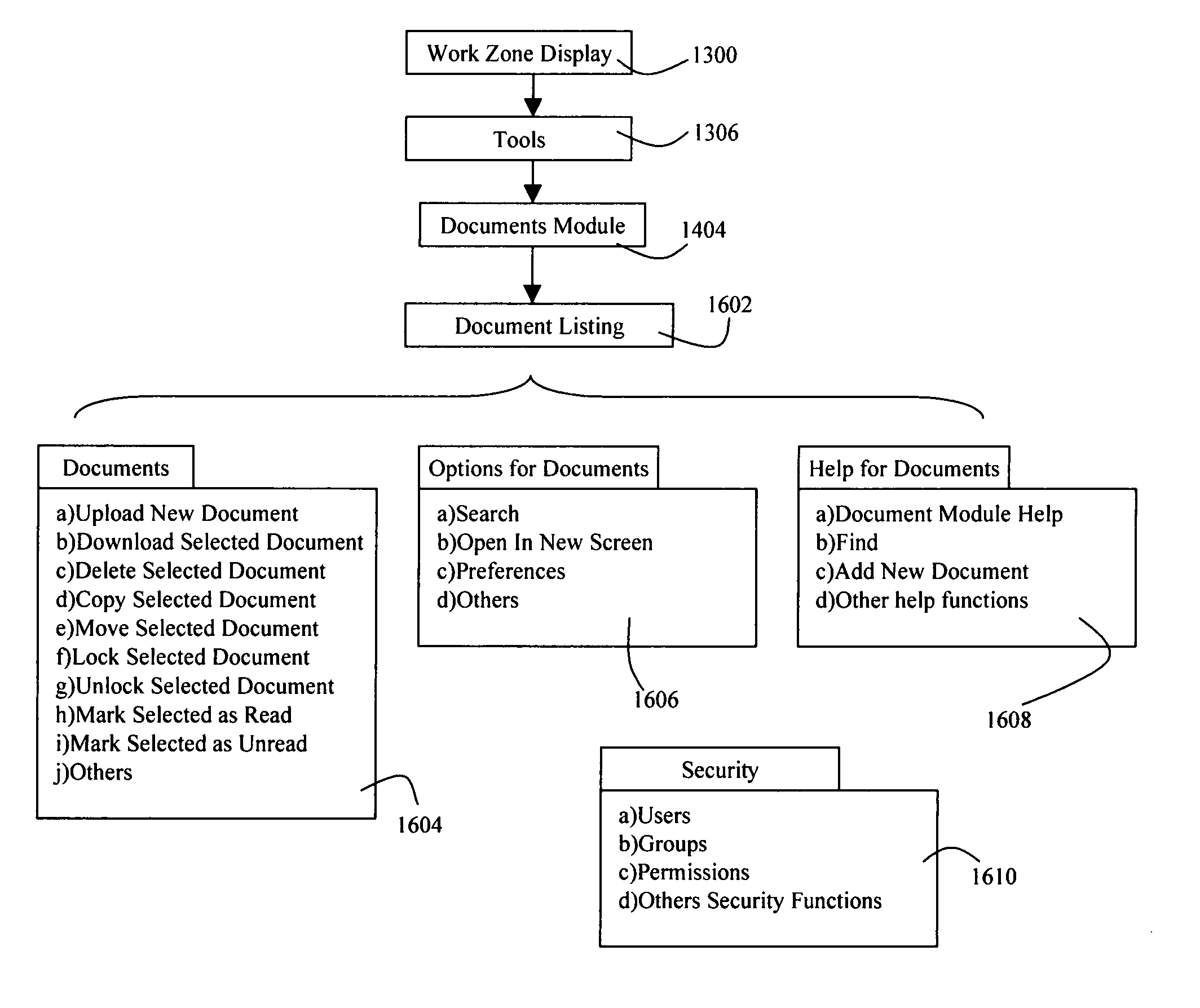
Patents
Literature
158results about How to "Avoid uploading" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
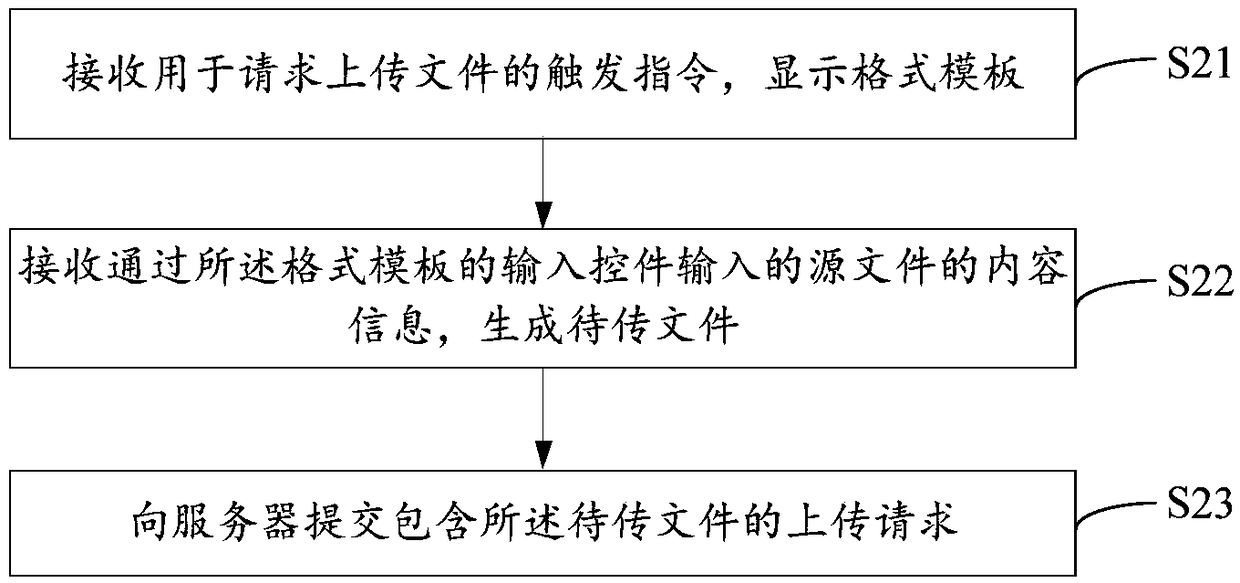
Method and system for collaboration
InactiveUS20050097440A1Eliminate needAvoid uploadingDigital computer detailsOffice automationEngineeringHuman–computer interaction
A scalable and reliable collaborative software application that provides an information hub that serves as a single portal to using applications in an aggregated, collaborative manner, thereby eliminating the need for constant transmission / reception of information to achieve collaboration, is presented. The present invention creates a portal for all entities, and enables access, storage, sharing, and response to related information from anywhere at anytime on any access unit in a collaborative and collective methodology. The present invention also provides object-based security and object-based threaded discussion sessions for all objects generated by the various applications.
Owner:LUSK RICHARD +2
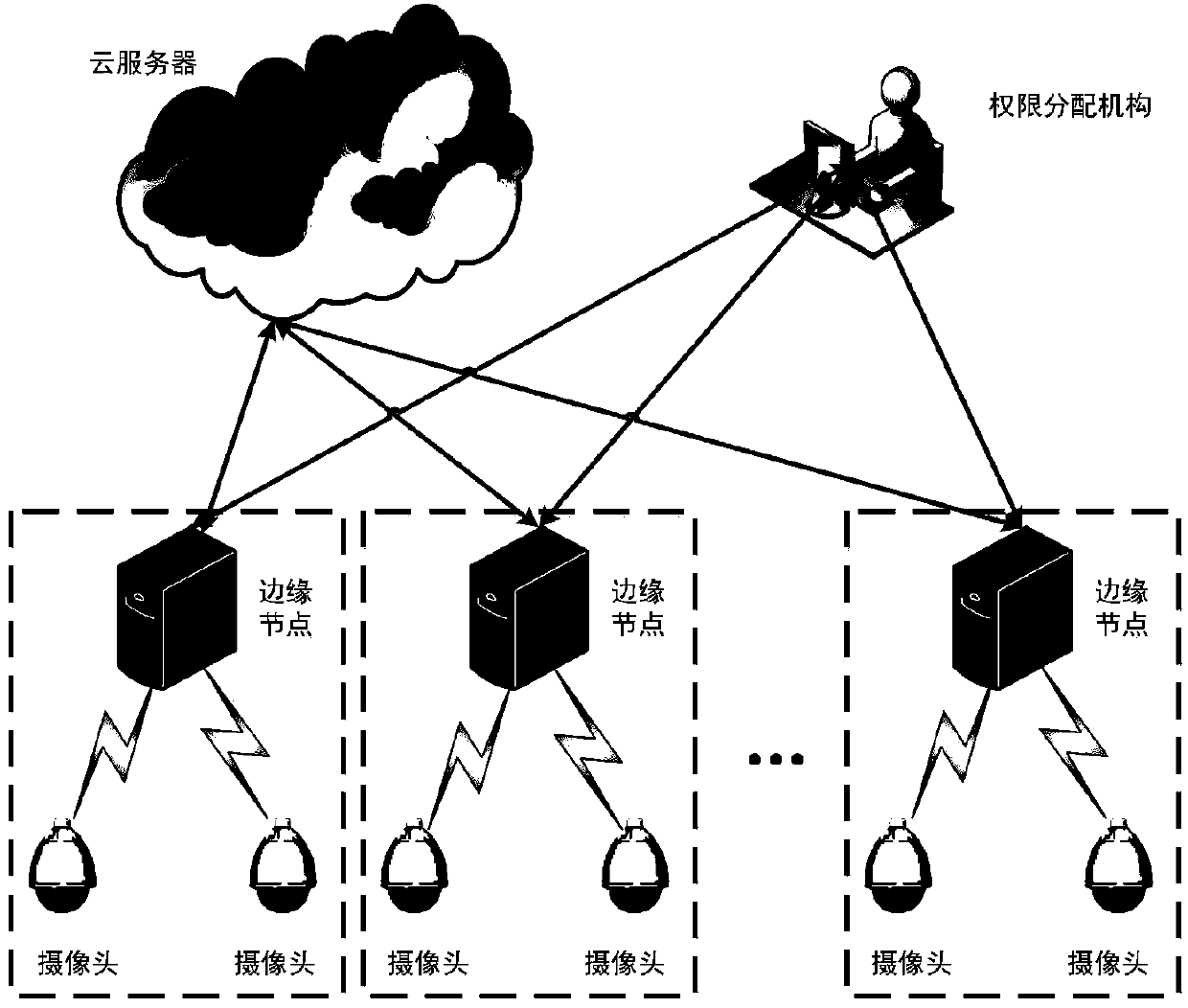
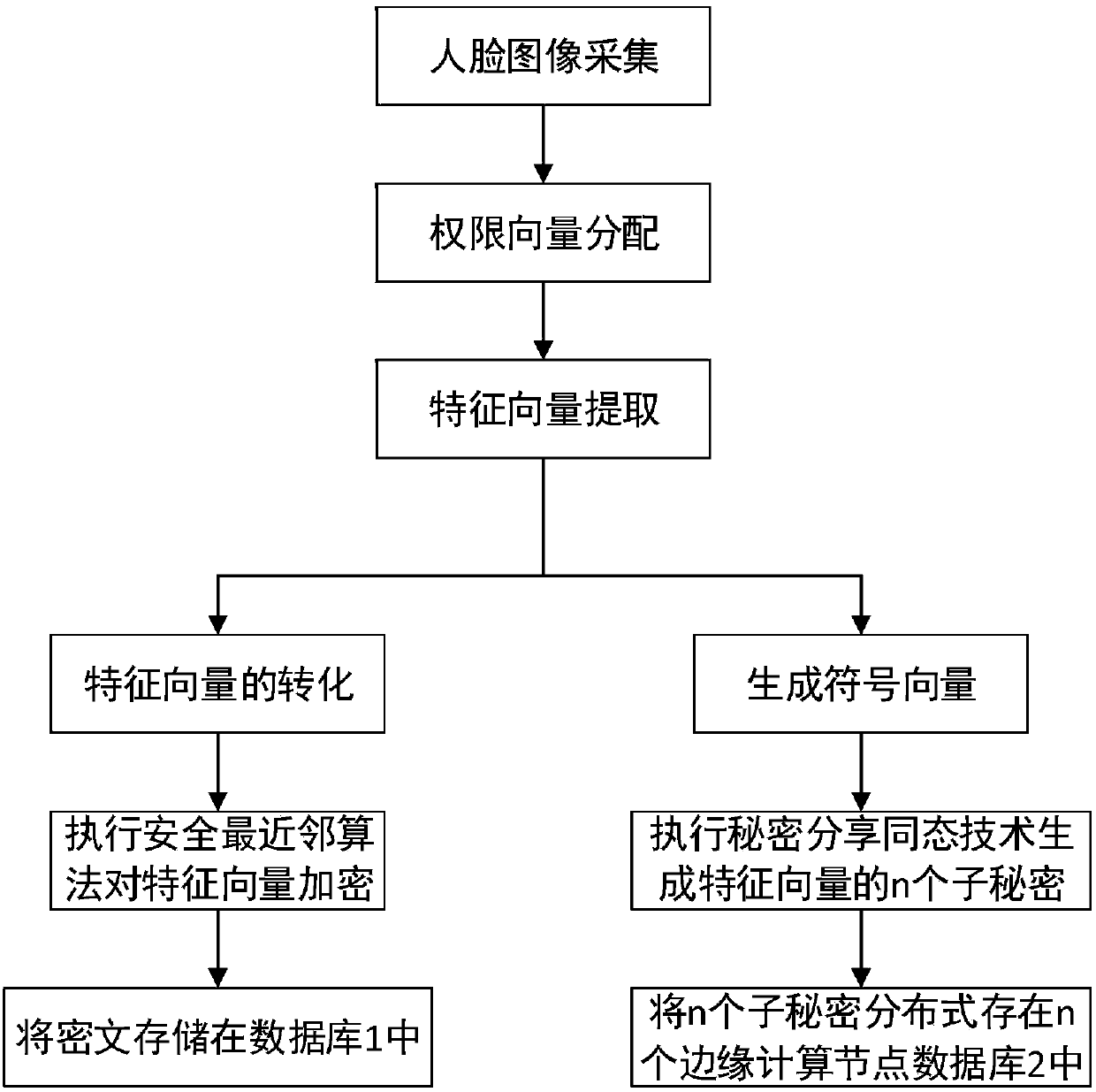
Privacy protection method in face authentication system based on edge calculation
ActiveCN108446680APrivacy protectionProtect face recognition functionCharacter and pattern recognitionTransmissionPlaintextFault tolerance
The invention belongs to the technical field of privacy protection in cloud computing and discloses a privacy protection method in face authentication system based on edge calculation. The method comprises the steps that: a camera collects a face image and uploads the face image to a connected edge computing node, an authority assigning mechanism sends a permission vector Li of a user to the edgecomputing node after collecting user face information, an edge computing device carries out feature extraction on a face image of a user requesting registration to obtain a feature vector by using a method based on a deep convolutional neural network, a safe nearest neighbor algorithm is performed to encrypt the feature vector of a registered user, and a secret sharing homomorphic algorithm is performed and n sub-secrets are generated according to the feature vector and are distributively stored in n edge computing devices. The direct upload of sensitive data to a cloud server is avoided, theprivacy of the face data is protected, and the fault tolerance of a system is improved. Results prove that the accuracy of face recognition under a ciphertext of the present invention is completely equal to the accuracy of face recognition under a plaintext.
Owner:XIDIAN UNIV
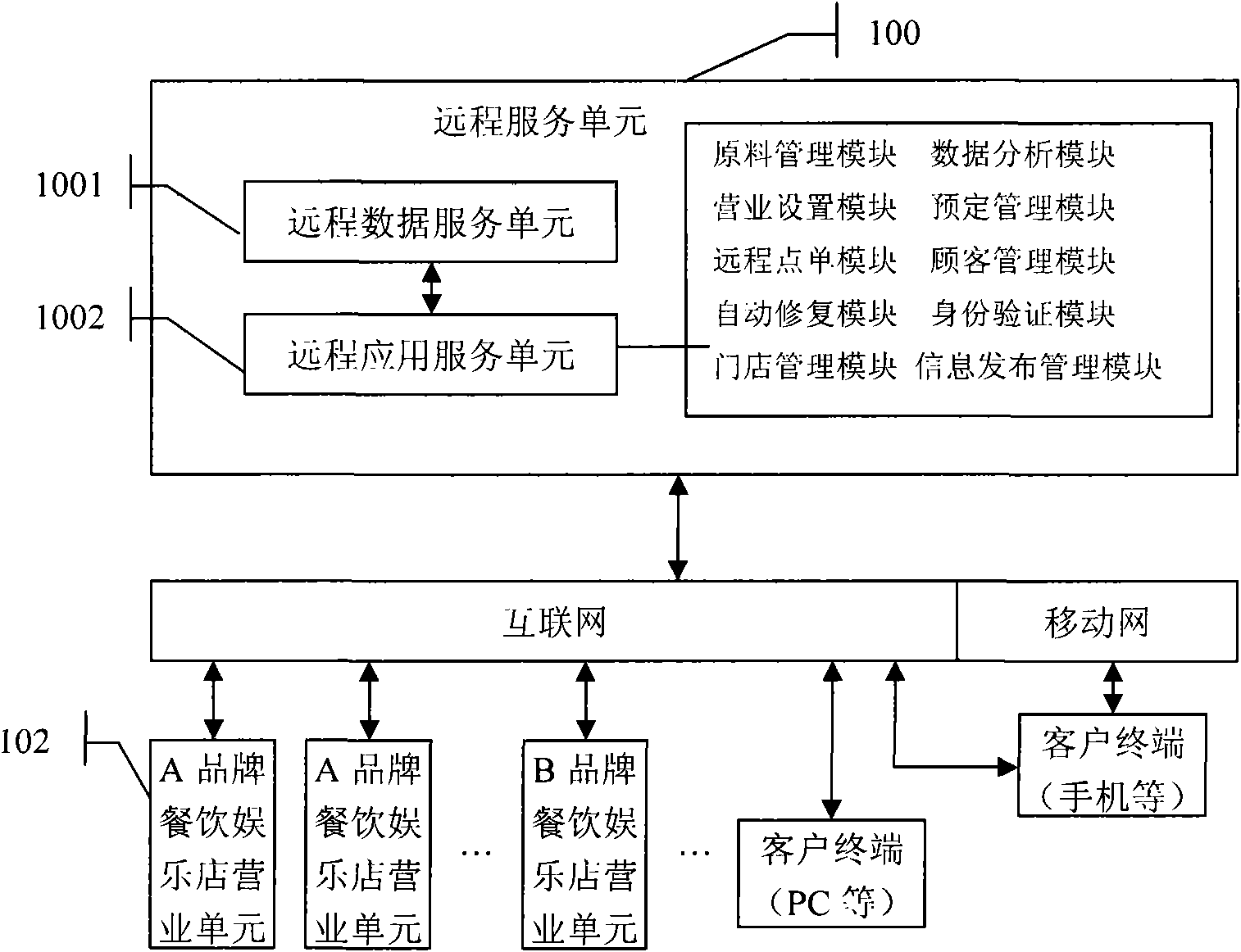
Internet-based catering and amusement management system and electronic menu and ordering method thereof
InactiveCN101540026AConfiguration highImprove performanceCommerceSpecial data processing applicationsDaily operationSystem maintenance
The invention discloses a catering and amusement management system and a special electronic menu and a self-help ordering method thereof. The internet-based catering and amusement management system comprises a remote data service unit, a remote application service unit, at least one catering and amusement shop operating unit and an access terminal unit, wherein the remote data service unit is used for the collective and concentrated storage of data from the units in the system; the remote application service unit is used for acquiring the data from the units, analyzing and processing the data collectively, distributing the data to the units and providing an internet-based catering management application service module; the at least one catering and amusement shop operating unit is used for the daily operation of a catering and amusement shop and the data interaction with the remote data service unit; and the access terminal unit is used for accessing the corresponding catering management application service module according to the right distributed by the remote application service unit. The system has high data safety, remote management, convenient and quick maintenance, low system maintenance cost and good augmentability, and can be simultaneously applied to the management of a plurality of catering and amusement shops with different brands.
Owner:杭州因餐信息技术有限公司
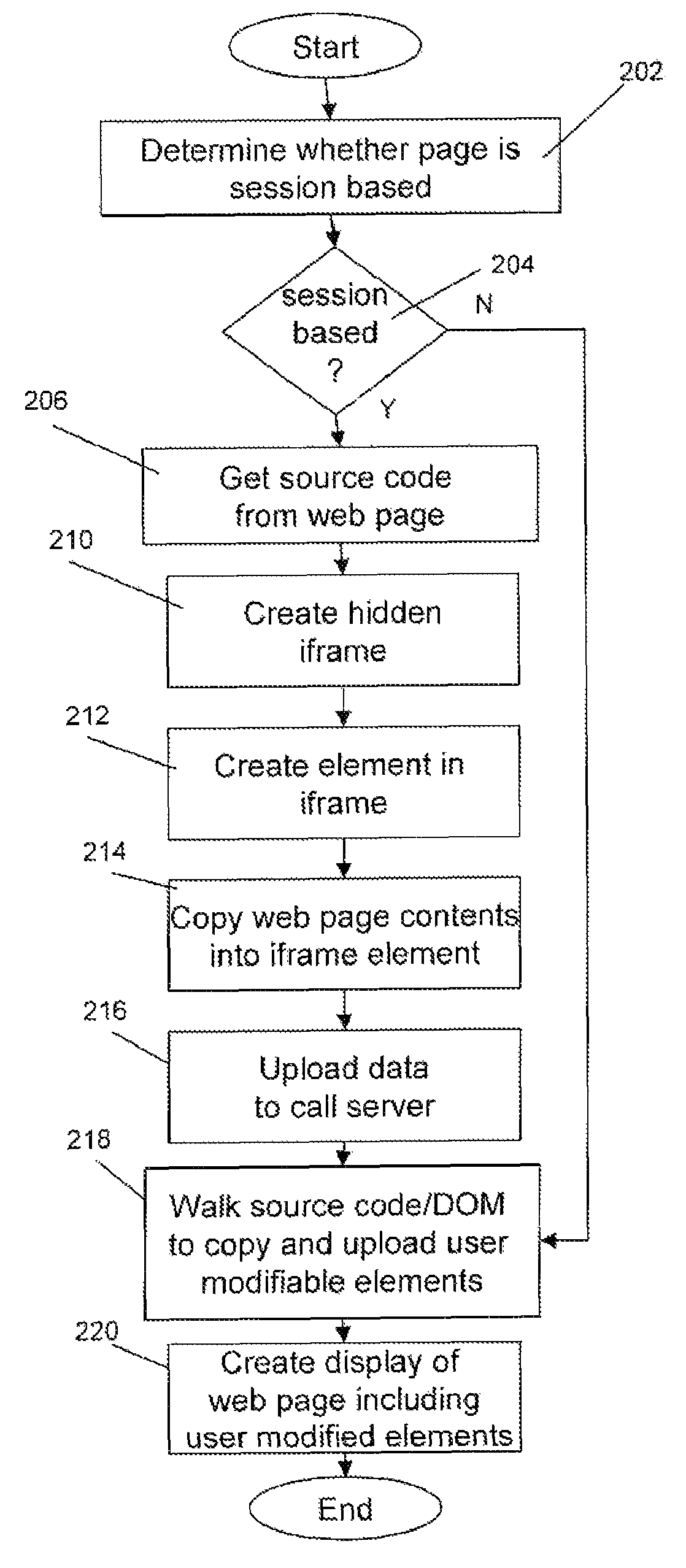
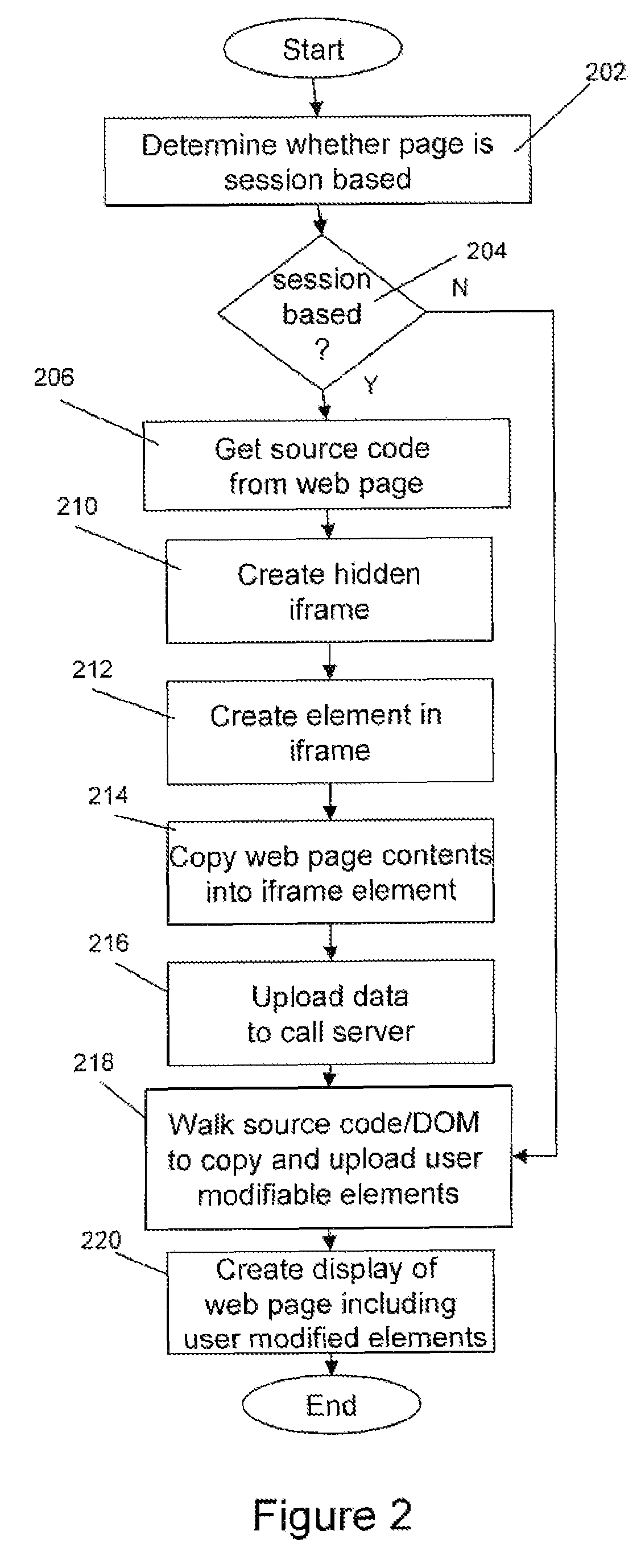
Method and apparatus for web page co-browsing
A method and apparatus for extracting information from a web page on a standard end user browser without plug-ins, includes the steps of dynamically creating an element on a web page being viewed by an end user, copying at least a portion of the contents of the web page or form field values, and uploading the data to a target domain, wherein the target domain may be different from the domain of the web page. In co-browsing applications, the data uploaded is used to create a copy of the website for display to a third party.
