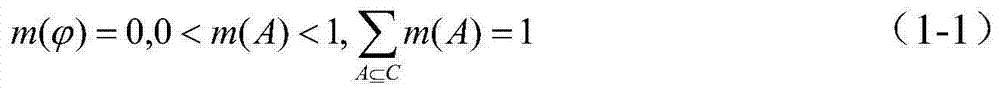Patents
Literature
353 results about "Data level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
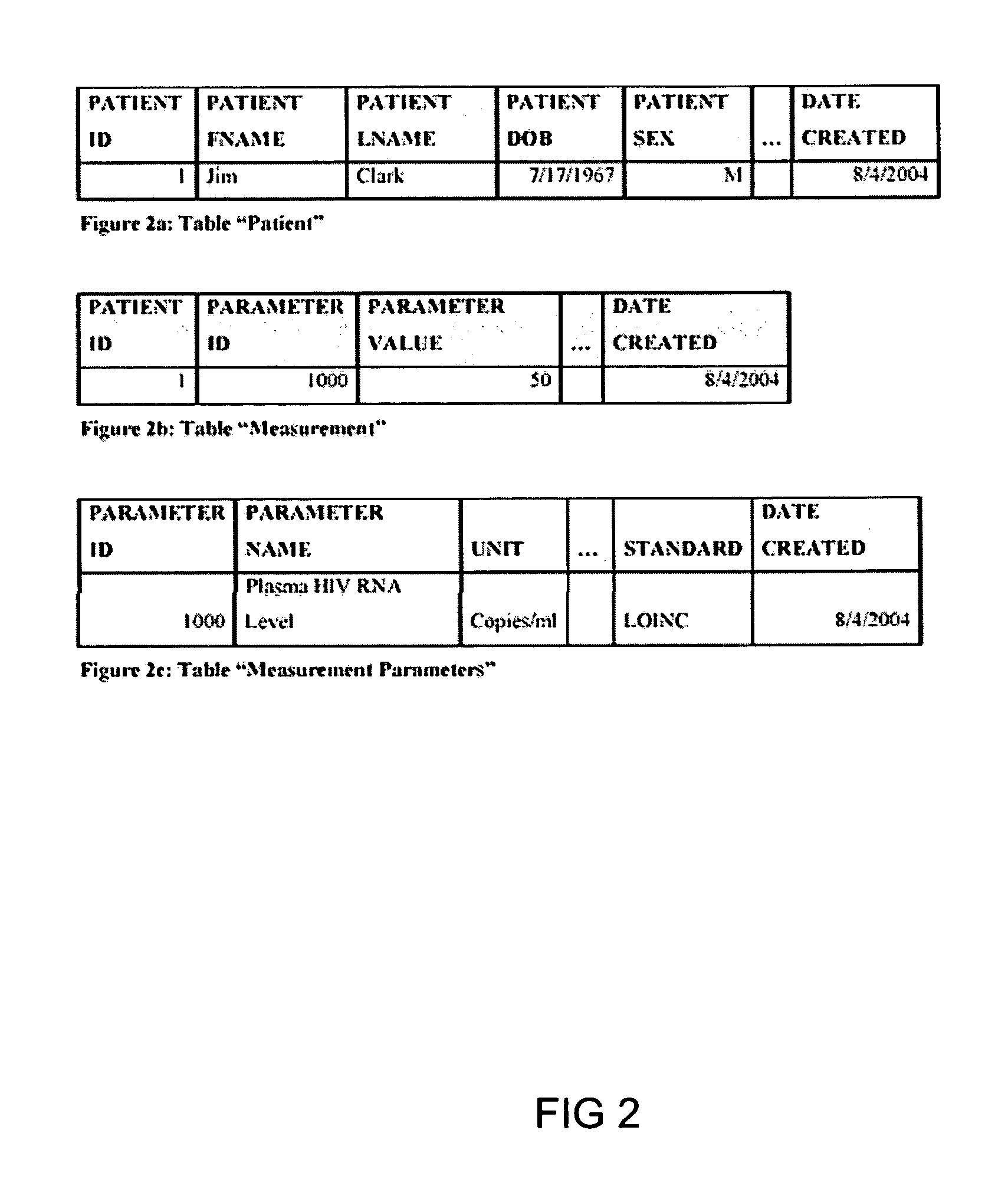
Data Levels of Measurement. A variable has one of four different levels of measurement: Nominal, Ordinal, Interval, or Ratio. (Interval and Ratio levels of measurement are sometimes called Continuous or Scale).
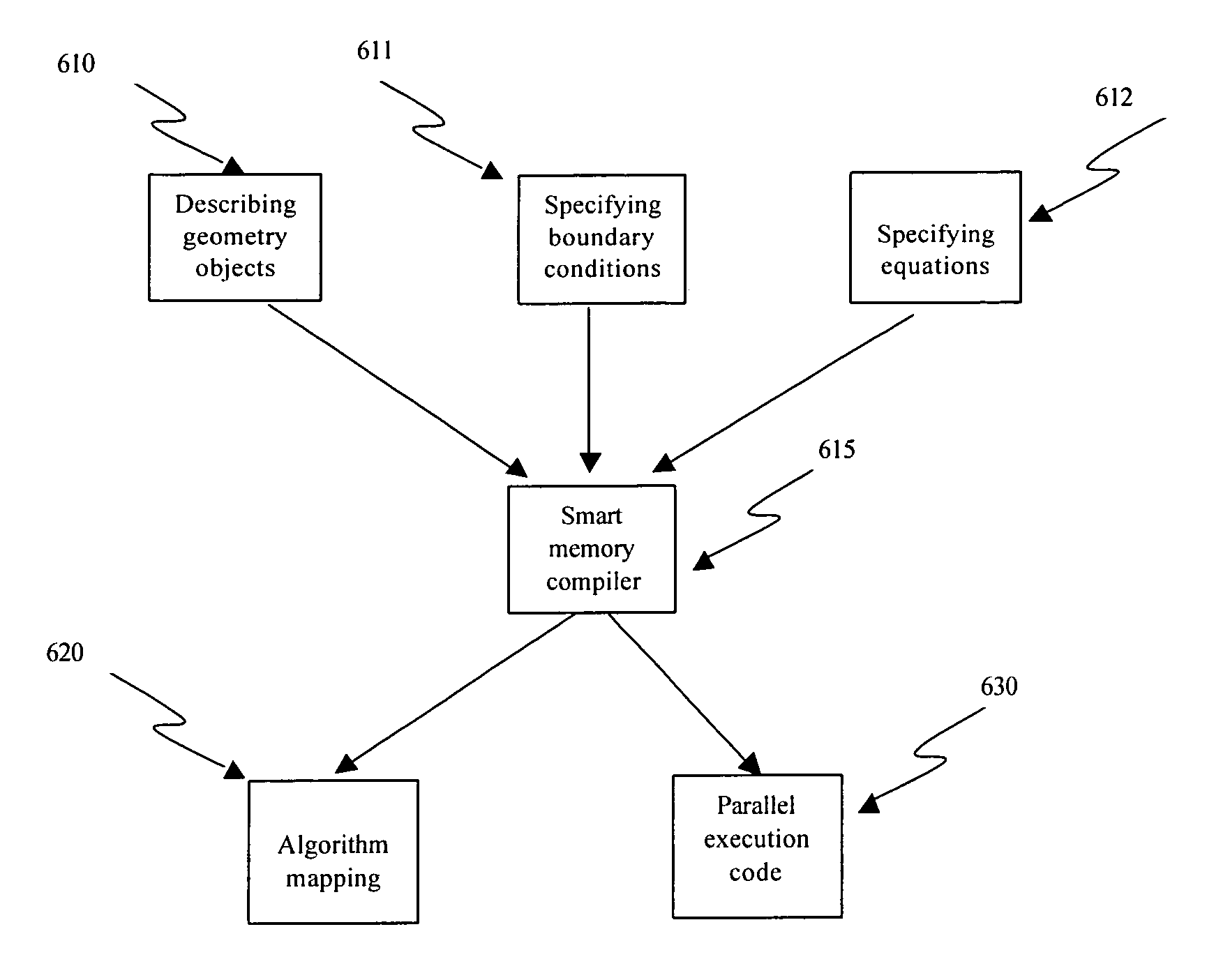
Algorithm mapping, specialized instructions and architecture features for smart memory computing
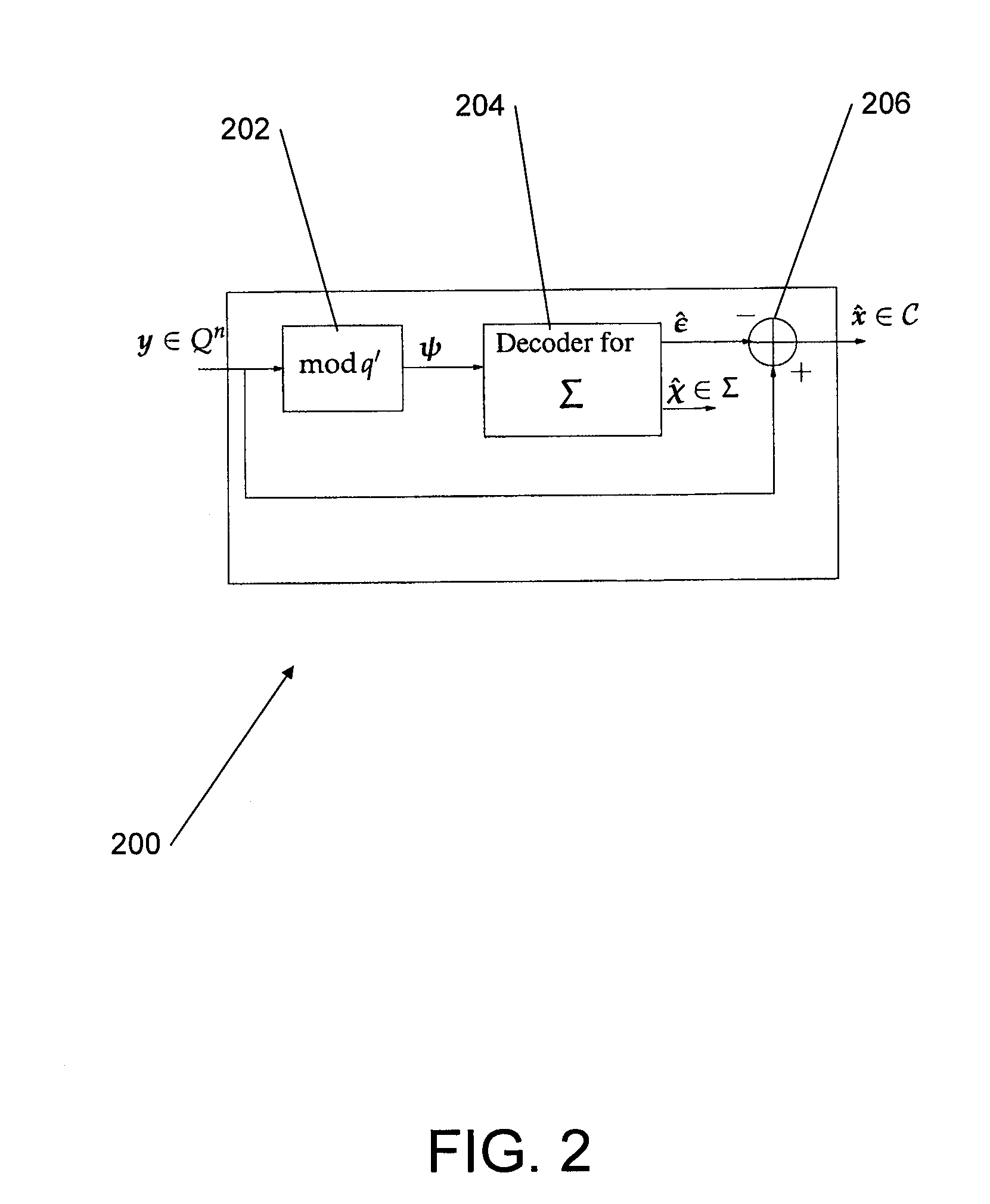
InactiveUS7546438B2Improve performanceLow costMultiplex system selection arrangementsDigital computer detailsSmart memoryExecution unit
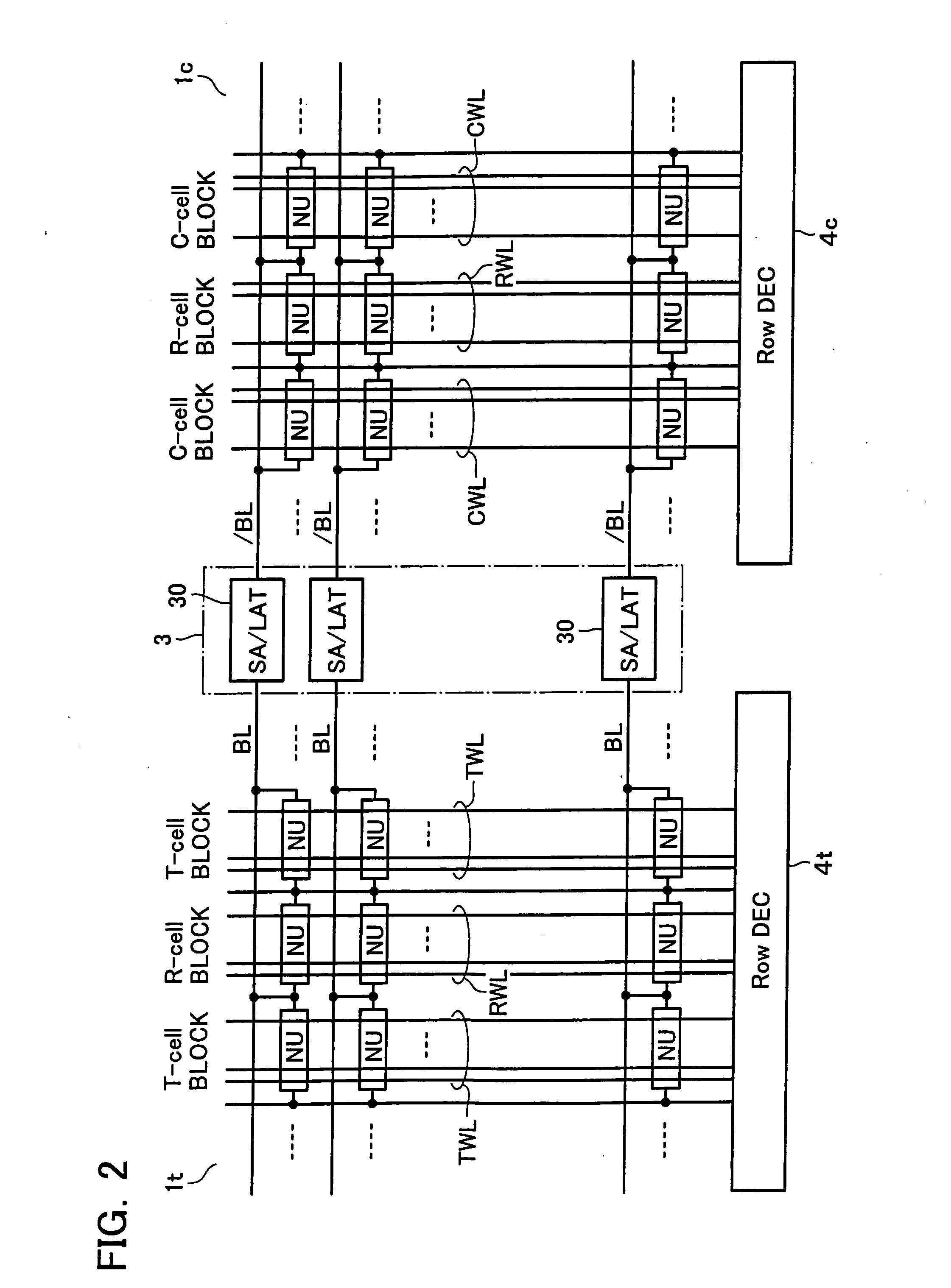
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
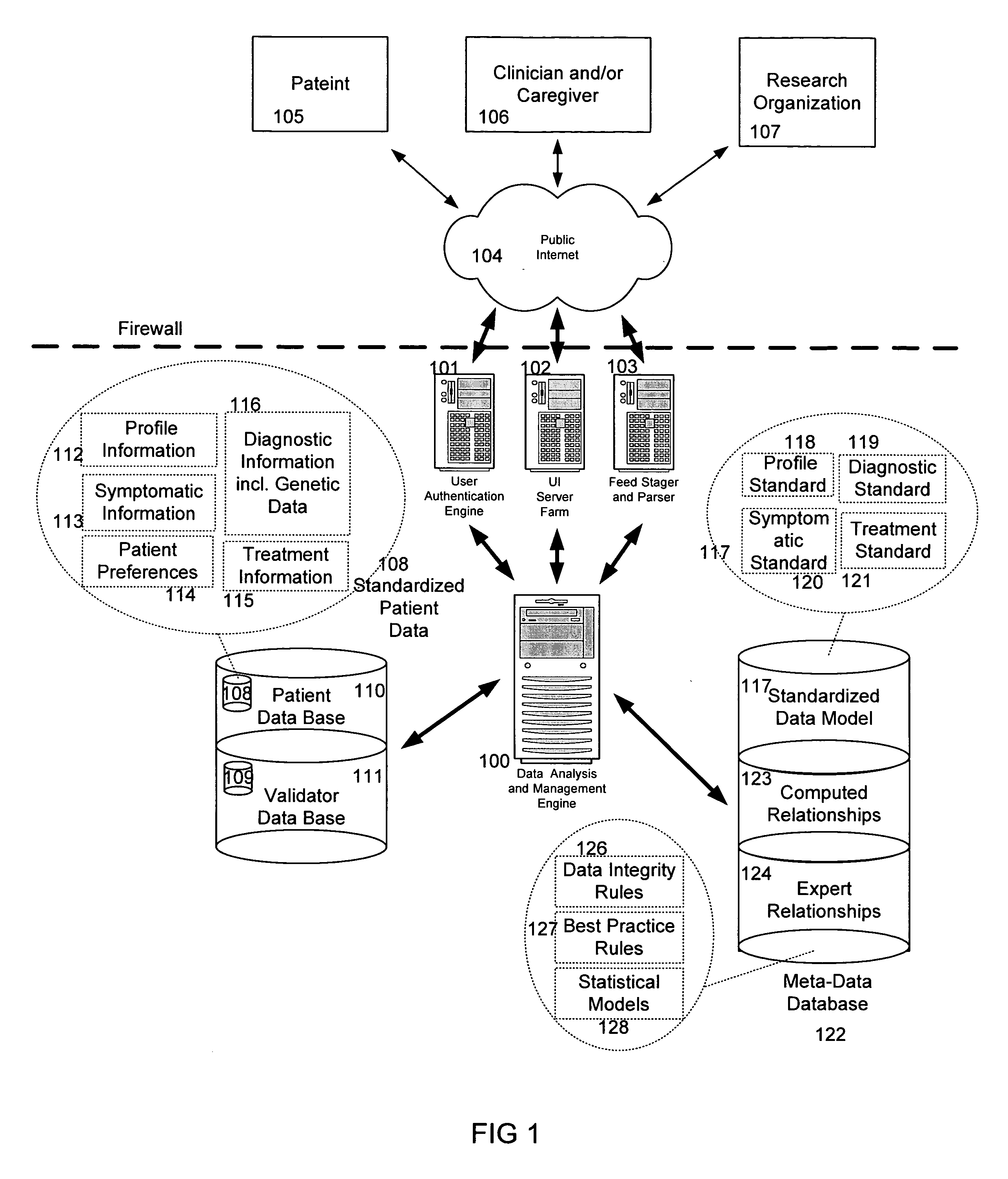
System and method for improving clinical decisions by aggregating, validating and analysing genetic and phenotypic data
The information management system disclosed enables caregivers to make better decisions, faster, using aggregated genetic and phenotypic data. The system enables the integration, validation and analysis of genetic, phenotypic and clinical data from multiple subjects who may be at distributed facilities. A standardized data model stores a range of patient data in standardized data classes that encompass patient profile information, patient symptomatic information, patient treatment information, and patient diagnostic information including genetic information. Data from other systems is converted into the format of the standardized data classes using a data parser, or cartridge, specifically tailored to the source system. Relationships exist between standardized data classes that are based on expert rules and statistical models. The relationships are used both to validate new data, and to predict phenotypic outcomes based on available data. The prediction may relate to a clinical outcome in response to a proposed intervention by a caregiver. The statistical models may be inhaled into the system from electronic publications that define statistical models and methods for training those models, according to a standardized template. Methods are described for selecting, creating and training the statistical models to operate on genetic, phenotypic and clinical data, in particular for underdetermined data sets that are typical of genetic information. The disclosure also describes how security of the data is maintained by means of a robust security architecture, and robust user authentication such as biometric authentication, combined with application-level and data-level access privileges.
Owner:NATERA
Codes For Limited Magnitude Asymetric Errors In Flash Memories
ActiveUS20080168320A1Increase speedReach levelError preventionTransmission systemsReduced sizeErrors and residuals
Error correction is tailored for the use of an ECC for correcting asymmetric errors with low magnitude in a data device, with minimal modifications to the conventional data device architecture. The technique permits error correction and data recovery to be performed with reduced-size error correcting code alphabets. For particular cases, the technique can reduce the problem of constructing codes for correcting limited magnitude asymmetric errors to the problem of constructing codes for symmetric errors over small alphabets. Also described are speed up techniques for reaching target data levels more quickly, using more aggressive memory programming operations.
