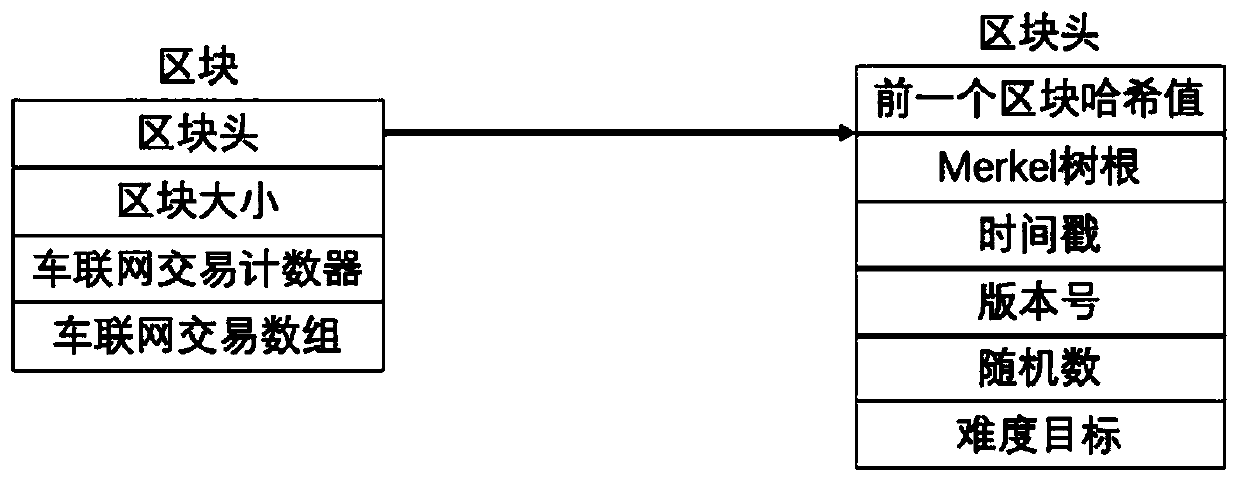
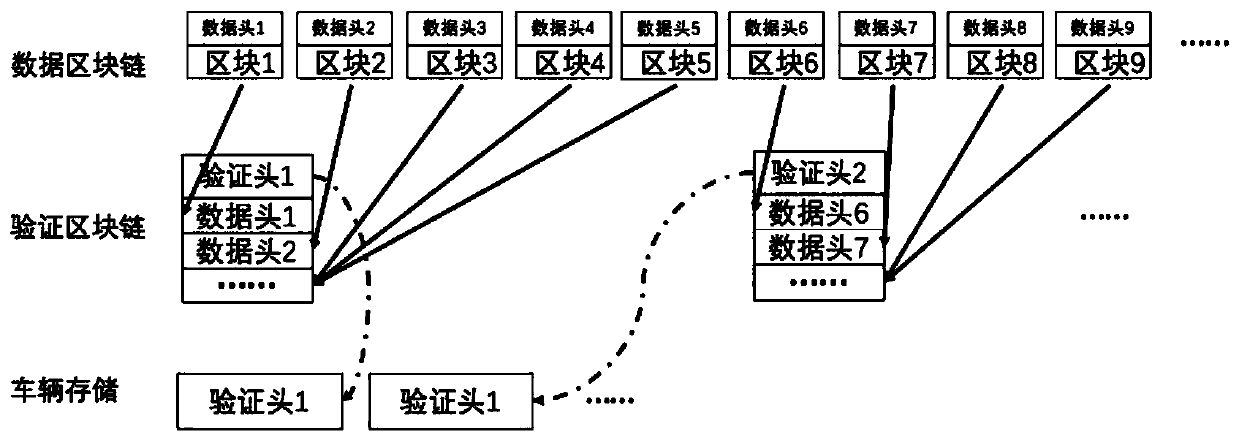
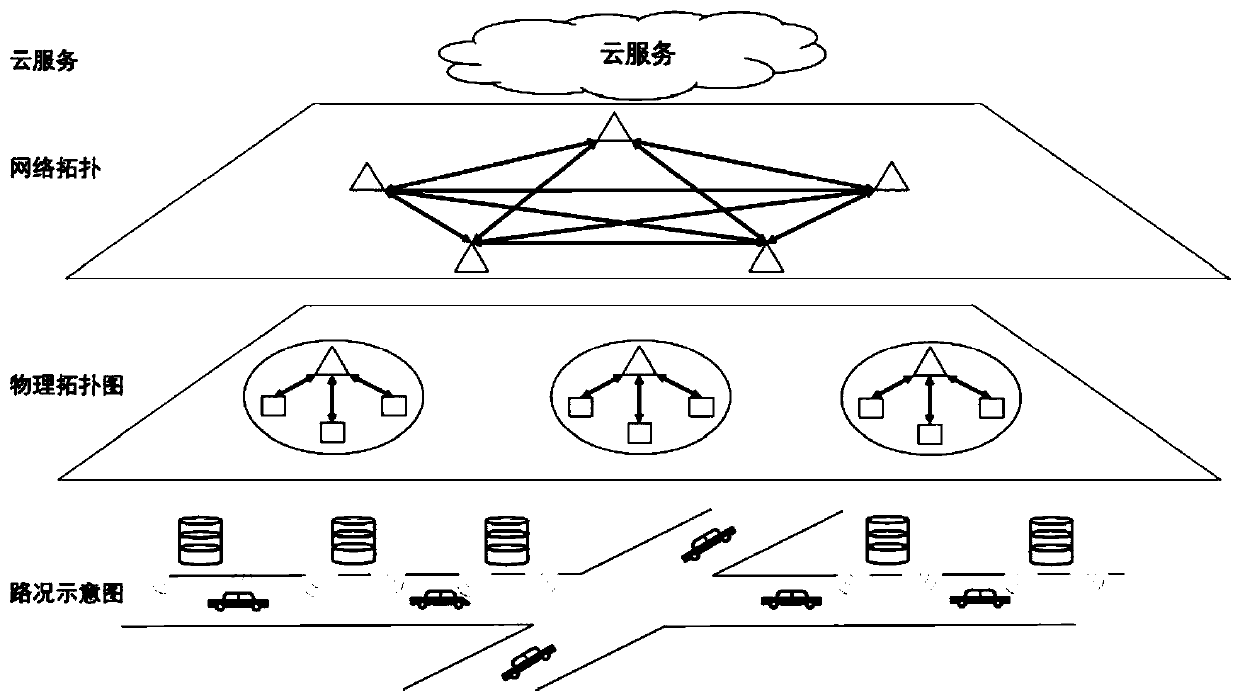
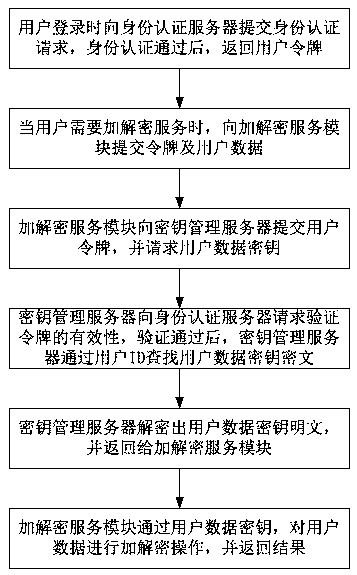
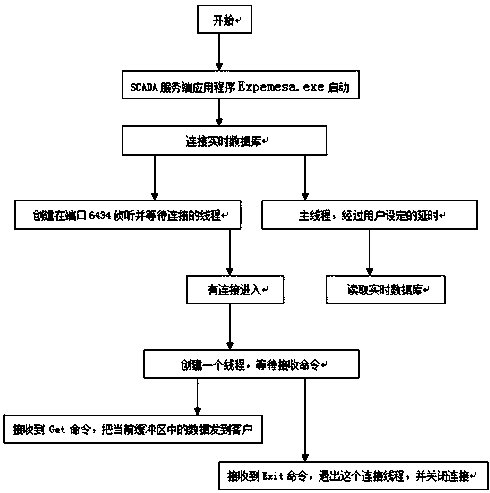
Patents
Literature
117results about How to "Solve data security issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
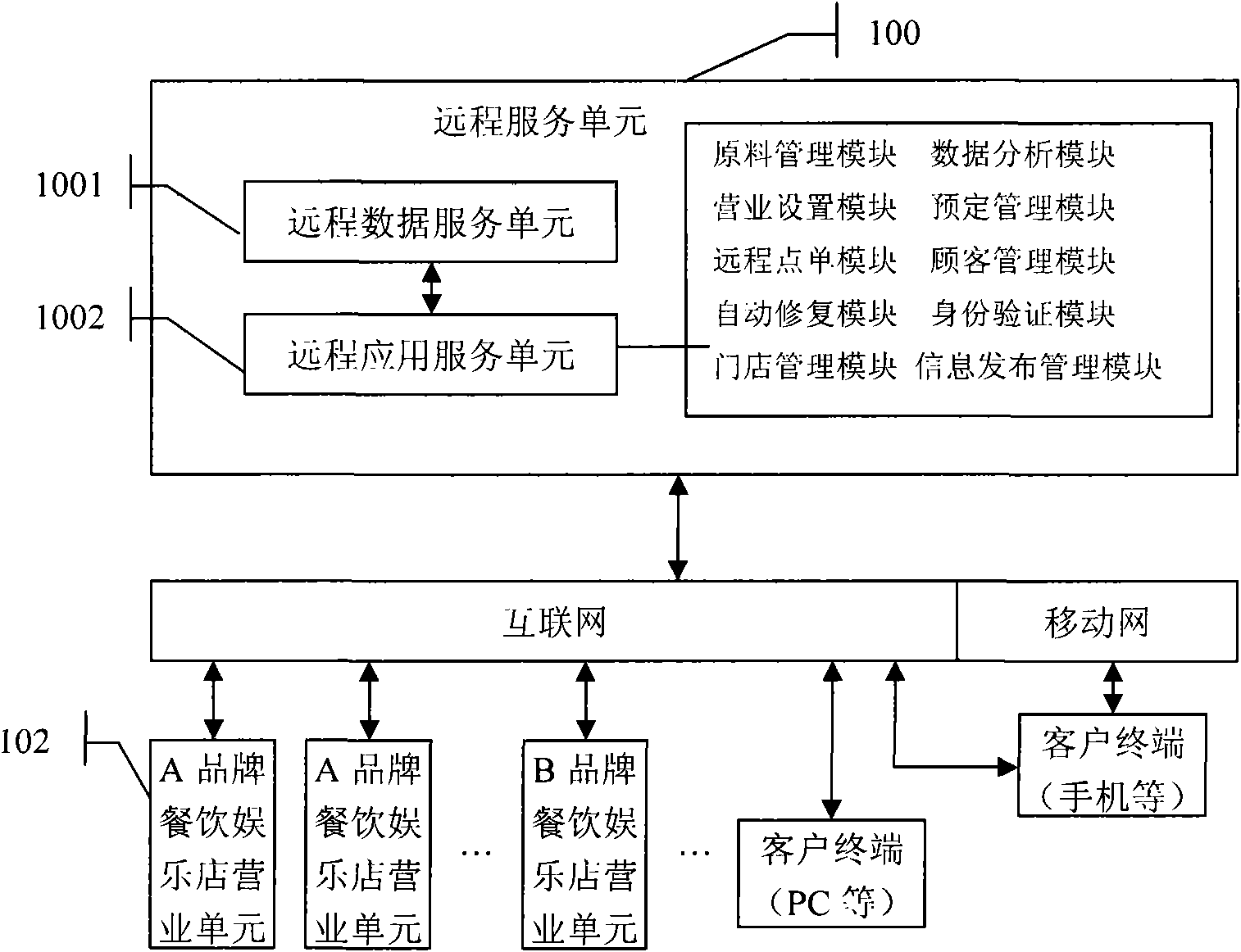
Internet-based catering and amusement management system and electronic menu and ordering method thereof
InactiveCN101540026AConfiguration highImprove performanceCommerceSpecial data processing applicationsDaily operationSystem maintenance
The invention discloses a catering and amusement management system and a special electronic menu and a self-help ordering method thereof. The internet-based catering and amusement management system comprises a remote data service unit, a remote application service unit, at least one catering and amusement shop operating unit and an access terminal unit, wherein the remote data service unit is used for the collective and concentrated storage of data from the units in the system; the remote application service unit is used for acquiring the data from the units, analyzing and processing the data collectively, distributing the data to the units and providing an internet-based catering management application service module; the at least one catering and amusement shop operating unit is used for the daily operation of a catering and amusement shop and the data interaction with the remote data service unit; and the access terminal unit is used for accessing the corresponding catering management application service module according to the right distributed by the remote application service unit. The system has high data safety, remote management, convenient and quick maintenance, low system maintenance cost and good augmentability, and can be simultaneously applied to the management of a plurality of catering and amusement shops with different brands.
Owner:杭州因餐信息技术有限公司
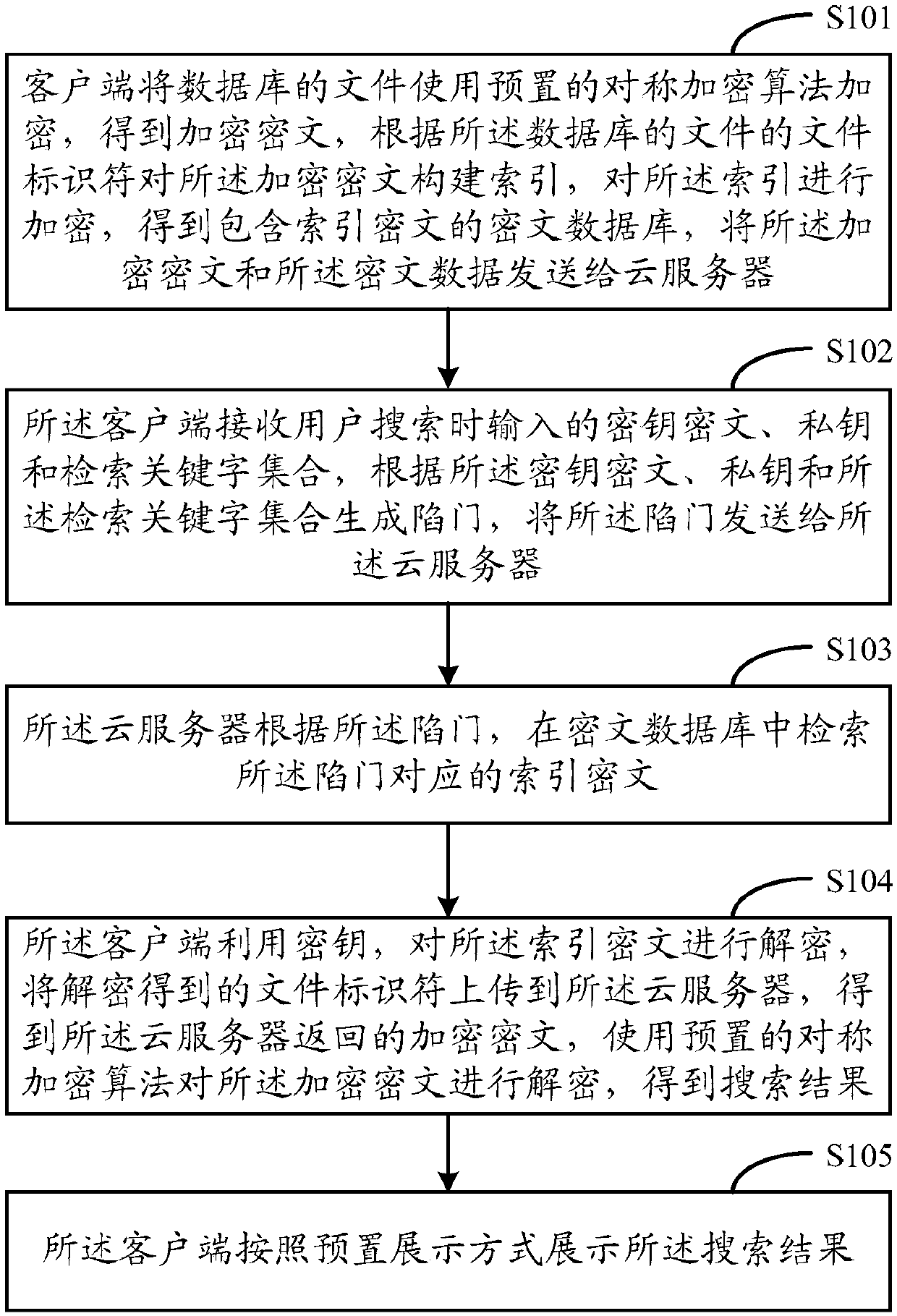
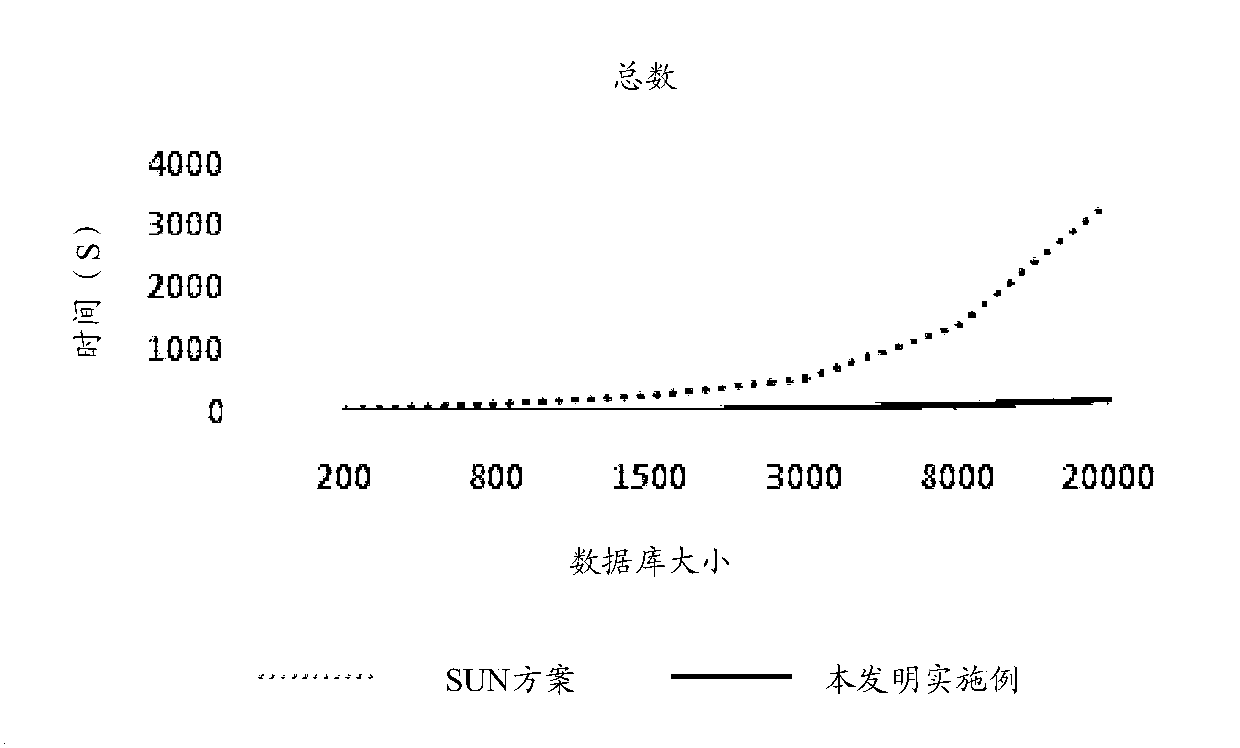
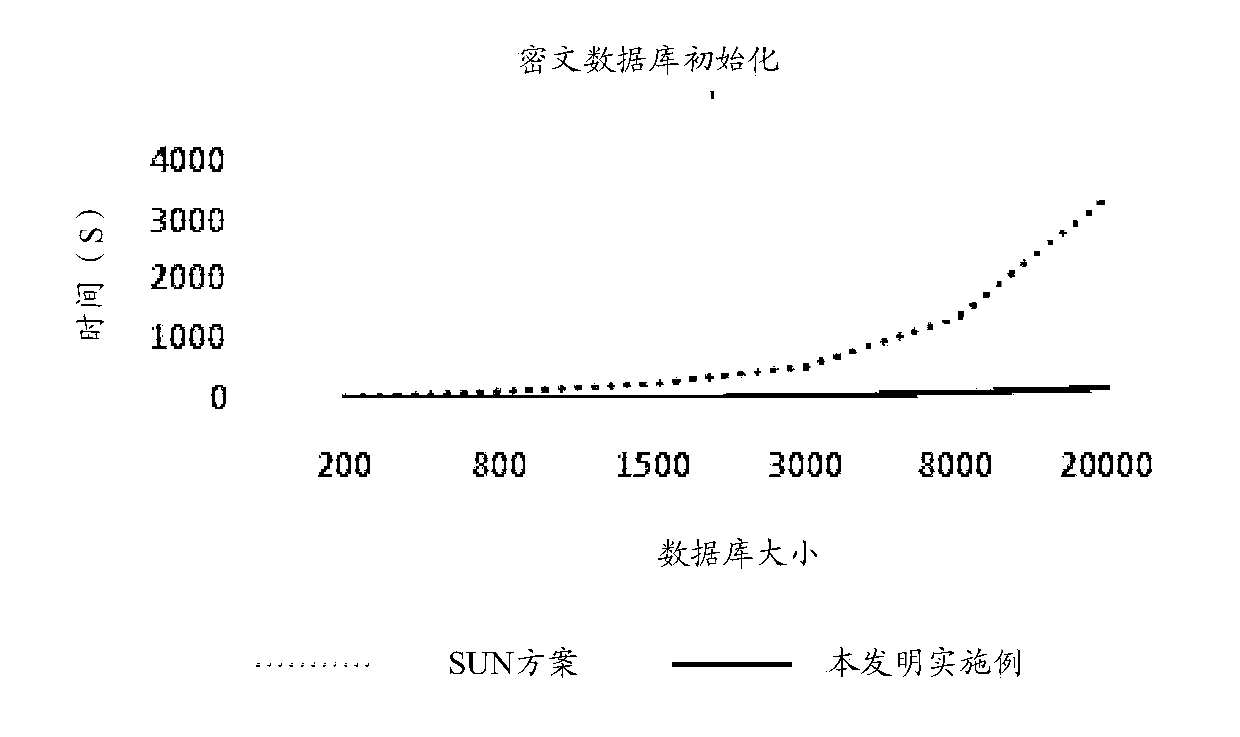
Ciphertext searching method and system supporting access control
ActiveCN108494768ASolve data security issuesReduce computational overheadTransmissionSpecial data processing applicationsAttribute-based encryptionCiphertext
The invention is applicable to the field of data processing, and provides a searching method supporting access control. The searching method comprises the steps that: a client encrypts files of a database to obtain encrypted ciphertexts, and indexes are established and encrypted according to file identifiers to obtain a ciphertext database; the client receives a key ciphertext, a private key and aretrieval keyword set to generate a trap door; a cloud server retrieves the corresponding index ciphertext according to the trap door; the client carries out decryption on the index ciphertext by utilizing a key, uploads the file identifier obtained by decryption to the cloud server to obtain the encrypted ciphertext, and the encrypted ciphertext is decrypted to obtain a search result; and the client shows the search result according to a preset showing mode. In the implementation process of the embodiment of the invention, the ability of a searching client for data access is controlled by adopting attribute-based encryption, but access control is set to be carried out in the overall database instead of the indexes, so that calculation cost when a data owner encrypts the database can be greatly reduced; and meanwhile, in the process that a user acquires the search trap door, the data owner does not need to participate in.
