Transaction data-based anti-fraud monitoring method and device
A transaction data and transaction technology, which is applied in the field of data processing, can solve the problems that USBKey cannot meet the security needs of online banking business transactions, and cannot know the legal users of the initiator of the digital signature, so as to improve security and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
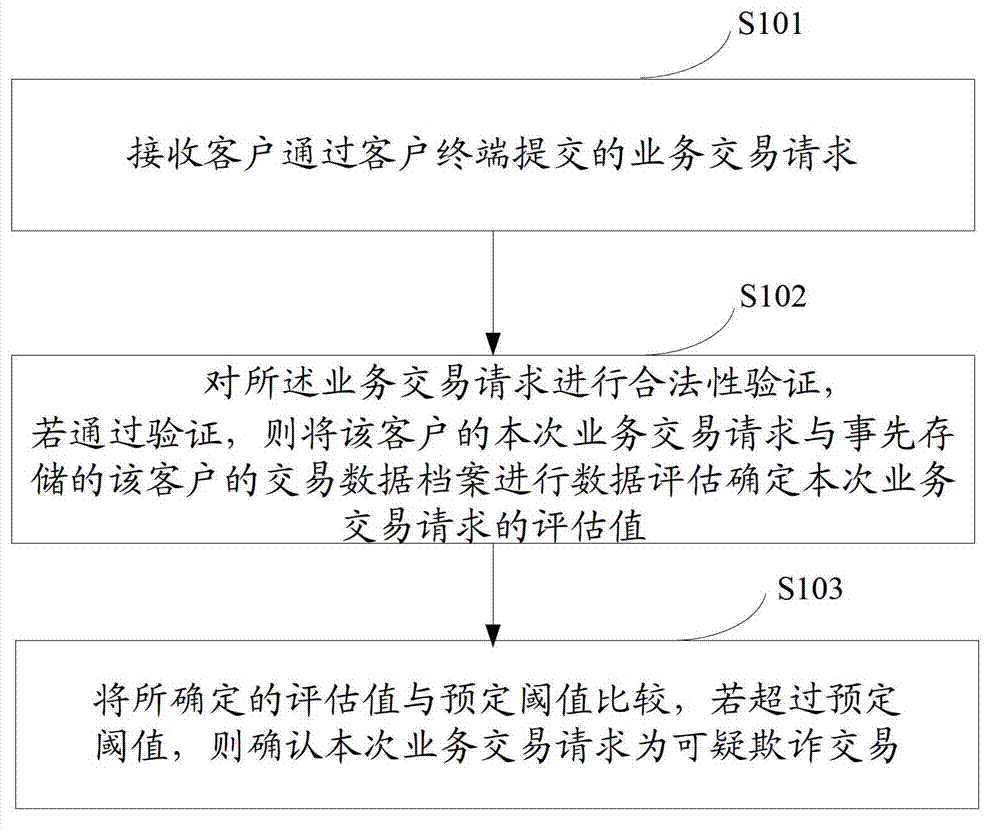
[0019] see figure 1 , which illustrates a schematic flowchart of an anti-fraud monitoring method based on transaction data according to an embodiment of the present invention, the method may specifically include:
[0020] S101, receiving a business transaction request submitted by a client through a client terminal;
[0021] S102, verifying the legality of the business transaction request,
[0022] If the verification is passed, perform data evaluation on the customer's current business transaction request and the previously stored customer's transaction data file to determine the evaluation value of this business transaction request;
[0023] S103, comparing the determined evaluation value with a predetermined threshold, and if it exceeds t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com