Method for enhancing multicast security
A security and multicast technology, applied in the field of network security, can solve problems such as denial of service, difficulty in secure multicast, network congestion, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Specific embodiments of the present invention are described below for a better understanding of the present invention. It should be noted that in the following description, when detailed descriptions of known functions and designs may dilute the main content of the present invention, these descriptions will be omitted here.
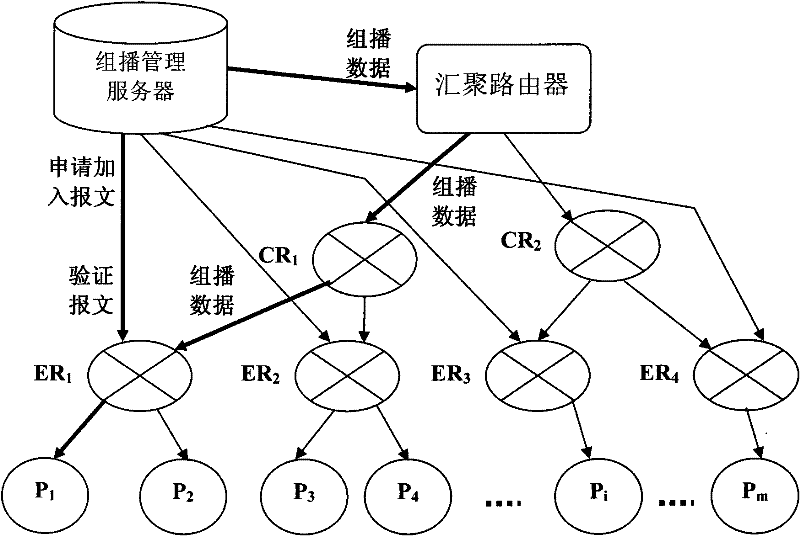
[0021] figure 1 It is a schematic diagram of a specific implementation of the method for enhancing multicast security in the present invention.
[0022] The multicast management server passes through the aggregation router and the core router CR 1 、CR 2 , the edge router ER 1 、ER 2 、ER 3 、ER 4 form a multicast network. Multicast user P 1 ,P 2 ,P 3 ,P 4 ----P i ----P n Access to the multicast network through the edge router.
[0023] (1), for multicast management server, edge router ER 1 、ER 2 、ER 3 、ER 4 and convergence server to perform initialization settings, in this embodiment, also includes the core router CR 1 、CR 2 Perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com