Token parameter filling equipment, filling data processing equipment and filling method
A technology for data processing equipment and filling equipment, applied in the field of confidential or secure communication devices and token parameter filling equipment, can solve problems such as no seed key definition, and achieve data security problems, filling data integrity, The effect of improving filling efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
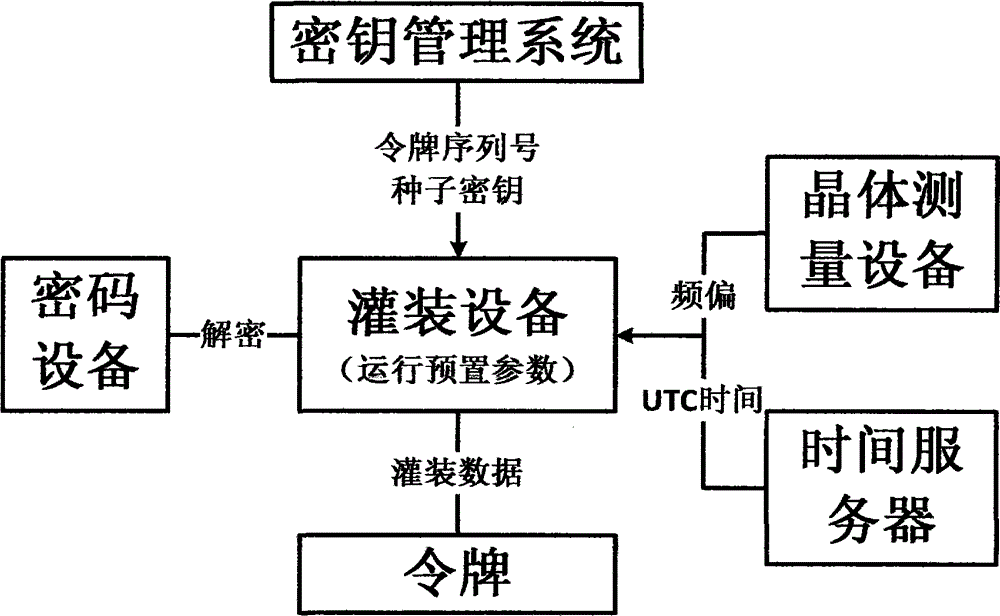
[0063] A token parameter filling equipment, the filling equipment includes:
[0064] The dynamic token uses the seed key to generate a dynamic password based on the current time, challenge code or event counter value. The seed key is used to encrypt or digest the input time, challenge code or event counter, and output 6-8 digits to the display screen after a transformation operation (usually a modular operation) as a dynamic password.
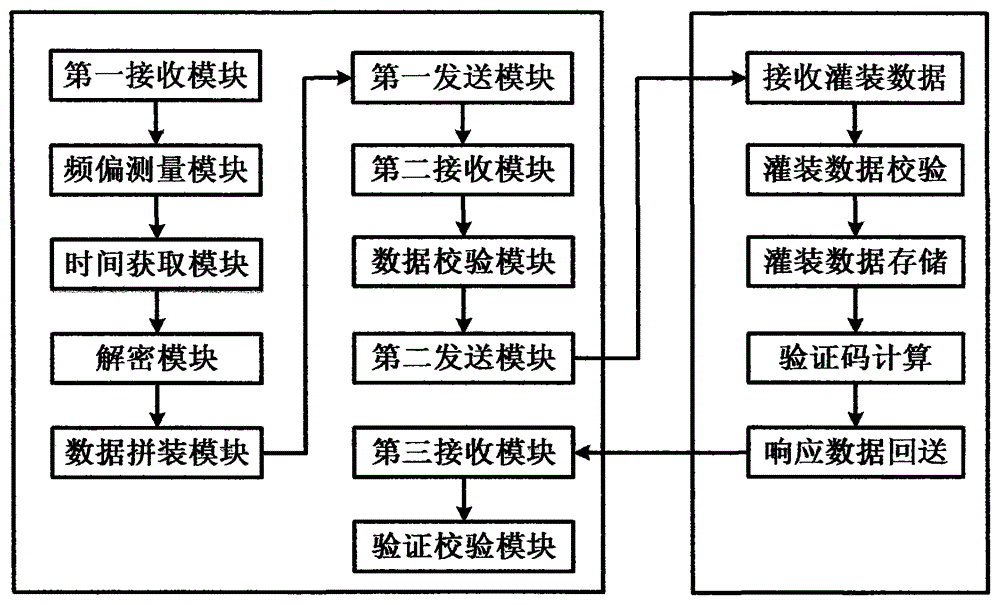
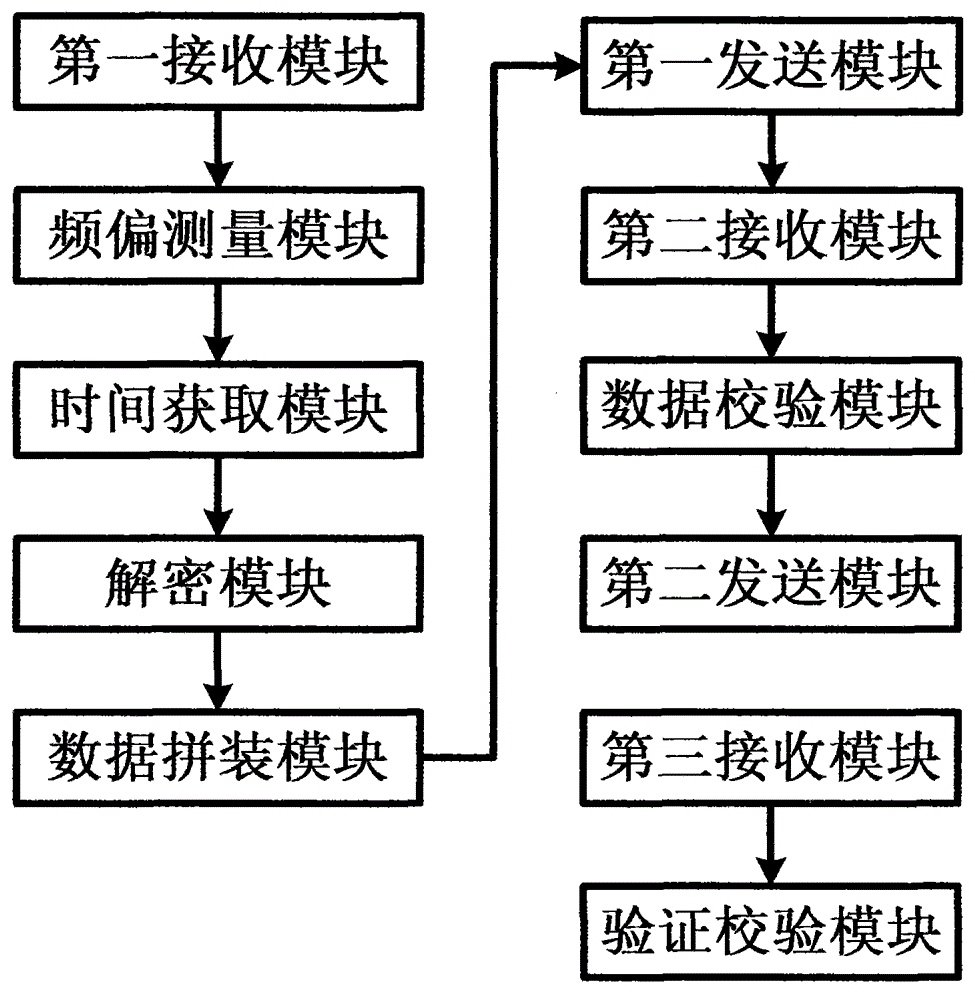
[0065] The first receiving module is used to obtain the token serial number and the encrypted seed key from the key management system, and encrypt them into the filling equipment, where the seed key corresponds to the serial number one to one; the dynamic token and the authentication server software system The fixed factors shared between the keys include the key KEY and the variable IV, and the variable IV is used to transform the key KEY or input variable factors. The fixed factor (KEY, IV) is called the dynamic token and the seed key of the auth...
Embodiment 2
[0081] Embodiment 2: A token filling data processing equipment, the token filling data processing equipment includes:
