Patents
Literature
797 results about "Operational behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An operational definition of behavior is a tool for understanding and managing behaviors in a school setting. It is an explicit definition that makes it possible for two or more disinterested observers to identify the same behavior when observed, even when it occurs in very different settings.
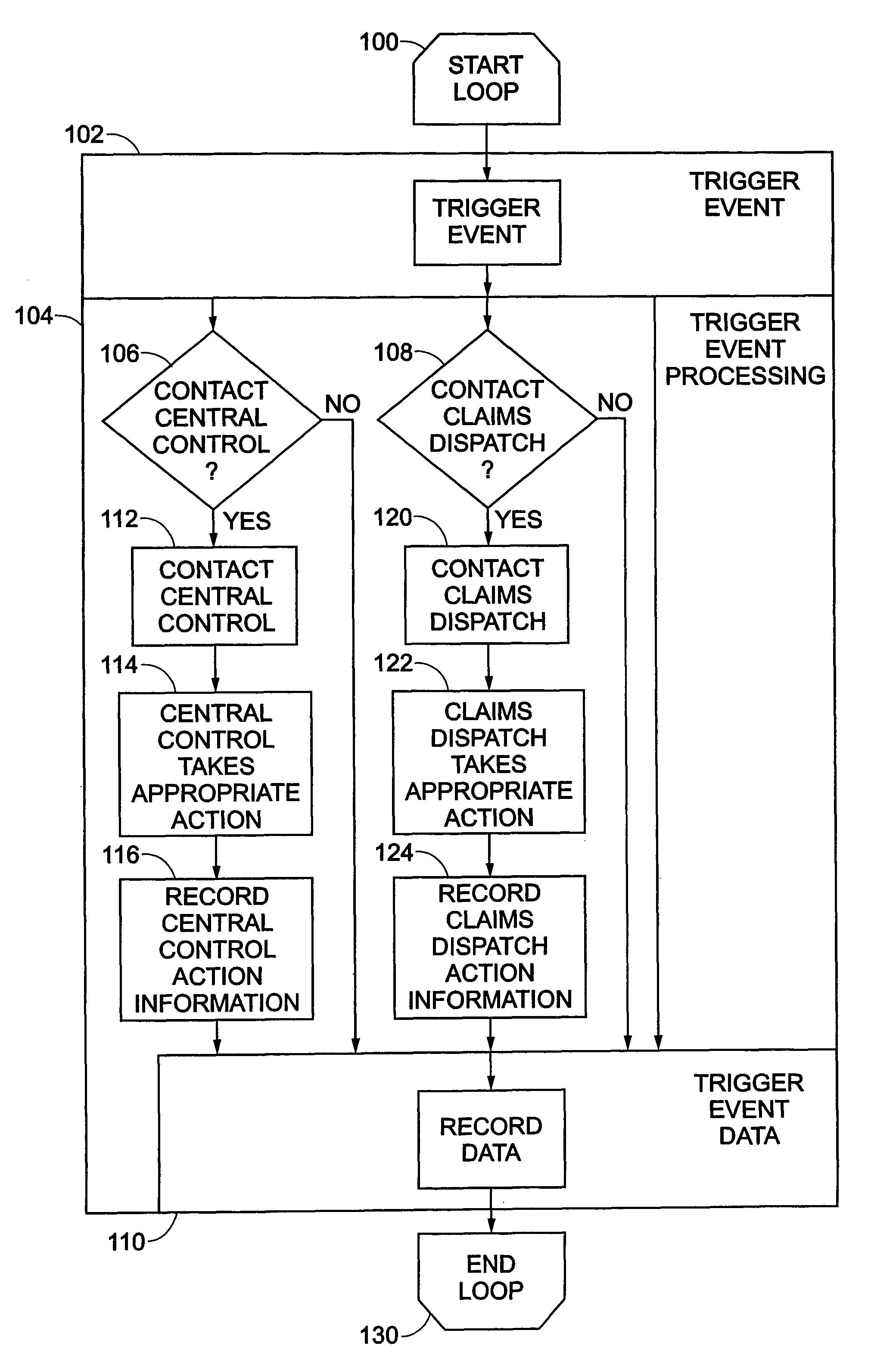
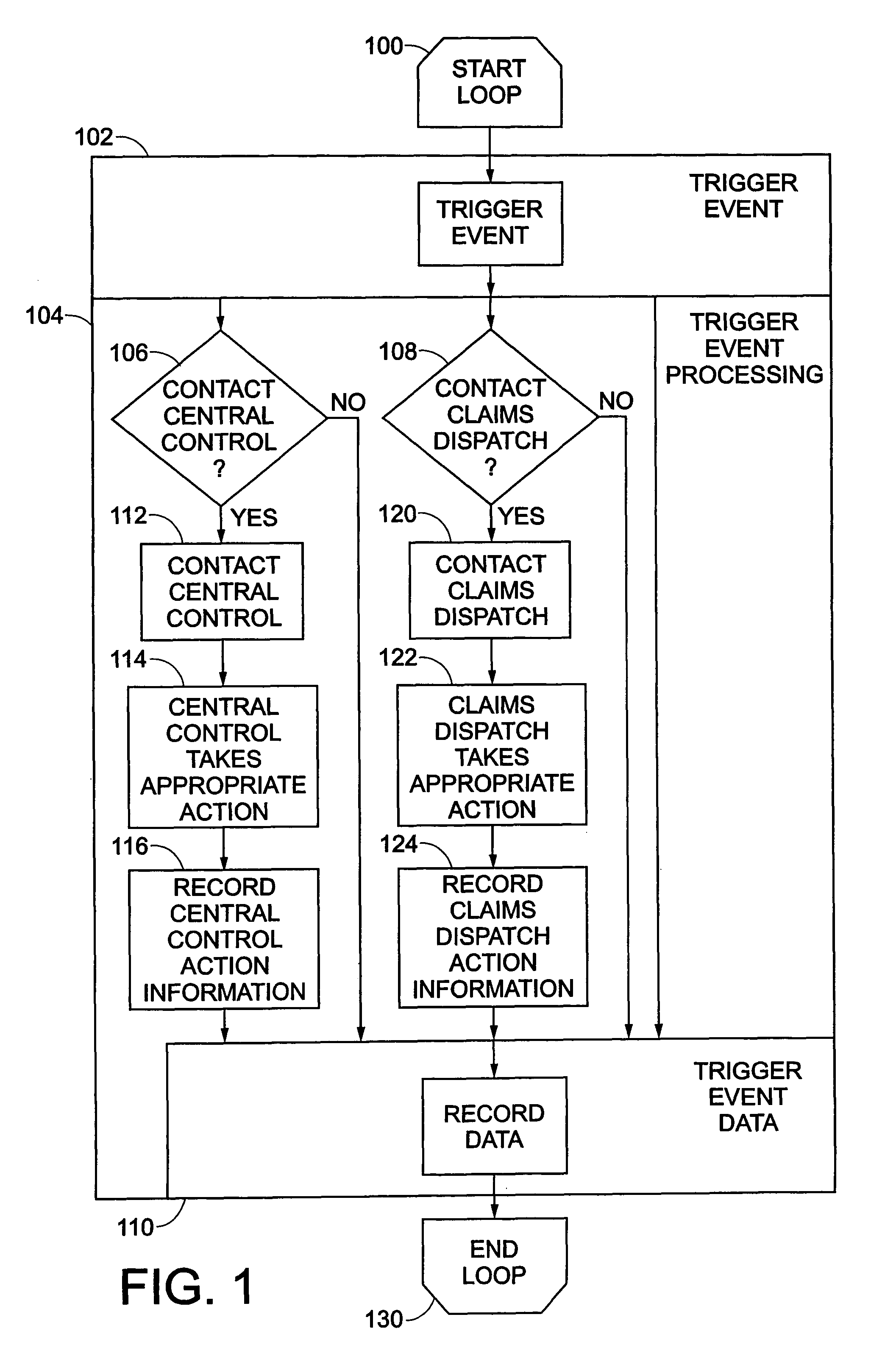
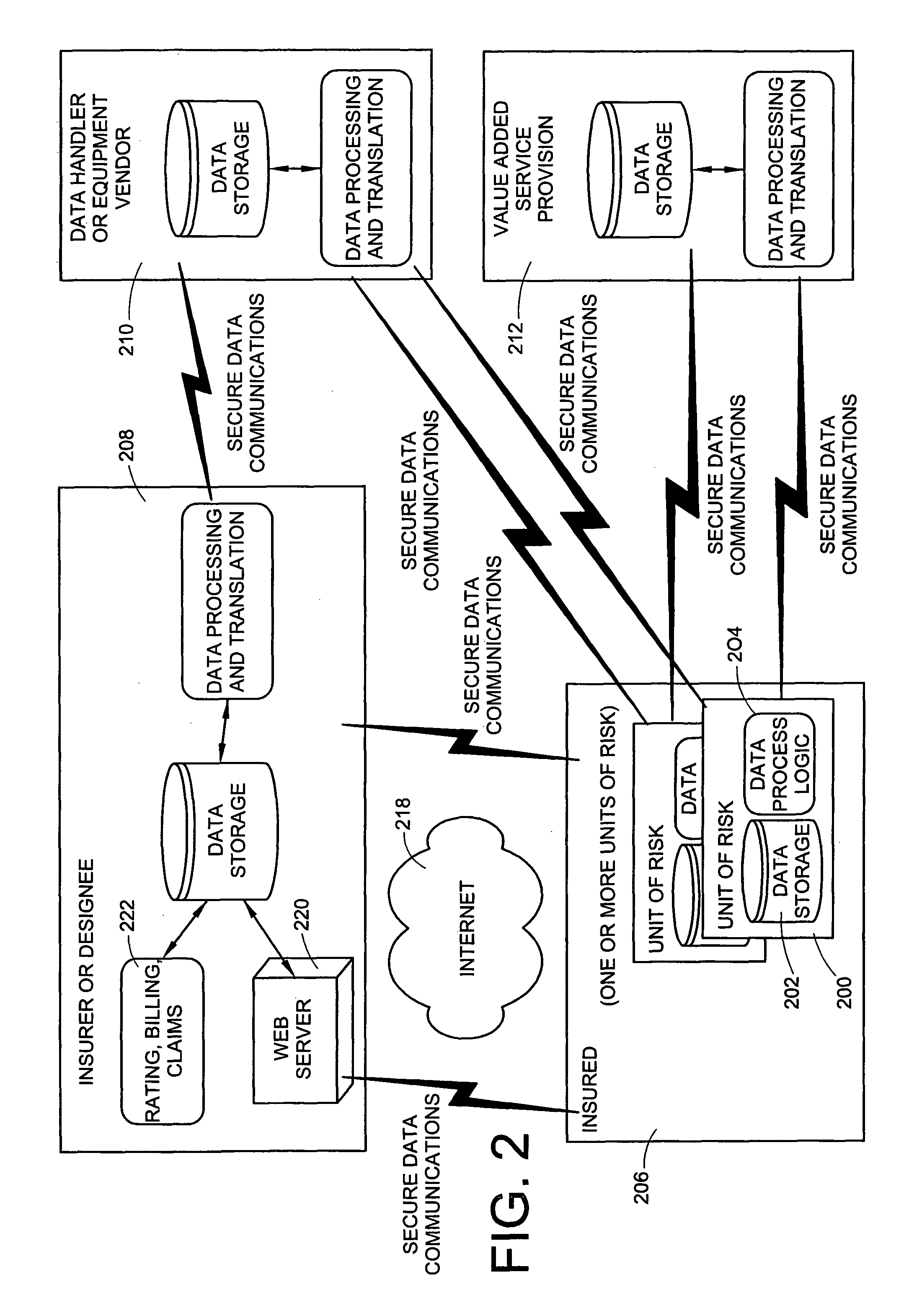
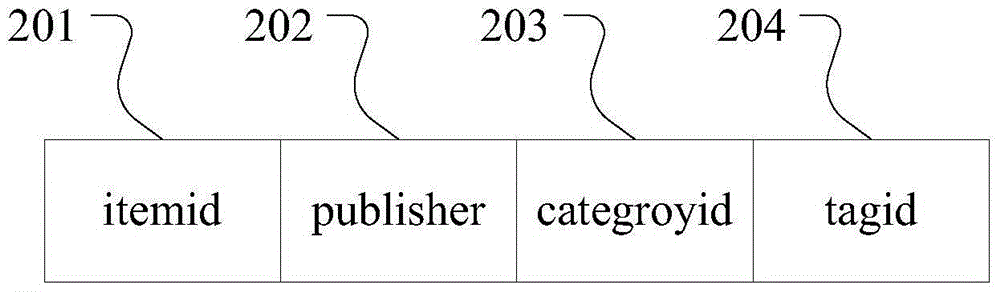
Monitoring system for determining and communicating a cost of insurance
InactiveUS8090598B2Easy to analyzeAnalogue computers for vehiclesAnalogue computers for trafficWeb siteMonitoring system
Means are provided for recording, storing, calculating, communicating and reviewing one or more operational aspects of a machine. Insurance costs are based, in part, on activities of the machine operator. A discount may be provided in exchange for recording the operational aspects and providing the recorded information to the insurer. The party may review information and decide whether to provide it to the insurer. The means for reviewing may present comparative information. Information that causes insurance costs to vary may be highlighted. Provided data may be used to verify insurance application information, generate actuarial information or determine insurance rates. Operating data may be reviewed on a computer, a Web site or other display medium so a party can observe how his operating behavior compares to that of other operators of similar machines and may be manipulated so a party can understand how changes in operating behavior can affect his insurance rates.
