Patents
Literature
36results about How to "Limited data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Managed peer-to-peer applications, systems and methods for distributed data access and storage
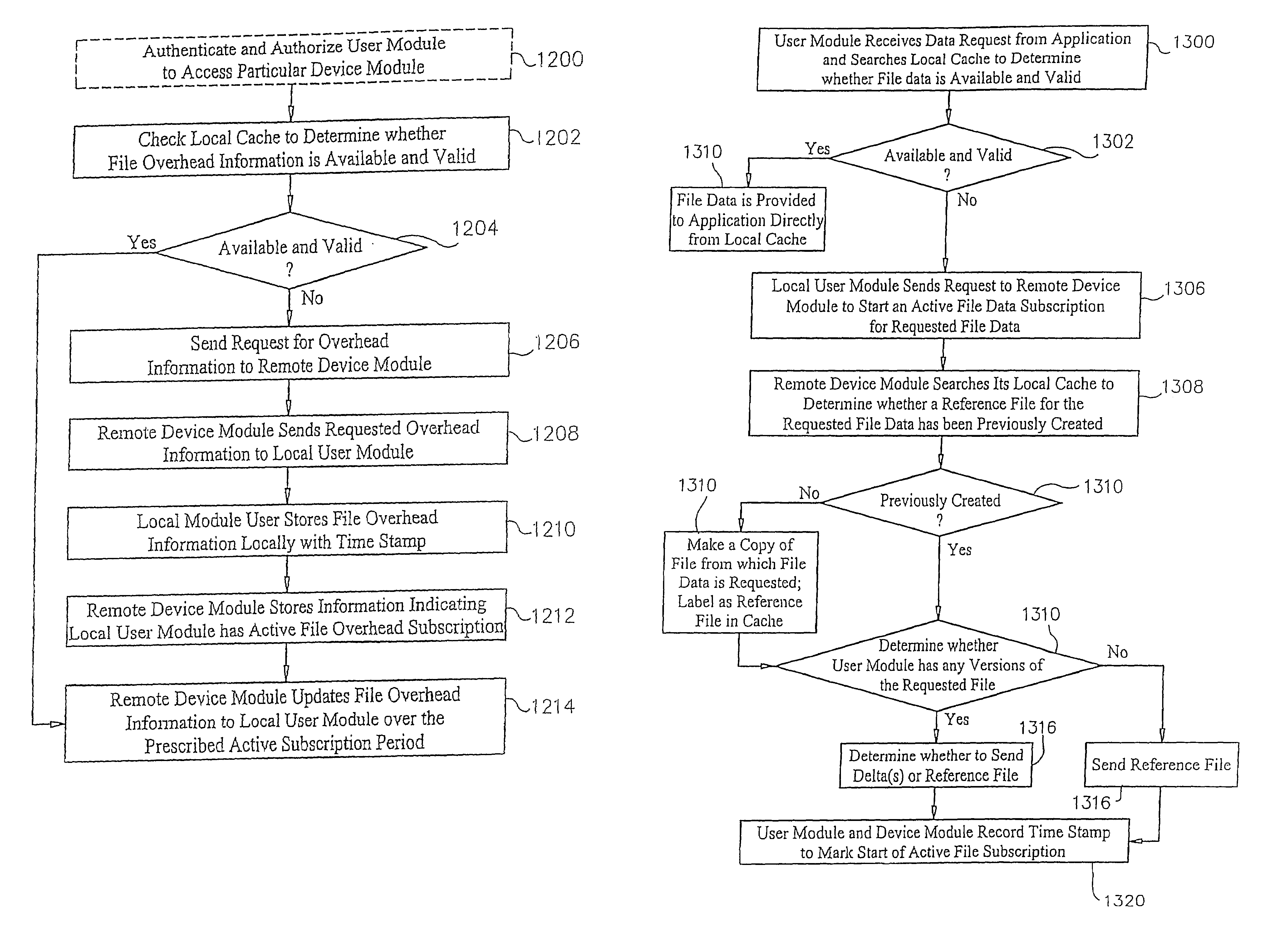
InactiveUS7546353B2Reduce bandwidth requirementsLimited dataDigital data processing detailsUser identity/authority verificationNetwork connectionData access
Applications, systems and methods for efficiently accessing data and controlling storage devices among multiple computers connected by a network. Upon receiving a request for access to data originally stored in a remote storage device, determining whether the data is already available and valid in a local storage device. Accessing the data from the local storage device if the data is available and valid. Authenticating a request for a secure connection between a local computer associated with the local storage device and a remote computer associated with the remote storage device. Securely connecting the local computer with the remote computer. Requesting the data from the remote storage device, over the network, if the data is not locally available and valid. Receiving data over the network from the remote storage device, and storing the data in the local storage device for direct local access thereto.
Owner:WESTERN DIGITAL TECH INC
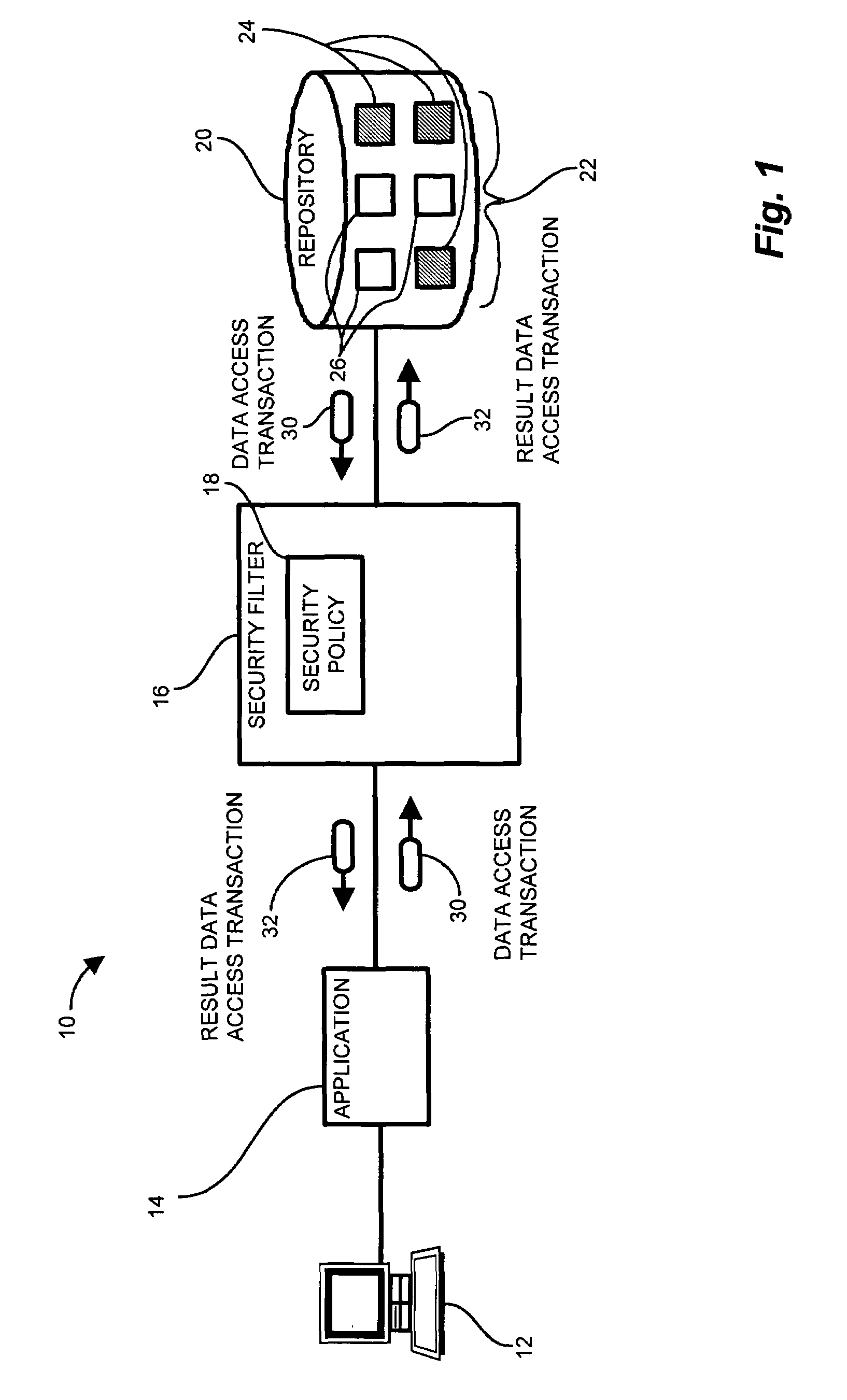
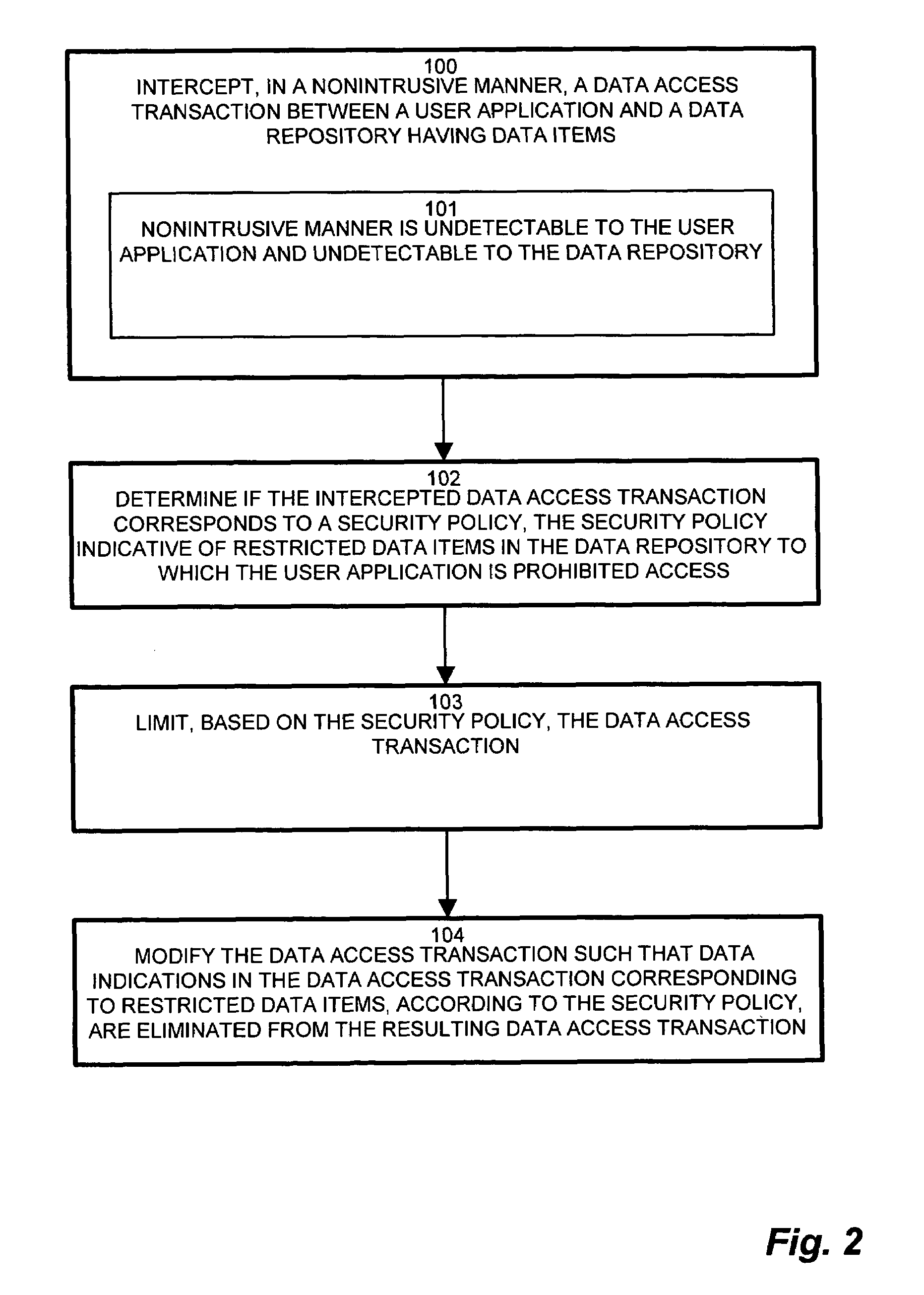
System and methods for nonintrusive database security
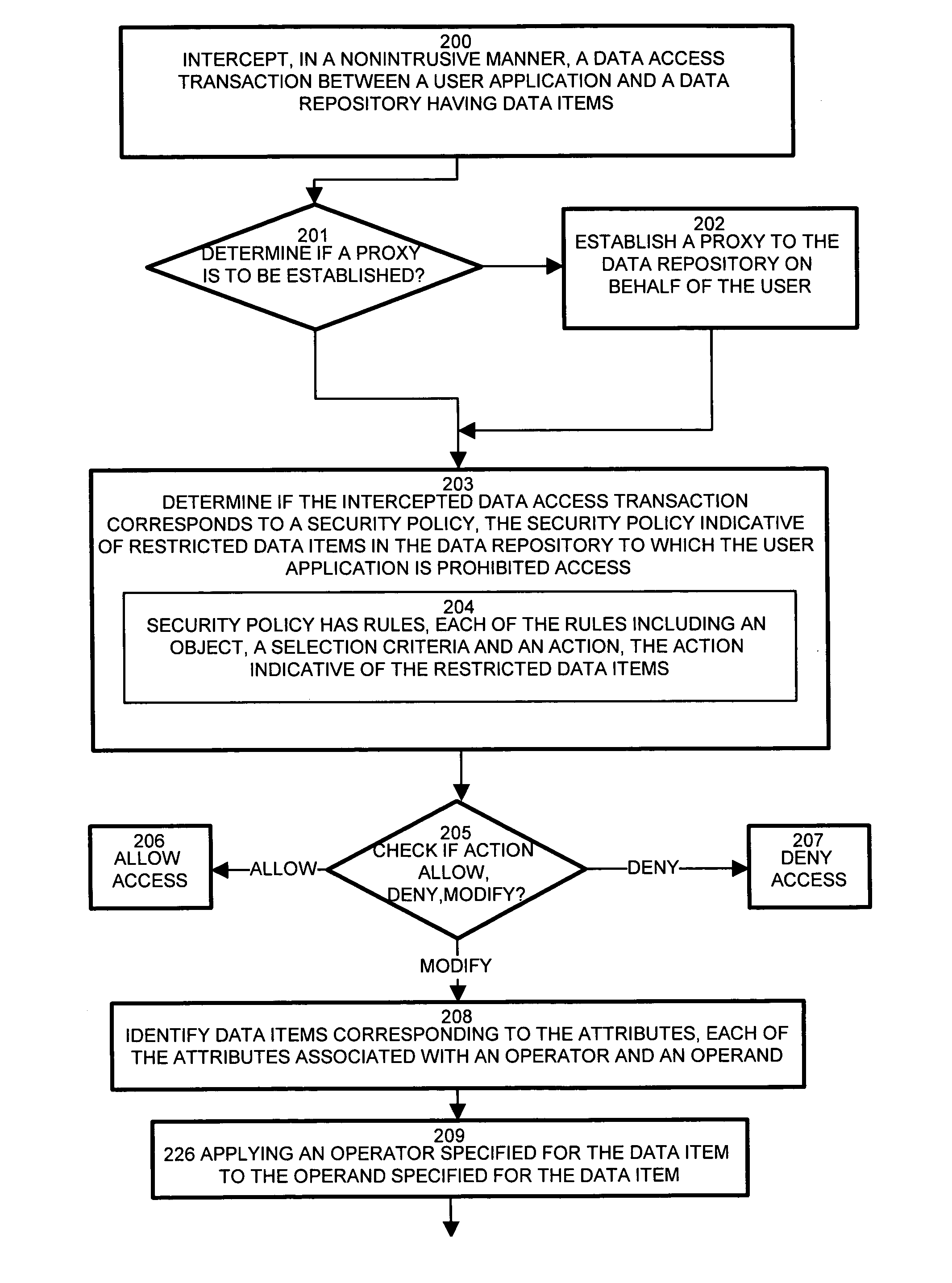
InactiveUS7437362B1Reduce the burden onOvercome deficienciesDigital data processing detailsComputer security arrangementsRelational databaseData access
Typical conventional database security scheme mechanisms are integrated in either the application or database. Maintenance of the security scheme, therefore, such as changes and modifications, impose changes to the application and / or database. Configurations of the invention employ a security filter for intercepting database streams, such as data access transactions, between an application and the a data repository, such as a relational database. A security filter deployed between the application and database inspects the stream of transactions between the application and the database. The security filter, by nonintrusively interrogating the transactions, provides a content-aware capability for seamlessly and nondestructively enforcing data level security. A security policy, codifying security requirements for the users and table of the database, employs rules concerning restricted data items. The filter intercepts transactions and determines if the transaction triggers rules of the security policy. If the transactions contain restricted data items, the security filter modifies the transaction to eliminate the restricted data items.
Owner:IBM CORP
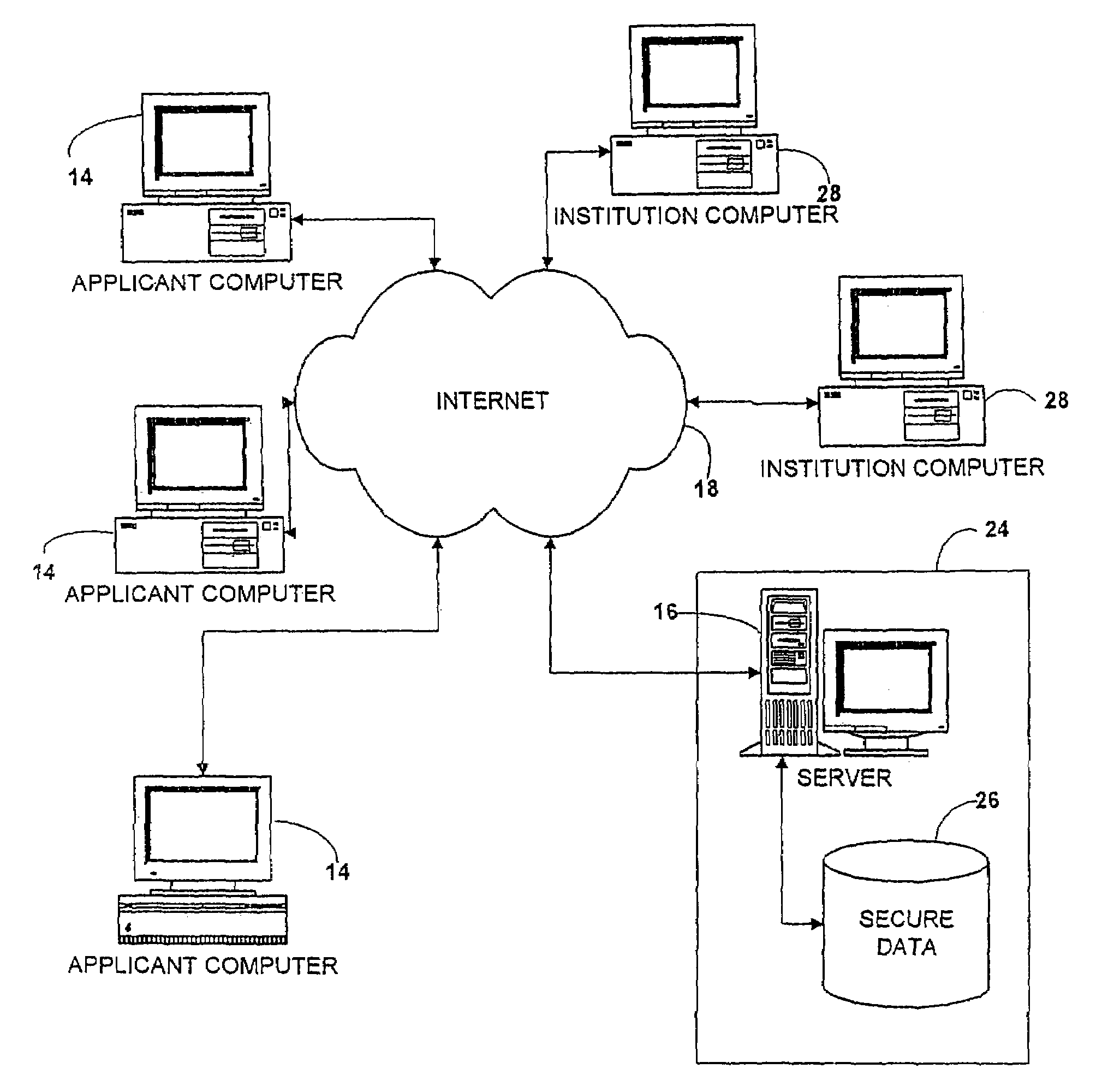
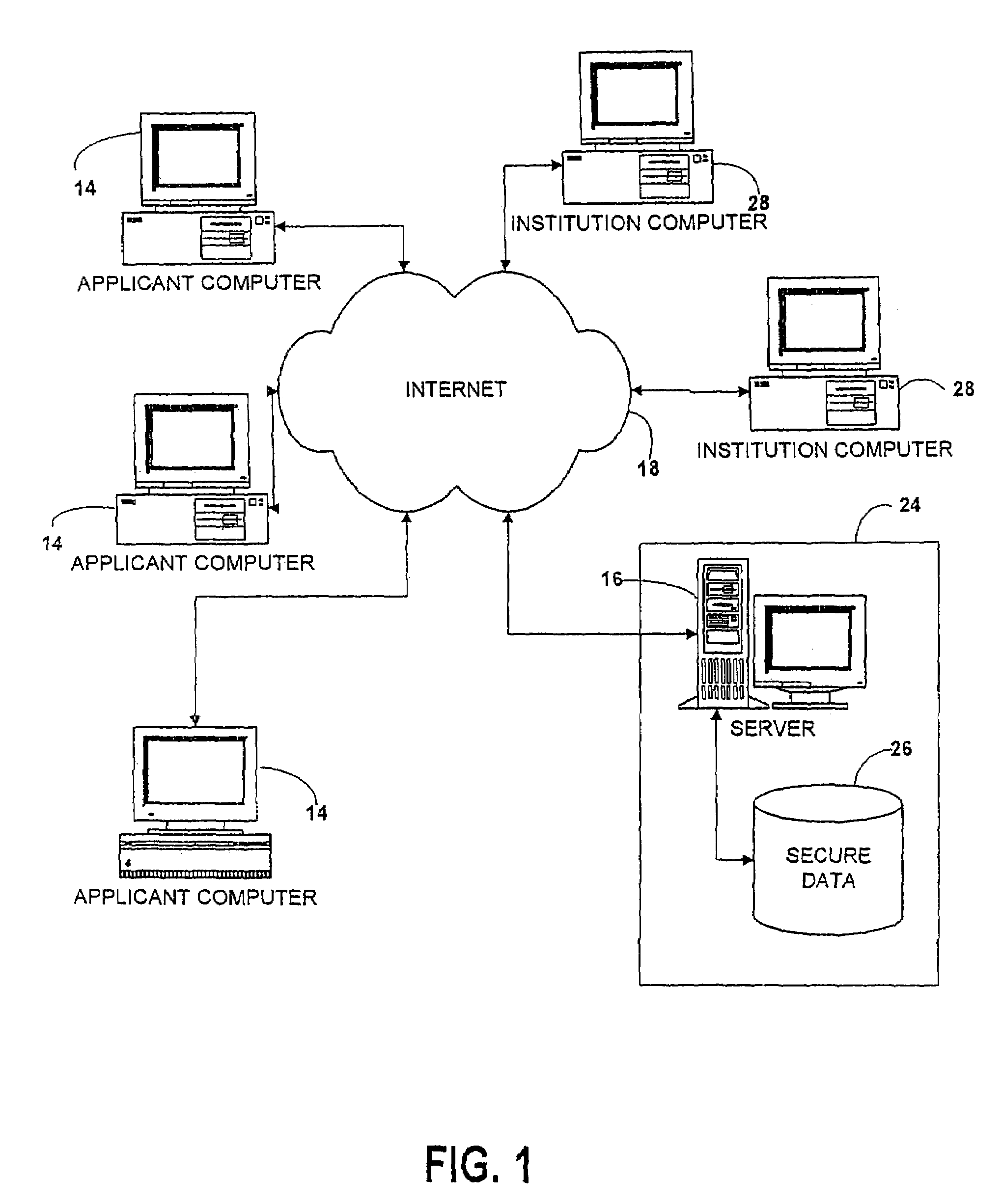
Universal forms engine
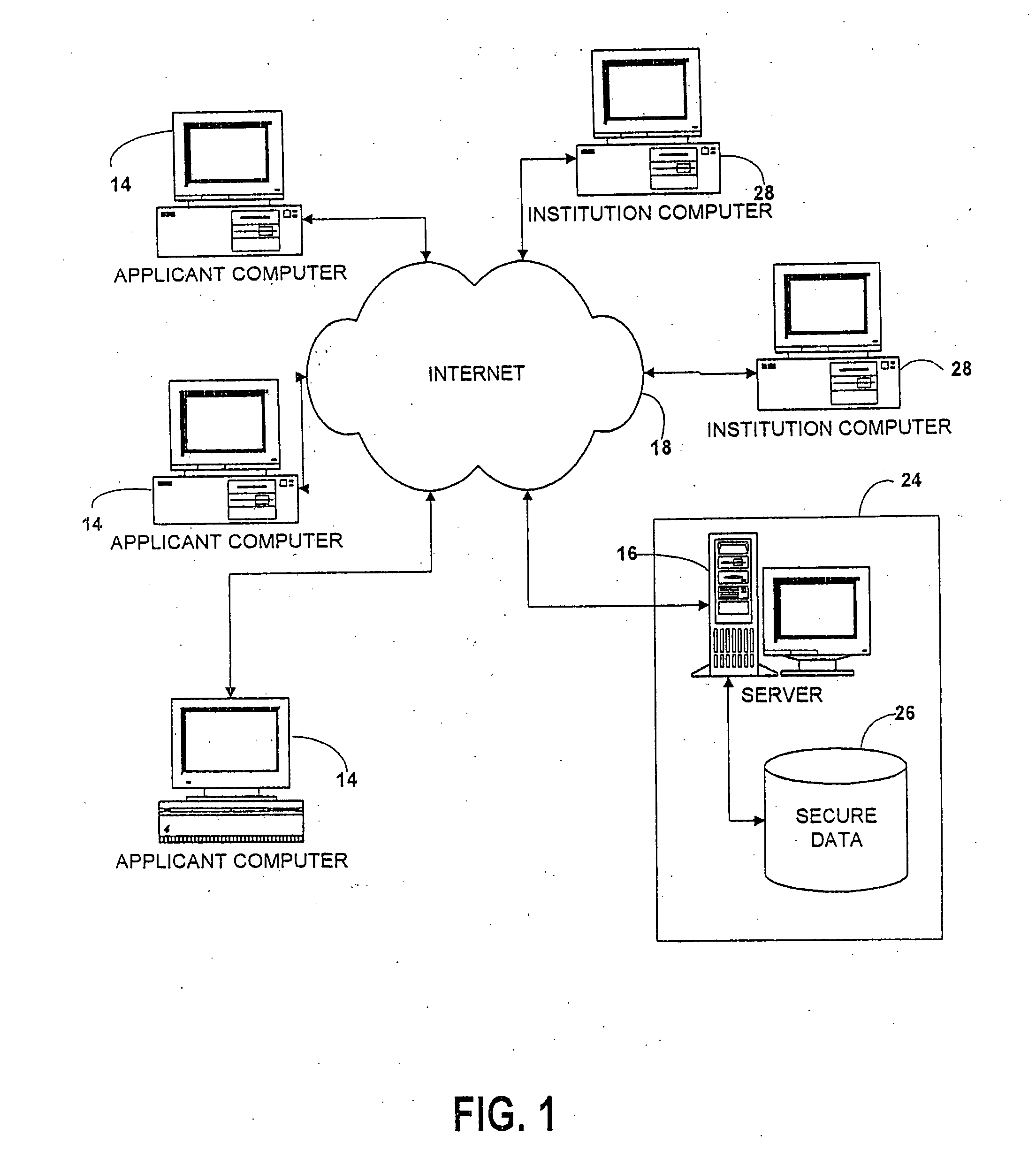
InactiveUS7376891B2Simple methodSpeed up the processData processing applicationsNatural language data processingData validationThird party
A forms engine allows data sharing between customizable on-line forms, such as college admissions applications. Before applying, an applicant opens an account with a third party application servicer. After the applicant completes an application for one institution, the data is saved in a data base and automatically populates fields in subsequent application forms. The form for each institution is created from a form description file. Each form is branded for its institution and forms for different institutions differ in appearance and content so that the presence of the third party servicer is transparent to the applicant.The system is extensible without programming, allowing new applicant attributes to be readily incorporated into the system and allowing the content and appearance of the application to be readily changed by changing the description file. The use of aliases for applicant attributes permits data to be readily shared between forms even though labeled and arranged differently on different forms. Information stored about each attribute allows the specification of data validation rules and data sharing and grouping rules, as well as dependency rules that permit application page content to depend on applicant's responses on a previous page.
