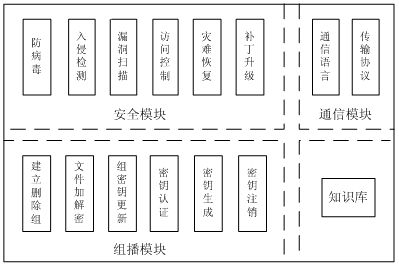
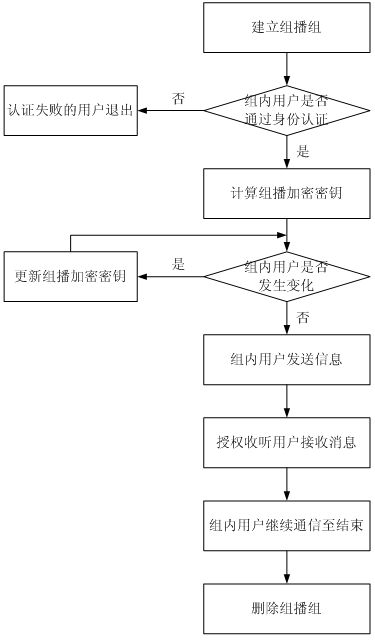
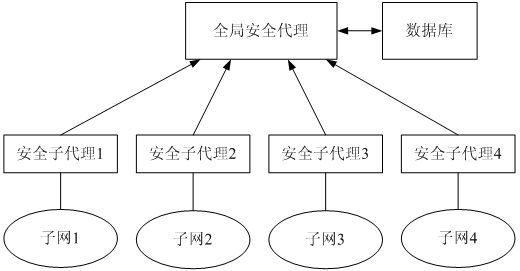
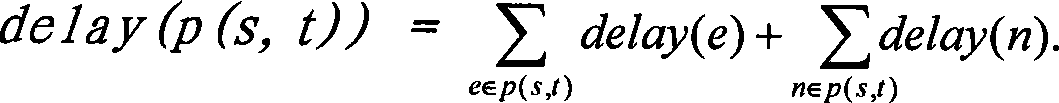Patents
Literature
36 results about "Multicast security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
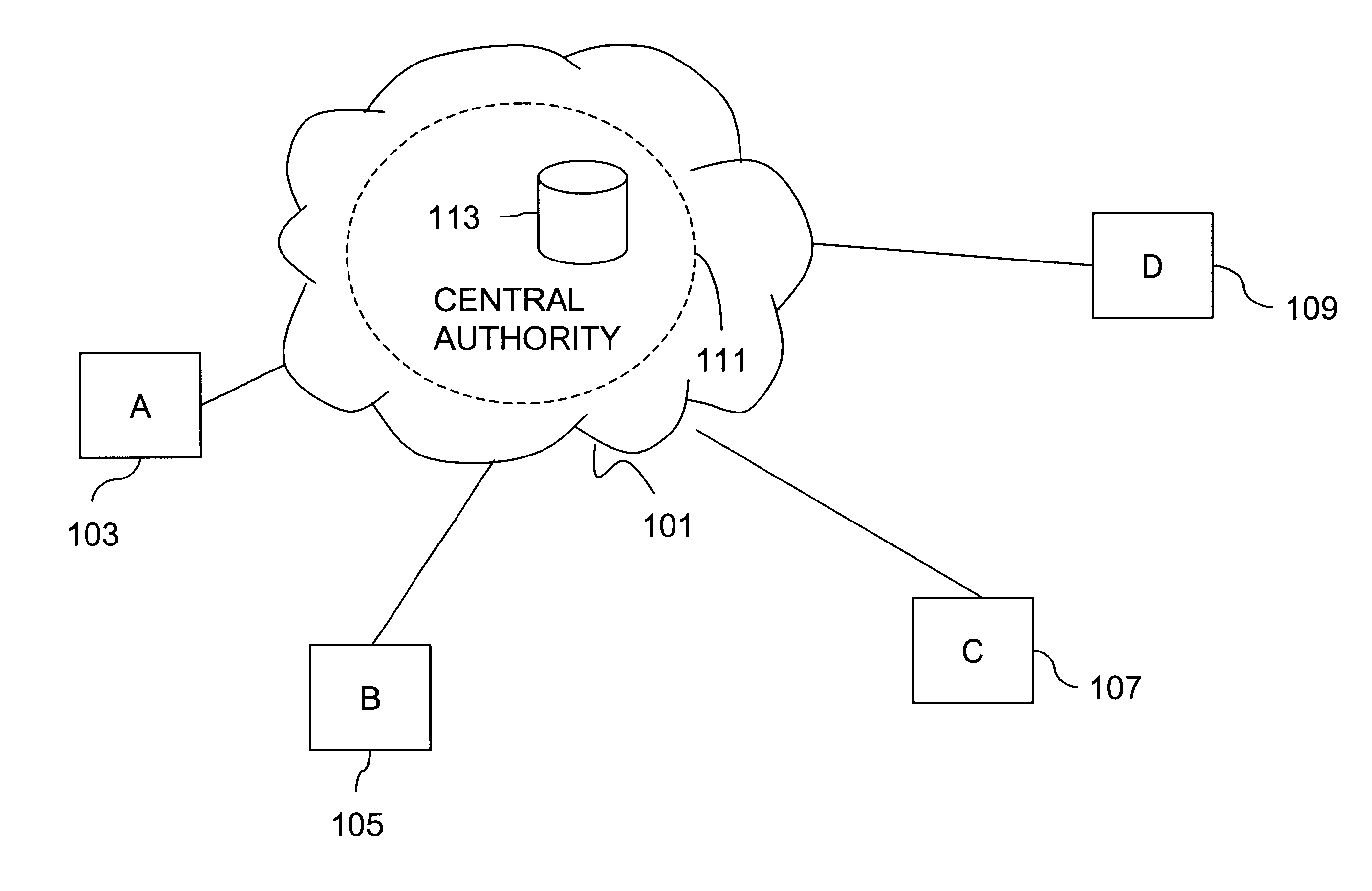
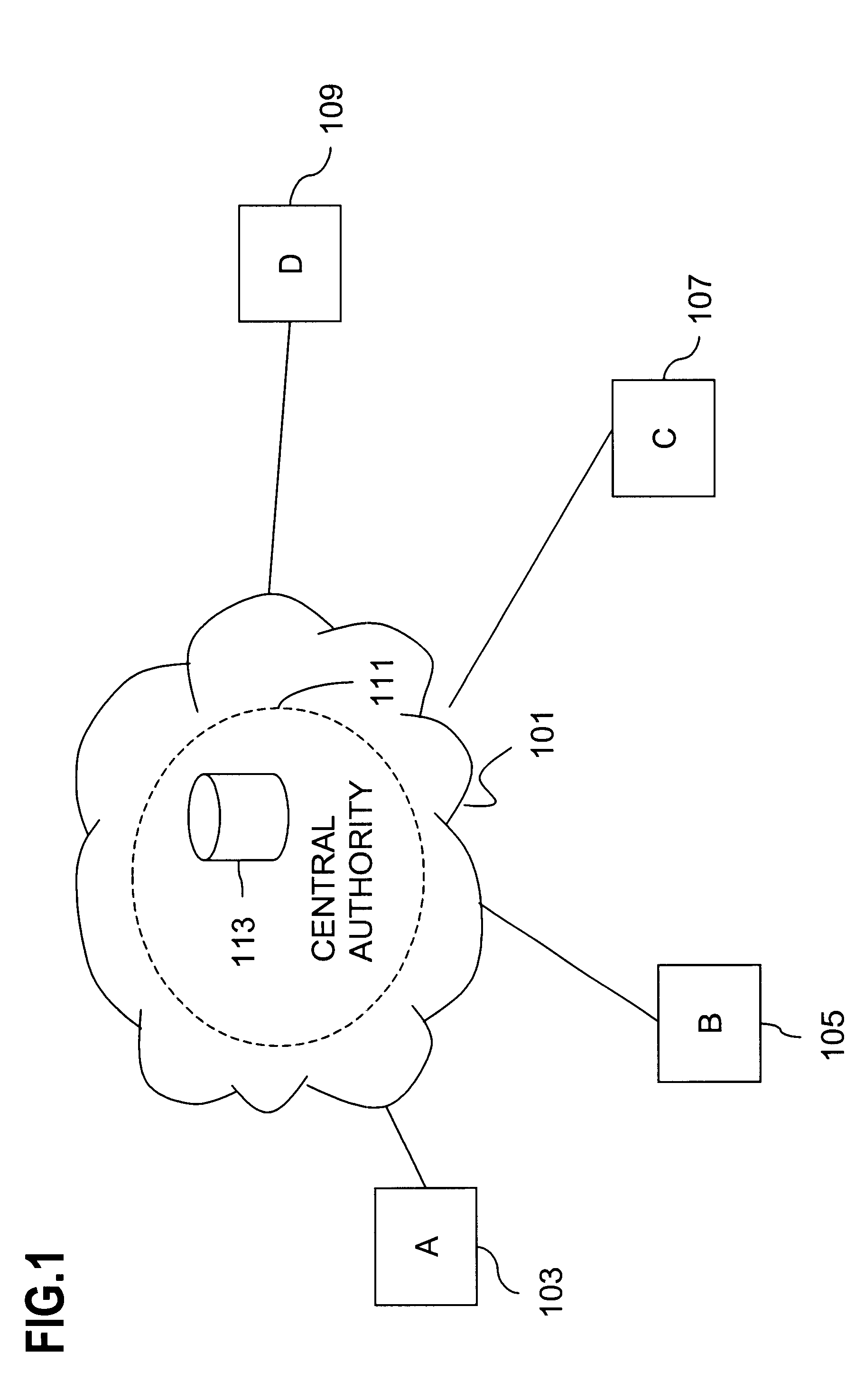
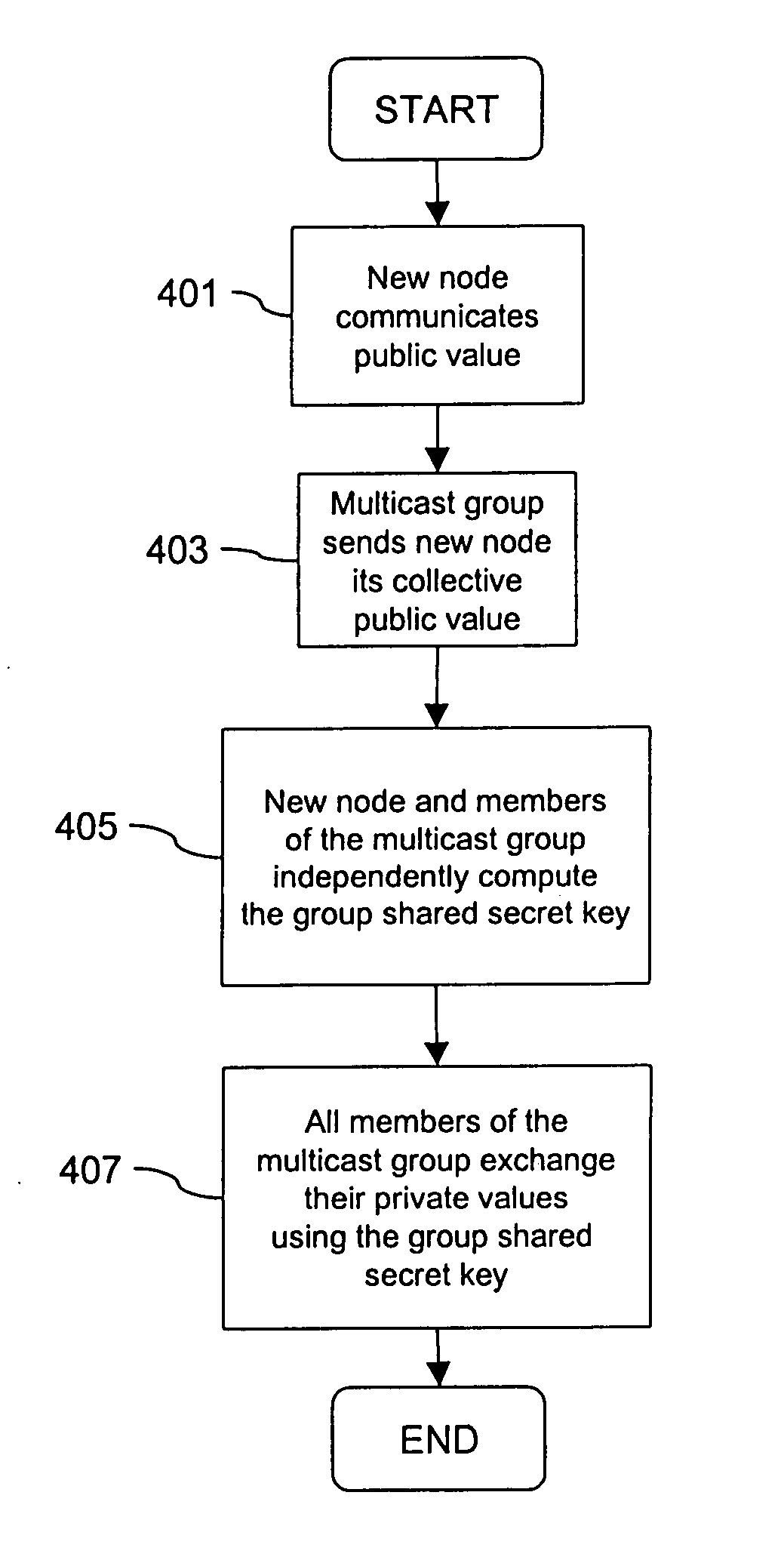
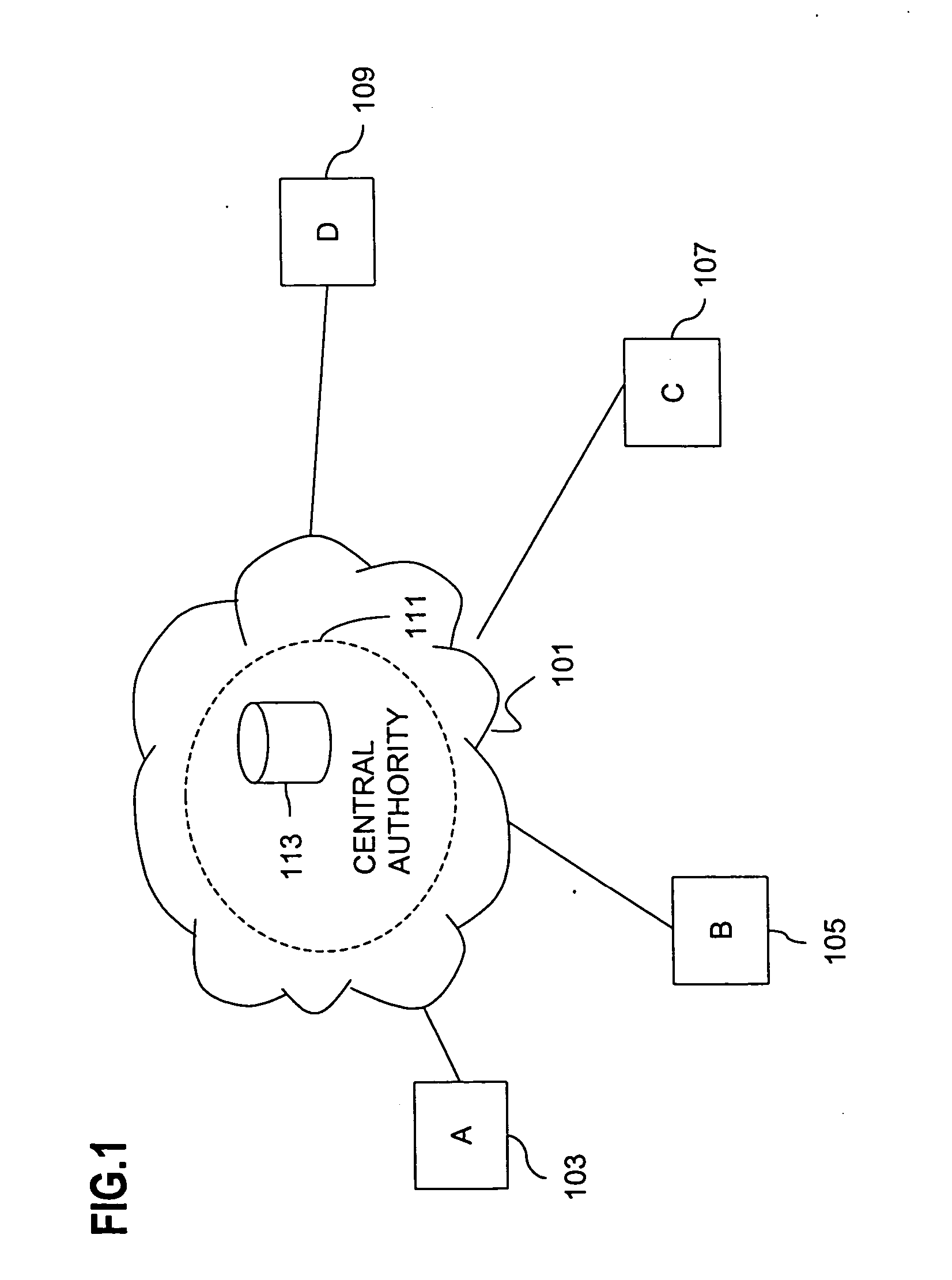
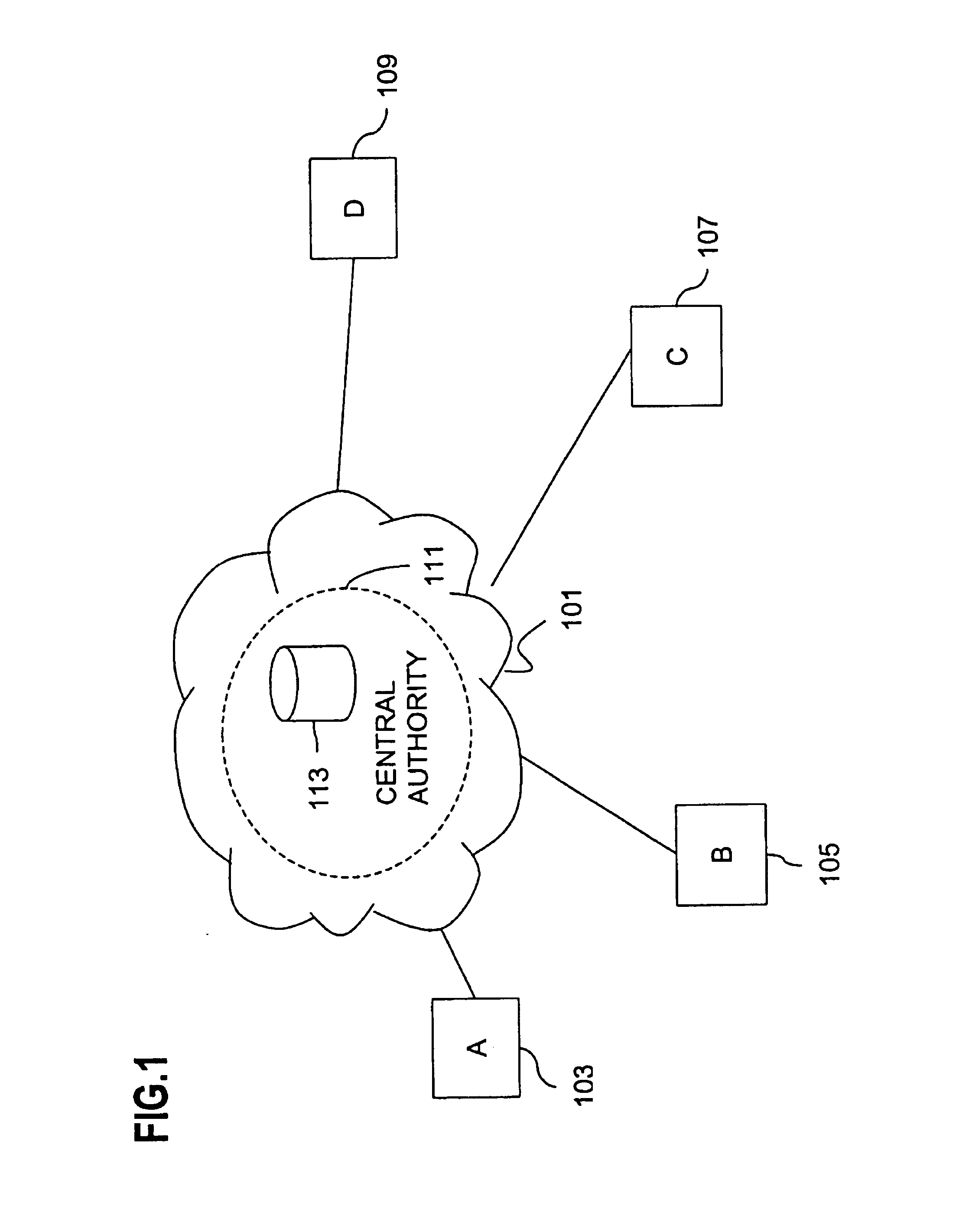
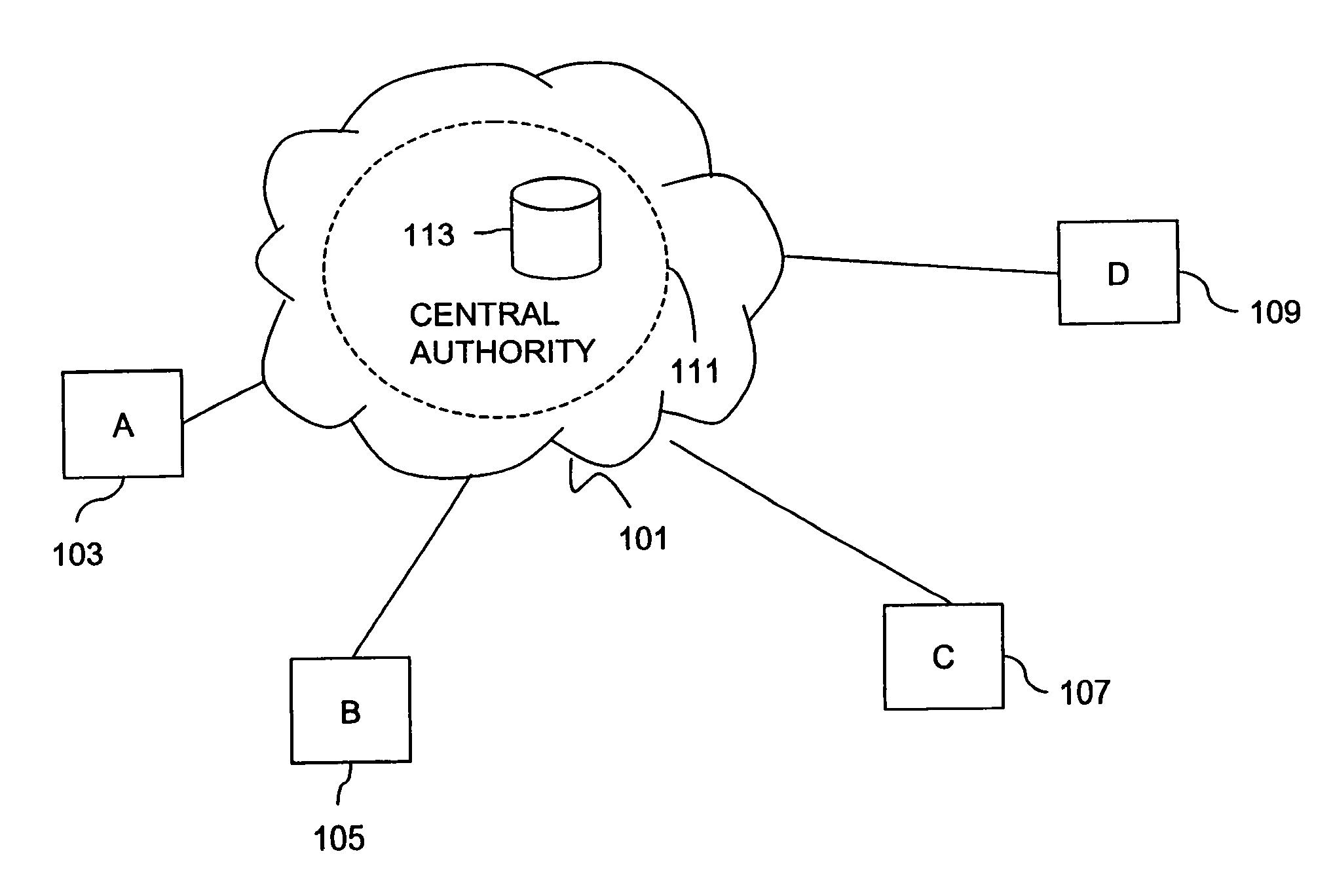
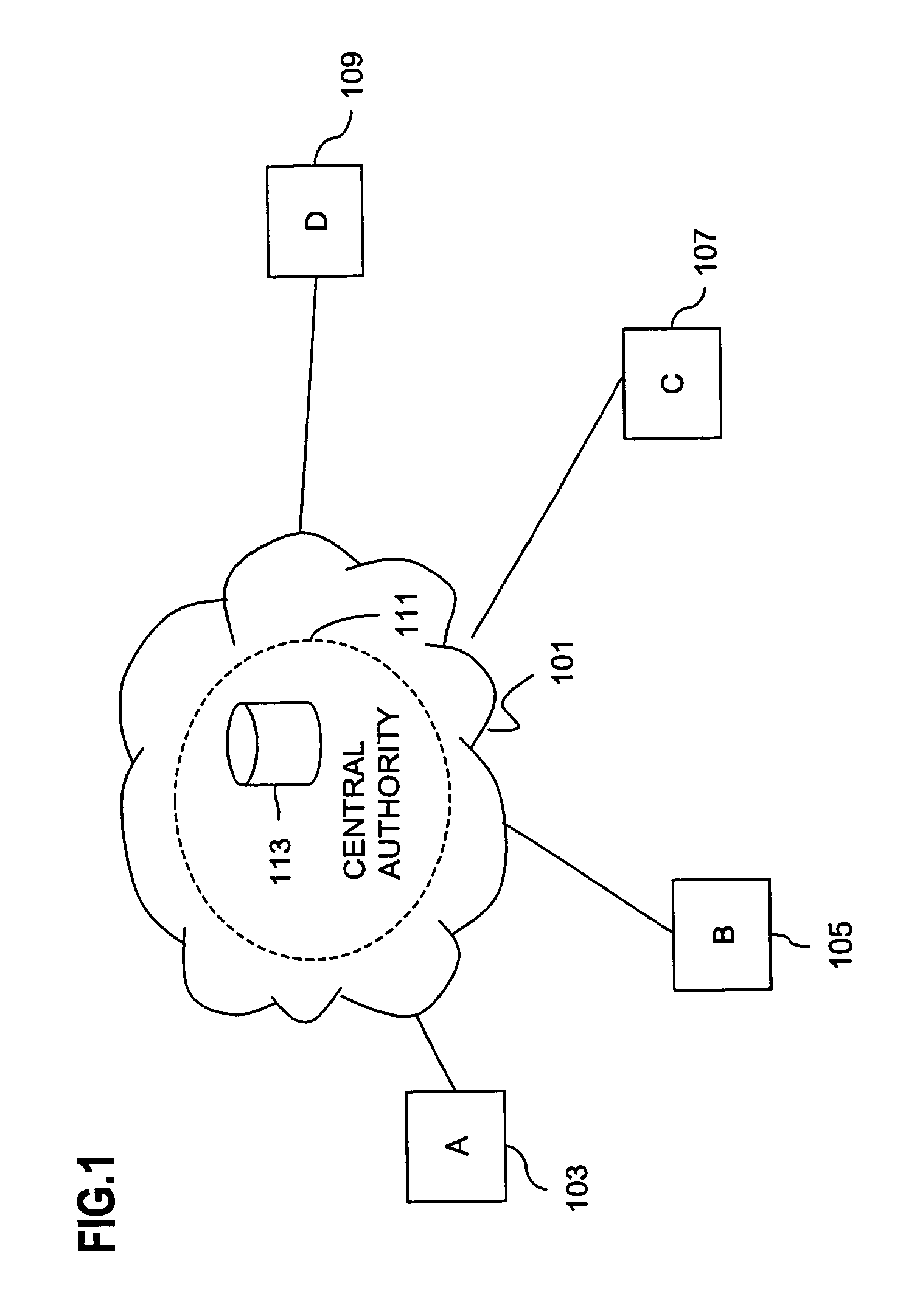
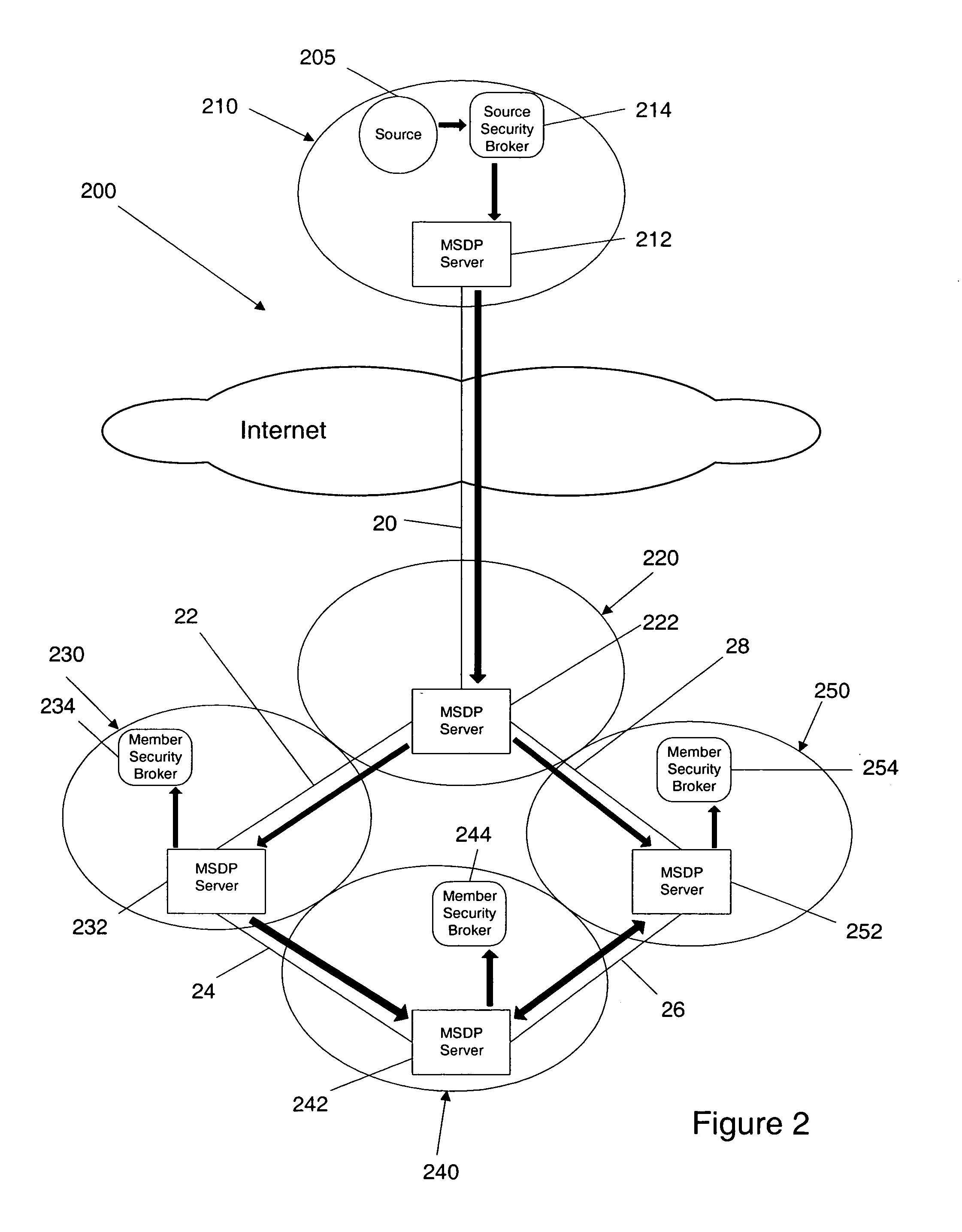
Method and apparatus for creating a secure communication channel among multiple event service nodes
InactiveUS7013389B1Easy to scaleUser identity/authority verificationSecure communicationGroup session
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Event service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
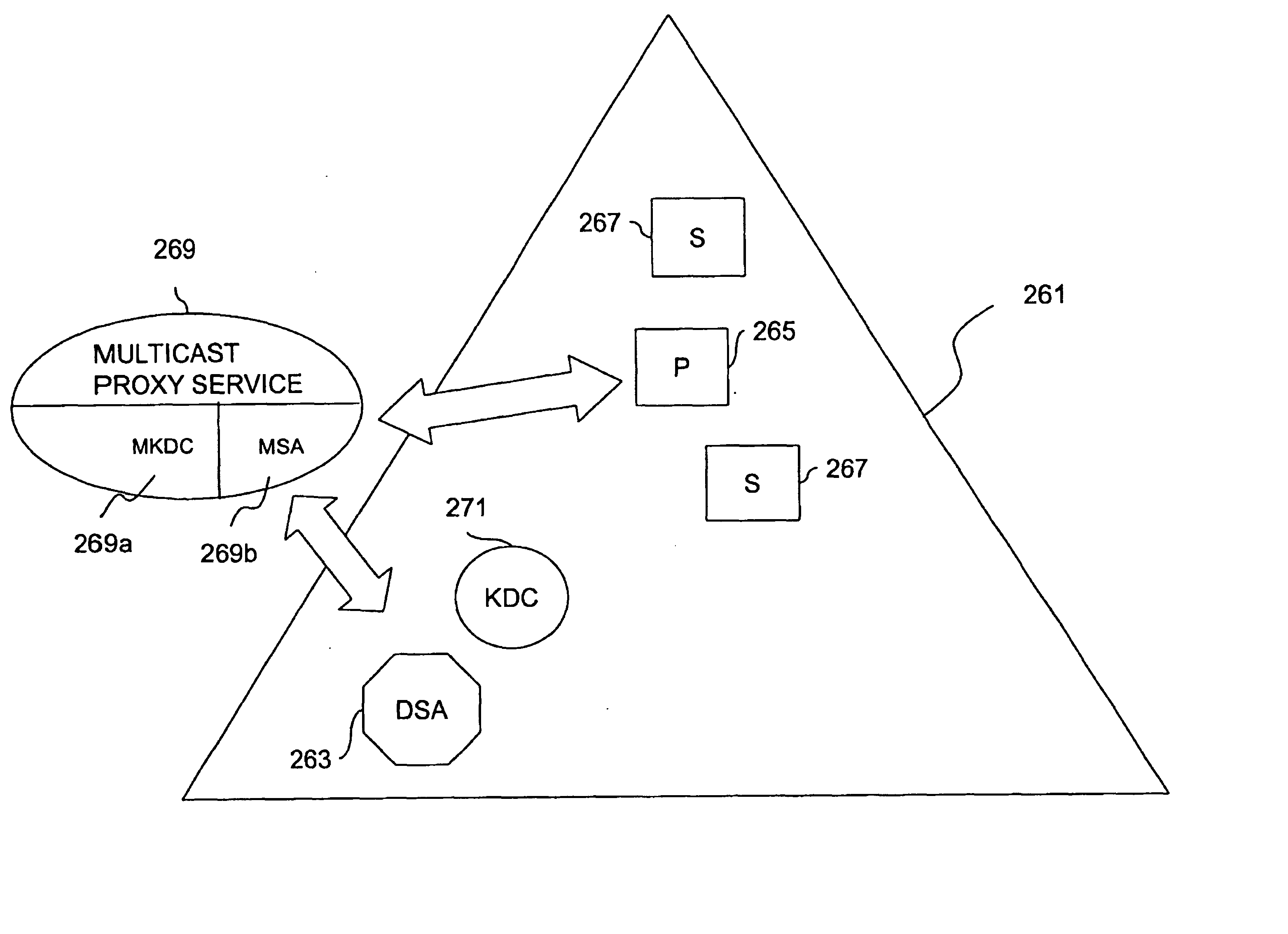
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
InactiveUS20050044356A1Optimize allocationKey distribution for secure communicationGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session keys that are members of the secure multicast or broadcast groups. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
InactiveUS7103185B1Optimize allocationKey distribution for secure communicationSynchronising transmission/receiving encryption devicesGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session key and the private keys of the multicast proxy service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the multicast proxy service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
Method and apparatus for creating a secure communication channel among multiple event service nodes
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service.
