Patents
Literature
63results about How to "Information leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
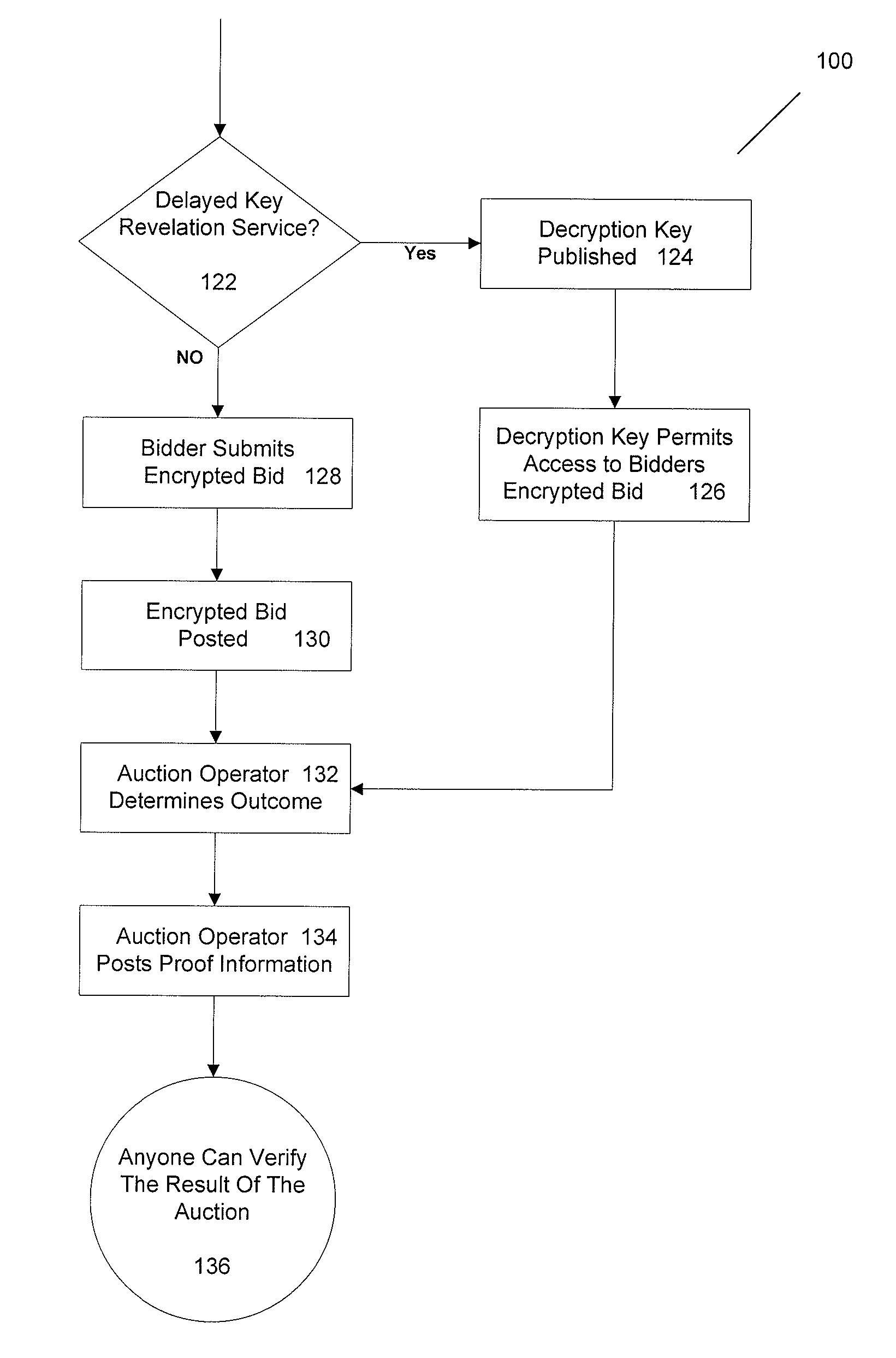
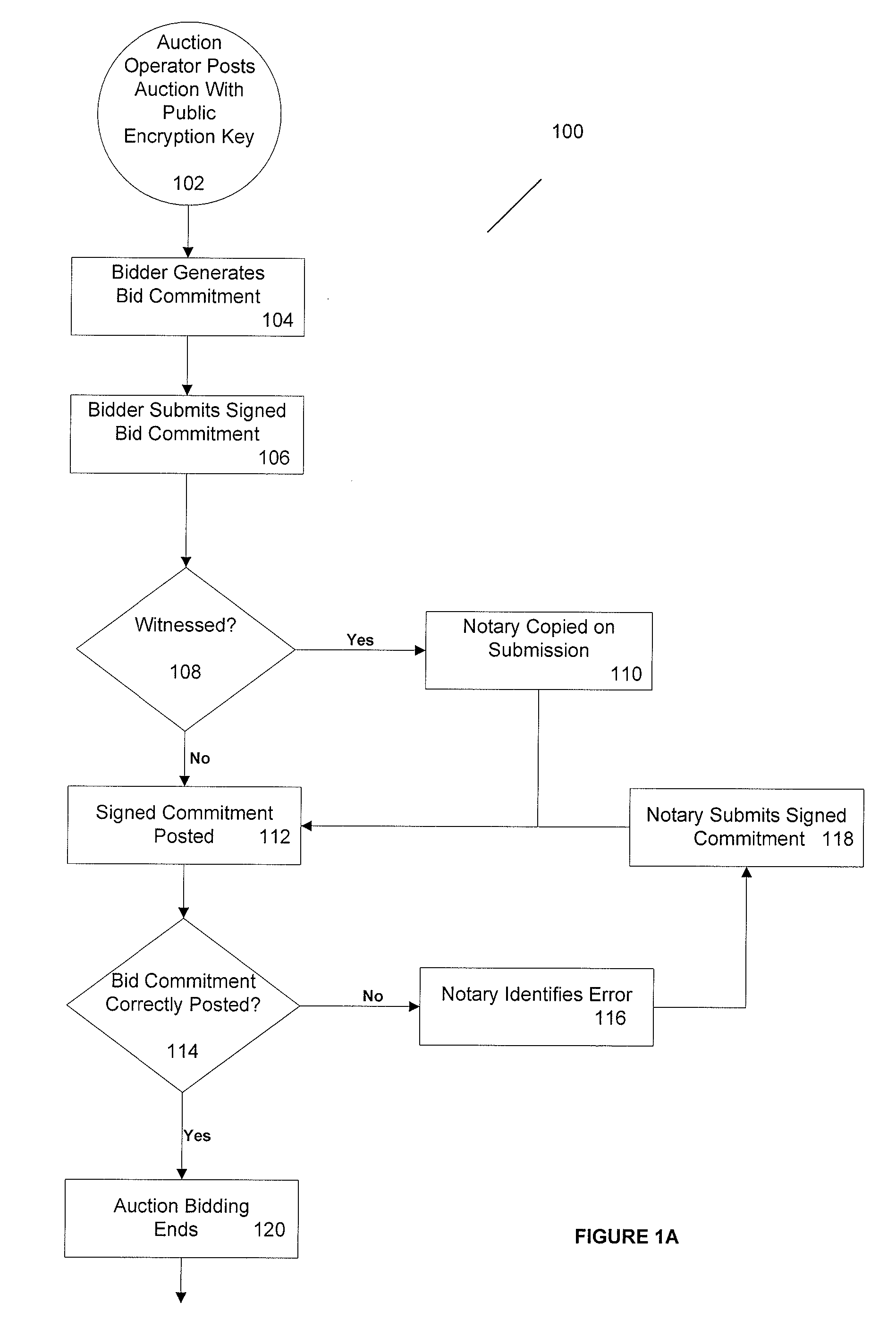
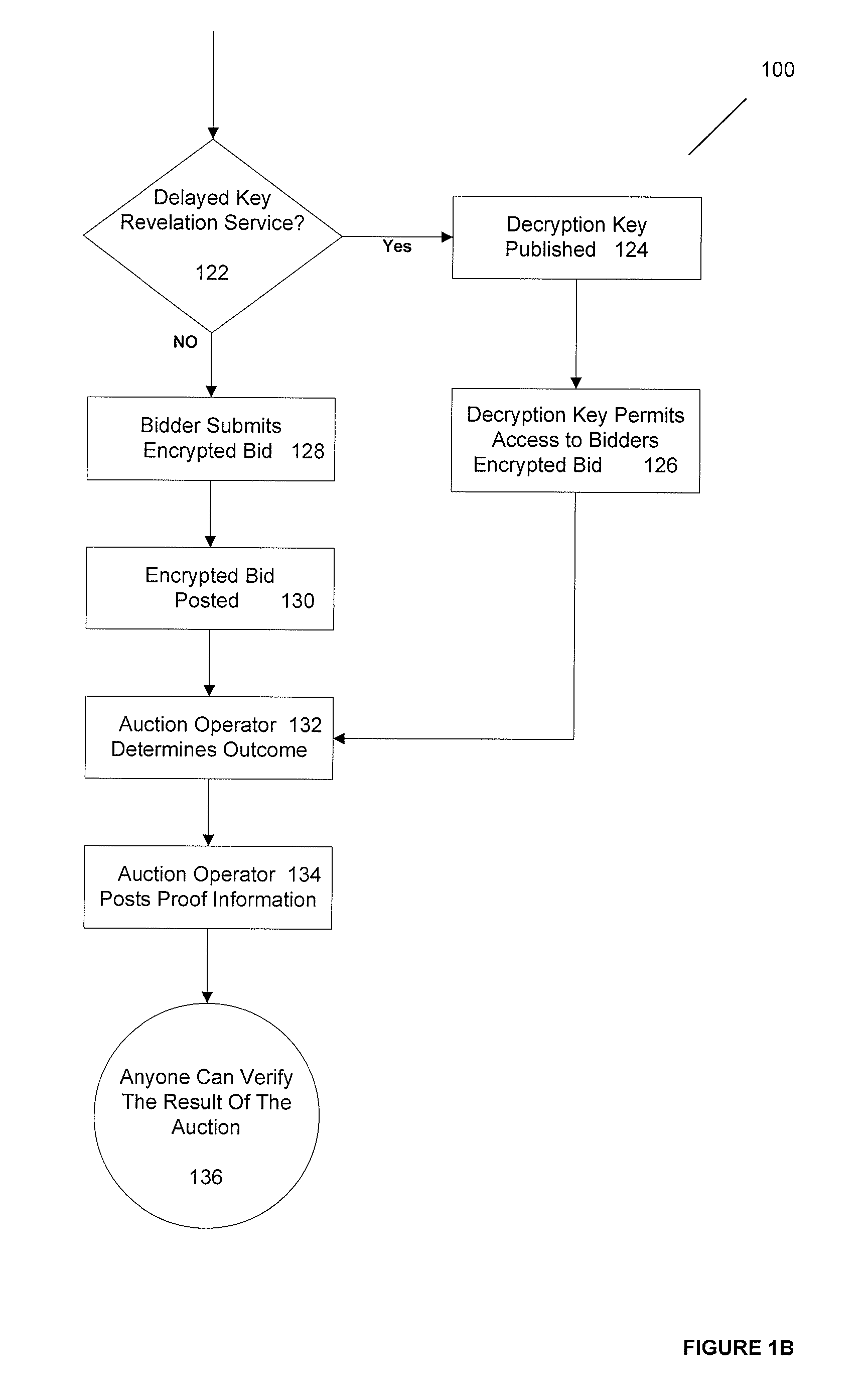
Practical secrecy-preserving, verifiably correct and trustworthy auctions
ActiveUS20090182667A1Ensure safetyImprove simplicityMultiple keys/algorithms usageUser identity/authority verificationCorrectness proofsTheoretical computer science
A system and method for conducting verifiably correct auctions that preserves the secrecy of the bids while providing for verifiable correctness and trustworthiness of the auction is disclosed. Some of the elements of the method and apparatus are that the auction operator accepts all bids submitted and follows the published rules of the auction. In one embodiment, the bids are maintained secret from the auctioneer and all bidders until the auction closes and no bidder is able to change or repudiate her bid. In another embodiment, the auction operator computes the auction results and publishes proofs of the results' correctness. In yet another embodiment, any party can check these proofs of correctness via publicly verifiable computations on encrypted bids.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE
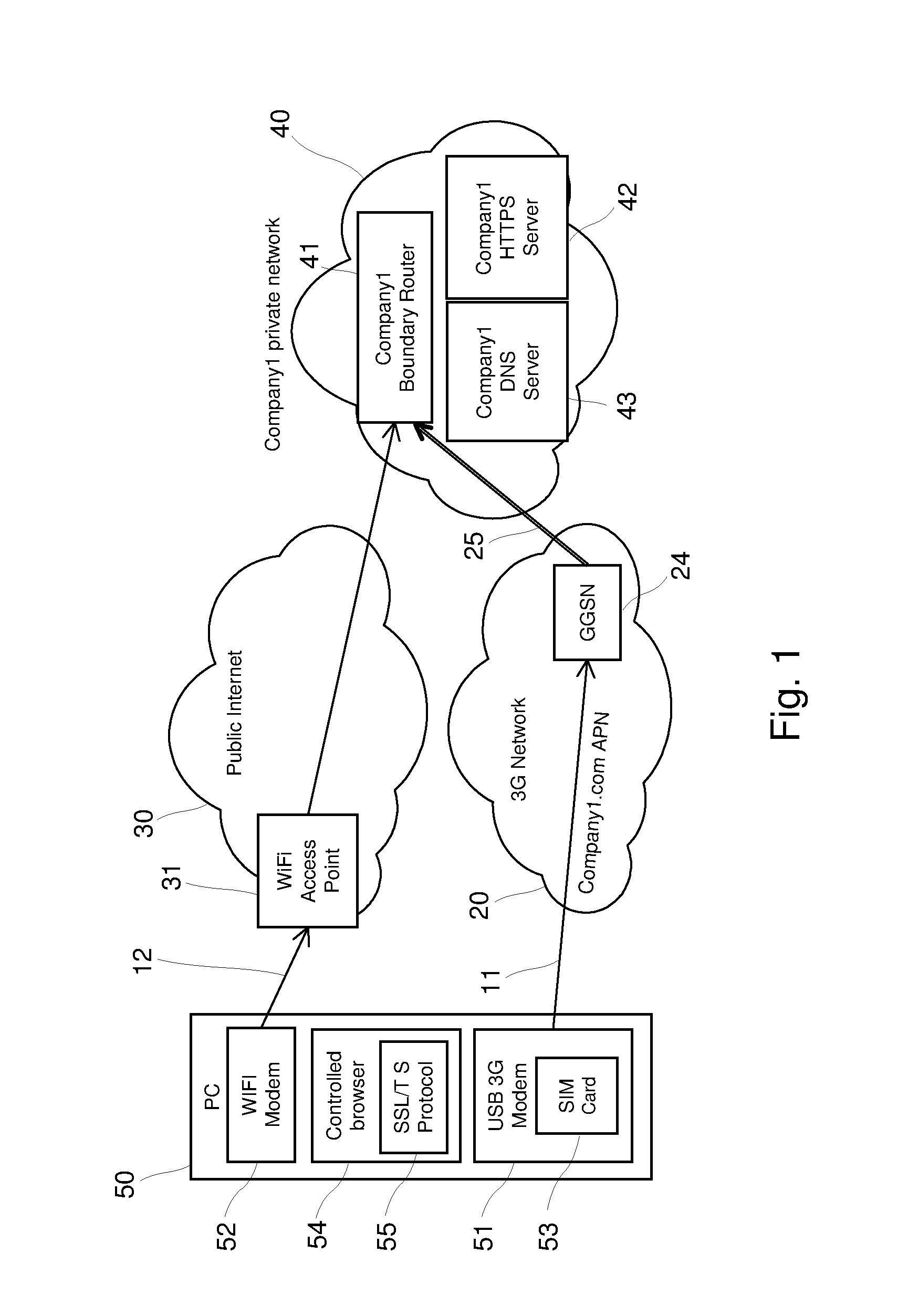
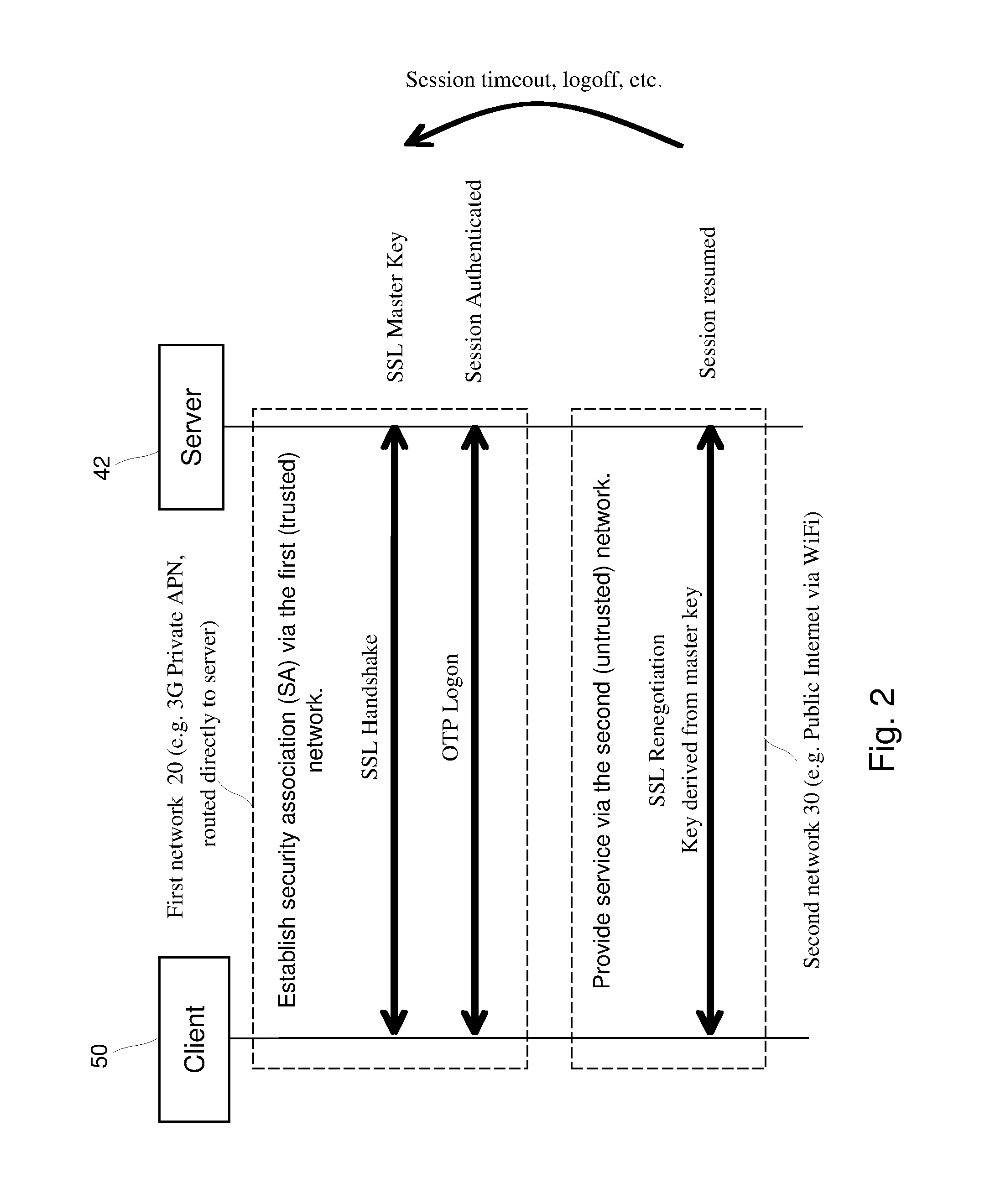
Establishing a communication session
InactiveUS20140289826A1Information leakageImprove trustDigital data processing detailsMultiple digital computer combinationsSecure communicationShared secret
A secure communication session is established between a first endpoint and a second endpoint. The first endpoint can contact the second endpoint via a first communication network and via a second communication network. The first communication network is more trusted than the second communication network. The first endpoint determines that a secure communication session is required. A security association is established between the endpoints for the communication session on a connection via the first communication network. Service is received on a connection via the second communication network using the previously established security association. The step of establishing a security association can comprise authenticating the second endpoint and negotiating a shared secret and the step of receiving service on a connection via the second communication network can occur without any further negotiation of key material or authentication between the endpoints via the second communication network.
Owner:OPTION NV
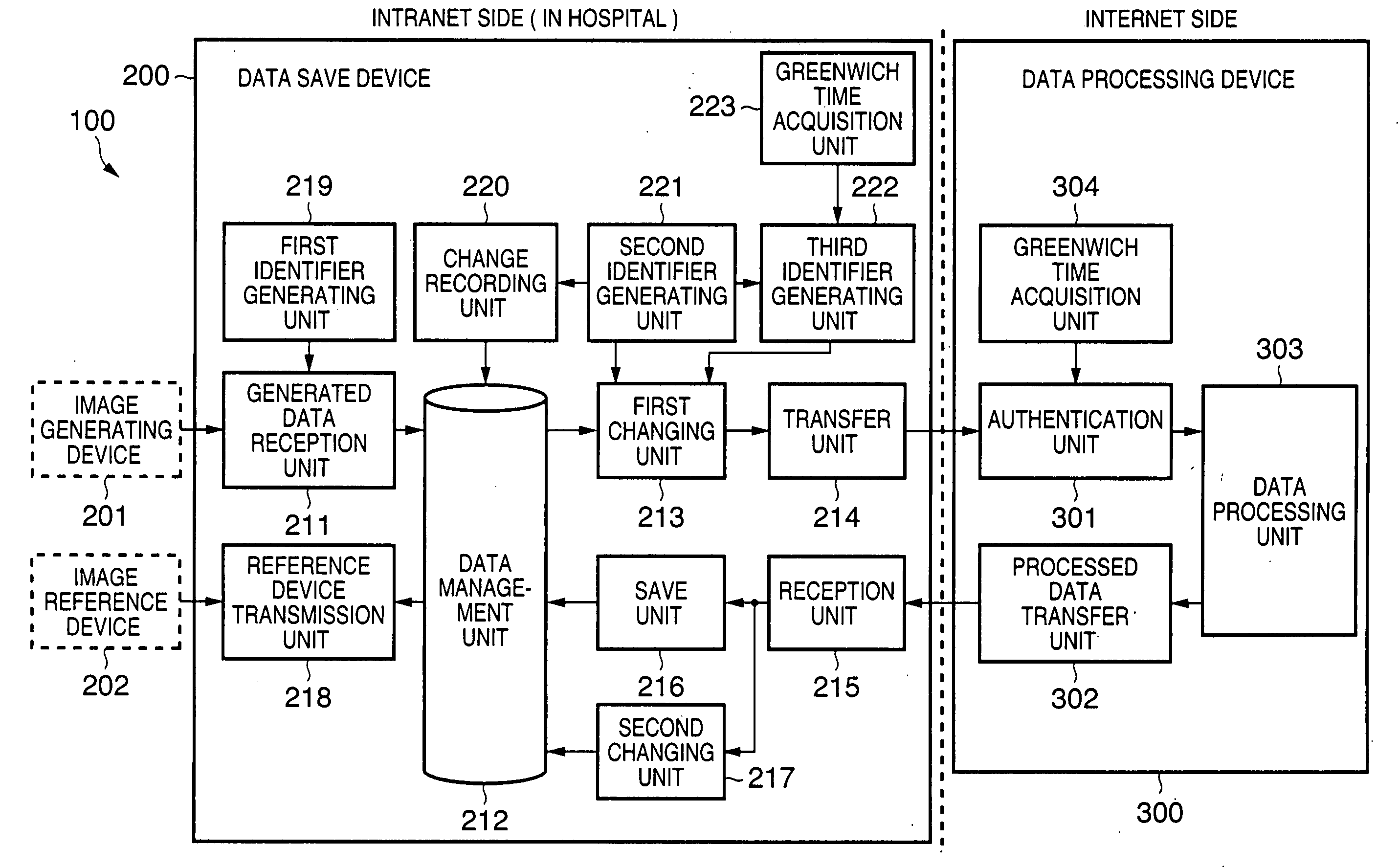
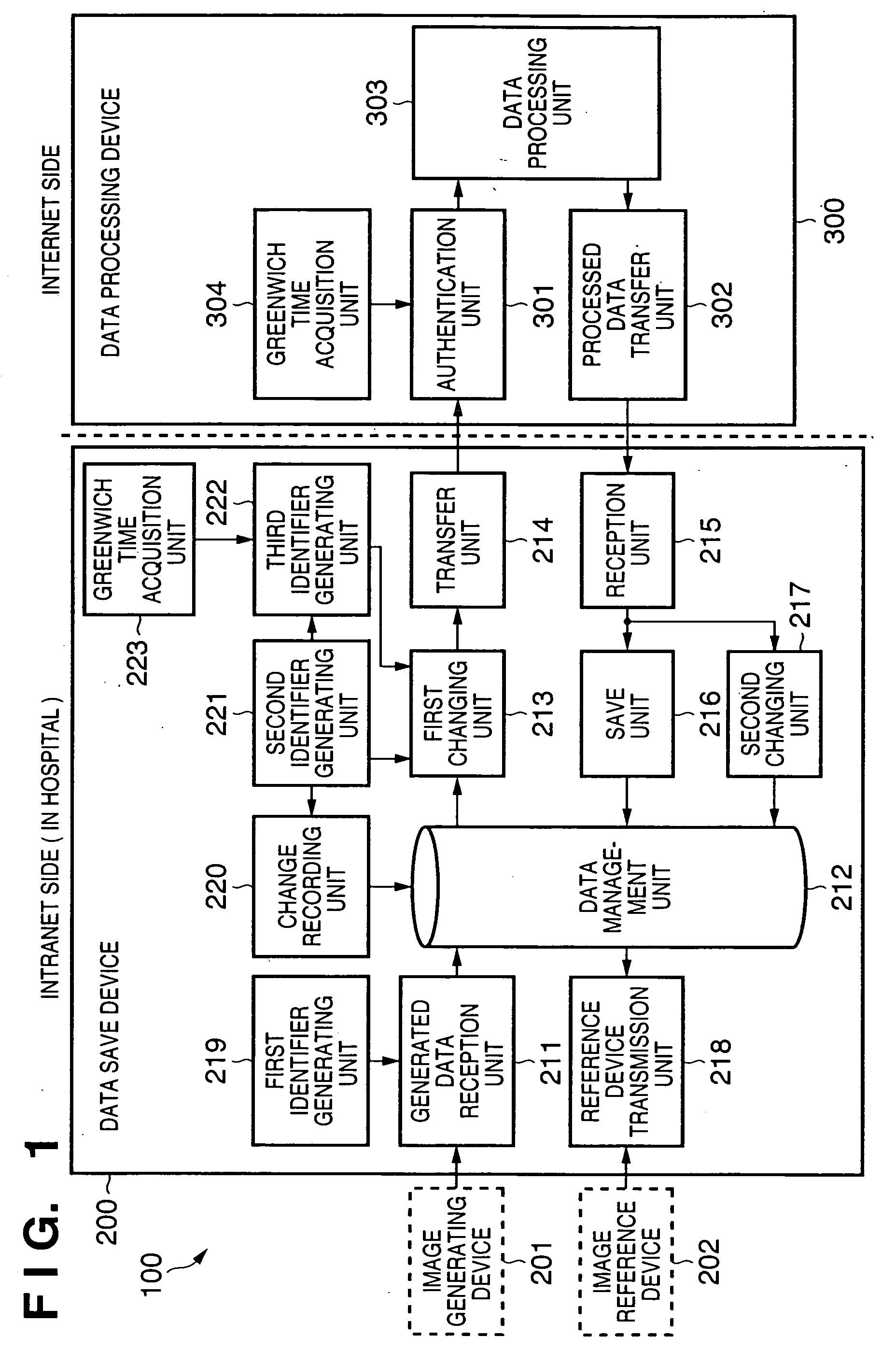
Information processing apparatus, information processing system, information processing method, storage medium, and program
InactiveUS20050086720A1Inhibition of informationProtect informationUltrasonic/sonic/infrasonic diagnosticsDigital data processing detailsInformation processingManagement unit
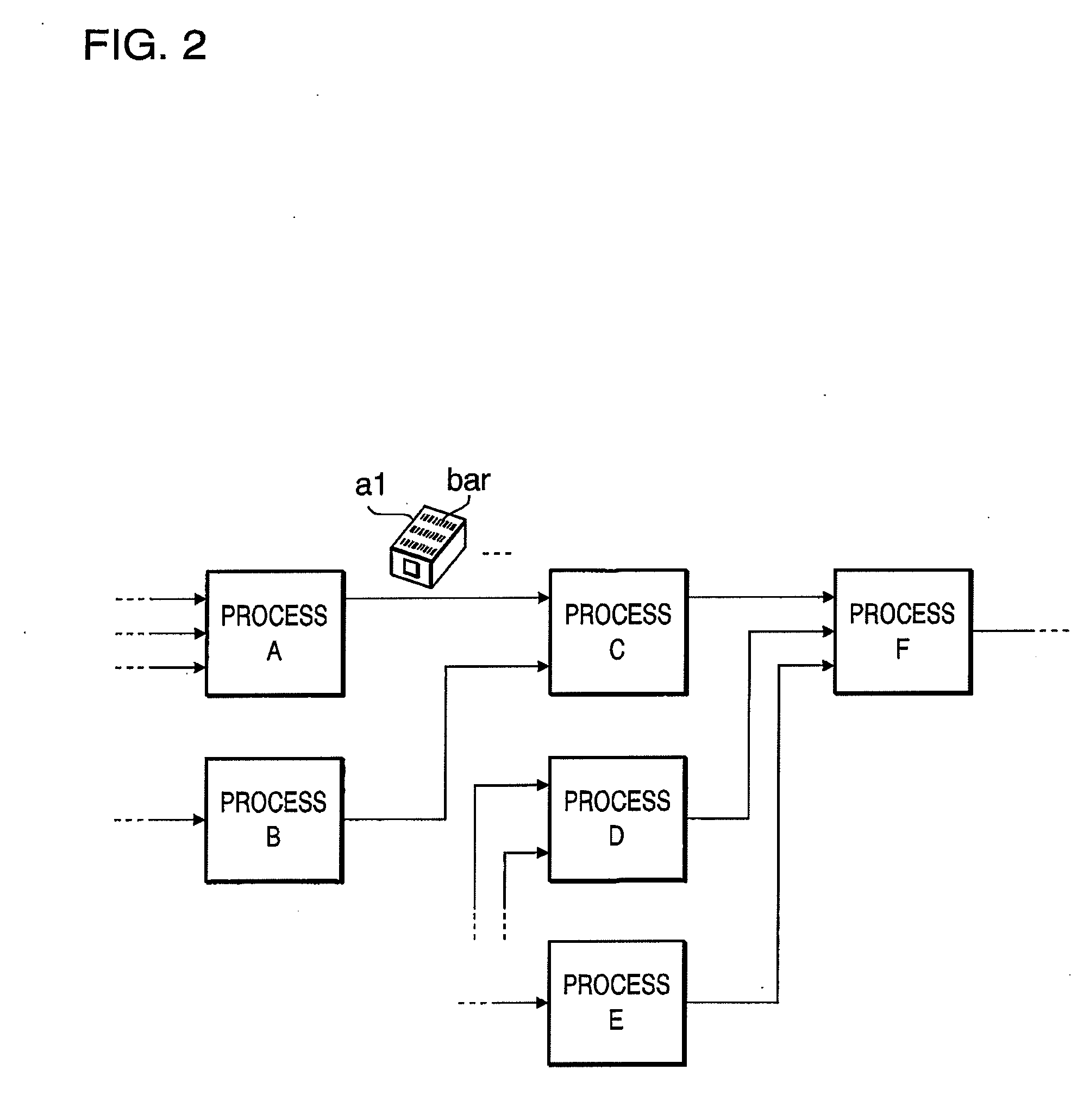
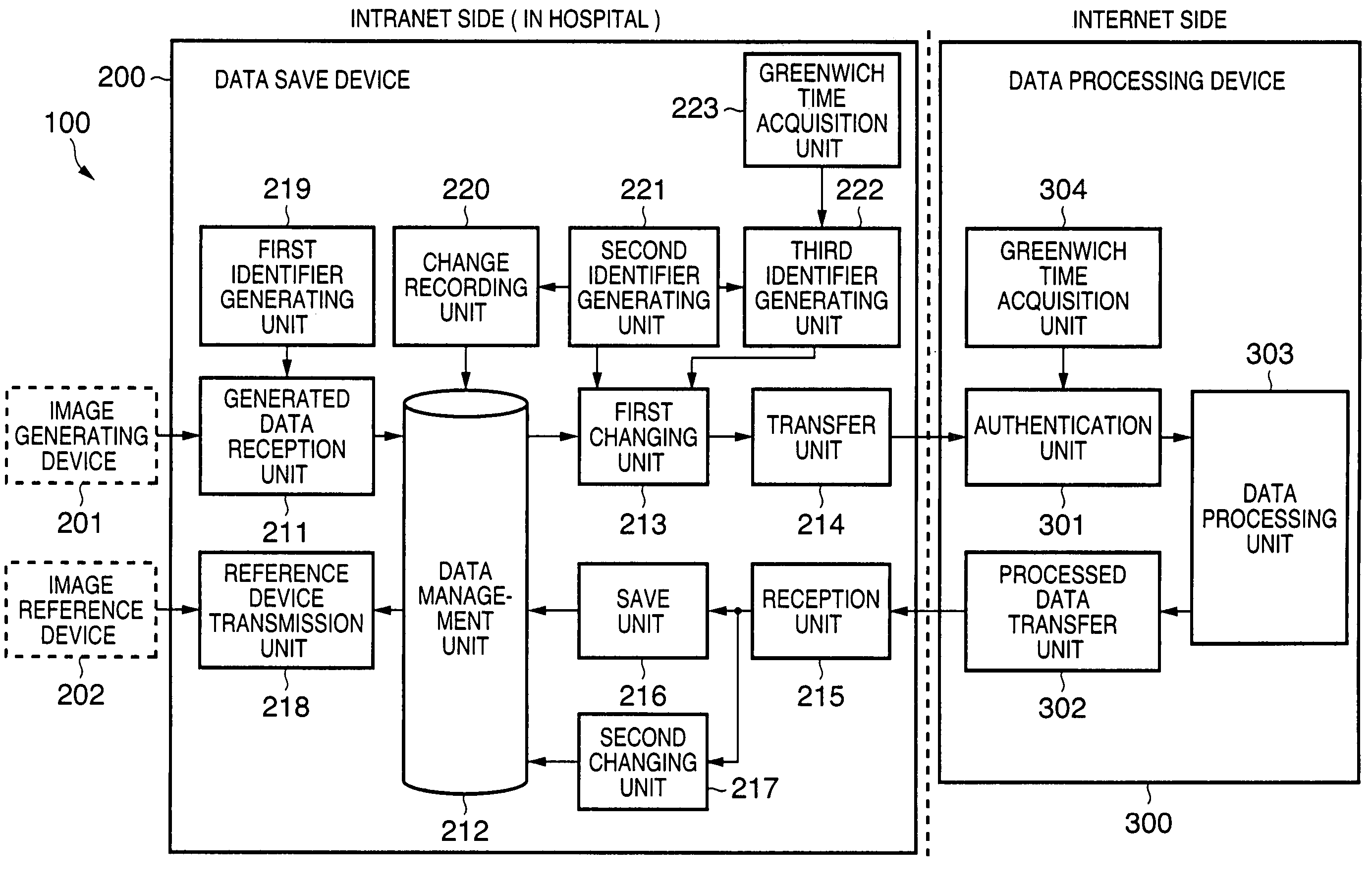
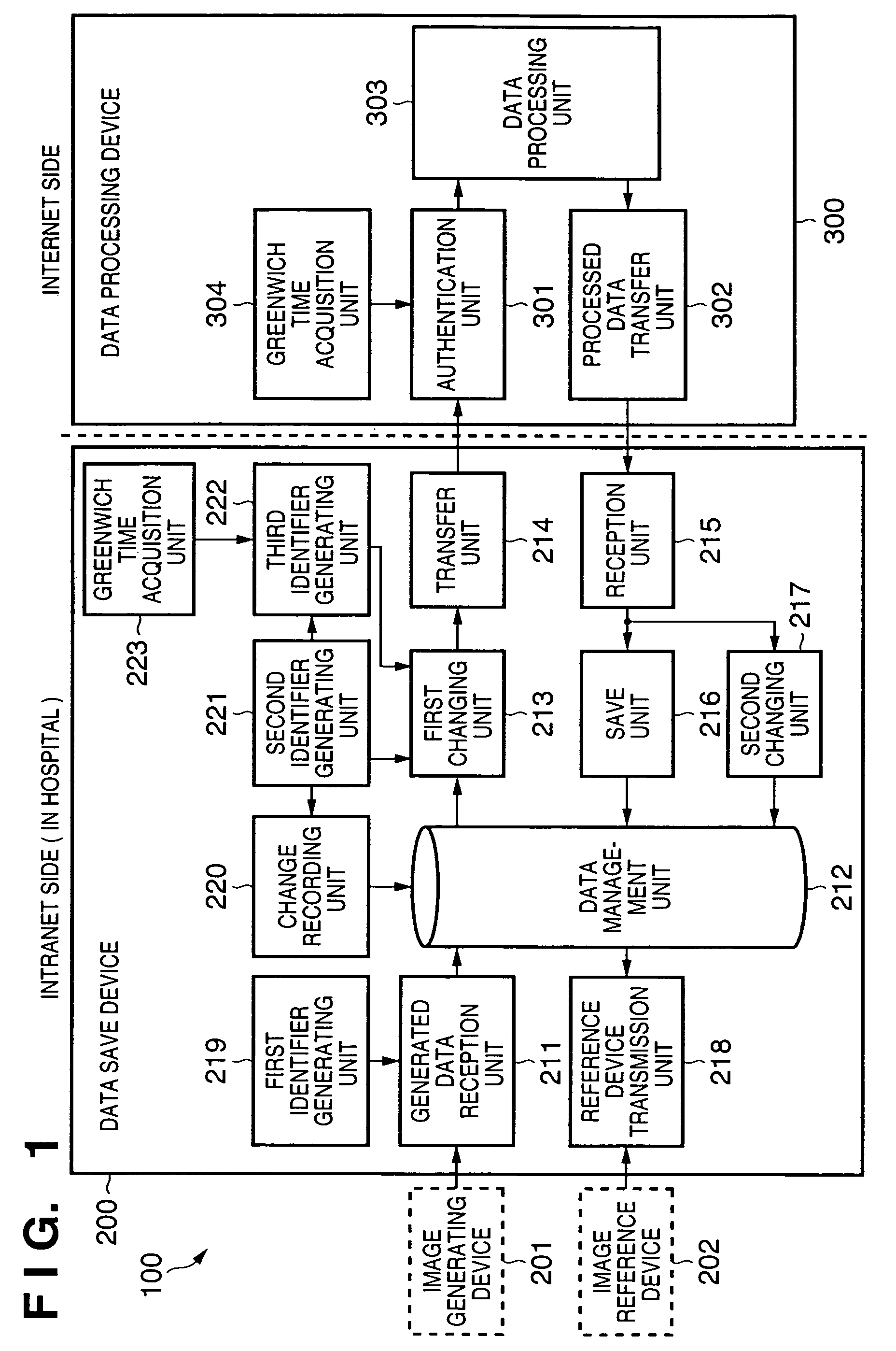
In an information processing apparatus which transfers target information to an external data processing device to process the information, and saves the processed information, a data management unit stores second identification information corresponding to the target information in association with the target information to which first identification information is attached. The first changing unit deletes the first identification information from the target information and adds the corresponding second identification information to the target information in the data management unit. The transfer unit transfers the target information processed by the first changing unit to the external data processing device.
