Patents
Literature
189results about How to "Improve verification accuracy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
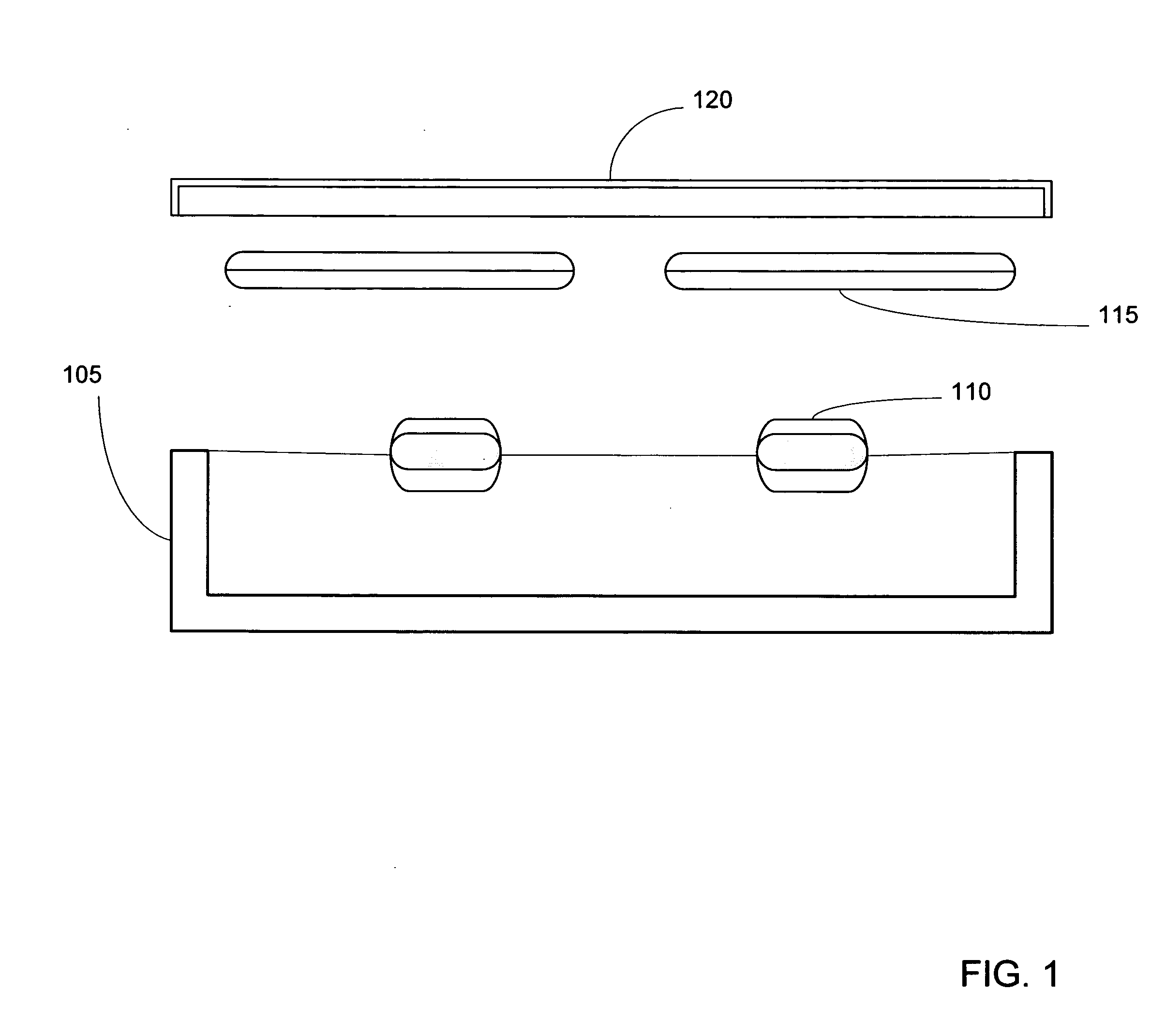
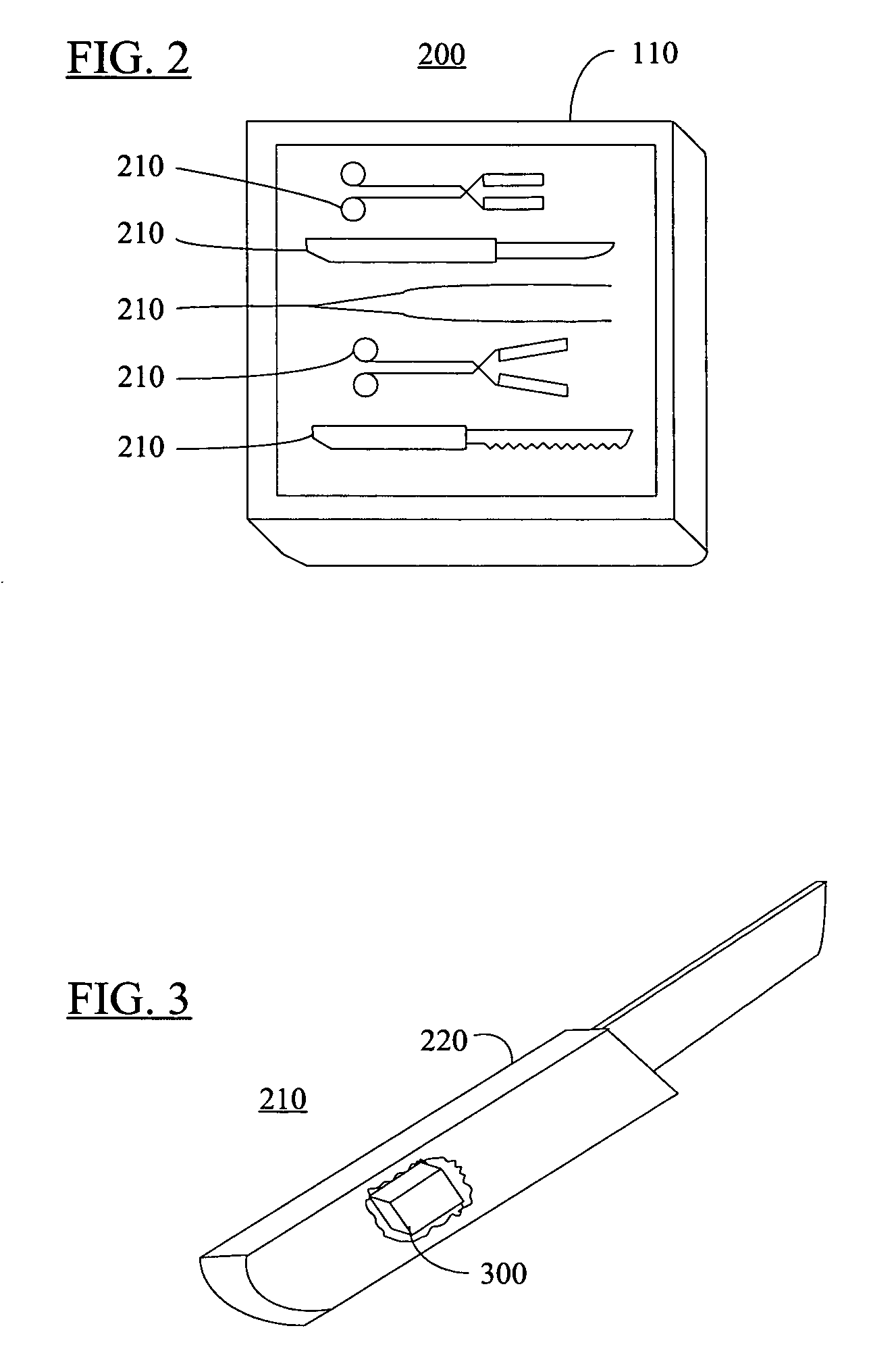
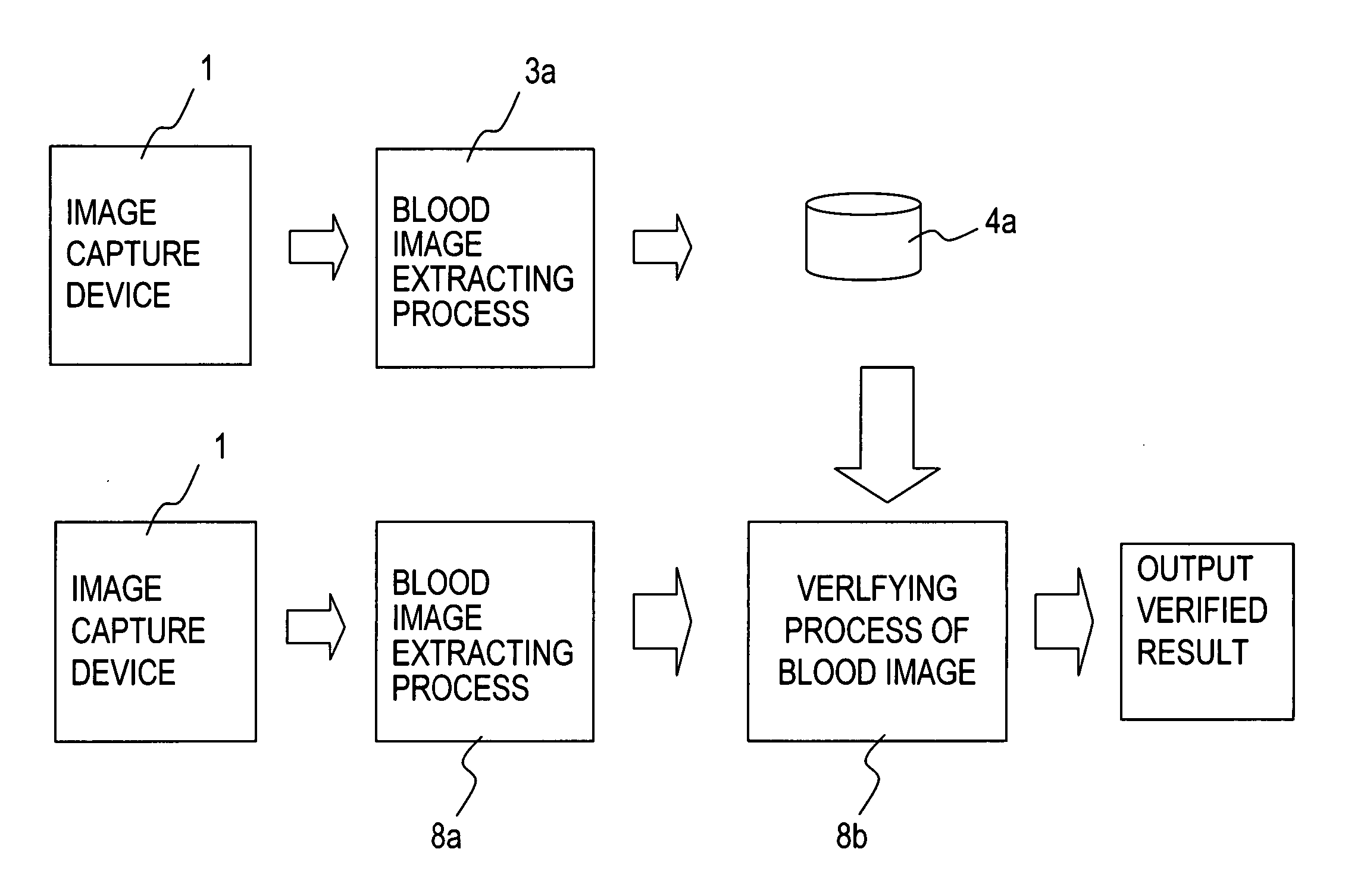
Smart instrument tray RFID reader
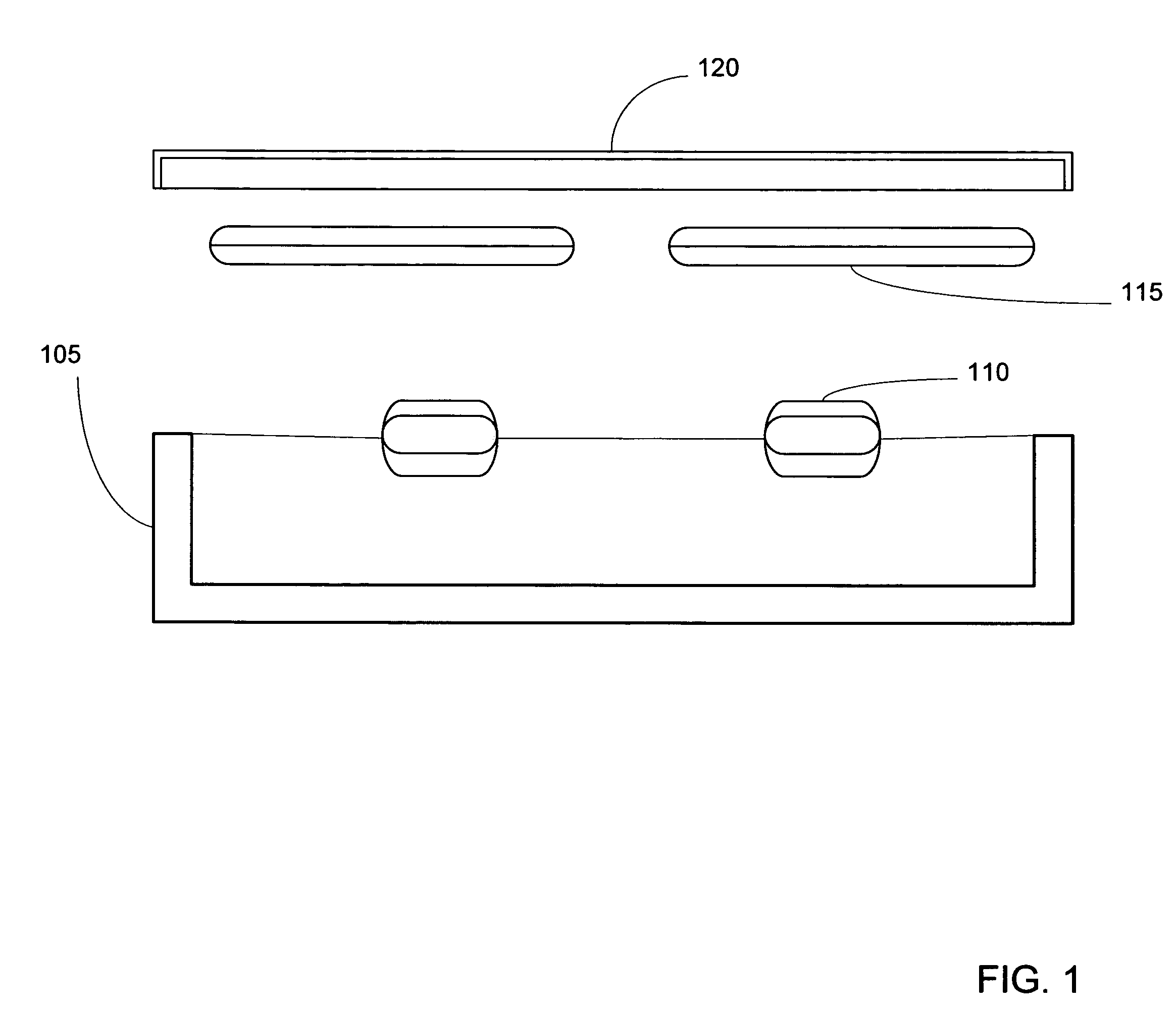
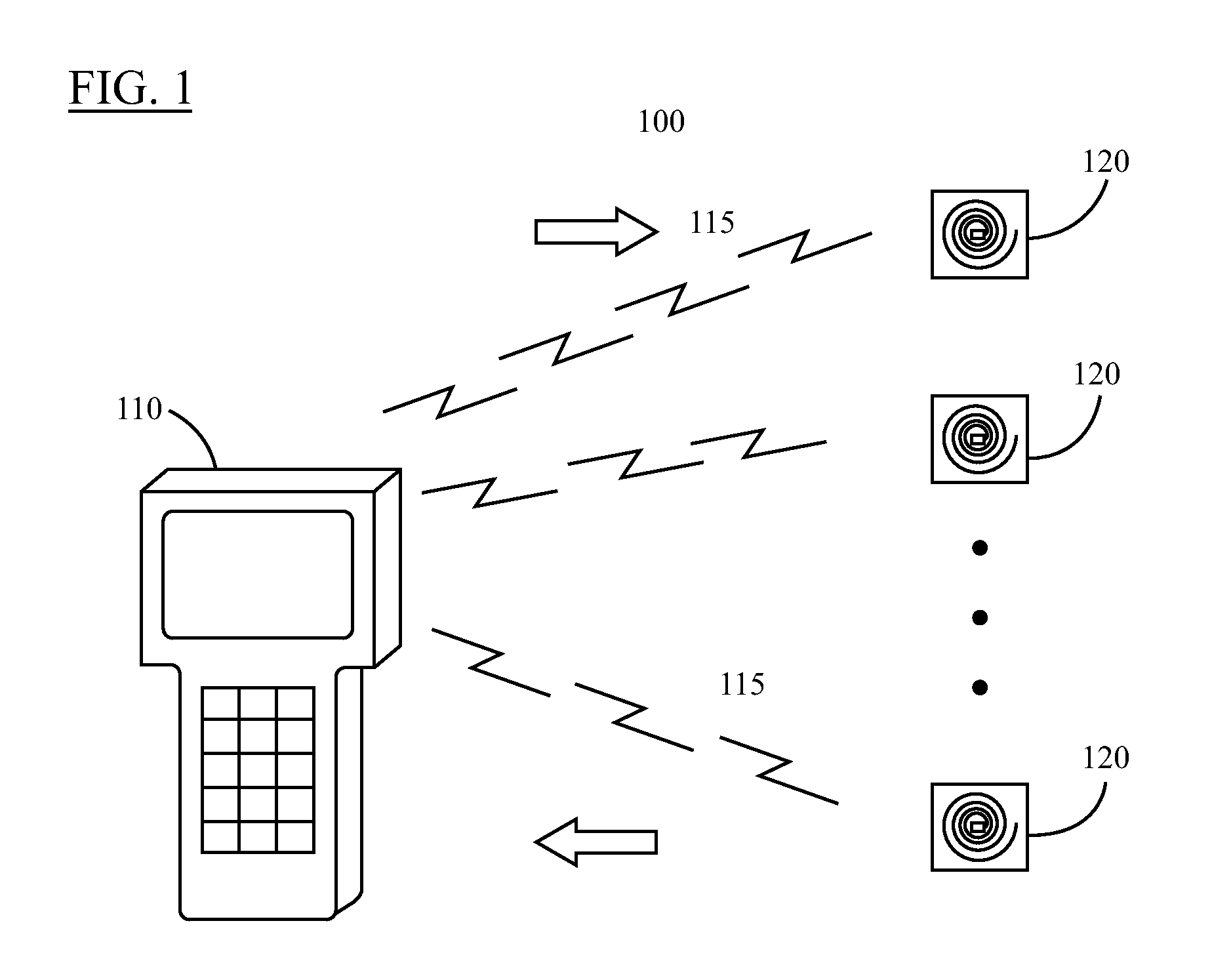
ActiveUS7118029B2Reduce processing costsImprove verification accuracySurgical furnitureDiagnosticsWireless lanEngineering
Owner:WARSAW ORTHOPEDIC INC
Smart instrument tray RFID reader
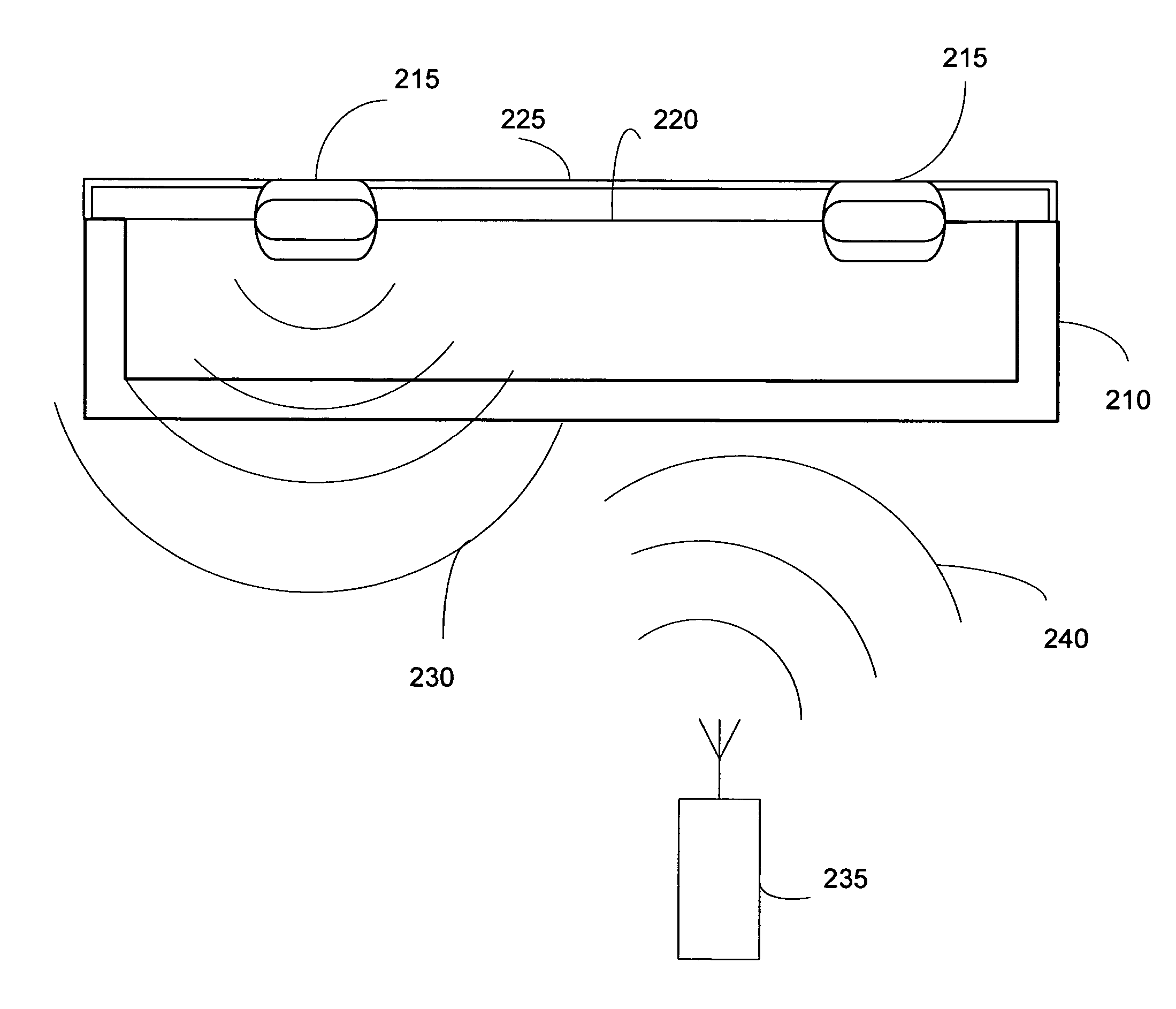
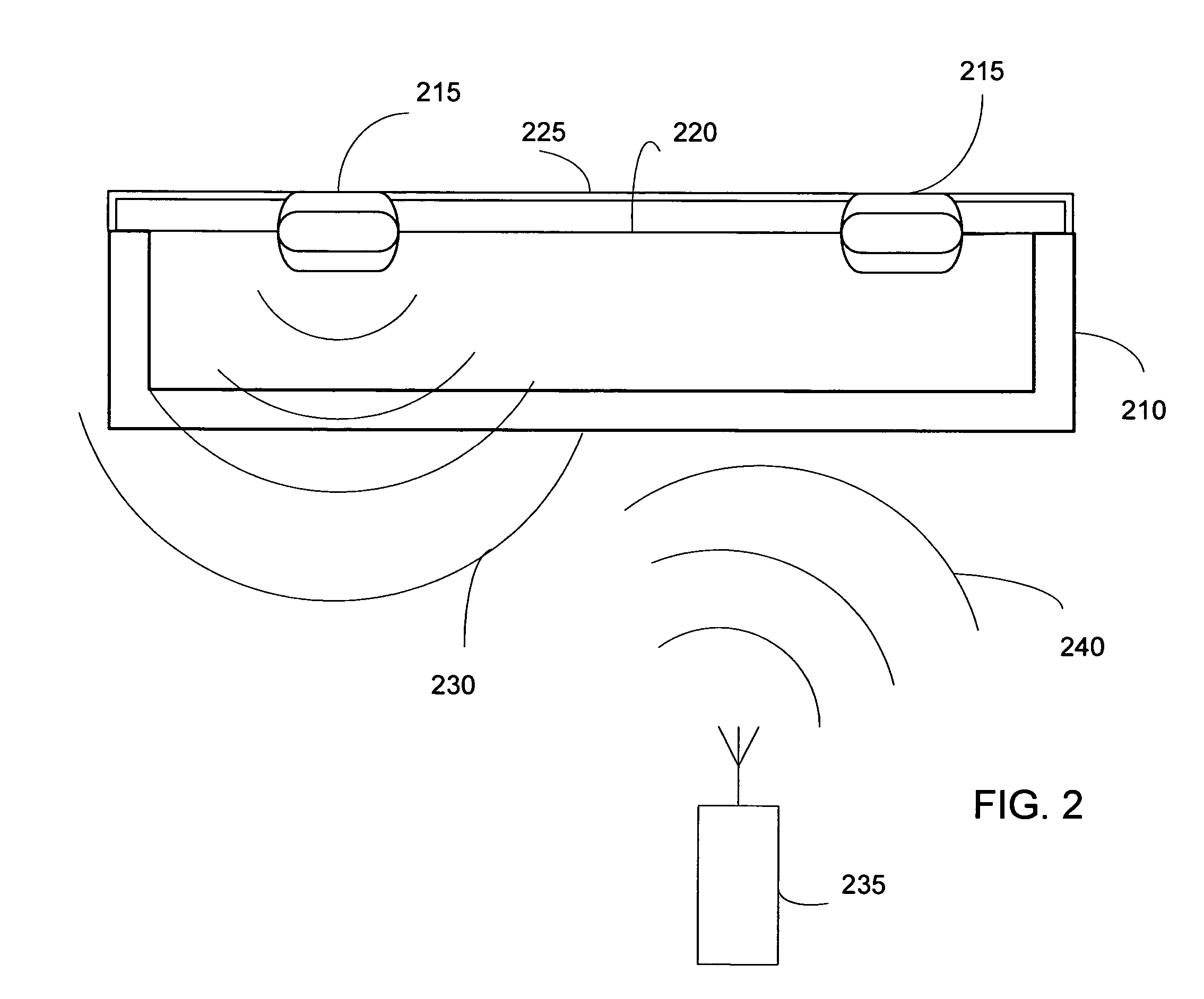
ActiveUS20060043179A1Reduce processing costsInterference problemSurgical furnitureDiagnosticsEngineeringElectromagnetic field
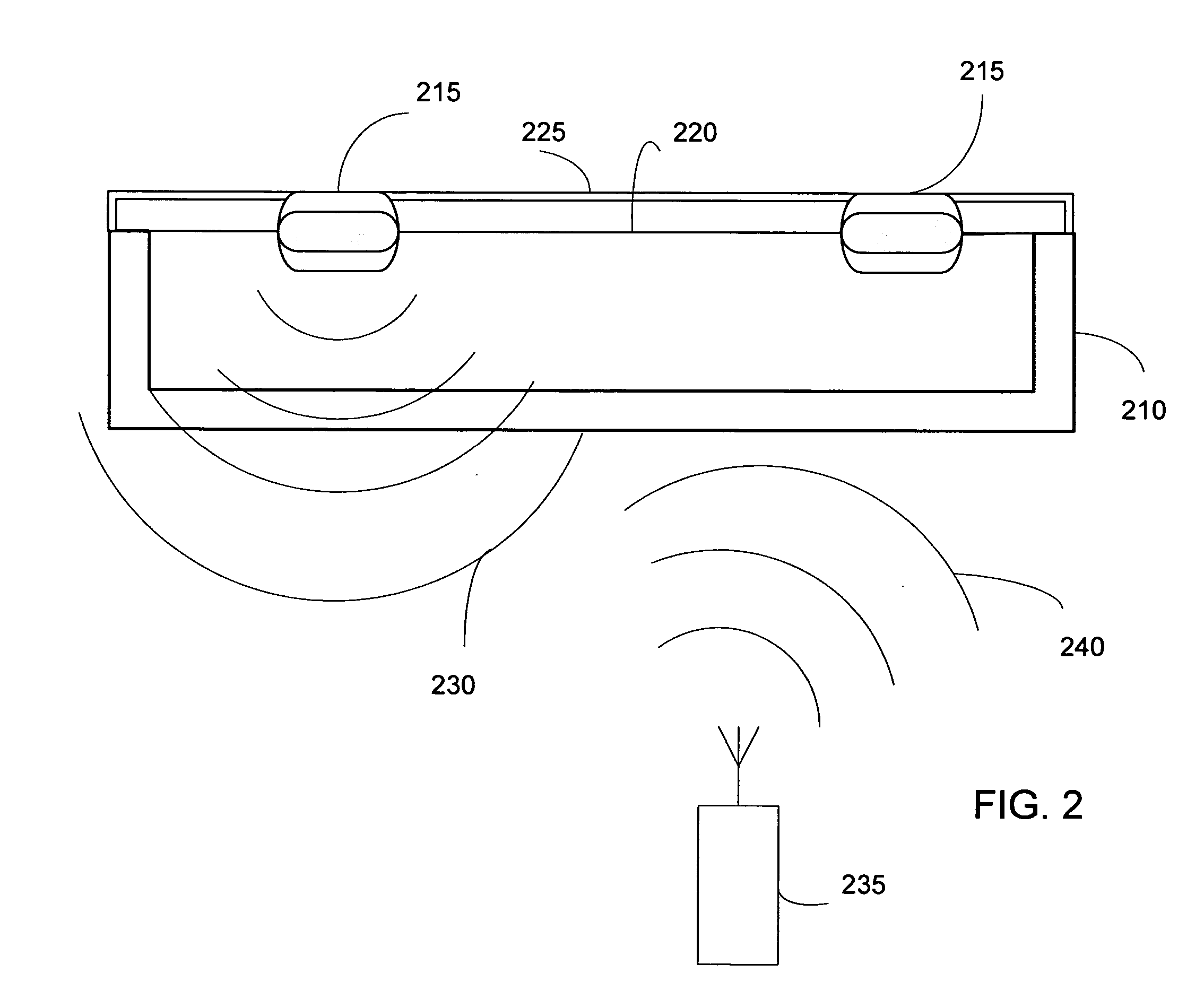
A method and apparatus for automatically identifying the contents of an instrument tray by use of a radio-frequency tag (RFID) is disclosed. The method, apparatus, and system enable the instrument tray to receive an interrogation signal from a reader and to respond to the interrogation signal with a code comprised of its identifying information as well as its contents of radio frequency tagged instruments. Both the instrument tray and / or the reader may be coupled by a proximity electromagnetic field, an inductive coupling, or may be units of a wireless LAN system such as a wireless fidelity local area network. The interrogation signal interrogates the tray to ascertain its contents, and the tray in turn transmits a signal to the reader to inform the reader of its contents. The method, apparatus, and system can track, inspect, and verify inbound and outbound surgical instrument trays and kits, to assess, for example, the surgical instruments' and trays' duty life cycle usage.
