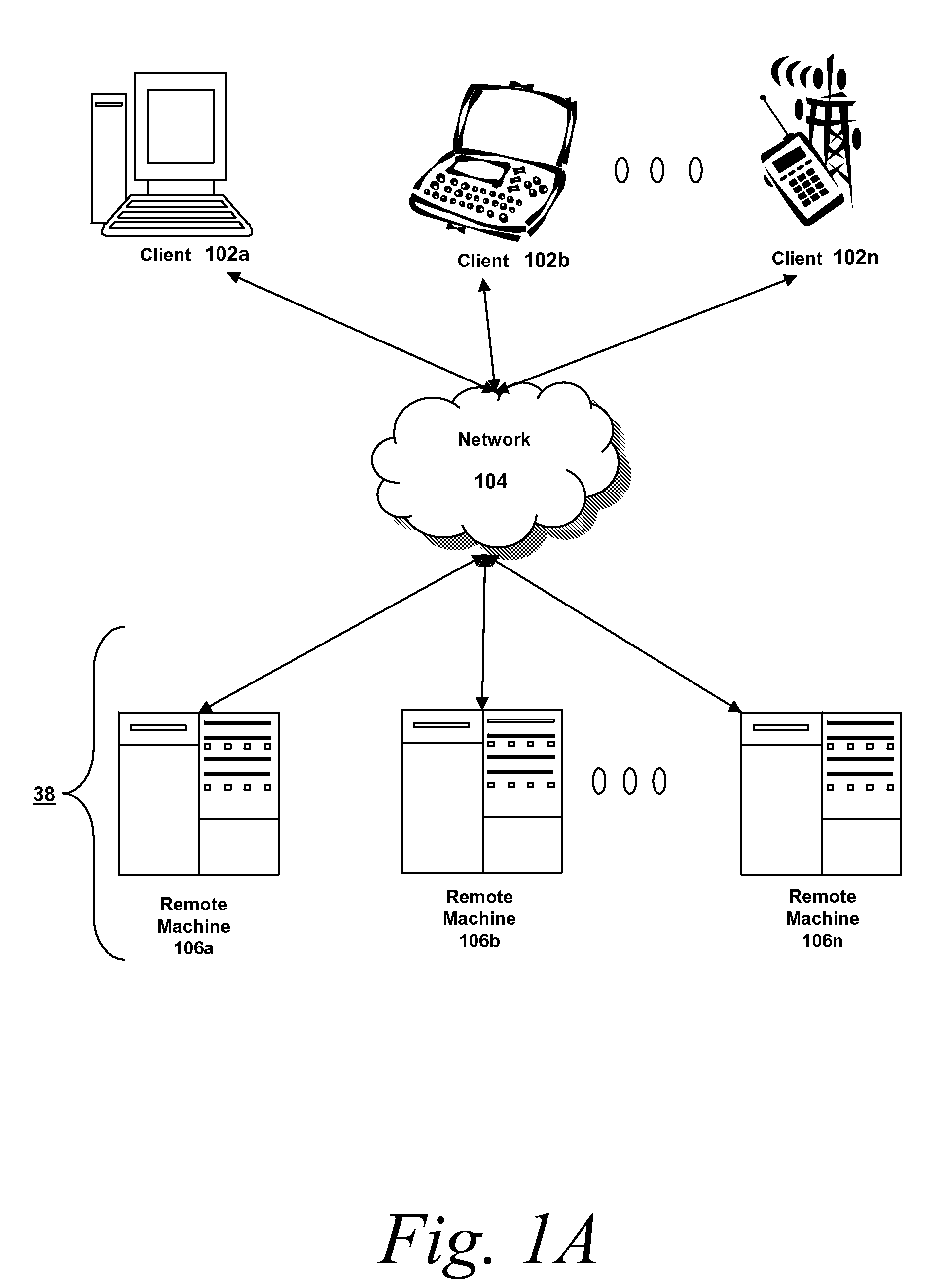
Patents
Literature
1057 results about "Proxy service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
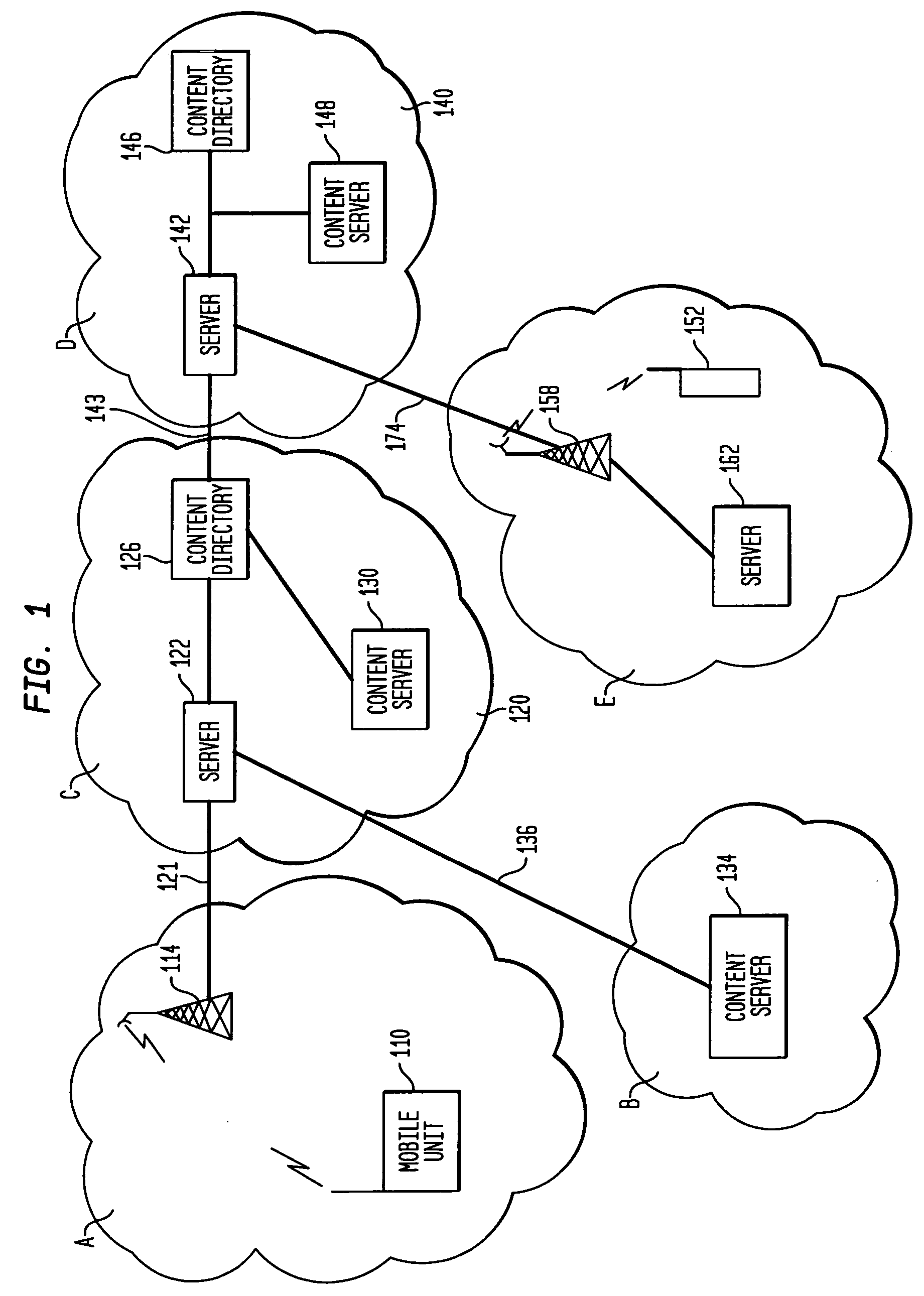
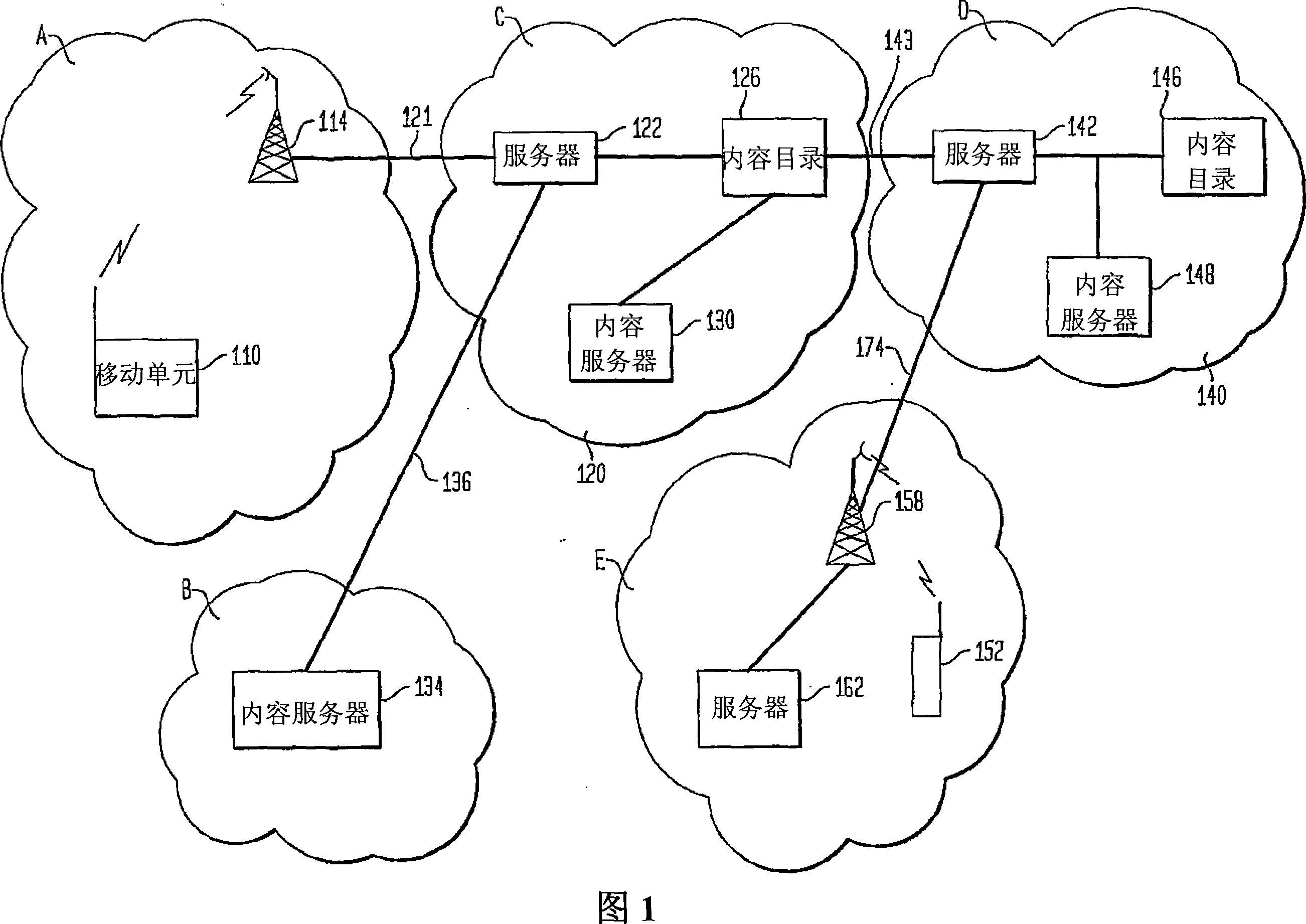
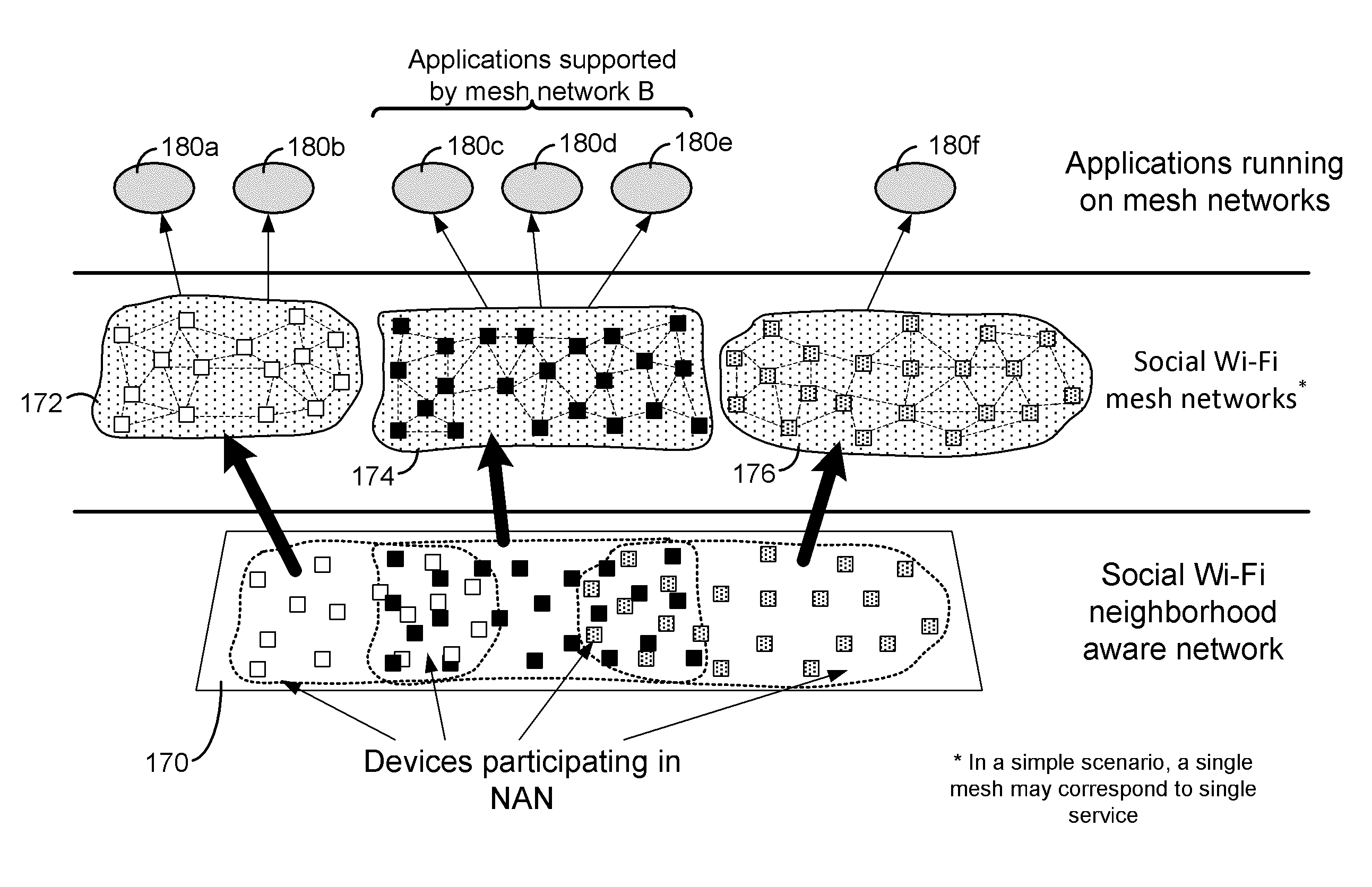
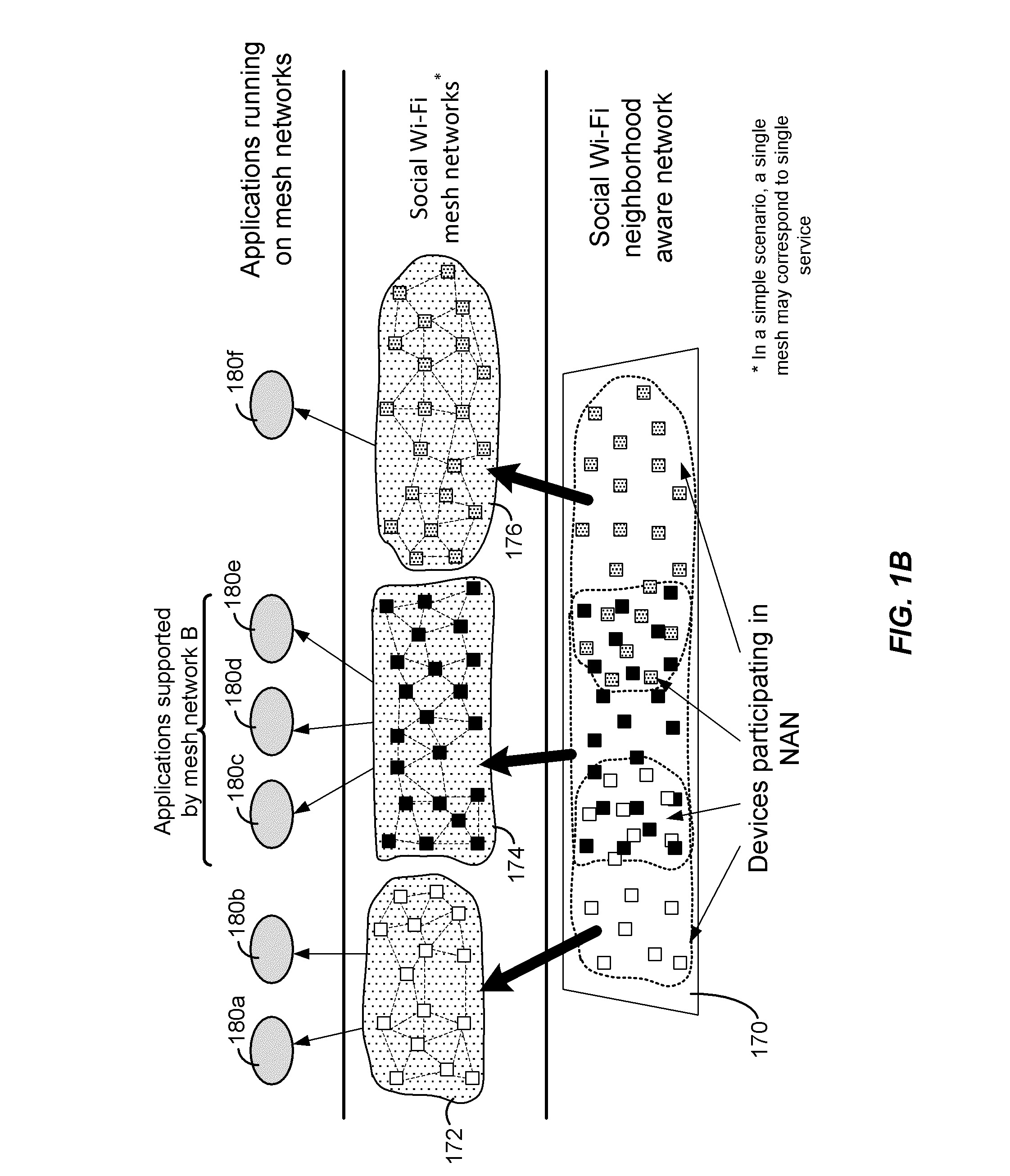
A proxy service is an intermediary role played by software or a dedicated computer system between an endpoint device and a client which is requesting the service. The proxy service may exist on the same machine or on a separate server.
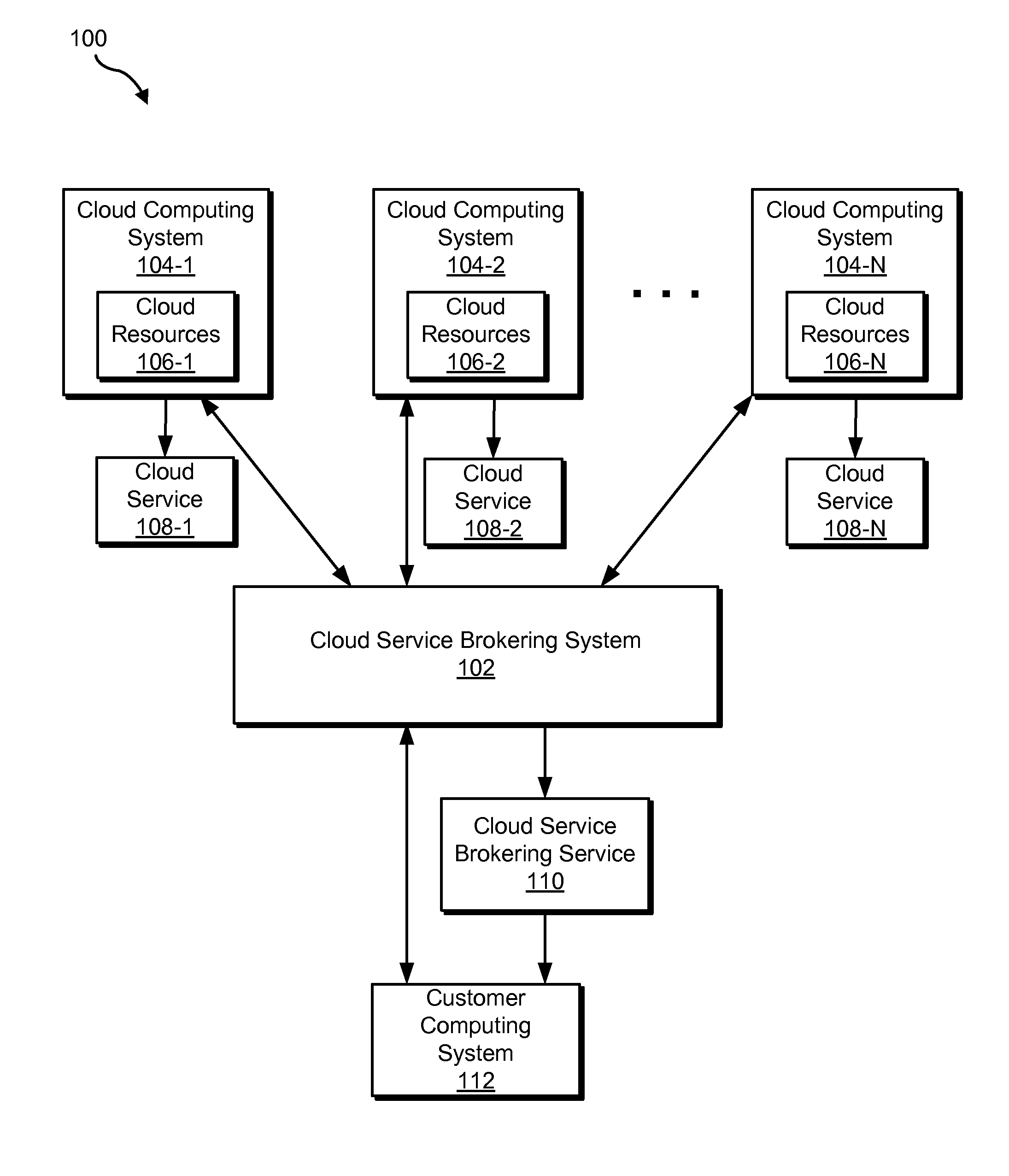
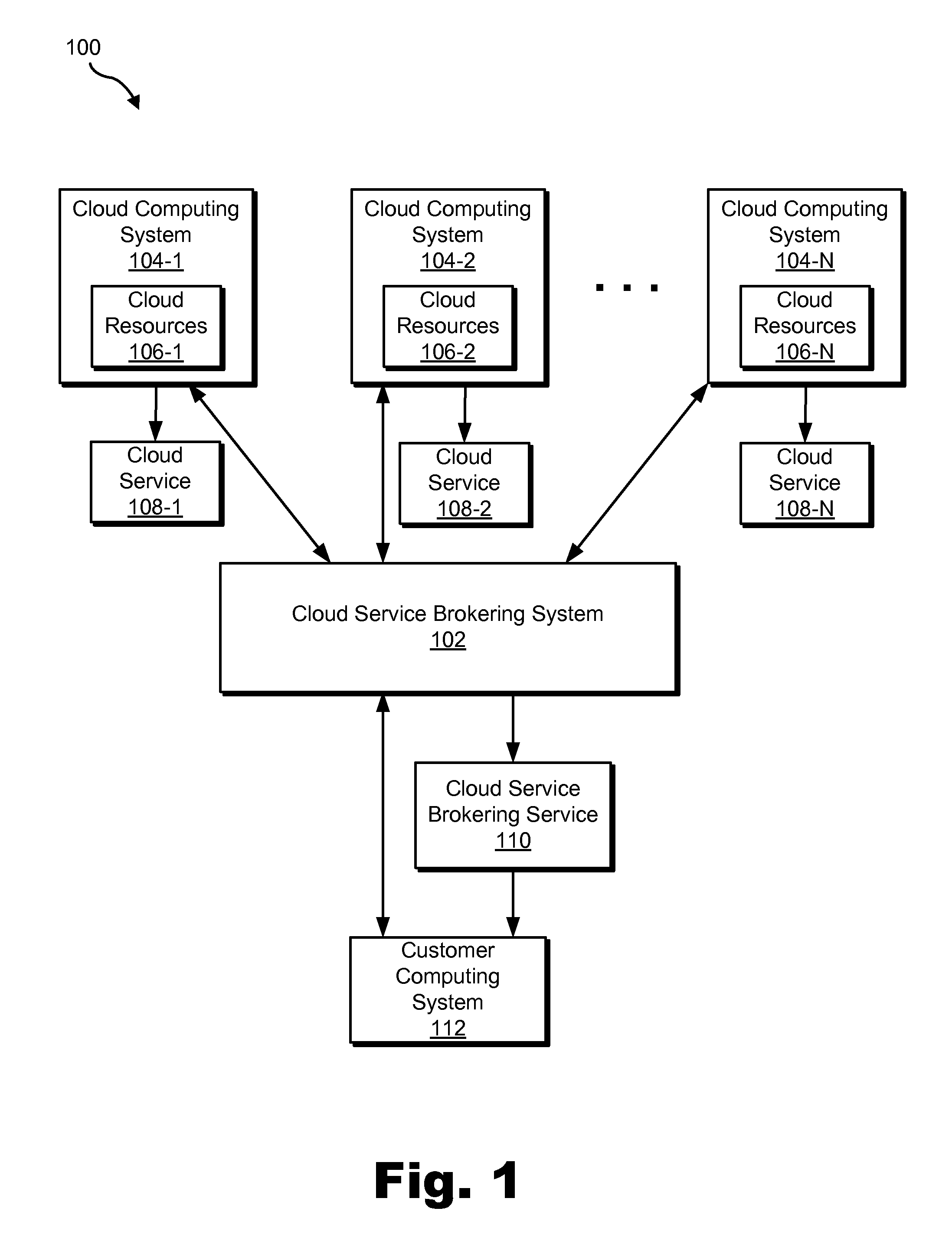
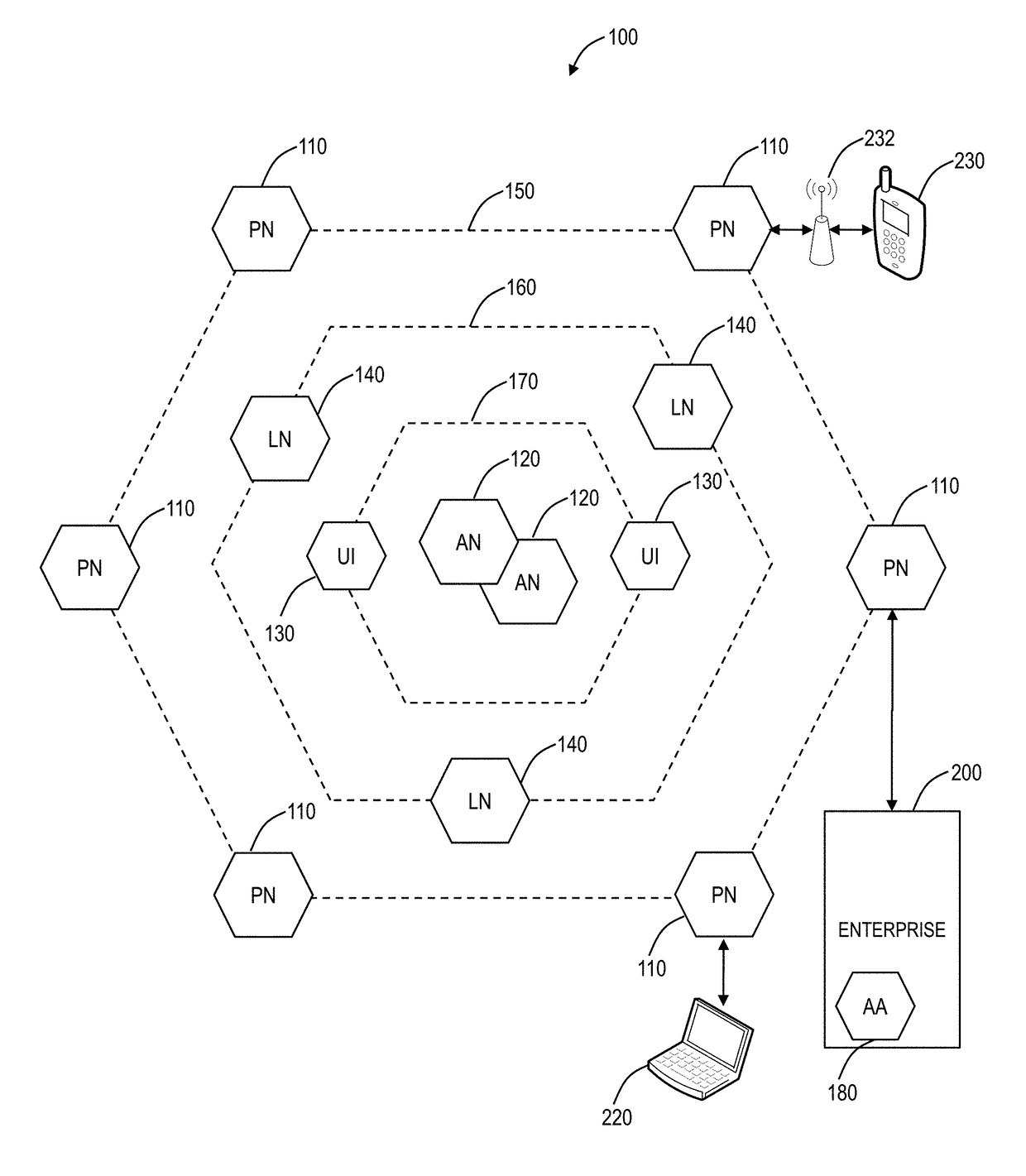
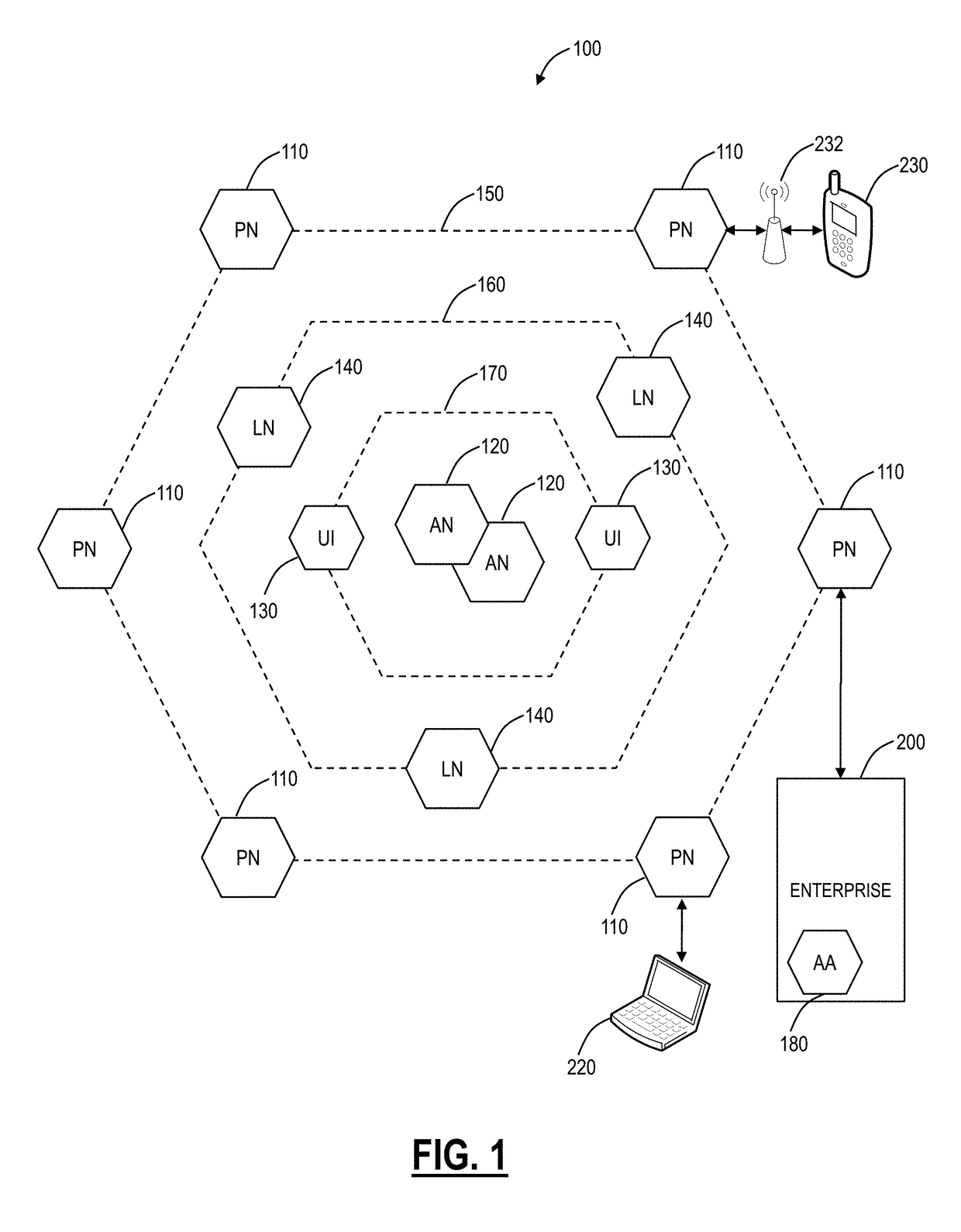
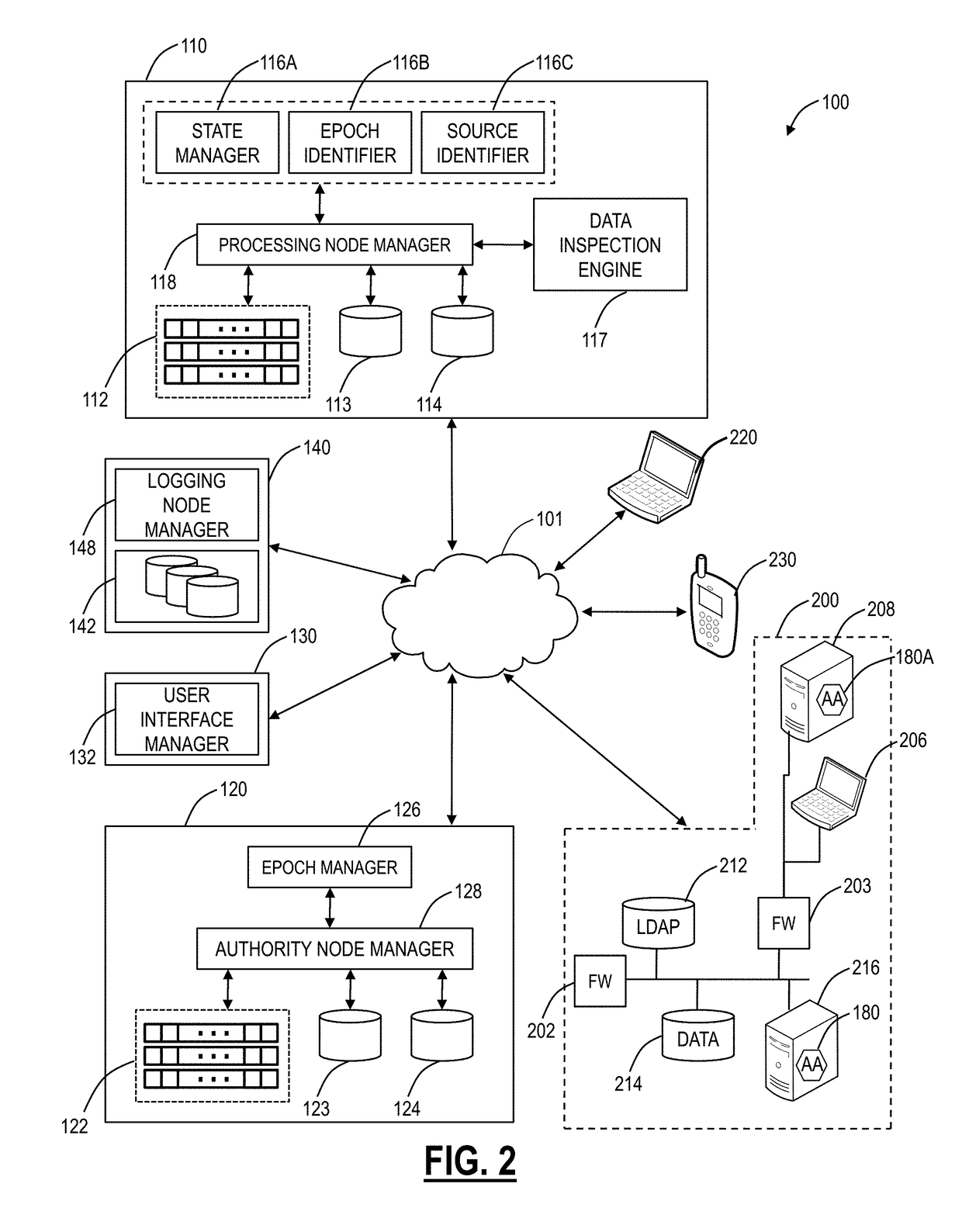
Cloud service brokering systems and methods
An exemplary method includes a computer-implemented cloud service brokering system that provides a cloud service brokering service 1) registering a plurality of cloud services with the cloud service brokering service, the plurality of cloud services provided by a plurality of cloud service providers and configured to provide distinct sets of cloud computing resources as a service, 2) receiving, from a customer of the cloud service brokering service, cloud service request information, 3) selecting, based on the cloud service request information, a cloud computing resource from the distinct sets of cloud computing resources provided by the plurality of cloud services registered with the cloud service brokering service, and 4) allocating the selected cloud computing resource for use by the customer. In certain examples, the allocating may be supported by the system configuring a customer network to support implicit and / or explicit transport requirements. Corresponding systems and methods are also described.