Owner:CANON KK
Reduction of side-channel information by interacting crypto blocks
ActiveUS20100095133A1Reduce the ratioProtection attackEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionComputer hardwareControl unit
A cryptography device which reduces side channel information including a first computing block adapted to either encrypt or decrypt received first input data and to output the encrypted or decrypted first input data as first output data at a first data output, a second computing block adapted to either encrypt or decrypt received second input data and to output the encrypted or decrypted second input data as second output data at a second data output, and a control unit connected to the first and second computing blocks and adapted in a first operating condition on the one hand to partially or completely assign the first output data to the first computing block as the first input data and on the other hand to completely or partially assign the first output data to the second computing block as part of the second input data.
Owner:IHP GMBH INNOVATIONS FOR HIGH PERFORMANCE MICROELECTRONICS INST FUR INNOVATIVE MIKRELEKTRONIK
Storage device and storage method, and information-processing device and information-processing method
InactiveUS20080034223A1Reduction of informationInformation leakageUnauthorized memory use protectionHardware monitoringInformation processingComputer hardware
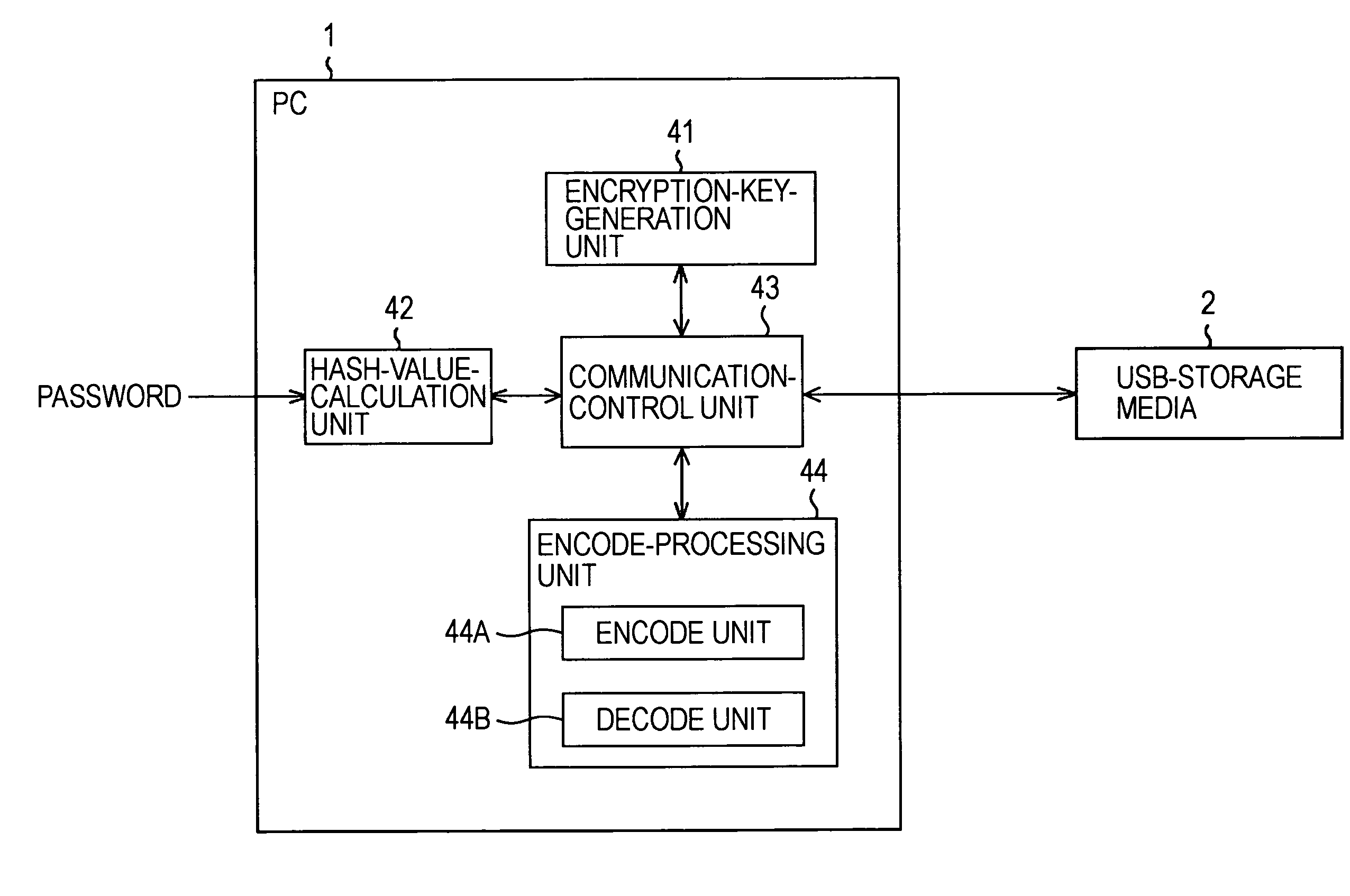
A storage device that can be attached and / or detached to and / or from an information-processing device is provided. The storage device includes a storage unit including a first area provided to store an encryption key used to encode first information and first authentication information used to perform authentication, and a second area storing second information encoded by the information-processing device by using the encryption key, an authentication unit configured to authenticate a user based on second authentication information generated by the information-processing device based on third information input by the user and the first authentication information, a transmission unit configured to transmit the encryption key to the information-processing device when validity of the user is confirmed through the authentication, and a control unit configured to have control over writing and / or reading the encoded second information into and / or from the second area.
Owner:SONY CORP
Facsimile machine
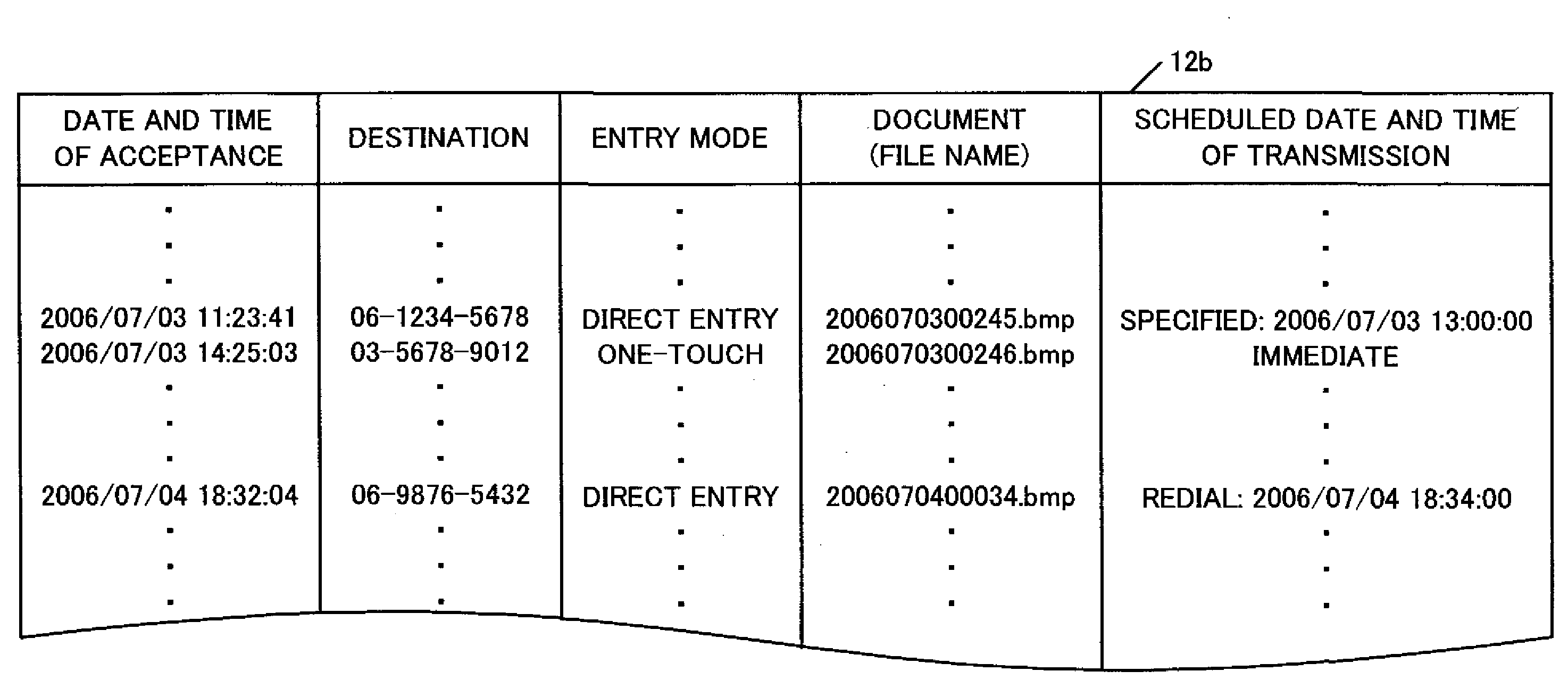
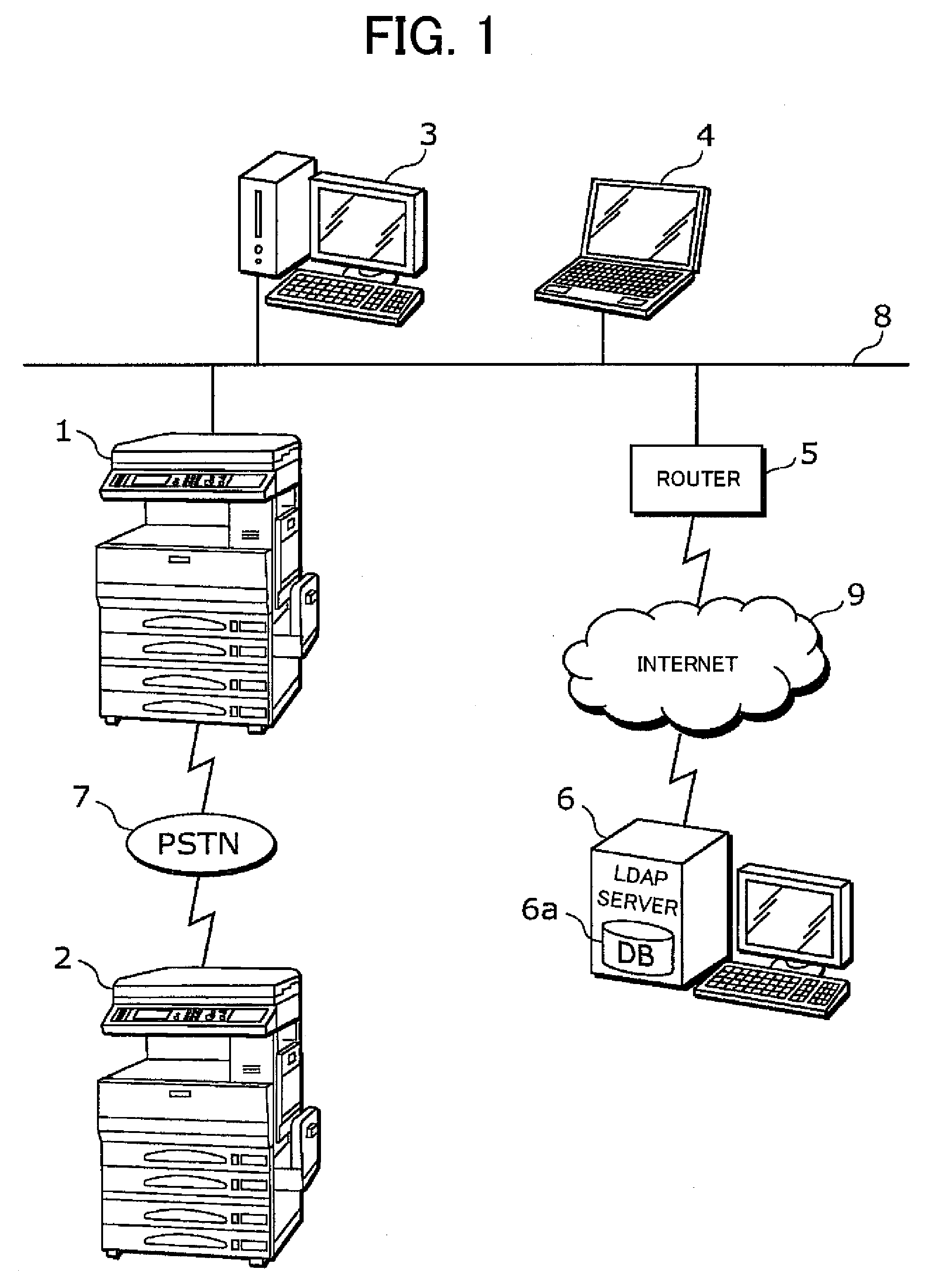
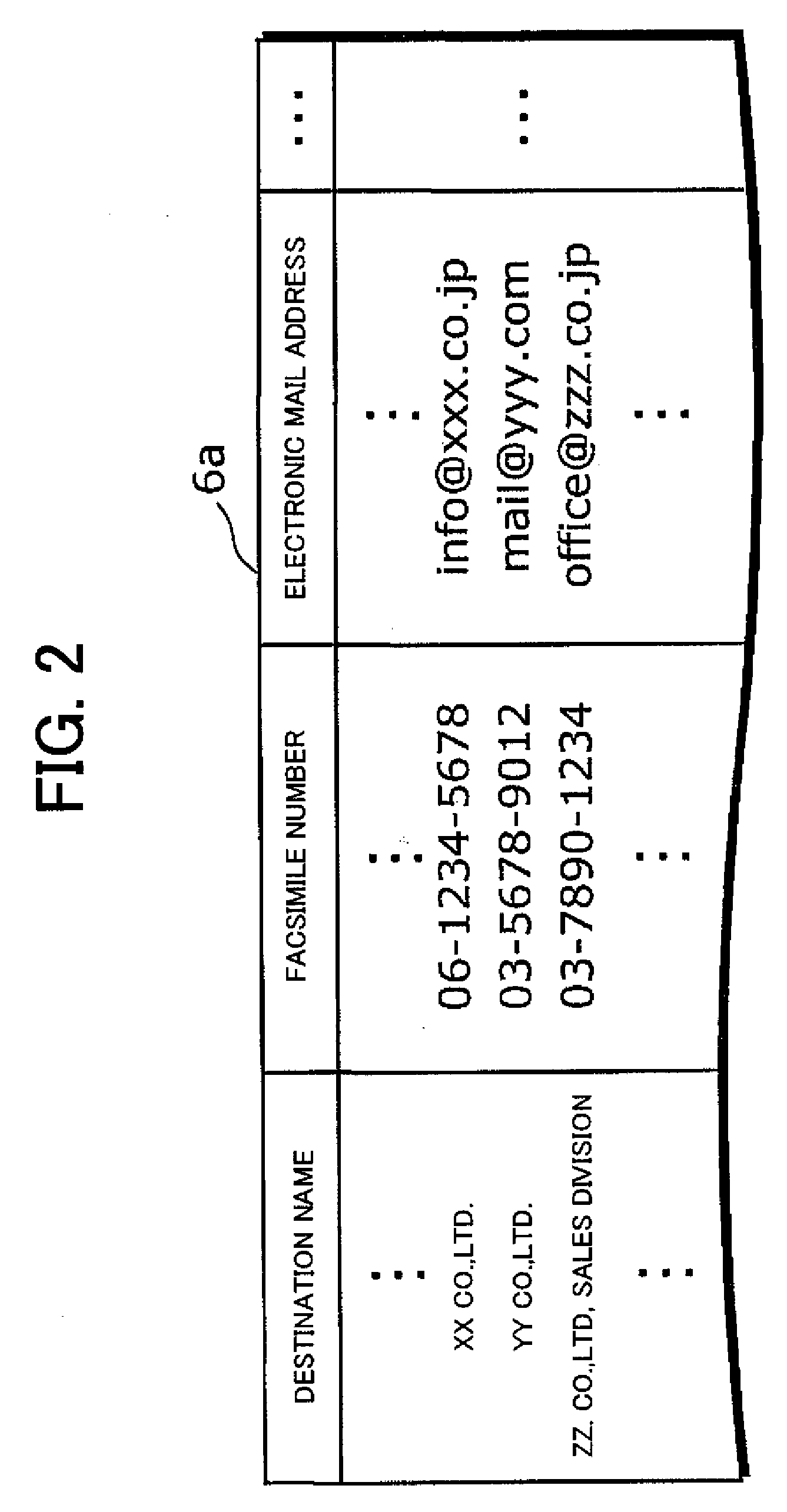
InactiveUS20080024833A1Information leakageHigh practical valuePictoral communicationFacsimile transmissionComputer science
A facsimile machine includes an entry unit, a searching unit, a transmitting unit and a control unit. The entry unit accepts a transmission instruction including a destination. The searching unit searches the destination information in a database held by an external database device with the destination as a search key. The transmitting unit executes the facsimile transmission. The control unit causes the searching unit to execute searching for the first time immediately after the acceptance of the transmission instruction by the entry unit and for the second time immediately before the facsimile transmission in the case in which the entry unit accepts the time-specified transmission instruction or immediately before the redialing facsimile transmission and, when it is found that the destination information including the search key exists in the database by the searches for the first time and the second time, causes the transmitting unit to execute the facsimile transmission for the corresponding destination.
Owner:MURATA MASCH LTD
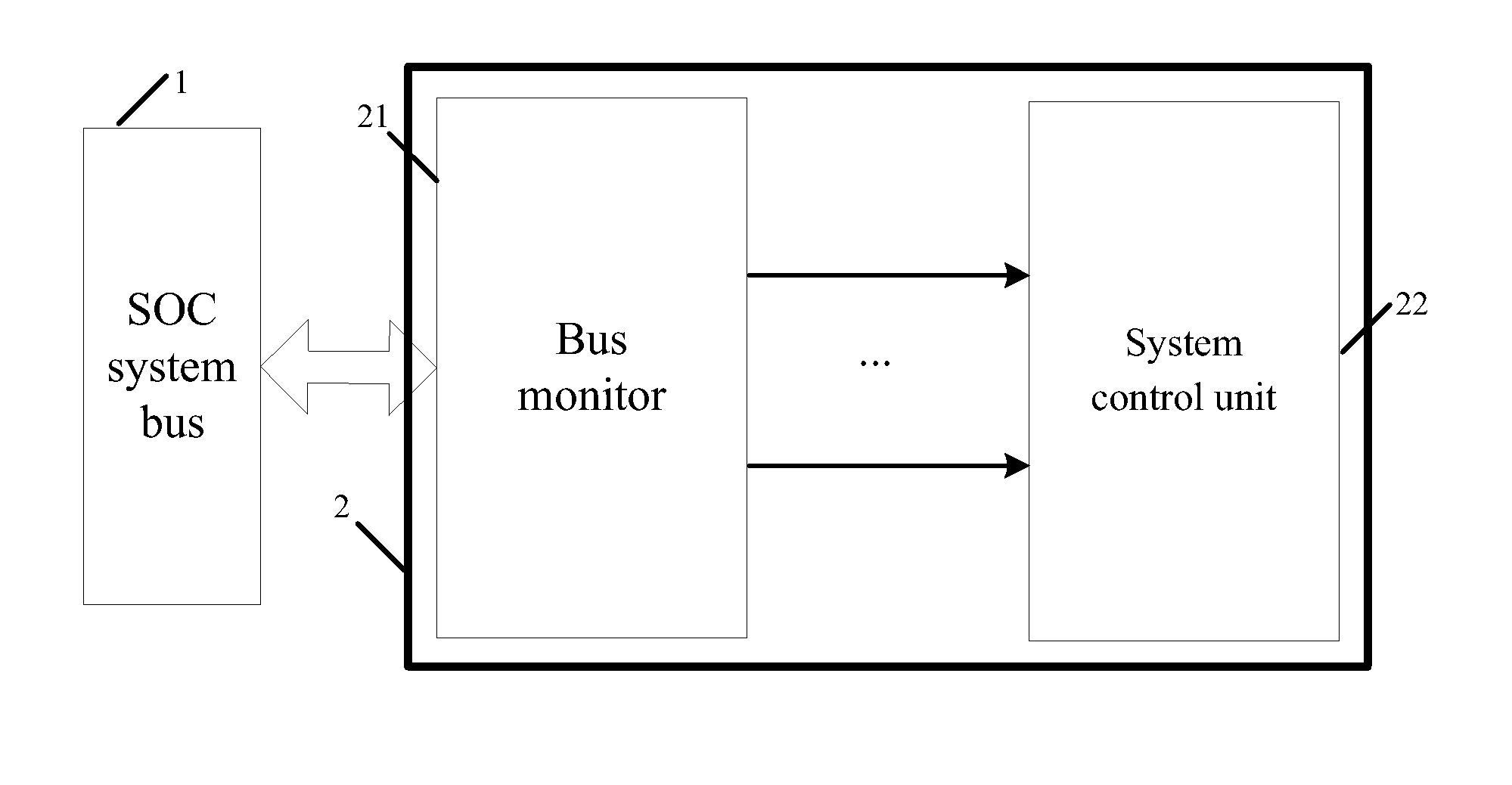
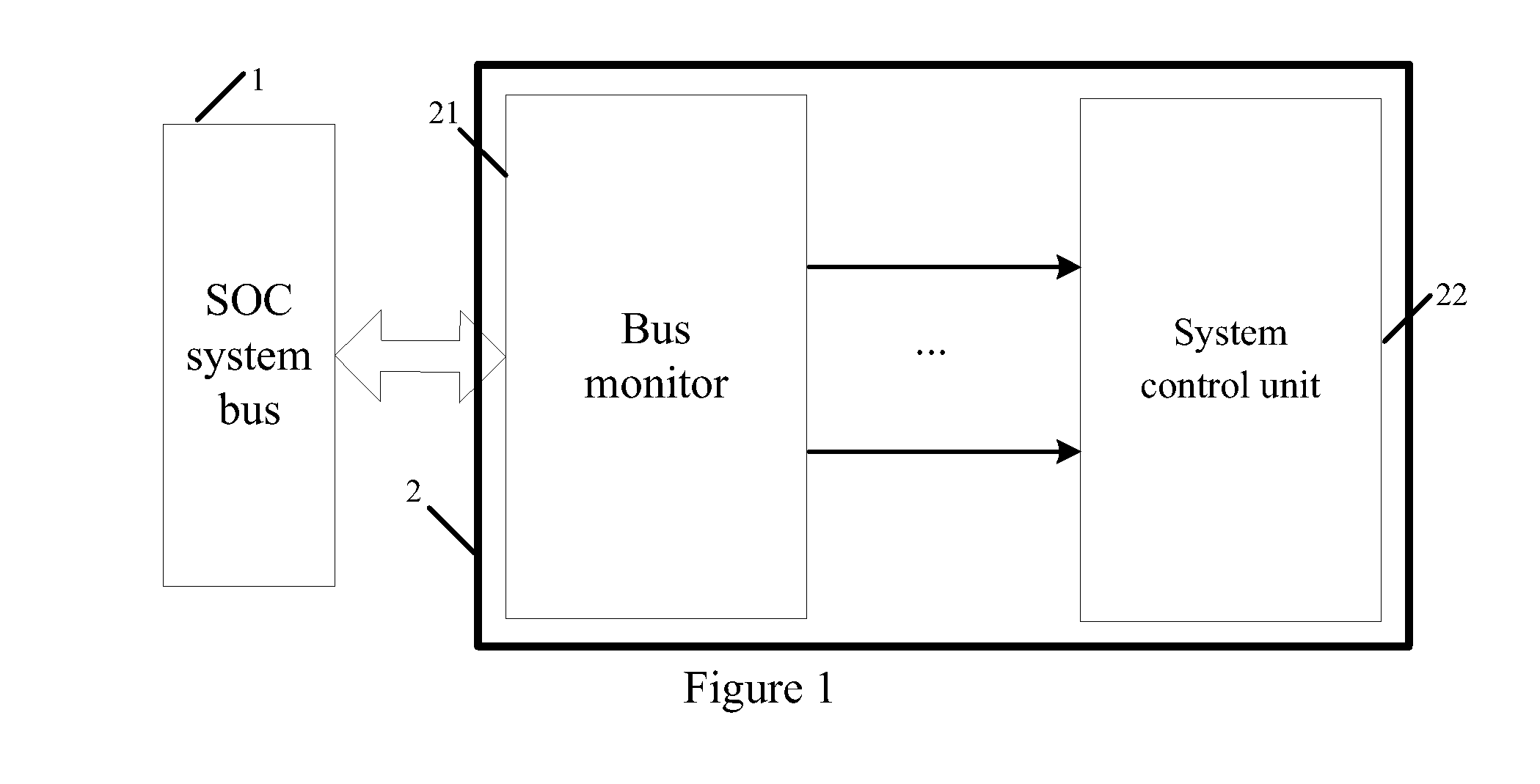
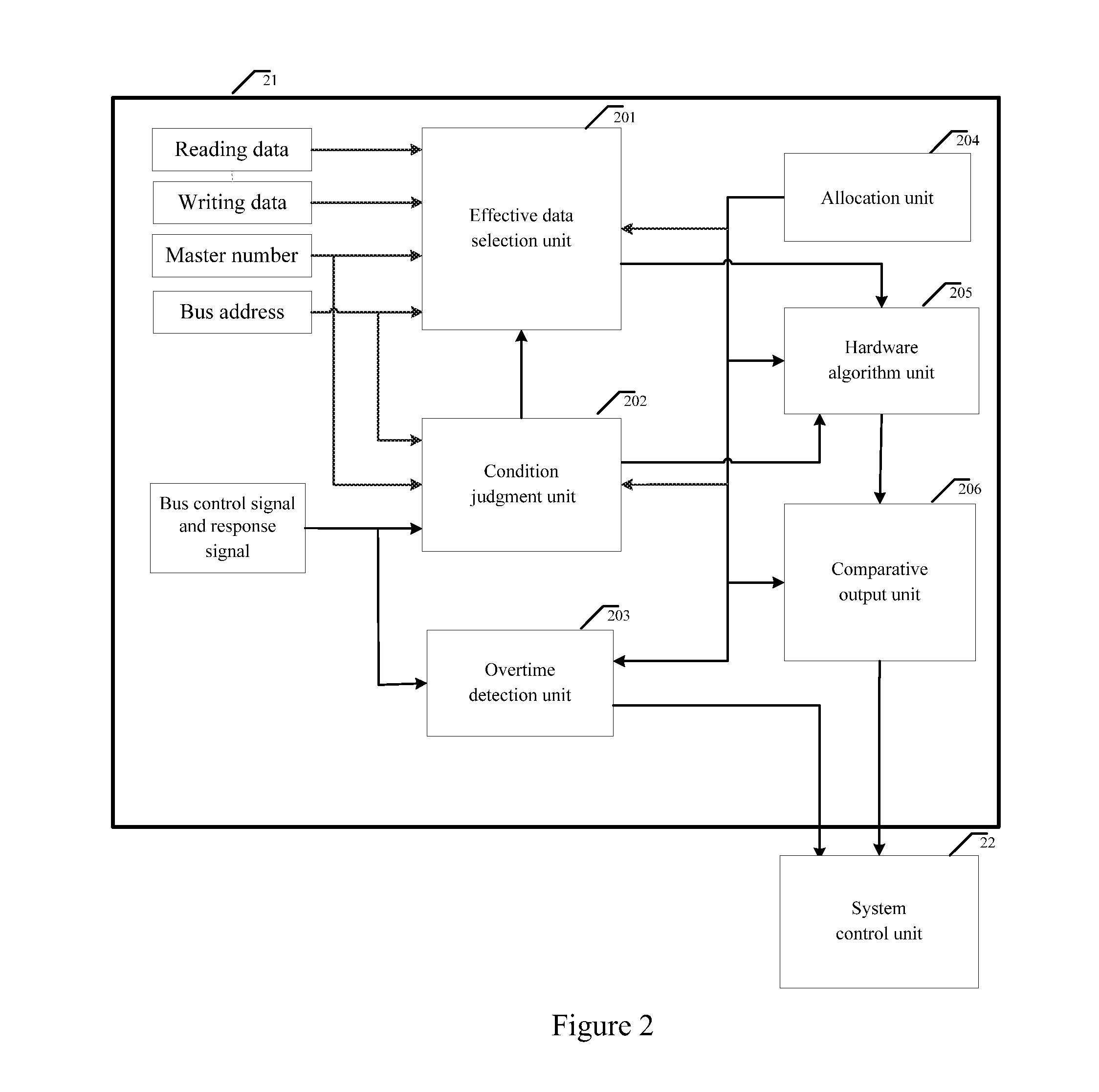
Bus monitor for enhancing soc system security and realization method thereof
InactiveUS20130219452A1Improve information securityInformation leakageMemory loss protectionError detection/correctionClassified informationData selection
The present invention discloses a bus monitor for enhancing SOC system security and a realization method thereof. The bus monitor disposed between a system bus and a system control unit includes a configuration unit, a condition judgment unit, an effective data selection unit, a hardware algorithm unit and a comparative output unit. Without affecting the bus access efficiency, the present invention provides the method capable of immediately monitoring the bus behavior, and the detection system notices whether a particular bus access serial behavior is changed due to an accidental fault or intentional attacking fault. If the particular bus access serial behavior is changed, the present invention warns the system to adopt a suitable security measure to prevent the security hidden trouble and leakage of classified information due to the incorrect system security process.