Owner:WARSAW ORTHOPEDIC INC
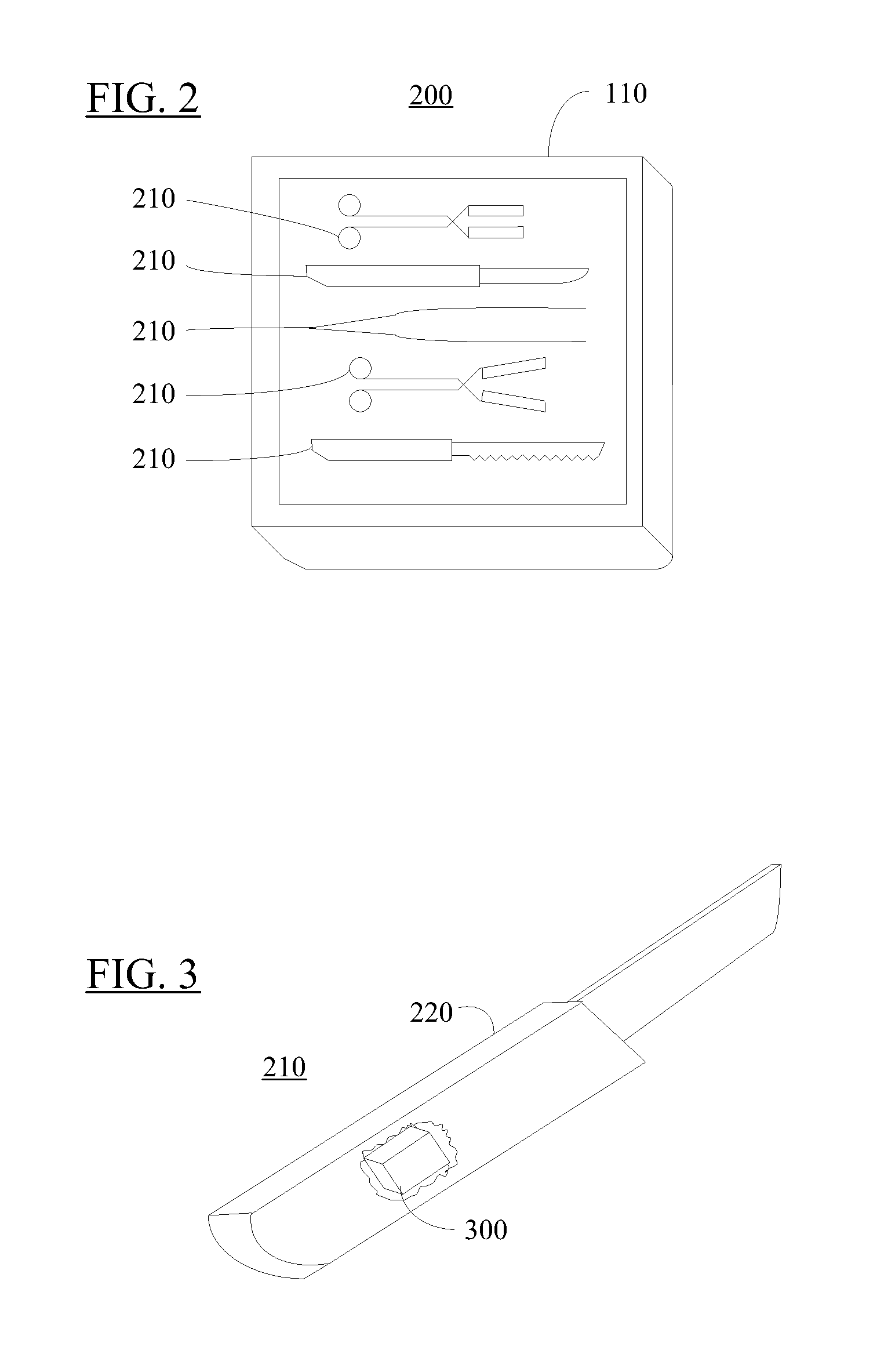
Method and apparatus for surgical instrument identification
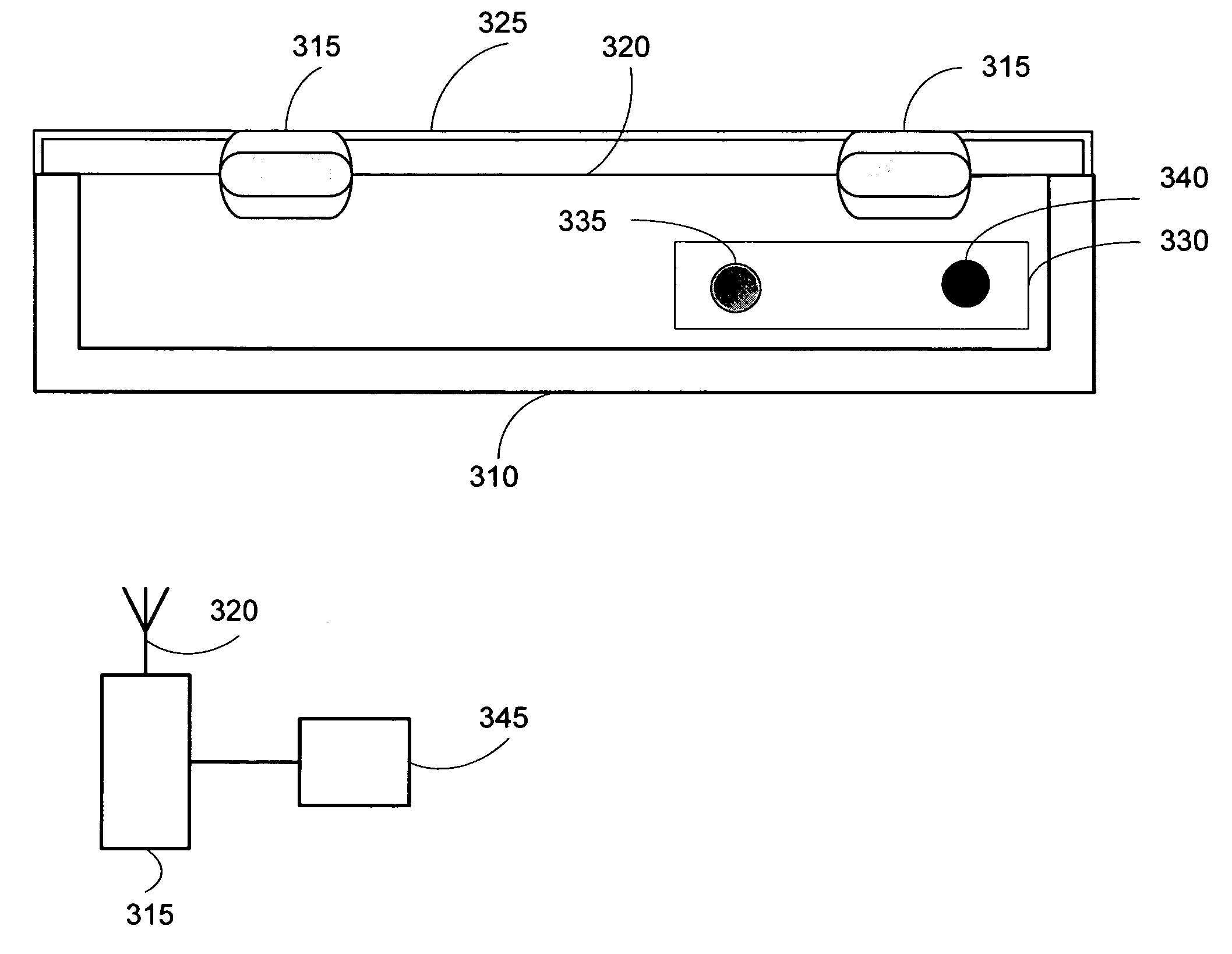
ActiveUS20060244652A1Reduce processing costsOvercomes shortcomingSurgical furnitureDiagnosticsEngineeringOperating life
Systems and methods for identifying surgical instruments by use of radio-frequency identification tags (RFID) are disclosed. In the systems and methods, each of a plurality of surgical instruments is provided with at least one RFID transponder tag storing identification information associated with the corresponding instrument. The tag may be adhered to, embedded, or potted within a portion of the instrument. Using an RFID reading device, a user may interrogate the tag, thereby identifying the particular instrument. This identification information may be used to index a database and retrieve a data record unique to that instrument. The systems and methods allow a user to track, inspect, and verify inbound and outbound surgical instruments, to assess, for example, the surgical instruments' duty life cycle usage.
Owner:WARSAW ORTHOPEDIC INC
Biometrics-based device for detecting indentity of people and identification
InactiveCN101669824AReduce work intensityReduce error ratePerson identificationCharacter and pattern recognitionFace detectionProcess module
The invention discloses a biometrics-based device for detecting identity of people and identification, which comprises an omni-directional vision sensor used for acquiring the facial image of an ID card holder, an ID card reader used for reading the photograph information in a bulit-in chip of the second-generation ID card and a microprocessor used for comparing whether the facial photograph imagestored in the built-in chip of the second-genration ID card and the facial images acquired by the omni-directional vision sensor are consistent or not, wherein the microprocessor comprises a data module used for reading photograph image in the ID card, a first facial detecting module, a first facial feature extraction module, a panoramicpicture reading module, a second facial detecting module, animage expanding module, a second facial feature extraction module, an identity detecting module for the biological feature of people and the ID card and a decision-layer voting and processing module.The device adopts biometrics identification technology, can greatly improve the efficiency for validating the ID card, and reduce the working strength and error rate of office personnels.
Owner:ZHEJIANG UNIV OF TECH
Biometrics authentication system registration method, biometrics authentication system, and program for same
InactiveUS20060078170A1Effectively pluralityImprove verification accuracyWriting implementsDigital data authenticationData setDegree of similarity
A biometrics authentication system utilizes information of the palm of the hand of a body to perform individual authentication. A processing unit obtains an image of the palm of the hand of the same body a plurality of times from an image capture unit, judges the degrees of similarity among the characteristic data sets of the plurality of images of the palm of the hand, and registers a plurality of characteristic data sets with a high degree of similarity in a storage unit. And the shape of the hand in the image is checked from the outlines in the image of the palm of the hand, so it is possible to rapidly judge whether image capture has been successful and extract characteristic data, and registration processing can be executed in a short length of time.
Owner:FUJITSU LTD +1
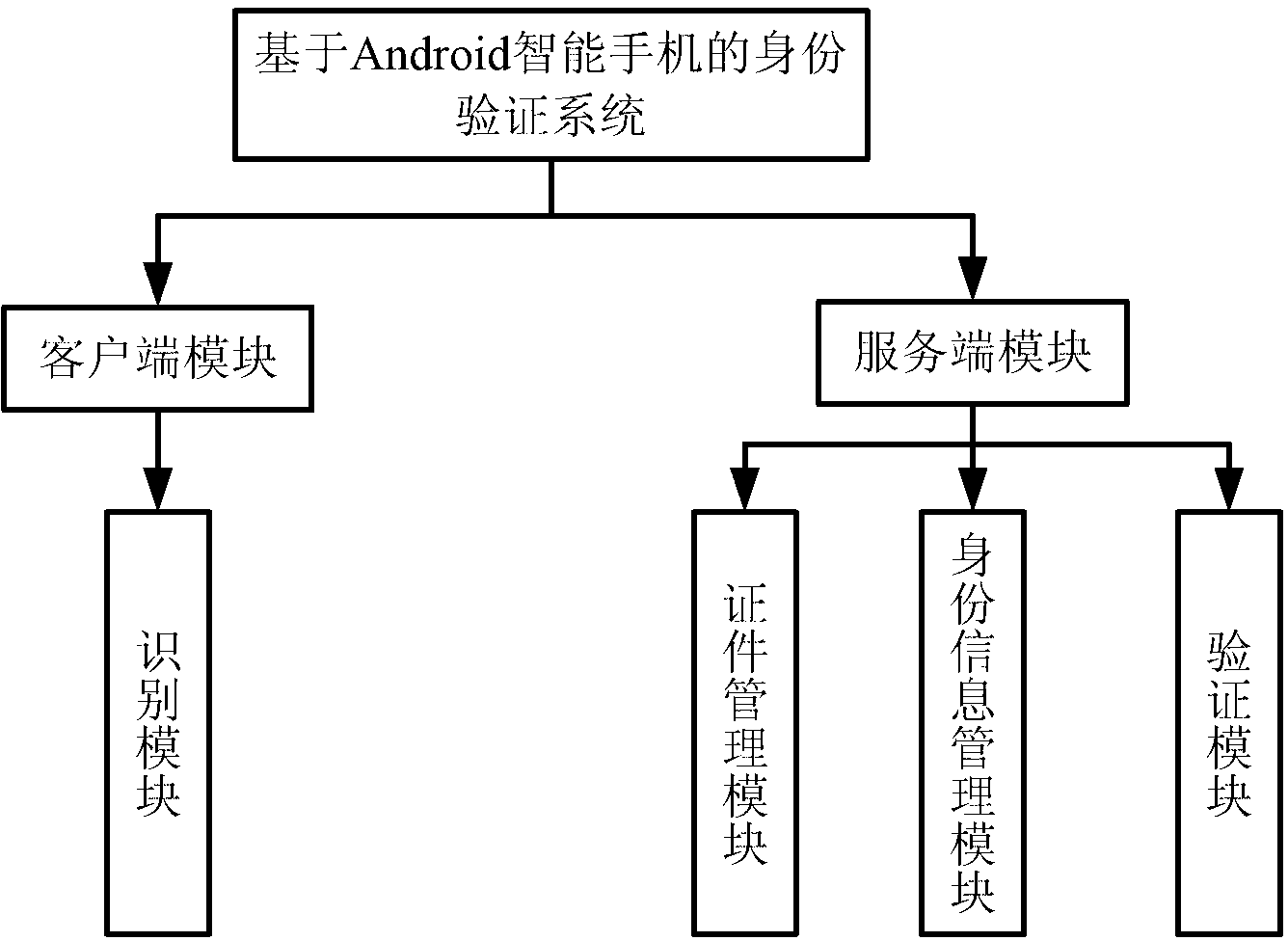
Authentication system and method based on intelligent mobile communication equipment
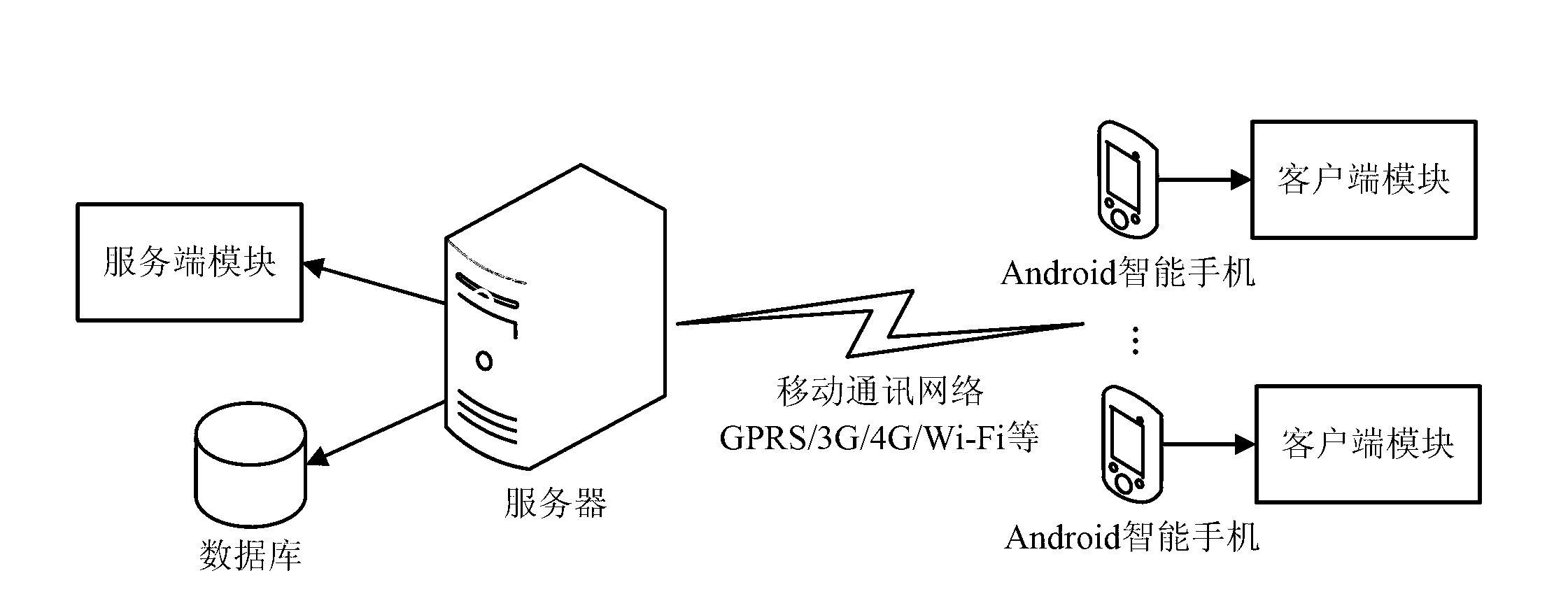
InactiveCN102801528AVerification is achieved quicklyRealize verificationUser identity/authority verificationSecurity arrangementComputer moduleE communication
The invention provides an authentication system based on intelligent mobile communication equipment. The authentication system comprises more than one intelligent mobile communication equipment, more than one server, a client-side module and a server-side module; the client-side module is arranged in the intelligent mobile communication equipment and comprises an identification module, wherein the identification module is used for submitting an authentication request, acquiring identity information, identifying elements in the identity information and querying an authentication result; the server-side module is arranged in the server and comprises a certificate management module, an identity information management module and an authentication module and is used for realizing format and content management of various certificates, management of the identity information and authentication of effectiveness of the elements; the identity information comprises at least one element; and the client-side module and the server-side module are in data communication through a mobile communication network. The invention further provides an authentication method based on the intelligent mobile communication equipment. Due to adoption of the authentication system and method, the identity authentication can be rapidly, conveniently and accurately carried out.