Owner:COLLEGENET
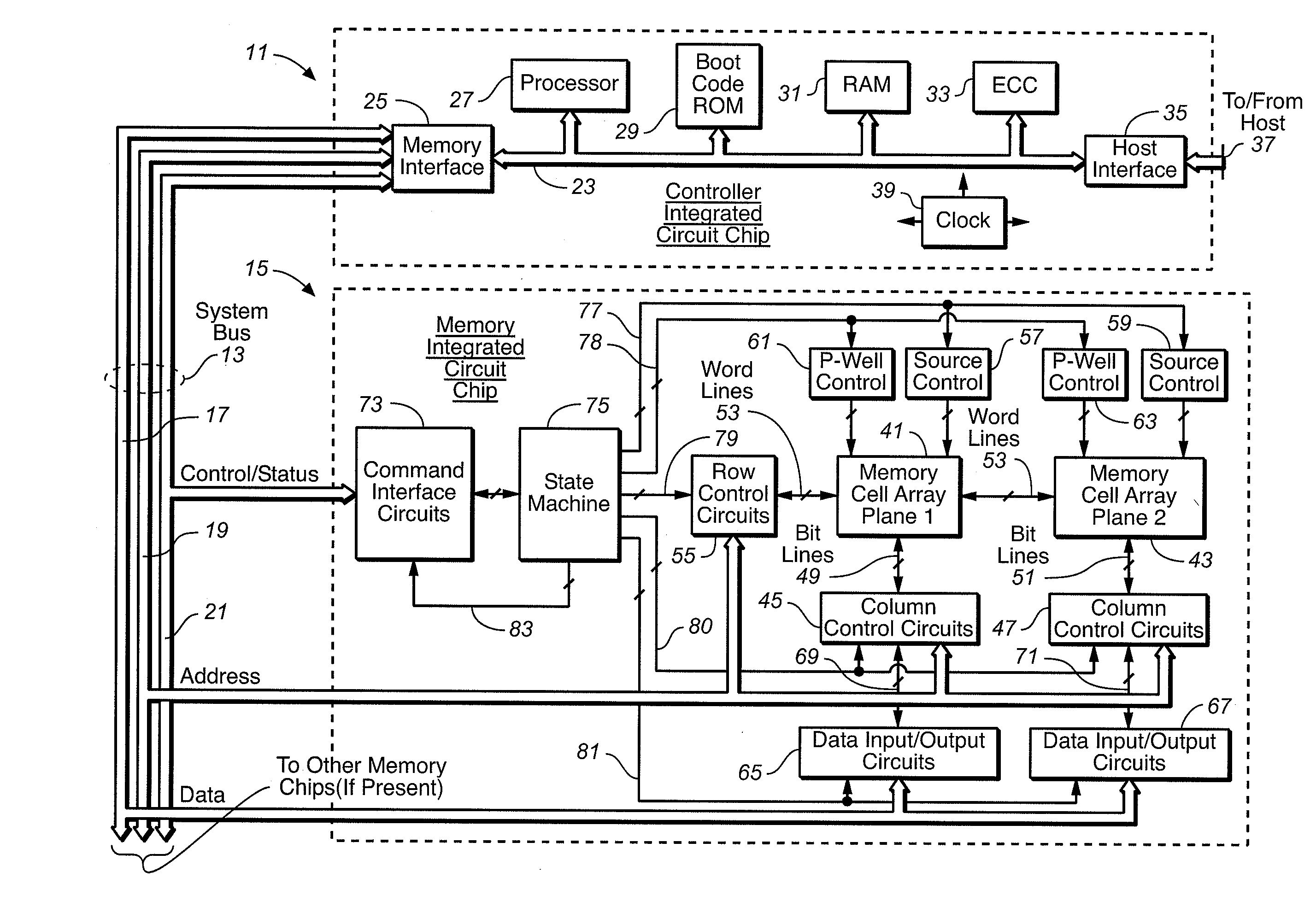
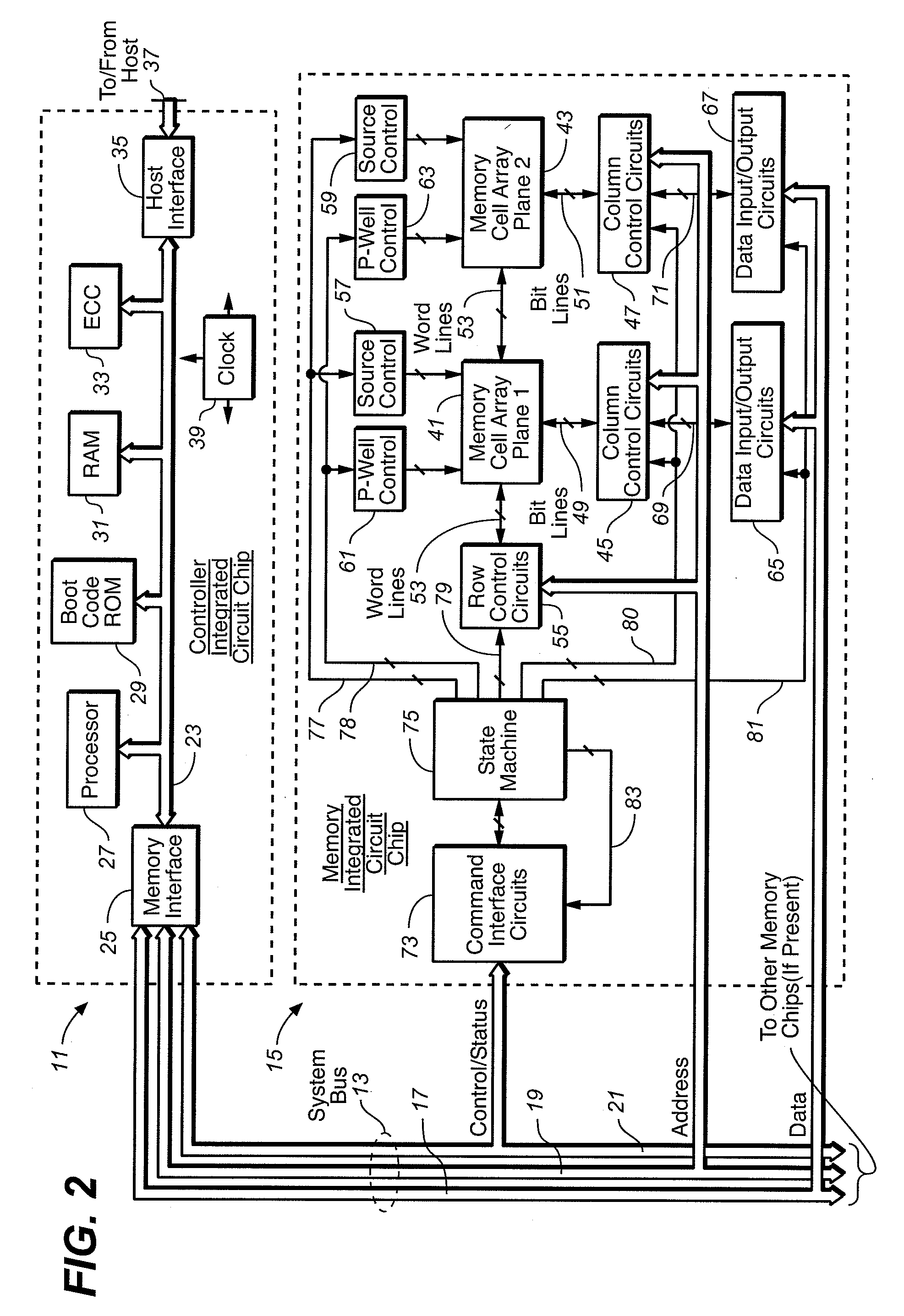
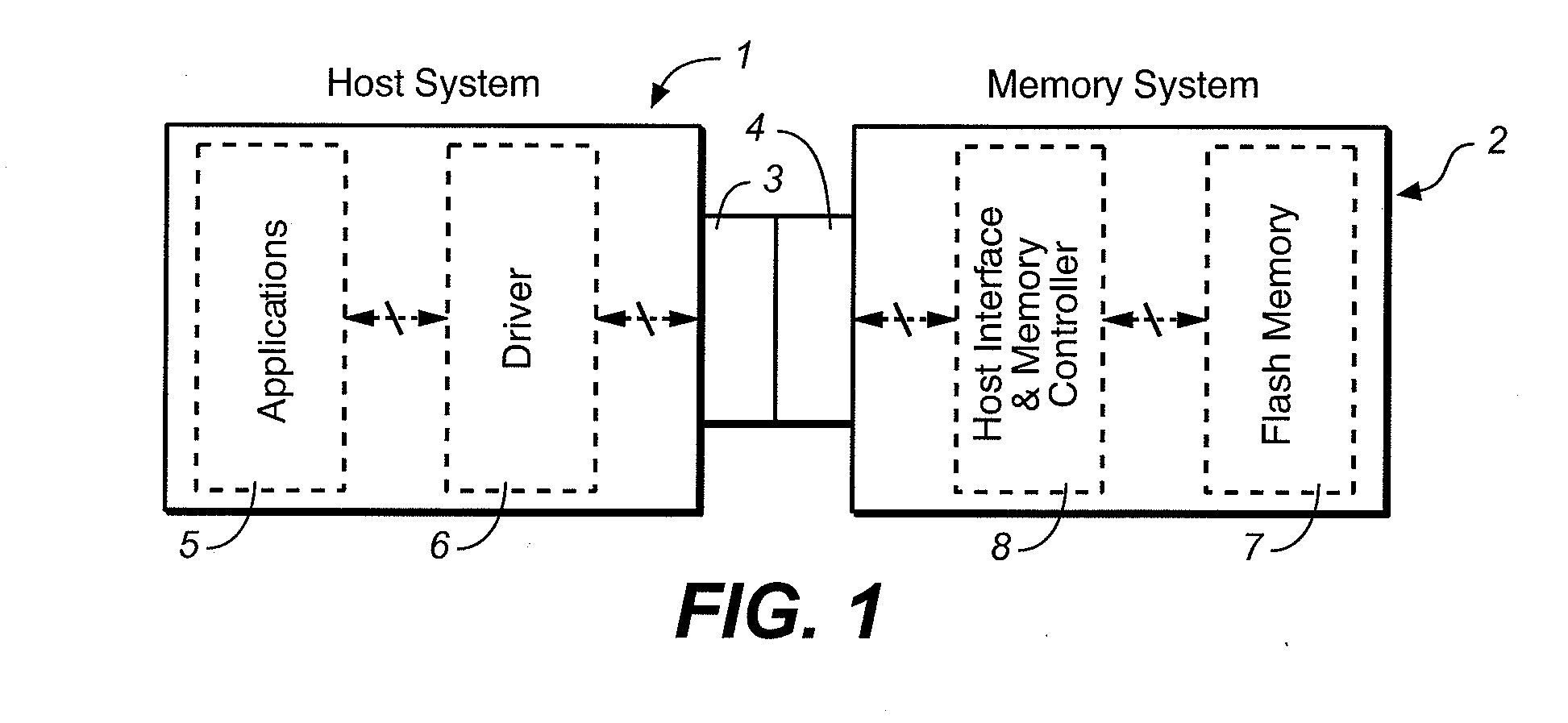
Host System That Manages a LBA Interface With Flash Memory
InactiveUS20080155175A1Minimized volumeImprove performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationData fileLogical address
Owner:SANDISK TECH LLC
Data communications
InactiveUS6996722B1Easy to detectImprove reliabilitySpecial service provision for substationKey distribution for secure communicationCommunications systemThe Internet
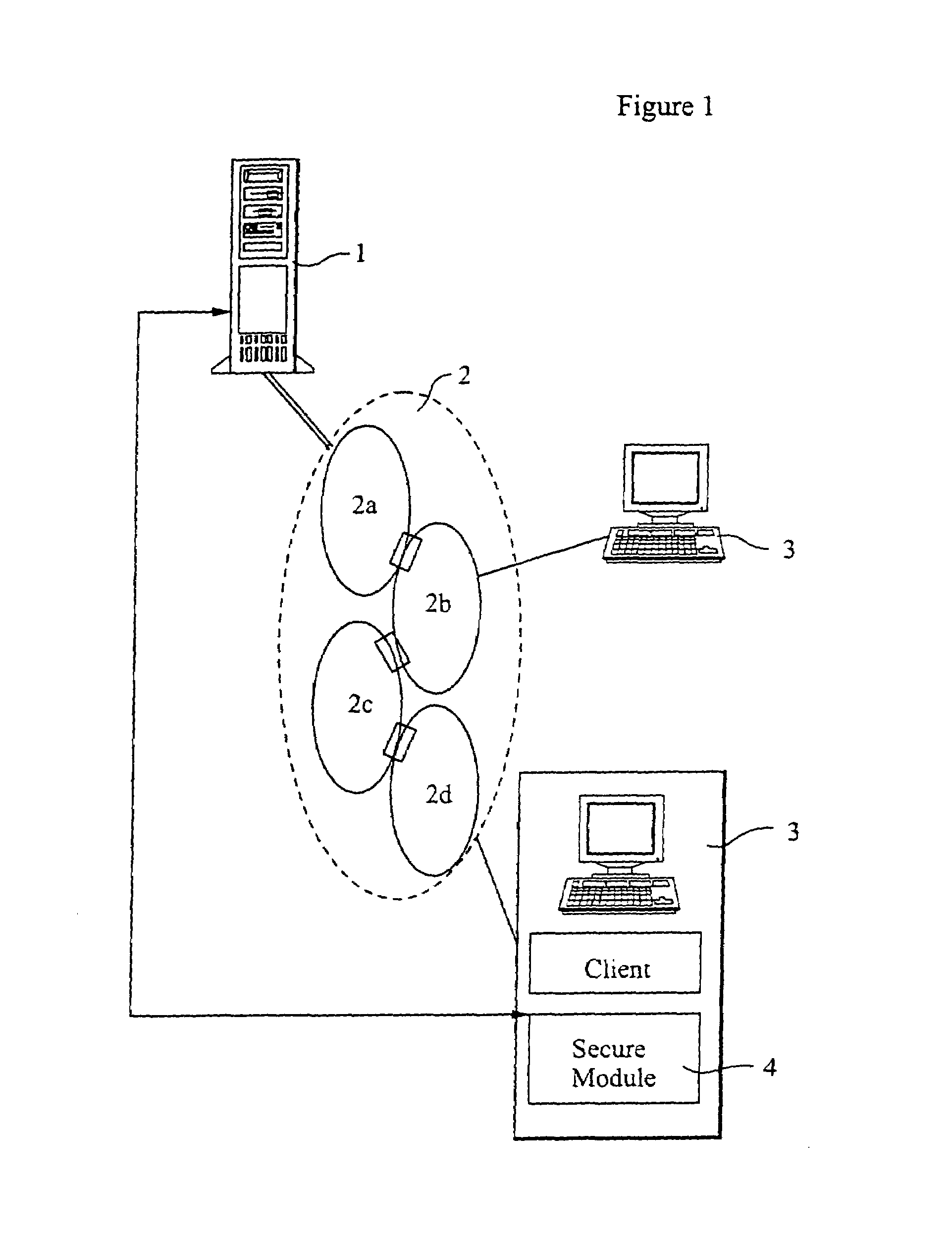
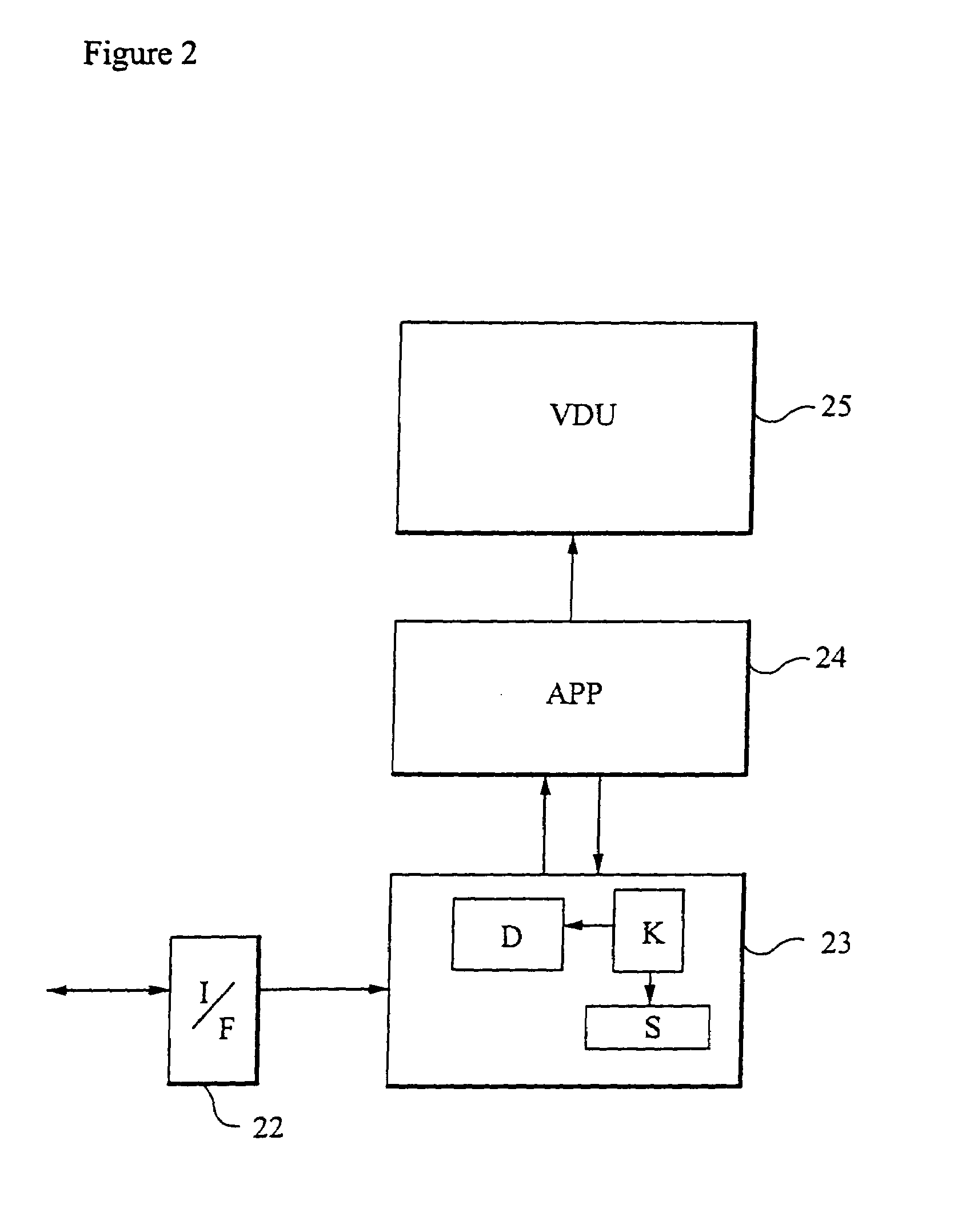
In a data communications system a remote data source outputs data as a series of application data units (ADUs). Each ADU is individually encrypted with a different key. The keys are transmitted (for example using Internet multicasting) via a communications network to one or more customer terminals. At the terminals a sequence of keys is generated for use in decrypting the ADUs. A record is kept of the keys generated, and this record may subsequently be used to generate a receipt for the data received by the customer. The keys may be generated, and the record stored within a secure module such as a smartcard.
Owner:BRITISH TELECOMM PLC
Universal forms engine
InactiveUS20050080756A1Easy to controlEasy accessData processing applicationsDigital data processing detailsData validationThird party
A forms engine allows data sharing between customizable on-line forms, such as college admissions applications. Before applying, an applicant opens an account with a third party application servicer. After the applicant completes an application for one institution, the data is saved in a data base and automatically populates fields in subsequent application forms. The form for each institution is created from a form description file. Each form is branded for its institution and forms for different institutions differ in appearance and content so that the presence of the third party servicer is transparent to the applicant. The system is extensible without programming, allowing new applicant attributes to be readily incorporated into the system and allowing the content and appearance of the application to be readily changed by changing the description file. The use of aliases for applicant attributes permits data to be readily shared between forms even though labeled and arranged differently on different forms. Information stored about each attribute allows the specification of data validation rules and data sharing and grouping rules, as well as dependency rules that permit application page content to depend on applicant's responses on a previous page.
Owner:COLLEGENET
Managing a LBA Interface in a Direct Data File Memory System
ActiveUS20080155227A1Minimized volumeImprove performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationData fileAddress space
Owner:SANDISK TECH LLC
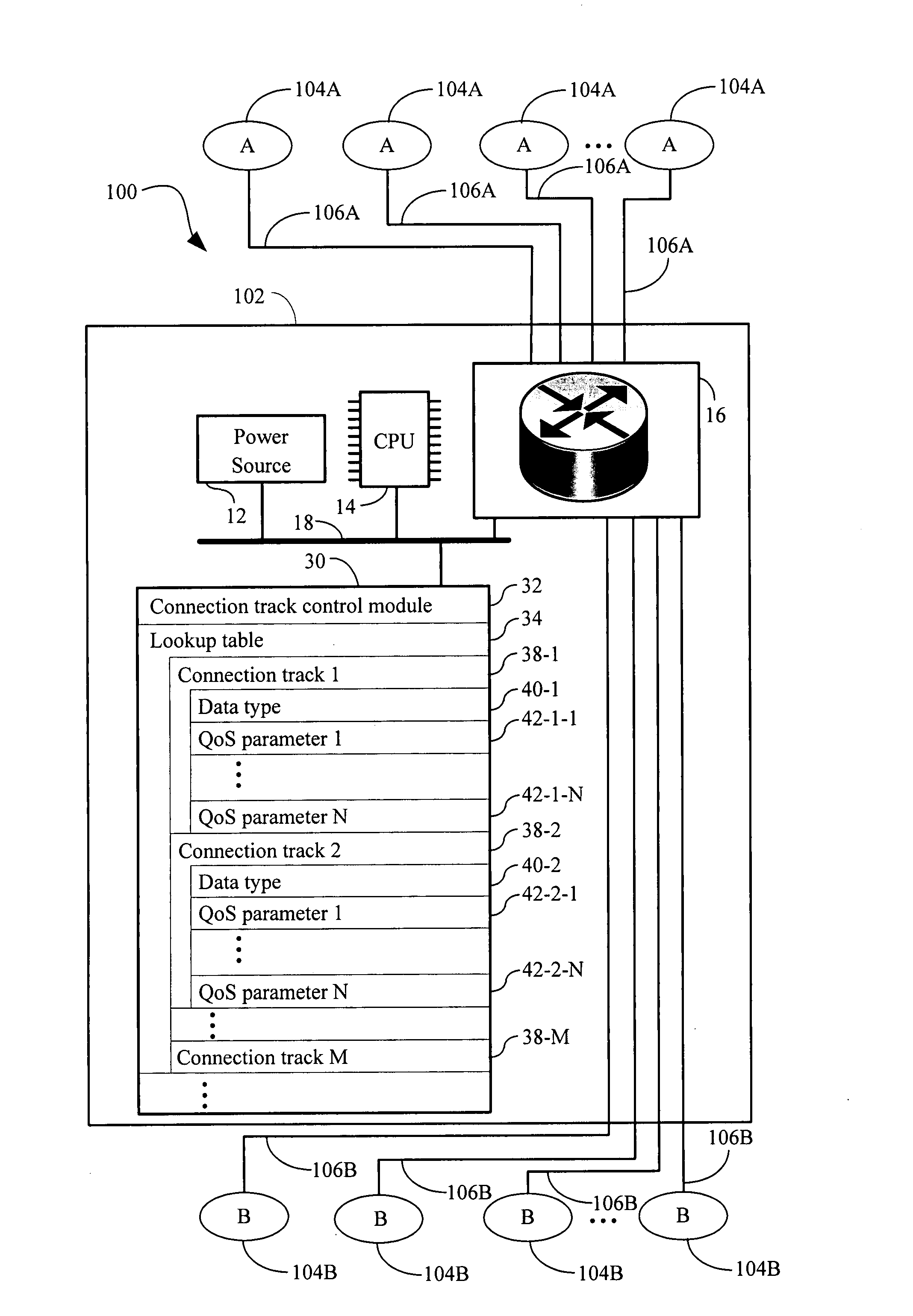
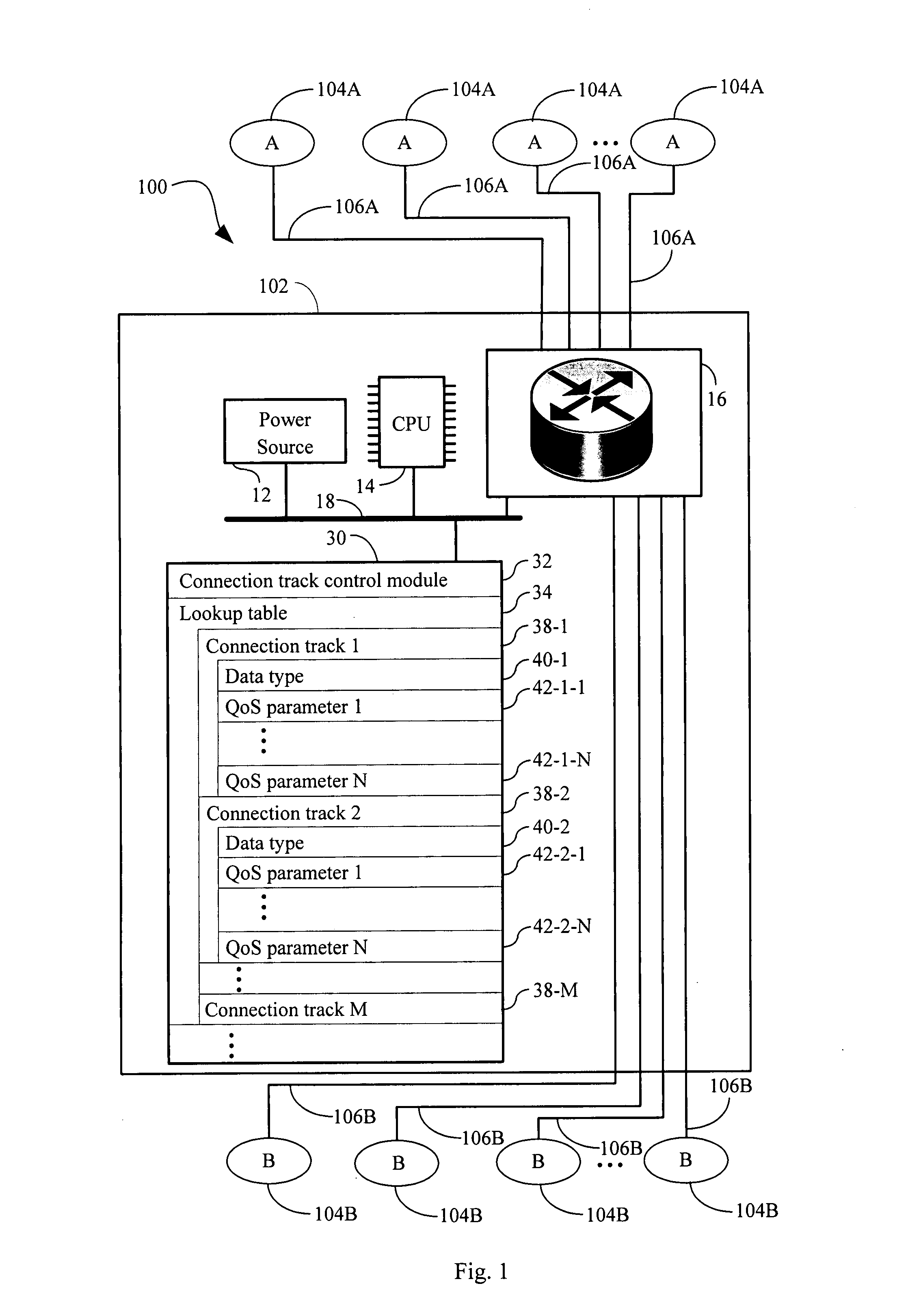
Systems and methods for dynamic quality of service
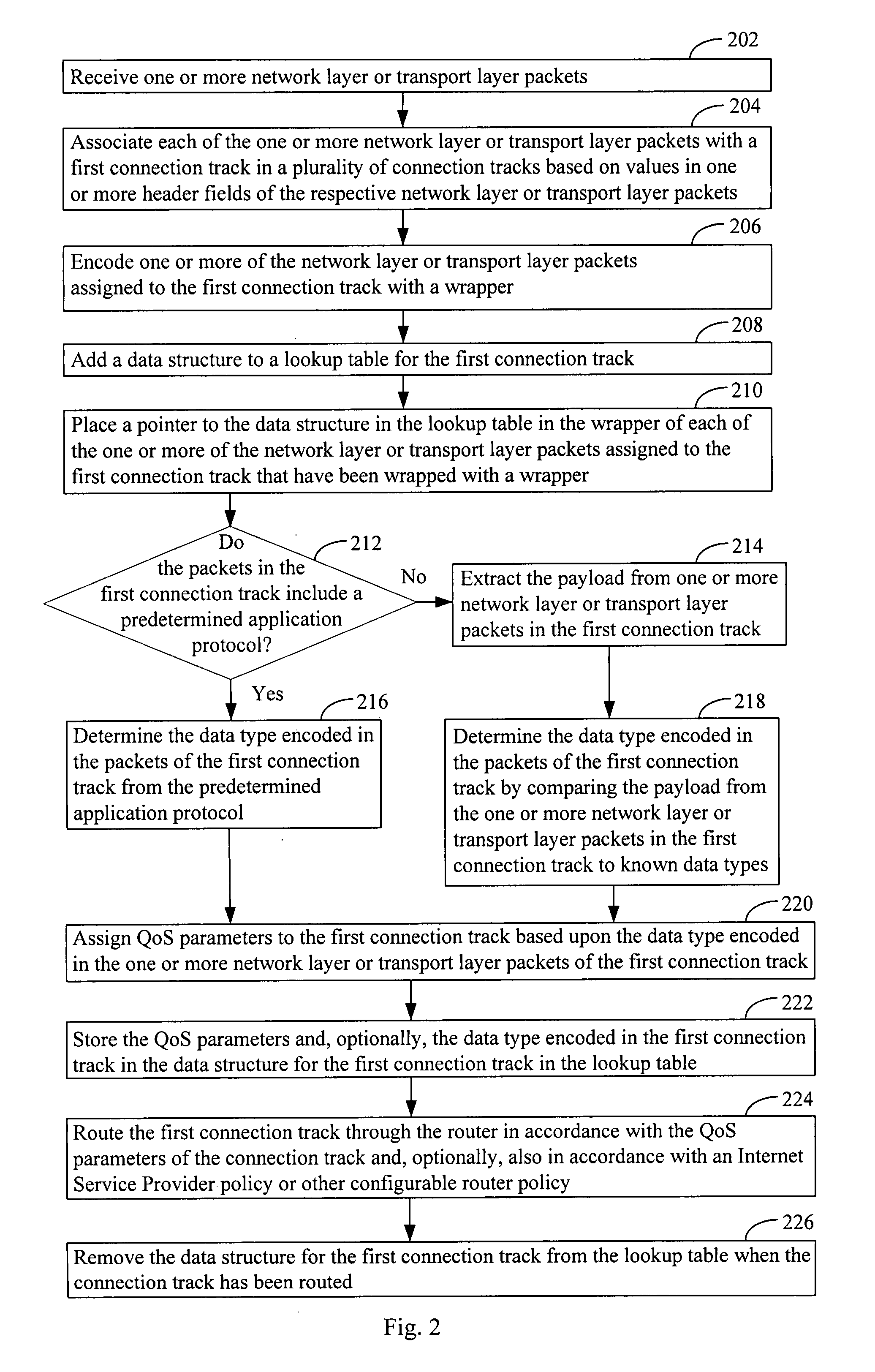
ActiveUS20080291827A1Improve performanceLimited dataError preventionFrequency-division multiplex detailsQuality of serviceTransport layer
Systems, methods, and apparatus for routing are provided in which a connection track comprising a plurality of network or transport layer packets, received by a router, is identified by examination of header fields of one or more first packets in the plurality of packets. One or more quality of service (QoS) parameters is associated with the connection track by determining whether the track encodes a data type by (i) an identification of a predetermined application protocol used within the one or more first packets and / or (ii) a comparison of a payload of one or more packets in the plurality of packets to known data type formats. A first QoS parameter is set to a first value in a first value range when the connection track contains the first data type. The connection track is routed through the router in accordance with the one or more QoS parameters assigned to the connection track.
