Patents
Literature
49results about How to "Address privacy concerns" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
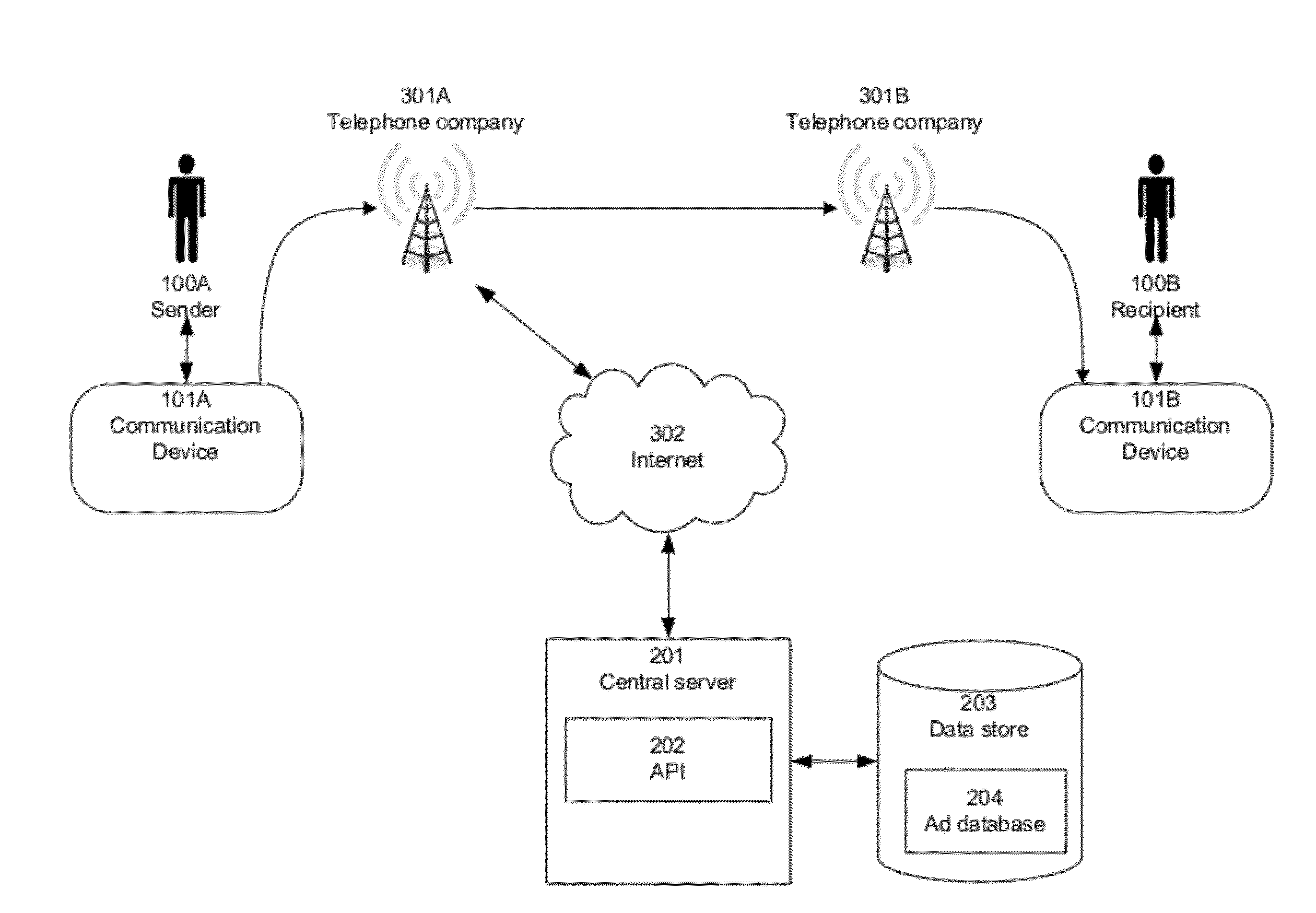
System and Method For Including Advertisements In Electronic Communications
InactiveUS20120284093A1Improve efficiencyAddress privacy concernsServices signallingMessaging/mailboxes/announcementsMessage passingElectronic communication
Improved techniques for targeting advertisements are provided, which take into account the content of electronic communications delivered via text messaging and / or other forms of communications. The system may automatically select advertisements based on message content, and the selected advertisements may then be displayed alongside messages, and / or embedded in or included in messages, for presentation to the sender and / or recipient of the message. Overall conversational context, including content of past messages between the parties, can be taken into account in selecting advertisements. In at least one embodiment, the content of a displayed advertisement can change dynamically in response to changes in the subject of a text conversation. Senders of messages can be rewarded for allowing advertisements to be embedded and / or displayed in connection with their messages.
Owner:EVANS MICHAEL SHEPHERD
Method and system for biometric authentication and encryption
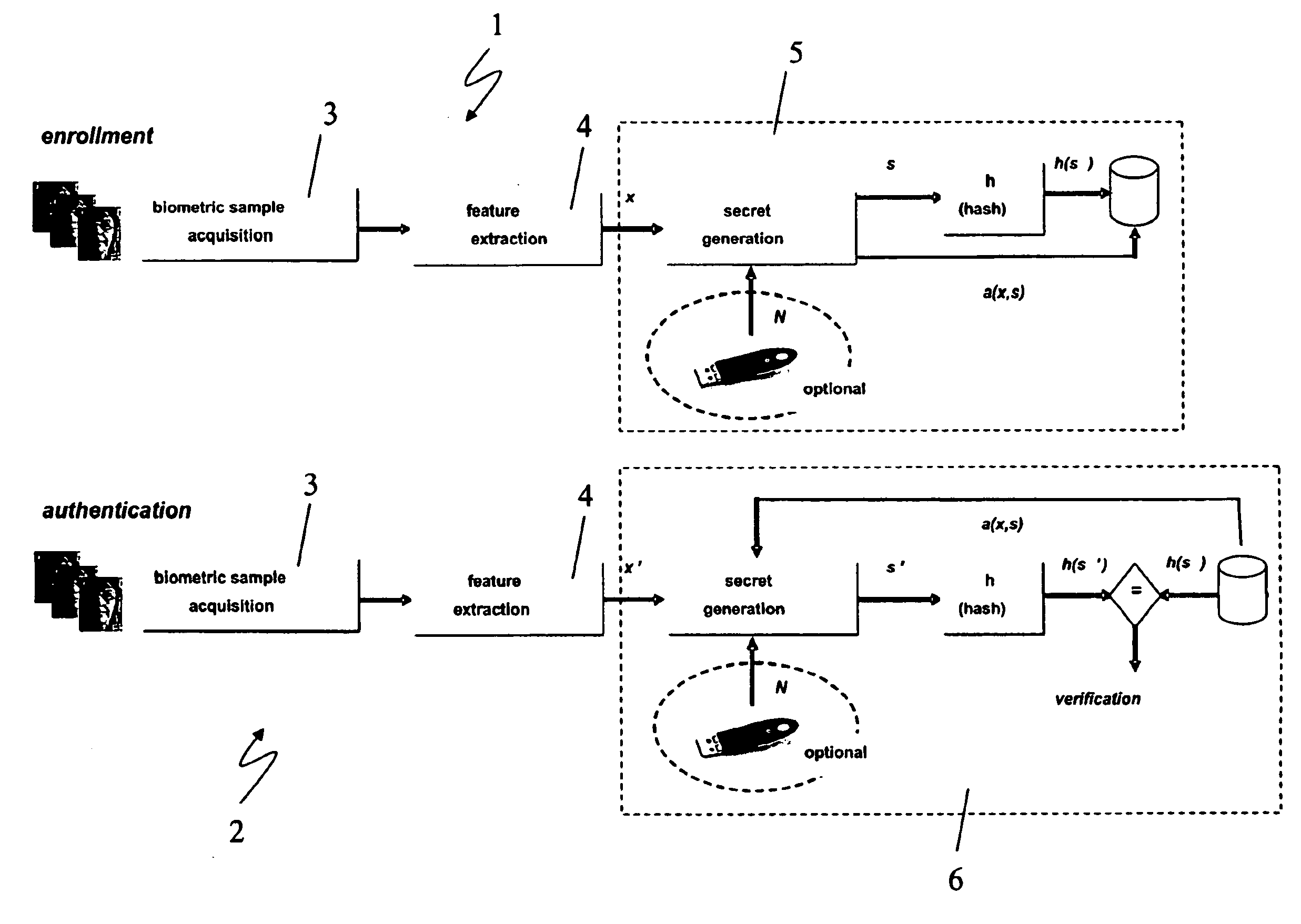
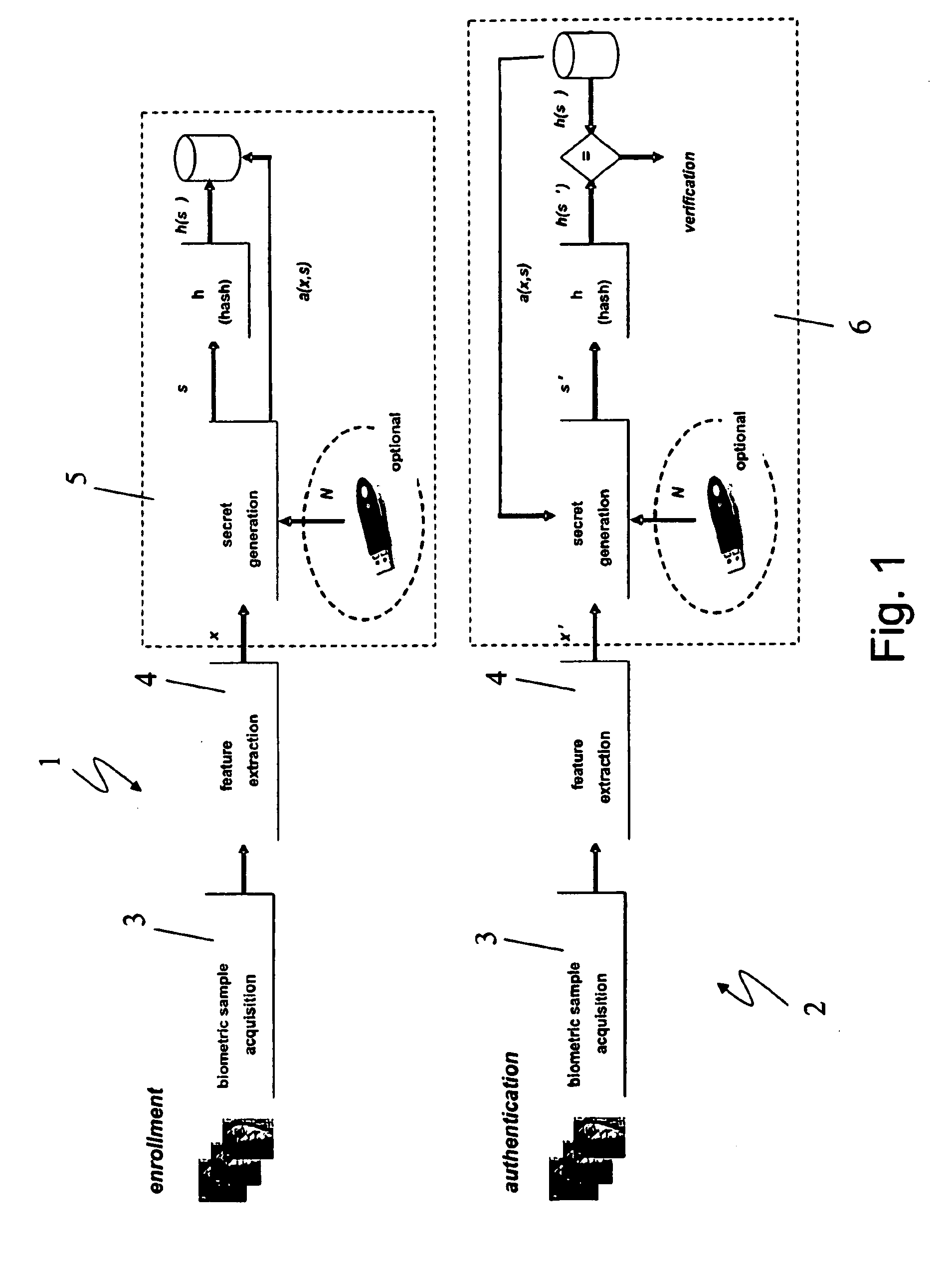
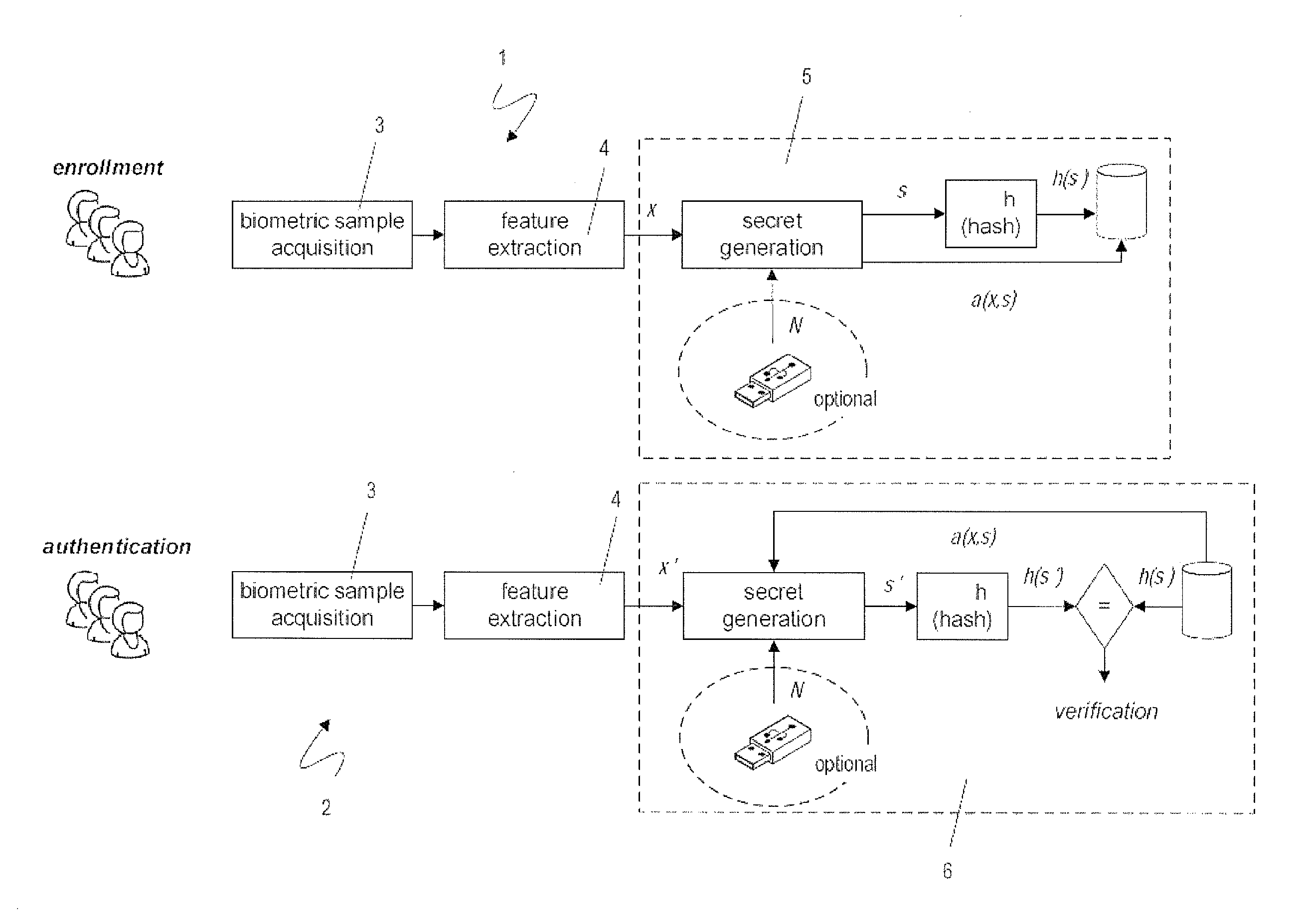
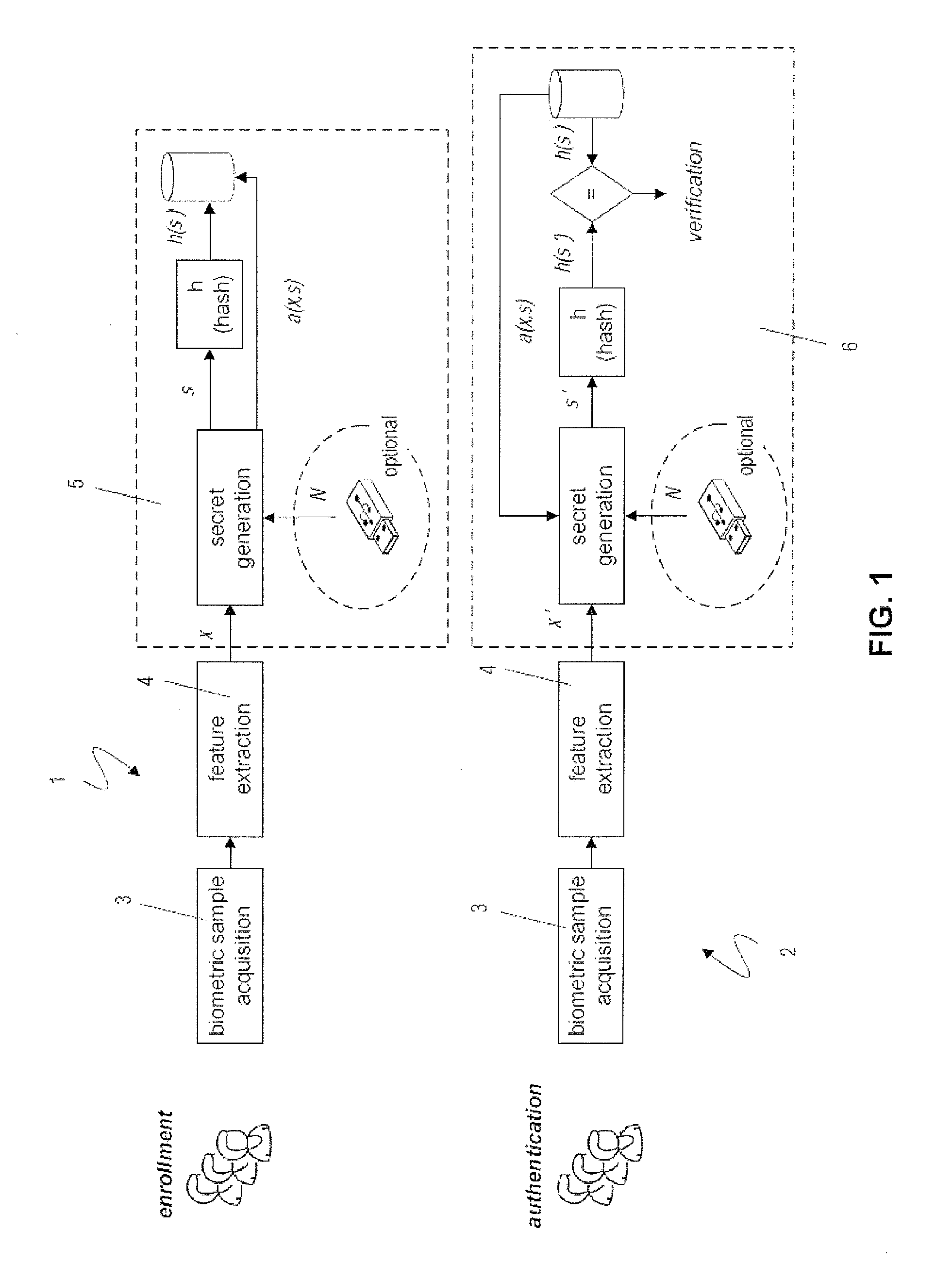
ActiveUS20100017618A1Privacy protectionAddress privacy concernsDigital data processing detailsUser identity/authority verificationFeature vectorMean vector
A biometric user authentication method, includes enrolling a user based on user's biometric samples to generate user's reference data; and authenticating the user based on a user's live biometric sample and the user's reference data; wherein enrolling a user includes acquiring the user's biometric samples; extracting an enrollment feature vector from each user's biometric sample; computing a biometric reference template vector as a mean vector based on the enrollment feature vectors; computing a variation vector based on the enrollment feature vectors and the mean vector; randomly generating an enrollment secret vector; computing an enrollment code vector based on the enrollment secret vector and the variation vector; computing a difference vector as a wrap-around difference between the enrollment code vector and the mean vector; computing an error correction vector based on the enrollment secret vector to enable error correction during the user authentication phase according to a given error tolerance level, wherein the error correction vector is not computed if the error tolerance level is equal to zero; and storing the variation vector, the difference vector, and the error correction vector as a part of the user's reference data to be used during the user authentication phase.
Owner:TELECOM ITALIA SPA
Method and system for biometric authentication and encryption
ActiveUS8312291B2Address privacy concernsEasily changeableDigital data processing detailsUser identity/authority verificationFeature vectorMean vector
A biometric user authentication method, includes enrolling a user based on user's biometric samples to generate user's reference data; and authenticating the user based on a user's live biometric sample and the user's reference data; wherein enrolling a user includes acquiring the user's biometric samples; extracting an enrollment feature vector from each user's biometric sample; computing a biometric reference template vector as a mean vector based on the enrollment feature vectors; computing a variation vector based on the enrollment feature vectors and the mean vector; randomly generating an enrollment secret vector; computing an enrollment code vector based on the enrollment secret vector and the variation vector; computing a difference vector as a wrap-around difference between the enrollment code vector and the mean vector; computing an error correction vector based on the enrollment secret vector to enable error correction during the user authentication phase according to a given error tolerance level, wherein the error correction vector is not computed if the error tolerance level is equal to zero; and storing the variation vector, the difference vector, and the error correction vector as a part of the user's reference data to be used during the user authentication phase.
