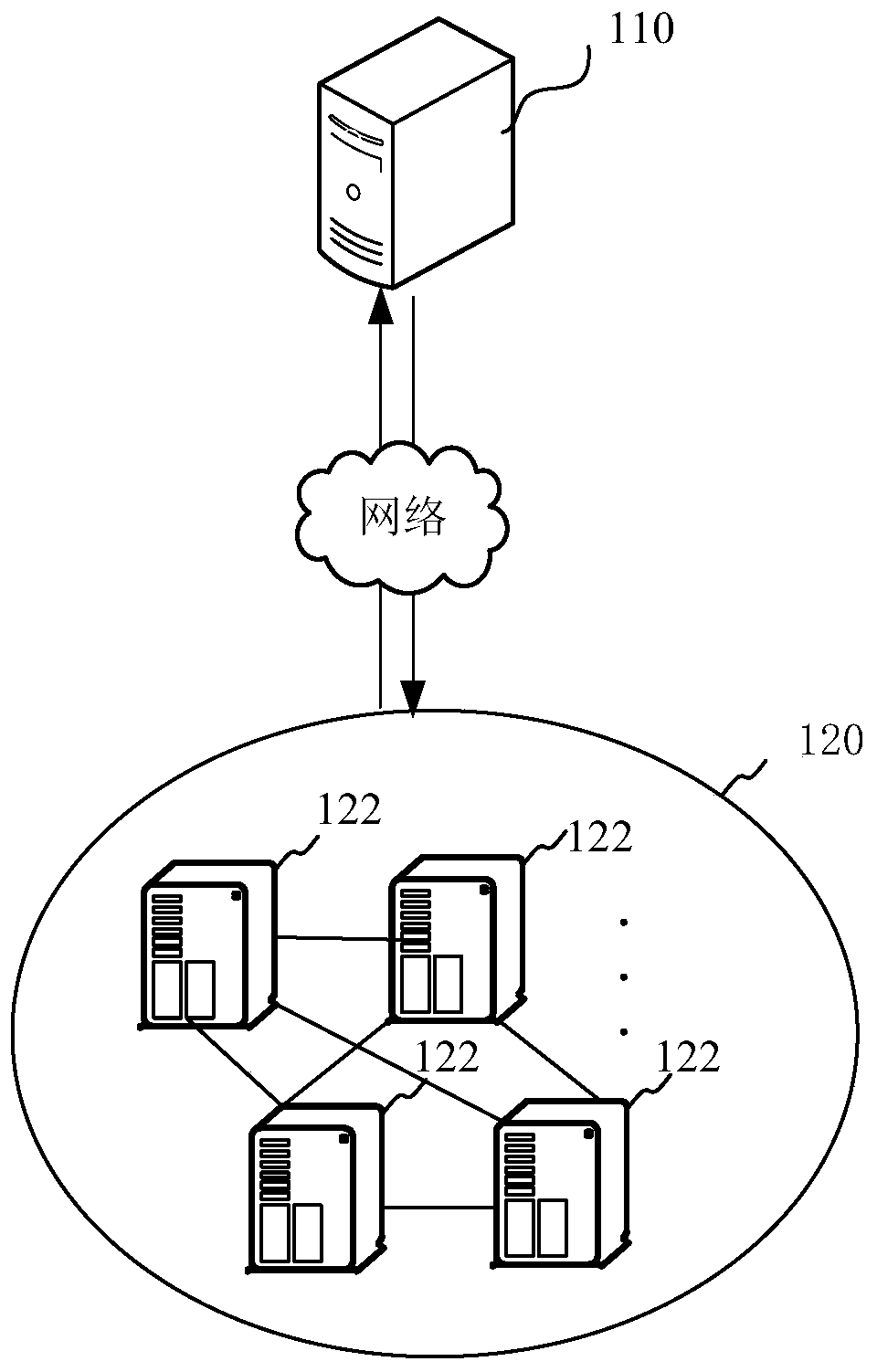
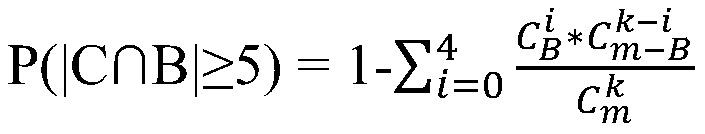Patents
Literature
48results about How to "Avoid evil" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
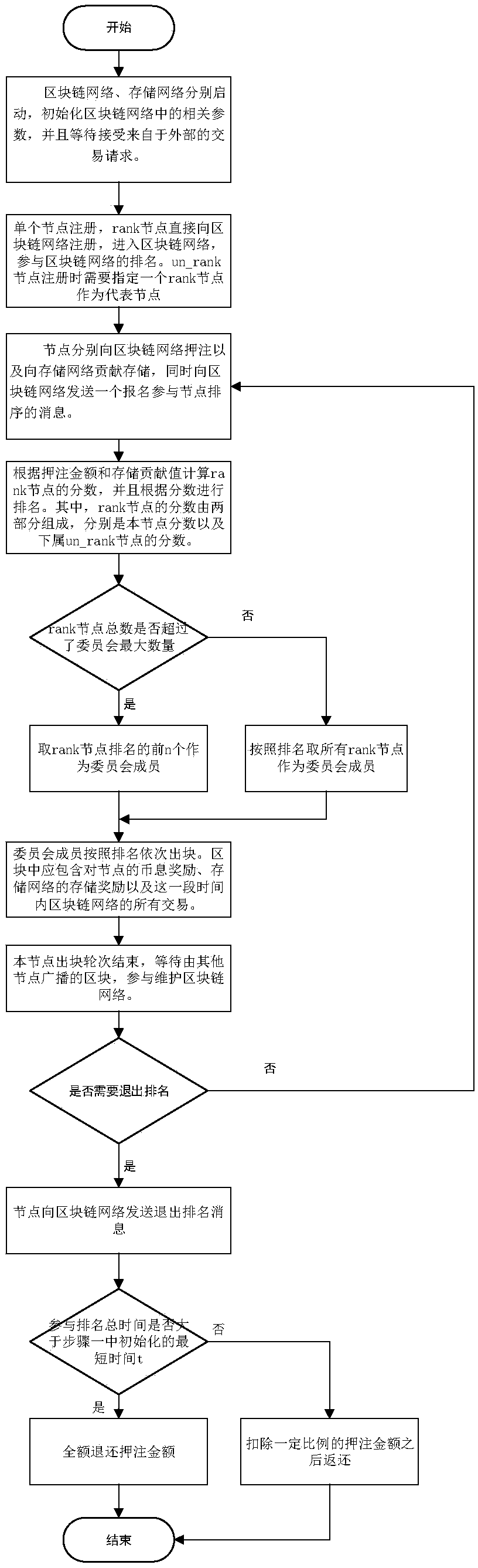
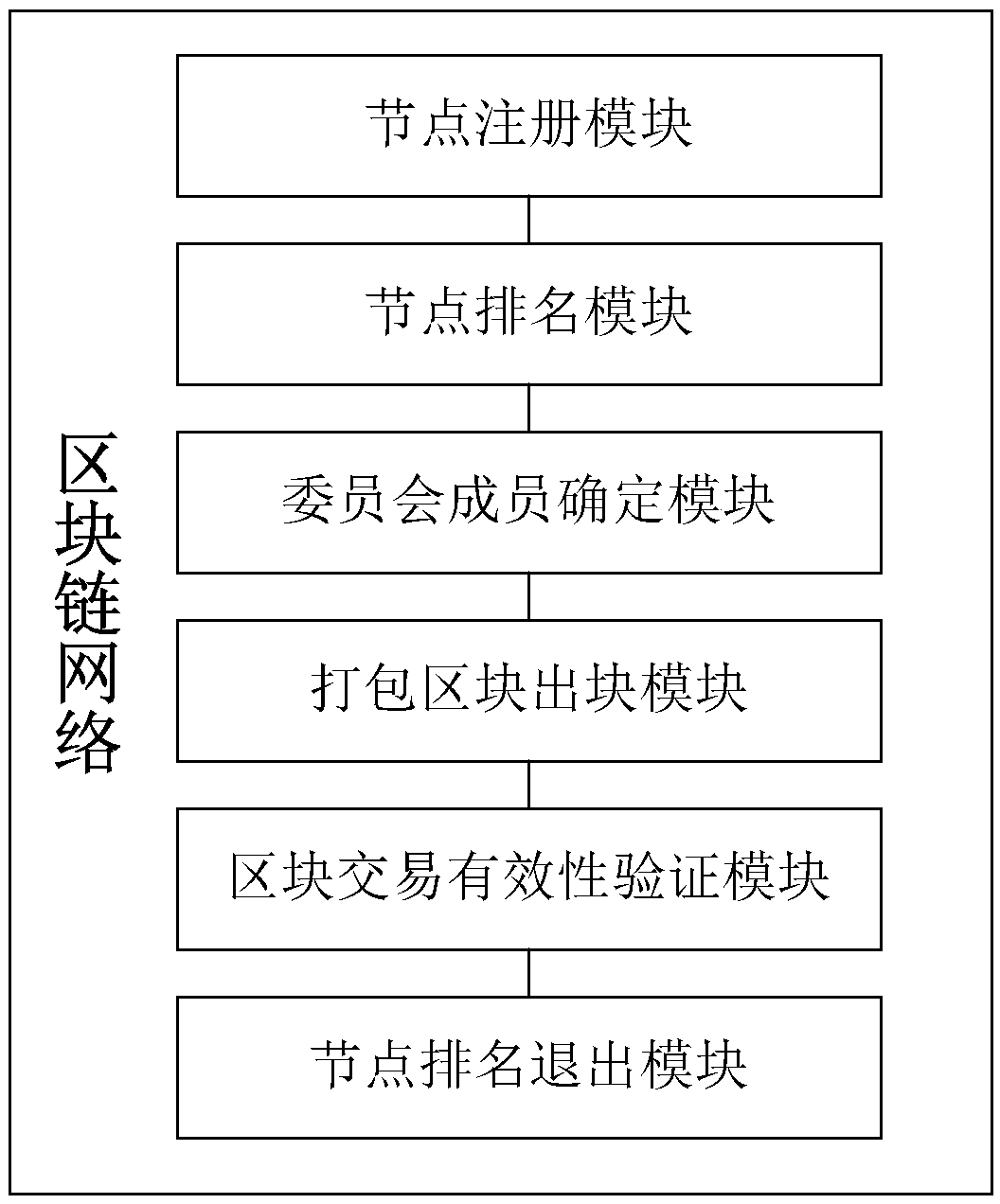
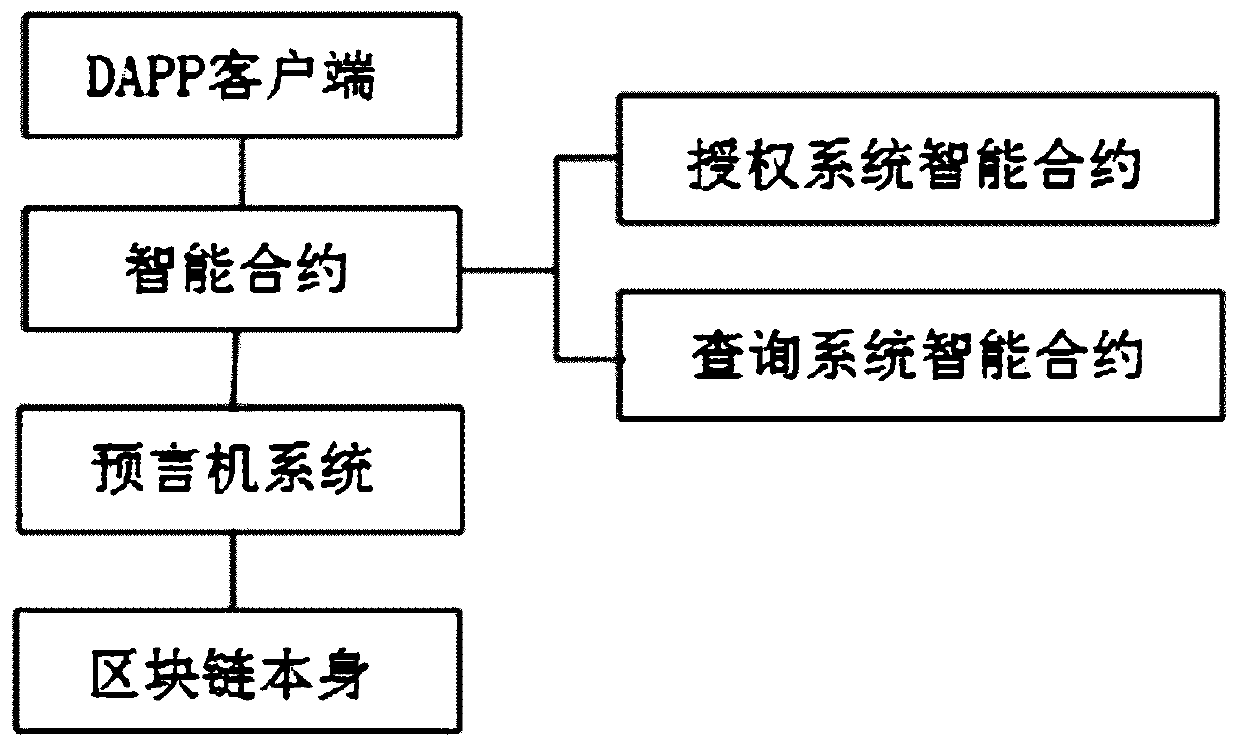
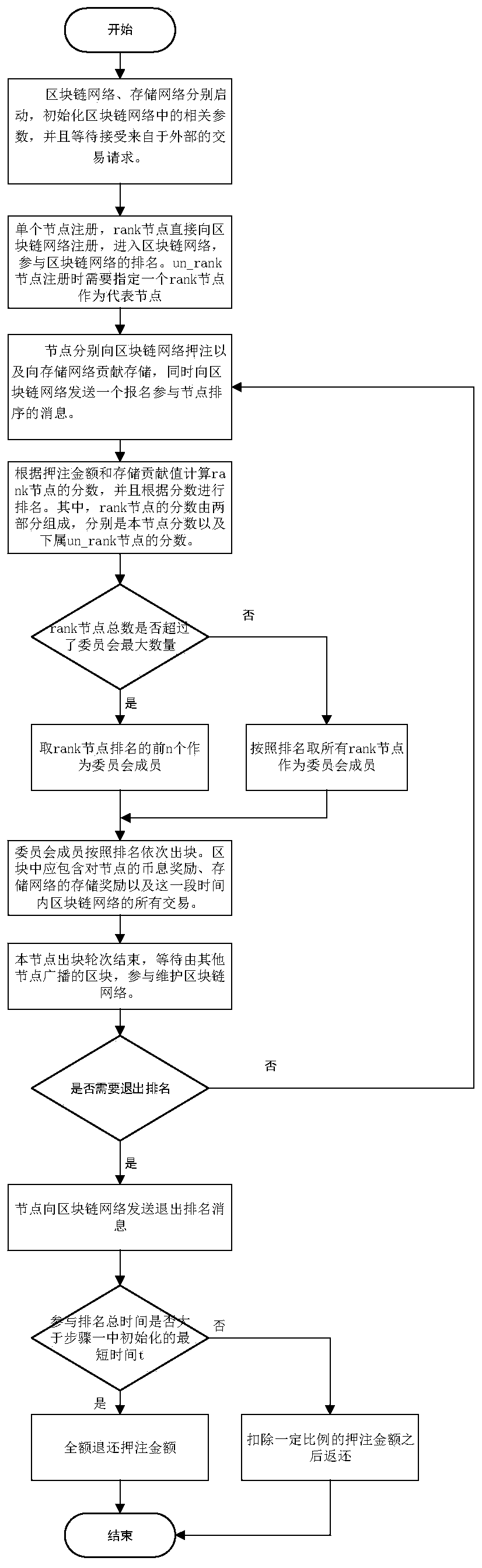
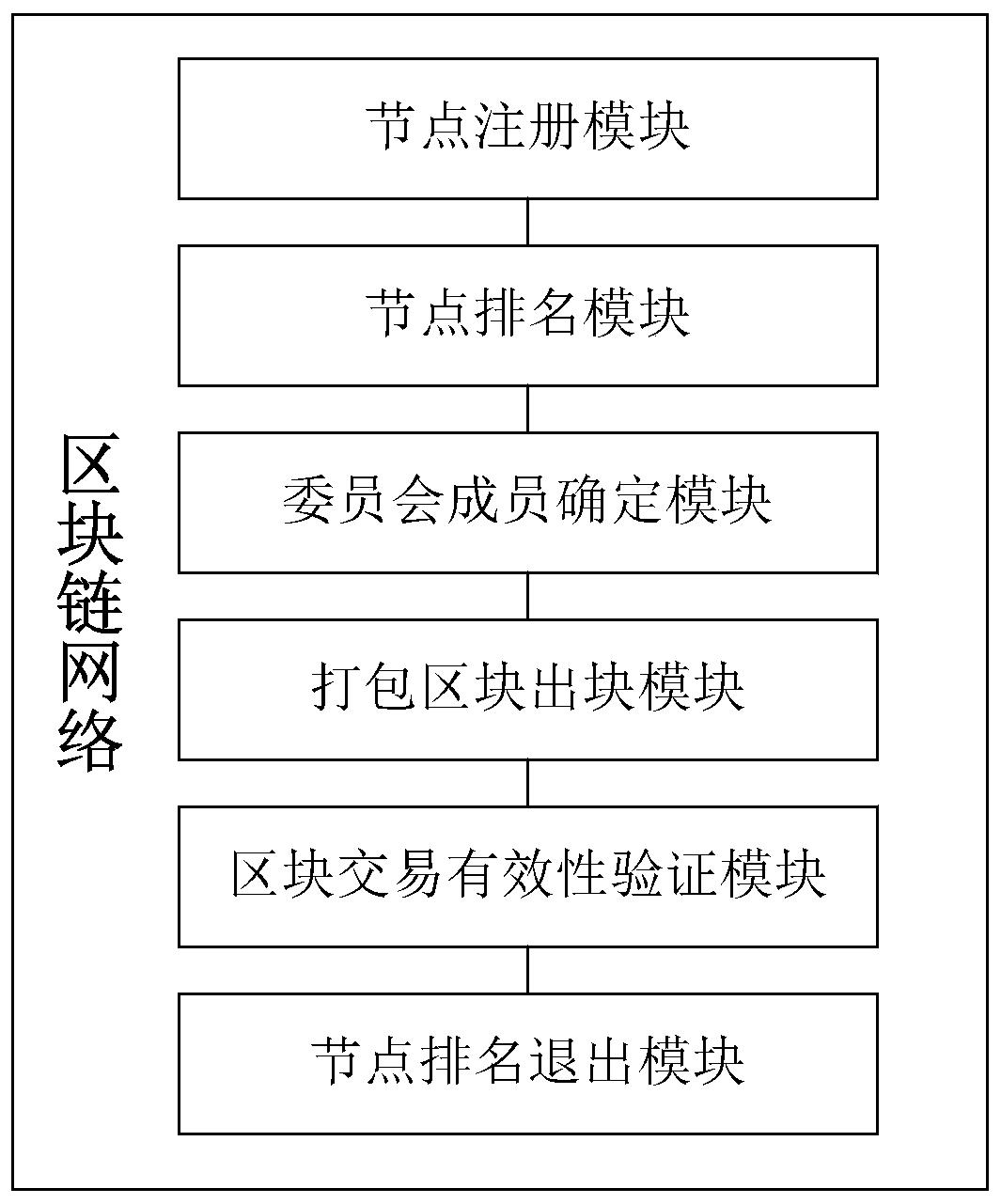
Storage-based block chain excitation method, block chain network and storage network
ActiveCN109325746ASolve the problem that malicious nodes cannot be effectively reducedAvoid evilFinancePayment protocolsSystem maintenanceRanking
The invention discloses a storage-based block chain excitation method, a block chain network and a storage network. The method of the invention comprises the following steps that a ranking algorithm of the block chain nodes is proposed. The total contribution value is calculated by the storage contribution and the betting amount of the block chain nodes, and the contribution of the nodes to the whole system in the storage contribution and the betting is effectively evaluated. In this paper, a method of ranking un_rank nodes is proposed, in which the nodes of the whole network participate in the ranking as much as possible, and the un_rank nodes can also get the block chain reward by storing their contribution. A method of incentive based on storage reward and wager amount is proposed, which effectively motivates the node to maintain the whole block chain system continuously and ensure the safety of the block chain system. The method of the invention is suitable for rewarding nodes according to the storage contribution, can effectively evaluate the storage contribution of nodes, motivates all nodes to participate in the system maintenance of the block chain, and rewards the nodes based on the storage contribution.
