Decentralized private data authorization method and system based on block chain
A private data, decentralized technology, applied in the field of private data authorization, can solve the problems of encrypted data leakage, heavy workload of authorization center, system paralysis, etc., to avoid evil or failure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
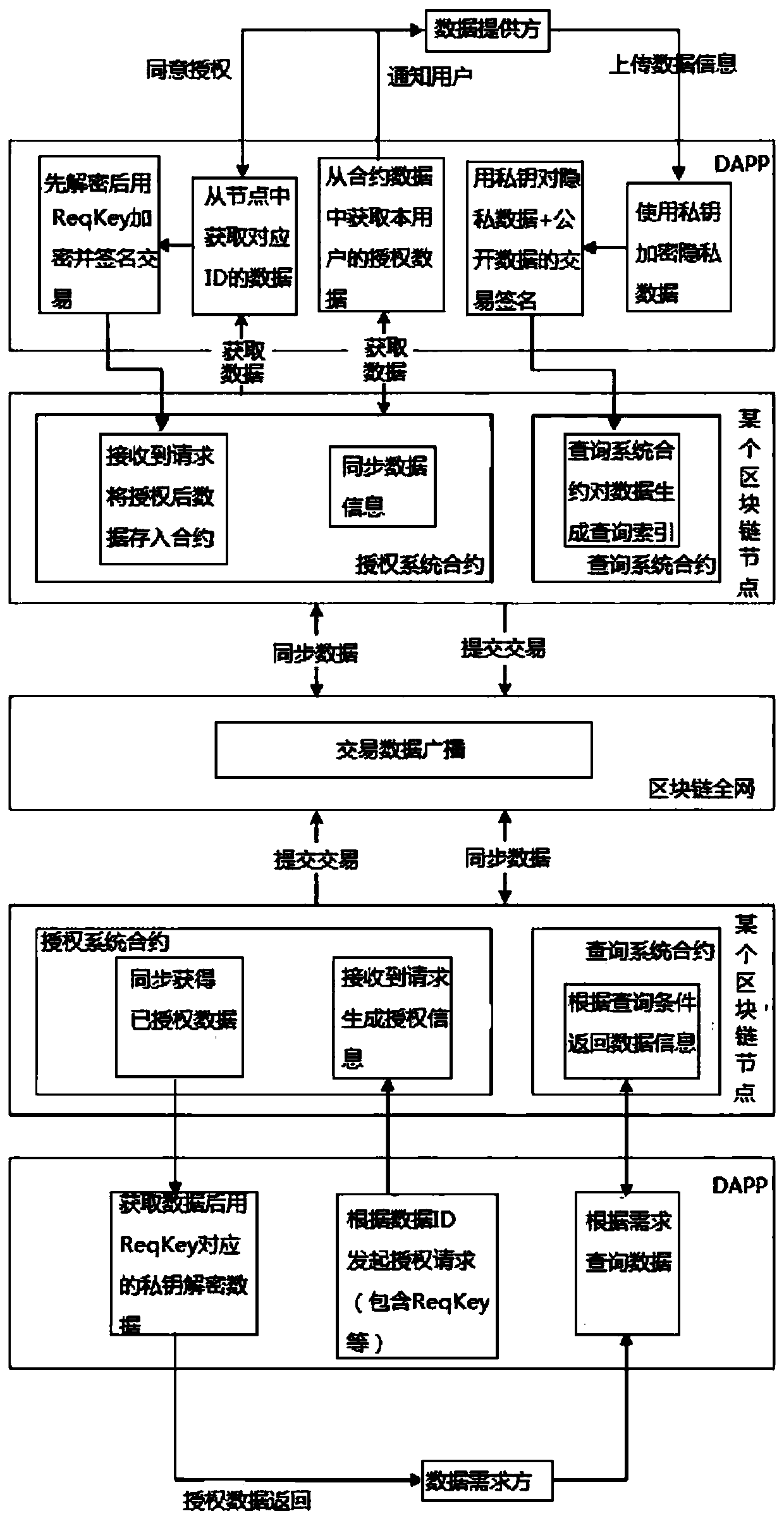
[0042] Such as figure 1 As shown, this embodiment provides a decentralized private data authorization method based on blockchain, and the specific workflow is as follows:
[0043] (1) The data provider inputs the data information that needs to be submitted to the blockchain system according to the business needs, and the privacy data that needs to be encrypted is selected by the system or by the data provider itself;
[0044] (2) After the data provider confirms the private data that needs to be encrypted, the data provider uses the private key of the provider to encrypt the private data using asymmetric encryption, and collects open data to generate a data set I= {E,D}, where E={E1,E2,E3,…}, that is private data, D={D1,D2,D3,…}, that is open data; then, sign the transaction data set I, And submit it to a blockchain node;
[0045] (3) After the transaction is submitted to the blockchain node, establish a query system smart contract, preset index fields according to different...