Owner:SHENZHEN UNIV
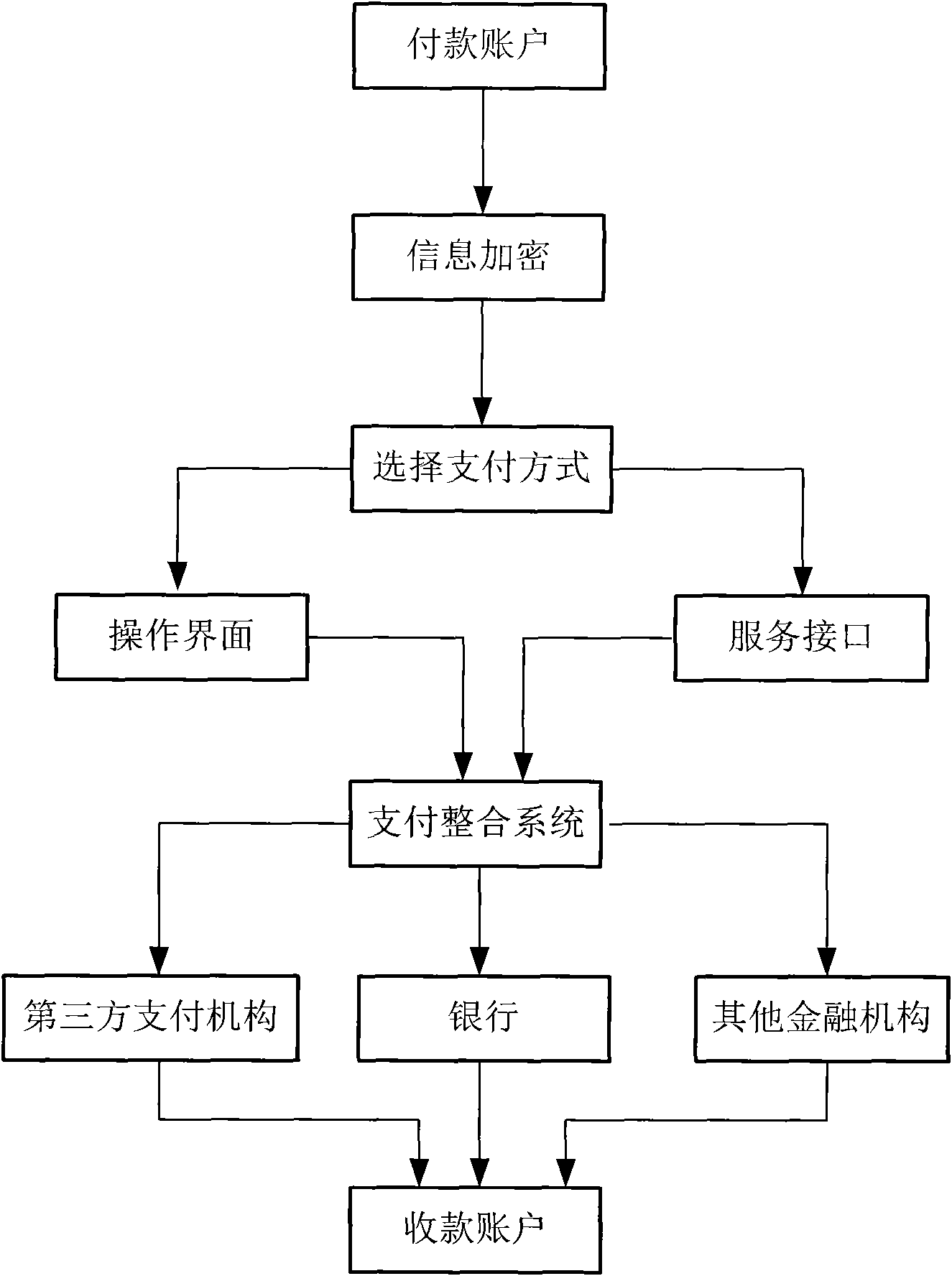
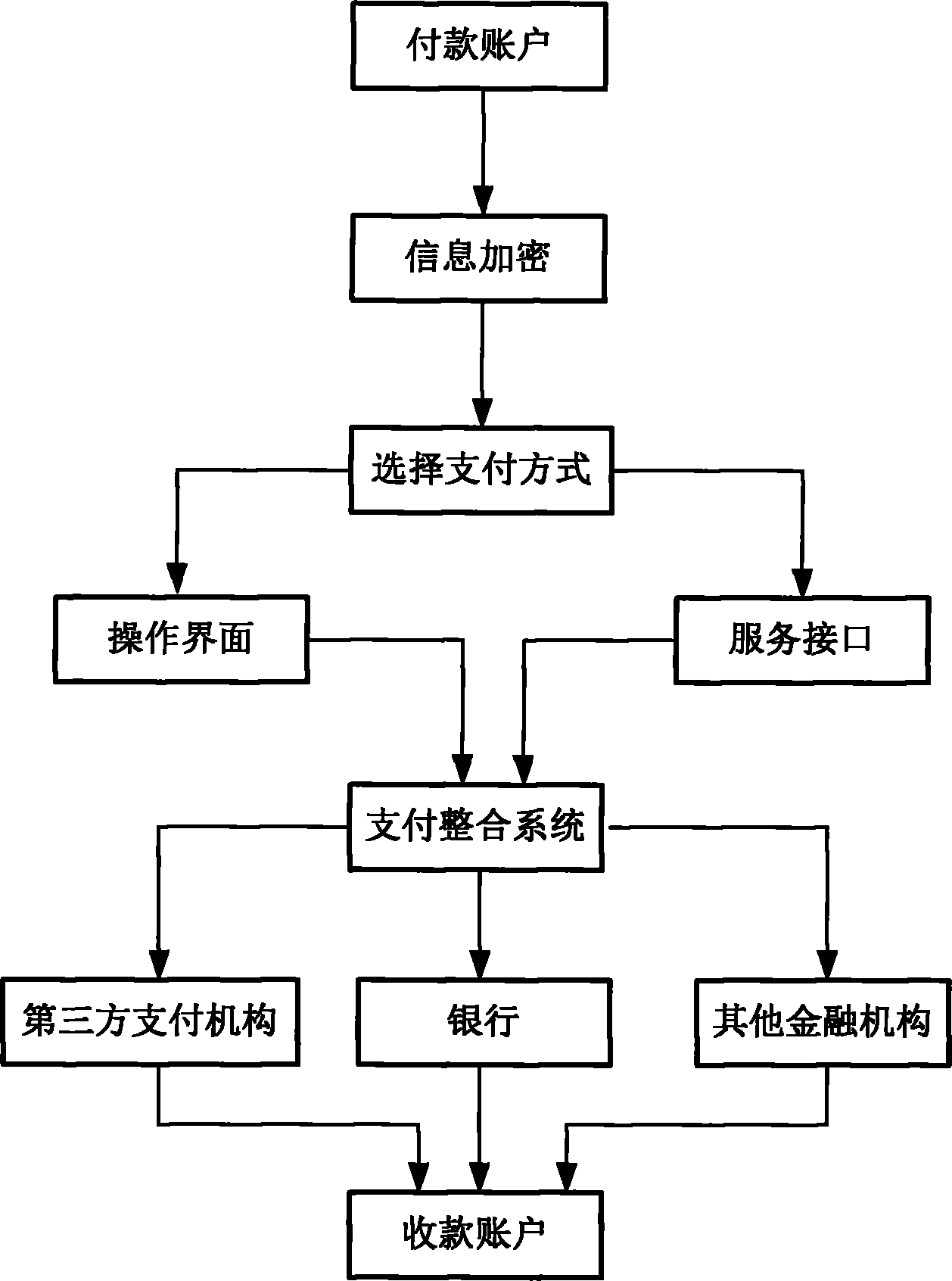
Internet-based payment channel integrating method
InactiveCN102646238AAvoid wanderingAvoid round tripPayment architectureMerchant servicesPrivate network
The invention relates to an Internet-based payment channel integrating method which is characterized by comprising the following steps: firstly, a customer accesses an Internet for selecting goods, and selects a payment settlement mode; secondly, the customer encrypts relevant order information and submits an order; thirdly, a merchant sever checks and confirms purchasing information of the customer and ensures that electronic money issuers such as a bank check the purchasing information to obtain authentication of payment fund; fourthly, after the bank checks and confirms the purchasing information, confirming and payment settlement information is transmitted back to the merchant server through an encrypting communication channel; fifthly, settlement is carried out by means of a financial private network, and payment settlement success information is sent; and finally, the merchant server sends network payment success information and delivery release to the customer. Therefore, all modes of global payment can be completed on the provided payment platform. From different aspects and different links, data security of a user using a payment channel is strictly protected, and the problem of information data security of the user is solved.
Owner:TONGCHENG NETWORK TECH
Collaborative caching method based on lightweight block chain in Internet of Vehicles environment
ActiveCN110535687AMaximize utilizationLower latencyData switching networksSource Data VerificationEngineering
The invention discloses a collaborative caching method based on a lightweight block chain in an Internet of Vehicles environment, and belongs to the field of Internet of Vehicles. The lightweight block chain architecture is applied to an Internet of Vehicles environment, and the underlying vehicle layer undertakes a lightweight node role, reports driving data to the intermediate layer, requests Internet of Vehicles data from the intermediate layer and verifies the data; the middle roadside node layer is responsible for a full-node role, storing blockchain data, providing request data service for bottom-layer vehicles, reporting Internet of Vehicles data to the cloud server, and cooperatively caching the blockchain data by using multiple roadside nodes; and the top cloud service layer undertakes a full-node role, stores blockchain data, provides services for the intermediate roadside node layer, and participates in the cooperative cache initialization process of the intermediate roadside node layer. According to the method, the data security problem is solved, a light data verification mode is provided, maximum utilization of storage resources of the roadside nodes is achieved through cooperative caching among the multiple roadside nodes, and the delay of communication between the roadside nodes and vehicles is reduced.
Owner:DALIAN UNIV OF TECH
Identity-based closed key management method and system
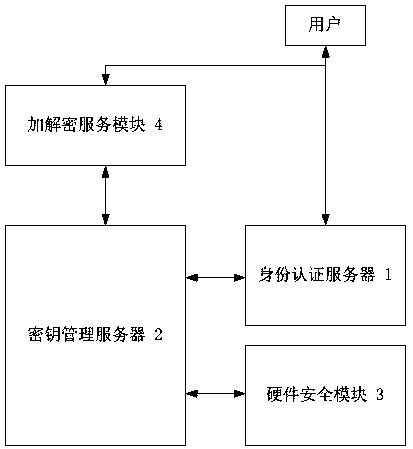
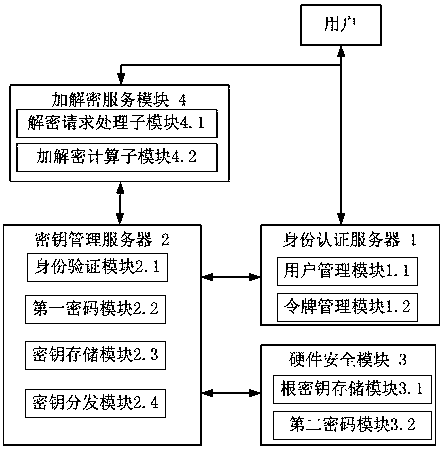
ActiveCN107948156ASimplify the management processAvoid cumbersomeKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention provides an identity-based closed key management method and system. The method comprises the following steps: 1, an identity authentication request is submitted to an identity authentication server when a user logs in, and a user token is returned upon successful identity authentication; 2, when the user requires encryption / decryption service, the token and user data are submitted toan encryption / decryption service module; 3, the encryption / decryption service module submits the user token to a key management server, and requests a user data key; 4, the key management server requests the identity authentication server to verify the validity of the token, and the key management server searches for user data key ciphertext through a user ID upon successful verification; 5, thekey management server obtains user data key plaintext through decryption and returns the user data key plaintext to the encryption / decryption service module; and 6, the encryption / decryption service module carries out encryption / decryption operation on the user data through the user data key, and returns an encryption / decryption result. The system comprises the identity authentication server, thekey management server, a hardware security module, and the encryption / decryption service module.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Data safety storage method and system under cloud computing environment
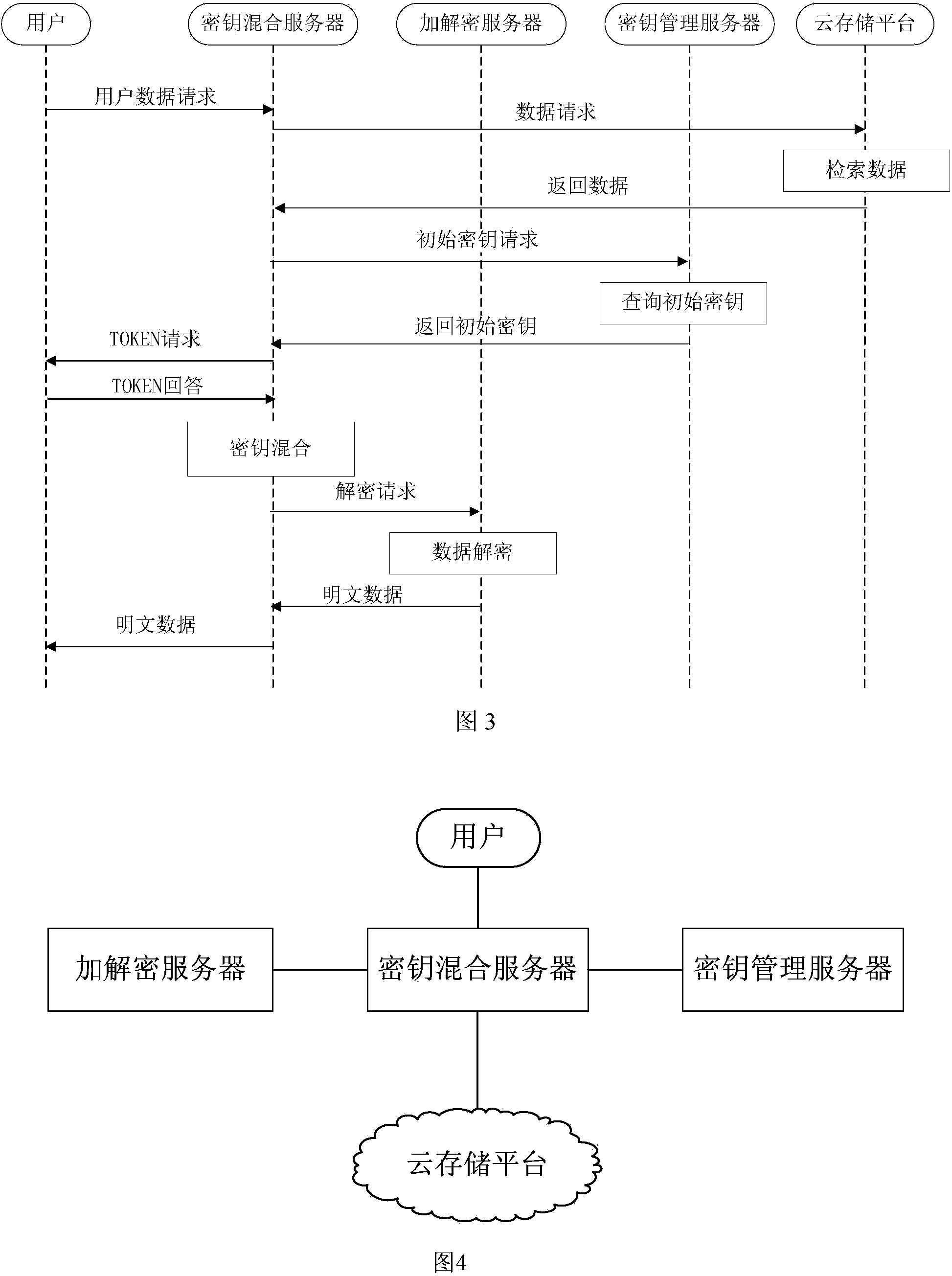
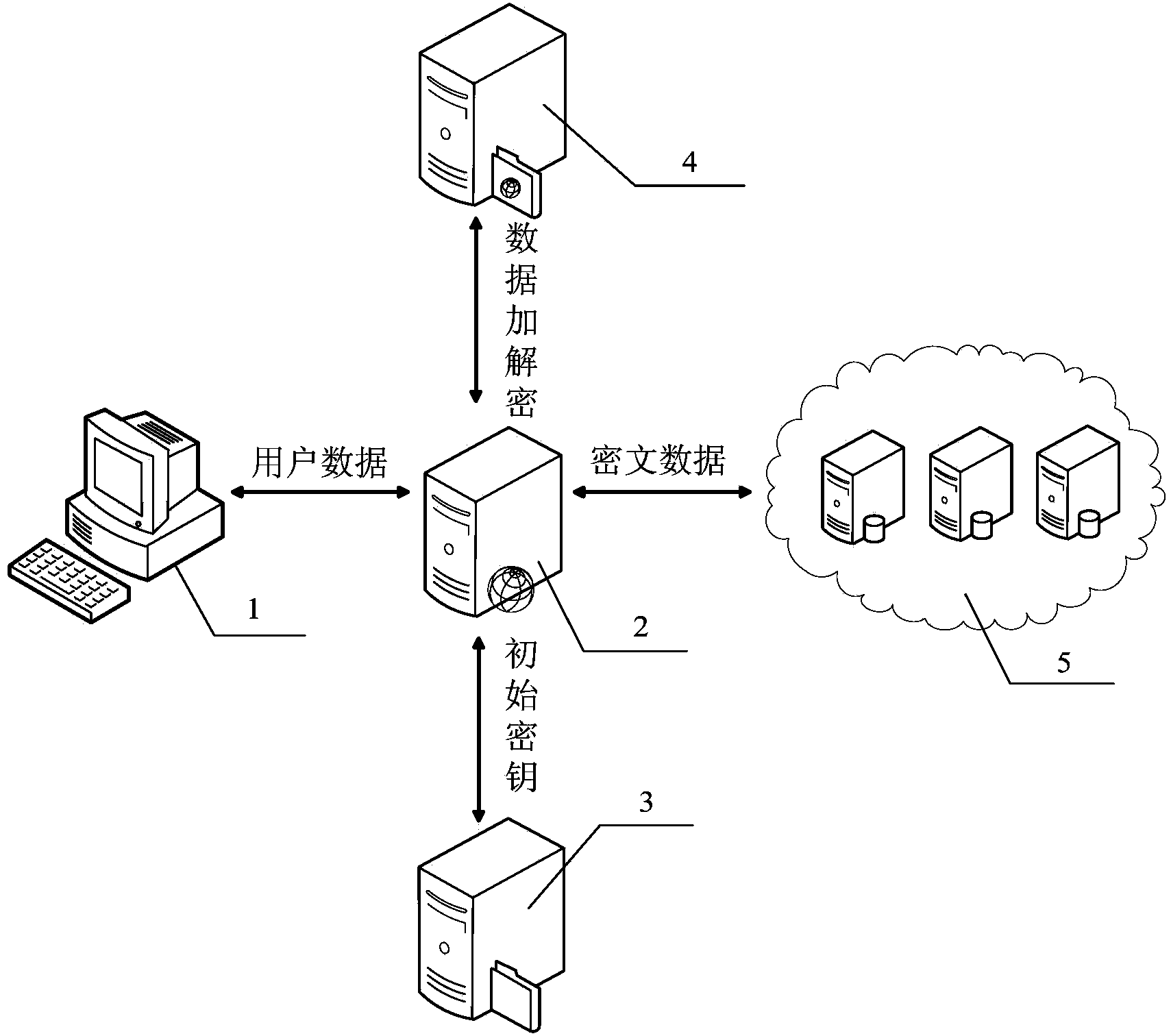
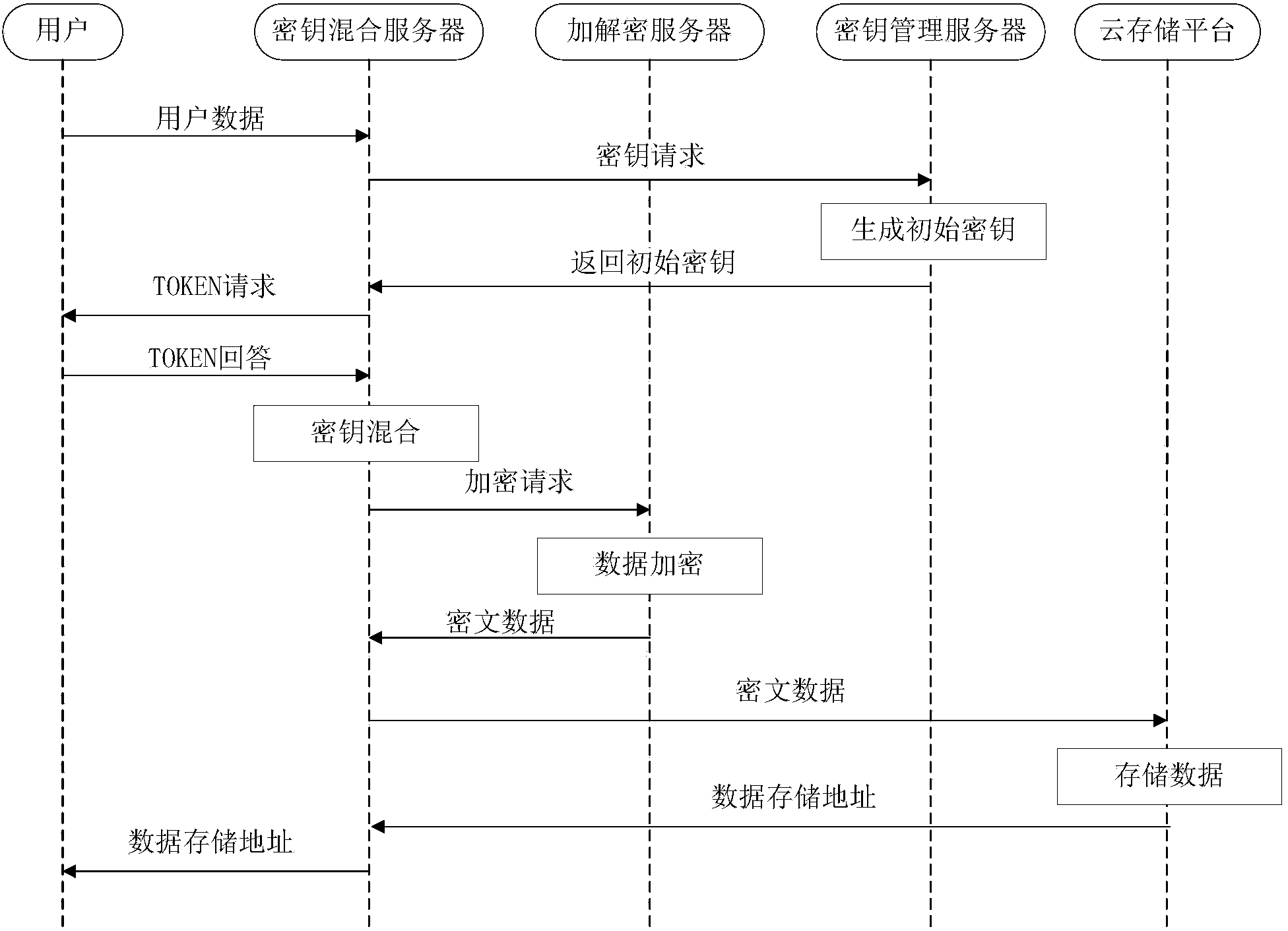
ActiveCN103457932AFix the leakGuaranteed safe storageSecuring communicationCloud storageKey management
The invention relates to a data safety storage method and system under the cloud computing environment. The method comprises the steps that a secret key mixed server is interacted with a user to obtain an encryption and decryption token, the secrete key mixed technology is adopted in the secret key mixed server to enable the encryption and decryption token to be mixed with an initial secrete key provided by a secrete key management server so as to obtain a data encryption and decryption secrete key, encryption and decryption are carried out on data by an encryption and decryption server according to the encryption and decryption secrete key, and after being encrypted, the data are stored in a cloud storage platform. According to the data safety storage method and system, the secret key mixed server is introduced, the secrete key mixed technology is applied, the data leakage problem caused by conspiring of a secrete key management party and a data storage party can be solved, and the data safety storage under the cloud computing environment is effectively achieved.