Owner:HUAZHONG UNIV OF SCI & TECH +1
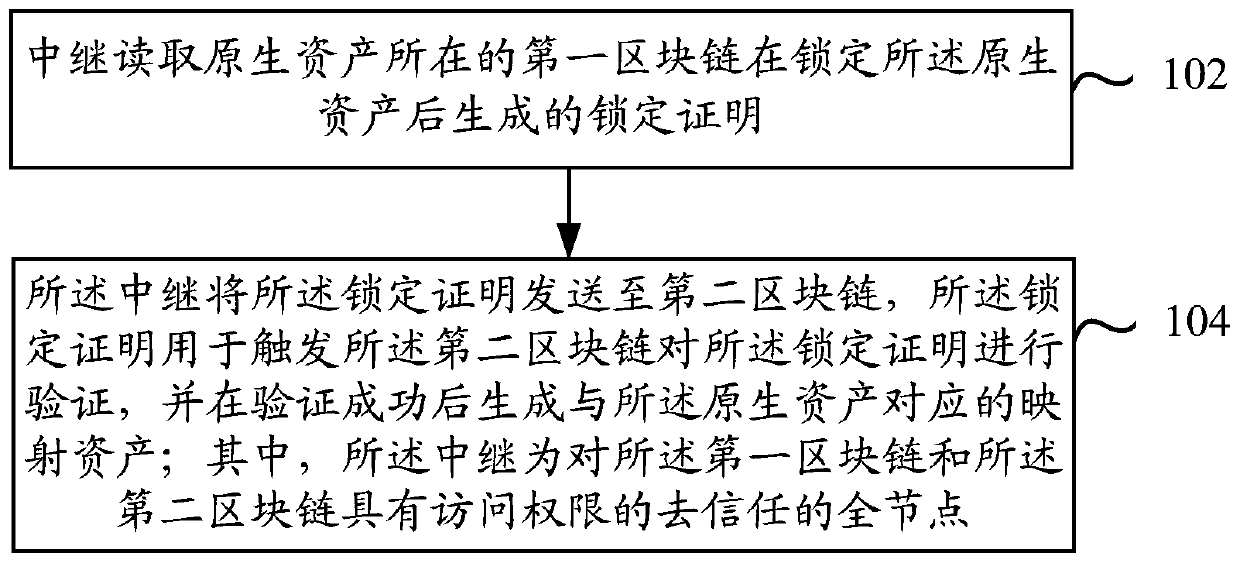
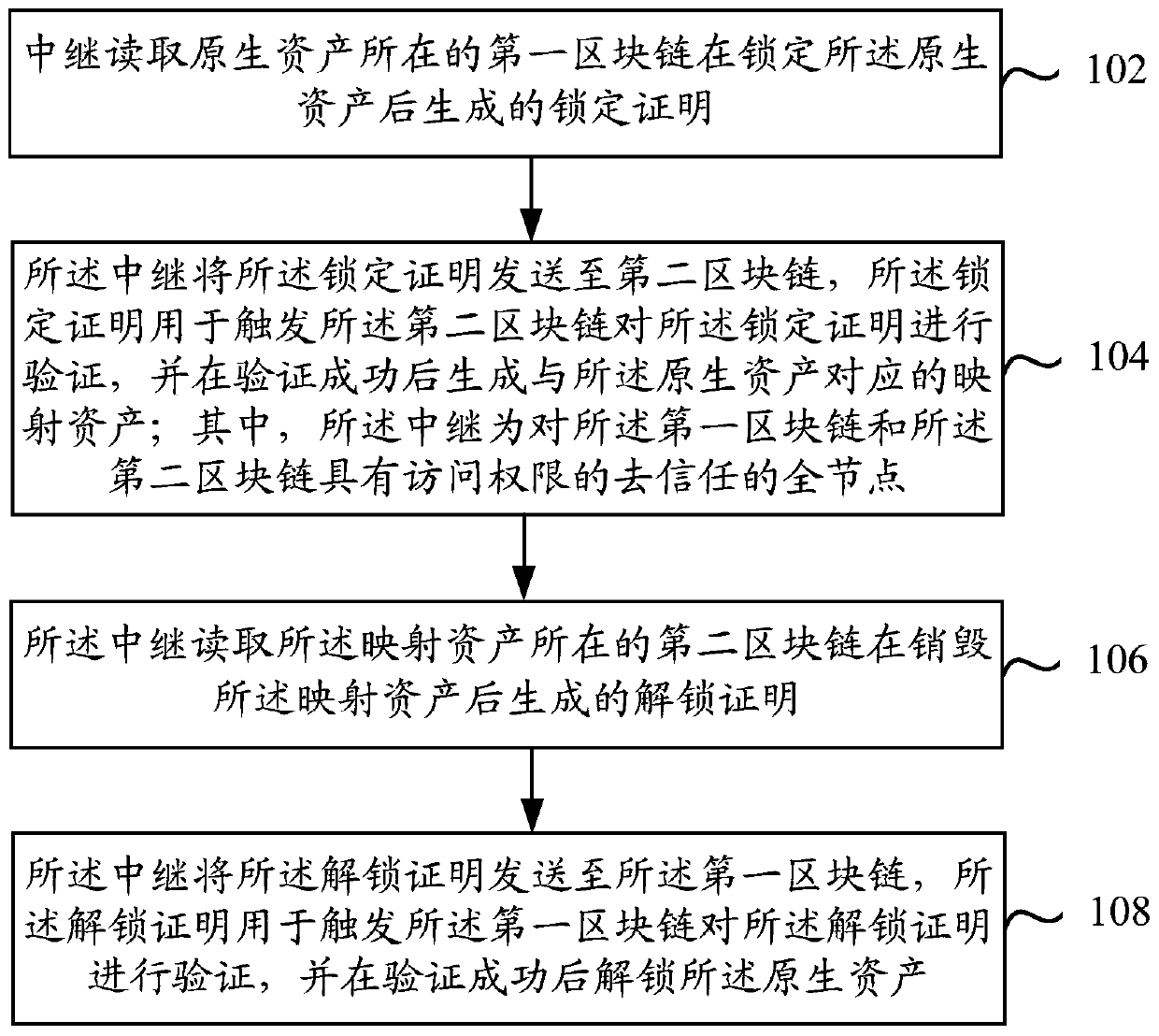
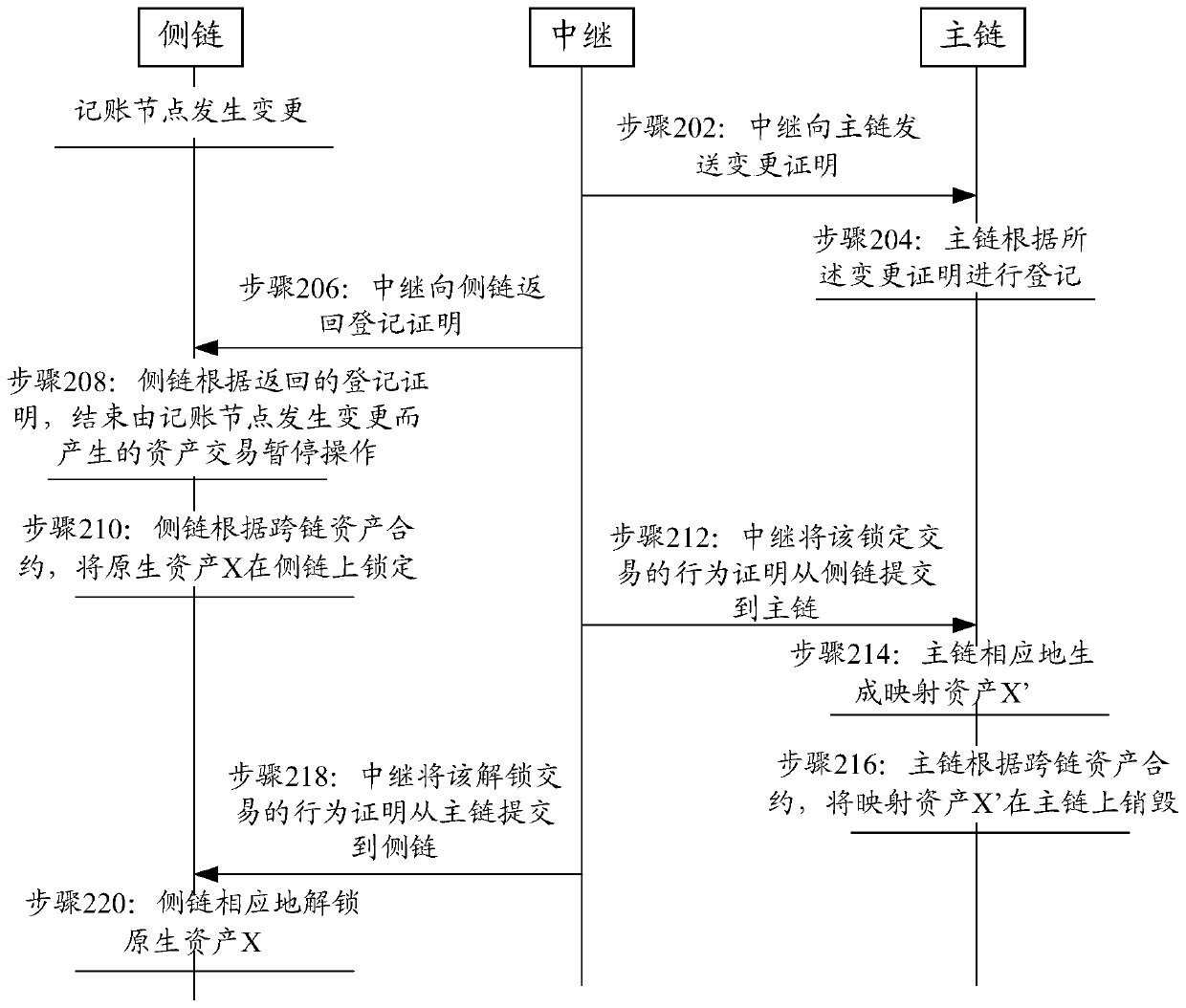
Block chain cross-chain method, device and system and electronic device
InactiveCN110245517AEnsure safetyAvoid evilFinanceDatabase distribution/replicationChain systemBlockchain
Owner:杭州秘猿科技有限公司
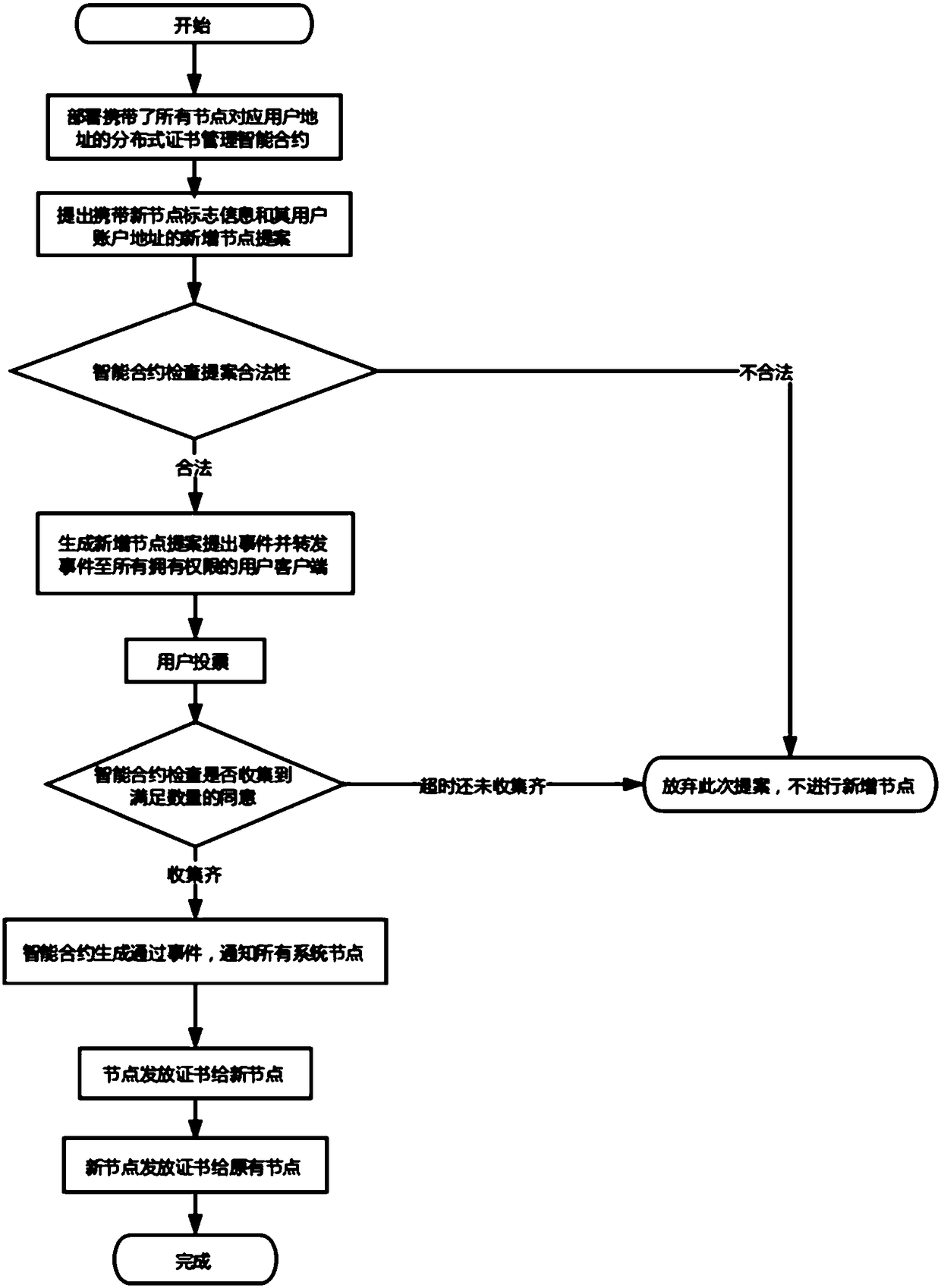
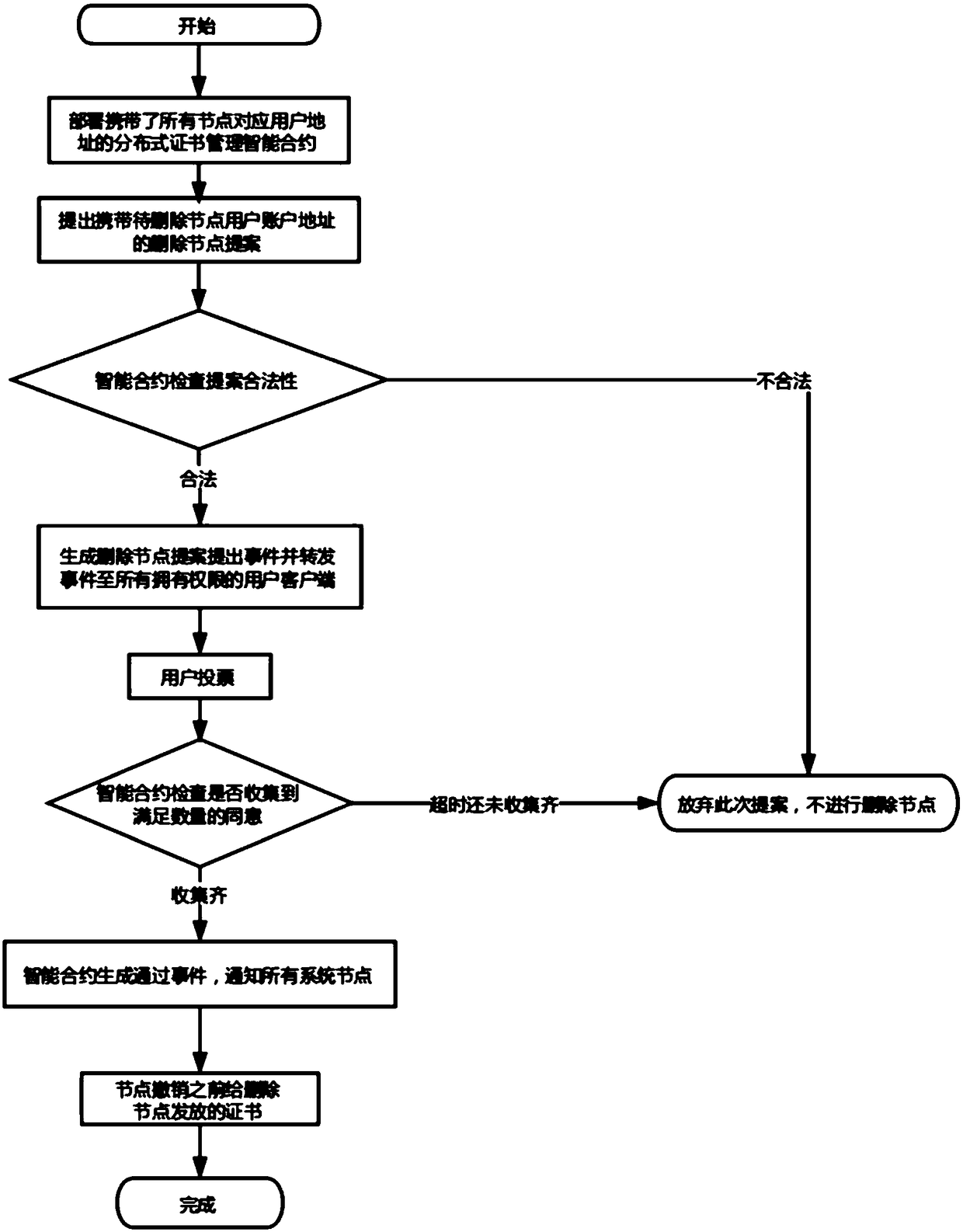
A block chain distributed certificate management method based on intelligent contract
ActiveCN109067553AImprove the authority mechanismAvoid evilUser identity/authority verificationTrusted clientClient-side
The invention discloses a block chain distributed certificate management method based on intelligent contract. In the system start-up stage, each system node corresponds to a user with system authority, and all users provide their own addresses to initialize the distributed certificate management intelligent contract. The new node should join the system, or the system should delete a node, and putforward the corresponding proposal; after the smart contract checks the validity of the proposal, the proposed event is forwarded to all user clients with system privileges; after receiving the proposal event, the client notifies the user to vote, and the user votes and feeds back to the intelligent contract. When a sufficient number of consents are gathered for a smart contract, the proposal ispassed and applied, and the system issues or revokes the certificate. The invention solves the centralization problem of the traditional certificate system, solves the problem of a single point of failure, and improves the safety.