Owner:ORACLE OTC SUBSIDIARY
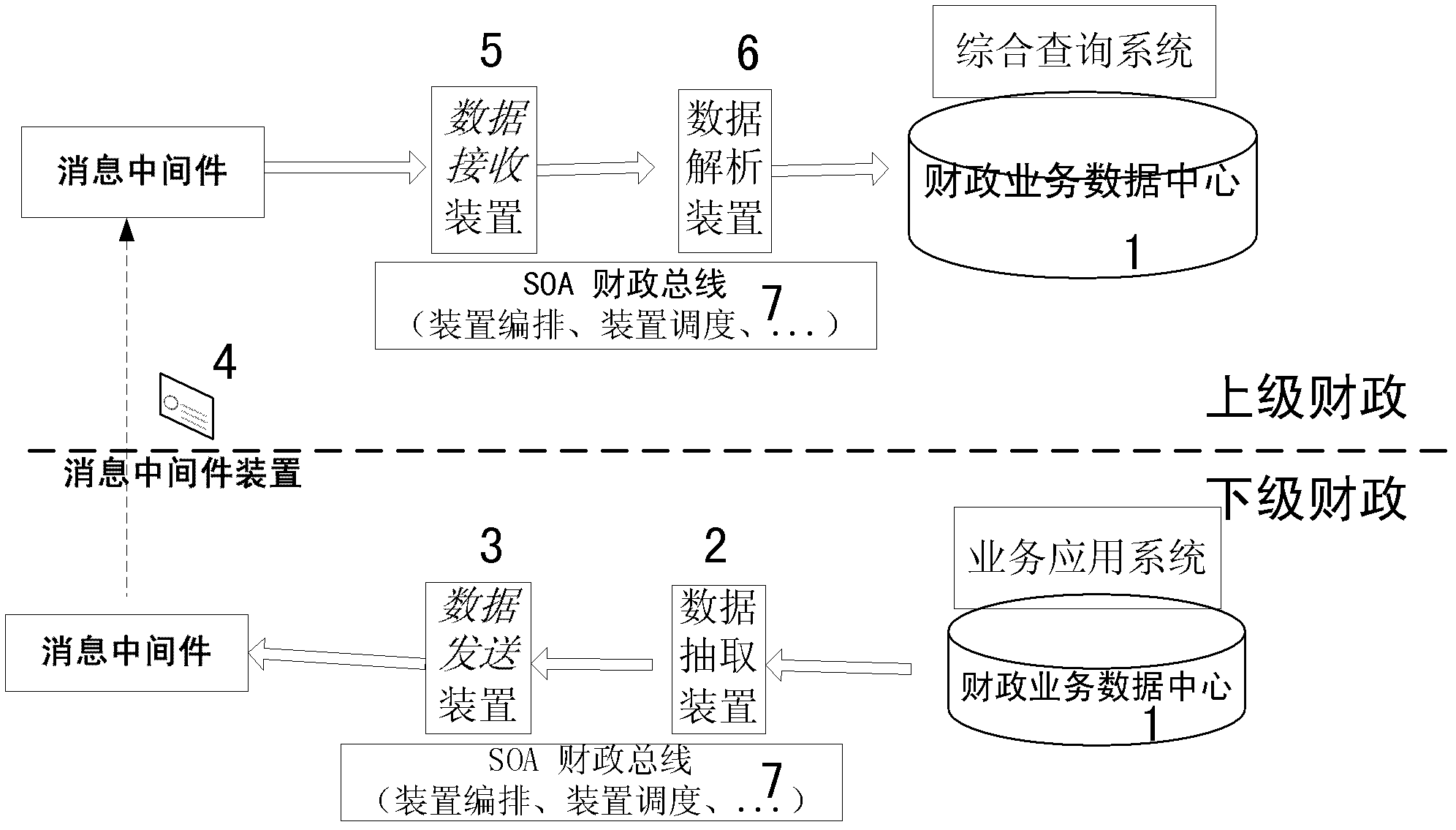
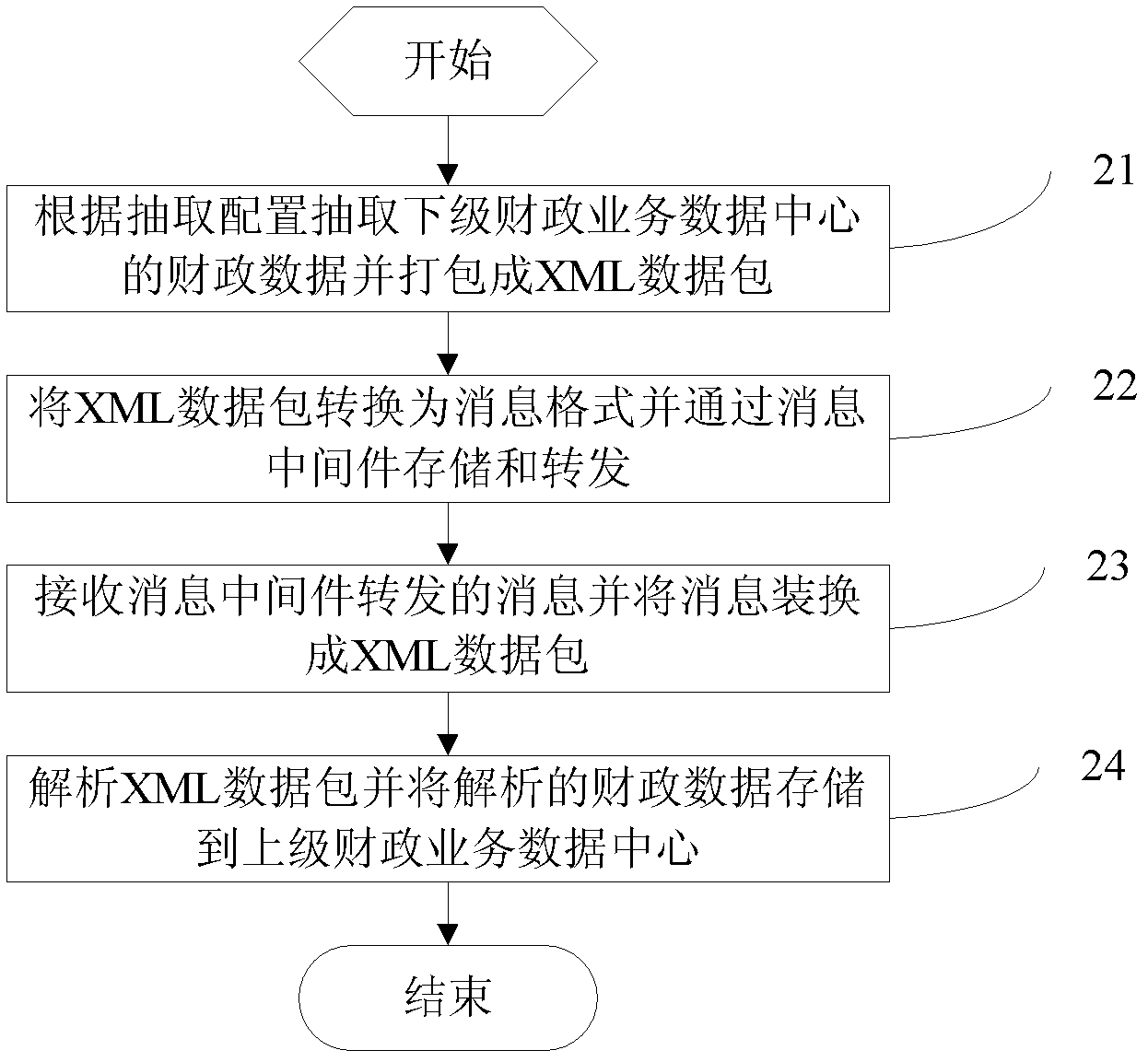
Method for acquiring subordinate financial business data and system for acquiring subordinate financial business data
ActiveCN102508908AImprove collection efficiencyAvoid uploadingSpecial data processing applicationsData warehouseData center
The invention discloses a method for acquiring subordinate financial business data and a system for acquiring the subordinate financial business data, which relate to the field of ETL (extraction-transformation-loading) of a data warehouse, and realize automatic acquisition of the subordinate financial business data based on an SOA (service-oriented architecture) and a message-oriented middleware. The method includes the steps of firstly, extracting financial business data needing to be uploaded according to extracting configuration; and then uploading the extracted data to a superior financial business data center by the aid of the message-oriented middleware and utilizing the uploaded extracted data as a basic data source for integrative query. The method provides two data acquiring modes including overall extracting and data extracting in the extracting configuration, and a user can extract changed data in a data sheet without changing an original business data sheet by the acquiring mode of data extracting, so that data extracting efficiency is improved, only data meeting the requirements can be acquired by setting up access conditions, and acquisition and upload of unnecessary data is avoided.
Owner:北京用友政务软件股份有限公司
Live-broadcasting room video stream synthesis method and apparatus, and terminal equipment
ActiveCN106792245AGuaranteed simultaneityAvoid uploadingTransmissionSelective content distributionSynthesis methodsTerminal equipment
Owner:GUANGZHOU HUADUO NETWORK TECH
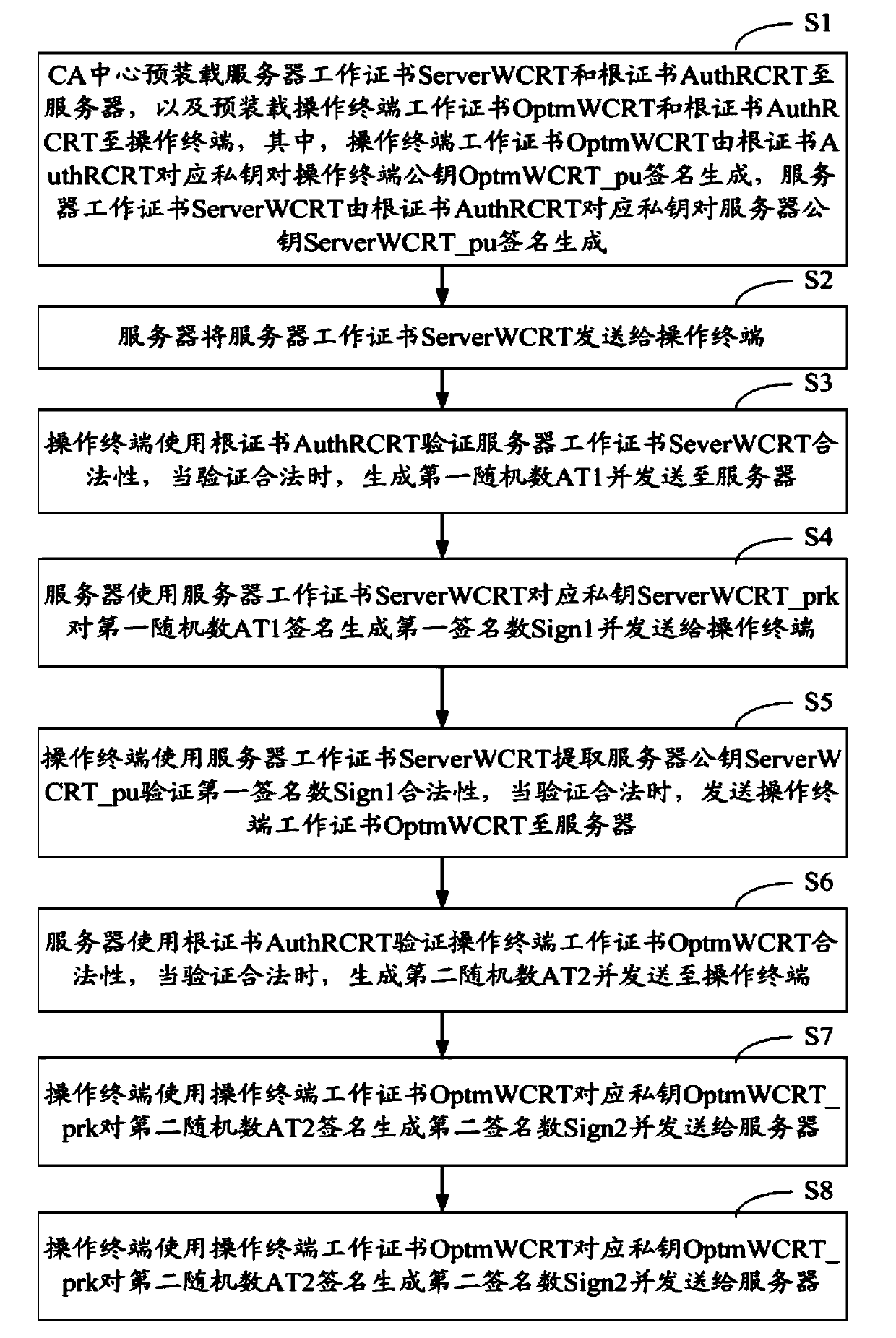
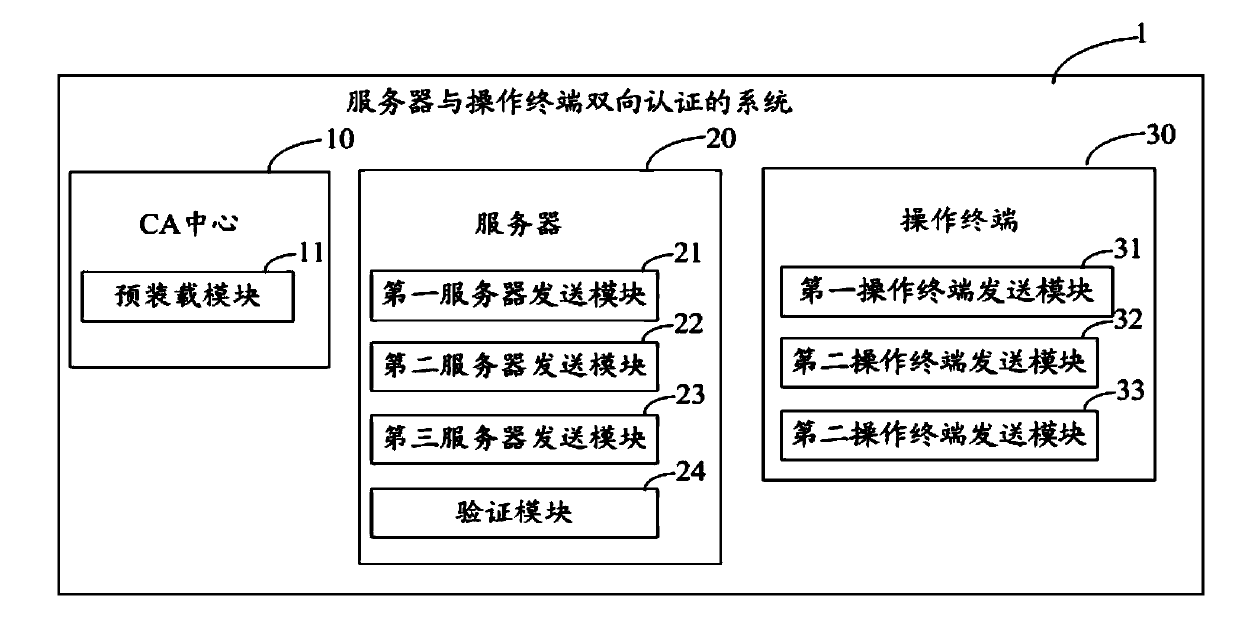
Bidirectional authentication method and system for server and operating terminal
ActiveCN103701609AImprove uploadImprove download securityKey distribution for secure communicationUser identity/authority verificationRoot certificateEncryption
The invention discloses a bidirectional authentication method and system for a server and an operating terminal. The bidirectional authentication method comprises the following steps that: the server sends a server public key to a CA (Certificate Authority) center, and the CA center signs the server public key by using a corresponding private key of a root certificate AuthRCRT to generate a server work certificate ServerWCRT; the CA center sends the work certificate ServerWCRT and the root certificate AuthRCRT to the server to store in a database; the operating terminal sends the public key to the CA center, the CA center signs the public key of the operating terminal by using the corresponding private key of the root certificate AuthRCRT to generate a work certificate OptmWCRT, and sends the OptmWCRT and the AuthRCRT to the operating terminal to store in an encryption module; bidirectional authentication is performed by using the generated certificates and the preset root certificate in a remote master private key download scheme, so that the system security is improved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
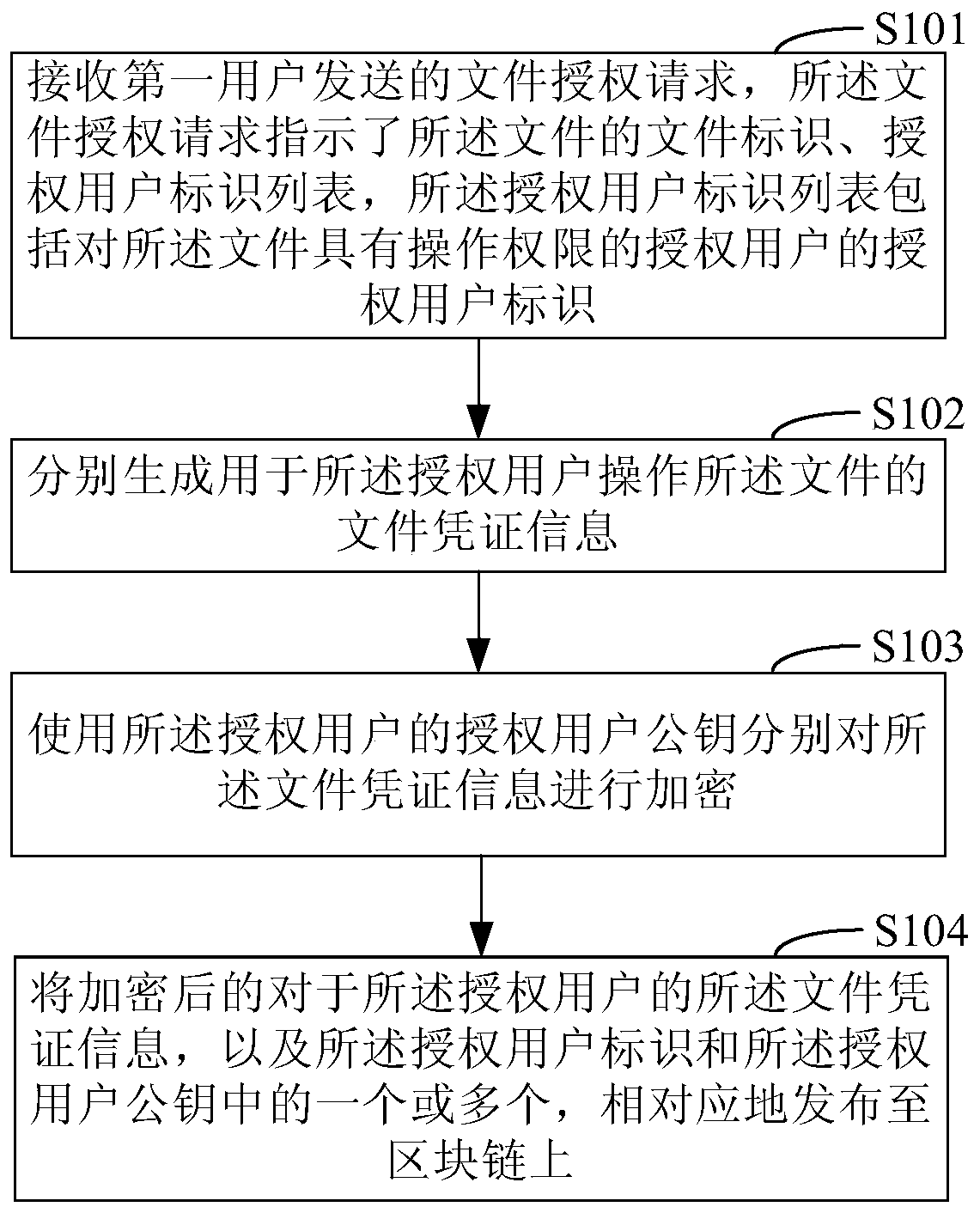
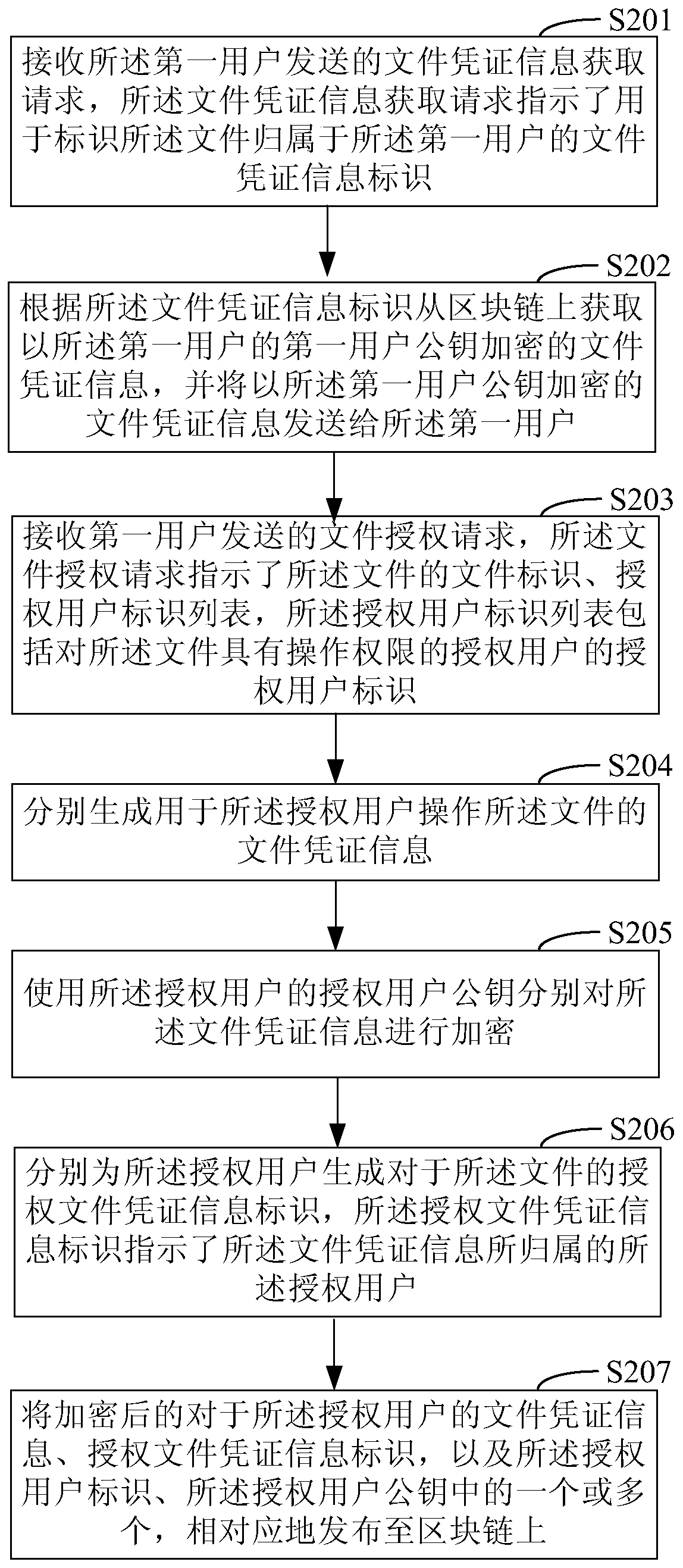
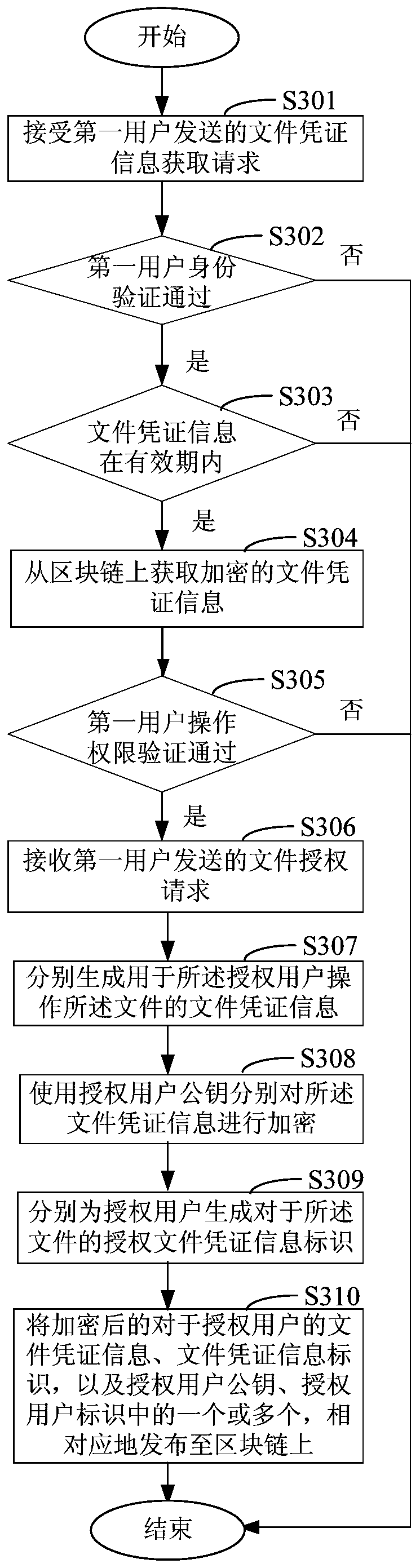
File authorization access method, device and system based on block chain
InactiveCN110636043AAvoid uploads and downloadsImprove securityUser identity/authority verificationBlockchainUser identifier
The invention discloses a file authorization access method, device and system based on a block chain, and relates to the technical field of computers. One specific embodiment of the method comprises the following steps: receiving a file authorization request sent by a first user, wherein the file authorization request indicates an authorized user identifier list and a file identifier of the file,and the authorized user identifier list comprises an authorized user identifier of an authorized user having an operation authority for the file; respectively generating file certificate information for the authorized user to operate the file; respectively encrypting the file certificate information by using an authorized user public key of the authorized user; and correspondingly publishing the encrypted file certificate information for the authorized user and one or more of the authorized user identifier and the authorized user public key to a block chain. According to the embodiment, file uploading or downloading in the file authorization process is avoided, the file security is improved, and network resources are saved.