Owner:VERIZON PATENT & LICENSING INC
Method, apparatus and system for a location-based uniform resource locator
InactiveUS20060206586A1Data processing applicationsMultiple digital computer combinationsThe InternetClient-side
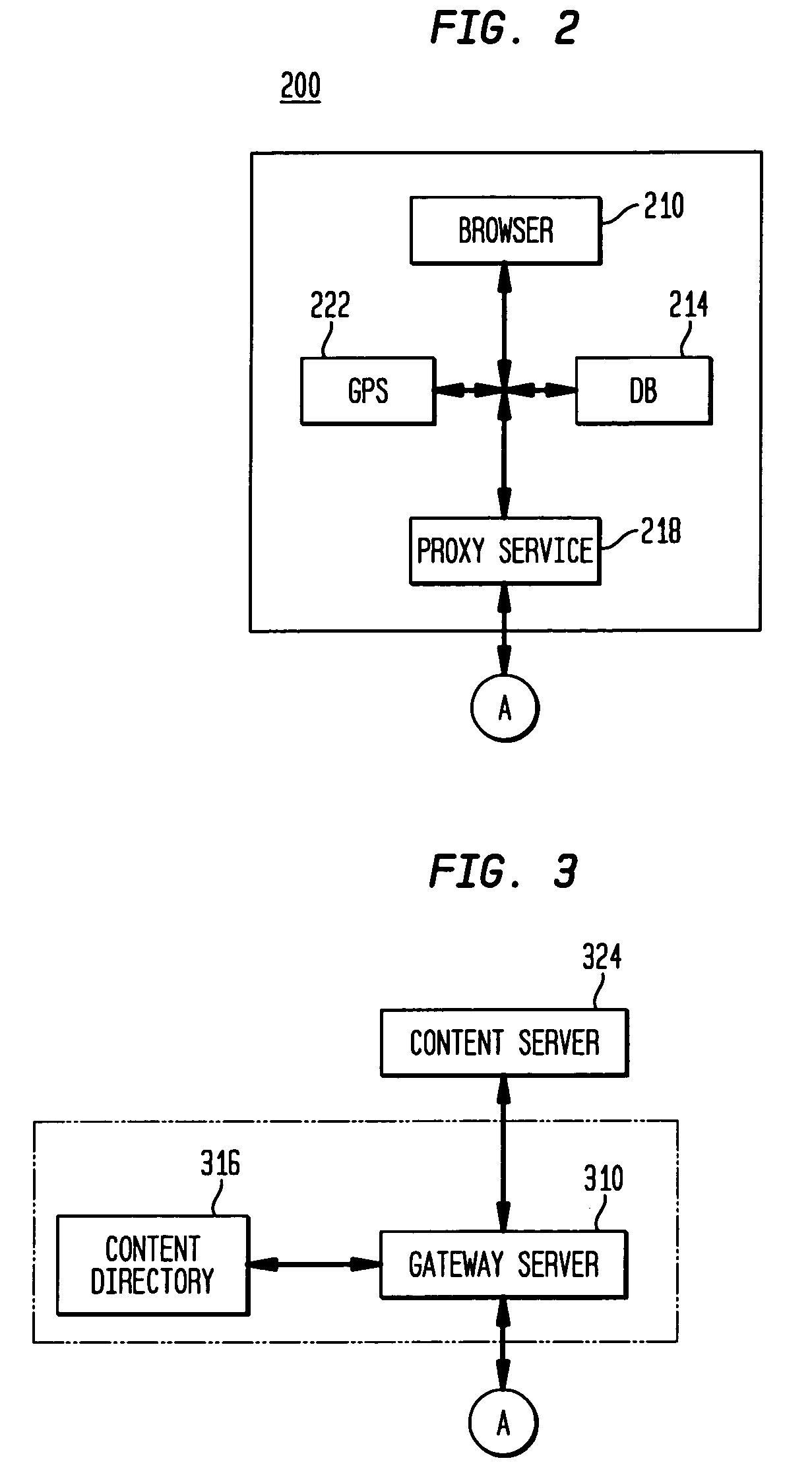
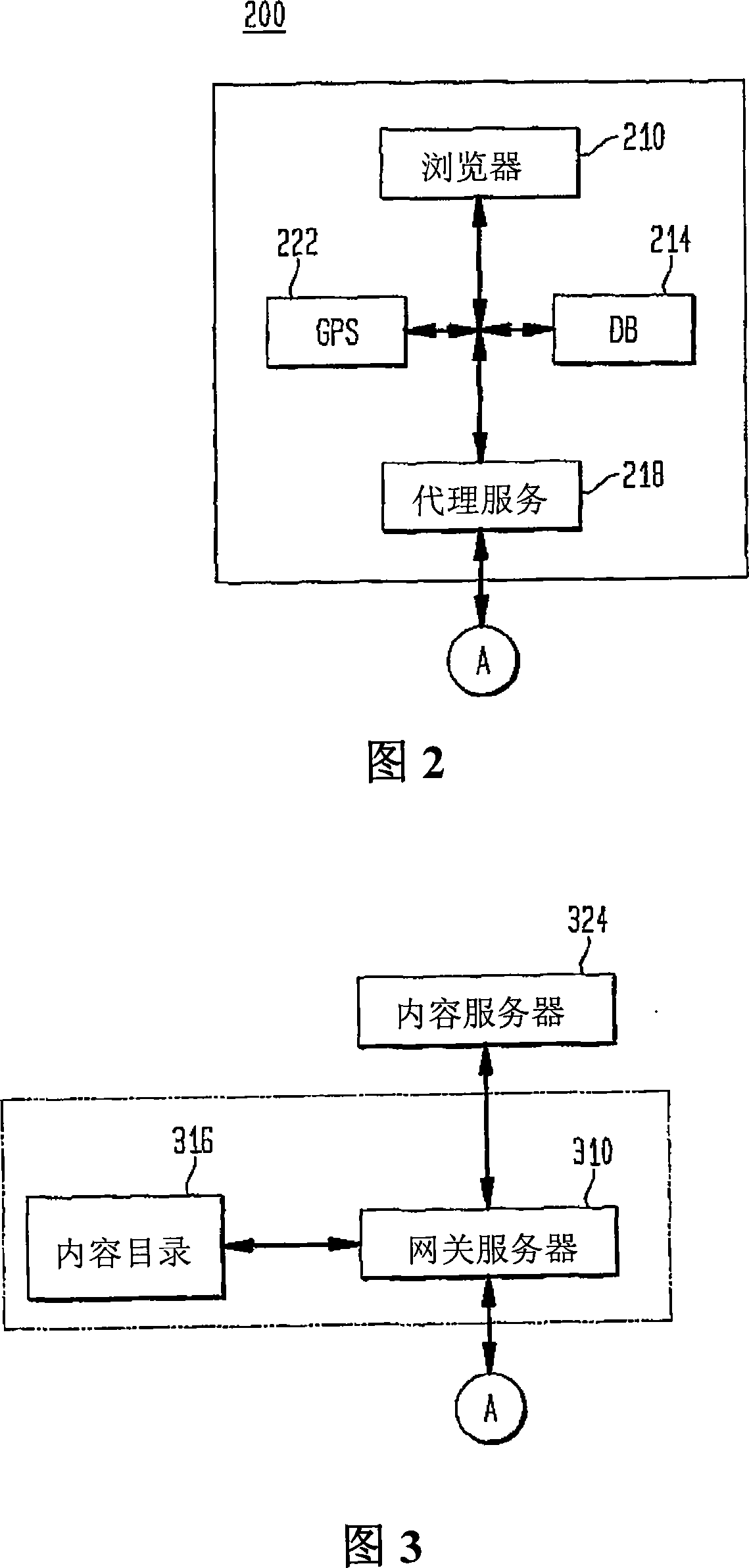
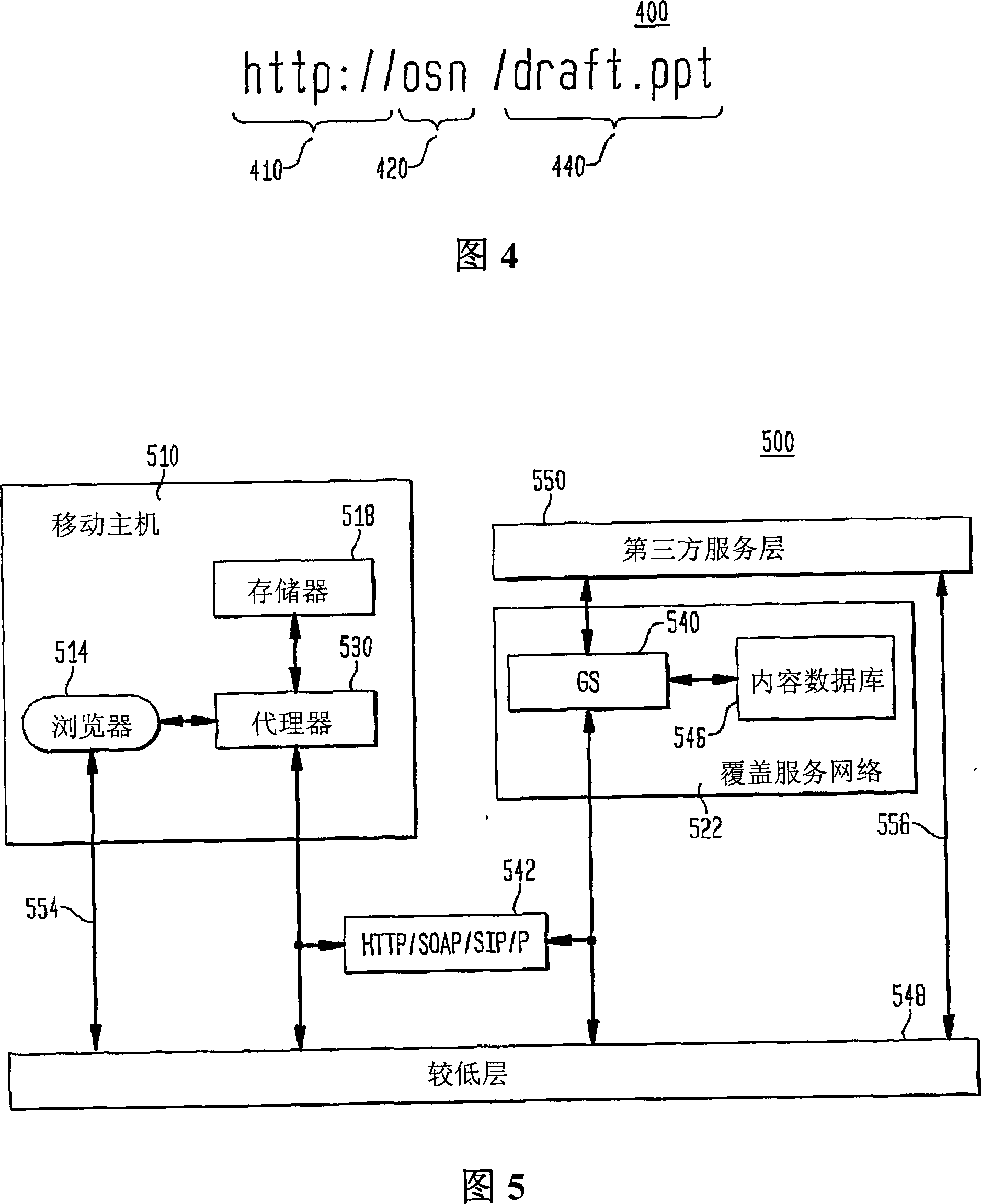
An aspect of the present invention is a method for routing content information to a mobile user or client application. The method preferably comprises re-directing a user request to one or more gateway servers provided via an overlay network. In another aspect, the present invention is an apparatus that includes a proxy service that intercepts content information requests to the Internet and re-directs the content requests to an overlay. Another aspect of the present invention comprises a location-based Uniform Resource Locator that includes a protocol semantic portion and a location-based resolver address portion that identifies one or more resources on a network based on the geographical location of the resources.
Owner:TELCORDIA TECHNOLOGIES INC +1
Method, apparatus and system for a location-based uniform resource locator
An aspect of the present invention is a method for routing content information to a mobile user or client application. The method preferably comprises re-directing a user request to one or more gateway servers provided via an overlay network. In another aspect, the present invention is an apparatus that includes a proxy service that intercepts content information requests to the Internet and re-directs the content requests to an overlay. Another aspect of the present invention comprises a location-based Uniform Resource Locator that includes a protocol semantic portion and a location-based resolver address portion that identifies one or more resources on a network based on the geographical location of the resources.
Owner:TELCORDIA TECHNOLOGIES INC +1
Method and apparatus for offline cooperative file distribution using cache nodes
InactiveUS20060224687A1Digital data information retrievalMultiple digital computer combinationsDistribution systemOperating system
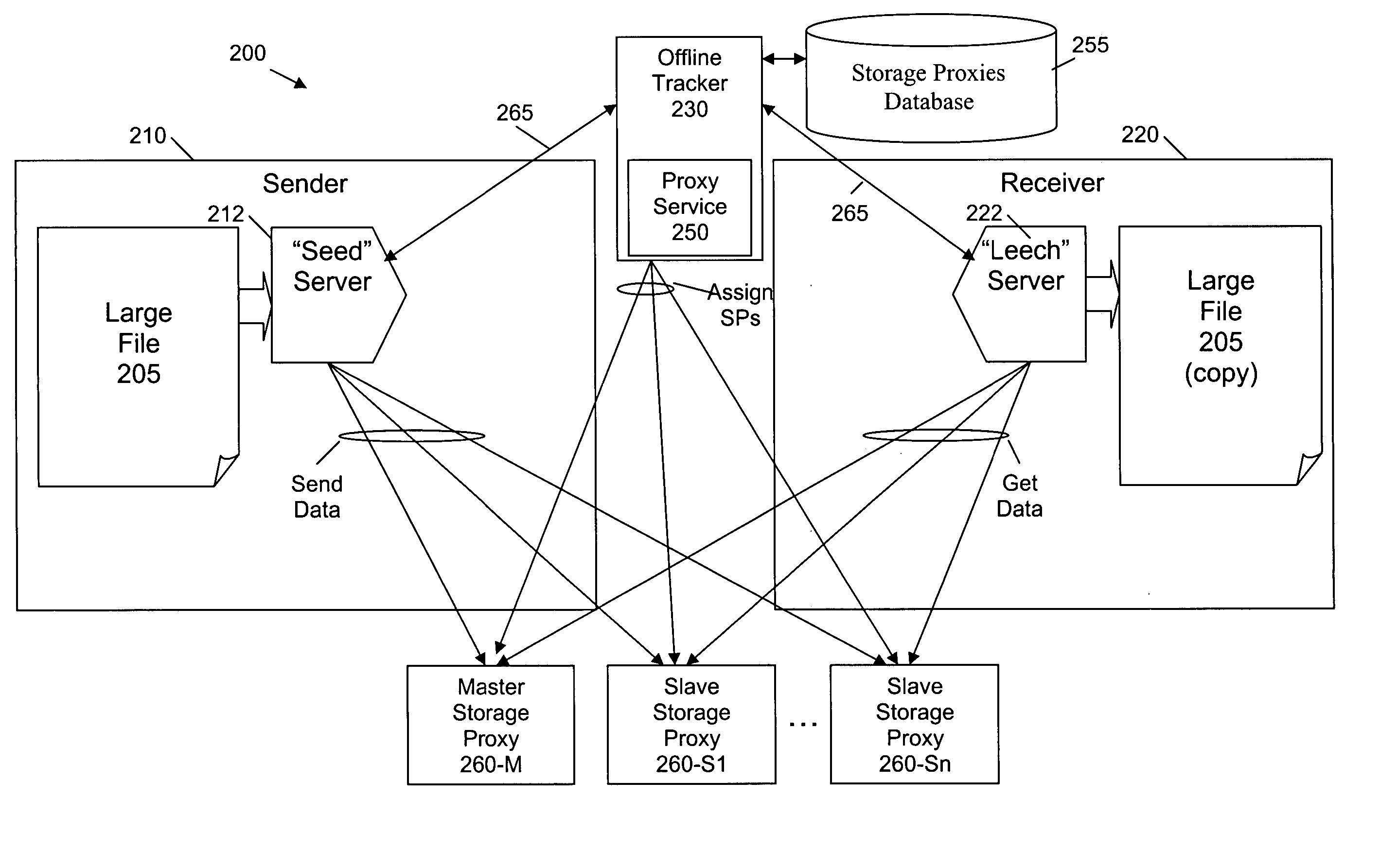
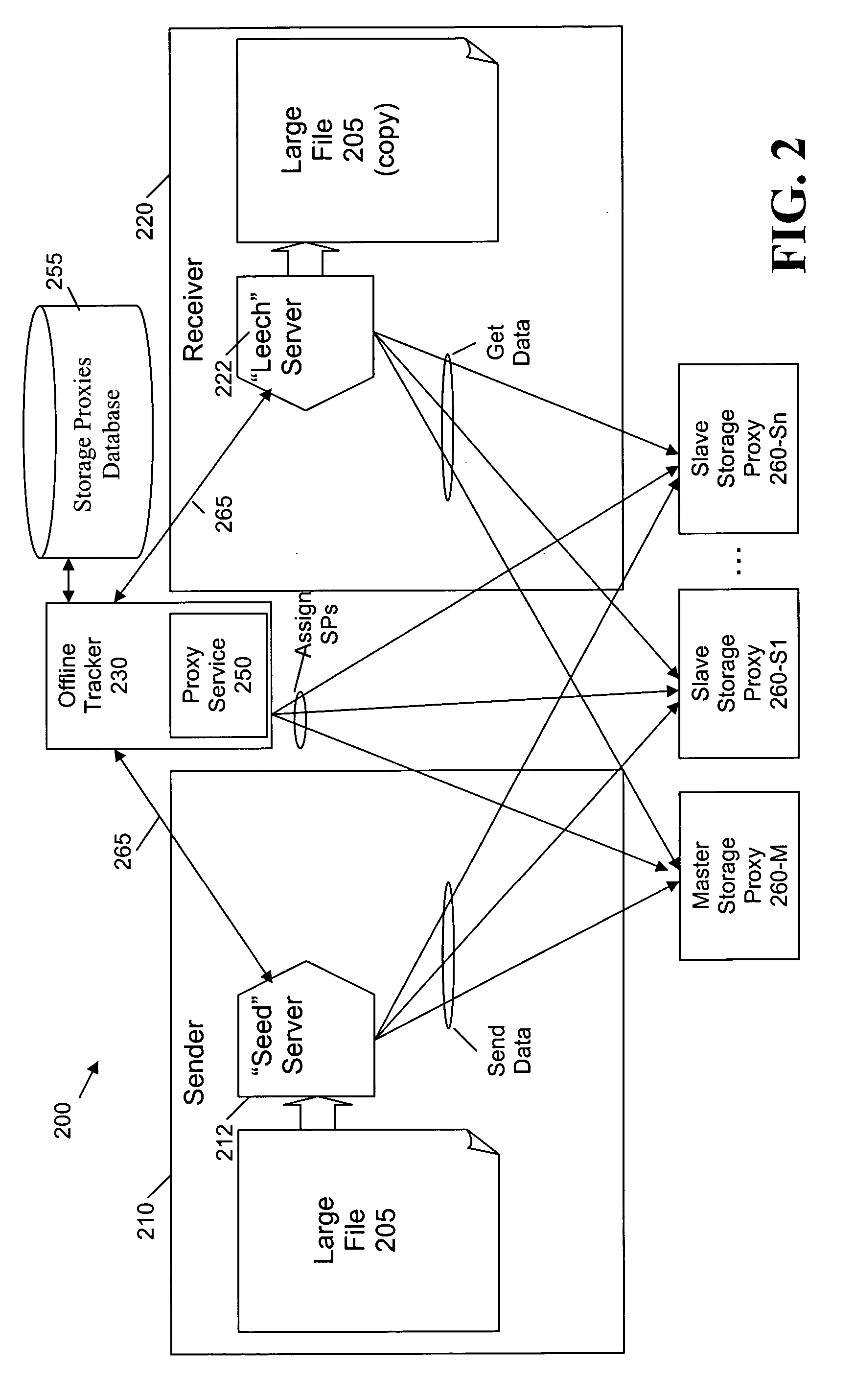
Methods and apparatus are provided for cooperative file distribution system employing one or more storage proxies to allow an offline receiver to obtain files or pieces thereof when the receiver comes online. A central tracker receives an indication from the sender that the sender has the file; determines if the receiver is online; and initiates a storage of the file on one or more storage proxies if the receiver is not online. A proxy service can identify one or more potential storage proxies that can store the file and that each satisfy one or more predefined resource criteria. The sender can send a request to one or more of the storage proxies from the list of storage proxies to act as a storage proxy for the communication between the sender and the receiver. The potential storage proxies compare one or more resource measures to predefined criteria; and provide an acceptance if the one or more resource measures satisfy the predefined criteria.
Owner:MICROSOFT TECH LICENSING LLC +1
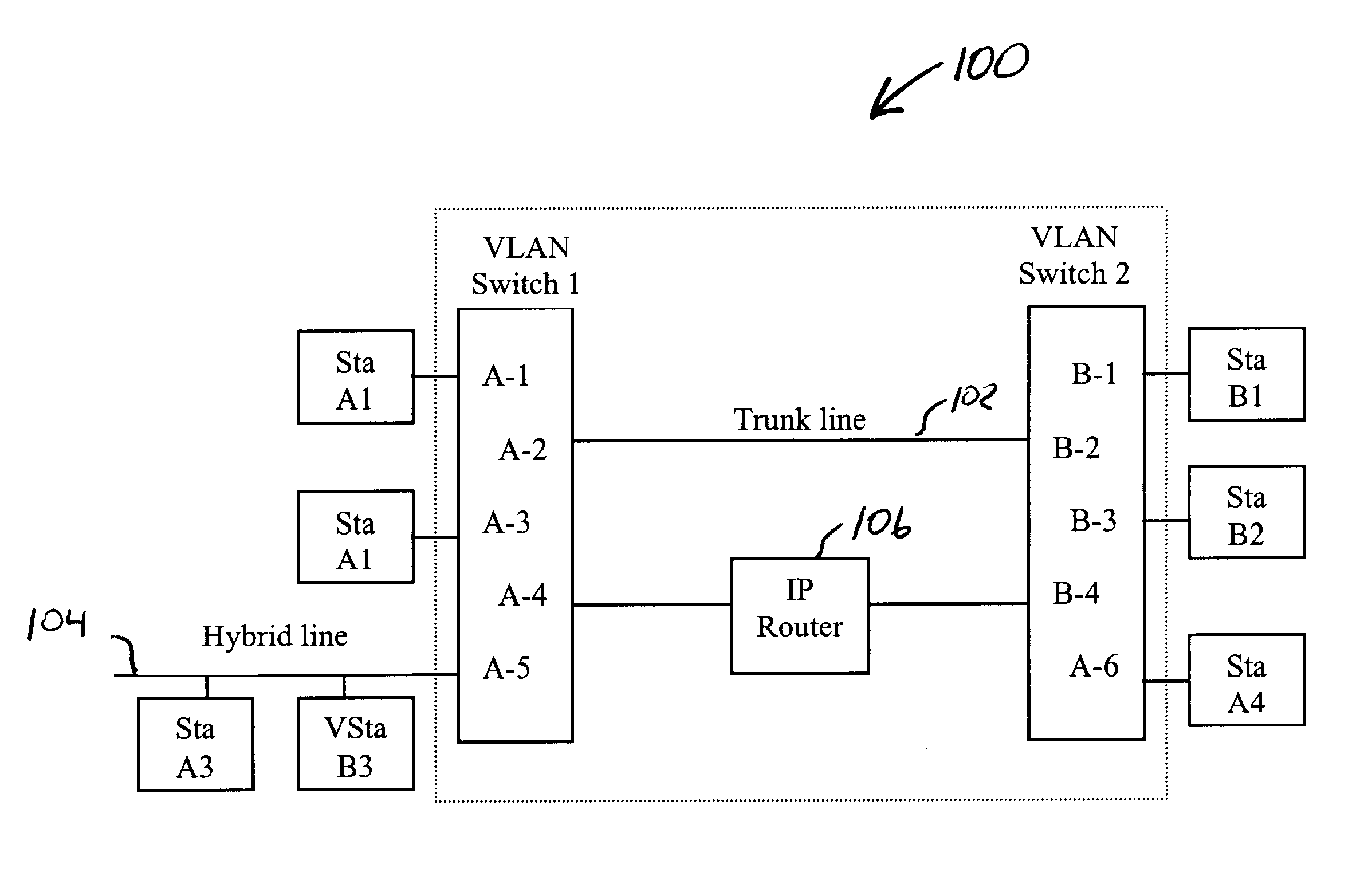
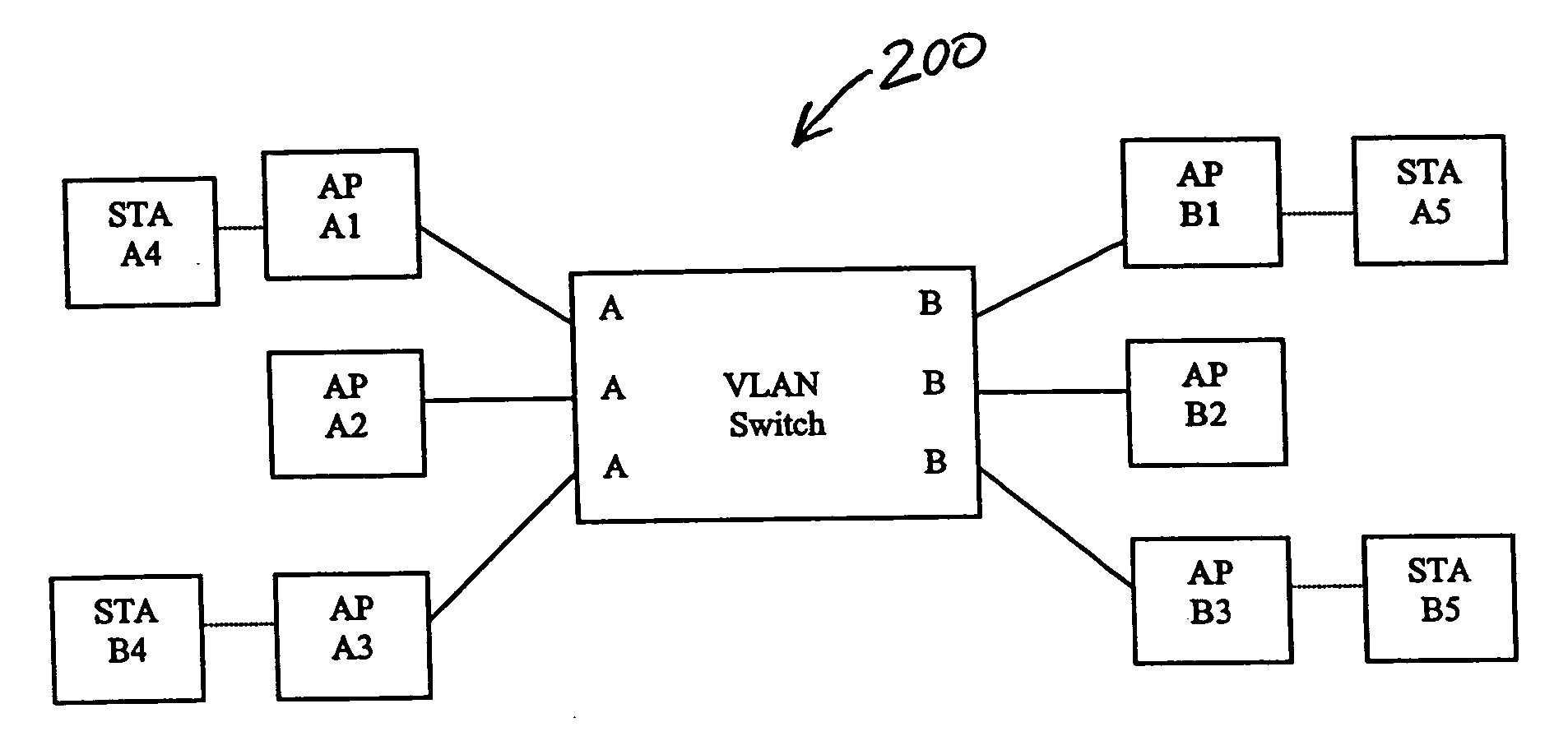
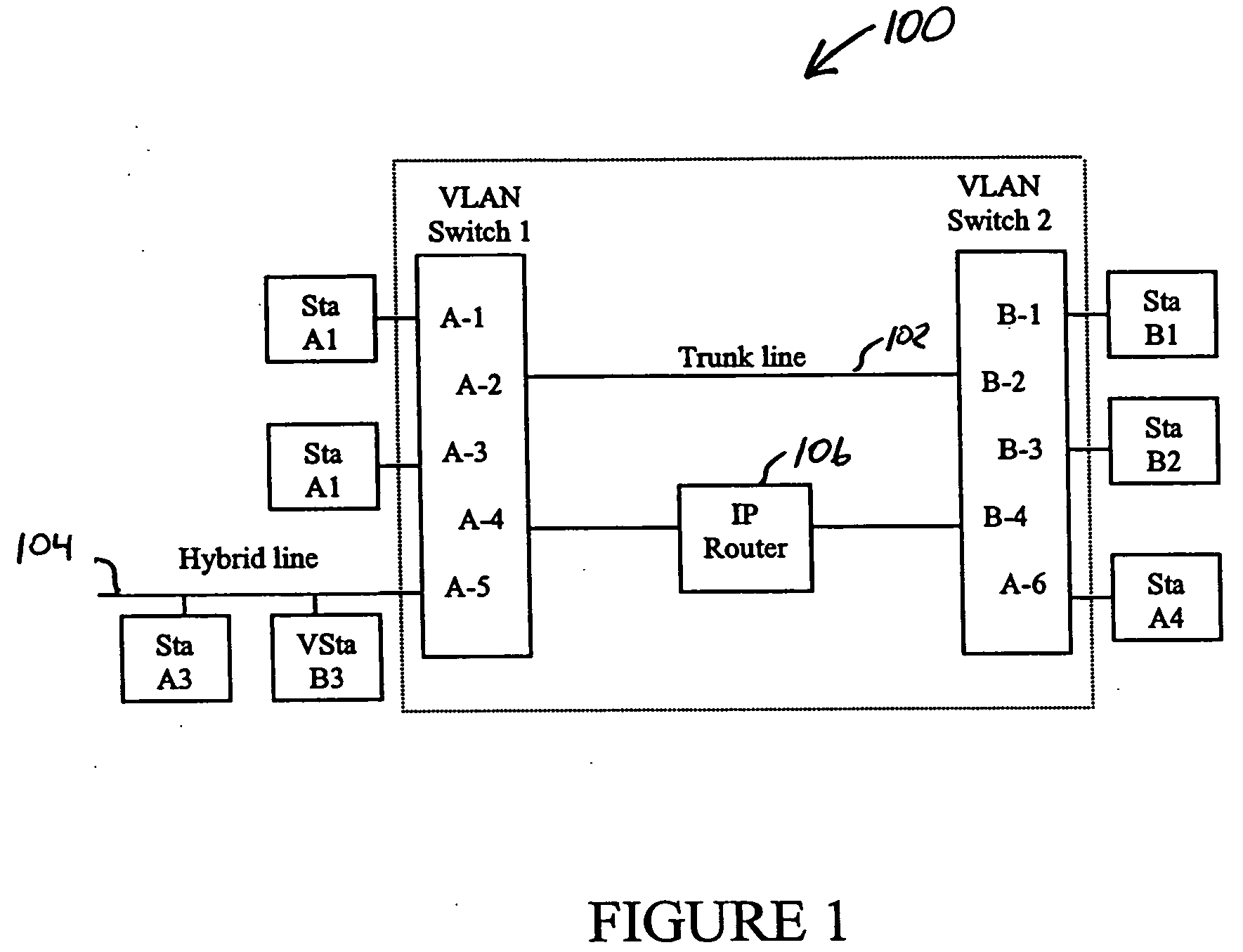
Mobile virtual LAN
InactiveUS6847620B1Not burdened with associated computational overheadNetwork topologiesWireless network protocolsCommunications systemVirtual LAN
A communication system in which multiple protocols and proxy services are executed by an access point. In one embodiment of the invention, GVRP and GMRP registrations are combined in a single packet when a wireless device roams to a different VLAN. In addition, outbound GVRP and GMRP multicast messages are handled by an access point (also referred to as a GVRP and GMRP “gateway”) such that the wireless device is not burdened with the associated computational overhead. In a further embodiment, a wireless device may dynamically switch between a VLAN-aware state and a VLAN-unaware state depending on the nature of a detected access point. For example, if a relevant access point supports GVRP, the wireless device may operate as a VLAN terminal. If a wireless device is not attached to an access point with a matching VLAN ID, the wireless device sends and receives VLAN tagged frames. If a wireless device configured with a VLAN ID is attached to an access point with a matching VLAN ID, or if the wireless device is attached to a non-VLAN access point, then the wireless device may send and receive raw / untagged frames. In addition to the gateways described below, the ability of a wireless device to detect when it can send untagged frames is considered novel. In another embodiment of the invention, a special ID that is different than the native VLAN ID for a switch port is used for VLAN-unaware devices. This allows such devices that do not issue tagged frames to belong to a single VLAN ID.
Owner:AVAGO TECH INT SALES PTE LTD
System and method for establishing universal real time protocol bridging
InactiveUS20070171898A1Exemption stepsSpecial service for subscribersNetwork connectionsTime-division multiplexingConference call
An apparatus and methods for Real Time Protocol (RTP) based bridging to create calls to and From any communication devices connected to the Public Switched Telephone Network (PSTN) or any public or private Internet Protocol network. The methods are represented in controls residing either in an RTP Bridge apparatus or as middleware on a service creation platform, softswitch, or SIP proxy services incorporating SIP bridging and SIP call relay technologies, with an interface to a TDM (Time Division Multiplexing) switch operated by a Local Exchange Carrier (LEC) or Competitive LEC (CLEC), or hosted by an Internet Telephony Service Provider (ITSP) with connectivity to the PSTN through media gateways. The method permits a party to request an on demand conference call by either dialing into the apparatus from the PSTN or from any type of RTP communication device such as an IP phone; or using a form of signaling from RTP translation device. The moderator initiates the request, enters the participant(s) to be included in the call, and the launch sequence is initiated and the apparatus makes contact with the phone / end point and uses RTP bridging to interlace the packet streams and deliver one stream back to all the devices. The advantage is an on demand conference call to one or many participants, on similar or different communications platforms.