Owner:PROGRESSIVE CASUALTY INSURANCE
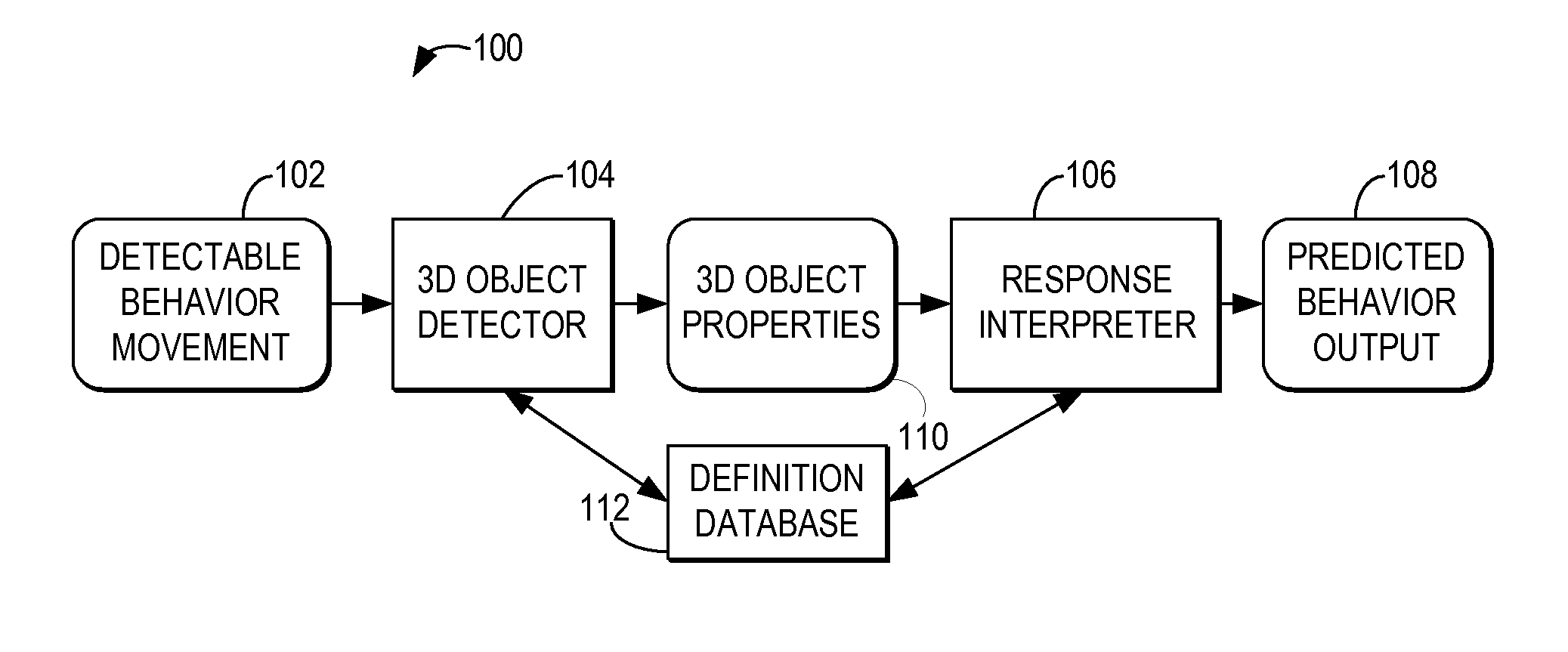