Owner:HANGZHOU QULIAN TECH CO LTD
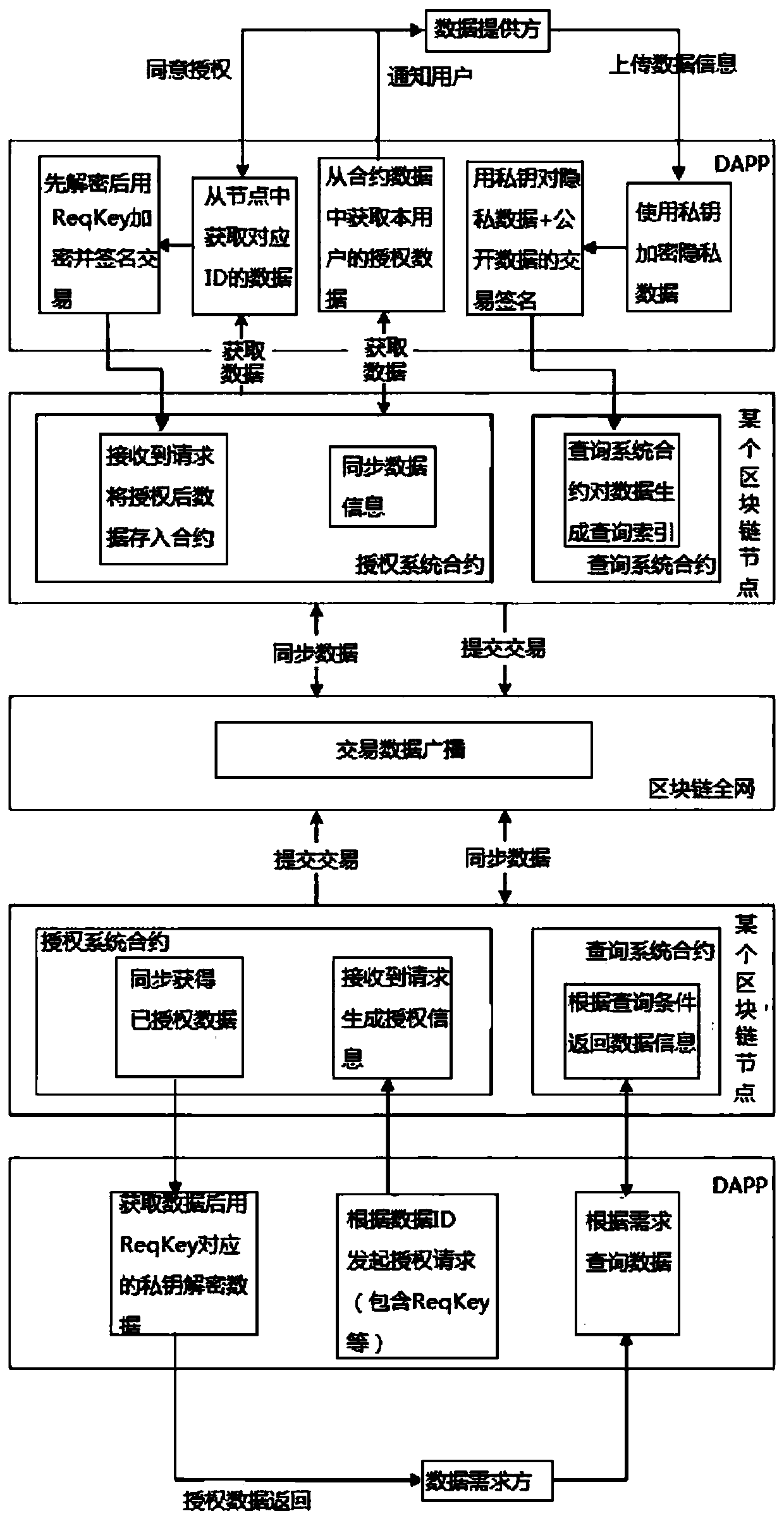
Decentralized private data authorization method and system based on block chain
PendingCN111310225AAvoid evilProblems posed by Avoidor FaultsDigital data protectionAuthorization ModeData provider
The invention relates to the technical field of privacy data authorization, and discloses a decentralized privacy data authorization method and system based on a blockchain, and the method specifically comprises the steps that a data provider selects privacy data needing to be encrypted in data information; encrypting the private data by using a provider private key, and submitting data information to the blockchain node; decrypting the private data by using the provider private key, and encrypting the private data through the demander public key; and the data demander decrypts the private data through the demander private key corresponding to the demander public key to obtain the content of the private data. The problems of large workload, difficult management and centralized rights of acentralized authorization mode and an authorization center are solved; the method solves the technical problems that in the prior art, hierarchical authorization is adopted, a system lacks flexibility, and if a data requester of a certain layer is disgusted, access permission of the data requester is disclosed, and all encrypted data of the layer can be leaked.
Owner:北京众信易保科技有限公司
Fish feed additive
InactiveCN106387509AAvoid evilAvoid fearFood processingClimate change adaptationDisease occurrenceCyprinus
The present invention discloses a fish feed additive. The fish feed additive comprises the following components inparts by weight: 10-15 parts of semen lablab album, 3-15 parts of dried tangerine peels, 3-12 parts of fruits of russianolive, 6-15 parts of flos celosiae cristatae, 5-10 parts of radix aconiti carmichaeli, 6-15 parts of radix codonopsis, 6-15 parts of rhizoma atractylodis macrocephalae, 5-12 parts of dried gingers and 9-18 parts of prepared radix licorice. The fish feed additive can enhance the body constitution of cyprinus carpio, reduce the disease occurrence, improve the disease resistance of the fish schools on the whole, reduce the occurrence of climate stress responses, significantly reduce the incidence of diseases such as enteritis, saprolegniasis, bleeding diseases, spring viraemia, etc. of the cyprinus carpio, and ensure the breeding efficiency.
Owner:GUANGZHOU NUTRIERA BIOTECH CO LTD +1
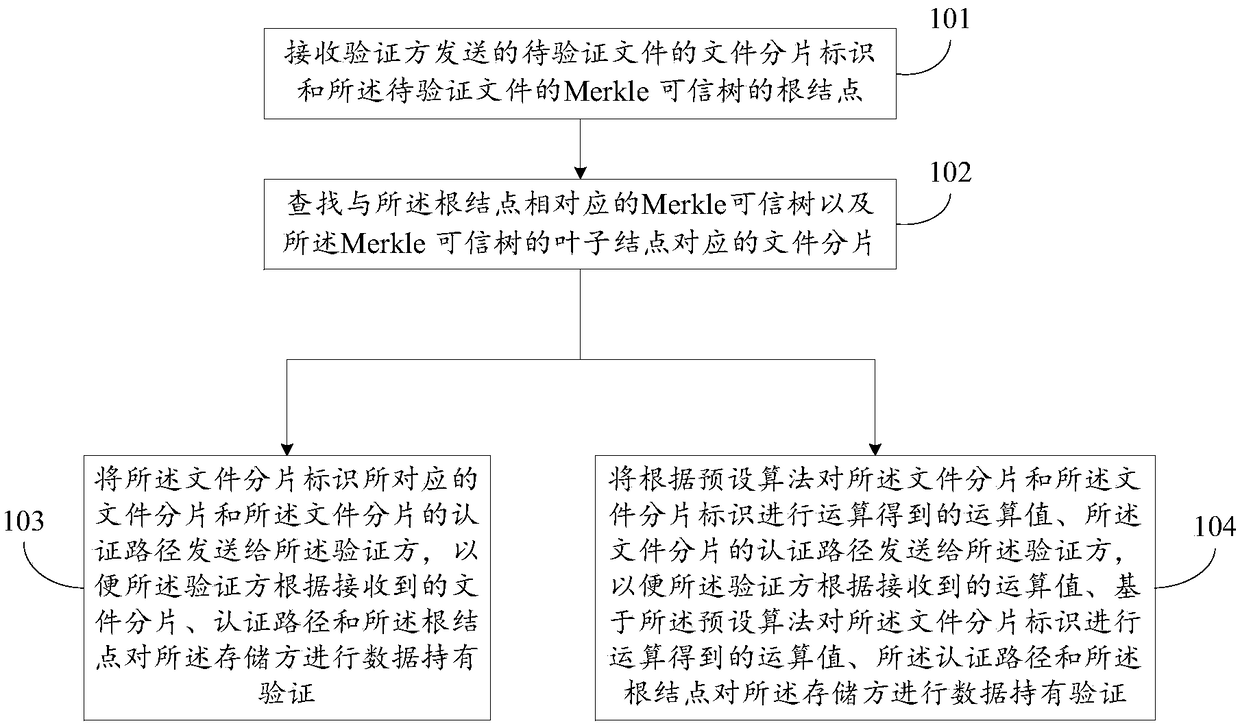
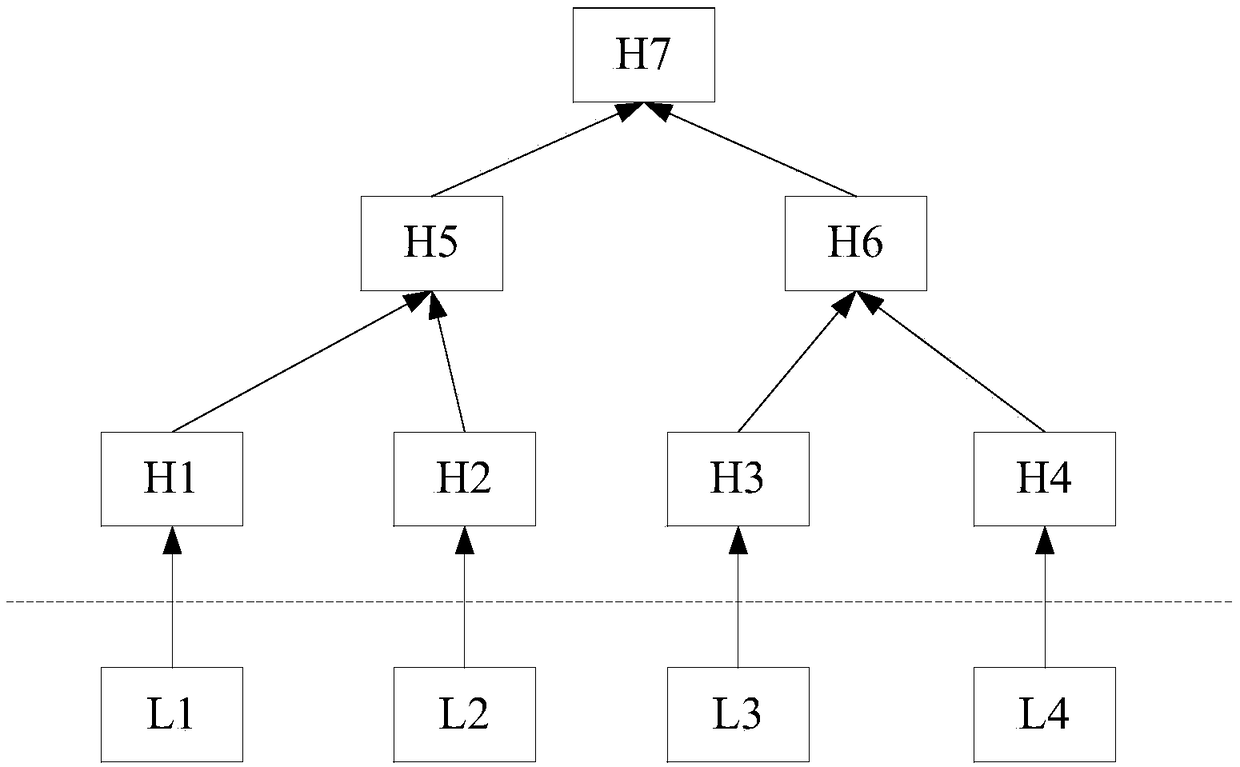
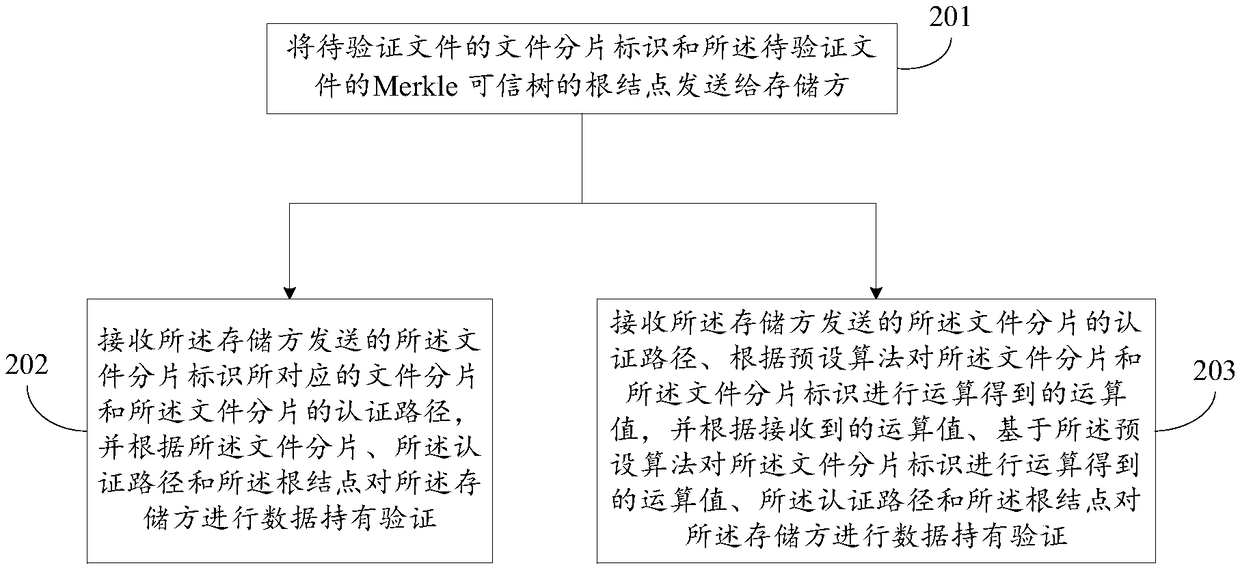
Data holding proving method, device and system
InactiveCN108629040AAvoid evilAvoid damageInternal/peripheral component protectionSpecial data processing applicationsAuthenticationBlockchain
The invention discloses a data holding proving method, device and system. The problem that there is no data holding proving mechanism for existing personal storage can be solved. The method includes the steps of receiving file segment identifiers of a to-be-verified file and a root node of a Merkle trusted tree; searching for the Merkle trusted tree corresponding to the root node and file segmentscorresponding to leaf nodes of the Merkle trusted tree; sending the file segments corresponding to the file segment identifiers and authentication paths of the file segments to a verification side sothat the verification side can conveniently conduct data holding verification on a storage side according to the file segments, the authentication paths and the root node; or sending operation values, calculated according to a preset algorithm, of the file segments and file segment identifiers and the authentication paths of the file segments to the verification side so that the verification sidecan conduct data holding verification on the storage side according to the operation values, calculated on the basis of the preset algorithm, of the file segments, the operation values, calculated onthe basis of the preset algorithm, of the file segment identifiers, the authentication paths and the root node. The data holding proving method, device and system are mainly applicable to scenes in which data is stored on the basis of a blockchain.
Owner:BEIJING QIHOO TECH CO LTD
Zhikening
InactiveCN105770075AAvoid evilAvoid fearDispersion deliveryAnthropod material medical ingredientsPeriostracumOral medication
The invention discloses an oral traditional Chinese medicine preparation for treating intractable cough. The oral traditional Chinese medicine preparation is characterized by comprising the following traditional Chinese medicine raw materials by weight: 12 g of radix adenophorae, 10 g of platycodon grandiflorum, 10 g of semen armeniacae amarae, 5 g of herba ephedrae, 8 g of periostracum cicada, 12 g of radix scutellariae, 12 g of gnaphalium affine, 10 g of schisandra chinensis, 9 g of herba plantaginis and 8 g of radix glycyrrhizae preparata. The raw medicinal materials selected in the oral traditional Chinese medicine preparation are complementary in medicine effect; mutual inhibition, mutual restraint and mutual detoxication of compatibility among drugs are avoided, so that the drugs are obvious in mutual promotion and mutual assistance effects; the oral traditional Chinese medicine preparation has the effects of dispersing the lung, clearing interior heat, purifying and descending, and relieving cough. The oral traditional Chinese medicine preparation is used for treating the intractable cough after oral administration and is definite in curative effect.
Owner:吴金霞
Multi-party secure computing implementation method based on block chain technology
PendingCN112115204AEnhanced authenticationImprove audit effectDatabase updatingFinanceData securitySmart contract
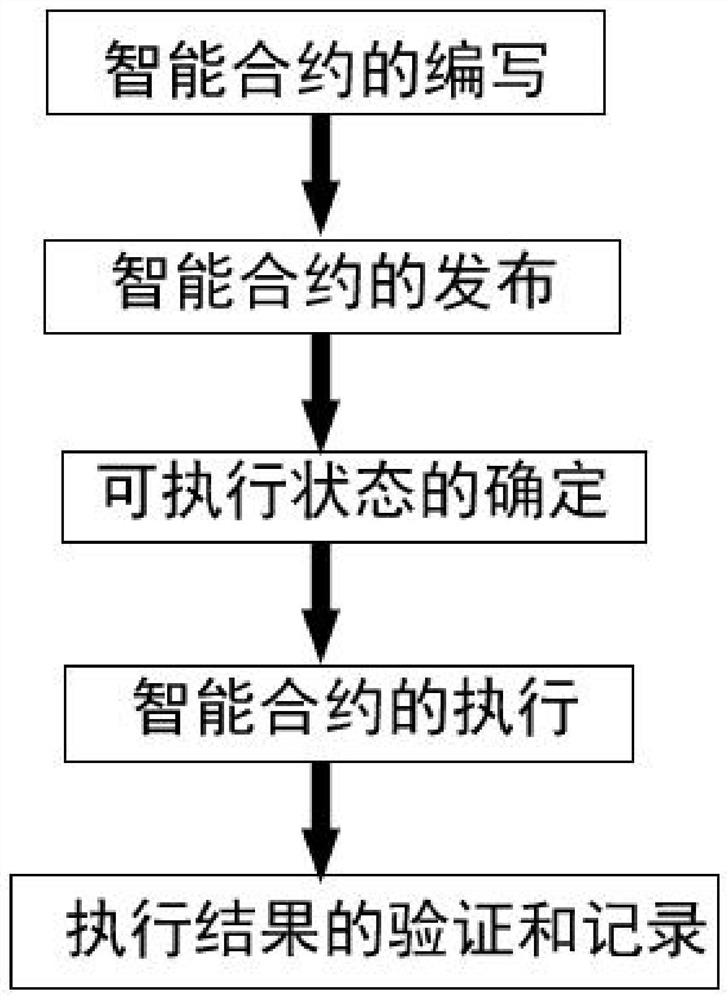
The invention discloses a multi-party security computing implementation method based on a blockchain technology. The method specifically comprises the following steps: step 1, compiling an intelligentcontract, wherein the intelligent contract comprises node information of each contract party, tasks of each contract party for executing the intelligent contract and task execution relationships among the tasks; step 2, publishing the intelligent contract: publishing the intelligent contract on the block chain; 3, determining an executable state: after the intelligent contract is authorized by related nodes of each contract party of the intelligent contract, determining the intelligent contract as the executable state; step 4, executing the intelligent contract, wherein different contract parties have own unique business accounts, log in node servers of nodes through node accounts of the nodes and execute tasks of the intelligent contract on the blockchain; and step 5, carrying out verification and recording of an execution result, wherein the nodes which do not participate in the intelligent contract carry out verification and state recording of the contract execution result. According to the invention, the problems of data security and privacy in the data cooperation process are solved.