Owner:ZHUHAI ZAIZHOU SOFTWARE TECH
Speaker verification
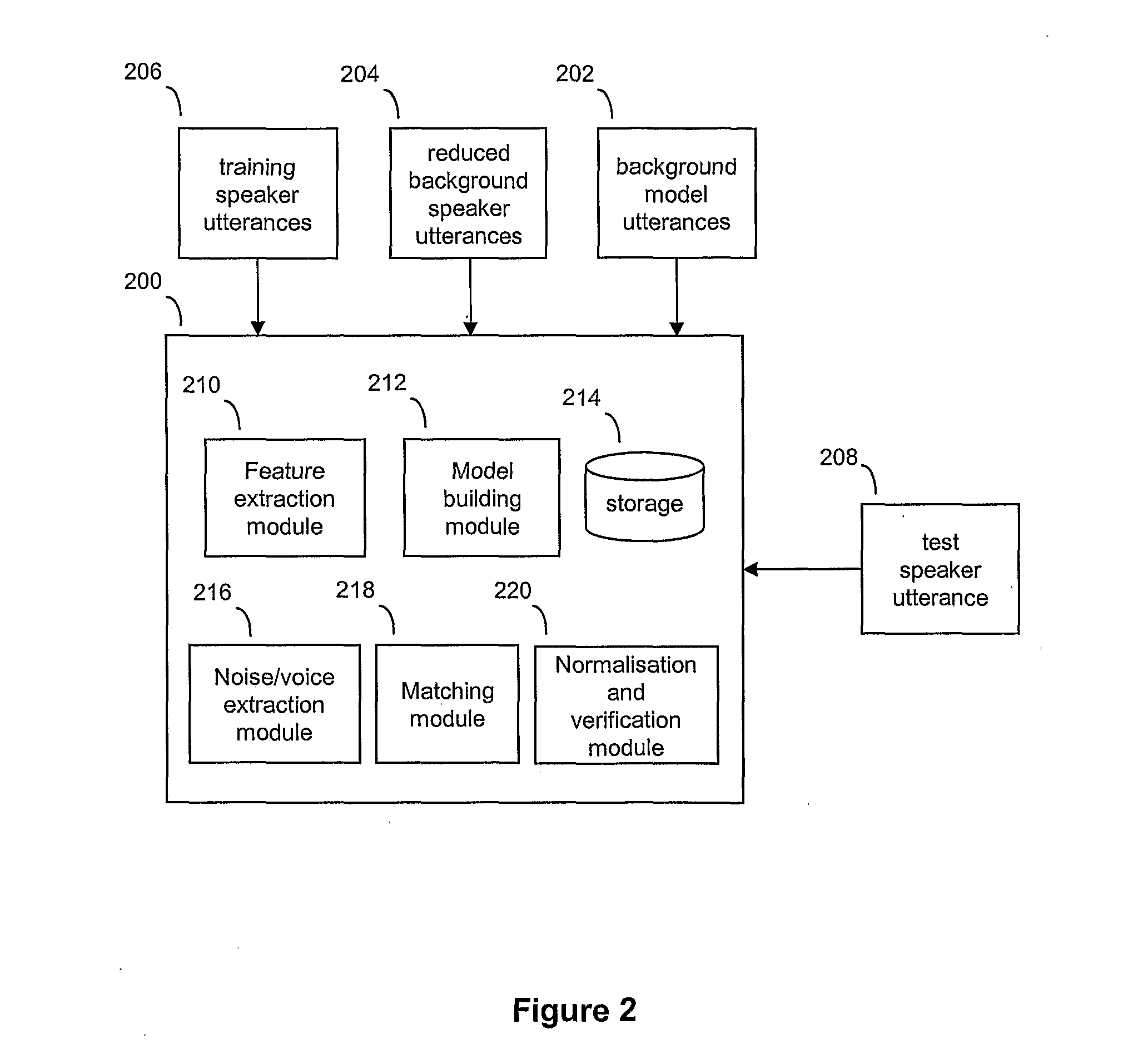
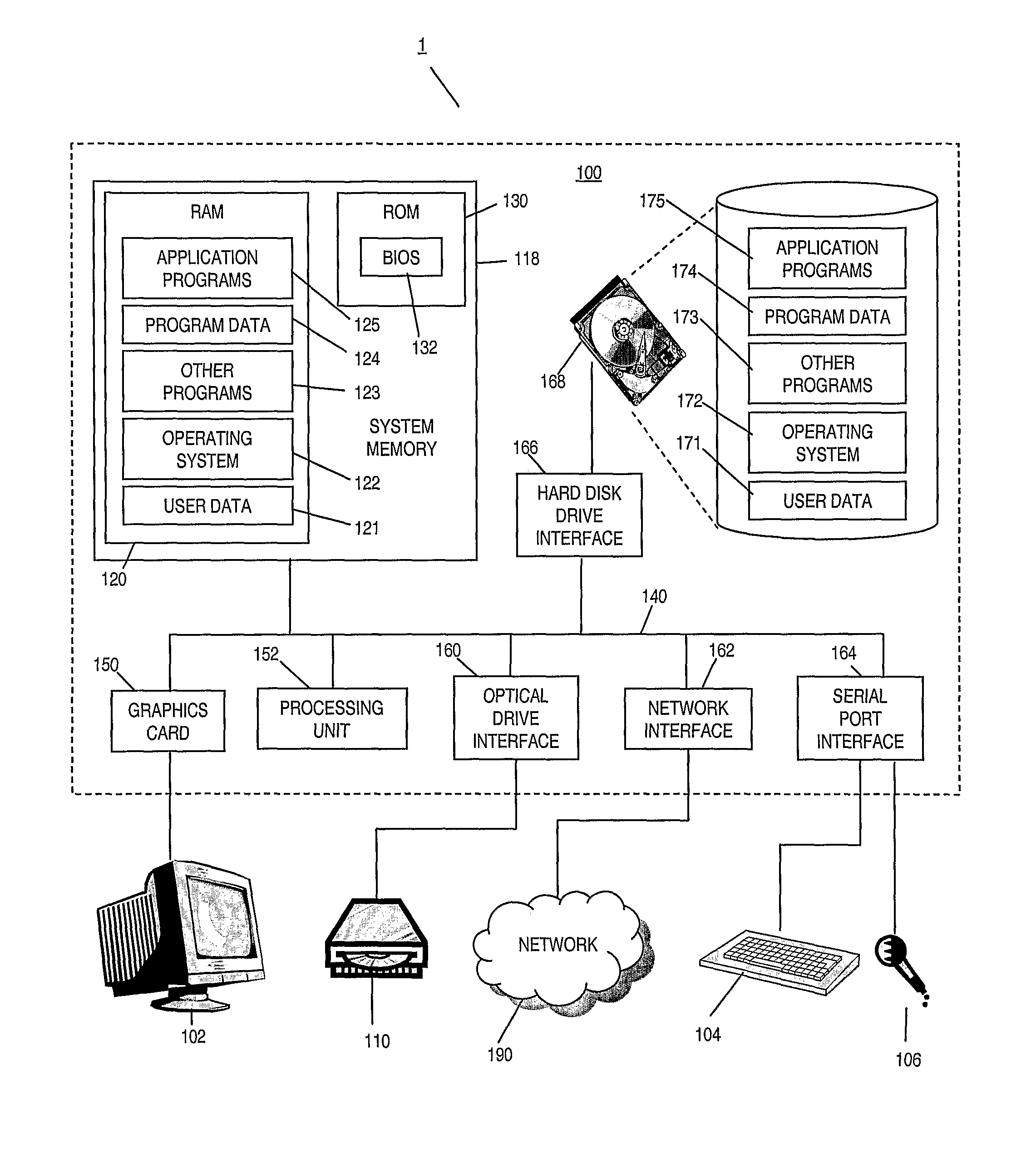
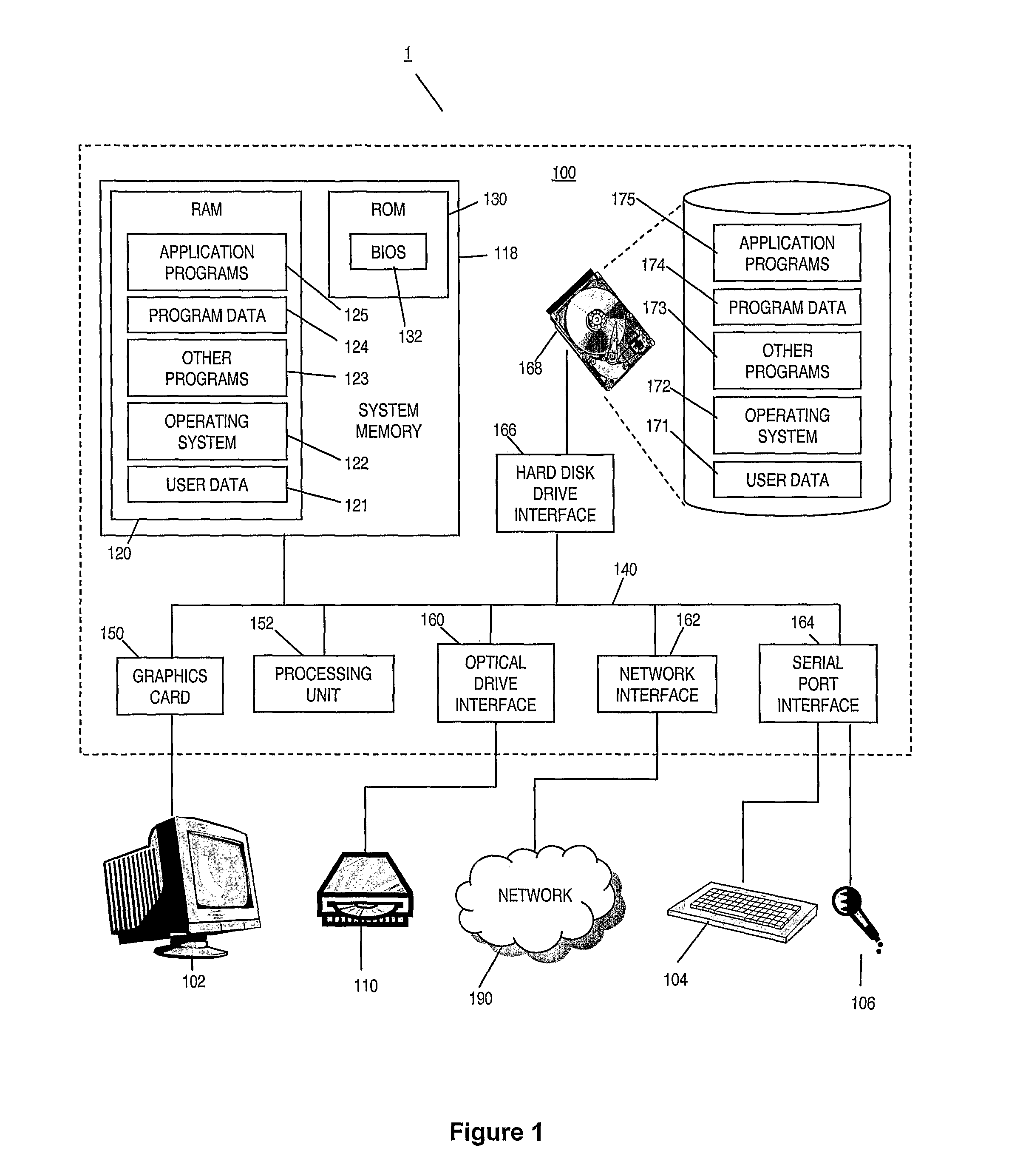
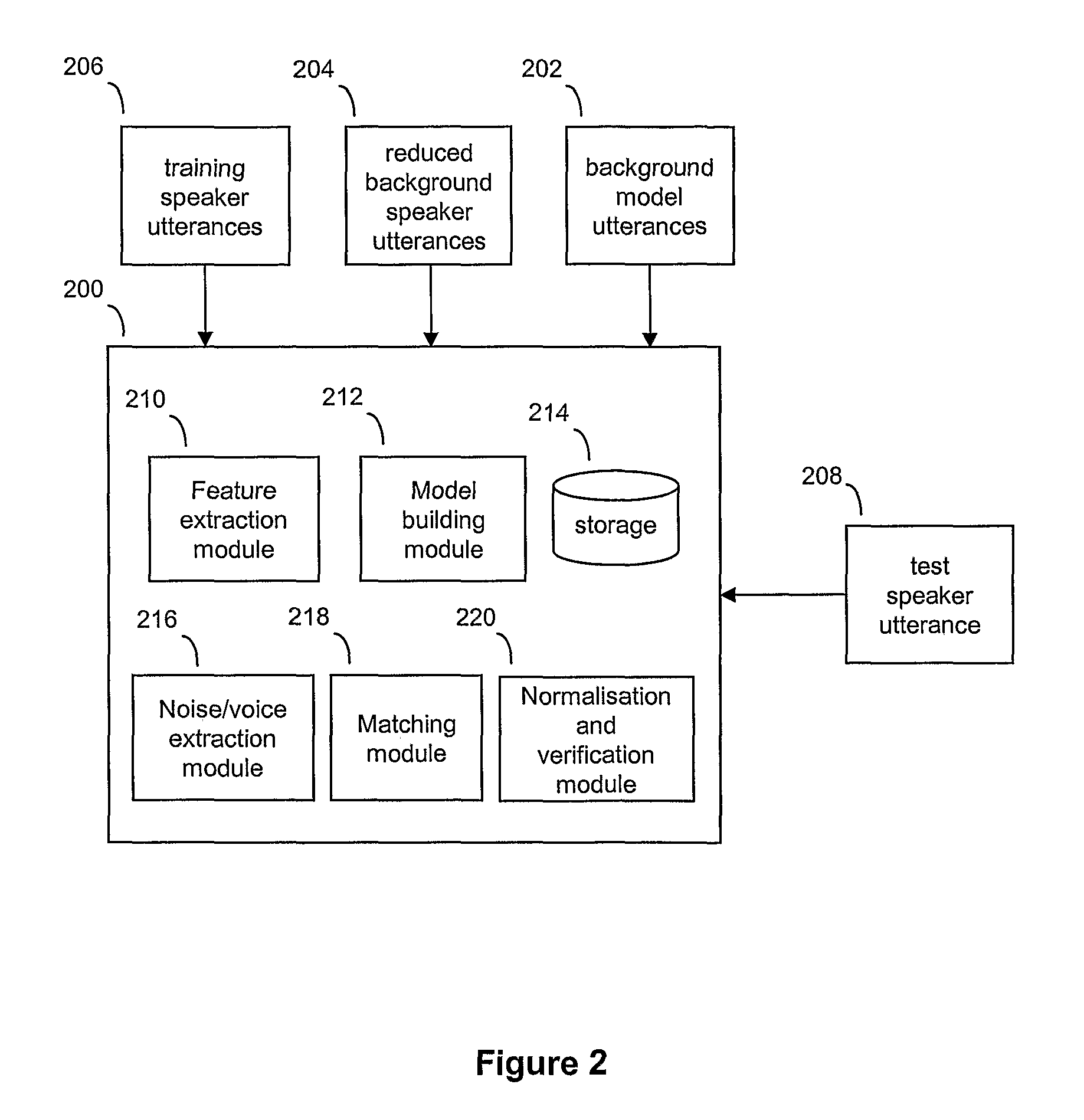
ActiveUS20110202340A1Simple methodImprove verification accuracySpeech recognitionPassphraseFeature vector
A speaker verification method is proposed that first builds a general model of user utterances using a set of general training speech data. The user also trains the system by providing a training utterance, such as a passphrase or other spoken utterance. Then in a test phase, the user provides a test utterance which includes some background noise as well as a test voice sample. The background noise is used to bring the condition of the training data closer to that of the test voice sample by modifying the training data and a reduced set of the general data, before creating adapted training and general models. Match scores are generated based on the comparison between the adapted models and the test voice sample, with a final match score calculated based on the difference between the match scores. This final match score gives a measure of the degree of matching between the test voice sample and the training utterance and is based on the degree of matching between the speech characteristics from extracted feature vectors that make up the respective speech signals, and is not a direct comparison of the raw signals themselves. Thus, the method can be used to verify a speaker without necessarily requiring the speaker to provide an identical test phrase to the phrase provided in the training sample.
Owner:BRITISH TELECOMM PLC
Biometrics authentication system registration method, biometrics authentication system, and program for same
InactiveUS8000503B2Effectively pluralityImprove verification accuracyElectric signal transmission systemsDigital data processing detailsData setDegree of similarity
A biometrics authentication system utilizes information of the palm of the hand of a body to perform individual authentication. A processing unit obtains an image of the palm of the hand of the same body a plurality of times from an image capture unit, judges the degrees of similarity among the characteristic data sets of the plurality of images of the palm of the hand, and registers a plurality of characteristic data sets with a high degree of similarity in a storage unit. And the shape of the hand in the image is checked from the outlines in the image of the palm of the hand, so it is possible to rapidly judge whether image capture has been successful and extract characteristic data, and registration processing can be executed in a short length of time.
Owner:FUJITSU LTD +1
Software behavior modeling device, software behavior modeling method, software behavior verification device, and software behavior verification method
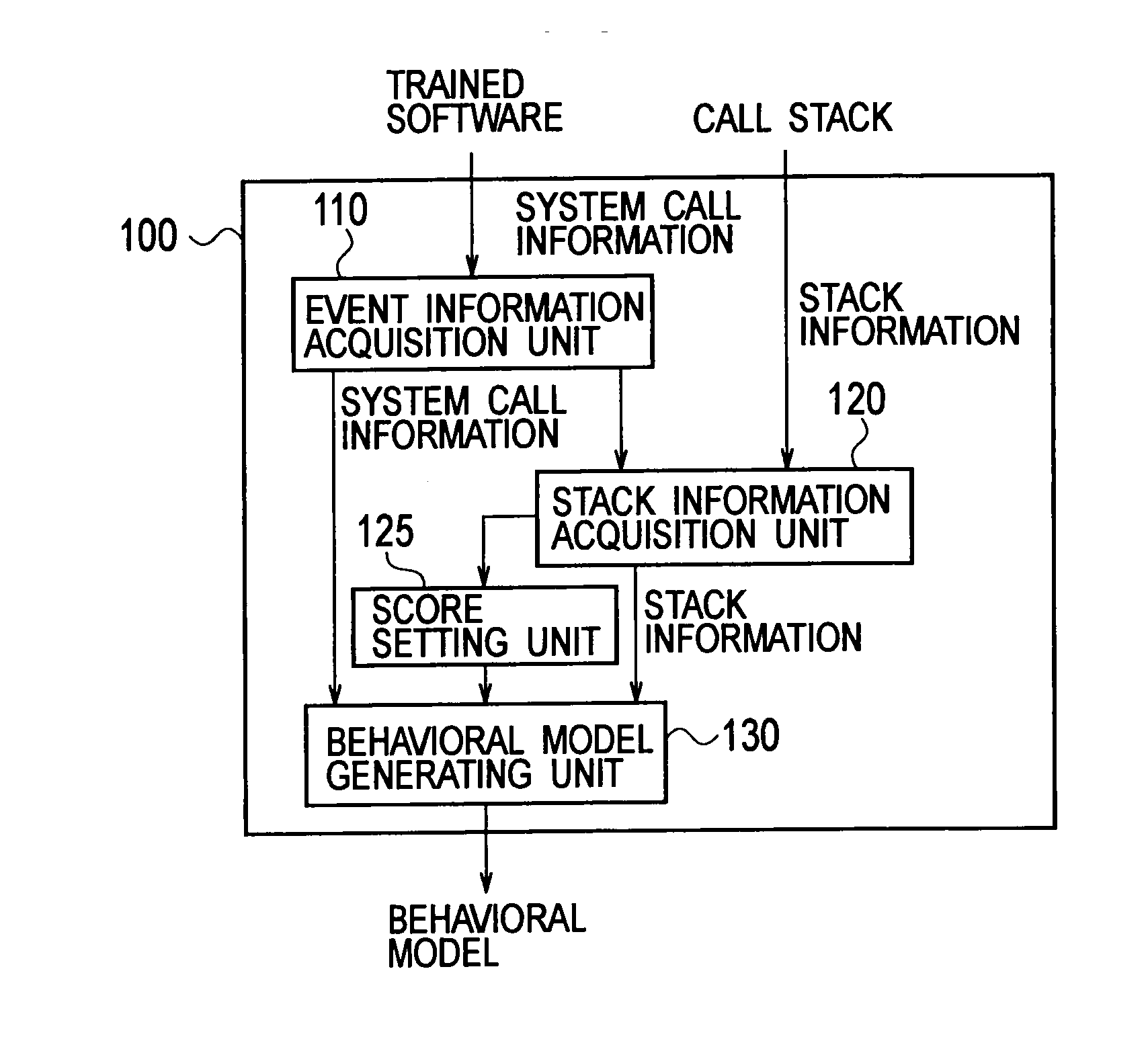
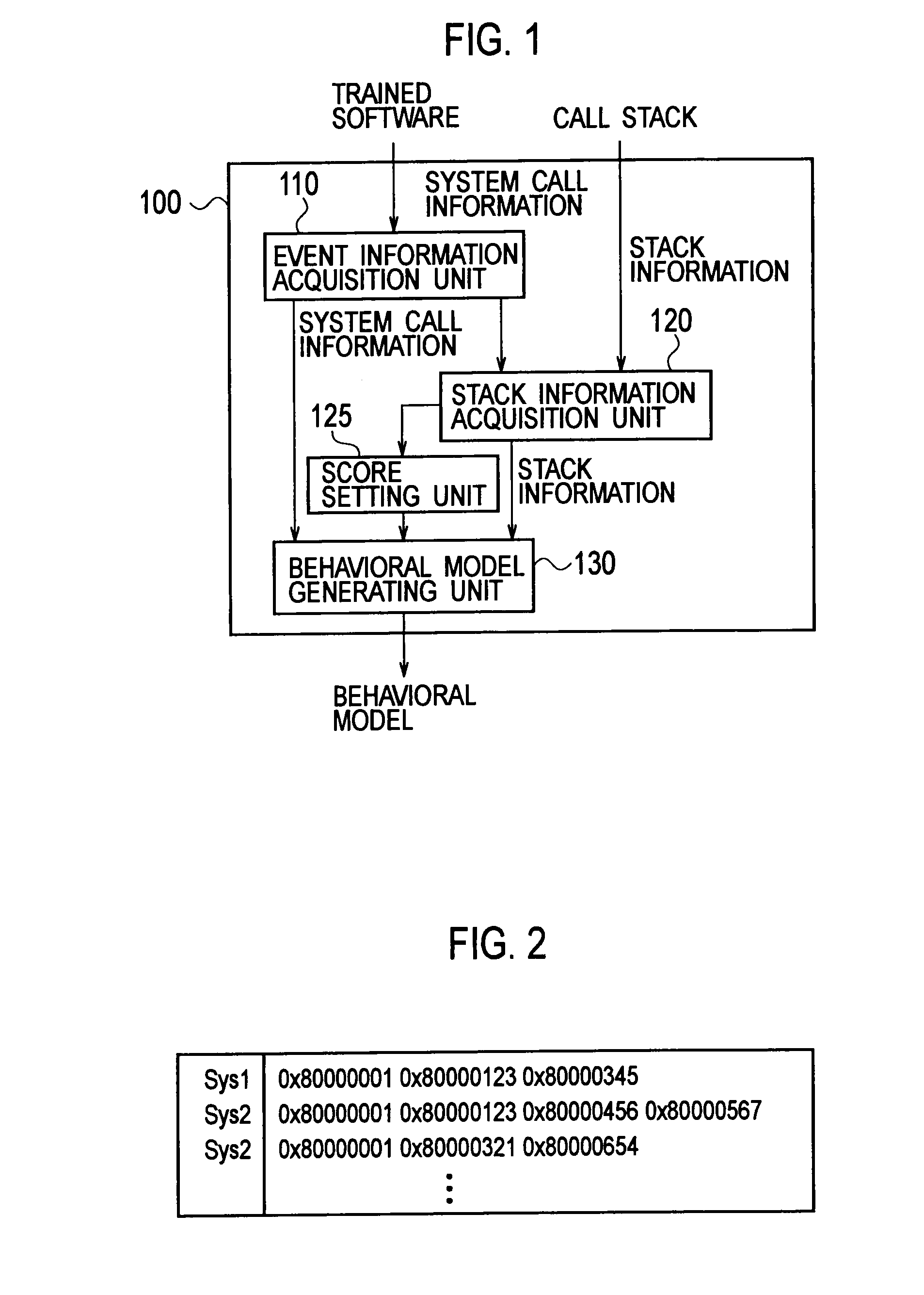
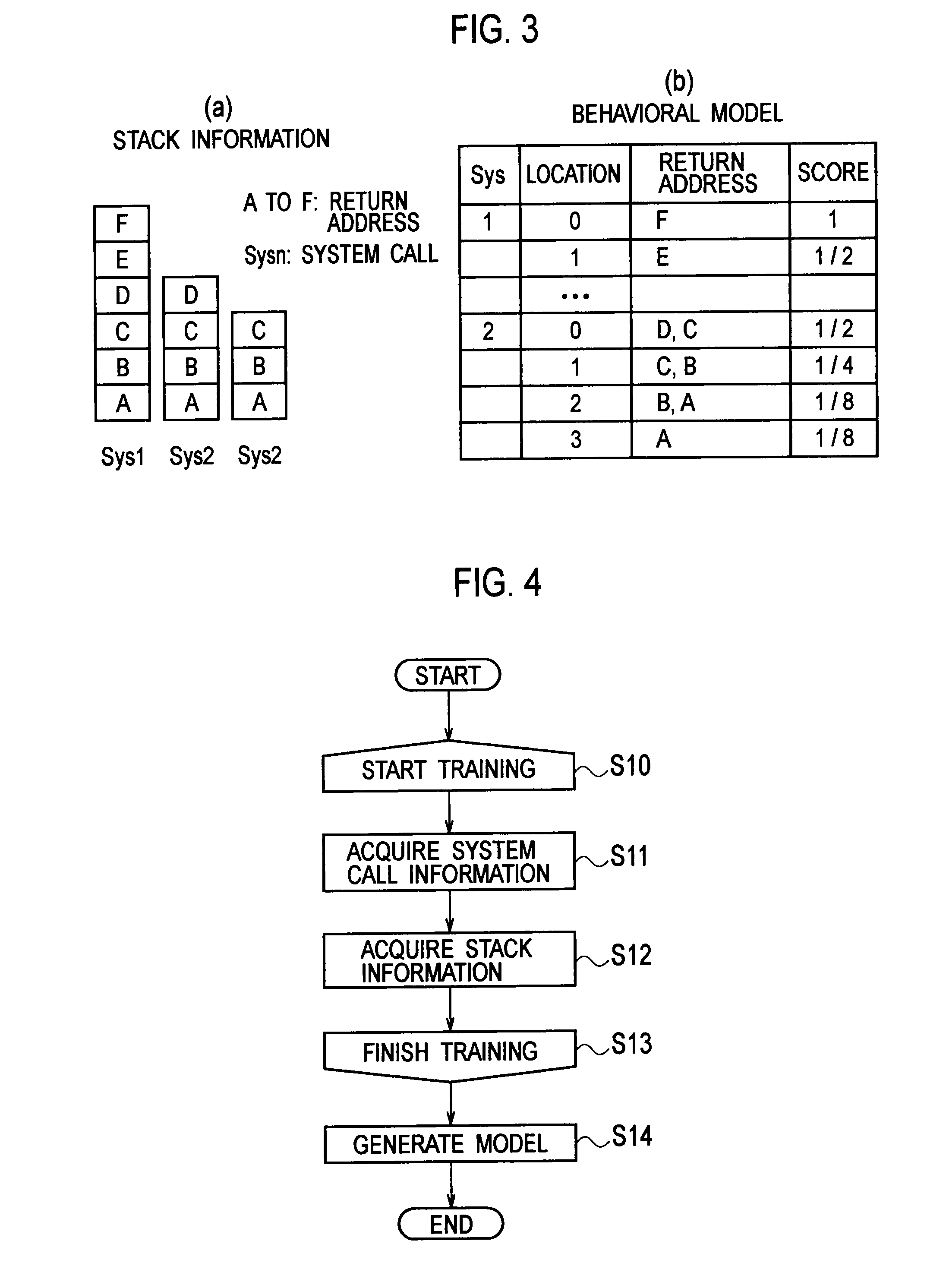
InactiveUS20110154487A1Improve accuracyReduce processing loadMemory loss protectionError detection/correctionCall stackSoftware engineering
A software behavior modeling device which forms a model of a behavior of software includes; an event information acquisition unit configured to acquire event information indicating a specific event which occurs during execution of the software; a stack information acquisition unit configured to acquire stack information stored in a call stack at a time of occurrence of the specific event; a score setting unit configured to set a score in accordance with a storage location in which each element included in the stack information is stored in the call stack; and a model generating unit configured to form a model of a relationship between the specific event and the element by using the score, and to generate a behavior model of the software.
