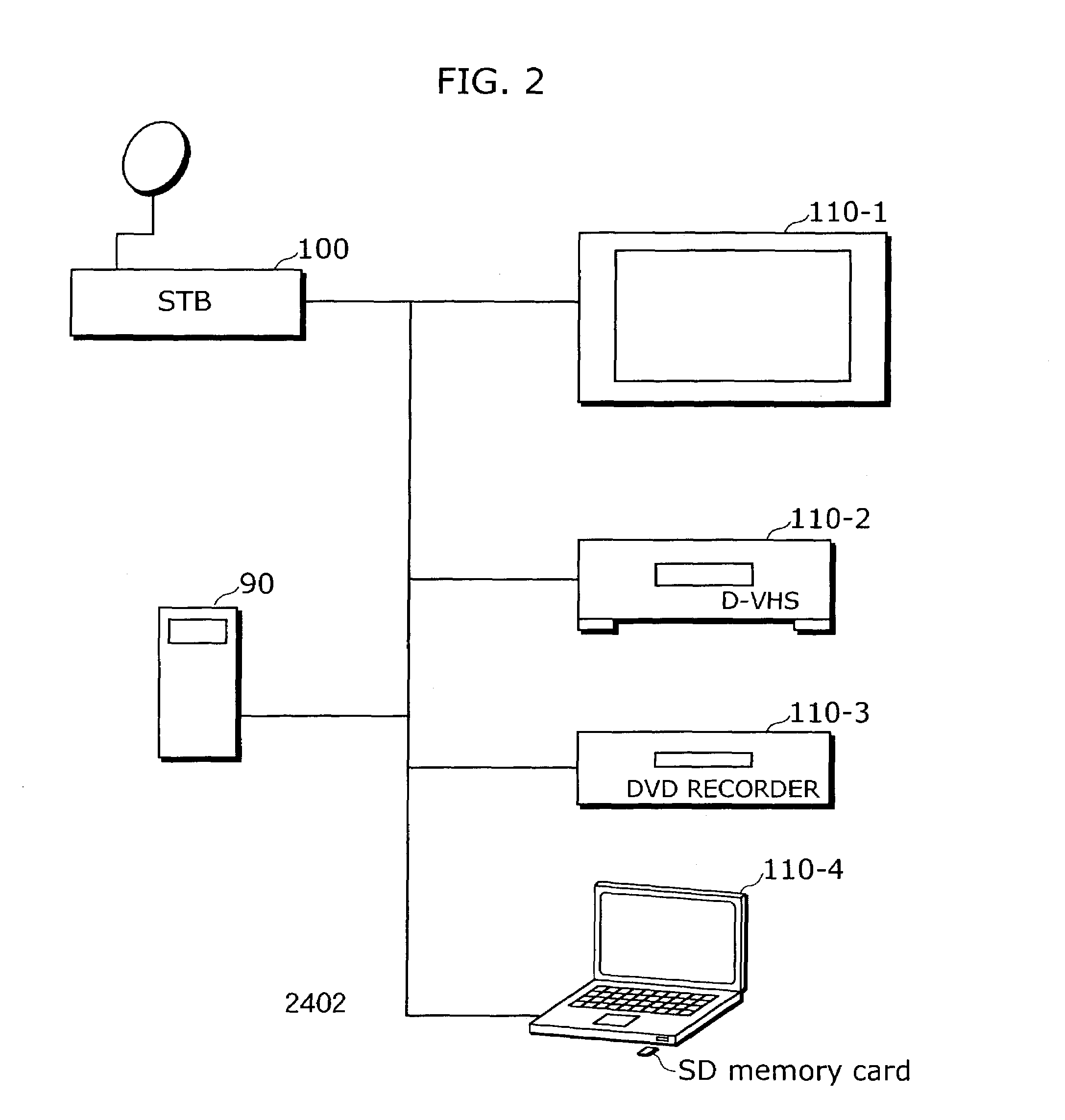
Content using system
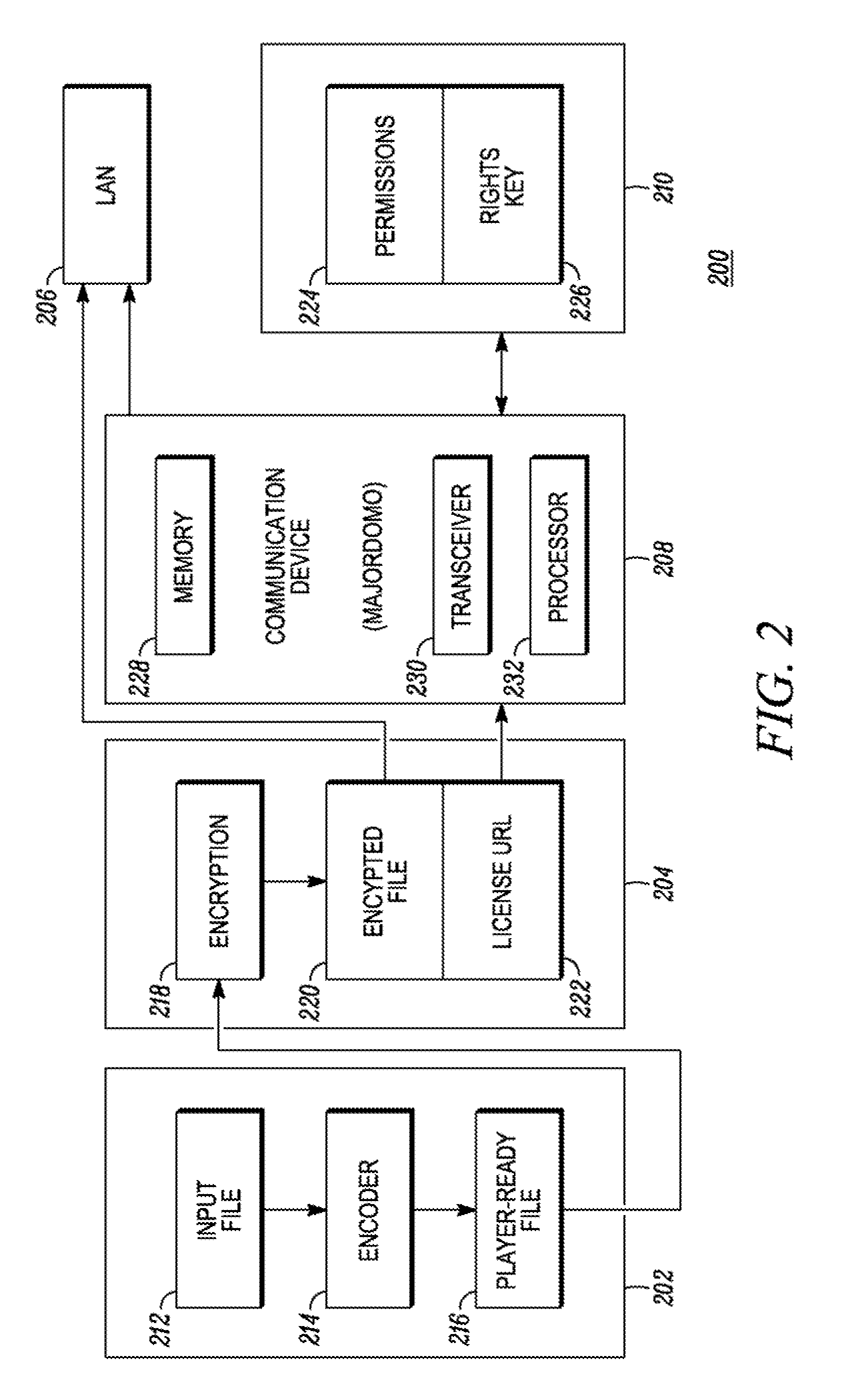
ActiveUS7194091B2Unlimited writing of contentsProtected contentSynchronising transmission/receiving encryption devicesDigital data processing detailsManagement unitMobile content
A content using system is composed of a content importing apparatus and at least one content using apparatus. The content importing apparatus includes a content ID generating unit that generates a content ID, and a content key information encryption converting unit that converts the encryption of content key information by using an encryption key (“network key”) that is shared in advance on the network. The content using apparatus includes a content key information decrypting unit that decrypts the content key information, whose encryption has been converted, by using the network key, a moved content list storing unit for storing a moved content list (MCL) in which the content IDs of contents that have been written onto a storage medium are written, and a moved content list managing unit that judges whether the writing of a content is permitted or prohibited based on the MCL.