Owner:CALIFORNIA INST OF TECH
Algorithm mapping, specialized instructions and architecture features for smart memory computing
InactiveUS6970988B1Improve performanceLow costMultiplex system selection arrangementsProgram controlSmart memoryExecution unit
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
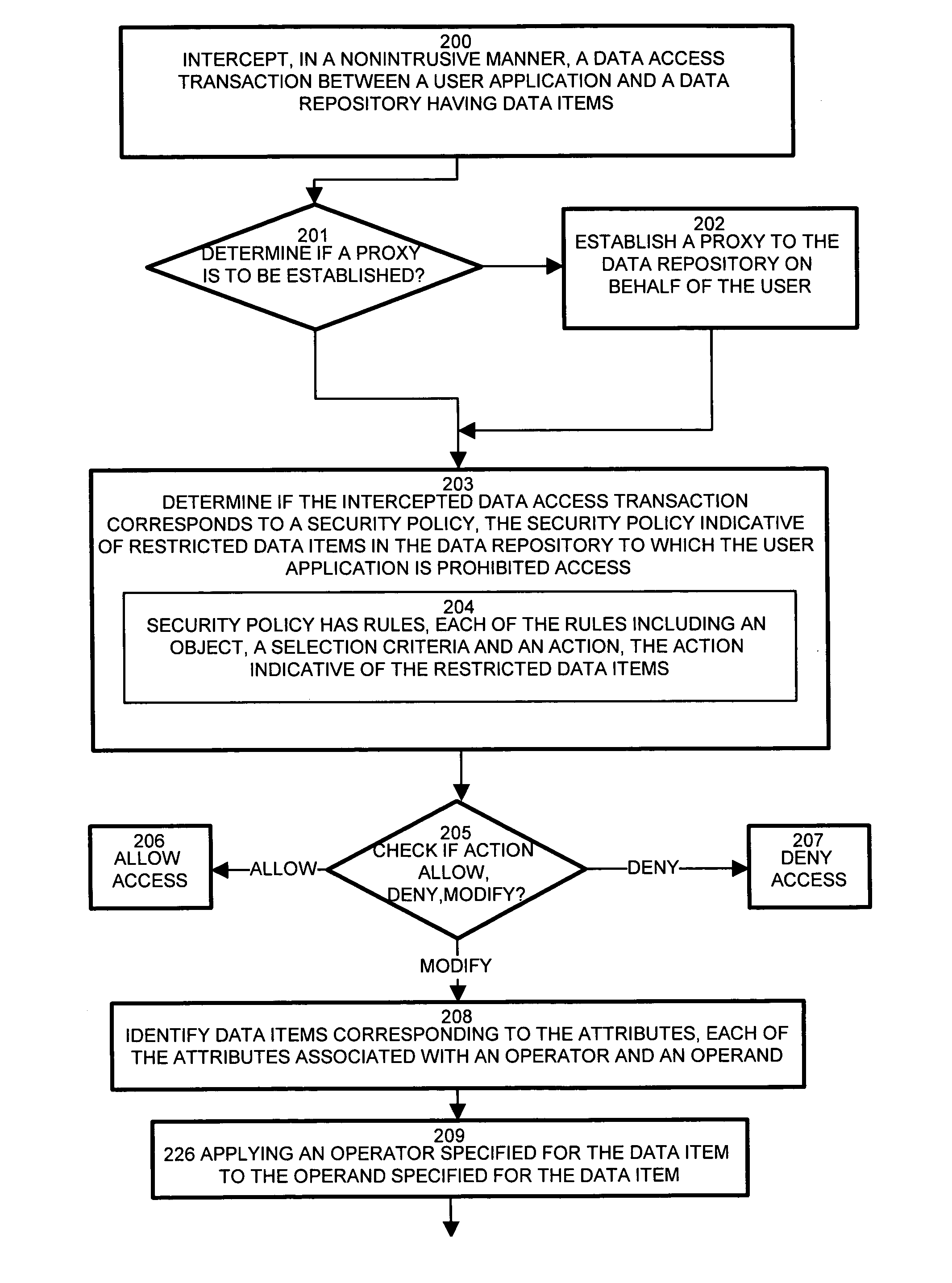
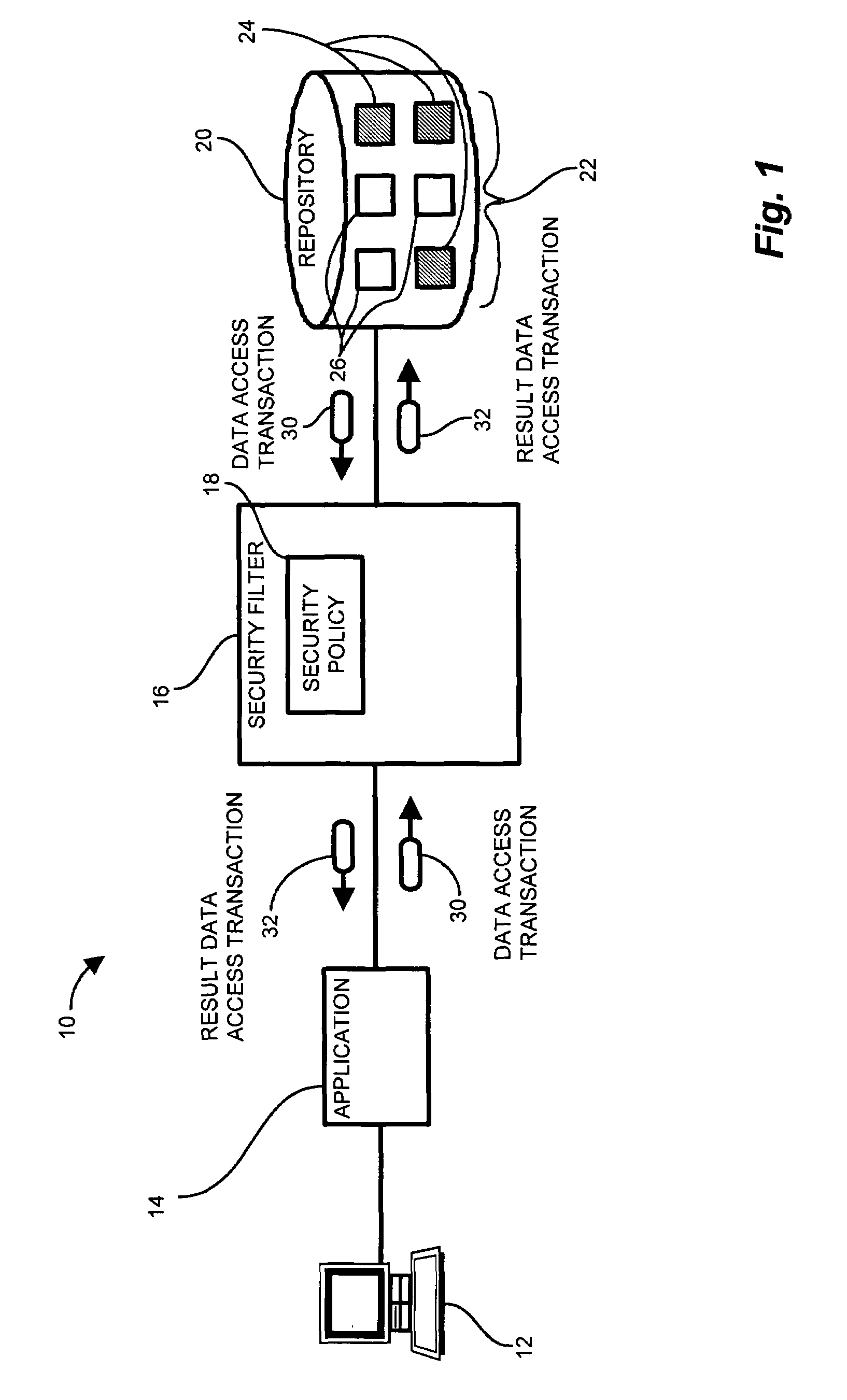
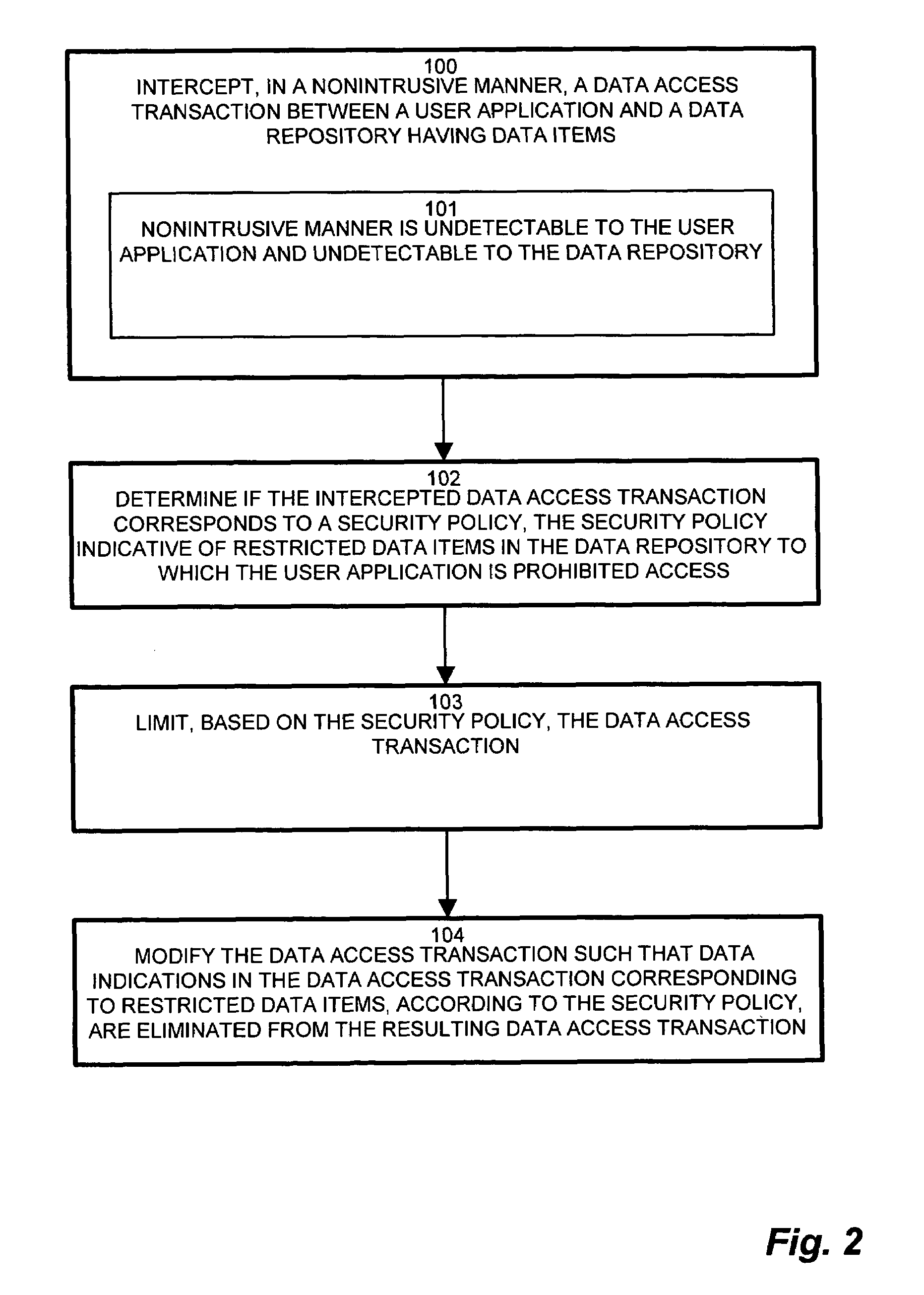
System and methods for nonintrusive database security
InactiveUS7437362B1Reduce the burden onOvercome deficienciesDigital data processing detailsComputer security arrangementsRelational databaseData access
Typical conventional database security scheme mechanisms are integrated in either the application or database. Maintenance of the security scheme, therefore, such as changes and modifications, impose changes to the application and / or database. Configurations of the invention employ a security filter for intercepting database streams, such as data access transactions, between an application and the a data repository, such as a relational database. A security filter deployed between the application and database inspects the stream of transactions between the application and the database. The security filter, by nonintrusively interrogating the transactions, provides a content-aware capability for seamlessly and nondestructively enforcing data level security. A security policy, codifying security requirements for the users and table of the database, employs rules concerning restricted data items. The filter intercepts transactions and determines if the transaction triggers rules of the security policy. If the transactions contain restricted data items, the security filter modifies the transaction to eliminate the restricted data items.
Owner:IBM CORP
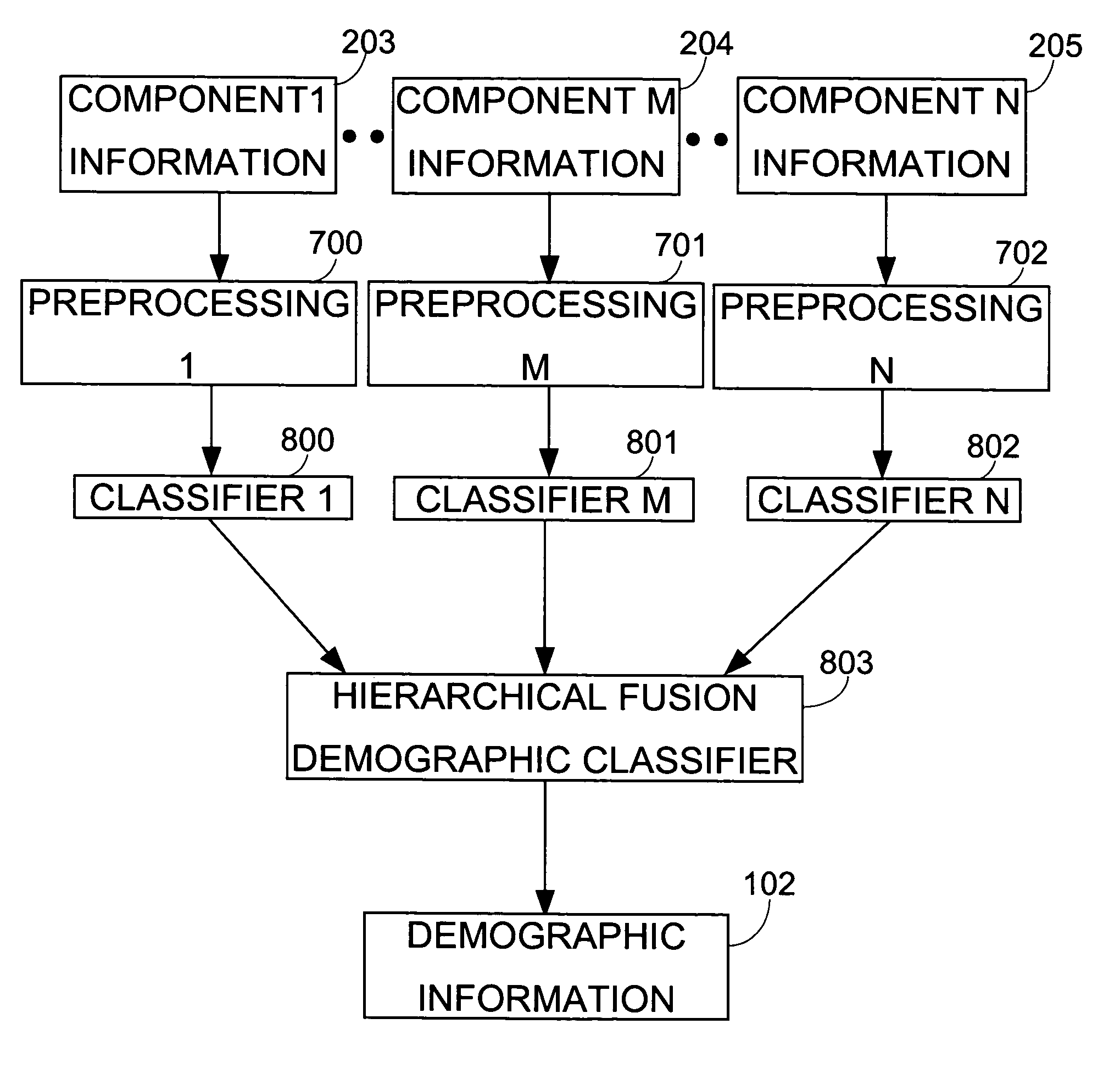
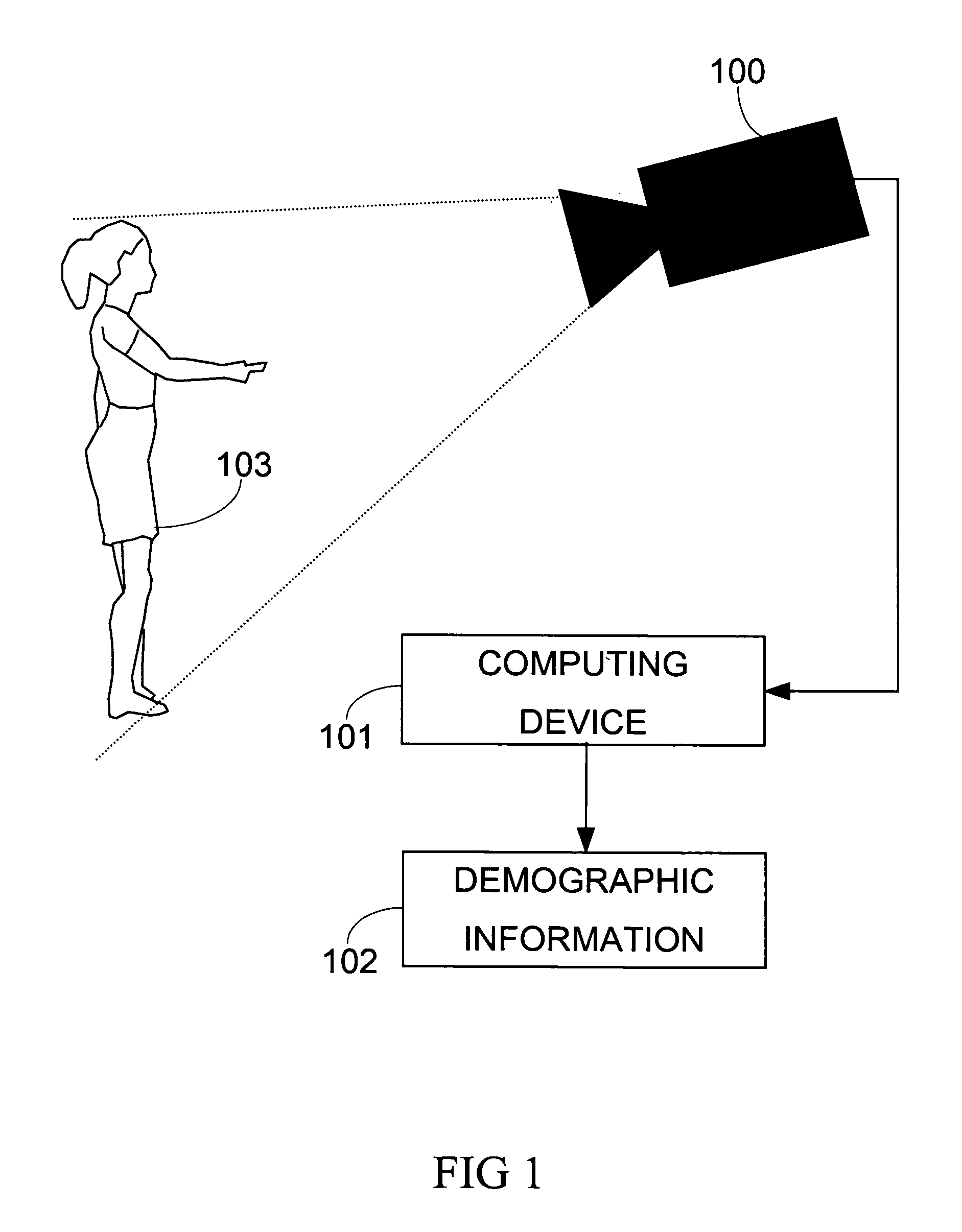
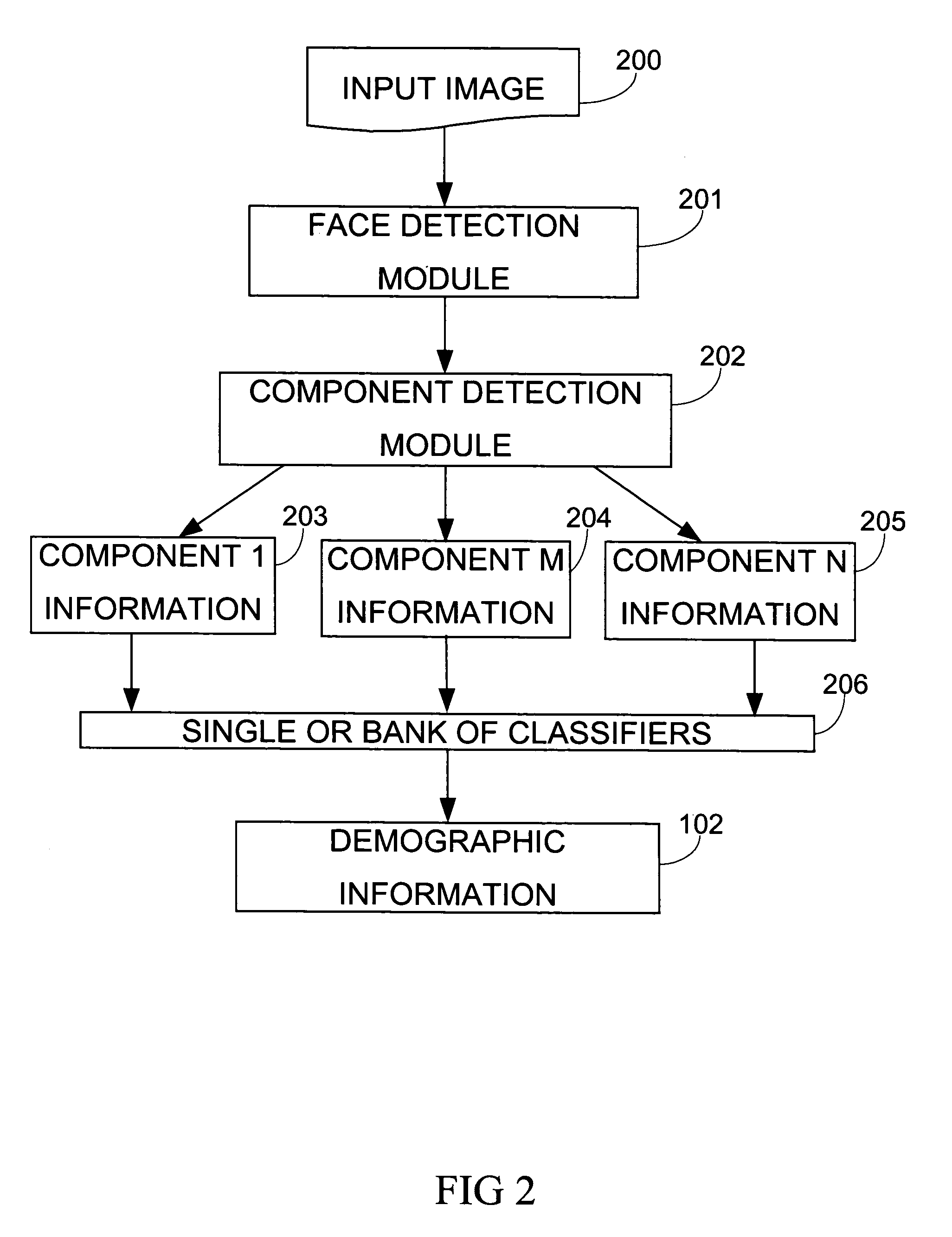
Demographic classification using image components
The present invention includes a system and method for automatically extracting the demographic information from images. The system detects the face in an image, locates different components, extracts component features, and then classifies the components to identify the age, gender, or ethnicity of the person(s) in the image. Using components for demographic classification gives better results as compared to currently known techniques. Moreover, the described system and technique can be used to extract demographic information in more robust manner than currently known methods, in environments where high degree of variability in size, shape, color, texture, pose, and occlusion exists. This invention also performs classifier fusion using Data Level fusion and Multi-level classification for fusing results of various component demographic classifiers. Besides use as an automated data collection system wherein given the necessary facial information as the data, the demographic category of the person is determined automatically, the system could also be used for targeting of the advertisements, surveillance, human computer interaction, security enhancements, immersive computer games and improving user interfaces based on demographic information.
Owner:VIDEOMINING CORP
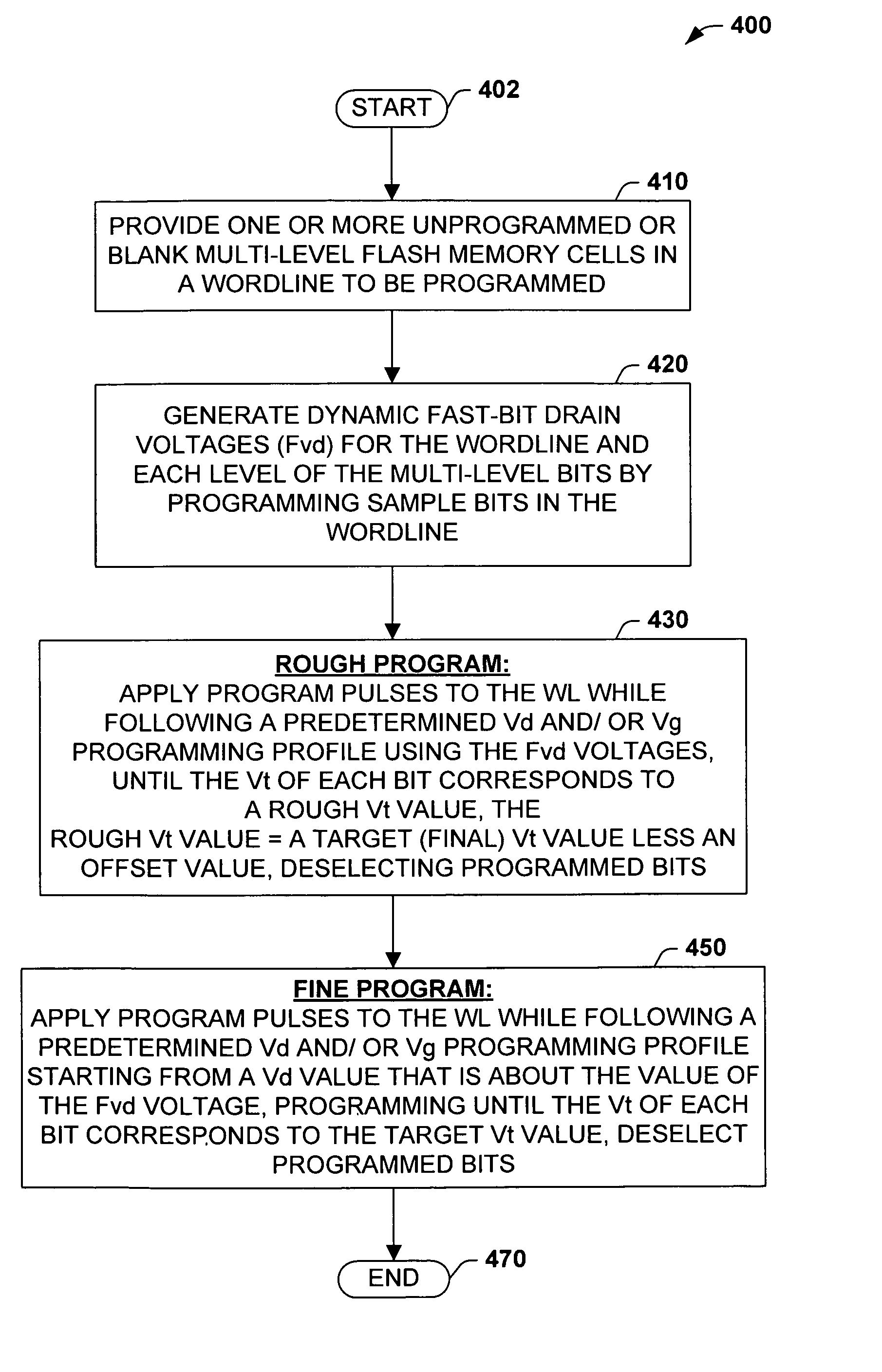
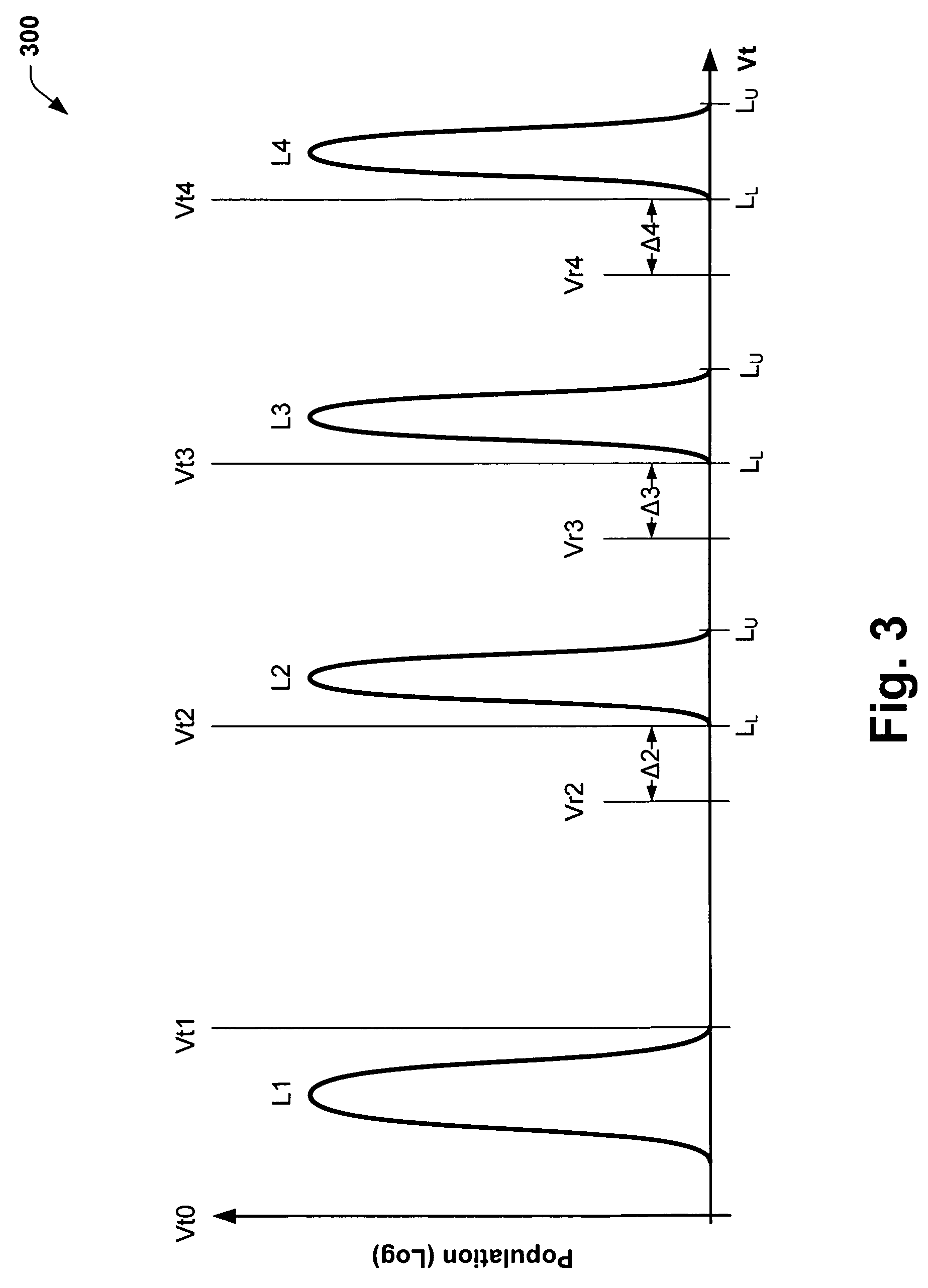
Multi-level ONO flash program algorithm for threshold width control
Methods of programming a wordline of multi-level flash memory cells (MLB) having three or more data levels per bit corresponding to three or more threshold voltages are provided. The present invention employs an interactive program algorithm that programs the bits of the wordline of memory cells in two programming phases, comprising a rough programming phase and a fine programming phase to achieve highly compact Vt distributions. In one example, cell bit-pairs that are to be programmed to the same program pattern are selected along a wordline. Groups of sample bits are chosen for each wordline to represent each possible program level. The sample bits are then programmed to determine a corresponding drain voltage at which each sample group is first programmed. This fast-bit drain voltage (Fvd) for each program level essentially provides a wordline specific program characterization of the Vt required for the remaining bits of that wordline. In the rough programming phase, the bits of core cells are then programmed from a starting point that is relative to (e.g., slightly less than or equal to) the fast-bit Vd and according to a predetermined Vd and Vg profile of programming pulses. The bits of the complementary bit-pairs are alternately programmed in this way until the Vt of the bits attains a rough Vt level, which is offset lower than the final target threshold voltage level. Then in the second fine programming phase, the bits of the MLB cells of the wordline are further programmed with another predetermined Vd and Vg profile of programming pulses until the final target threshold voltage is achieved. The Vd and Vg profiles of programming pulses may further be tailored to accommodate the various bit-pair program pattern combinations possible. In this way, the bits of each wordline are fine-tune programmed to a data state to achieve a more precise Vt distribution, while compensating for the effects of complementary bit disturb.