Owner:NTT DOCOMO INC
Capacitance measurement circuit
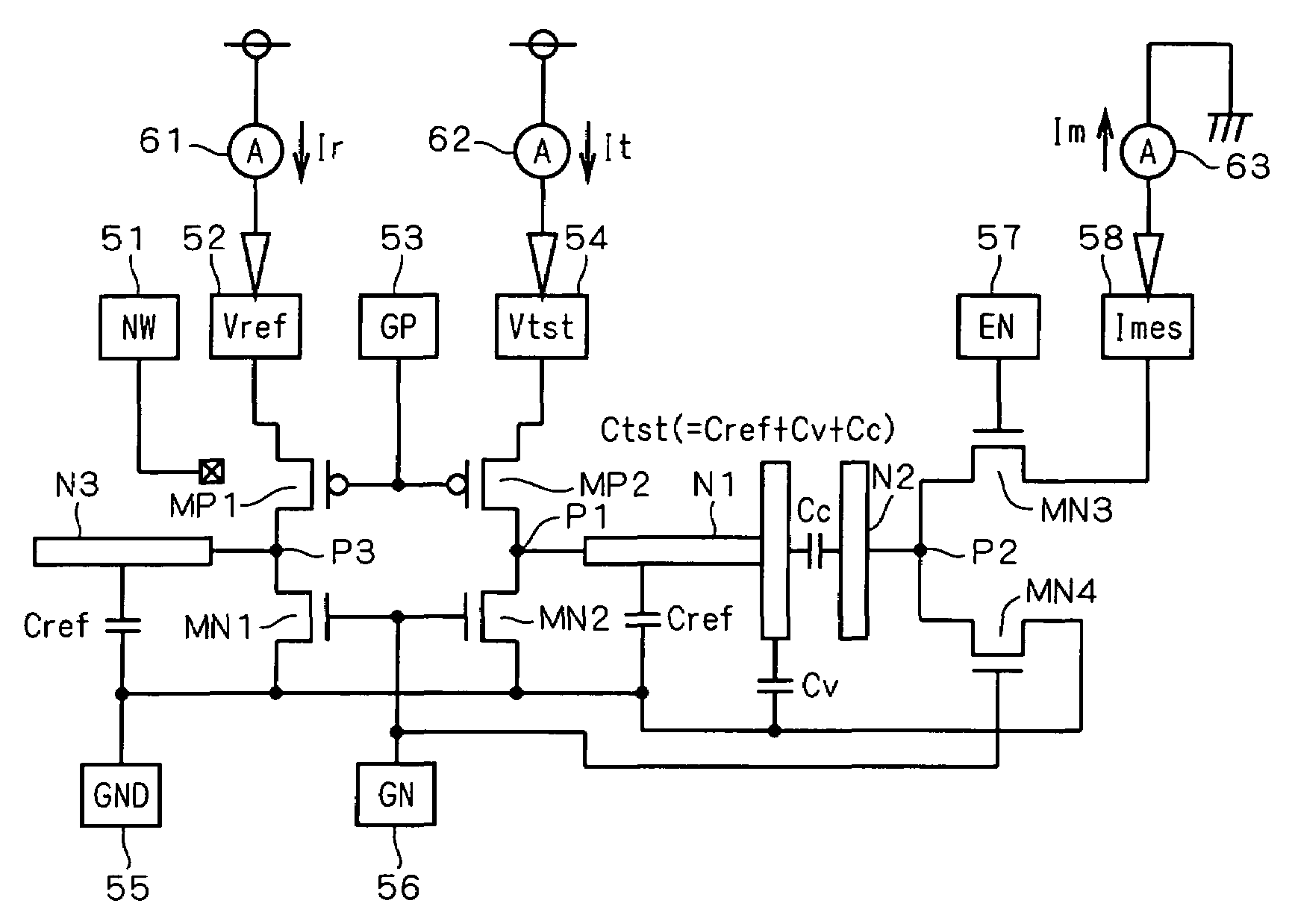
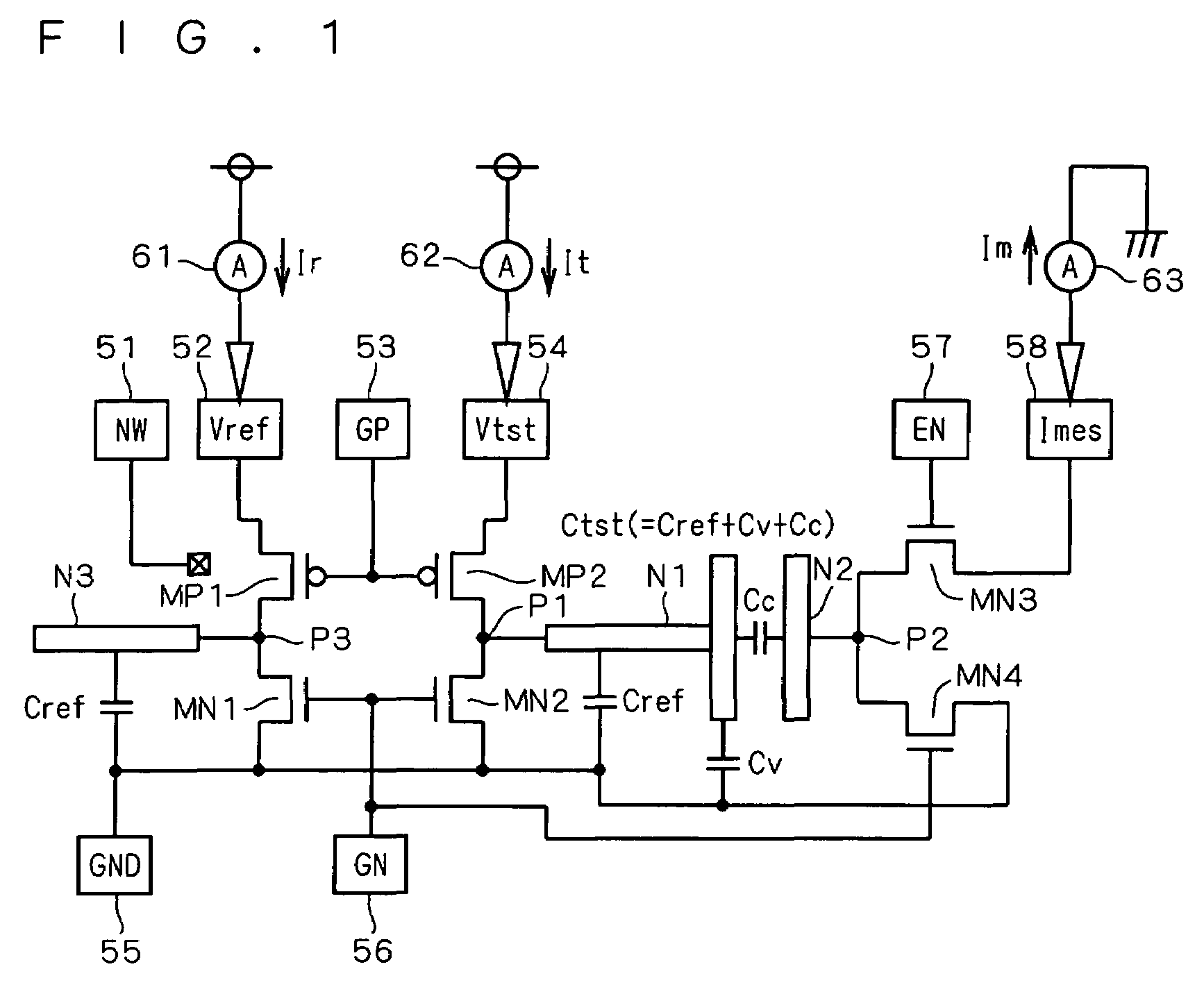
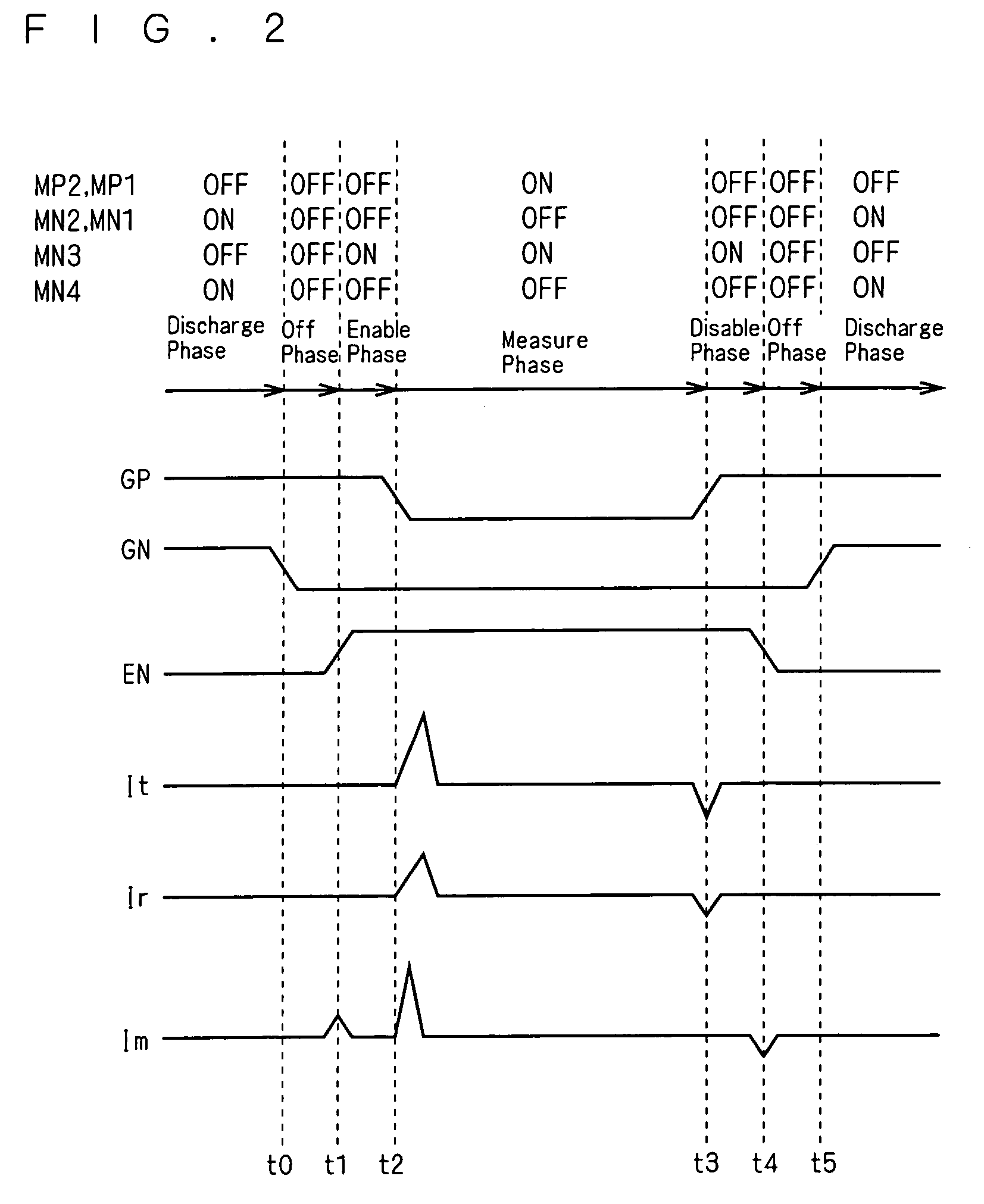
InactiveUS7230435B2Verify accuracyImprove verification accuracyCapacitance measurementsCurrent meterEngineering
A CBCM circuit is capable of separately measuring each component of a measuring target capacitance. A node (N1) is electrically connected to a terminal (P2) between the drains of PMOS and NMOS transistors (MP2, MN2). As a target capacitance forming part, a coupling capacitance (Cc) is formed between the node (N1) and a node (N2). The node (N2) is connected to a pad (58) through the terminal (P2) and an NMOS transistor (MN3), and a node (N3) is connected to a terminal (P3) between the drains of PMOS and NMOS transistors (MP1, MN1). A reference capacitance (Cref) is formed at the node (N3) as a dummy capacitance. Currents (Ir, It) supplied from a power source to the nodes (N3, N1) are measured with current meters (61, 62), respectively and a current (Im) induced from the node (N2) and flowing to a ground level is measured with a current meter (63).
Owner:RENESAS ELECTRONICS CORP +1
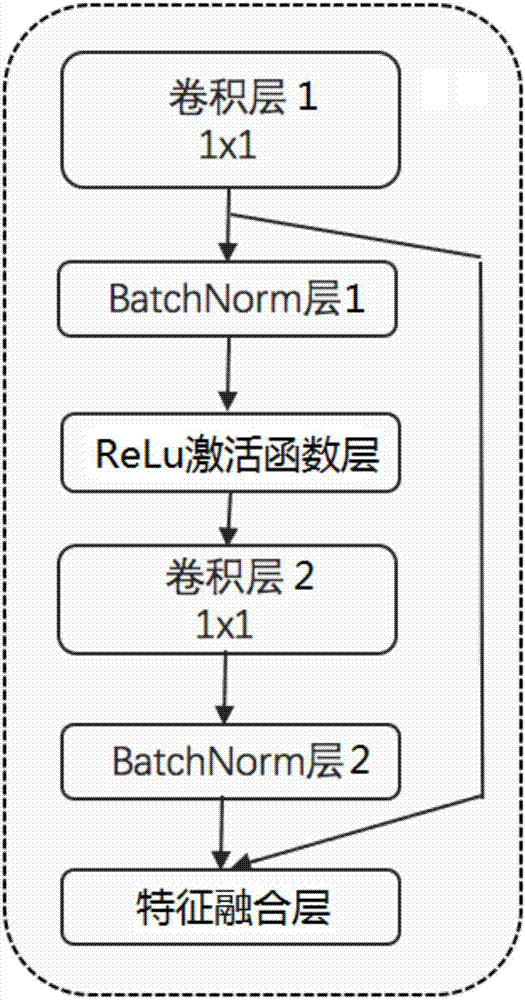
Image watermark removal device
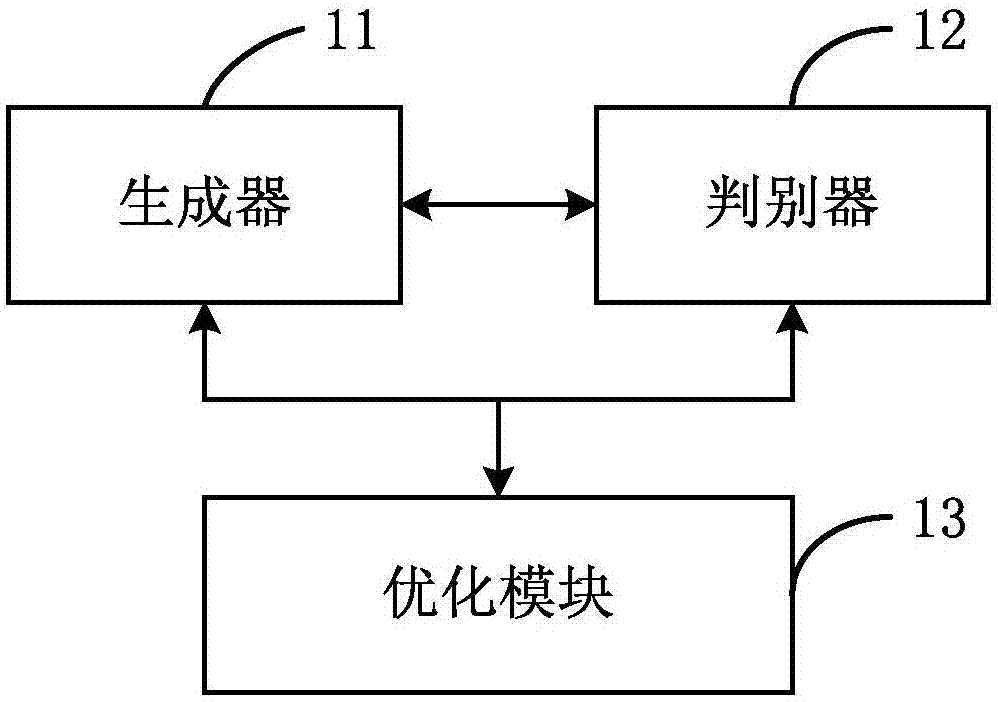
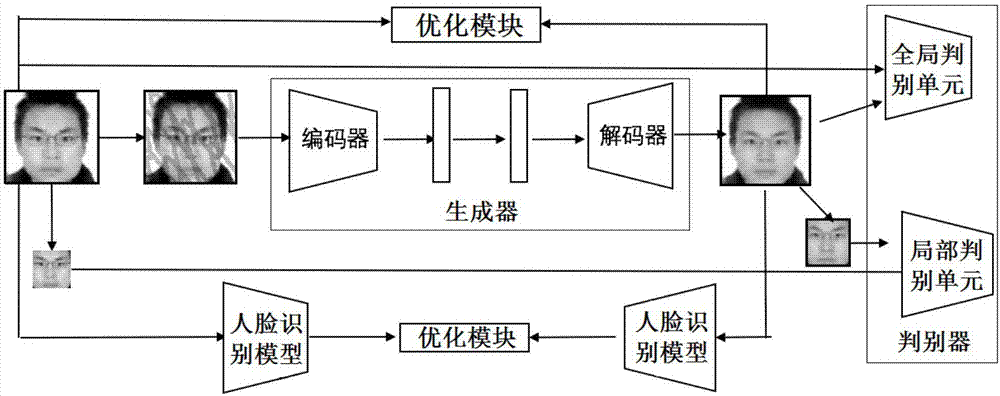
ActiveCN107993190AQuality improvementImprove verification accuracyGeometric image transformationCharacter and pattern recognitionGenerative adversarial networkDiscriminator
The invention relates to the technical field of image processing, in particular to an image watermark removal device. The image watermark removal device aims to provide a way of solving the technicalproblem that the picture quality of a restored image and face verification accuracy are low. In order to realize the purpose, the image watermark removal device can carry out watermark removal processing on a face image on the basis of a generative adversarial network model, wherein a generator in the generative adversarial network model can generate a corresponding watermark-free image corresponding to the face image, a discriminator can judge whether the integral image and the local image of the watermark-free image are true images or not; and an optimization module optimizes the generator and the discriminator. Furthermore, the device comprises a face recognition model to extract the face feature of a watermark-free original image and the face feature of the watermark-free image generated by the generator, and the generator and the discriminator are further optimized. By use of the technical scheme of the invention, while the high-quality watermark-free image can be obtained, information contained in the image is effectively protected.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
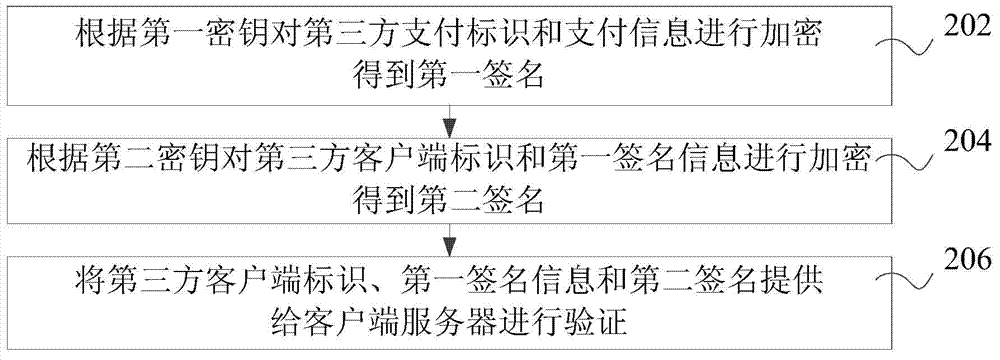
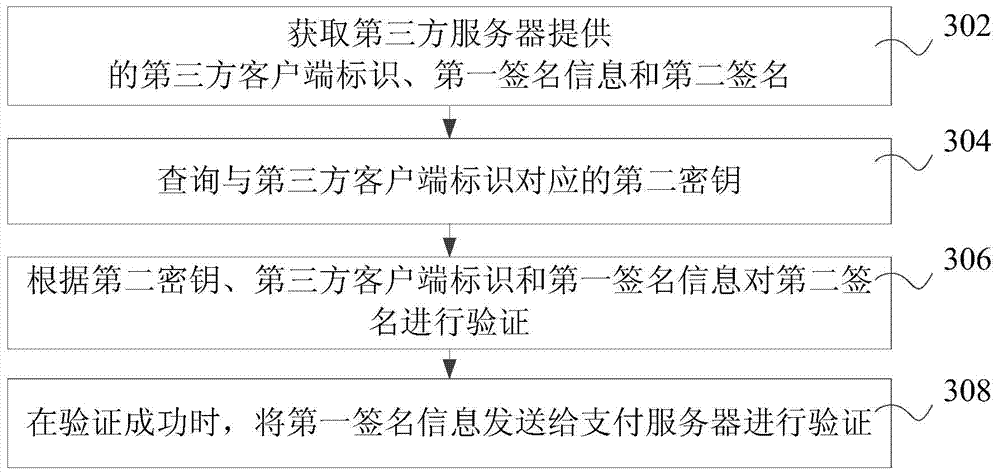
Signature verification method, device and system
ActiveCN104767613AImprove securityImprove verification accuracyCryptography processingUser identity/authority verificationThird partyInformation transmission
Owner:TENCENT TECH (SHENZHEN) CO LTD
Systems and methods for privacy-enabled biometric processing
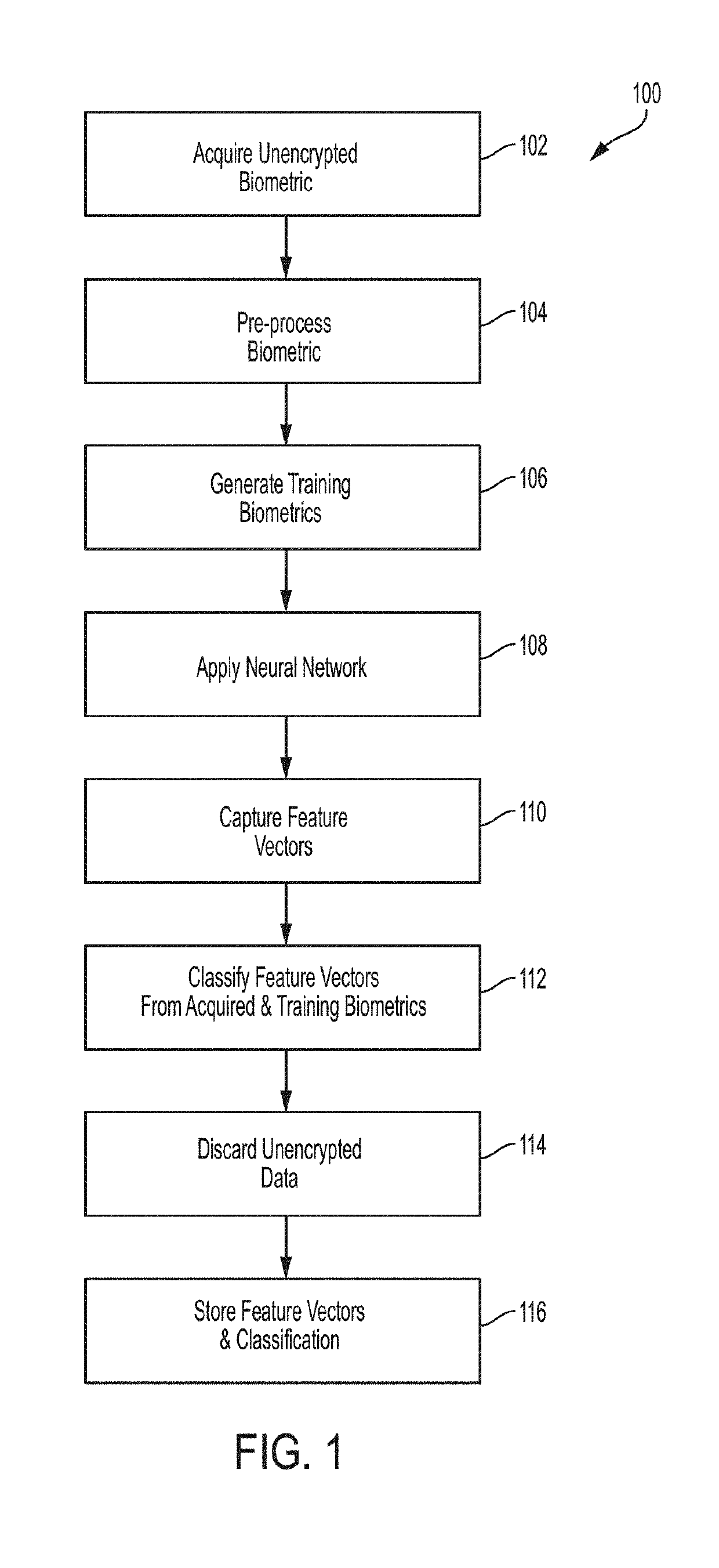
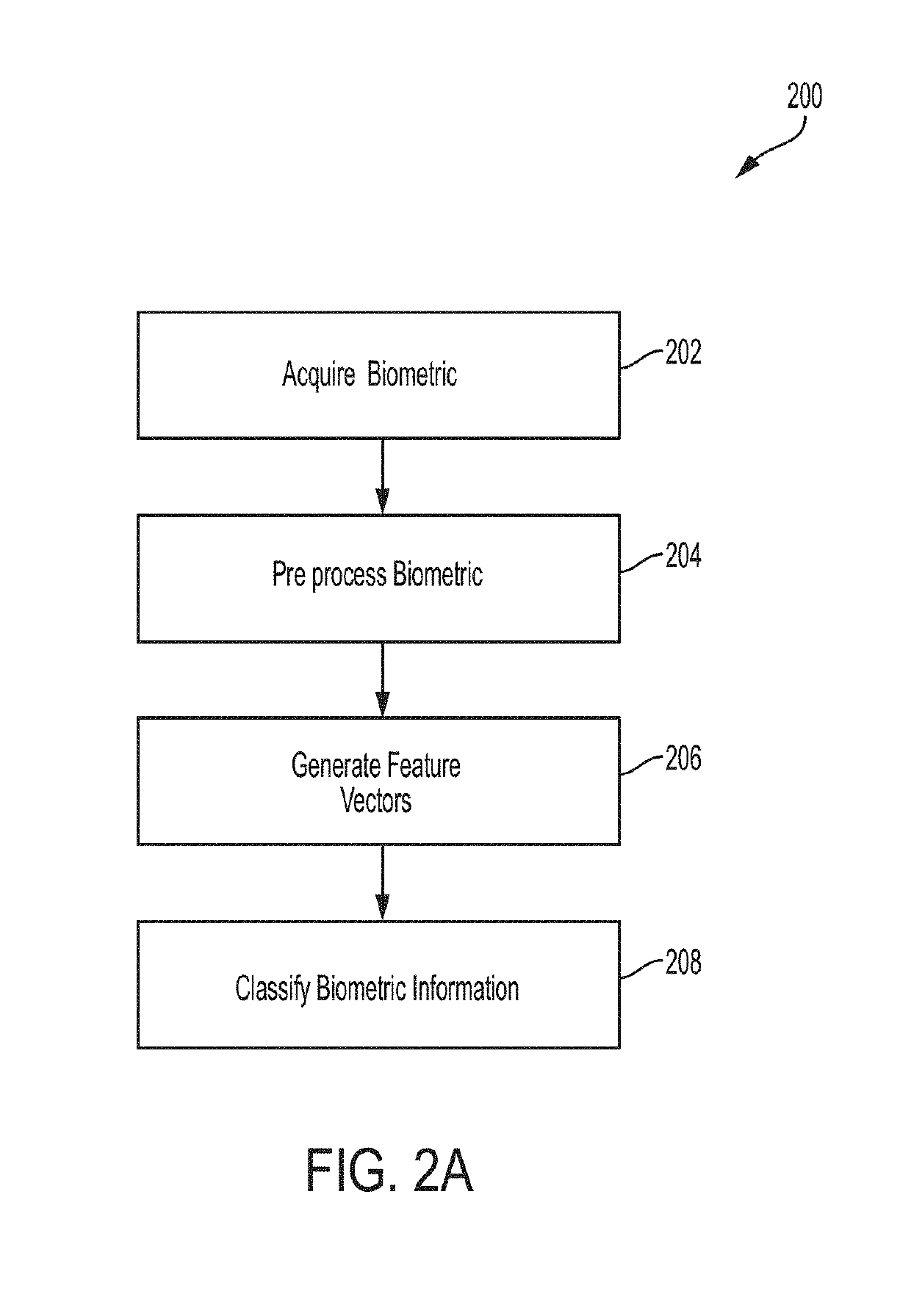
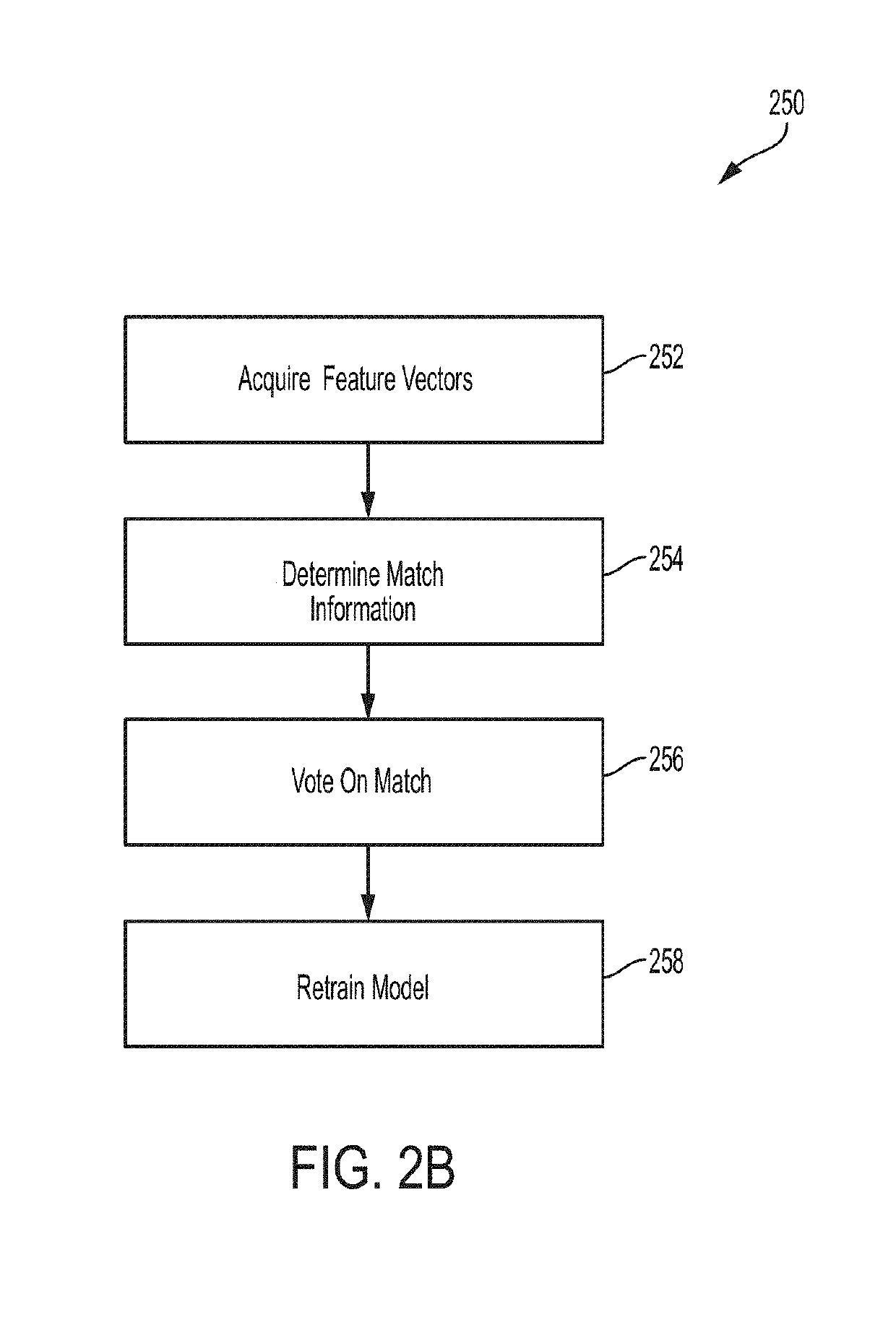
ActiveUS20190278937A1Improve accuracyImprove securityKernel methodsCharacter and pattern recognitionFeature vectorBiometric data
