Multicast security agent assembly and multicast encryption management method
A security proxy and multicast technology, applied in the field of key management, can solve the problems that users cannot access current and future communication content, users cannot access communication content, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
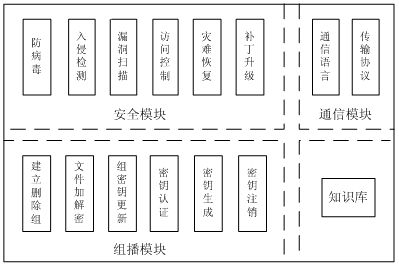
[0030] one, Multicast Security Agent Component
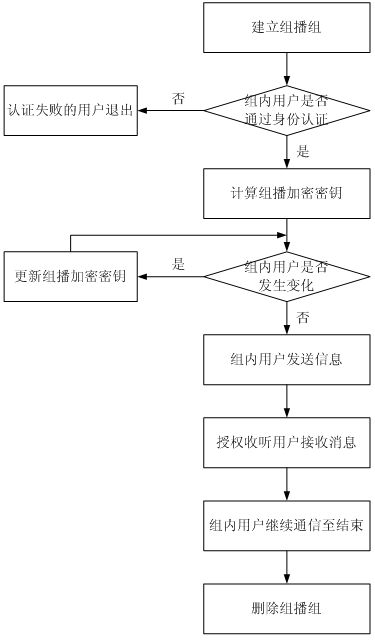
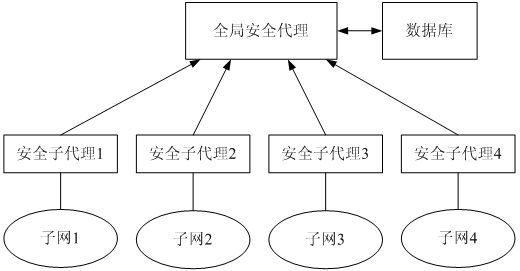
[0031] In general, agents are characterized by autonomy, adaptability, and cooperation [3] , can decide what to do next according to its state, without human or other external intervention. The multicast security agent (Security Agent) component is mainly composed of four modules: security module, communication module, multicast module and knowledge base module.
[0032] (1) Security module
[0033] The security module provides services related to intranet security in the area where the agent is located, and the valuable information it collects is stored in the knowledge base. The security module is composed of sub-modules such as anti-virus, intrusion detection, vulnerability scanning, access control, disaster recovery and patch upgrade.
[0034] (2) Communication module
[0035] The communication module is mainly used for exchanging information between agents, intranet hosts and agents. The sent request information inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com