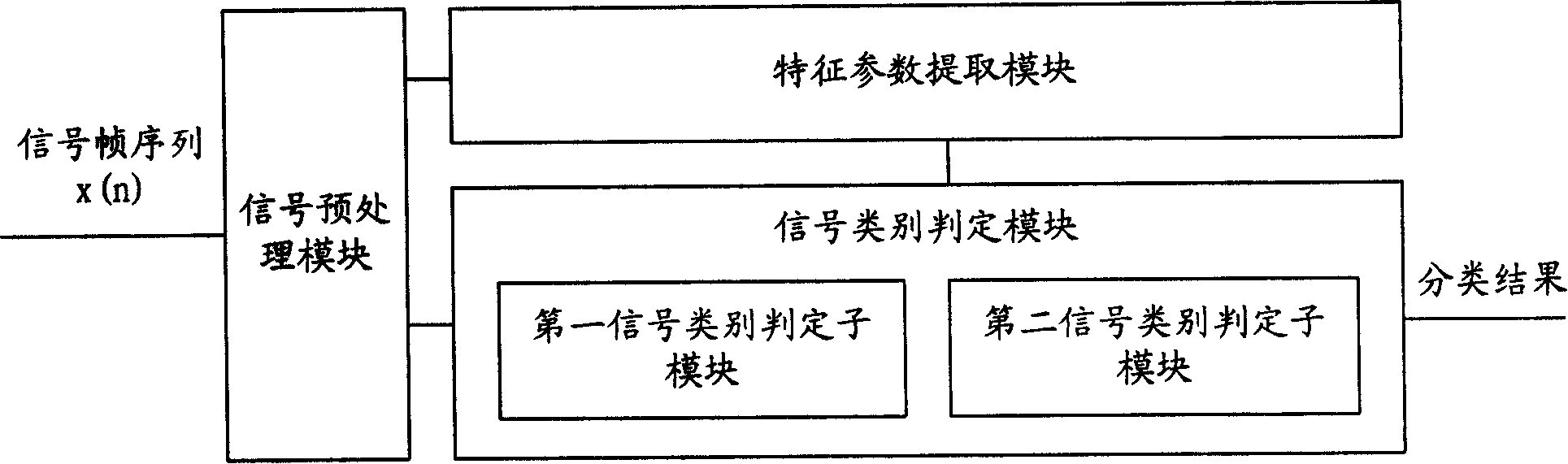
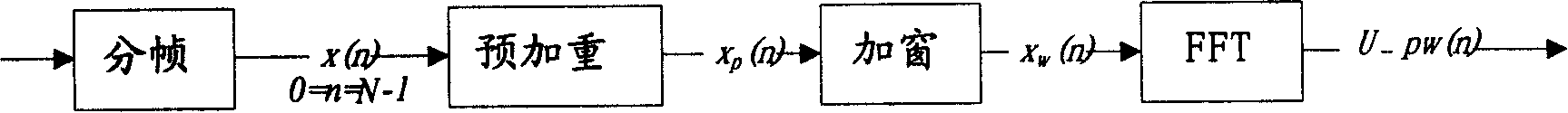Patents
Literature
953 results about "Activity detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
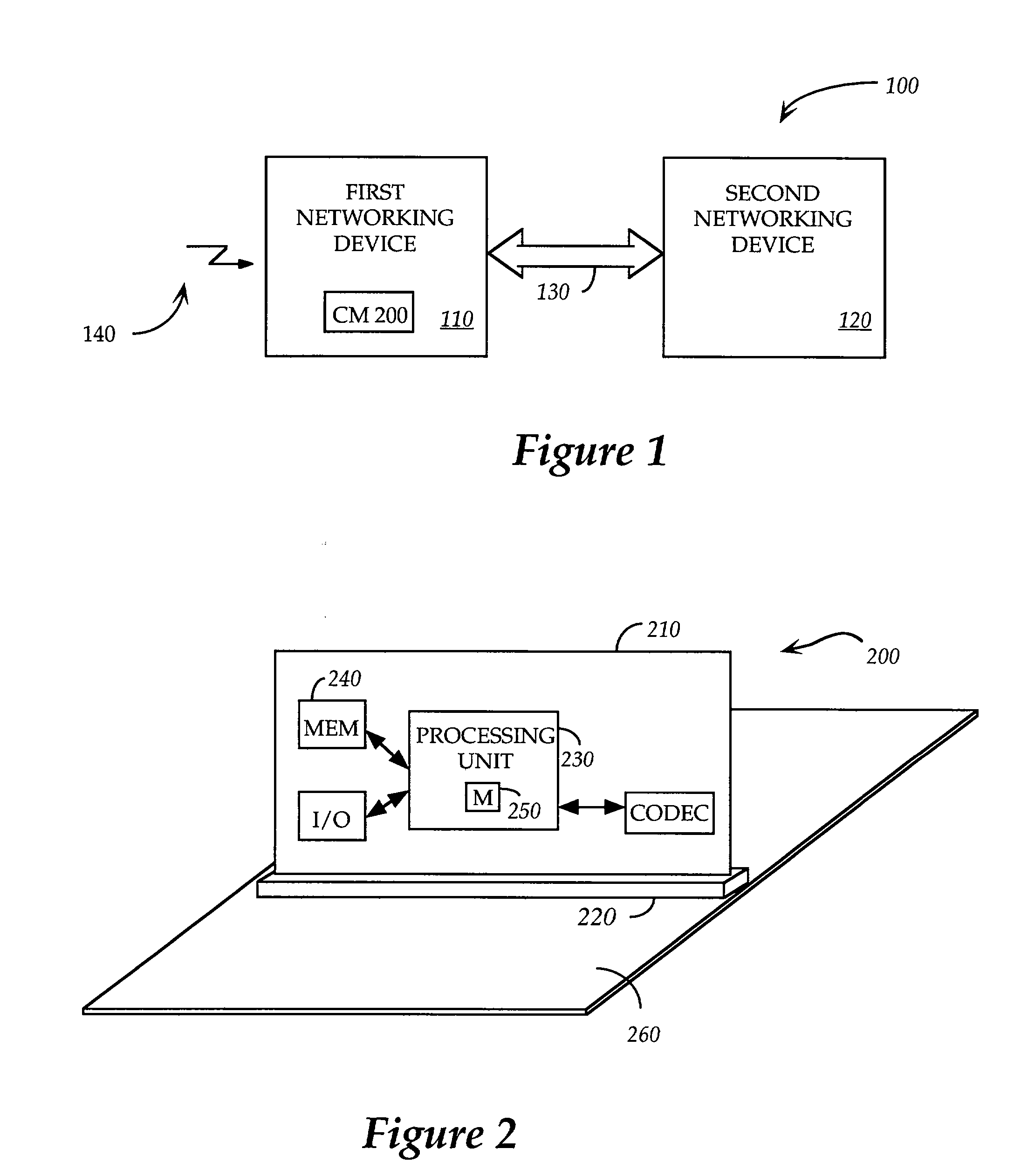
Terminal and associated method and computer program product for monitoring at least one activity of a user
InactiveUS20050172311A1Inertial sensorsAnalogue secracy/subscription systemsEngineeringAcceleration Unit
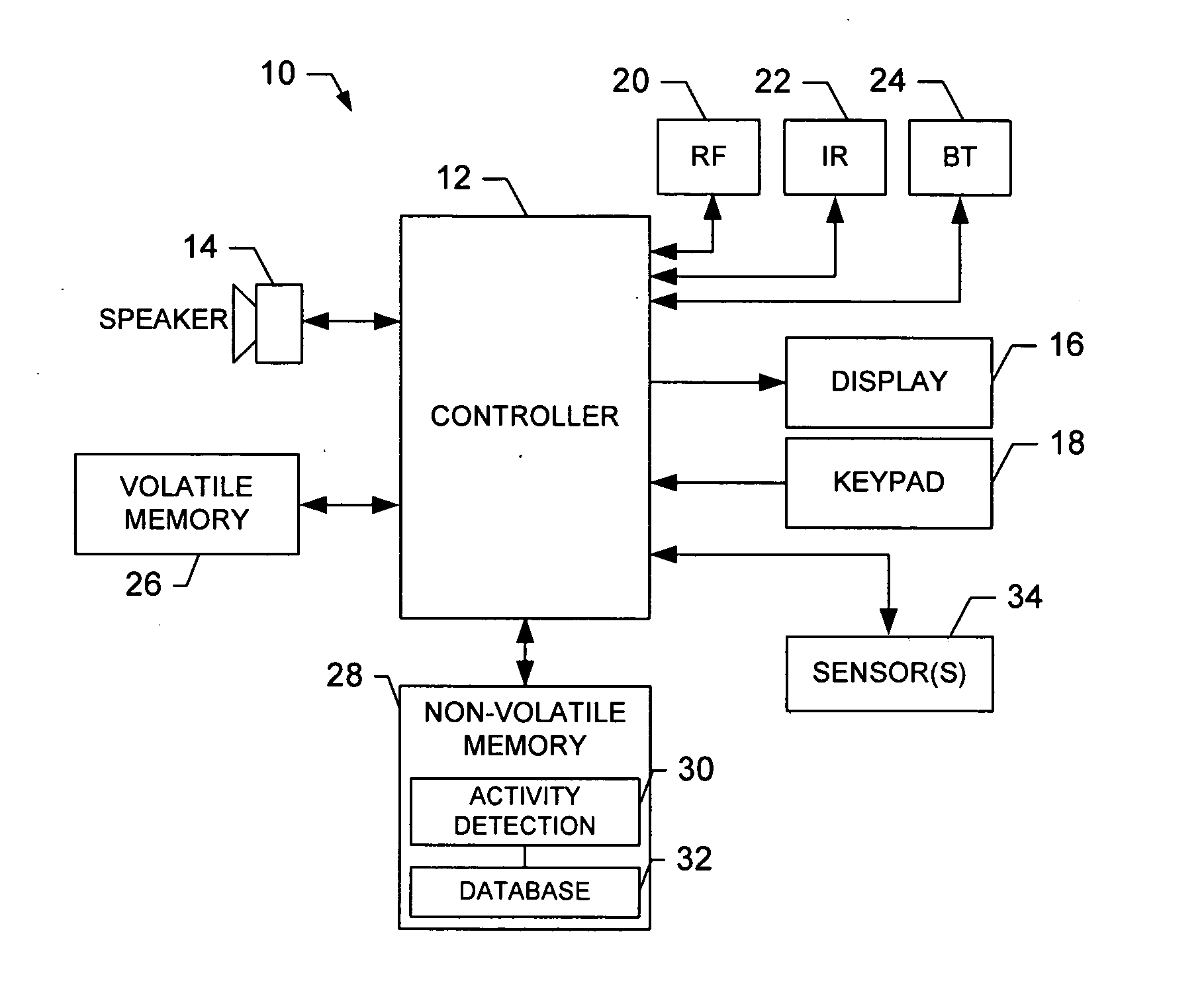
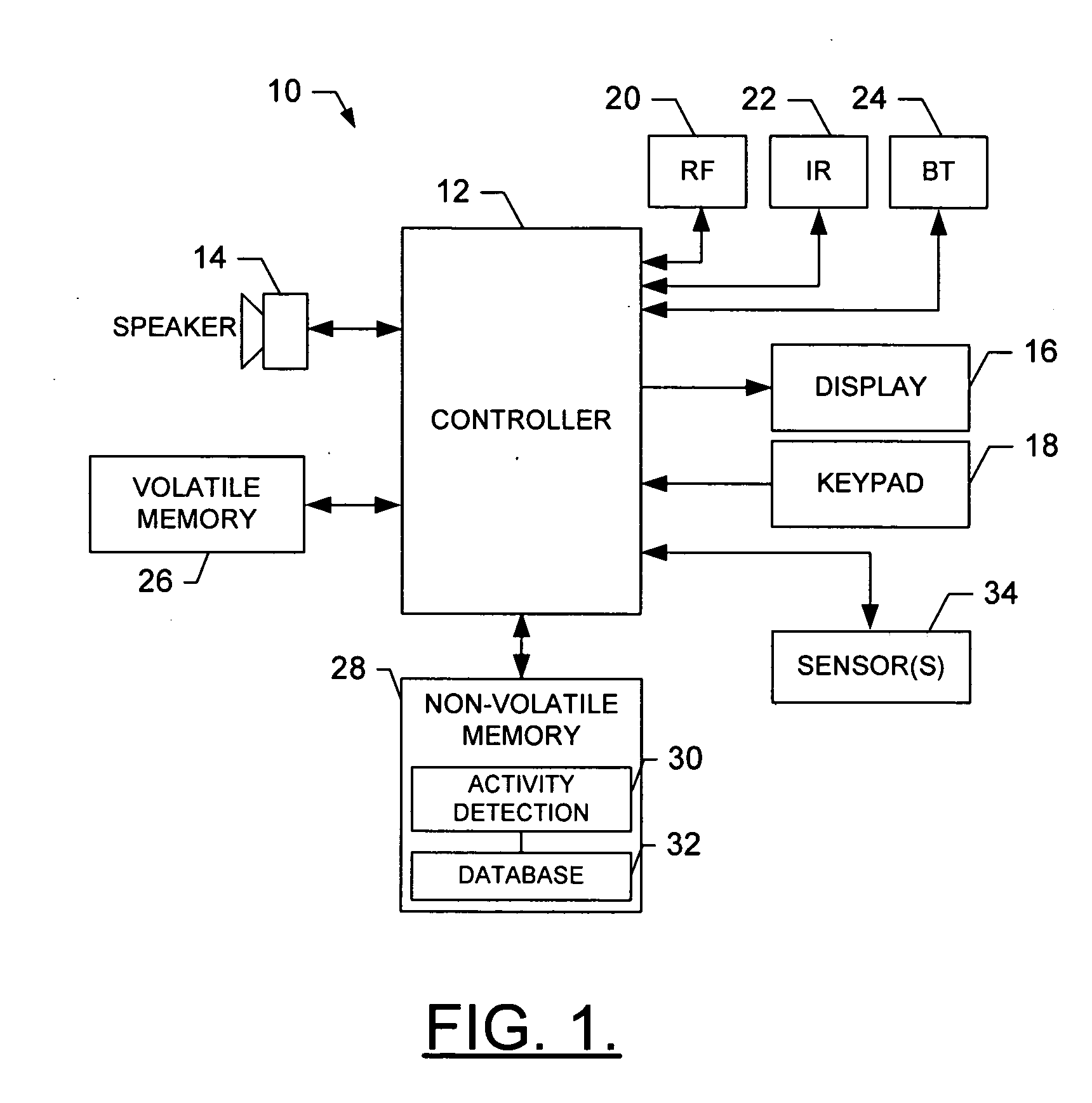
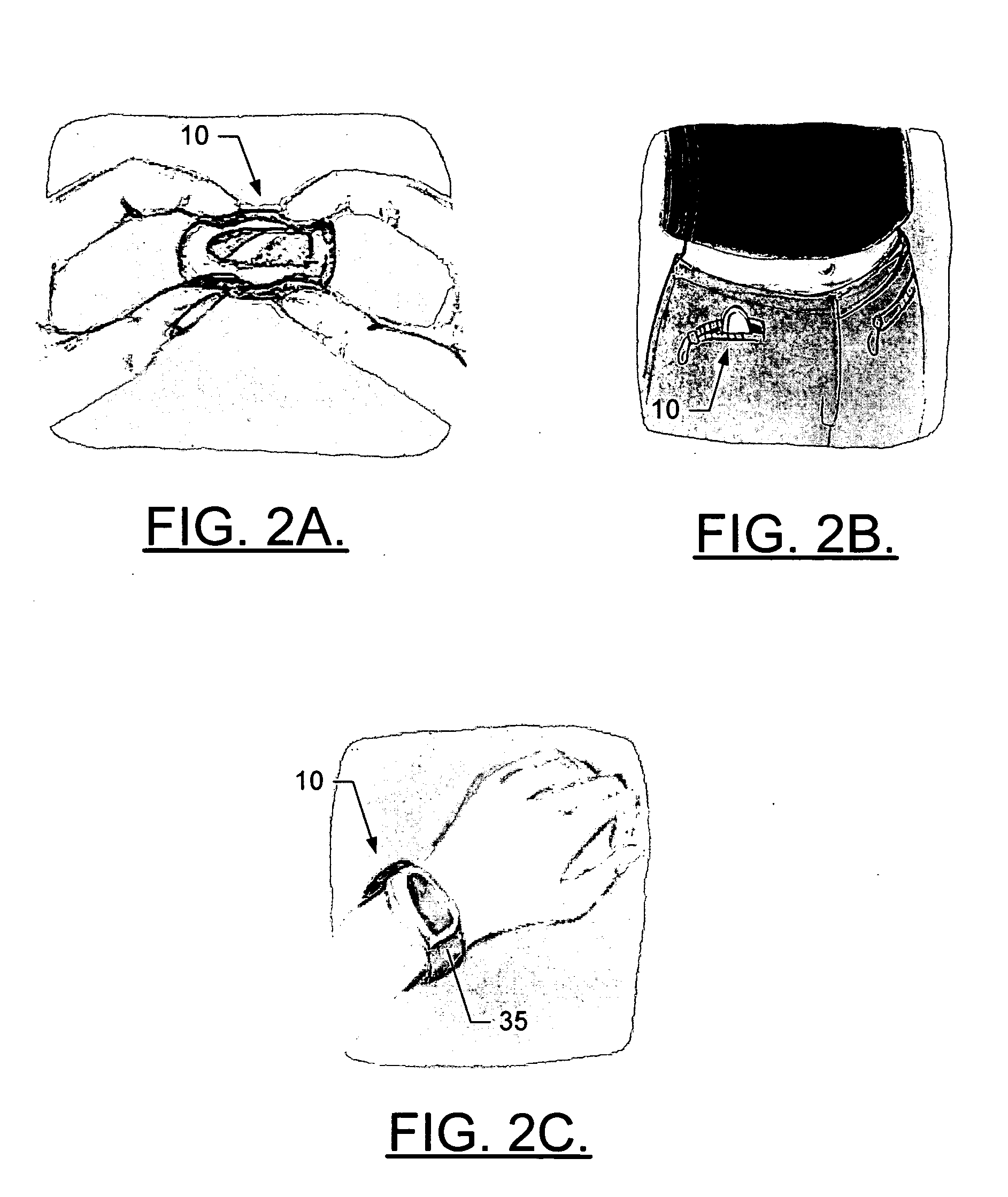
A terminal is provided for monitoring at least one activity of a user. The terminal includes a connecting means, at least one acceleration sensor and a controller. The connecting means, which can include a strap, belt, clip, lanyard or the like, is adapted for attaching the terminal onto a body of the user. The acceleration sensor(s) are capable of measuring and providing acceleration measurement signals representative of movement of the user in performing an activity. And the controller is capable of operating an activity detection application, which is capable of receiving at least a portion of the measurement signals. The activity detection application is also capable of determining at least one value related to the user performing the selected activity based upon the acceleration measurement signals, the at least one value being an intensity value representing an intensity with which the user performs the activity.
Owner:NOKIA CORP
Sensor based activity detection
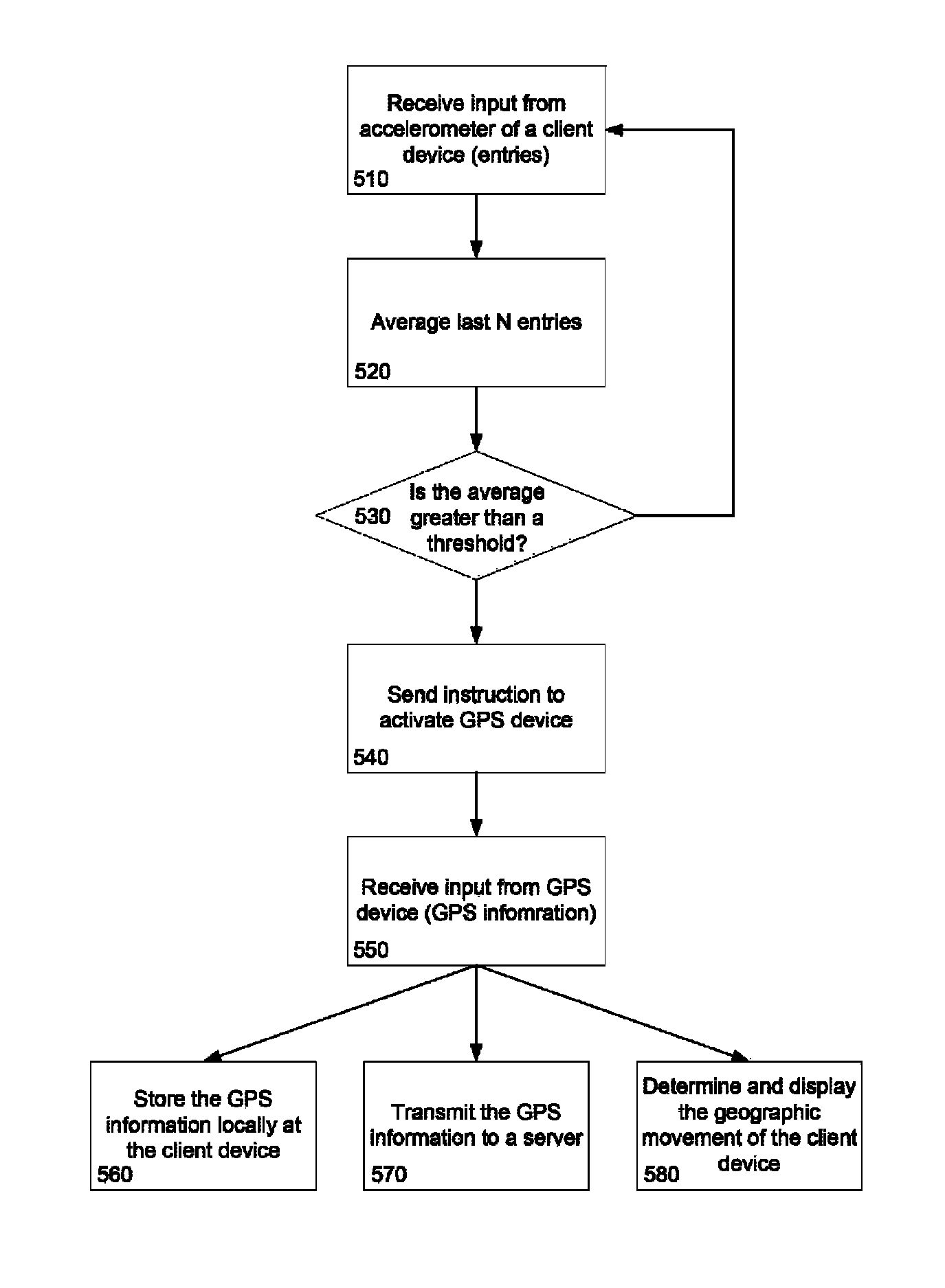
ActiveUS8560229B1Maximize utilizationMinimizing power useInstruments for road network navigationNavigational calculation instrumentsAccelerometerGps receiver
A sensor is used to detect movement of a mobile device. For example, data received from an accelerometer may be averaged together and compared to a threshold value. If the average of the data is greater than a threshold value, the mobile device may be assumed to be moving. This information may be used to control the frequency of data collection by, for example, a GPS receiver in order to maximize utility and minimize power use.
Owner:GOOGLE LLC
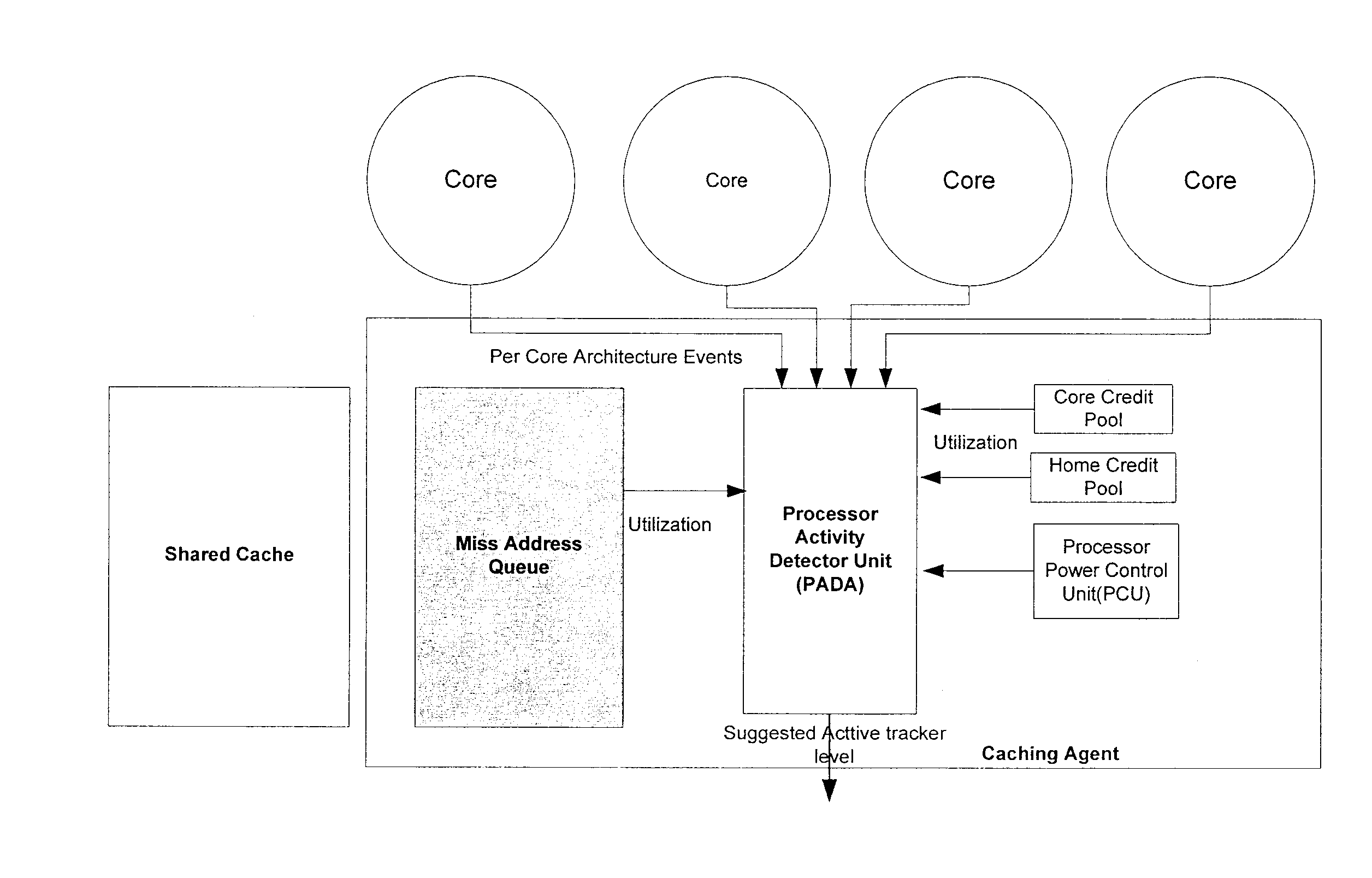
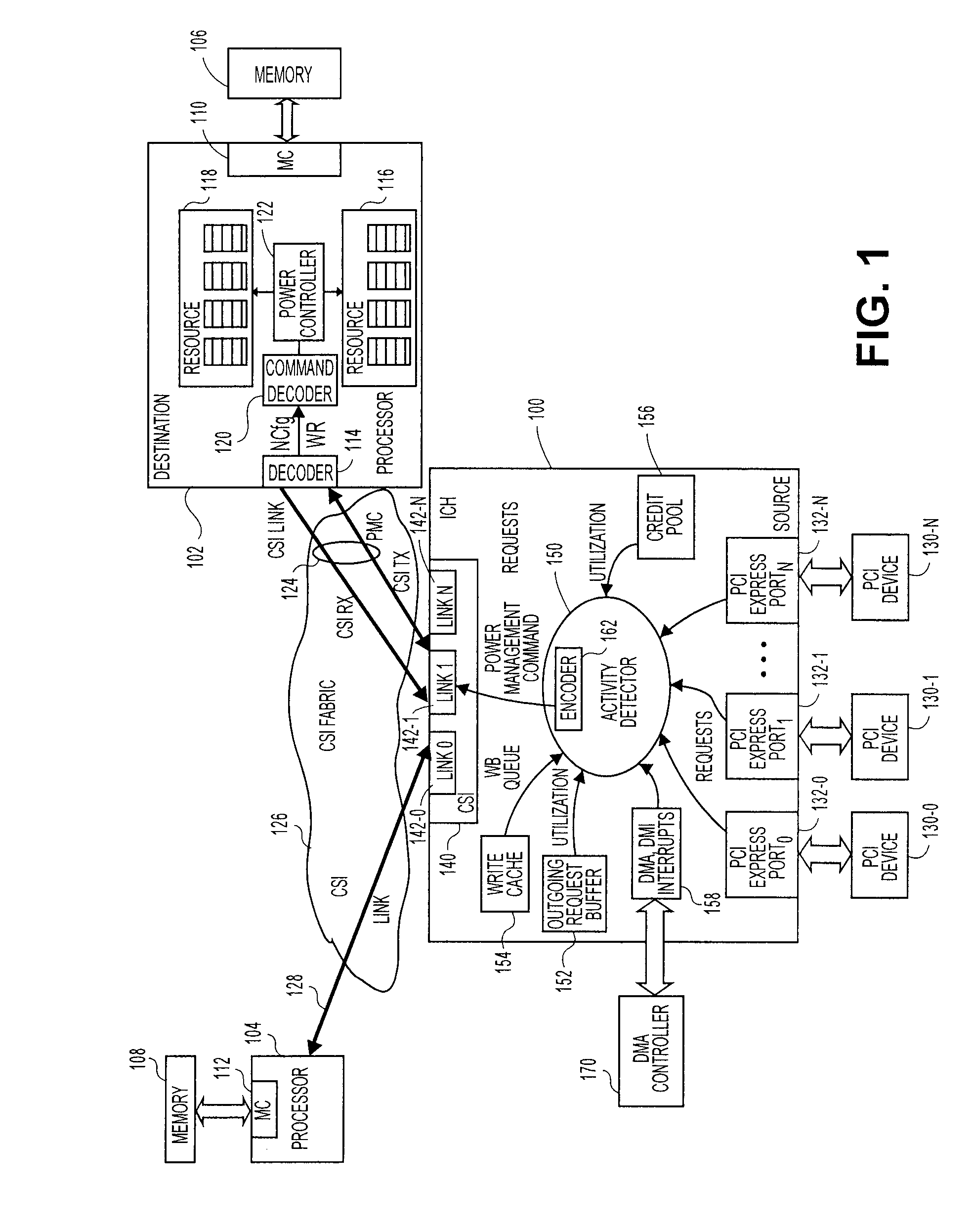
Method, system, and apparatus for a core activity detector to facilitate dynamic power management in a distributed system
A system and method to provide source controlled dynamic power management. An activity detector in a source determines expected future resource usage. Based on that expected usage, the source generates a power management command and sends that command to a destination. The destination then adjusts the power level of the resource based in the command.