Owner:SHENZHEN STATE MICRO TECH CO LTD
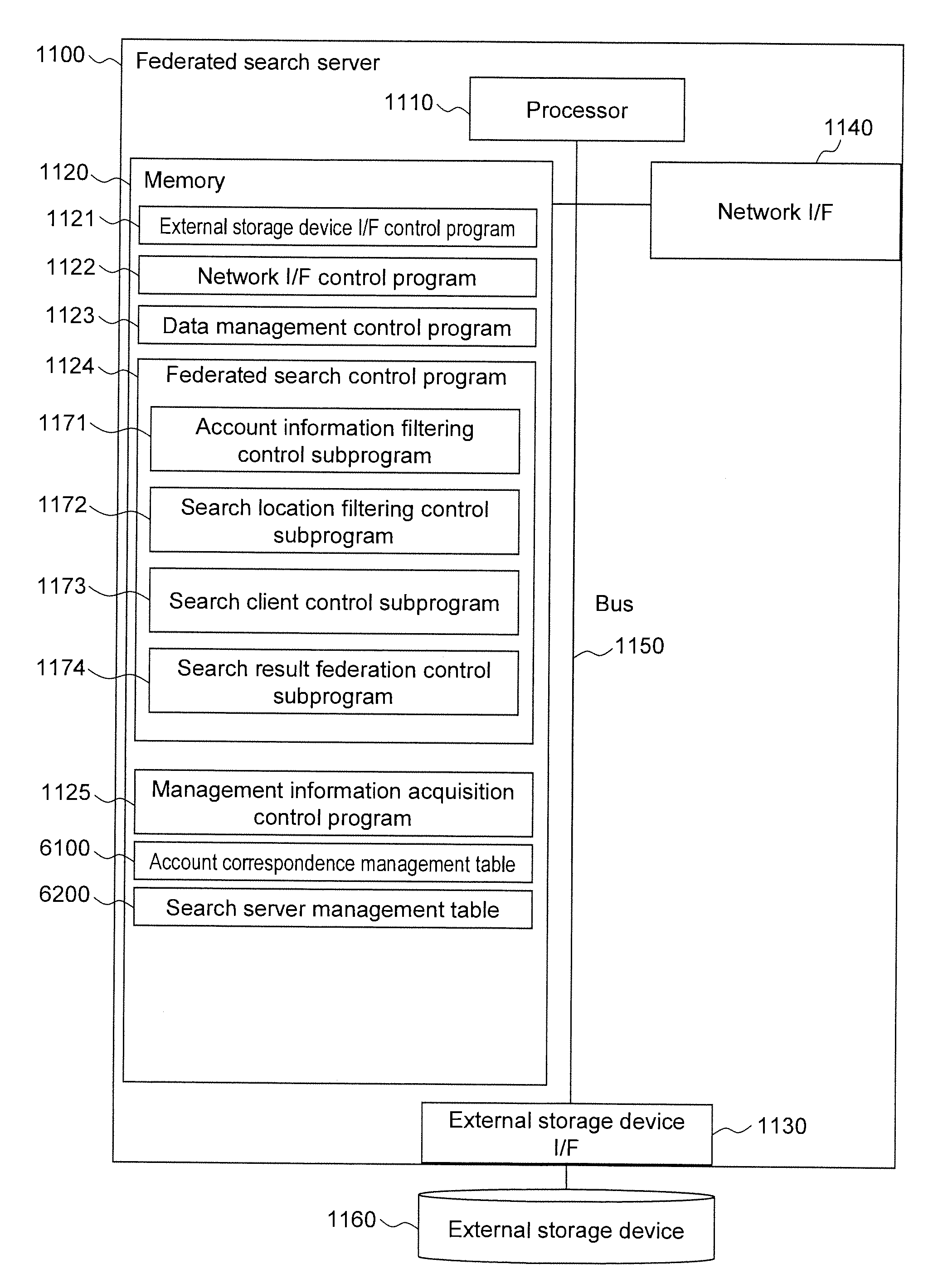
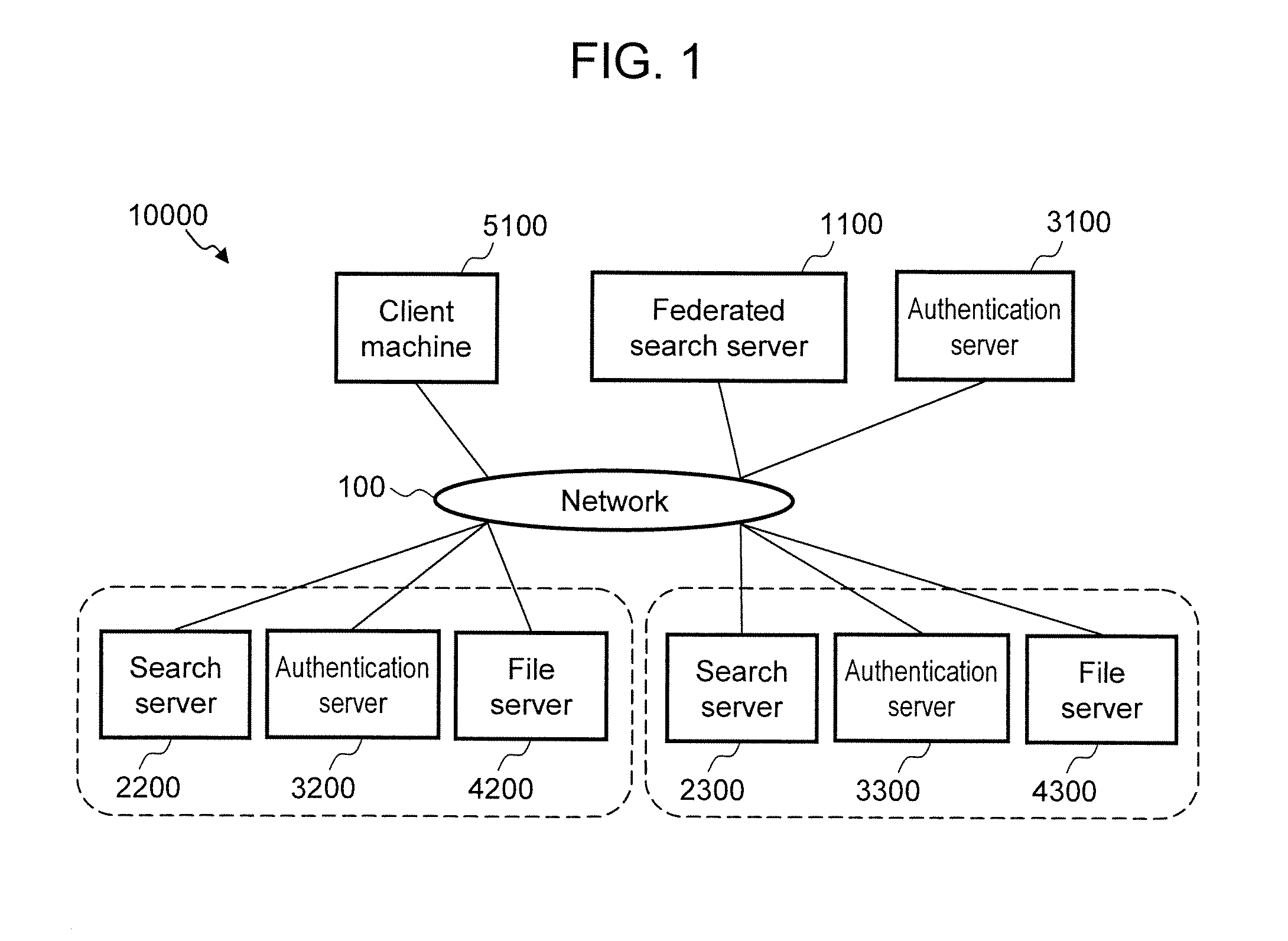
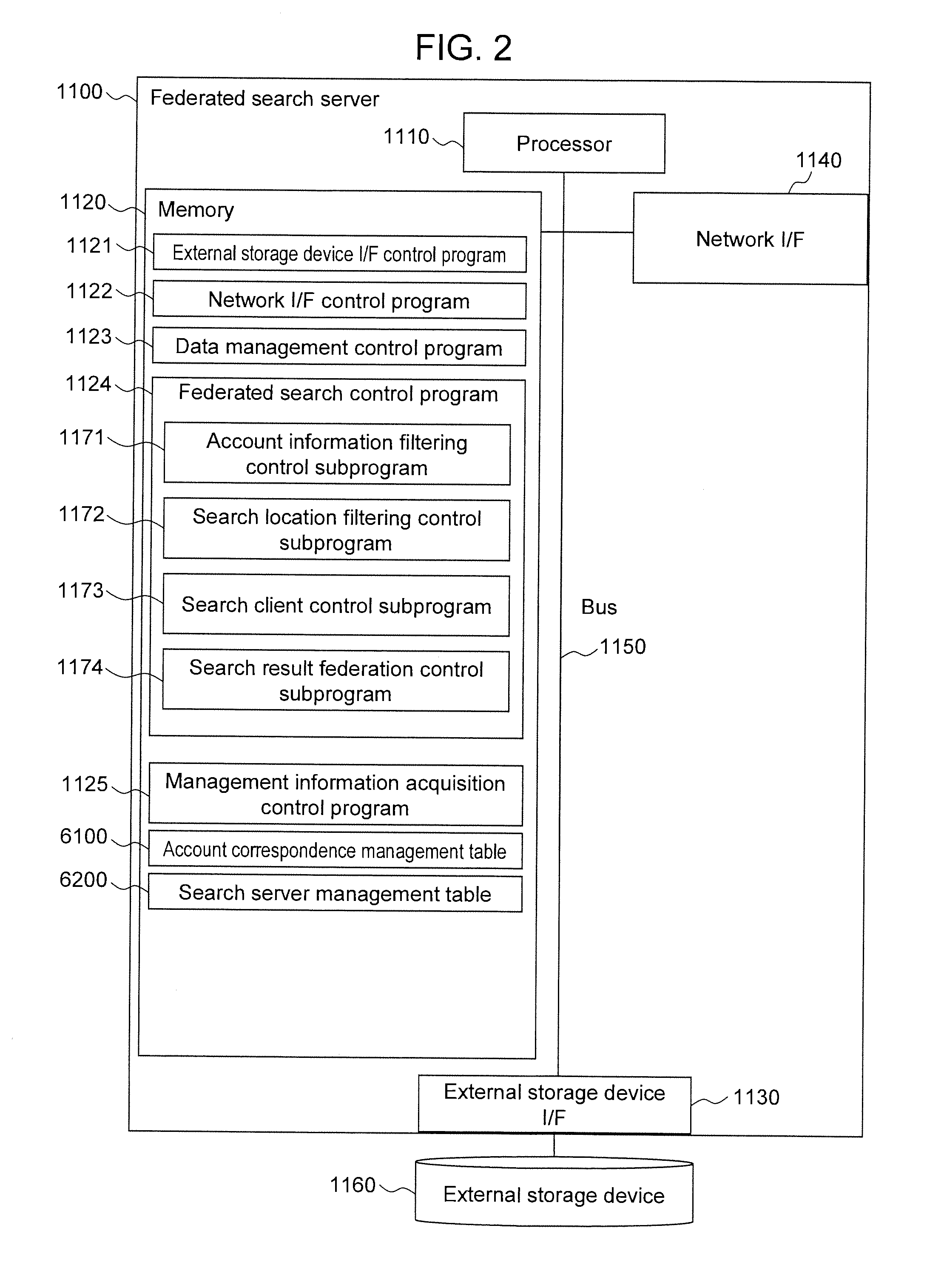
Federated search apparatus, federated search system, and federated search method
InactiveUS20120290592A1Prevent leakagePrevent transmissionDigital data information retrievalDigital data processing detailsFederated searchDatabase
Provided is a technique that can control a federated search apparatus to prevent transmission of access account information, which is not necessary to carry out security trimming, to search servers in the execution of federated search. The federated search apparatus according to the present invention includes an account correspondence table describing a correspondence between a first access account that issues a first search request for requesting federated search and second access accounts that issue a second search request to the search apparatuses. The federated search apparatus specifies the second access account corresponding to the first access account in accordance with the description of the account correspondence table, designates, as a search condition, a range that can be accessed by the second access account, and issues the second search request to the search servers.
Owner:HITACHI SOFTWARE ENG
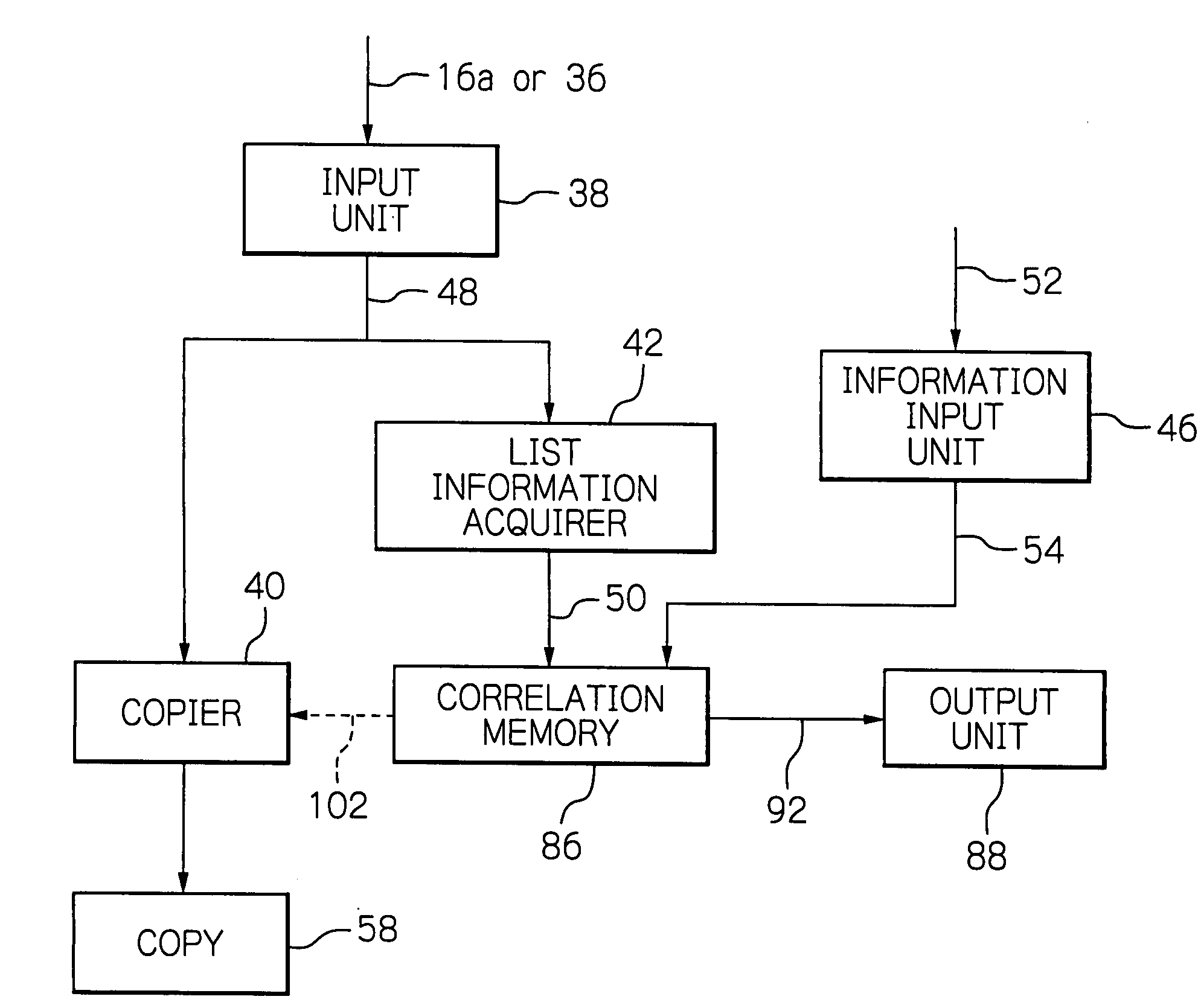
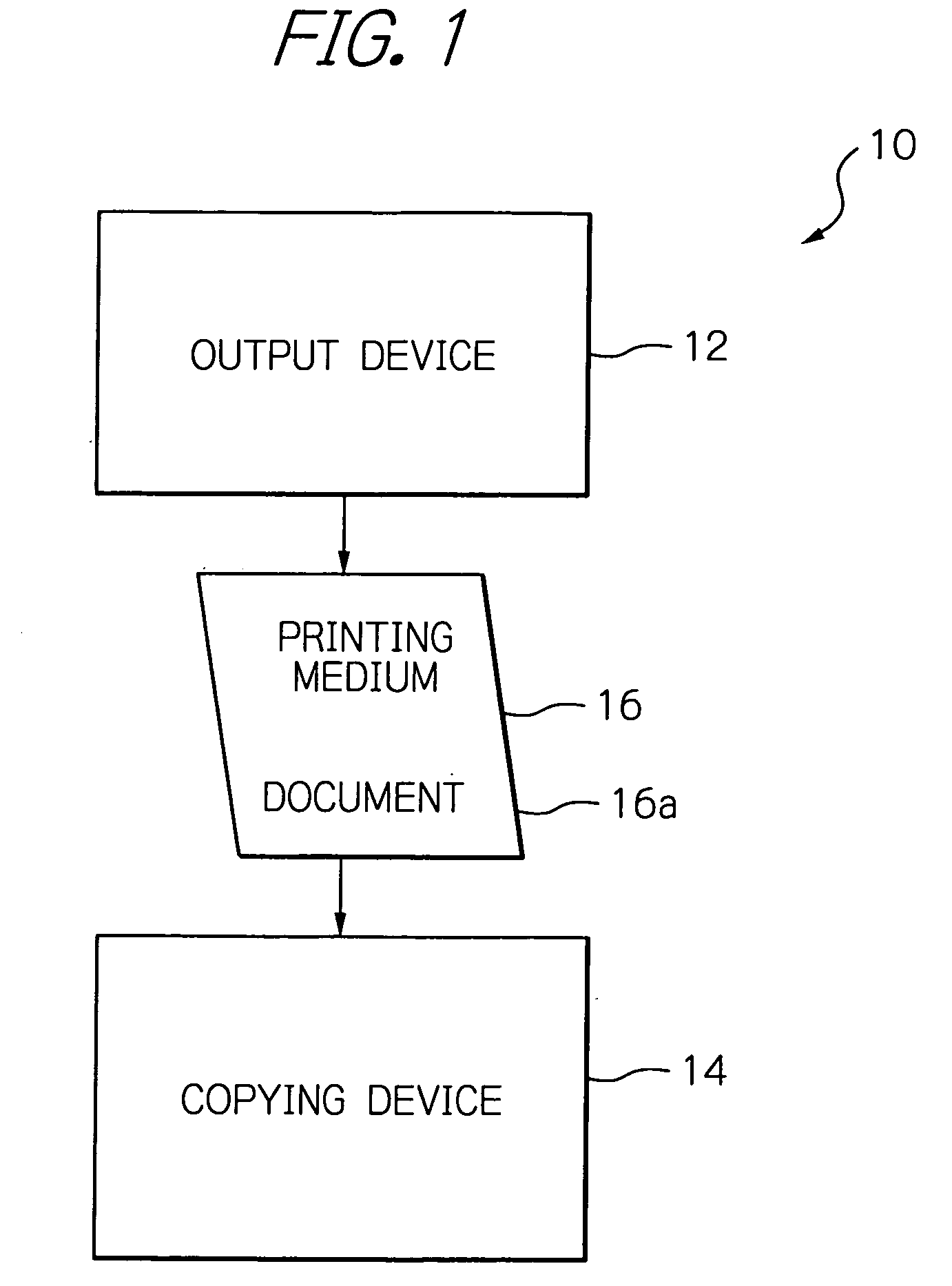
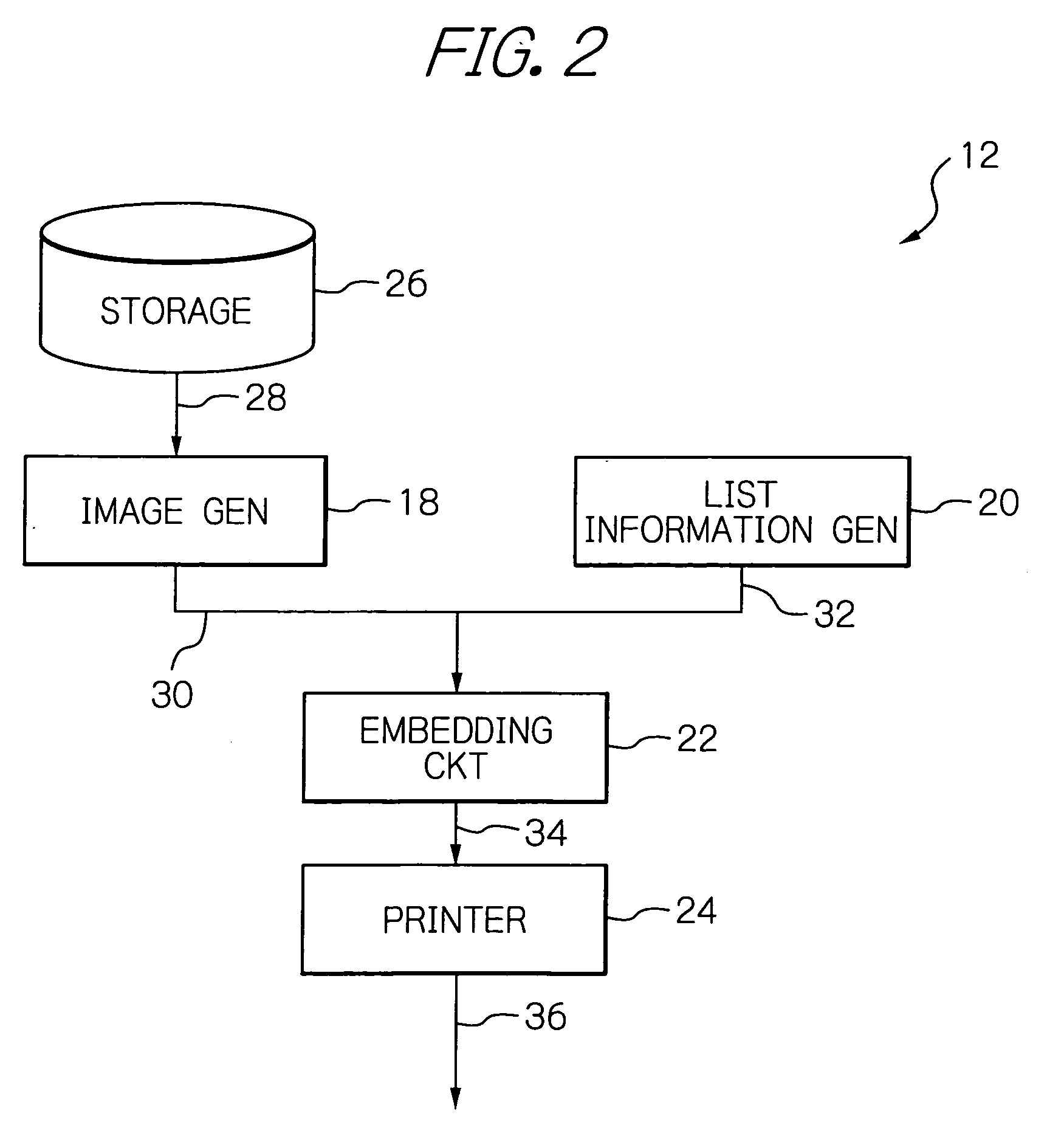
System for managing flexible copying with information leakage prevented and/or detected
InactiveUS20080180753A1Information leakageFlexible managementCharacter and pattern recognitionComputer security arrangementsManagement systemInformation leakage
In a copy management system, an output device generates a print image, and list information including identification information identifying a person authorized for printing. The list information is converted to a specific code, which is in turn embedded in a print image. The code-embedded print image is output by a printer on a printing medium. The code-embedded print image on the printing medium is received by a copying device of the system. The copying device also receives and accepts copier identification information identifying a copying person. The list information is acquired from the code-embedded print image. The identification information in the list information acquired is compared to the copier identification information accepted. Allowance / non-allowance of copying is determined based on whether or not the above information coincides with each other. The copying device outputs a printed copy subject to decision for allowance of copying.