Owner:XTELTEK
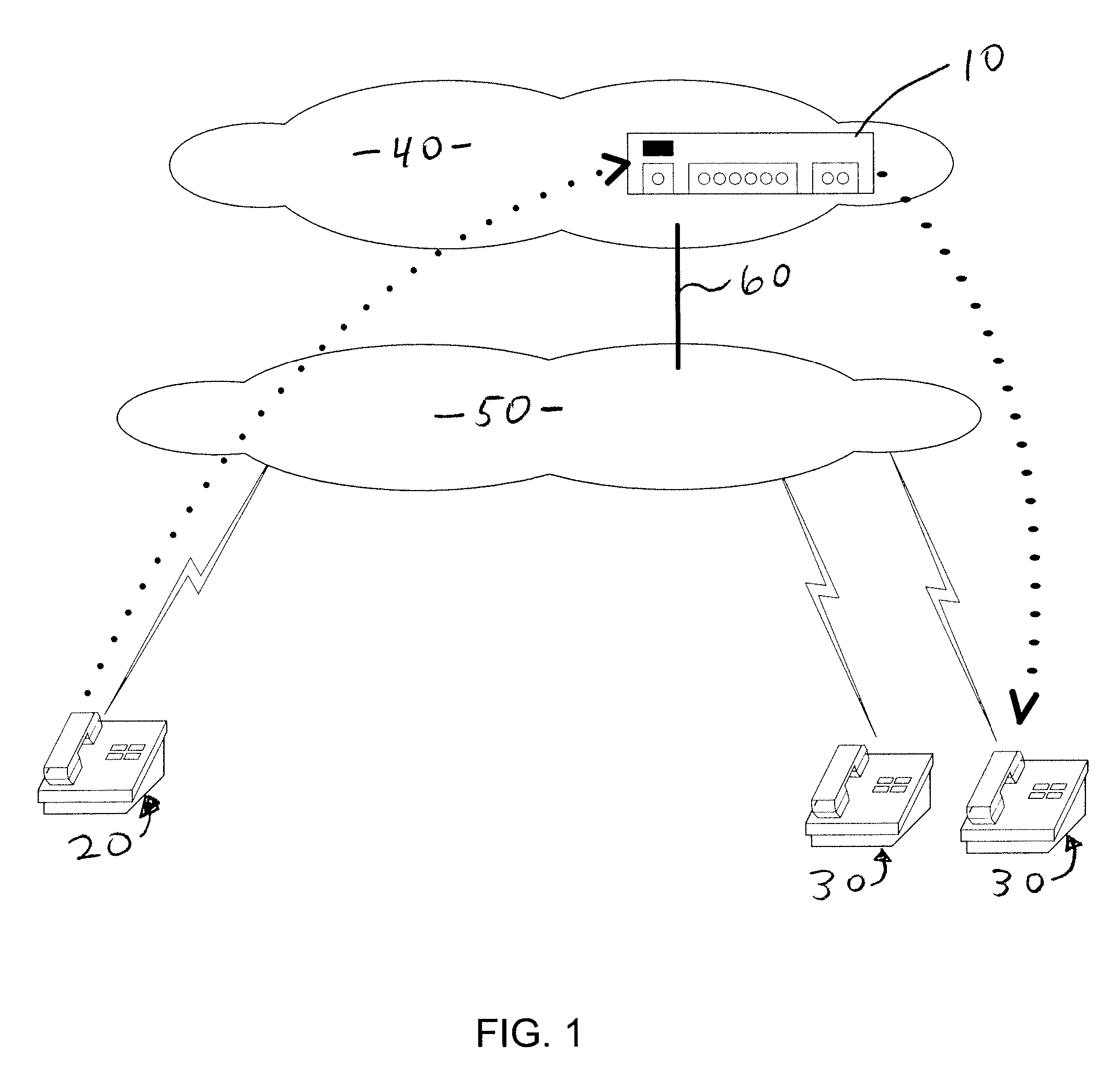
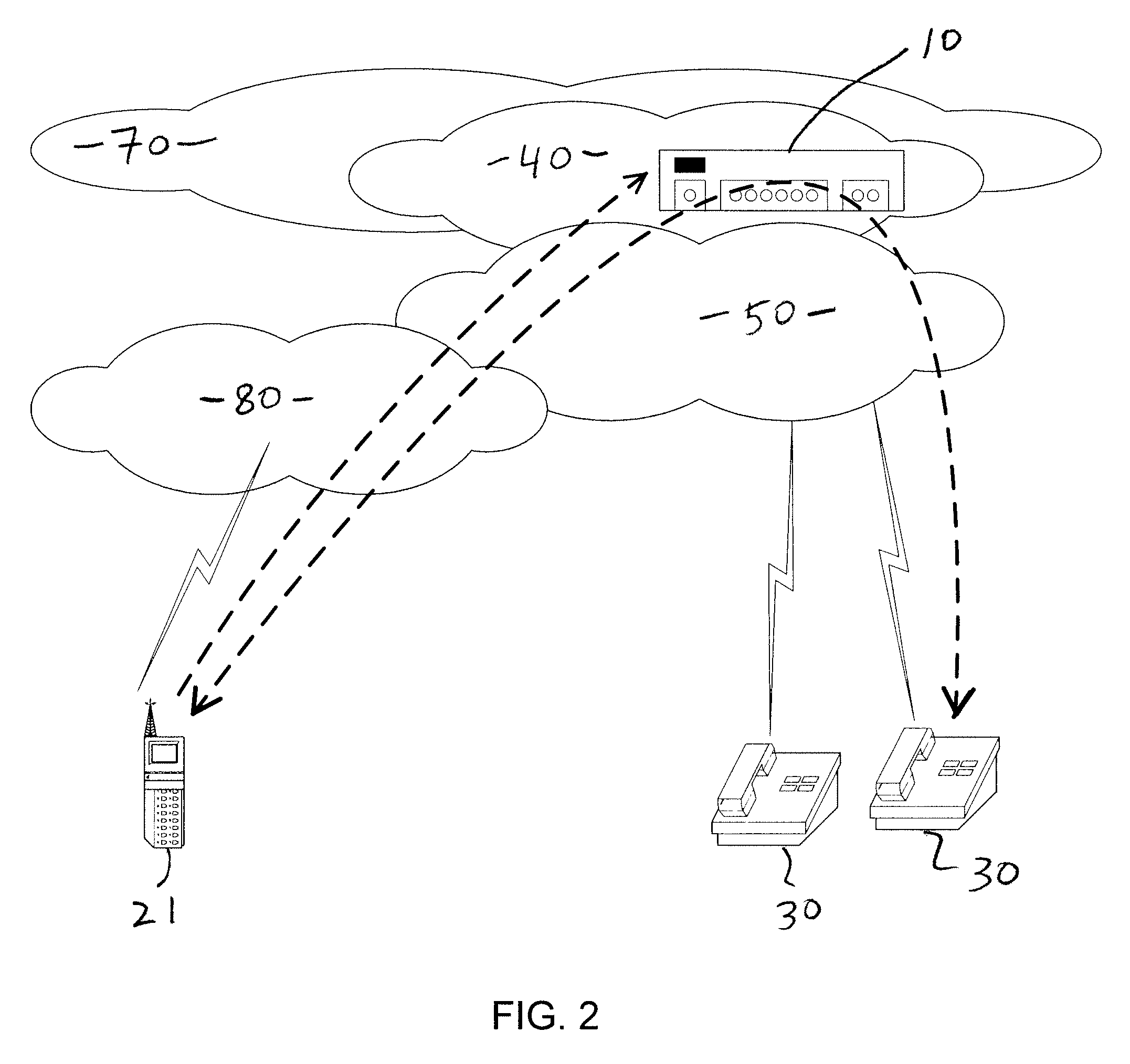
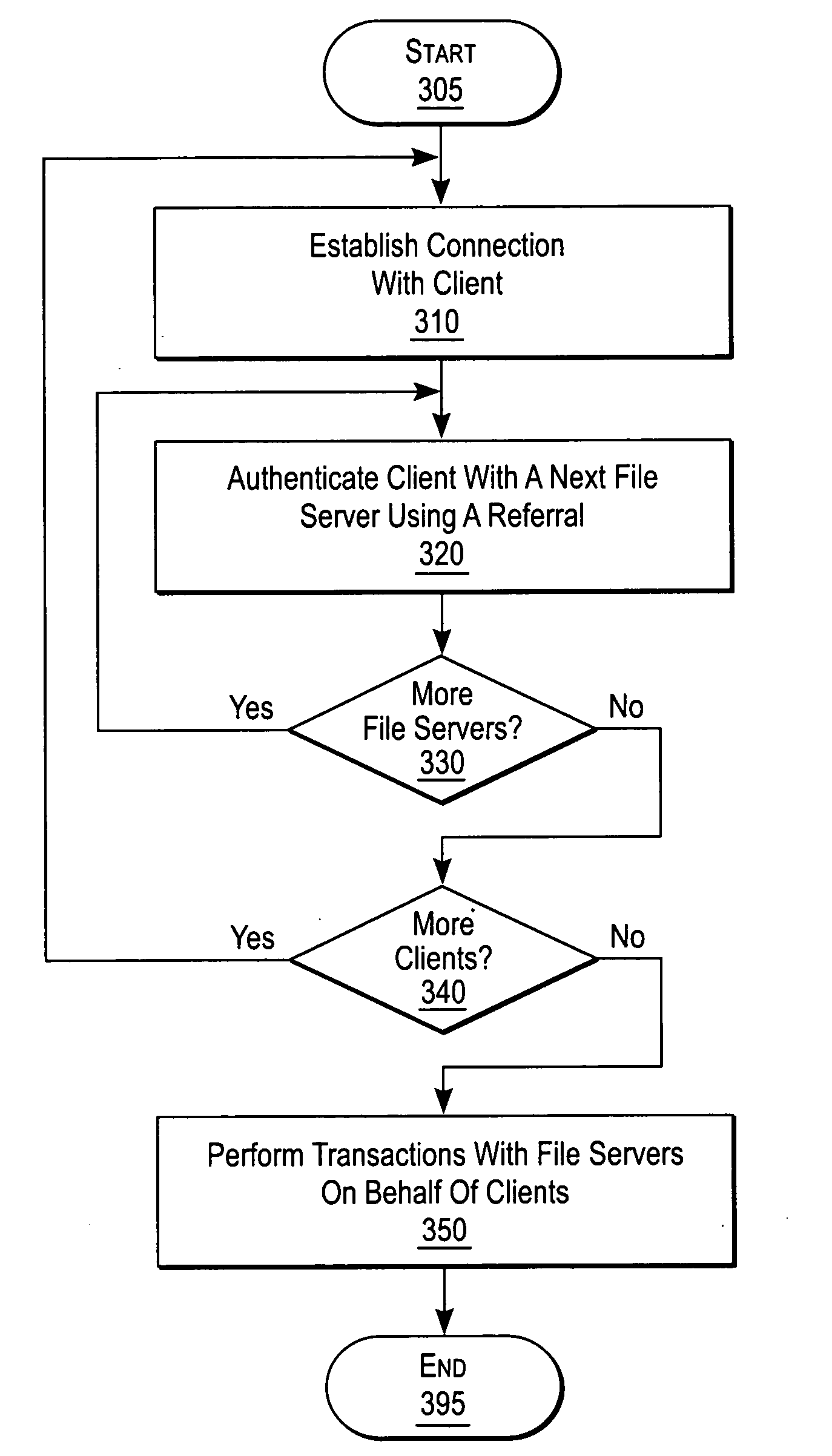
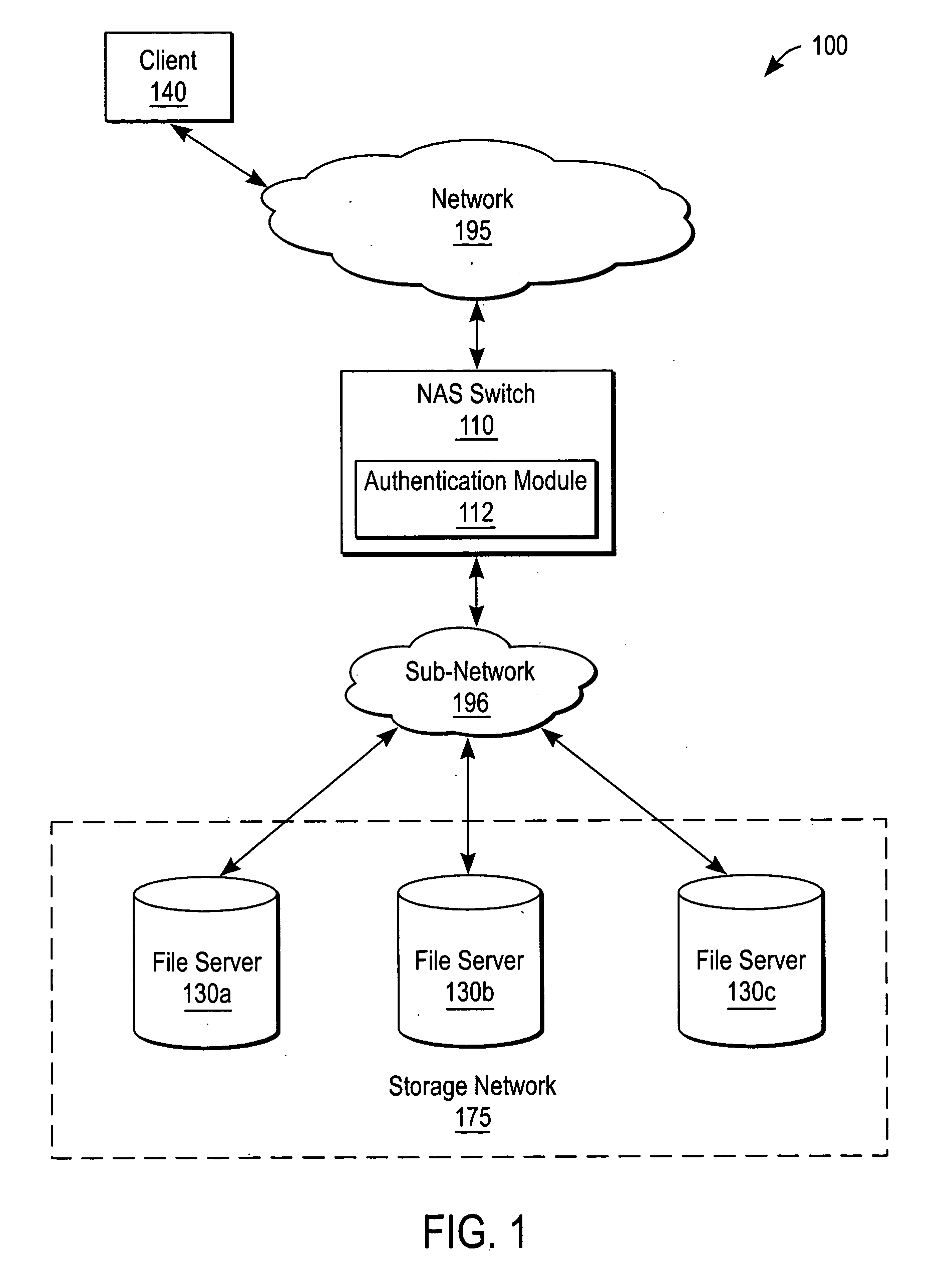
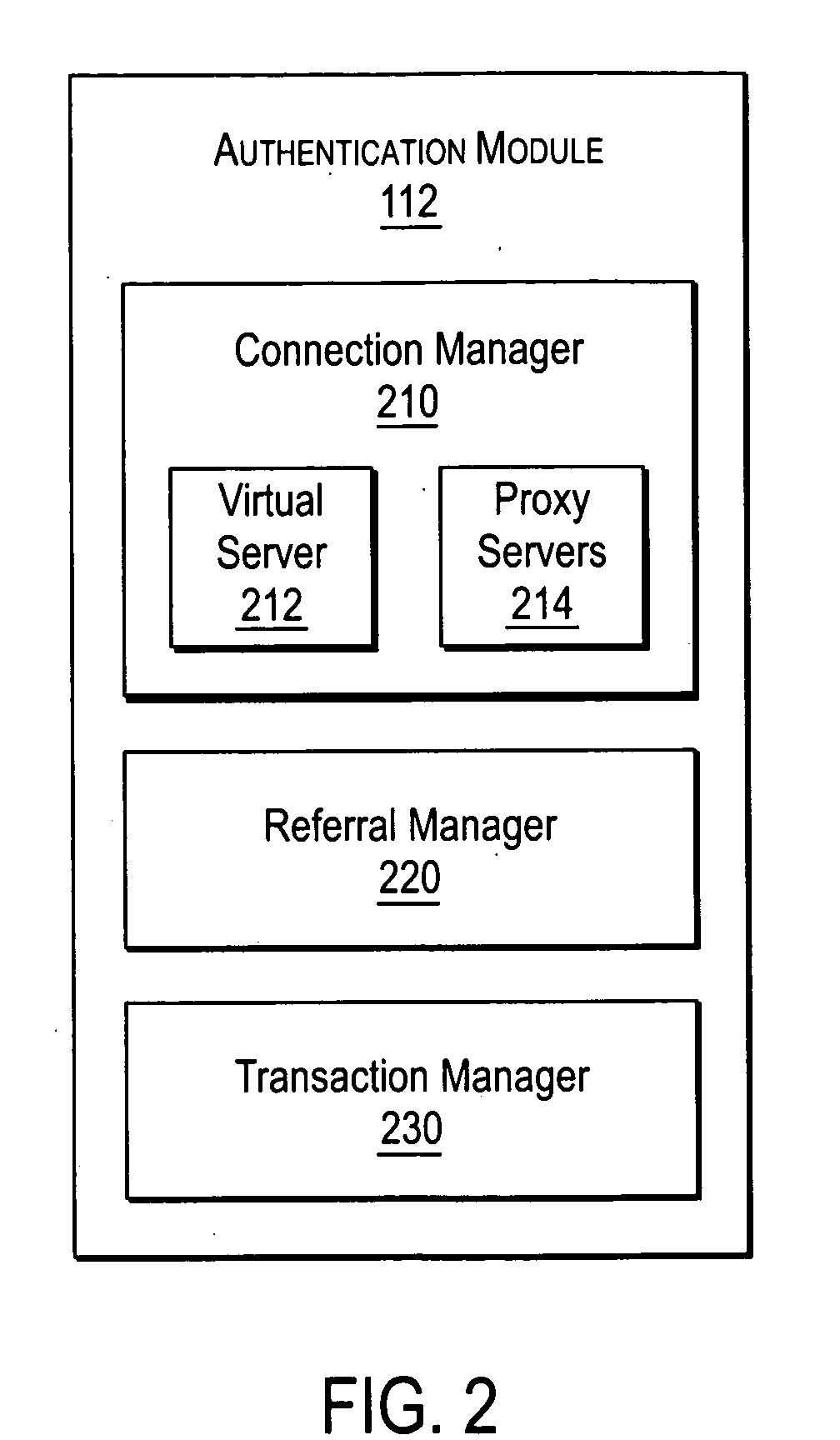
Enabling proxy services using referral mechanisms
ActiveUS20050125503A1Maintaining safety standardMultiple digital computer combinationsSecuring communicationNetwork connectionDistributed File System
A NAS (Network Attaches Storage) switch authenticates a client on multiple file servers for proxy services. The NAS switch enables proxy services by successively authenticating the client on the file servers using referrals. The NAS switch further comprises a connection manager to establish connections to the client and the file servers, a referral manager to redirect the client for successive authentications, and a transaction manager to perform data transfers with the file servers on behalf of the client. The system components support DFS (Distributed File System), and communicate using a protocol dialect that supports referral mechanisms such as NFSv4 (Network File Server version 4) or CIFS (Common Internet File System). The transaction manager also performs a protocol dialect translation service when the connection manager negotiates one protocol dialect with the client, and a different protocol dialect with the file server.
Owner:CISCO TECH INC
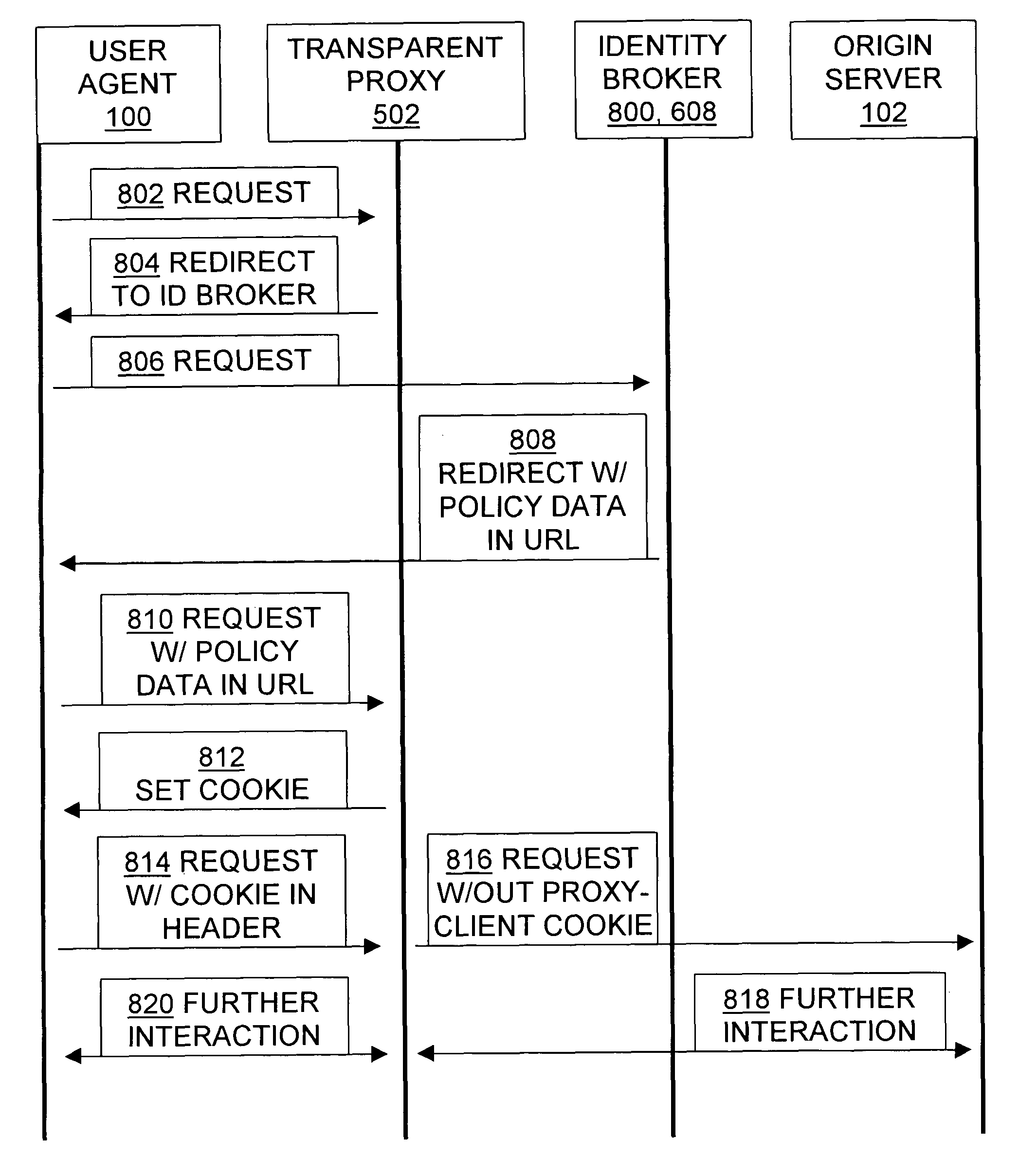
Brokering state information and identity among user agents, origin servers, and proxies
InactiveUS7954144B1Easy to useGuaranteed to continue to useDigital data processing detailsUser identity/authority verificationPerformance enhancementClient-side
Methods, signals, devices, and systems are provided for using proxy servers to transparently forward messages between clients and origin servers if, and only if doing so does not violate network policies. In some systems, a transparent proxy uses a combination of standard-format HTTP commands, embedding auxiliary information in URLs and other tools and techniques to redirect an initial client request to one or more policy modules, such as a login server or an identity broker or an access control server. The policy module authenticates the request, and uses HTTP redirection to have the client transmit authorization data to the proxy. The proxy extracts the authorization data, directs the client to use a corresponding cookie, and subsequently provides the implicitly requested proxy services to the client in response to the client's subsequently providing the authorization data in a cookie. This is accomplished without requiring installation of any invention-specific software or hardware on either the client or the origin server, and also works with proxy servers that are known to the client. Unless the client request violates network policy, a person using the client will generally perceive no reduction of services, and will instead benefit from the proxy's caching and / or other performance enhancements.
Owner:RPX CORP
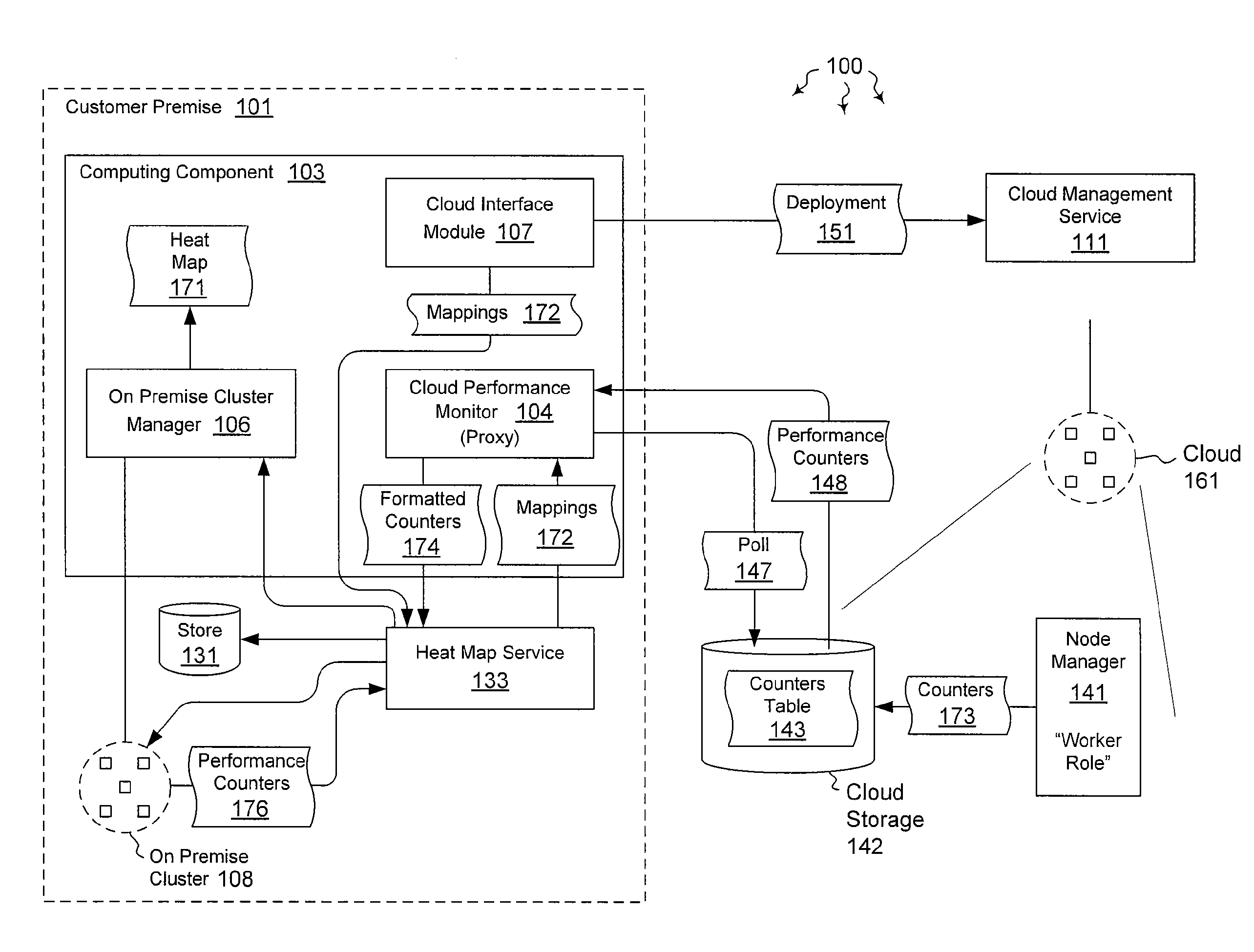
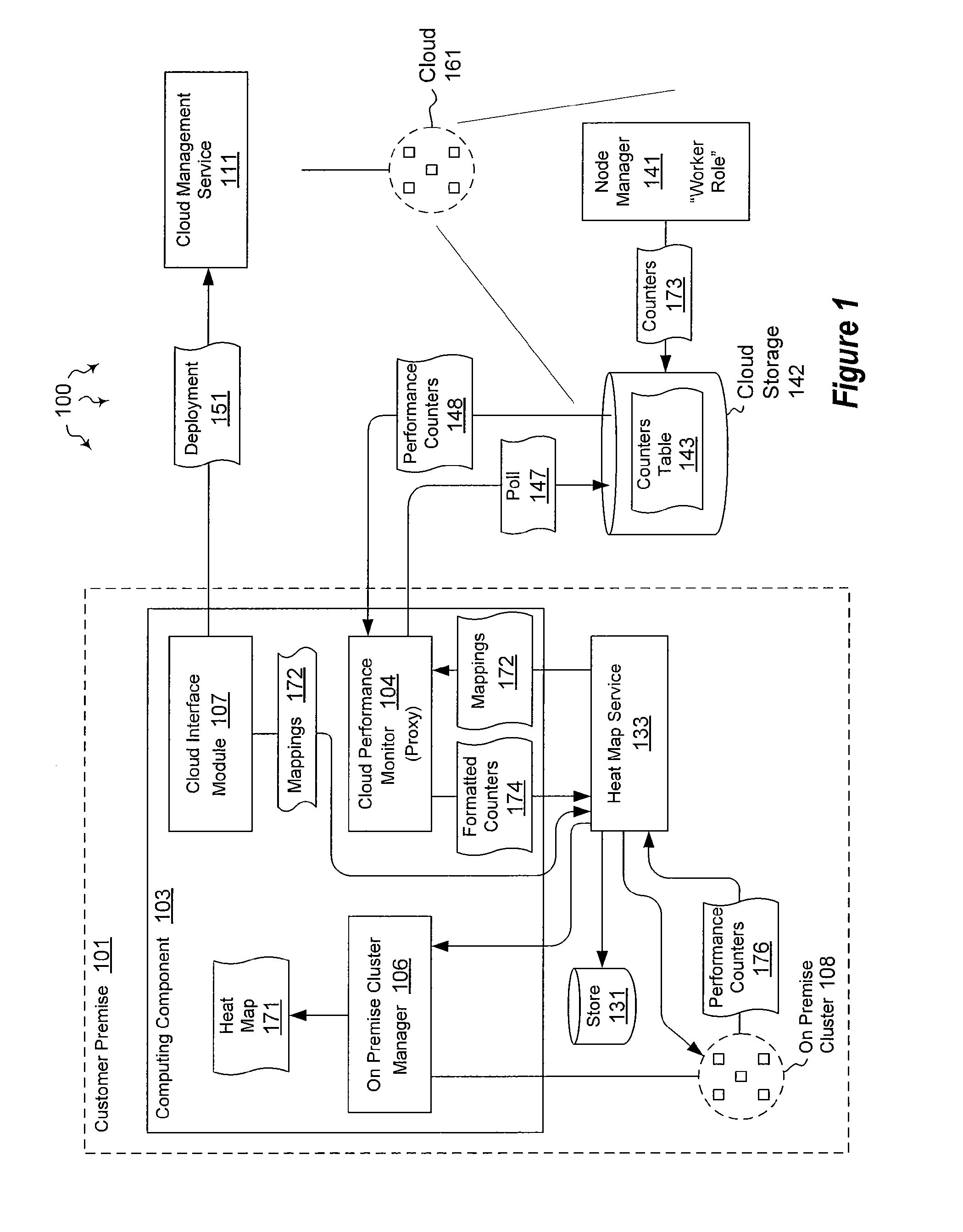
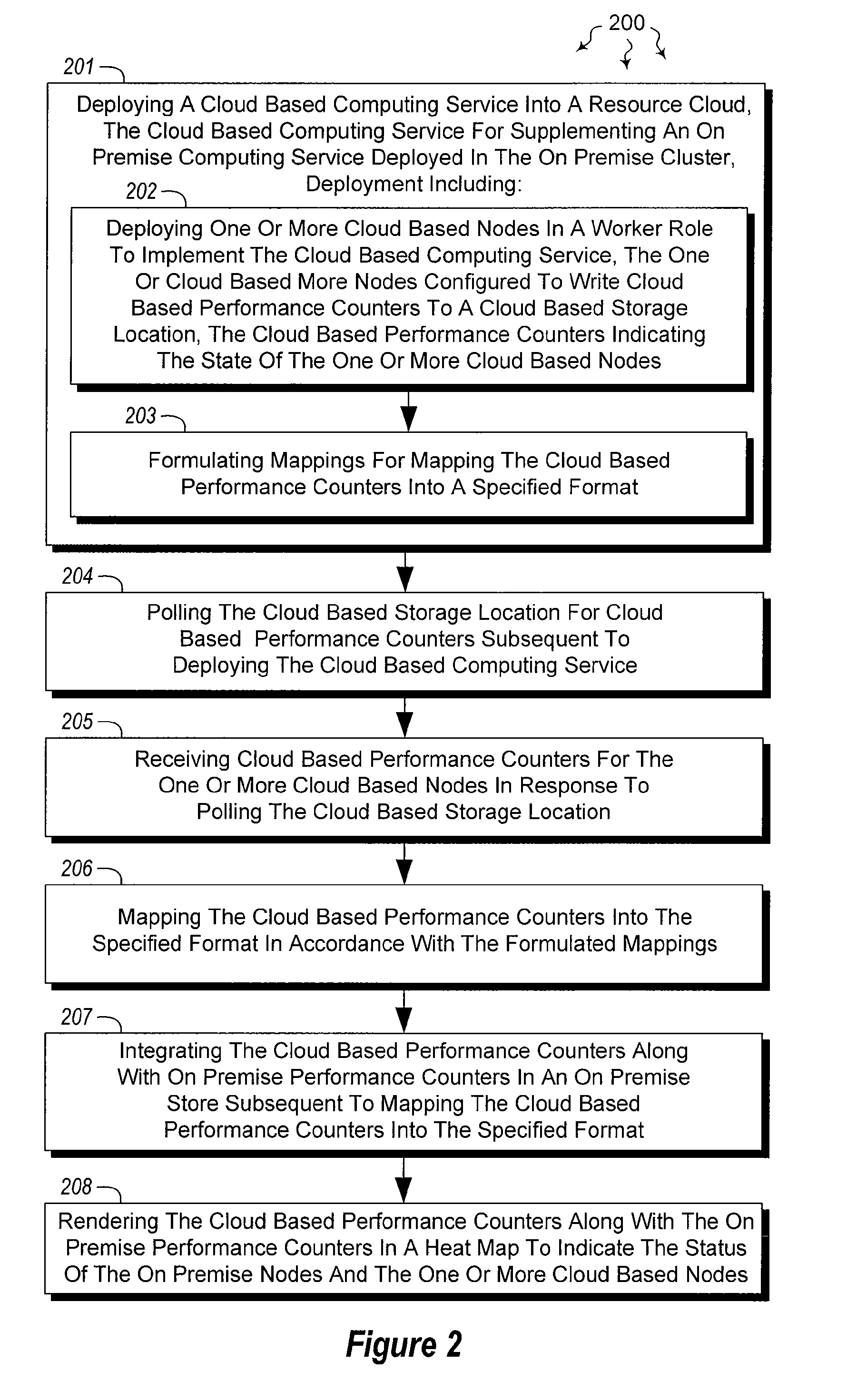
Integrating external and cluster heat map data
ActiveUS20120072578A1Well formedError detection/correctionMultiple digital computer combinationsTimestampHeat map
The present invention extends to methods, systems, and computer program products for integrating external and cluster heat map data. Embodiments of the invention include a proxy service that manages (e.g., asynchronous) communication with cloud nodes. The proxy service simulates packets to on-premise services to simplify the integration with an existing heat map infrastructure. The proxy maintains a cache of performance counter mappings and timestamps on the on-premise head node to minimize the impact of latency into heat map infrastructure. In addition, data transfer is minimized by mapping a fixed set of resource based performance counters into a variable set of performance counters compatible with the on premise heat map infrastructure.