Owner:INTEL CORP
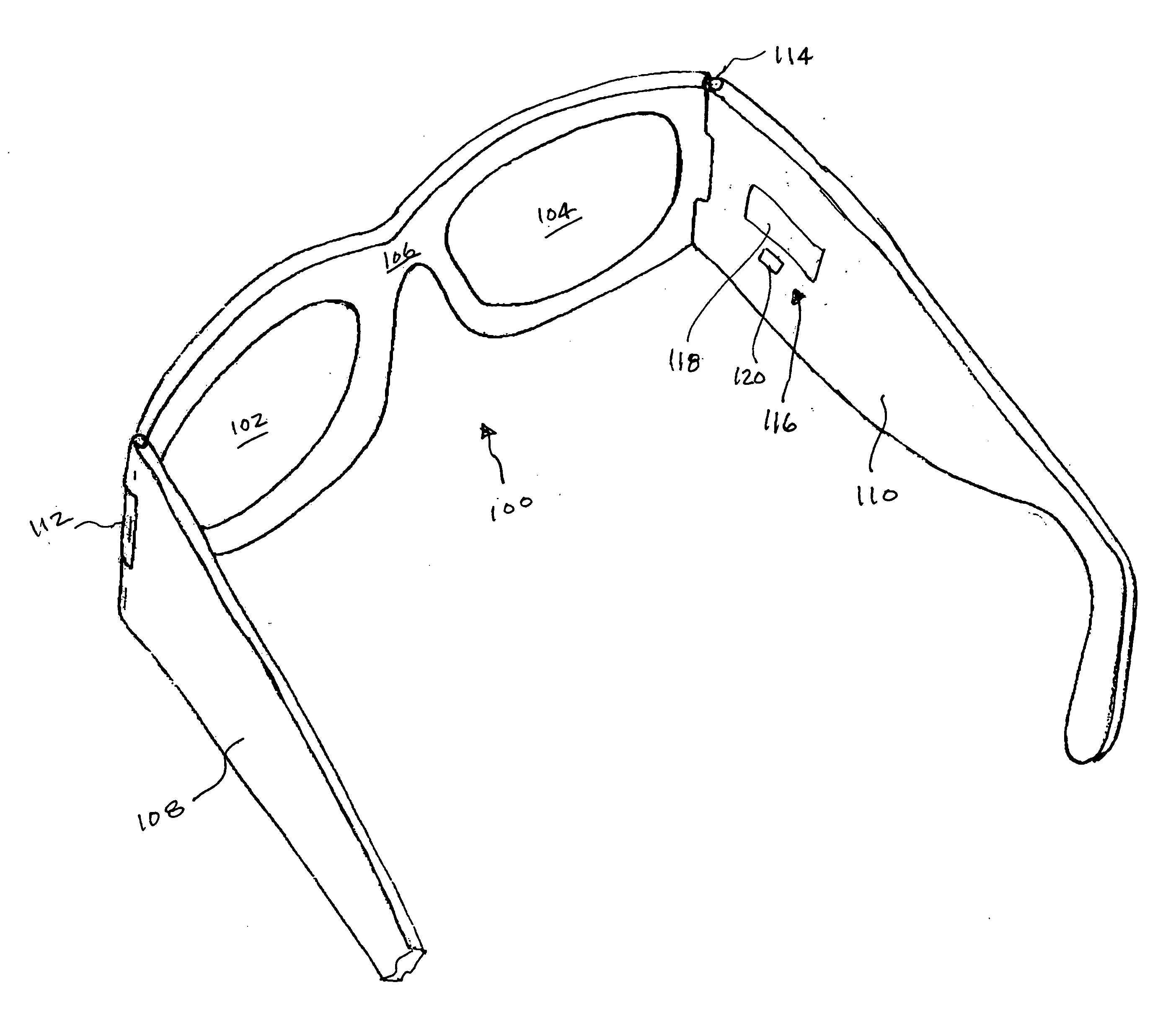
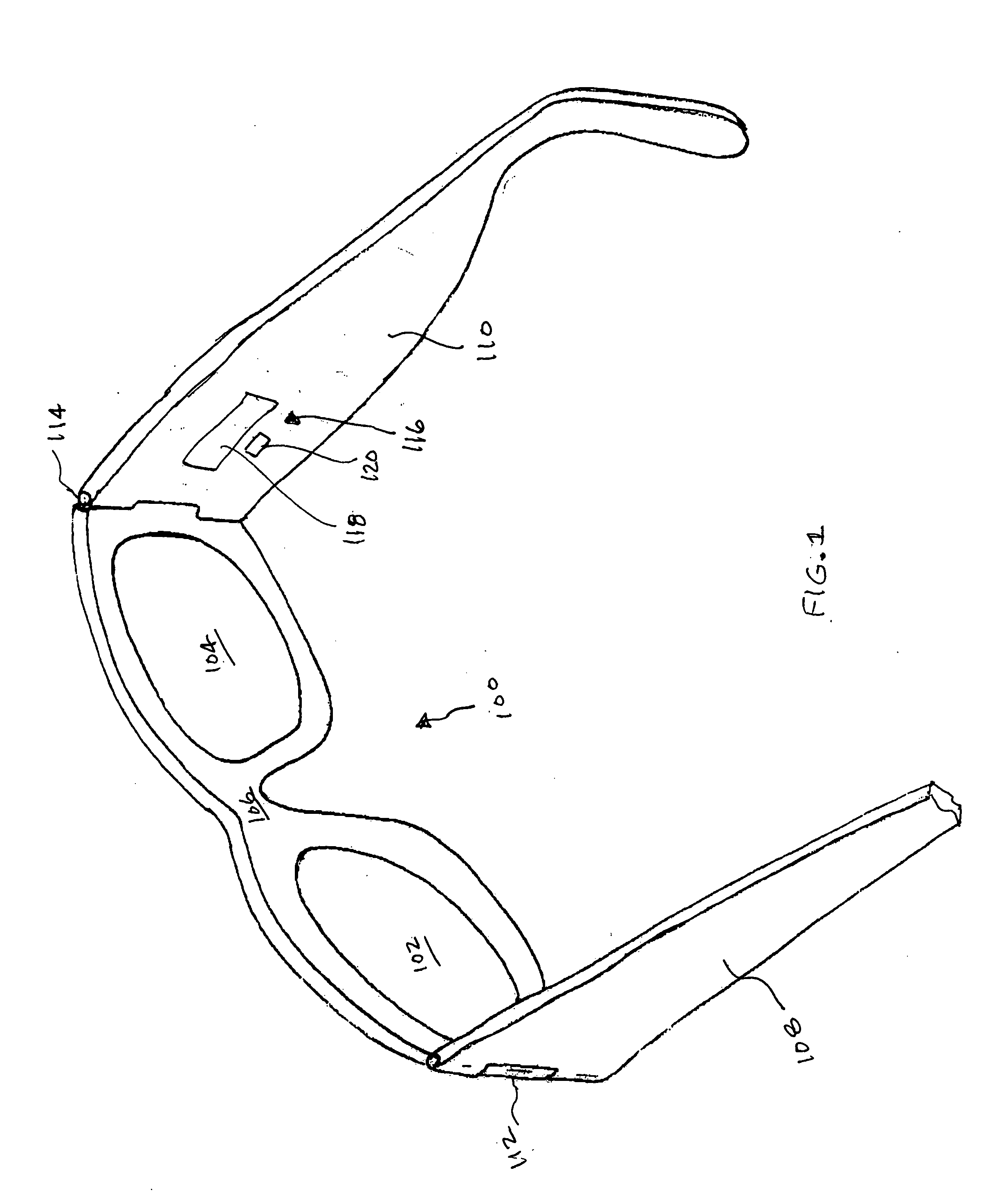
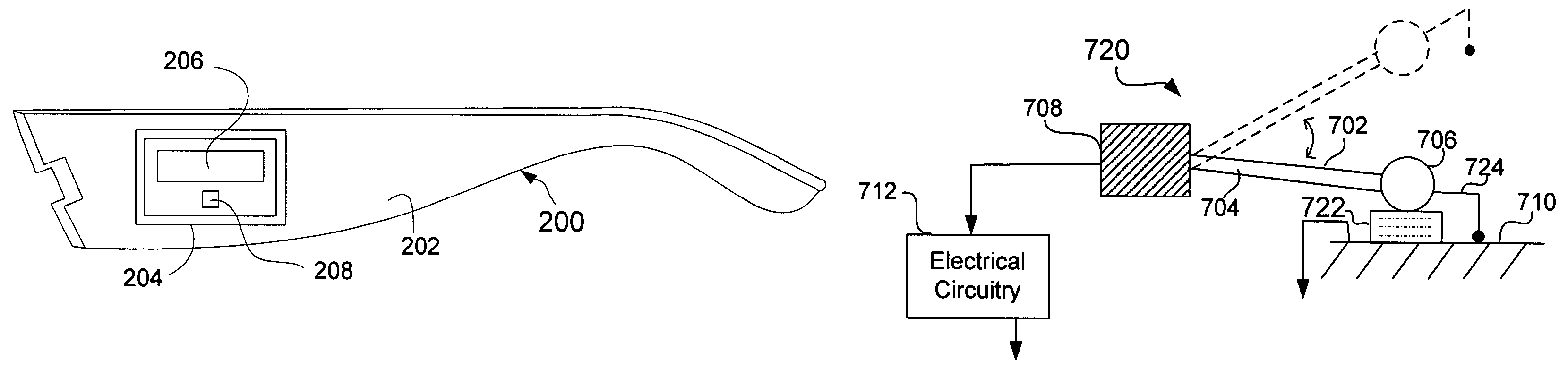
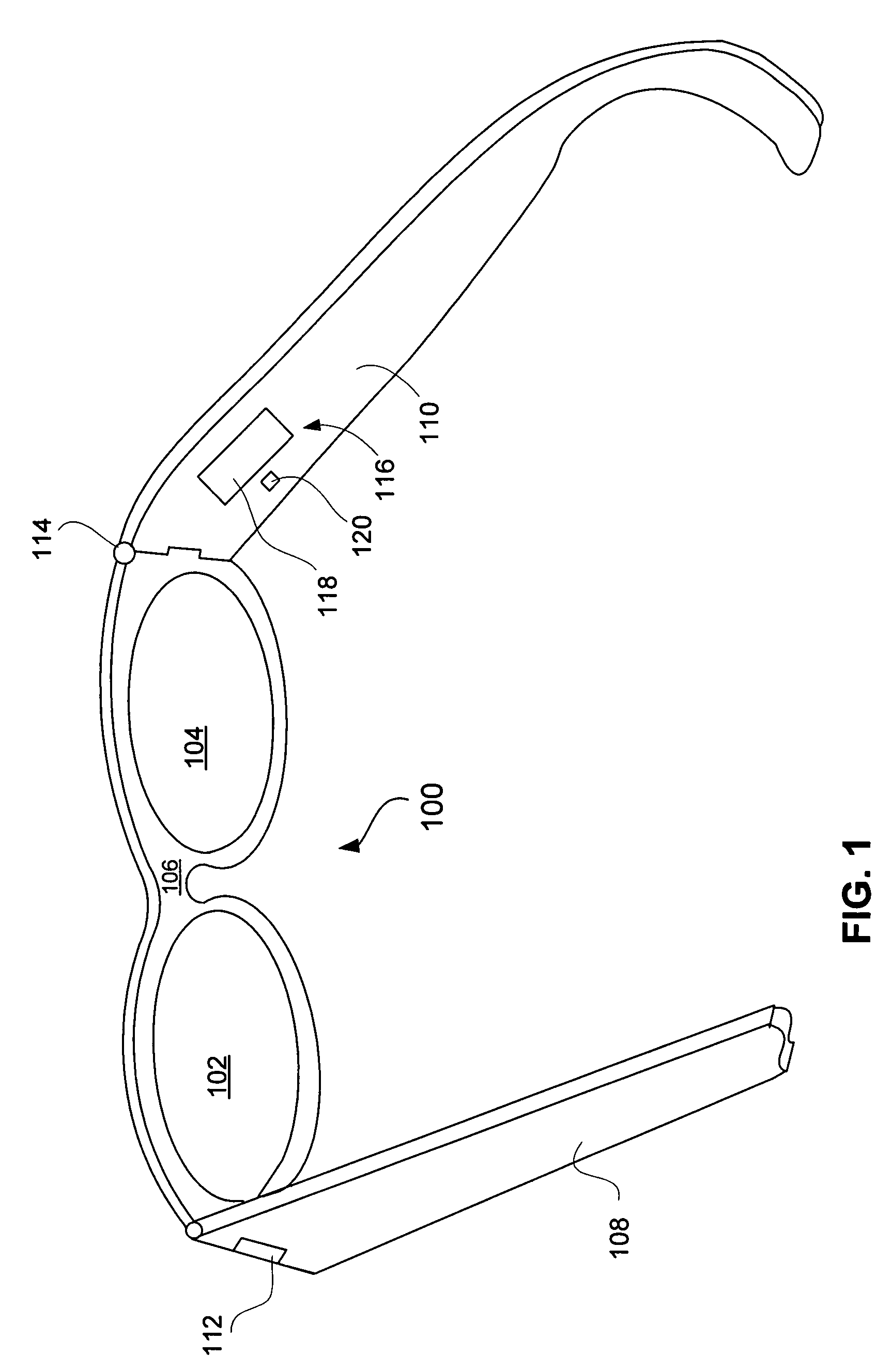
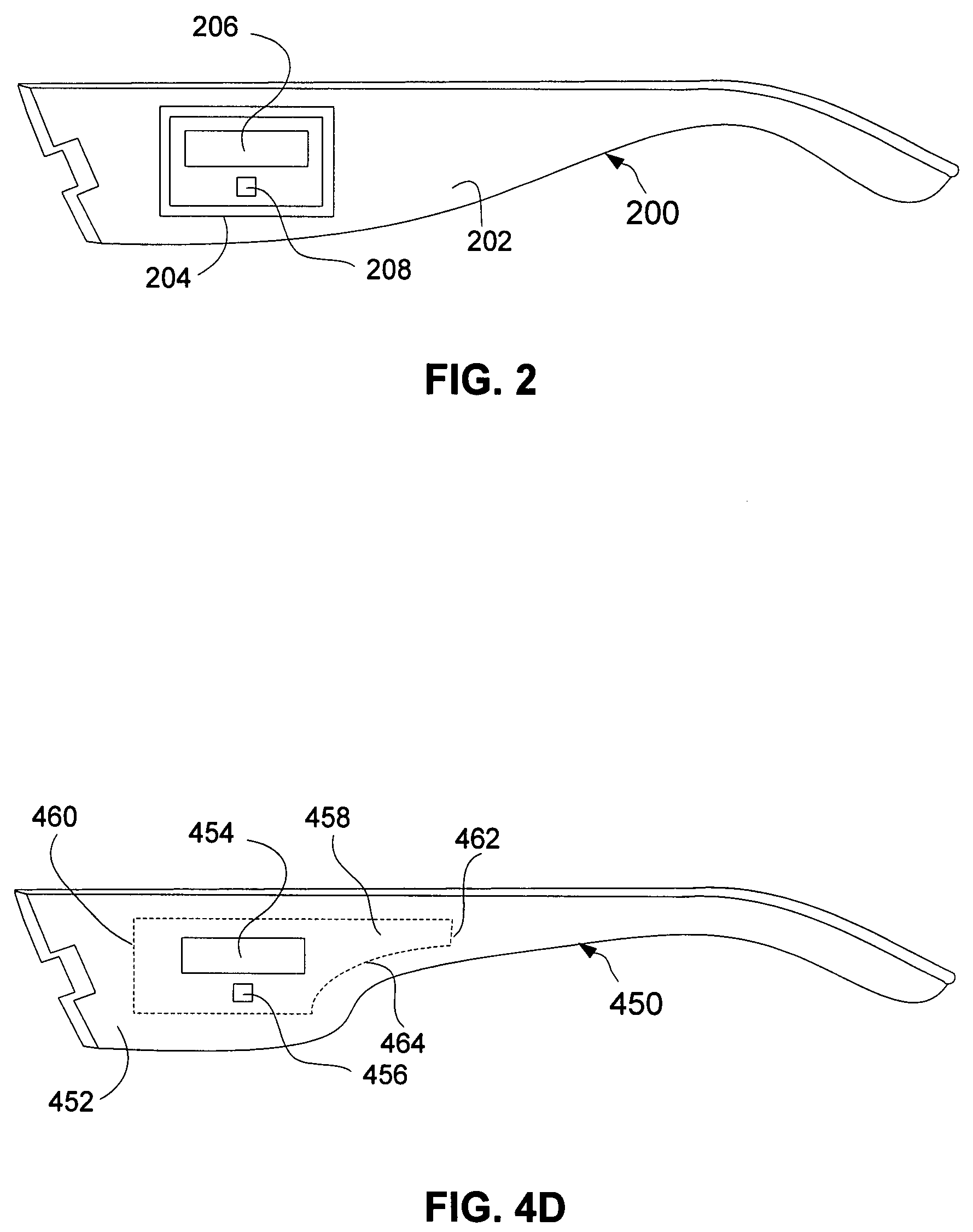
Eyeglasses with activity monitoring
In one embodiment, eyewear having an activity monitoring capability is disclosed. Activity, such as motion, steps or distance, can be measured by an activity detector. The measured activity can then be used in providing activity-related information to a user of the eyewear. Advantageously, the user of the eyewear is able to easily monitor their degree of activity.
Owner:INGENIOSPEC
Eyeglasses with activity monitoring
ActiveUS20050248718A1Easily degree of activityEasy to monitorNon-optical adjunctsNon-optical partsEyewearActivity monitoring
In one embodiment, eyewear having an activity monitoring capability is disclosed. Activity, such as motion, steps or distance, can be measured by an activity detector. The measured activity can then be used in providing activity-related information to a user of the eyewear. Advantageously, the user of the eyewear is able to easily monitor their degree of activity.
Owner:INGENIOSPEC
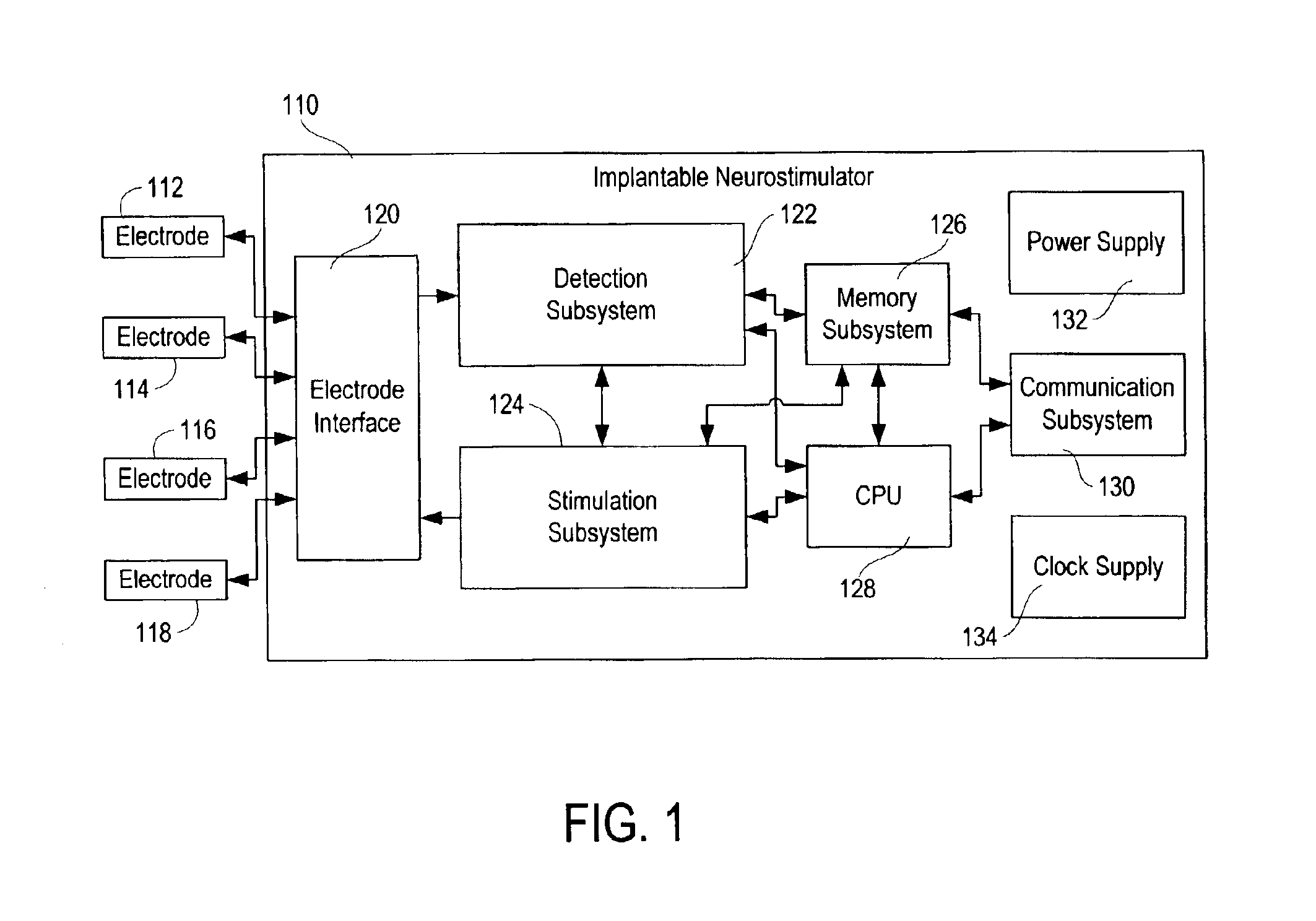
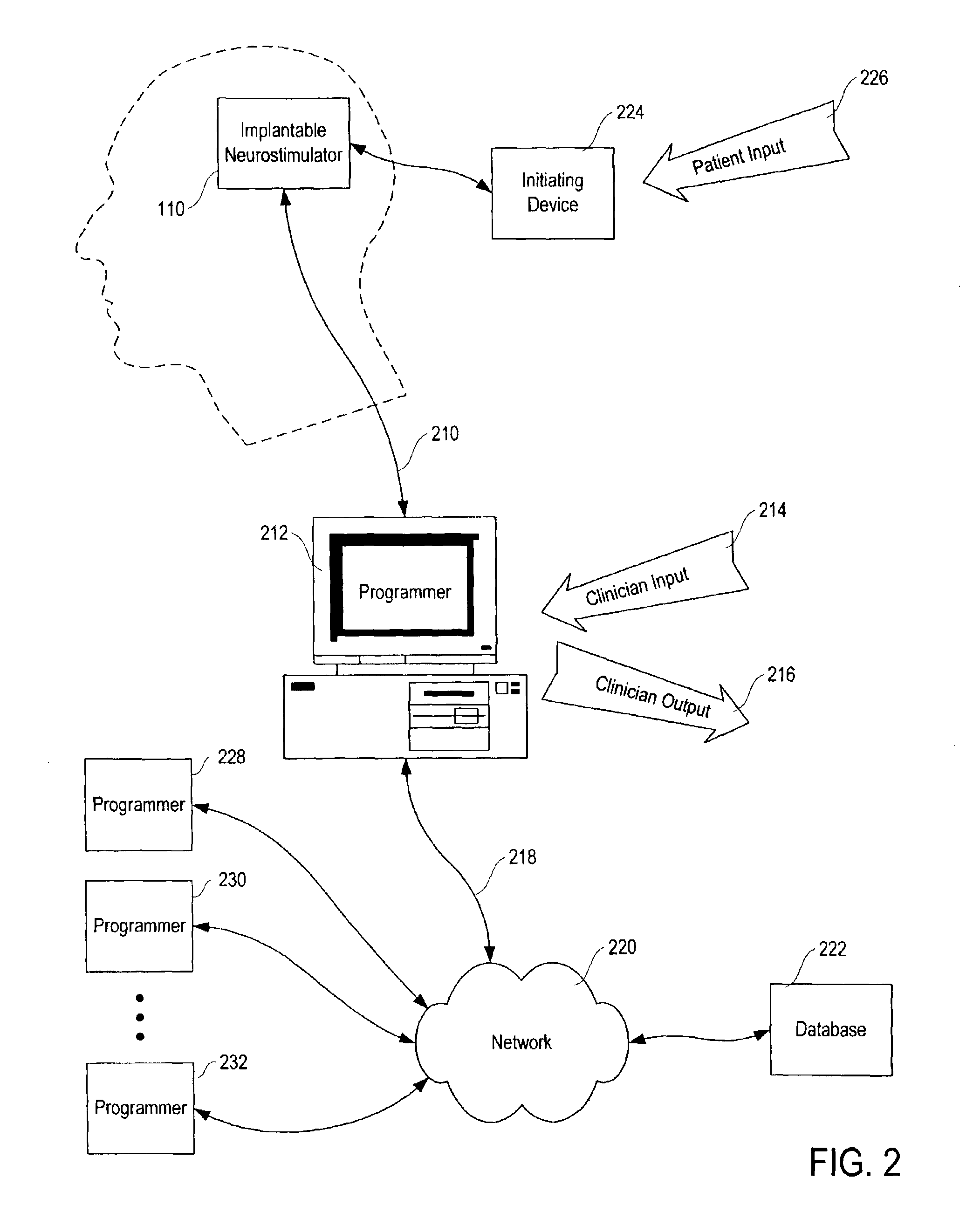
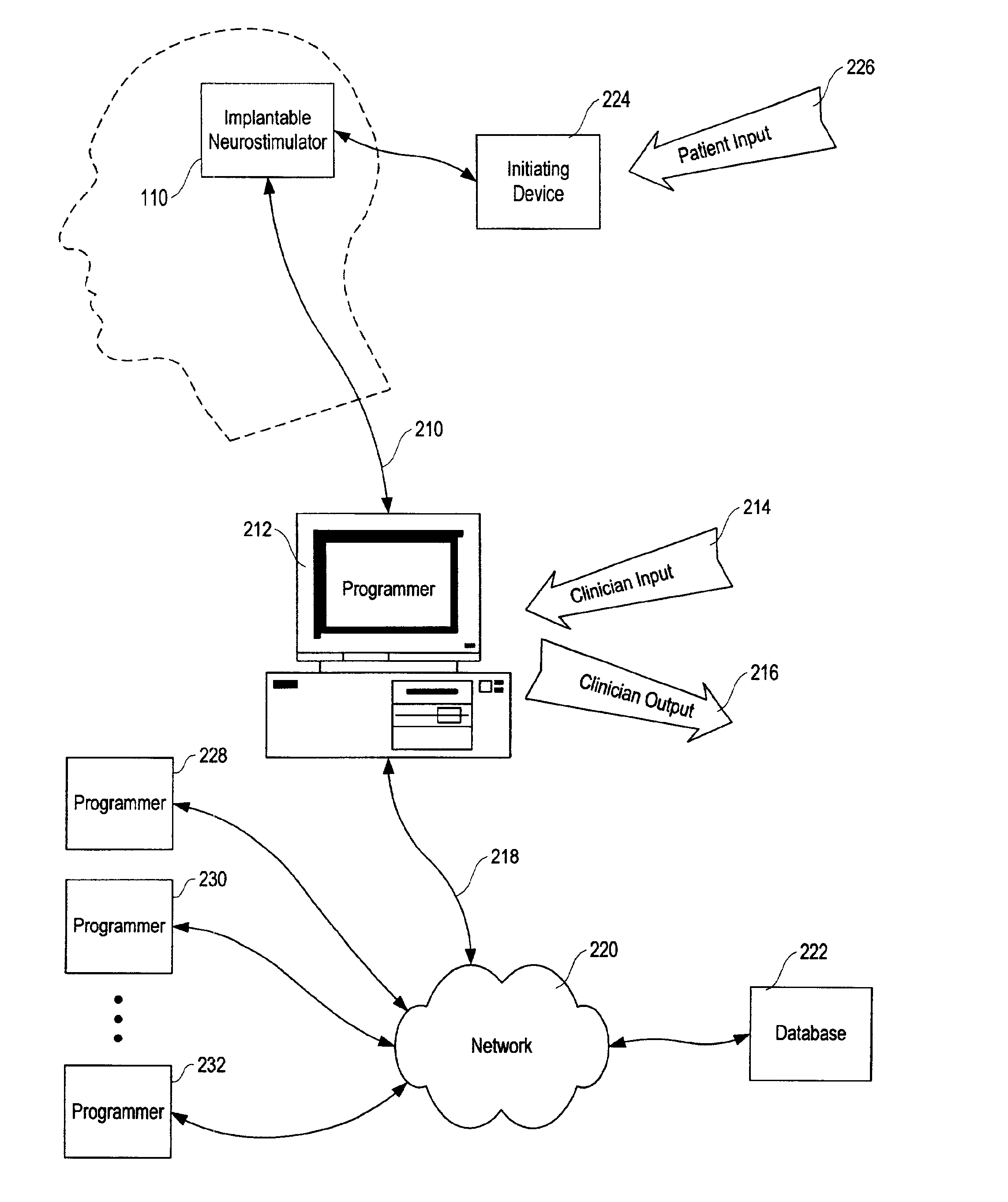
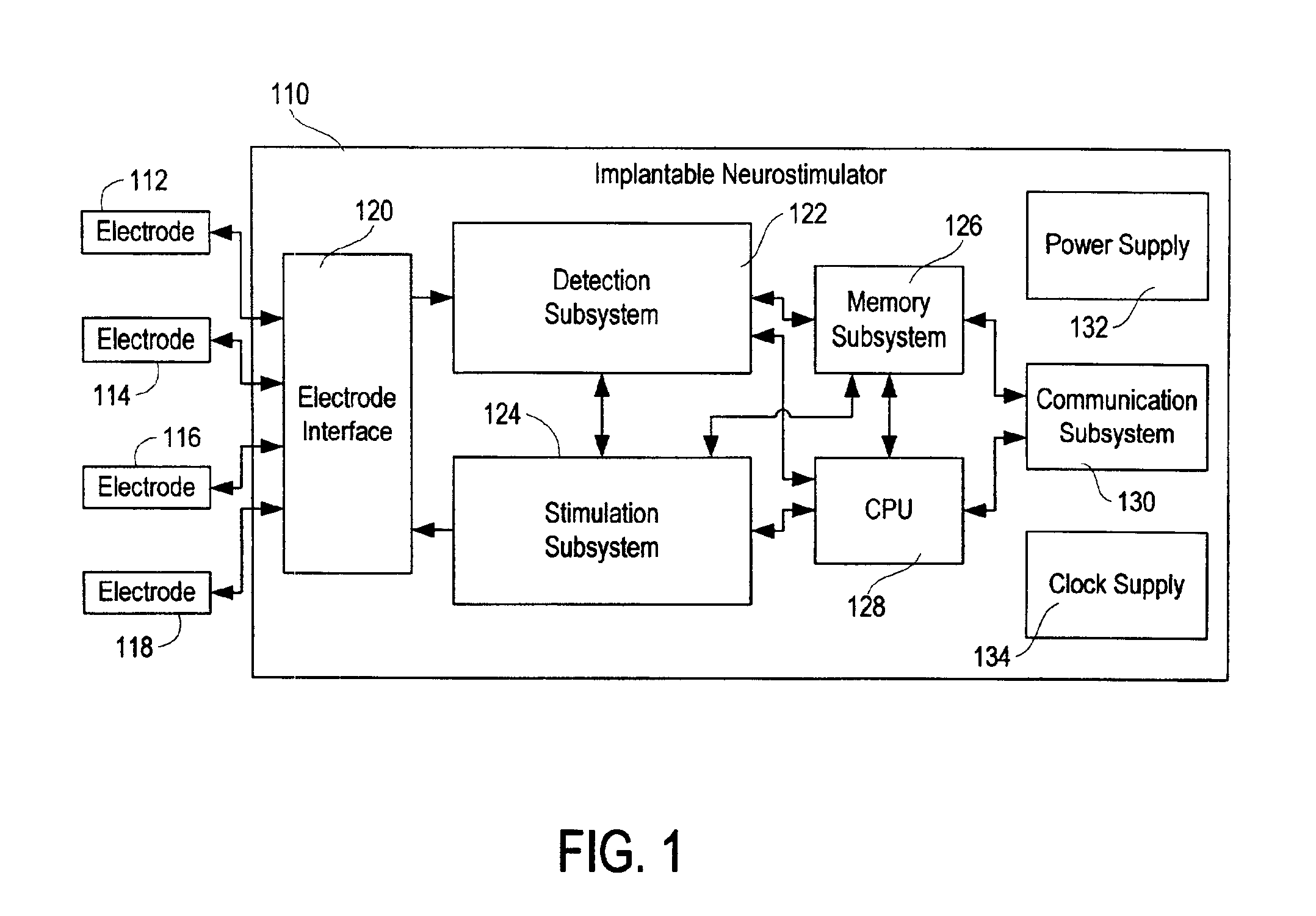
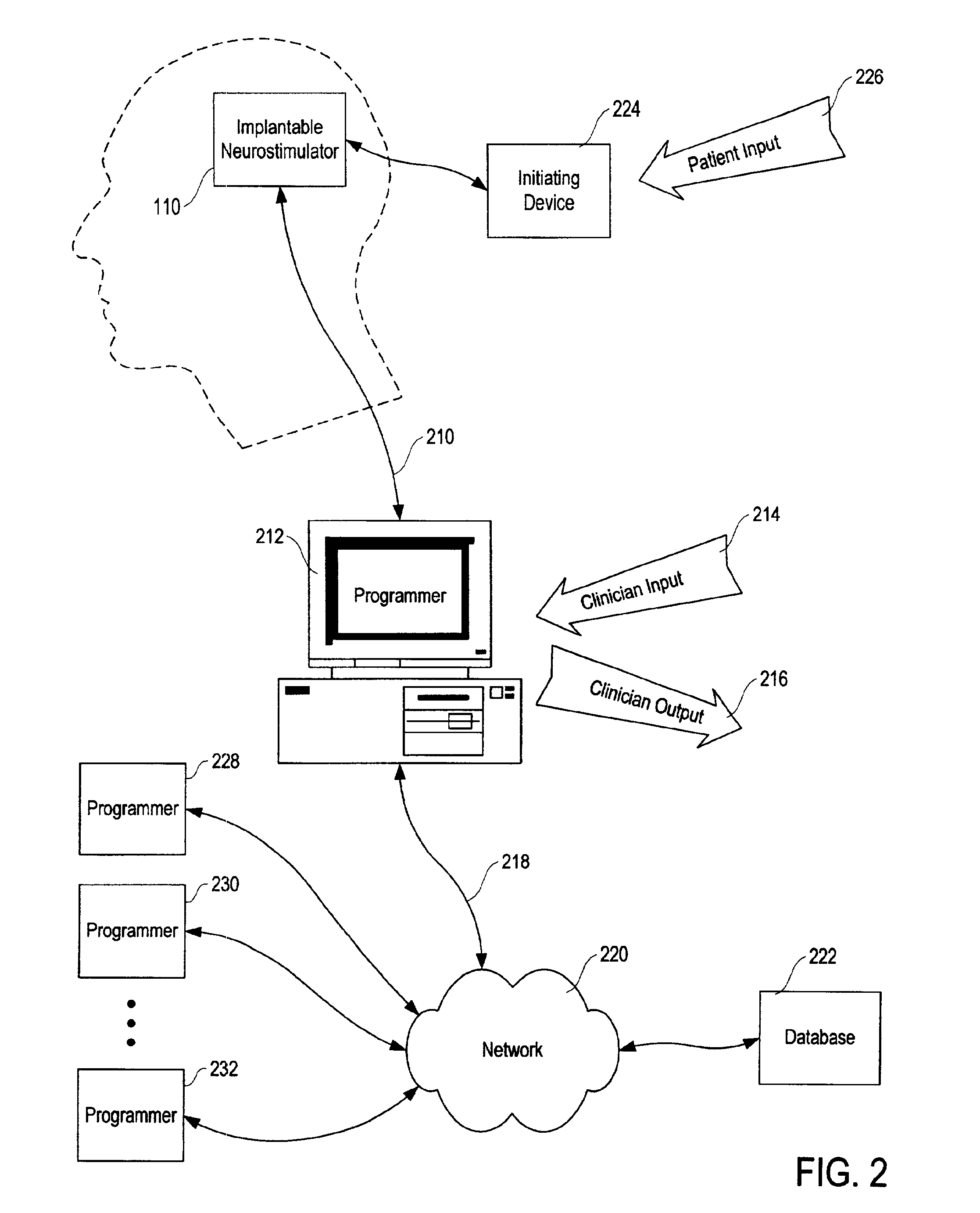
Patient-specific parameter selection for neurological event detection
InactiveUS7177674B2Efficient developmentPhysical therapies and activitiesElectroencephalographyEeg dataLine search
An epileptiform activity patient-specific template creation system permits a user to efficiently develop an optimized set of patient-specific parameters for epileptiform activity detection algorithms. The epileptiform activity patient template creation system is primarily directed for use with an implantable neurostimulator system having EEG storage capability, in conjunction with a computer software program operating within a computer workstation having a processor, disk storage and input / output facilities for storing, processing and displaying patient EEG signals. The implantable neurostimulator is operative to store records of EEG data when neurological events are detected, when it receives external commands to record, or at preset or arbitrary times. The computer workstation operates on stored and uploaded records of EEG data to derive the patient-specific templates via a single local minimum variant of a multidimensional greedy line search process and a feature overlay process.
Owner:NEUROPACE
Personalized Voice Activity Detection
ActiveUS20080255842A1Reduce transmission bandwidthLeveling precisionSpeech recognitionPersonalizationVoice activity
A method of transferring a real-time audio signal transmission, including: registering voice patterns (or other characteristics) of on more users to be used to identify the voices of the users, accepting an audio signal as it is created as a sequence of segments, analyzing each segment of the accepted audio signal to determine if it contains voice activity (314), determining a probability level that the voice activity of the segment is of a registered user (320&322); and selectively transferring the contents, of a segment responsive to the determined probability level (324).
Owner:SHIMHI SHAUL
Eyeglasses with activity monitoring and acoustic dampening
InactiveUS20080068559A1Easy to monitorNon-optical adjunctsDigital computer detailsEyewearActivity monitoring
