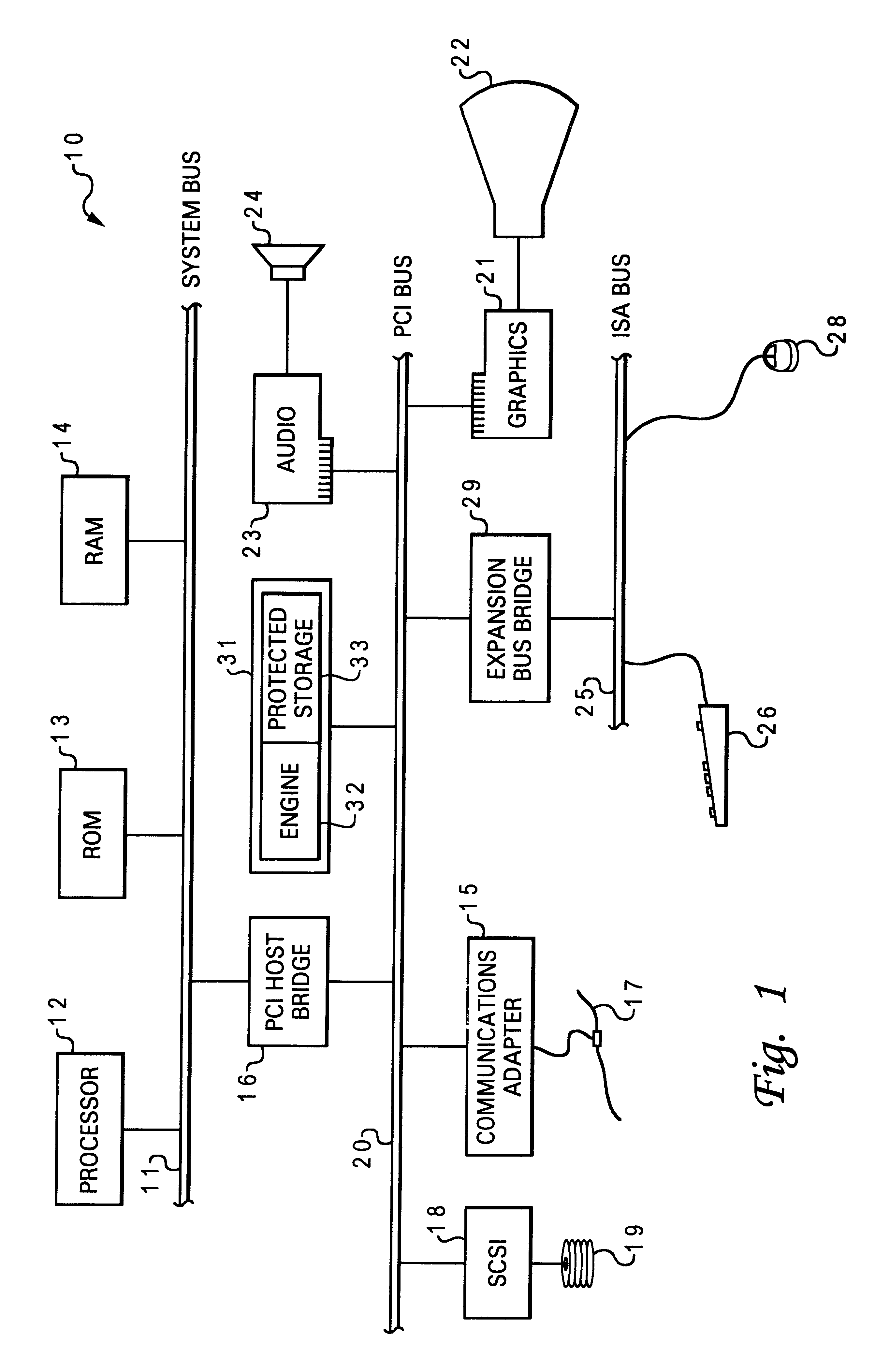
Patents
Literature
111 results about "Passphrase" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A passphrase is a sequence of words or other text used to control access to a computer system, program or data. A passphrase is similar to a password in usage, but is generally longer for added security. Passphrases are often used to control both access to, and operation of, cryptographic programs and systems, especially those that derive an encryption key from a passphrase. The origin of the term is by analogy with password. The modern concept of passphrases is believed to have been invented by Sigmund N. Porter in 1982.
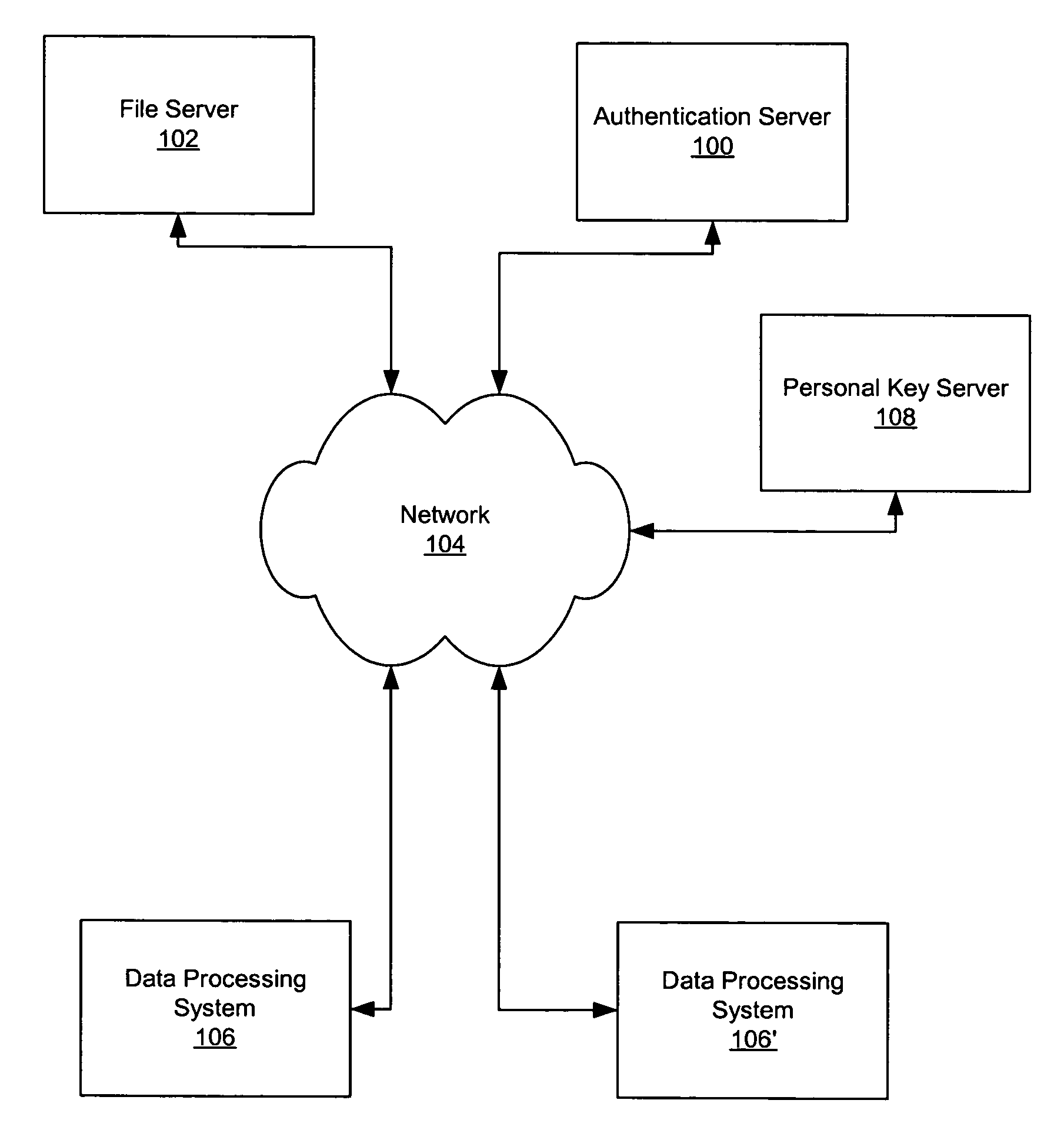
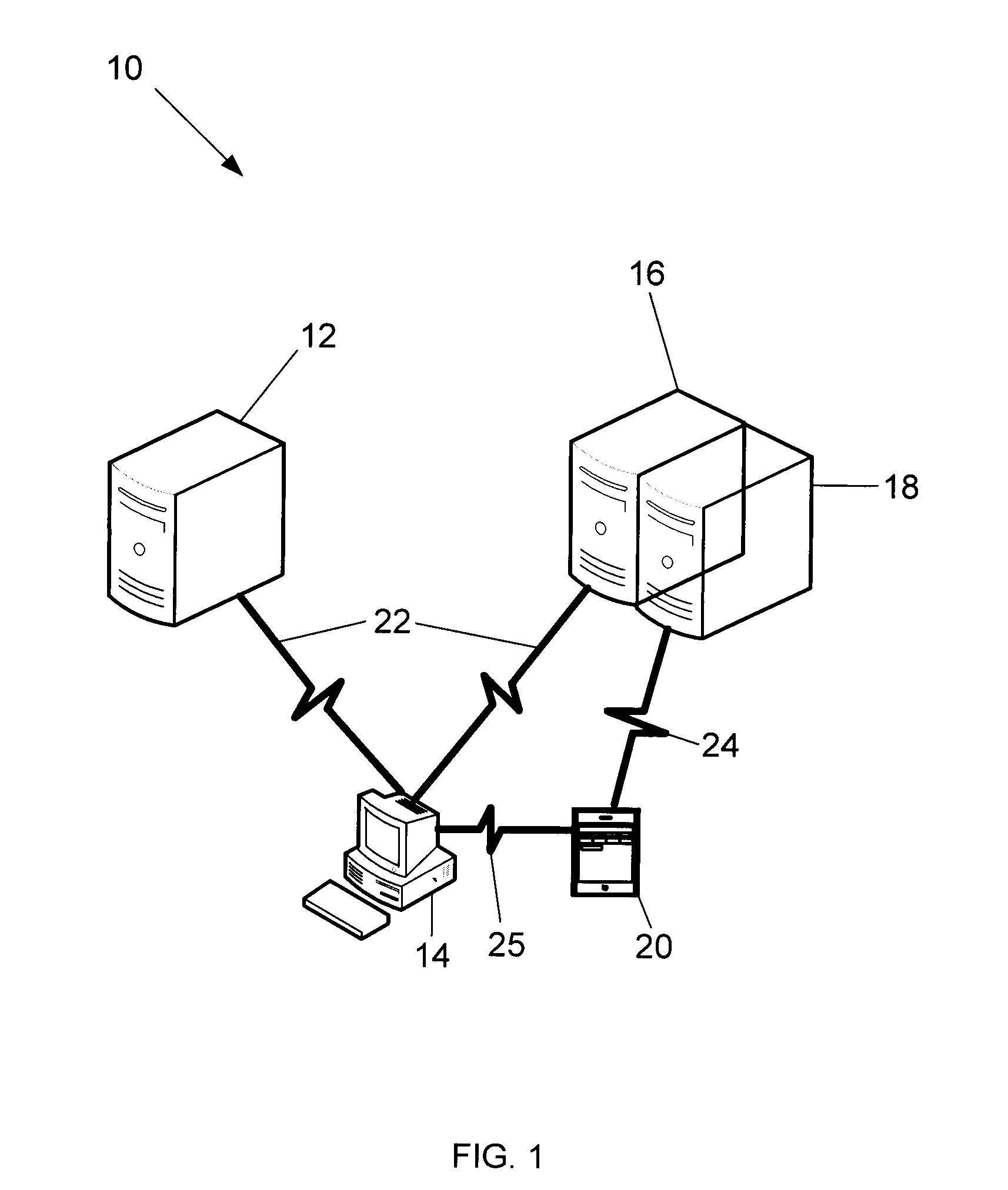
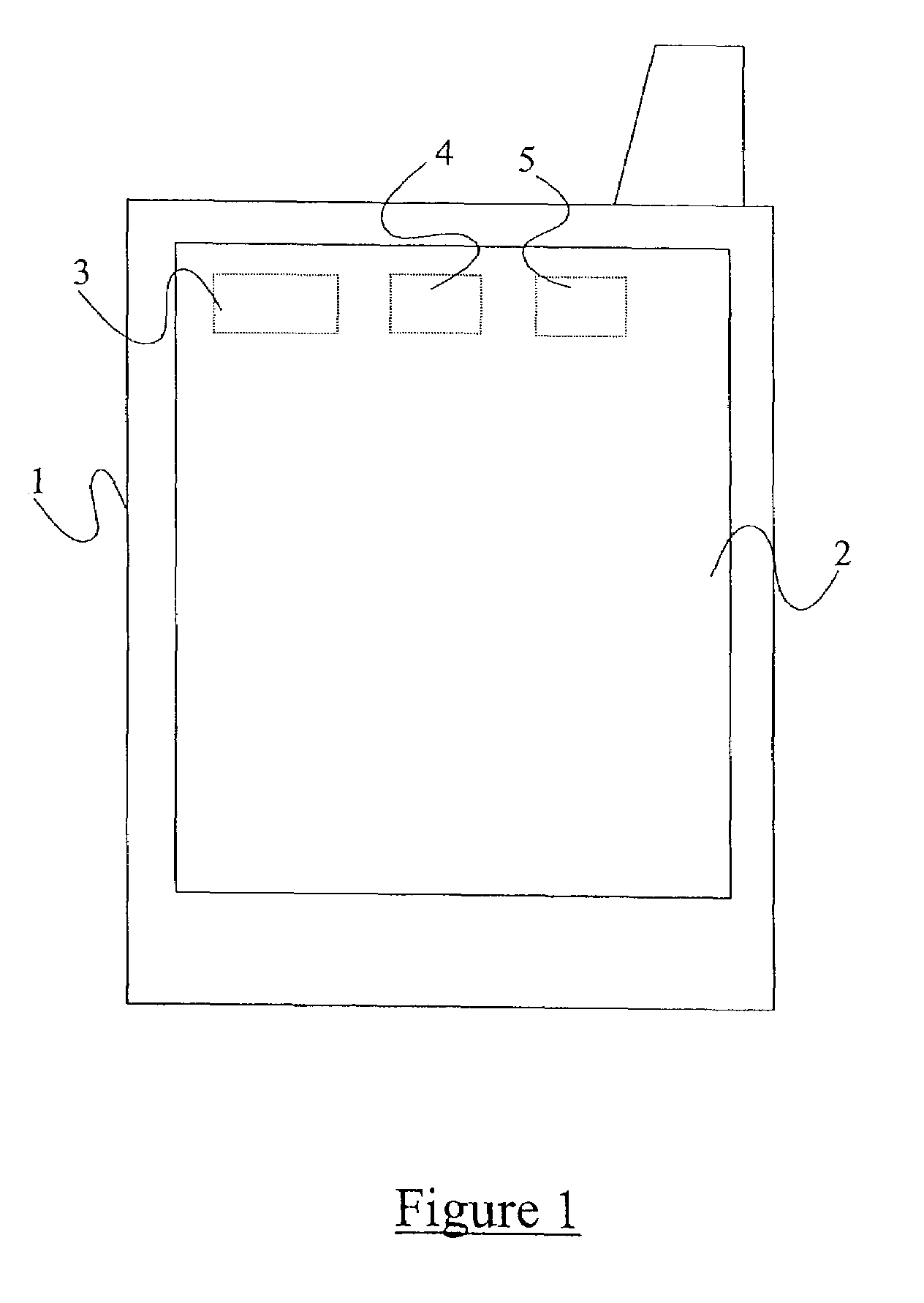
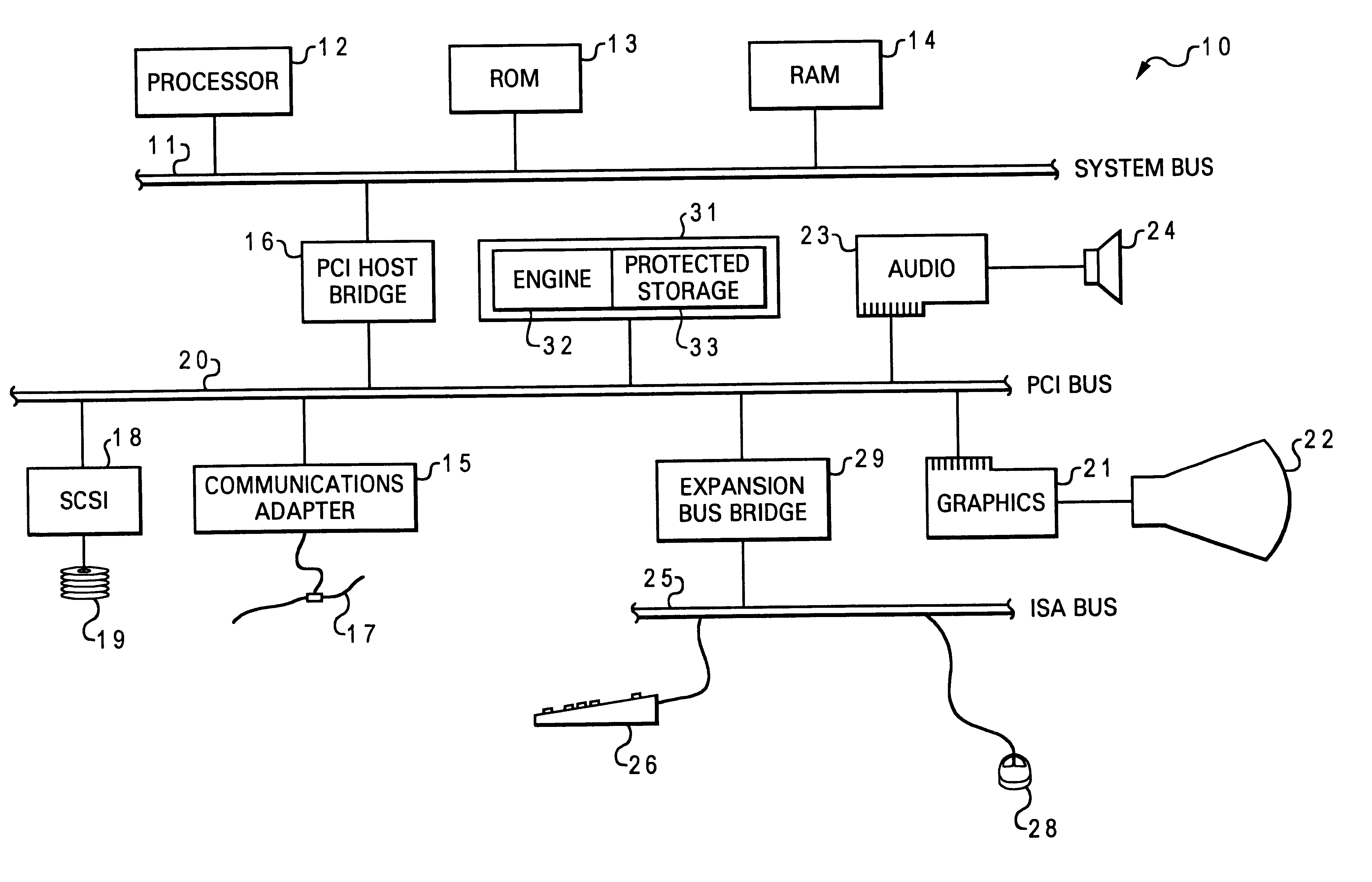
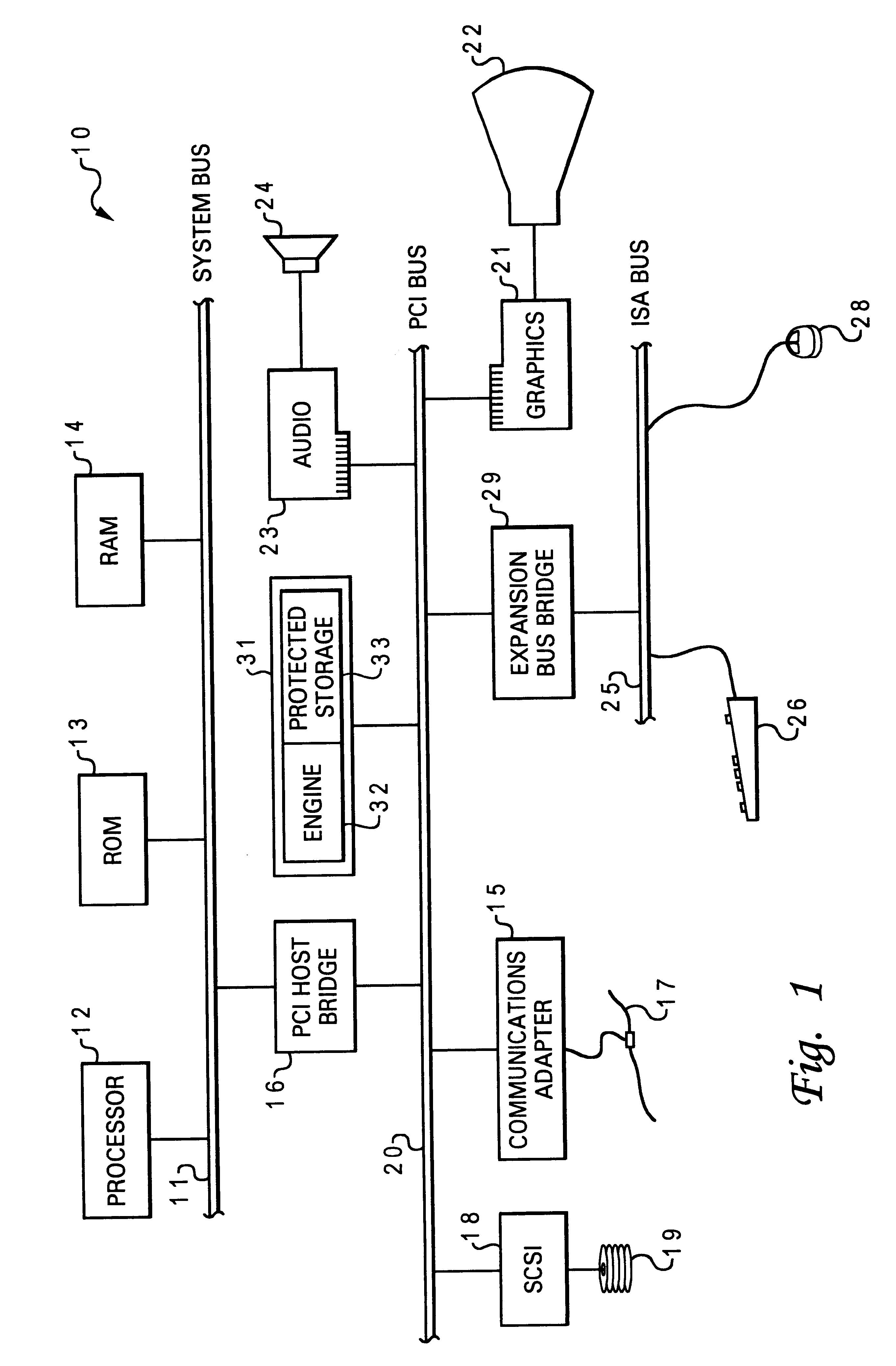
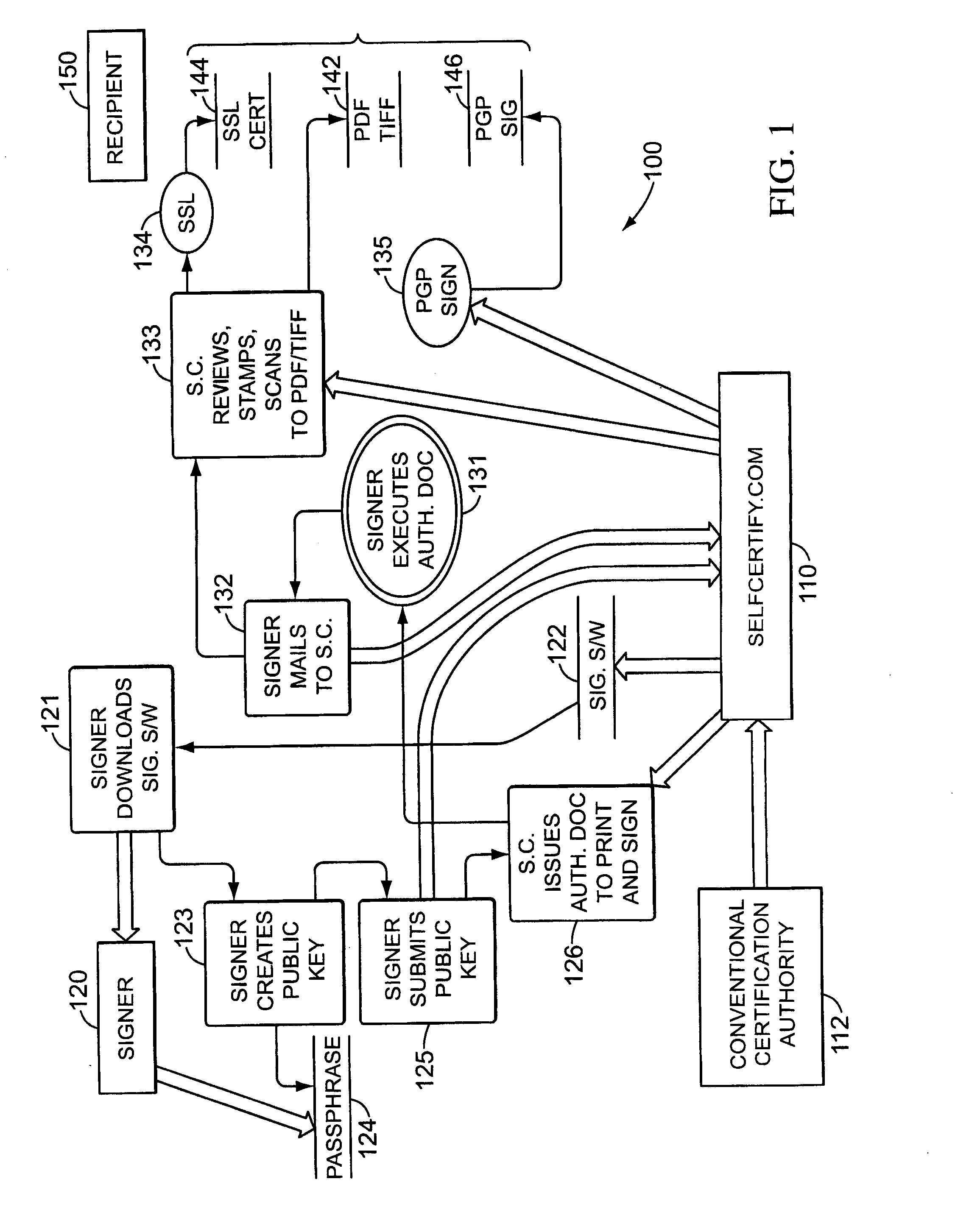
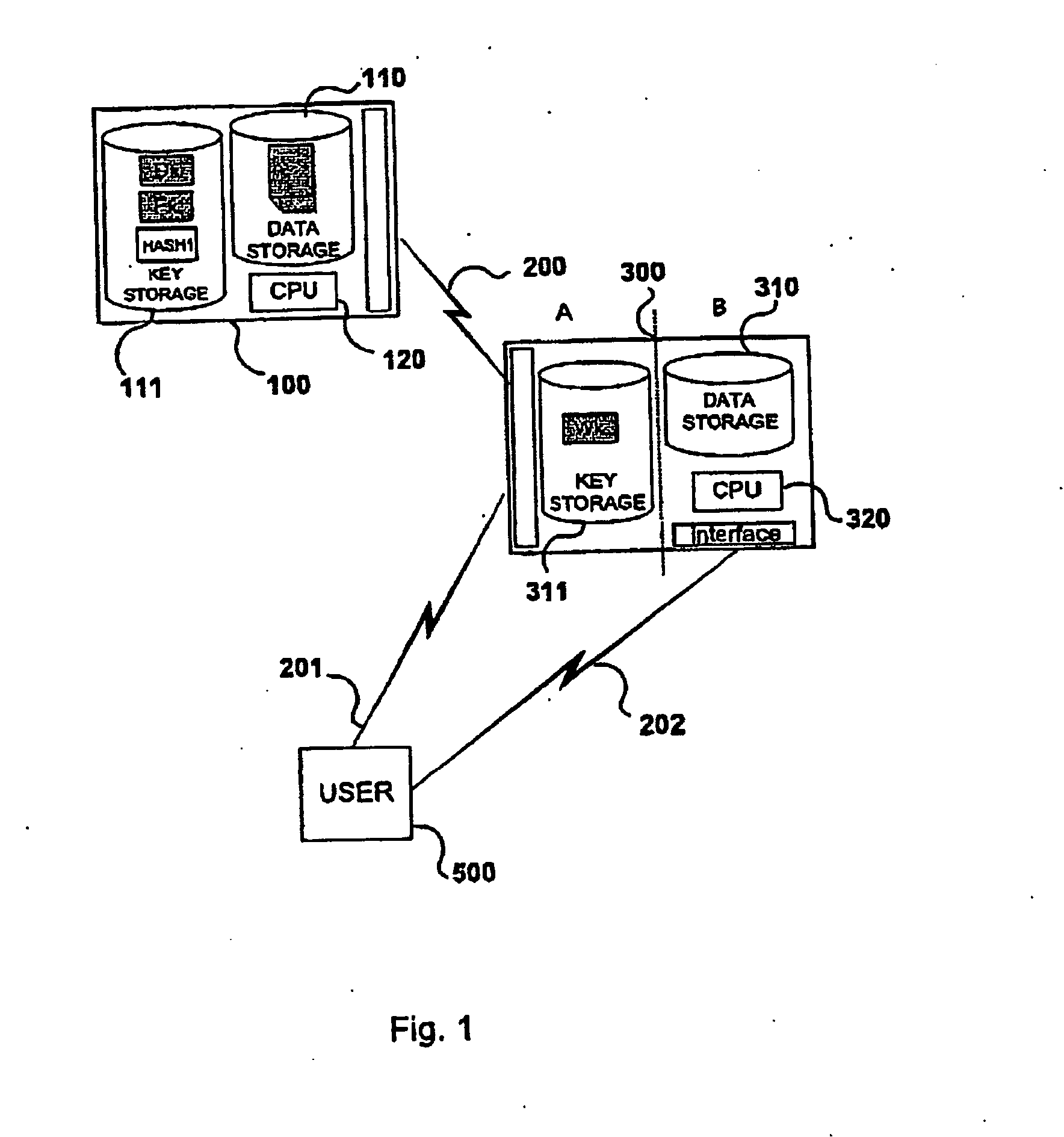
Secure data storage and retrieval with key management and user authentication
InactiveUS6947556B1Key distribution for secure communicationUser identity/authority verificationDigital dataPassphrase
Methods, systems and computer program products are provided which provide for controlling access to digital data in a file by encrypting the data with a first key, encrypting the first key with a second personal key generated from a password / passphrase associated with the file and further encrypting the encrypted first key with a control key which is managed by the system. In certain embodiments, user authentication may also be provided by issuing a ticket which is utilized to create, access and administer the files in the system.
