Patents
Literature
2014 results about "Remote computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
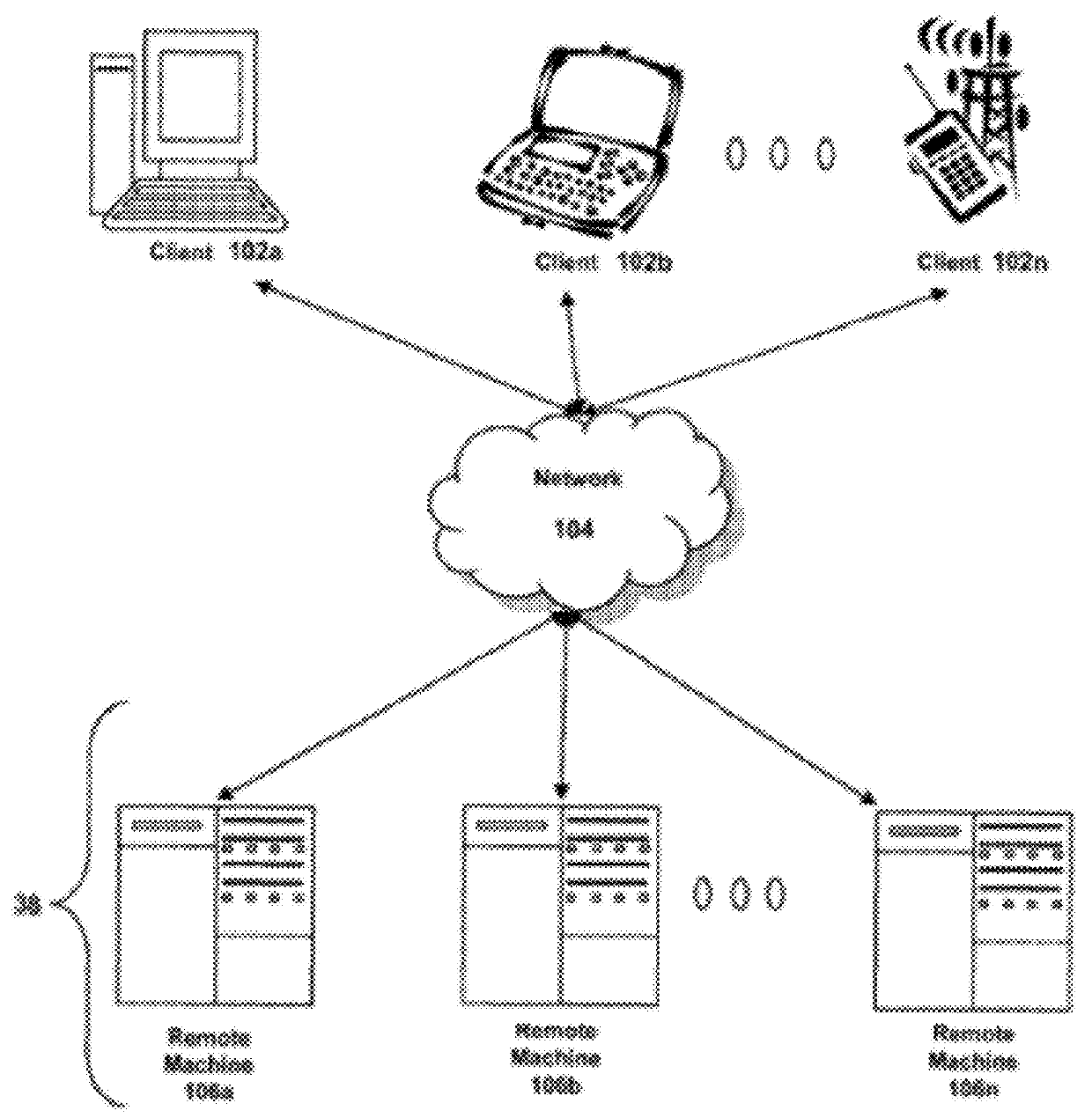
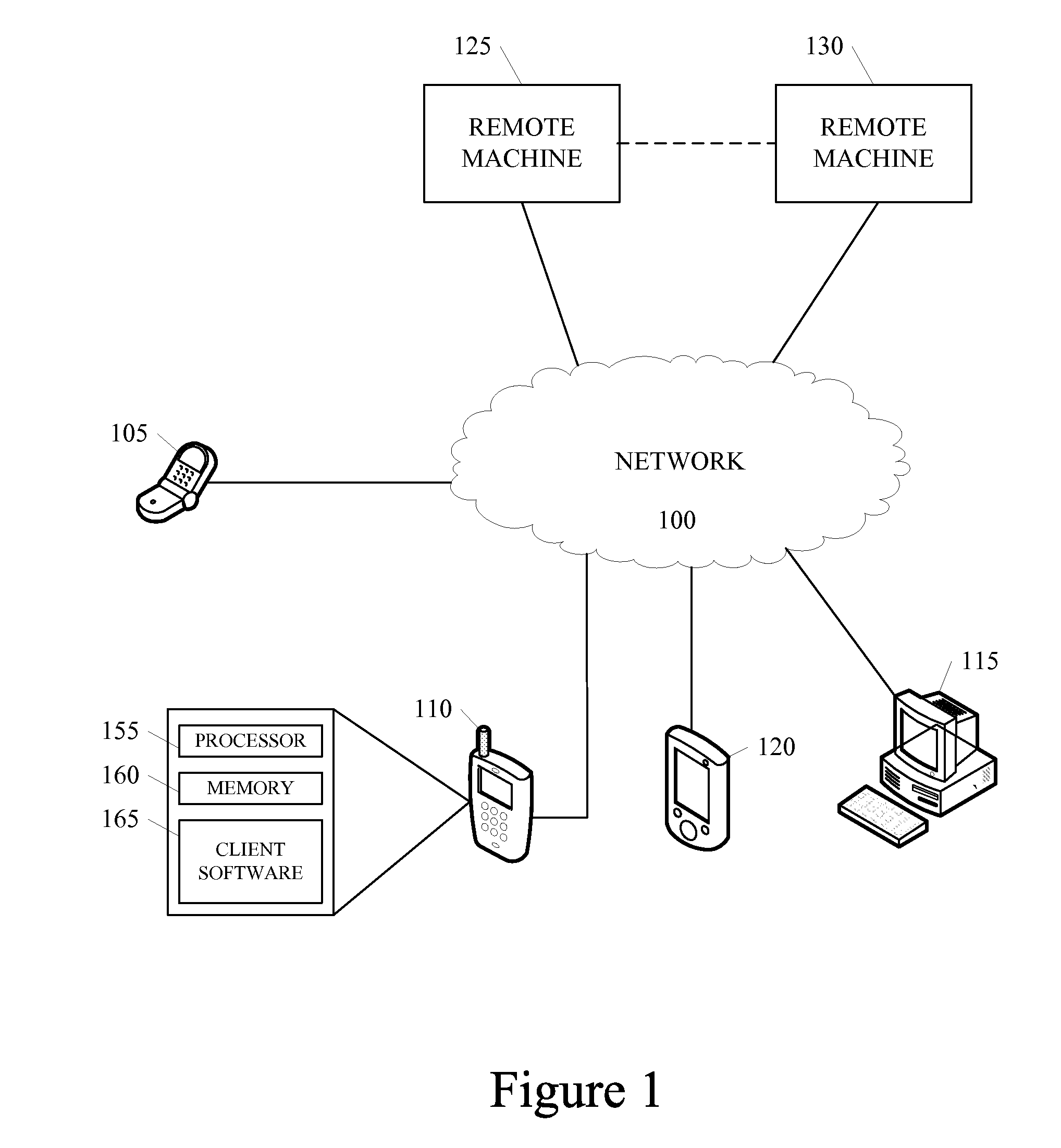
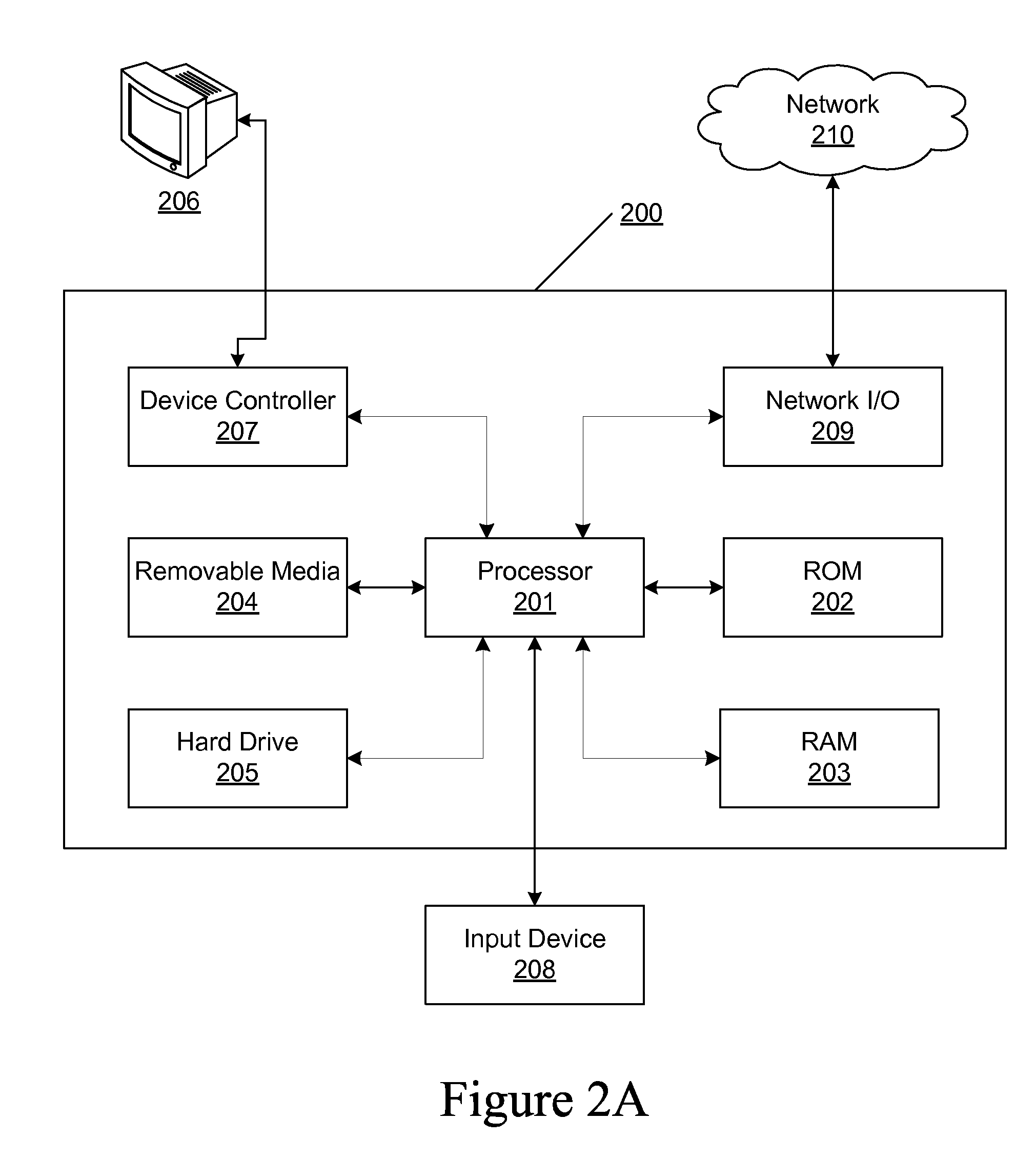
A remote computer is a computer that a user has no access to physically, but may be able to access it remotely via a network link from another computer. Remote connections are made through the use of a network which connects the computer and the device that is used to access it.
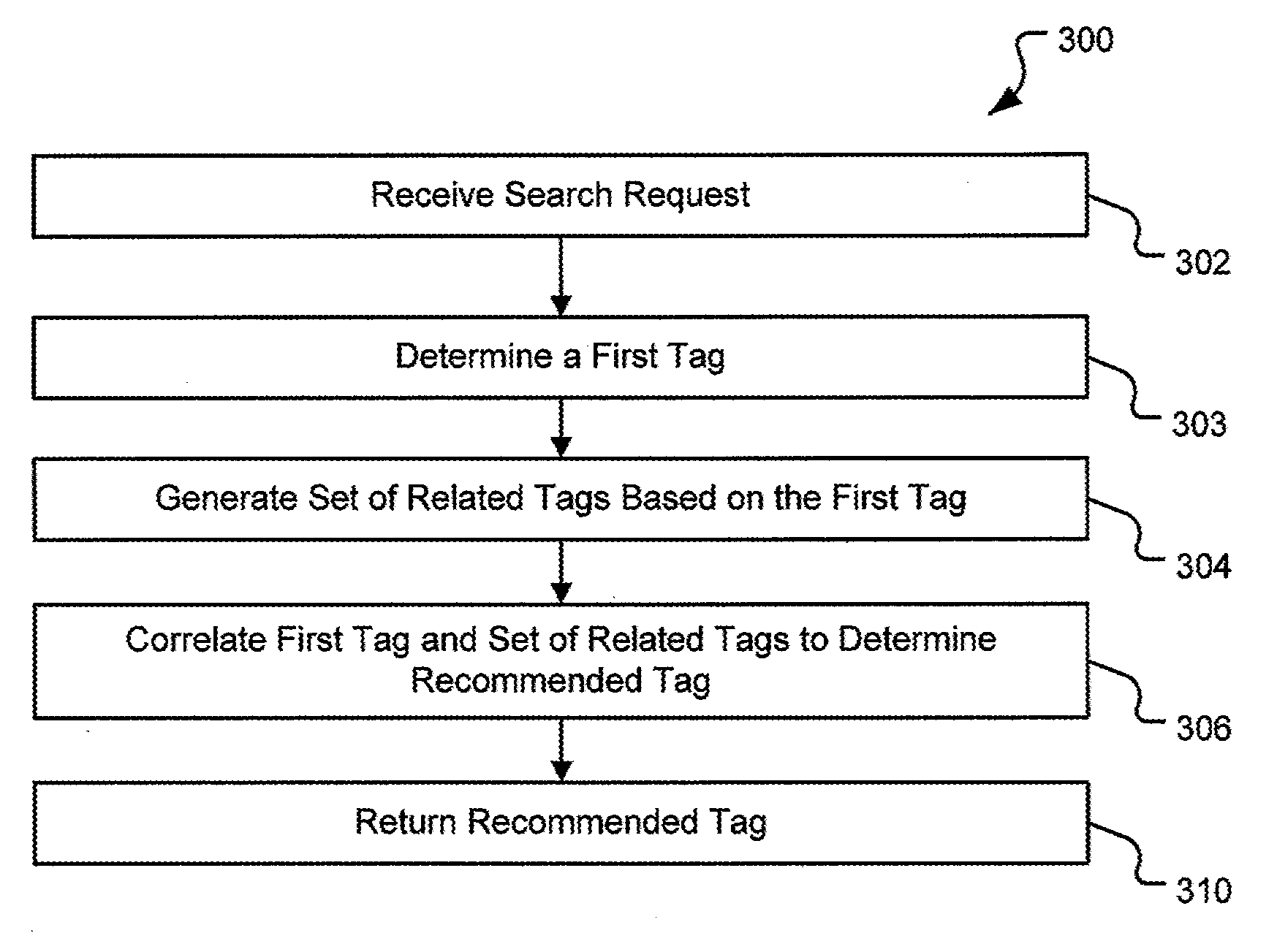
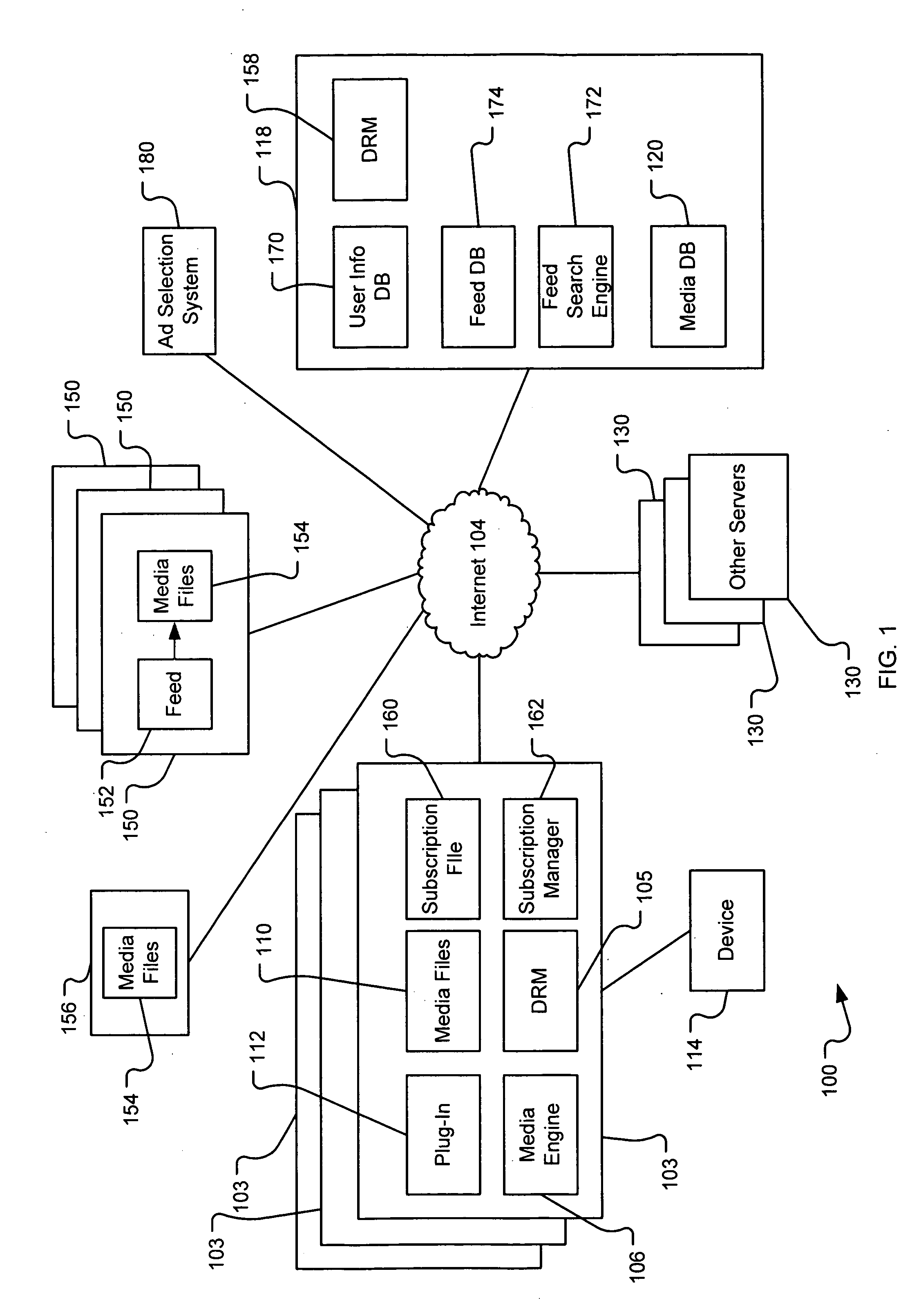
Method and system for using smart tags and a recommendation engine using smart tags
InactiveUS20070078832A1Effective marketingGenerate incomeDigital data information retrievalDigital data processing detailsRemote computingRecommender system
The present invention relates to a system and method for recommending tags and / or content items in response to requests received from remote computing devices. In one aspect, a content item recommendation system comprises a database configured to store an identifier of a first content item, a first tag and information from which a tag density associated with the first tag and with the first content item may be derived. The tag density may be a measure of times a tag has been associated with a content item by any user of a plurality of users who are members of a community. The system also comprises a recommendation engine configured to receive search results containing the first tag from a search engine and to correlate the first tag with information stored in the database. The recommendation engine may be further configured to determine a recommended tag, based on a recommendation threshold and a tag density, the tag density associated with both the recommended tag and the first content item.
Owner:OATH INC
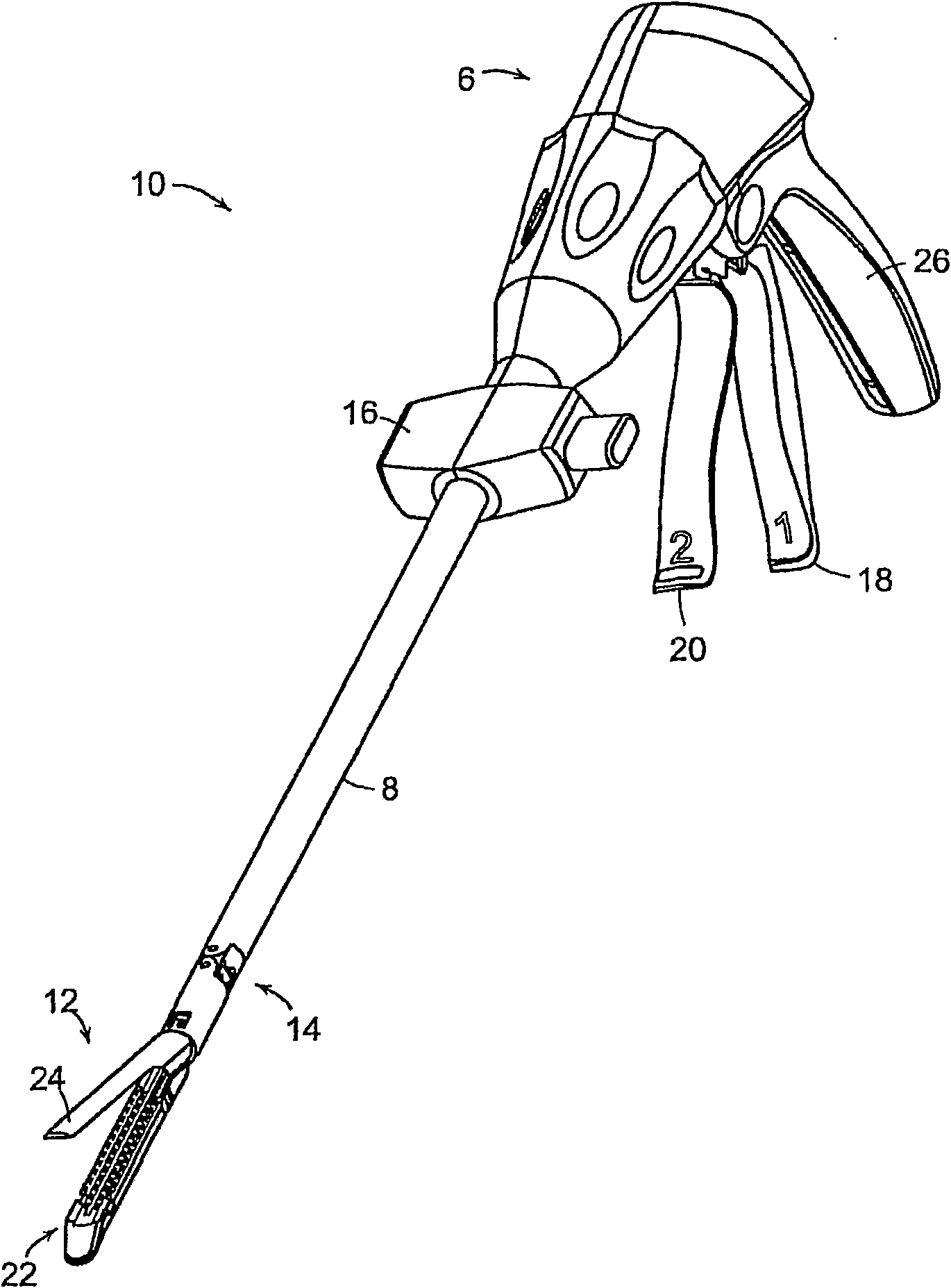
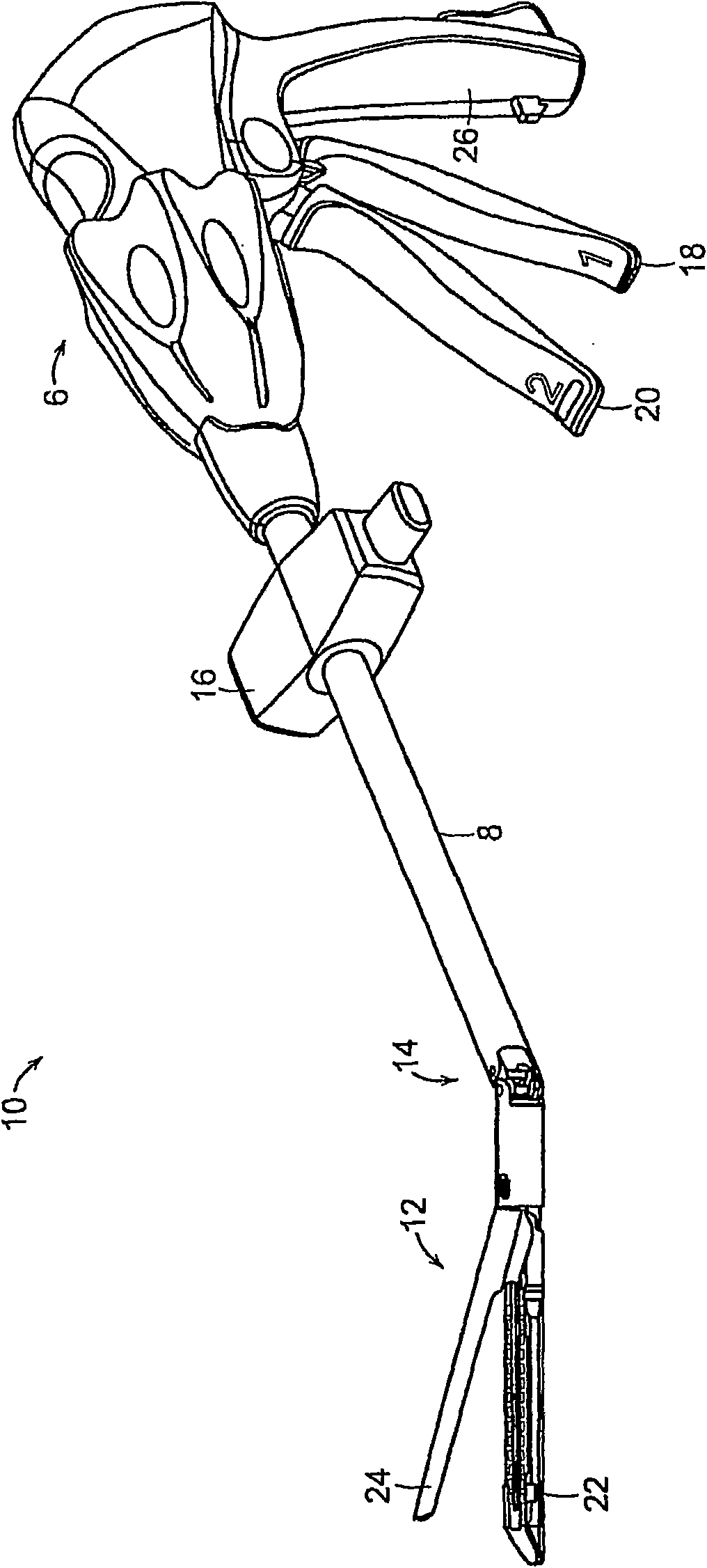
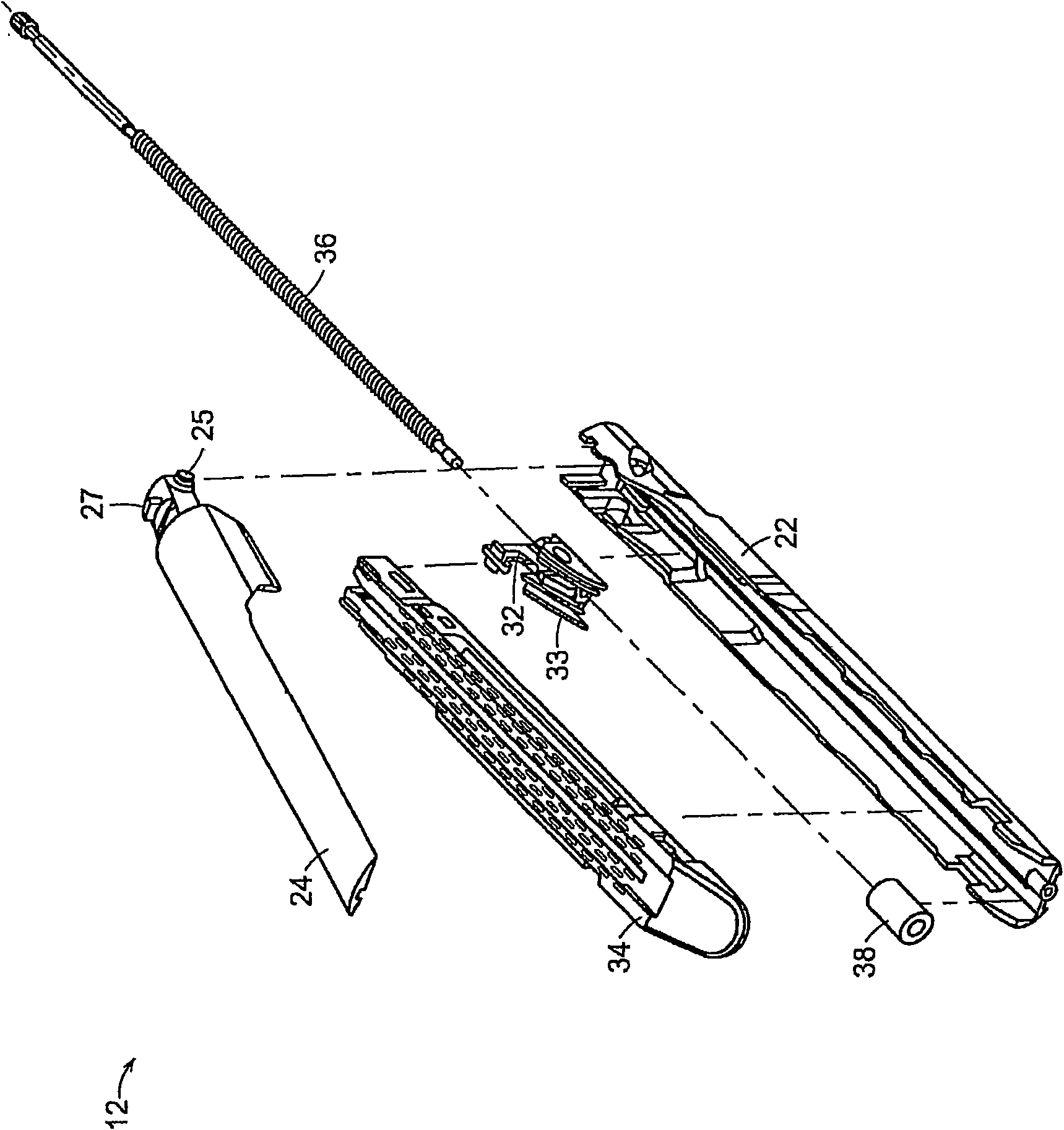
Accessing data stored in a memory of a surgical instrument
A process and system are disclosed for downloading sensor data, stored in a memory device of a surgical cutting and fastening instrument, to an external or remote computer device. The process may involve storing data from one or more sensors of a surgical cutting and fastening instrument in a memory device of a control unit of the surgical cutting and fastening instrument during a surgical procedure involving the surgical cutting and fastening instrument. Next, after the surgical procedure, a data link between the control unit and the remote computer device is established. Then, the sensor data can be downloaded from the control unit to the remote computer device.
Owner:ETHICON ENDO SURGERY INC
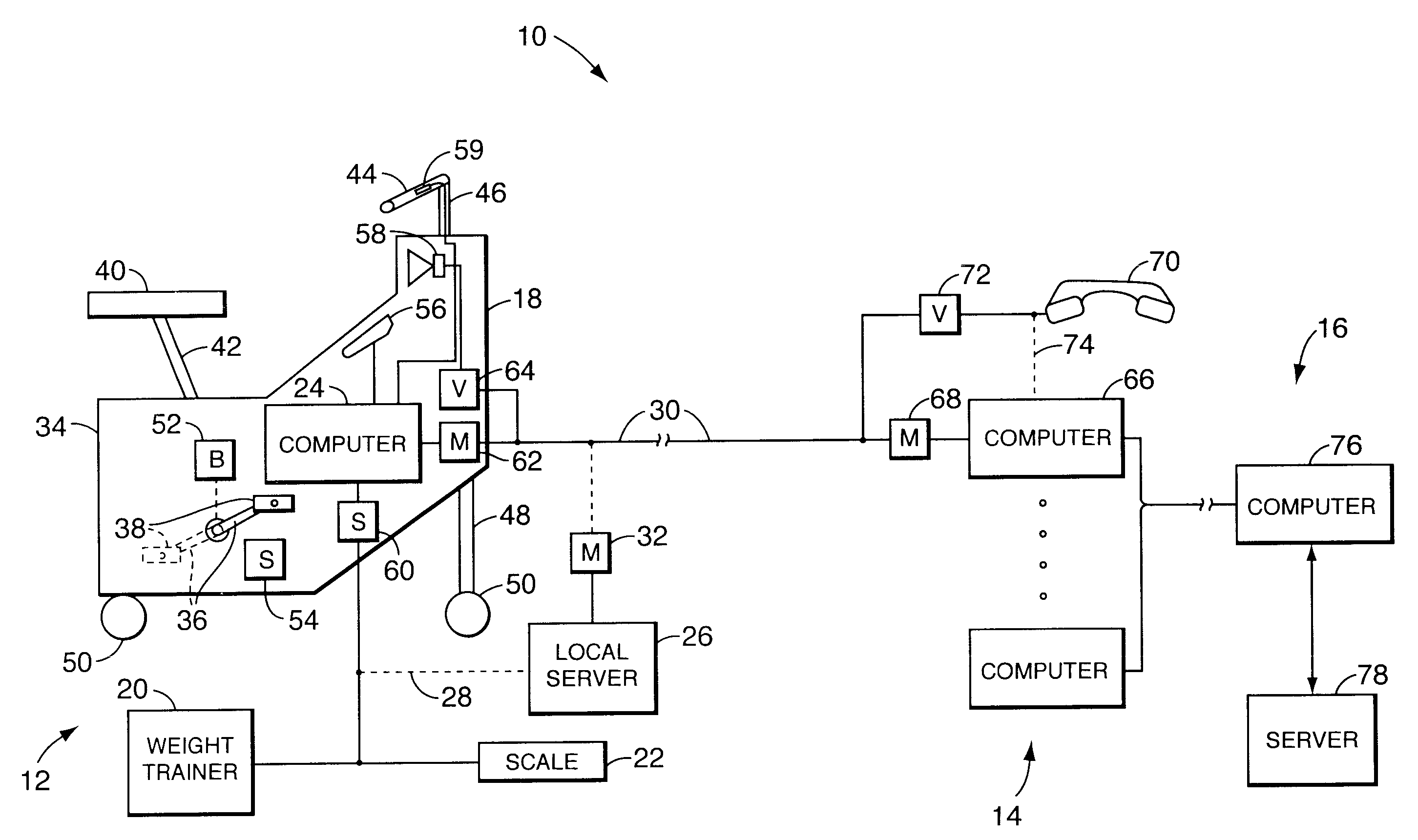
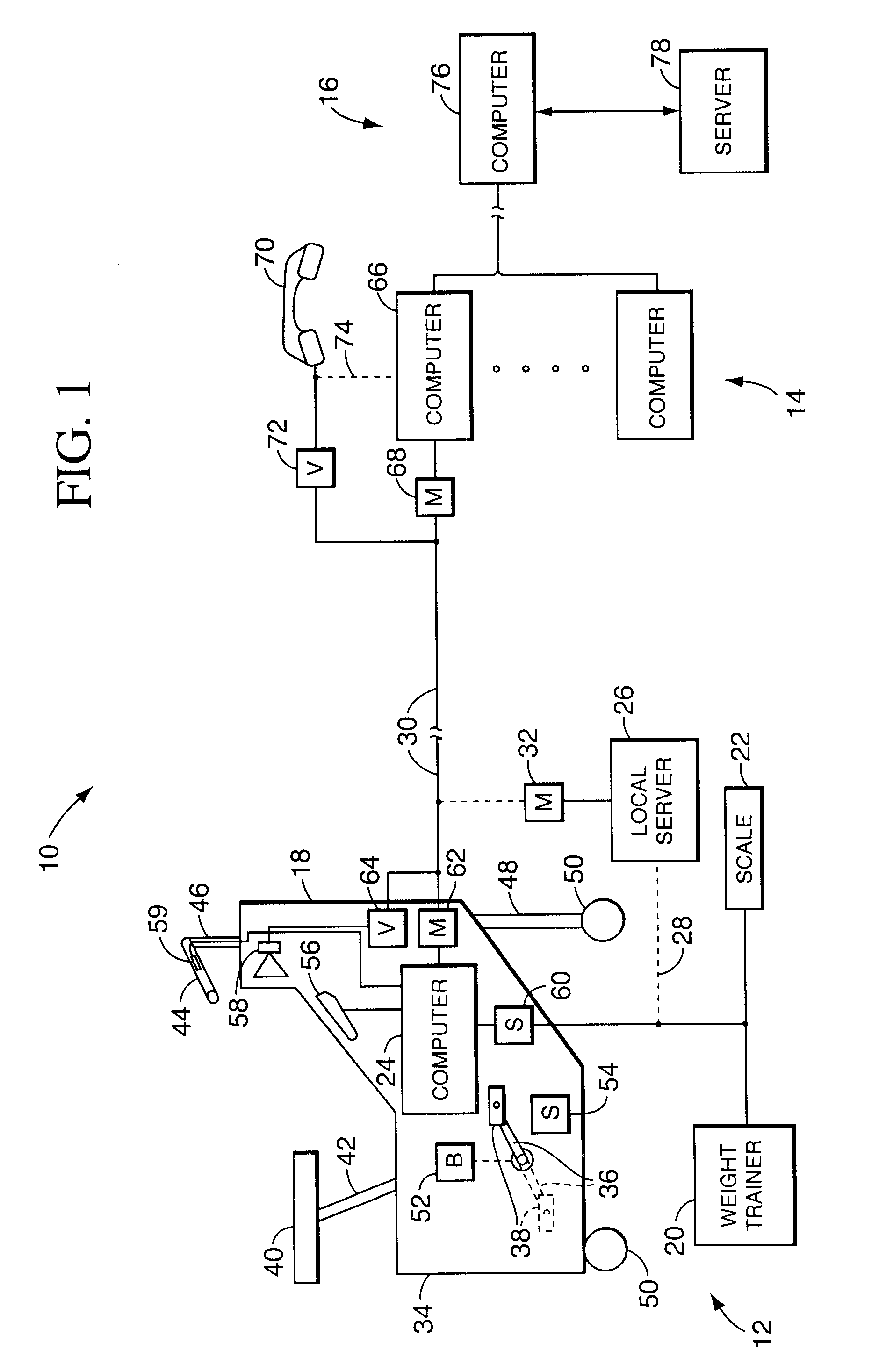
Method and apparatus for remote interactive exercise and health equipment
InactiveUS6921351B1Convenient and affordable and effectiveEffective exercise and dietary and health programPhysical therapies and activitiesWireless architecture usageRemote systemThe Internet
An exercise system includes a local system having an exercise apparatus and an associated local computer, where the local computer controls and monitors the operation and use, respectively, of the exercise apparatus. The system further includes a remote system having a remote computer, and a transmission medium preferably including the Internet that couples the local system to the remote system for data communication between the local system and the remote system. The remote system may receive local system data from the local system concerning the use of the exercise apparatus, and the local system may receive remote system data from the remote system concerning the operation of the exercise apparatus. The local computer preferably controls the operation of the exercise apparatus based upon a modifiable script stored in a read / write memory of the local computer, which can be updated by the remote system. A method for controlling an exercise apparatus includes running a modifiable script on a local computer to control the use and to monitor the operation of an exercise apparatus, and communicating with a remote system, preferably via the Internet, to provide the remote system with data concerning the use of the exercise apparatus. The script is stored in read / write memory of the local computer and remote system data received from the remote system may include at least a portion of a new script to be stored in the read / write memory of the local computer.