Owner:TELECOM ITALIA SPA
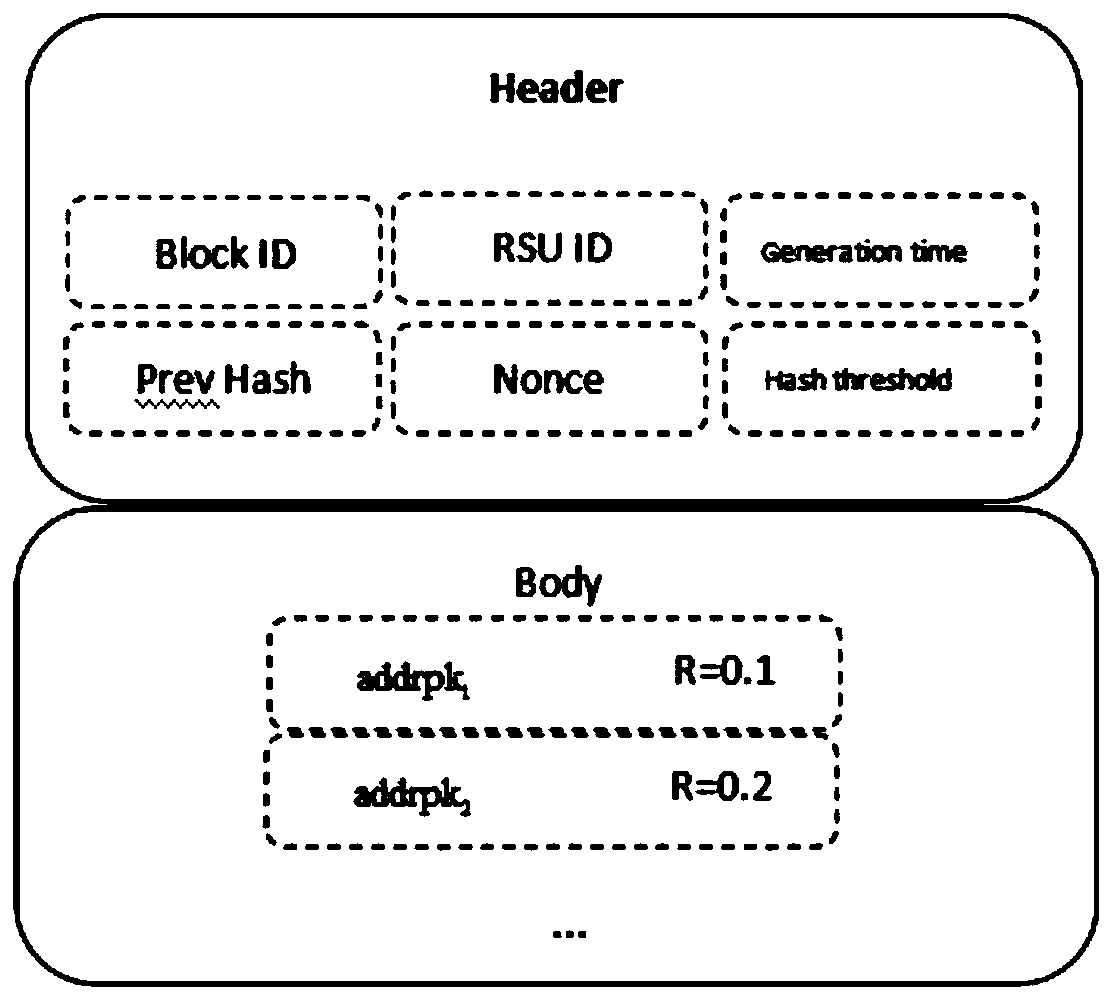
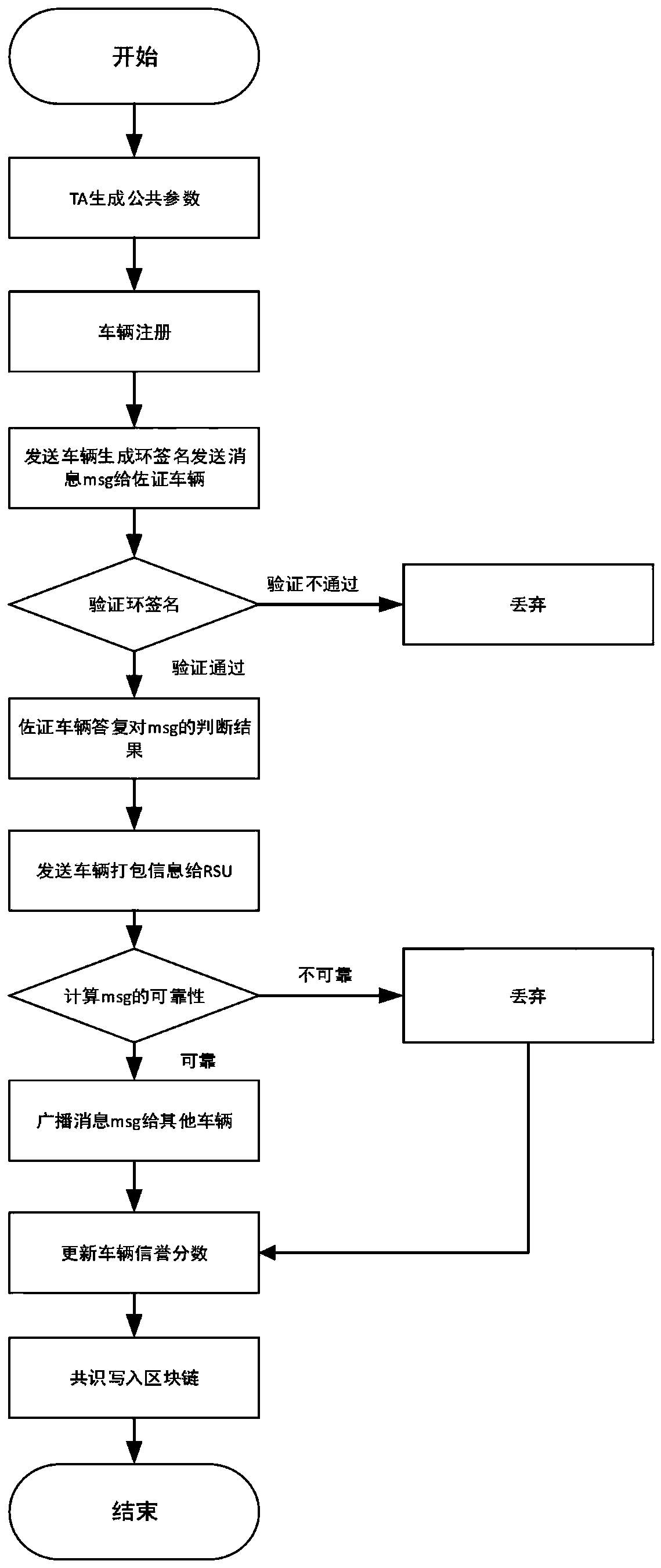
Internet of Vehicles privacy protection trust model based on block chain
ActiveCN110300107AAddress privacy concernsResolve trust issuesUser identity/authority verificationRing signaturePrivacy protection
The invention provides an Internet of Vehicles privacy protection trust model based on a block chain. Vehicles on the road generate and broadcast messages through the vehicle-mounted ad hoc network toshare surrounding traffic information so as to improve the traffic efficiency and safety. However, due to the untrusted network environment of the vehicle-mounted ad hoc network, the privacy of the vehicle is easy to expose, and whether the received message is reliable cannot be judged. The message is anonymously sent by the vehicle through the ring signature technology, so that the vehicle is prevented from being tracked by a malicious vehicle. Messages sent by the vehicle are evaluated and screened through a reputation evaluation mechanism based on the block chain technology, and forged information in the messages is filtered. Based on the characteristics of the block chain, it is guaranteed that the vehicle reputation is not maliciously tampered, real-time synchronous updating of the vehicle reputation is achieved, and the safety and usability of the vehicle-mounted ad hoc network are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
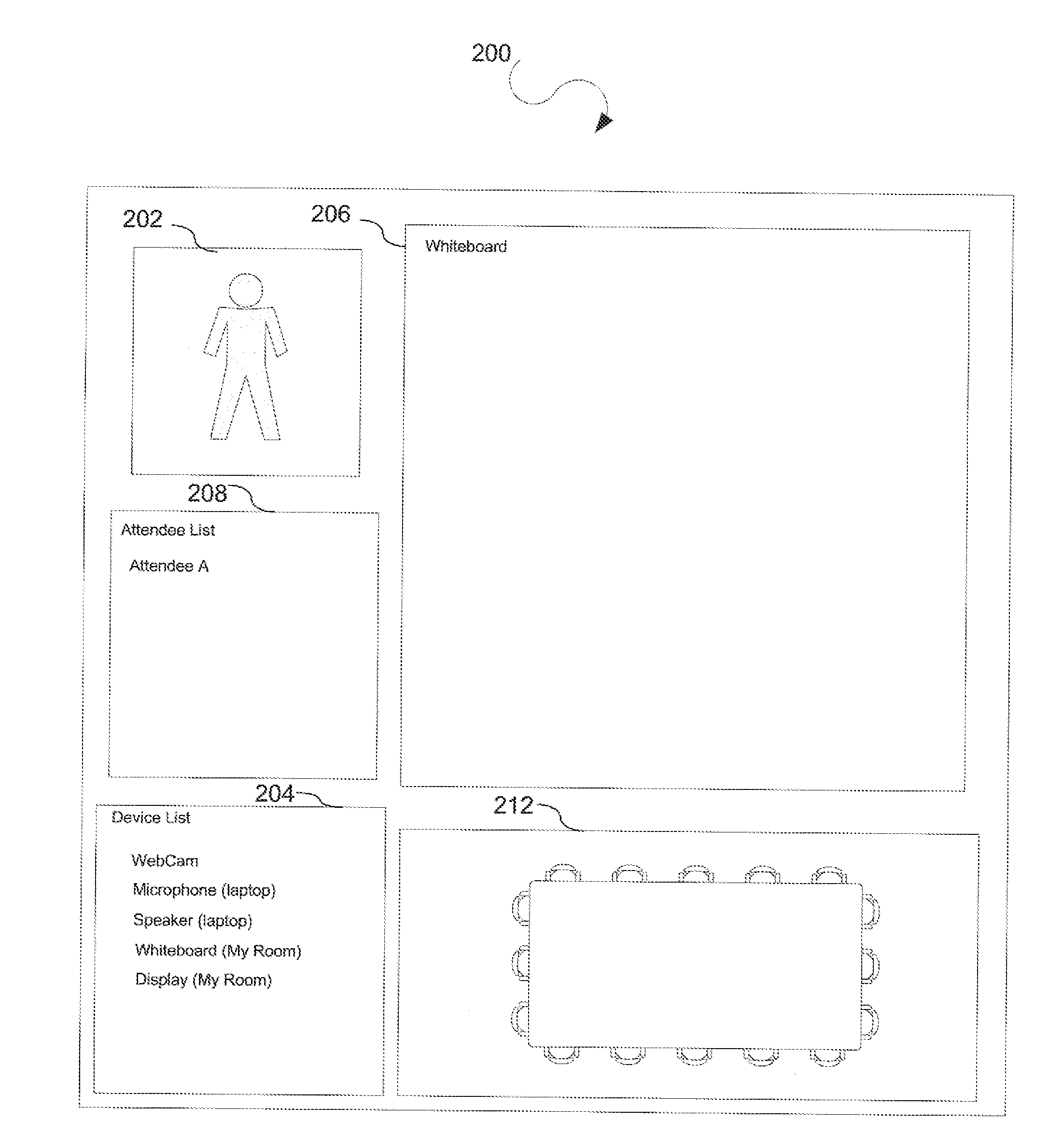
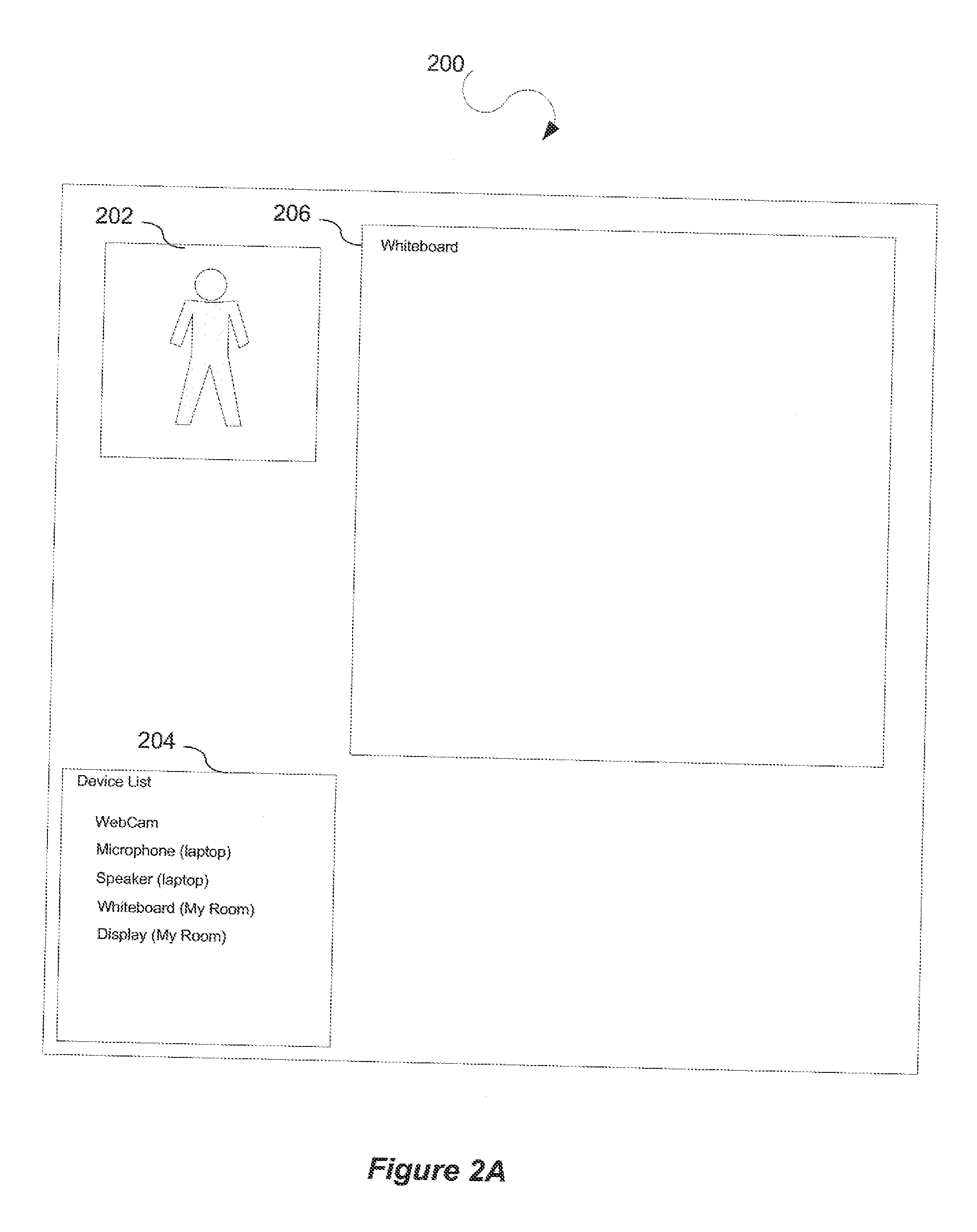
Device information index and retrieval service for scalable video conferencing
ActiveUS20130127979A1Efficient use ofFirmly connectedTelevision conference systemsAutomatic exchangesInformation indexConnected device
A video conference invitation is sent from a computing device in a first conference room to a second conference room for a video conference. Further, an acceptance of the invitation is received at the computing device. In addition, a list of available devices for video conferencing is retrieved from a device information database. The list of available devices indicates a locally connected device and a remotely connected device. The computing device is connected to the video conference through a platform independent interface. Further, the computing device locally controls operation of the locally connected device through a platform independent interface during the video conference and remotely controls operation of the remotely connected device during the video conference.
Owner:ADOBE INC
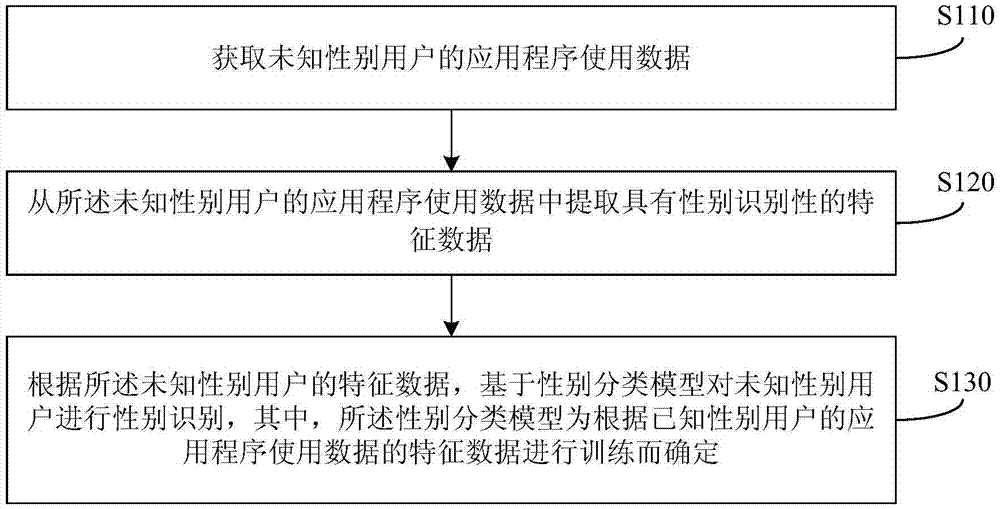
Method and device for recognizing user gender
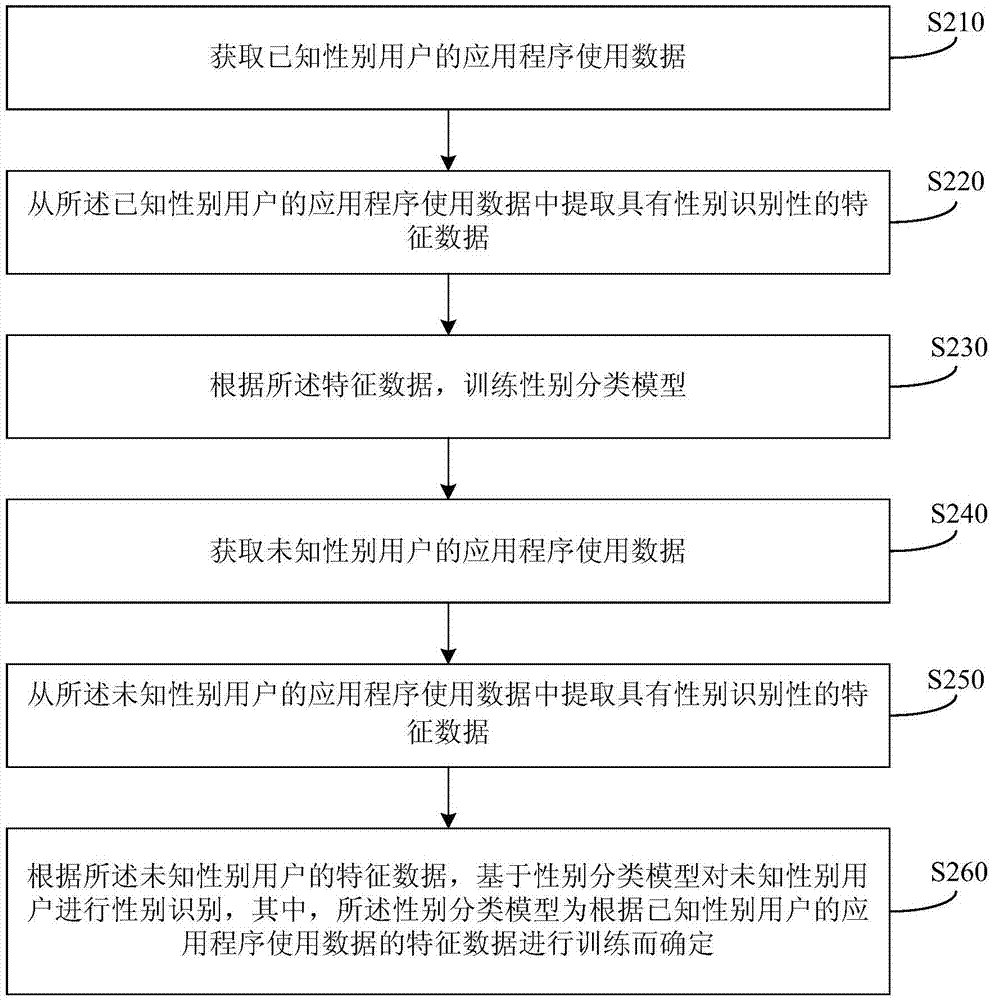
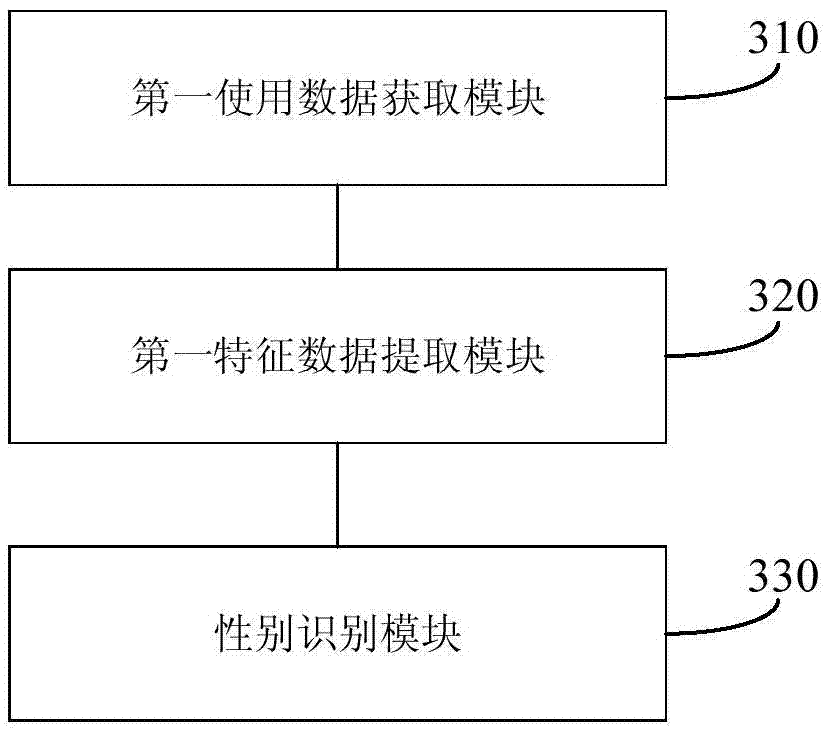
InactiveCN106897727AAddress privacy concernsSolve the costCharacter and pattern recognitionBiometric pattern recognitionFeature dataUsage data