Owner:SOVEREIGN PEAK VENTURES LLC
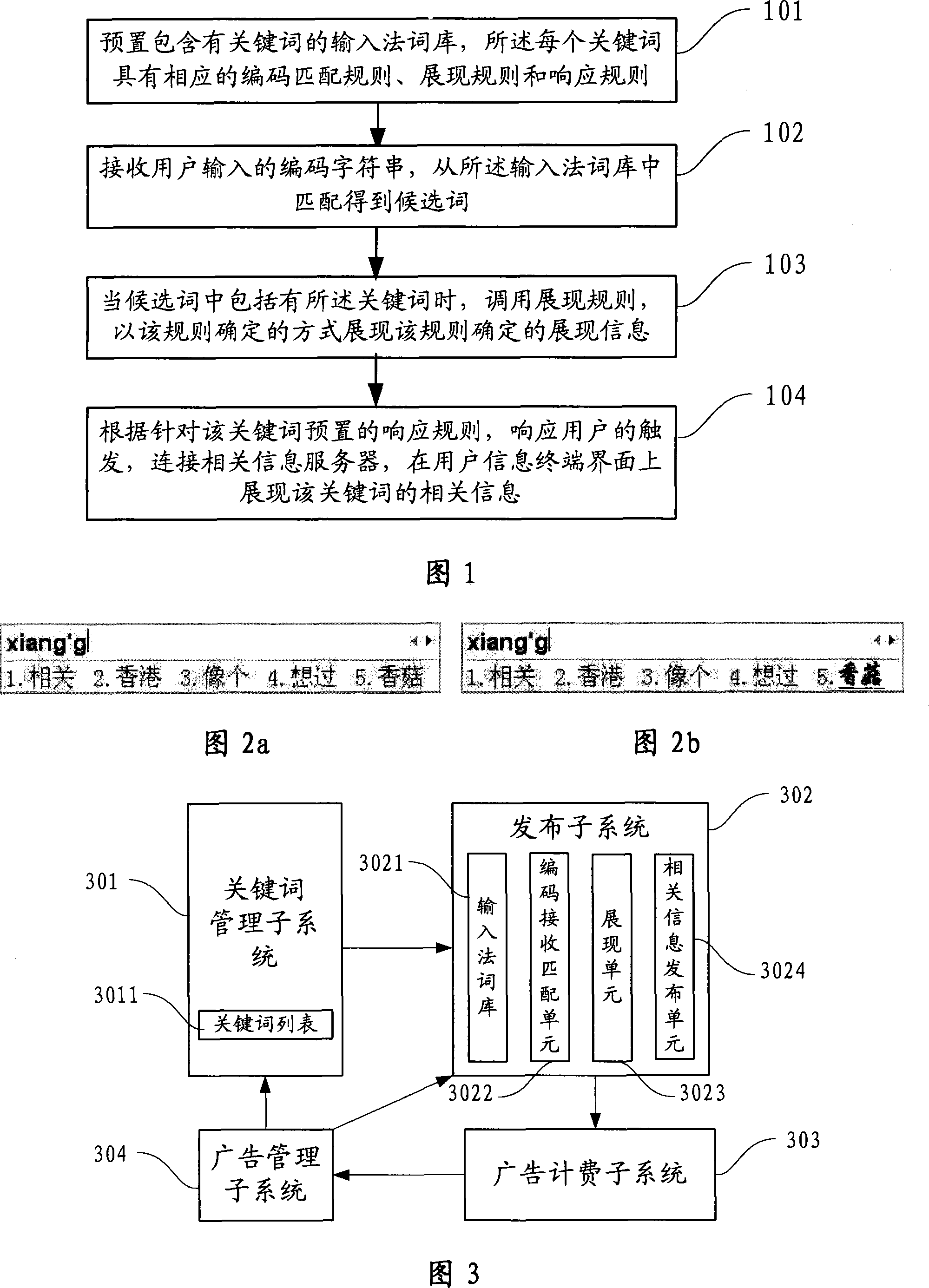
Method and system for publishing information related to internet key character
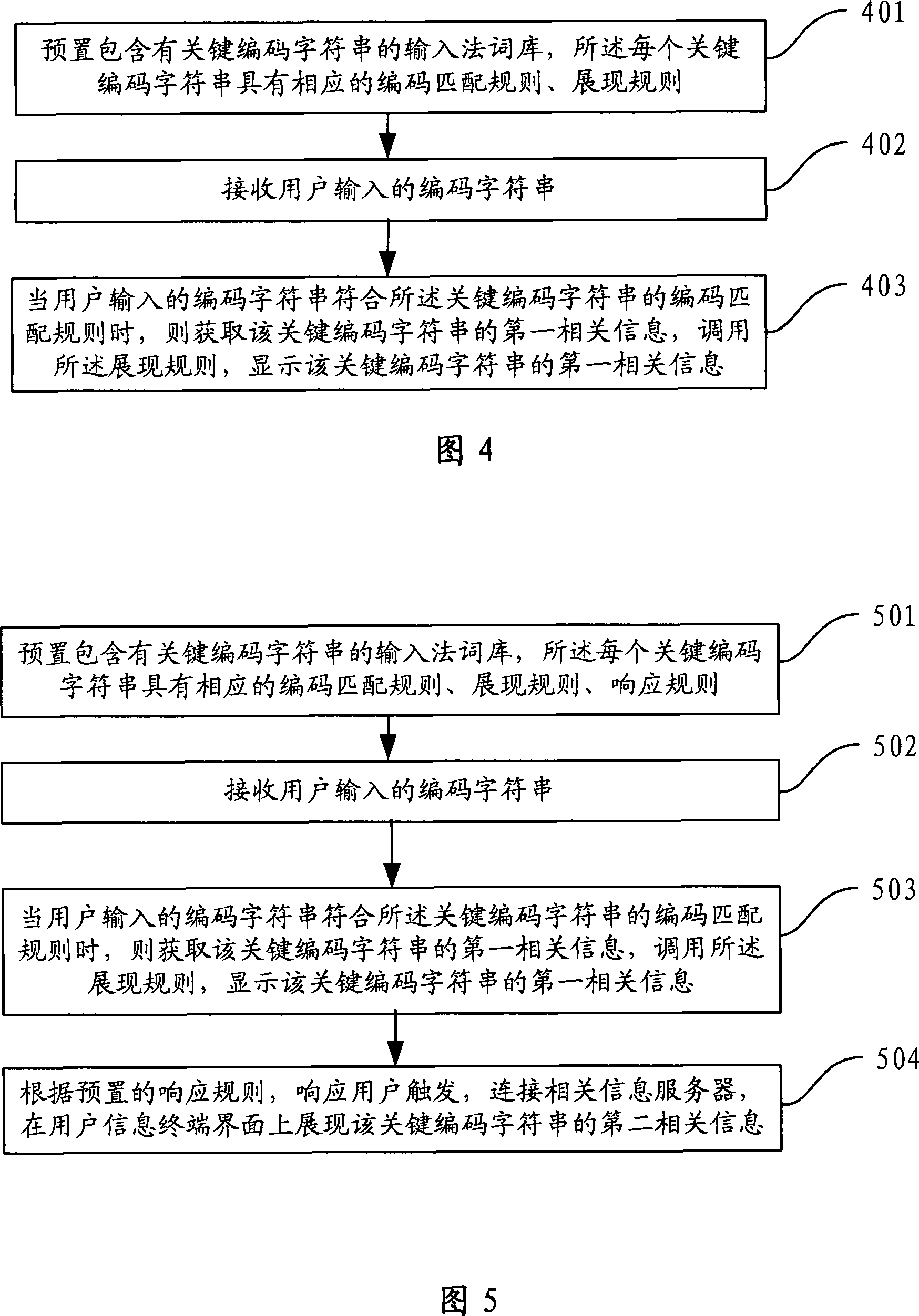
ActiveCN101178737ABroaden the way to connectMeet needsSpecial data processing applicationsRelevant informationUser input
The invention provides an issuing method of a network key character related information and comprises steps below: the invention presets an input method word base containing key words, each key word has corresponding coding matching rule and exhibiting rule; the invention receives a coding character string inputted by users and obtains candidate words in a matching way from the input method word base; when the candidate words comprise the key word, the invention transfers the exhibiting rule and exhibits the confirmed exhibiting information in a method confirmed by the rule. The method also can be used in the related information for issuing the key coding character string. The invention cuts an issuing method and system of new network key character related information, and widens a connecting path between the key character relative information and the users. The invention can reduce the applying experience of the users in a smallest degree, prevents the key word related information which is not needed by the users, is invalid and useless from being largely downloaded to the users local and elevates the using efficiency of the network communication resource.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Urban area road network operating state evaluation method considering critical degree of road section
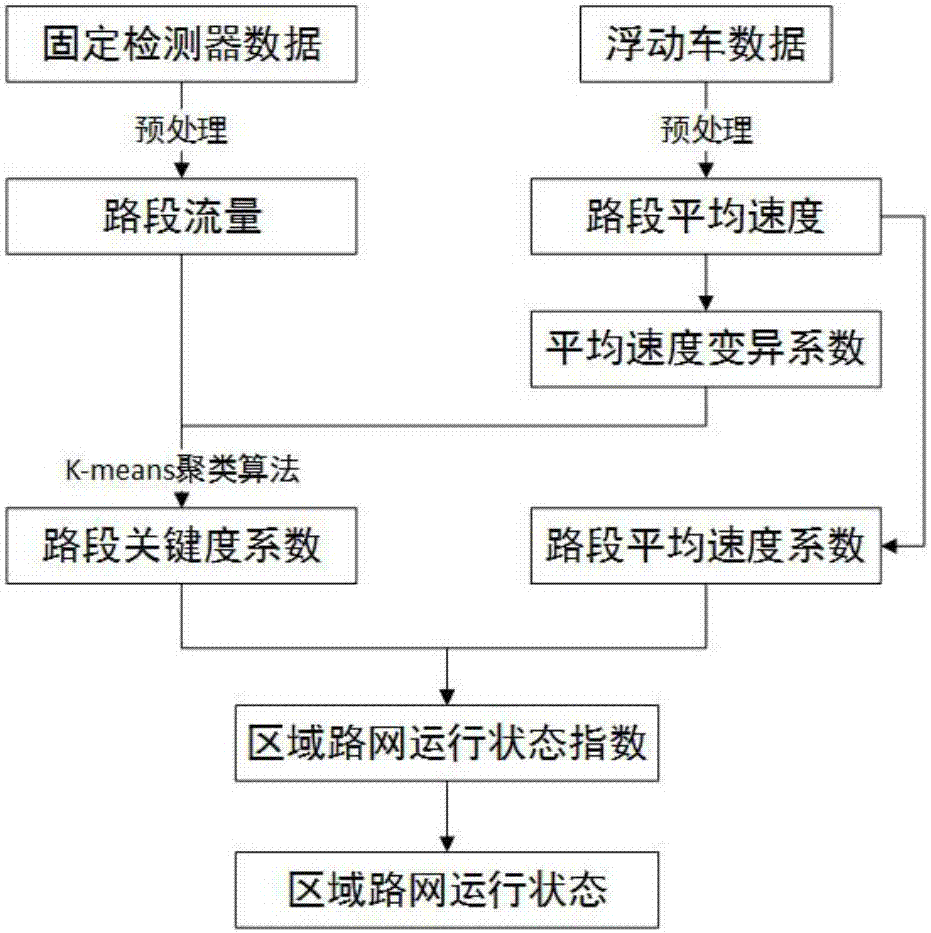
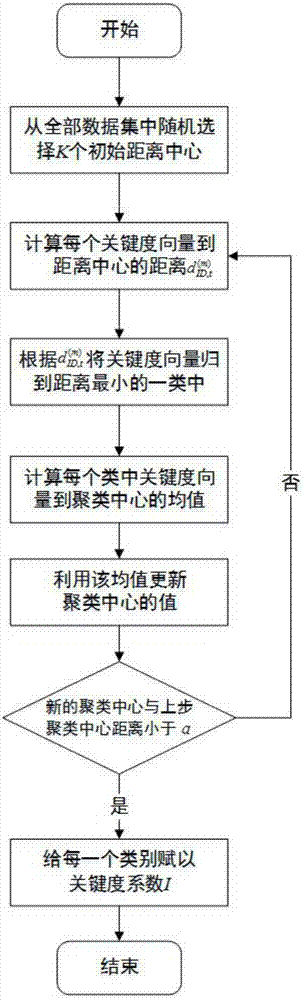
InactiveCN107248283ACongestion evaluation fits realitySensitive to congestion evaluationDetection of traffic movementCharacter and pattern recognitionRoad networksNetwork key
The invention discloses an urban area road network operating state evaluation method considering the critical degree of a road section. The method comprises the following steps that: step 1, floating vehicle GPS data and fixed detector data are obtained and preprocessed; step 2, urban road network important road section identification is performed; step 3, urban road network weak road section identification is performed; step 4, urban road network key road section identification is performed, and critical degree vectors are divided into different levels; and step 5, urban road network operating state index construction is performed. According to the method of the invention, a traffic flow rate which measures the critical degree of the road section and an average velocity variation coefficient which measures the weak degree of the road section are both considered, the critical degrees of the road section are clustered and divided, and therefore, the evaluation of the congestion of a road network is more realistic and more sensitive.