Owner:THE PEOPLES BANK OF CHINA DIGITAL CURRENCY INST
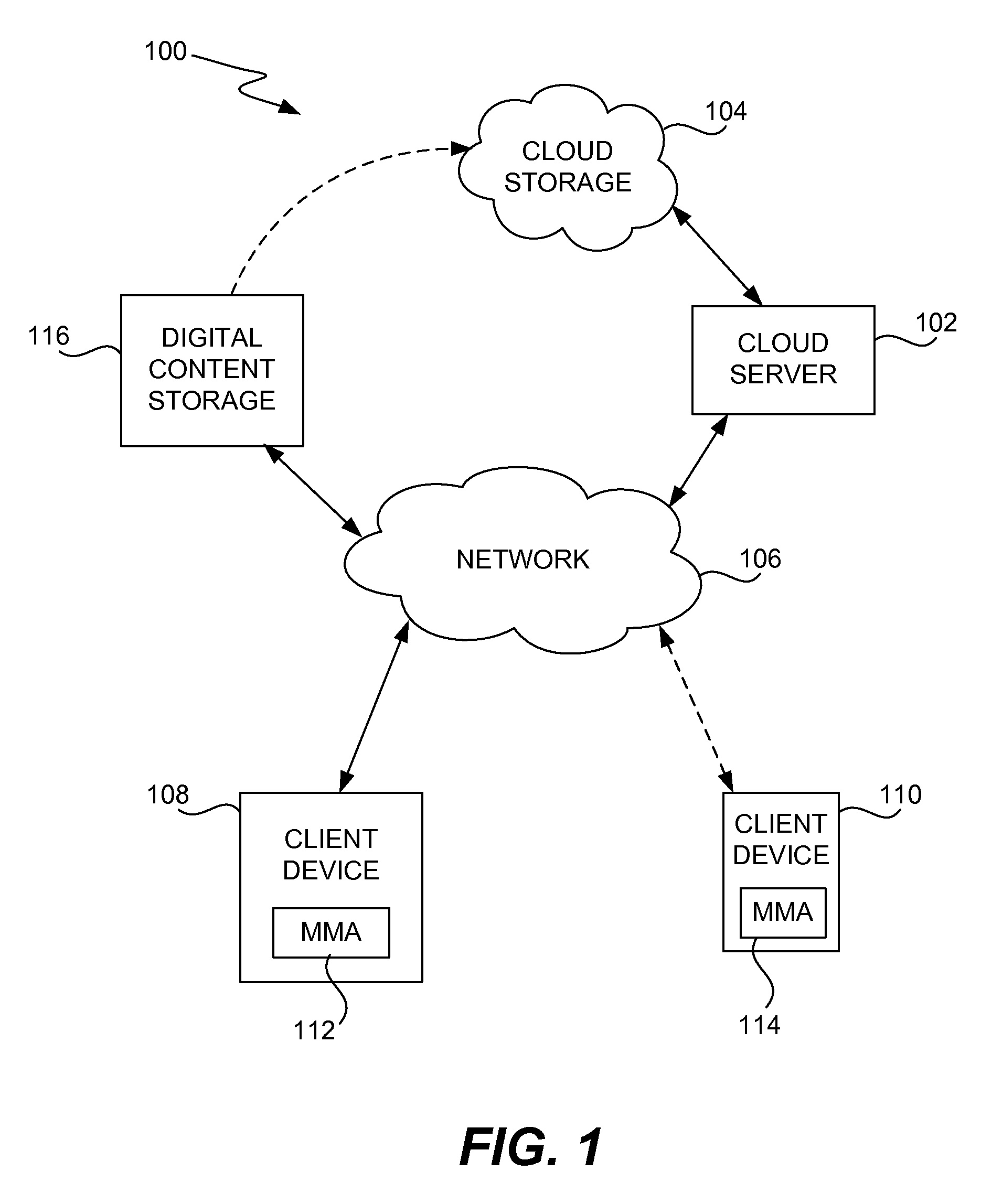
Management of Network-Based Digital Data Repository
InactiveUS20120311081A1Avoid uploadingDigital data information retrievalMultiple digital computer combinationsDigital dataUser device
Improved techniques and systems for storage, delivery and acquisition of digital assets are disclosed. The techniques and systems are suitable and useful for storing, delivering and accessing digital assets (e.g., media assets) that have been acquired from online stores. The techniques and systems are also suitable and useful for storing, delivering and accessing digital assets that have been acquired from other than from online stores. Regardless, the digital assets become accessible from a network-based digital data repository (e.g., cloud data storage) via electronic devices (e.g., user devices) and thus usable by the electronic devices. The digital assets can include media assets and / or non-media assets.
Owner:APPLE INC
Product service data uploading method and device, product service data evidence storage method and device, equipment and medium
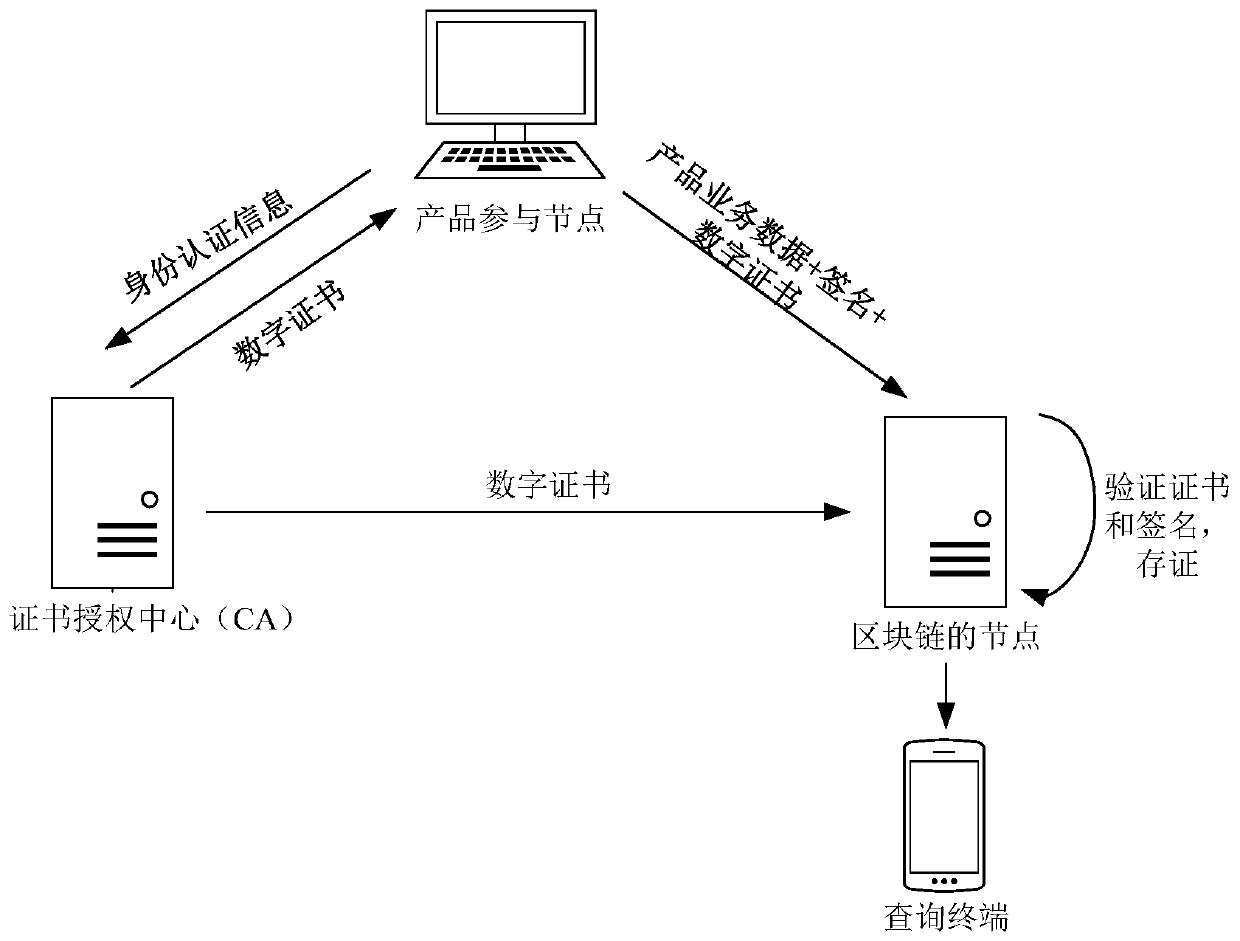
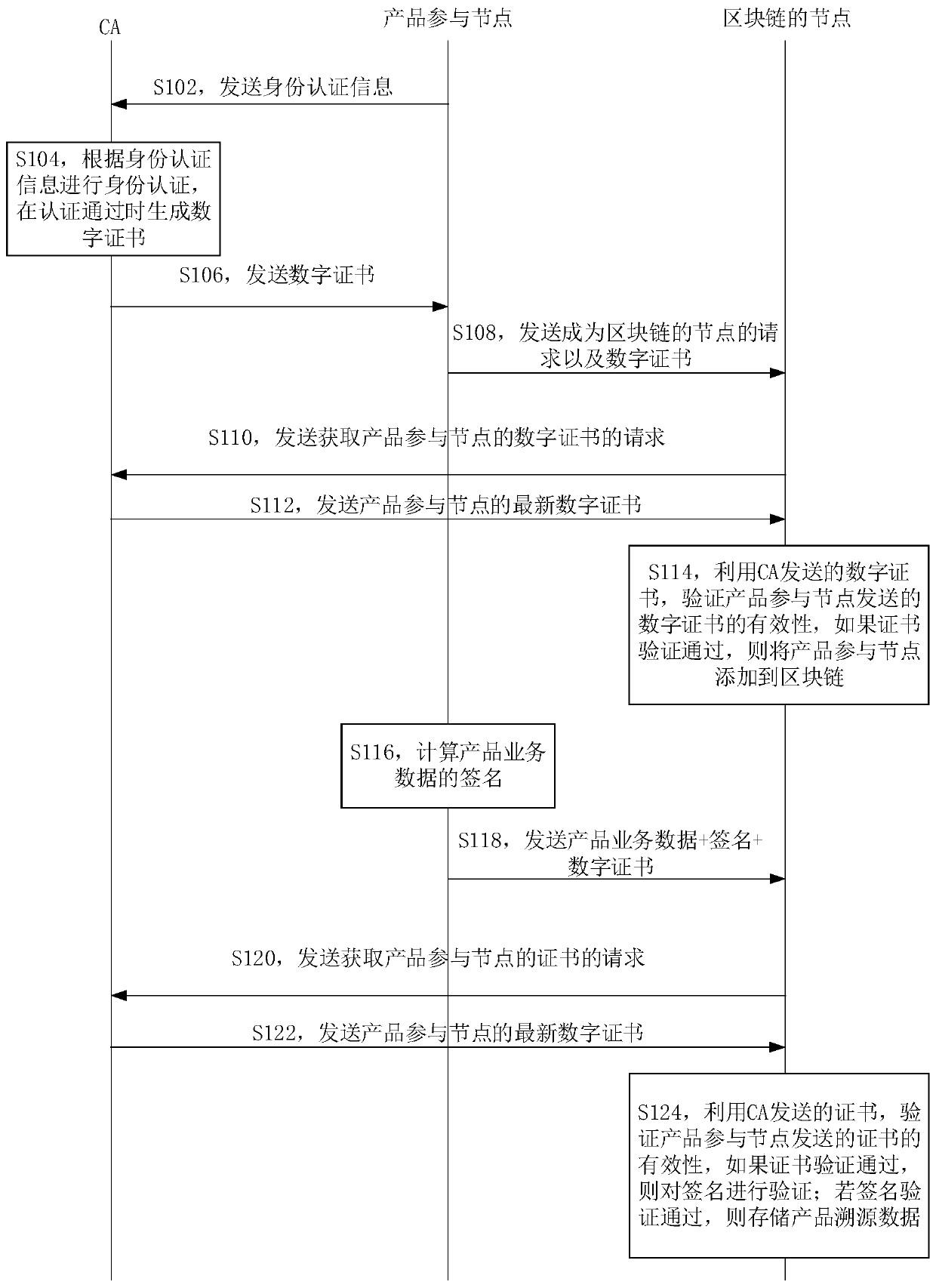
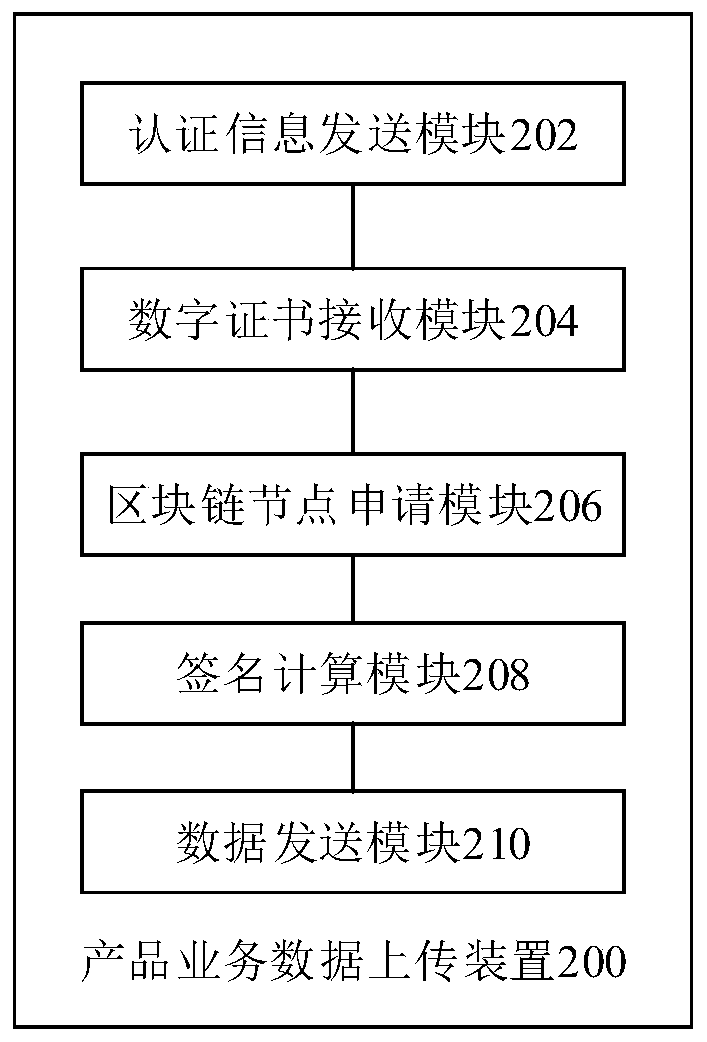
PendingCN110874747AThe certification result is accurateAbundant resourcesUser identity/authority verificationDatabase distribution/replicationBlockchainEngineering
One or more embodiments of the invention disclose a product service data uploading method, a product service data storage method, a product service data storage device, product service data storage equipment and a medium. The product service data uploading method comprises the following steps: sending identity authentication information of a product participation node to a certificate authority CA; receiving a digital certificate sent by the CA, wherein the digital certificate is generated by authenticating the product participation node by the CA according to the identity authentication information; according to the digital certificate, applying for the product participation node to become a node of a block chain; and after the product participation node becomes the node of the block chain, calculating the signature of the product service data for the product service data to be uploaded each time, and sending the product service data, the signature and the digital certificate to the nodes of the block chain except the product participation node.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
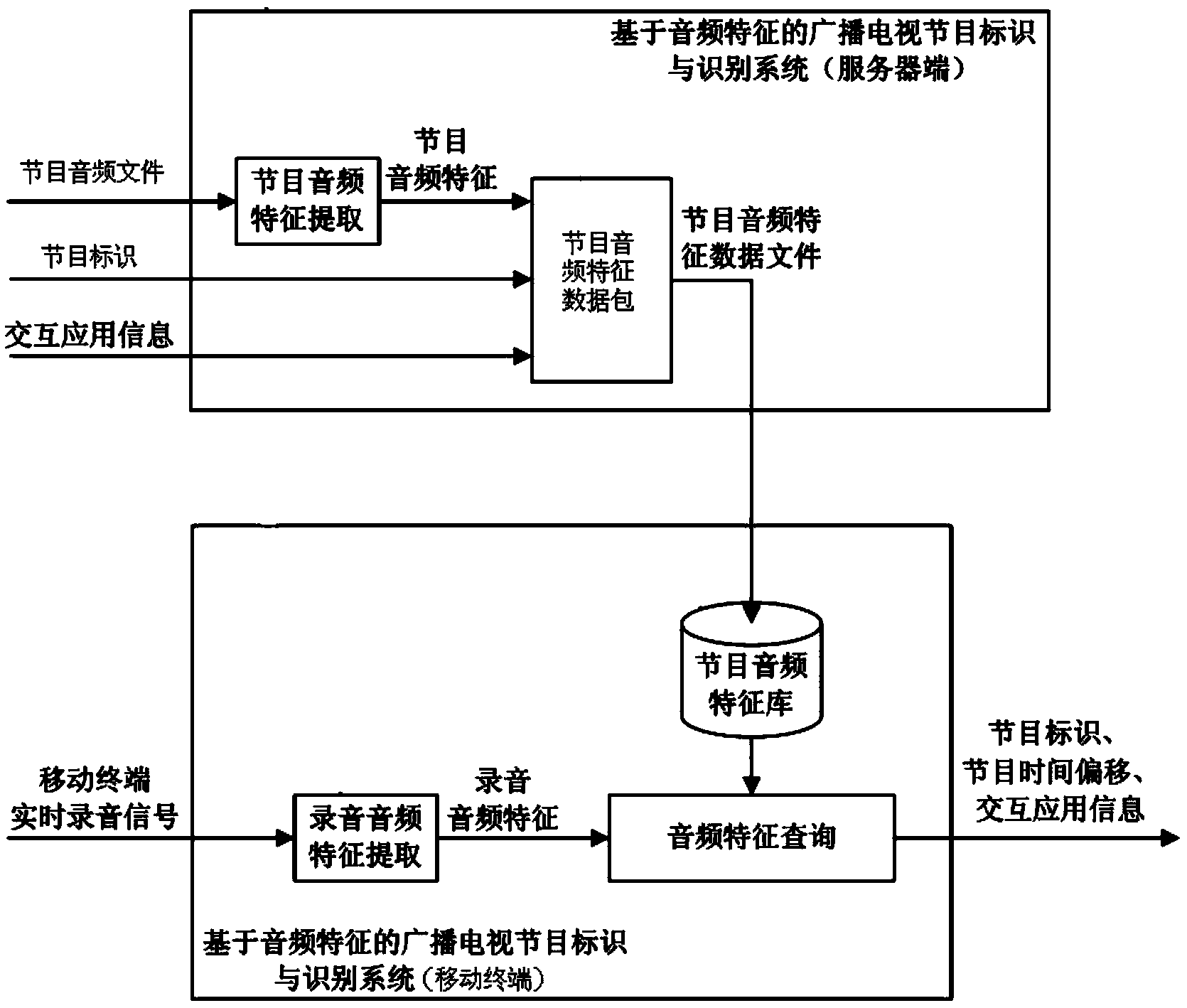
Audio frequency feature based method and system for marking and identifying broadcast television program
ActiveCN103618953AImprove recognition accuracyAccurate positioning time offsetSelective content distributionComputer terminalFeature data
The invention provides an audio frequency feature based method and system for marking and identifying a broadcast television program. The method includes steps of extracting feature data of a program audio frequency file through a server-side to obtain program audio frequency feature data; merging the program audio frequency feature data, a program identifier and interactive applications, and the transmitting to a mobile terminal; recording a record audio signal of the program through the mobile terminal; extracting the audio frequency feature of the record audio signal to obtain record audio frequency feature data; determining whether there is program audio frequency feature data matching with the record audio frequency data in a program audio frequency feature database or not, and outputting a matched program identifier, playing time and corresponding interactive applications, if the program audio frequency feature data exists; and further, calculating time difference of the program and outputting the calculated time difference of the program. By adopting the audio frequency feature based method and system for marking and identifying the broadcast television program, a user can enjoy various interactive applications corresponding to a broadcast television program being watched at present through just easily operating the mobile terminal, and privacy of the user can be effectively protected so as to raise user experience.
