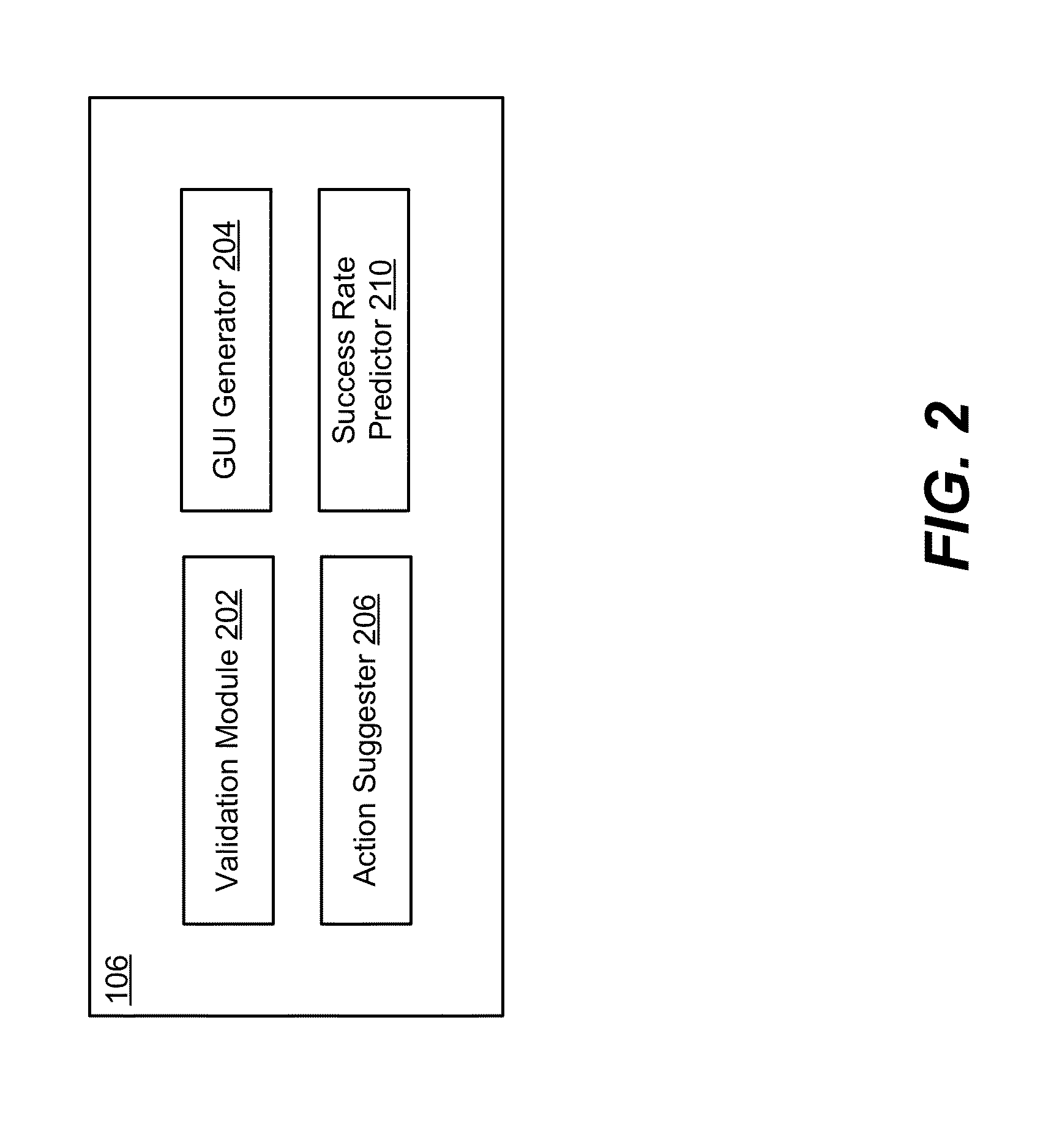
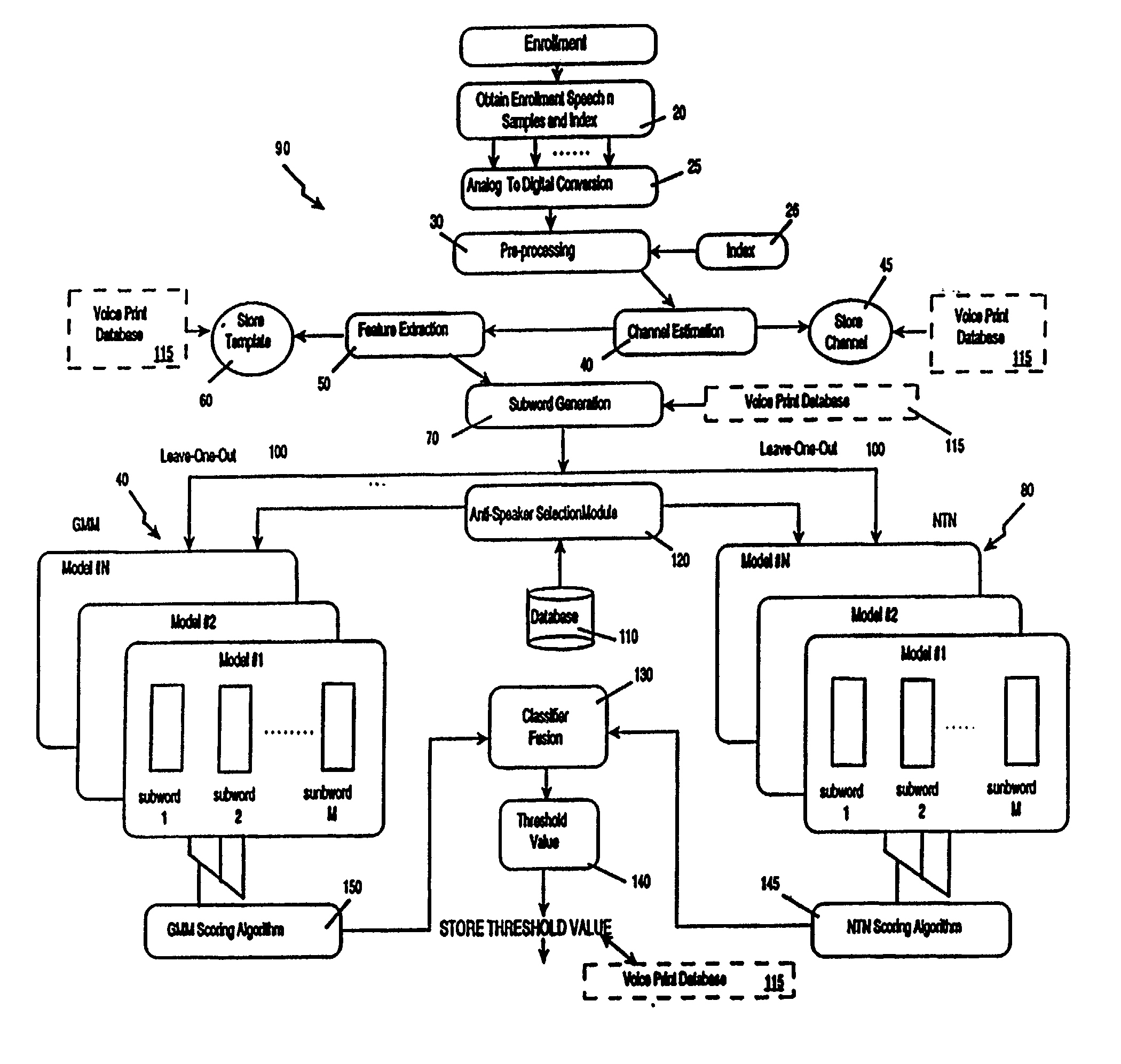
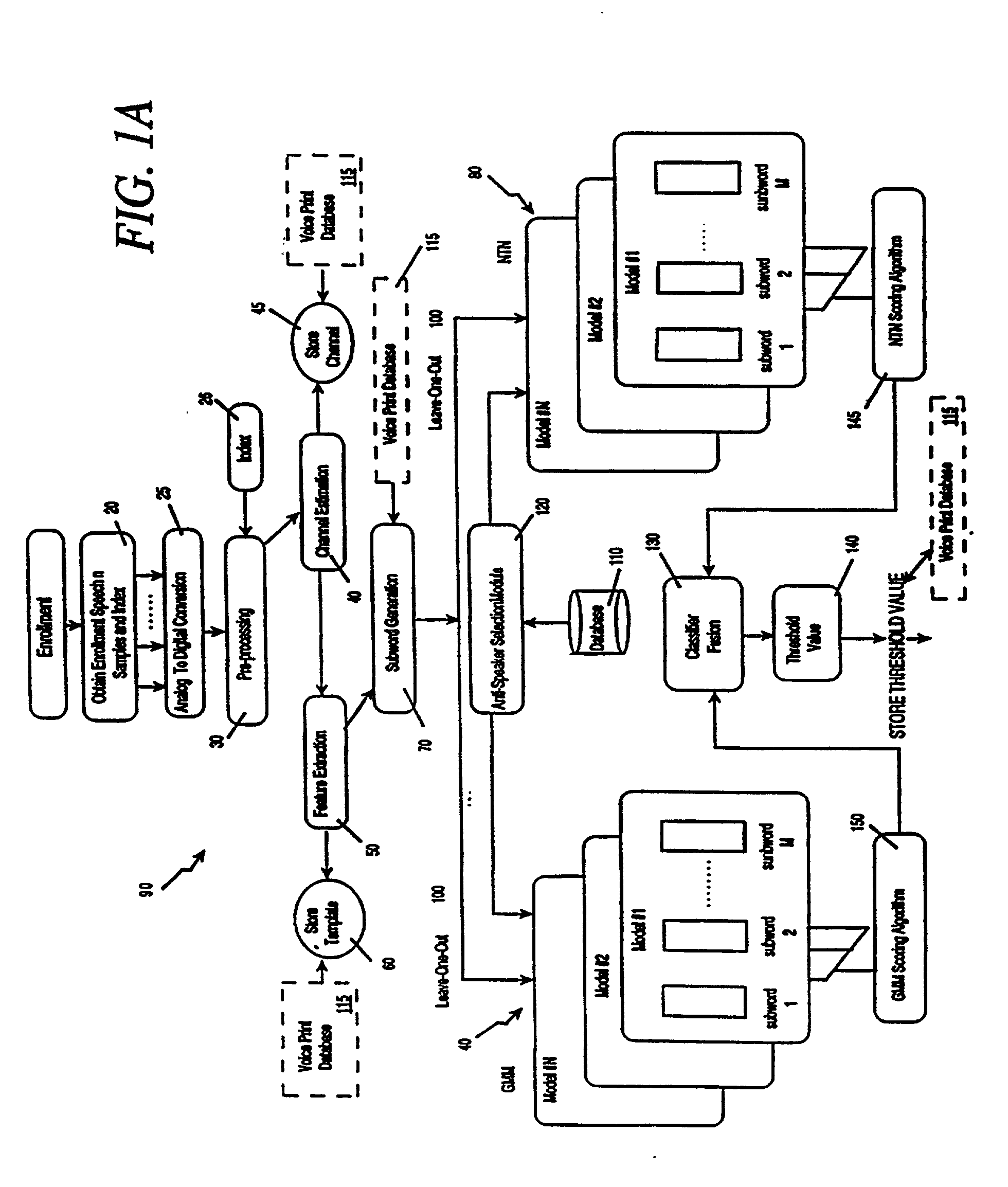
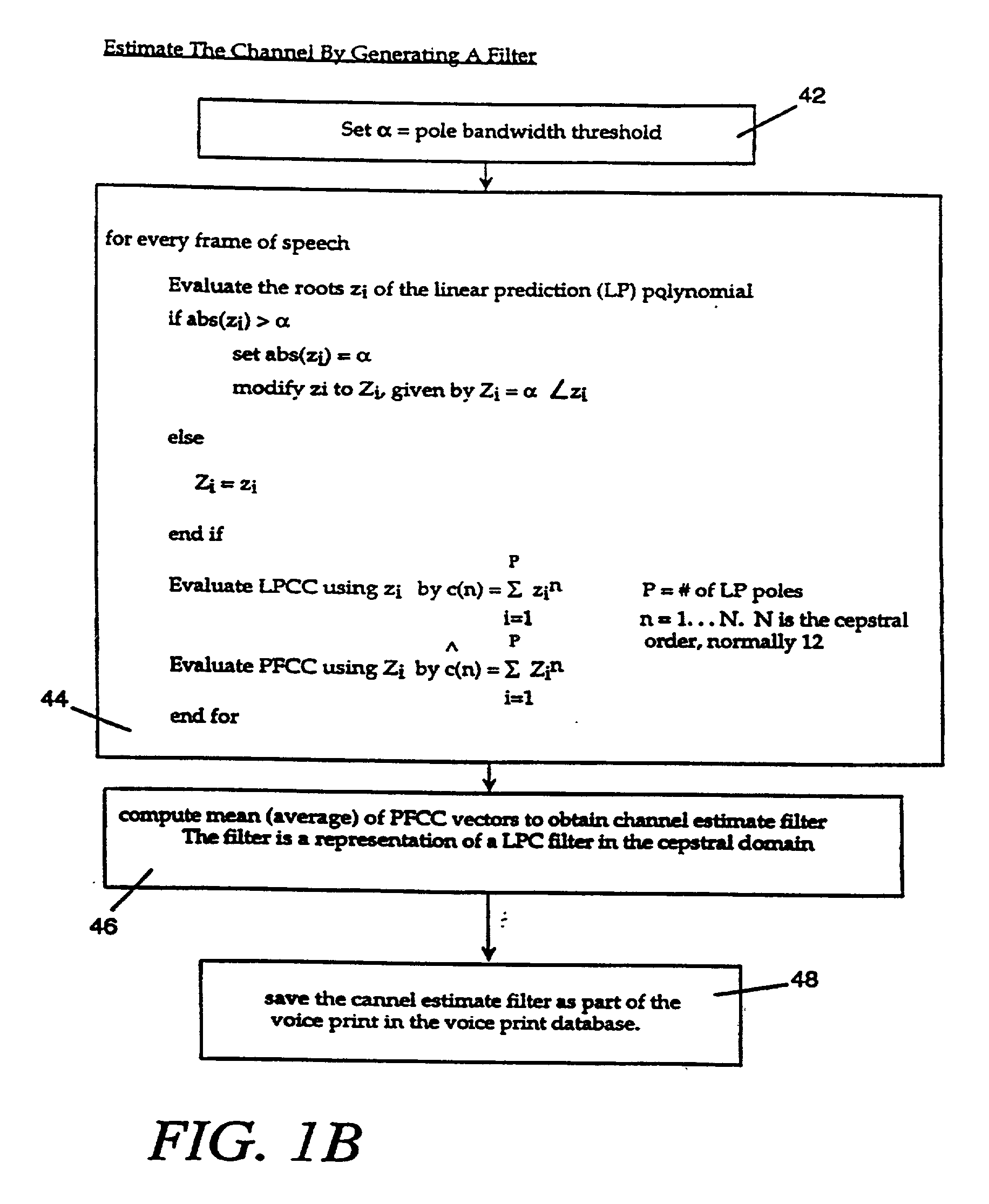
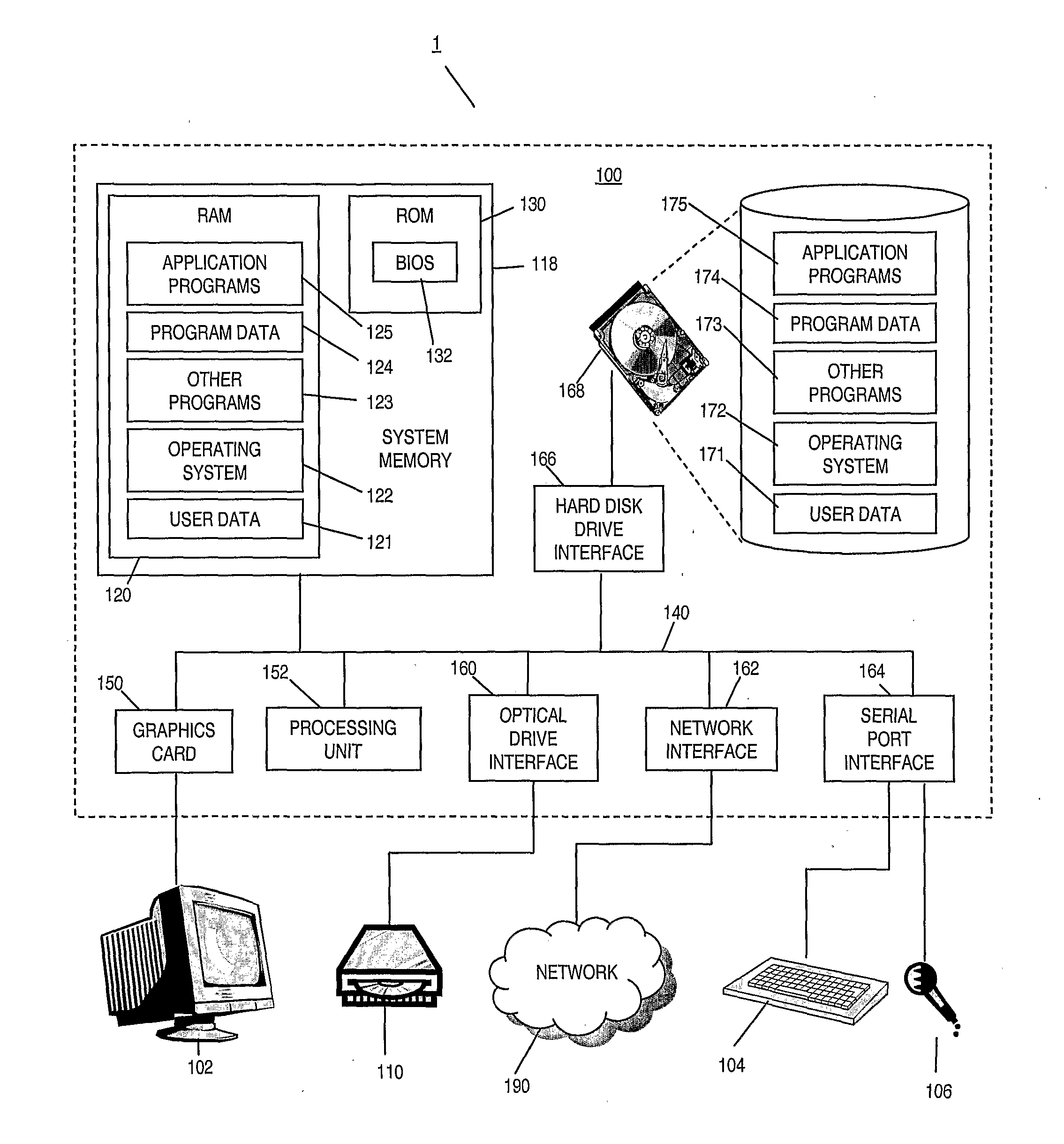
Patents
Literature
141 results about "Speaker verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
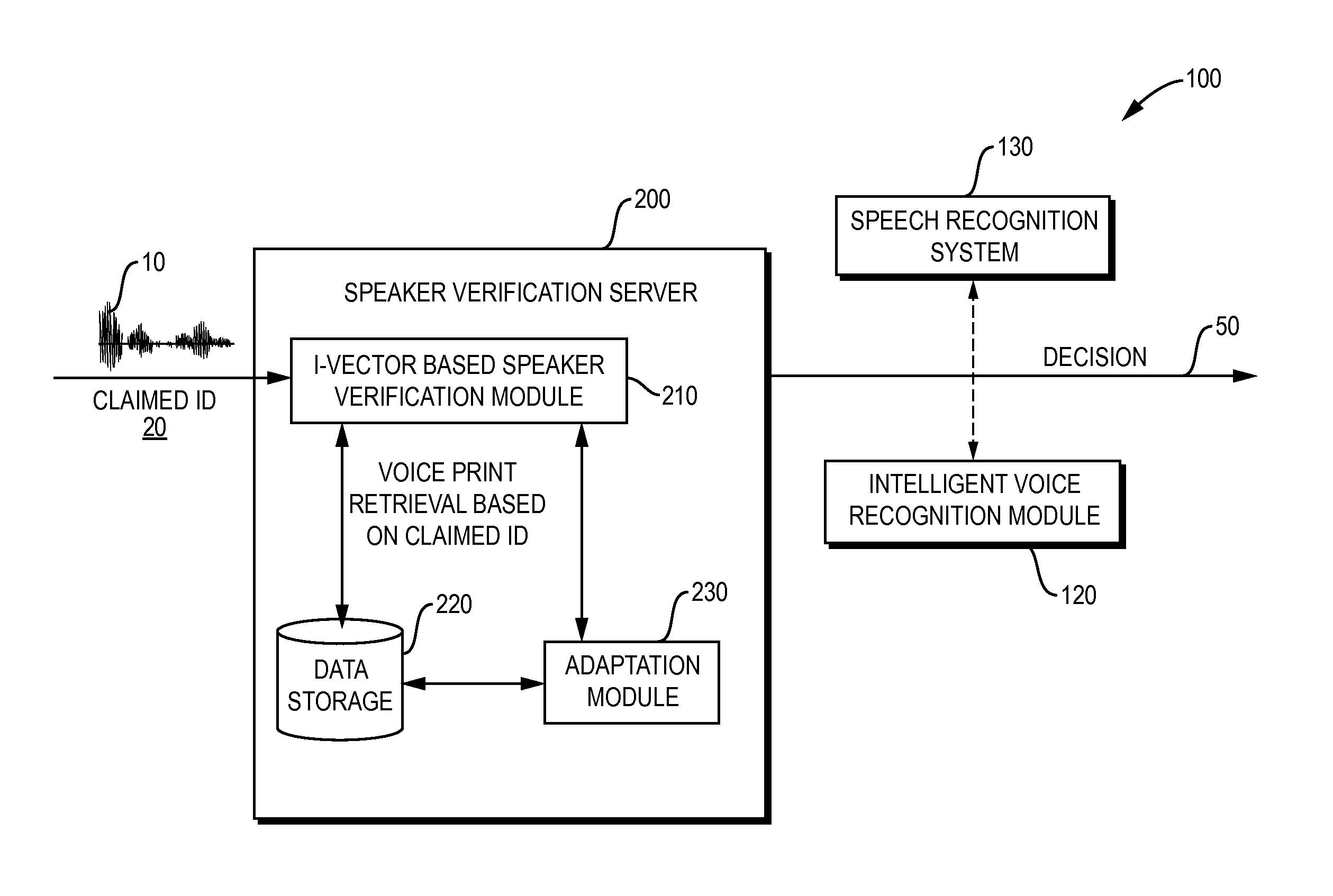
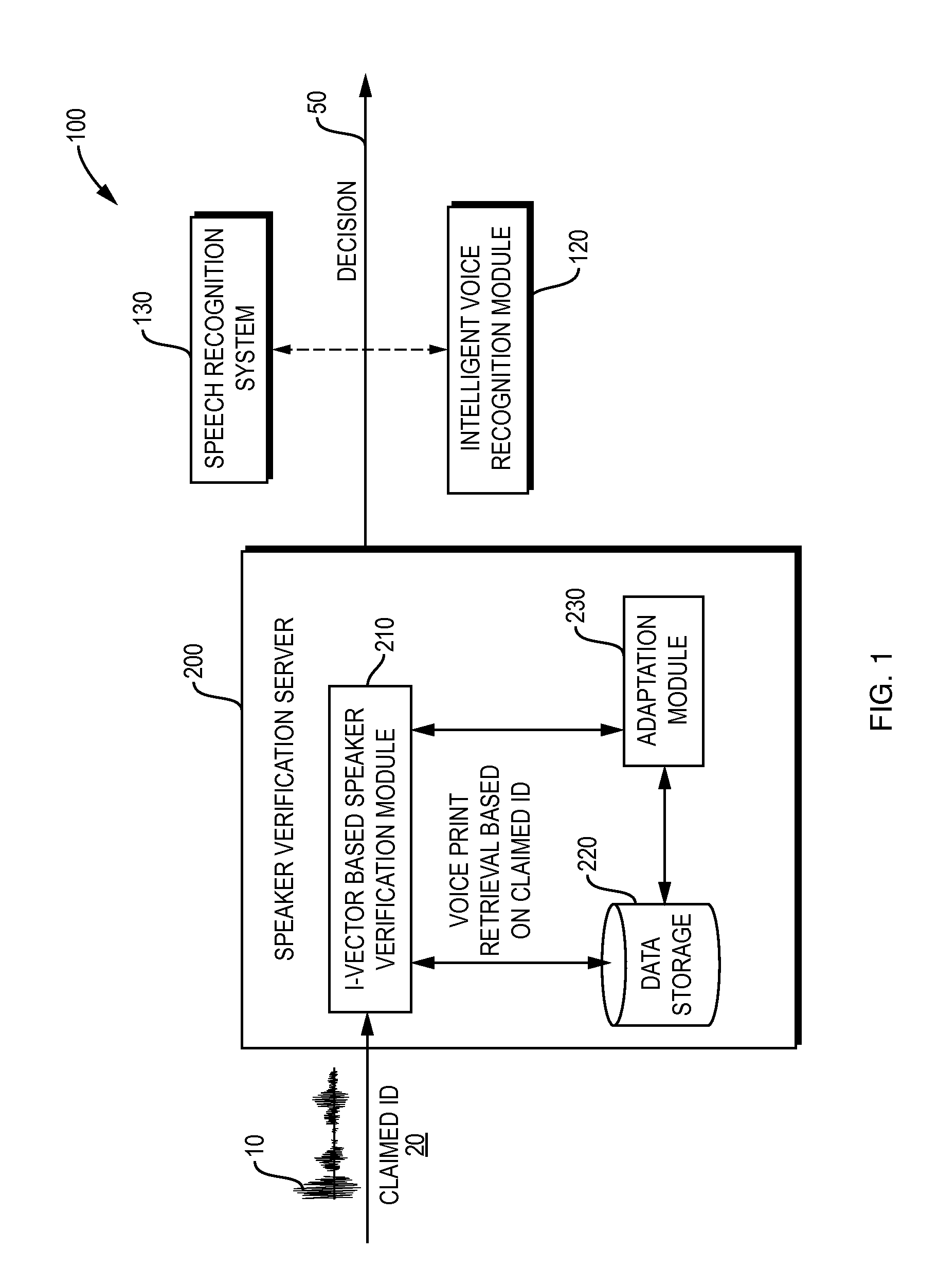
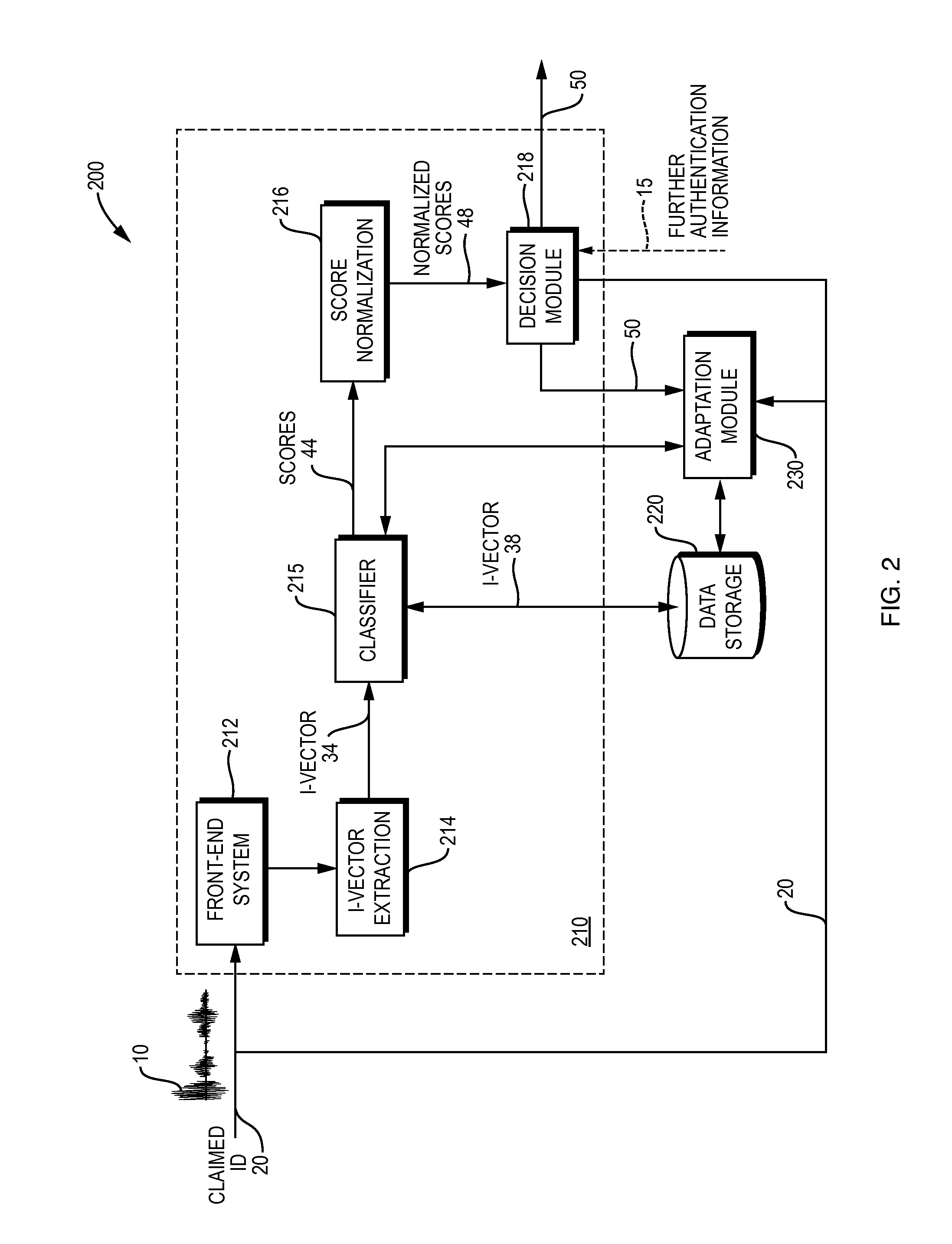
Method and Apparatus for Automated Speaker Parameters Adaptation in a Deployed Speaker Verification System
Typical speaker verification systems usually employ speakers' audio data collected during an enrollment phase when users enroll with the system and provide respective voice samples. Due to technical, business, or other constraints, the enrollment data may not be large enough or rich enough to encompass different inter-speaker and intra-speaker variations. According to at least one embodiment, a method and apparatus employing classifier adaptation based on field data in a deployed voice-based interactive system comprise: collecting representations of voice characteristics, in association with corresponding speakers, the representations being generated by the deployed voice-based interactive system; updating parameters of the classifier, used in speaker recognition, based on the representations collected; and employing the classifier, with the corresponding parameters updated, in performing speaker recognition.
Owner:NUANCE COMM INC
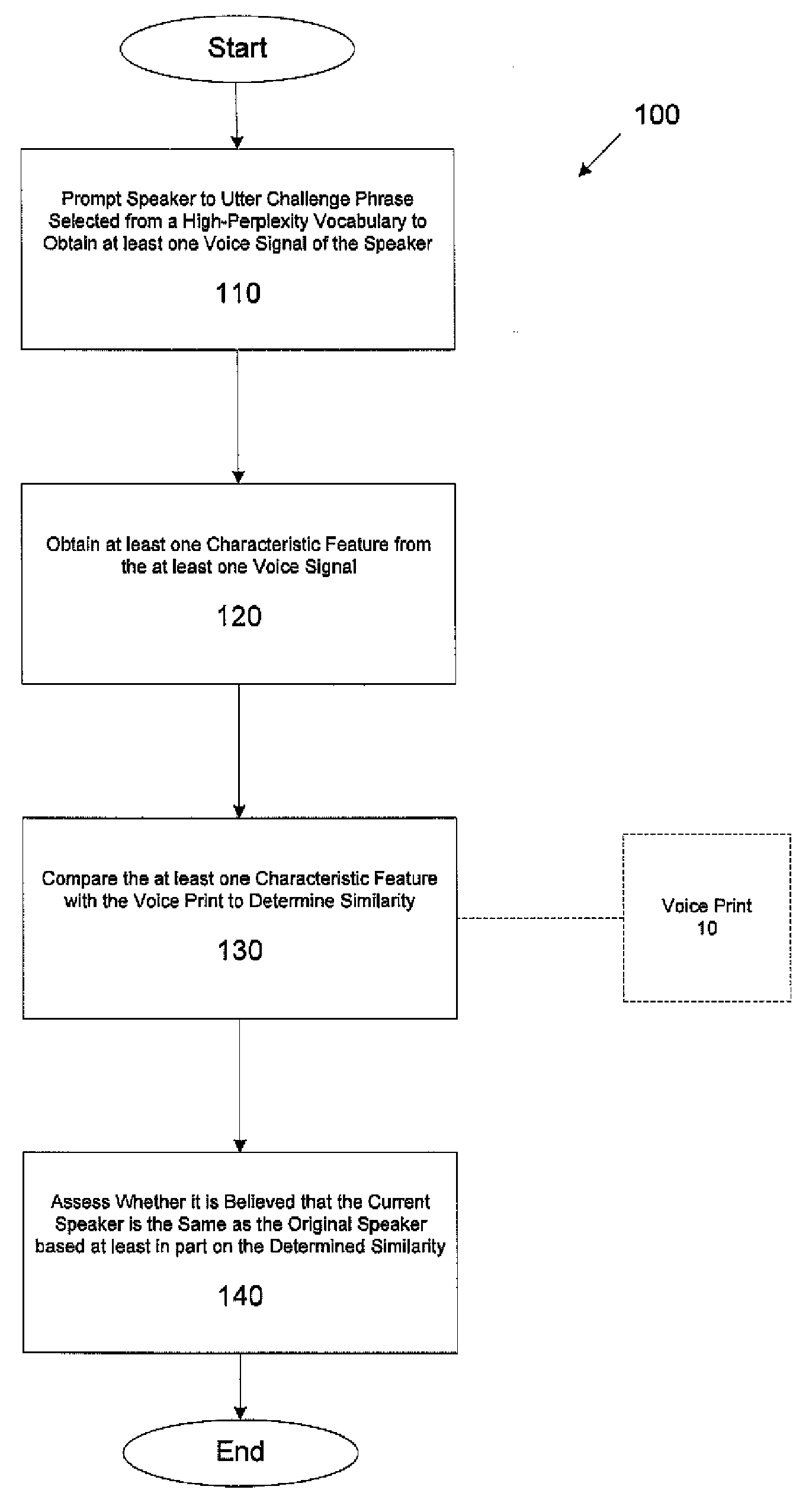
Speaker verification methods and apparatus
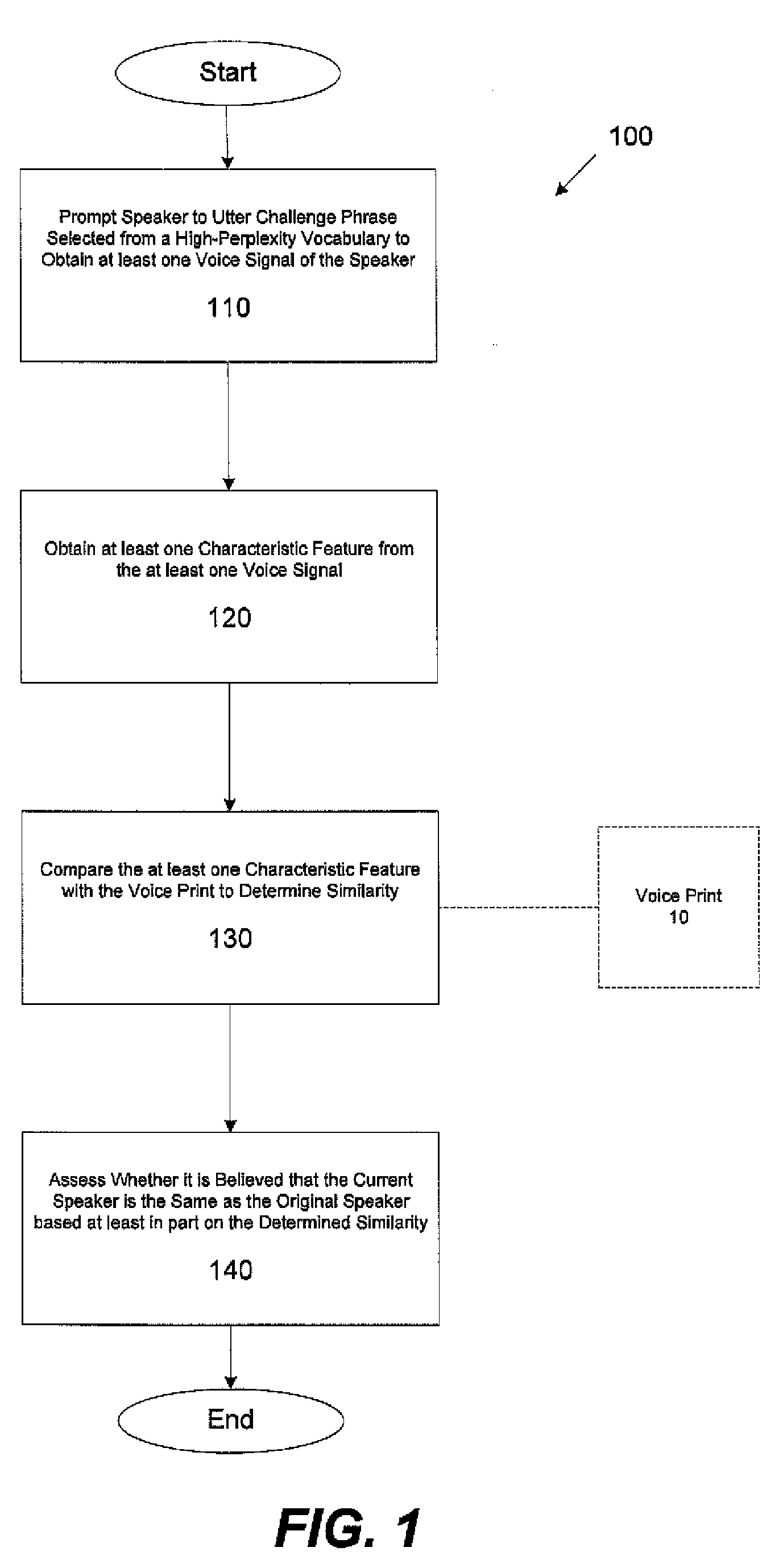
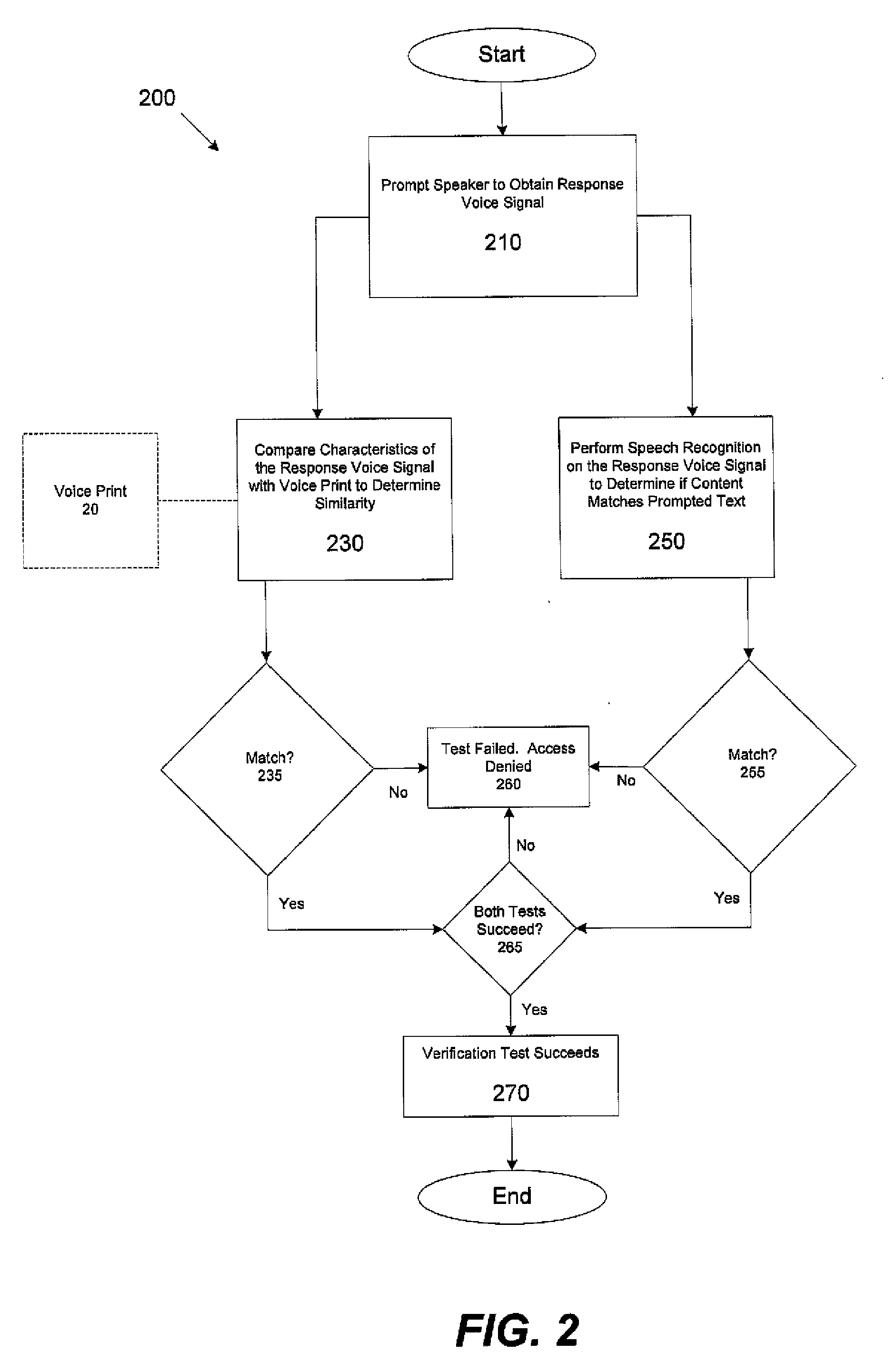
In one aspect, a method for determining a validity of an identity asserted by a speaker using a voice print that models speech of a user whose identity the speaker is asserting is provided. The method comprises acts of performing a first verification stage comprising acts of obtaining a first voice signal from the speaker uttering at least one first challenge utterance; and comparing at least one characteristic feature of the first voice signal with at least a portion of the voice print to assess whether the at least one characteristic feature of the first voice signal is similar enough to the at least a portion of the voice print to conclude that the first voice signal was obtained from an utterance by the user. The method further comprises performing a second verification stage if it is concluded in the first verification stage that the first voice signal was obtained from an utterance by the user, the second verification stage comprising acts of adapting at least one parameter of the voice print based, at least in part, on the first voice signal to obtain an adapted voice print, obtaining a second voice signal from the speaker uttering at least one second challenge utterance, and comparing at least one characteristic feature of the second voice signal with at least a portion of the adapted voice print to assess whether the at least one characteristic feature of the second voice signal is similar enough to the at least a portion of the adapted voice print to conclude that the second voice signal was obtained from an utterance by the user.