The invention discloses a method and a device for recognizing a user gender. The method comprises steps: application usage data of a user with an unknown gender are acquired, feature data with gender recognition are extracted from the application usage data of the user with an unknown gender, and according to the feature data of the user with an unknown gender, based on a gender classification model, gender recognition is carried out on the user with an unknown gender, wherein the gender classification model is determined through training feature data of application usage data of a user with a known gender. By adopting the method of the invention, the technical problem that in the case of user gender recognition in the prior art, the privacy of the user is possibly involved or the cost is high can be solved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method for registration and verification of Internet of Things identity based on blockchain
ActiveCN109639714AAchieve decentralizationAddress privacy concernsEncryption apparatus with shift registers/memoriesPublic key for secure communicationDigital signatureValidation methods
Owner:ZHEJIANG WANLI CONSTR ENG
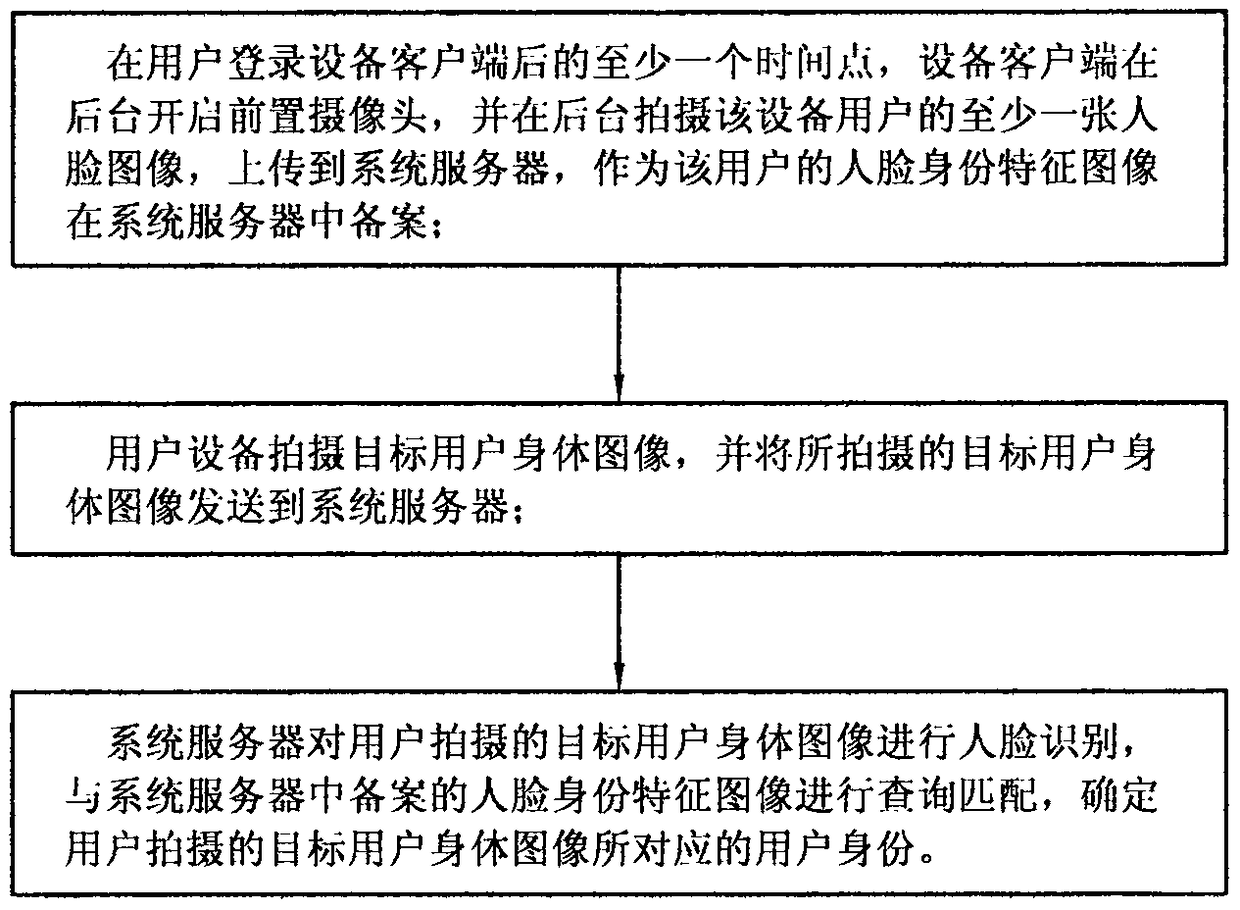
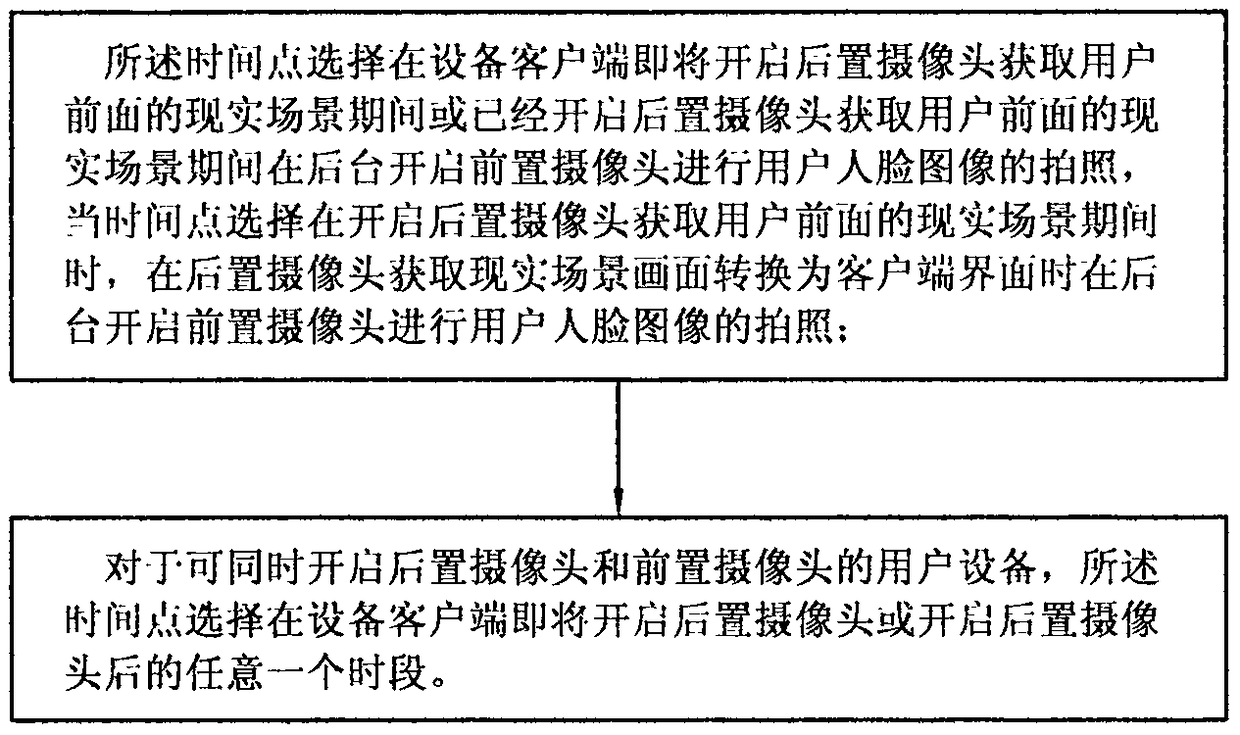
User identity recognition and matching method based on face recognition technology
PendingCN108573201AFast experienceImprove experienceCharacter and pattern recognitionSpecial data processing applicationsPattern recognitionUser device
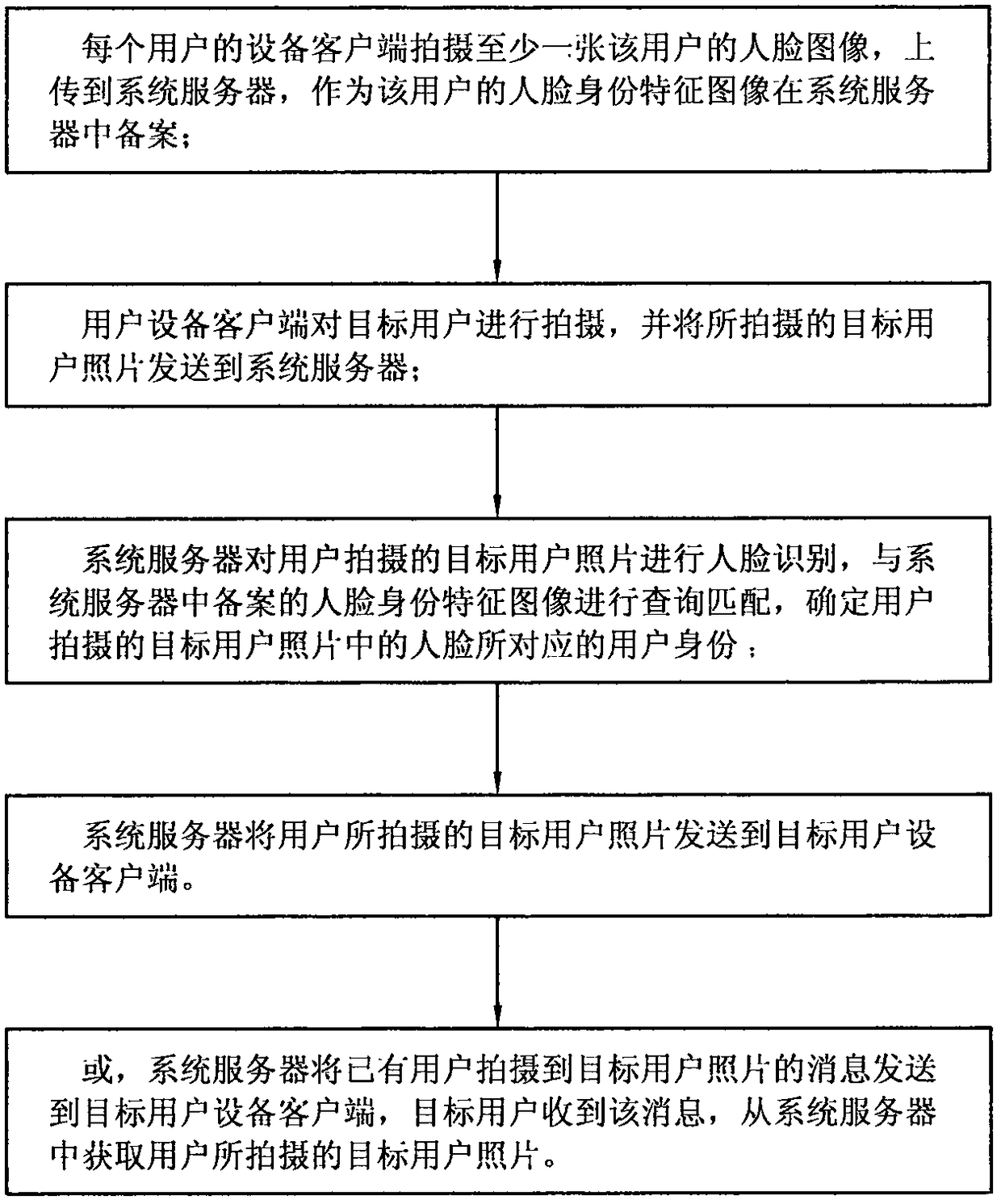
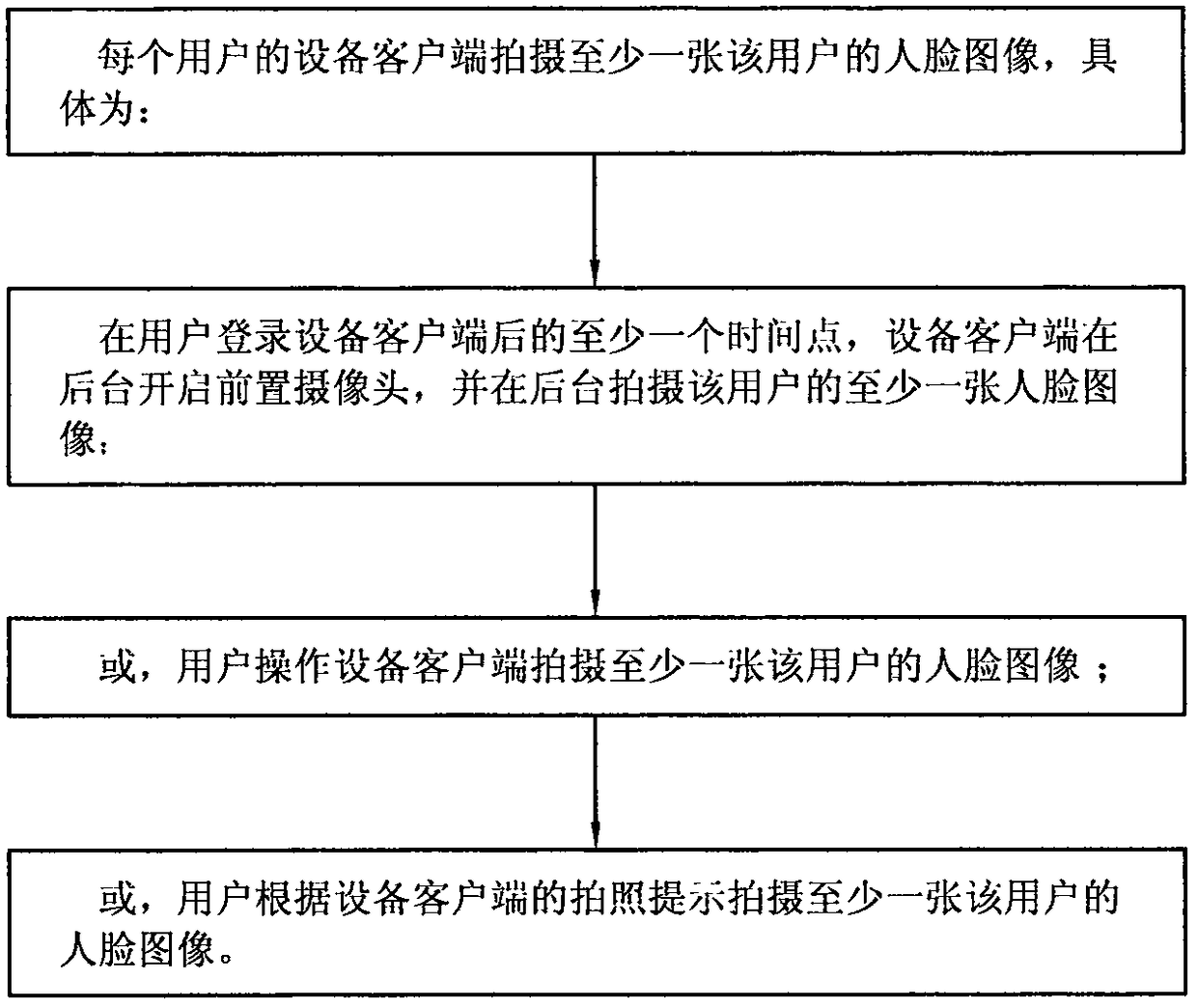
The invention relates to a user identity recognition and matching method based on face recognition technology. Through user device clients, faces of users are automatically acquired to serve as face identity characteristic images which are recorded in a system server. Target user identity images shot by user devices are allowed to match the face identity characteristic images recorded in the system server and user identities corresponding to the target user identity images are determined. According to the invention, by searching the face identity characteristic images which are recorded in thesystem server and match all users in position regions where the users are located, the searching range is shortened, search speed is improved and accuracy of recognition and matching is improved.
Owner:金德奎
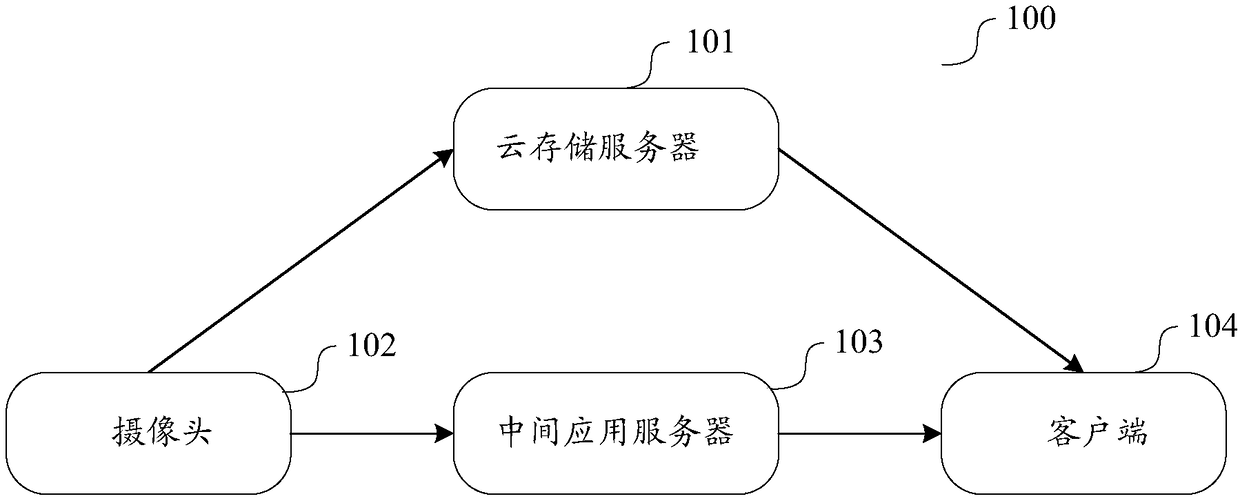
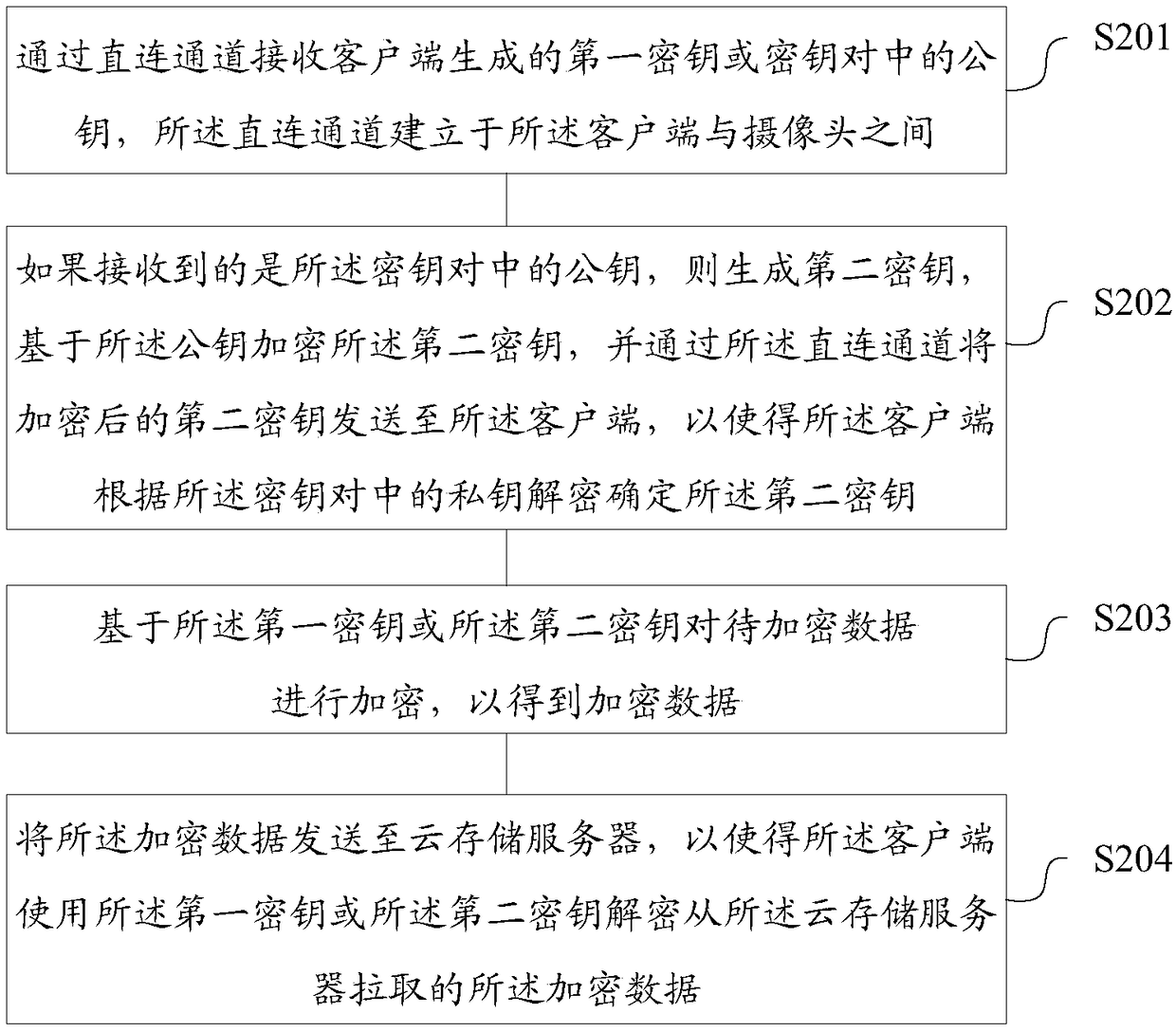
Cloud storage data safety protection method and device, storage medium, camera and computing device
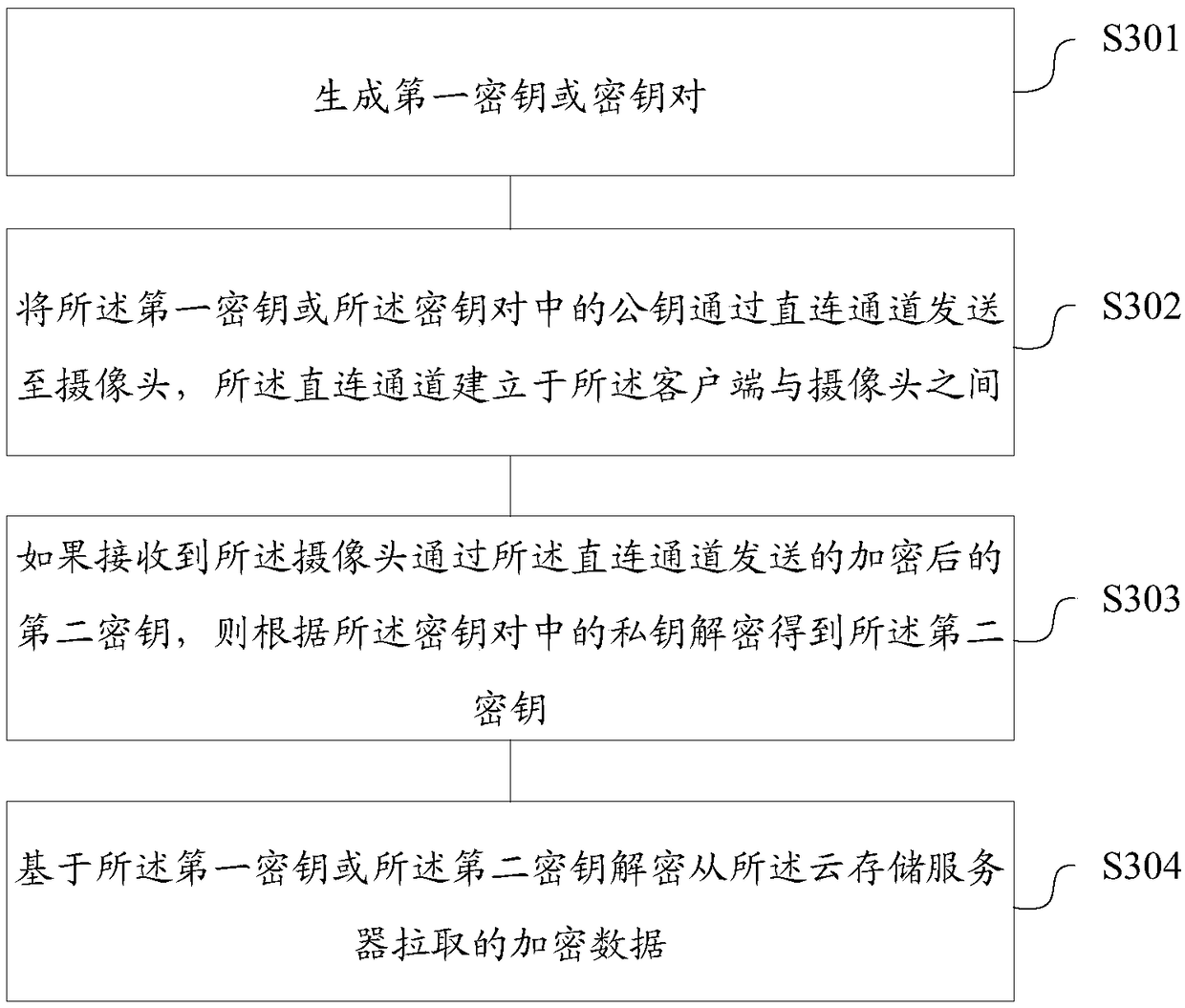
InactiveCN108777677AImprove securityImprove protectionKey distribution for secure communicationPrivacy protectionClient-side
The invention relates to a cloud storage data safety protection method and device, a storage medium, a camera and a computing device. The method comprises steps that a first key generated by a clientor a public key in a key pair is received through a direct connection channel, and the direct connection channel is established between the client and the camera; if the public key in the key pair isreceived, a second key is generated, the second key is encrypted based on the public key, the encrypted second key is sent to the client through the direct connection channel to make the client decrypt and determine the second key based on a private key in the key pair; to-be-encrypted data is encrypted based on the first key or the second key to obtain encrypted data; the encrypted data is sent to a cloud storage server to make the client decrypt the encrypted data obtained from the cloud storage server through the first key or the second key. The method is advantaged in that safety protection and privacy protection for the cloud storage data can be enhanced.