Owner:CISCO TECH INC
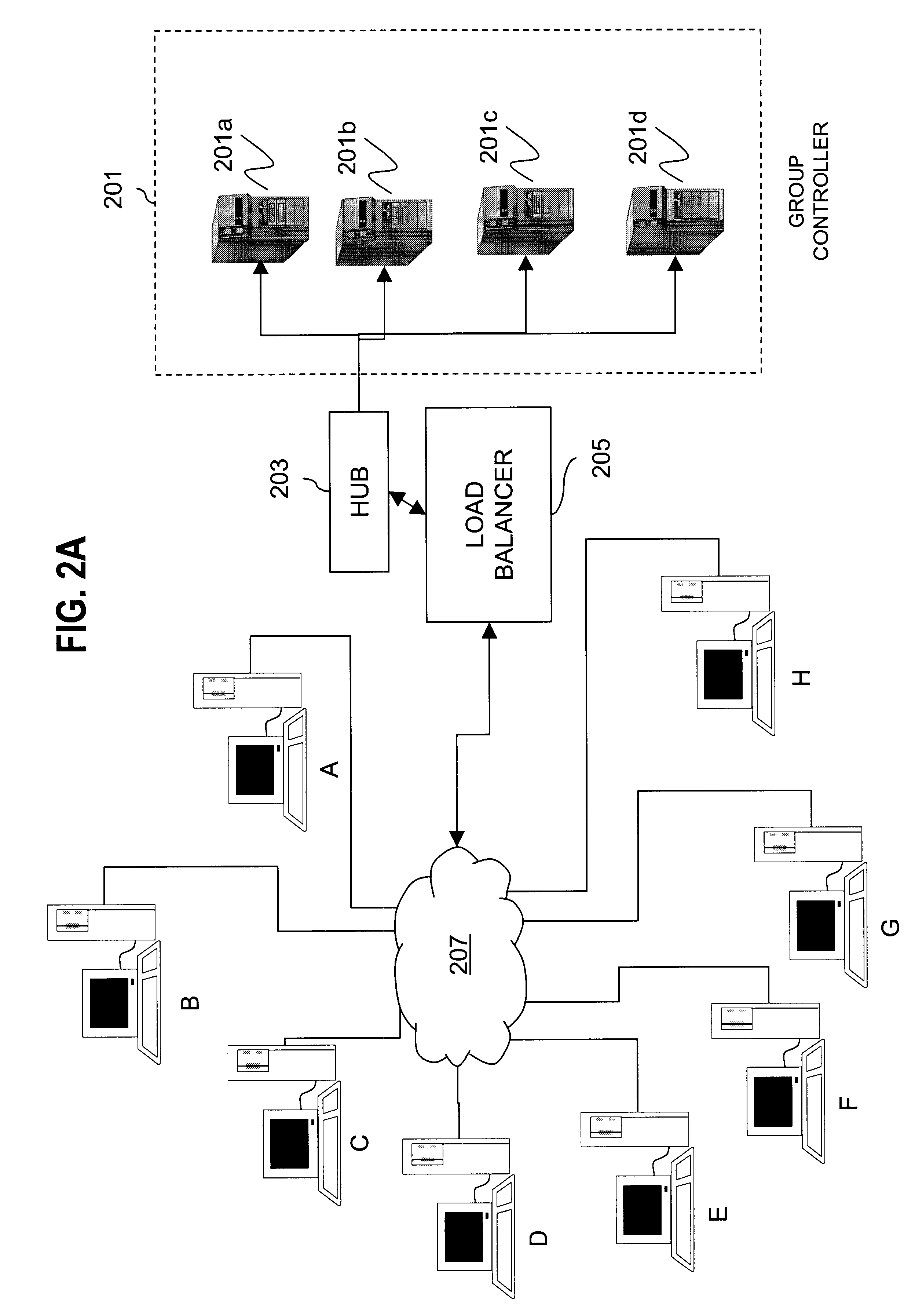
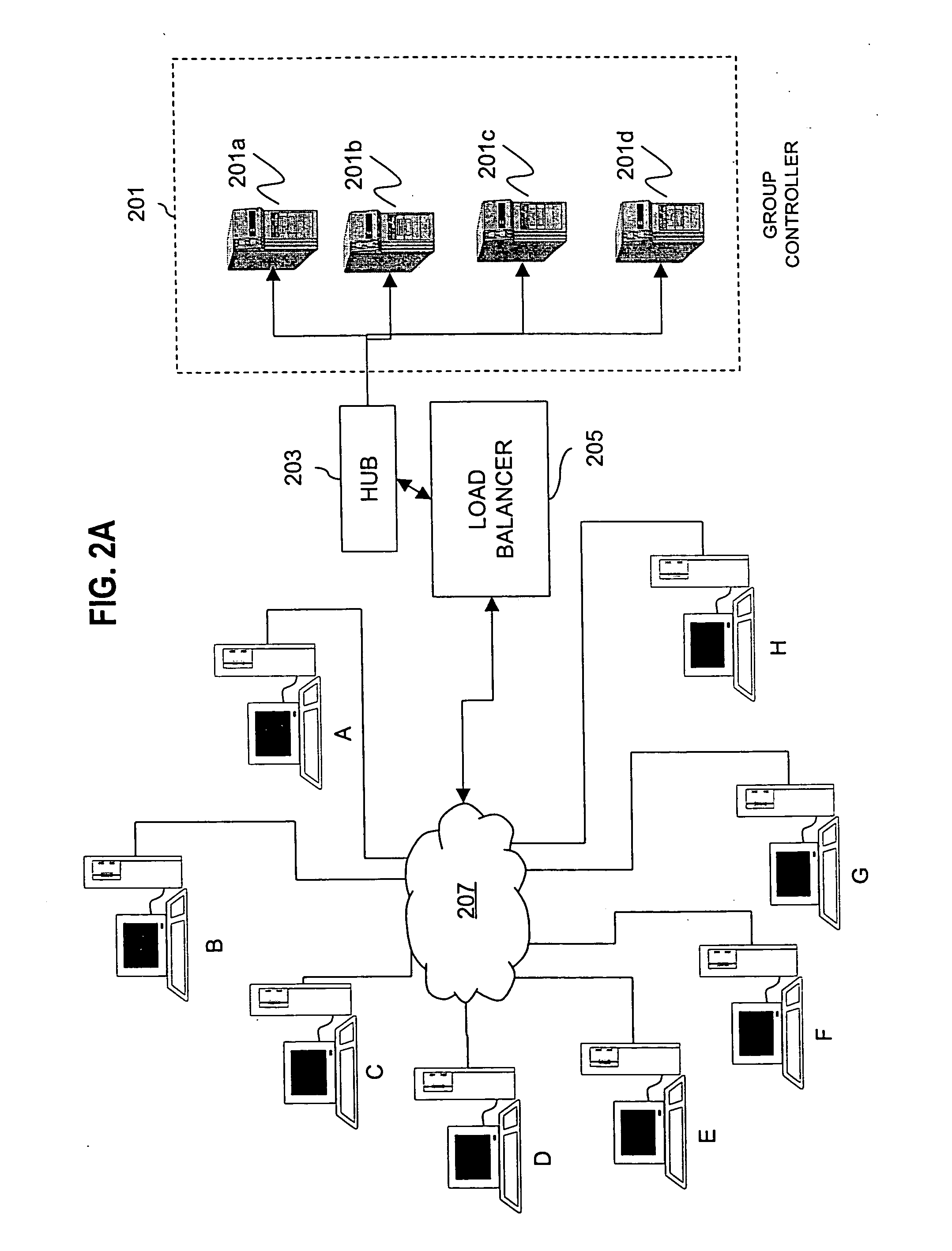
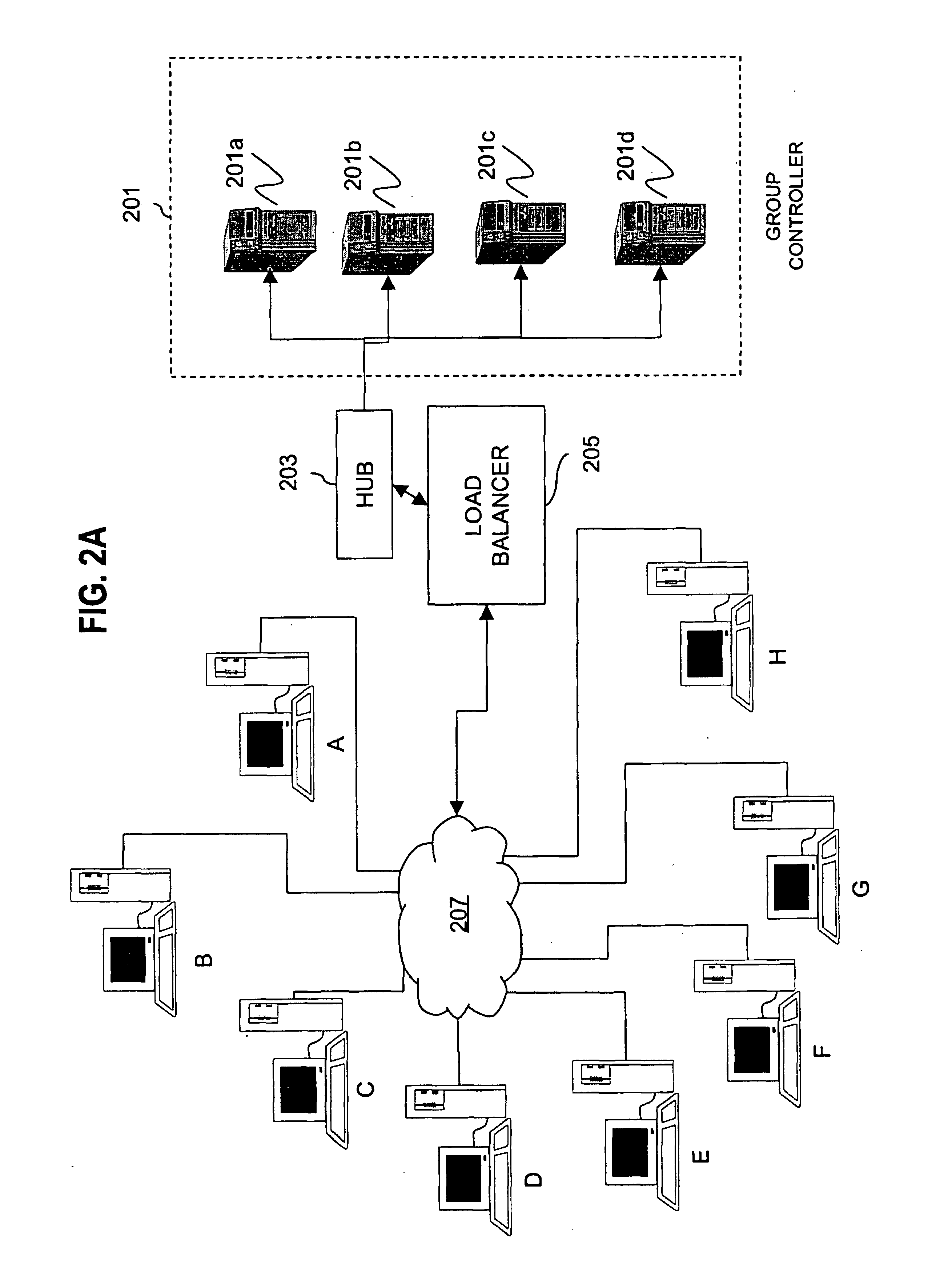
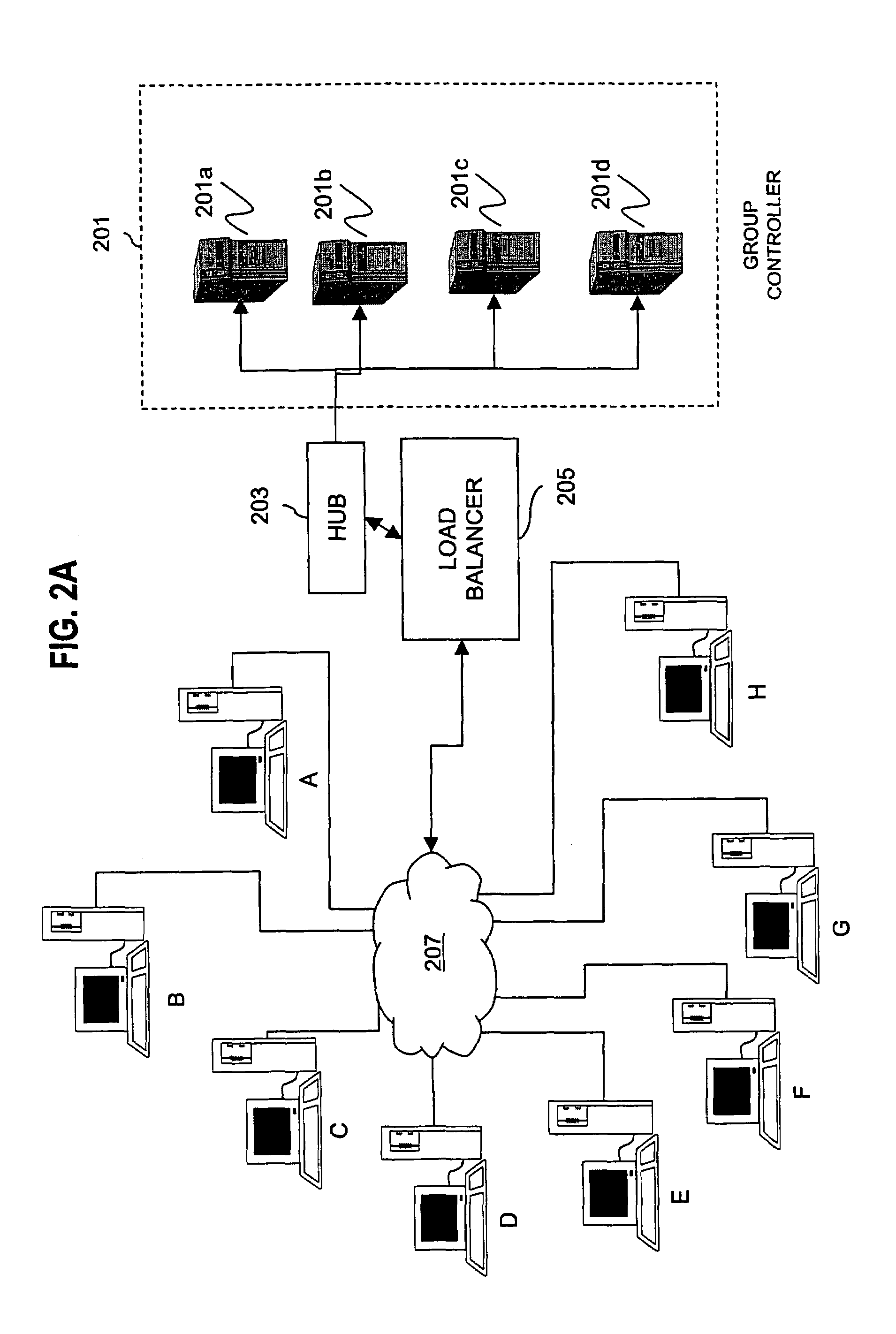
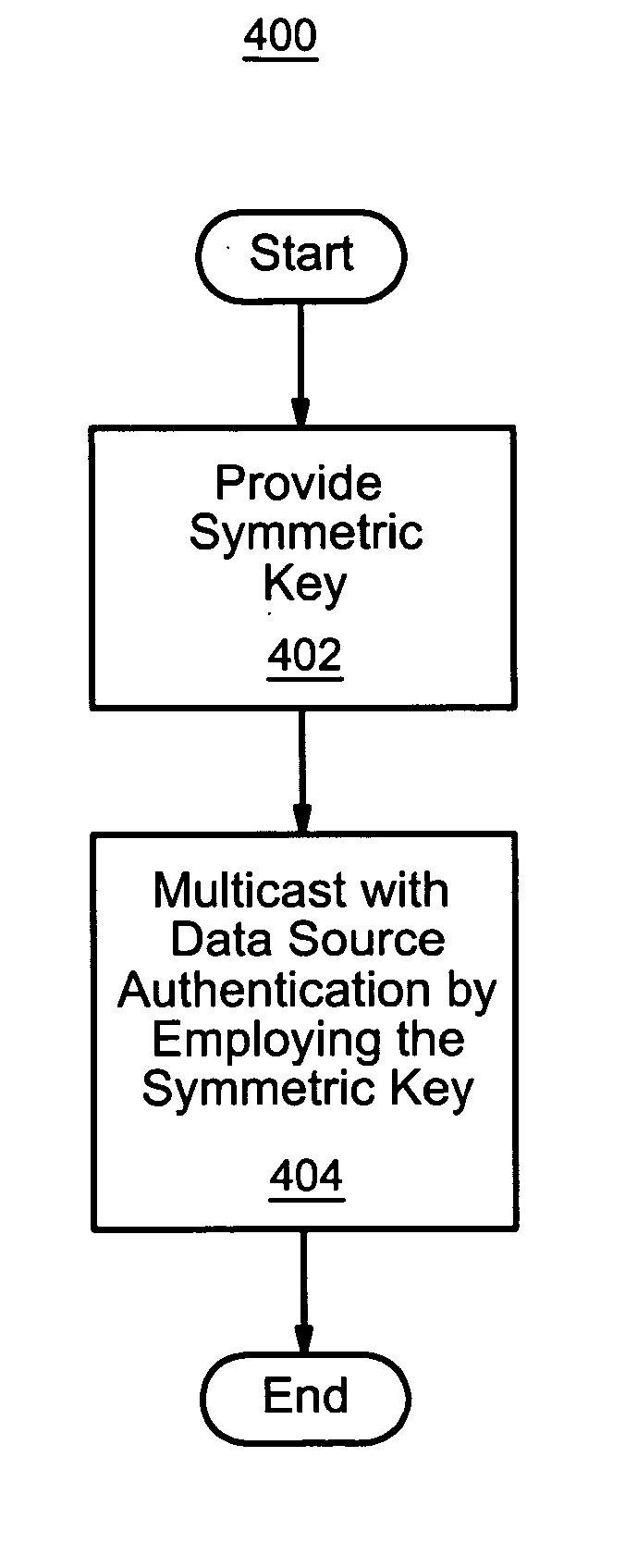
Apparatus and method for data source authentication for multicast security
A method and apparatus for data source authentication in multicast communications is provided. Multicasting a packet may be divided into two actions. The first action includes unicasting the packet from a sending member to a group controller. The second action includes multicasting the packet from the group controller to the multicast group. The packet may be unicast to the group controller with a message authentication code (MAC) that may be generated by encrypting the packet with a symmetric key that is intended to be known only to the sending member and the group controller. After authenticating the MAC, the group controller multicasts the packet to the multicast group. The group controller includes with the packet a separate MAC for substantially each receiving member of the multicast group, each encrypted by a separate symmetric key. Each symmetric key may be intended to be known only by the receiving member and the group controller.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Multi-cast method and multi-cast system and multi-cast device
InactiveCN101145900AImprove securityReduce the burden onSpecial service provision for substationSecuring communicationComputer networkGroup Label
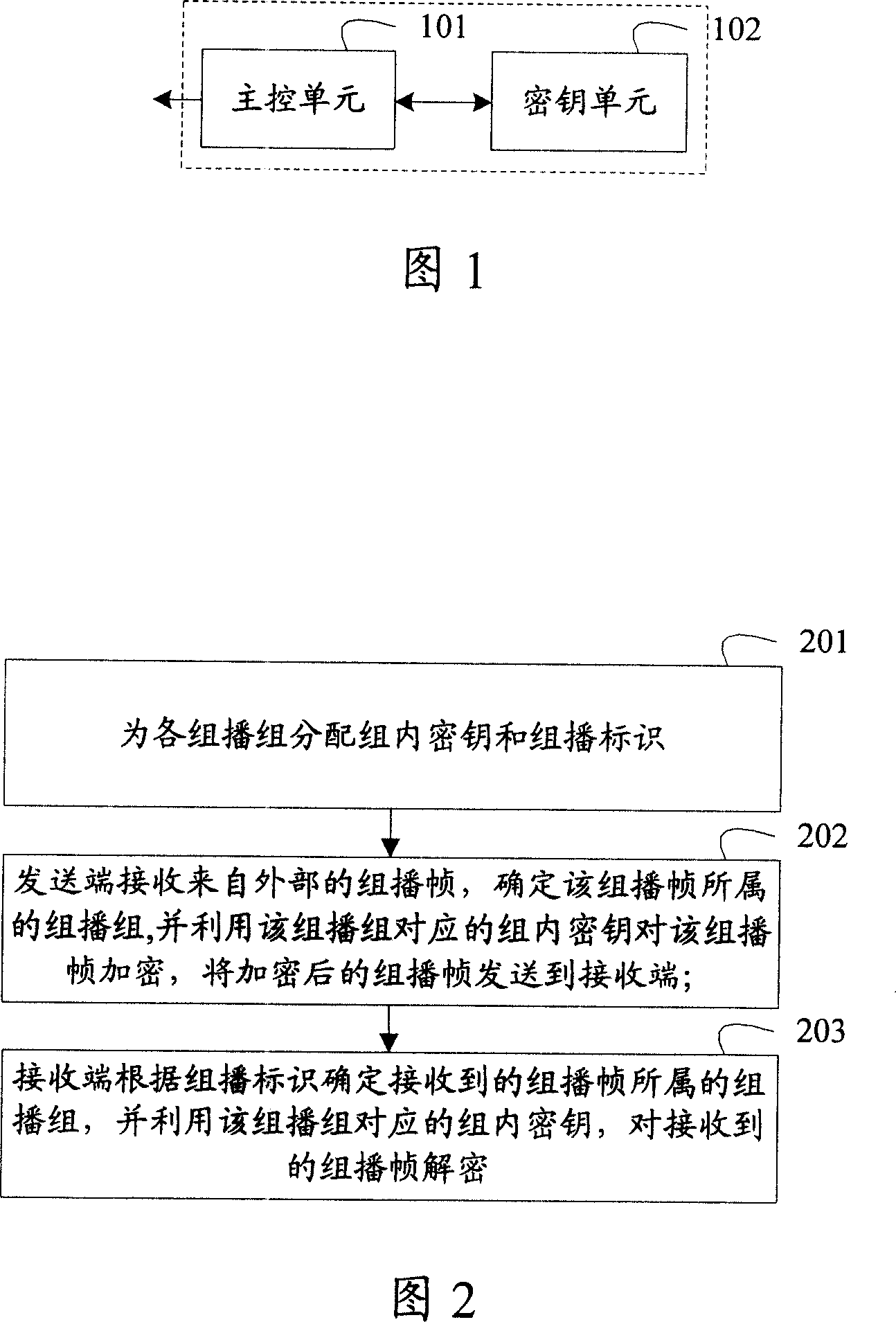
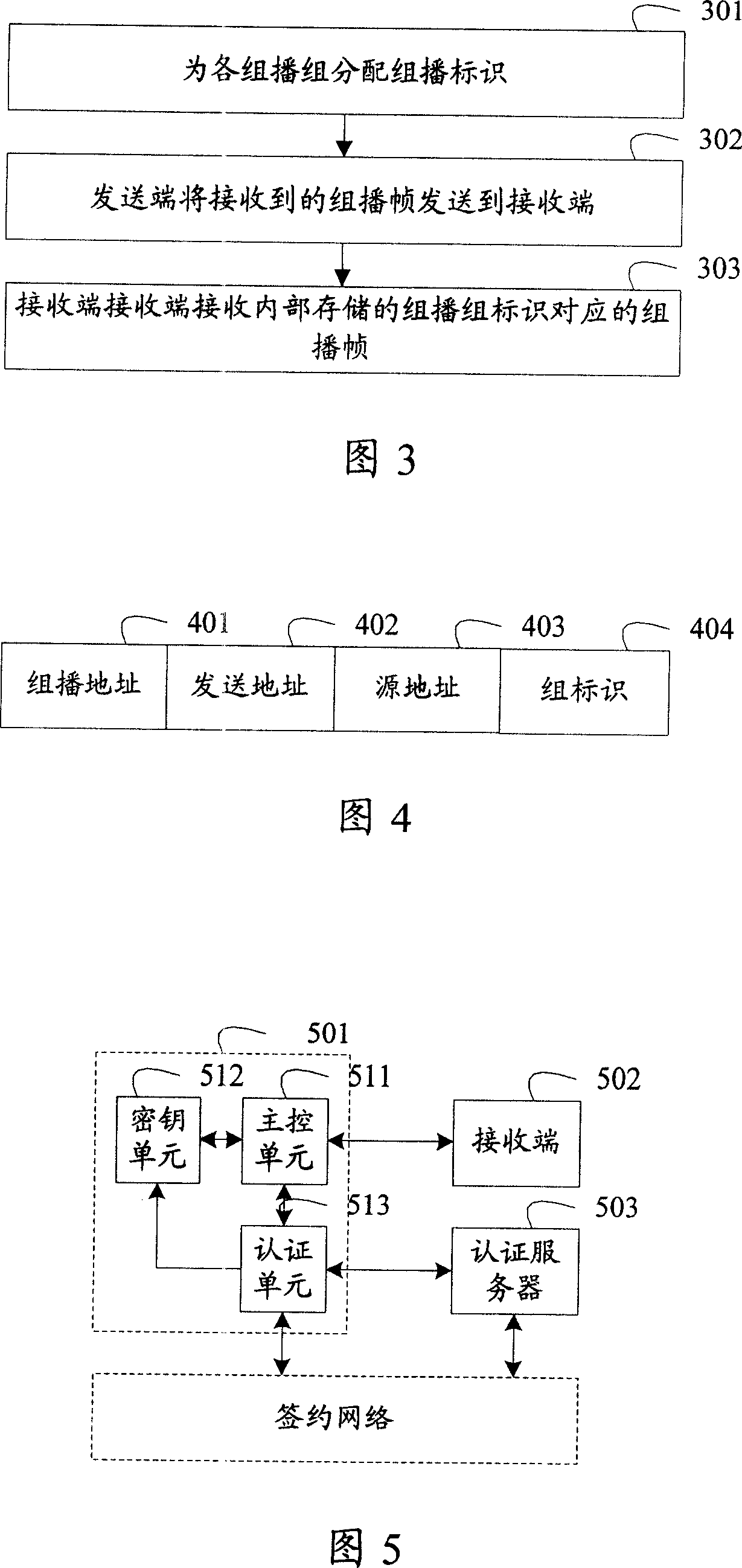
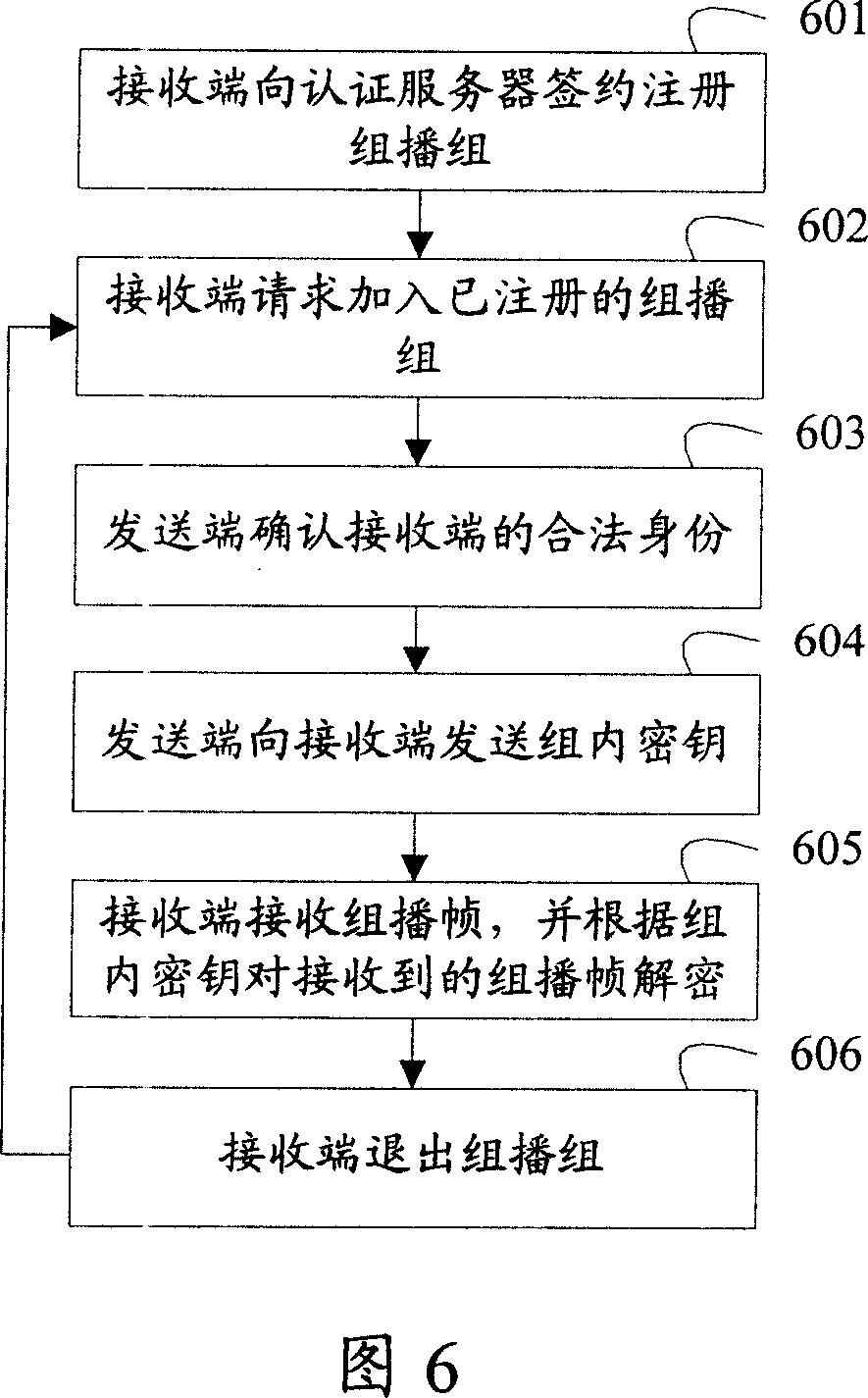
The invention discloses a multicast method, which includes the steps as follows: distribute intragroup keys and multicast group labels to all multicast groups; a sending end receives a multicast frame from the outside, the multicast group which the multicast frame belongs to is determined, the multicast frame is encrypted by using the intragroup key corresponding to the multicast group, and the encrypted multicast frame is sent to a receiving end; the receiving end identifies the multicast group which the multicast frame belongs to according to the multicast group labels, and decrypts the received multicast frame by using the intragroup key corresponding to the multicast group. The invention discloses a multicast system, multicast equipment, another multicast method and aother multicast equipment. The technical proposal of the invention improves the multicast security and reduces the system burden.
Owner:HUAWEI TECH CO LTD
Realizing system of multicast routing based on mark and method thereof
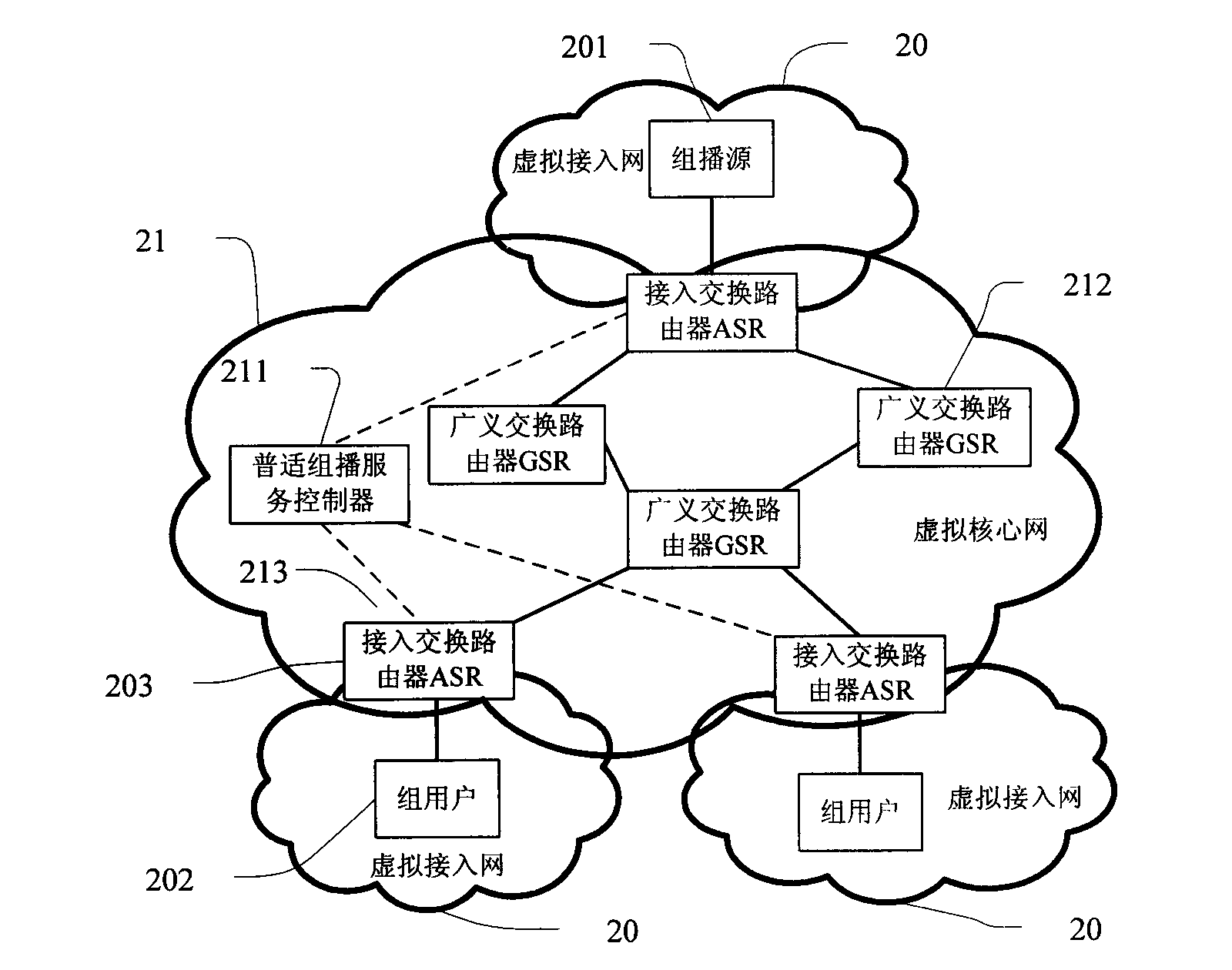
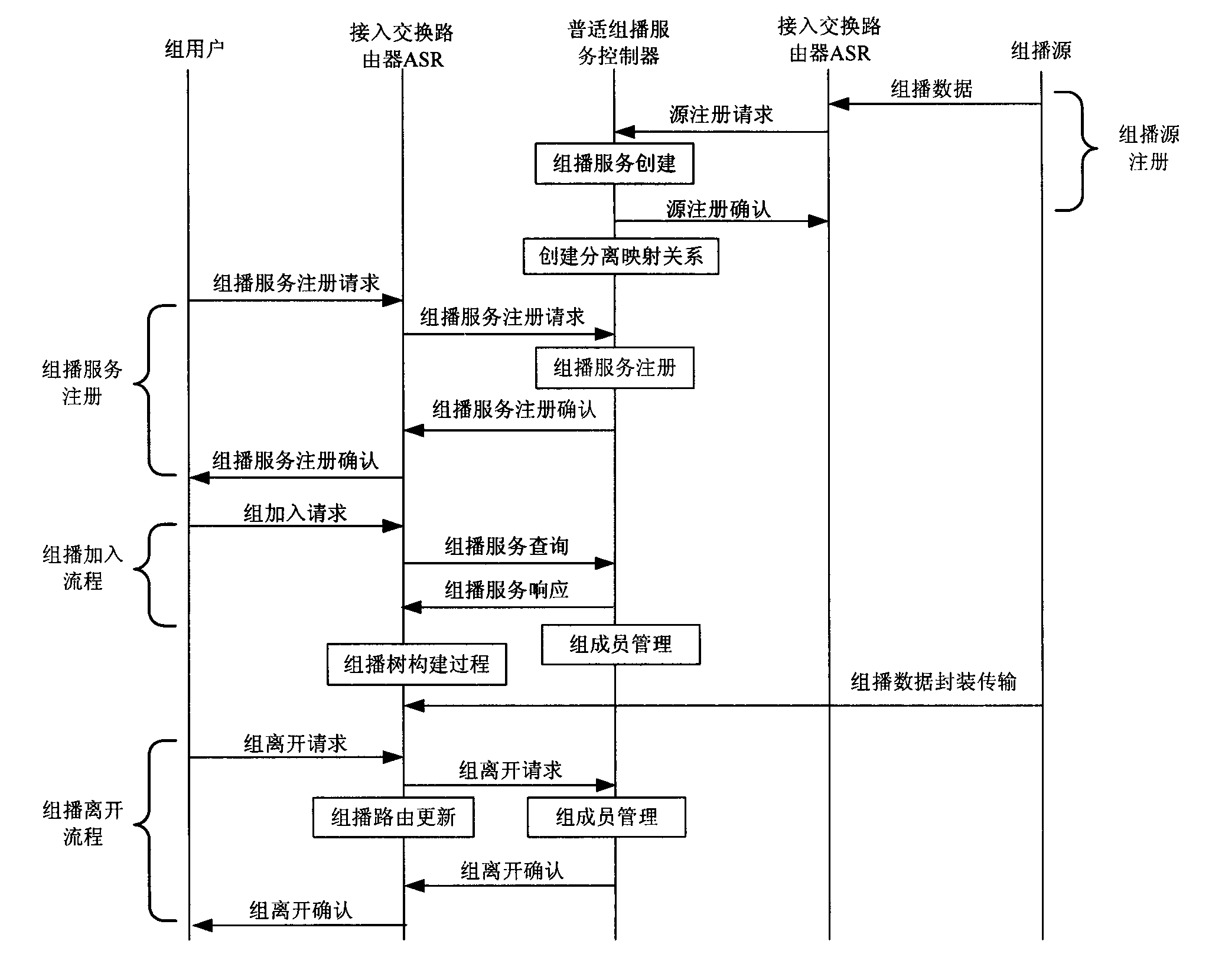
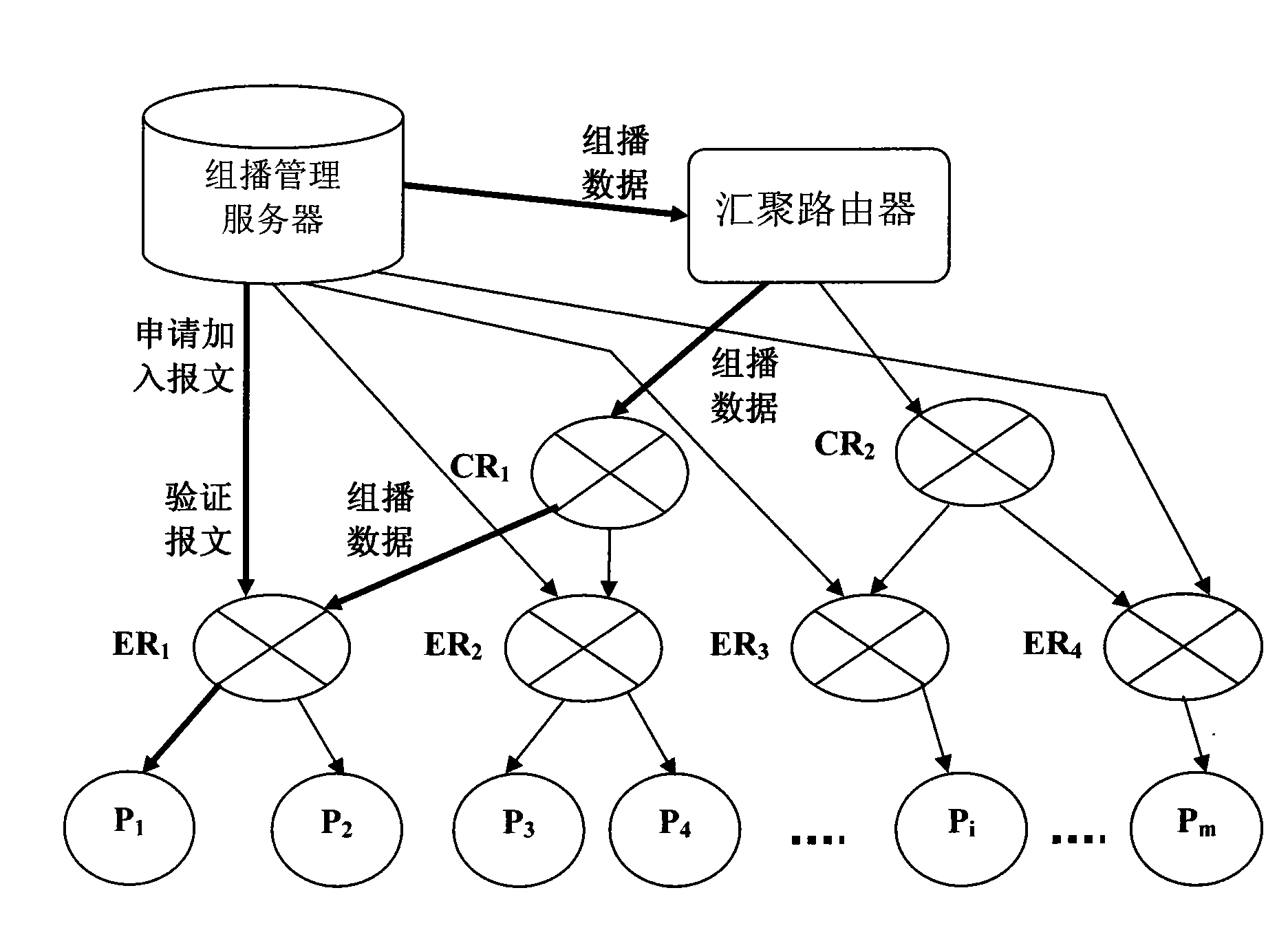