In one embodiment, eyewear having an activity monitoring capability is disclosed. Activity, such as motion, steps or distance, can be measured by an activity detector. The measured activity can then be used in providing activity-related information to a user of the eyewear. Advantageously, the user of the eyewear is able to easily monitor their degree of activity. For quieter operation, acoustic dampening can be employed. In other embodiments, activity monitoring capability can be provided to products other than eyewear.
Owner:INGENIOSPEC
Patient-specific template development for neurological event detection
InactiveUS7136695B2Easy to set upEfficient developmentPhysical therapies and activitiesElectroencephalographyEeg dataWorkstation
An epileptiform activity patient-specific template creation system permits a user to efficiently develop an optimized set of patient-specific parameters for epileptiform activity detection algorithms. The epileptiform activity patient template creation system is primarily directed for use with an implantable neurostimulator system having EEG storage capability, in conjunction with a computer software program operating within a computer workstation having a processor, disk storage and input / output facilities for storing, processing and displaying patient EEG signals. The implantable neurostimulator is operative to store records of EEG data when neurological events are detected, when it receives external commands to record, or at preset or random times. The computer workstation operates on stored and uploaded records of EEG data to derive the patient-specific templates.
Owner:NEUROPACE
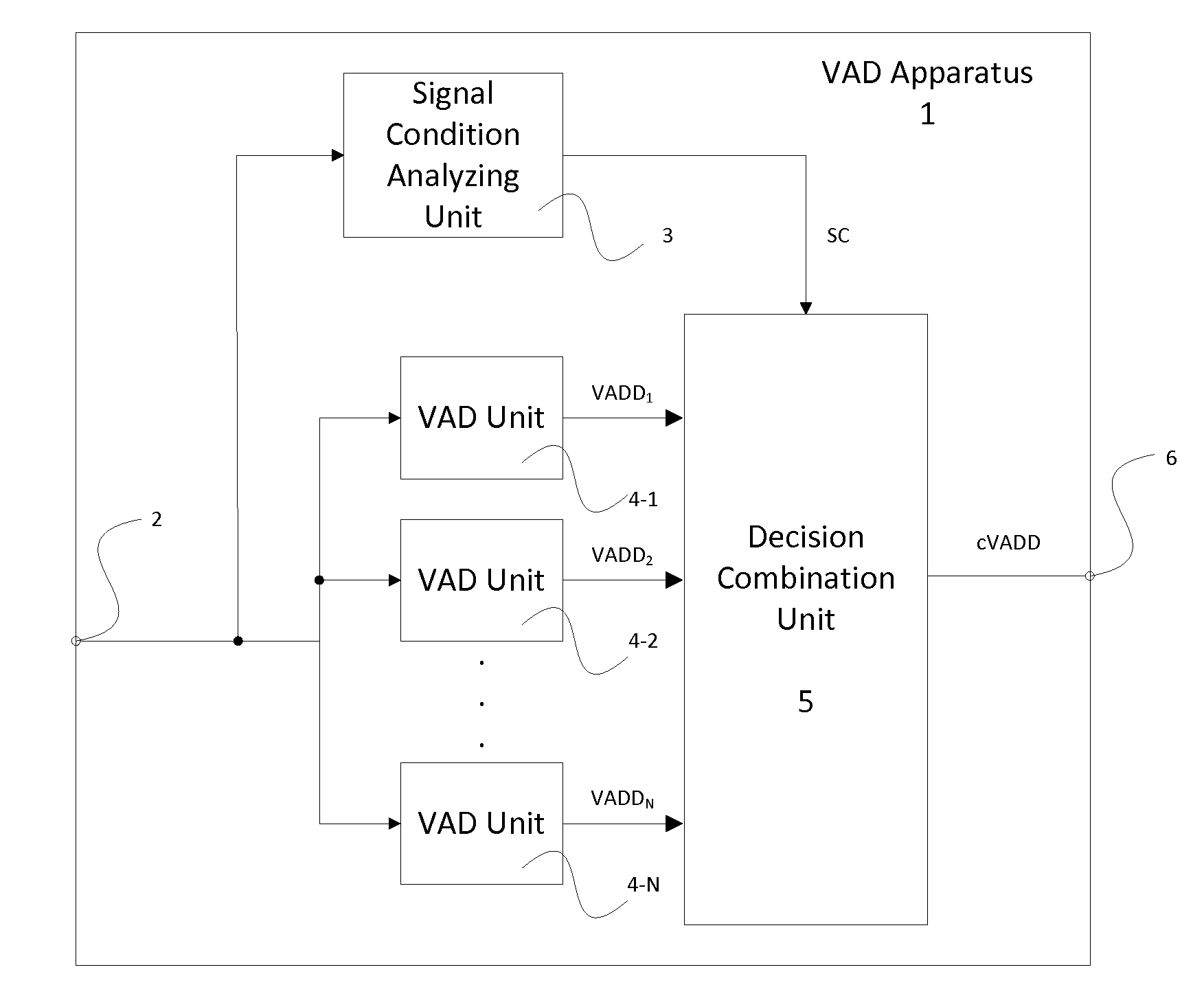
Method and an apparatus for voice activity detection
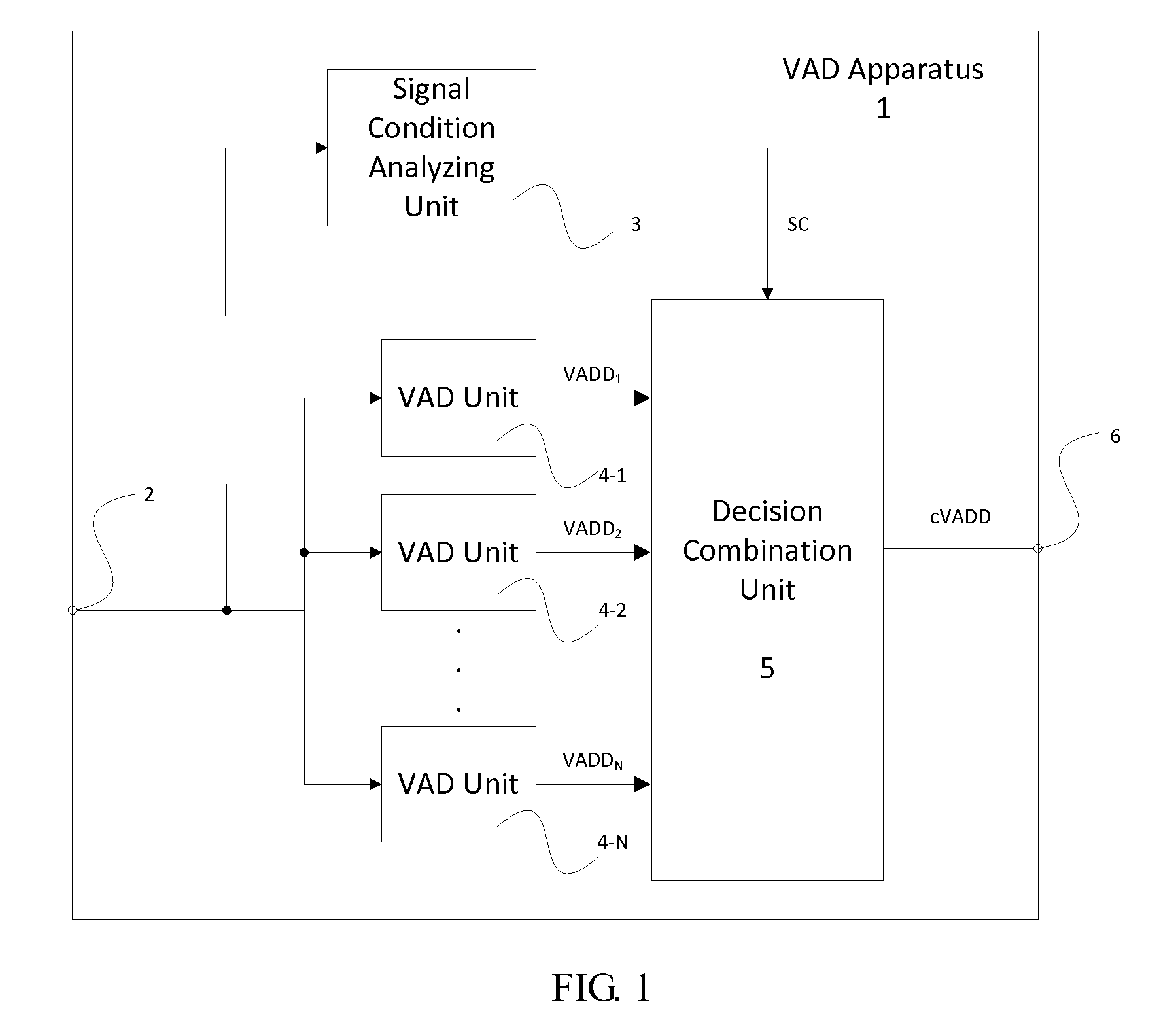
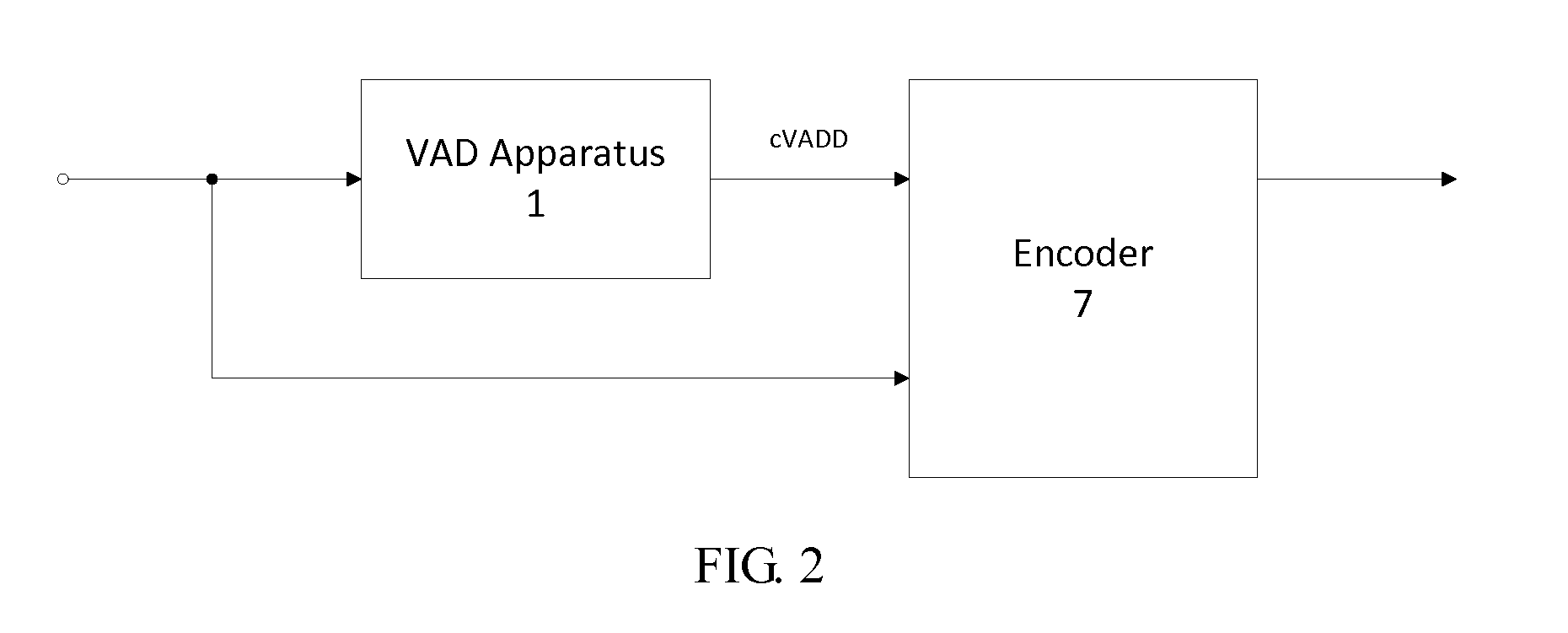
InactiveUS20120232896A1Easy to adaptFast processingSpeech recognitionDecision combinationSpeech sound
A voice activity detection apparatus (1) comprising: a signal condition analyzing unit (3) which analyses at least one signal parameter of an input signal to detect a signal condition SC of said input signal; at least two voice activity detection units (4-i) comprising different voice detection characteristics, wherein each voice activity detection unit (4-i) performs separately a voice activity detection of said input signal to provide a voice activity detection decision VADD; and a decision combination unit (5) which combines the voice activity detection decisions VADDs provided by said voice activity detection units (4-i) depending on the detected signal condition SC to provide a combined voice activity detection decision cVADD.
Owner:HUAWEI TECH CO LTD
Eyeglasses with activity monitoring and acoustic dampening
InactiveUS7543934B2Easy to monitorNon-optical adjunctsDigital computer detailsEyewearActivity monitoring
In one embodiment, eyewear having an activity monitoring capability is disclosed. Activity, such as motion, steps or distance, can be measured by an activity detector. The measured activity can then be used in providing activity-related information to a user of the eyewear. Advantageously, the user of the eyewear is able to easily monitor their degree of activity. For quieter operation, acoustic dampening can be employed. In other embodiments, activity monitoring capability can be provided to products other than eyewear.
Owner:INGENIOSPEC
Anomalous activity detection
ActiveUS20110202500A1Increase valueFocused and direct monitoringMemory loss protectionDigital data processing detailsData feedTime segment
The disclosure addresses the detection of anomalous activity. Some embodiments are directed towards consolidating information from multiple data feeds. Exemplary information may relate to: extrusion violations, failed logins, sensitive fields access, sensitive objects access, escalation of privileges, or activity during a specific time frame within a time period, and combinations of one or more of these. In one embodiment, duplicate data may be removed or consolidated.