Owner:SHANGHAI XIAOYI TECH CO LTD
Radio frequency identification tag security systems
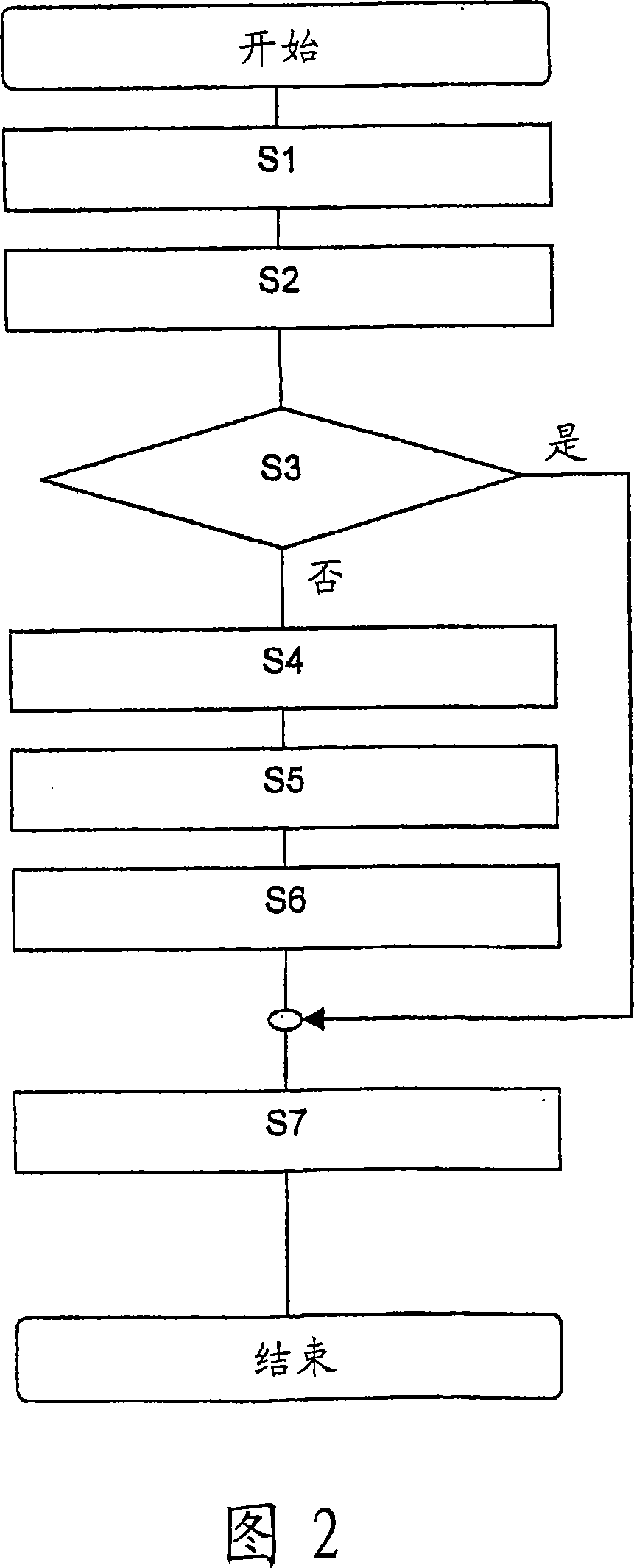
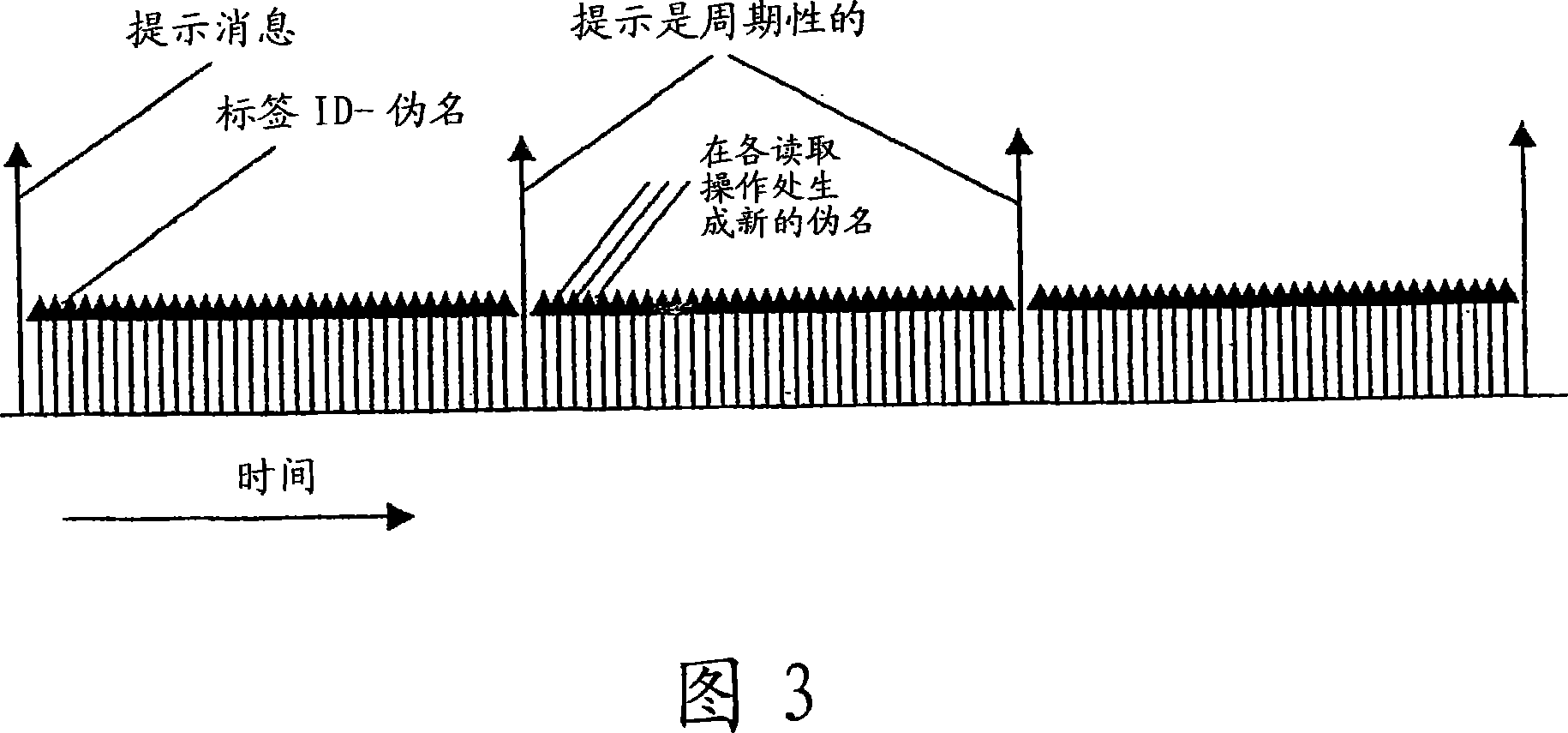
ActiveCN101103365AAddress privacy concernsFix security issuesUser identity/authority verificationMemory record carrier reading problemsLimited accessHash function
Security and privacy of tag information in an RFID-based system can be achieved through the usage of pseudonyms generated based on one-way hash functions. A system based on binary one-way trees allows for the scalable generation and decoding of authentication keys to obtain access to tag identities. The apparatus and methods described can also be adapted to provide limited access for readers to tag information.
Owner:BRITISH TELECOMM PLC
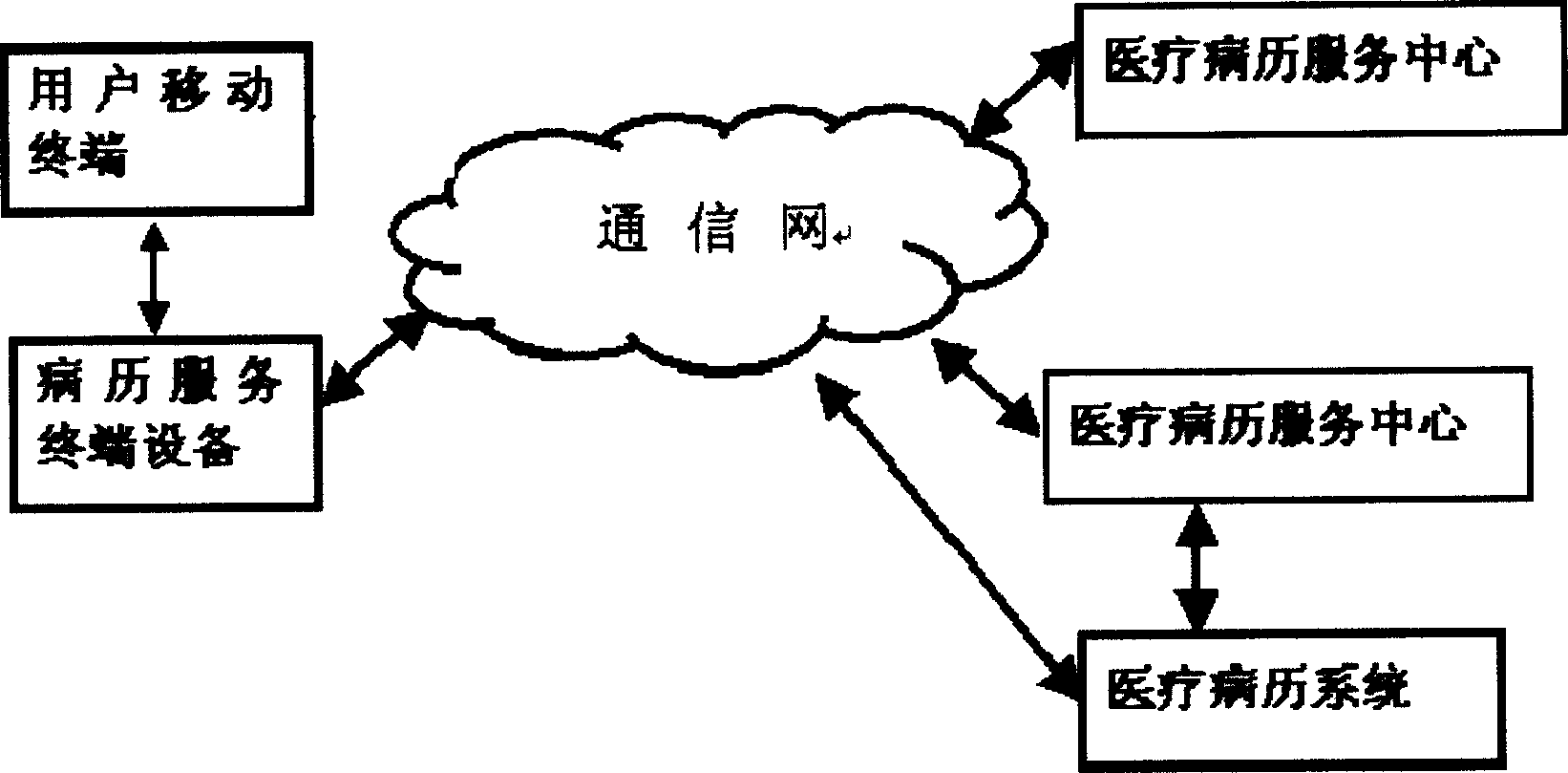
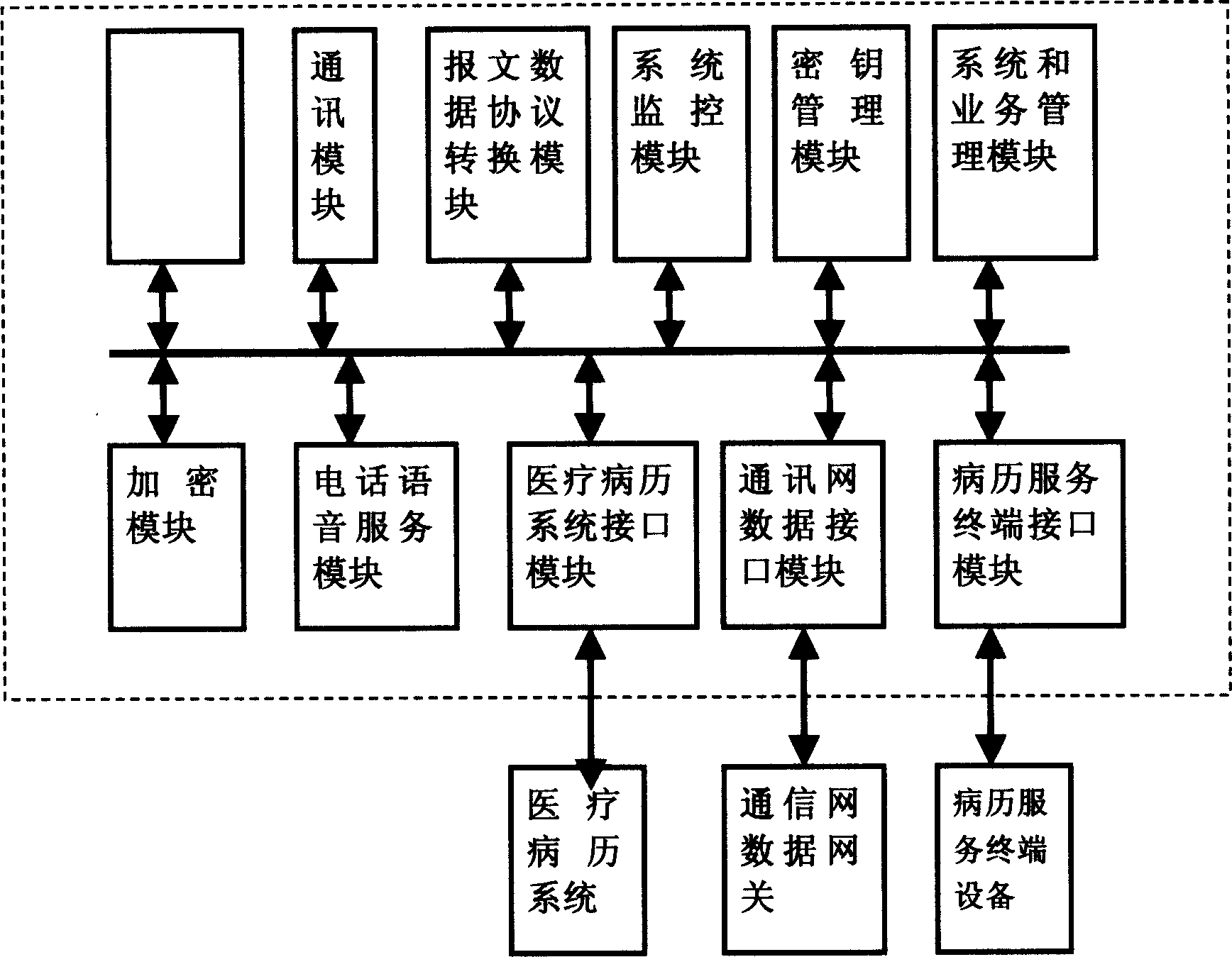
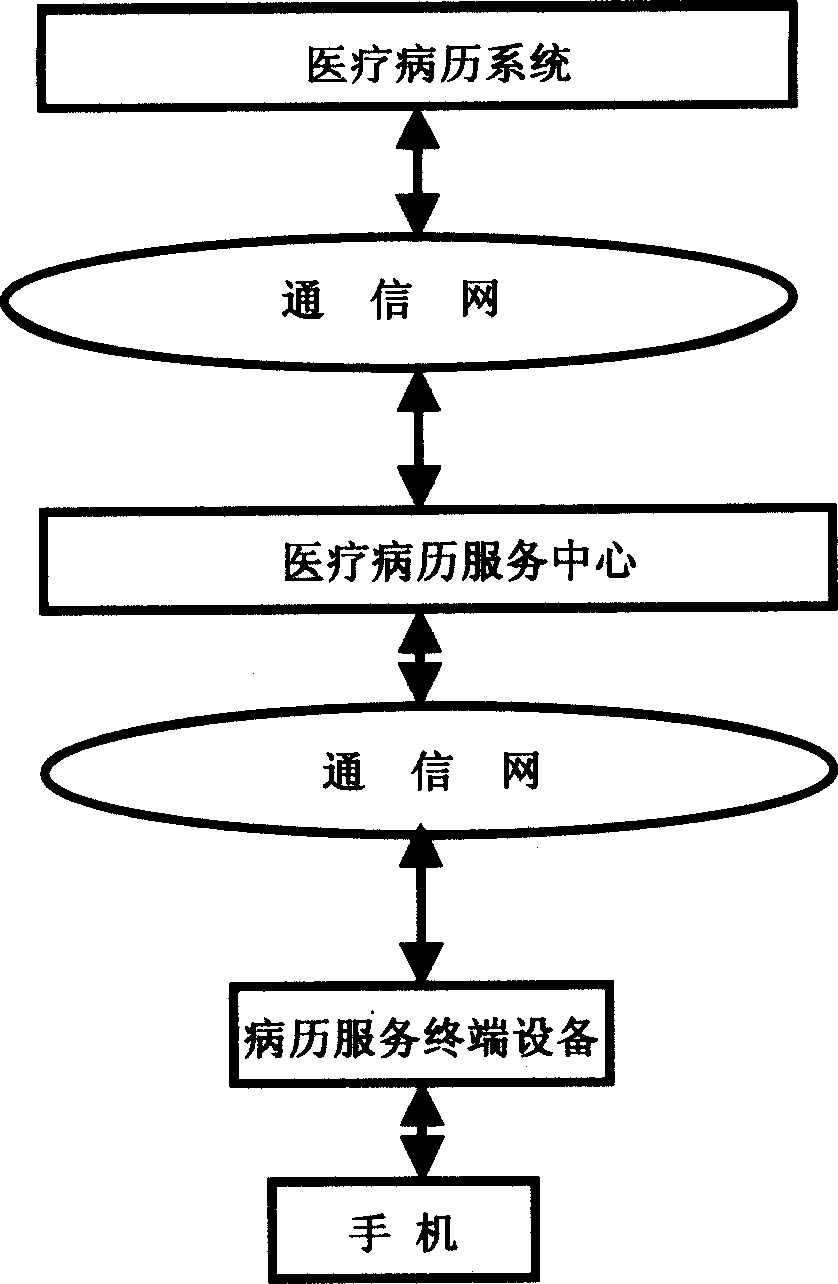
A method for mobile medical record service and system thereof
InactiveCN1570944AAddress privacy concernsSpecial data processing applicationsLibrary scienceCases history
A kind of mobile case history service method. It comprises: user mobile terminal sends user case history identification information to the medical case history service terminal device. The medical case history service terminal device receives user case history identification information from user mobile terminal, and sends case history service request information to the case history service center. The medical case history service center receives and process the case history service request information from medical service terminal device, and verify the validity of medical service request. The case history service center provides case history service by working with case history service terminal device and / or medical case history system. By using the unique number of user's mobile terminal, this invention can provide case history service to case history terminal device by the relevancy of mobile case history service center and case history accounts.