Owner:LONGITUDE FLASH MEMORY SOLUTIONS LTD
Parallel object detection method for heterogeneous multithreaded microarchitectures
ActiveUS20130243329A1Improve performanceTime-consuming to improveCharacter and pattern recognitionObject detectionMicroarchitecture
A parallel object detection method for heterogeneous microarchitectures. The method is designed for increasing the throughput of object detection in a computer system that is equipped with an array of cores including a shared memory, a constant memory, and functional units. Latency reduction is achieved through a multilevel parallelization method that exploits fine-grain data-level parallelism using multithreaded SIMD computations, and coarse-grain parallelism by relying on concurrent kernel execution.
Owner:HERTA SECURITY
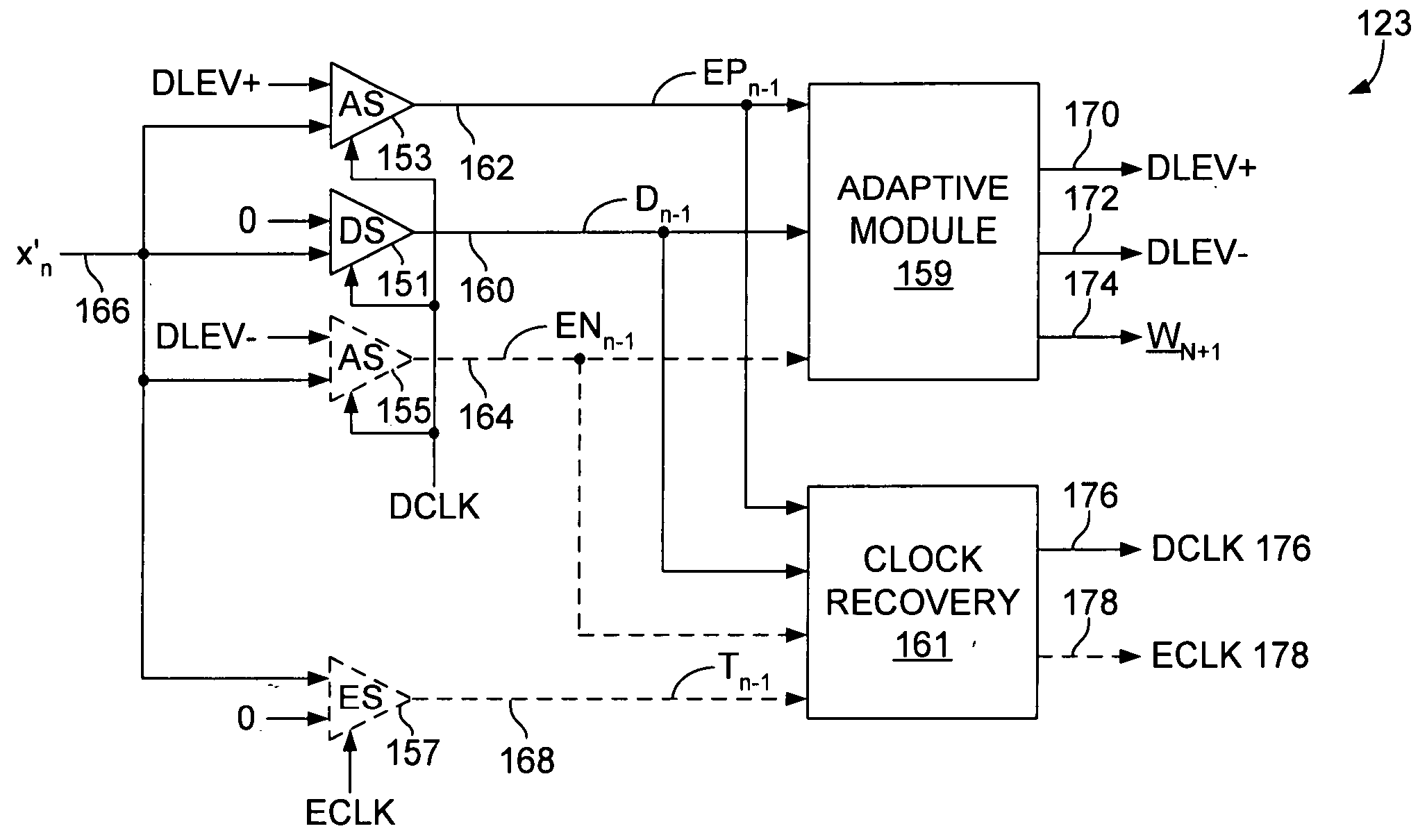
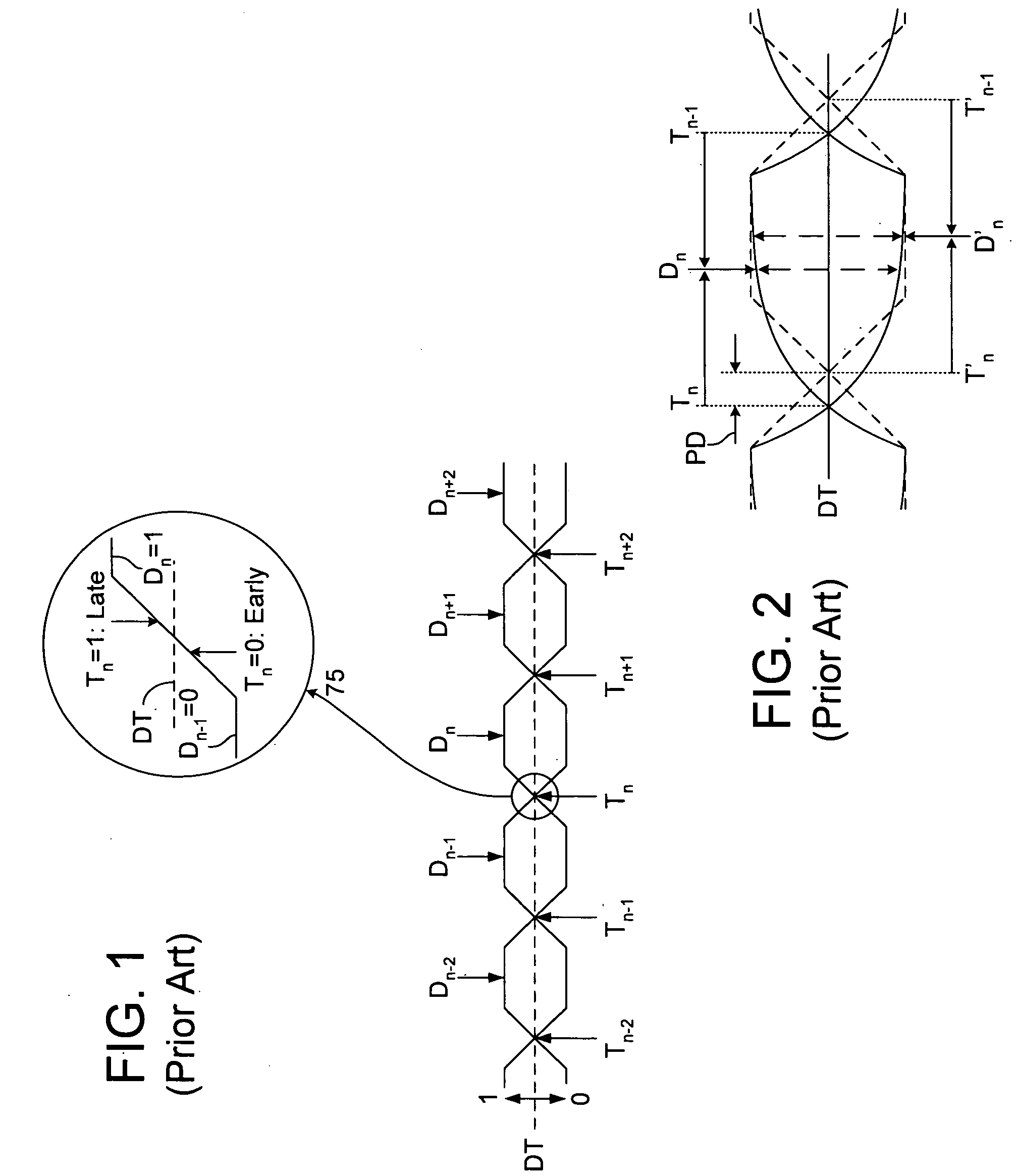
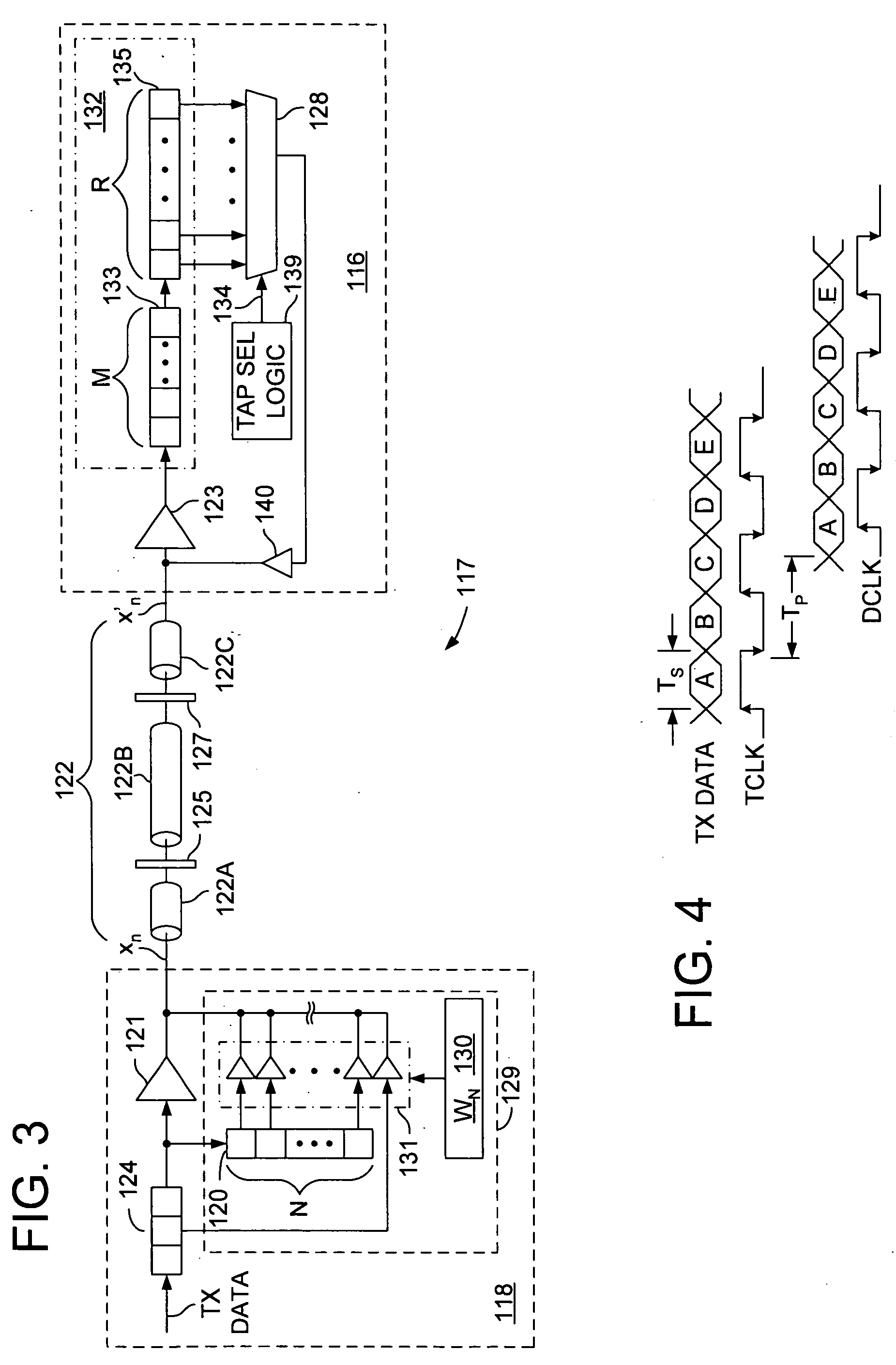
Data-level clock recovery
ActiveUS20050058234A1Angle demodulation by phase difference detectionSynchronising arrangementPattern matchingClock recovery
A circuit for adjusting the phase of a clock signal. A first sampling circuit generates a sequence of data samples in response to transitions of the clock signal, each of the data samples having either a first state or a second state according to whether an incoming signal exceeds a first threshold. An second sampling circuit generates an error sample in response to one of the transitions of the clock signal, the error sample having either the first state or the second state according to whether the incoming signal exceeds a second threshold. A phase adjust circuit adjusts the phase of the clock signal if the sequence of data samples matches a predetermined pattern and based, at least in part, on whether the error sample has the first state or the second state.
Owner:K MIZRA LLC
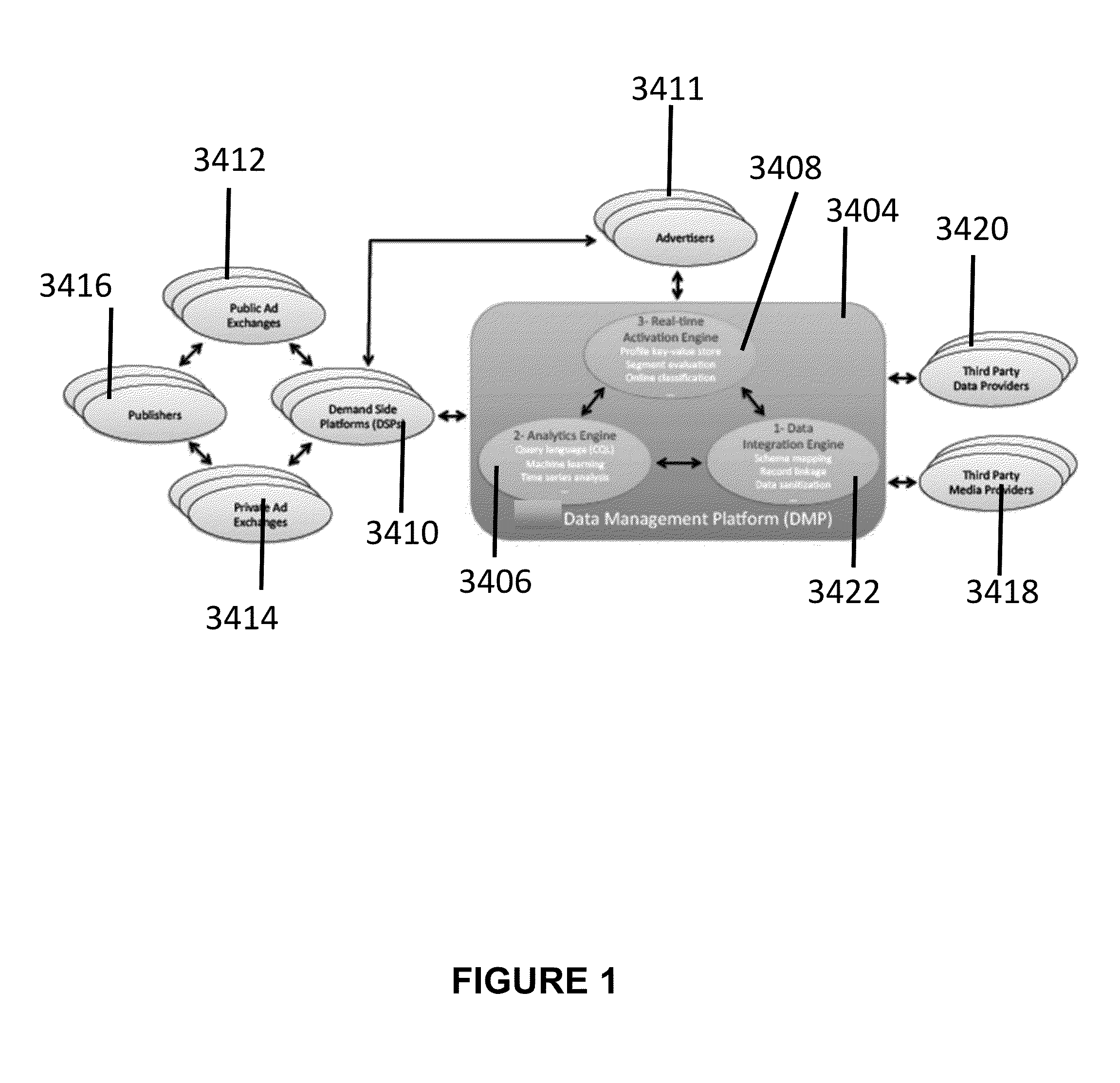
Data management platform for digital advertising
InactiveUS20140279074A1Improve customer experienceAdvertisementsNatural language data processingDigital advertisingData management
A data management apparatus for digital advertising includes a data integration processor for collecting and storing data from providers, resolving heterogeneity of the data at schema and data levels, and performing validity checks of the data; an analytics processor for receiving validated data from the data integration processor and providing to users custom, nesting-aware, SQL-like query language and a library of data mining methods, machine learning models, and analytical user profiles (AUP); and an activation processor for encapsulating complex computations performed in real-time, segment evaluation, and online user classification using runtime user profiles (RUP).
Owner:TURN
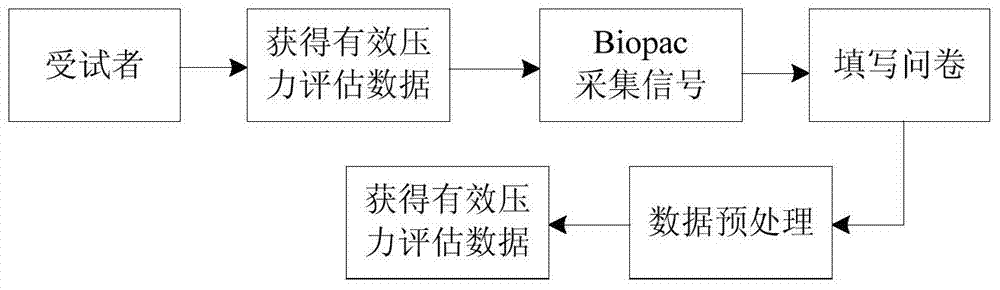
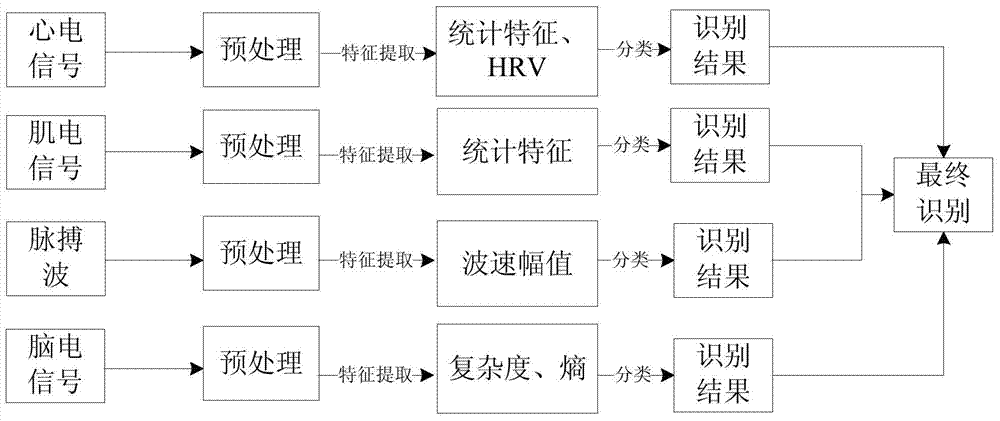
Psychological stress assessment method based on multi-physiological-parameter integration
InactiveCN103584872AEfficient integrationImprove recognition rateSensorsPsychotechnic devicesData informationCrowds
The invention discloses a psychological stress assessment method based on multi-physiological-parameter integration. The method includes: designing a reasonable stimulation program, acquiring four types of electrophysiological signals, namely electrocardiogram signals, electromyographic signals, pulse wave signals and electroencephalogram signals from people suffering psychological stress; extracting affective features of the four types of electrophysiological signals; subjecting the extracted features to feature selection by means of Relief algorithm, genetic algorithm optimization and the like; acquiring related integration functions on the basis of basic probability assignment mass. According to the method, multi-parameter signals are subjected to acquisition, preprocessed, feature selection and psychological stress affective recognition and are integrated; compared to single-parameter classified recognition or multi-parameter data-level or feature-level integration, the method allows data information to be more fully utilized and psychological stress emotions to be more accurately recognized.