Owner:IBM CORP
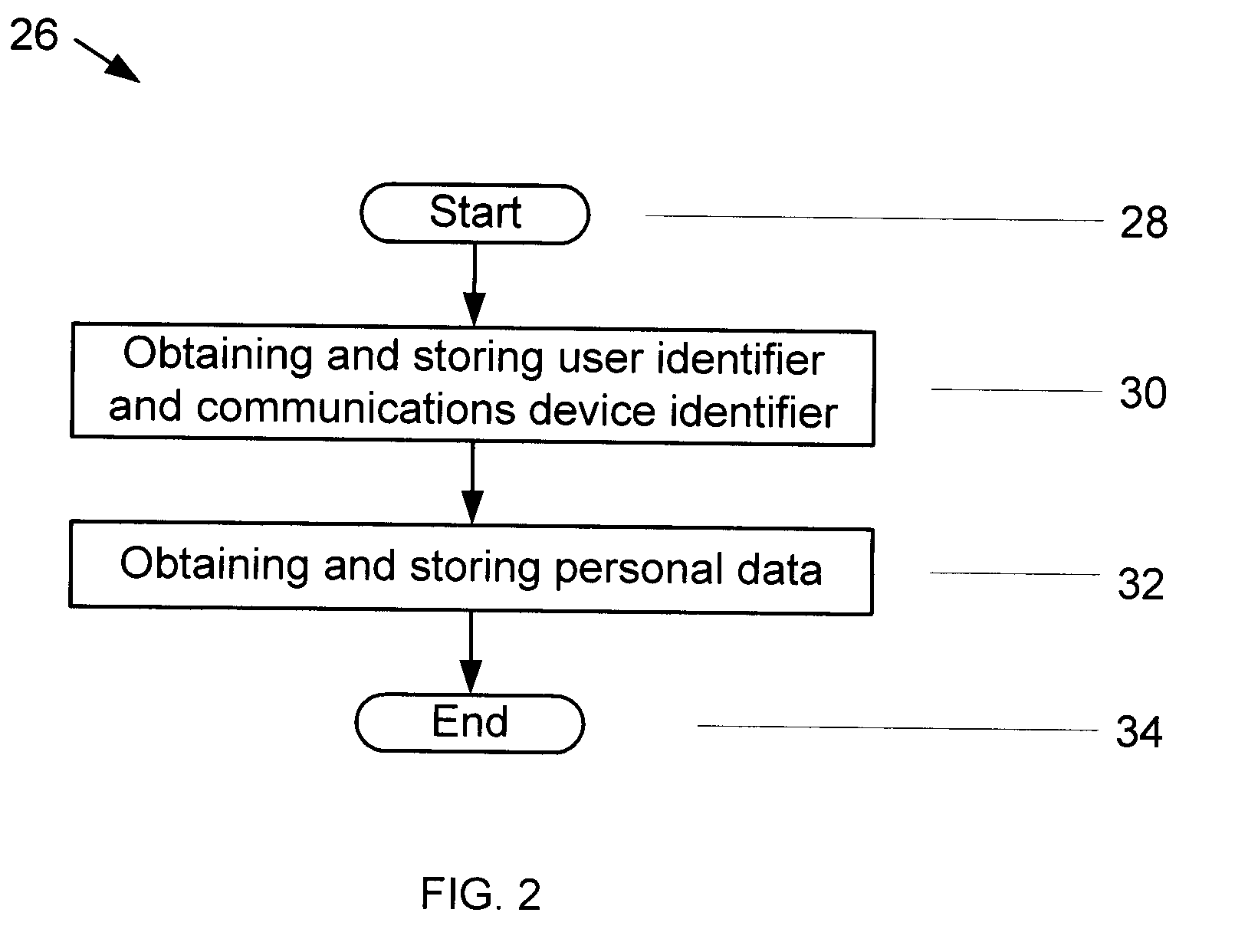
Methods and systems for authenticating users
ActiveUS20110035788A1Reduce transaction riskReduce riskDigital data processing detailsUser identity/authority verificationWorkstationOne-time password
A method of authenticating users to reduce transaction risks includes indicating a desire to conduct a transaction, inputting information in a workstation, and determining whether the inputted information is known. Moreover, the method includes determining a state of a communications device when the inputted information is known, and transmitting a biometric authentication request from a server to an authentication system when the state of the communications device is enrolled. Additionally, the method includes obtaining biometric authentication data in accordance with a biometric authentication data capture request with the communications device, biometrically authenticating the user, generating a one-time pass-phrase and storing the one-time pass-phrase on the authentication system when the user is authenticated, comparing the transmitted one-time pass-phrase against the stored one-time pass-phrase, and conducting the transaction when the transmitted and stored one-time pass-phrases match.
Owner:DAON TECH
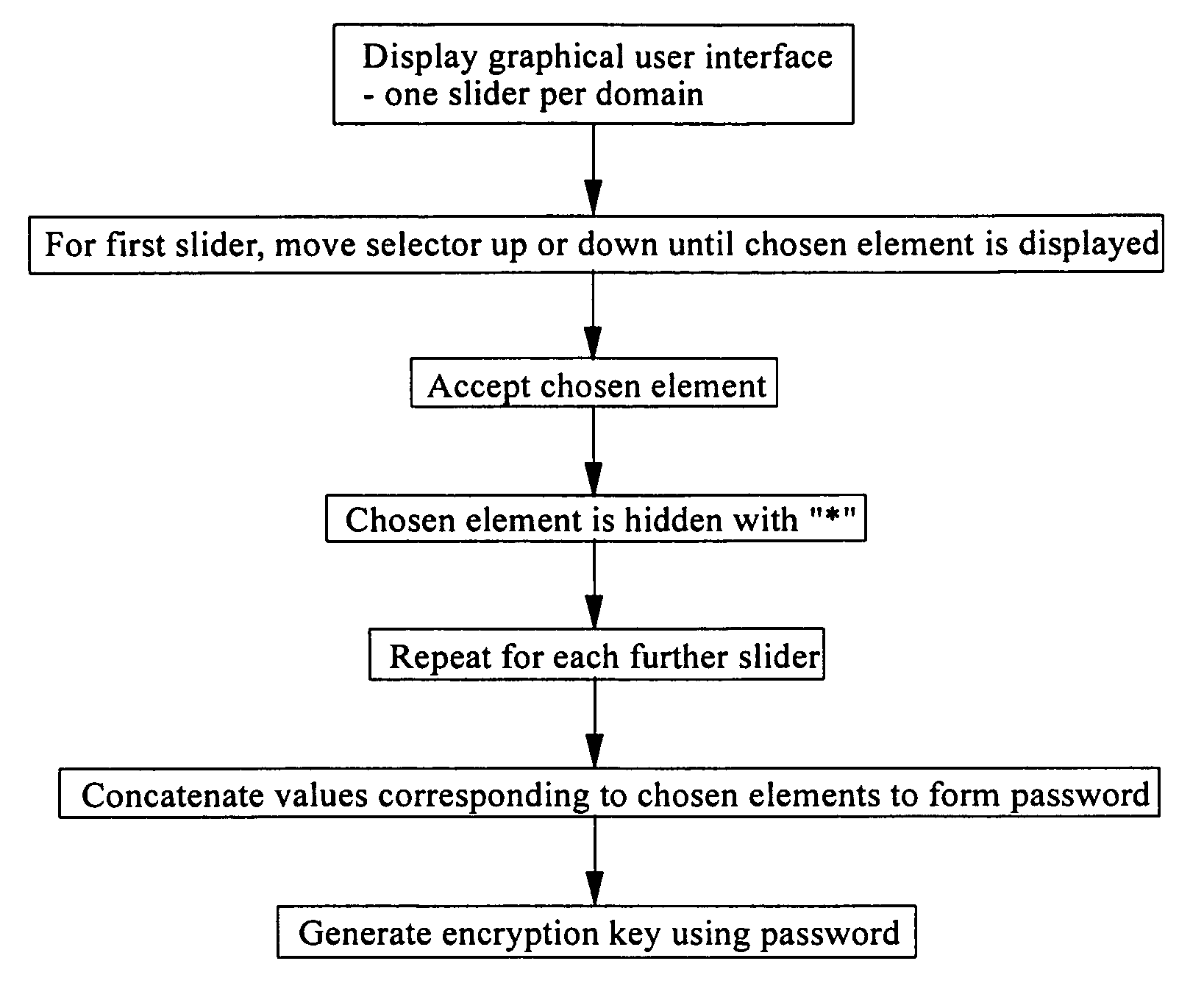
Method and apparatus for selecting a password
ActiveUS20050044425A1Easy to correctImprove recallDigital data processing detailsUnauthorized memory use protectionComputer hardwarePassphrase
A method of generating or entering a password or passphrase on a computer system 1. The method comprises storing a plurality of sets of values in a memory 5 of the system 1, the values of each set defining respective elements which belong to a common domain, the domains of respective sets being distinct from one another, selecting at least one value from each stored set or from each of a plurality of the stored sets, and combining the selected values or elements thereof to form a password or passphrase.
Owner:F SECURE CORP
System and method for automatic wireless network authentication in an internet of things (IOT) system
A system, apparatus, and method are described for a secure IoT wireless network configuration. For example, one embodiment of an Internet of Things (IoT) hub comprises: a local wireless communication interface to establish local wireless connections with one or more IoT devices and / or IoT extender hubs; a network router to establish network connections over the Internet on behalf of the IoT devices and / or IoT extender hubs; an authentication module pre-configured with a passphrase and a hidden service set identifier (SSID), the authentication module to receive a connection requests from the IoT devices and / or an IoT extender hubs and to grant the connection requests when the IoT devices and / or IoT extender hubs use the pre-configured passphrase and hidden SSID; and a firewall of the IoT hub to block all outgoing and incoming connection requests other than those directed to designated servers of an IoT service with known host names.
Owner:AFERO
Multiple choice challenge-response user authorization system and method
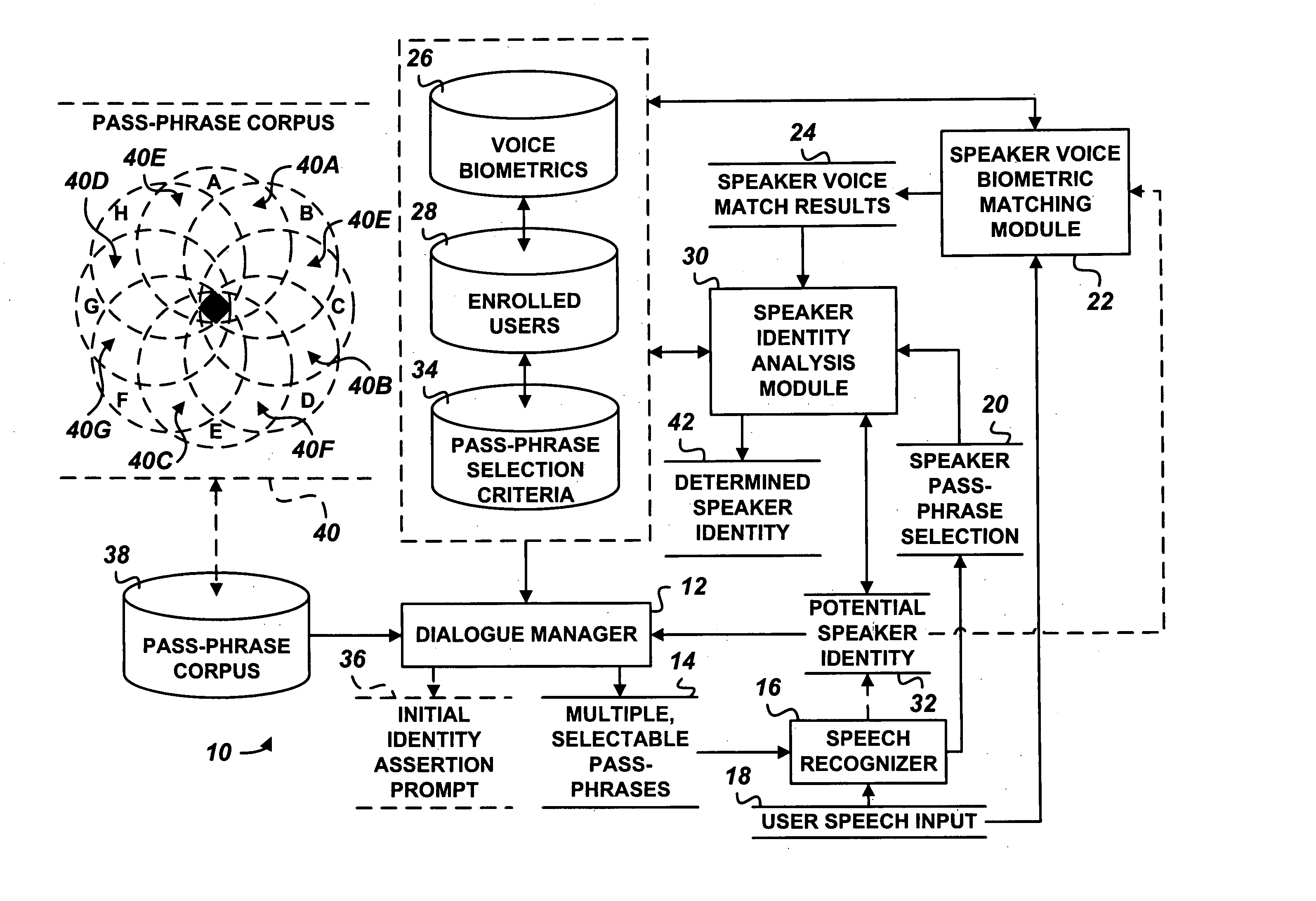
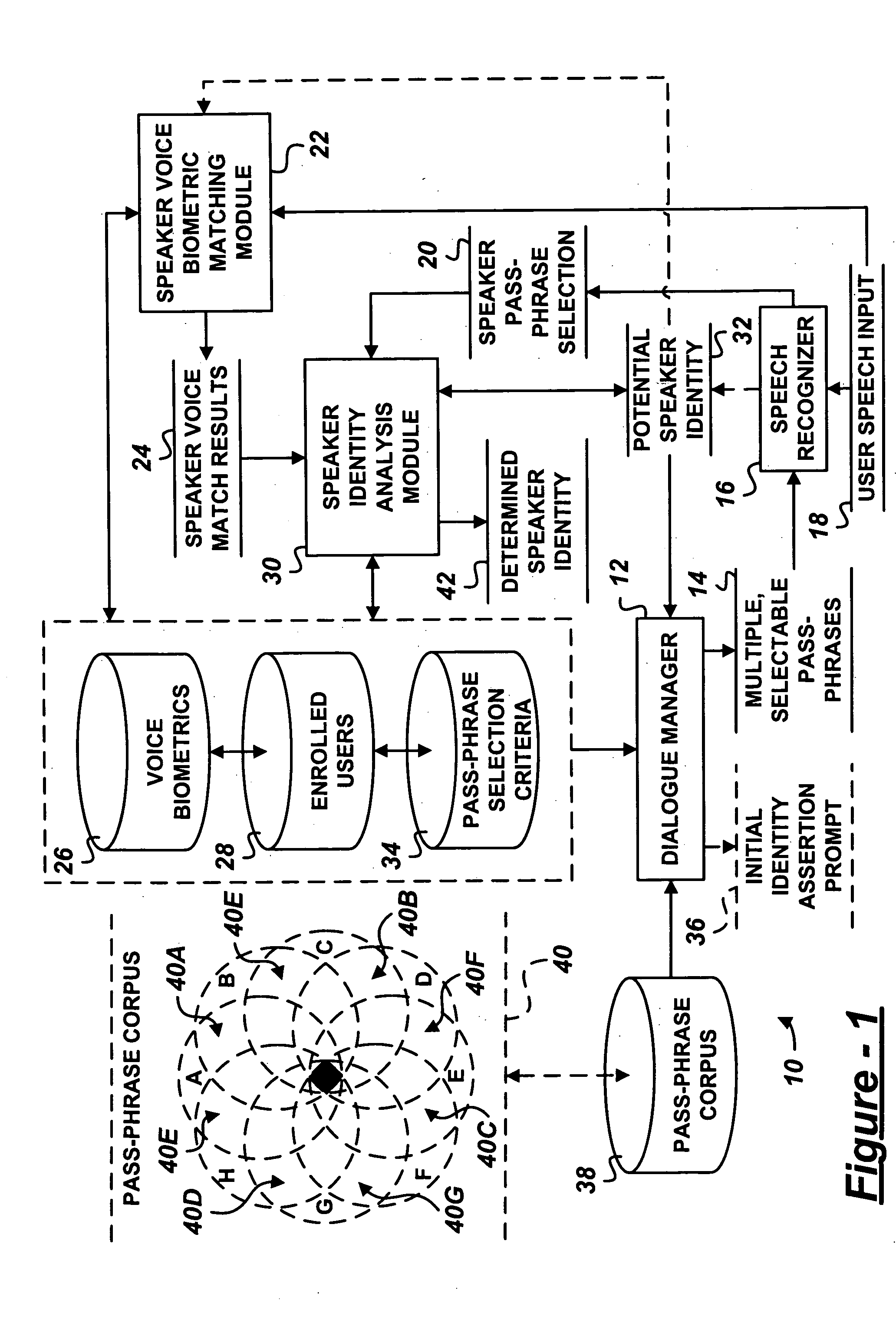
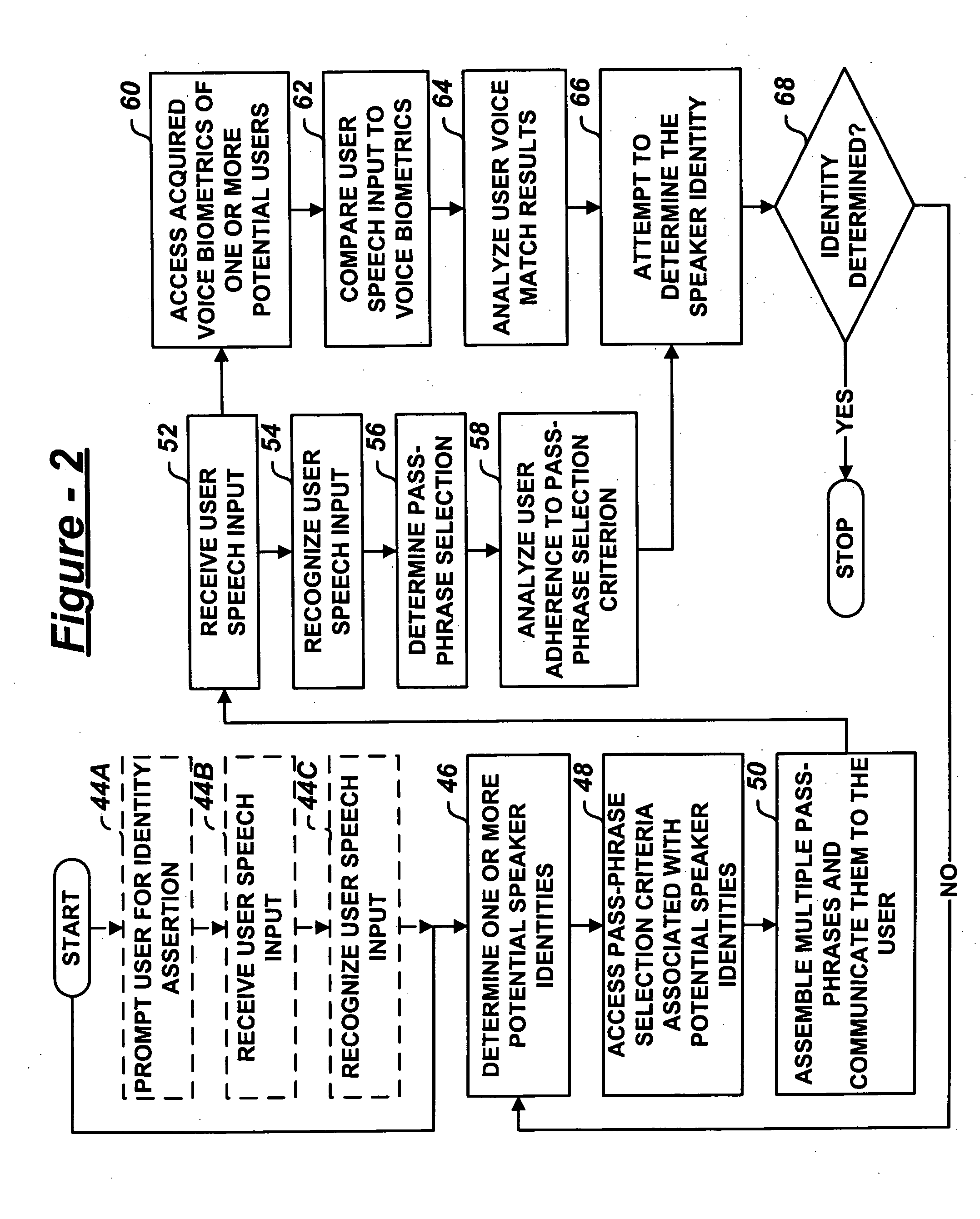
ActiveUS20050171851A1Digital data processing detailsUnauthorized memory use protectionPassphraseSelection criterion
A user authentication system includes a dialogue manager adapted to prompt the user with multiple, selectable pass-phrases. A selection recognizer recognizes user selection of at least one of the multiple, selectable pass-phrases. A user identity analysis module analyzes one or more potential user identities based on adherence of user selection of the pass-phrase to predetermined pass-phrase selection criteria assigned one or more enrolled users.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
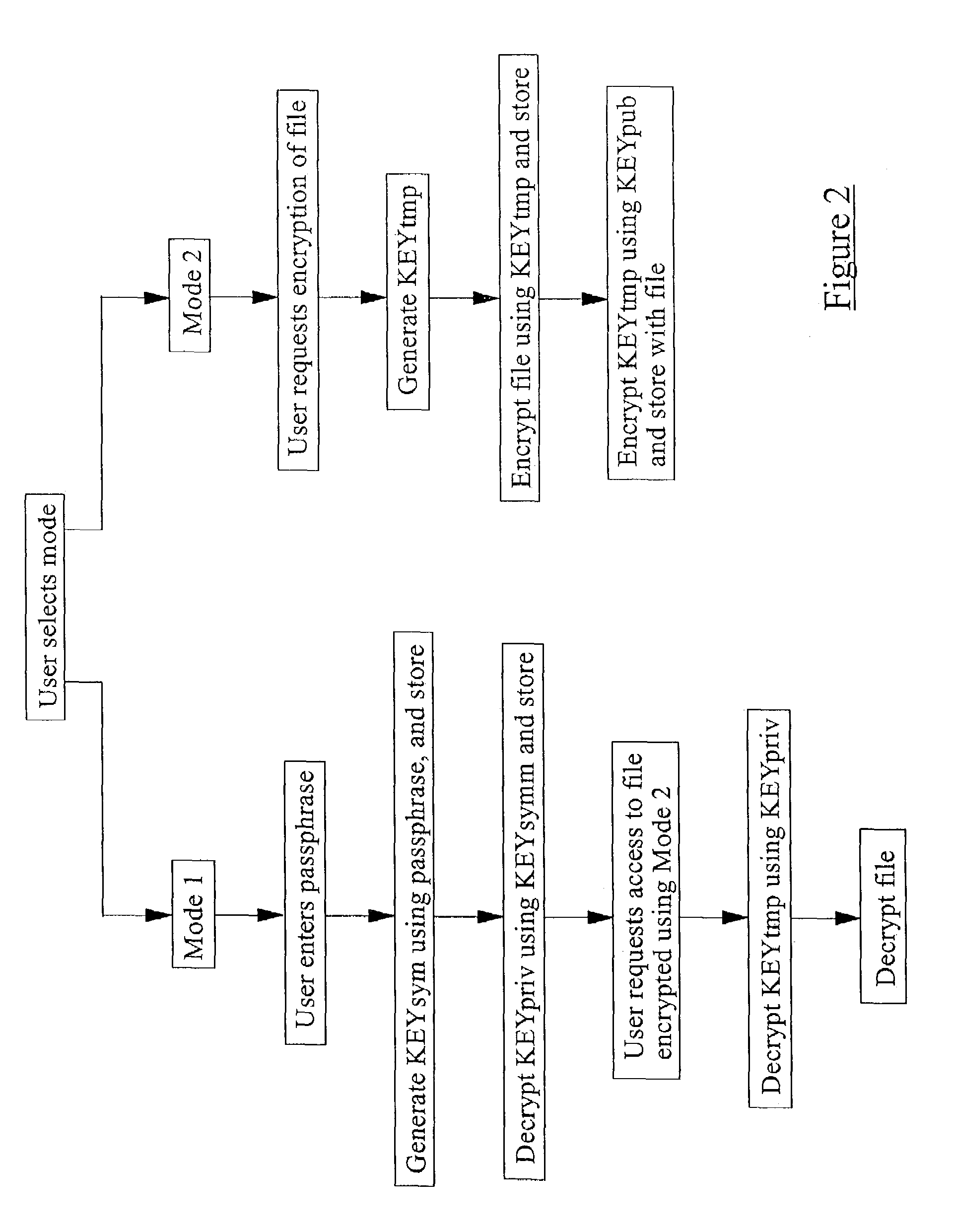
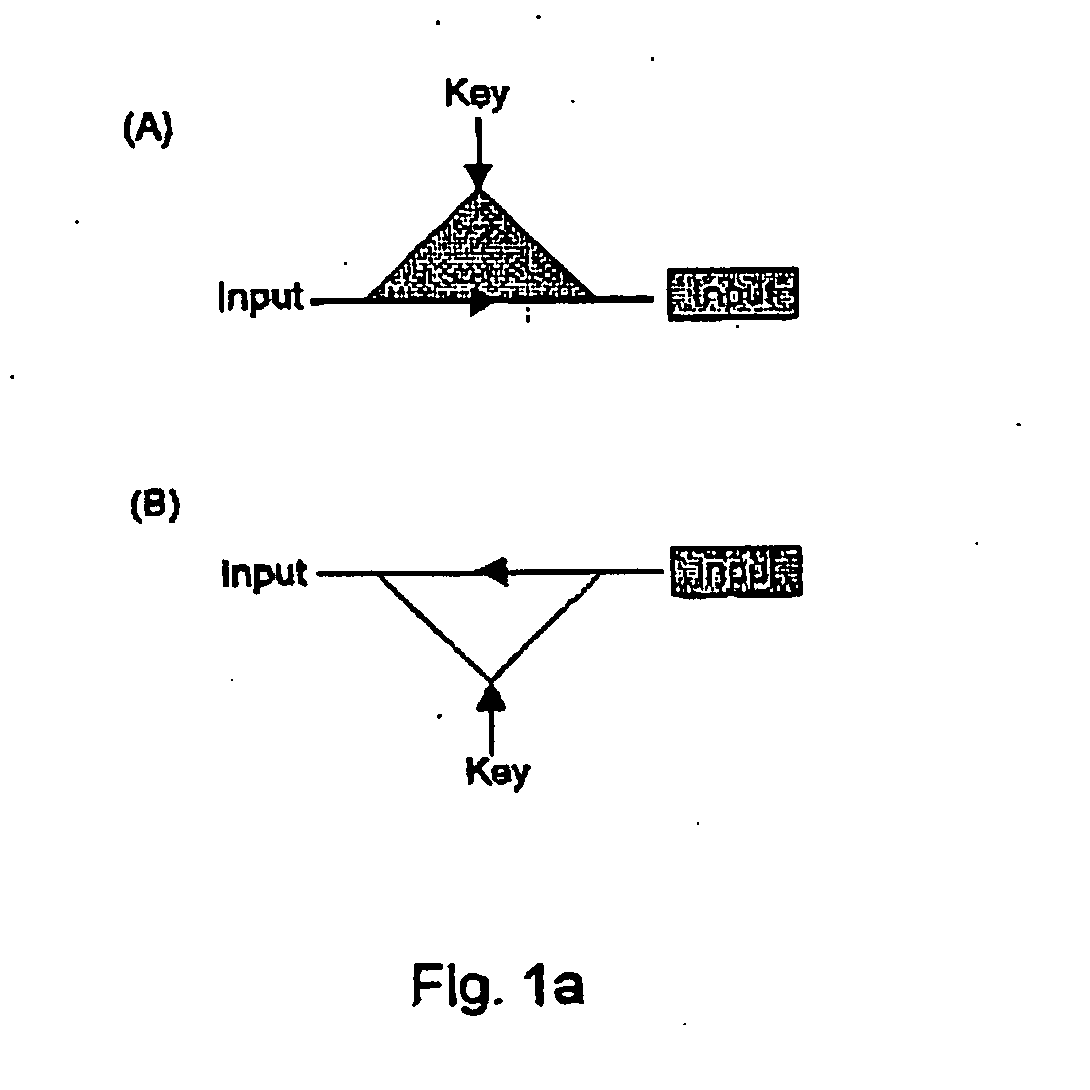
Method and apparatus for encrypting data
InactiveUS7529374B2Reduce riskKey distribution for secure communicationPublic key for secure communicationPassphraseSecret code
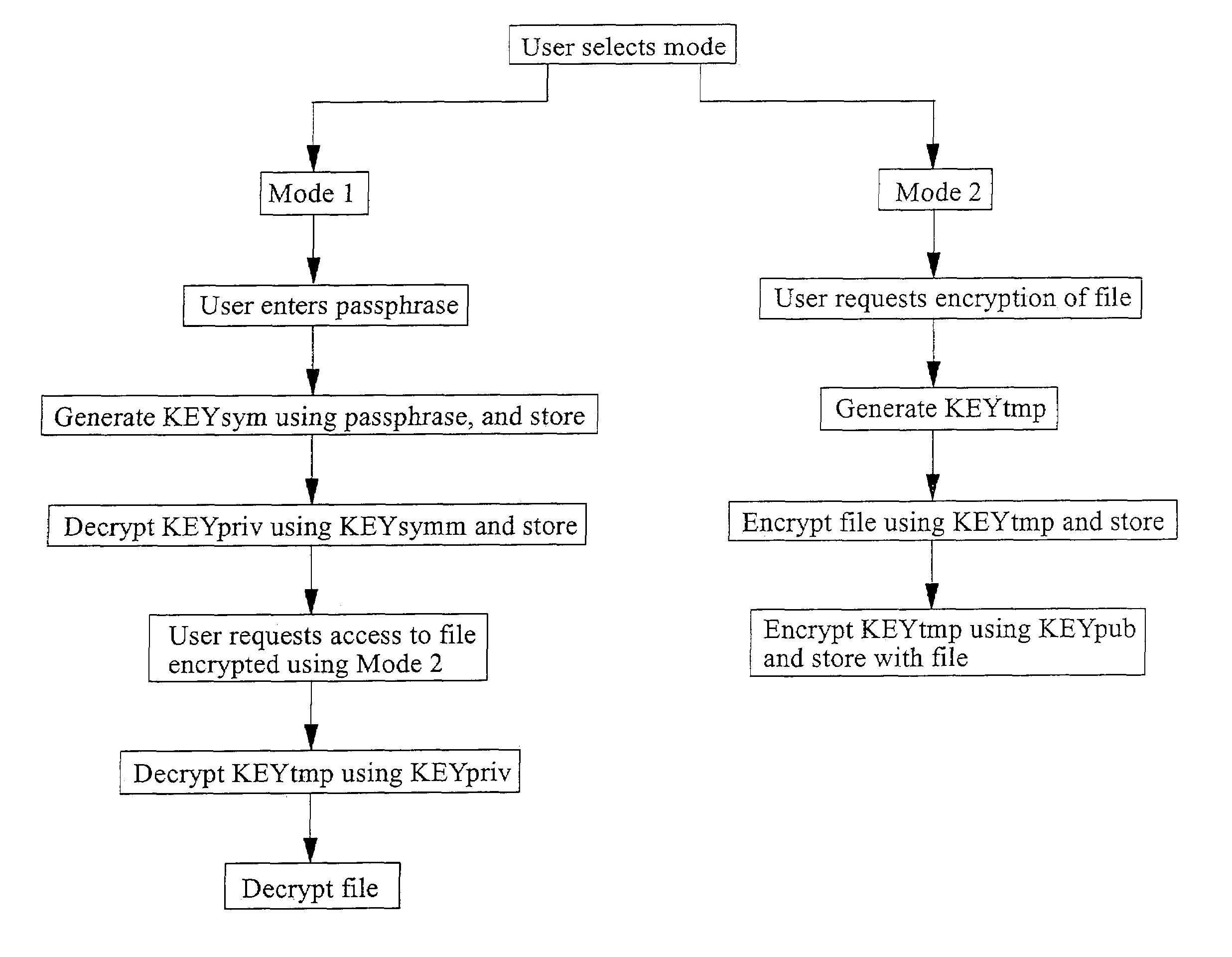
A method of securing data on an electronic device comprises allowing a user of the device to select one of an encryption and decryption operating mode and an encryption only operating mode. The encryption and decryption operating mode requires that the device have access to a user passphrase, and the encryption only operating mode does not require that the device have access to the passphrase.