Owner:MICROSOFT TECH LICENSING LLC
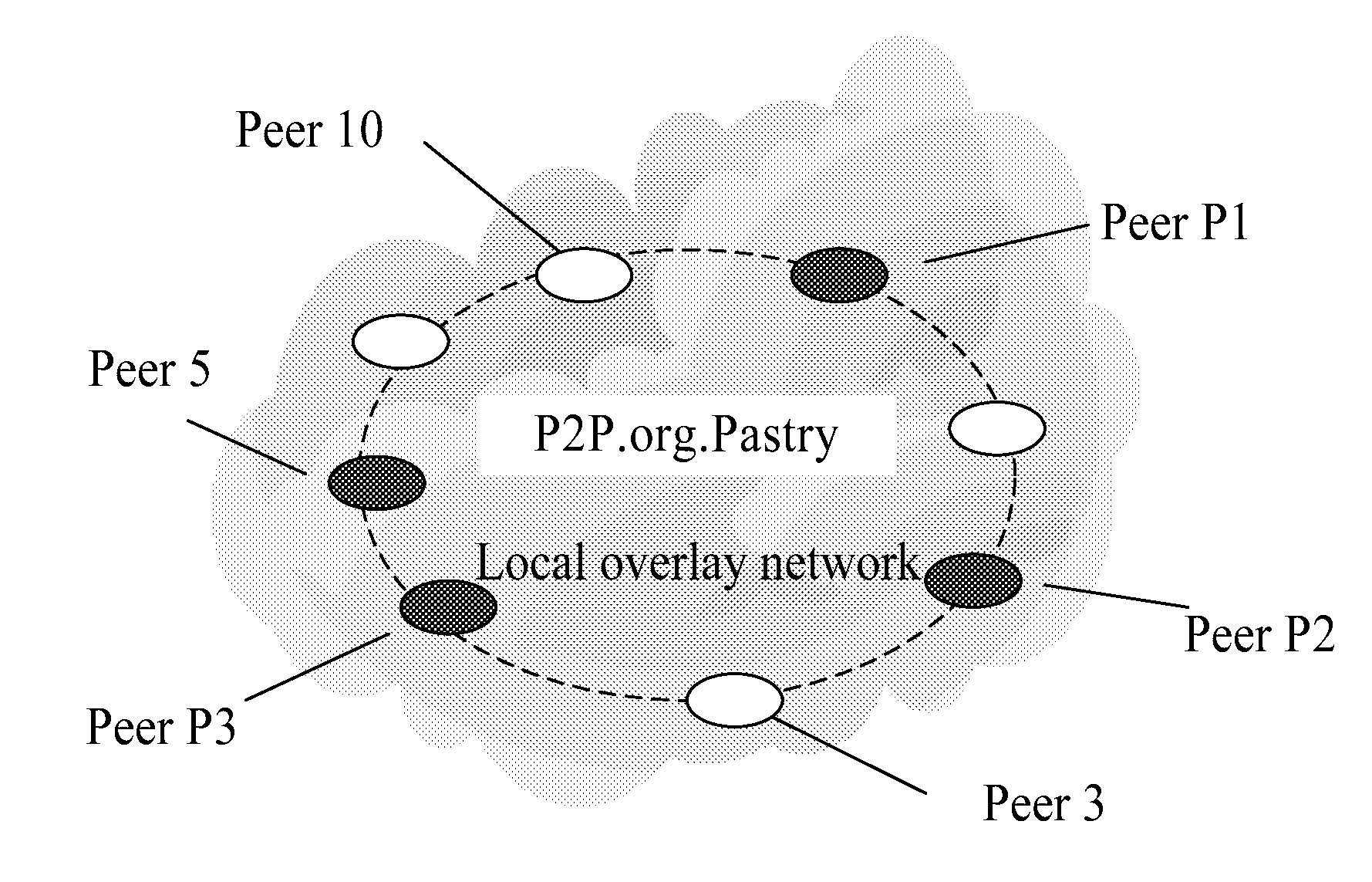
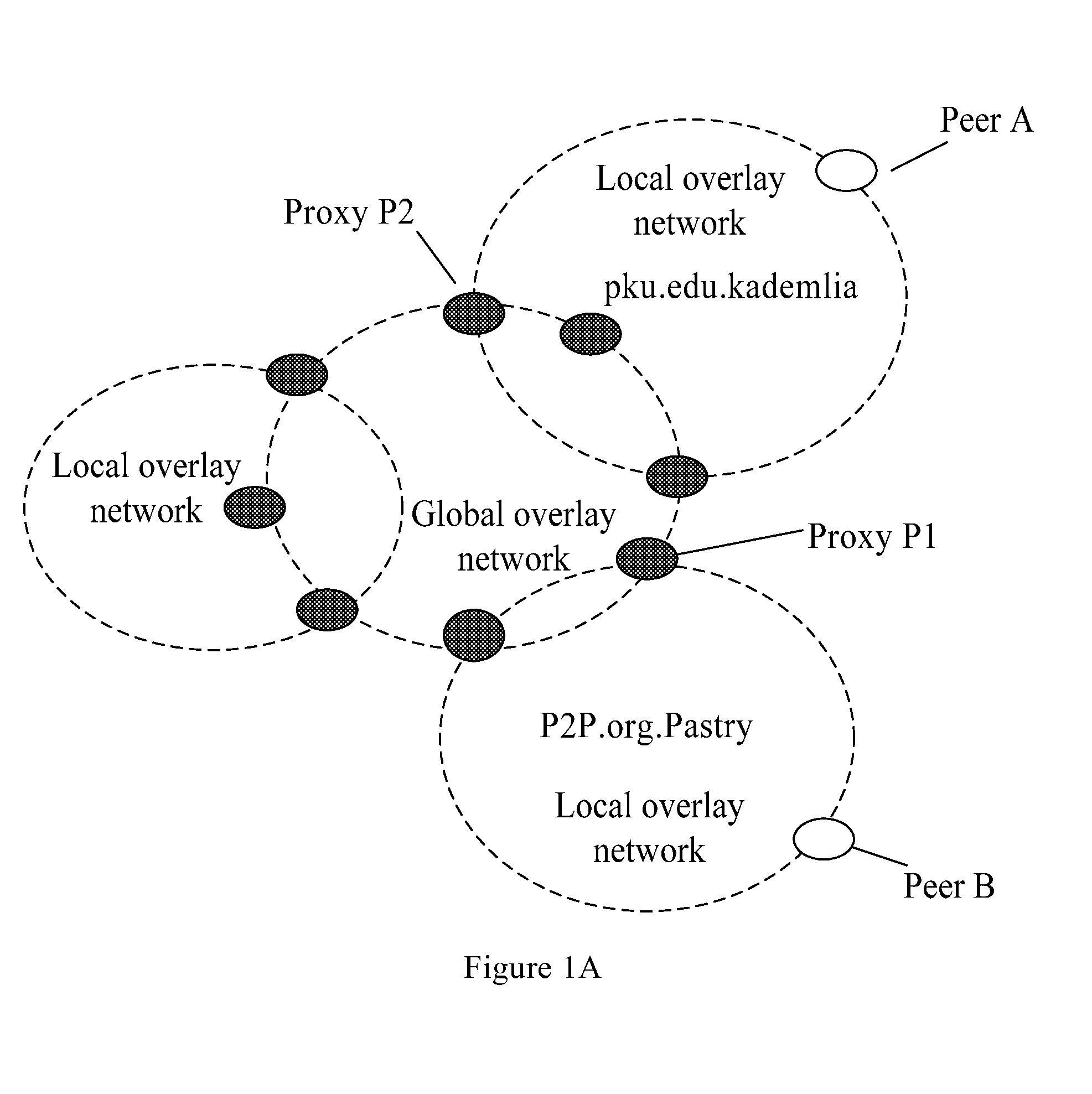
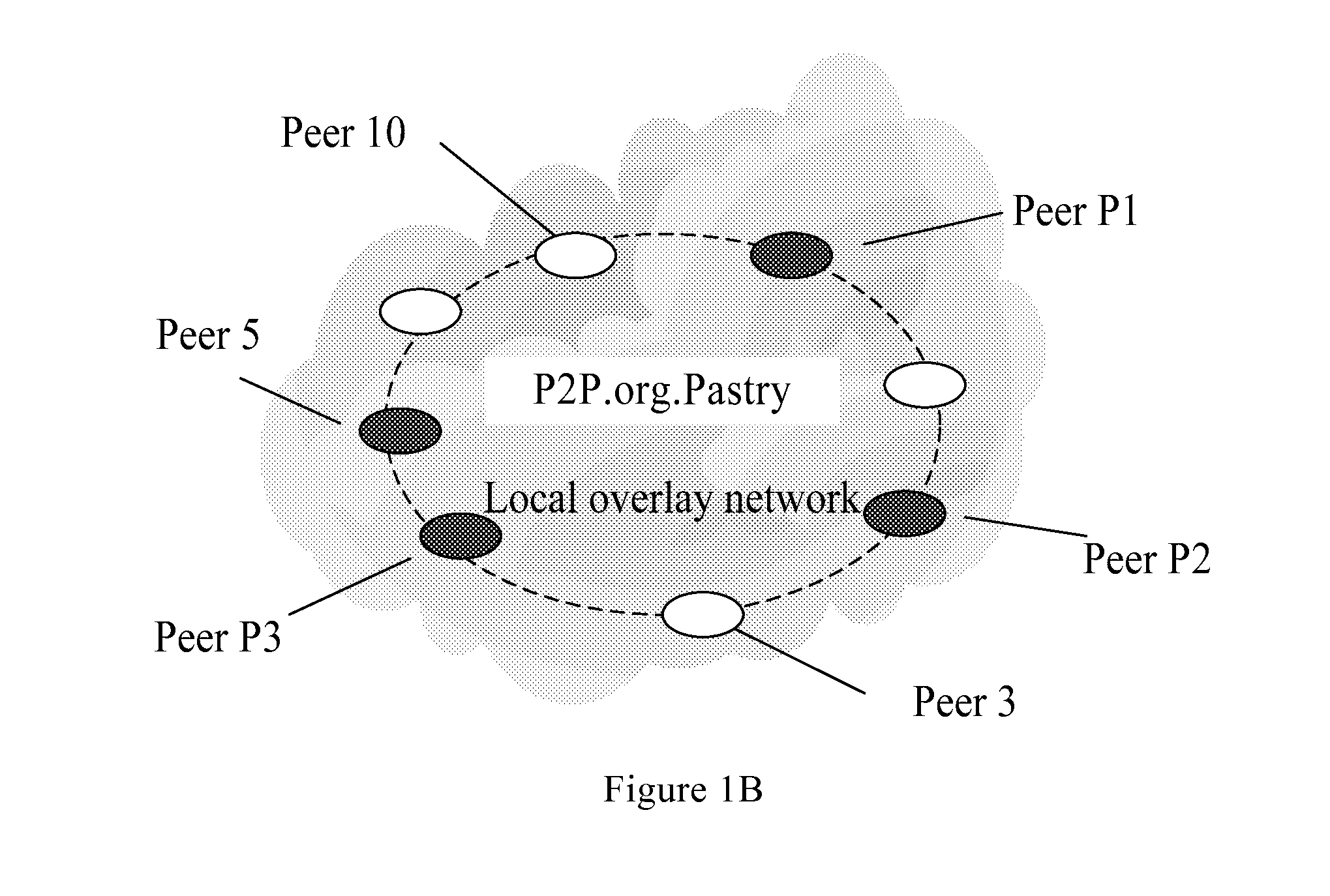
Peer-to-peer network system, proxy service peer, and method for peer interworking between overlay networks
ActiveUS20100064008A1Reduce loadImprove response speedUser identity/authority verificationMultiprogramming arrangementsPeer-to-peerOverlay network
The present invention relates to a P2P network system. The P2P network system includes: multiple local overlay networks, each comprising multiple proxy service peers; a global overlay network composed of the proxy service peers of all local overlay networks. The proxy service peer is adapted to respond to the request of the requesting peer, query the local overlay network or global overlay network, and return the address information of the requested peer or the requested proxy service peer to the requesting peer. The present invention also relates to a proxy service peer applicable to the foregoing network system, and a method of peer interworking between P2P overlay networks based on the foregoing system. The present invention relieves the load of the proxy service peer, avoids blindness of the requesting peer in selecting the proxy service peer, and achieves load balance between proxy service peers.
Owner:XFUSION DIGITAL TECH CO LTD
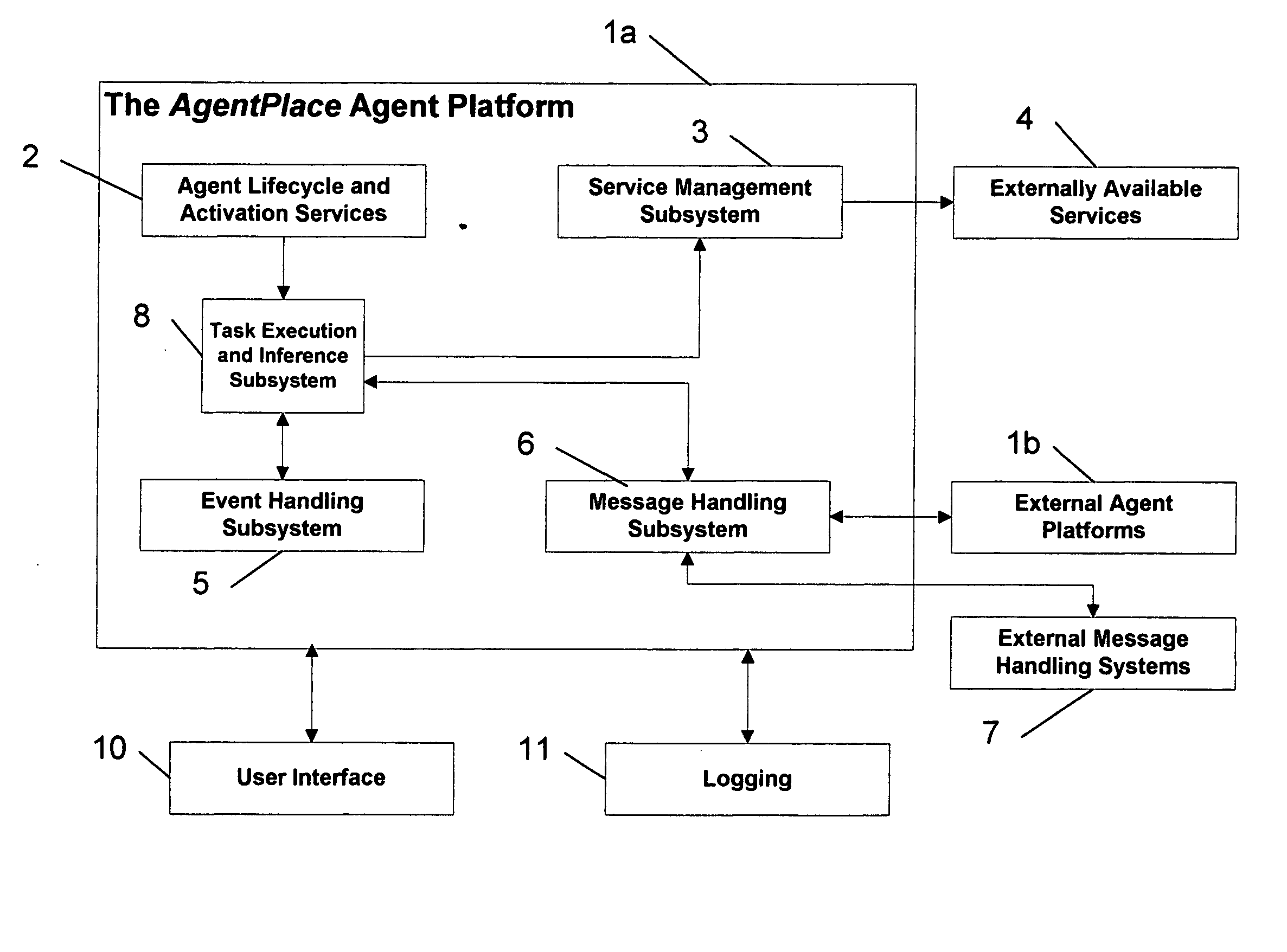
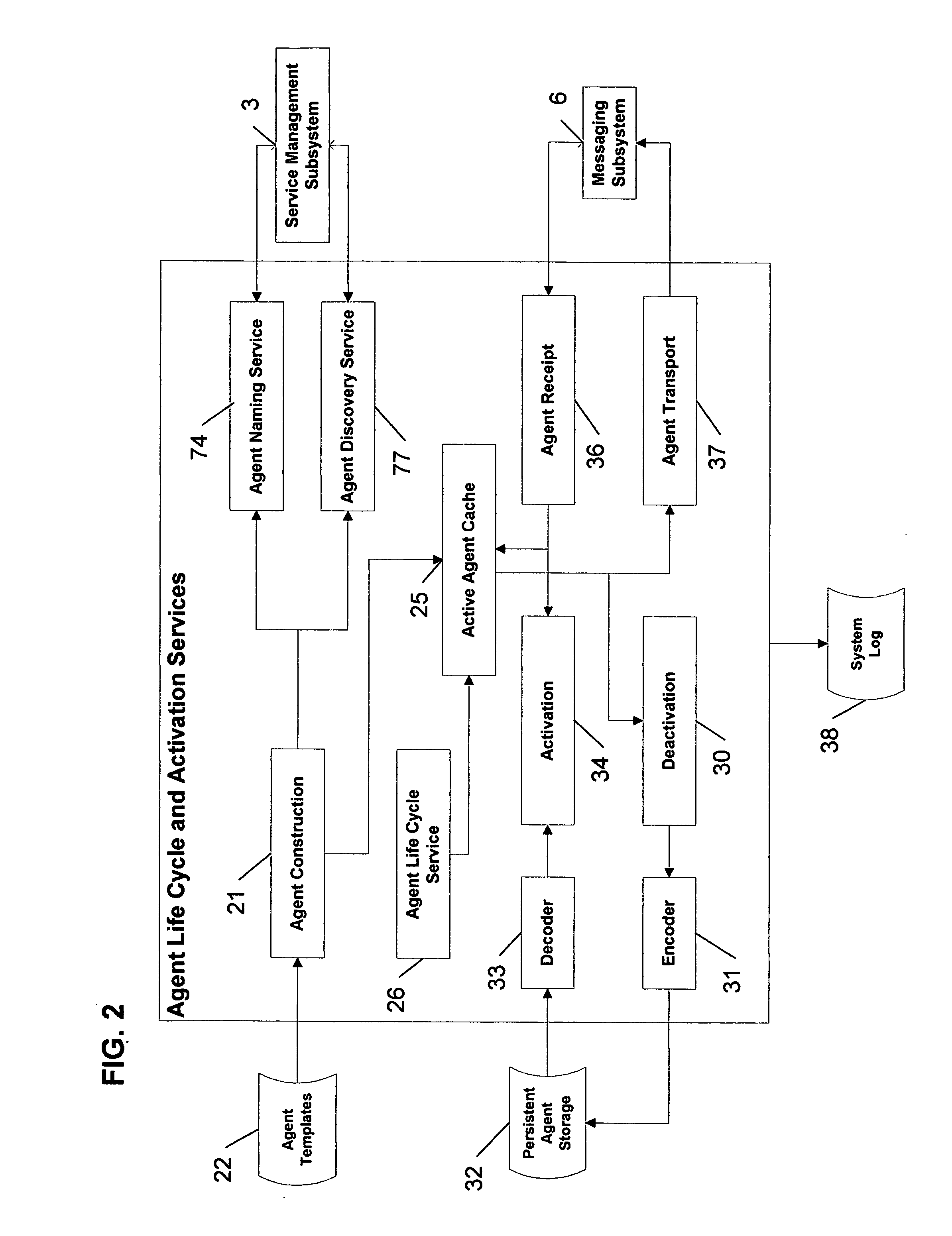
Extendible software platform for the construction and deployment of intelligent agents
InactiveUS20050144218A1Easy to specifyEasy to useResource allocationMultiple digital computer combinationsHandling systemUser interface
A system and methods for building and executing intelligent agents are disclosed. This system allows the automatic invocation of computerized software services using Boolean conditions to determine if and when a specific service or task is executed. Intelligent agents within the platform can communicate with each other through a message-handling infrastructure. The message-handing system includes methods for data encoding / decoding, encryption and transport across multiple protocols. This system also includes methods for event handling, task selection, agent mobility, and agent persistence. A graphical user interface helps individuals define and monitor agent activity. This system is highly extendible, providing methods for the addition or inclusion of alternative agent services, message-handling approaches, event-handling systems and task-handling approaches.
Owner:HEINTZ TIMOTHY JAMES
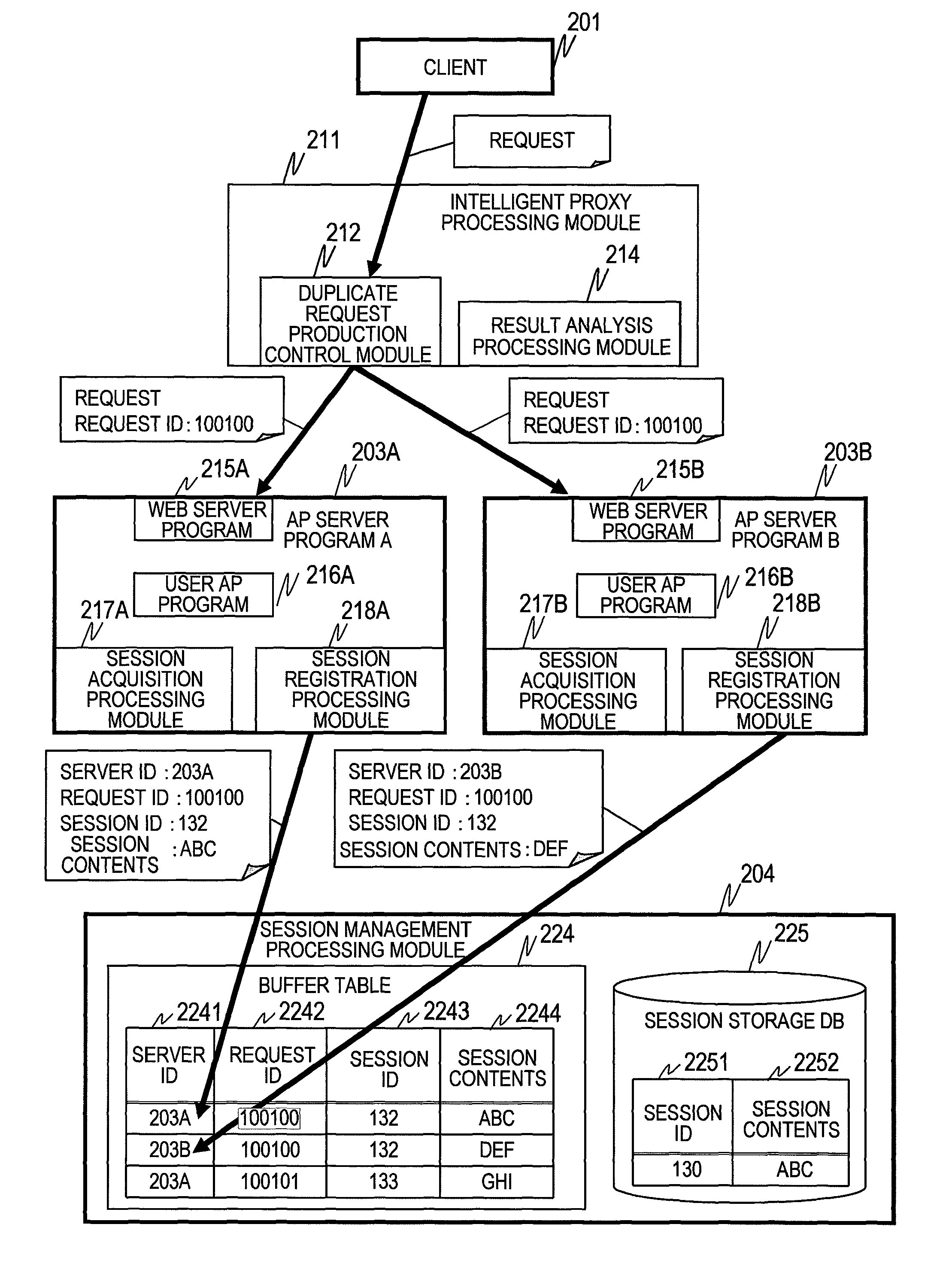
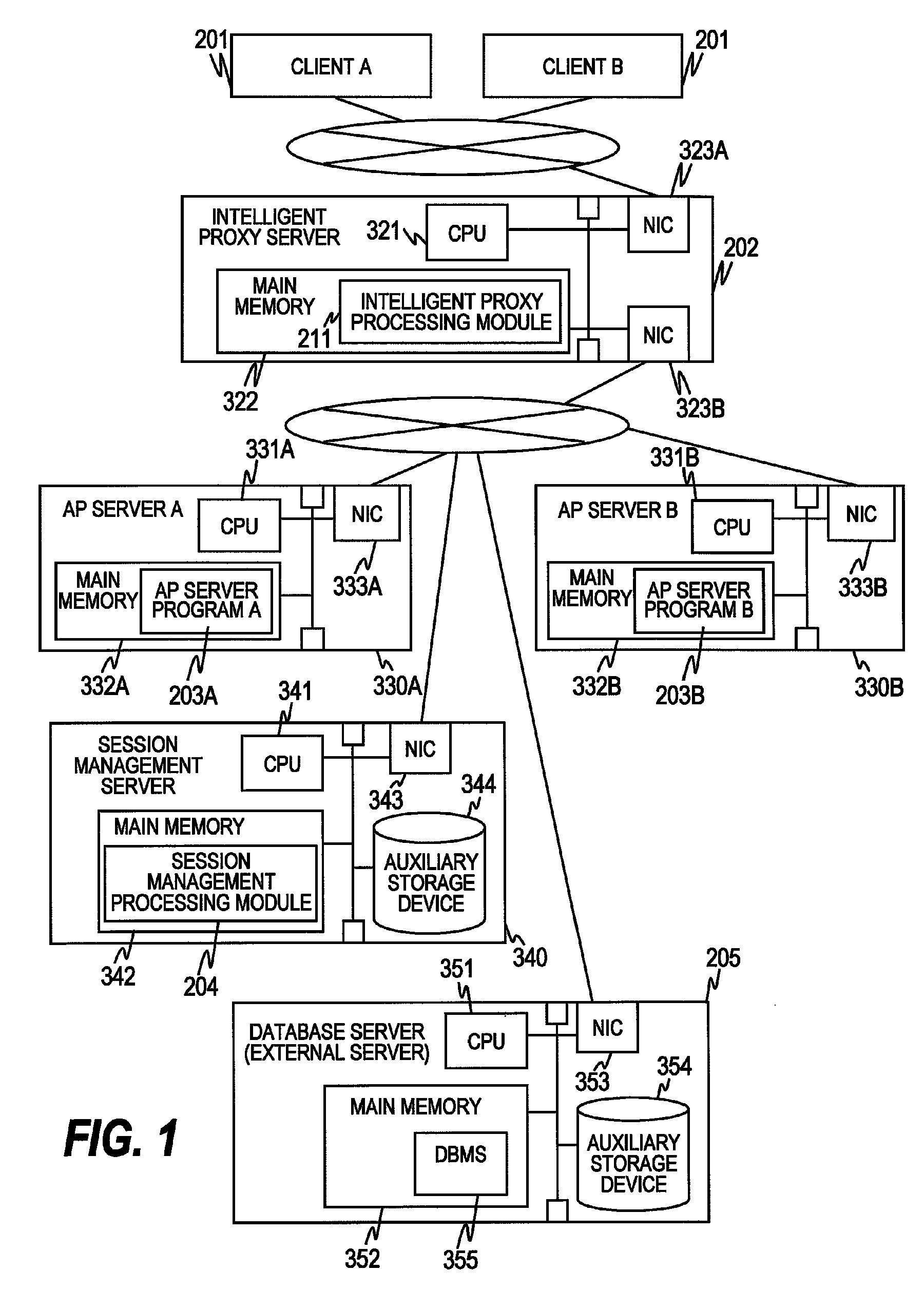
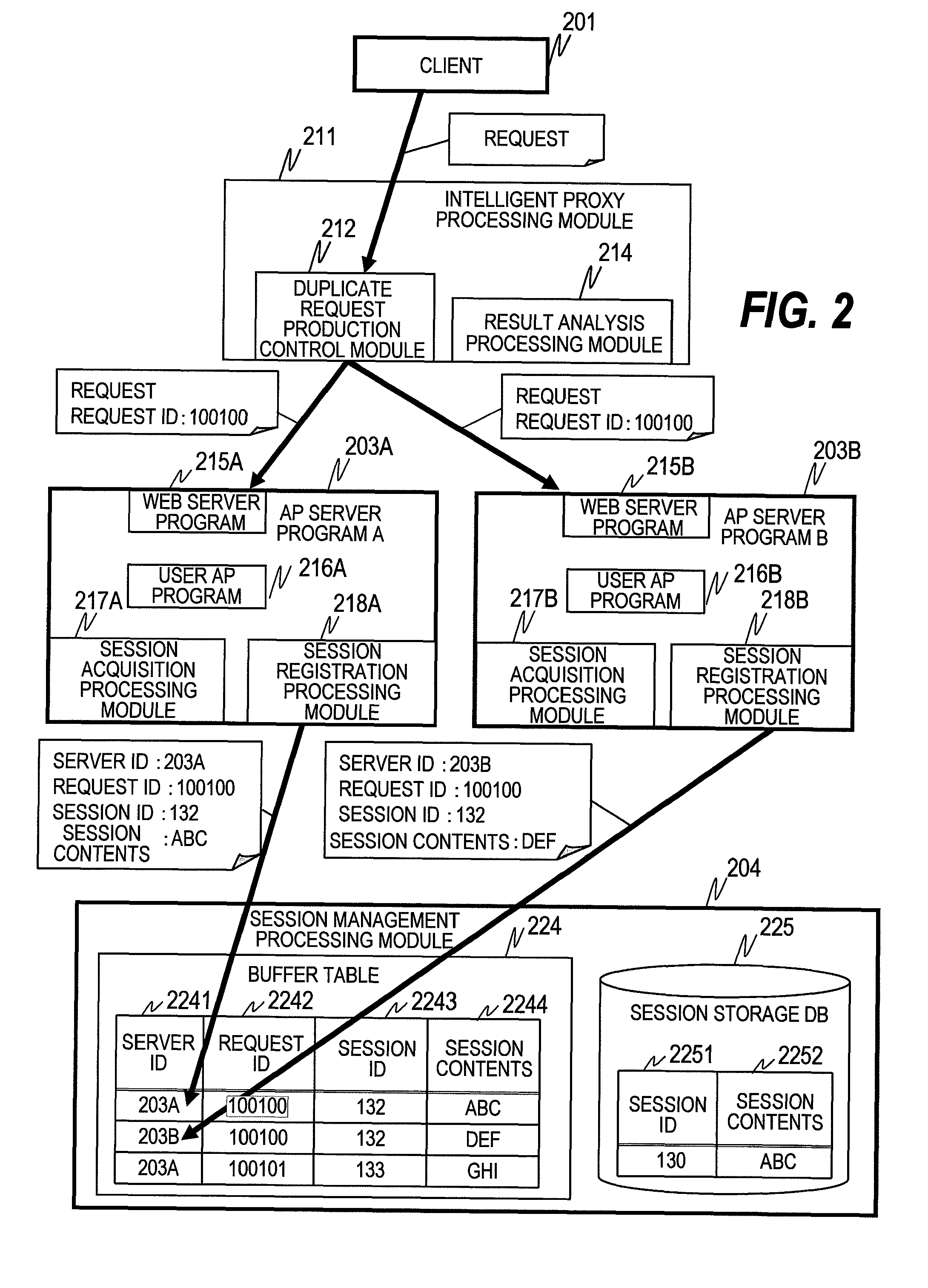
Method and apparatus for processing a request using proxy servers
InactiveUS7937437B2Error detection/correctionMultiprogramming arrangementsSession managementApplication server
Provided is a request processing method of processing a request requesting task processing in a computer system including the steps of: transmitting, by a proxy server, a first requests which is one of duplicate and original requests to application servers; transmitting, by the application servers, a result of processing of the first requests to the proxy server; notifying, by the application servers, a session management server of session information including identifiers of the application servers and identifiers of the first requests; determining, by the proxy server, a result of the processing used for responding to a client computer upon receiving the result of the processing of the first requests; and notifying, by the proxy server, the session management server of the identifiers of the application servers which have transmitted the determined processing result and an identifier of the request transmitted from the client computer.
Owner:HITACHI LTD
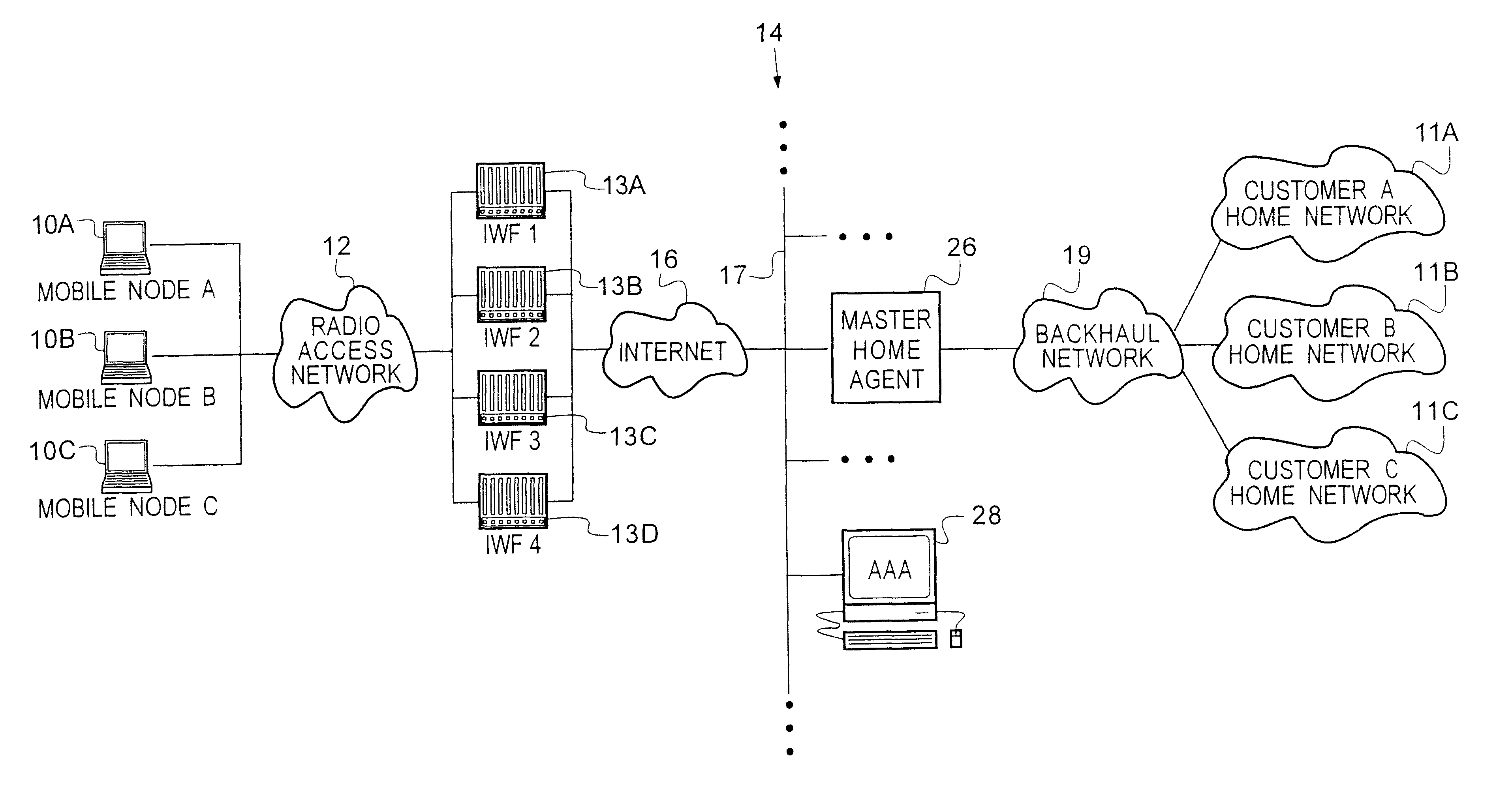
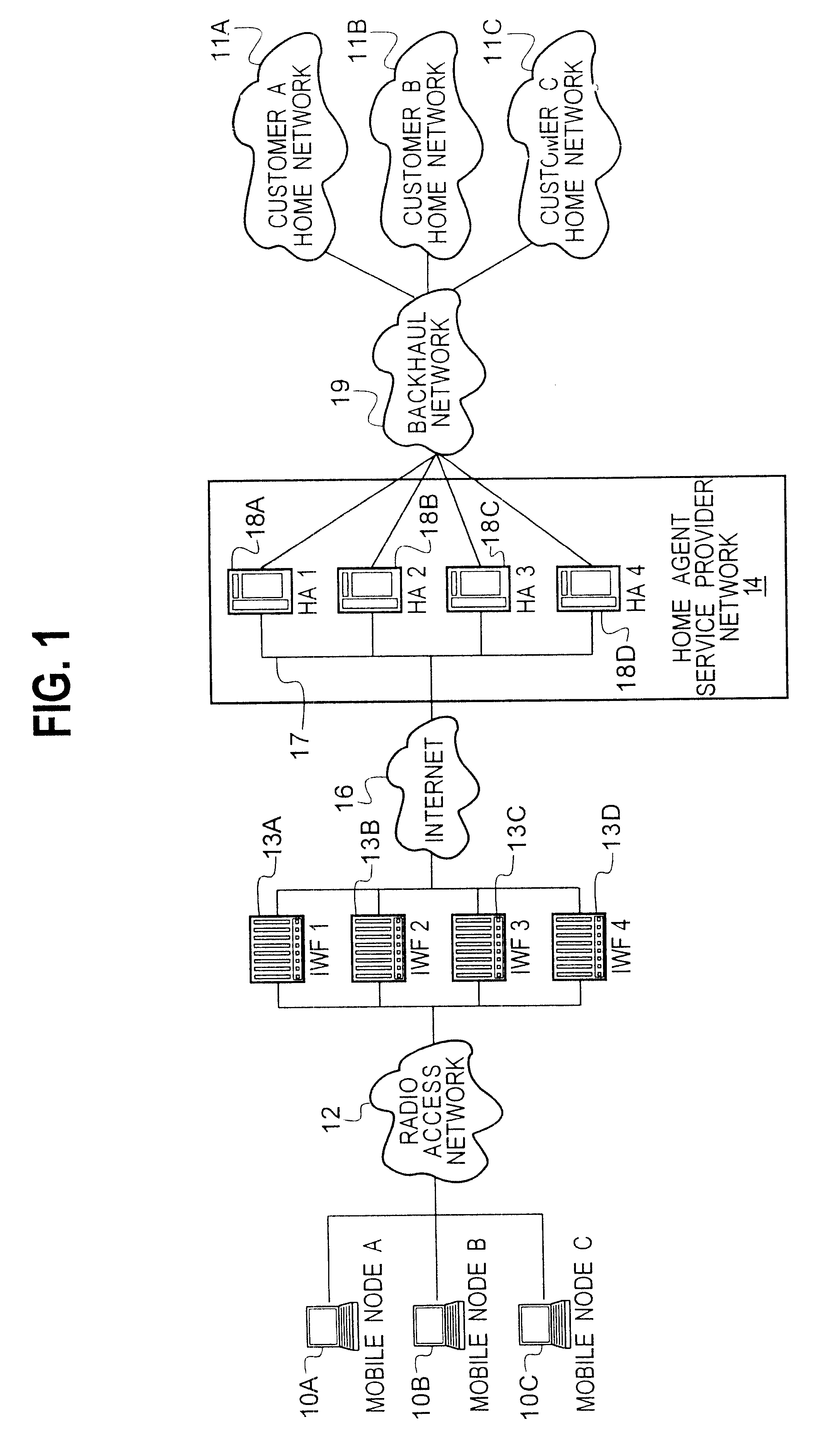
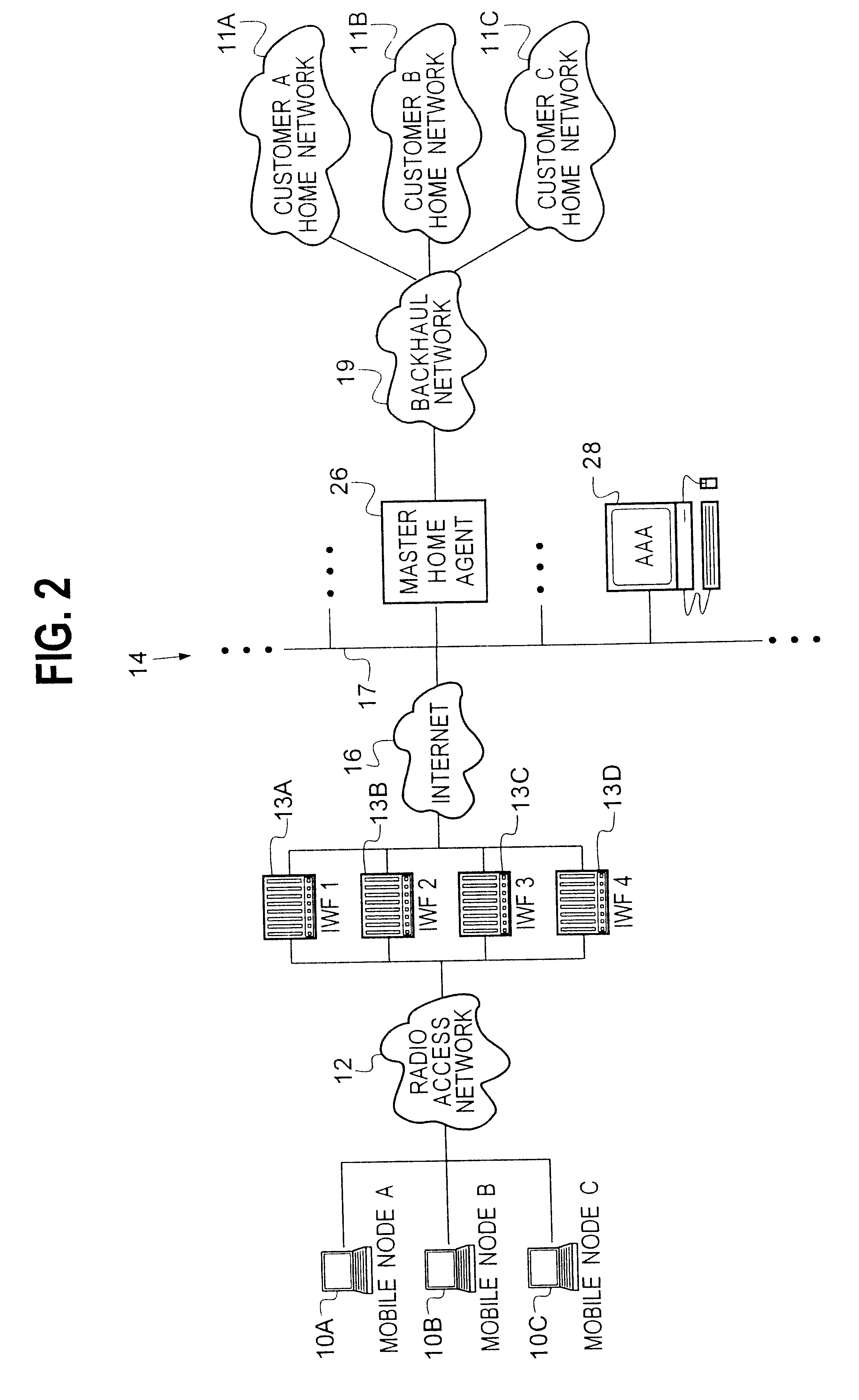
Virtual home agent service using software-replicated home agents
InactiveUS6560217B1Easy to manageMore fault tolerantData switching by path configurationMultiple digital computer combinationsPrivate networkIp address
Multiple home agents for a home agent service provider network are implemented in a single computing platform in software as multiple virtual home agents. Each home agent is assigned or dedicated to a single virtual private network. Any number of home agents can be realized in the computing platform by multiple instantiations of a home agent program or code, and by providing unique IP addresses for each instantiation. Each home agent runs independently, and is independently configured and managed by the subscriber of the virtual private network service, freeing the service provider of having to manage and supervise low level processing tasks and customization features that the subscribers may want. In a representative embodiment, the computing platform comprises a router having a general purpose-computing platform.