In one embodiment, a set of feature vectors can be derived from any biometric data, and then using a deep neural network (“DNN”) on those one-way homomorphic encryptions (i.e., each biometrics' feature vector) can determine matches or execute searches on encrypted data. Each biometrics' feature vector can then be stored and / or used in conjunction with respective classifications, for use in subsequent comparisons without fear of compromising the original biometric data. In various embodiments, the original biometric data is discarded responsive to generating the encrypted values. In another embodiment, the homomorphic encryption enables computations and comparisons on cypher text without decryption. This improves security over conventional approaches. Searching biometrics in the clear on any system, represents a significant security vulnerability. In various examples described herein, only the one-way encrypted biometric data is available on a given device. Various embodiments restrict execution to occur on encrypted biometrics for any matching or searching.
Owner:OPEN INFERENCE HLDG LLC
Method and apparatus for acquiring images, and verification method and verification apparatus
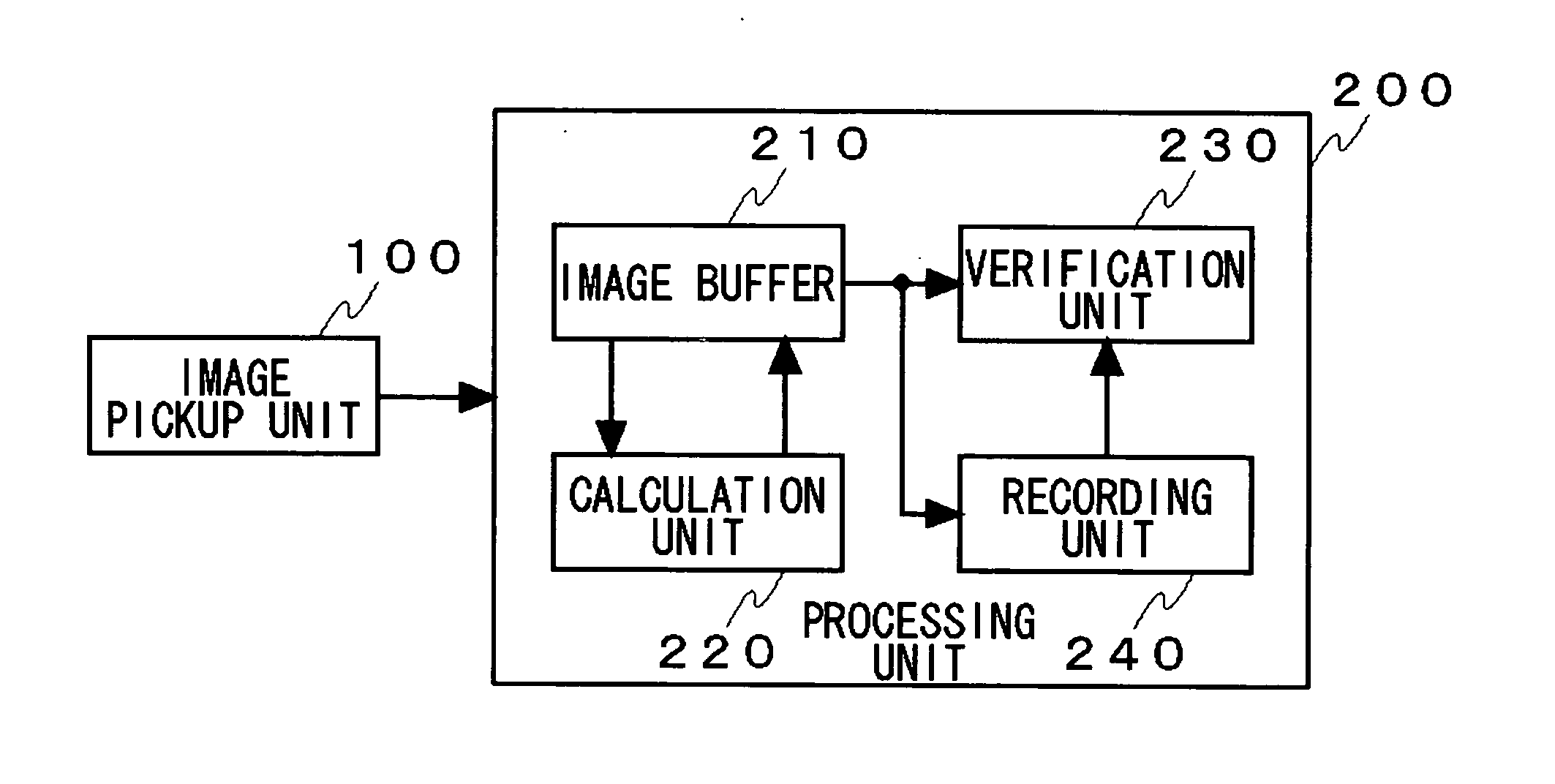
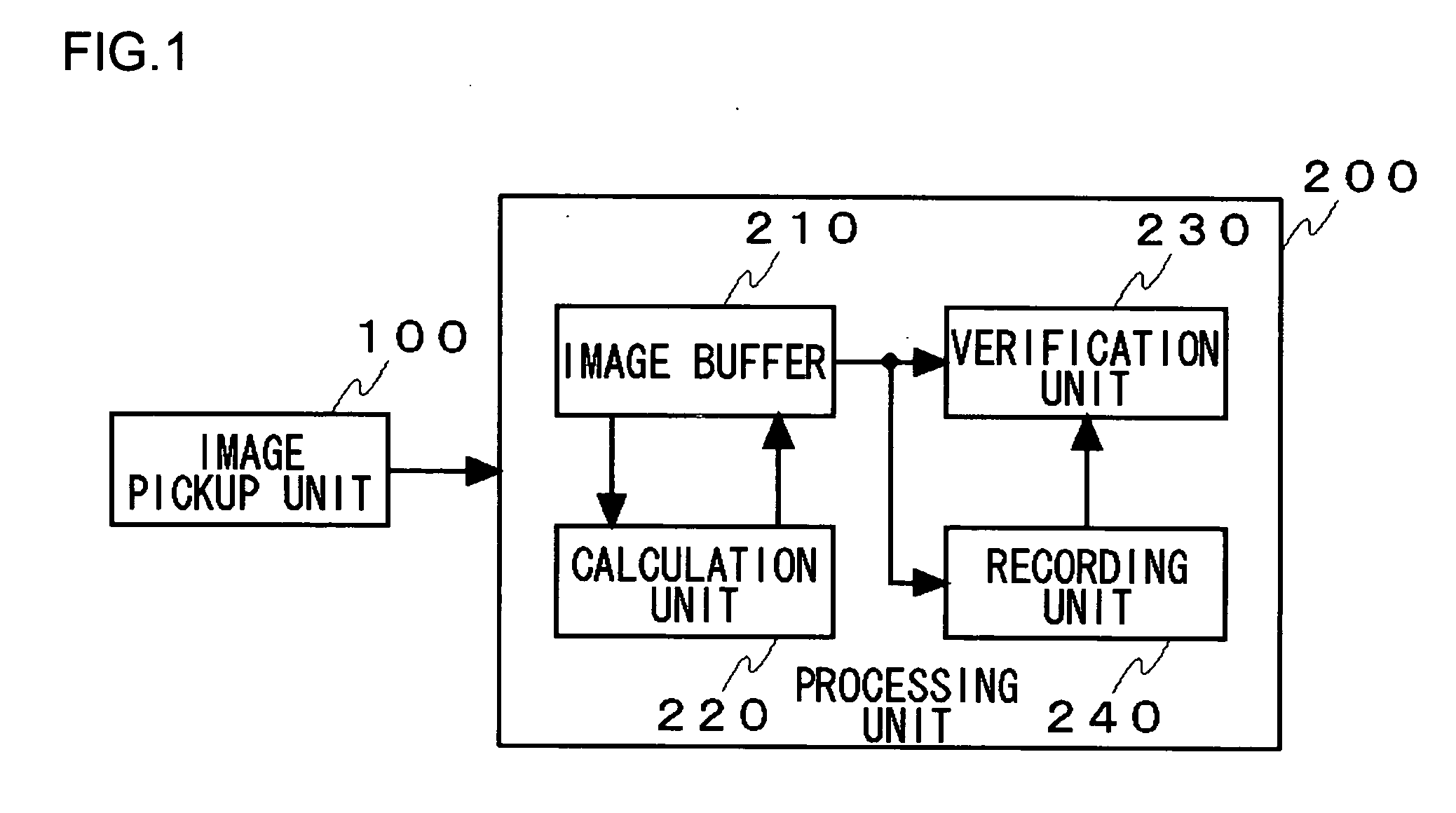
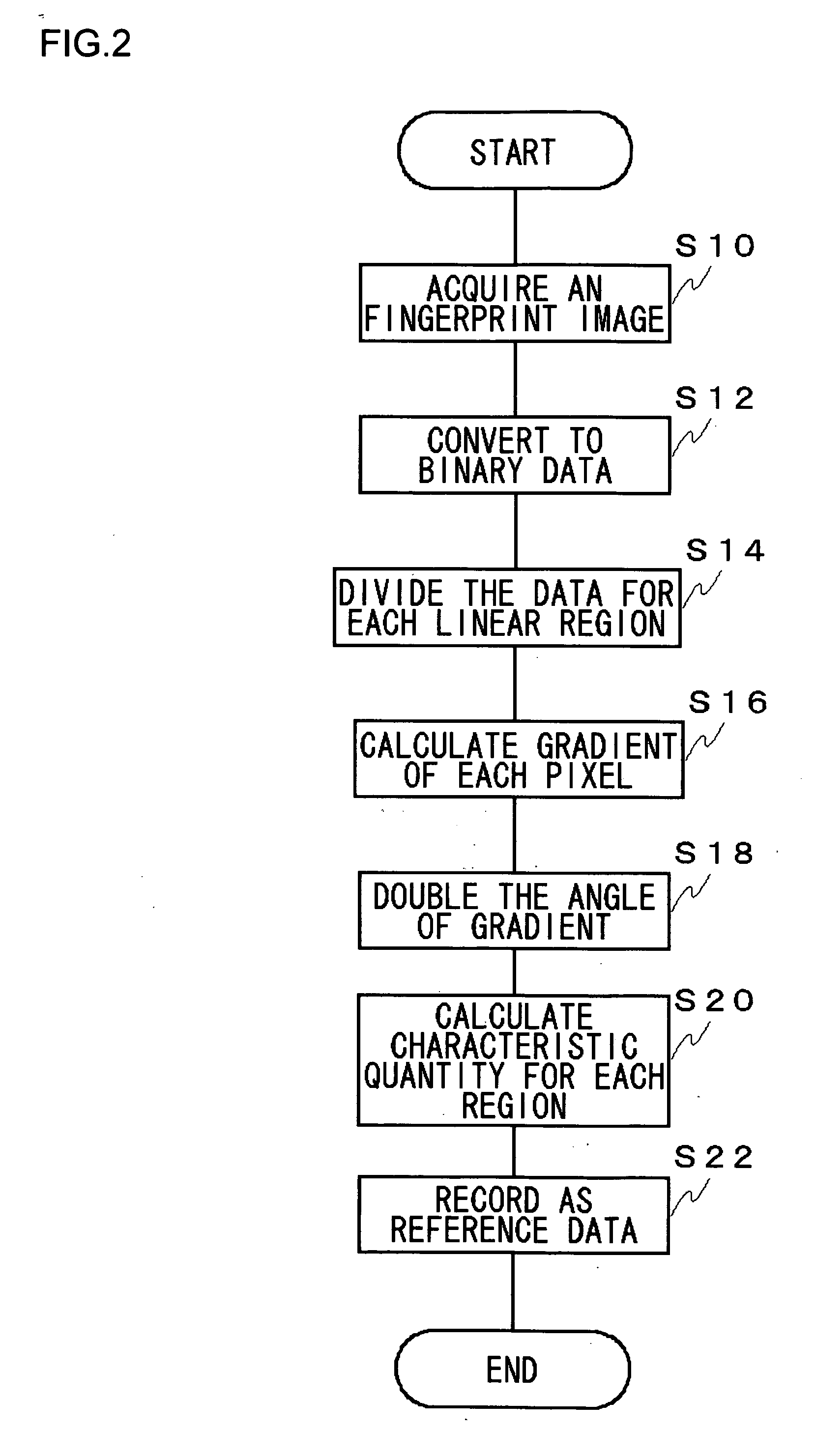
InactiveUS20060165264A1Small amount of calculationSolve large capacityAcquiring/recognising eyesPhysical quantityReference image
In a verification apparatus, an image pickup unit picks up an image of an object to be verified. A calculation unit calculates, from the captured object image, a characteristic quantity that characterizes a direction of lines within the object image along a first direction or a characteristic quantity that characterizes the object image as a single physical quantity. Then a region from which data are to be acquired is set by referring to a characteristic quantity of the object image and, from this region, a characteristic quantity that characterizes a direction of lines within the object image along a second direction different from the second direction or a characteristic quantity that characterizes the object image as a single physical quantity is calculated. A verification unit at least verifies the characteristic quantity of the object image against that of a reference image along the second direction.
Owner:SANYO ELECTRIC CO LTD
Action recognition based living body face recognition method and system
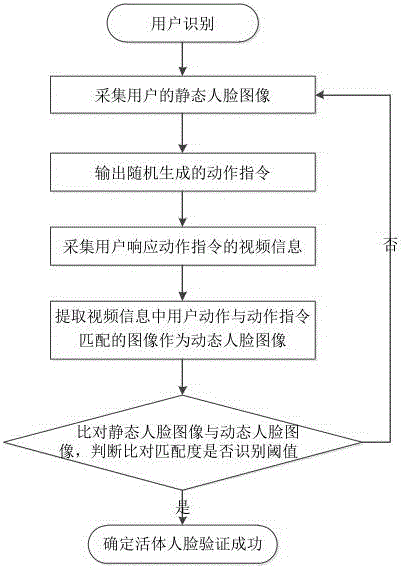
InactiveCN106650646AEasy to implementImprove verification accuracySpoof detectionActivity recognitionLiving body
The invention discloses an action recognition based living body face recognition method and system. The method includes steps of collecting a static face image of a user; outputting an action command generated randomly; collecting video information of the user responding to the action command; extracting an image in which the action of the user is matched with the action command in the video information as a dynamic face image; comparing the static face image with the dynamic face image, determining living body face recognition success when the matching degree is greater than a recognition threshold value or else determining living body face recognition failure.
Owner:南京合荣欣业金融软件有限公司
Method and Apparatus for Surgical Instrument Identification
InactiveUS20100176925A1Reduce processing costsOvercomes shortcomingSurgical furnitureDiagnosticsEngineeringSurgical device
Systems and methods for identifying surgical instruments by use of radio-frequency identification tags (RFID) are disclosed. In the systems and methods, each of a plurality of surgical instruments is provided with at least one RFID transponder tag storing identification information associated with the corresponding instrument. The tag may be adhered to, embedded, or potted within a portion of the instrument. Using an RFID reading device, a user may interrogate the tag, thereby identifying the particular instrument. This identification information may be used to index a database and retrieve a data record unique to that instrument. The systems and methods allow a user to track, inspect, and verify inbound and outbound surgical instruments, to assess, for example, the surgical instruments' duty life cycle usage.
