Method for realizing burglary prevention and data protection of hard disk
A data protection and hard disk technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems of loss, easy theft, security threats of hard disk use, etc., to achieve the effect of protecting data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0071] The method for realizing hard disk theft prevention and data protection in this embodiment includes the following steps:
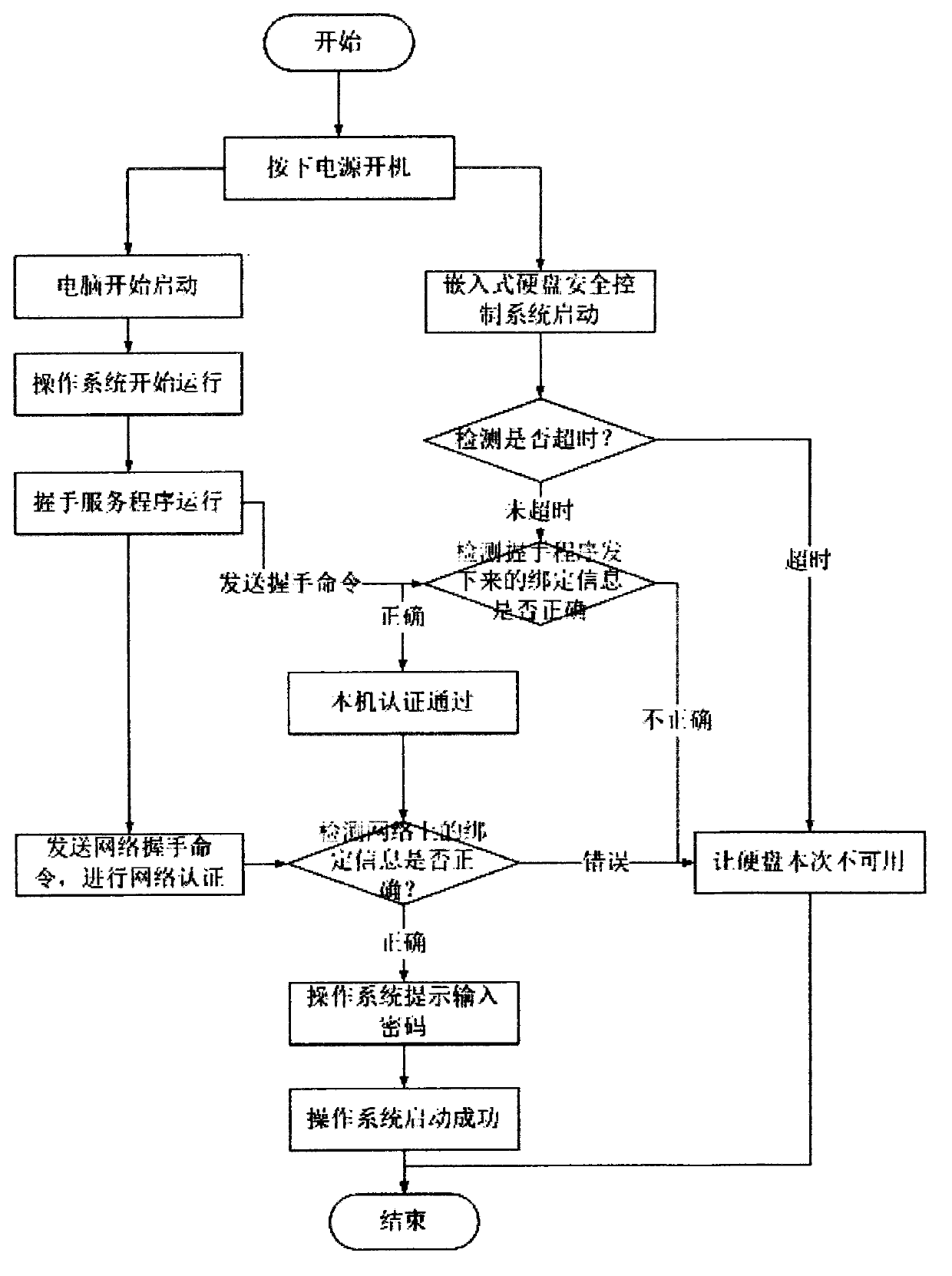
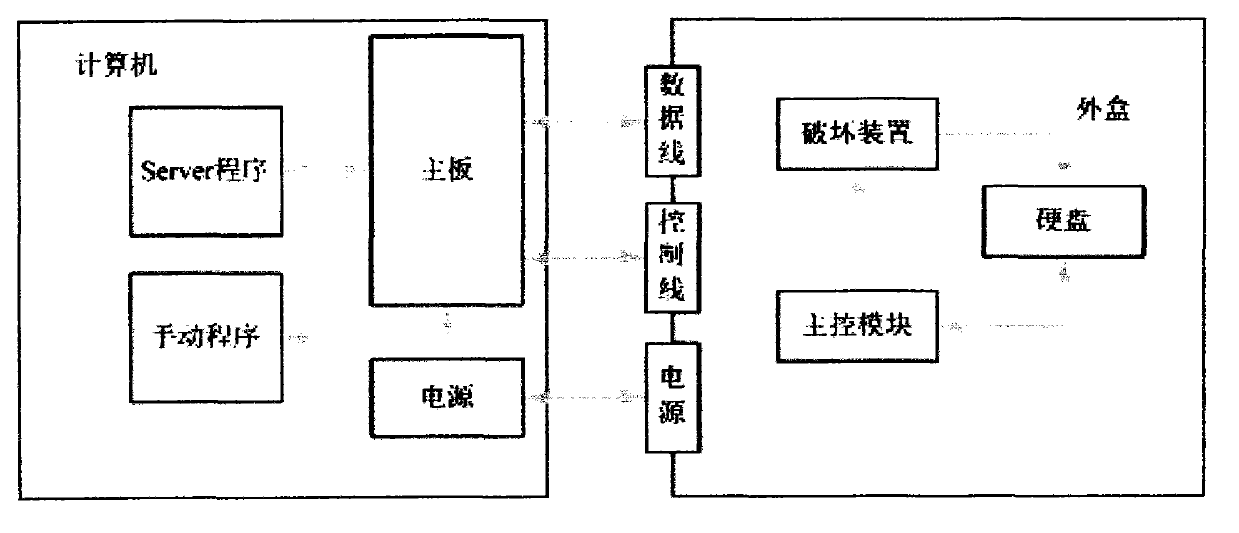
[0072] (1) Bind the hard disk and the computer through a manual program, that is, read the computer feature code, and send it to the embedded main control module through the control line and save it in the embedded memory;
[0073] (2) When the system is started, it is authenticated through the server program or manual program or network, that is, the system feature code is read, sent to the embedded main control module through the control line, and compared with the computer feature code held in the memory , Pass it to make the dedicated hard drive available, and if it fails, it will restrict the dedicated hard drive from being unavailable.