Owner:BEIHANG UNIV
Method for managing network key and updating session key
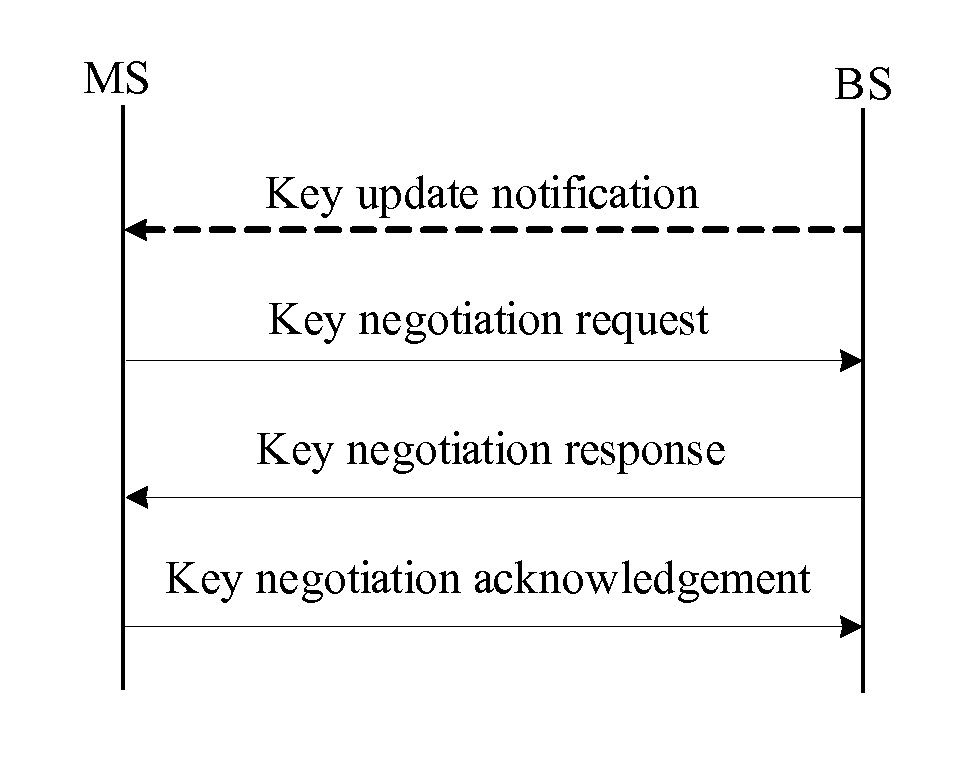
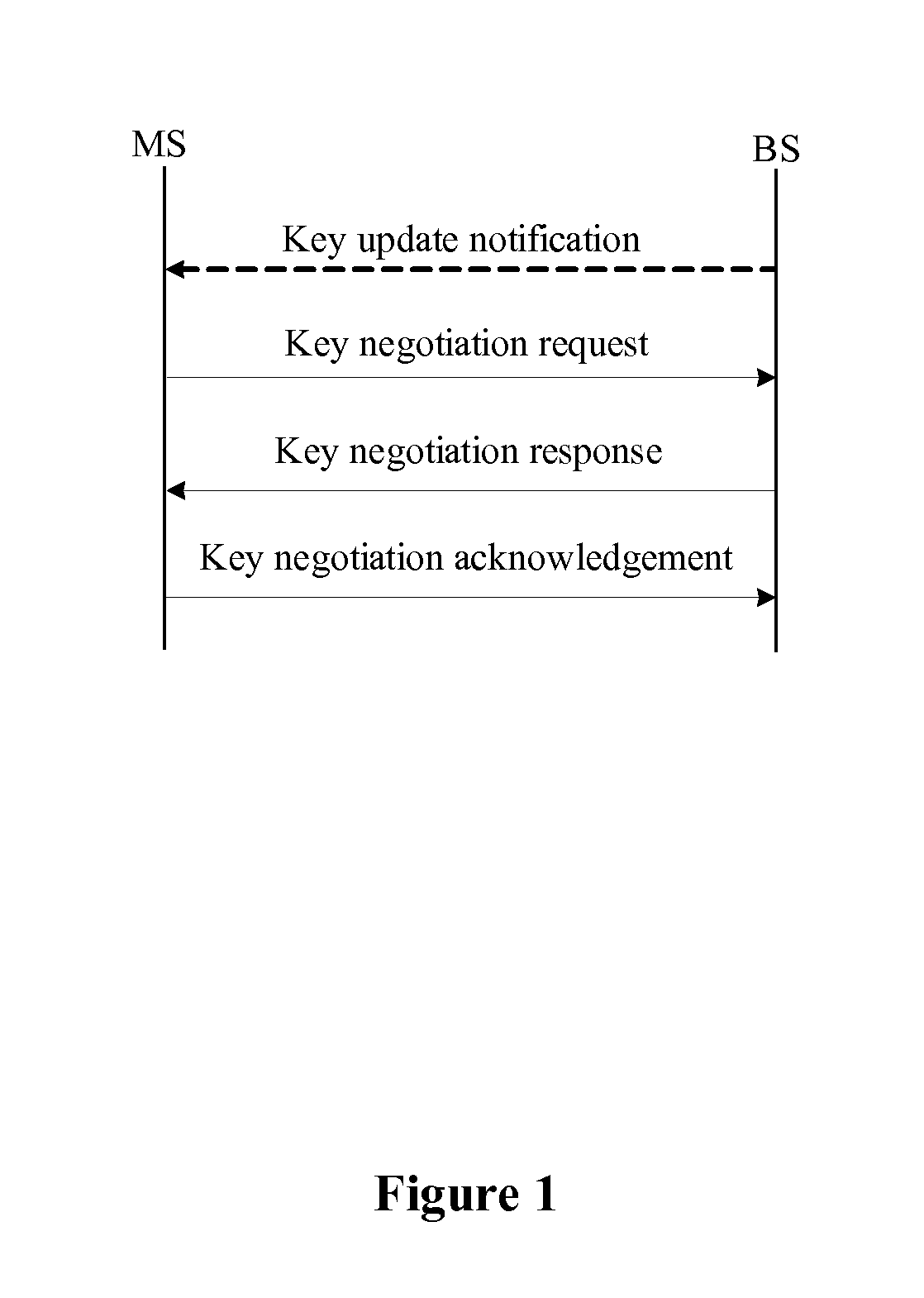
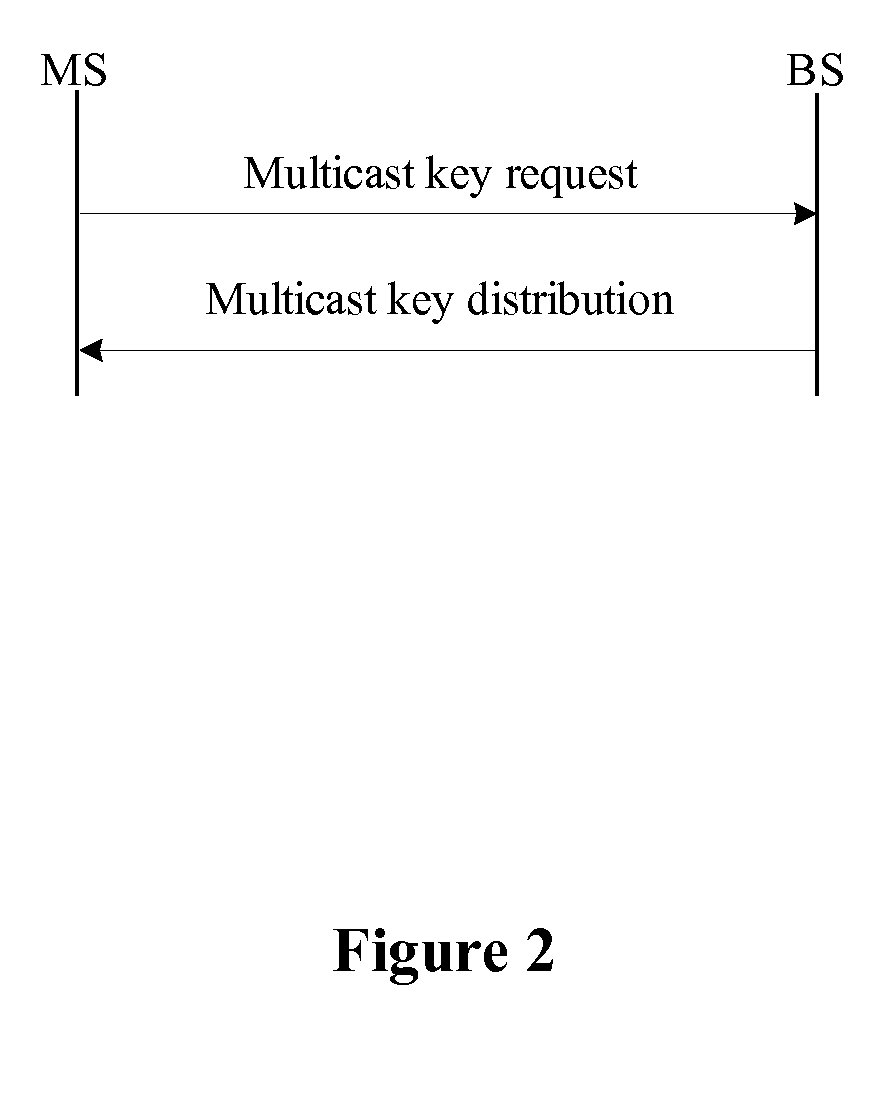
ActiveUS20090300358A1Improve performanceSimplifies state managementKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey-agreement protocolNetwork key
A method for managing network key and updating session key is provided. The step of the key management includes: constructing key request group, constructing key negotiation response group, and constructing key negotiation acknowledgement group. The step of multicasting key management method includes multicasting main key negotiation protocol and multicasting session key distribution protocol. The multicasting main key negotiation protocol comprises key updating informs group, constructing encryption key negotiation request group, constructing key negotiation response group and constructing key negotiation acknowledgement group. The multicasting session key distribution protocol comprises multicasting session key request and multicasting session key distribution.
Owner:CHINA IWNCOMM
Method of establishing authentication keys and secure wireless communication
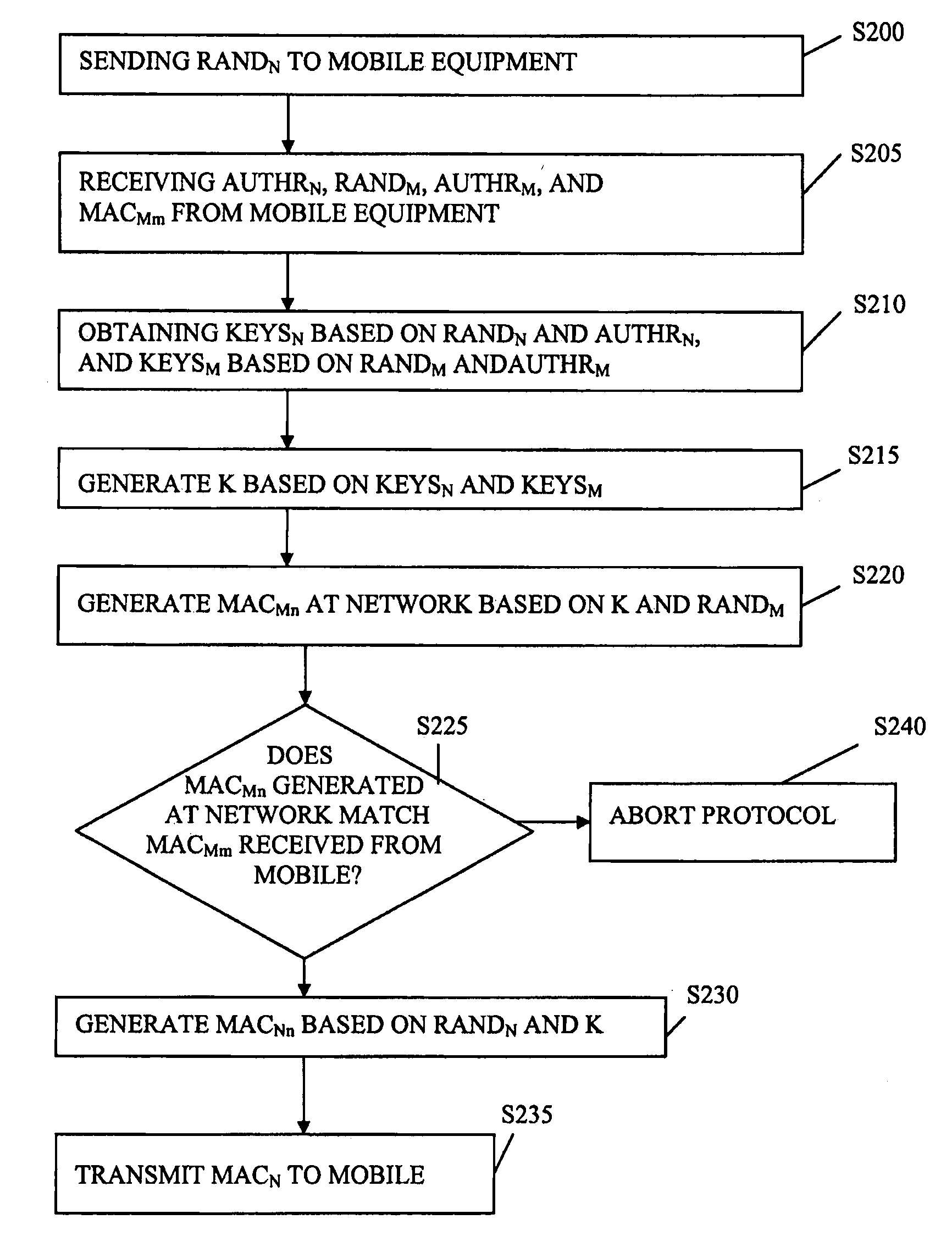
ActiveUS20090089583A1User identity/authority verificationSecret communicationNetwork generationNetwork key
A method of establishing authentication keys at both a network and mobile equipment are provided. The authentication key generated by the mobile equipment is based on both mobile keys and network keys, which are each calculated by the mobile equipment. The authentication key generated by the network is based on both mobile keys and network keys, which are each calculated by the network. The mobile keys are calculated from a challenge generated by the mobile equipment and the network keys generated by the mobile based on a challenge generated by network.