Owner:OKI DATA CORP
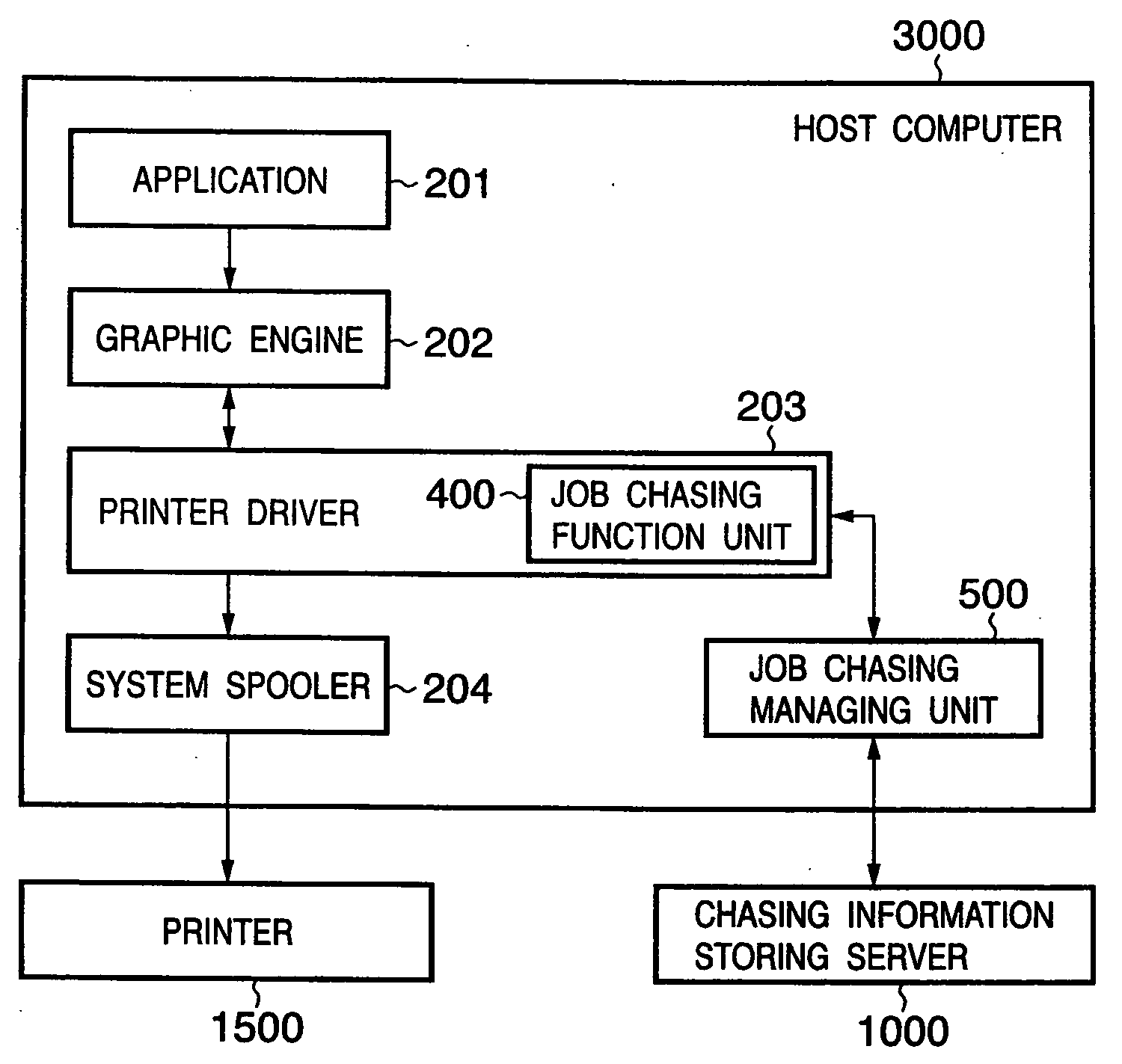
Method of protecting leakage of information and information processing apparatus and driver program implementing the same
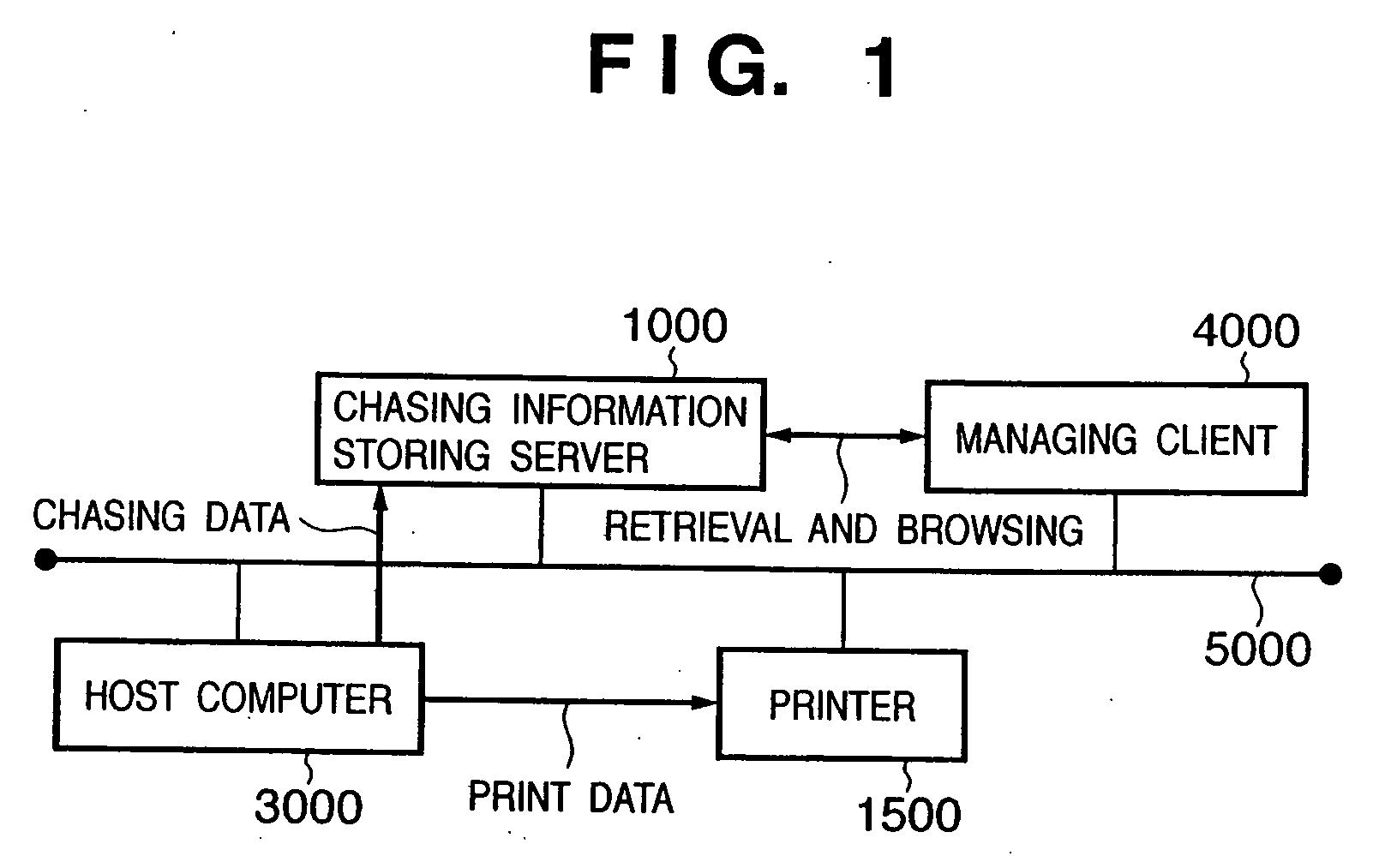
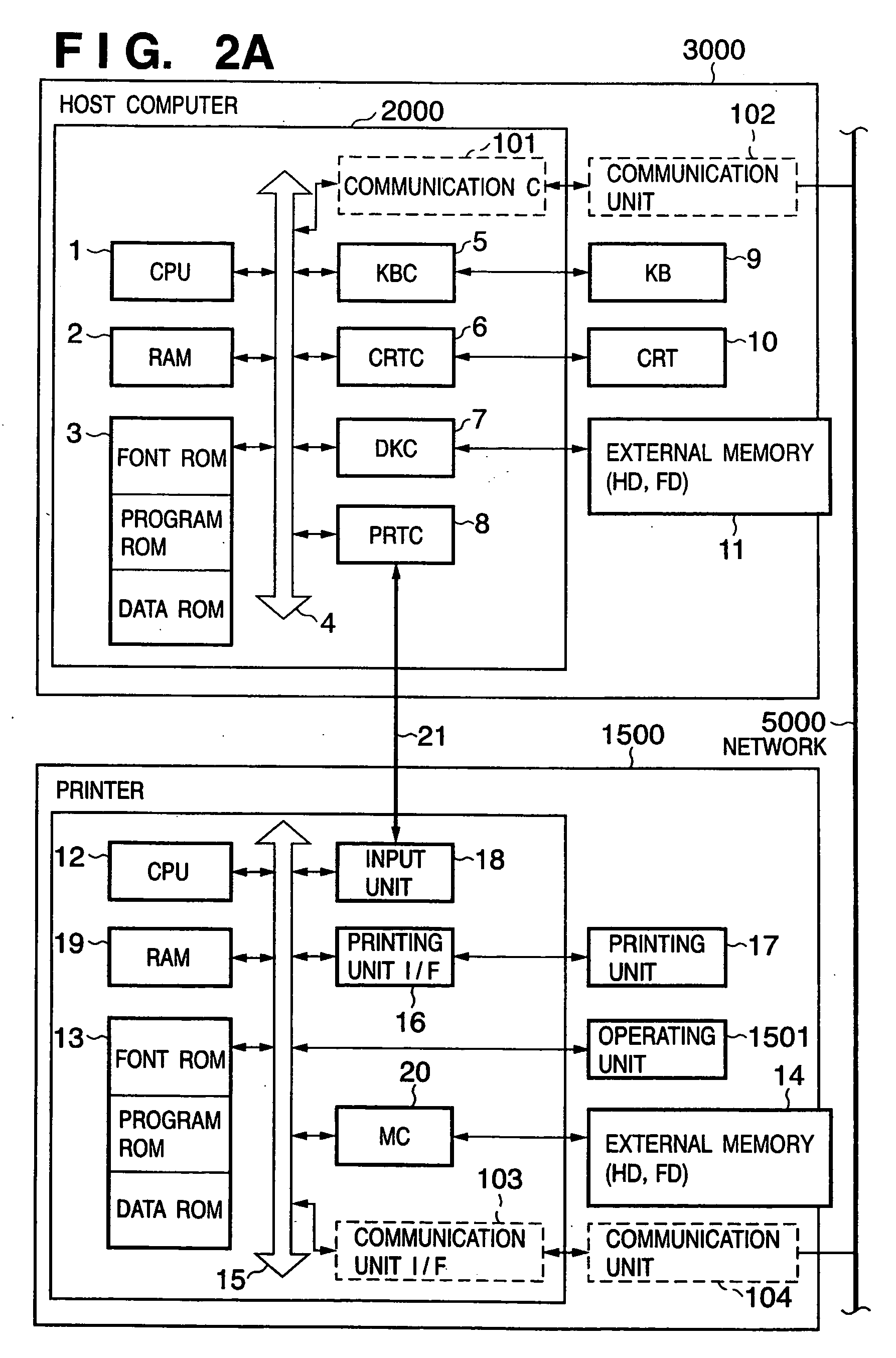
InactiveUS20060215202A1Prevent leakageInformation leakageVisual presentationDigital output to print unitsInformation processingImaging processing
To generate print jobs to be executed by a printing device, an image processing apparatus edits drawing commands output by applications and stored in storage means, in accordance with editing instructions input through input means, executes a process of generating chasing data using the drawing commands, the process including the edition, and then executes a process of generating print data, the process including the edition. The editing instructions for the drawing commands include an instruction to combine a plurality of drawing commands, an instruction to separate a drawing command into a plurality of subcommands, and an instruction to delete a drawing command. The chasing data is generated so as to have a layered data structure indicating the combinative relationship among the plurality of drawing commands if the editing instruction instructs a plurality of drawing commands to be combined together.
Owner:CANON KK
System and method for allocating electronic trade orders among a plurality of electronic trade venues
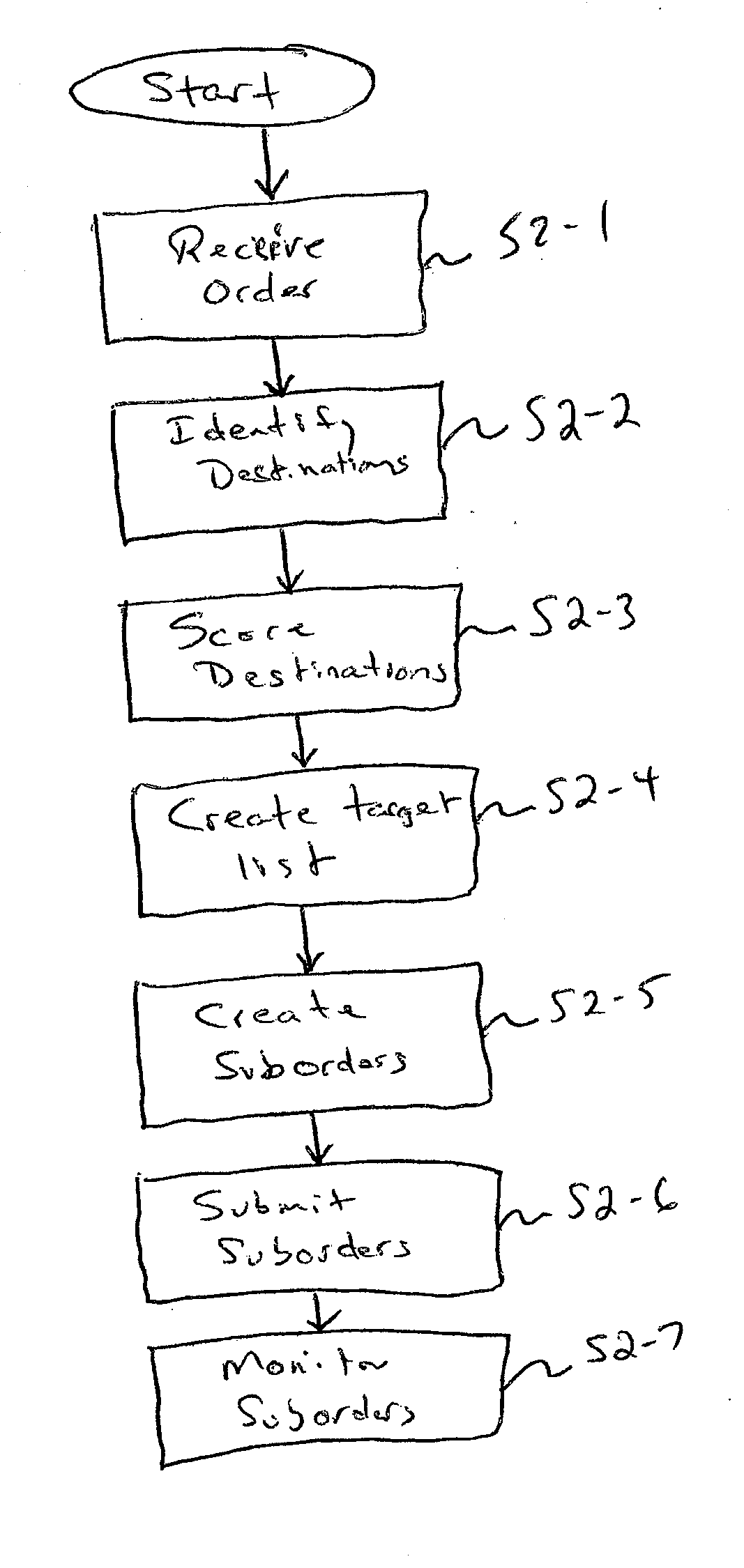
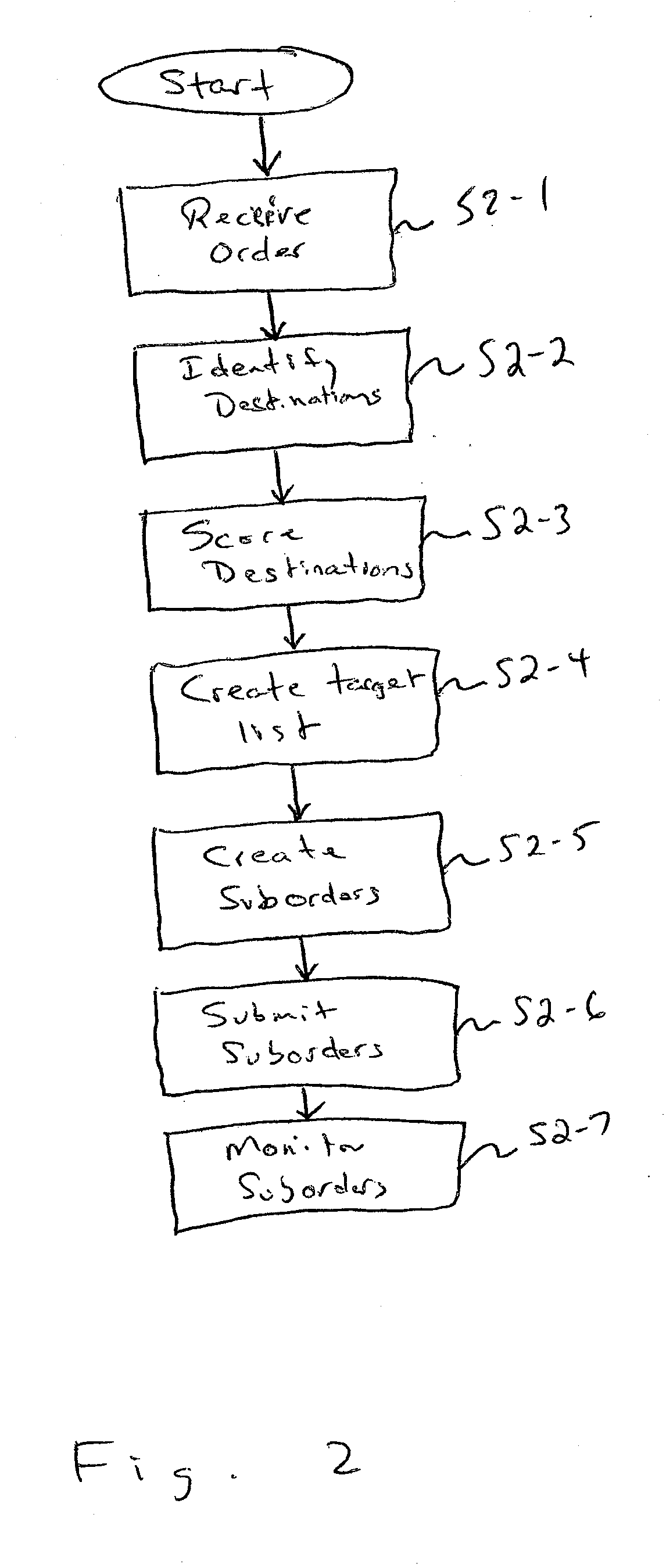
A method and system for optimizing allocation of large block orders for a security for maximum fill rate and minimum information leakage. The invention includes a process by which a block order for a security is allocated to a number of suborders which are then submitted to various electronic trading destinations to be filled. This allocation process involves ranking the suborders on the basis of a quality measurement, calculating and assigned a liquidity expectation to each suborder, determining a maximum target execution rate for the security that will not result in market impact, assigning orders to a trade list beginning with the higher rank suborder until the sum of shares represented in the list is equal to the maximum target execution rate, allocating the suborders not assigned to the trade list, and submitting the suborders to the corresponding electronic trading destination.
Owner:ITG SOFTWARE SOLUTIONS INC
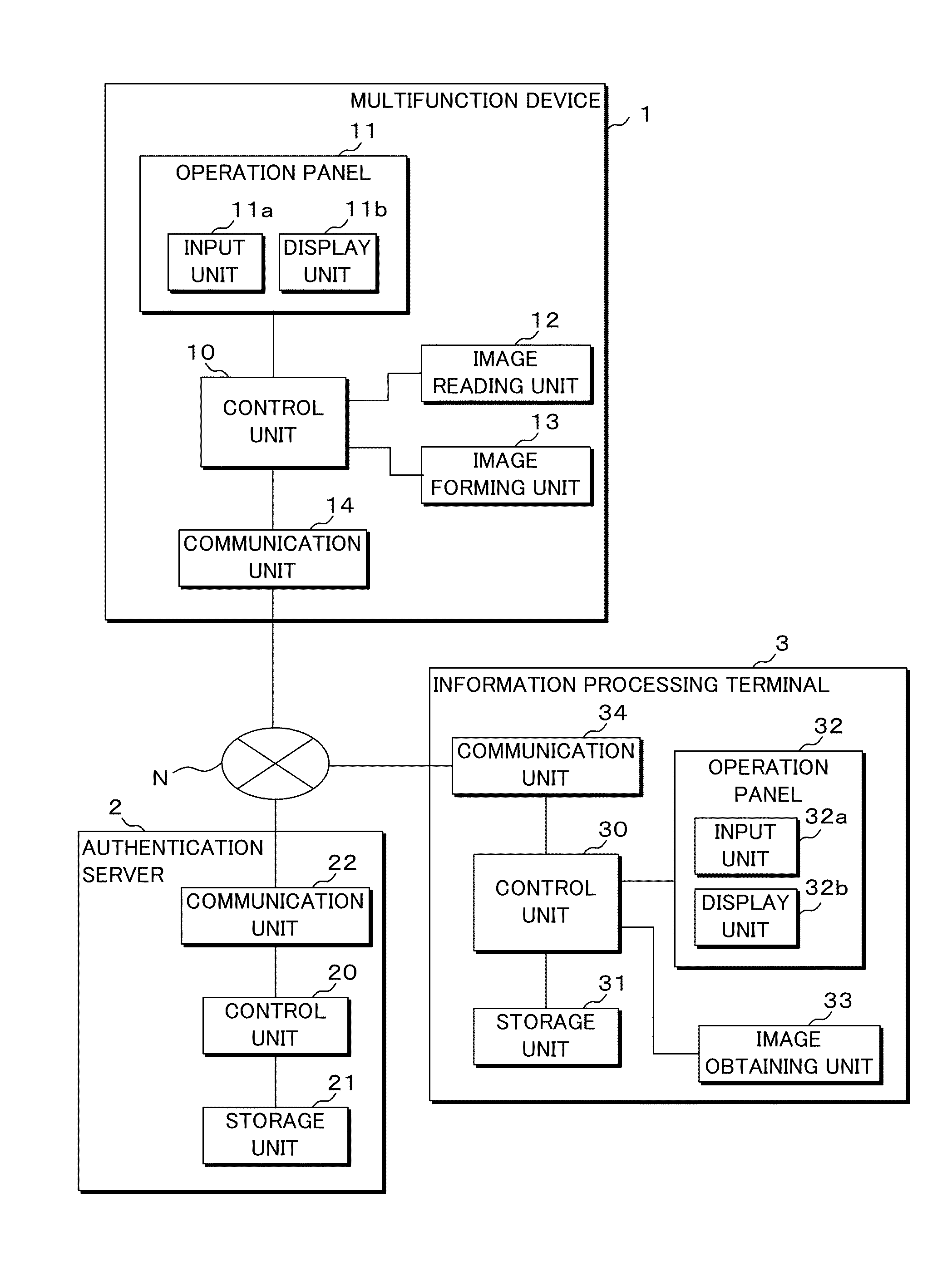
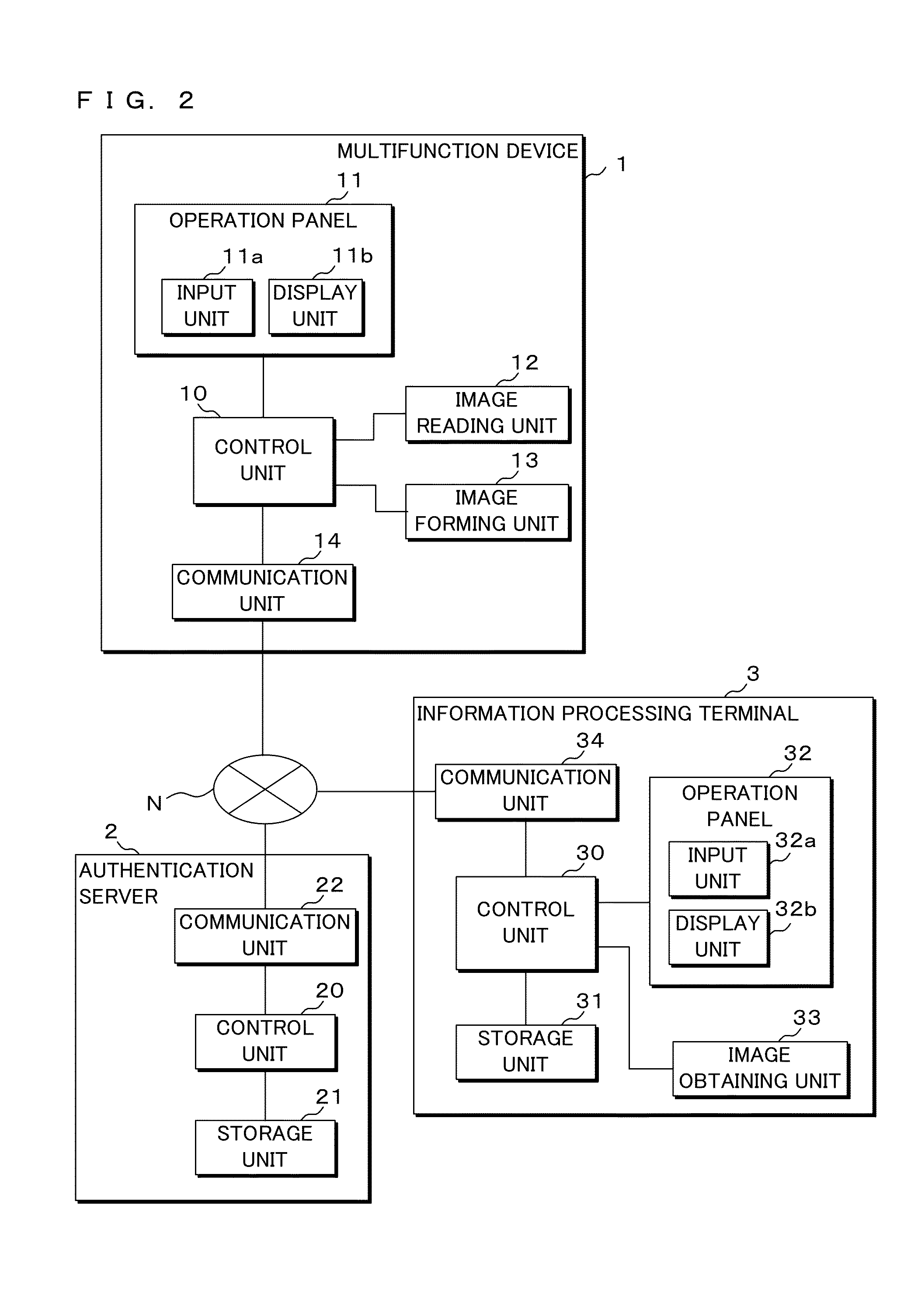
Image output system, information processing device, and authentication device
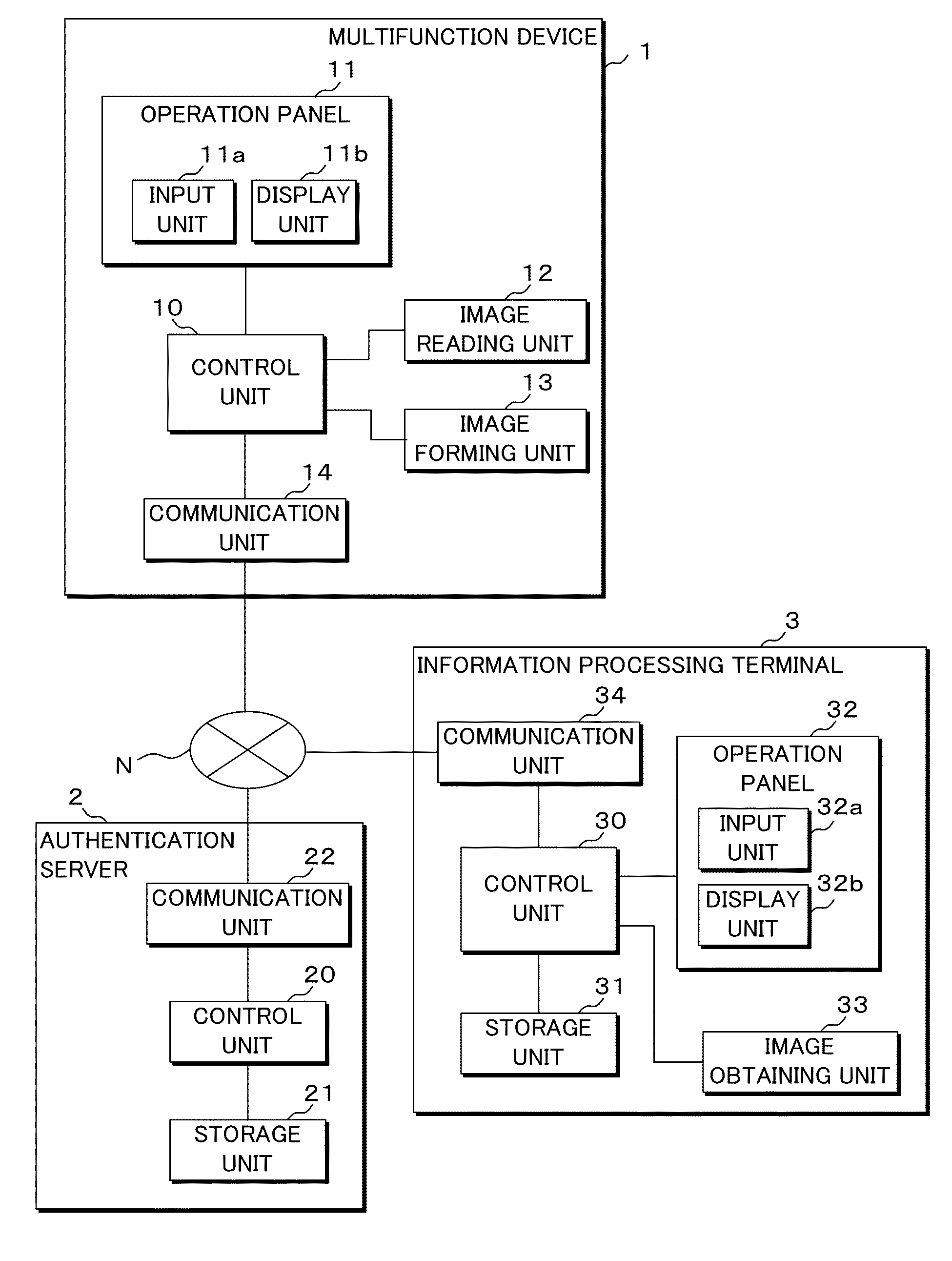
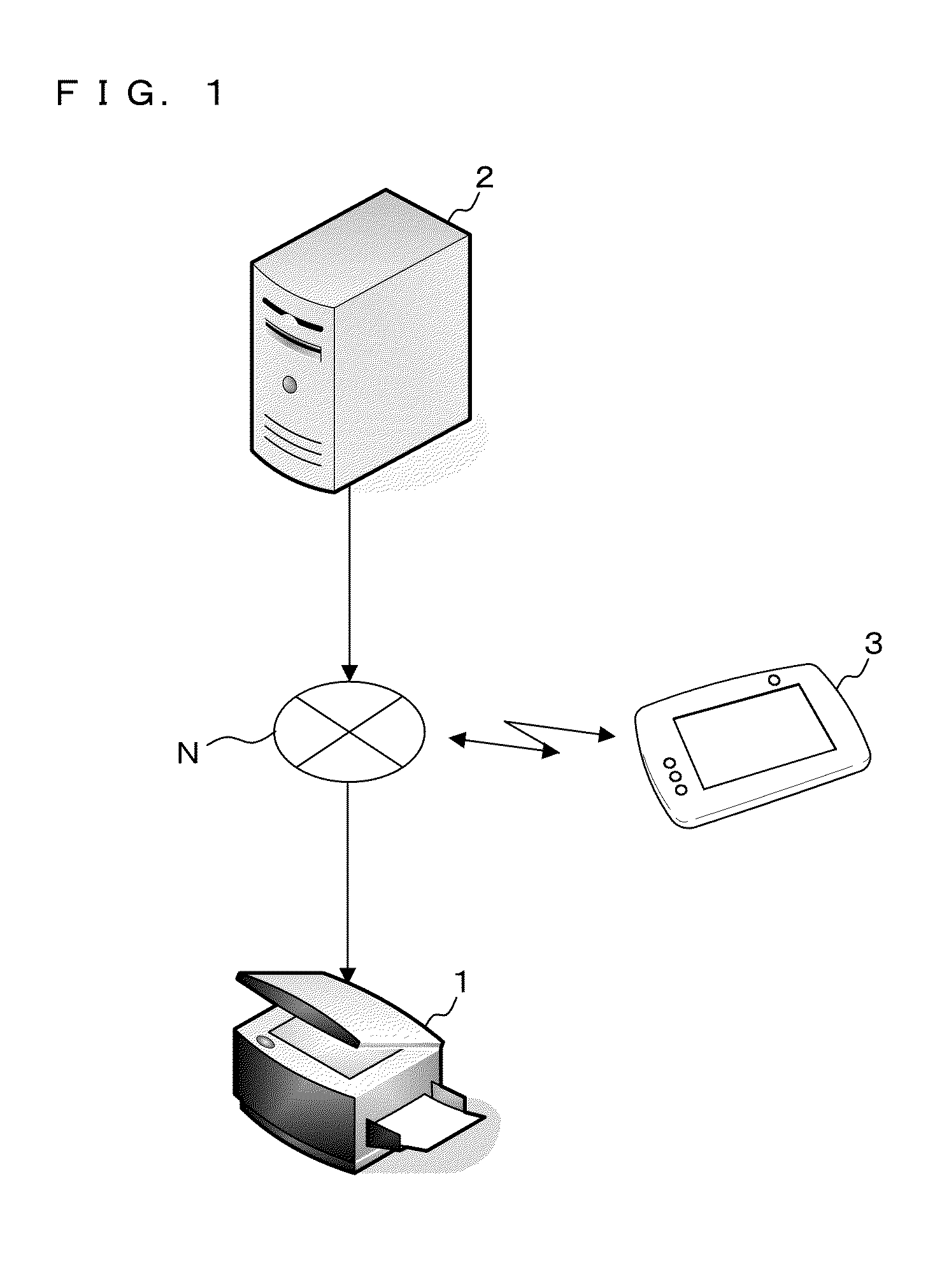
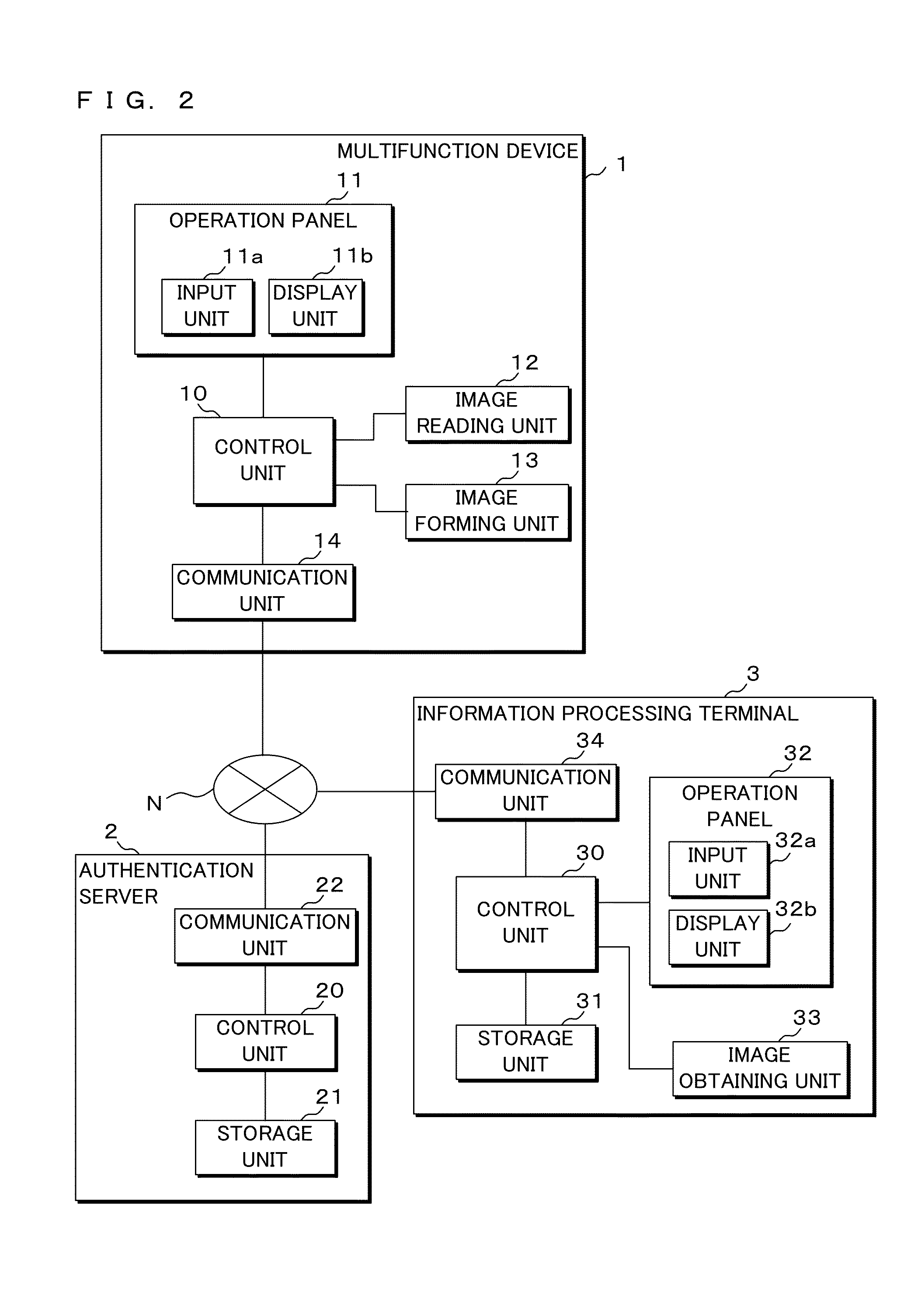
ActiveUS20140355039A1Information leakageDigital data authenticationVisual presentationUser authenticationMultiple function
An information processing terminal transmits, to an authentication server, information obtained by imaging a code pattern of multifunction device information, and authentication information inputted by a user. The authentication server performs user authentication based on the received authentication information and specifies a multifunction device based on the received information of the code pattern. If the user has been authenticated, the authentication server transmits print data corresponding to the user to the multifunction device and prescribes the execution of print processing to the multifunction device. The multifunction device executes print process based on the obtained print data.