Owner:YANSHAN UNIV
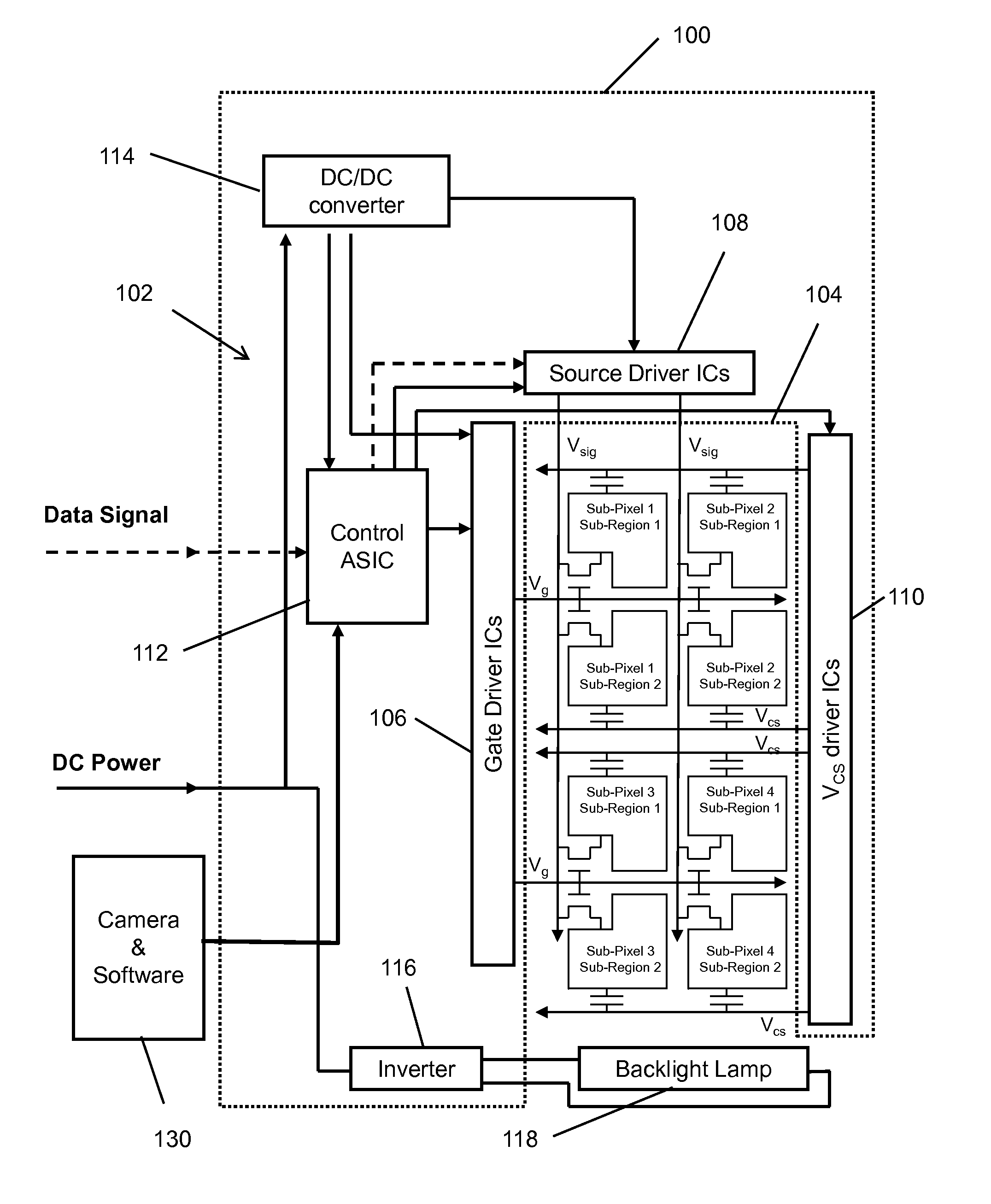
Display having split sub-pixels for multiple image display functions
InactiveUS20110234605A1High resolutionReduce spacingStatic indicating devicesImage data processing detailsCapacitanceDisplay device
A display which includes a plurality of sub-pixels each split into a plurality of sub-regions. Each sub-pixel includes a single gate line and a single signal line, and each sub-region within a given sub-pixel includes a corresponding storage capacitor line. An optical element cooperatively combines with the plurality of sub-pixels to create distinct angularly dependent brightness functions in association with corresponding sub-regions within the sub-pixels. Control electronics are configured to provide image data levels in the form of signal data voltages to each sub-region included within each sub-pixel via the gate line and signal line included within the sub-pixel; and to independently modify the signal data voltages provided to each sub-region within the sub-pixels via the corresponding storage capacitor lines whereby the display operates in accordance with at least two different image functions.
Owner:SHARP KK
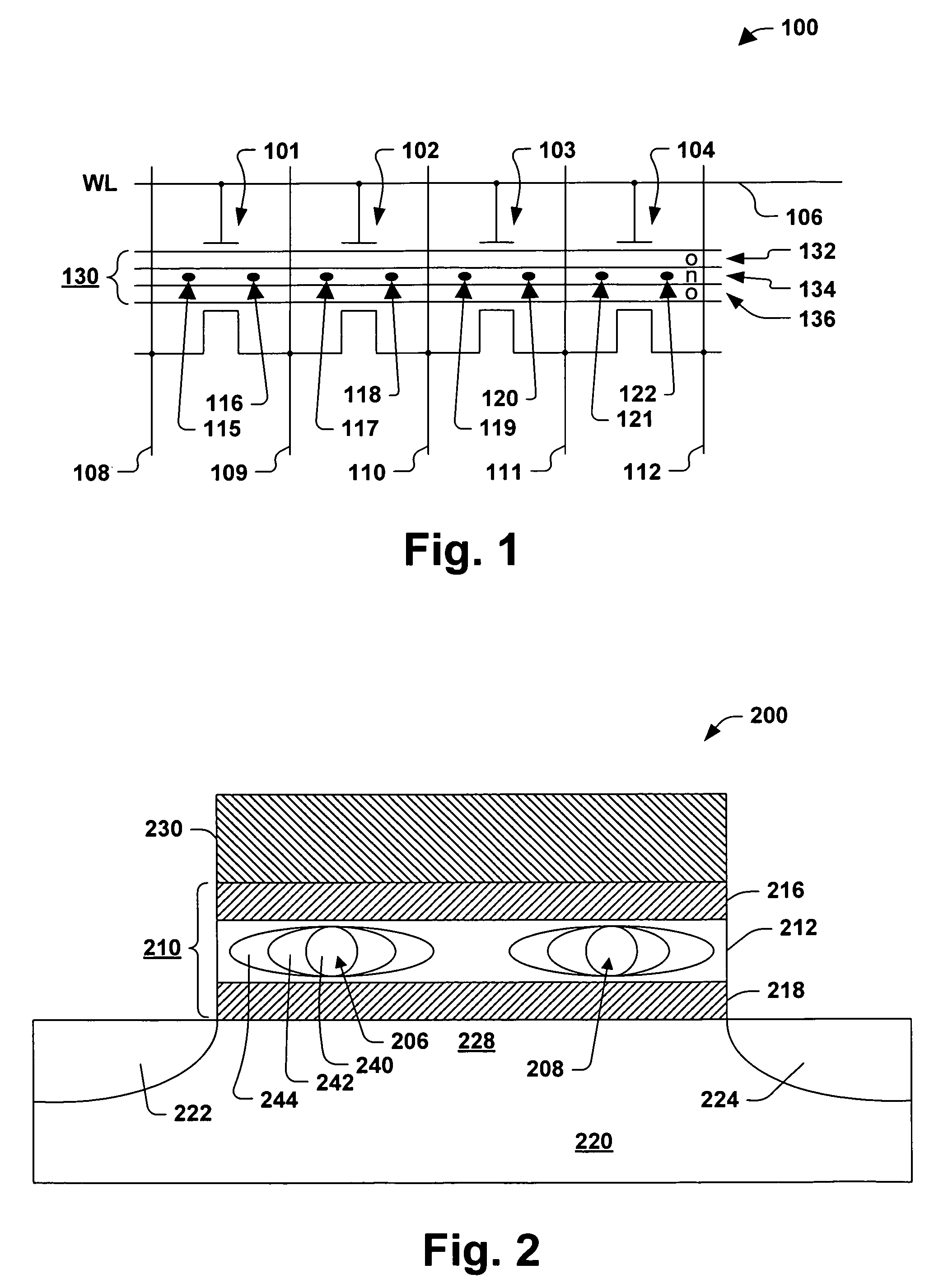
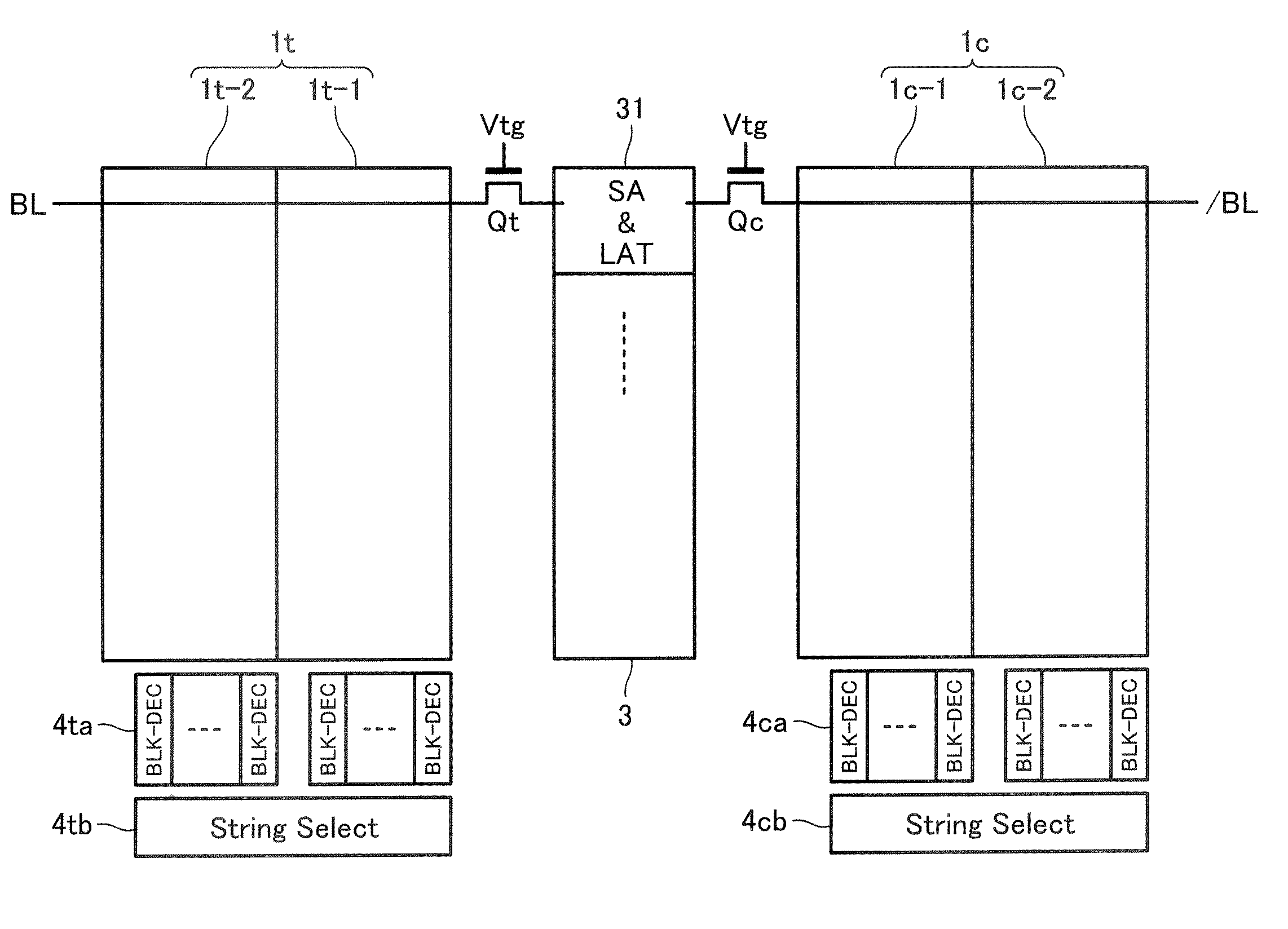
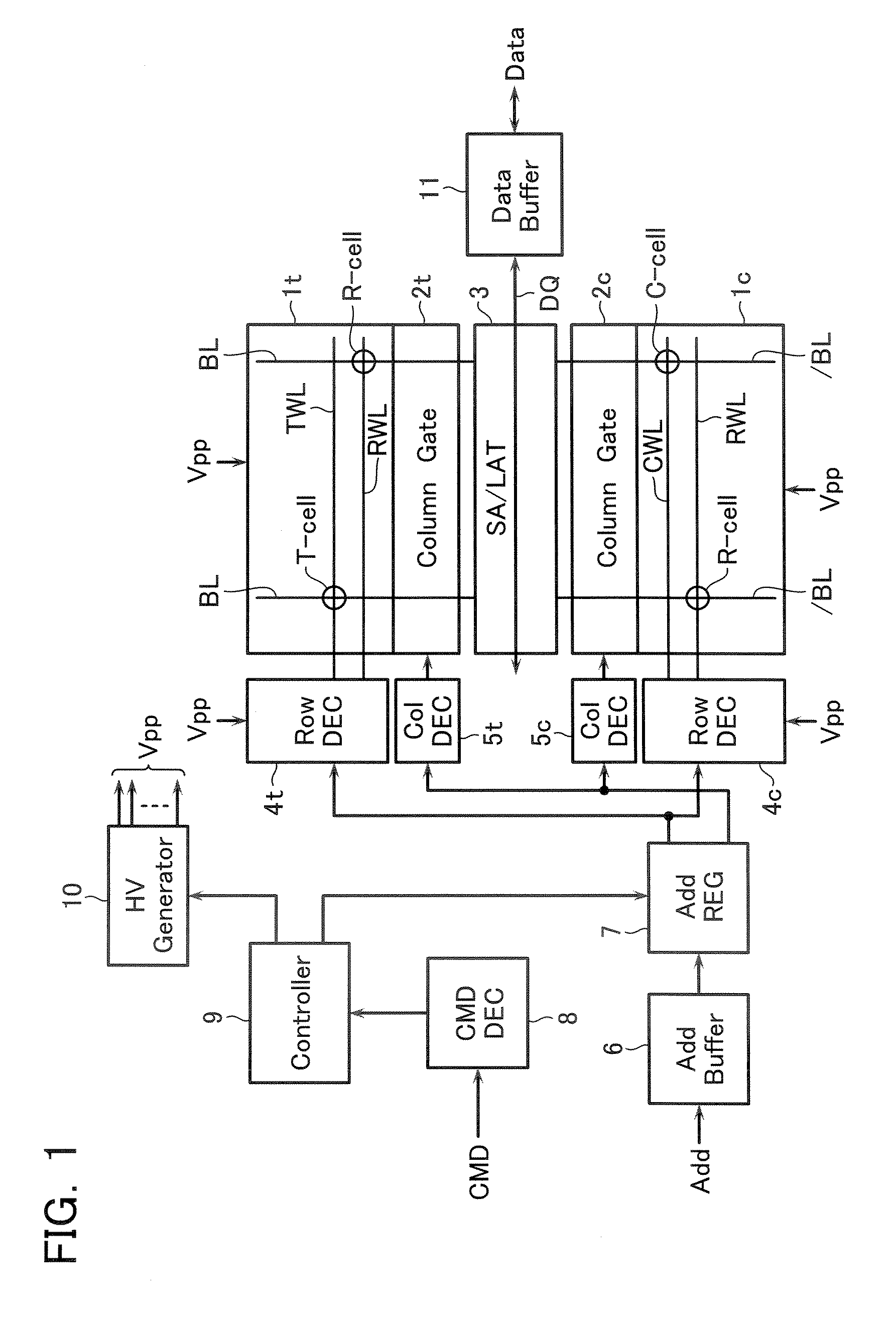
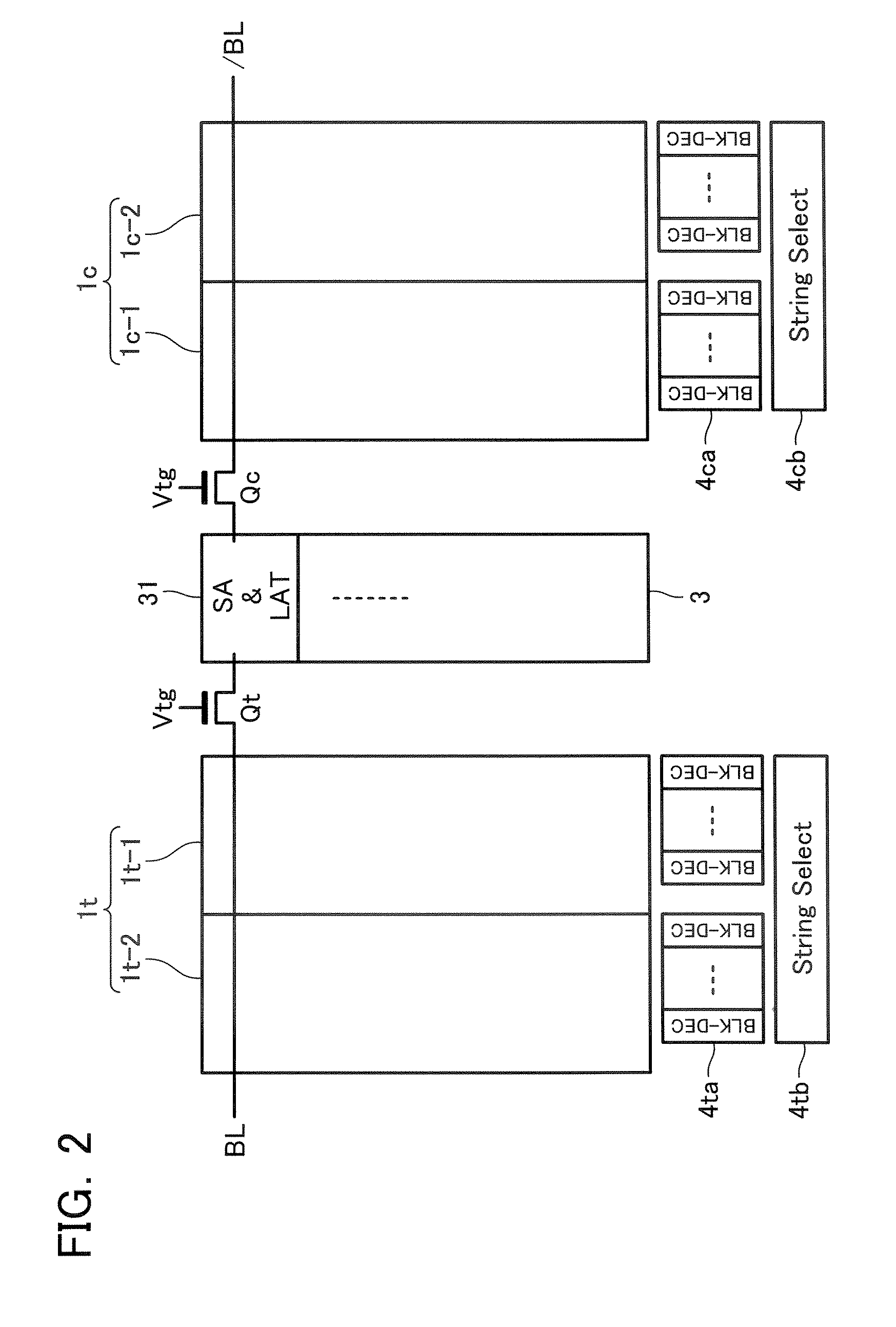
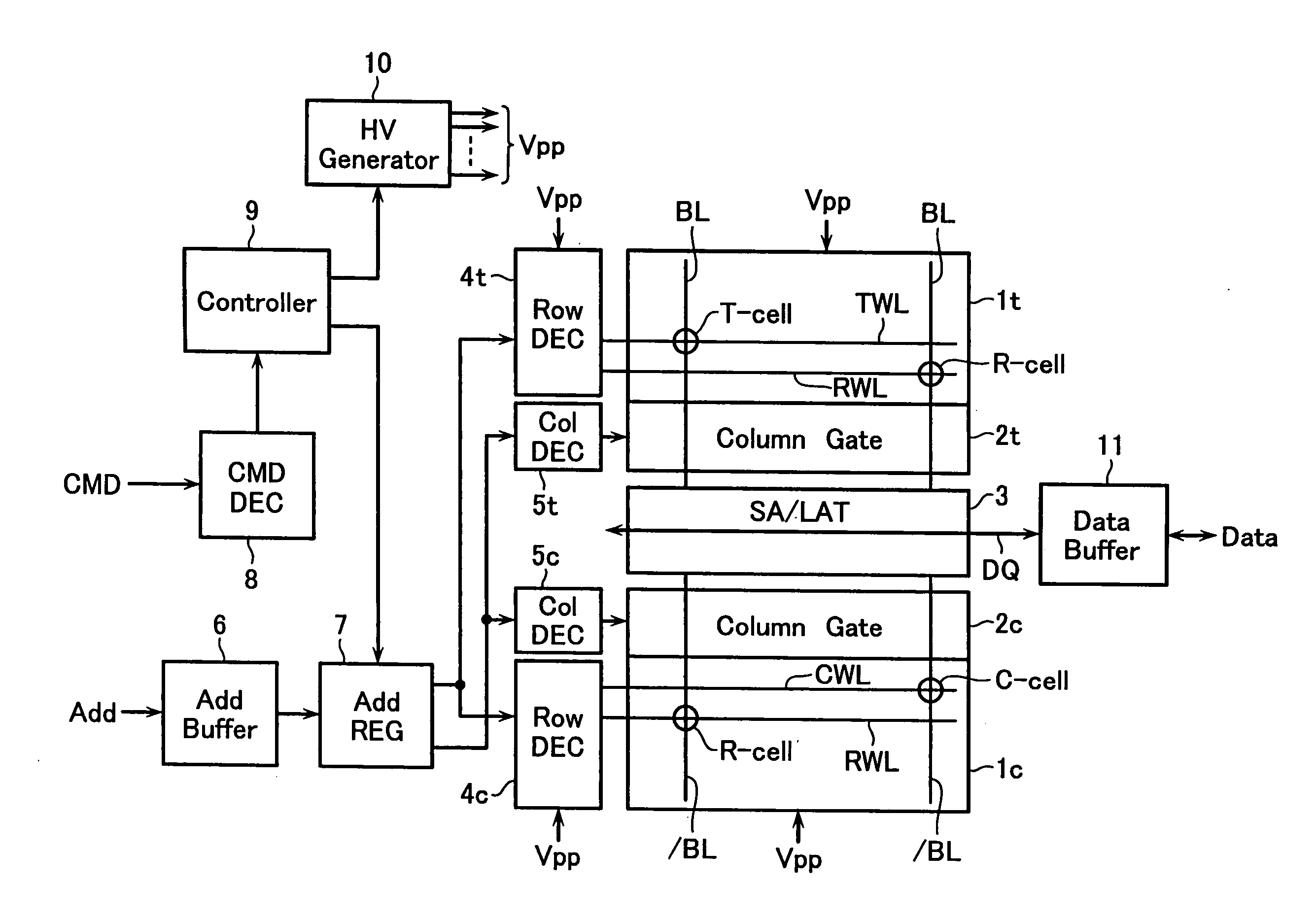
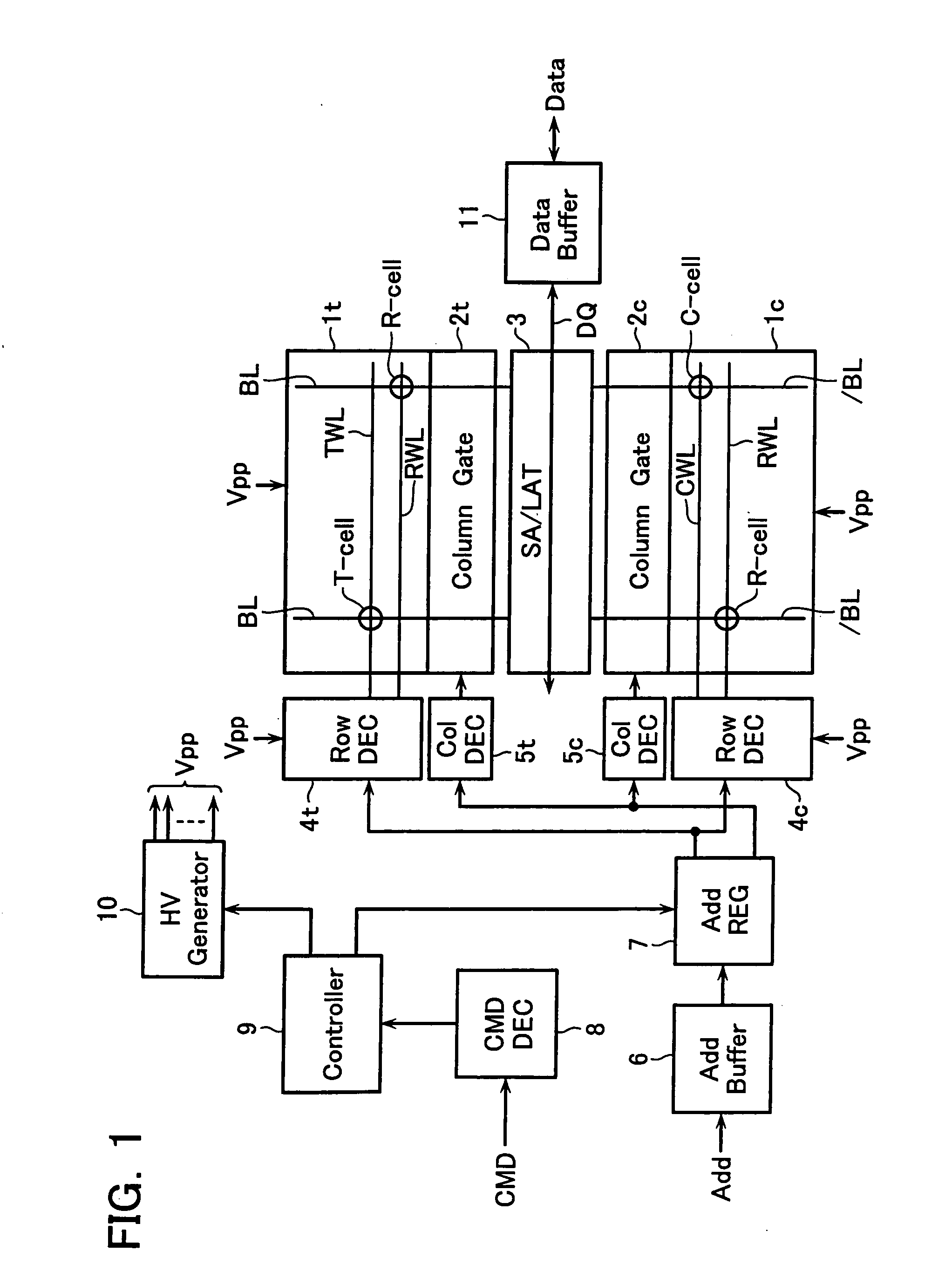
Semiconductor memory device and data write method thereof
A semiconductor memory device including a memory cell array and a sense amplifier, wherein the memory cell array includes: a plurality of information cells, in each of which either one of multi-level data is written; a first reference cell with the same structure and the same connection state as the information cell, in which a reference data level is written for generating a first reference current; and a second reference cell, which serves for generating a second reference current used for setting the lowest data level of the multi-level data and for setting the reference data level of the first reference cell.