Owner:NUANCE COMM INC
Speaker verification
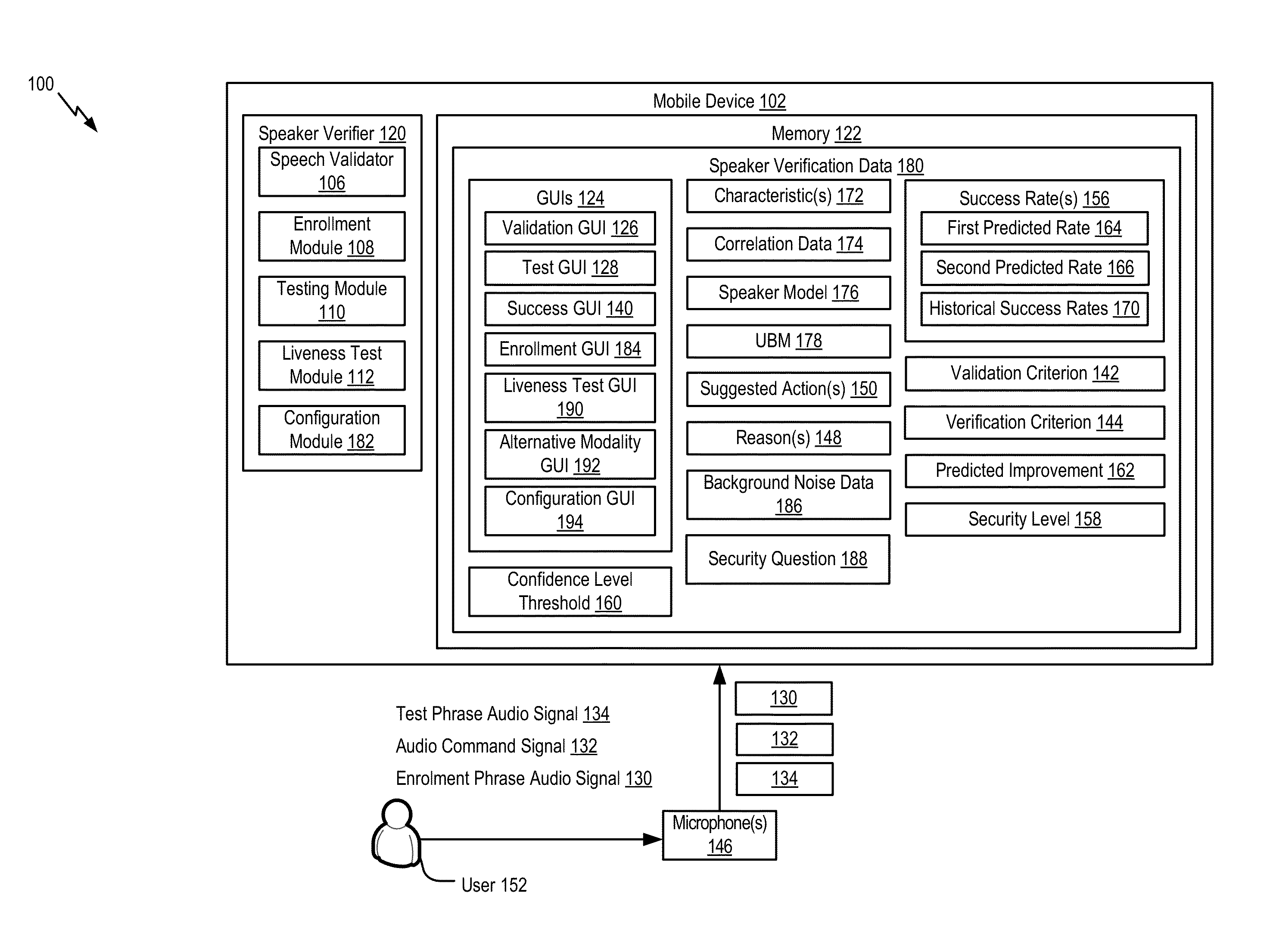
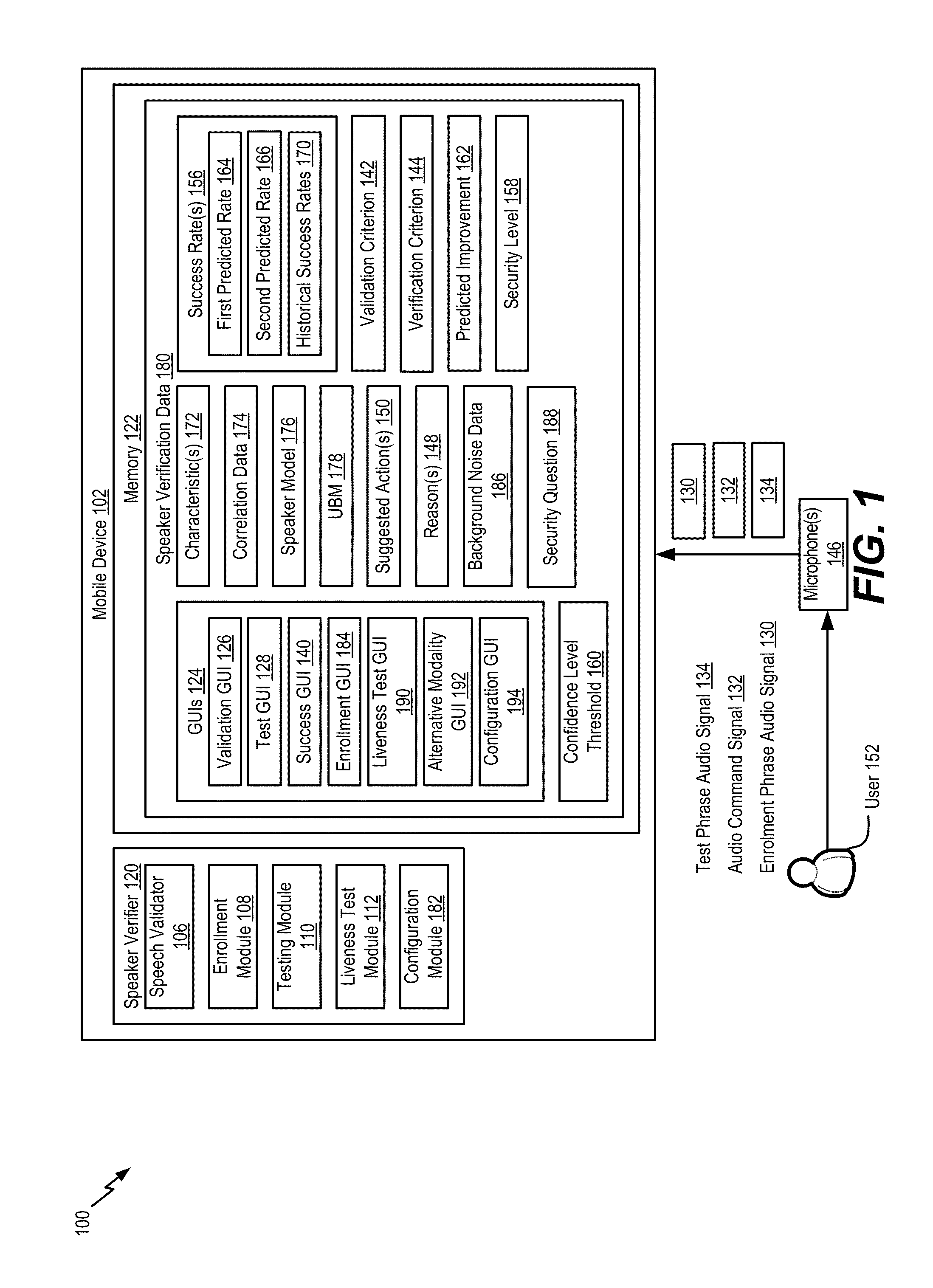
A device includes a memory, a receiver, a processor, and a display. The memory is configured to store a speaker model. The receiver is configured to receive an input audio signal. The processor is configured to determine a first confidence level associated with a first portion of the input audio signal based on the speaker model. The processor is also configured to determine a second confidence level associated with a second portion of the input audio signal based on the speaker model. The display is configured to present a graphical user interface associated with the first confidence level or associated with the second confidence level.
Owner:QUALCOMM INC
Voice print system and method
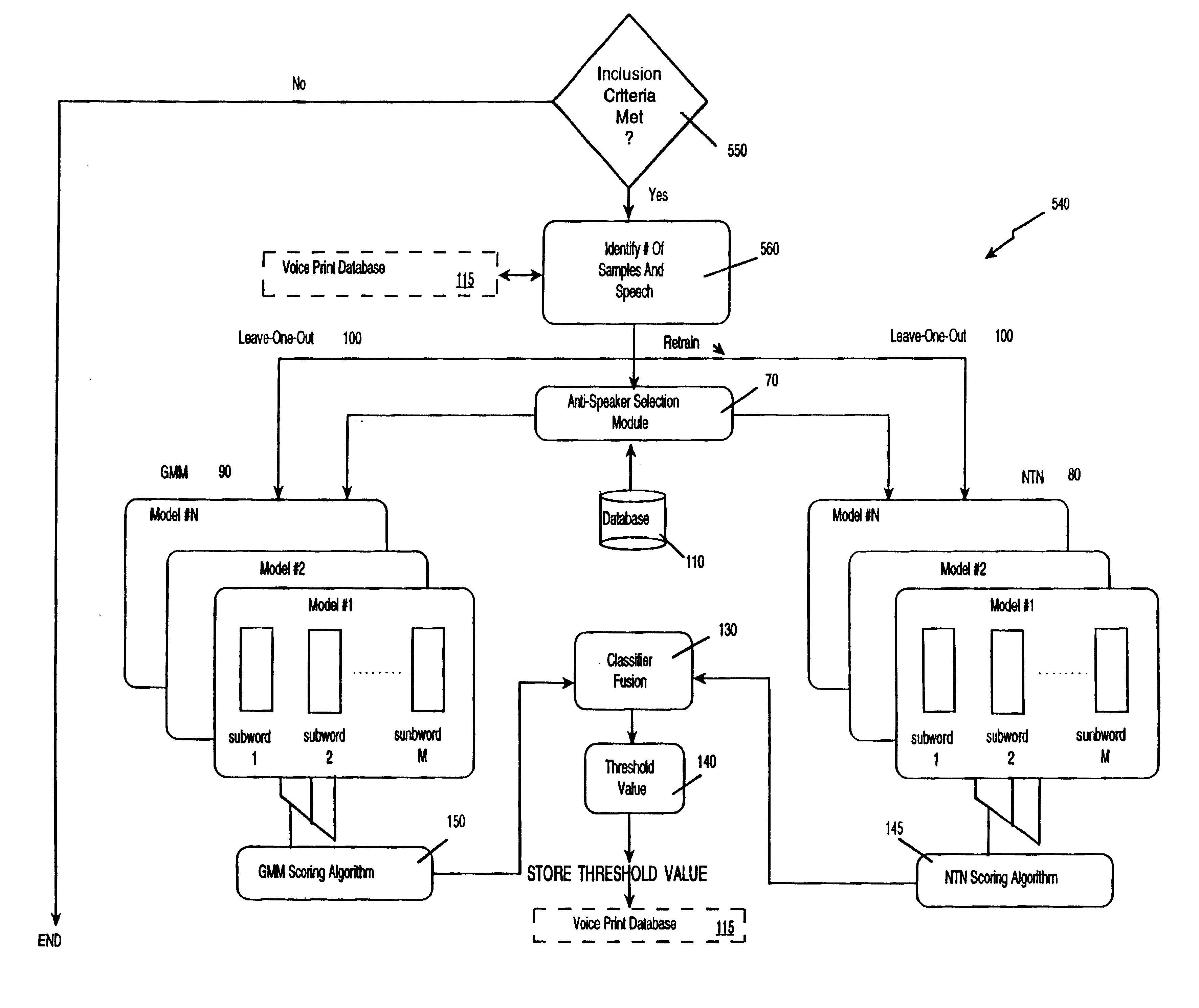
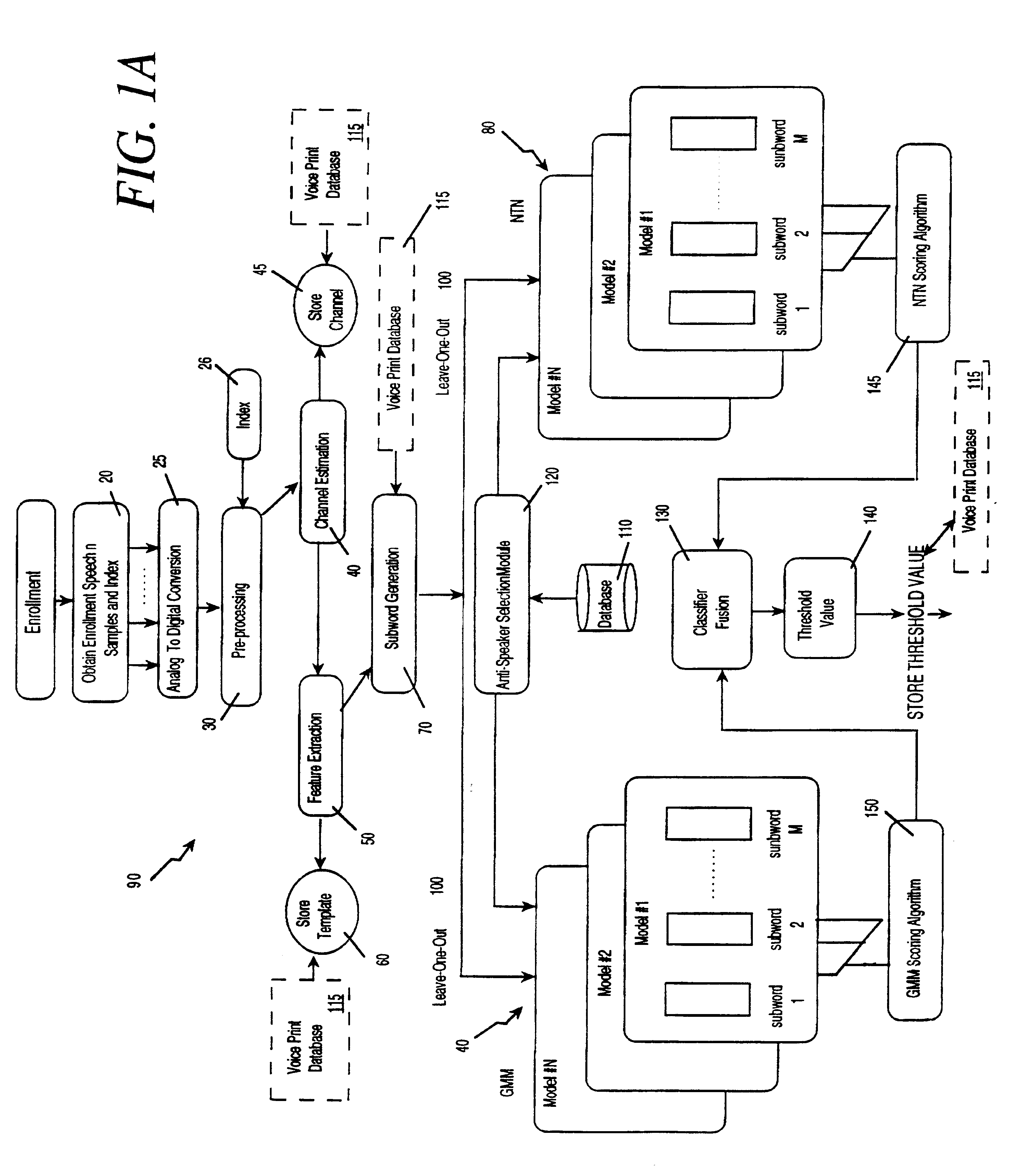
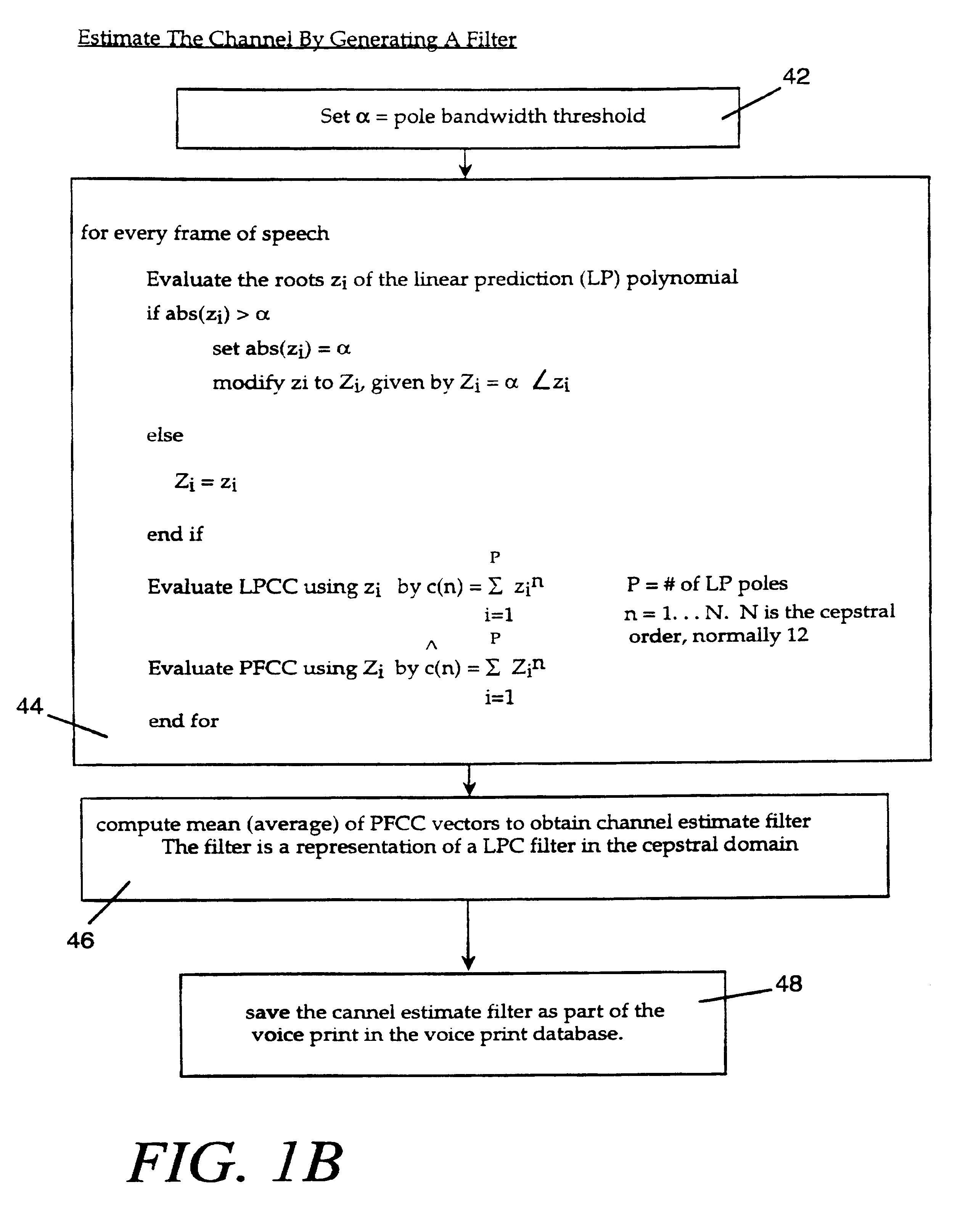
InactiveUS20030009333A1Increase in sizeImprove generalization abilitySpeech recognitionSpeech segmentationSpeaker verification
The voice print system of the present invention is a subword-based, text-dependent automatic speaker verification system that embodies the capability of user-selectable passwords with no constraints on the choice of vocabulary words or the language. Automatic blind speech segmentation allows speech to be segmented into subword units without any linguistic knowledge of the password. Subword modeling is performed using a multiple classifiers. The system also takes advantage of such concepts as multiple classifier fusion and data resampling to successfully boost the performance. Key word / key phrase spotting is used to optimally locate the password phrase. Numerous adaptation techniques increase the flexibility of the base system, and include: channel adaptation, fusion adaptation, model adaptation and threshold adaptation.
Owner:SPEECHWORKS INT
Speaker verification system
ActiveUS20100268537A1High precisionLess-powerful microprocessorProgramme controlElectric signal transmission systemsFeature extractionPattern matching
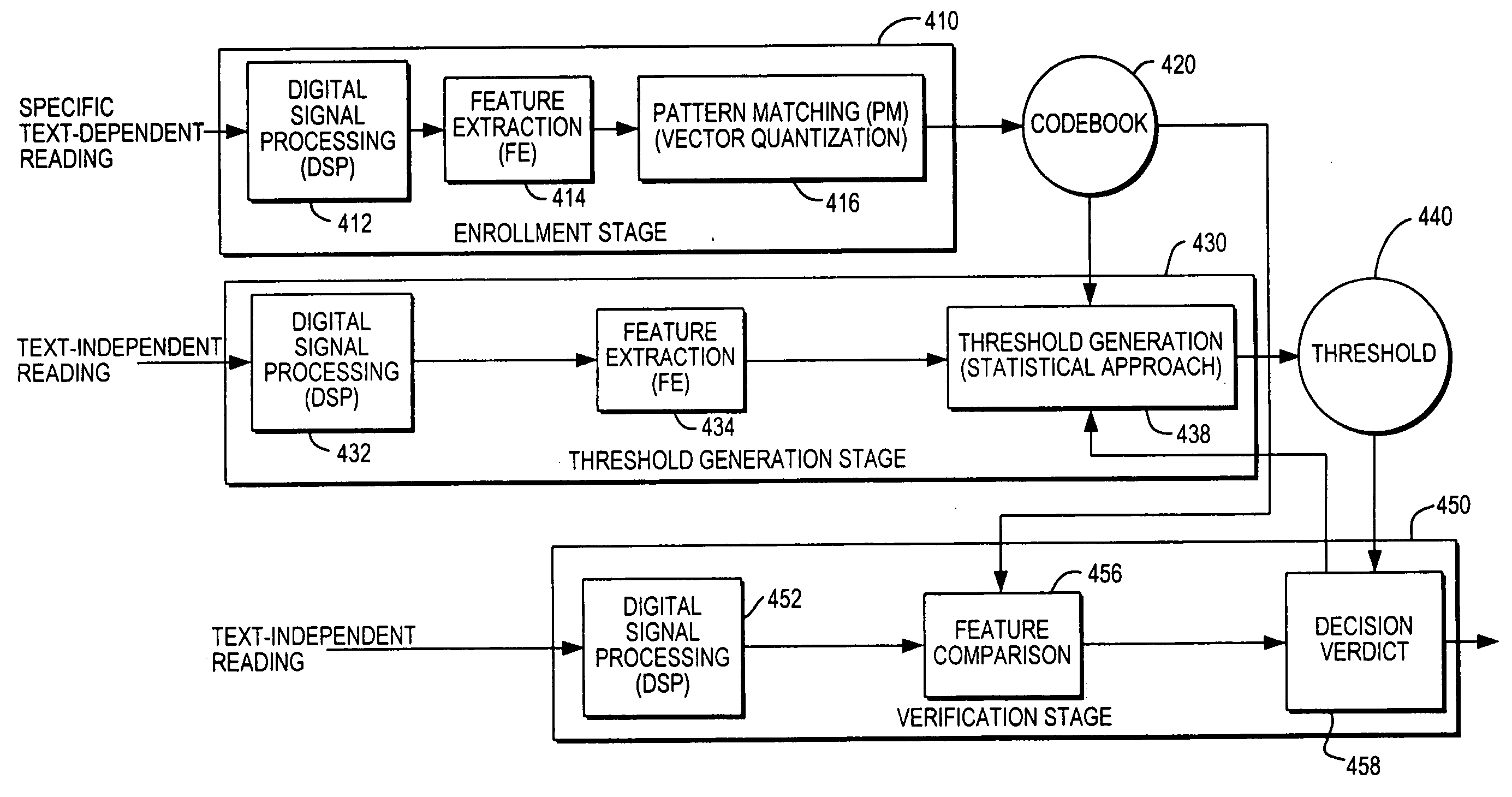
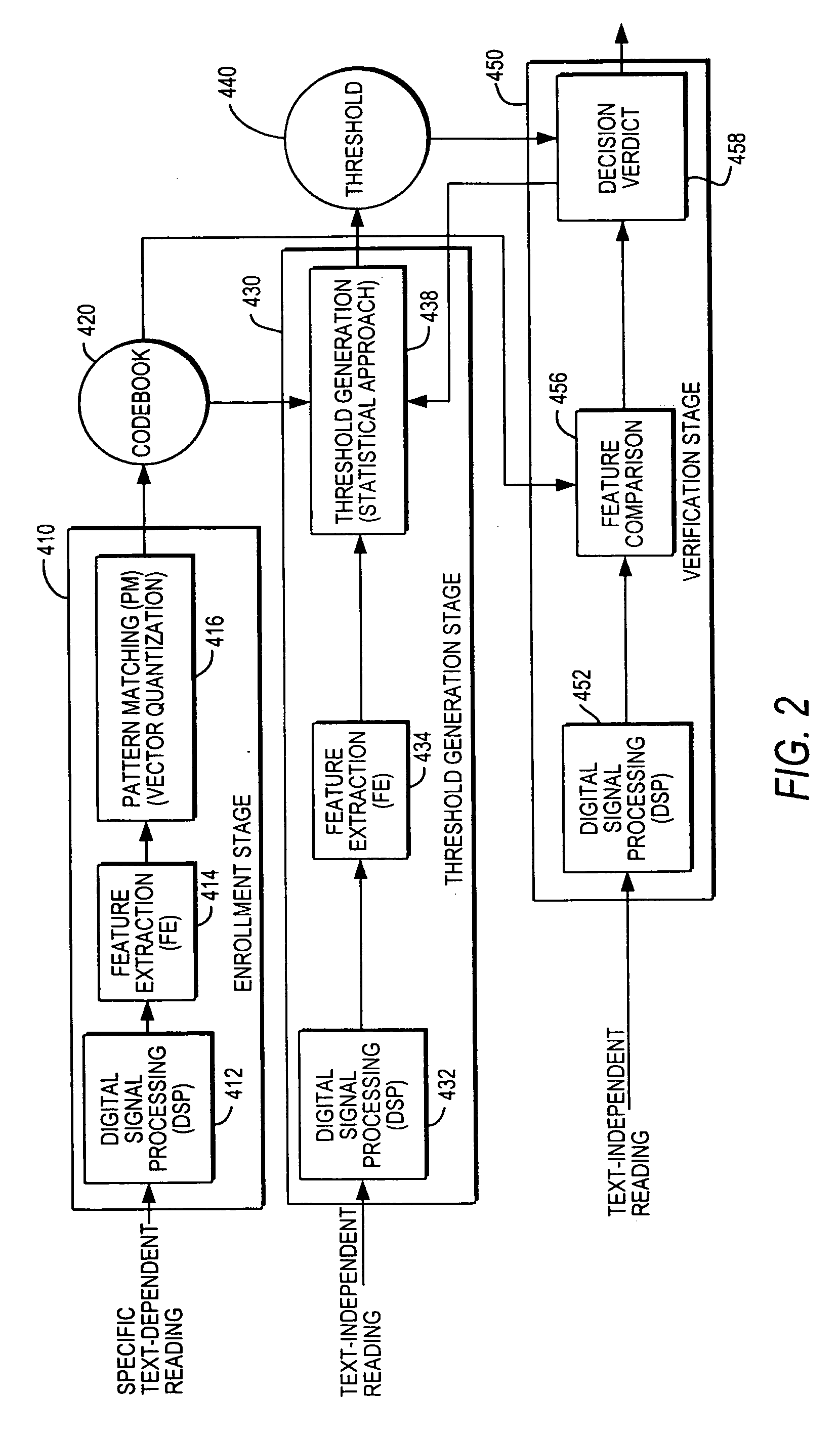
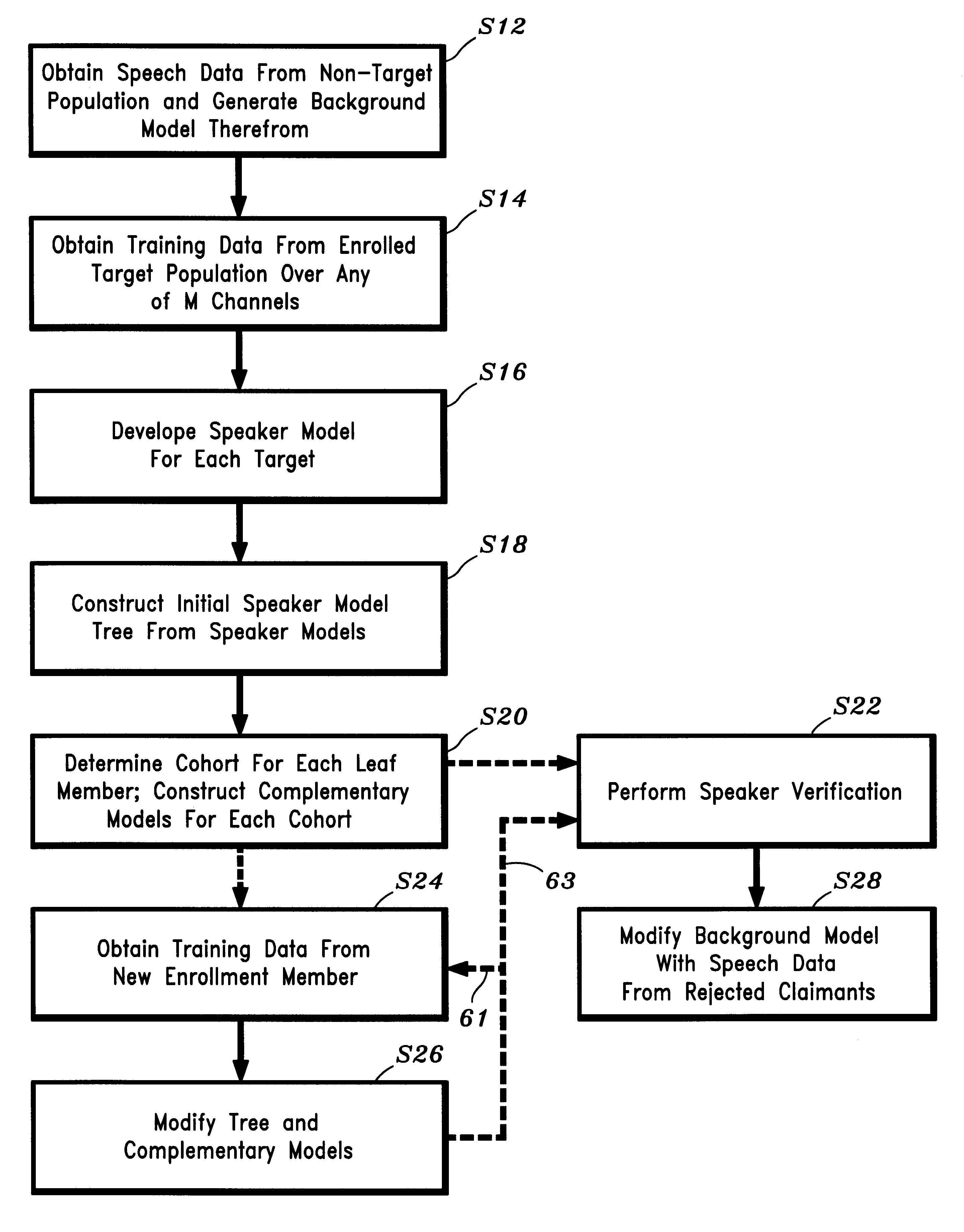
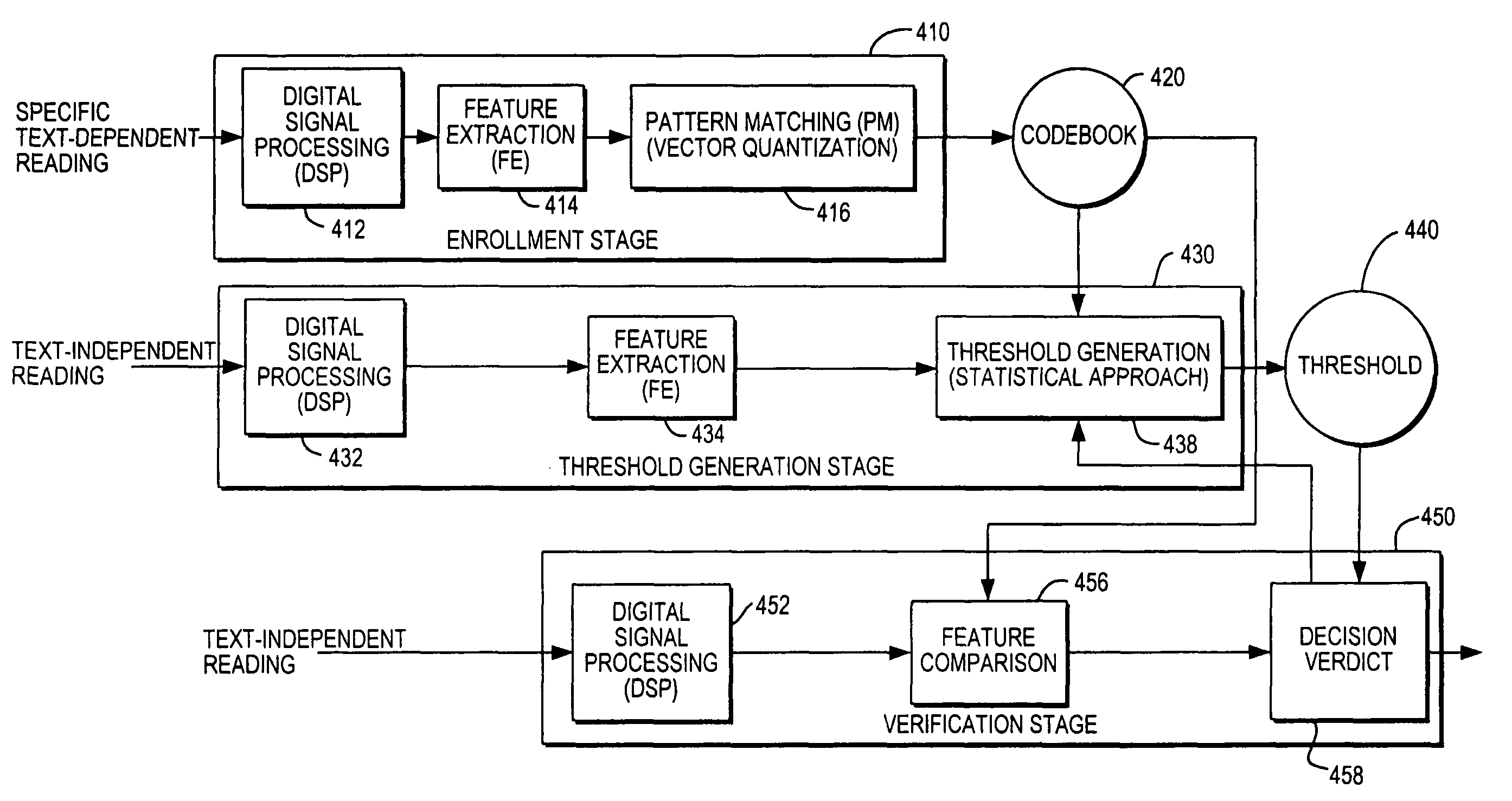
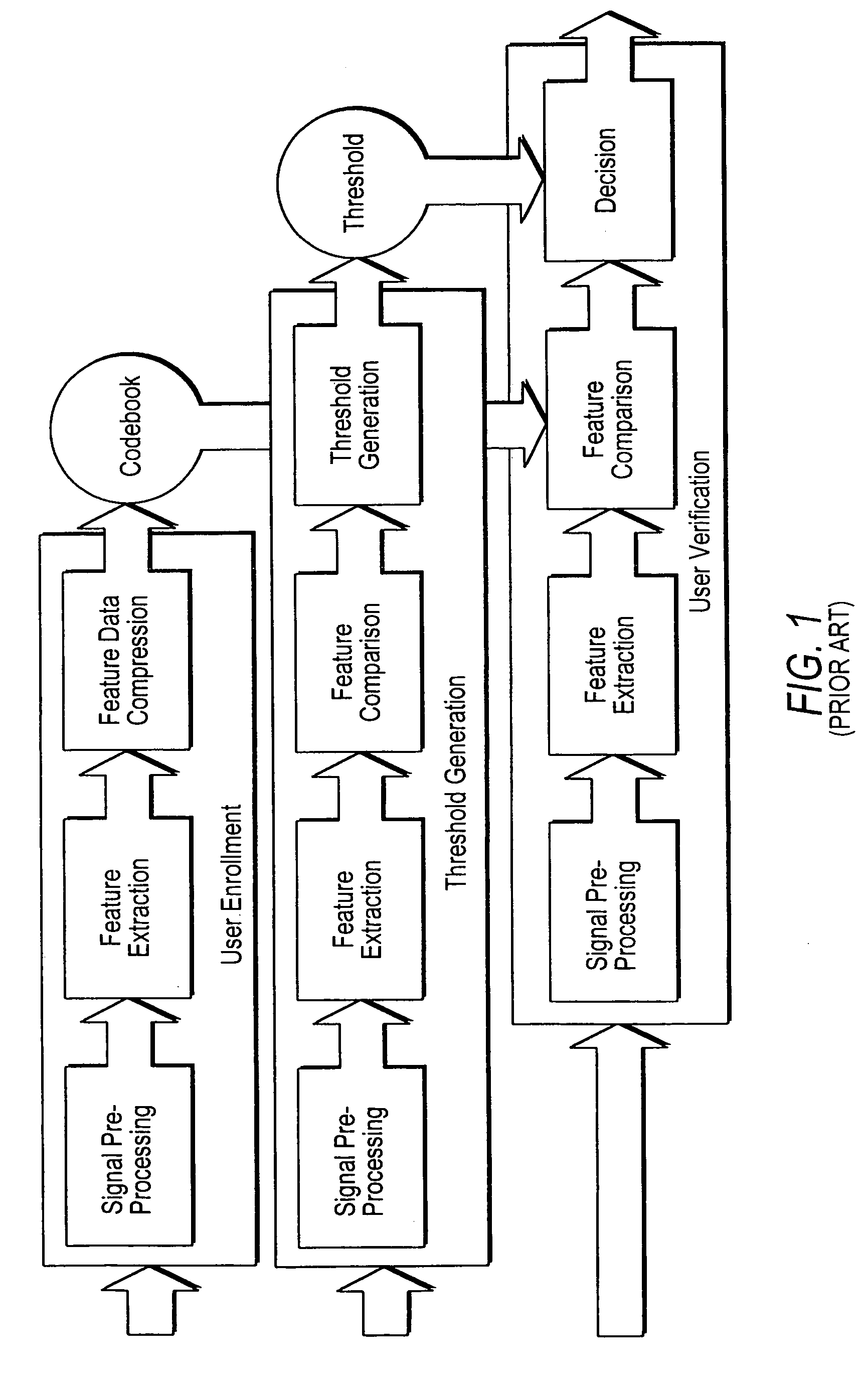
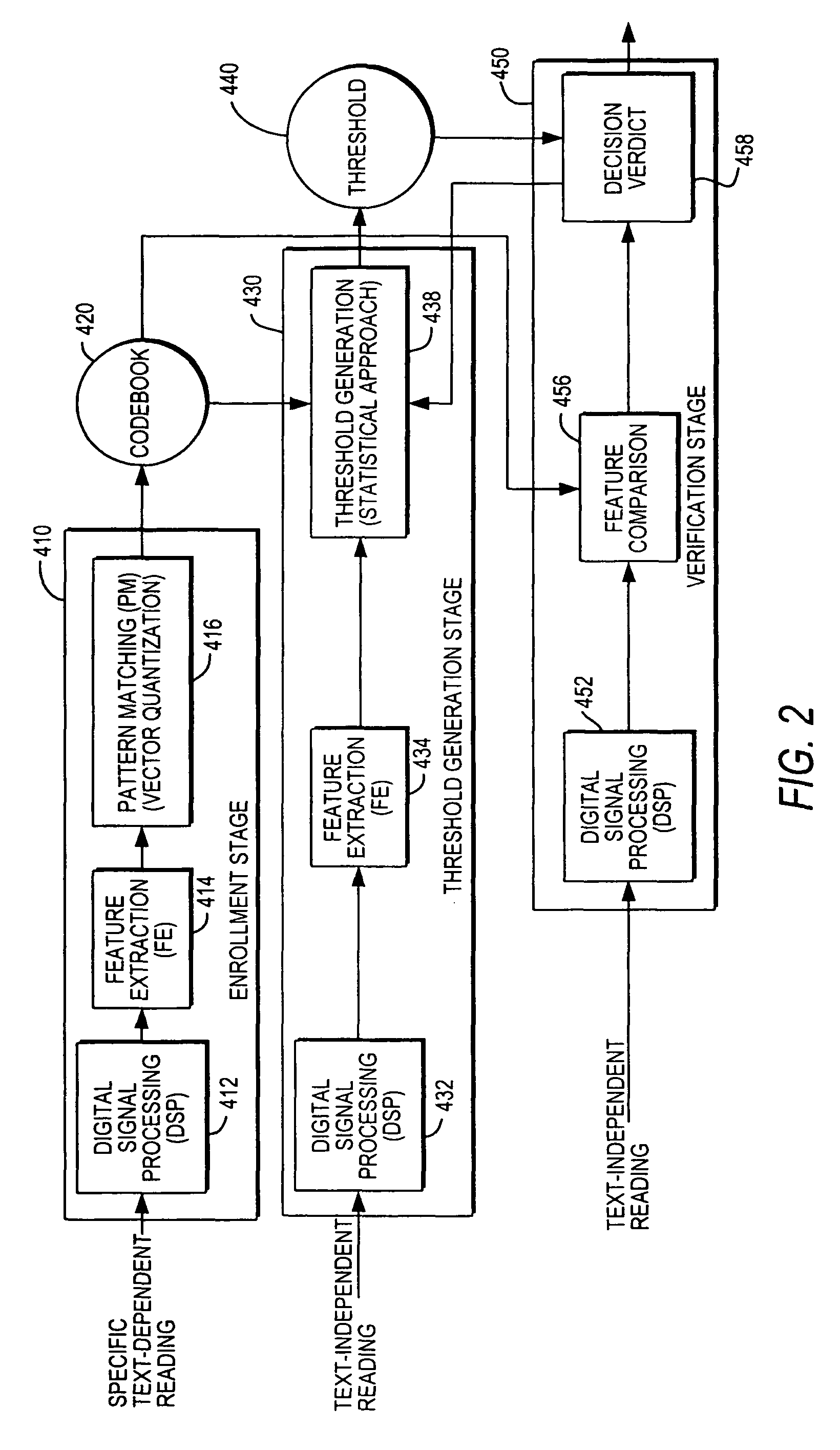
A text-independent speaker verification system utilizes mel frequency cepstral coefficients analysis in the feature extraction blocks, template modeling with vector quantization in the pattern matching blocks, an adaptive threshold and an adaptive decision verdict and is implemented in a stand-alone device using less powerful microprocessors and smaller data storage devices than used by comparable systems of the prior art.