[0074] In the step (2), during the set time, if there is no authentication or the authentication fails, the use of the dedicated hard disk is also restricted. The set time is 5 seconds.
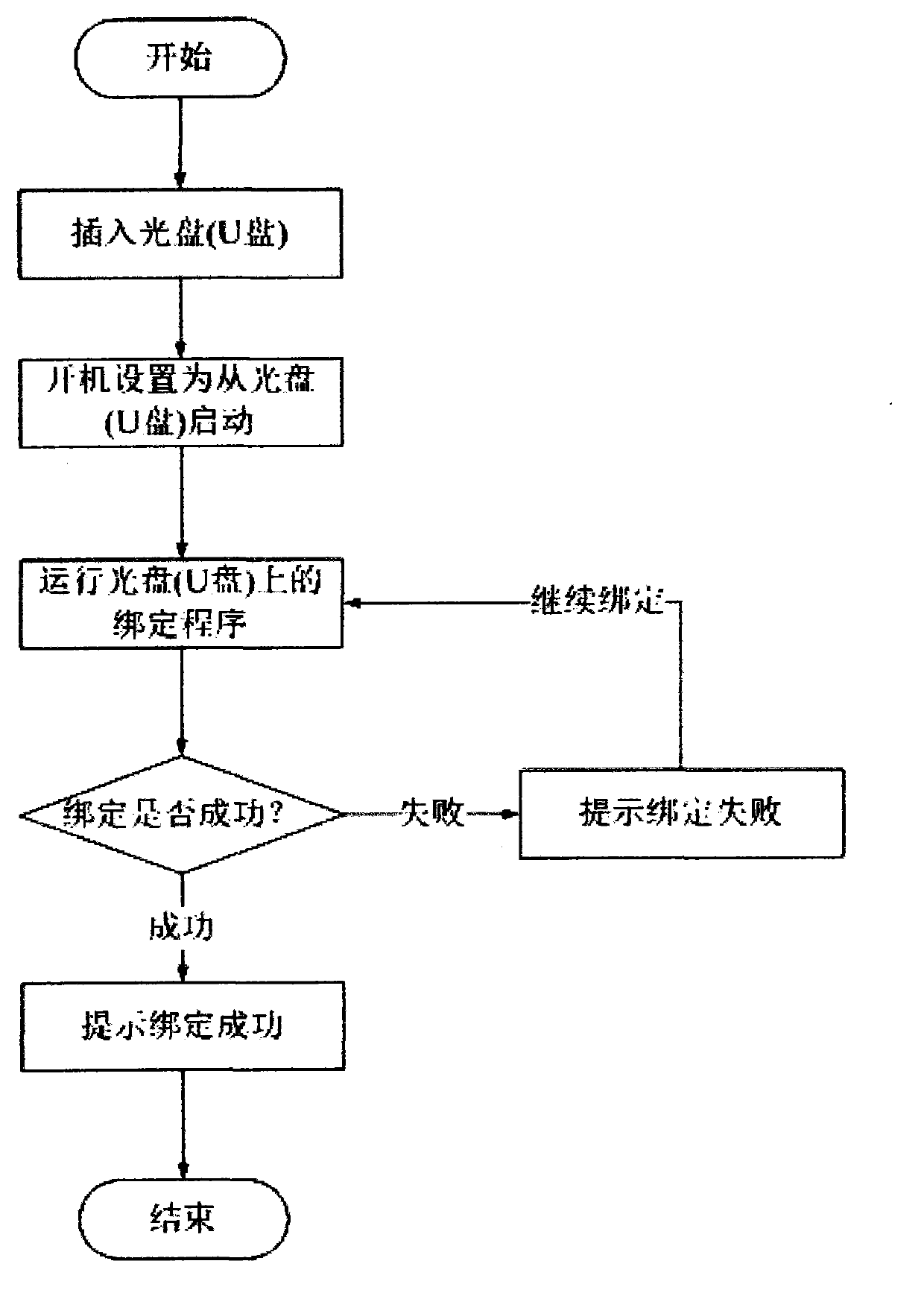
[0075] The described binding...
Embodiment 2
[0078] The method for realizing hard disk theft prevention and data protection in this embodiment includes the following steps:
[0079] (1) Bind the hard disk and the computer through a manual program, that is, read the computer feature code, and send it to the embedded main control module through the control line and save it in the embedded memory;
[0080] (2) When the system is started, it is authenticated through the server program or manual program or network, that is, the system feature code is read, sent to the embedded main control module through the control line, and compared with the computer feature code held in the memory , Pass it to make the dedicated hard drive available, and if it fails, it will restrict the dedicated hard drive from being unavailable.
[0081] In the step (2), during the set time, if there is no authentication or the authentication fails, the use of the dedicated hard disk is also restricted. The set time is 8 seconds.
[0082] The described binding...
Embodiment 3
[0085] The method for realizing hard disk theft prevention and data protection in this embodiment includes the following steps:
[0086] (1) Bind the hard disk and the computer through a manual program, that is, read the computer feature code, and send it to the embedded main control module through the control line and save it in the embedded memory;
[0087] (2) When the system is started, it is authenticated through the server program or manual program or network, that is, the system feature code is read, sent to the embedded main control module through the control line, and compared with the computer feature code held in the memory , Pass it to make the dedicated hard drive available, and if it fails, it will restrict the dedicated hard drive from being unavailable.
[0088] In the step (2), during the set time, if there is no authentication or the authentication fails, the use of the dedicated hard disk is also restricted. The set time is 10 seconds.
[0089] The described bindin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com