Owner:张亮 +2
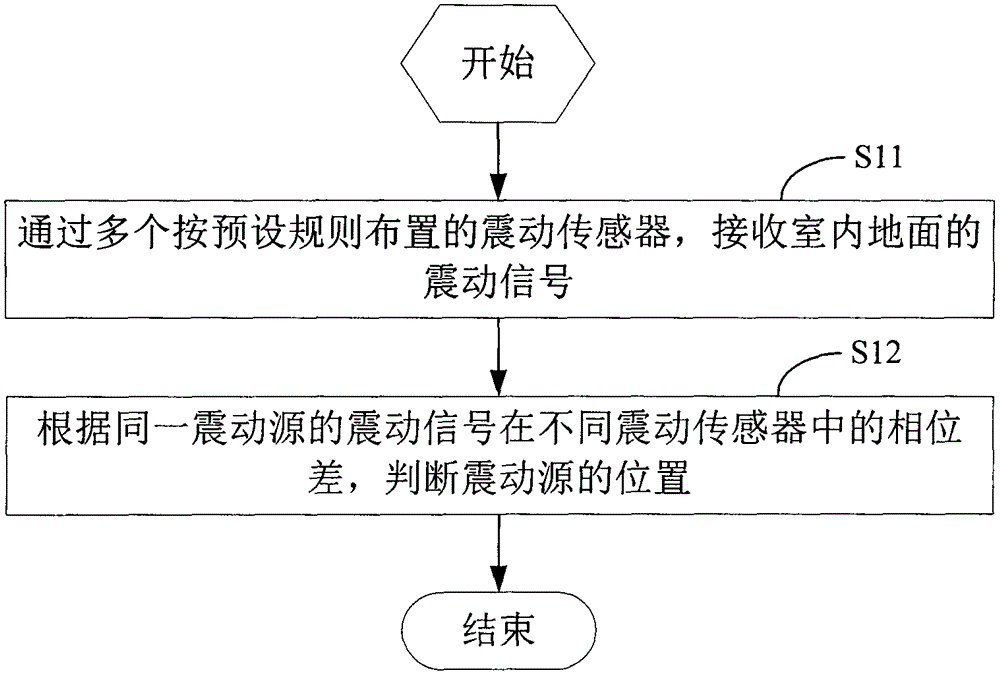
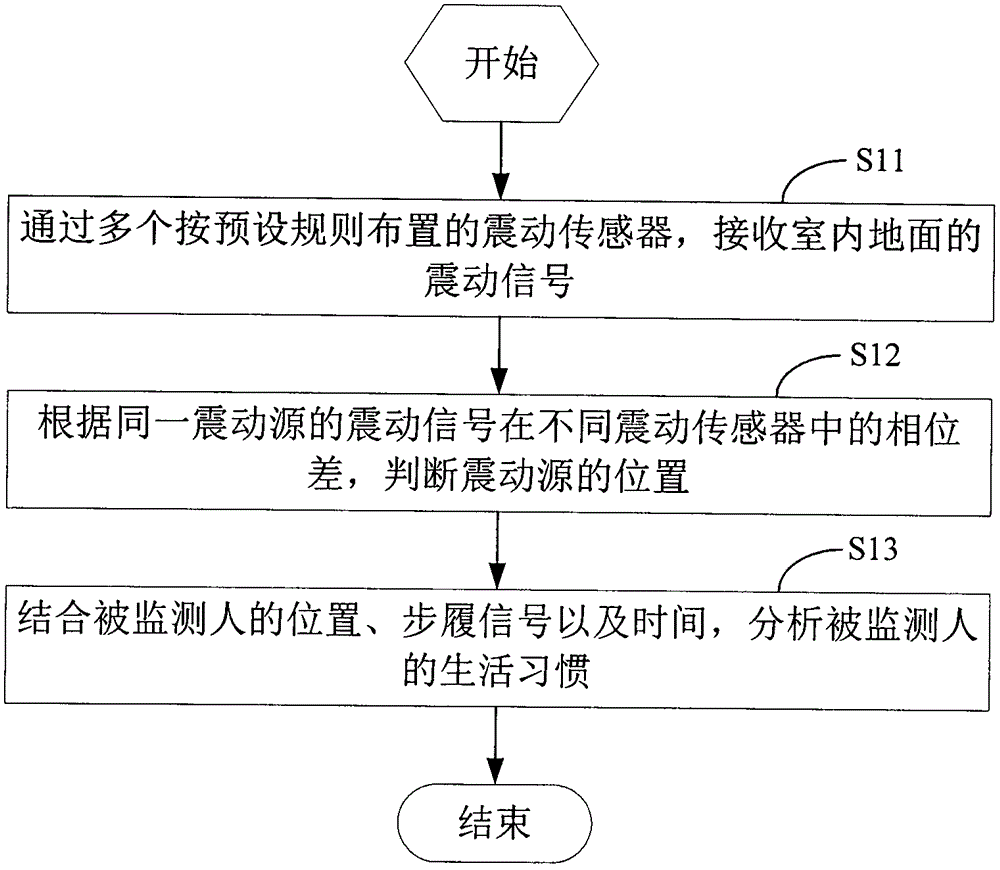
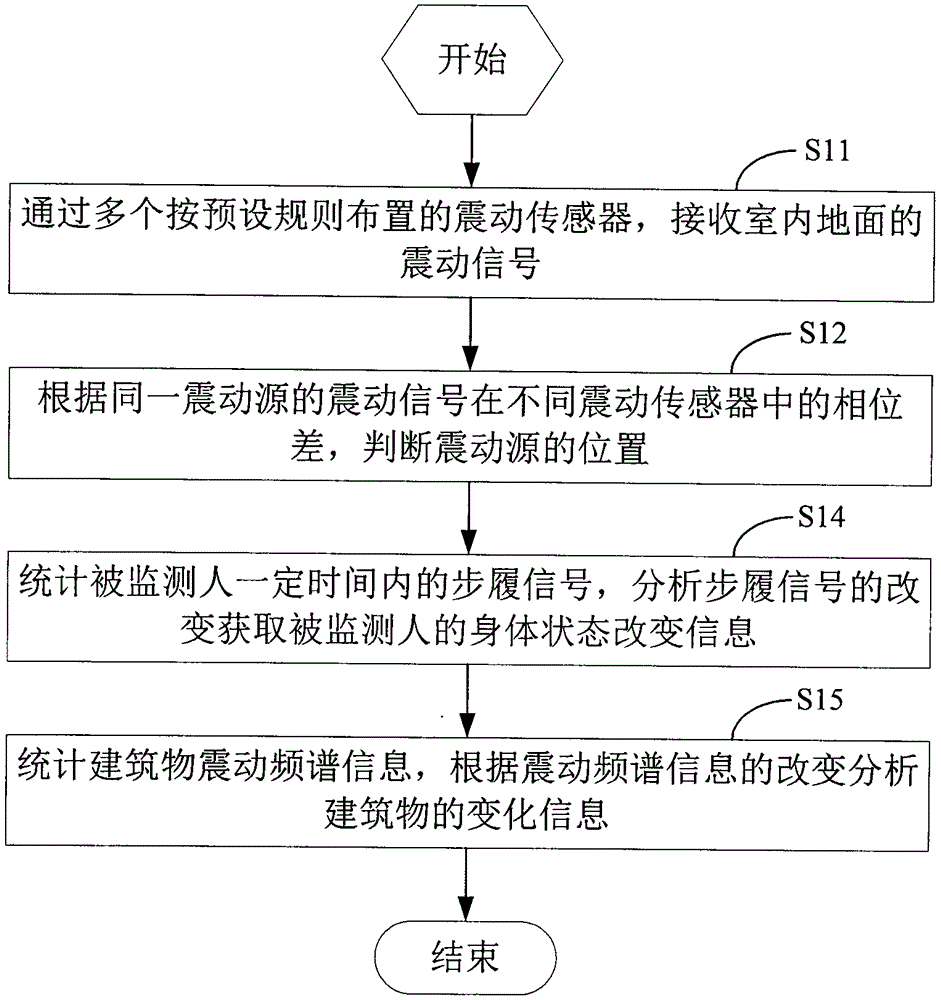
Method and device for accurately sensing indoor activities
InactiveCN103558851AAddress privacy concernsAcoustic presence detectionAcoustic sensorsPhase differenceComputer science
The invention discloses a method and device for accurately sensing indoor activities. The method comprises the steps that shake signals of the indoor floor are received through a plurality of shake sensors distributed according to a preset rule; the position of a shake source is judged according to the phase difference, in the different shake sensors, of the shake signals of the same shake source. By means of the method and device for accurately sensing the indoor activities, the indoor activities can be monitored on the premise of not disturbing a monitored person, and concern about leakage of the privacy of the monitored person can be eliminated.
Owner:杨松
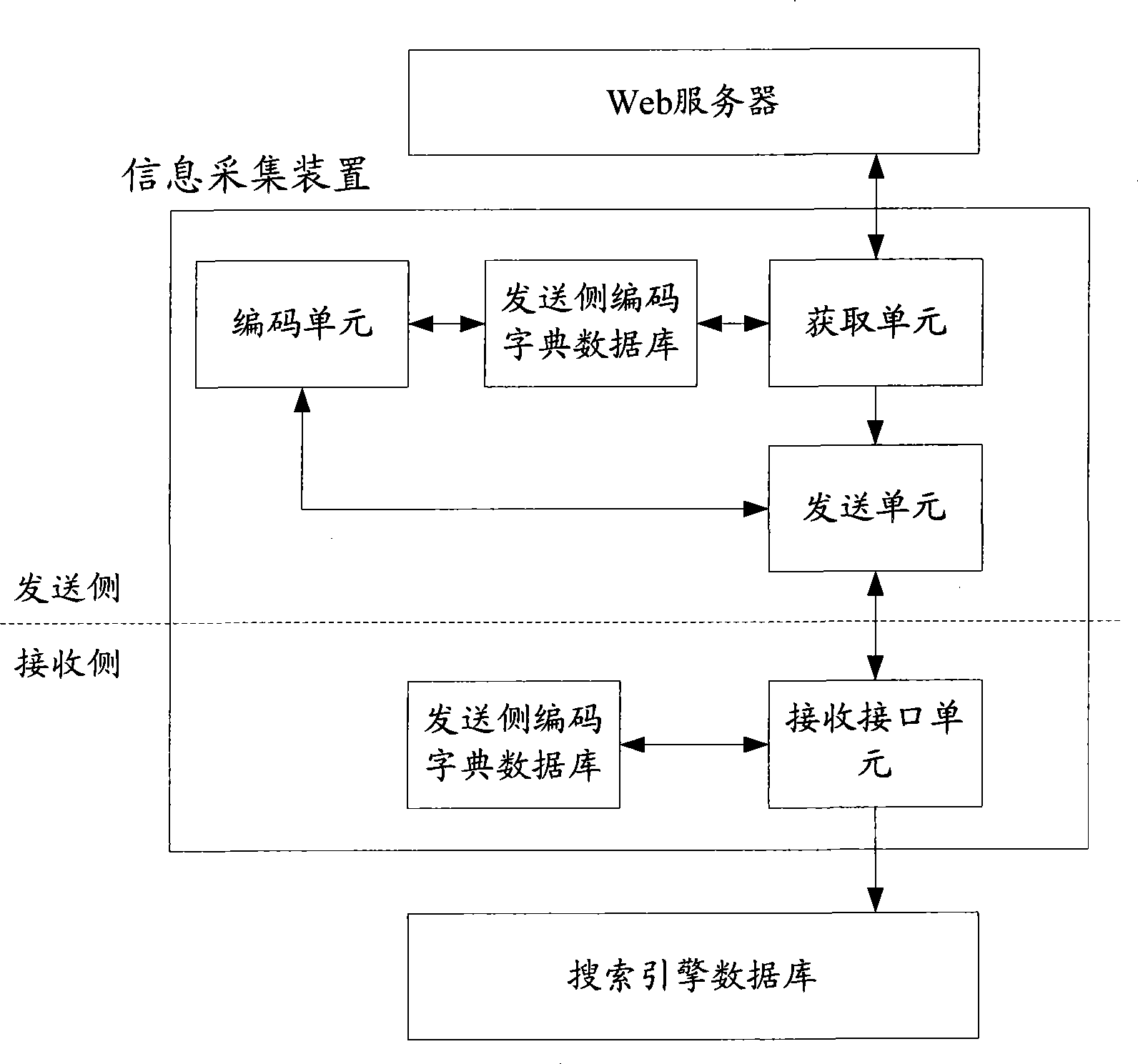
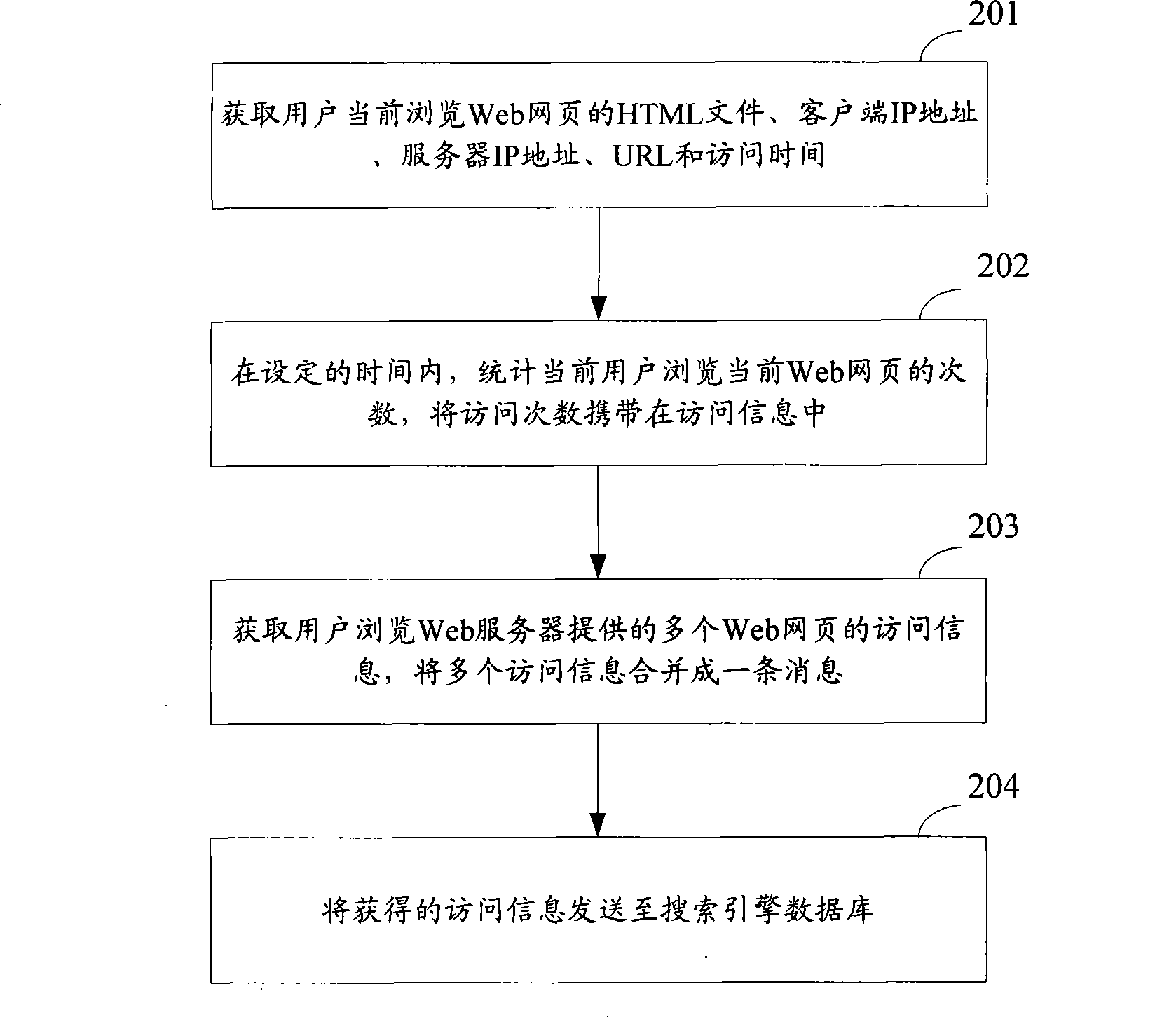
Information acquisition method and device
InactiveCN101477539AExact search contentSearch content in timeWeb data indexingWebsite content managementService conditionInformation acquisition
The invention discloses a method and a device for collecting information. The invention adopts the technical scheme that access information of browsing Web pages by users is transmitted to a database for searching engine, so as to realize the purpose of collecting dynamic Web pages through the database for searching engine. In addition, in the technical scheme of the invention, the information of browsing the Web pages the by users is obtained, so that service conditions of the users of the Web pages can be truly mastered. Therefore, the method and the device for collecting information also plays a significant referential role of ordering the Web pages for searching engine.
Owner:NEW H3C TECH CO LTD
Block chain technology-based fine-grained cloud storage access control method, system and device
PendingCN114065265ASolve the costAddress privacy concernsKey distribution for secure communicationDatabase distribution/replicationCiphertextTheoretical computer science
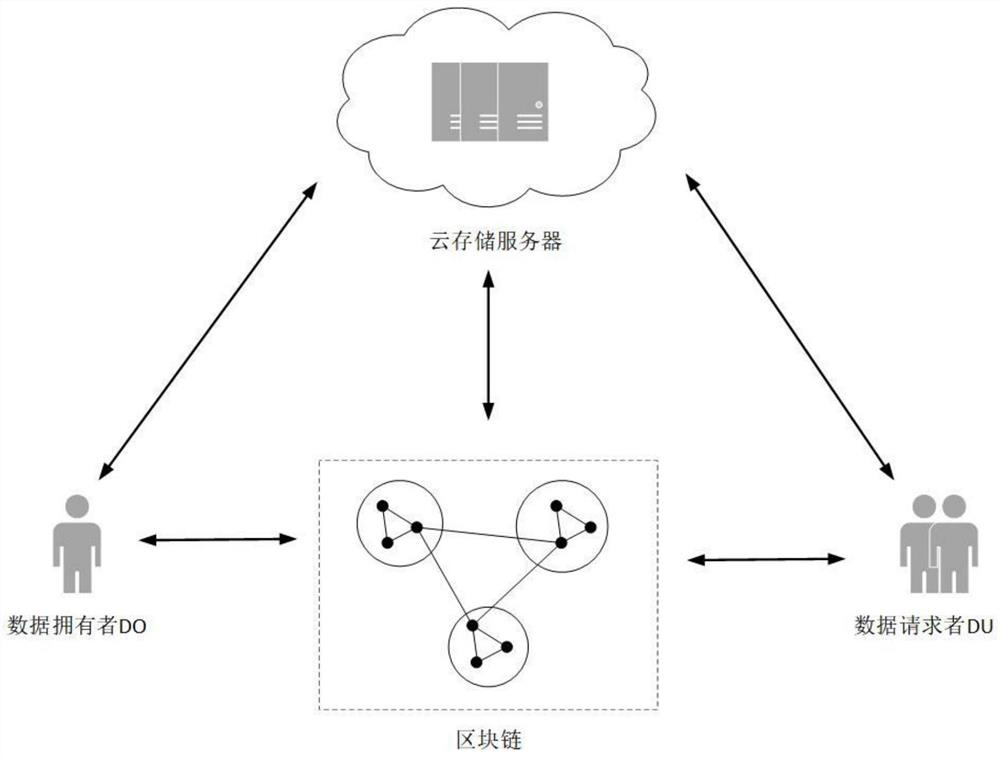
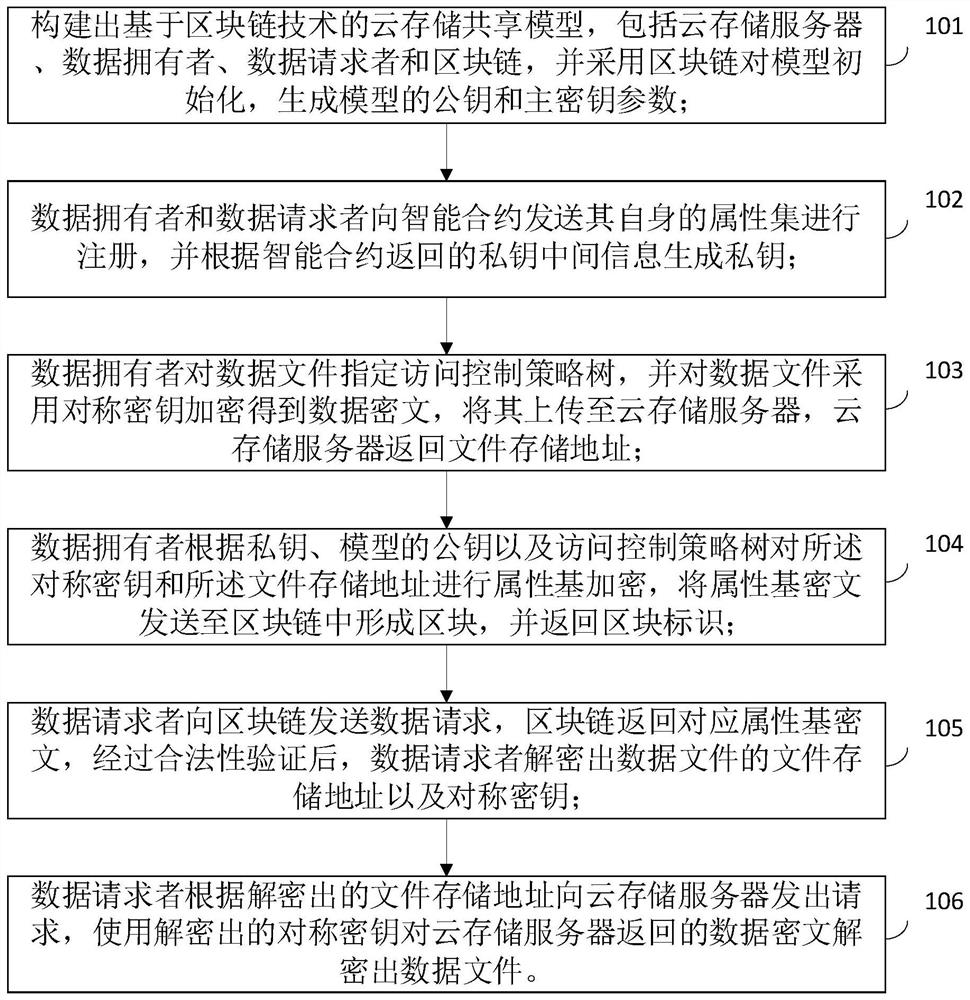
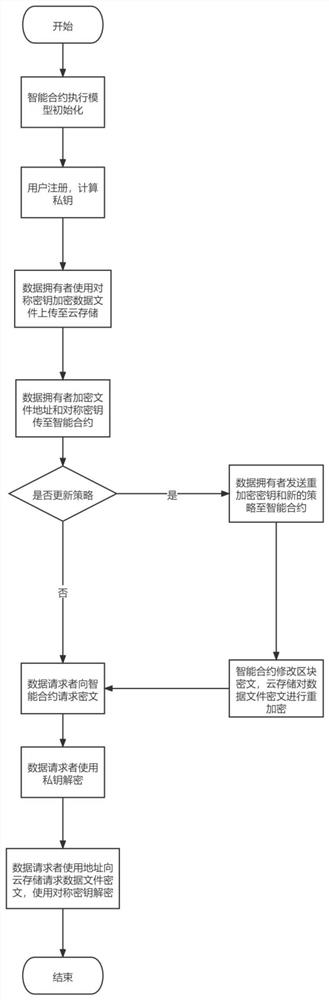
The invention relates to the field of data security, and relates to a block chain technology-based fine-grained cloud storage access control method, system and device. The method comprises the following steps: constructing a cloud storage sharing model based on a block chain technology, registering a DO and a DU to an intelligent contract and generating a private key; the DO encrypting the data file with a symmetric key to obtain a data ciphertext, uploading the data ciphertext to the CSP, and the CSP returning a file storage address; the DO performing attribute-based encryption on the symmetric key and the file storage address according to the private key, the model public key and the access control policy tree, sending an attribute-based ciphertext to the block chain to form a block, and returning a block identifier; the DU sending a data request to the block chain, returning a corresponding attribute base ciphertext, and decrypting a file storage address and a symmetric key of the data file; and the DU sending a request to the CSP according to the decryption address, and decrypting the data file from the data ciphertext returned by the CSP by using the decrypted symmetric key. According to the invention, the security of key transmission and data transmission is ensured.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A method and apparatus for the delivery of digital data
A method and apparatus for the delivery of digital data to an end user (902) from a network (900) comprising at least two different data sources (912as 912b) is disclosed. Each of the at least two different data sources (912a, 912b) can deliver the digital data to the end network at at least one parameter and the data sources (912a, 912b) have substantially identical copies of the digital data comprising portions and are connected to the end user (902). The method comprises receiving (1011) a list of a subset of the at least two data sources (912a, 912b) and selecting (1012) on the basis of the list one or more of the subset of at least two data sources (912a, 912b). At least a portion of the digital data from the selected ones of the at least two data sources (912a, 912b) is delivered to the end user (902). The parameter for the delivery of the digital data to the end user (902) is monitored and the configuration (913) of the selected ones of the at least two data sources (912a, 912b) is adjusted (1015) on the basis of the monitored parameter such that a combined configuration of the configurations (913) of the selected ones of the at least two data sources (912a, 912b) matches the specification (905).