Owner:CEC CYBERSPACE GREAT WALL
System and method for structure health monitoring based on block chain technology and smart contract
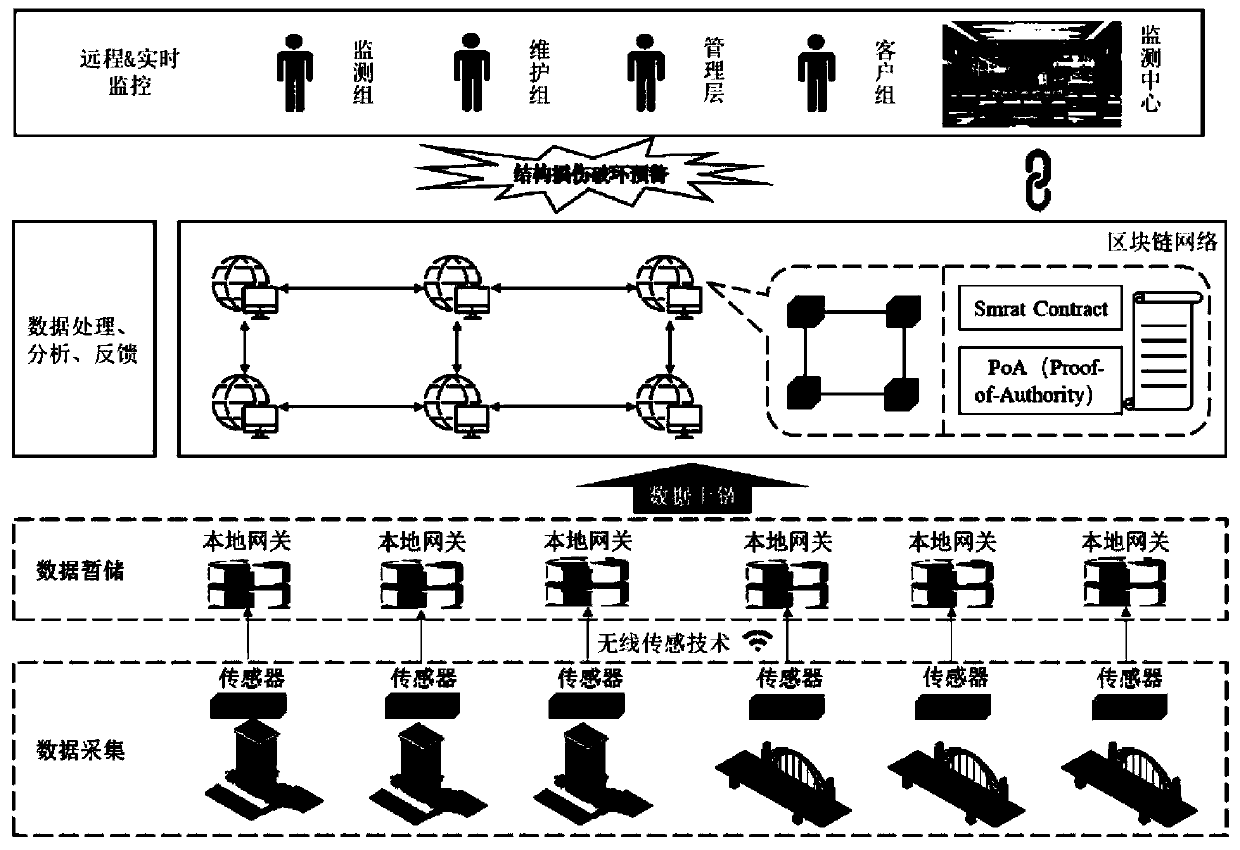
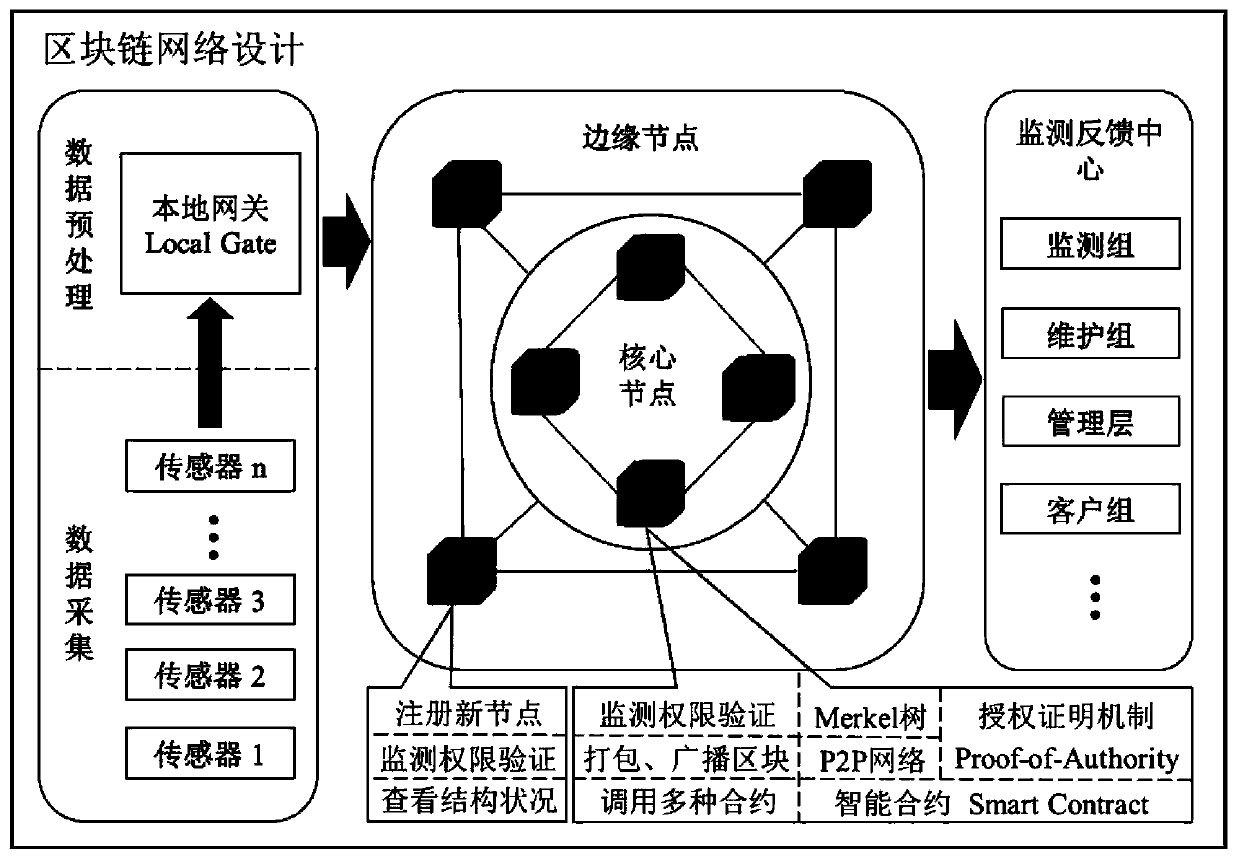
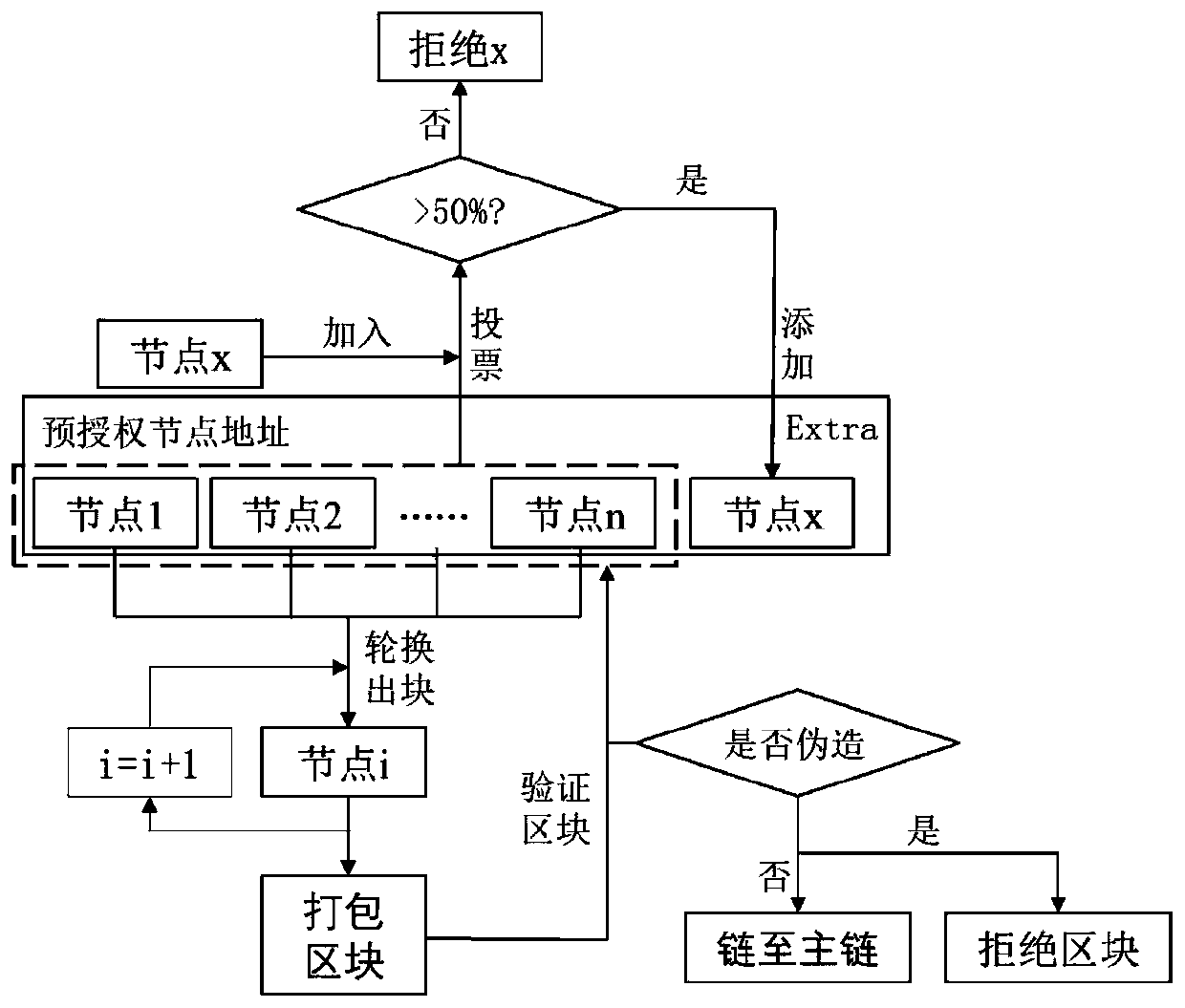
PendingCN111125468AGuarantee safe and reliableSolve the problem of mutual mistrustData processing applicationsOther databases browsing/visualisationOriginal dataData acquisition
The invention provides a system and a method for structural health monitoring based on a block chain technology and a smart contract. The system comprises a data acquisition module, a data temporary storage and transmission module, a data analysis module and an intelligent monitoring module; the data acquisition module comprises a sensor and a digital camera which are arranged on a building structure, and the sensor and the digital camera are used for acquiring original data; the data temporary storage and transmission module comprises a local gateway, and the local gateway is in wireless connection with the data acquisition module and the data analysis module; and the data analysis module comprises a block chain network system and the health monitoring smart contract deployed in the blockchain network system. The information among the participants is accurate, efficient and shared, and the operation efficiency of the whole system is improved from the perspective of data management and application. The structure health monitoring system is effectively prevented from being paralyzed under the condition of a server fault or a network fault.
Owner:TIANJIN UNIV
Method of speech sound used as secret key to achieve data resource cloud storage management
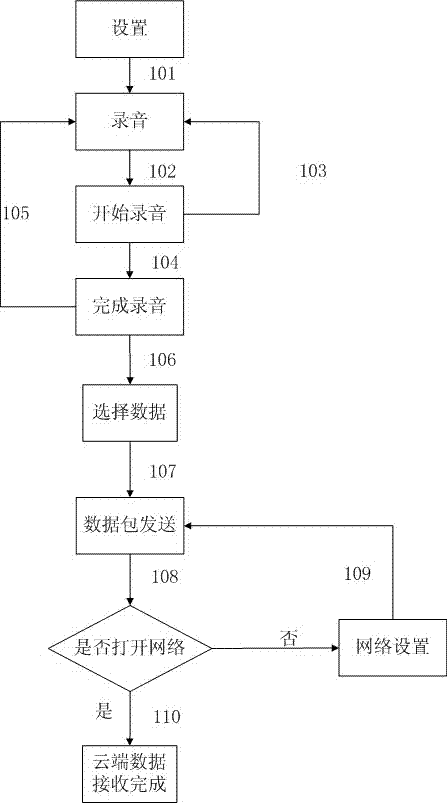
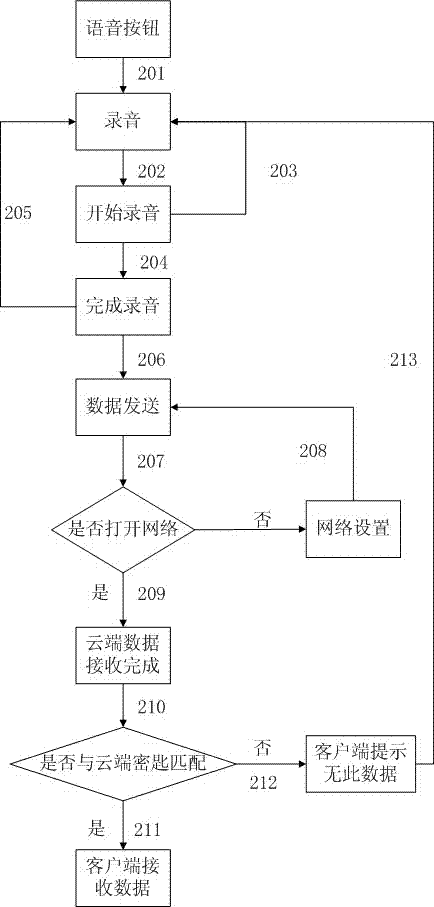
InactiveCN103118002ASolve data security issuesSimple experienceSpeech recognitionTransmissionEnvironmental noiseComputer hardware
The invention discloses a method of speech sound used as a secret key to achieve data resource cloud storage management. The method of speech sound used as a secret key to achieve the data resource cloud storage management is characterized in that after users complete recording under a recording interface, recording files can be encrypted and compressed, and then the recording files can be sent to a cloud server. The cloud server can be used for doing voice frequency analysis for the received records and the whole stored records and extracting sound features. The influence caused by environmental noise, information channel and speakers can be reduced as soon as possible. The analyzed speech sound information features are matched with backup speech sound information features. After the matching is succeeded, data resources backup by the speech sound secret key of a cloud storage server is returned to a corresponding client side. The client side can be used for receiving the backup data resources. When the matching is failed, error messages can be returned, and then the client side can be used for reminding users. A speech recognition technology can be used for resolving the safe problems of user registration, code management and the like. The user experience can be improved. A cloud server storage technology is used for reducing to occupy individual equipment resource occupying and overcoming the shortcomings of data loss and the like.
Owner:北京飞漫软件技术有限公司
Encrypted data storage system based on key other-place storage and method
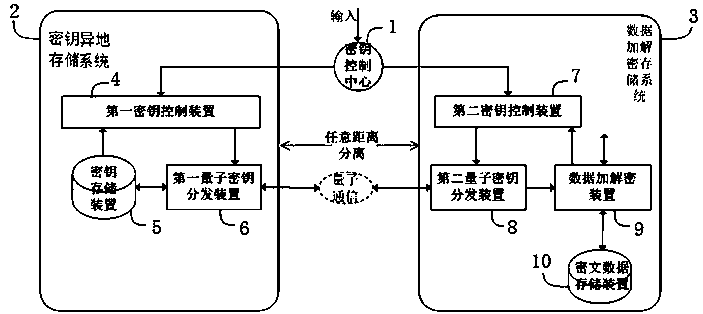
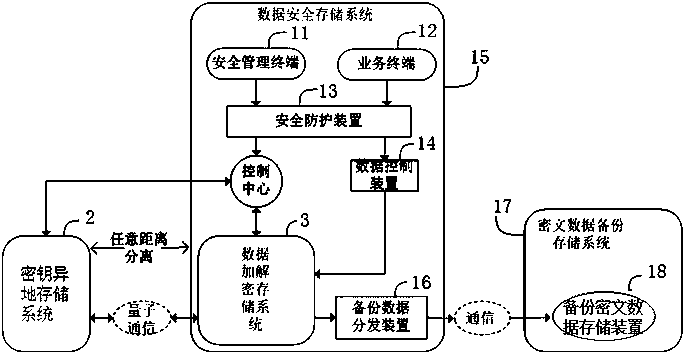
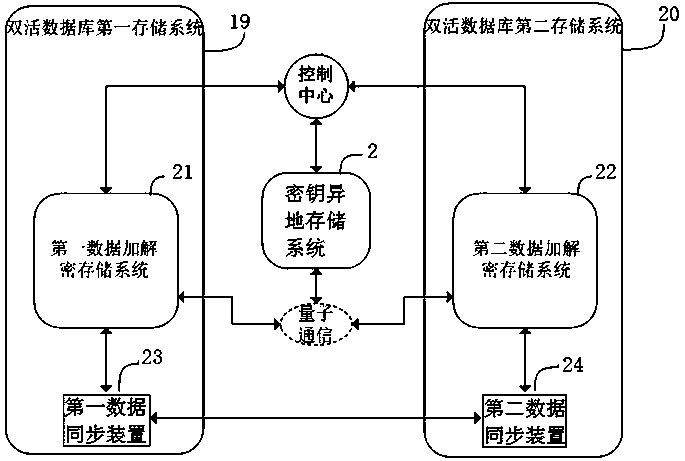
ActiveCN109561047AAvoid easy theftImprove data storage securityKey distribution for secure communicationError detection/correctionComputer hardwareKey storage
The invention discloses an encrypted data storage system based on key other-place storage and method. The encrypted data storage system based on key other-place storage comprises a key control center,a key other-place storage system and a data encryption and decryption storage system, wherein the key other-place storage system comprises a first key control device, a key storage device and a firstquantum key distribution device; the data encryption and decryption storage system comprises a second key control device, a data encryption and decryption storage device and a second quantum key distribution device; the first quantum key distribution device and the second quantum key distribution device are in quantum communication connection; the first key control device is in communication connection with the key storage device and the first quantum key distribution device respectively; and the second key control device is in communication connection with the data encryption and decryptionstorage device and the second quantum key distribution device respectively. The key other-place storage system and the data encryption and decryption storage system can be separated at any distance safely and reliably, and other-place separate and safe storage between encryption and decryption keys and data can be realized.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
Instant messaging system incorporating block chain technology, method and application
ActiveCN109274573ASolve data security issuesAchieve mutual trustFinanceDigital data protectionThird partyConfidentiality
The invention provides a design method of an instant messaging system architecture incorporating a block chain technology, and an application realization method oriented to financial services based onthe system architecture. The instant messaging system is deployed in different organizations, and the mutual trust between peer organizations is realized. The method ensures the security of session data in instant messaging system, including confidentiality and non-tampering, and provides shielding privacy protection and real-time clearing service for transactions embedded in instant messaging session.