Owner:KIOXIA CORP
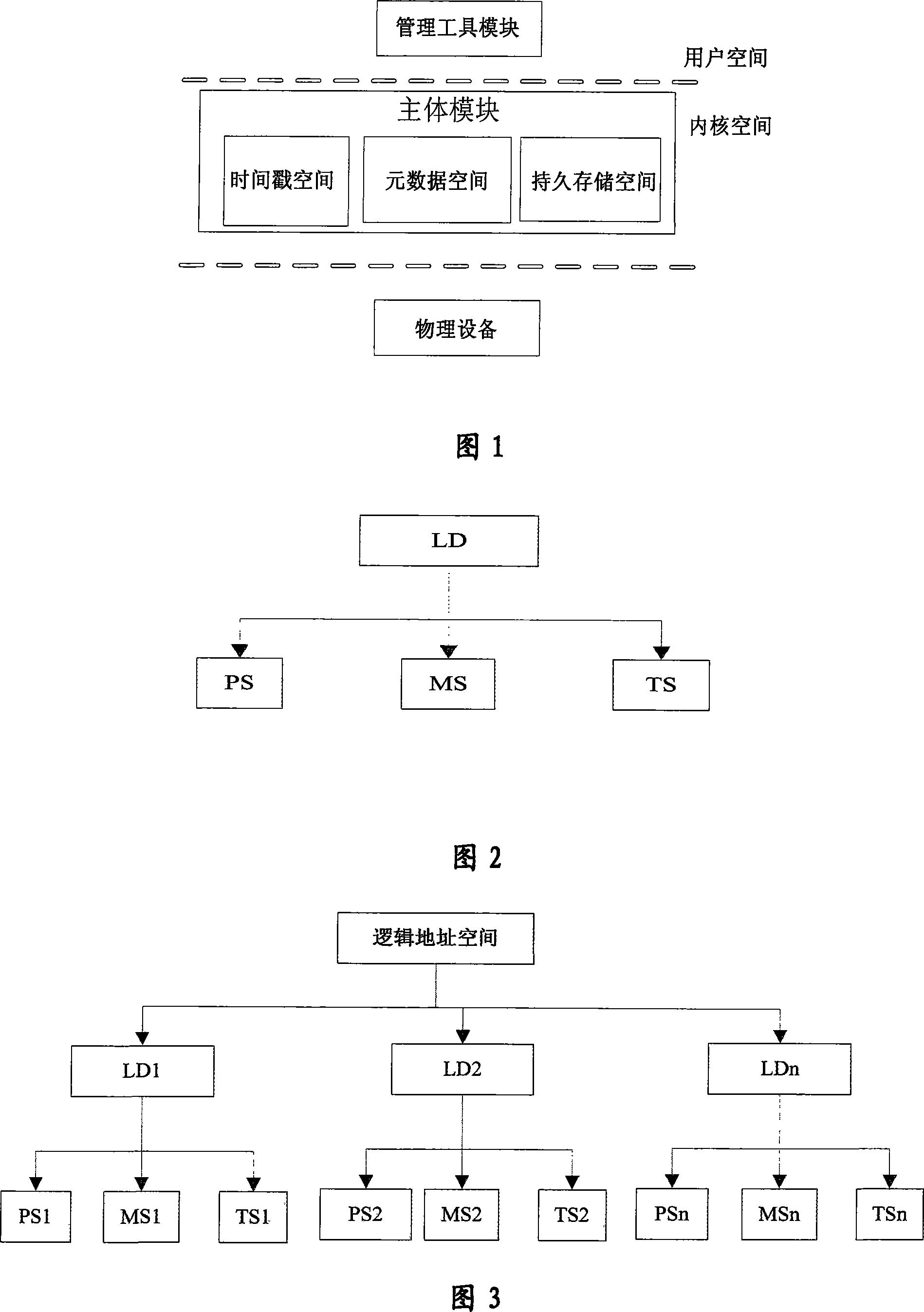
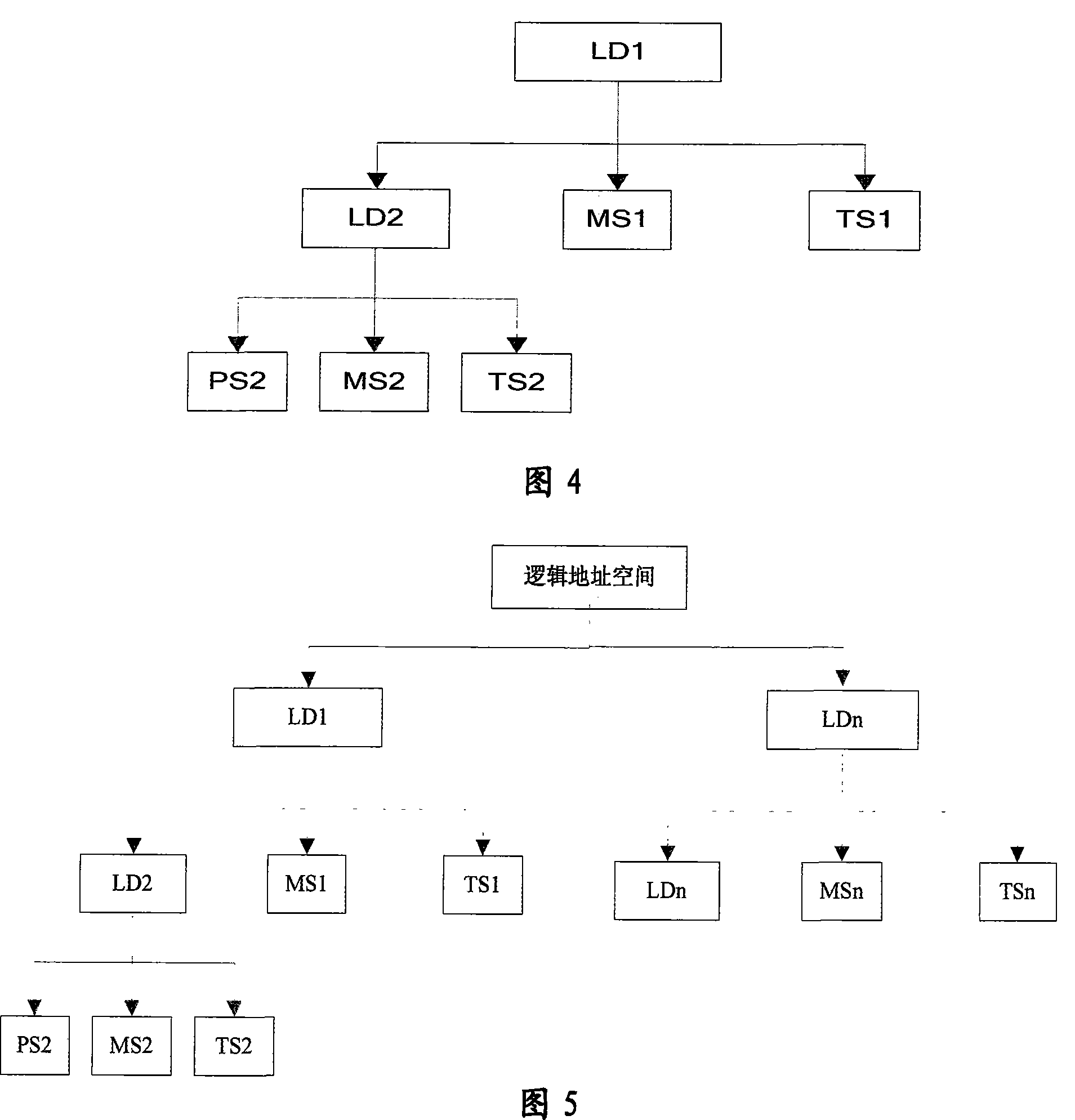
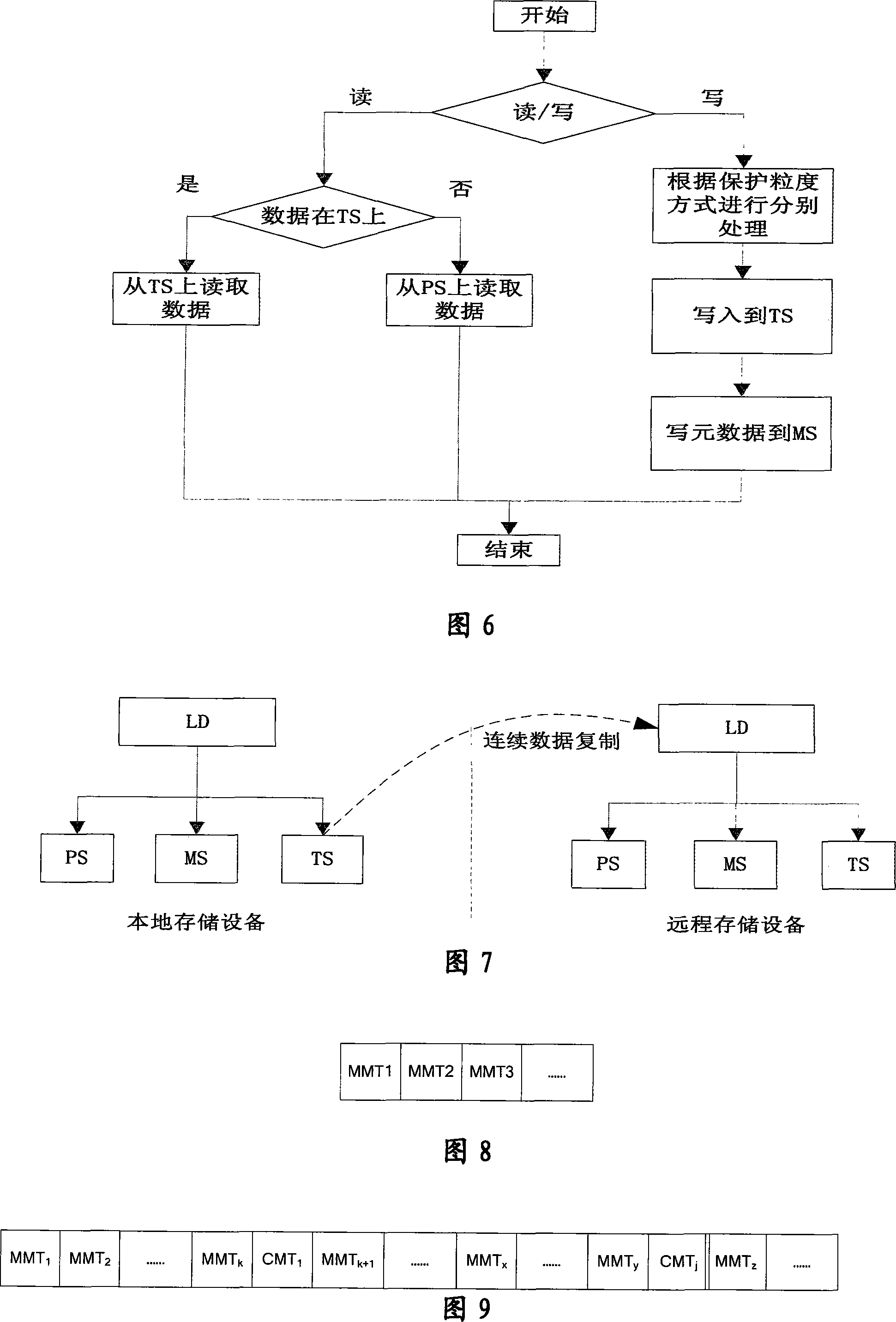
A continuous data protection system and its realization method
ActiveCN101187948AReliability is not reducedRedundant operation error correctionSpecial data processing applicationsManagement toolGranularity
The invention provides a Continuous Data Protection CDP system and the realizing method thereof. The system comprises a management tool module, a main body module and physical equipment. The system can perform flexible stack. The management tool module is used for building the main body module with a temporal point, and performing the operations of reading, writing and storing to the main body module, according to the difference of the data access frequency and the data level, the important data which is accessed recently adopts a CDP technique with a fine grit, the non-important data which is not accessed often adopts a back-up protection technique with a coarse particle size, thereby the invention can support continuous data protection of different protection granularities, through the flexible stack structure, the requirement of the data memory capacity is reduced, while the reliability for the data continuous protection is not reduced.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
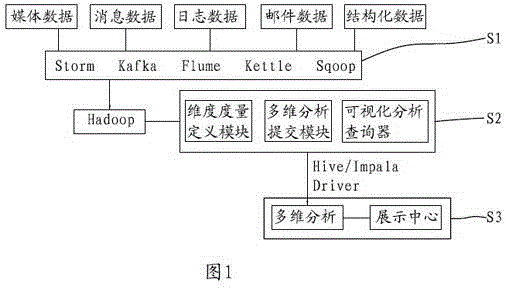
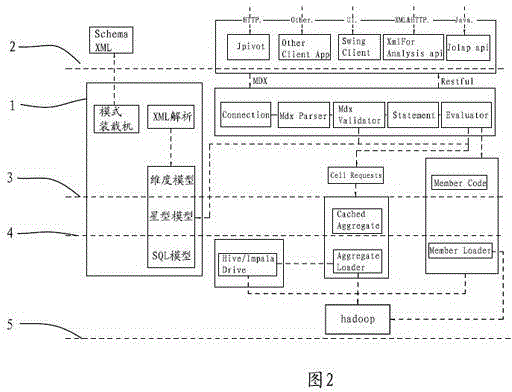
Visualized on-line analytical processing (OLAP) application realizing method and system
ActiveCN103955502ASolve performance shortcomingsFix performance issuesMulti-dimensional databasesSpecial data processing applicationsStatistical analysisBusiness data
The invention discloses a visualized on-line analytical processing (OLAP) application realizing method and a visualized OLAP application realizing system. The visualized OLAP application realizing method and the visualized OLAP application realizing system store business data analyzed by OLAP in Hadoop cluster which supports the distributed and column-oriented mode, and the effective dock of an on-line analytical platform and a Hadoop storage platform is realized through a structured query language (SQL) query engine supported by Hive and Impala. The visualized OLAP application realizing method and the visualized OLAP application realizing system increase the storage volume, improve the storage expansibility and safety, and effectively operate the hundred billion or even thousand billion data level on-line multidimensional statistical analysis and machine learning.
Owner:科技谷(厦门)信息技术有限公司
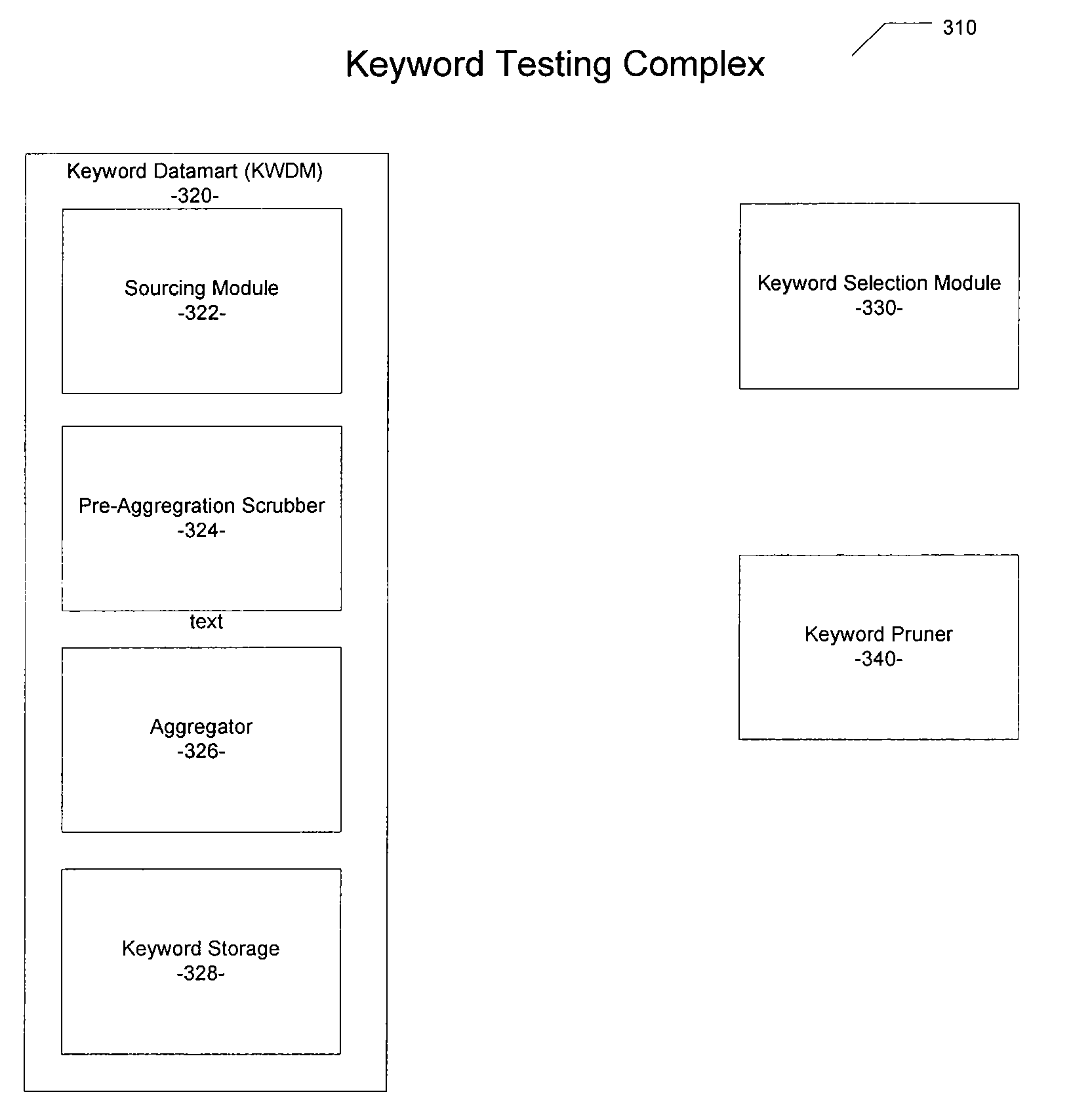
Computer-implemented method and system for enabling the automated selection of keywords for rapid keyword portfolio expansion
A computer-implemented method and system for enabling the automated selection of keywords for rapid keyword portfolio expansion are disclosed. Various embodiments are operable to normalize a plurality of keywords received from a source, filter the normalized plurality of keywords against one or more keyword filtration lists, produce site-specific variants of the filtered plurality of keywords, associate at least one level of dimension data with each of the plurality of keywords, and store the processed plurality of keywords and dimension data in a keyword database.
Owner:EBAY INC
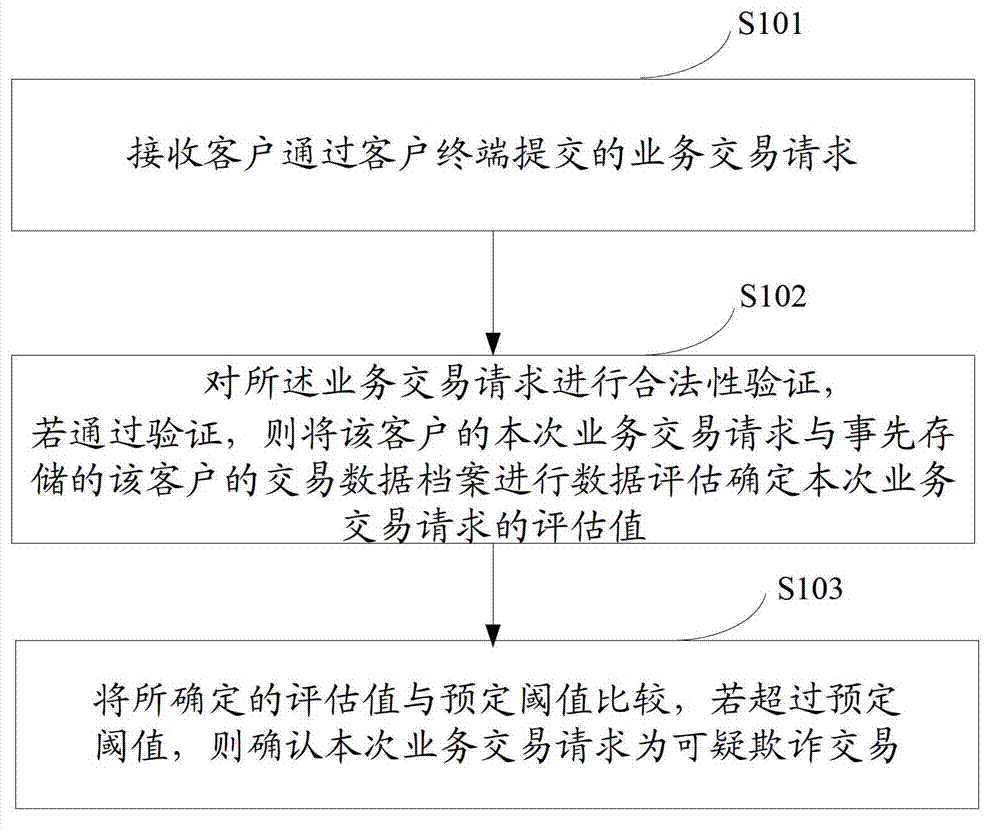
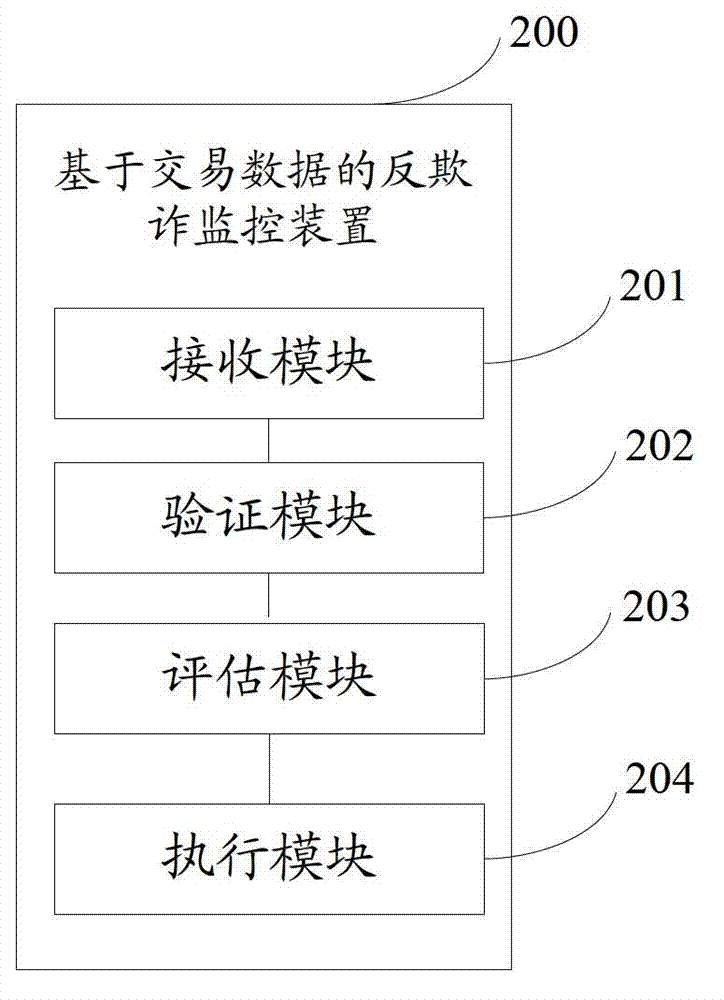
Transaction data-based anti-fraud monitoring method and device
The invention provides a transaction data-based anti-fraud monitoring method, which comprises the following steps of: receiving a business transaction request submitted by a client through a client terminal; verifying legality of the business transaction request; if the verification is passed, performing data evaluation on the current business transaction request of the client and a previously stored transaction data file of the client to determine an evaluation value of the current business transaction request; comparing the determined evaluation value with a predetermined threshold value; and determining that the current business transaction request is suspicious fraudulent transaction if the determined evaluation value exceeds the predetermined threshold value. The invention also provides a corresponding device. By implementing the method and the device provided by the invention, the security of business transaction can be improved on the data level of business transaction data analysis.