InactiveCN101631274AEnsure safetyGuaranteed Multicast Service StatusBroadcast service distributionData switching networksMulticast securityMulticast
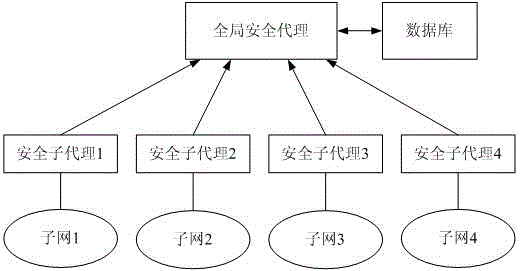
The invention relates to a realizing system of multicast routing based on a mark and a method thereof. The realizing system at least comprises a group user, an access switching router, an universal multicast service controller, a generalized switching router, and the like, to realize the member management, the counting management and the safe relative function of a multicast user. The invention comprises a management method of a group member, a multicast adding and separating method and a multicast tree building method, wherein the management method of the group member records the multicast user and multicast group information and provides a multicast counting function and a multicast security mechanism; the multicast adding and separating method relates to the group member relationship, counting, security, and the like, of the group user, and is used for controlling the update and the maintainace of a multicast tree; and the multicast tree building method intensively builds the tree with the universal multicast service controller, as to realize the transmission of the data in a core net.
Owner:BEIJING JIAOTONG UNIV
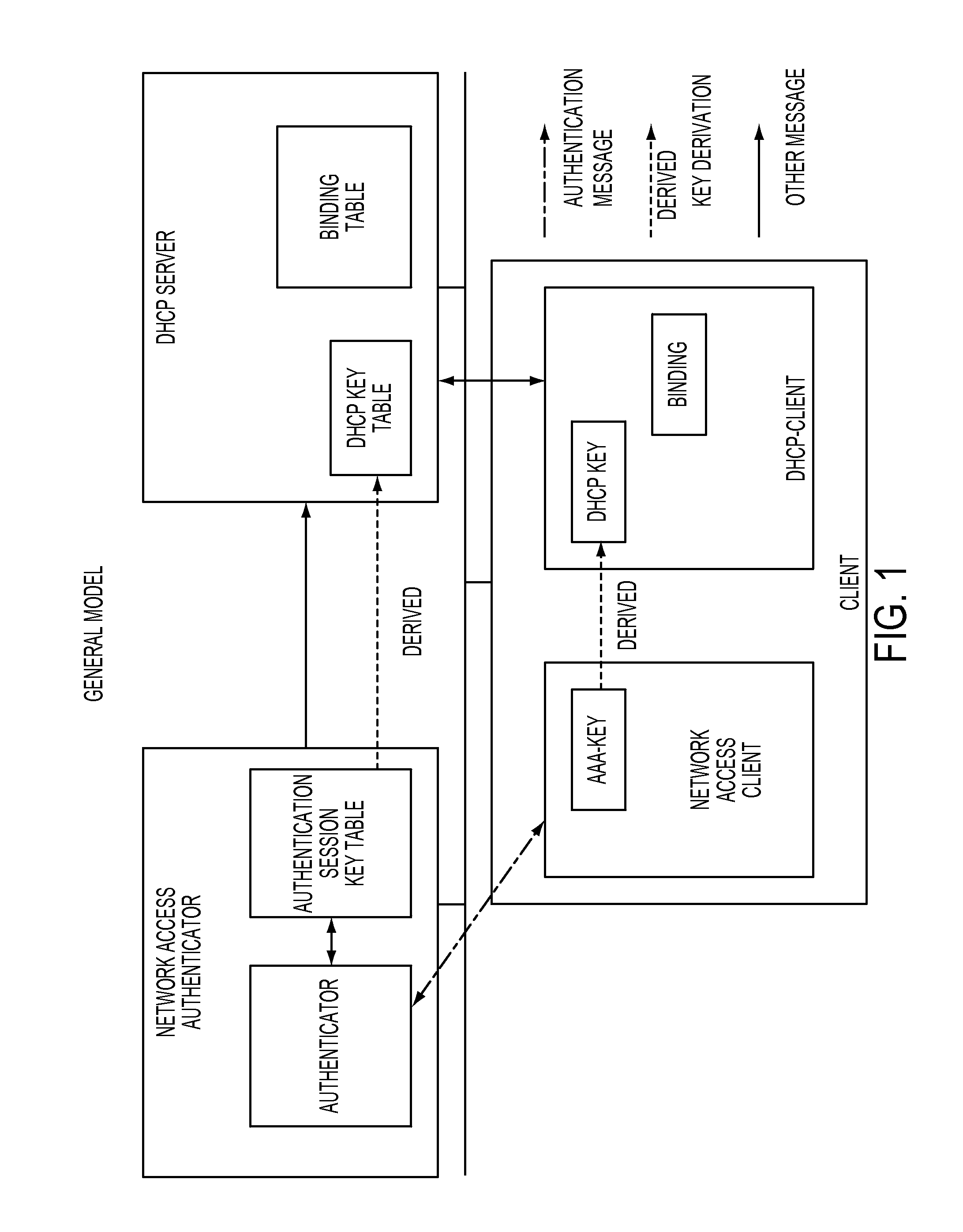
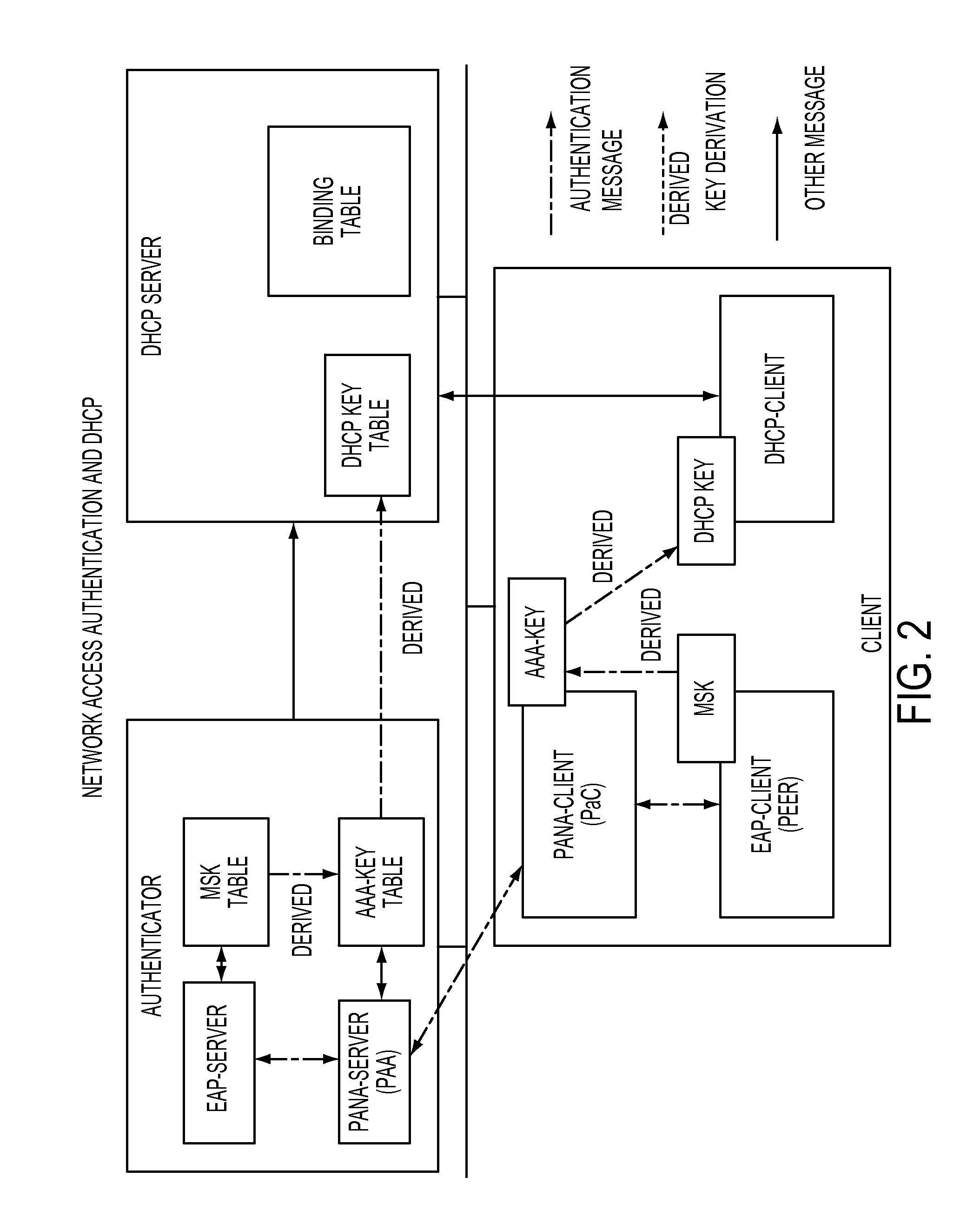
Dynamic host configuration and network access authentication
InactiveUS8688834B2Multiple digital computer combinationsProgram controlProtocol for Carrying Authentication for Network AccessMAC address
According to some embodiments, systems and methods for binding dynamic host configuration and network access authentication are provided related to, inter alia, interactions between a PAA (PANA Authentication Agent) and a DHCP (Dynamic Host Configuration Protocol) server, such as, e.g., for synchronization between the PANA SA state and the DHCP SA state, such as, e.g., maintaining synchronization when a connection is lost. In some embodiments, systems and methods for binding network bridge and network access authentication are also provided related to, inter alia, interactions between a PAA and a layer-2 switch, such as, e.g., for avoiding service thefts and the like (such as, e.g., MAC address and / or IP address spoofing) in the context of, e.g., the above. In some other embodiments, systems and methods for bootstrapping multicast security from network access authentication protocol are also provided related to, inter alia, key management for protected IP multicast streams, such as, e.g., to avoid IP multicast streams unnecessarily received and / or processed by unauthorized receivers connected to the same layer 2 segment as authorized receivers in the context of, e.g., the above.
