Business method for secure installation of a credit authorization key on a remote tcpa compliant system
a credit authorization key and remote installation technology, applied in the field of data processing systems, can solve the problems of stealing a large amount of credit cards and losing half of the monetary loss of credit card companies, and achieve the effect of reducing the amount of fraud and being easy to check
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
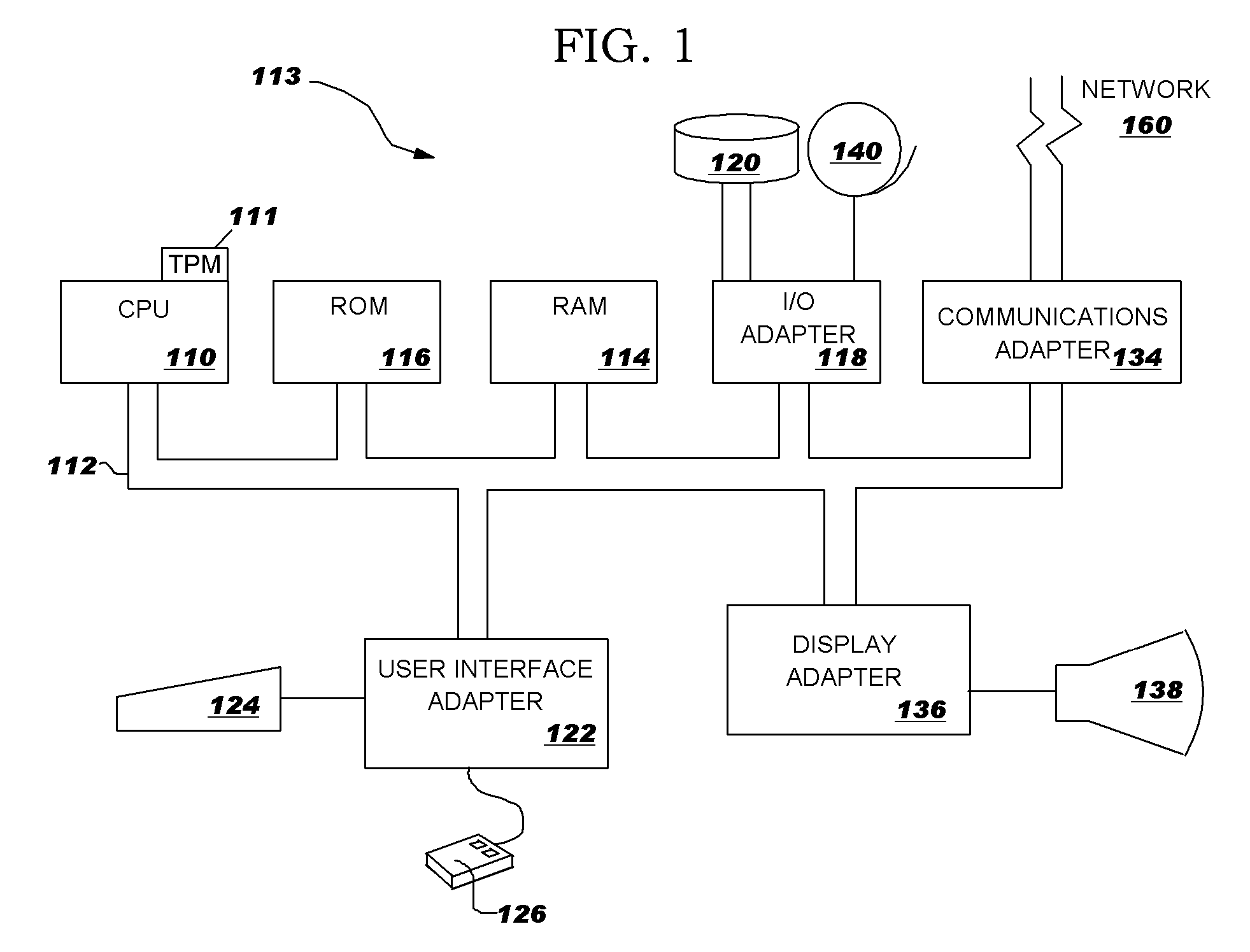
[0016] In the following description, numerous specific details are set forth such as encryption methods or key lengths, etc. to provide a thorough understanding of the present invention. However, it will be obvious to those skilled in the art that the present invention may be practicedwithout such specific details. In other instances, well-known circuits have been shown in blockdiagram form in order not to obscure the present invention in unnecessary detail. For the mostpart, details concerning timing considerations and the like have been omitted in as much as suchdetails are not necessary to obtain a complete understanding of the present invention and arewithin the skills of persons of ordinary skill in the relevant art.