Owner:RPX CORP
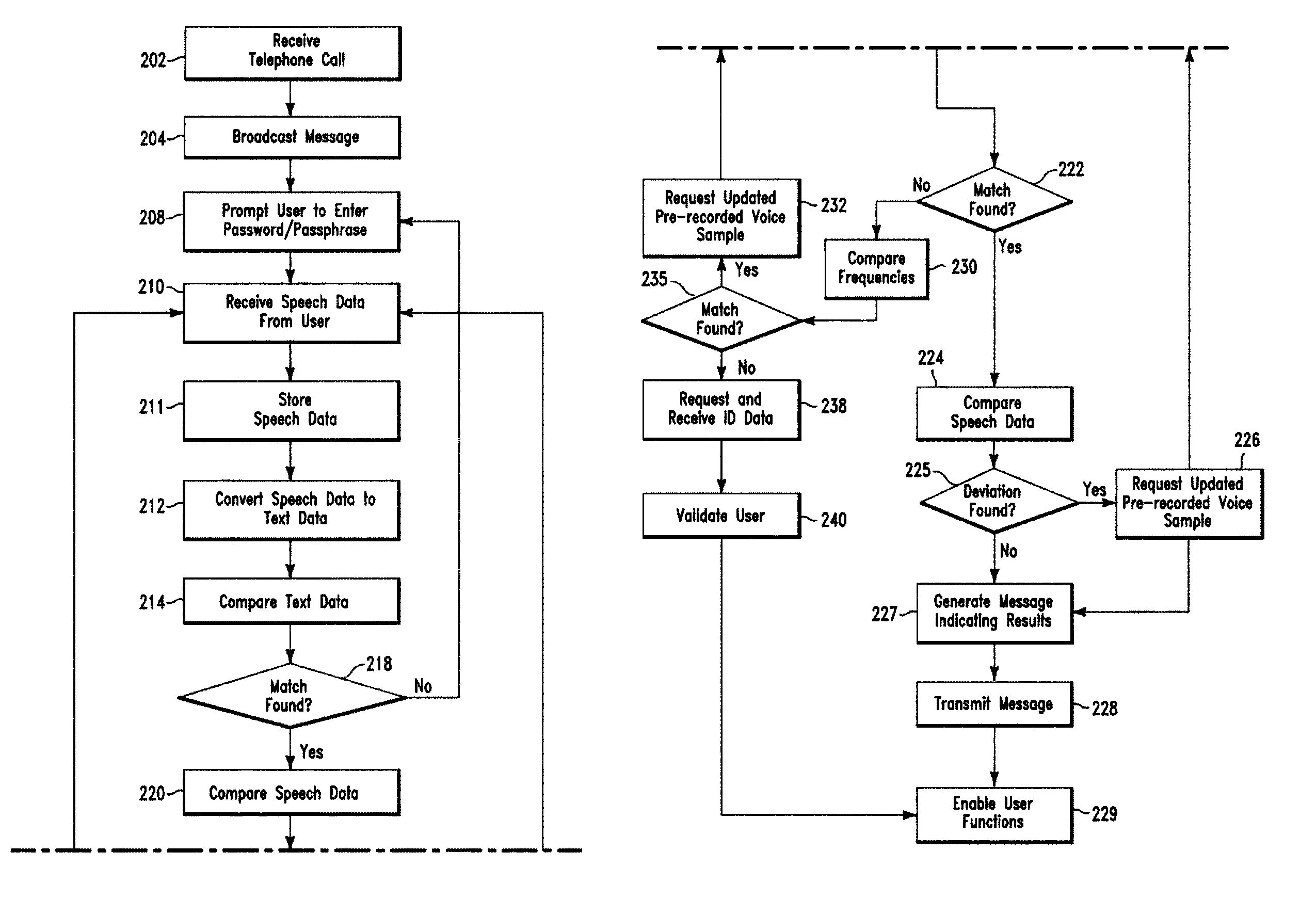
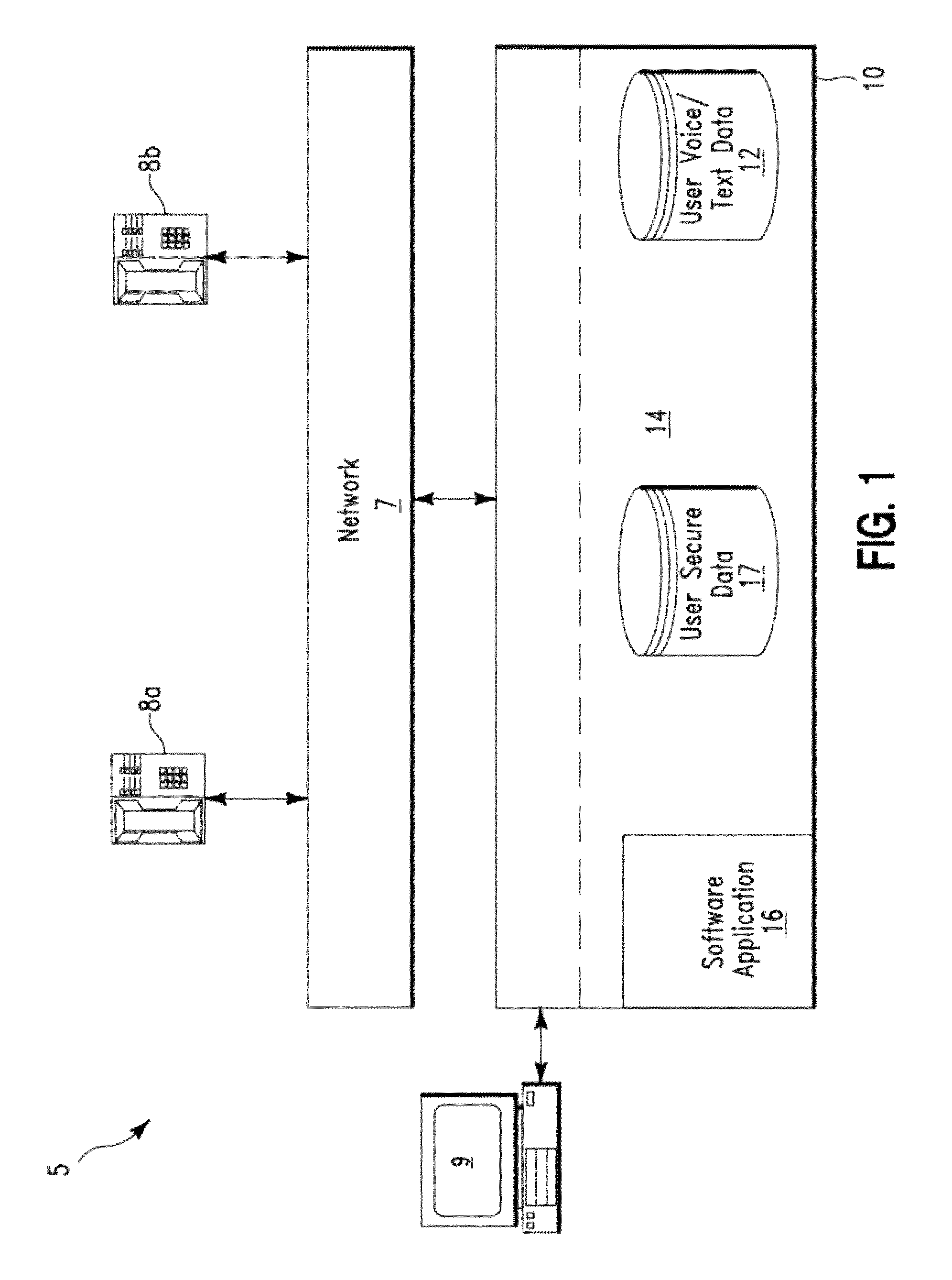
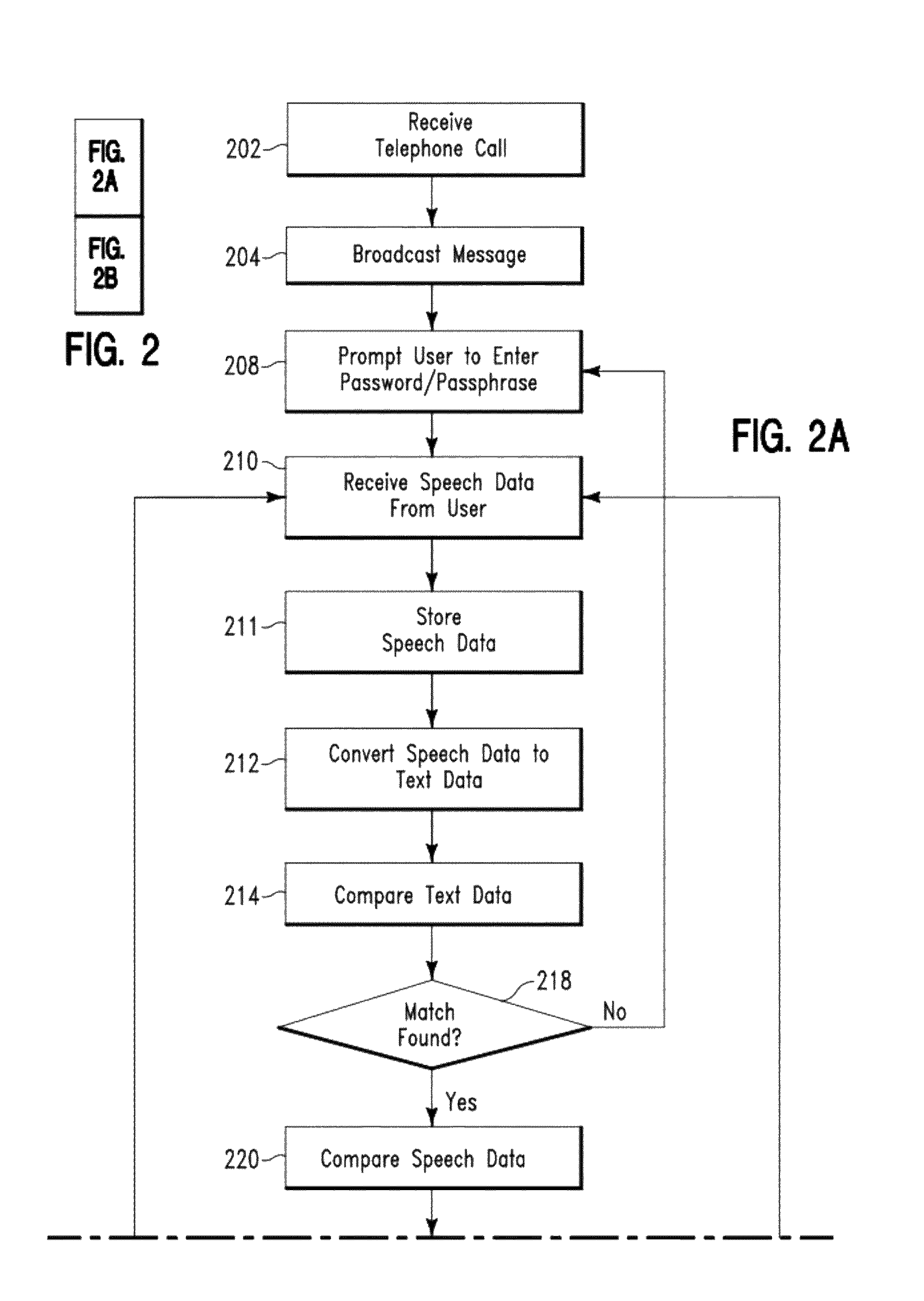
Secure voice transaction method and system
ActiveUS8194827B2Communication securityUnauthorised/fraudulent call preventionDigital data processing detailsPassphraseFrequency spectrum
A security method and system. The method includes receiving by a computing system, a telephone call from a user. The computing system comprises an existing password / passphrase and a pre-recorded voice sample associated with the user. The computing system prompts the user to enter a password / passphrase using speech. The computing system receives speech data comprising a first password / passphrase from the user. The computing system converts the speech data to text data. The computing system first compares the text data to the first password / passphrase and determines a match. The computing system compares the speech data to the pre-recorded voice sample to determine a result indicating whether a frequency spectrum associated with the speech data matches a frequency spectrum associated with the pre-recorded voice sample. The computing system transmits the result to the user.
Owner:MICROSOFT TECH LICENSING LLC
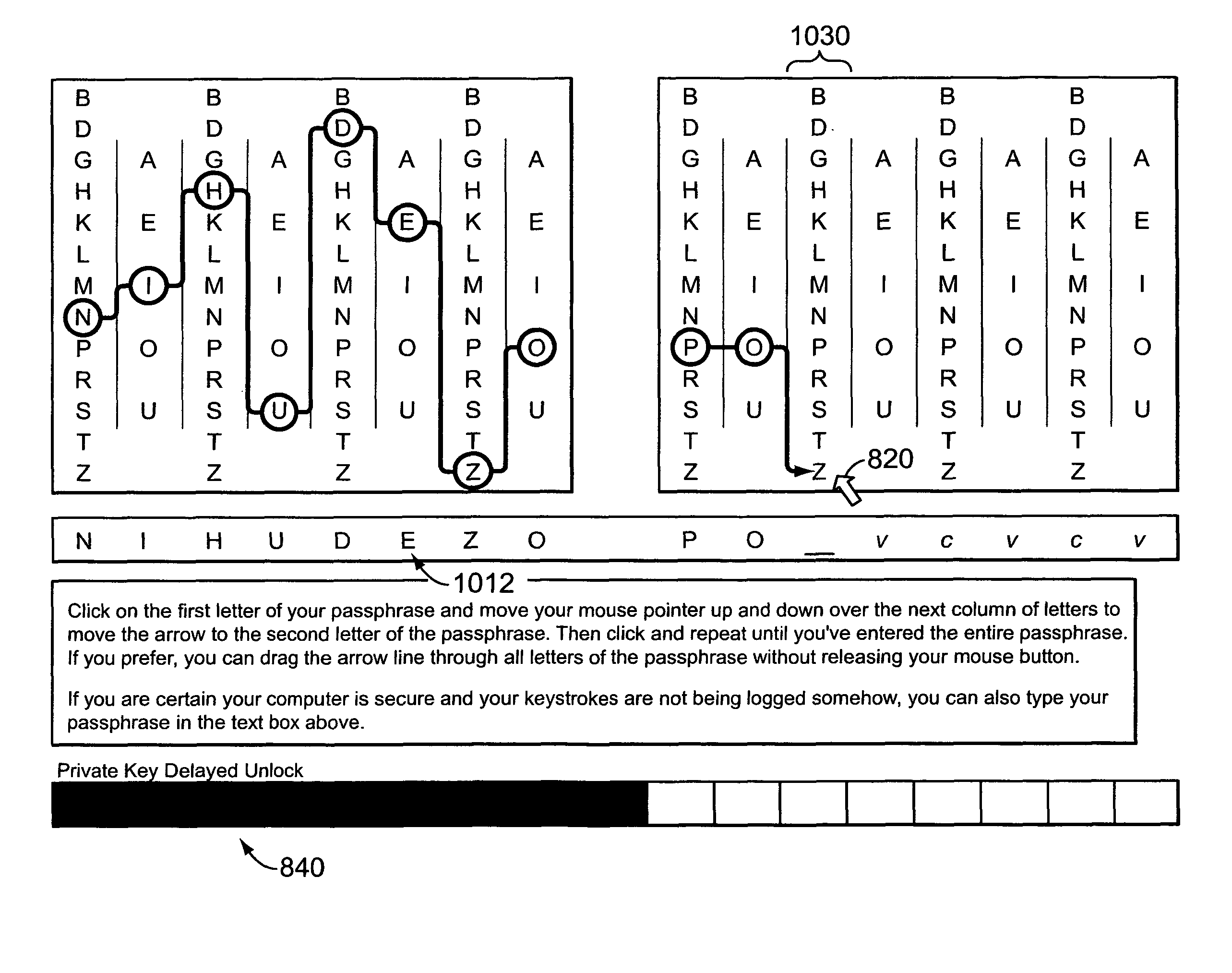
Encryption and authentication systems and methods
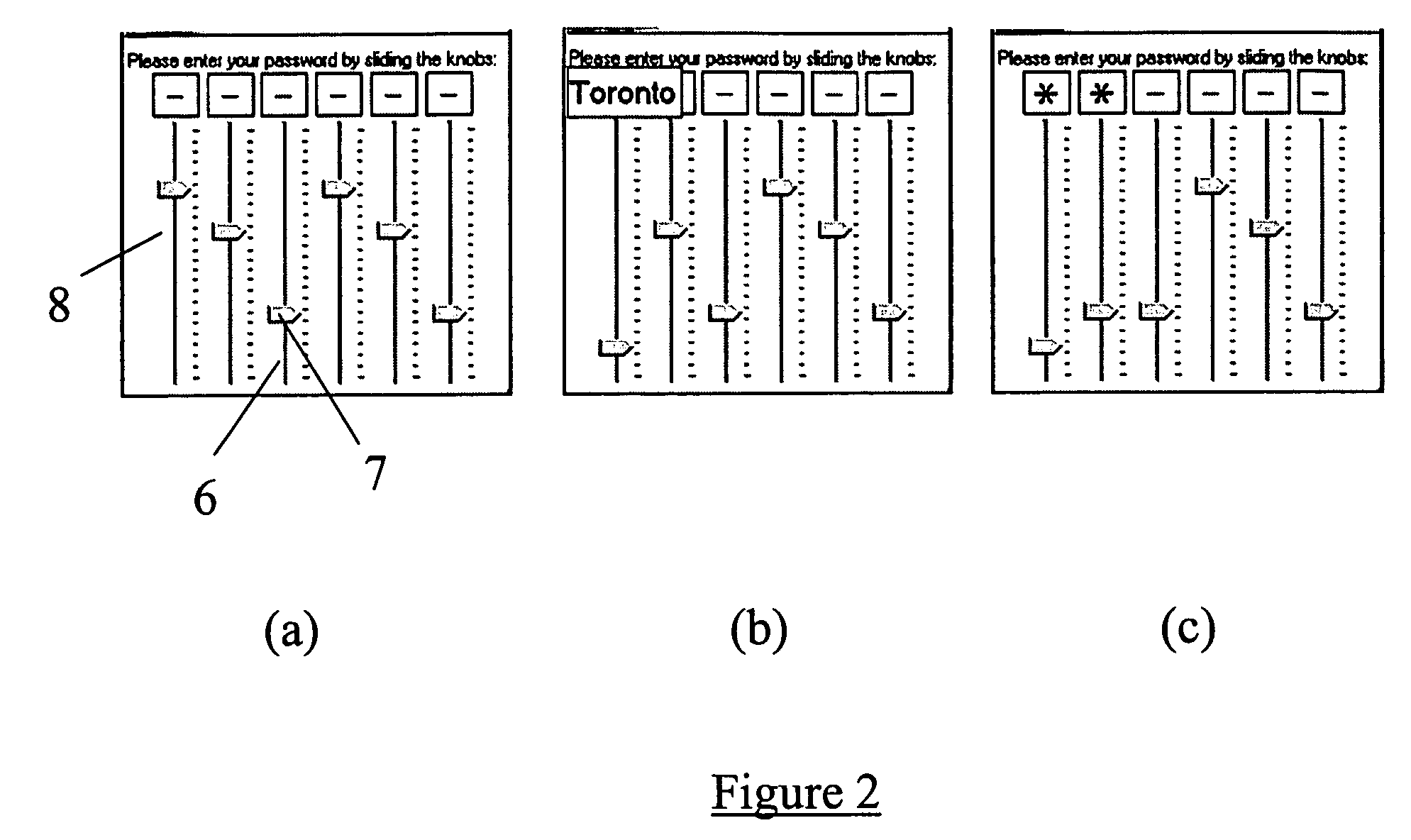
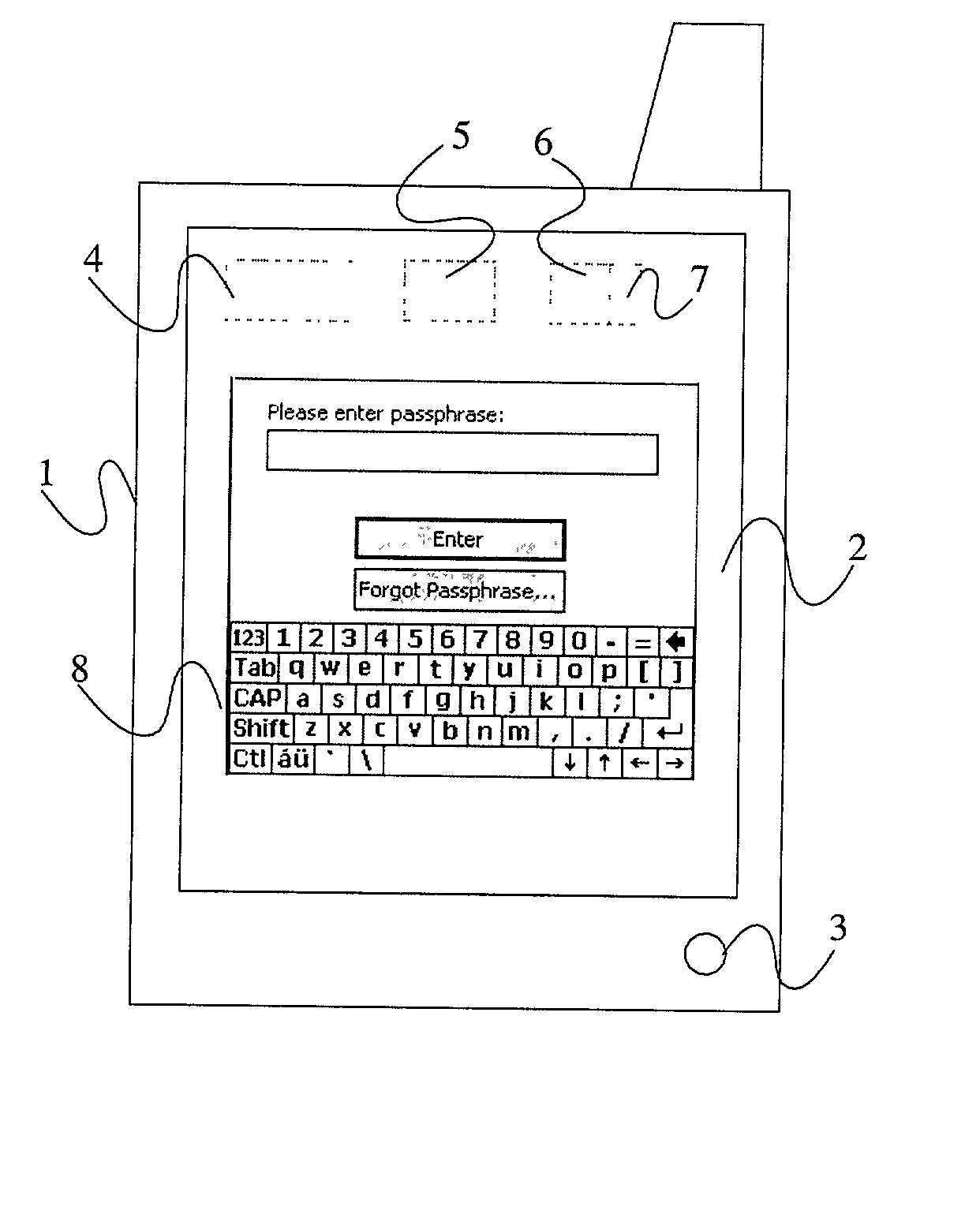
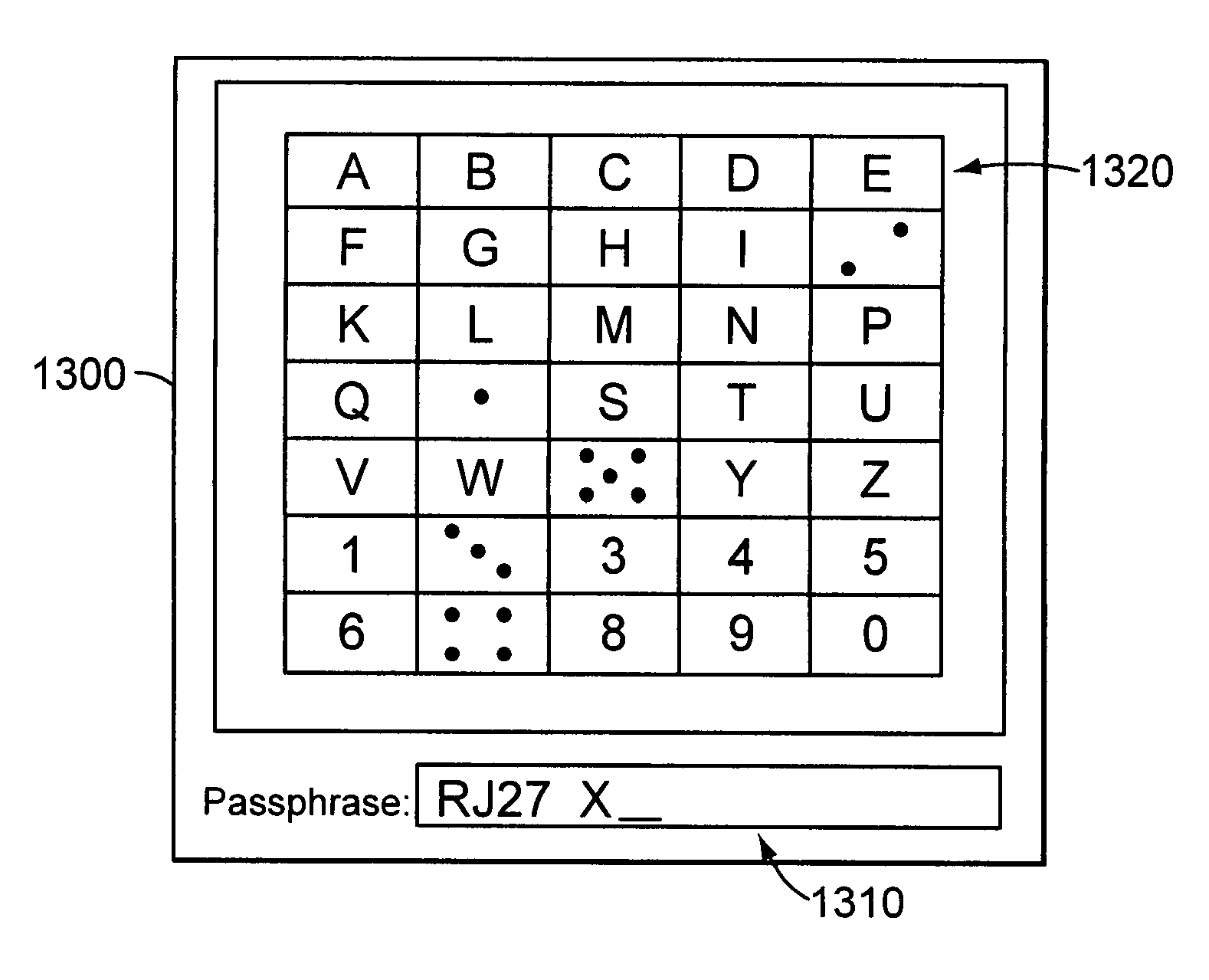
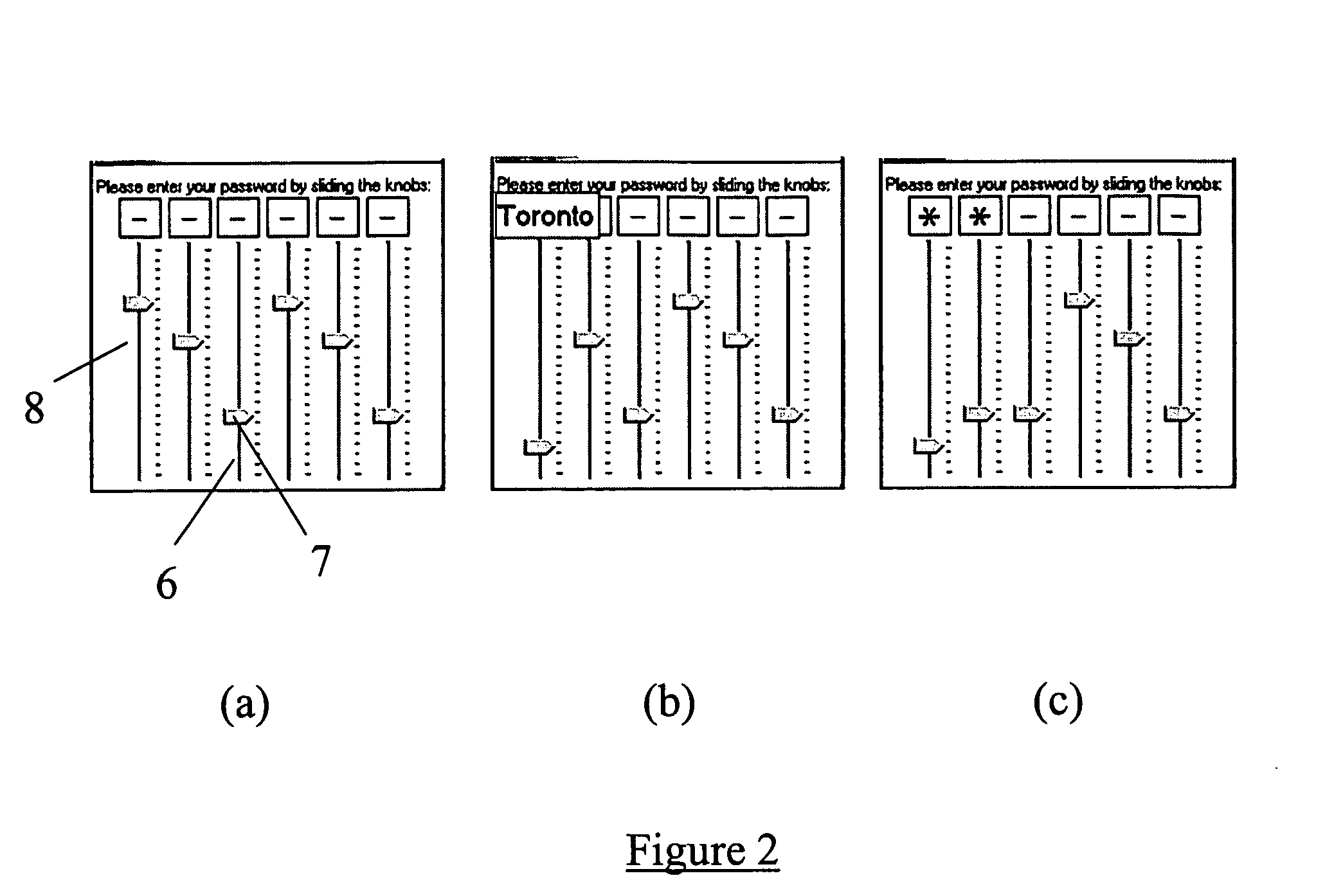
InactiveUS8006299B2Digital data processing detailsUser identity/authority verificationElectronic documentGraphics
Methods, apparatus, and systems are disclosed for, among other things, passphrase input using secure delay, passphrase input with characteristic shape display, user authentication with non-repeated selection of elements with a displayed set of elements, document authentication with embedding of a digital signature stamp within a graphical representation of the electronic document wherein the stamp comprises digits of a digital signature, and sub-hash computation using secure delay.
