Multi-party secure computing implementation method based on block chain technology
An implementation method, blockchain technology, applied in the field of multi-party security computing based on blockchain technology, can solve problems such as easy data leakage, low collaboration efficiency, and low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The technical solutions of the present invention will be clearly and completely described below in conjunction with the accompanying drawings. Apparently, the described embodiments are part of the embodiments of the present invention, rather than all of them.
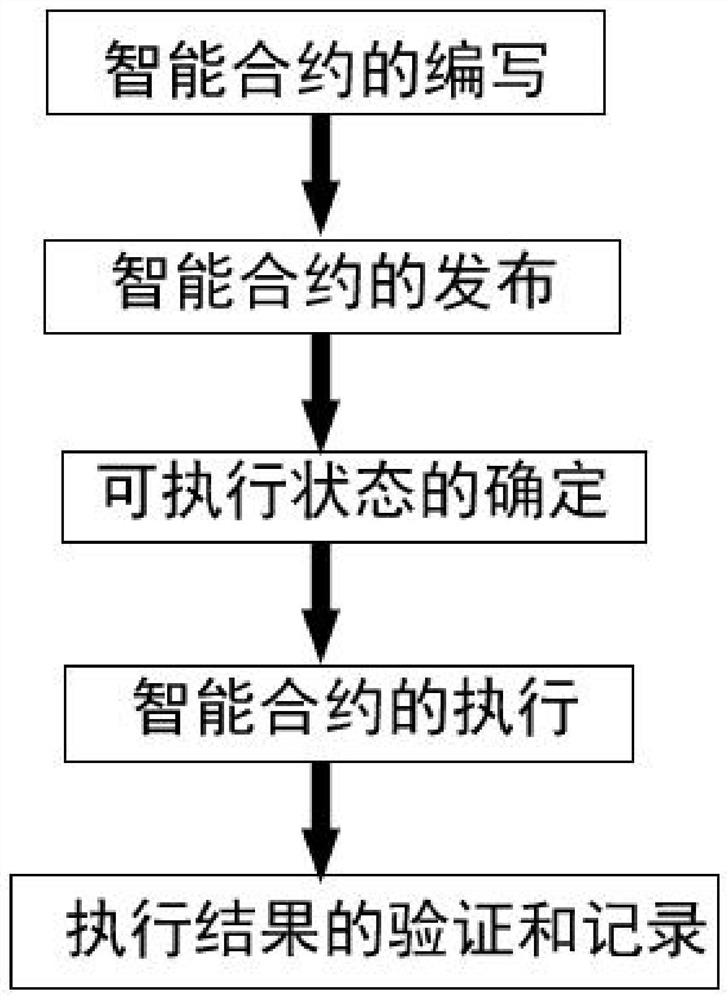
[0031] An embodiment of a multi-party secure computing implementation method based on blockchain technology as shown in the present invention, specifically includes the following steps:
[0032] Step 1. Compilation of smart contracts: The contract party corresponding to any demand side node that writes the smart contract acts as the initial initiator to write the smart contract. The smart contract written includes the node information of each contracting party, and each contracting party executes the contract. The tasks of the smart contract and the task execution relationship between the tasks; the content of the smart contract includes the state preservation and access interface of the ledger data, and the tasks...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com