Owner:ACTIONTEC ELECTRONICS
Controlling an influence on a user in a rendering environment
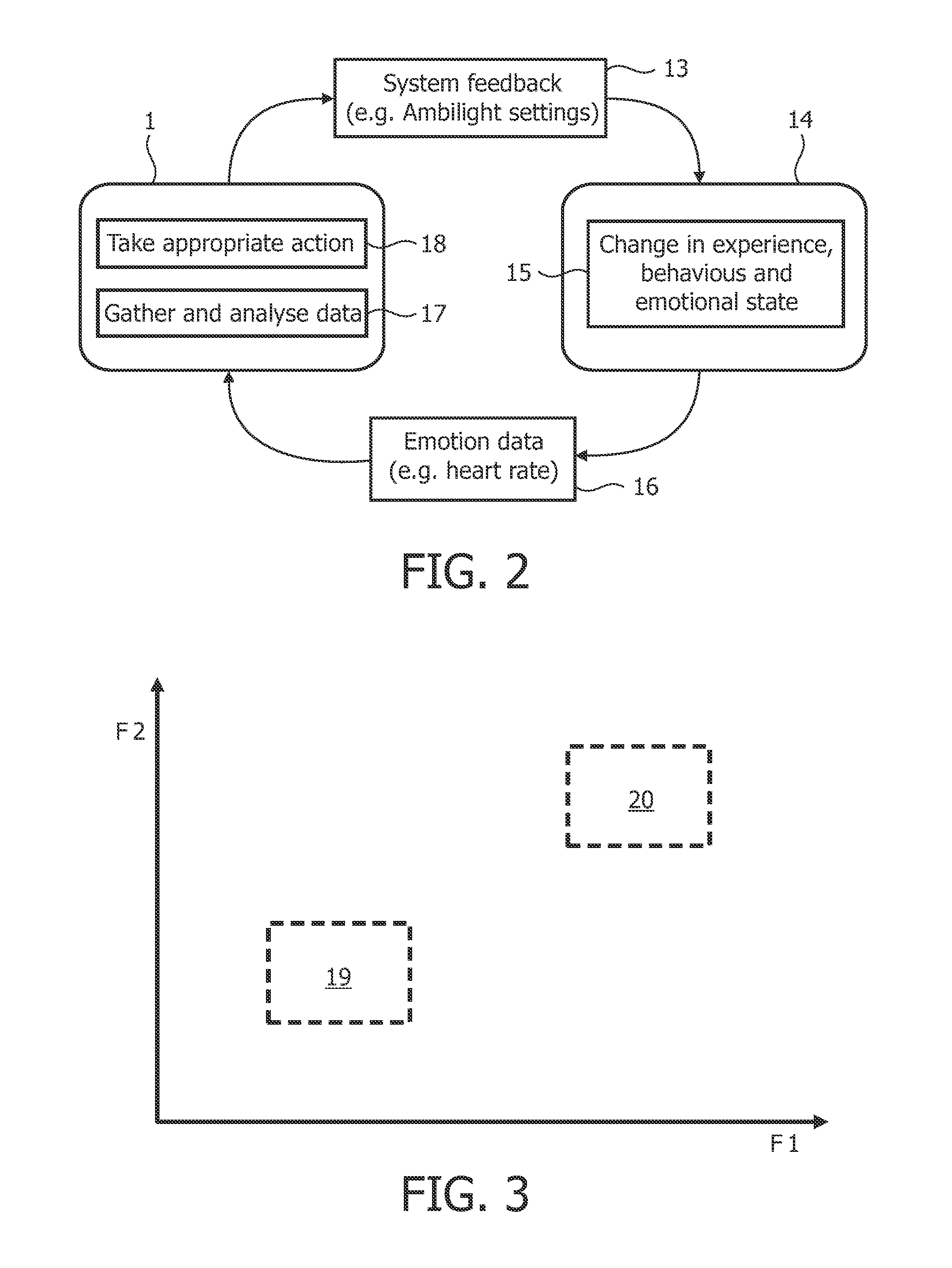
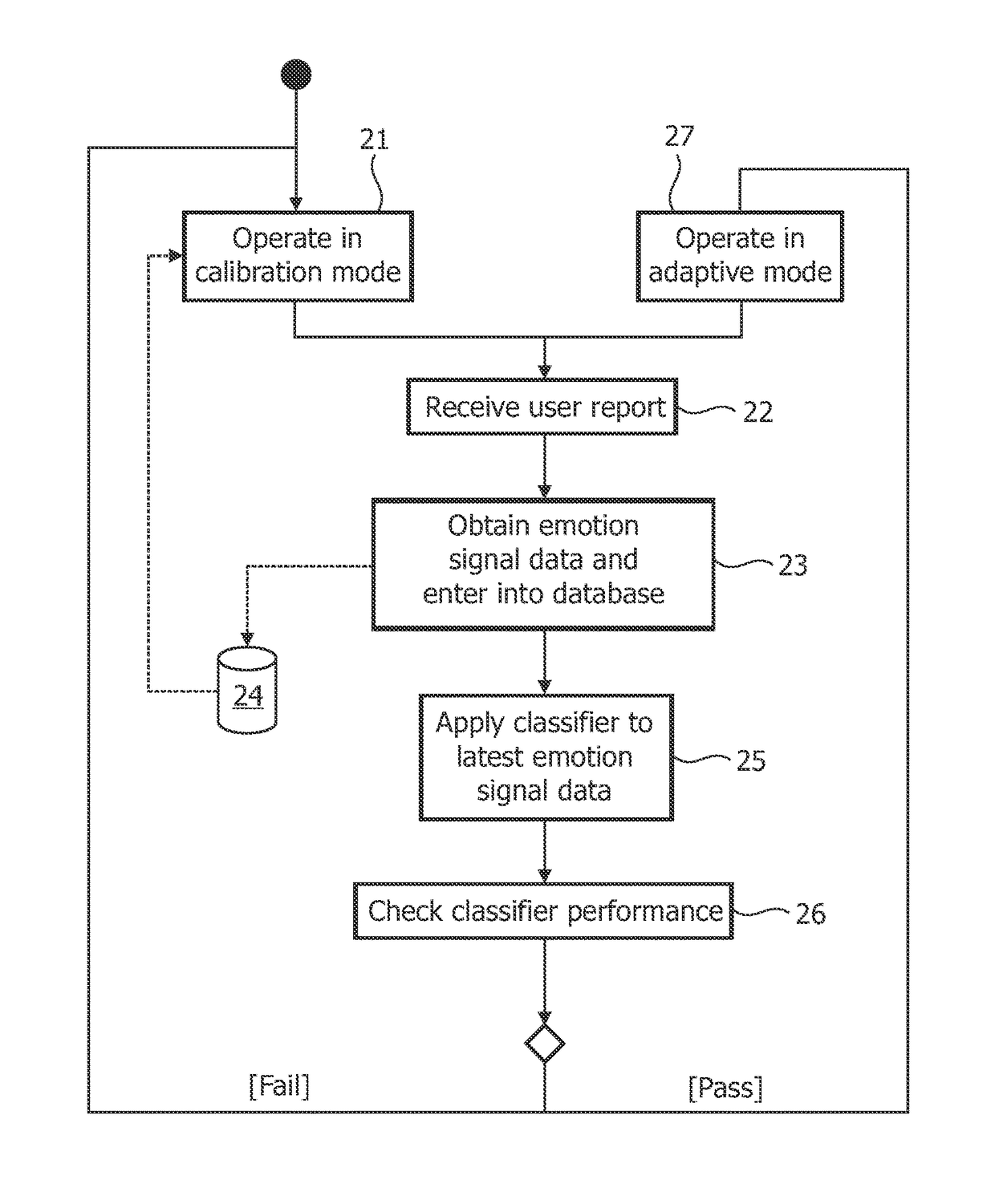
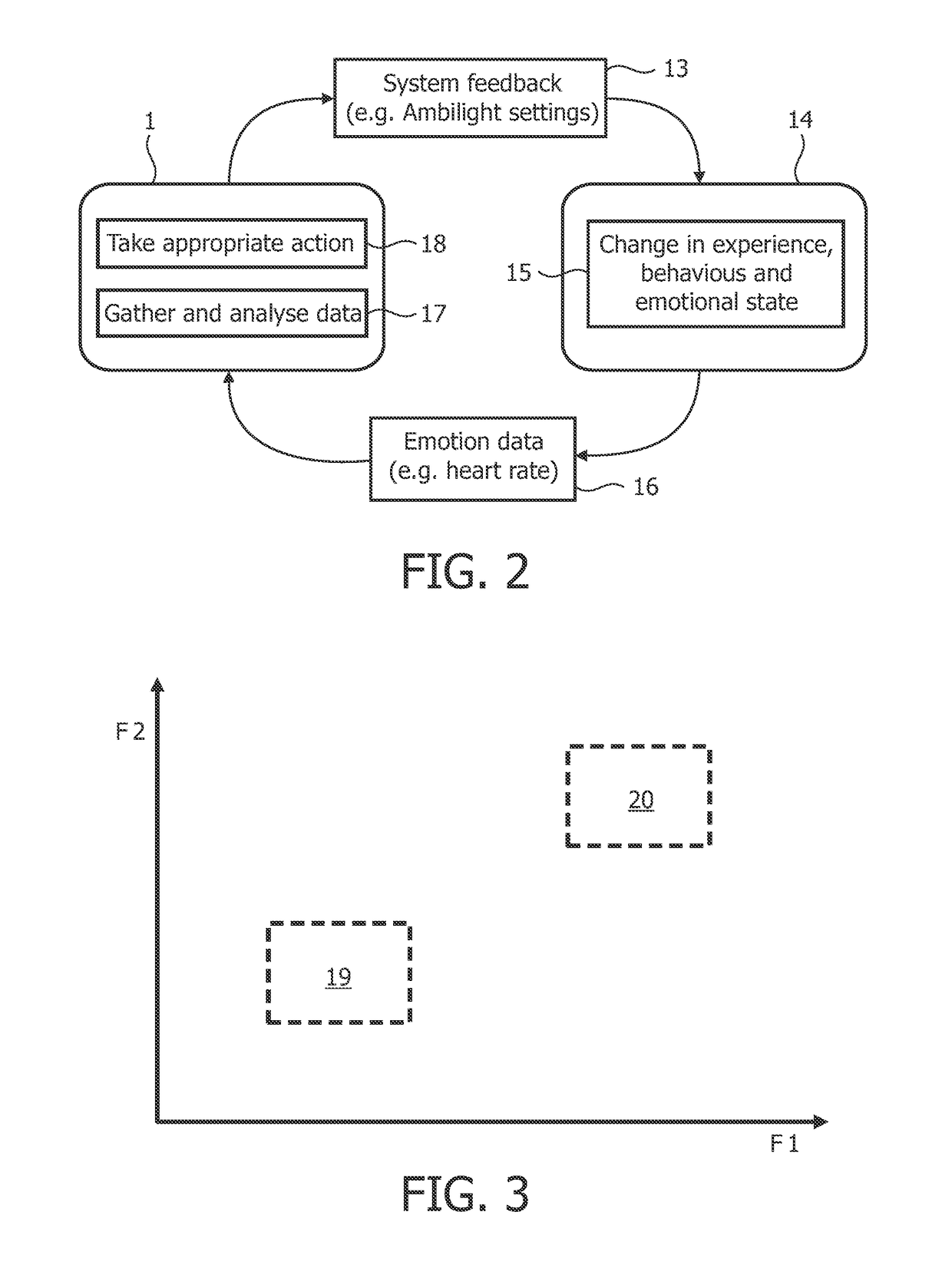
ActiveUS20110207100A1Optimize the player's enjoymentSimple processTeaching apparatusInput/output processes for data processingSelf reportUser expectations
A method of controlling an influence on a user (14) in a rendering environment comprises: obtaining signal data (16) representing one or more physiological conditions of a user (14) in response to an influence caused by system feedback (13) of the rendering environment; obtaining data corresponding to a user's desired emotional state (19,20;32-36), which data is based on the user's self-reports and data representative of accompanying signal data (16) representing one or more physiological conditions of the user (14) over a last period before the accompanying self-report; —determining whether the desired emotional state (19,20;32-36) is reached; and if the state (19,20;32-36) is not reached, adapting the system feedback (16) provided by the rendering environment correspondingly.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Generating a distrubition package having an access control execution program for implementing an access control mechanism and loading unit for a client
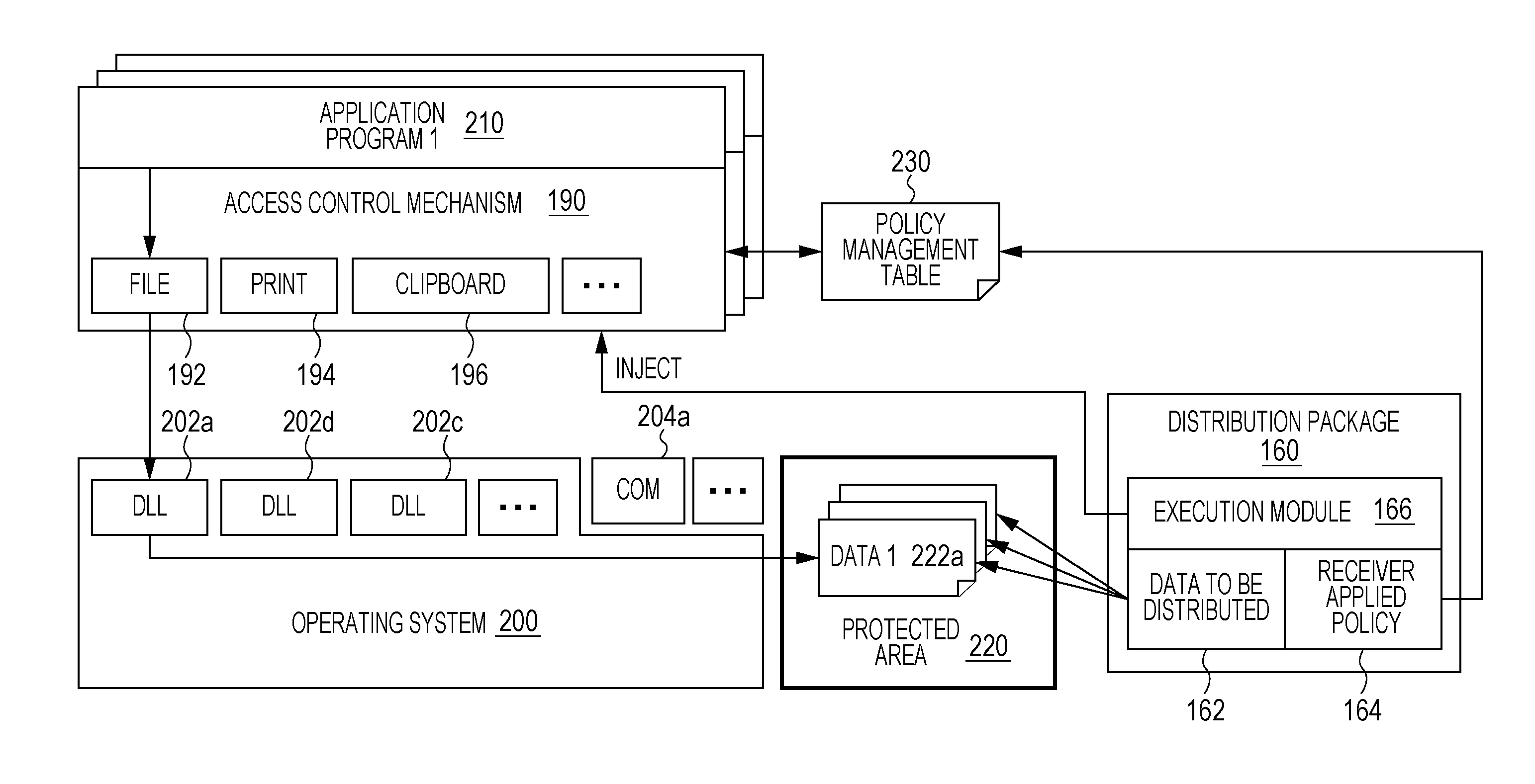
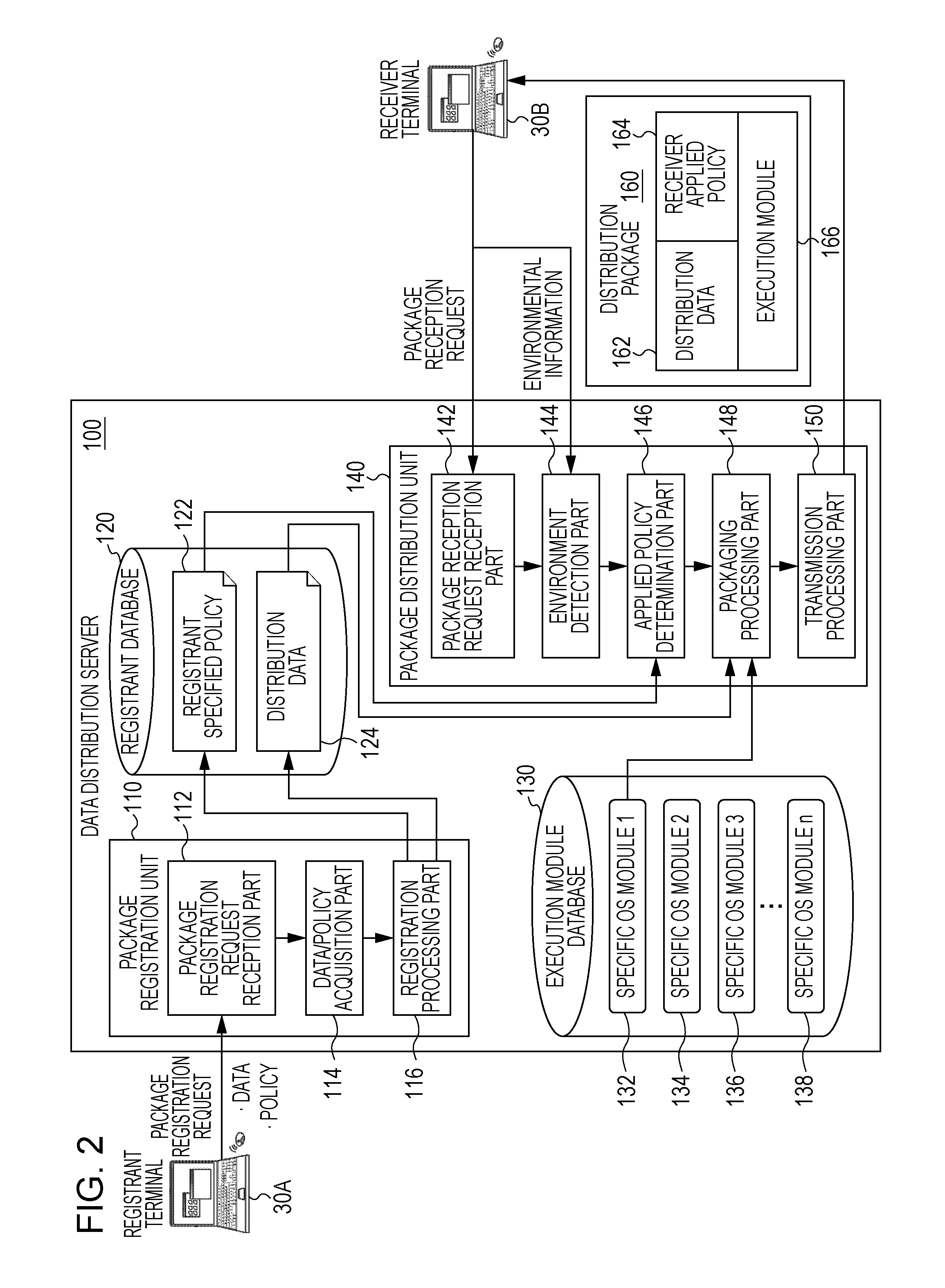
InactiveUS20130219462A1Limited dataLimited rangeDigital data protectionPlatform integrity maintainanceUnit loadDistribution system
A data distribution system, method and program for generating a distribution package for distribution data to a client. An environment of a requesting client requesting distribution data is detected. A determination is made of an access control execution program for implementing an access control mechanism and a loading unit on the requesting client. The access control execution program is adapted to the detected environment of the requesting client and control access to a resource from a process in the client. The loading unit loads the distribution data to a protected storage area of the client. A determination is made of a security policy specified for the distribution data. A distribution package is generated including the distribution data, the security policy, the loading unit, and the access control execution program adapted to the environment of the requesting client; and transmitting the generated distribution package to the requesting client.
Owner:IBM CORP
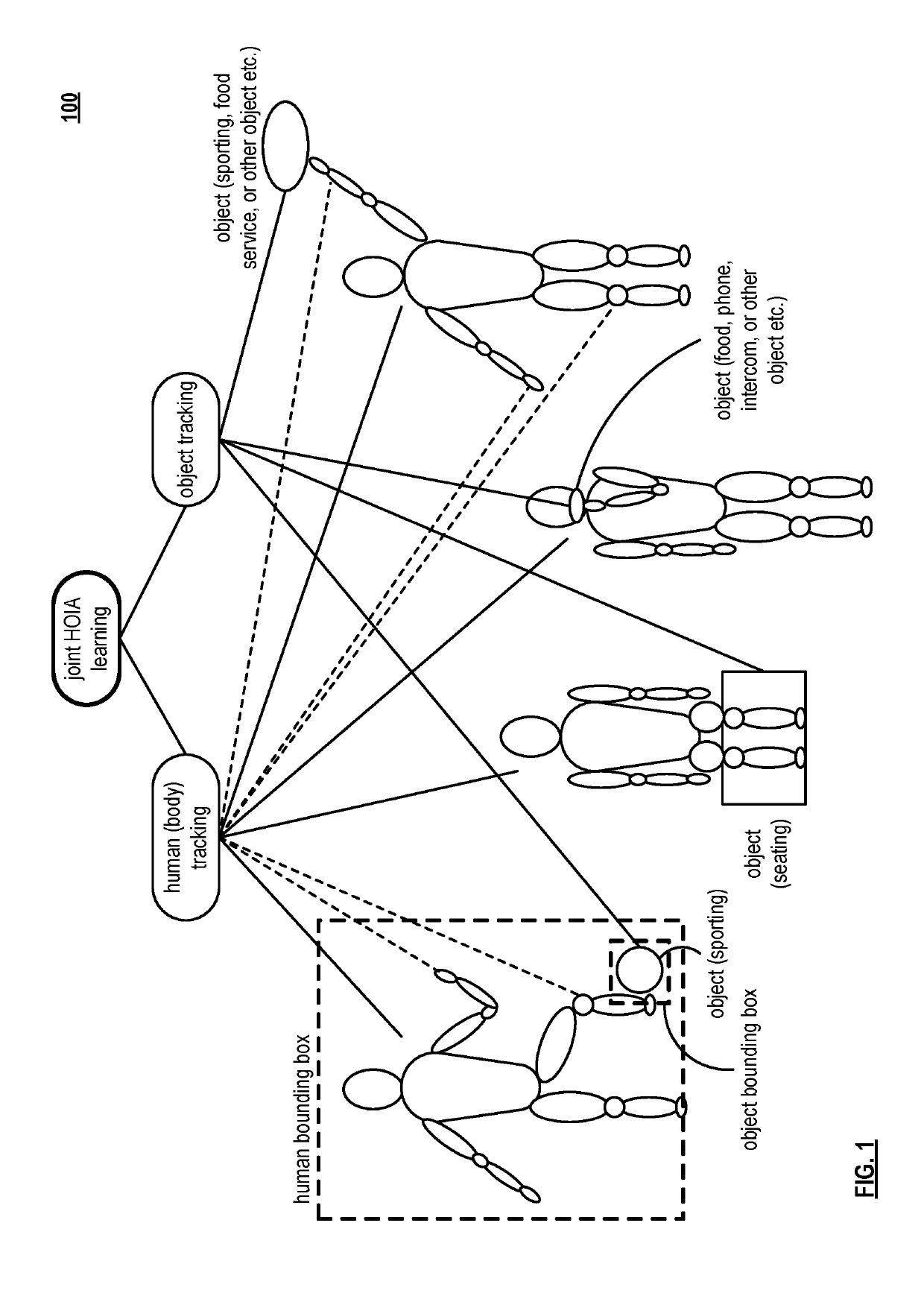
Activity detection by joint human and object detection and tracking
ActiveUS20190180090A1Efficient network trainingLimited dataImage enhancementMedical data miningCommunication interfaceObject detection
A computing device includes a communication interface, a memory, and processing circuitry. The processing circuitry is coupled to the communication interface and to the memory and is configured to execute the operational instructions to perform various functions. The computing device is configured to process a video frame of a video segment on a per-frame basis and based on joint human-object interactive activity (HOIA) to generate a per-frame pairwise human-object interactive (HOI) feature based on a plurality of candidate HOI pairs. The computing device is also configured to process the per-frame pairwise HOI feature to identify a valid HOI pair among the plurality of candidate HOI pairs and to track the valid HOI pair through subsequent frames of the video segment to generate a contextual spatial-temporal feature for the valid HOI pair to be used in activity detection.
