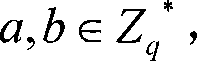Bidirectional authentication method, system and network terminal
A network terminal and two-way authentication technology, applied in the field of network information security, can solve problems such as certificate management complexity and occupation, and achieve the effect of avoiding additional calculations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
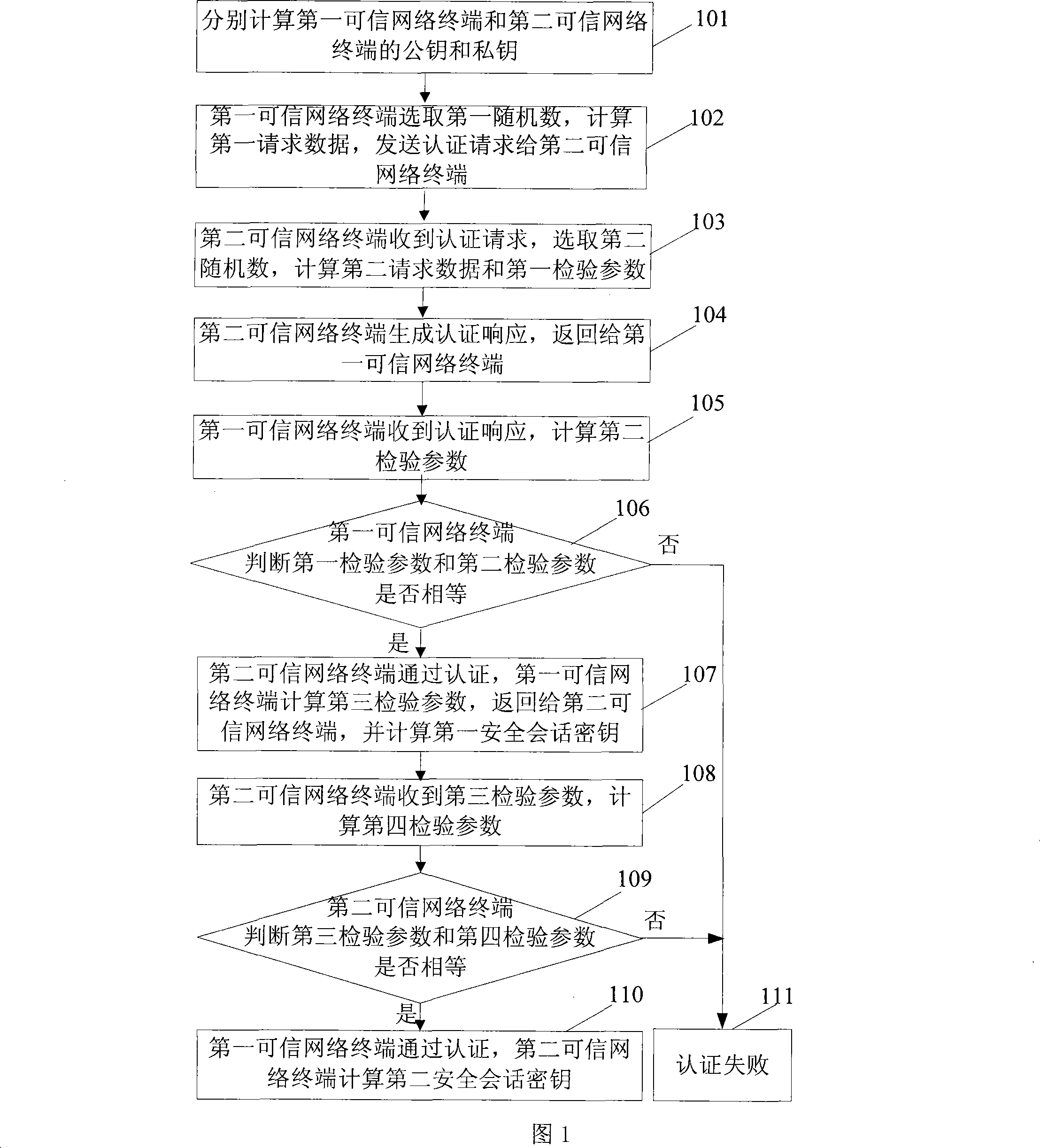
Examples
Embodiment 2
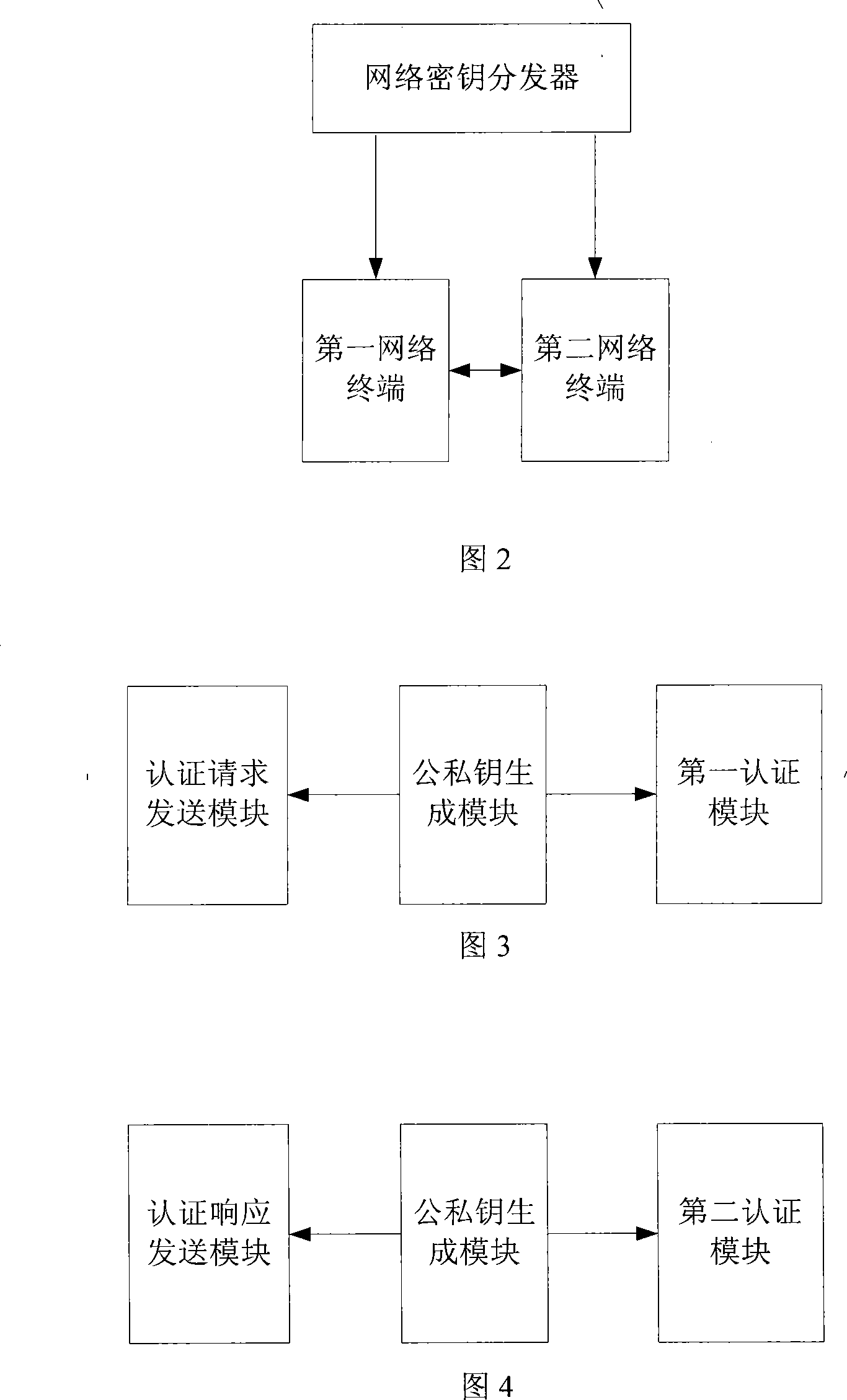
[0067] Referring to FIG. 2, an embodiment of the present invention provides a two-way authentication system, including: a network key distributor, a first network terminal, and a second network terminal, wherein,
[0068] The network key distributor is used to generate system parameters and group keys, and generate the private key of the network terminal according to the network terminal identification;
[0069] The first network terminal is used to generate the public key of the network terminal according to the network terminal identifier; it is also used to generate the second verification parameter according to the public key of the second network terminal and the private key of the first network terminal, and according to the first verification parameter and the second verification parameter The second verification parameter verifies the second network terminal; generates a third verification parameter according to the public key of the second network terminal and the priv...
Embodiment 3
[0072] Referring to FIG. 3 , an embodiment of the present invention provides a network terminal, including: a public-private key generation module, an authentication request sending module, and a first authentication module, wherein,
[0073] A public-private key generating module, configured to generate a public key and a private key of the network terminal according to the network terminal identifier;
[0074] An authentication request sending module, configured to send an authentication request to a peer network terminal;
[0075] The first authentication module is configured to generate a second verification parameter according to the public key of the peer network terminal and the private key of the local network terminal, and verify the peer network terminal according to the first verification parameter and the second verification parameter sent by the peer network terminal. Perform verification; generate a third verification parameter according to the public key of the ...
Embodiment 4
[0082] Referring to FIG. 4 , an embodiment of the present invention provides a network terminal, including: a public-private key generation module, an authentication response sending module, and a second authentication module, wherein,
[0083] A public-private key generating module, configured to generate a public key and a private key of the network terminal according to the network terminal identifier;
[0084] An authentication response sending module, configured to generate a first verification parameter according to the public key of the peer network terminal and the private key of the local network terminal, and return an authentication response including the first verification parameter to the peer network terminal;
[0085] The second authentication module is configured to generate a fourth verification parameter according to the public key of the peer network terminal and the private key of the local network terminal, and verify the peer network terminal according to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com