Owner:WSOU INVESTMENTS LLC
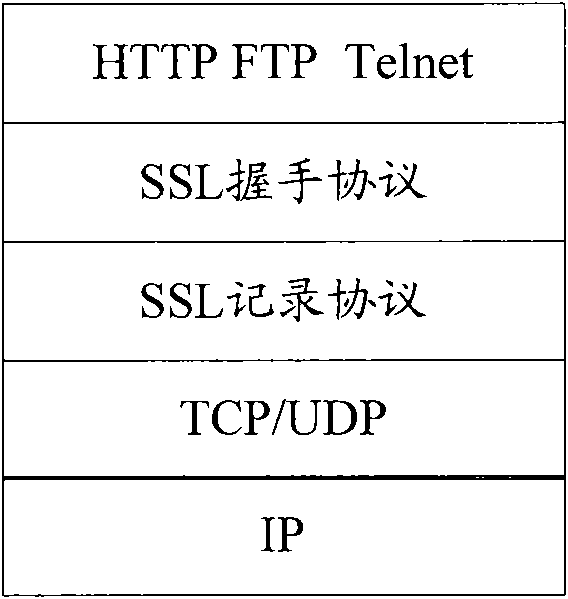
Method and device for detecting SSL enciphered data safety
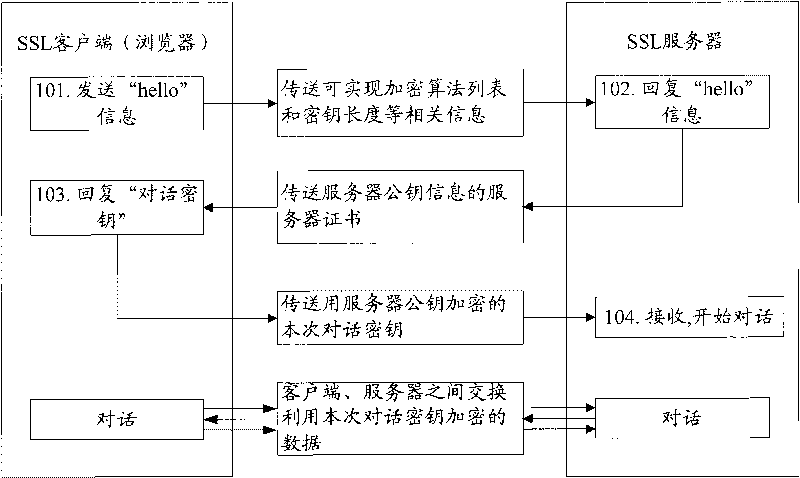
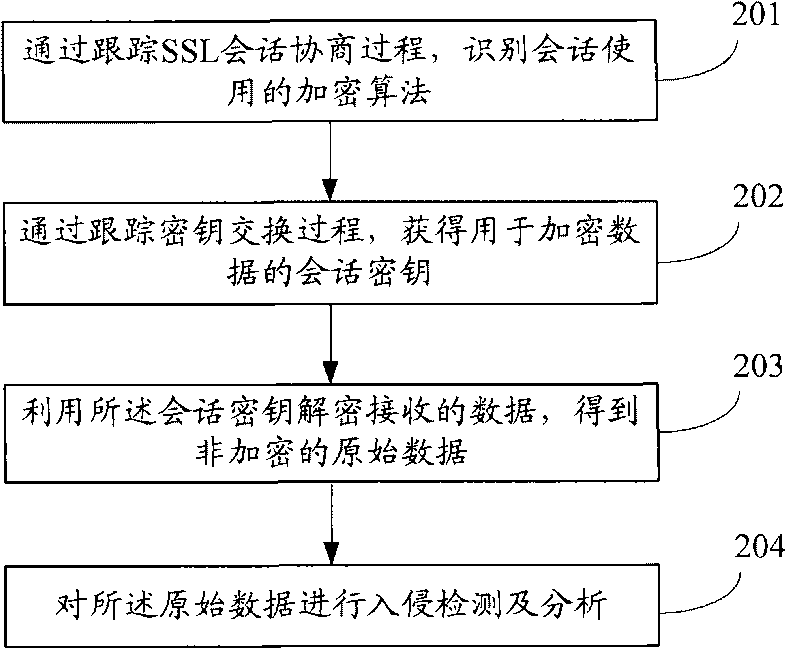
InactiveCN101695038AEnsure safetyUser identity/authority verificationData switching networksKey exchangeOriginal data
The invention relates to the network safety technology, and discloses a method and a device for detecting SSL enciphered data safety, wherein the method comprises identifying conversation-used encryption algorithms through tracing SSL conversation negotiation process, obtaining conversation key for enciphered data through tracing the key exchange process, utilizing the conversation key to decrypt received data to get non-encrypted original data, and conducting inversion detections and analysis for the original data. The invention can be utilized to detect and analysis SSL enciphered data through by-pass arrangement on network key nodes, and guarantees the safety of SSL enciphered data.
Owner:BEIJING LEADSEC TECH
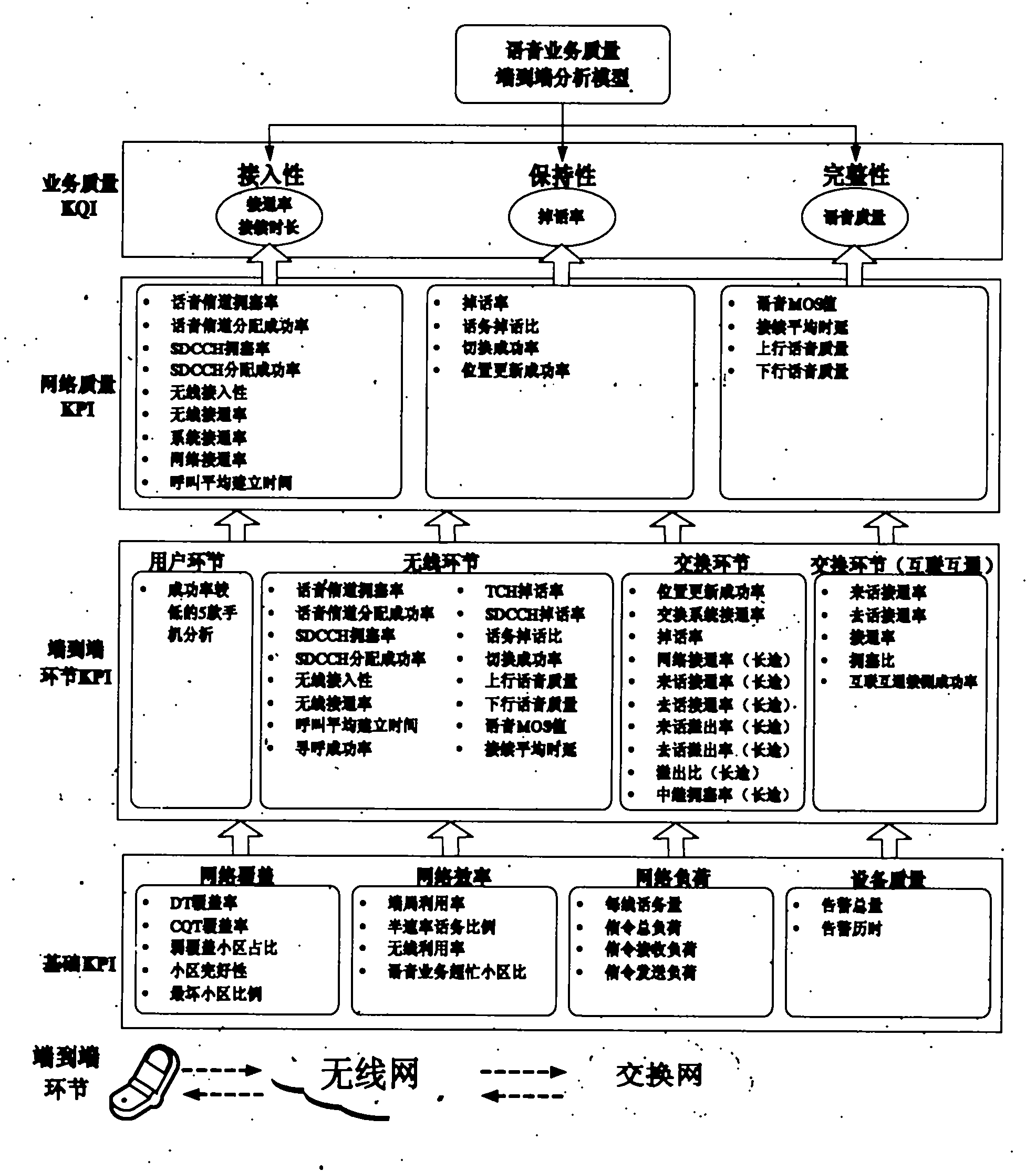
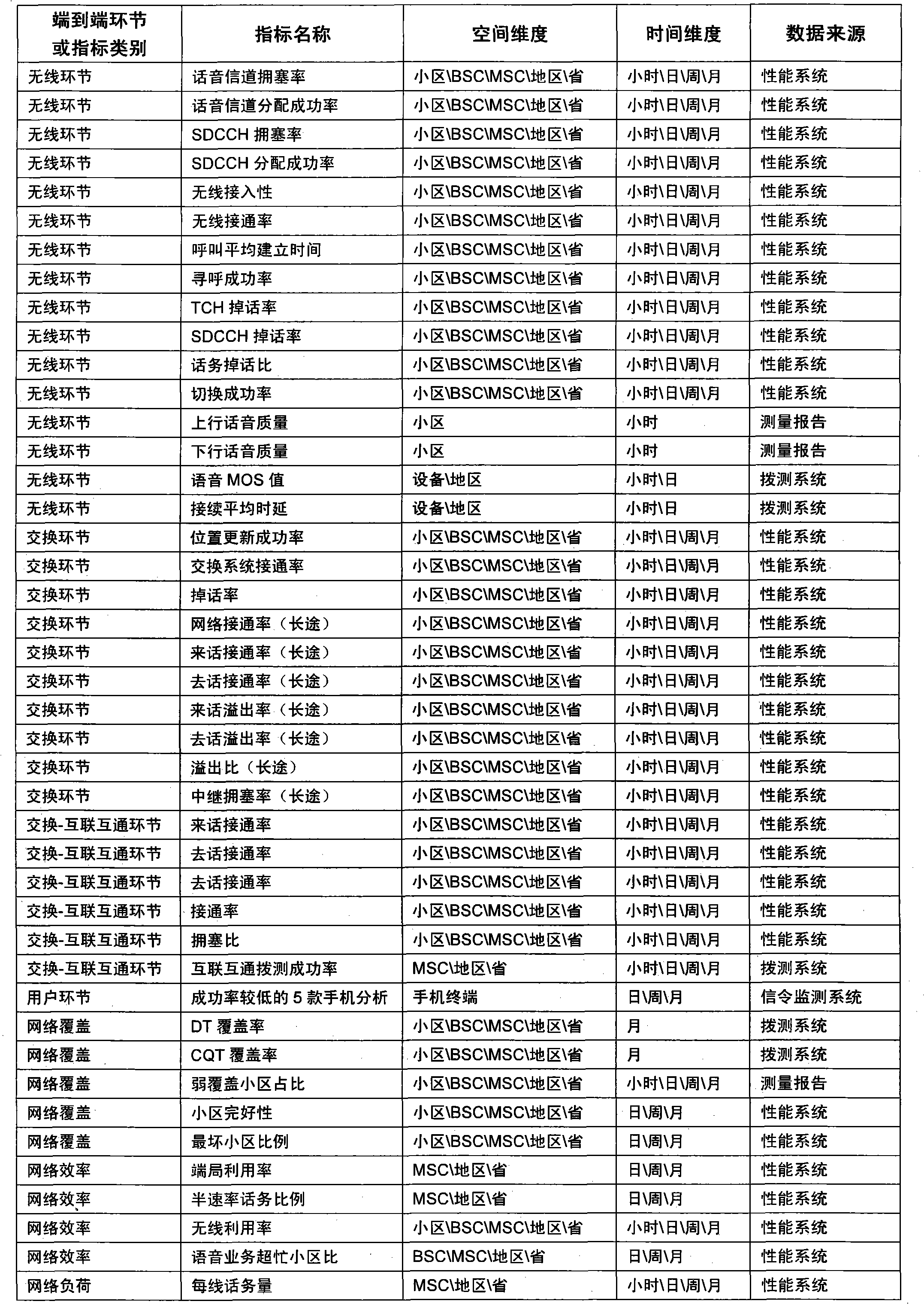
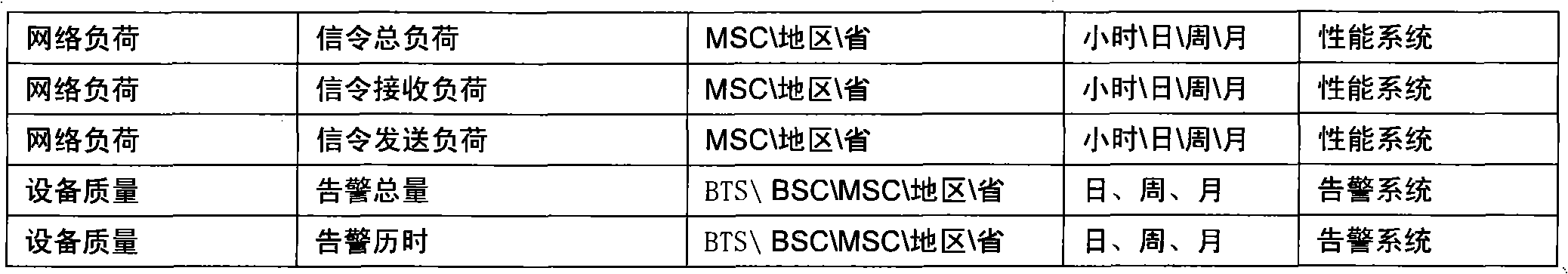
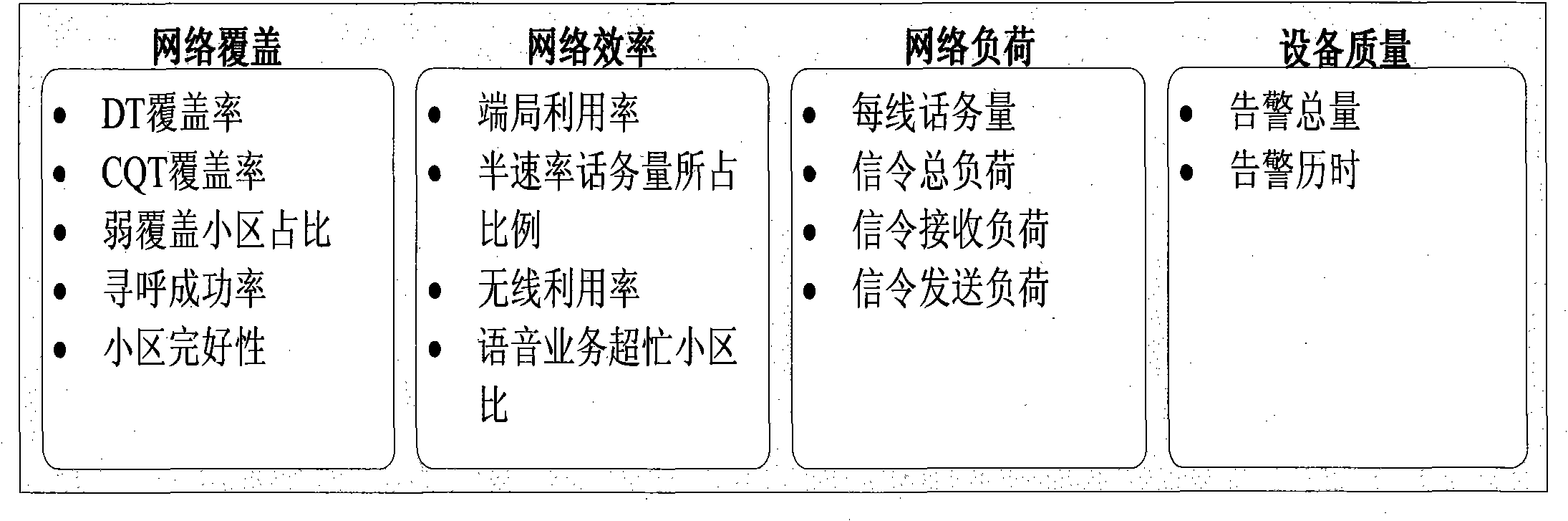
Speech service quality end-to-end analyzing method
InactiveCN102149119AImprove business service qualityAnalysis route is clearWireless communicationNetwork keyService quality
The invention relates to the field of service quality analysis in mobile communication, and provides a voice service quality-based end-to-end analyzing method. The indicators of voice service quality is evaluated multi-dimensionally, a method for correlating service key quality indicators (KQI) with related network key performance indicators (KPI) is established, a method for correlating and carrying indicators from a service to a network and to equipment is established, voice