Owner:FOUR BATONS WIRELESS LLC
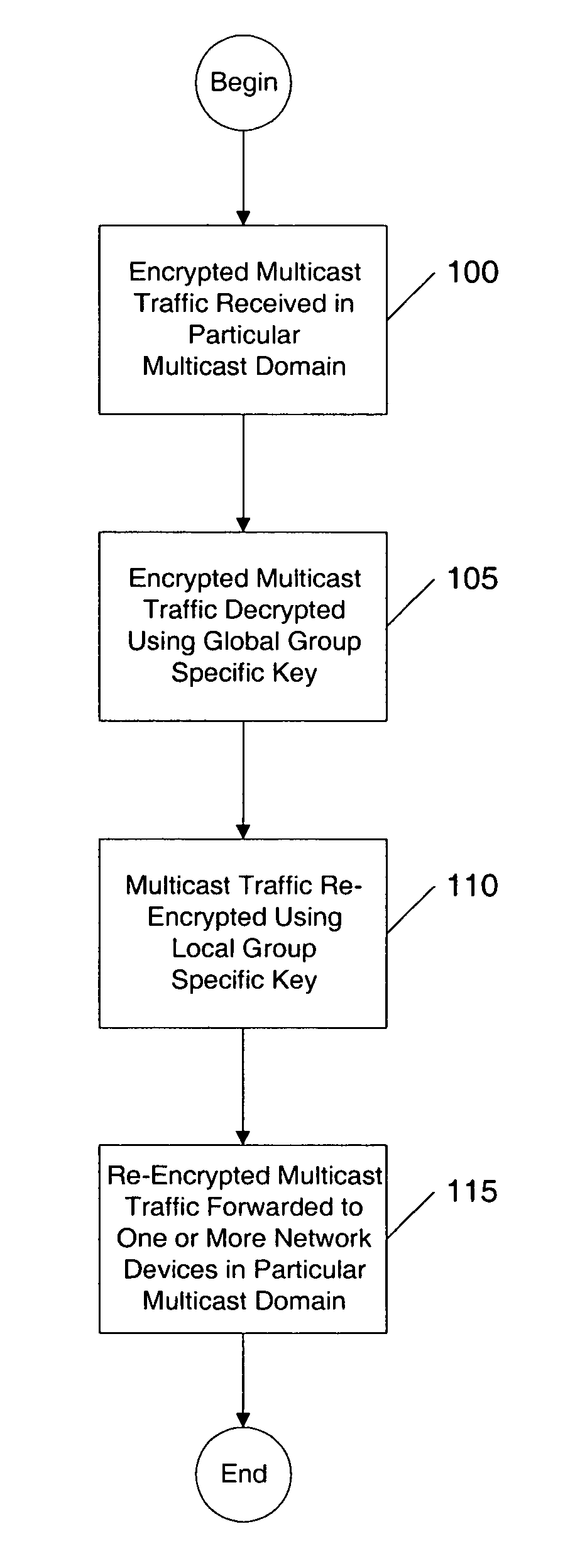
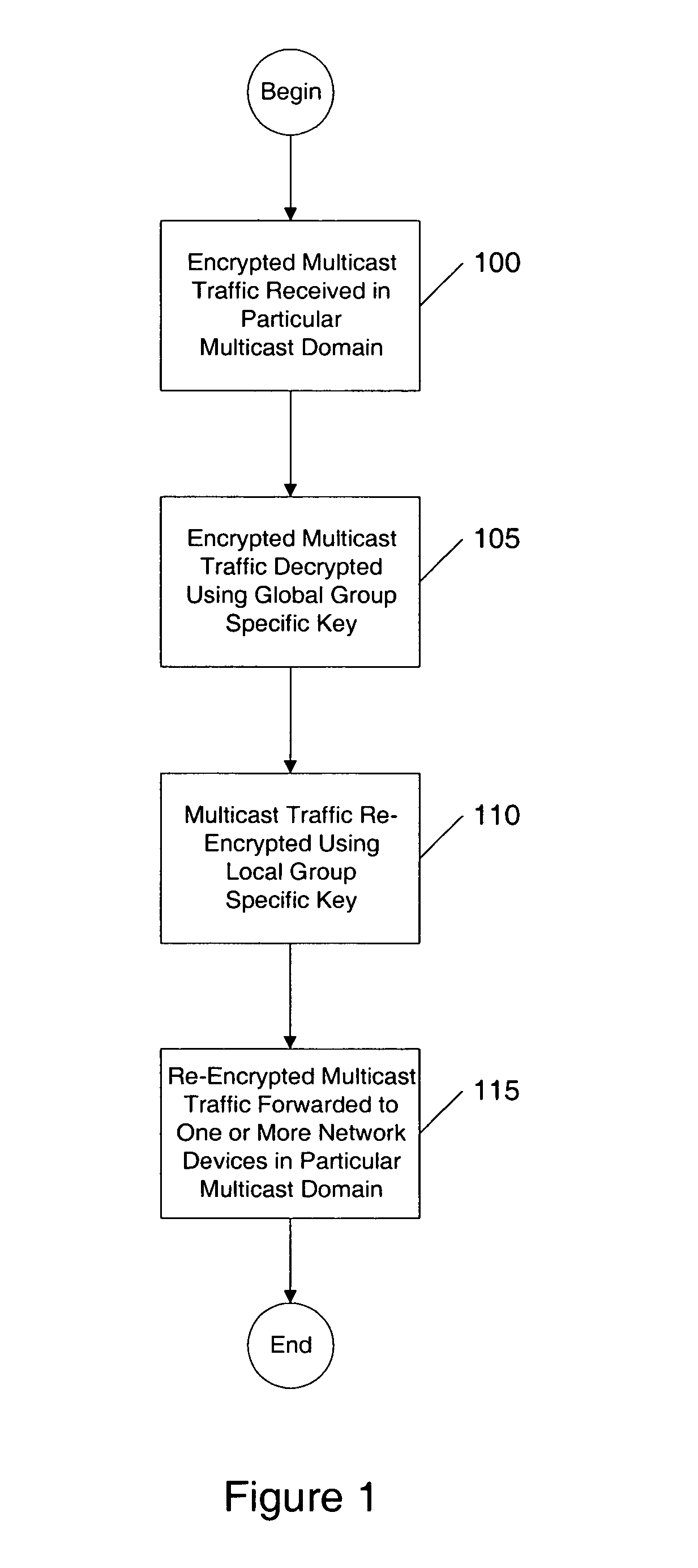
Apparatus and method of implementing multicast security between multicast domains
InactiveUS7127610B1Special service provision for substationDigital data processing detailsTraffic capacityComputer network
An apparatus and method of implementing multicast security in a given multicast domain, the given multicast domain having one or more network devices, receives multicast traffic that is encrypted with a global key, the global key being available to the given multicast domain and one or more other multicast domains, decrypts the received multicast traffic with the global key to produce decrypted multicast traffic, encrypts the decrypted multicast traffic with a local key to produce local encrypted multicast traffic, the local key being available to the given multicast domain, and forwards the local encrypted multicast traffic to the one or more network devices in the given multicast domain. In a further embodiment, the apparatus and method for implementing multicast security in a given multicast domain first receives a global key message that identifies the global key.
Owner:RPX CLEARINGHOUSE
A method, system and device for securing multi-party communication
InactiveCN101127595AVersatileMulti-party communication security implementationKey distribution for secure communicationSynchronising transmission/receiving encryption devicesGroup sessionCryptographic protocol
Owner:HUAWEI TECH CO LTD
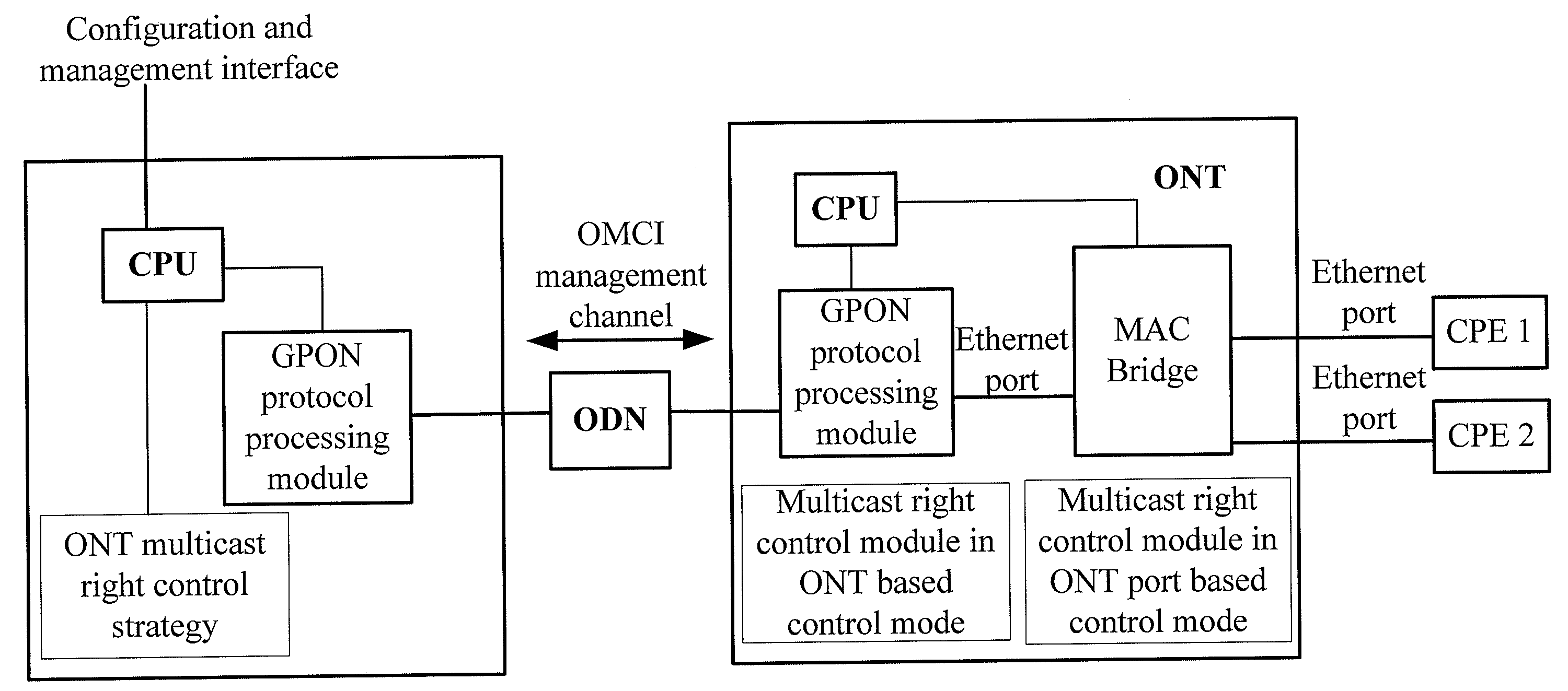
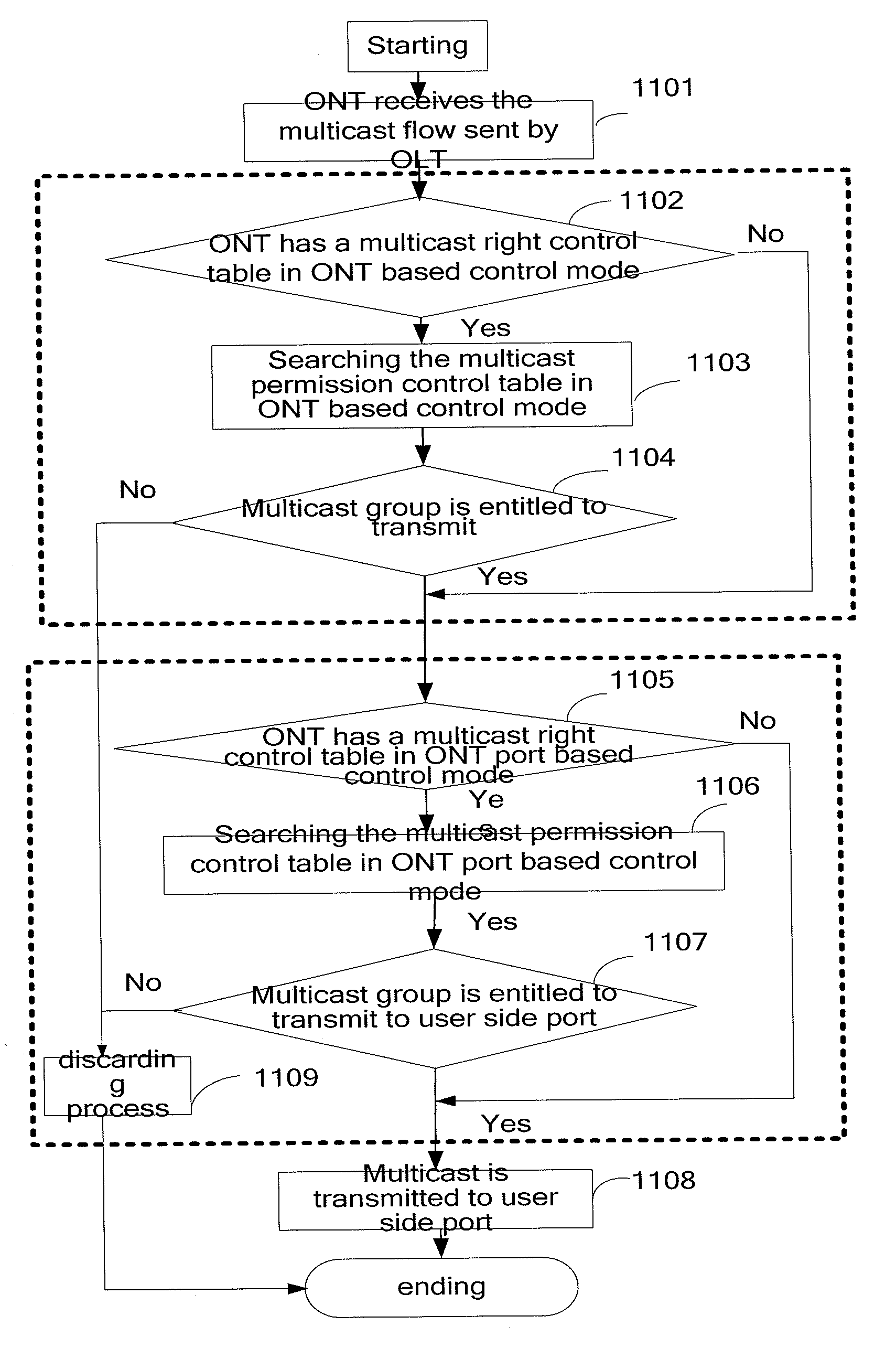
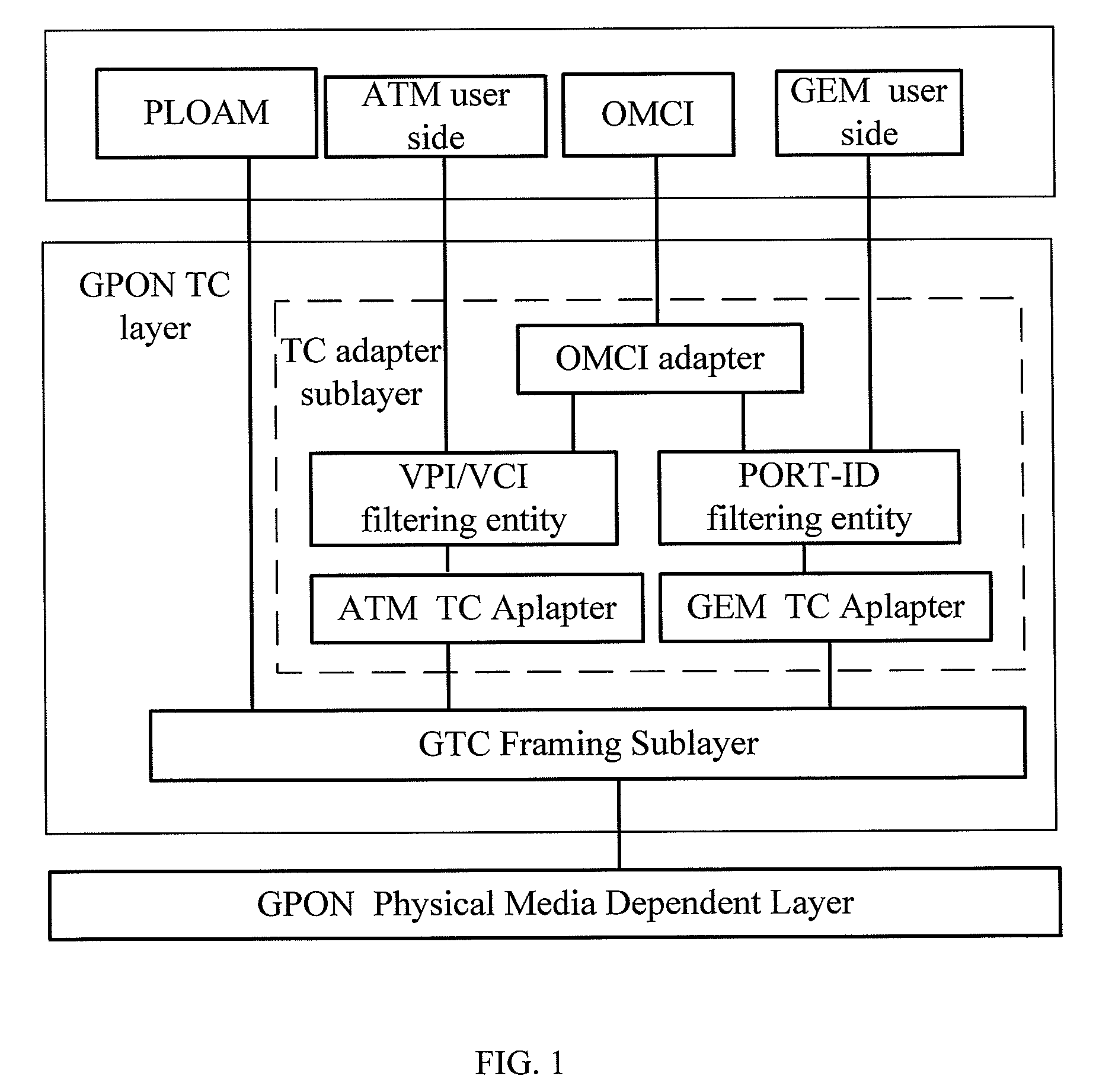
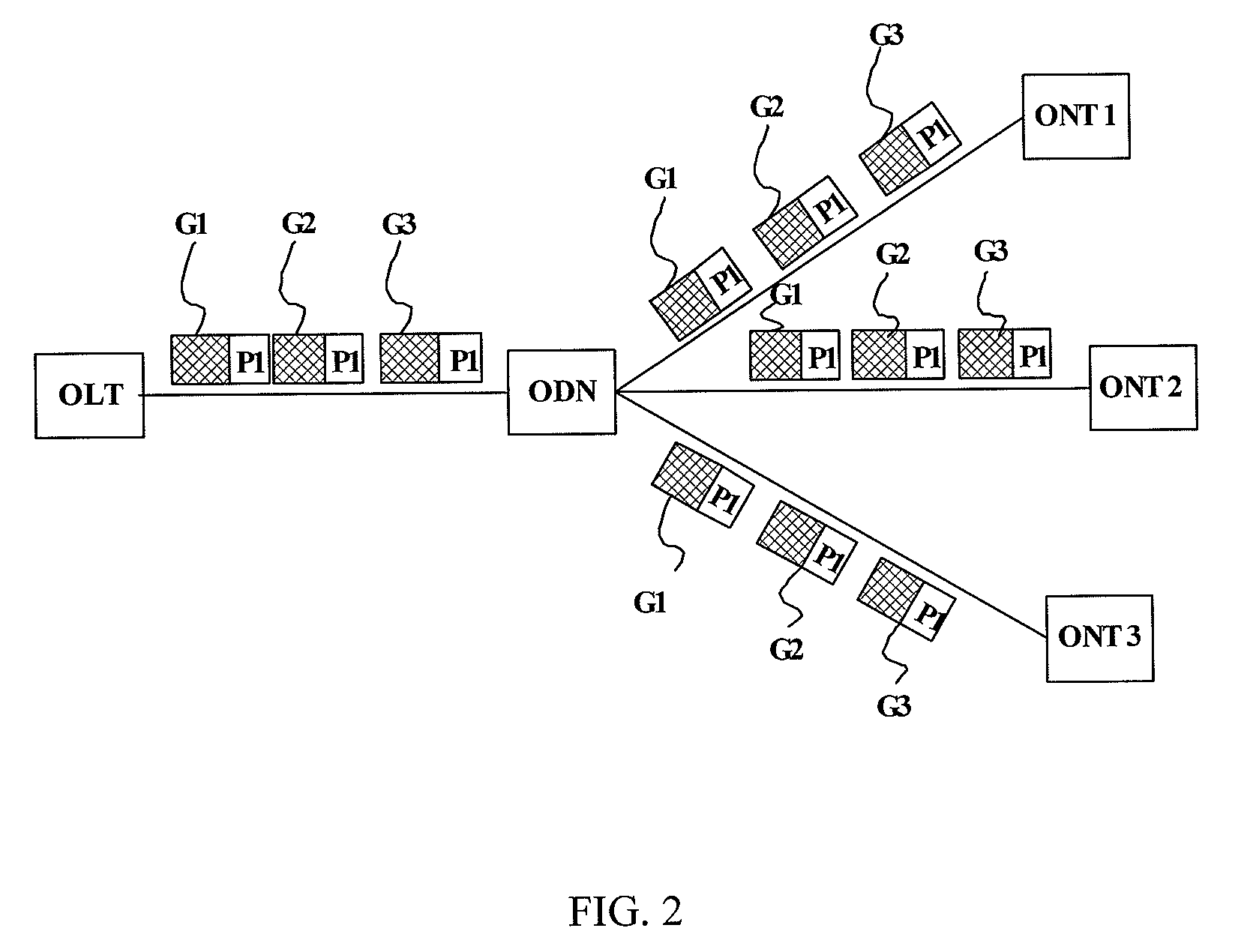
System, apparatus and method for controlling multicast flow in passive optical network
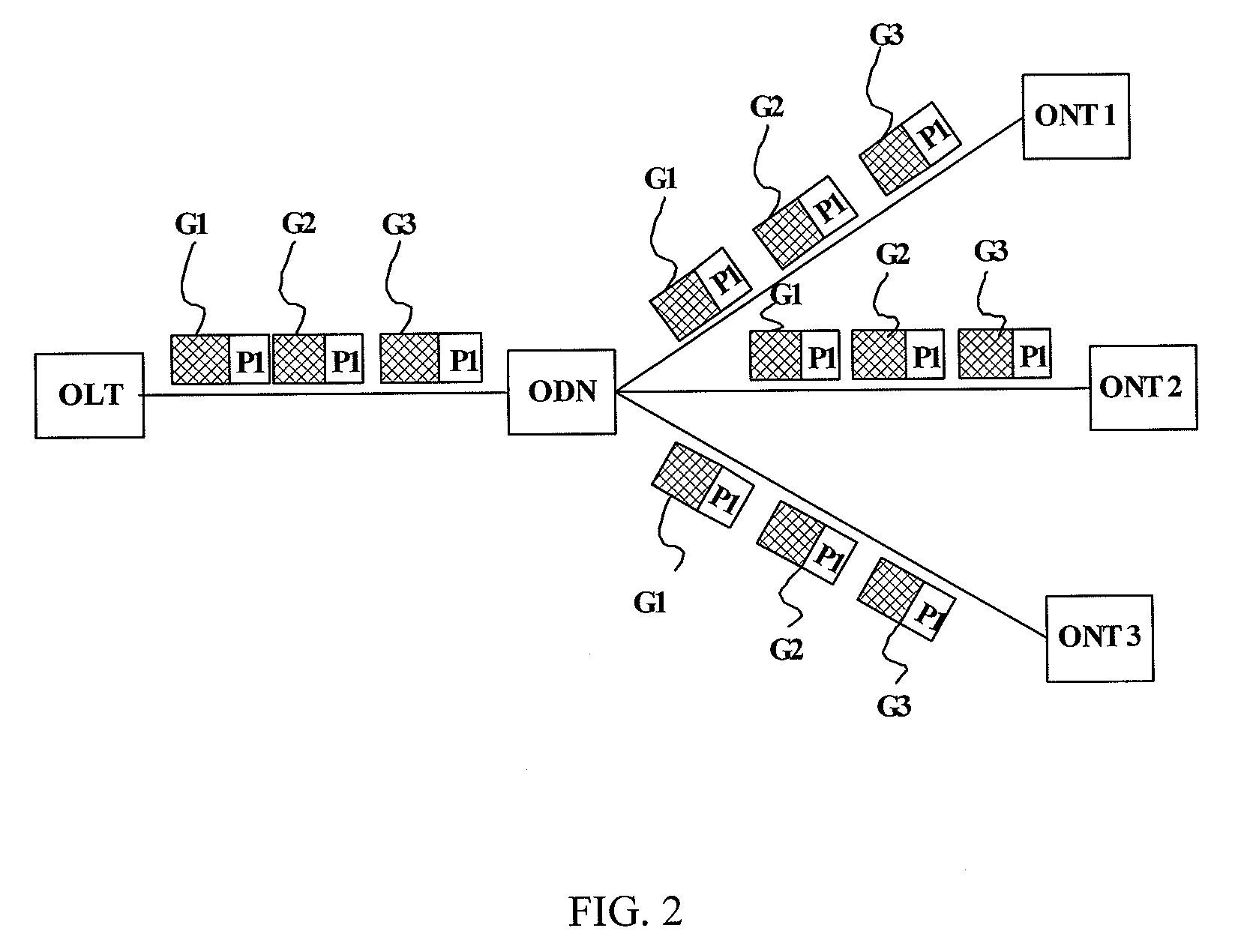
ActiveUS20080267626A1Enhances multicast securityIncrease operating incomeMultiplex system selection arrangementsOptical multiplexComputer networkOptical network terminal
The present invention discloses a method for controlling multicast flow in passive optical network includes: receiving multicast data from the optical line terminal, determining whether the received multicast data satisfies a multicast right control condition, transmitting the multicast data to the user side if the received multicast data satisfies the multicast right control condition, or discarding the multicast data if the received multicast data does not satisfy the multicast right control condition. The present invention also discloses an optical network terminal, an optical line terminal, and a system consisting of an optical network terminal and an optical line terminal and an optical distribute network, which implement the above mentioned method. The present invention could prevent the optical network terminal from receiving illegal multicast data and enhance the multicast security of the whole passive optical network system.