Owner:KIOBA PROCESSING LLC
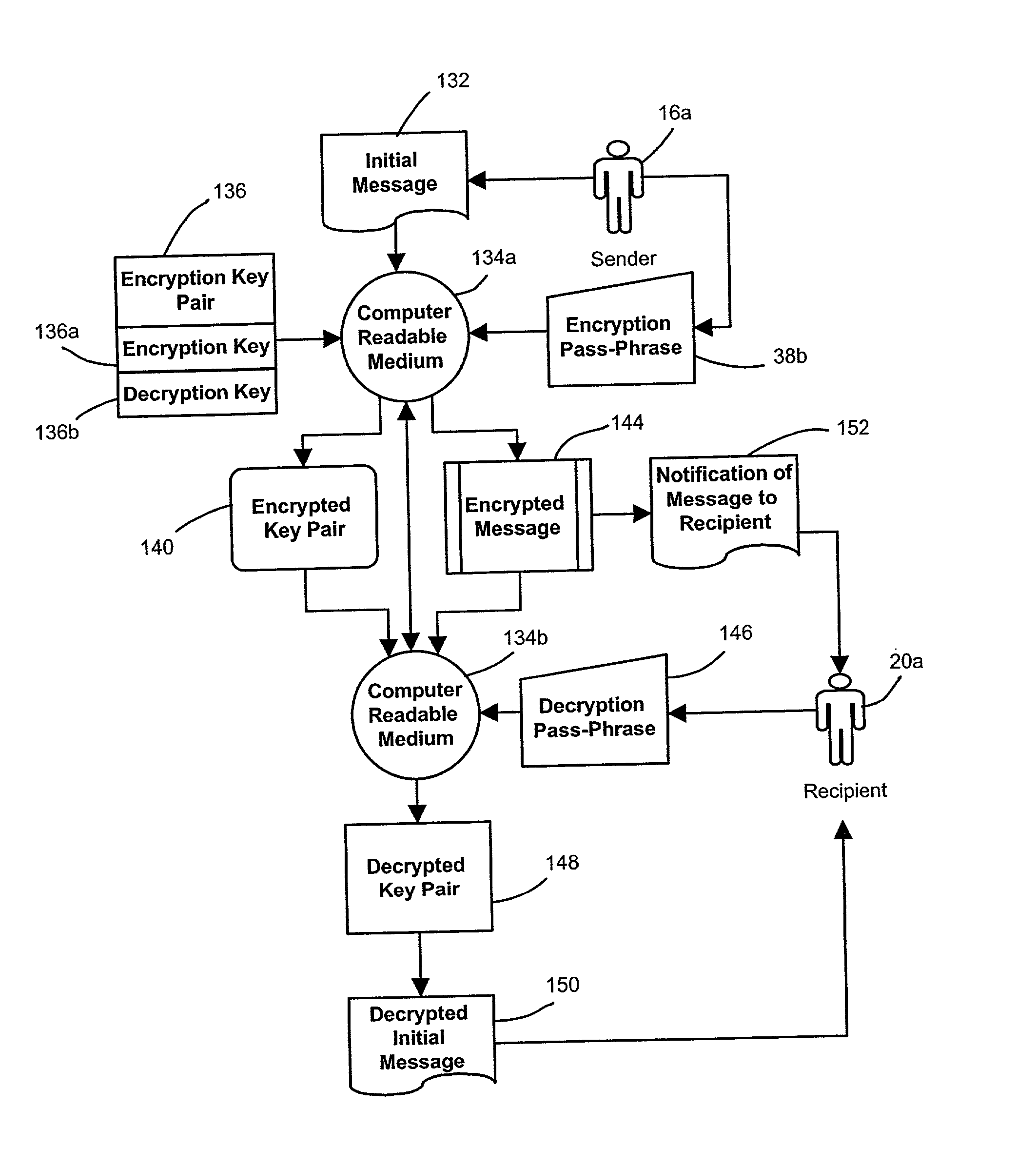
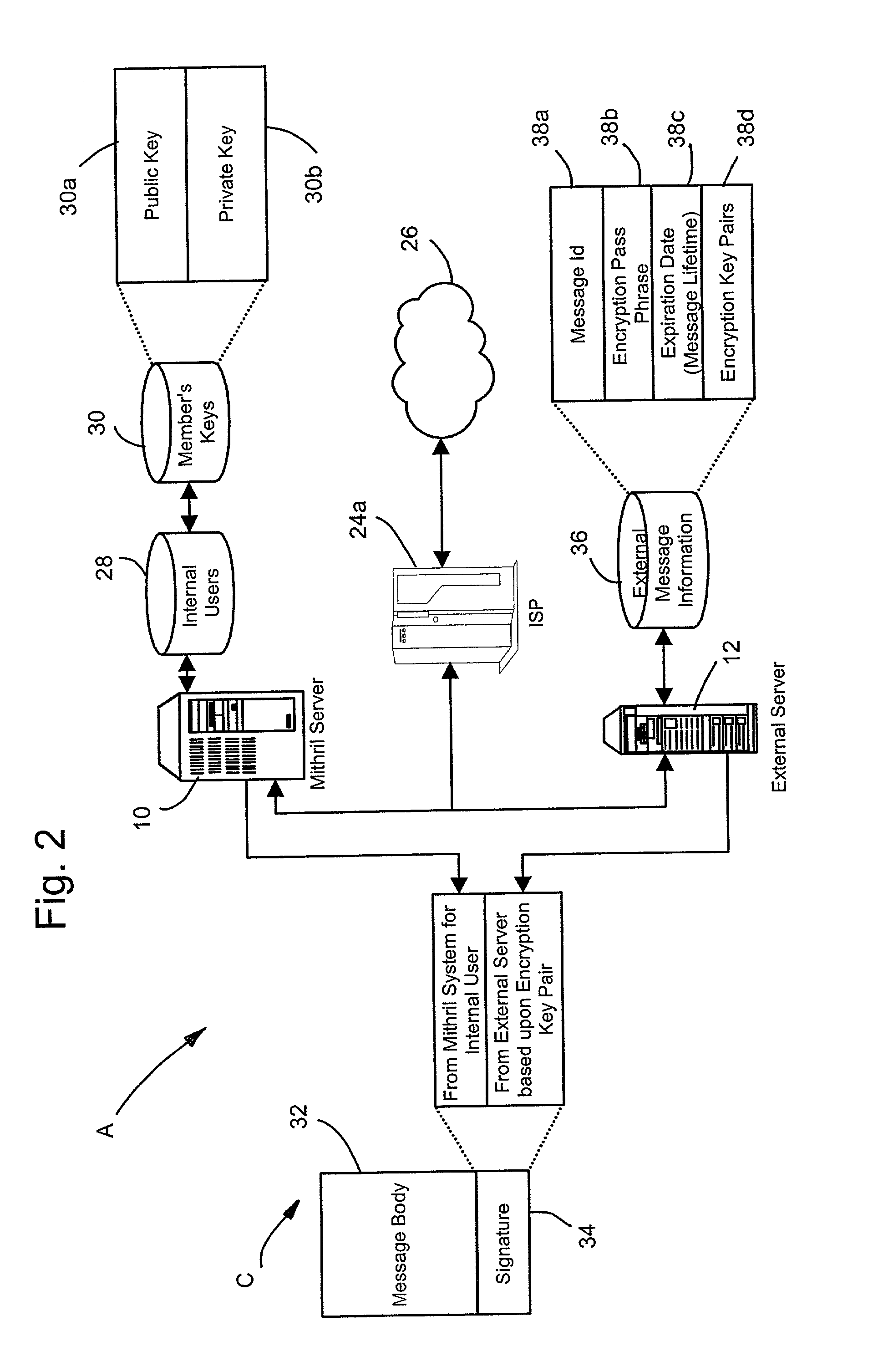
System and method for computerized global messaging encryption
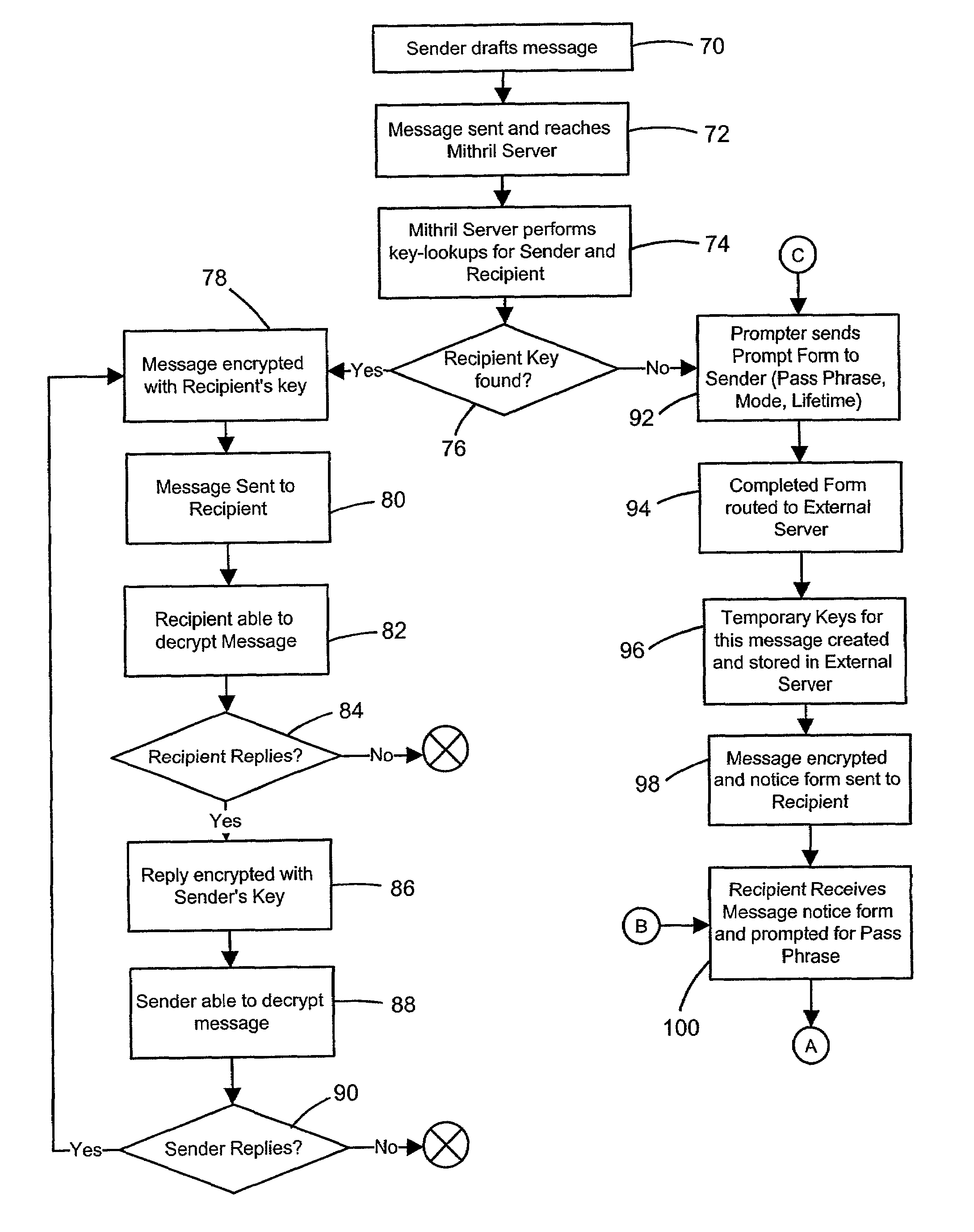
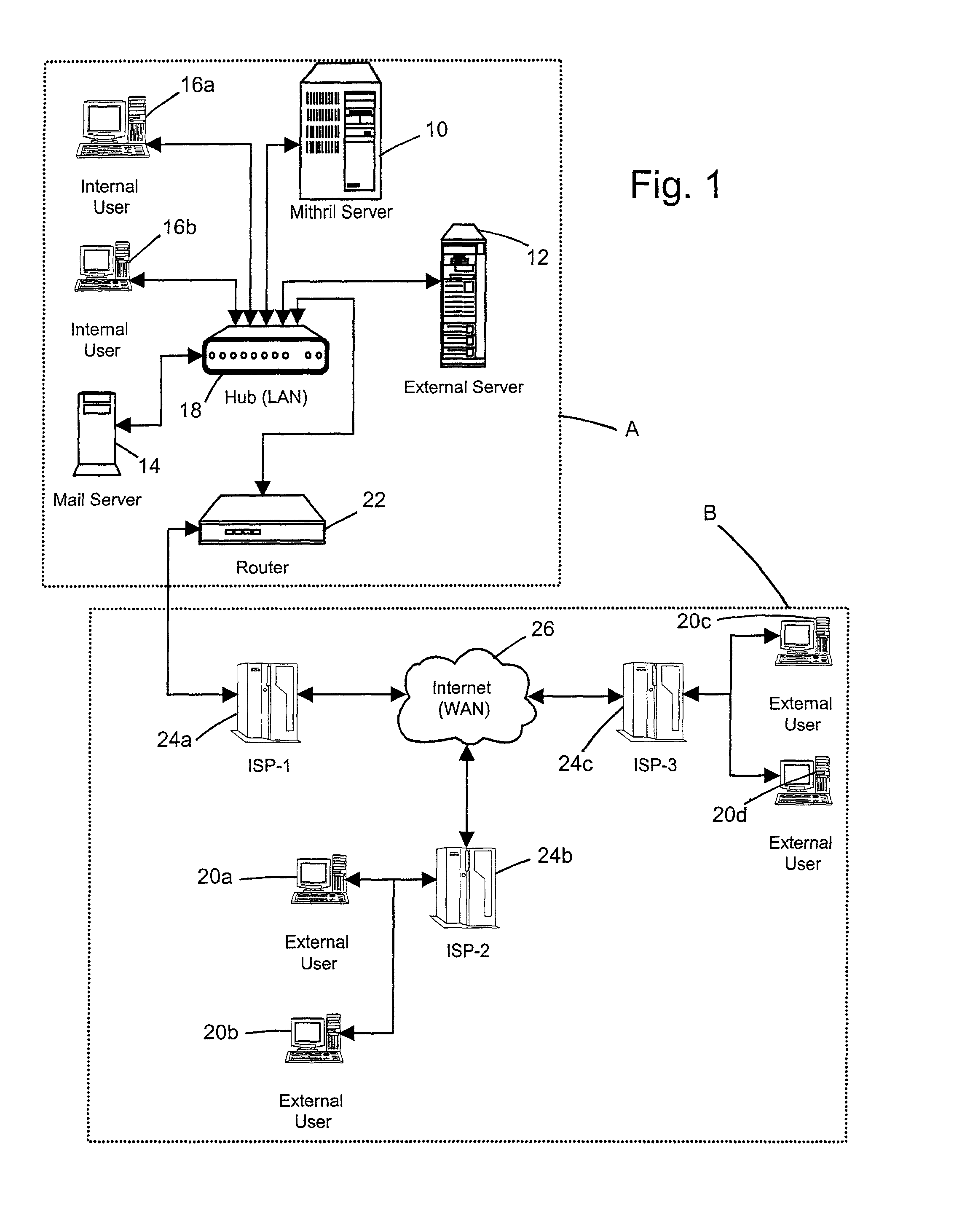
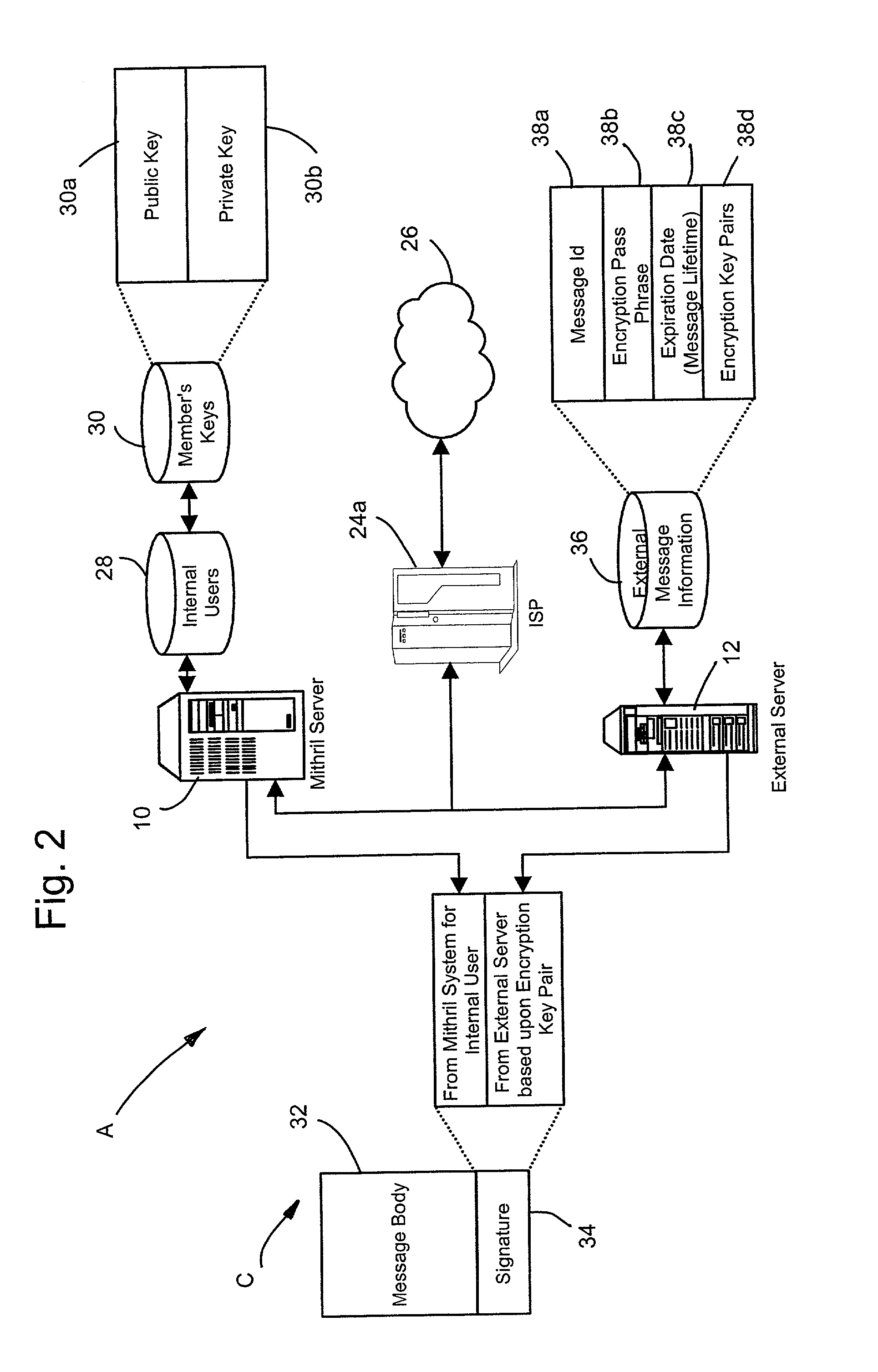
InactiveUS7082536B2Key distribution for secure communicationPublic key for secure communicationPassphrasePhrase
A computer based message encryption system for transmitting encrypted message between a sending member of an internal messaging system and a receiving non-member or receiving member external user without requiring the sender or recipient member to maintain and support encryption key pairs themselves. An internal system that contains an external server for creating key pairs for message encryption between the senders and receives for the encryption of messages. The key pairs are encrypted themselves according to an encryption pass-phrase so that the pass-phrase may used to decrypt the key pair which in turn may be used to decrypt the message. In response to a predetermined time or destroy command, said encryption key pairs are destroyed.
Owner:GLOBALCERTS LLC
Mutual authentication
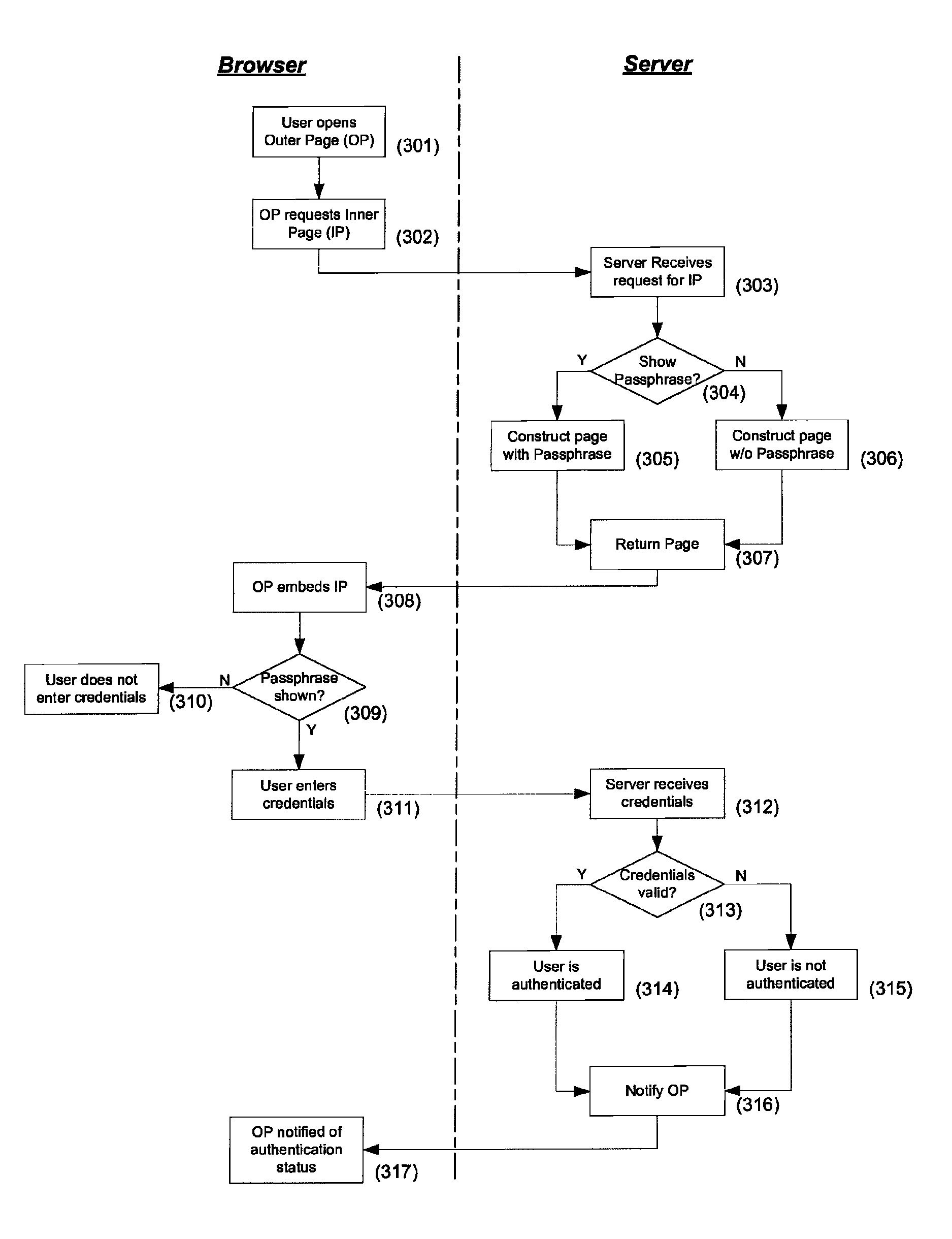
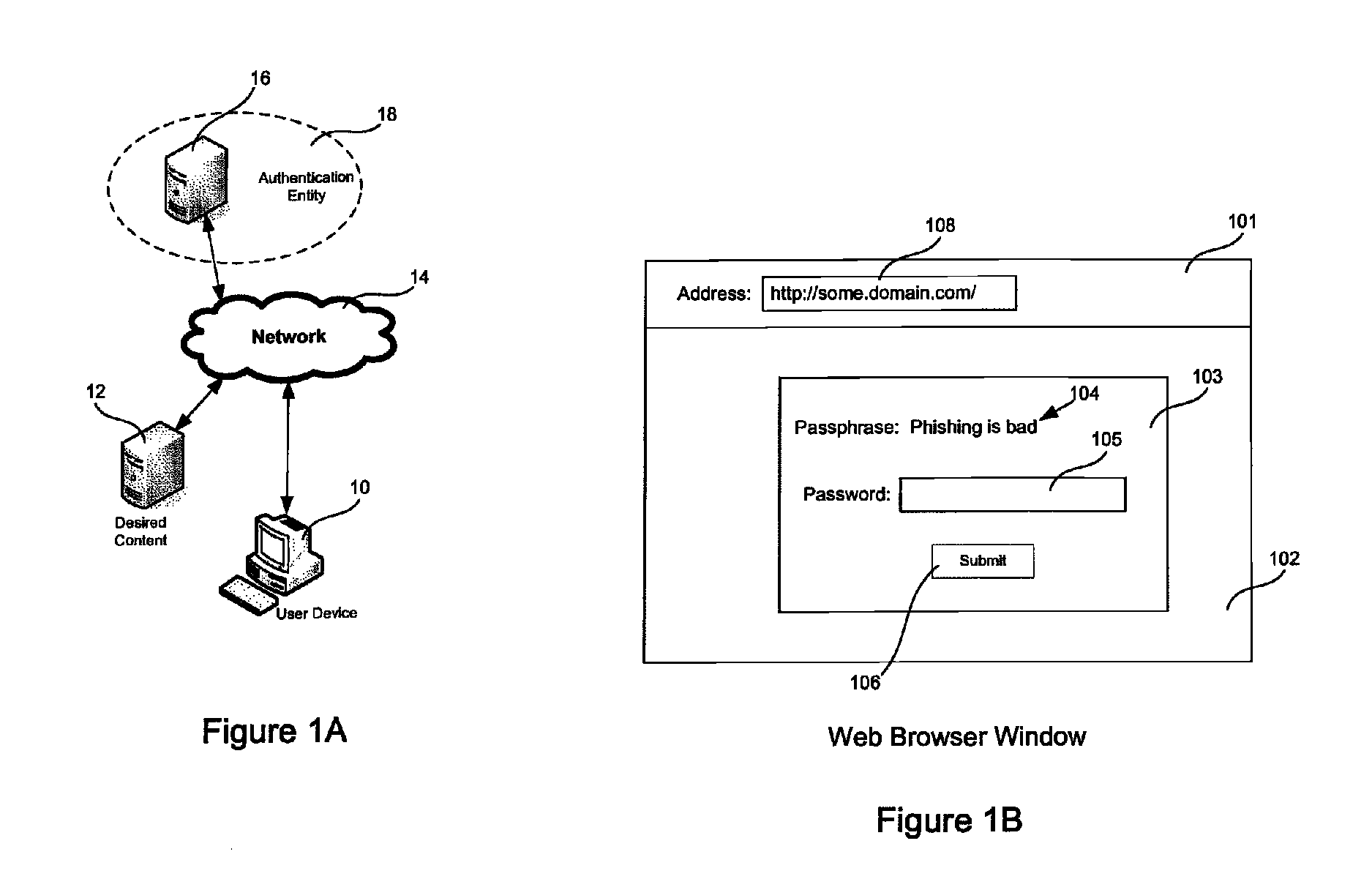
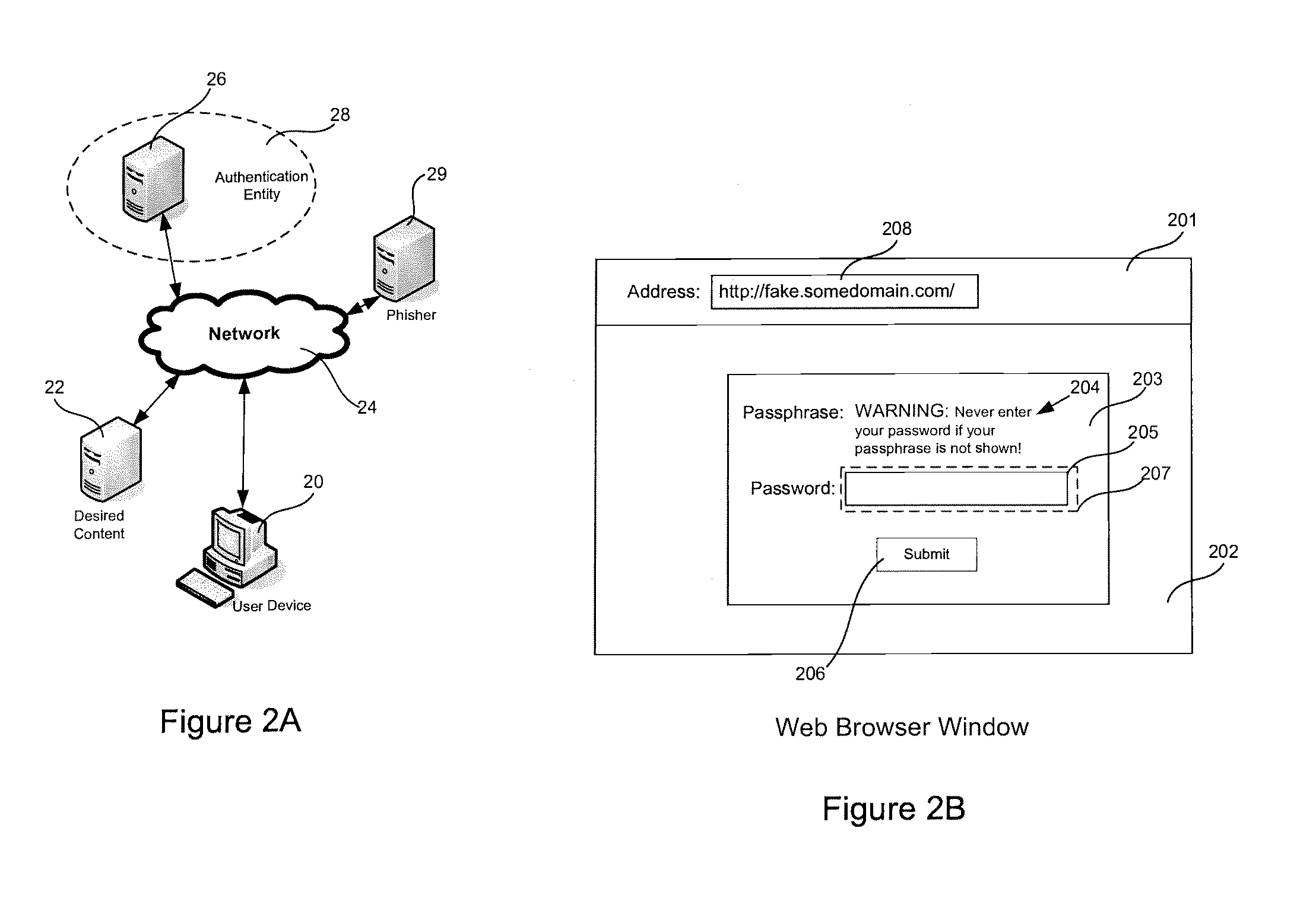
ActiveUS8332627B1Thwart common phishing attackCommon phishing attackMemory loss protectionDigital data processing detailsPassphraseUser device
Mutual authentication systems and methods are described that comprise an authenticating server that is available across a network and capable of authenticating a user based on credentials provided by the user. An embeddable object provided by the authenticating server and containing a passphrase that identifies the server to the user. A credentials entry mechanism identifies the user to the authenticating server. A user device displays an Outer Page that can request authentication. The authenticating server verifies the source of the request and provides the passphrase to the user device. The display of the passphrase confirms the identity of the authenticating server to the user. The source of the request can be verified using a secure cookie. The embeddable object can be provided in a second page and can prevent display of the passphrase if user input is not directed to the second page.
Owner:CISCO TECH INC
Computer security method and apparatus
InactiveUS20030074566A1Internal/peripheral component protectionDigital data authenticationPassphrasePassword
A method of securing data stored on an electronic device 1, the method comprising encrypting the data using a cryptographic key derivable from or accessed using a passphrase, requiring the entry into the device of the passphrase when a user wishes to access the data, subsequently inhibiting access to the data whilst the device 1 remains active, and requiring the entry into the device of a predefined password when a user wishes to access the data, the password being different from the passphrase.