Owner:ICON HEALTH & FITNESS INC
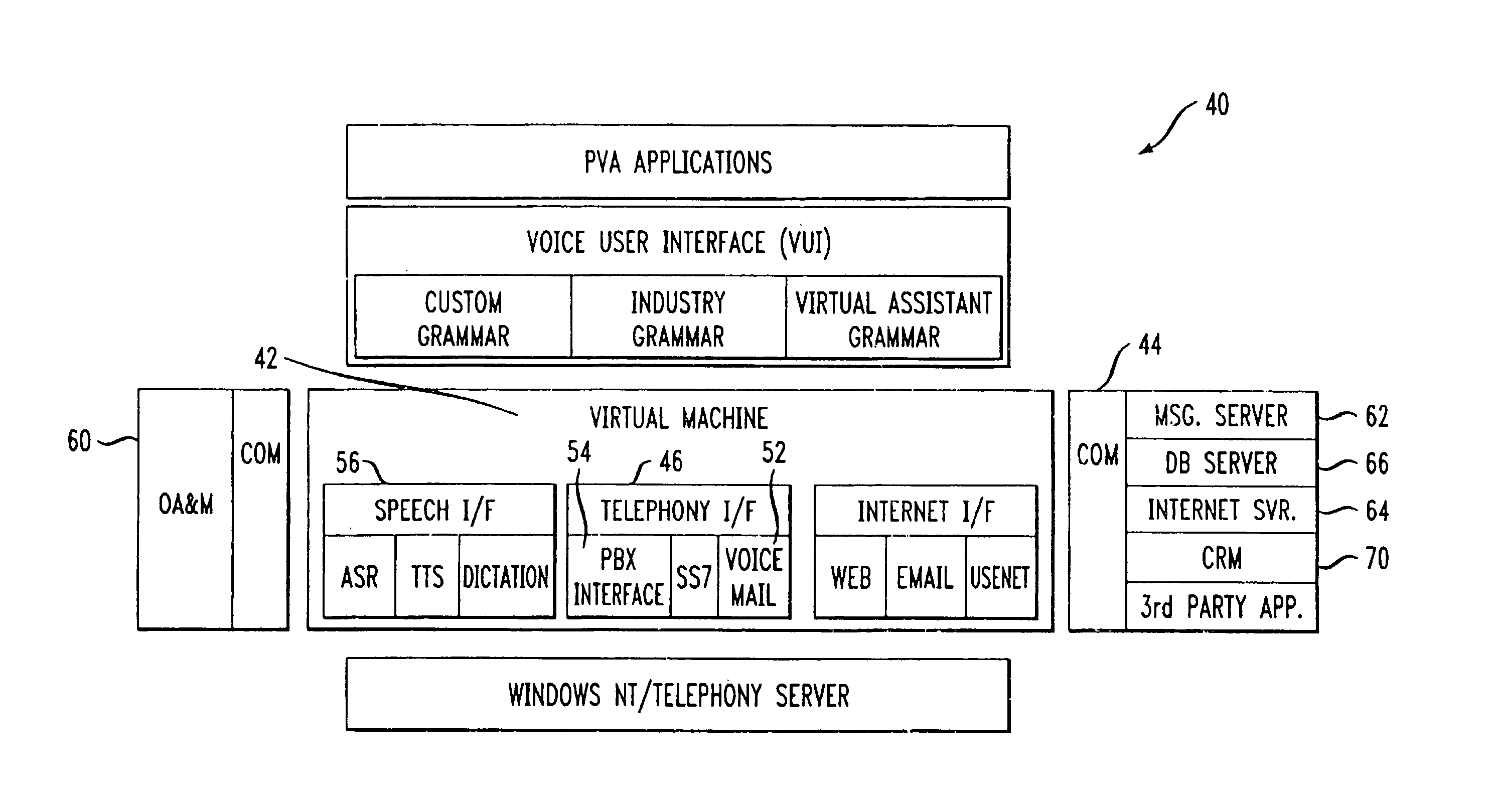
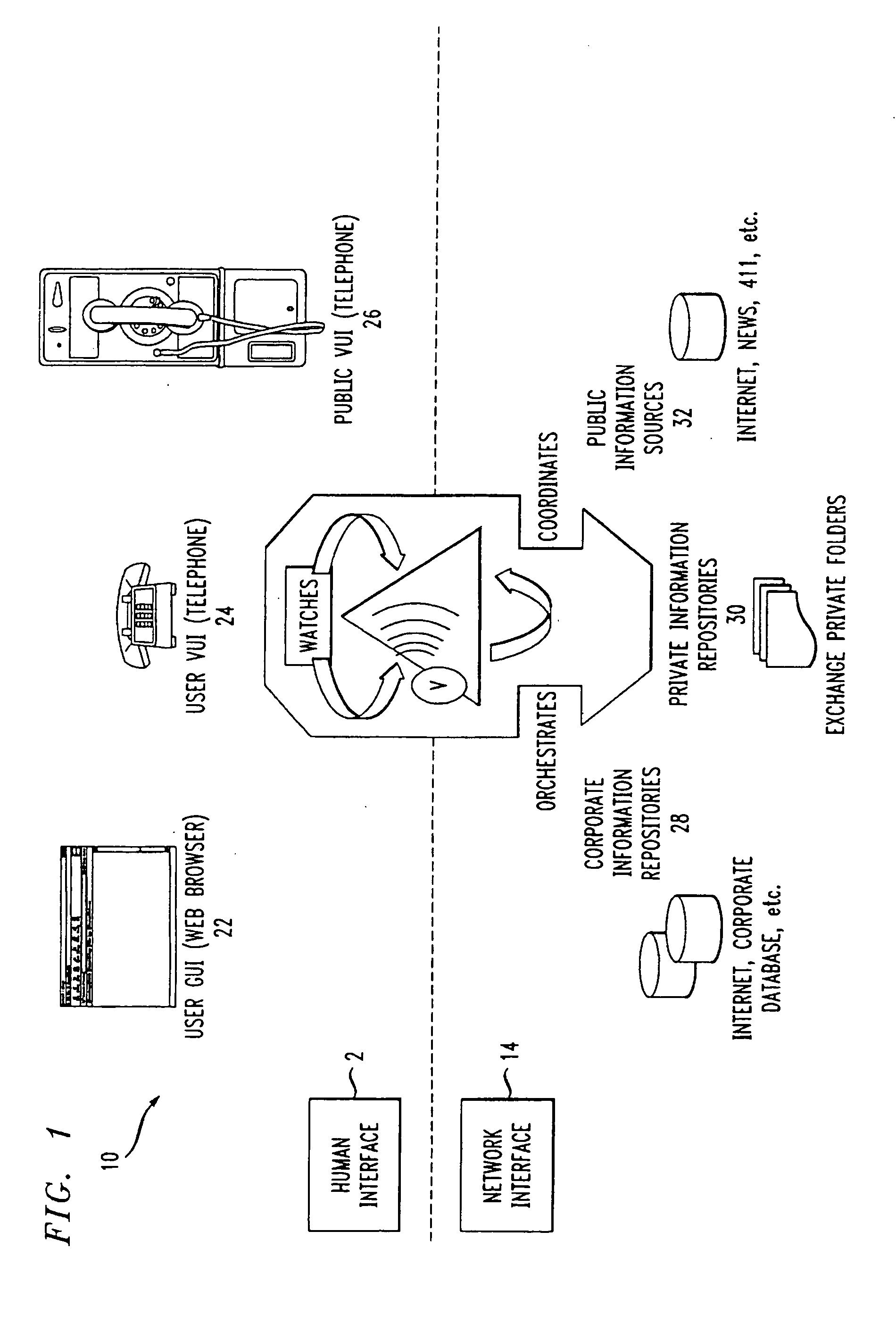
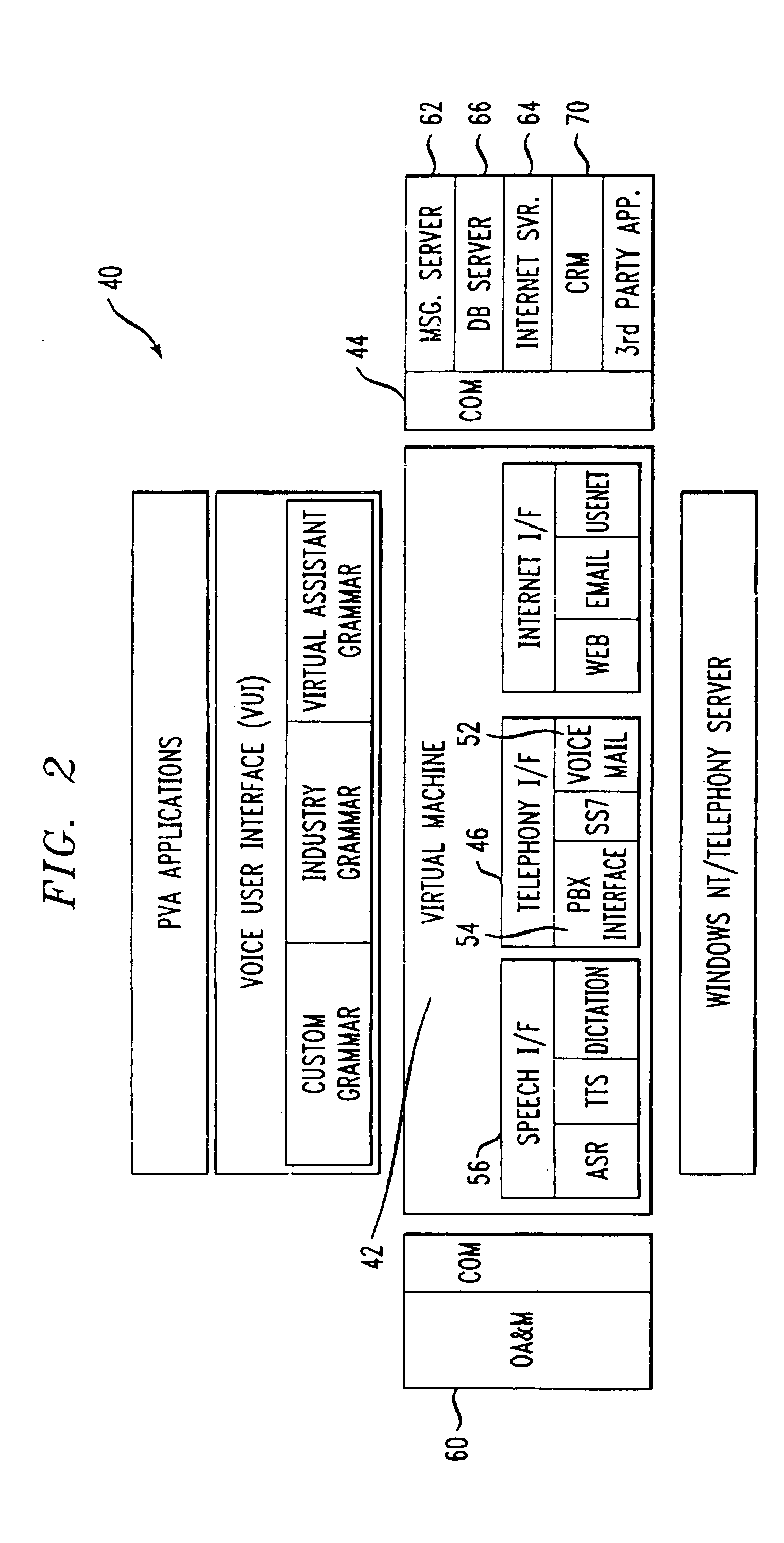
Personal virtual assistant
InactiveUS7415100B2Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesUser inputZoom
A computer-based virtual assistant the behavior of which can be changed by the user, comprising a voice user interface for inputting information into and receiving information from the virtual assistant by speech, a communications network, a virtual assistant application running on a remote computer, the remote computer being electronically coupled to the user interface via the communications network, wherein the behavior of the virtual assistant changes responsive to user input. A computer-based virtual assistant that also automatically adapts its behavior is disclosed, comprising a voice user interface for inputting information into and receiving information from the virtual assistant by speech, a communications network, a virtual assistant application running on a remote computer, the remote computer being electronically coupled to the user interface via the communications network, wherein the remote computer is programmed to automatically change the behavior of the virtual assistant responsive to input received by the virtual assistant. As detailed below, the virtual assistant adapts to the user in many different ways based on the input the virtual assistant receives. Such input could be user information, such as information about the user's experience, the time between user sessions, the amount of time a user pauses when recording a message, the user's emotional state, whether the user uses words associated with polite discourse, and the amount of time since a user provided input to the virtual assistant during a session.
Owner:AVAYA TECH LLC
Remote computer virus scanning
InactiveUS20010005889A1Improve network securityLower the volumeMemory loss protectionDigital data processing detailsRemote computerVirus
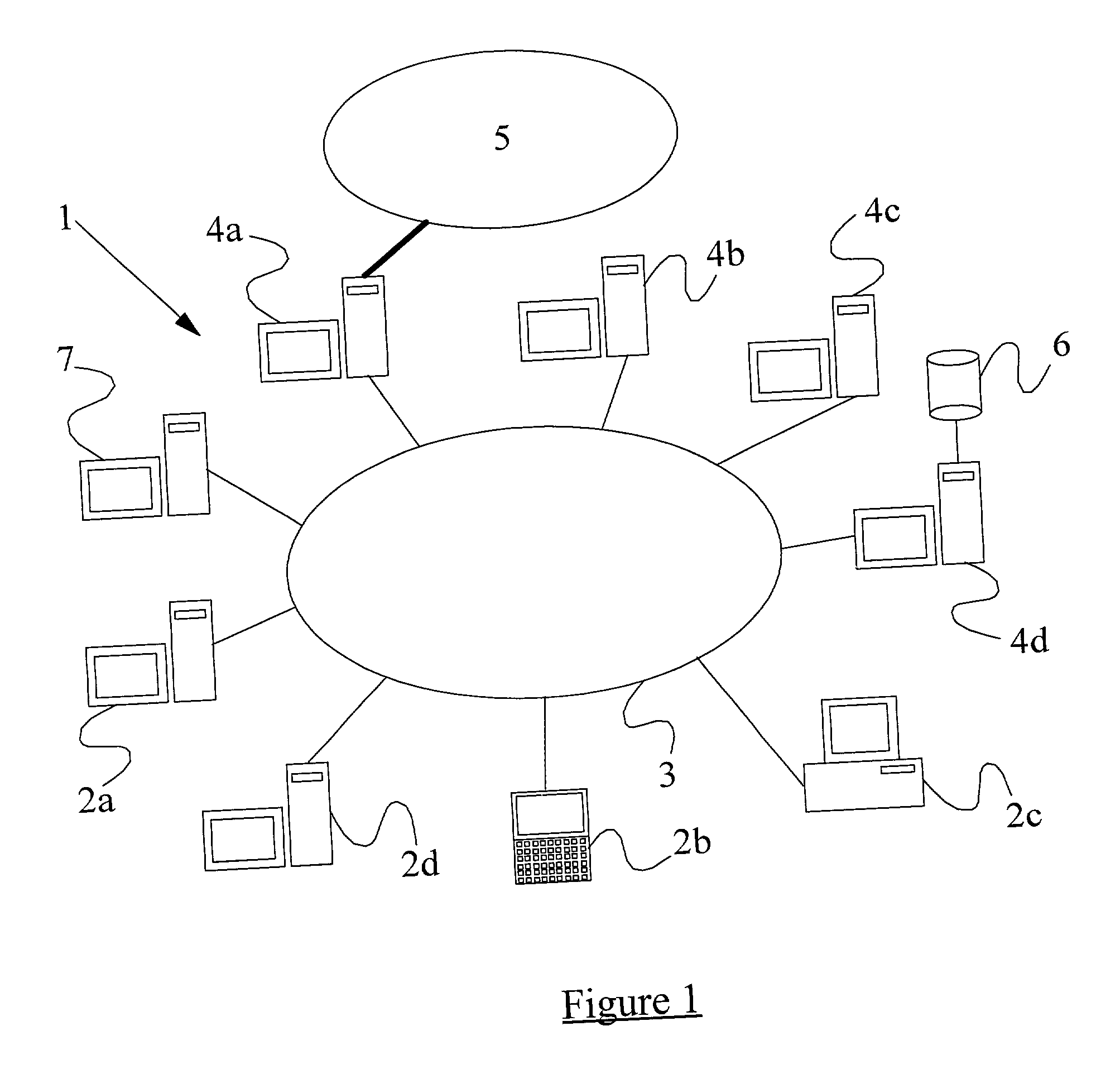
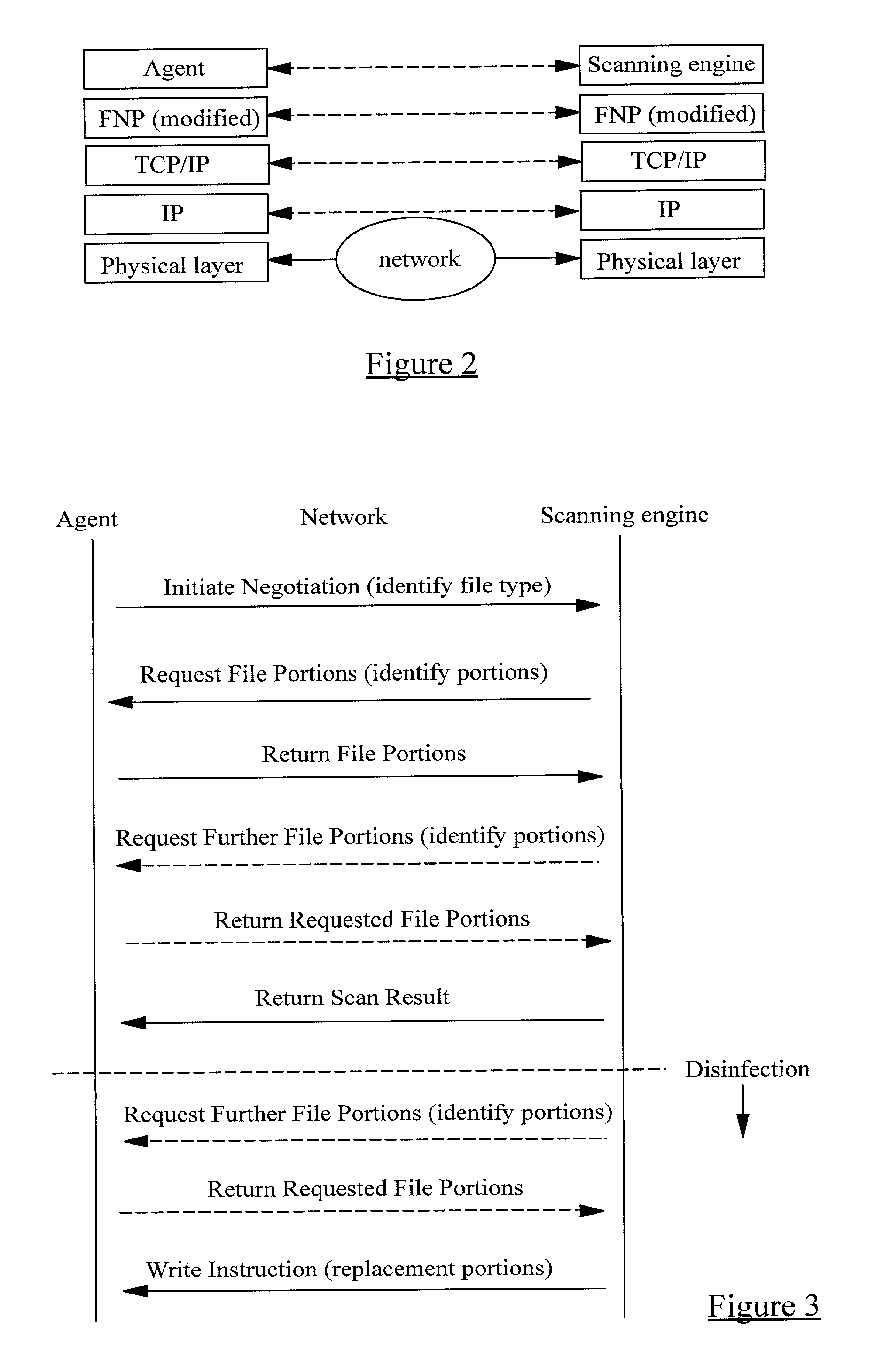
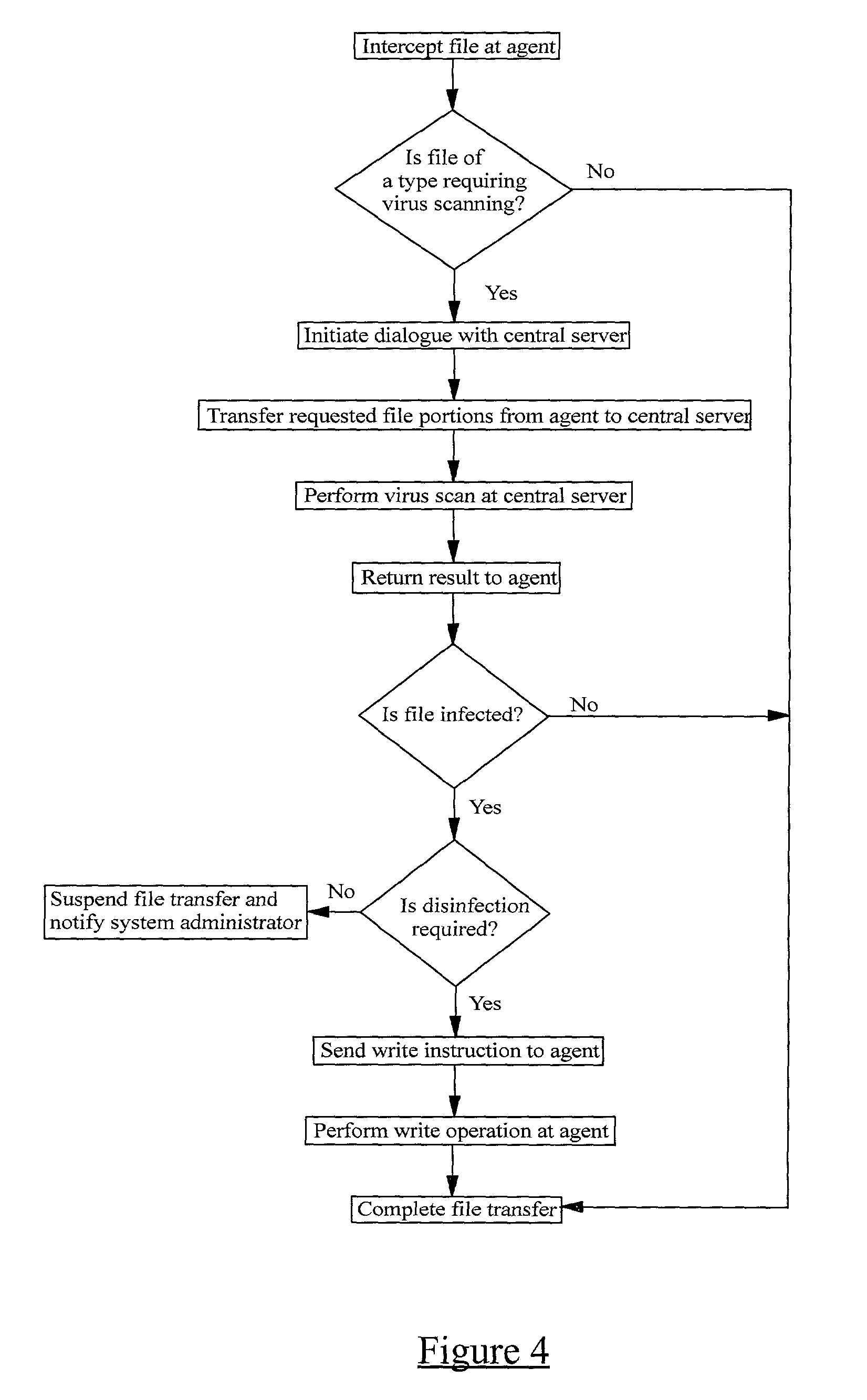
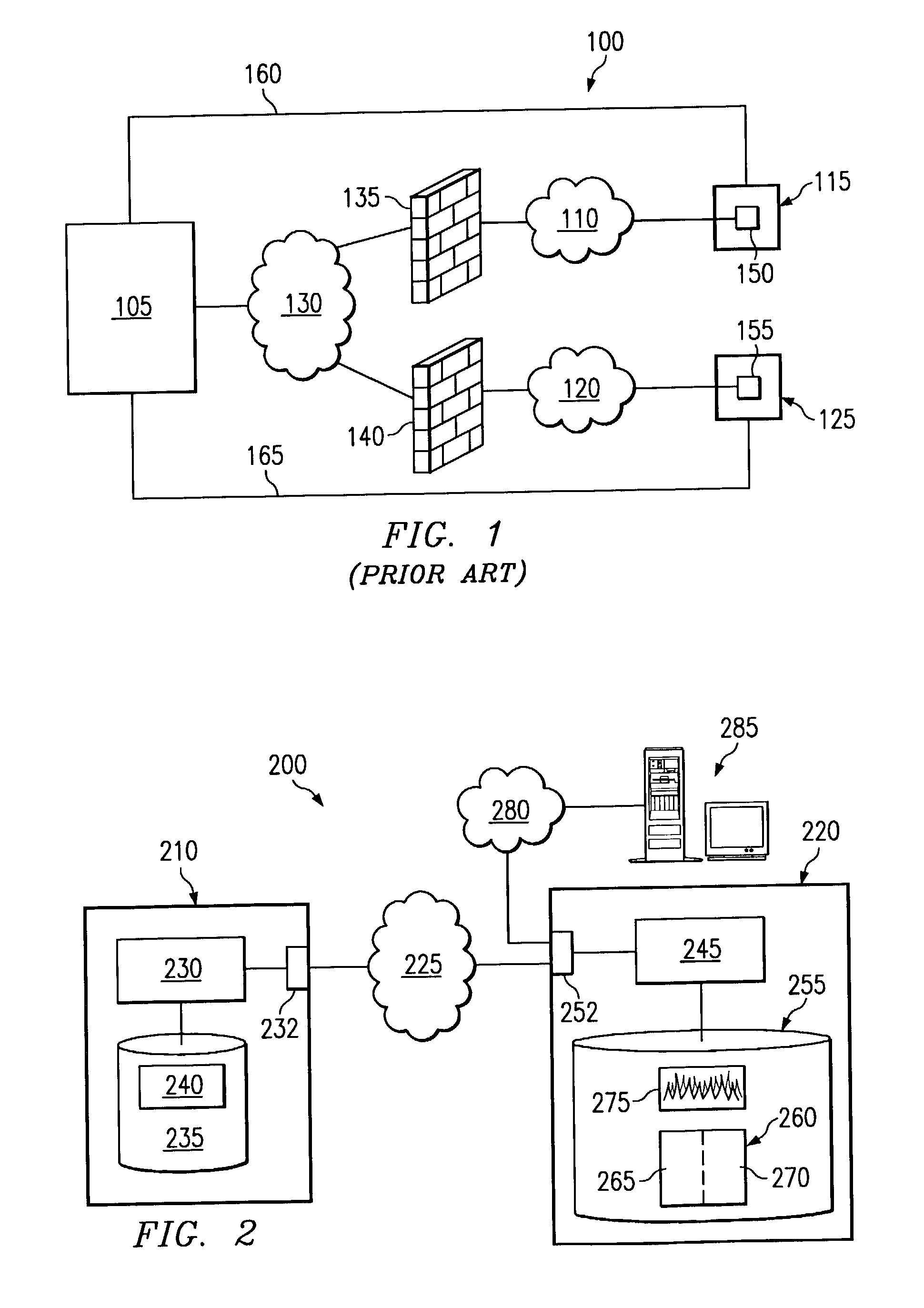
A method of scanning electronic files for computer viruses comprises identifying at a first node 4 of a computer network 1, electronic files which require to be scanned for computer viruses. The first node 4 initiates a dialogue with a second node 7 of the network 1, the second node comprising a virus scanning application. During the dialogue, the second node 7 identifies to the first node 4 one or more portions of the electronic file required by the virus scanning application. The first node 4 transfers the identified portions to the second node 7 which then carries out a virus scanning operation. The result of this operation is then returned to the first node 4.