Owner:CHINA TELEVISION INFORMATION TECH BEIJINGCO
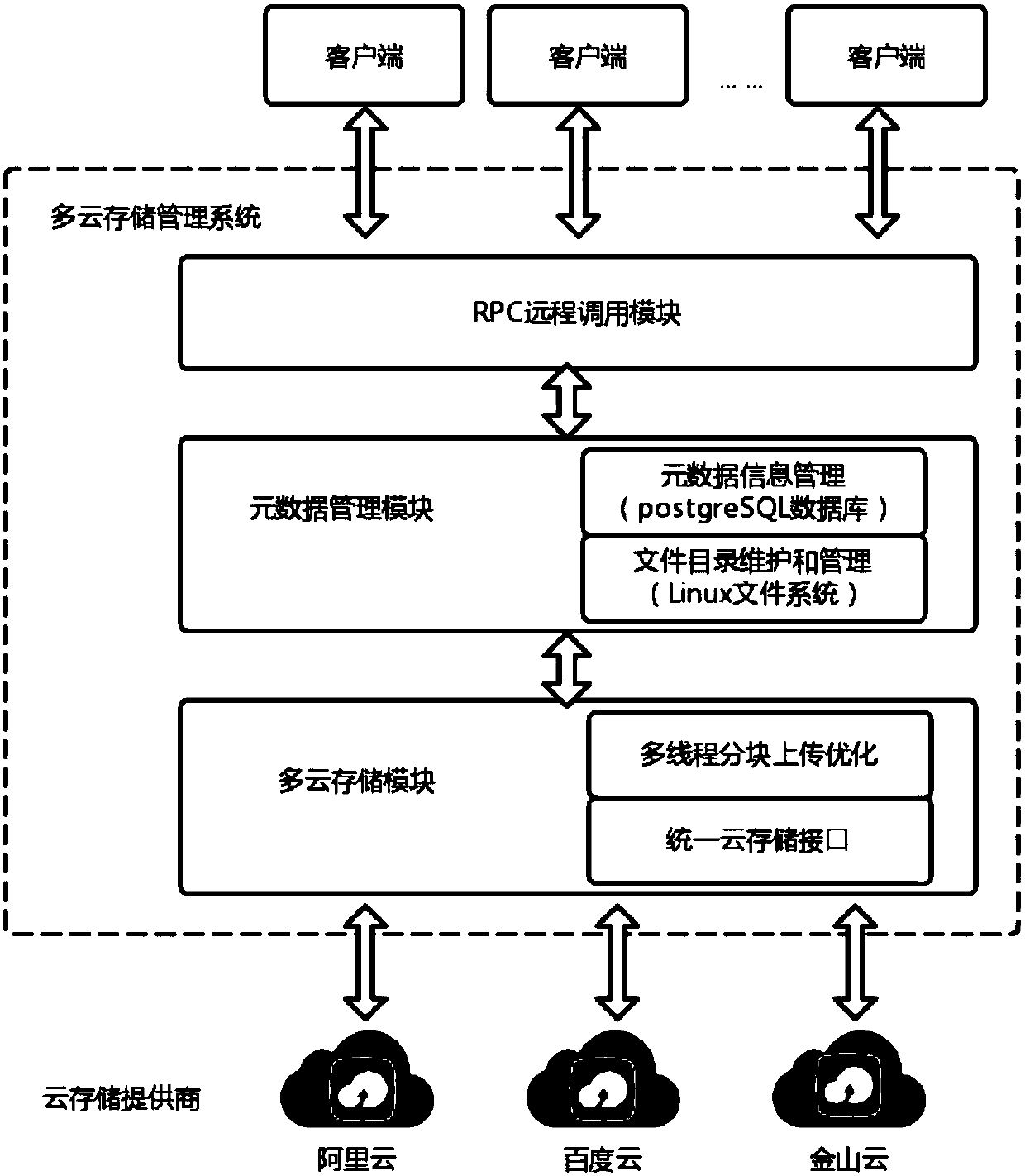
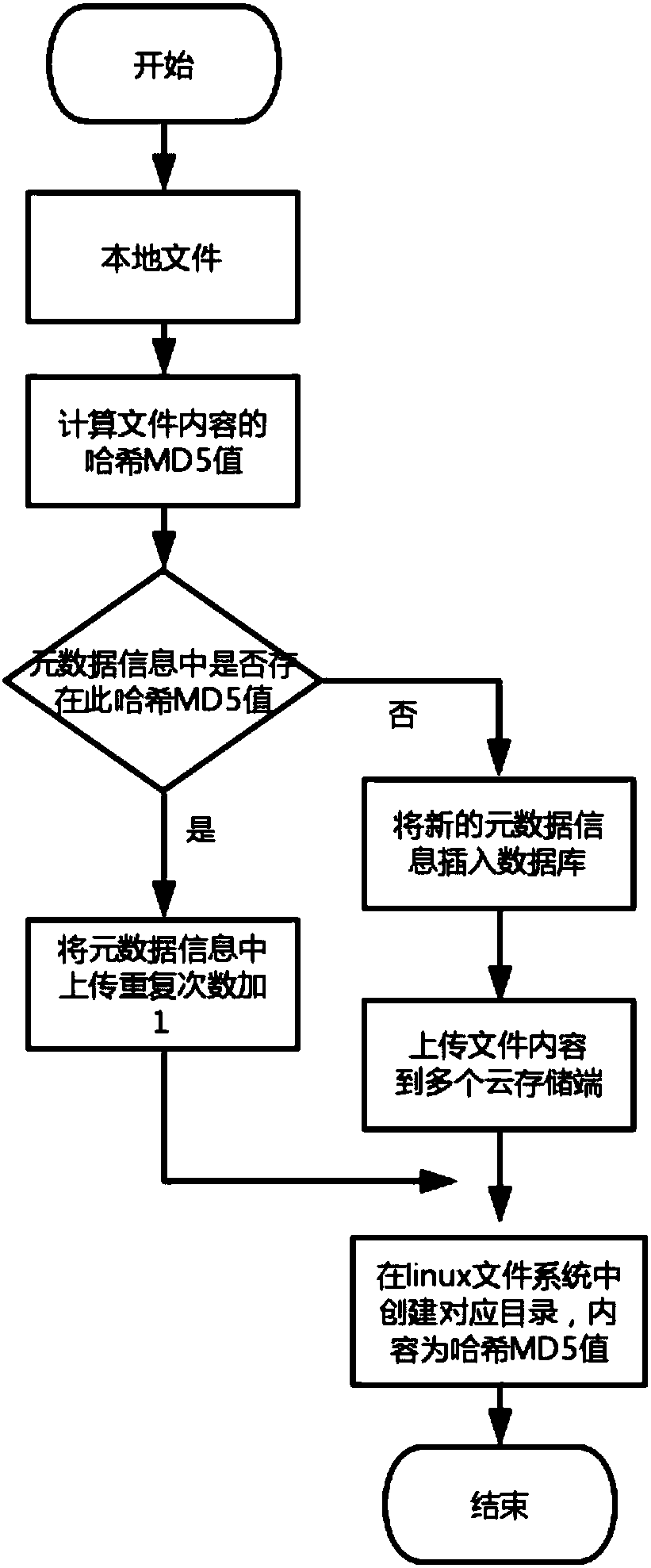
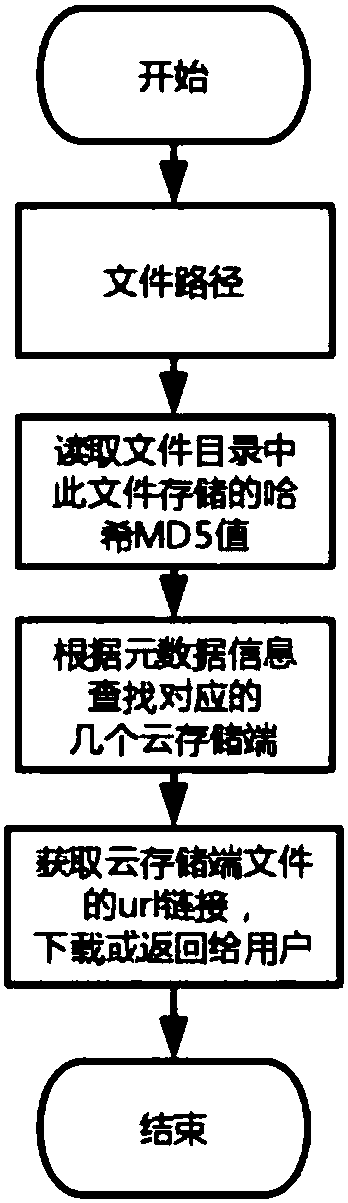
Multi-cloud-storage management system capable of improving storage availability
ActiveCN107566463AAchieve redundancyImprove reliabilityTransmissionSpecial data processing applicationsDirectory structureData management
The invention provides a multi-cloud-storage management system capable of improving storage availability. In order to overcome defects in the existing cloud storage uploading interface and multi-cloud-storage data management, the invention puts forward a multi-cloud-storage management system capable of improving storage availability, thereby improving data reliability, optimizing an uploading rate, eliminating repeated data in cloud storage, and providing a convenient directory structure management.
Owner:BEIHANG UNIV
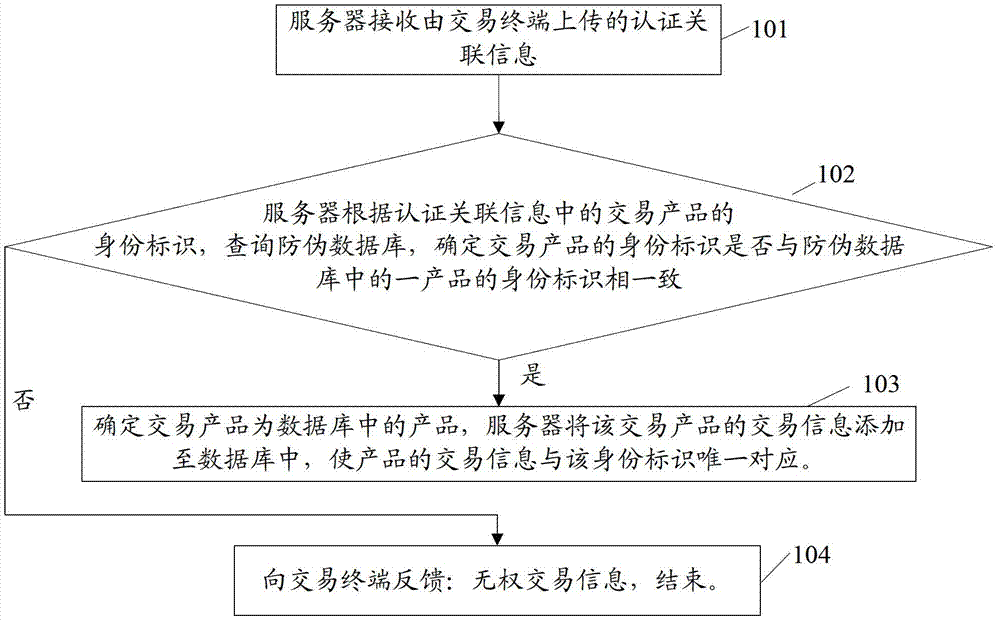
Anti-counterfeiting authentication processing method, transaction terminal and processing system
InactiveCN103177367AEnsure authenticity and uniquenessImprove anti-counterfeiting effectCommerceInternet privacyData library
The invention relates to the field of anti-counterfeiting authentication, and discloses an anti-counterfeiting authentication processing method, a transaction terminal and a processing system. The method mainly comprises the following steps: receiving authentication associated information uploaded by a transaction terminal through a server; according to an identity in the authentication associated information, determining whether the identity of a transaction product is consist with the identity of a product in an anti-counterfeiting database through the server; if so, adding transaction information in the authentication associated information into the anti-counterfeiting database, and uniquely corresponding the transaction information of the product to the identity. After receiving an authentication request of any one user, the server inquires whether the identity of a product to be authenticated is consist with the identity of a product in the anti-counterfeiting database, and if so, acquiring the transaction information of the product from the anti-counterfeiting database, and feeding back the transaction information to the user. Through the technical scheme disclosed by the invention, anti-counterfeiting effect of product is enhanced, and uniqueness and authenticity of authentication information acquired by customers are guaranteed.
Owner:欧家奇
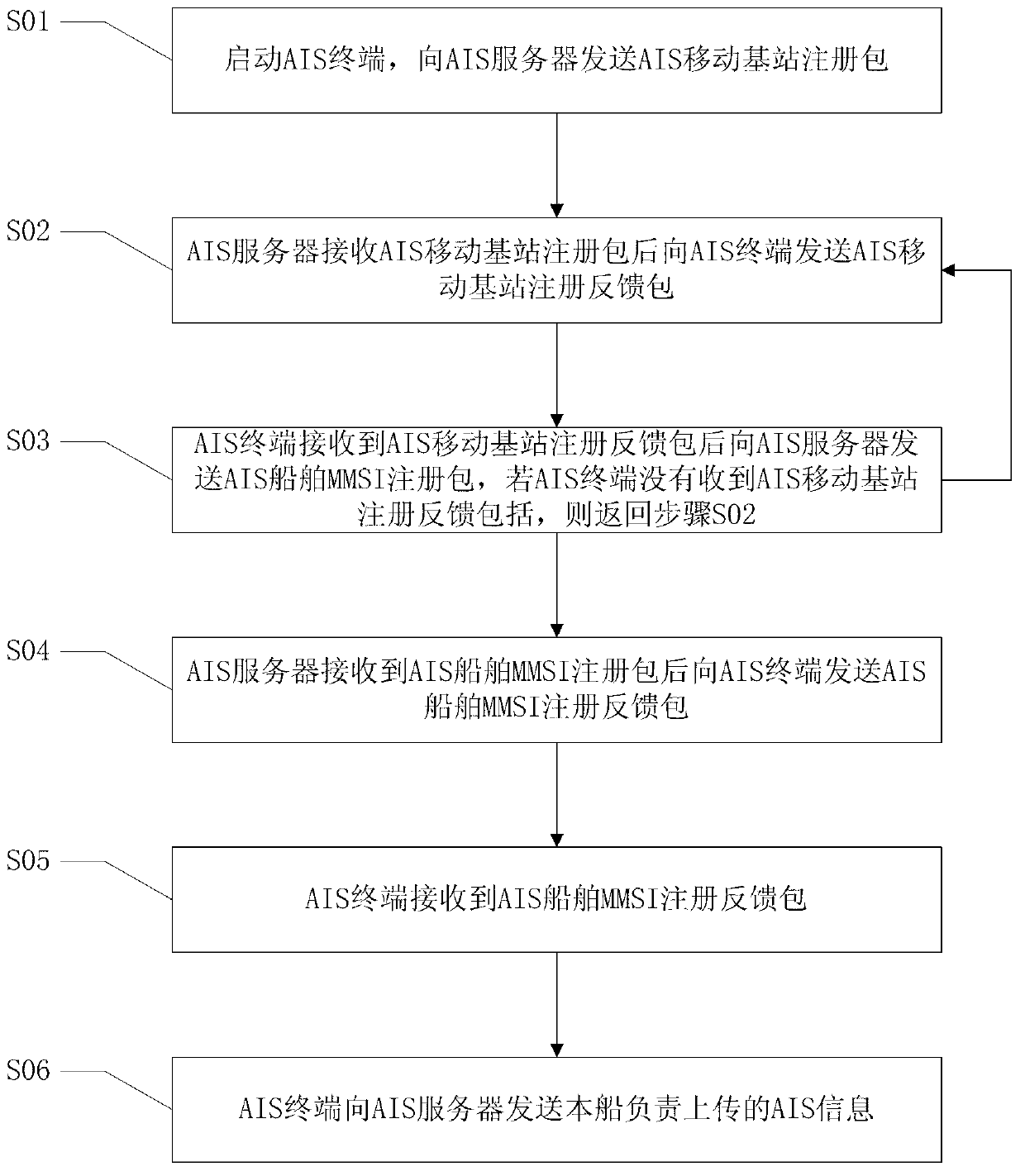
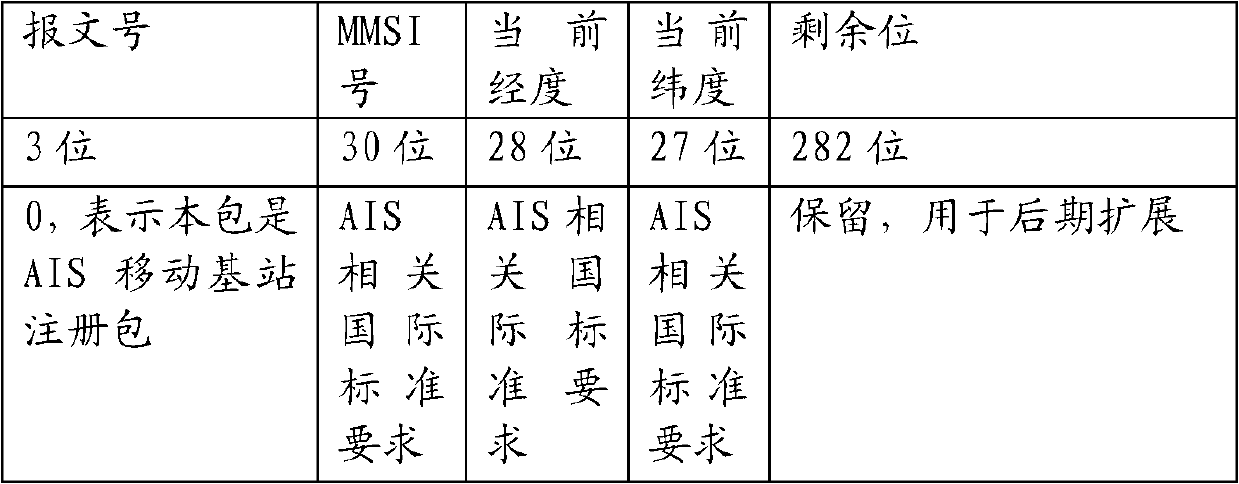
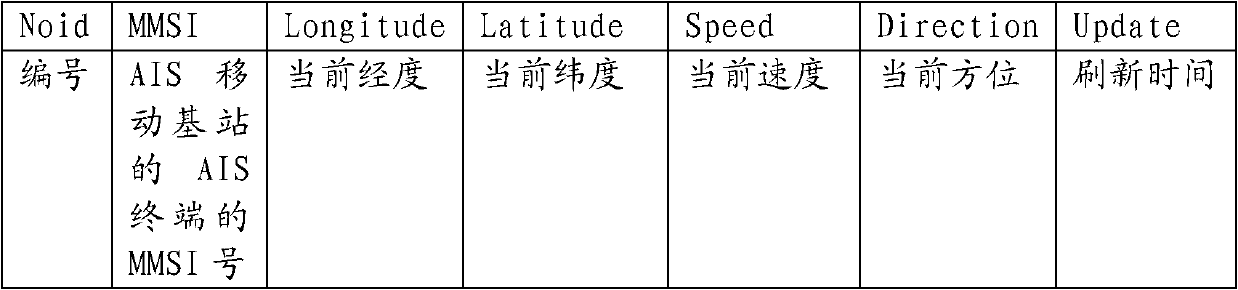
Data transmission method for automatic identification system (AIS) mobile base station
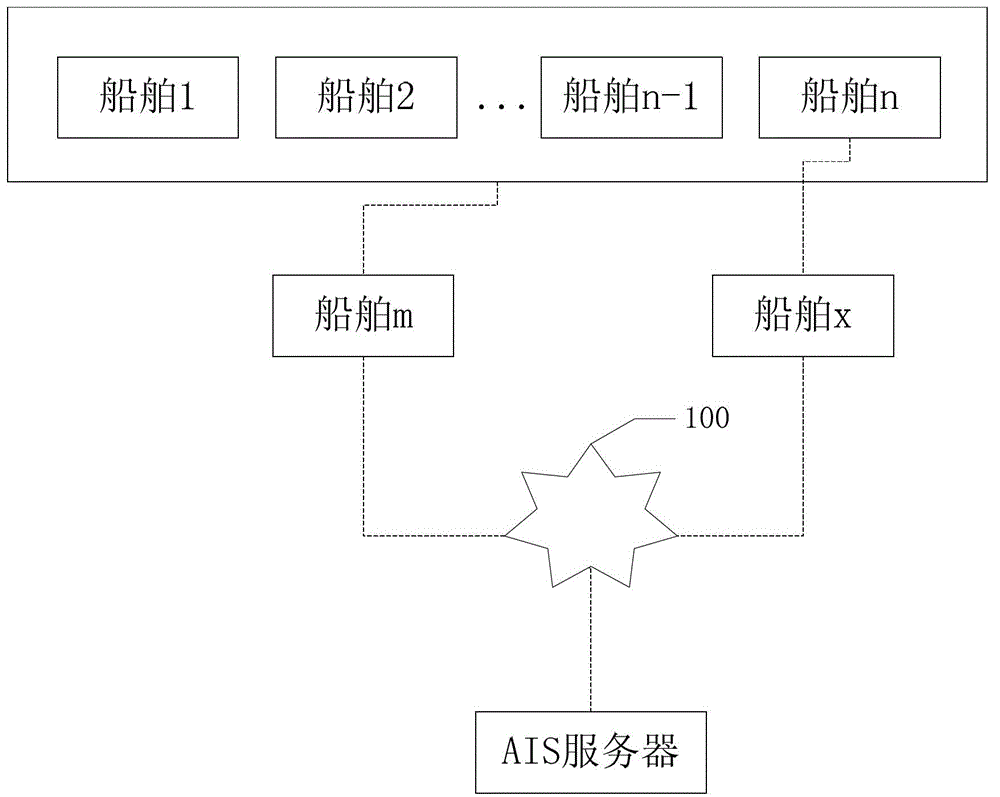
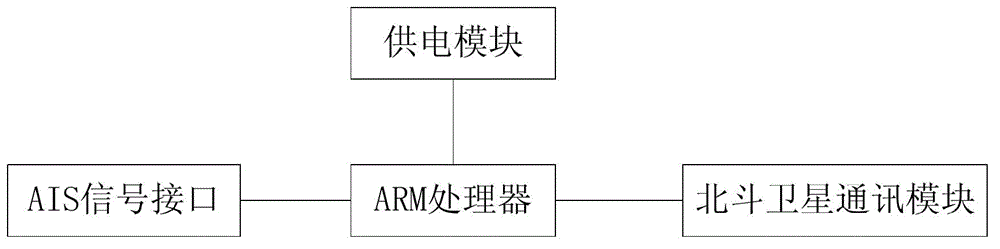
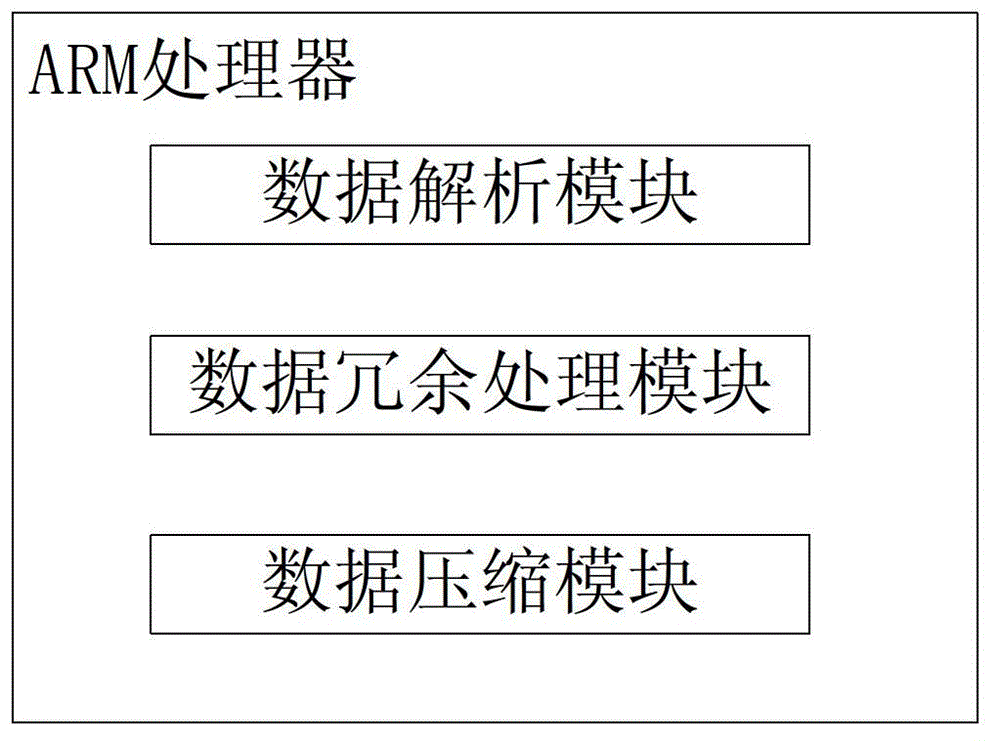
InactiveCN103002565AAvoid Duplicate Upload IssuesAvoid uploadingWireless communicationComputer terminalE communication
The invention relates to a data transmission method for an automatic identification system (AIS) mobile base station. According to the method, a ship with an AIS terminal can obtain AIS information of an AIS device of the ship through an AIS signal interface, the AIS information is transmitted to an AIS server through a Beidou satellite communication system and undergoes uniform processing after received by the AIS server, and accordingly the ship with the AIS terminal is equivalent to the AIS mobile base station on the sea. The Beidou satellite communication system is adopted to serve as a communication mode, and the data transmission method has the advantages of communication timeliness, high frequency and low total cost. Besides, according to the method, the problem that the AIS information is uploaded repeatedly after a plurality of AIS mobile base station receives the AIS information of the same ship can be solved, uploading of plenty of redundant data is avoided, and effective utilization of a bandwidth of the Beidou satellite communication system is reinforced.