Owner:UTSTARCOM INC
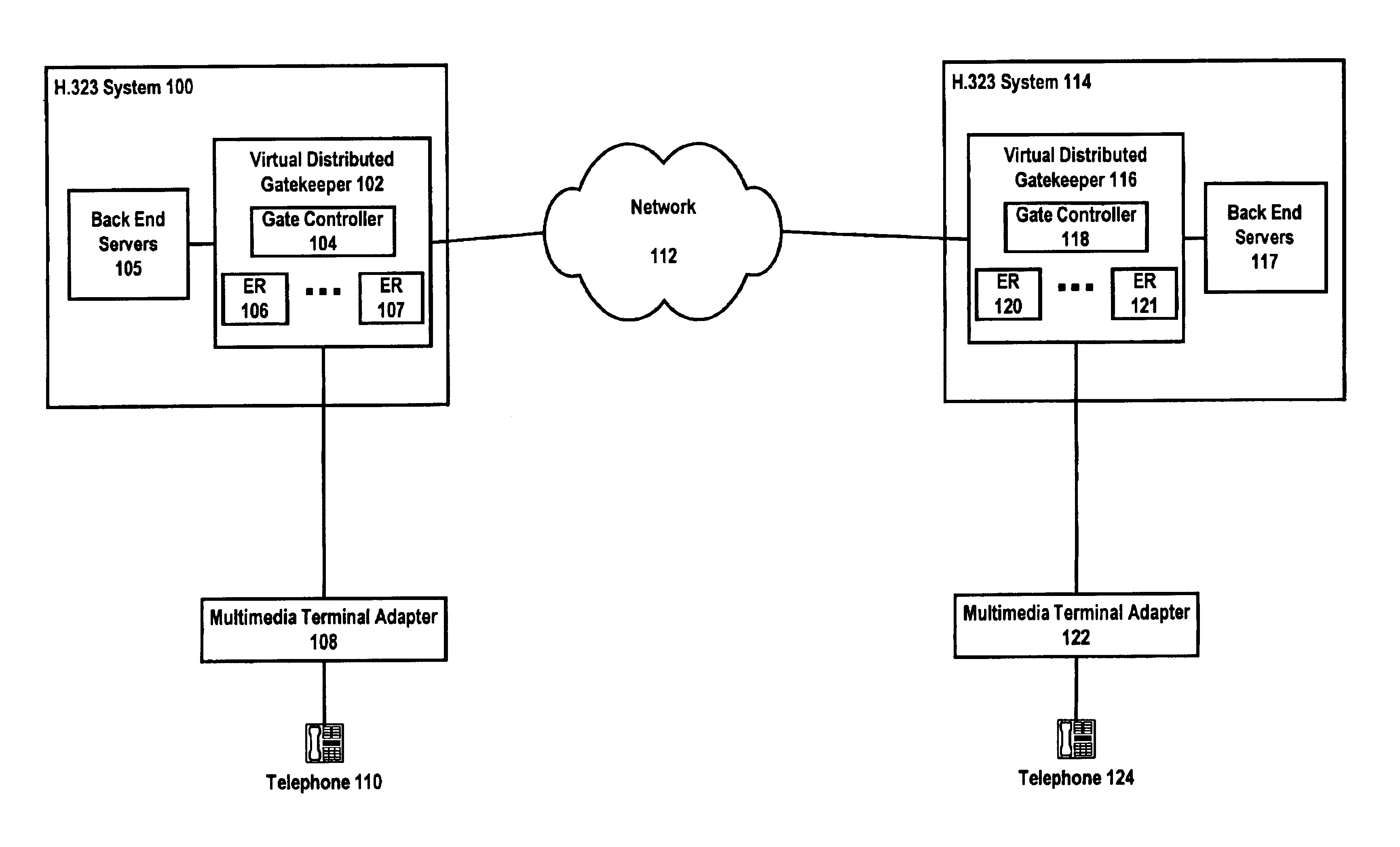
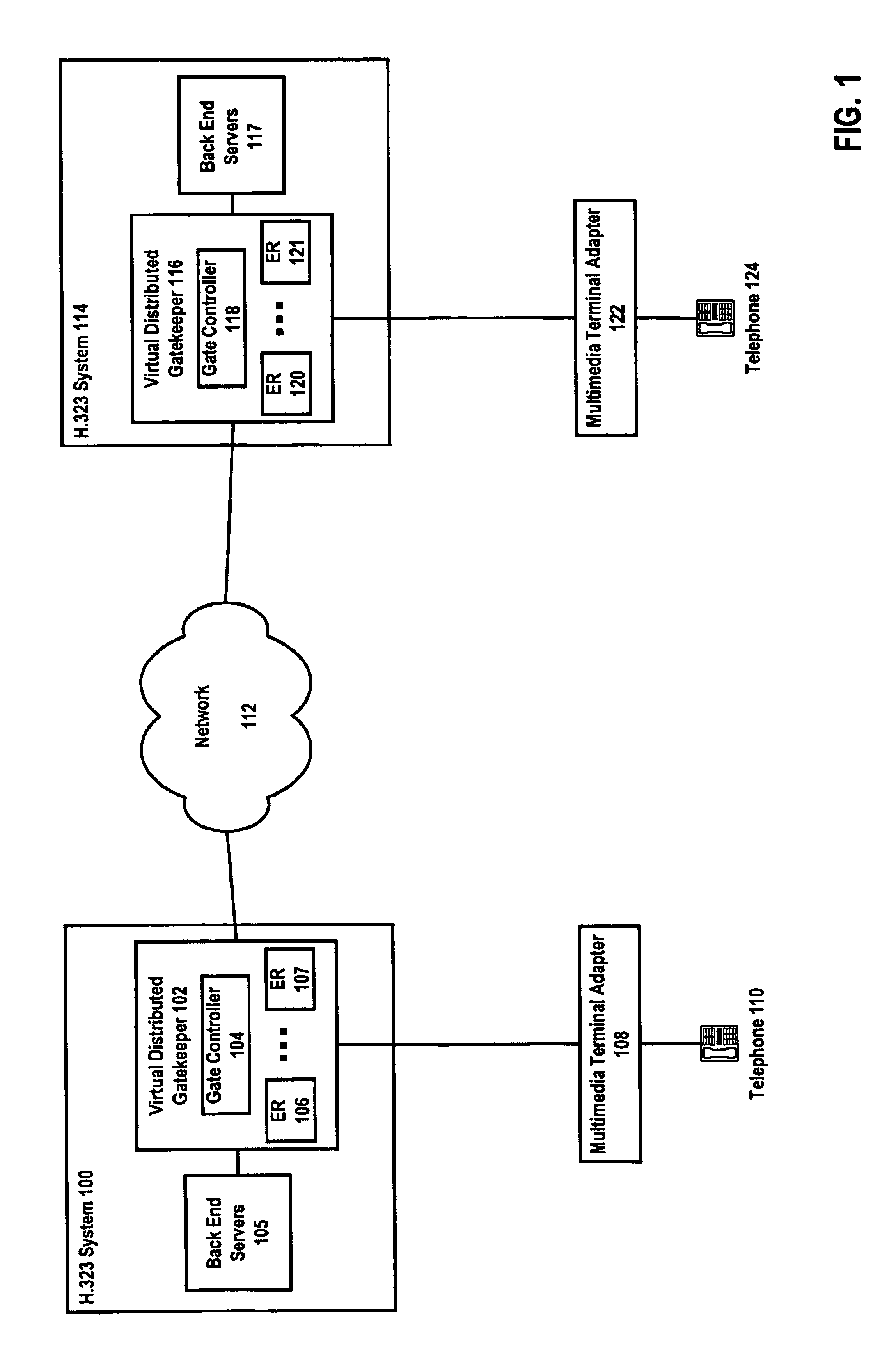
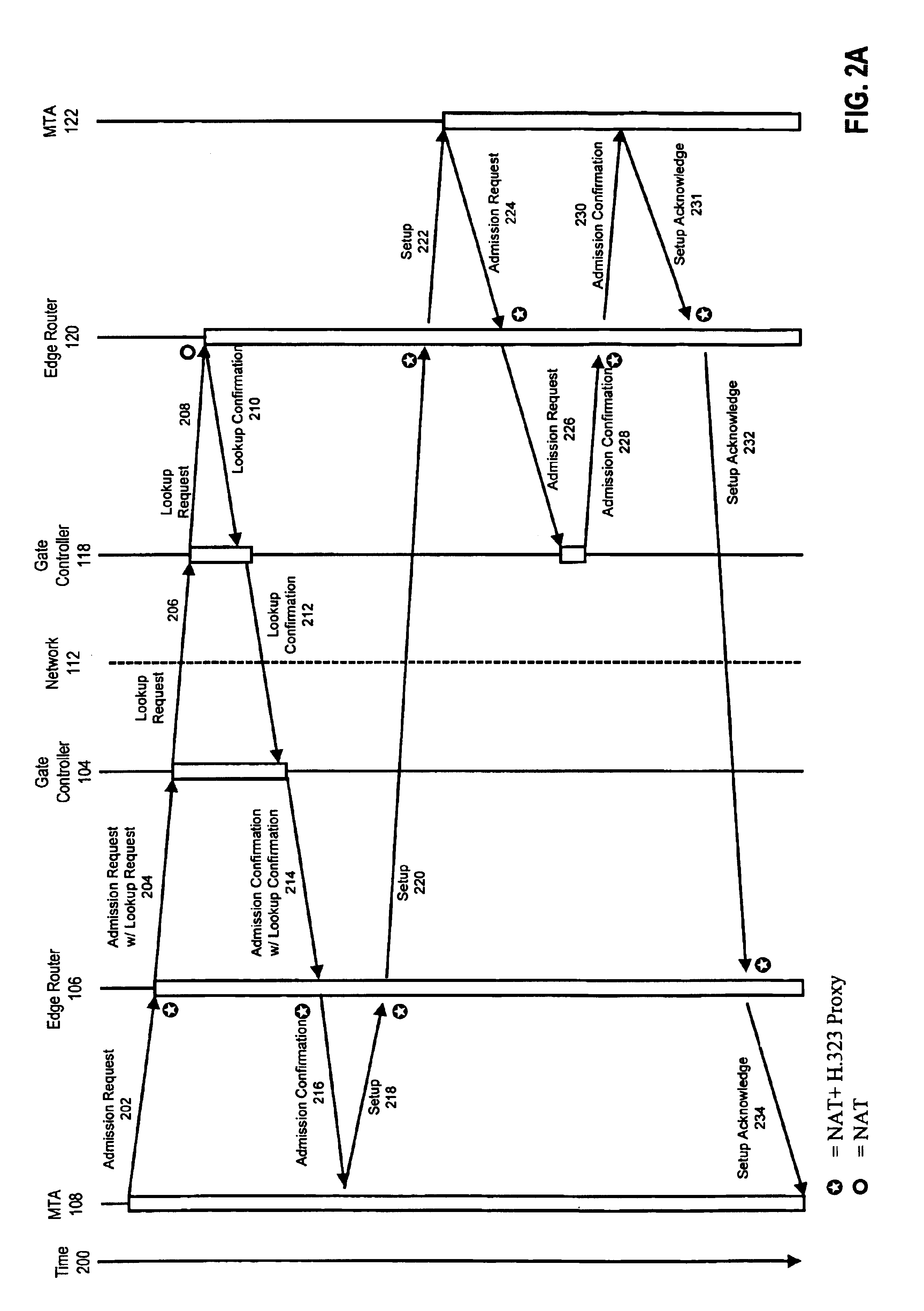
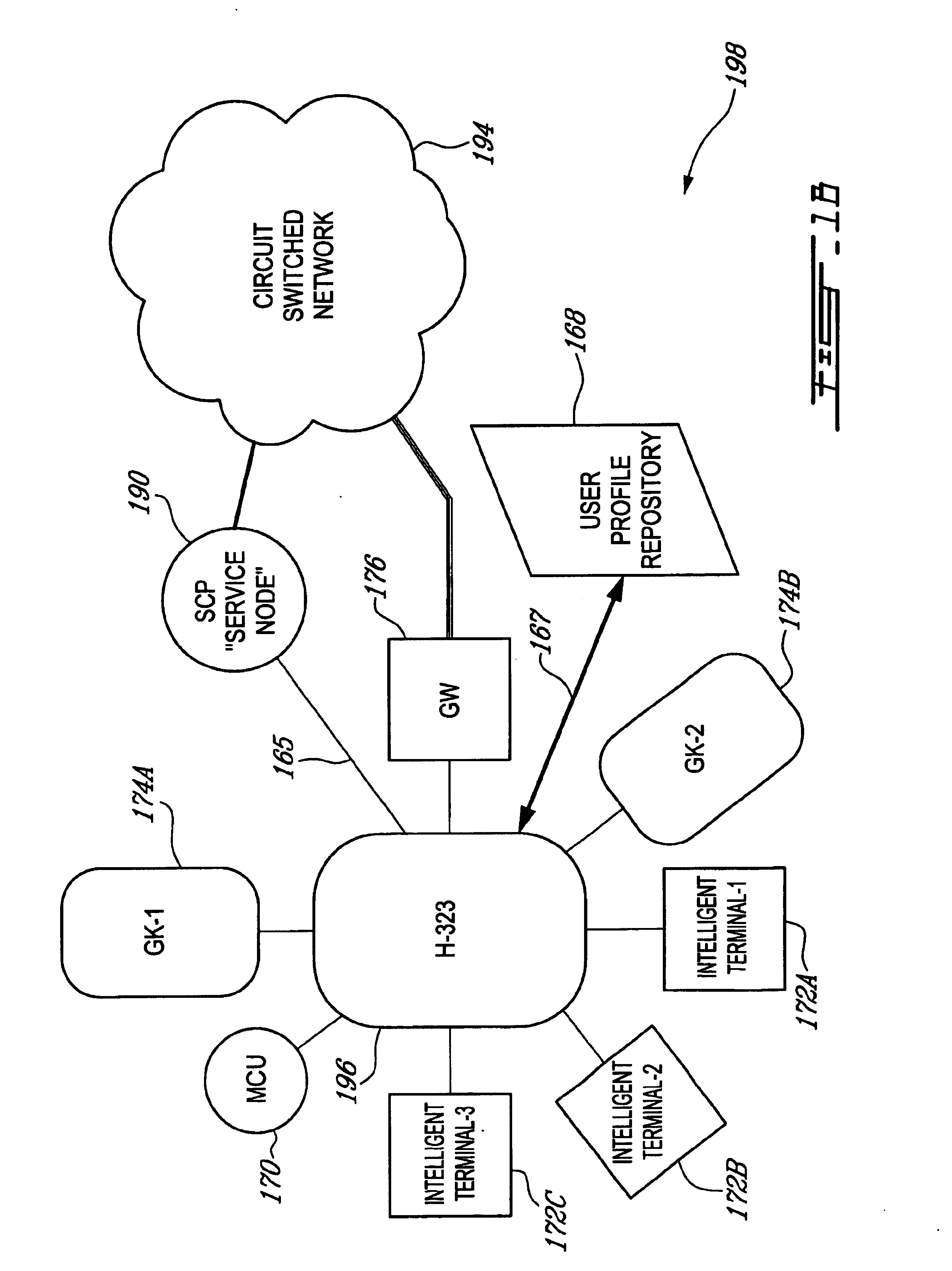
Method and apparatus for providing a virtual distributed gatekeeper in an H.323 system
InactiveUS6925076B1Improve scalabilityData switching by path configurationNetwork connectionsExtensibilityIp address
A method and apparatus for improving the scalability of H.323 systems is described. An H.323 gateway can be modified to store call state information associated with a call on at least one of the ports of the modified H.323 gateway. The modified H.323 gateway can send registration, admission, and status requests to a modified H.323 gatekeeper. This relieves the modified H.323 gatekeeper of the need to maintain call status information for that call. If the modified H.323 gatekeeper fails, there is no disruption of the call or the billing information associated with the call. The modified H.323 gateway and the modified H.323 gatekeeper can be embodied in interface cards suitable for IP telephony gateways. Additionally, the modified H.323 gateway can support a standard network address translation protocol and an H.323 proxy service. These features help prevent users of the modified H.323 gateway from bypassing the billing and user authentication systems while also conserving the IP address space.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
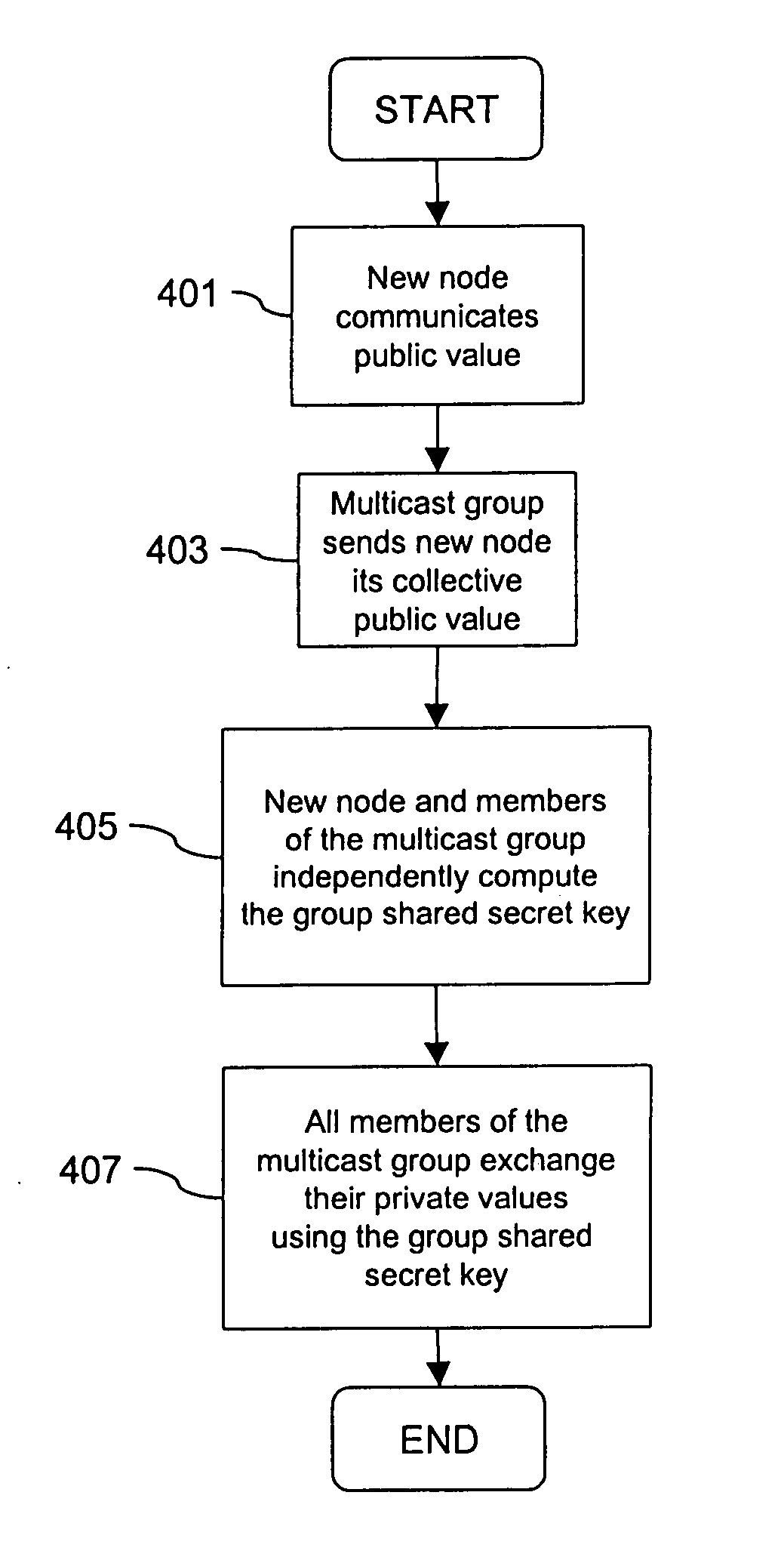
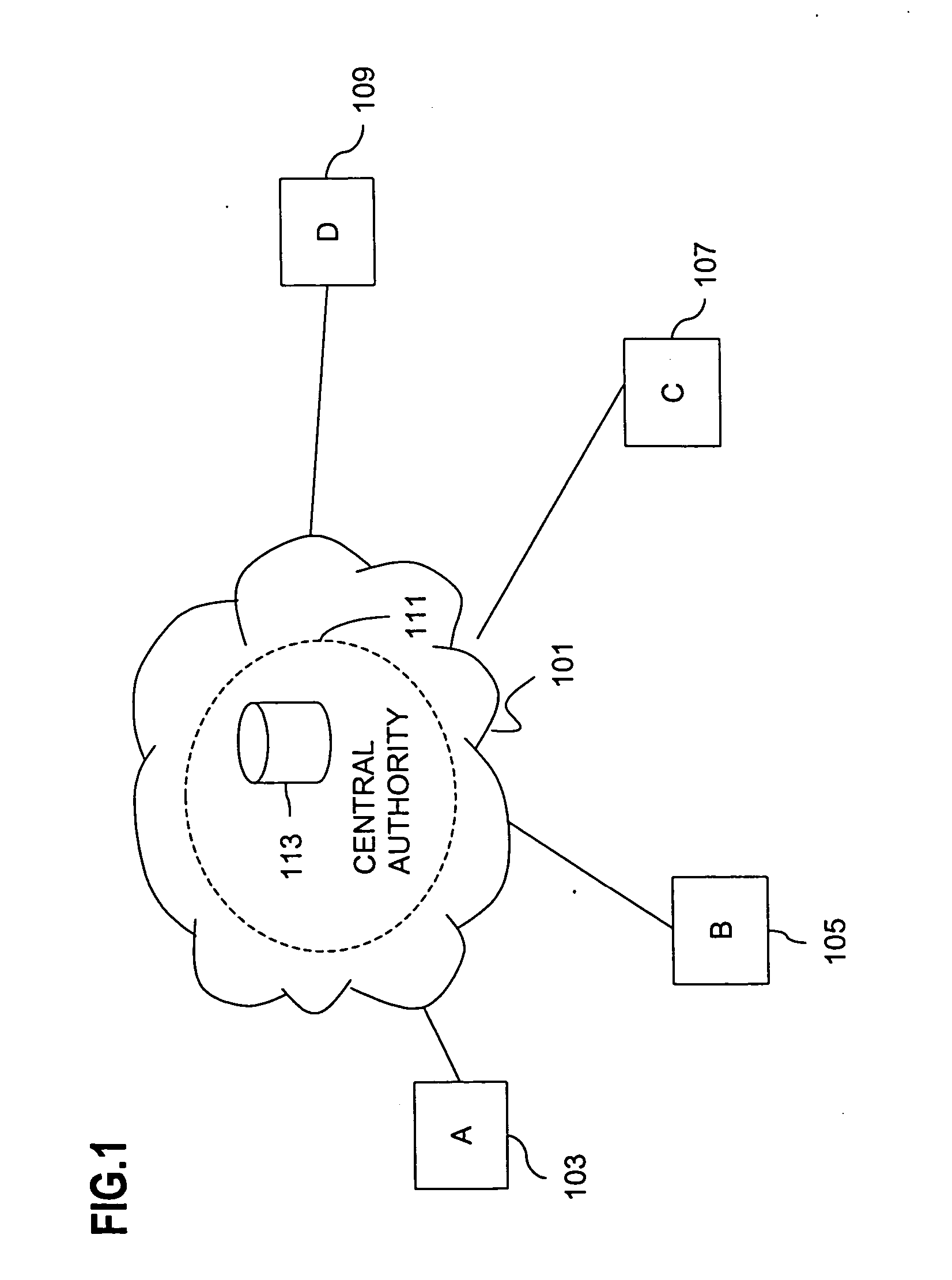
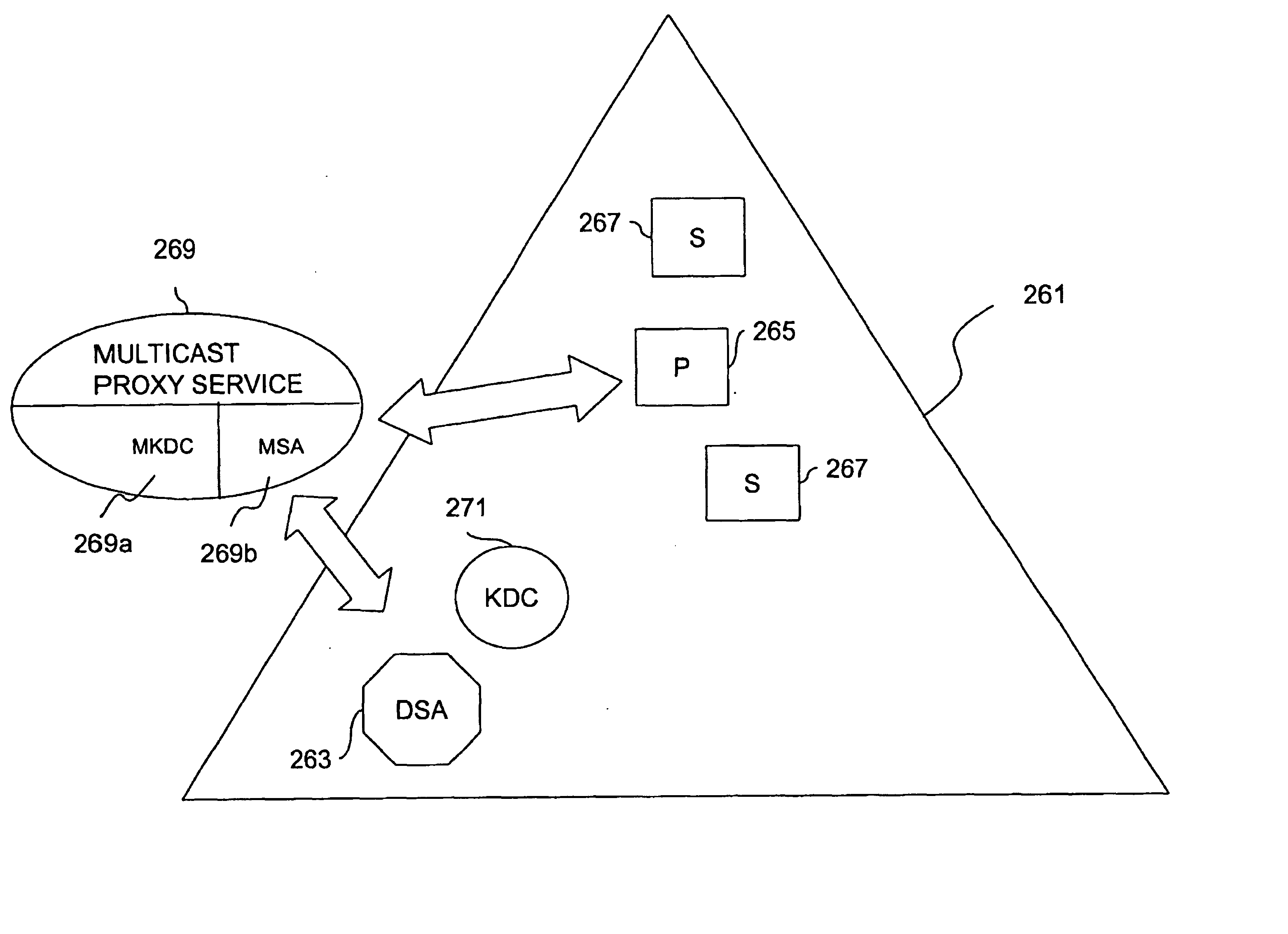
InactiveUS20050044356A1Optimize allocationKey distribution for secure communicationGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session keys that are members of the secure multicast or broadcast groups. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
System and method for providing a representational state transfer proxy service for a blockchain cloud service
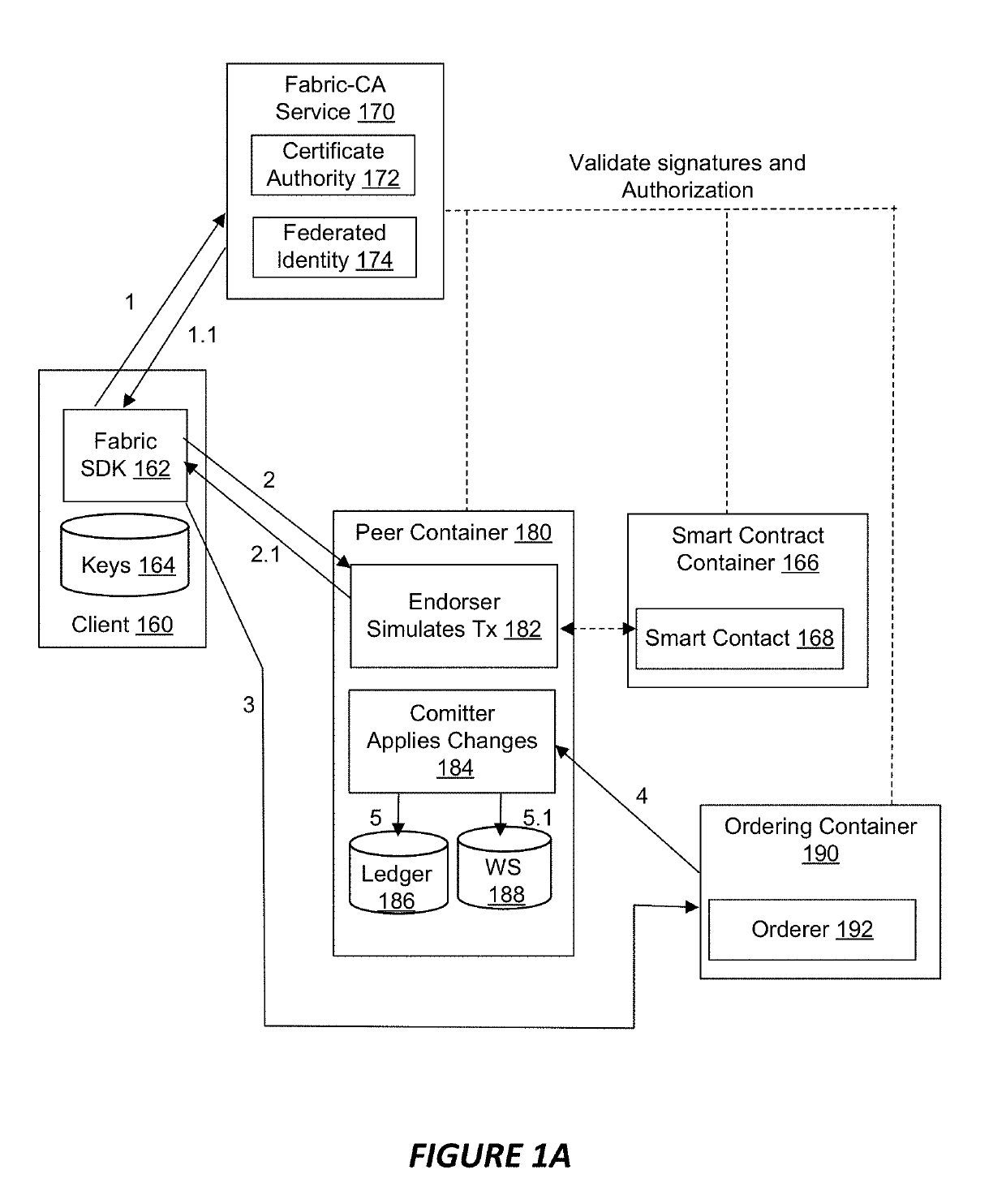
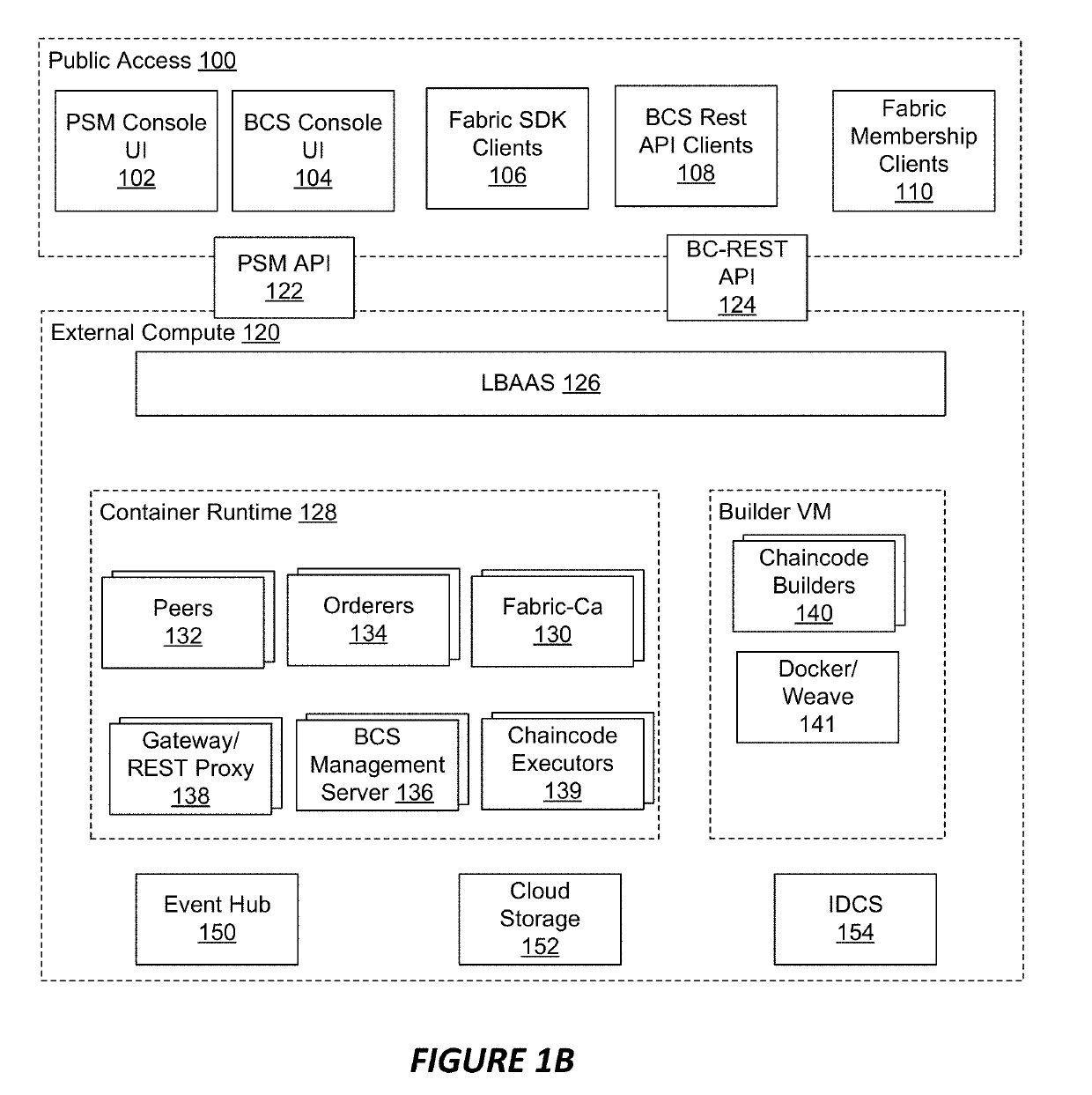
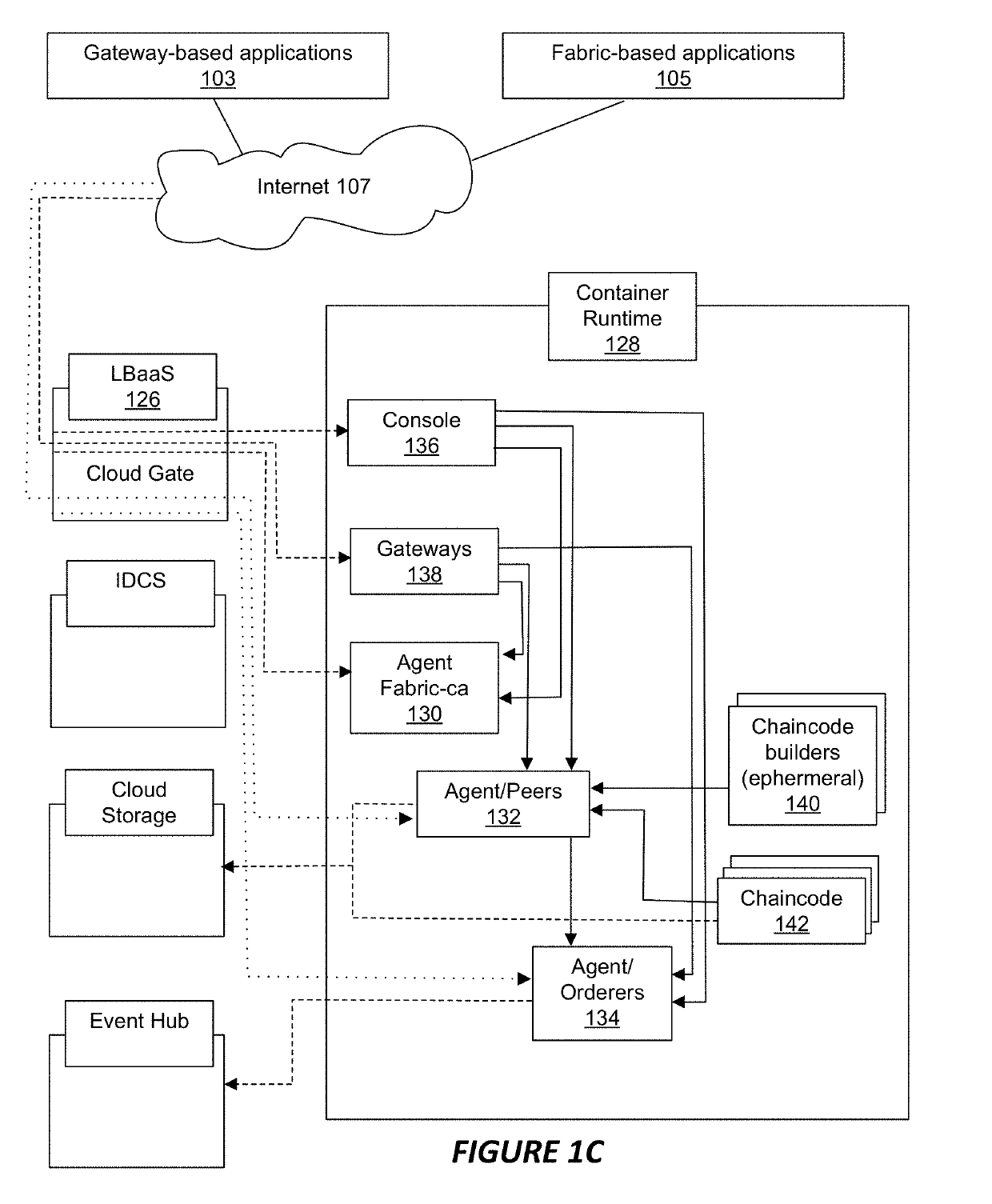
ActiveUS20190104196A1Key distribution for secure communicationResource allocationRepresentational state transferEngineering
In accordance with an embodiment, described herein are systems and methods for implementing a distributed ledger a blockchain cloud service. The blockchain cloud service can include nodes of the distributed ledger and a REST proxy service component. The REST proxy service uses a service development kit for the distributed ledger to communicate with the distributed ledger, and can provide REST APIs for use by client applications to query through chaincodes, synchronously or asynchronously invoke transactions through the chaincodes, get transaction statuses, and get BCS proxy versions. The REST proxy service component can authenticate REST calls, and translate the REST calls into remote procedural calls, for use in interfacing with the distributed ledger. The REST proxy service component can further provide REST APIs that support the same functions which are provided by the BCS management console component, and provide a user interface for client applications to consume the BCS instance.