Owner:DATANG NETWORK CO LTD
Data encoding method and system supporting data ownership certification and data restoration
ActiveCN111104694AIntegrity guaranteedGuaranteed reliabilityDatabase distribution/replicationDigital data protectionEngineeringData encoding
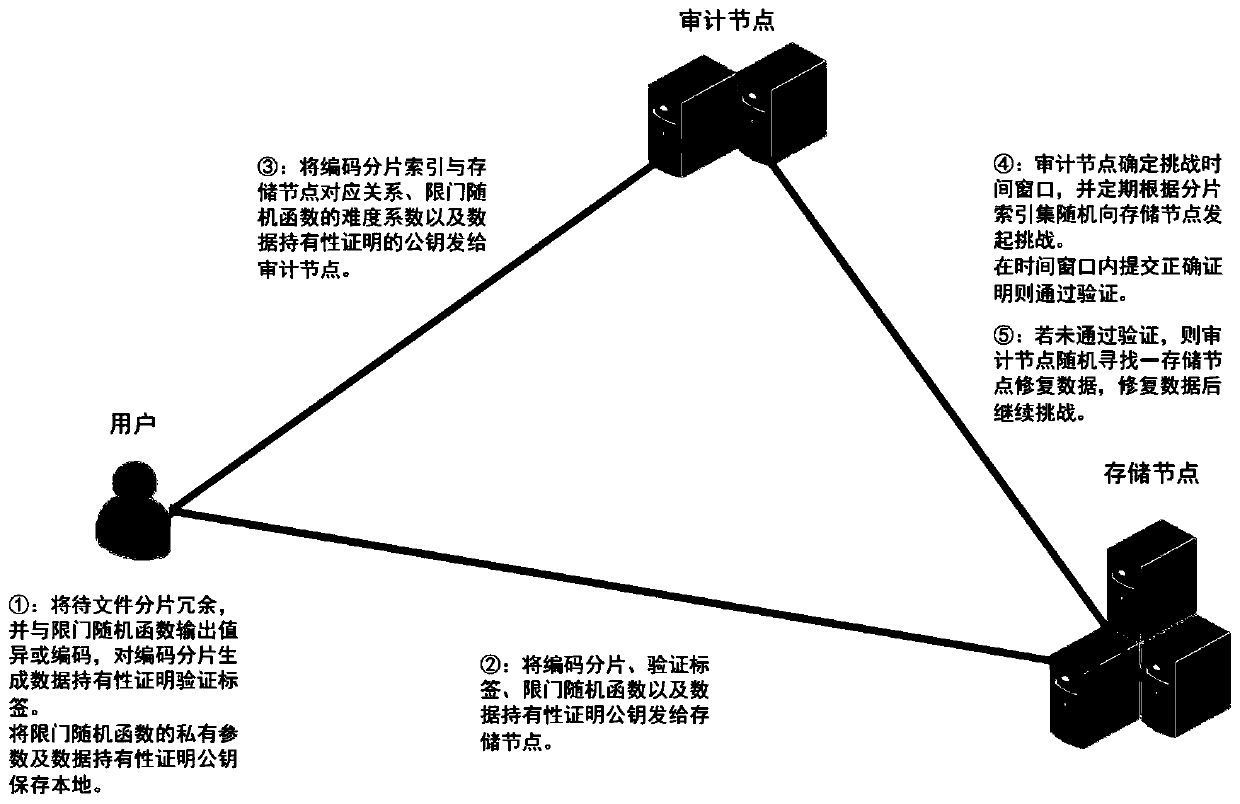
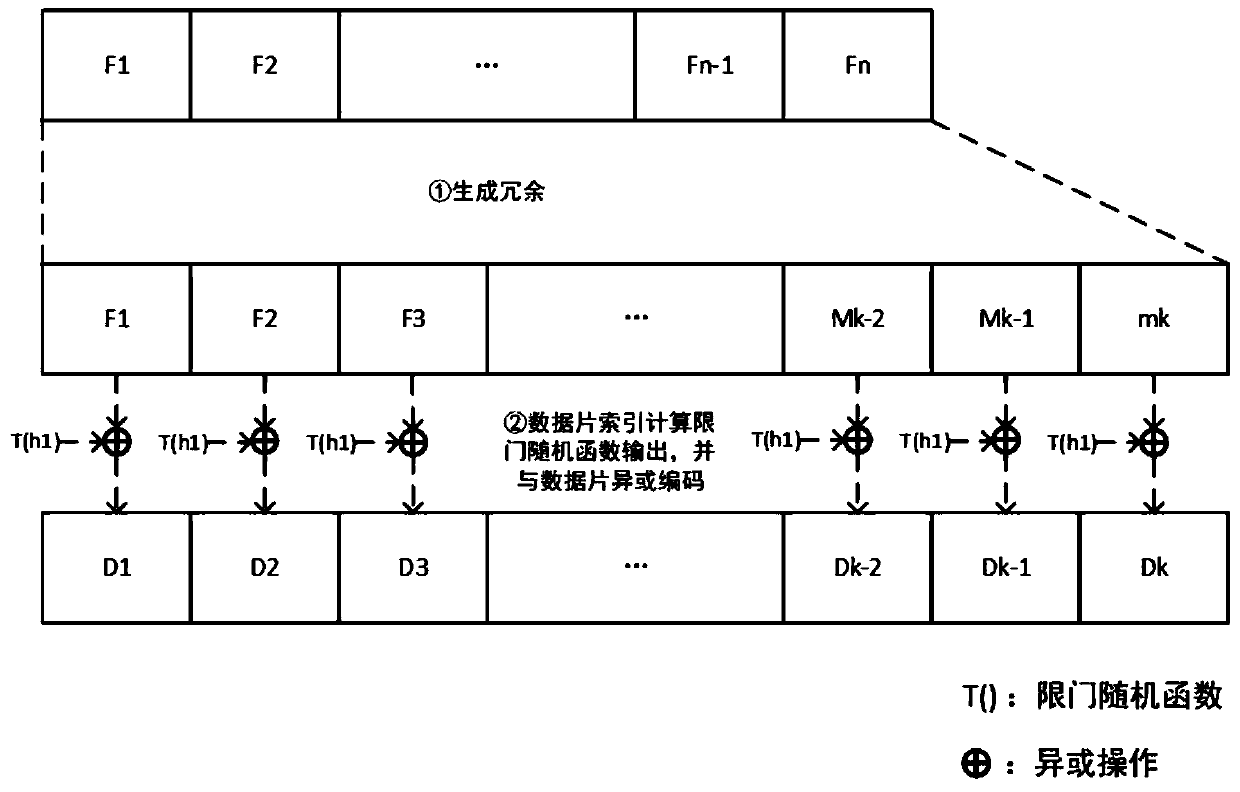
The invention discloses a data encoding method supporting data ownership certification and data restoration and belongs to the field of information security. The method comprises the following steps:after a client fragments a file, a coding fragment and a verification label thereof are generated according to a redundancy strategy R, a trap door random function T and a data ownership proving scheme S, the coding fragment and the verification label are sent to a storage node, and a corresponding relationship is sent between a coding fragment index and the storage node to an auditing node; the private parameters are stored locally at the client, and the public parameters are sent to the storage node and the auditing node; after randomly selecting the challenge node and the challenge set, theauditing node initiates a challenge, so that the challenge node obtains the corresponding coding fragment and the verification label thereof, generates a data ownership certificate according to the Sand returns the data ownership certificate; if the auditing node receives the data ownership proof in the challenge time window and passes the verification, the challenge succeeds; otherwise, challenge failure. According to the invention, the integrity and reliability of the data can be ensured in the distributed storage system.
Owner:HUAZHONG UNIV OF SCI & TECH
Block chain incentive method and system based on shared integrals
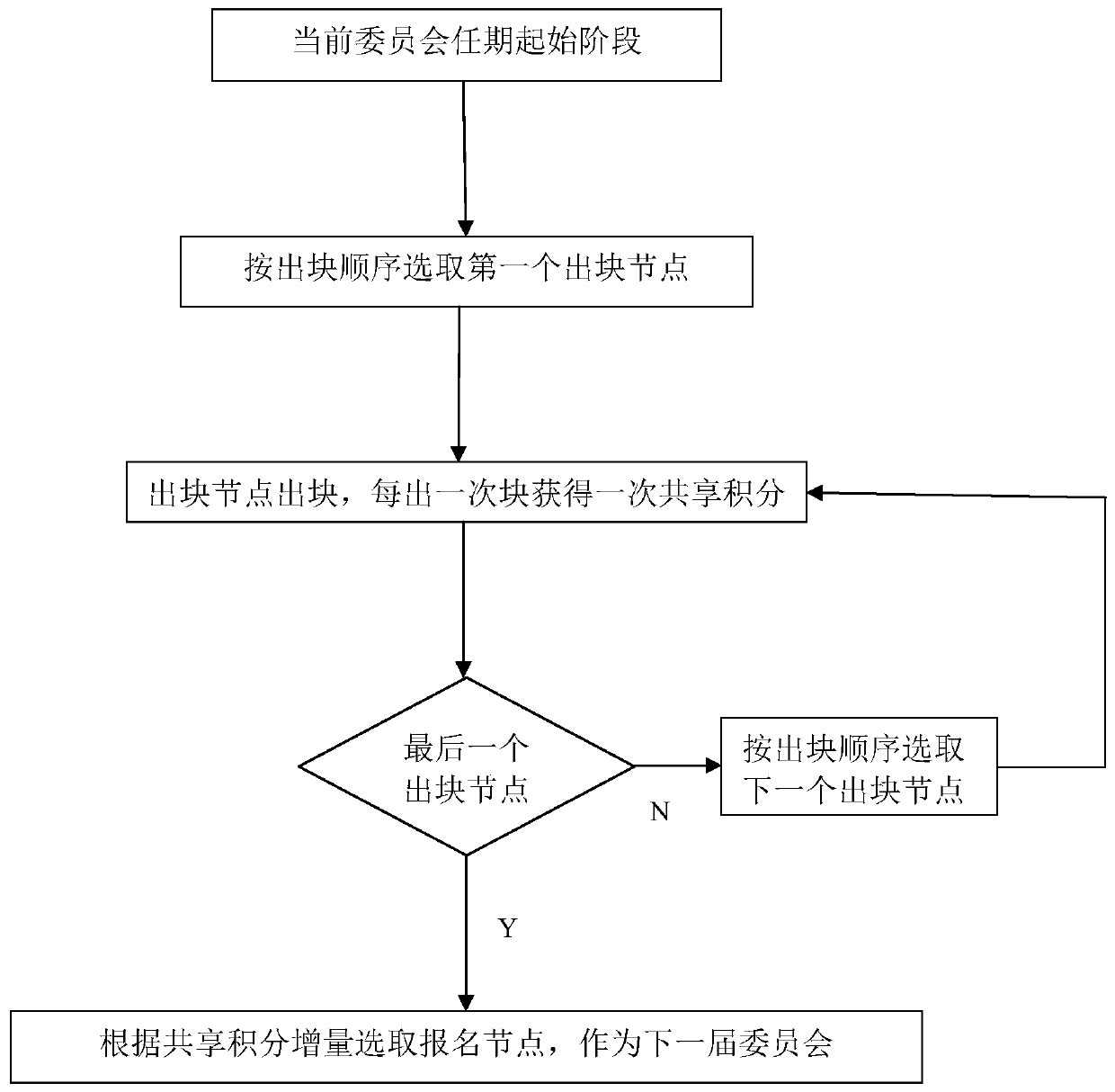
ActiveCN110175867AShared incentivesSolve problems that consume a lot of energyDigital data protectionMarketingChain networkPurchasing
The invention discloses a blockchain incentive method and system based on shared integrals, and belongs to the field of blockchain. The method comprises the steps that within the valid period of the current committee, enabling all block output nodes to output blocks in turn, wherein each block output node obtains a shared score reward every time; when the last outbound node of the current committee finishes outbound, selecting an application node as a next outbound committee according to the shared integral increment; enabling a node in the block chain network to obtain a shared point by selling a shared marketing label or purchasing currency, obtain a shared point reward by becoming a block output node, and use the shared point when purchasing the shared marketing label. According to theinvention, merchants are stimulated to share marketing tags with other merchants to obtain shared points, a certain number of nodes are selected from high to low as committee members according to theincrement of the shared points of the nodes, and the committee members are blocked in turn. According to the increment of the shared score in the current time period of the outblock node, issuing a shared score reward to the outblock node.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Symmetrical searchable encryption method based on PBFT consensus mechanism
ActiveCN112861172AEnsure openness and transparencyGuarantee a fair dealDigital data protectionPlatform integrity maintainanceSource Data VerificationData retrieval
The invention discloses a symmetric searchable encryption method based on a PBFT consensus mechanism, and relates to the technical field of data processing methods. The method comprises the following steps: a preparation stage, a retrieval stage, a consensus stage and an updating stage. According to the method, a block chain technology and a searchable encryption technology are combined, so that the disclosure, transparency and traceability of a data retrieval process can be ensured; a symmetric searchable encryption method including data verification, data updating and node behavior supervision is established through an improved PBFT consensus, so that the transaction fairness between the user and the server can be ensured, the one-to-one correspondence between the user retrieval request and the retrieval result provided by the cloud server is ensured, and the method is real and reliable. And the credibility between the user and the cloud server can be effectively improved.
Owner:SHIJIAZHUANG TIEDAO UNIV
Consensus method of alliance chain based on hierarchical model
ActiveCN113191772AImprove performancePrevent behaviorUser identity/authority verificationProtocol authorisationComputer networkLayered model
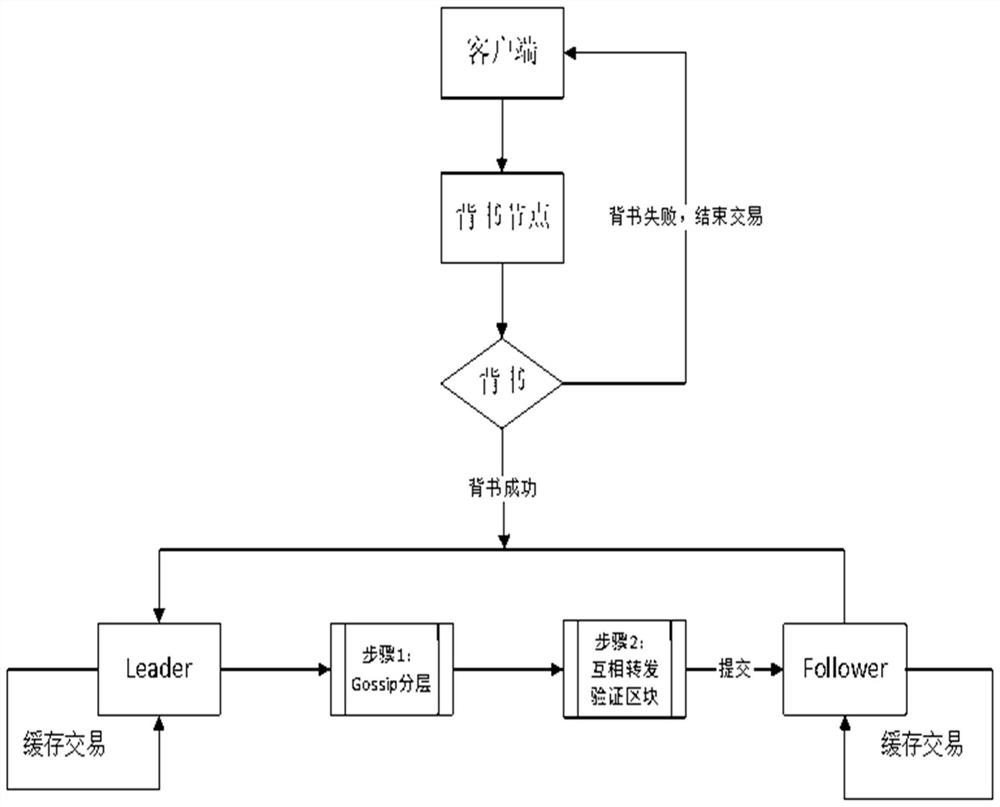
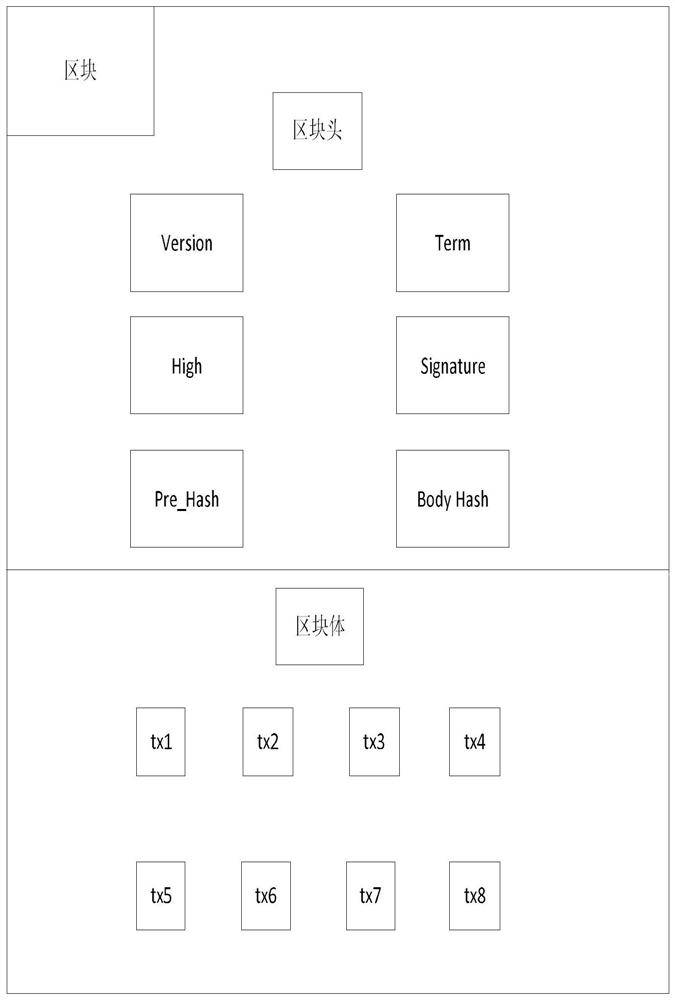
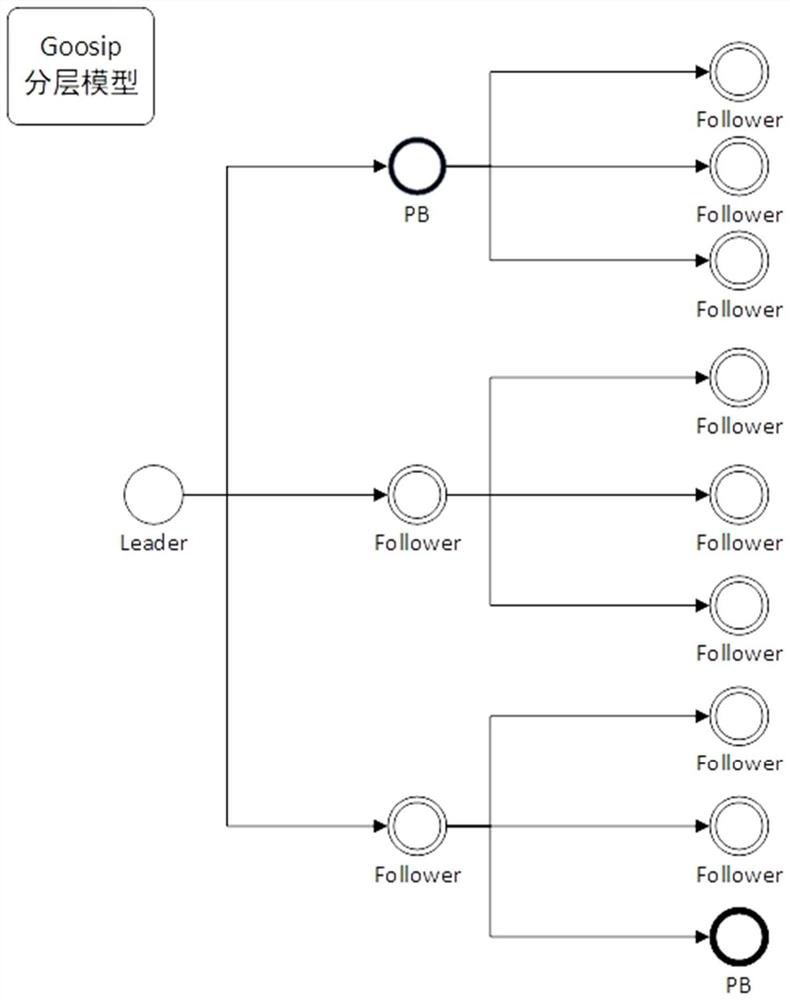
The invention discloses an alliance chain consensus method based on a hierarchical model, and the method comprises the steps: carrying out the dynamic division of nodes in a chain: the nodes are no longer used as common peer nodes or sorting nodes, layering the alliance chain according to a Goosip protocol propagation mode, and selecting proxy nodes, and if the previous node finds that the block sent by the previous layer of node does not accord with the local cache transaction, determining that the previous layer of node has the Byzantine node, and if not, performing block copying on the node of the layer communicating with the PB node of the upper layer of the Byzantine node and then continuing the propagation to the next layer; if it is found that the Leader of the first layer do evil, completing, by the PB of each layer, the preparatory work locally and competing for the Leader; then forwarding the messages passing the verification mutually, and carrying out the next verification after messages passing the verification of most nodes are received; and carrying verification according to local transaction cache, main node signature, previous block hash, block height and read-write set conflict; and completing block submission if the verification is passed. Therefore, the consensus process of the alliance chain is optimized.