Owner:F SECURE CORP
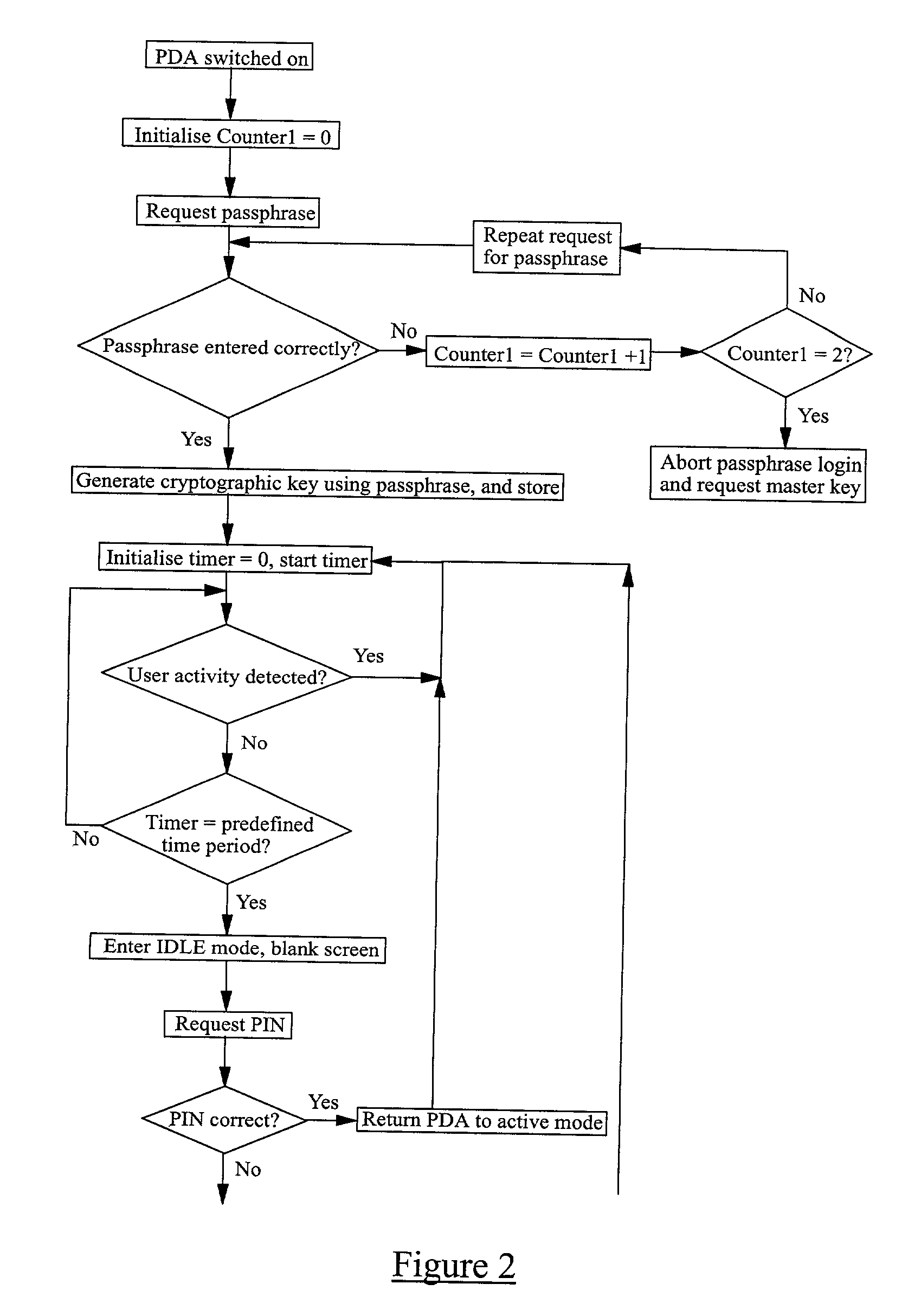
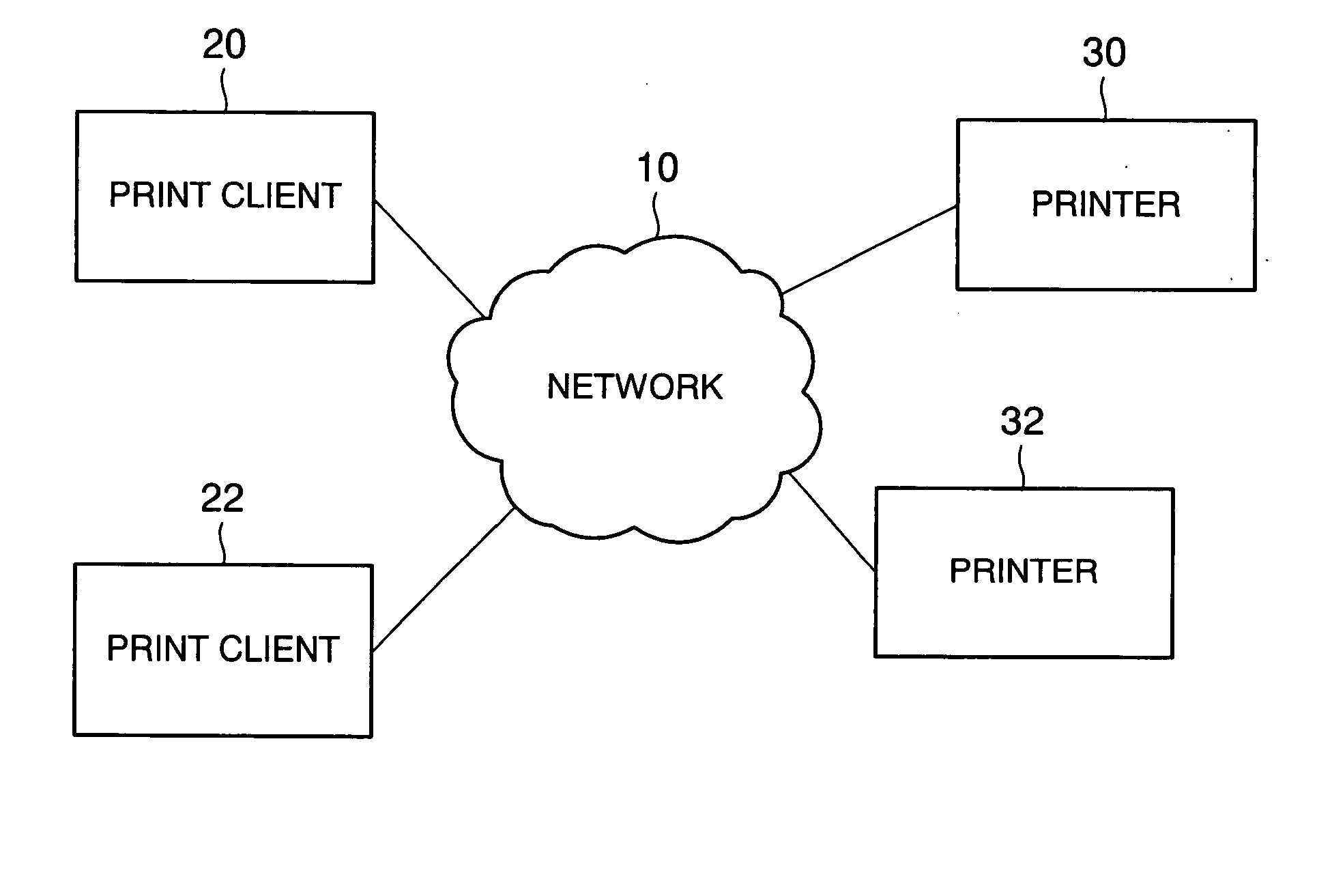
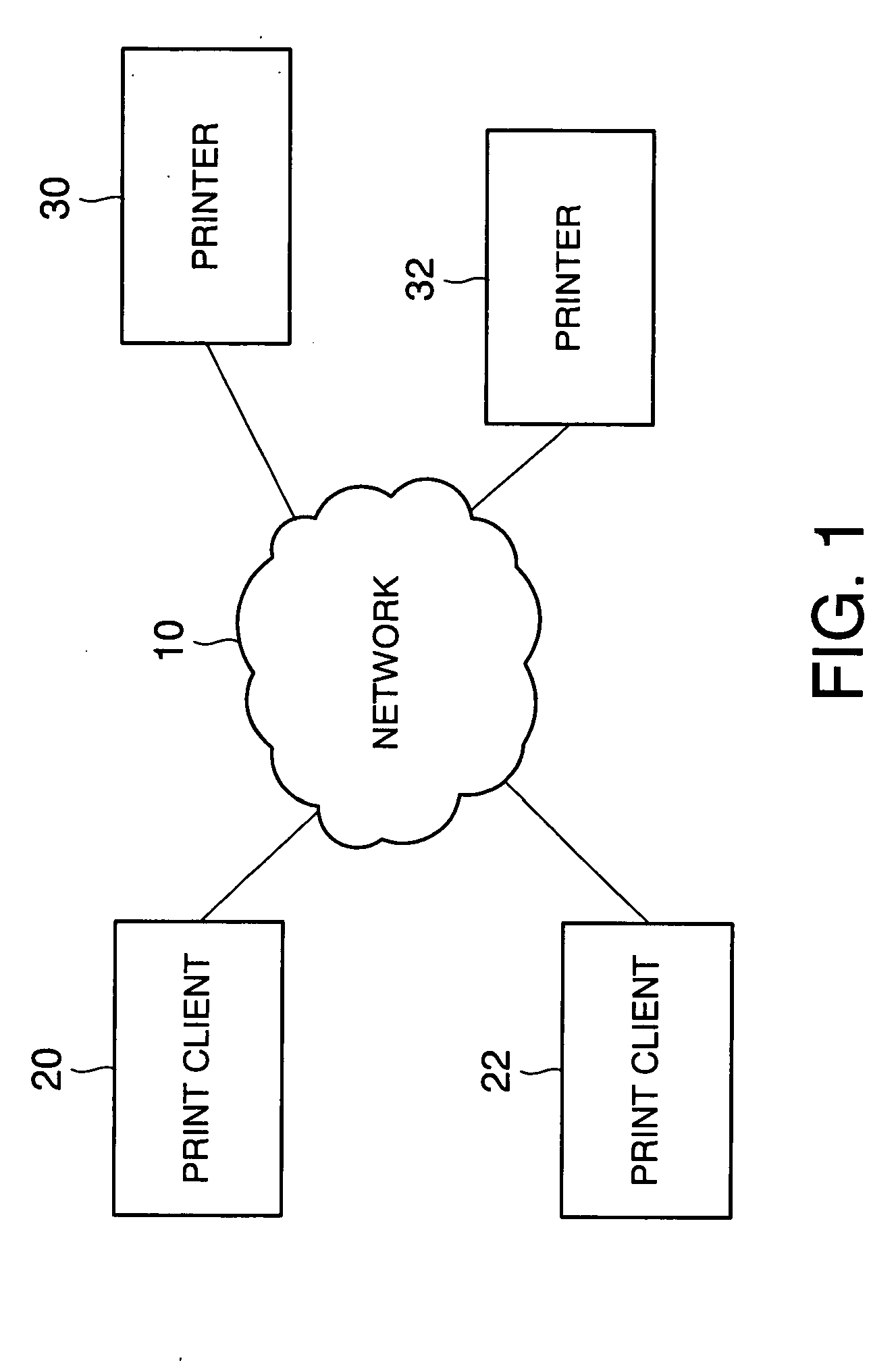
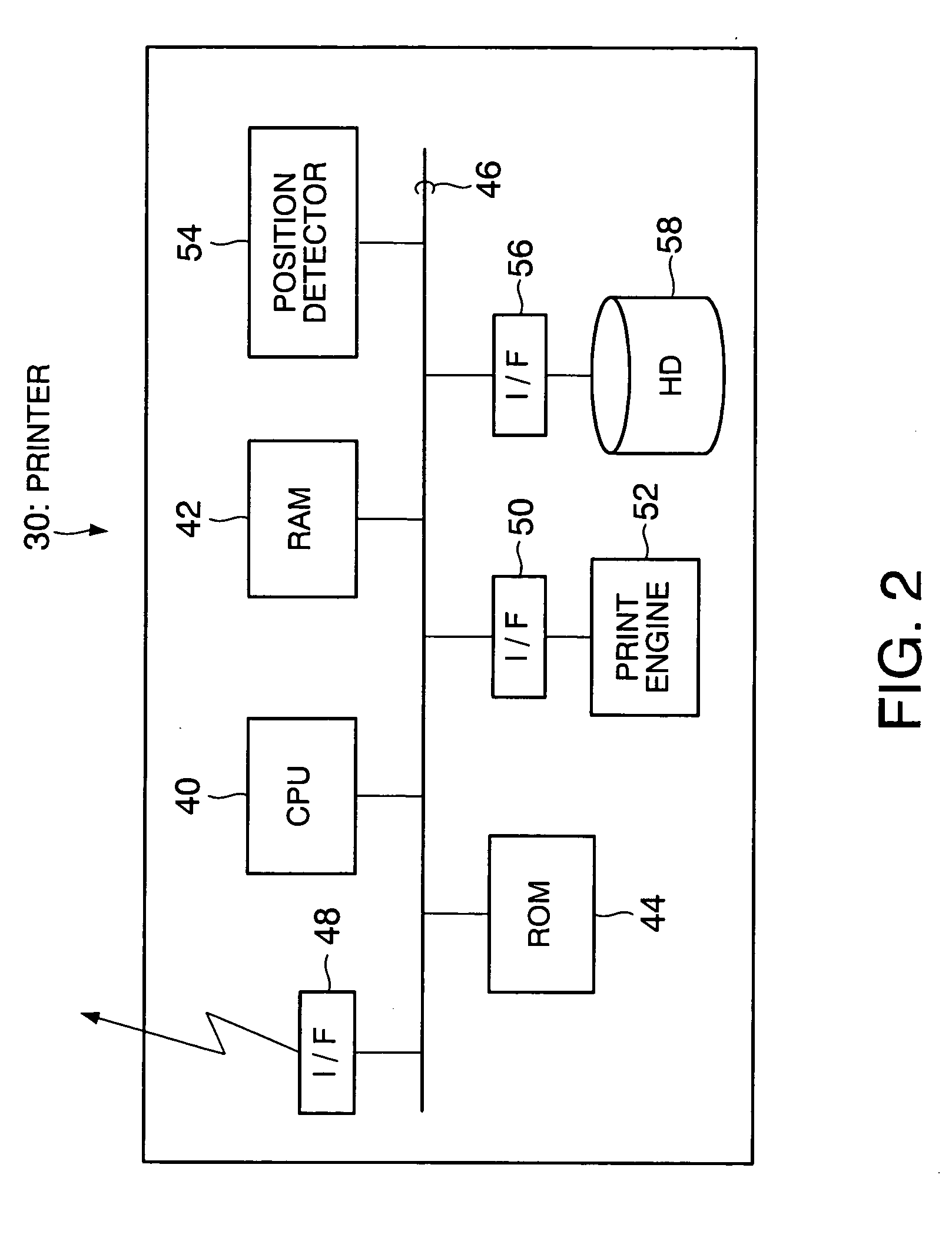
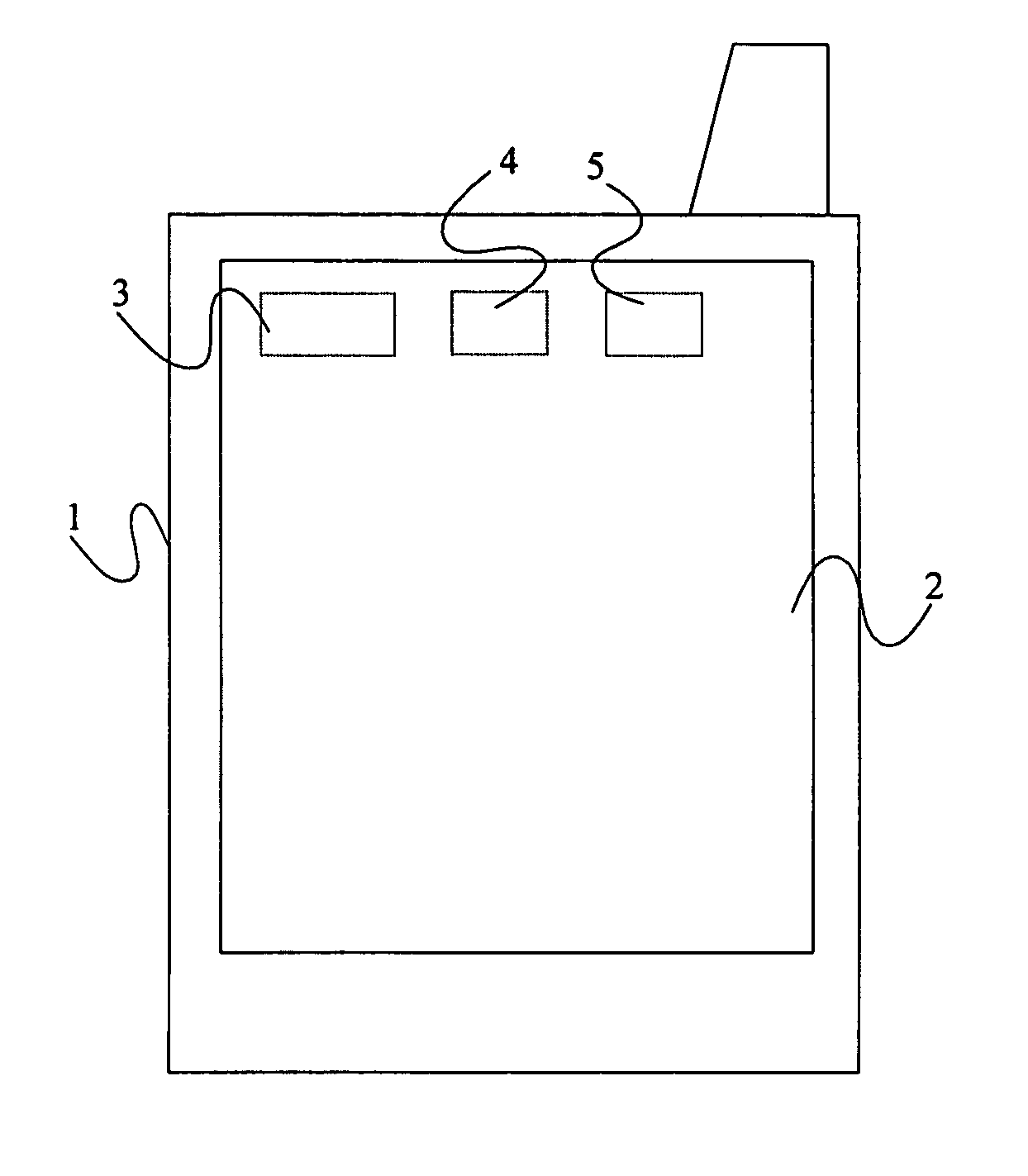
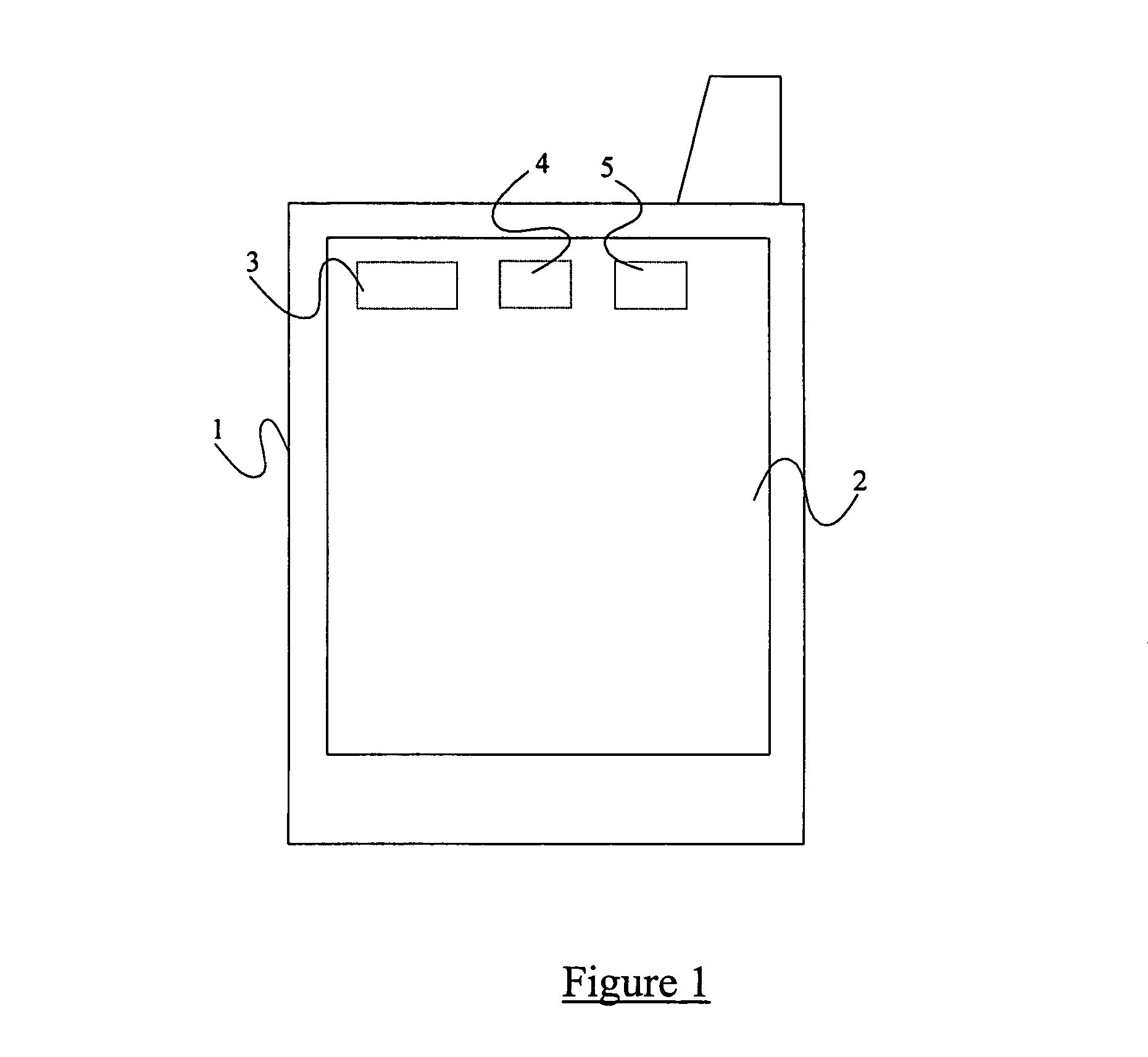
Printer and print system, and data receiving device and data transmitting and receiving system
InactiveUS20050163549A1Character printing data arrangement from carrierError detection/correctionPassphraseComputer printing
A printer generates a public key with a passphrase containing at least printer position information and a random number by a public key cryptography, and holds this random number. A print client previously acquires the public key from the printer. When transmitting print data to the printer, the print client encrypts the print data in advance with the acquired public key and transmits the encrypted print data as print transmitting data. The printer which has received the print transmitting data generates a private key with a passphrase containing at least printer position information and the held random number by the public key cryptography. The printer then decrypts the received print transmitting data with the private key. Consequently, the security of the print data transmitted from the print client to the printer via a network is ensured.
Owner:SEIKO EPSON CORP
Computer security method and apparatus
InactiveUS6986050B2Sufficient entropyEasy and fast entryUnauthorized memory use protectionInternal/peripheral component protectionPassphrasePassword
A method of securing data stored on an electronic device 1, the method comprising encrypting the data using a cryptographic key derivable from or accessed using a passphrase, requiring the entry into the device of the passphrase when a user wishes to access the data, subsequently inhibiting access to the data whilst the device 1 remains active, and requiring the entry into the device of a predefined password when a user wishes to access the data, the password being different from the passphrase.
Owner:F SECURE CORP
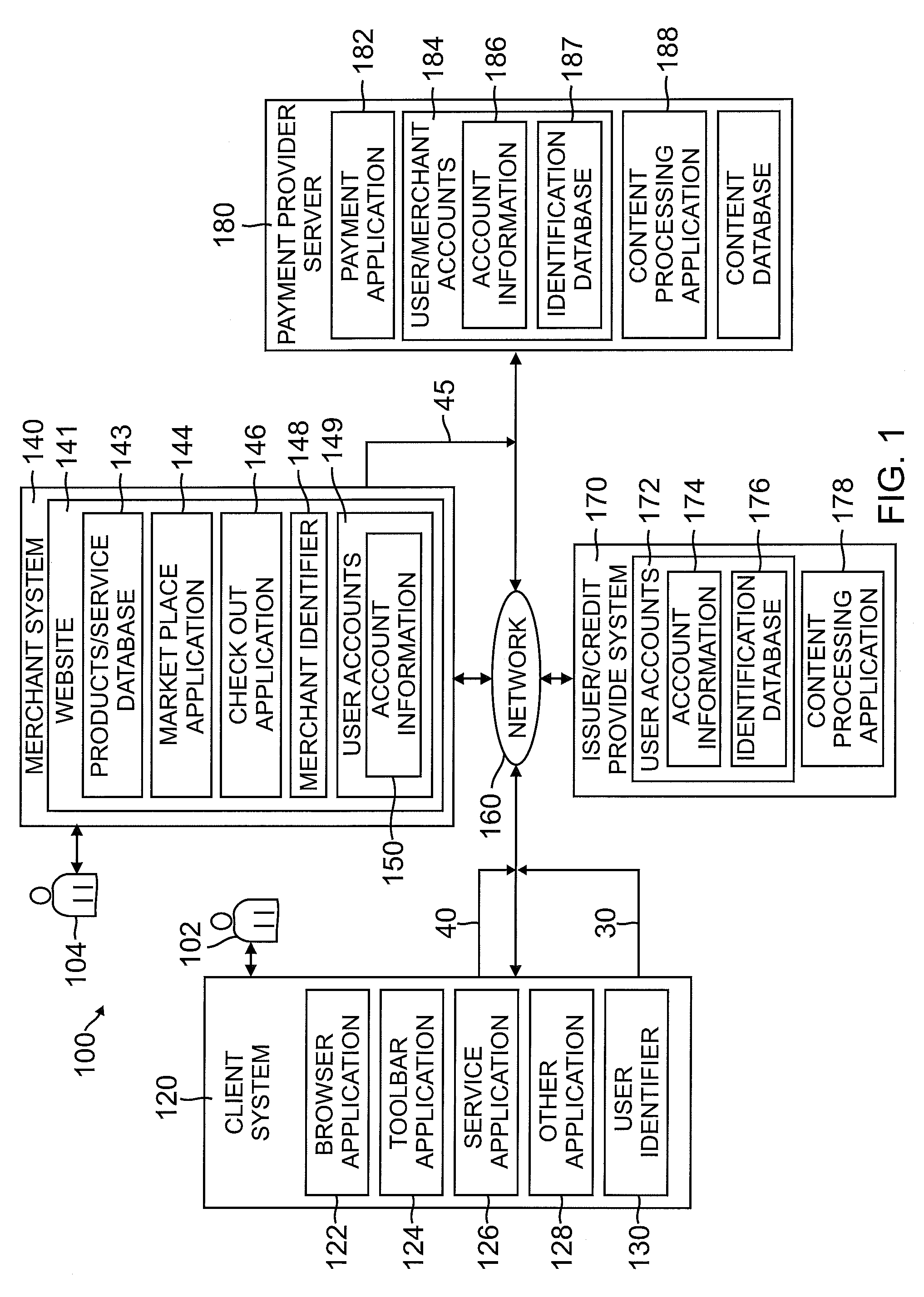
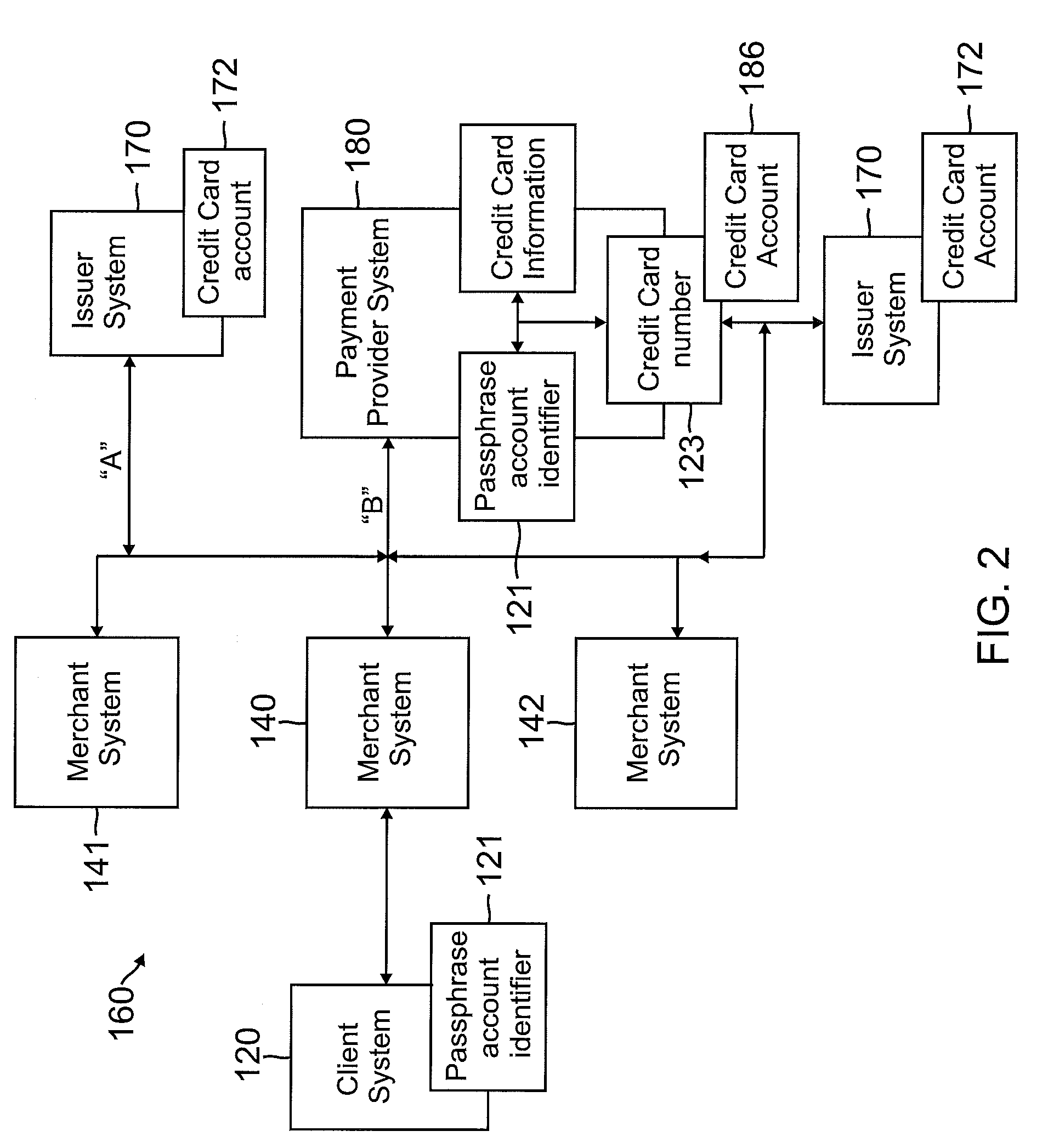
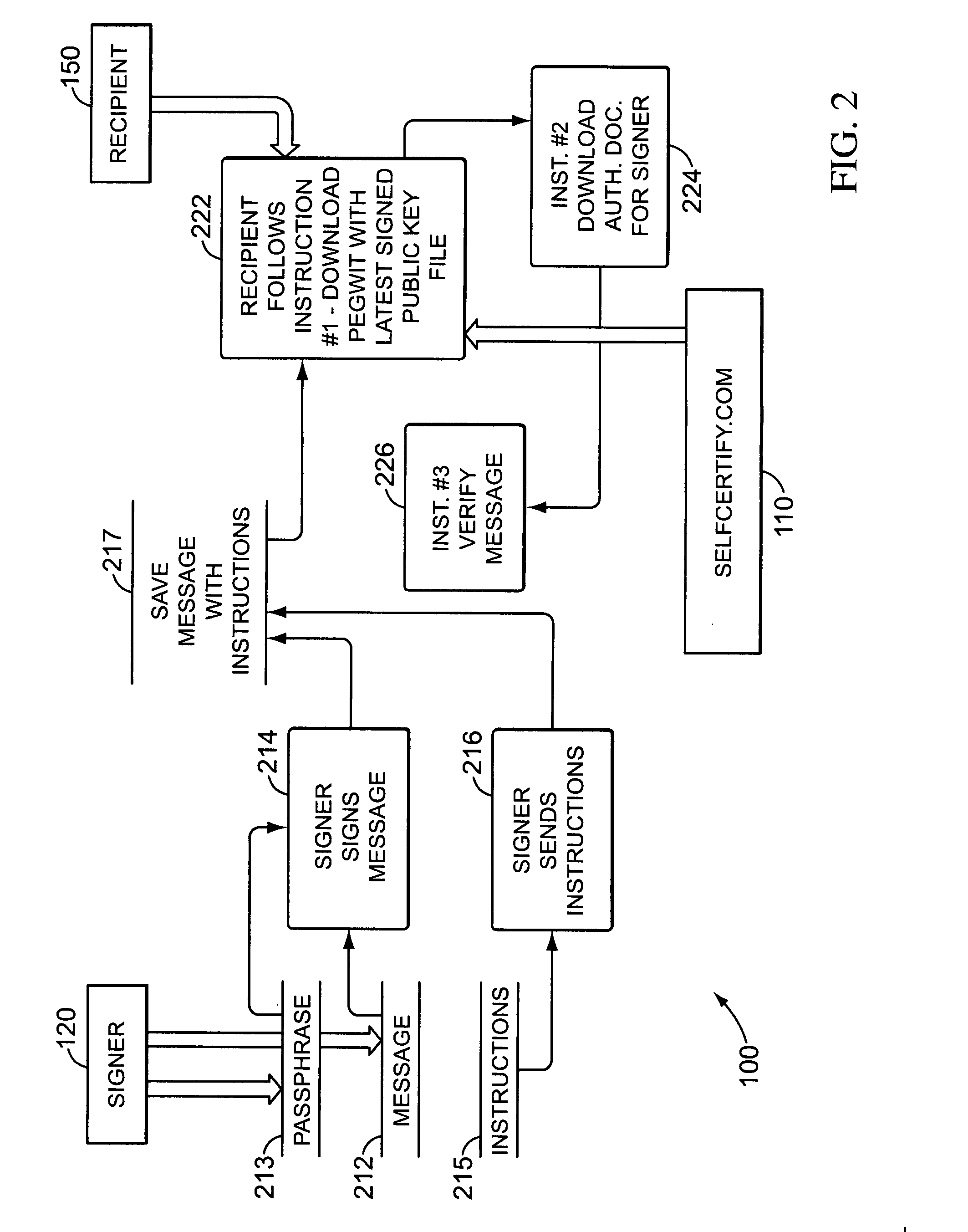
System and method of a passphrase account identifier for use in a network environment
Owner:PAYPAL INC
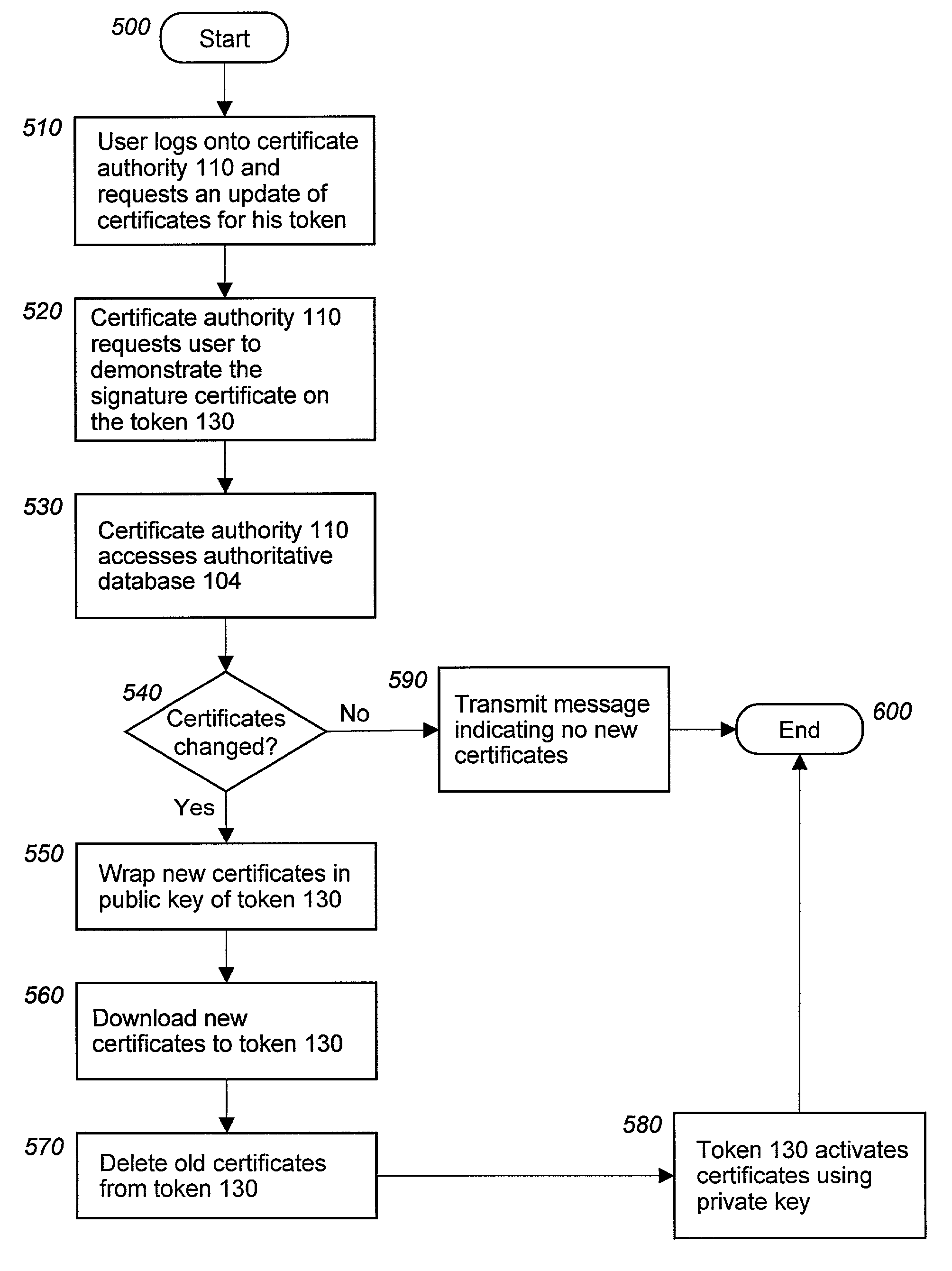
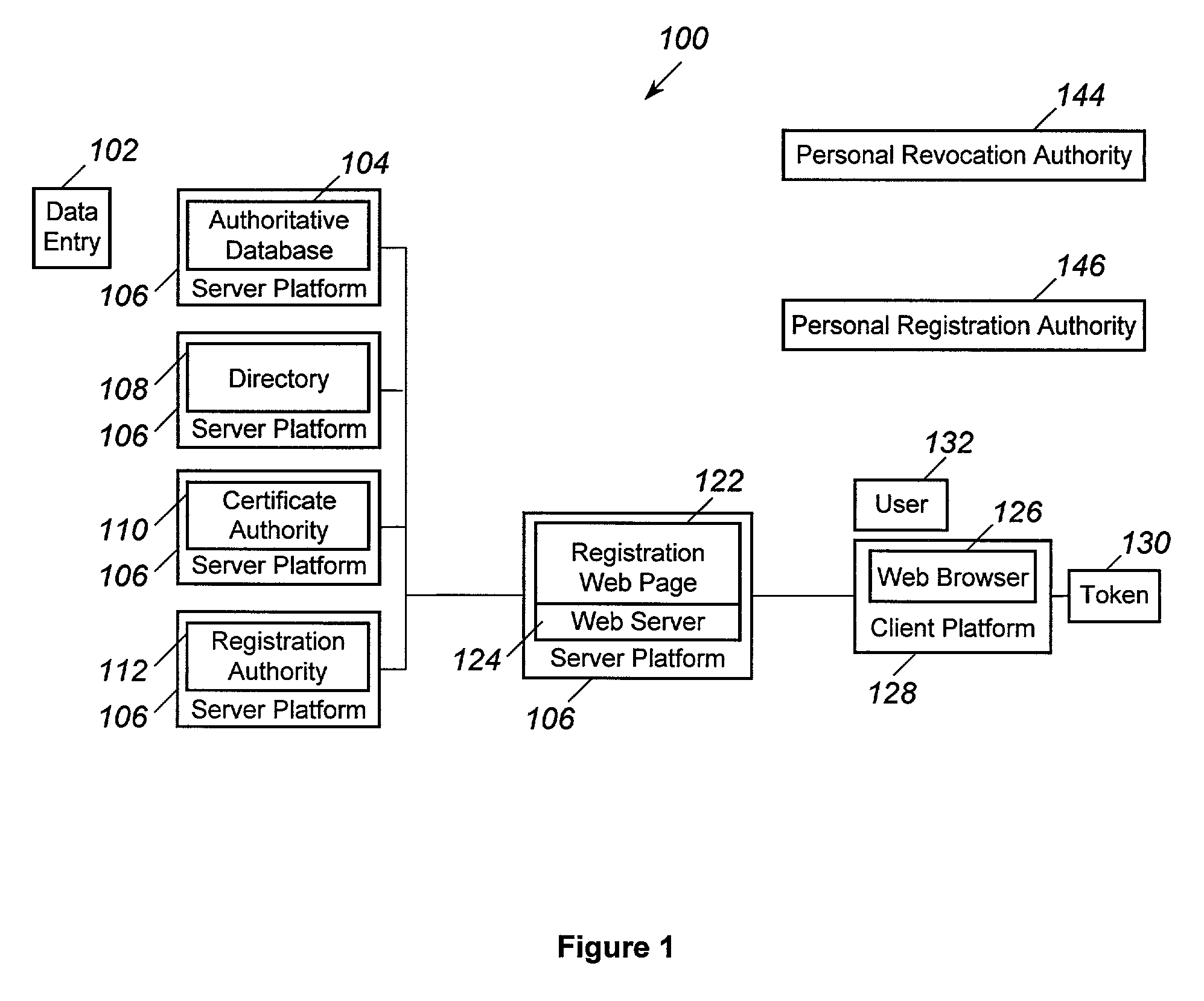
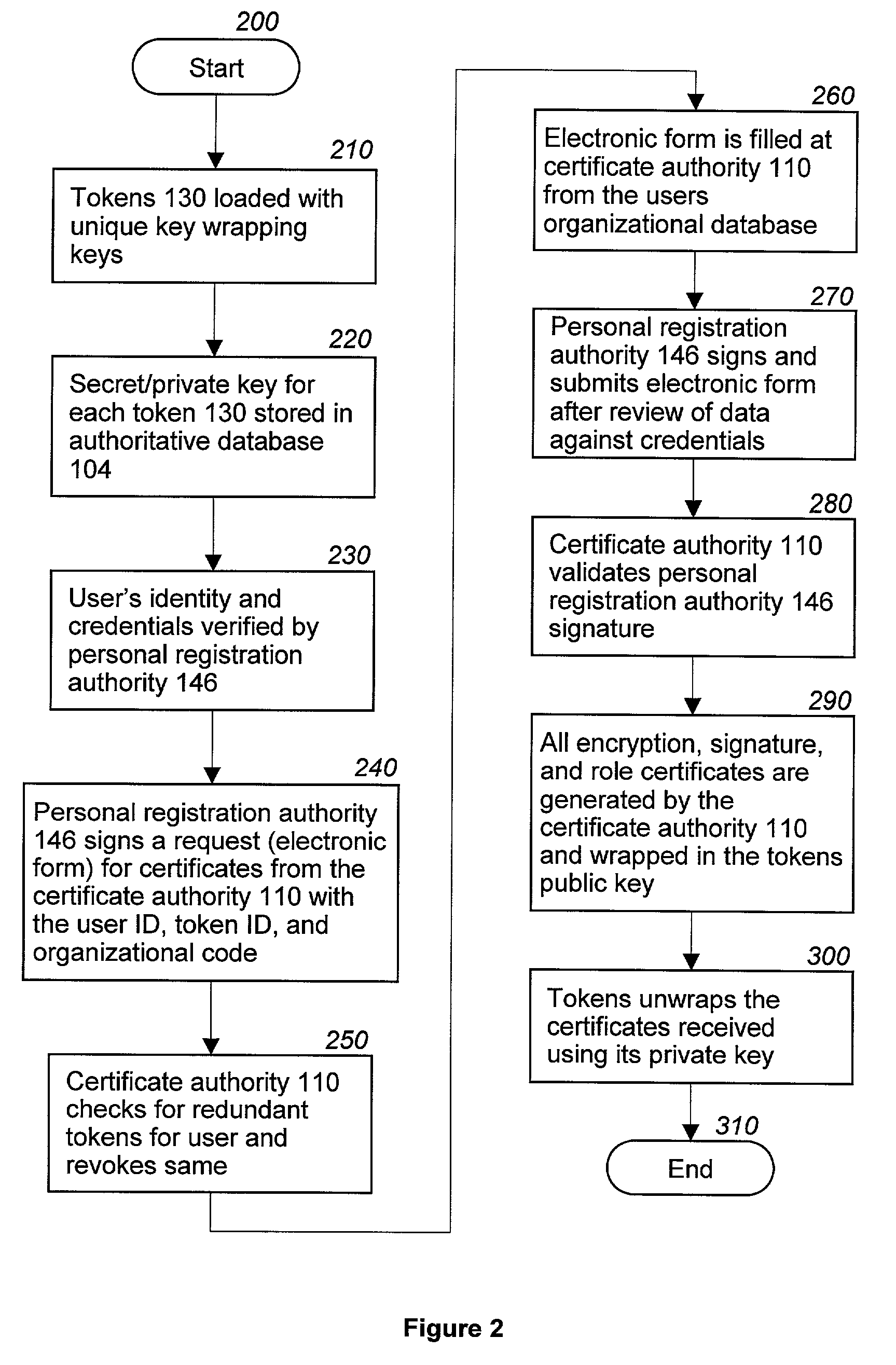
Revocation and updating of tokens in a public key infrastructure system
ActiveUS7206936B2Key distribution for secure communicationDigital data processing detailsPassphraseUser input
A method and computer program to revoke and update a token (130) having several encryption, signature and role certificates / private keys contained in the token (130). The certificates / private keys in the token 130 are transmitted wrapped by a public key and may only be activated by a private key contained in the token (130). The activation of any certificate / private key requires the entry of a passphrase by a user (132). Further, all certificates / private keys contained in a token (130) are stored in an authoritative database 104. In the event that a token (130) is lost then all certificates / private keys associated with the token (130) are revoked. Further, when new certificates / private keys are issued to a user (132) these certificates / private keys are encrypted using the token's (130) public key and downloaded to the token (130).
Owner:NORTHROP GRUMMAN SYST CORP
Secure unlocking and recovery of a locked wrapped app on a mobile device
InactiveUS20140040622A1Key distribution for secure communicationUnauthorised/fraudulent call preventionPassphraseApplication software