Owner:ORACLE INT CORP
Proxy server, communication system, communication method and program
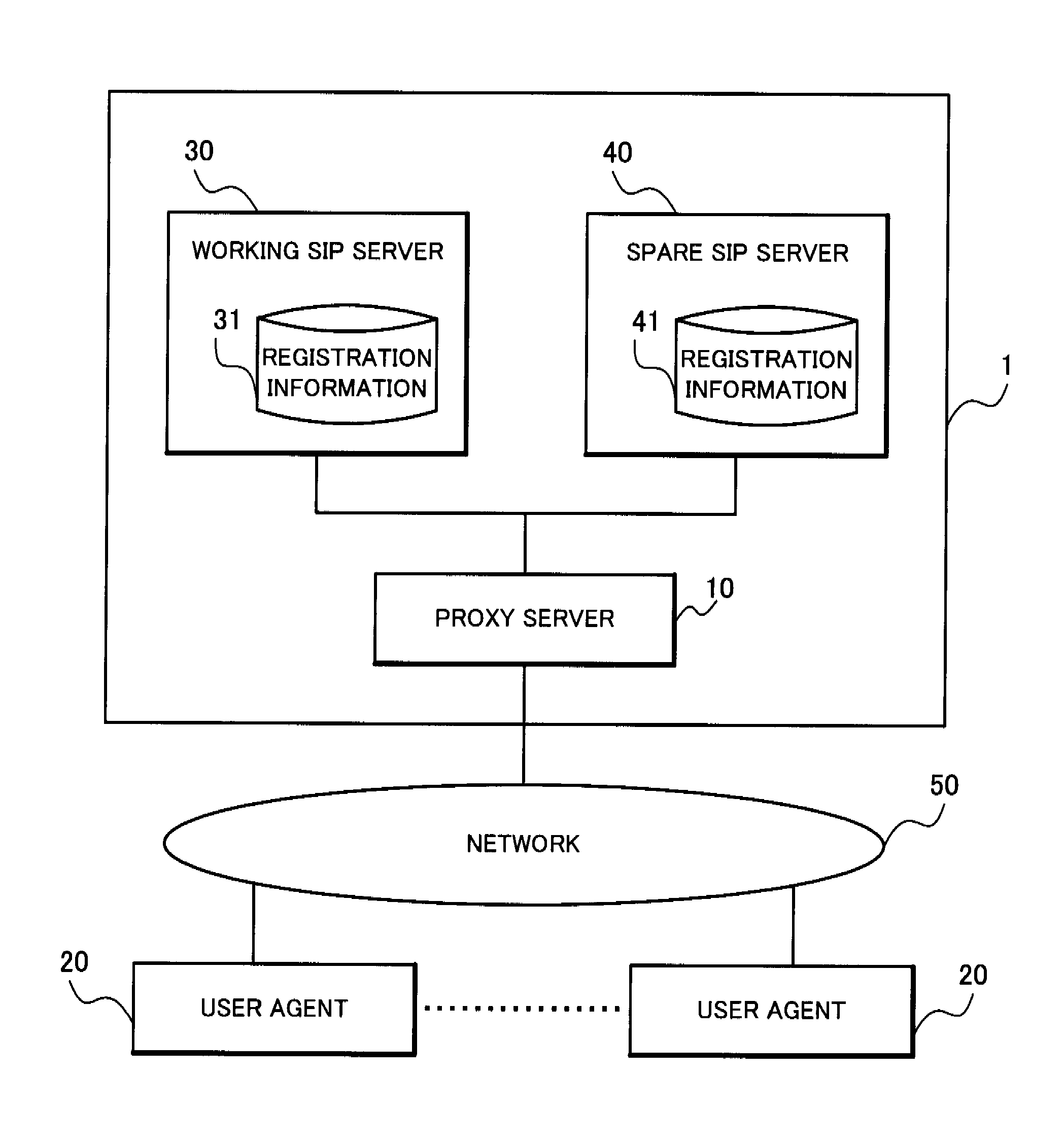
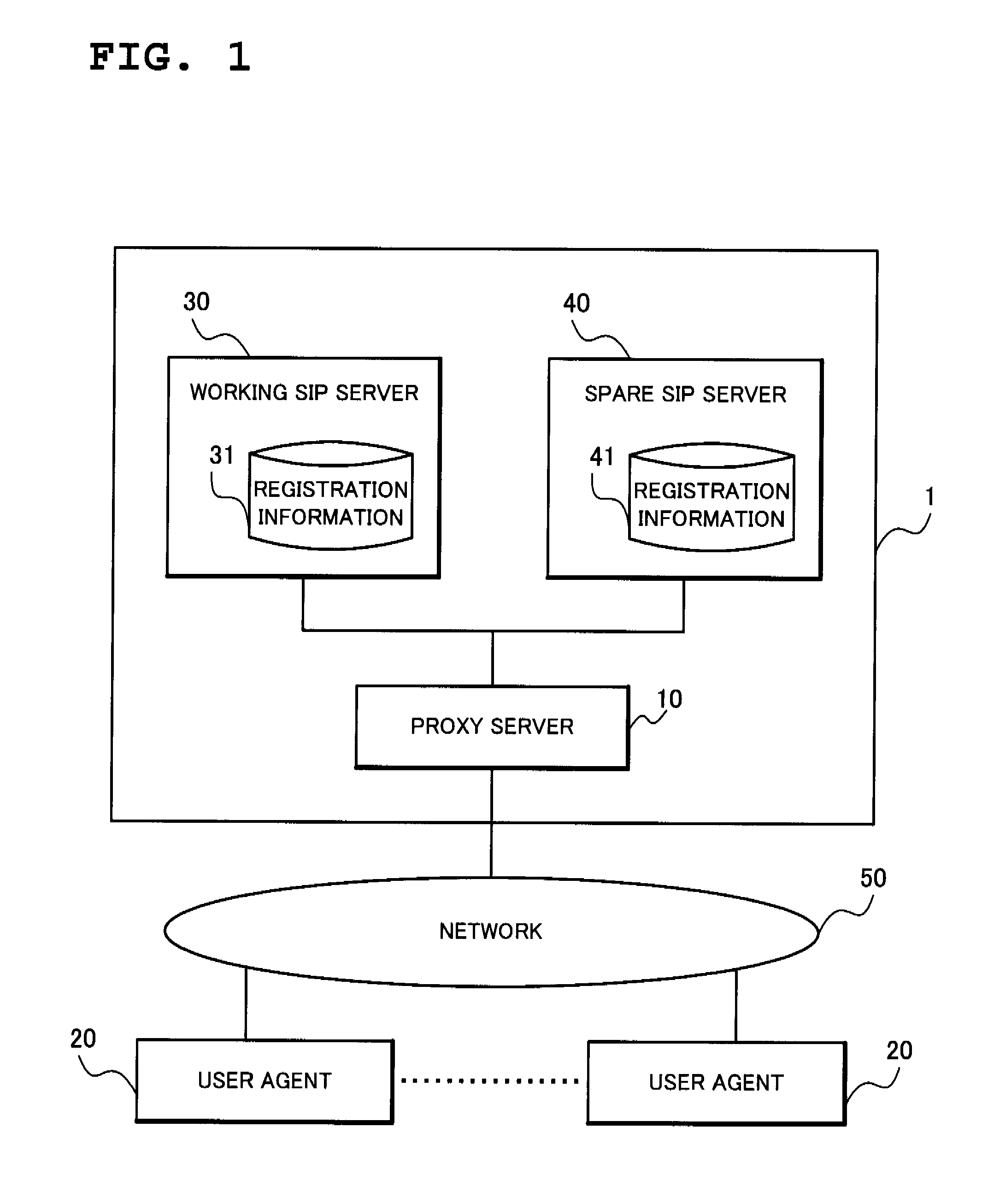
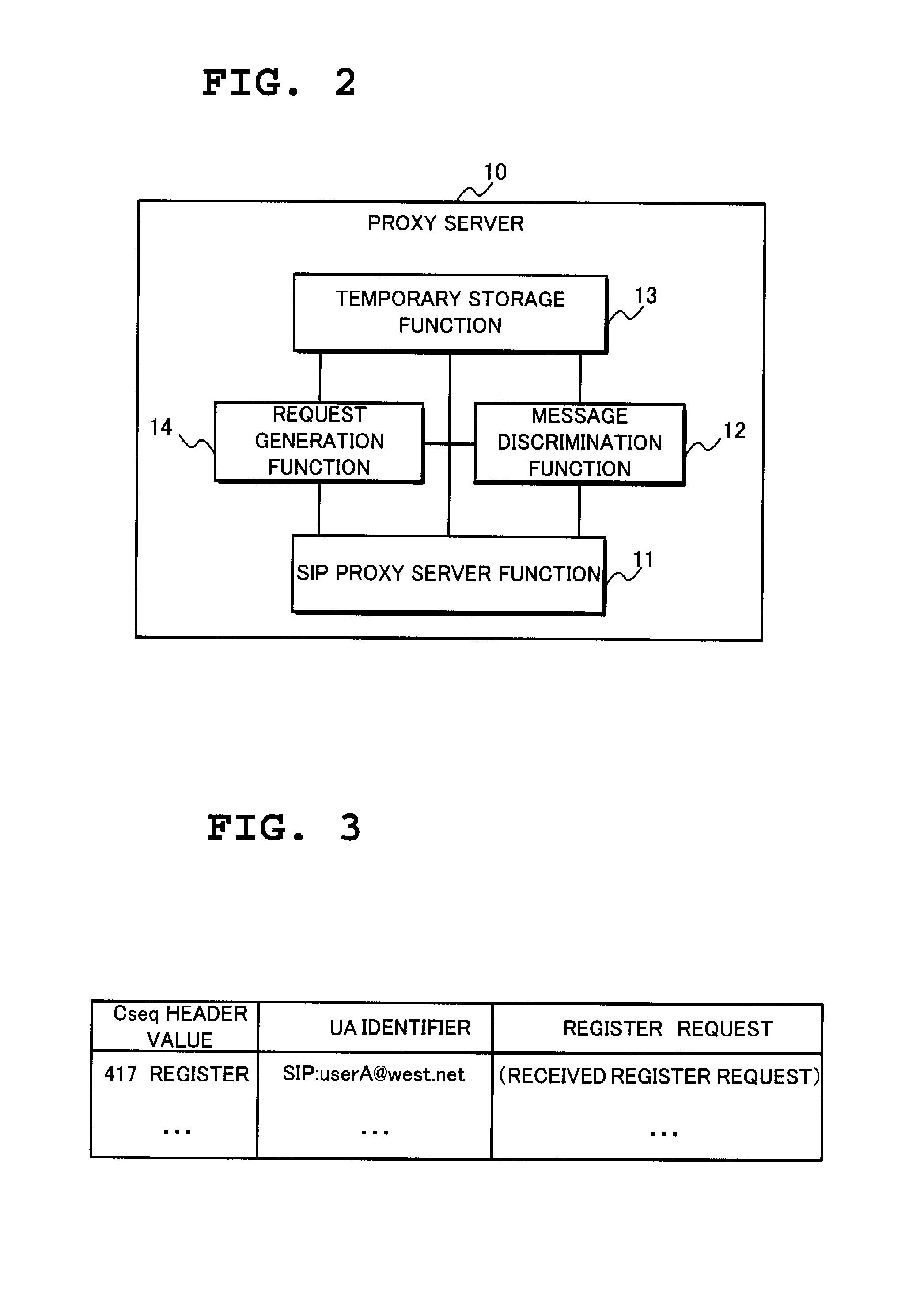
Provided in a proxy server which enables a plurality of SIP servers to copy registration information after presenting, to an SIP server requesting SIP Digest authentication, properness of one who makes an access and of a REGISTER request to be transmitted. With a REGISTER request generation function provided in addition to a function that a common SIP proxy server holds, a proxy server disposed between a user agent and an SIP server generates a REGISTER request to a spare SIP server and transmits the same to the spare SIP server, thereby realizing registration information copying, and holds a user identifier and a password of the proxy server to execute Digest authentication with the spare SIP server. Moreover, after confirming a REGISTER request processing completion response (200 OK) from a working SIP server from which registration information is copied, the proxy server transmits a copied REGISTER request to the spare SIP server.
Owner:NEC CORP
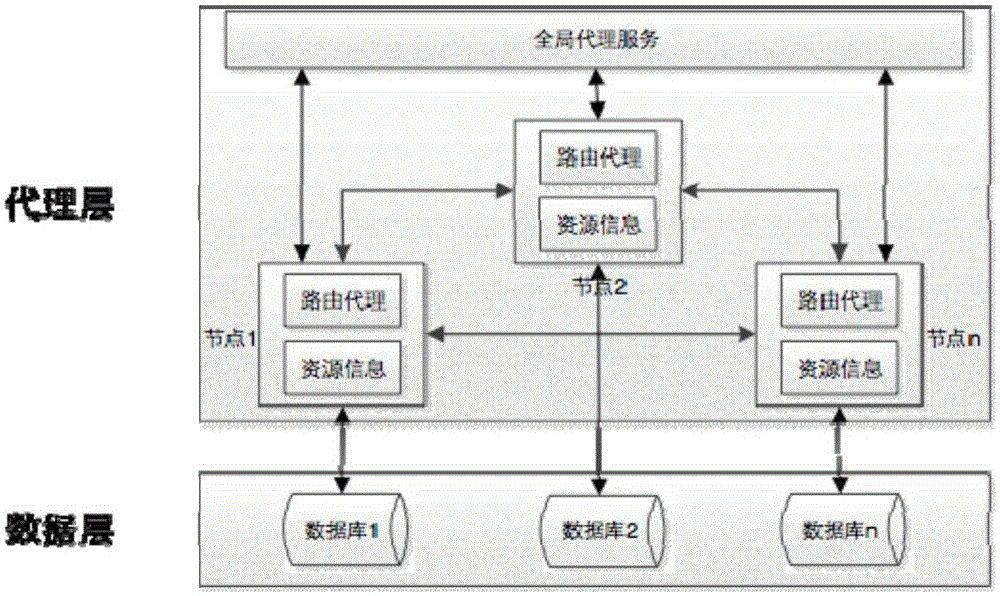
Peer-to-peer network-based heterogeneous database synchronization method
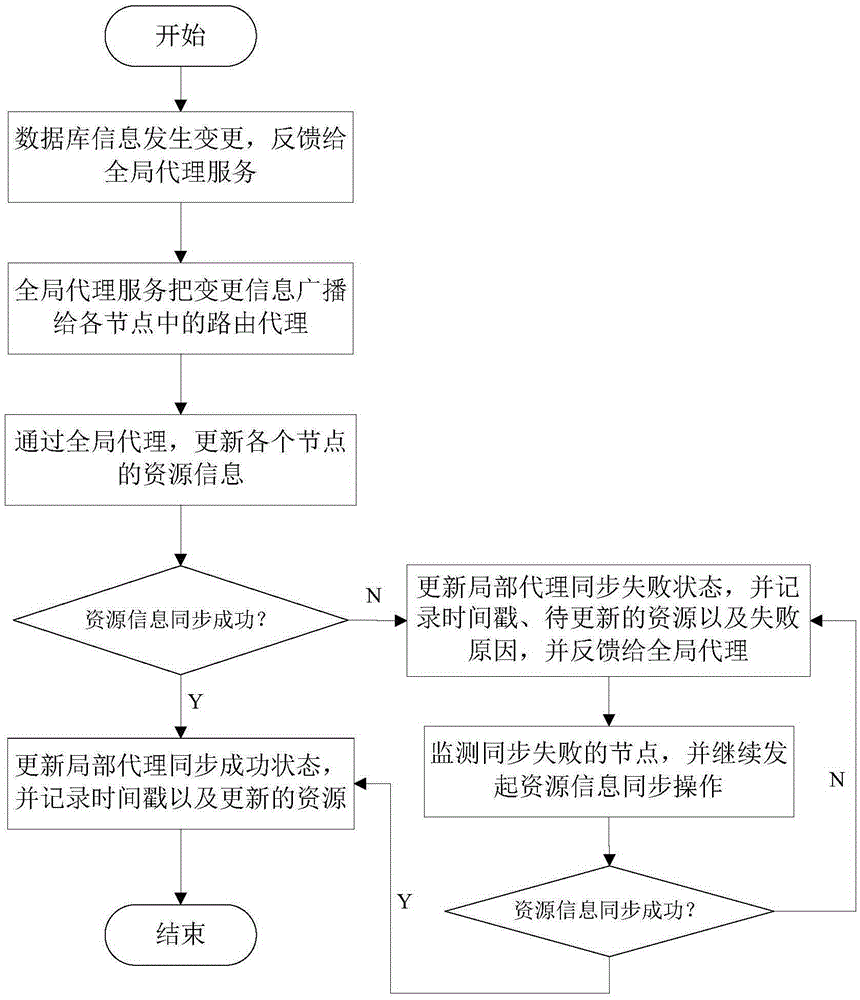
ActiveCN105404701AImprove reliabilityImprove usabilityTransmissionSpecial data processing applicationsTimestampUsability
The invention discloses a peer-to-peer network-based heterogeneous database synchronization method. The method is realized based on a heterogeneous database synchronization device composed of routing nodes and a global proxy server. The method comprises the steps of detecting the information charging condition of a database, feeding back the information changing condition to the global proxy server, broadcasting the changed information to the routing proxies of all nodes by the global proxy server, updating the resource information of each node, recording the timestamp of the updated information, updating the recorded timestamp in a block chain, updating the proxy synchronization state of each node, recording the timestamp thereof and the-be-changed information, and feeding back the updating state to a global proxy. According to the invention, through the decentration process, the self-management of each node is realized. Therefore, the reliability and the usability of database synchronization are greatly improved. The above method is conducted based on the block chain technology and enables the complete data exchange record. Meanwhile, the problem in the prior art that the data exchange in the traditional goal-centered approach cannot be traced is solved.
Owner:浙江图讯科技股份有限公司
Systems and methods for cloud based unified service discovery and secure availability
Systems and methods implemented by a unified agent application executed on a mobile device, for unified service discovery and secure availability include authenticating a user into a plurality of cloud services including a proxy service and a Virtual Private Network (VPN) service, wherein the proxy service is utilized for Internet traffic and the VPN service is for Intranet traffic; creating and operating a link local network at the mobile device with a virtual network interface and multiple listening sockets; and intercepting traffic at the virtual network interface from one or more client applications on the mobile device and splitting the traffic between the proxy service, the VPN service, and the Internet based on a type of the traffic, a destination, and the one or more client applications.
Owner:ZSCALER INC
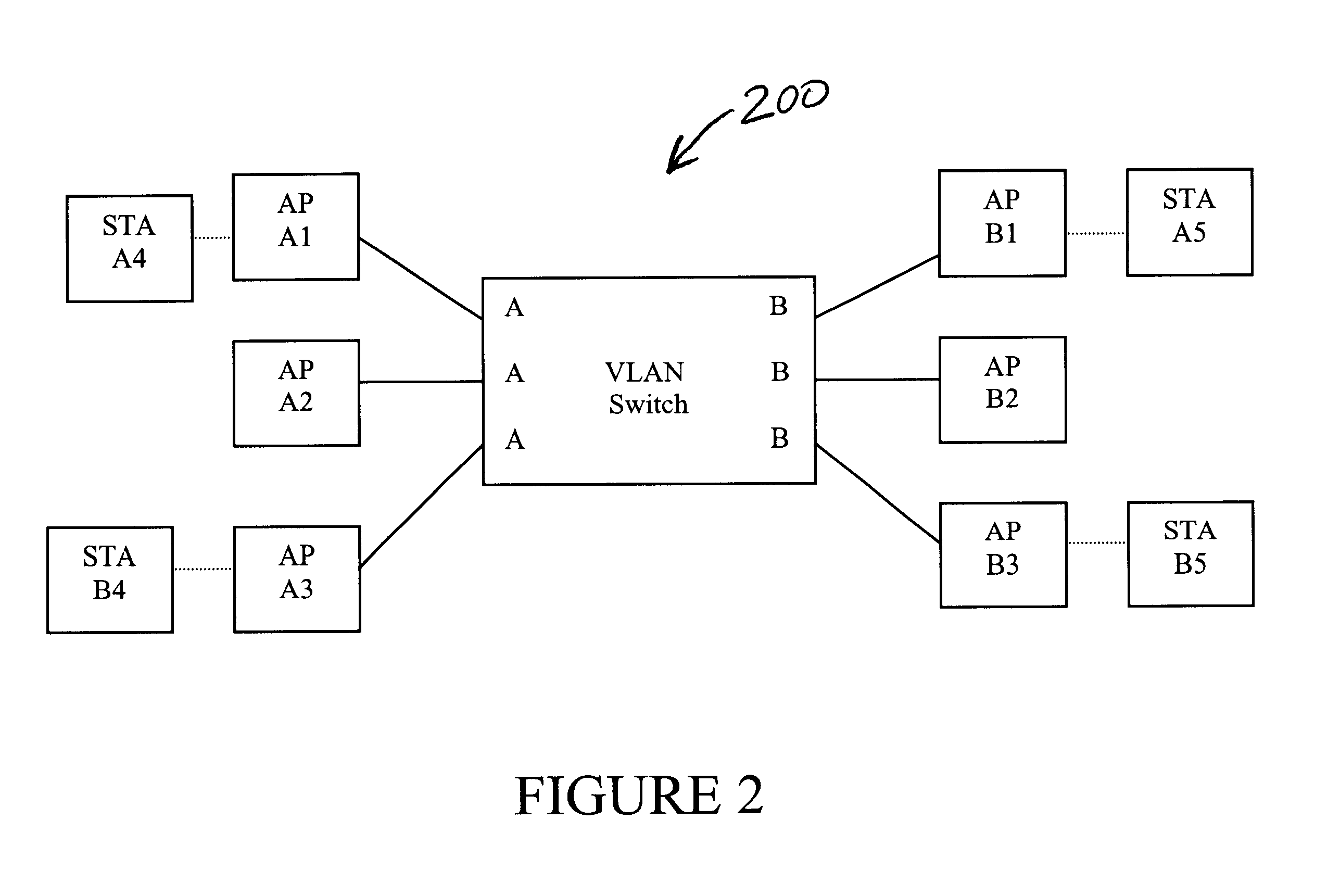
System and method for multihop service discovery with member station proxy service advertisements
InactiveUS20150081840A1Network topologiesMultiple digital computer combinationsTelecommunicationsMobile device
Systems and methods for multi-hop service discovery within a mobile device cluster are disclosed. A seeker station may be seeking or may have found a desired service available from a provider station. The seeker station may receive the service announcement from the provider station, and become a proxy station, expanding the service area of the provider station. The proxy station may selectively transmit services and advertisements for services on behalf of the provider station based on restrictions placed on selection as a proxy station. Restrictions or conditions may be placed on the proxy station limiting the number of stations that may become proxy stations, limiting traffic within the cluster. Some restrictions may require a proxy station to be a member of the cluster or a member of a group within the cluster. Selection as a proxy station and frequency of transmission of service announcements by proxy stations may also be conditioned on various specific parameters or combinations of parameters as specified by the provider station.
Owner:QUALCOMM INC
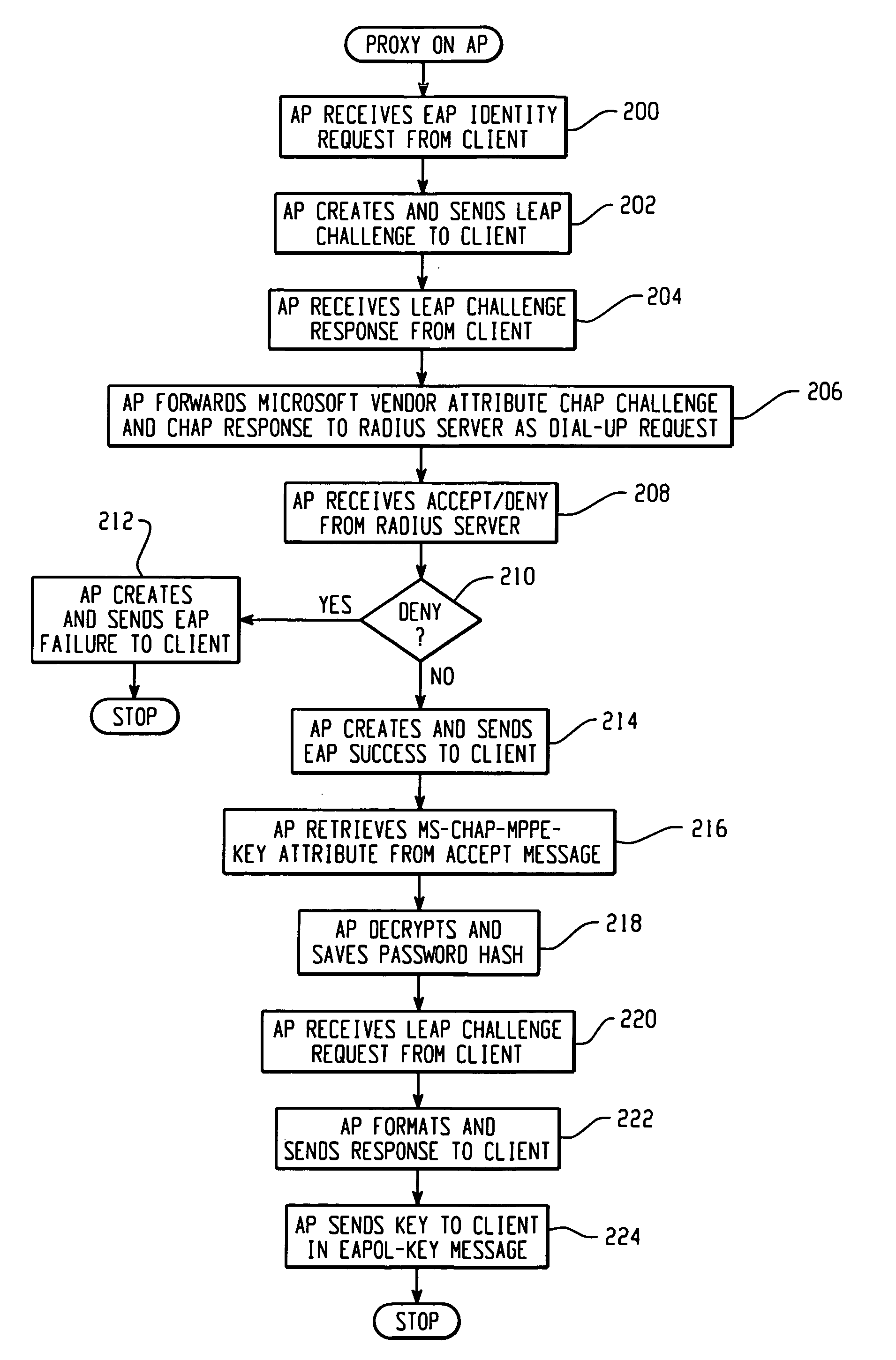
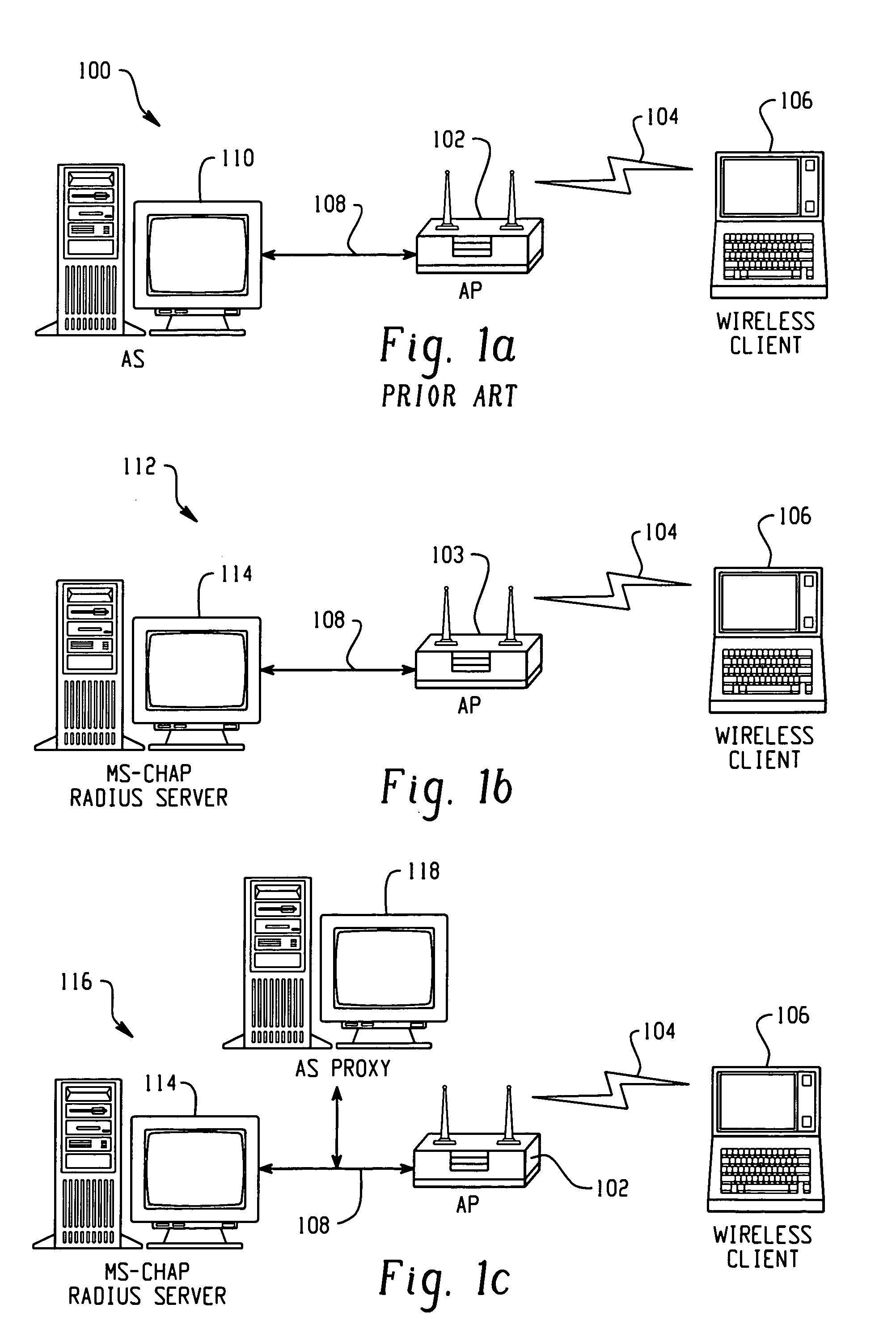
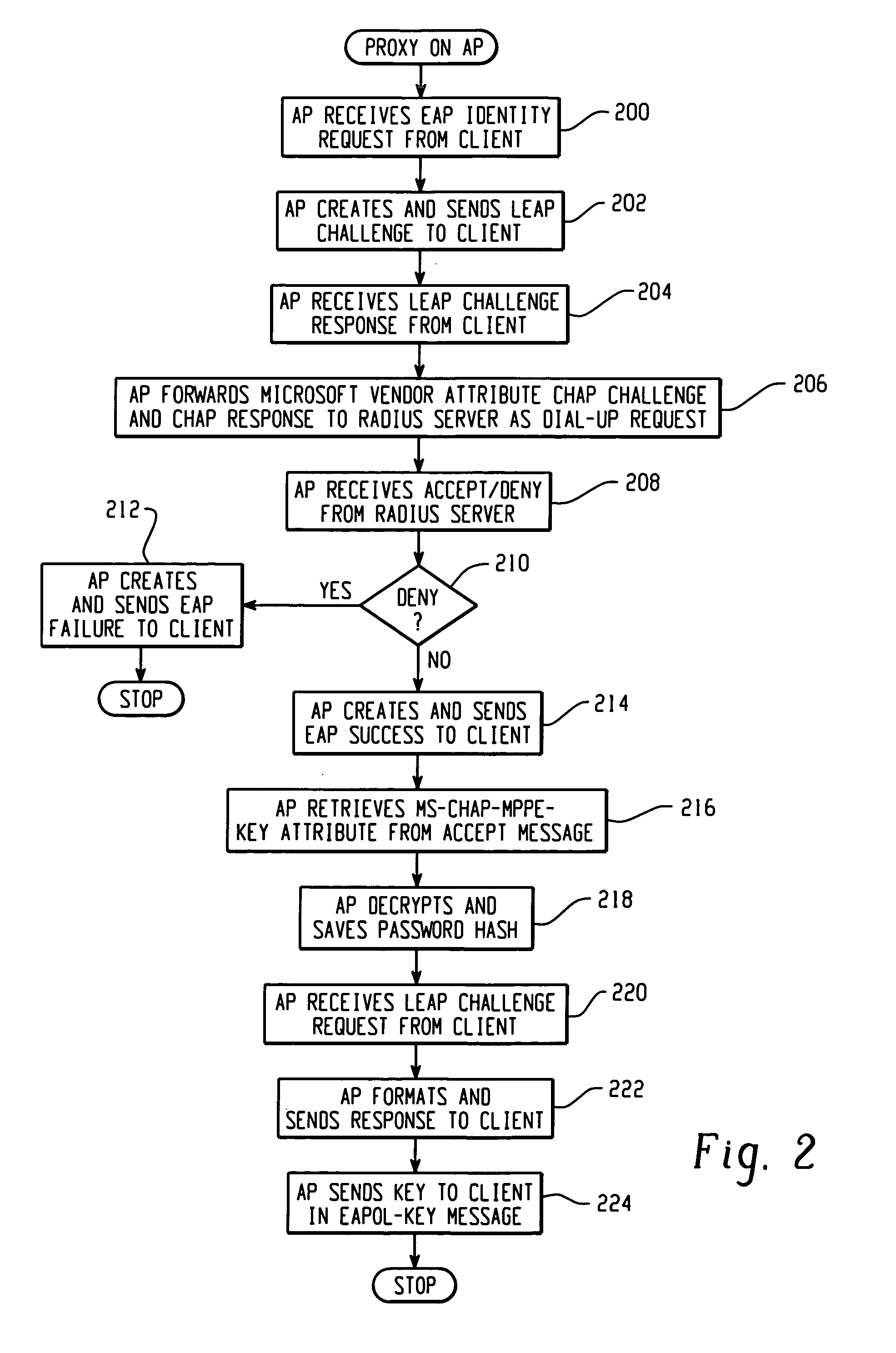
System and method of controlling access by a wireless client to a network that utilizes a challenge/handshake authentication protocol
Architecture for controlling access by a Light Extensible Authentication Protocol (LEAP)-compatible wireless client to a network that utilizes a challenge / handshake authentication protocol (CHAP). A proxy service is hosted on a network server disposed on the network, and accessed in response to receiving access information from the client. The access information is processed with the proxy service into CHAP-compatible access information, and forwarded to a CHAP-based access control server disposed on the network to determine whether to grant network access to the client.