Owner:广州联物网络科技有限公司
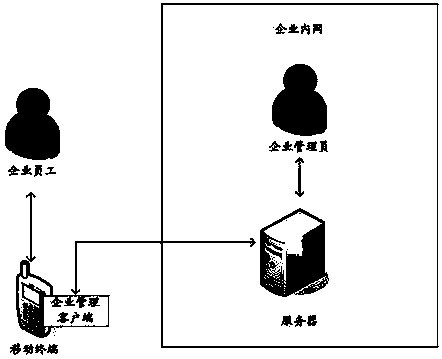
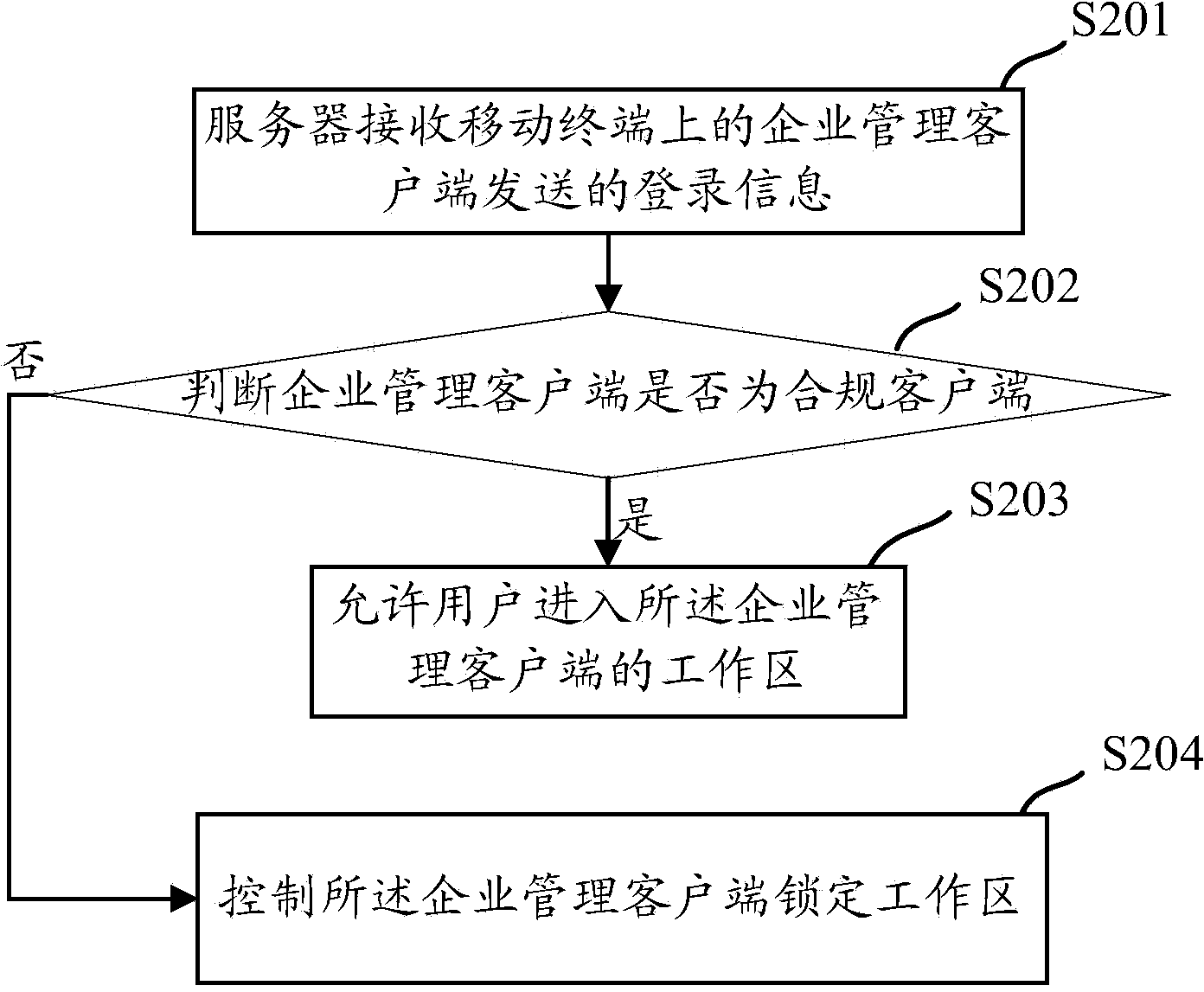
Method, system and device for locking working region of mobile terminal
InactiveCN103646198AAvoid uploadingProtection securityDigital data authenticationTransmissionComputer terminalClient-side
The invention provides a method for locking a working region of a mobile terminal, which is used for guaranteeing the information safety of the working region. According to the method, a server determines whether an enterprise management client is a compliant client according to a compliance detection rule stored by the server after receiving login information transmitted by the enterprise management client on the mobile terminal, and controls the enterprise management client to lock the working region when determining that the enterprise management client is non-compliant client. The embodiment of the invention also provides a corresponding device and system. In the embodiment of the invention, when the enterprise management client logins in every time, the server detects whether the enterprise management client is the compliant client, so that illegal users can be prohibited from entering the working region, uploading, sharing and leakage of data of the working region under the illegal condition can be avoided, and the safety of enterprise information is effectively protected.
Owner:BEIJING QIHOO TECH CO LTD +1
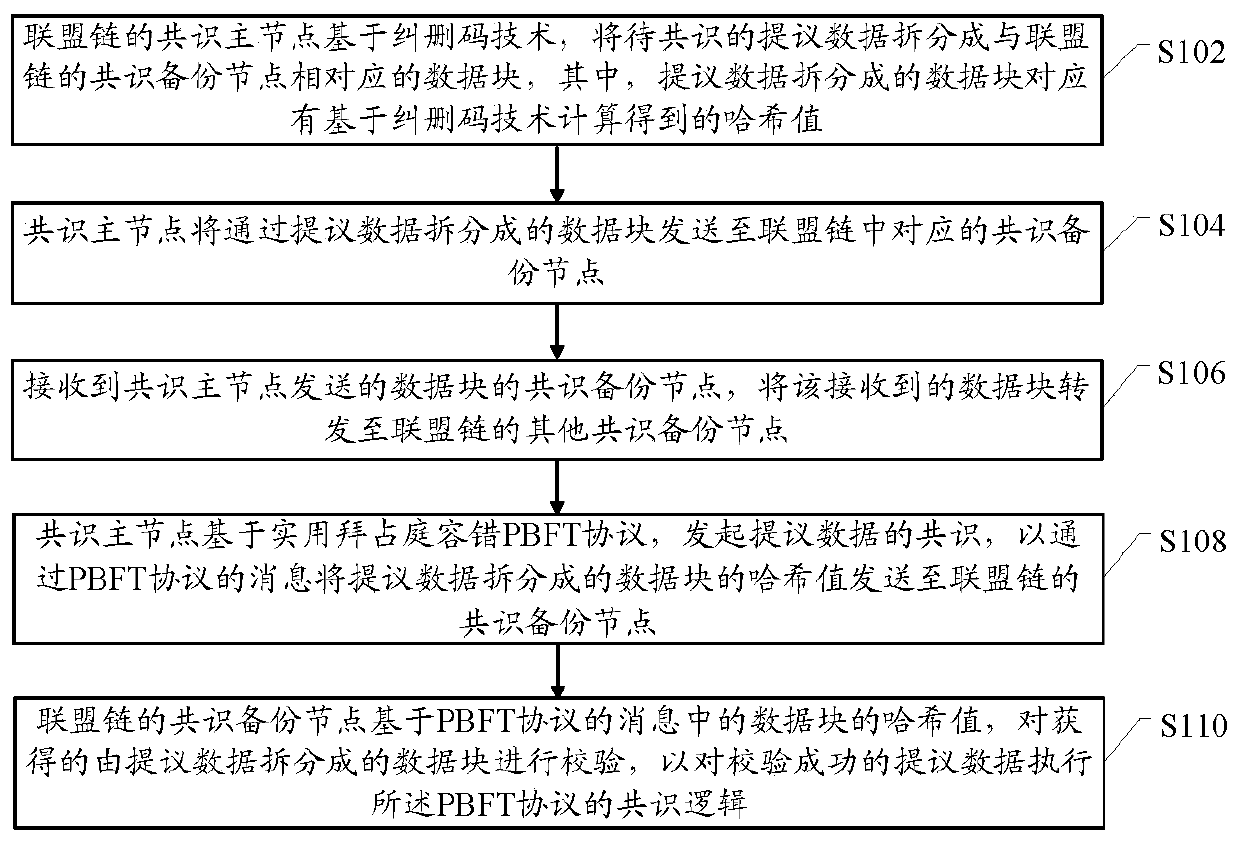
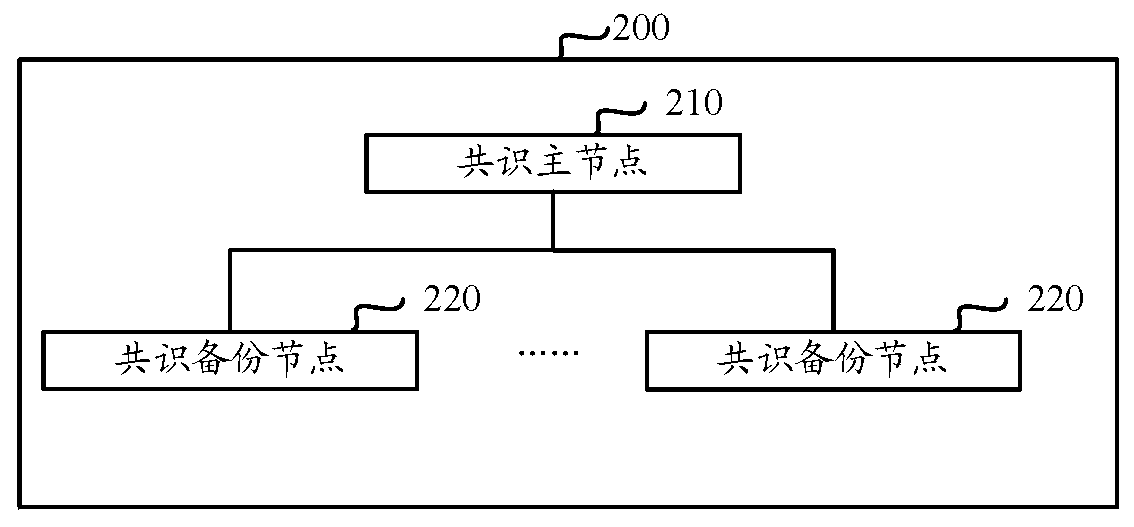
Alliance chain consensus method and alliance chain system
ActiveCN111526219ATo achieve fault toleranceAvoid uploadingUser identity/authority verificationForward error control useVIA protocolConsensus method
The embodiment of the invention provides an alliance chain consensus method and an alliance chain system. The method comprises the steps that a consensus main node splits proposed data to be consensusinto data blocks corresponding to consensus backup nodes based on an erasure code technology, and the data blocks split from the proposed data correspond to hash values obtained through calculation based on the erasure code technology; the consensus master node sends the data blocks split by the proposed data to the corresponding consensus backup nodes, receives the consensus backup node of the data block sent by the consensus main node, and forwards the data block to other consensus backup nodes; the consensus master node initiates consensus of the proposed data based on a practical Byzantine fault-tolerant PBFT protocol so as to send hash values of data blocks obtained by splitting the proposed data to the consensus backup node through a message of the PBFT protocol; the consensus backup node verifies the obtained data blocks split by the proposed data based on the hash values of the data blocks in the message of the PBFT protocol so as to execute the consensus logic of the PBFT protocol on the proposed data which is successfully verified.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
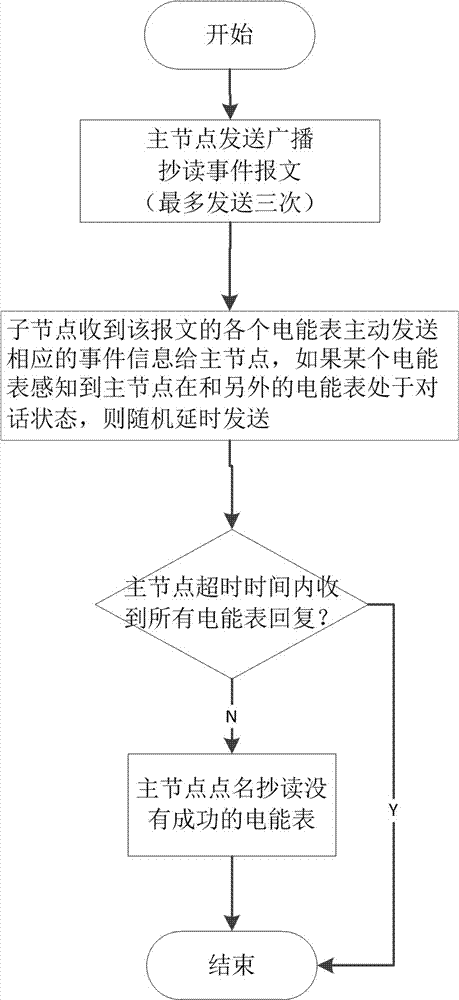
Electric energy meter event information copying and reading method
InactiveCN107464412AImprove efficiencyEasy accessElectric signal transmission systemsBus networksData transmissionCollection methods
The invention discloses an electric energy meter event information copying and reading method, and relates to a collection method. At present, a master node can only achieve control by sending information frames to slave nodes, namely electric energy meters, one by one in a periodically polling way. The electric energy meter event information copying and reading method comprises the following steps: sending a broadcast reading event information message on a bus by the master node; actively sending corresponding event information to the master node by each electric energy meter receiving the message, and if a certain electric energy meter senses that the master node is in a conversation with another electric energy meter, randomly delaying sending; if the master node does not receive the information replied by all the smart electric energy meters within the receiving timeout period, sending the broadcast reading event information message again; if the master node still does not receive the information replied by any of the smart electric energy meters, copying and reading the unsuccessful smart electric energy meters in a roll call manner. According to the technical scheme, abnormal event information query is performed in a broadcast mode, so that the efficiency is high; when the master node is in data transmission with one electric energy meter slave node, the other slave nodes send random delay so as to avoid congestion.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
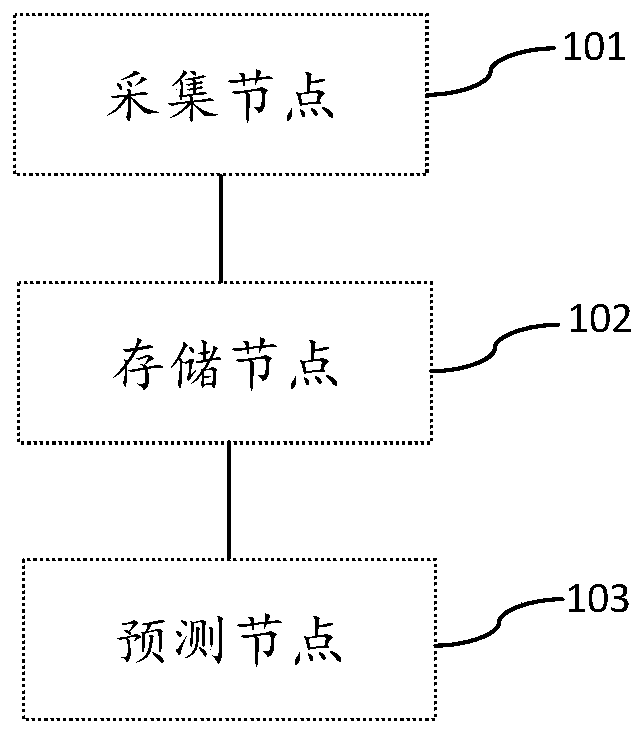
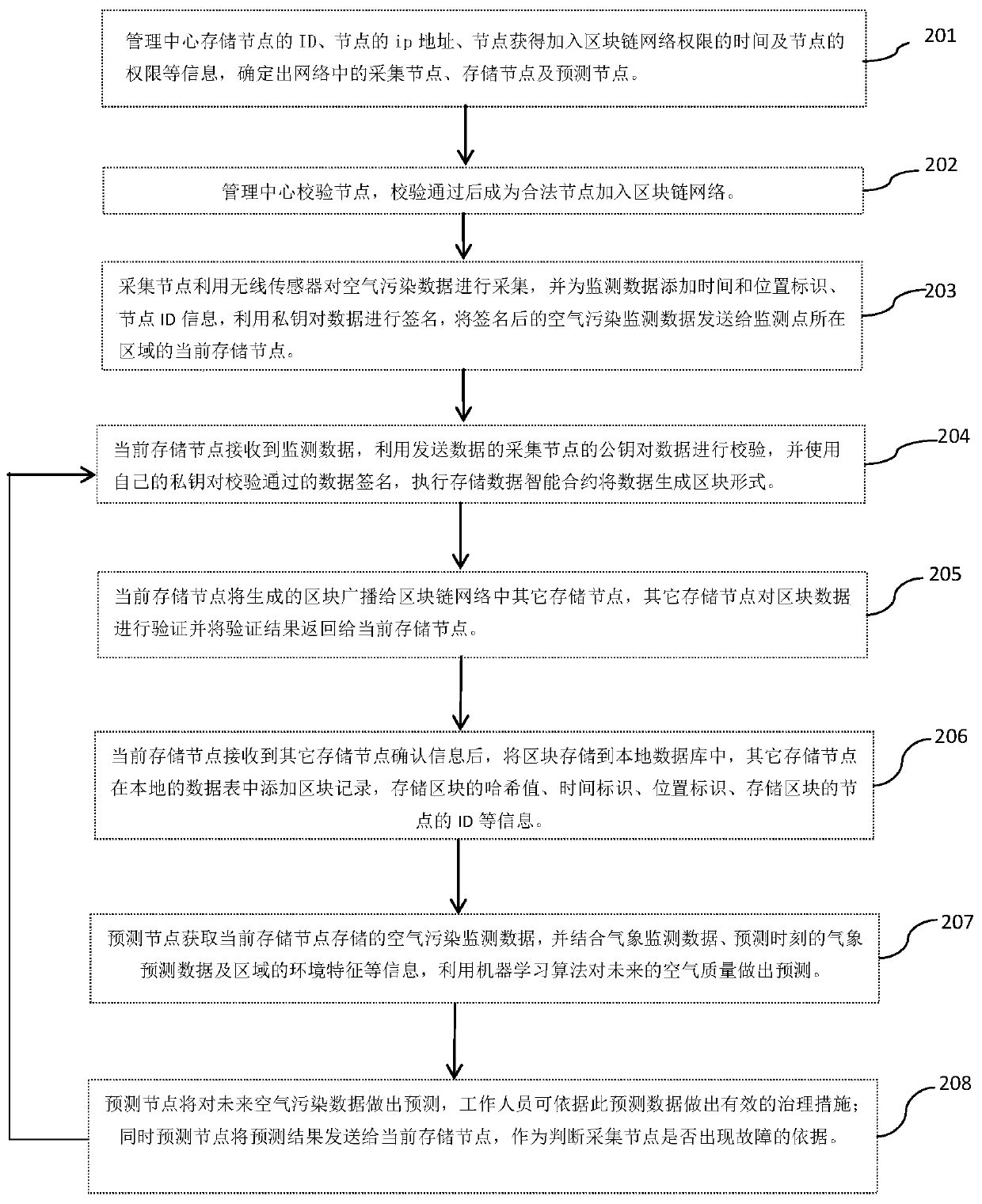
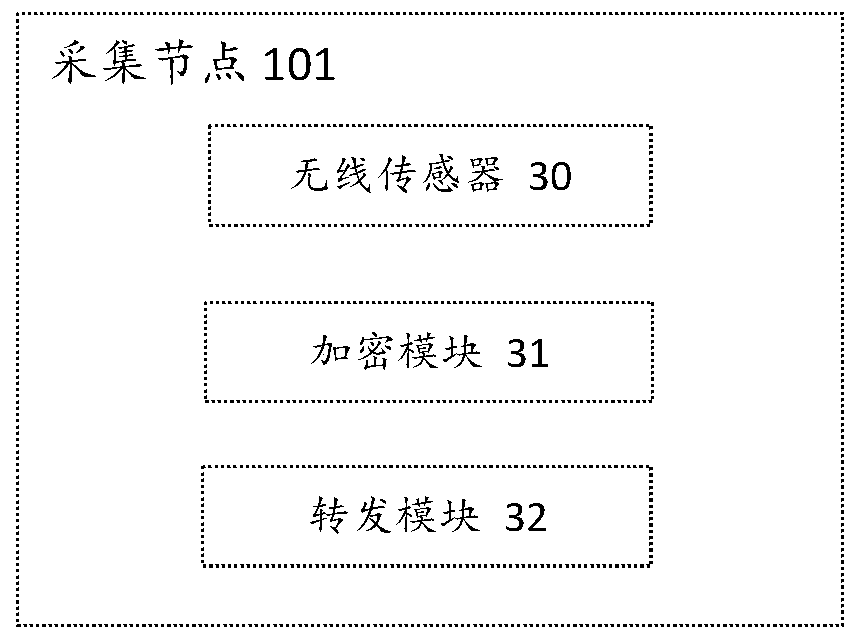
Air quality monitoring and predicting system and method
PendingCN111157682APrevent forgeryPrevent tamperingWeather condition predictionMaterial analysisMonitoring sitePrediction system
The invention provides an air quality monitoring and prediction system and method, and the system comprises a collection node, a storage node, and a prediction node, and the collection node, the storage node, and the prediction node form a blockchain network. The collection nodes are used for acquiring air pollution monitoring data and sending the monitoring data to the storage nodes in the area where the monitoring points are located. After receiving the monitoring data, the storage node verifies the data, generates a block from the data after passing the verification, and broadcasts the block in the system. Other storage nodes verify the blocks, and after the blocks pass the verification, the current storage node receives verification information of the other storage nodes and stores theblocks locally according to a time sequence to form a chain structure. Other storage nodes store the hash value, the time identifier and the position identifier of the block and the information of the storage node of the block locally for monitoring and querying the monitoring data, and the prediction nodes acquire monitoring data and predict future air quality in combination with a machine learning algorithm.