Owner:SAUDI ARABIAN OIL CO
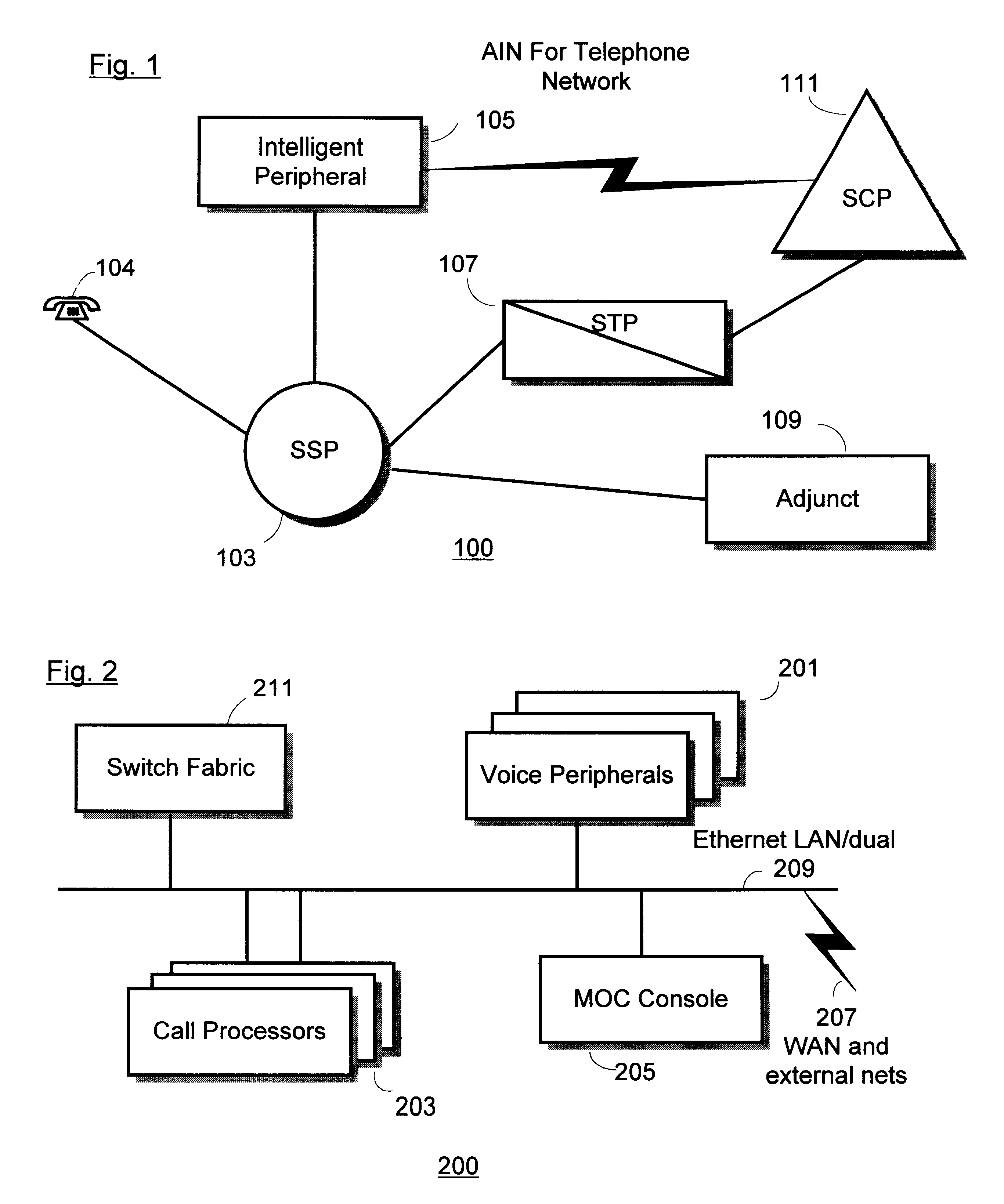
Speaker verification for authorizing updates to user subscription service received by internet service provider (ISP) using an intelligent peripheral (IP) in an advanced intelligent network (AIN)
InactiveUS6337899B1Multiplex system selection arrangementsSpecial service provision for substationFrequency spectrumMatch algorithms
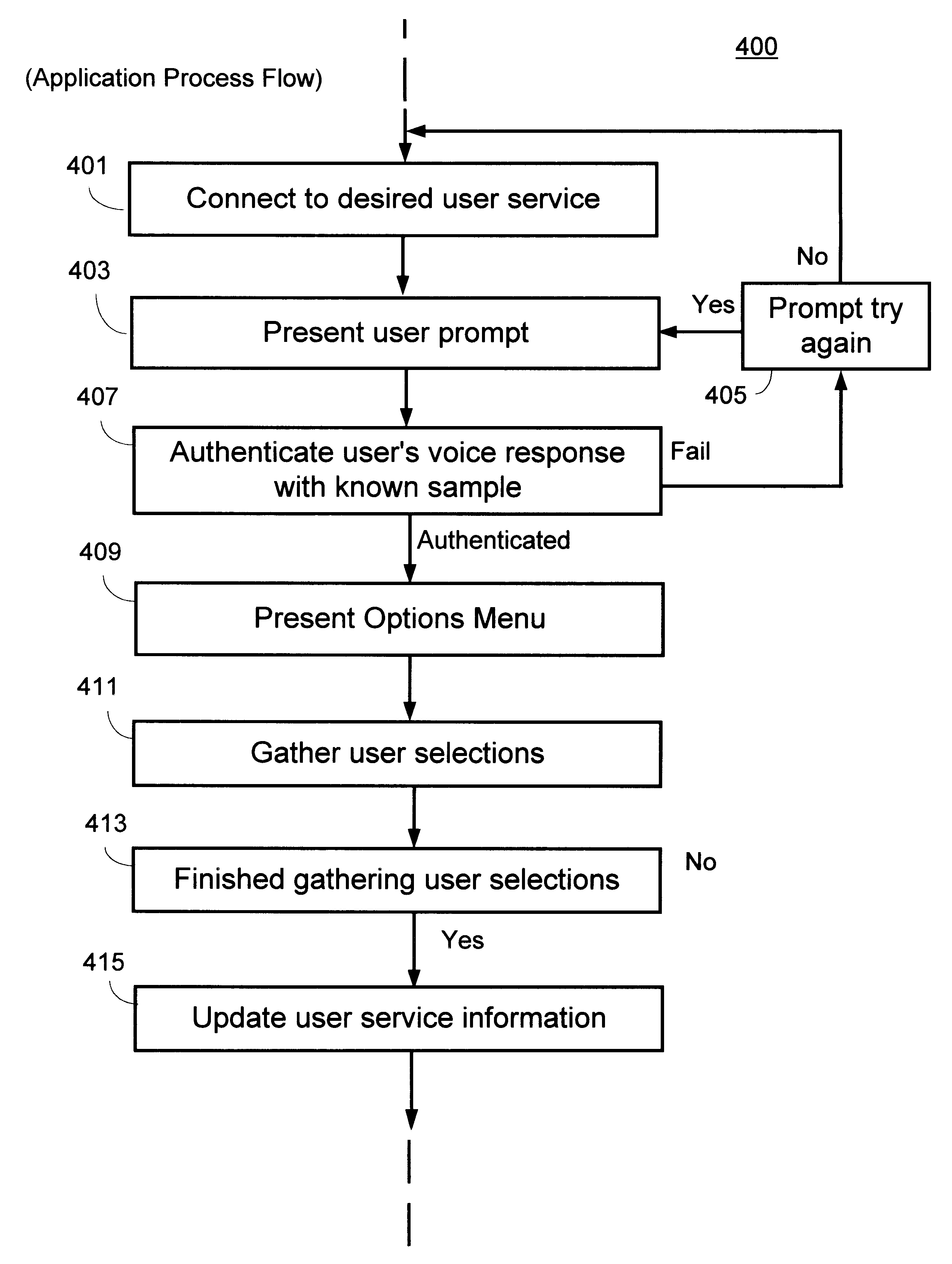
A method for controlling subscription services delivered to a user by an Internet Service Provider (ISP) coupled to an Automated Intelligent Network (AIN) telephone system with at least one central office switching system. An intelligent peripheral subsystem is connected to the central office switching system, via a call connection channel. The intelligent peripheral subsystem providing at least one auxiliary call processing capability via the call connection channel and provides a telephony speaker authentication method for selectively authorizing updates to user subscription services types provided by the ISP, wherein each of the subscription services types include one or more service options. The method for controlling subscription services including: a) prompting for a voice response; b) authenticating a user's voice response pattern by performing a speaker-dependent cepstrum matching algorithm with previously stored samples of the user's voice response, and if the user's voice response pattern is positively authenticated with previously stored samples, then performing the steps of: c) presenting a menu of user subscription types, each with available AIN service options; and d) responding to a user selection of at least one user subscription types, each with service option, by activating a service option selected by the user, wherein the service option is governed by said ISP by regulating one or more Uniform Resource Locator (URL) addresses received by a user subscriber device from said ISP over a telecommunication line.
Owner:IBM CORP
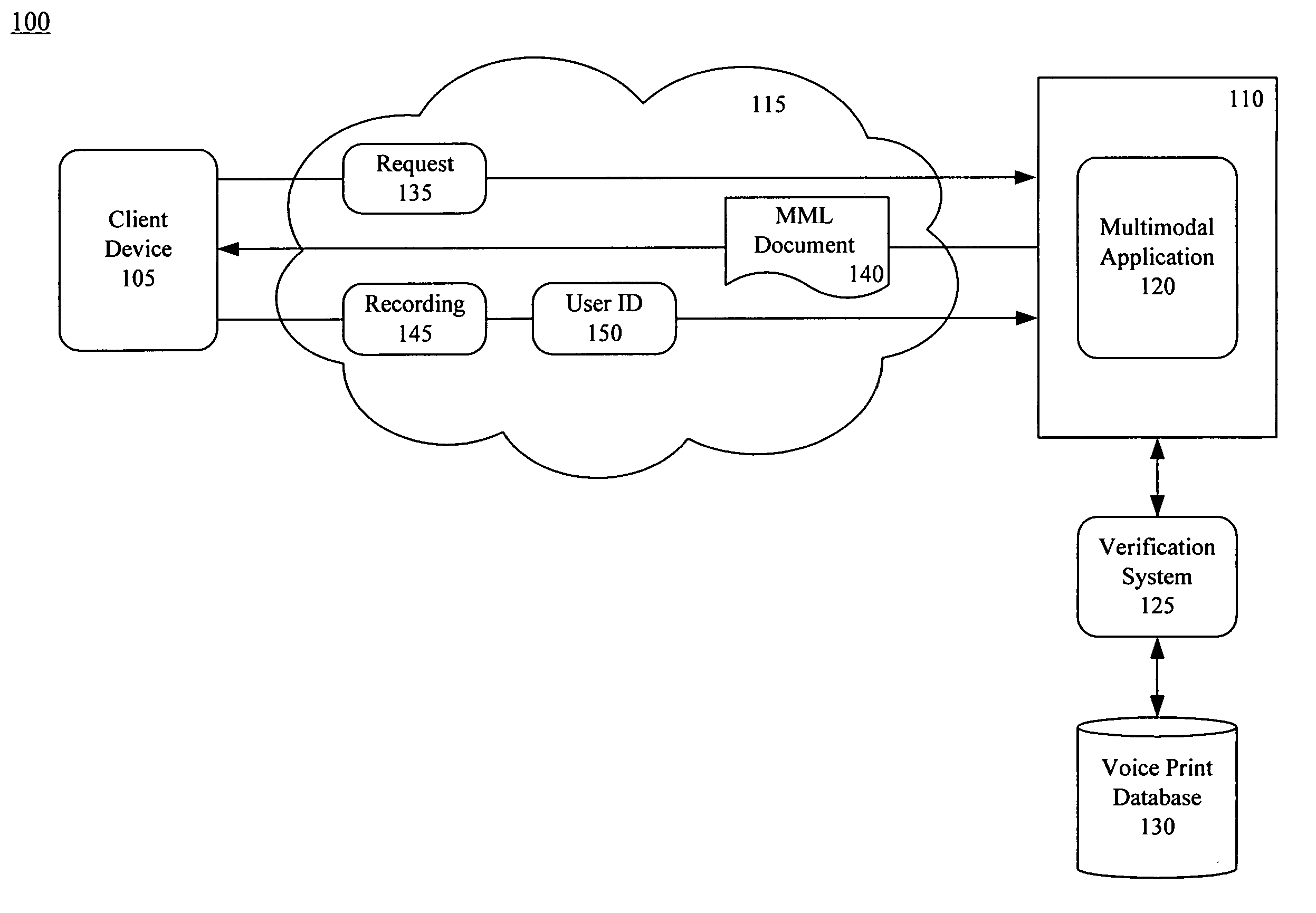
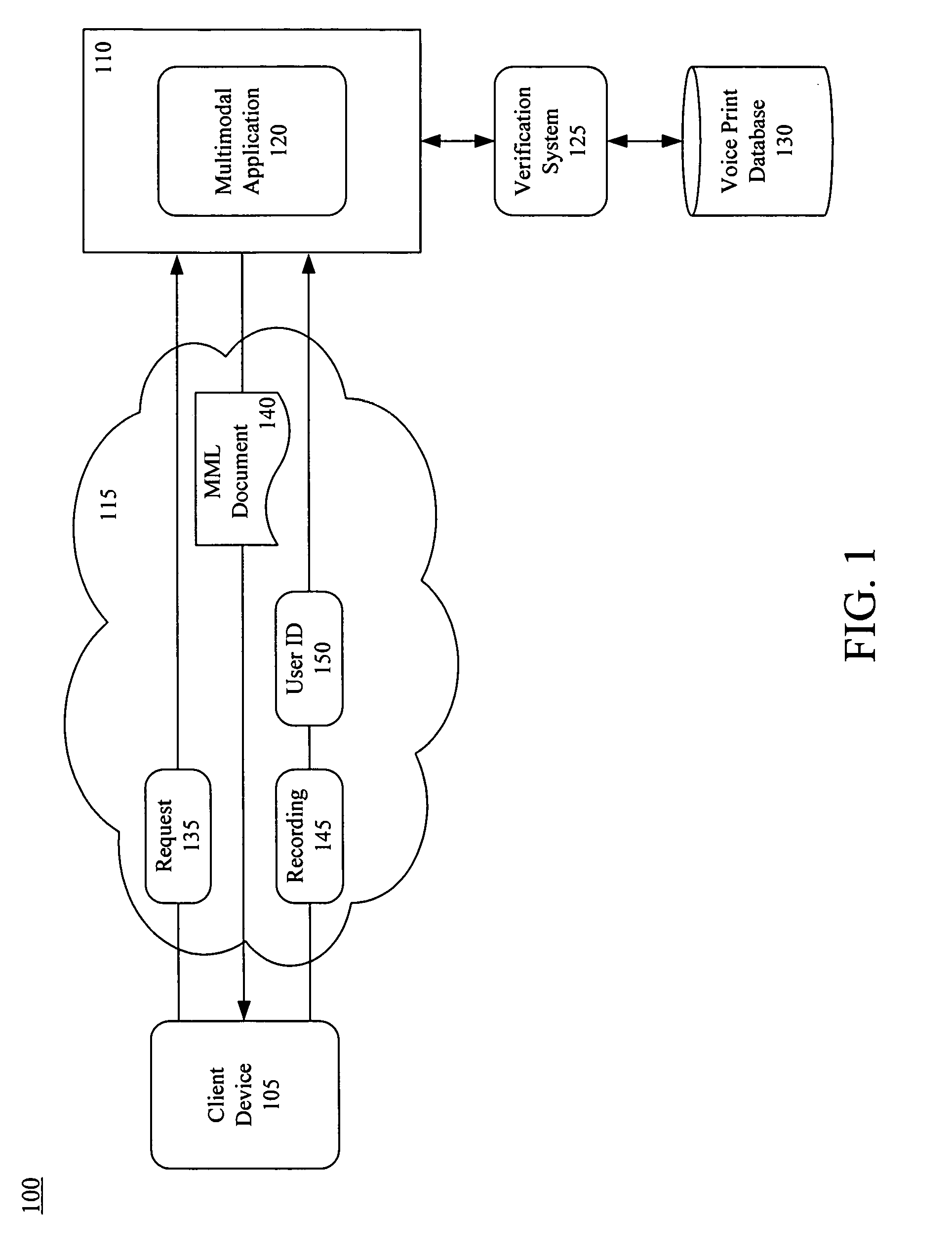
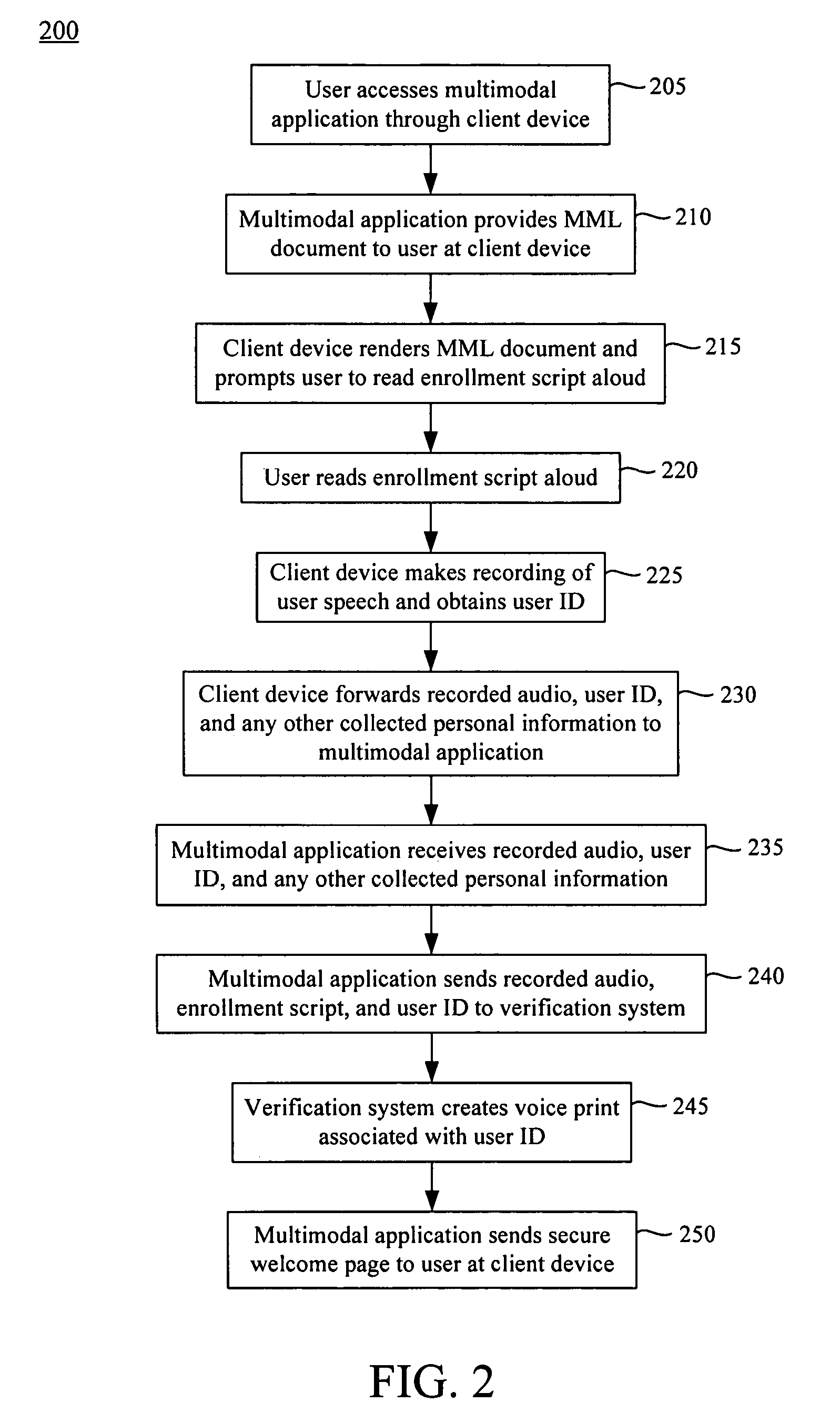
Verifying a user using speaker verification and a multimodal web-based interface
A method of verifying a user identity using a Web-based multimodal interface can include sending, to a remote computing device, a multimodal markup language document that, when rendered by the remote computing device, queries a user for a user identifier and causes audio of the user's voice to be sent to a multimodal, Web-based application. The user identifier and the audio can be received at about a same time from the client device. The audio can be compared with a voice print associated with the user identifier. The user at the remote computing device can be selectively granted access to the system according to a result obtained from the comparing step.
Owner:NUANCE COMM INC
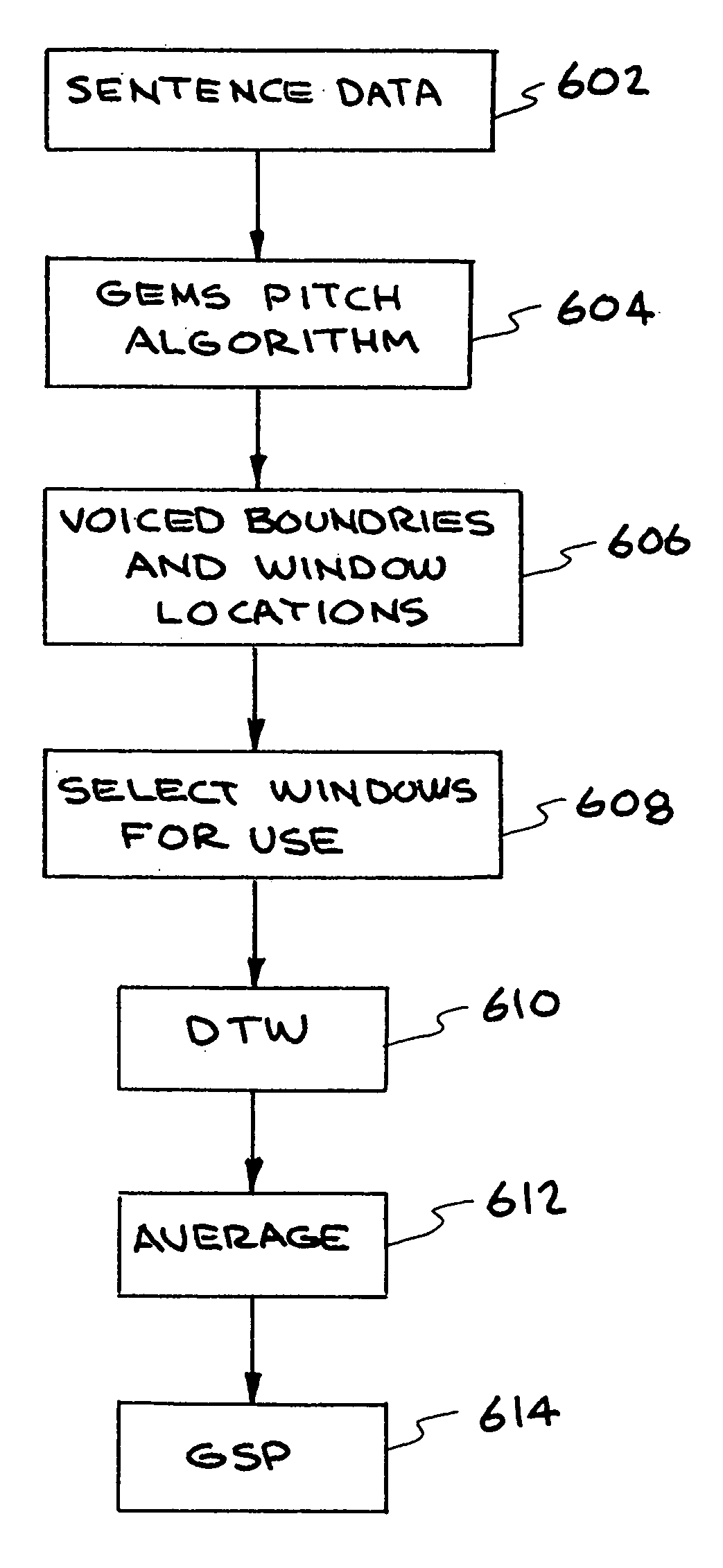
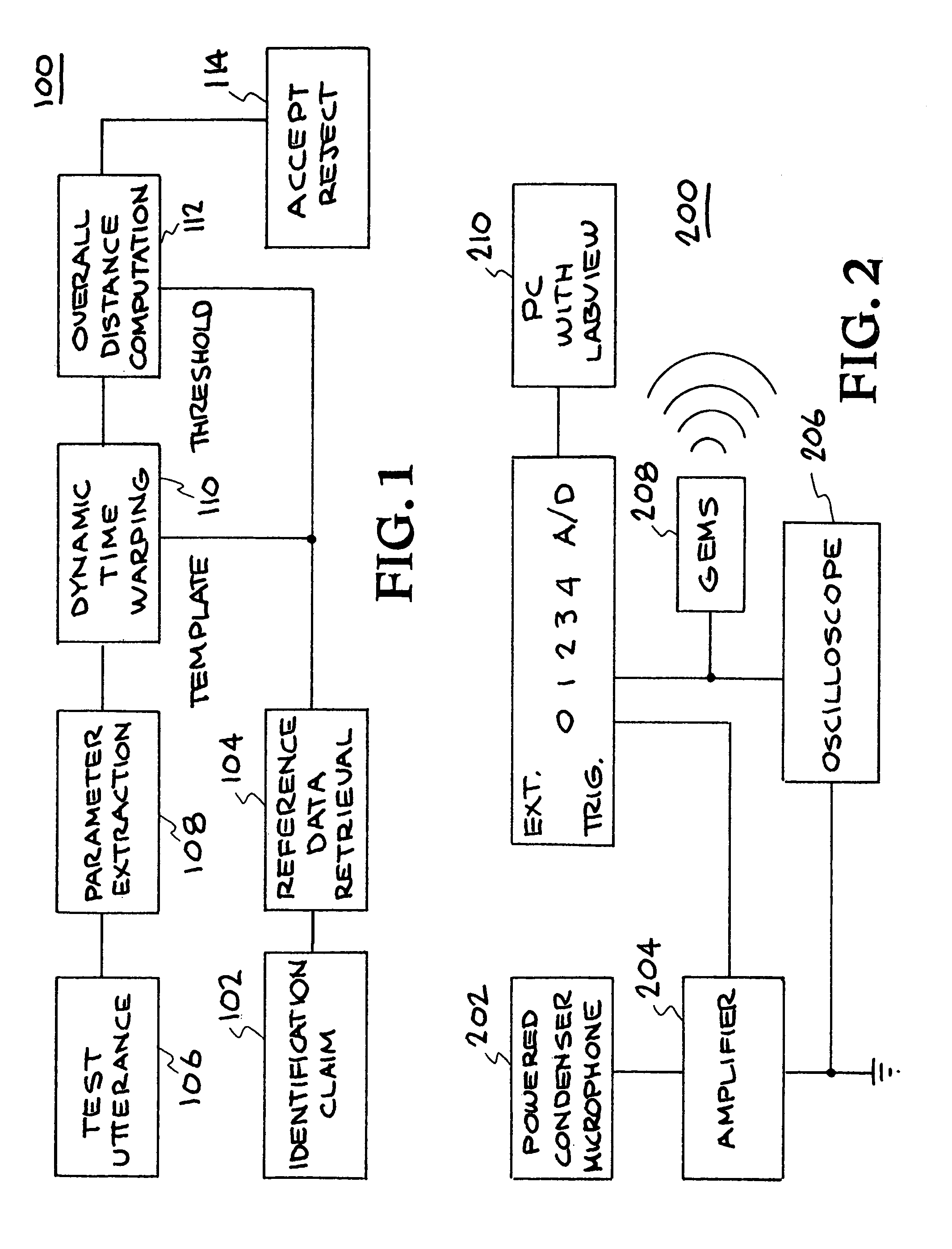
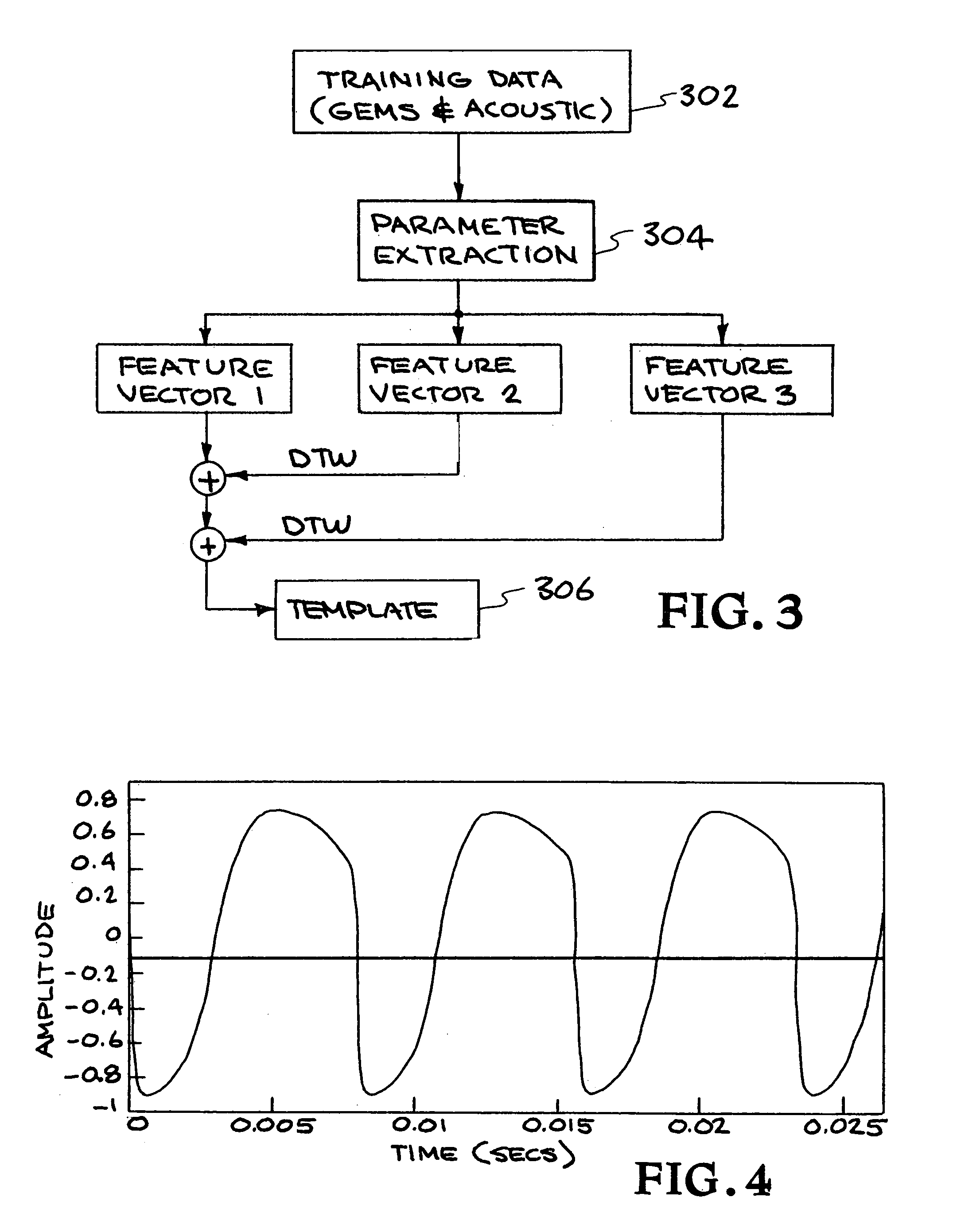
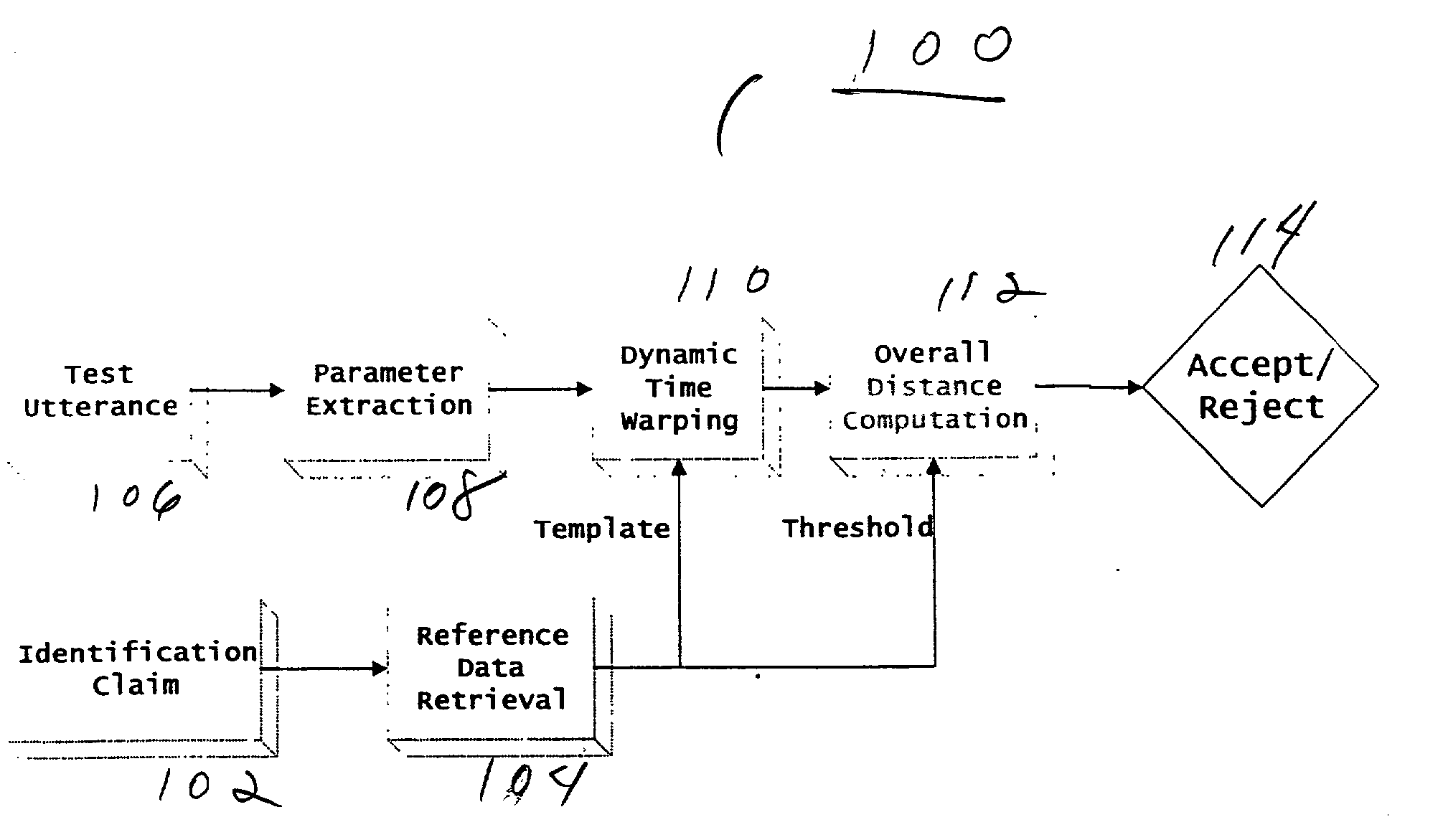
Speaker verification system using acoustic data and non-acoustic data
A method and system for speech characterization. One embodiment includes a method for speaker verification which includes collecting data from a speaker, wherein the data comprises acoustic data and non-acoustic data. The data is used to generate a template that includes a first set of “template” parameters. The method further includes receiving a real-time identity claim from a claimant, and using acoustic data and non-acoustic data from the identity claim to generate a second set of parameters. The method further includes comparing the first set of parameters to the set of parameters to determine whether the claimant is the speaker. The first set of parameters and the second set of parameters include at least one purely non-acoustic parameter, including a non-acoustic glottal shape parameter derived from averaging multiple glottal cycle waveforms.