Owner:SHARP KK
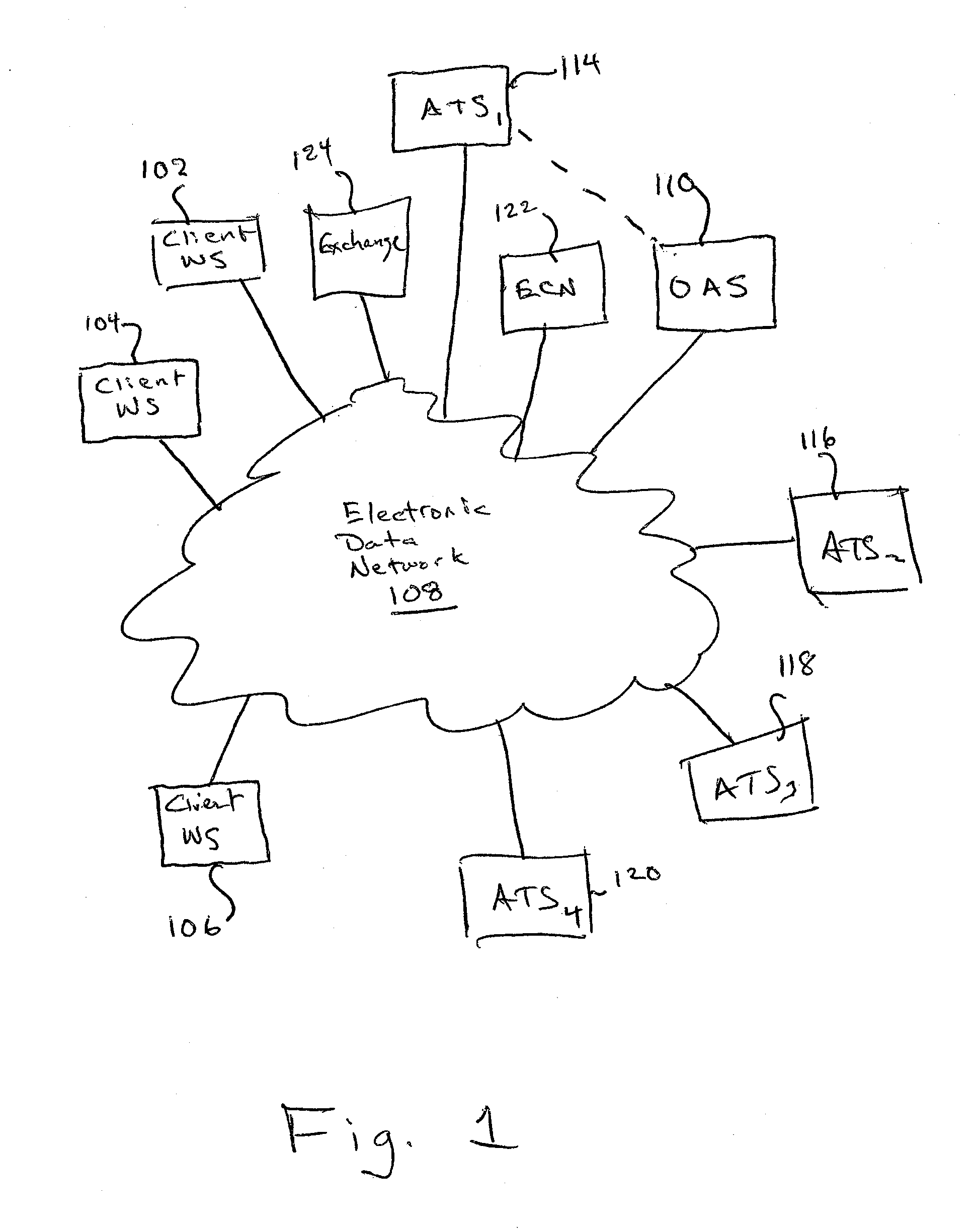
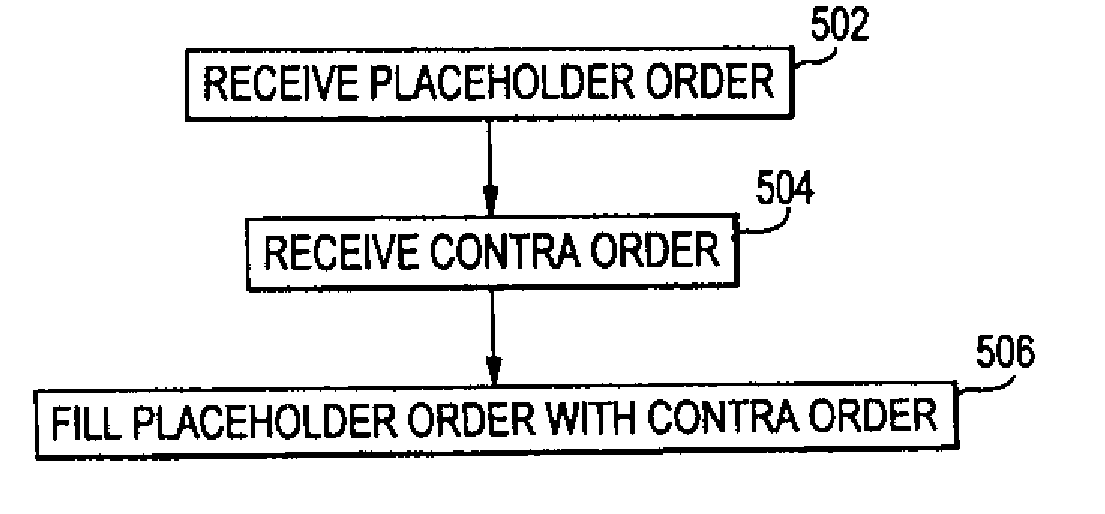
Block trading system and method providing price improvement to aggressive orders
InactiveUS20090076961A1Improve trading experienceImprove experienceFinanceComputer security arrangementsOrder management systemComputer science
In a trading system for trading securities or the like, Contra Targeting is performed by enabling users to expose the liquidity within their order management system without divulging order management system information to a central trading server. Also, virtual orders can be placed and executed which give users price-time priority on an order without reserving the shares until the moment of execution.
Owner:ITG SOFTWARE SOLUTIONS INC
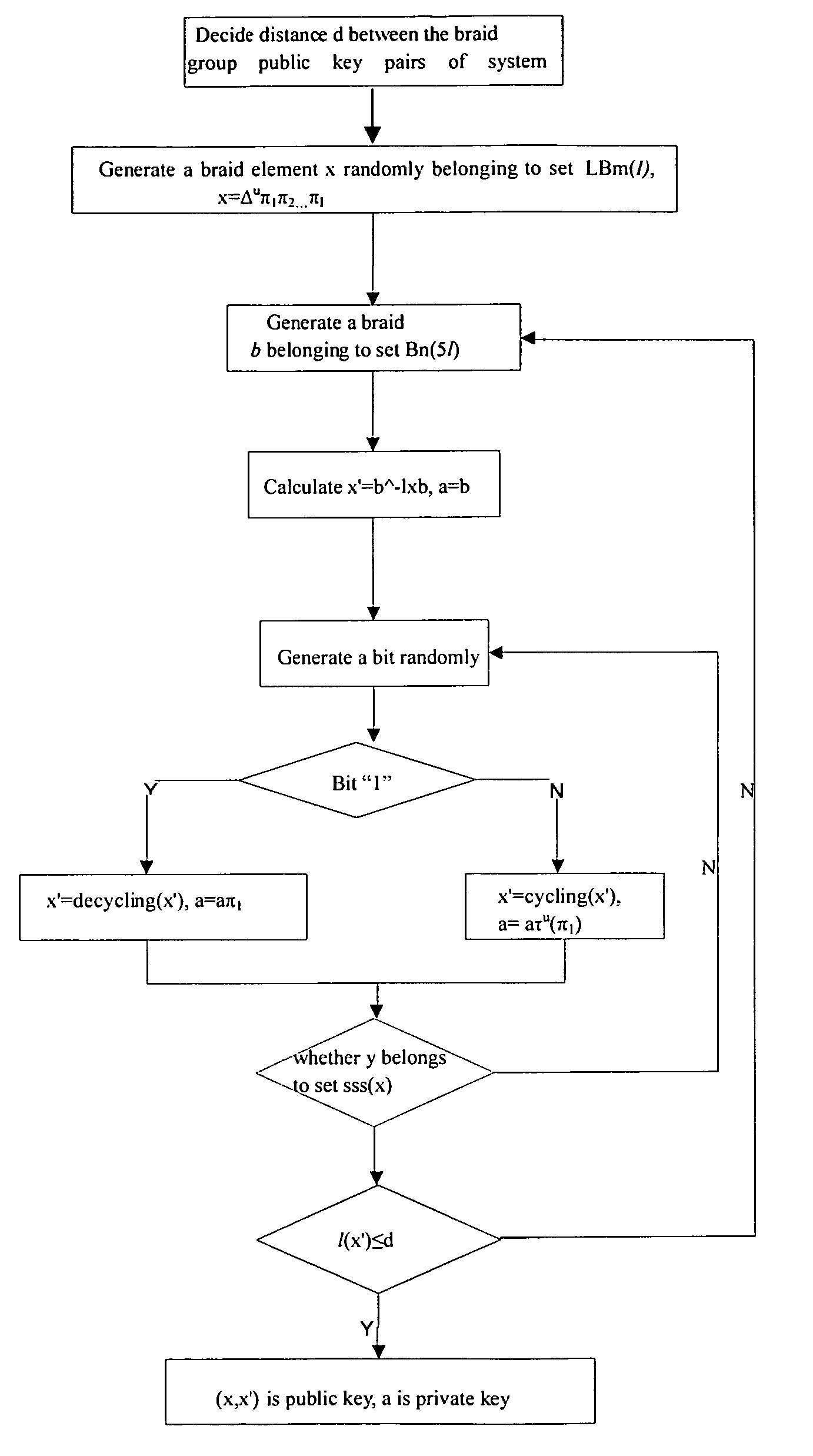
Digital signature method based on braid groups conjugacy and verify method thereof
InactiveUS7725724B2Improve efficiencyMany timesPublic key for secure communicationUser identity/authority verificationHash functionDigital signature
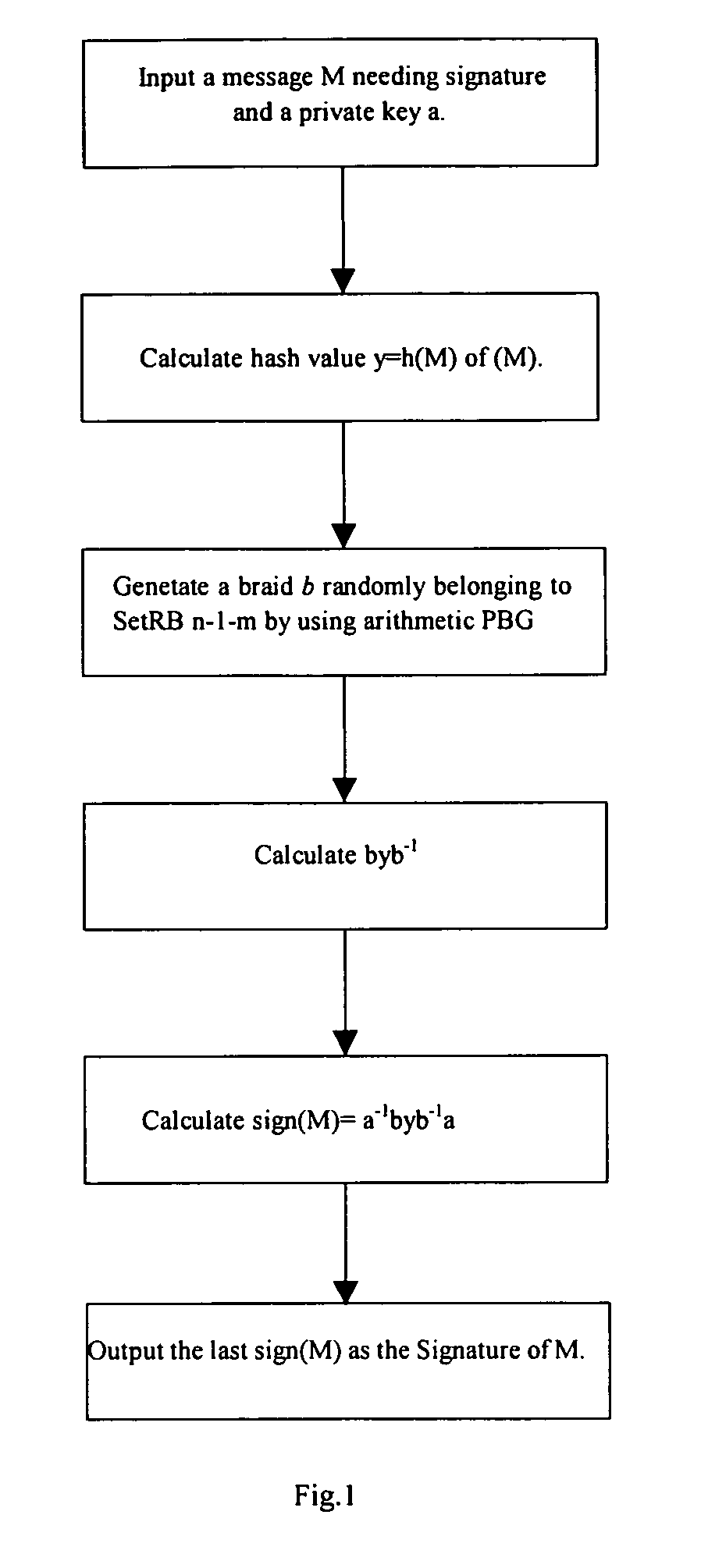
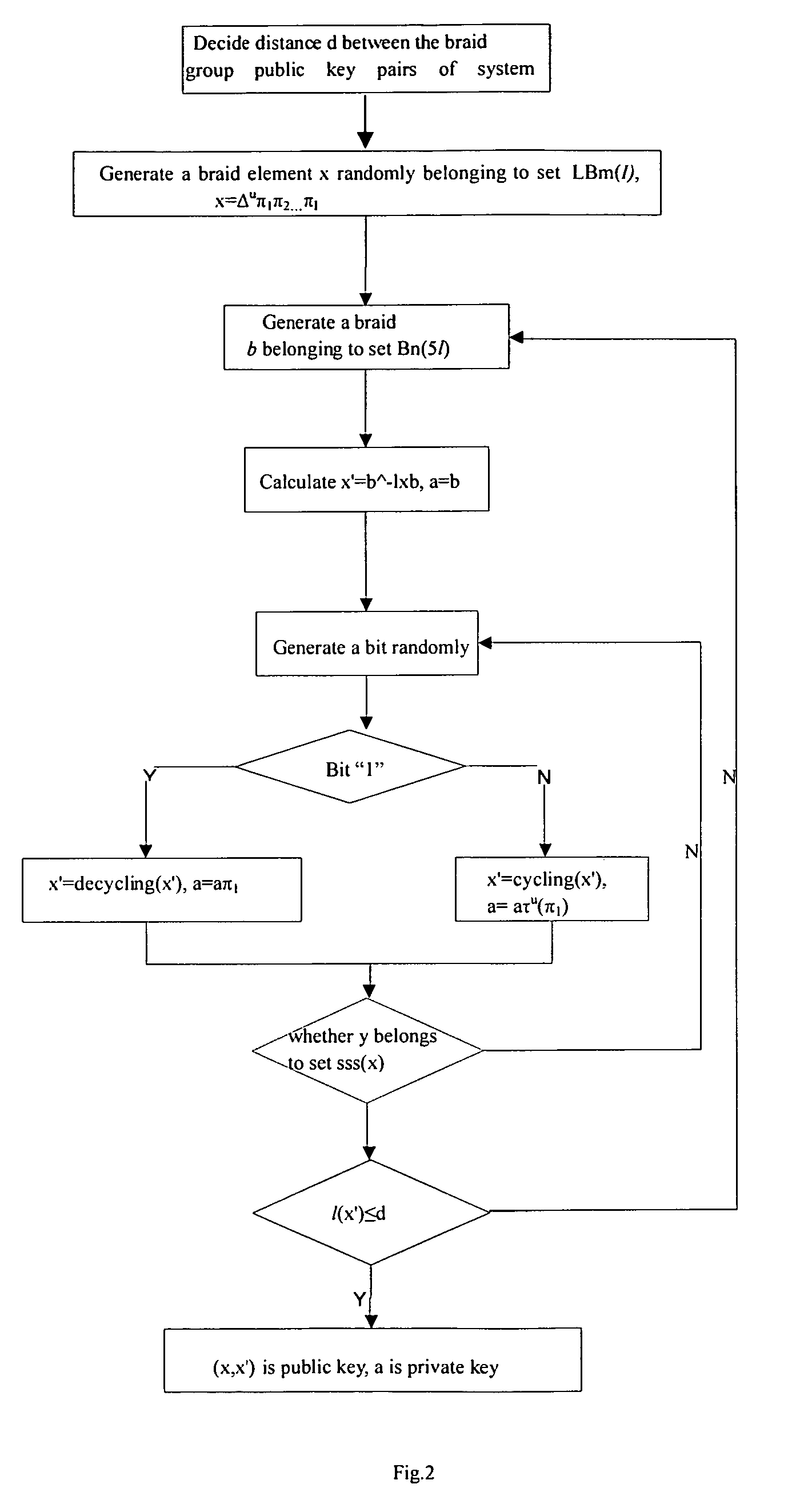
The present invention discloses a digital signature scheme based on braid group conjugacy problem and a verifying method thereof, wherein a signatory S selects three braids xεLBm(l), x′εBn(l), aεBn(l), and considers braid pair (x′,x) as a public key of S, braid a as a private key of S; Signatory S uses hash function h for a message M needing signature to get y=h(M)εBn(l); generating a braid bεRBn−1−m(l) randomly, then signing M with a and b to obtain Sign(M)=a−1byb−1a; a signature verifying party V obtains the public key of S, calculating the message M by employing hash function h, obtaining the y=h(M); judging whether sign(M) and y, sign(M)x′ and xy are conjugate or not, if yes, sign(M) is a legal signature of message M; the present invention reduces the number of braids involved and the number for conjugacy decision without reducing security, thereby improving the operation efficiency of signature.
Owner:ZTE CORP
Communication system, communication apparatus, communication method, and program
InactiveUS20090037587A1Remove the burdenInformation leakageMultiple digital computer combinationsSecuring communicationCommunications systemEncryption
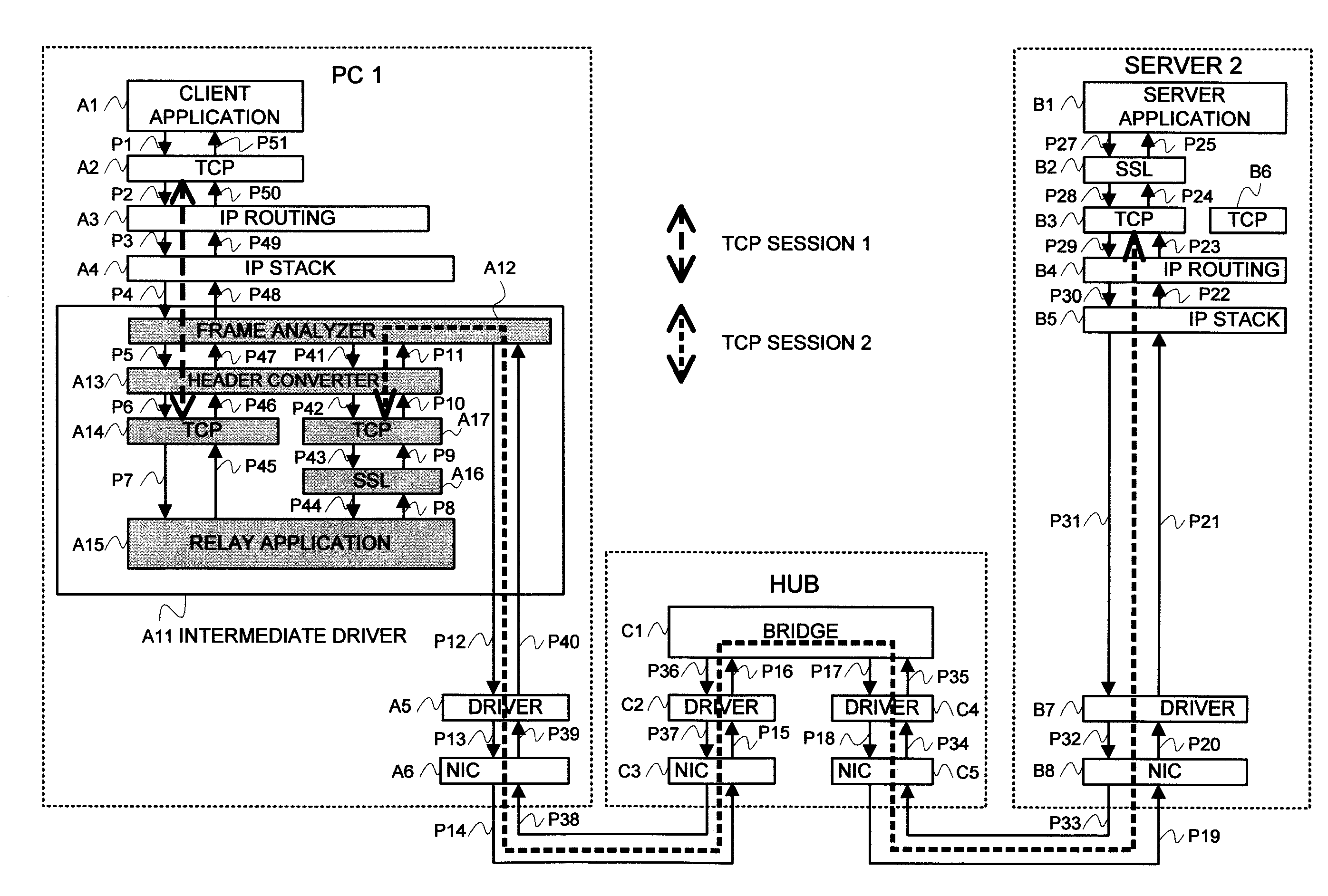
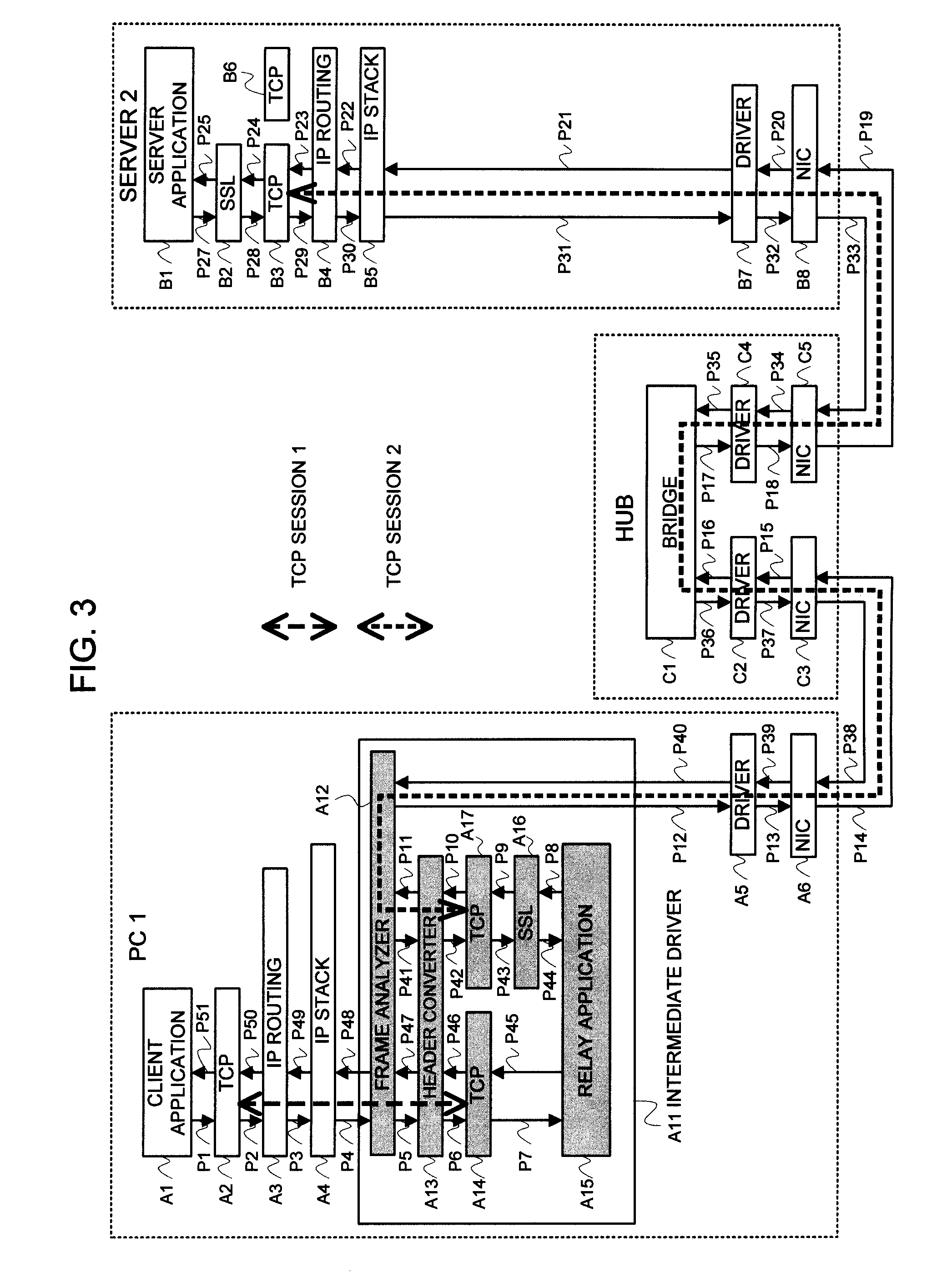
Out of data being transmitted from a client application A1 to a server application B1, data of which encryption has been determined to be necessary in a frame analyzing means within an intermediate driver A11 of s PC 1 is relayed by use of a total of two TCP sessions consisting of a TCP session 1 between a TCP A14 and a TCP A2, and a TCP session 2 between a TCP A17 and a TCP B3. Relaying the TCP sessions in such a manner makes it possible to achieve a coincidence of a TCP / IP protocol hierarchy between an SSL A16 within the intermediate driver A11 and an SSL B2 within a server 2, which enables certificate information, an encryption algorithm, etc. necessary for starting an SSL session to be automatically exchanged therebetween. As a result, secret data being sent out from the PC can be encrypted without changing the setting of the server or installing any software.