Owner:F SECURE CORP
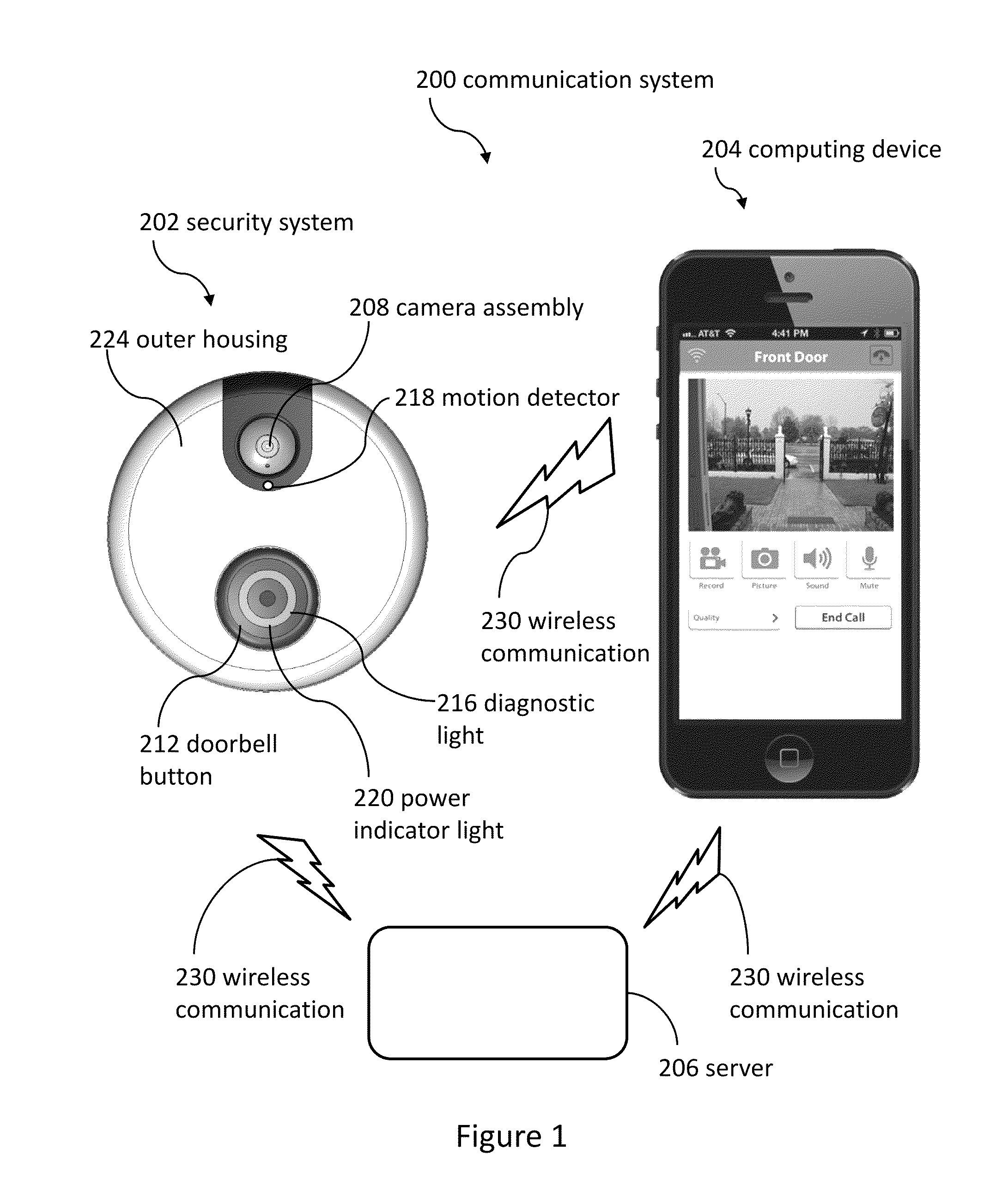
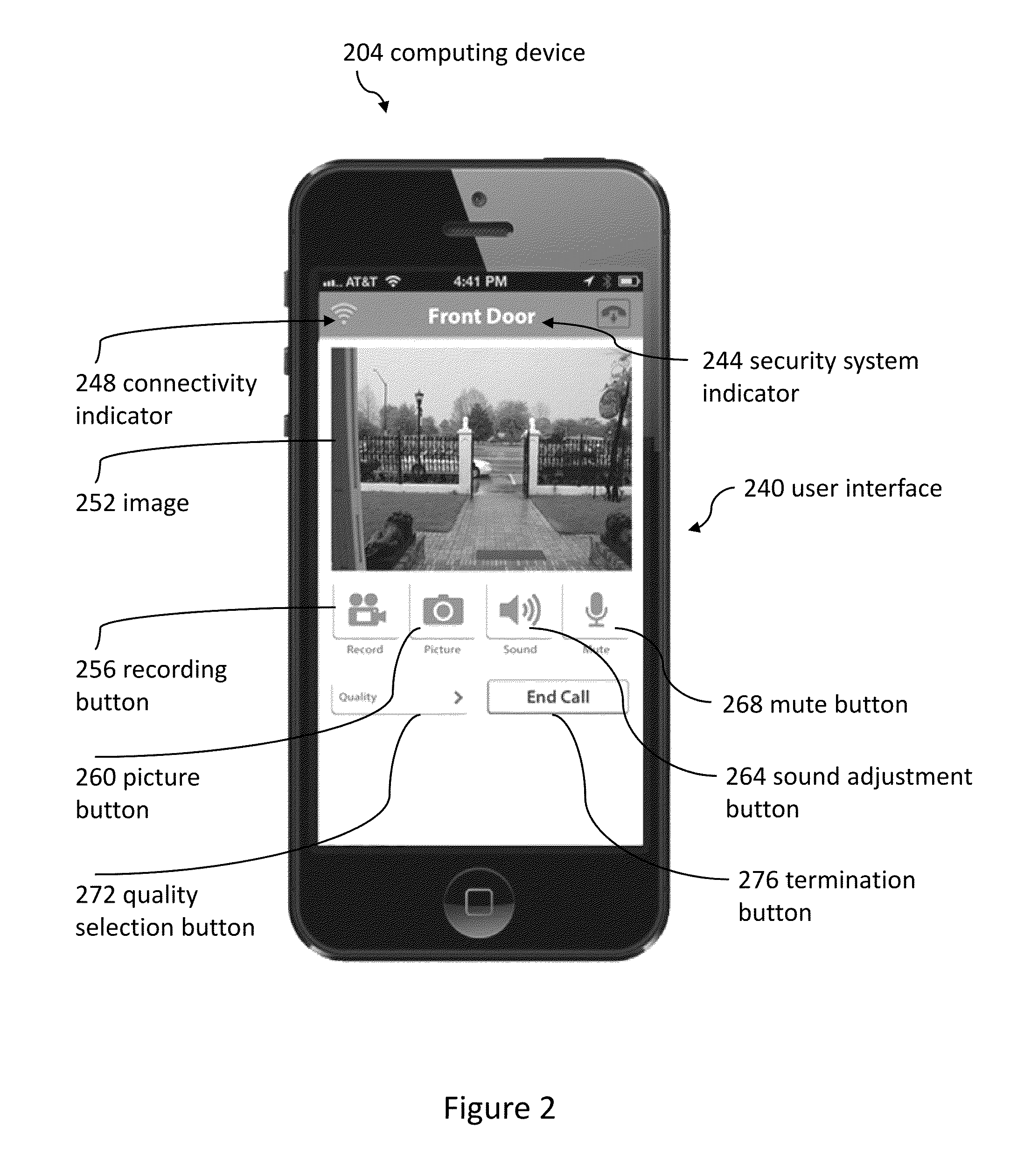
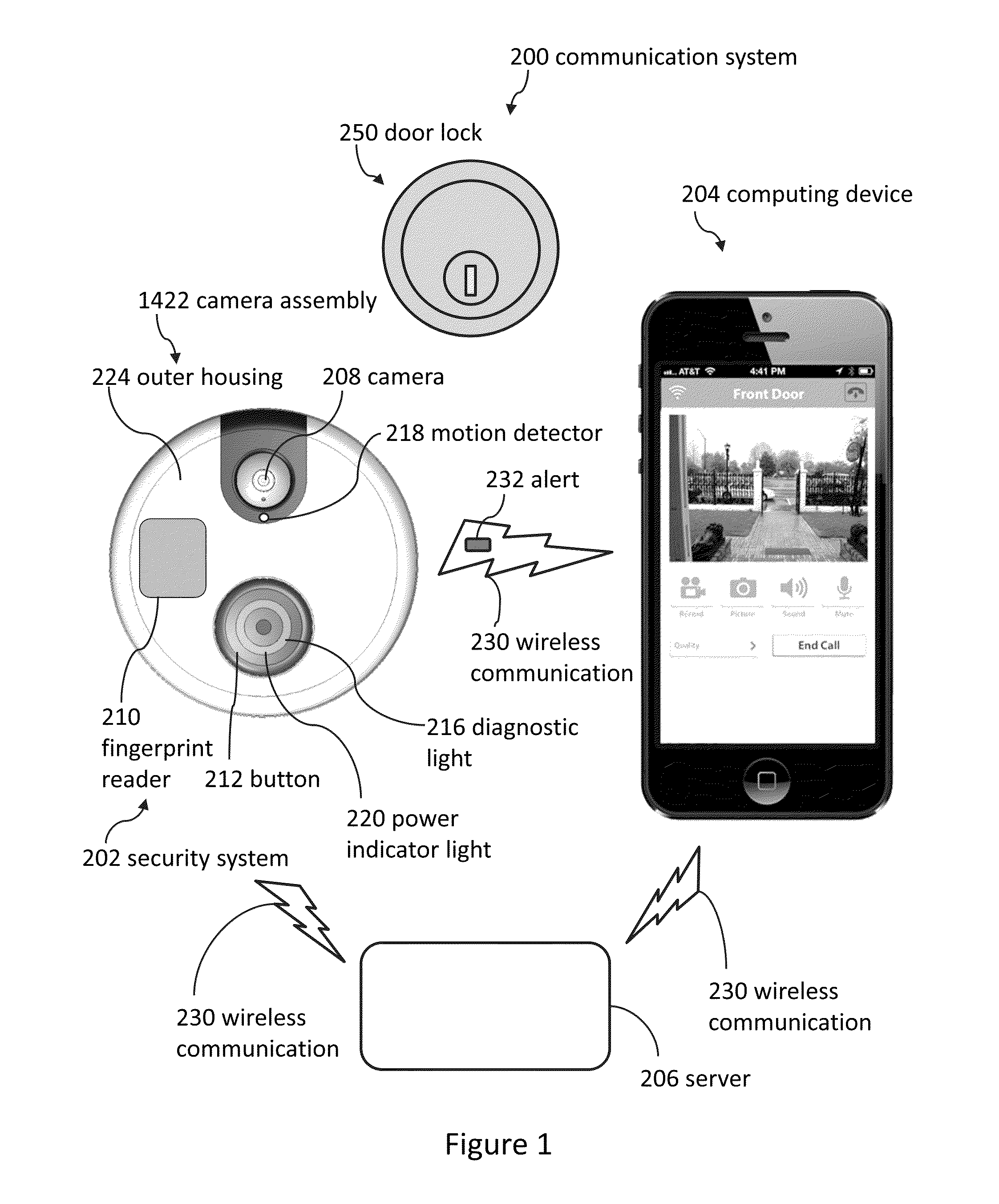
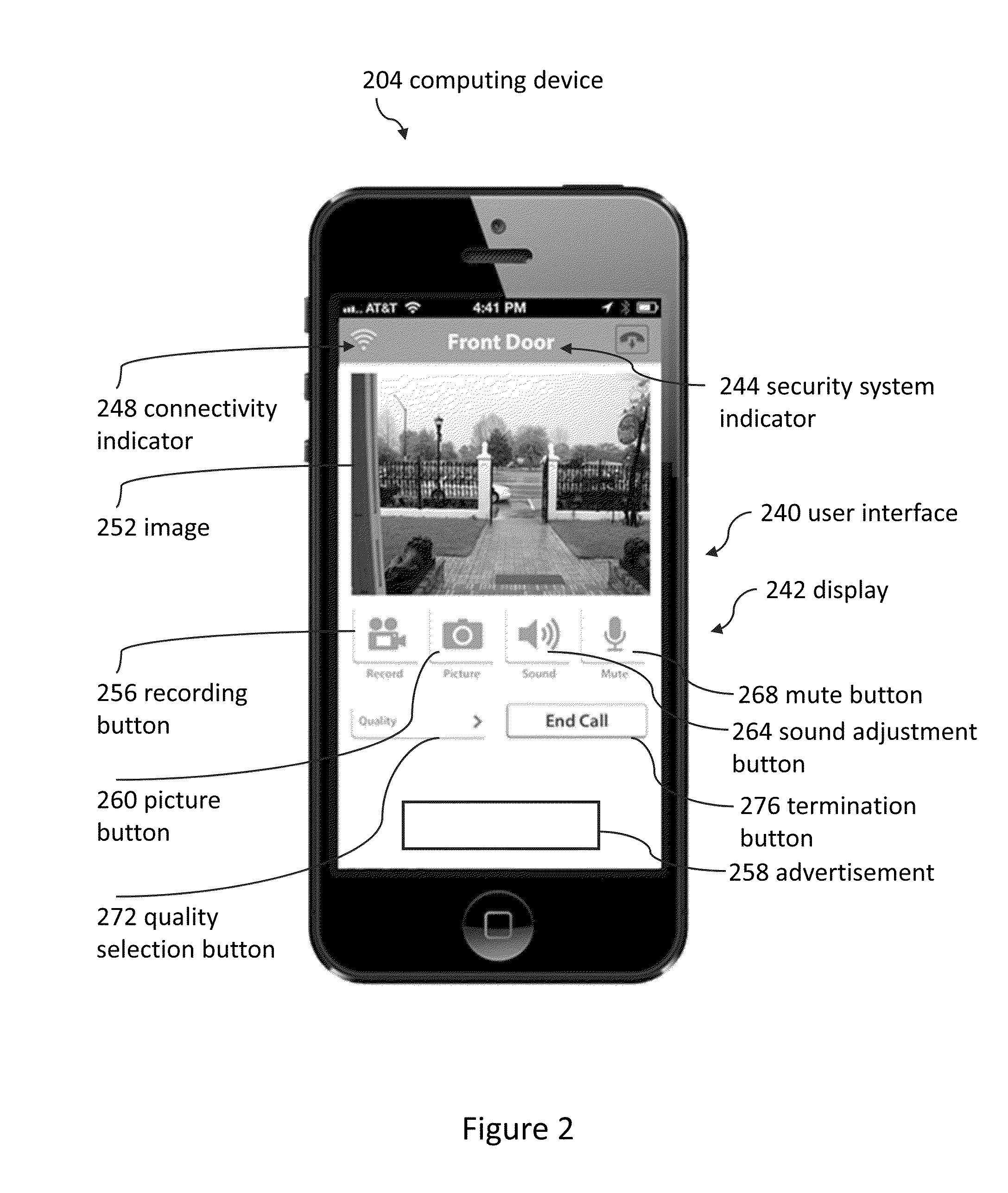
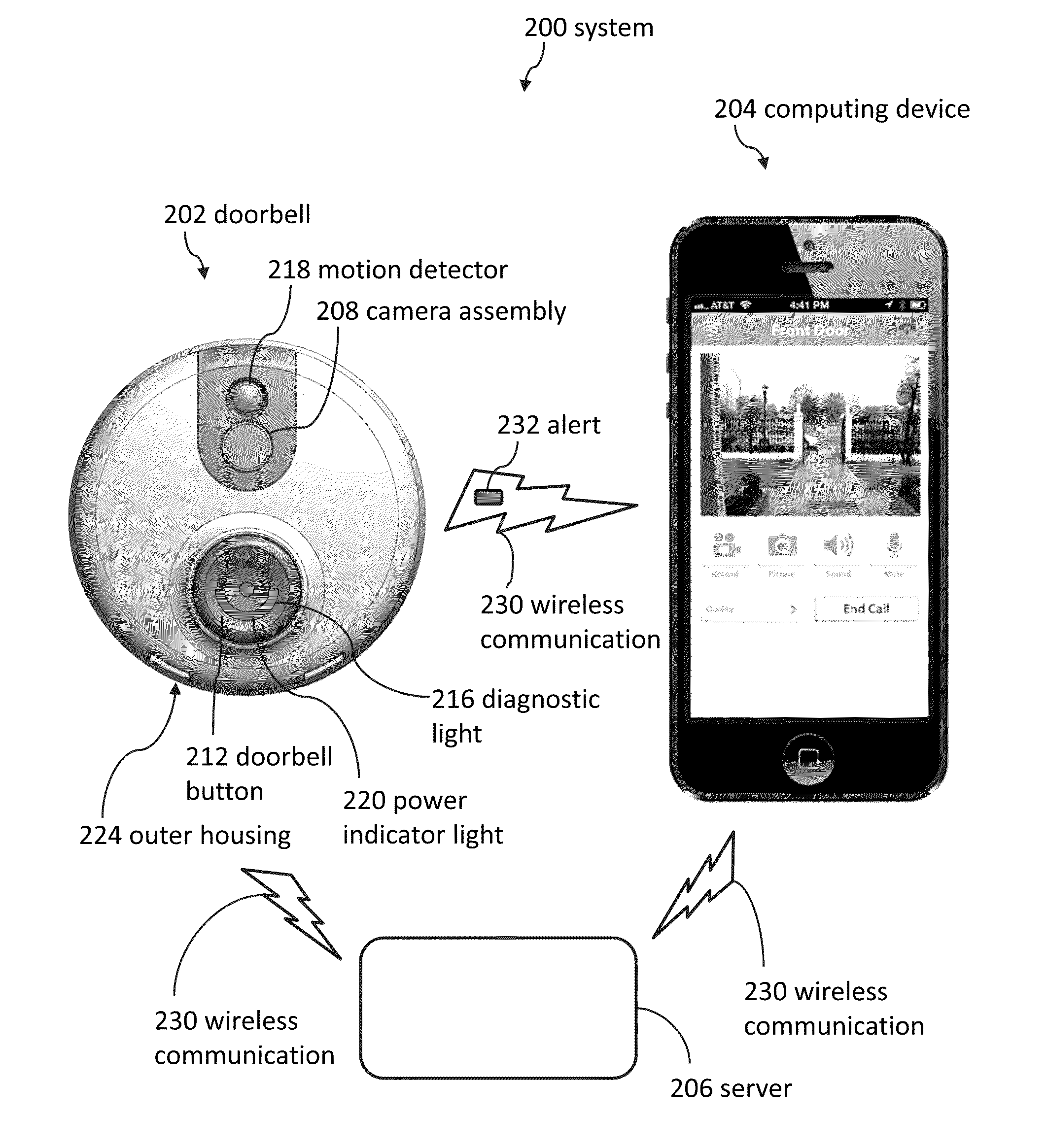
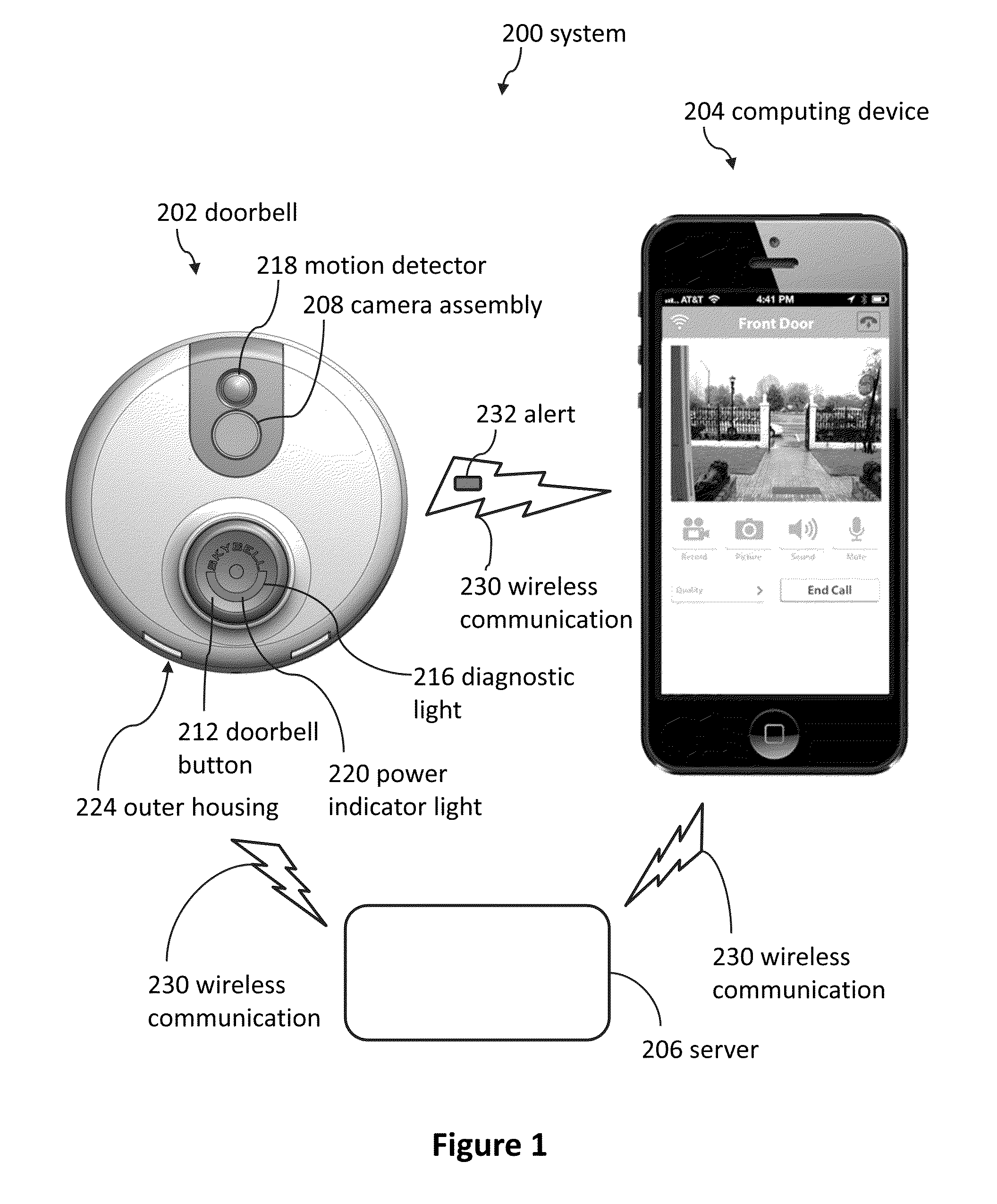
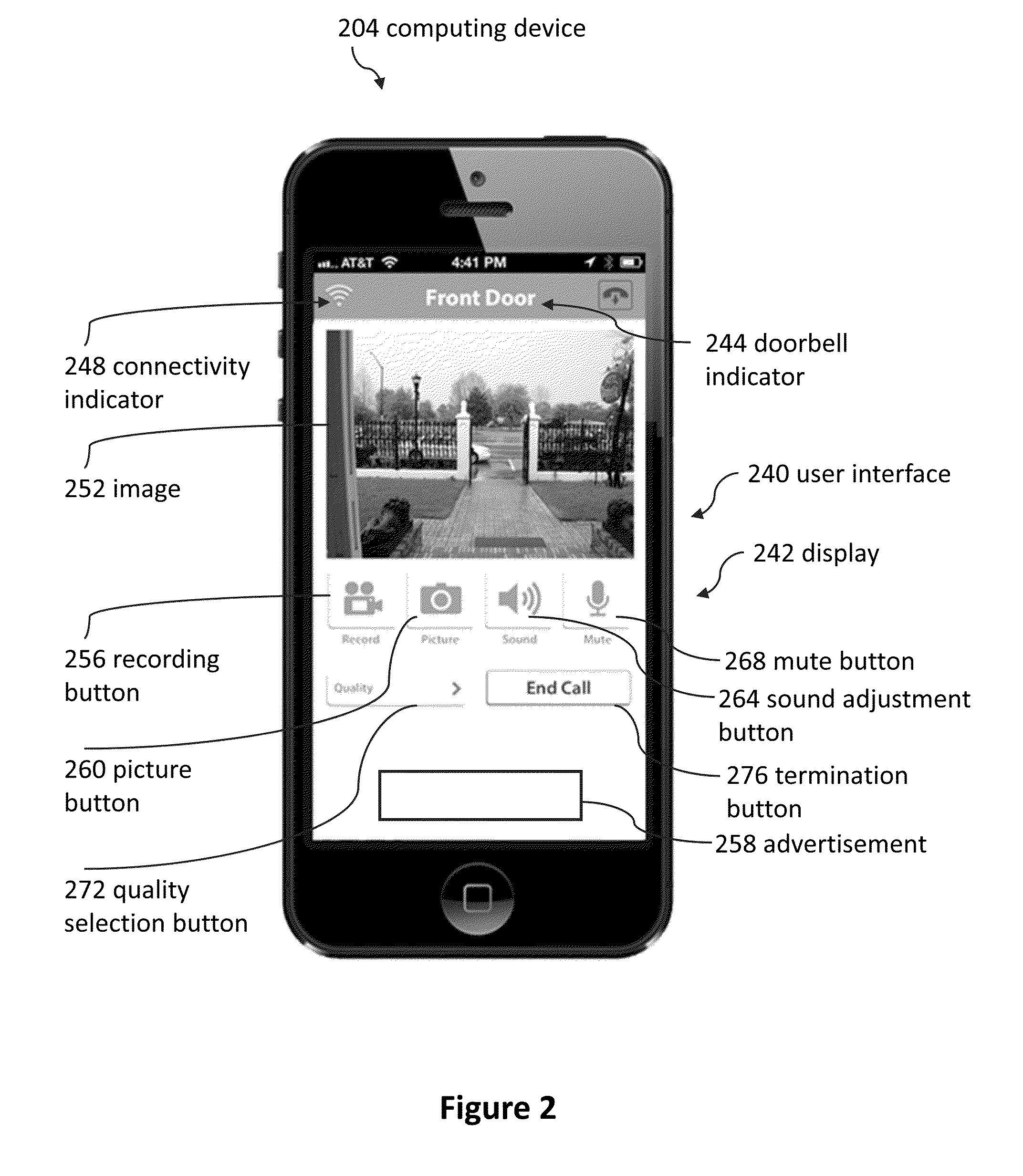
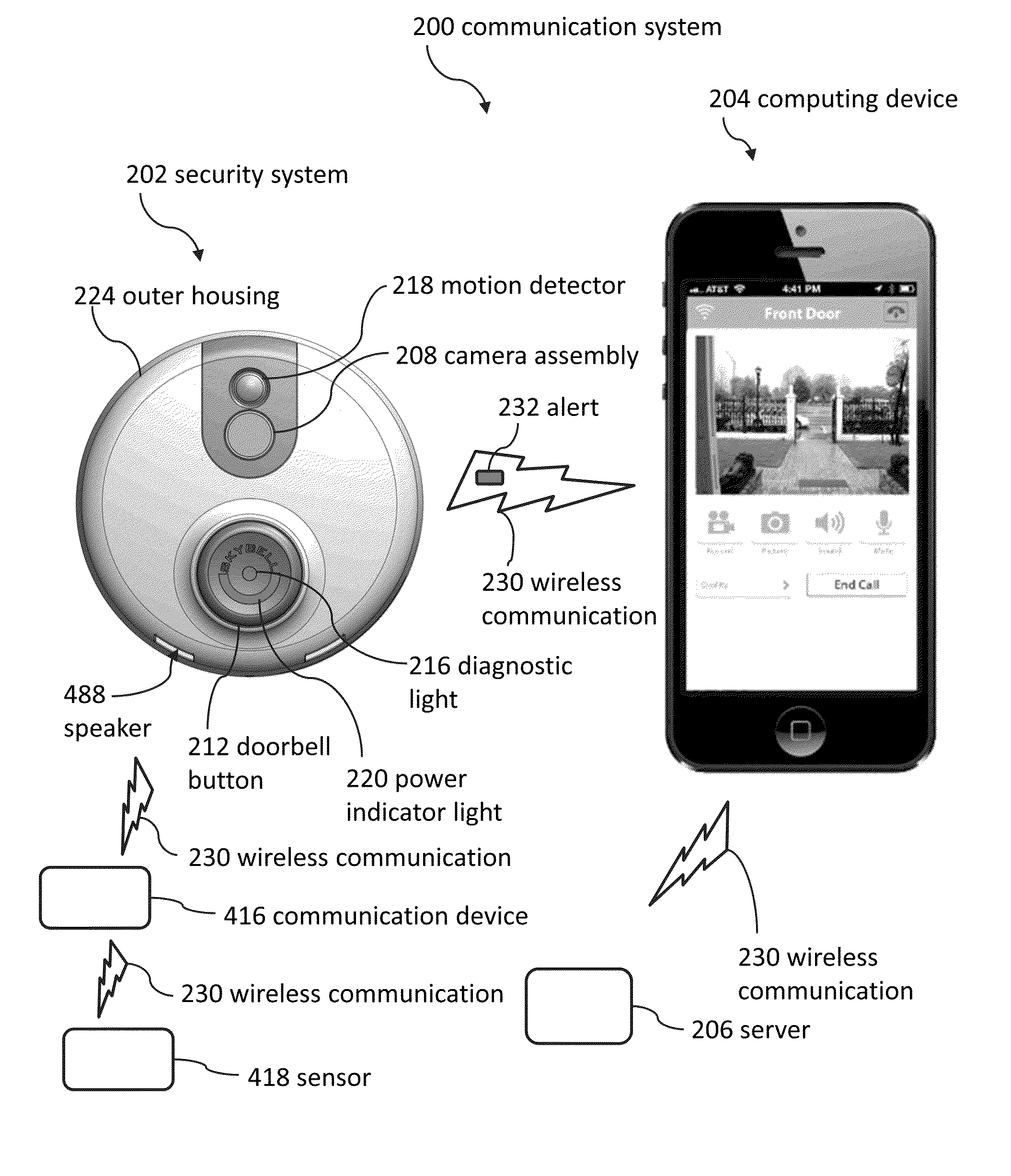
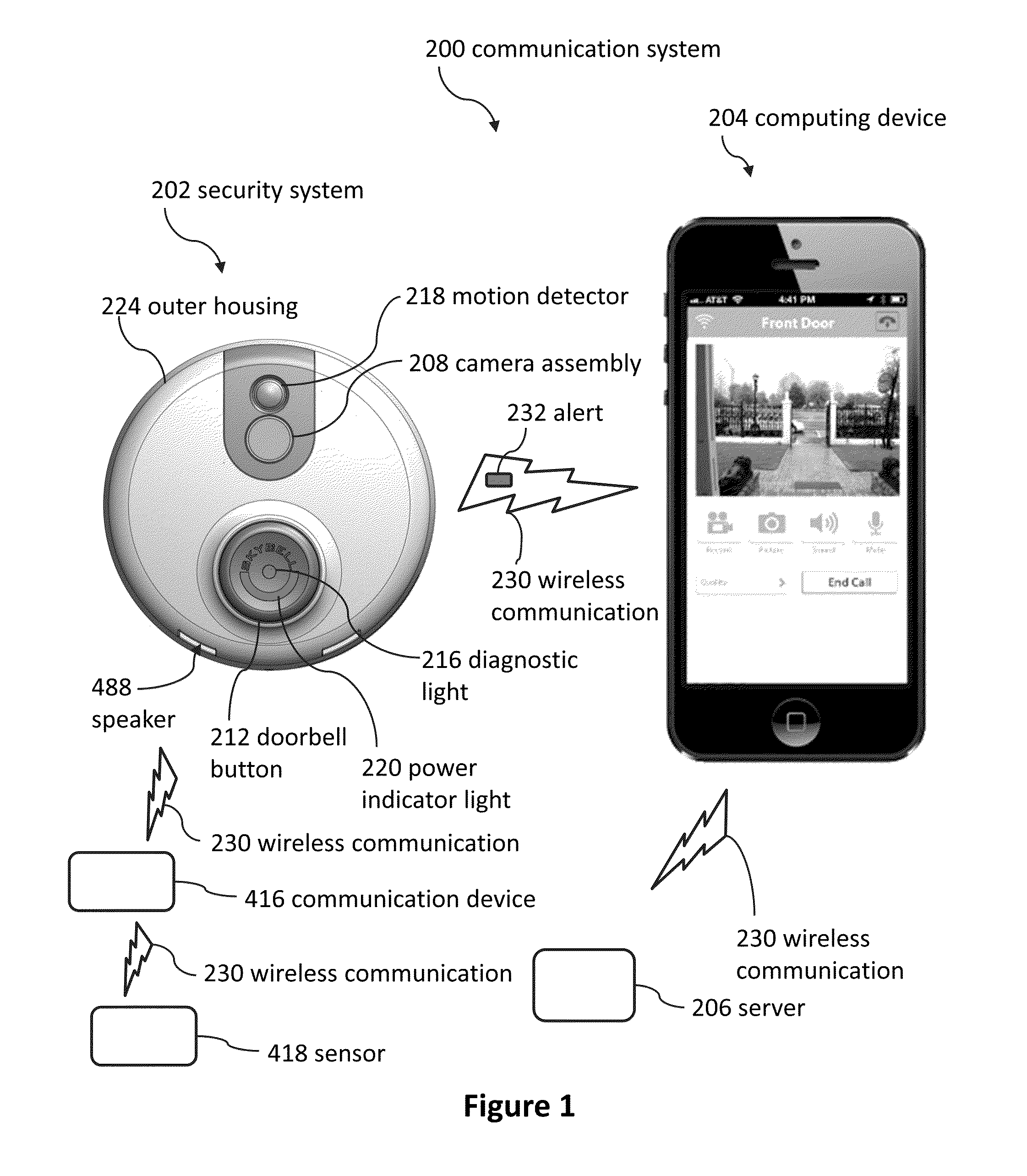
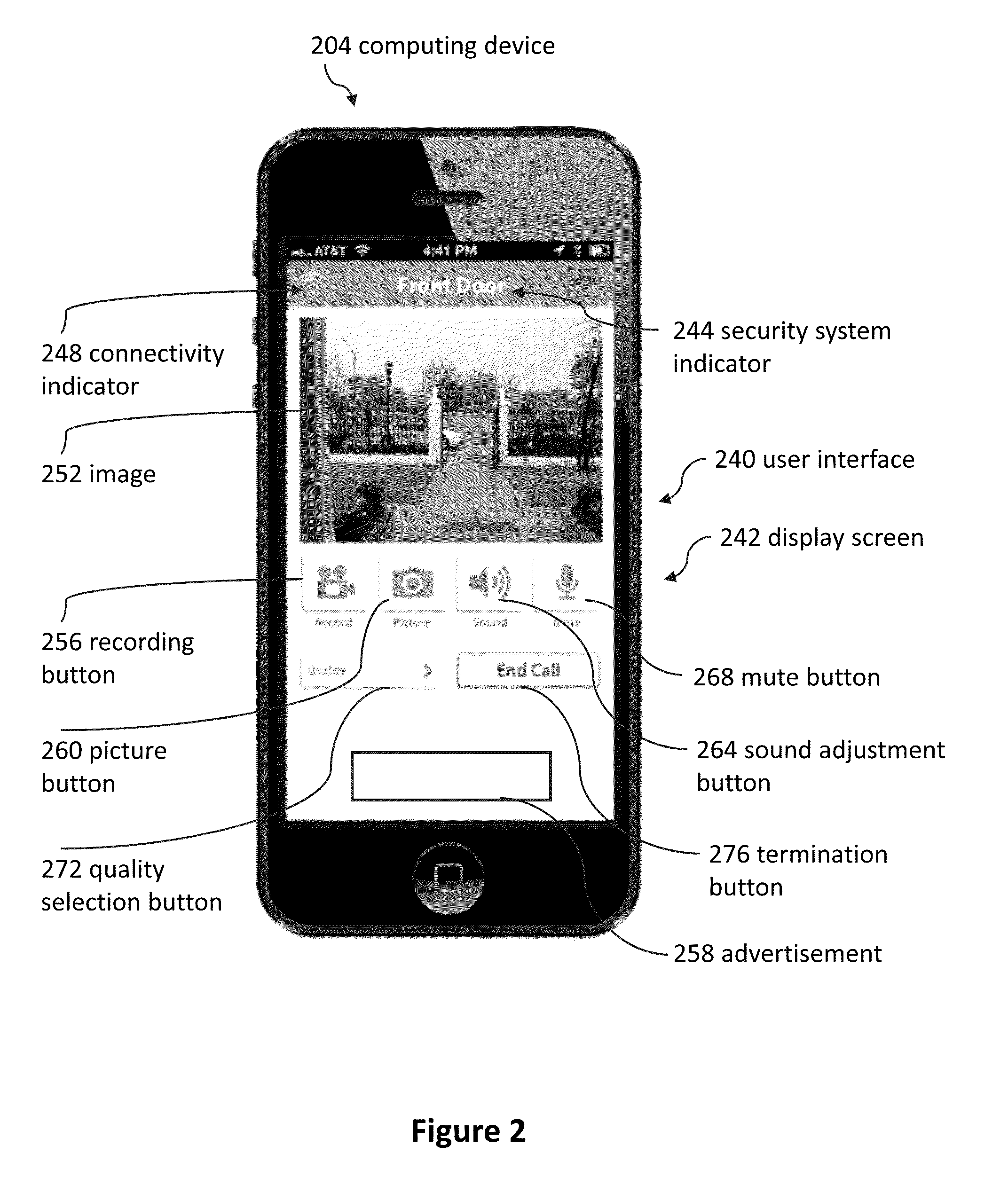
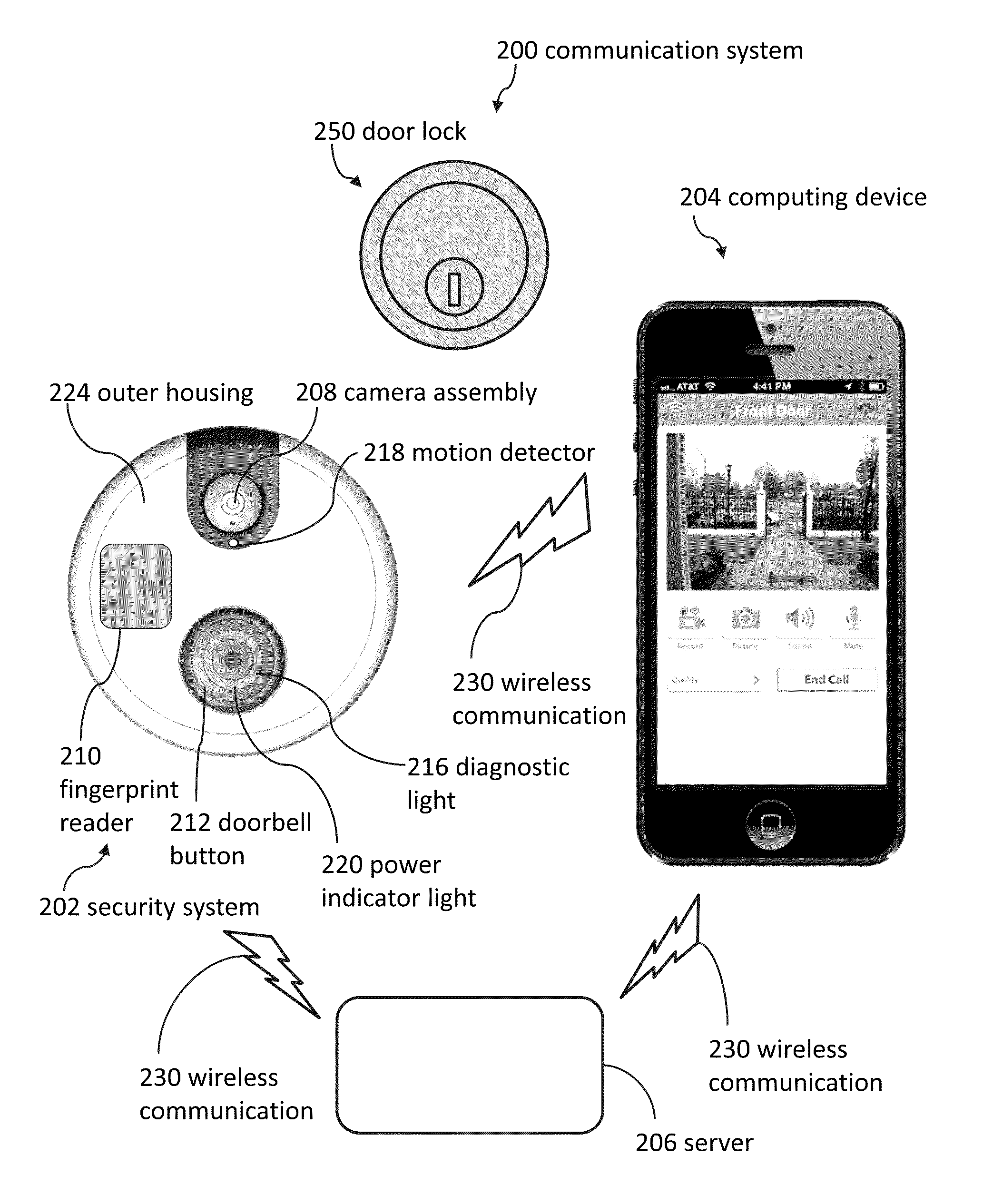
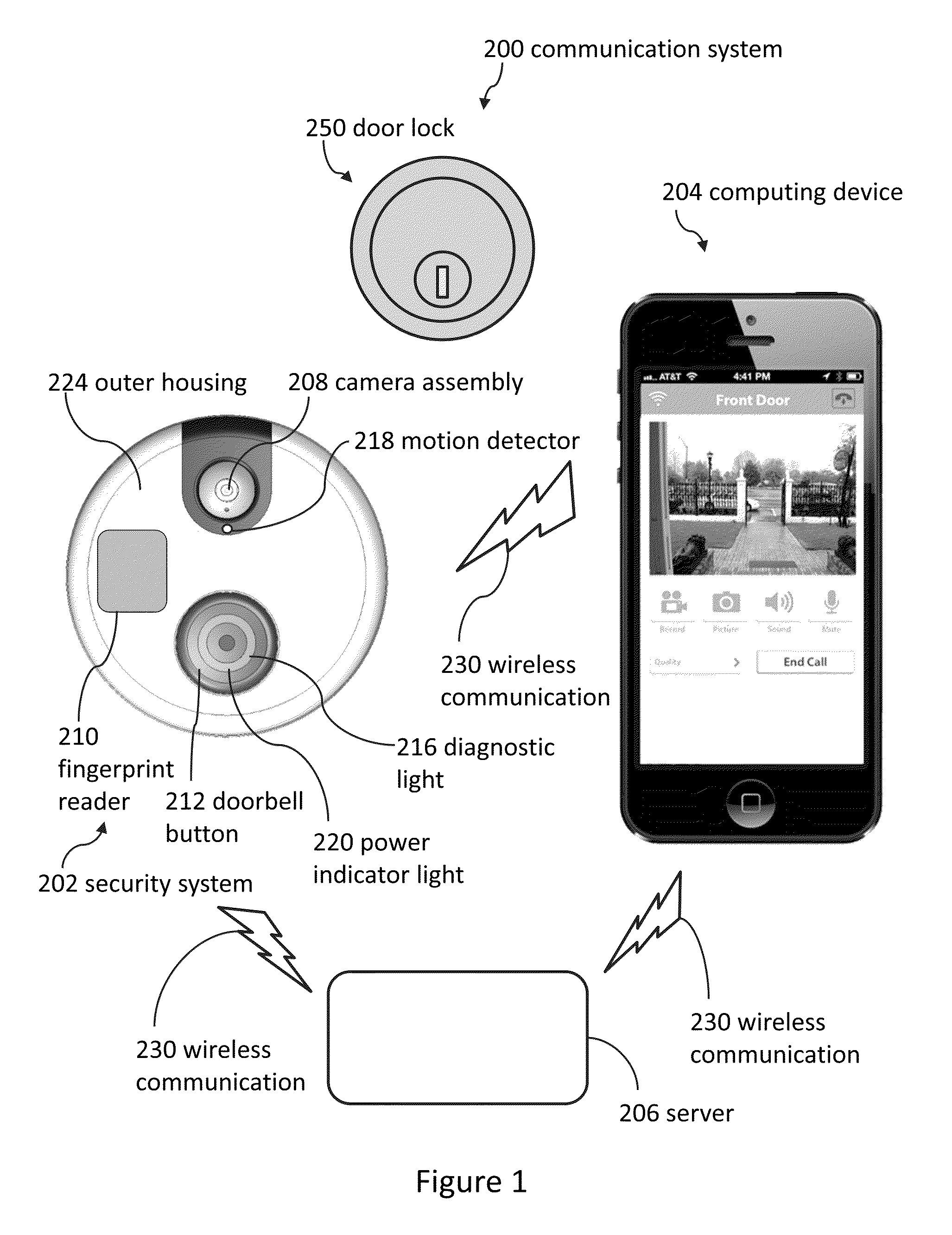
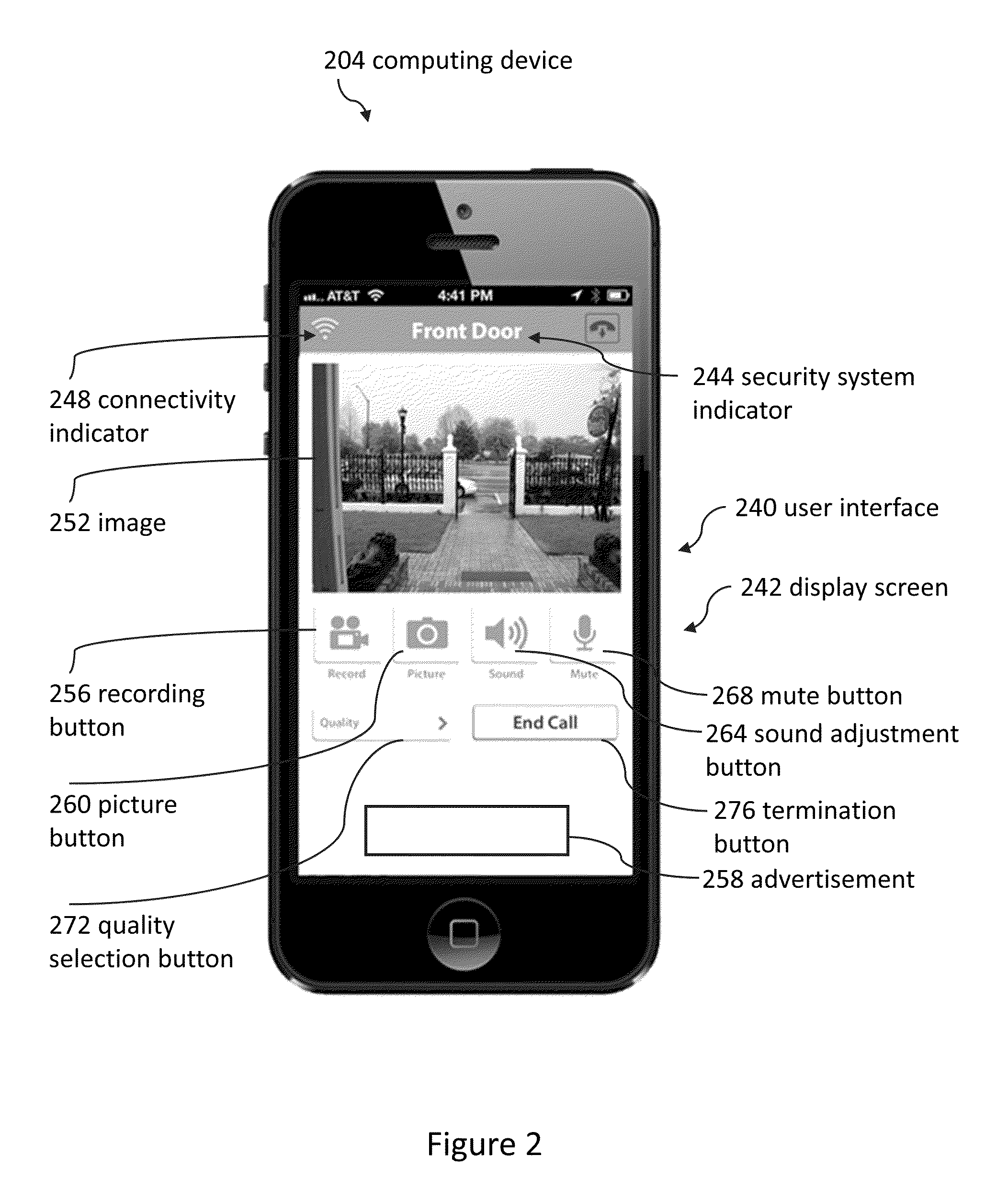
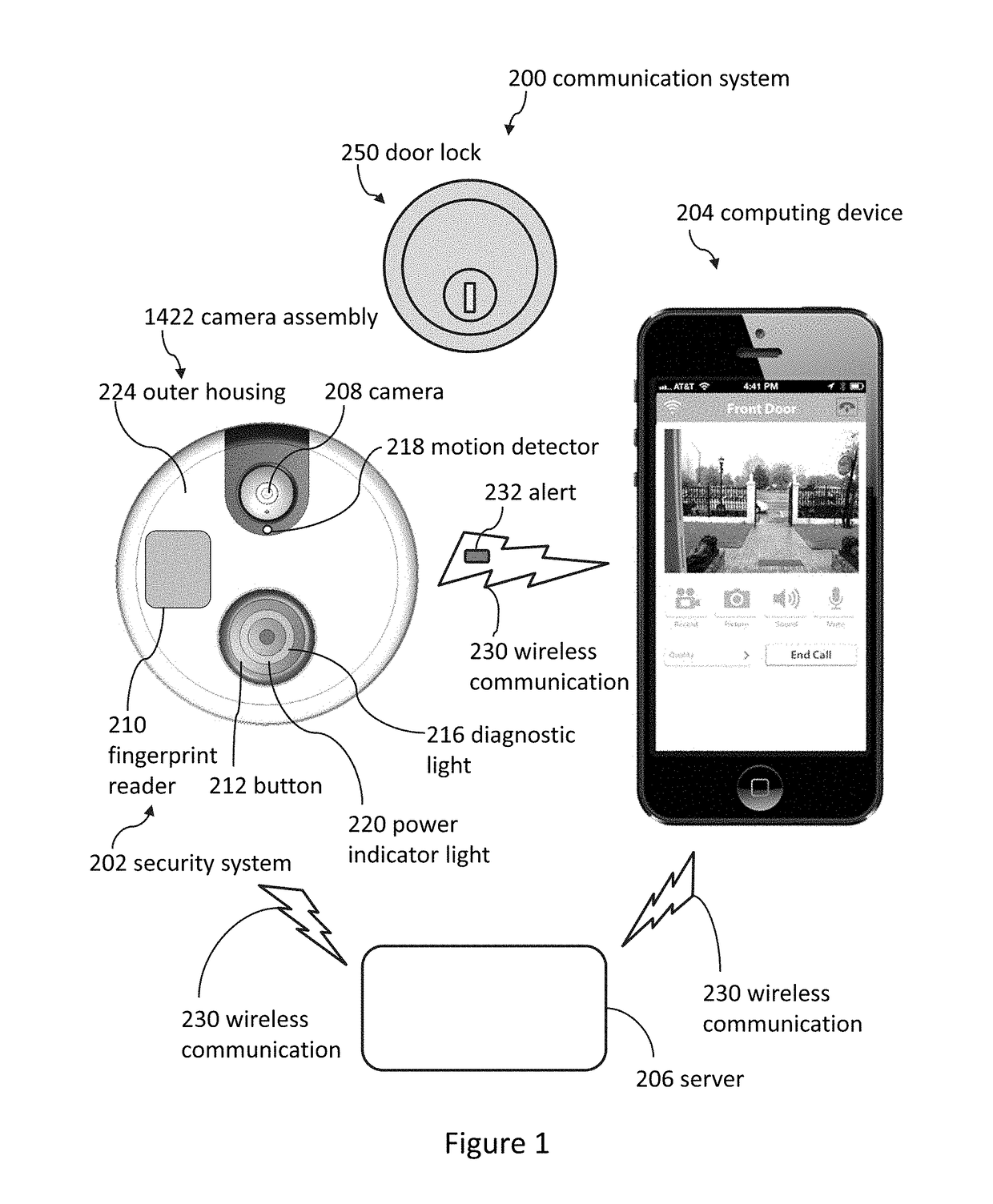