Owner:VELOCIX LTD
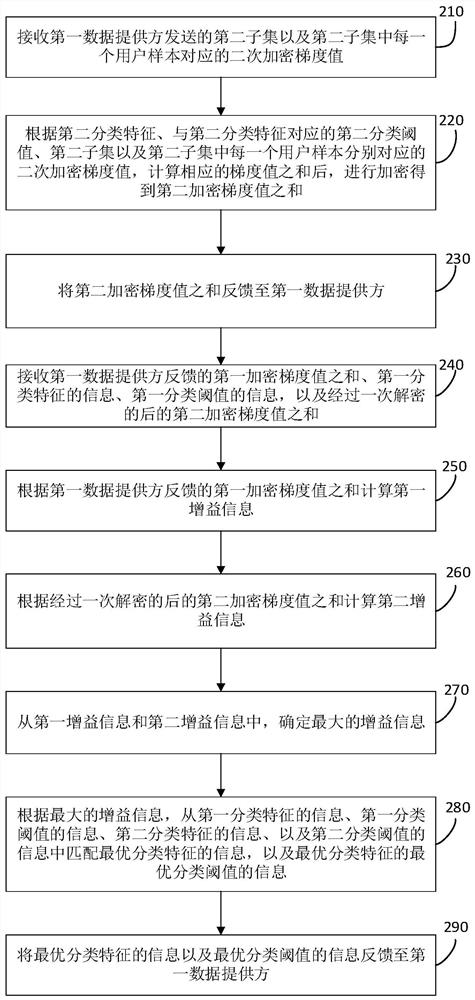
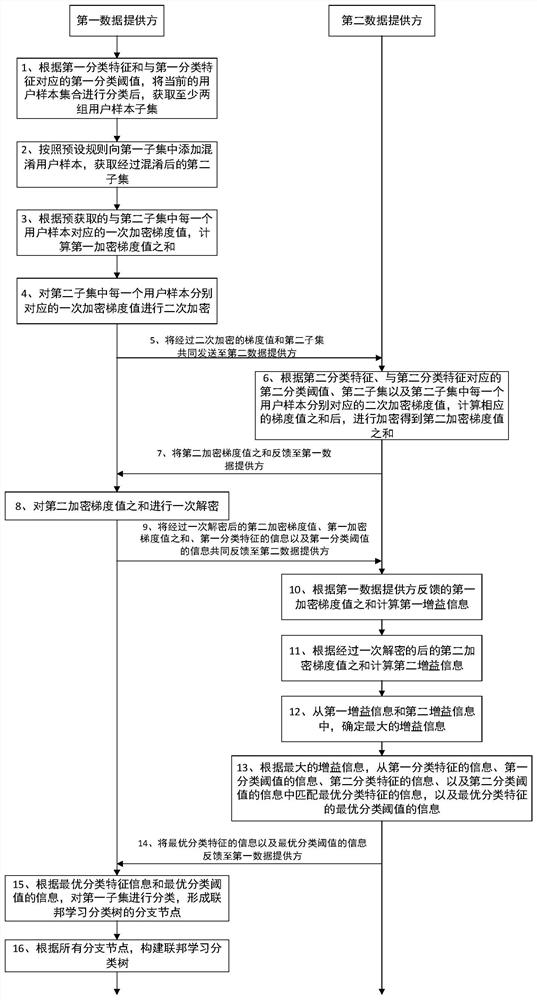
Federated learning classification tree construction method, model construction method and terminal equipment
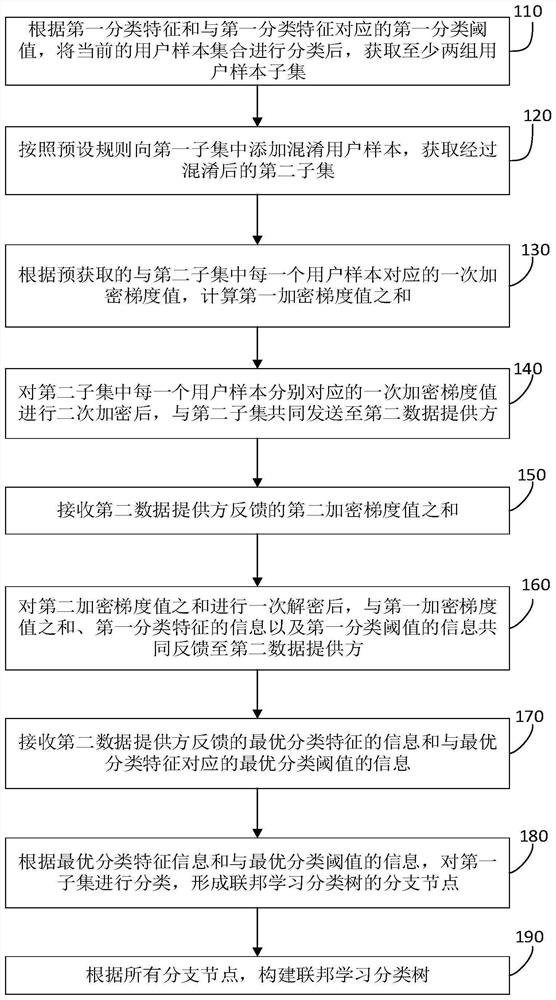
PendingCN111783139AProtection from prying eyesPrevent leakageEnsemble learningCharacter and pattern recognitionData providerMachine learning
The embodiment of the invention relates to a federated learning classification tree construction method, a model construction method and terminal equipment. The method comprises the steps of carryingout the classification of a user sample set according to a first classification feature and a first classification threshold, and obtaining at least two groups of user sample subsets; adding confuseduser samples into the first subset to obtain a second subset; calculating the sum of the first encryption gradient values corresponding to the second subset; after the primary encryption gradient value is subjected to secondary encryption, sending the primary encryption gradient value and the second subset to a second data provider together; receiving the sum of the second encryption gradient values; performing primary decryption on the sum of the second encryption gradient values, and feeding back the sum of the second encryption gradient values, the sum of the first encryption gradient values, the information of the first classification feature and the information of the first classification threshold to the second data provider; receiving information of the optimal classification feature and information of an optimal classification threshold corresponding to the optimal classification feature; and classifying the first subset according to the information of the optimal classification feature and the information of the optimal classification threshold corresponding to the optimal classification feature to form branch nodes of a federated learning classification tree, and constructing the federated learning classification tree.
Owner:JINGDONG TECH HLDG CO LTD
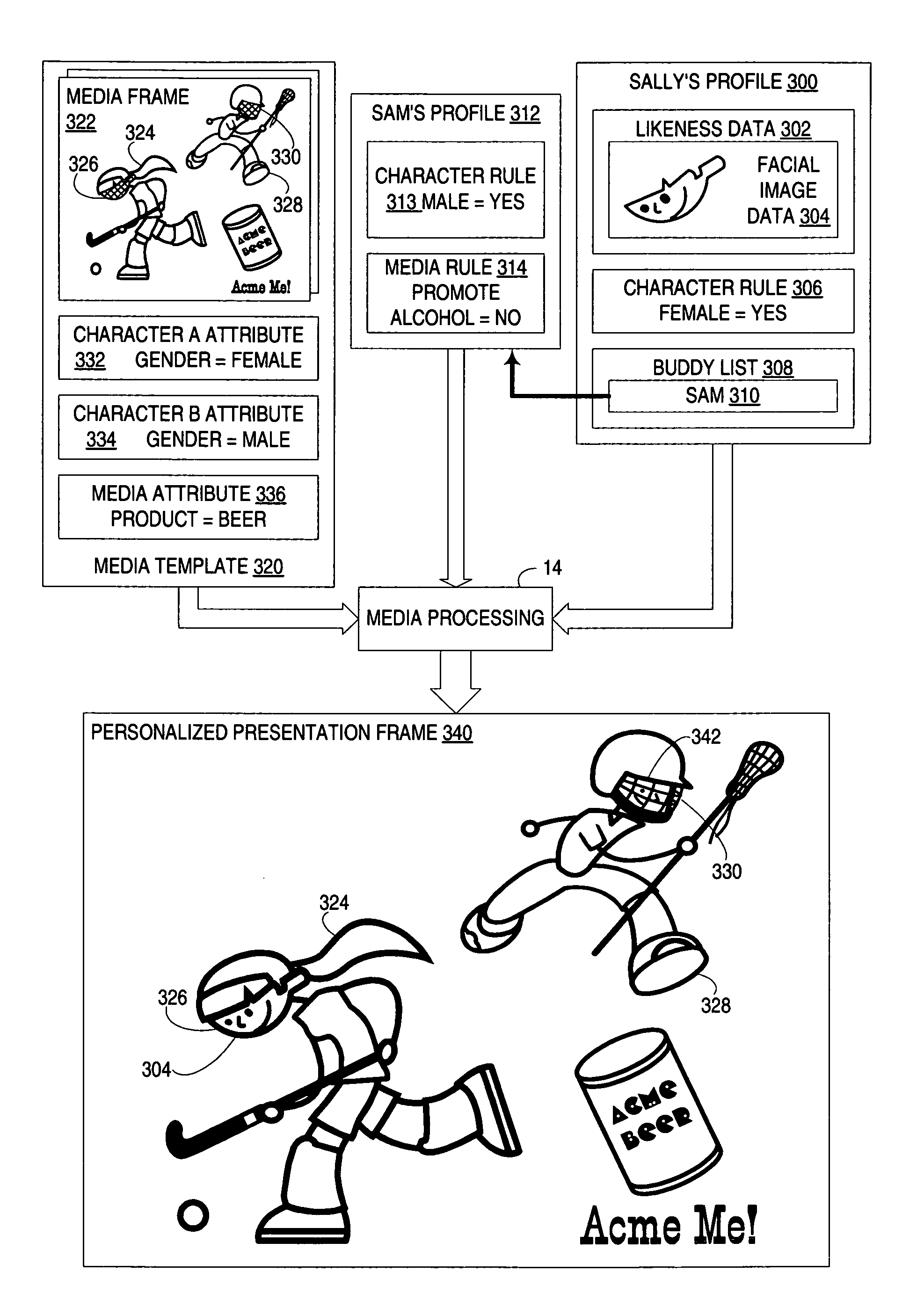
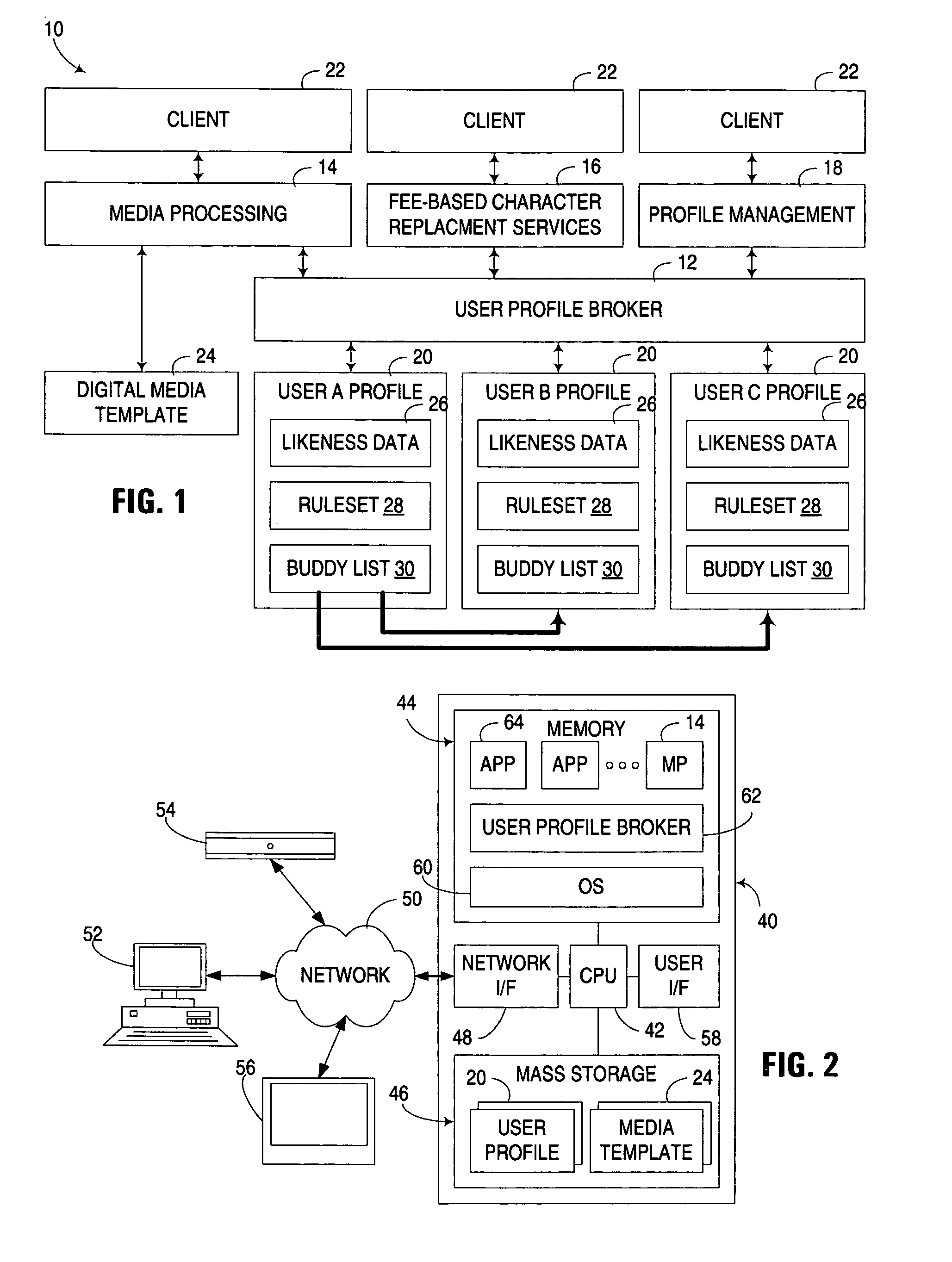
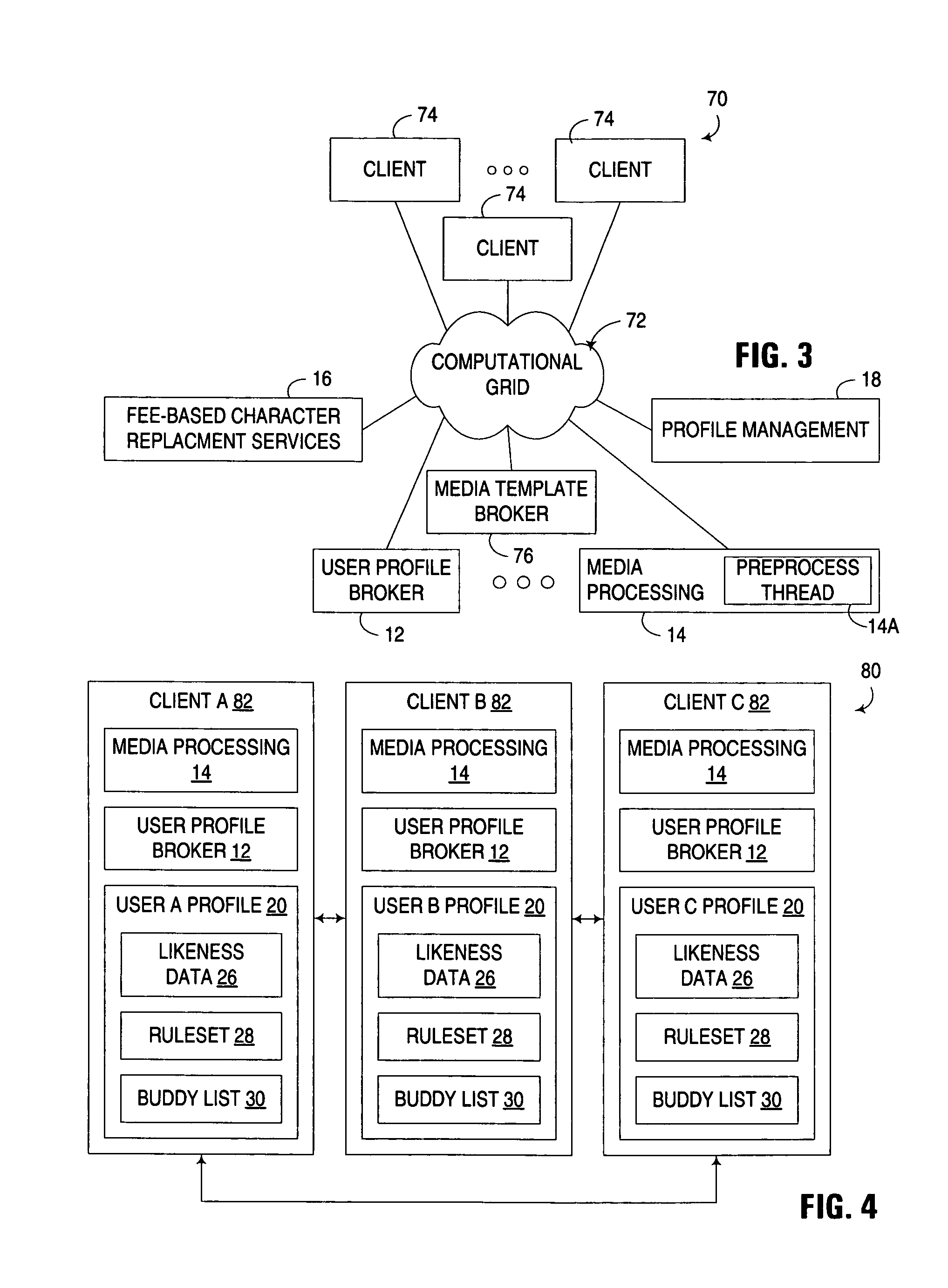
Brokering of personalized rulesets for use in digital media character replacement
ActiveUS8683333B2Address privacy concernsIncrease useTelevision system detailsProgram control using stored programsPersonalizationRule sets
An apparatus, program product and method utilize a brokering service for use in controlling the incorporation of likeness data for an individual into a media presentation. The brokering service maintains a plurality of rulesets respectively associated with a plurality of individuals. Each ruleset is used to restrict or otherwise control the incorporation of likeness data associated with an associated individual into media presentations, typically through the inclusion of one or more rules configured to define conditions under which the likeness data for the associated individual may or may not be incorporated into a media presentation. The brokering service is capable of responding to requests for selected rulesets for different individuals by communicating the rulesets to various requesting entities.