service quality problems are analyzed end to end in the overall process, and the reasons of the voice service quality problems can be quickly and effectively positioned, so that a basis can be provided for service quality-based network optimization, and the perception and satisfaction degree of users can be promoted.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
Method and device for evaluating mobile data service quality oriented to user experience
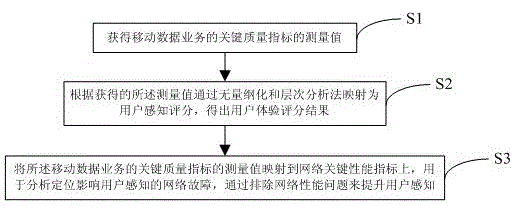
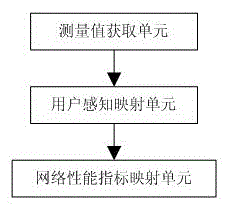
ActiveCN105050125AGuaranteed validityGuaranteed accuracyWireless communicationService experienceNetwork key
The invention discloses a method and device for evaluating mobile data service quality oriented to user experience and belongs to the field of mobile wireless network performance evaluation. In view of eight current main mobile data services of the mobile Internet, a key quality indicator system for both subjective quantitative evaluation and objective quantitative evaluation is provided. The measured value of the key quality indicator system may perform objective quantitative evaluation on user subjective service experience by means of a nondimensionalized and analytic hierarchy process and can be mapped to a network performance indicator to be used for analyzing and positioning a network fault influencing user awareness and improving the user awareness by eliminating network performance problems. The method and the device solve a problem that a network key performance indicator based on network elements, which is still mainly taken by network operators, for evaluating the network performance, cannot reflect the real feeling of a user using mobile data service so as to cause disjunction between the service using experience of the user and network performance evaluation optimization.