Owner:XI AN JIAOTONG UNIV
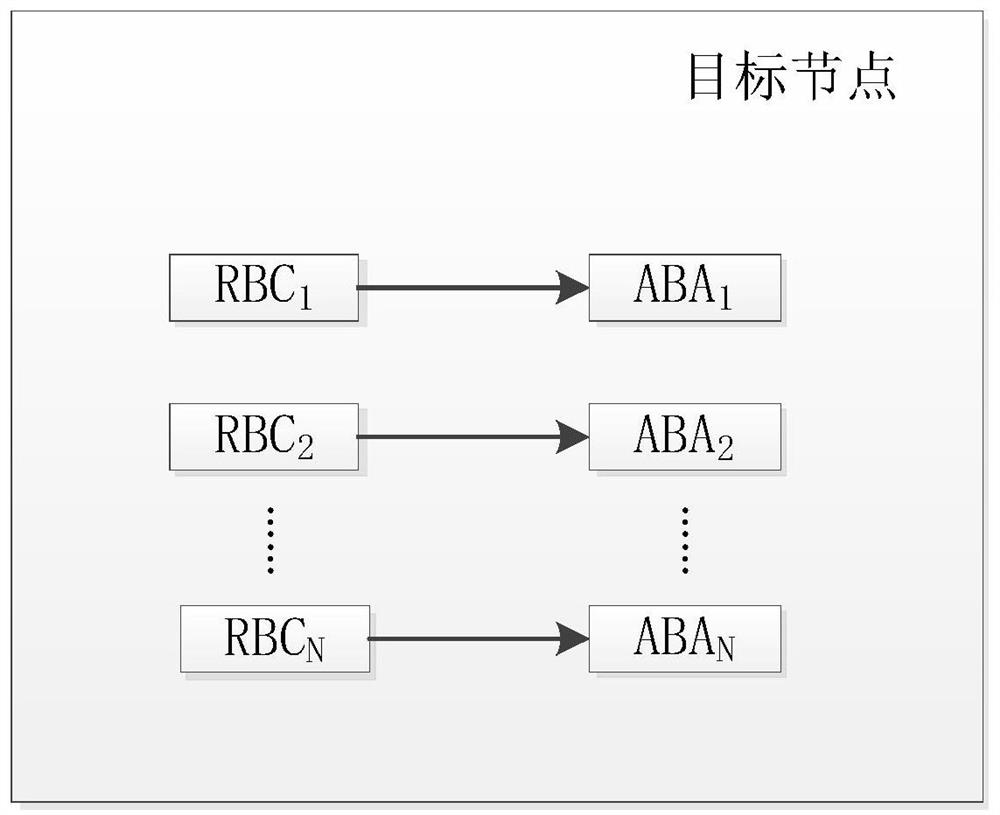
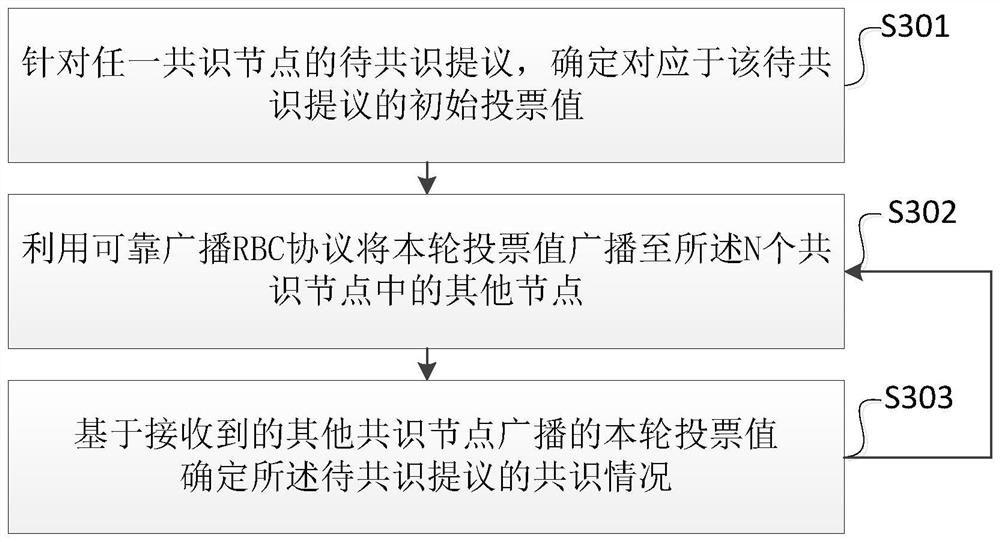
Binary consensus method and device based on reliable broadcast
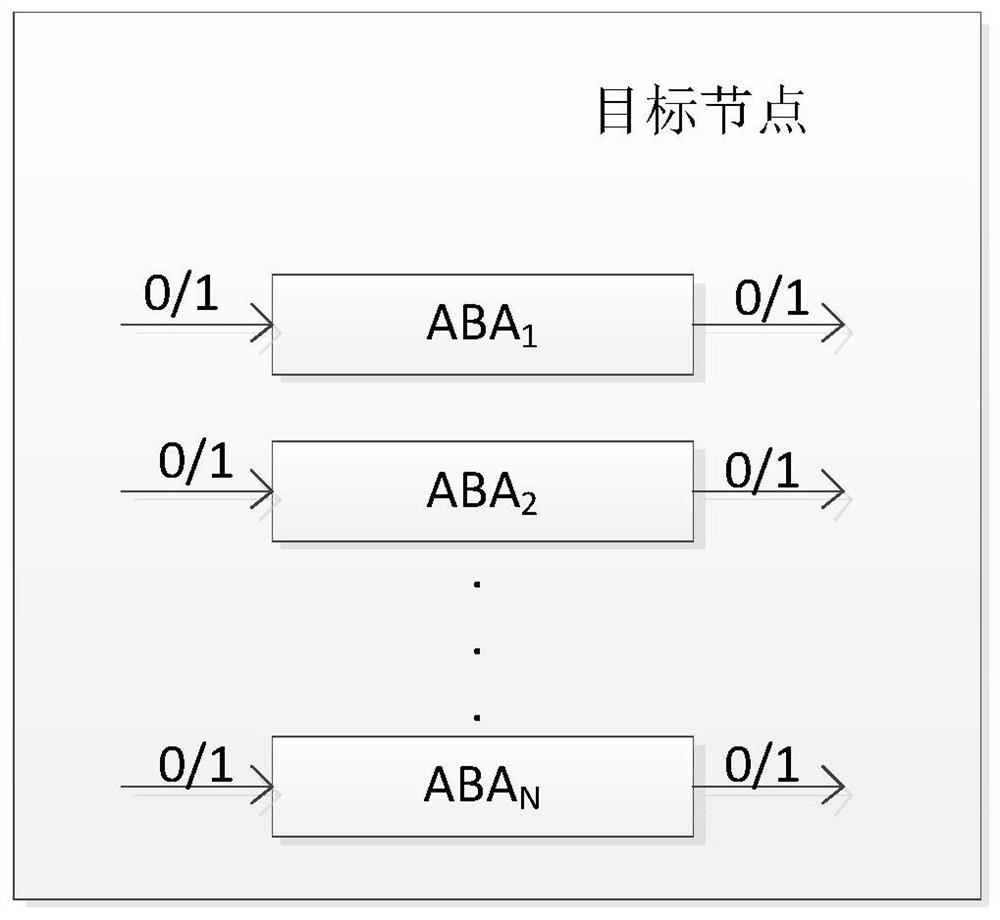
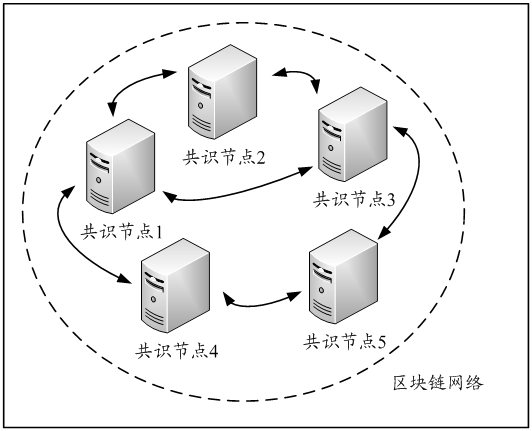
The embodiment of the invention provides a binary consensus method based on reliable broadcast, which is characterized by being applied to any consensus node in a distributed system, and comprises the following steps: aiming at a to-be-consensus proposal of any consensus node, determining an initial voting value corresponding to the to-be-consensus proposal; wherein the initial voting value is a first voting value or a second voting value; circularly executing each round of consensus step until a preset stop condition is met, and each round of consensus step comprising the step of broadcasting the voting value of the round to other nodes in the N consensus nodes by using a reliable broadcast (RBC) protocol; and determining the consensus condition of the to-be-proposed consensus based on the received voting value broadcasted by other consensus nodes. By adopting the method, each consensus node broadcasts the voting value through the reliable broadcast RBC protocol, and determines the consensus result based on the received voting values broadcasted by other consensus nodes, so that each consensus node can quickly reach the consensus about the to-be-consensus proposal, and the security of the consensus process is improved.
Owner:TSINGHUA UNIV +1
Traditional Chinese medicine for treating amygdalitis
InactiveCN105125835ALow costAvoid Compatibility ProblemsHydroxy compound active ingredientsRespiratory disorderFritillaria cirrhosaCurative effect
Traditional Chinese medicine for treating amygdalitis is characterized by comprising, by weight, 2-5 parts of borneol, 6-9 parts of snakegourd seed, 2-4 parts of mint, 15-25 parts of radix aristolochiae, 3-8 parts of indigo naturalis, 4-6 parts of achyranthes bidentata, 12-18 parts of radix scutellariae, 3-6 parts of alum and 6-10 parts of unibract fritillary bulb. The traditional Chinese medicine for treating amygdalitis has effects of clearing away heat and toxic materials, invigorating blood circulation and eliminating swelling and resisting bacteria and inflammation and is good in clinical curative effect on the amygdalitis, simple to prepare, convenient to use and low in medicinal material cost.
Owner:陈志玛
Blockchain-based data consensus method, related equipment and storage medium
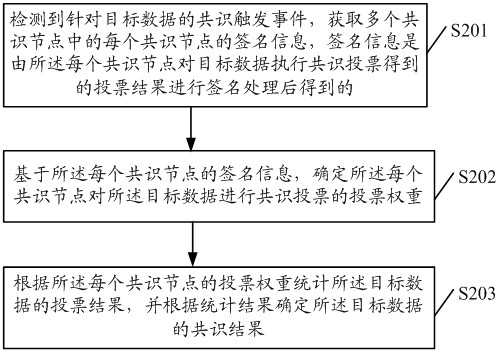
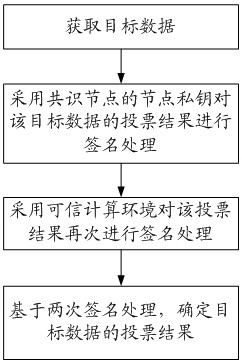
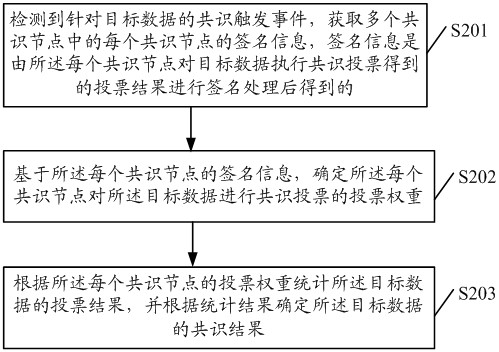
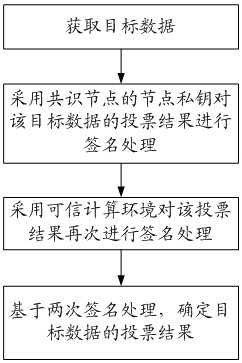
ActiveCN111814204AAvoid evilImprove accuracyDatabase distribution/replicationDigital data protectionComputer networkTrusted Computing
The embodiment of the invention discloses a blockchain-based data consensus method, related equipment and a storage medium. The method comprises the steps of: detecting a consensus triggering event for target data, and obtaining signature information of each consensus node in a plurality of consensus nodes; based on the signature information of each consensus node, determining a voting weight of each consensus node for performing consensus voting on the target data; in the plurality of consensus nodes, enabling the voting weight corresponding to the consensus node which performs signature processing in a trusted computing environment to be greater than the voting weight corresponding to the consensus node which performs signature processing outside the trusted computing environment; and calculating the voting result of the target data according to the voting weight of each consensus node, and determining the consensus result of the target data according to the calculating result. Thus,the accuracy of the consensus result obtained by performing consensus processing on the target data (transaction data) can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Multi-input verifiable pseudo-random number generation method
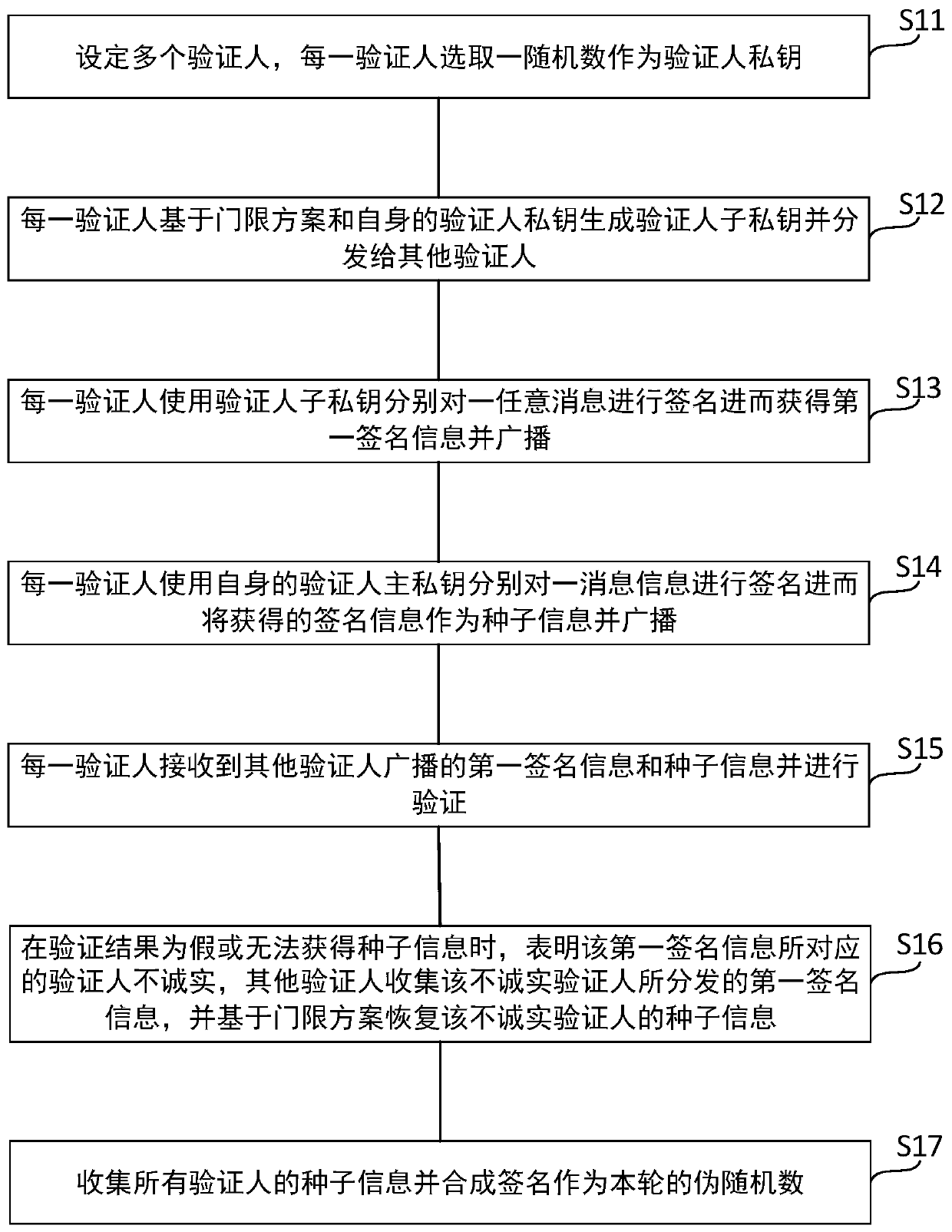
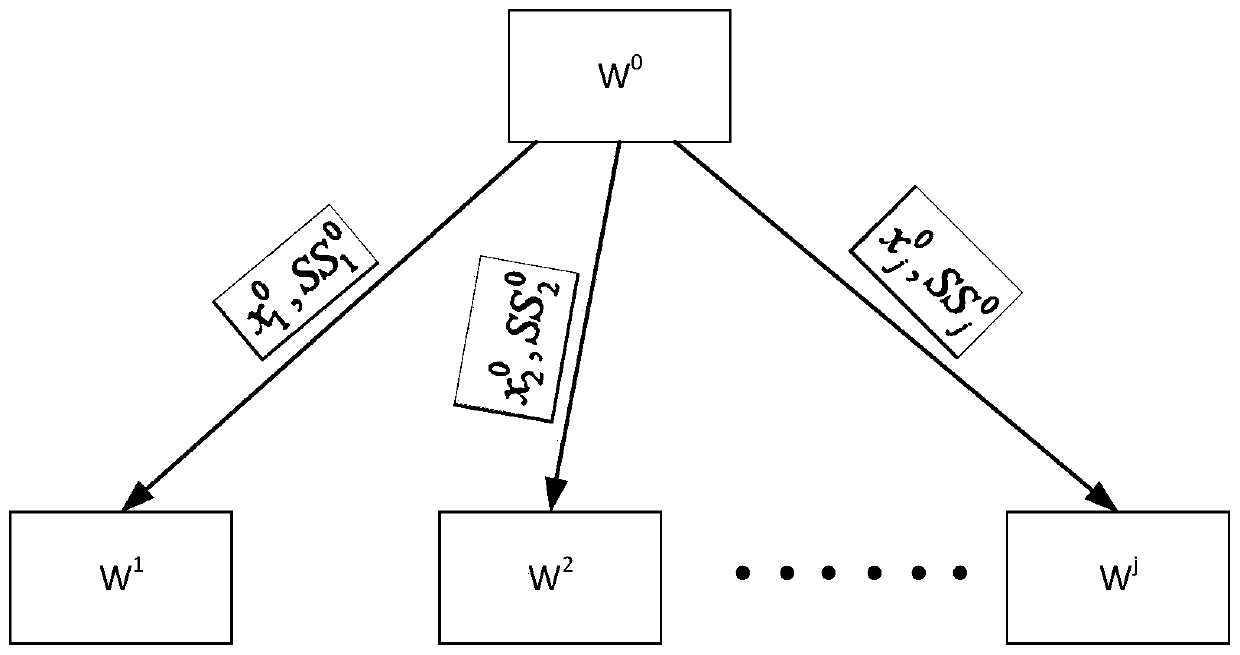
ActiveCN110113173AViolation of verifiabilityAvoid evilKey distribution for secure communicationRandom number generatorsMulti inputPseudo random number generation
The invention relates to a multi-input verifiable pseudo-random number generation method. The method comprises the following steps of enabling a verifier to select a random number as a main private key; generating the sub-private keys based on a threshold scheme and the main private key and distributing the sub-private keys; signing any message by using a verifier sub-private key so as to obtain the first signature information and broadcasting the first signature information; signing the message information by using an own verifier main private key to form the seed information and broadcastingthe seed information; receiving the first signature information and the seed information broadcasted by other verifiers and verifying the first signature information and the seed information; when the verification result is false or the seed information cannot be obtained, enabling the other verifiers to collect the first signature information distributed by the dishonest verifier, and recoveringthe seed information of the dishonest verifier based on the threshold scheme; and collecting the seed information of all verifiers, and synthesizing a signature as a pseudo-random number of the round. According to the present invention, when the verifier is judged to be dishonest, the signature of the dishonest verifier is published, so that the verifiability of the random number is prevented from being damaged, and the last person is completely prevented from doing evil.