Owner:BANK OF AMERICA CORP
Monitoring system, monitoring device and method, recording medium, and program
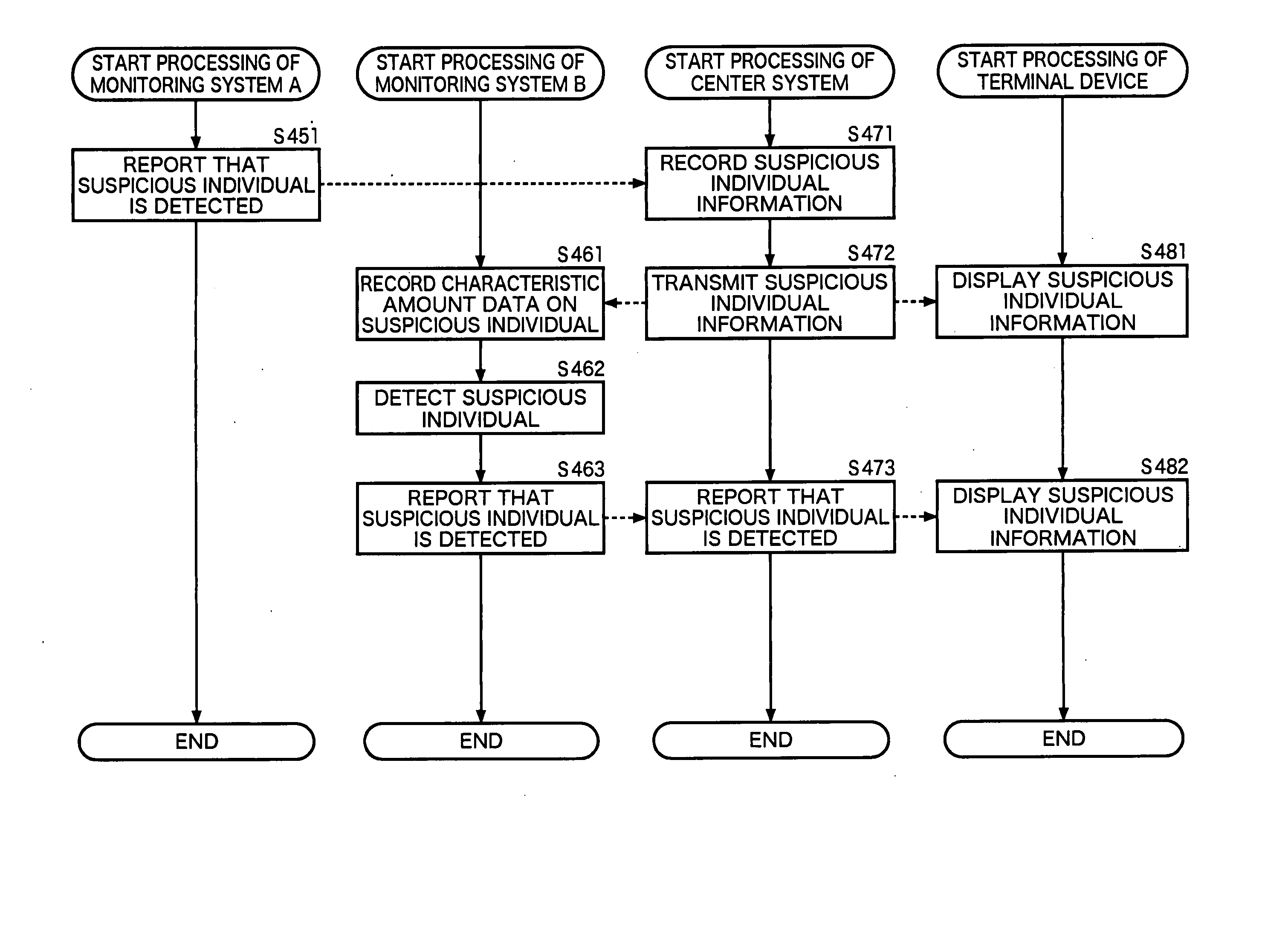
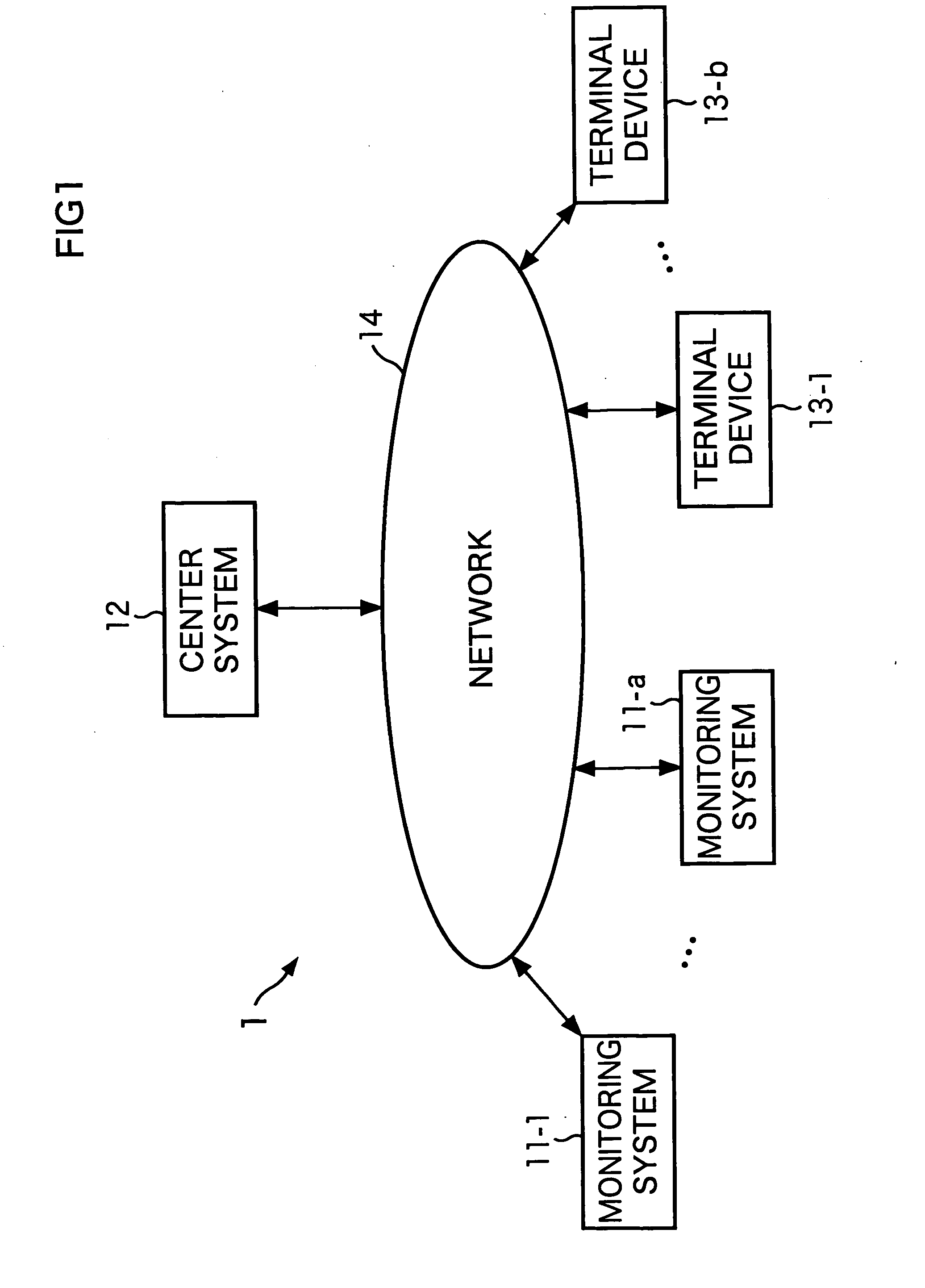
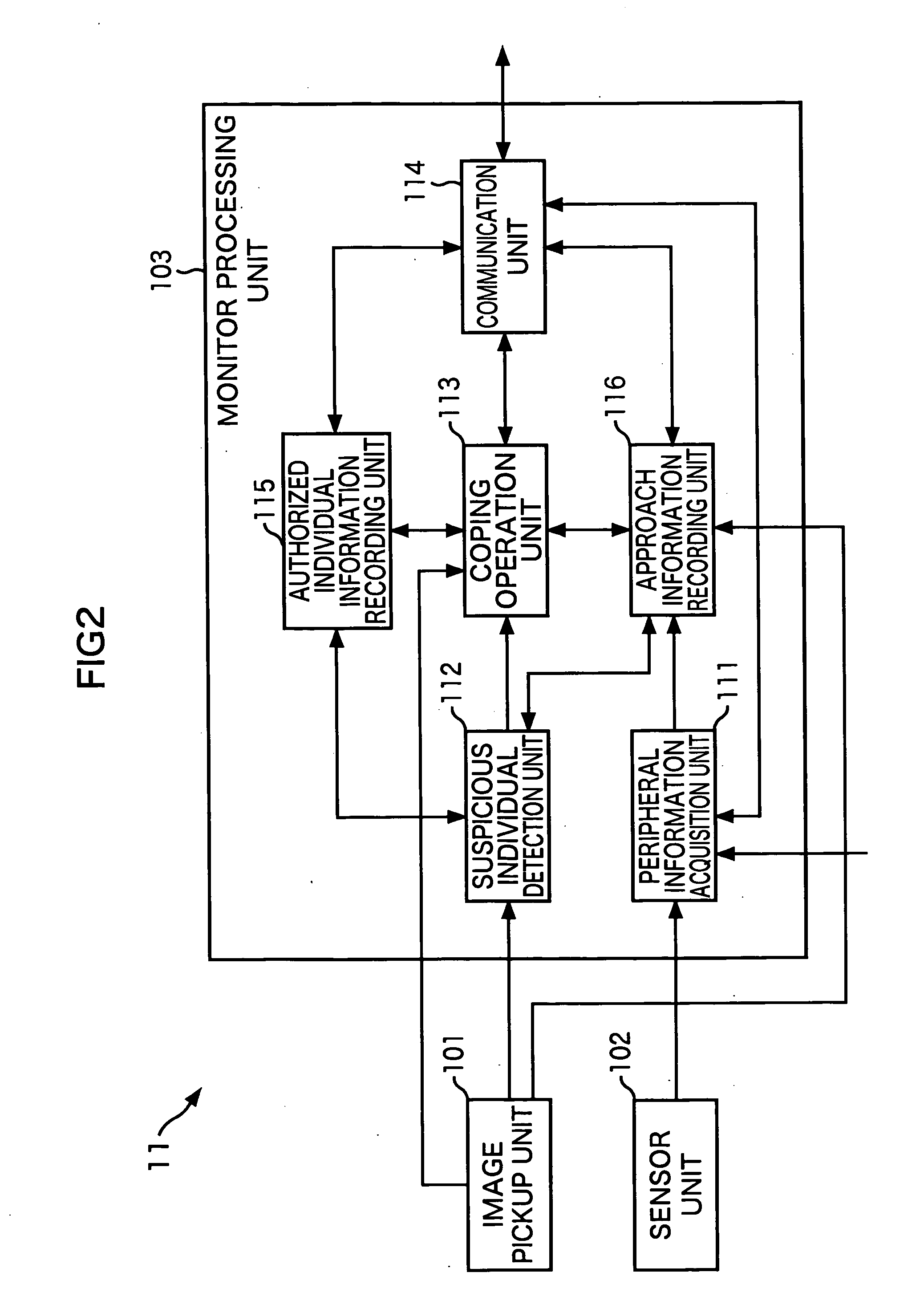
InactiveUS20070014439A1Accurate detectionAvoid expansionCharacter and pattern recognitionBurglar alarmPersonal recordMonitoring system
A suspicious individual can be detected more accurately. A face detecting unit detects a face image of an approaching individual from a monitor image, and a characteristic amount detecting unit detects the characteristic amount of the approaching individual from the face image. A collating unit identifies an approaching individual by collating the characteristic amount of the approaching individual with the characteristic amount of an authorized individual which is recorded in an authorized individual information recording unit and the characteristic amount of a previously detected individual which is recorded in an approach information recording unit. An approaching activity detecting unit and an abnormal activity detecting unit compute the degree of suspiciousness of the approaching individual on the basis of the frequency with which the approaching individual approaches a target of monitoring, time at which the approaching individual approaches a target of monitoring, distance by which the approaching individual approaches a target of monitoring, and the like. A suspiciousness degree judgment unit judges whether the approaching individual is a suspicious individual or not, on the basis the degree of suspiciousness. The present invention can be applied to an on-vehicle monitoring system.
Owner:ORMON CORP
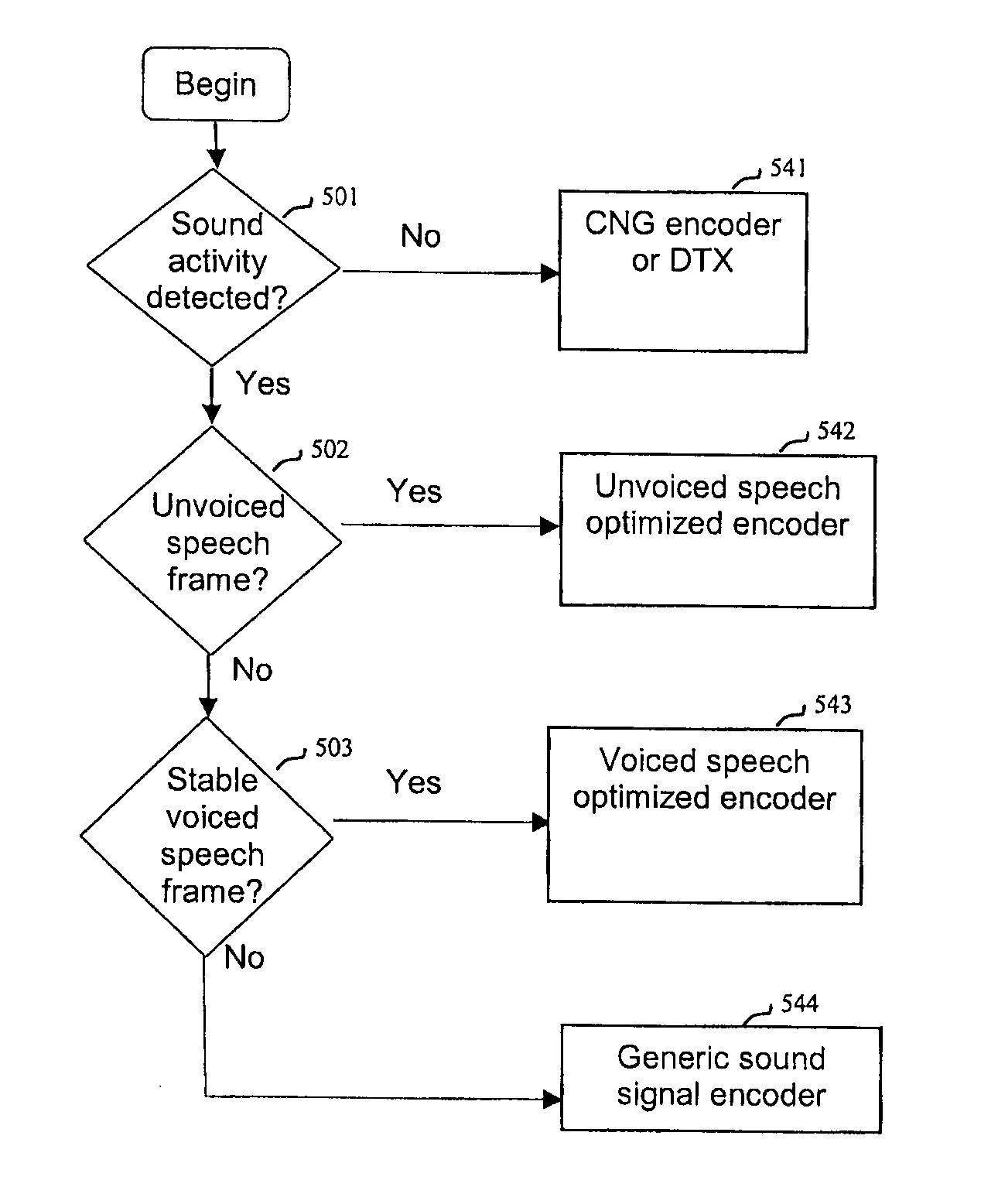
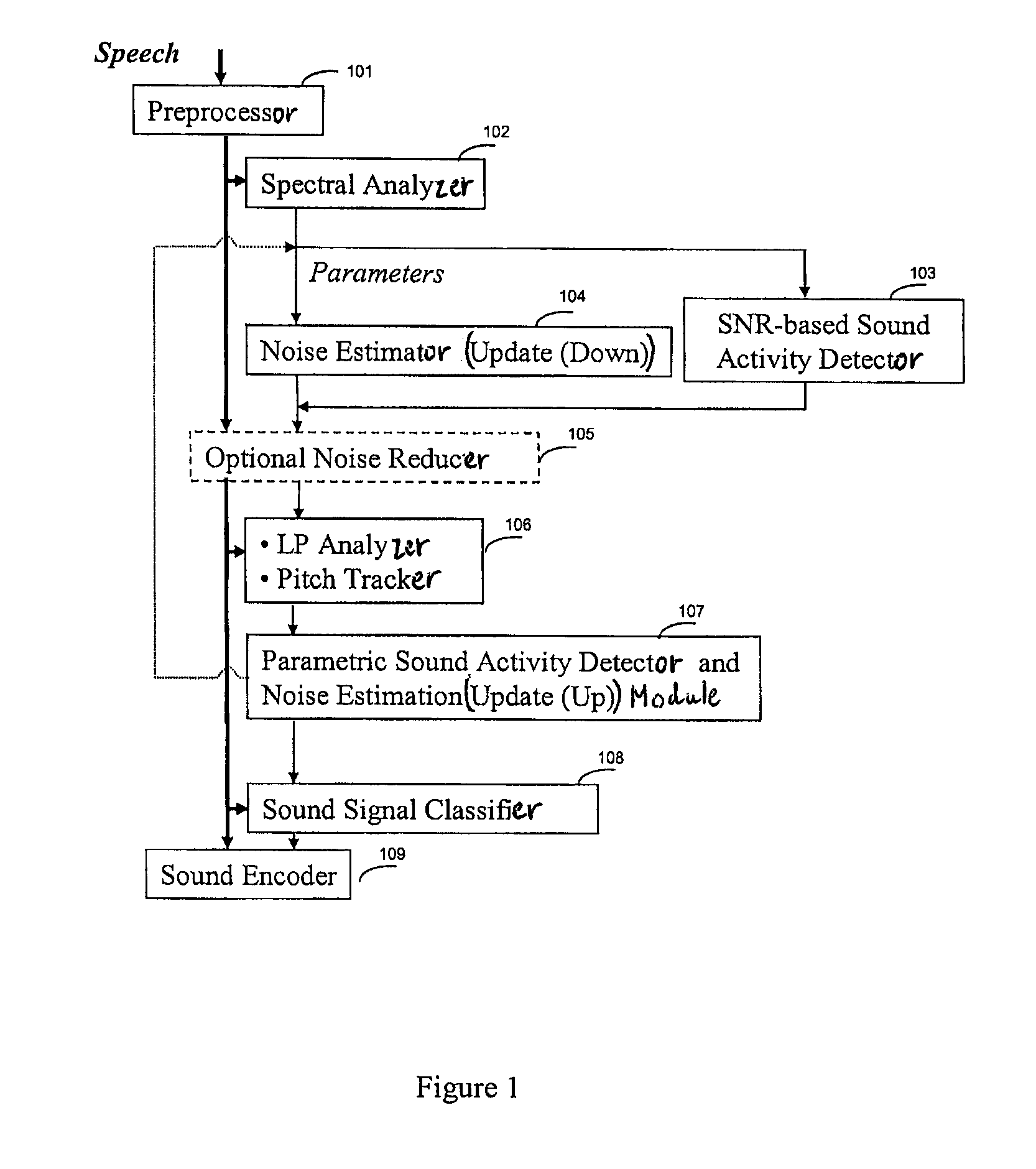
Method and Device for Sound Activity Detection and Sound Signal Classification
A device and method for estimating a tonality of a sound signal comprise: calculating a current residual spectrum of the sound signal; detecting peaks in the current residual spectrum; calculating a correlation map between the current residual spectrum and a previous residual spectrum for each detected peak; and calculating a long-term correlation map based on the calculated correlation map, the long-term correlation map being indicative of a tonality in the sound signal.
Owner:VOICEAGE EVS LLC
Clock control of functional units in an integrated circuit based on monitoring unit signals to predict inactivity
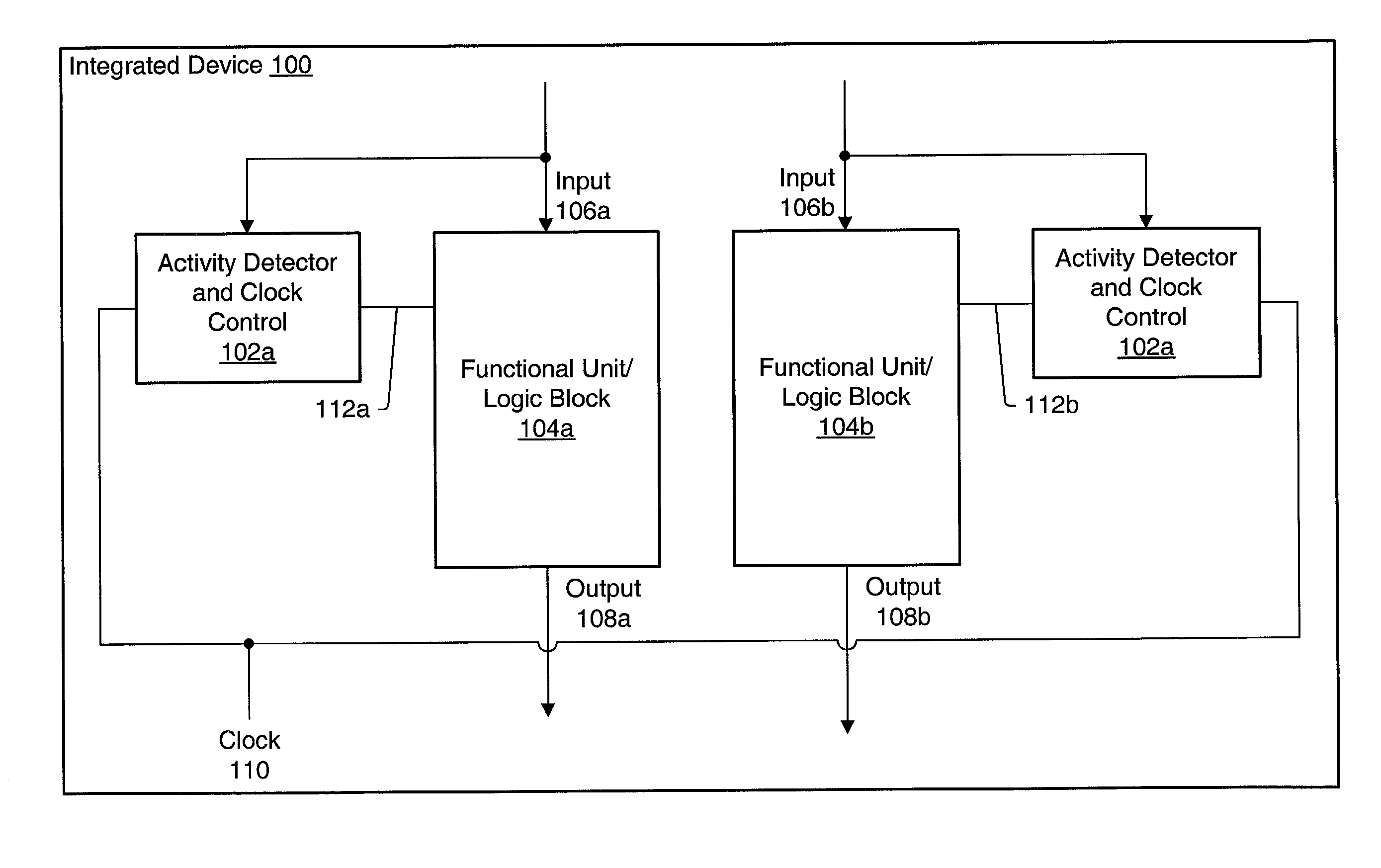
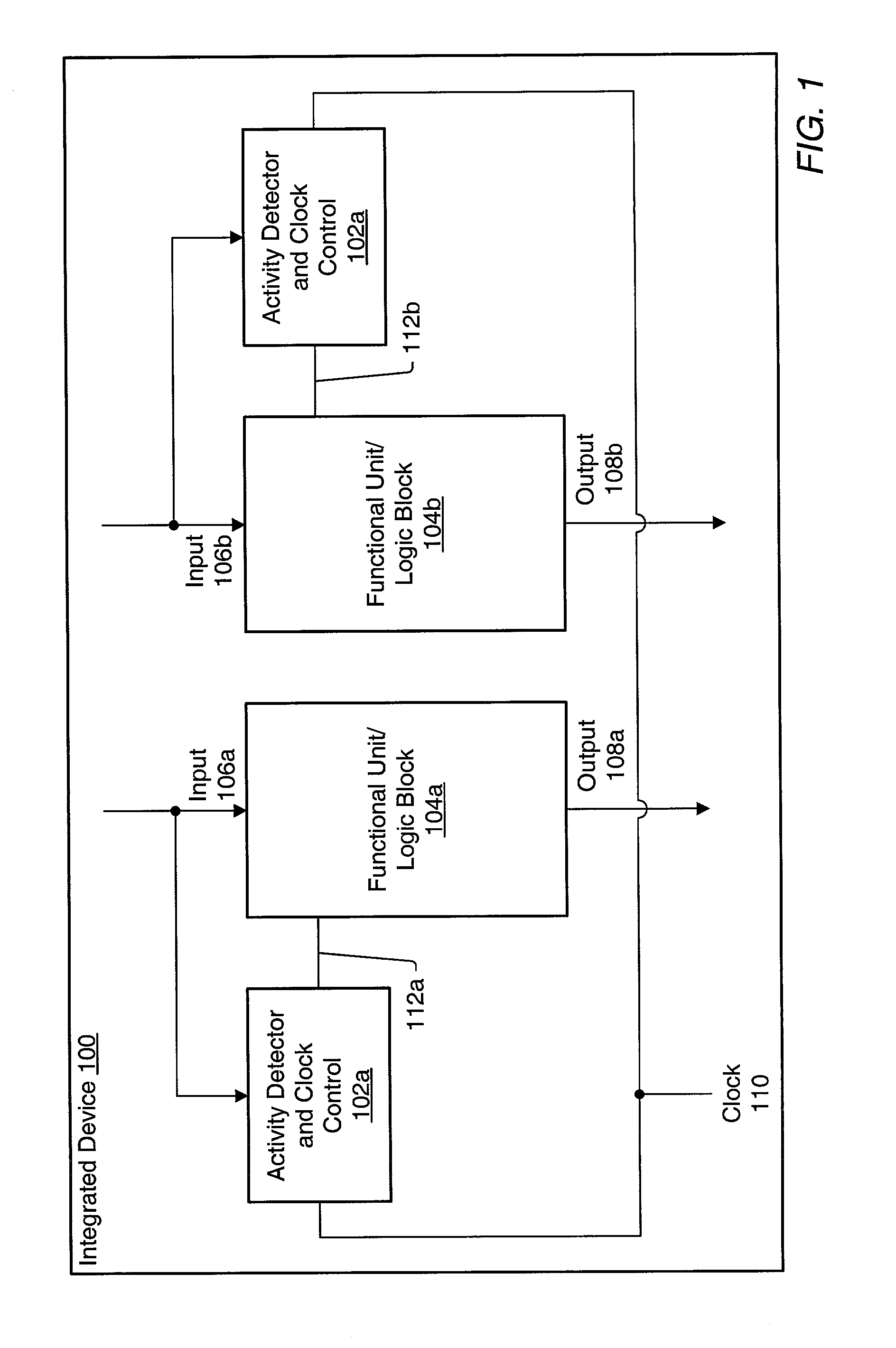
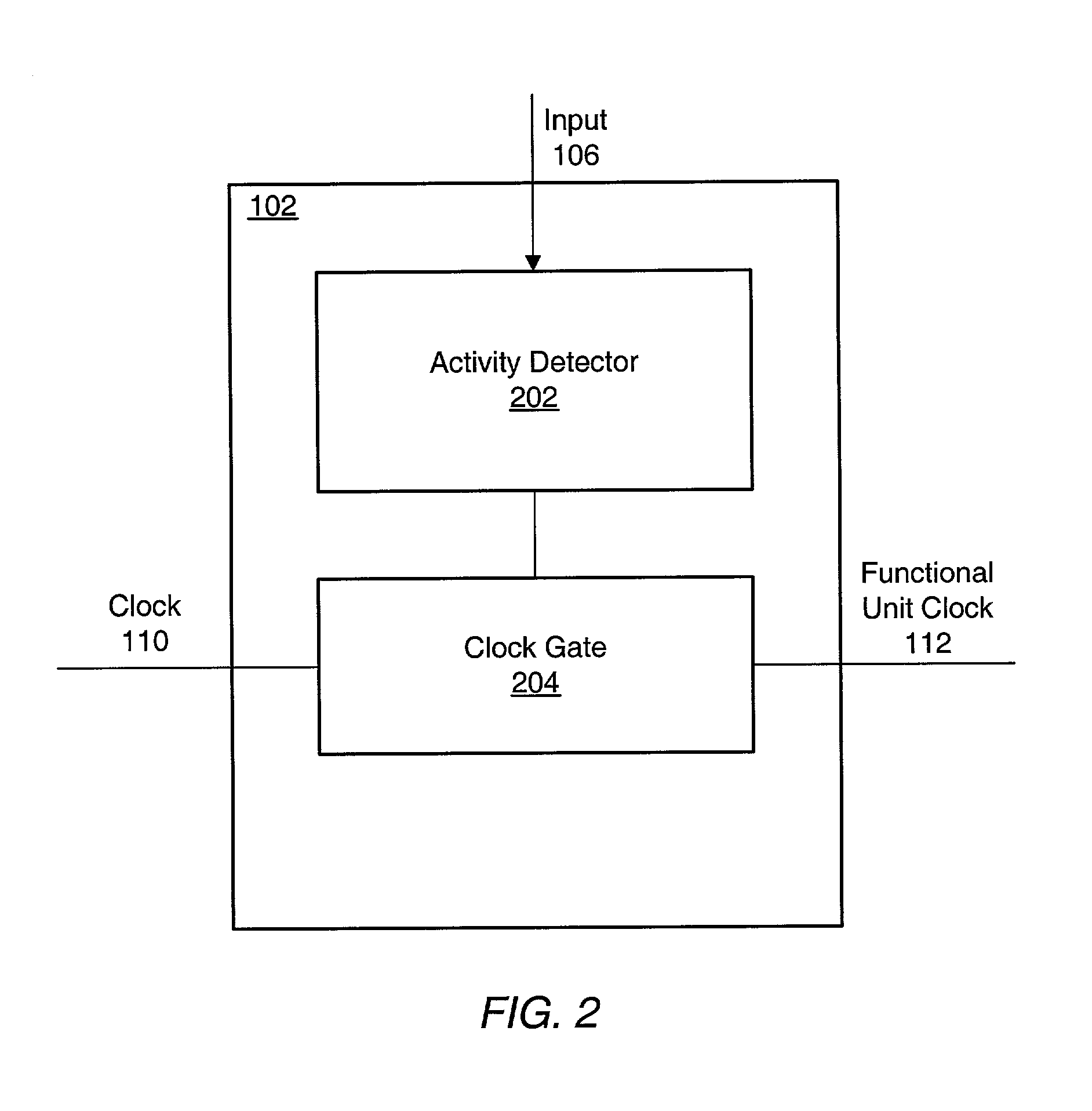
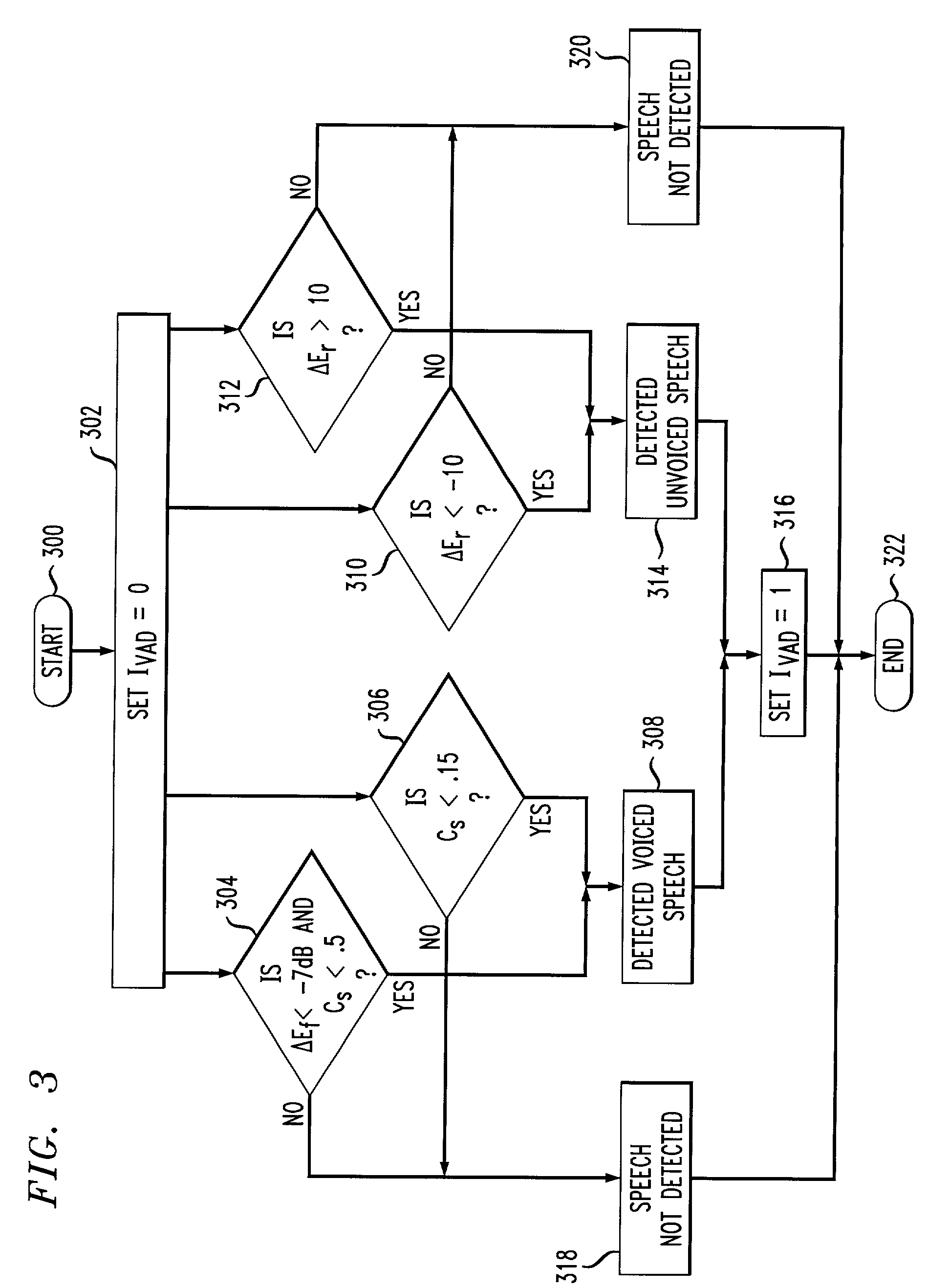
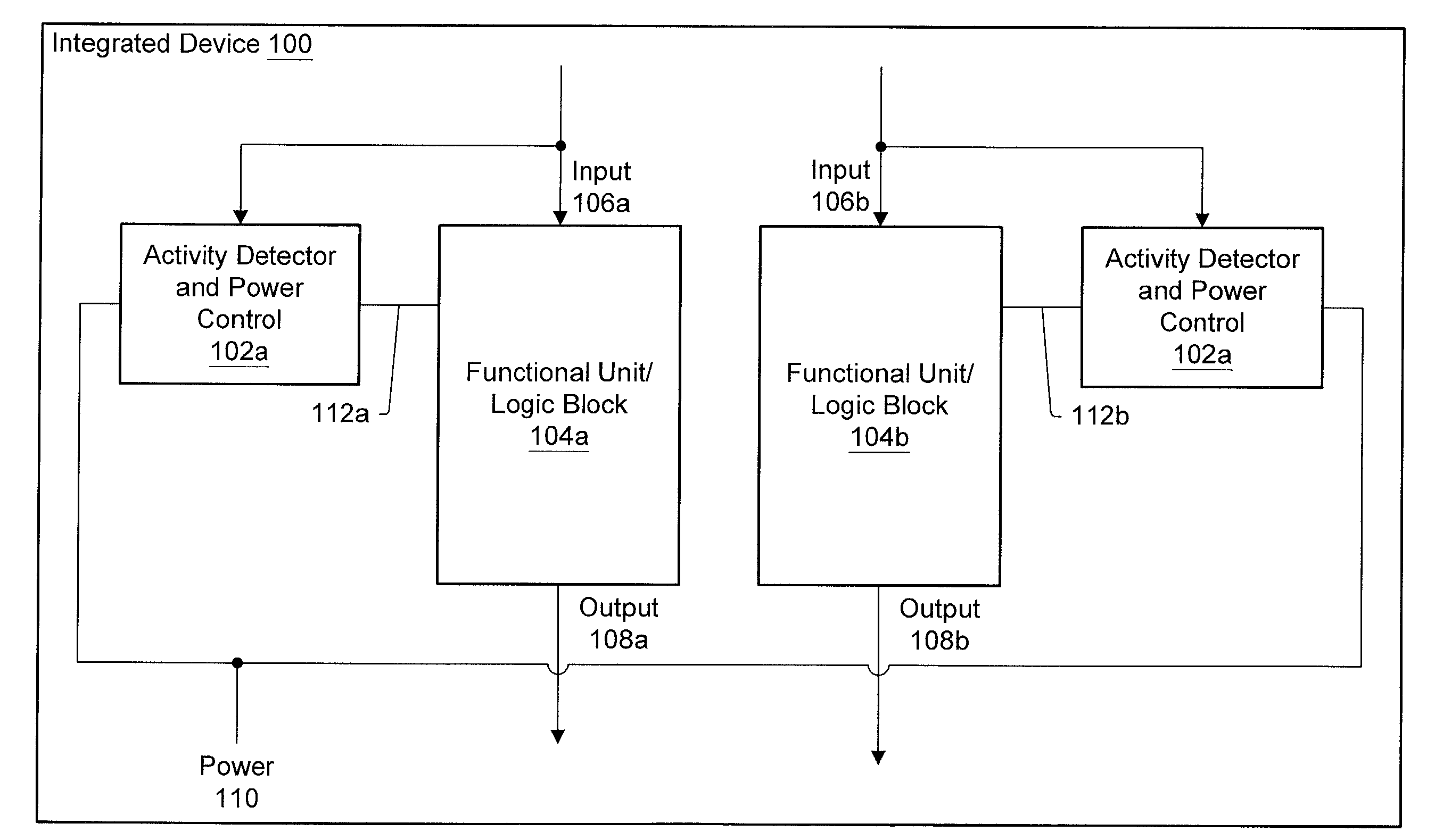
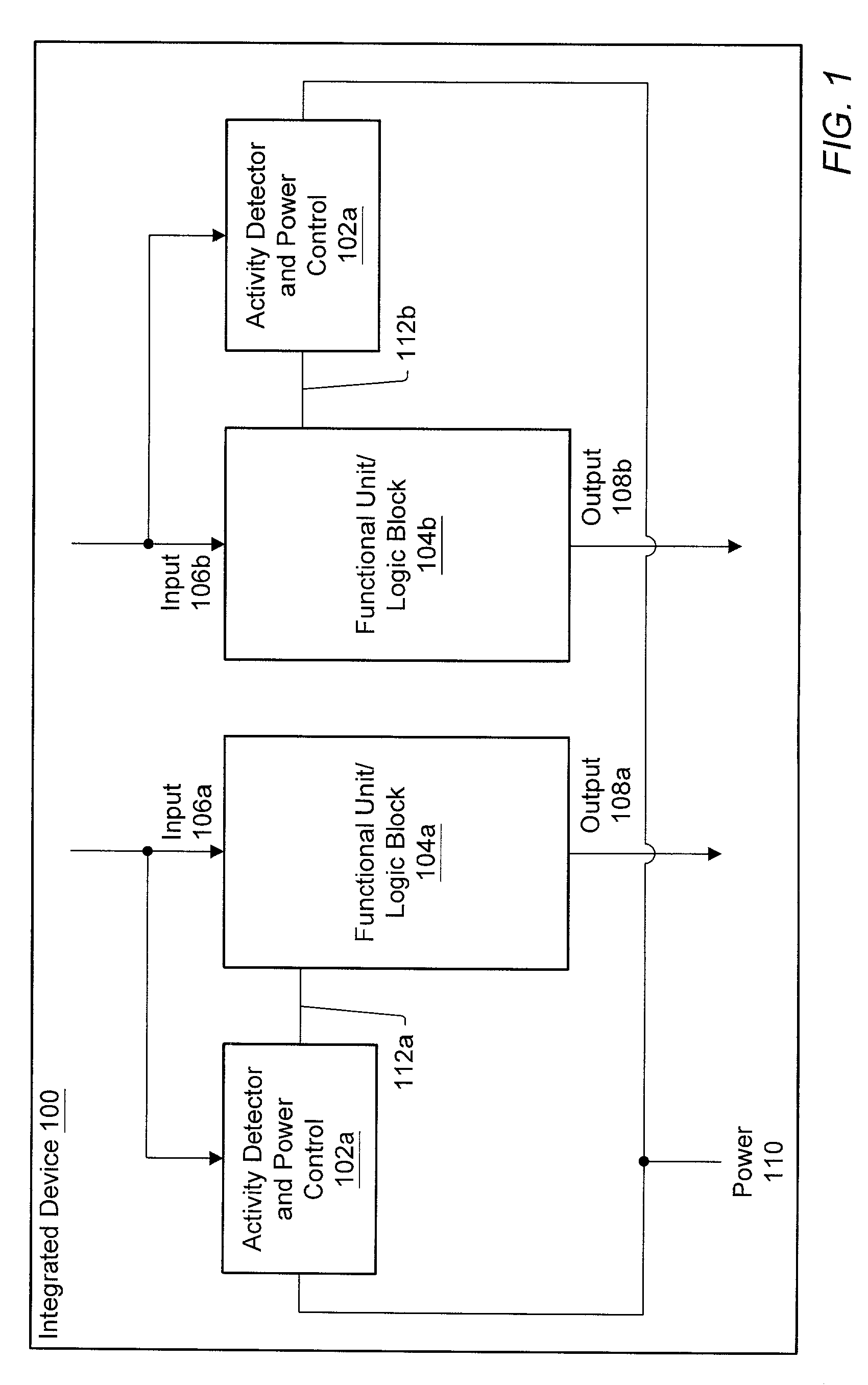
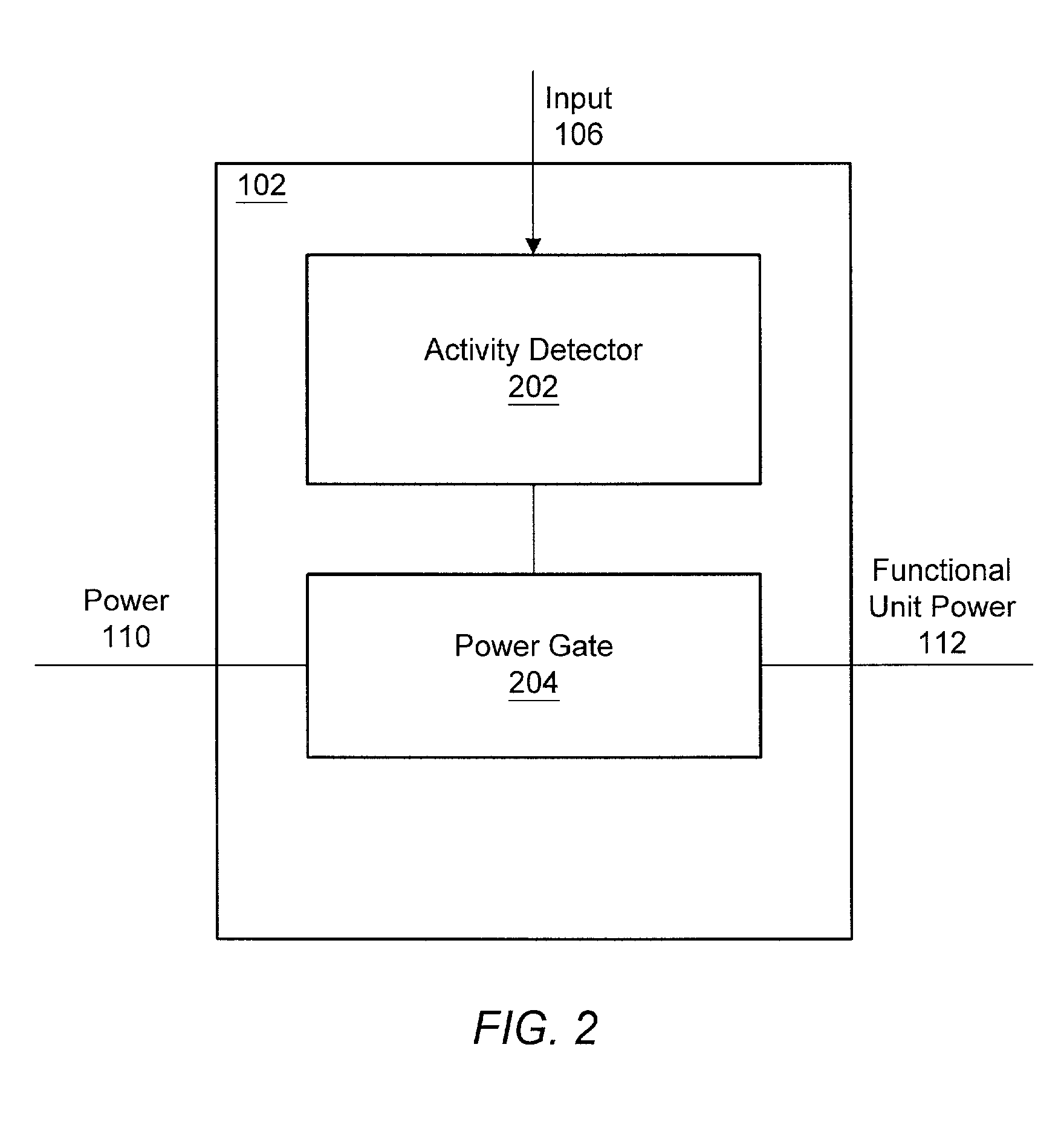
ActiveUS6983389B1Reduce overall static and dynamic power consumptionEnergy efficient ICTPower supply for data processingEngineeringEmbedded system