Owner:FUTUREWEI TECH INC
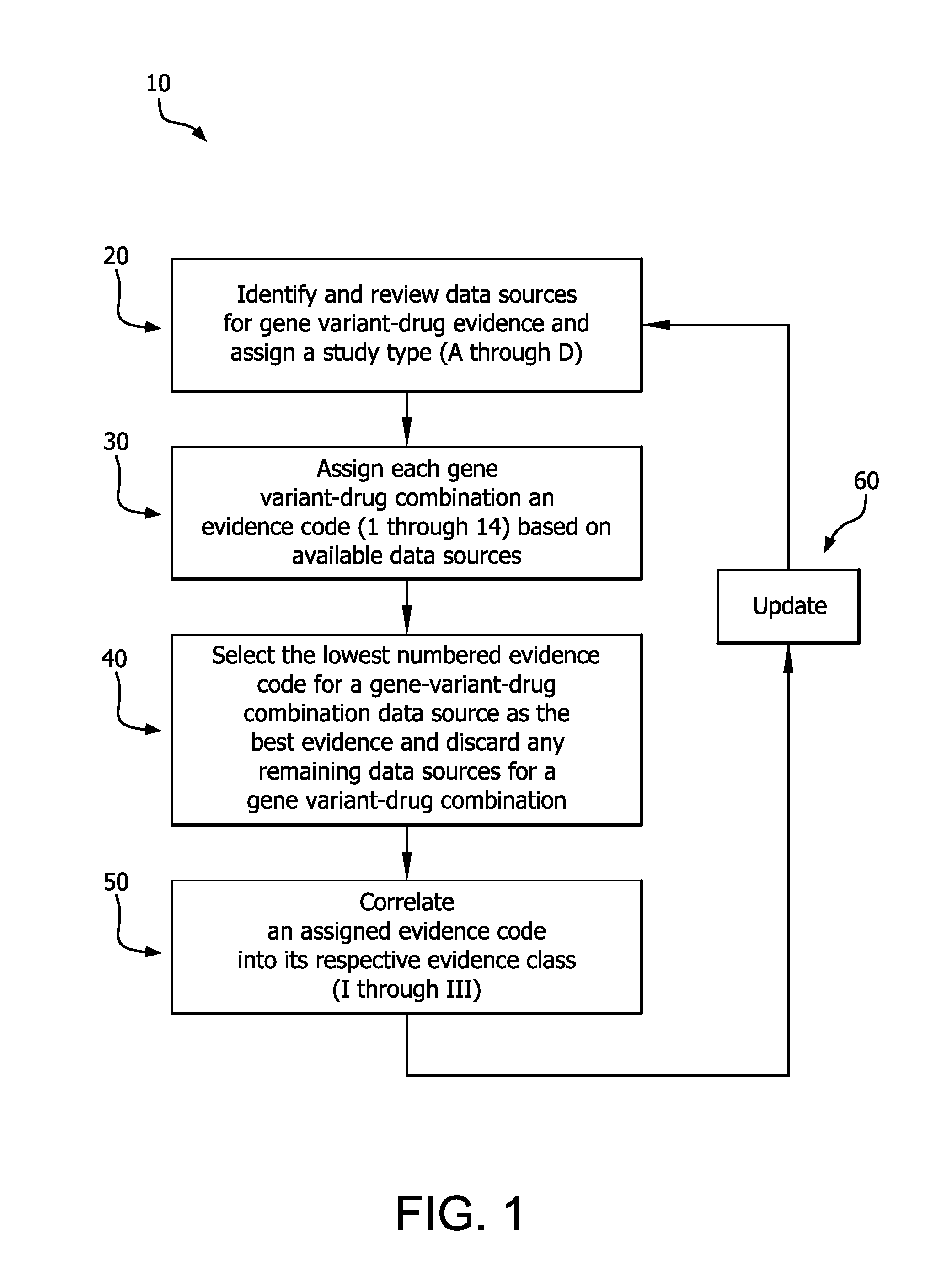
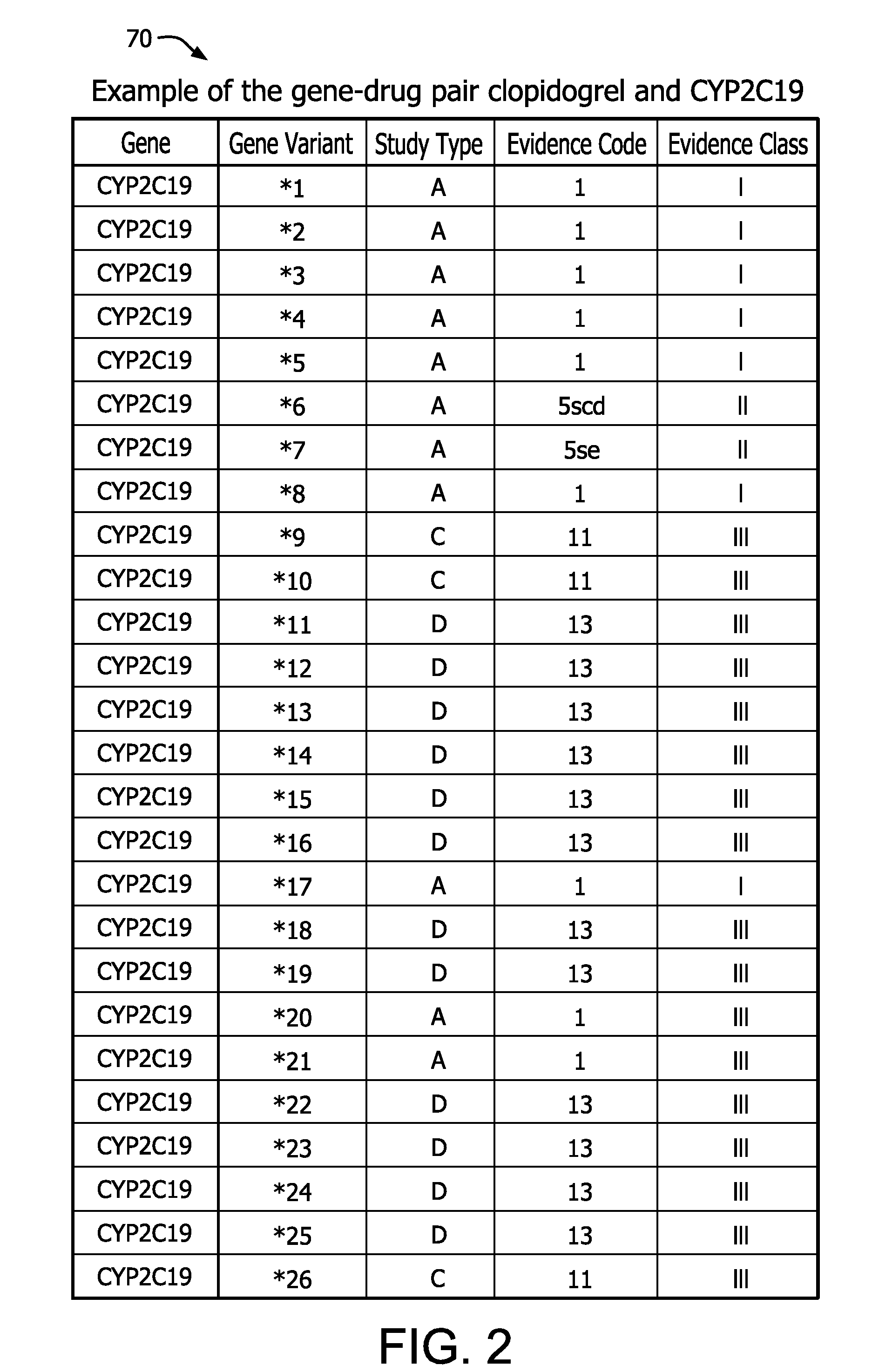
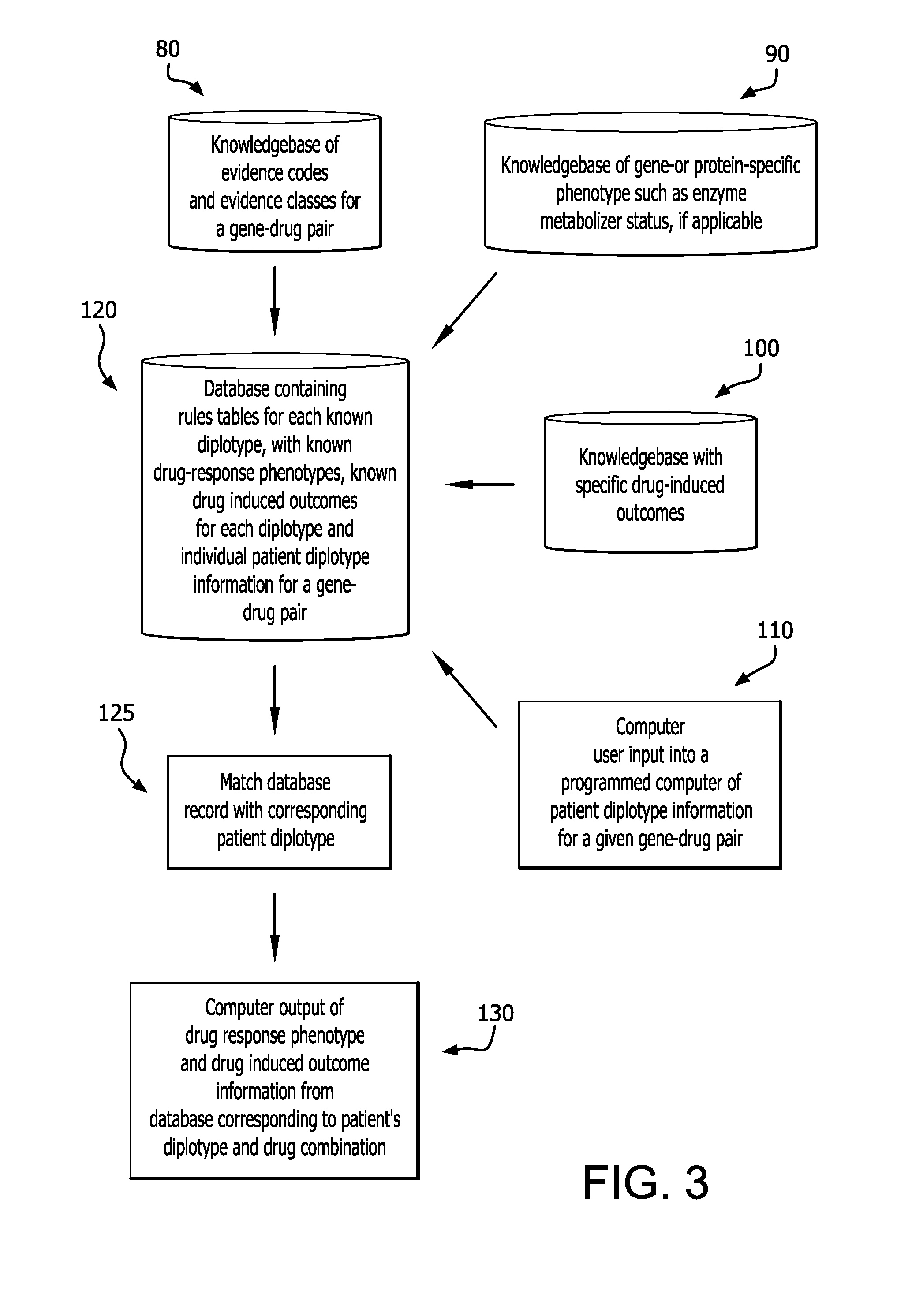
Method for translating genetic information for use in pharmacogenomic molecular diagnostics and personalized medicine research
A gene-drug specific system for classifying individual genetic variants based on strength-of-evidence of clinical utility from published scientific and clinical data that support their effect on modifying drug response and behavior. This allows categorization of the genetic variants into evidence classes that have a wide range of uses such as pharmacogenomic molecular diagnostics and personalized medicine research designed to guide the clinical implementation of PGx. Furthermore, this information can be combined with a knowledgebase of drug-response phenotypes, a knowlegebase of specific drug-induced outcomes and individual patient diplotype information for a gene-drug combination into a programmed computer to output corresponding patient-specific predicted drug responses.
Owner:CORIELL INST FOR MEDICAL RES
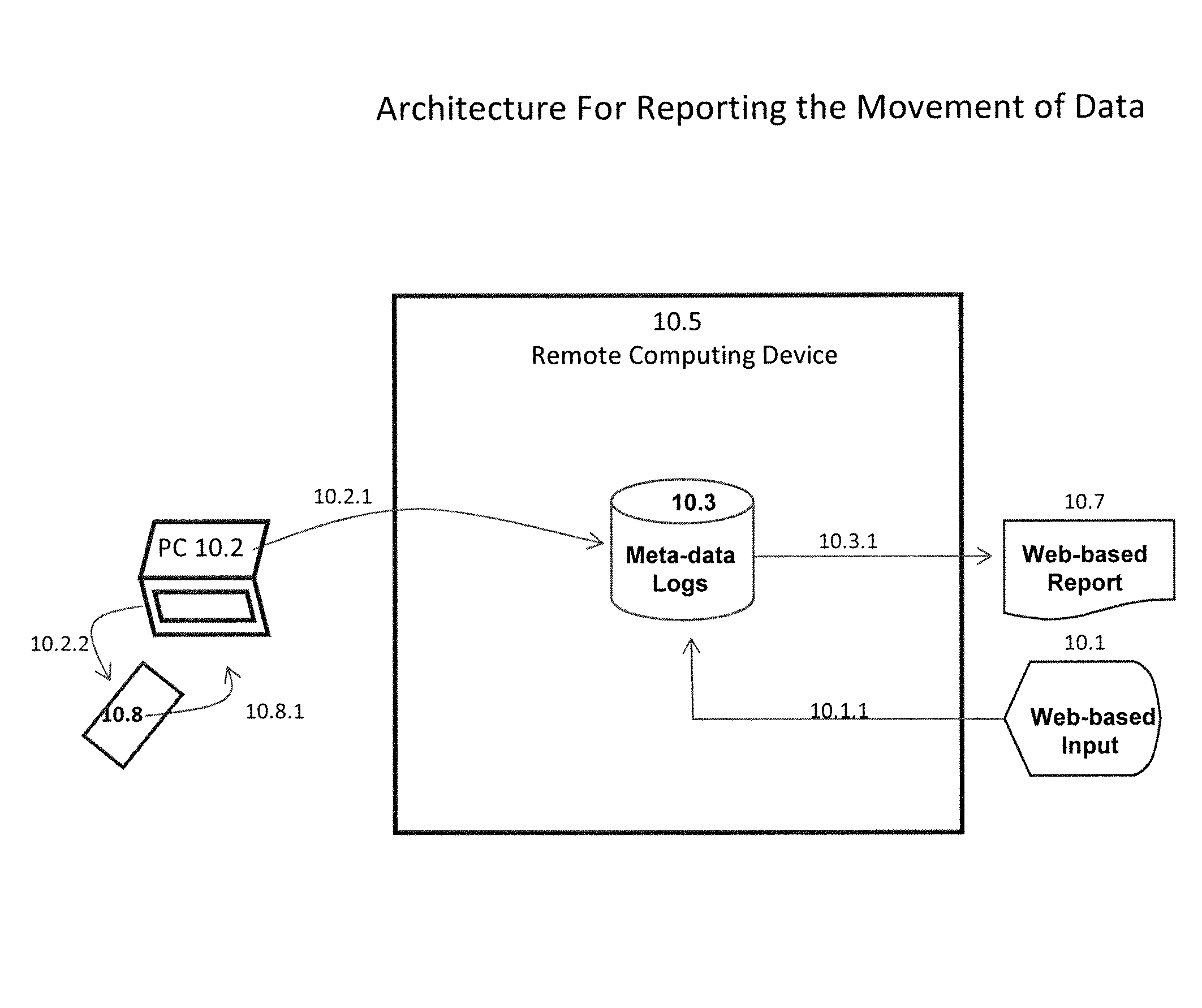
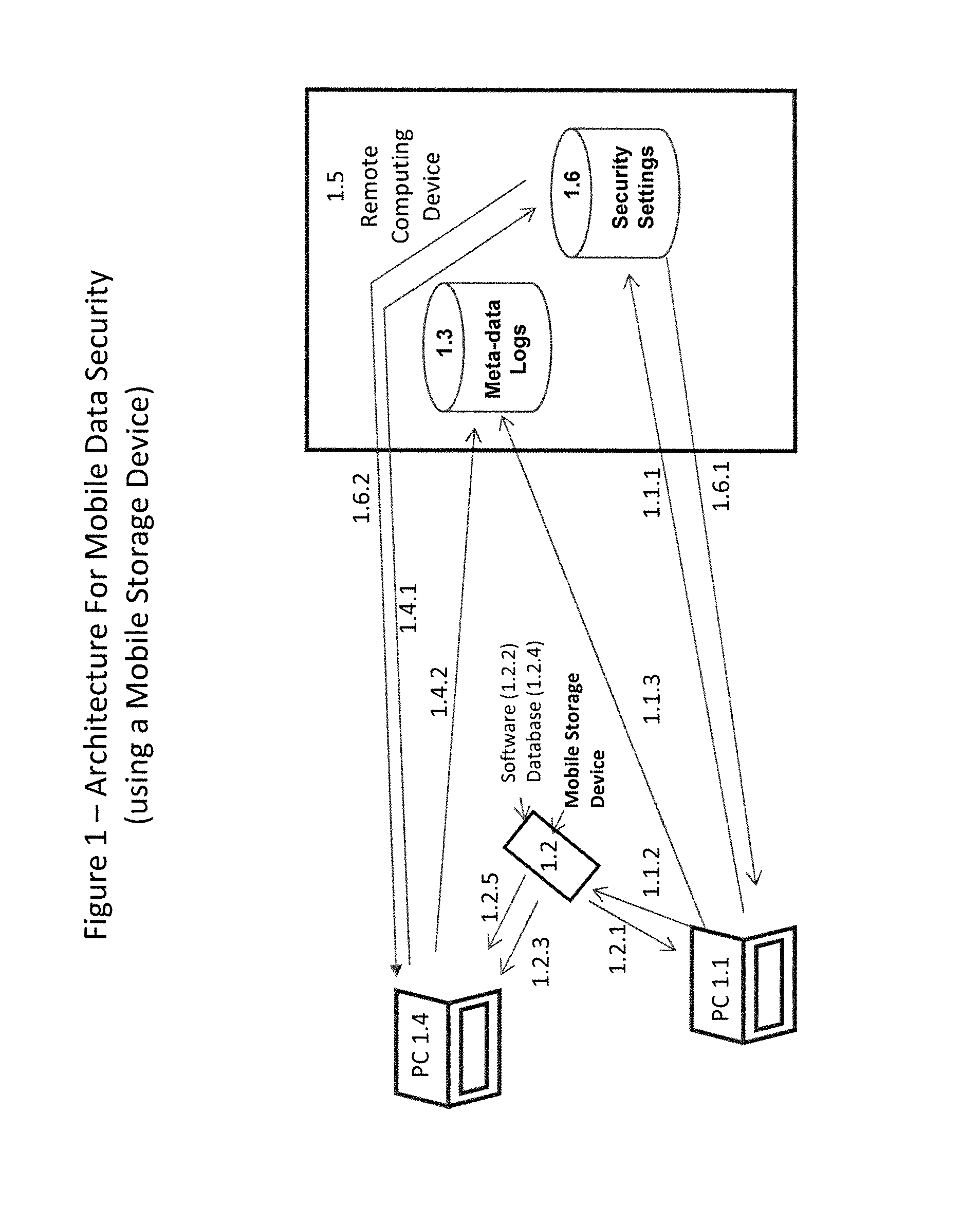
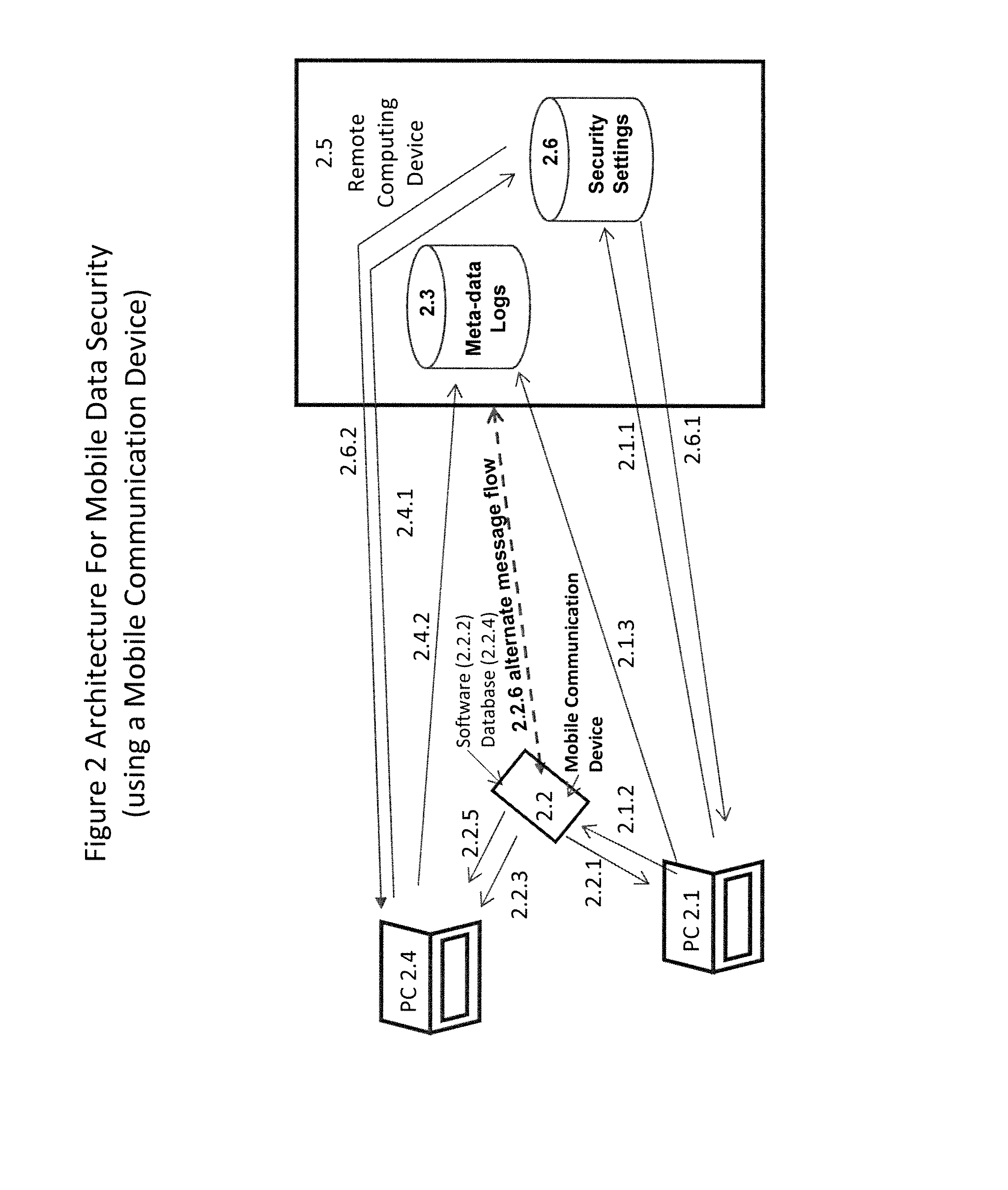
Method and system for mobile data security
ActiveUS8086688B1Limited dataDigital data processing detailsUnauthorized memory use protectionMobile deviceData security
A system and method for securely storing, retrieving and sharing data using PCs and mobile devices and for controlling and tracking the movement of data to and from a variety of computing and storage devices.
Owner:QUICKVAULT
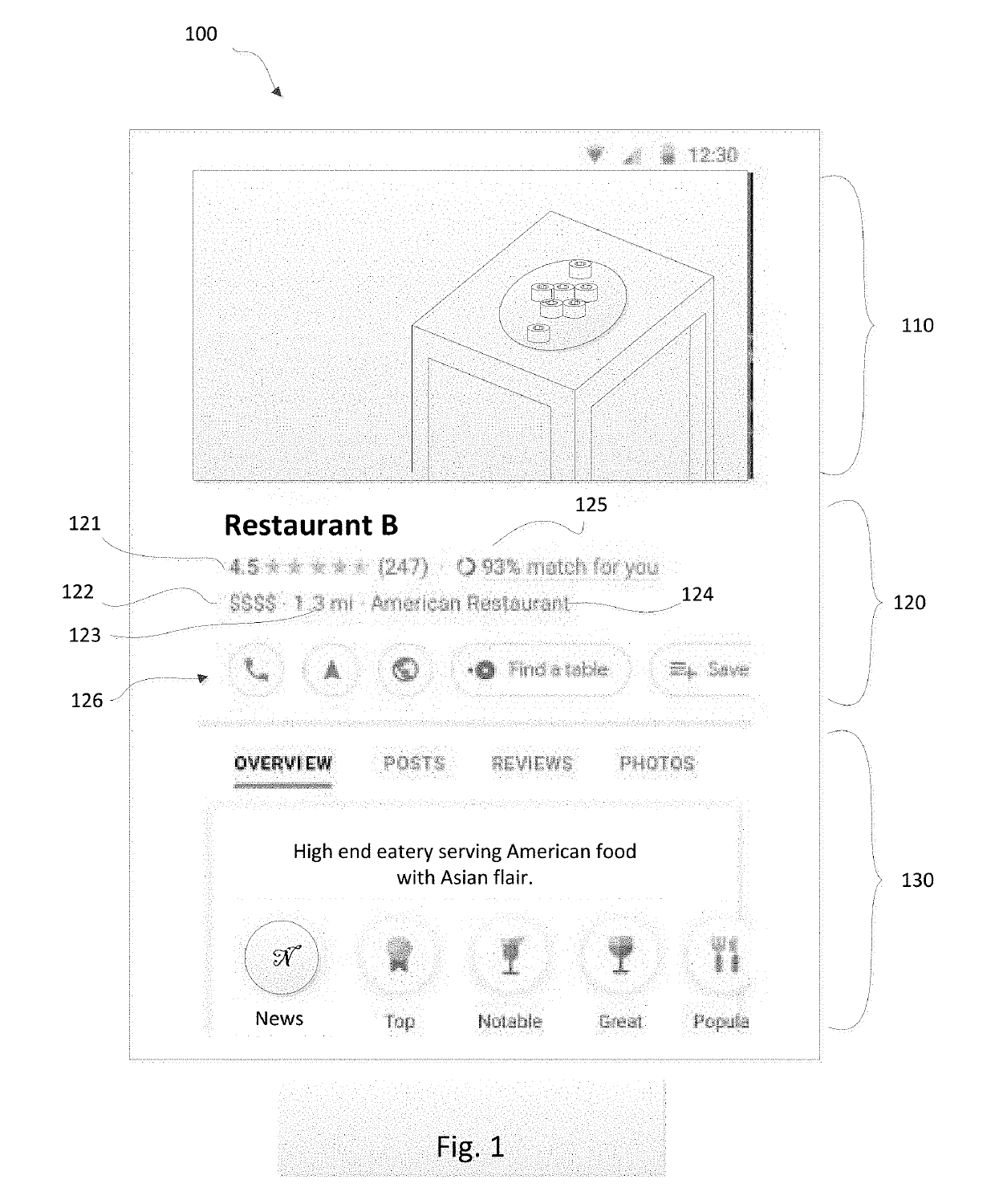
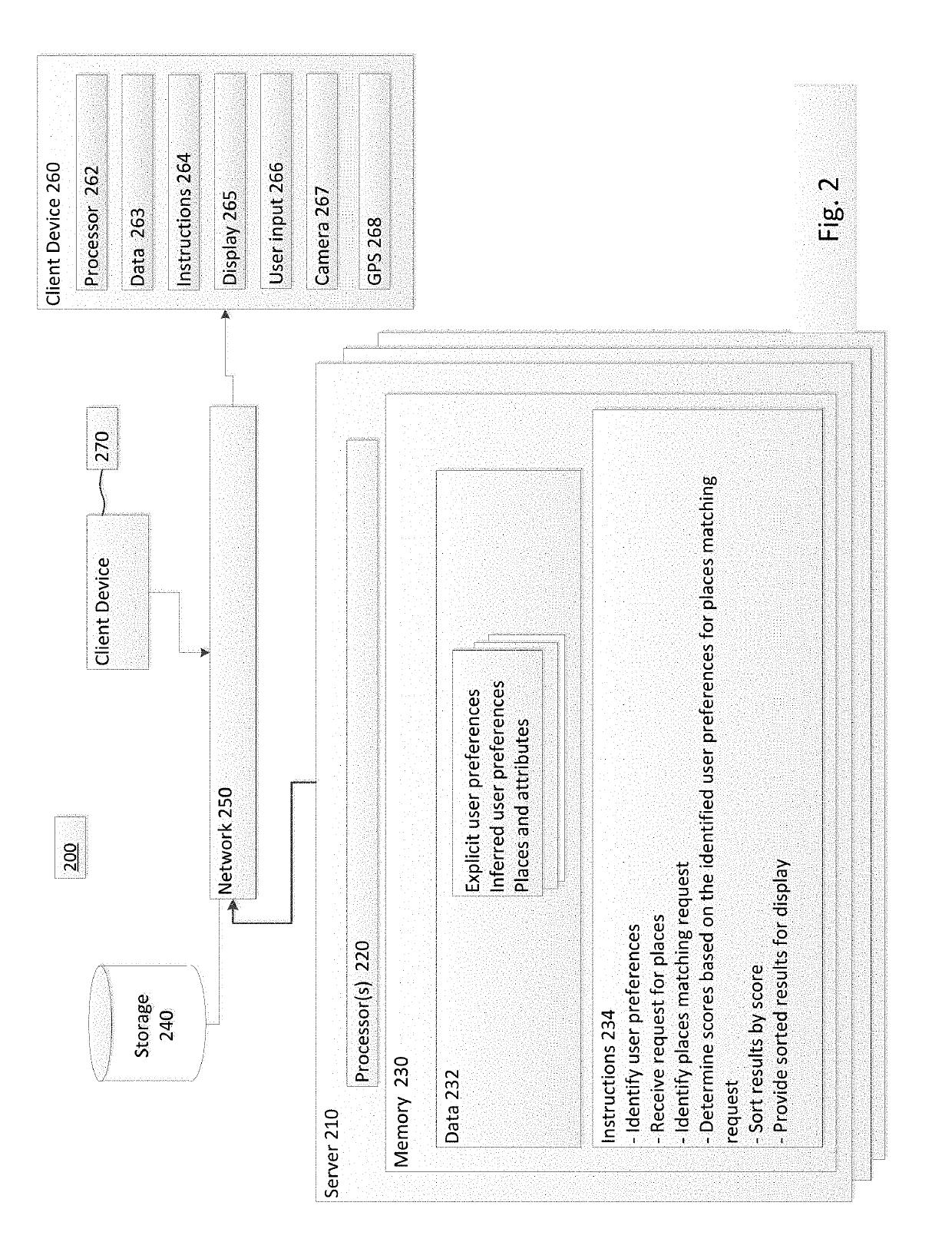
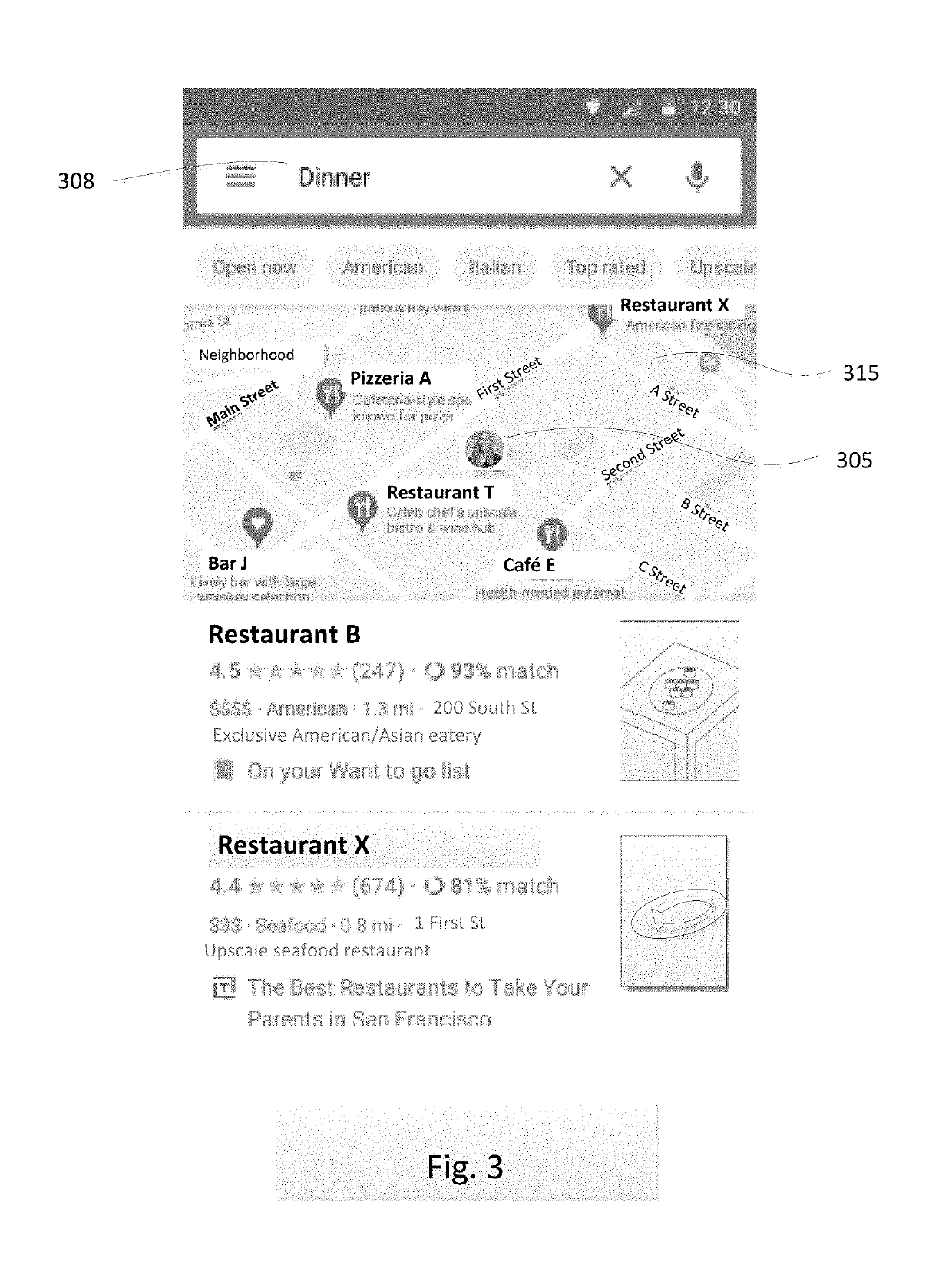
Personalized Match Score For Places
PendingUS20190340537A1Improve accuracyLimited dataCharacter and pattern recognitionMachine learningPersonalizationMultimedia
A personalized score for a place that a user may want to visit is computed and displayed to the user. The score is computed based on at least one of inferred or explicit parameters, using machine learning. The score may be displayed to the user in connection with the place, and in some examples explanations of the underlying factors that resulted in the score are also displayed. Because each user is unique, the score may be different for one person than for another. Accordingly, when a group of friends are deciding on a place to visit, such as a place to eat, the personalized score for a given restaurant may be higher for a first user than for a second user.