Owner:SHANGHAI INST OF TECH
Automatic identification system (AIS) mobile base station system based on Beidou satellite communication system
InactiveCN103067452AHigh frequencyLow costError preventionRadio transmissionComputer terminalMobile station
The invention relates to an automatic identification system (AIS) mobile base station system based on a Beidou satellite communication system. A ship with an AIS terminal can be enabled to acquire the AIS information of an AIS device of the ship through an AIS signal interface, the Beidou satellite communication system is used for enabling the AIS information to be transmitted to an AIS server, and the AIS server processes uniformly after receiving. Thus, the ship with the AIS terminal is equivalent to an AIS mobile base station on the sea. The Beidou satellite communication system is used as a communication mode, the maximum effects of communication timeliness and high frequency are achieved, and the advantage of being low in total cost is also achieved. The AIS server can achieve the fact that the AIS information is updated in 3-10 minutes.
Owner:广州联物网络科技有限公司
Processing System for Generating a Playlist from Candidate Files and Method for Generating a Playlist
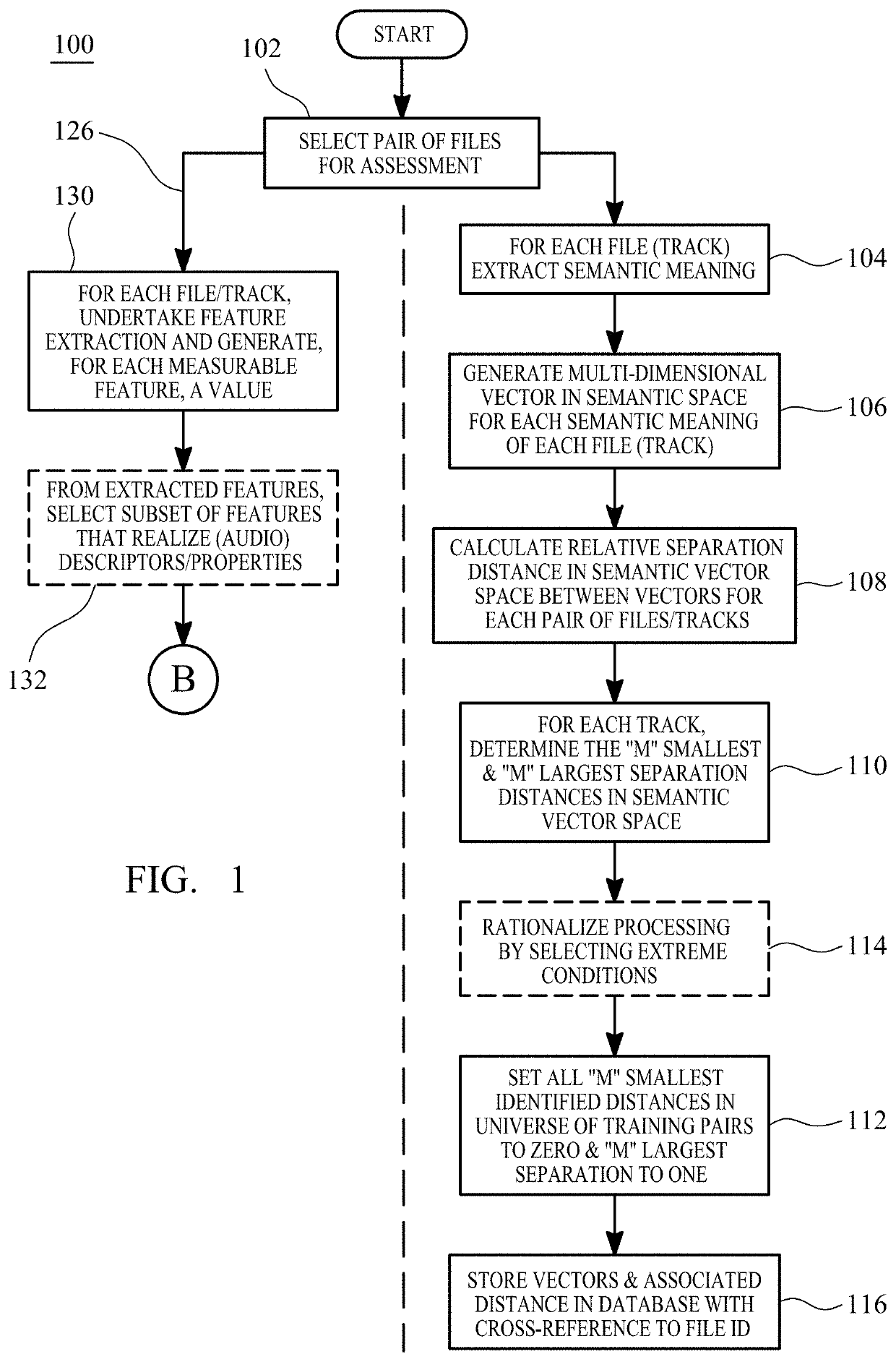
ActiveUS20220107975A1Rapid assimilationReduce search spaceElectrophonic musical instrumentsMathematical modelsData fileSource data
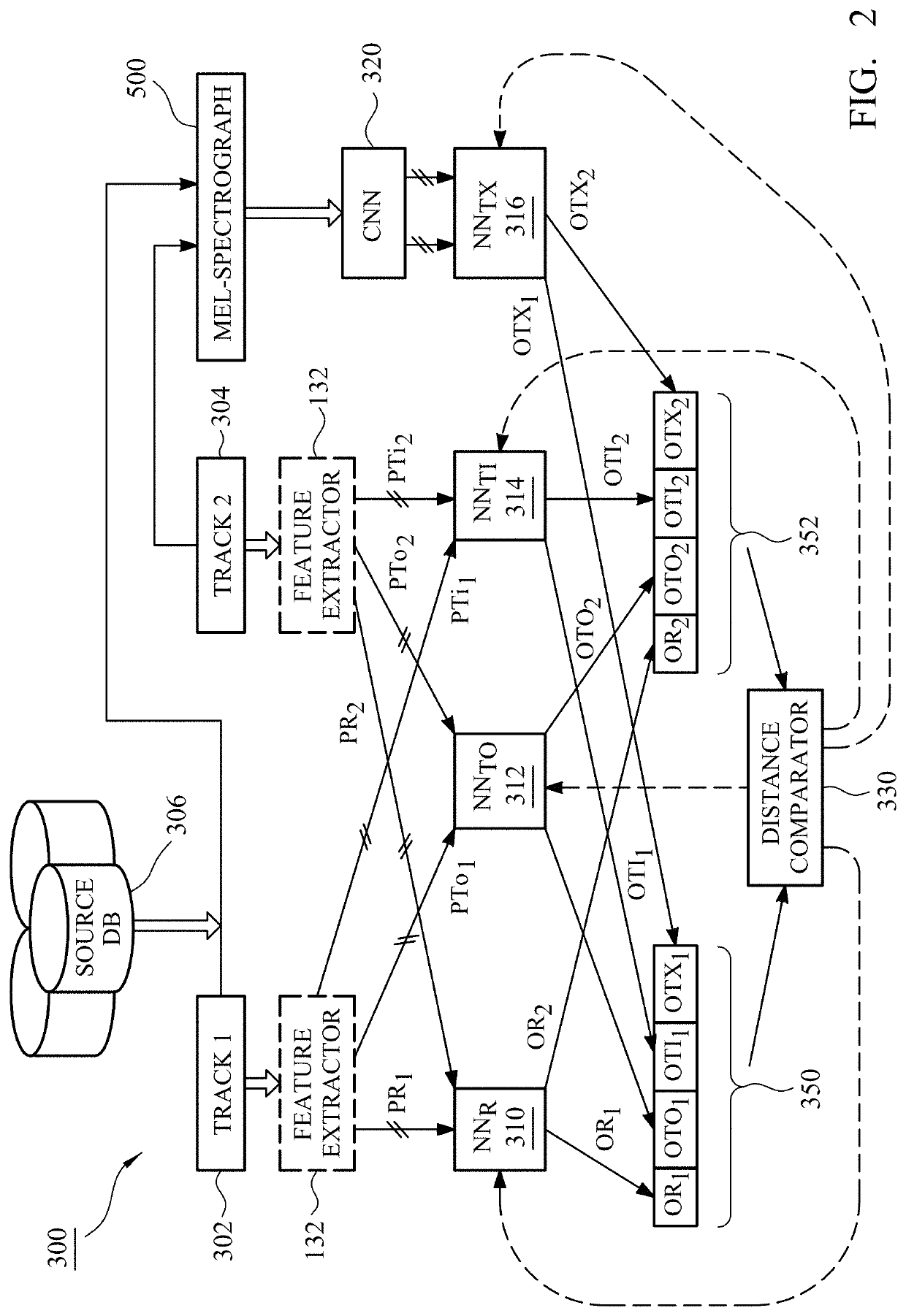
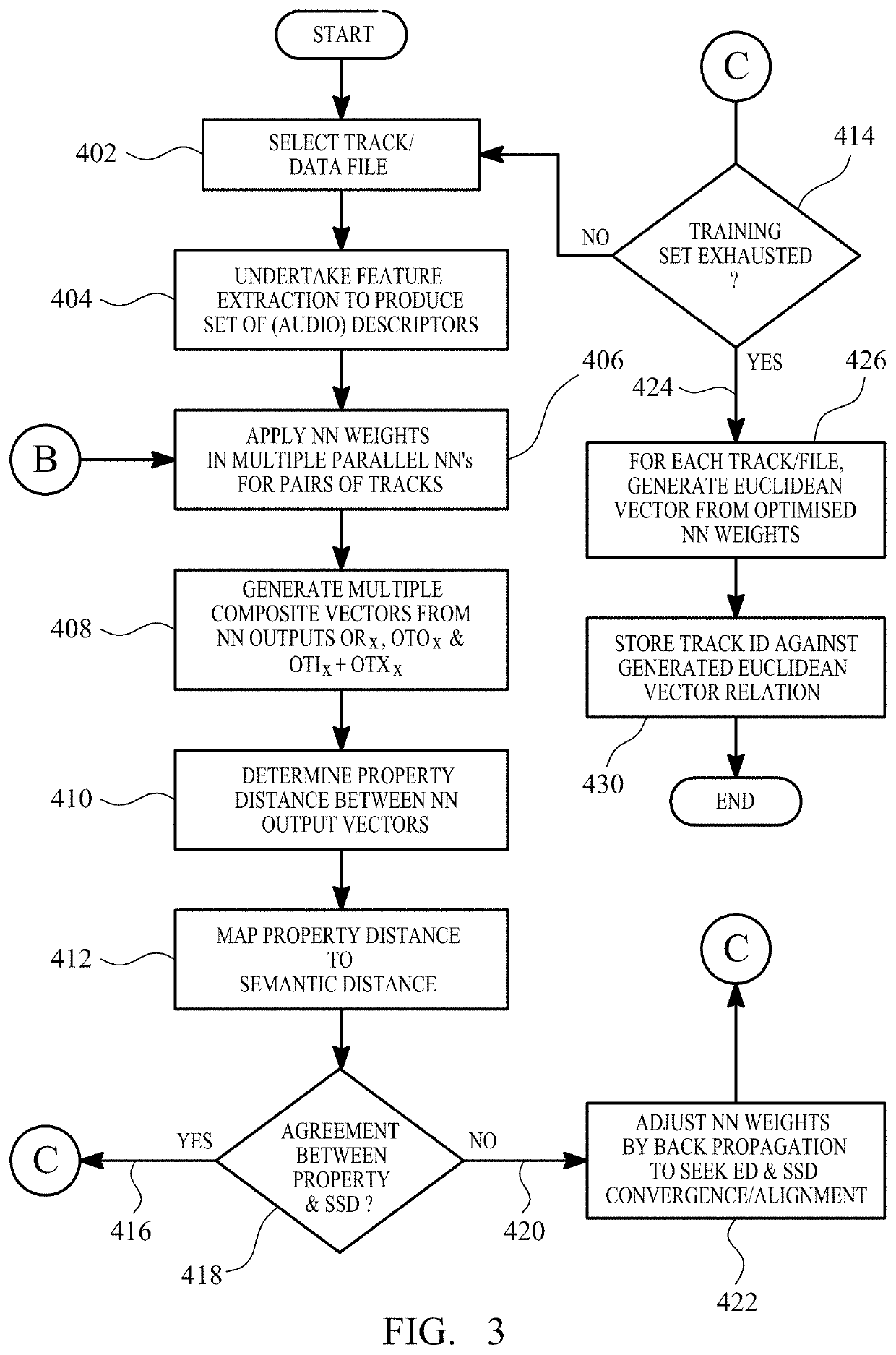
The invention provides for the evaluation of semantic closeness of a source data file relative to candidate data files. The system includes an artificial neural network and processing intelligence that derives a property vector from extractable measurable properties of a data file. The property vector is mapped to related semantic properties for that same data file and such that, during ANN training, pairwise similarity / dissimilarity in property is mapped, during towards corresponding pairwise semantic similarity / dissimilarity in semantic space to preserve semantic relationships. Based on comparisons between generated property vectors in continuous multi-dimensional property space, the system and method assess, rank, and then recommend and / or filter semantically close or semantically disparate candidate files from a query from a user that includes the data file. Applications apply to search and compilation tools and particularly to recommendation tools that provide a succession of logical progressive associations that link between disparate file content in source and destination files.
Owner:EMOTIONAL PERCEPTION AI LTD
Method and system for determining electricity utilization maturity of regional users
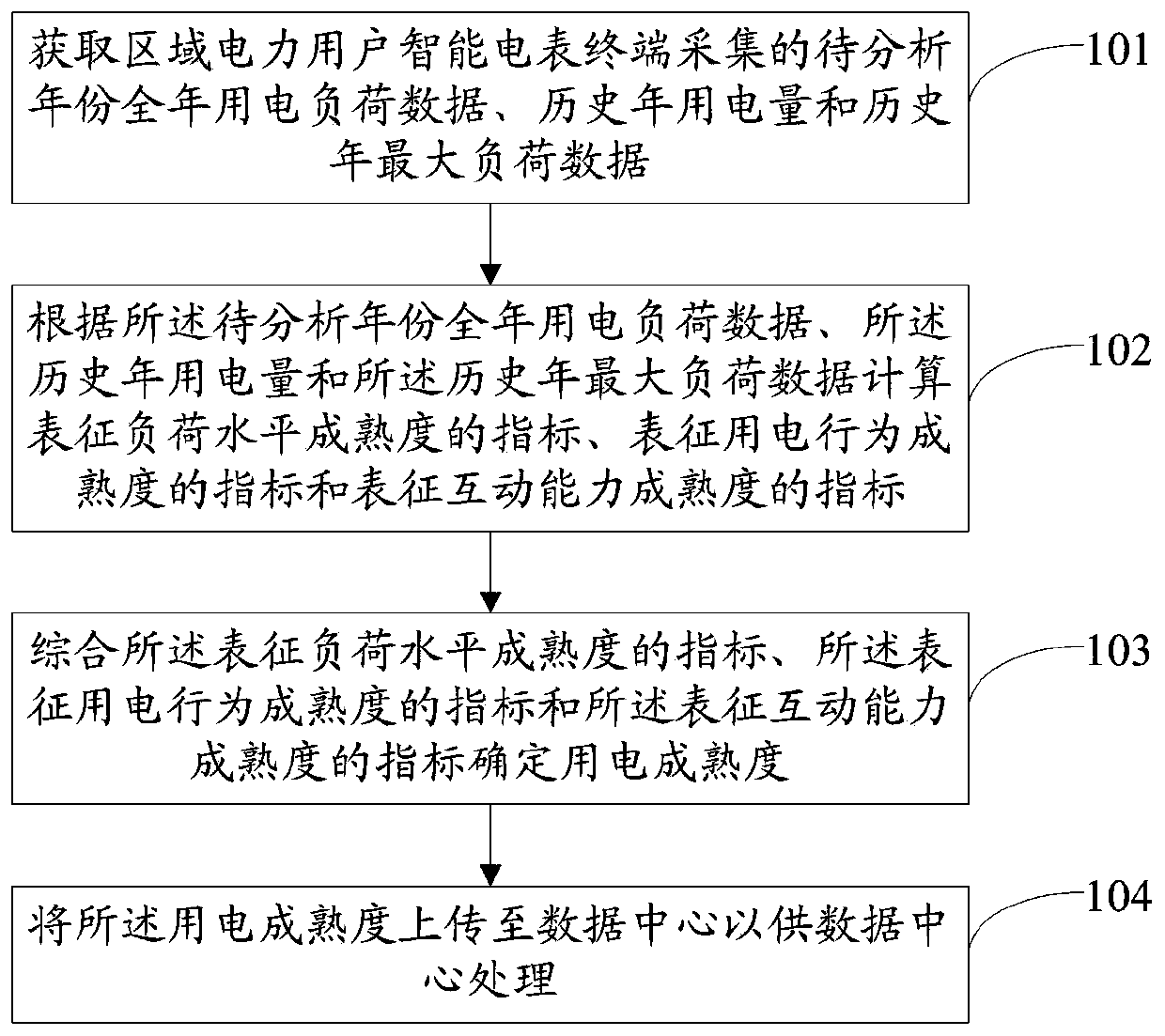
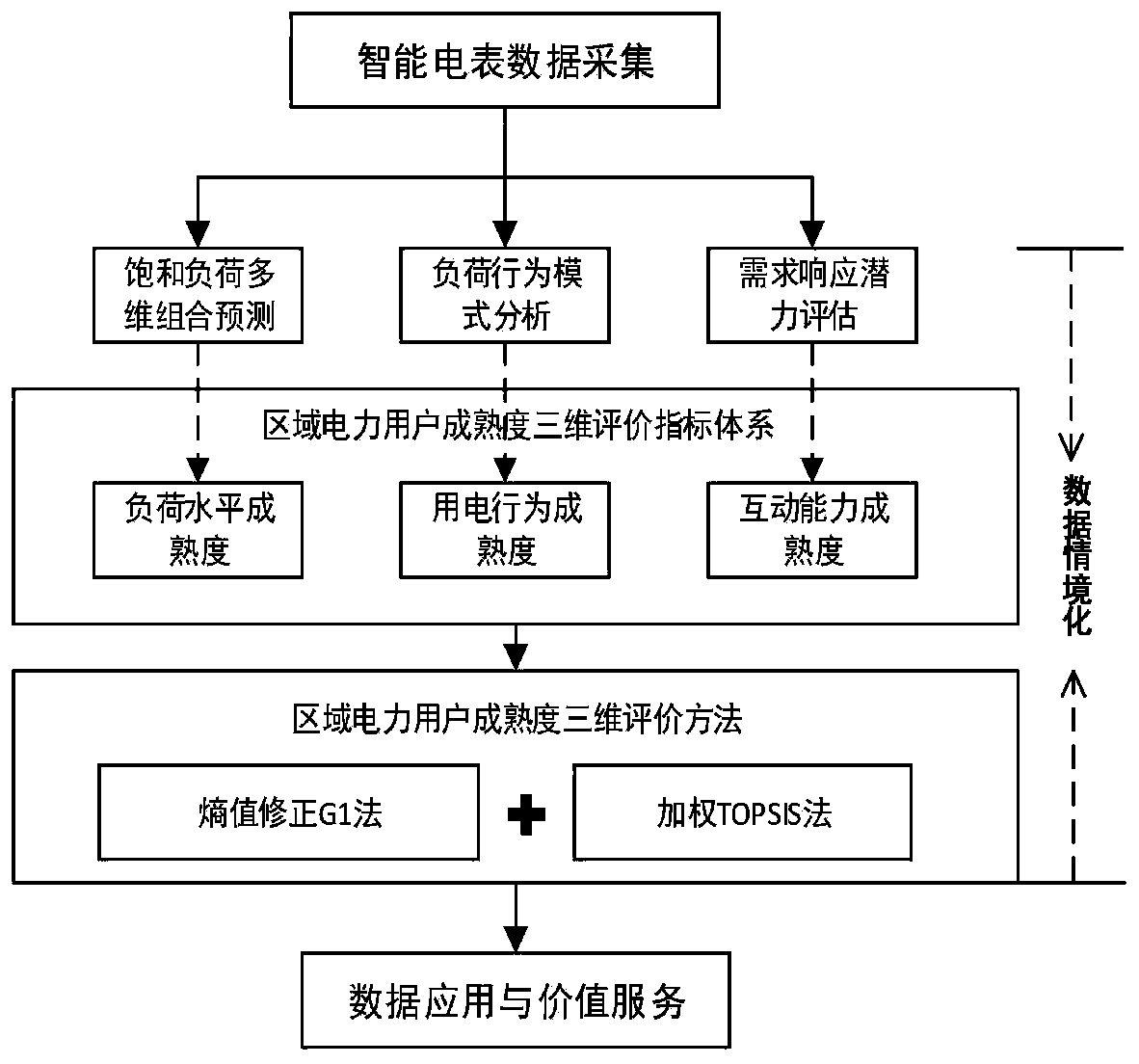
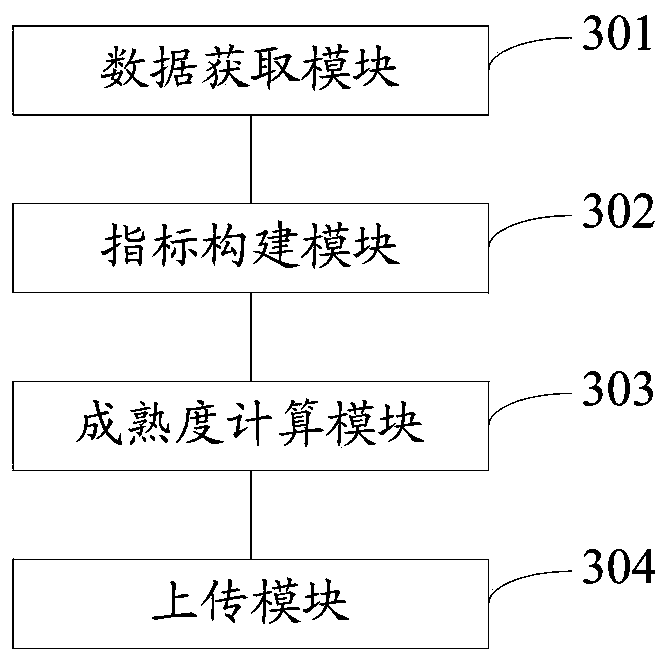
ActiveCN111027872AImprove processing efficiencyAvoid uploadingForecastingResourcesAgricultural scienceData center
The invention discloses a method and a system for determining the electricity utilization maturity of regional users. The method comprises the following steps: acquiring annual power consumption loaddata, historical annual power consumption and historical annual maximum load data of a year to be analyzed collected by a regional power consumer intelligent electric meter terminal; calculating an index representing load level maturity, an index representing power consumption behavior maturity and an index representing interaction capability maturity according to the annual power consumption loaddata, the historical annual power consumption and the historical annual maximum load data of the year to be analyzed; determining the power utilization maturity by comprehensively representing the index of the load level maturity, the index of the power utilization behavior maturity and the index of the interactive capability maturity; and uploading the power utilization maturity to a data centerfor processing by the data center. According to the method and the system for determining the electricity utilization maturity of the regional users, electricity utilization maturity analysis can becarried out on the regional power users, a large amount of data is prevented from being uploaded to a data center, and the data processing efficiency is improved.