A security-wrapped app that is locked and inaccessible is unlocked and recovered using a secure and user-friendly protocol. Apps that are security wrapped are passphrase protected. The app security keystore on the device becomes locked. The keystore is encrypted with a recovery key which is only in an encrypted form on the device and cannot be decrypted or otherwise accessed by the user. As such, the user cannot unlock the keystore on the device and therefore is not able to unlock the app. The app can be unlocked using a recovery mechanism that is highly secure in all communications between the mobile device and the service provider server. At the same time the recovery mechanism is easy for the end user to carry out.
Owner:BLUE CEDAR NETWORKS INC
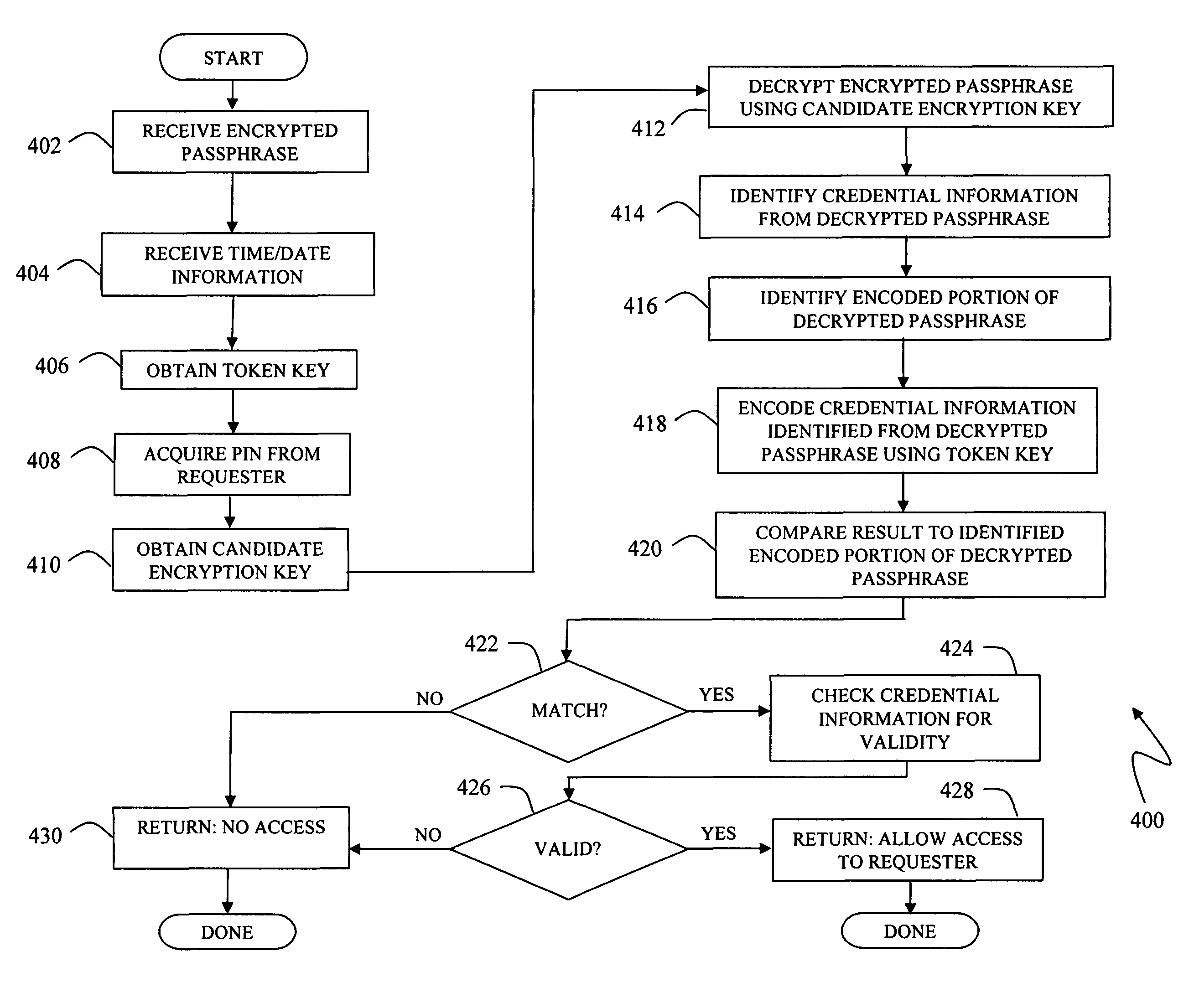
Securing a passphrase
Access to a target system is secured by use of an encrypted passphrase that is supplied on-site at the target system by a user requesting access. The encrypted passphrase includes an access credential portion and a one-way encoded portion. The one-way encoded portion is an encoded version of at least some of the access credential portion. A validator at the target system receives and decrypts the encrypted passphrase and identifies the access credential portion and one-way encoded portion. The validator one-way encodes the identified access credential portion and compares the result to the identified one-way encoded portion from the decrypted passphrase. If the results do not match, the validator denies access to the user requesting access. The encoding and decrypting of the passphrase may be performed using keys generated from a secret key / seed related to the target system, unencrypted information such as time / date information, and a user PIN.
Owner:EMC IP HLDG CO LLC
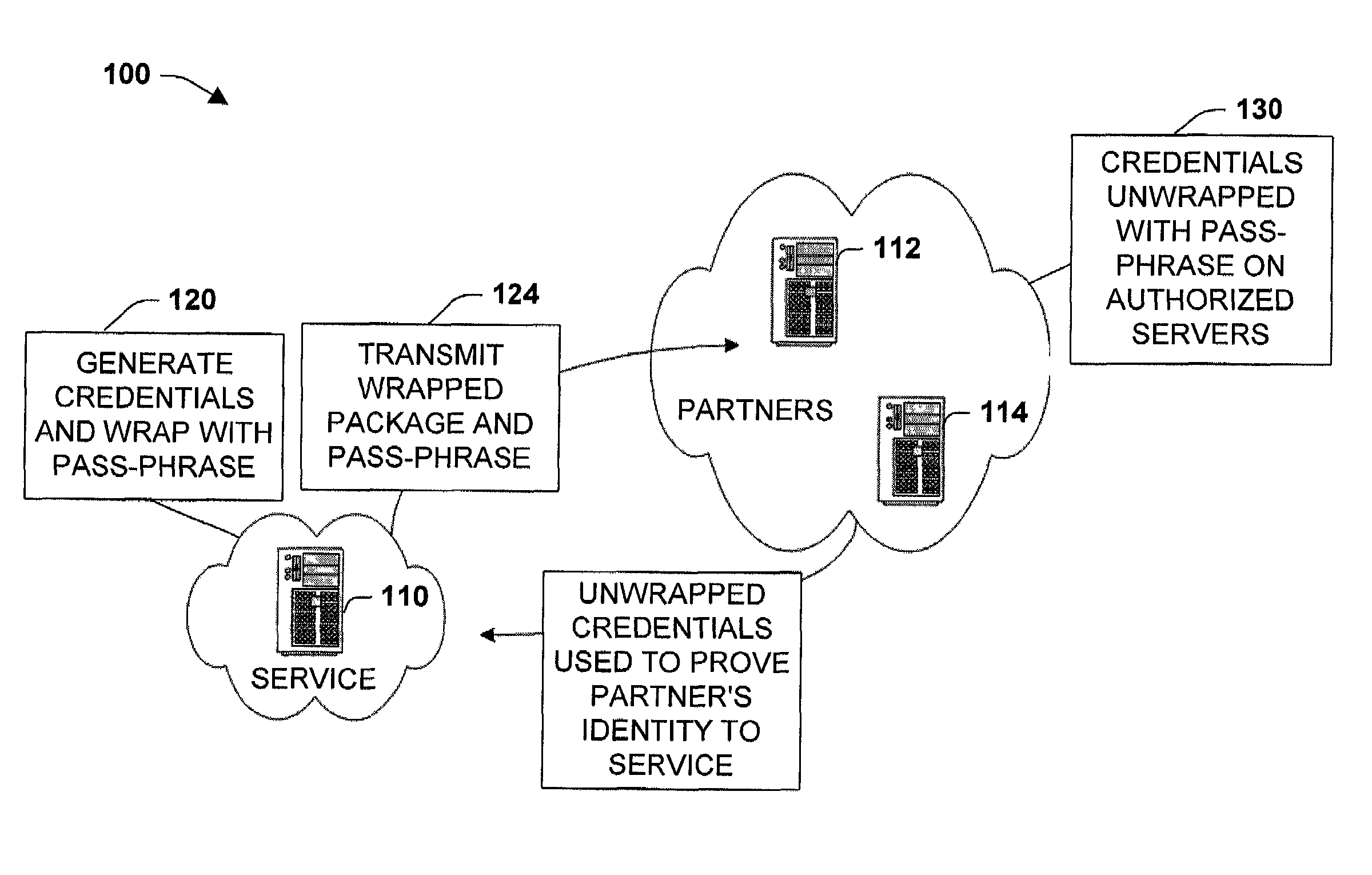
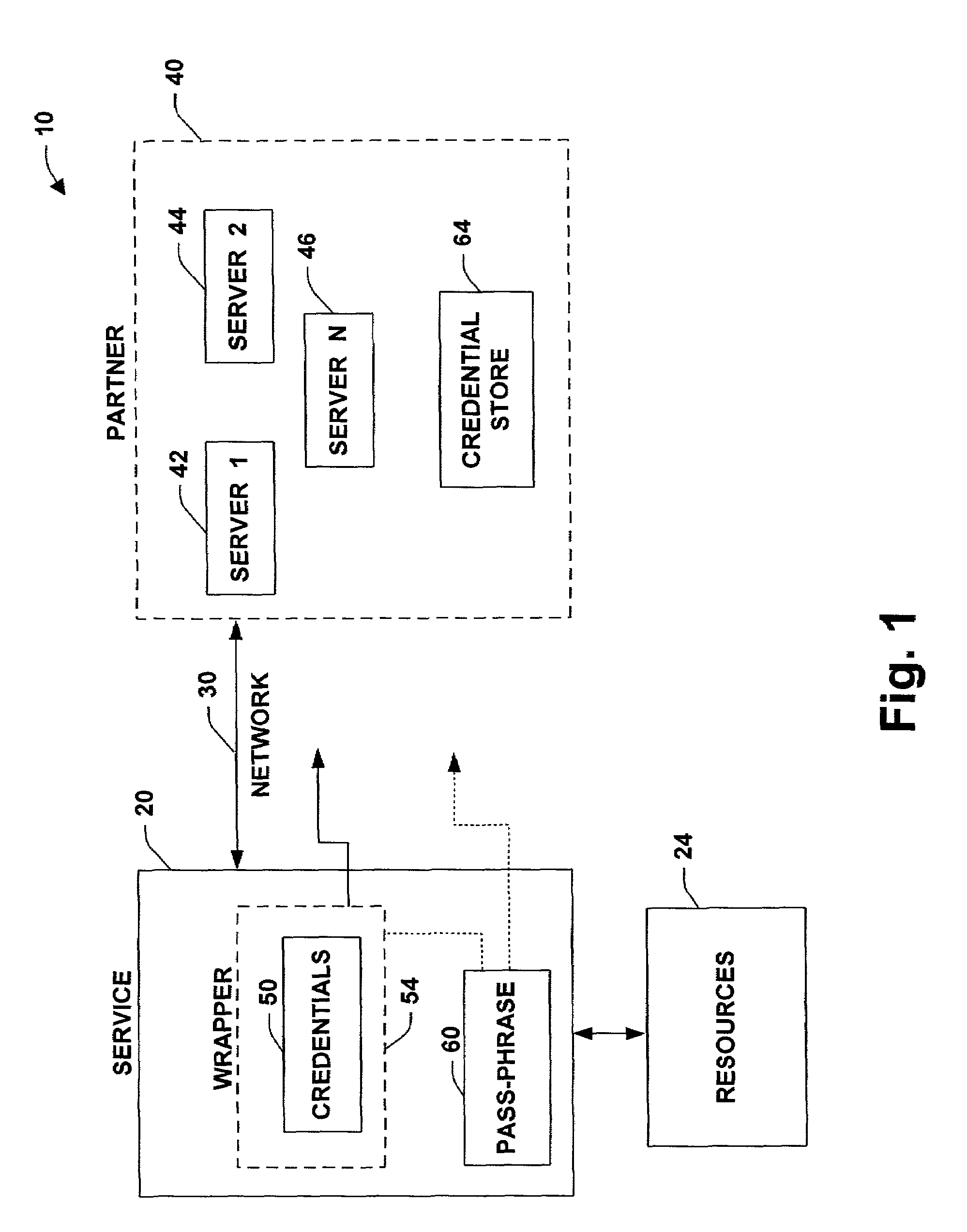
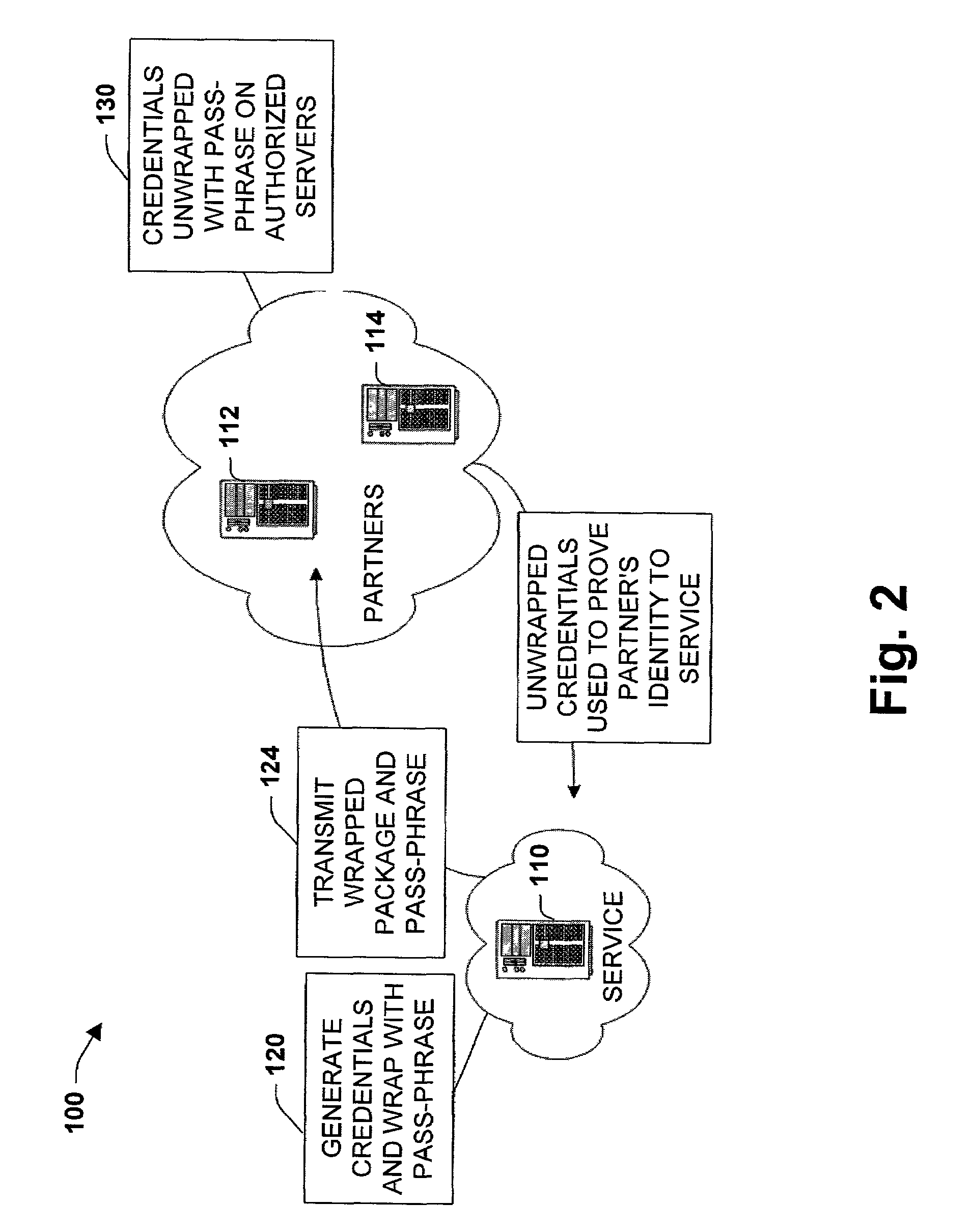
System and method to package security credentials for later use
InactiveUS7571467B1Facilitate secure network communicationFacilitates secure communicationDigital data processing detailsAnalogue secracy/subscription systemsCommunications securityPassphrase
The present invention relates to a system and methodology to facilitate communications security in a distributed computing and applications environment. A pass-phrase is generated to wrap a strong set of security credentials that are employed to establish trusted relationships between entities such as a service provider and one or more partners seeking access to the provider. The pass-phrase is generally constructed from weaker cryptographic material and is generally transported or communicated separately from the wrapped security credentials. When the partner desires to access service resources, the pass-phrase is employed to unlock the strong set of security credentials contained within the wrapper. The unlocked security credentials are then utilized to establish encrypted communications channels between the service provider and the partner.
Owner:MICROSOFT TECH LICENSING LLC
System and method for computerized global messaging encryption
ActiveUS20020112168A1Key distribution for secure communicationPublic key for secure communicationPassphraseMessage delivery
A computer based message encryption system for transmitting encrypted message between a sending member of an internal messaging system and a receiving non-member or receiving member external user without requiring the sender or recipient member to maintain and support encryption key pairs themselves. An internal system that contains an external server for creating key pairs for message encryption between the senders and receives for the encryption of messages. The key pairs are encrypted themselves according to an encryption pass-phrase so that the pass-phrase may used to decrypt the key pair which in turn may be used to decrypt the message. In response to a predetermined time or destroy command, said encryption key pairs are destroyed.