Owner:WUHAN HONGXIN TECH DEV CO LTD
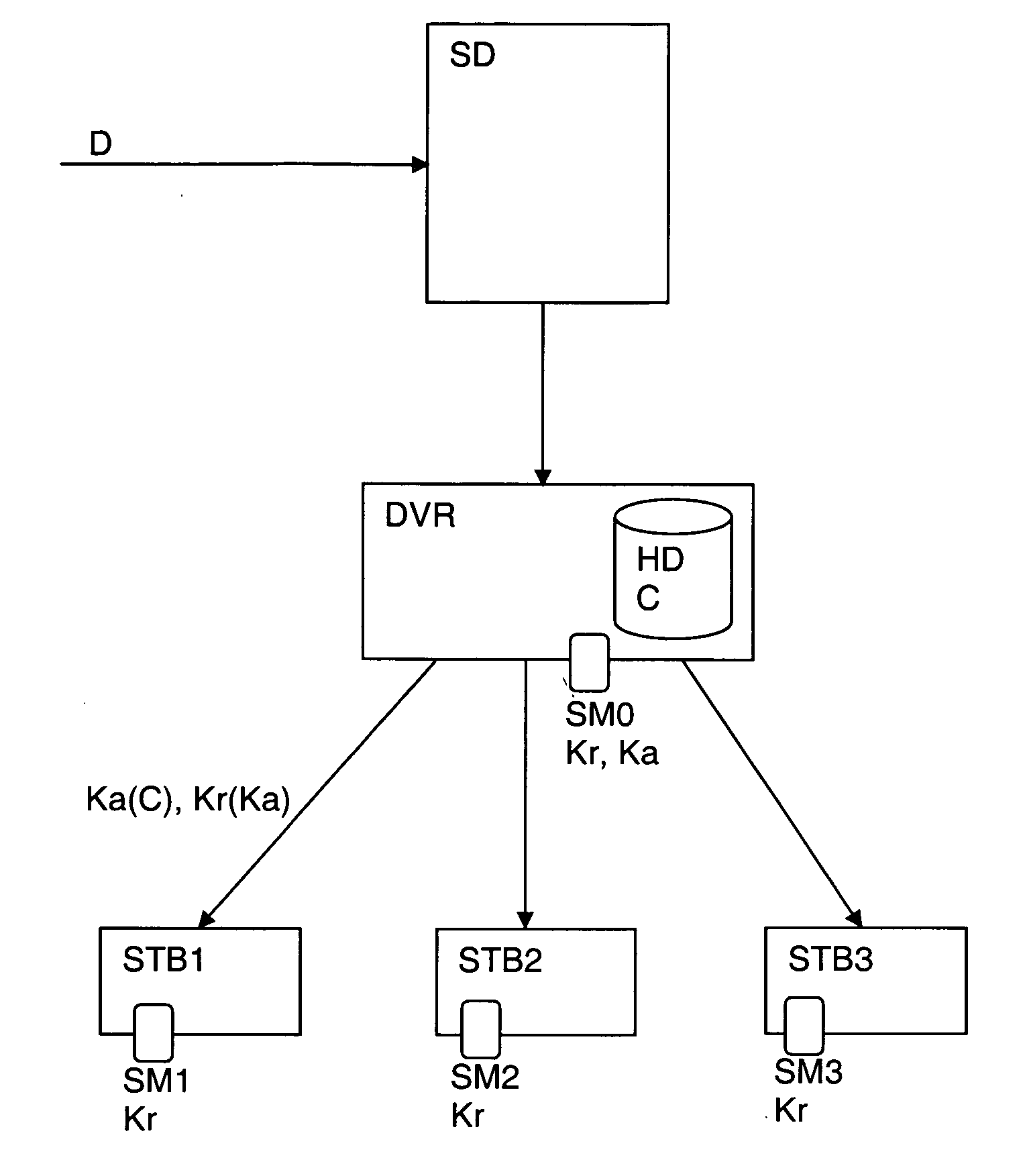
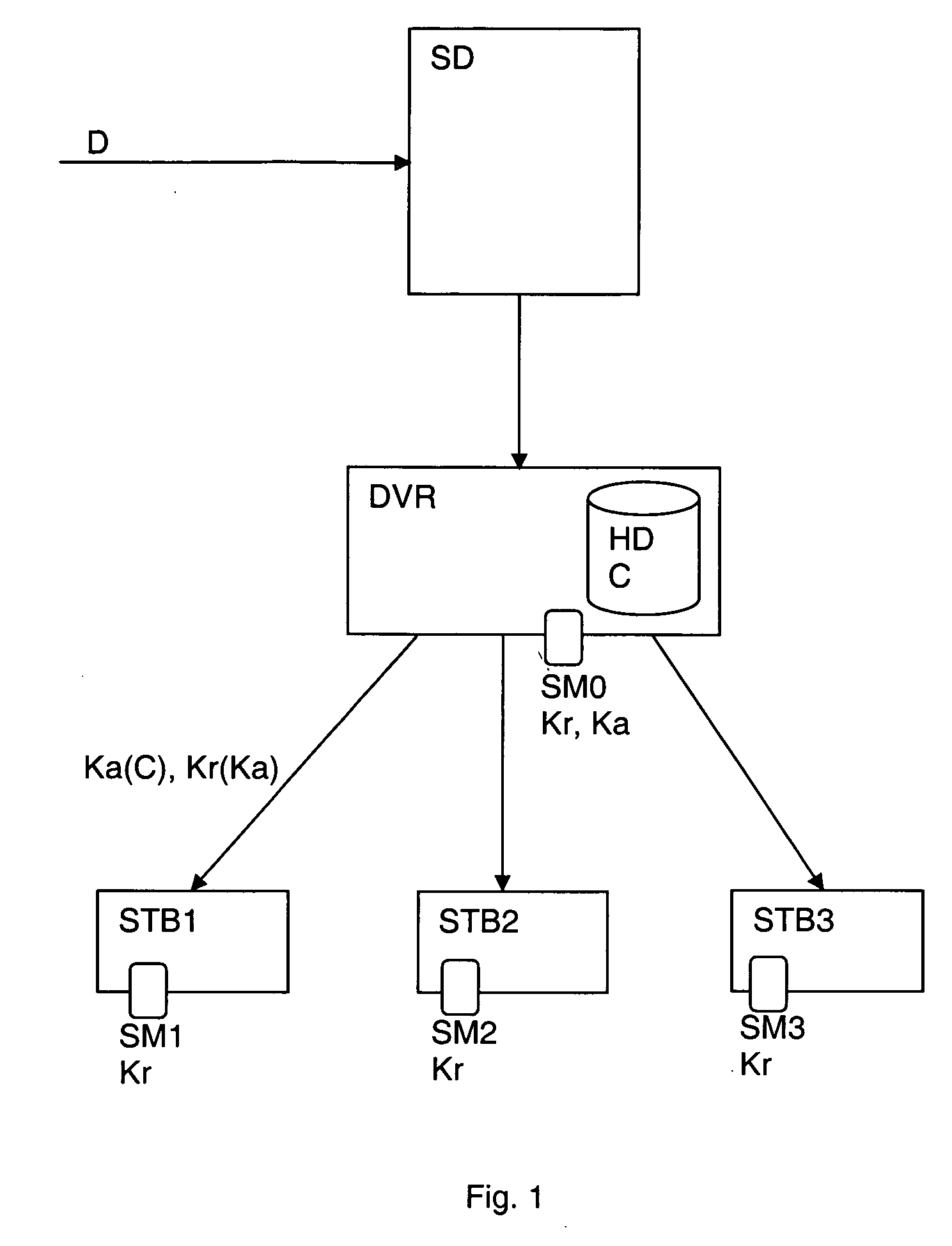
Method for generating and managing a local area network
ActiveUS20060161969A1Random number generatorsUser identity/authority verificationData streamNetwork key
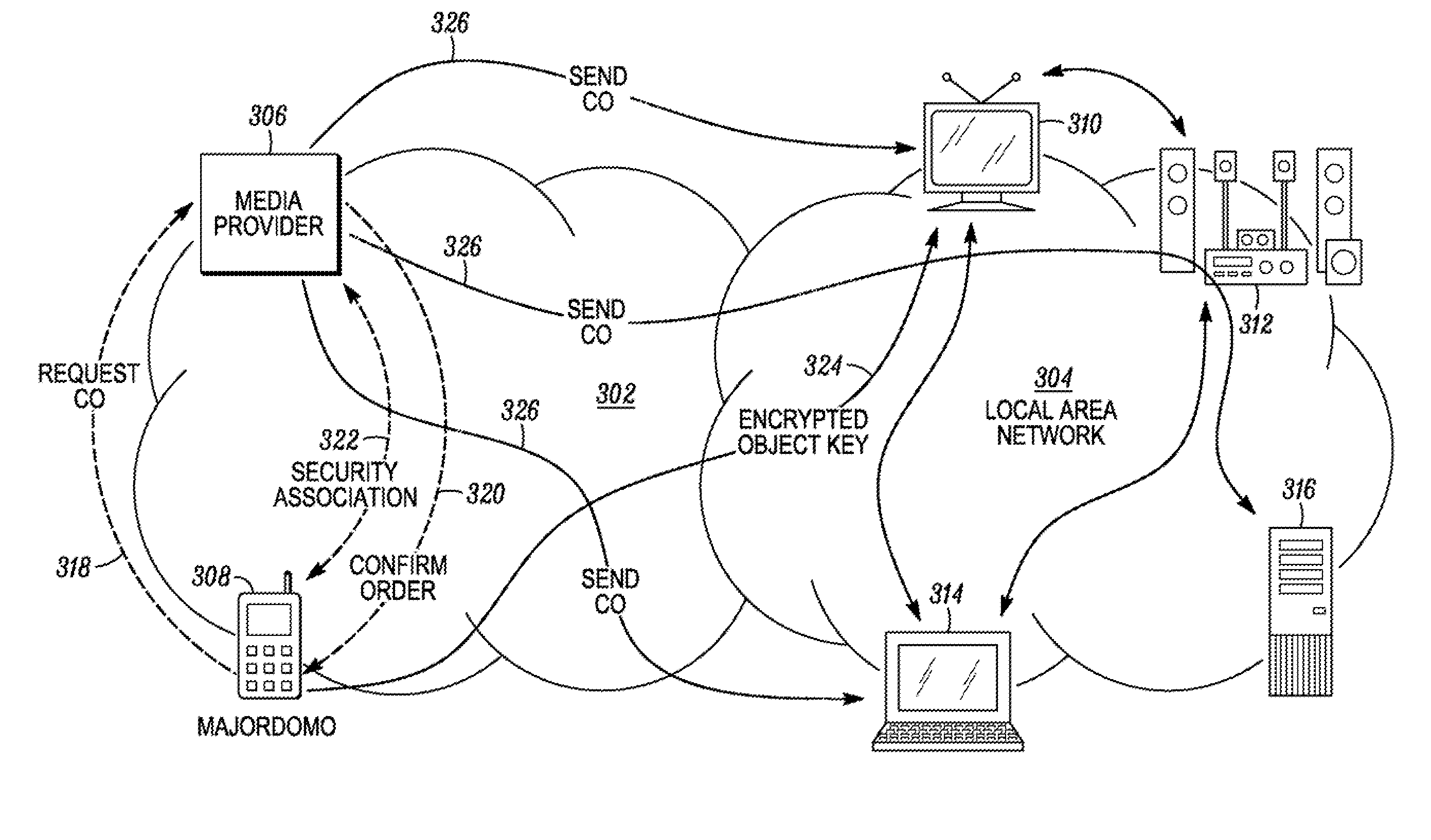
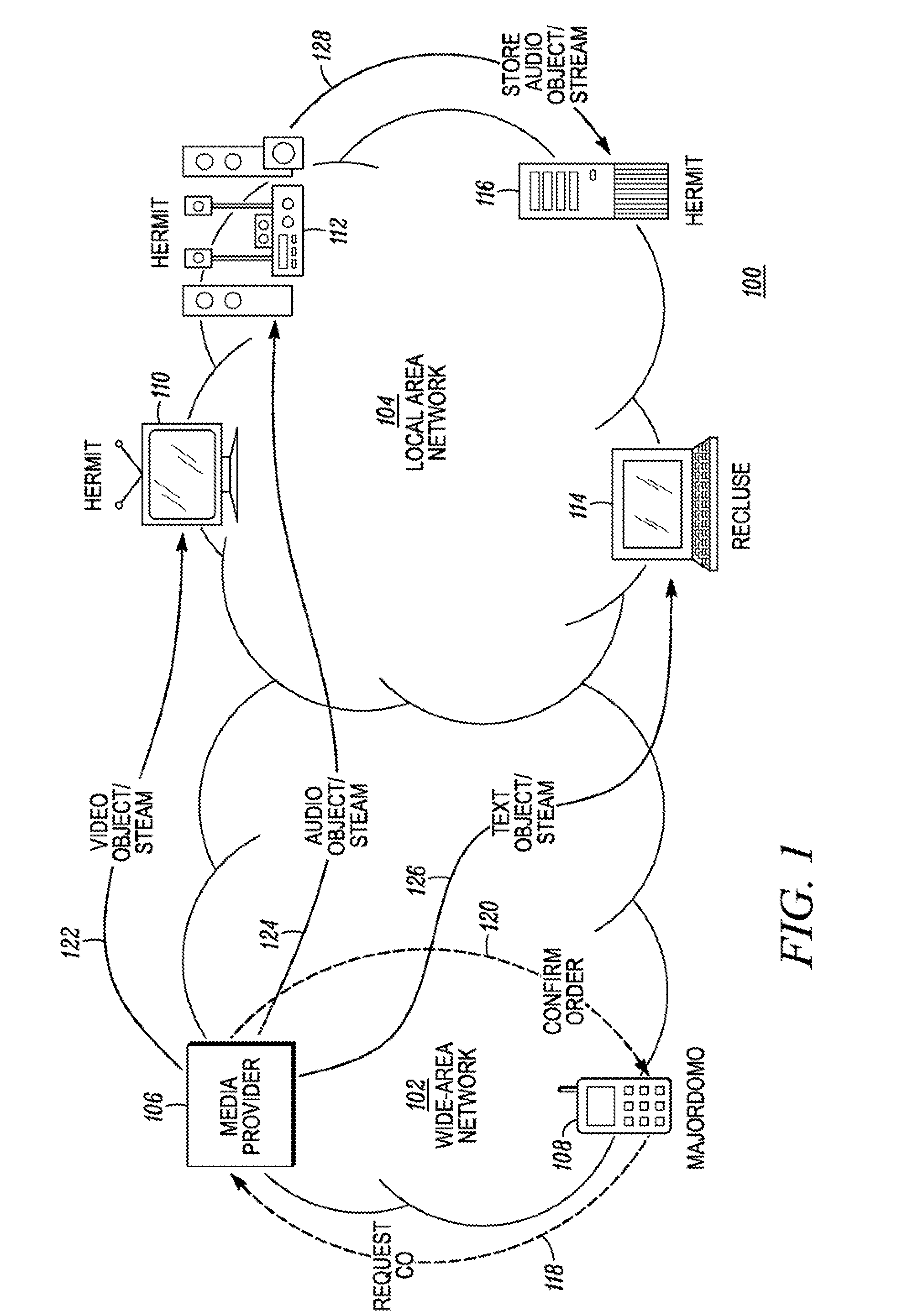
The present invention relates to a method for creating and managing a local area network including at least one device for reproducing an encrypted data flow and a device for transmitting and re-encrypting all or part of said encrypted data, which devices include security modules. The method includes the steps of connecting a so-called master security module in one of the devices connected to the local area network, causing the master security module to generate a network key, securely transmitting the network key to one or more so-called user security modules, decrypting the data encrypted by the transmission and re-encryption device, re-encrypting the data with said device by means of a local key, transmitting the re-encrypted data to the reproduction device, and holding the reproduction device to perform decryption using the user security module associated therewith and provided with means for locating the local key.