Owner:STATE GRID CORP OF CHINA +1
POI (Point Of Interest) offline method and related equipment
ActiveCN108833527AAvoid uploadingThe update process is fastTransmissionLocation information based serviceTerminal equipmentData mining
The embodiment of the invention discloses a POI (Point Of Interest) offline method and related equipment. The method comprises the steps of: sending an identifier of a first POI to terminal equipment;receiving request information sent by the terminal equipment, wherein the request information comprises a to-be-determined image; according to the request information, judging whether the terminal equipment has a permission of carrying out shooting on a second POI; and if determining that the terminal equipment has the permission of carrying out shooting on the second POI and if determining thatthe identifier of the first POI is different from that of the second POI, deleting the identifier of the first POI in target map data. By adopting the method disclosed by the embodiment, accuracy thata server carries out statistics on identifiers of POIs in a target region is promoted.
Owner:LINKTECH NAVI TECH +1
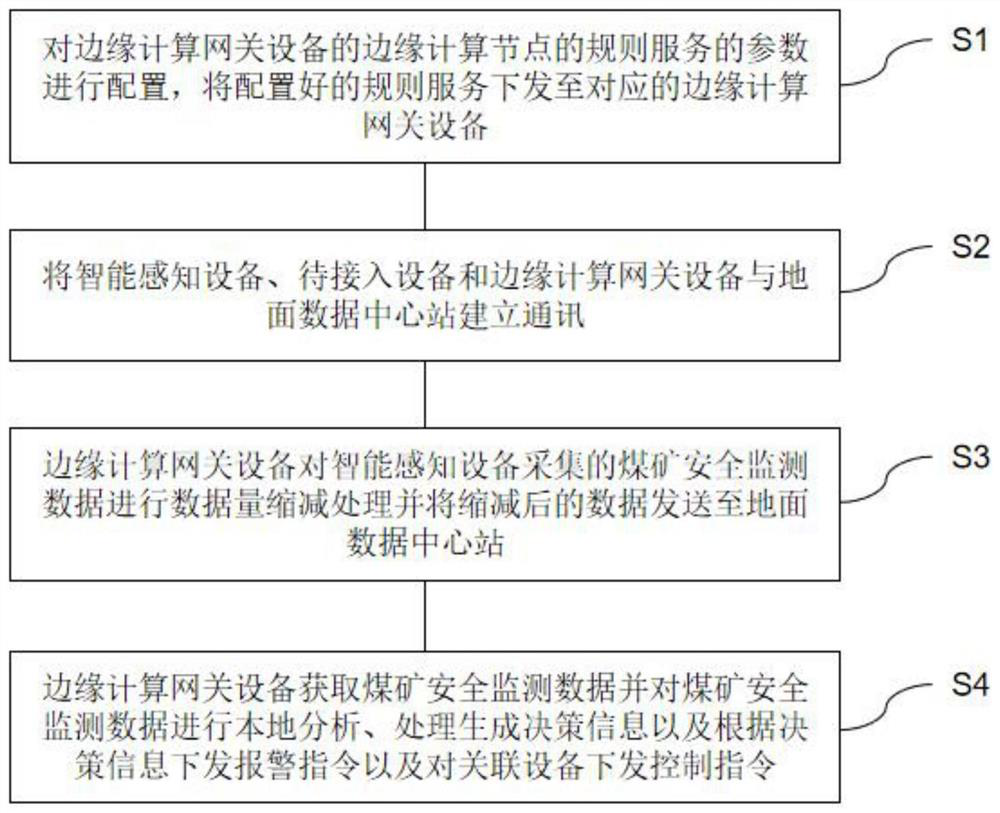
Coal mine monitoring system and method and computer storage medium
PendingCN112165511AAvoid large data uploadsRelieve stressMining devicesTransmissionMonitoring dataEnvironmental geology
The invention provides a coal mine monitoring system and method and a computer storage medium, and the system comprises intelligent sensing equipment which is disposed in a well and can collect coal mine safety monitoring data in real time; edge computing gateway equipment which is connected with the intelligent sensing equipment, can acquire the coal mine safety monitoring data, carry out local analysis and processing to generate decision information, gives an alarm instruction according to the decision information and sends a control instruction to associated equipment; a plurality of coal mine safety monitors which monitors the environmental information in the coal mine; and a group-layer safety monitor which acquires safety monitoring information of each coal mine. According to the system provided by the embodiment of the invention, the pressure of a ground data processing center is reduced, the timeliness of data analysis is improved by changing a mode where the data is transmitted to a ground central station to be processed into a mode of processing the data underground, and the service response capability is enhanced.
Owner:TIANDI CHANGZHOU AUTOMATION +1
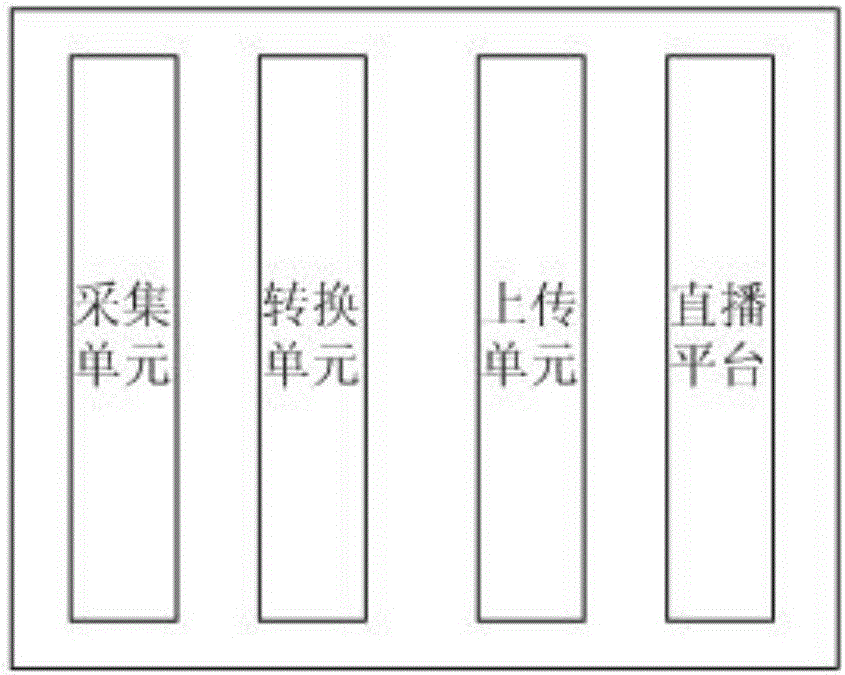
Scenic spot streaming media live system
ActiveCN106534804AReasonable designThe need for reduced speedClosed circuit television systemsSelective content distributionLiving systemsSystems design
The present invention discloses a scenic spot streaming media live system. The scenic spot streaming media live system comprises an acquisition unit, a conversion unit, an uploading unit and a live platform. The acquisition unit is used for deploying an RTSP video service in an intranet network of scenic spot monitoring, and capturing real-time monitoring information from the internal network to video; the conversion unit is used for acquiring a monitored rtsp protocol flow, the rtsp protocol flow is converted to an hls protocol flow which is stored locally in a TS way, and is encapsulated as an M3U8 format; the uploading unit is used for uploading information locally stored to the live platform; and the live platform is used for providing a user with monitoring information of the scenic spot according to the user right. The technical effects that the system design is reasonable and the user can acquire real-time scenic spot monitoring information through the live system are realized.
Owner:成都中科大旗软件股份有限公司
Frying pan for electromagnetic oven
The invention relates to a griddle applicable for induction cooker, which is characterized in that: a plurality of downward extended ferruginous fin structures or protuberant structures are arranged on the bottom of the inner arc griddle body or the small pan body with great part arc, at the middle of the griddle bottom, the heights of the structures increase gradually from inside to outside; the upper ends of the structures, that are the basal parts, are either connected with the griddle body as a whole, or connected with the bottom of the griddle body through a panel integrated and arranged in the bottom of the griddle; a support is arranged at the lower ends of the fin structures or the protuberant structures, the plane of the fulcrum of the support, that is the supporting surface, is parallel with the surface of the griddle port. The invention has the advantages of rational structure, lighter weight, high heat efficiency, convenient use, and edible oil saving and oil fume reduction when used for frying.
Owner:万平
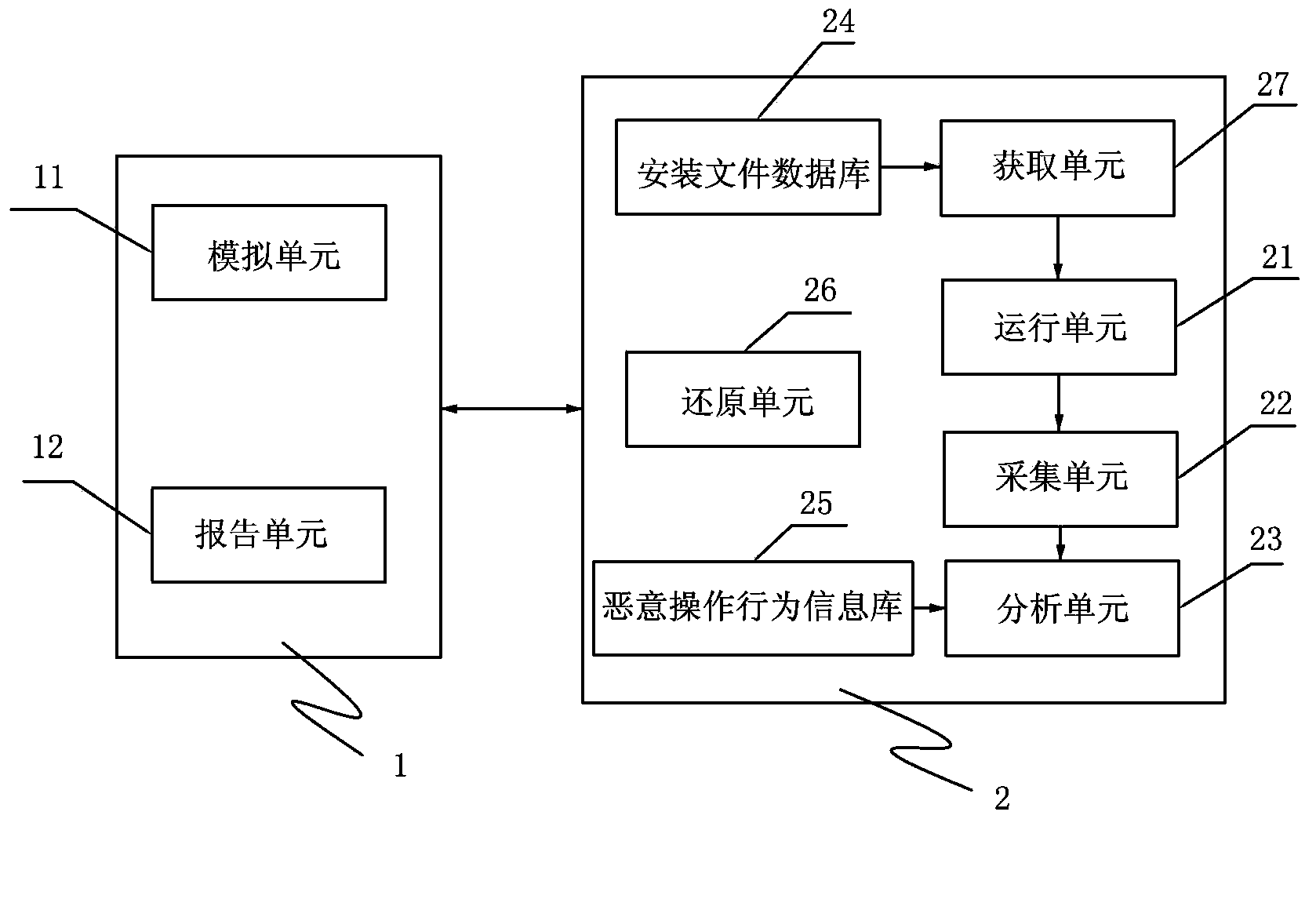
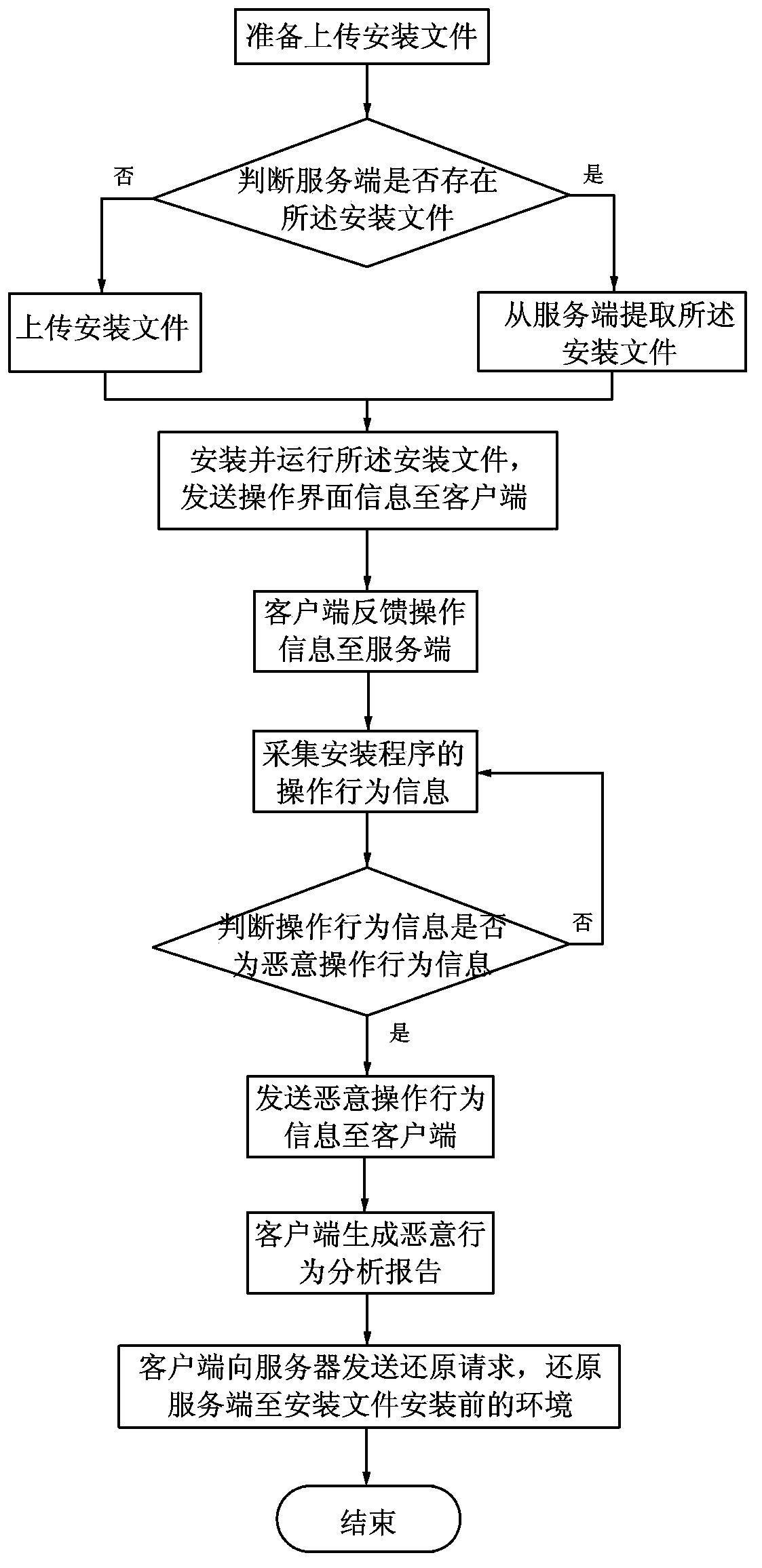
Virtual installing device and method for mobile phone programs
InactiveCN103677882AImprove experienceAvoid uploadingComputer security arrangementsProgram loading/initiatingBehavioral analyticsClient-side
The invention discloses a virtual installing device and method for mobile phone programs. The virtual installing device comprises an obtaining unit provided with the server-side, a running unit arranged on the server-side and used for executing file installation, running installation programs and sending operating interfaces of the installation programs to the client-side, a simulation unit arranged on the client-side and used for receiving operation instructions with respect to the operating interfaces and sending the operation instructions to the server-side, an acquisition unit arranged on the server-side and used for acquiring operation behavior information of the installation programs, and an analysis unit arranged on the server-side and used for judging whether the operation behavior information is malicious operation behavior information or not and sending the malicious operation behavior information to the client-side. The operation non-required programs are directly installed in a mobile phone is avoided through the programs installed on the server-side and by simulating and experiencing functions on the mobile phone. In addition, program behaviors are further detected, behavior analysis reports are generated, and malicious programs are prevented from being directly installed in the mobile phone.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH +3
Blockchain-oriented Internet of Things chip lightweight data encryption method
ActiveCN111740989AData source is credibleAvoid uploadingKey distribution for secure communicationUser identity/authority verificationKey exchangeData Origin
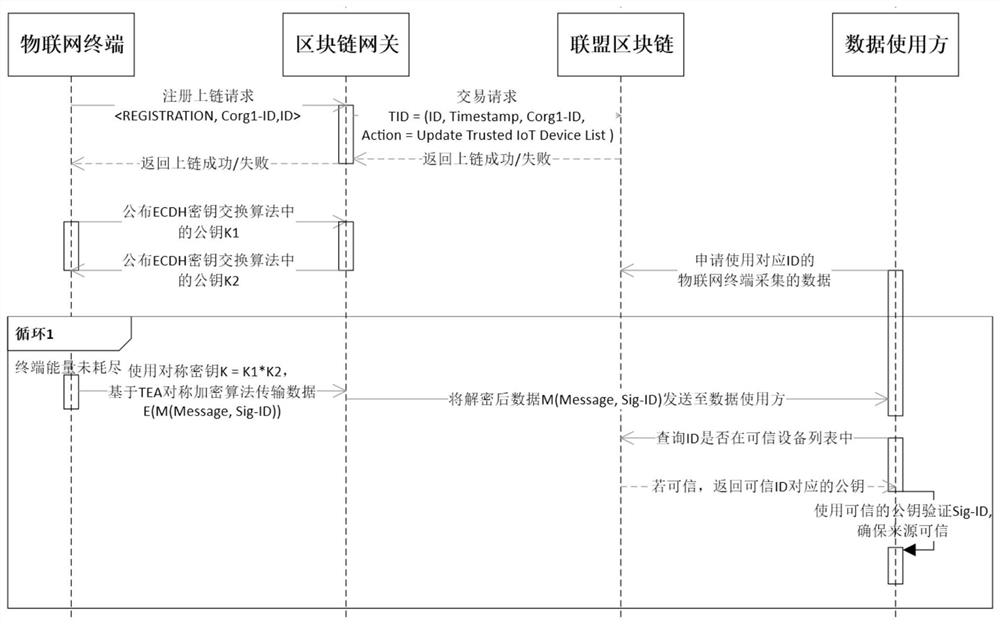
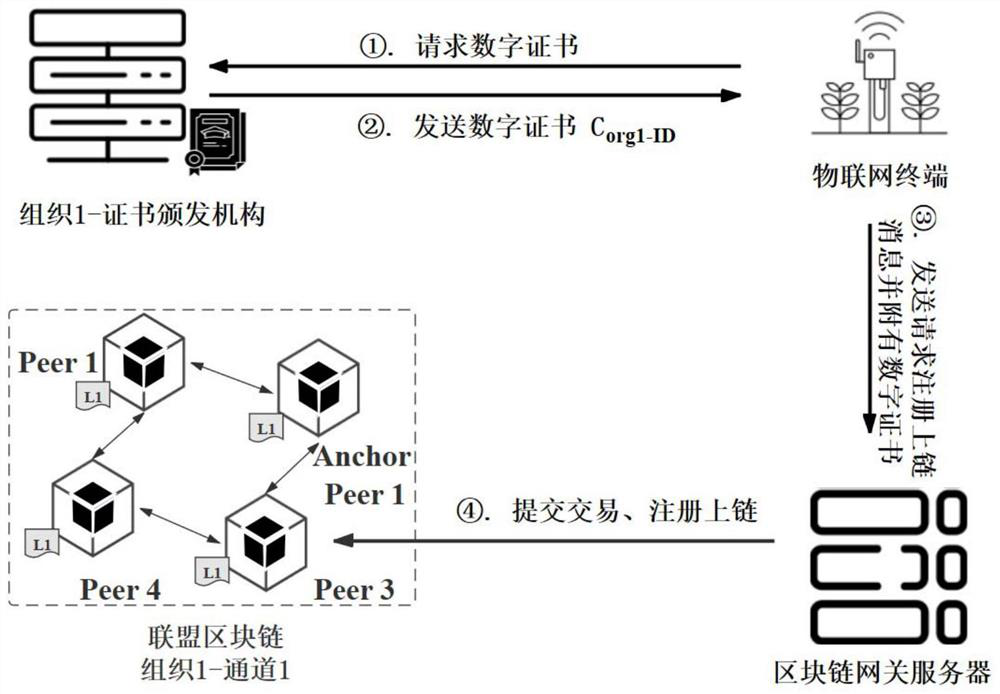
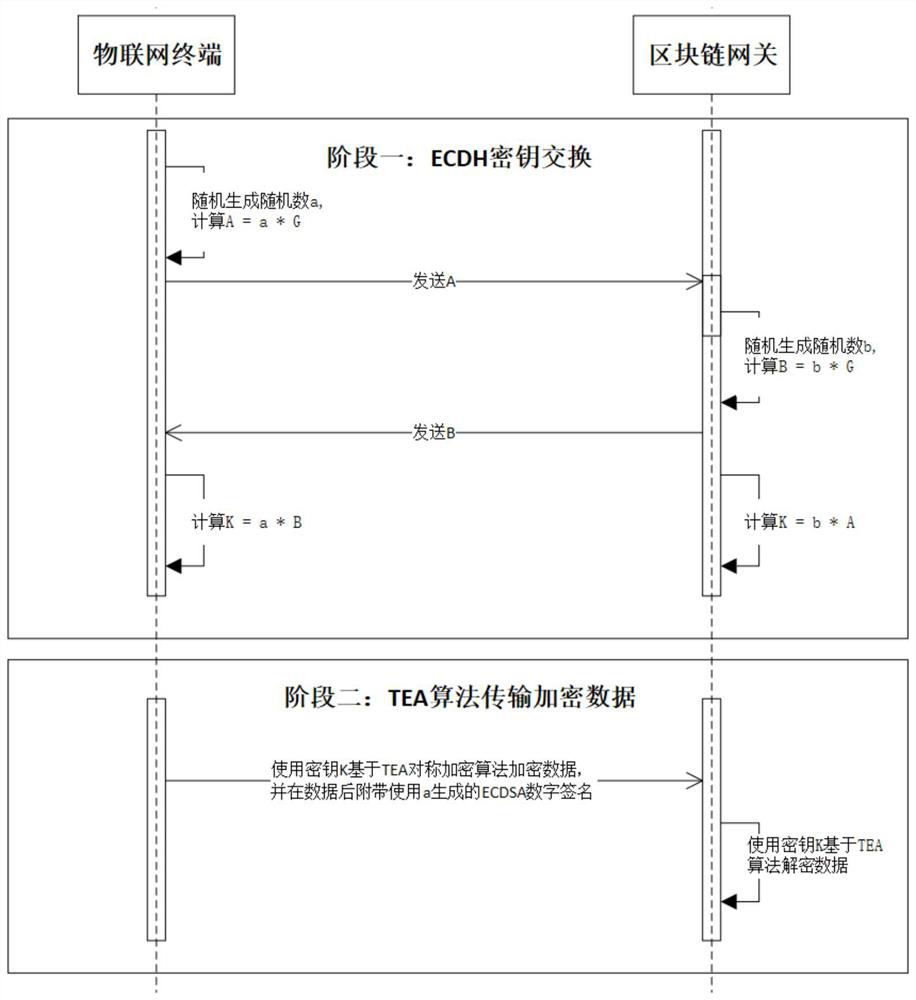
The invention belongs to the technical field of Internet of Things information security, and particularly relates to a blockchain-oriented Internet of Things chip lightweight data encryption method. The method specifically comprises the following steps: an Internet of Things terminal generates a public and private key by using a true random number, obtains a digital certificate through a certificate issuing mechanism, and exchanges a symmetric key with a block chain gateway by using an ECDH key exchange algorithm; and the blockchain gateway receives the digital certificate and the public key from the Internet of Things terminal and submits a transaction request to the alliance blockchain. And the alliance block chain uplinks the trusted device list after endorsement and sorting. And if thedata user requests to use the data, the Internet of Things terminal sends the ciphertext data to the block chain gateway and attaches an ECDSA digital signature, and the block chain gateway forwardsthe ciphertext data to the data user. And the data user queries the trusted device list on the chain and verifies the digital signature by using the trusted public key so as to ensure that the data source is real and trusted. According to the invention, credible data source, safe data transmission and credible sharing on the data link can be realized.