Owner:LAWRENCE LIVERMORE NAT SECURITY LLC
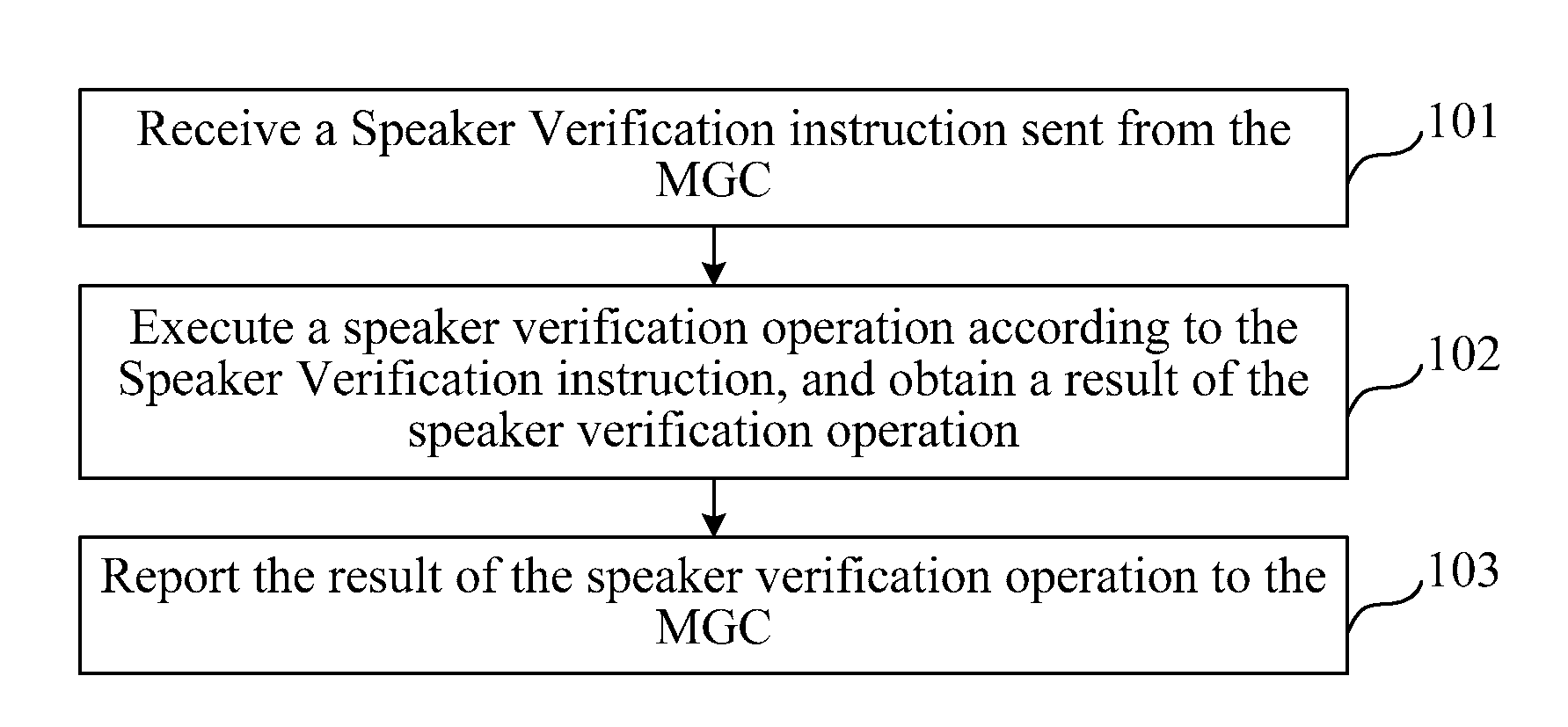
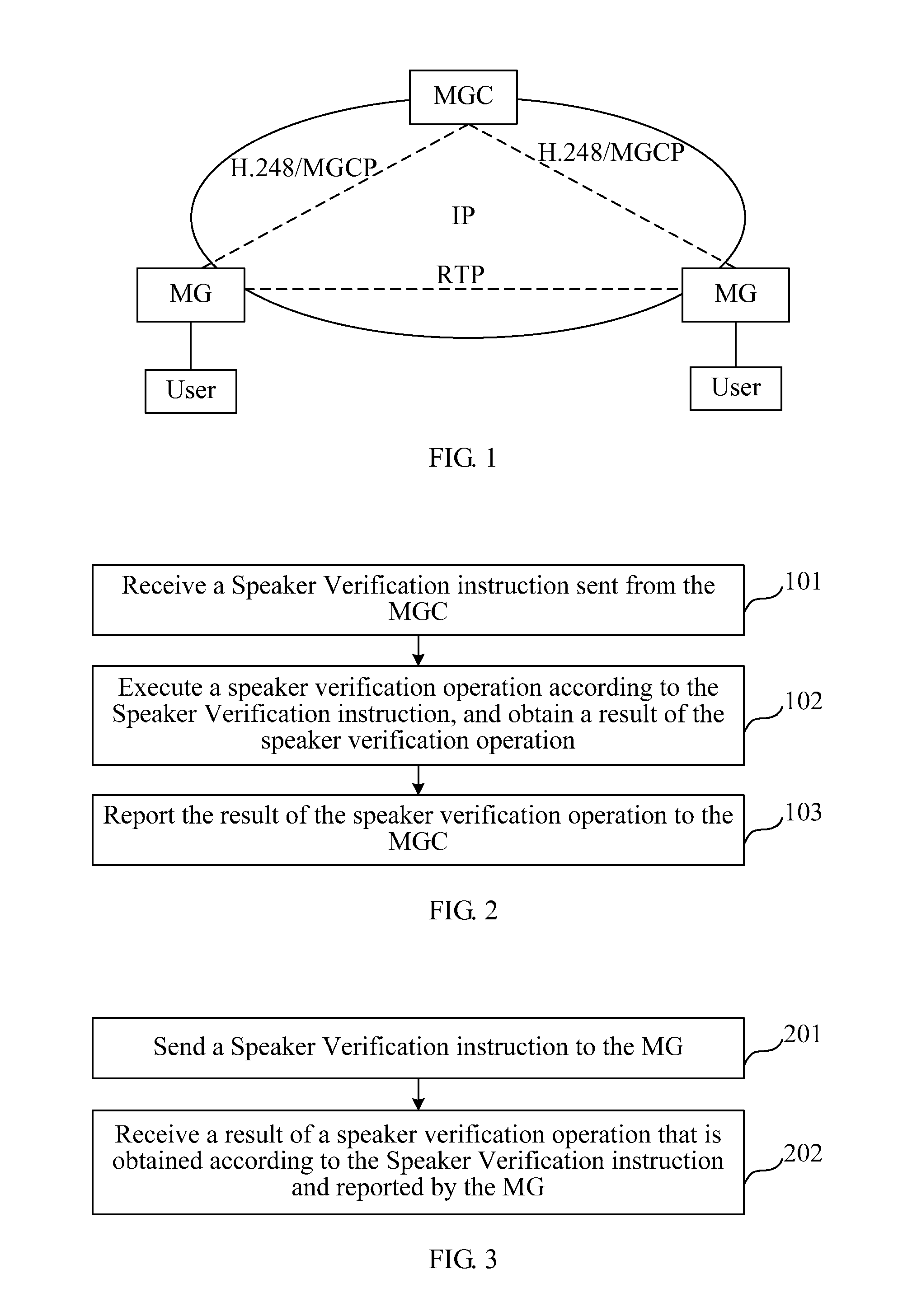
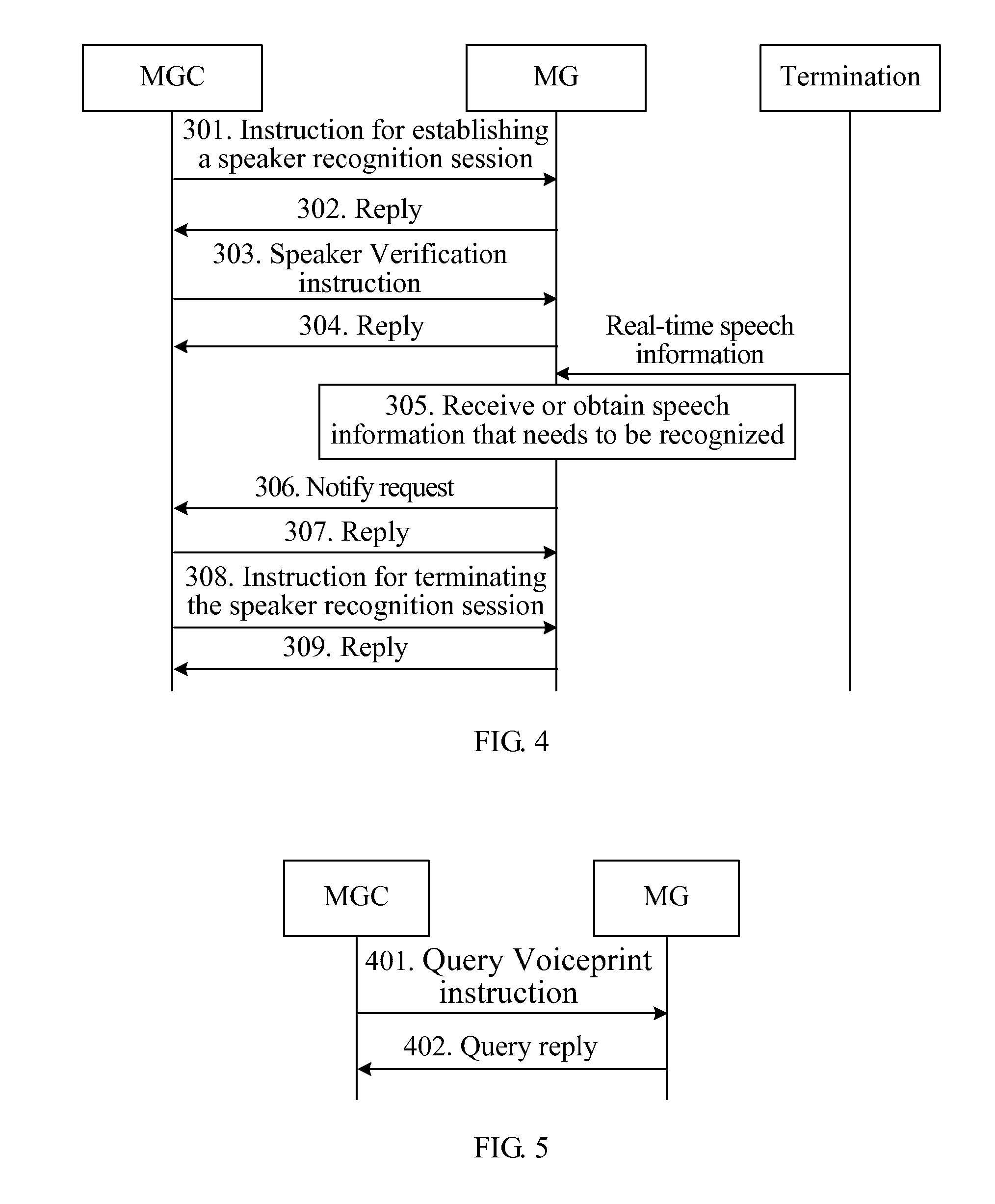
Method, device, and system for speaker recognition
A method, device, and system for speaker recognition are provided. The method includes: receiving a Speaker Verification instruction sent from a Media Gateway Controller (MGC) (101); executing a speaker verification operation according to the Speaker Verification instruction, and obtaining a result of the speaker verification operation (102); and reporting the result of the speaker verification operation to the MGC (103).
Owner:HUAWEI TECH CO LTD
Voice controlled messaging system and processing method
InactiveUS6088428AImprove noise immunityRobust error handlingUnauthorised/fraudulent call preventionSpecial service for subscribersPasswordSpeaker verification
A voice controlled voice-messaging systems permits manipulation of voice messages over the telephone without the need for keypressed commands. Manipulation includes playback of messages, deletion of messages, saving messages, and sending a new message to a recipient from a user-defined list. Access to the messaging system is by spoken password. Voice input also allows the following functions: enrollment of a spoken password; granting or refusing user access to the system based on verification of the user speaking a password; recognition of spoken utterances of "yes" and "no" in response to prompts by the VMS; recognition of "stop" to interrupt and stop a voice message during playback; enrollment of a spoken personal directory of names of potential message recipients; and recognition of names in the spoken personal directory. The invention uses speaker verification, speaker-independent recognition (SIR) of "yes / no", speaker-independent recognition of "stop" during message playback, and speaker-dependent recognition (SDR) of a limited vocabulary of short phrases such as a list of message recipients' names.
Owner:DIGITAL SOUND CORP
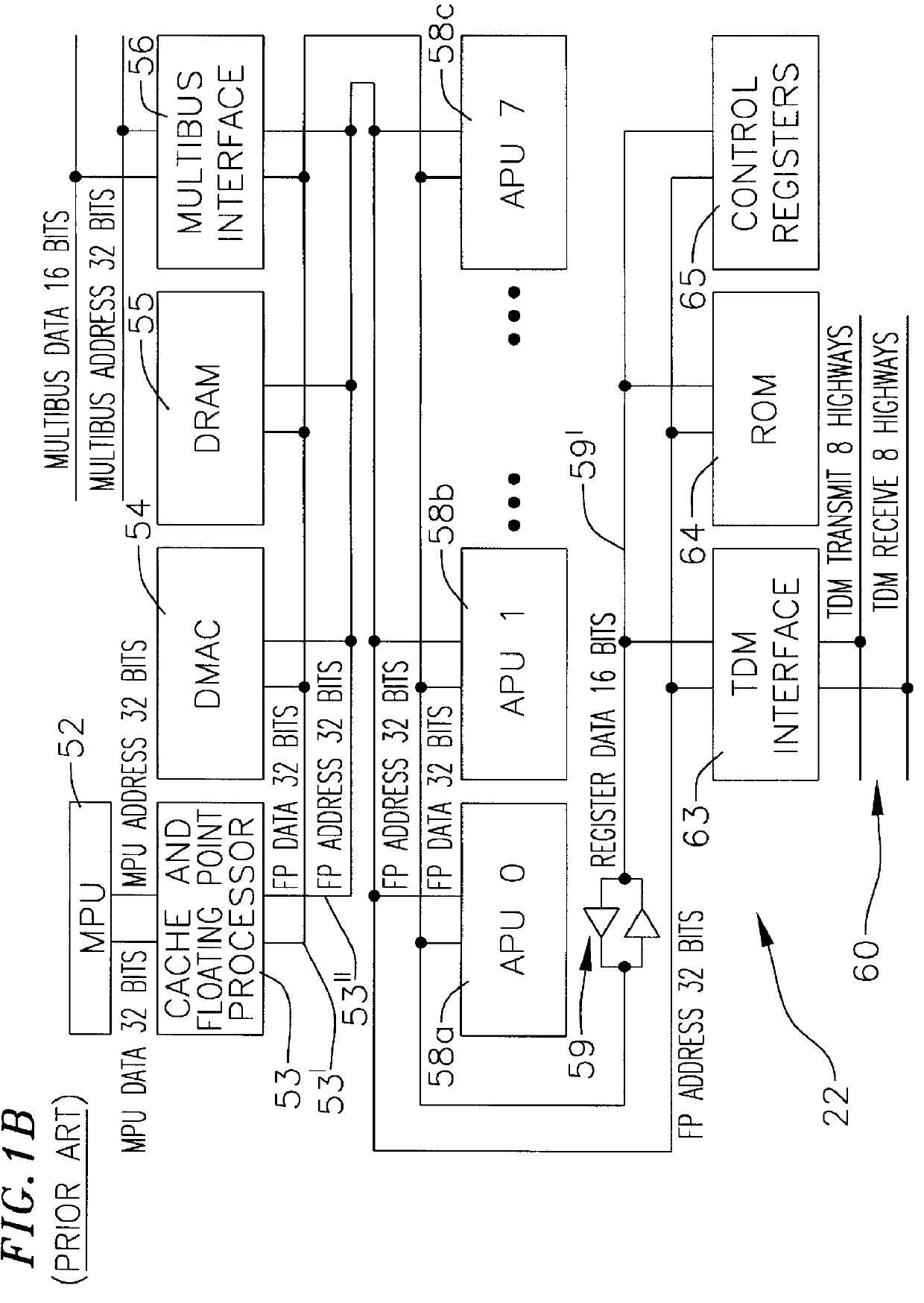
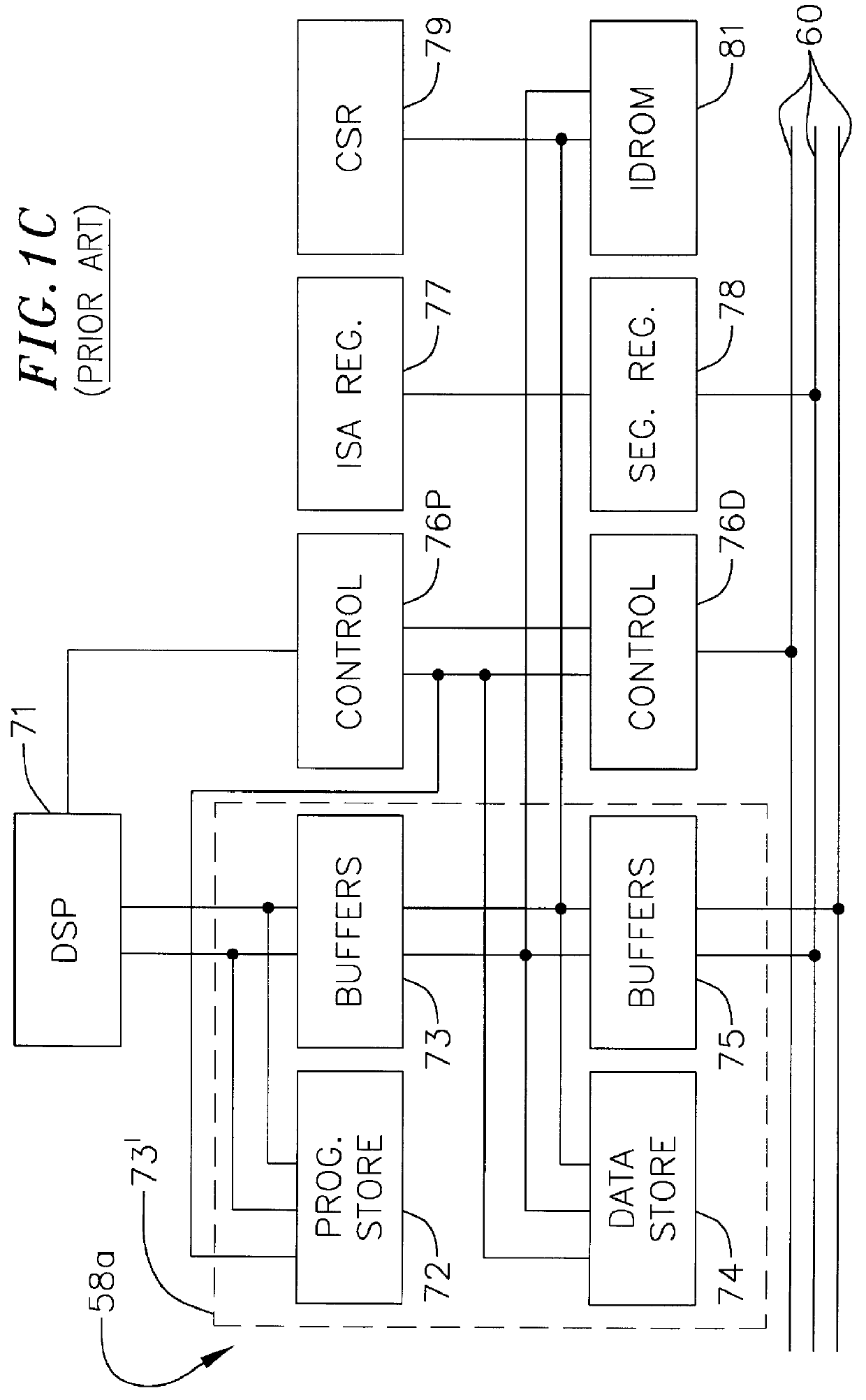
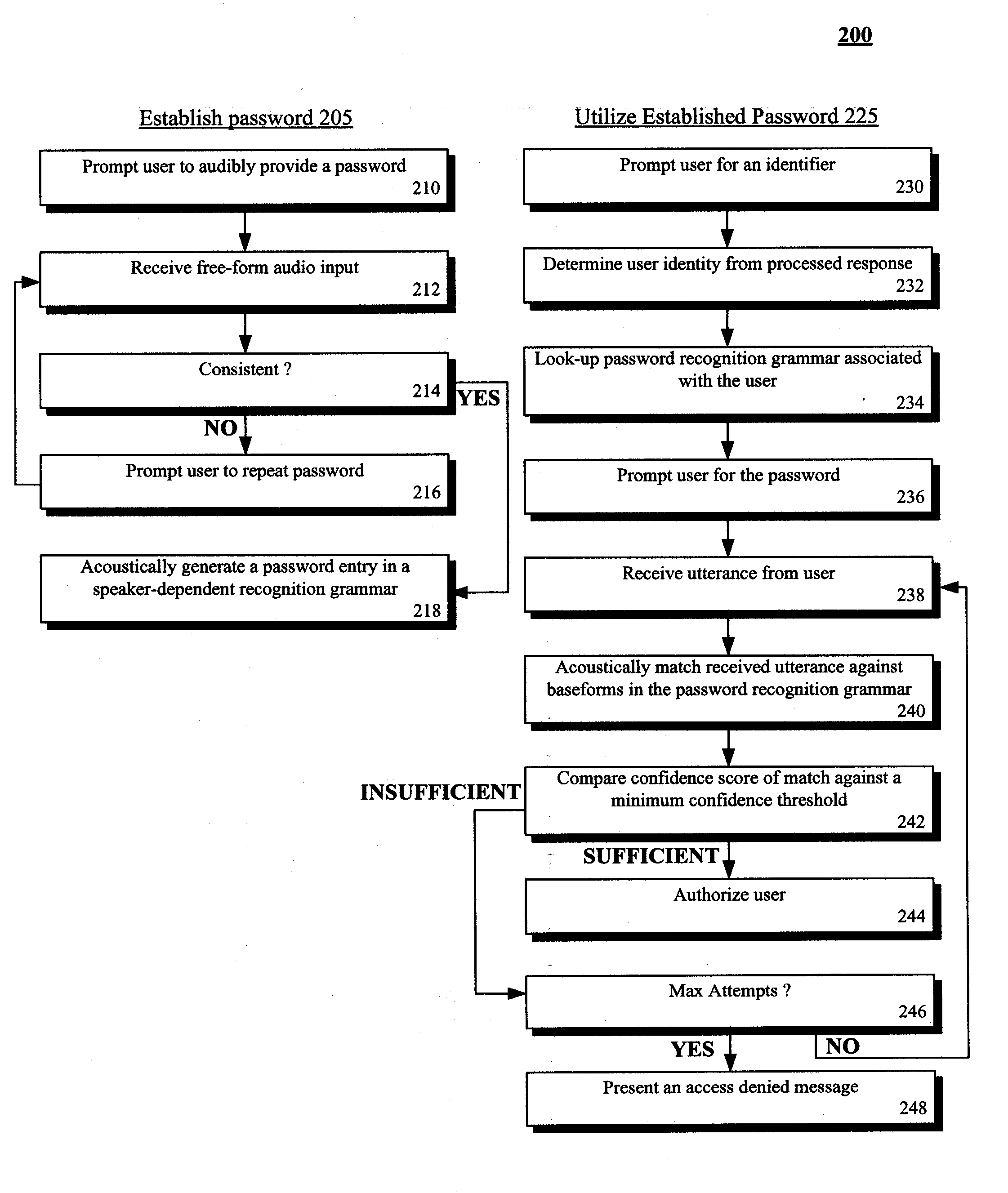
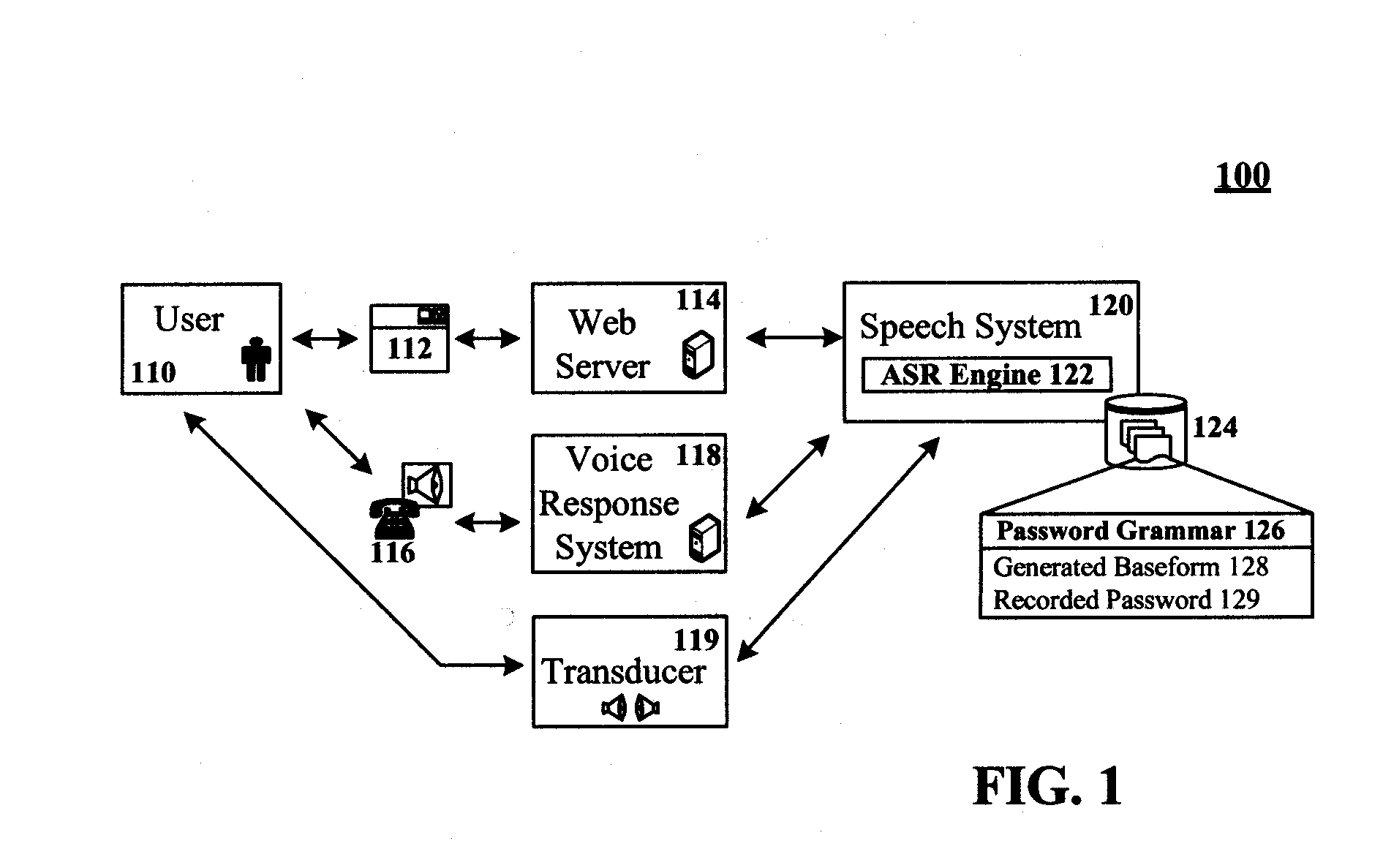
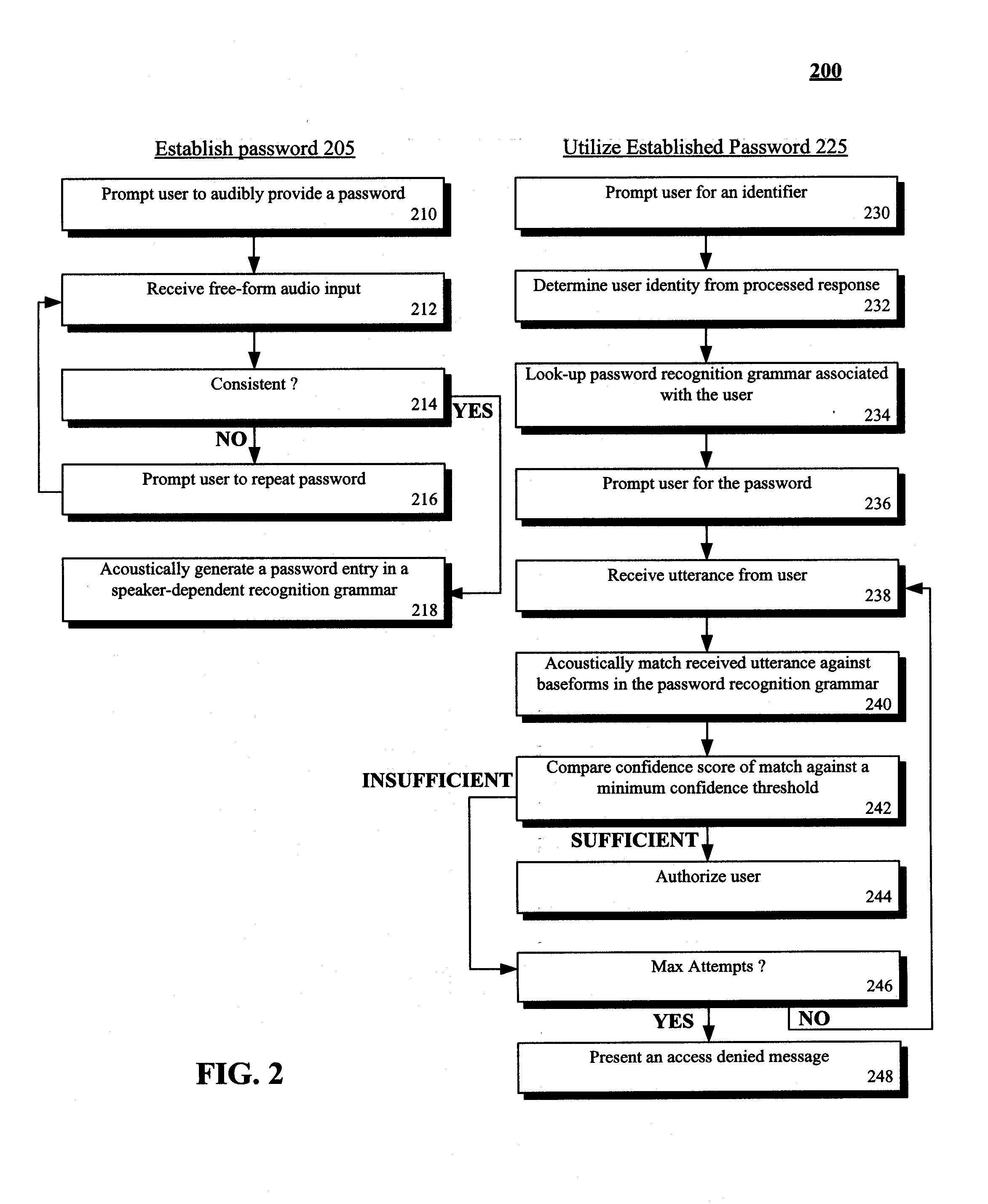
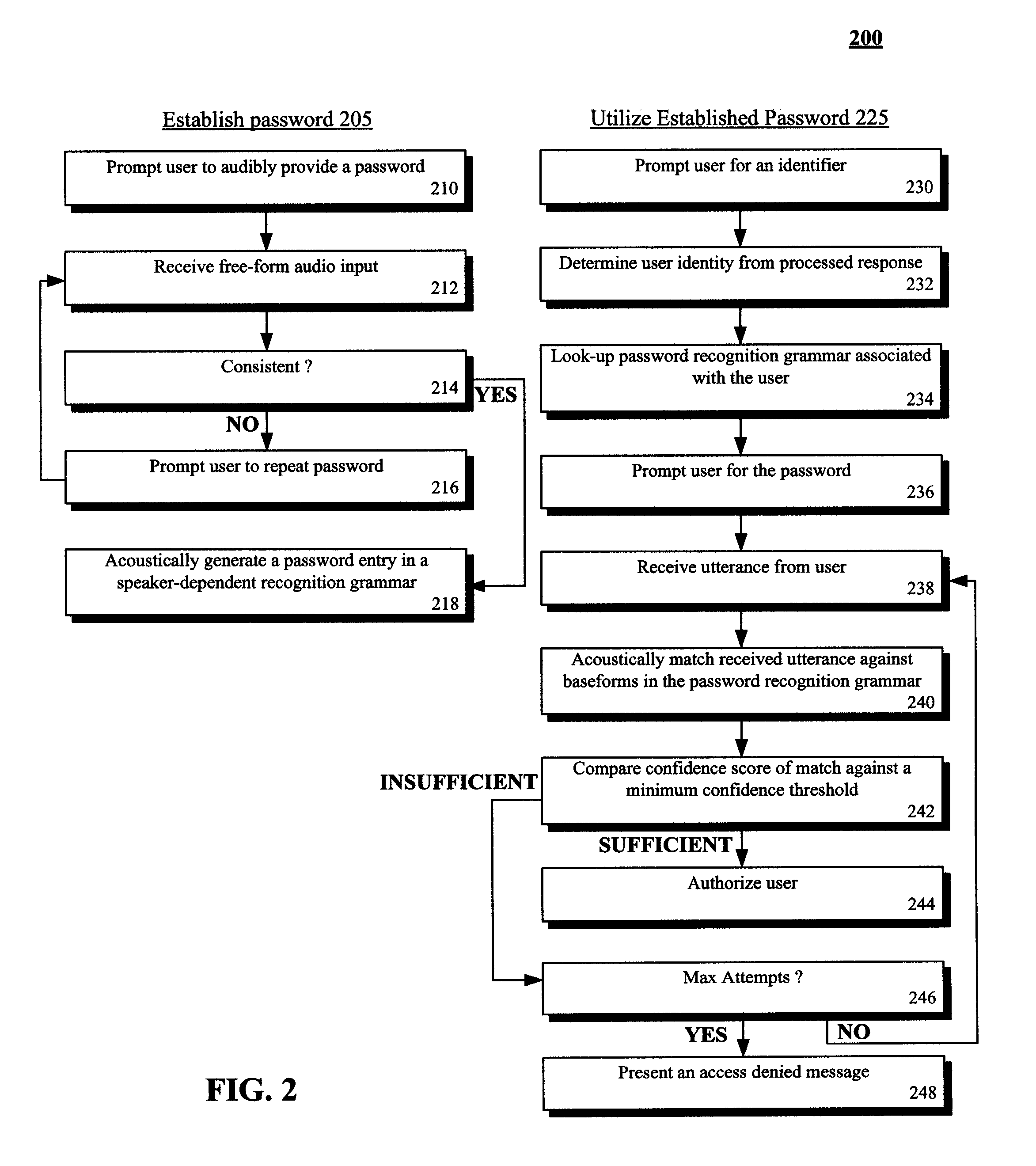
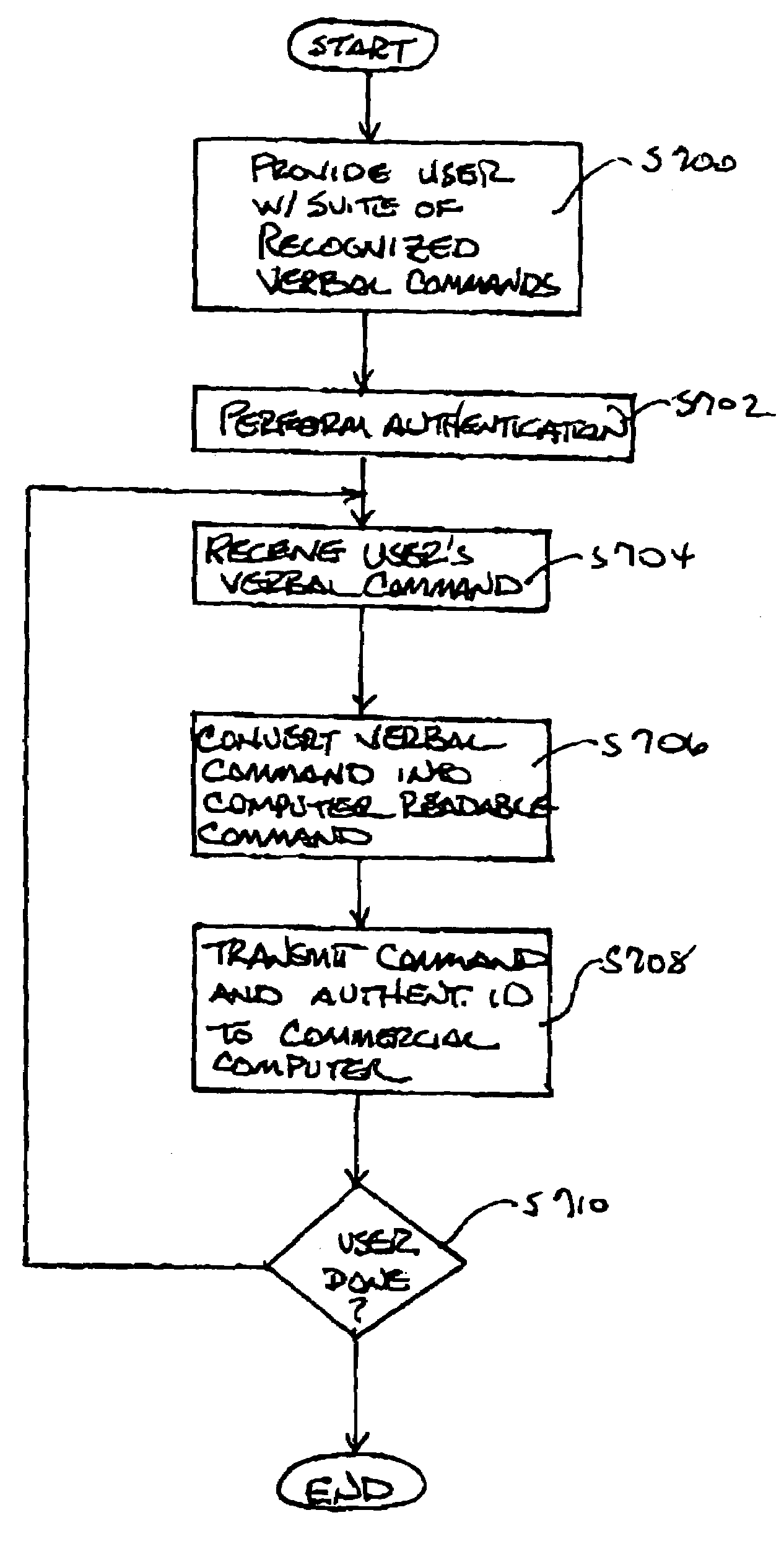
Spoken free-form passwords for light-weight speaker verification using standard speech recognition engines
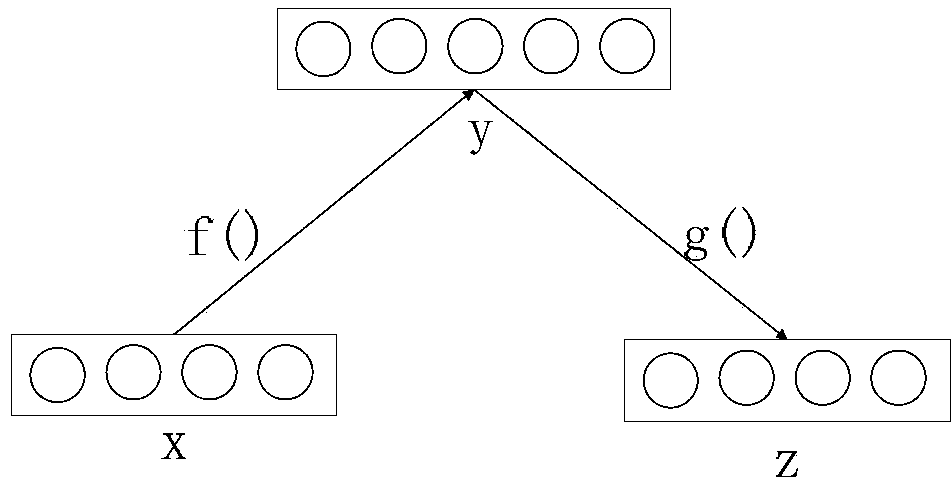
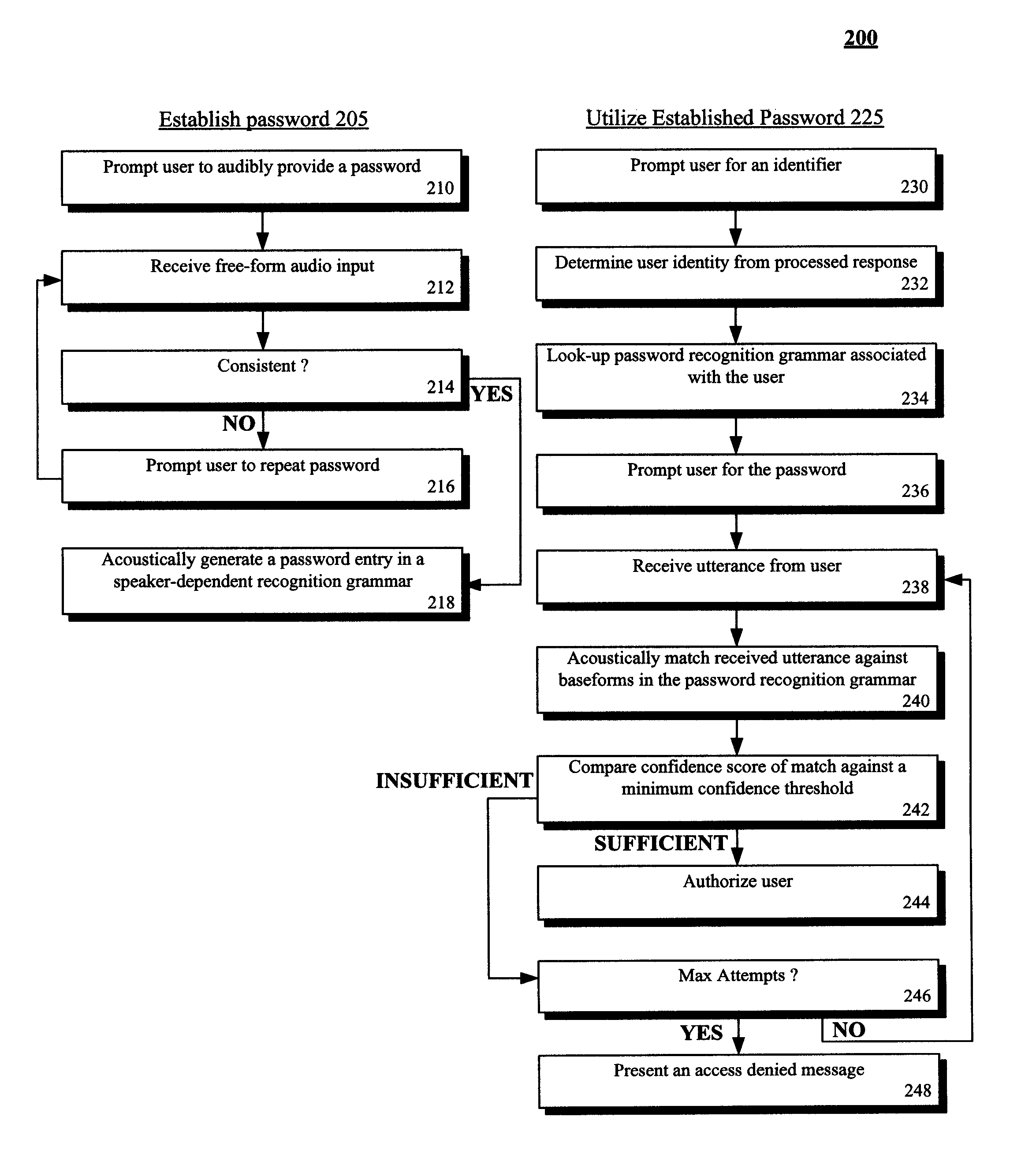
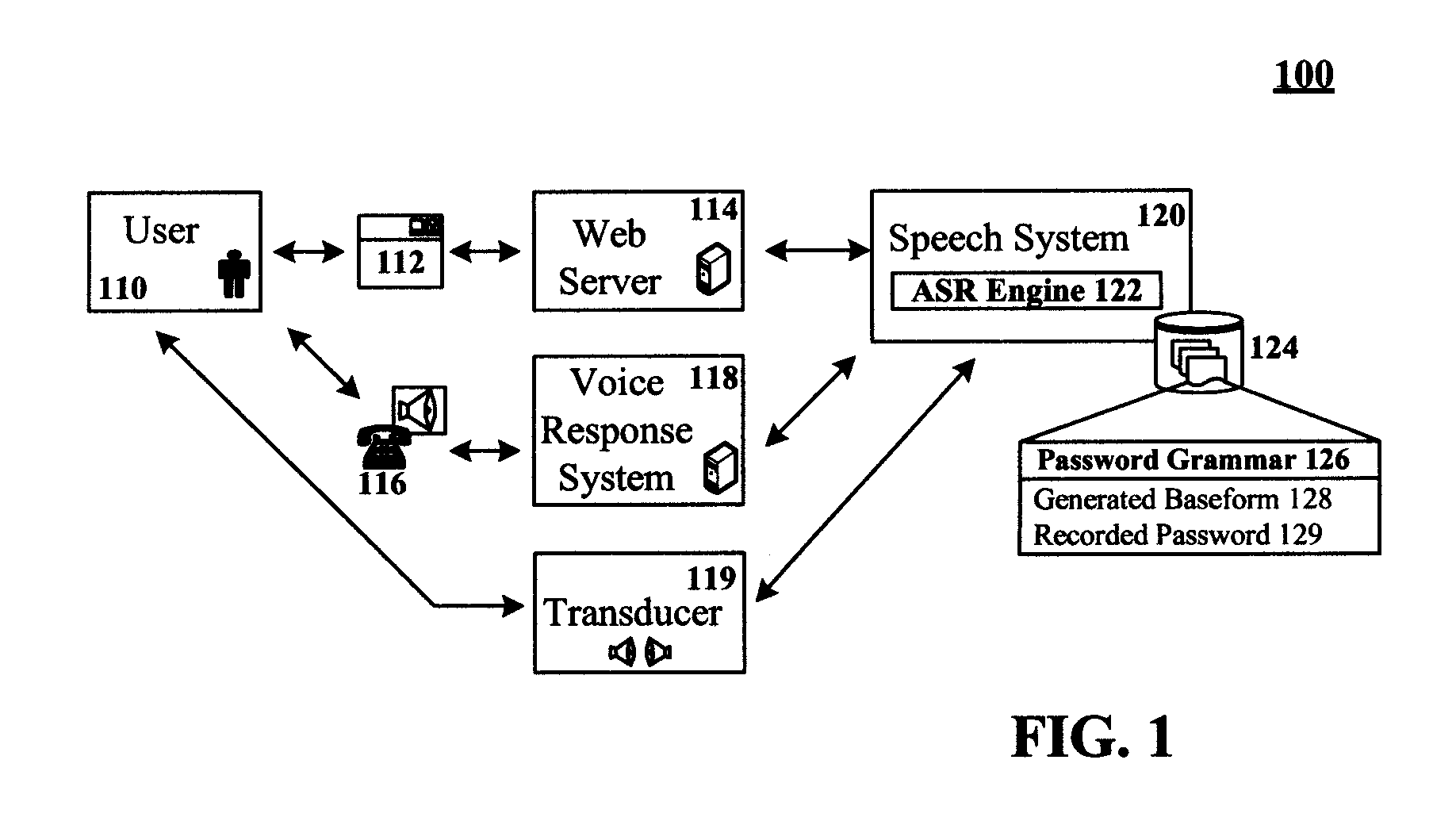
The present invention discloses a system and a method for authenticating a user based upon a spoken password processed though a standard speech recognition engine lacking specialized speaker identification and verification (SIV) capabilities. It should be noted that the standard speech recognition grammar can be capable of acoustically generating speech recognition grammars in accordance with the cross referenced application indicated herein. The invention can prompt a user for a free-form password and can receive a user utterance in response. The utterance can be processed through a speech recognition engine (e.g., during a grammar enrollment operation) to generate an acoustic baseform. Future user utterances can be matched against the acoustic baseform. Results from the future matches can be used to determine whether to grant the user access to a secure resource.
Owner:NUANCE COMM INC
Method and appratus for speech characterization