Owner:NAGRAVISION SA
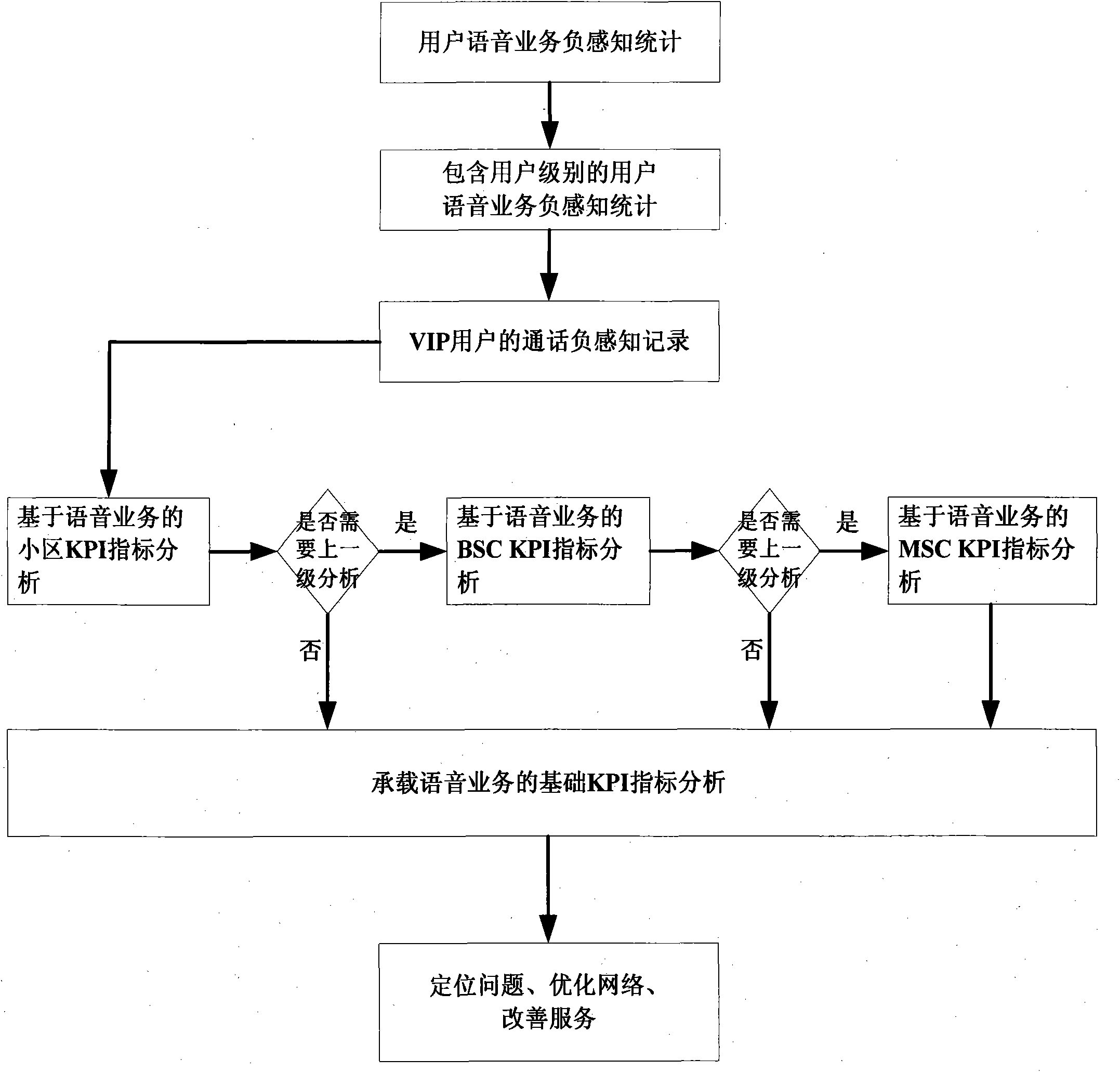
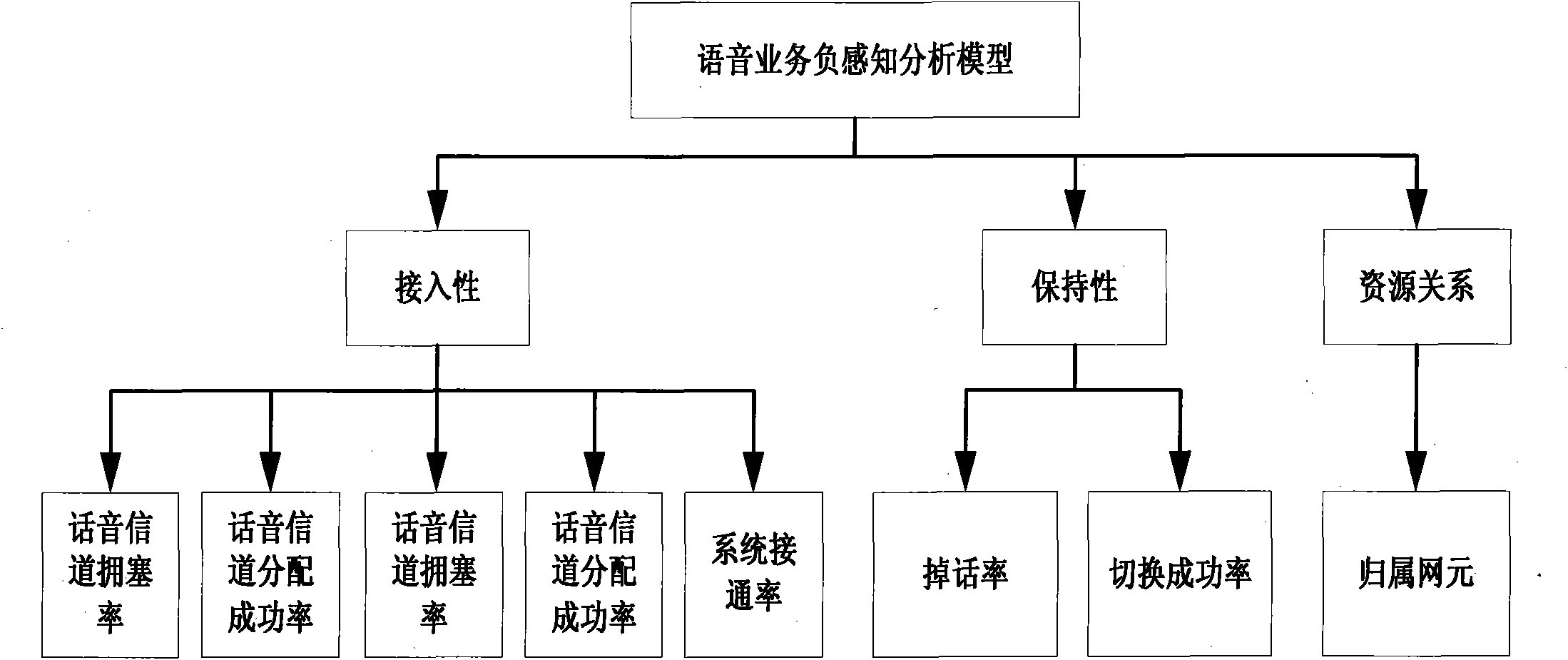
Voice service user negative perception-based network problem analysis method
ActiveCN102075978AImprove service qualityImprove satisfactionWireless communicationNetwork keyUser perception
The invention provides a voice service user negative perception-based network problem analysis method, which relates to the field of analysis of a client perception QoE index in a mobile network. In the method, index association analysis is performed on voice service-based negative perception of a terminal user (particularly a very important person (VIP) user), and a user perception situation is effectively associated with a network key performance indicator (KPI) index, so that the cause of a network problem can be positioned quickly and effectively. Therefore, the trouble of poor user perception under the condition of good network index is solved for an operator, a passive complaint handing mode is replaced by an active problem finding mode, bases are provided for service-oriented and customer-oriented network optimization, service quality is enhanced and customer satisfaction is enhanced.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
Specially adapted serving networks to automatically provide personalized rapid healthcare support by integrating biometric identification securely and without risk of unauthorized disclosure; methods, apparatuses, systems, and tangible media therefor
ActiveUS10984128B1Improve privacyReconcile and reduce and resolve mismatchMedical data miningWeb data indexingCyber operationsBiometric data
These solutions concern transforming a communication network into a scalable network to also automate personalized rapid healthcare support. They integrate biometric identification capabilities into a network entity of, or a resource communicably connectible with, a serving network by using computers to mediate biometric identification and location data. Network operators will provide always on enhanced emergency connectivity for mobility and roaming for user equipment to leverage biometric identification for rapid healthcare support and to produce a unified result set, without risk of undue disclosure of raw biometric data or of selected portions of health profile information. These techniques also support personalized, urgency-supported, healthcare to optimize biometrically-link identifiers / network keys (PUSH TO BLINK), even over a visited operator's IP services. Some facilitate backwardly compatibility across 2G, 3G, 4G, and other networks, whether a mission critical communication, even one with intermodal content via backhaul, is sent via a network that is wireless in any part, or not.