Owner:NEC CORP
Information leakage-aware computer aided cyber-physical manufacturing
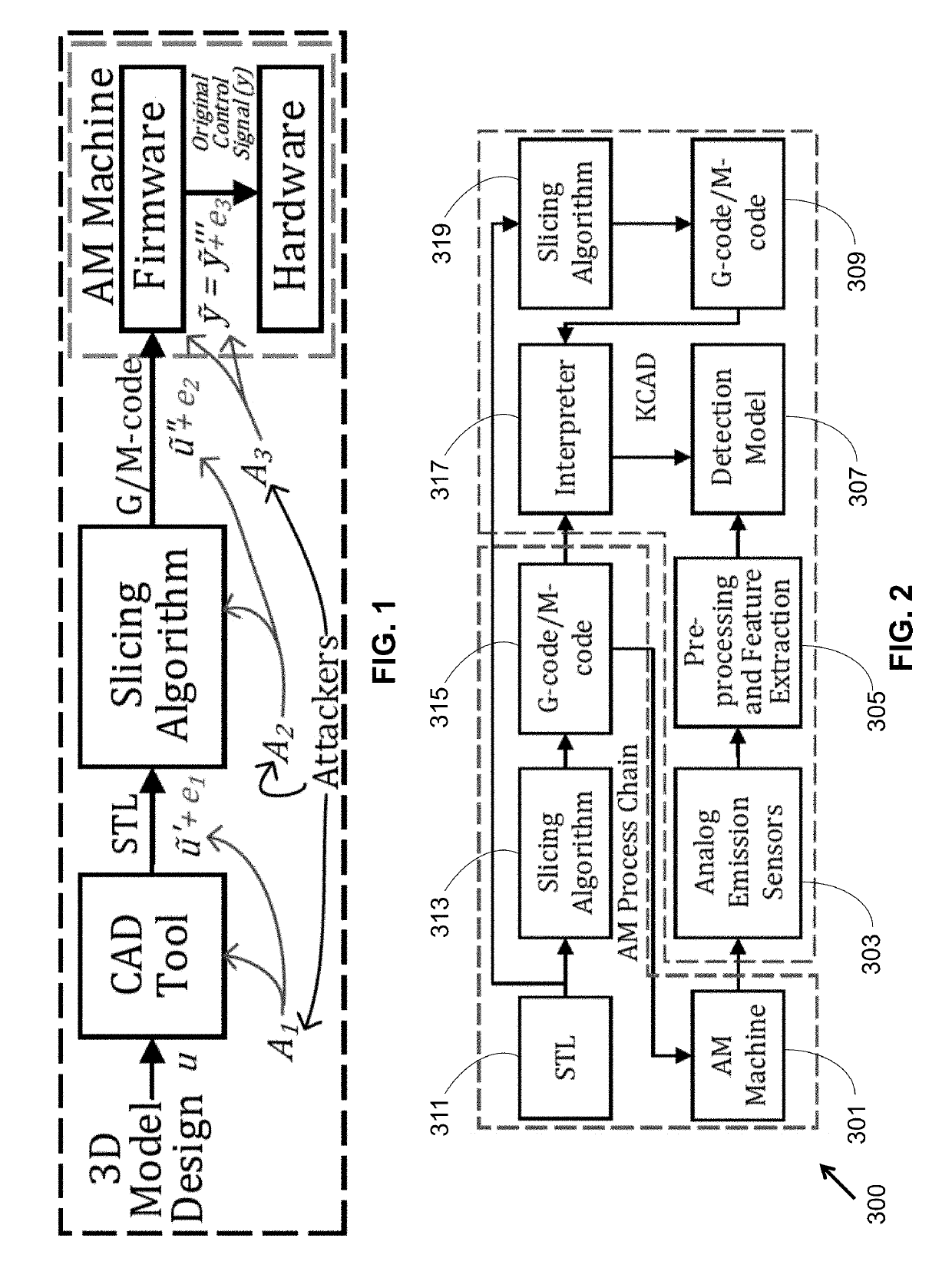
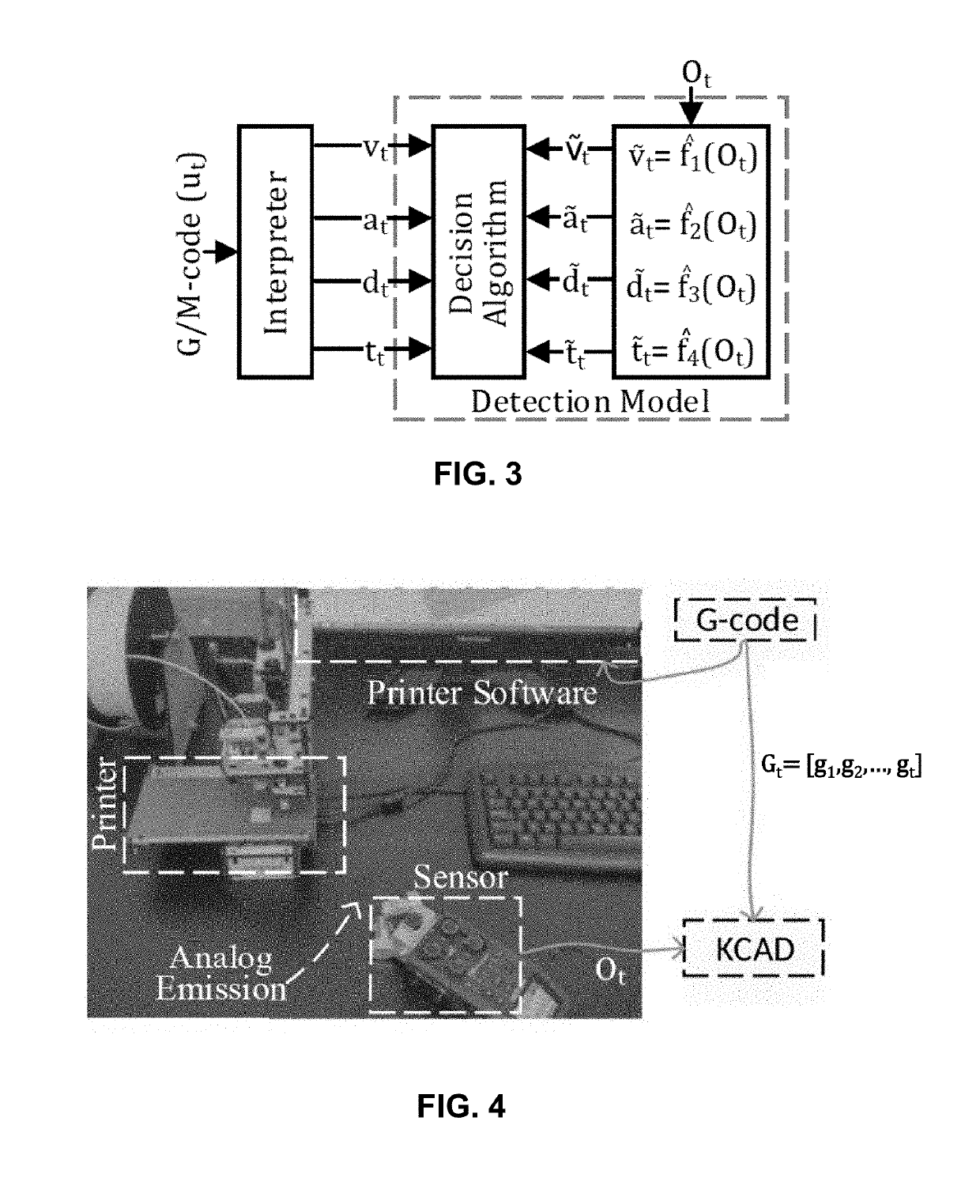
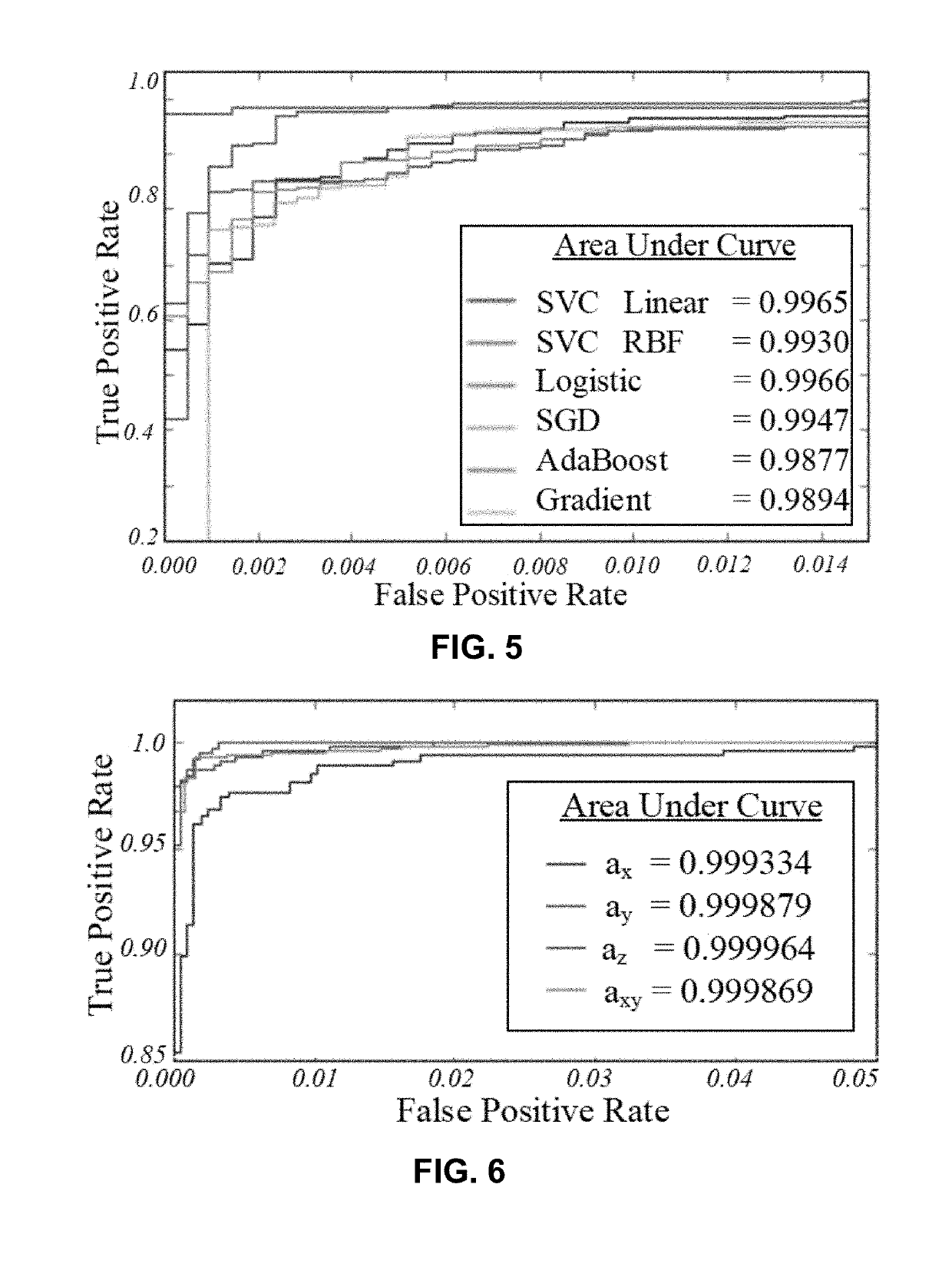
ActiveUS20190230113A1Prevent leakageMinimize information leakageAdditive manufacturing apparatusTransmissionSecurity solutionComputer aid
A methodology as described herein allows cyber-domain tools such as computer aided-manufacturing (CAM) to be aware of the existing information leakage. Then, either machine process or product design parameters in the cyber-domain are changed to minimize the information leakage. This methodology aids the existing cyber-domain and physical-domain security solution by utilizing the cross-domain relationship.
Owner:RGT UNIV OF CALIFORNIA
Information processing apparatus, information processing method, information processing program and computer readable recording medium
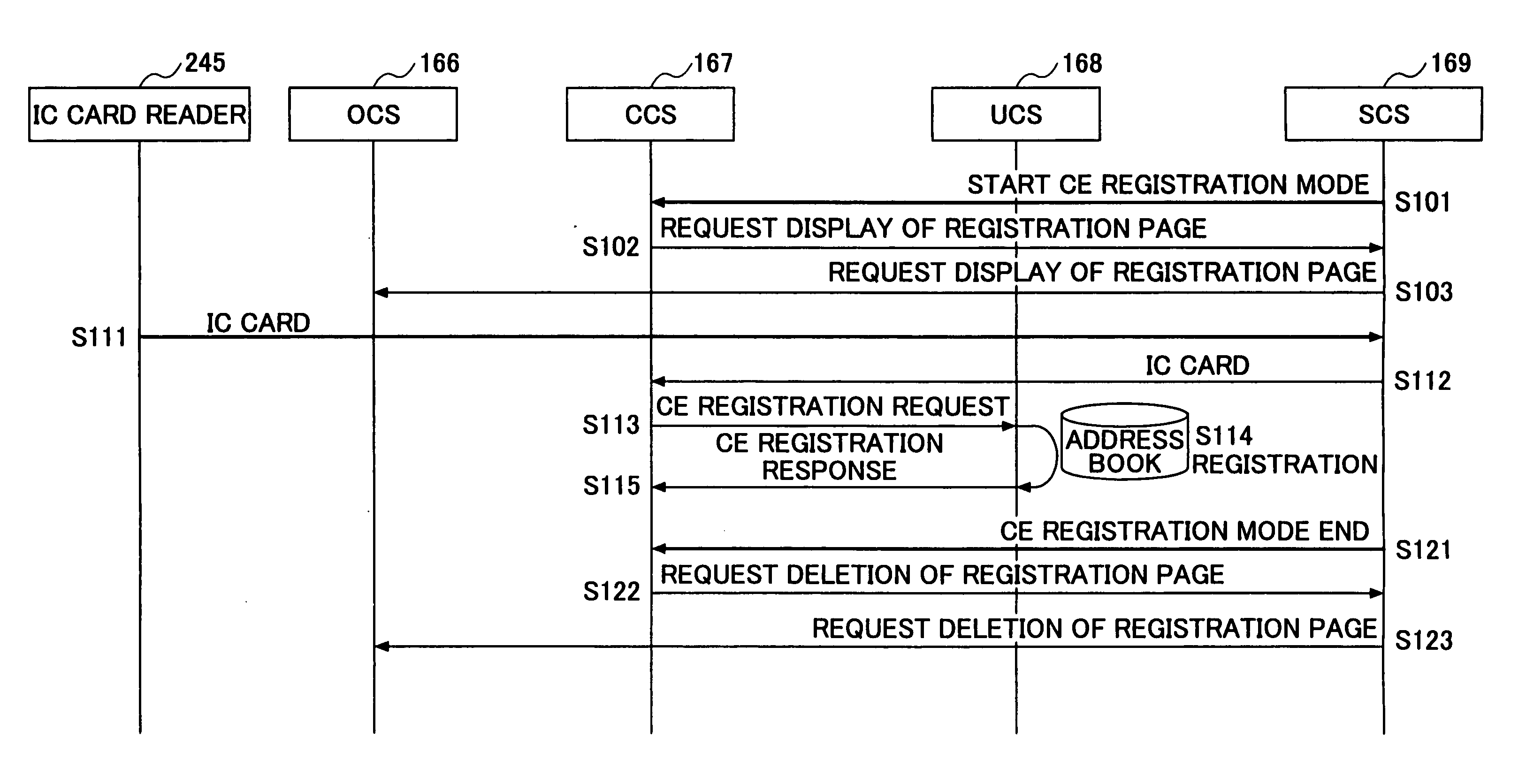
InactiveUS20050259288A1Interest be increaseInformation leakageElectric signal transmission systemsDigital data processing detailsService workerOperating system
In an information processing apparatus having a service mode for a service person to carry out maintenance of the apparatus enters for carrying out the maintenance, a registration page is provided for registering the service person as a service person in charge of the maintenance of the apparatus, and an input page is provided for inputting authentication information required for the service person that is registered in the registration page as a person in charge of the maintenance of the apparatus to enter the service mode.
Owner:RICOH KK
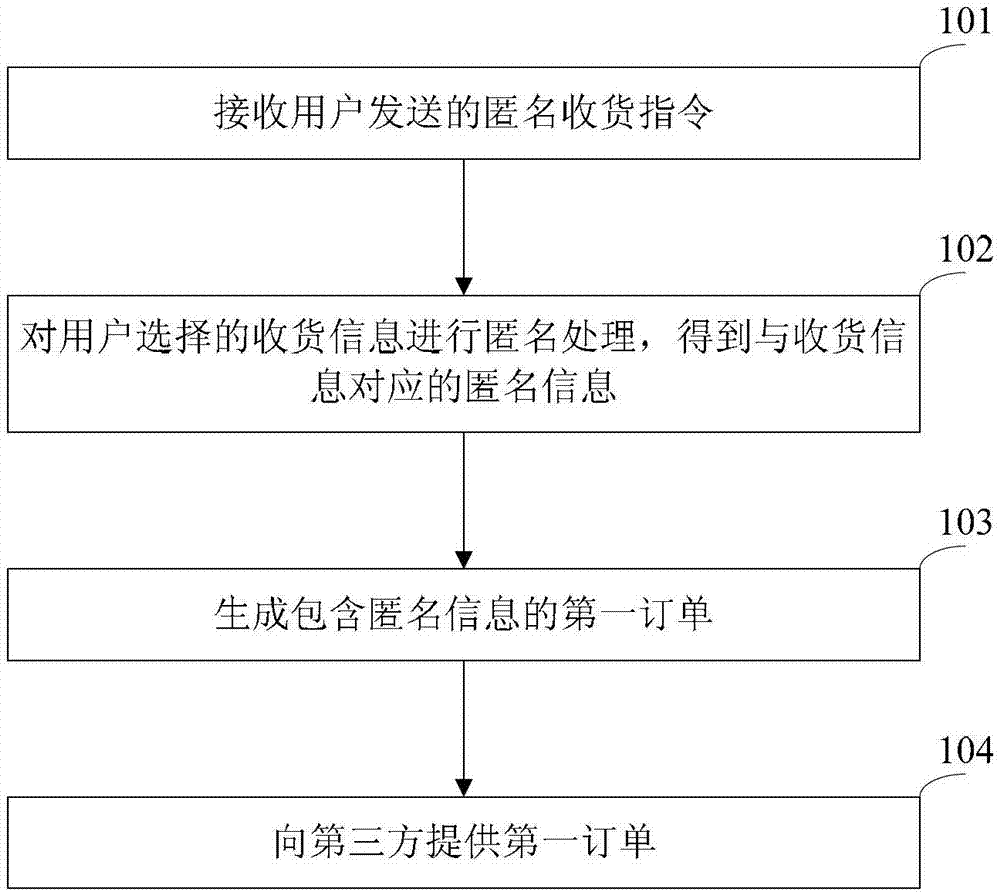
Receiving information processing method and device
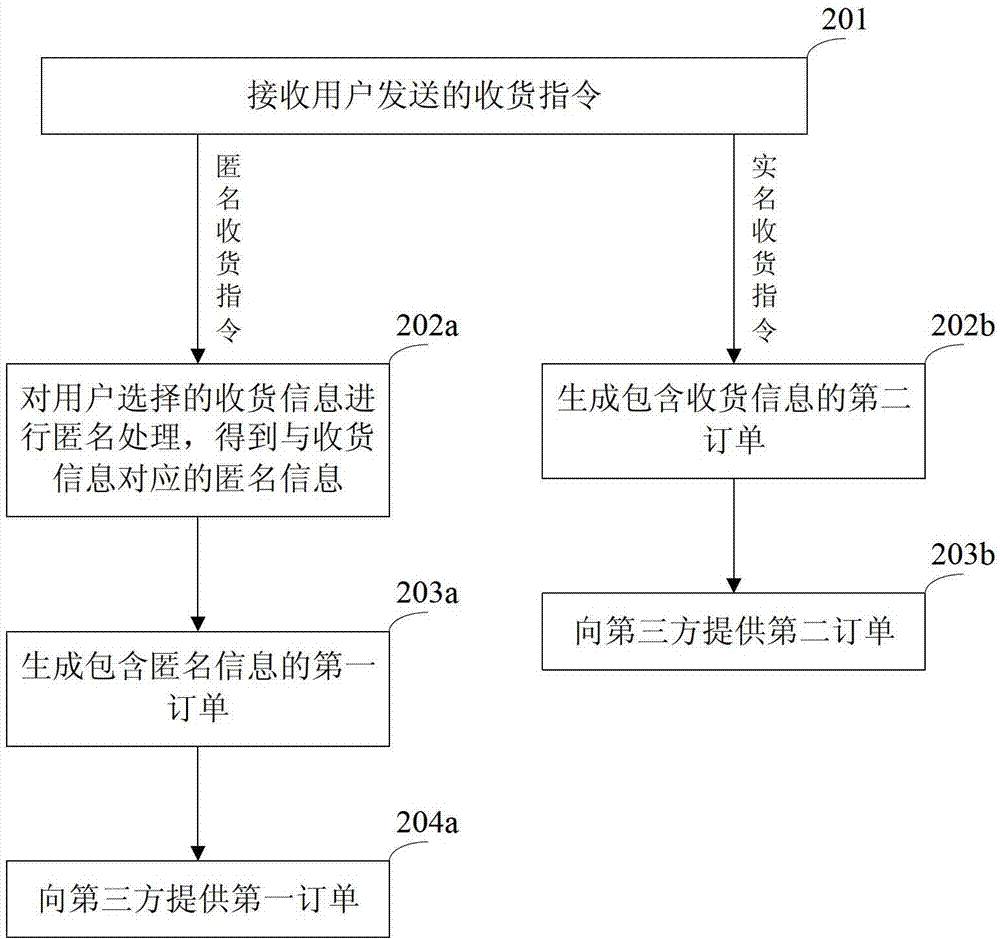
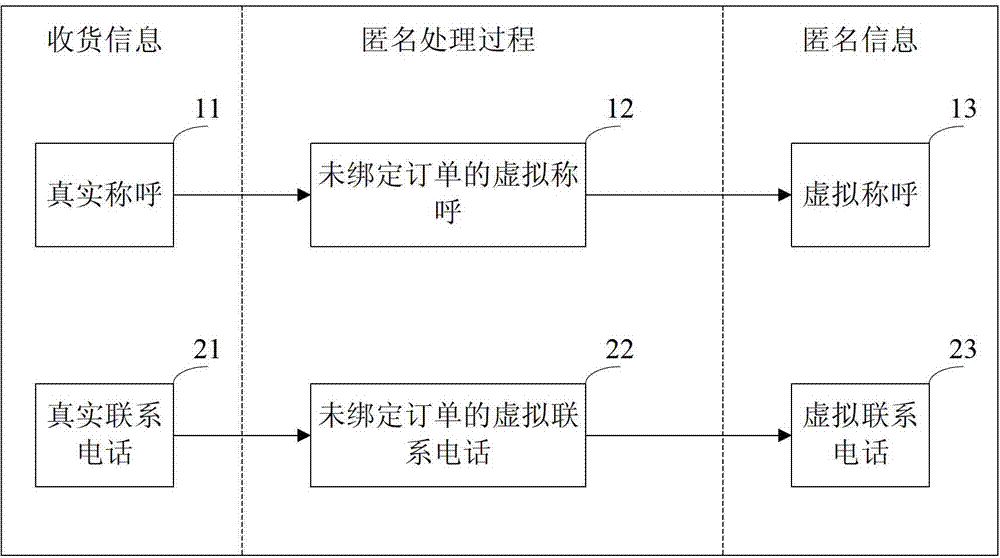
The invention discloses a receiving information processing method and a receiving information processing device, belonging to the field of e-business. The method comprises the steps of receiving an anonymous receiving instruction transmitted by a user; performing the anonymous process on the receiving information selected by the user so as to obtain anonymous information corresponding to the receiving information; generating a first order containing the anonymous information; and providing the first order to a third party. The device comprises a receiving module, an anonymous processing module, an order generating module and a providing module; the receiving module is used for receiving the anonymous receiving order of the user; the anonymous processing module is used for performing the anonymous process on the receiving information selected by user so as to obtain the anonymous information corresponding to the receiving information; the order generating module is used for generating the first order of the anonymous information containing the anonymous processing module; and the providing module is used for providing the first order generated by the order generating module for the third party. According to the receiving information processing method and the receiving information processing device, the anonymous information of the user instead of the receiving information of the user is provided for the third party so as to protect the privacy of the user.
Owner:XIAOMI INC
Electronic cassette and electronic cassette apparatus
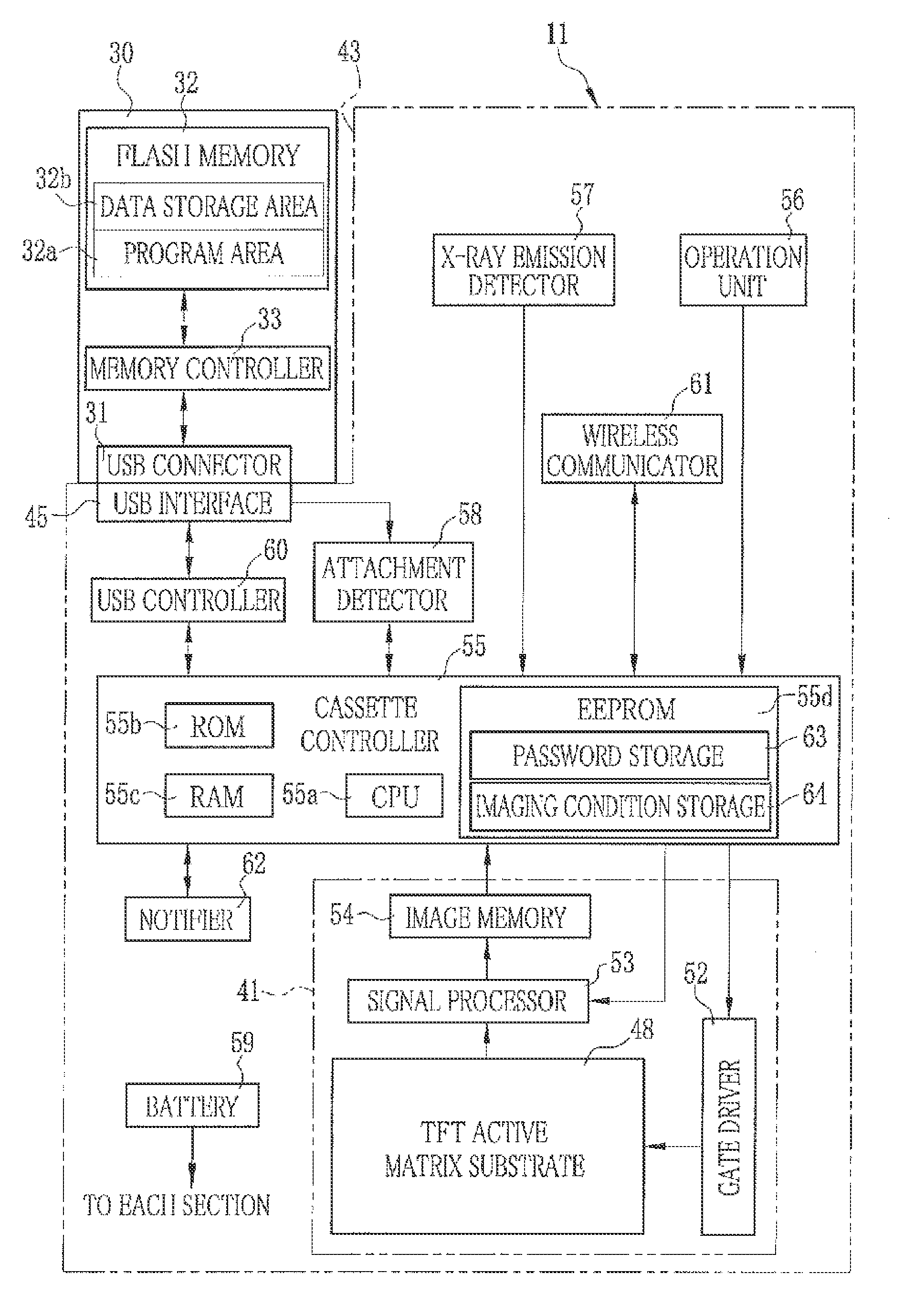
InactiveUS20130214157A1Improve usabilityInformation leakagePhotometryMaterial analysis by optical meansPasswordMemory controller
A USB memory device incorporates a flash memory and a memory controller. An access lock is placed on a data storage area of the flash memory. When the USB memory device is attached to an electronic cassette, a cassette controller controls a USB controller to input an unlock password to the USB memory device. The memory controller unlocks the access lock on the data storage area when the unlock password matches a password stored in a program area of the flash memory in advance.