Owner:GOOGLE LLC
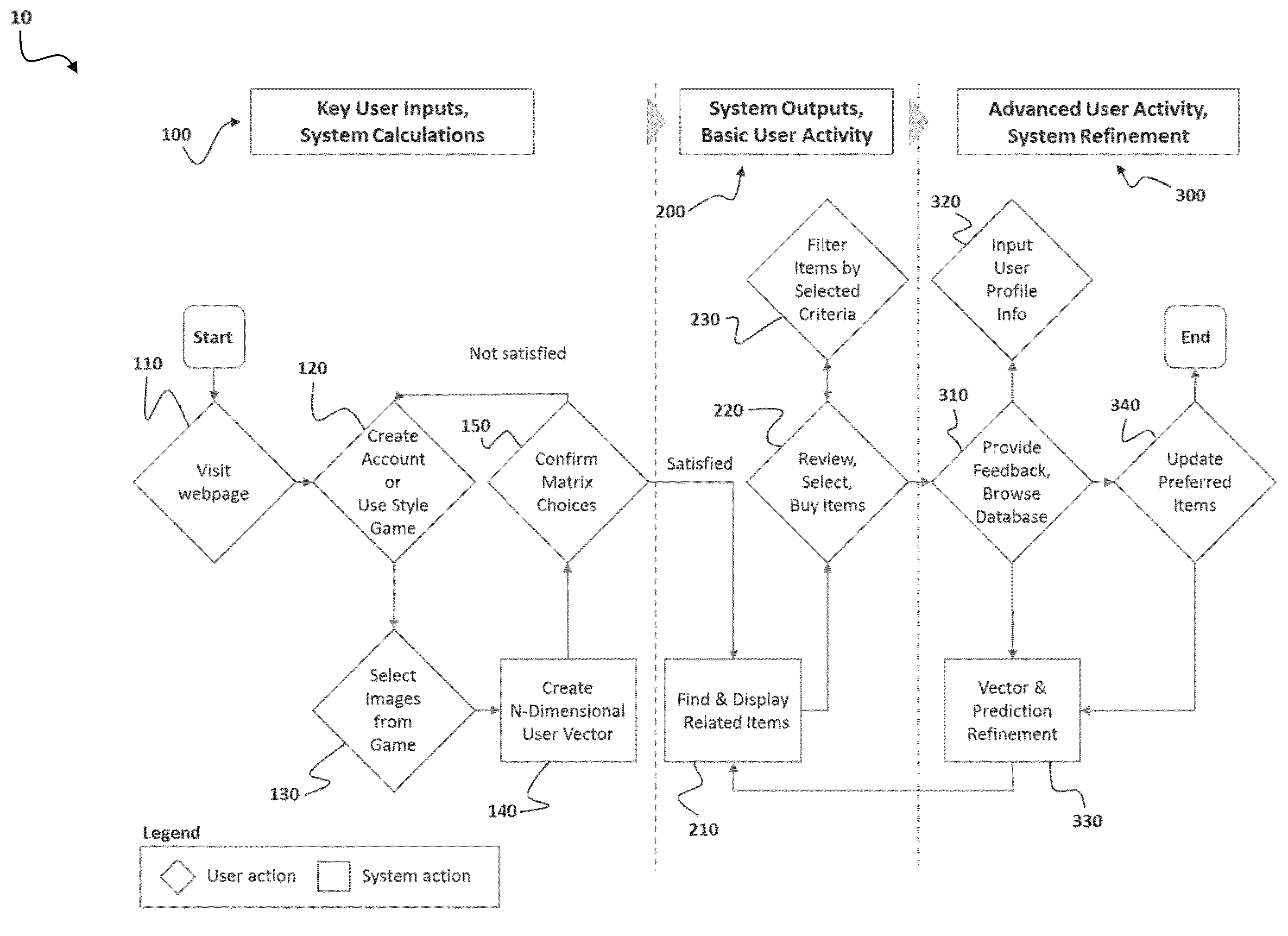
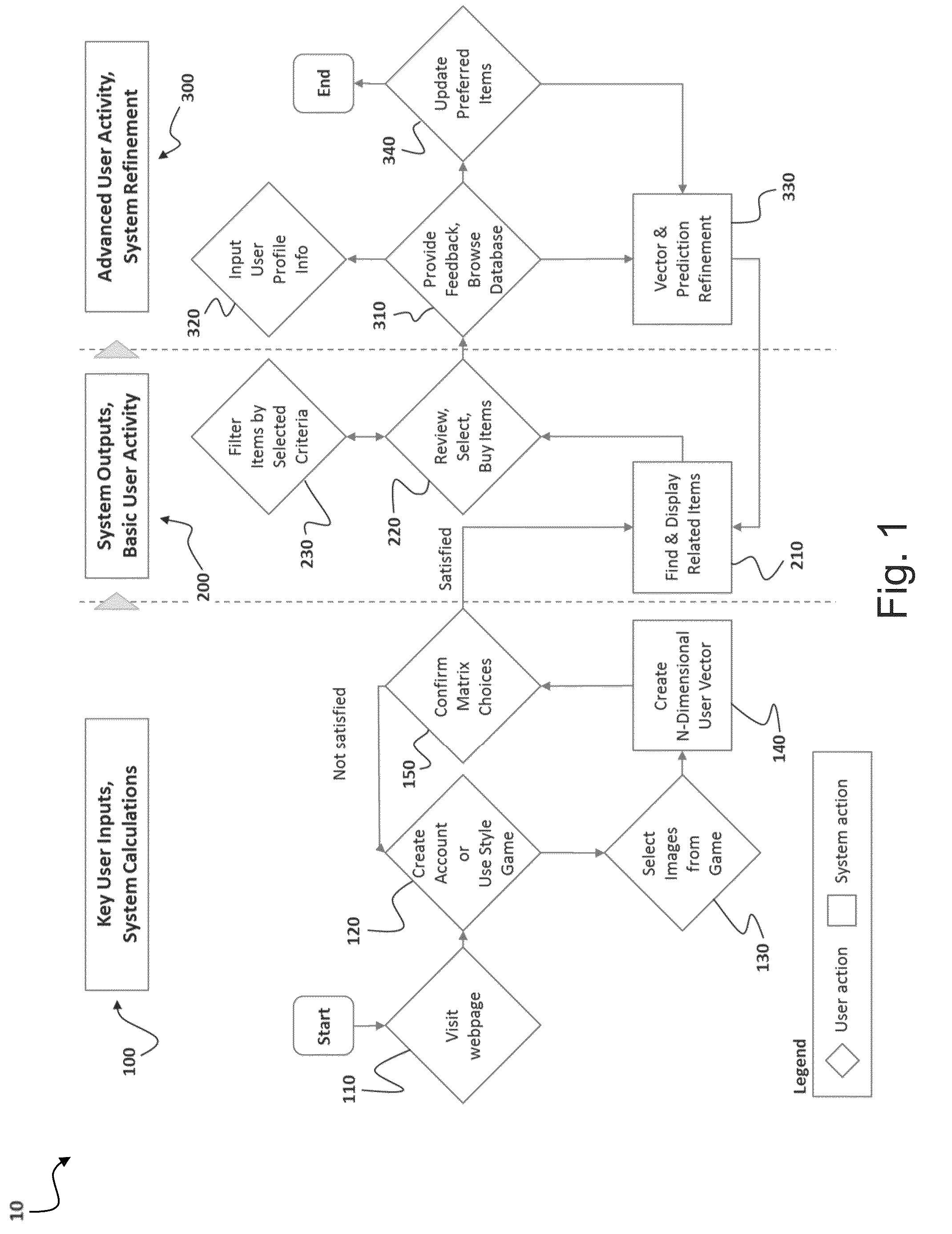
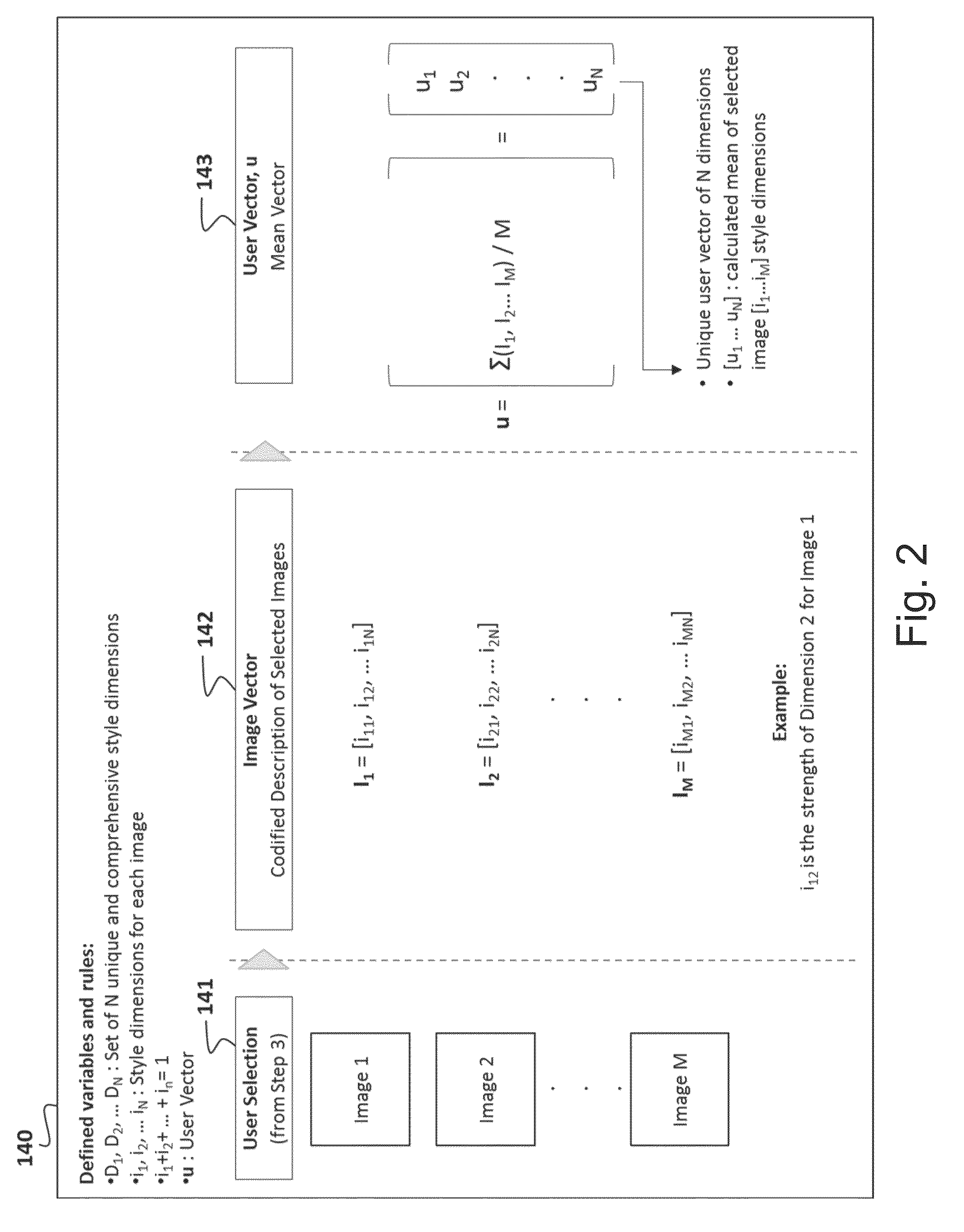
Method and system for personalized recommendation of lifestyle items
ActiveUS9183510B1Straightforward and non data-intensiveRelevant and accurate resultDigital computer detailsMachine learningPersonalizationComputer science
A browser-based personalized recommendation system and method for lifestyle items comprising style dimension mapping, inputs, outputs, and a computer-algorithm is described. The system gathers information about a user's unique lifestyle preferences, which is then correlated to clothing and lifestyle items. The recommendation system uniquely and directly matches users to discrete items without the need for historic user data.
Owner:RAISE MARKETPLACE LLC
Label applicator with RFID antenna
InactiveUS20050194442A1Small and inexpensiveLimited range , resolution and data storage capacitySensing record carriersBurglar alarm by hand-portable articles removalPatch antennaComputer science
A label applicator with a patch antenna or in the label applicator. The antenna is able to read and / or write to an RFID tag embedded in the label as the label is being applied to an object. The antenna can write the most current information to the RFID tag as the label is being applied. The antenna also can read the RFID tag and identify failed or damaged tags so they can be disguarded.
Owner:INTERMEC IP
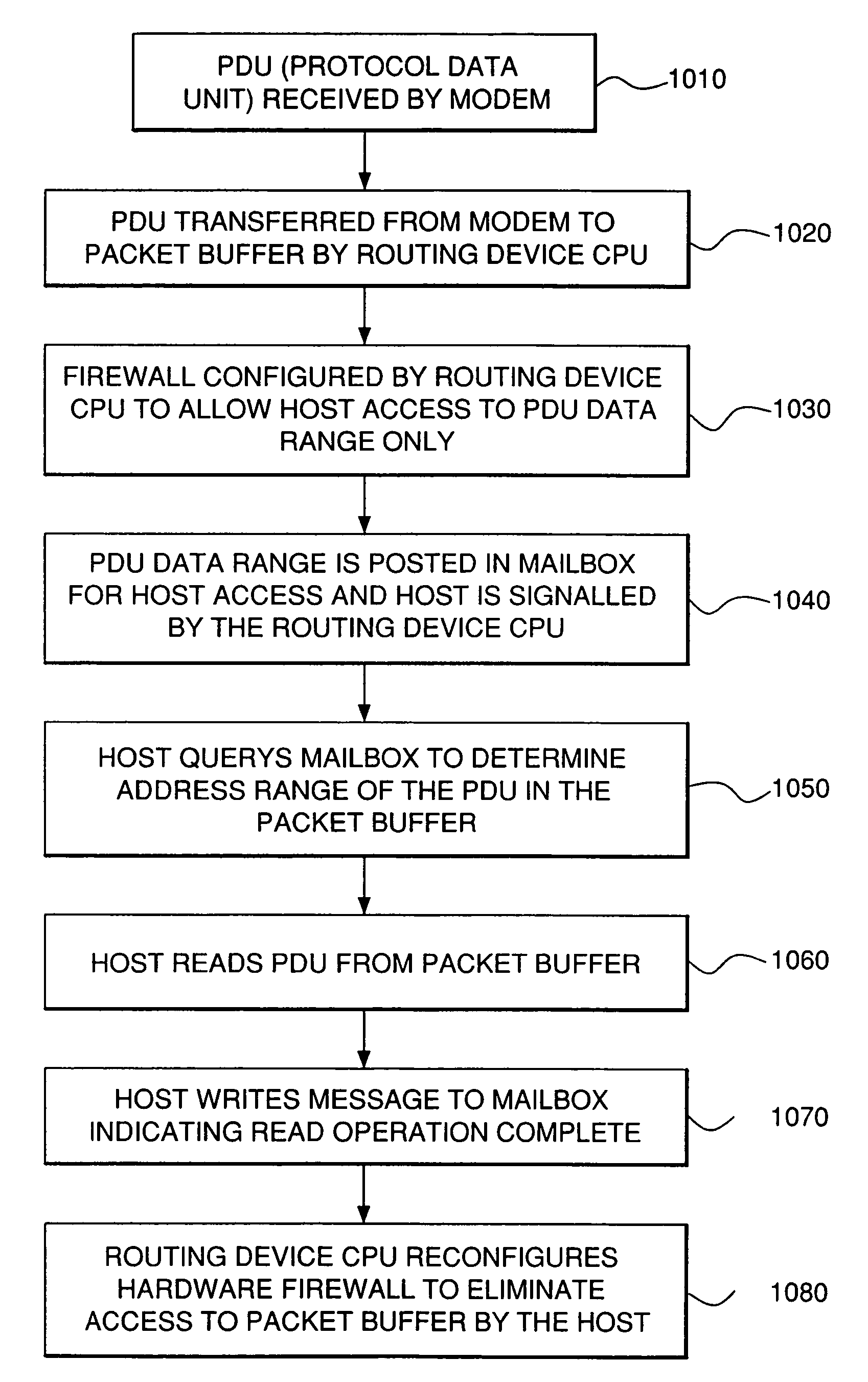
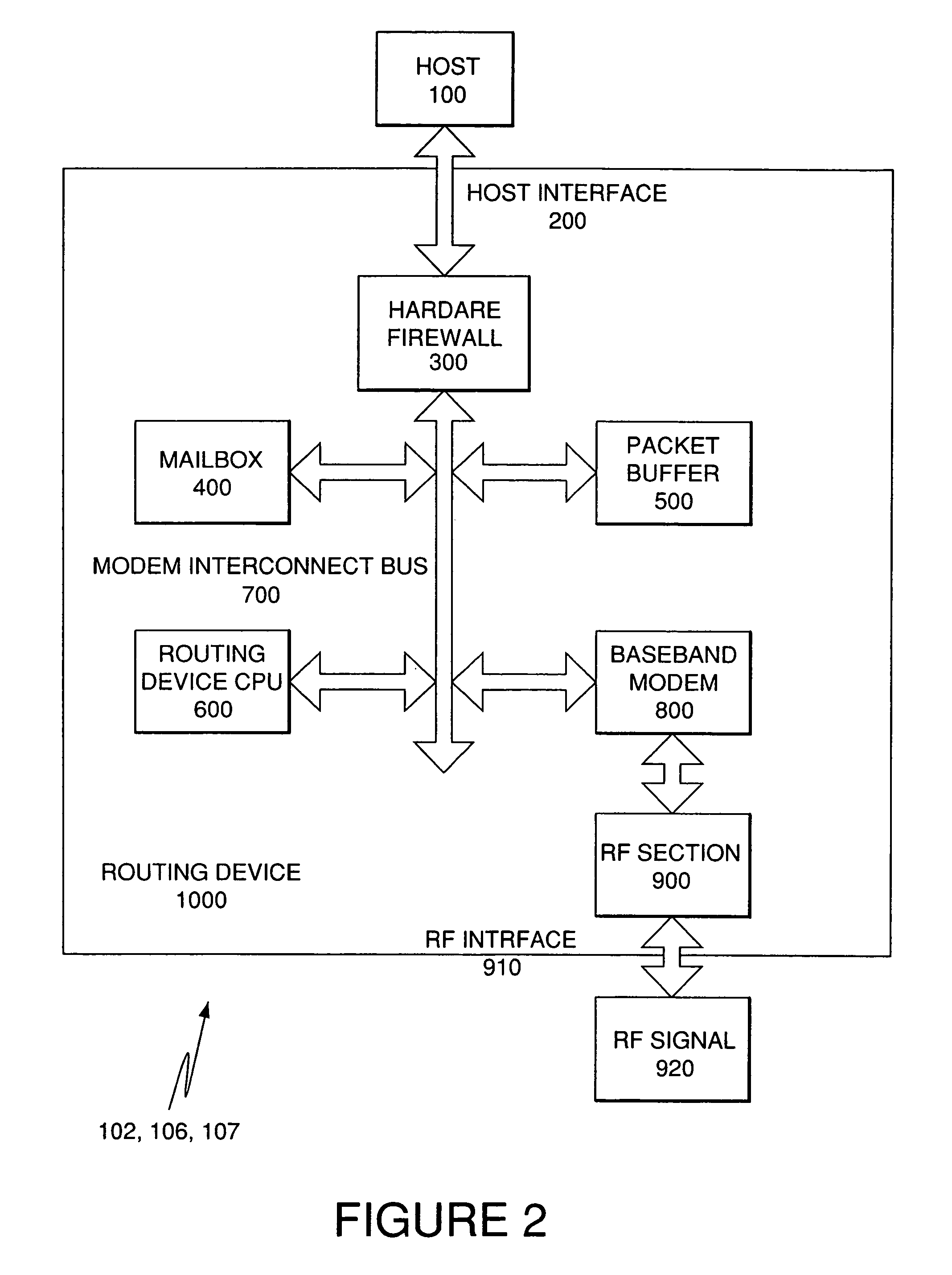
System and method for a routing device to securely share network data with a host utilizing a hardware firewall
ActiveUS7284268B2Limited dataPrevent unauthorized accessData taking preventionDigital data processing detailsNetwork packetNetwork data
A system and method for providing the ability to selectively share data in a network routing device with an associated host. The system and method employs a hardware firewall in the routing device which restricts the host such that it can only access areas in shared memory which contains data destined for the host. The routing device CPU notifies the host of pending data and the location of that data in the shared memory. The hardware firewall is also notified of the location in shared memory which the host may access. When the host attempts to read the data, the firewall ensures that only the stated memory area or areas are accessed by the host. Once the data has been read by the host, the firewall is notified to cancel the host's ability to access the shared memory until such time as a new packet destined for the host arrives in the routing device.
Owner:ARRIS ENTERPRISES LLC
Method for simultaneous characterization and expansion of reference libraries for small molecule identification
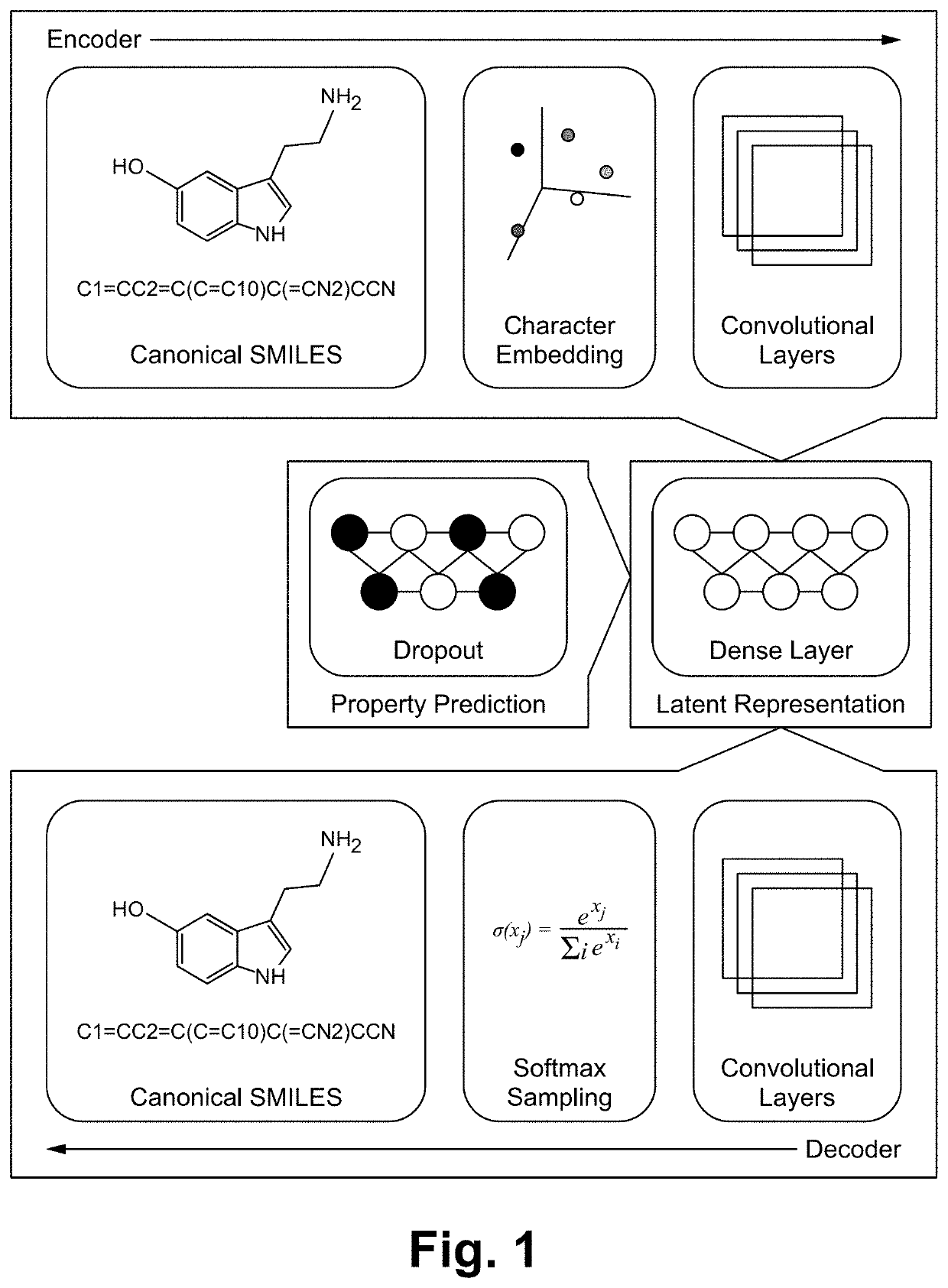
ActiveUS20200176087A1Increase percentageImprove discriminationChemical property predictionMathematical modelsData setAlgorithm
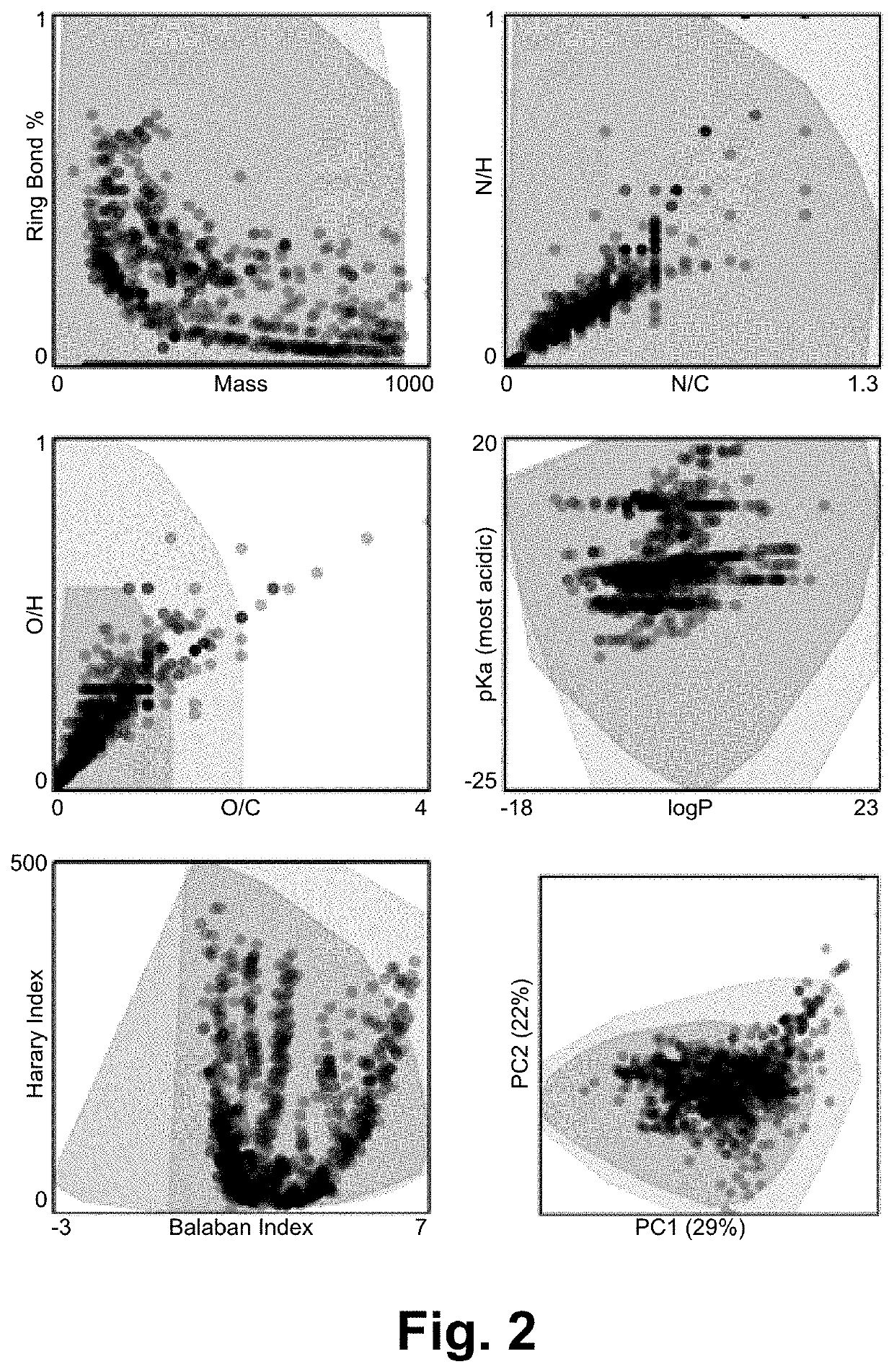
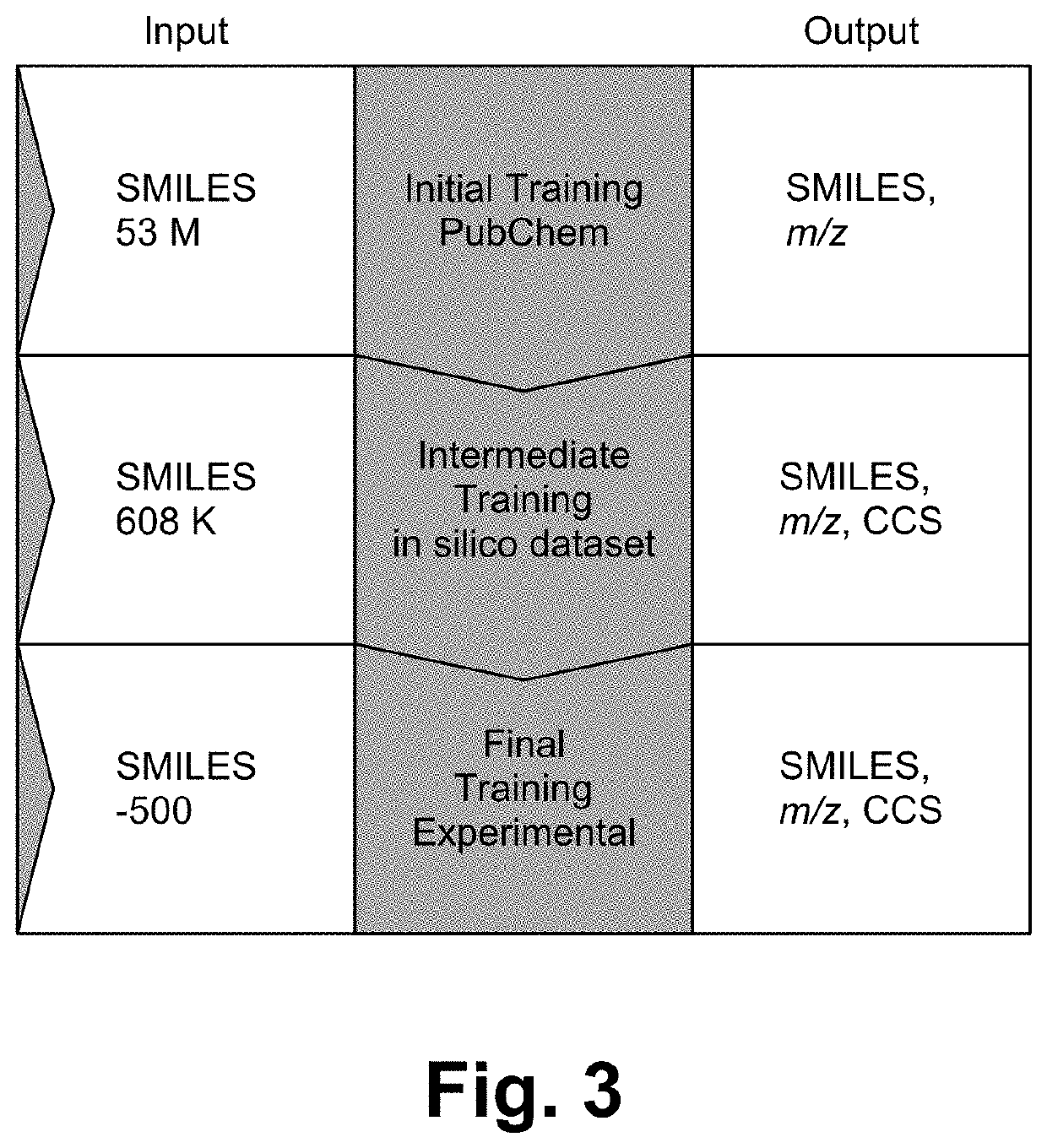
A variational autoencoder (VAE) has been developed to learn a continuous numerical, or latent, representation of molecular structure to expand reference libraries for small molecule identification. The VAE has been extended to include a chemical property decoder, trained as a multitask network, to shape the latent representation such that it assembles according to desired chemical properties. The approach is unique in its application to metabolomics and small molecule identification, focused on properties that are obtained from experimental measurements (m / z, CCS) paired with its training paradigm, which involves a cascade of transfer learning iterations. First, molecular representation is learned from a large dataset of structures with m / z labels. Next, in silico property values are used to continue training. Finally, the network is further refined by being trained with the experimental data. The trained network is used to predict chemical properties directly from structure and generate candidate structures with desired chemical properties. The network is extensible to other training data and molecular representations, and for use with other analytical platforms, for both chemical property and feature prediction as well as molecular structure generation.