Owner:CISCO TECH INC
System and method for providing access to service nodes from entities disposed in an integrated telecommunications network
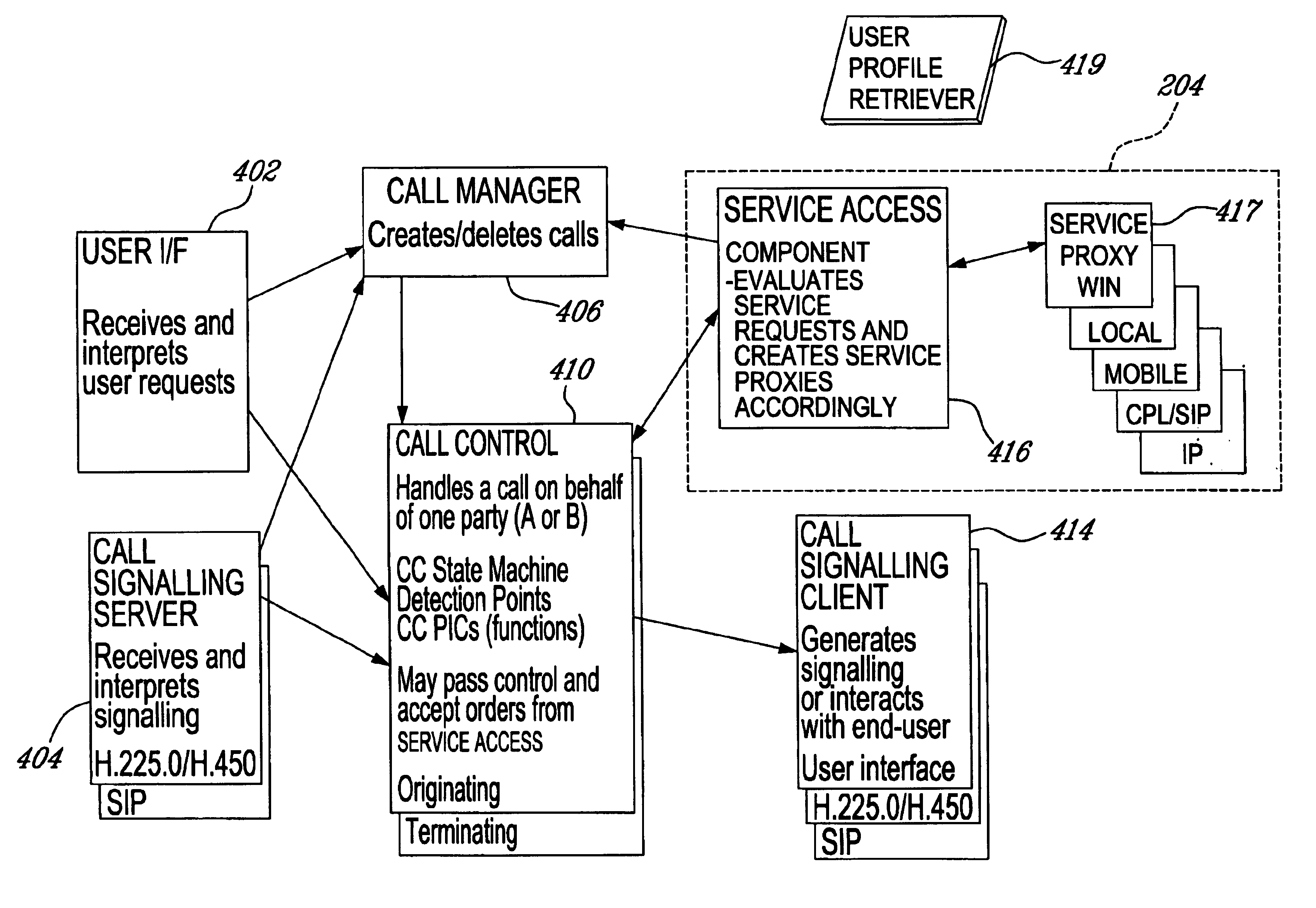
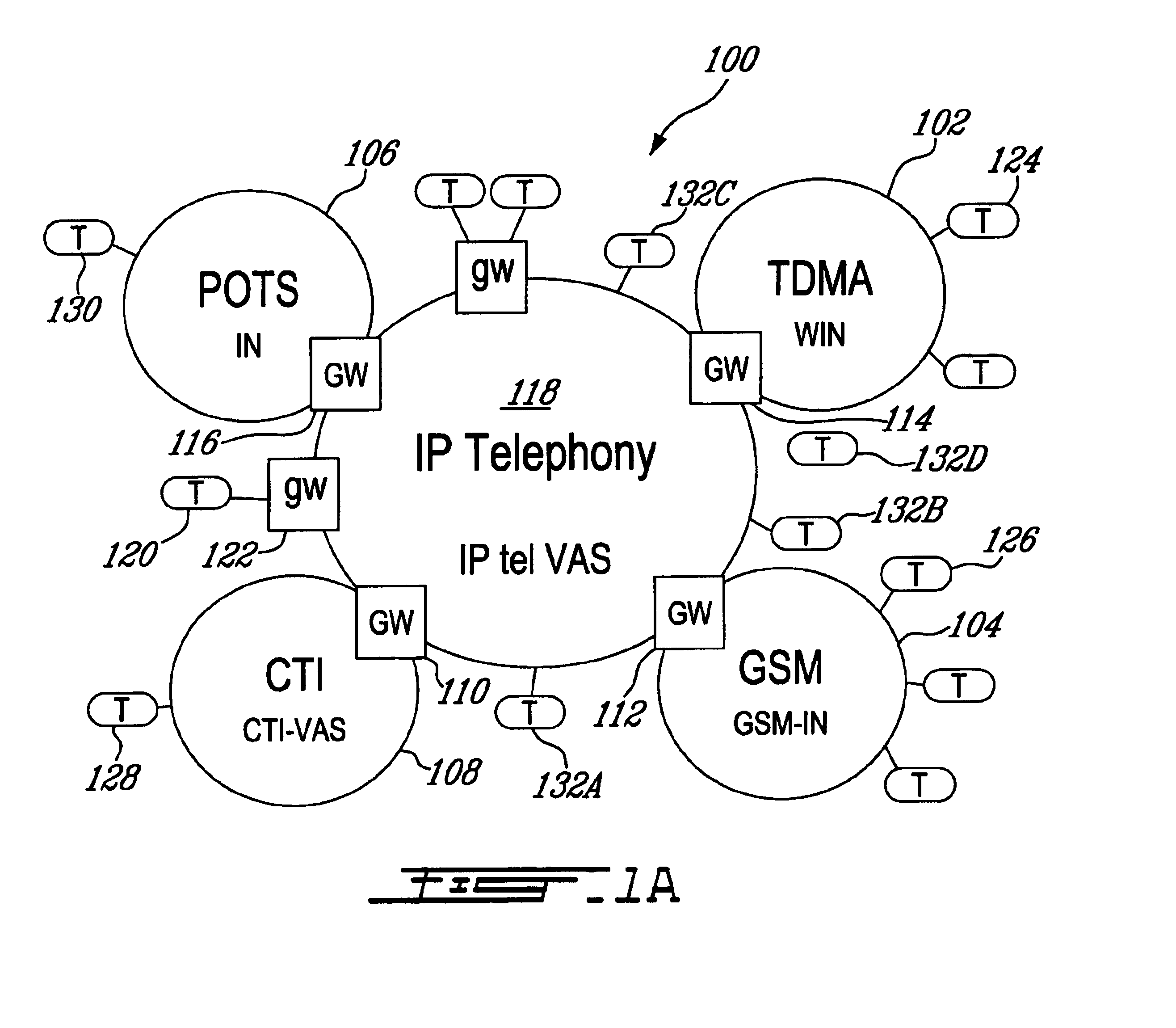
InactiveUS6940847B1Interconnection arrangementsTime-division multiplexTelecommunications networkComputer module
A system and method of accessing services from end terminals disposed in an integrated telecommunications network having a packet-switched network (PSN) portion such as, for example, a network portion using the Internet Protocol (IP) and a circuit-switched network (CSN) portion such as, for example, a wireless telephony network portion. A generalized service invocation and realization architecture includes one or more call control modules modified to include service-related Detection Points (DPs), a Service Access component or instance that is created when a new DP is encountered, and one or several service proxies which invoke services on behalf of the Service Access component and mediate between the call control modules and services. A common Service Logic Environment is implemented for local services, mobile agent services, and remote services. The PSN portion is preferably realized as a Voice-over-IP (VoIP) network having a gateway connected to the CSN portion.
Owner:OPTIS WIRELESS TECH LLC
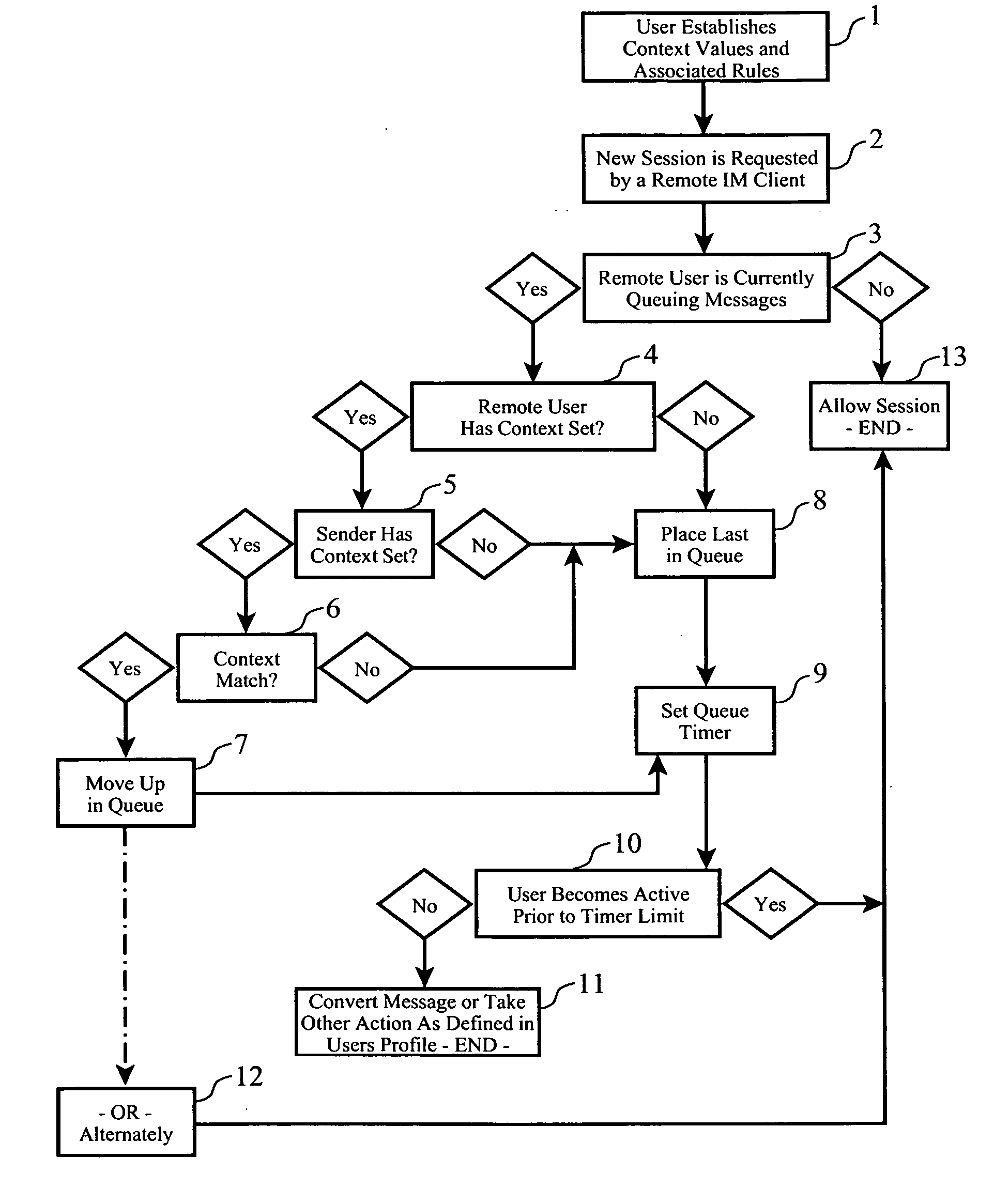
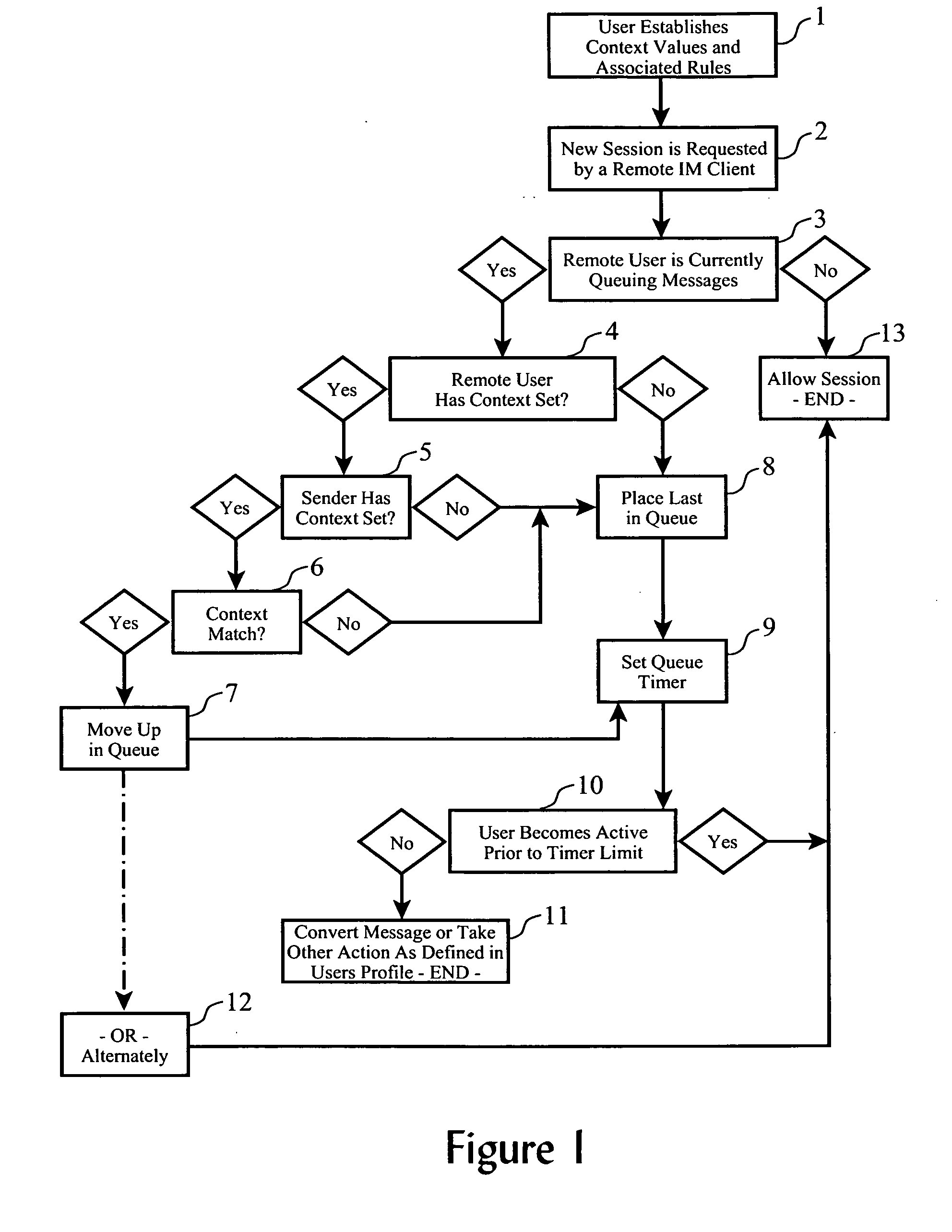
Active session queue management using contextual systems with an instant messaging proxy service
InactiveUS20070016643A1Manager chat sessionAvoid delayComputer security arrangementsMultiple digital computer combinationsUser interfaceInstant messaging
A system and method for providing implementing proxy handling of instant messages and the like, wherein proxy recipients are designated by an original recipient, and one or more redirection rules are established indicating conditions under which said designated proxy recipients are to be sent redirected messages. When an instant message is received directed towards the original recipient, the redirection rules are evaluated and the message is redirect to a designated proxy recipient according to the redirection rules, with the display of the received message being suppressed or blocked on the intended original recipient's user interface.
Owner:SNAP INC
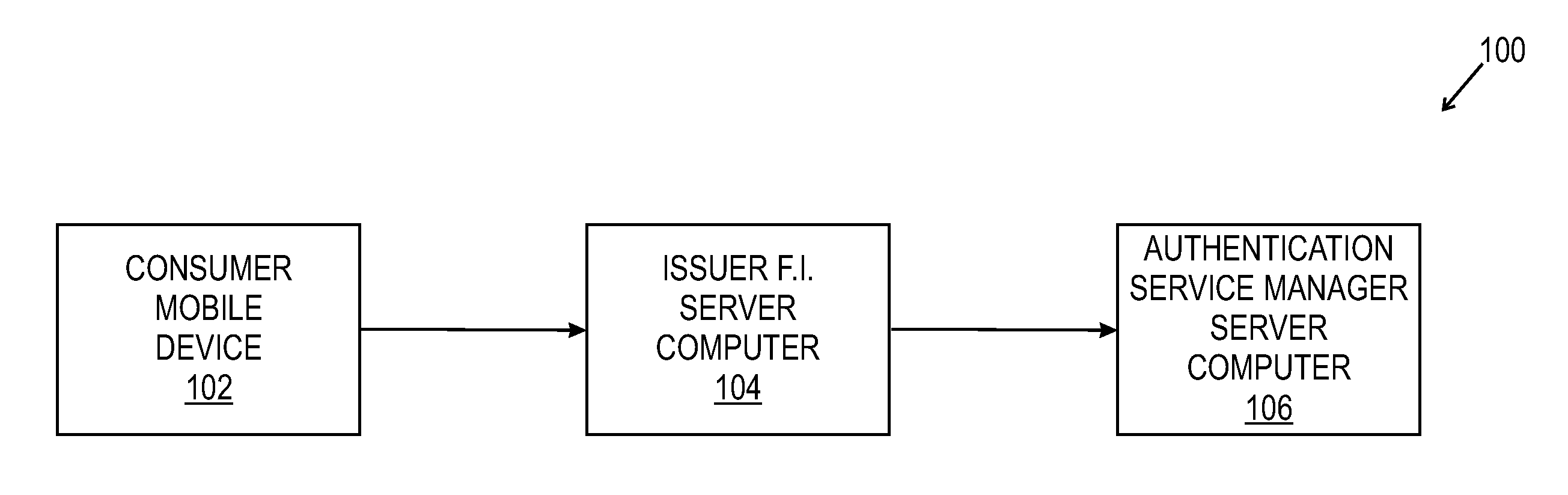
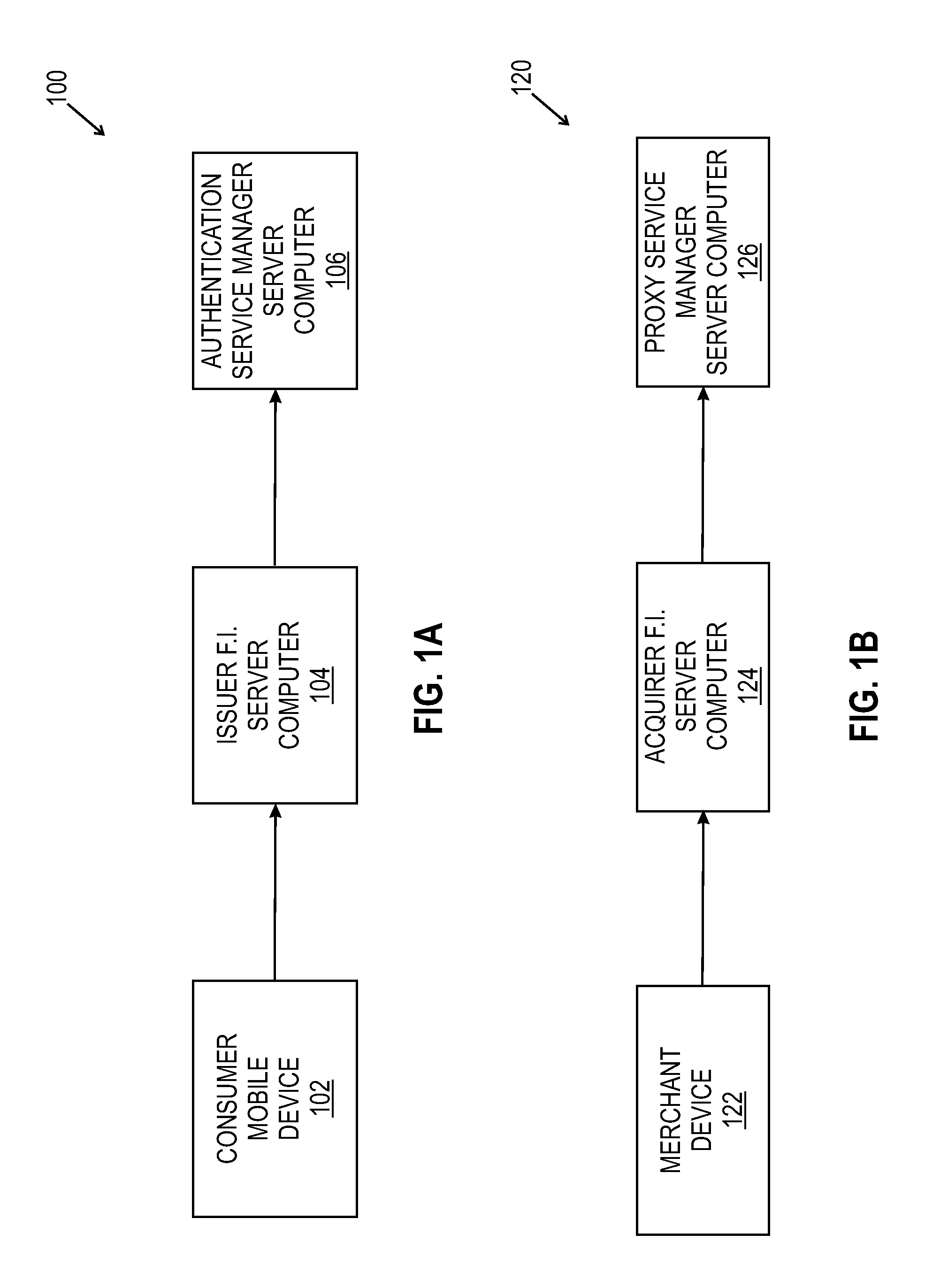
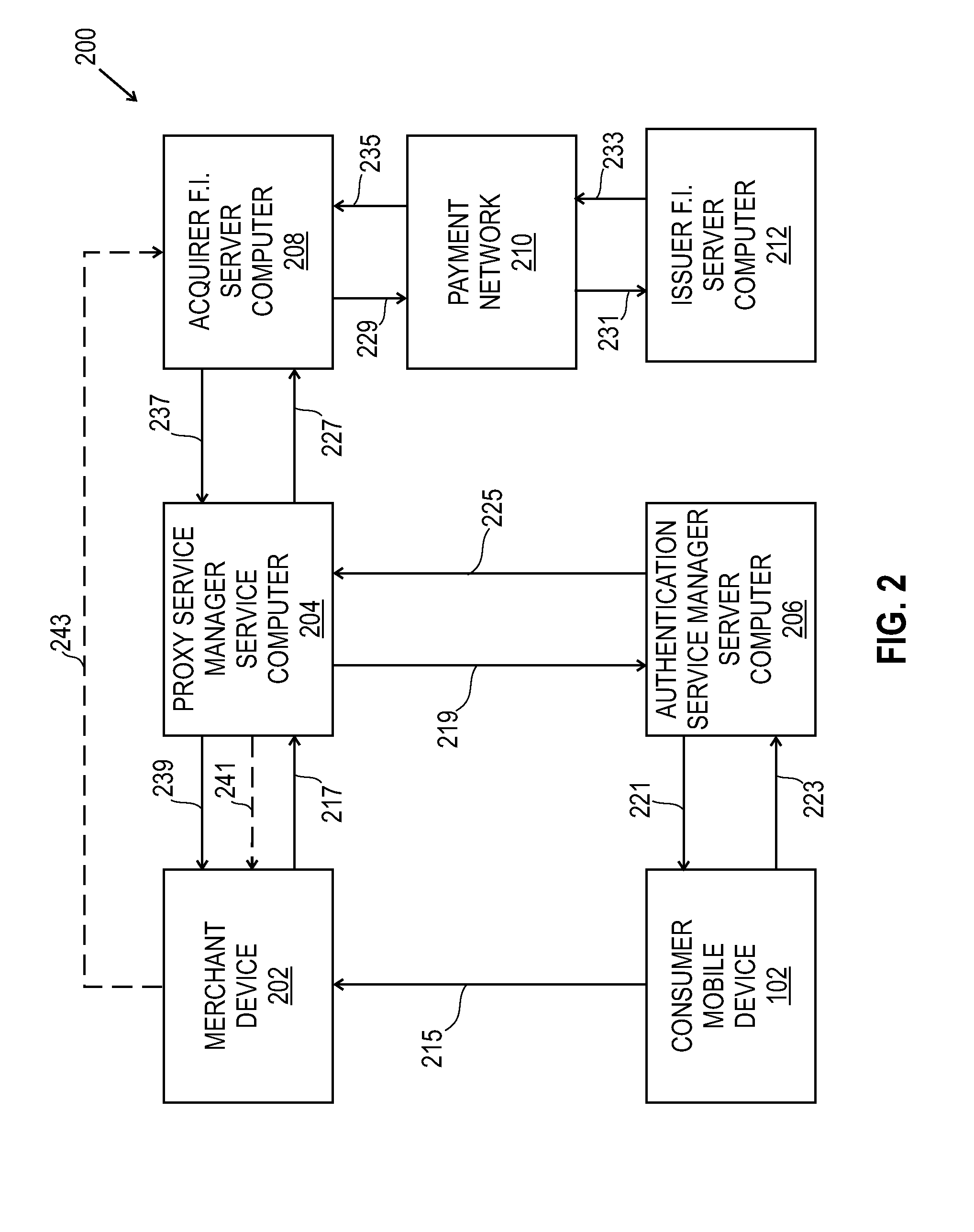
Methods and systems for payments assurance
Payments assurance methods and systems are described. In some embodiments, a Proxy Service Manager Server computer receives a consumer authentication request from a merchant device, and transmits that request to an Authentication Service Manager Server computer. The Proxy Service Manager Server computer then receives a non-repudiable accountholder authentication value (“AAV”) token, generates a payment authorization request that includes the AAV token, and transmits the payment authorization request to an Acquirer financial institution (FI) Server computer. The Proxy Service Manager Server computer is then operable to receive a payment authorization message, and to transmit the payment authorization message to the merchant device to enable a merchant to complete a purchase transaction with a consumer.