Owner:FUJIFILM CORP
Anonymous transaction platform
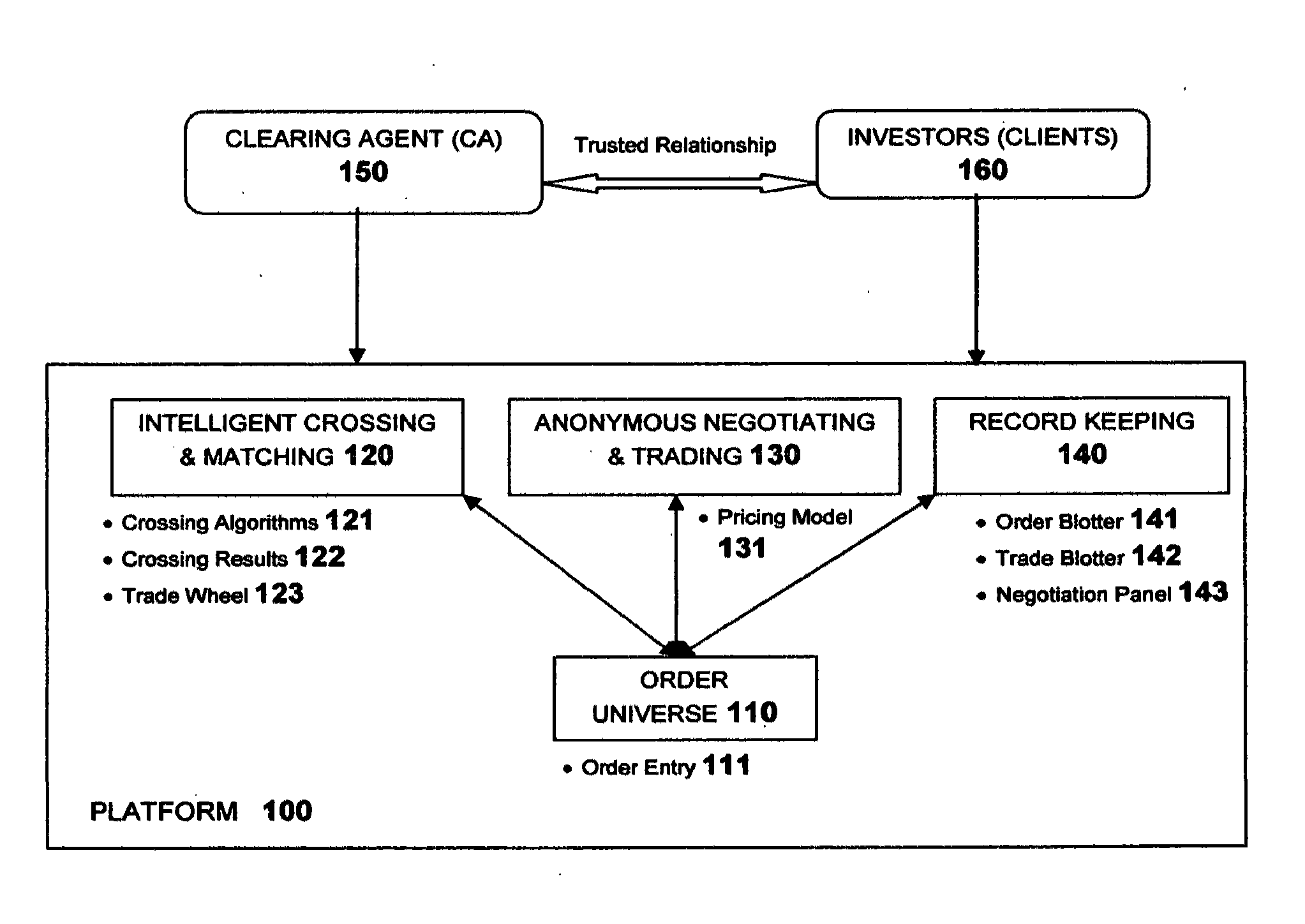
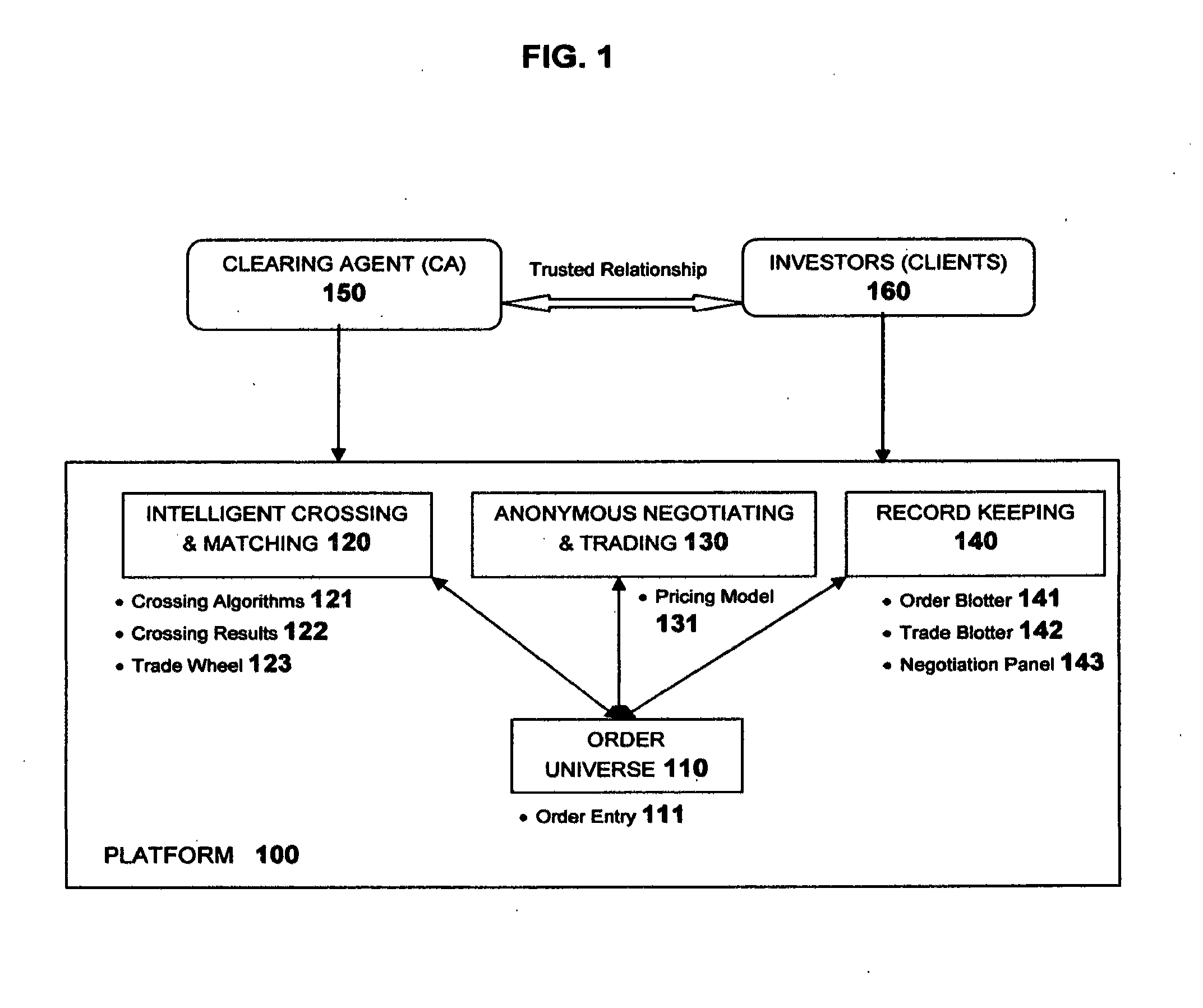
InactiveUS20130325686A1Reduce disruption and disruptionImprove liquidityFinanceClearing AgentTransaction data
A computer implemented method to anonymise transactions conducted via a trading platform between a clearing agent in communication with a trading database, and a client terminal, the method comprising: identifying the client terminal with an anonymised client identifier; the clearing agent receiving from a client terminal, as an order, a request to buy or sell a quantity of financial instrument and assigning an anonymised order identifier to the request; for each anonymised order identifier the trading database identifying identical or similar financial instruments, and their quantity, offered by a plurality of other users for the financial instrument in the request and assigning a weighted score of the likelihood of a match between the identified instruments and the requested instrument; presenting on the client terminal, as a trade offer anonymised information of the weighted score of the likelihood of a match between the requested and each of a plurality of identified financial instruments; and indicating via the client terminal if one or more of the trade offers is to be negotiated or accepted.
Owner:ALGOMI
Encrypted data verification system, method and recording medium
ActiveUS20150195090A1Avoid Information LeakageInformation leakagePublic key for secure communicationDigital data authenticationComputer hardwarePlaintext
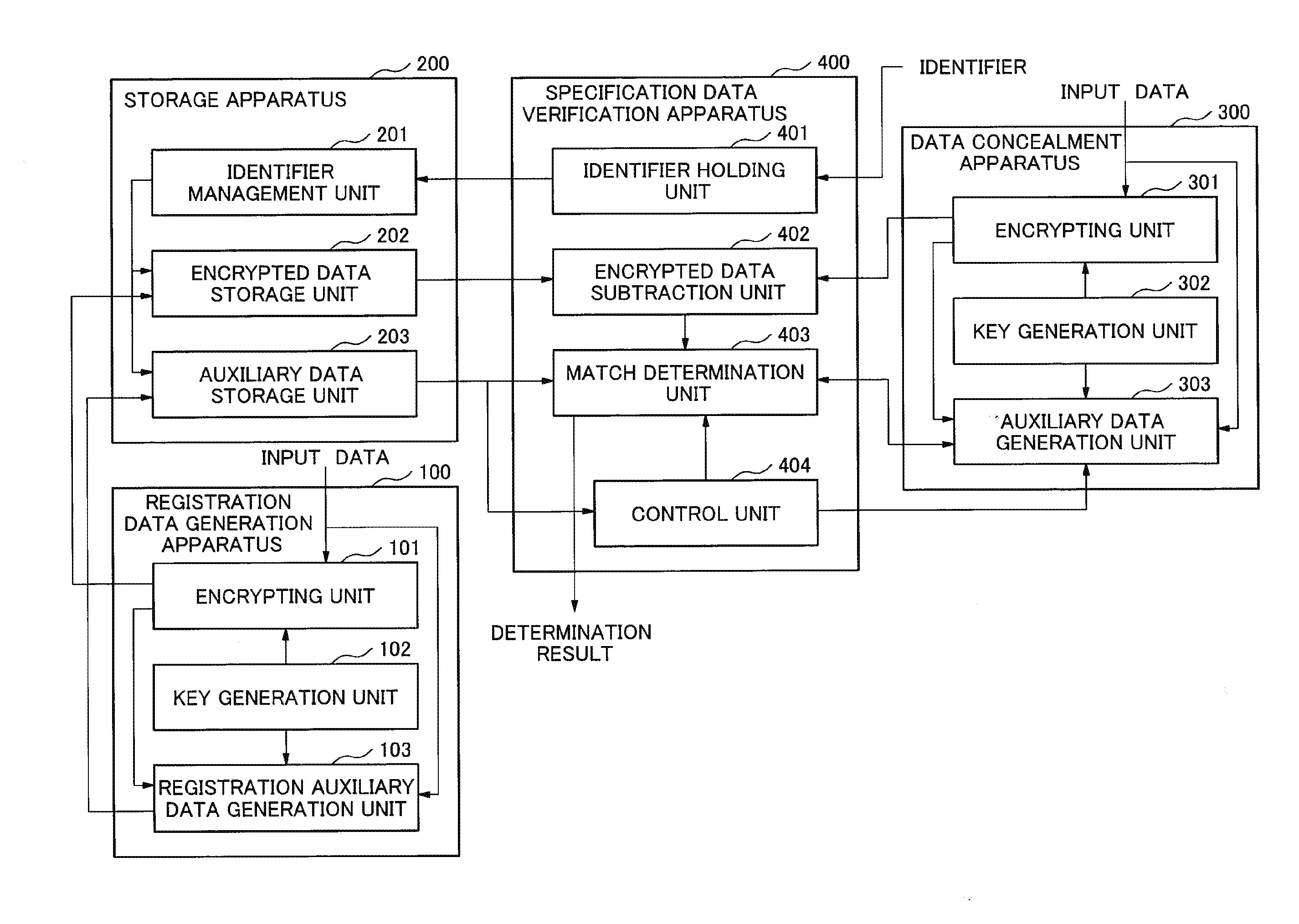
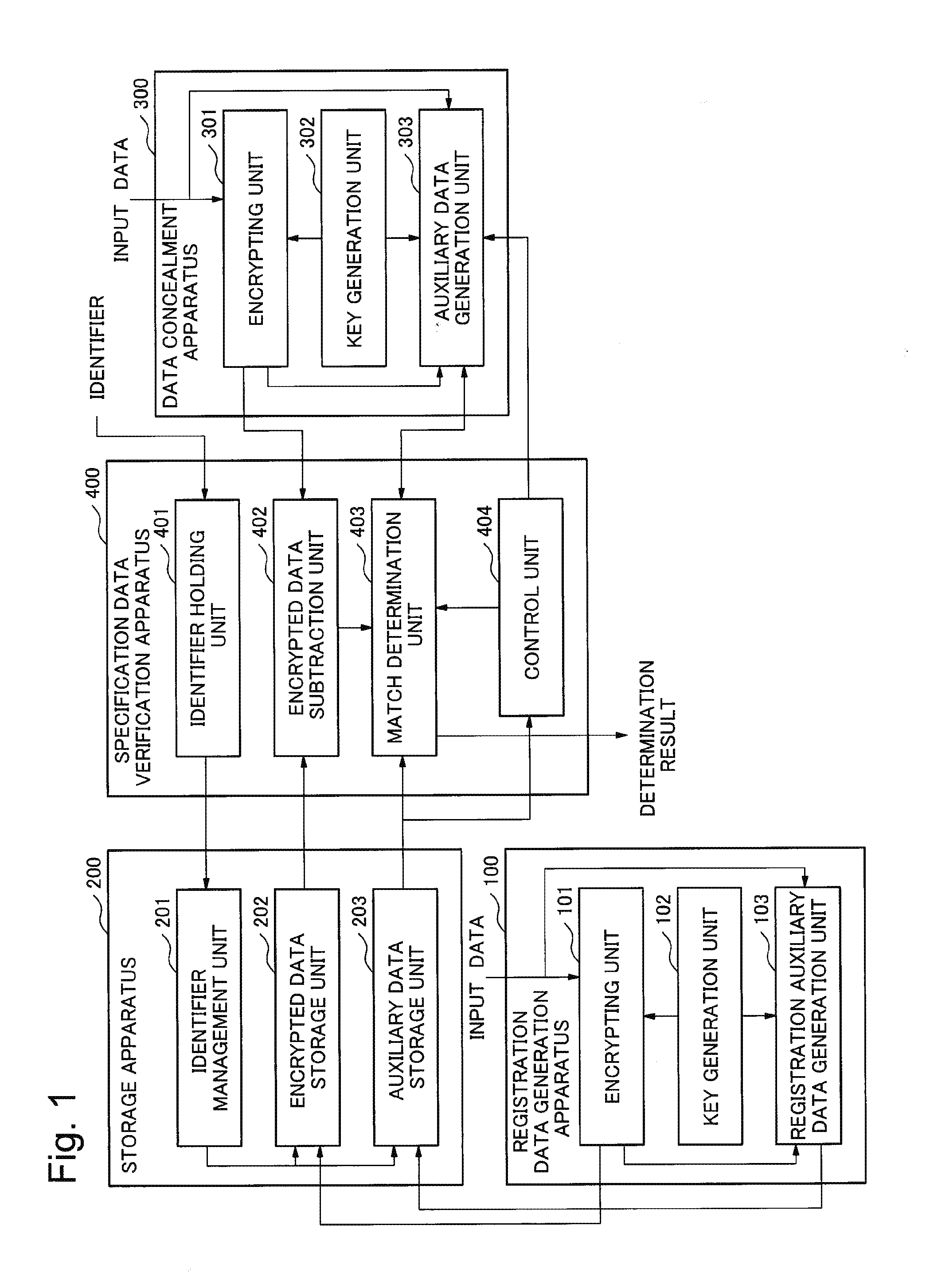
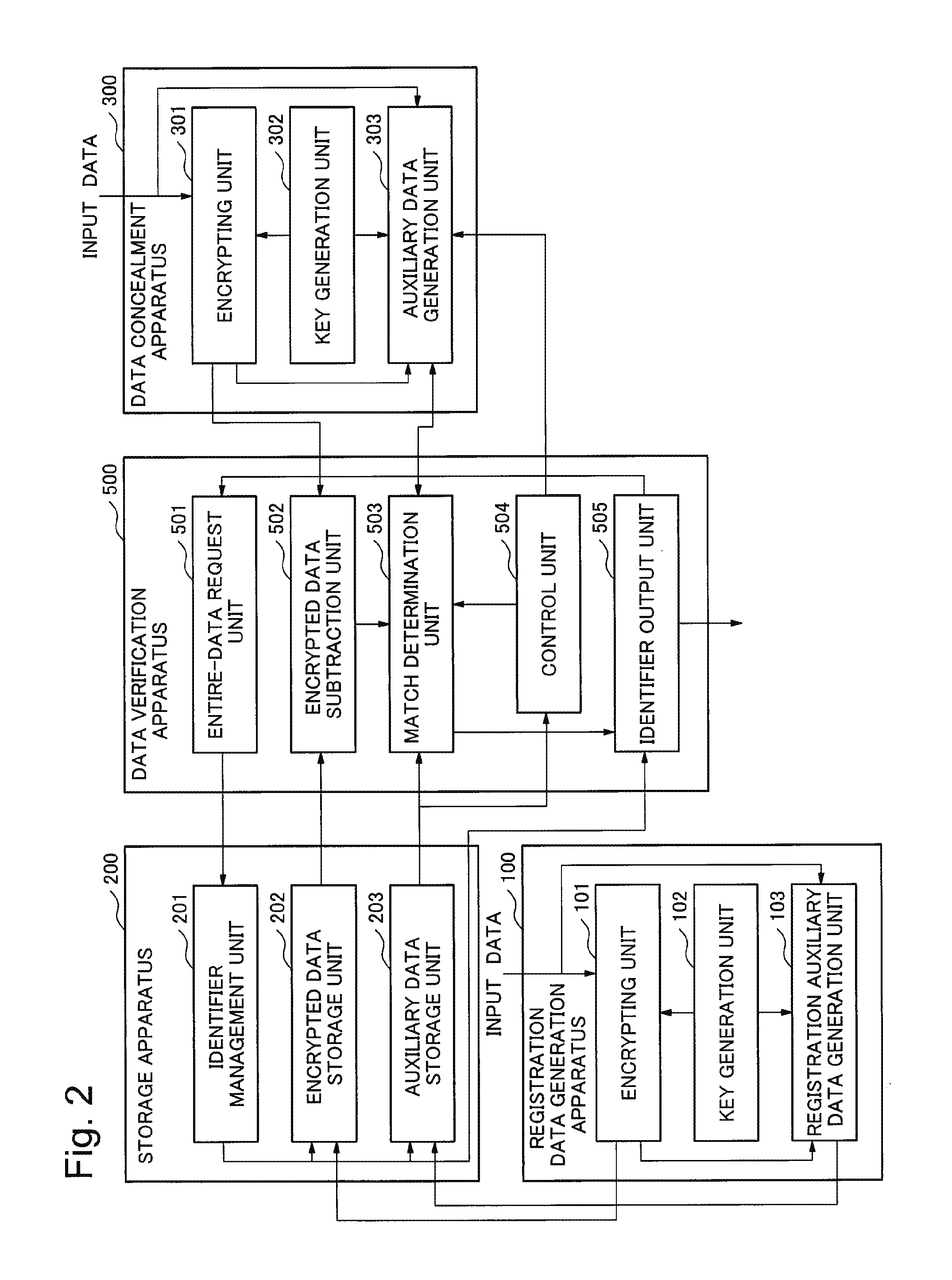
The present invention makes it possible, in encrypted data verification, to avoid the leaking of information related to the original plaintext, thereby ensuring safety. The system of the present invention is provided with: means (103 in FIG. 1) for generating first and second auxiliary data for verifying whether or not the Hamming distance of a plaintext between a first encrypted data in which input data is encrypted and is recorded in a storage device, and a second encrypted data obtained by encrypting input data of a target to be checked is equal to or less than a predetermined value; and means (402 and 403 in FIG. 1) for taking the difference between the first encrypted data recorded in the storage device, and the second encrypted data, and determining, using the first and second auxiliary data, whether or not the Hamming distance of the plaintext corresponding to the difference between the first encrypted data and the second encrypted data is equal to or less than the predetermined value.
Owner:NEC CORP
Heating cooker for commercial use
ActiveUS20050011881A1Improve securityInformation leakageElectric heatingCooking vesselsPasswordMonitoring system
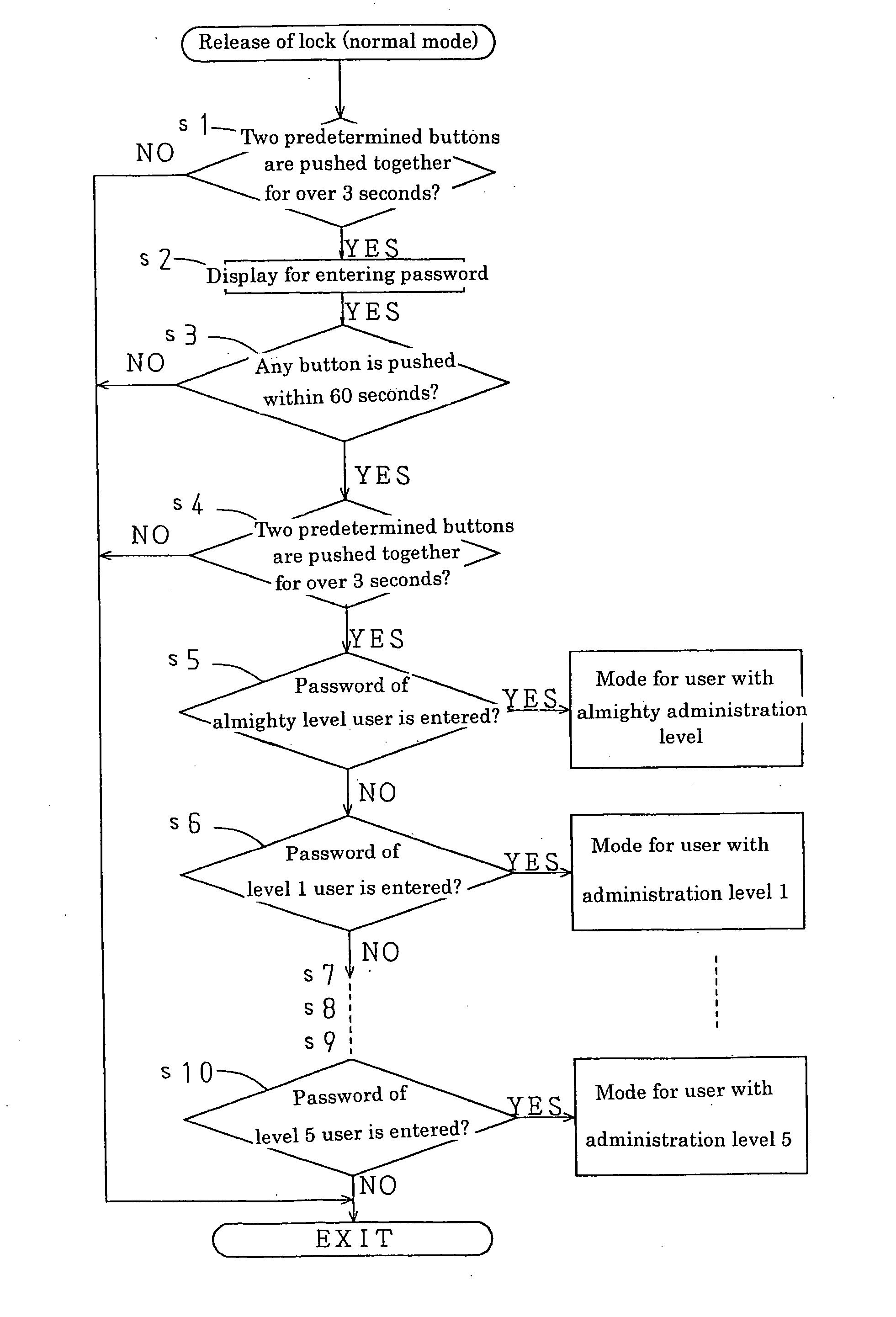
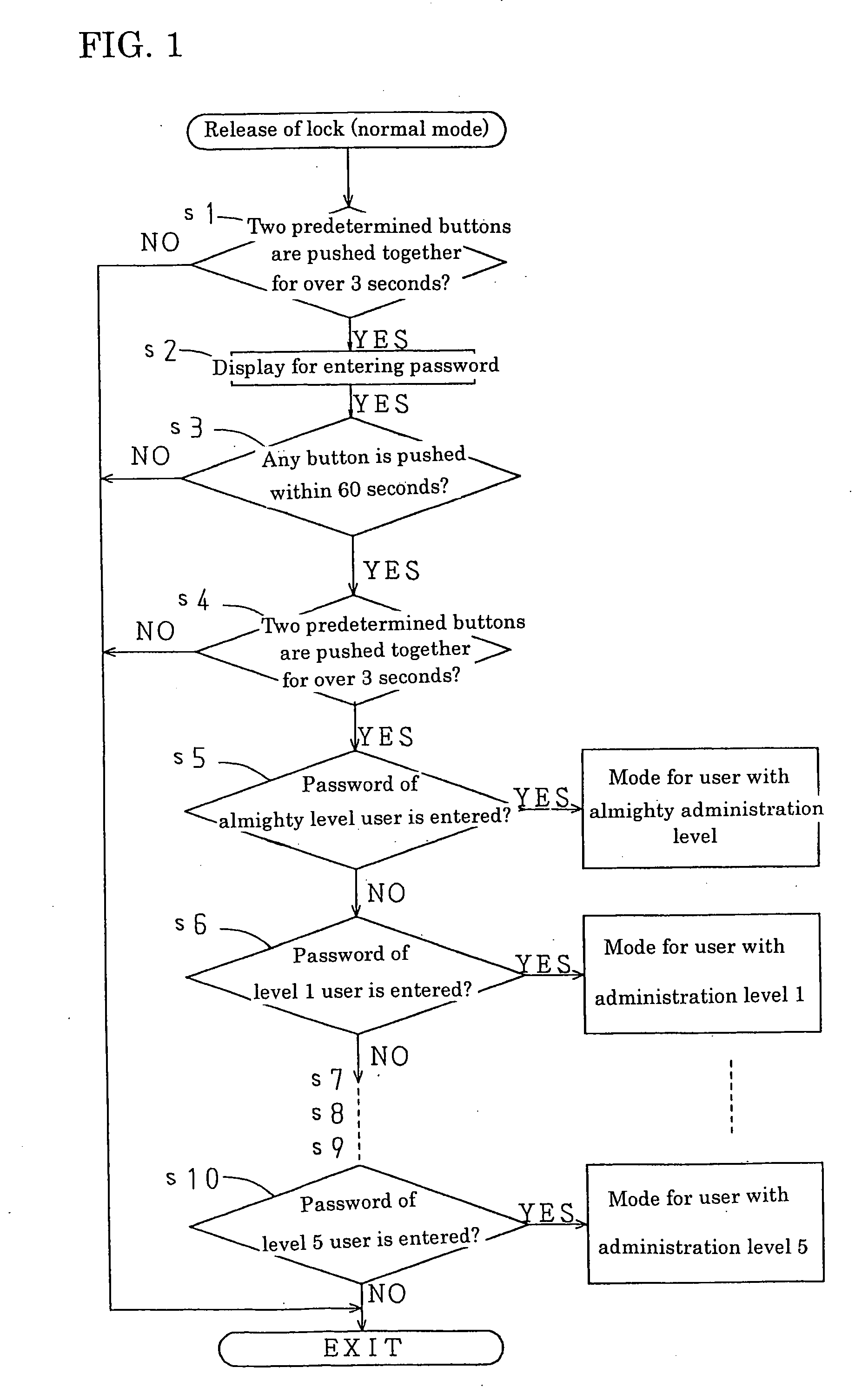
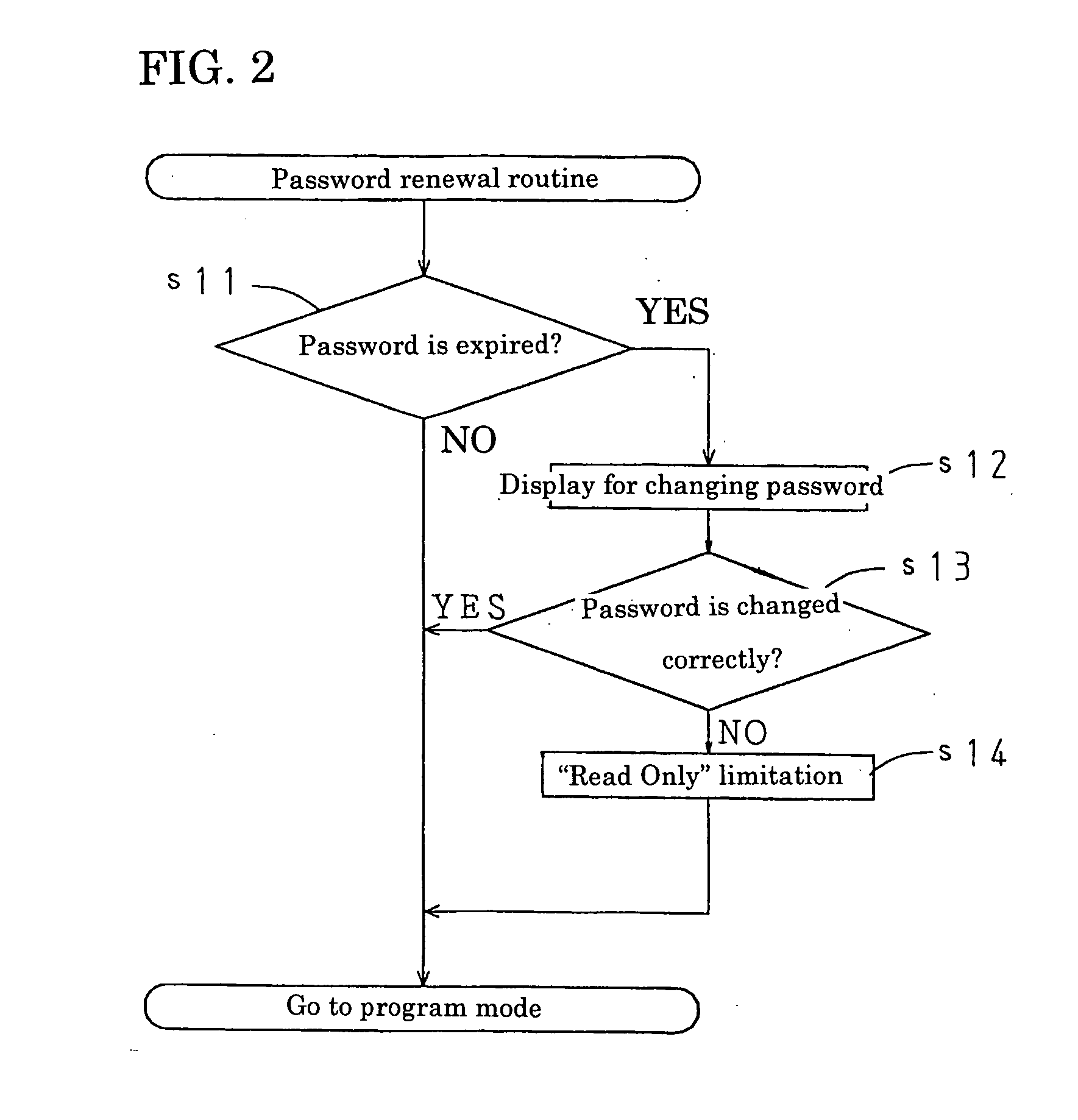
A heating cooker for commercial use is provided in which heating control is conducted based on cooking parameter according to each cooking menu and an unauthorized user is prevented from changing the cooking parameter easily. In the heating cooker, cooking parameter can be changed only when a password is entered. Moreover, a user's administration level is determined by the entered password and information which can be changed is selected according to the user's administration level. The password entry can be carried out not only in an operation display panel provided with the heating cooker but in a remote central monitoring system which operates the heating cooker from a distant place.