Owner:上海链朗信息科技有限公司
Data safety collaborative calculation method and system
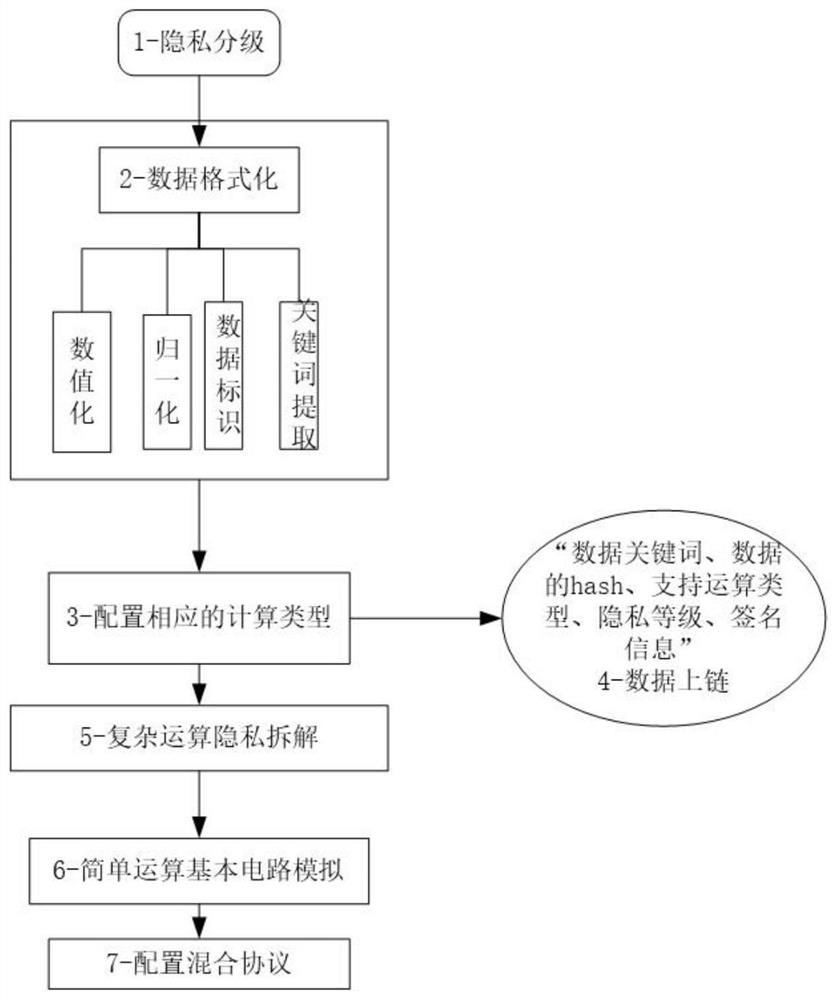
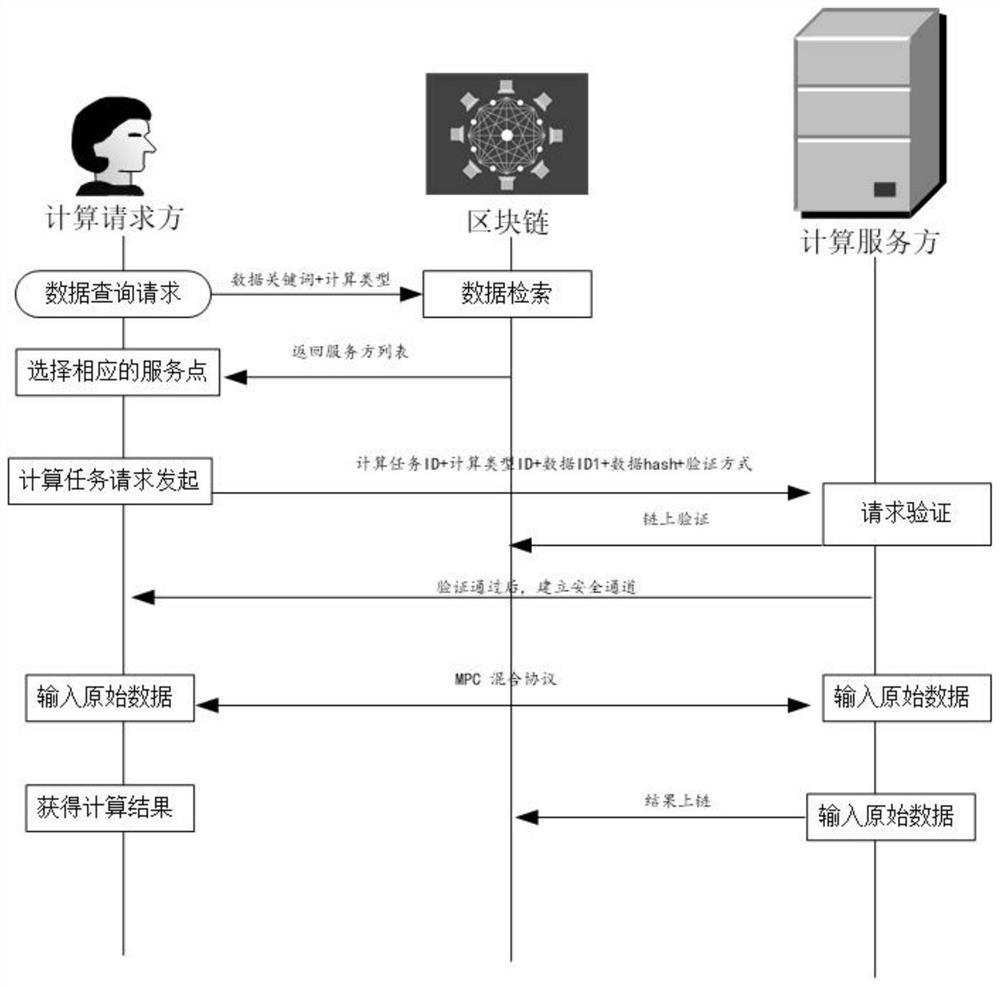
ActiveCN113438237AAvoid interactionAvoid evilEnergy efficient computingSecuring communicationData miningData transmission
The invention provides a data safety collaborative calculation method and system. The method comprises the steps: 1, extracting data features, carrying out the privacy grading of data, configuring a calculation type, formulating a calculation protocol, and carrying out the uplink of the data features, the privacy grade, the calculation type and the calculation protocol; 2, after selecting an online node, a data calculation requester initiates an HTTP request and links request information, a calculation service party verifies the information on the link, establishes a secure channel after verification, carries out data transmission and calculation, and links a calculation result; and 3, verifying the calculation result. According to the method, the block chain technology is combined, the data hash before calculation and the result after calculation are chained, verification is carried out in a regular public or zero knowledge mode, and it is guaranteed that the data of the double-sending participants are real and cannot be tampered.
Owner:SHANGHAI WANXIANG BLOCK CHAIN CO LTD
Bupleurum pulling-right preparation
InactiveCN108201592AAvoid evilAvoid fearNervous disorderDispersion deliveryGLYCYRRHIZA EXTRACTChinese licorice
The invention discloses an orally-taken traditional Chinese medicine preparation which is used for treating facial paralysis caused by neuritis, the preparation is characterized by being prepared fromthe selected traditional Chinese medicine raw materials respectively, by weight, of 30 g of bupleurum, 17 g of scutellaria baicalensis, 14 g of schizonepeta, 15 g of saposhnikovia divaricata root, 15g of rhizoma typhonii, 15 g of rhizoma gastrodiae, 15 g of scorpion, 10 g of liquorice, 15 g of garden balsam stem, 20 g of incised notopterygium and 20 g of lumbricus. The drug properties of the selected traditional Chinese medicine raw materials are mutually complementary, selection of mutual inhibition, mutual restraint and mutual detoxication of the compatibility of the drugs is avoided, themutual promotion and mutual assistance actions of the drugs are remarkable, and the preparation has the efficacy of expelling wind and dredging collat and reconciling exterior and interior. The preparation is taken orally to treat the facial paralysis caused by neuritis and has definite efficacy.
Owner:HENAN CREATION TECH SERVICE CO LTD
Anxiety-proof decoction
InactiveCN108210779AAvoid evilAvoid fearNervous disorderDispersion deliveryFructus aurantii immaturusDrug
The invention discloses anxiety-proof decoction and an orally-taken Chinese traditional medicinal preparation for treating symptoms such as dizziness and nausea, vexation and less sleep and difficultyin falling asleep. The orally-taken Chinese traditional medicinal preparation is characterized by being prepared from the following traditional Chinese medicinal raw materials in parts by weight: 8gof rhizoma coptidis, 5g of cortex cinnamomi, 20g of pericarpium citri reticulatae, 12g of rhizoma pinelliae, 15g of caulis bambusae in taeniam, 16g of fructus aurantii immaturus, 18g of radix paeoniaealba, 19g of radix rehmanniae, 12g of radix rehmanniae preparata, 20g of fried wild jujube seed, 12g of radix polygalae, 15g of rhizoma acori graminei, 35g of crude dragon bone, 35g of raw oyster shell, 20g of flos rosae rugosae and 15g of semen cannabis. The medicinal effects of raw herbal materials selected by the invention are complementary with one another, so that mutual inhibition, mutual restraint and mutual detoxication among drugs are avoided; in addition, the effects of mutual promotion and mutual assistance are enabled to be obvious; the anxiety-proof decoction has the efficacy ofregulating the center and reducing phlegm and clearing heat and soothing the nerves. The anxiety-proof decoction has definite effects for treating the symptoms such as the dizziness and nausea, the vexation, the less sleep and difficulty in falling asleep by orally taking.
Owner:侯春华
Transaction realization method in alliance block chain system
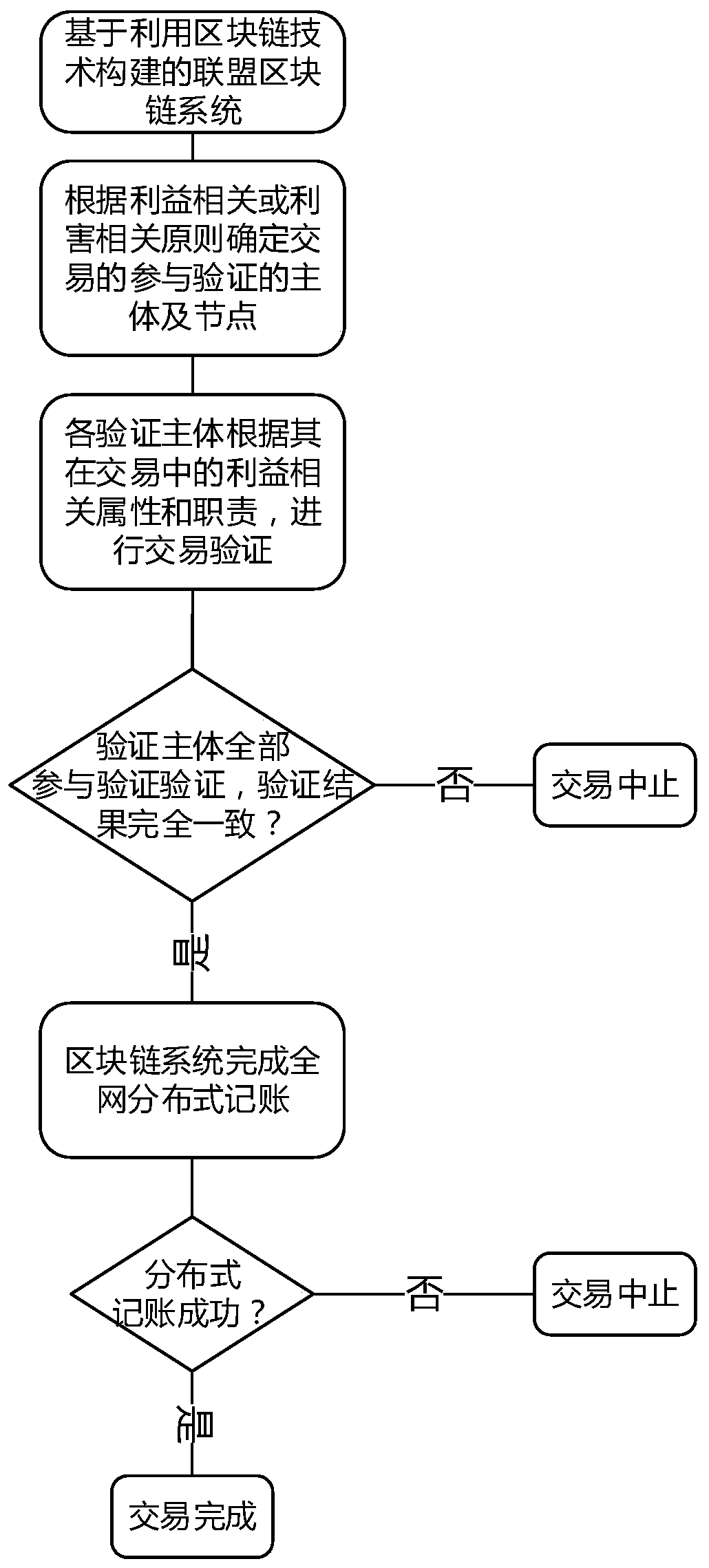
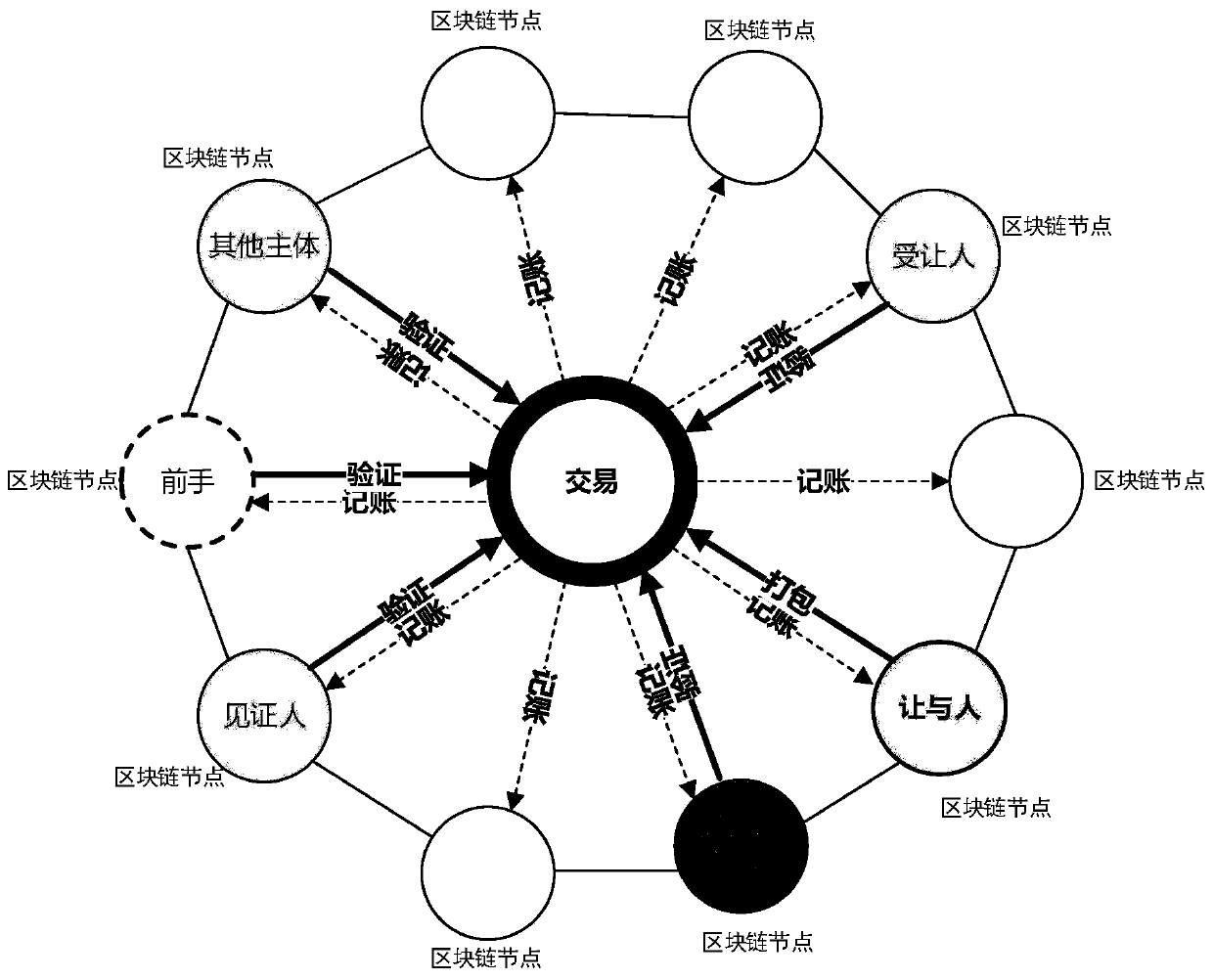
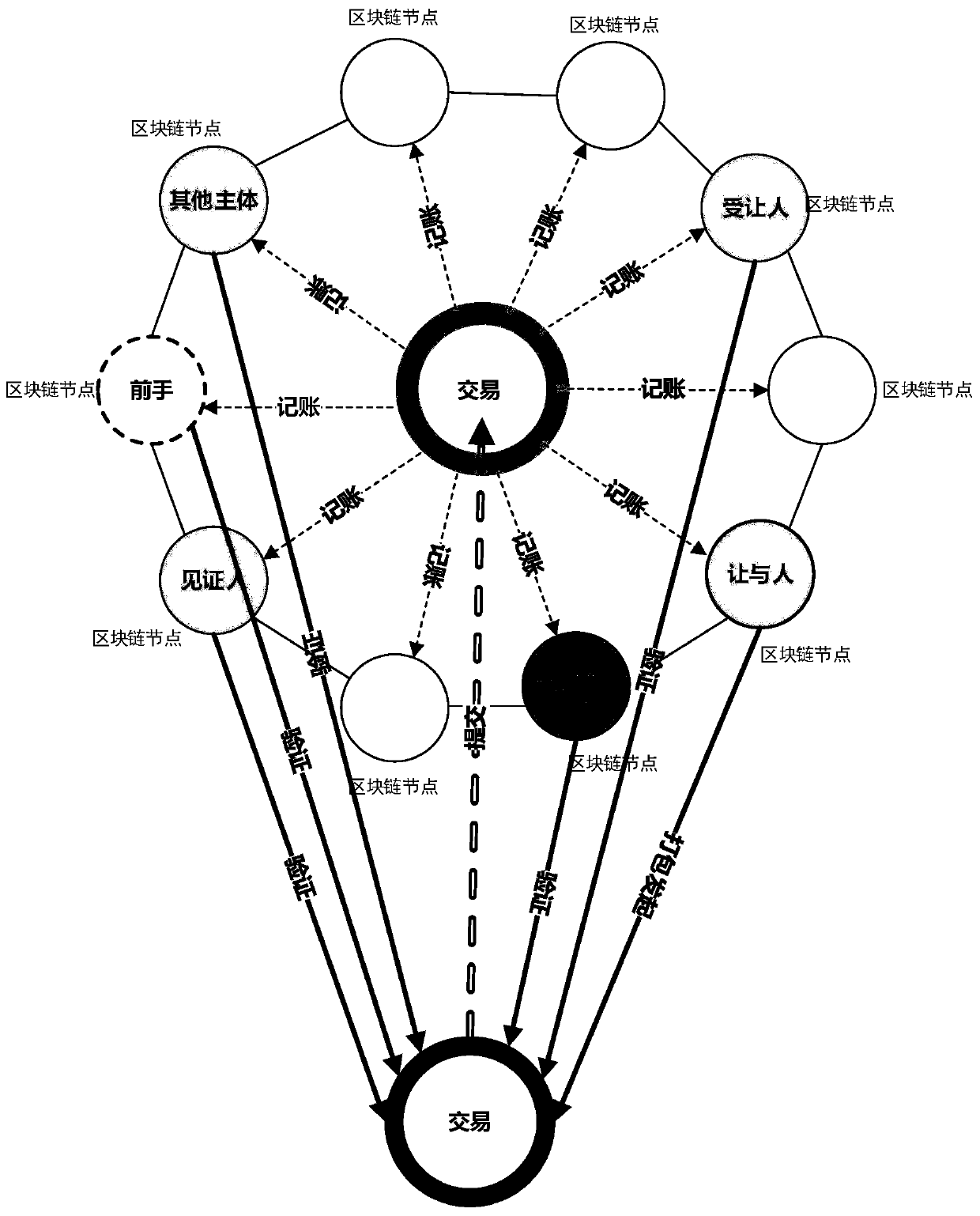
InactiveCN110232572AProtection of rights and interestsLow efficiencyFinanceProtocol authorisationChain systemBlockchain
The invention provides a transaction realization method in an alliance block chain system. The transaction realization method comprises the following steps: based on a supply chain, ecologically constructing an alliance block chain system consisting of a block chain and an auxiliary service system thereof; determining subjects participating in transaction verification and nodes of the subjects according to benefit-related or benefit-related principles of commercial transactions, wherein the subjects participating in the transaction verification and the nodes thereof completely participate in the verification, and the transaction verification result is 100% consistent; and submitting to the block chain system to complete the whole network distributed accounting, thereby ensuring that the rights and interests of all interest-related subjects involved in the transaction are guaranteed.