Owner:GLOBALCERTS LLC
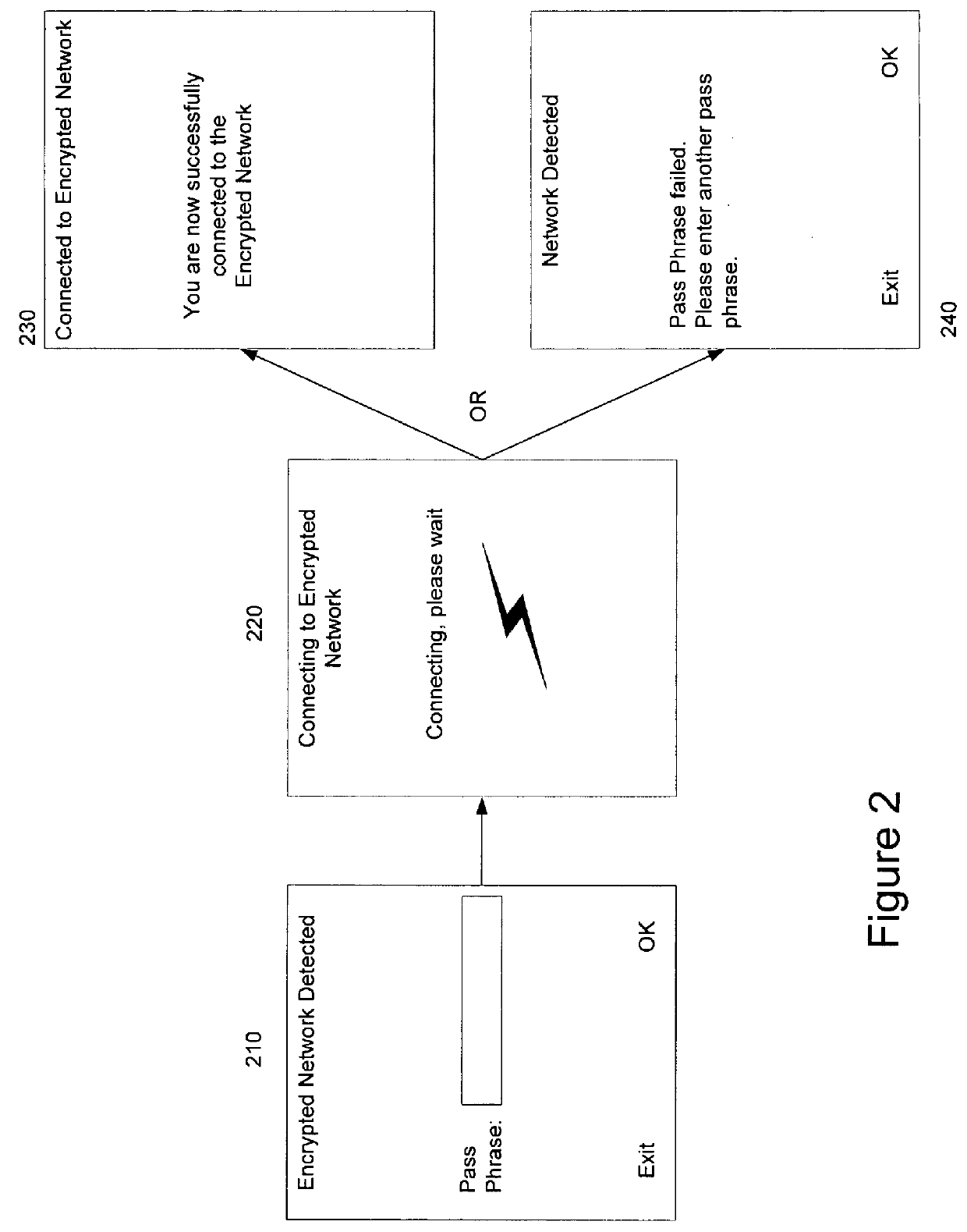
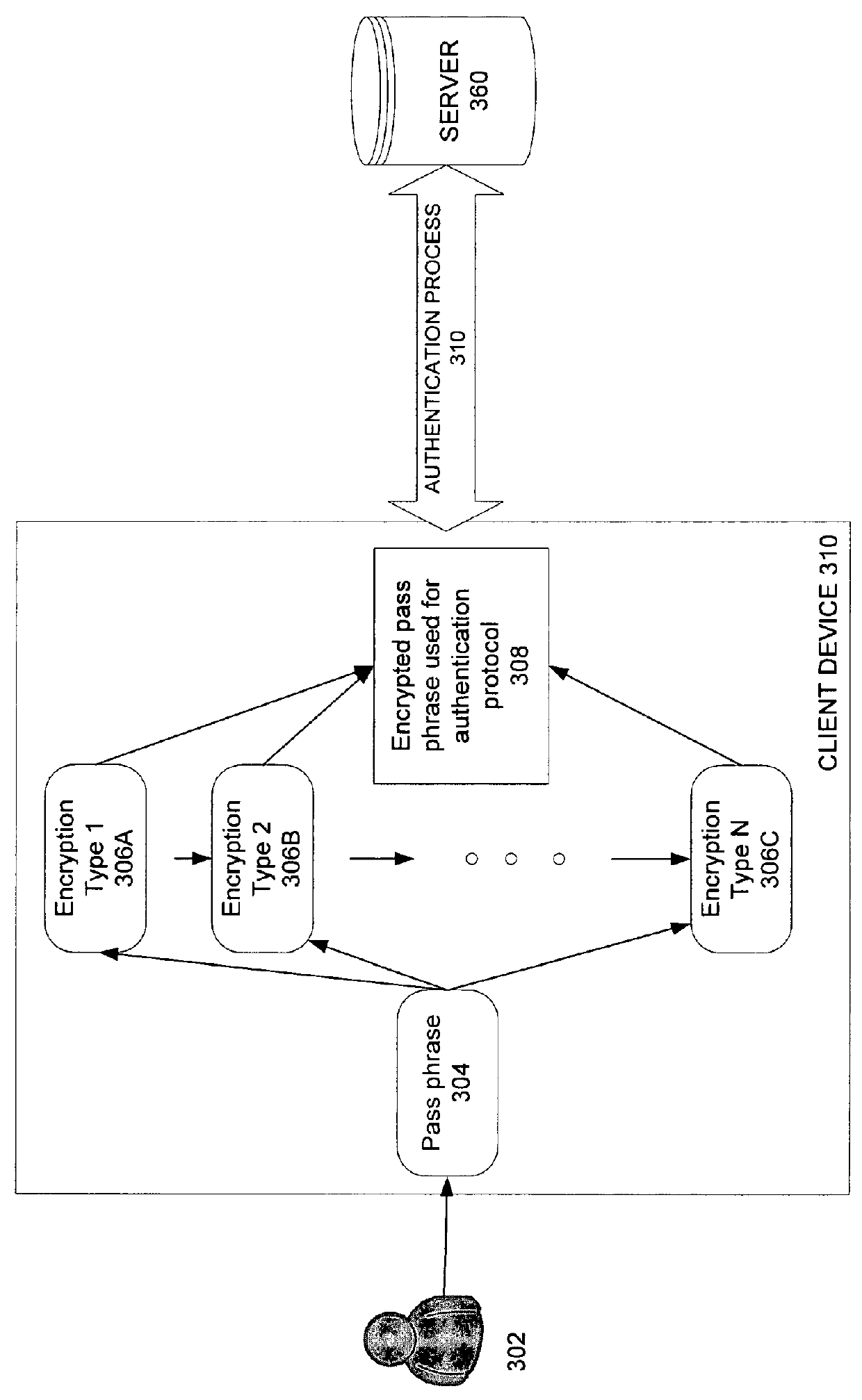
Automatic detection of required network key type
ActiveUS9378343B1User identity/authority verificationDigital data authenticationPassphraseUser input
Methods and apparatuses in automatic detection of a required network key type are described. In one embodiment, a client device prompts a user for a pass phrase, receives a pass phrase and automatically determines the encryption type for the pass phrase to connect to a network. The client device then communicates with a server to authenticate the client device.
Owner:QT +1
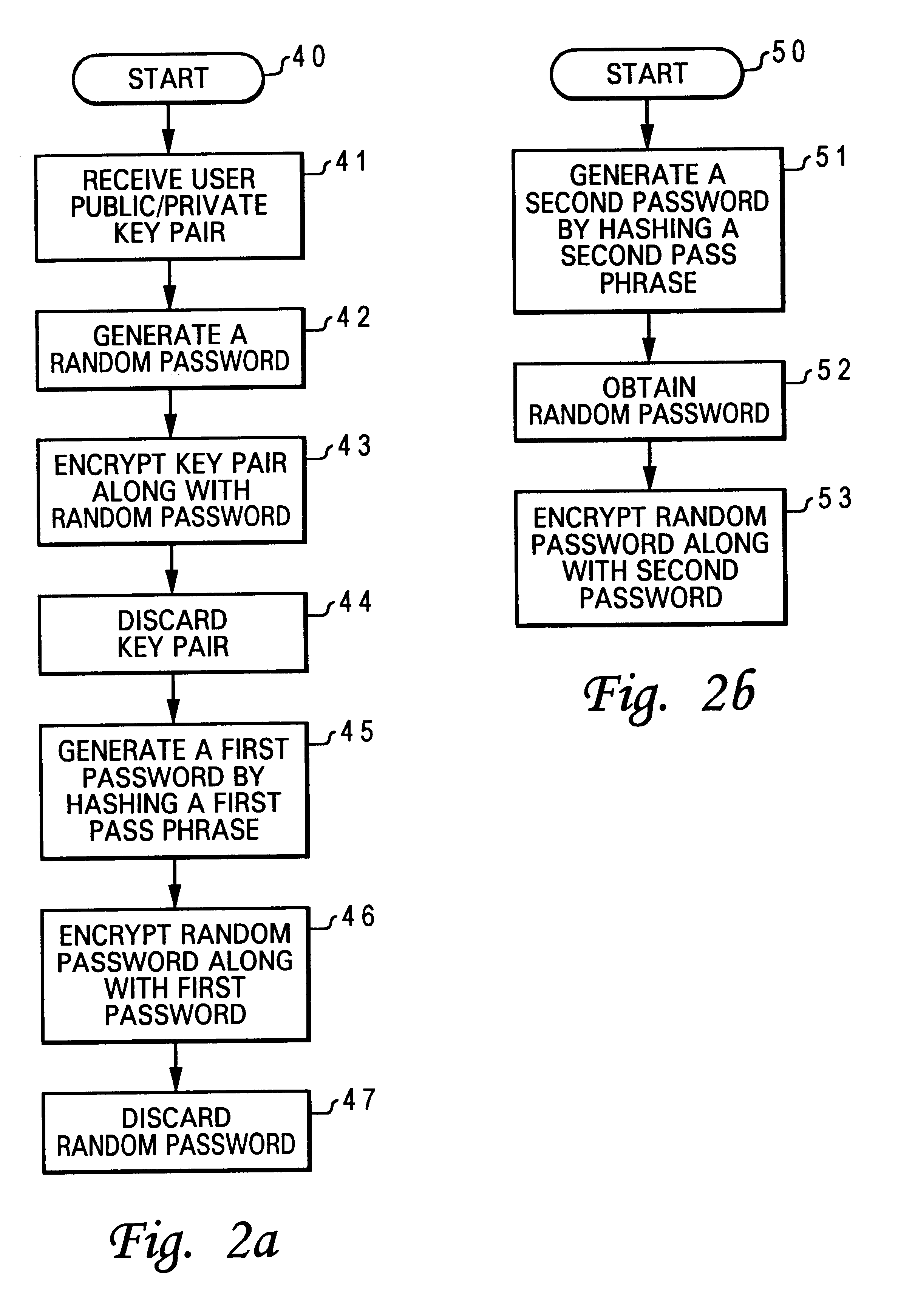
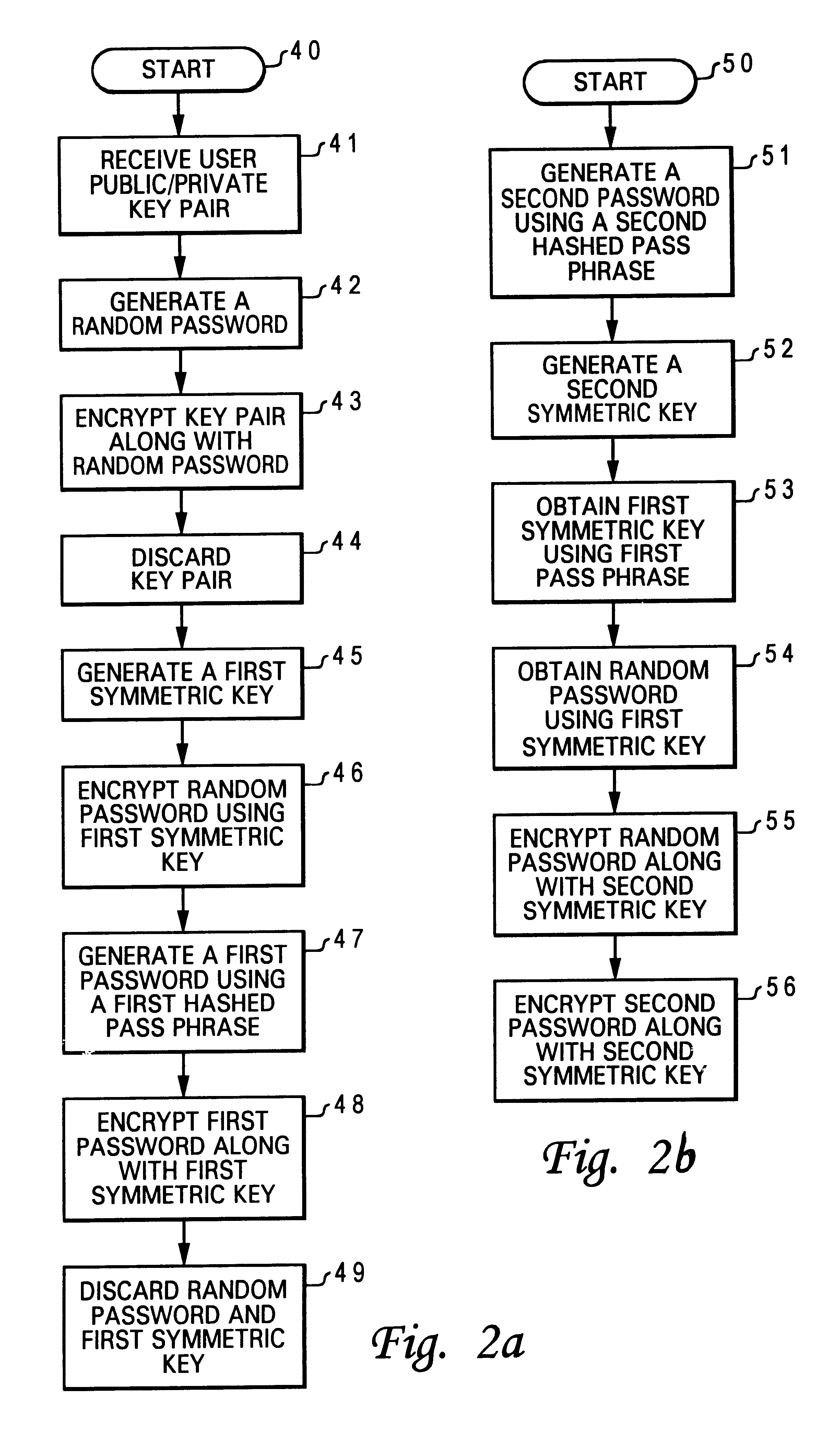
Method for associating a password with a secured public/private key pair
InactiveUS6718468B1Public key for secure communicationDigital data processing detailsPassphrasePassword
A method for associating a password with a secured public / private key pair is disclosed. A user public / private key pair is first established for a user. The user public / private key pair includes a user public key and a user private key. Then, the user public / private key pair is encrypted along with a random password, utilizing a chip public key. Next, a first password is generated by hashing a pass phrase. Finally, the random password is encrypted along with the first password, also utilizing the chip public key. As a result, a user can assess the user private key to perform an authentication function by providing the pass phrase.
Owner:LENOVO PC INT
Speaker verification
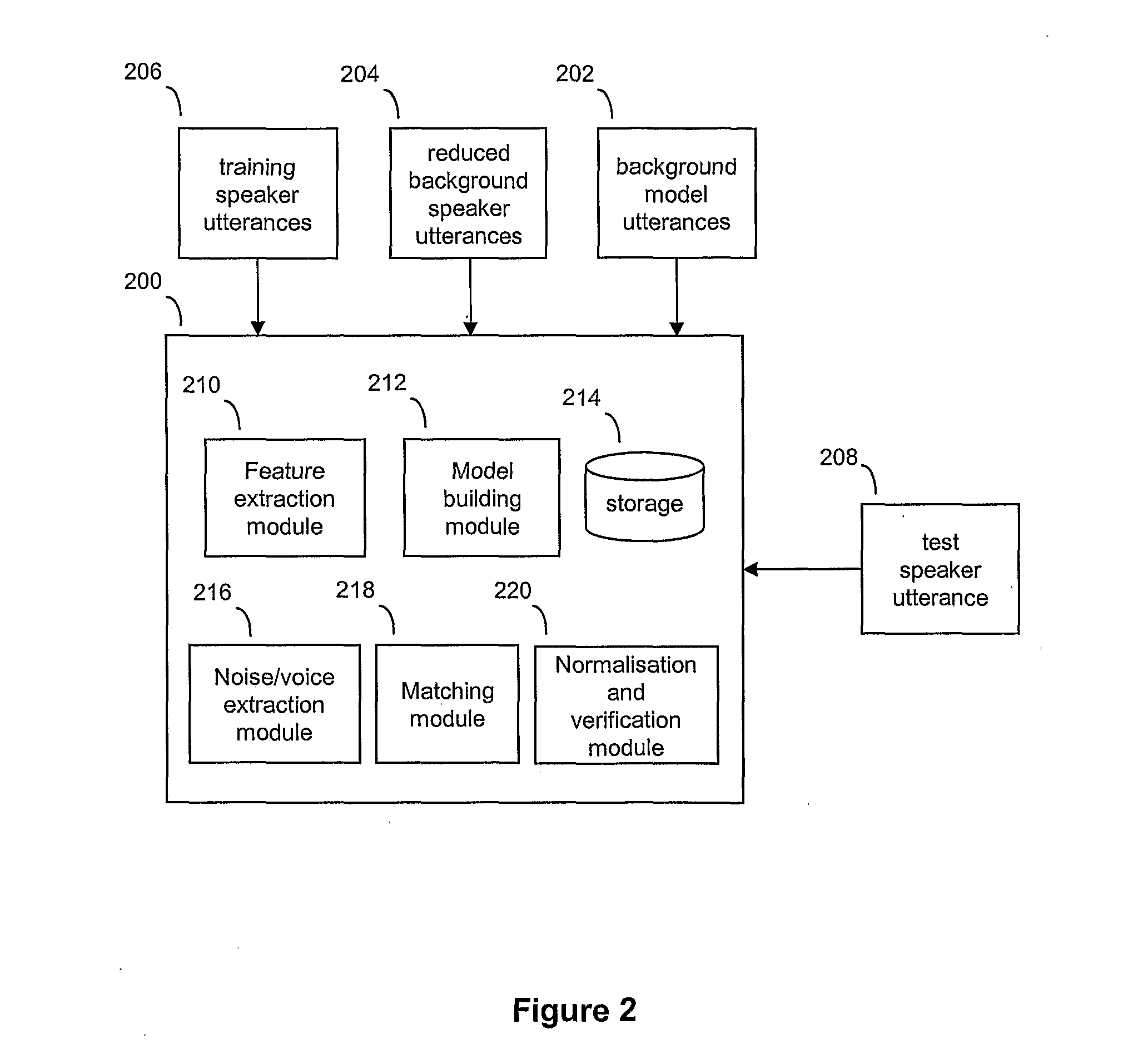
ActiveUS20110202340A1Simple methodImprove verification accuracySpeech recognitionPassphraseFeature vector
A speaker verification method is proposed that first builds a general model of user utterances using a set of general training speech data. The user also trains the system by providing a training utterance, such as a passphrase or other spoken utterance. Then in a test phase, the user provides a test utterance which includes some background noise as well as a test voice sample. The background noise is used to bring the condition of the training data closer to that of the test voice sample by modifying the training data and a reduced set of the general data, before creating adapted training and general models. Match scores are generated based on the comparison between the adapted models and the test voice sample, with a final match score calculated based on the difference between the match scores. This final match score gives a measure of the degree of matching between the test voice sample and the training utterance and is based on the degree of matching between the speech characteristics from extracted feature vectors that make up the respective speech signals, and is not a direct comparison of the raw signals themselves. Thus, the method can be used to verify a speaker without necessarily requiring the speaker to provide an identical test phrase to the phrase provided in the training sample.
Owner:BRITISH TELECOMM PLC
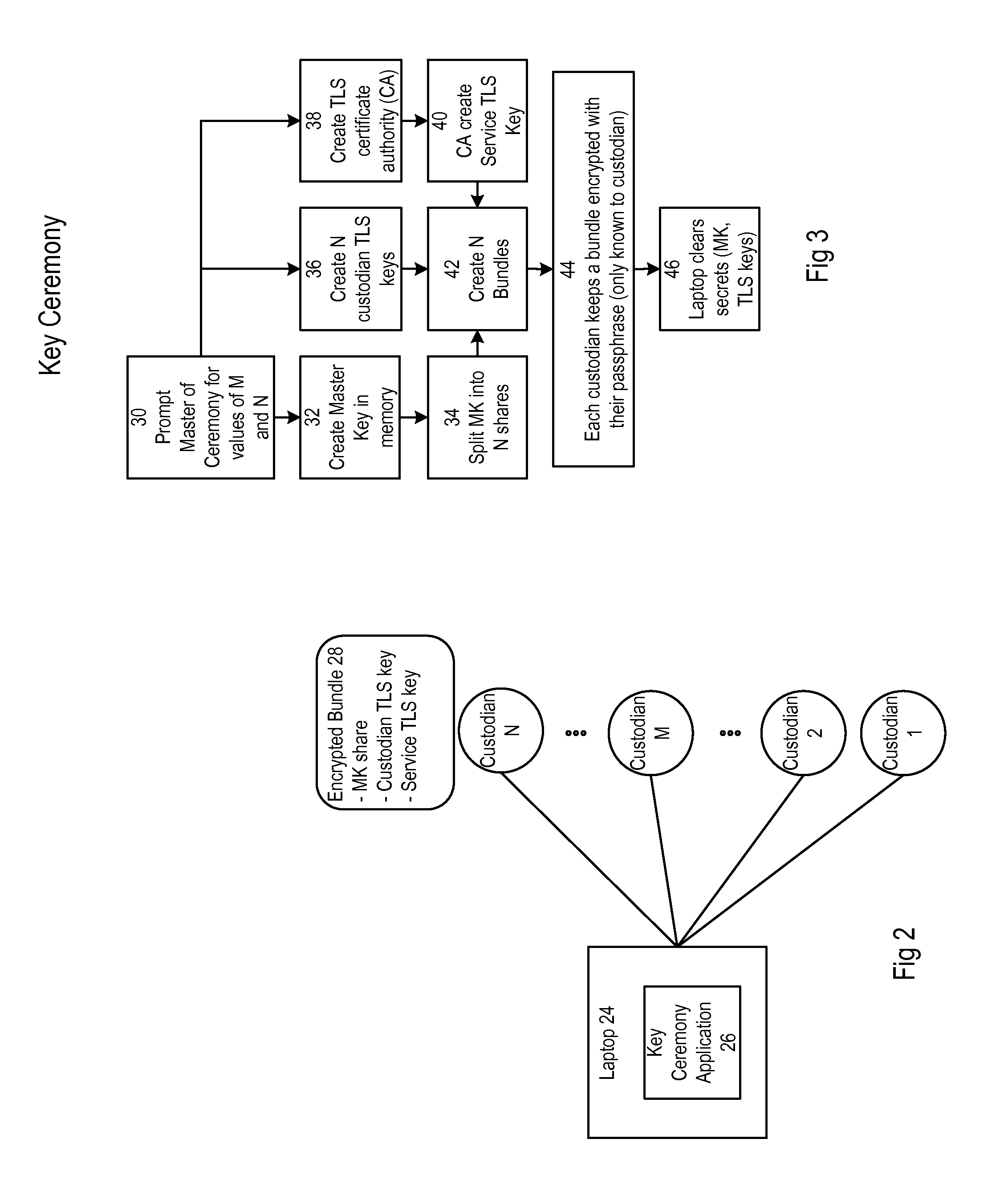
Security system forming part of a bitcoin host computer
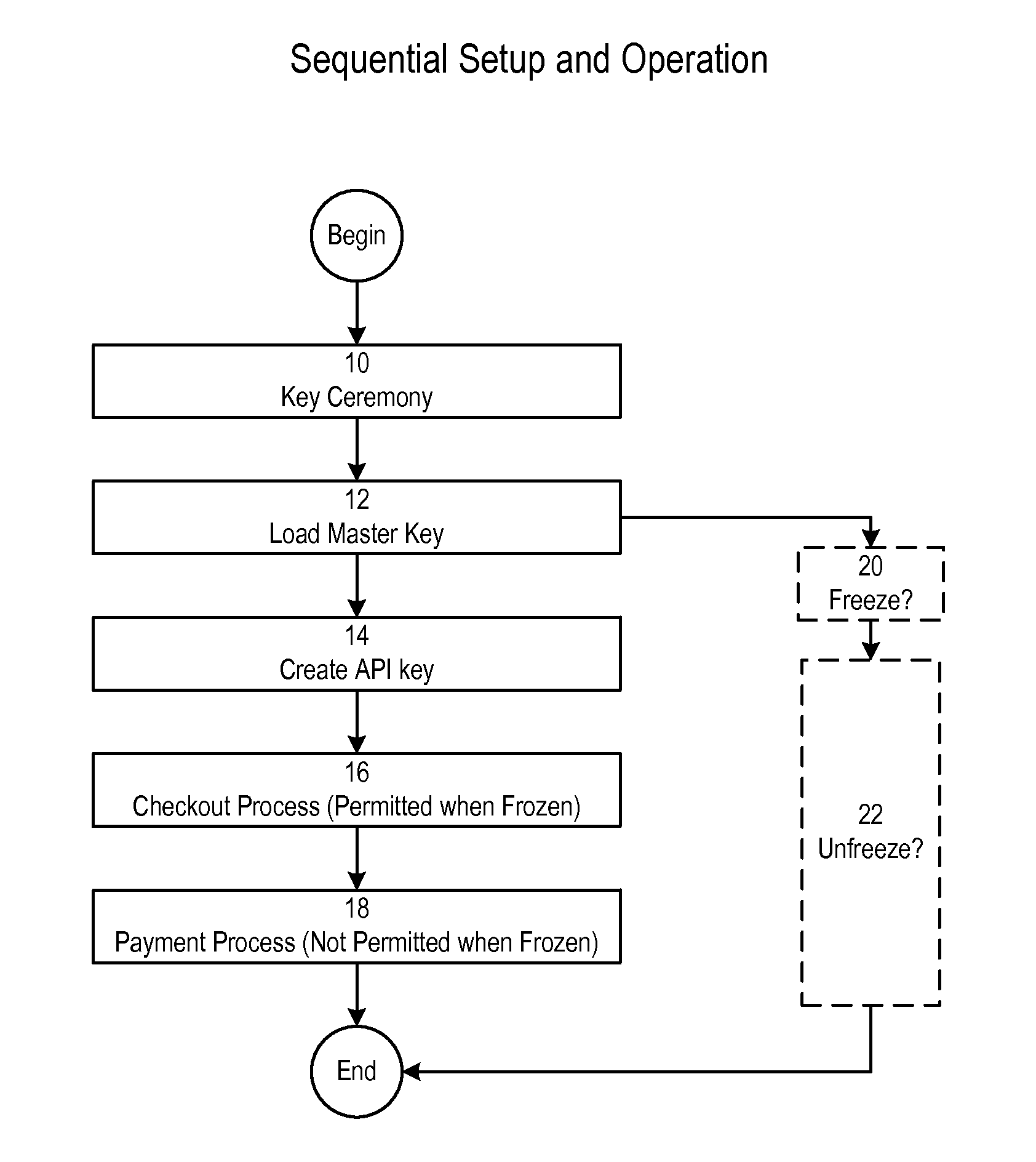
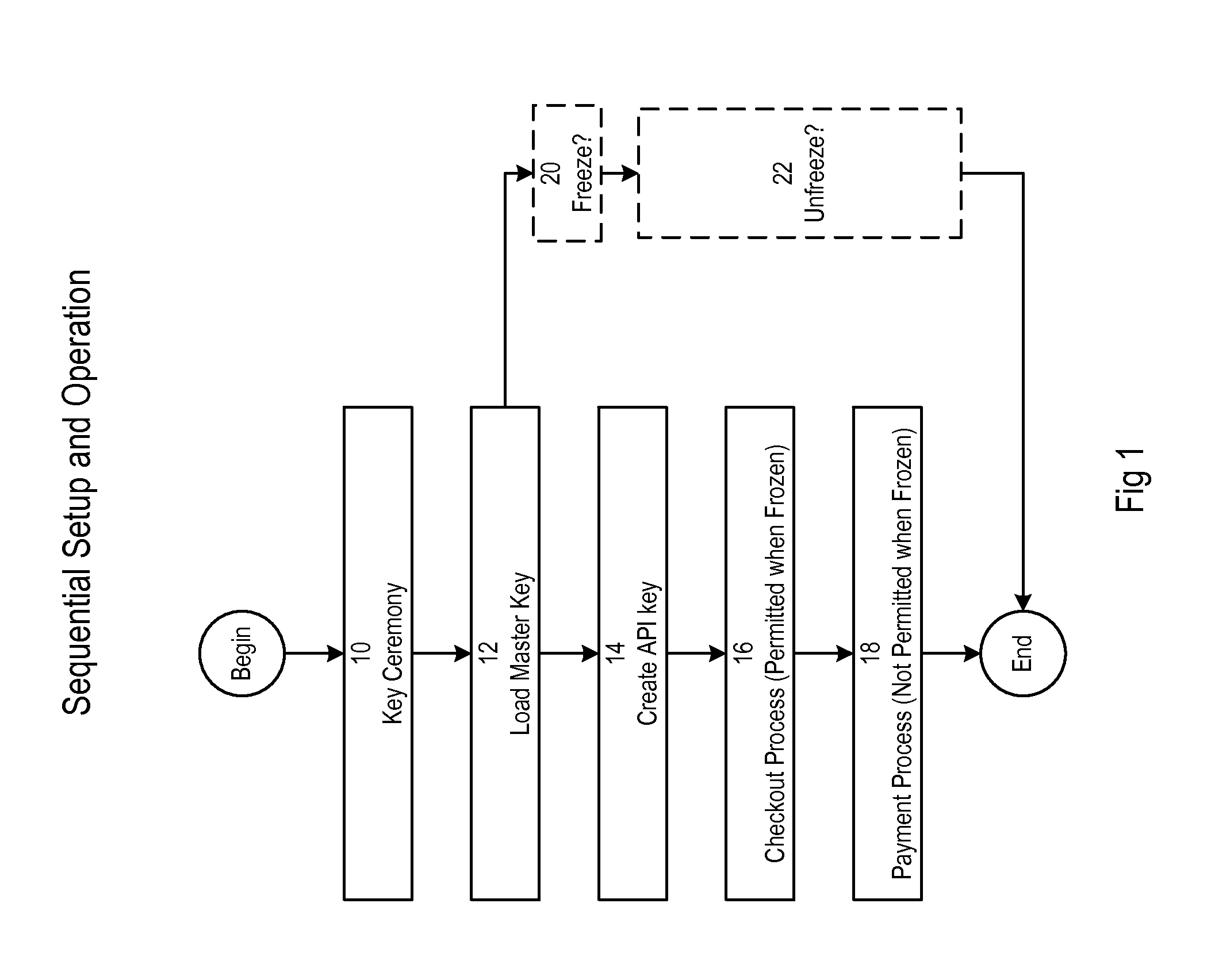
A key ceremony application creates bundles for custodians encrypted with their passphrases. Each bundle includes master key share. The master key shares are combined to store an operational master key. The operational master key is used for private key encryption during a checkout process. The operational private key is used for private key decryption for transaction signing in a payment process. The bundles further include TLS keys for authenticated requests to create an API key for a web application to communicate with a service and to unfreeze the system after it has been frozen by an administrator.