Owner:WARSAW ORTHOPEDIC INC
Lens module
InactiveUS20080273255A1Prevent interferenceImprove verification accuracyInking apparatusPaper-money testing devicesCamera lensEngineering
A lens module includes a holder base, which is affixed to a circuit board and has bottom receiving holes for receiving LEDs or sensors on the circuit board and a top flange with a foolproof notch, a lens device press-fitted into the top flange and secured to the foolproof notch to ensure accurate positioning and having flat protrusions engaged into respective through holes in the holder base in alignment with the LEDs or sensors, and a top cover capped on the holder base to hold down the lens device and having through holes that receive convex portions of the lens device respectively.
Owner:INT CURRENCY TECH
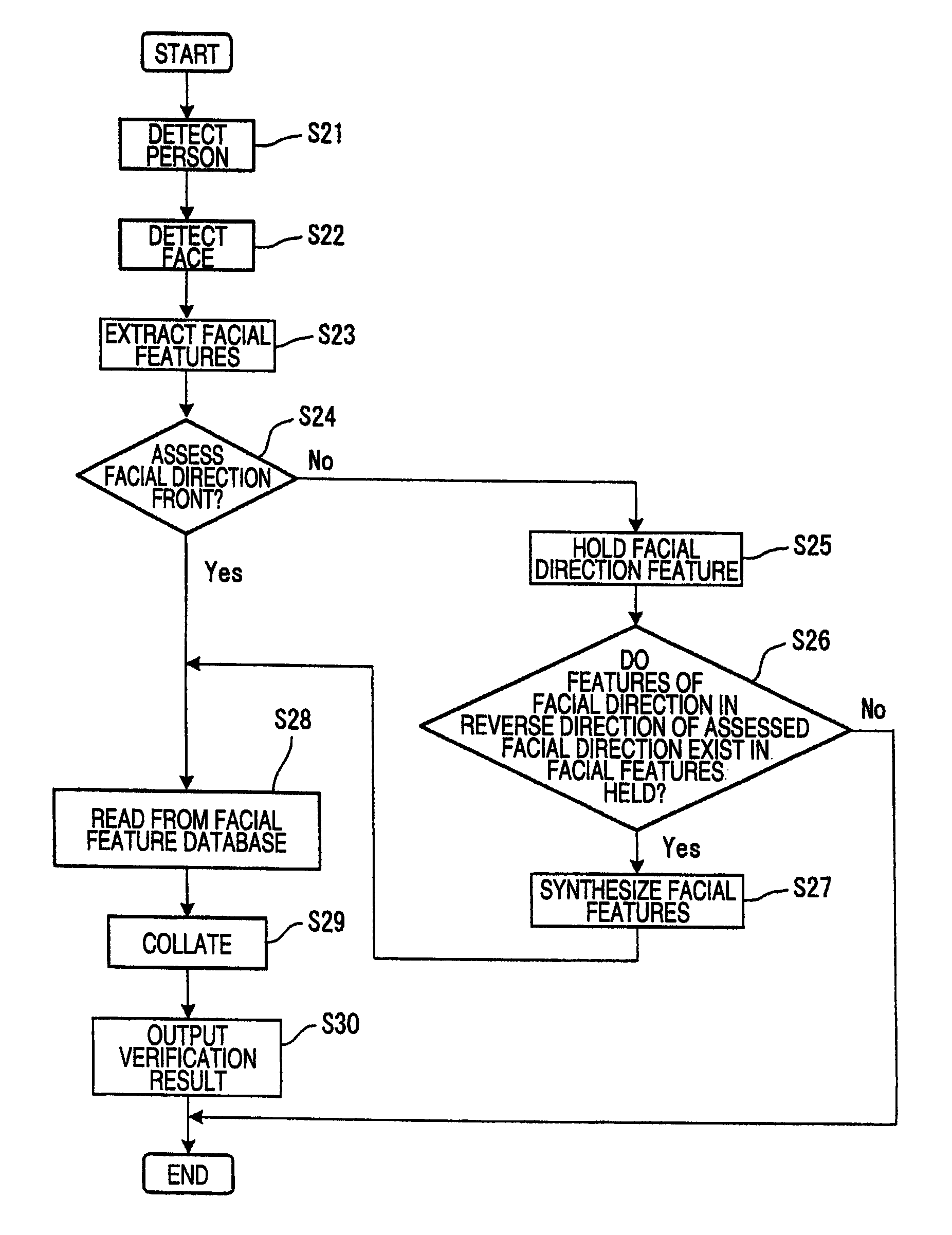
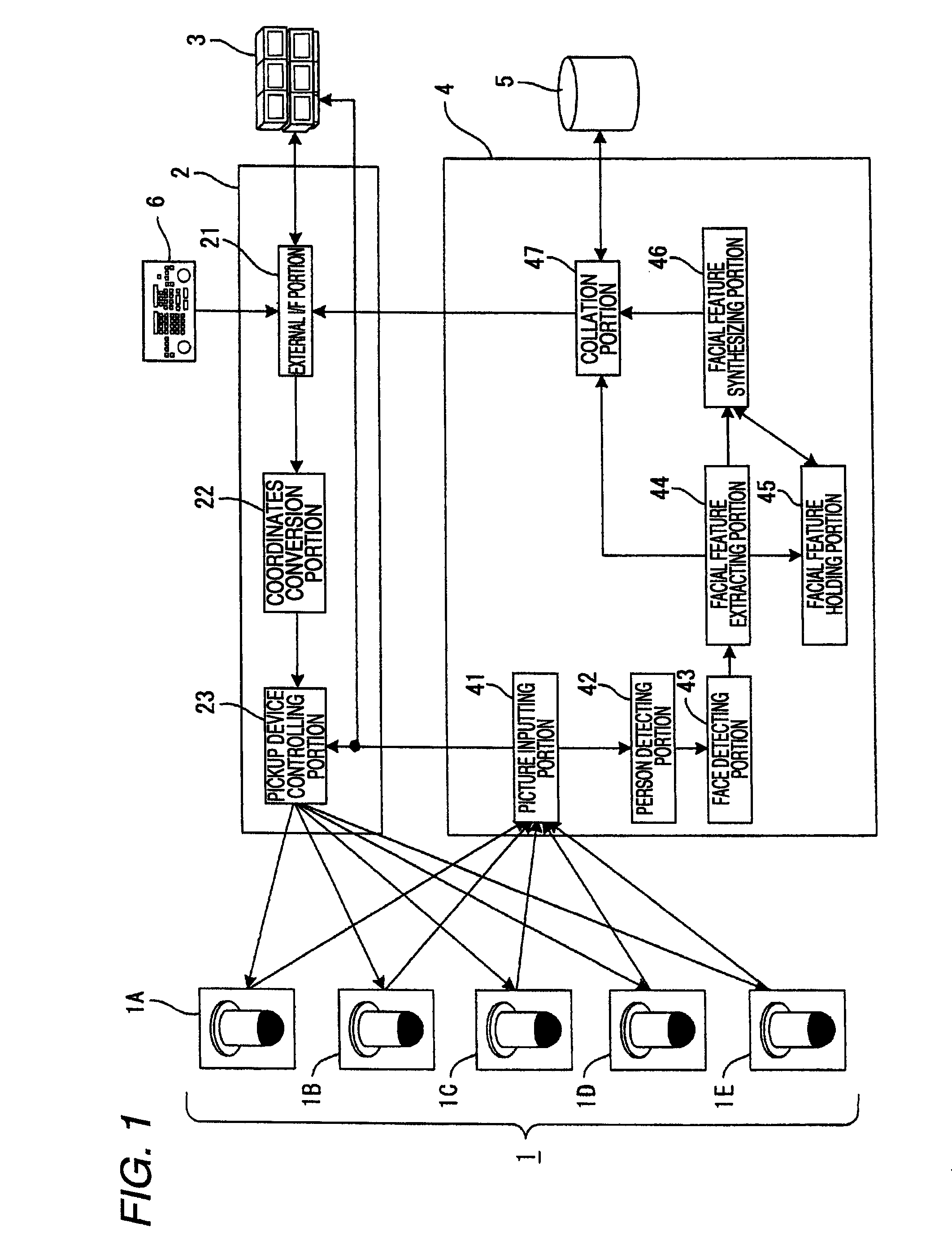
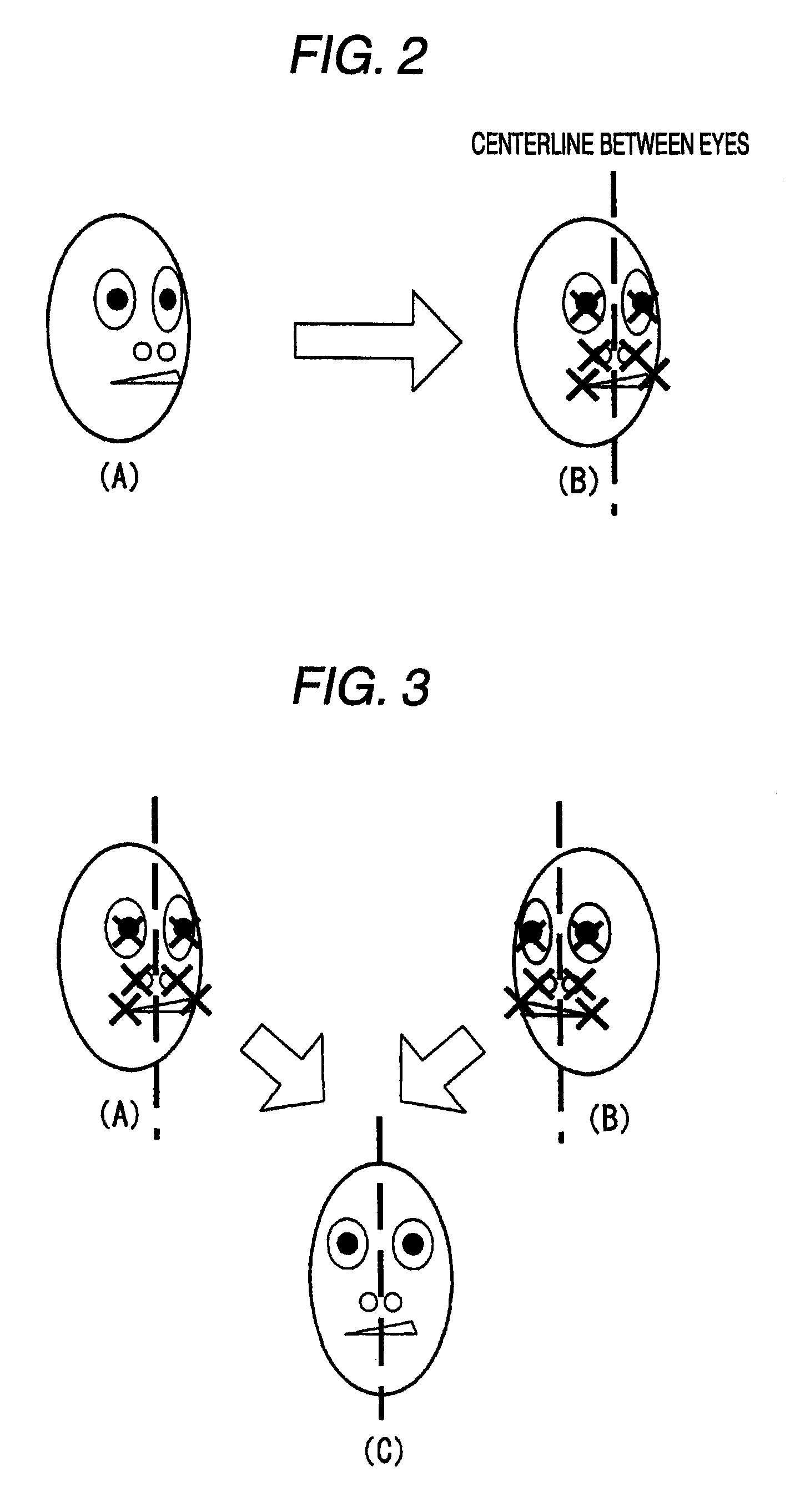
Face feature collator, face feature collating method, and program
InactiveUS20090052747A1Improve verification accuracyImprove accuracyCharacter and pattern recognitionColor television detailsImage databaseFacial characteristic
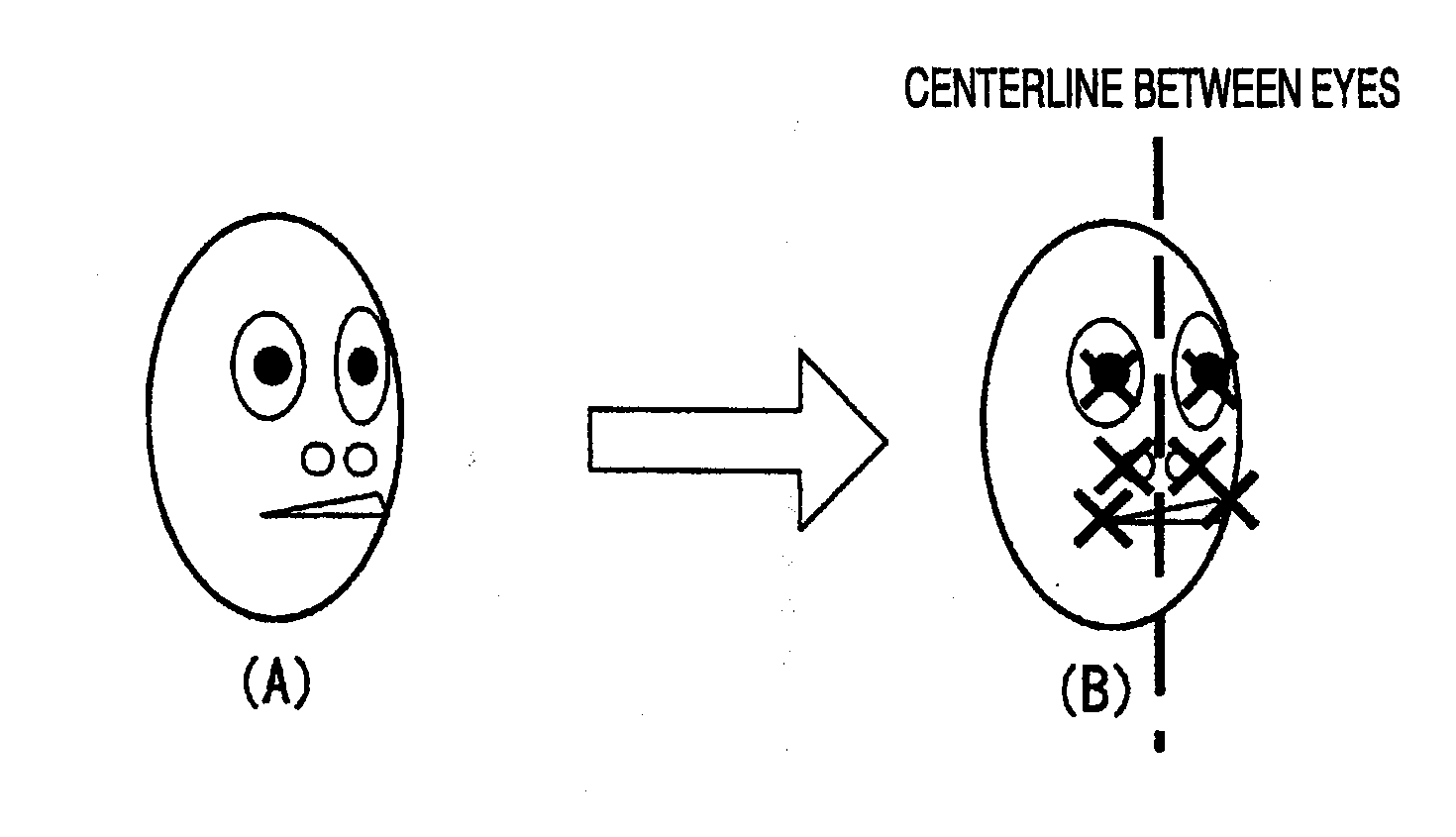
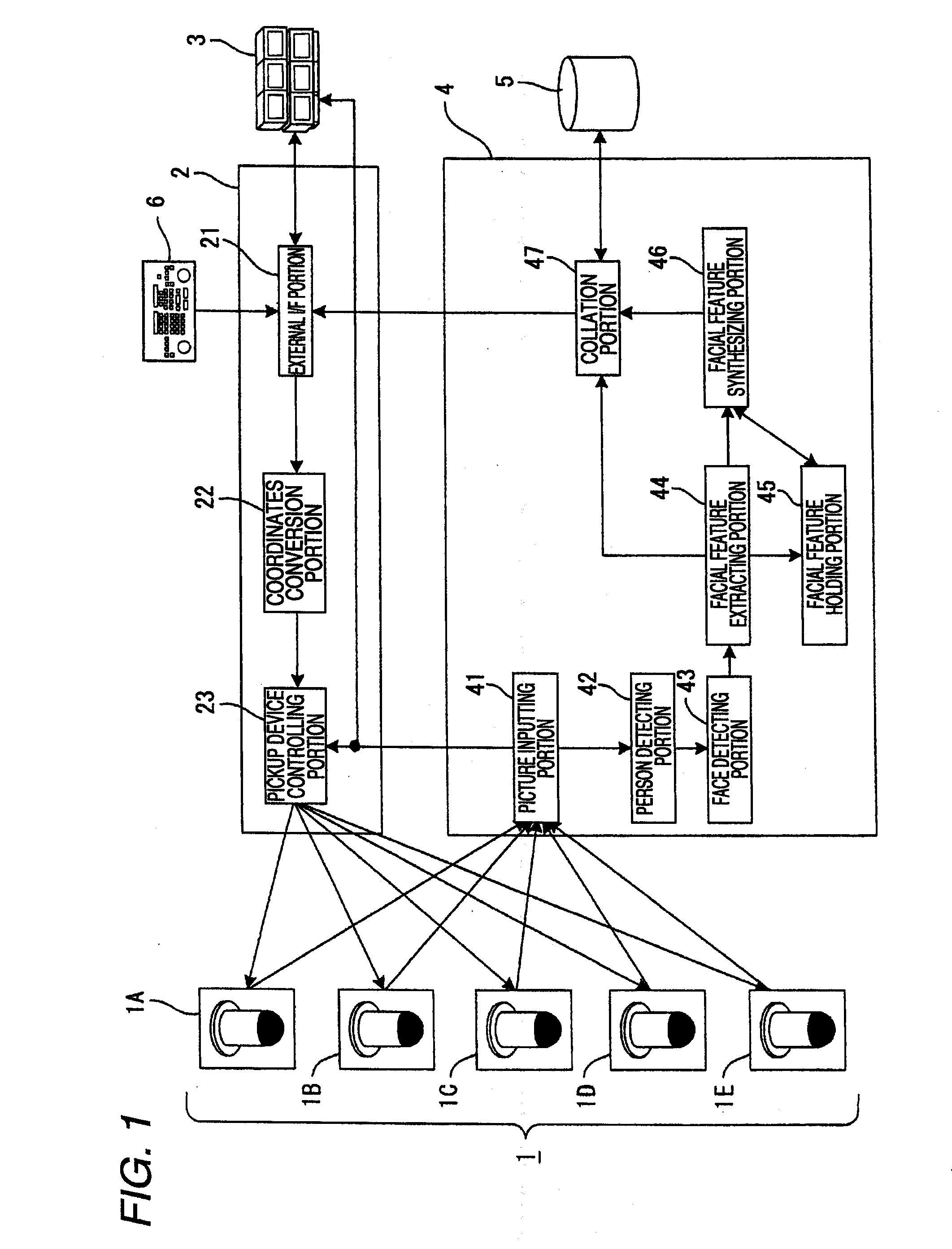
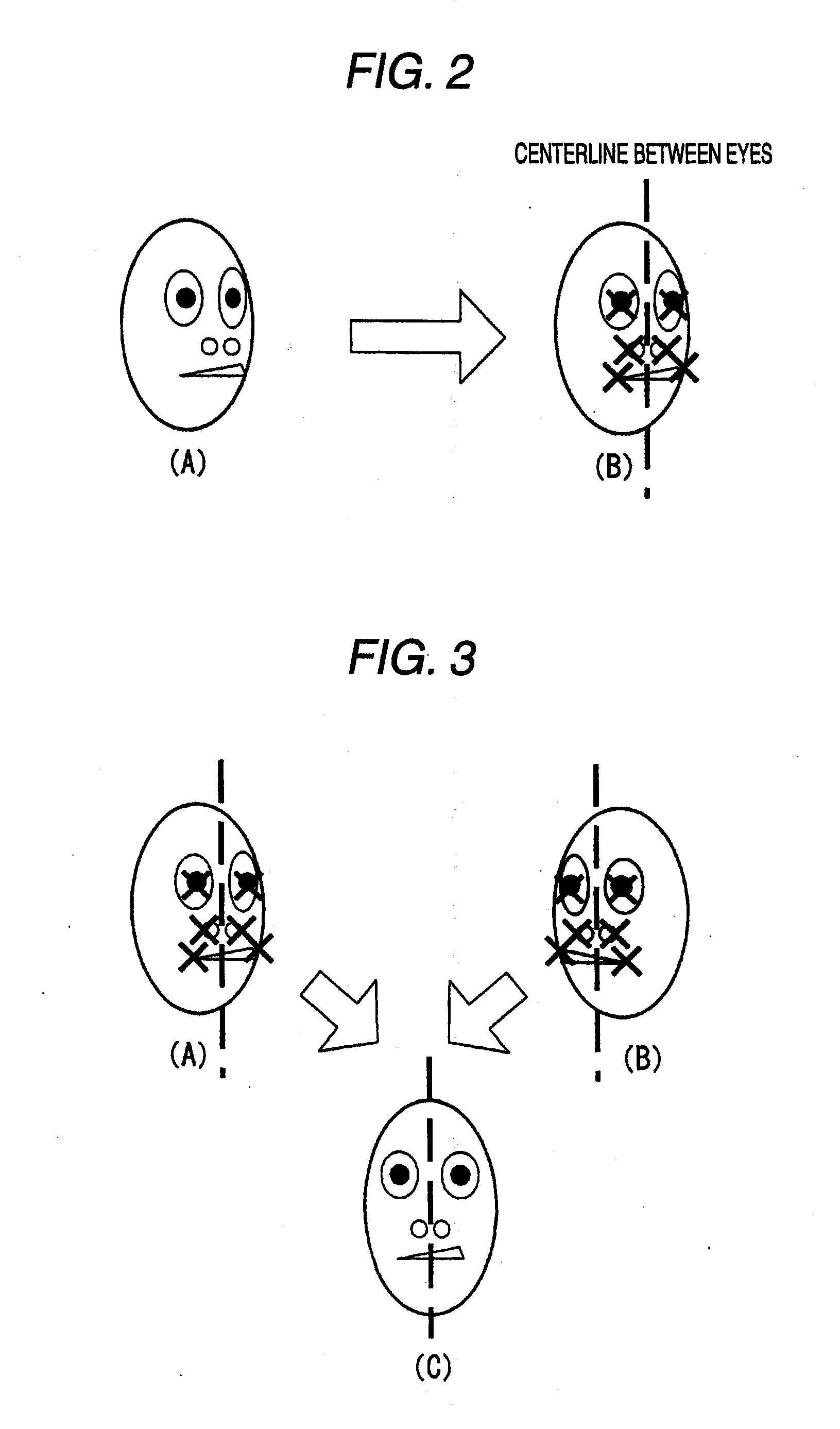
The invention provides a facial feature verification apparatus capable of synthesizing an image suitable for verification to identify a person subjected to surveillance whom surveillance staff desires to watch. The facial feature verification apparatus includes a plurality of pickup units 1, a pickup controlling unit 2 for controlling the pickup units 1, a displaying unit 3 for displaying images picked up by the pickup units 1, and a verifying unit 4 for detecting a person from the picked up images, extracting a facial image by determining a face area of the person, extracting a facial image from the images picked up by the pickup units 1, synthesizing a plurality of facial features by extracting facial features from the extracted facial images, and verifying the synthesized facial features with the facial features enrolled in advance in a facial image database 5.
Owner:PANASONIC CORP
Speaker verification
ActiveUS9343067B2Simple methodImprove verification accuracySpeech recognitionPassphraseFeature vector
A speaker verification method is proposed that first builds a general model of user utterances using a set of general training speech data. The user also trains the system by providing a training utterance, such as a passphrase or other spoken utterance. Then in a test phase, the user provides a test utterance which includes some background noise as well as a test voice sample. The background noise is used to bring the condition of the training data closer to that of the test voice sample by modifying the training data and a reduced set of the general data, before creating adapted training and general models. Match scores are generated based on the comparison between the adapted models and the test voice sample, with a final match score calculated based on the difference between the match scores. This final match score gives a measure of the degree of matching between the test voice sample and the training utterance and is based on the degree of matching between the speech characteristics from extracted feature vectors that make up the respective speech signals, and is not a direct comparison of the raw signals themselves. Thus, the method can be used to verify a speaker without necessarily requiring the speaker to provide an identical test phrase to the phrase provided in the training sample.
