Safety multicast method based on protocol of conversation initialization
An initialization protocol and secure multicast technology, applied in the field of secure multicast, can solve problems such as inability to adapt to complex network environments and scalability requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
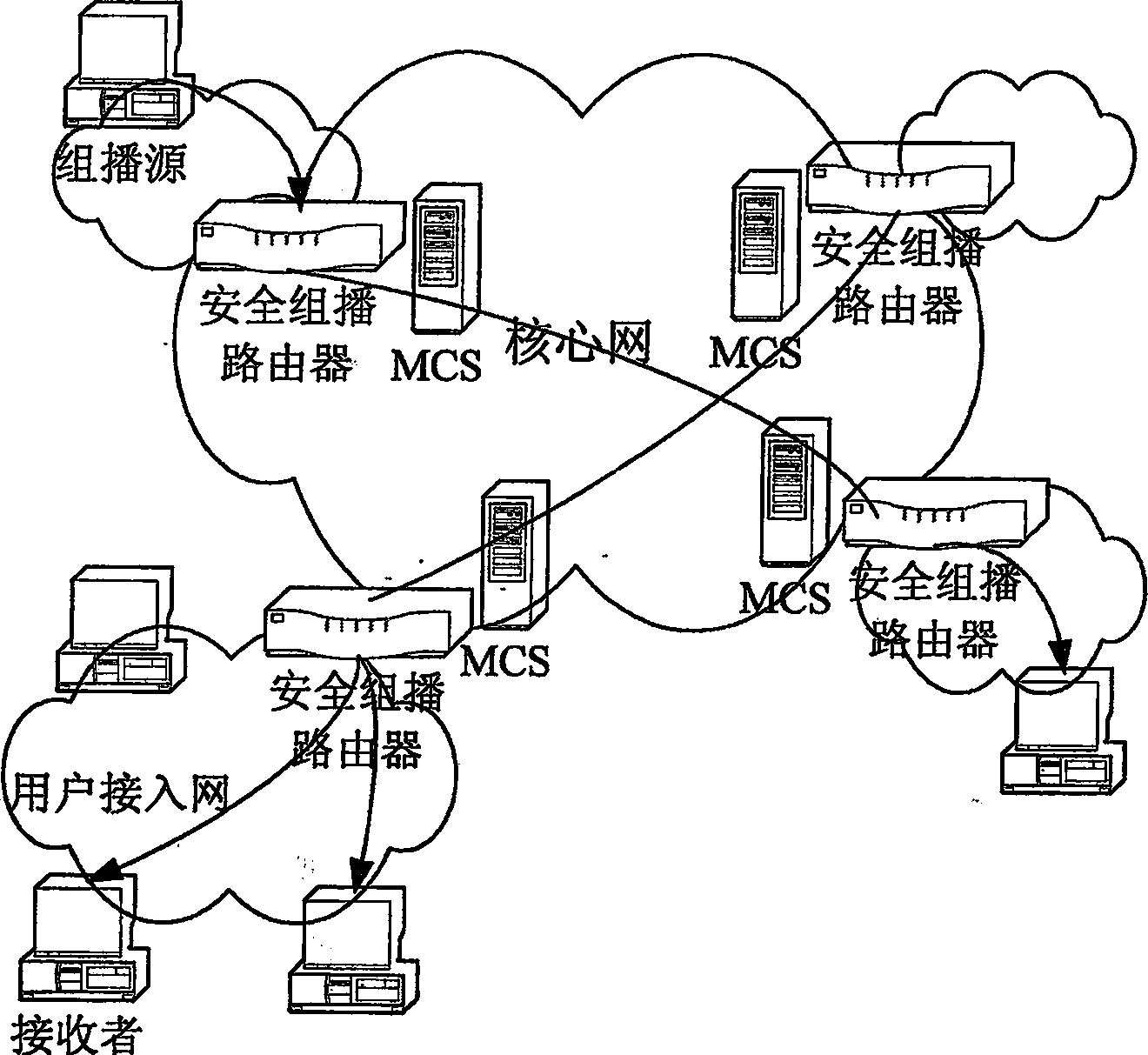
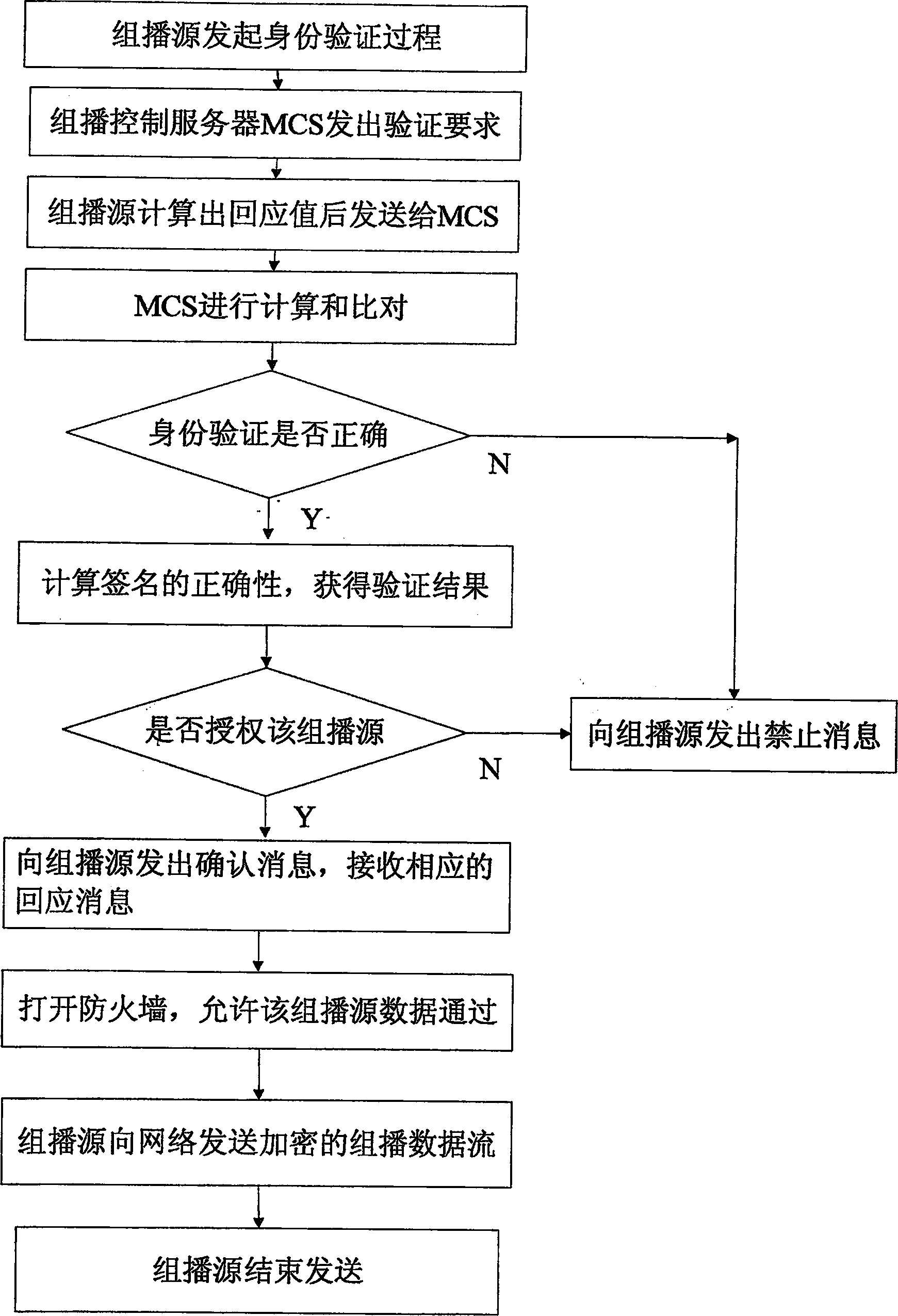
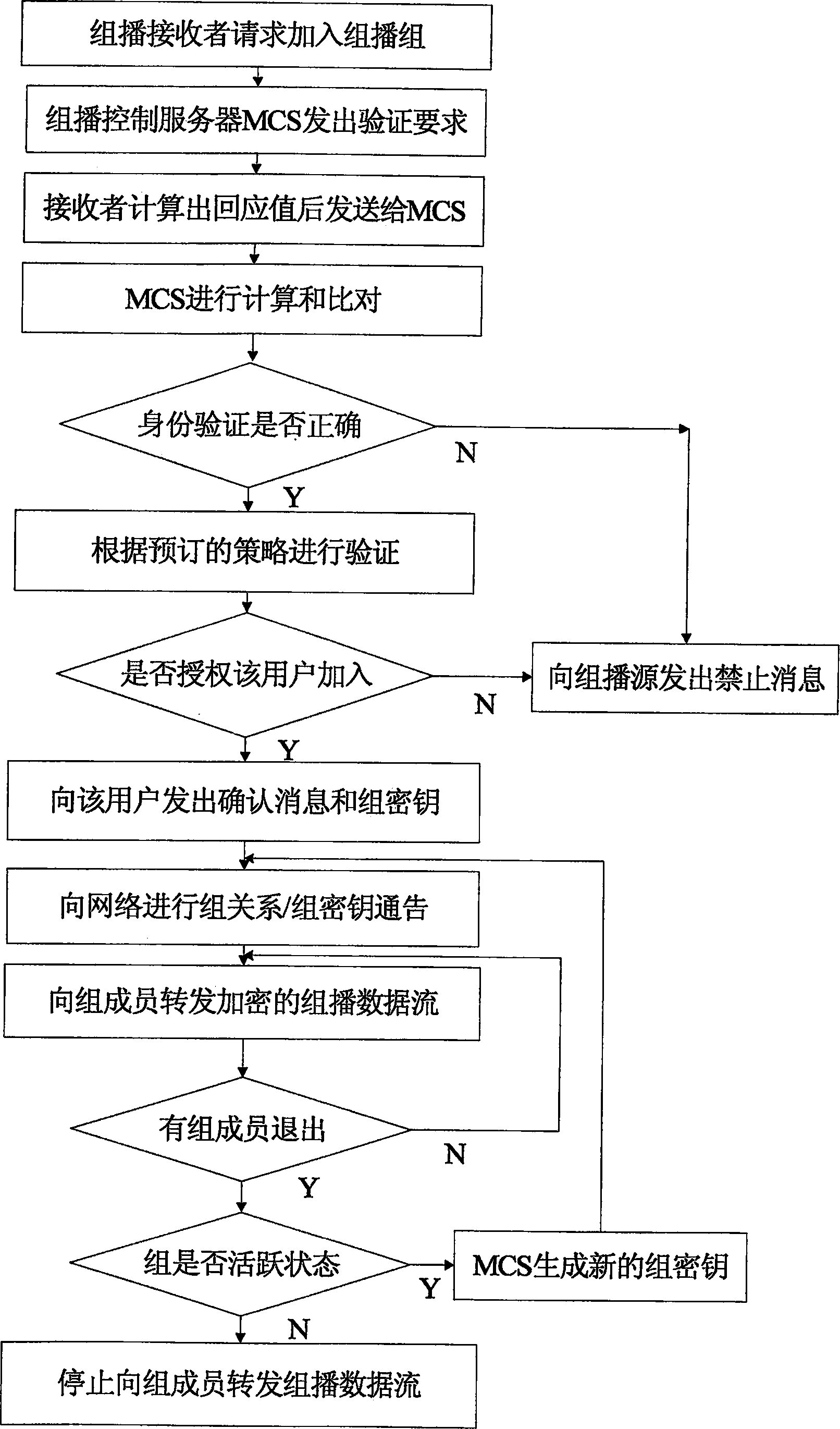
[0071] The solution of the present invention consists of three parts: multicast source and receiver access control and group key management, Internet Group Management Protocol / Multicast Receiver Discovery Protocol (IGMP / MLD) adapter, and regional MCS deployment, specifically as follows:
[0072] 1. Multicast source and receiver access control and group key management
[0073] MSSIP source authentication adopts a two-stage scheme according to the hierarchical characteristics of the network. Since the core network is usually a WAN, with large traffic and a wide geographical area, although the link bandwidth of the recently constructed core network has reached 10G, there are still a large number of packet losses on the network, and the impact of packet loss is even greater. Therefore, MSSIP adopts the HMAC authentication method in the core network; while the user access network has the characteristics of high speed and low packet loss rate, and can use multicast source authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com