Owner:INT BUSINESS MASCH CORP
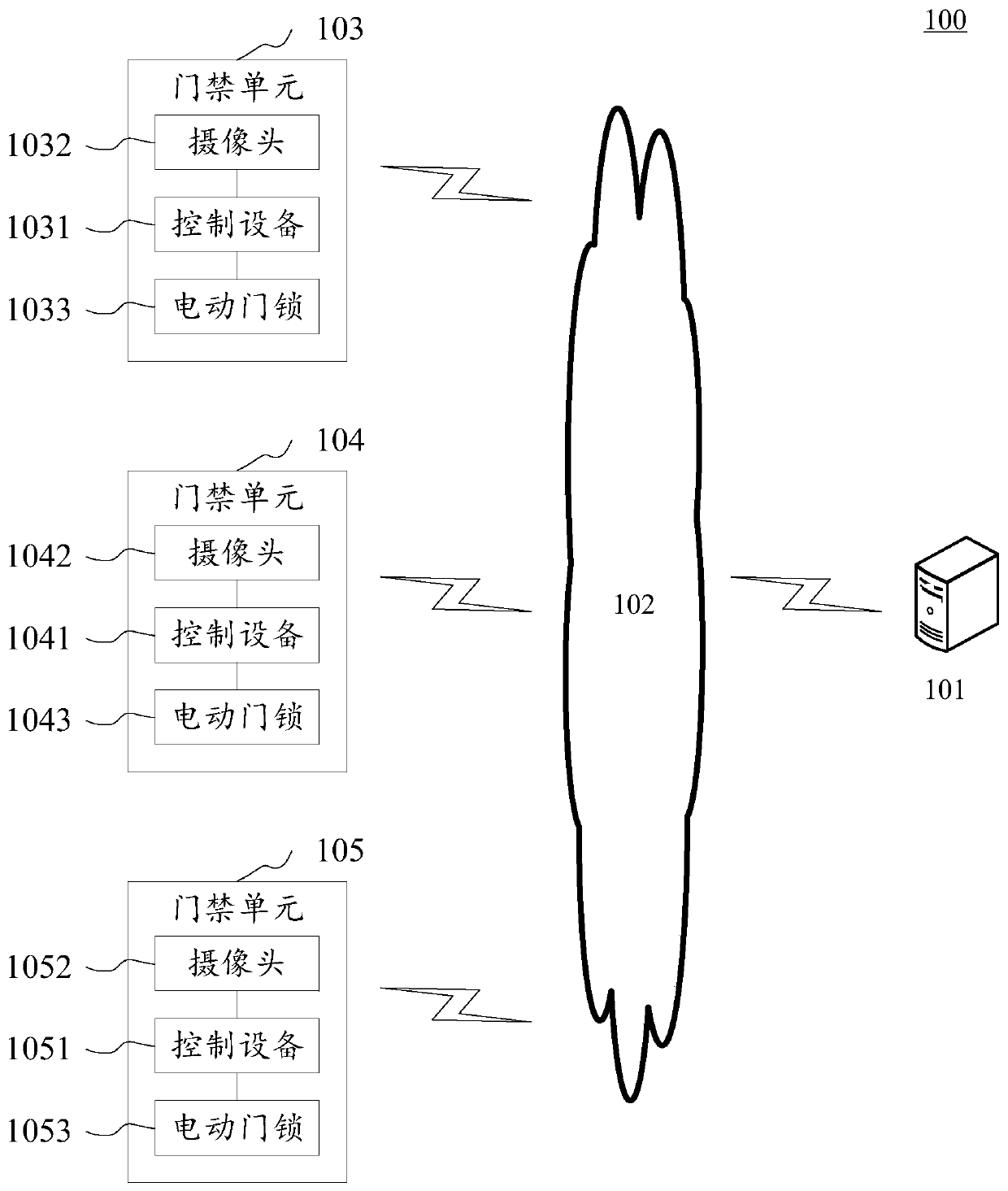
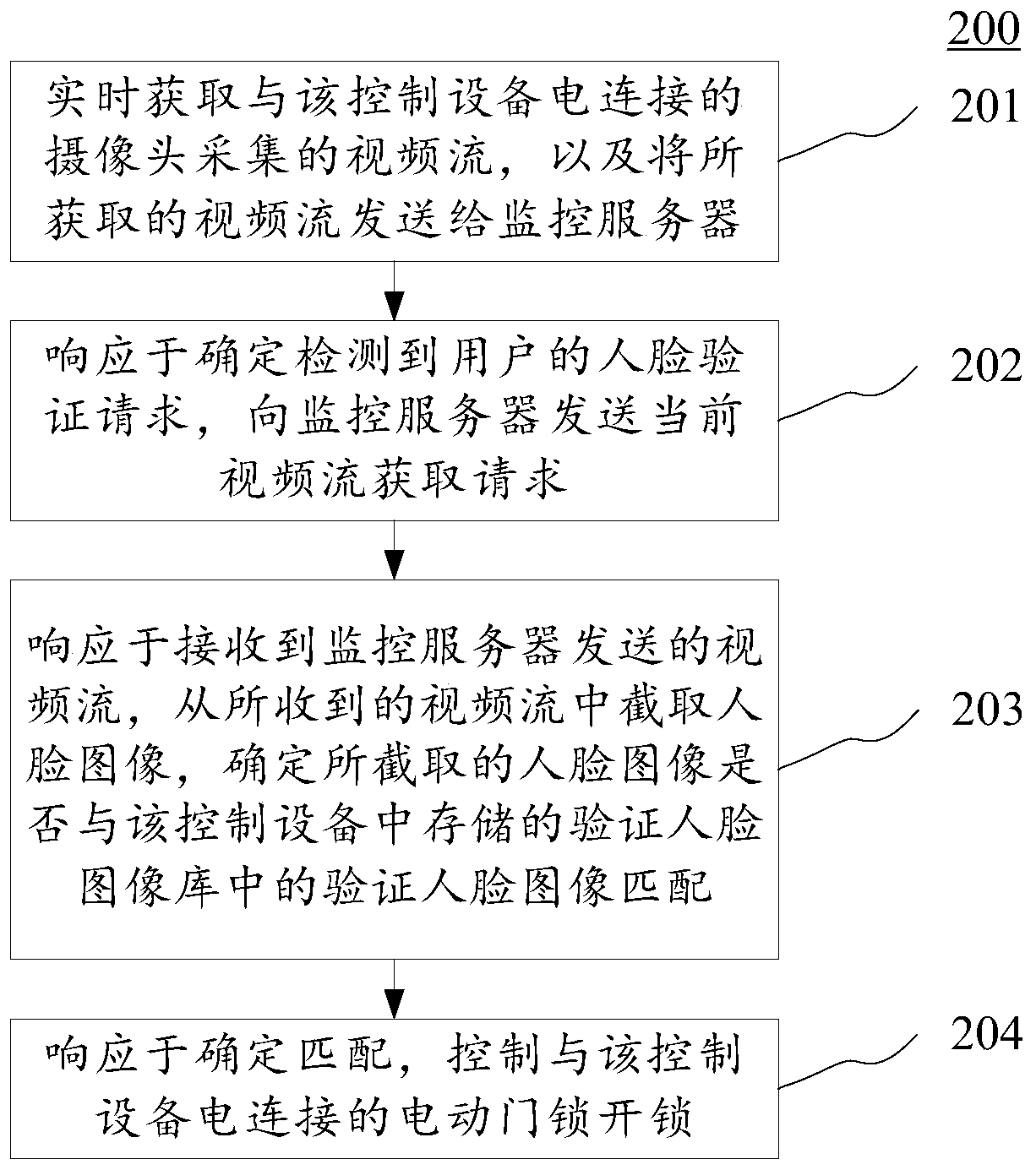
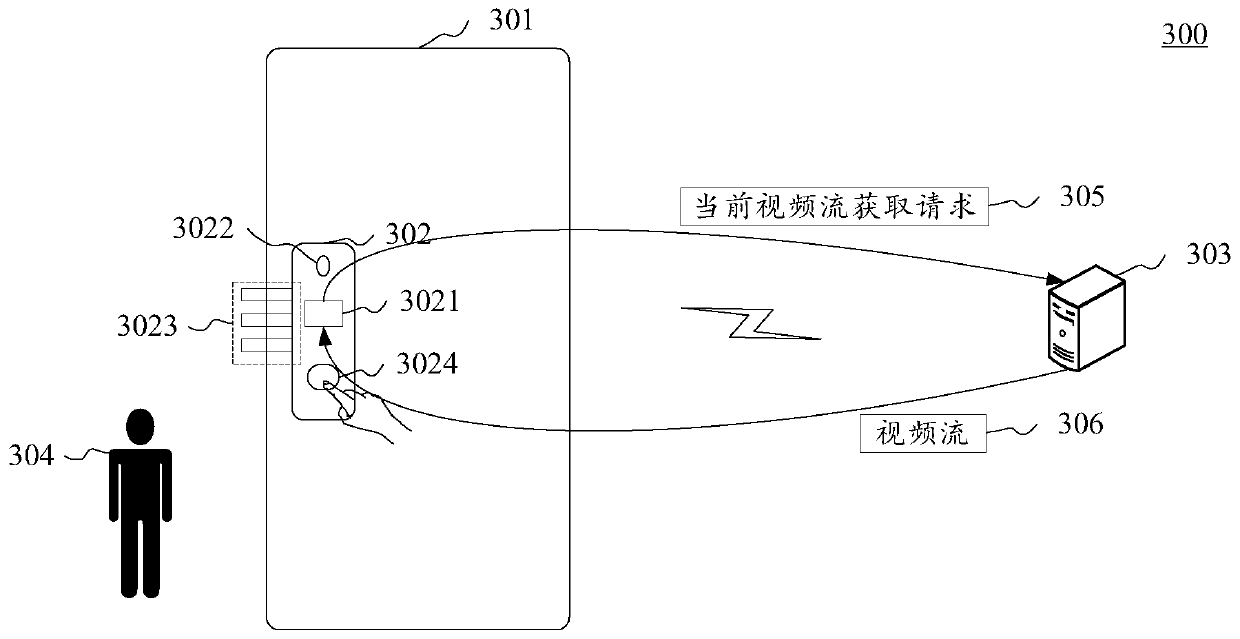
Community access control system, access control method and device, access control unit and medium
InactiveCN111583485AAddress privacy concernsEasy to updateClosed circuit television systemsIndividual entry/exit registersComputer hardwareNetwork connection
The invention provides a community access control system, an access control method and device and an access control unit. The community access control system comprises a monitoring server and at leastone access control unit, wherein the access control units are in network connection with the monitoring server, each access control unit comprises control equipment, a camera and an electric door lock, the camera and the electric door lock are electrically connected with the control equipment, the control equipment sends a video stream acquired by the camera to the monitoring server for storage in real time, if the control device detects a face verification request of a user, the control device requests a current video stream from a monitoring server and intercepts a face image from the current video stream, and then determines whether the intercepted face image is matched with a verification face image in a verification face image database stored in the control device or not; in responseto the determination of matching, an electric door lock electrically connected with the control equipment is controlled to be unlocked. The system is advantaged in that the face recognition part is specifically managed and controlled by the user on the premise of ensuring the community security, and privacy worry of the user is solved.
Owner:北京澎思科技有限公司
Activity management method
InactiveCN1625743AAddress privacy concernsImprove accuracyResourcesPoint-of-sale network systemsUser profileComputer science
The present invention provides a method of managing an event comprising the steps of: a user making a request to attend an event of a first provider among a plurality of providers; and the user presenting a personal data storage device to the first provider , the device is provided with: identification data to identify the user, and user profile information, the user profile information comprising multiple sets of user profile data, each of the multiple sets of user profile data being associated with at least one of a plurality of providers; wherein , evaluating the user's request to participate in the campaign against one or more sets of user profile data.
Owner:ONEEMPOWER PTE LTD
Notebook computer
PendingCN110262629ASolve the problem of camera privacyAddress privacy concernsDetails for portable computersTerminal equipmentComputer terminal
The invention relates to the technical field of terminal equipment, and discloses a notebook computer which comprises a front frame, a camera and a camera shielding device located between the front frame and the camera. A light transmission part opposite to the camera is formed on the front frame so as to transmit light required by the camera, the camera shielding device comprises a shielding plate movably mounted on the front frame, and the shielding plate comprises a light shielding area used for shielding the light and a light transmission area used for transmitting the light; wherein the shielding plate is provided with a first station and a second station in a moving path, and when the shielding plate is located at the first station, a shading area of the shielding plate is opposite to the camera; when the shielding plate is located at the second station, the light-transmitting area of the shielding plate is opposite to the camera; and the handle is used for manually shifting the shielding plate to move, is connected with the shielding plate and is positioned on the outer side of the front frame. According to the notebook computer, the shielding plate can be manually adjusted to move to the station where the camera is shielded, the problem of privacy of the camera of the notebook computer is solved, and safety is high.
Owner:WUXI RUIQIN TECH CO LTD
Federal learning model training method, client, server and storage medium
PendingCN113298229AAddress privacy concernsImprove training effectEnsemble learningNeural architecturesEngineeringNetwork model
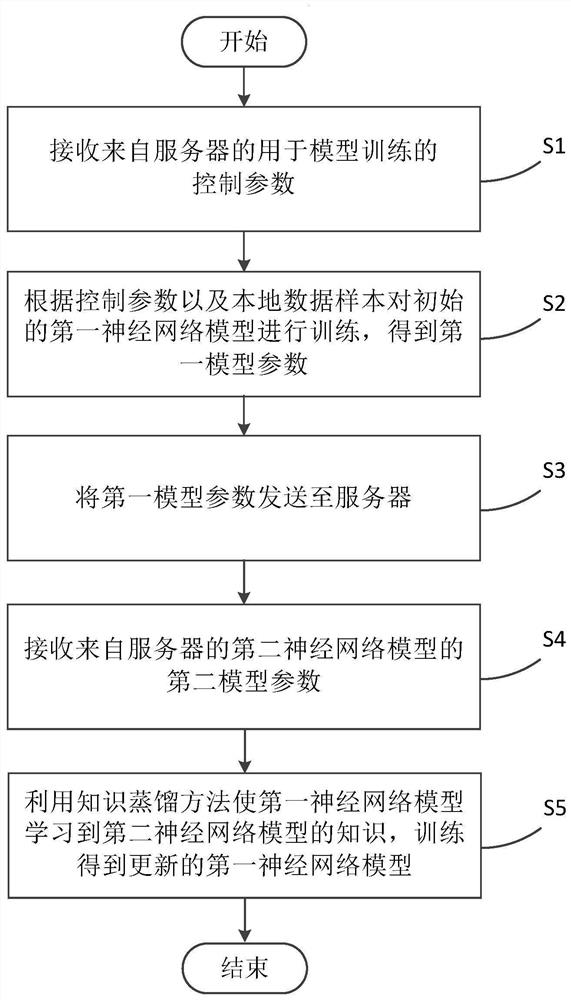
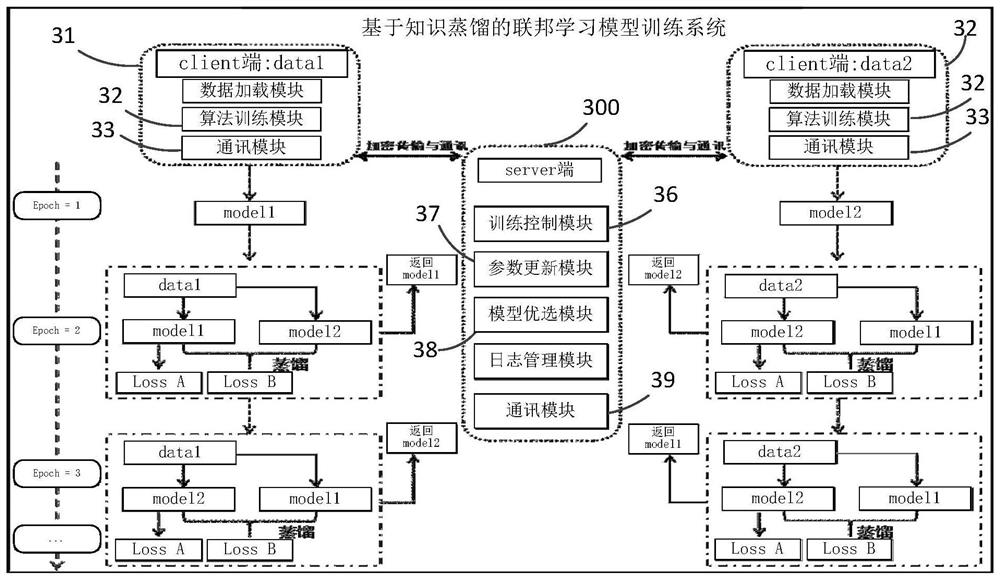
The invention relates to the technical field of artificial intelligence algorithms, and particularly provides a federated learning model training method based on knowledge distillation, which comprises the following steps: receiving control parameters for model training from a server; training the initial first neural network model according to the control parameter and the local data sample to obtain a first model parameter; sending the first model parameter to the server; receiving a second model parameter of a second neural network model from the server; and utilizing a knowledge distillation method to enable the first neural network model to learn knowledge of the second neural network model, and training to obtain an updated first neural network model. According to the method, the existing data island problem is effectively solved by constructing the federated learning system, and meanwhile, the knowledge distillation module is added in the federated learning framework system, so that the algorithm model can be trained and optimized on the basis of knowledge of all training data at the same time; and the training effect of the federal learning framework system is further improved.
Owner:GUANGZHOU YUNCONG INFORMATION TECH CO LTD
Hardware cipher-based mobile phone data protection method and device
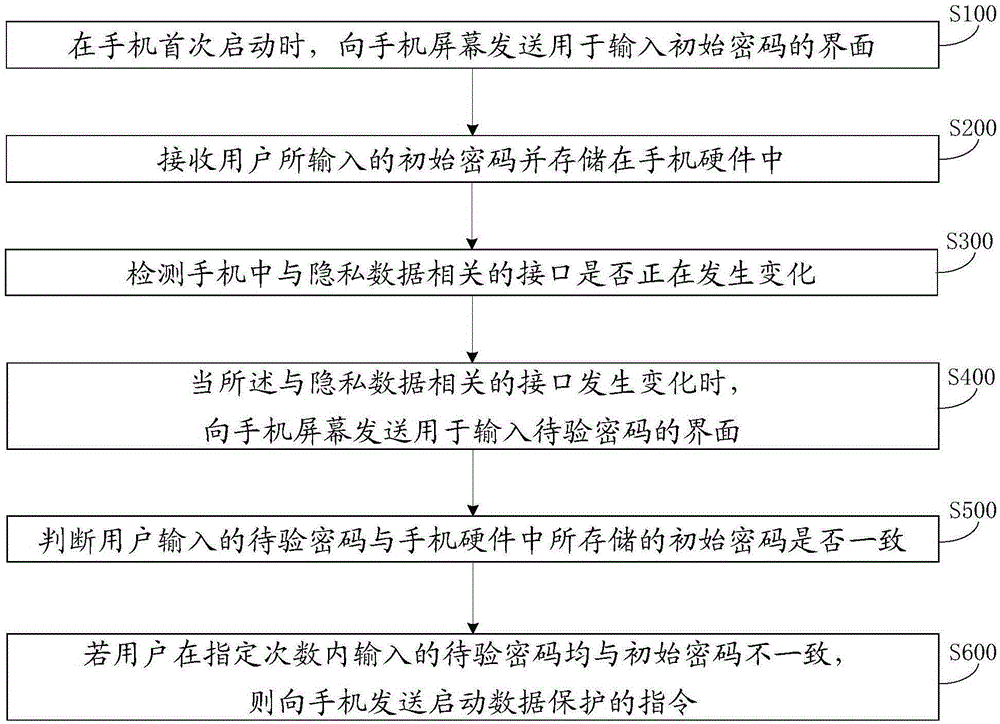
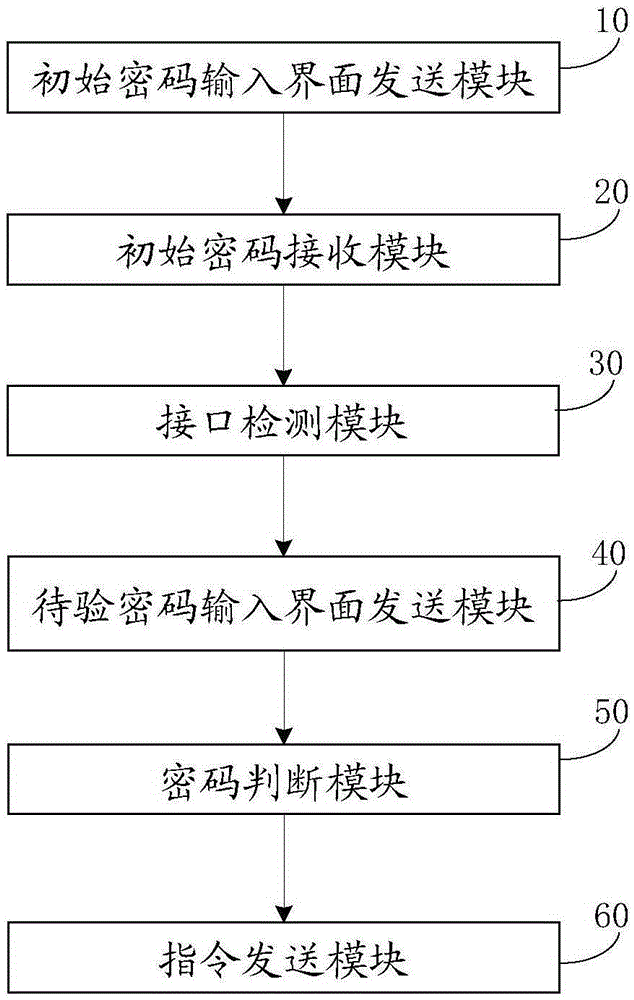
InactiveCN105898011AEnsure safetyImprove performanceSubstation equipmentSecurity arrangementUser inputMobile phone
The invention discloses a hardware cipher-based mobile phone data protection method and device. The mobile phone data protection method comprises the following steps: whether a private data-related interface in a mobile phone changes is detected; if the private data-related interface changes, an interface used for inputting ciphers to be verified is sent to a screen of the mobile phone; whether the ciphers to be verified which are input by a user are consistent with an initial cipher stored in mobile phone hardware is determined; if the ciphers to be verified which are input by the user are inconsistent with the initial cipher for a designated number of times, an instruction of starting data protection is sent to the mobile phone. The mobile phone data protection device comprises an interface detection module, a cipher to be verified input interface sending module, a cipher verifying module and an instruction sending module that are respectively used for taking the above steps. Via use of the hardware cipher-based mobile phone data protection method and device provided in the invention, operation steps are simplified, user experience is improved, software decryption can be prevented, and data safety can be ensured.
Owner:LETV INFORMATION TECH BEIJING
Video face changing method and device
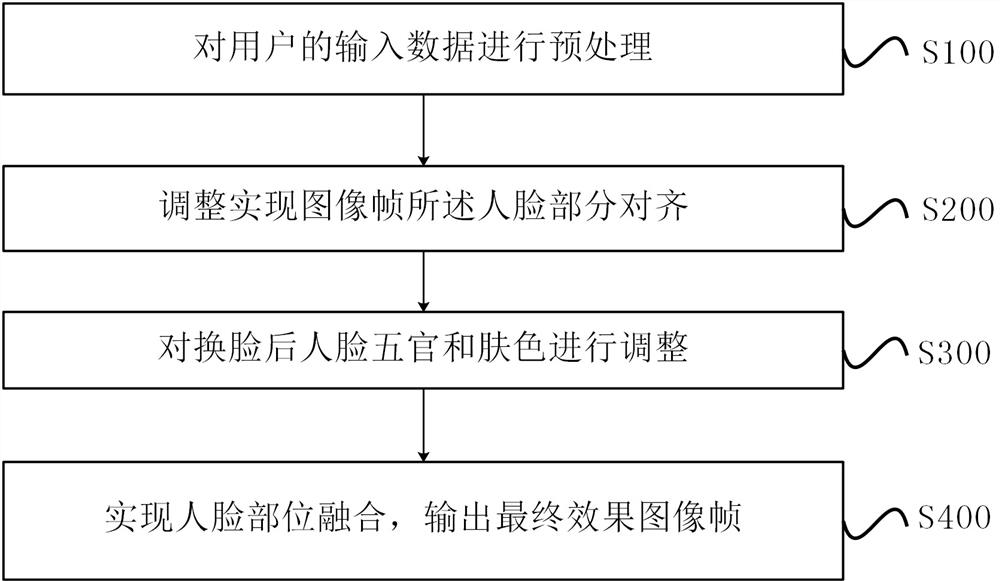
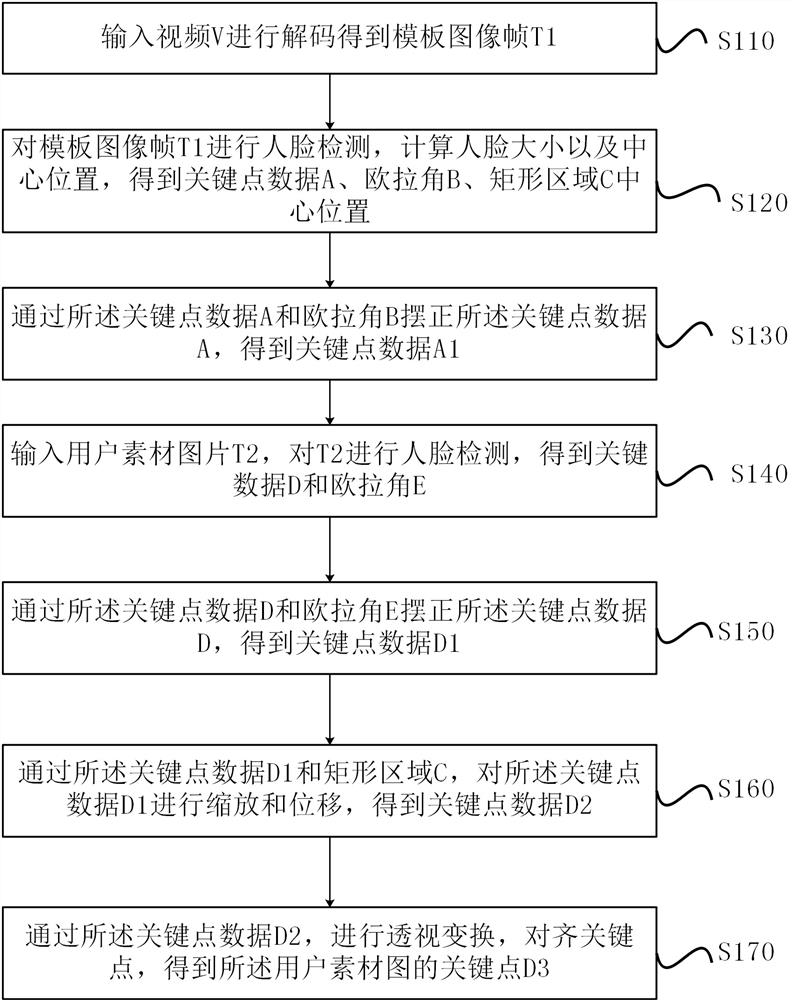
PendingCN112949360ASettlement of portrait rightsAddress privacy concernsCharacter and pattern recognitionPattern recognitionSkin colour
The invention provides a video face changing method and device. The video face changing method comprises the steps of obtaining a to-be-processed image frame, performing key detection on a template image and a to-be-processed user image, adjusting key points to achieve alignment and superposition, migrating fusion of areas such as a face and skin color, restoring other parts, fusing a face contour mask image to a template, and performing replacement to obtain a face-changed image frame. The method can be realized locally, the privacy can be better protected, and the shape problems of light, skin color, five sense organs and the like are solved.