Owner:BATTELLE MEMORIAL INST
Information processing device and method, program, and recording medium
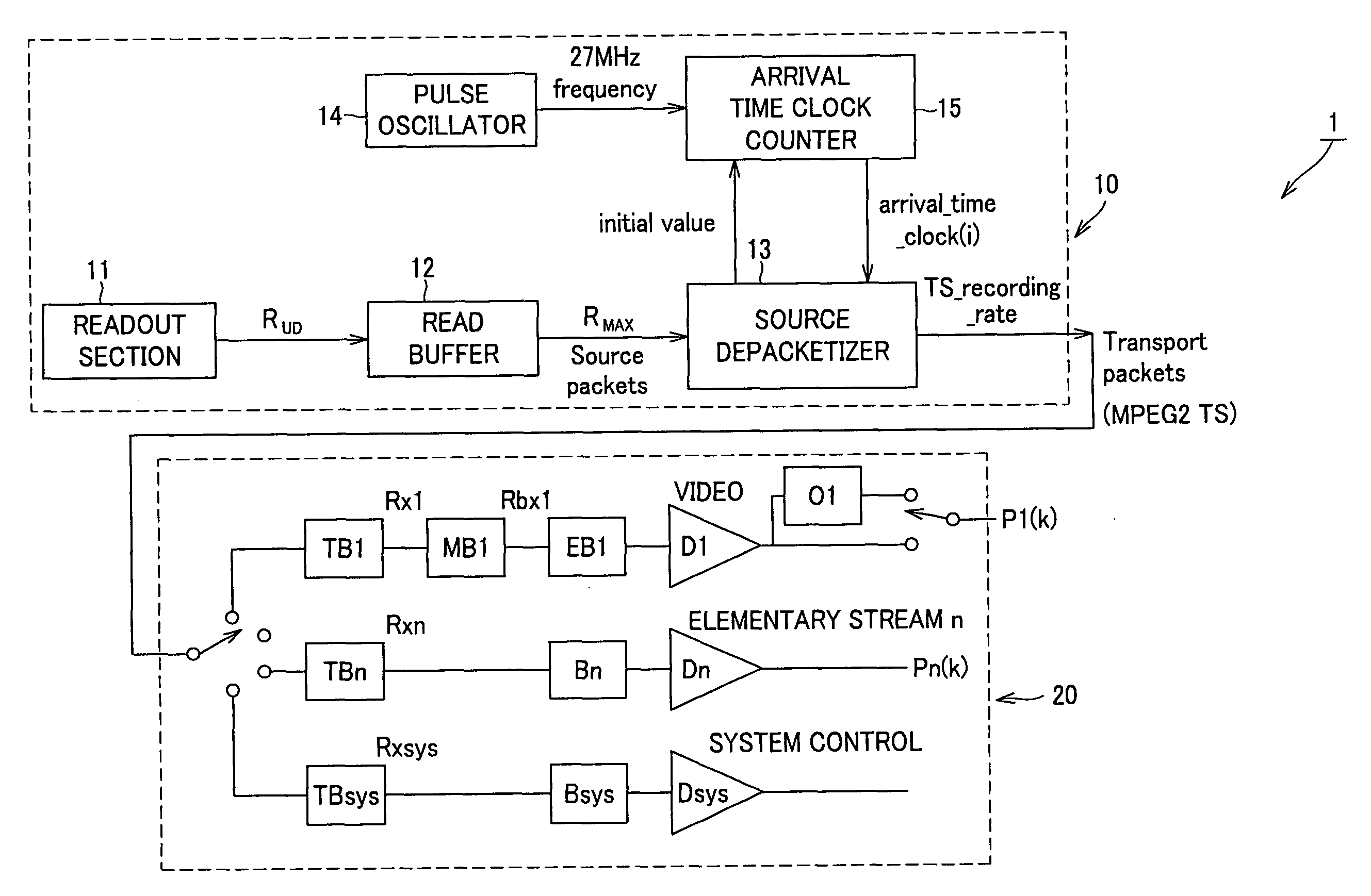
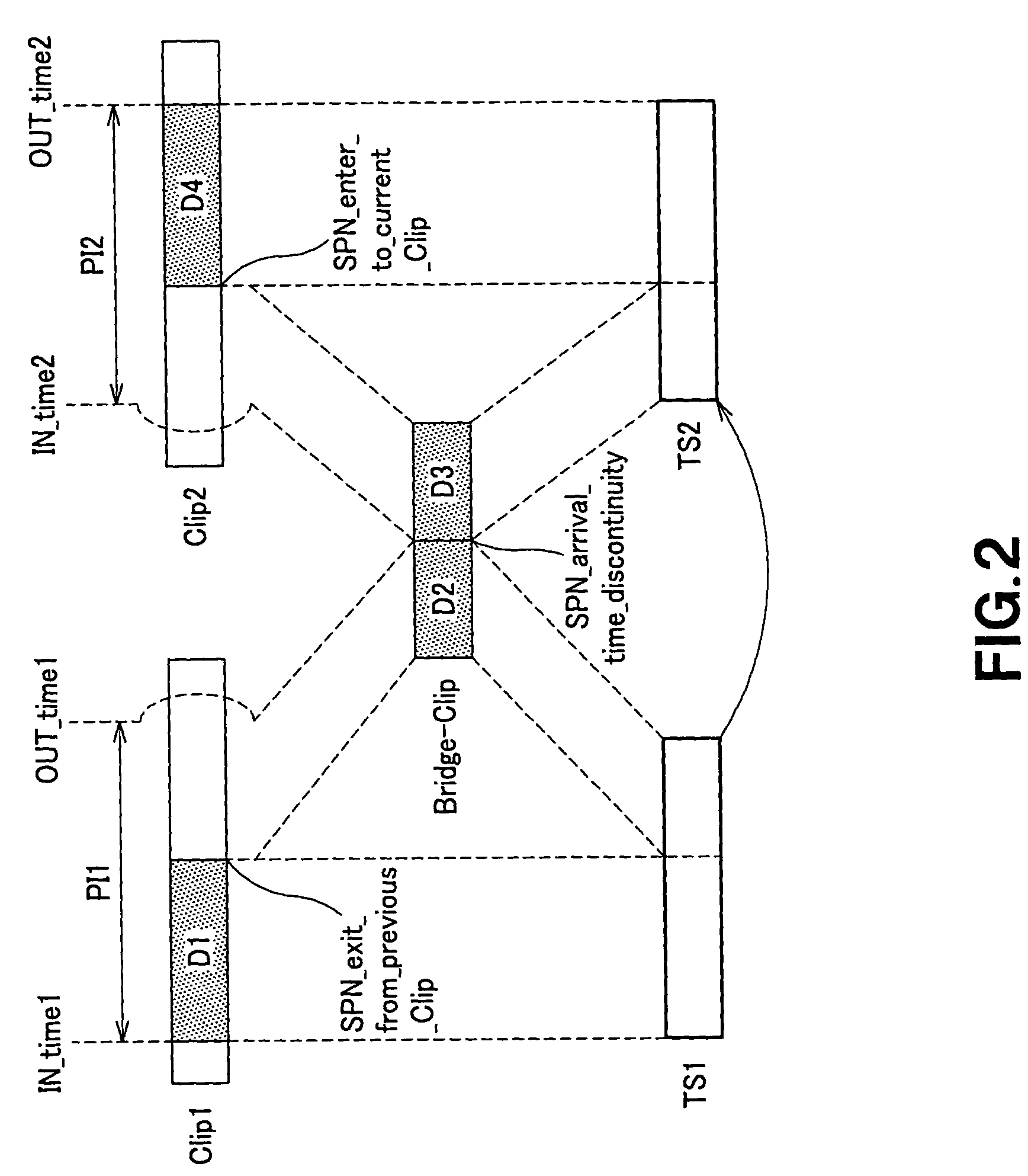
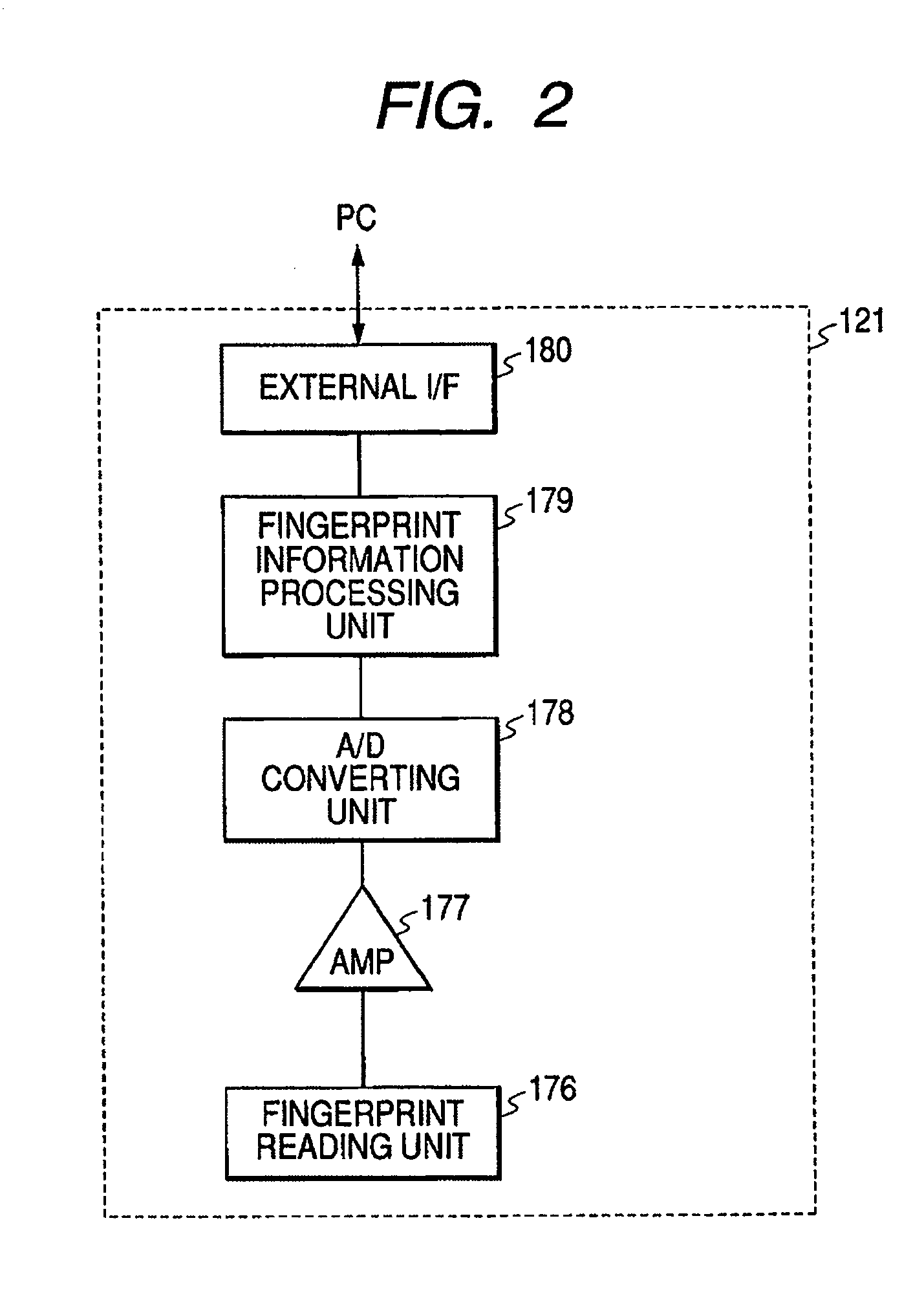
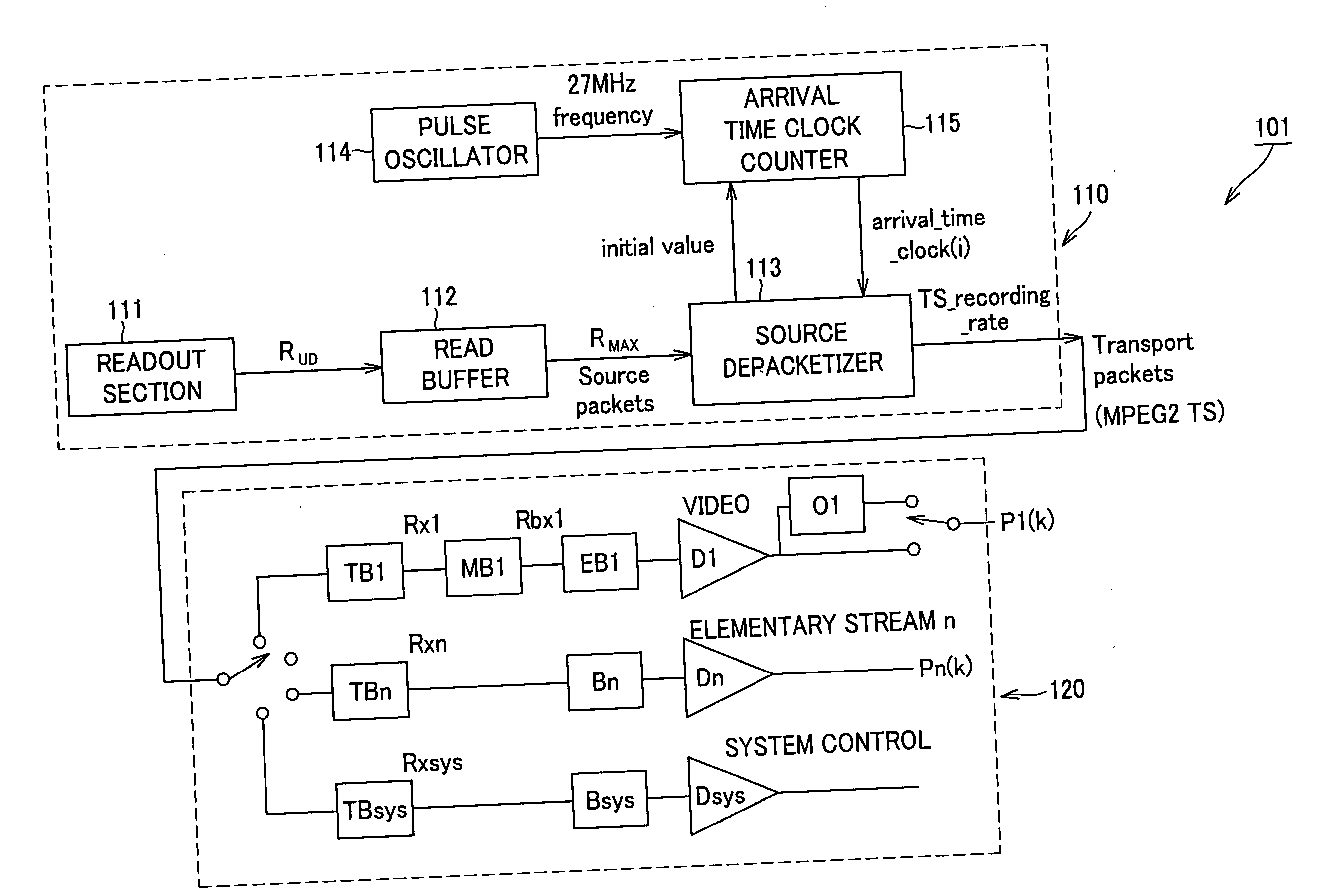
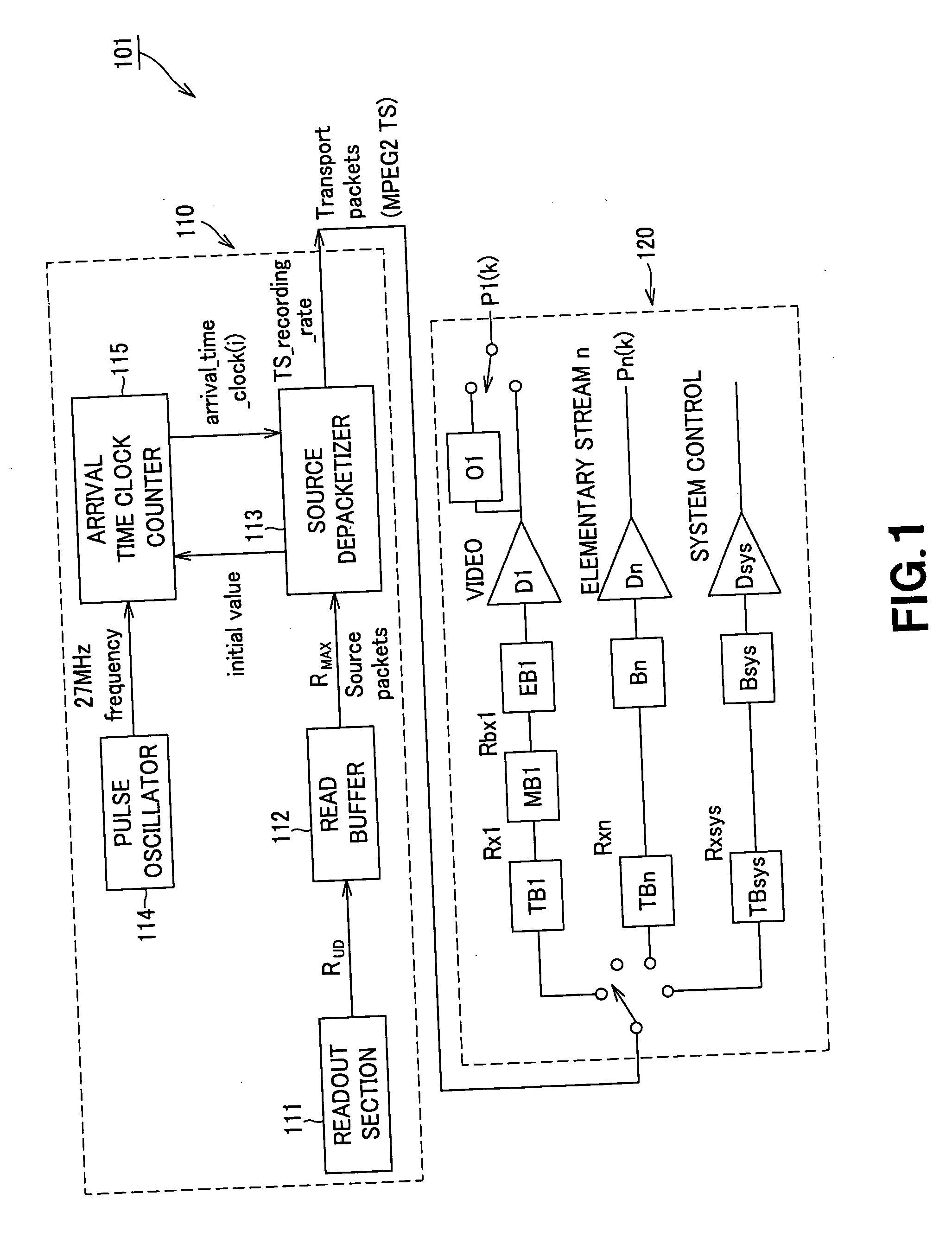
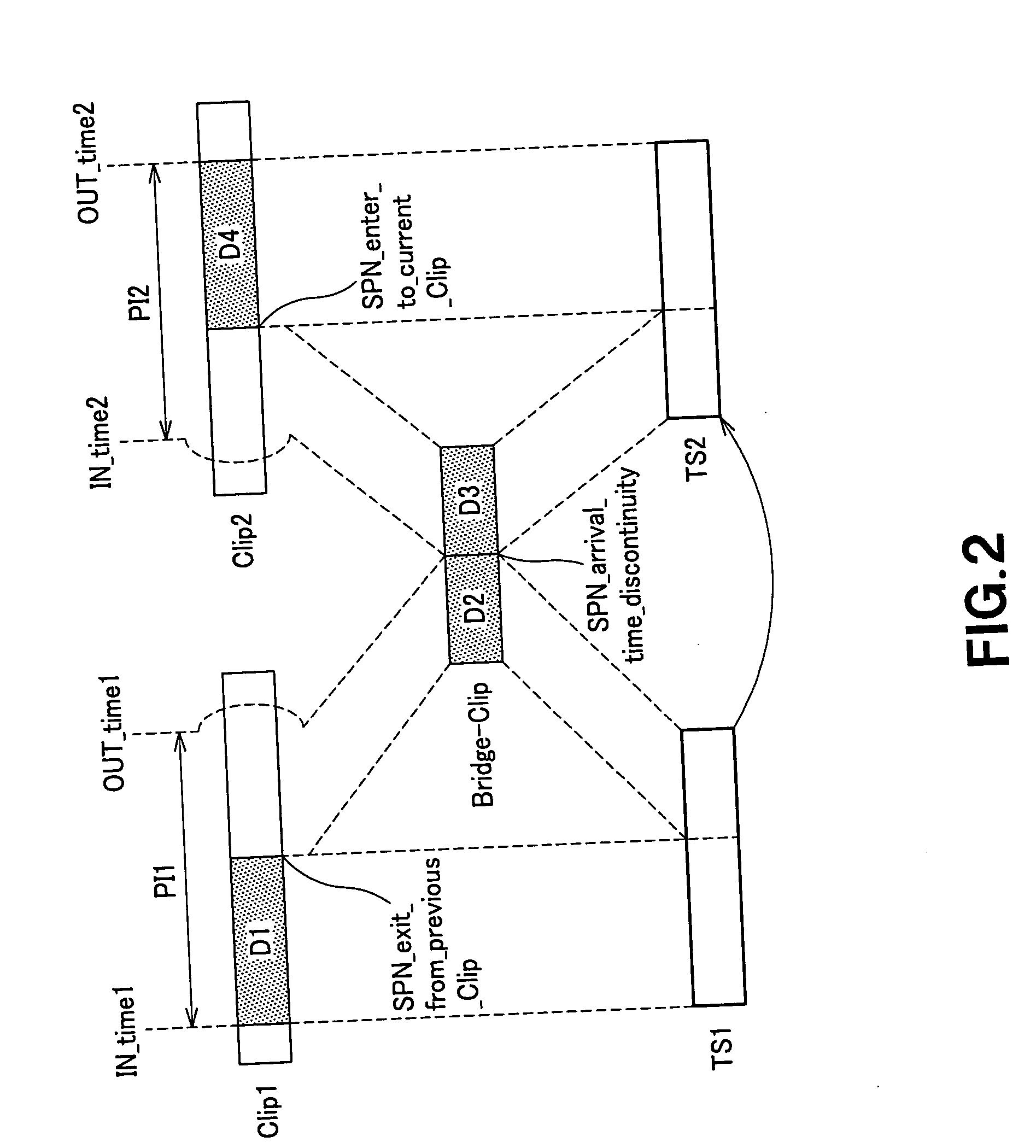
ActiveUS8086087B2Limited dataReduce restrictionsTelevision system detailsRecording carrier detailsInformation processingArrival time
A player model (1) includes an output section (10) that reads out a source packet having a transport packet and arrival time stamp from TS1 and TS2 connected seamlessly to each other and outputs the transport packet according to the arrival time stamp, and a decoder (20) that decodes the transport packet. The output section (10) inputs the transport packet according to the arrival time stamp of the source packet to the decoder (20). The decoder (20) includes an audio buffer TBn having a capacity capable of buffering the audio data corresponding to the time required for inputting I picture, which is the first picture of TS2, to a video buffer TB1.