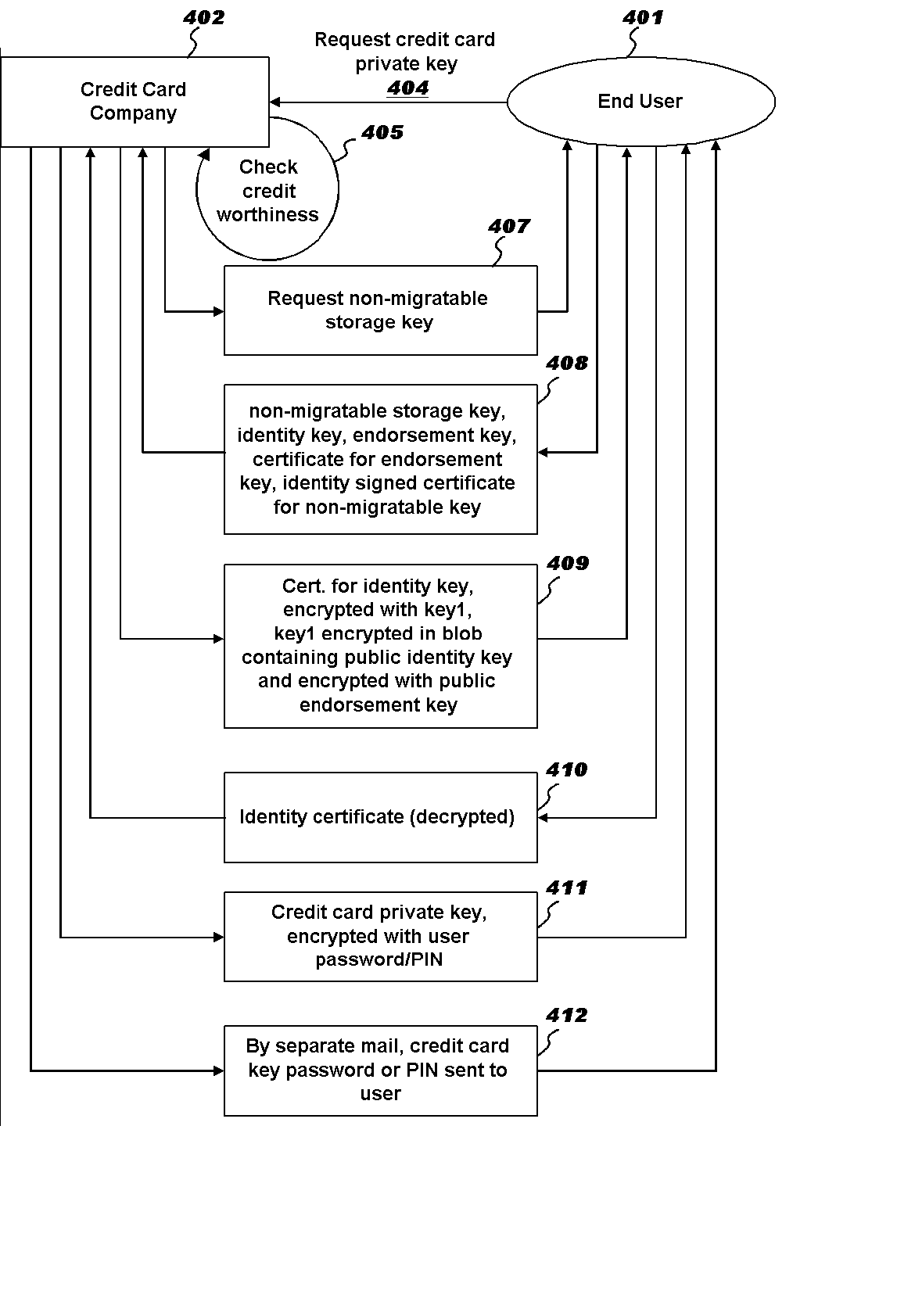
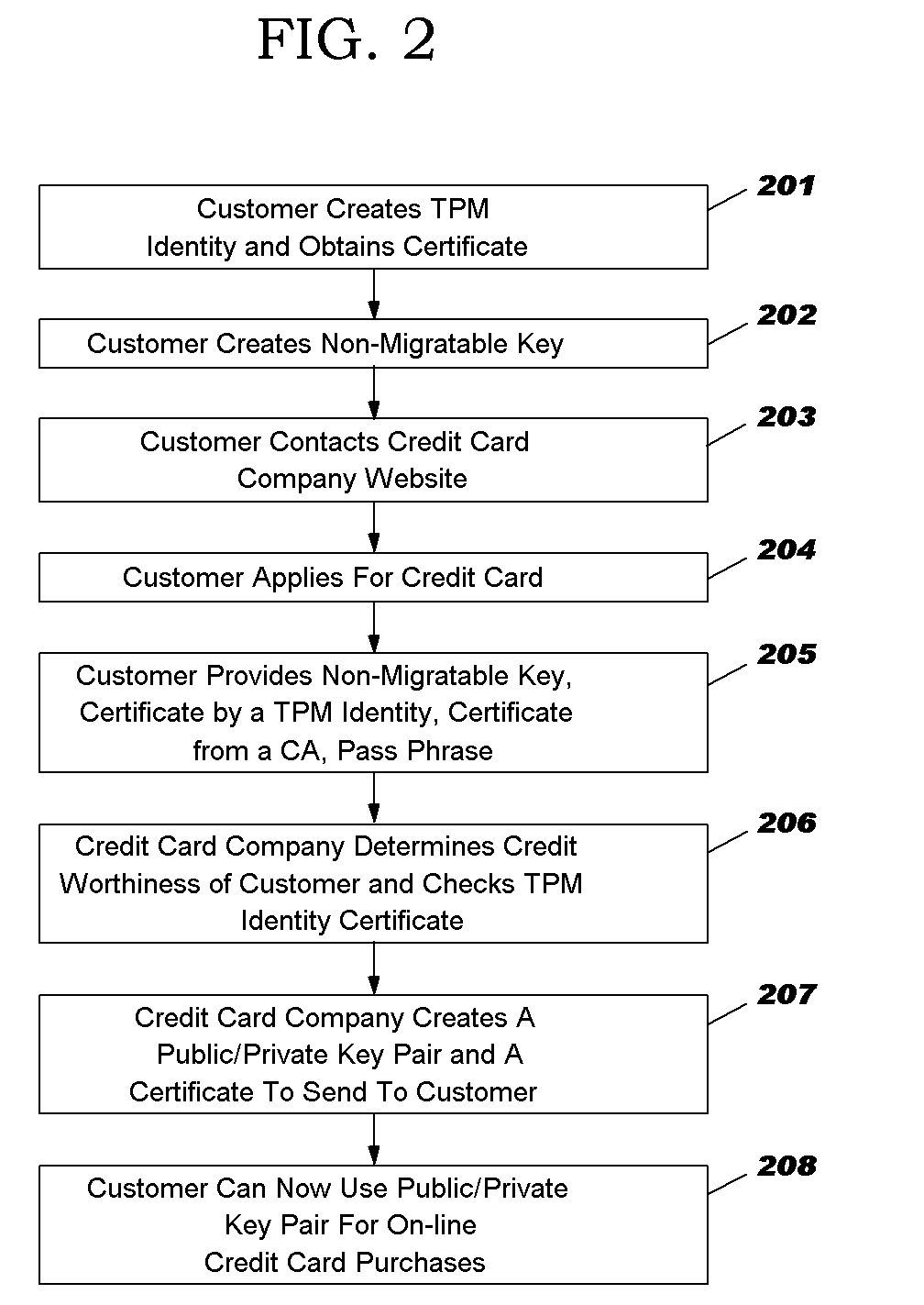
[0017] Referring to FIGURE 3, there is illustrated a configuration of a network 300 in accordance with the present invention where a user (customer) computer 301 applies for a creditcard authorization from a credit card company server 302 over the Internet 303.
[0018...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com