Owner:JIANGSU SECURITIES
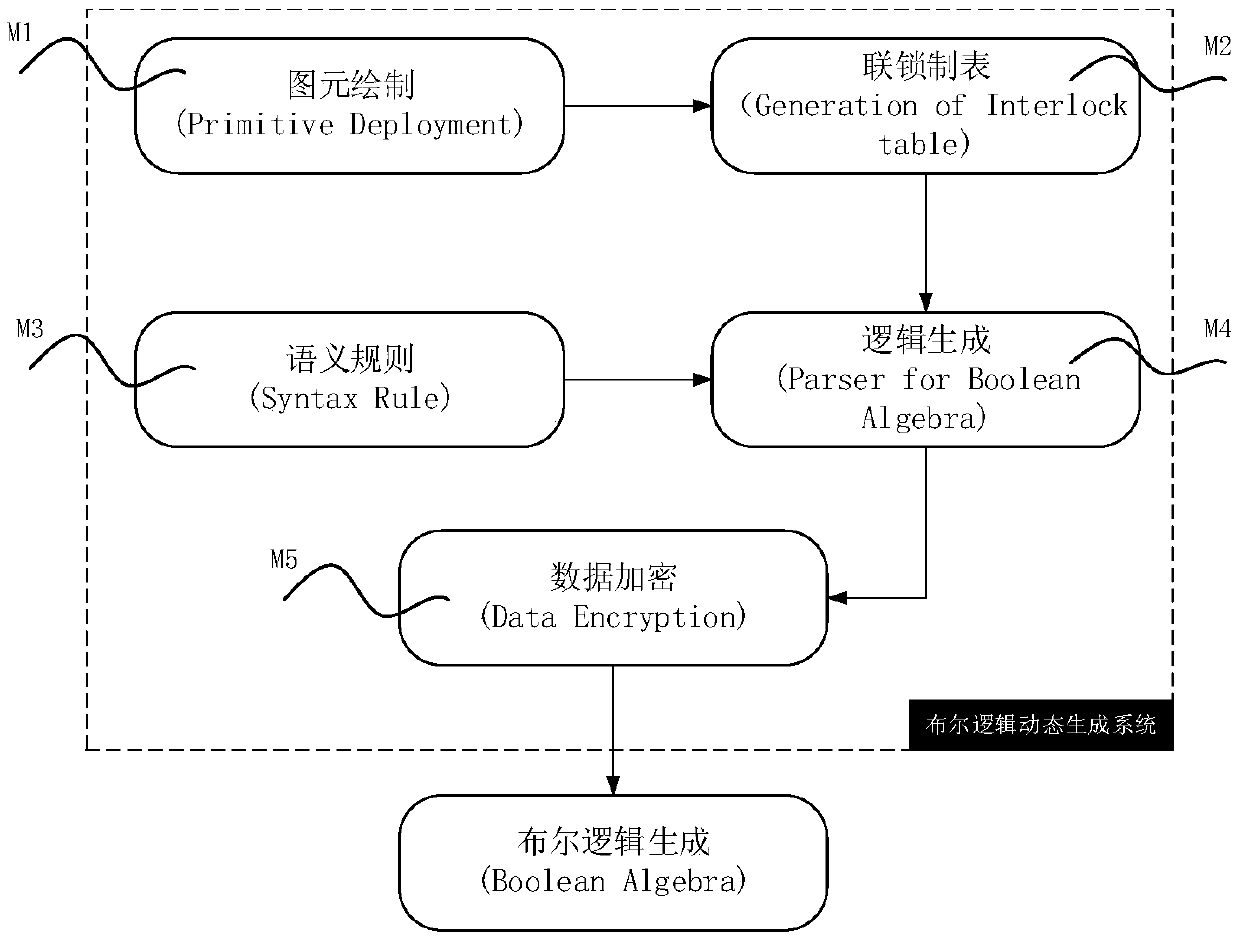
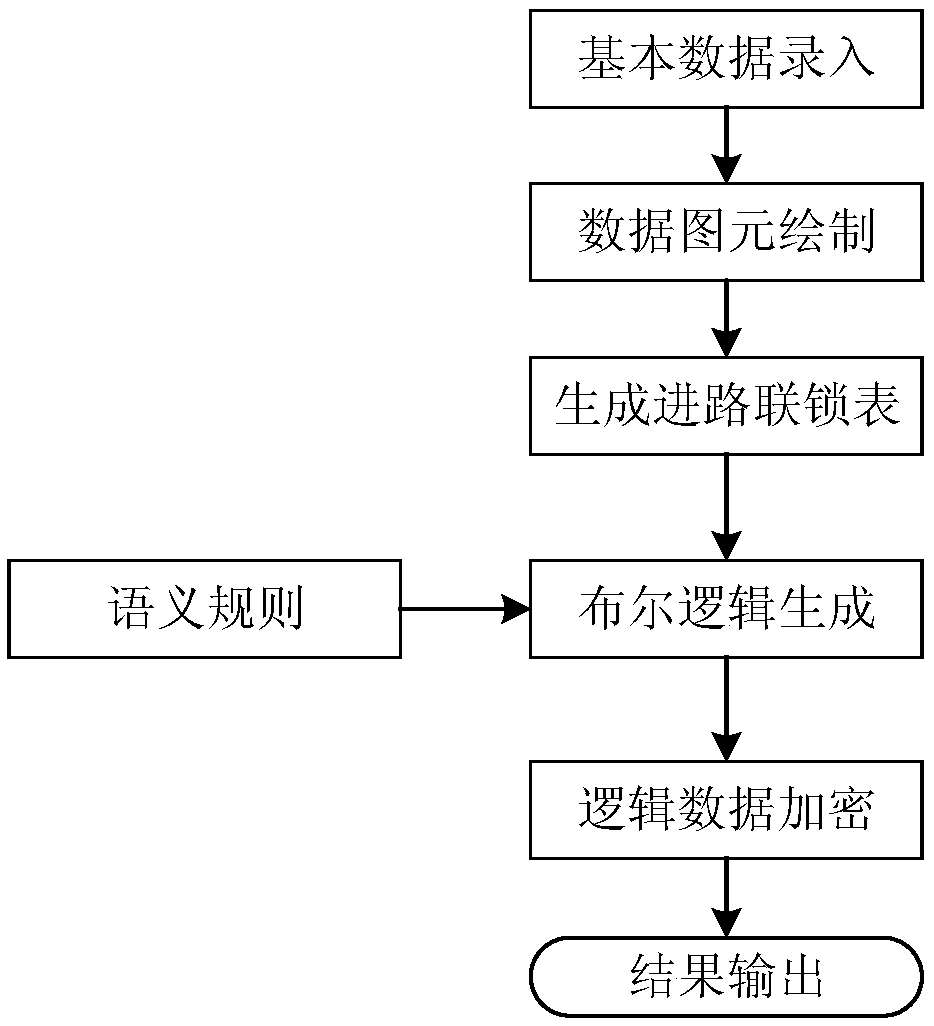
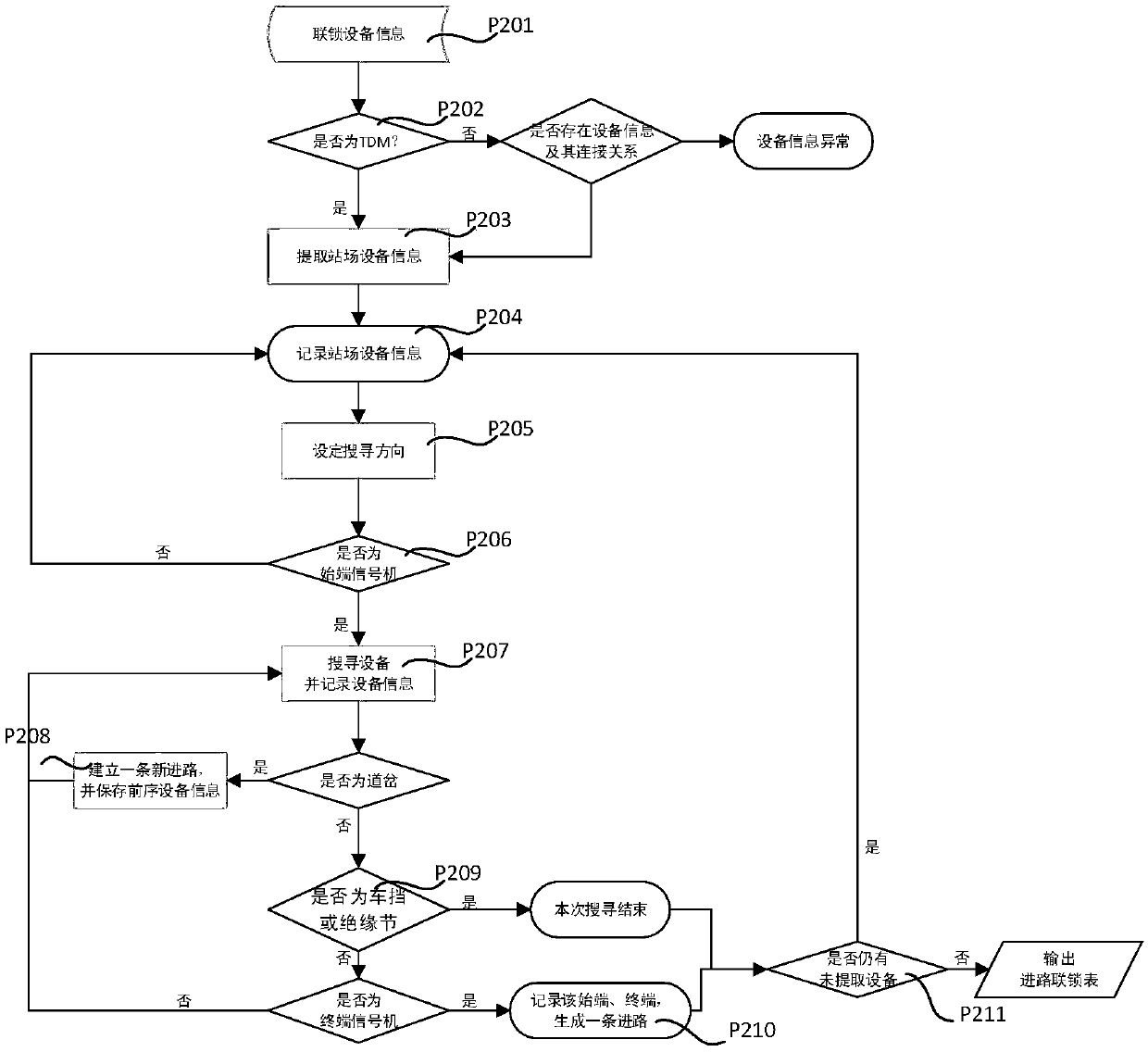
An LL (K)-based interlocking Boolean logic dynamic generation system and a dynamic generation method
ActiveCN109558634AEnsure safetyImplement rule customizationGeometric CADDigital data protectionComputer moduleDependability
The invention discloses an interlocking Boolean logic dynamic generation system and a dynamic generation method in the field of urban rail transit. The system comprises a component deployment module,an interlocking tabulation module, a semantic rule module and a logic generation module by which the Boolean logic data are dynamically generated; and a data encryption module which is used for carrying out data encryption rearrangement according to the generated logic data to generate a Boolean logic file. According to the present invention,the misoperation of the file in the later period is prevented, and the data security is ensured. According to the technical scheme of the invention, a context-independent LL (K) mode is adopted to analyze interlocking logic and dynamically generate and output the interlocking logic; the interlocking developers only need to modify the interlocking logic according to a predetermined grammar rule in the later period, so that the latest Boolean logic can be dynamically generated in real time without changing any code, the rule and generation decoupling is achieved, the workload of signal technicians is greatly reduced, the safety of logic data is ensured through introduction of the encryption technology, the reliability is high, and the working efficiency is improved.
Owner:NARI TECH CO LTD
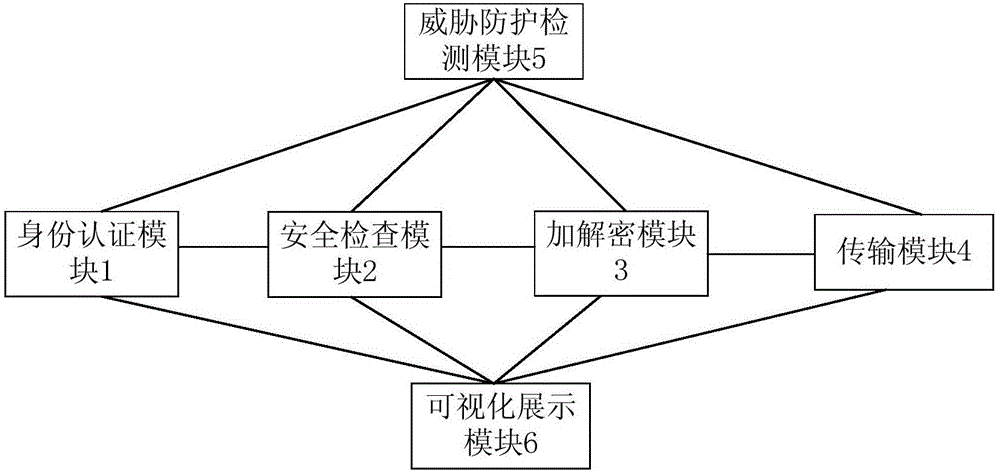
Cloud storage safety gateway and access method thereof
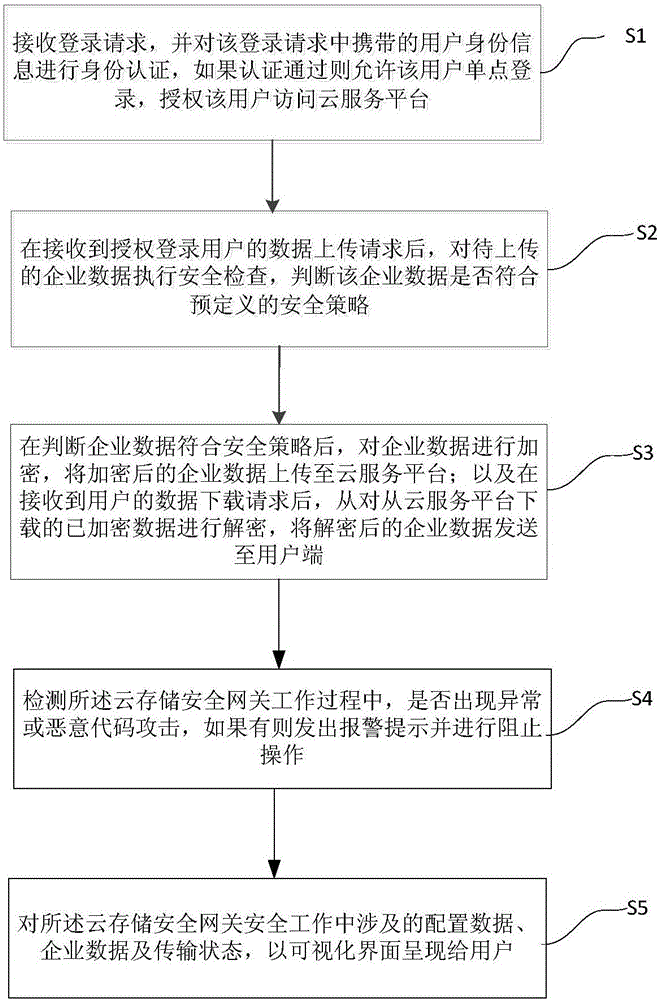
InactiveCN107438071ACompliance Threat PreventionDiscover and analyze job statusTransmissionSecurity checkSingle point
The invention provides a cloud storage safety gateway and an access method thereof. The method comprises steps that identity authentication of the user identity information is carried out by an identity authentication module, if authentication passes, a user is permitted to realize single-point login; safety check on to-be-uploaded enterprise data is carried out through a safety check module, and whether the enterprise data is consistent with pre-defined safety strategy is determined; the enterprise data is encrypted through an encryption module, after a data download request of the user is received, the encrypted data downloaded from a cloud service platform is decrypted; the enterprise data after encryption is uploaded by a transmission module to the cloud service platform, and the enterprise data after decryption is sent to a user terminal; a threat protection detection module is used for detecting whether abnormality or malicious code attack exists in the cloud storage safety gateway work process, if yes, alarm prompt is emitted, and blocking operation is further carried out. The method is advantaged in that visualization, data safety, compliance and threat prevention requirements can be satisfied.
Owner:北京信安世纪科技股份有限公司
Public entrepreneurship e-commerce platform
InactiveCN107833098ASolve data security issuesFinanceAdvertisementsNetwork terminationData synchronization
The invention relates to a public entrepreneurship e-commerce platform comprising a network server, a network terminal, a server background monitoring terminal and a server data synchronous backup cloud disk. The network server includes a network server end and a server end monitoring module. The network terminal includes a network client and a display processor. The server background monitoring terminal includes a portable remote monitoring terminal. The network service end includes a mall module, a personal center module, a merchant center module, and a background management module. The network client includes a registration / login module. The registration / login module includes a personal registration / login module, a merchant registration / login module, and an agent registration / login module. The personal registration / login module, the merchant registration / login module, the agent registration / login module, the mall module, the personal center module, and the merchant center module exchange information. The public entrepreneurship e-commerce platform uses a remote monitoring and cloud synchronous backup scheme, and has the characteristics of high safety and high efficiency.
Owner:上海誉风信息科技有限公司
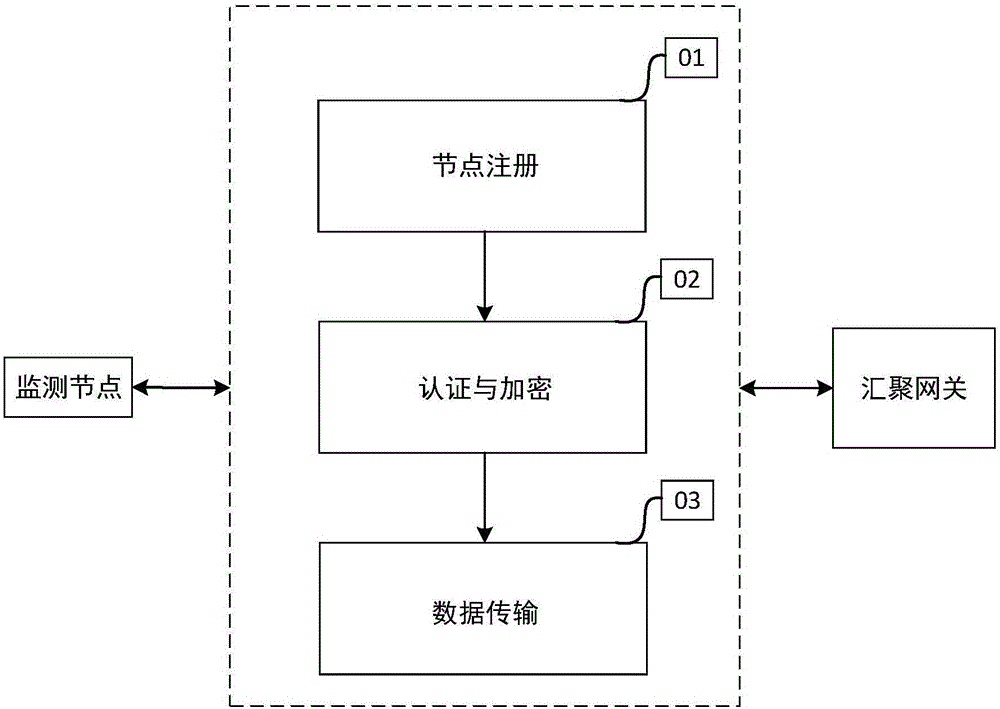
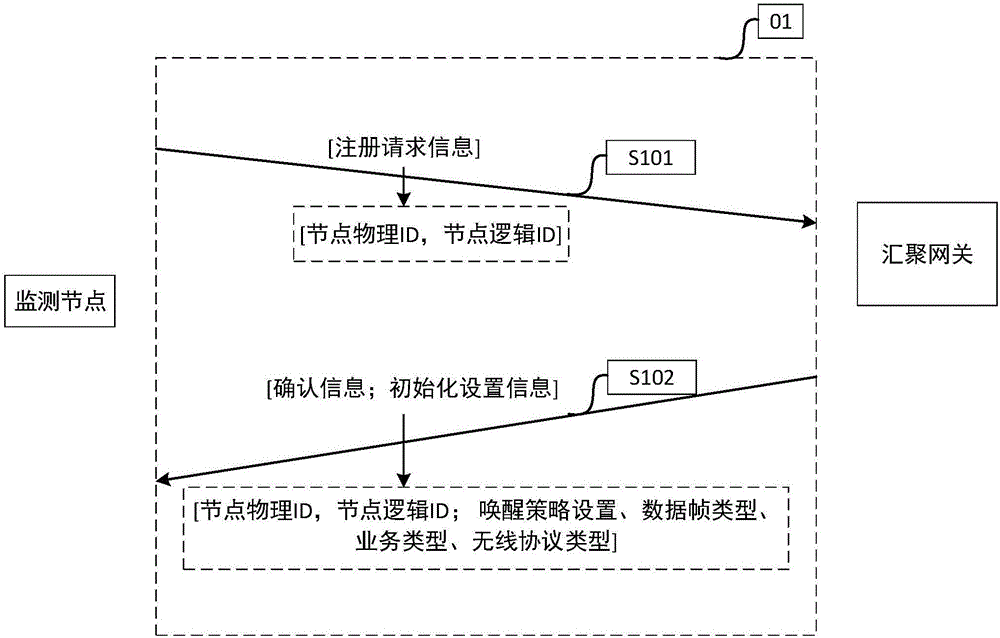
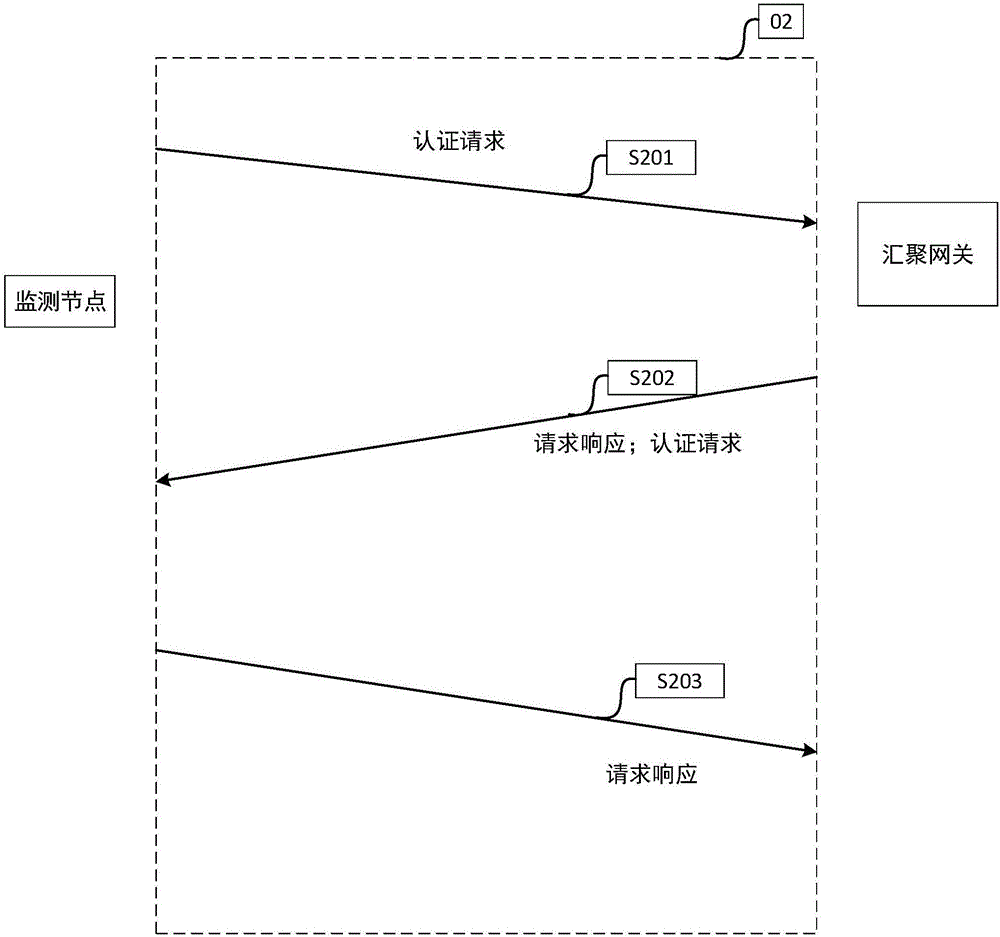
Method of low-power consumption wireless communication between monitoring node and convergence gateway
ActiveCN106230645ALower energy consumption levelsConvenient power supplyData switching networksActivity timeRadio frequency
The invention discloses a method of low-power consumption wireless communication between a monitoring node and a convergence gateway. The method at least comprises three stages of monitoring node registration, authentication and encryption and data transmission. In the data transmission stage, the monitoring node organizes and stores acquired sensor data in a data grouping mode. In order to improve the transmission efficiency and reduce the power consumption, grouped sensor data are firstly segmented or merged to adapt to the characteristics of monitoring business; and then, wireless transmission protocol adaptation is carried out on business data frames to select the best wireless transmission protocol, and the best transmission performance and the energy-saving efficiency are thus acquired. In order to acquire better energy-saving efficiency, the monitoring node continuously learns and improves a sleep awakening control strategy of a node radio frequency unit according to safety assessment and energy consumption assessment results to reduce the activity time of the radio frequency unit. The sleep awakening control with a learning ability can better adapt to various different intelligent security application scenes, and the energy consumption efficiency and the system performance are thus maximized.
