Multicast security control method, system and transmission node
A transmission node and security control technology, applied in the field of communication, to achieve the effect of ensuring security, avoiding attacks, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
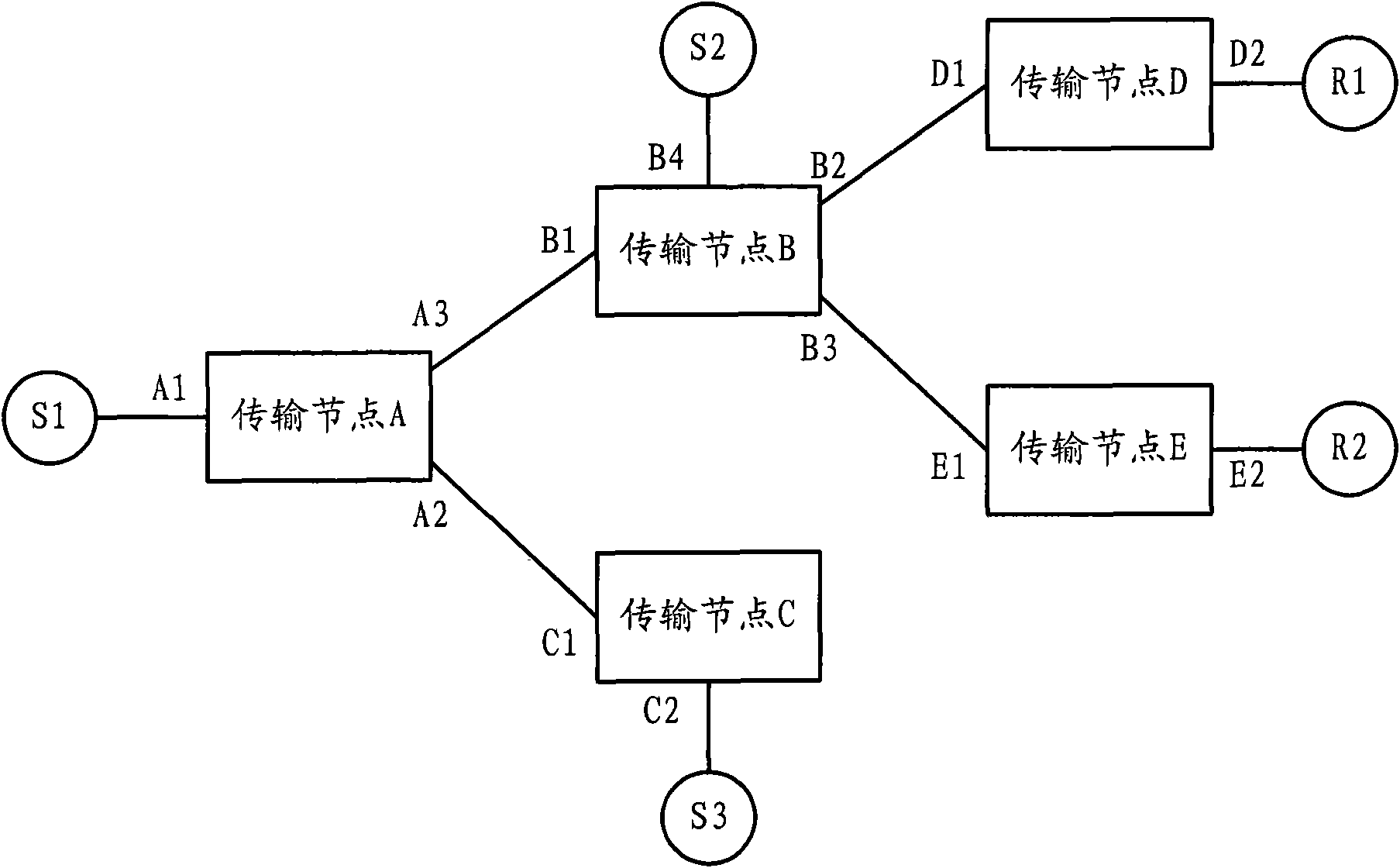
[0032] The multicast security control system provided by the embodiment of the present invention may include: a multicast source, a transmission node, and a receiver. Wherein, the multicast source is used to provide multicast flow data packets, and send them to the transmission nodes connected to itself. The transmission node is used to transmit the received multicast flow data message to the downstream node or the receiving end. The receiving end is used to receive the multicast flow data message sent by the transmission node.