Owner:DALIAN UNIV OF TECH
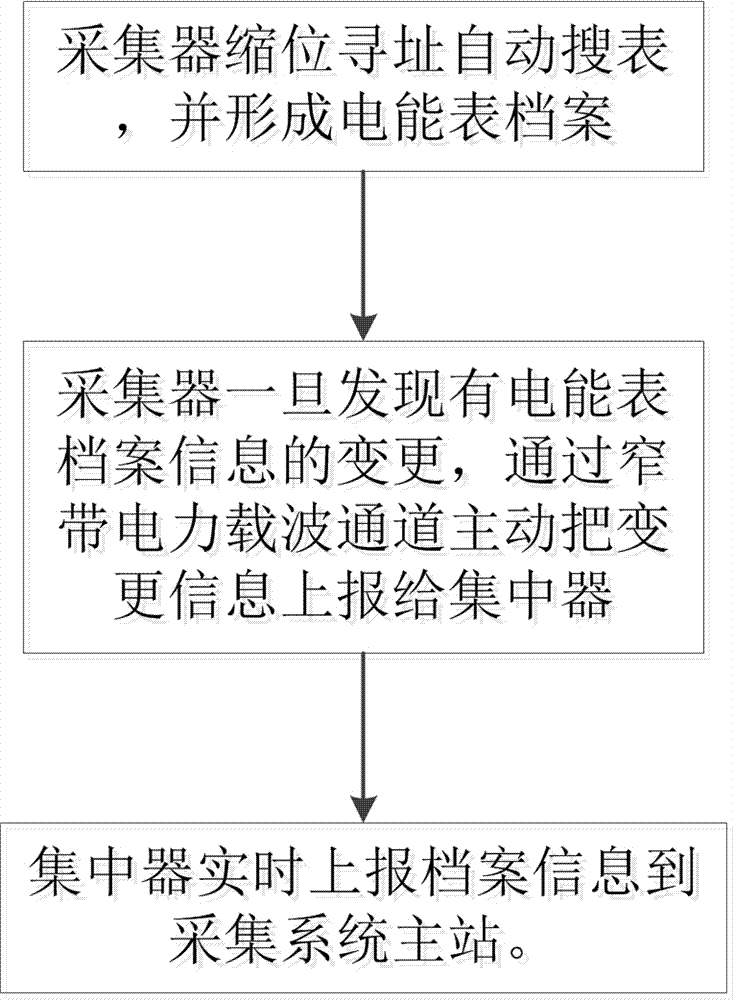
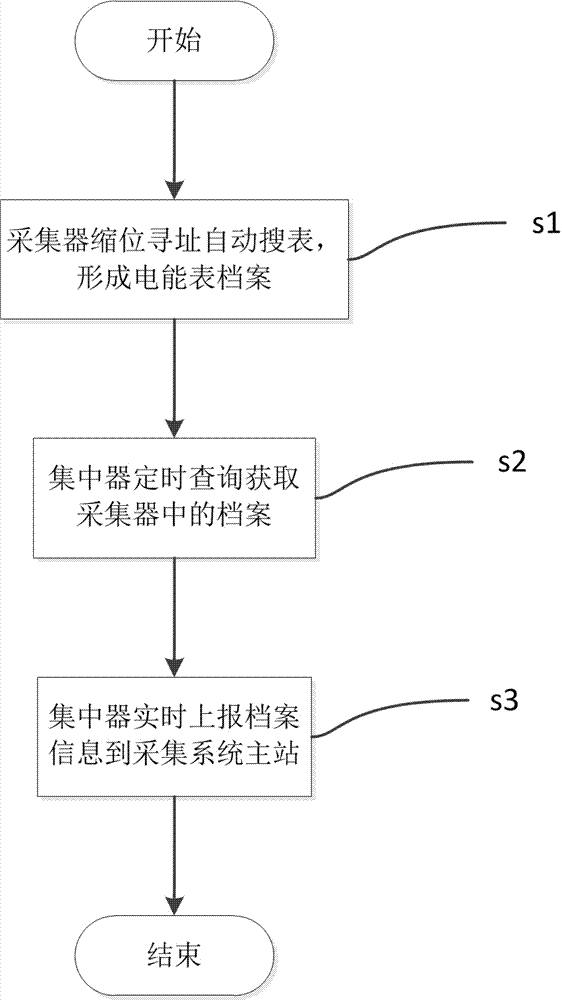
Electricity consumption information collection system electric energy meter sensing method based on narrow band power line carrier wave
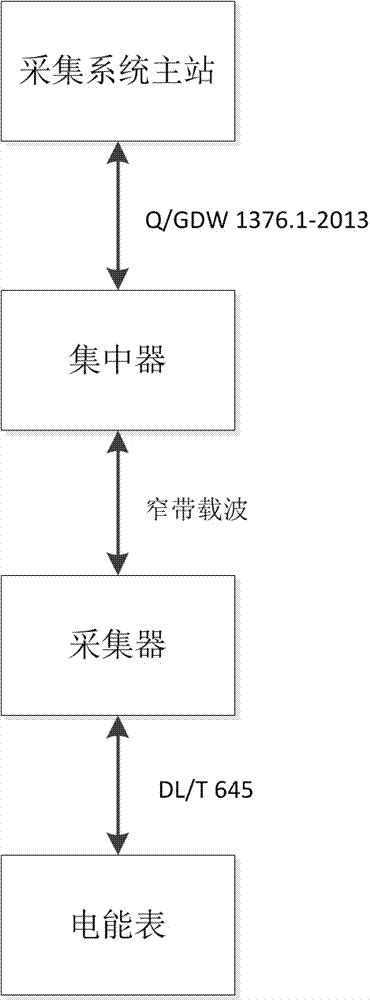
InactiveCN107516409AImprove replacement efficiencyIncrease pressure limitedElectric signal transmission systemsElectricityPrimary station
The invention discloses an electricity consumption information collection system electric energy meter sensing method based on narrow band power line carrier wave, and relates to a collection method. During the application process, if electric energy meters are increased or replaced, the change of the electric energy meter archive information cannot be reported to the main station of the collection system in time. The method comprises the following steps: (11) carrying out abbreviated addressing and automatic table searching by a collector, and forming an electric energy meter archive; (12) once the change of the electric energy meter archive is sensed by the collector, actively reporting the change information to a concentrator by a narrow band power line carrier wave channel; and (13) reporting the archive information to the main station of a collection system in time by the concentrator. The automatic sensing of carrier wave is adopted, the assembly and disassembly of electric energy meters can be found out in time, other incidents are not taken into account, and the processing is real-time. After a meter or collector is installed, the information can be reported in several seconds. The active reporting is realized, and the information replacement efficiency is improved effectively.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
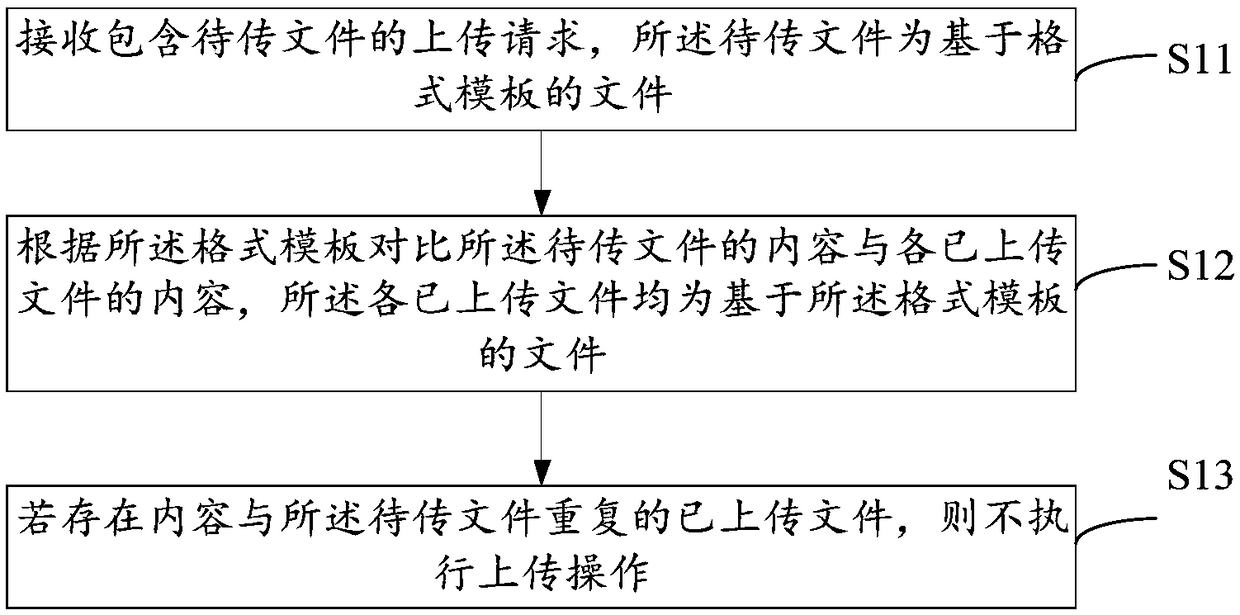
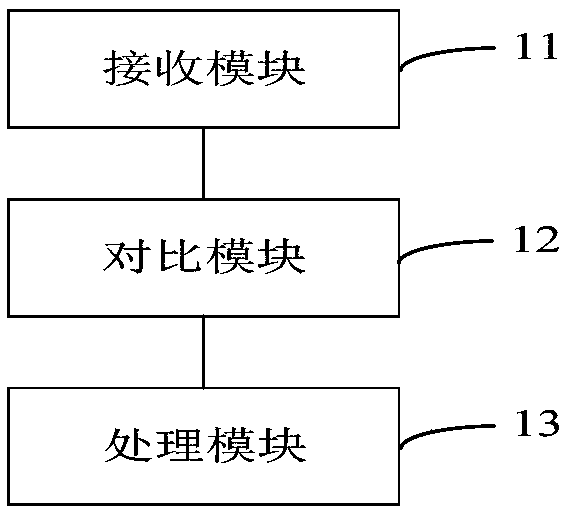
Method for preventing file from being uploaded repeatedly, and control method and device thereof
PendingCN109241009AAvoid duplicate uploadsReduce riskDigital data information retrievalNatural language data processingOperating system
Owner:CHINA PING AN LIFE INSURANCE CO LTD
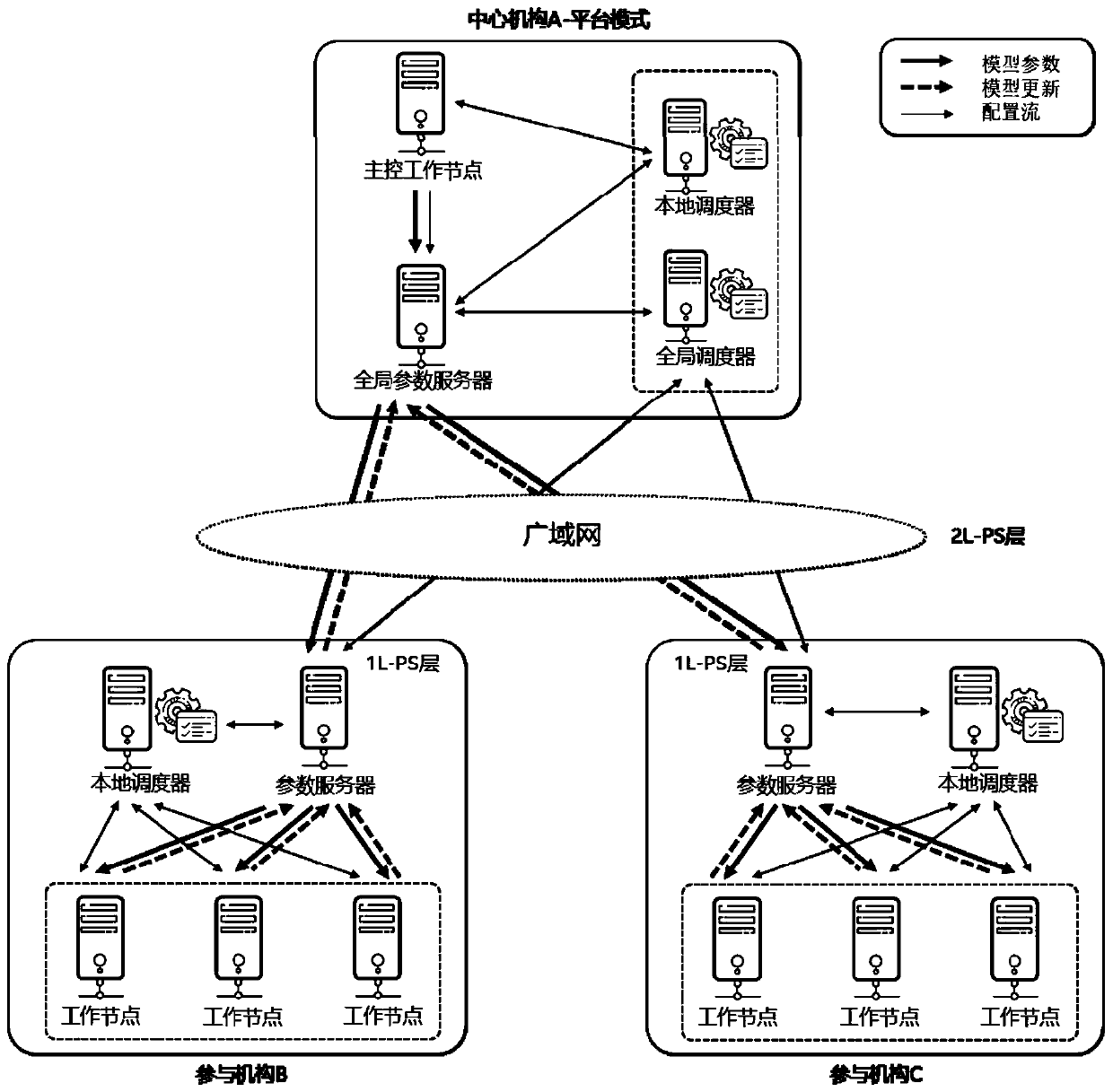
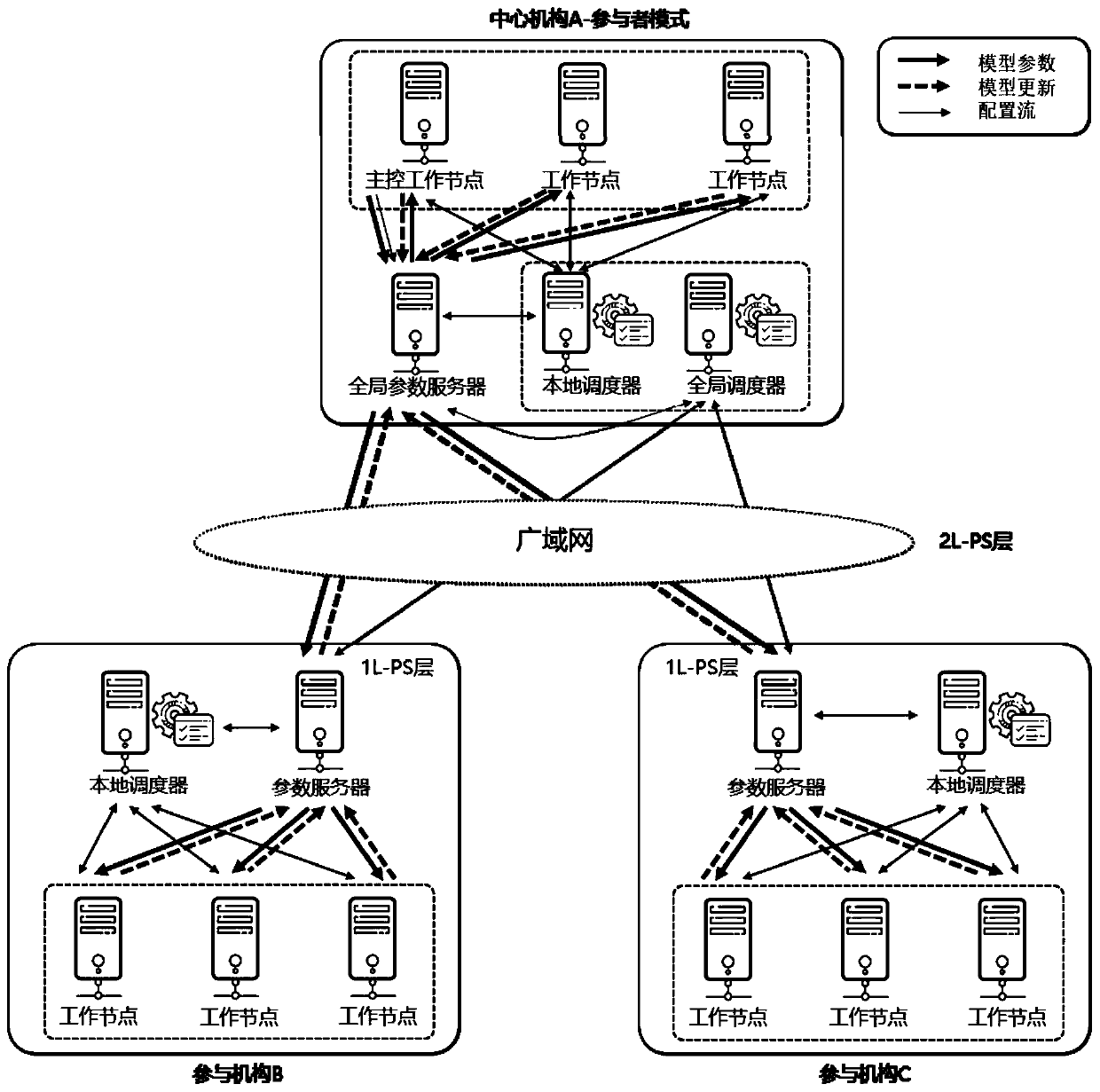
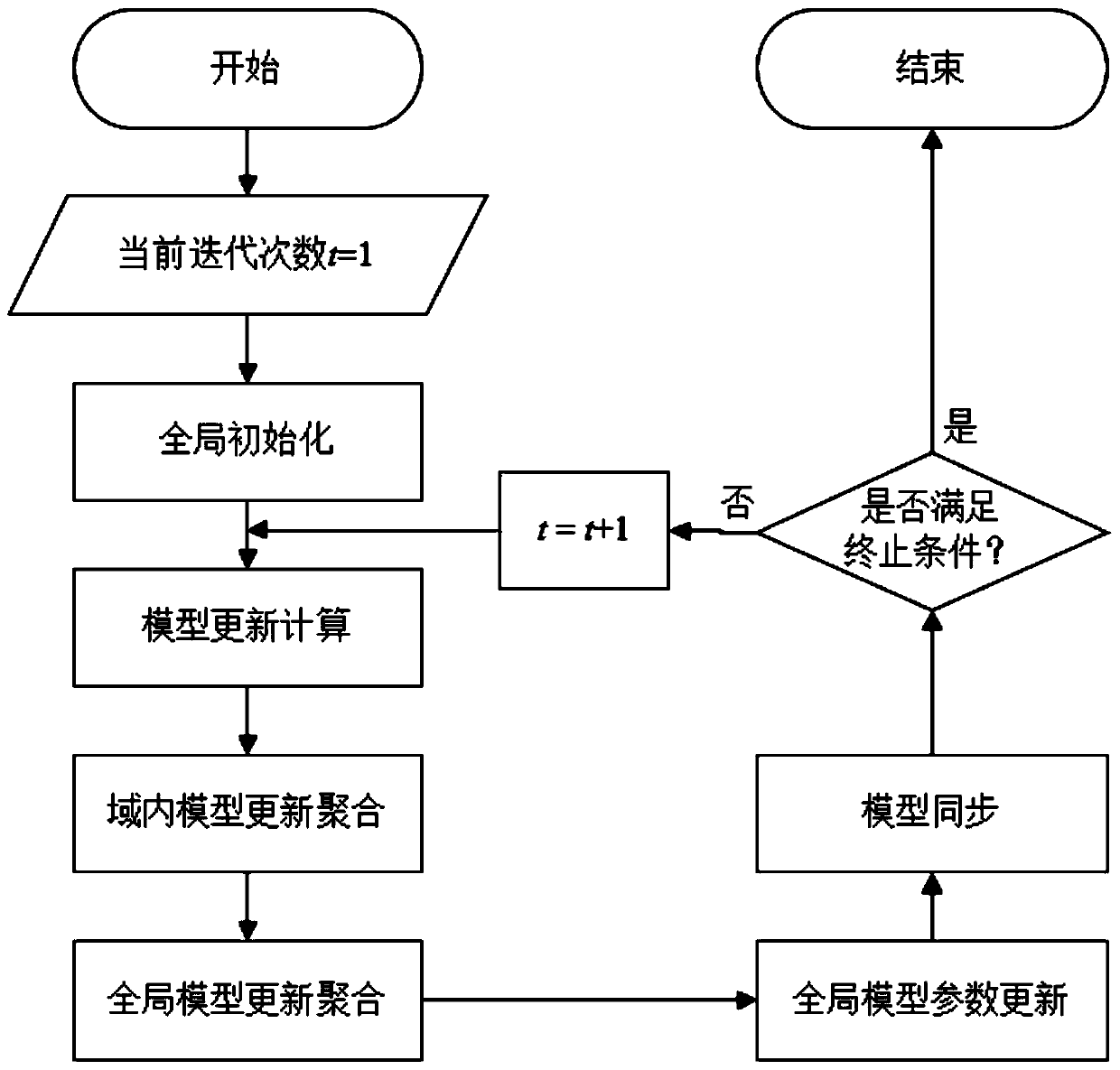
Multi-mechanism collaborative learning system and method based on hierarchical parameter server
ActiveCN110995488AComputationally efficientEfficient communicationData switching networksResource utilizationEngineering
The invention discloses a multi-mechanism collaborative learning system based on a hierarchical parameter server. The multi-mechanism collaborative learning system comprises a central mechanism and aplurality of participation mechanisms connected with the central mechanism through a WAN network. Based on the system, the invention further discloses a multi-mechanism collaborative learning method based on the hierarchical parameter server. According to the method, the data island problem of big data is solved, the data privacy safety problem during multi-party cooperation is solved, and the problems of high communication cost, high maintenance cost, high safety risk and low resource utilization rate of an existing system are solved. On the premise of ensuring data privacy safety, efficientcommunication and efficient calculation multi-party collaborative learning is realized, and the method is suitable for cross-domain interconnection of multiple independent mechanisms and multiple datacenters. The system provided by the invention supports a platform mode and a participation mode, can be used as a platform to provide multi-party knowledge fusion service, and can also be used as a tool to support sharing cooperation among a plurality of independent mechanisms.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com