A method and system for speech characterization. One embodiment includes a method for speaker verification which includes collecting data from a speaker, wherein the data comprises acoustic data and non-acoustic data. The data is used to generate a template that includes a first set of “template” parameters. The method further includes receiving a real-time identity claim from a claimant, and using acoustic data and non-acoustic data from the identity claim to generate a second set of parameters. The method further includes comparing the first set of parameters to the set of parameters to determine whether the claimant is the speaker. The first set of parameters and the second set of parameters include at least one purely non-acoustic parameter, including a non-acoustic glottal shape parameter derived from averaging multiple glottal cycle waveforms.
Owner:LAWRENCE LIVERMORE NAT SECURITY LLC
Subword-based speaker verification with multiple-classifier score fusion weight and threshold adaptation
InactiveUS6539352B1Increase in sizeImprove generalization abilitySpeech recognitionSpeech segmentationSpeaker verification
The voice print system of the present invention is a subword-based, text-dependent automatic speaker verification system that embodies the capability of user-selectable passwords with no constraints on the choice of vocabulary words or the language. Automatic blind speech segmentation allows speech to be segmented into subword units without any linguistic knowledge of the password. Subword modeling is performed using a multiple classifiers. The system also takes advantage of such concepts as multiple classifier fusion and data resampling to successfully boost the performance. Key word / key phrase spotting is used to optimally locate the password phrase. Numerous adaptation techniques increase the flexibility of the base system, and include: channel adaptation, fusion adaptation, model adaptation and threshold adaptation.
Owner:BANK ONE COLORADO NA AS AGENT +1
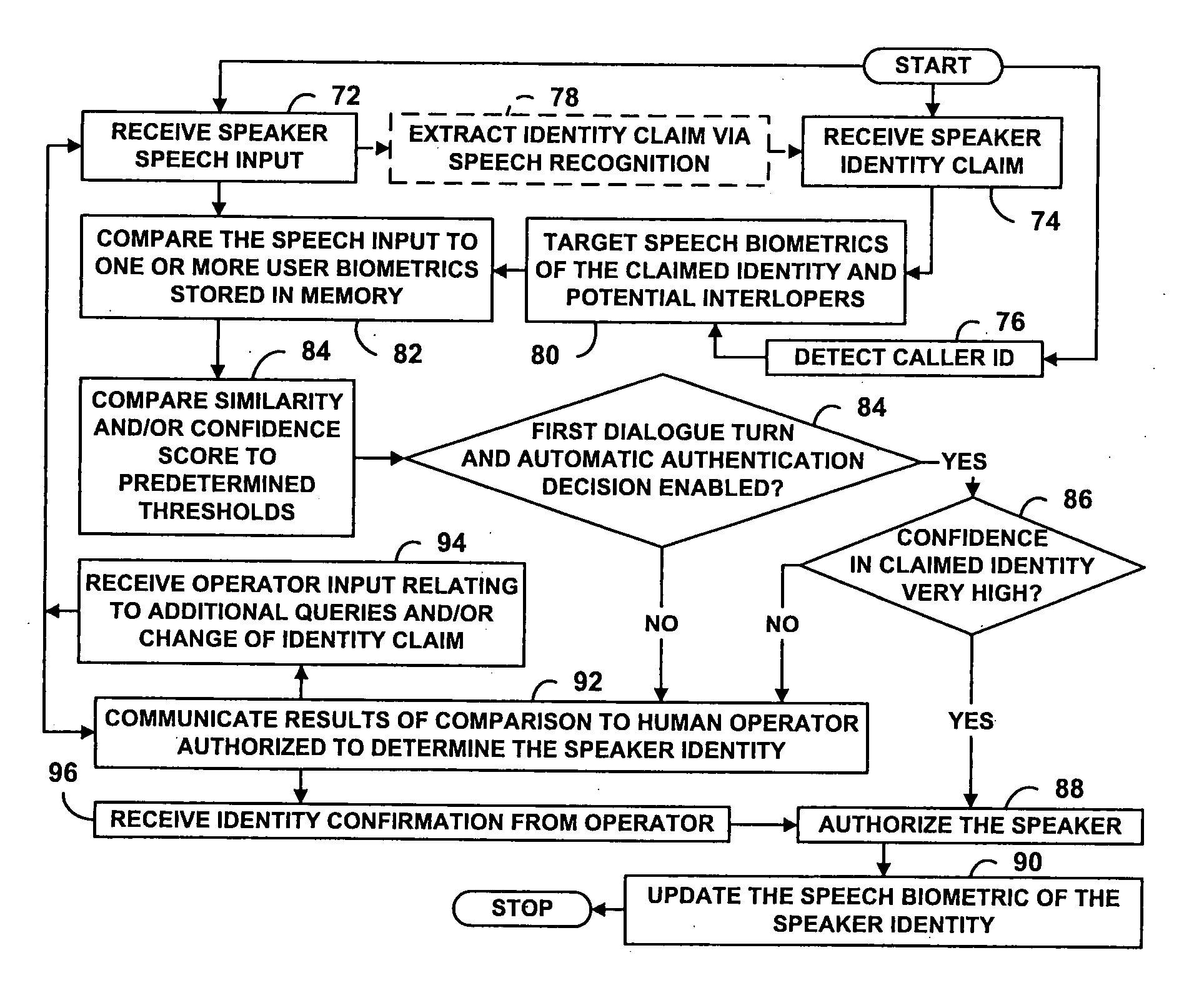
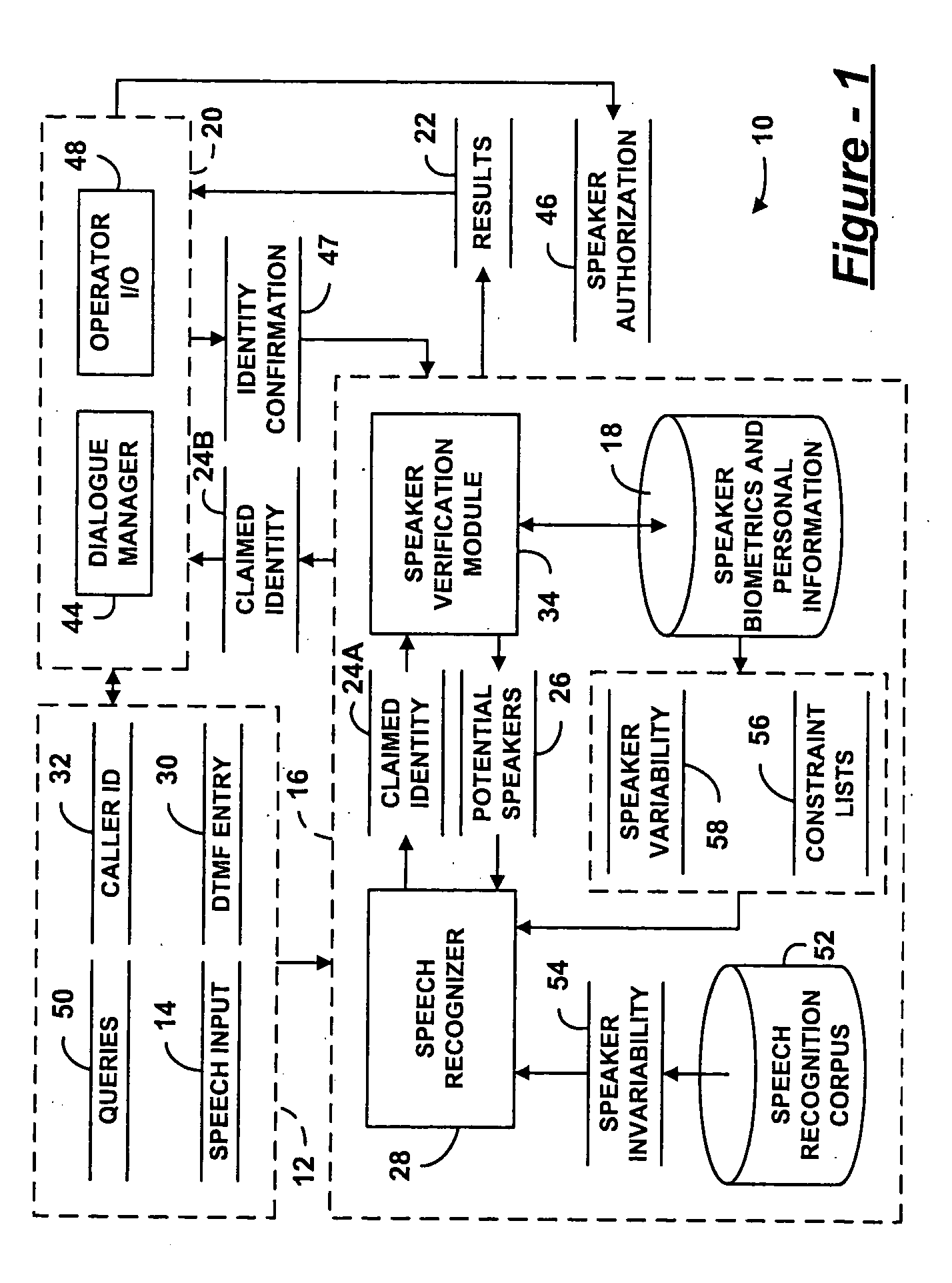
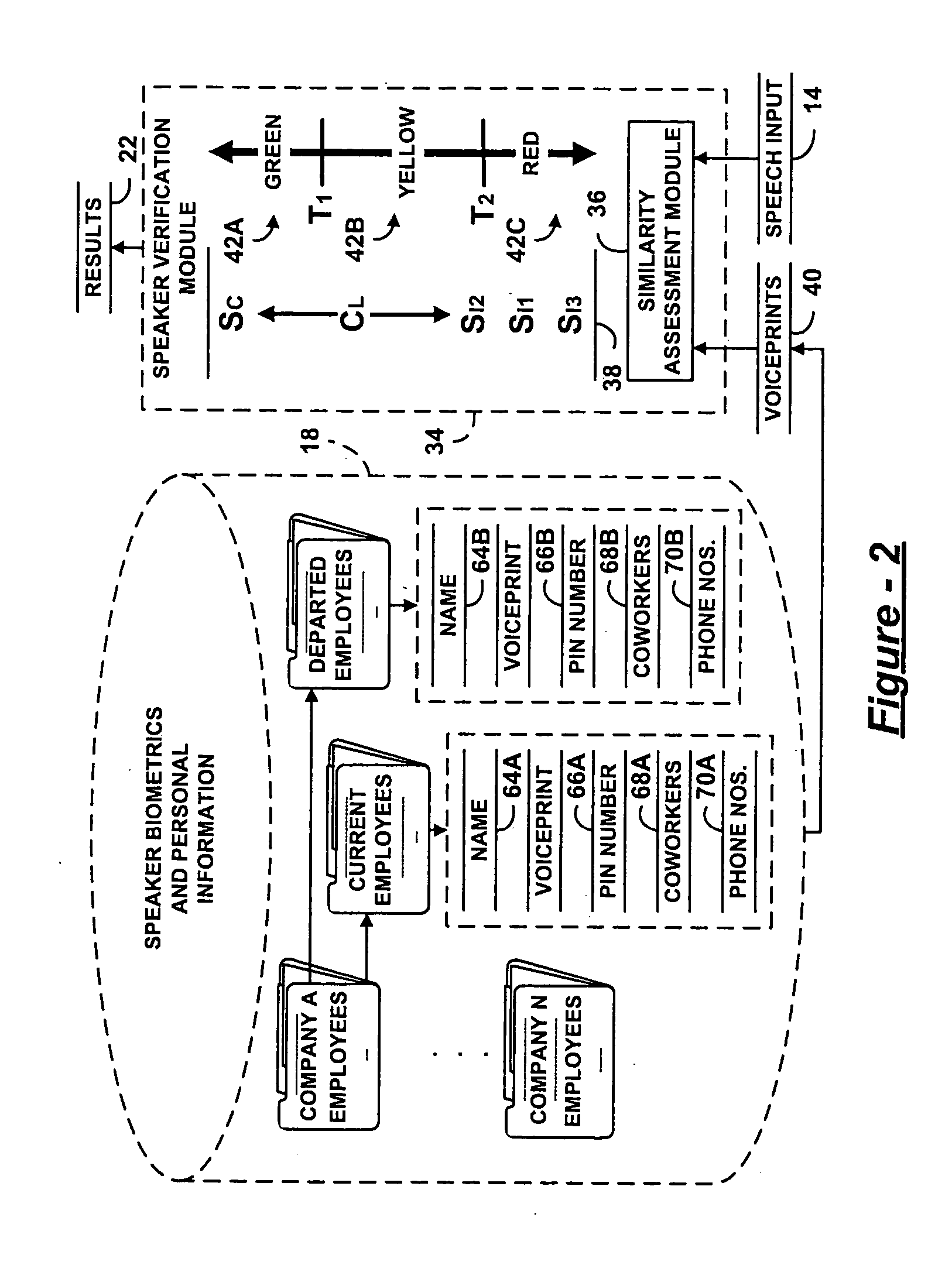
Speaker verification for security systems with mixed mode machine-human authentication
The central concept underlying the invention is to combine the human expertise supplied by an operator with speaker authentication technology installed on a machine. Accordingly, a speaker authentication system includes a speaker interface receiving a speech input from a speaker at a remote location. A speaker authentication module performs a comparison between the speech input and one or more speaker biometrics stored in memory. An operator interface communicates results of the comparison to a human operator authorized to determine identity of the speaker.
Owner:PANASONIC CORP
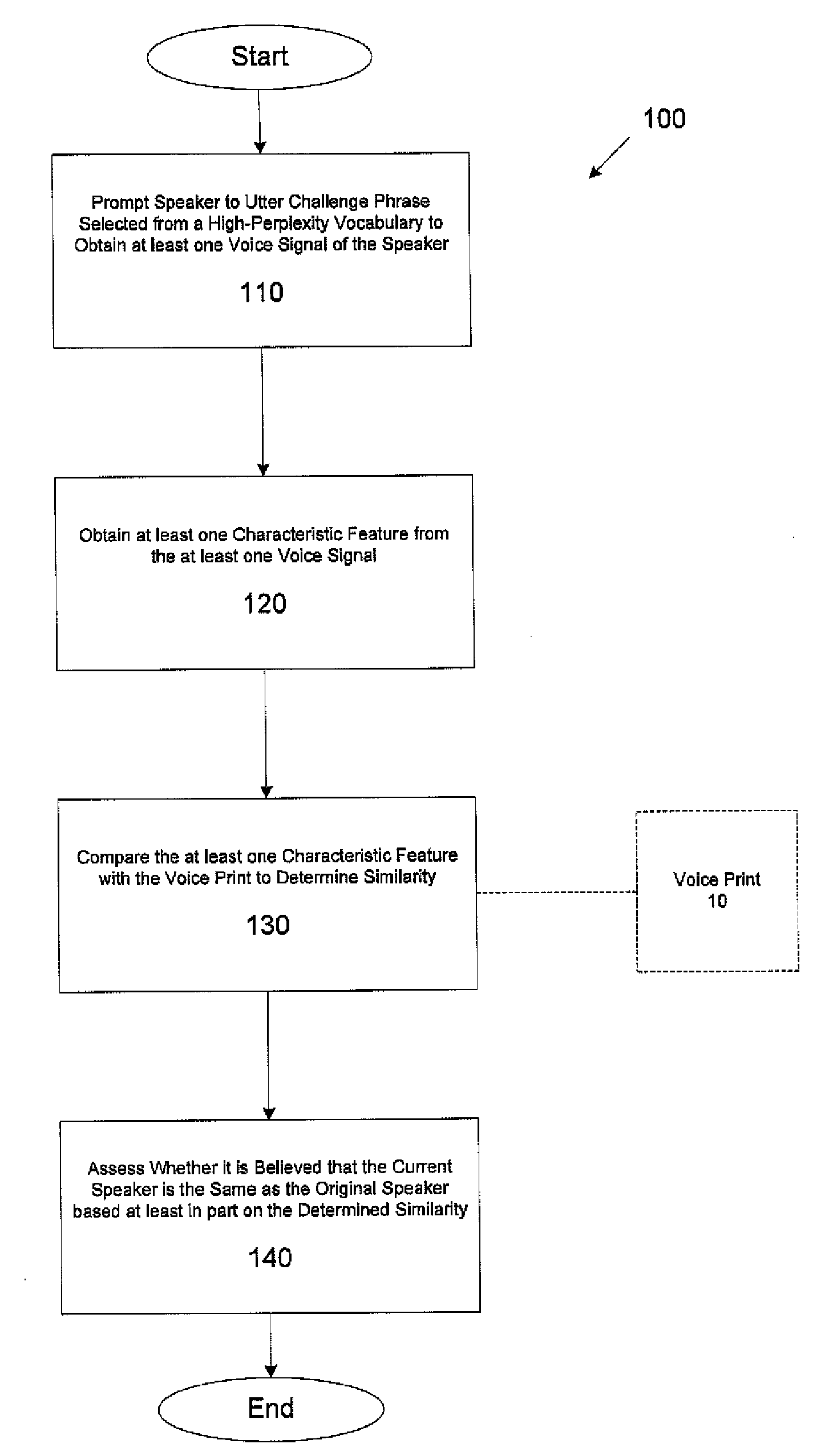
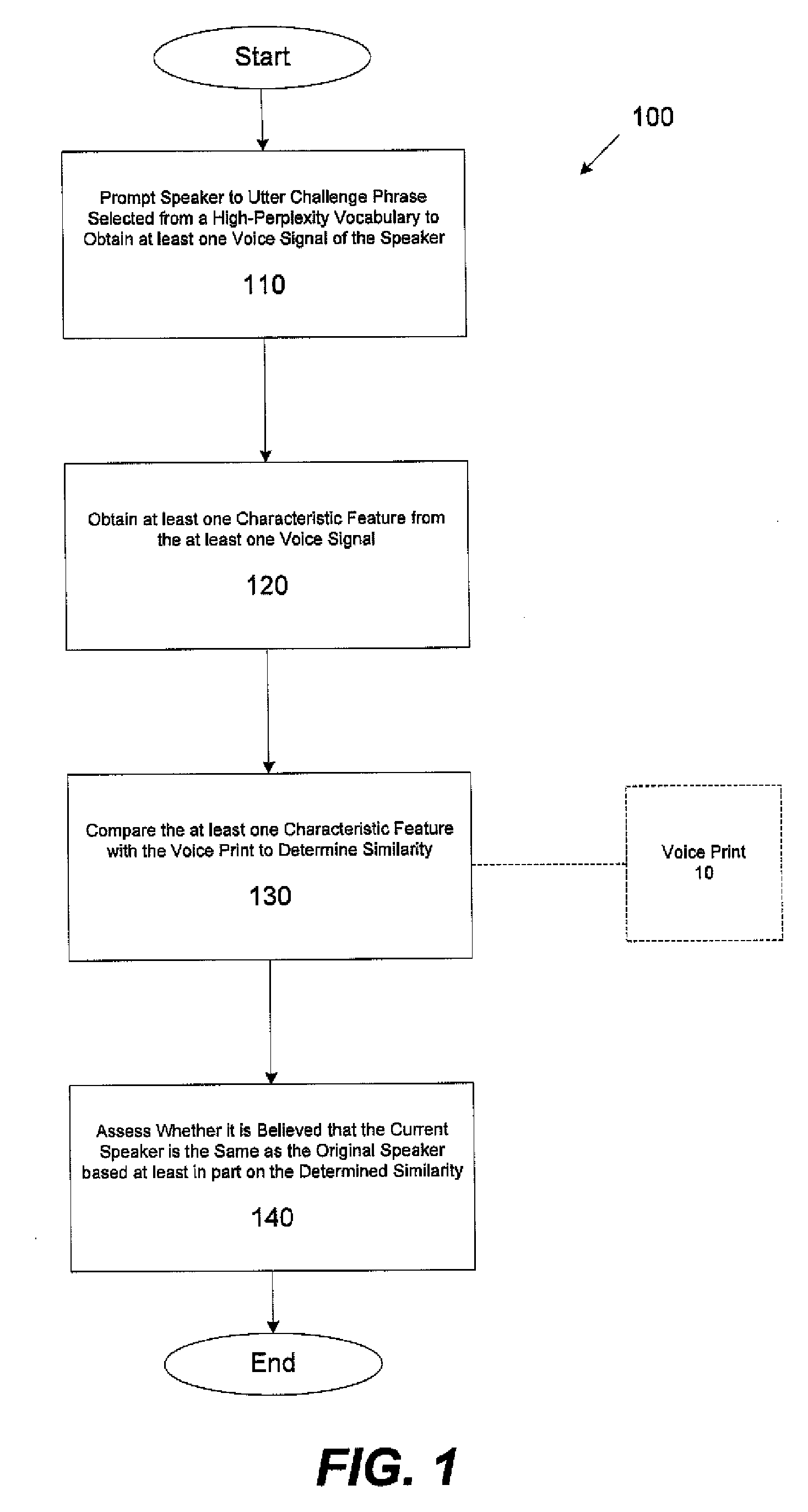
Speaker verification methods and apparatus
ActiveUS20100106502A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSpeaker verificationLoudspeaker
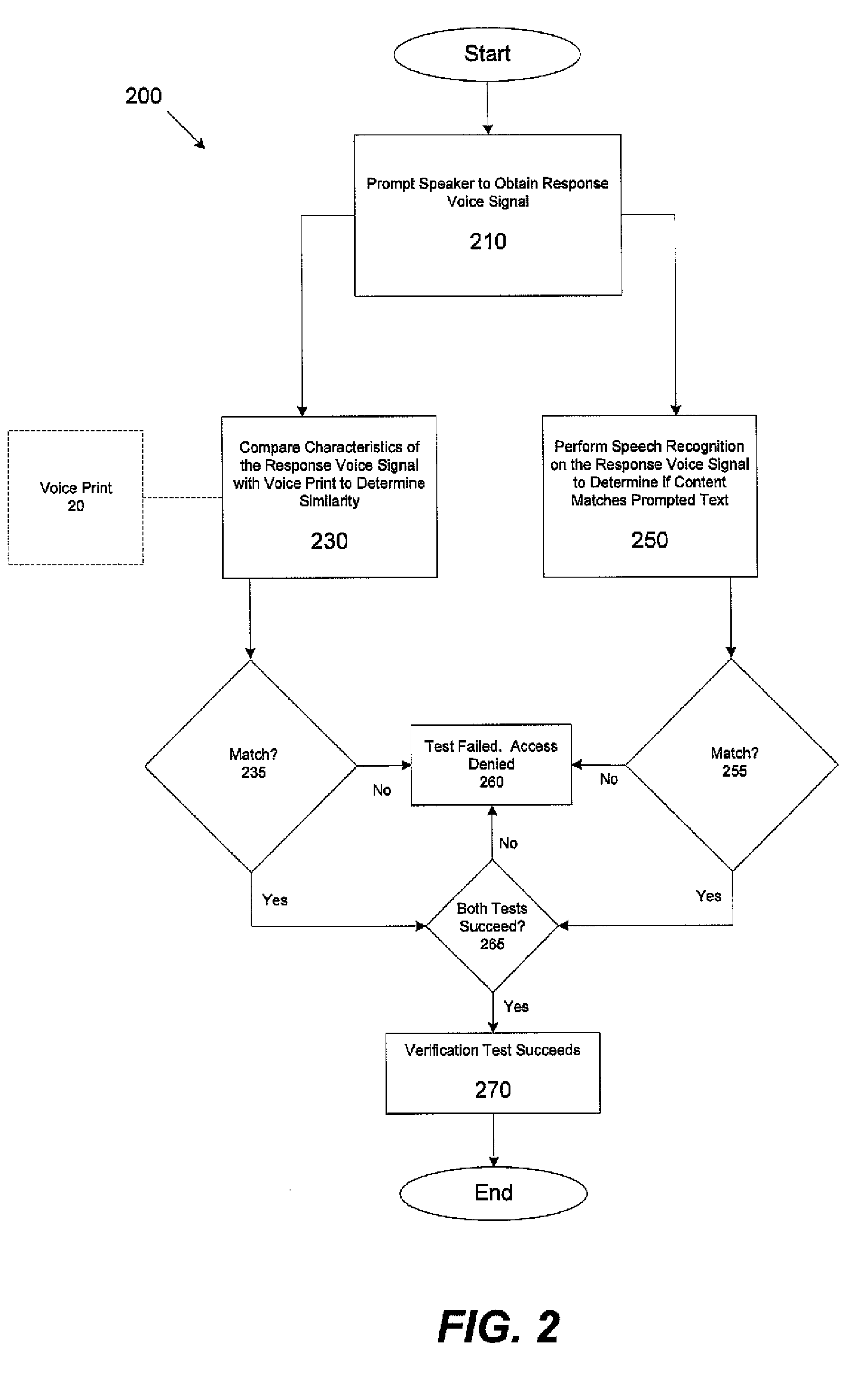
In one aspect, a method for determining validity of an identity asserted by a speaker using a voice print associated with a user whose identity the speaker is asserting, the voice print obtained from characteristic features of at least one first voice signal obtained from the user uttering at least one enrollment utterance including at least one enrollment word is provided. The method comprises acts of obtaining a second voice signal of the speaker uttering at least one challenge utterance, wherein the at least one challenge utterance includes at least one word that was not in the at least one enrollment utterance, obtaining at least one characteristic feature from the second voice signal, comparing the at least one characteristic feature with at least a portion of the voice print to determine a similarity between the at least one characteristic feature and the at least a portion of the voice print, and determining whether the speaker is the user based, at least in part, on the similarity between the at least one characteristic feature and the at least a portion of the voice print.