Owner:HUAWEI TECH CO LTD
Safety multicast method based on protocol of conversation initialization
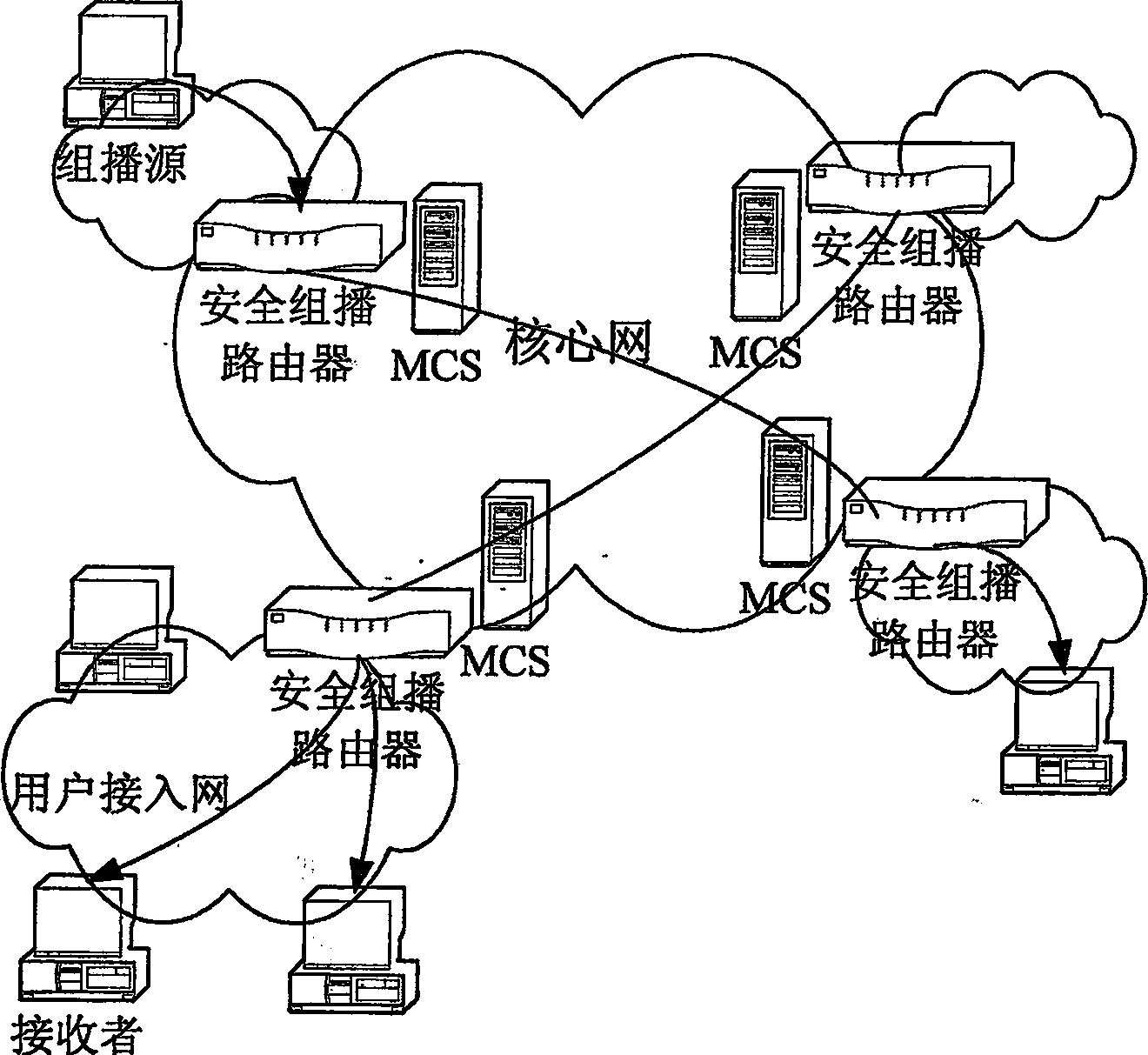
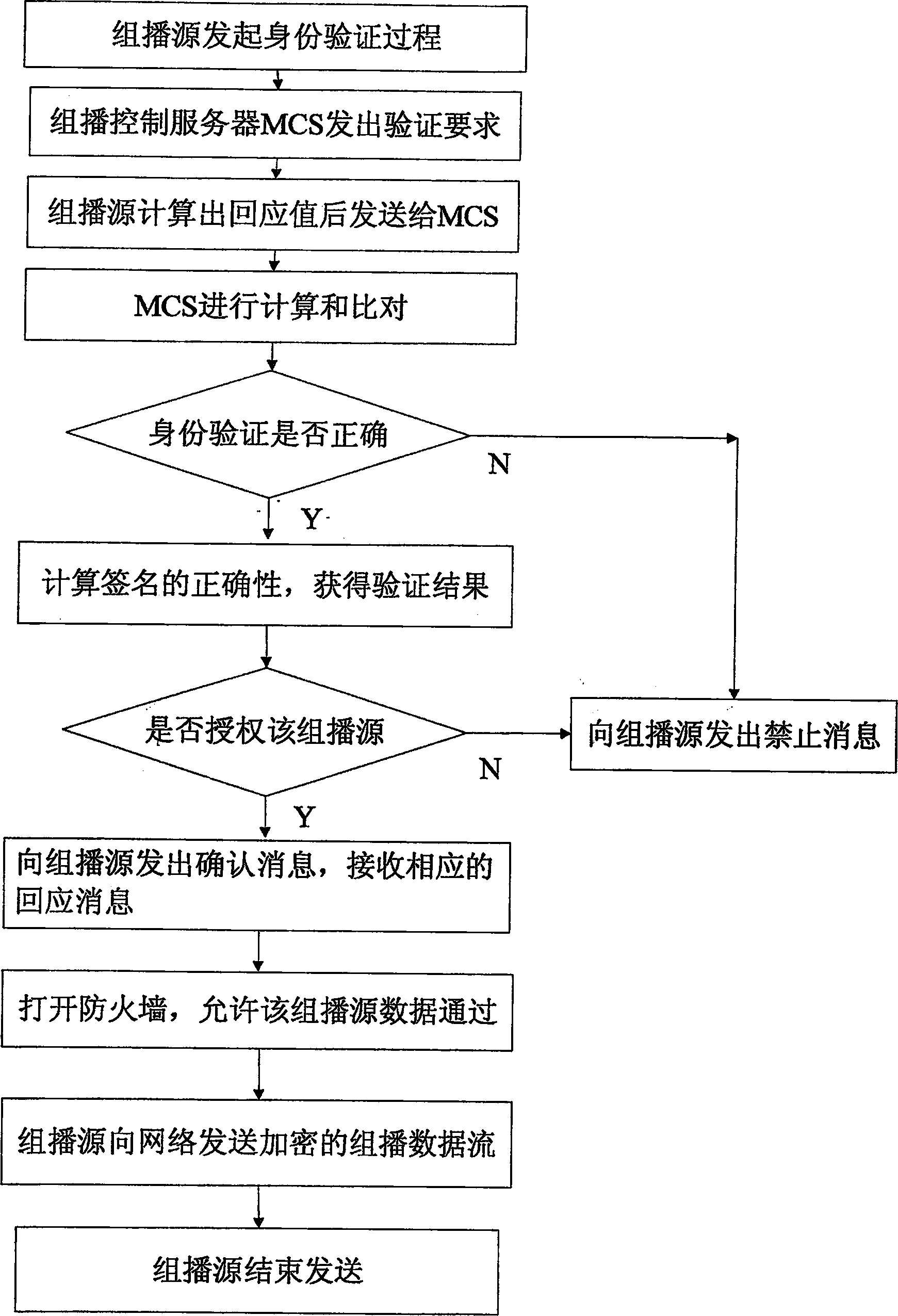
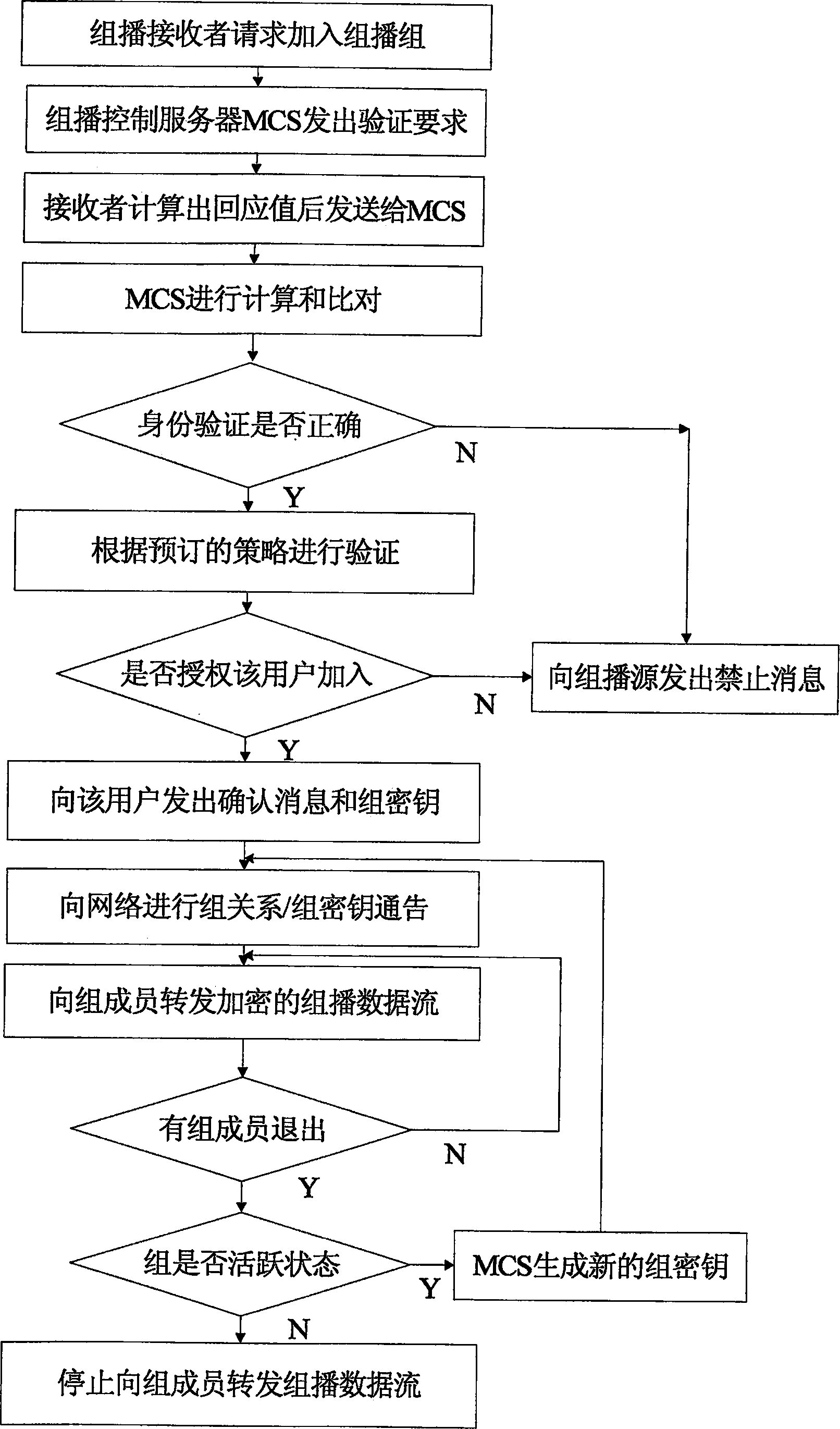
InactiveCN1874224ASolve the requestSolve the statistical billing abilityUser identity/authority verificationSecure communicationMethod selection
The safe multicast method is a first method of using the protocol of conversation initialization to implement operation of safe multicast. The method presents a set of scheme for solving issue of safe multicast including access control of multicast source, access control for receiver, management of group key, authentication of multicast source, service statistics, and charging capability. The method includes procedures: using route in network to encrypt data of multicast to guarantee access control of service, and safe comm.; method for authenticating multicast source in two stages is adopted; when IGMP / MLD adapter layer implements the method, working mode of traditional multicast route system does not need to be changed; three expansion techniques including cluster of regional multicast control server, regional physical and logical segmentations. The expansibility is suitable to large-scale network environment, and concurrent use. The invention does not change core network.
Owner:SOUTHEAST UNIV
Multicast security control method, system and transmission node
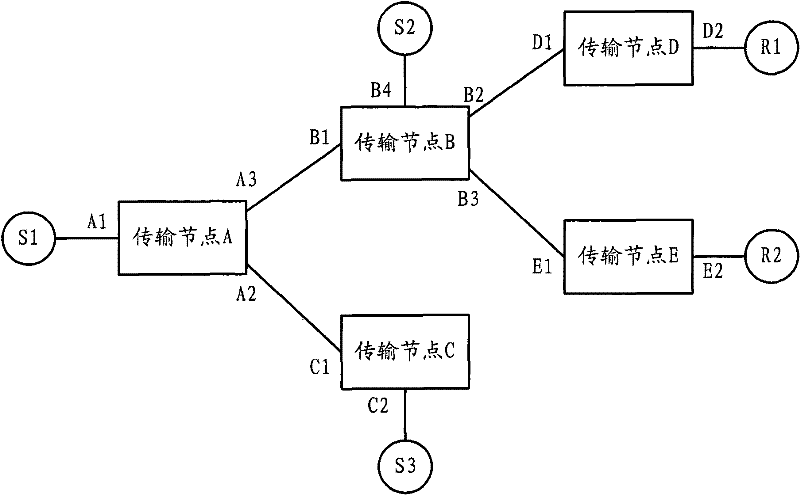
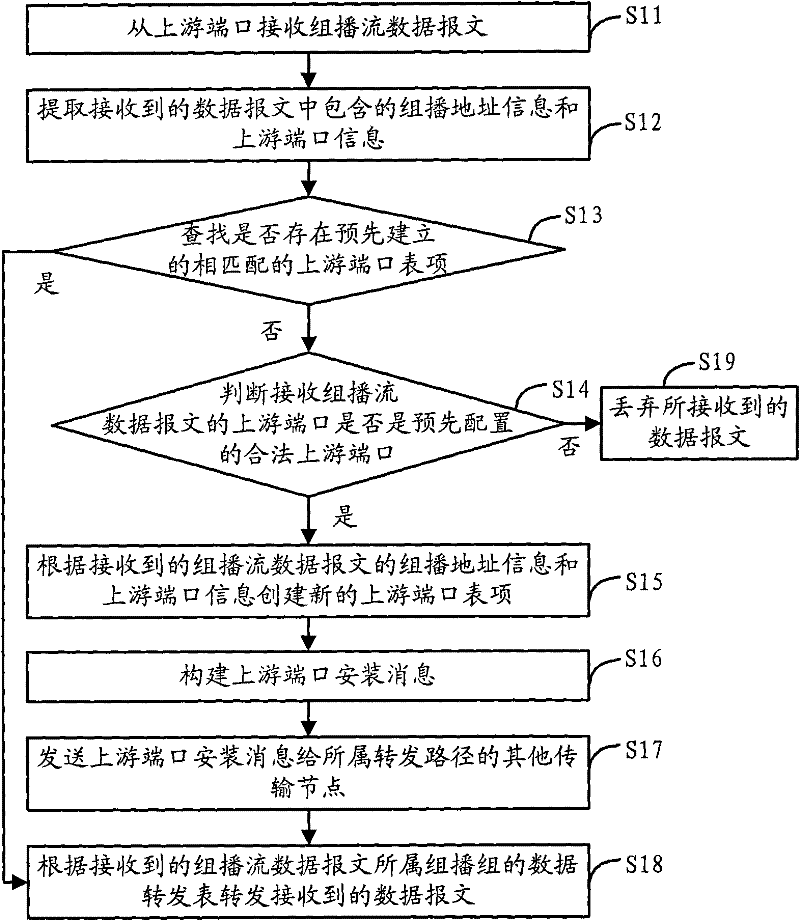
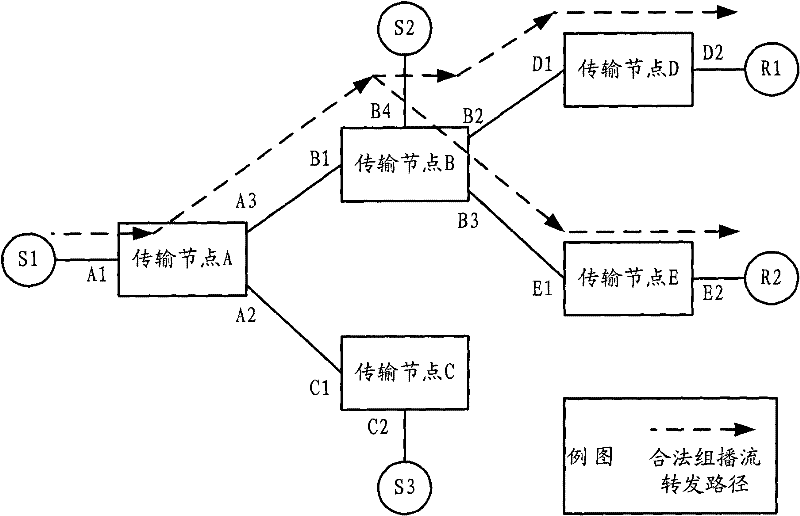
ActiveCN101795223AEnsure safetyAvoid attackSpecial service provision for substationStream dataMulticast address
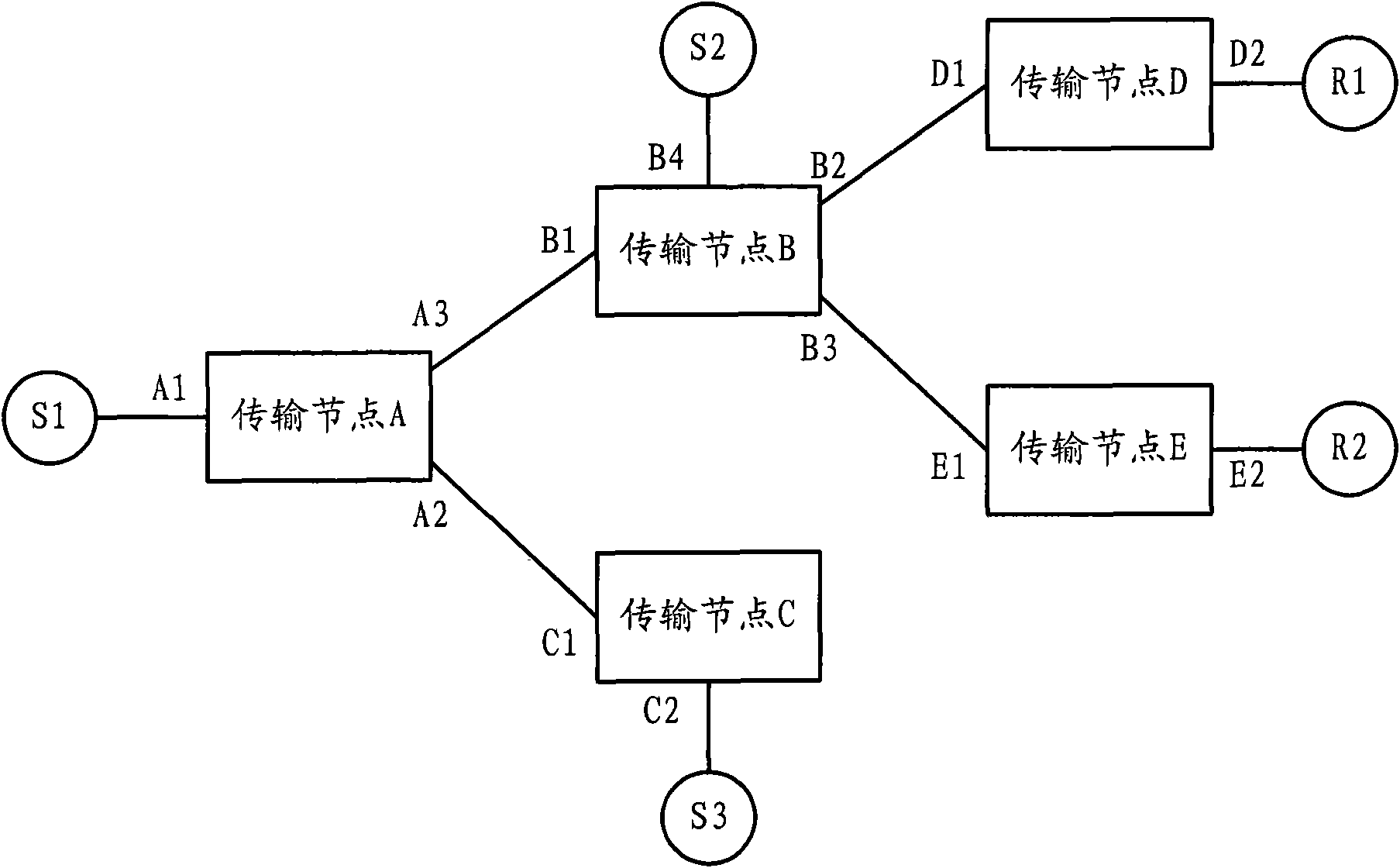
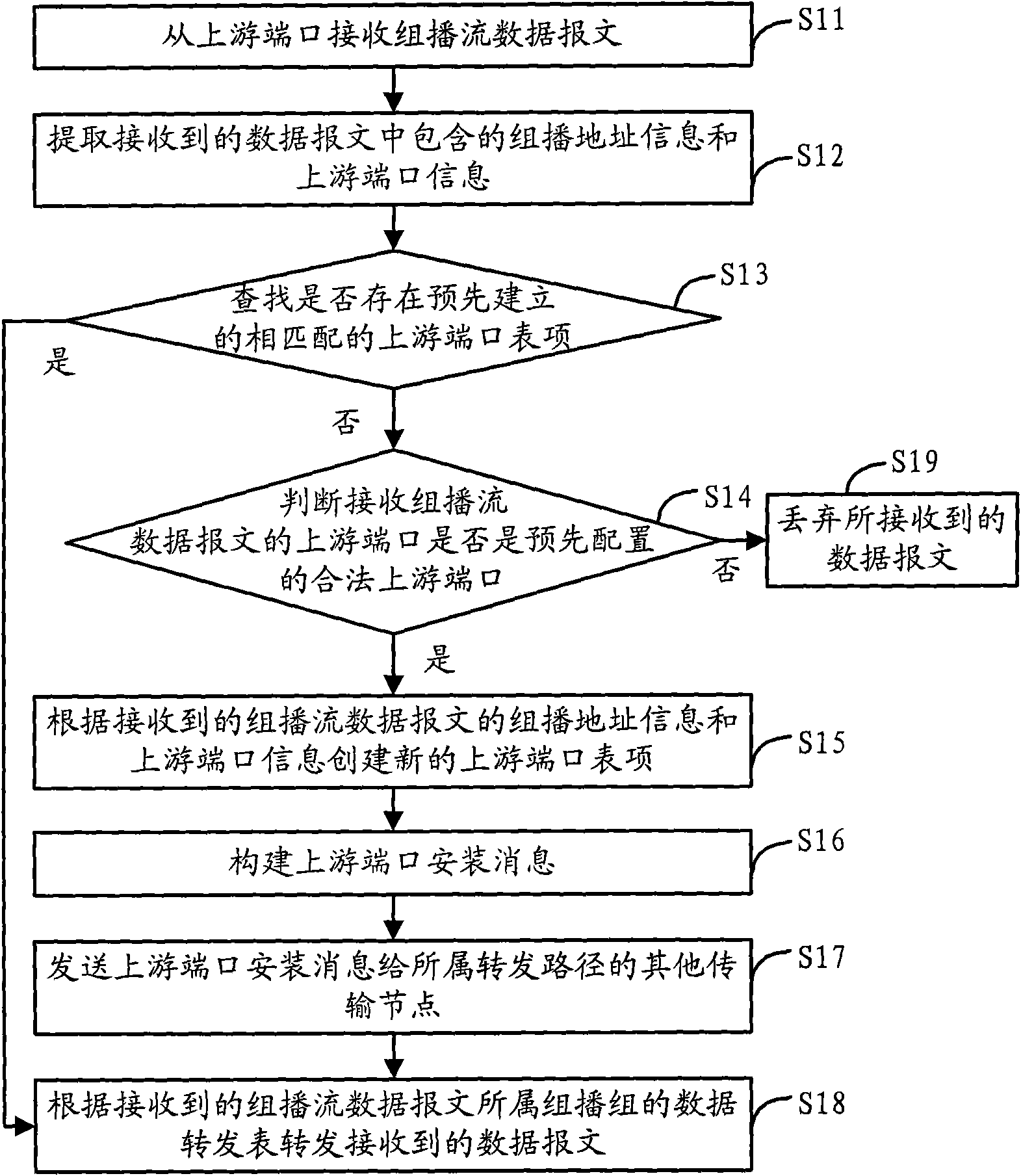
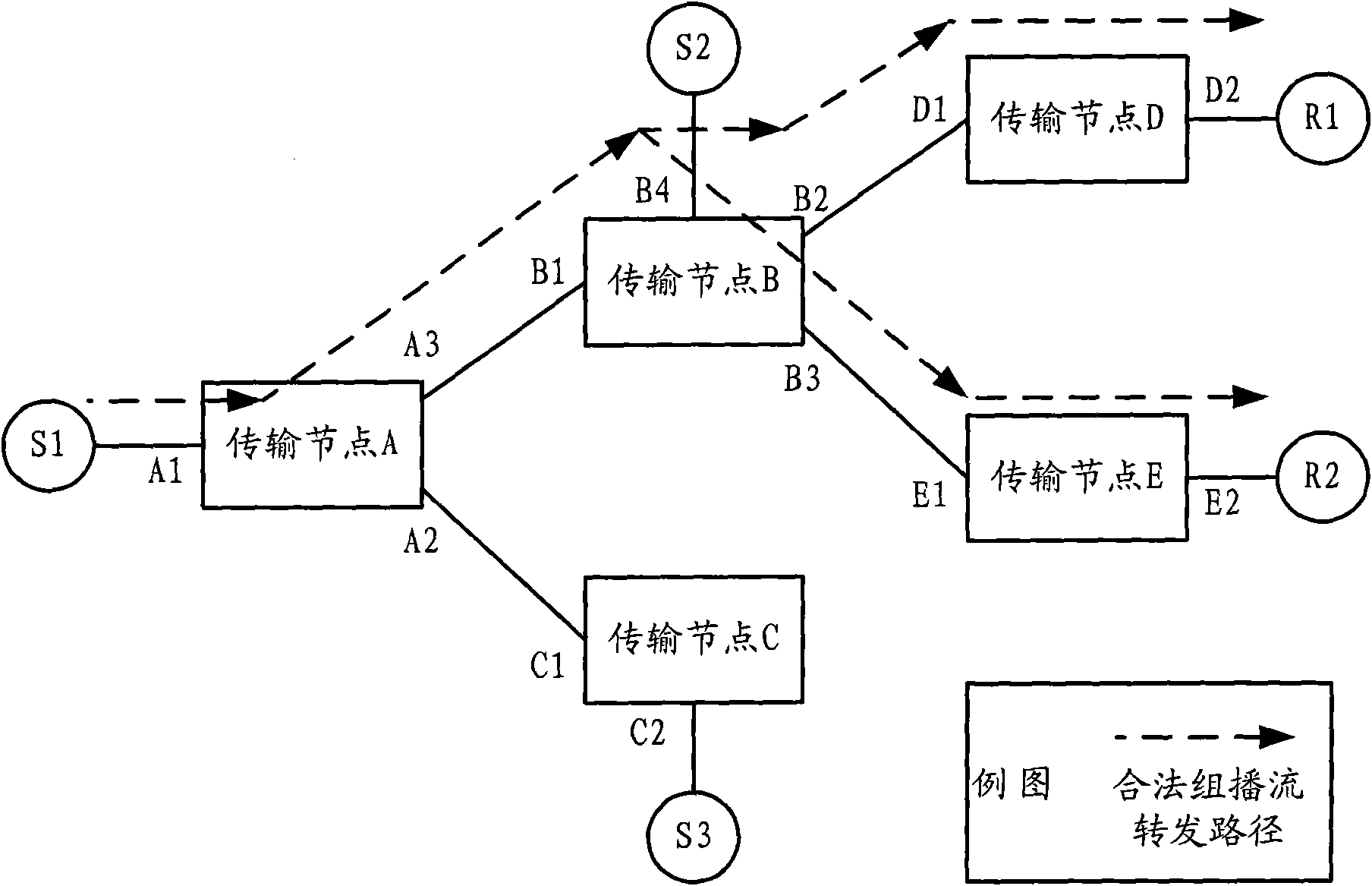
The invention discloses a multicast security control method, a system and a transmission node. The method includes the following steps that: the transmission node receives a multicast stream data message from an upstream port; according to multicast address information and upstream port information contained in the data message, a preestablished matched upstream port item containing the multicast address information and the upstream port information are queried; if the upstream port item exists, the data message is forwarded according to a data forwarding table of a multicast group owning the data message; if the upstream port item does not exist, whether the upstream port is a preconfigured valid upstream port is judged, if yes, a new upstream port item is created according to the multicast address information and the upstream port information, the data message is forwarded according to a data forwarding table of a forwarding path corresponding to the multicast group owning the data message, and if no, the data message is discarded. The invention effectively ensures the security of an upstream node of a multicast stream and prevents the attack of invalid multicast sources on transmission nodes.