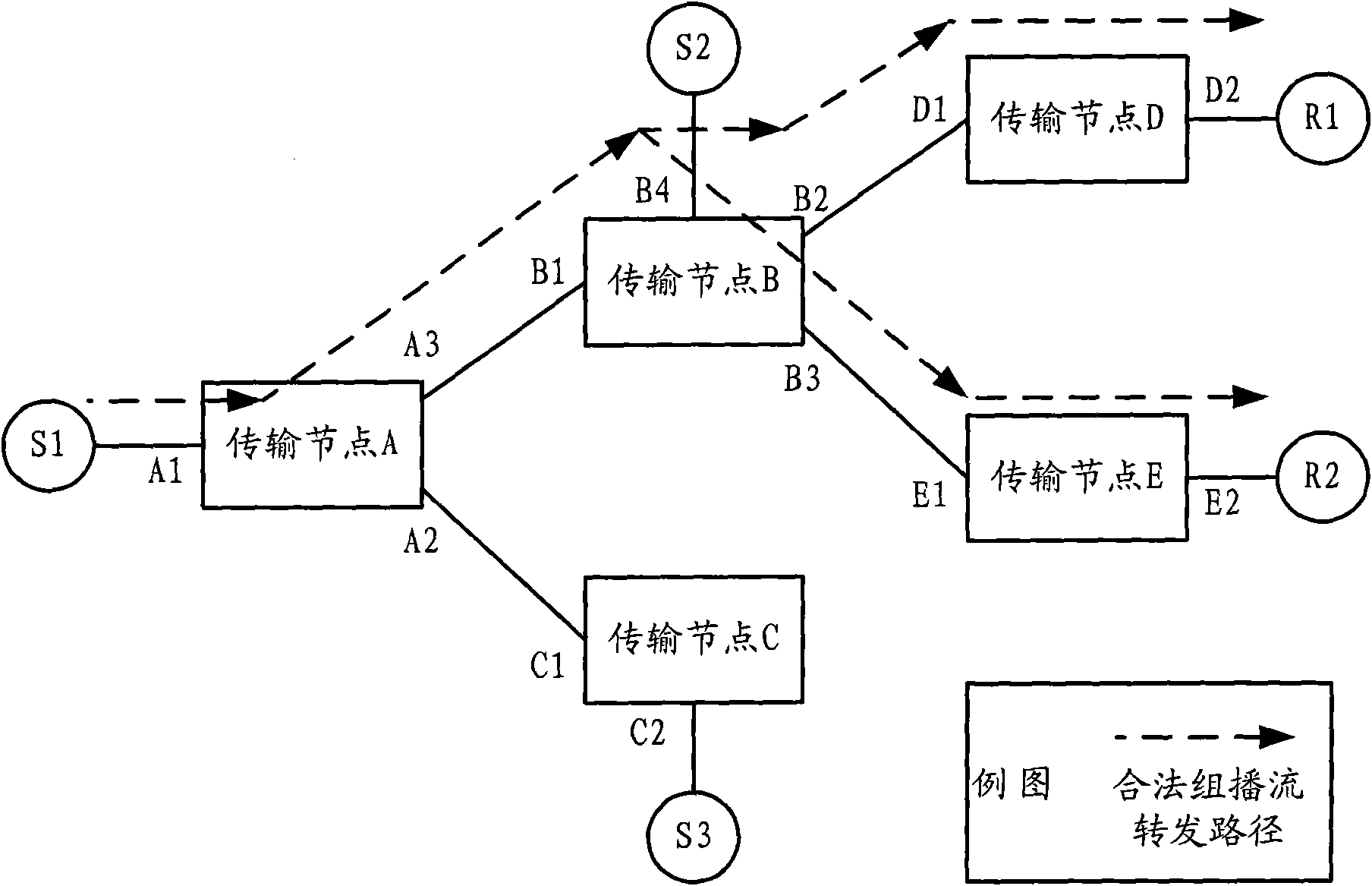
[0033] Such as figure 1 Shown is a structural example of the multicast security control system. figure 1 The multicast sources shown in include: legal multicast sources S1, illegal multicast sources S2 and S3, etc.; transmission nodes include: transmission nodes A, B, C, D, E, etc.; and receivers include: receivers R1 and R2 etc.