Owner:NUANCE COMM INC
Multi-resolution system and method for speaker verification
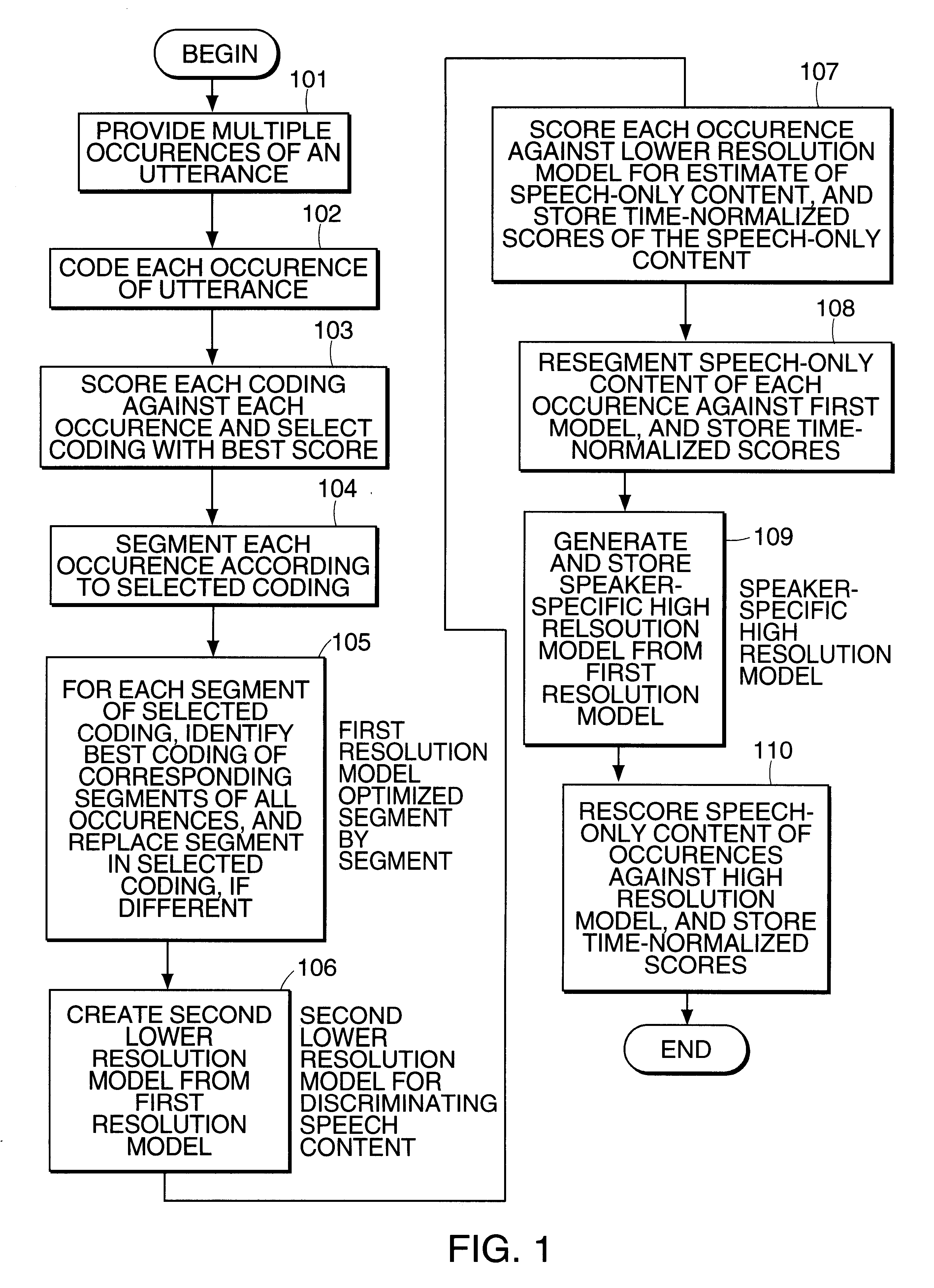
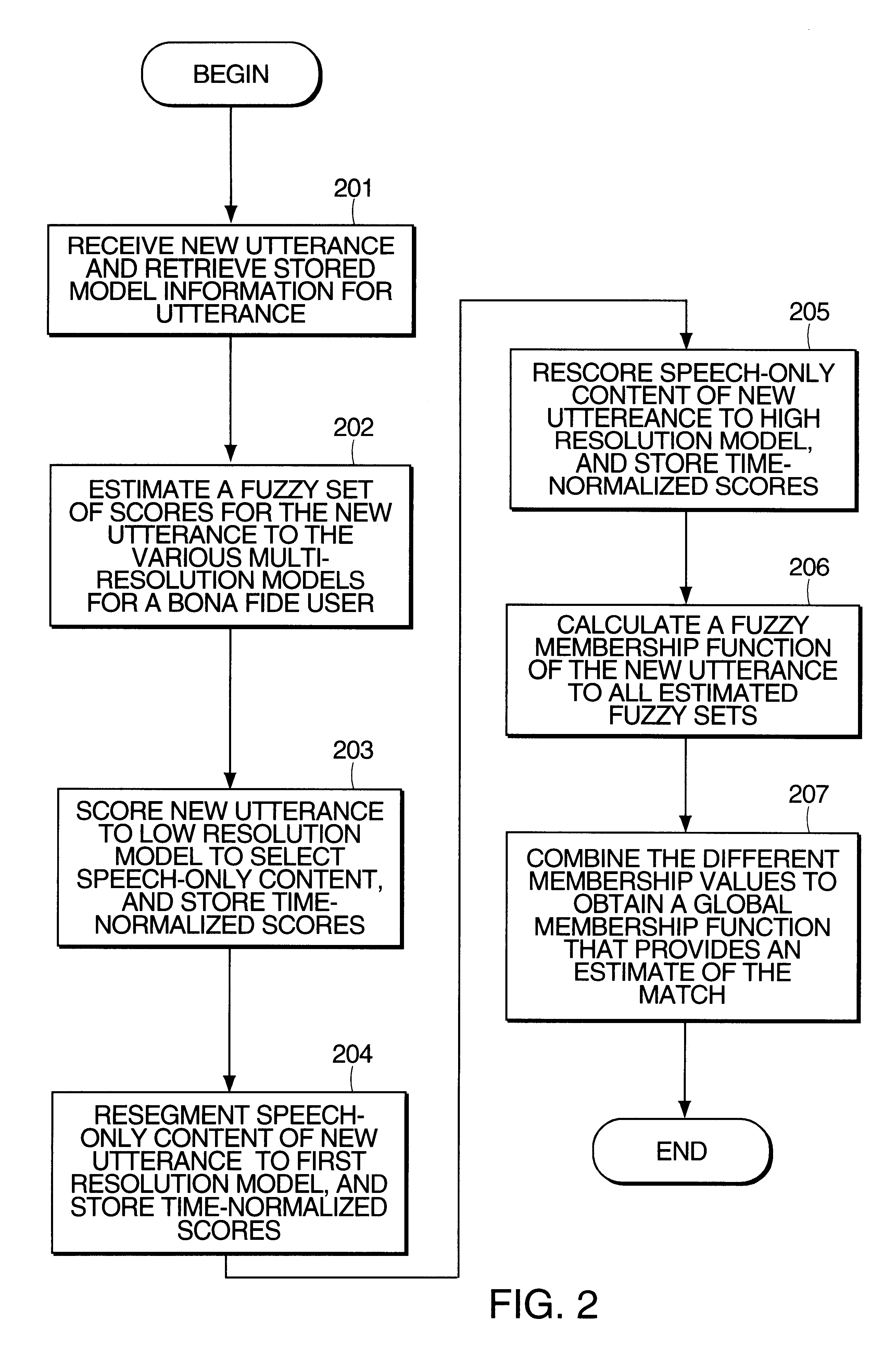
A method is given for generating a speaker-dependant model of an utterance that has at least one occurrence. The method includes generating an initial model, having a first resolution, that encodes each of the occurrences of the utterance; and generating at least one additional speaker-specific model, having a different resolution from that of the initial model, of all occurrences of the utterance.
Owner:NUANCE COMM INC
Method and device for voiceprint recognition
ActiveUS20140214417A1Reduce noise disturbanceFunction increaseSpeech recognitionSpeaker verificationLoudspeaker
Owner:TENCENT TECH (SHENZHEN) CO LTD
Voiceprint recognition method and device
InactiveCN103971690AResistance to noise interferenceImprove performanceSpeech analysisSpeaker verificationSpeech sound
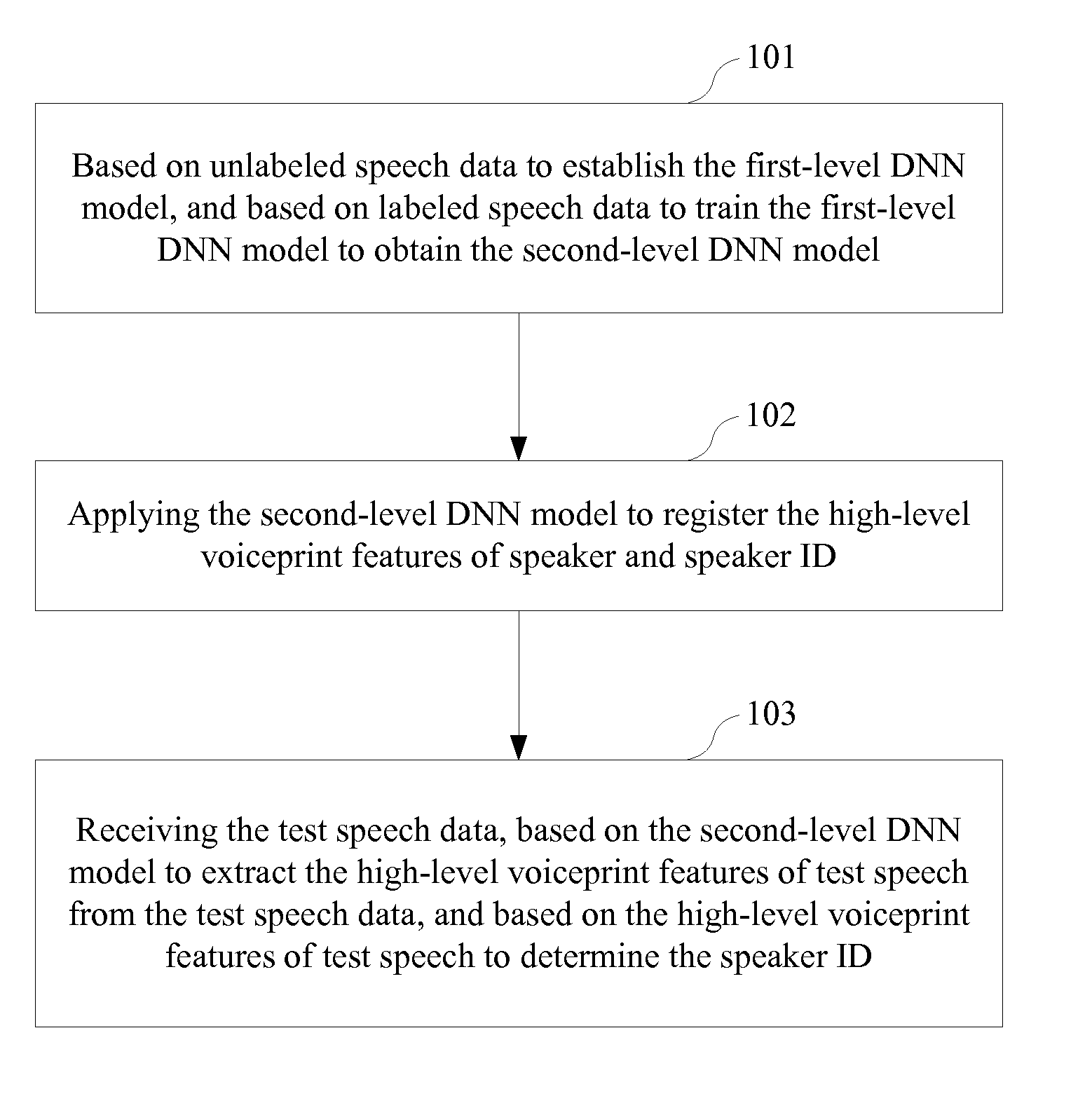
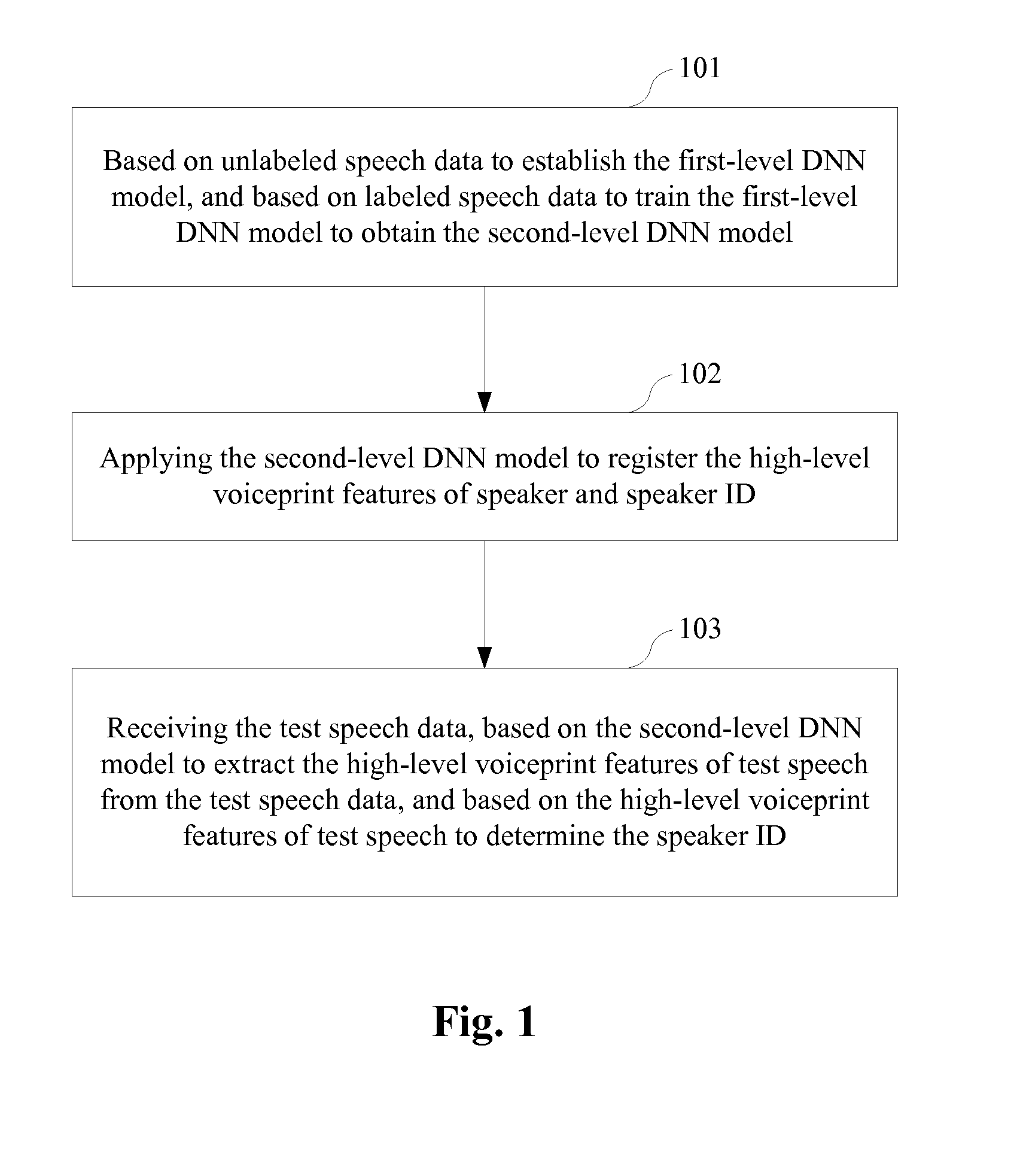
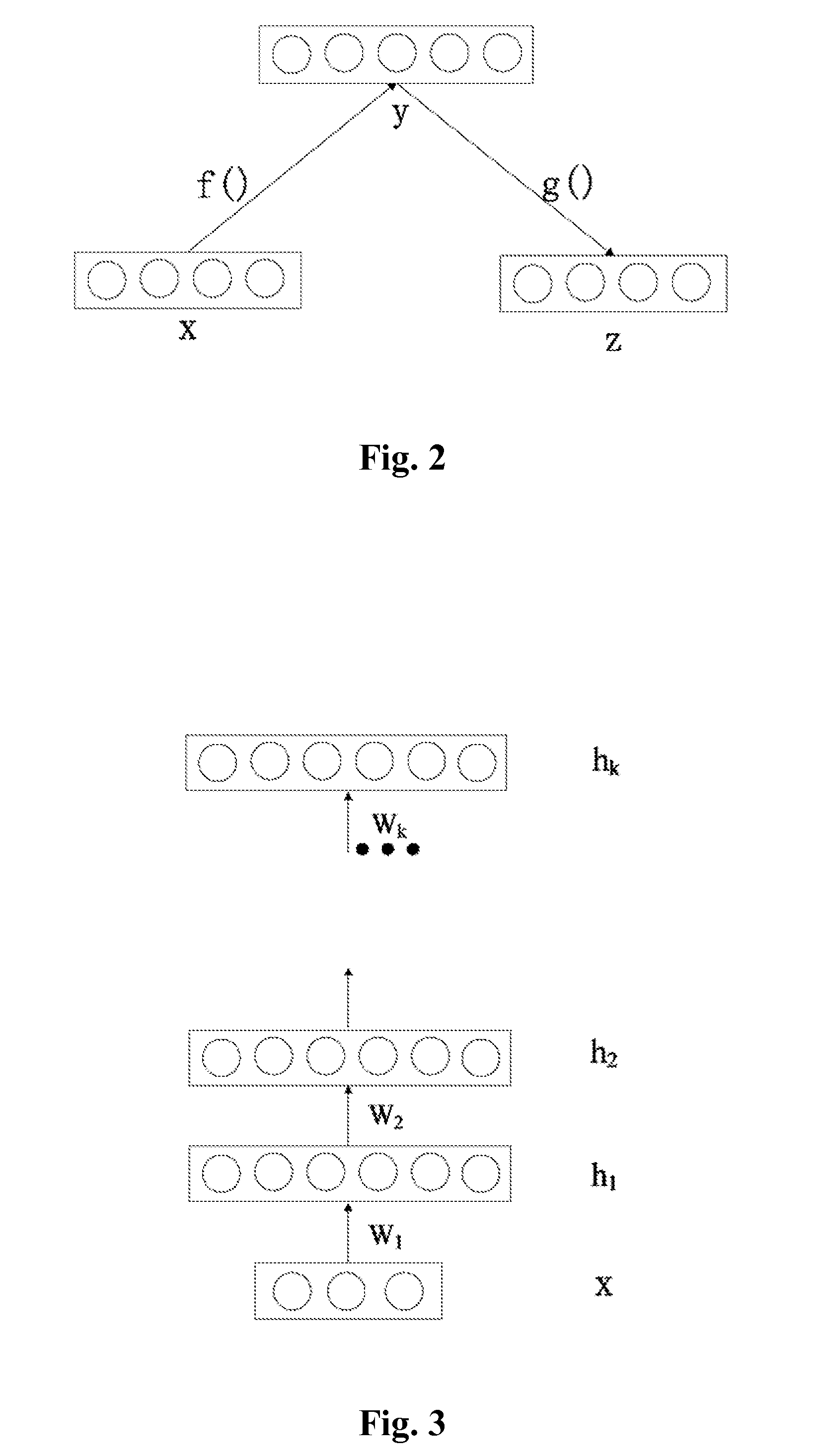
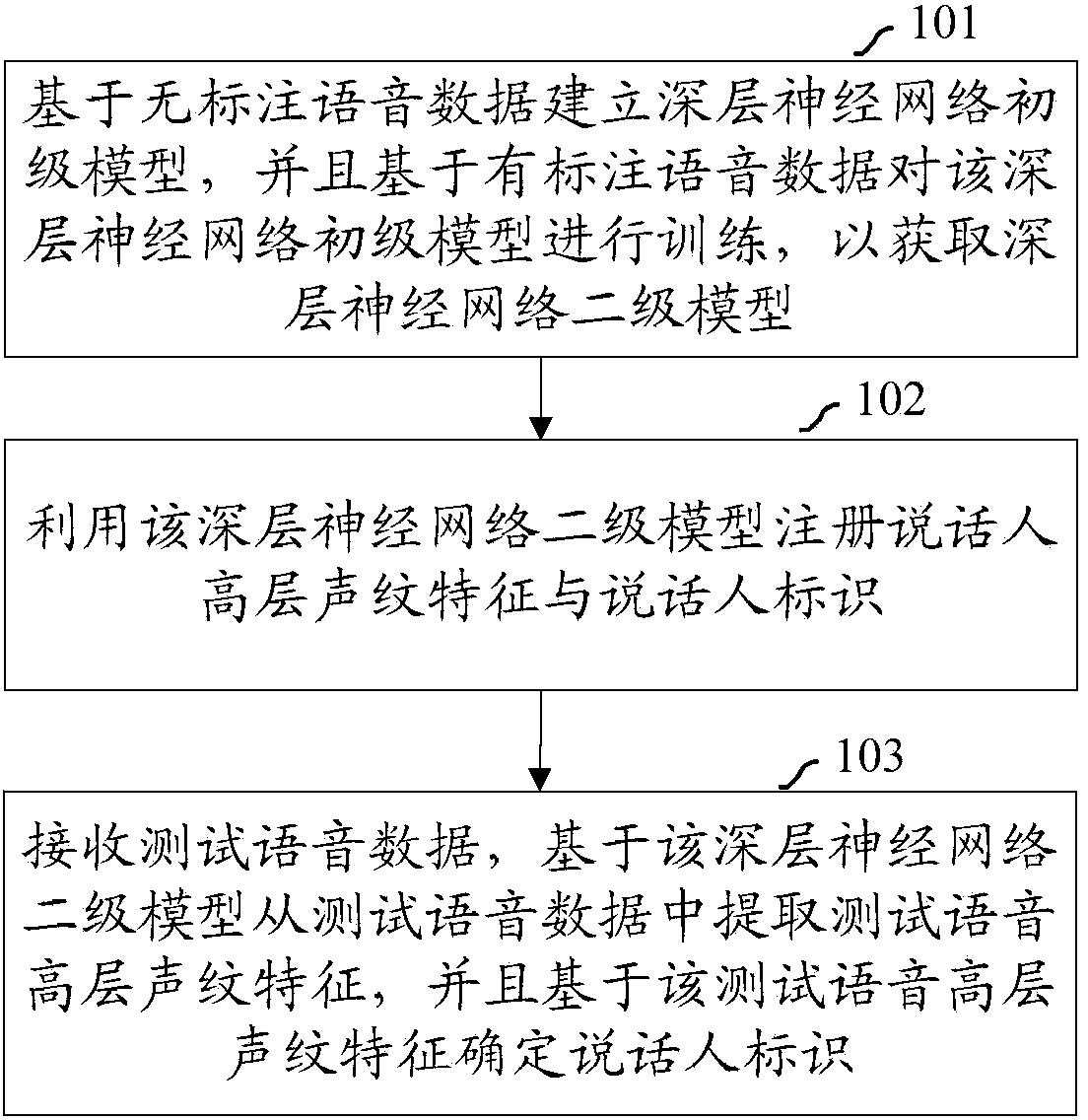
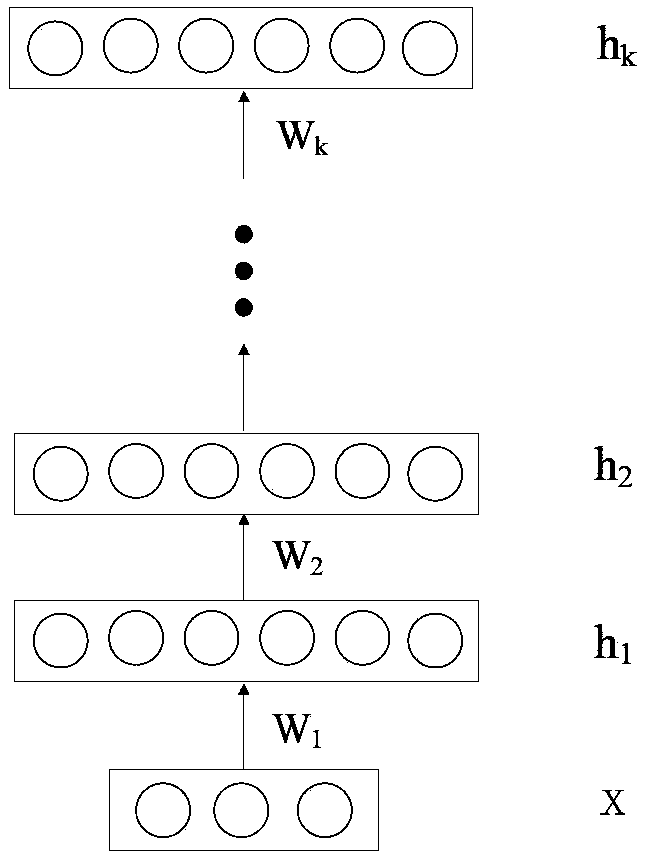
A method and system (800) for voiceprint recognition, include: establishing a first-level Deep Neural Network (DNN) model based on unlabeled speech data, the unlabeled speech data containing no speaker labels and the first-level DNN model specifying a plurality of basic voiceprint features for the unlabeled speech data; obtaining a plurality of high-level voiceprint features by tuning the first-level DNN model based on labeled speech data, the labeled speech data containing speech samples with respective speaker labels, and the tuning producing a second-level DNN model specifying the plurality of high-level voiceprint features; based on the second-level DNN model, registering a respective high-level voiceprint feature sequence for a user based on a registration speech sample received from the user; and performing speaker verification for the user based on the respective high-level voiceprint feature sequence registered for the user.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Spoken free-form passwords for light-weight speaker verification using standard speech recognition engines
The present invention discloses a system and a method for authenticating a user based upon a spoken password processed though a standard speech recognition engine lacking specialized speaker identification and verification (SIV) capabilities. It should be noted that the standard speech recognition grammar can be capable of acoustically generating speech recognition grammars in accordance with the cross referenced application indicated herein. The invention can prompt a user for a free-form password and can receive a user utterance in response. The utterance can be processed through a speech recognition engine (e.g., during a grammar enrollment operation) to generate an acoustic baseform. Future user utterances can be matched against the acoustic baseform. Results from the future matches can be used to determine whether to grant the user access to a secure resource.
Owner:NUANCE COMM INC
User authentication by combining speaker verification and reverse turing test
ActiveUS20060136219A1Digital data processing detailsSpeech analysisInternet privacySpeaker verification
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for multi-environment speaker verification
InactiveUS6253179B1Reduce false acceptanceSpeech recognitionTelecommunications linkSpeaker verification
Owner:NUANCE COMM INC
Speaker verification system
ActiveUS8209174B2High precisionLess-powerful microprocessorProgramme controlElectric signal transmission systemsFeature extractionPattern matching
A text-independent speaker verification system utilizes mel frequency cepstral coefficients analysis in the feature extraction blocks, template modeling with vector quantization in the pattern matching blocks, an adaptive threshold and an adaptive decision verdict and is implemented in a stand-alone device using less powerful microprocessors and smaller data storage devices than used by comparable systems of the prior art.