Owner:MASTERCARD INT INC
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
InactiveUS7103185B1Optimize allocationKey distribution for secure communicationSynchronising transmission/receiving encryption devicesGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session key and the private keys of the multicast proxy service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the multicast proxy service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
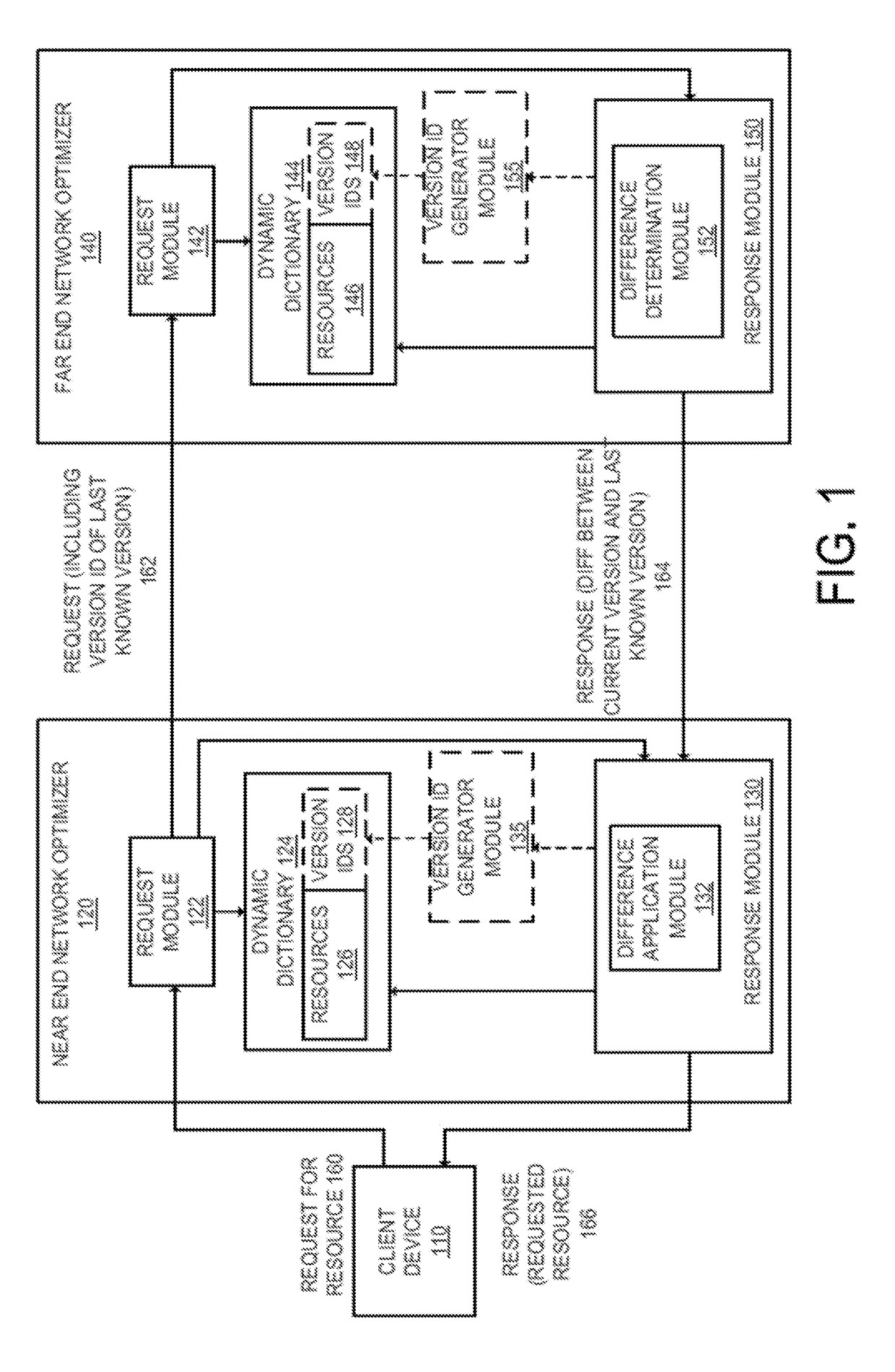
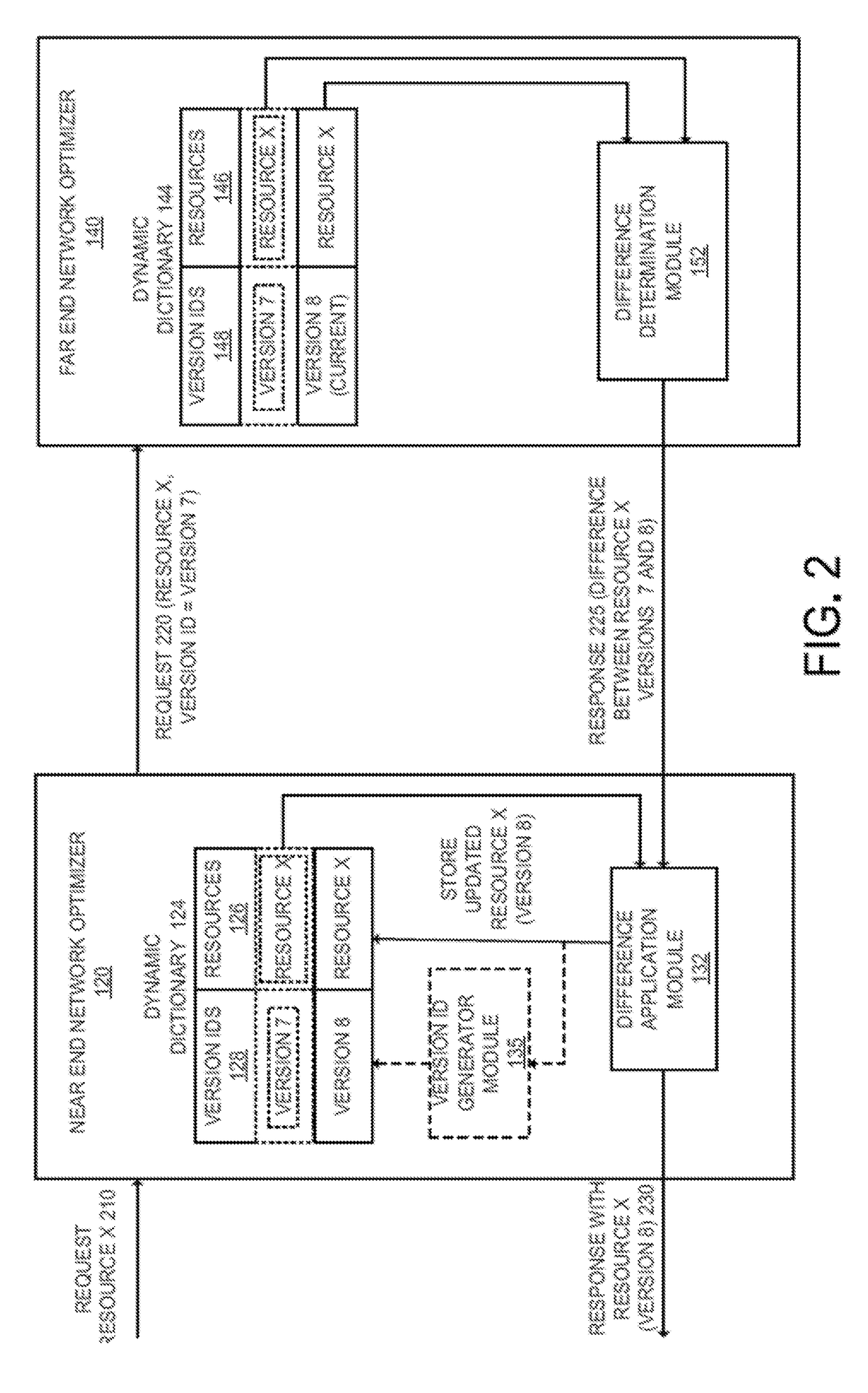
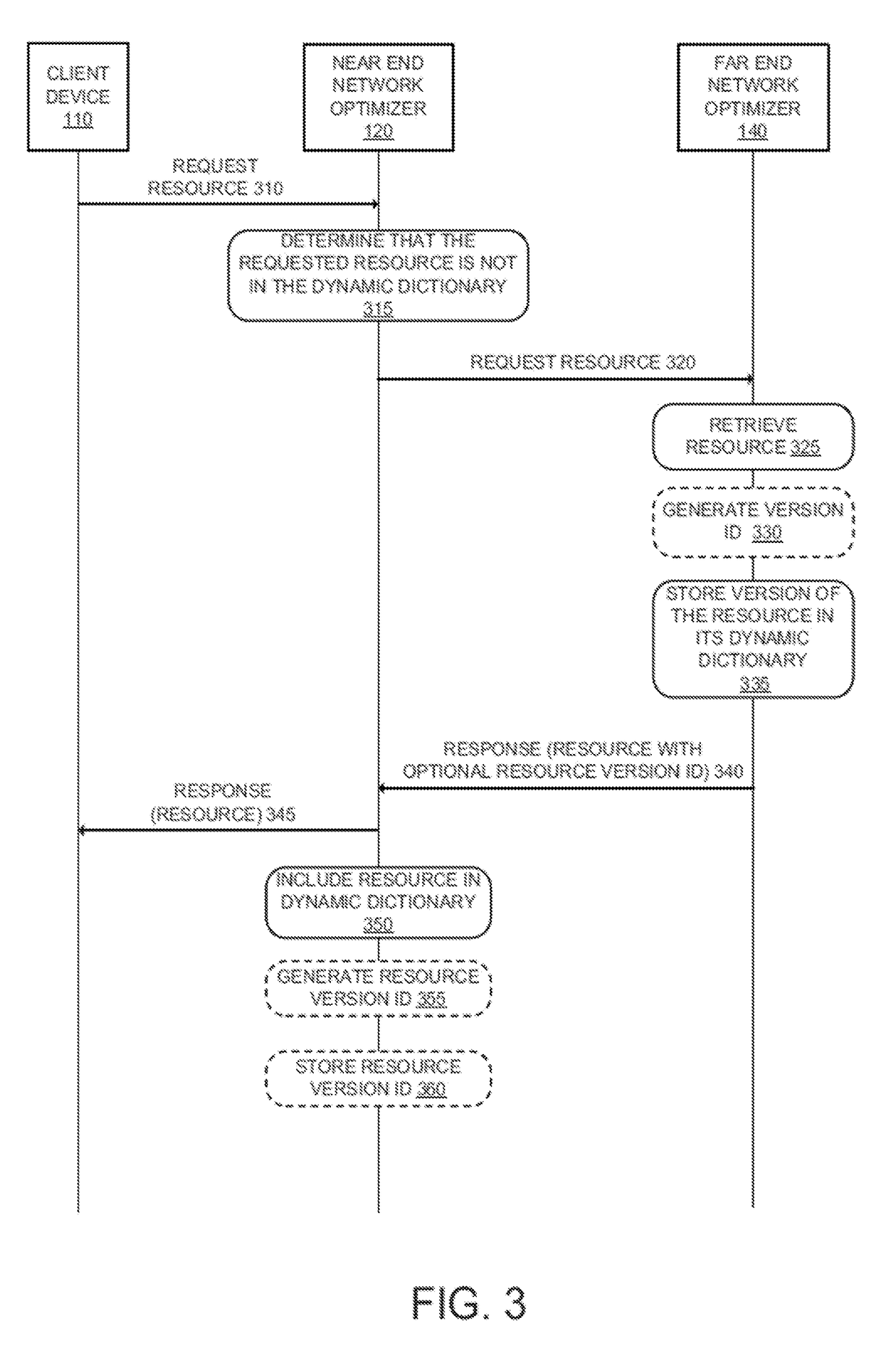
Method and apparatus for reducing network resource transmission size using delta compression
A near end point of presence (PoP) of a cloud proxy service receives, from a client device, a request for a network resource. A far end PoP from a plurality of PoPs of the cloud proxy service is identified. Responsive to determining that a version of the network resource is stored in the near end PoP, a request for the network resource is transmitted to the far end PoP with a version identifier that identifies that version. The far end PoP receives, from the near end PoP, a response that includes difference(s) between the version of the network resource stored in the near end PoP with a most current version of the network resource. The response does not include the entire network resource. The near end PoP applies the specified difference(s) to the version that it has stored to generate an updated version of the network resource, and transmits it to the client device.
Owner:CLOUDFLARE
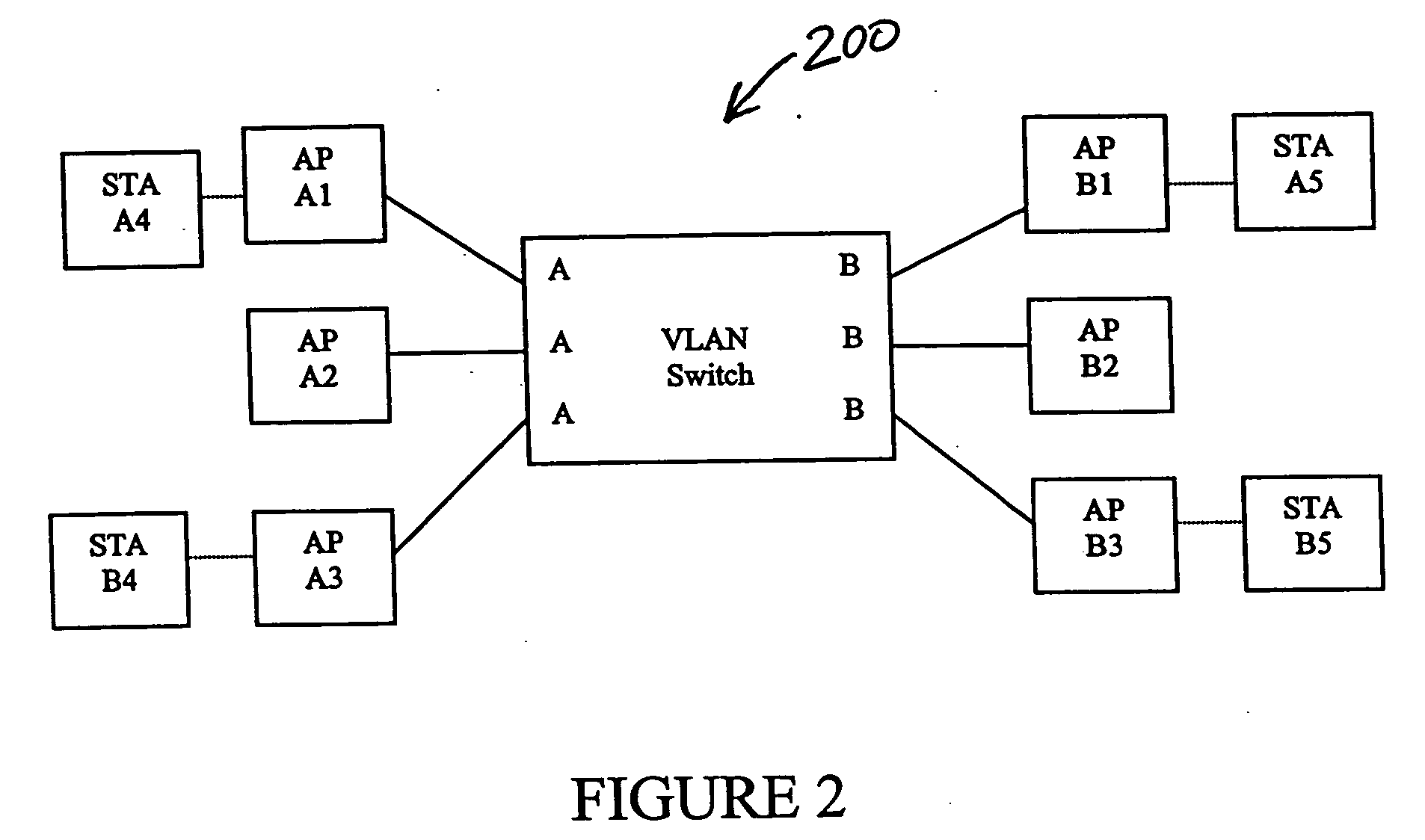
Mobile virtual LAN
InactiveUS20050180345A1Not burdened with associated computational overheadNetwork topologiesWireless network protocolsCommunications systemVirtual LAN
A communication system in which multiple protocols and proxy services are executed by an access point. In one embodiment of the invention, GVRP and GMRP registrations are combined in a single packet when a wireless device roams to a different VLAN. In addition, outbound GVRP and GMRP multicast messages are handled by an access point (also referred to as a GVRP and GMRP “gateway”) such that the wireless device is not burdened with the associated computational overhead. In a further embodiment, a wireless device may dynamically switch between a VLAN-aware state and a VLAN-unaware state depending on the nature of a detected access point. For example, if a relevant access point supports GVRP, the wireless device may operate as a VLAN terminal. If a wireless device is not attached to an access point with a matching VLAN ID, the wireless device sends and receives VLAN tagged frames. If a wireless device configured with a VLAN ID is attached to an access point with a matching VLAN ID, or if the wireless device is attached to a non-VLAN access point, then the wireless device may send and receive raw / untagged frames. In addition to the gateways described below, the ability of a wireless device to detect when it can send untagged frames is considered novel. In another embodiment of the invention, a special ID that is different than the native VLAN ID for a switch port is used for VLAN-unaware devices. This allows such devices that do not issue tagged frames to belong to a single VLAN ID.
Owner:AVAGO TECH INT SALES PTE LTD
Single sign-on system and implementation method thereof
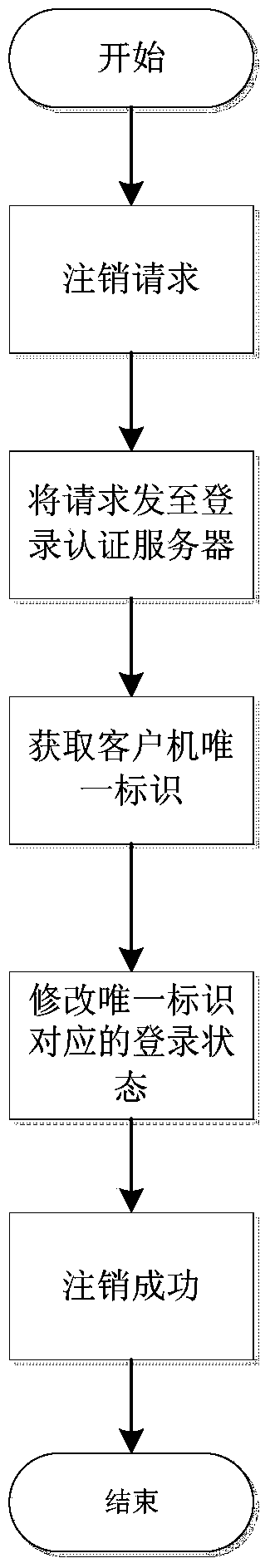
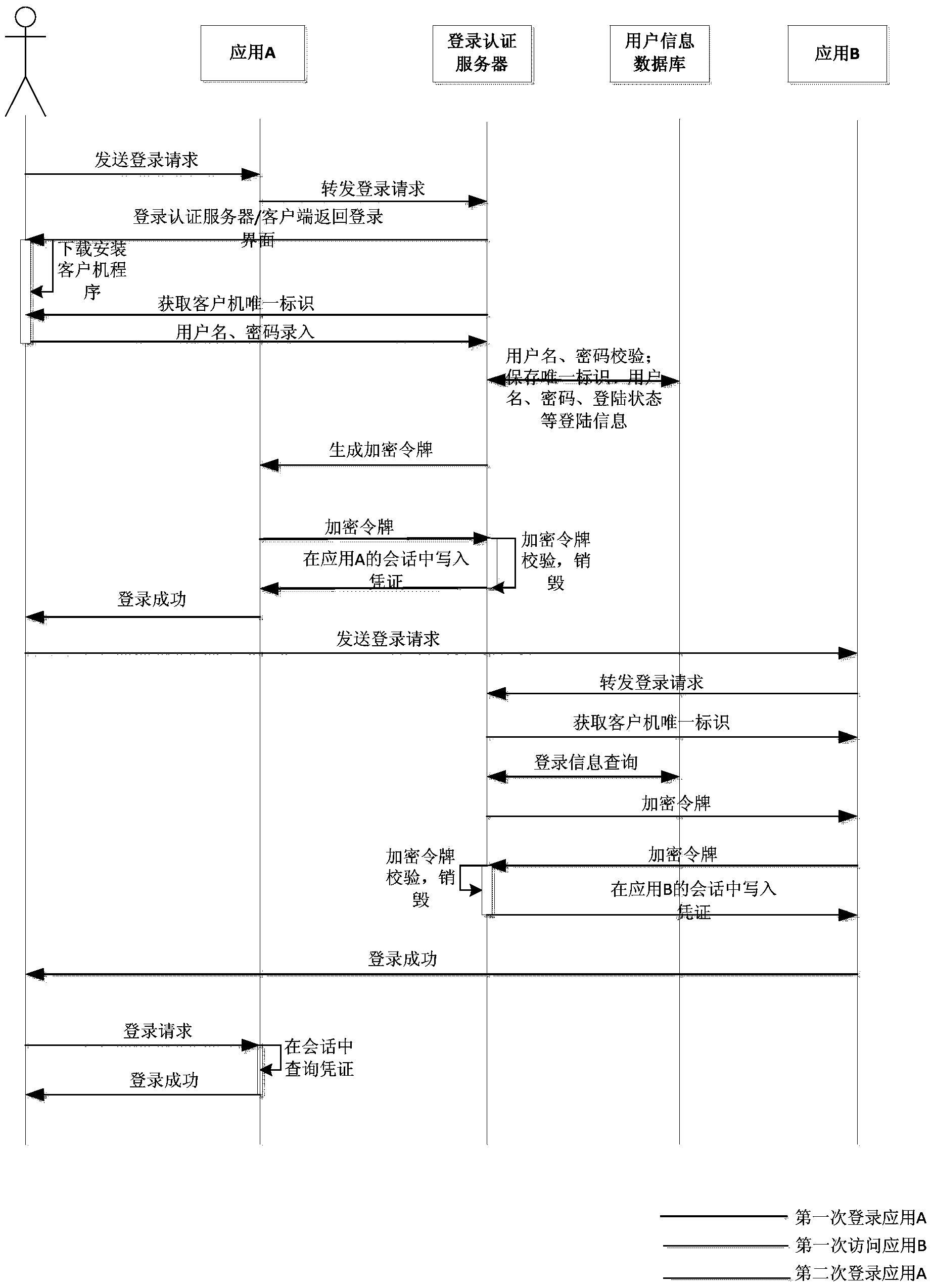
The invention discloses a single sign-on system and an implementation method of the single sign-on system. The method comprises the following steps that a client sends a sign-on request to an application server, a sign-on authentication client integrated on the application server forwards the request to a sign-on authentication server, the sign-on authentication server obtains the unique identification of the client through a sign-on agency service, the sign-on information such as the unique identification, a username, a password and the sign-on status is saved in or updated to a user information database, the sign-on authentication server queries the user sign-on information according to the unique identification and assigns an encryption token to the application server, and the application server queries the sign-on situation of the user according to the token. According to the single sign-on system and the implementation method of the single sign-on system, the sign-on authentication server obtains the unique identification of the client through the sign-on agency service installed on the background of the client, and safe and reliable cross-browser and cross- architecture (B / S, C / S) single sign-on between multiple application systems is achieved.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Systems and Methods for Secure Handling of Secure Attention Sequences
ActiveUS20090210934A1Digital data processing detailsUser identity/authority verificationTrusted componentsInternet privacy
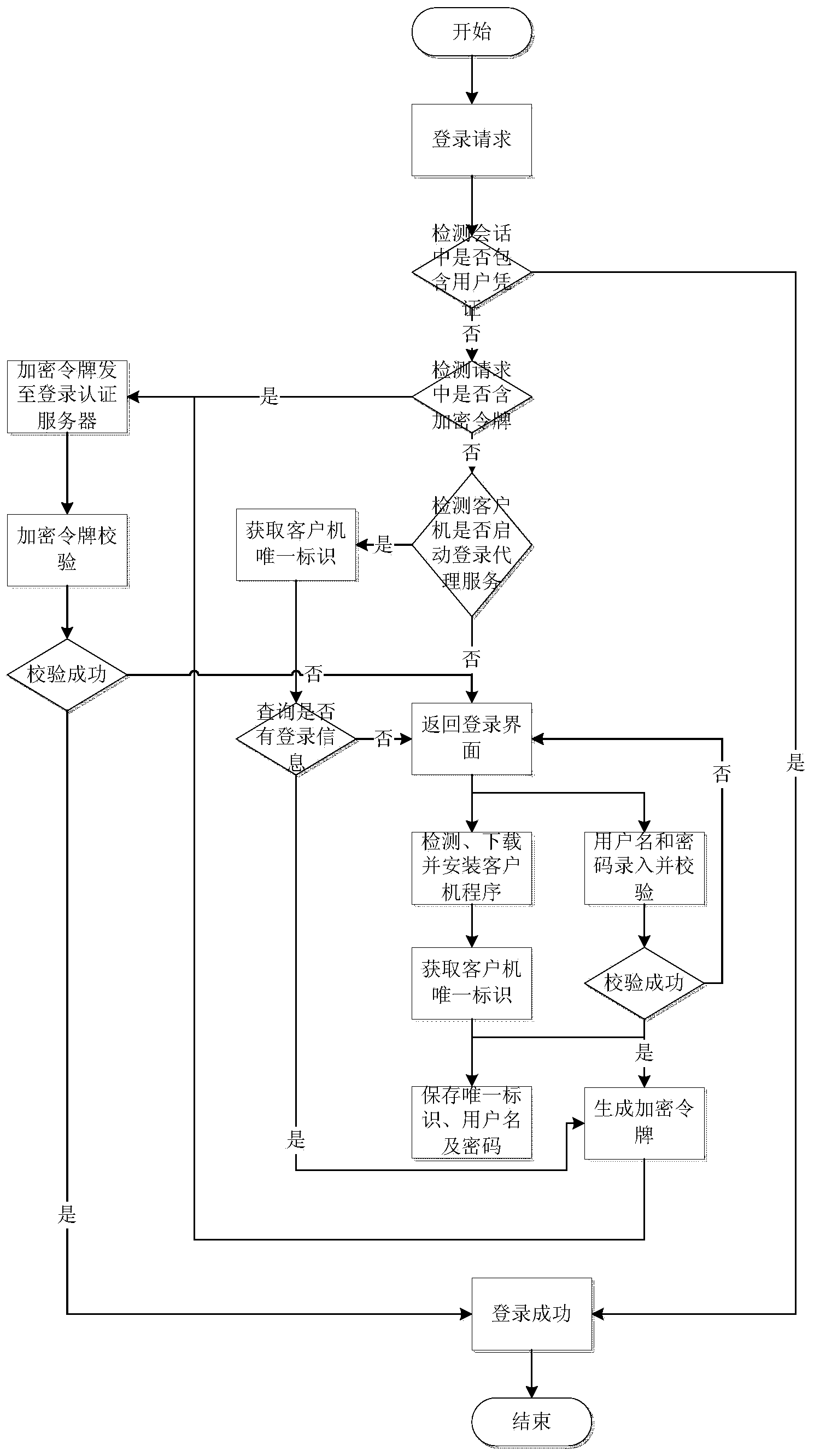
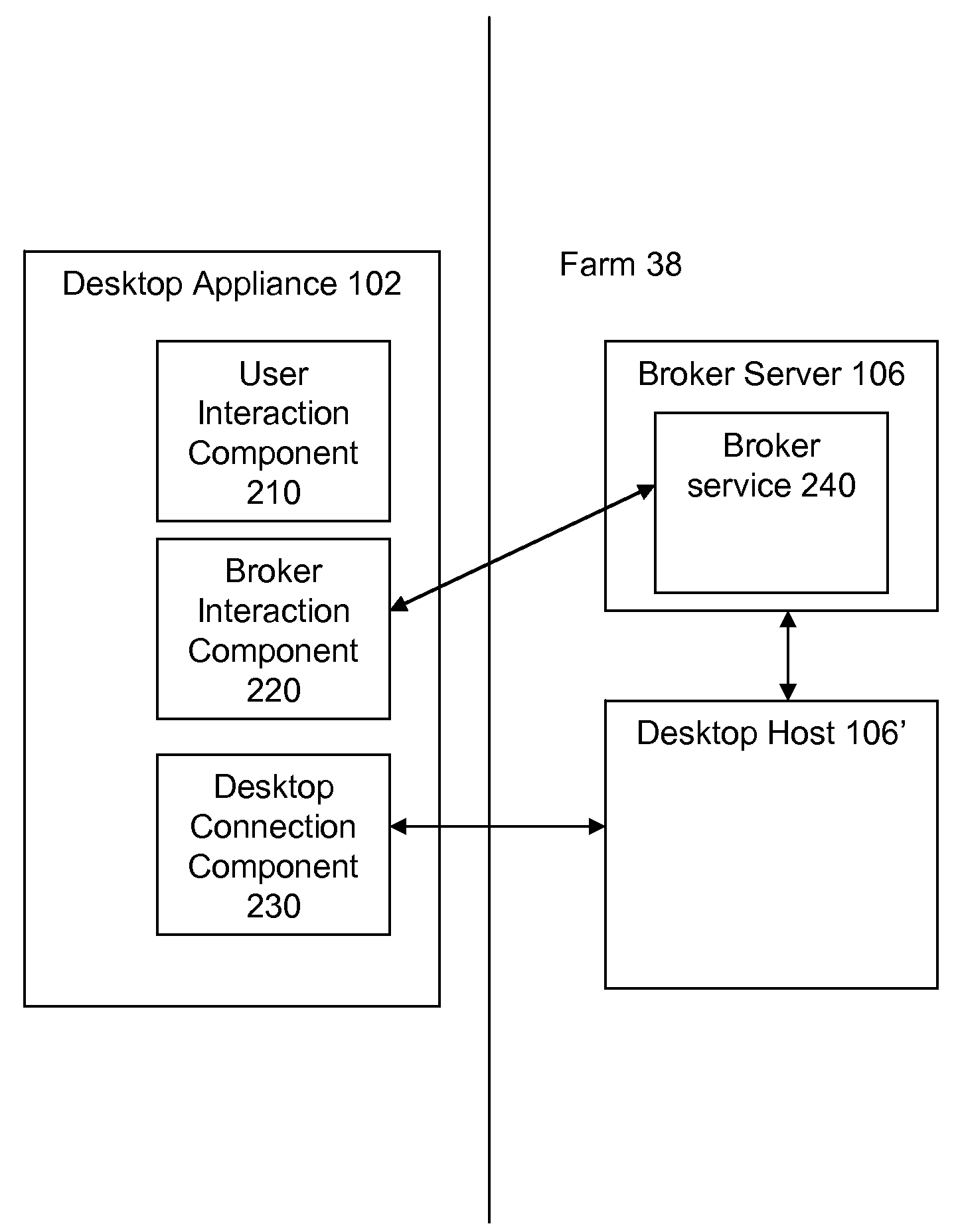
A method for authenticating, by a trusted component, a user of a desktop appliance to a remote machine includes executing, by a desktop appliance, a user interaction component, responsive to receiving a secure attention sequence from a user. The user interaction component receives authentication credentials associated with the user. The desktop appliance transmits, to a broker service, the received authentication credentials. The broker service authenticates the user, responsive to the received authentication credentials. The broker service transmits, to a remote machine, authentication data associated with the received authentication credentials. The remote machine authenticates the user, responsive to the received authentication data. The remote machine provides, to the desktop appliance, access to a resource requested by the user. In another aspect, a trusted component provides, to a user of a desktop appliance, access to secure desktop functionality provided by a remote machine.
Owner:CITRIX SYST INC
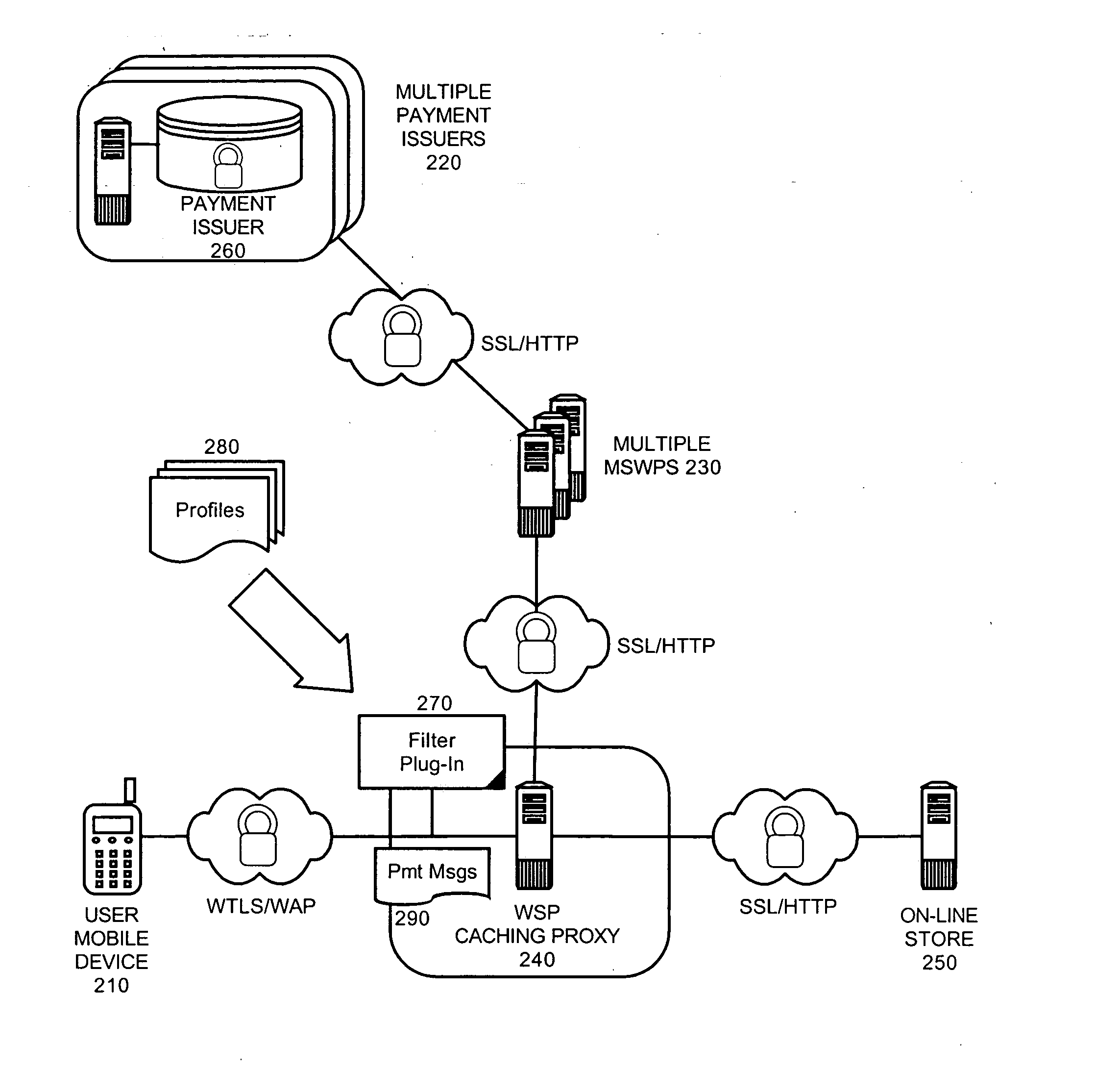
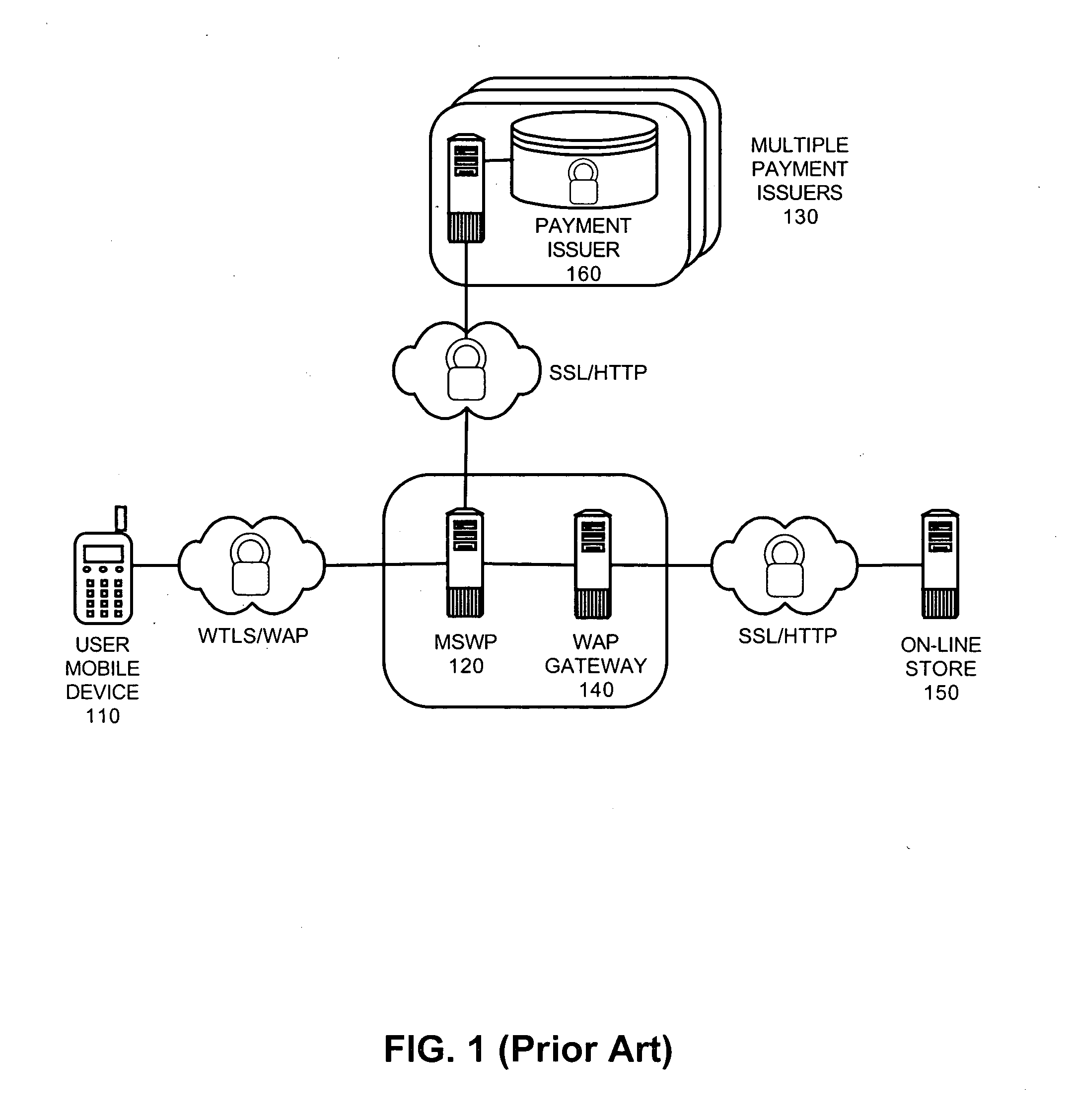
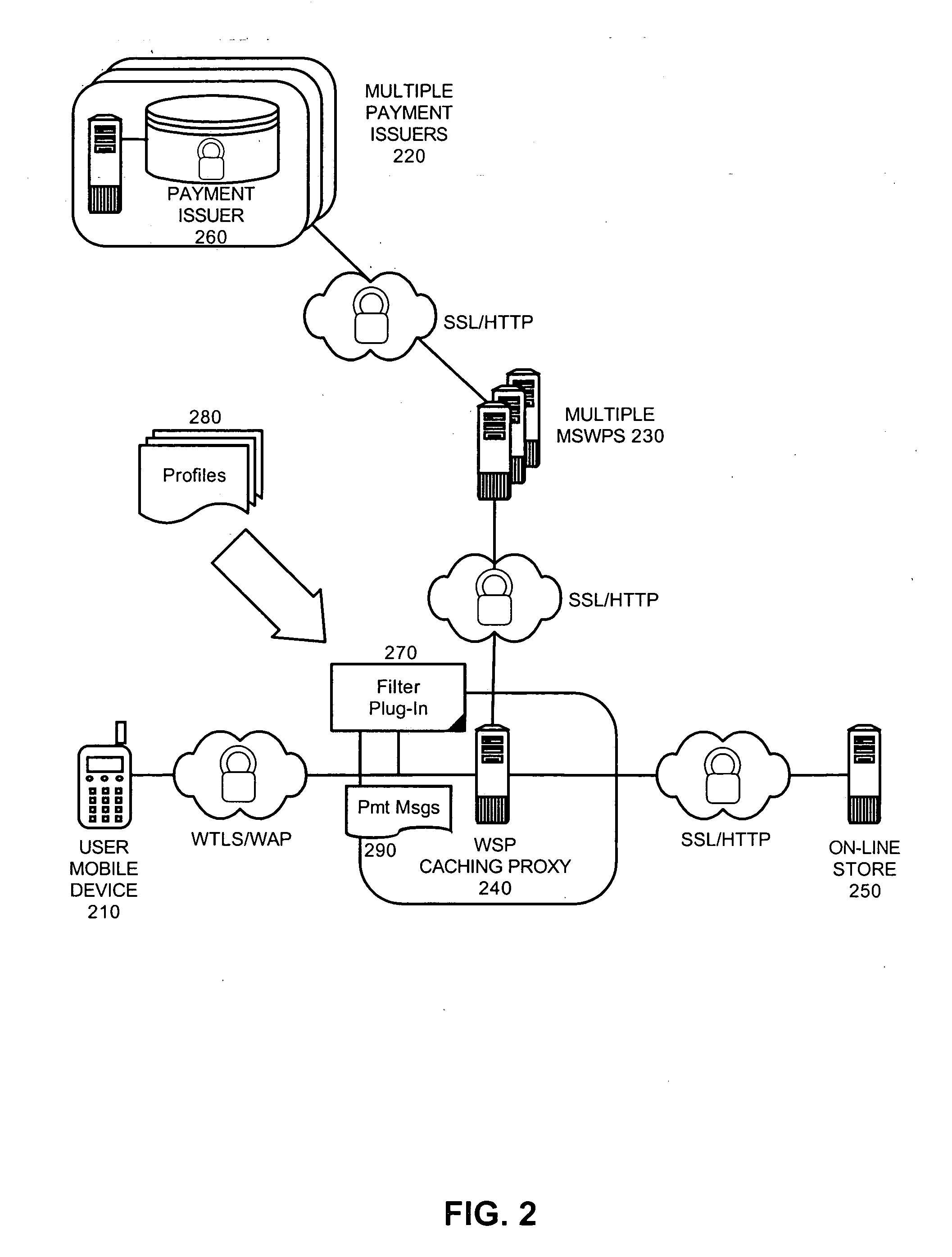
Dynamic processing of payment requests for mobile commerce transactions
A mobile commerce system which has been configured in accordance with the present invention can include a multiplicity of mobile server wallets. Each wallet can have an association with a corresponding subscriber in a wireless service provider network. A proxy server can be disposed in the wireless service provider network. Finally, a filter plug-in can be coupled to the proxy server and configured to intercept selected payment messages flowing through the proxy server. The filter plug-in further can be configured to route the payment messages to selected ones of the mobile server wallets.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com