[0082] The receiving filling data module is used to obtain binary-coded filling data from the data line according to the clock line signal provided by the filling equipment and the filling frequency of the filling equipment. The data header and data tail are used for data synchronization;
[0083] Filling data verification module, used to confirm the integrity of the issued filling data after receiving the filling data;
[0084] The filling data storage module is used to store the seed key, UTC time, token product frequency offset, and running preset parameters of the token into the token's corresponding key area, audit area and data area for The token is used for dynamic password calculation and operation;
[0085] Verification code calculation module. After the filling is successful, assign the result code to 00, use SM3 algorithm, and calculate the verification co...
Embodiment 3
[0090] A token parameter filling method, the method includes the following steps:
[0091] Obtain the token serial number and encryption seed key from the key management system, the seed key corresponds to the serial number one to one, and the encryption enters the filling device, including encryption algorithms including SM2, SM1, and SM4;
[0092] Real-time measurement obtains three times of token product frequency deviation, calculates the average deviation, and the frequency deviation accuracy is 0.01PPM;
[0093] Run preset parameters. The preset parameters include: seed key length, expiration time, number of failed power-on passwords, number of automatic unlocking, and algorithm selection; it has been successfully preset according to user needs before production. It can be performed according to user needs. Parameter expansion;
[0094] Obtain the current UTC time; in this embodiment, the preferred method is to obtain the current UTC time through GPS or a time server.
[0095] De...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com