Owner:SAUDI ARABIAN OIL CO
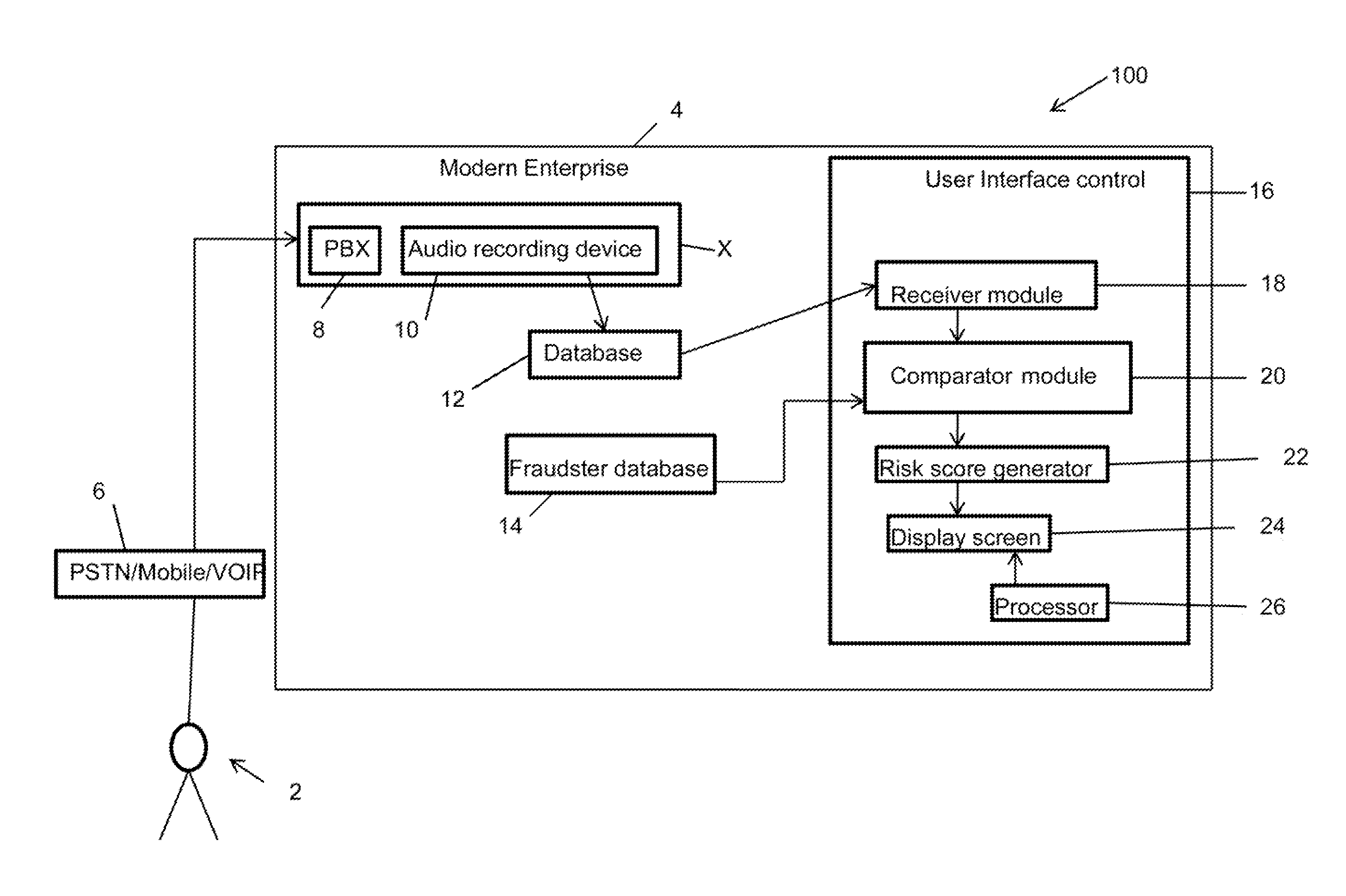
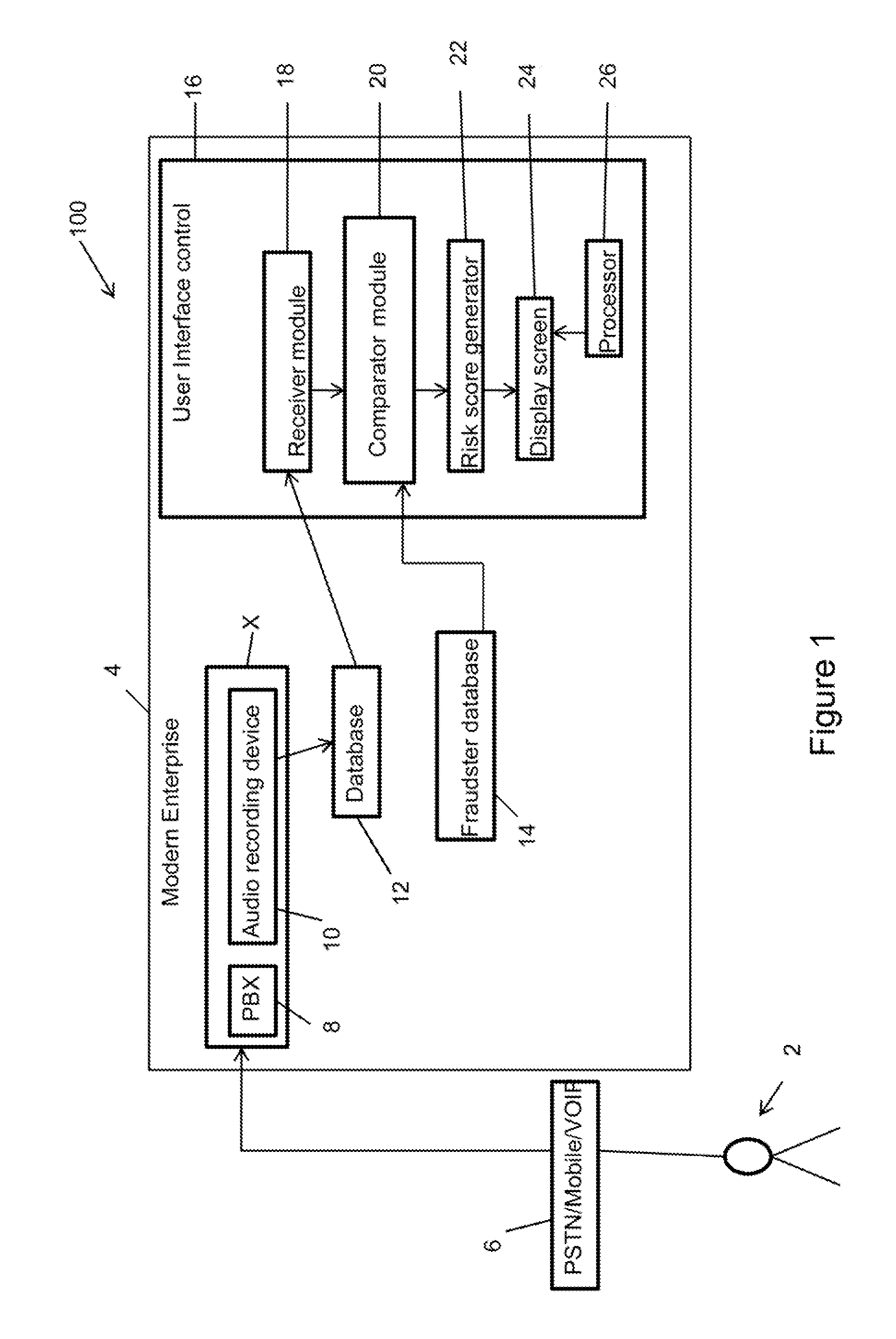
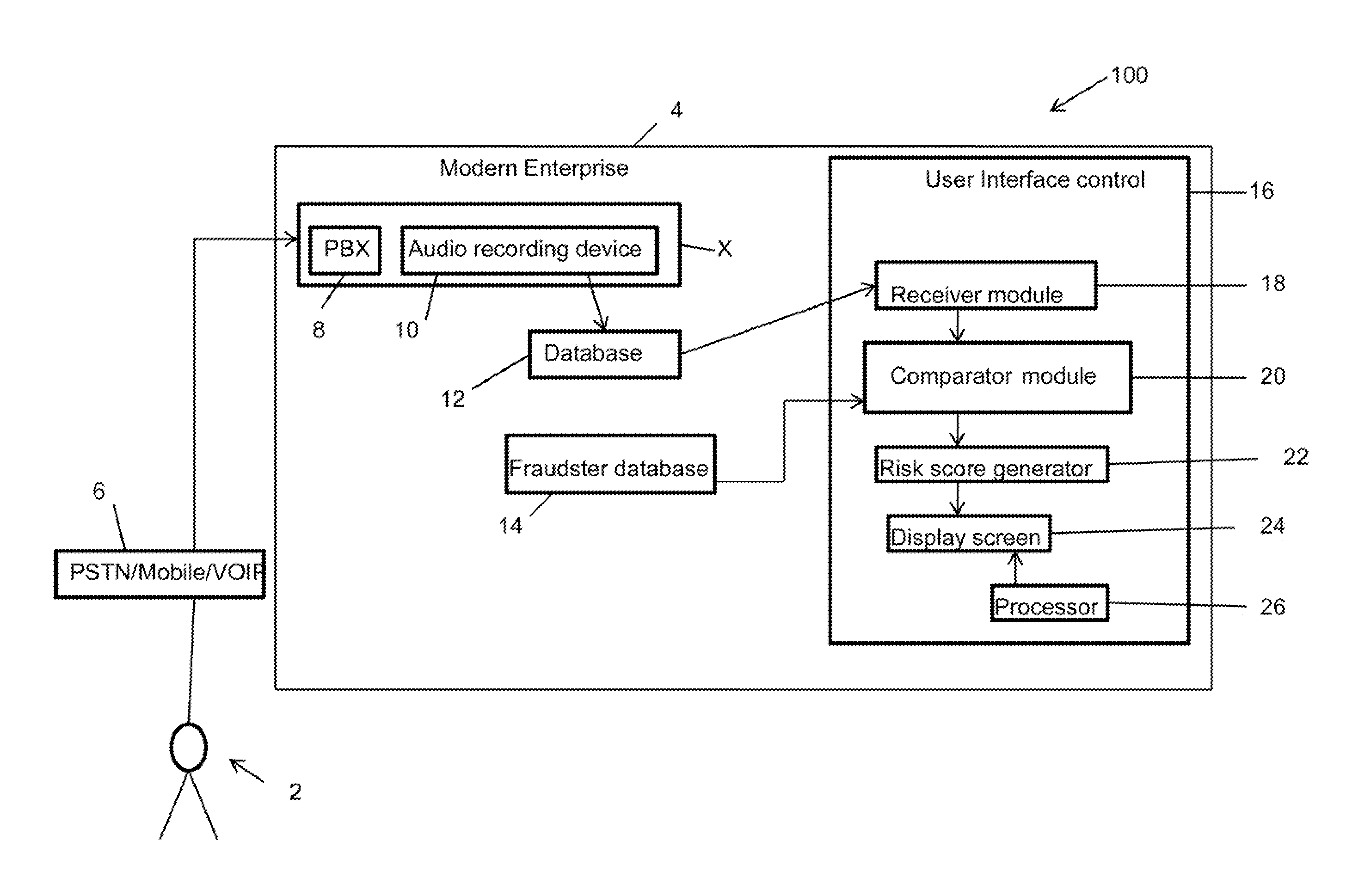
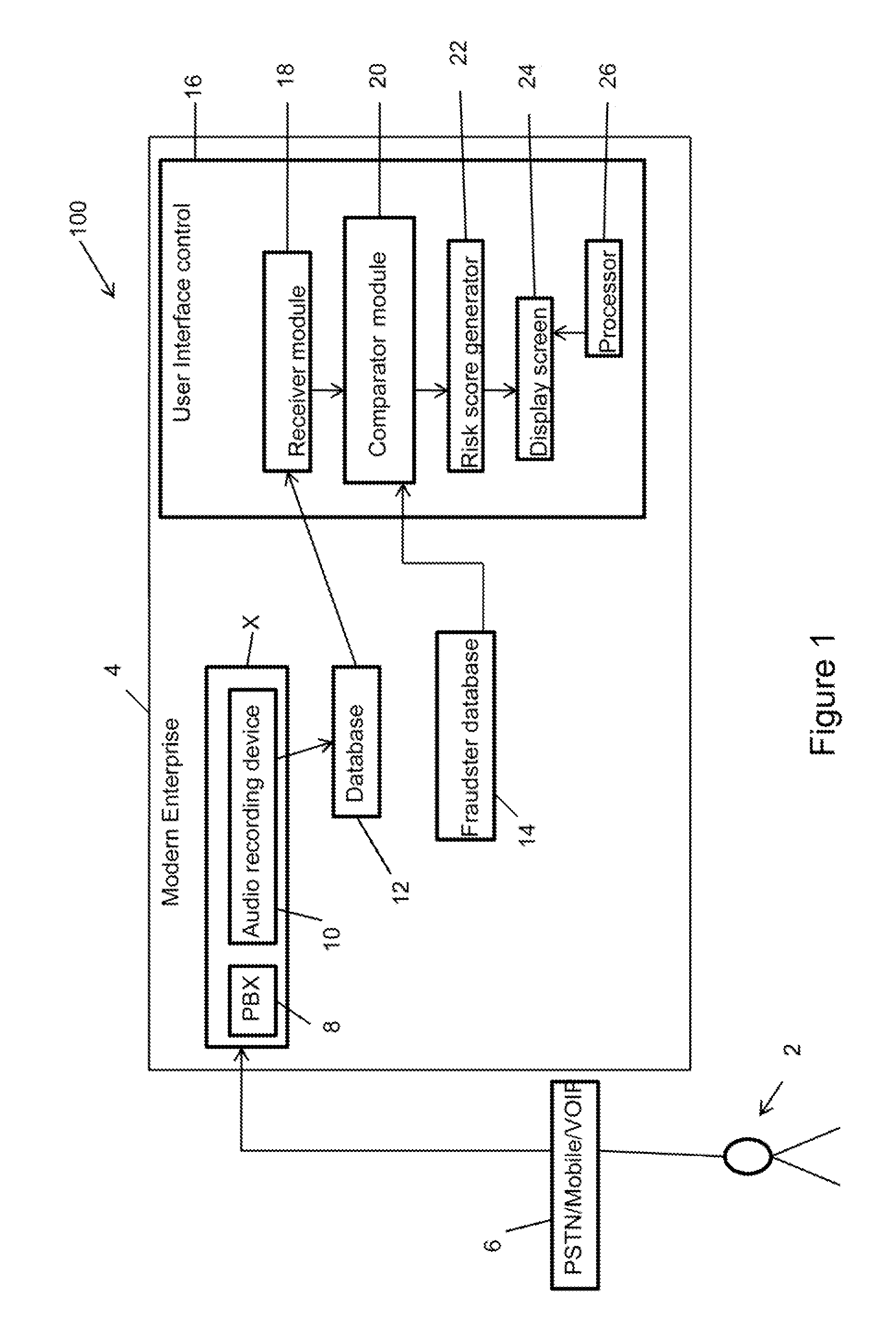
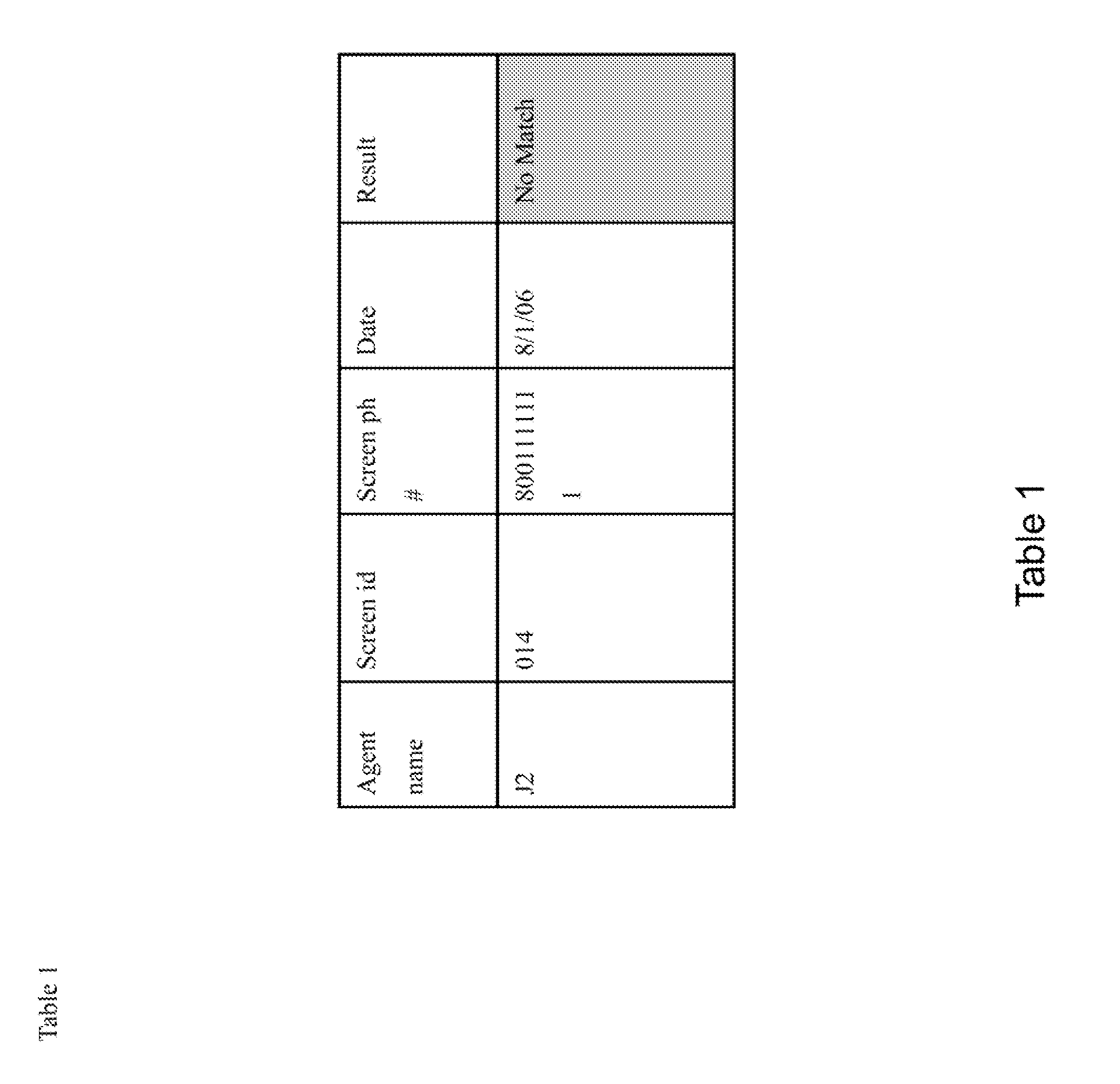
Speaker verification-based fraud system for combined automated risk score with agent review and associated user interface
Disclosed is method for screening an audio for fraud detection, the method comprising: providing a User Interface (UI) control capable of: a) receiving an audio; b) comparing the audio with a list of fraud audios; c) assigning a risk score to the audio based on the comparison with a potentially matching fraud audio of the list of fraud audios; and d) displaying an audio interface on a display screen, wherein the audio interface is capable of playing the audio along with the potentially matching fraud audio, and wherein the display screen further displays metadata for each of the audio and the potentially matching fraud audio thereon, wherein the metadata includes location and incident data of each of the audio and the potentially matching fraud audio.
Owner:VERINT AMERICAS
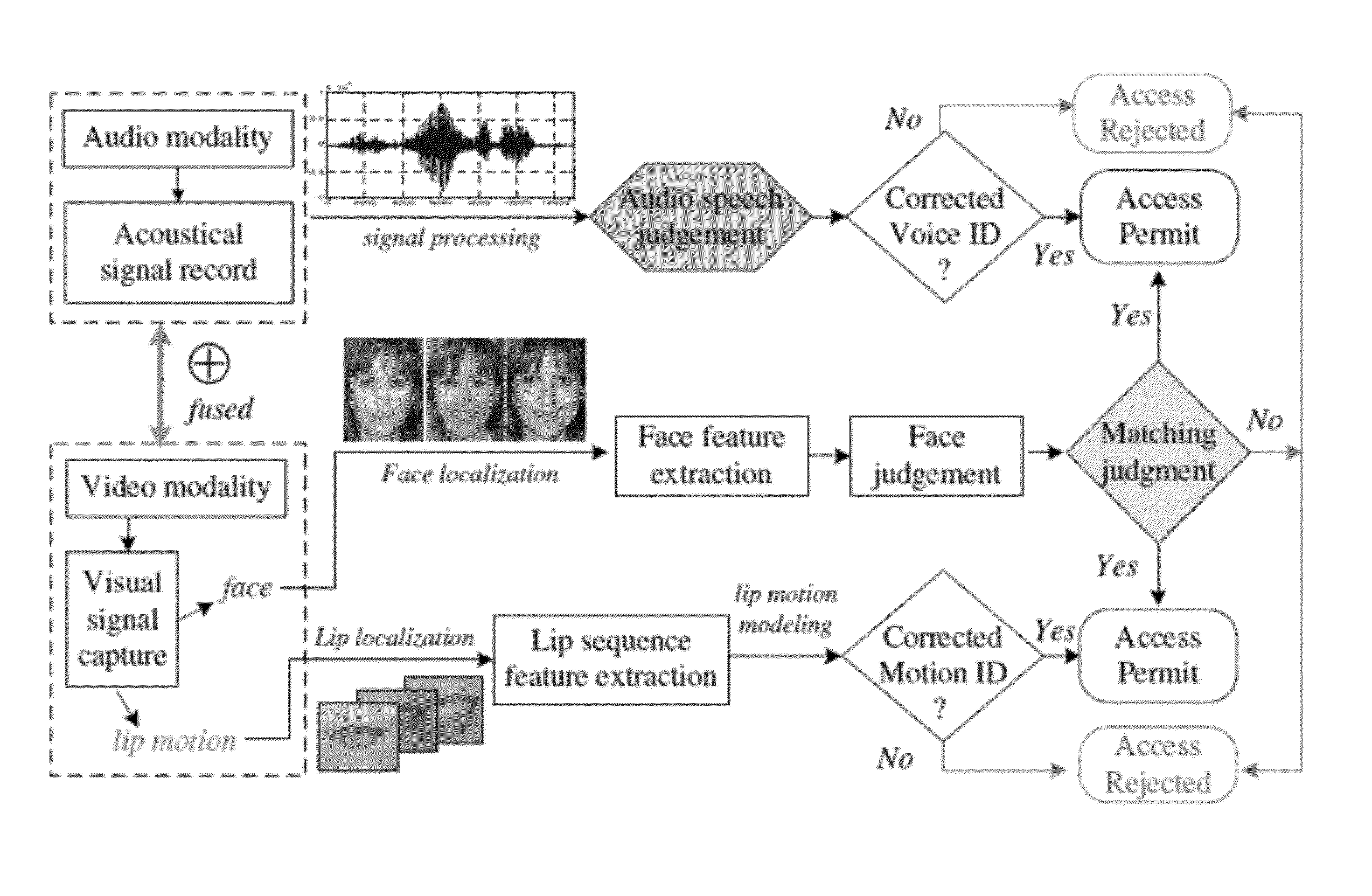
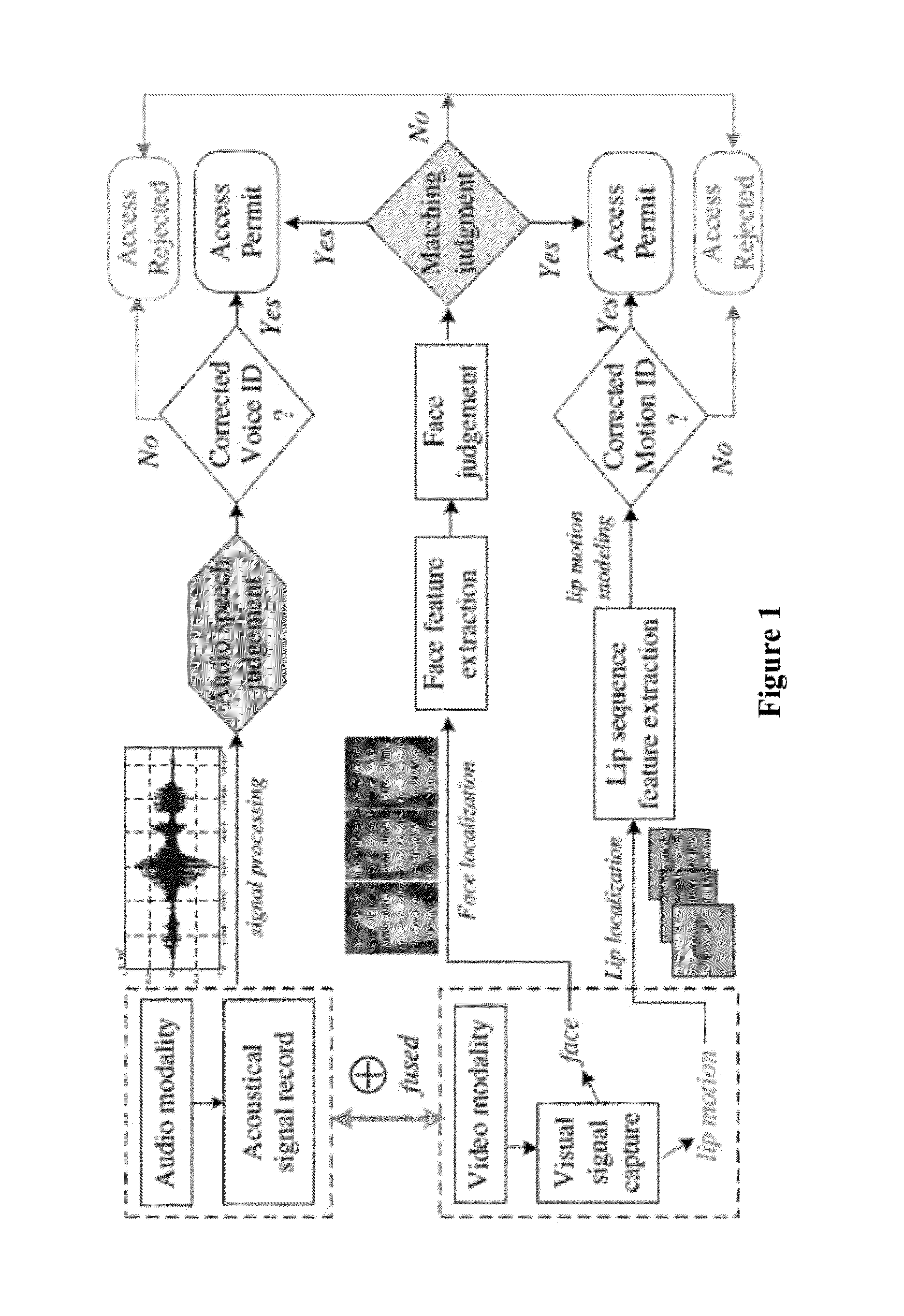
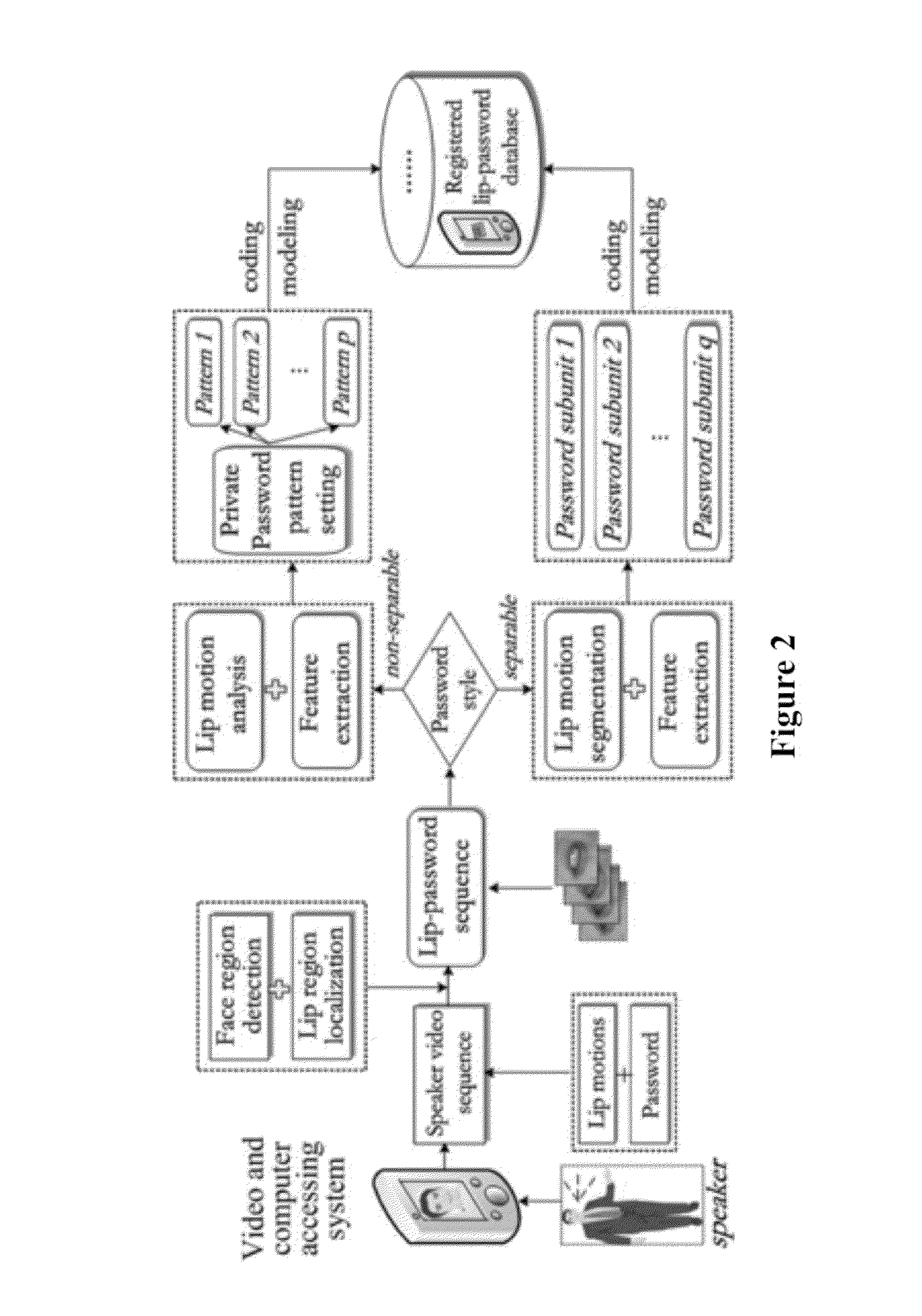
Lip-password Based Speaker Verification System
ActiveUS20130226587A1Easy to implementEasy to useCharacter and pattern recognitionSpeech recognitionIdentification keyPassword
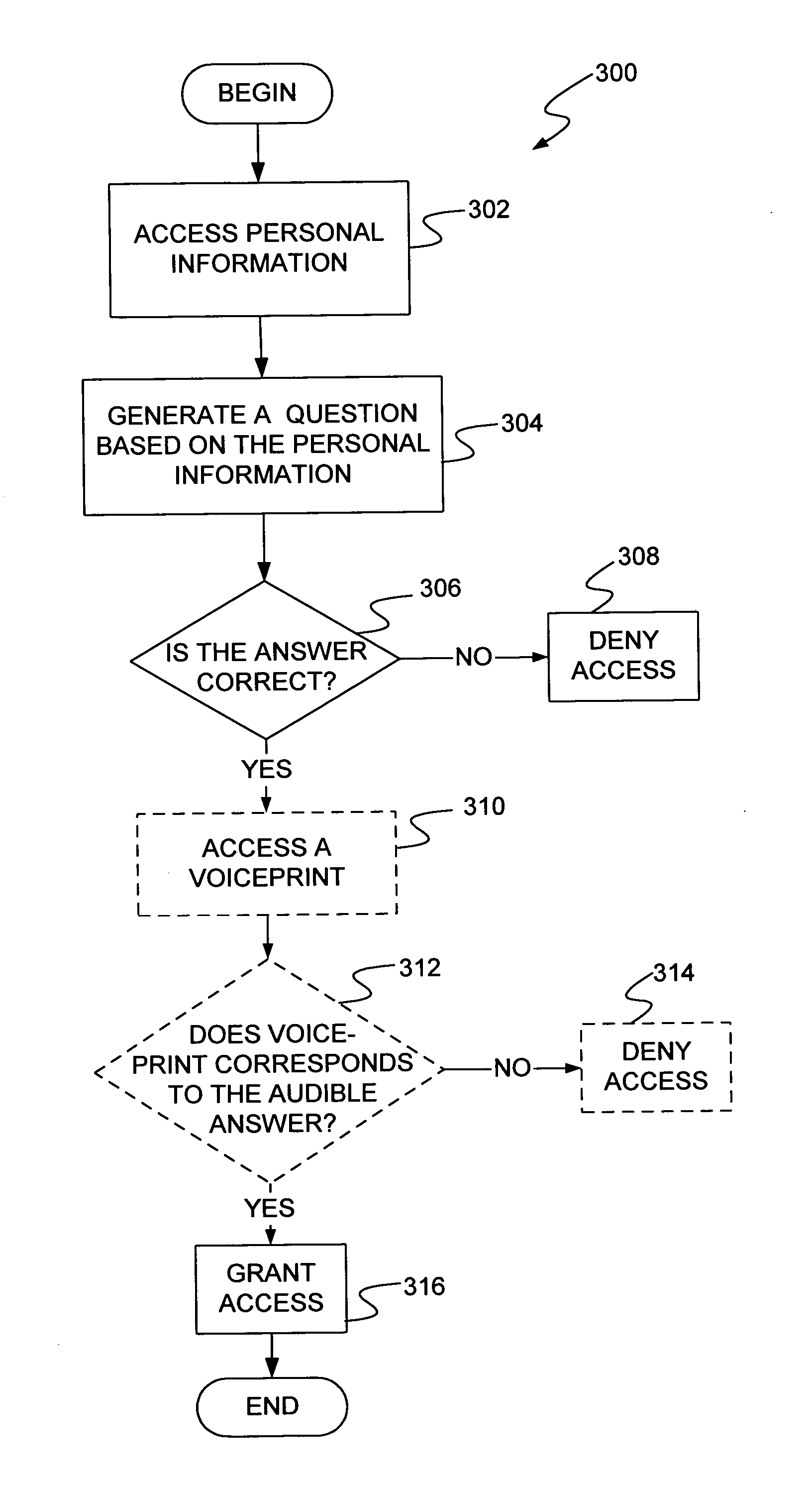
A lip-based speaker verification system for identifying a speaker using a modality of lip motions; wherein an identification key of the speaker comprising one or more passwords; wherein the one or more passwords are embedded into lip motions of the speaker; wherein the speaker is verified by underlying dynamic characteristics of the lip motions; and wherein the speaker is required to match the one or more passwords embedded in the lip motions with registered information in a database. That is, in the case where the target speaker saying the wrong password or even in the case where an impostor knowing and saying the correct password, the nonconformities will be detected and the authentications / accesses will be denied.
Owner:HONG KONG BAPTIST UNIV
Speaker verification-based fraud system for combined automated risk score with agent review and associated user interface
Owner:VERINT AMERICAS
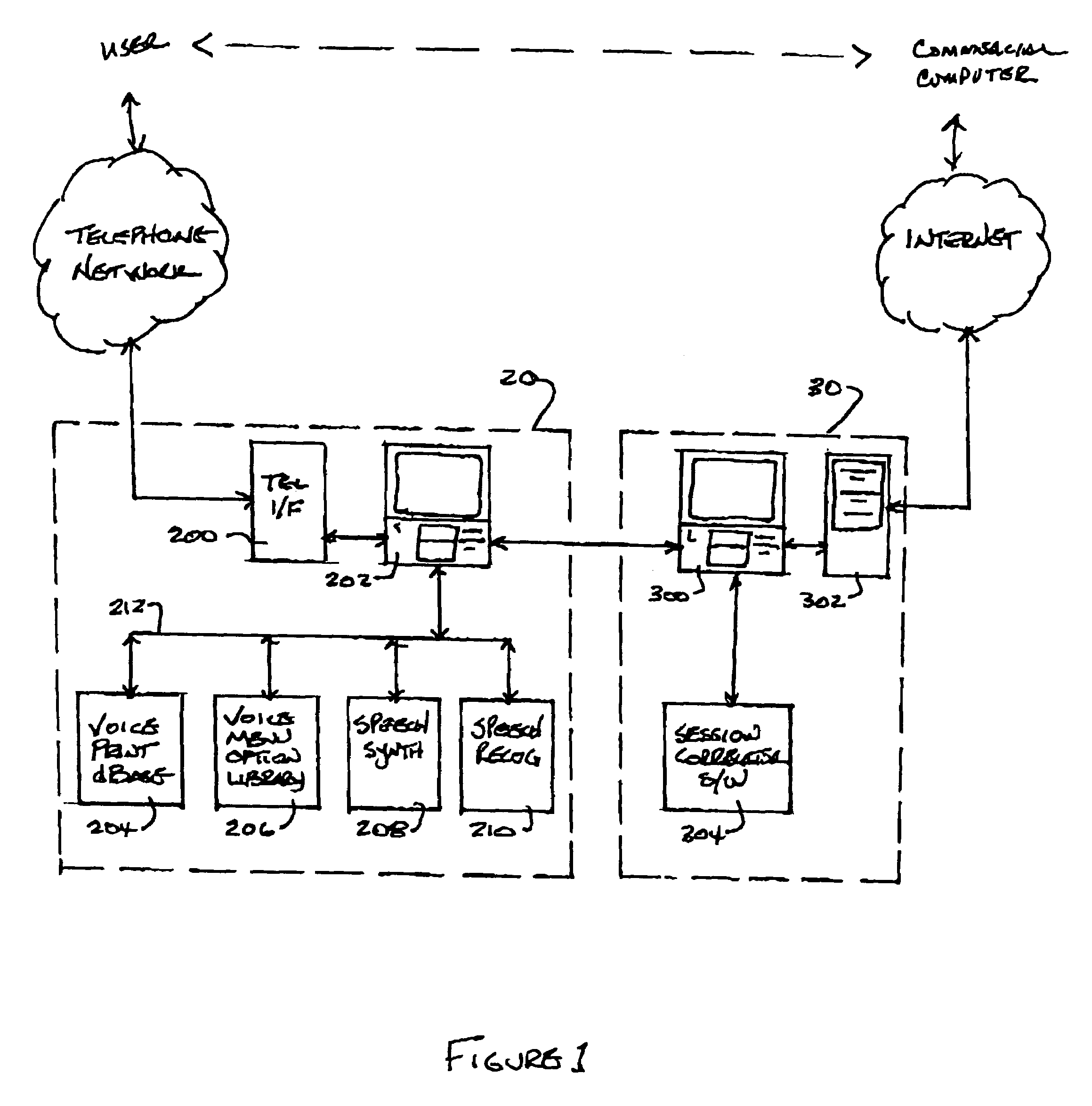
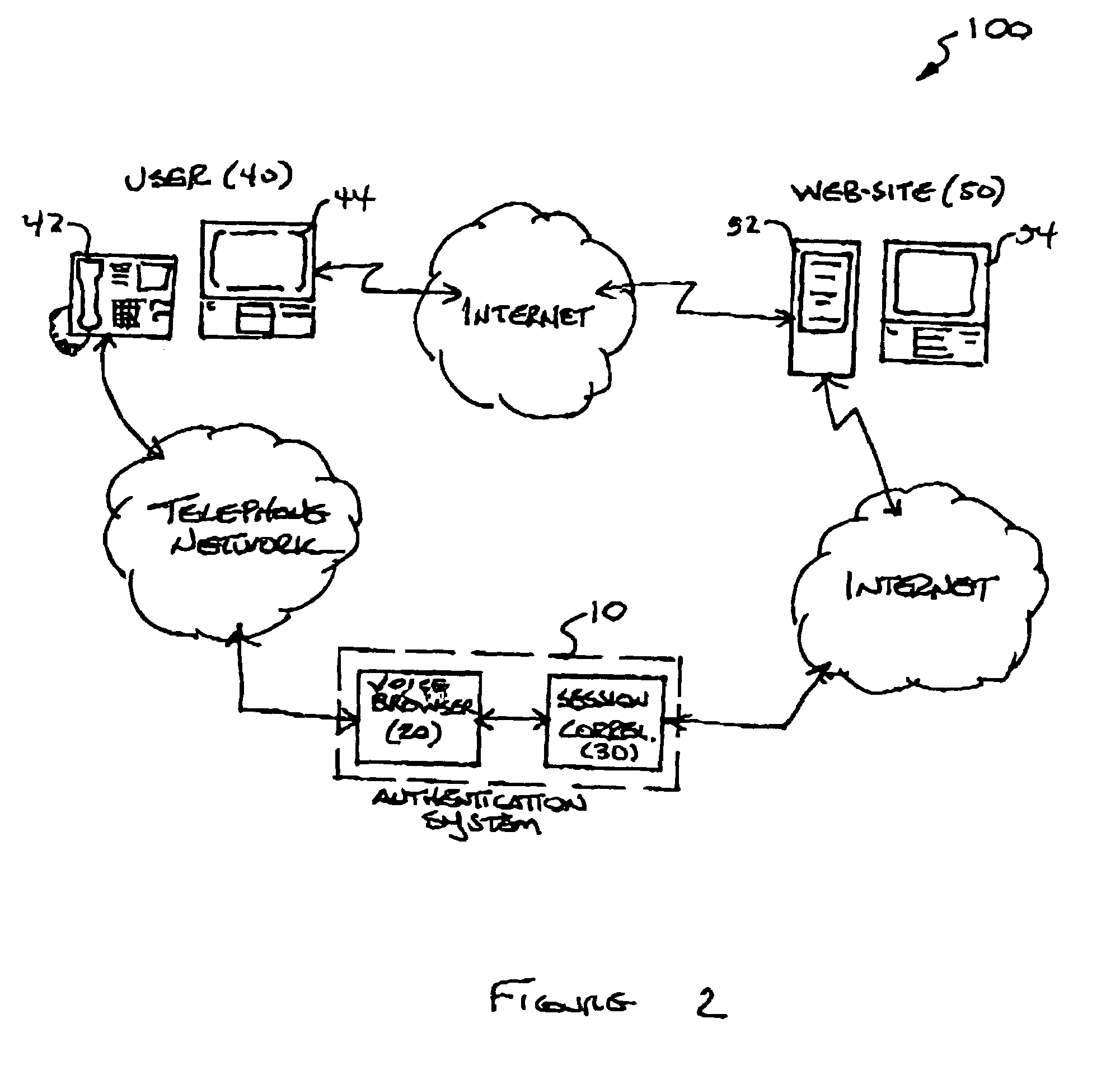
System and method for multi-modal authentication using speaker verification
ActiveUS7174323B1User identity/authority verificationDigital computer detailsSpeaker verificationComputer science
A system authenticates an electronic transaction between a first user-operated device and a computer. The computer is configured to conduct electronic transactions. The system includes a voice browser and a session correlator. The voice browser is configured to receive and process user-spoken information from a second user-operated device, where the voice browser is programmed to compare a user-spoken transaction identifier to a computer generated transaction identifier, and to compare a user-spoken verification identifier to a voice print of the user. The session correlator is coupled to the voice browser and is configured to transmit an authentication message to the computer if the user-spoken transaction identifier matches the computer transaction identifier, and if the user-spoken verification identifier matches the voice print.