Owner:RUIJIE NETWORKS CO LTD
Method and apparatus for supporting security in muliticast communication
A method of supporting a security for a multicast communication is provided in a mobile station. The mobile station shares an MAK with a base station, derives a prekey based on a first parameter including the MAK, and derives a multicast security key including an MTEK based on a second parameter including the prekey, and decrypts a multicast traffic using the multicast security key.
Owner:ELECTRONICS & TELECOMM RES INST
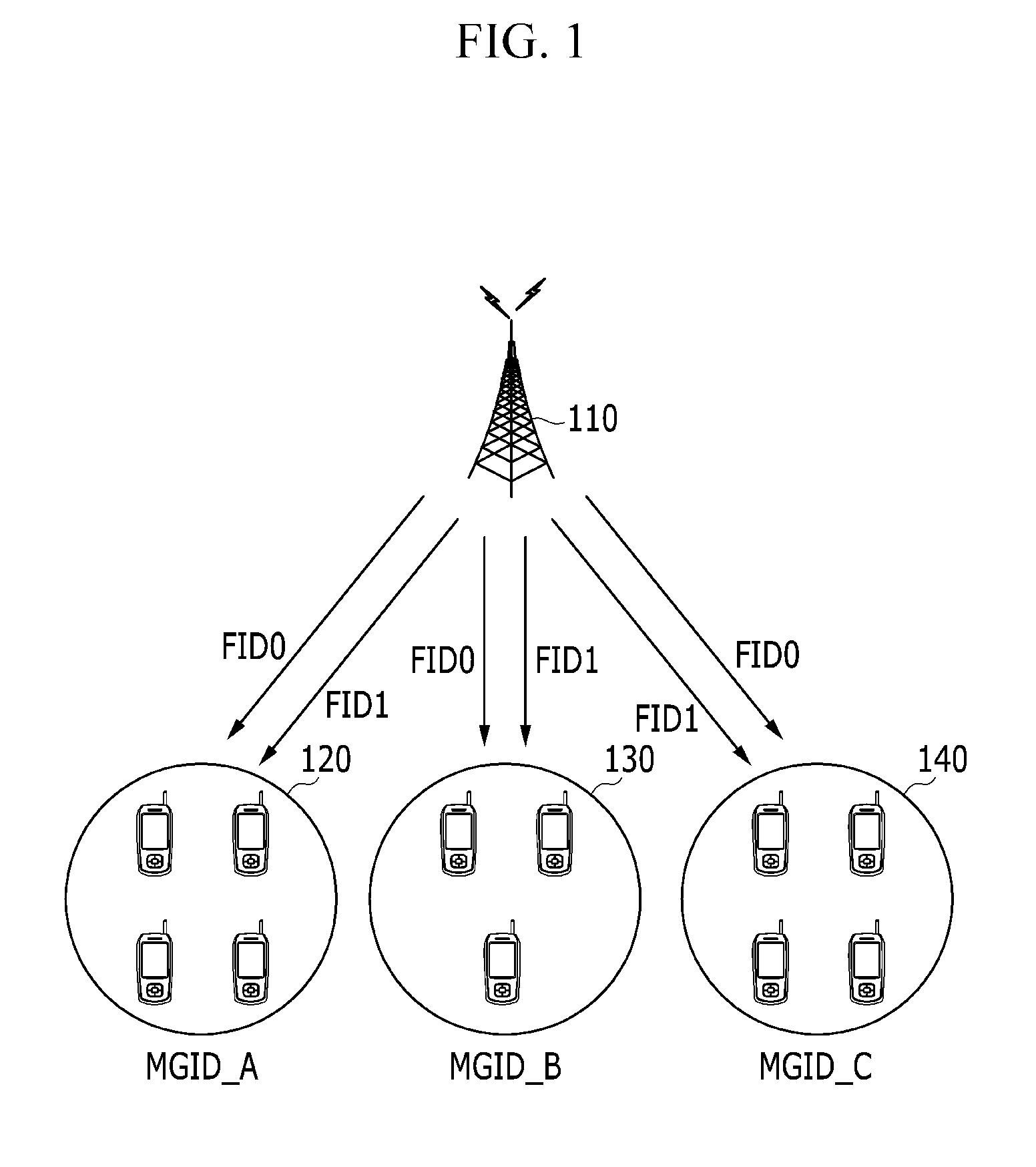
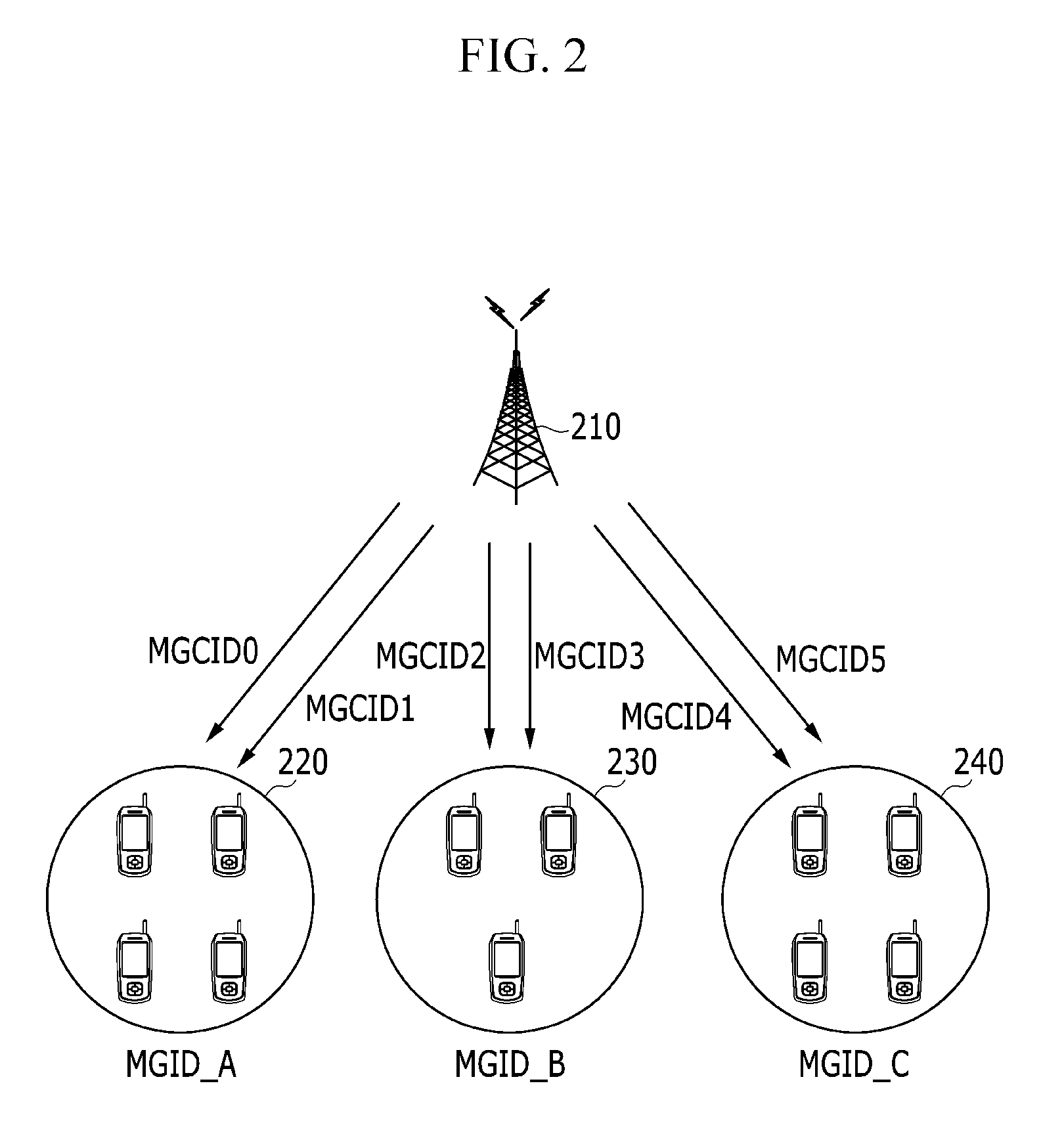
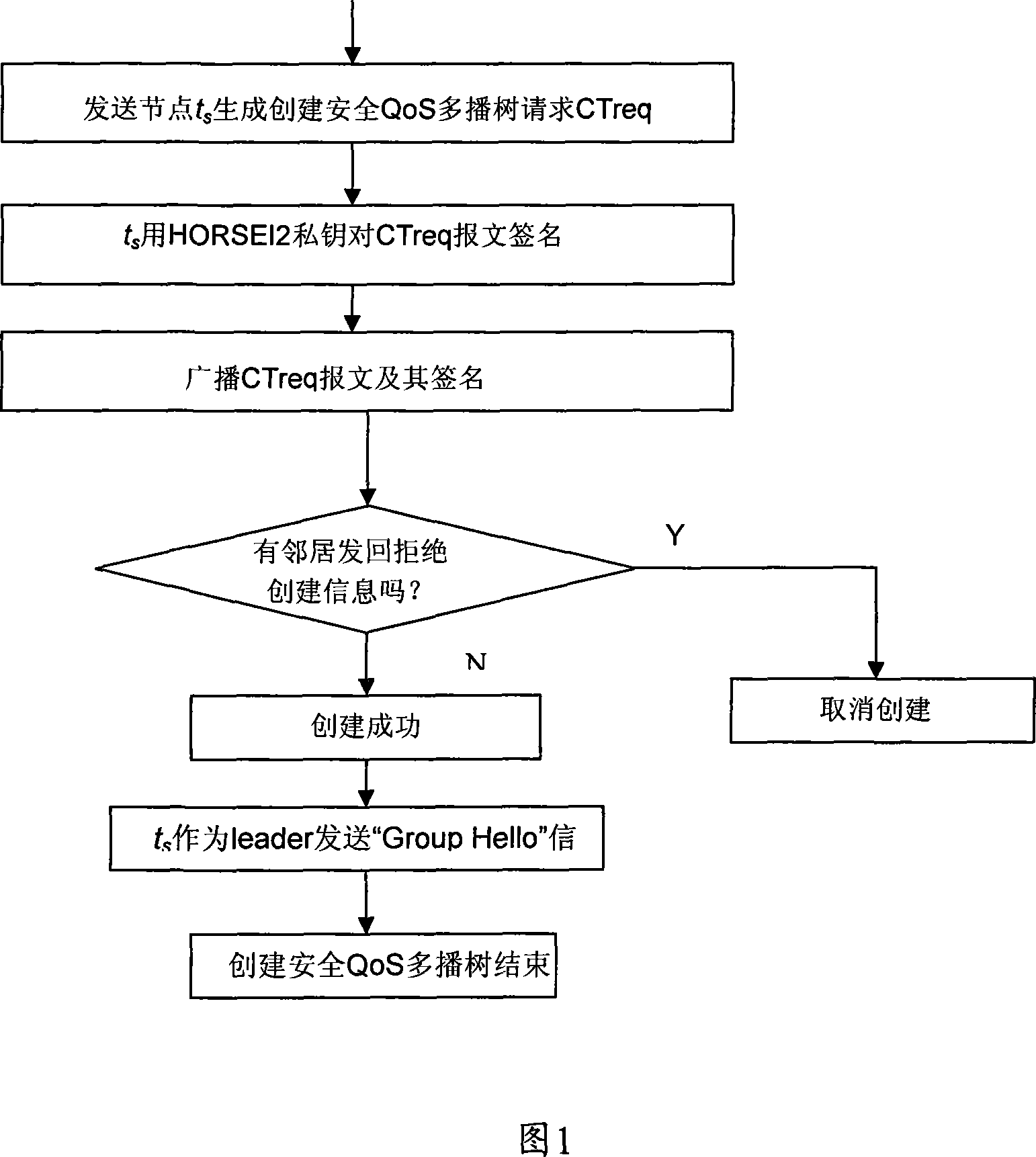
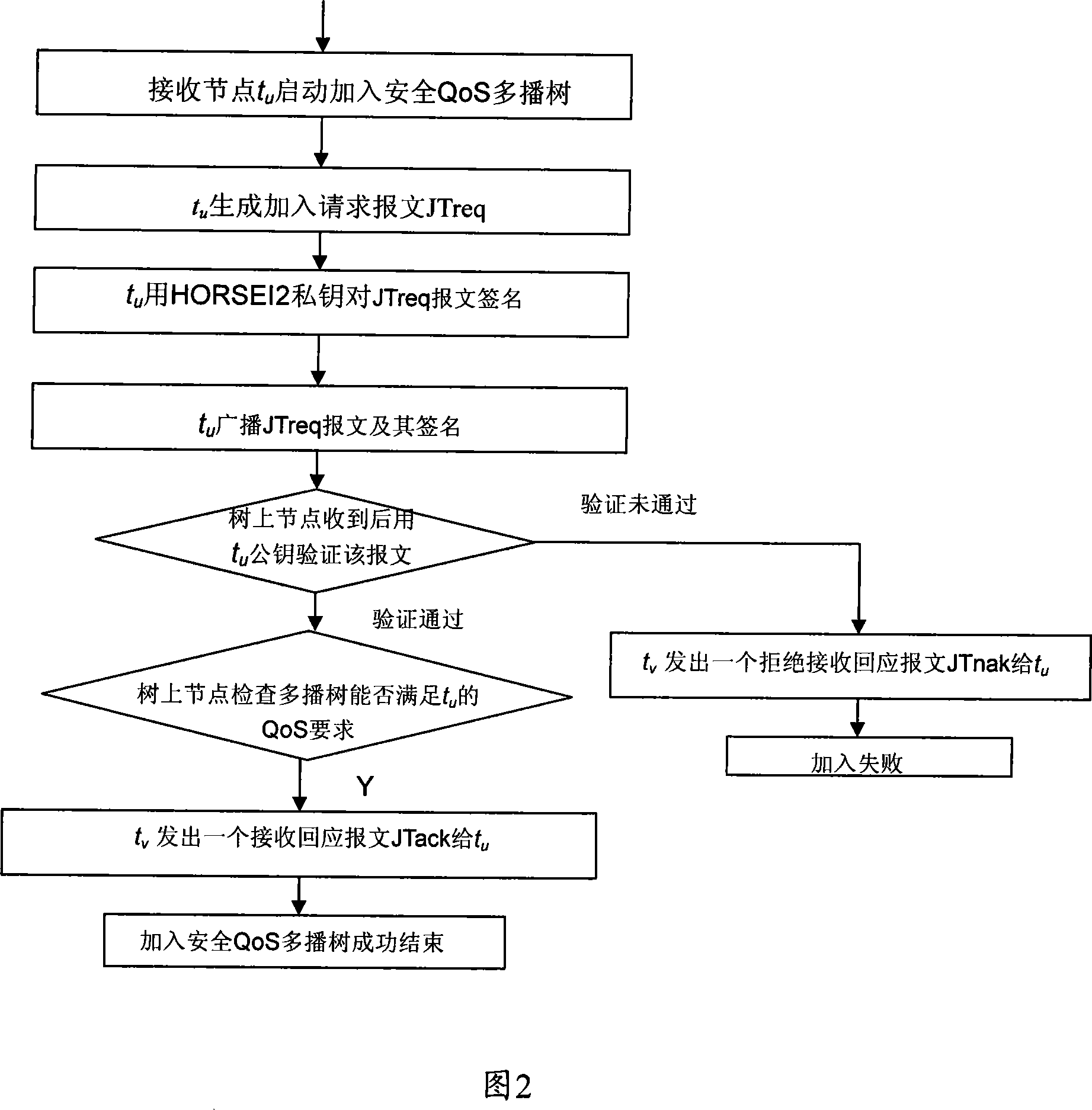
HORSEI2-based mobile self-organized network safety QoS multicast route creating method
InactiveCN101060480AReduce consumptionImprove efficiencyPublic key for secure communicationUser identity/authority verificationSelf-organizing networkSecure authentication
The related HORSEI2 based building method for self-organizing network security QoS multicast route comprises: every transmitter and receiver can add the multicast security group only being checked by visits control mechanism to obtain the private and public key of HORSEI2; every node requiring for creating / receiving new security multicast dialogue data creates / adds safe QoS multicast tree, wherein the transmitter applies signature on the message generated by HORSEI2, and the receiver uses the public key for verification.
Owner:WUHAN UNIV OF TECH
System, apparatus and method for controlling multicast flow in a passive optical network
ActiveUS7792112B2Improve securityData being receivedMultiplex system selection arrangementsTime-division multiplexComputer networkOptical network terminal
The present invention discloses a method for controlling multicast flow in passive optical network includes: receiving multicast data from the optical line terminal, determining whether the received multicast data satisfies a multicast right control condition, transmitting the multicast data to the user side if the received multicast data satisfies the multicast right control condition, or discarding the multicast data if the received multicast data does not satisfy the multicast right control condition. The present invention also discloses an optical network terminal, an optical line terminal, and a system consisting of an optical network terminal and an optical line terminal and an optical distribute network, which implement the above mentioned method. The present invention could prevent the optical network terminal from receiving illegal multicast data and enhance the multicast security of the whole passive optical network system.