Owner:深圳市链联科技有限公司
Traditional Chinese medicine preparation for treating influenza and preparation method of traditional Chinese medicine preparation for treating influenza
The invention discloses a traditional Chinese medicine preparation for treating influenza and a preparation method of the traditional Chinese medicine preparation for treating influenza. The traditional Chinese medicine preparation for treating influenza is characterized by being prepared from, by weight, 15 parts of herba corydalis bungeanae, 20 parts of folium isatidis, 35 parts of radix isatidis, 15 parts of honeysuckle, 15 parts of radix astragali, 20 parts of fructus forsythiae, 20 parts of radix platycodi, 35 parts of herba taraxaci, 20 parts of rhizoma et radix polygoni cuspidati, 20 parts of radix scrophulariae, 10 parts of radix glycyrrhizae, 20 parts of herba houttuyniae and 20 parts of herba artemisiae apiaceae. Due to property complementation of raw medicinal materials, mutual inhibition, mutual restraint and mutual detoxication in compatibility of the raw medicinal materials are avoided, and remarkable functions of mutual promotion and mutual enhancement are achieved. The traditional Chinese medicine preparation for treating influenza has efficacies of heat clearing, detoxifying, inflammation resisting, sterilizing, swelling relieving and heat dissipating and is a pure orally-taken herbal medicine preparation for treating influenza.
Owner:景金发
Interactive zero knowledge proof method and device, computer equipment and storage medium
PendingCN111277416AImprove securityAvoid evilFinancePublic key for secure communicationZero-knowledge proofComputer equipment
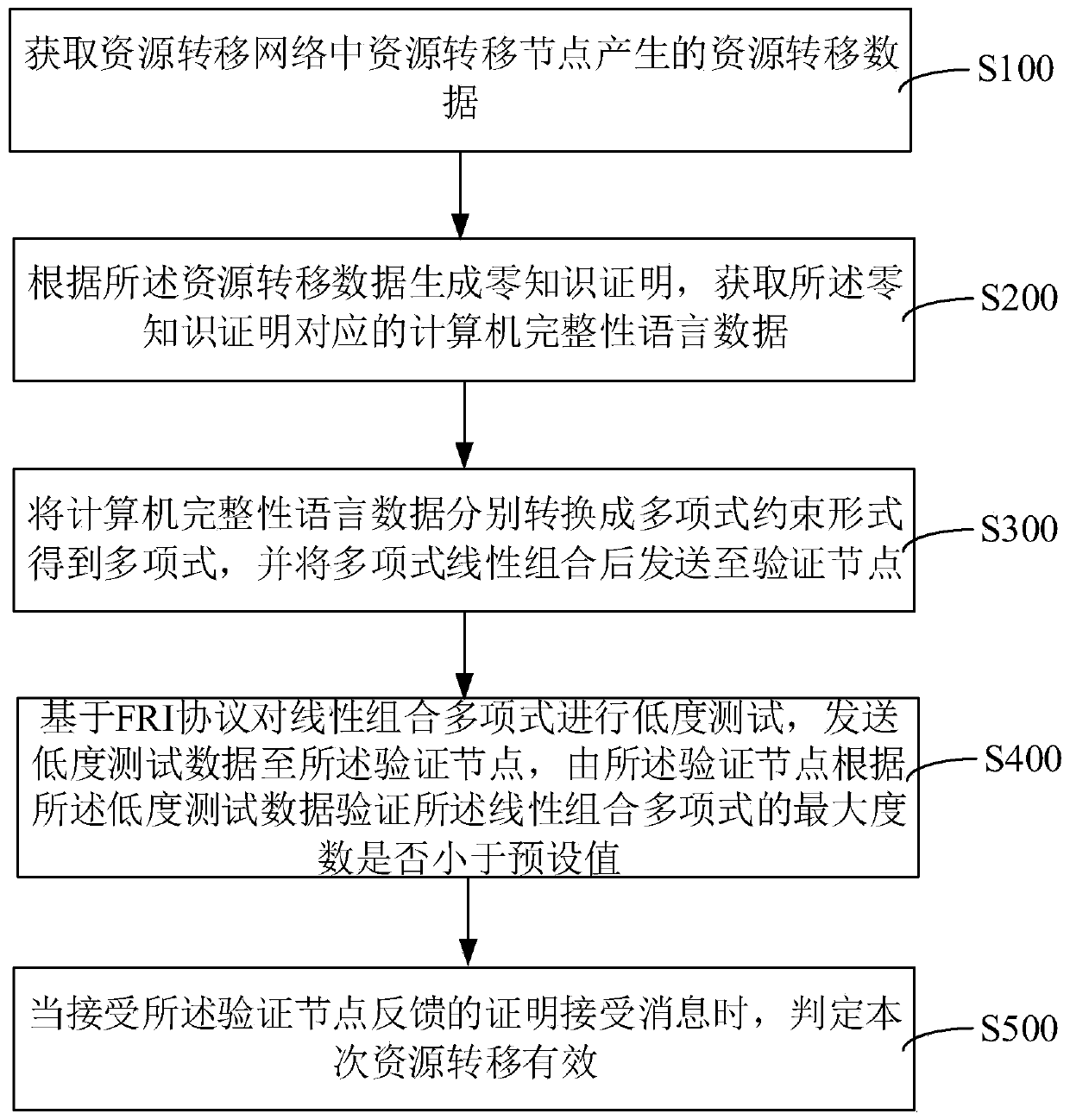
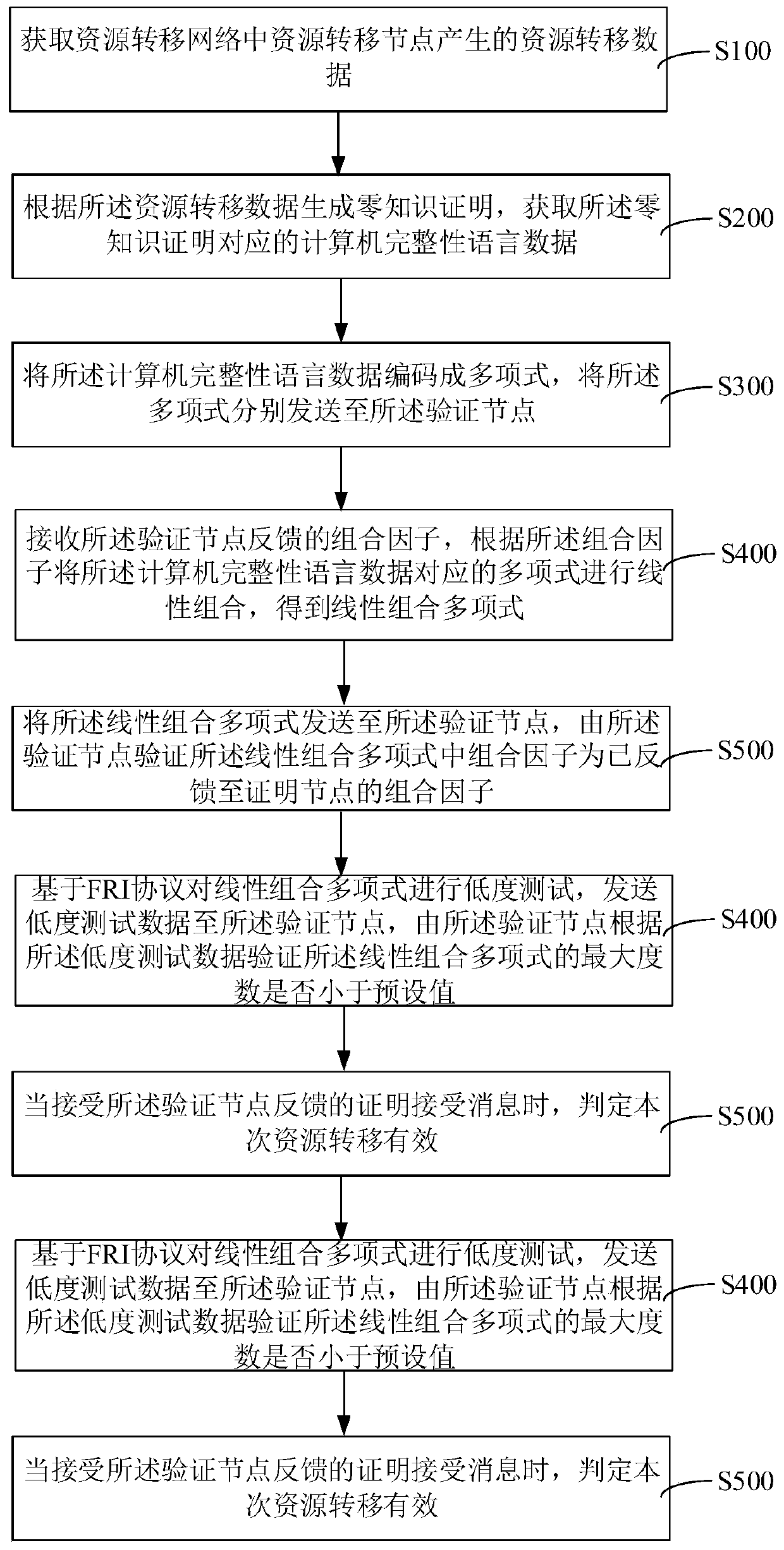
The invention relates to an interactive zero knowledge proof method and device, computer equipment and a storage medium. The method comprises the following steps: converting the resource transfer datainto zero knowledge proof; obtaining computer integrity language data corresponding to the zero knowledge proof; converting the computer integrity language data into a polynomial constraint form; performing a low-degree test on the linear combinatorial polynomial based on an FRI protocol; and sending low-degree test data to the verification node, verifying whether the maximum degree of the linearcombinatorial polynomial is smaller than a preset value or not by the verification node according to the low-degree test data, and judging that the resource transfer is valid when receiving a certification acceptance message fed back by the verification node. In the whole process, a third party does not need to set public parameters, the content needing to be proved is converted into a linear combinatorial polynomial based on the FRI protocol to carry out a low-degree test process, the third party is prevented from being disgusted, and the zero-knowledge proof safety is remarkably improved.
Owner:PINGAN YIQIANBAO E COMMERCE CO LTD
Block chain service execution method and device based on multi-signature smart contract
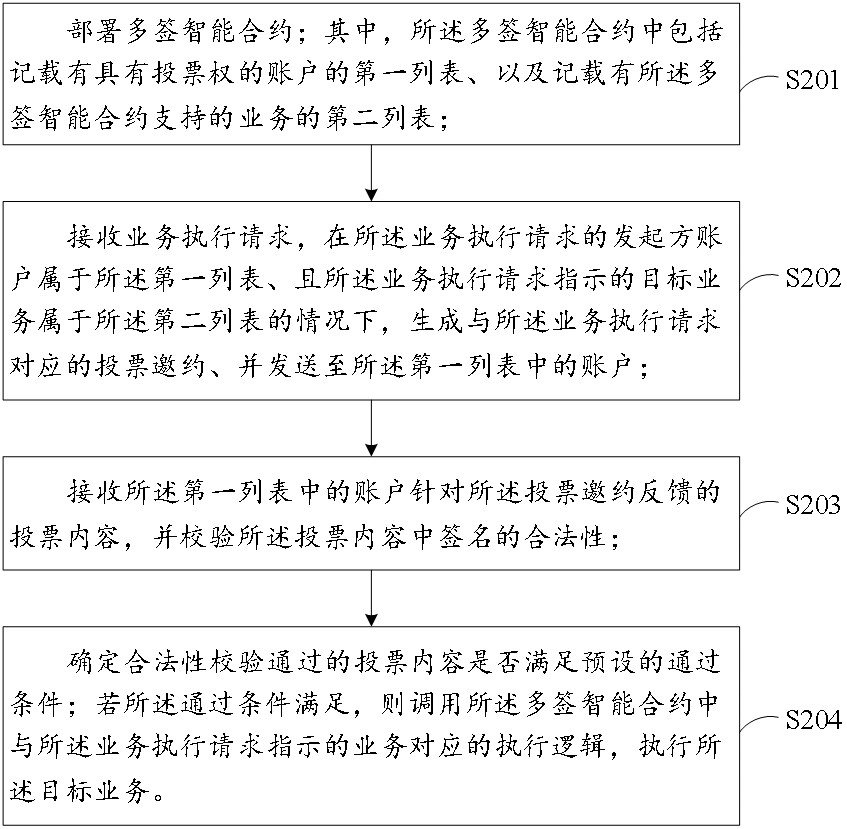
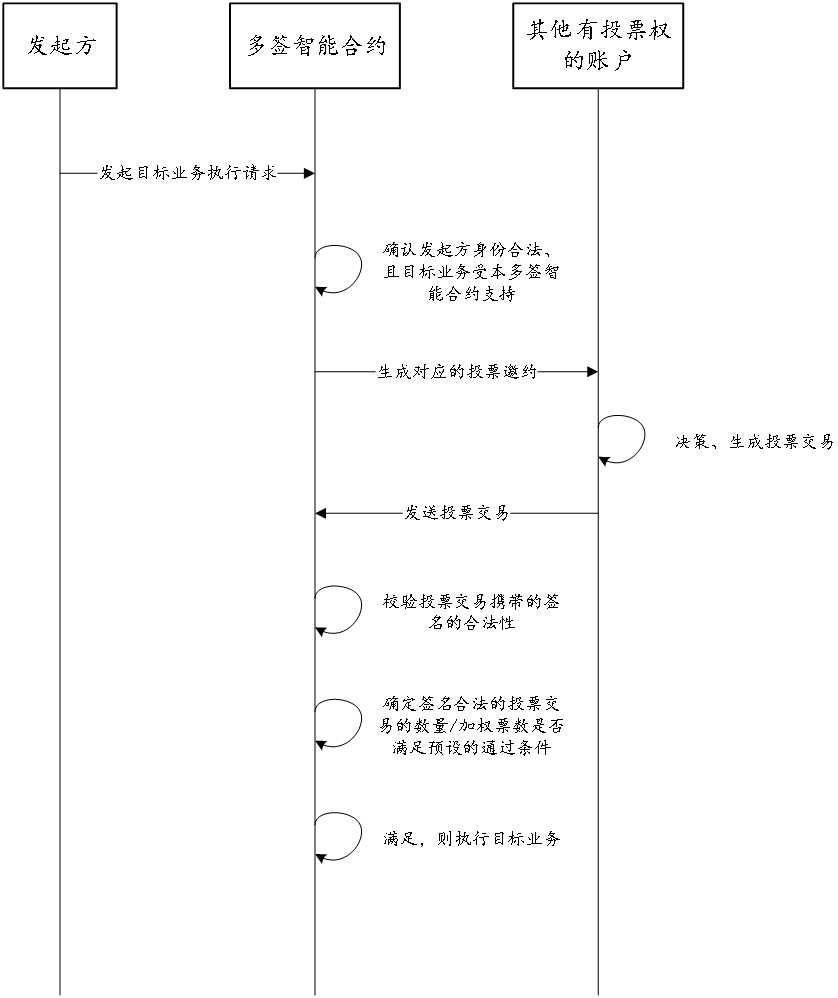
PendingCN114372280AImplement a distributed implementationAvoid evilFinanceDigital data protectionComputer networkSmart contract
The invention discloses a block chain service execution method and device based on a multi-signature smart contract. The method is applied to any block chain node. Comprising the steps of deploying a multi-signature smart contract; receiving a service execution request, generating a voting invitation corresponding to the service execution request under the condition that an initiator account of the service execution request belongs to the account with the voting right and a target service indicated by the service execution request belongs to the service supported by the multi-signature smart contract, and sending the voting invitation to the account with the voting right; receiving voting content fed back by the account with the voting right for the voting invitation, and verifying the legality of a signature in the voting content; determining whether the voting content passing the legality verification meets a preset passing condition or not; and if the passing condition is satisfied, calling an execution logic corresponding to the service indicated by the service execution request in the multi-signature smart contract, and executing the target service. By applying the scheme, the reliability of group decision service execution can be improved.
Owner:HANGZHOU RIVTOWER TECH CO LTD
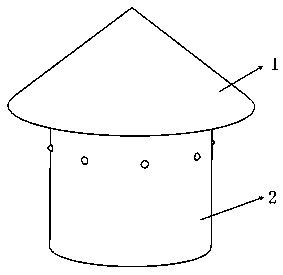
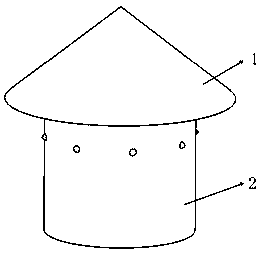
Anti-blocking boiler air cap applied to power station field
ActiveCN108800114AAvoid evilExtended service lifeFluidized bed combustionApparatus for fluidised bed combustionCoalPower station
The invention belongs to the technical field of air caps, and particularly relates to an anti-blocking boiler air cap applied to the power station field. The anti-blocking boiler air cap comprises anair cap conical cover, an air cap sleeve, air cap holes and an executing mechanism, wherein a turbine drives a rotary shaft to rotate after being blown by air, and volute spiral springs are compressedfor energy storage; after the turbine rotates after being blown by air, executing rods in an anti-blocking mechanism can be quickly separated from the air cap holes, and normal ventilation of the aircap is achieved. After the air cap stops air blowing, the volute spiral springs release energy; the release speed of the volute spiral springs can be decreased through a fly wheel, and the effect that the rotary shaft can drive annular sleeves to slowly rotate through a first shaft sleeve, connection plates and a gear ring; and the executing rods in the anti-blocking mechanism can slowly penetrate through the air cap holes in a rotary mode, thus, the effect that high-temperature small-particle coal in the air cap holes can be discharged through the executing rods is ensured, in addition, a small space without the high-temperature small-particle coal can be formed through rotation of the rotary executing rods, and the situation that the air cap is blocked is avoided.