Owner:SONY CORP
Integrated circuit apparatus
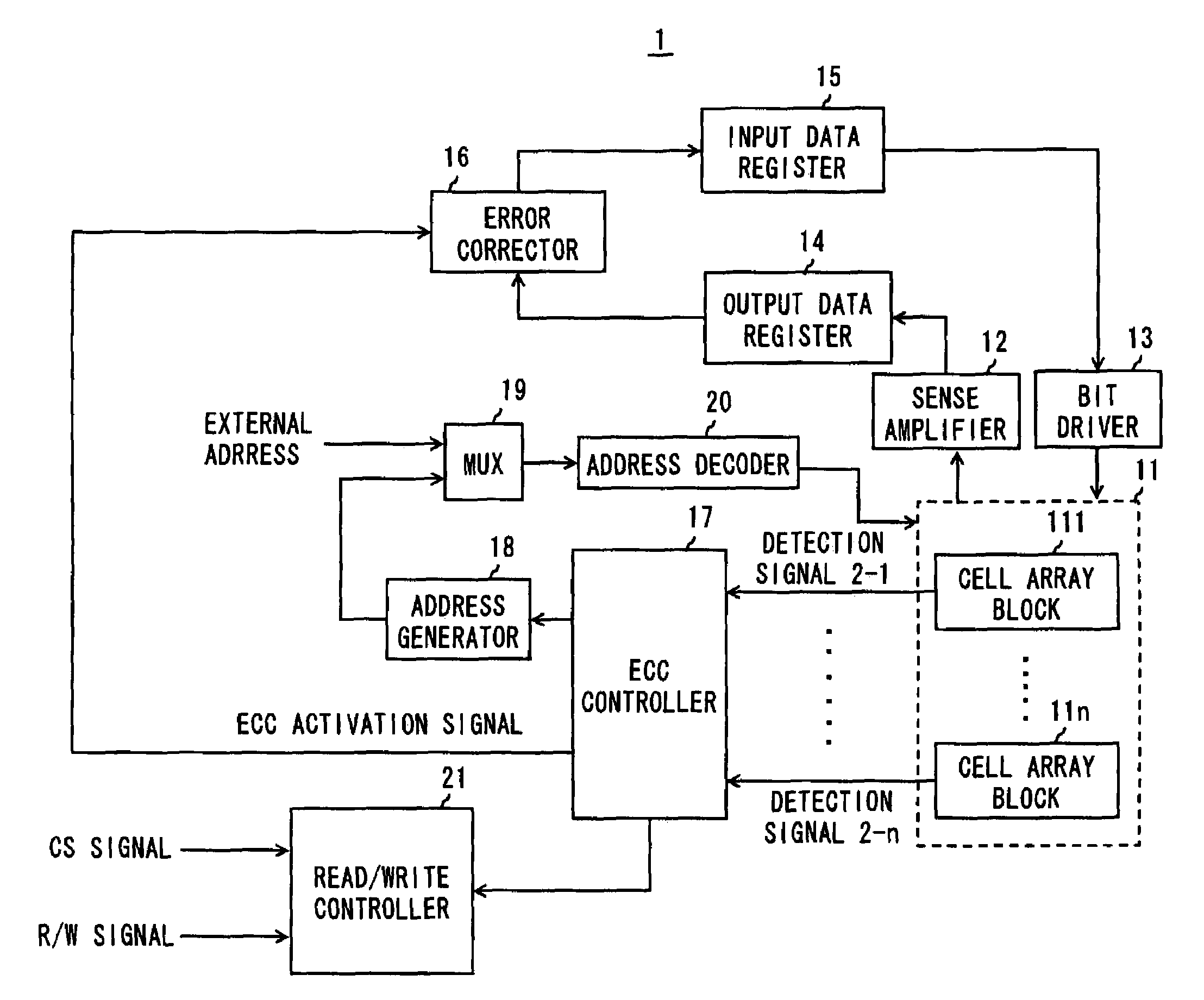
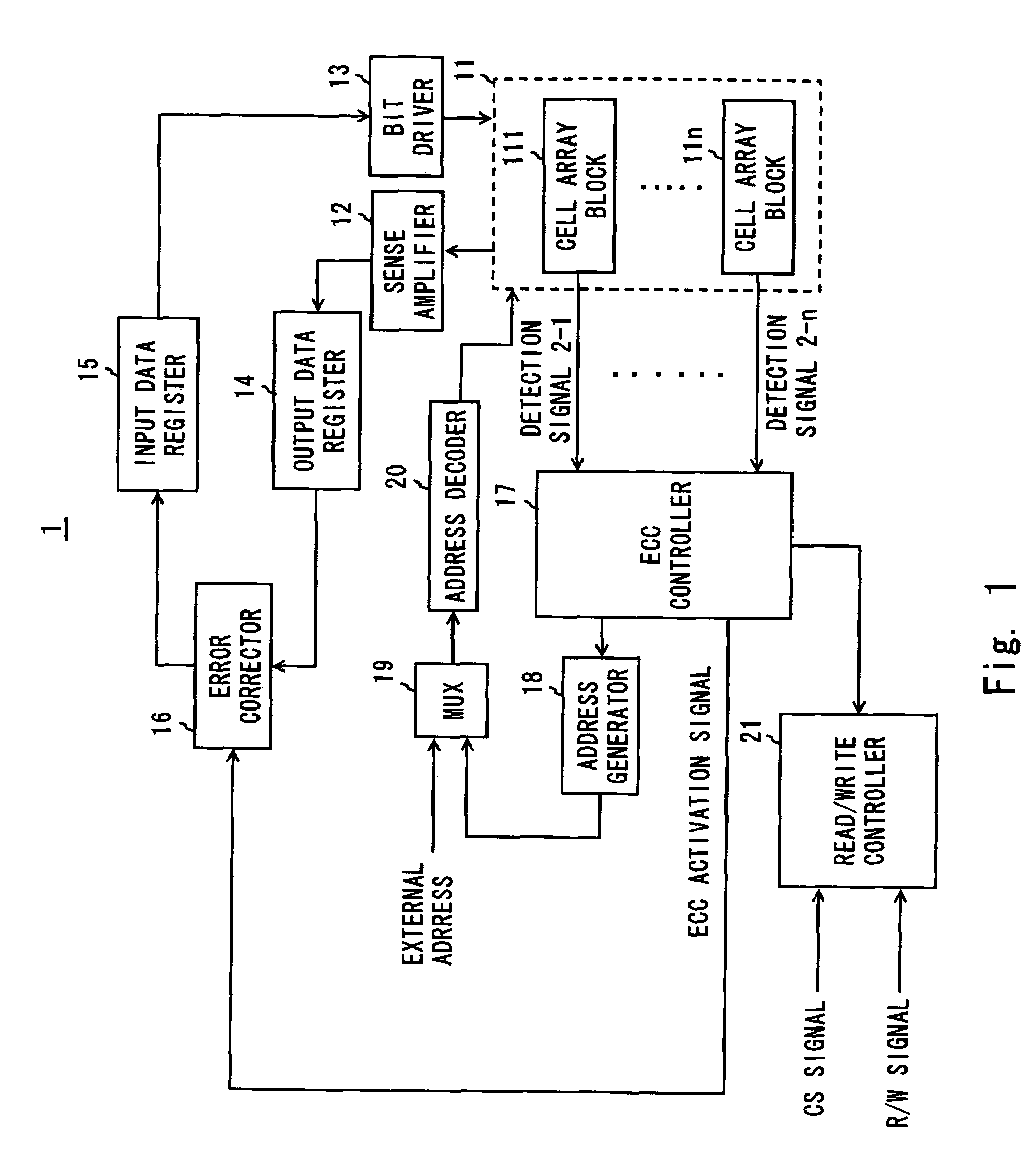
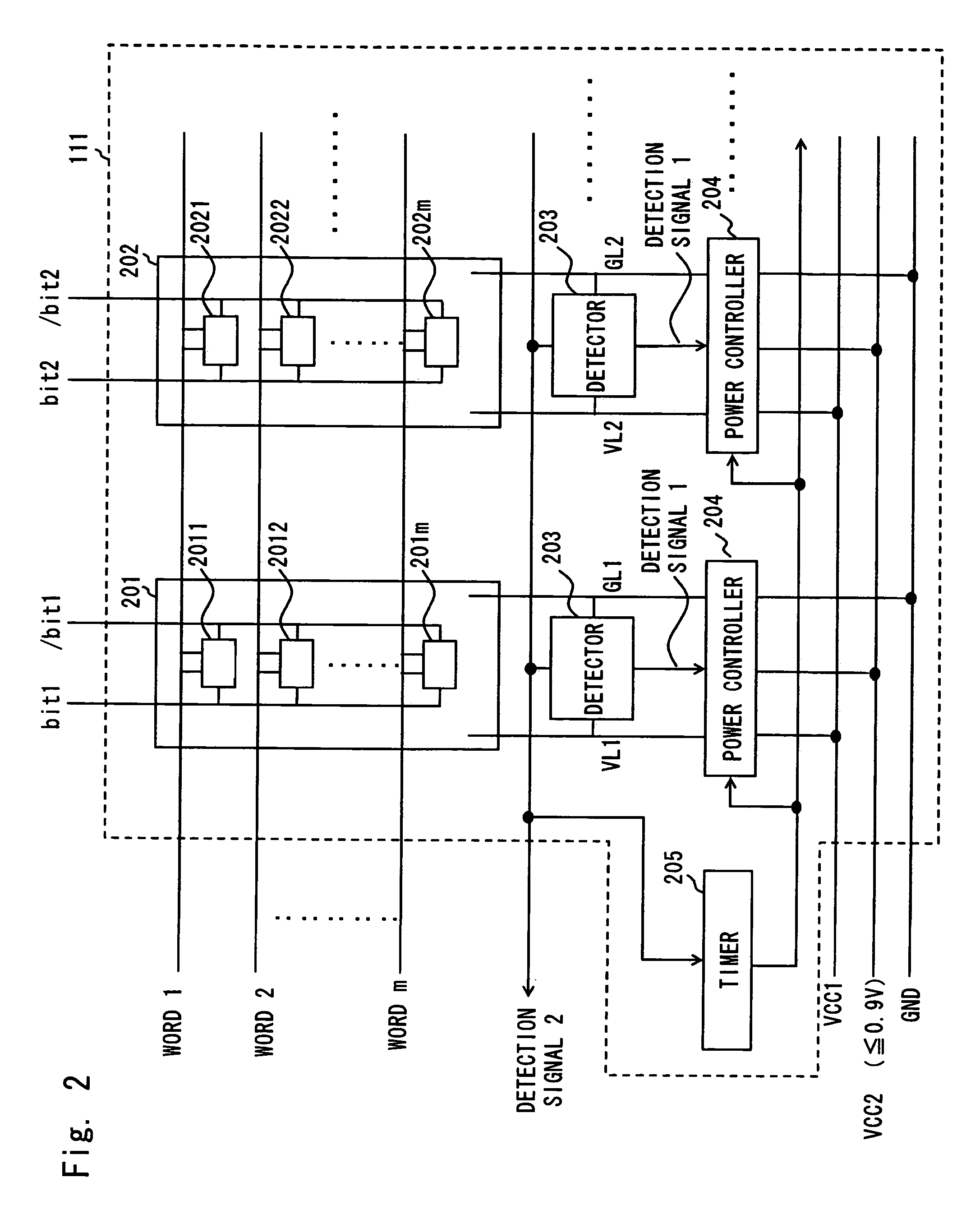
An integrated circuit apparatus includes a SRAM cell array having a plurality of memory cells formed of CMOSFET arranged lattice-like. The SRAM cell array has a pair of power line and ground line in each of 1-bit sequences. The integrated circuit apparatus also includes a detector detecting the occurrence of latch-up for each 1-bit sequence and outputting a detection signal, and a power controller controlling a power supply voltage to the power line for each 1-bit sequence. The power controller reduces a voltage to be supplied to the power line in the 1-bit sequence where latch-up is occurring down to a predetermined value according to the detection signal.
Owner:RENESAS ELECTRONICS CORP
Controlling an influence on a user in a rendering environment
ActiveUS9612654B2Optimize the player's enjoymentSimple processInput/output for user-computer interactionVideo gamesUser expectationsComputer science
Owner:KONINK PHILIPS ELECTRONICS NV
Learning method, corresponding system, device and computer program product
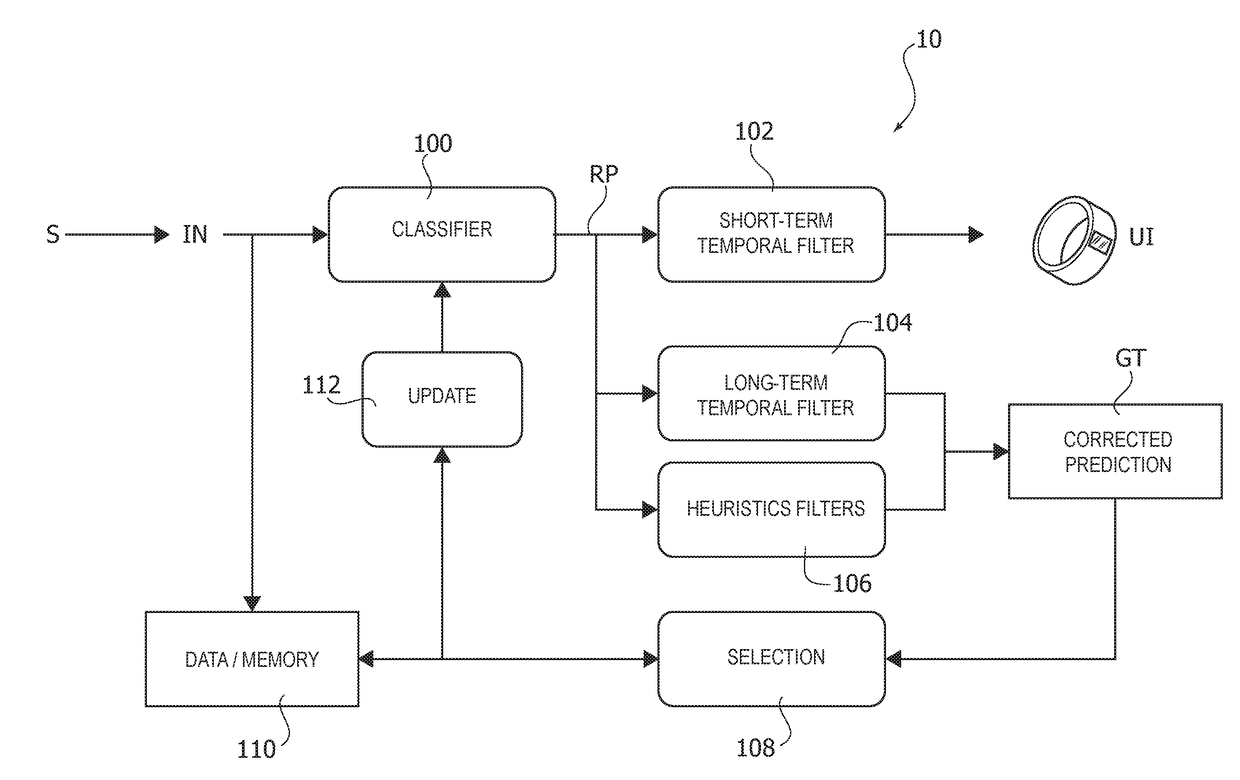
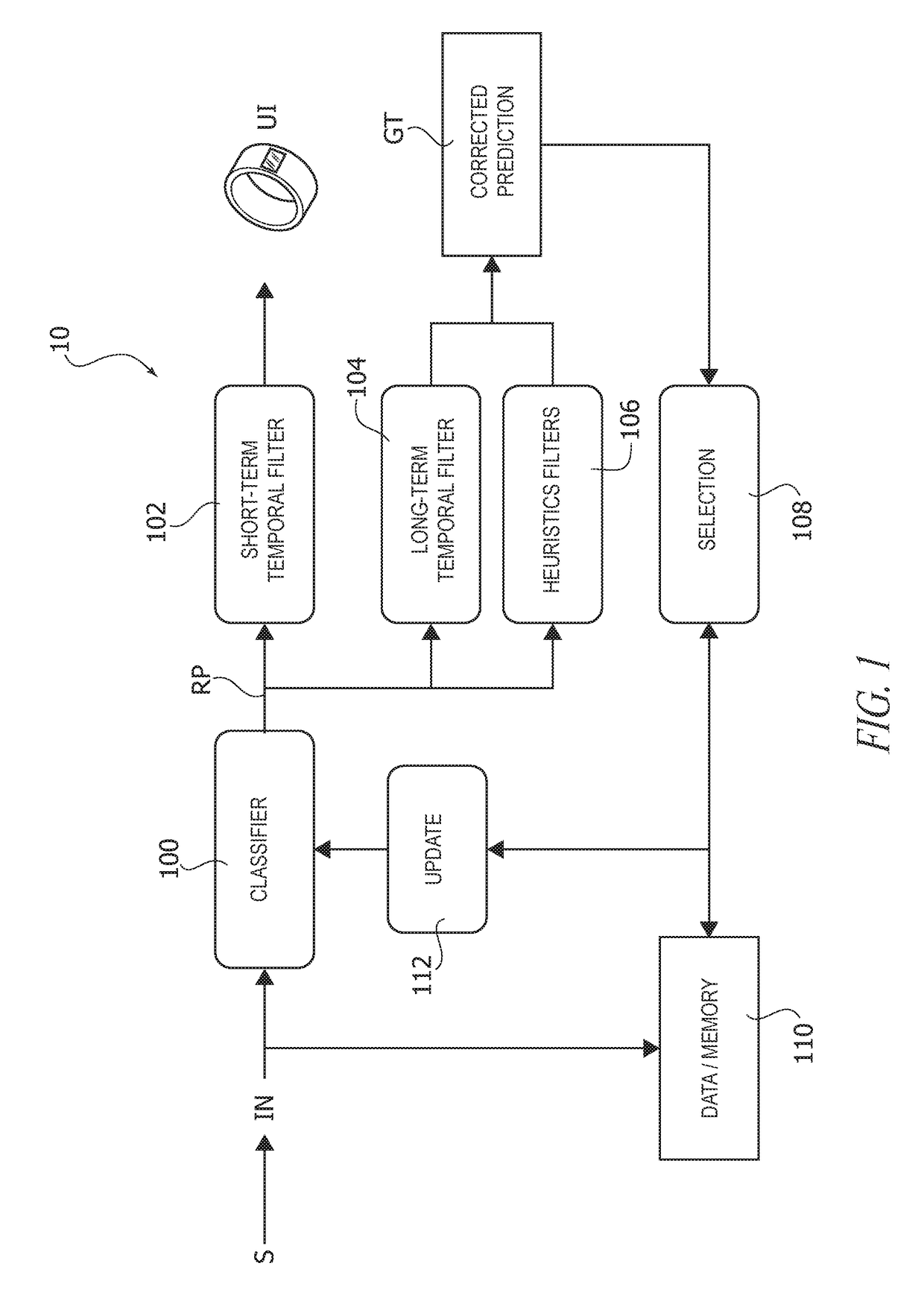
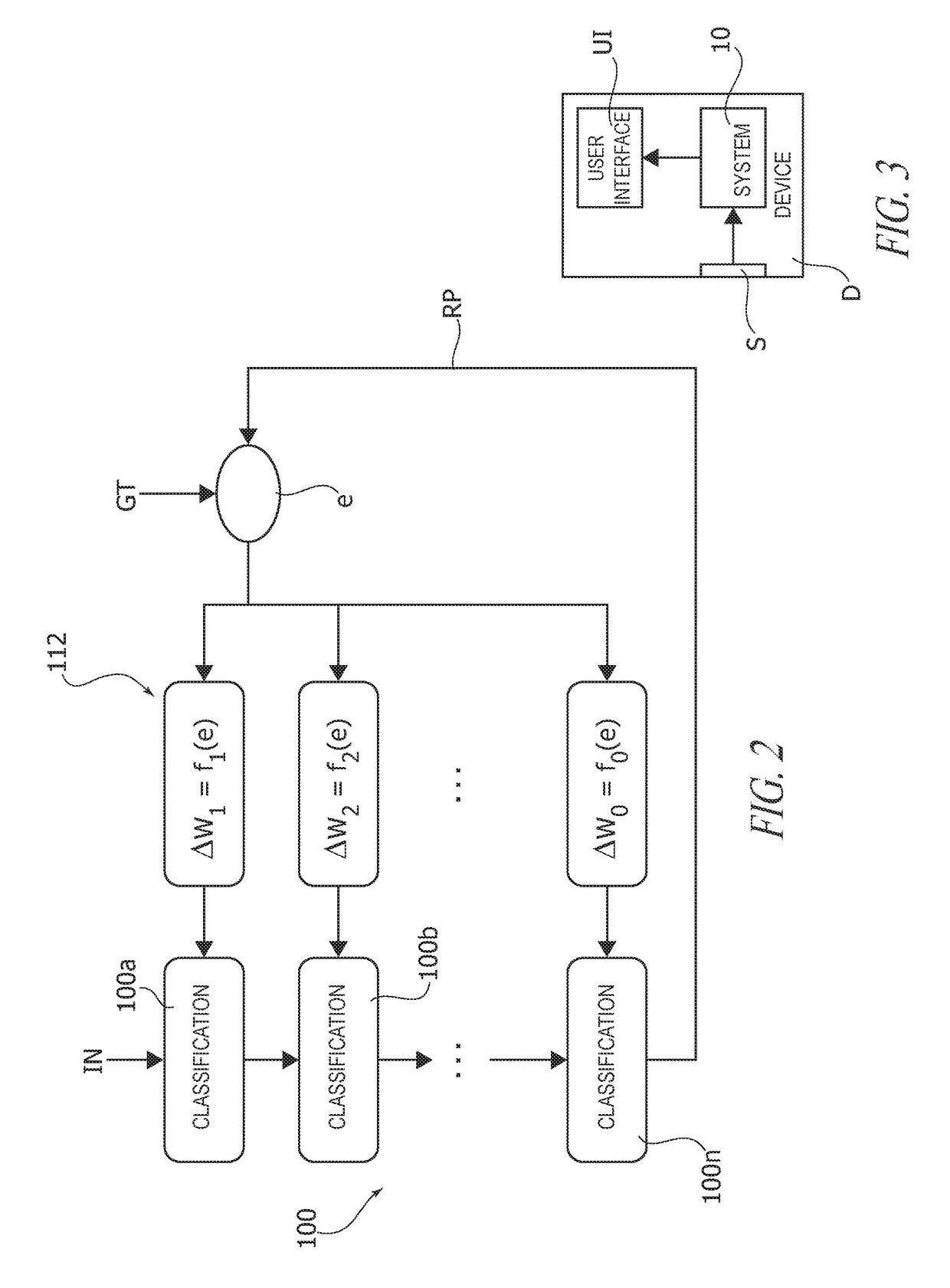
PendingUS20180247194A1Easy to predictAvoid communicationProbabilistic networksNeural learning methodsContext classificationModel parameters
A classification device receives sensor data from a set of sensors and generates, using a context classifier having a set of classifier model parameters, a set of raw predictions based on the received sensor data. Temporal filtering and heuristic filtering are applied to the raw predictions, producing filtered predictions. A prediction error is generated from the filtered predictions, and model parameters of the set of classifier model parameters are updated based on said prediction error. The classification device may be a wearable device.
Owner:STMICROELECTRONICS SRL
Information processing apparatus, information processing method, computer program, and image forming system
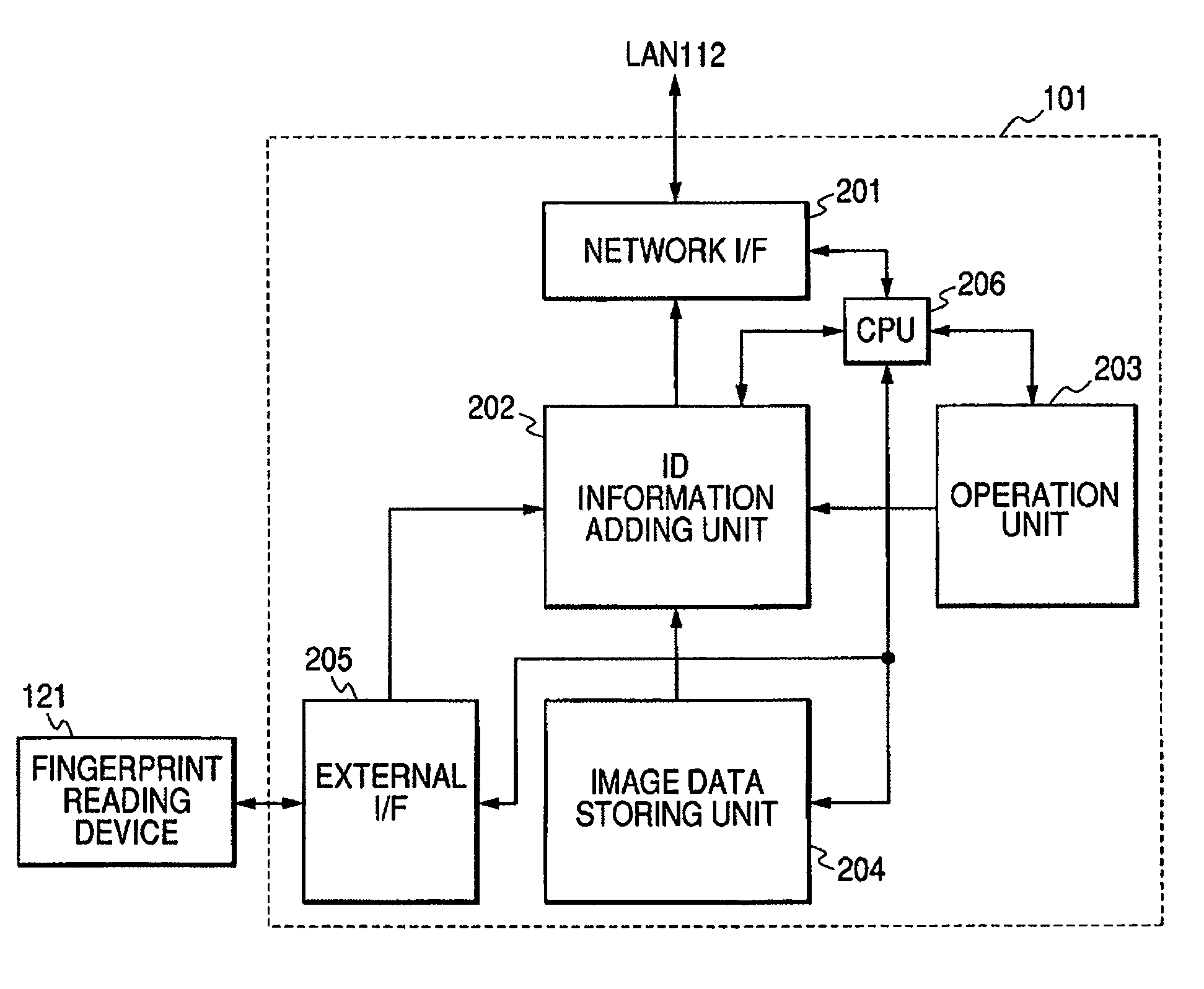
InactiveUS20060250635A1Improve securityLimited dataCharacter and pattern recognitionComputer security arrangementsInformation processingImage formation
The invention provides an information processing apparatus in which print data is inputted, whether or not authentication information has been added to the print data is discriminated, and an output destination of the print data is controlled on the basis of the discrimination result, thereby making it possible to prevent the print data from being sent to an image output apparatus of a low security level.
Owner:CANON KK
Information processing device and method, program, and recording medium
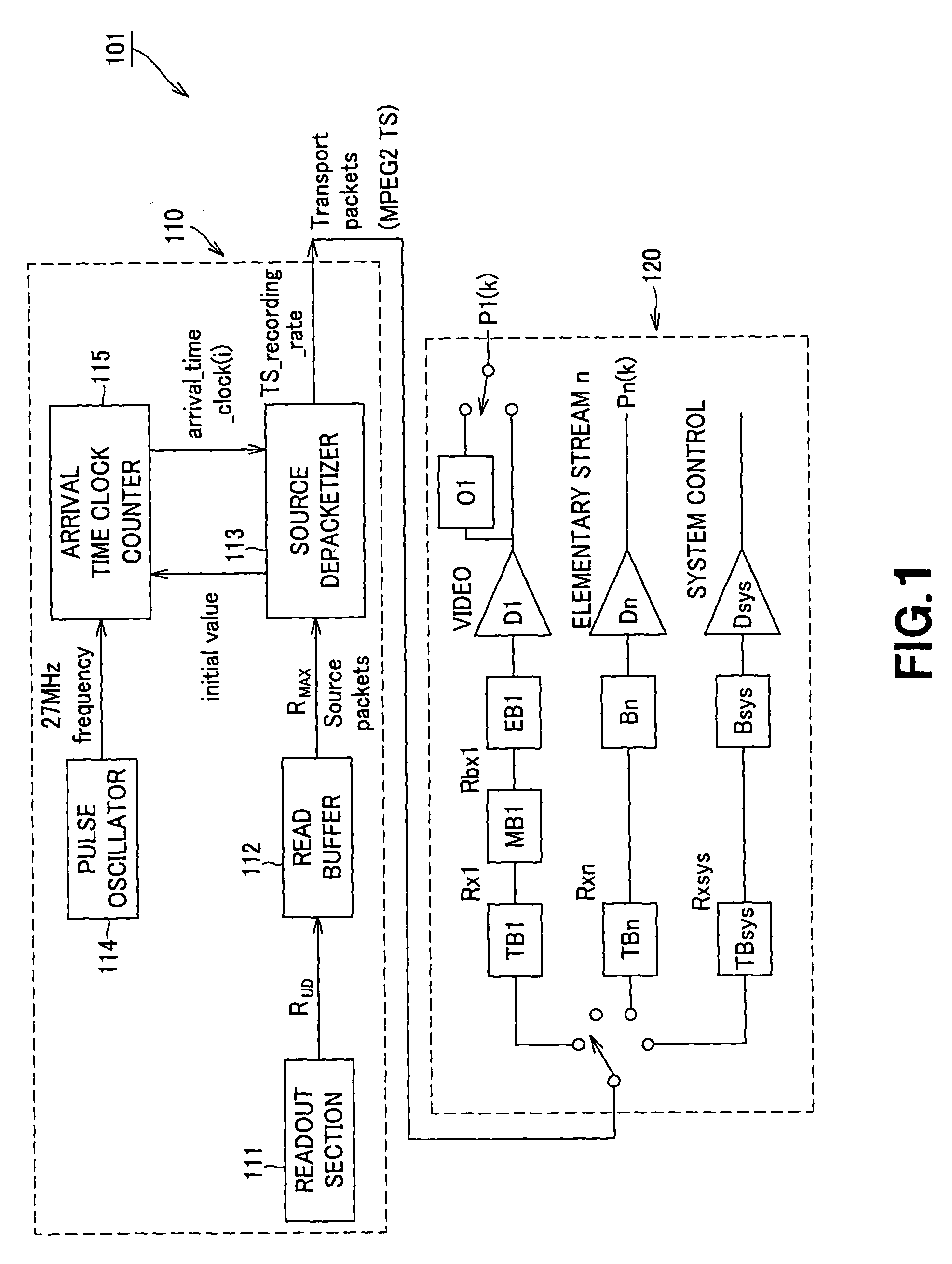
ActiveUS20050249202A1Easy to codeLimited dataTelevision system detailsRecording carrier detailsInformation processingArrival time
A player model (1) includes an output section (10) that reads out a source packet having a transport packet and arrival time stamp from TS1 and TS2 connected seamlessly to each other and outputs the transport packet according to the arrival time stamp, and a decoder (20) that decodes the transport packet. The output section (10) inputs the transport packet according to the arrival time stamp of the source packet to the decoder (20). The decoder (20) includes an audio buffer TBn having a capacity capable of buffering the audio data corresponding to the time required for inputting I picture, which is the first picture of TS2, to a video buffer TB1.
Owner:SONY CORP
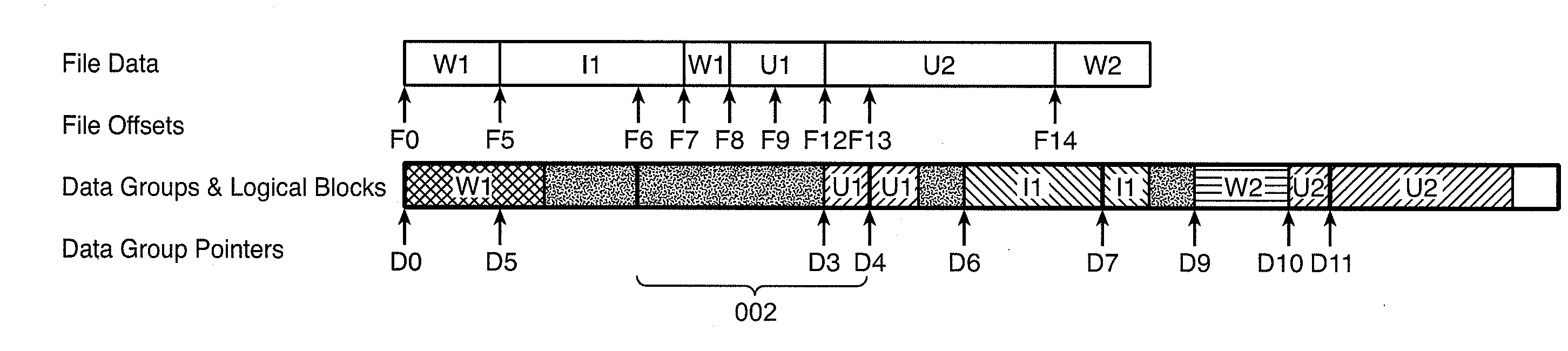
Stream compression and decompression
InactiveUS20130144850A1Simple accessIncrease the compression ratioDigital data information retrievalDigital data processing detailsBlock codeComputer science
Owner:IBM CORP
Stream compression and decompression
InactiveUS20130024434A1High data efficiencyLimited dataDigital data information retrievalDigital data processing detailsBlock codeComputer science
A method for compressing a sequence of records, each record comprising a sequence of fields, comprises steps of buffering a record in a line of a matrix, reordering the lines of the matrix according to locality sensitive hash values of the buffered records such that records with similar contents in corresponding fields are placed in proximity, and consolidating fields in columns of the matrix into a block of codes. In this, consolidating yields codes of one of a first type comprising a sequence of individual fields and a second type comprising a sequence of fields with at least one repetition. The second type of code comprises a presence field indicating repeated fields and an iteration field indicating a number of respective repetitions. Decompression of the records from the block codes compressed above is also described.