Owner:COINBASE
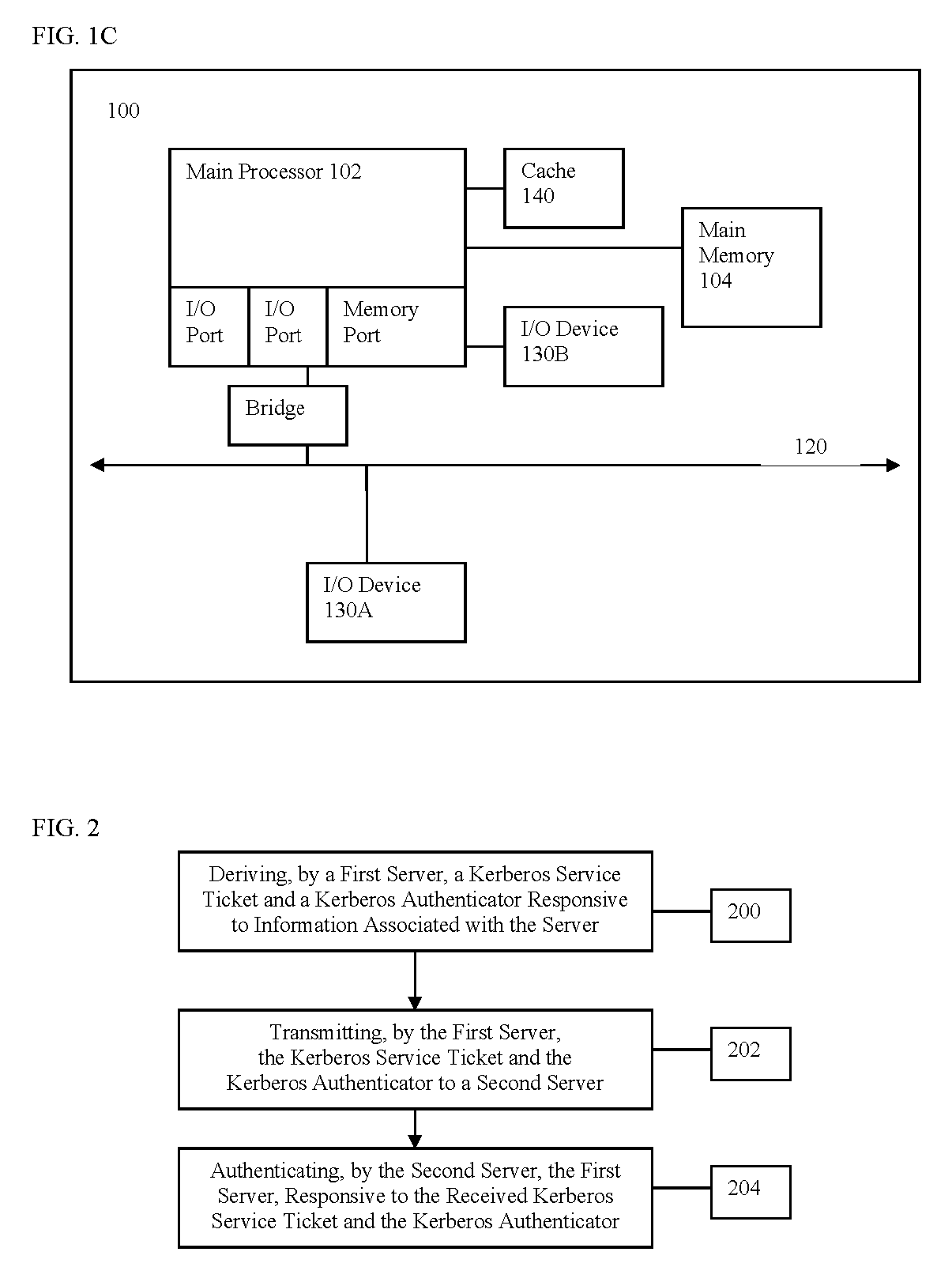
A method and system for requesting and granting membership in a server farm
ActiveUS20060161974A1Digital data processing detailsUser identity/authority verificationPassphraseAuthentication
A server transmits to a server in a server farm a request for membership in the server farm and a first nonce. The server derives a Kerberos service ticket and a Kerberos authenticator, responsive to generating a hash of the server farm name, a passphrase, the name of the server, the name of the server in the server farm, the first nonce, and a second nonce. The server transmits the Kerberos service ticket and the Kerberos authenticator to the server in the server farm. The server in the server farm authenticates the requesting server responsive to the received Kerberos service ticket and the Kerberos authenticator and a generated hash. The server in the server farm transmits, responsive to the authentication, a secret to the requesting server.
Owner:CITRIX SYST INC
Method and system for secure distribution of subscription-based game software
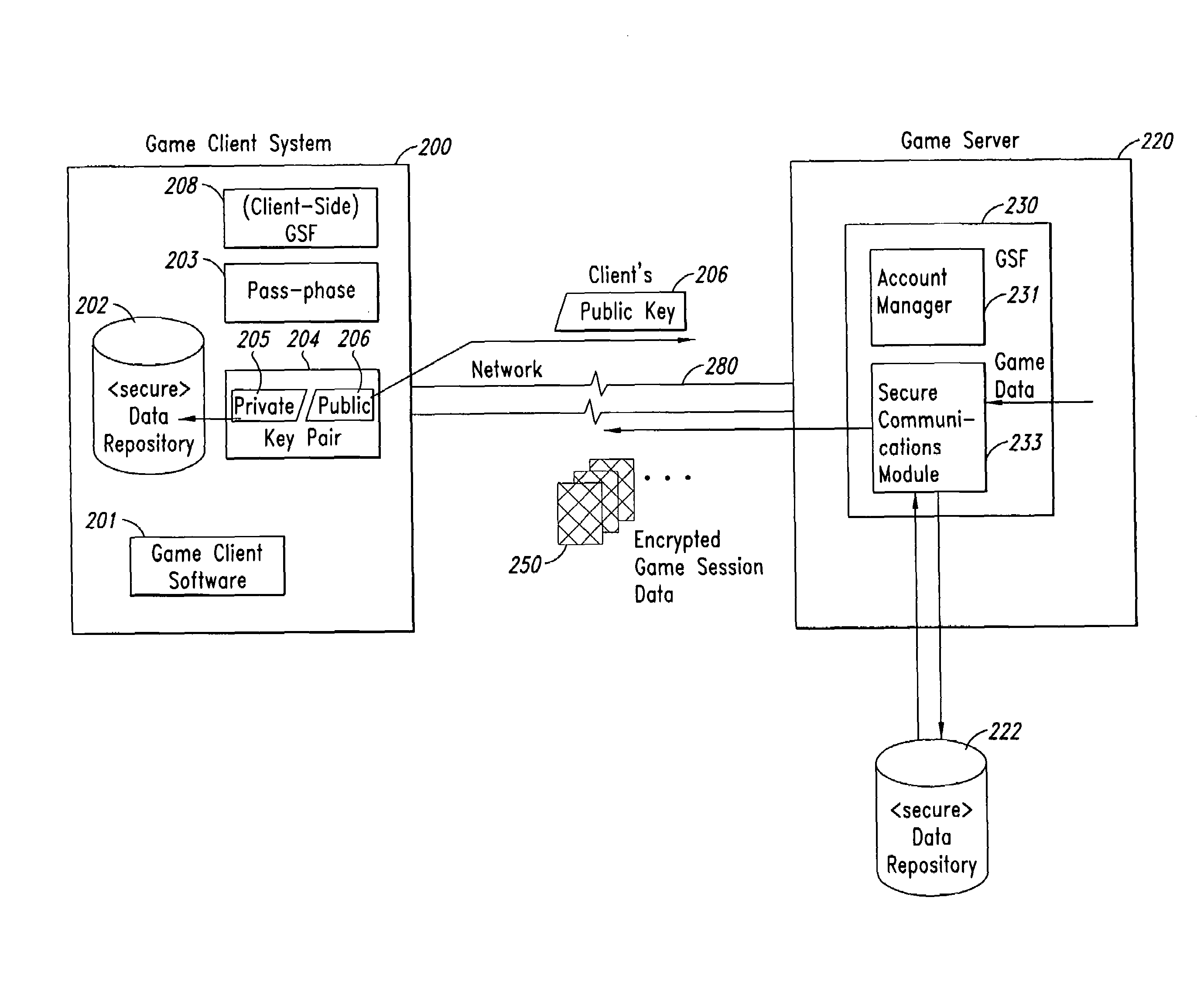
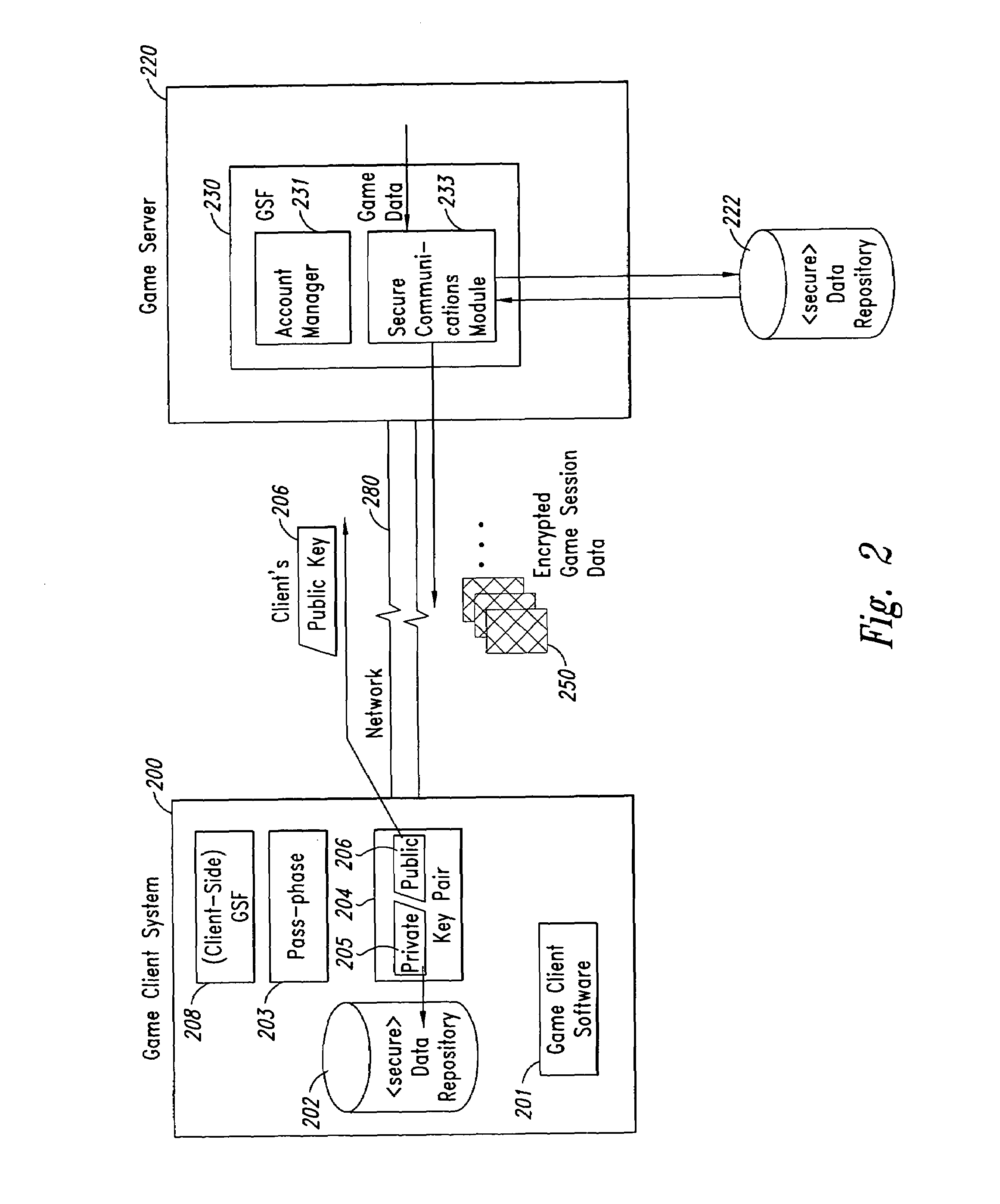
ActiveUS7409061B2Secure distributionCommunication securityKey distribution for secure communicationPublic key for secure communicationGame serverCopying
Methods and Systems for securely distributing software in a subscription-based environment are provided. In an example embodiment, a Game Security Facility (“GSF”) associated with a game server is used to manage secure communications with game clients. The GSF typically manages secure communication of the accounting and billing information and secure communication of game session data. In typical operation, the game client generates a pass-phrase that transparently includes a unique identifier of the machine upon which the subscription software will reside. RSA-type key pairs that are then generated using this pass-phrase will be associated uniquely with both the game player and with the machine upon which the software resides, thus preventing unauthorized copying to another machine or unauthorized use by a third party. A public key generated using this pass-phrase is forwarded to the GSF, which uses it to generate a unique one-time random session key (for use as a symmetric key) for each session with the game client. The session key is then encrypted for the game client using the public key of the client. Session data, including the original game files downloaded upon successfully subscribing, are then transmitted between the game server and the game client using encrypted versions of the session key. In one embodiment, the game client can upgrade the machine upon which the subscription data resides, cause the session keys to be reissued using a new public key, and retain access to previously downloaded data.
Owner:CLOUDROCK LLC
Encryption and authentication systems and methods
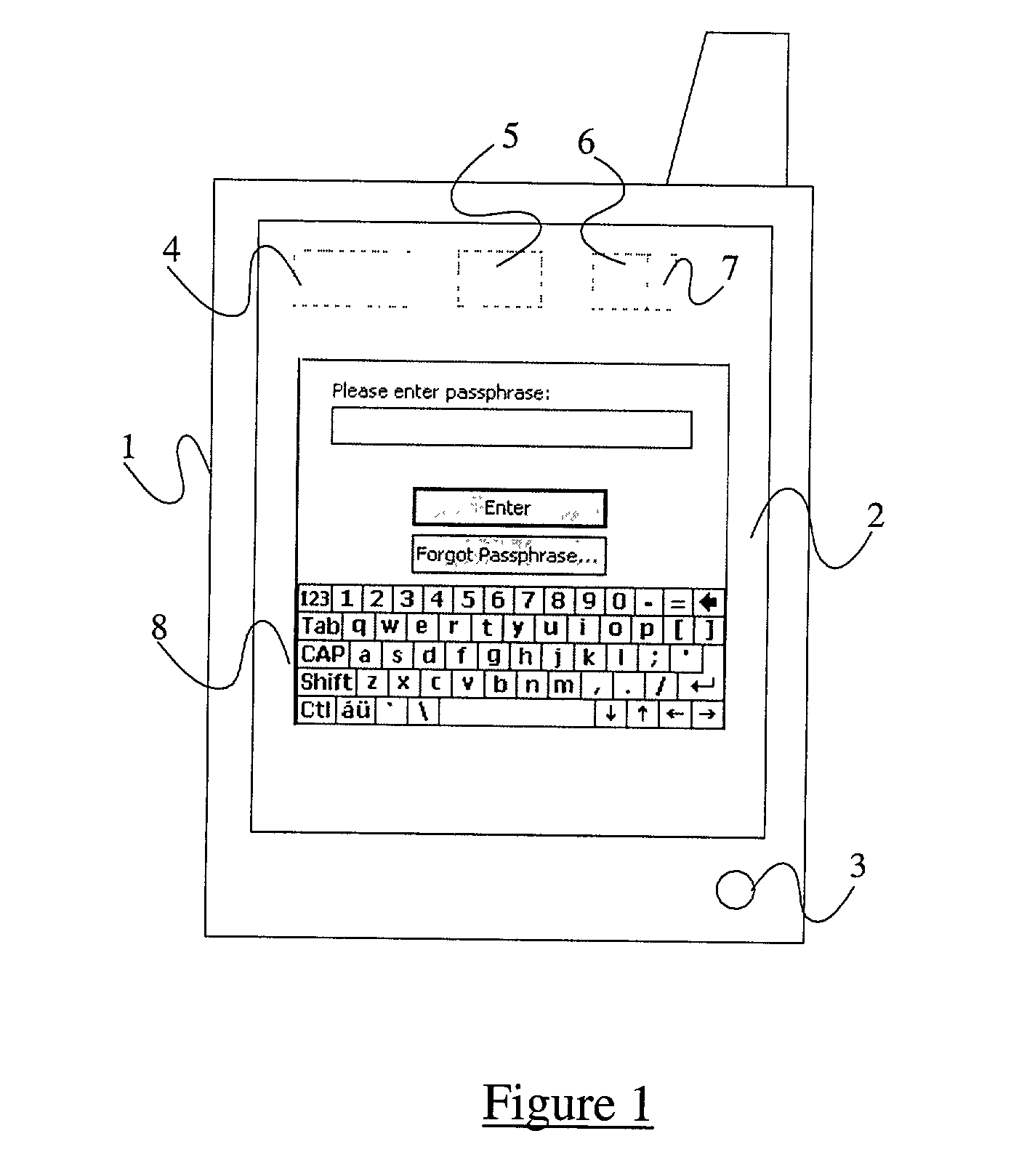
InactiveUS20070174629A1Digital data processing detailsUser identity/authority verificationUser verificationElectronic document
Methods, apparatus, and systems are disclosed for, among other things, passphrase input using secure delay, passphrase input with characteristic shape display, user authentication with non-repeated selection of elements with a displayed set of elements, document authentication with embedding of a digital signature stamp within a graphical representation of the electronic document wherein the stamp comprises digits of a digital signature, and sub-hash computation using secure delay.
Owner:KIOBA PROCESSING LLC
Method and apparatus for selecting a password
ActiveUS8127141B2Easy to listImprove recallDigital data processing detailsAnalogue secracy/subscription systemsPassphrasePassword
A method of generating or entering a password or passphrase on a computer system 1. The method comprises storing a plurality of sets of values in a memory 5 of the system 1, the values of each set defining respective elements which belong to a common domain, the domains of respective sets being distinct from one another, selecting at least one value from each stored set or from each of a plurality of the stored sets, and combining the selected values or elements thereof to form a password or passphrase.
Owner:F SECURE CORP
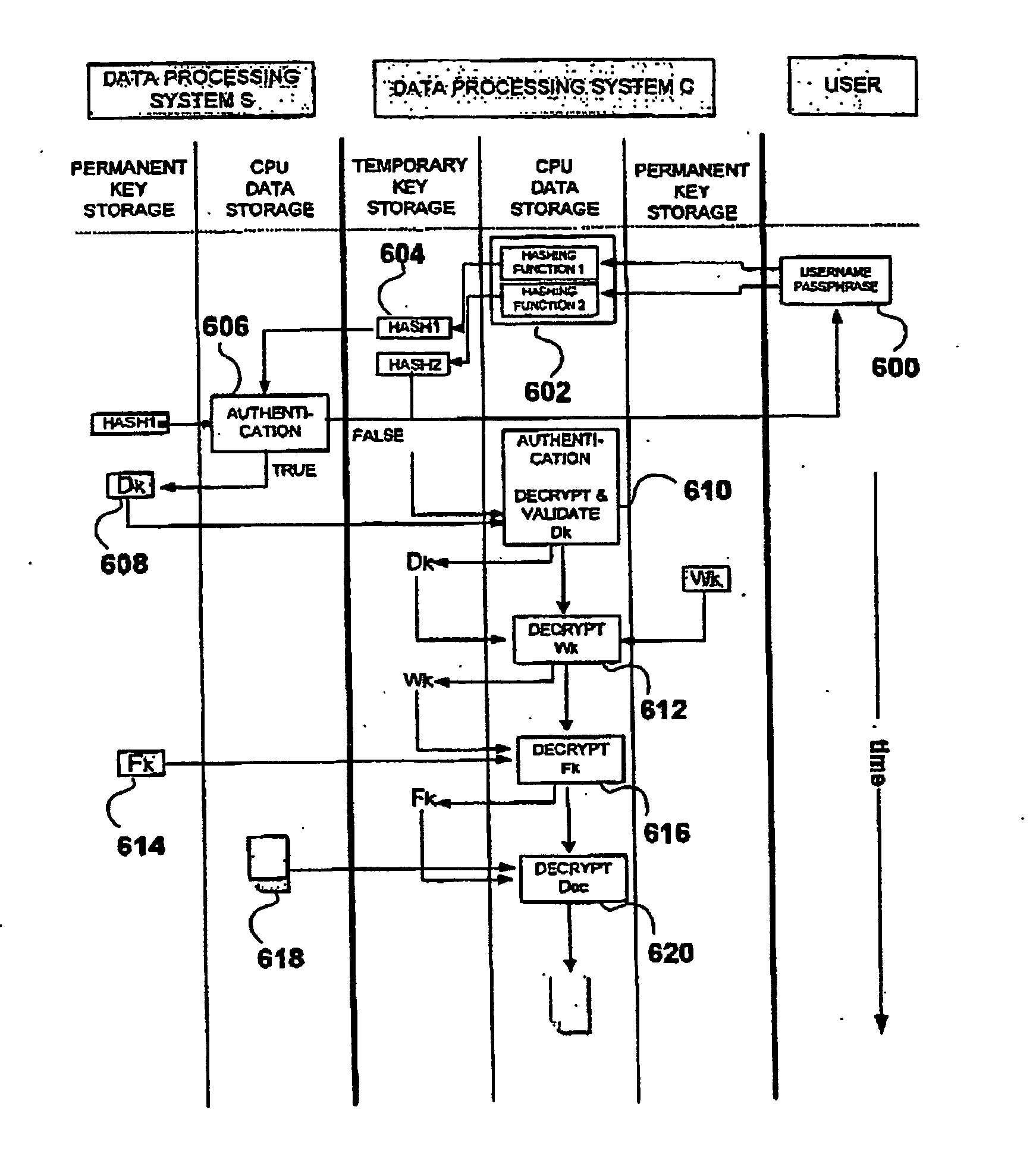
Method and system for authentication, data communication, storage and retrieval in a distributed key cryptography system
InactiveUS20050033963A1Improve securityUser identity/authority verificationPassphraseData processing system
A method for protecting the transfer and storage of data by encryption using a private key encrypted with a first key encrypting key, which is encrypted using a second key encrypting key. This latter key is encrypted using a hashed passphrase value, obtained by hashing a passphrase known only to the authorized user. Upon receipt of a request initiated by the user by entering a passphrase, a first hashed passphrase is transferred to a first data processing system, where it is compared with a predefined hash string. If they match, the first data processing system transfers to a second data processing system the encrypted second key encrypting key. A candidate key is obtained by decrypting the encrypted second key encrypting key using a second hashed passphrase. Upon successful validation of the candidate key, the passphrase is verified and the user is authenticated. After the user has been authenticated, the first data processing system transmits to the second data processing system the encrypted private key and the encrypted data. The second processing system then decrypts the encrypted first key encrypting key using the second key encrypting key, decrypts the encrypted private key using the first key encrypting key and finally decrypts the data using the private key.
Owner:EISST
Business method for secure installation of a credit authorization key on a remote tcpa compliant system
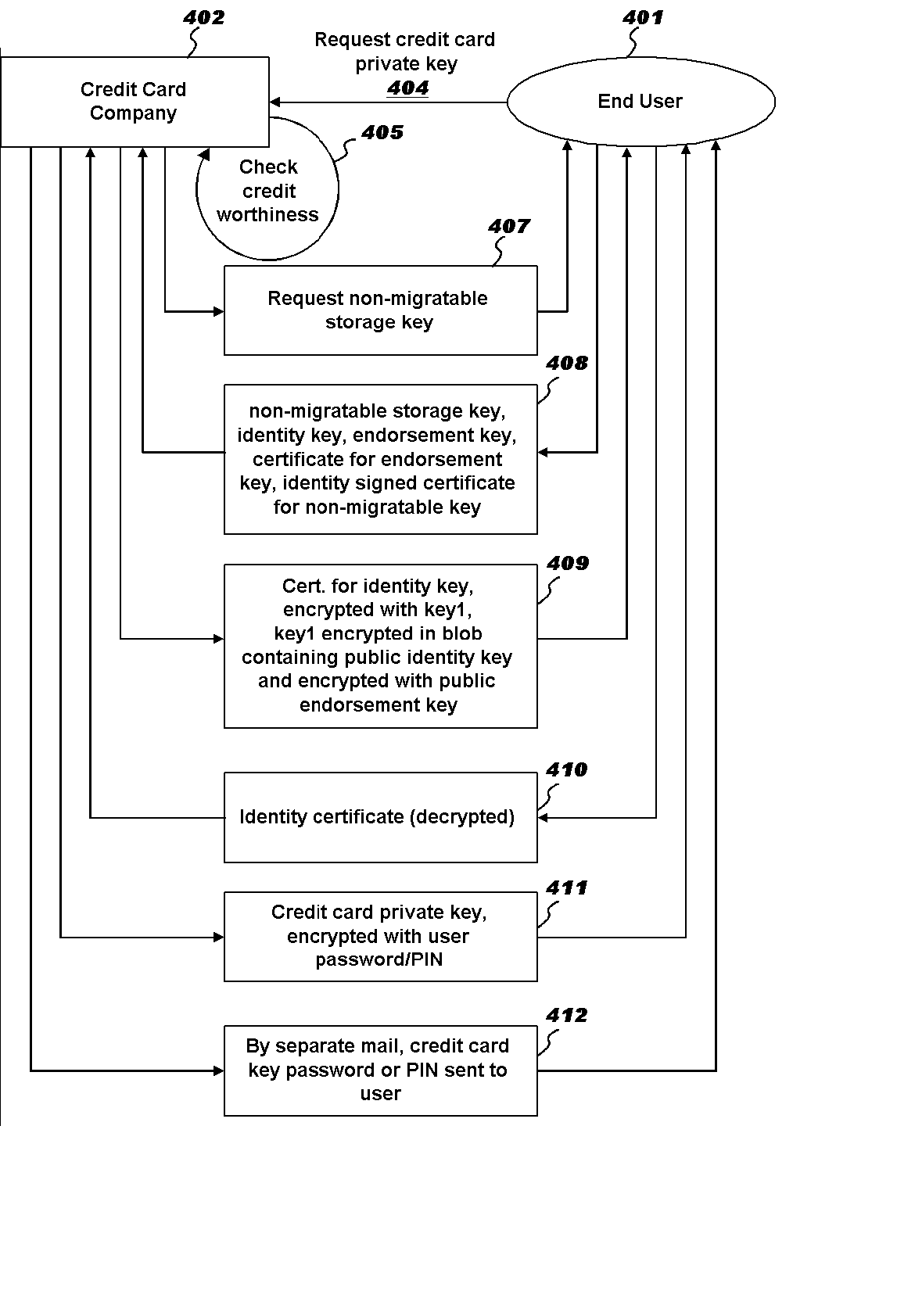
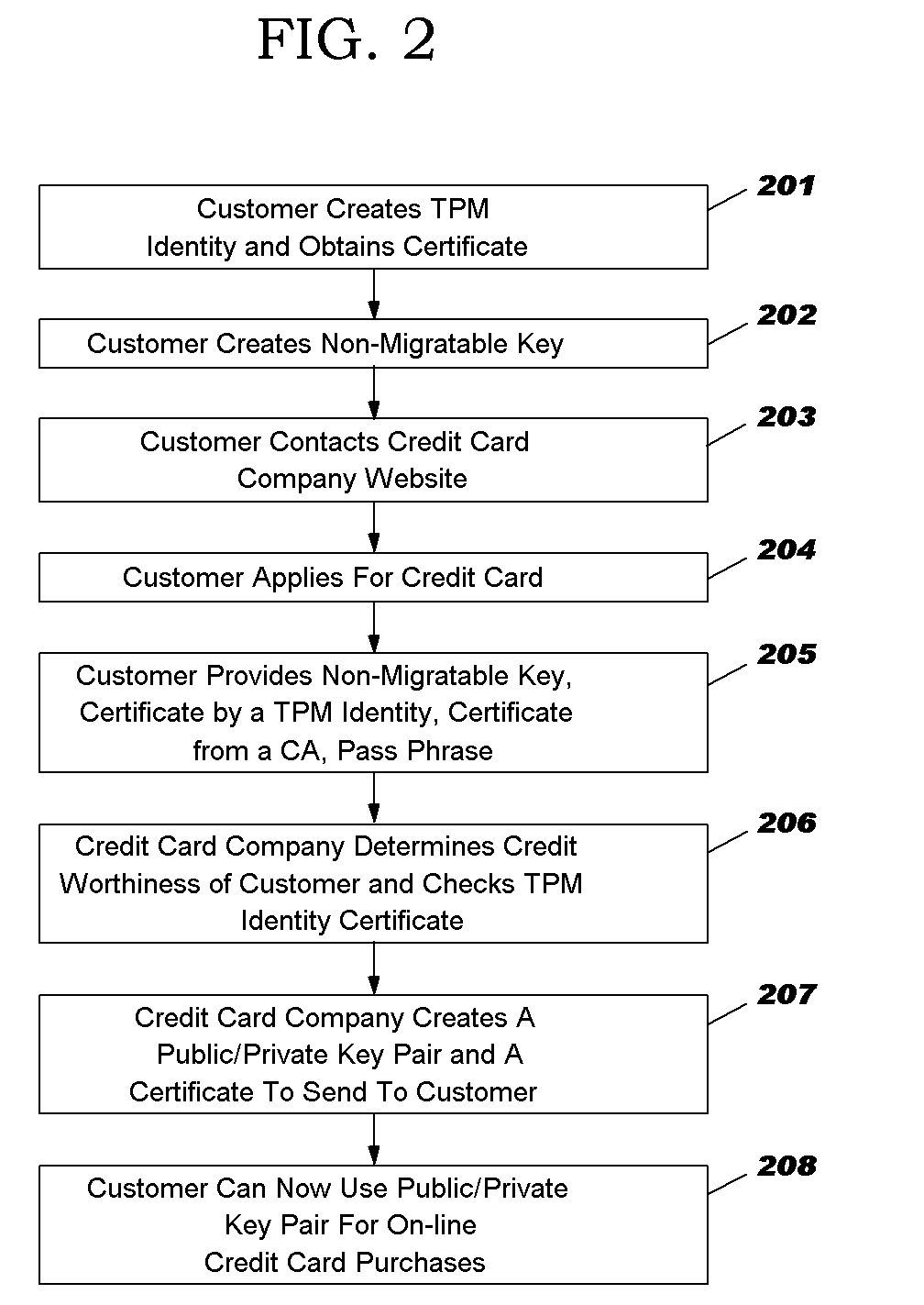
InactiveUS20030105965A1Reduce the amount requiredEasy to checkCredit registering devices actuationFinanceComputer hardwareCredit card
Abstract of the Disclosure A business method employing hardware complaint to the Trusted Computing Platform Alliance (TCPA) Specification is implemented to allow a credit card company to remotely install a credit card private key into a TCPA module to create a Trusted Platform Module (TPM). More specifically, when a credit worthy user applies for a credit card, the user will send the credit card company a public portion of a "non-migratable storage key," which is accredited a TPM endorsed by a Certification Authority. The credit card company will create its own public / private key pair according to the TCPA Specification, to create a TCPA header, and wrap the full structure by encrypting it with the public portion of the TCPA non-migratable storage key. The credit card company then sends by email the encrypted bundle with a certificate for it, and sends a corresponding pass phrase by regular mail.
Owner:LENOVO (SINGAPORE) PTE LTD
Method for associating a pass phase with a secured public/private key pair
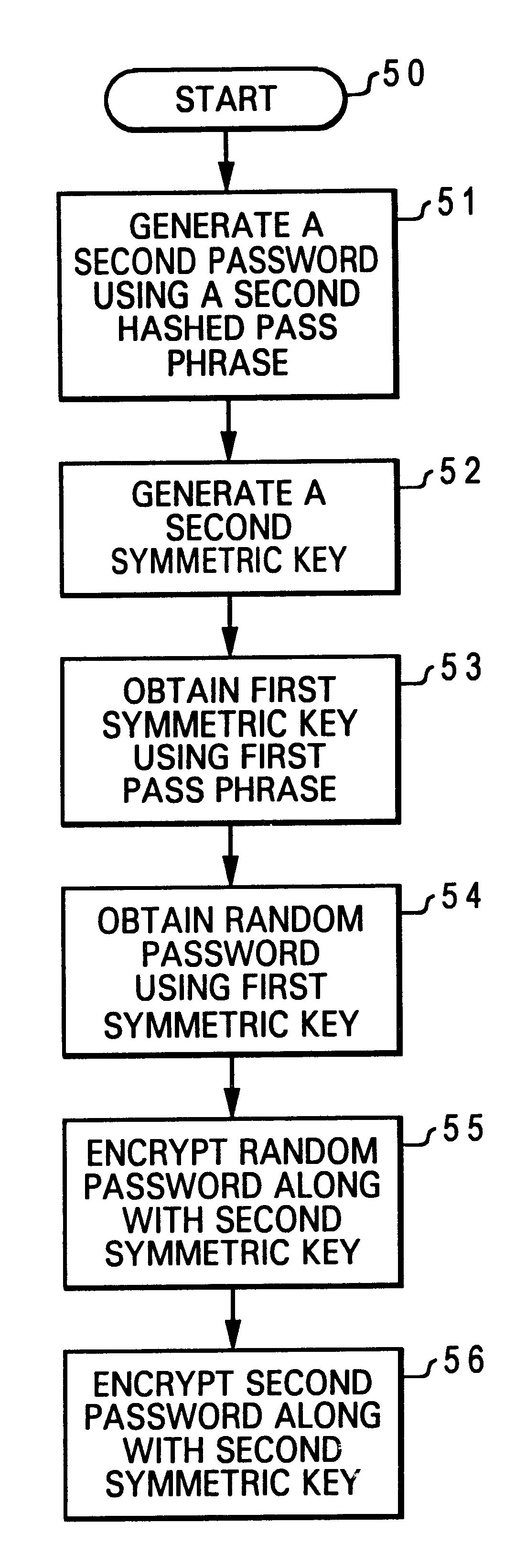
InactiveUS6704868B1Digital data processing detailsUser identity/authority verificationPassphrasePassword
A method for associating a pass phrase with a secured public / private key pair is disclosed. A user public / private key pair is first established for a user. The user public / private key pair includes a user public key and a user private key. Then, the user public / private key pair is encrypted along with a random password, utilizing a chip public key. Next, a first symmetric key is generated. The random password is encrypted utilizing the first symmetric key. A first password is generated by hashing a first pass phrase. Finally, the first password is encrypted along with the first symmetric key, also utilizing the chip public key. As a result, a user can access the user private key to perform an authentication function by providing the first pass phrase.
Owner:LENOVO PC INT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com