Owner:PALOMA
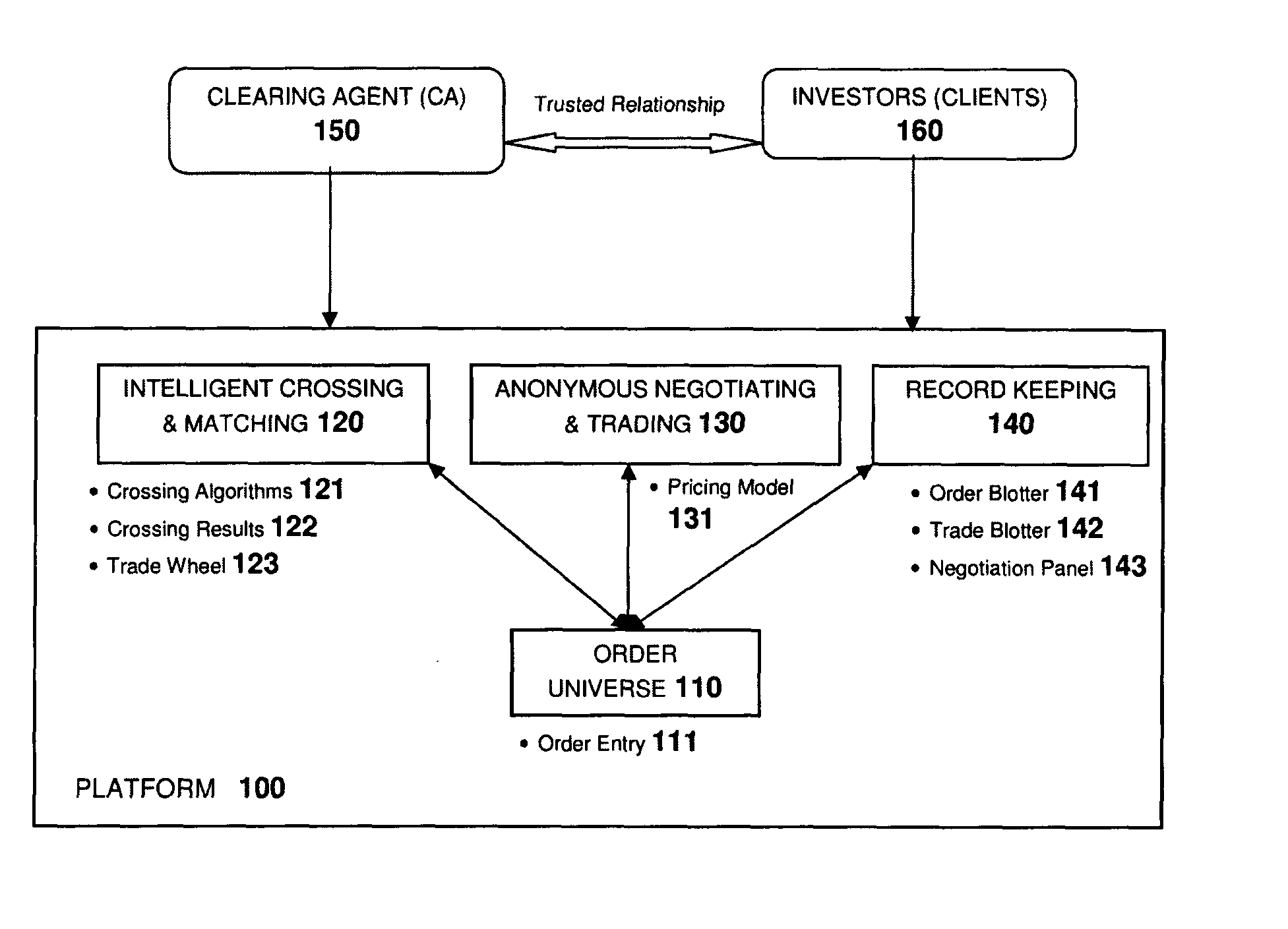
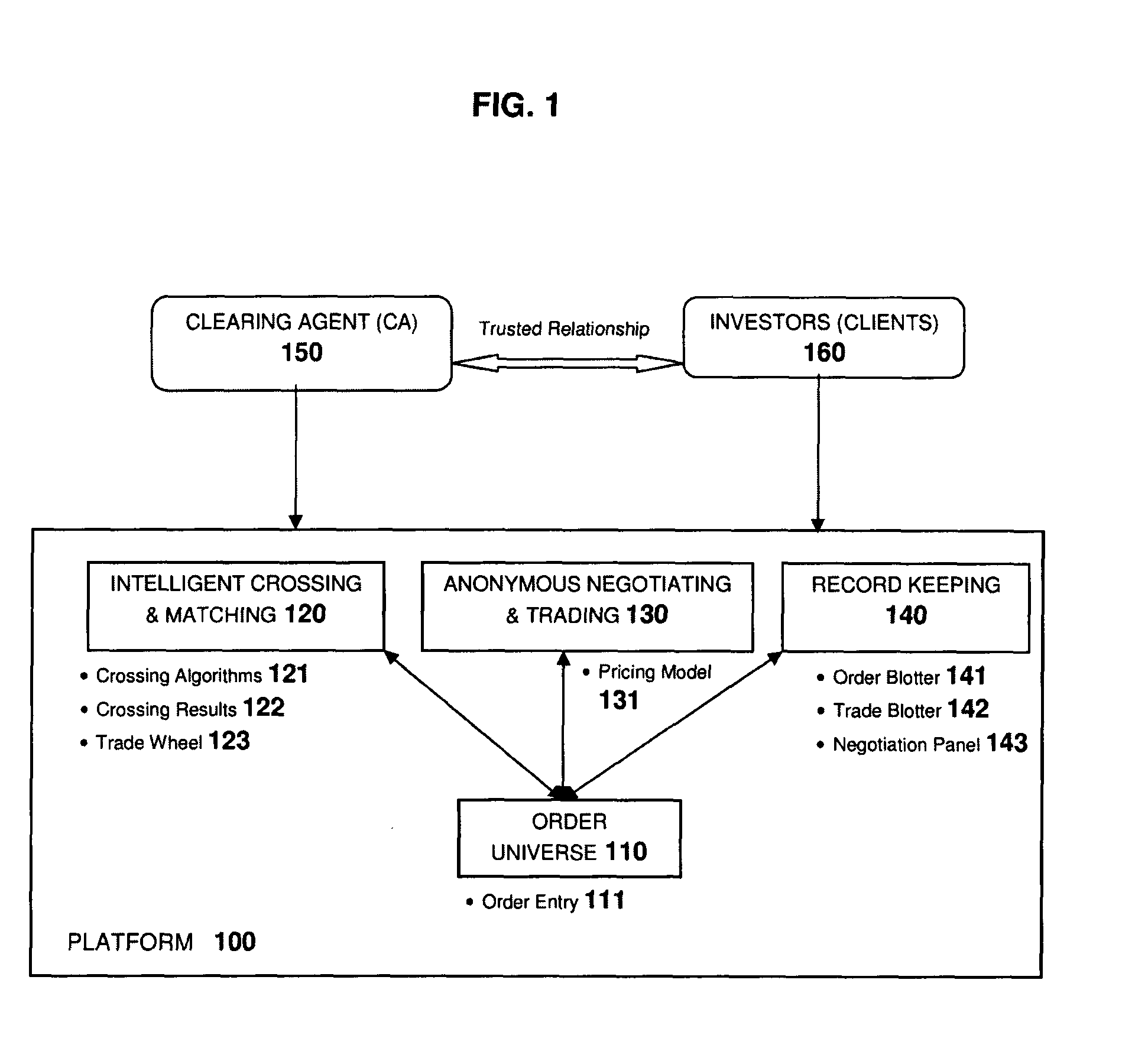
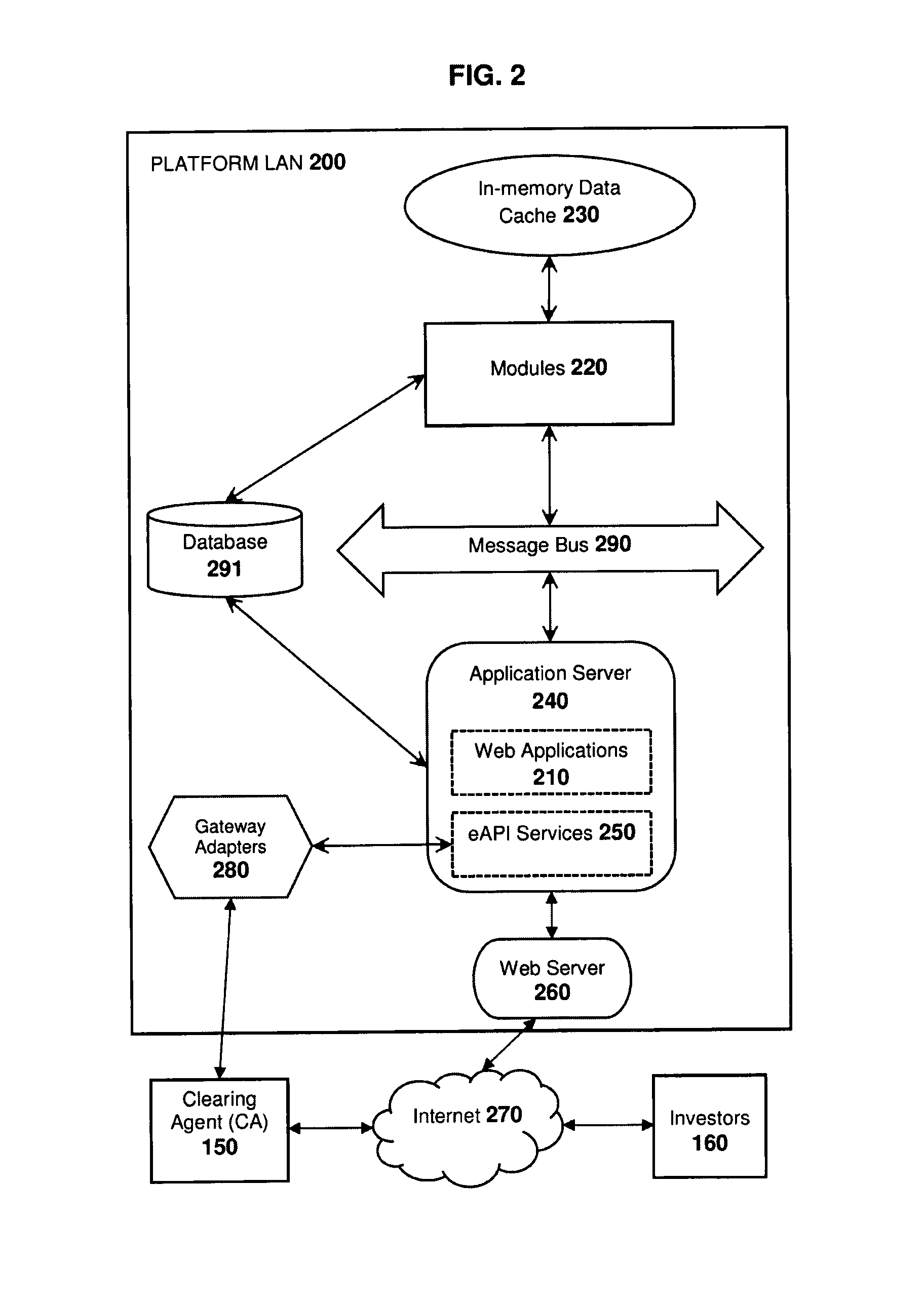
Intelligent order matching platform for anonymously negotiating and trading financial instruments
InactiveUS20120221453A1Minimizes information leakageReduce disruptionFinanceIntelligent designClearing Agent
This software enables a financial institution acting as a clearing agent to offer a liquidity pool where their clients can anonymously submit orders for a financial instrument. Many financial markets suffer from reduced liquidity, the causes for which include: 1) fragmentation across multiple markets, 2) fragmentation across a large instrument universe and 3) attempting to trade an illiquid instrument. The software has been developed to uniquely improve available liquidity using crossing algorithms that intelligently identify orders for similar instruments as relevant execution opportunities, and applies a quantitative scoring of their propensity to trade on which clients can anonymously negotiate and execute. As crossing algorithms are not constrained by the conventional restriction that orders must be for identical instruments, the system is able to increase liquidity by identifying execution opportunities that existing markets cannot, while employing an anonymous negotiation process that minimizes information leakage to mitigate disruption to market prices.
Owner:HOWES ROBERT +1
Semiconductor device
InactiveUS20080169467A1Avoid Information LeakagePrevent leakageSemiconductor/solid-state device testing/measurementSemiconductor/solid-state device detailsSemiconductorSemiconductor device
A transistor of a characteristic checking element has a gate electrode connected to a measurement pad disposed in a dicing line and to an internal measurement pad disposed inside a semiconductor device. In a P / W process, a gate insulating film of the transistor is broken by an electric voltage applied via the internal measurement pad. Since the gate insulating film of the transistor is broken, a new current path is formed. Thus, measurement of accurate characteristics of the characteristic checking element is inhibited.
Owner:LONGITUDE SEMICON S A R L
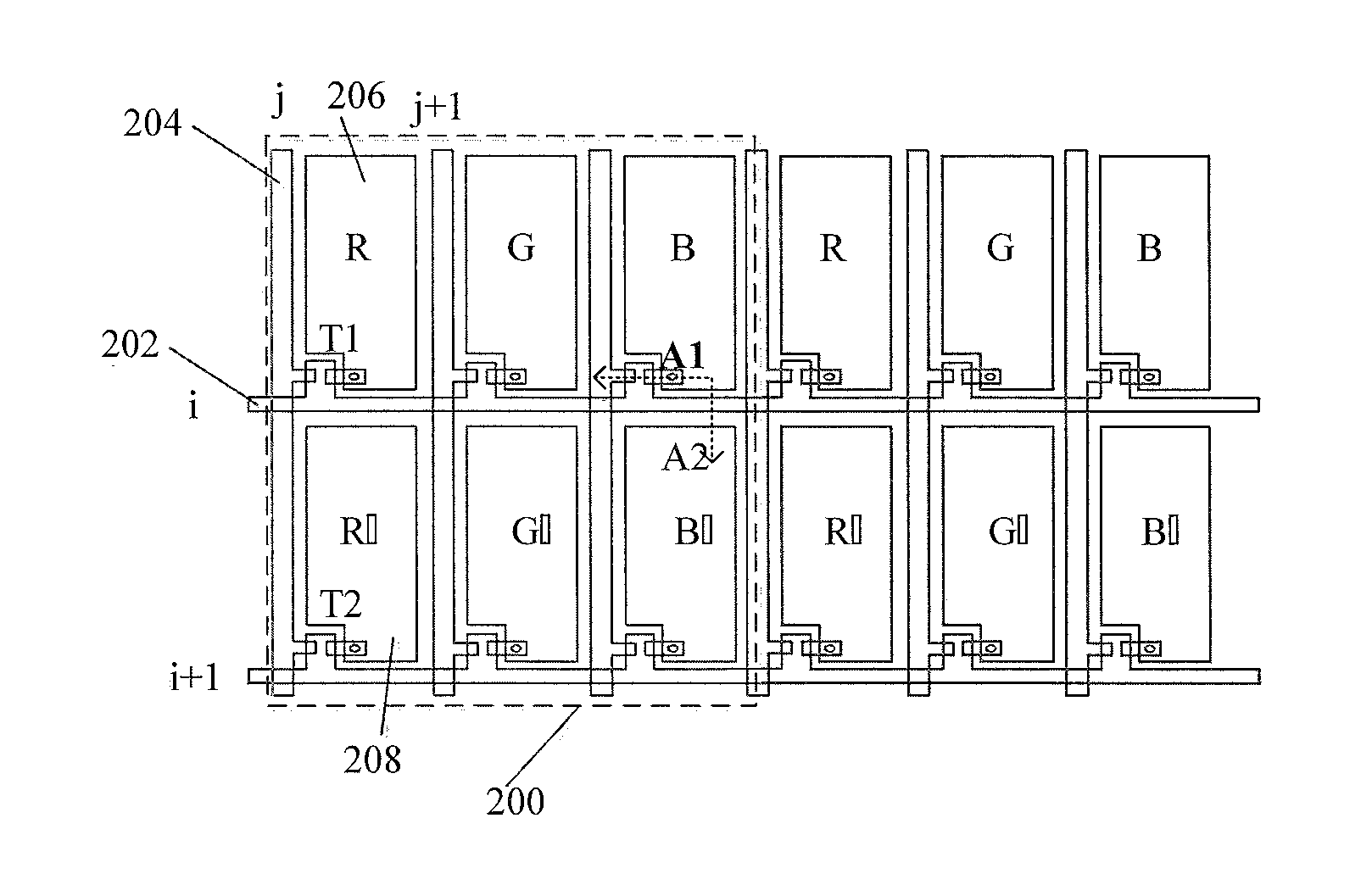
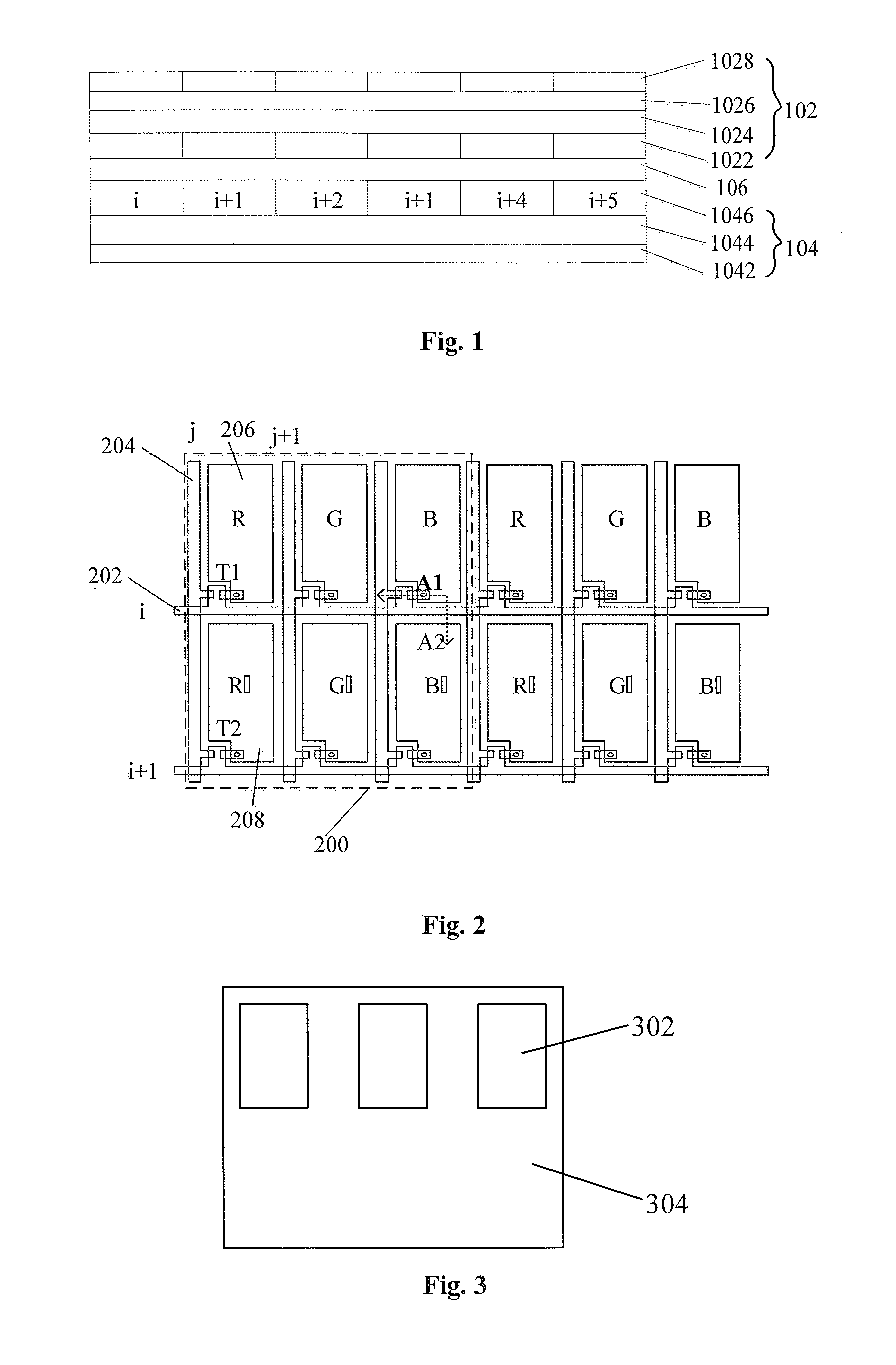
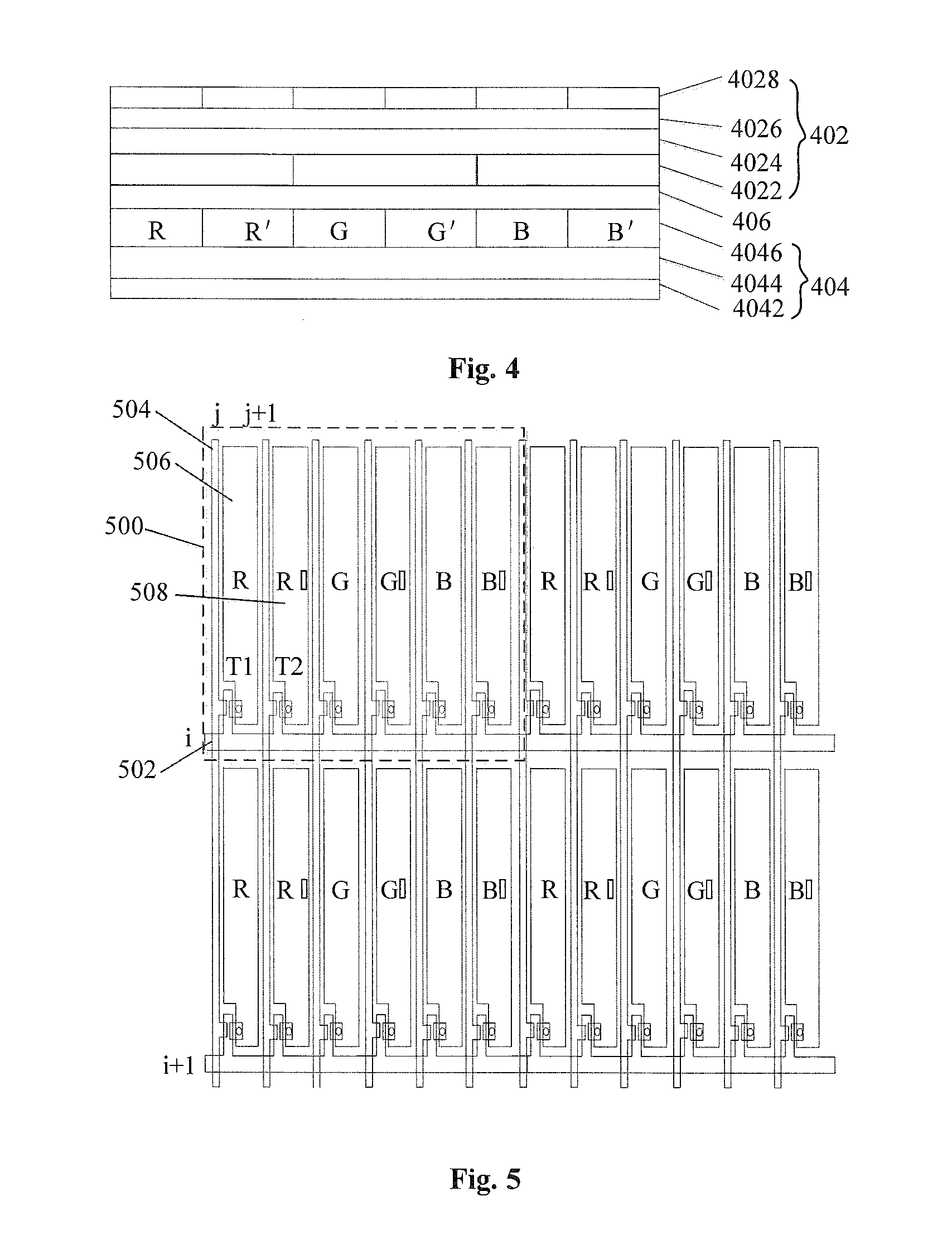
Display panel, displayer and driving method
ActiveUS20160011450A1Information leakageSolid-state devicesSemiconductor/solid-state device manufacturingDisplay deviceComputer science
The present invention discloses a display panel, a displayer and a drive method for an array substrate in a display panel. The display panel comprises a cell substrate and an array substrate. Sub-pixel units of the array substrate are classified into first type of sub-pixel units for displaying an original image and second type of sub-pixel units for displaying an interference image. The outermost side of the cell substrate is provided with a FPR film array, wherein, first FPR films are in correspondence to the first type of sub-pixel units so as to convert emitting light of the first type of sub-pixel units into polarized light in a first direction; and a second FPR film is in correspondence to the second type of sub-pixel units so as to convert emitting light of the second type of sub-pixel units into polarized light in a second direction different from the first direction. The displayer may show the original image as well as the interference image simultaneously, and only wearing glasses for filtering interference image can the user observes the normal original image so as to prevent the original image from being observed by a peeper with his / her naked eyes.
Owner:BOE TECH GRP CO LTD
Semiconductor device
InactiveUS8704223B2Avoid Information LeakagePrevent leakageSemiconductor/solid-state device testing/measurementSemiconductor/solid-state device detailsEngineeringSemiconductor
A transistor of a characteristic checking element has a gate electrode connected to a measurement pad disposed in a dicing line and to an internal measurement pad disposed inside a semiconductor device. In a P / W process, a gate insulating film of the transistor is broken by an electric voltage applied via the internal measurement pad. Since the gate insulating film of the transistor is broken, a new current path is formed. Thus, measurement of accurate characteristics of the characteristic checking element is inhibited.
Owner:LONGITUDE SEMICON S A R L
Distributed Traceability Management System
InactiveUS20080098007A1Function increaseInformation leakageStacking articlesResourcesComputer scienceData store
The distributed traceability management system includes a management data creation unit and a data storage unit. When the final products are produced, final management data is transmitted to the downstream side vendor. When the final management data is received from an upstream side vendor, the final management data is stored in the data storage unit. When it is judged that the same final management data as that stored in a system's data storage unit is stored in the data storage unit of a communication party vendor through communication with the communication party vendor, it is confirmed that the communication party vendor is an upstream side vendor or a downstream side vendor to which the final products are to be distributed. Tracing of products in a sequence of processes is executed based on each f pieces of management data created by the management data creation unit.
Owner:ASAHI KOGAKU KOGYO KK
Information processing apparatus, information processing system, information processing method, storage medium, and program
InactiveUS7450742B2Inhibition of informationProtect informationUltrasonic/sonic/infrasonic diagnosticsDigital data processing detailsInformation processingManagement unit
Owner:CANON KK
Image output system, information processing device, and authentication device
ActiveUS9131093B2Information leakageDigital data authenticationTransmissionInformation processingUser input
Owner:SHARP KK
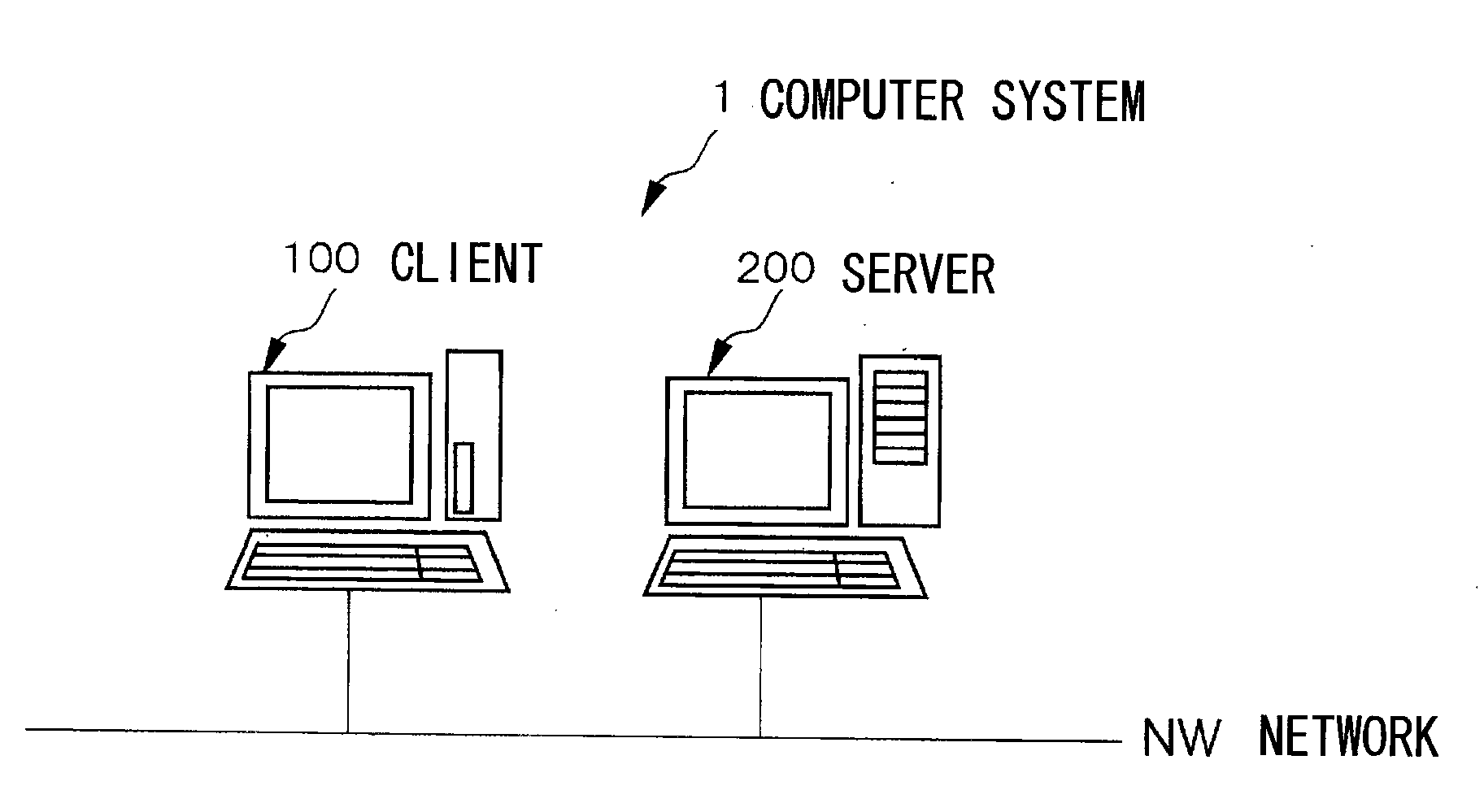
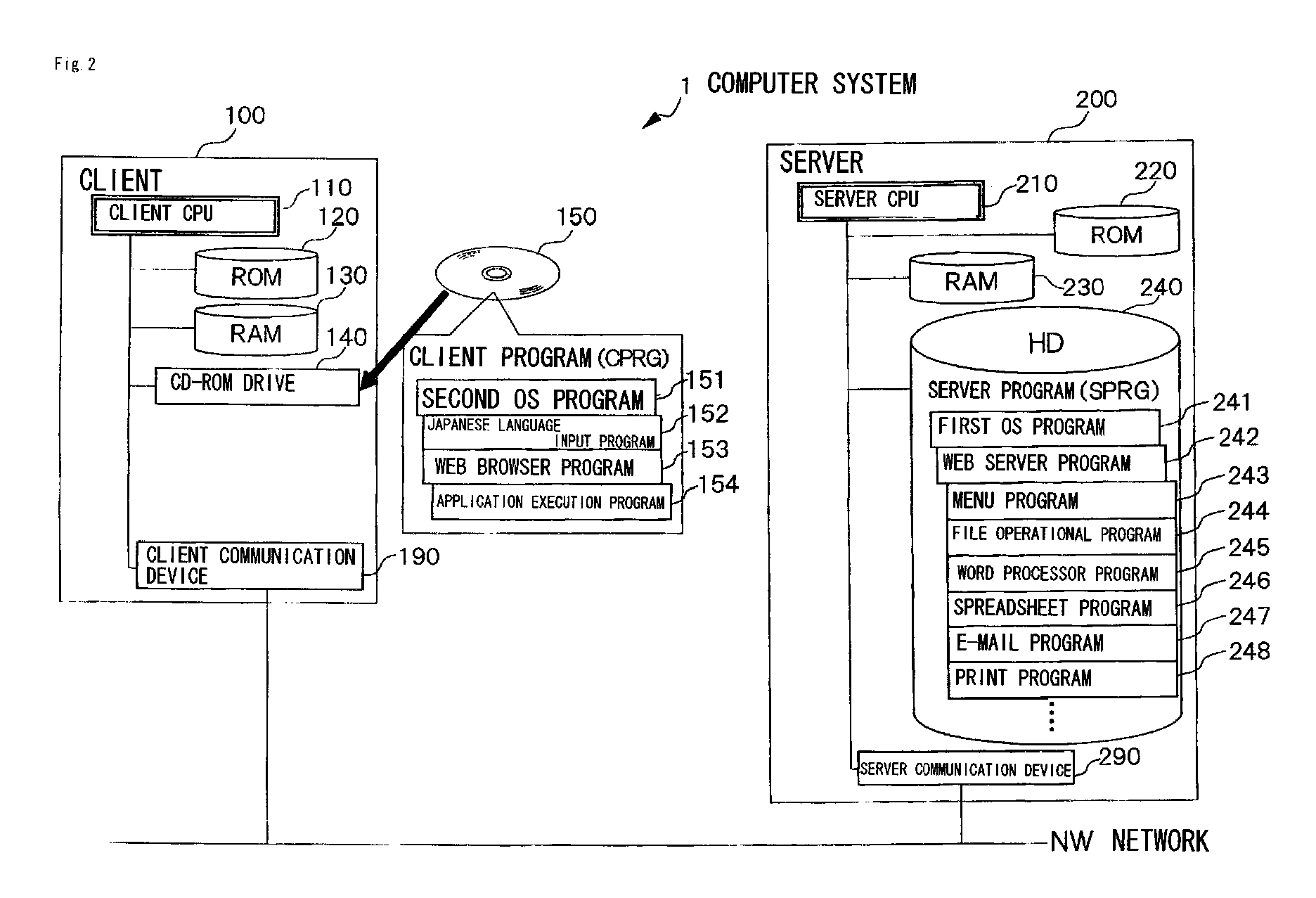
Centralized management type computer system
InactiveUS20090030908A1Easy system managementInhibition of informationDigital data protectionProgram/content distribution protectionWeb browserClient-side
A computer system for an easy system / information management. A client (100) and a server (200) are connected through a network (NW) so that a hard disk (240) or a server storage device is stored with a server holding type application program such as a menu program (243) to be operated on the web browser of the client (100). The server (200) has a web server program (242) and provides a file in response to the request of the client (100). After having started a second OS program (151), the client (100) starts a web browser program (153) in a full-screen display, and gains access to the file which is set for each client (100) or user and expressed in URL.
Owner:IZE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com