Owner:陕西哥莱信息科技有限公司
Method for realizing burglary prevention and data protection of hard disk
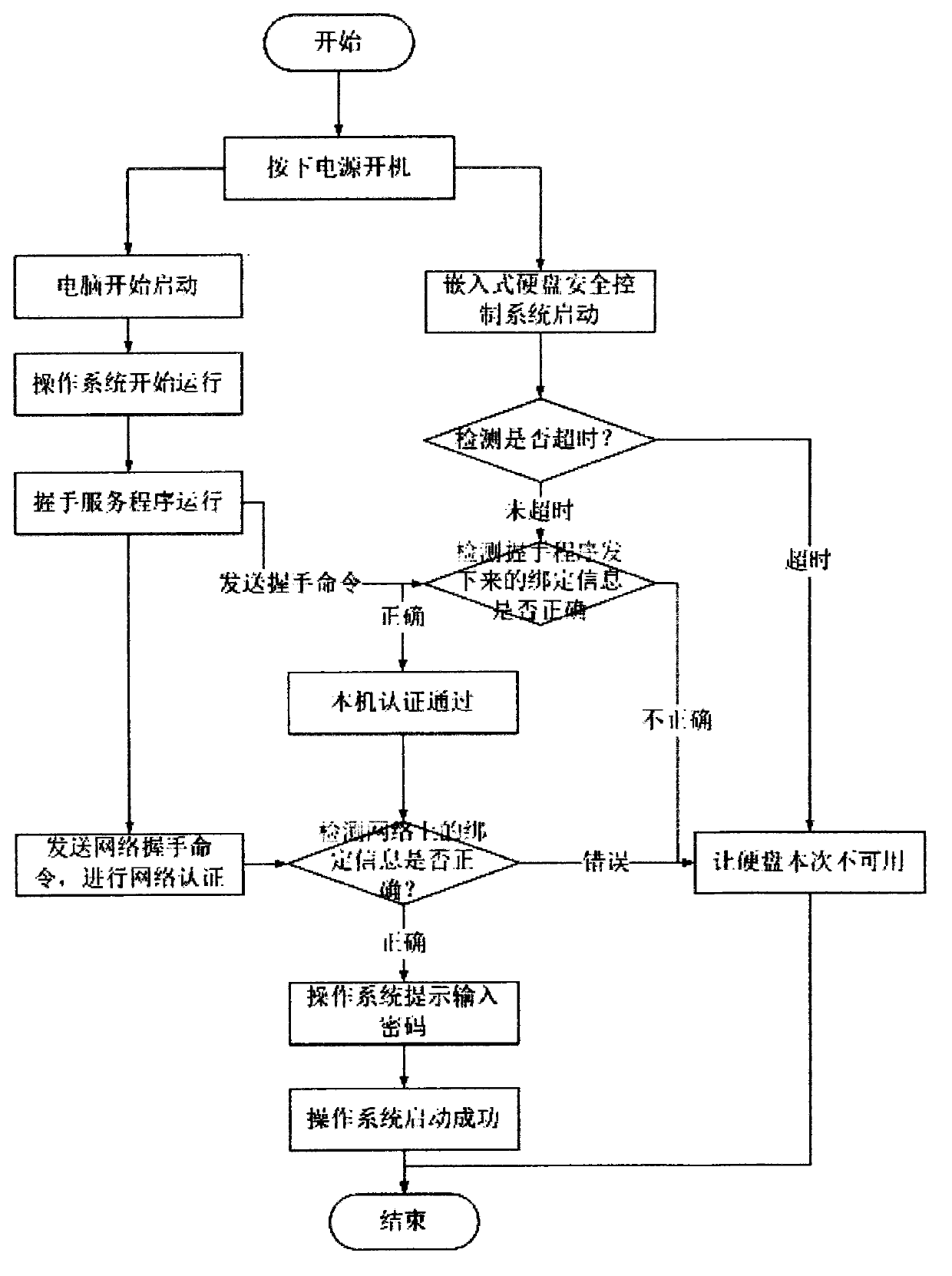
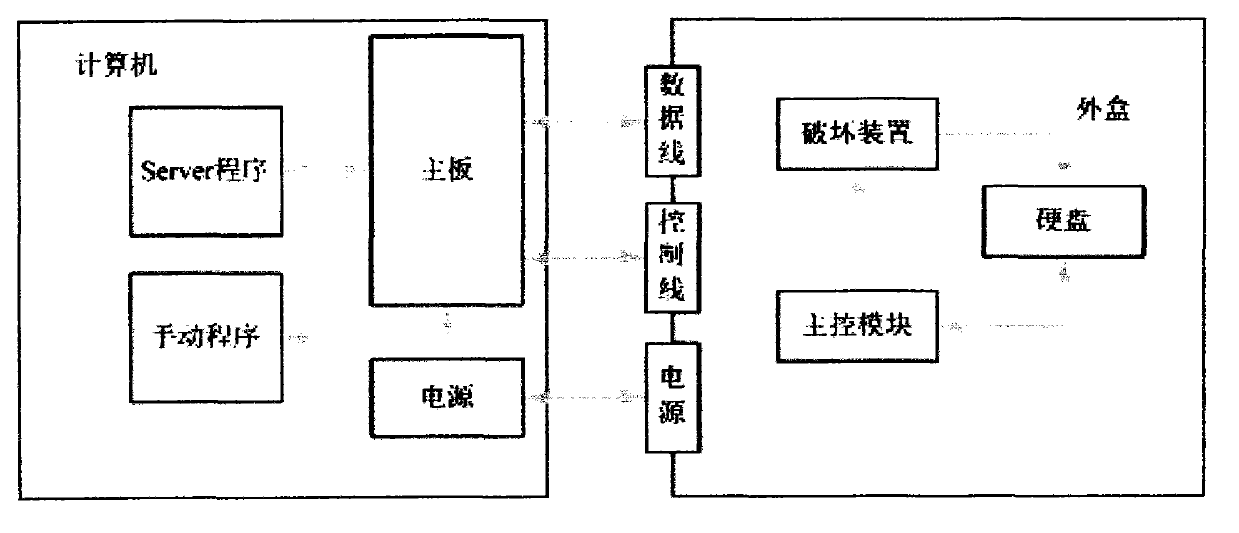
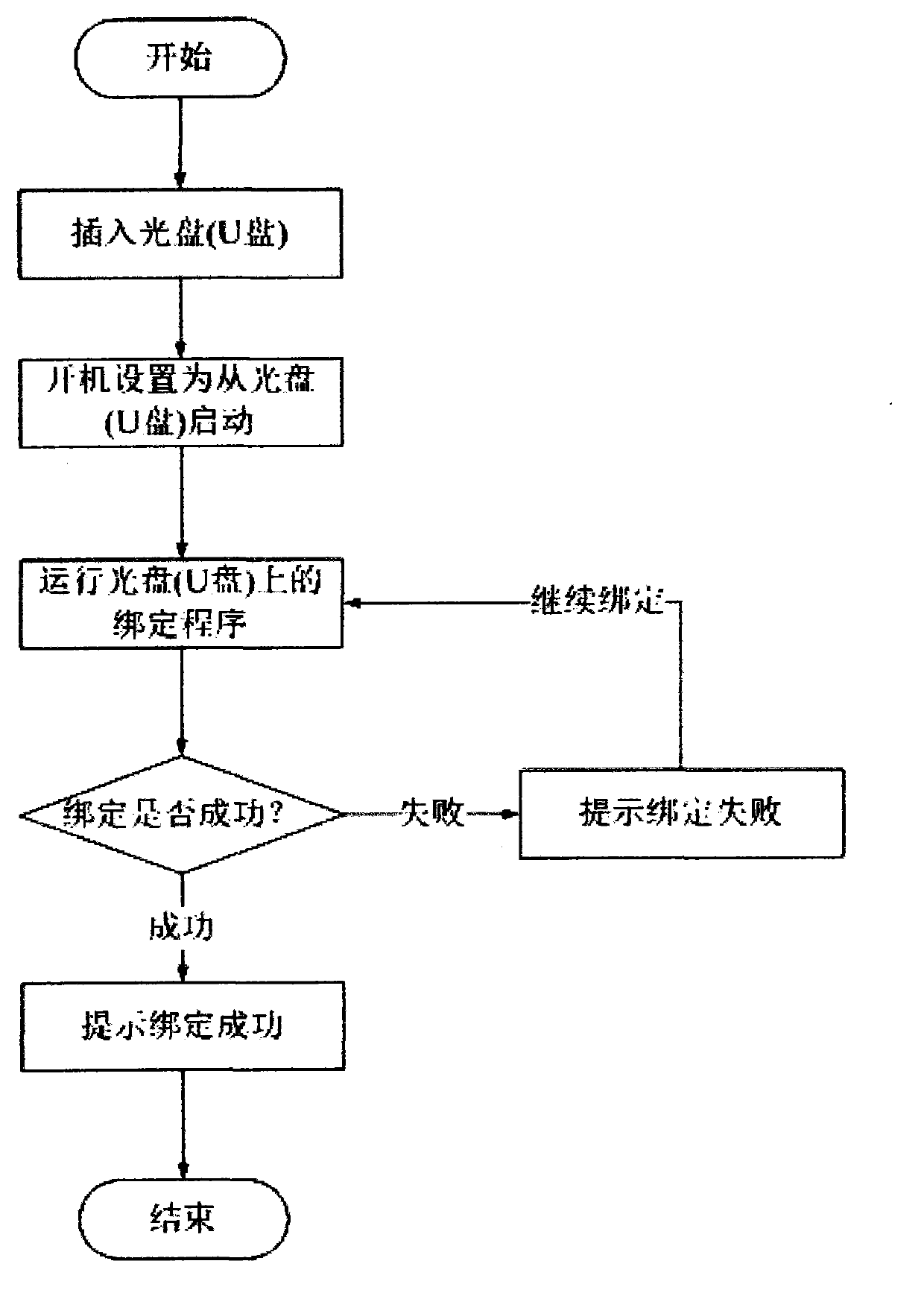
InactiveCN103294971AProtection reachedSolve data security issuesInternal/peripheral component protectionControl lineStart up
The invention provides a method for realizing burglary prevention and data protection of a hard disk. The method can effectively prevent the hard disk from being burgled. The method comprises the following steps of (1) binding the hard disk with a computer by a manual program: reading a computer feature code, transmitting to an embedded master control module through a control line, and storing in an embedded memorizer, and (2) performing authentication with a server program or the manual program when a system is started up: reading a system feature code, transmitting to the embedded master control module through the control line, comparing with the computer feature code stored in the memorizer, allowing the dedicated hard disk to be available if the feature code passes, and allowing the dedicated hard disk to be unavailable if the computer feature code fails. According to the method for realizing the burglary prevention and the data protection of the hard disk, the data interaction between a mainboard and the hard disk is conducted by a data line, so that the data security purposes such as the burglary prevention of the hard disk, and prevention of starting from win pe, an optical disk or a slave disk are achieved, and the purpose of the data protection is achieved.
Owner:XIAN CHENAN ELECTRONICS TECH
Mobile integrated test server
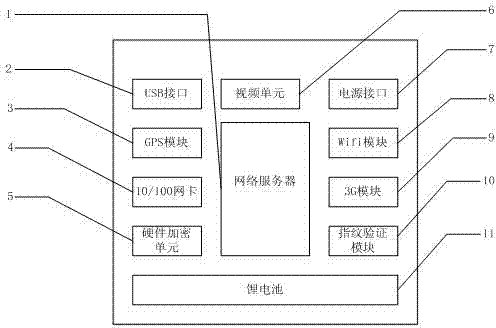
InactiveCN102880246AAddress reliabilityGuaranteed to workDigital data processing detailsWireless communicationInternal memoryThird generation
A mobile integrated test server takes a network server as a center, and integrates a USB interface, a GPS module, a 10 / 100 Mbit / s self-adaptive network card, a hardware encryption unit, a video unit, a power supply interface, a 3G module, a Wi-Fi module, a fingerprint verification module, and a lithium battery. The network server includes a CPU, an internal memory, and an SSD solid state disk; the hardware encryption unit is internally provided with an encryption algorithm chip, a clock chip and a digital certificate; the video unit outputs standard VGA videos; the power supply interface supports access of a 12 V direct-current power supply; the Wi-Fi module is used for providing an AP with the wireless routing function; and the fingerprint verification module is used for scanning and recognizing fingerprints. The mobile integrated test server solves the data safety problem, the server reliability problem and the network reliability problem.
Owner:陈思宁
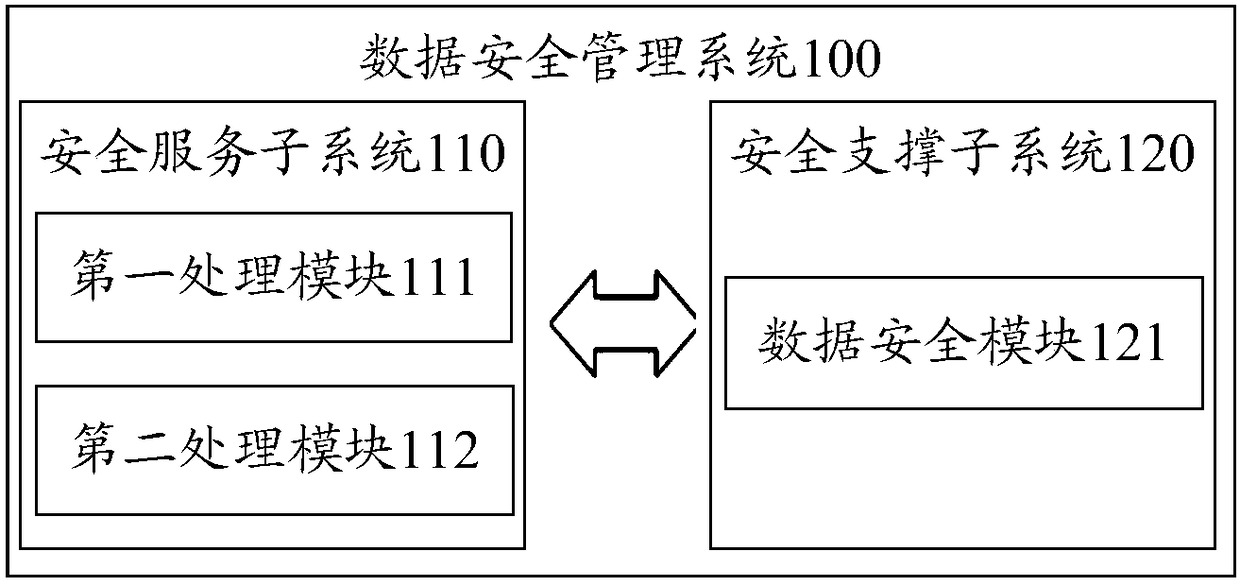
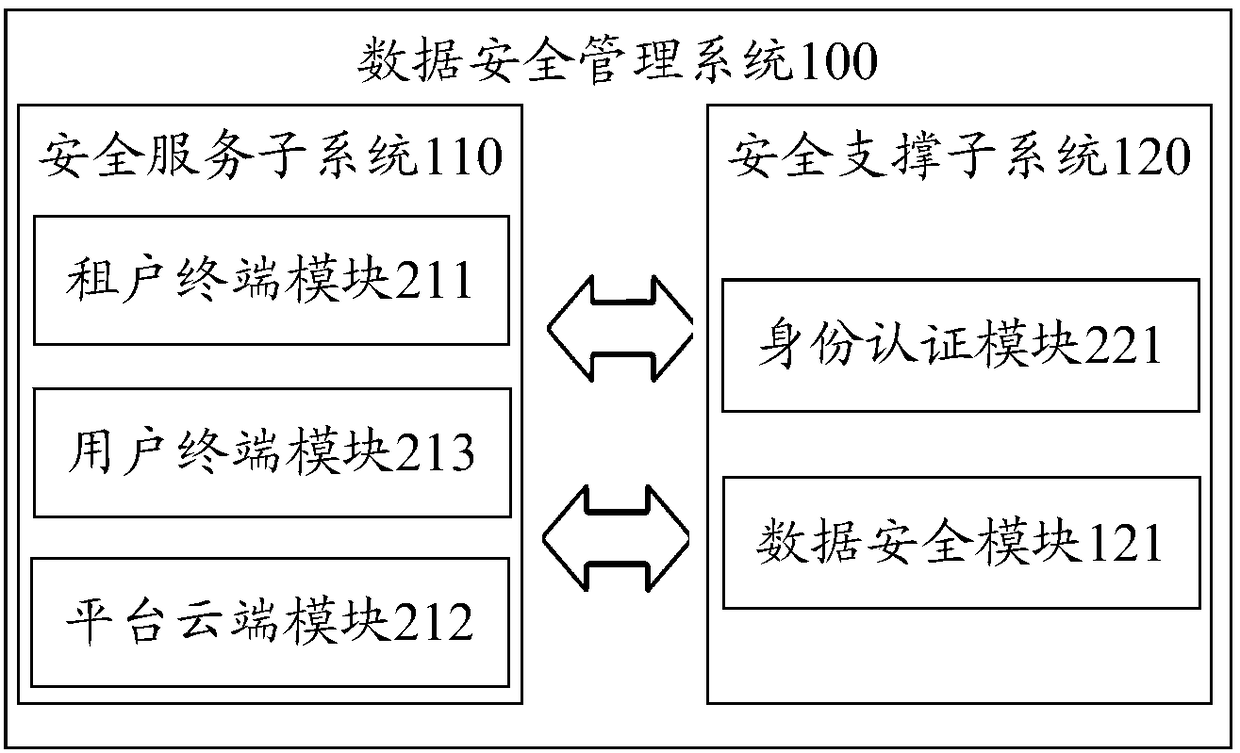
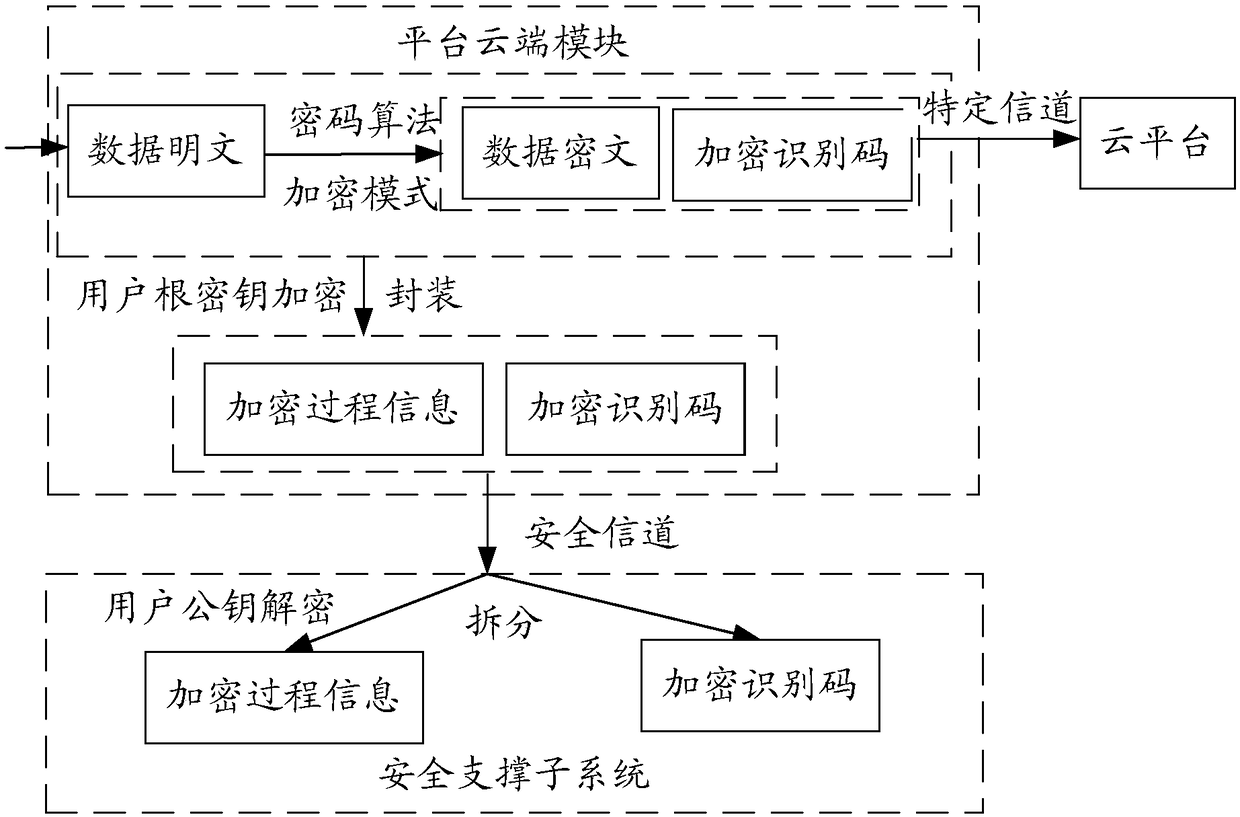
Data security management system and method
ActiveCN108183899ASolve data security problems caused by inability to protect independentlySolve data security issuesTransmissionPlaintextSafety management systems
The invention provides a data security management system and method. The system comprises a security service subsystem and a security support subsystem; a first processing module of the security service subsystem is used for encrypting data plaintext according to encryption configuration information to obtain data ciphertext and an encryption identification code to send to a receiving end; the encryption process information is encrypted by using a preconfigured user root key, and the encrypted encryption process information and the encryption identification code are sent to the security support subsystem; the security support subsystem is used for decrypting the encrypted encryption process information by using a user public key corresponding to the first processing module; the encryptionidentification code is mapped according to a decryption request to correspond to the decrypted encryption process information, the encryption process information is processed to generate decryption configuration information, and the decryption configuration information is fed back to a second processing module of the security service subsystem, so that the second processing module can generate thedata plaintext corresponding to the data ciphertext according to the decryption configuration information; the data plaintext is provided for the receiving end to use, and the service demand is satisfied.
Owner:北京明朝万达科技股份有限公司
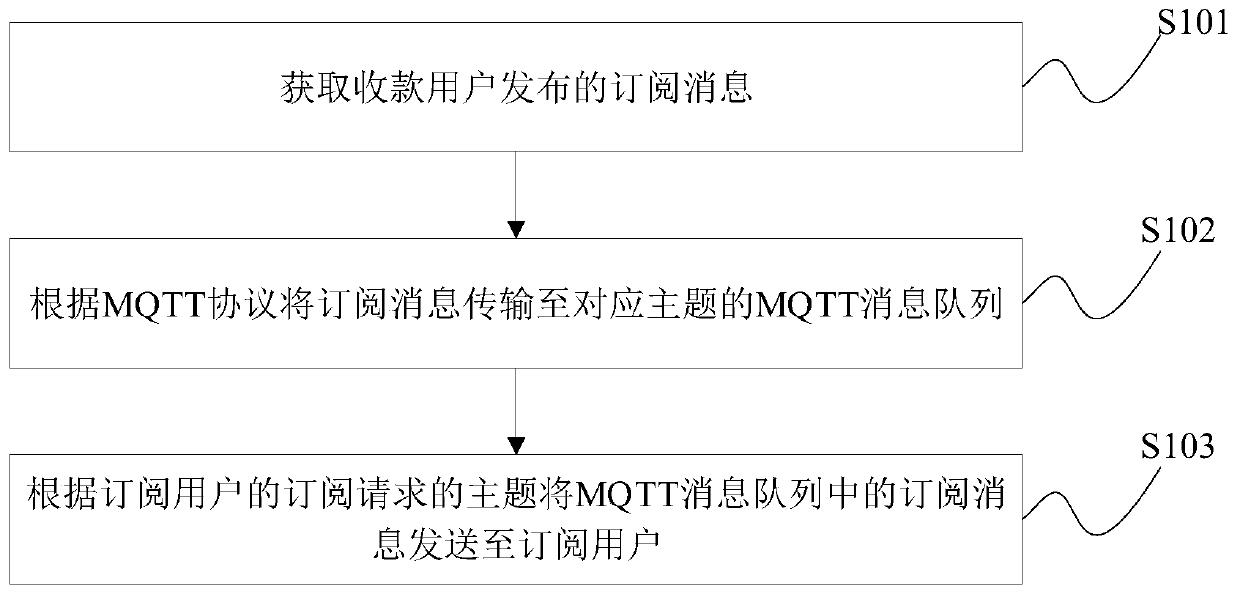
Collection information subscription method and device and collection system
InactiveCN110417795AImprove experienceSolve data security issuesFundraising managementData switching networksMessage queueCollection system
The invention provides a collection information subscription method and device, and a collection system. The method comprises the steps of obtaining a subscription message published by a collection user; transmitting the subscription message to an MQTT message queue of a corresponding theme according to an MQTT protocol; and sending the subscription message in the MQTT message queue to the subscriber according to the theme of the subscription request of the subscriber. Electronic collection information subscription, publishing and collection based on MQTT real-time subscription are realized, the user experience in the collection process is improved, the collection efficiency is improved, resources are saved, meanwhile, the problems of network bandwidth delay and data security are solved, and an online and offline linkage solution in the collection process is provided.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method for encrypting and decrypting information by means of ciphertext storage gateway
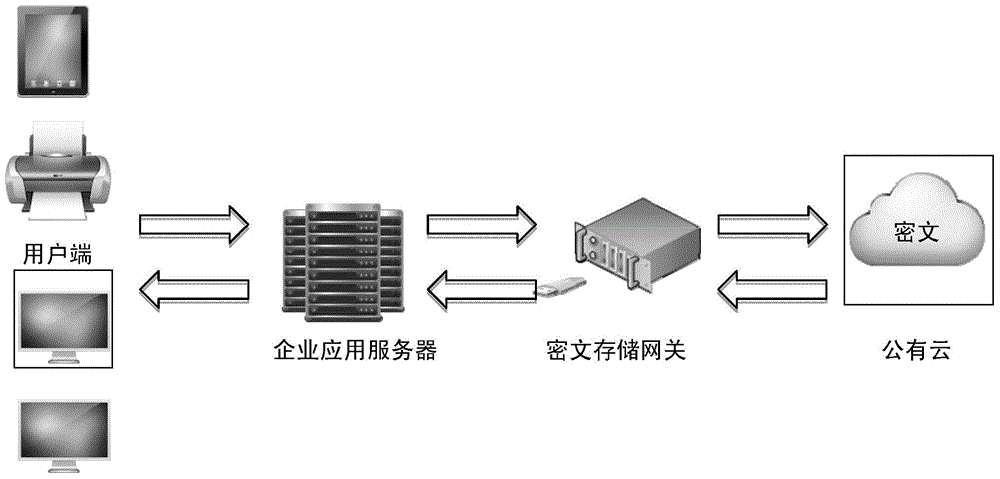
InactiveCN104092672ASolve data security issuesDoes not affect work efficiencyTransmissionComputer hardwarePlaintext
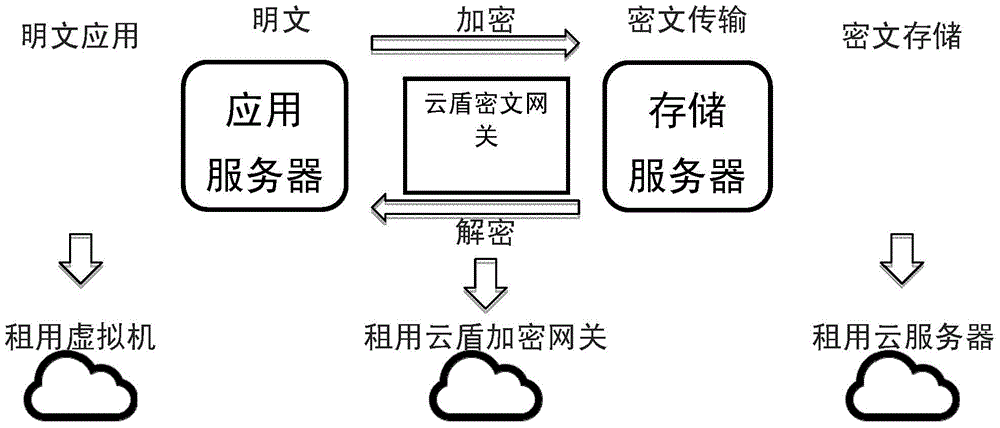
The invention relates to a method for encrypting and decrypting information by means of a ciphertext storage gateway. According to the method for encrypting and decrypting information by means of the ciphertext storage gateway, data read by a client side are in a plaintext form, and the data are stored in a storage server in a ciphertext mode through the ciphertext storage gateway; the data are read out from the storage server in a ciphertext mode and are converted into data in a plaintext form on the client side application server through the ciphertext storage gateway. The method for encrypting and decrypting information by means of the ciphertext storage gateway specifically comprises the steps that (1) a storage space is mounted to the ciphertext storage gateway; (2) the ciphertext storage gateway is mounted to a cloud computing server; (3) a driving program is installed on the ciphertext storage gateway, and the driving program is called during access to all / mnt / oss files. The method for encrypting and decrypting information by means of the ciphertext storage gateway has the advantages that the cloud shield ciphertext storage gateway is used by enterprises for encrypting data during data storage, and data encryption is independent of carriers and containers; data leakage protection and enterprise application systems are combined perfectly, and the data security of the enterprises are effectively guaranteed; the method can be flexibly applied to various complicated kinds of network architecture more effectively and more flexibly.