An integrated circuit may have separate clock control for a number of different functional units. Ancillary to some of the functional units may be an activity detector and clock control unit which monitors input to its functional unit to determine when the functional unit will be inactive. When an activity detector and clock control unit determines that a particular functional unit is or will be inactive, it may disable clocking to its functional unit while the functional unit is inactive. When activity detector and clock control unit determines that activity will resume for its functional unit, it enables clocking to its functional unit. Thus, the activity detector and clock control unit for each such functional unit functions to control clocking to its respective functional unit so that during periods of inactivity, inactive functional units are not clocked to reduce the overall static and / or dynamic power consumption for the integrated device.
Owner:ADVANCED SILICON TECH
Method of controlling an object by user motion for electronic device
ActiveUS20090295738A1Minimize shielding effectInput/output for user-computer interactionAssess restrictionCMOSControl signal
The present invention provides a method of controlling a virtual object or instruction for a computing device comprising: detecting a user activity by a detecting device; generating a control signal in responsive to the user activity detection; controlling an object displayed on a display in responsive to the control signal to execute the instruction. The user activity is detected by CMOS or CCD. The user activity includes facial motion, eye motion, or finger motion.
Owner:TAIWAN SEMICON MFG CO LTD
Remote continuous seizure monitor and alarm
InactiveUS20110270117A1Improve accuracyEasy to explainElectroencephalographySensorsRadio receptionElectroencephalography
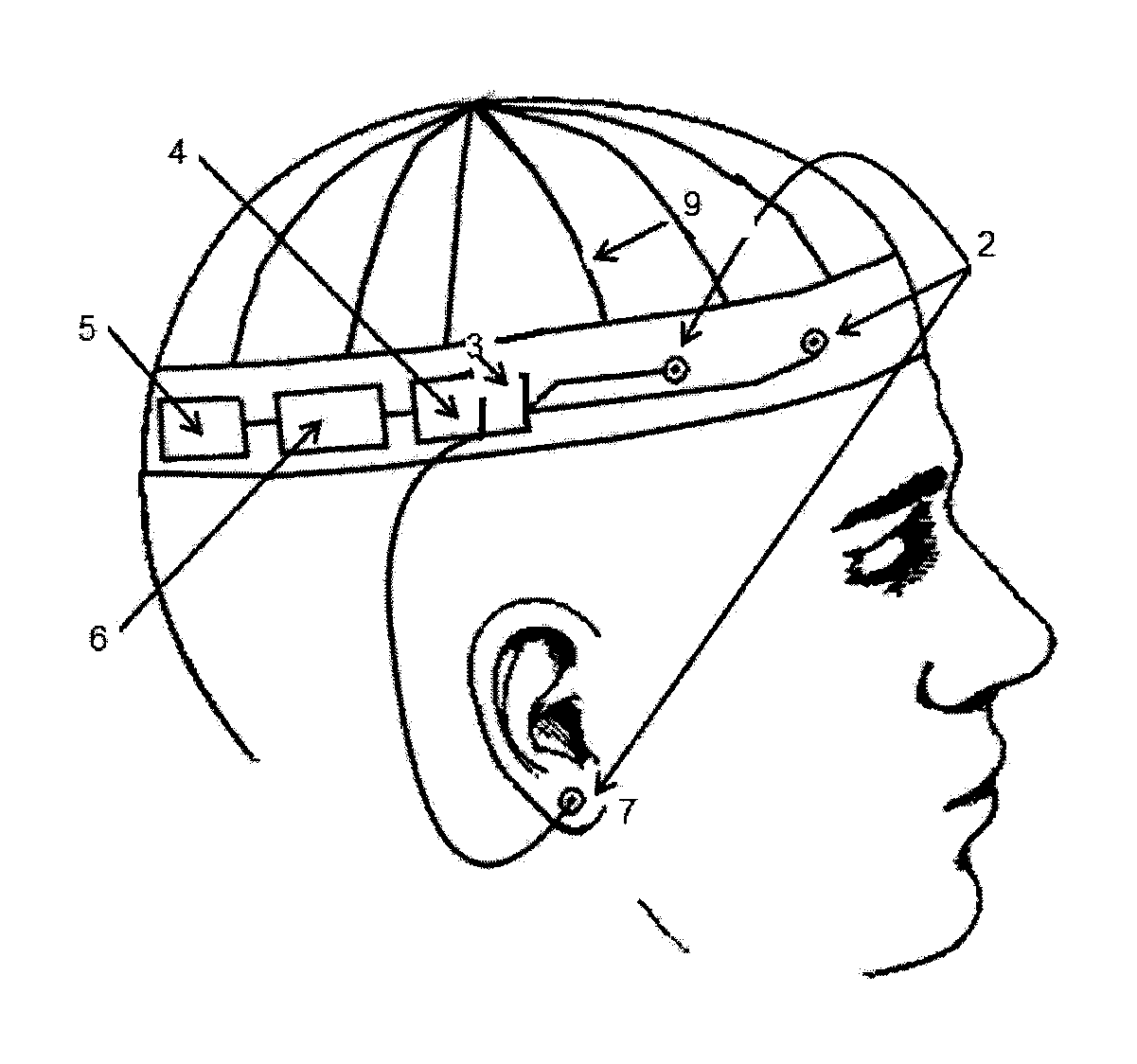
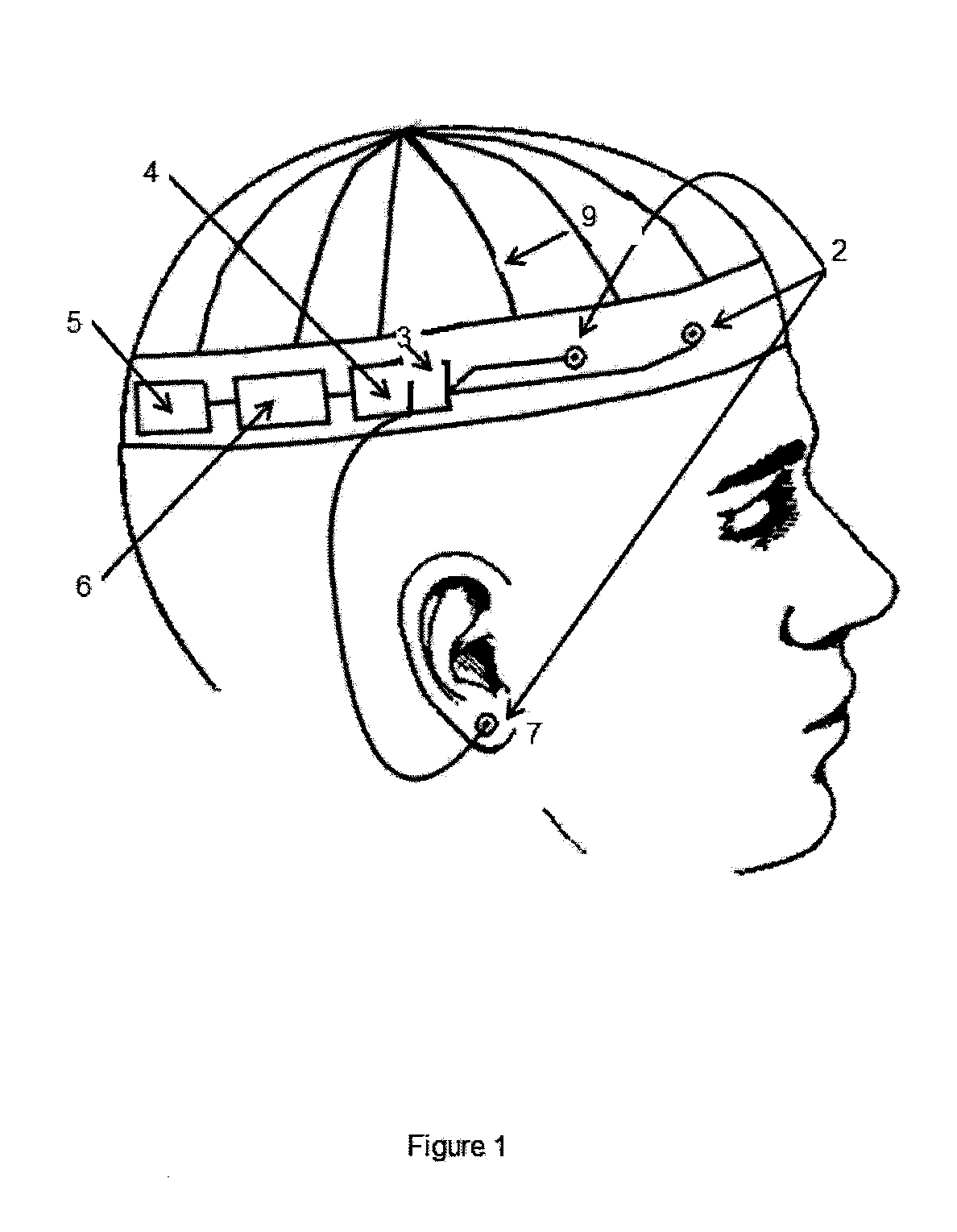
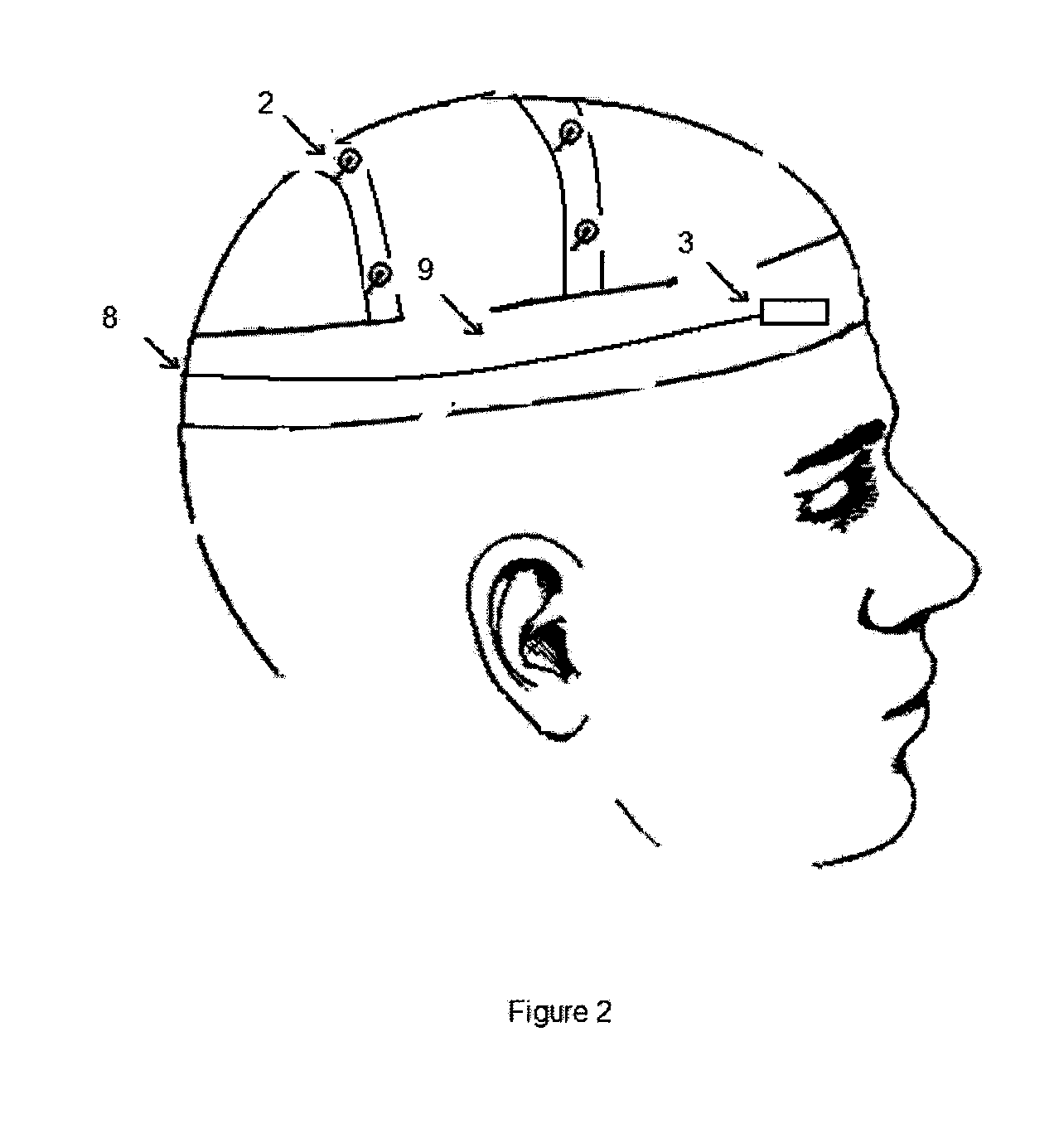
An electroencephalogram (EEG) utilizing epileptiform activity detection, warning and recording system adapted for use by non-healthcare professionals or healthcare professionals. The system is simple enough for use by untrained personnel and will be self-contained, not requiring technical setup or point of use maintenance. The system includes a small number of passive or active scalp electrodes for capturing the electrical signals in the subject's brain allowing for detection of epileptiform activity. The system will recognize epileptiform activity and will either transmit signals upon detection of epileptiform activity to either a localized warning device or to a cellular or radio receiving device. The system will note epileptiform activity in a recording component and allow for review of the epileptiform data to allow non-clinical and clinical personnel to verify such activity.