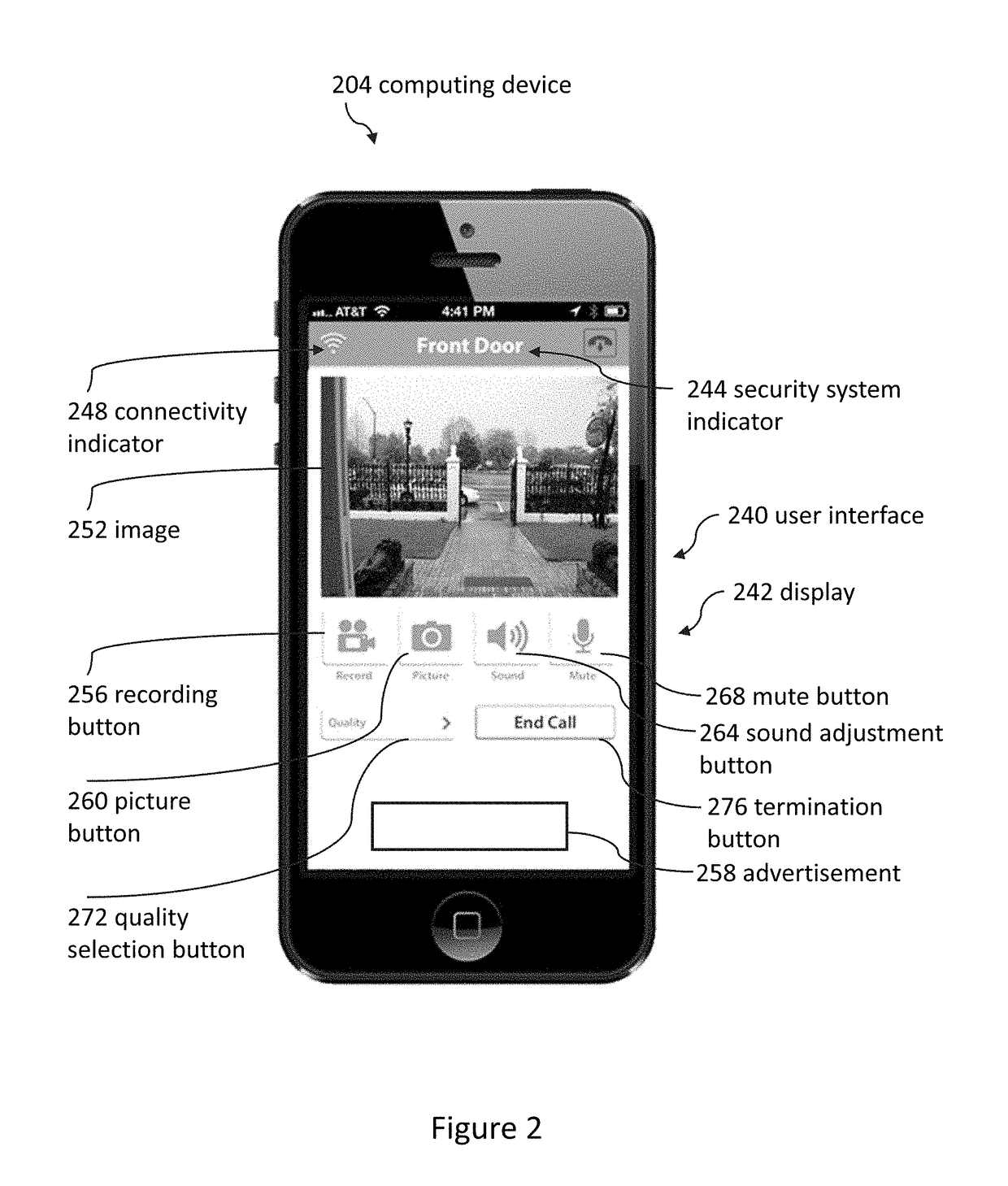
Doorbell communication systems and methods
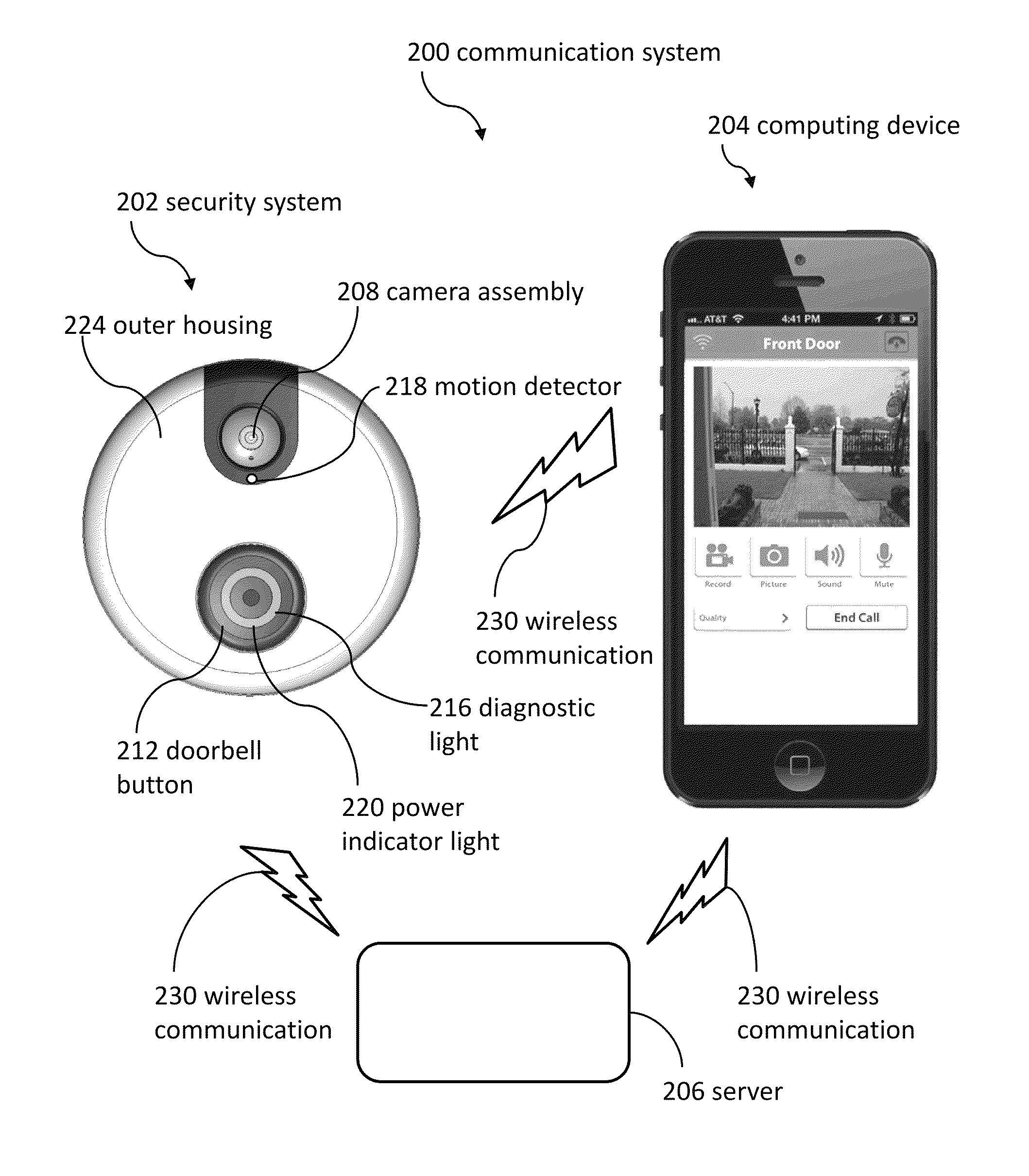
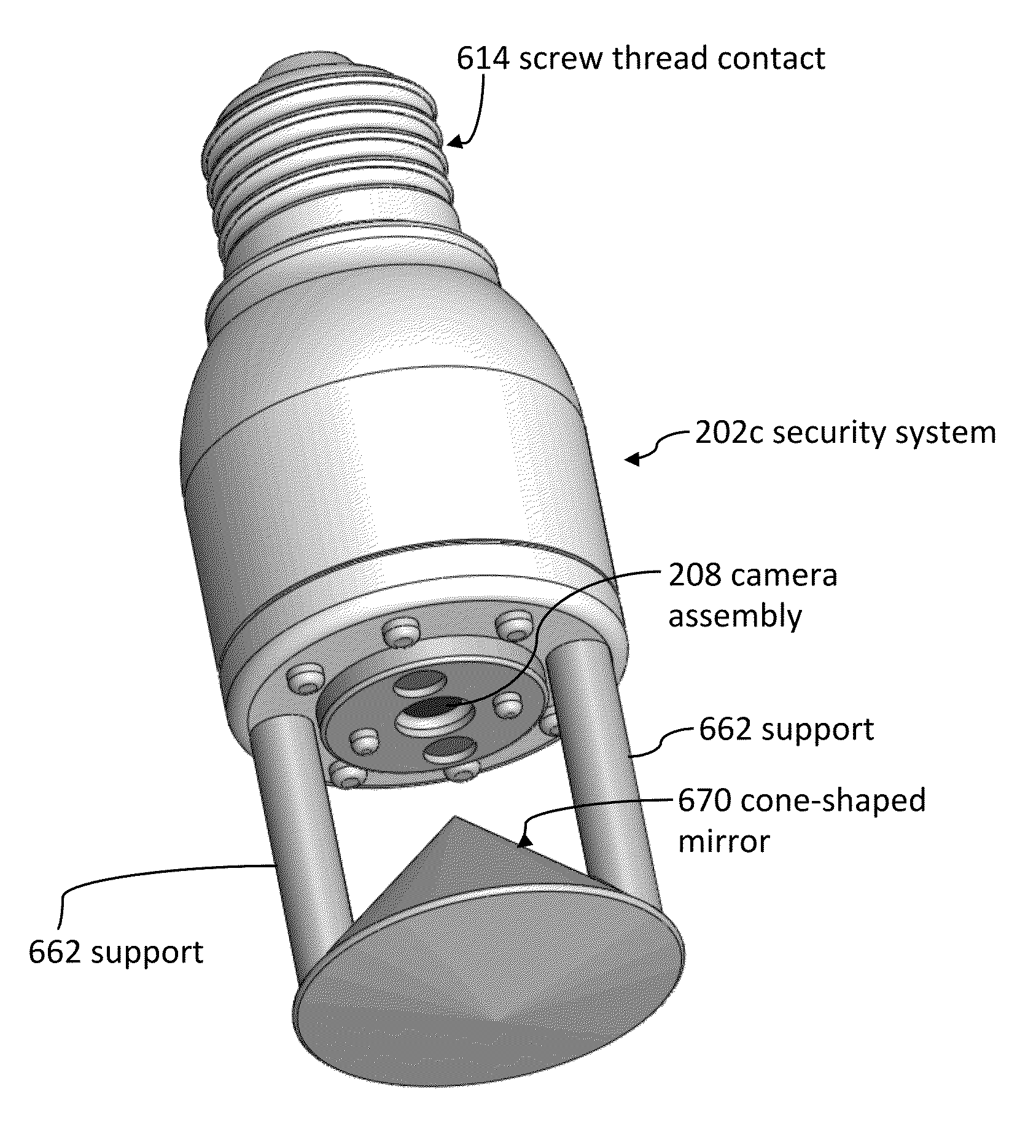
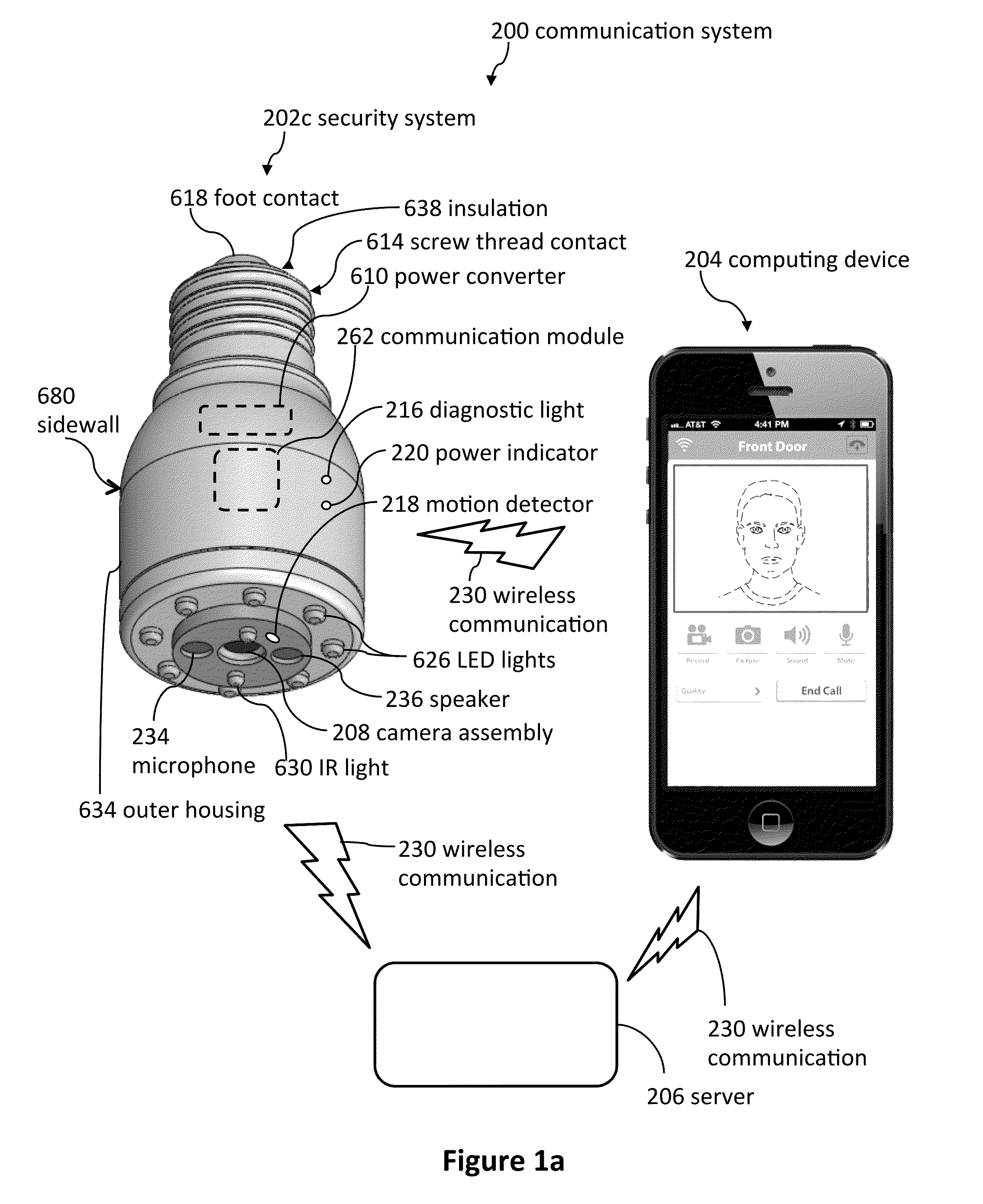
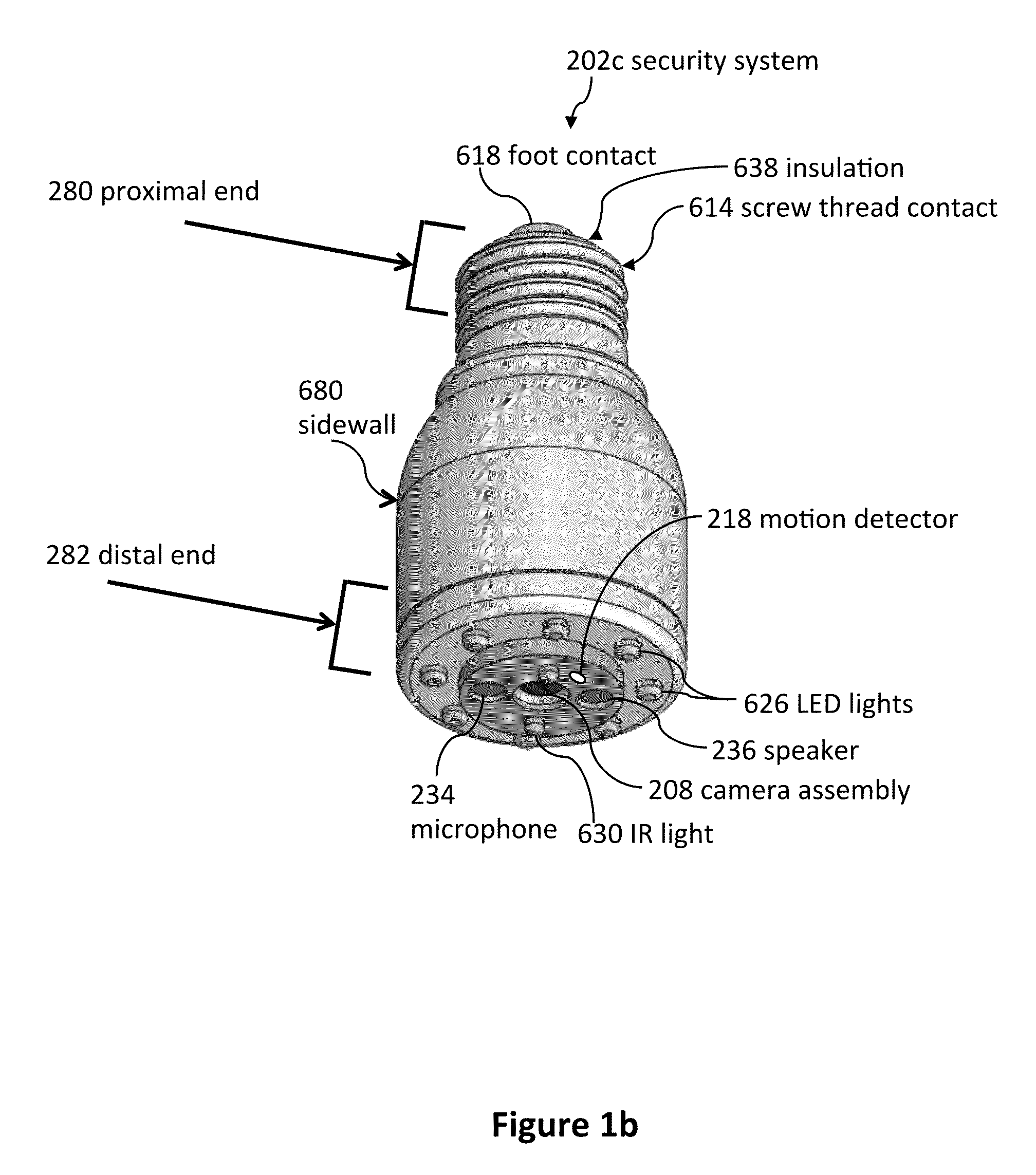
ActiveUS8823795B1High activityLess powerColor television detailsClosed circuit television systemsDoorbellEntryway
Communication systems configured to monitor an entryway to a building can include a security system configured to wirelessly communicate with a remote computing device. The security system can include a doorbell that comprises a camera, a speaker, and a microphone.