Owner:HOFFER STEVEN MILES
Spark environment-based microblog network key user mining system and method
ActiveCN108509551ACalculation speedFast executionData processing applicationsSpecial data processing applicationsEvaluation resultNetwork key
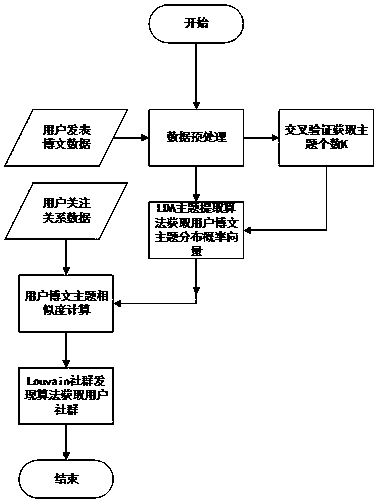
The invention discloses a Spark environment-based microblog network key user mining system and method. The system integrates contents in two aspects of a social network topology structure and user comprehensive information, and proposes an integral framework of key user mining in a large-scale social network. The user topic similarity is introduced for representing the strength of a community relationship among users, and a Louvain community discovery algorithm is applied, so that high efficiency of community discovery is ensured and a division result is relatively accurate; according to fourevaluation indexes of authority, transmissibility, interactivity and linkability of microblog users, compared with an existing user influence evaluation method, the diversity of the evaluation indexesis expanded and the comprehensiveness of an evaluation result is enhanced; and a mainstream Spark big data computing platform is introduced in computing, so that the whole key user mining has not only a complete implementation process but also environment conditions of actual application.
Owner:NORTHWEST UNIV
Method for managing security keys utilized by media devices in a local area network
A method of an existing media device for distributing a media key to a new media device joining a local area network or revoking an existing media key. For distributing a media key, a set of key generation counter (“KGC”) values are received from the media devices (1010). Each value is then voted on based on the network keys utilized by the existing media device (1012). Next, all votes for each value are gathered from the media devices (1012). A popular values is determined from the set of values (1014). To revoke a media key, a NONCE is encrypted with the network key (1104). The encrypted NONCE is then distributed to media devices of the local area network (1108). Next, votes are gathered from the media devices of the local area network (1110). All votes are received from media devices that are able to decrypt the NONCE using the media key.
Owner:MOTOROLA INC
Mass subscriber management
ActiveUS7325133B2Key distribution for secure communicationRandom number generatorsNetwork connectionNetwork key
Owner:KOOLSPAN
VPN system based on dynamic encryption algorithm
ActiveCN1972237AEnhanced defenses against hackers attacking its encrypted systemsImprove efficiencyUser identity/authority verificationNetworks interconnectionRandom combinationPrivate network
This invention relates to VPN system based on dynamic code formula, which uses keys, chips and network technique and designs one set of dynamic symmetric code formula to make each formula with different virtual special networks in each data coding, wherein, each code system only adopts one symmetric code keys such as network keys, pack keys and channel keys through establishing code formula to generate formula and symmetric key generation formula.
Owner:北京中电数安科技有限责任公司
Control system and multicast communication method
InactiveUS20080175388A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesSecure communicationMutual authentication
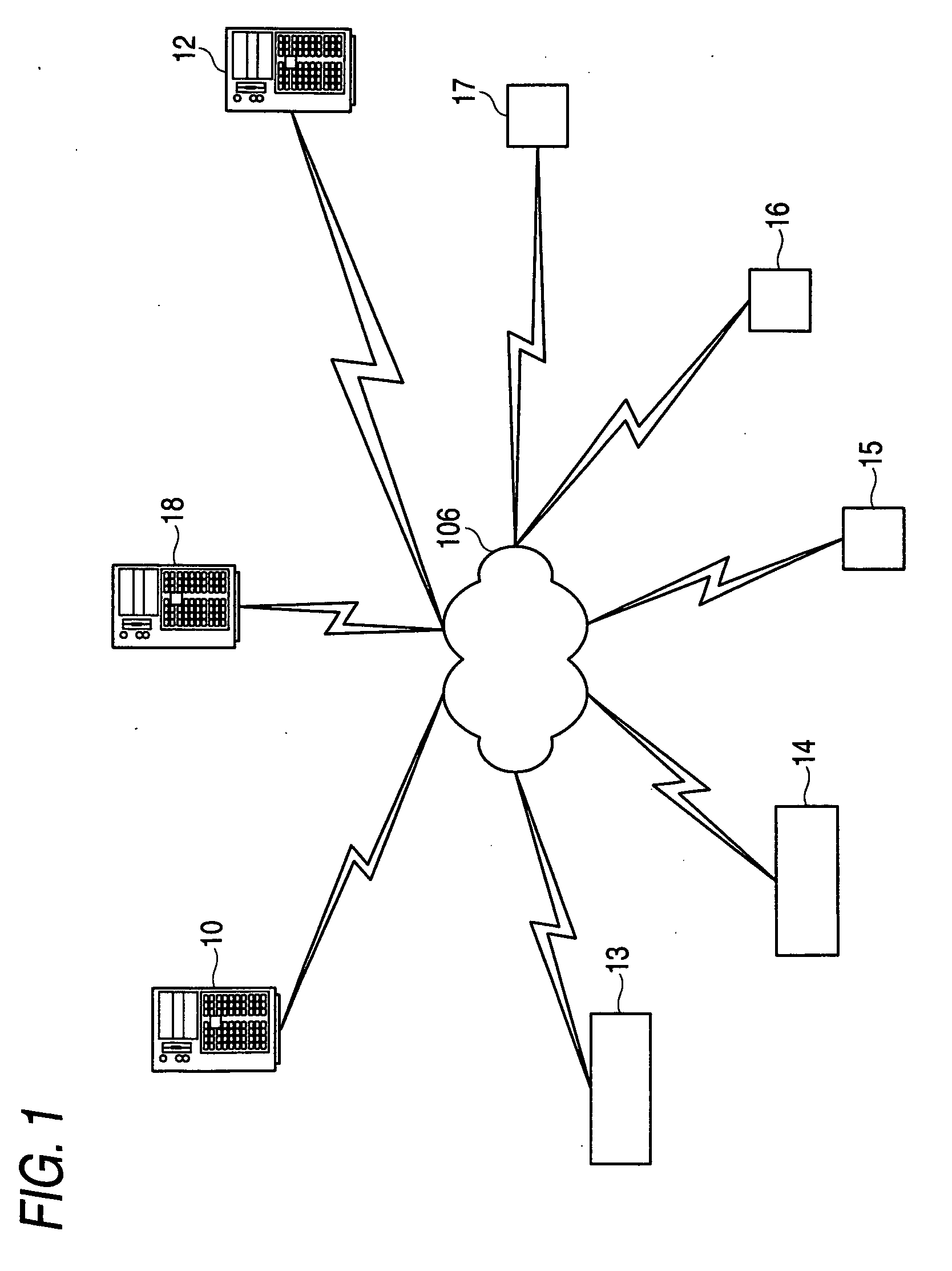
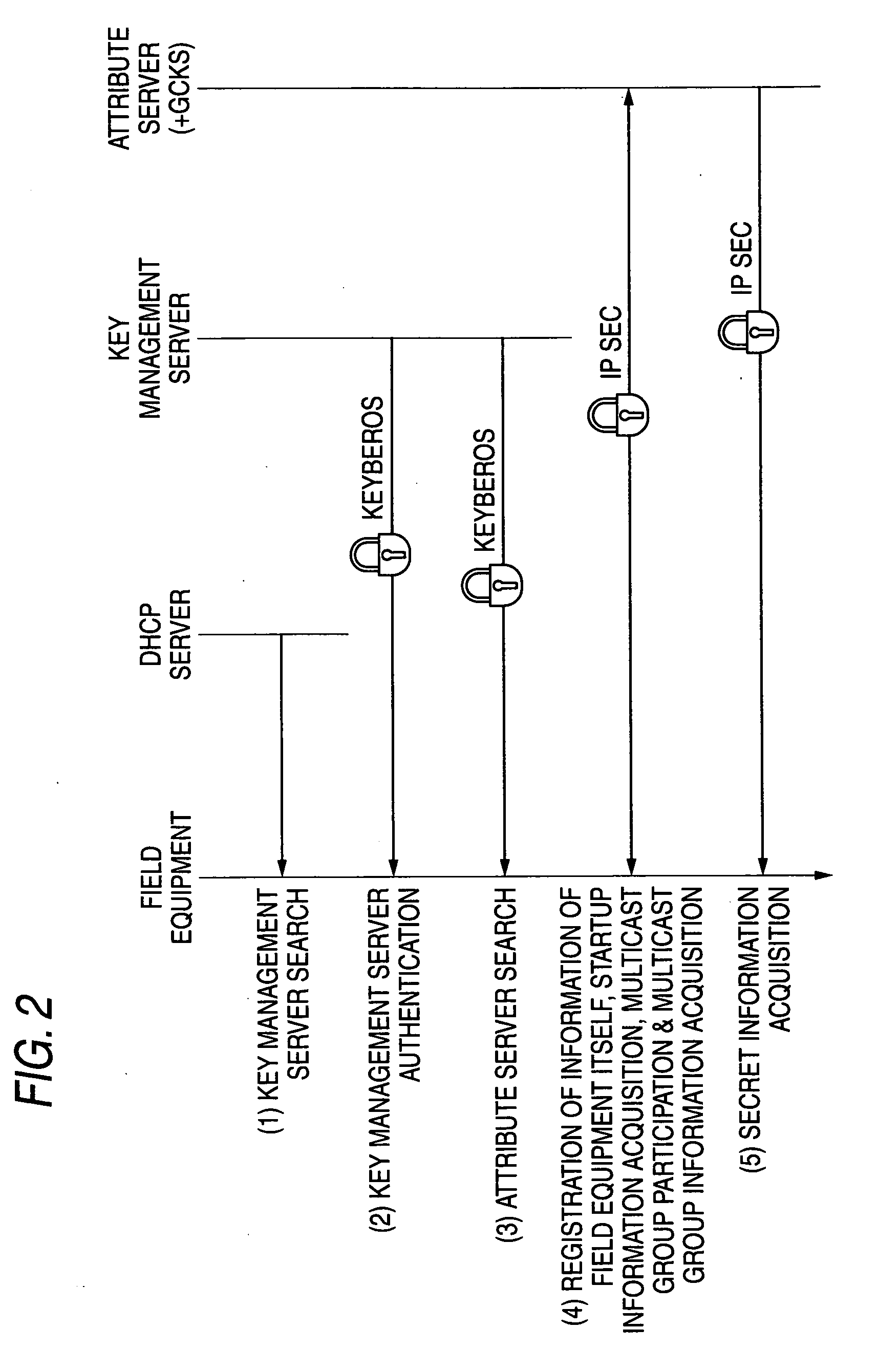
A control system includes: a plurality of field equipments that are connected mutually to an IP network; a key management server that is connected mutually to the IP network and issues key information for authentication of the plurality of field equipments and security communication; and an attribute server having a GCKS server function, which is connected mutually to the IP network, and manages or provides attribute information for mutual authentication between the field equipments, and contains preset group information for multicast communication in a particular multicast group, wherein each of the field equipments is operable to: make authentication of the key management server; acquire information of the attribute server existing on the IP network; register information of each of the field equipments itself in the attribute server; acquire startup information from the attribute server; receive a notification of the group information from the attribute server; participate in a particular multicast group using the GCKS server function; receive a distribution of secret information from the GCKS server function; and perform multicast communication based on the group information and the secret information.
Owner:YOKOGAWA ELECTRIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com