Owner:HUAWEI TECH CO LTD
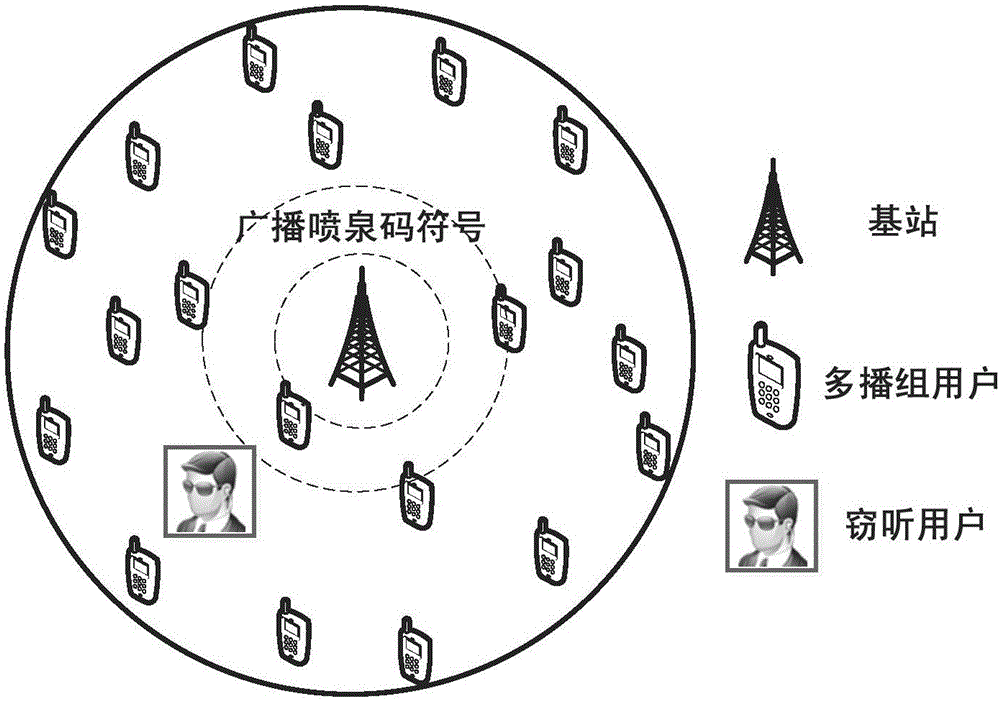
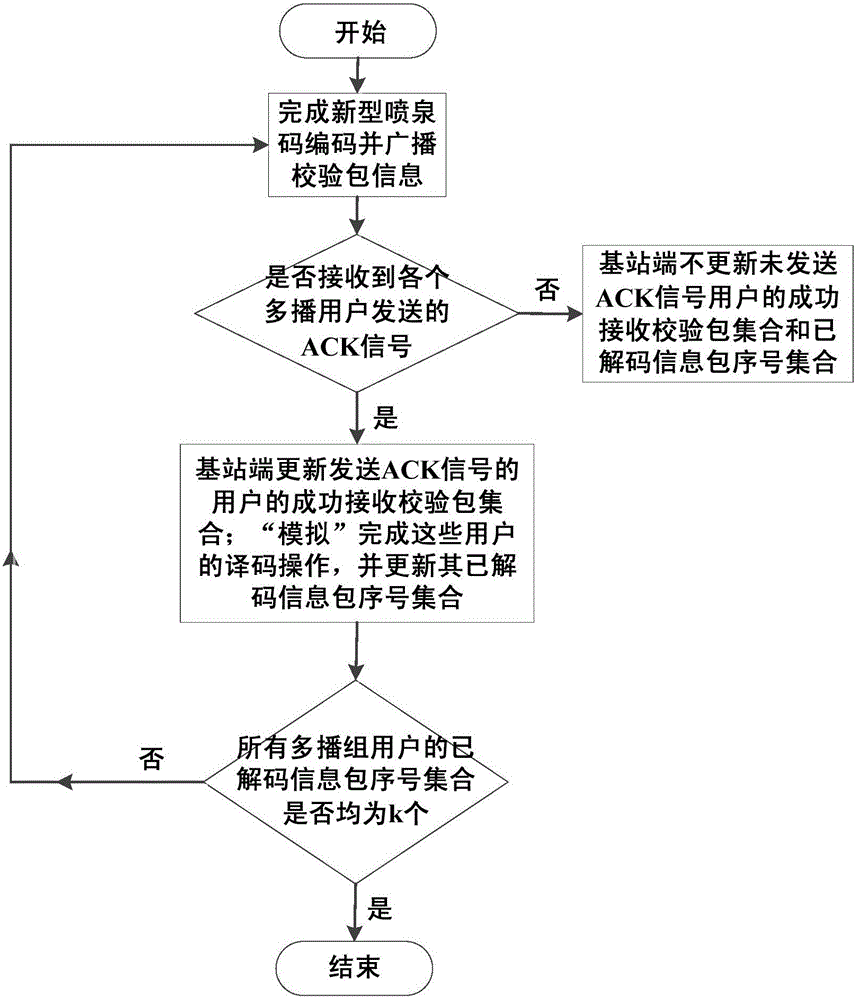
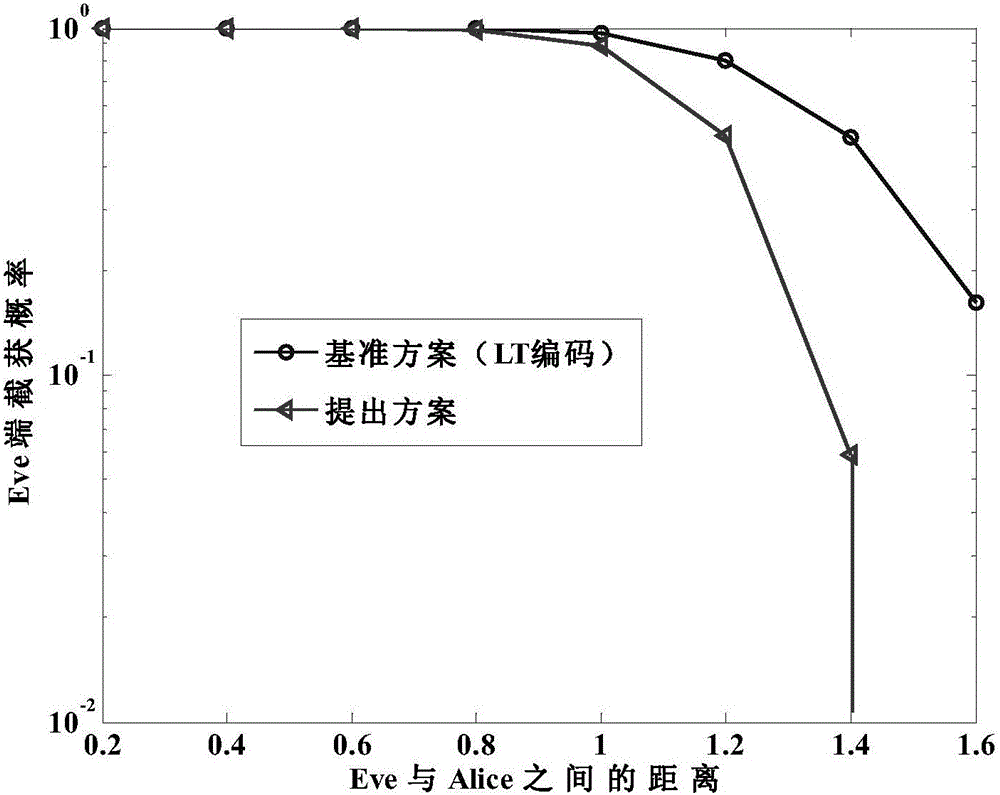
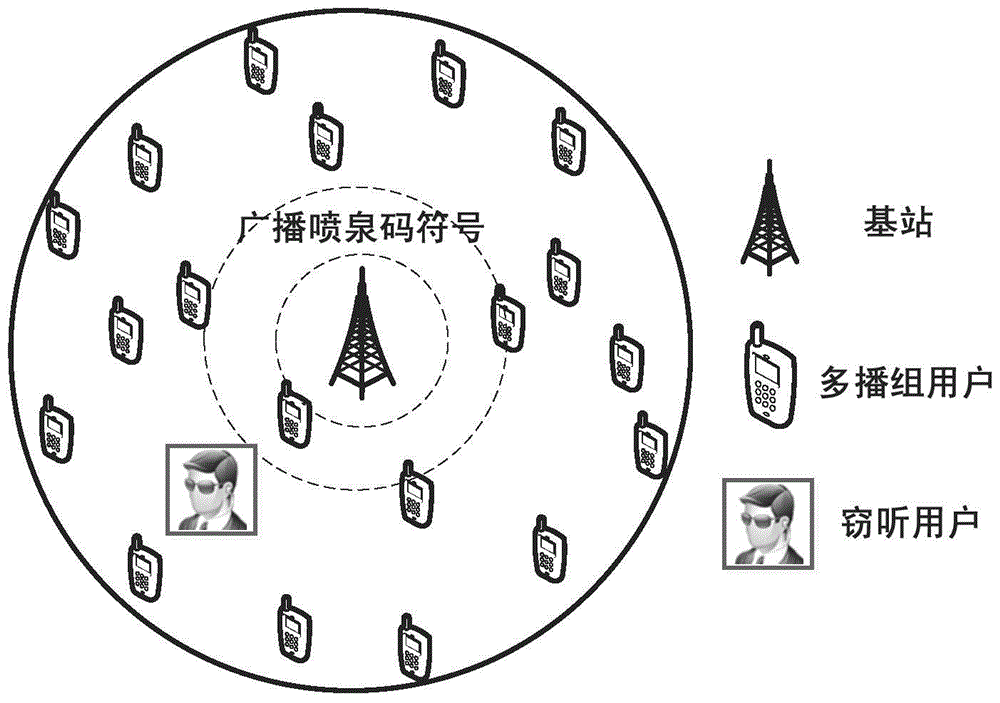
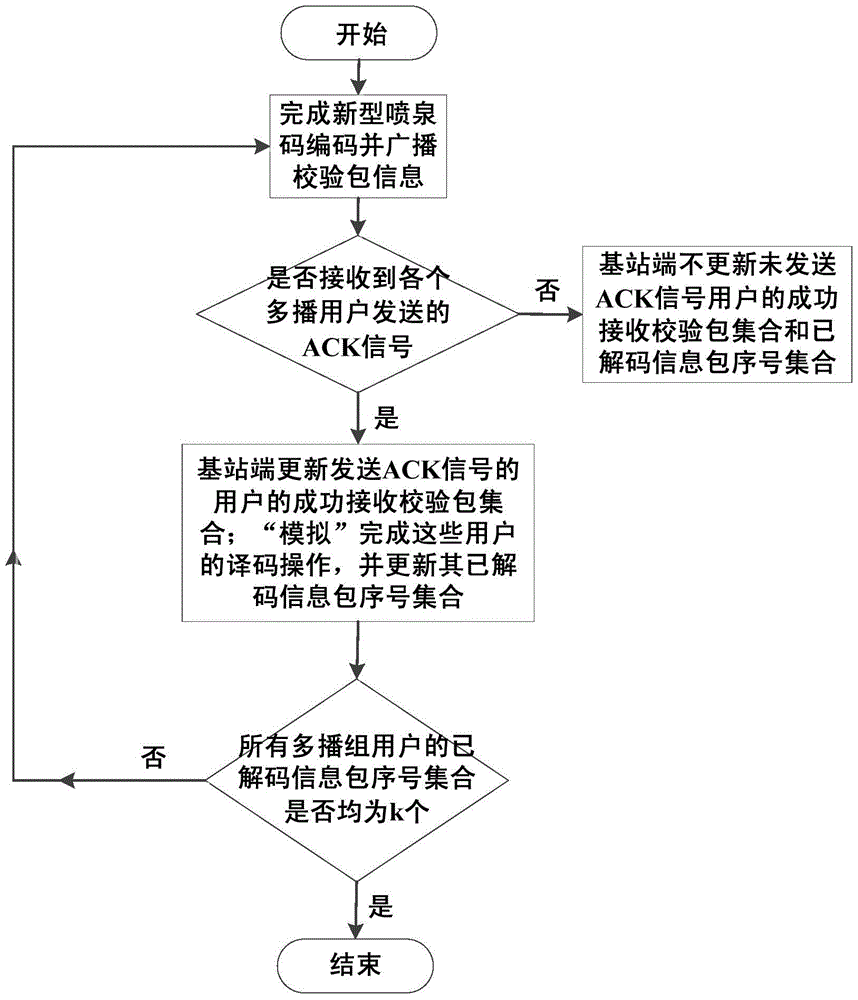
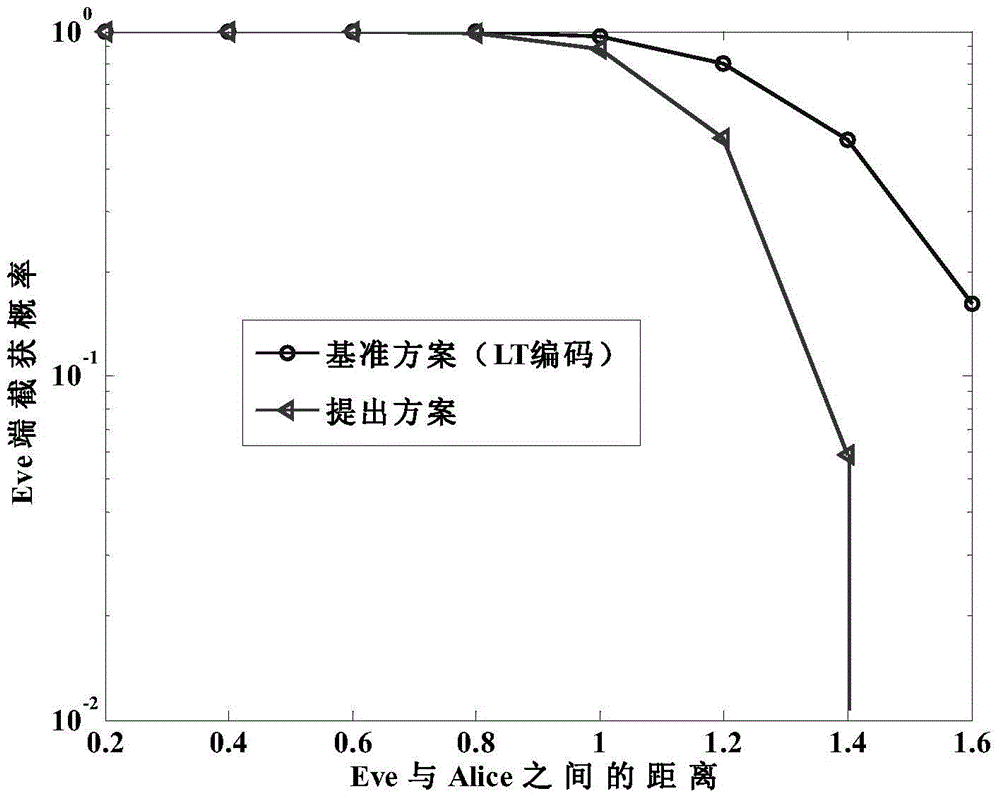
Fountain-coding-based method for ensuring multicast security transmission of multimedia
ActiveCN105141412ASmooth transmissionImprove transmission efficiencySecurity arrangementSecuring communicationService flowFountain code
The invention discloses a fountain-coding-based method for ensuring the multicast security transmission of multimedia. The method comprises the steps of 1) dividing the to-be-transmitted multimedia service flow into k information packets; 2) within a current transmission interval Ts, coding an information packet corresponding to the transmission interval at a base station based on the fountain-coding method to obtain a validation packet; 3) within the current transmission interval Ts, broadcasting the validation packet obtained in the step 2) to the users of a multicast group by the base station; 4) adding the validation packet successfully received by the first user of the multicast group into a successfully received validation packet set by the base station, decoding the validation packet successfully received by the first user at the same time, and adding the decoded information into a decoded information packet sequence number set Di; 5) repeating the steps 2), 3) and 4) till the transmission completion of the k formation packets; 6) completing the transmission of the multimedia service flow upon detecting k sequence numbers in the decoded information packet sequence number set. The fountain-coding-based method is high in transmission efficiency, high in security and high in reliability.
Owner:广西南宁修瑾电子科技有限公司
Routing protocol security alliance management method, device and system
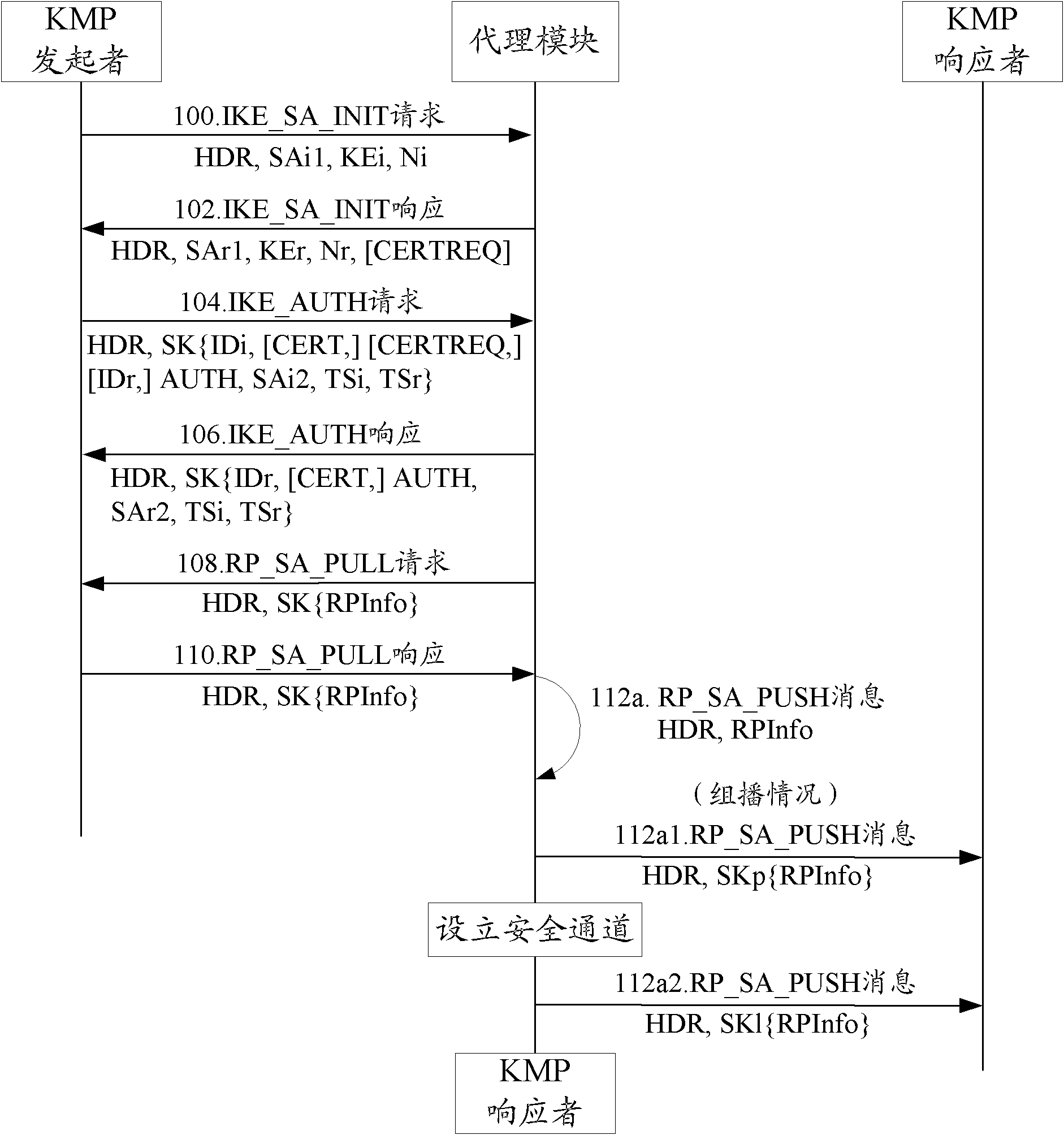
InactiveCN102469063AThe solution can only be manually configuredFix security issuesData switching networksManagement systemSecure channel
The invention discloses a routing protocol security alliance management method, which comprises the following steps that: an agent module for negotiating a routing protocol security alliance is arranged in a network element; the element provided with the agent module and a negotiation initiator of the routing protocol security alliance establish a security alliance; under the protection of the established security alliance, the element provided with the agent module and the negotiation initiator of the routing protocol security alliance negotiate the routing protocol security alliance; and the network element provided with the agent module transmits the negotiated routing protocol security alliance through a preset or set security channel. The invention also discloses a routing protocol security alliance management device and a routing protocol security alliance management system. By the invention, the routing protocol unicast and multicast security alliance can be negotiated, updated and managed, so that the problems that the routing protocol security alliance only can be configured manually and potential safety hazards are large are solved, and routing information is transmitted more safely and reliably.
Owner:ZTE CORP
Method for enhancing multicast security
InactiveCN101588361AEnhanced Multicast SecuritySpecial service provision for substationNetworks interconnectionStructure of Management InformationThe Internet
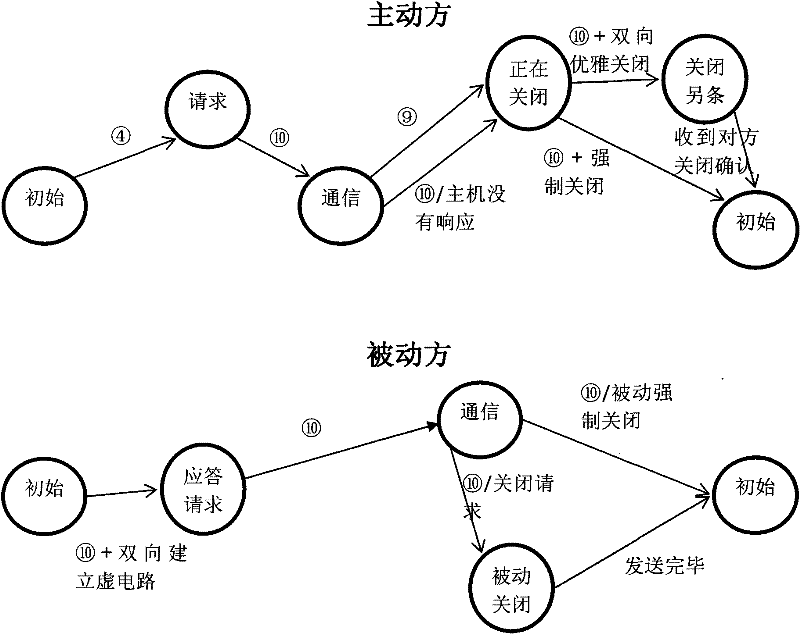
The invention discloses a method for enhancing the multicast security. For the structural security, building an end-to-end virtual circuit from a multicast user to a server not only supports the existing security mechanism of Internet, but also has a unique security mechanism based on the network structure, namely, security is embedded. Using a virtual circuit indicator and hiding multicast address during the multicast process cause the attacker difficult to attack, so as to efficiently manage and control multicast data transmission. In addition, the multicast user qualification is validated, so the attacker cannot imitate a qualified member in a group to receive multicast data, so as to enhance the security of the multicast network.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Multicast security agent assembly and multicast encryption management method
InactiveCN102684875AEnsure safetyMulticast Security GuaranteeSpecial service provision for substationKey distribution for secure communicationAttackEngineering
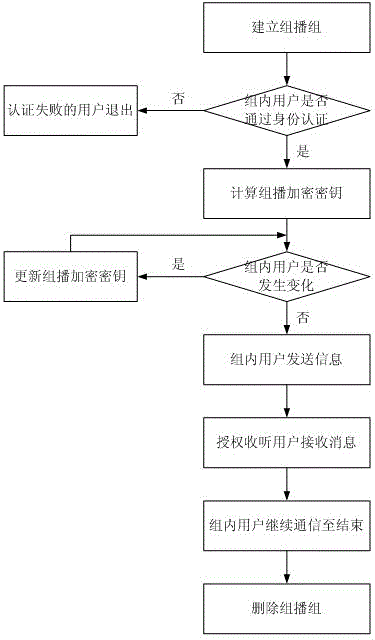
The invention relates to a multicast security agent assembly and a multicast encryption management method. File encryption and decryption submodules in a multicast module serve as specific execution modules for multicast users to encrypt / decrypt messages or files, an RSA (Rivest-Shamir-Adleman) algorithm is adopted as a multicast encryption / decryption algorithm, and private keys of the users are taken as decryption keys. After system authentication, if some users in an intranet need intra-group communication, a group key formed by a product of the private keys of all the members can ensure multicast security; and when new users participate in the intranet or the old users exit the intranet, the new users can not access communication contents before accessing and the exited users can not access the communication contents after exiting through updating the group key, therefore, the functions of encryption with one key and decryption with multiple keys in a multicast group are realized. When group members change, the keys (namely the private keys) of the other users in the group do not need to be updated, thereby realizing the encryption on the multicast information, and achieving important forward secrecy, backward secrecy, inner attack resistance and the like in security multicast.
Owner:HENAN UNIV OF SCI & TECH
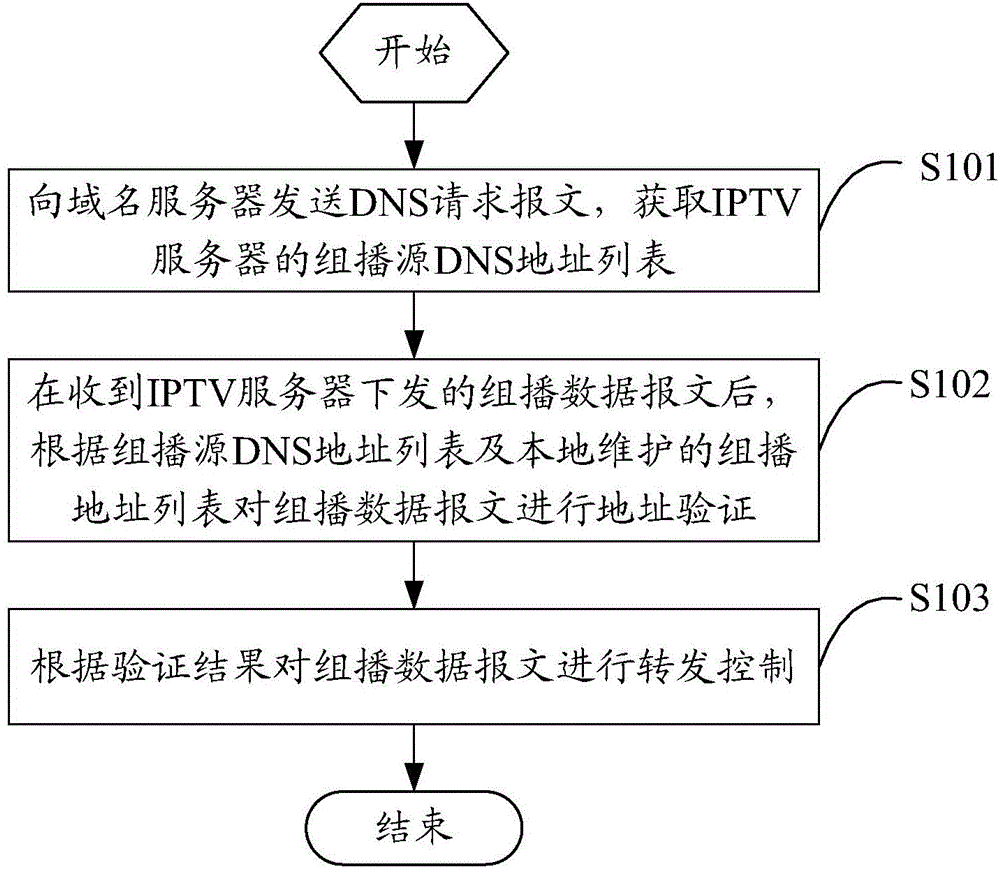
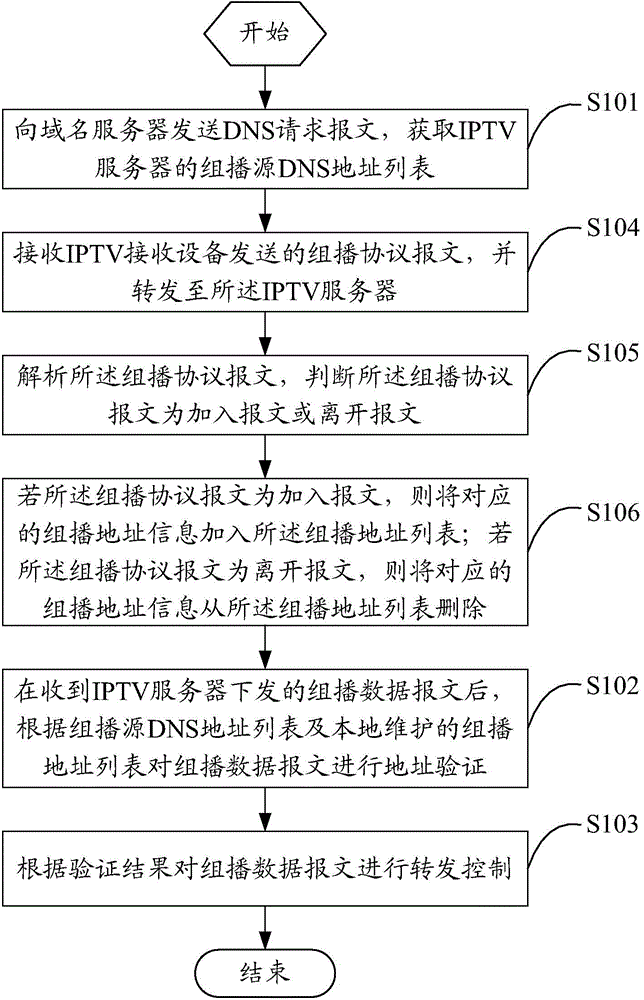
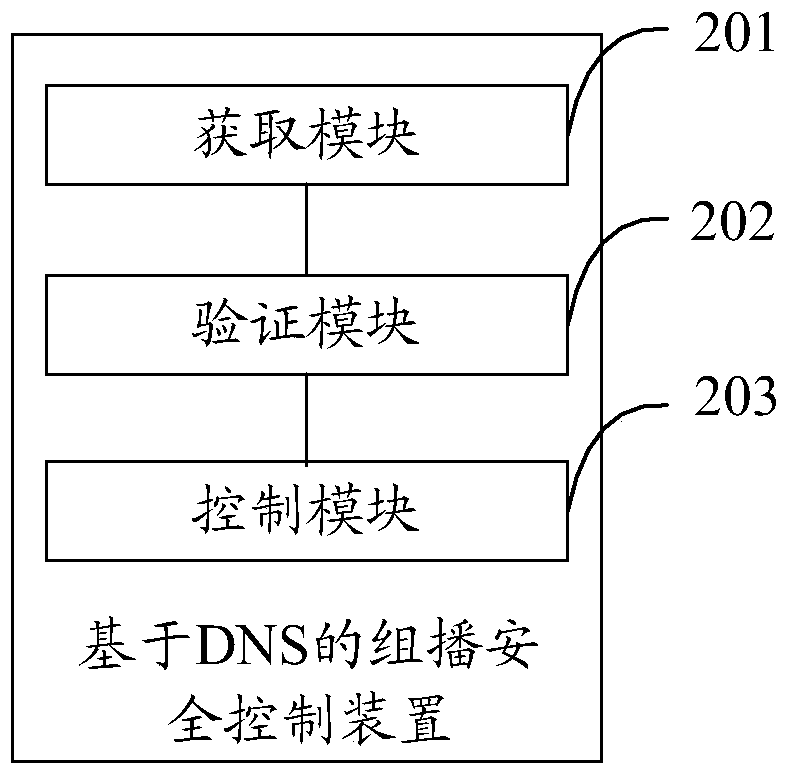
Domain name service (DNS) based multicast security control method and apparatus
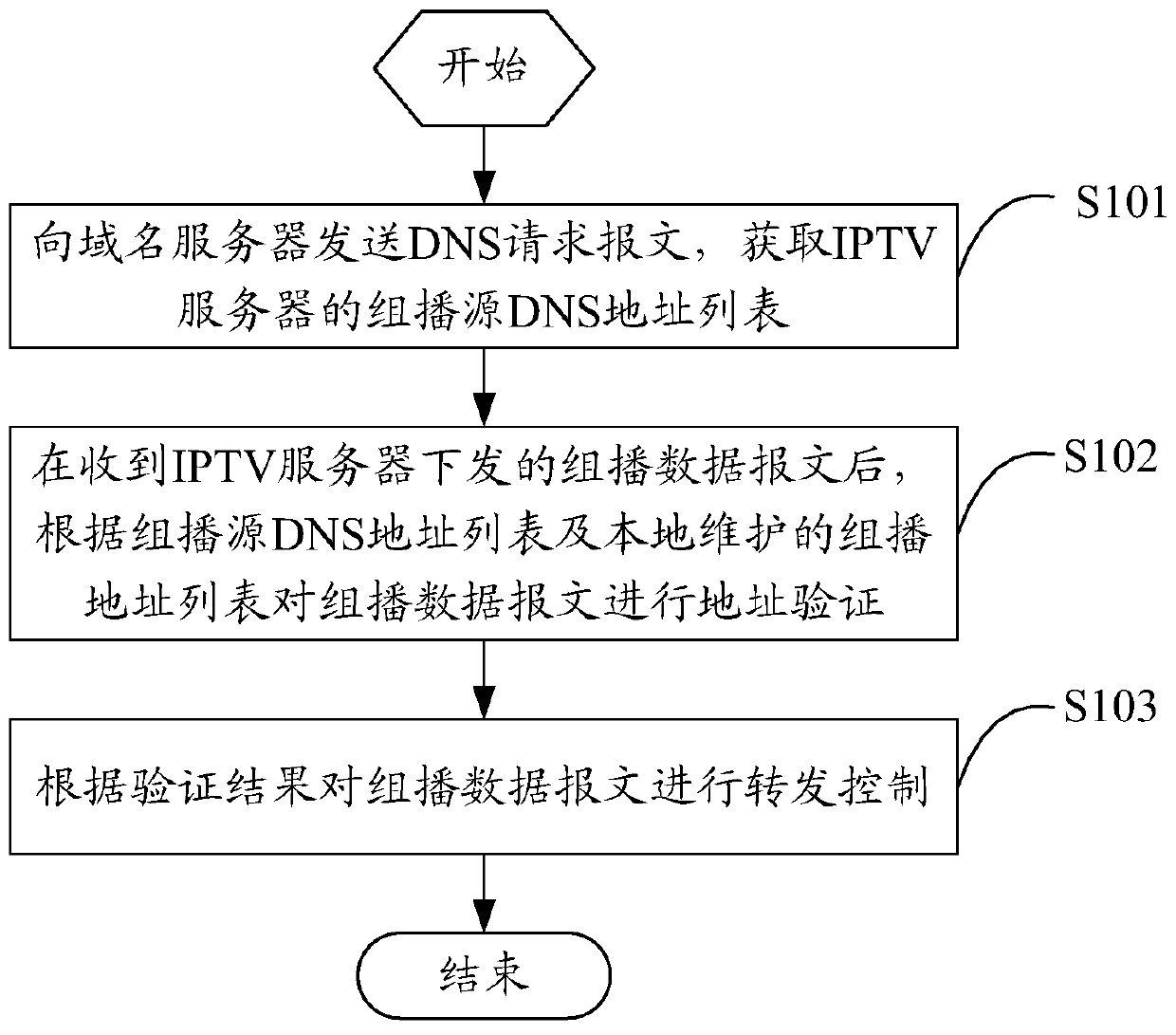
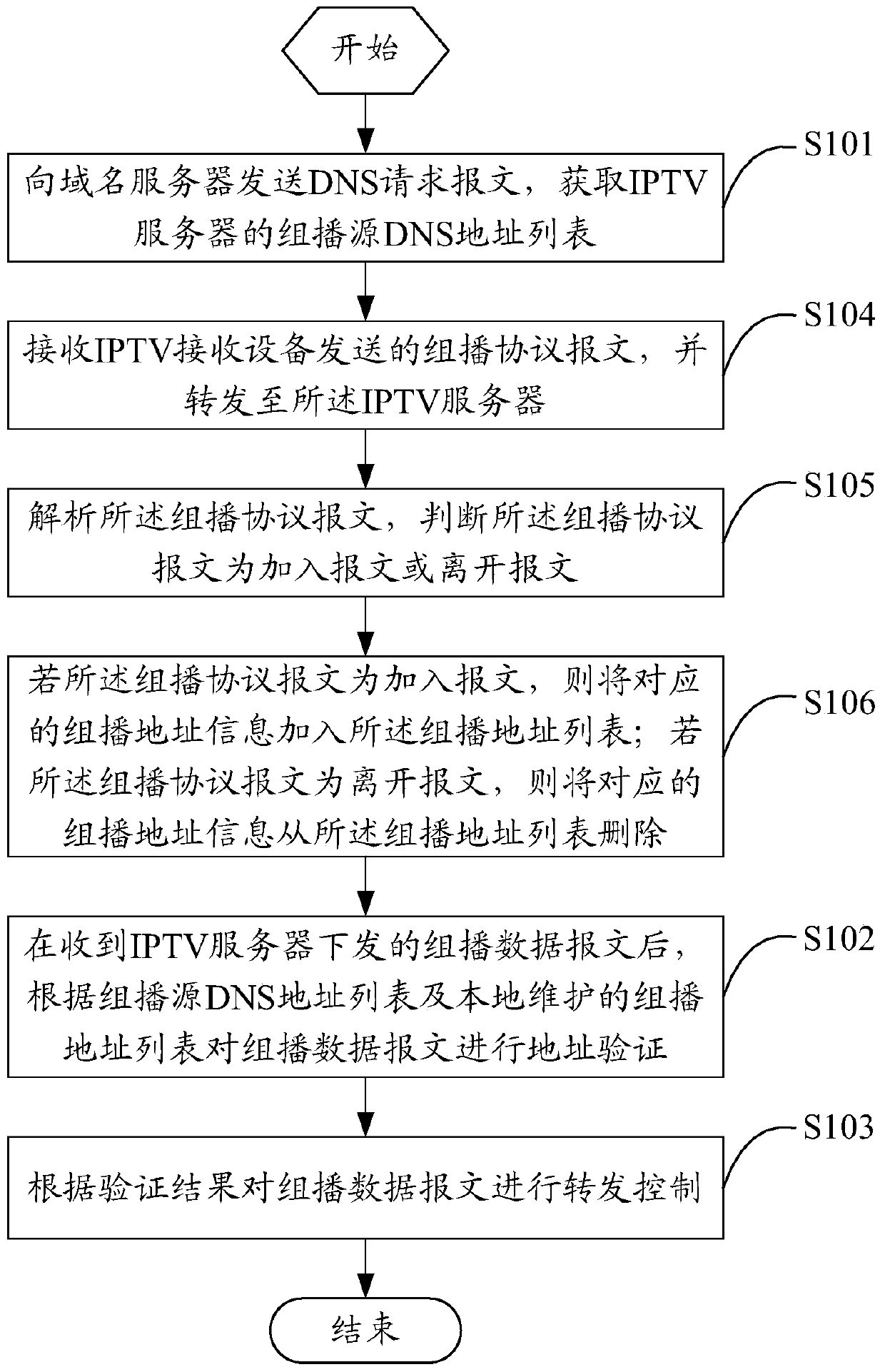
ActiveCN105491460ASimplify and filter complex processingReduce attackSelective content distributionSecuring communicationDomain nameName server
The invention relates to a domain name service (DNS) based multicast security control method and apparatus. The method comprises the steps of sending a DNS request message to a domain name server, and acquiring a multicast source DNS address list of an internet protocol television (IPTV) server; after a multicast data message delivered by the IPTV server is received, performing address verification on the multicast data message according to the multicast source DNS address list and a multicast address list maintained locally; and performing forwarding control on the multicast data message according to a verification result. Through adoption of the method, multicast source verification can be carried out effectively, multicast service streams can be controlled effectively and safely, the multicast services are guaranteed to be stable, network attacks are reduced, a complicated filtering process of the multicast source is simplified, and engineering implementation and deployment are easy.