Owner:GLKK
Dynamic multidimensional risk-weighted suspicious activities detector
InactiveUS20080021801A1Avoid negative effectsImprove accuracyFinanceMultidimensional scalingImage resolution
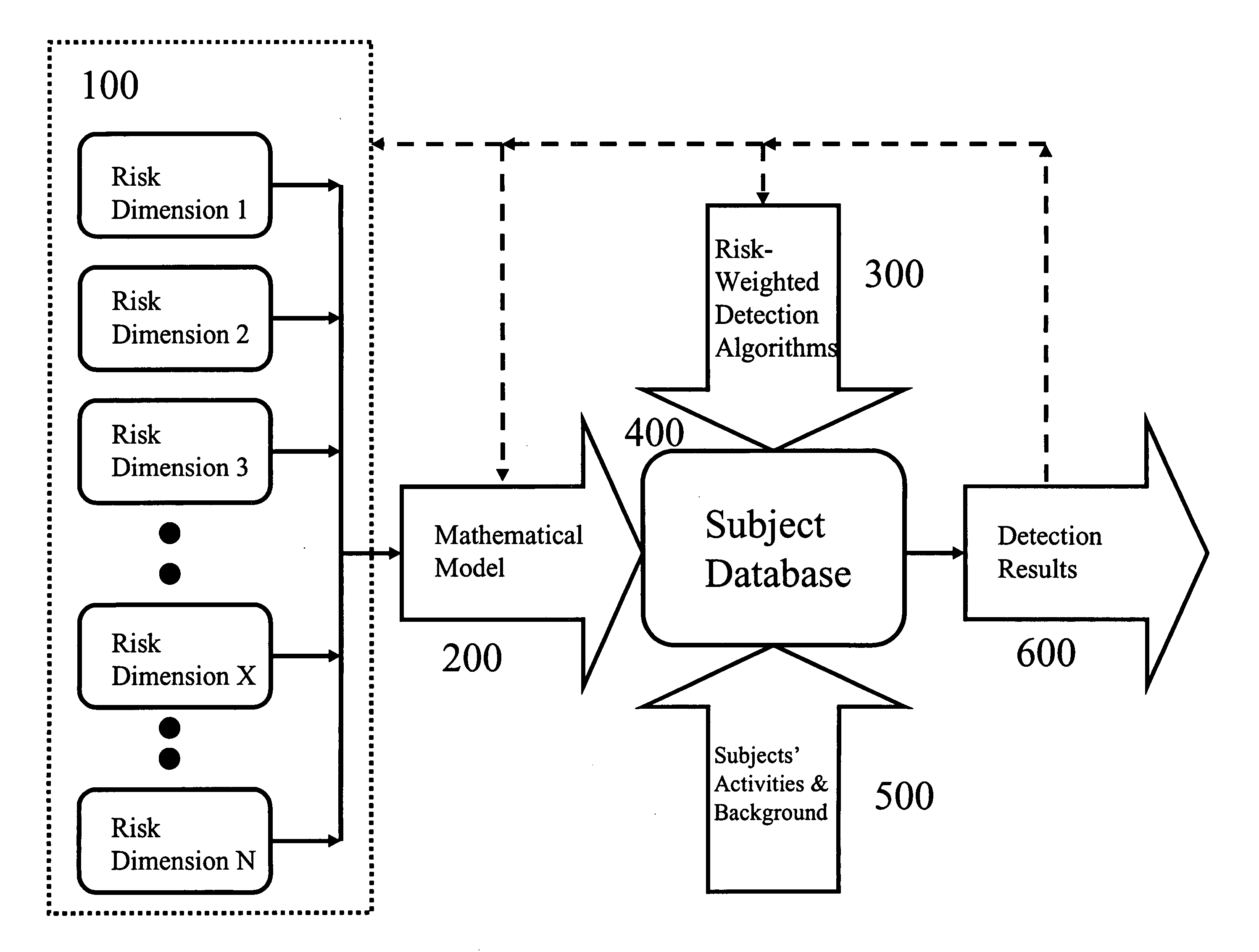
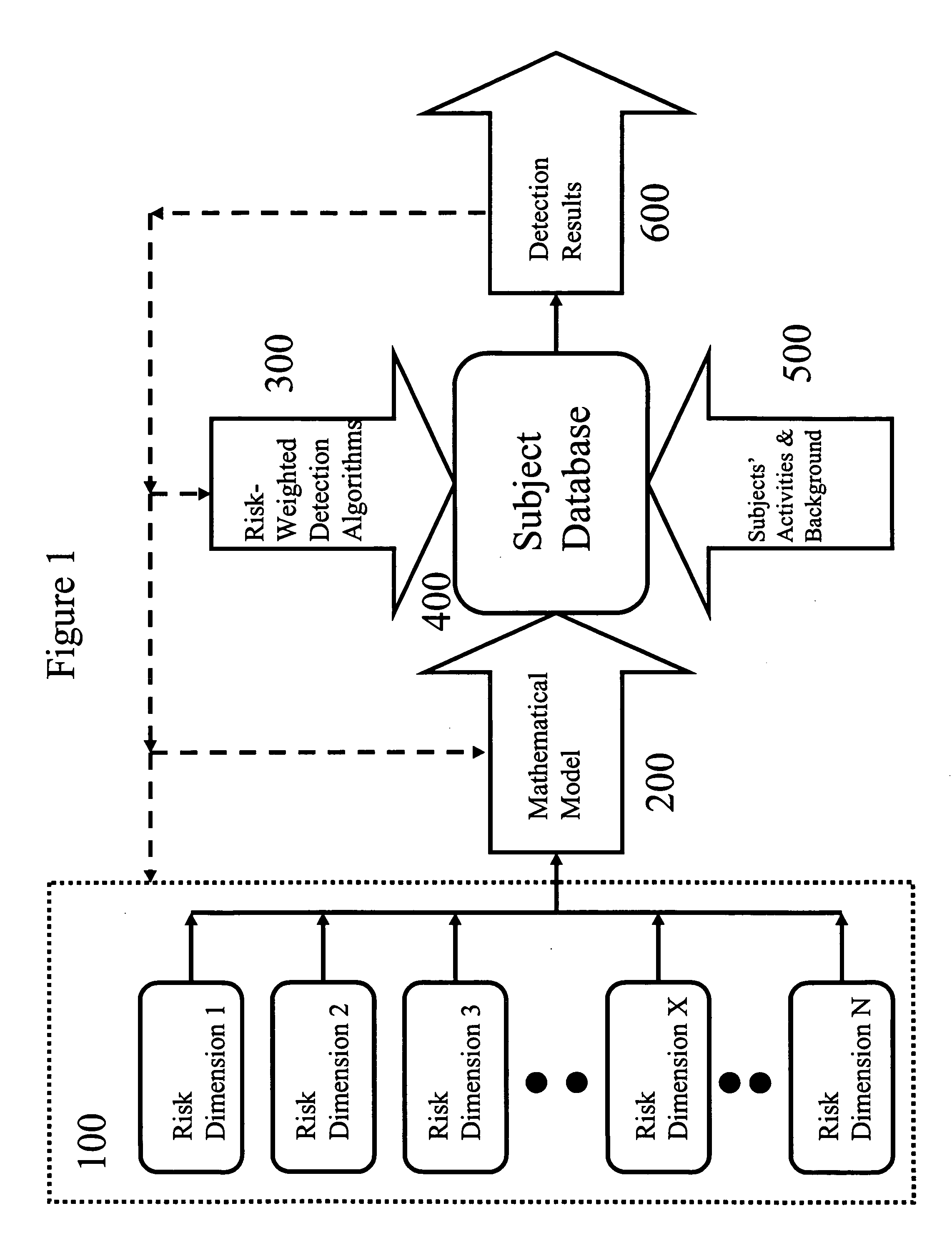
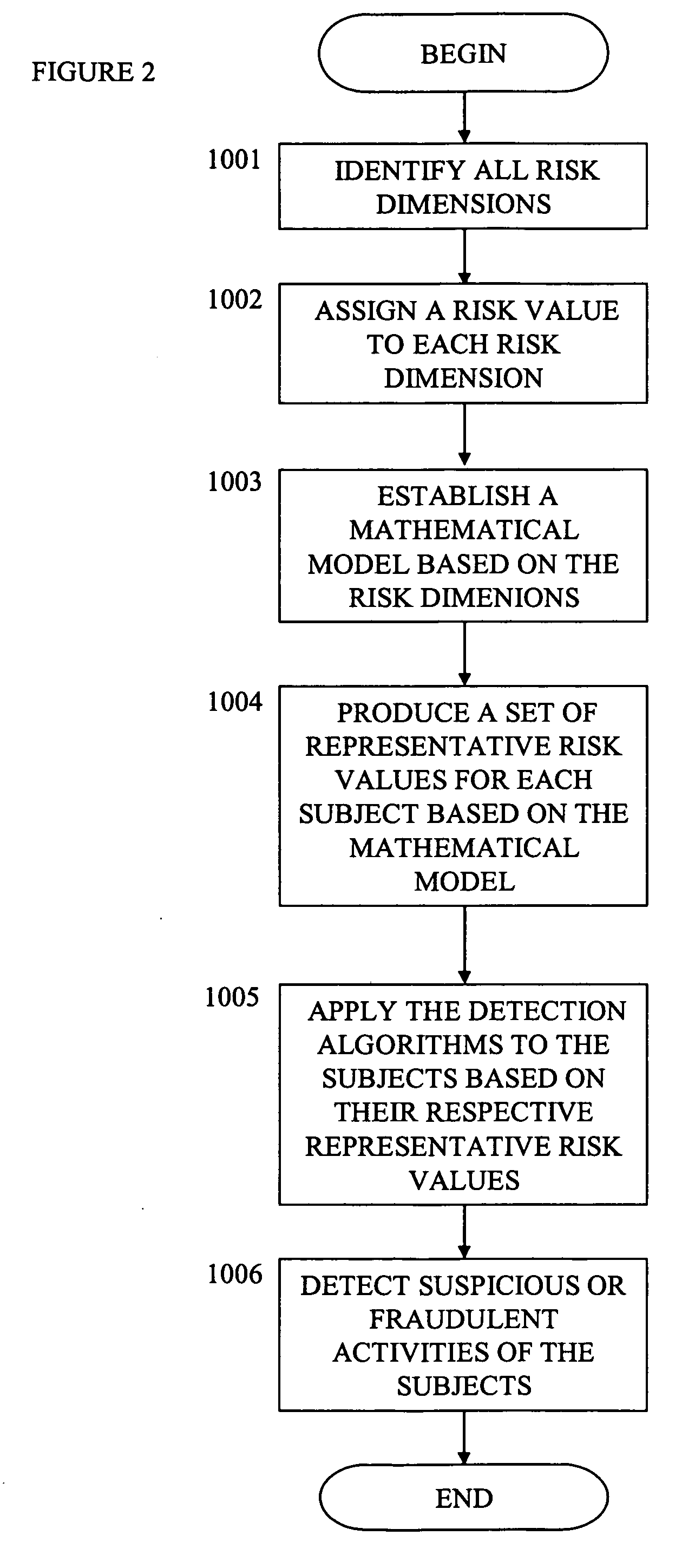
A computerized method is established to detect suspicious and fraudulent activities in a group of subjects by defining and dynamically integrating multidimensional risks, which are based on the characteristics of the subjects, into a mathematical model to produce a set of the most up-to-date representative risk values for each subject based on its activities and background. These multidimensional risk definitions and representative risk values are used to select a subset of multidimensional risk-weighted detection algorithms so that suspicious or fraudulent activities in the group of subjects can be effectively detected with higher resolution and accuracy. A priority sequence, which is based on the set of detection algorithms that detect the subject and the representative risk values of the detected subject, is produced to determine the priority of each detected case during the investigation process. To assist the user to make a more objective decision, any set of multidimensional risks can be used to identify a group of subjects that contain this set of multidimensional risks so that group statistics can be obtained for comparison and other analytical purposes. Furthermore, to fine-tune the system for future detections and analyses, the detection results are used as the feedback to adjust the definitions of the multidimensional risks and their values, the mathematical model, and the multidimensional risk-weighted detection algorithms.
Owner:SONG YUH SHEN +3
System and method for detecting unauthorized call activity
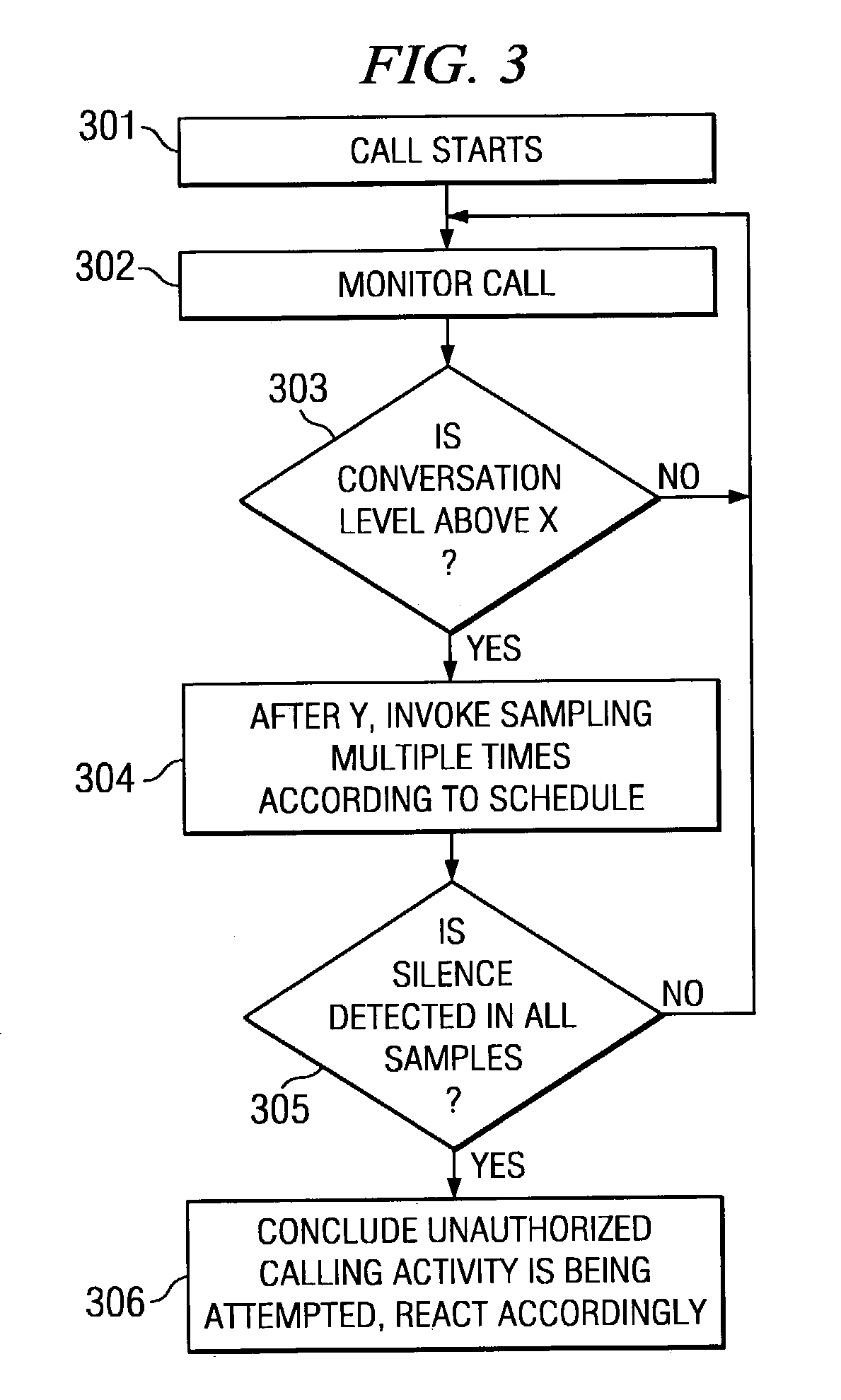
ActiveUS7079637B1Create noiseImprove experienceUnauthorised/fraudulent call preventionSpecial service for subscribersComputer scienceActivity detection
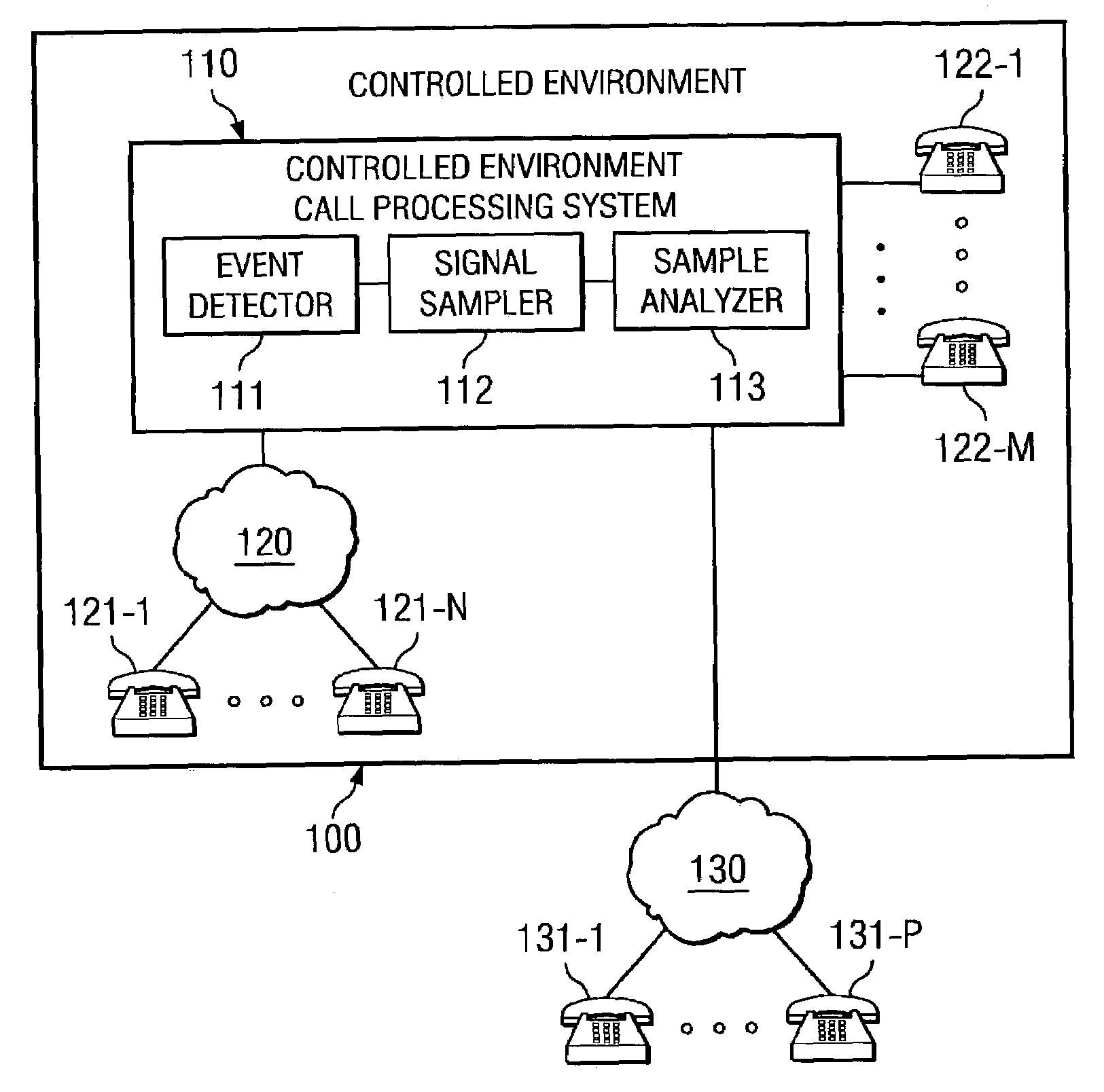
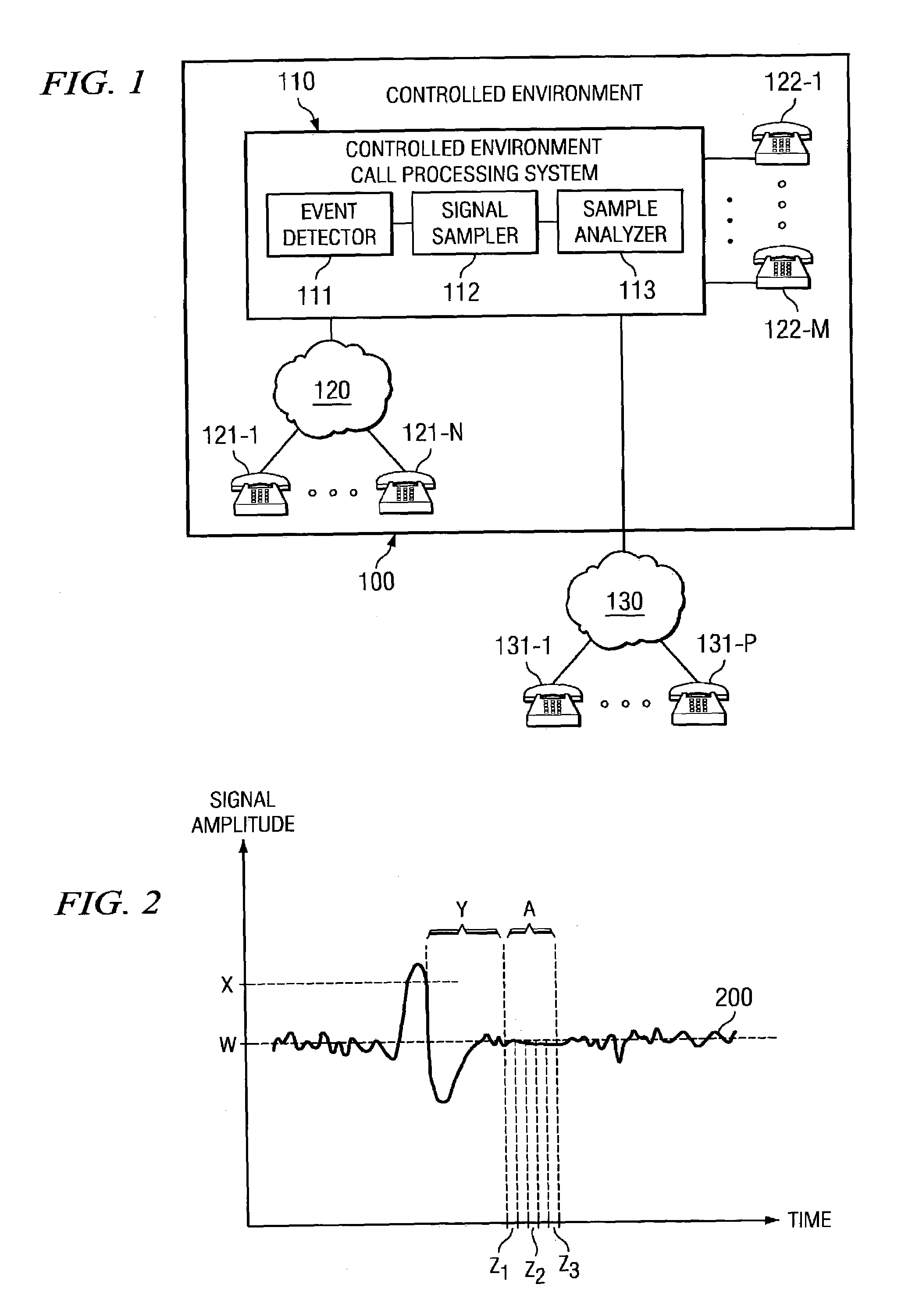
Disclosed are systems and methods which detect unauthorized, impermissible, or otherwise undesired call activity through a silence detection technique employing multiple samples. One embodiment monitors a call in progress to detect an event such as might be indicative of unauthorized call activity. Thereafter, a sampling process may be invoked which analyzes multiple samples of the call to make a determination as to whether or not a particular unauthorized call activity is being attempted. A party to the call may be muted to thereby prevent that party from thwarting the unauthorized call activity determination. Embodiments implement techniques for defeating parties to calls learning the unauthorized call activity detection system in order to avoid detection, such as by implementing a plurality of detection techniques.
Owner:SECURUS TECH HLDG
Post-Recording Data Analysis and Retrieval
InactiveUS20080263012A1Digital data information retrievalModulated-carrier systemsDigital dataData compression
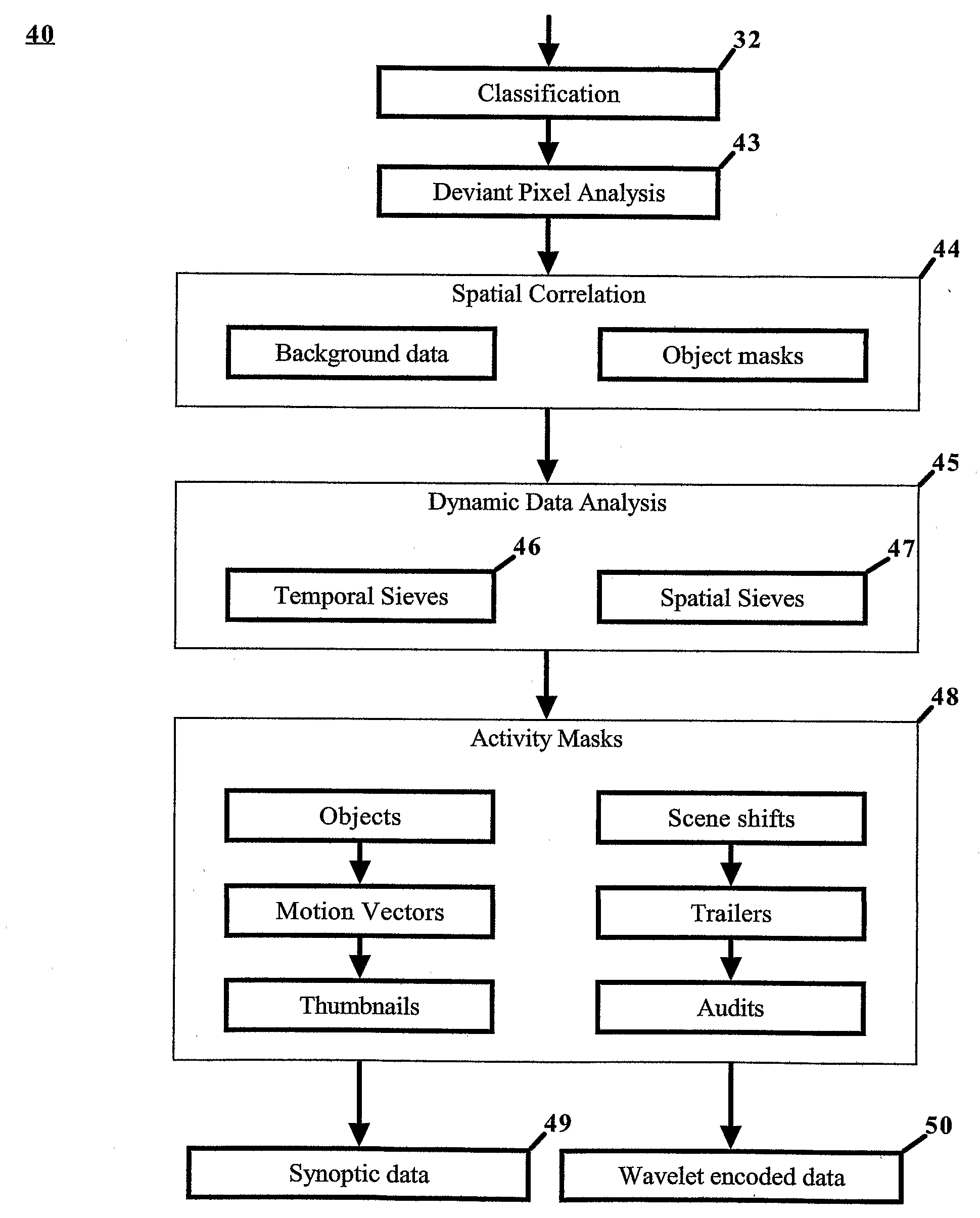
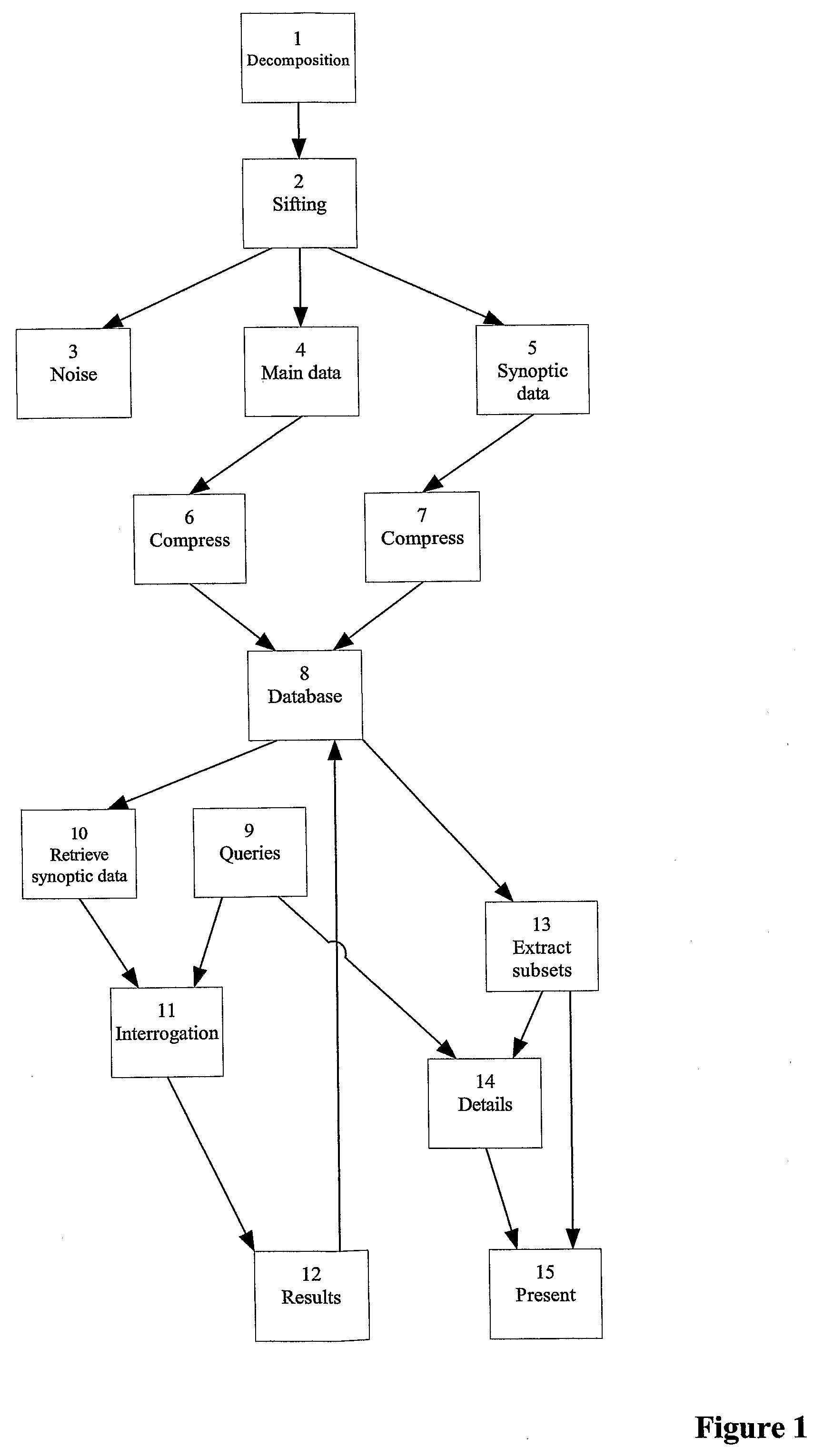
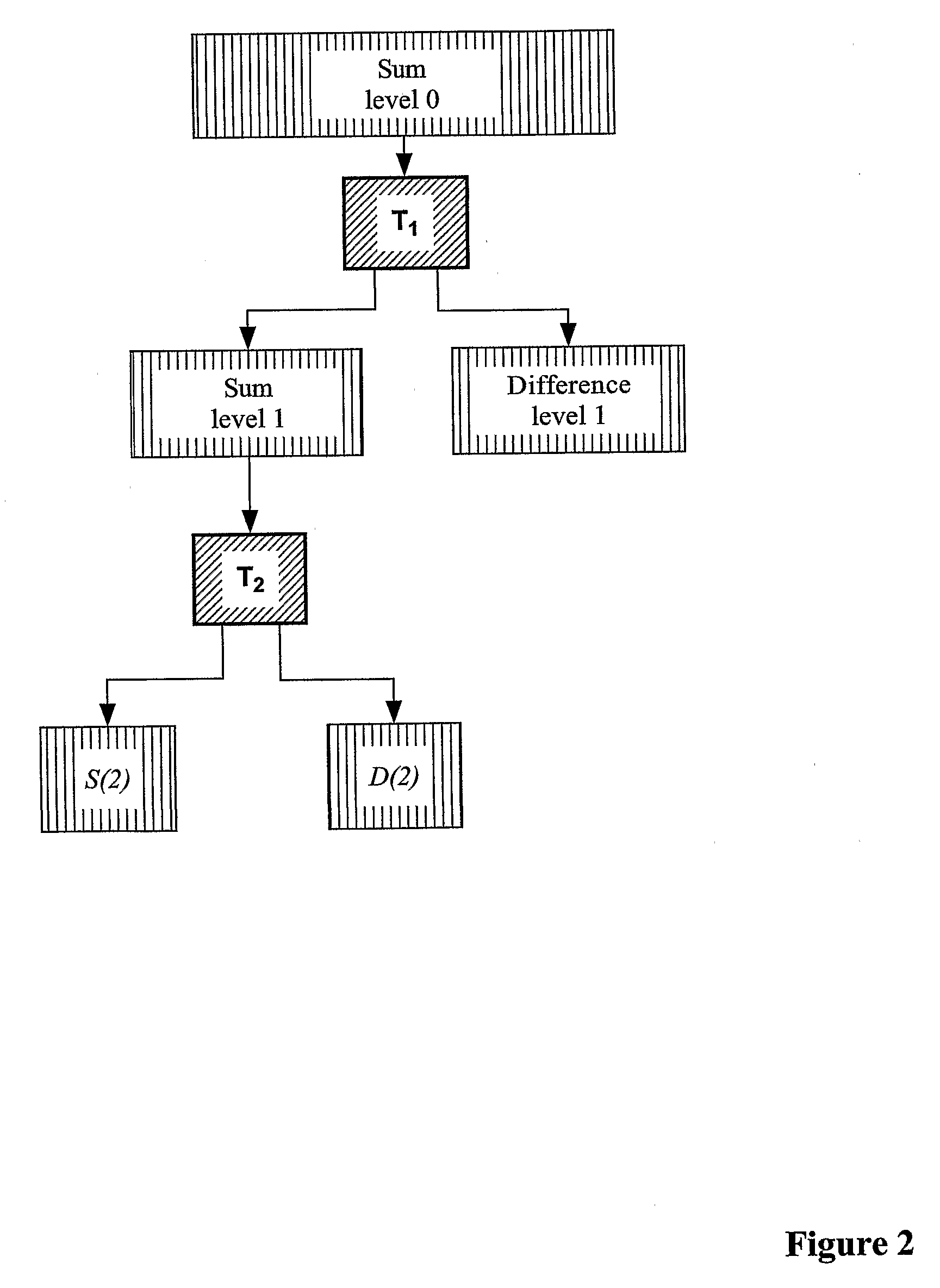
When making digital data recordings using some form of computer or calculator, data is input in a variety of ways and stored on some form of electronic medium. During this process calculations and transformations are performed on the data to optimize it for storage. This invention involves designing the calculations in such a way that they include what is needed for each of many different processes, such as data compression, activity detection and object recognition. As the incoming data is subjected to these calculations and stored, information about each of the processes is extracted at the same time. Calculations for the different processes can be executed either serially on a single processor, or in parallel on multiple distributed processors. We refer to the extraction process as “synoptic decomposition”, and to the extracted information as “synoptic data”. The term “synoptic data” does not normally include the main body of original data. The synoptic data is created without any prior bias to specific interrogations that may be made, so it is unnecessary to input search criteria prior to making the recording. Nor does it depend upon the nature of the algorithms / calculations used to make the synoptic decomposition. The resulting data, comprising the (processed) original data together with the (processed) synoptic data, is then stored in a relational database. Alternatively, synoptic data of a simple form can be stored as part of the main data. After the recording is made, the synoptic data can be analyzed without the need to examine the main body of data. This analysis can be done very quickly because the bulk of the necessary calculations have already been done at the time of the original recording. Analyzing the synoptic data provides markers that can be used to access the relevant data from the main data recording if required. The nett effect of doing an analysis in this way is that a large amount of recorded digital data, that might take days or weeks to analyze by conventional means, can be analyzed in seconds or minutes. This invention also relates to a process for generating continuous parameterised families of wavelets. Many of the wavelets can be expressed exactly within 8-bit or 16-bit representations. This invention also relates to processes for using adaptive wavelets to extract information that is robust to variations in ambient conditions, and for performing data compression using locally adaptive quantisation and thresholding schemes, and for performing post recording analysis.