Owner:RAKUTEN GRP INC
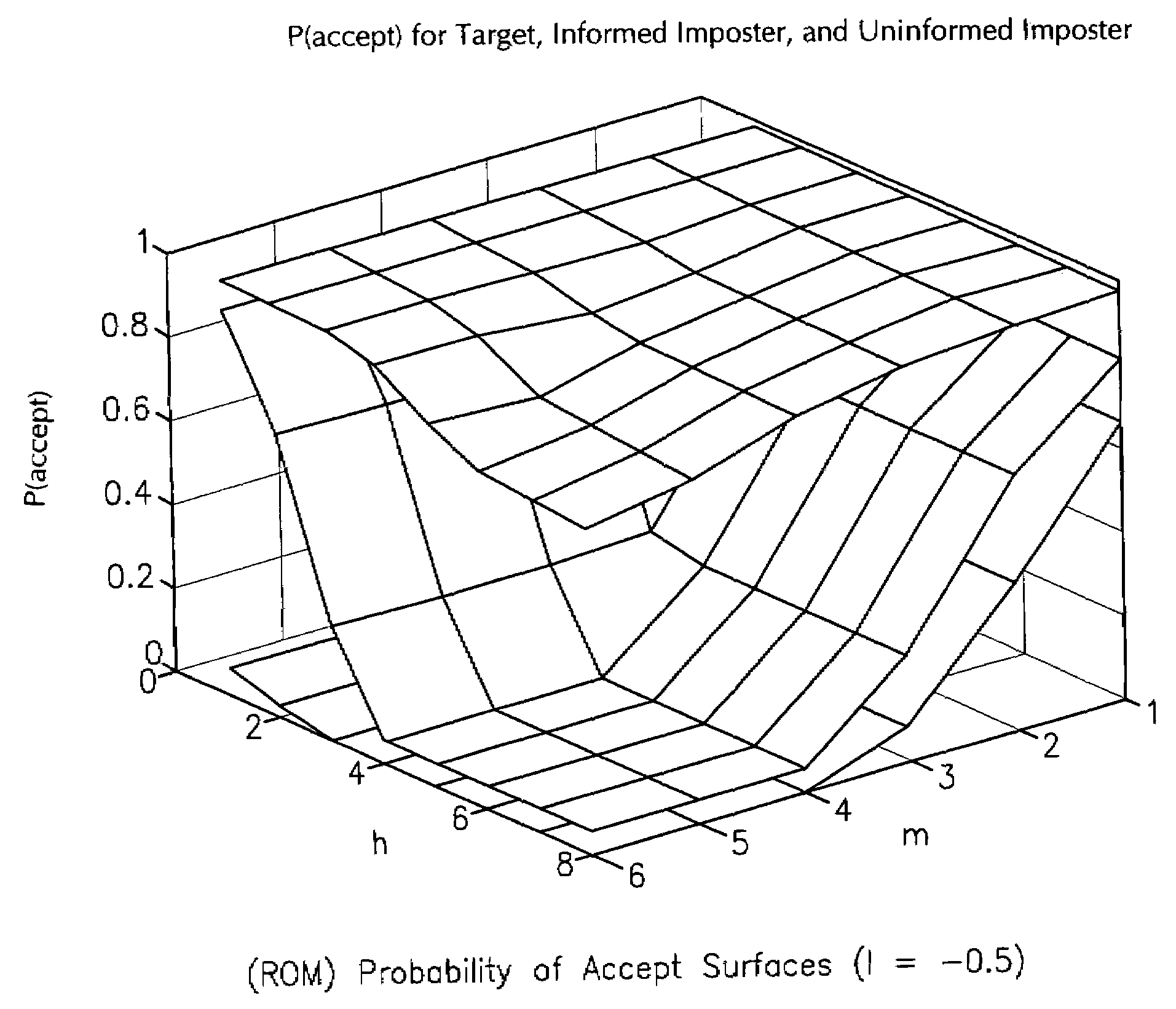
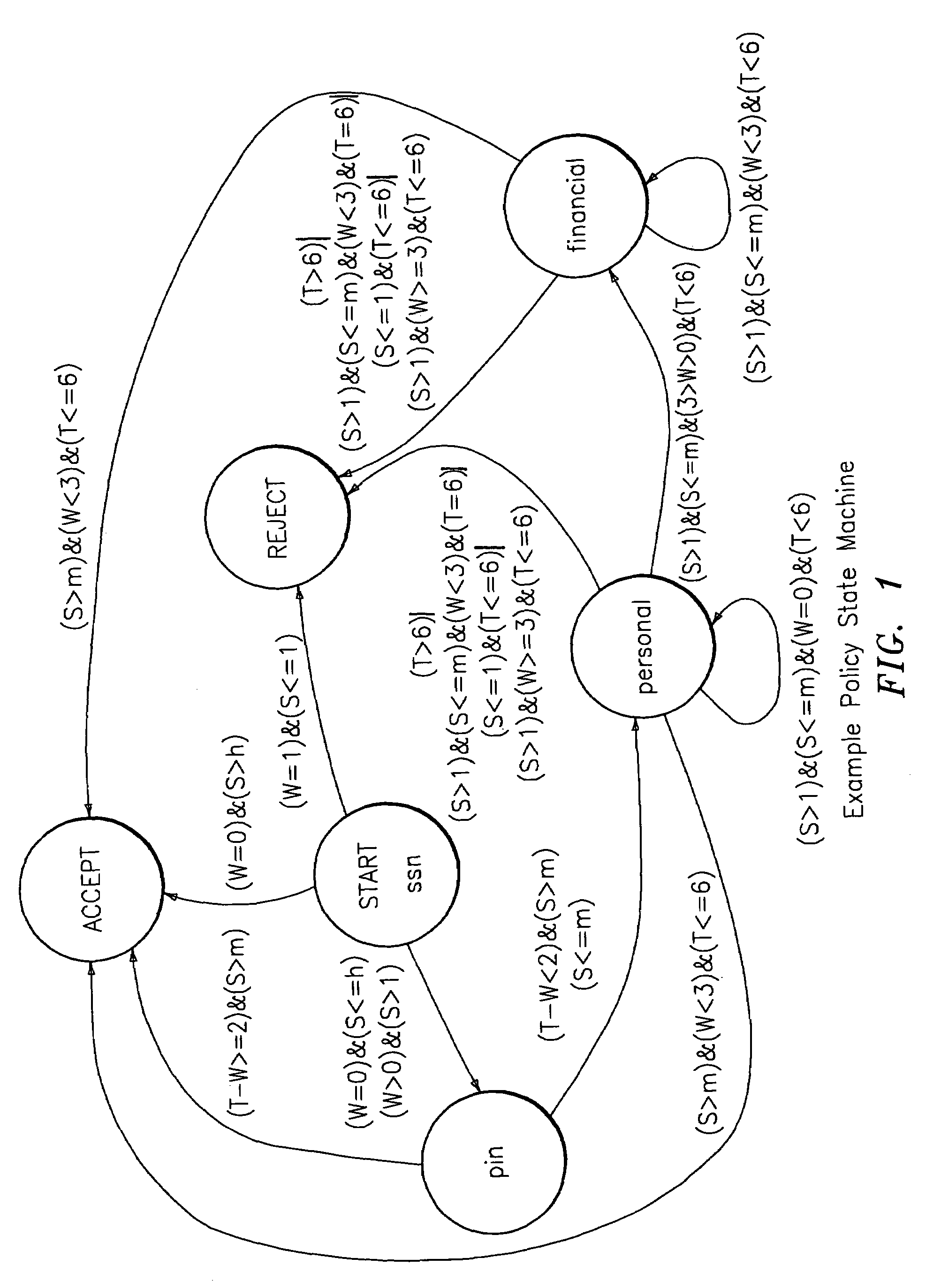
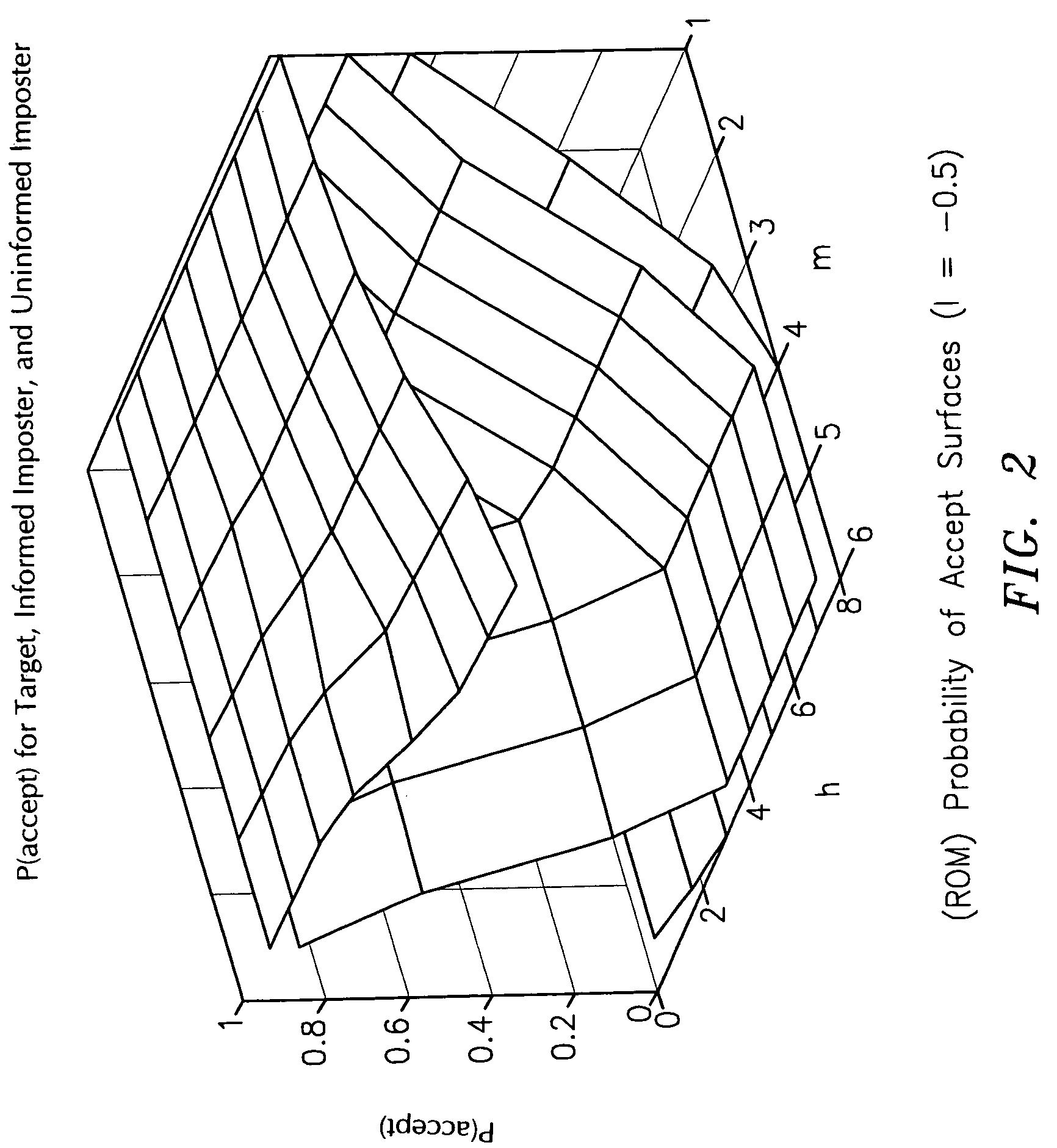
Policy analysis framework for conversational biometrics
InactiveUS7363223B2Digital data processing detailsMultiple digital computer combinationsSpeaker verificationFinite-state machine
The present invention describes a framework for the analytical and visual analysis and tuning of complex speaker verification systems guided by a policy finite state machine. The Receiver Operating Curve associated with the acoustic speaker recognition task is transformed into a multi-dimensional Receiver Operating Map (ROM), which results from a probabilistic analysis of the policy state machine. A Detection Cost Function (DCF) Map can be similarly generated. Results indicating that optimization over this surface (or the ROM) is an appropriate way to set thresholds are given.
Owner:GOOGLE LLC
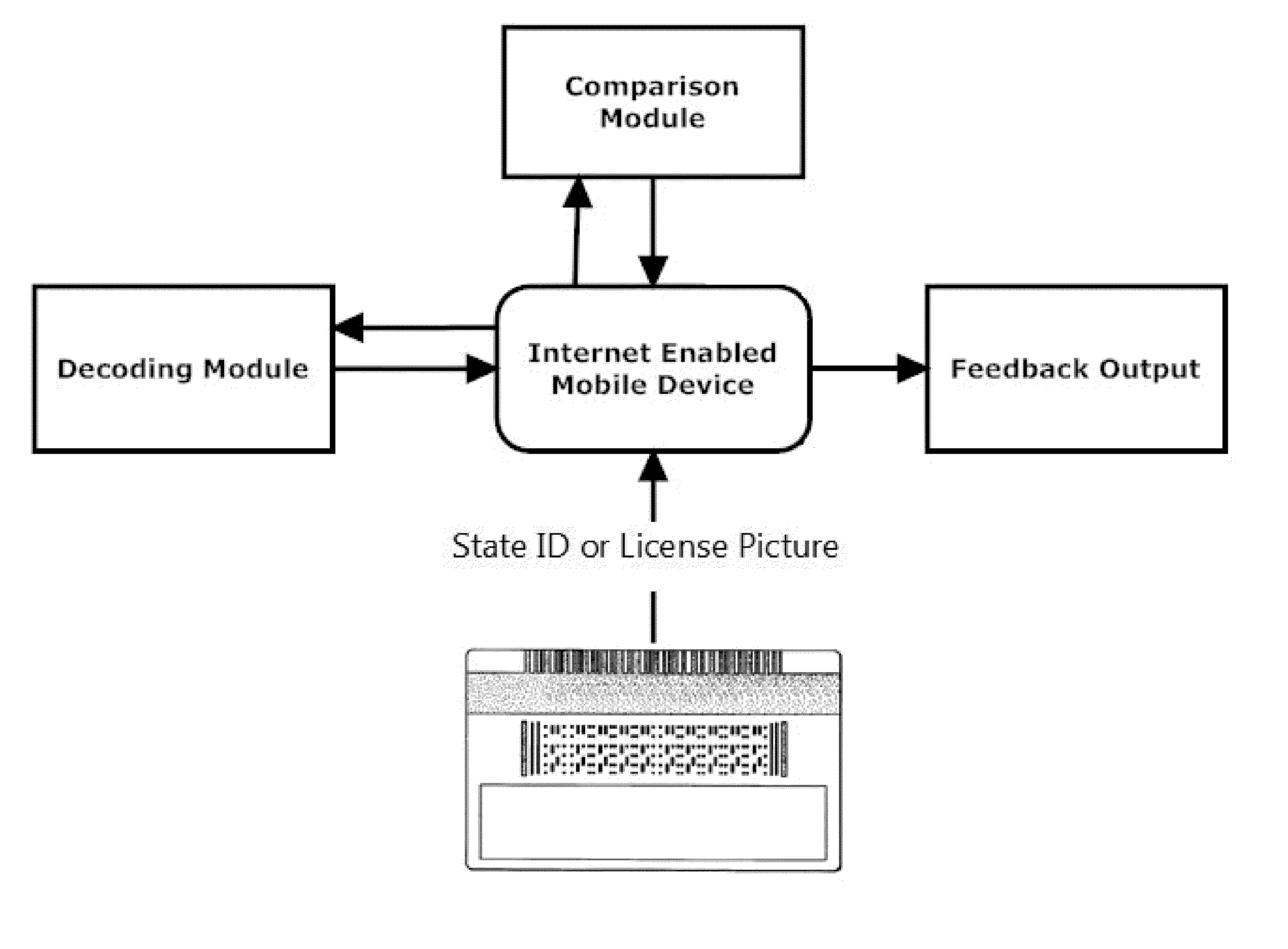
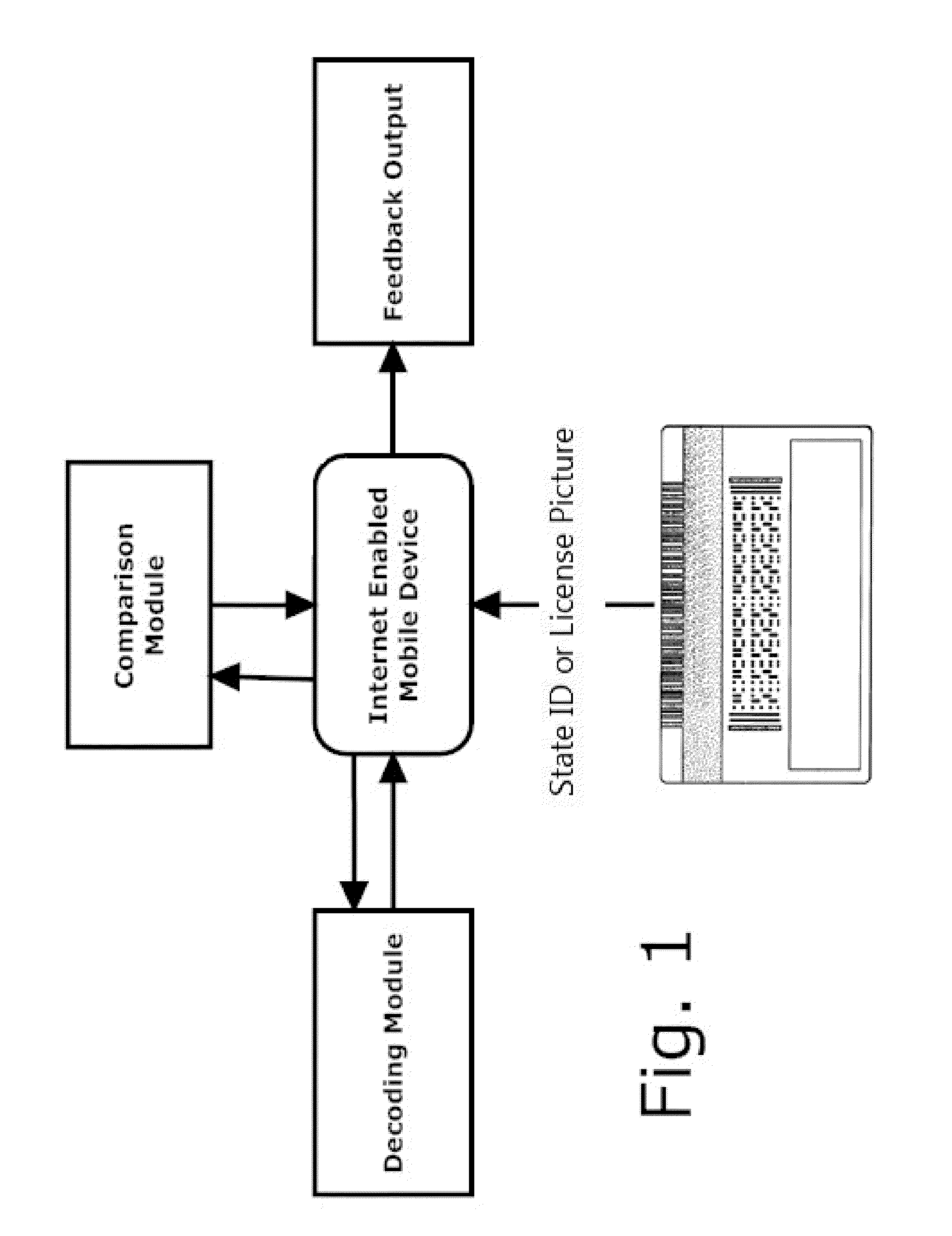
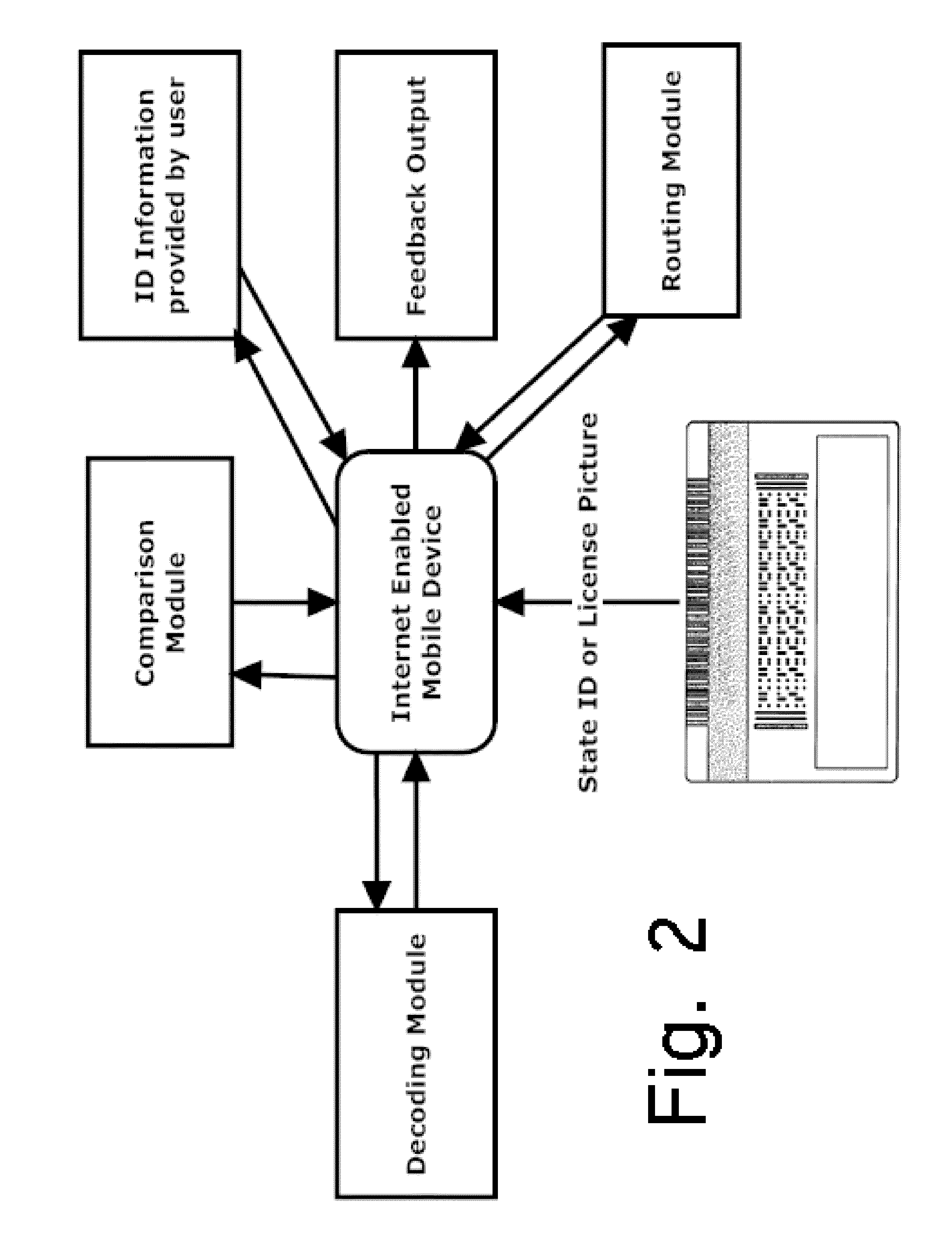
Alcohol Delivery Management System
A system for management of age verification using an internet enabled mobile device. The system provides ID verification using identification information comparison. The system further optionally provides display of completed and pending orders, routing to delivery destination, and prioritizing of deliveries.
Owner:BEERDROPPER
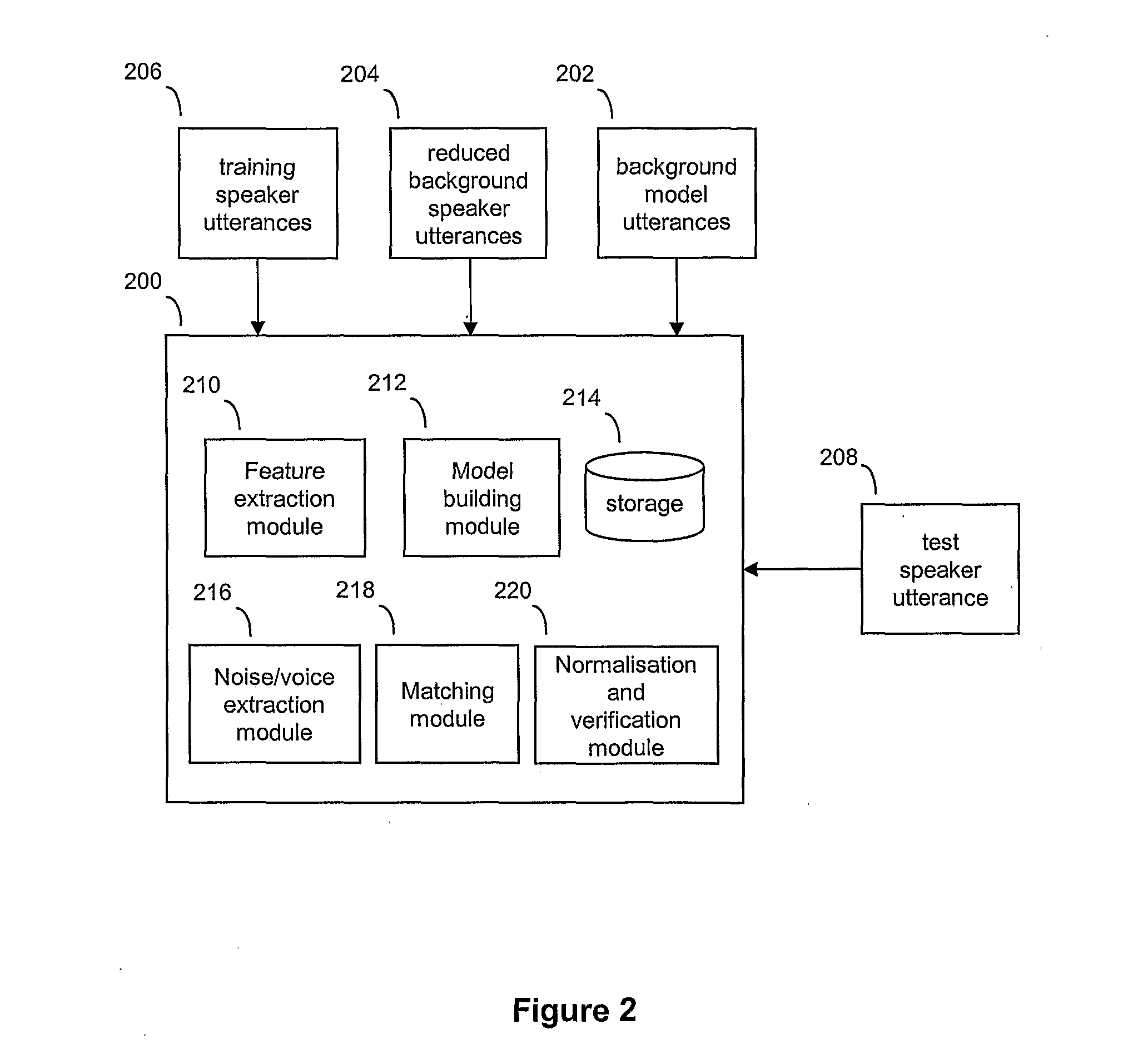
Speaker verification
ActiveUS20110202340A1Simple methodImprove verification accuracySpeech recognitionPassphraseFeature vector
A speaker verification method is proposed that first builds a general model of user utterances using a set of general training speech data. The user also trains the system by providing a training utterance, such as a passphrase or other spoken utterance. Then in a test phase, the user provides a test utterance which includes some background noise as well as a test voice sample. The background noise is used to bring the condition of the training data closer to that of the test voice sample by modifying the training data and a reduced set of the general data, before creating adapted training and general models. Match scores are generated based on the comparison between the adapted models and the test voice sample, with a final match score calculated based on the difference between the match scores. This final match score gives a measure of the degree of matching between the test voice sample and the training utterance and is based on the degree of matching between the speech characteristics from extracted feature vectors that make up the respective speech signals, and is not a direct comparison of the raw signals themselves. Thus, the method can be used to verify a speaker without necessarily requiring the speaker to provide an identical test phrase to the phrase provided in the training sample.
Owner:BRITISH TELECOMM PLC
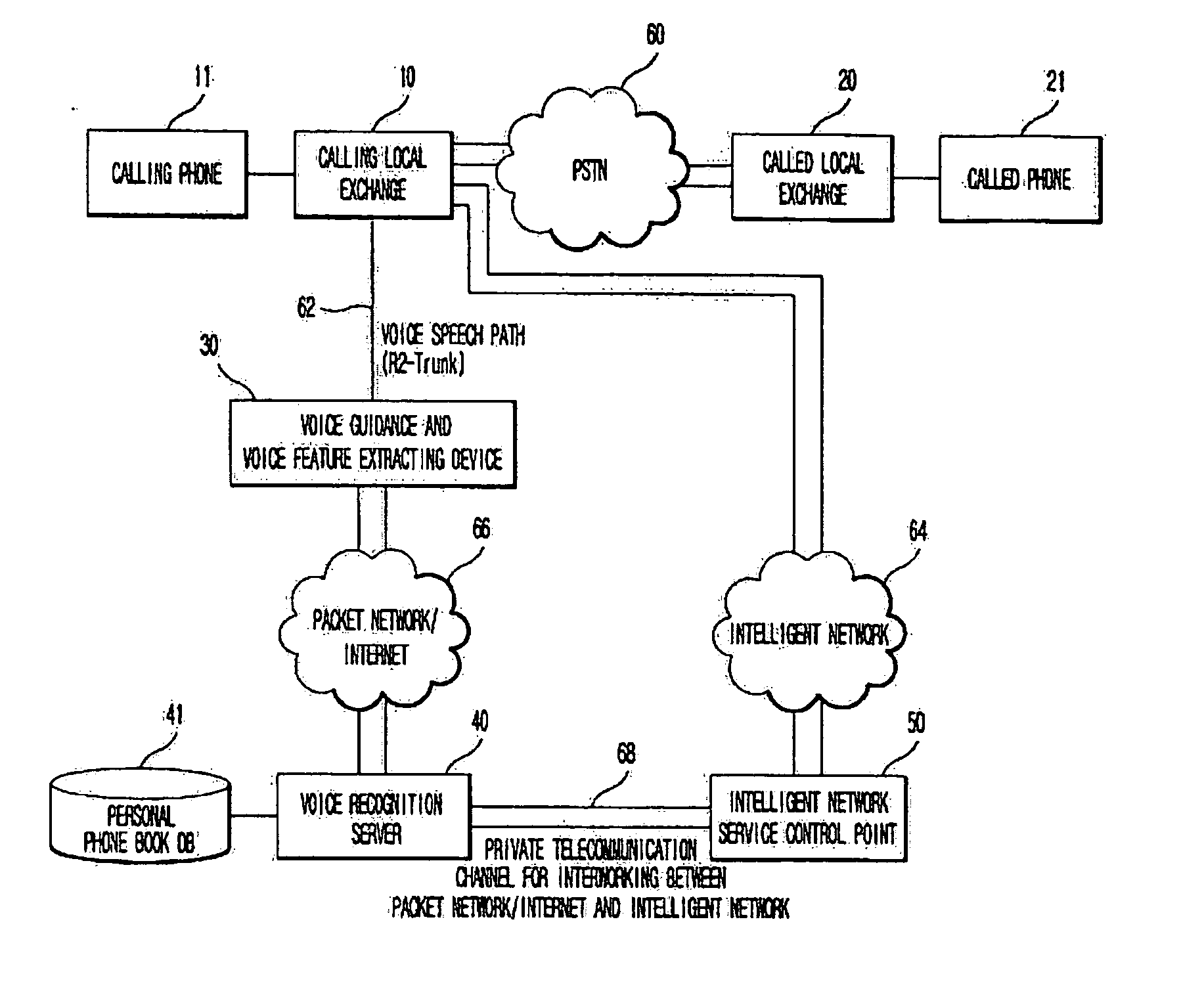
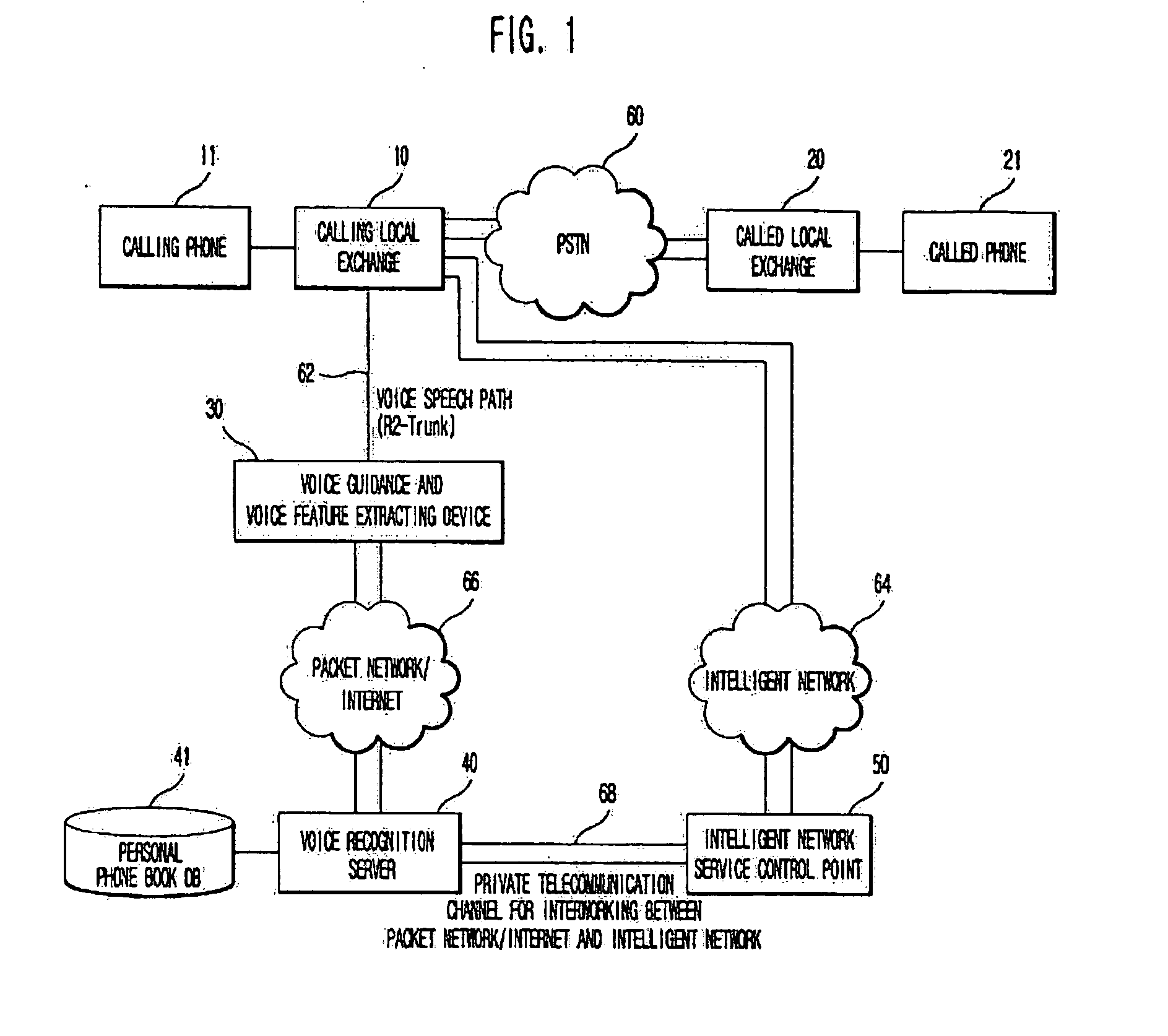
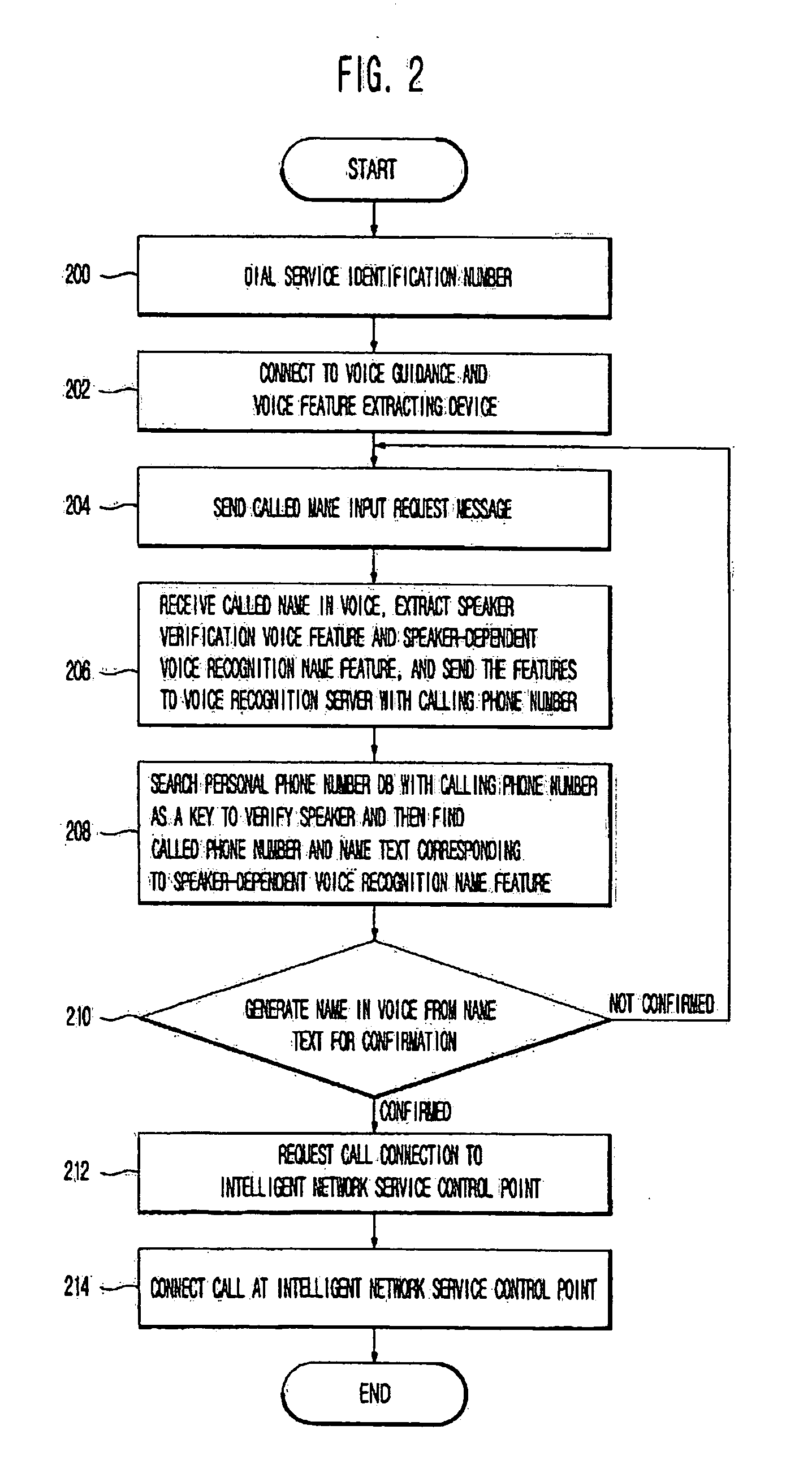
Automatic voice call connection service method using personal phone book databse constructed through voice recognition
ActiveUS20040247088A1Conveniently madeSpecial service for subscribersAutomatic call-answering/message-recording/conversation-recordingSpeaker verificationSpeech identification
Disclosed is an automatic voice call connection service method using a personal phone book database constructed through voice recognition, which includes the steps of allocating personal databases corresponding to phone number to each service user; storing name text, speaker verification feature, speaker-dependent voice recognition name feature and called phone number to the personal database; extracting the speaker verification feature when the speaker requires a phone call and then sending the feature to a voice recognition server / database; verifying the speaker with the feature and searching a name text and a called phone number with the speaker-dependent voice recognition name feature; checking the searched name text and sending the text as a voice to the user; and connecting the call through a public switched telephone network (PSTN).
Owner:LEE MOON SEUB
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com