Embodiment 2
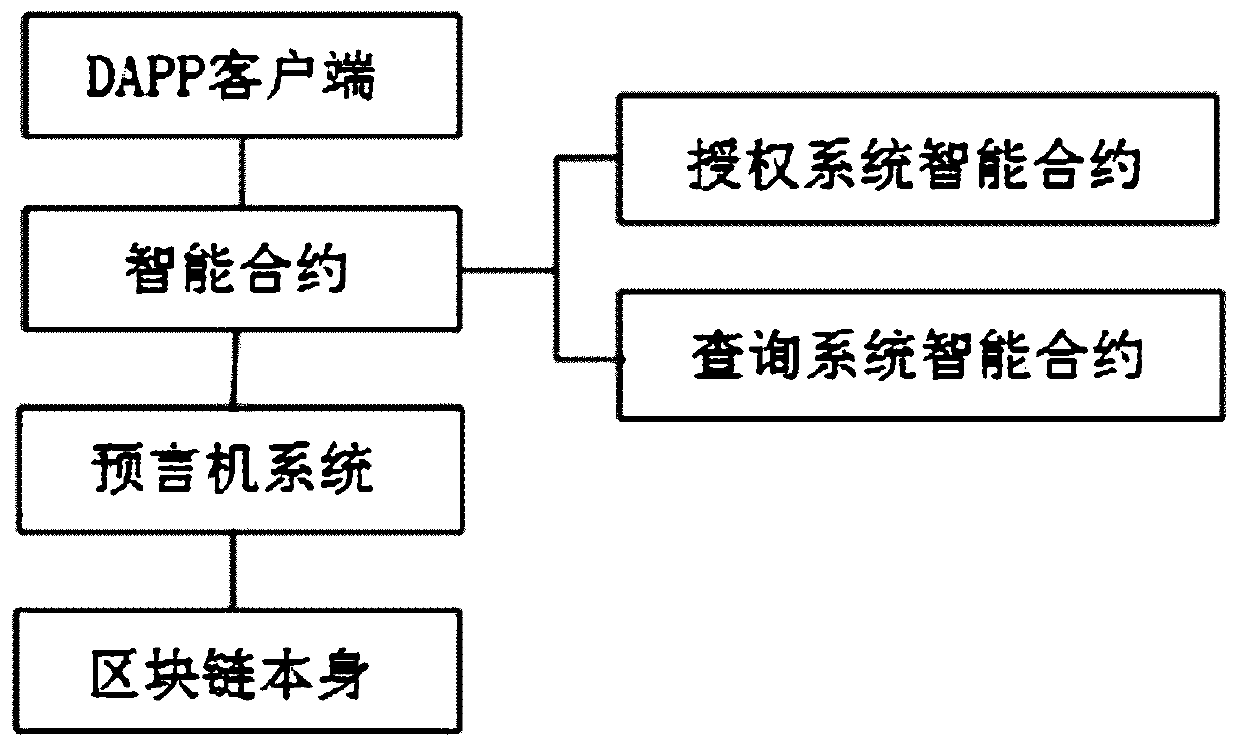
[0054] Such as figure 2 As shown, in order to implement the method in Embodiment 1, this embodiment provides a blockchain-based decentralized privacy data authorization system, including a DAPP client, a smart contract, and the blockchain itself;
[0055] The DAPP client includes any form of APP, desktop application, and web page. It is used to provide a platform for user nodes including data providers and data demanders to operate, and to manage the keys of the user nodes, access blockchain interfaces and asymmetric encryption algorithms (including all Encryption algorithms that can be applied to the block chain, such as ECC elliptic curve encryption algorithm, RSA algorithm, Elgamal algorithm, etc.), realize the encryption and decryption functions of the asymmetric encryption algorithm; the encryption function can use the encryption framework of ECC (ECIES, Elliptic Curve Integrated Encryption Schema).
[0056] The smart contract is used to provide the user node for trans...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com