Owner:安徽云盾信息技术有限公司
State monitoring device and forewarning method for distribution network low-voltage cable branch box
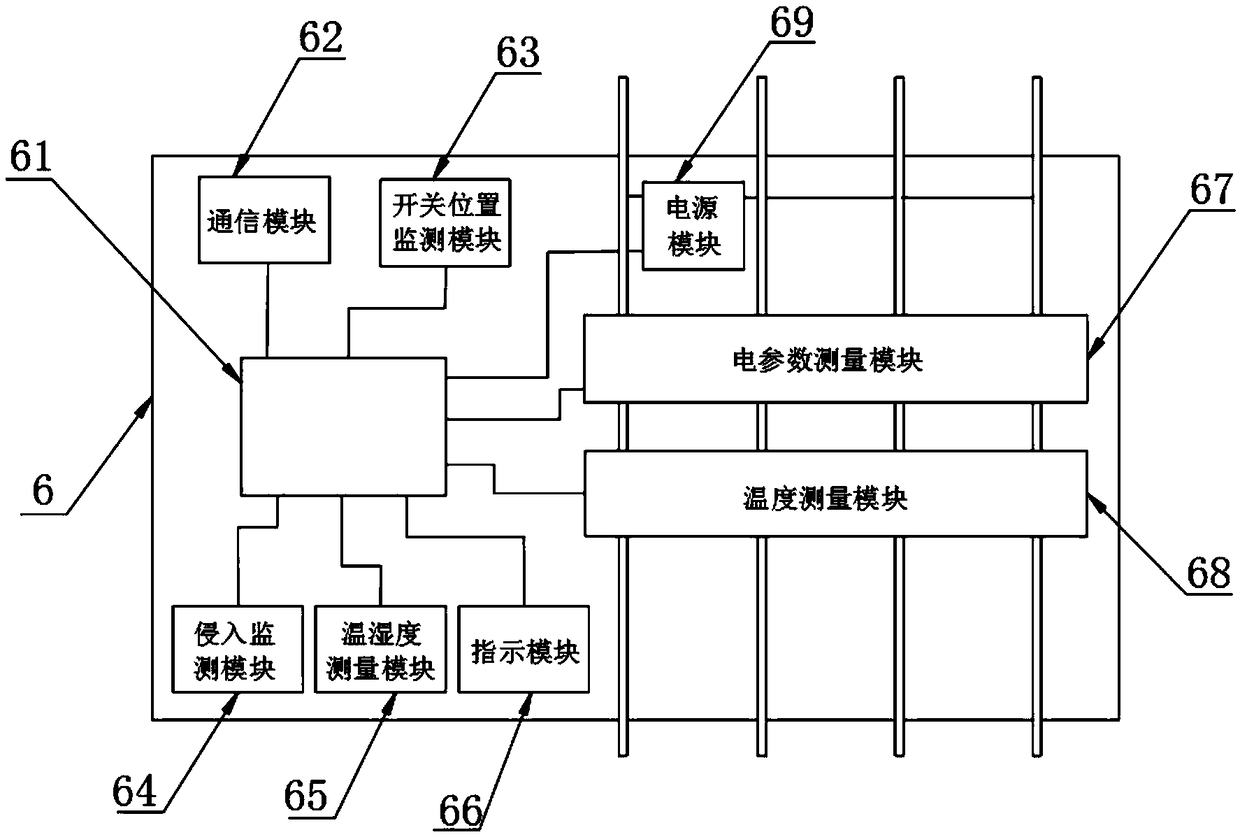
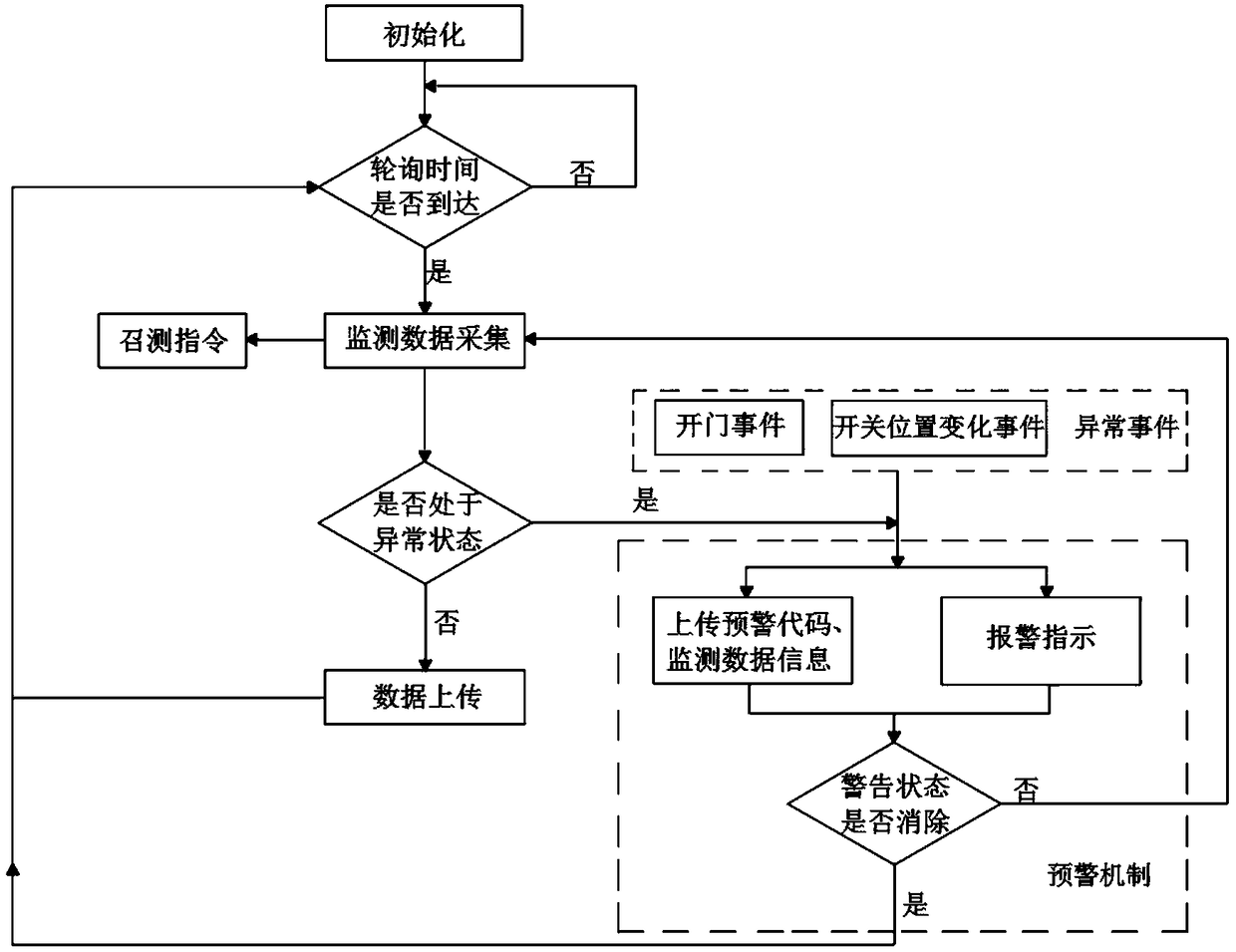
PendingCN109470995ARealize remote active early warningImprove work efficiencyFault location by conductor typesInterference (communication)Busbar
The invention discloses a state monitoring device for a distribution network low-voltage cable branch box. The state monitoring device comprises a main control module, a communication module, a switching position monitoring module, an intrusion monitoring module, a temperature and humidity measuring module, an indicating module, an electrical parameter measuring module, a temperature measuring module and a power module; a low-power-dissipation MCU is adopted for the main control module and is used for keeping alarm informing for a period of time after a circuit loses power, a communication mode that a physical layer is LoRa is adopted for the communication module, on this basis, obstacle avoidance, distance, anti-interference and power dissipation are optimized, and an upper-layer protocolis encapsulated; the electrical parameter measuring module comprises CT, PT and electrical parameter metering unit modules, and the power module comprises a power supply and a stand-by power supply.By means of the state monitoring device, remote active forewarning on the branch box is achieved through monitoring and combined analysis of power losing, overcurrent, leakage protection switching motions of the low-voltage cable branch box, over-temperature of busbars, switching cabinet door events and environment anomaly states, problems are timely found and solved, and the working efficiency ofoperation and maintenance personnel and the power supply reliability are improved.
Owner:武汉特试特科技有限公司
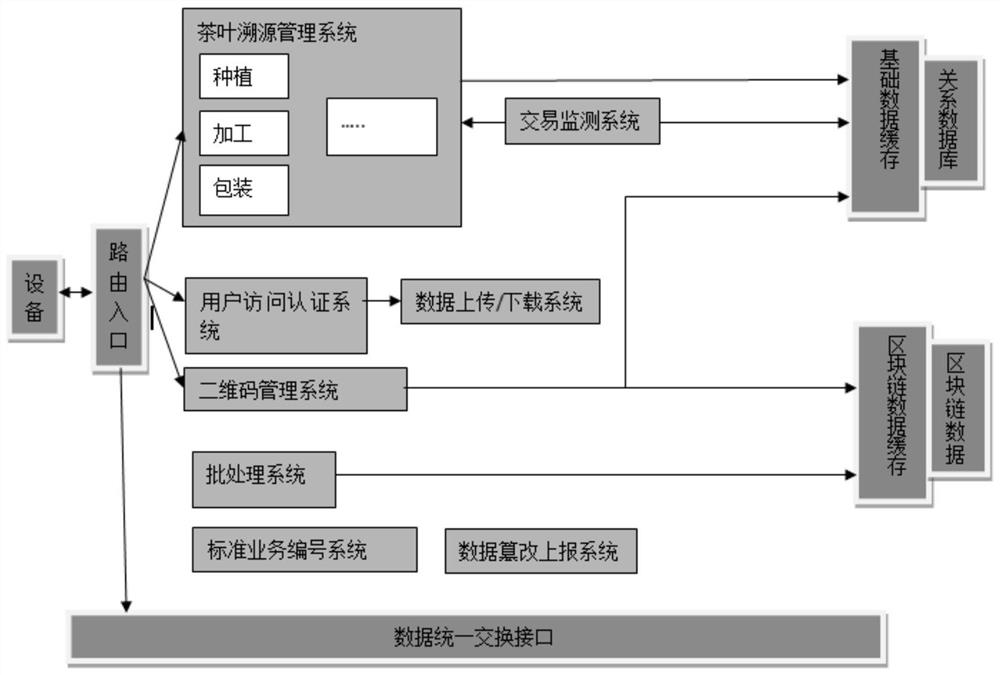
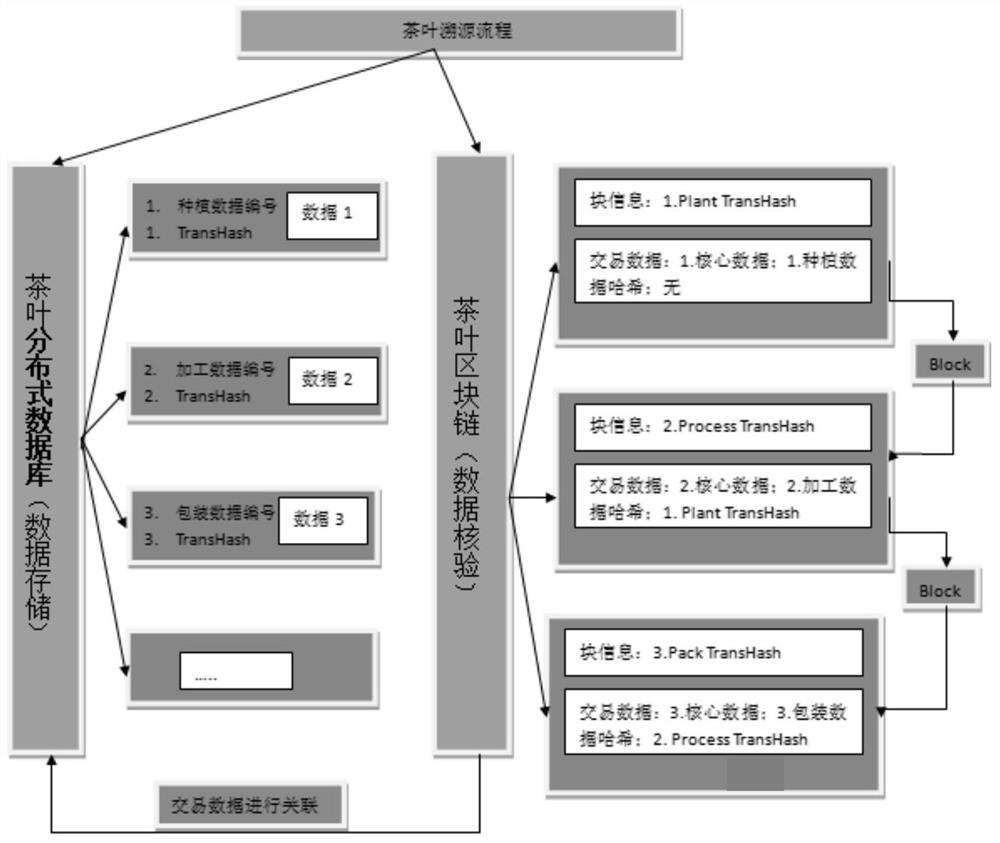
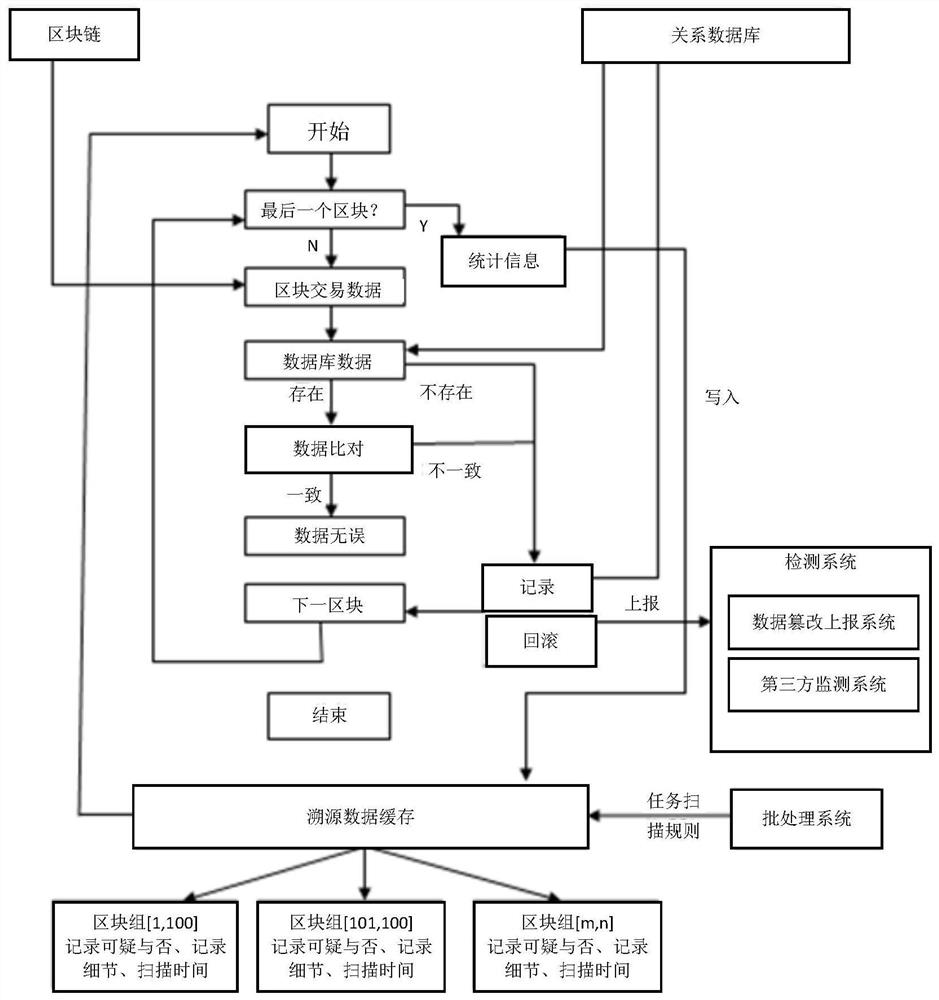
Tea credible tracing system based on decentralization and centralization cooperation
ActiveCN111612483ASolve the centralization problemSolve the problem of susceptibility to tamperingCommerceSpecial data processing applicationsData informationTerm memory
The invention relates to a tea credible tracing system based on decentralization and centralization cooperation. According to the method, a database model is reconstructed, a distributed relational database and blockchain data storage collaboration technology is adopted, a novel traceability system with distributed storage, collaborative verification storage, data scanning monitoring, data rollback and self credit evaluation is established, distributed storage of the system is completed, and the system is difficult to tamper. Blocks are scanned in a blocked mode based on multiple tasks of a memory database, and system transaction data information in a block chain is scanned more quickly. According to the method and the system, the deletion and tampering behaviors of the system are recordedand reported, the trustworthiness degree of the system in a certain period of time can be counted by formulating a reasonable rule, and the security of the system in the period of time is scored, sothat a user is informed that the blockchain technology has the characteristic of data tampering prevention, and the system also has the trustworthiness degree. The problem of a credit mechanism of a traditional tea leaf tracing information system is solved.
Owner:ANHUI AGRICULTURAL UNIVERSITY
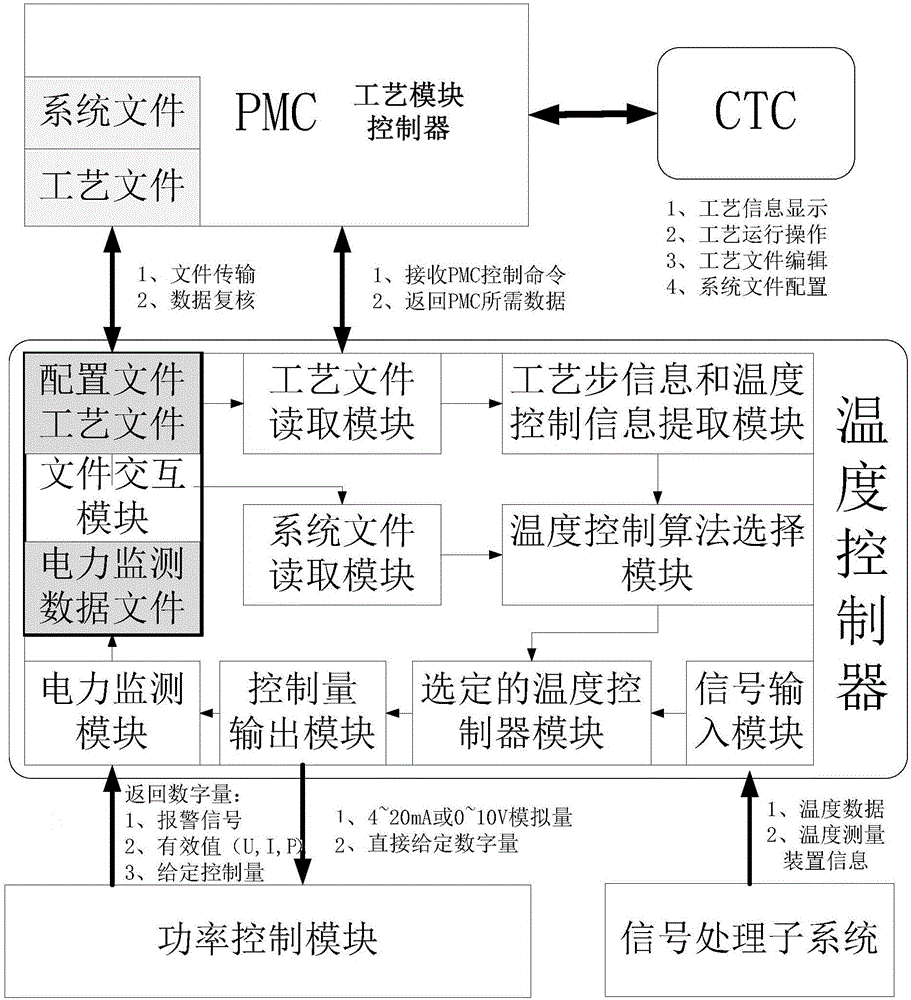
Heat treatment equipment process control device and heat treatment equipment process control method with multiple main process steps
ActiveCN106384723AImprove work efficiencyHigh working reliabilitySemiconductor/solid-state device manufacturingTemperature control using electric meansProcess moduleEngineering
The invention provides a heat treatment equipment process control device and a heat treatment equipment process control method with multiple main process steps. The heat treatment process control device comprises the components of a heater, an electric power supply unit which supplies electric power to the heater, a temperature measuring unit which measures temperature of a reacting chamber, a signal processing unit, a power control unit which is included in the electric power supply unit, a specialized temperature controller and a process module controller. The heat treatment equipment process control method comprises the steps of before the process is started, introducing process parameters of at least two main process steps in a process file and process parameter information of all auxiliary process files which correspond with the main process steps into a buffer area of the temperature controller by the process module controller; and in main process step switching, actively transmitting a switching controlling semaphore by the process module controller, introducing a to-be-updated process parameter from the buffer area into the operating power control unit by the specialized temperature controller in a pointer manner or memory position jumping manner, and realizing control information updating of the electric power supply unit together with the signal processing unit.