Owner:IBM CORP
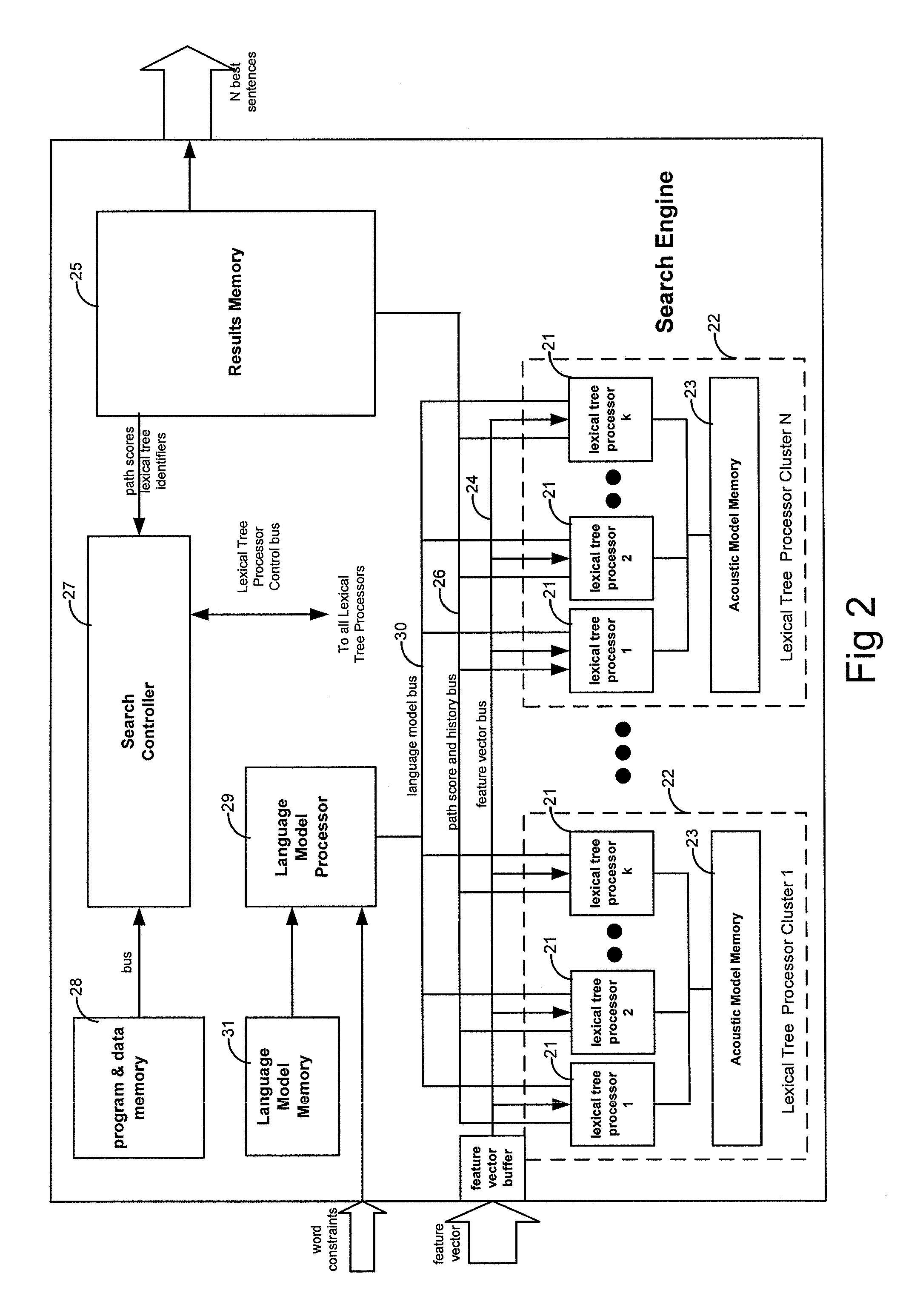
Speech recognition circuit using parallel processors
ActiveUS20120022871A1Effective process managementImprove accuracySpeech recognitionLexical itemSpeech identification
A speech recognition circuit comprises a memory containing lexical data for word recognition, the lexical data comprising a plurality of lexical data structures stored in each of a plurality of parts of the memory; and a parallel processor structure connected to the memory to process speech parameters by performing parallel processing on a plurality of the lexical data structures.
Owner:ZENTIAN
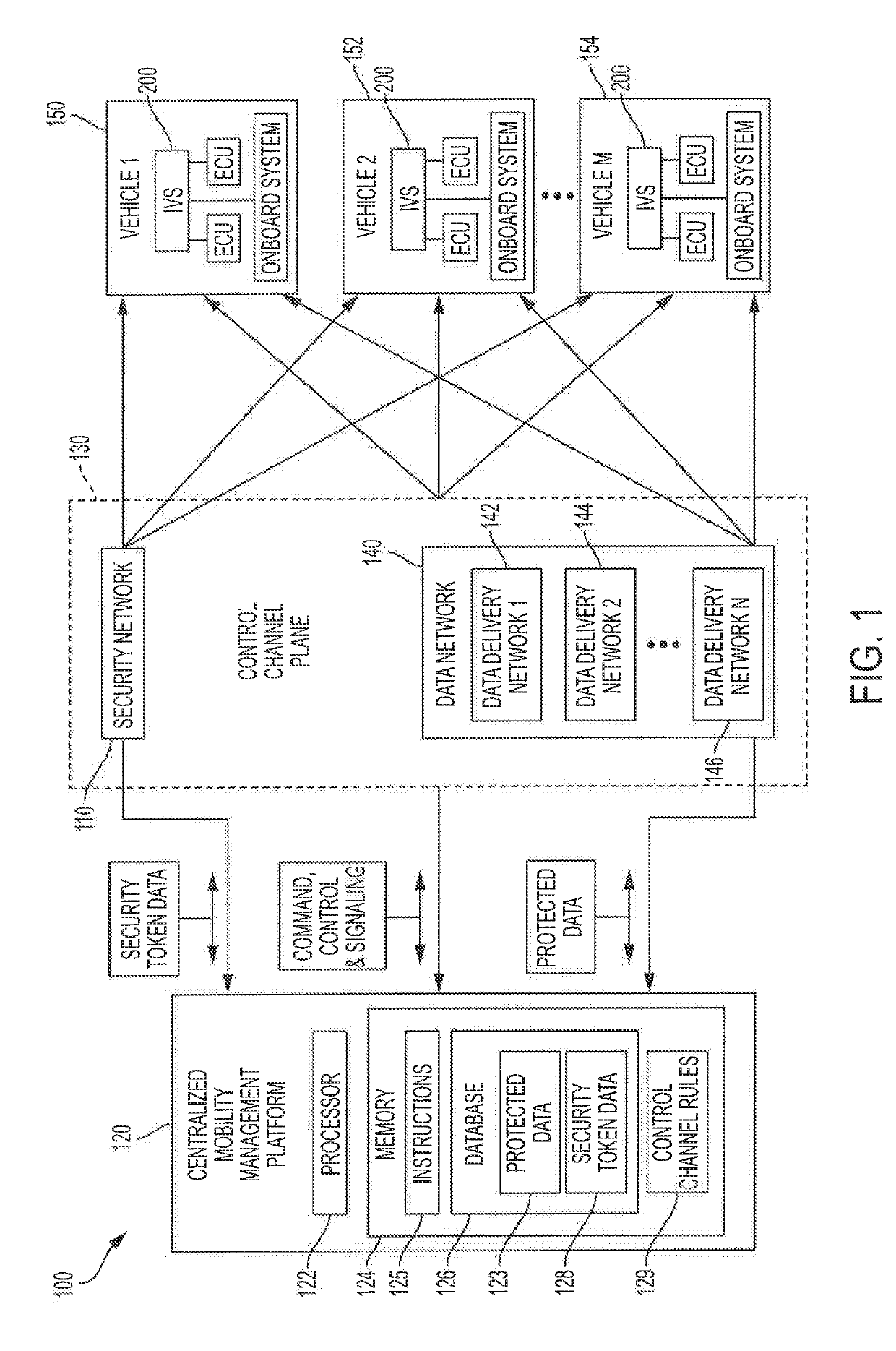
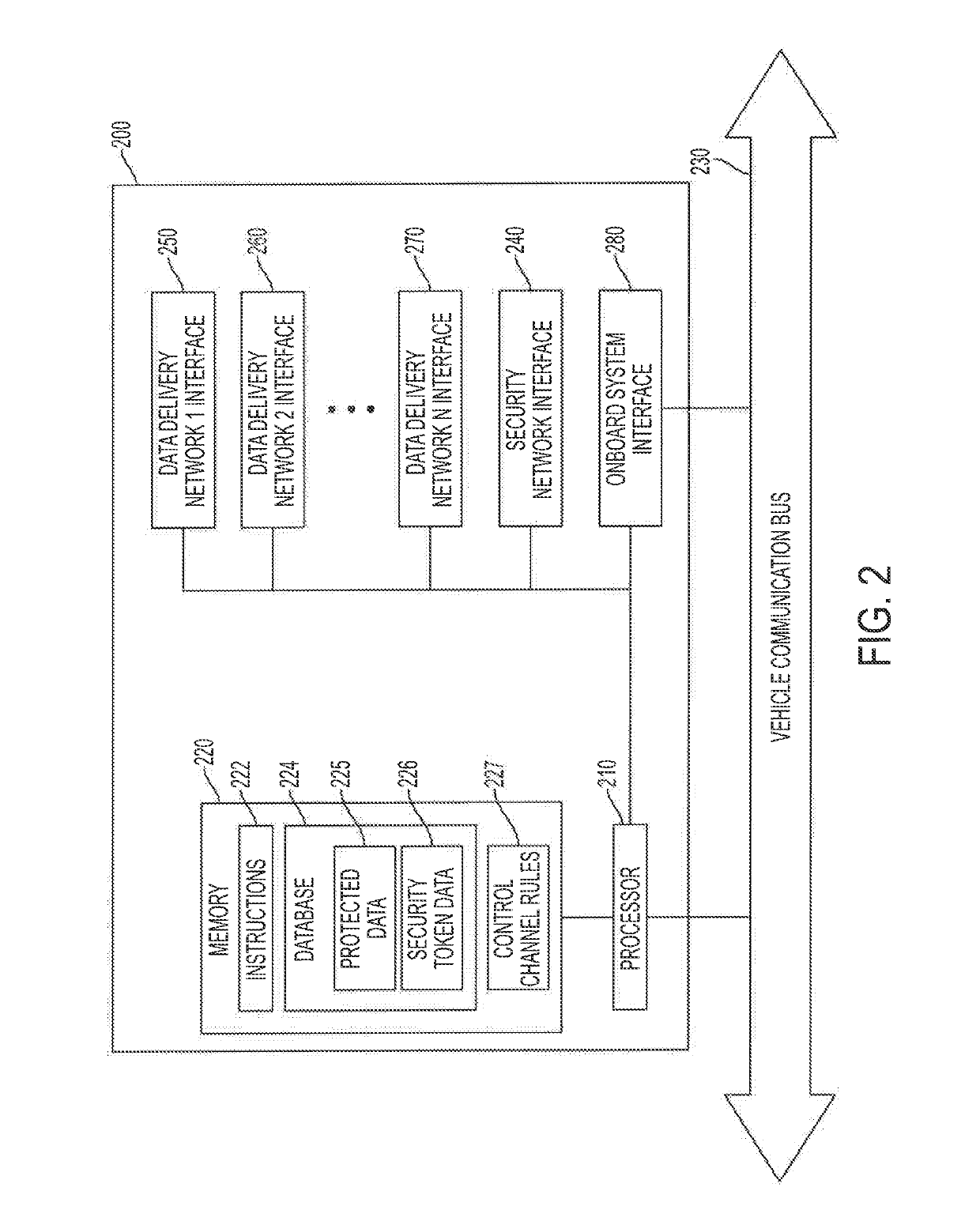
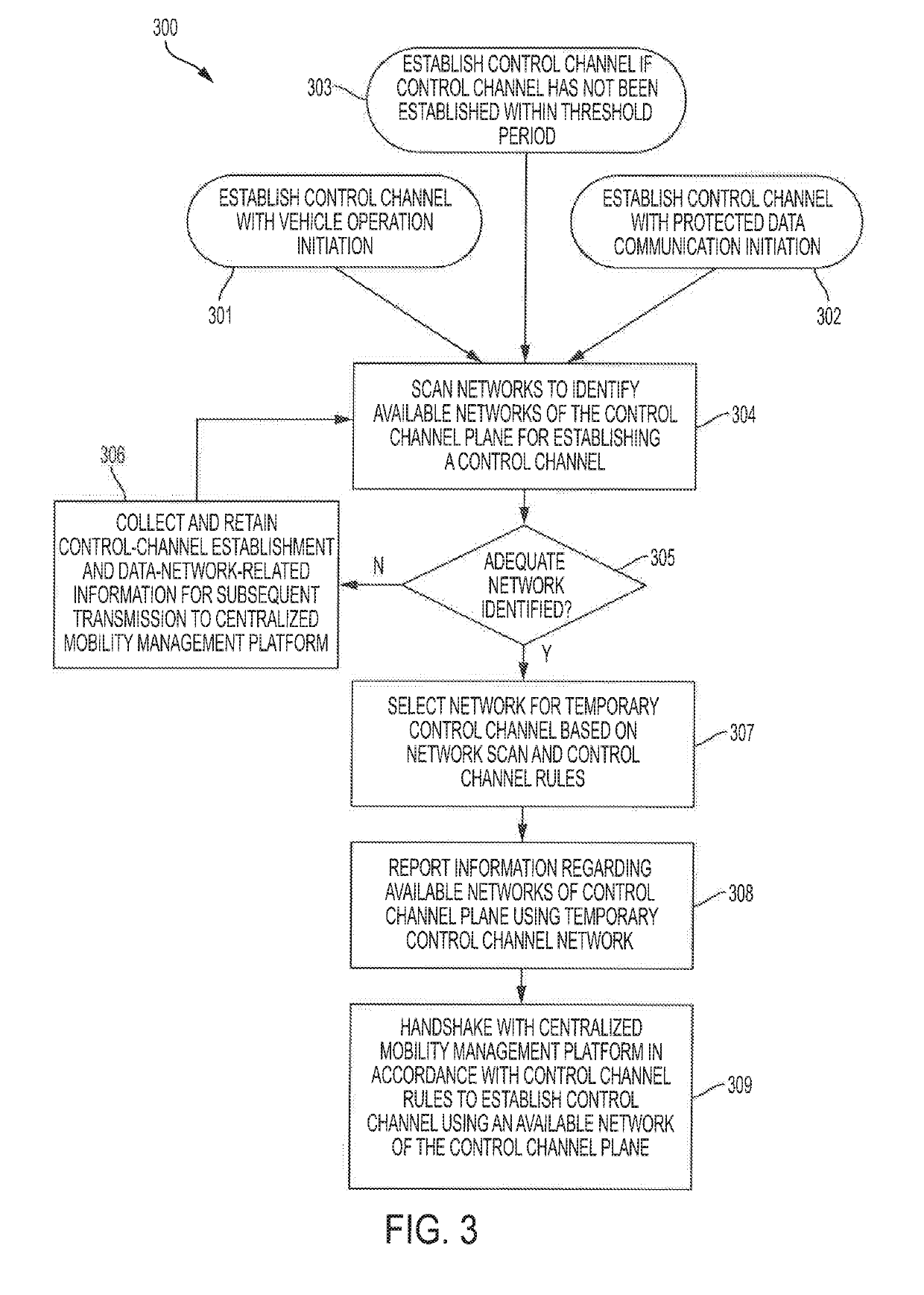
Systems and methods for reliably providing a control channel for communicating control information with automotive electronic control units
ActiveUS20190208420A1Facilitate communicationImprove securityParticular environment based servicesIn-vehicle communicationControl signalIn vehicle
Systems and methods which provide reliable and resilient control channels for communicating control information with vehicle onboard systems using a control channel plane supporting migration of a control channel among various networks forming the control channel plane are described, The control channel plane of embodiments includes at least one data delivery network of a data network and at least one out-of-band network of a security network. Embodiments introduce an in-vehicle system into vehicles facilitating secure data communication between a centralized mobility management platform and the vehicles using a data network for data content communication and a security network for security enhancement with respect to the data network. The centralized mobility management platform and IVS may utilize the aforementioned control channel for control signaling with respect to such operations, wherein the control channel is migrated between various networks of the control channel plane to provide a reliable and resilient control channel.
Owner:AUTON INC
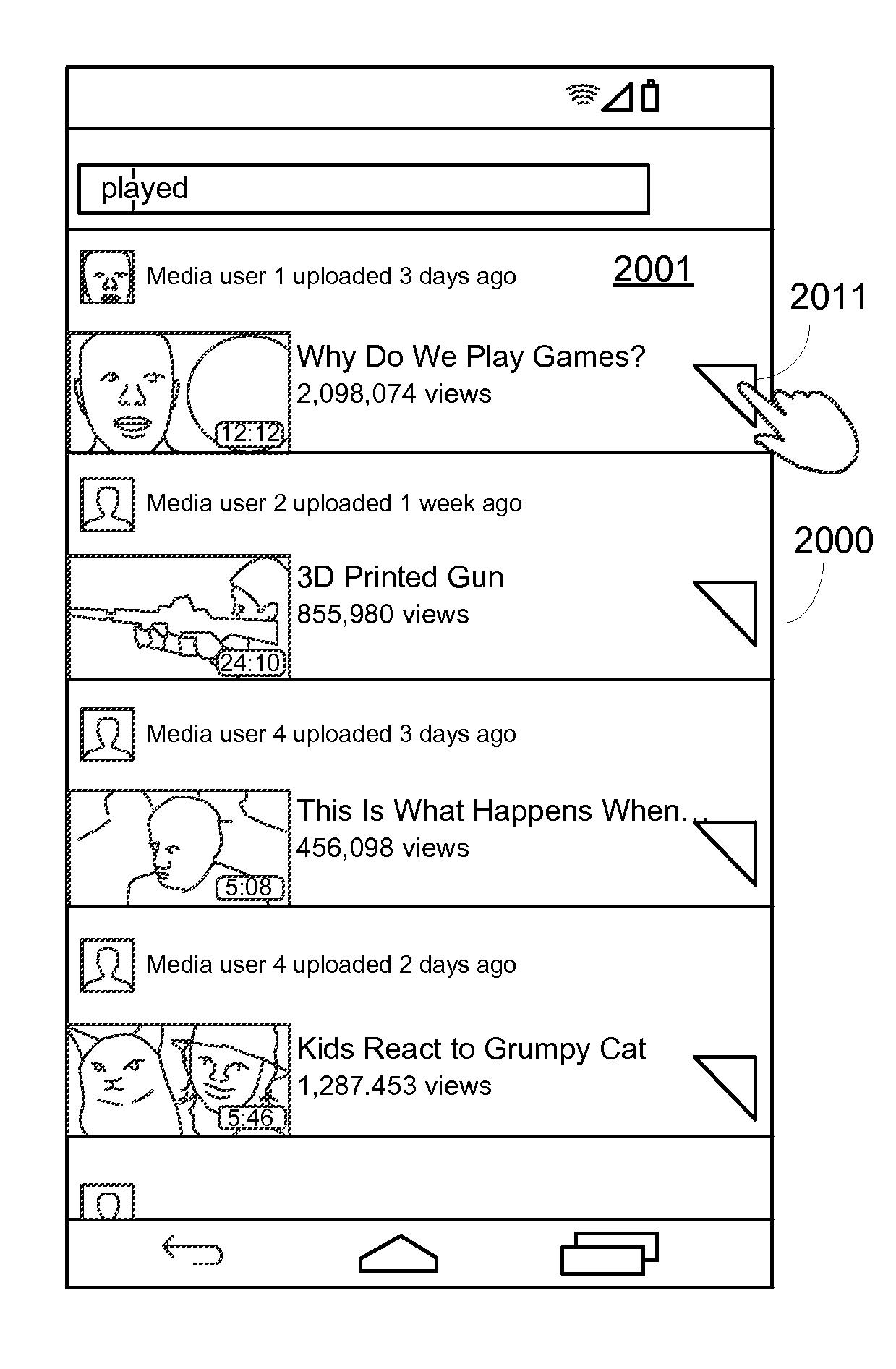
Methods and systems for displaying text using RSVP
ActiveUS9483109B2Enhanced informationLimited bandwidthInput/output for user-computer interactionCathode-ray tube indicatorsRapid serial visual presentationDisplay device
The disclosure describes systems and methods related to moving object content that is enhanced with textual content presented using rapid serial visual presentation (“RSVP”). In one embodiment, video content is enhanced with RSPV content. Related embodiments provide systems and methods for displaying, creating, and editing such content. A particular embodiment provides for RSPV enhanced video previews. In another embodiment, augmented reality content is enhanced with RSVP content. In some embodiments, RSPV enhanced moving object content is provided on various end user electronic devices including smart phones, smart watches, and head mounted displays. These and other embodiments are disclosed further herein.
Owner:SPRITZ HLDG LLC
Dynamic Assembly and Dispatch of Controlling Software
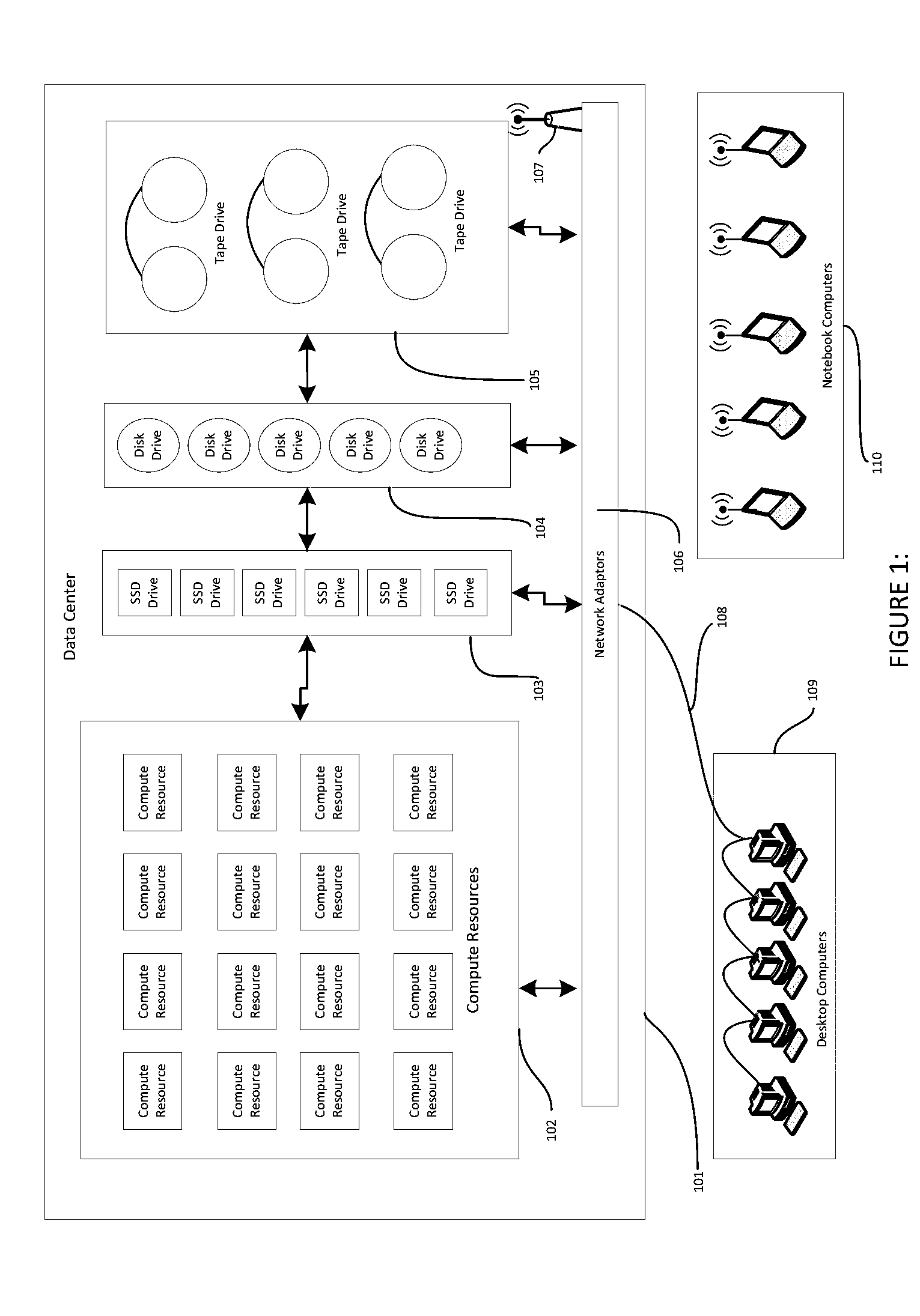
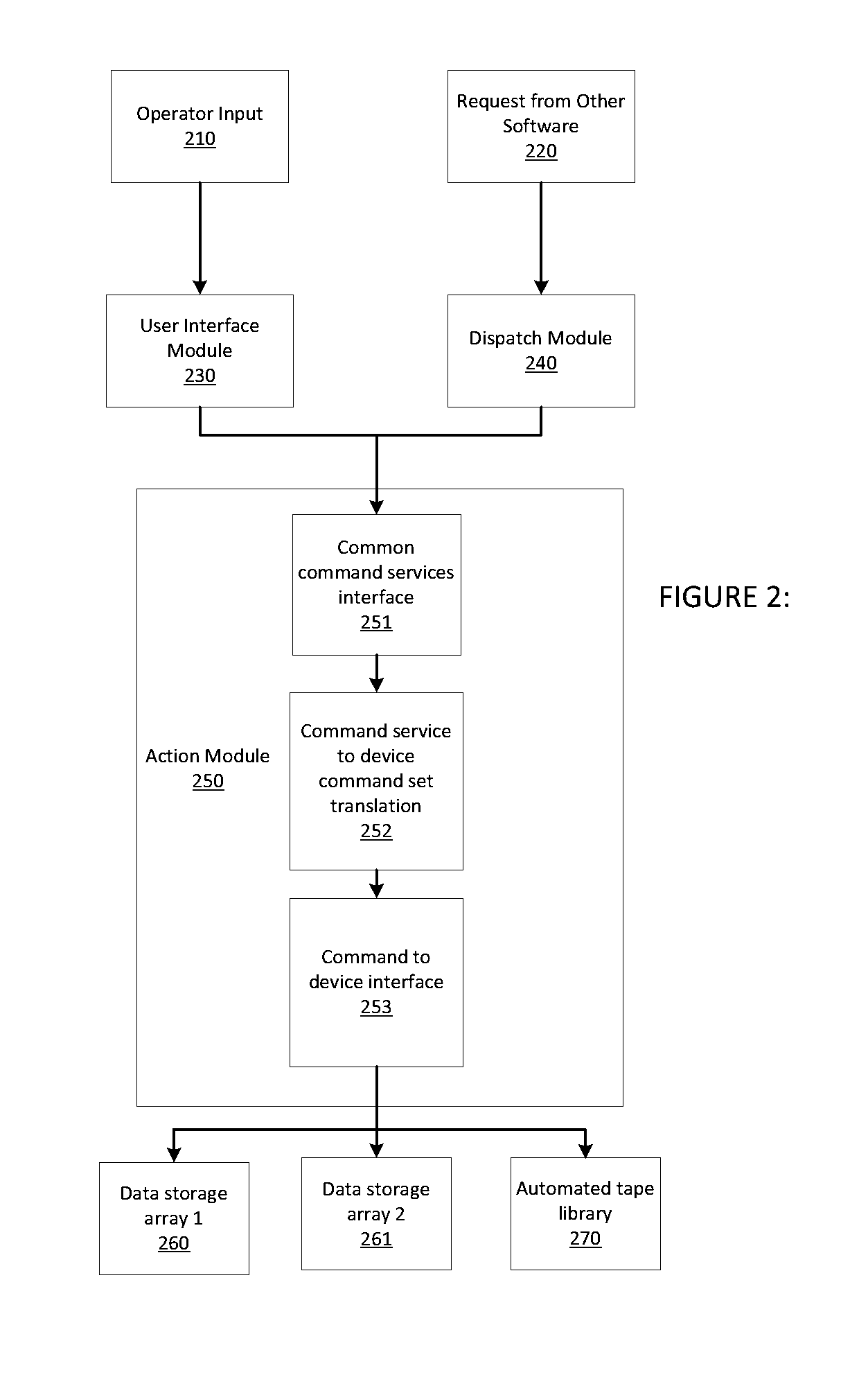
InactiveUS20140280957A1Limited dataSimple equipmentDigital computer detailsData switching networksData centerControl software
Embodiments of the invention include software that provides an operator or a system service the ability to access, control, or configure a plurality of different data center resources using common sets of functions or commands even though those data center resources natively require different commands to access, control, or configure them. The invention is configured to accept common commands and then translate them from a common command format into device specific commands or command sets. The invention simplifies how data center equipment is controlled and configured.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com