Owner:CHINA CONSTRUCTION BANK
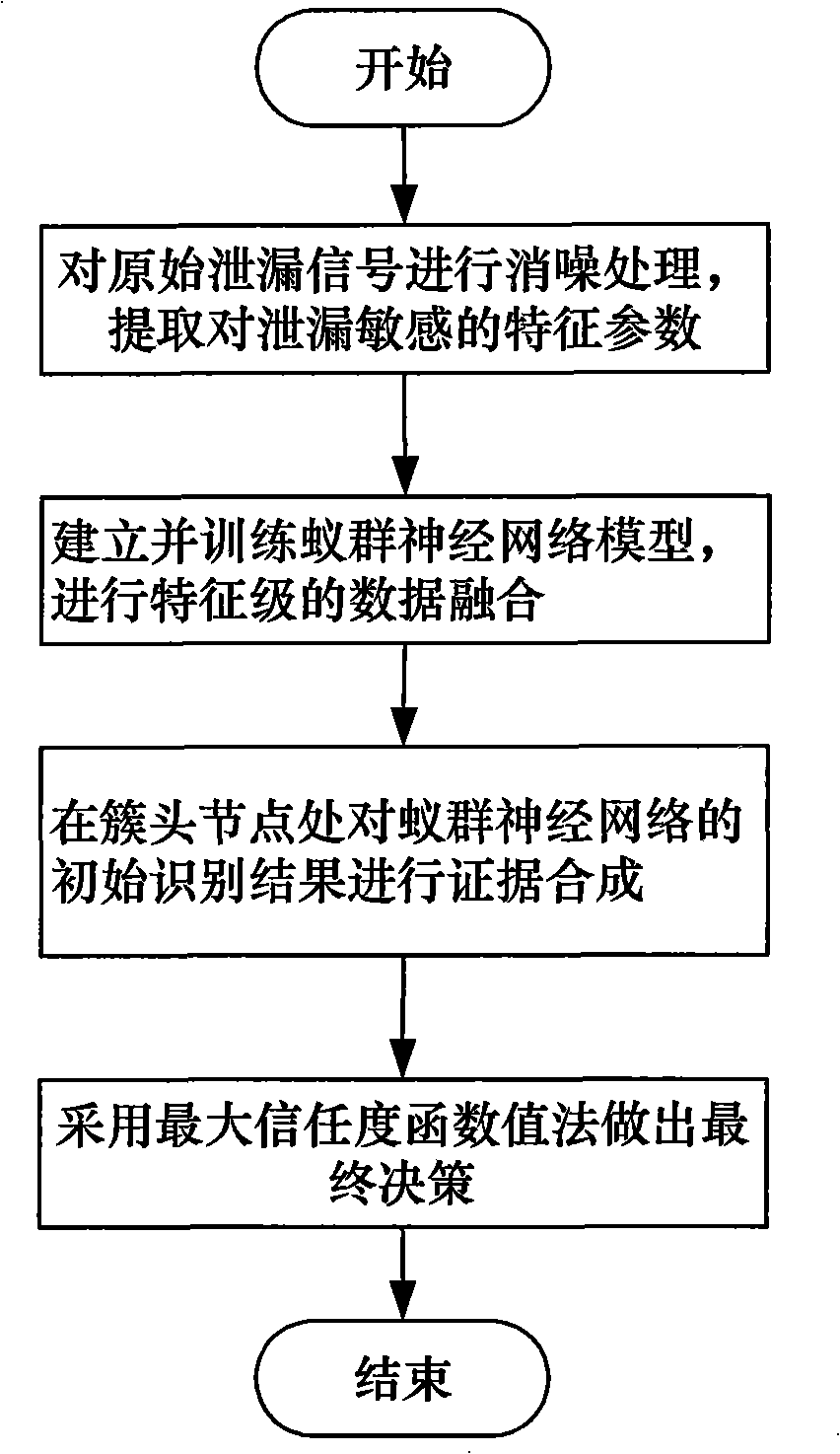
Hierarchical multi-source data fusion method for pipeline linkage monitoring network
InactiveCN101539241AImprove accuracyAccurate removalCharacter and pattern recognitionPipeline systemsLevel dataBasic probability
The invention discloses a hierarchical multi-source data fusion method for a pipeline linkage monitoring network, which comprises the following steps: carrying out data level preprocessing for various primary linkage detection signals acquired by a sensor at a common node of the monitoring network by using wavelet transformation, and extracting leakage-sensitive characteristic parameters; establishing a characteristic level data fusion model based on an ant colony neural network, processing the leakage characteristic parameters extracted by various sensors on the node, and constructing an elementary probability assignment function of evidence according to the output result of the ant colony neural network; and carrying out evidence synthesis at a cluster-head node according to an evidence combination rule, and making final decisions according to a maximum trust value method. The invention provides the hierarchical multi-source linkage detection data fusion method from the data level and characteristic level to decision level, and solves the multi-source data processing problem of the pipeline linkage monitoring network; and the method utilizes the linkage detection information acquired by various sensors in the network so as to effectively improve the accuracy rate of leakage identification.
Owner:BEIHANG UNIV
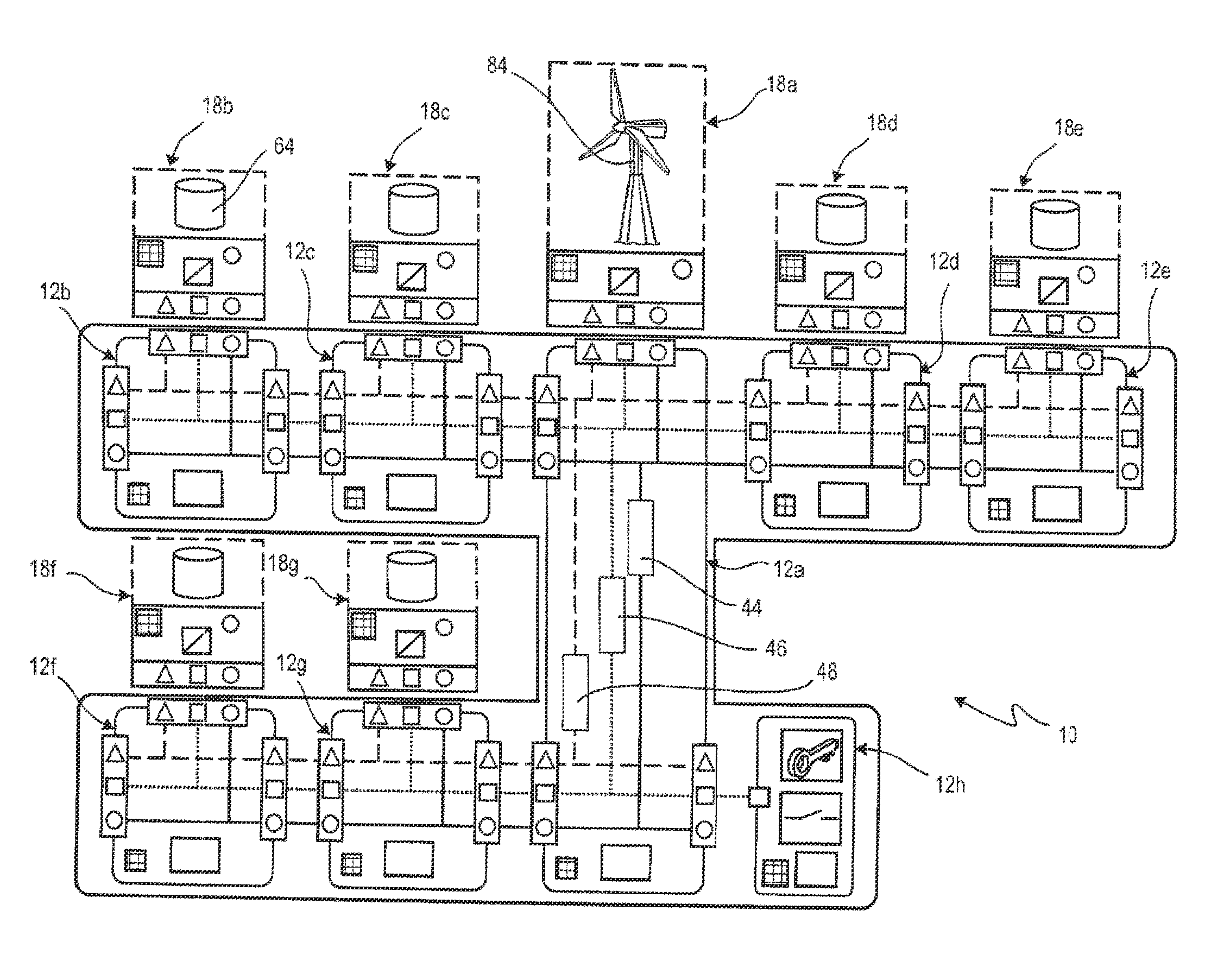
Network infrastructure component, network system having a plurality of network infrastructure components, and use of the network system
InactiveUS20140368032A1Function increaseHighly self-configuringAc-dc network circuit arrangementsDc source parallel operationNetworked systemControl equipment
The invention relates to a network infrastructure component and a distributed network system for supply purposes comprising a plurality of network infrastructure components, wherein the network infrastructure component comprises at least one contact unit for connection to a further network infrastructure component, and at least one coupling module for coupling a functional group, wherein the network infrastructure component is designed to communicate with a coupled functional group at least at a supply level, wherein the network infrastructure component is designed to communicate with at least one further network infrastructure component at least at the supply level and / or a data level, such that a self-configured network system for linking a plurality of functional groups can be produced with a network of a plurality of network infrastructure components. Preferably, the network infrastructure component comprises a control device for controlling operating parameters, in particular for load control at the supply level.
Owner:UNICORN ENERGY GMBH
Semiconductor memory device
InactiveUS20070019467A1Difference can be detectedRead-only memoriesDigital storageAudio power amplifierHemt circuits
A semiconductor memory device includes: first and second cell arrays each having a plurality of memory cells; and a sense amplifier circuit for reading out data of the first and second cell arrays, wherein plural information cells and at least one reference cell are set in each of the first and second cell arrays, one of four data levels L0, L1, L2 and L3 (where, L0<L1<L2<L3) being written into the information cell, reference level Lr (where, L0<Lr<L1) being written into the reference cell to used for detecting the data level of the information cell, and wherein the sense amplifier circuit detects a cell current difference between the information cell and the reference cell simultaneously selected from the first and second cell arrays.
Owner:KK TOSHIBA
Shutdowns and data recovery to avoid read errors weak pages in a non-volatile memory system
ActiveUS20140304560A1Avoid reading errorsPrevent read error of dataMemory architecture accessing/allocationMemory adressing/allocation/relocationData recoveryPage buffers
A memory apparatus and methods are provided for preventing read errors on weak pages in a non-volatile memory system. In one example, a method includes identifying a weak page in a non-volatile memory device along a word line, wherein the weak page is partially written with at least some data; buffering data associated with the weak page to a weak page buffer that is coupled in communication with the non-volatile memory device; determining that an amount of data in the weak page buffer has reached a predetermined data level; and writing the data from the weak page buffer into the weak page along the word line in the non-volatile memory device.
Owner:WESTERN DIGITAL TECH INC
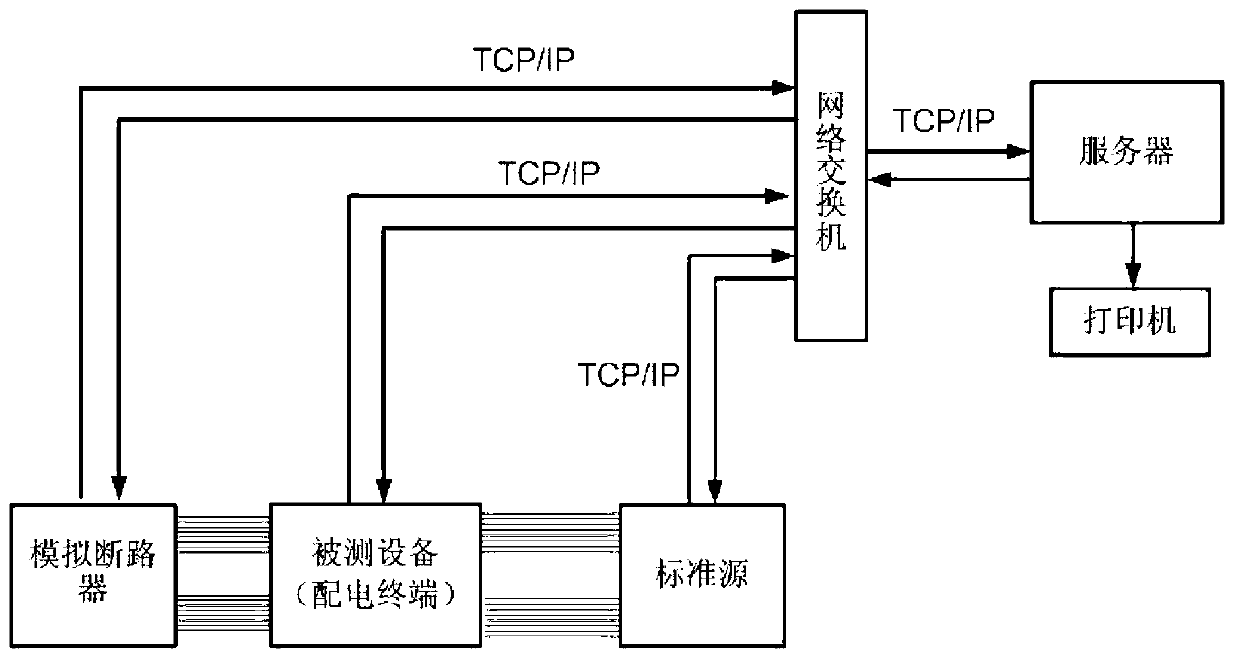
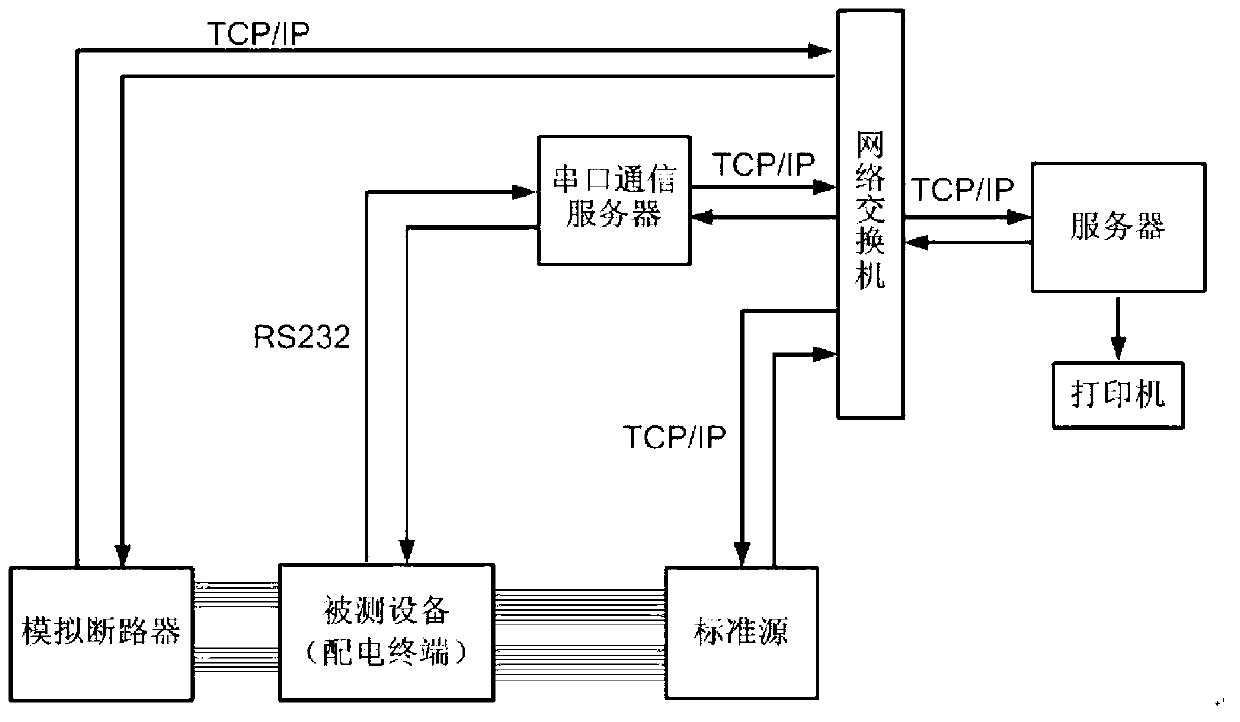
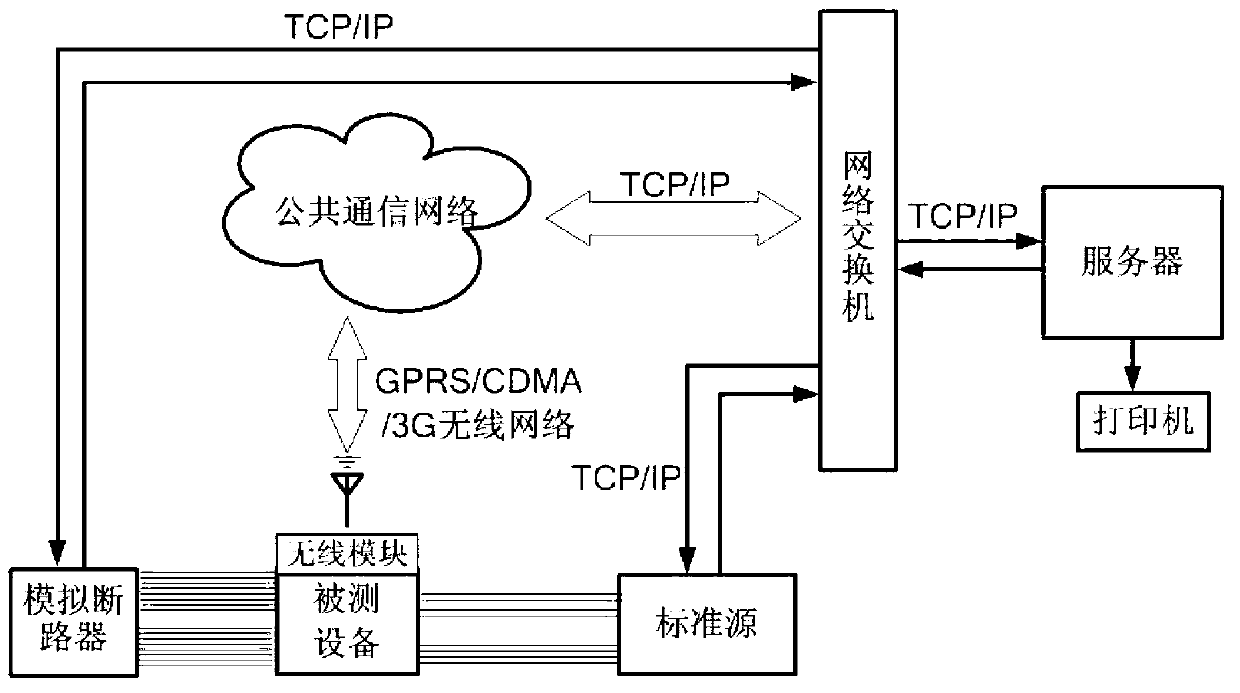
Detection method of function and performance of power distribution automation terminal device
The invention discloses a detection method of the function and the performance of a power distribution automation terminal device. The detection method includes a function test portion and a performance test portion. The function test portion comprises a remote control function test, a remote signaling collection function test, a data grade test and a power supply low voltage protection alarming function test. The performance test portion comprises a remote measuring accuracy test and an SOE anti-shaking test. By means of the detection method, tests of various function and performance parameters of a power distribution terminal can be finished comprehensively and quickly in development of access network detection work to ensure that the power distribution terminal runs safely, reliably and stably.
Owner:ELECTRIC POWER RES INST OF GUANGXI POWER GRID CO LTD
Method and system for validating information
ActiveUS20130090803A1Simplification potentialLow production costVehicle testingRegistering/indicating working of vehiclesCommunication deviceData level
A method for validating information, wherein a first information item is detected essentially continuously, at least for the duration of its relevance, by a vehicle-to-X communication device, wherein a second information item is detected at the same time as the first information item by at least an individual sensor or a group of sensors, wherein the at least one individual sensor or the group of sensors is coupled at the data level to the vehicle-to-X communication device and wherein the first and / or second information items are validated by reconciling an information content of the first and second information items in the case of corresponding information content. The method is distinguished by the fact that the second information item is detected in an essentially discontinuous fashion.