Owner:SKYBELL TECH IP LLC
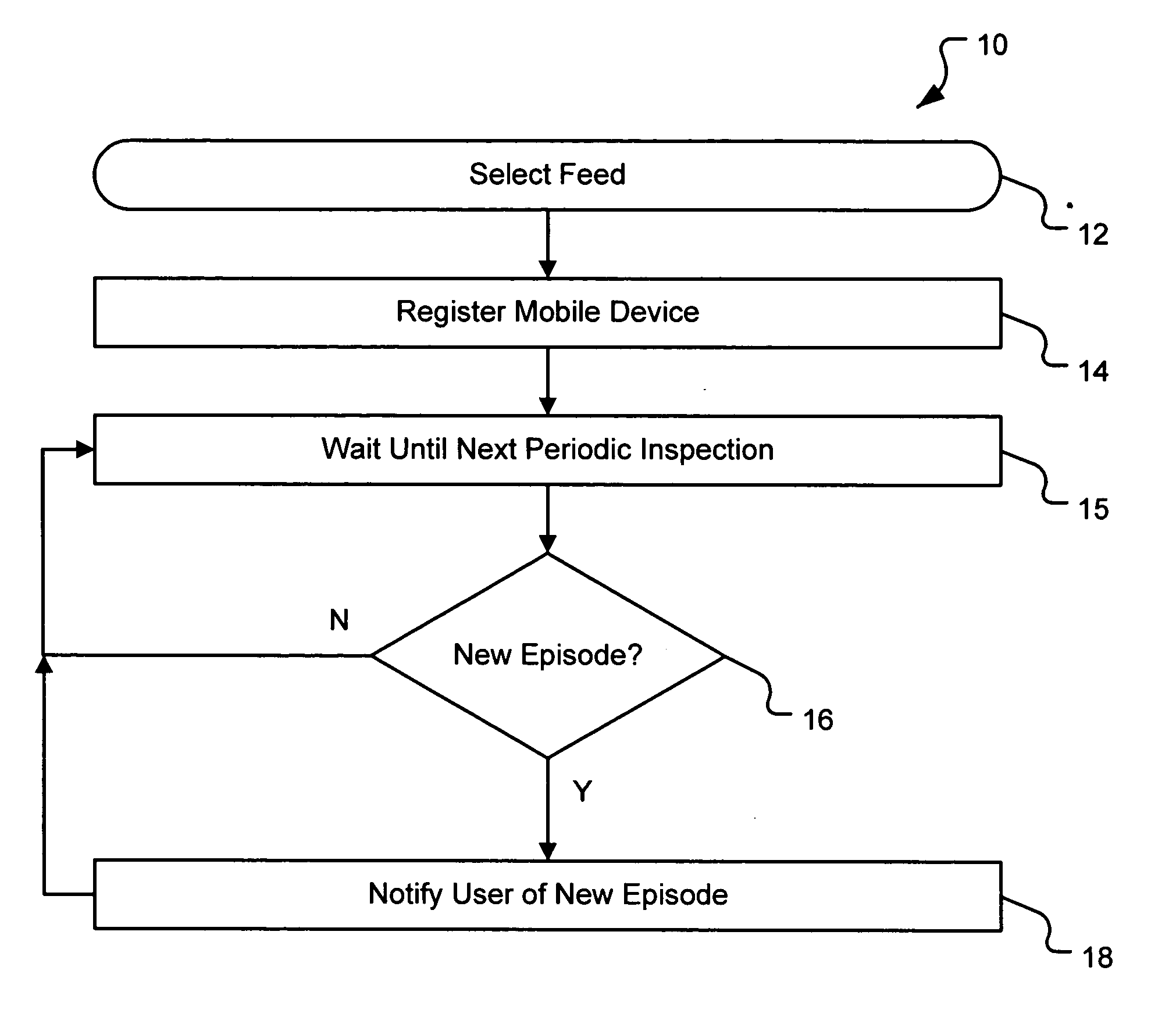
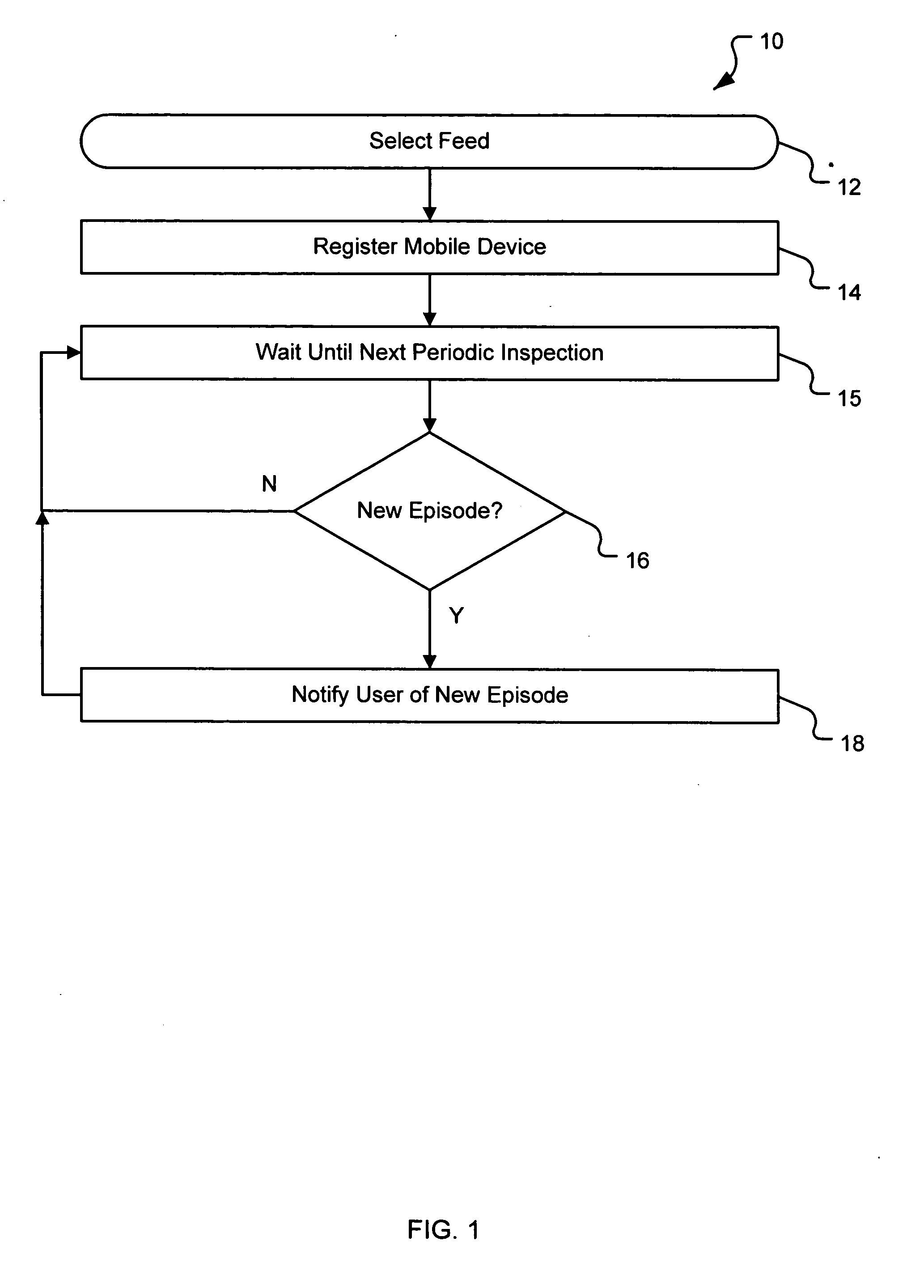
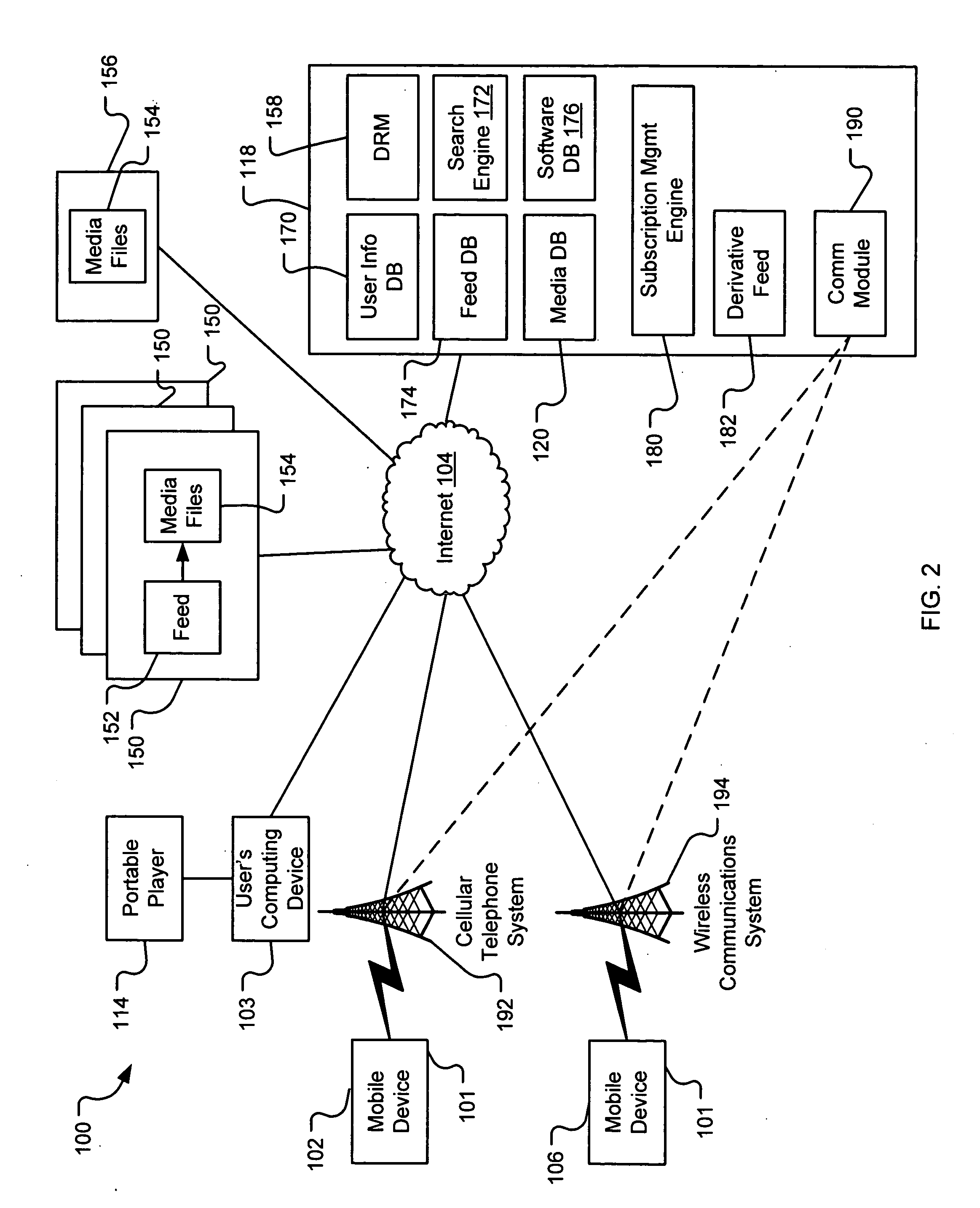
Pushing podcasts to mobile devices
InactiveUS20070077921A1Simple methodSpecial service for subscribersRadio/inductive link selection arrangementsTelecommunicationsNew episode
The present invention relates to a system and method for pushing podcasts to mobile devices, such as cellular phones, from a remote subscription management system. A subscription management system is described that is adapted to retrieve episodes from one or more remote computing devices and transmit retrieved episodes to a mobile device over a wireless network. The transmissions are made via a telephone number associated with the mobile device. The system includes a datastore, in communication with the server, containing at least one telephone number of a mobile device associated with a user and at least one podcast subscription associated with the user. The podcast lists episodes that are located on one or more of the remote computing devices. When a search module identifies a new episode, the system retrieves the new episode and transmits it to the mobile device using the telephone number to address the transmission.
Owner:OATH INC
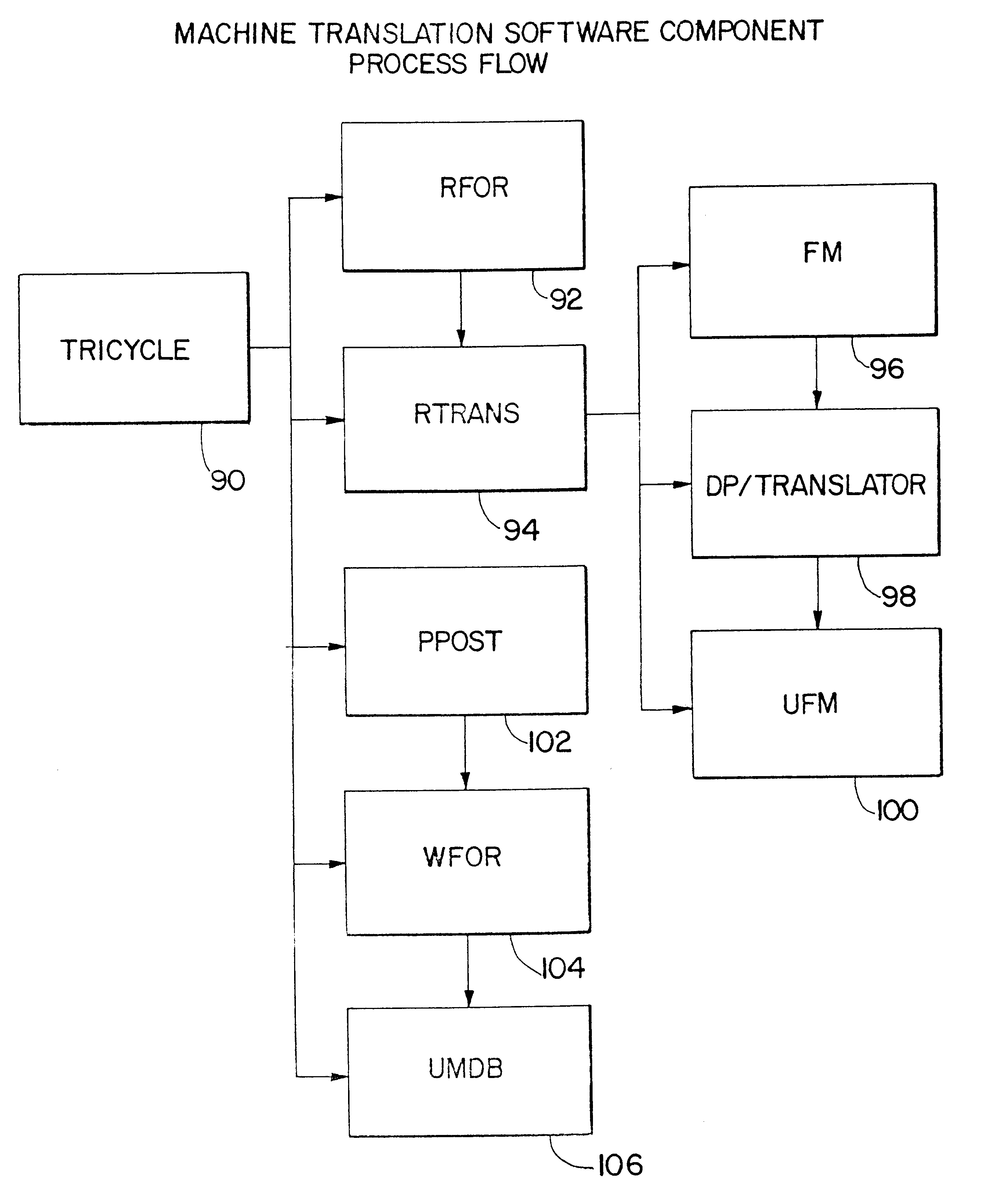
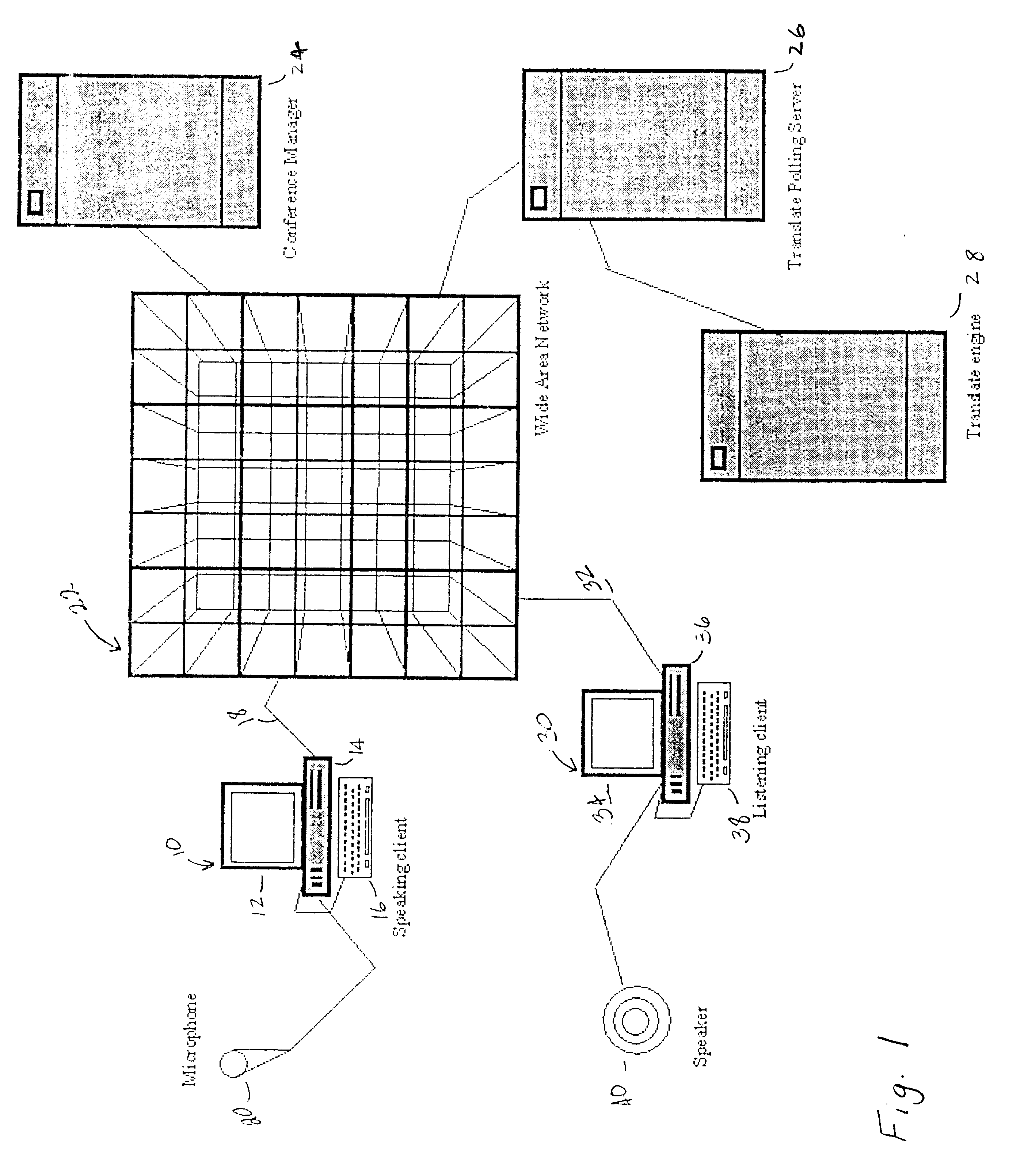
System for automated translation of speech
InactiveUS6339754B1Natural language translationAutomatic exchangesSpeech to speech translationRemote computing
The present invention allows subscribers to an online information service to participate in real-time conferencing or chat sessions in which a message originating from a subscriber in accordance with a first language is translated to one or more languages before it is broadcast to the other conference areas. Messages in a first language are translated automatically to one or more other languages through language translation capabilities resident at online information service host computers. Access software that subscribers use for participating in conference is integrated with speech recognition and speech generation software such that a subscriber may speak the message he or she would like to share with other participants and may hear the messages from the other participants in the conference. Speech-to-speech translation may be accomplished as a message spoken into a computer microphone in accordance with a first language may be recited by a remote computer in accordance with a second language.
Owner:META PLATFORMS INC
Methods and systems for updating a dock with a user interface element representative of a remote application
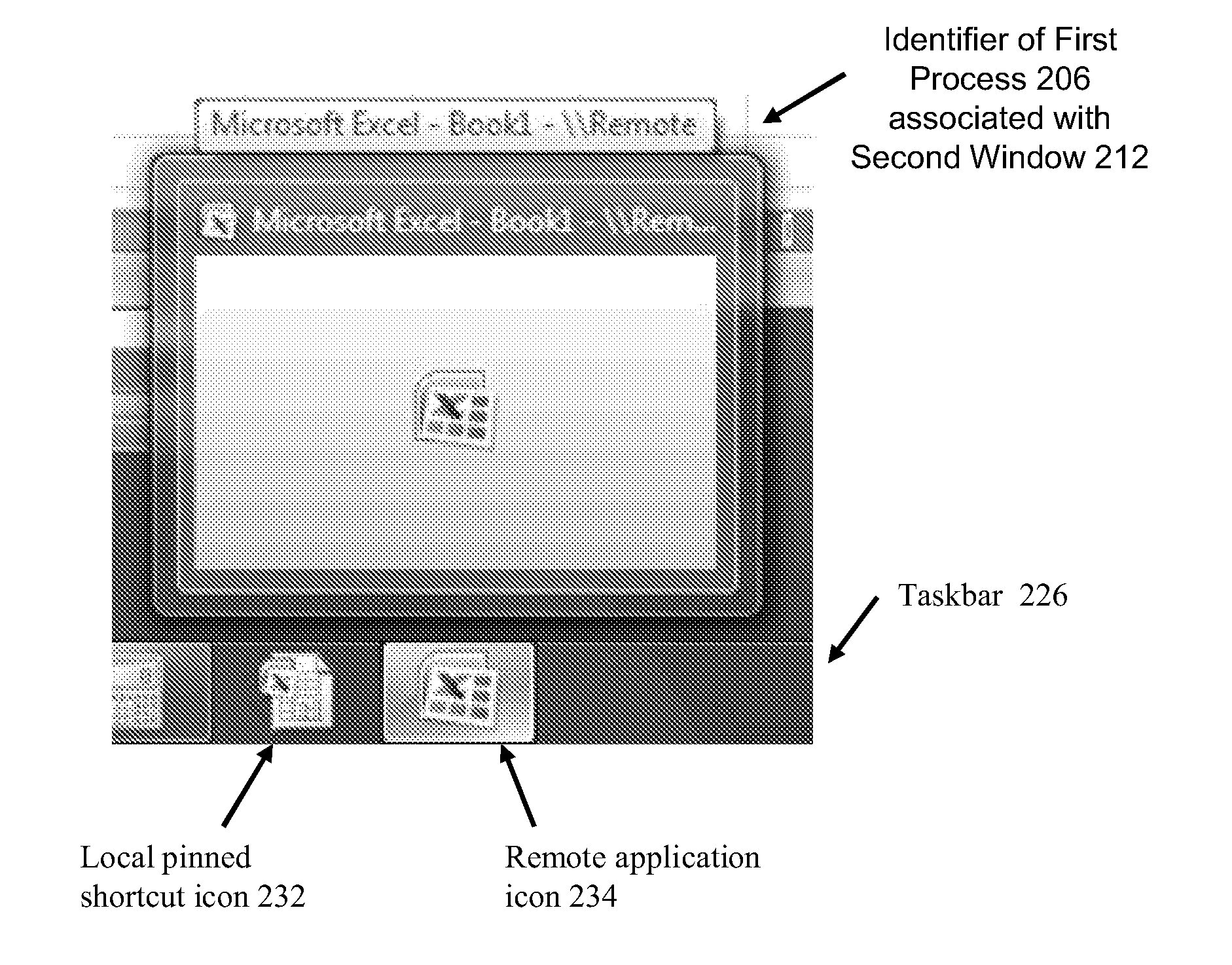
ActiveUS20110138295A1Input/output for user-computer interactionCathode-ray tube indicatorsRemote computerApplication software
The present disclosure features methods and systems for updating an application-centric interface or dock, generated and displayed by a local computer, with a user interface element representative of a remote application executing on a remote computer to provide integration between remote (“published”) applications and their local counterparts. This functionality provides a seamless, unified user experience by allowing hosted applications to appear as if they are running locally in a dock interface, in the same way that local applications appear.
Owner:CITRIX SYST INC
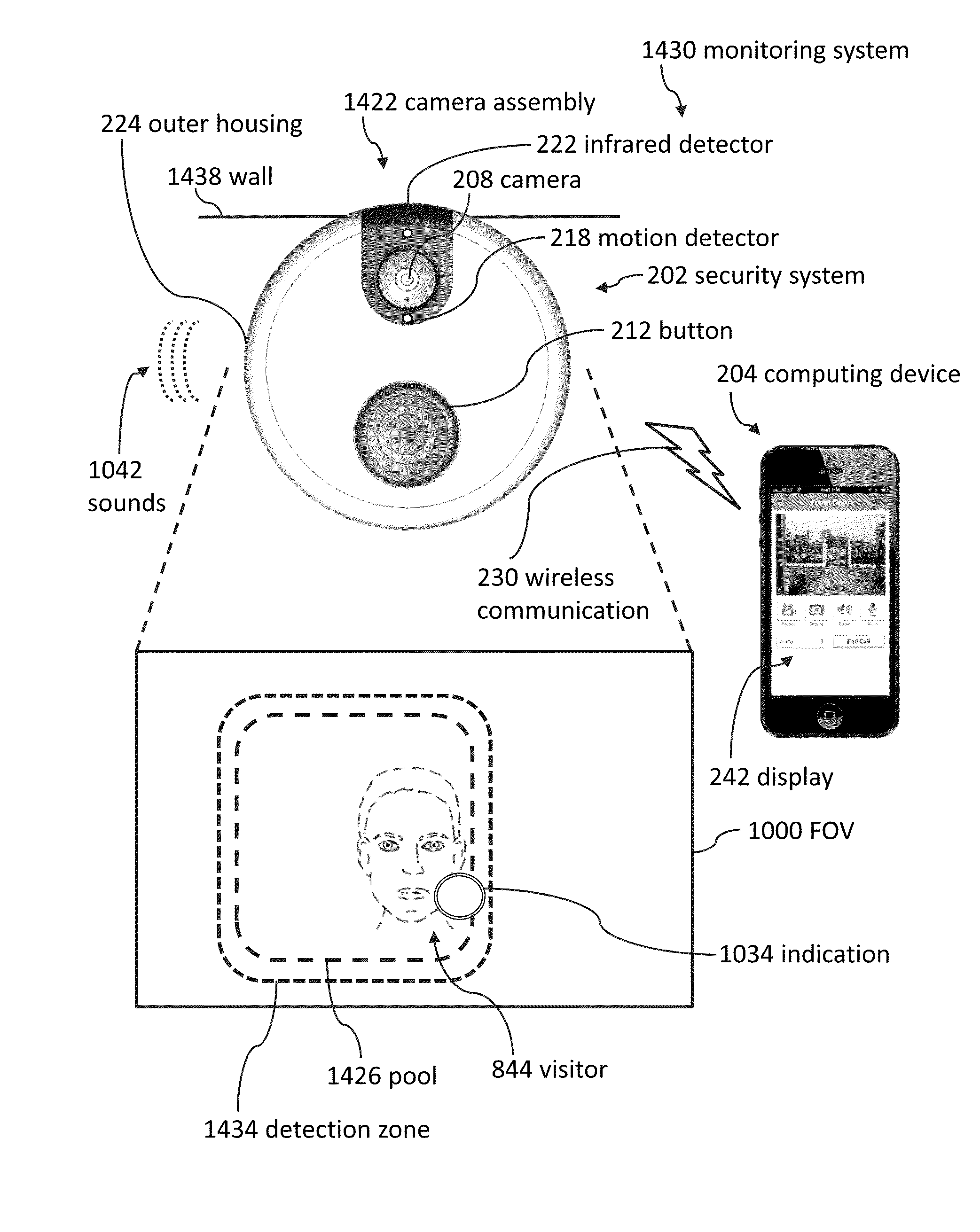
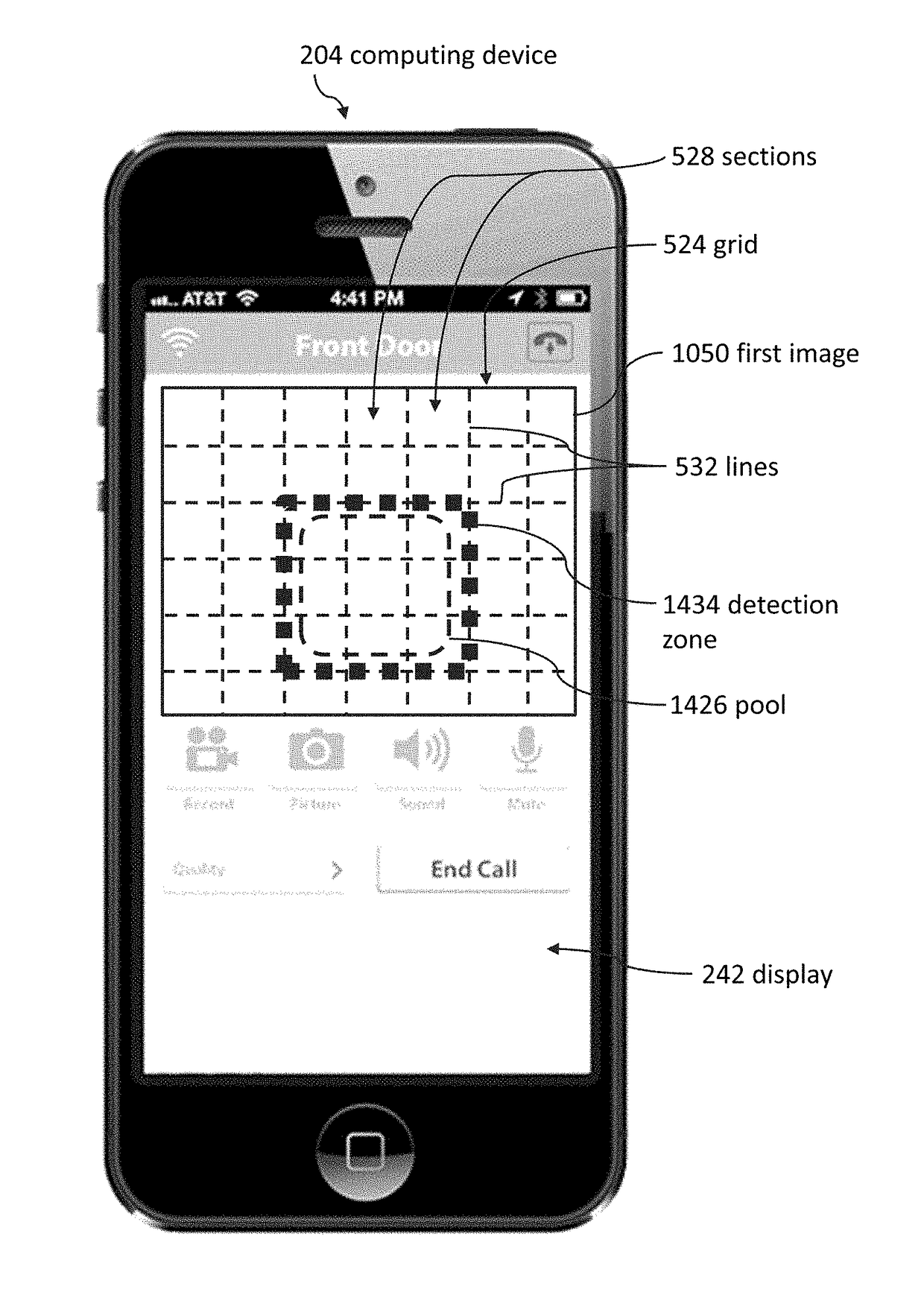
Pool monitor systems and methods
ActiveUS9049352B2Reduce false positivesTelephonic communicationColor television detailsRemote computingField of view
Cameras can be used to detect if unauthorized visitors enter pool areas. Cameras can send alerts to remote computing devices regarding unauthorized pool entry. Several embodiments include using a camera to take an image of a pool area, sending the image from the camera to a remote computing device, displaying the image on the remote computing device, and using the remote computing device to select a detection zone. Some embodiments include ignoring certain portions of the camera's field of view in response to detection zone selections.
Owner:SKYBELL TECH IP LLC
Methods and systems for securing sensitive information using a hypervisor-trusted client
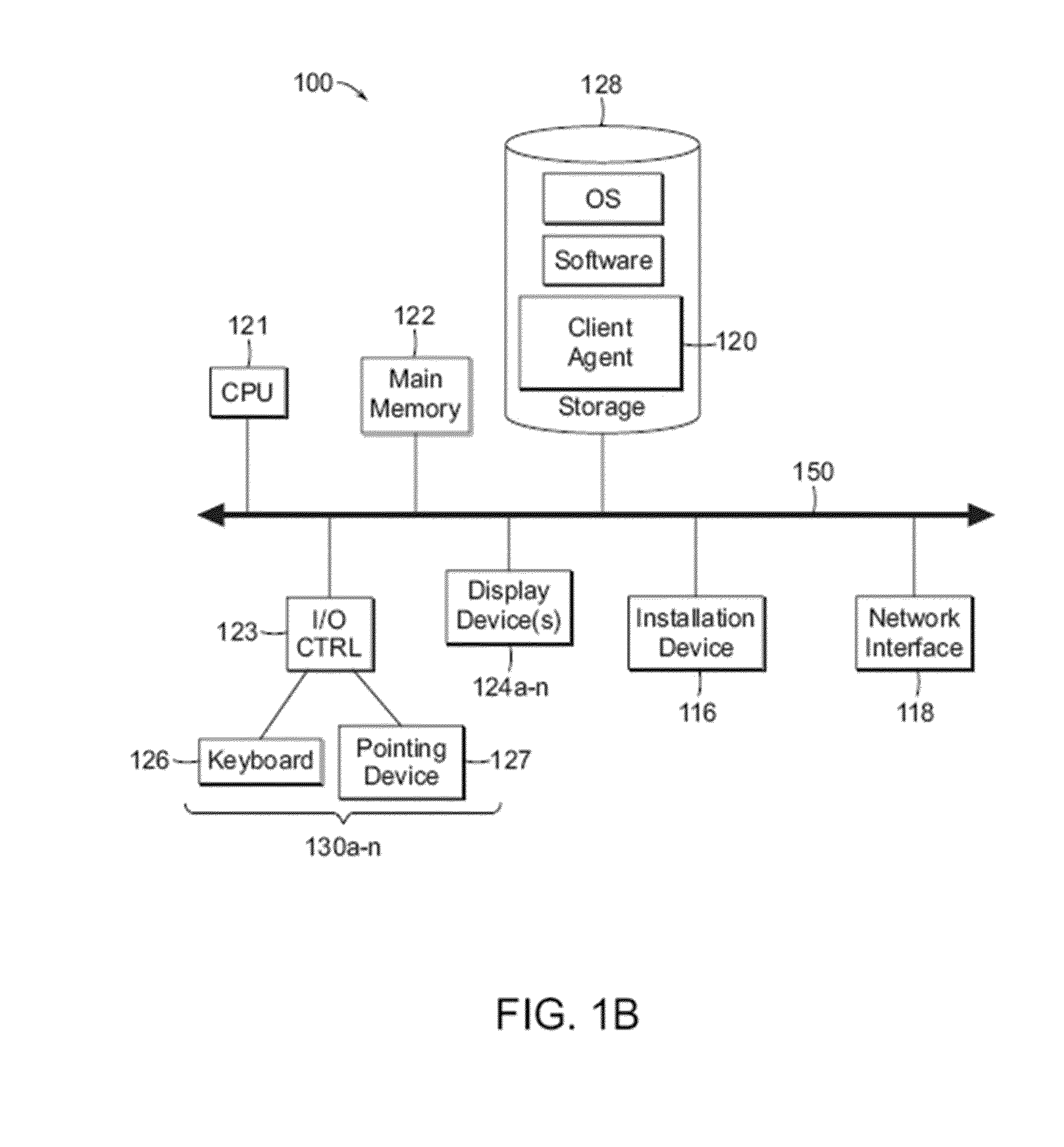
ActiveUS20110141124A1Internal/peripheral component protectionDigital data authenticationClient agentGraphics
The methods and systems described herein provide for securing sensitive information using a hypervisor-trusted client, in a computing device executing a hypervisor hosting a control virtual machine and a non-trusted virtual machine. A user of a non-trusted virtual machine requests to establish a connection to a remote computing device. Responsive to the request, a control virtual machine launches a client agent. A graphics manager executed by the processor of the computing device assigns a secure section of a memory of a graphics processing unit of the computing device to the client agent. The graphics manager renders graphical data generated by the client agent to the secure section of the graphics processing unit memory.
Owner:CITRIX SYST INC
Personal virtual assistant
InactiveUS20040225650A1Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesUser inputZoom
A computer-based virtual assistant the behavior of which can be changed by the user, comprising a voice user interface for inputting information into and receiving information from the virtual assistant by speech, a communications network, a virtual assistant application running on a remote computer, the remote computer being electronically coupled to the user interface via the communications network, wherein the behavior of the virtual assistant changes responsive to user input. A computer-based virtual assistant that also automatically adapts its behavior is disclosed, comprising a voice user interface for inputting information into and receiving information from the virtual assistant by speech, a communications network, a virtual assistant application running on a remote computer, the remote computer being electronically coupled to the user interface via the communications network, wherein the remote computer is programmed to automatically change the behavior of the virtual assistant responsive to input received by the virtual assistant. As detailed below, the virtual assistant adapts to the user in many different ways based on the input the virtual assistant receives. Such input could be user information, such as information about the user's experience, the time between user sessions, the amount of time a user pauses when recording a message, the user's emotional state, whether the user uses words associated with polite discourse, and the amount of time since a user provided input to the virtual assistant during a session.