Owner:BEIJING NAURA MICROELECTRONICS EQUIP CO LTD
Multi-party secure computing implementation method based on block chain technology
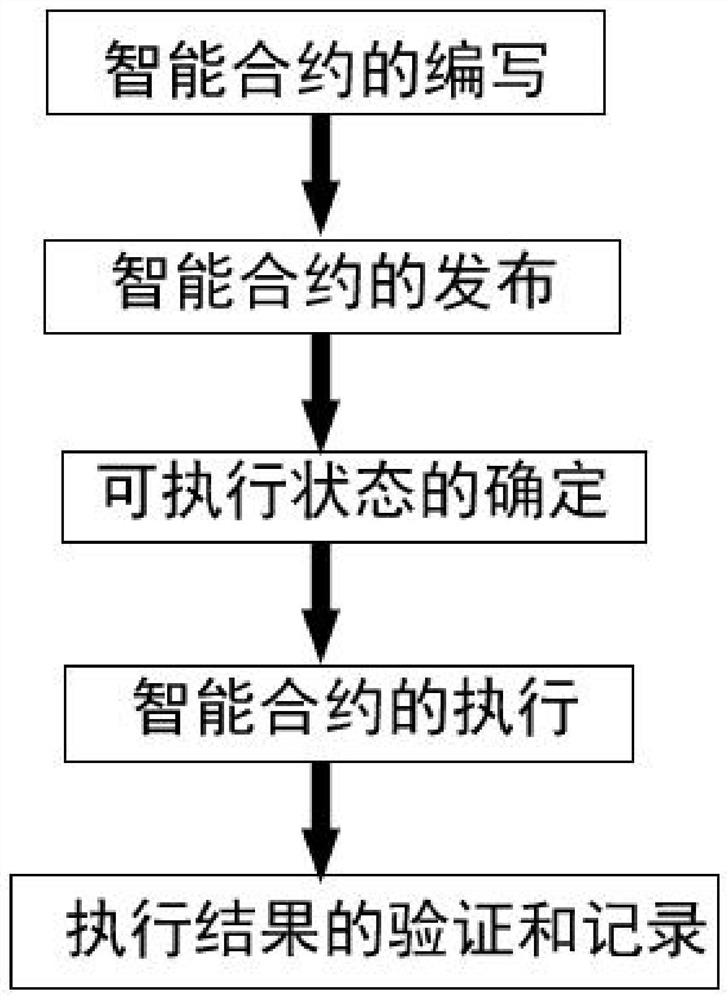
PendingCN112115204AEnhanced authenticationImprove audit effectDatabase updatingFinanceData securitySmart contract
The invention discloses a multi-party security computing implementation method based on a blockchain technology. The method specifically comprises the following steps: step 1, compiling an intelligentcontract, wherein the intelligent contract comprises node information of each contract party, tasks of each contract party for executing the intelligent contract and task execution relationships among the tasks; step 2, publishing the intelligent contract: publishing the intelligent contract on the block chain; 3, determining an executable state: after the intelligent contract is authorized by related nodes of each contract party of the intelligent contract, determining the intelligent contract as the executable state; step 4, executing the intelligent contract, wherein different contract parties have own unique business accounts, log in node servers of nodes through node accounts of the nodes and execute tasks of the intelligent contract on the blockchain; and step 5, carrying out verification and recording of an execution result, wherein the nodes which do not participate in the intelligent contract carry out verification and state recording of the contract execution result. According to the invention, the problems of data security and privacy in the data cooperation process are solved.
Owner:DATANG NETWORK CO LTD
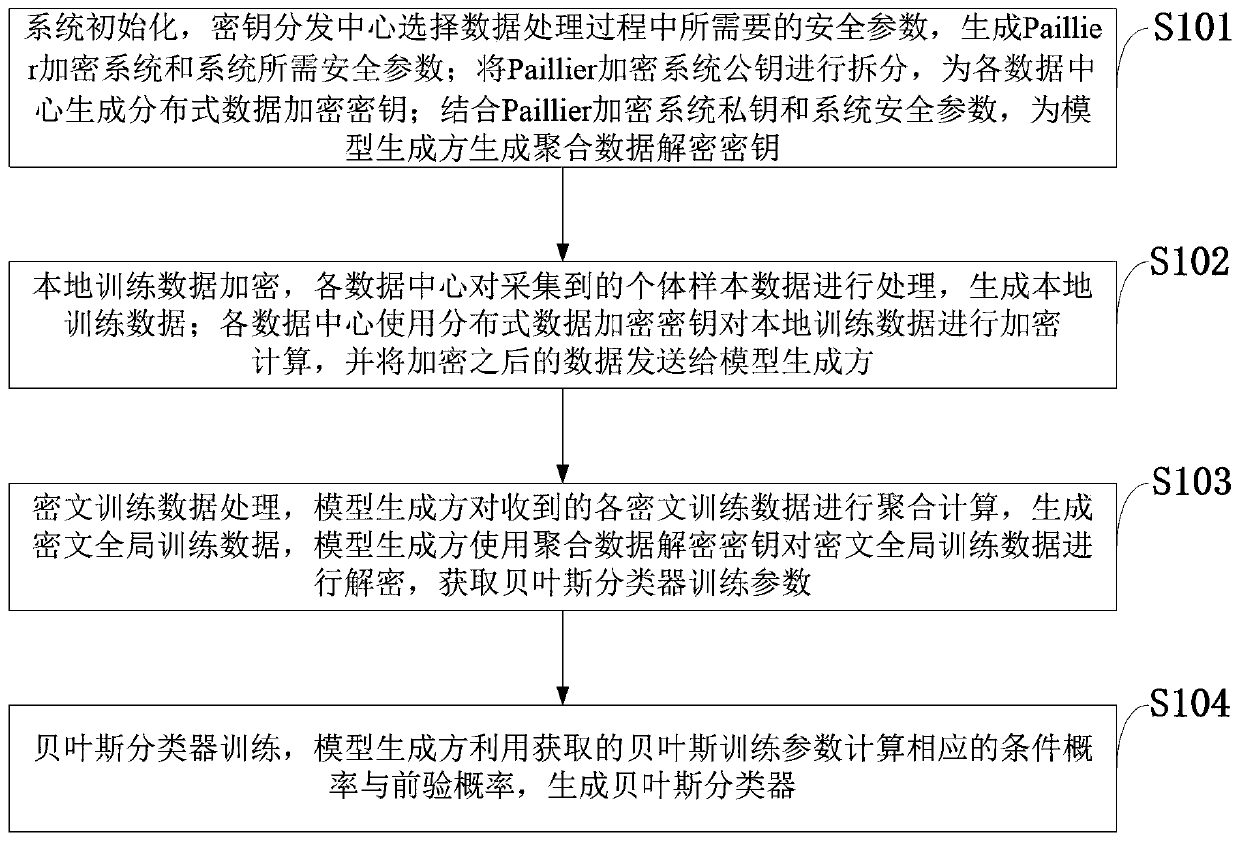
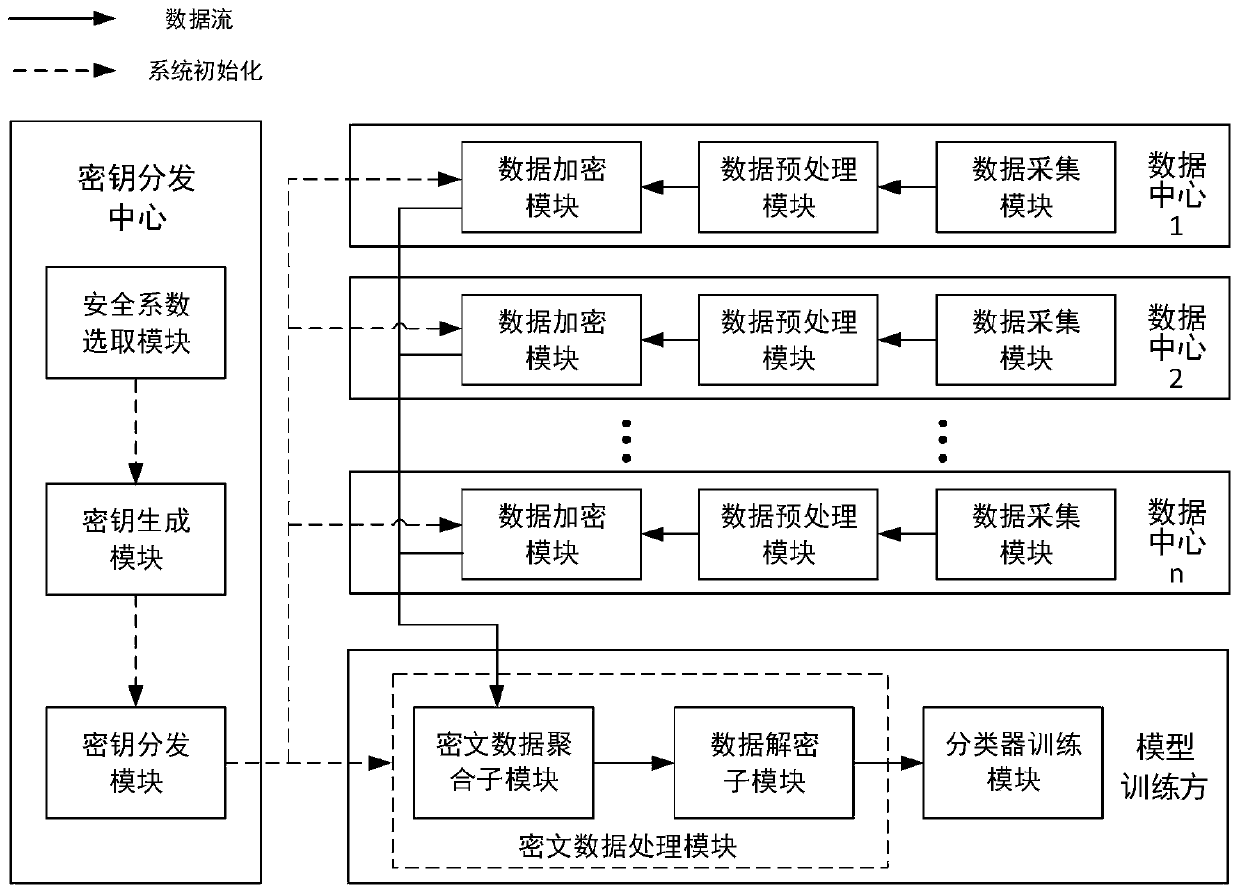
Bayesian classifier security generation system and method for multi-party collaboration
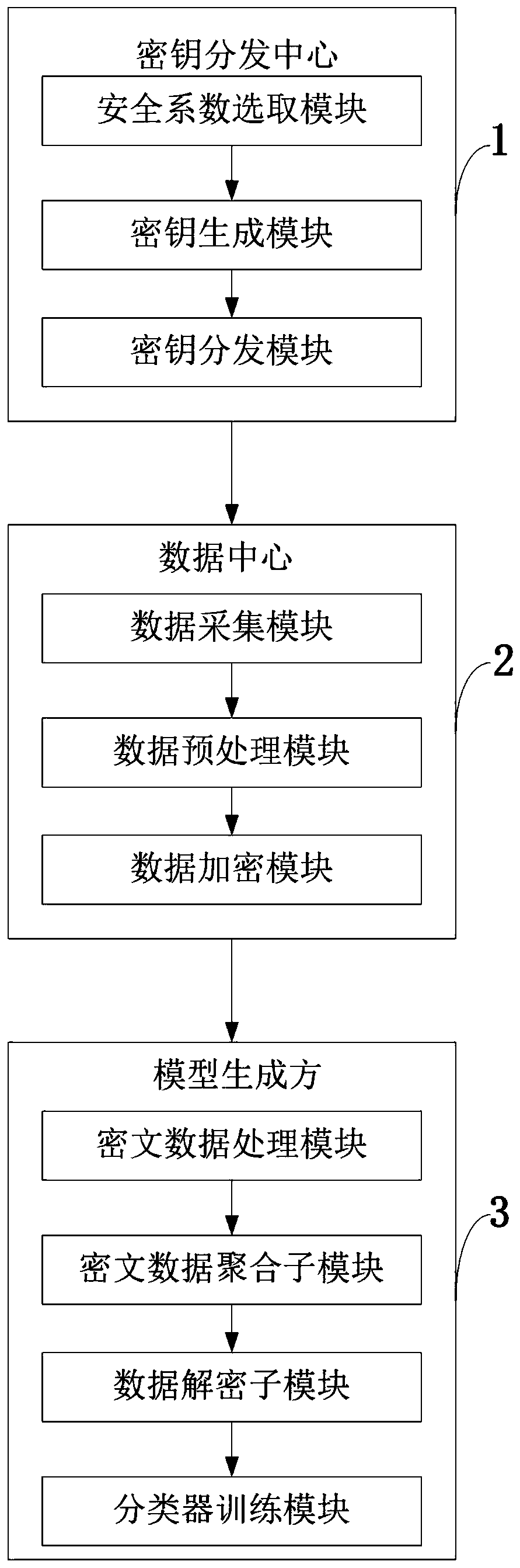
ActiveCN111159727AAchieve securityAchieve protectionDigital data protectionCiphertextPrivacy protection
The invention belongs to the technical field of information security, and discloses a secure multi-party Bayesian classifier generation system and a method, and the method comprises system initialization, system security parameter generation by a key distribution center, a distributed data encryption key and an aggregated data decryption key. Encrypting the local training data, and sending the encrypted data to a model generator; the model generator performs aggregation calculation on the received ciphertext training data to generate ciphertext global training data, and decrypts the ciphertextglobal training data by using an aggregation data decryption key to obtain Bayesian classifier training parameters; and the Bayesian classification model generator uses the obtained Bayesian trainingparameters to calculate a corresponding conditional probability and a corresponding preamble probability, and generates a Bayesian classifier. The method can be used for generating and training the Bayesian classifier in a distributed scene, and can realize safe aggregation and privacy protection of sensitive data of multiple data centers while ensuring that a model generator acquires the high-precision Bayesian classifier.
Owner:THE FIRST AFFILIATED HOSPITAL OF MEDICAL COLLEGE OF XIAN JIAOTONG UNIV +1
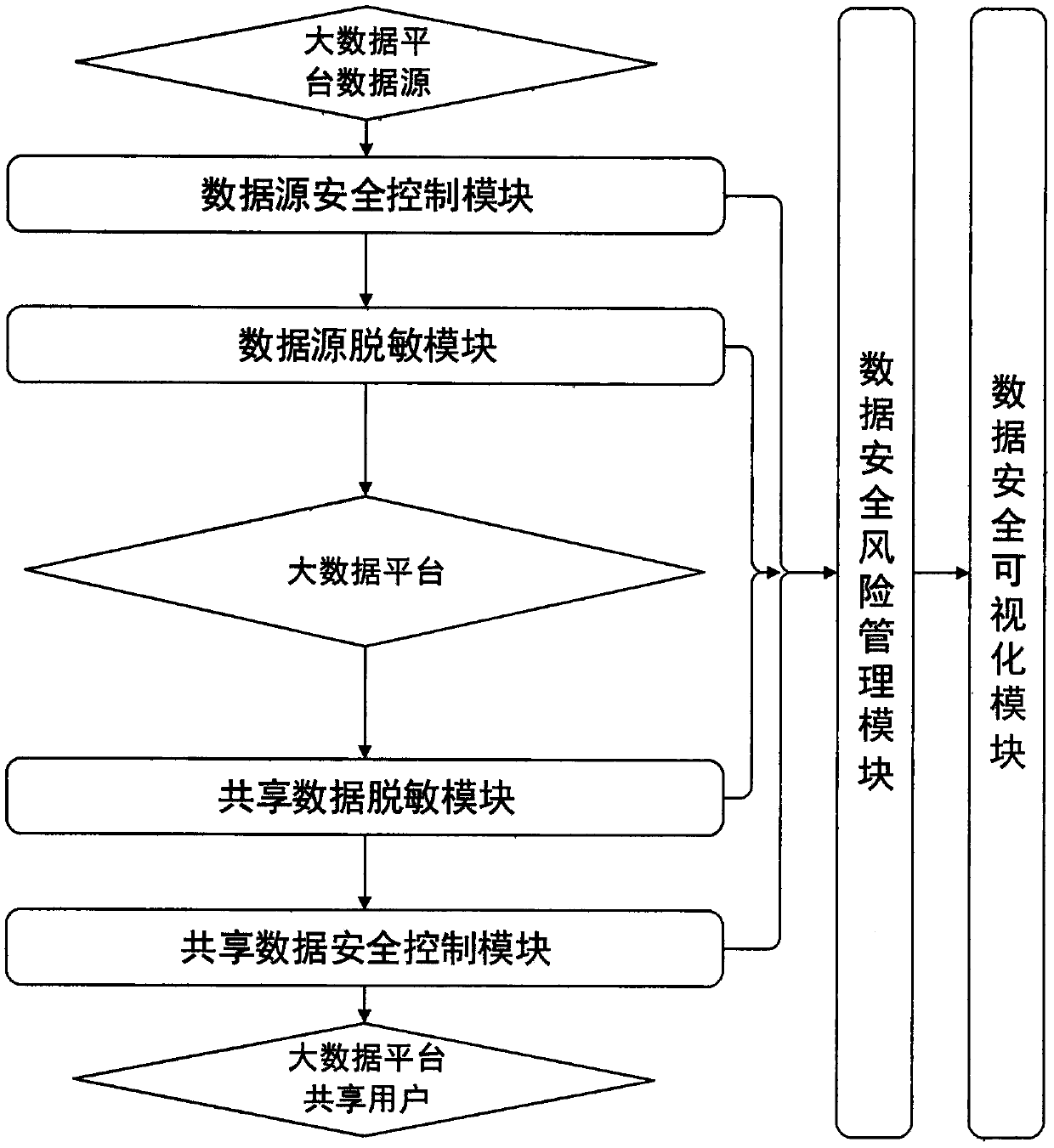
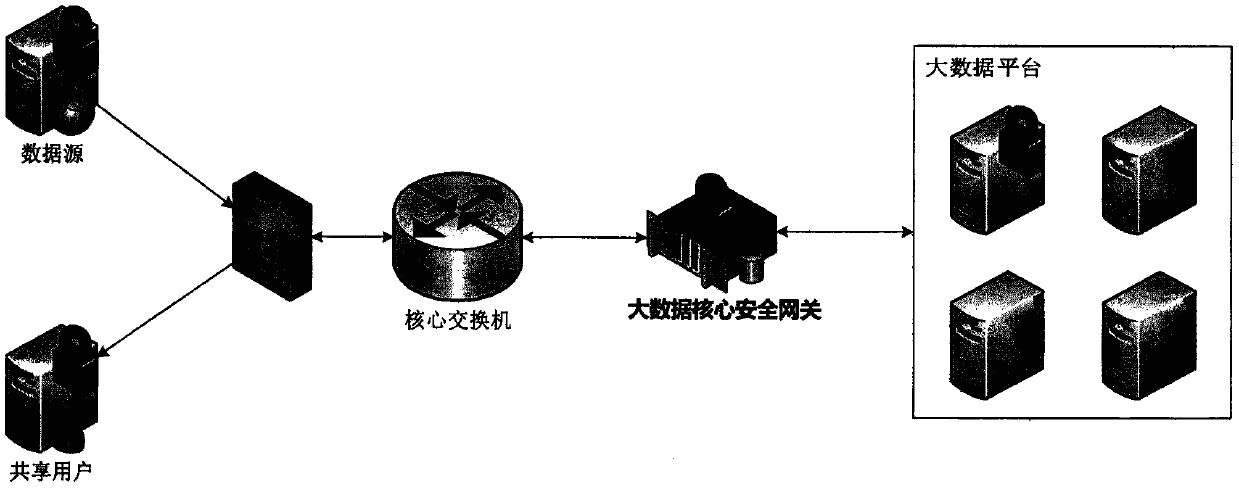
System and method for protecting data security in big data platform data exchange process
The invention provides a system and a method for protecting data security of a big data platform in a data exchange process. The system comprises a data source security control module, a data source desensitization module, a shared data desensitization module, a shared data security control module, a data security risk management module and a data security visualization module. Based on a data exchange process of a current big data platform, the data security problem of the whole exchange process is solved through a multi-factor authentication technology, a dynamic data desensitization technology, a data modeling technology, a machine learning technology and a data visualization technology, illegal data is prevented from being mixed into the platform to influence a calculation result, anddata leakage caused by a data sharing process is prevented.
Owner:慧盾信息安全科技(苏州)股份有限公司
Industrial internet terminal encrypted traffic data security detection method, device and equipment
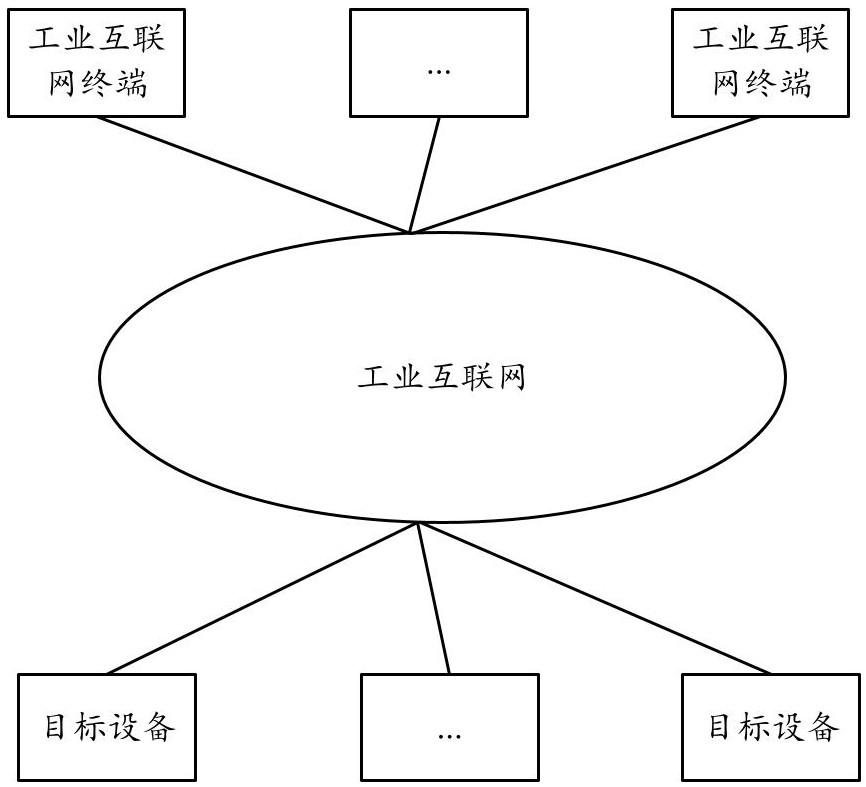
ActiveCN114465823AEnsure safetyLeakage avoidance or reductionCharacter and pattern recognitionSecuring communicationThe InternetTrunking
The invention provides an industrial internet terminal encrypted traffic data security detection method, device and equipment, and the method comprises the steps: carrying out the mirroring storage of traffic data interacted between an industrial internet terminal and target equipment if a proxy service request sent by a traffic proxy relay client is received; based on the traffic data stored in the mirroring manner, if the traffic feature corresponding to the traffic data is matched with the traffic feature in a configured traffic feature library, determining the traffic data as the traffic data of potential sensitive operation; for the traffic data of the potential sensitive operation, inputting the traffic data to a first classifier to obtain a first classification result; and determining that the traffic data has sensitive information based on the first classification result, or determining that the traffic data does not have sensitive information based on the first classification result. Through the technical scheme of the application, the traffic data with the sensitive information can be found in time, so that the leakage of the sensitive information is avoided or reduced, and the data security problem is solved.