[0034] The multicast source is used to provide multicast flow data packets to the transit nodes.
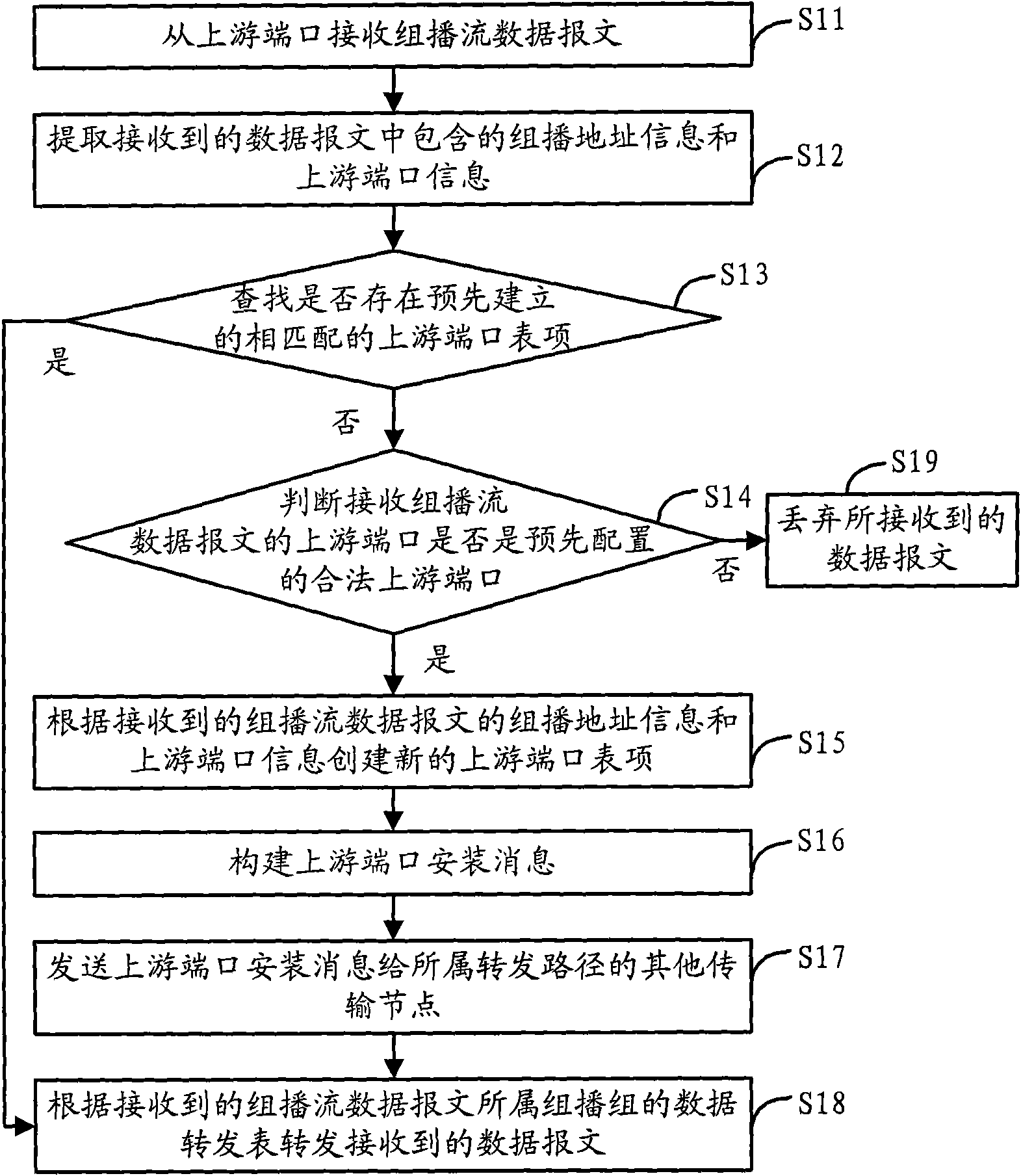
[0035] The transm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com