Owner:GUANGZHOU JIUBANG DIGITAL TECH
Multi-party secure computing implementation method based on block chain technology
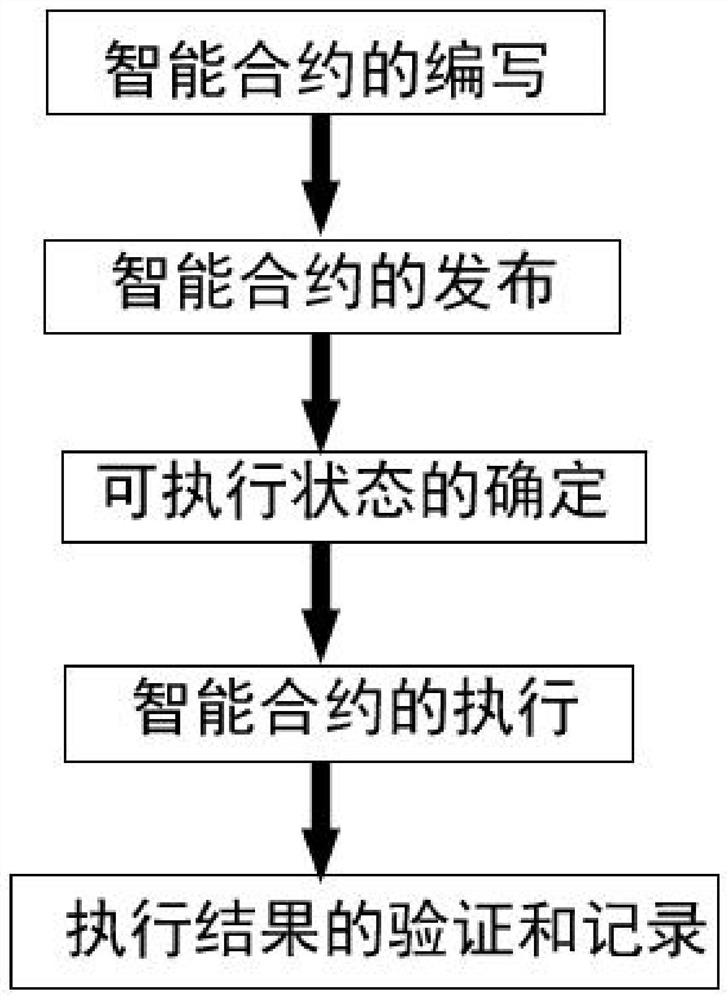
PendingCN112115204AEnhanced authenticationImprove audit effectDatabase updatingFinanceData securitySmart contract
The invention discloses a multi-party security computing implementation method based on a blockchain technology. The method specifically comprises the following steps: step 1, compiling an intelligentcontract, wherein the intelligent contract comprises node information of each contract party, tasks of each contract party for executing the intelligent contract and task execution relationships among the tasks; step 2, publishing the intelligent contract: publishing the intelligent contract on the block chain; 3, determining an executable state: after the intelligent contract is authorized by related nodes of each contract party of the intelligent contract, determining the intelligent contract as the executable state; step 4, executing the intelligent contract, wherein different contract parties have own unique business accounts, log in node servers of nodes through node accounts of the nodes and execute tasks of the intelligent contract on the blockchain; and step 5, carrying out verification and recording of an execution result, wherein the nodes which do not participate in the intelligent contract carry out verification and state recording of the contract execution result. According to the invention, the problems of data security and privacy in the data cooperation process are solved.
Owner:DATANG NETWORK CO LTD
Multi-target tracking and respiration detection method and device based on millimeter wave radar
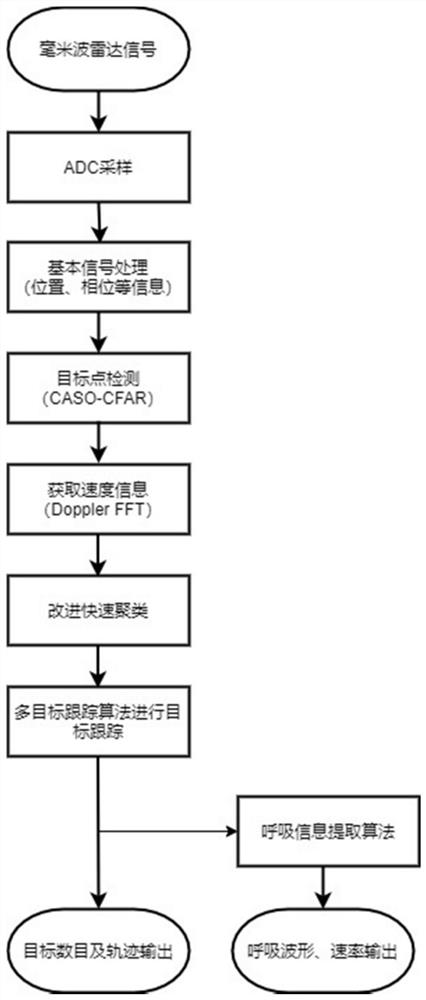
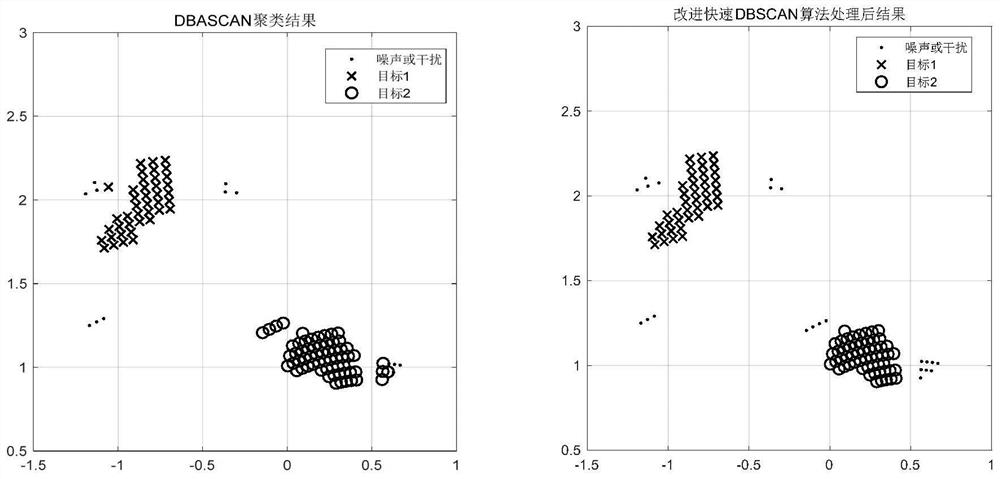
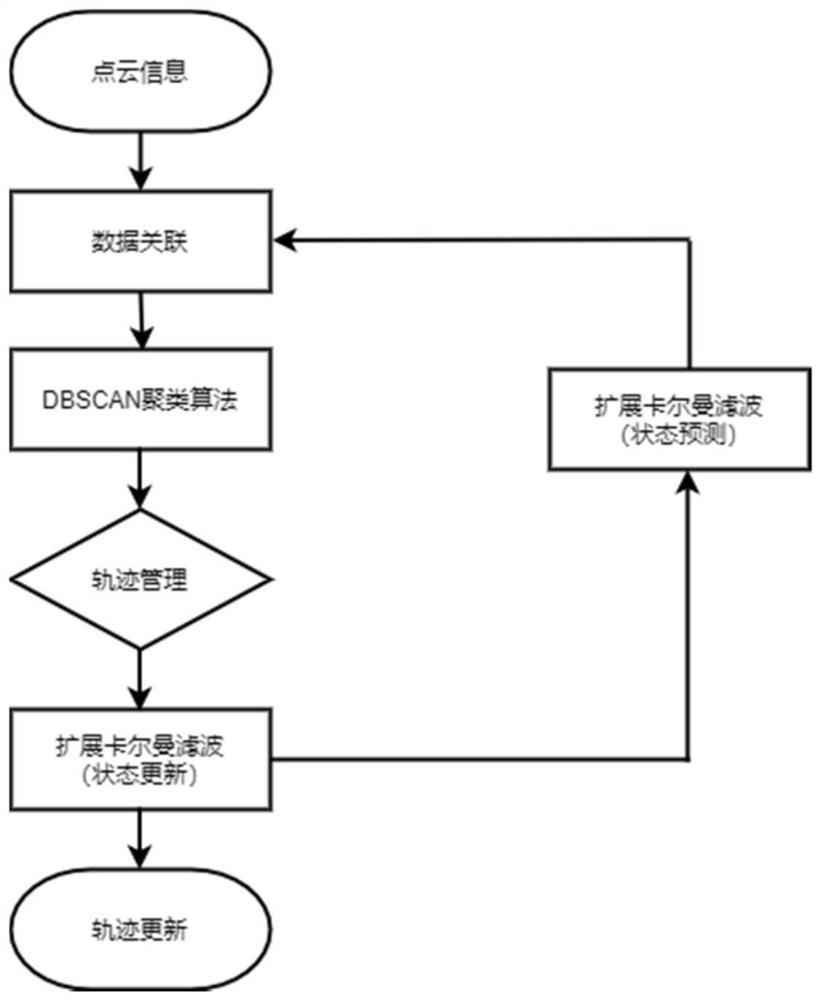
PendingCN114236525AAddress privacy concernsConvenient breath detectionRespiratory organ evaluationRadio wave reradiation/reflectionPoint cloudMulti target tracking
The invention discloses a multi-target tracking and breathing detection method and device based on a millimeter wave radar. The method comprises the following steps: acquiring distance, speed, angle and phase information from a sampled signal and completing detection of a target point; clustering the point clouds by using the provided improved fast DBSCAN algorithm; using a multi-target tracking algorithm to track the target and manage the trajectory; phase information corresponding to a plurality of targets is accurately obtained by using a target phase information extraction algorithm based on secondary clustering and statistical information provided by the invention; and on this basis, respiration information is extracted. According to the invention, a set of multi-target tracking and breathing detection system is designed and integrated on a set of device, and the system has the advantages of high real-time performance, high integration level, high engineering value and the like. Through the device, the number and the positions of the targets can be detected in real time on the end, the targets can be accurately tracked, and the breathing information of each target can be detected in the process.
Owner:ZHEJIANG UNIV
Photo shooting and acquiring method and social method thereof
PendingCN108734595AFast experienceImprove experienceData processing applicationsCharacter and pattern recognitionSocial circleSystem service
The invention provides a photo shooting and acquiring method and a social method thereof. Photos are shot between users and sent to a system server, the system server performs face recognition according to the photos and queries the user identity matched with the photos, and sends the photos to users on the photos. The users can initiate text, voice, and video sessions through the photos and a photo shooting user to create a social relationship, and the users can also comment, score, reward and rank the photos and the photo shooting user, and send the photos to a social circle. Privacy leakagecan be effectively prevented during photo shooting and acquiring processes.
Owner:金德奎
Fall-down alarm equipment and method
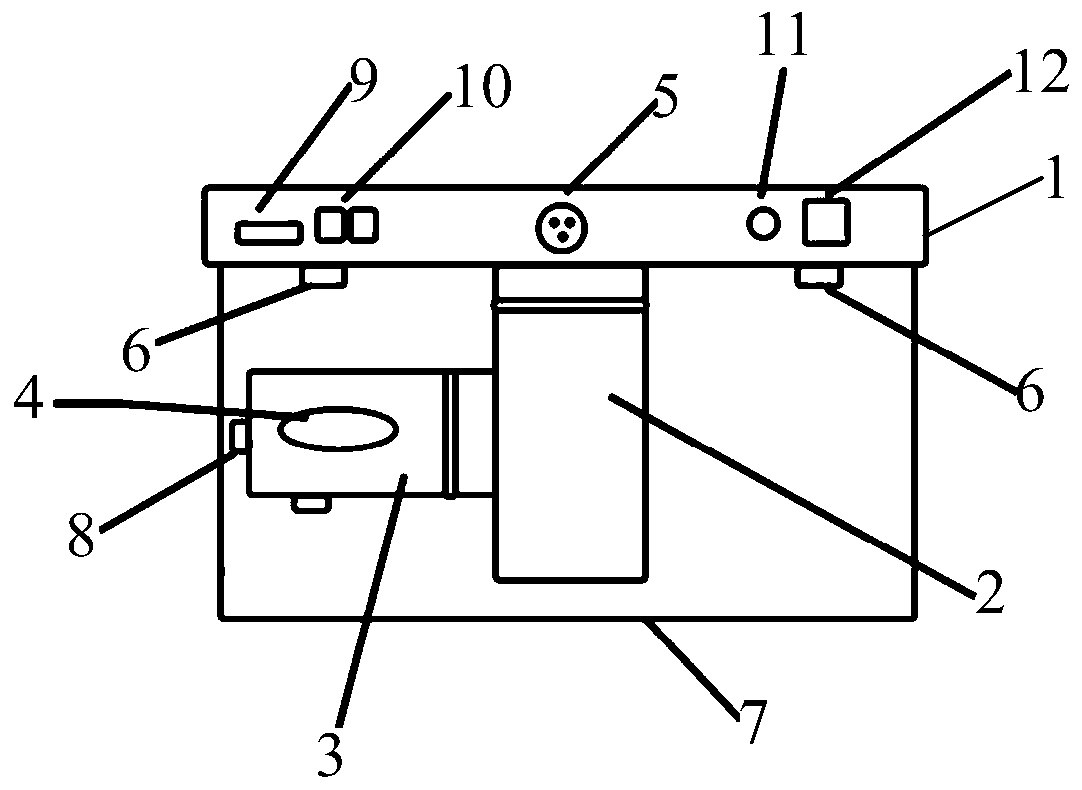
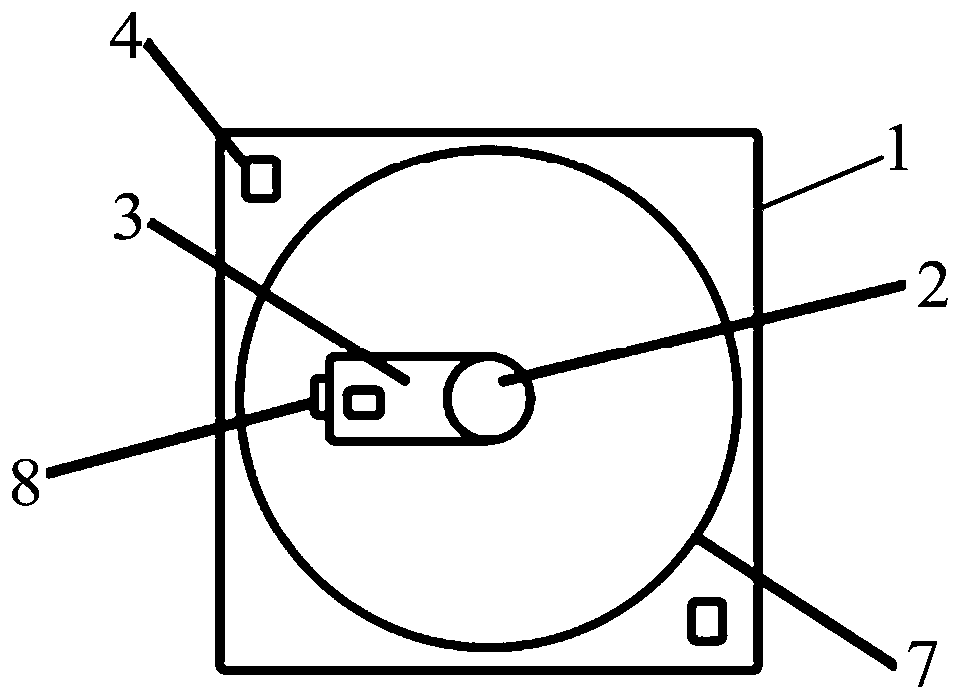
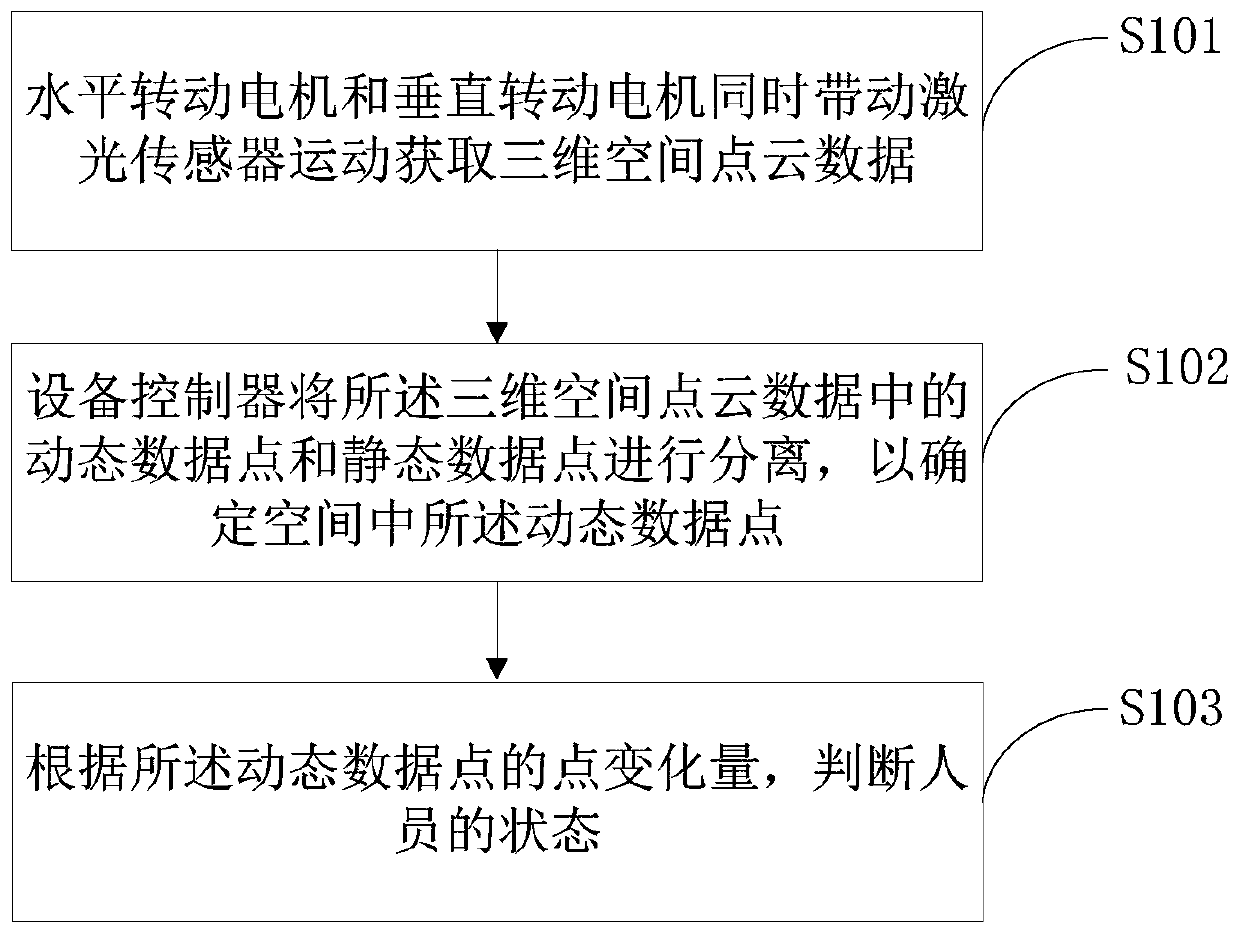
The application discloses fall-down alarm equipment and method, and relates to the technical field of the radar detection. The fall-down alarm equipment comprises an equipment controller, and a horizontal rotating motor is arranged on the equipment controller, a vertical rotating motor is fixedly arranged at a rotating end of the horizontal rotating motor, a laser sensor is arranged on the rotating end of the vertical rotating motor, and the laser sensor is electrically connected with the equipment controller; alarm equipment is further arranged on the equipment controller; and the alarm equipment is electrically connected with the equipment controller. The horizontal rotating motor, the vertical rotating motor and the laser sensor form a three-dimensional laser radar, thereby realizing the collection of three-dimensional point cloud data, and then the dynamic data point of the corresponding personnel is determined through the equipment controller; and a personnel state is judged according to the point variation quantity of the dynamic data point. if judging that the personnel falls down, the alarm equipment is controlled to give an alarm and notify other people that the personnelfalls down; and meanwhile, the boundedness that the alarm can be given only when the traditional wearable equipment or sensor is carried on the body and the phenomenon that video type alarm is easilyinvolved to the privacy are solved.
Owner:NANJING LINKSAINT TECH CO LTD
Apparatus and method for mobile communications and computing
InactiveCN104813327AAddress privacy concernsFix security issuesService provisioningHardware monitoringCommunications managementSecurity domain
A wireless computing and communications device comprises a baseband processor configured to implement operations providing access to a wireless communications network, and an application processor configured to execute user applications. A communications management processor communicates with the baseband processor and the application processor by respective first and second communications channels. The communications management processor is configured to operate in a separate security domain from the application processor, and to mediate all access to the wireless communications network by the user applications.
Owner:NETCOMM WIRELESS
Radio frequency identification transponder security
ActiveCN101103366AAddress privacy concernsFix security issuesMemory record carrier reading problemsCo-operative working arrangementsLimited accessHash function
Security and privacy of tag information in an RFID-based system can be achieved through the usage of pseudonyms generated based on one-way hash functions. A system based on binary one-way trees allows for the scalable generation and decoding of authentication keys to obtain access to tag identities. The apparatus and methods described can also be adapted to provide limited access for readers to tag information.
Owner:BRITISH TELECOMM PLC
Bidirectional authentication method of near field communication technology
ActiveCN110769404AIntegrity guaranteedGuaranteed confidentialityDigital data authenticationRecord carriers used with machinesCommunications securityData integrity
The invention discloses a bidirectional authentication method of a near field communication technology. The system comprises a real identity (ID) and a temporary identity (IDS) of a label held by thelabel and a back-end database together, and shared keys K1 and K2 of a current session, in addition, the label also needs to store a timestamp Tt required by authentication, and the back-end databasestores last and latest IDS and shared keys K1 and K2. The bidirectional authentication method has the advantages that the bidirectional authentication method for near field communication safety canbe provided, the safety of the bidirectional authentication method is proved through simple bit and exclusive OR operation without hash and other function encryption operation and BAN logic, bidirectional authentication can be achieved, and label anonymity, data integrity and confidentiality and non-traceability are guaranteed. Common attacks including denial of service attacks, asynchronous attacks, replay attacks, algebraic attacks and the like can be resisted. Compared with the traditional scheme, the protocol not only solves the security and privacy problems, but also reduces the calculation and storage cost.
Owner:ZHENGZHOU UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com