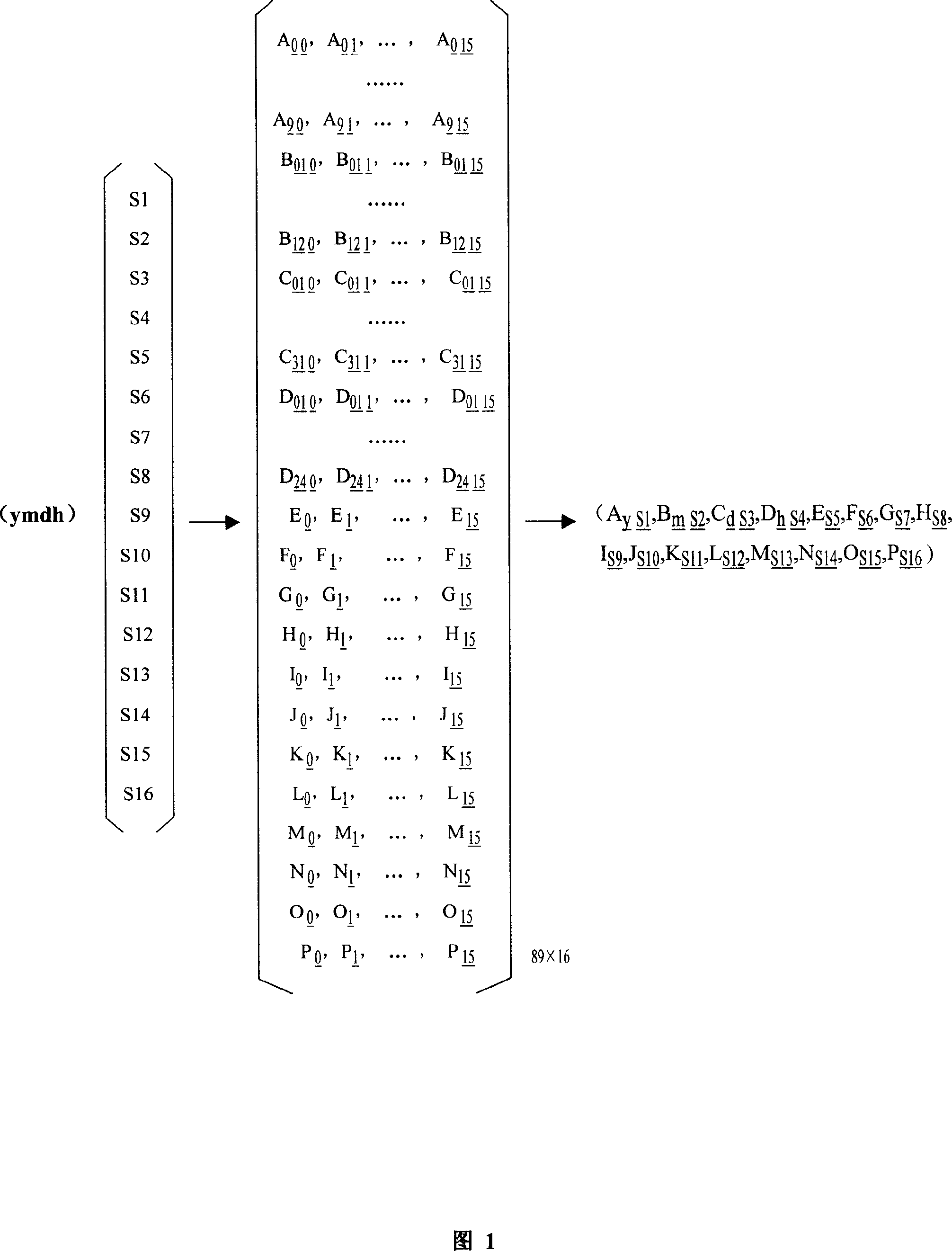VPN system based on dynamic encryption algorithm
A symmetric encryption algorithm and dynamic technology, applied in the field of information security, can solve problems such as slow speed, increased VPN system expenditure, and high price, and achieve the effect of enhancing the ability of the encryption system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
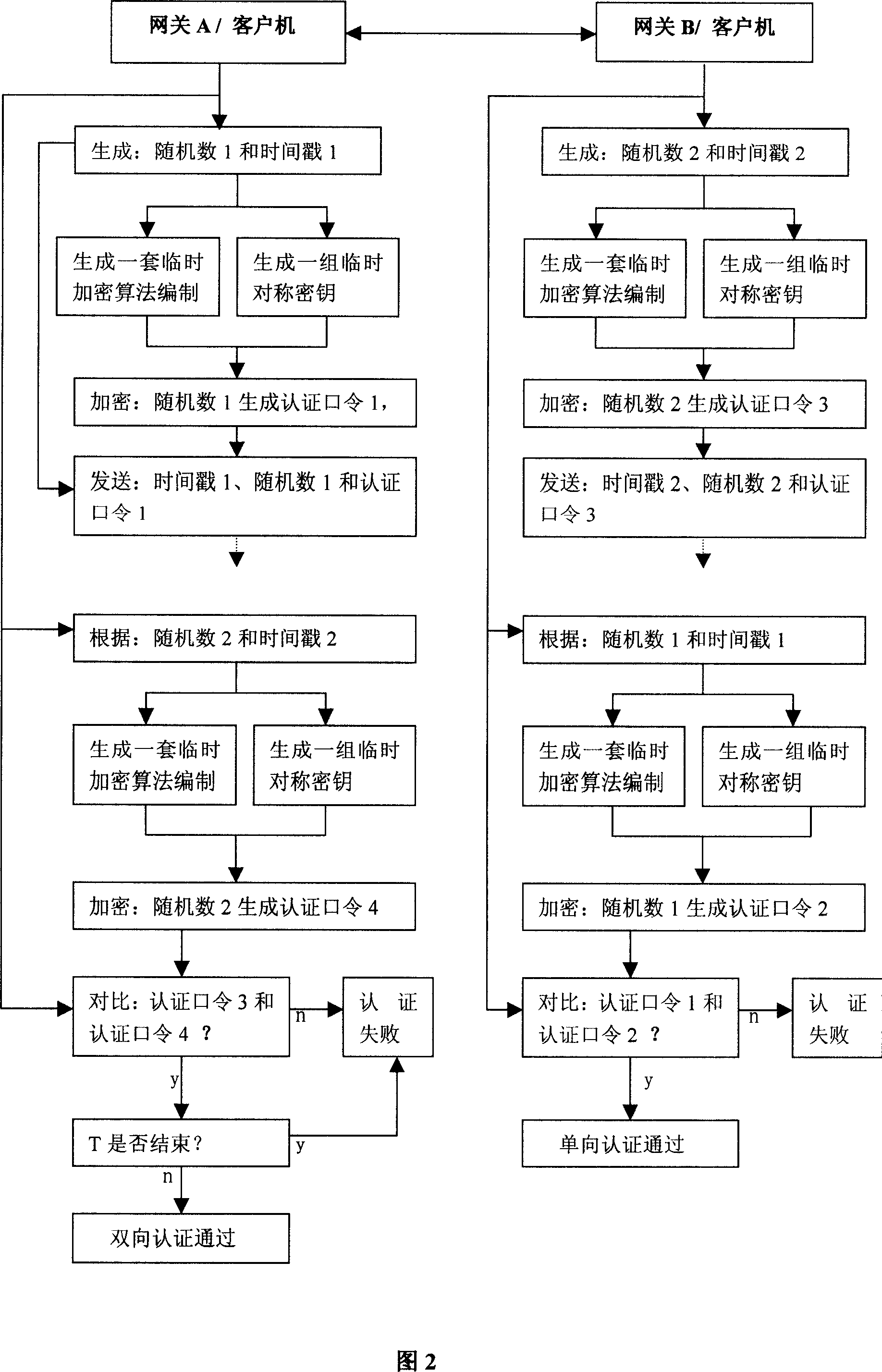
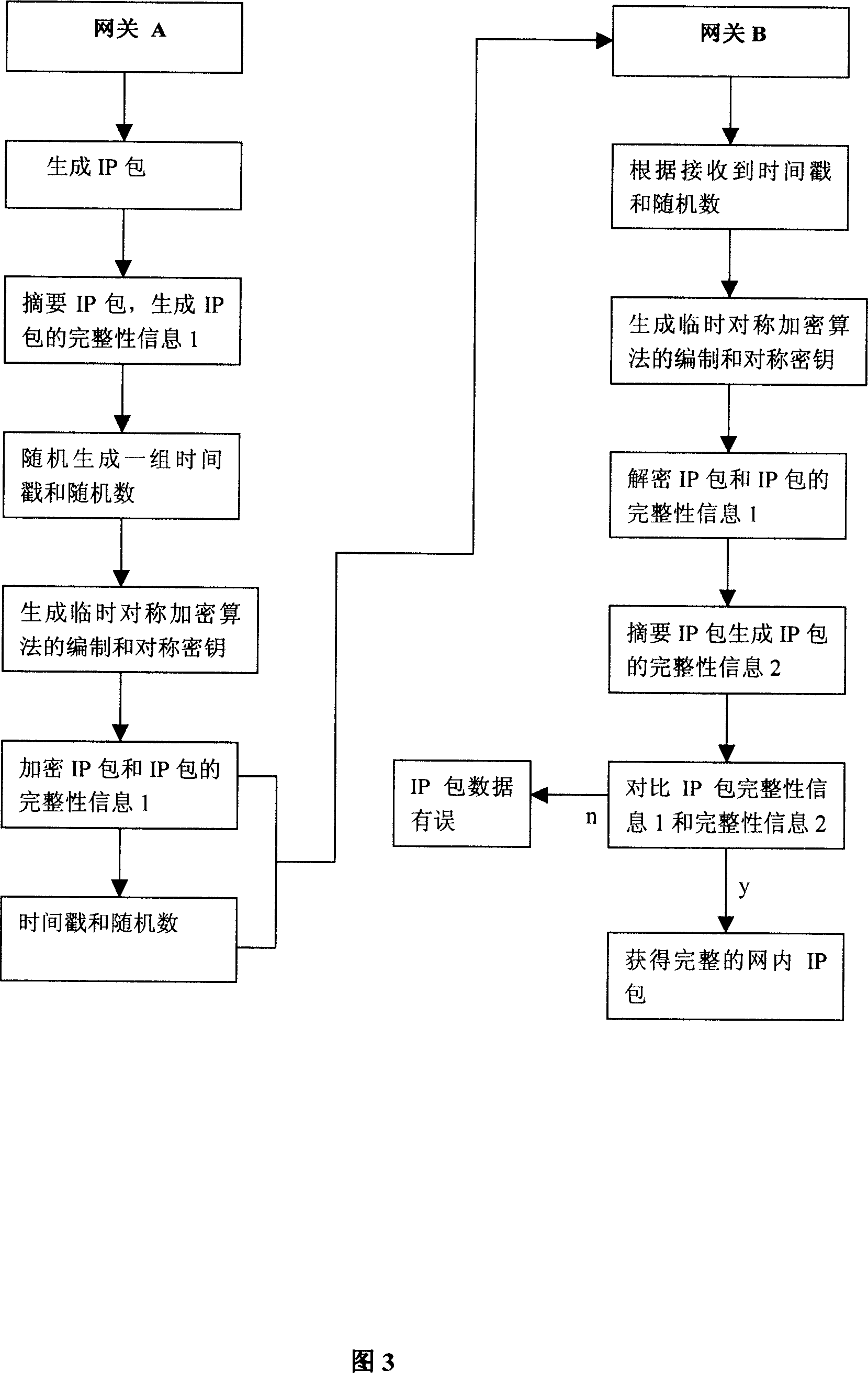
[0042] The VPN system implementation steps based on dynamic encryption algorithm are illustrated below in conjunction with accompanying drawings:
[0043] Figure 1: A structural diagram illustrating the selection algorithm for L×N matrix elements composed of random numbers and time stamps, where: L=89, N=16,
[0044] 1. Establish the "encryption element seed" matrix of the symmetric encryption algorithm and its selection rules for the elements of the matrix
[0045] (1) Take the timestamp as a 7-digit decimal number, set: timestamp: ymdh where: y represents "year" as a 1-digit number, m represents "month" as a 2-digit number, d represents "day" as a 2-digit number, h stands for "hour" with 2 digits,
[0046] (2) Take the random number as 16 hexadecimal numbers, set: random number: S1, S2, S3, S4, S5, S6, S7, S8, S9, S10, S11, S12, S13, S14, S15, S16,
[0047] (3) Taking the grouping algorithm SMS4 disclosed by the state in early 2006 as an example, to establish the "encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com