Owner:ZTE CORP
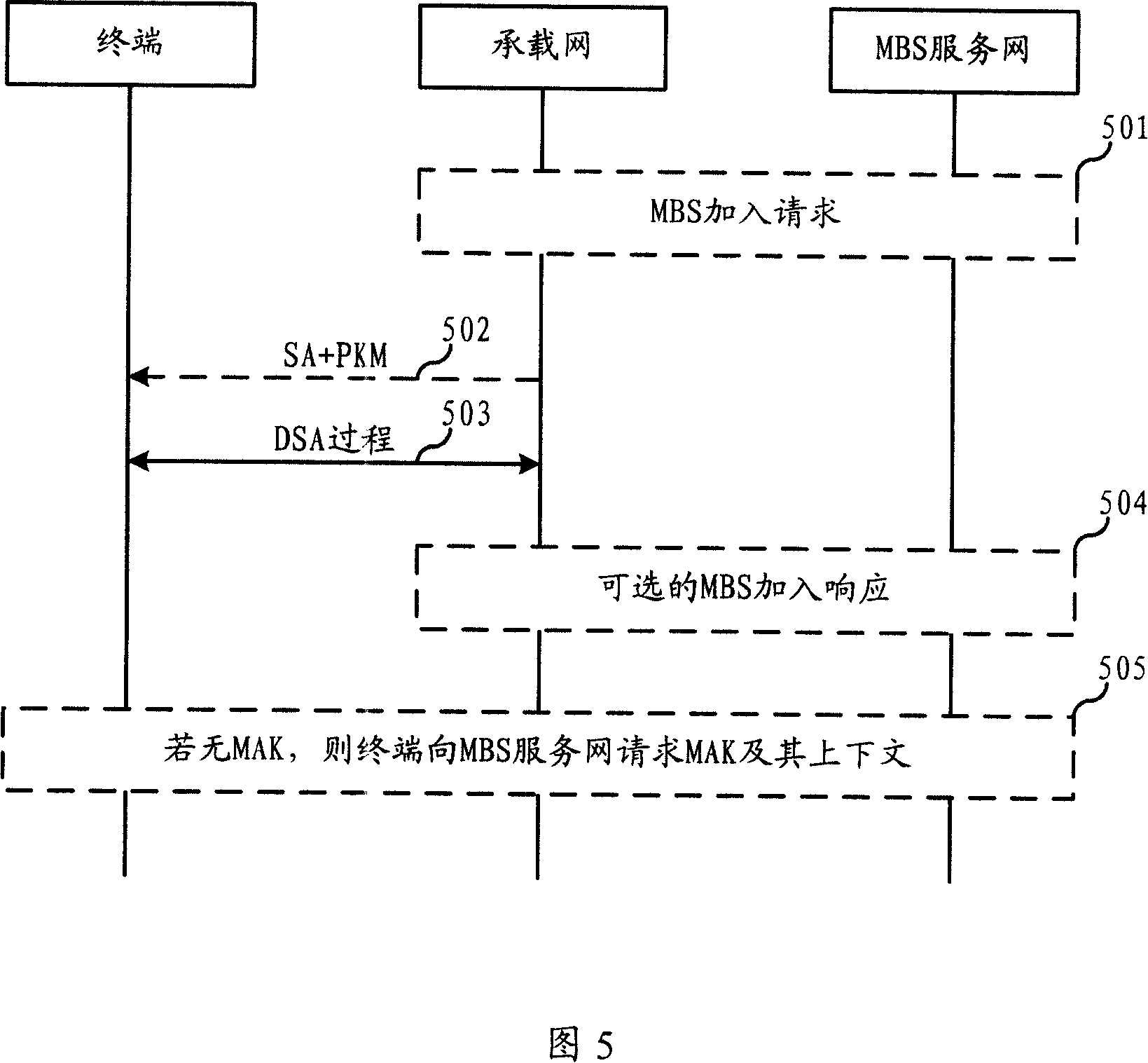
Method for adding multicast and broadcast service into communication system and terminal
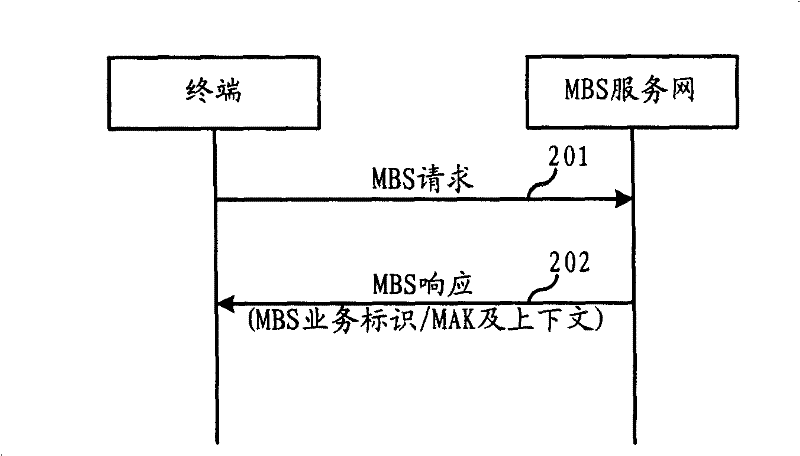
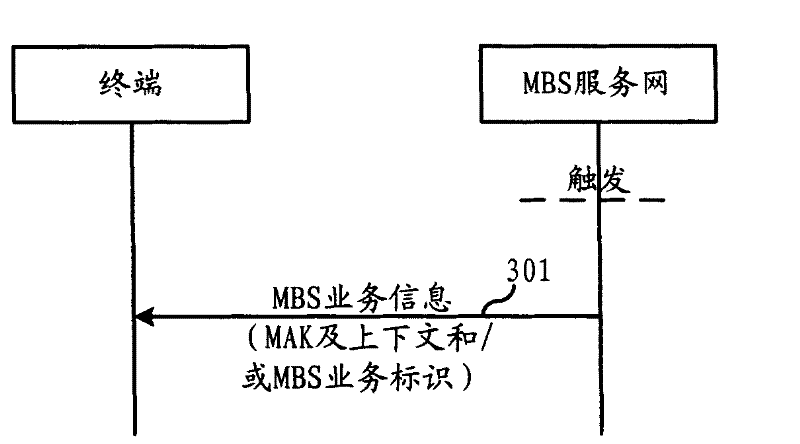
InactiveCN101150467AKey distribution for secure communicationData switching by path configurationCommunications systemBusiness data
The invention relates to the field of communications, which discloses a method for a communications system and a terminal to join a multicast broadcast service, which ensures that the terminal can be smoothly joined MBS business in order to receive the MBS business data. In the invention, the terminal acquires the MBS authorization key from an MBS service network then acquires the MBS multicast parameters and / or a multicast security key from the loading network in order to join the corresponding MBS business. Through the processes, the terminal can successfully receive the corresponding MBS business parameters based on the loading indicated by the multicast parameters, according to MBS security key that is generated by the MBS authorization key and the multicast security key. Before the MBS authorization key is issued, the MBS service network needs to certify the terminal and does not issue the MBS key to the terminal unless the certification is passed. The process that the terminal acquires the MBS multicast parameters and the multicast security key for joining the MBS business, from the loading network can be started either from the side of the network or directly from the terminal.
Owner:HUAWEI TECH CO LTD
Method and apparatus for supporting security in muliticast communication
ActiveUS8842832B2Key distribution for secure communicationSecret communicationTraffic capacityMobile station
A method of supporting a security for a multicast communication is provided in a mobile station. The mobile station shares an MAK with a base station, derives a prekey based on a first parameter including the MAK, and derives a multicast security key including an MTEK based on a second parameter including the prekey, and decrypts a multicast traffic using the multicast security key.
Owner:ELECTRONICS & TELECOMM RES INST
A Fountain Coding-Based Method for Guaranteeing the Secure Transmission of Multimedia Multicast
ActiveCN105141412BSmooth transmissionImprove transmission efficiencySecurity arrangementSecuring communicationService flowFountain code
The invention discloses a fountain-coding-based method for ensuring the multicast security transmission of multimedia. The method comprises the steps of 1) dividing the to-be-transmitted multimedia service flow into k information packets; 2) within a current transmission interval Ts, coding an information packet corresponding to the transmission interval at a base station based on the fountain-coding method to obtain a validation packet; 3) within the current transmission interval Ts, broadcasting the validation packet obtained in the step 2) to the users of a multicast group by the base station; 4) adding the validation packet successfully received by the first user of the multicast group into a successfully received validation packet set by the base station, decoding the validation packet successfully received by the first user at the same time, and adding the decoded information into a decoded information packet sequence number set Di; 5) repeating the steps 2), 3) and 4) till the transmission completion of the k formation packets; 6) completing the transmission of the multimedia service flow upon detecting k sequence numbers in the decoded information packet sequence number set. The fountain-coding-based method is high in transmission efficiency, high in security and high in reliability.
Owner:广西南宁修瑾电子科技有限公司
Multicast security agent component and multicast encryption management method
InactiveCN102684875BEnsure safetyImplement encryptionSpecial service provision for substationKey distribution for secure communicationEngineeringSecure multicast
The invention relates to a multicast security agent component and a multicast encryption management method. The file encryption and decryption sub-module in the multicast module is a specific execution module for multicast users to perform message or file encryption / decryption, and adopts the RSA algorithm as the multicast encryption / decryption algorithm, the user's private key is used as the decryption key. After the system is authenticated, if some users on the intranet need to communicate in the group, the group key composed of the product of all members' private keys can guarantee the security of the multicast. When a user joins or an old user exits, by updating the group key, the newly joined user cannot access the communication content before joining and the exiting user cannot access the communication content after exiting, realizing one-key encryption in the multicast group. With the function of decrypting the key, when the group members change, there is no need to update the keys (private keys) of other users in the group. Forward secrecy, backward secrecy, and collusion resistance.
Owner:HENAN UNIV OF SCI & TECH
DNS-based multicast security control method and device
ActiveCN105491460BSimplify and filter complex processingReduce attackSelective content distributionSecuring communicationDomain nameService flow
Owner:ZTE CORP
Service access method, device, and system
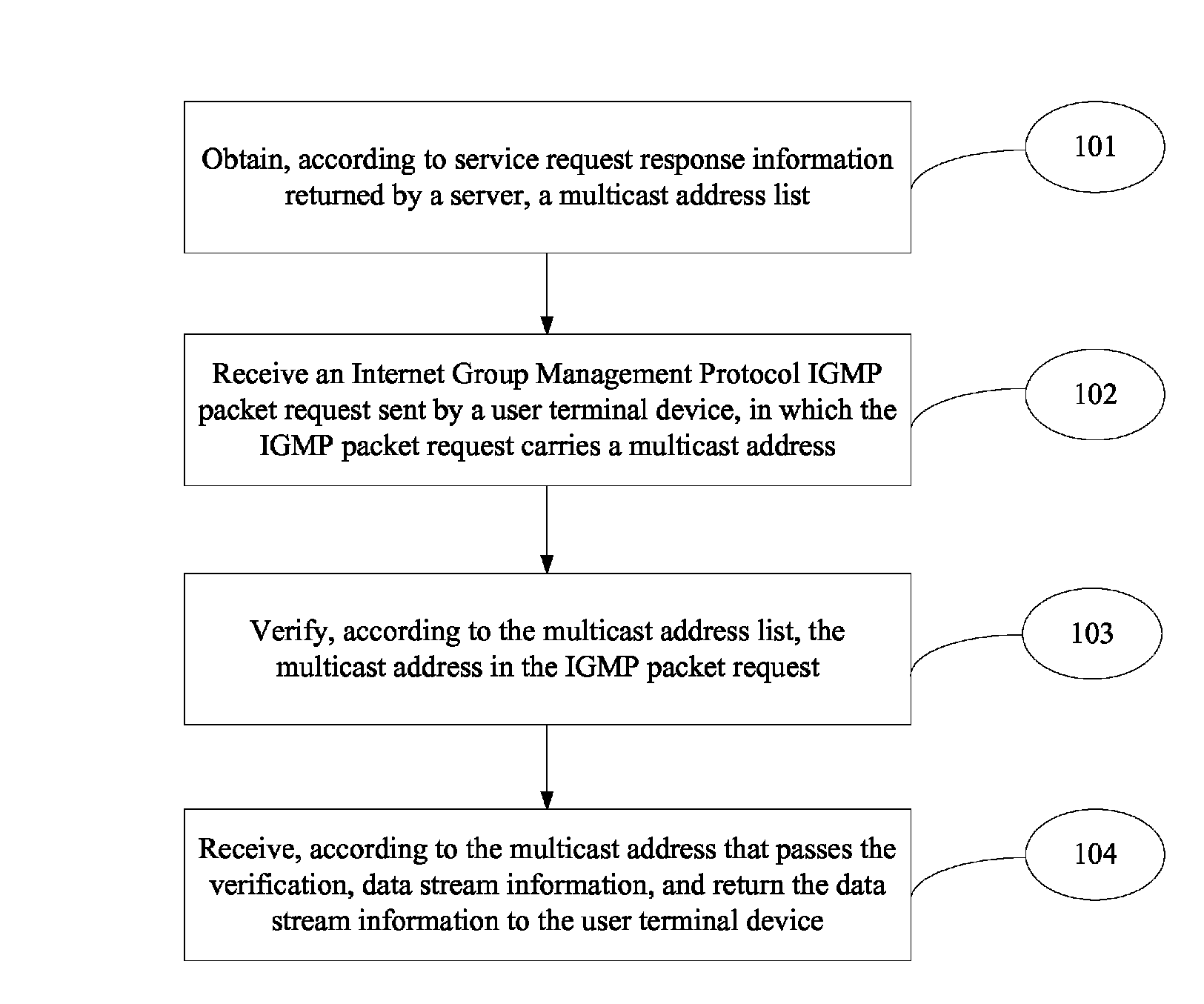
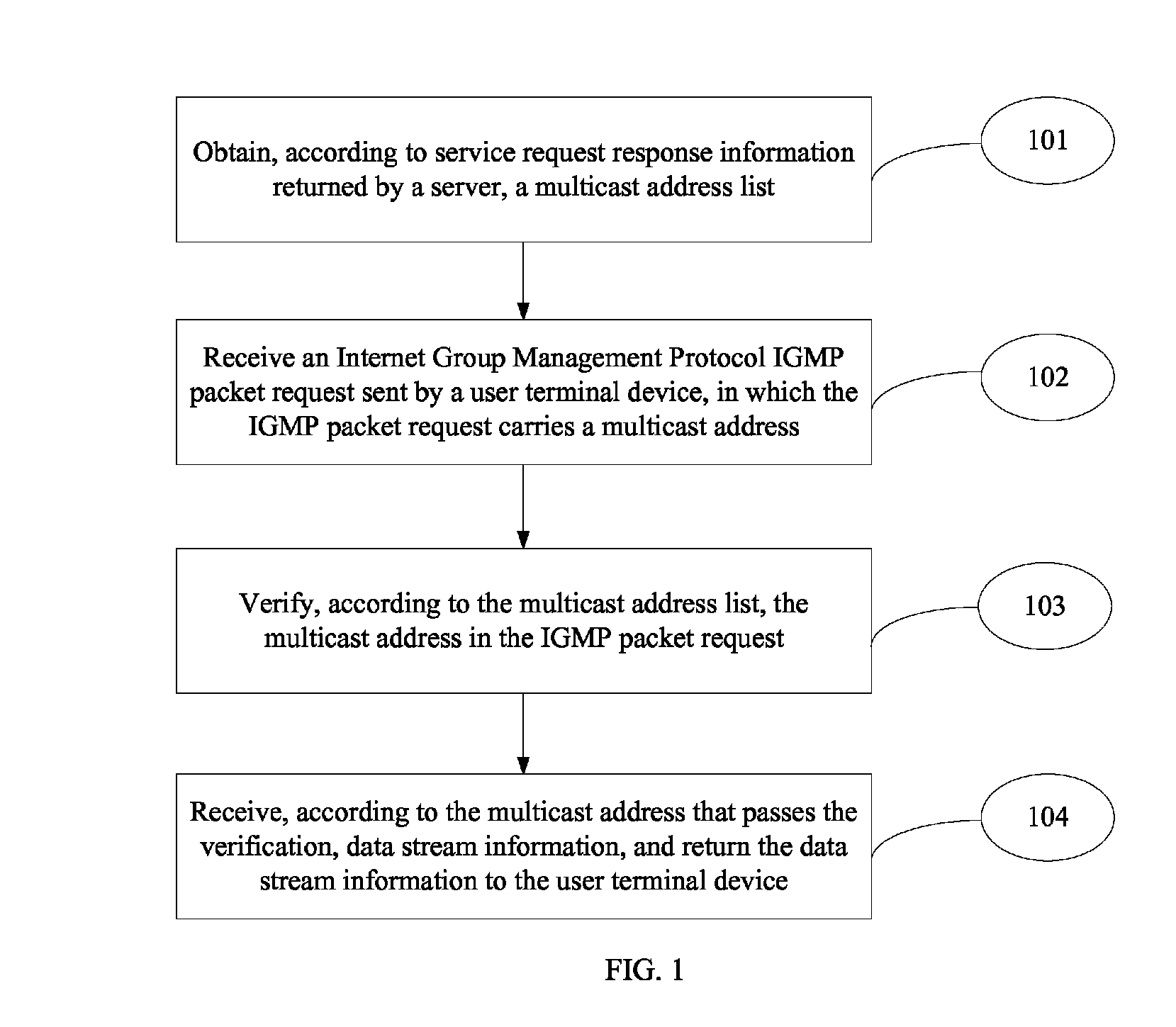
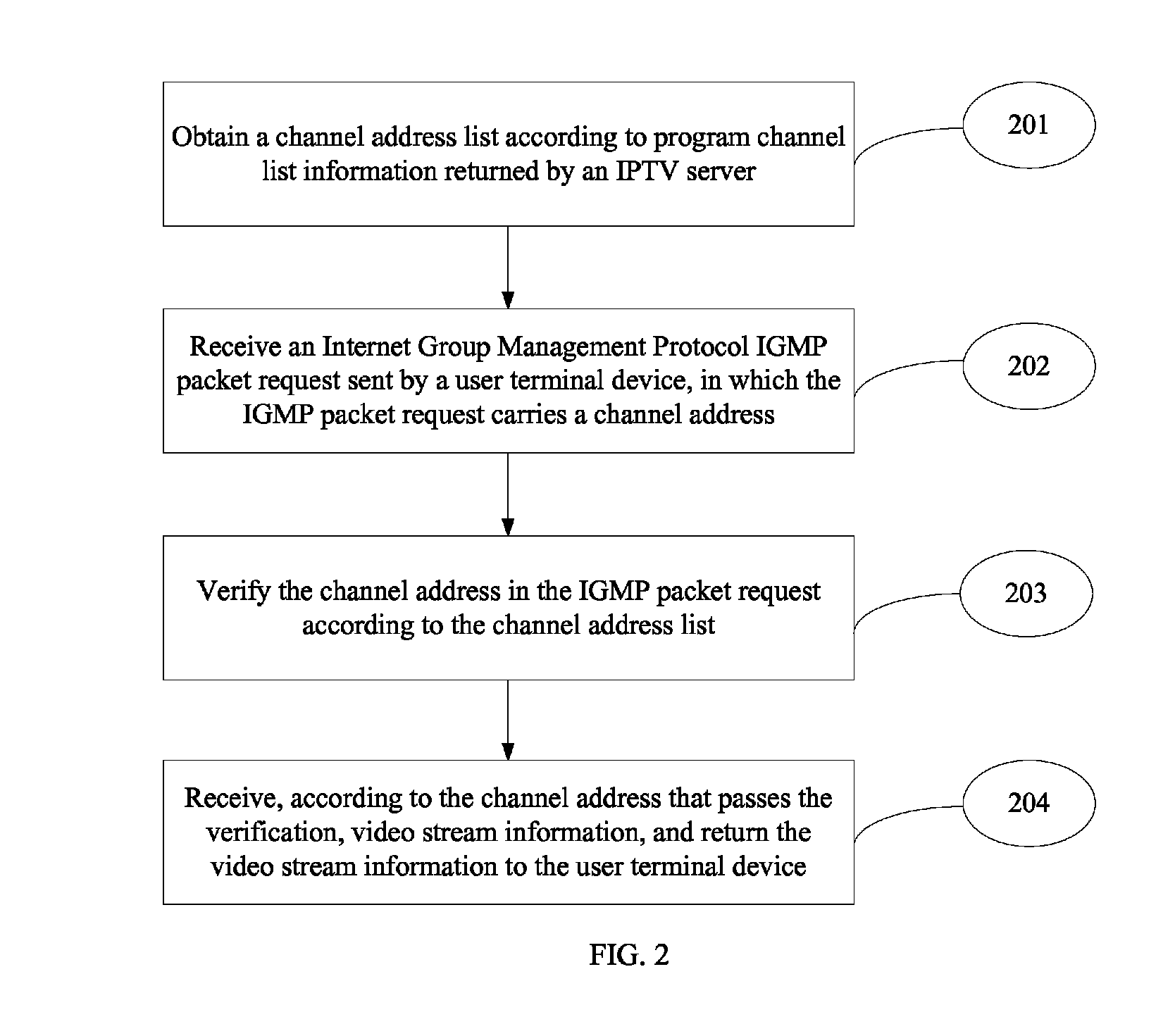
ActiveUS8813115B2Ensure safetyTelevision system detailsAnalogue secracy/subscription systemsData streamService domain
The present invention provides a service access method, device, and system, and relates to the field of television services, to guarantee multicast security of a network device. The method includes: obtaining an authorized multicast address list according to program channel list information provided by a server; receiving an Internet Group Management Protocol IGMP packet request sent by a user terminal device, where the IGMP packet request carries a multicast address; verifying the multicast address in the IGMP packet request according to the multicast address list; and sending a media data stream corresponding to the verified multicast address to the user terminal device. The solutions of the present invention are suitable for realizing the security of multicast of network device.
Owner:HUAWEI TECH CO LTD
Multicast security control method, system and transmission node
ActiveCN101795223BEnsure safetyAvoid attackSpecial service provision for substationMulticast addressStream data
The invention discloses a multicast security control method, system and transmission node. The method comprises: the transmission node receives a multicast flow data packet from an upstream port; Information, to find whether there is a pre-established matching upstream port entry containing the multicast address information and upstream port information; if it exists, forward the data according to the data forwarding table of the multicast group to which the data message belongs message; if it does not exist, it is judged whether the upstream port is a pre-configured legal upstream port, if so, a new upstream port entry is created according to the multicast address information and upstream port information, and a new upstream port entry is created according to the datagram The data forwarding table of the forwarding path corresponding to the multicast group to which the message belongs forwards the data message; if not, discards the data message. It effectively guarantees the security of the upstream node of the multicast flow, and avoids the attack of the illegal multicast source on the transmission node.
Owner:RUIJIE NETWORKS CO LTD
Method for enhancing multicast security
InactiveCN101588361BEnhanced Multicast SecuritySpecial service provision for substationNetworks interconnectionThe InternetMulticast network
The invention discloses a method for enhancing the multicast security. For the structural security, building an end-to-end virtual circuit from a multicast user to a server not only supports the existing security mechanism of Internet, but also has a unique security mechanism based on the network structure, namely, security is embedded. Using a virtual circuit indicator and hiding multicast address during the multicast process cause the attacker difficult to attack, so as to efficiently manage and control multicast data transmission. In addition, the multicast user qualification is validated,so the attacker cannot imitate a qualified member in a group to receive multicast data, so as to enhance the security of the multicast network.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com