Owner:CONTINENTAL TEVES AG & CO OHG
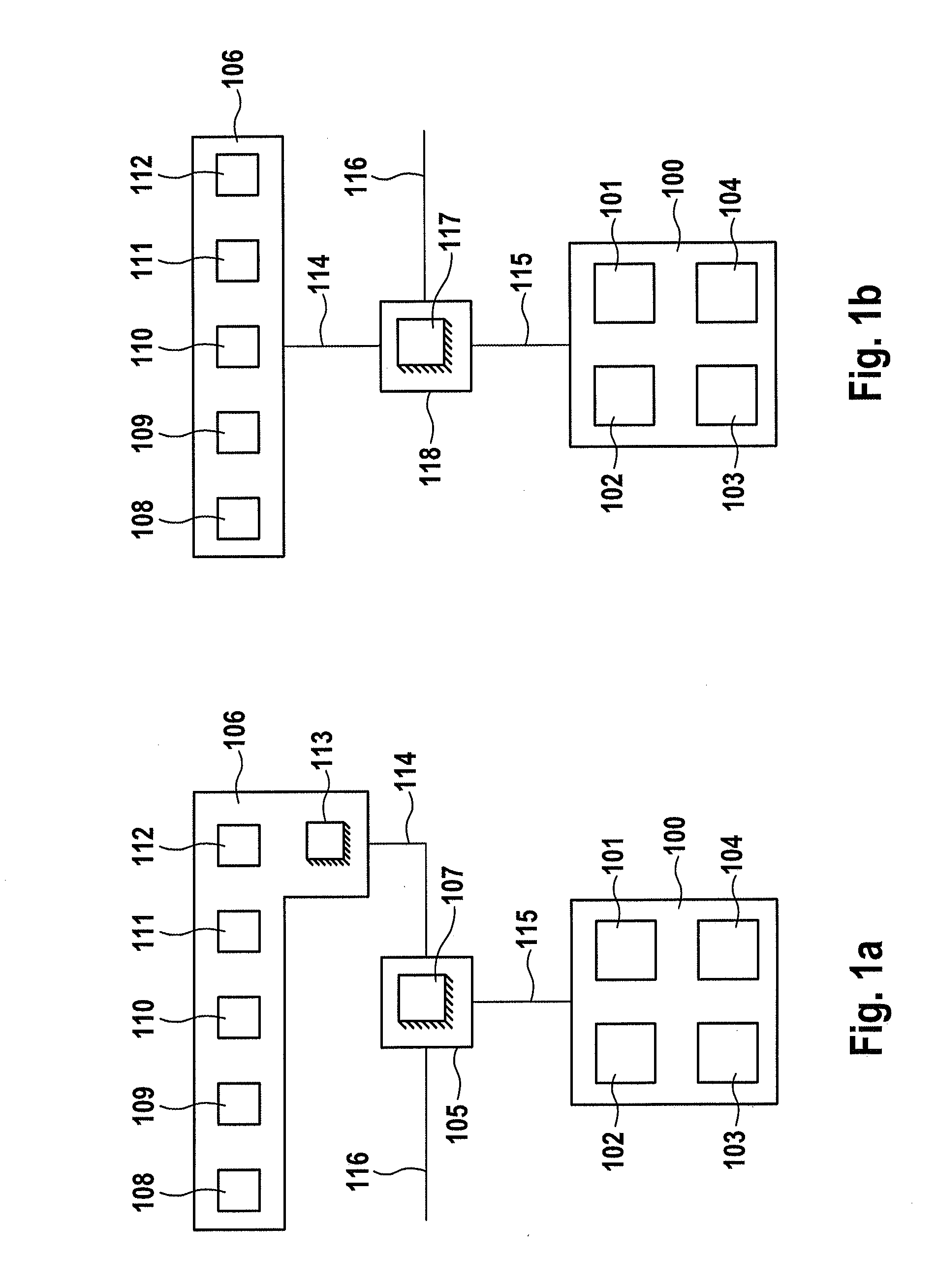
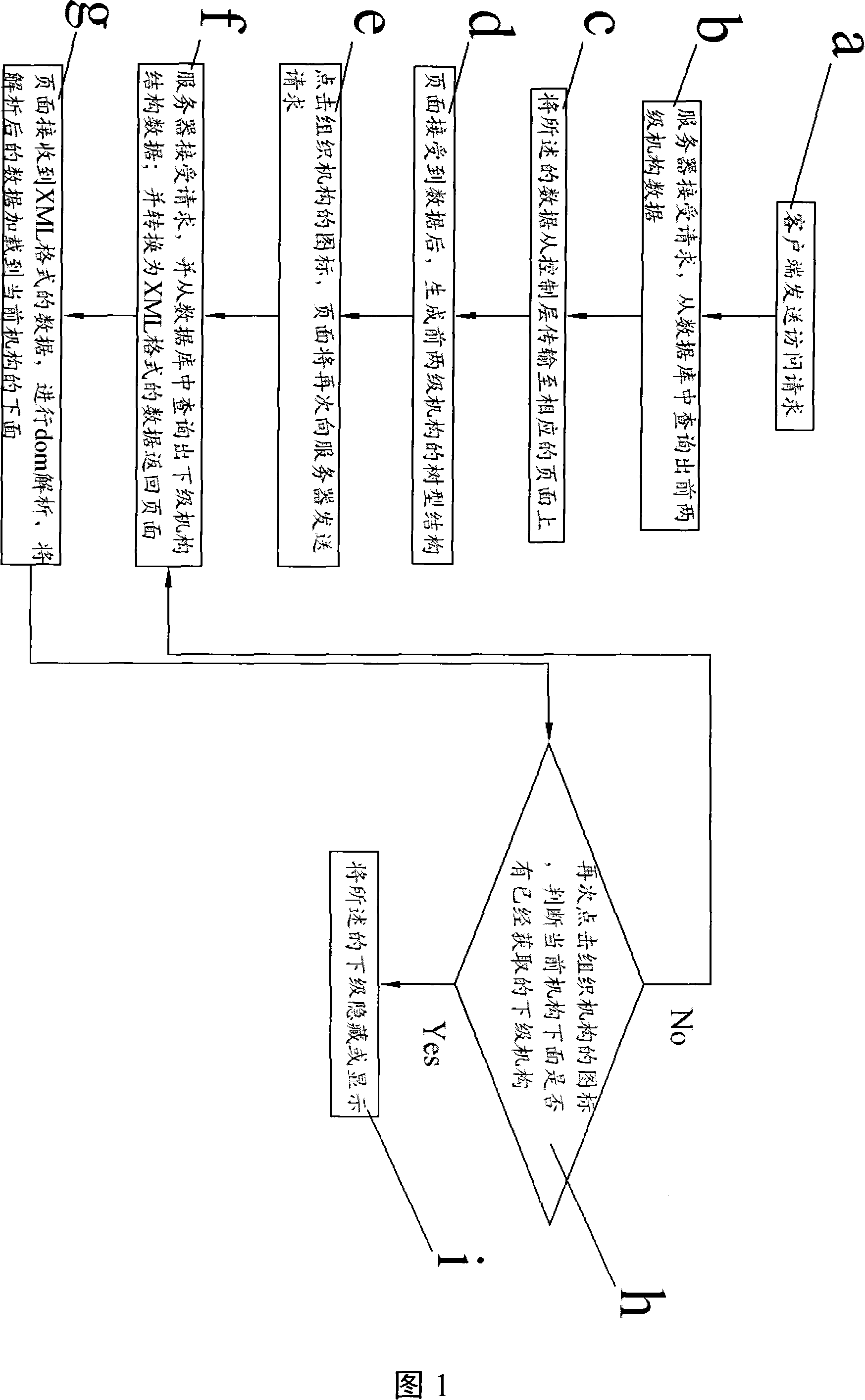
Method forming tree-shaped display structure based on ajax and html
InactiveCN101122921AImprove efficiencyTransmissionSpecial data processing applicationsData displayDynamic HTML
The invention is a method for forming a tree-shaped display structure based on ajax and html tags, and uses the combination of ajax technology and dynamic html tags and javaScript scripts to display data as a tree-shaped structure in the form of a list. And in order to improve efficiency, it is designed to display the data of level 2 first, and then display the lower level data of this level every time one level is clicked. Due to the use of ajax technology, the page can be partially refreshed so that users do not feel the refresh changes of the page, and the efficiency of the page is greatly improved.
Owner:北京意科能源技术有限公司
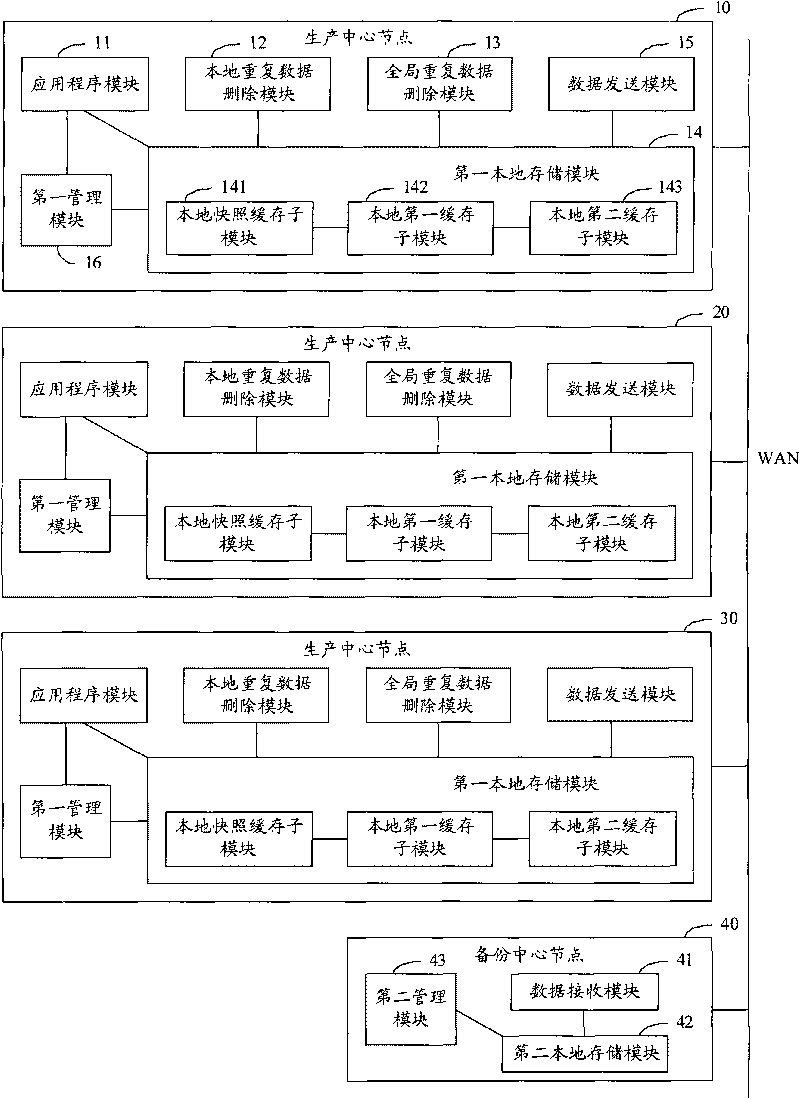
Data level disaster-tolerant method and system and production center node
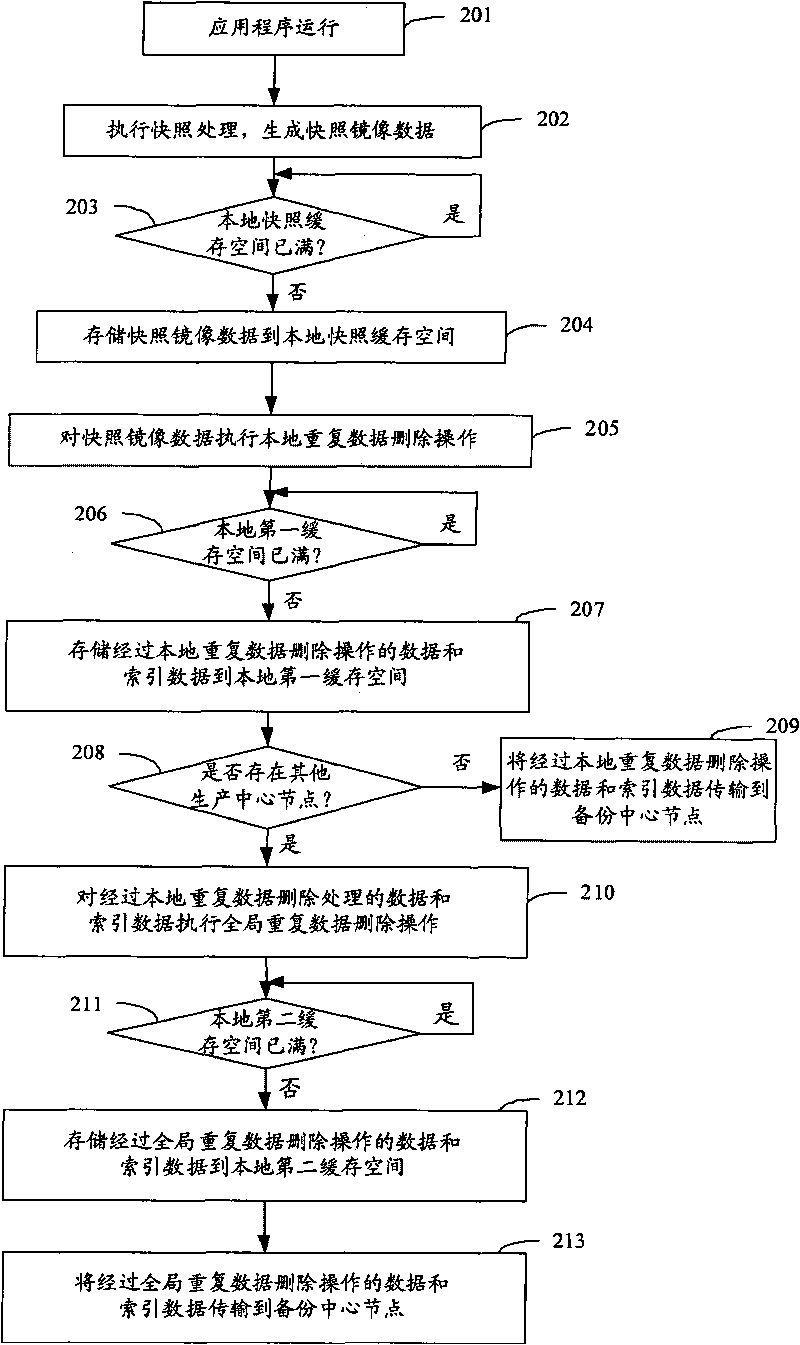
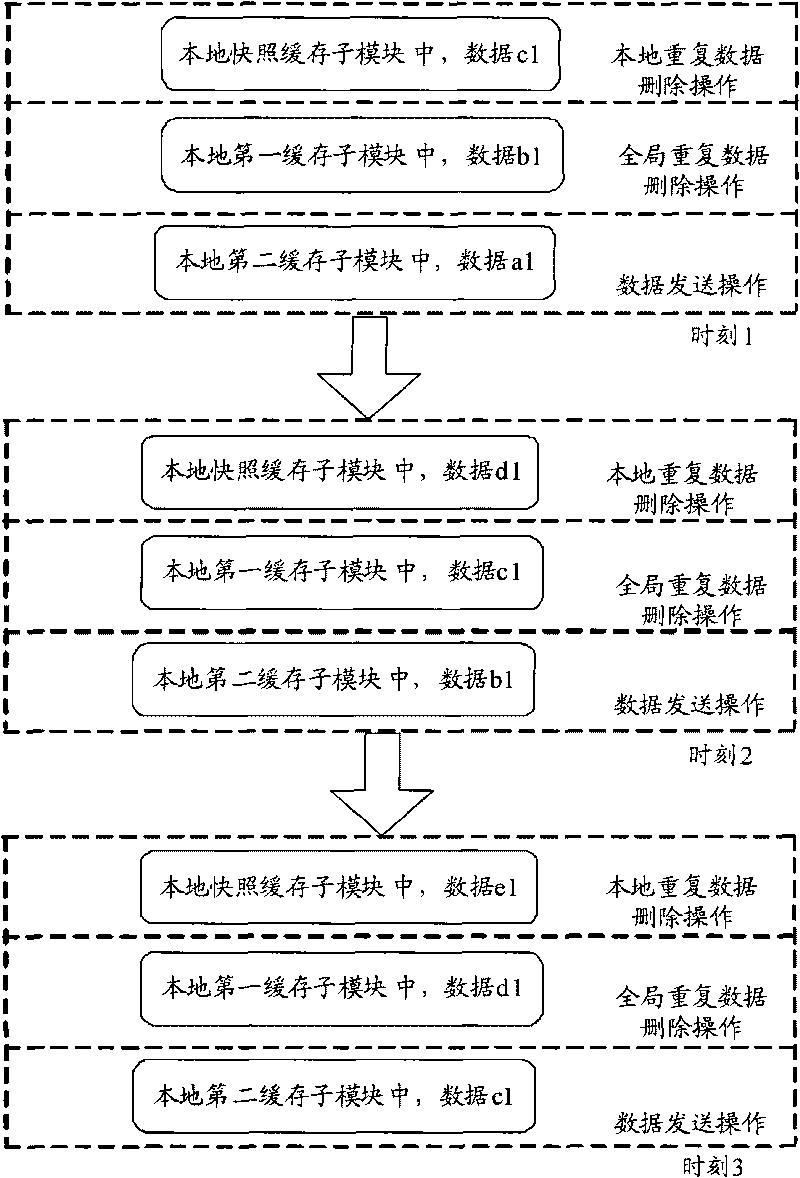
ActiveCN101741536ASpeed up data backupImprove reliabilityError preventionData capacityDependability
The invention discloses a data level disaster-tolerant method. The method comprises the following steps of: performing snapshot process on data generated through the operation of an application program to generate snapshot mirror data; performing local data de-duplication on the snapshot mirror data to generate the data processed through the local data de-duplication and the corresponding index data; performing global data de-duplication on the data processed through the local data de-duplication and the corresponding index data to generate the data processed through the global data de-duplication and the index data; and transmitting the data processed through the global data de-duplication and the index data to a backup center node. The invention also discloses a data level disaster-tolerant system and a production center node, which can reduce the capacity of the data transmitted between the production center node and the backup center node and the requirement on network bandwidth performance so as to realize the data level disaster tolerance more rapidly and effectively and enhance the reliability and availability of the disaster-tolerant system.
Owner:ZTE CORP
Road vision detection method combined with laser point cloud data
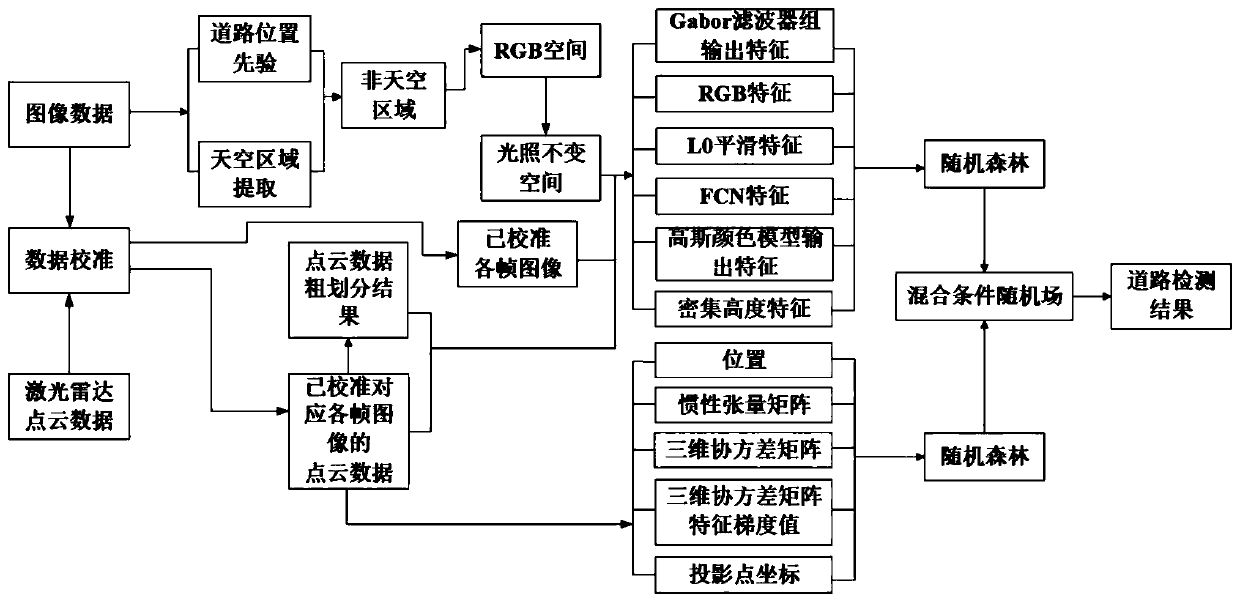
ActiveCN110378196AHigh precisionImprove robustnessCharacter and pattern recognitionNeural architecturesConditional random fieldFeature extraction
The invention discloses a road vision detection method combined with laser point cloud data, belongs to the field of unmanned driving, and solves the problem of multi-sensor fusion in the prior art. The method comprises the steps of performing data-level fusion on the point cloud data and the image data; performing road division on each frame of image in the image data, and performing conversion after division to obtain an illumination-invariant space image; according to the M estimation sample consistency, performing plane fitting on the point cloud data after data level fusion to obtain a point cloud data coarse division result; performing road feature extraction on each frame of image, the illumination-invariant space image and the point cloud data coarse division result of the image data after data level fusion and the point cloud data after data level fusion corresponding to each frame of image; respectively sending the extracted road features into two random forests for training,and obtaining probability output of each pixel point and probability output of each point cloud data; and constructing each point cloud-image mixed conditional random field to obtain a road area. Themethod is used for road vision detection.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
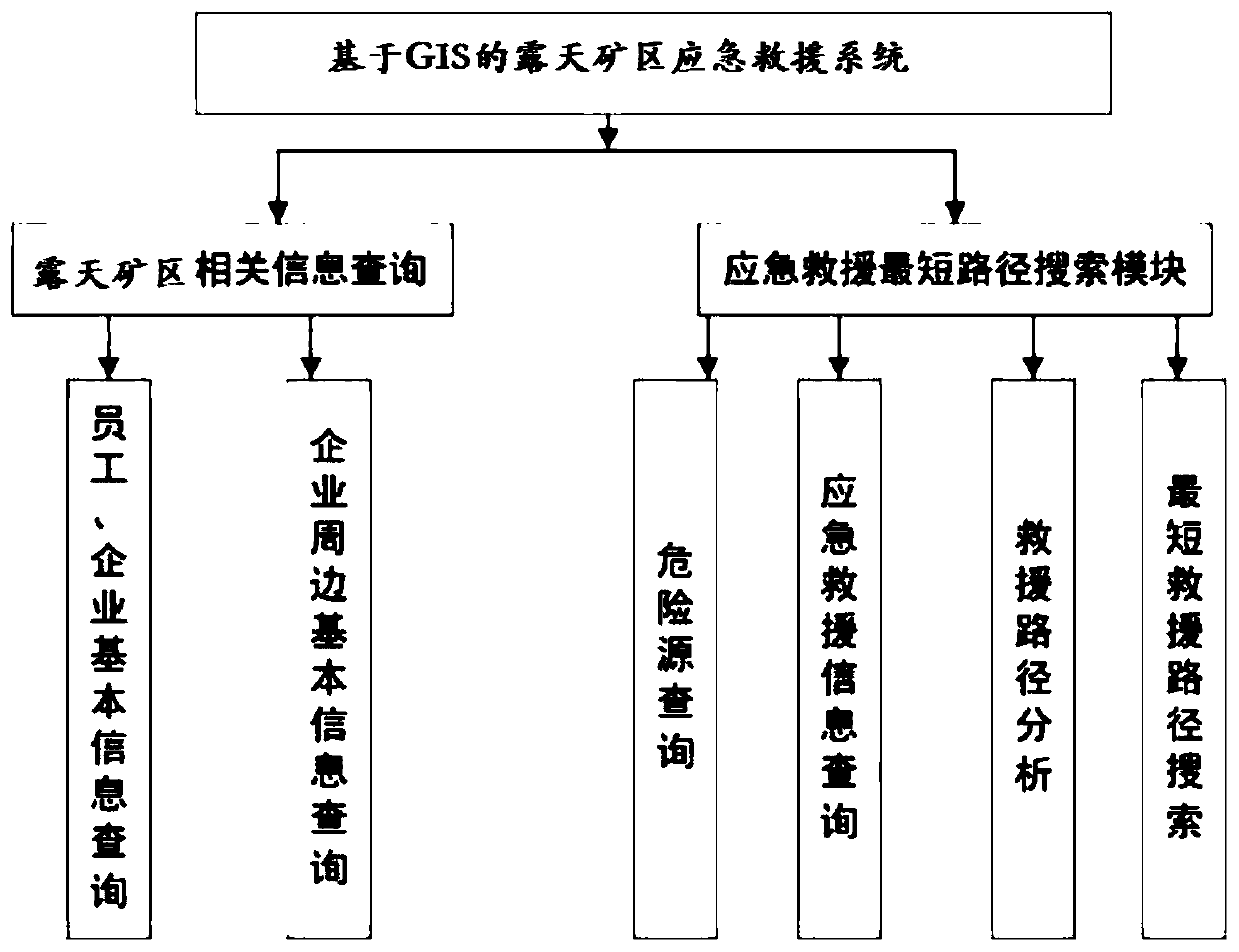
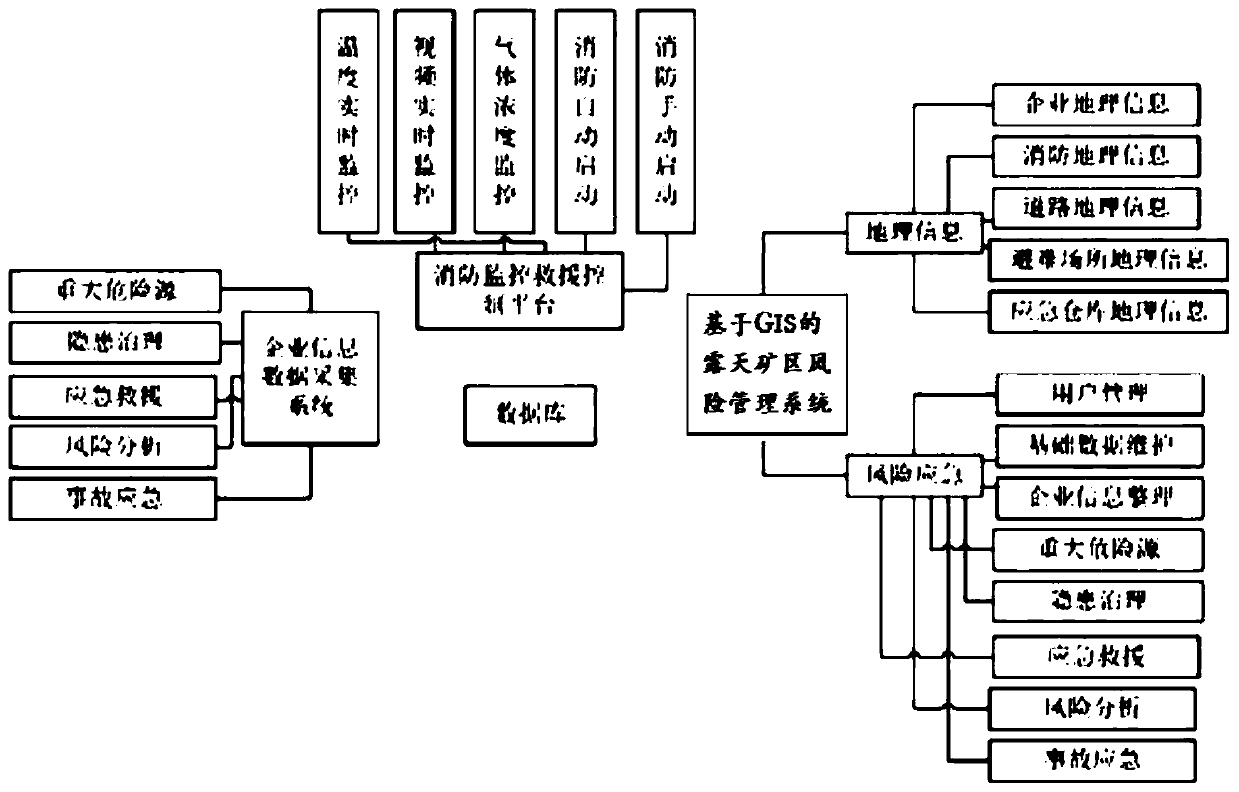
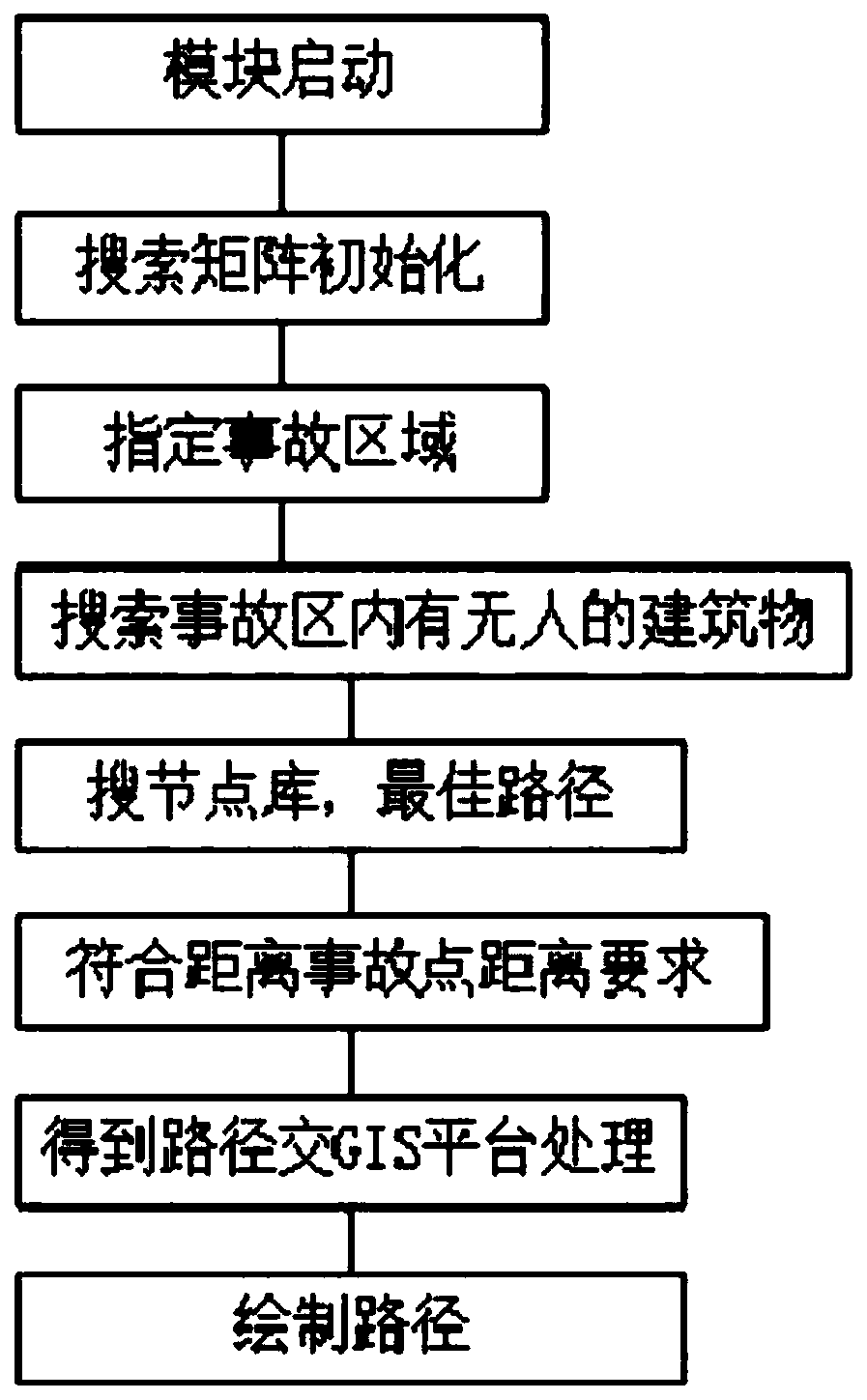
Emergency aid decision making system based on GIS and BIM
InactiveCN110008618ARealization of visual simulationStable supportData processing applicationsDesign optimisation/simulationDecision systemEmergency rescue
The invention provides an emergency aid decision making system based on a GIS and a BIM. According to the method, a GIS and a BIM are combined to realize interconnection and mutual homogeneity on a data level, a unified multi-scale open-pit mine area three-dimensional display platform is constructed, an emergency rescue management system based on the GIS is constructed, BIM model pipeline data isfused, and a risk management and emergency rescue aid decision making system is constructed. According to the method, two spatial information technologies of GIS and BIM are combined, interconnectionand mutual homogeneity of the two technologies on the data level are achieved, quantitative analysis is conducted on the strip mine area, and a designer is assisted in planning the strip mine area. Original data of a project site can be well stored for a designer, and the data can have a good supporting effect on later-period management such as planning, construction and operation maintenance.