Owner:HANGZHOU HIKVISION DIGITAL TECH
HTTP transmission protocol-based file reading and writing service downloading method
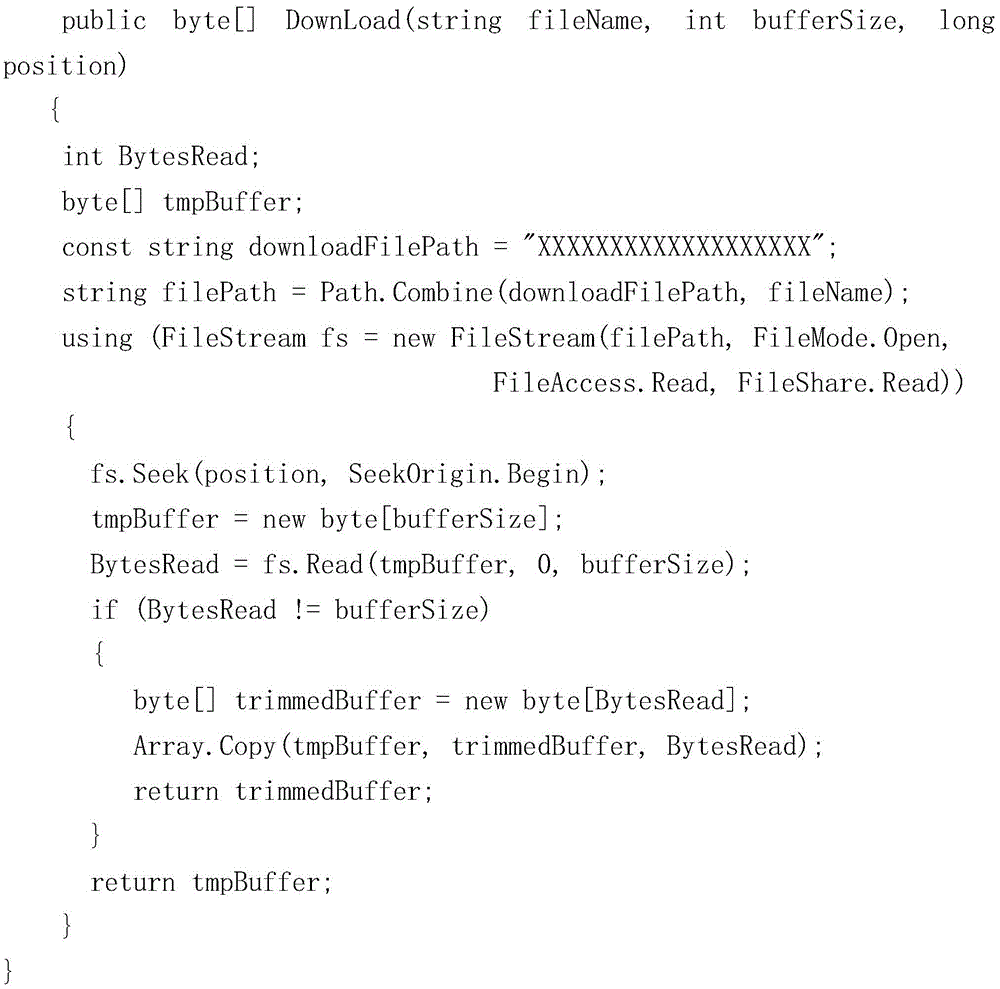
ActiveCN105635186AEnsure network securityEasy to downloadTransmissionTransmission protocolBatch processing
The invention discloses an HTTP transmission protocol-based file reading and writing service downloading method and belongs to the technical field of file downloading security in an Internet environment. The objective of the invention is to ensure the security of a file to be downloaded with convenience in downloading of a user ensured from the aspect of file management of attachments of an application system to. According to the technical schemes of the invention, the method includes the following steps that: (1), an application server end is provided with an IIS, the IIS is adopted as a web server, an application software system is deployed; (2) an application server end file reading and writing web services are deployed on the application software system; (3) a file reading and writing directory is set at the application server end; (4) the file to be downloaded is save under the path of the application server end; (5) the backstage of the application server end performs password compression processing on the file to be downloaded through batch processing; and (6) the download function module of the application software system calls the web services.
Owner:INSPUR COMMON SOFTWARE
Disaster recovery backup method and system for data service
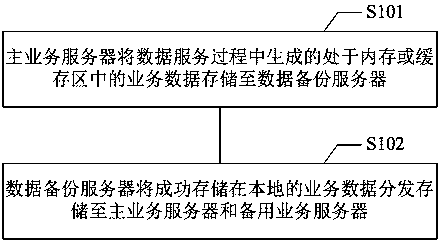
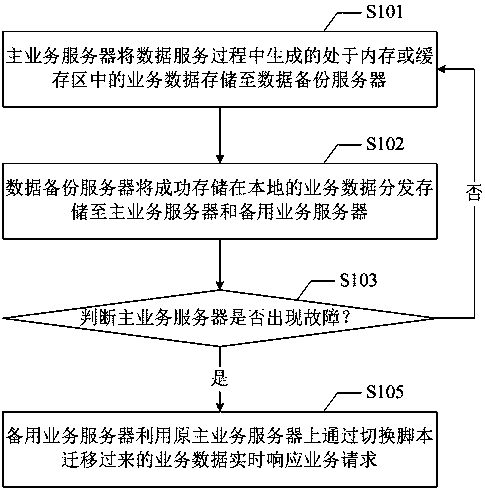
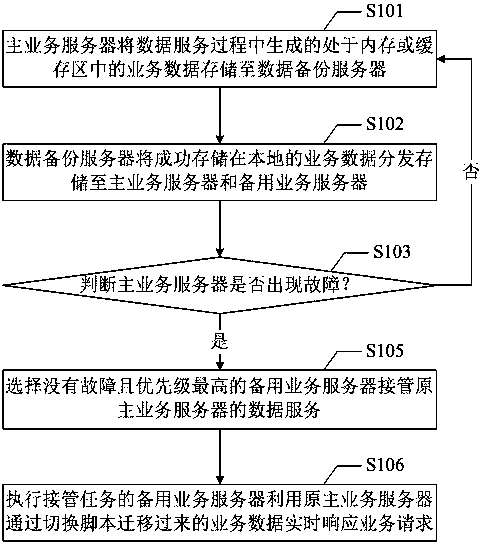
InactiveCN104158693BImprove usabilityIssues affecting service performanceData switching networksHigh availabilityBackup
The invention provides a method and a system for disaster recovery backup of data service. The system for executing the method includes a main service server, a standby service server, and a data backup server, which are connected over a network, and the method includes: the main service server stores service data generated during data service and located in a memory or cache region to the data backup server; and the data backup server distributes and stores the service data, which is stored successfully and locally, to the main service server and the standby service server. According to the invention, through the above means, service switching can be executed in real time, thus ensuring high availability of service, reducing service abnormality time delay, and improving greatly user experience.
Owner:LETV INFORMATION TECH BEIJING
Space test data transaction method
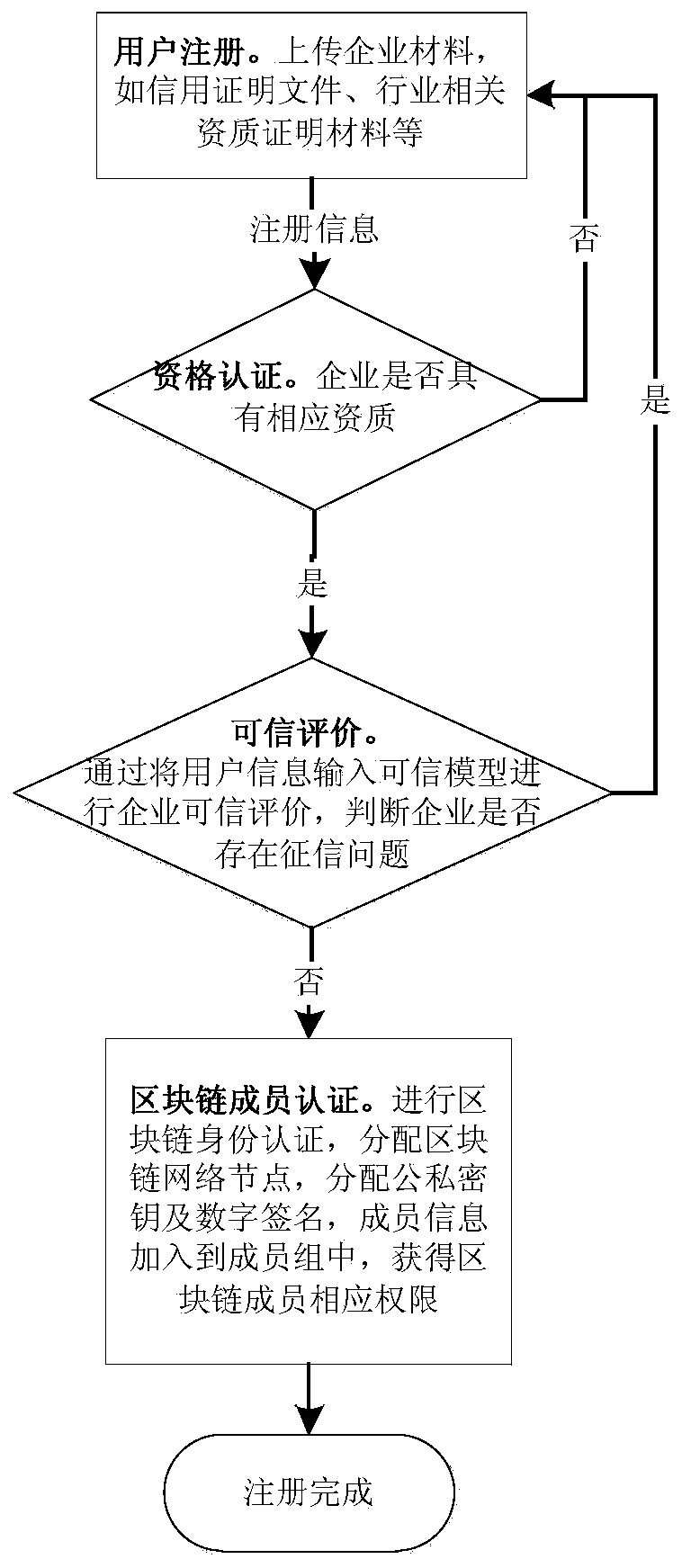
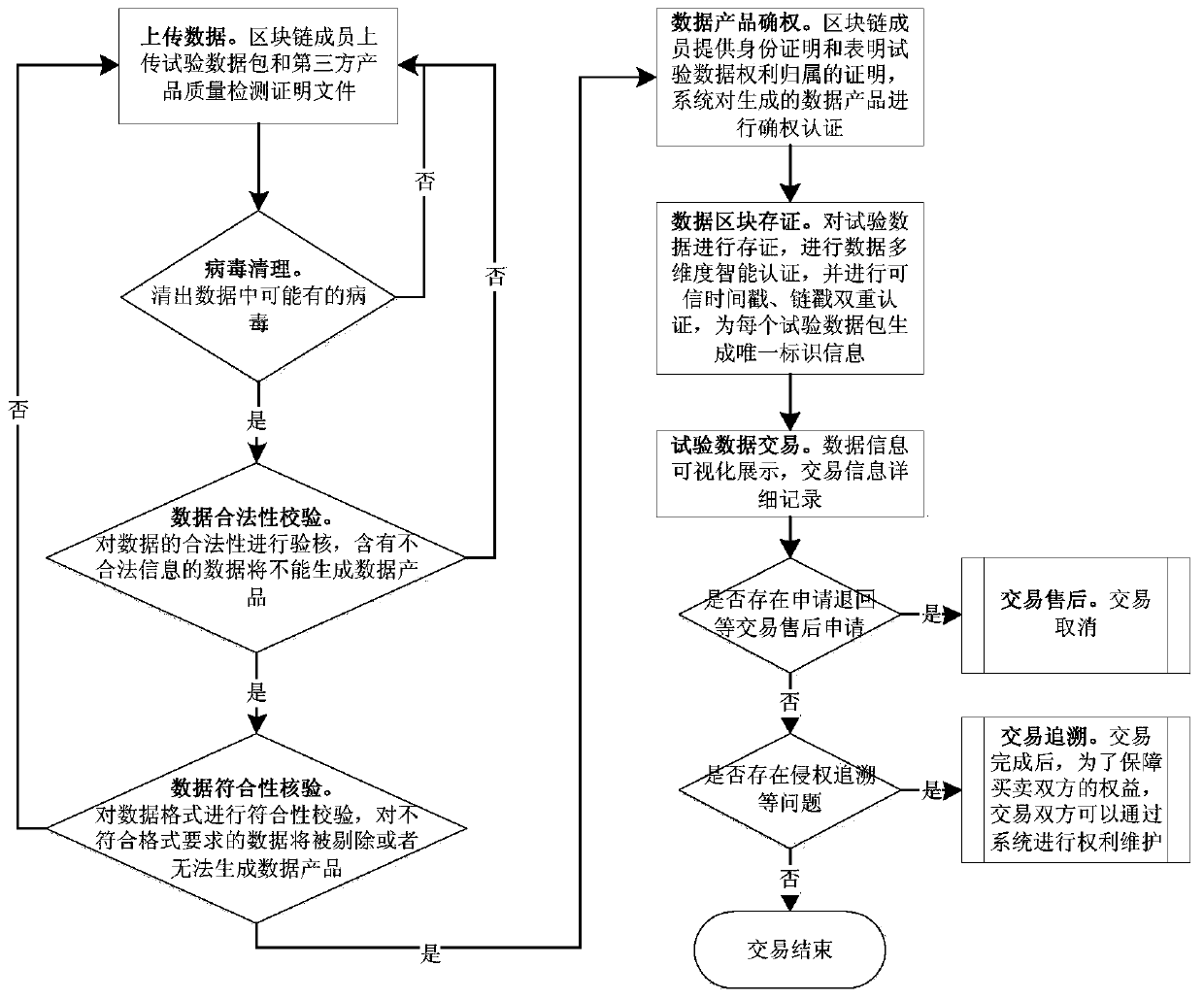
PendingCN111429198AEnsure legal complianceIncrease mutual trustFinanceDigital data protectionFinancial transactionChain network
The invention discloses an aerospace test data transaction method, and belongs to the technical field of aerospace test data transaction. According to the method, all related participants are added into a private block chain network through authorization to form a benefit association alliance and jointly maintain block chain operation, so that the legitimate compliance of each participant in a transaction system is ensured, the mutual trust among the participants is increased, an open cooperation environment is provided, and the benign circulation of aerospace industry resources is realized; the full-life-cycle processes of data product generation, data product right confirmation, data block evidence storage, data product transaction, transaction tracing and the like are covered, and a block chain technology is adopted, so that data credibility, data security and transaction traceability are guaranteed; and the problems of value proof, data security, network transaction trust and the like of aerospace test data are solved, the benefits of two transaction parties are guaranteed, and the application range of aerospace industry resources is effectively expanded.
Owner:中国航天系统科学与工程研究院
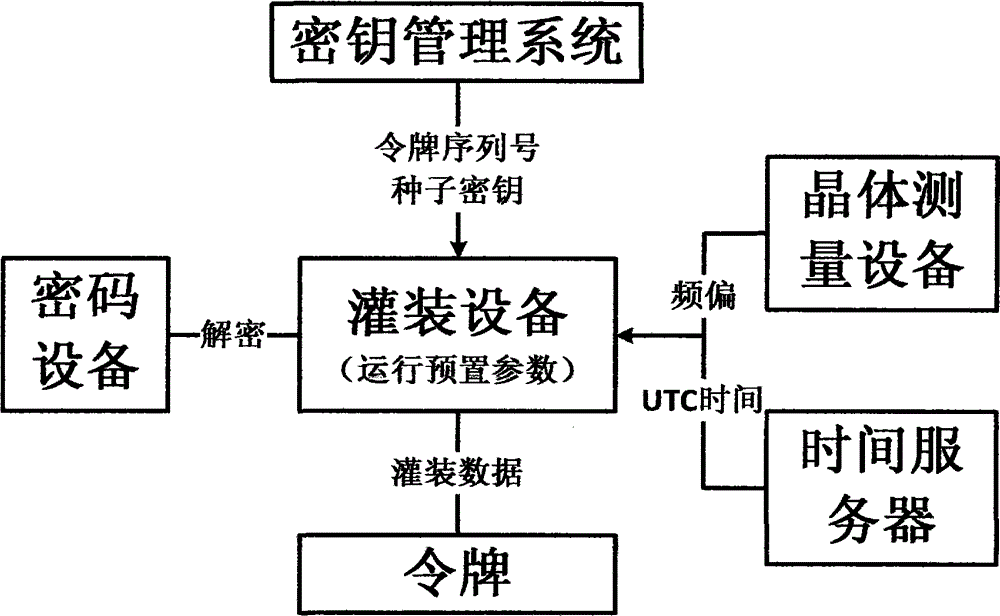
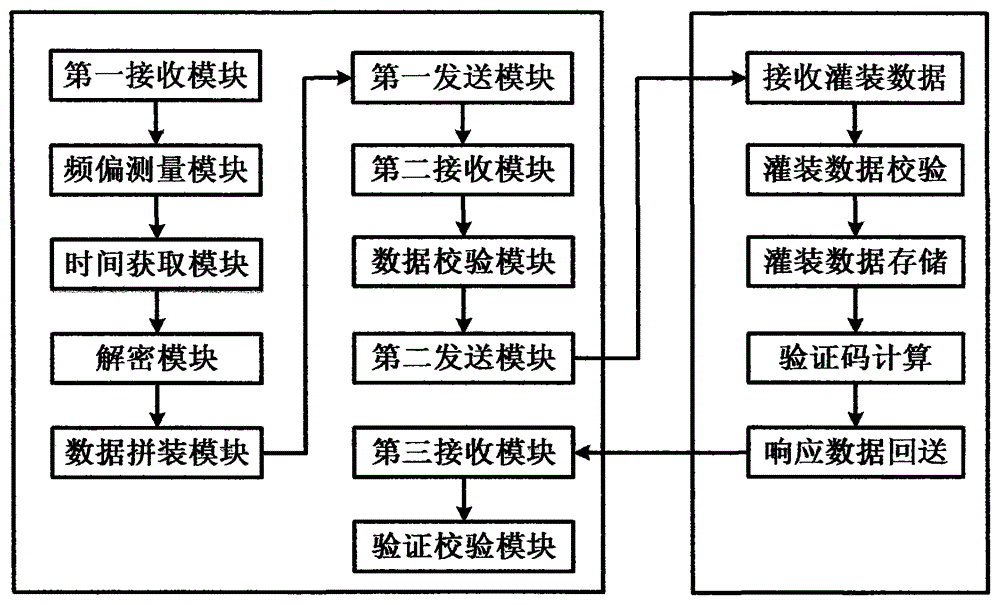
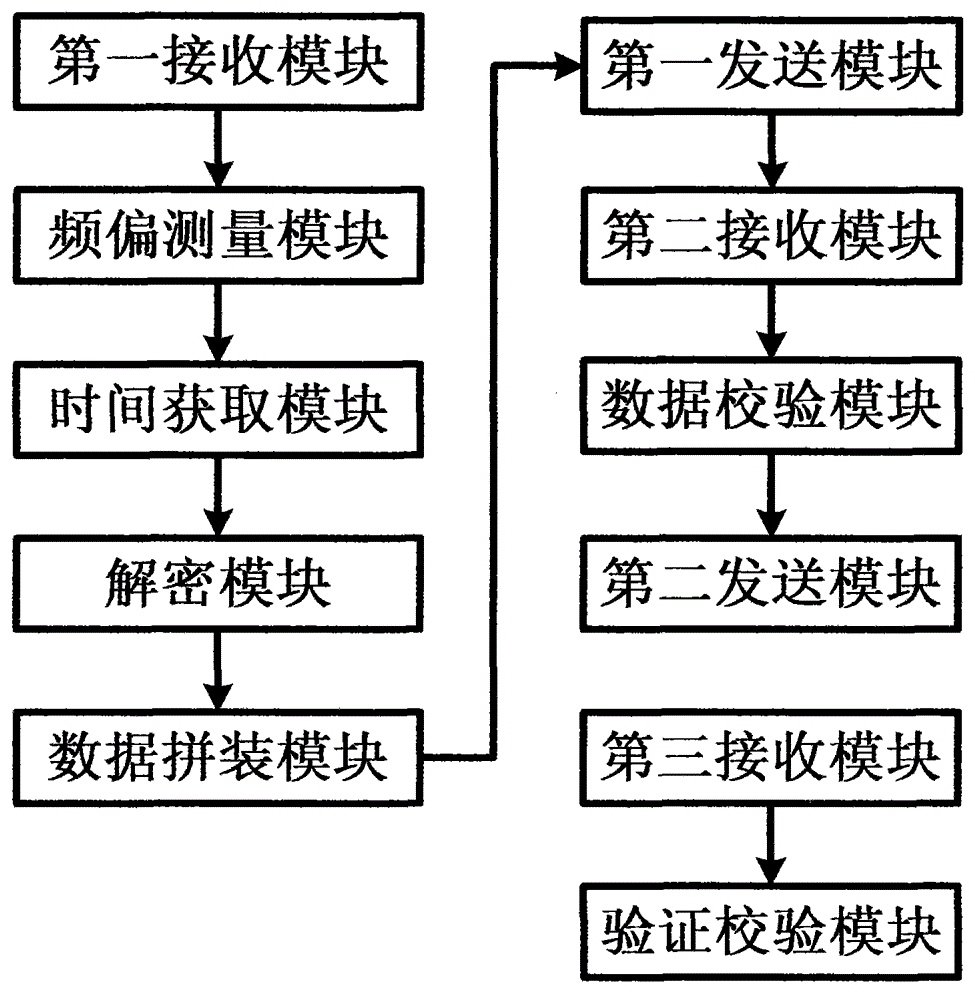
Token parameter filling equipment, filling data processing equipment and filling method
ActiveCN104660410ASolve data security issuesComplete filling dataUser identity/authority verificationMeasuring equipmentData security
The invention discloses token parameter filling equipment and filling data processing equipment and a filling method. The filling method comprises the following steps: sending token serial numbers and seed secret keys into the filling equipment by a secret key-management system, setting an operation preset parameter and performing filling on the token by the filling equipment, expanding preset parameter data according to the different configuration parameter requirements of users, performing decryption on the seed secret keys, obtaining three frequency deviations of a token product through the real-time measurement by adopting crystal measuring equipment, and performing calculation so as to obtain average deviation; then obtaining a current UTC time through a time server or a GPS (Global Position System) by a time obtaining module. The token parameter filling equipment, the filling data processing equipment and the filling method, disclosed by the invention, have the technical benefits that the problem of data security during filling process is solved, complete and reliable filling data is ensured, the filling efficiency is improved, and the product can be filled with the frequency deviation parameter of the dynamic token.
Owner:北京集联网络技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com