Owner:BRITISH TELECOMM PLC
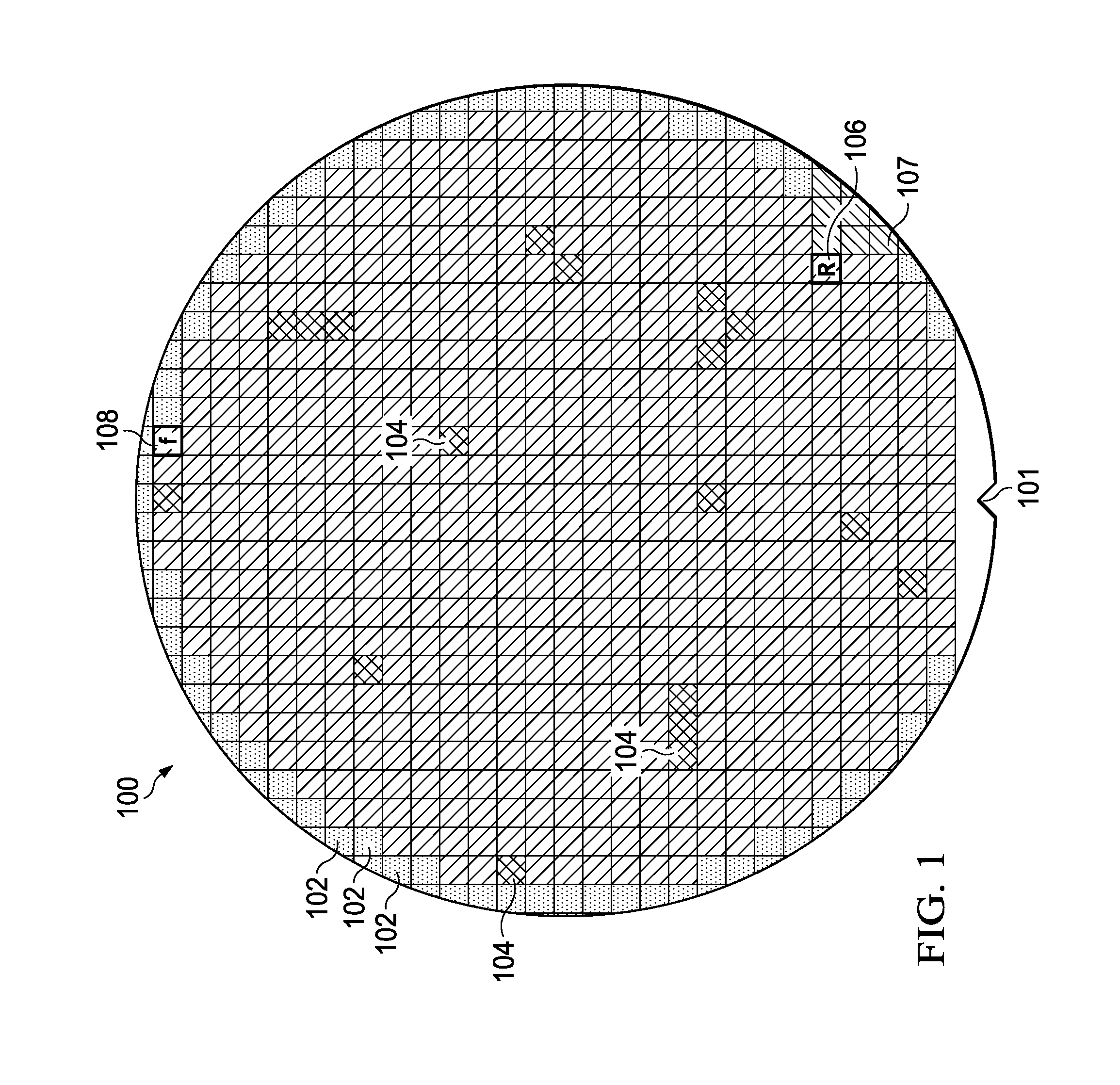
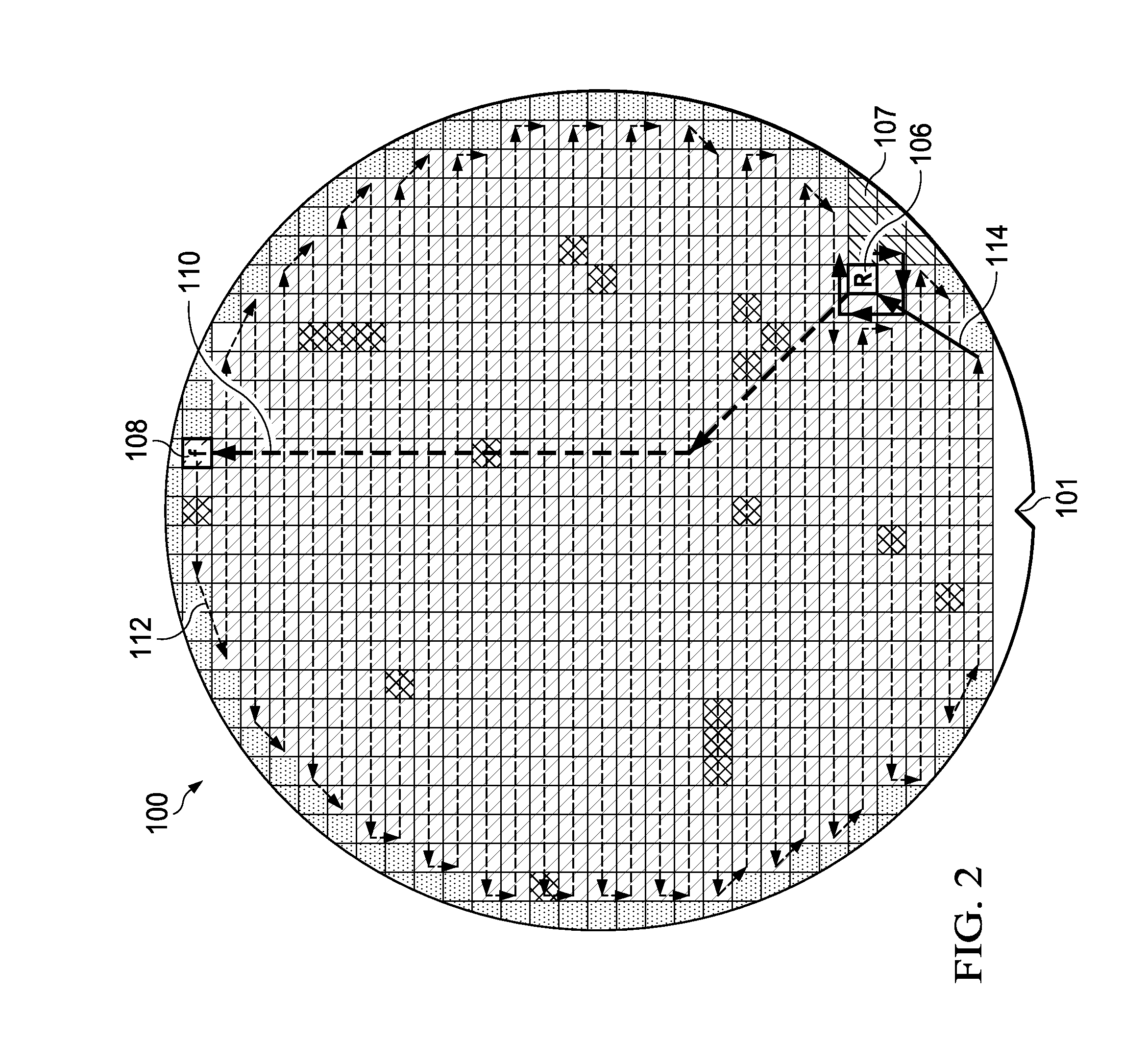
Die Attach Pick Error Detection
ActiveUS20140002128A1Improve verification accuracySemiconductor/solid-state device testing/measurementSemiconductor/solid-state device detailsEngineeringSemiconductor
Embodiments of the invention provide a method to detect pick and place indexing errors on each manufacturing batch (lot) of semiconductor wafer processed during a die attach process using a preselected skeleton of check die. The known locations of the check skeleton die are verified during picking of die from the wafer. If the check skeleton cannot be correctly verified at the known locations, then a pick error is indicated. The embodiments may be implemented on existing die attach equipment.
Owner:TEXAS INSTR INC
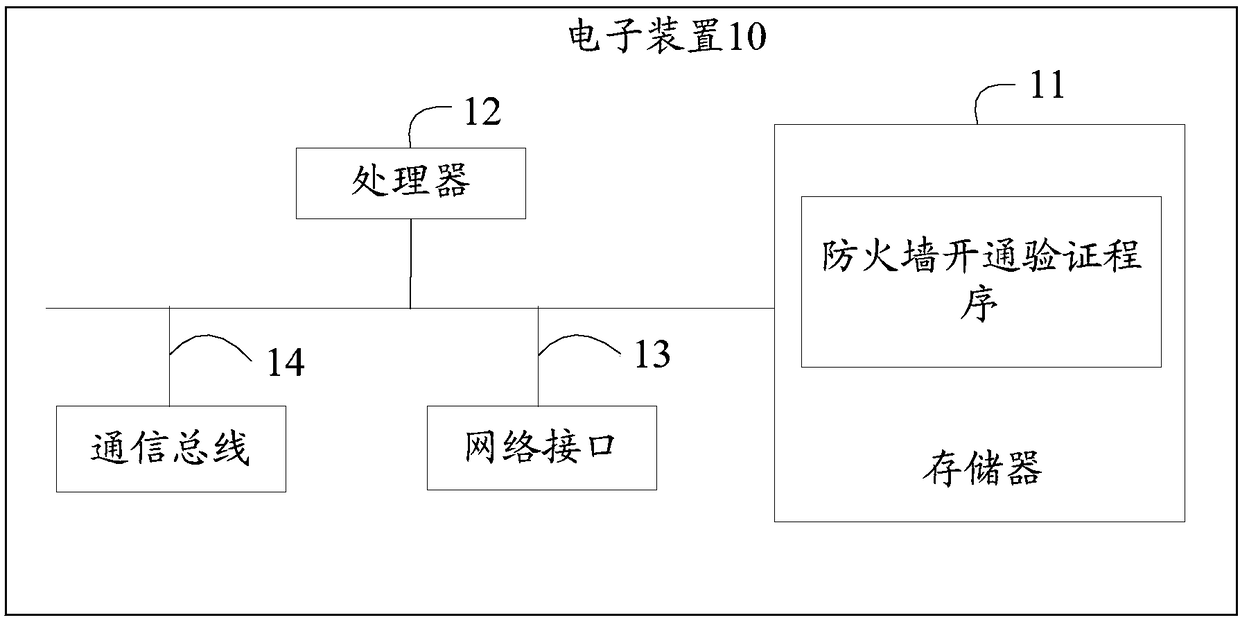
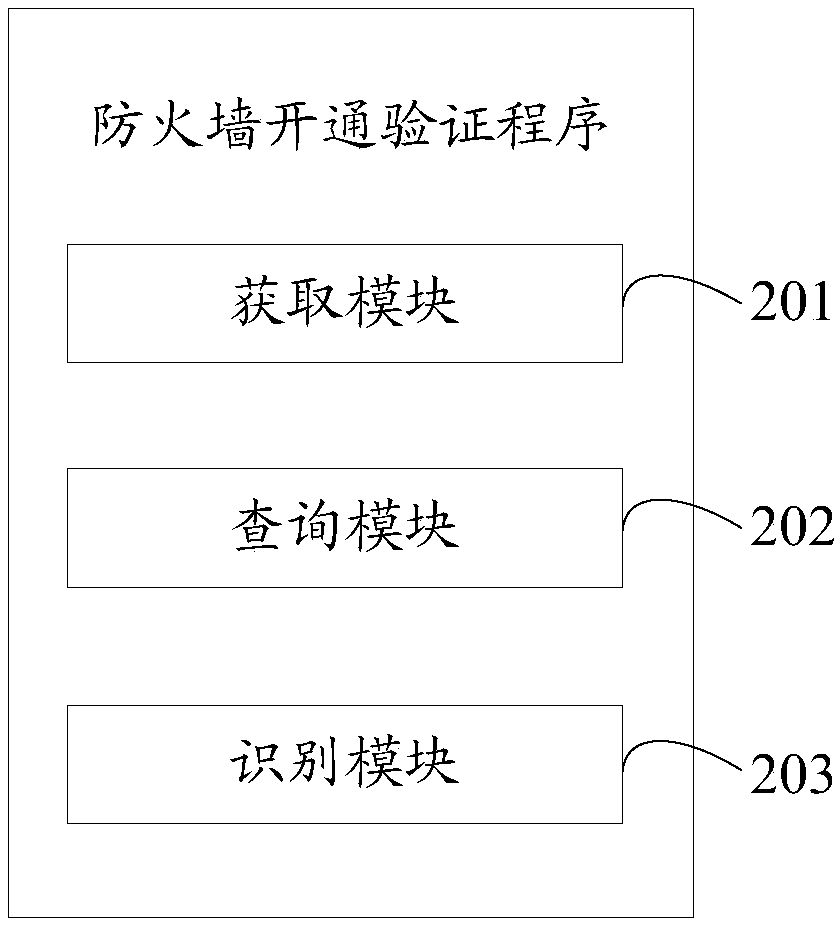
Electronic device, firewall operation verification method and storage medium
ActiveCN108494771AImprove efficiencyImprove verification accuracyTransmissionIp addressComputer security
The invention discloses an electronic device, a firewall operation verification method, and a storage medium. The verification method comprises the following steps: acquiring a source IP address and source port information of a client after receiving a request for acquiring service data sent by the client; traversing firewall white list generated in advance based on the source IP address and the source port information, querying a target IP address and target port information mutually mapped to the source IP address and the source port information in the firewall white list; executing an instruction for verifying the firewall operation by starting the corresponding thread count according to the mutually mapped target IP address and the target port information. The efficiency of verifying whether the firewall is in operation is improved, and the verification accuracy rate is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Station entrance identity authentication method based on two-dimensional code
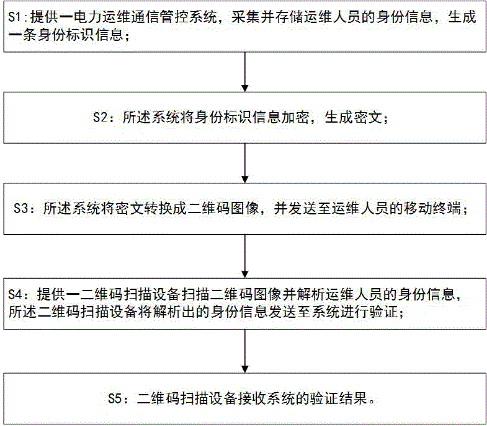
InactiveCN105844747AResolve authenticationAvoid safety hazardsData processing applicationsIndividual entry/exit registersControl systemCiphertext
The invention relates to a station entrance identity authentication method based on a two-dimensional code. The method particularly includes the following steps: S1) providing an electric operation and maintenance communication management and control system for collecting and storing identity information of operation and maintenance workers to generate identity identification information; S2) encrypting the identity identification information to generate a cipher text by a system; S3) converting the cipher text into a two-dimensional code image by the system and sending the two-dimensional code image to a mobile terminal of the operation and maintenance workers; S4) providing a two-dimensional code scanning device, so that when the operation and maintenance workers enter the station for maintenance and show the two-dimensional code image on the mobile terminal, the two-dimensional code scanning device scans the two-dimensional code and analyses the identity information of the workers, and sends the analyzed identity information to the system for identification; and S5) receiving the verification result from the system by the two-dimensional code scanning device. The method solves the problem of identity identification of the operation and maintenance workers through the two-dimensional code and data encryption technologies.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD +1
Data synchronization method, device and system for communication system
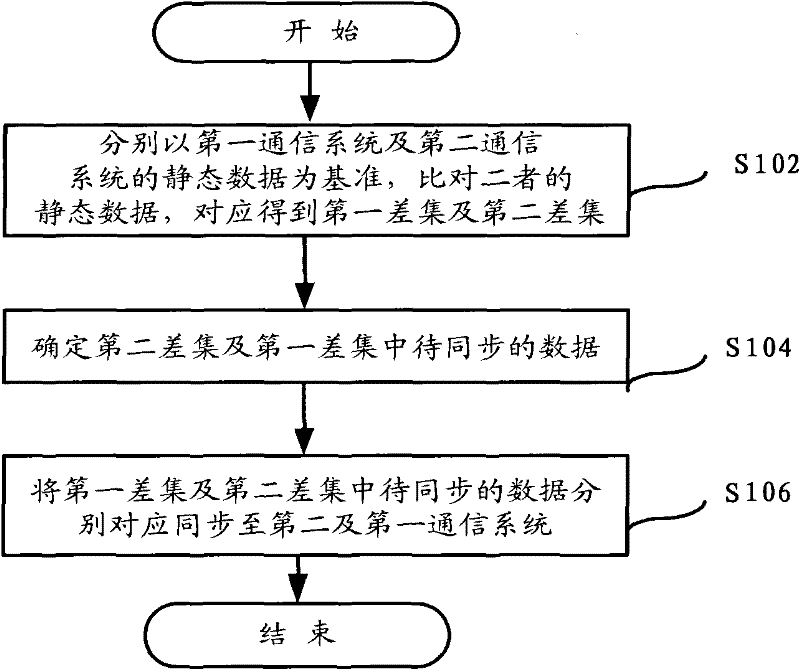
InactiveCN102263798AAvoid errorsImprove verification accuracyTransmissionBaseline dataData synchronization
The invention provides a data synchronization method, a data synchronization device and a data synchronization system for communication systems. The method comprises the following steps of: comparing first static data with second static data to correspondingly obtain a first difference set and a second difference set by taking the first static data of a first communication system and the second static data of a second communication system as references respectively; correspondingly determining data to be synchronized in the second difference set and the data to be synchronized in the first difference set according to a data track in the first communication system and the data track in the second communication system respectively; and correspondingly synchronizing the data to be synchronized in the first difference set and the data to be synchronized in the second difference set to the second communication system and the first communication system. By the method, the device and the system, errors caused by the inaccuracy of reference data are avoided to improve checkout accuracy, and the errors caused by the inaccuracy of single side reference data are simultaneously avoided to further improve the checkout accuracy.