Owner:AVAYA TECH LLC
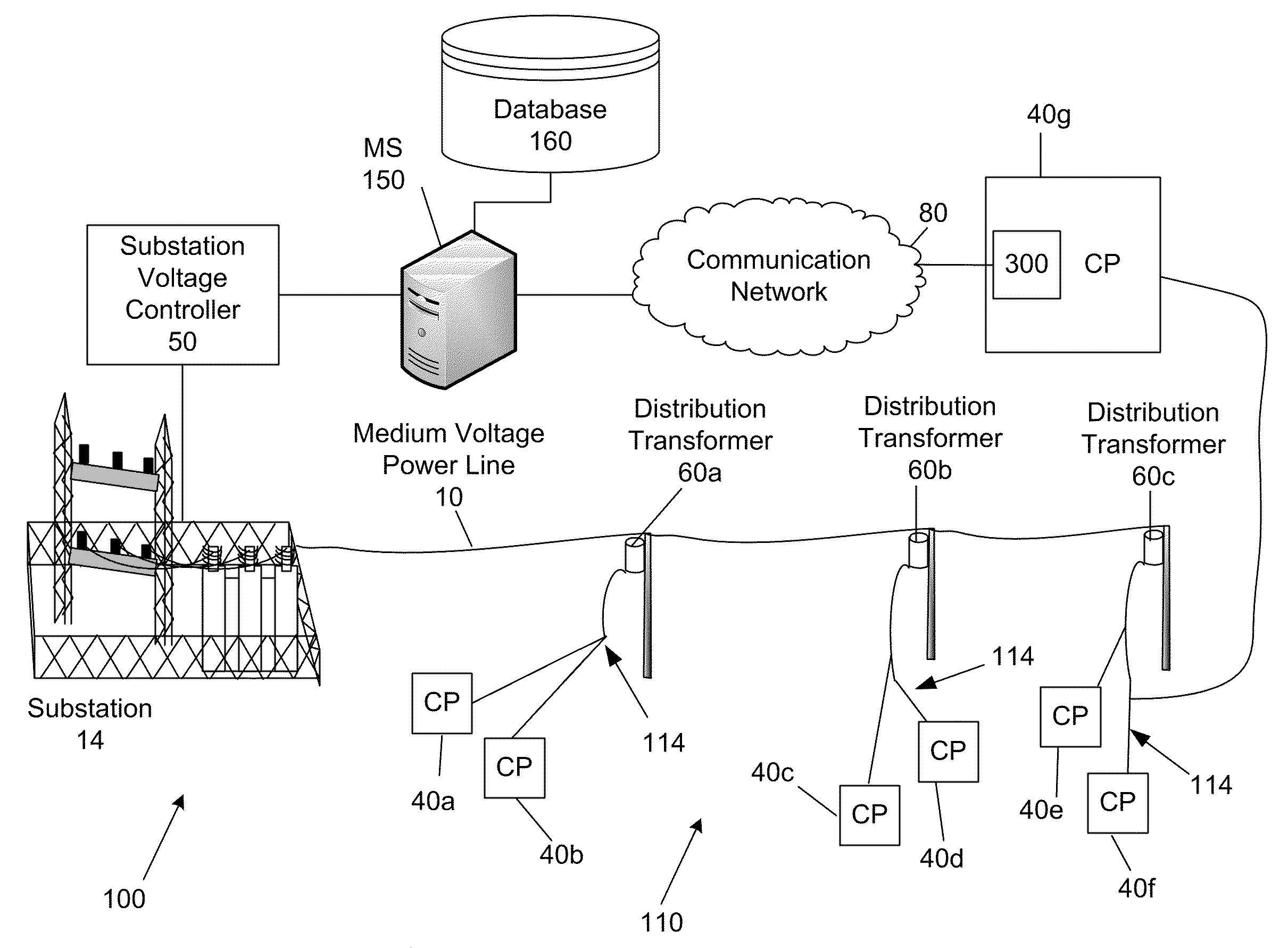
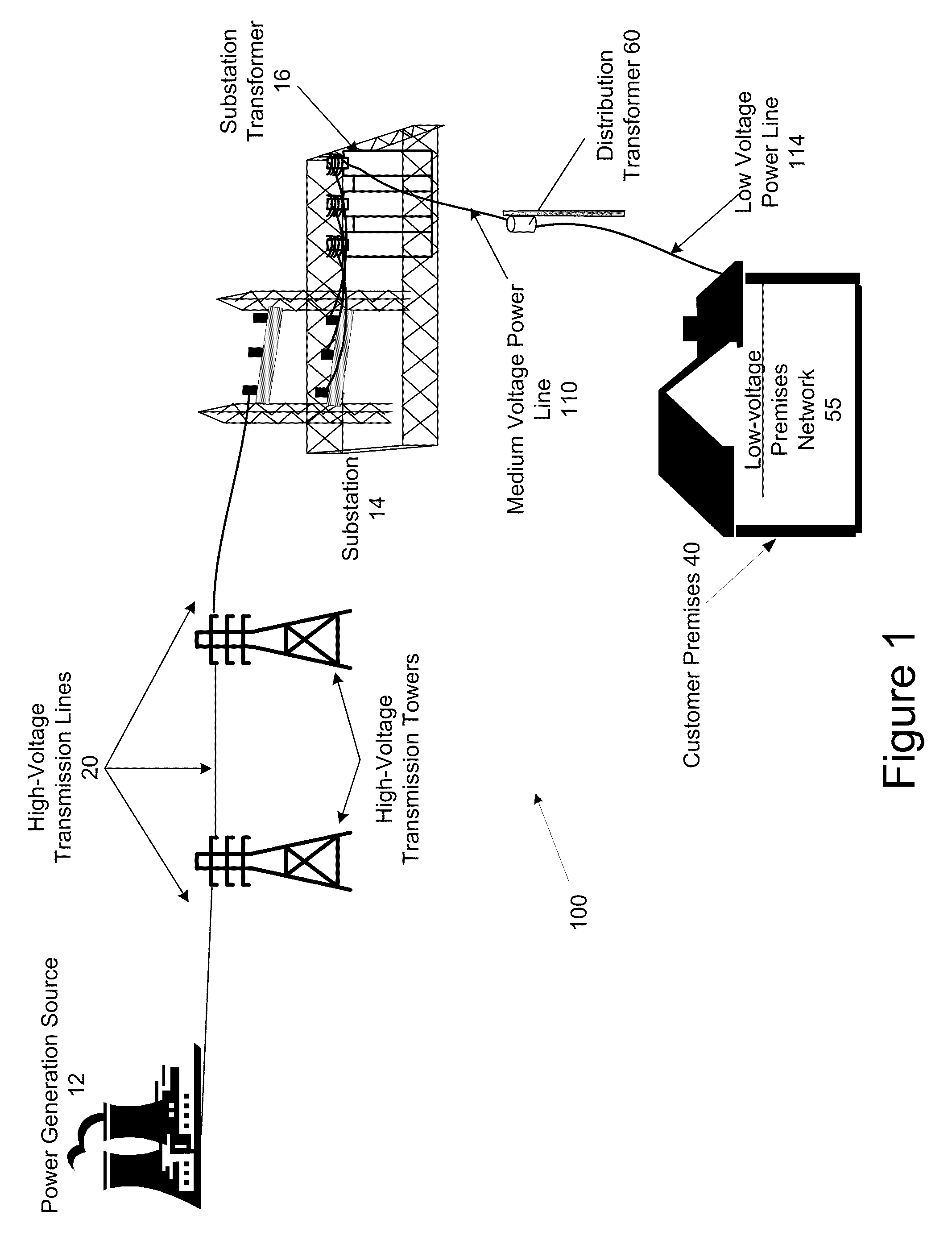
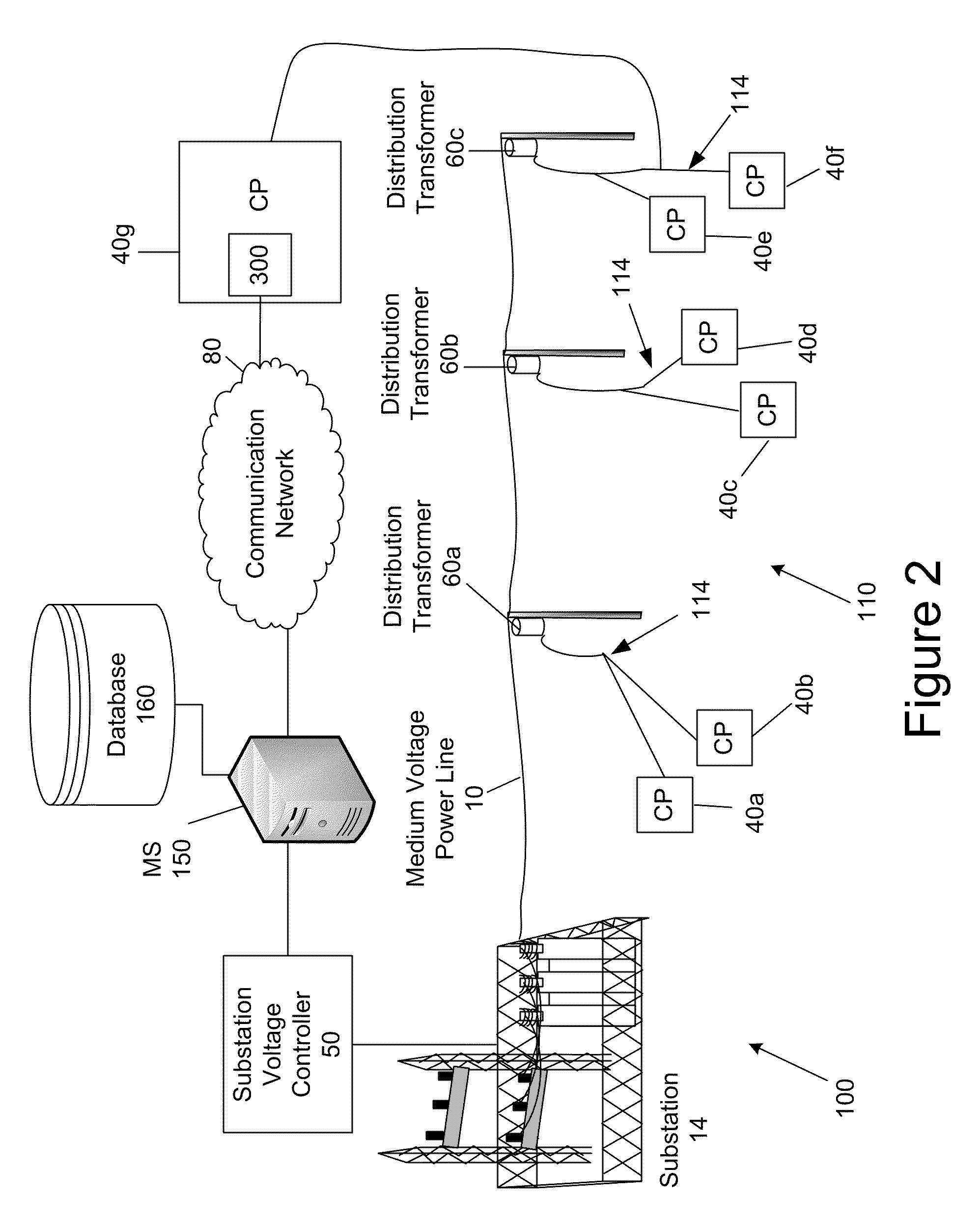
System and Method for Providing Voltage Regulation in a Power Distribution System
InactiveUS20090265042A1Mechanical power/torque controlDc network circuit arrangementsLow voltageDistribution power system
A system and method of regulating the voltage of the power supplied to a plurality of power customers via a power distribution system that includes low voltage power lines and medium voltage power lines is provided. In one embodiment, the method includes measuring the voltage of a plurality of low voltage power lines at a plurality locations in the power distribution system with a plurality of voltage monitoring devices; with the plurality of voltage monitoring devices, transmitting voltage data in real time to a remote computer system; receiving, with the computer system, the real time voltage data of the voltage measured from the voltage monitoring devices; comparing, with the computer system, the real time voltage data with a first threshold value; and if the real time voltage data is beyond the first threshold value, transmitting with the computer system a first voltage adjustment instruction to a voltage control device configured to adjust the voltage supplied to a low voltage power line.
Owner:S&C ELECTRIC
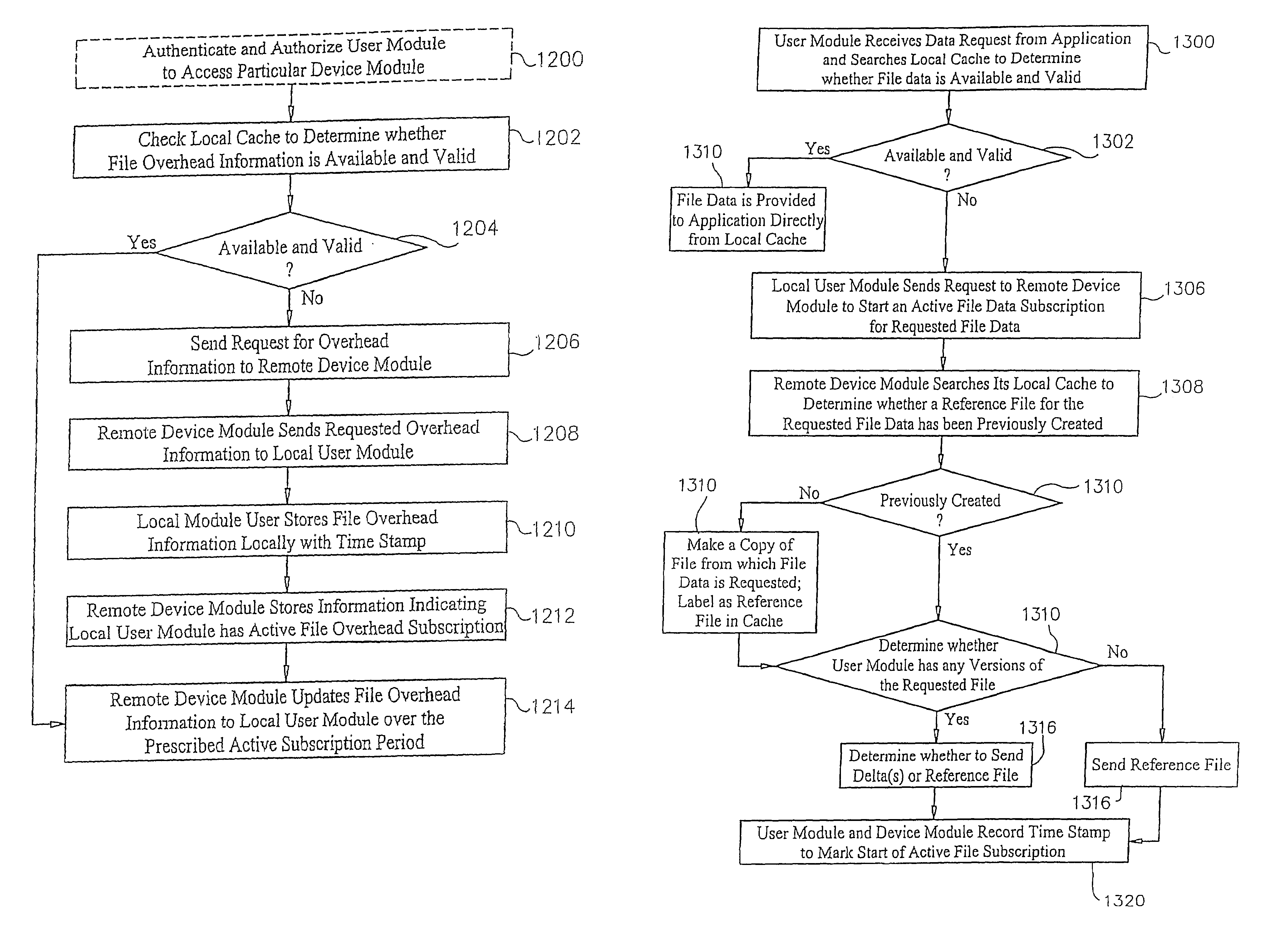
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS7546353B2Reduce bandwidth requirementsLimited dataDigital data processing detailsUser identity/authority verificationNetwork connectionData access
Applications, systems and methods for efficiently accessing data and controlling storage devices among multiple computers connected by a network. Upon receiving a request for access to data originally stored in a remote storage device, determining whether the data is already available and valid in a local storage device. Accessing the data from the local storage device if the data is available and valid. Authenticating a request for a secure connection between a local computer associated with the local storage device and a remote computer associated with the remote storage device. Securely connecting the local computer with the remote computer. Requesting the data from the remote storage device, over the network, if the data is not locally available and valid. Receiving data over the network from the remote storage device, and storing the data in the local storage device for direct local access thereto.
Owner:WESTERN DIGITAL TECH INC
Embedding cloud-based functionalities in a communication device
ActiveUS20160057619A1Improve securityPayment architectureDigital data authenticationCloud baseRemote computer
Techniques for enhancing the security of a communication device may include providing an application agent that executes in a trusted execution environment of the communication device, and a transaction application that executes in a normal application execution environment of the communication device. The application agent may receive, from the application, a limited-use key (LUK) generated by a remote computer, and store the LUK in a secure storage of the trusted execution environment. When the application agent receives a request to conduct a transaction from the application executing in the normal execution environment, the application agent may generate a transaction cryptogram using the LUK, and provides the transaction cryptogram to an access device.
Owner:VISA INT SERVICE ASSOC
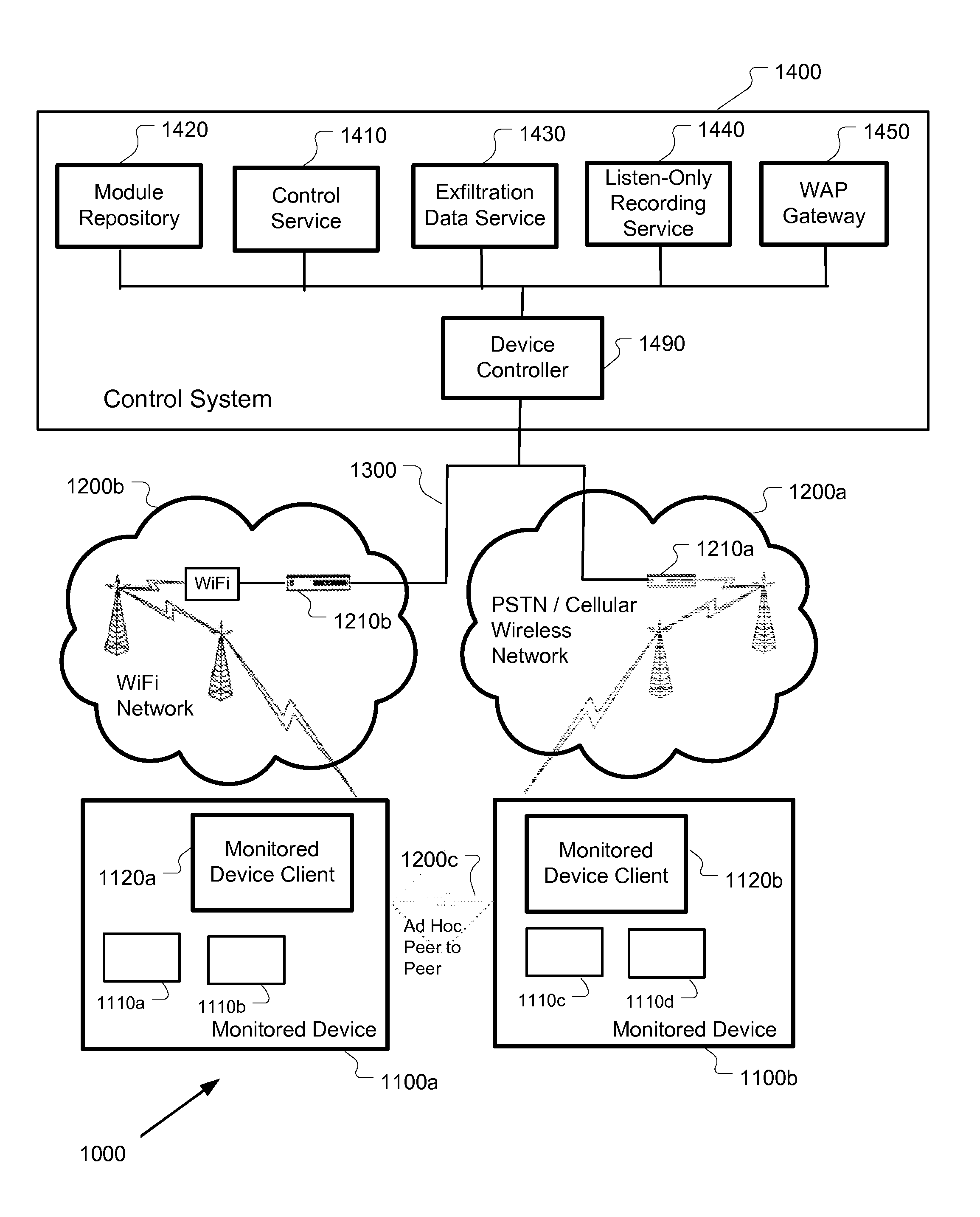
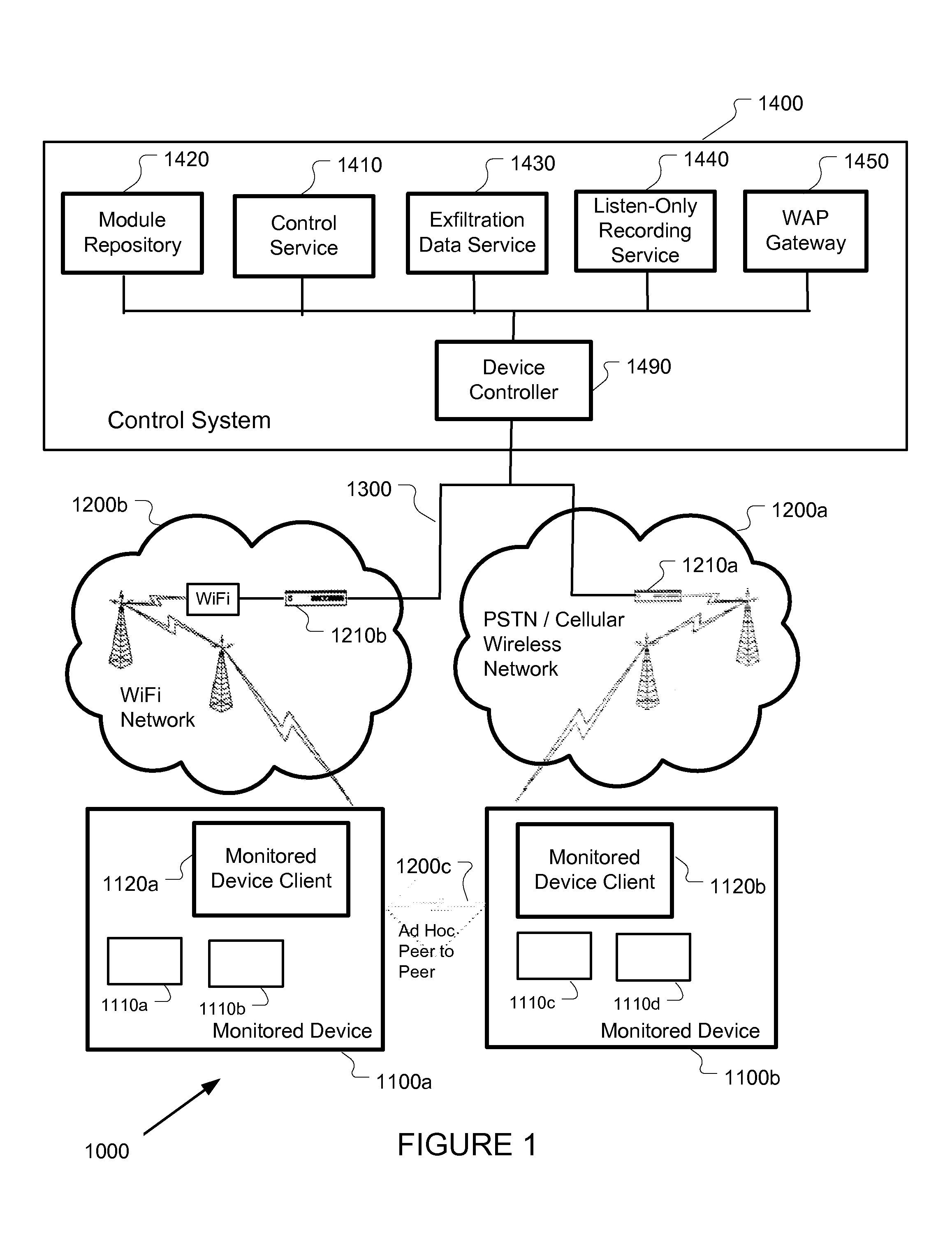
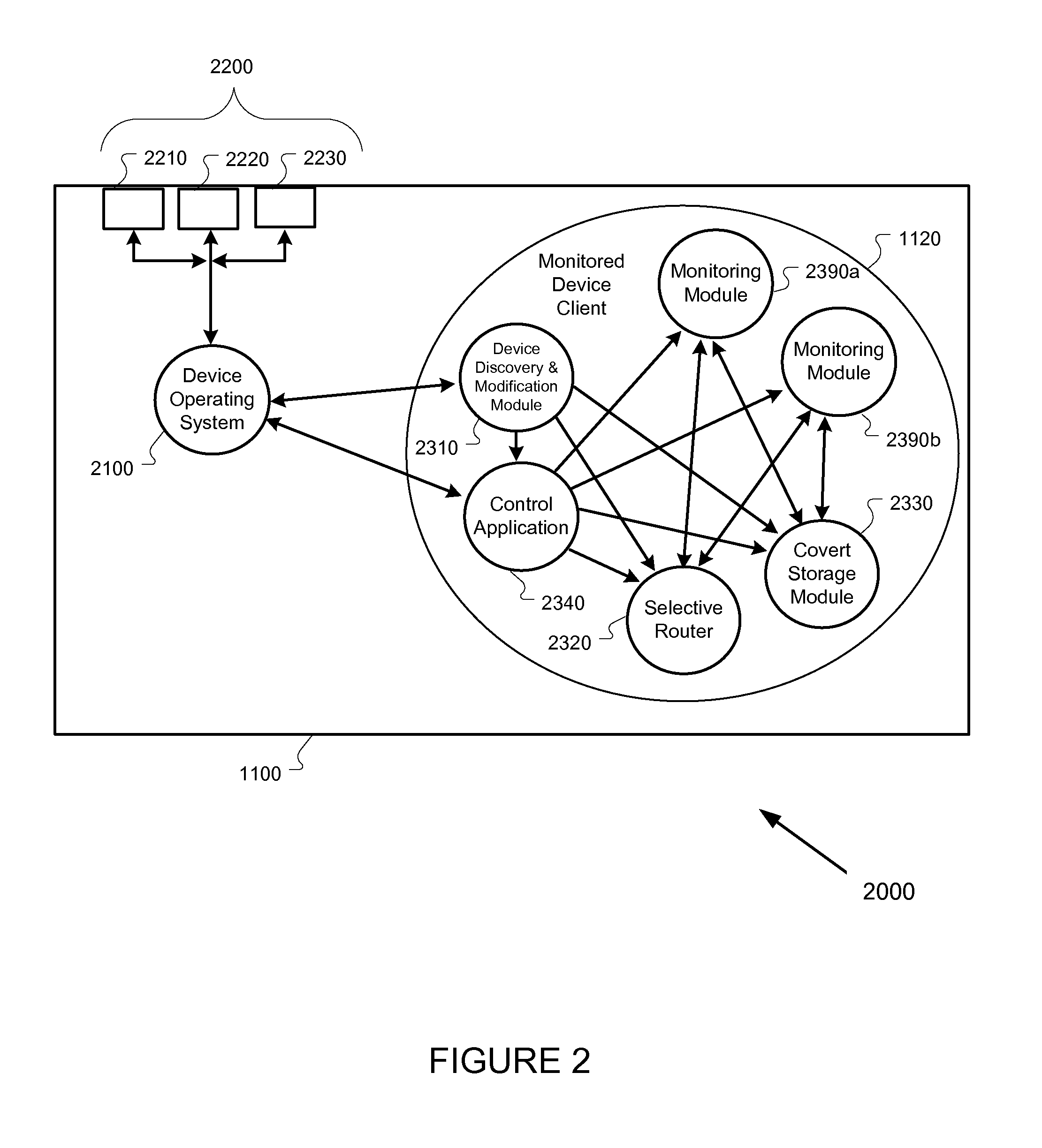
Mobile device monitoring and control system
Methods and apparatus, including computer program products, for surreptitiously installing, monitoring, and operating software on a remote computer controlled wireless communication device are described. One aspect includes a control system for communicating programming instructions and exchanging data with the remote computer controlled wireless communication device. The control system is configured to provide at least one element selected from the group consisting of: a computer implemented device controller; a module repository in electronic communication with the device controller; a control service in electronic communication with the device controller; an exfiltration data service in electronic communication with the device controller configured to receive, store, and manage data obtained surreptitiously from the remote computer controlled wireless communication device; a listen-only recording service in electronic communication with the device controller; and a WAP gateway in electronic communication with the remote computer controlled wireless communication device.
Owner:MANTECH ADVANCED SYST INT
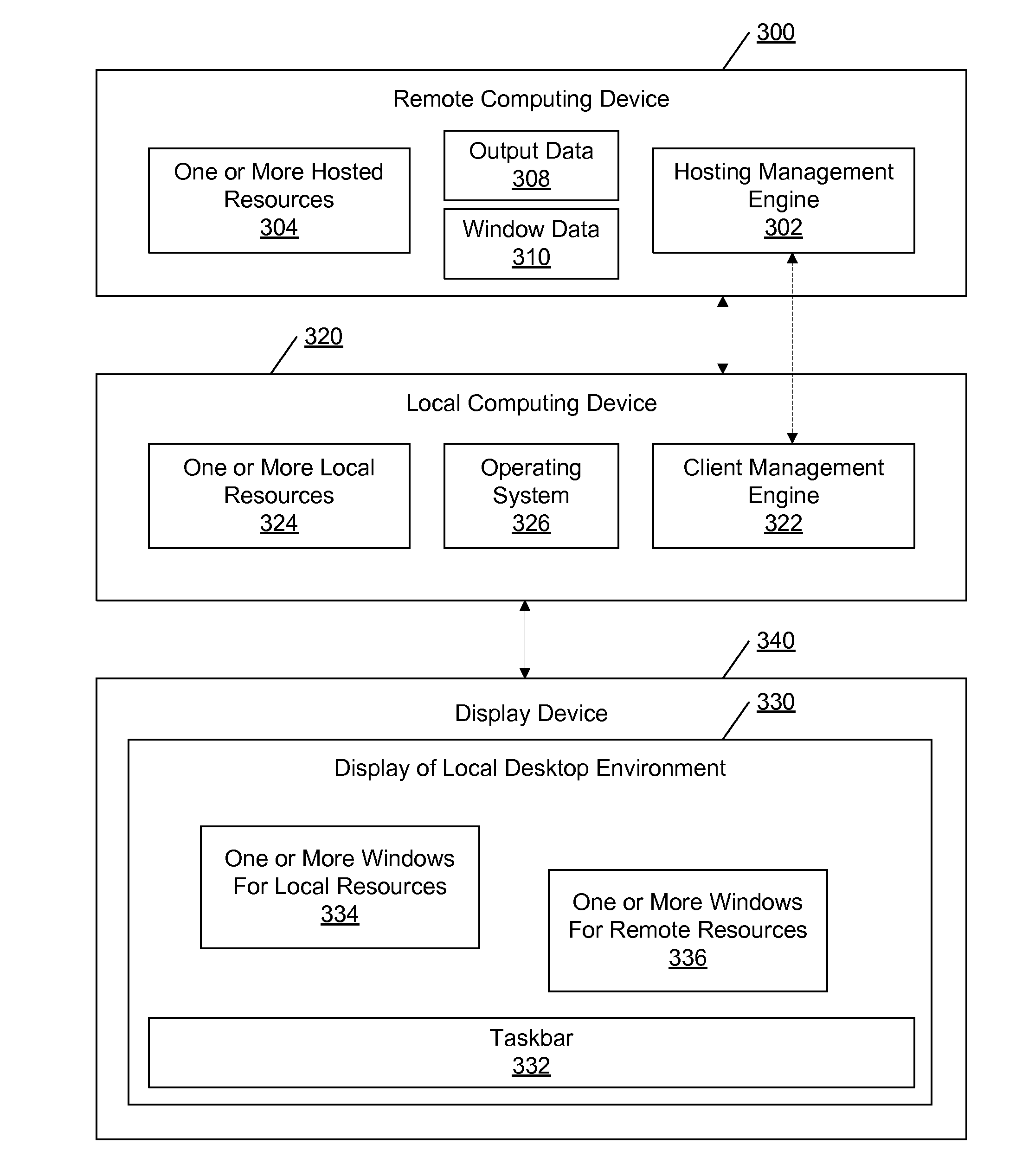
Transparent User Interface Integration Between Local and Remote Computing Environments
ActiveUS20120226742A1Enhance theme-integrationUnified and transparentStatic indicating devicesMultiple digital computer combinationsOperational systemRadio button
Methods and systems for transparent user interface integration between remote (“published”) applications and their local counterparts are described, providing a seamless, unified user experience, and allowing integration of a start menu, dock, taskbar, desktop shortcuts, windows, window and application switching, system tray elements, client-to-host and host-to-client file type association, URL redirection, browser cookie redirection, token redirection, status message interception and redirection, and other elements. These methods and systems further enhance theme-integration between a client and remote desktop or virtual machine by remoting all UI elements to a recipient for generation, including text controls, buttons, progress bars, radio buttons, list boxes, or other elements; presenting them with the receiver's product and OS-specific UI; and returning status back to the sender. This may achieve a more unified and transparent UI integration. Furthermore, international text may be correctly received in cross-language environments, or translated into the language of the presenting environment.
Owner:CITRIX SYST INC
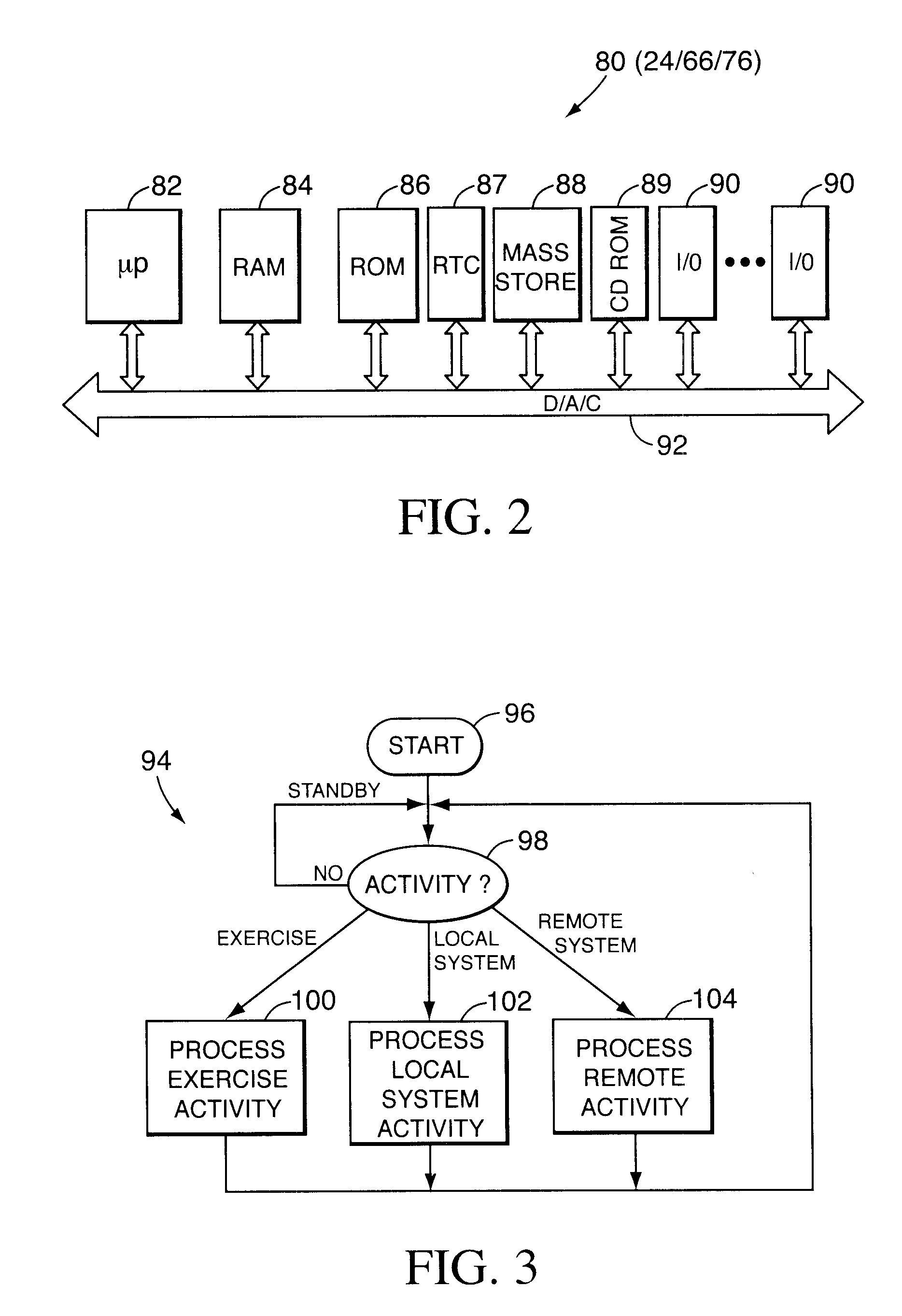
Providing User Interfaces and Window Previews for Hosted Applications
ActiveUS20120084713A1Execution for user interfacesInput/output processes for data processingGraphicsTaskbar
A local computing device may use a remote computing device to host various resources on behalf of the local computing device. The local computing device may receive data related to a graphical window of the remotely hosted resource and generate a graphical window on the local desktop environment for the remotely hosted resource. The local computing device may also update a taskbar to include the remote hosted resource. Window previews may also be generated by the local computing device and the window previews may include snapshots or dynamic images of the graphical window for the remotely hosted resource. In some instances, the snapshots may be provided to the local computing device from the remote computing device.