Owner:ASTRAGROUP AS
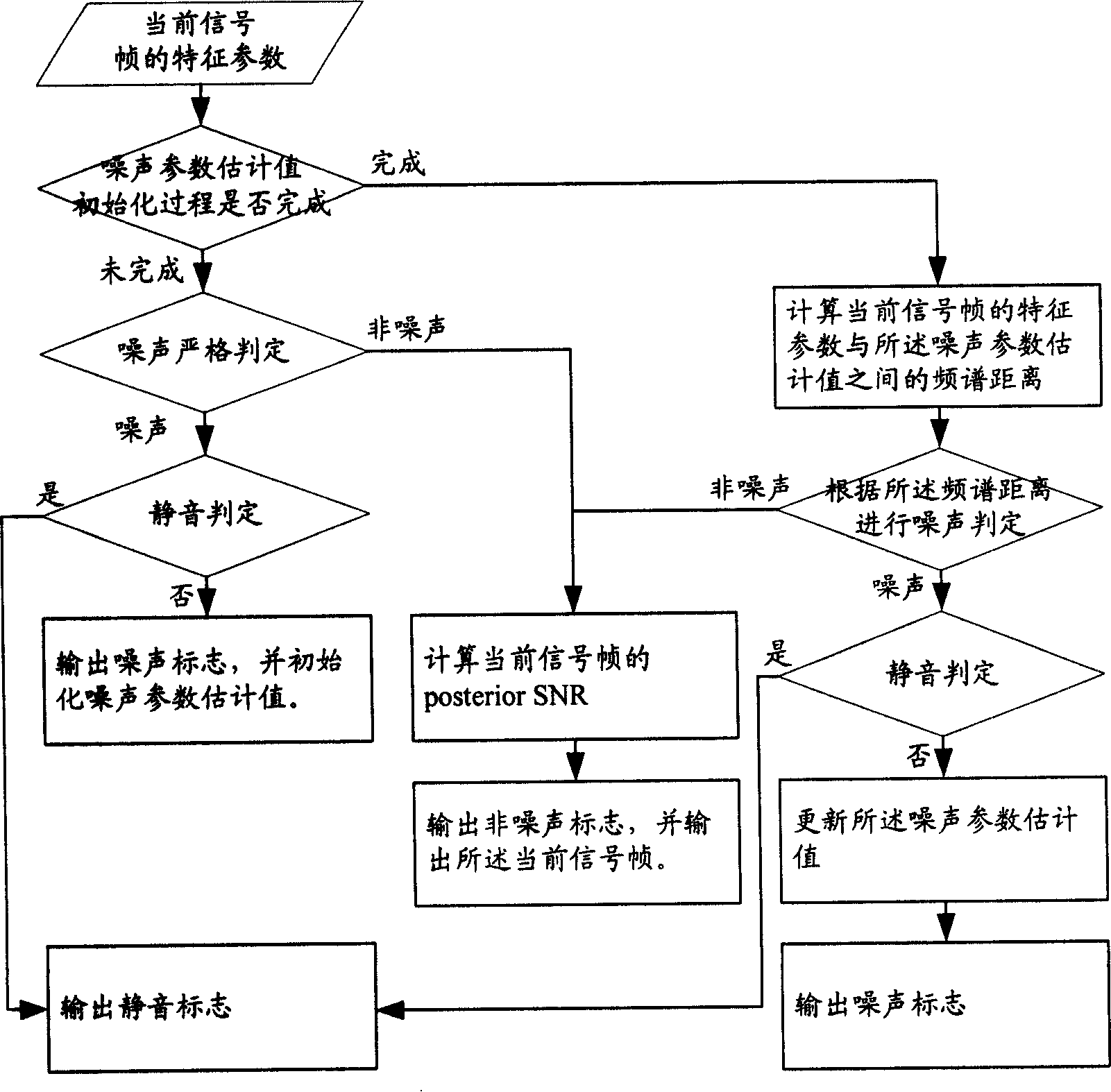
Sound activity detecting method and detector thereof
The invention discloses a sound activation detecting method and a sound activation detector, the core of which is: extracting the feature parameters of the current signal frame when the sound activation detection is needed; and determining the sound type of the current signal frame according to the feature parameters and the set parameter threshold. By the invention, the specific coding algorithm is not relied on when the used feature parameters in the classifying process are extracted, thus being convenient for maintenance and updating, and classifying the input signals into more sound types. When being used in the sound coding technical field, the invention can not only be used as new-opened variable rate sound frequency coding algorithm and standard rate selection foundation, but also provide foundation of rate selection for prior variable rate voice or sound frequency coding standard without VAD algorithm. The invention can be applicable to voice boosting, voice recognition, recognition of spoken person and other voice signal processing fields with strong commonality.
Owner:HUAWEI TECH CO LTD
Large Scale Recommendation Engine Based on User Tastes
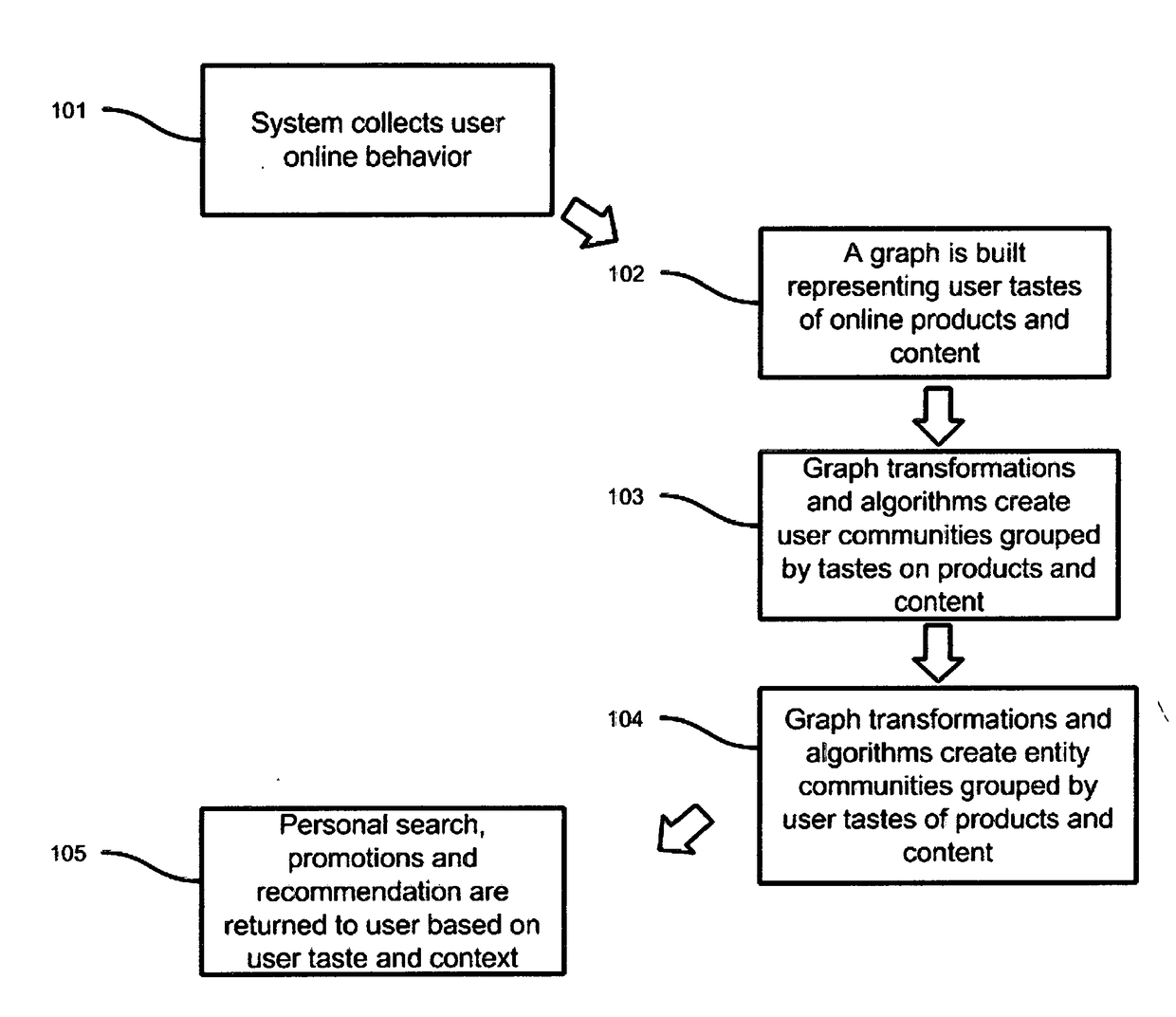
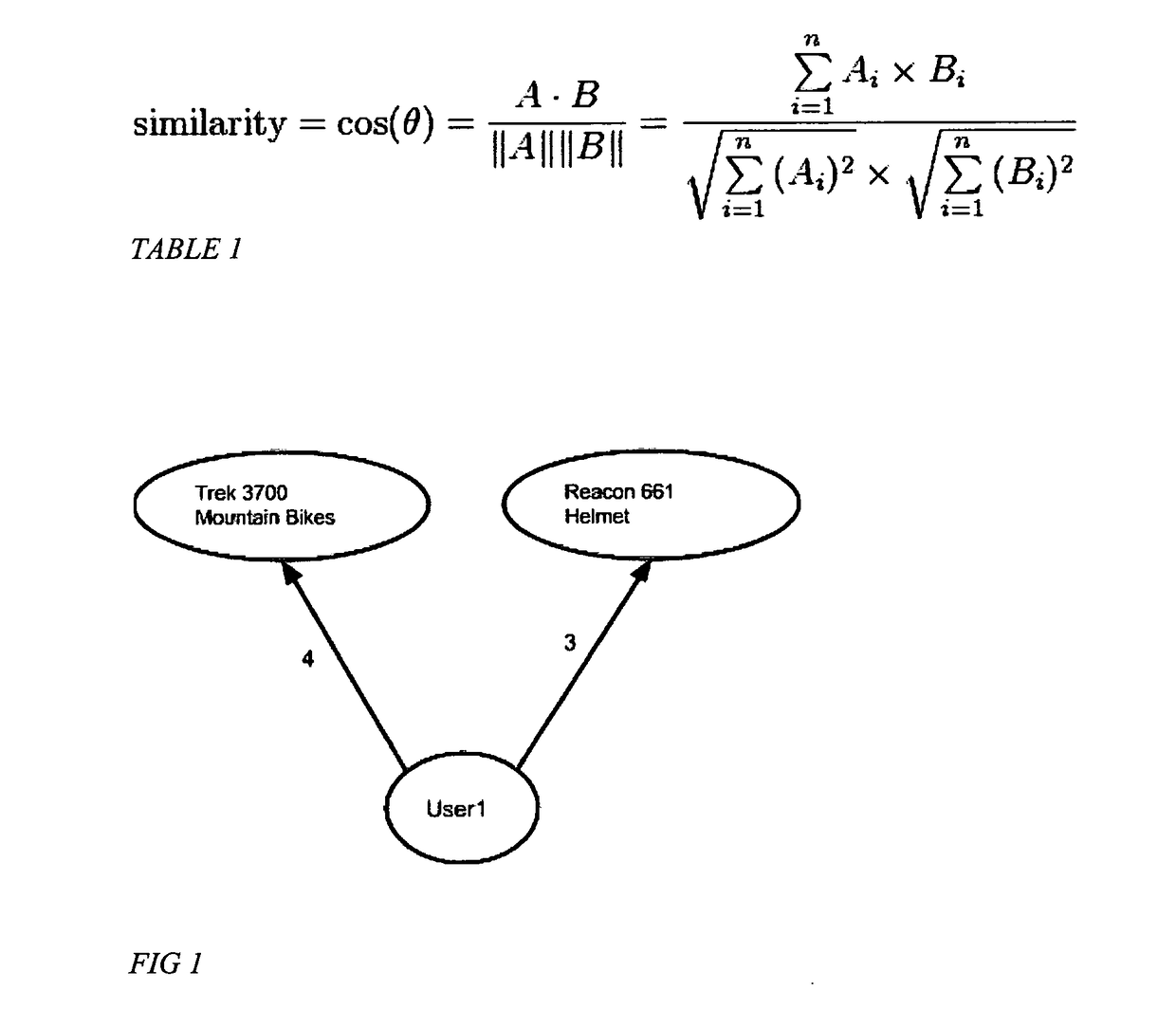
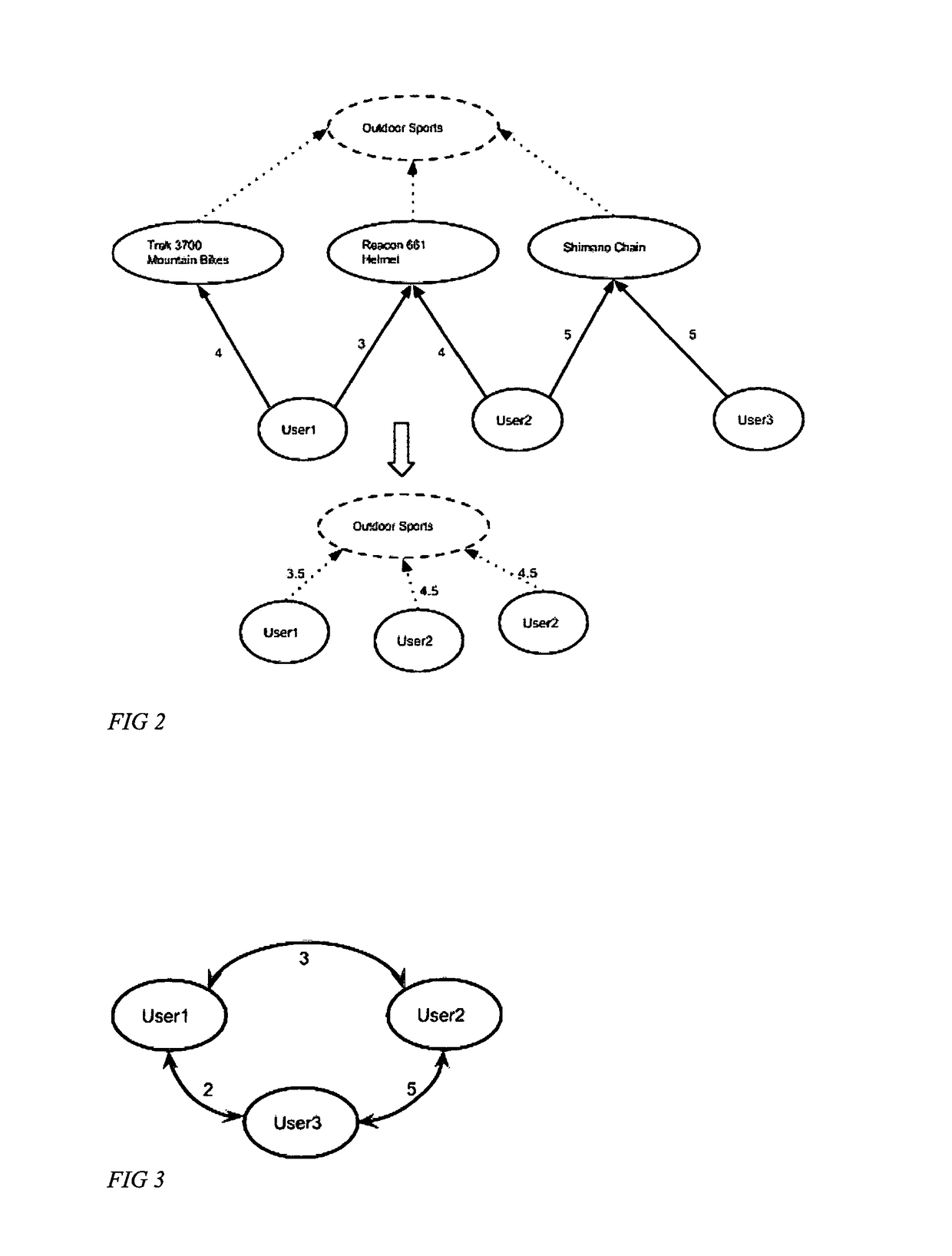
InactiveUS20170206276A1Handy search resultsRelational databasesSpecial data processing applicationsGraph generationEngineering
Computer-implemented processes are disclosed for creating predictive recommendations based on large scale analysis of users tastes. One process involves detecting users tastes based on online activity and organizing these users into groups of users with similar tastes by applying graph manipulation algorithms and applying a clustering method on these graphs. Another process is disclosed for generating from these sub-graphs of similar groups of users a list of items users are most likely to show interest in based on groups' interests. A large scale solution is disclosed capable of processing large volumes of data in parallel generated from the activities of users online to create these recommendations. A system is described that takes all these artifacts to create a large scale recommendation system and collaborative filtering system. Yet another process is disclosed on how to target these groups of users with promotions through advertising networks.
Owner:GILL IDDO
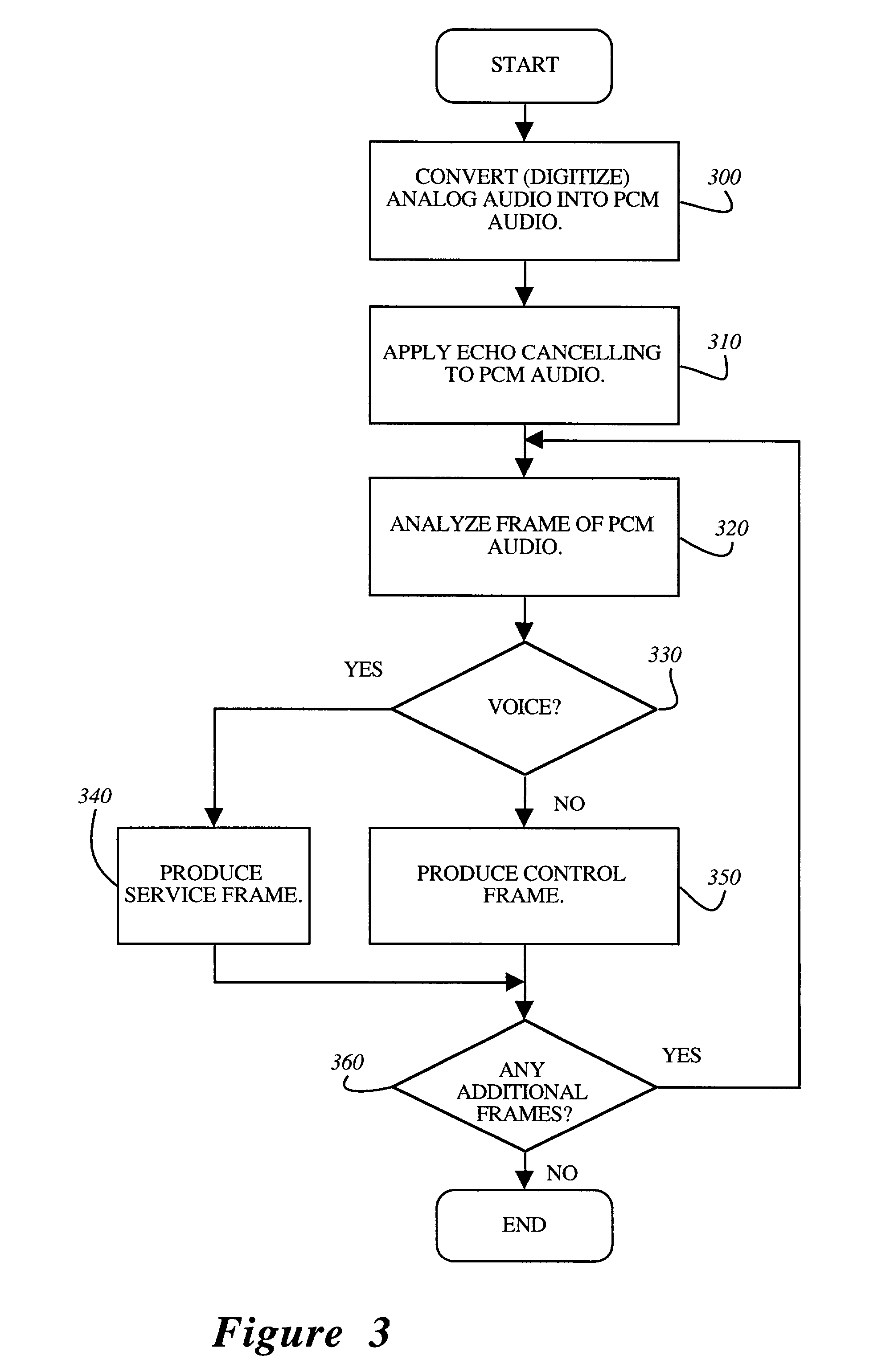
A voice activity detector for packet voice network
A voice activity detector to analyze a short-term averaged energy (STAE), a long-term averaged energy (LTAE), and a peak-to-mean likelihood ratio (PMLR) in order to determine whether a current audio frame being transmitted represents voice or silence. This is accomplished by determining whether a sum of the STAE and a factor is greater than the LTAE. If not, the current audio frame represents silence. If so, a second set of determinations is performed. Herein, a determination is made as to whether the difference between the LTAE and the STAE is less than a predetermined threshold. If so, the current audio frame represents voice. Otherwise, the PMLR is determined and compared to a selected threshold. If the PMLR is greater than the selected threshold, the current audio frame represents a voice signal. Otherwise, it represents silence.
Owner:NORTEL NETWORKS LTD
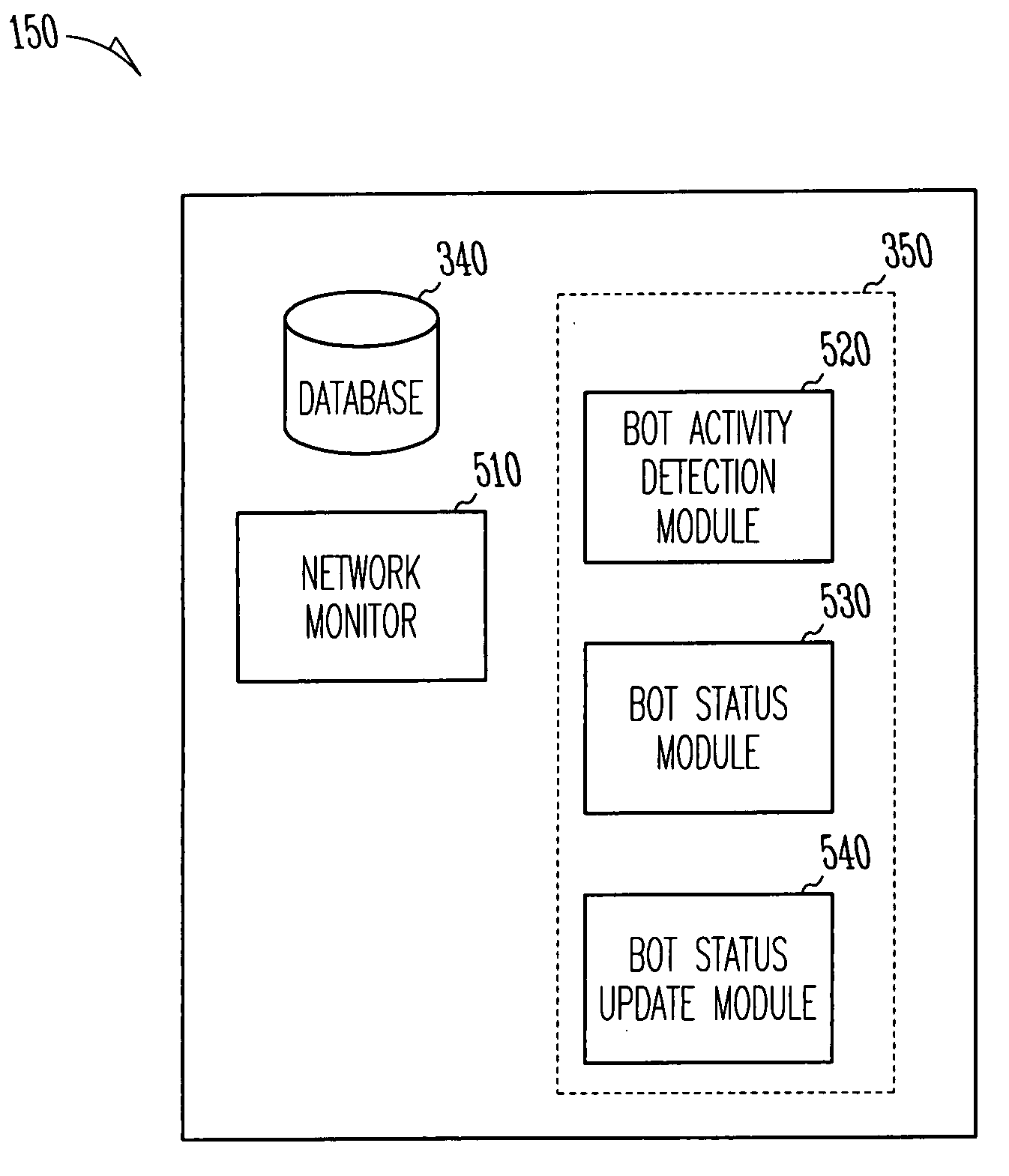
Method to perform botnet detection
A method and a system for monitoring network activities associated with a computer connected to a network are provided. The method may include detecting a bot activity associated with the computer; attributing a bot status to the computer, based on a bot activity type associated with the bot activity, prior detections of bot activities, and considering time stamps. The method may also include updating the bot status attributed to the computer, based upon detection of subsequent bot activities associated with the computer, the bot activity types associated with the subsequent bot activities, and one or more other criteria. In one example embodiment, the network activities may include network transmissions and behavioral patterns. According to example embodiments, the system may include a network monitor, a bot activity detection module, a bot status module, and a bot status update module.