Owner:聊城市开发区信远信息科技有限公司
Method for improving consensus efficiency of blockchain
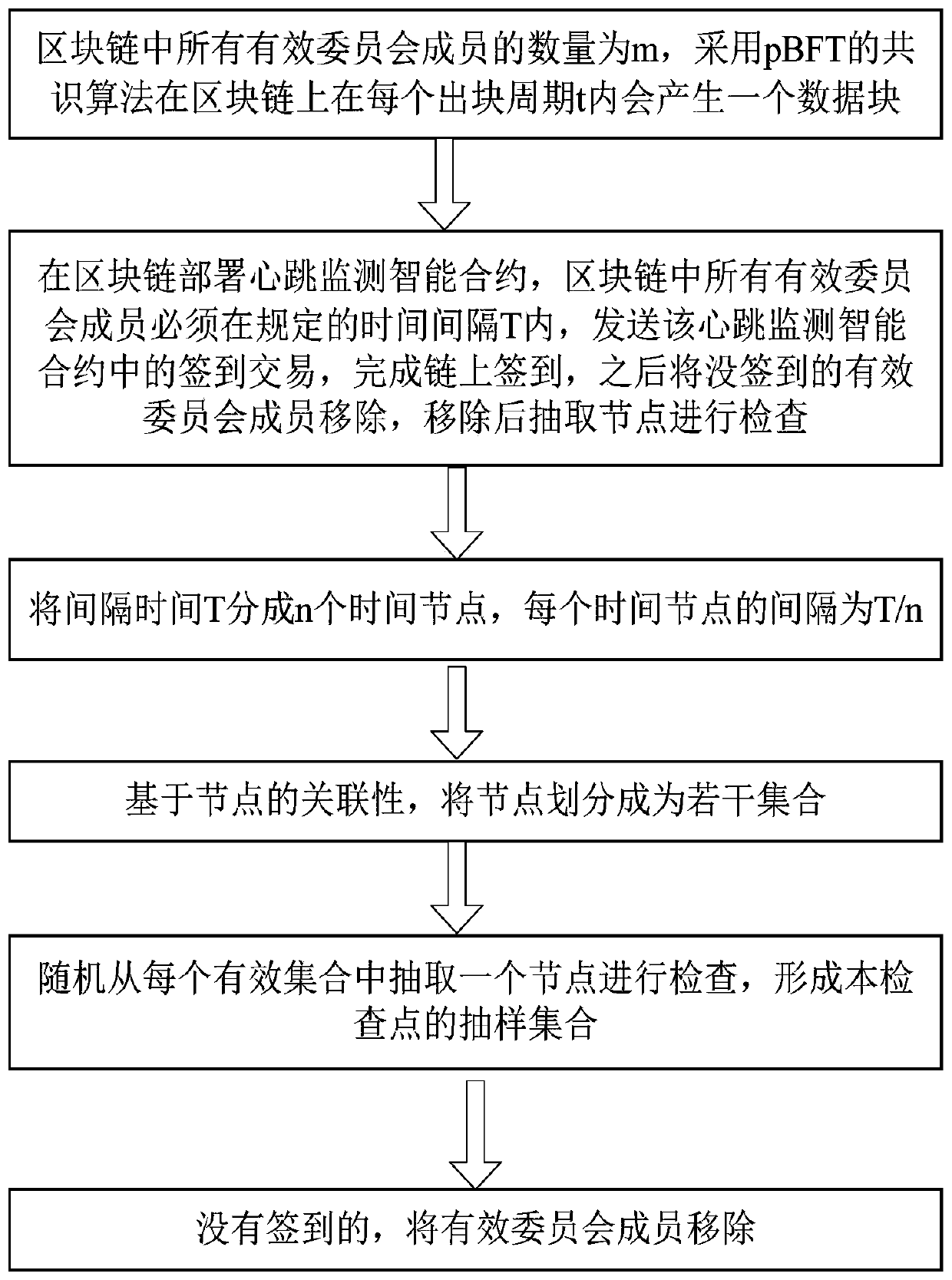
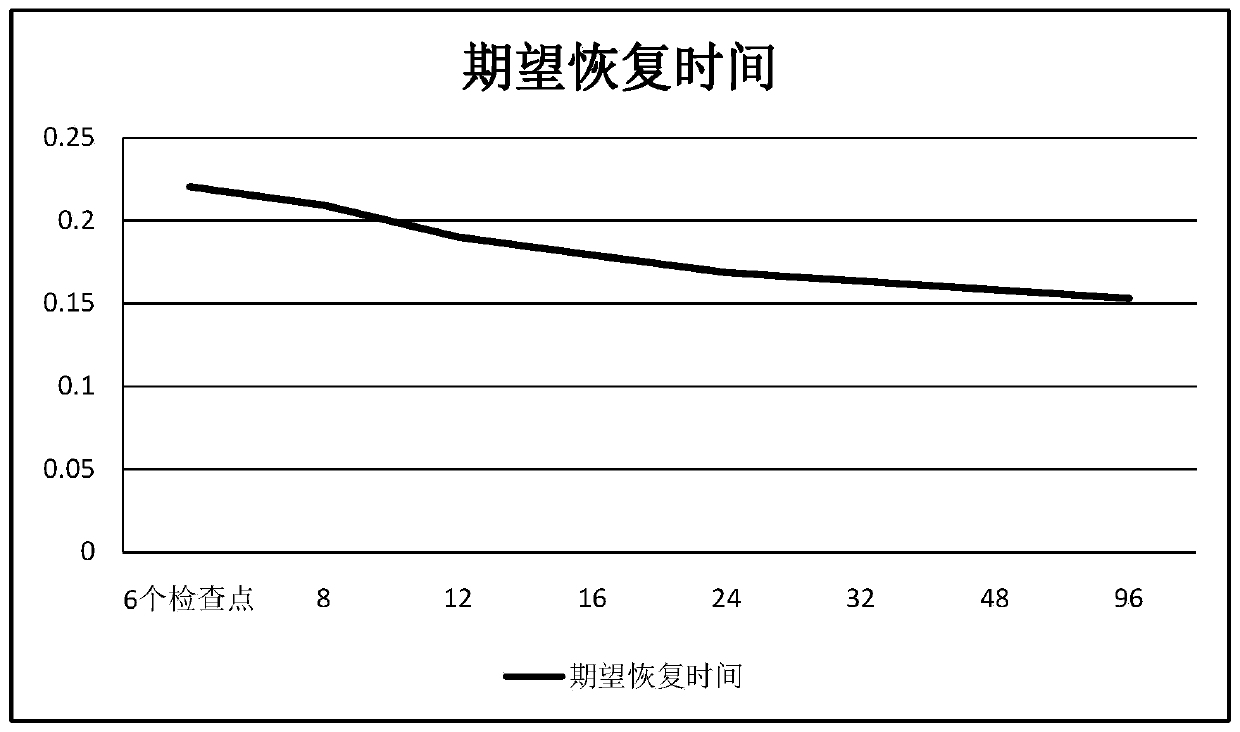
ActiveCN111510347AAvoid paralysisAvoid evilFinanceData switching networksFinancial transactionSmart contract
The invention discloses a method for improving the consensus efficiency of a blockchain, and the method comprises the steps: 1), enabling the number of all valid committee members in the blockchain tobe m, and generating a data block in each block output period t on the blockchain through a pBFT consensus algorithm; and 2) deploying a heartbeat monitoring smart contract in the blockchain, sendinga sign-in transaction in the heartbeat monitoring smart contract by all valid committee members in the blockchain within a specified time interval T, completing on-chain sign-in, then removing the valid committee members which are not signed in, and extracting nodes for inspection after removal. According to the invention, the valid committee members who do not sign in are removed, and differentcheck points are set for each group (one) of nodes, so that instant system paralysis caused by a herd effect can be effectively prevented.
Owner:北京链化未来科技有限公司
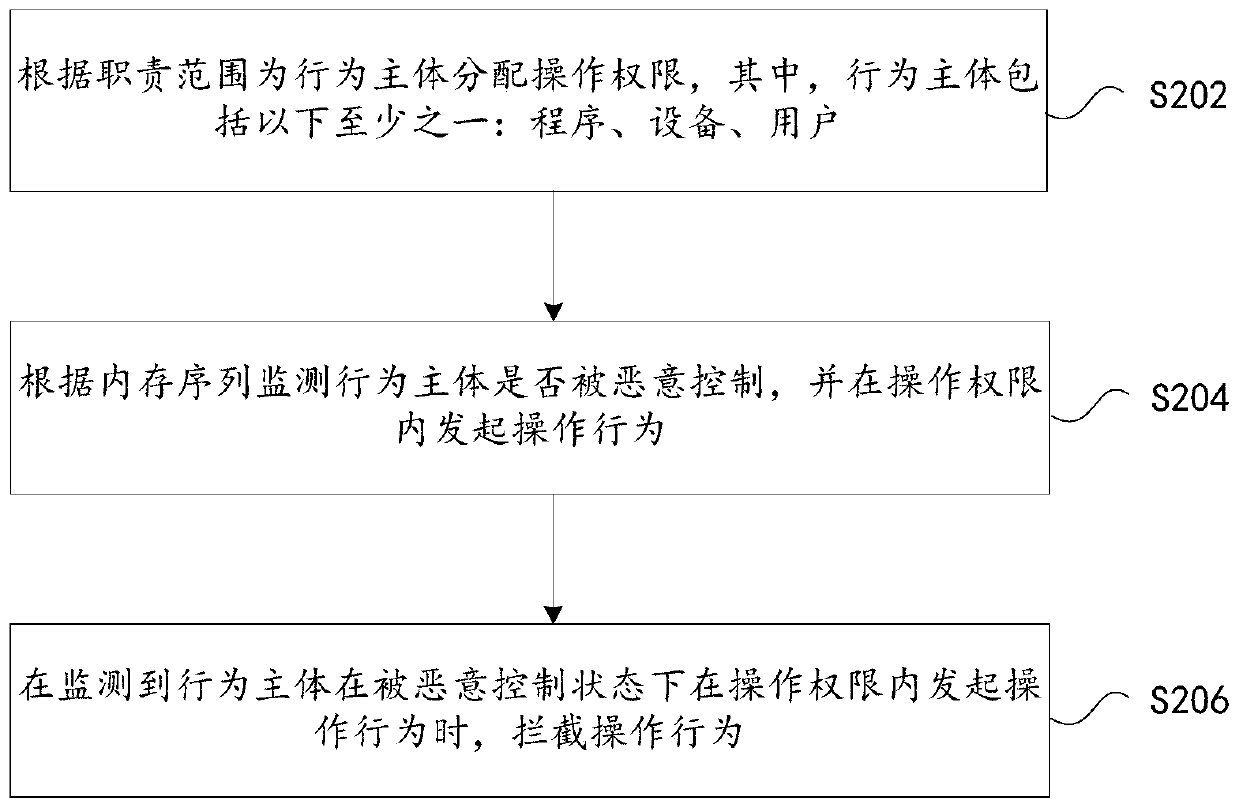
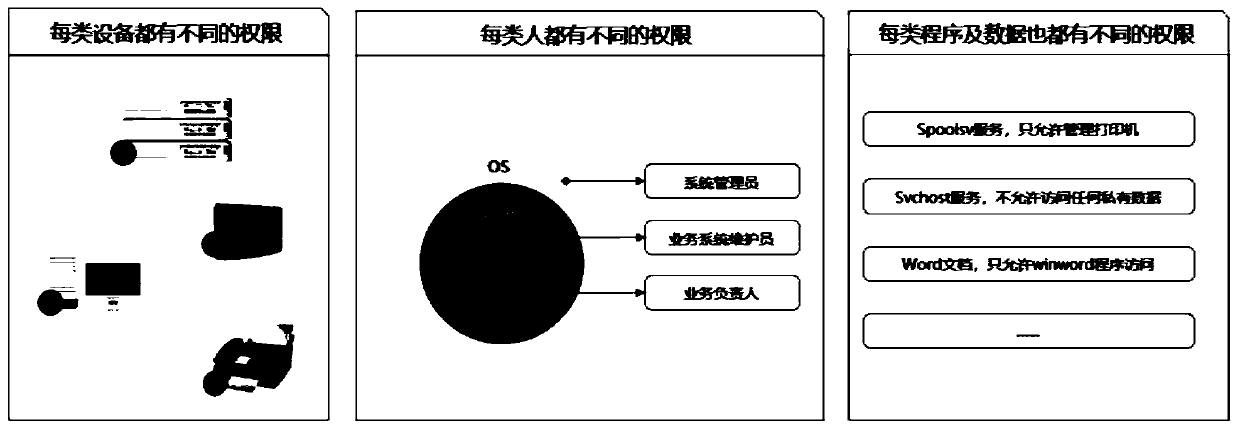
Operation behavior interception method and device, storage medium and electronic device
ActiveCN109766699AAvoid evilPrevent or minimize lossesPlatform integrity maintainanceOperational behaviorComputer science
The invention provides an operation behavior interception method and device, a storage medium and an electronic device, and the method comprises the steps of allocating operation authorities to a behavior subject according to a responsibility range, wherein the behavior subject comprises at least one of the following items of a program, equipment and a user; monitoring whether the behavior subjectis maliciously controlled or not according to the memory sequence, and initiating an operation behavior within the operation authority; and when it is monitored that the behavior subject initiates the operation behavior within the operation authority in the malicious control state, intercepting the operation behavior. Through the present invention, the risk that the system is maliciously controlled and the loss are prevented or reduced, and the technical problem of weak equipment safety in the prior art is solved.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
A storage-based blockchain incentive method, blockchain network, and storage network
ActiveCN109325746BAvoid evilReduce the number of malicious nodesFinancePayment protocolsSystem maintenanceEngineering
The invention discloses a storage-based block chain excitation method, a block chain network and a storage network. The method of the invention comprises the following steps that a ranking algorithm of the block chain nodes is proposed. The total contribution value is calculated by the storage contribution and the betting amount of the block chain nodes, and the contribution of the nodes to the whole system in the storage contribution and the betting is effectively evaluated. In this paper, a method of ranking un_rank nodes is proposed, in which the nodes of the whole network participate in the ranking as much as possible, and the un_rank nodes can also get the block chain reward by storing their contribution. A method of incentive based on storage reward and wager amount is proposed, which effectively motivates the node to maintain the whole block chain system continuously and ensure the safety of the block chain system. The method of the invention is suitable for rewarding nodes according to the storage contribution, can effectively evaluate the storage contribution of nodes, motivates all nodes to participate in the system maintenance of the block chain, and rewards the nodes based on the storage contribution.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Blockchain-based data consensus method, related equipment and storage medium
ActiveCN111814204BAvoid evilImprove accuracyDatabase distribution/replicationDigital data protectionComputer networkTrusted Computing
The embodiment of the present invention discloses a blockchain-based data consensus method, related equipment, and storage media, wherein the method includes: detecting a consensus trigger event for target data, and obtaining the signature of each consensus node among multiple consensus nodes information; based on the signature information of each consensus node, determine the voting weight of each consensus node for consensus voting on the target data; among multiple consensus nodes, the voting weight corresponding to the consensus node that performs signature processing in a trusted computing environment, It is greater than the voting weight corresponding to the consensus nodes that perform signature processing outside the trusted computing environment; according to the voting weight of each consensus node, the voting results of the target data are counted, and the consensus results of the target data are determined according to the statistical results, which can improve the accuracy of the target data. The accuracy of the consensus results obtained by consensus processing of data (transaction data).
Owner:TENCENT TECH (SHENZHEN) CO LTD
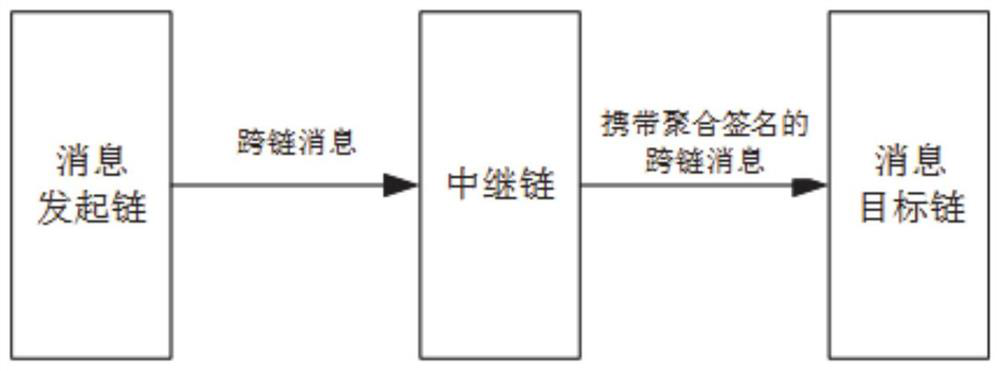
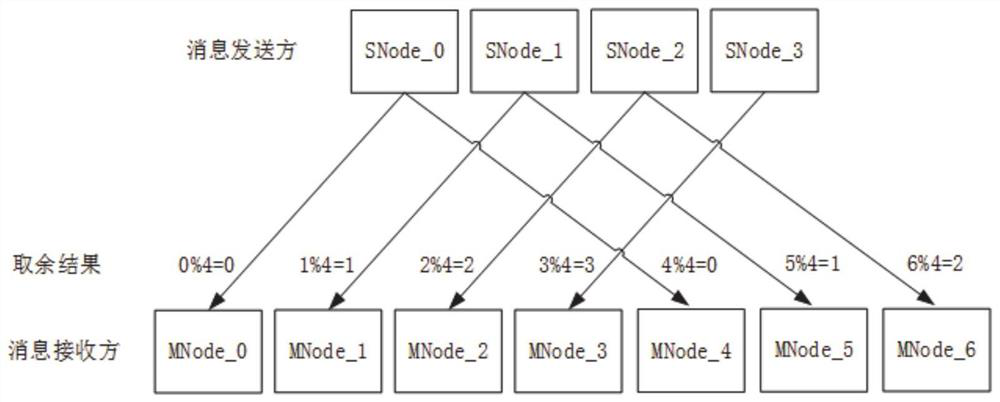
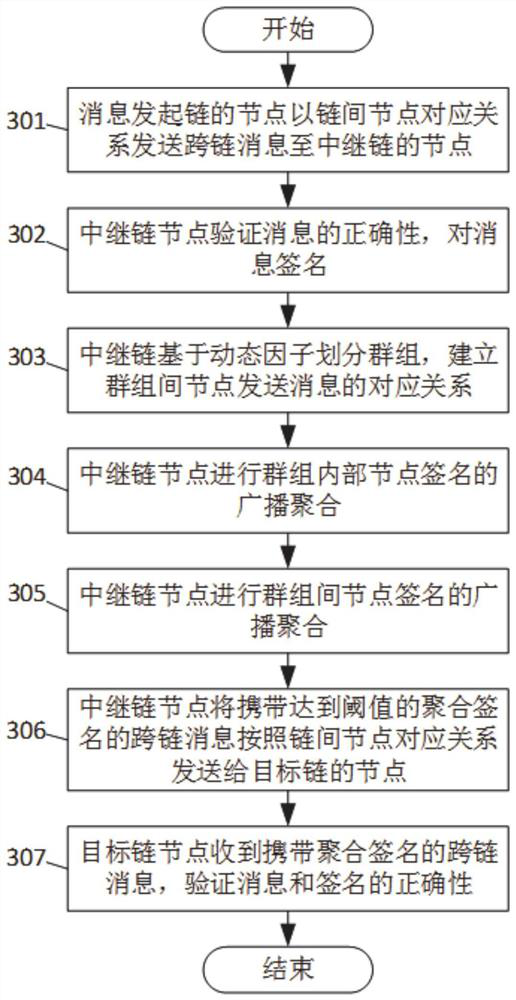
Dynamic cross-chain message forwarding method and system
PendingCN114362996APrevent malicious tampering and interceptionEnsure safetySpecial service provision for substationUser identity/authority verificationTrunkingEngineering
The invention provides a dynamic cross-chain message forwarding method and system. Each node of a message initiation chain sends a cross-chain message to a relay chain node according to an inter-chain node corresponding relationship; the relay chain node verifies the correctness of the cross-chain message, and signs the message passing the verification; the relay chain node divides groups based on the negotiated dynamic factor, and establishes a corresponding relation of message sending of the nodes among the groups; the relay chain node performs broadcast aggregation of group internal node signatures, and when the number of signatures reaches a set threshold value, broadcast aggregation of inter-group node signatures is performed until the total signature reaches a preset threshold value; the relay chain node sends a message carrying the aggregation signature reaching the preset threshold value to the node of the target chain according to the inter-chain node corresponding relation, and the node of the target chain verifies the correctness of the message and the aggregation signature; the method can ensure that the message is real and credible, is not tampered and is reliably transmitted; and the efficiency of verifying the message and aggregating the signature by the relay chain node can be improved.
Owner:DAREWAY SOFTWARE
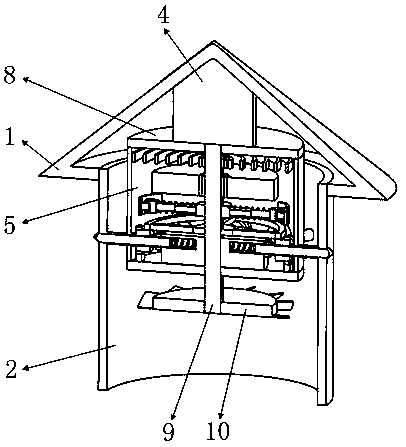
Boiler funnel cap used in power plant field
ActiveCN108800115AAvoid evilExtended service lifeFluidized bed combustionApparatus for fluidised bed combustionPower stationLow speed
The invention belongs to the technical field of funnel caps, and particularly relates to a boiler funnel cap used in the power plant field. The boiler funnel cap comprises a funnel cap conical cover,a funnel cap sleeve, funnel cap holes and an executing mechanism, a turbine drives a rotation shaft to rotate after being blown by wind, and volute spiral springs are compressed to store energy; and after the turbine is blown by wind to rotate, lead screws in an anti-blocking mechanism can be quickly separated from the funnel cap holes, and the funnel cap can be normally ventilated. After the funnel cap stops being blown by wind, the volute spiral springs release energy; the rotating speed of the rotation shaft can be limited through design of frictional arc-shaped plates in a gear shifting mechanism, then the effect of decreasing the releasing speed of the volute spiral springs is achieved, and it is guaranteed that the rotation shaft drives loop sleeves to rotate at low speed through a first shaft sleeve, connecting plates and a gear ring; and in addition, the lead screws in the anti-blocking mechanism can slowly penetrate through the funnel cap holes in a rotating mode, therefore, it is guaranteed that the lead screws can extrude out high-temperature small-particle coal in the funnel cap holes, it is guaranteed that high-temperature small-particle coal near the outer sides of the funnel cap holes can not enter the funnel cap holes, and the condition that the funnel cap holes are blocked is finally avoided.
Owner:JIANGSU JUJIE ELECTROMECHANICAL CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com