Owner:CITRIX SYST INC
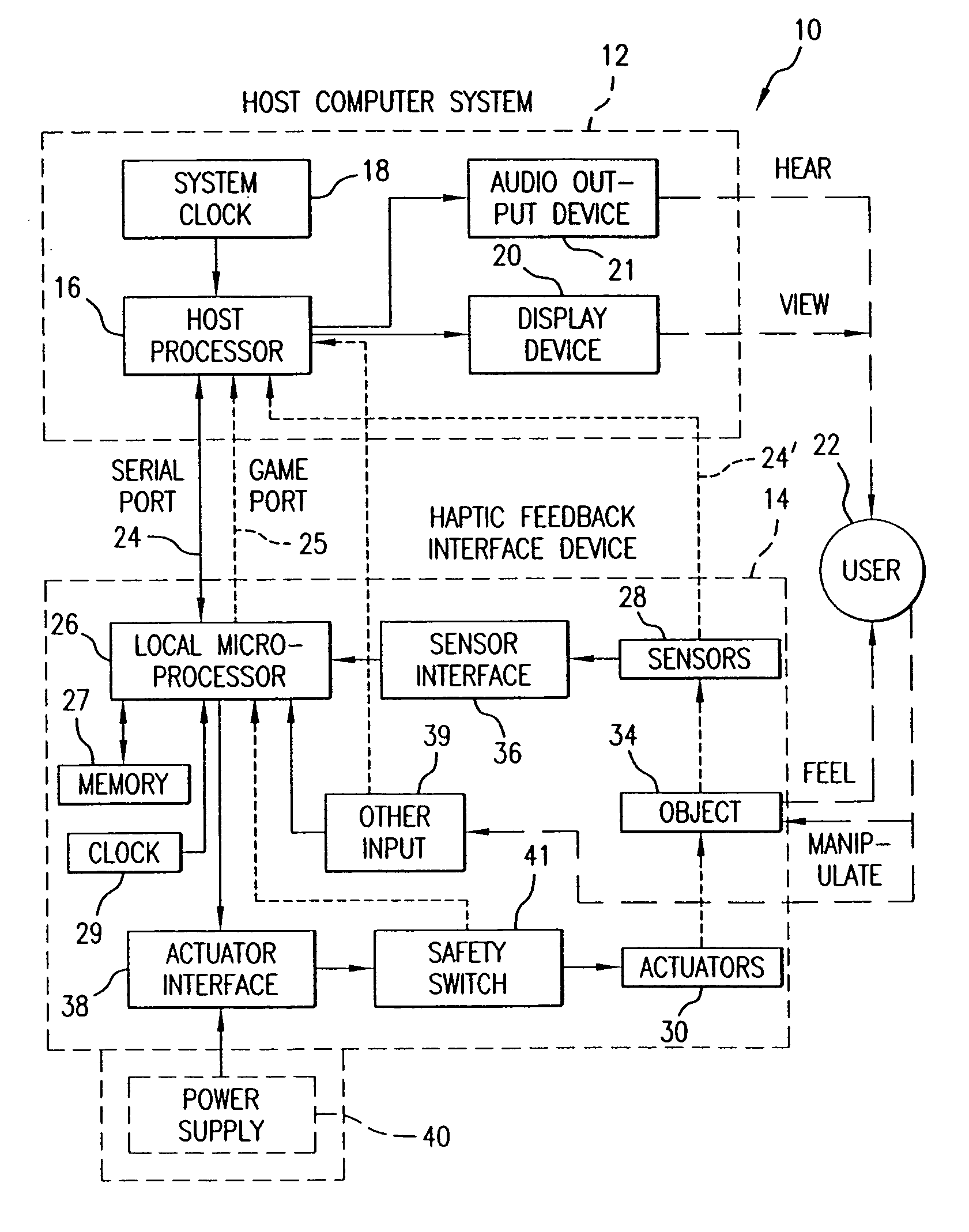
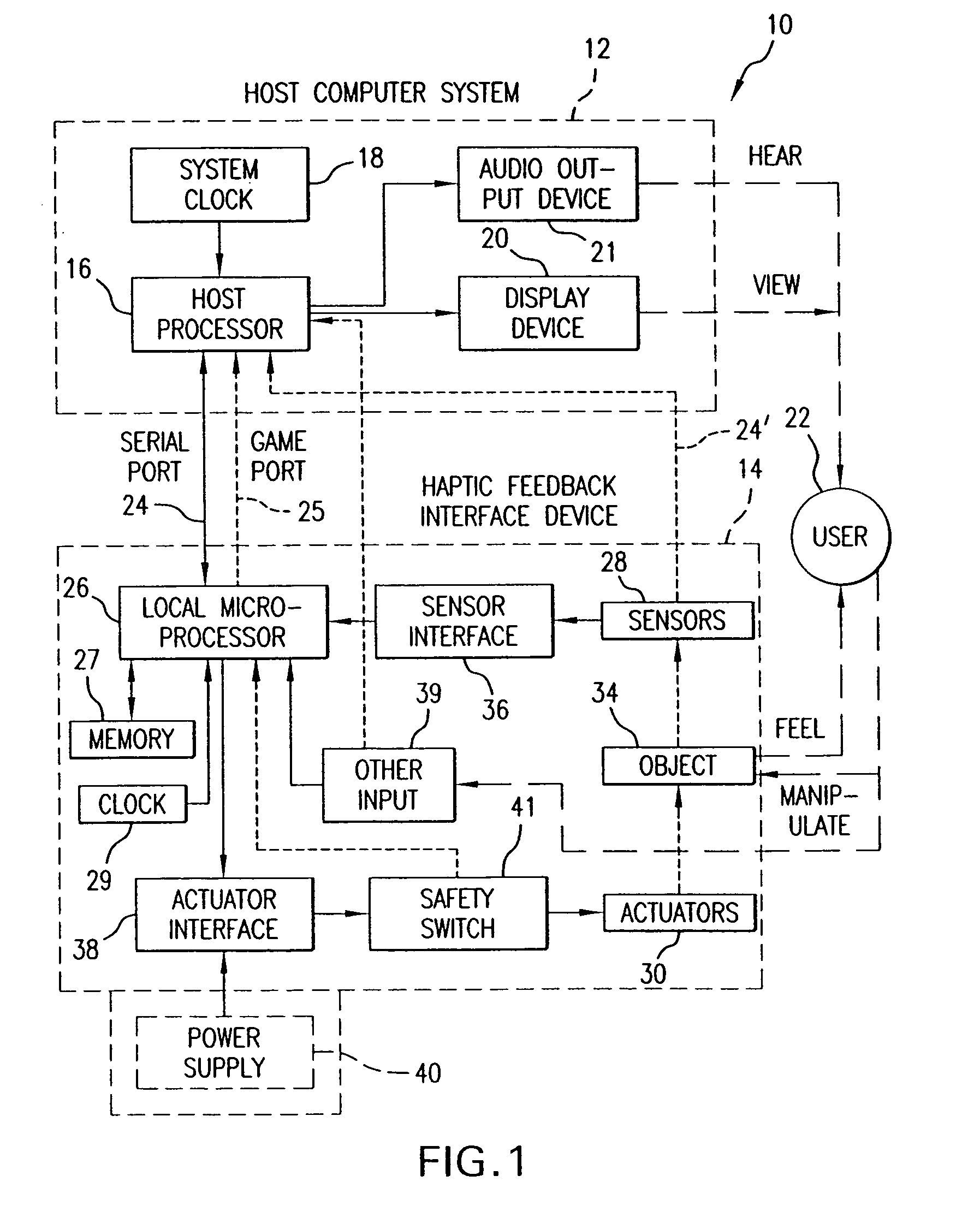
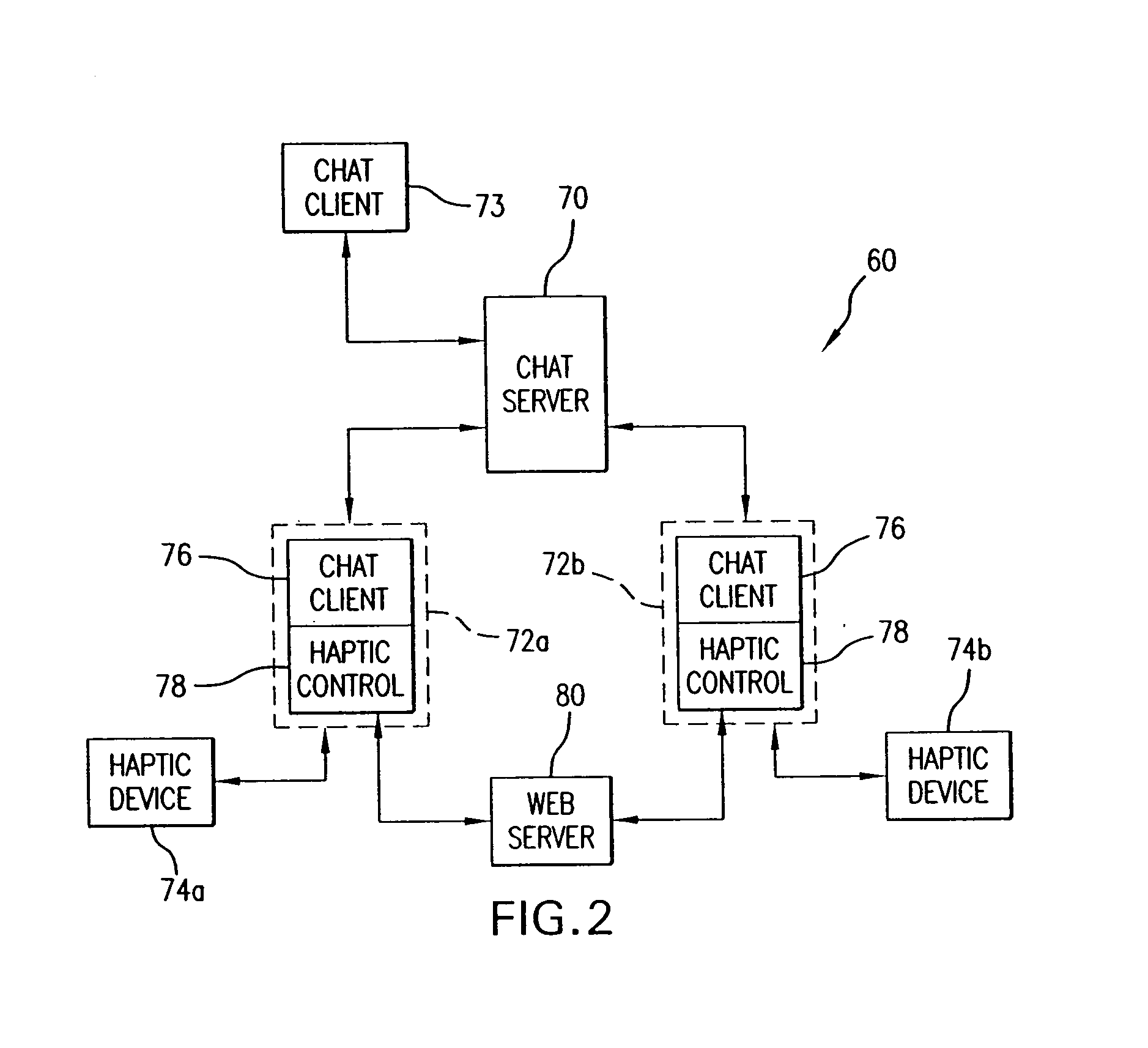
Chat interface with haptic feedback functionality
InactiveUS7159008B1Enhancements to chat messagesInput/output for user-computer interactionMultiple digital computer combinationsNetwork connectionDisplay device
A chat interface allowing a user to exchange haptic chat messages with other users in a chat session over a computer network. A chat interface can be displayed by a local computer and receives input data from a user of the local computer, such as text characters or speech input. The input data provides an outgoing chat message that can include sent force information. The outgoing chat message is sent to a remote computer that is connected to the local host computer via a computer network. The remote computer can display a chat interface and output a haptic sensation to a user of the remote computer based at least in part on the force information in the outgoing chat message. An incoming message from the remote computer can also be received at the chat interface, which may also include received force information. The incoming chat message is displayed on a display device to the user of the local computer. A haptic sensation can be output to the user of the local computer using a haptic device coupled to the local computer, where the haptic sensation is based at least in part on the received force information received from the remote computer.
Owner:IMMERSION CORPORATION
Doorbell communication systems and methods
ActiveUS9179109B1Television system detailsColor television detailsCommunications systemComputer vision
A doorbell system can include a remote computing device and a doorbell that has a camera. The doorbell can enter a camera sleep mode wherein the camera is configured not to record. The remote computing device can be used to override a power setting of the doorbell to enable the doorbell to record a video. Then, the remote computing device can receive the video that was recorded by the doorbell.
Owner:SKYBELL TECH IP LLC
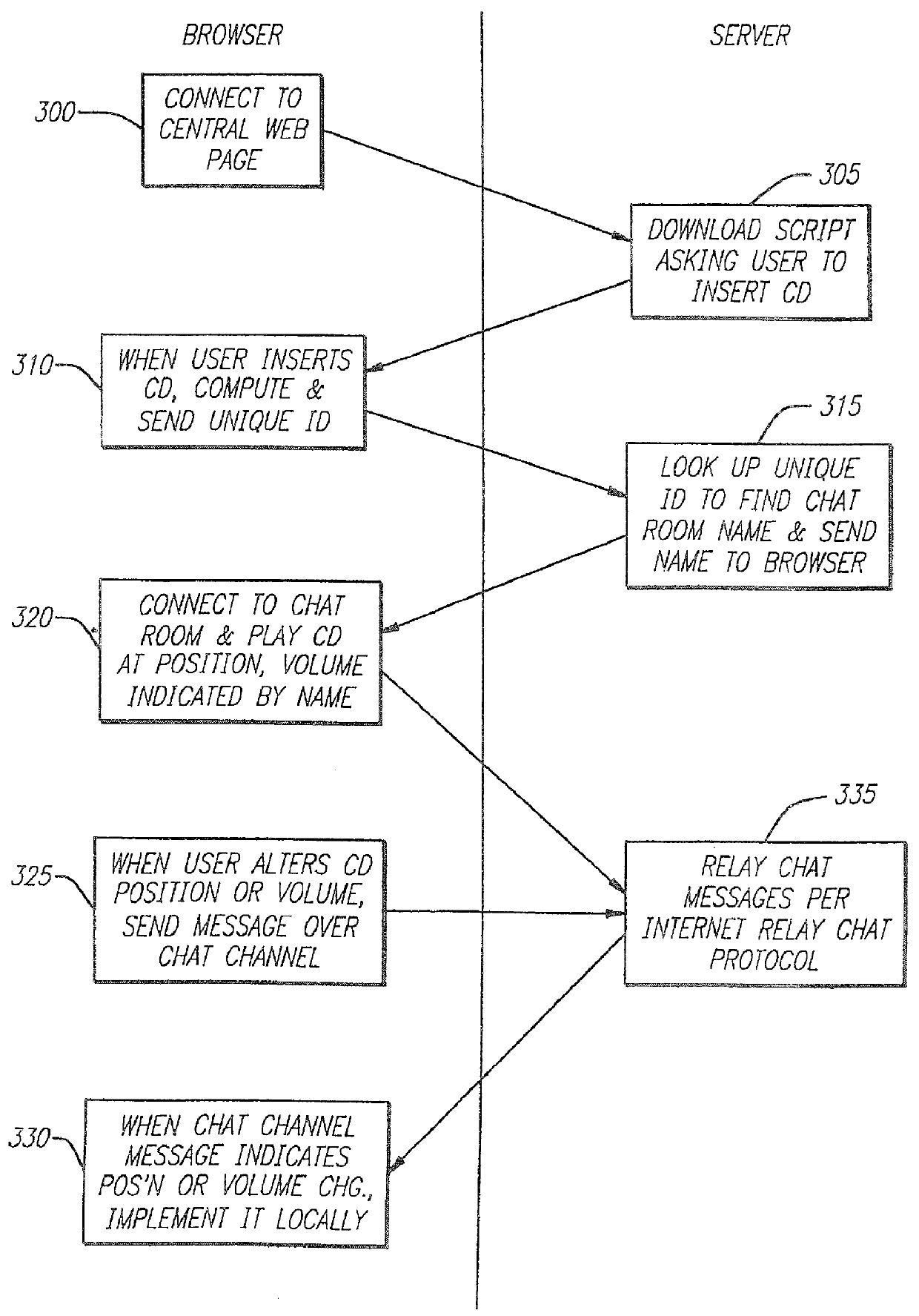
Method and system for finding approximate matches in database
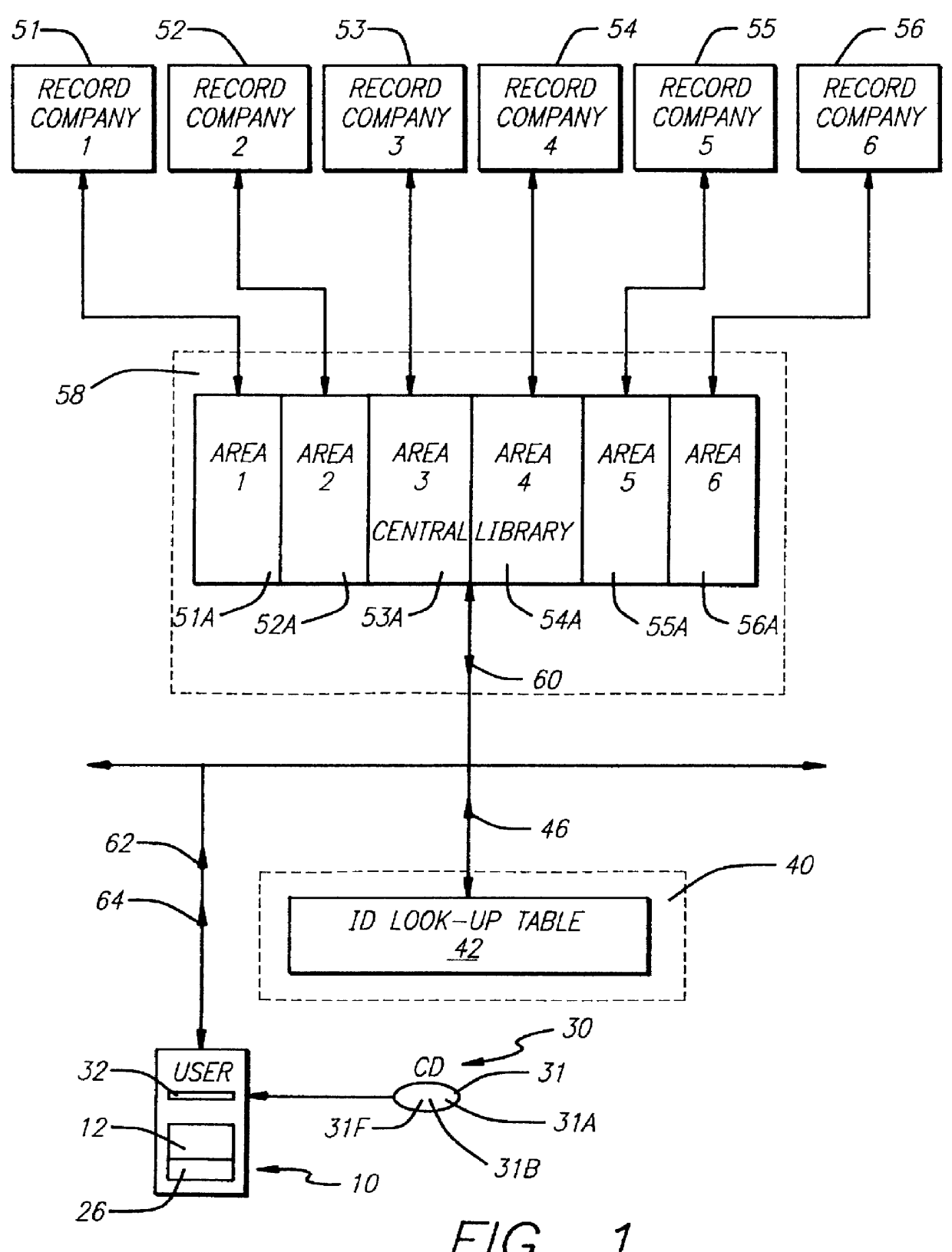
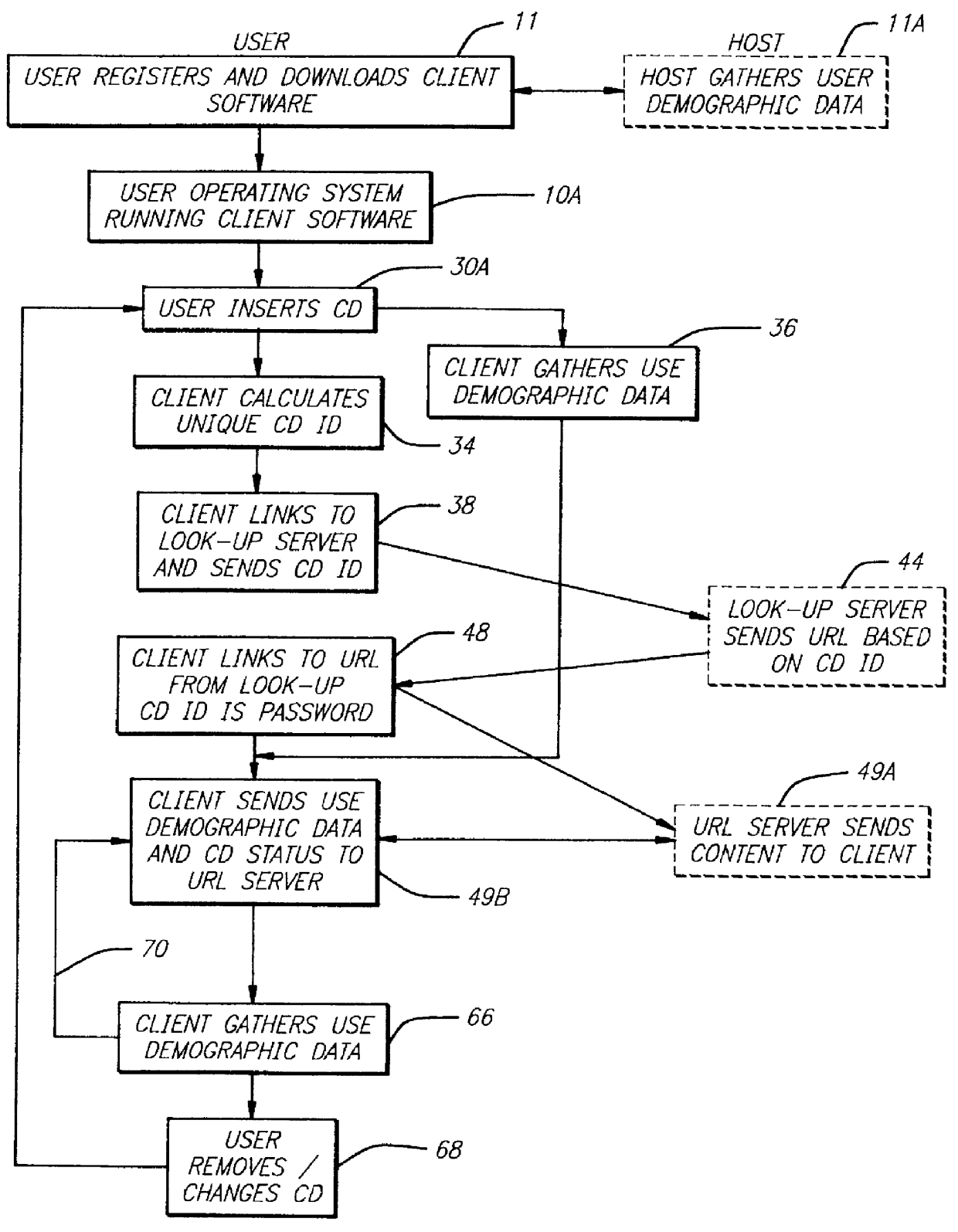
InactiveUS6061680A "chat roGood serviceDigital data processing detailsCoin-freed apparatusNetwork linkRemote computer
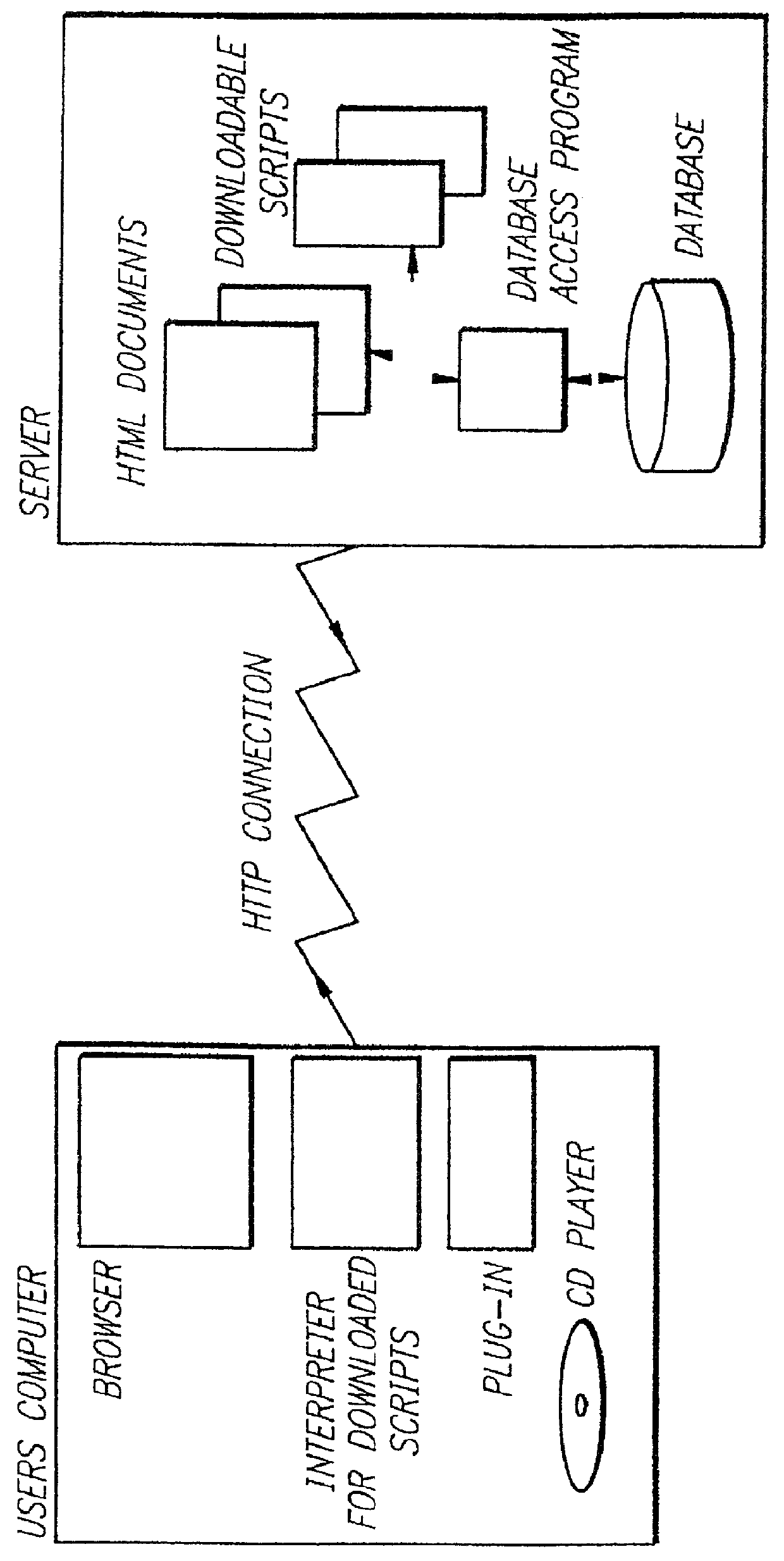
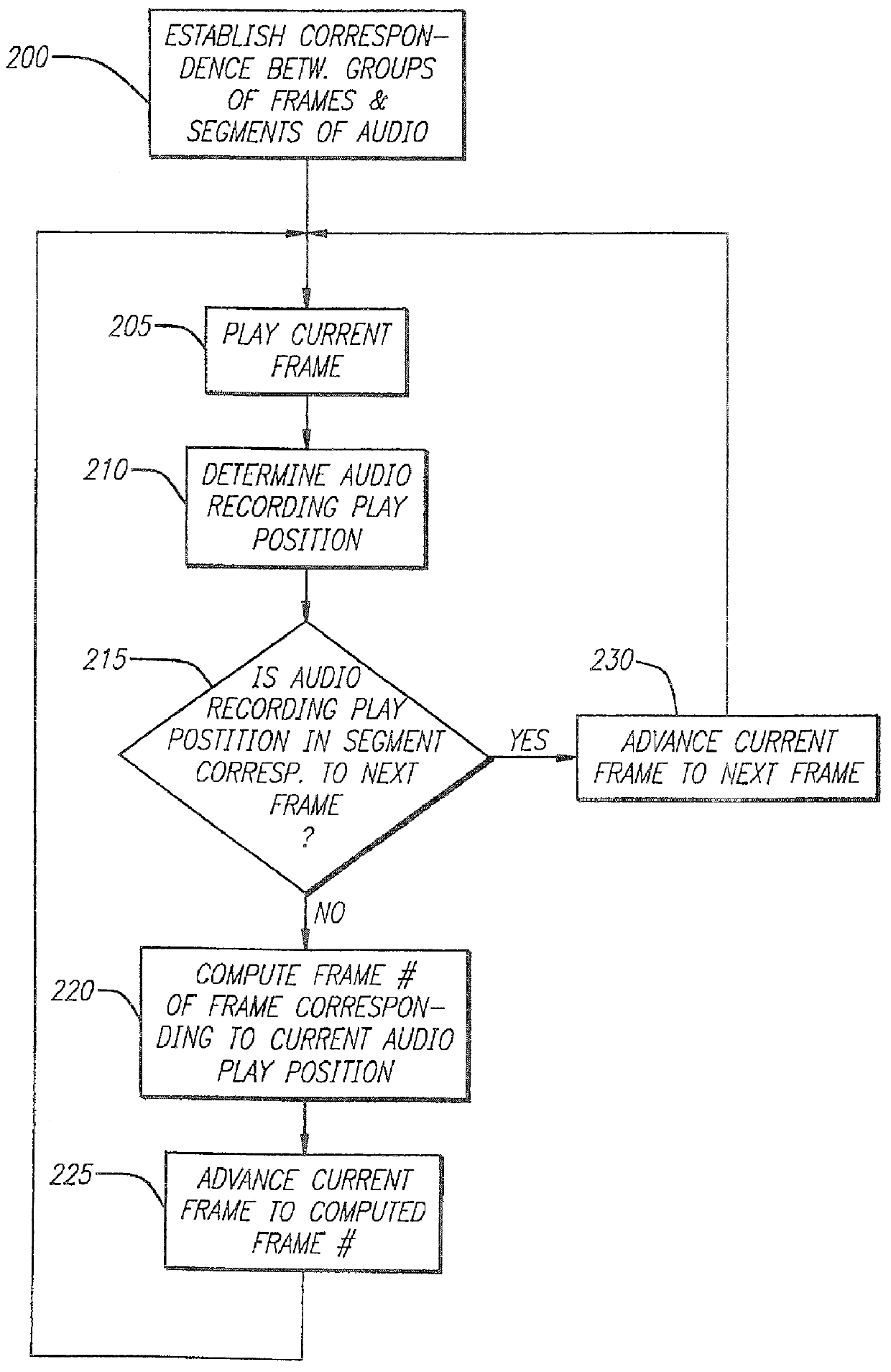
Entertainment content complementary to a musical recording is delivered to a user's computer by means of a computer network link. The user employs a browser to access the computer network. A plug-in for the browser is able to control an audio CD or other device for playing the musical recording. A script stored on the remote computer accessed over the network is downloaded. The script synchronizes the delivery of the complementary entertainment content with the play of the musical recording.