Owner:华夏天信物联科技有限公司
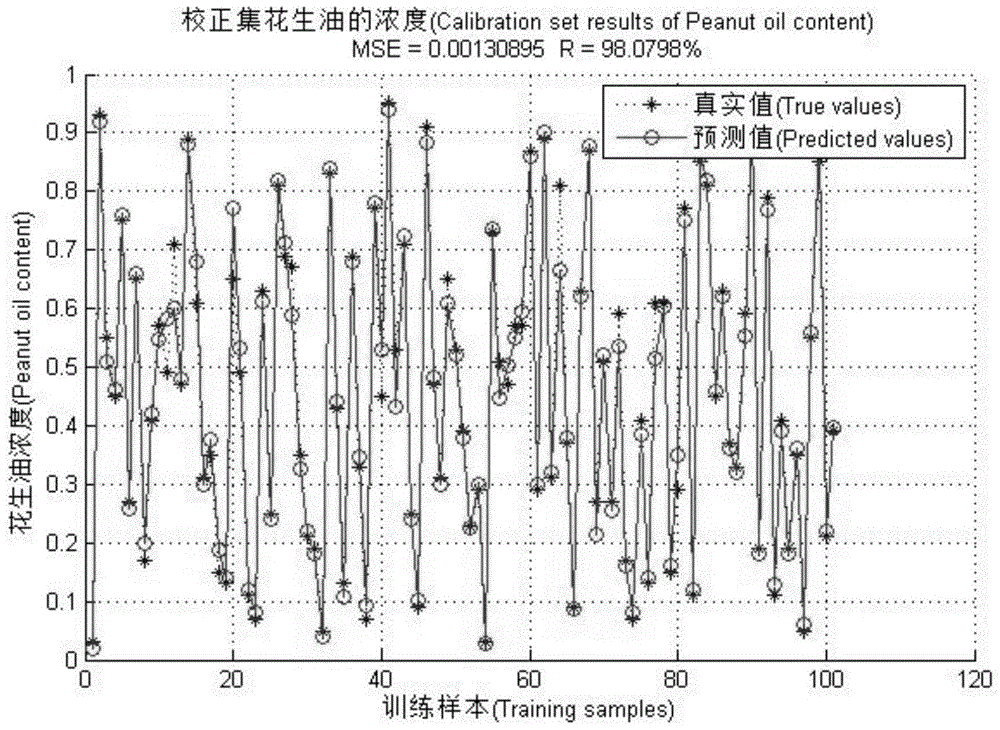
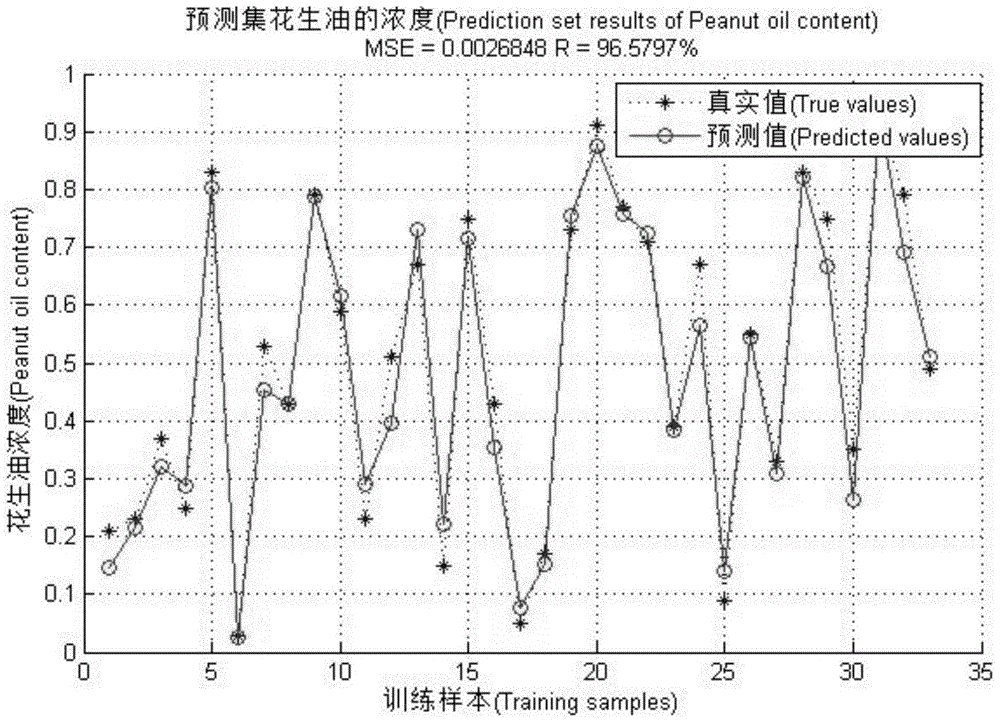
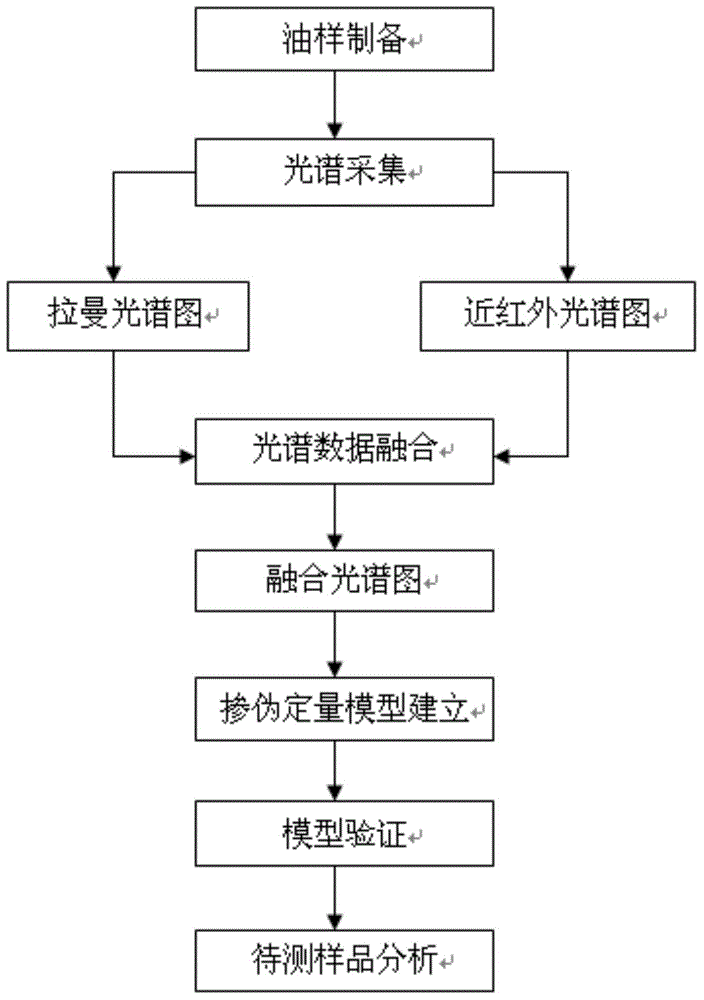
Quantitative adulteration detection method for peanut oil based on multiple-source spectroscopic data fusion
ActiveCN104807803AComprehensive Internal Characteristic InformationComprehensively reflect internal feature informationRaman scatteringNon destructiveQuantitative model
The invention discloses a quantitative adulteration detection method for peanut oil based on multiple-source spectroscopic data fusion. The quantitative adulteration detection method comprises the following steps: oil sample preparation; spectrum acquisition: respectively acquiring Raman spectrograms and near-infrared spectrograms of all adulterated oil samples; spectroscopic data fusion: performing data level fusion on the preprocessed Raman spectrograms and the preprocessed near-infrared spectrograms to obtain a fusion spectrogram; quantitative adulteration model establishment: extracting characteristic wavelengths of the fusion spectrogram, and establishing a quantitative peanut oil sample adulteration model through a multivariate quantitative calibration method; model verification: analyzing samples to be detected. The detection method performs data fusion on the edible oil spectrograms of two spectrums, has good complementarity, can reflect the inner characteristic information of edible oil more comprehensively, and is quick, convenient, efficient, non-destructive, free from preprocessing, high in accuracy, and strong in applicability.
Owner:WUHAN POLYTECHNIC UNIVERSITY
Distributed storage method based on KEY-VALUE pair
InactiveCN104657500AEasy to handleAvoid IO lossSpecial data processing applicationsSmall filesMetadata
The invention particularly relates to a distributed storage method based on a KEY-VALUE pair. The distributed storage method based on the KEY-VALUE pair comprises an operation receiving layer, a cache searching layer and an operation processing layer, wherein after receiving user data, the operation receiving layer of a server completes splicing of the key-value pair through internal data organization; a bottom layer is divided into different data levels for disk landing and is meanwhile responsible for analyzing and reading following data; since the access of the key value pair belongs to lightweight database type operation without metadata, and is appended to write in, time consumption brought by disk landing of random small files can be avoided. According to the distributed storage method based on the KEY-VALUE pair, the bottom layer storage is modified to be a key-value pair mode, so that the whole storage cluster can more quickly and efficiently process the small files, and IO loss caused by frequent addressing along with small file random write-in in a traditional distributed storage or local storage mode is avoided, and the storage efficiency under such scene is greatly improved.
Owner:INSPUR GROUP CO LTD
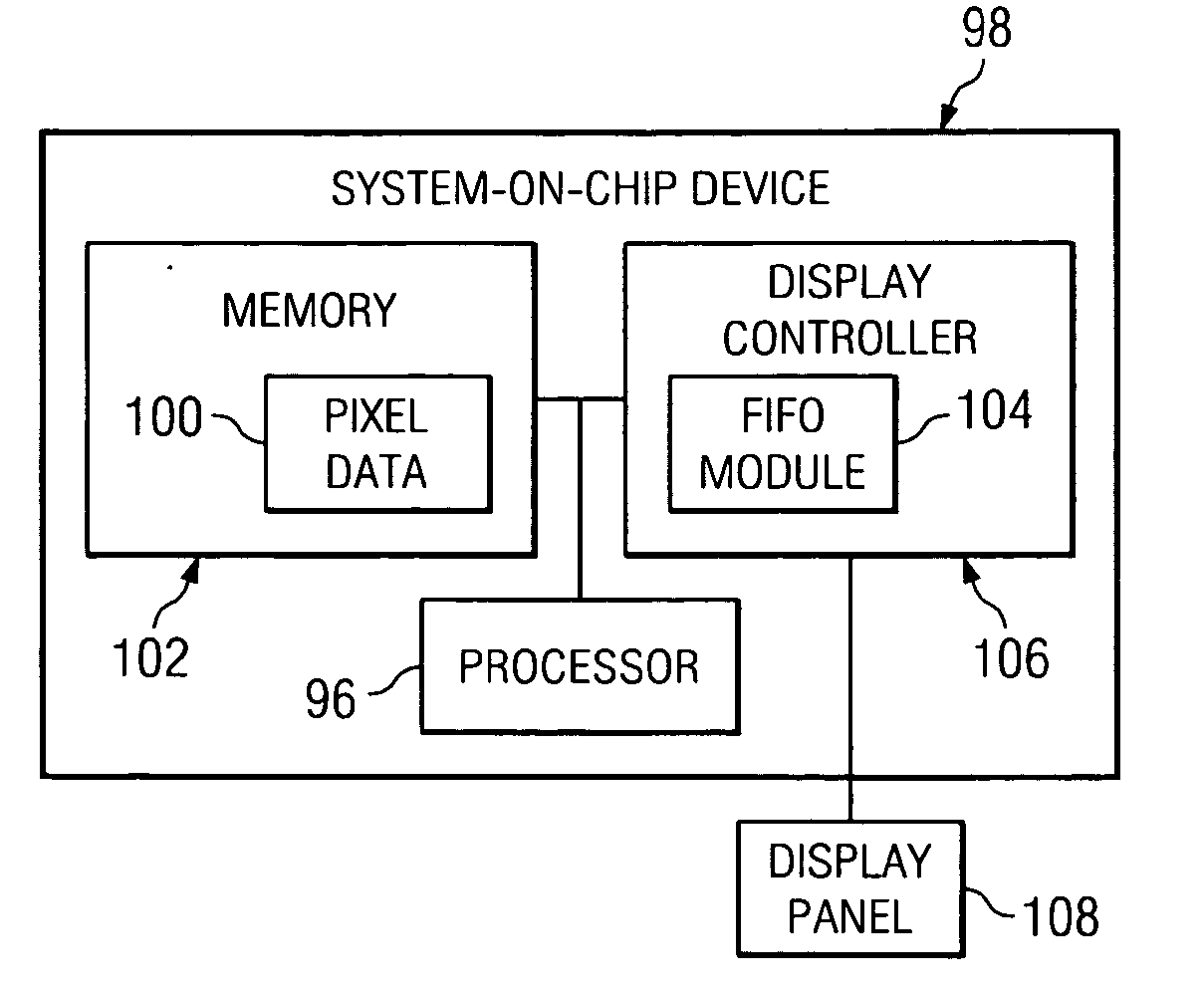
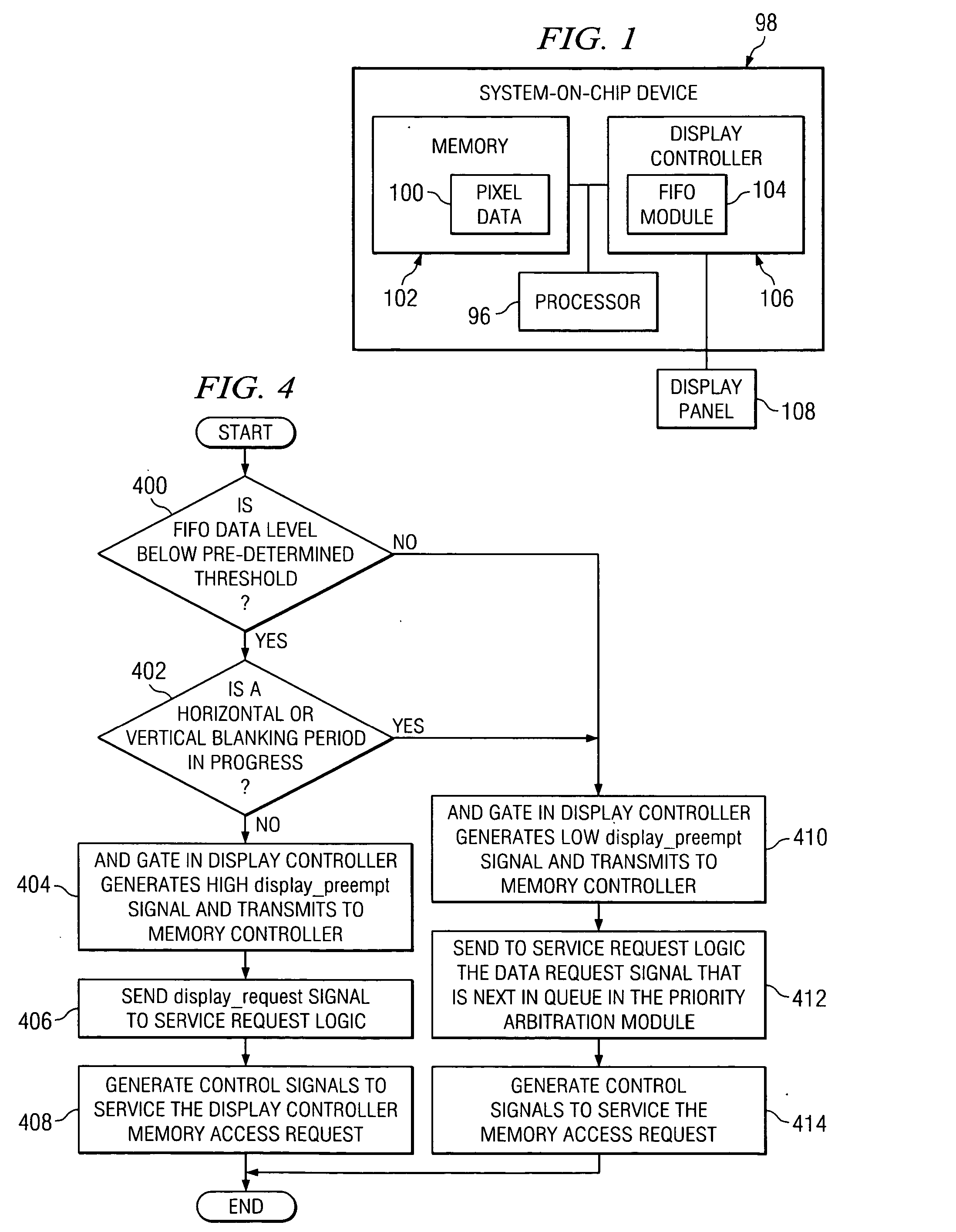
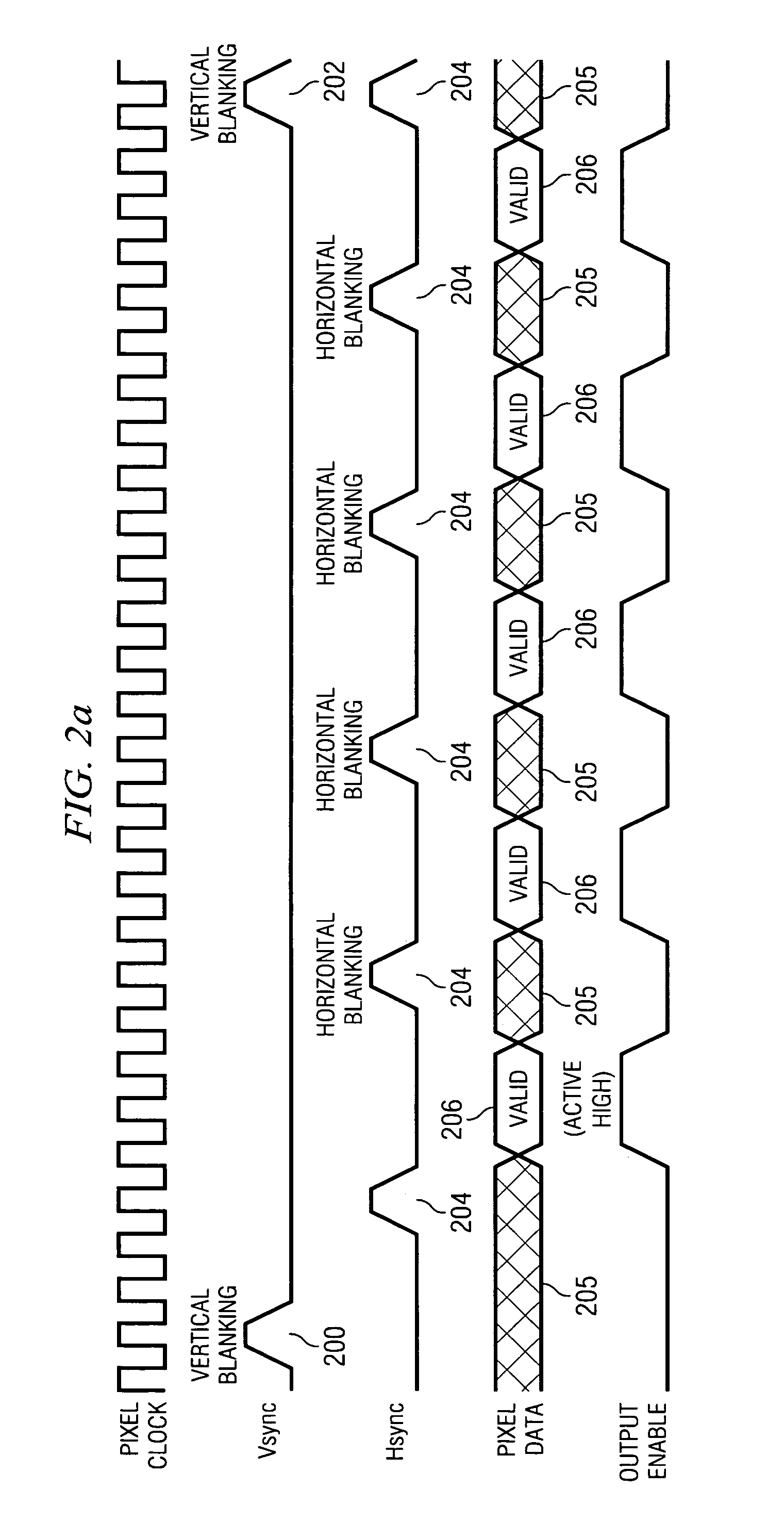
Preemptive rendering arbitration between processor hosts and display controllers
InactiveUS20060022985A1Cathode-ray tube indicatorsElectric digital data processingMemory controllerComputer science
A system comprises a display controller adapted to monitor a first-in, first-out module (“FIFO”) data level, a memory controller coupled to said display controller, and a memory coupled to said display controller and said memory controller. The memory controller permits the display controller to immediately access the memory when the FIFO data level drops below a pre-determined threshold level and no display panel horizontal or vertical blanking periods are in progress.
Owner:TEXAS INSTR INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com