Owner:中国移动通信集团甘肃有限公司
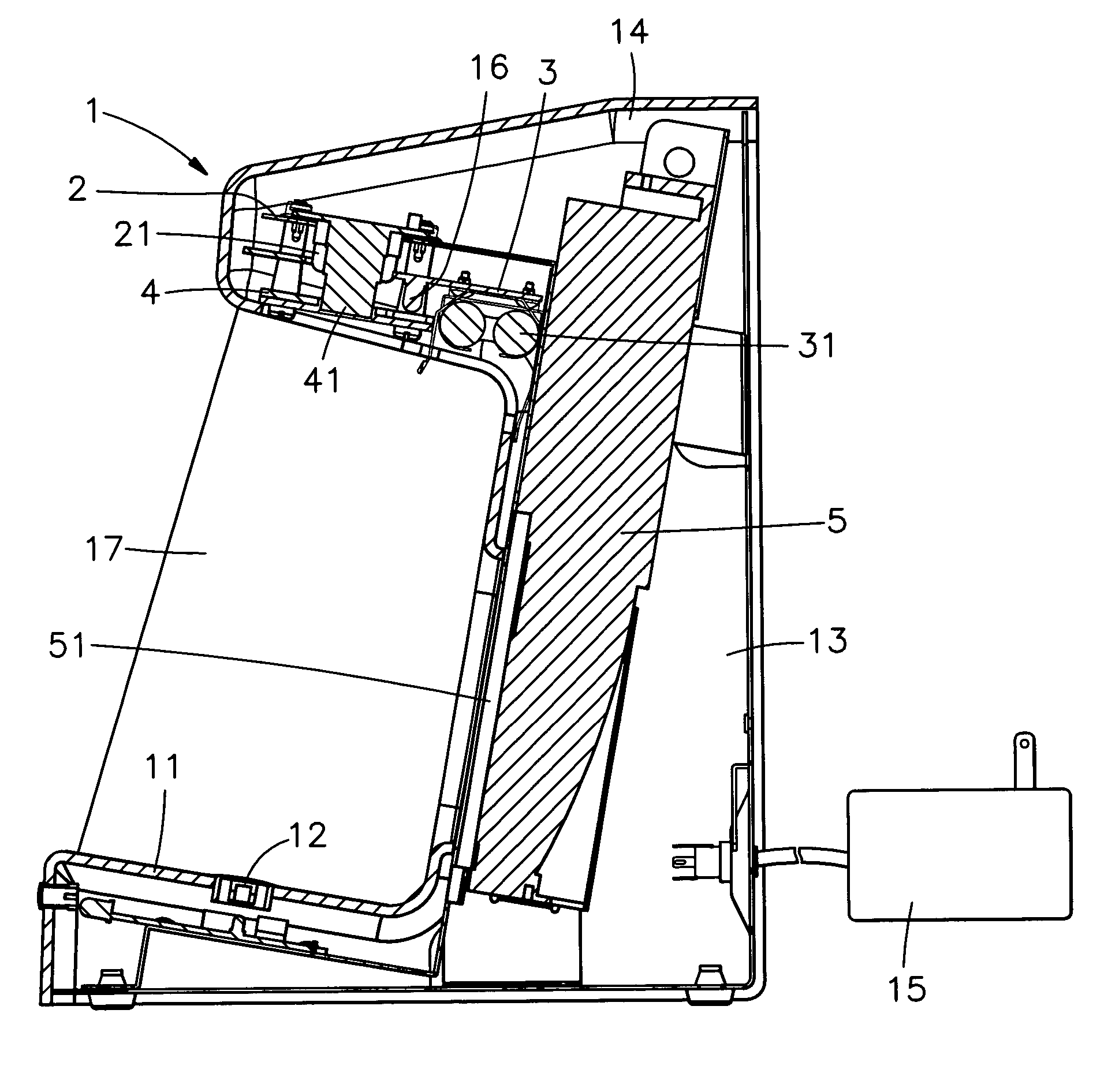
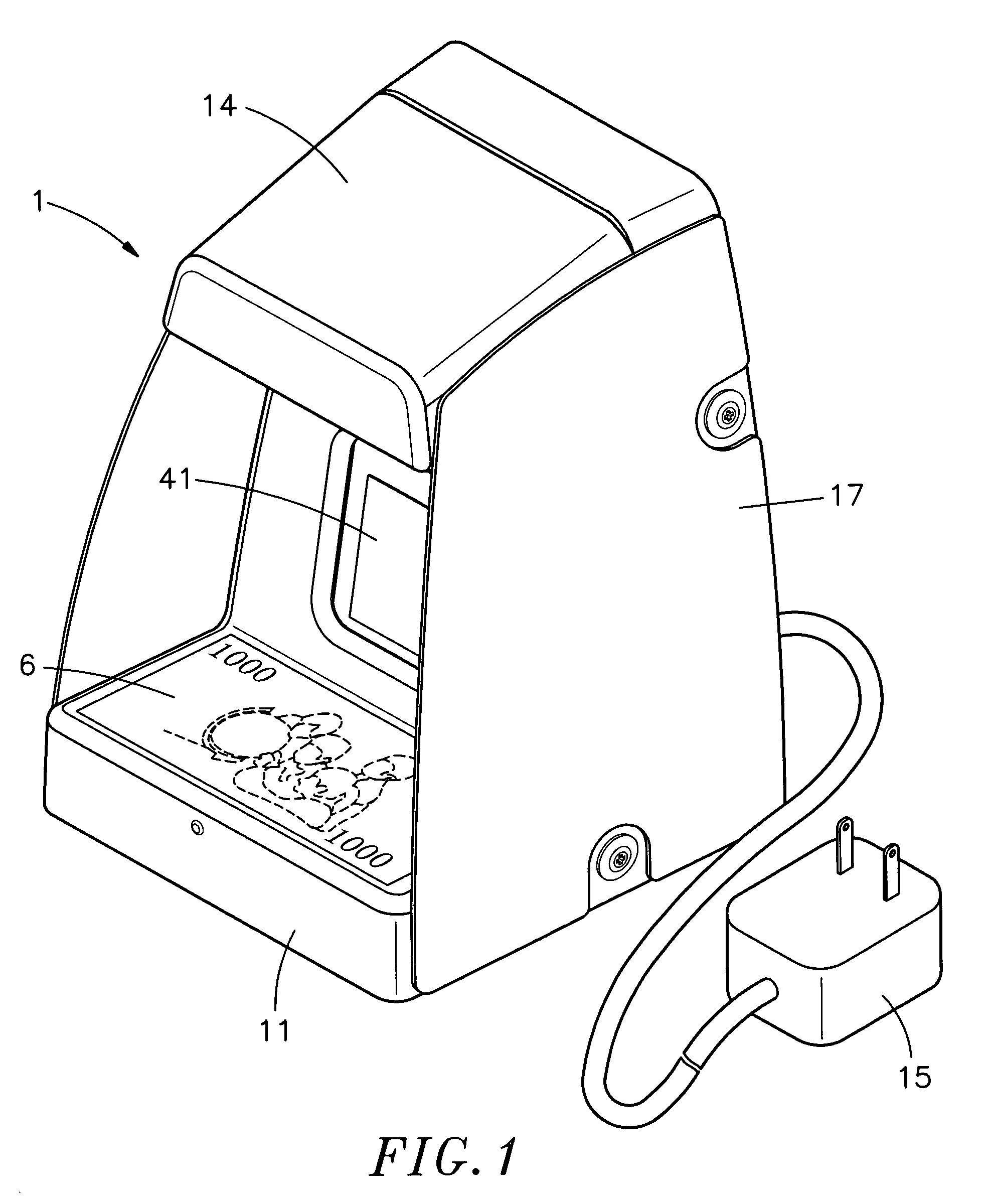
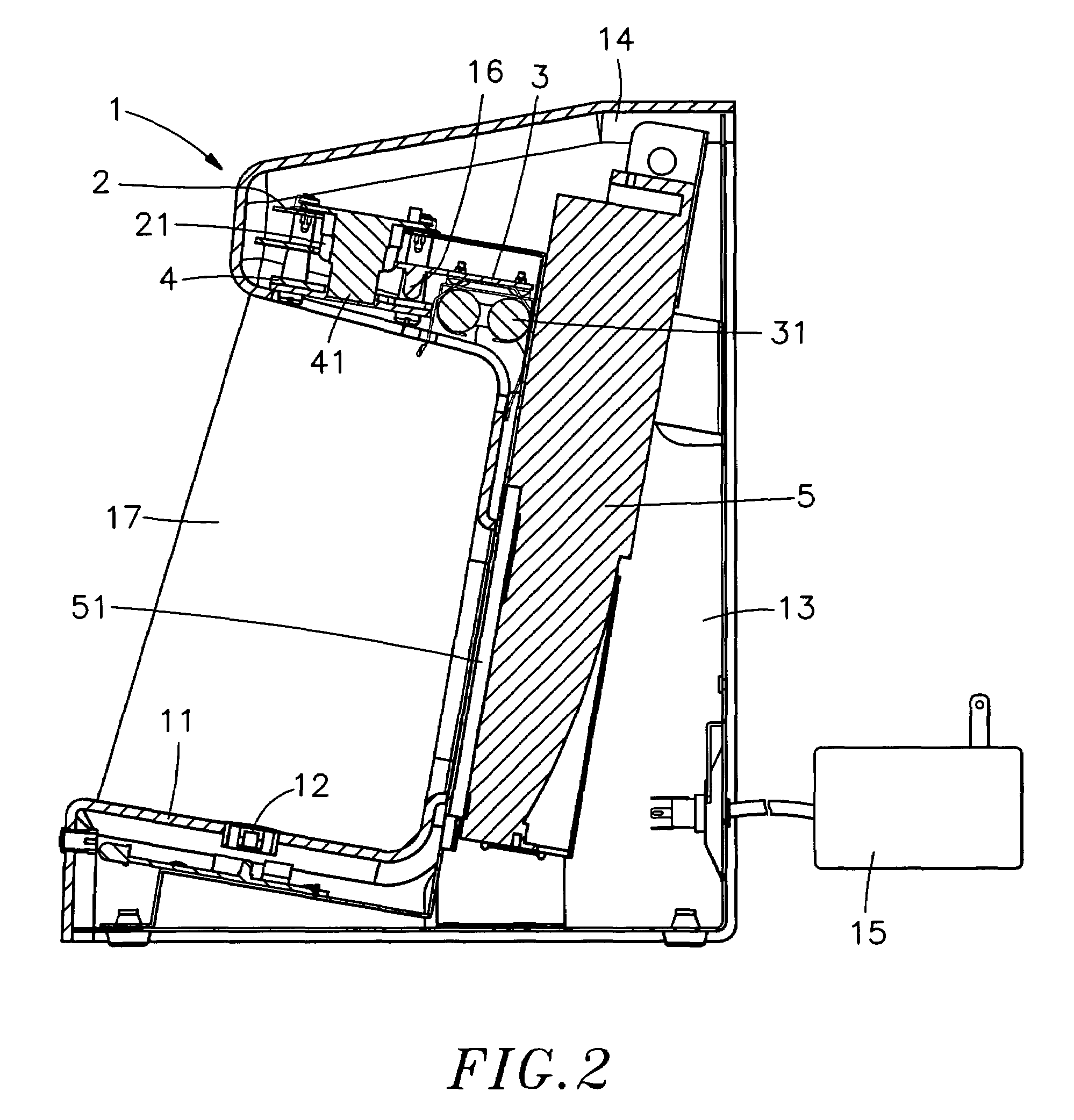
Bill acceptor
InactiveUS6994201B2Improve accuracyEliminate distractionsPaper-money testing devicesMaterial analysis by optical meansImage sensorEngineering
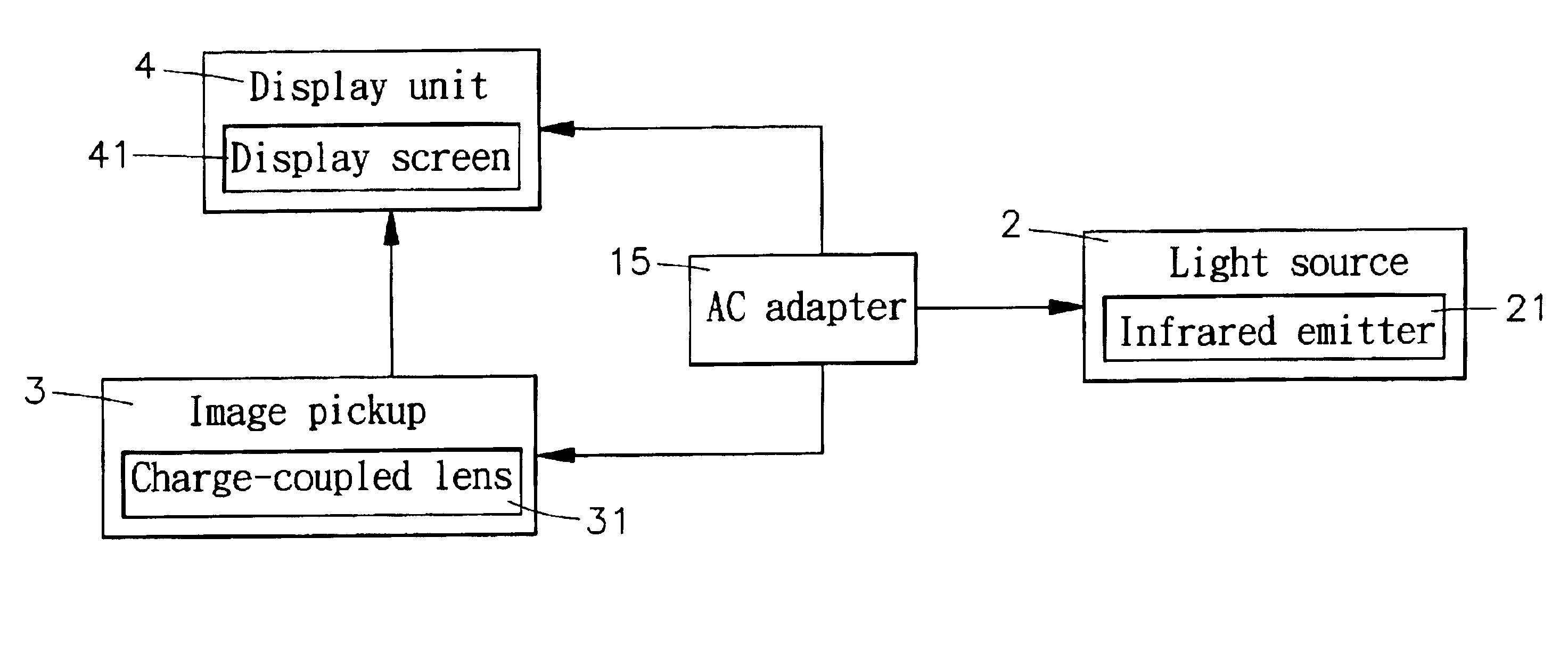
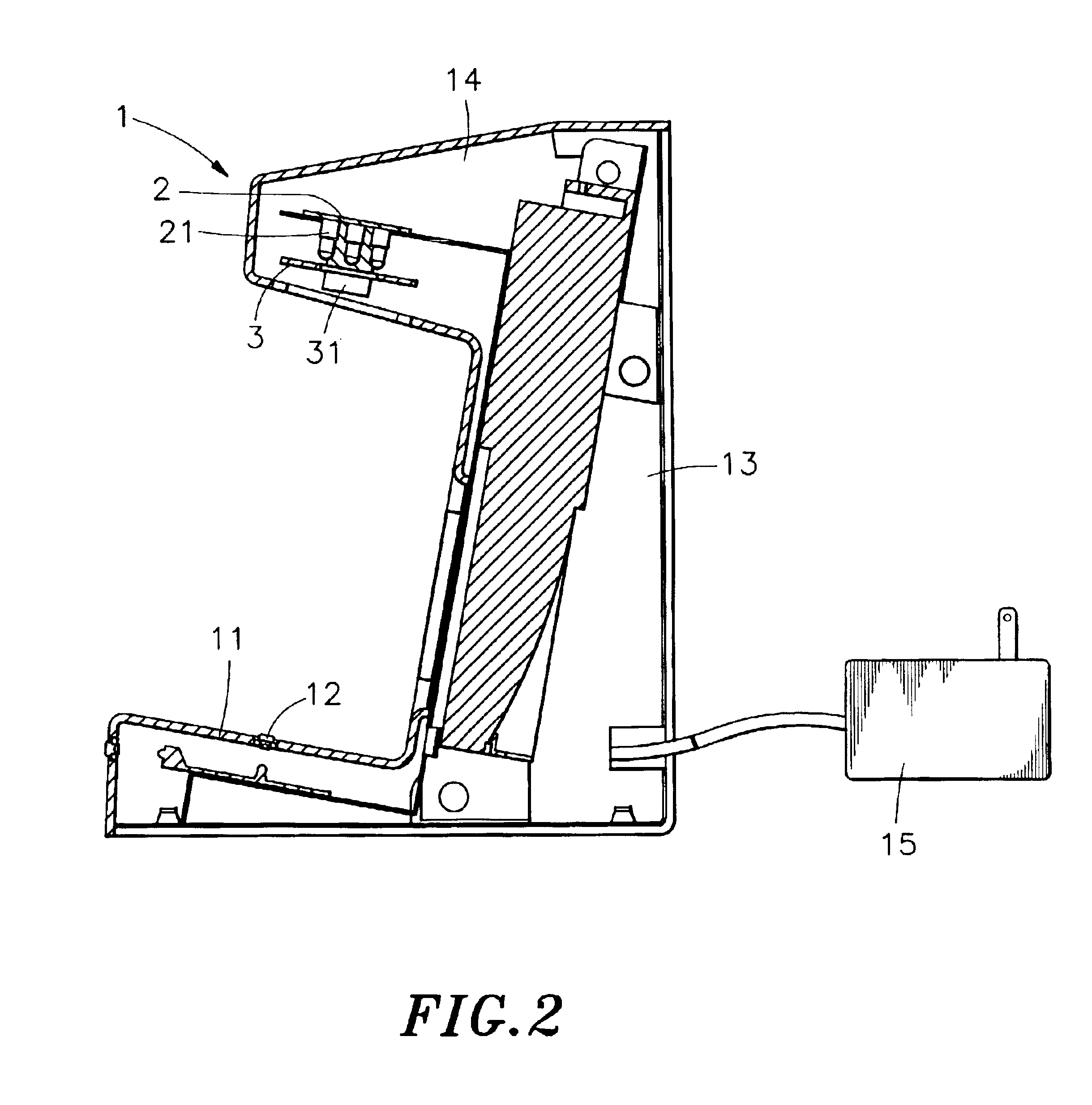
A bill acceptor is constructed to include a housing, the housing having a base for holding a banknote for examination, a first light emitter adapted to emit infrared light onto the banknote carried on the base of the housing for examination, a second light emitter adapted to emit ultraviolet light onto the banknote for visual examination, an image sensor adapted to pick up infrared light reflected from the banknote carried on the base of the housing and to convert received light signal into image signal, and a display adapted to display image signal obtained from the image sensor for verifying the authenticity of the banknote.
Owner:INT CURRENCY TECH
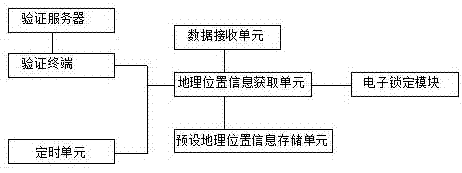
Dual wireless signal electronic lock and unlocking method thereof
PendingCN107248218AImprove securityPrevent findingIndividual entry/exit registersTransmissionEngineeringElectrical and Electronics engineering
The invention provides a dual wireless signal electronic lock and unlocking method thereof. The dual wireless signal electronic lock comprises a first lock and a second lock. The first lock and the second lock are fixedly connected. The first lock comprises a position information module, a safety locking module and an electronic locking module. The position information module is used for obtaining geographic position information of the position and comparing the geographic position information with preset geographic position information, if the geographic position information is matched with the preset geographic position information according to the comparison result, the electronic locking module is controlled to be unlocked, and if the geographic position information is not matched with the preset geographic position information according to the comparison result, data receiving is cut off; the safety locking module is used for verifying that a worker initiating the unlocking operation has the unlocking condition; the electronic locking module is used for locking the first lock. The dual locks are adopted for locking, the safety coefficient is high, the first lock performs unlocking by adopting the geographic position information unlocking mode, on the basis of control of the safety locking module, the safety is high, and damage is not likely to be caused.
Owner:林琳
Mutation analysis method and device for cell-free DNA (cfDNA) sequencing data
InactiveCN112111565AHigh mutation sensitivityImprove verification accuracyMicrobiological testing/measurementProteomicsRepetitive SequencesSomatic cell
The invention relates to a mutation analysis method and device for cell-free DNA (cfDNA) sequencing data. The method comprises the following steps: 1, preprocessing original sequencing data; 2, comparing the sequencing data with a reference standard genome, identifying and eliminating PCR repetitive sequences, and correcting comparison errors of sequences to obtain an accurate sequence comparisonfile; 3, identifying tumor-related somatic cell variation sites, adopting a Sentieon software TNScope tool, setting parameters to ensure that cfDNA variation sites higher than 5 / 10000 variation abundance can be detected, and obtaining a potential tumor-related somatic cell variation site table; and 4, analyzing and identifying the highly credible low-frequency variation, and finally obtaining an expected positive variation analysis result. The method can achieve ultrahigh mutation sensitivity detection and high verification accuracy.
Owner:上海其明信息技术有限公司
Banknote acceptor
InactiveUS6903342B2Improve verification accuracyEliminates the aforesaid drawbacksRadiation pyrometryPaper-money testing devicesLight beamEngineering
An infrared banknote acceptor for use to verify the authenticity of banknotes is constructed to include a housing, the housing having a base adapted to hold the banknote to be verified, a light source adapted to emit an infrared light beam onto the banknote carried on the base of the housing for verification, an image pickup adapted to receive infrared light reflected by the ink of the banknote carried on the base of the housing for verification and to convert received infrared light signal into video signal, and a display unit adapted to receive and display the video signal outputted from the image pickup.
Owner:INT CURRENCY TECH
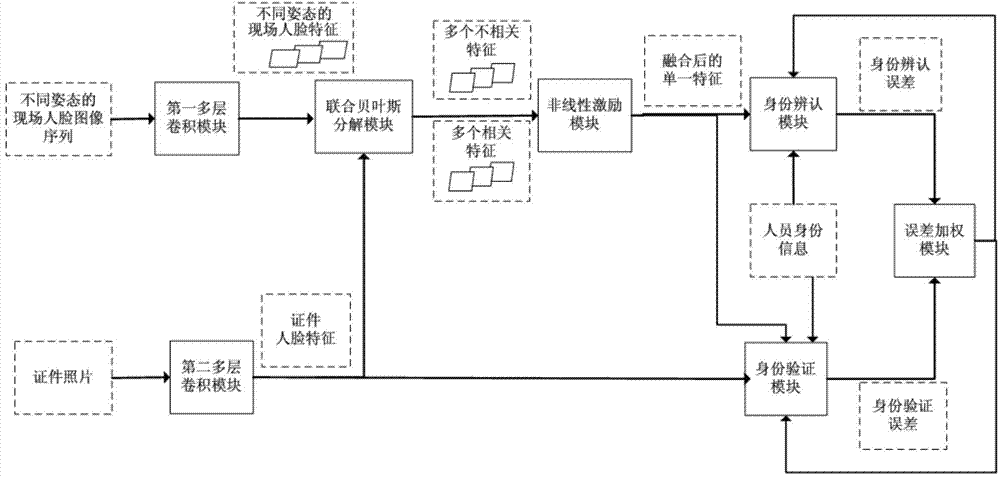
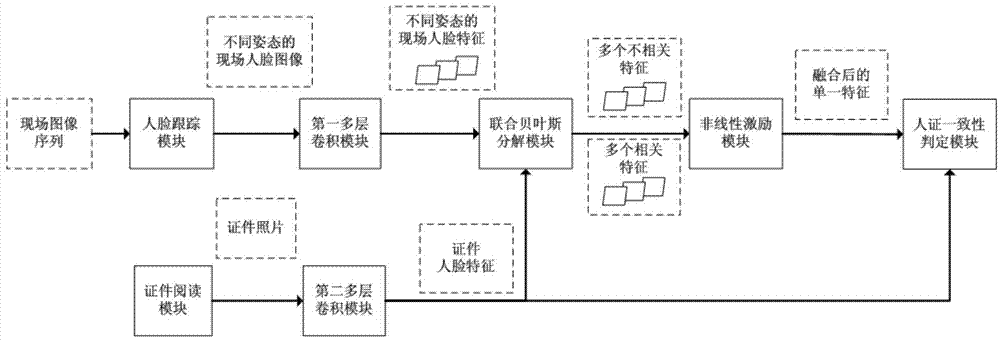
Person and credential verification system and method based on deep learning
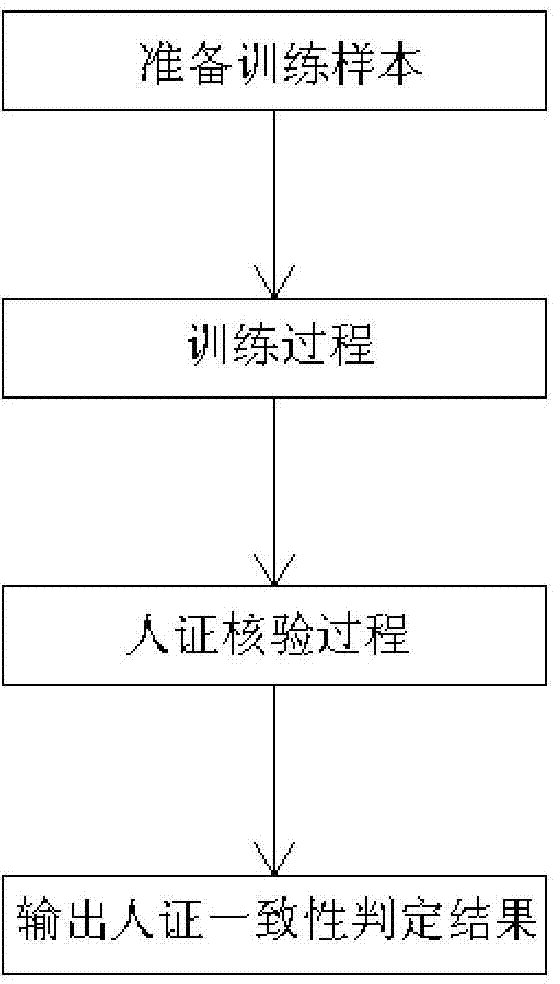
ActiveCN104751143AEffective comparisonImprove verification accuracyCharacter and pattern recognitionVideo monitoringSecurity guard
The invention relates to a person and credential verification system and method, in particular to a person and credential verification system and method based on deep learning and belongs to the field of security guarding. The system comprises a training subsystem and a person and credential verification subsystem; the method includes a training process and a person and credential verifying process; the training process includes adopting a plurality of on-site facial images of known identities and credential photos to train the training subsystem; the person and credential verifying process includes utilizing the module parameters acquired through the training process, comparing the plurality of on-site acquired images of a discharged person with the credential photos corresponding to the information acquired by a credential reading module, and outputting the verification result whether the person consistent with the credential or not automatically. By the aid of the system and method, the credential photos and a plurality of facial photos acquired through an on-site video monitoring device can be compared effectively, the adaptability to facial angles, on-site environment, light emission and other factors is high, the accuracy of person and credential verification is high, and the discharging speed is high.
Owner:BEIJING ZHONGDUN SECURITY TECH DEV
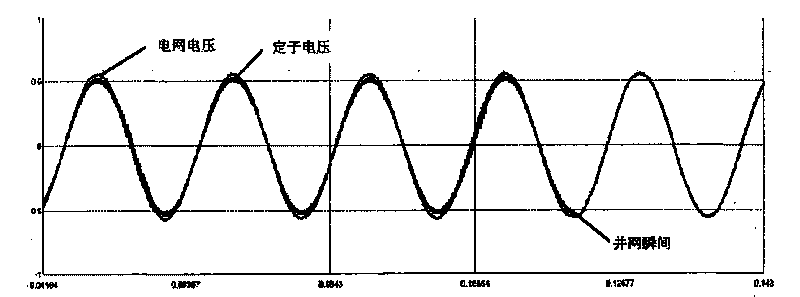
No-load cutting-in modeling and experimental method of double-fed type wind-driven generator
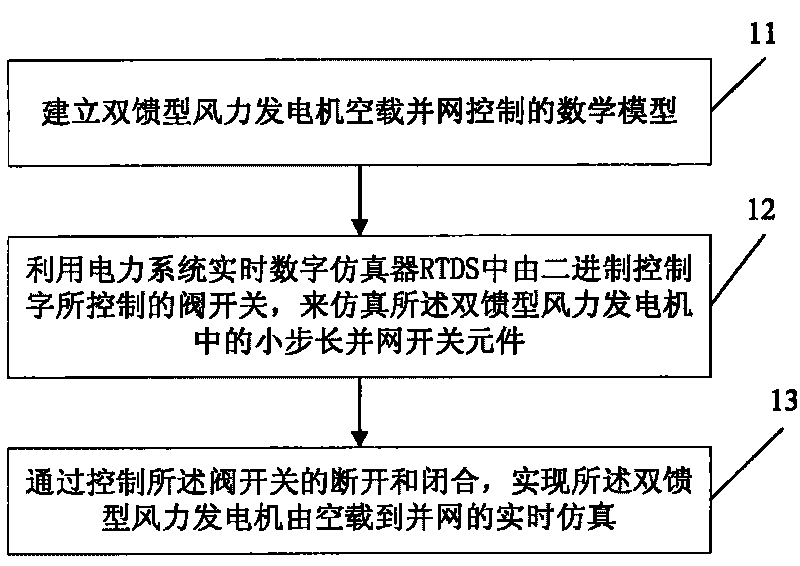
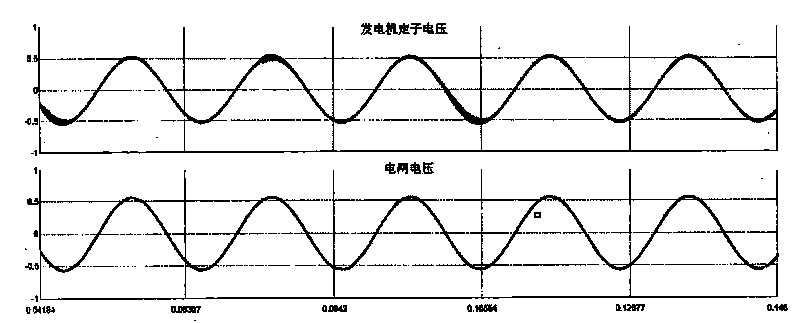
ActiveCN101719678AReal and accurate simulation environmentImprove verification accuracySingle network parallel feeding arrangementsSpecial data processing applicationsWind drivenReal-time simulation
The embodiment of the invention provides a no-load cutting-in modeling and experimental method of a double-fed type wind-driven generator. The modeling method comprises the following concrete steps: firstly, establishing a mathematical model for no-load cutting-in control of the double-fed type wind-driven generator; simulating a small-step cutting-in switch element in the double-fed type wind-driven generator by utilizing a valve switch which is controlled by binary control words in a real-time digital simulator (RTDS) of an electric power system; and realizing the simulation control of the double-fed type wind-driven generator from the no-load state to the cutting-in state by controlling the switching-on and the switching-off of the valve switch. The technical scheme of the invention can be implemented to realize the real-time simulation process of the double-fed type wind-driven generator from the no-load state to the cutting-in state, and the simulation model is used for carrying out the no-load cutting-in experiment on a variable-flow controller system of a practical double-fed type wind-driven generator, thereby providing real and accurate simulation environment and improving the verifying accuracy.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Face feature collator, face feature collating method, and program
InactiveUS8073206B2Improve verification accuracyImprove accuracyCharacter and pattern recognitionColor television detailsImage database
The invention provides a facial feature verification apparatus capable of synthesizing an image suitable for verification to identify a person subjected to surveillance whom surveillance staff desires to watch. The facial feature verification apparatus includes a plurality of pickup units 1, a pickup controlling unit 2 for controlling the pickup units 1, a displaying unit 3 for displaying images picked up by the pickup units 1, and a verifying unit 4 for detecting a person from the picked up images, extracting a facial image by determining a face area of the person, extracting a facial image from the images picked up by the pickup units 1, synthesizing a plurality of facial features by extracting facial features from the extracted facial images, and verifying the synthesized facial features with the facial features enrolled in advance in a facial image database 5.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com