Owner:GRACENOTE
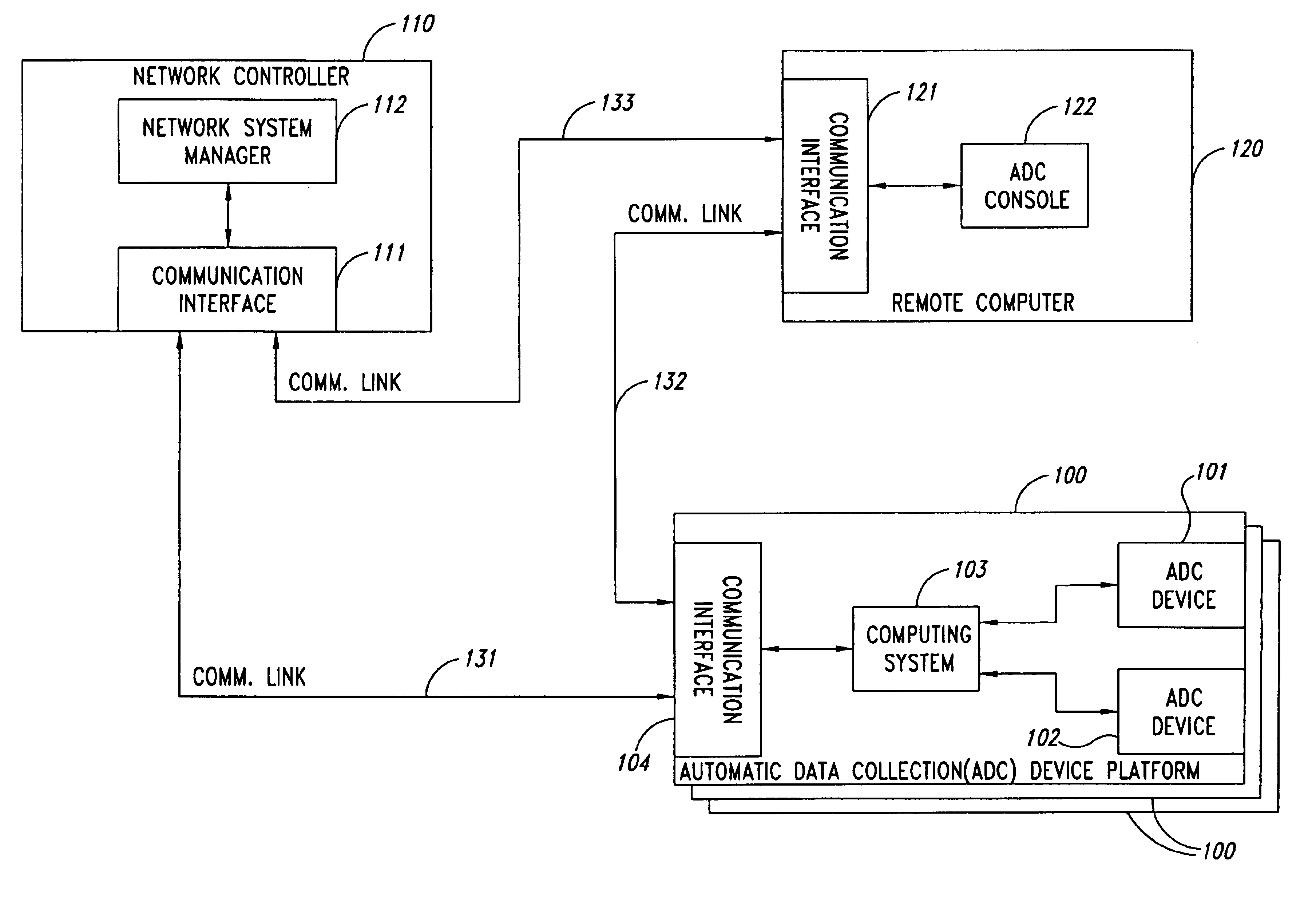
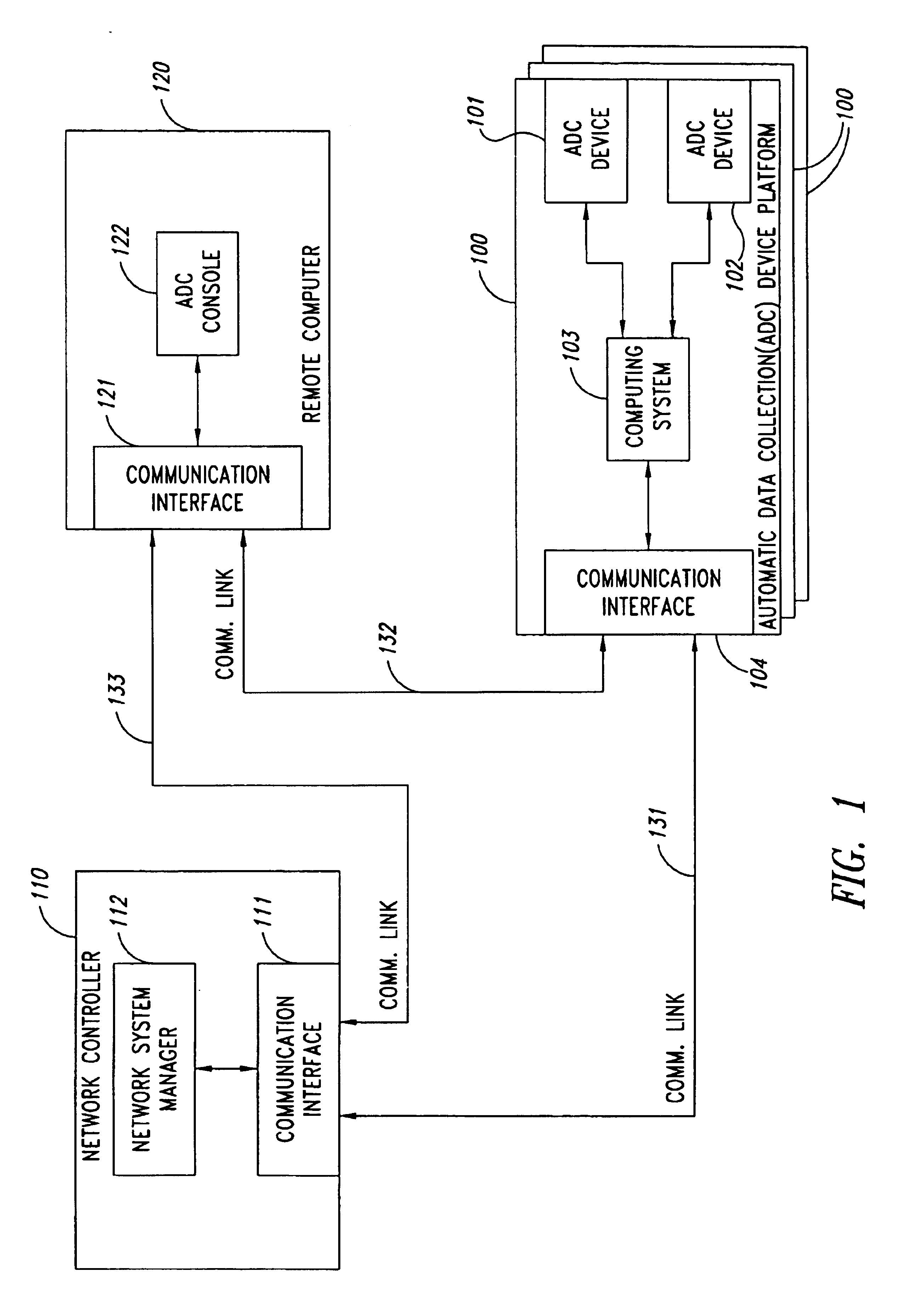
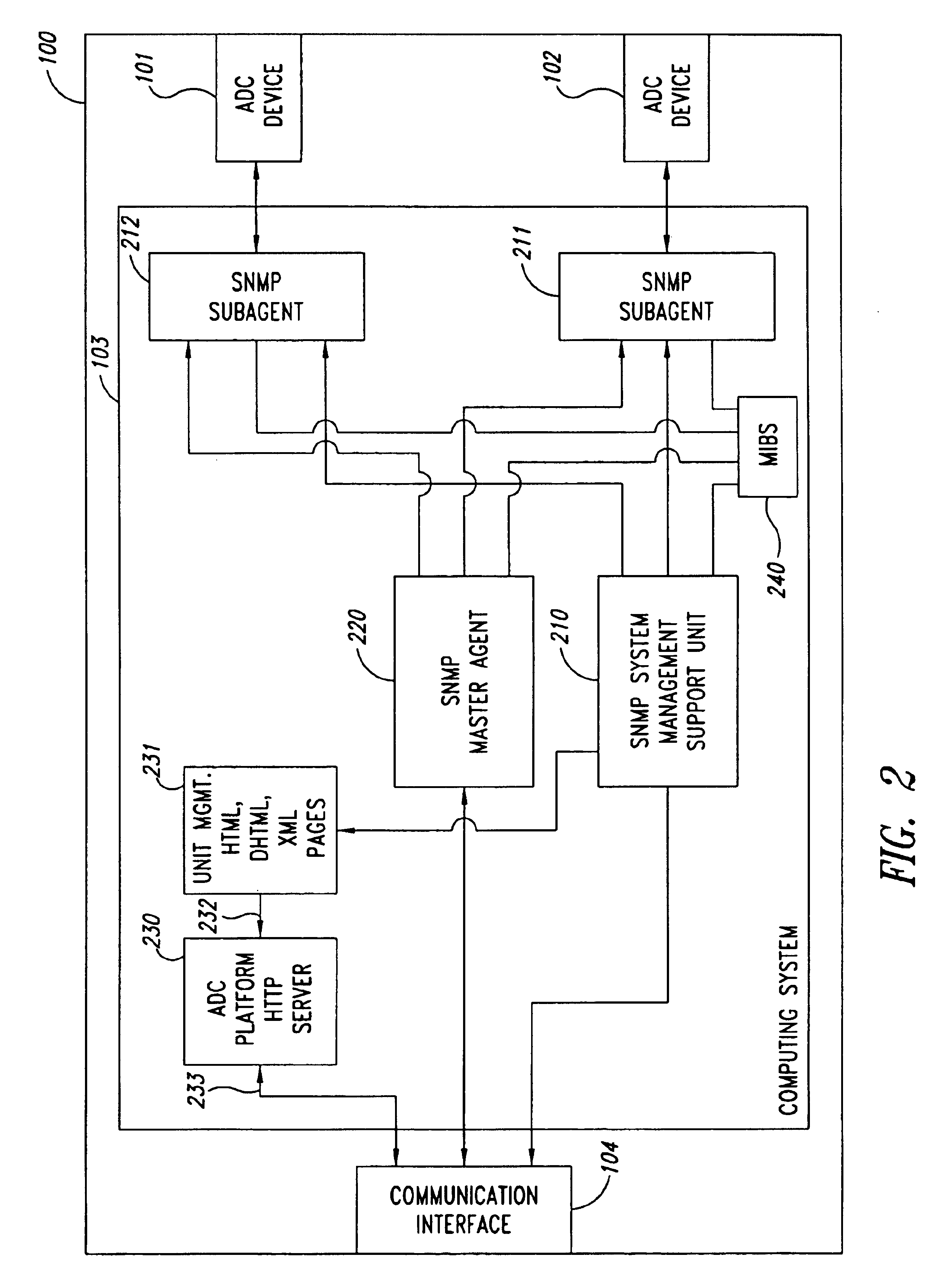
Remote anomaly diagnosis and reconfiguration of an automatic data collection device platform over a telecommunications network
InactiveUS6857013B2Detecting faulty hardware by remote testDigital computer detailsTelecommunications linkExtensible markup
Owner:INTERMEC IP CORP
Network delivery of interactive entertainment complementing audio recordings
InactiveUS6154773A "chat roGood serviceCoin-freed apparatusBroadcast transmission systemsNetwork linkRemote computer
Owner:GRACENOTE
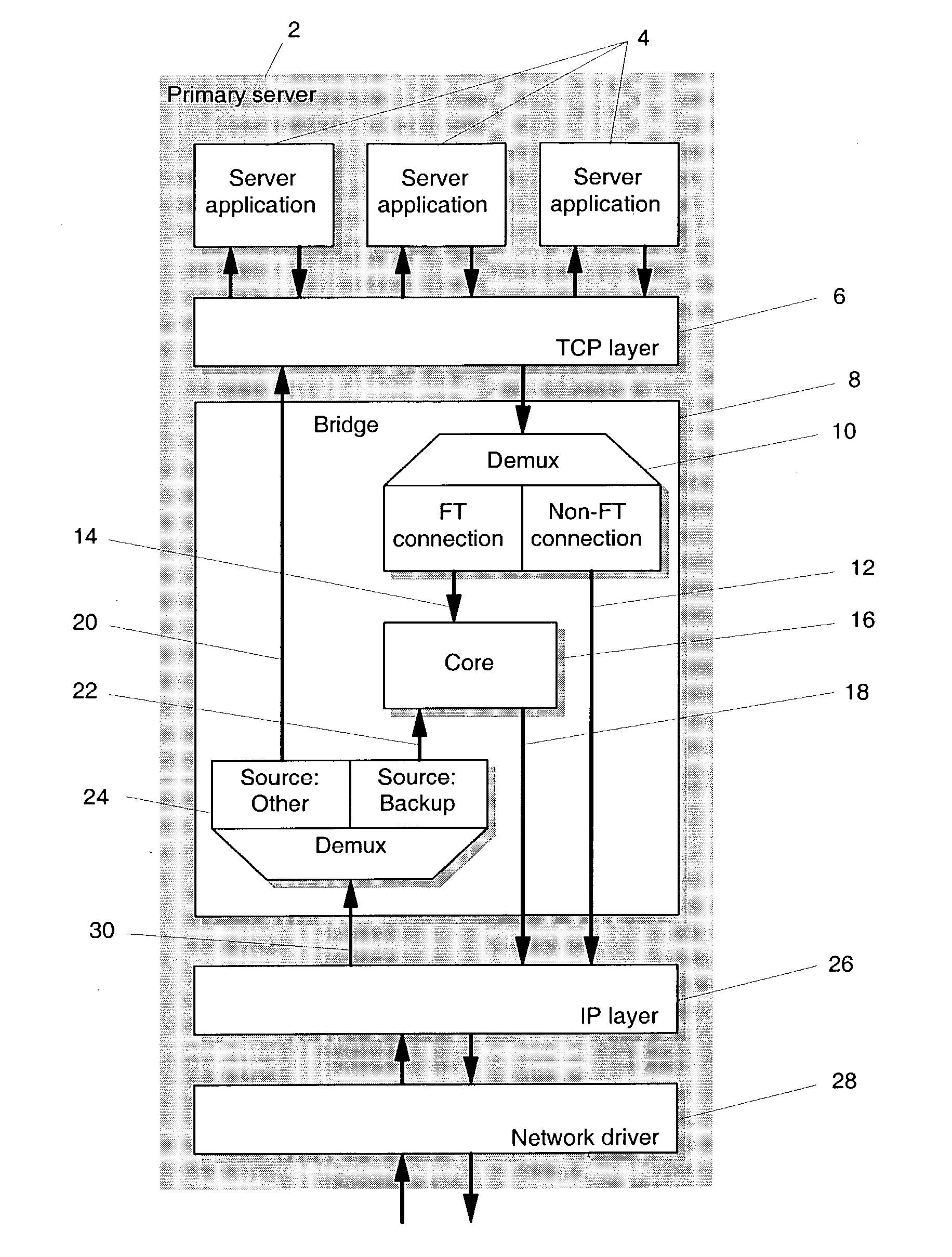
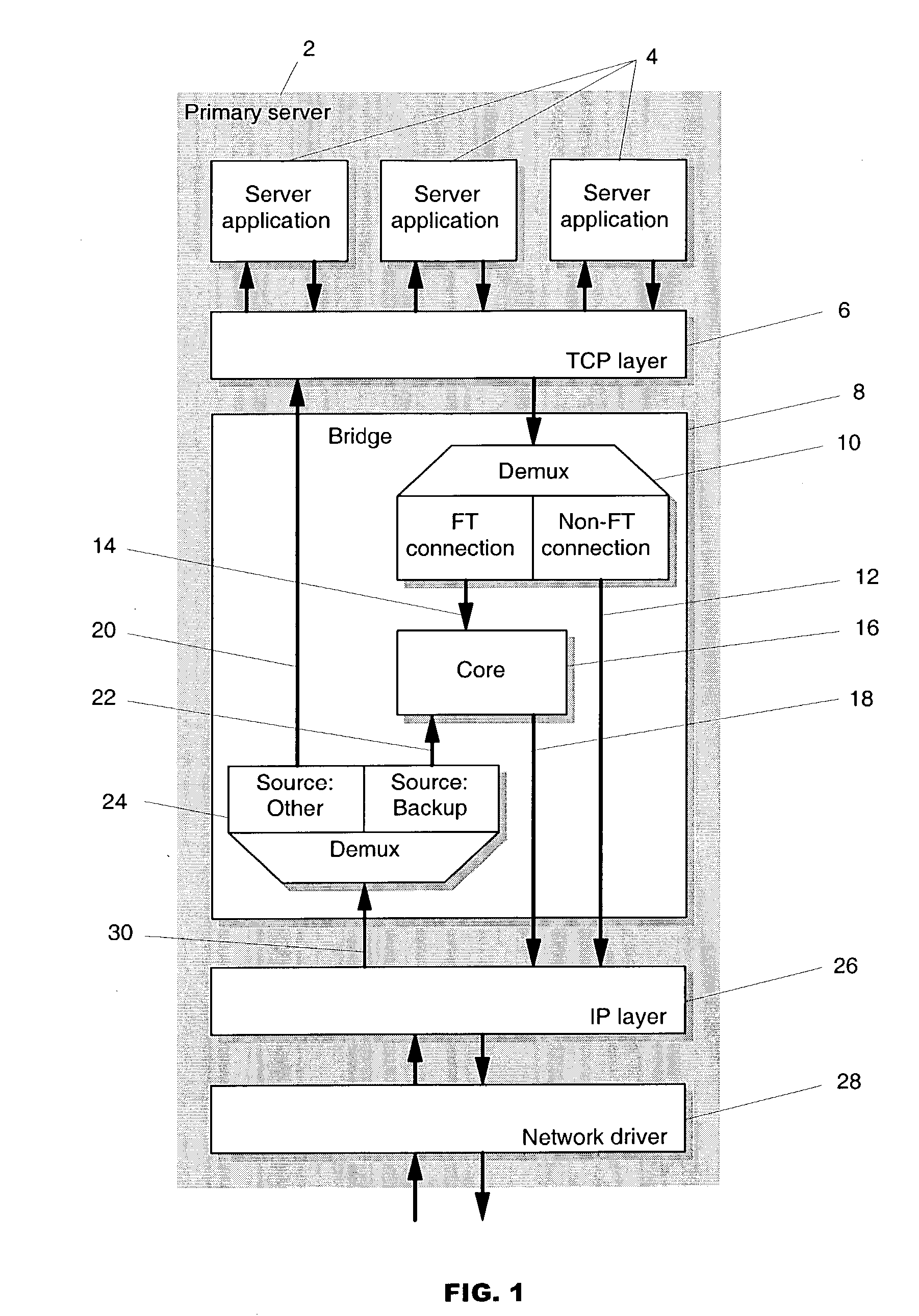
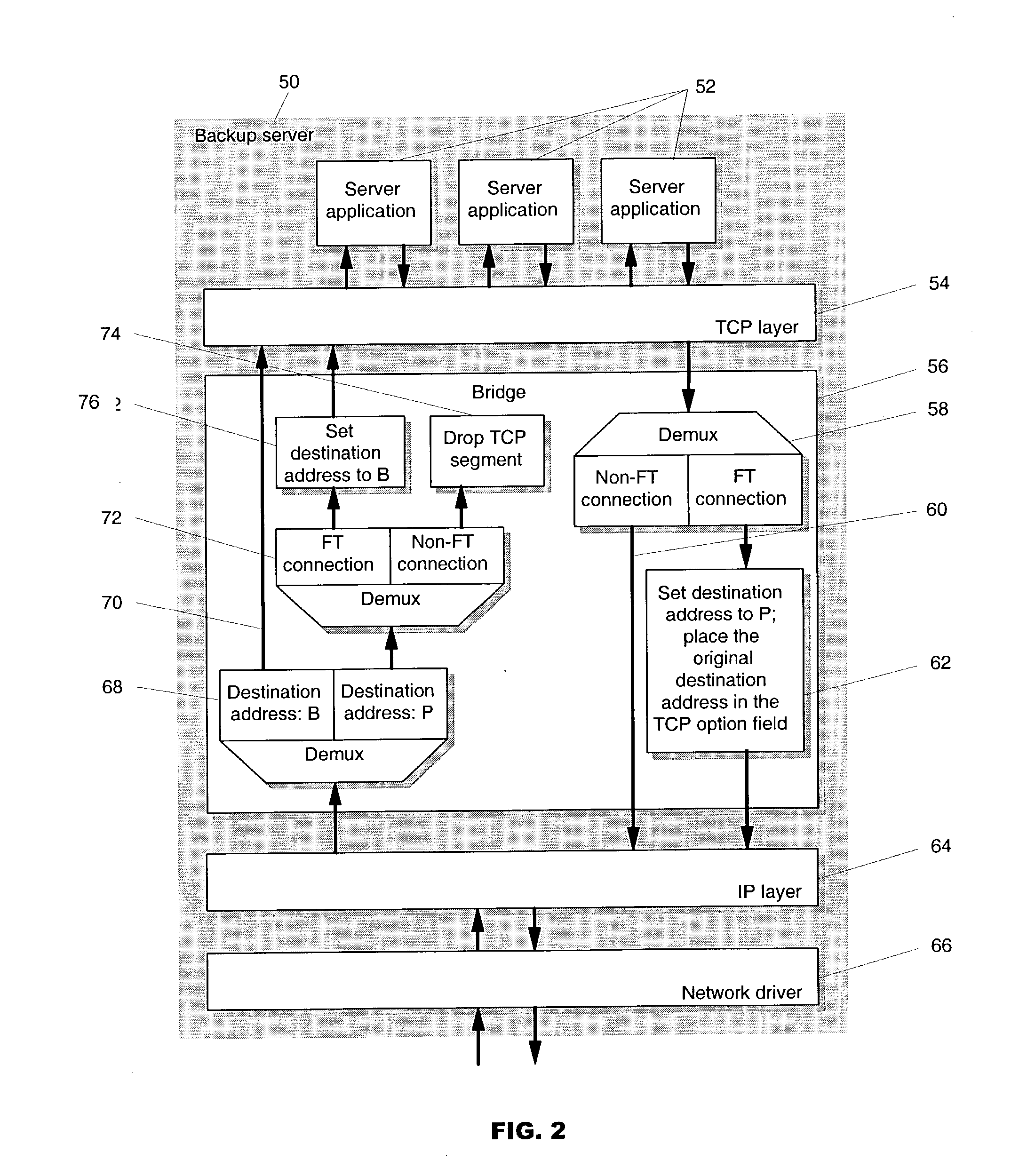
Transparent TCP connection failover
ActiveUS20040268175A1Emergency protective arrangements for automatic disconnectionTransmissionFailoverSemi active
Methods of transparent connection failover allowing a remote computer (i.e., a client), to continue to use a network connection to communicate with one of at least two or more other computers (i.e., the backup servers) over a network, when one of the other computers (i.e., the primary server) fails. With the mechanisms of this invention, there is no need for the client to establish a new connection to a backup server when the primary server fails. The failover is preferably executed within a bridge layer between the TCP layer and the IP layer of the server's TCP / IP stack. No modifications are required to the network infrastructure, the client's TCP / IP stack, the client application or the server application. The methods support active or semi-active replication of the server application, and do not require rollback of the application during failover. The invention also provides mechanisms for bringing up new backup servers.
Owner:SALESFORCE COM INC
Doorbell chime systems and methods
Doorbell systems can include a doorbell, a chime, and a remote computing device. In some embodiments, the remote computing device can select a sound. A data file comprising information that represents the sound can be sent to the doorbell that is communicatively coupled to the remote computing device. The doorbell can send the data file to the chime that is communicatively coupled to the doorbell and remotely located with respect to the doorbell.
Owner:SKYBELL TECH IP LLC
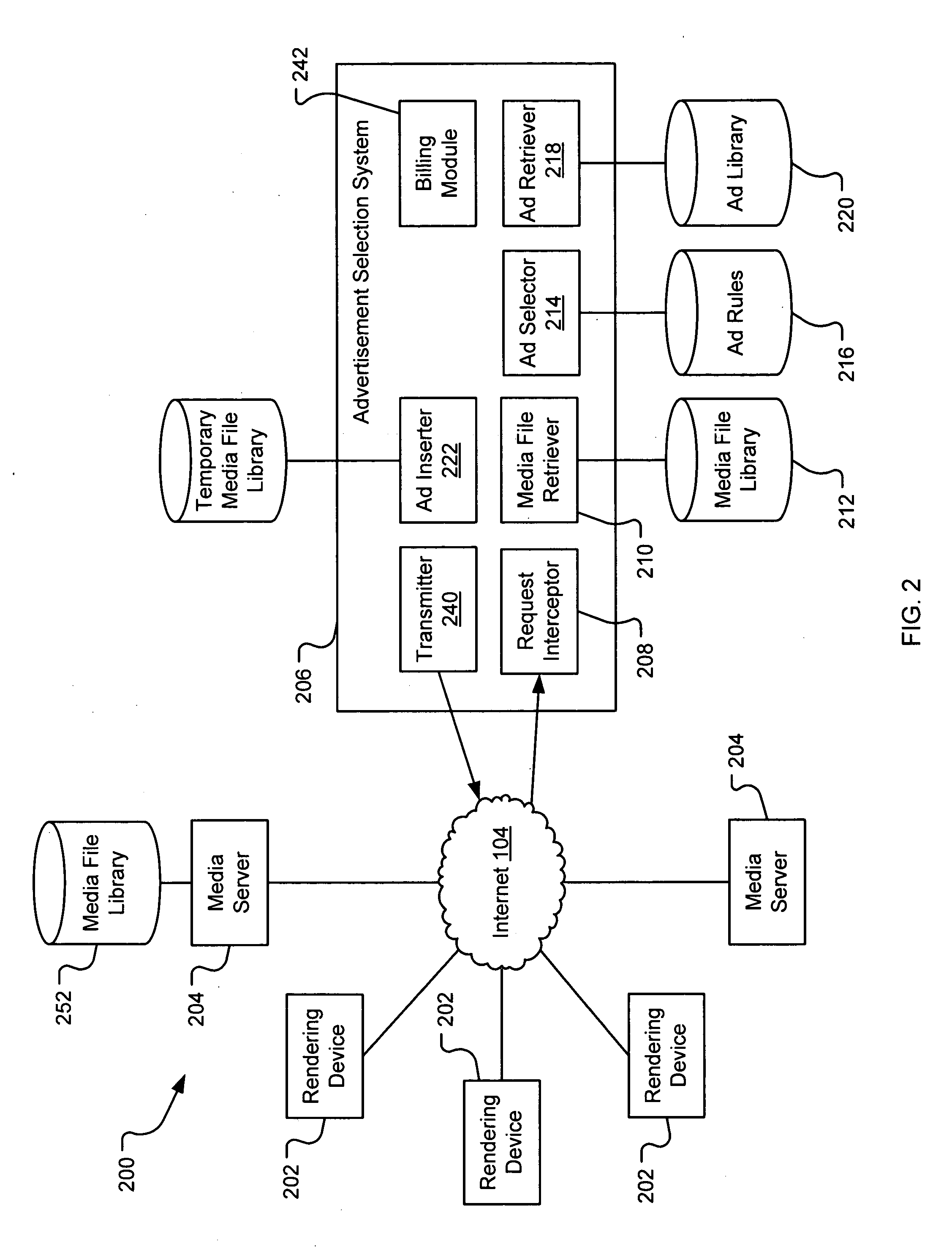
Automatically matching advertisements to media files
The present invention relates to a system and method for selecting advertisement for delivery over a network in response to requests received from remote computing devices. In one aspect, the present invention includes a method and system for automatically matching an advertisement with a media file, such as a podcast episode, when the media file has been requested by a consumer. Aspects of the present invention allow for automatic selection of advertisements after the creation of the media file, potentially without any interaction between the creator and the advertiser.
Owner:OATH INC
Doorbell diagnostics
ActiveUS9172920B1Reduce the impactReduce electrical effectPower network operation systems integrationColor television detailsDoorbellEngineering
A doorbell can be configured to wirelessly communicate with a remote computing device. In some cases, components that enable the doorbell to wirelessly communicate with the remote computing device could make the doorbell incompatible with certain types of chimes. In some embodiments, the doorbell is configured to diagnose chime compatibility issues.
Owner:SKYBELL TECH IP LLC
Monitoring systems and methods
ActiveUS9769435B2Television system detailsCharacter and pattern recognitionEngineeringComputer science
Cameras can be used to detect if a visitor enters a field of view. Cameras can be mounted in many different areas, including outside buildings, inside buildings, and near other items such as pools. Cameras can send alerts to remote computing devices regarding visitors. Thus, a user of a camera can see and even speak with visitors who are located far away from the user.
Owner:SKYBELL TECH IP LLC
Light socket cameras
InactiveUS9165444B2Television system detailsColor television detailsComputer graphics (images)Remote computing
Owner:SKYBELL TECH IP LLC
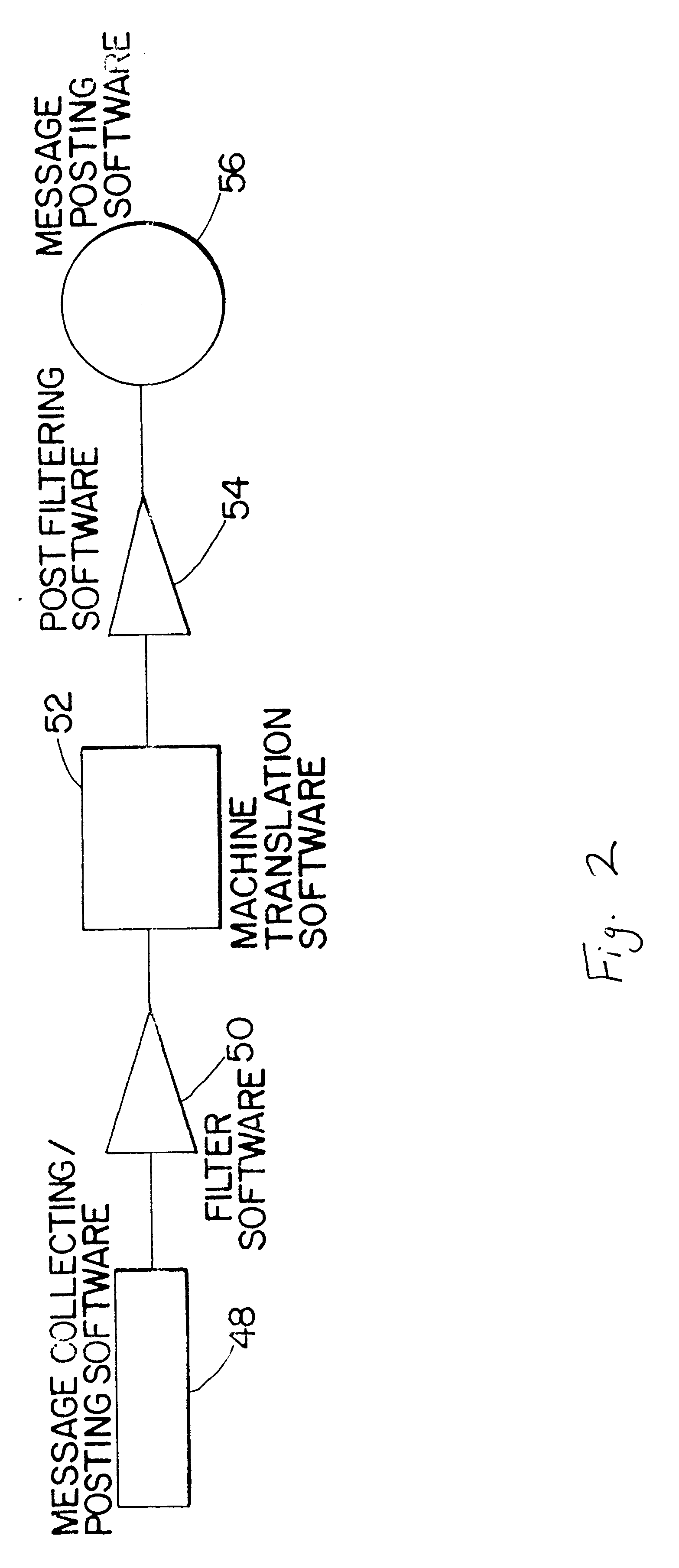
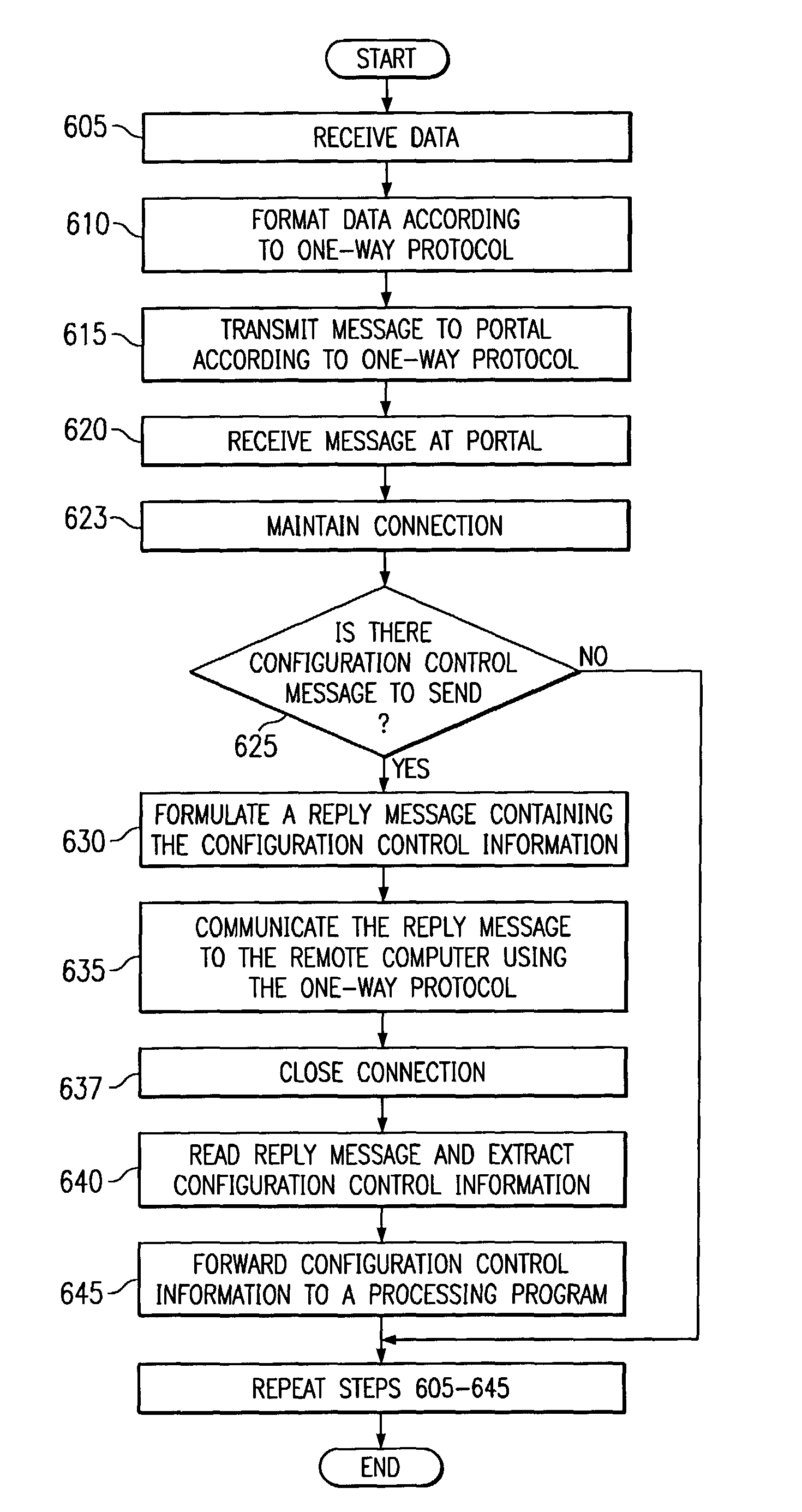
System and method for secure communications with a remote software program
ActiveUS7877783B1Communication securityAmount of timeDigital data processing detailsData switching networksSecure communicationLeased line
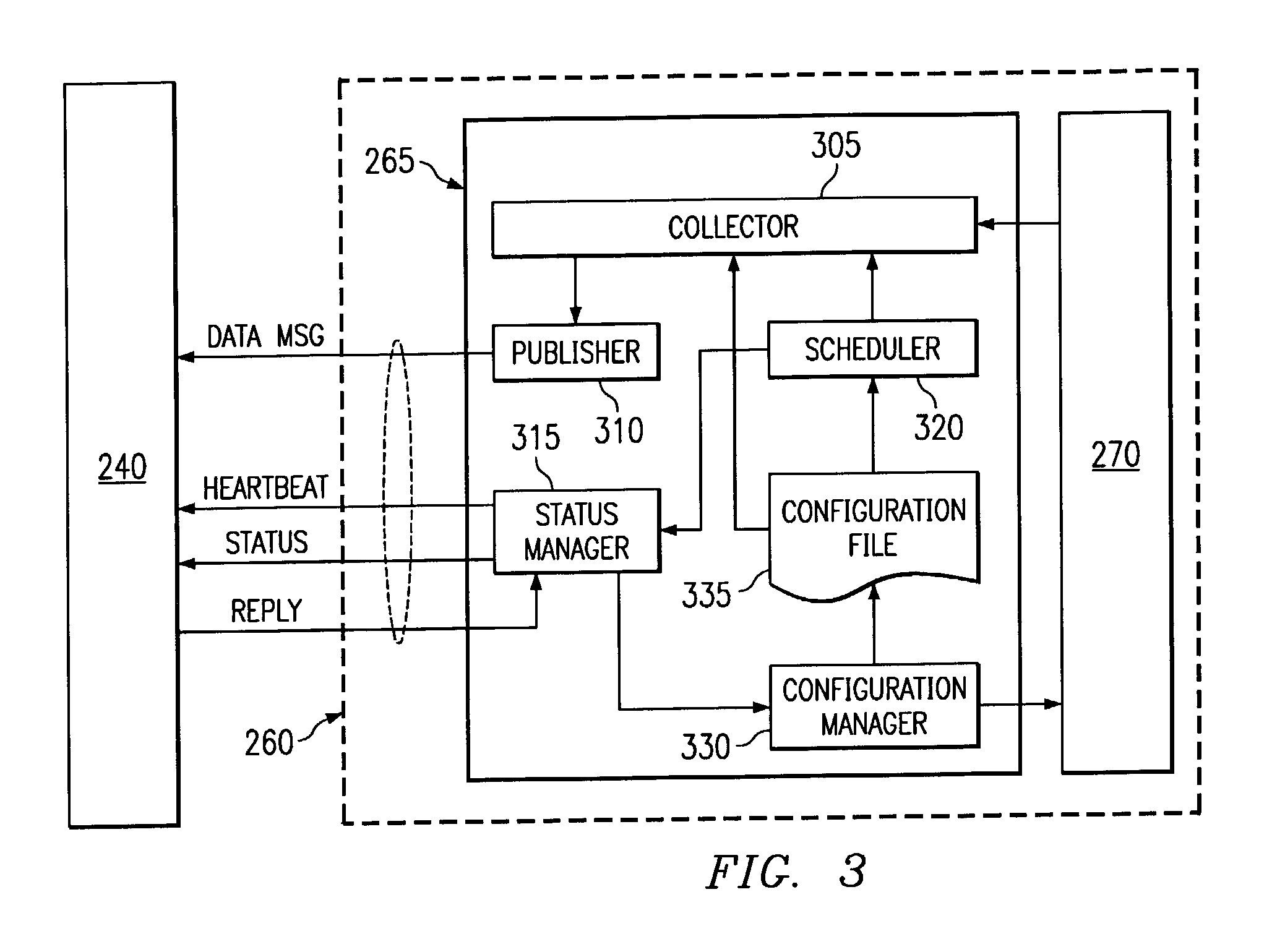
In one embodiment of the present invention, a messaging program at a remote computer can send a first message to a portal computer according to a one-way protocol such as HTTP. A portal program at the portal computer can receive the first message and determine if information should be sent to the portal computer. If so, the portal computer can generate a reply message that includes the information and send the reply message to remote computer on the same connection over which the first message was received. In this manner, the portal computer can send configuration control information and other information to the messaging program without requiring leased lines, dial-up connections or a VPN. Moreover, since the communication according to the one-way protocol was initiated at the remote computer, a firewall will allow the remote computer to receive the reply message.
Owner:BMC SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com