Owner:SYMANTEC CORP
Wireless Connectivity in a Radar Detector
ActiveUS20100214149A1Wave based measurement systemsRoad vehicles traffic controlData connectionNetwork Communication Protocols
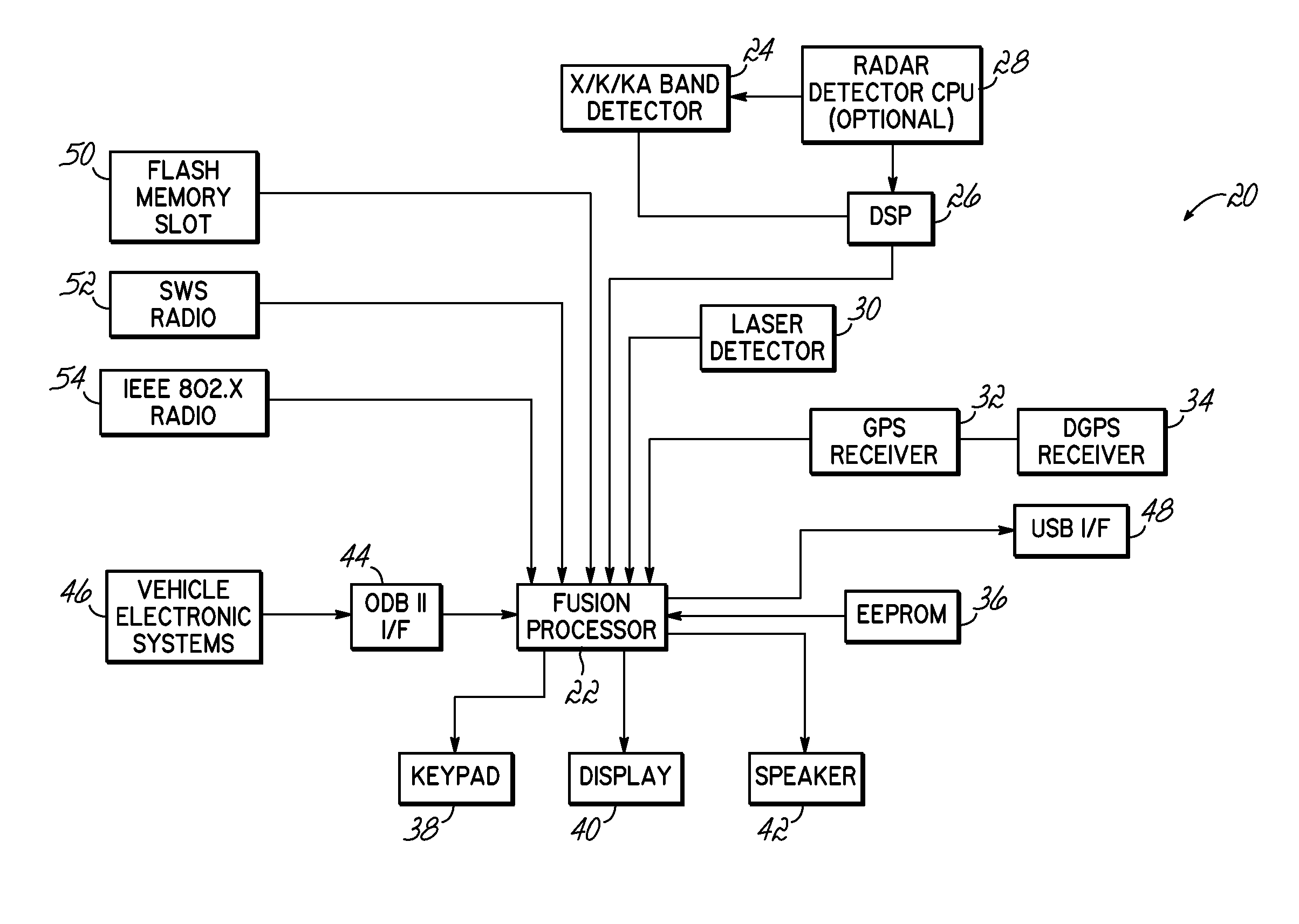
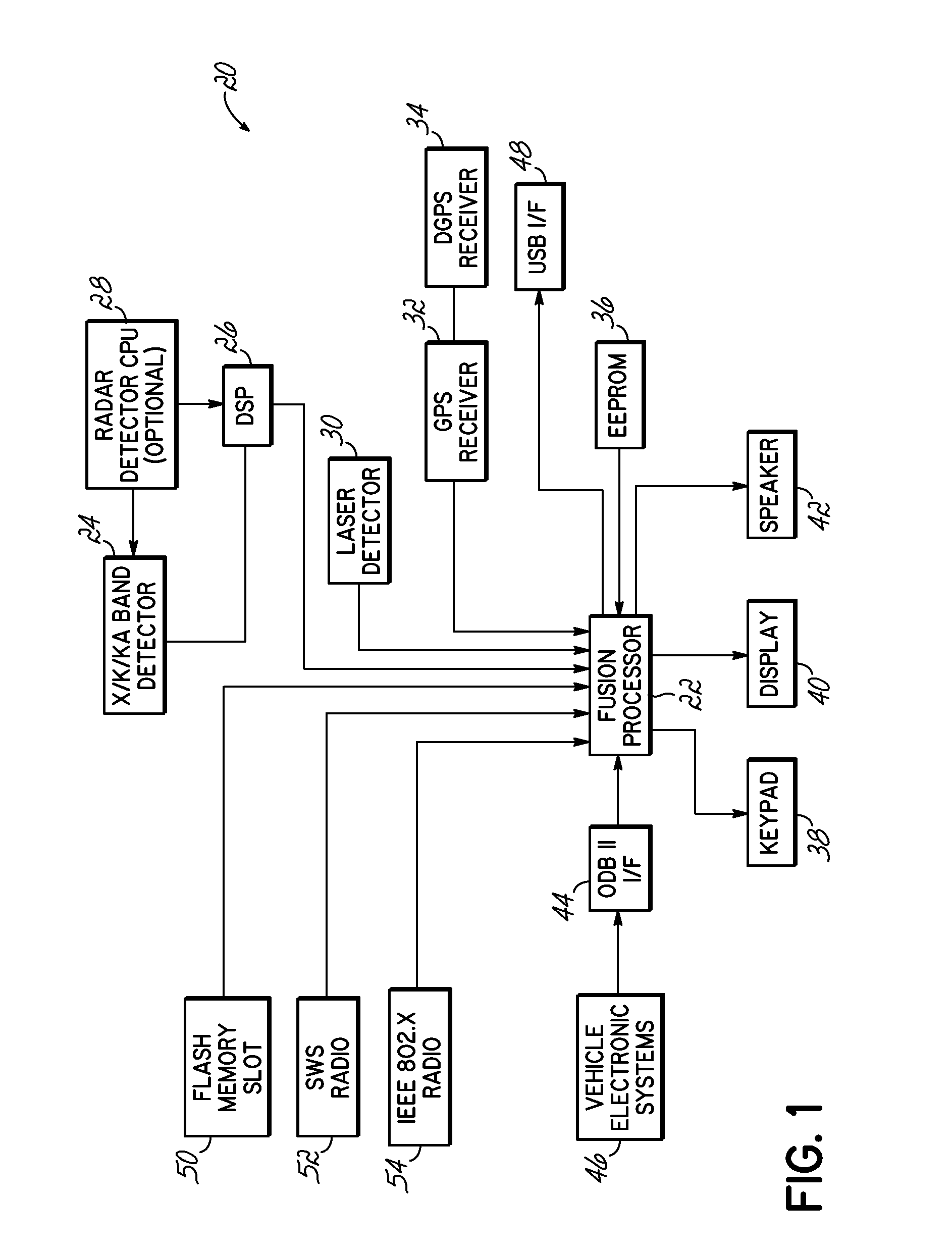
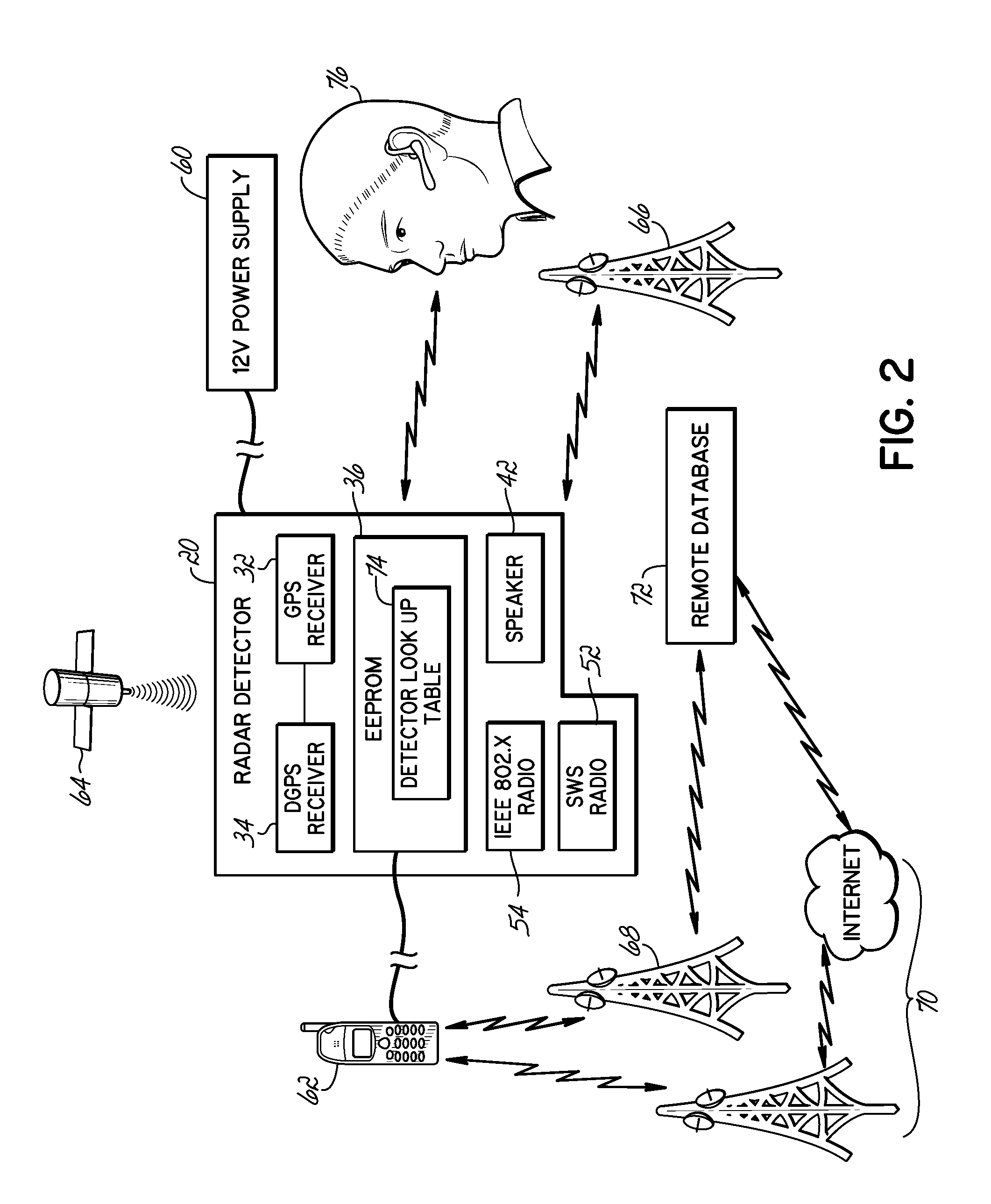
Wireless and other external connectivity technology is used in various ways to enhance or improve upon existing radar detector and police activity detection systems. External memory interfaces, such as SD cards or USB, provide external storage. Wireless interfaces such as Bluetooth, Zigbee, 802.11, and wireless personal area network communication protocols, allow a detector processor to interact wirelessly with external devices, such as a Bluetooth headset, a cellular network device providing a server connection, or toggle buttons used to indicate the presence of police activity at a current position. Further, radar detectors are upgraded to provide GPS capabilities, using the existing power / data connector of the radar detector.
Owner:ESCORT INC
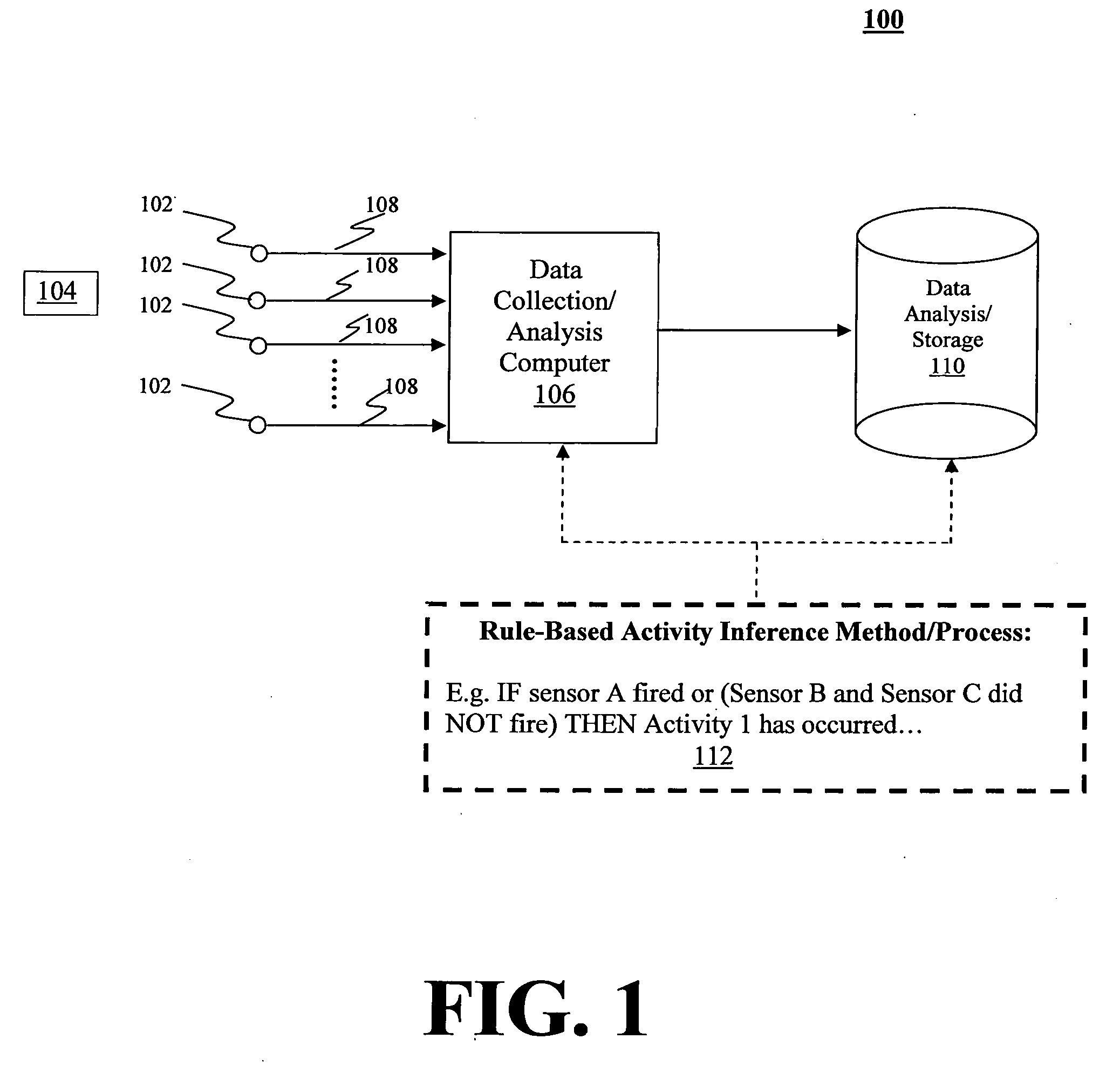
System and method for the inference of activities of daily living and instrumental activities of daily living automatically
InactiveUS20050234310A1Allow detectionPerson identificationTelemetric patient monitoringPersonalizationDisease
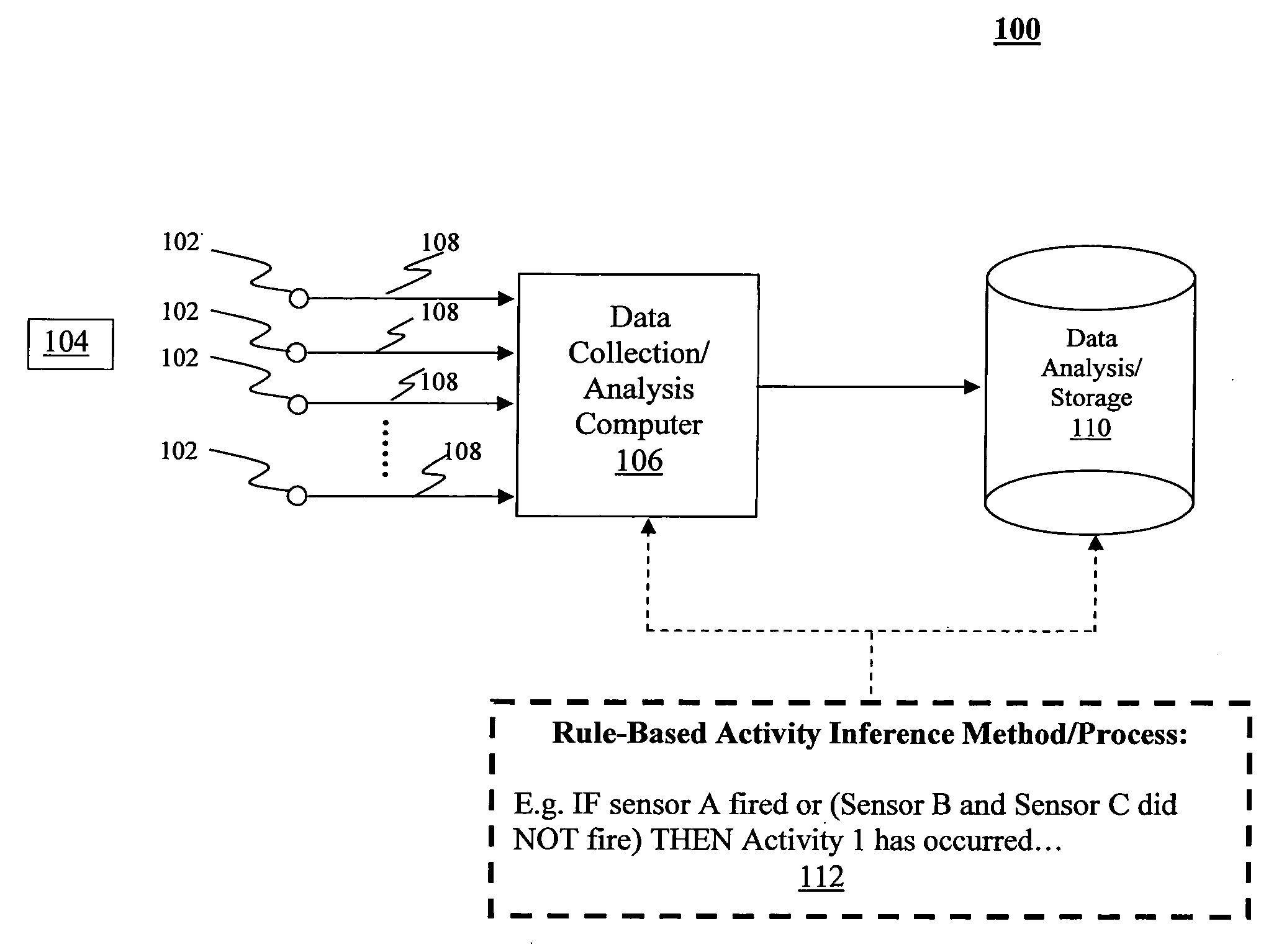
A method and related system to, among other things, automatically infer answers to all of the ADL questions and the first four questions of the IADL in the home. The inference methods detect the relevant activities unobtrusively, continuously, accurately, objectively, quantifiably and without relying on the patient's own memory (which may be fading due to aging or an existing health condition, such as Traumatic Brain Injury (TBI)) or on a caregiver's subjective report. The methods rely on the judicious placement of a number of sensors in the subject's place of residence, including motion detection sensors in every room, the decomposition of each relevant activity into the sub-tasks involved, identification of additional sensors required to detect the relevant sub-tasks and spatial-temporal conditions between the signals of sensors to formulate the rules that will detect the occurrence of the specific activities of interest. The sensory data logged on a computing device (computer, data logger etc.), date and time stamped, is analyzed using specialist data analysis software tools that check for the applicable task / activity detection rules. The methods are particularly useful for the continued in-home assessment of subjects living alone to evaluate their progress in response to medical intervention drug or physical therapy or decline in abilities that may be the indicator of the onset of disease over time. Measuring the frequency of each activity, the time required to accomplish an activity or a subtask and the number of activities / subtasks performed continuously over time can add extremely valuable quantification extensions to the existing ADL and IADL evaluation instruments, as it will not only reveal important information setting up a baseline for activity levels for each activity, but will also easily allow the detection of any drift from these personalized norms.
Owner:UNIV OF VIRGINIA ALUMNI PATENTS FOUND
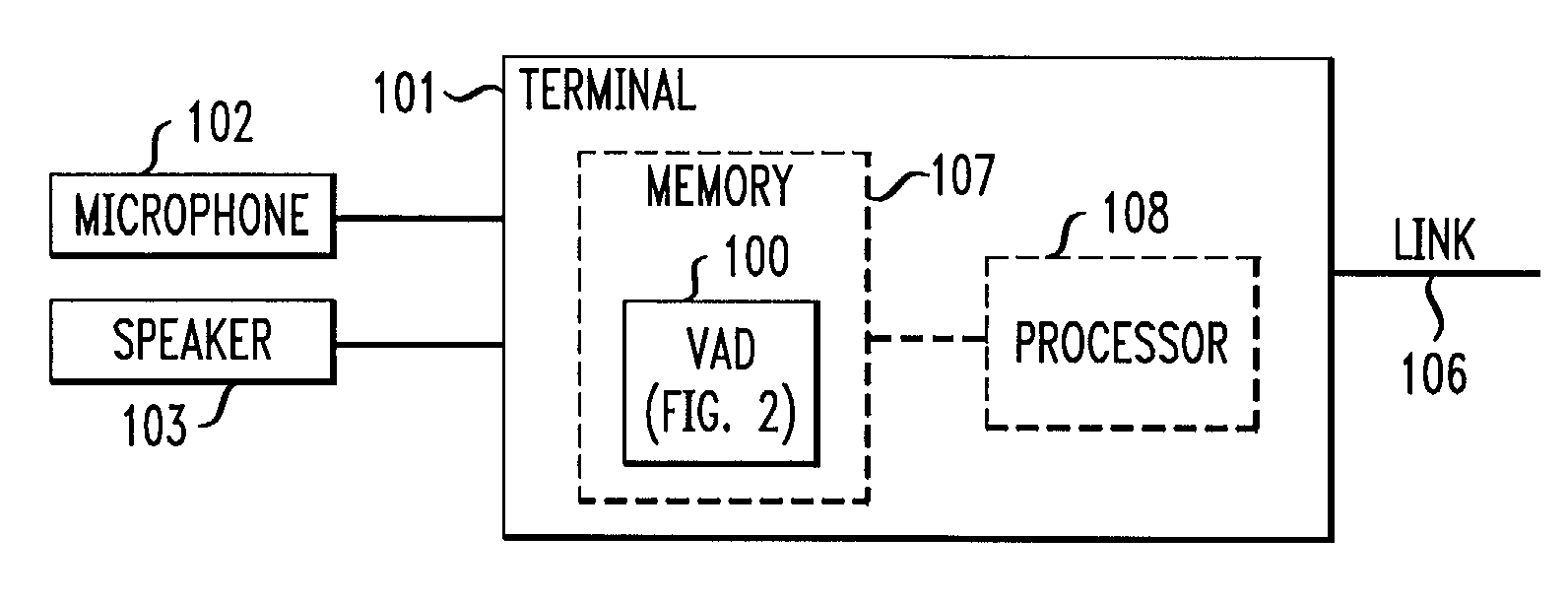
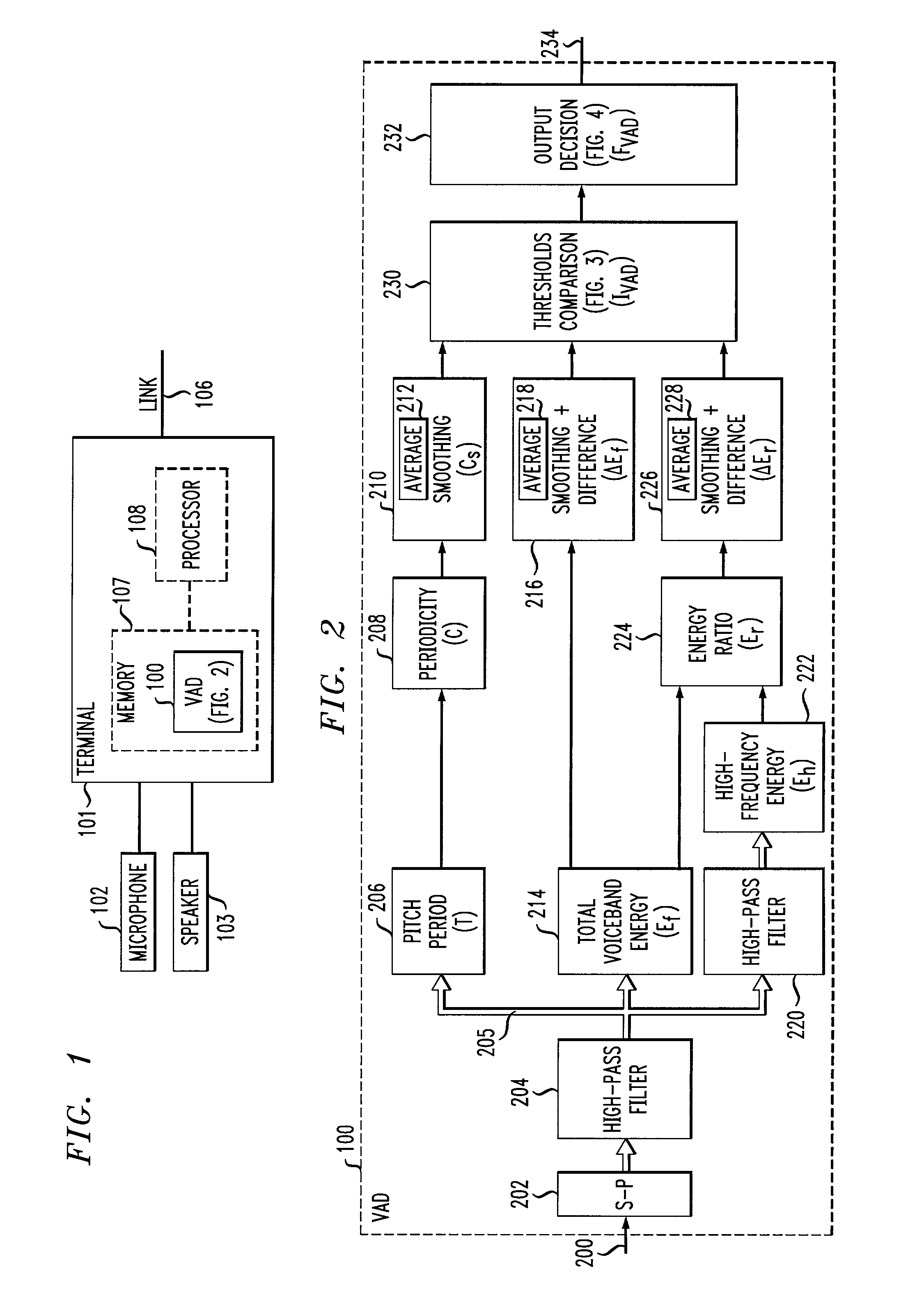
Voice-activity detection using energy ratios and periodicity
A voice activity detector (100) filters (204) out noise energy and then computes a high-frequency (2400 Hz to 4000 Hz) versus low-frequency (100 Hz to 2400 Hz) signal energy ratio (224), total voiceband (100 Hz to 4000 Hz) signal energy (214), and signal periodicity (208) on successive frames of signal samples. Signal periodicity is determined by estimating the pitch period (206) of the signal, determining a gain value of the signal over the pitch period as a function of the estimated pitch period, and estimating a periodicity of the signal over the pitch period as a function of the estimated pitch period and the gain value. Voice is detected (230–232) in a segment if either (a) the difference between the average high-frequency versus low-frequency signal energy ratio and the present segment's high-frequency versus low-frequency energy ratio either exceeds (310) a high threshold value or is exceeded (312) by a low threshold value, or (b) the average periodicity of the signal is lower (306) than a low threshold value, or (c) the difference between the average total signal energy and the present segment's total energy exceeds (304) a threshold value and the average periodicity of the signal is lower (304) than a high threshold value, or (d) the average total signal energy exceeds (412) a minimum average total signal energy by a threshold value and voice has been detected (410) in the preceding segment.
Owner:AVAYA INC
Method for targeted knockout of specific gene of Suqin yellow chicken embryonic stem cell
InactiveCN104805118ASimple methodGood repeatabilityVector-based foreign material introductionForeign genetic material cellsDual promoterExon
The invention discloses a method for targeted knockout of a specific gene of a Suqin yellow chicken embryonic stem cell. The method comprises the following steps: firstly, checking out an exon sequence of a gene, cloning the gene, sequencing to obtain a complete exon sequence, designing a CRISPR / Cas9 knockout target site on the sequence as gRNA, and constructing a CRISPR / Cas9 dual-promoter knockout vector; performing SSA activity detection on the constructed Cas9 vector, transfecting a control group with an empty vector, detecting a luciferase signal, and obtaining a result that the more the luciferase activity is increased relative to the control group, the higher the gRNA shearing activity is shown; transfecting the CRISPR / Cas9 vector which is high in SSA activity with ESCs, using flow cytometry to screen a GFP-positive cell, extracting genome DNA, and designing a primer.
Owner:YANGZHOU UNIV
Apparatus and method for decreasing power consumption in an integrated circuit
ActiveUS6976182B1Reduce overall static and dynamic power consumptionEnergy efficient ICTPower supply for data processingEngineeringEmbedded system
An integrated circuit may have separate power control for a number of different functional units. Ancillary to some of the functional units may be an activity detector and power control unit which monitors input to its functional unit to determine when the functional unit will be inactive. When an activity detector and power control unit determines that a particular functional unit is or will be inactive, it may disable power to its functional unit while the functional unit is inactive. When activity detector and power control unit determines that activity will resume for its functional unit, it enables power to its functional unit. Thus, the activity detector and power control unit for each such functional unit functions to control power to its respective functional unit so that during periods of inactivity, inactive functional units are powered down to reduce the overall static and / or dynamic power consumption for the integrated device.
Owner:ADVANCED SILICON TECH
Adaptive voice activity detection
ActiveUS20070265842A1Improve spectral efficiencyReduction in VAFSpeech recognitionSignal classificationVoice activity
Encoding audio signals with selecting an encoding mode for encoding the signal categorizing the signal into active segments having voice activity and non-active segments having substantially no voice activity by using categorization parameters depending on the selected encoding mode and encoding at least the active segments using the selected encoding mode.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com