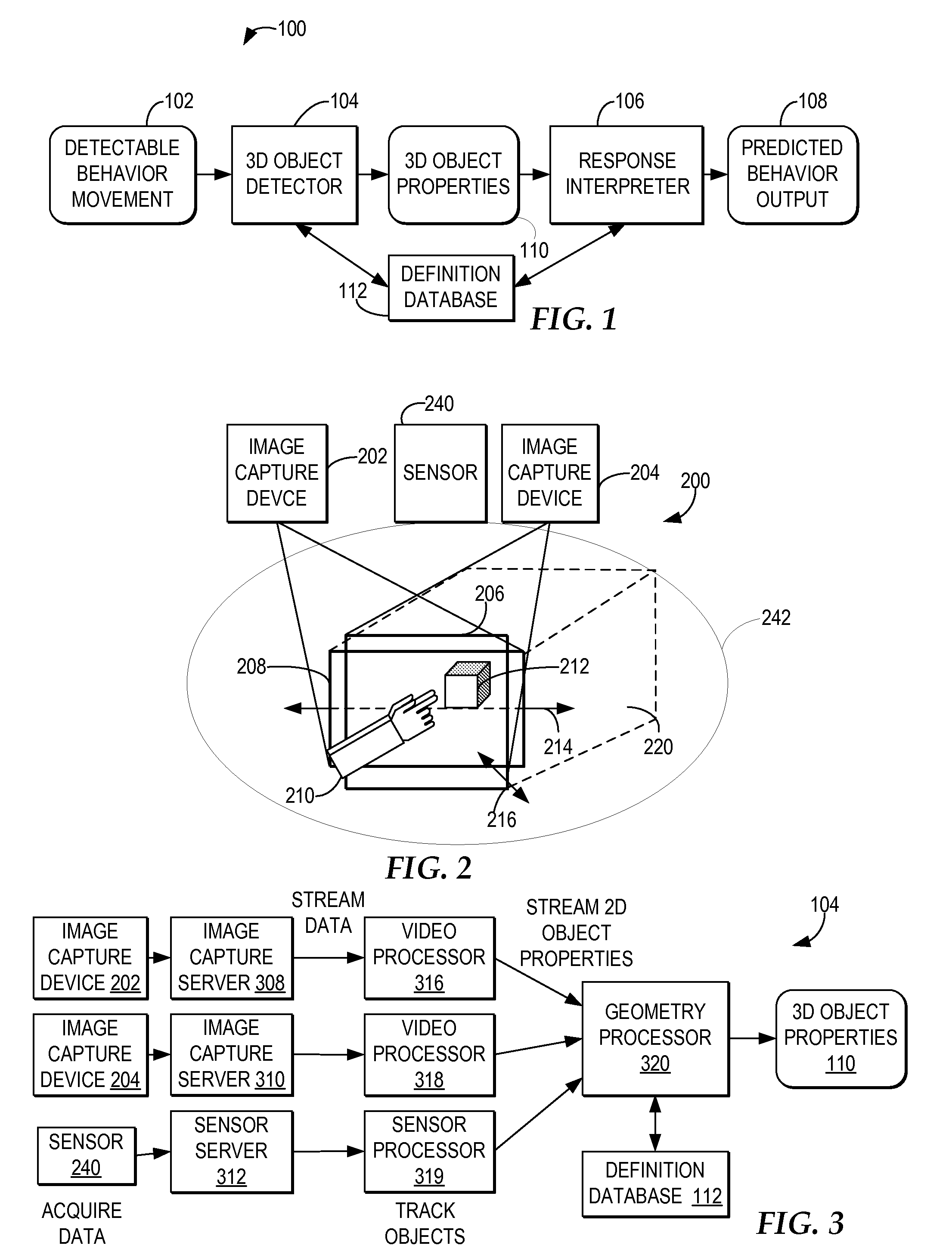
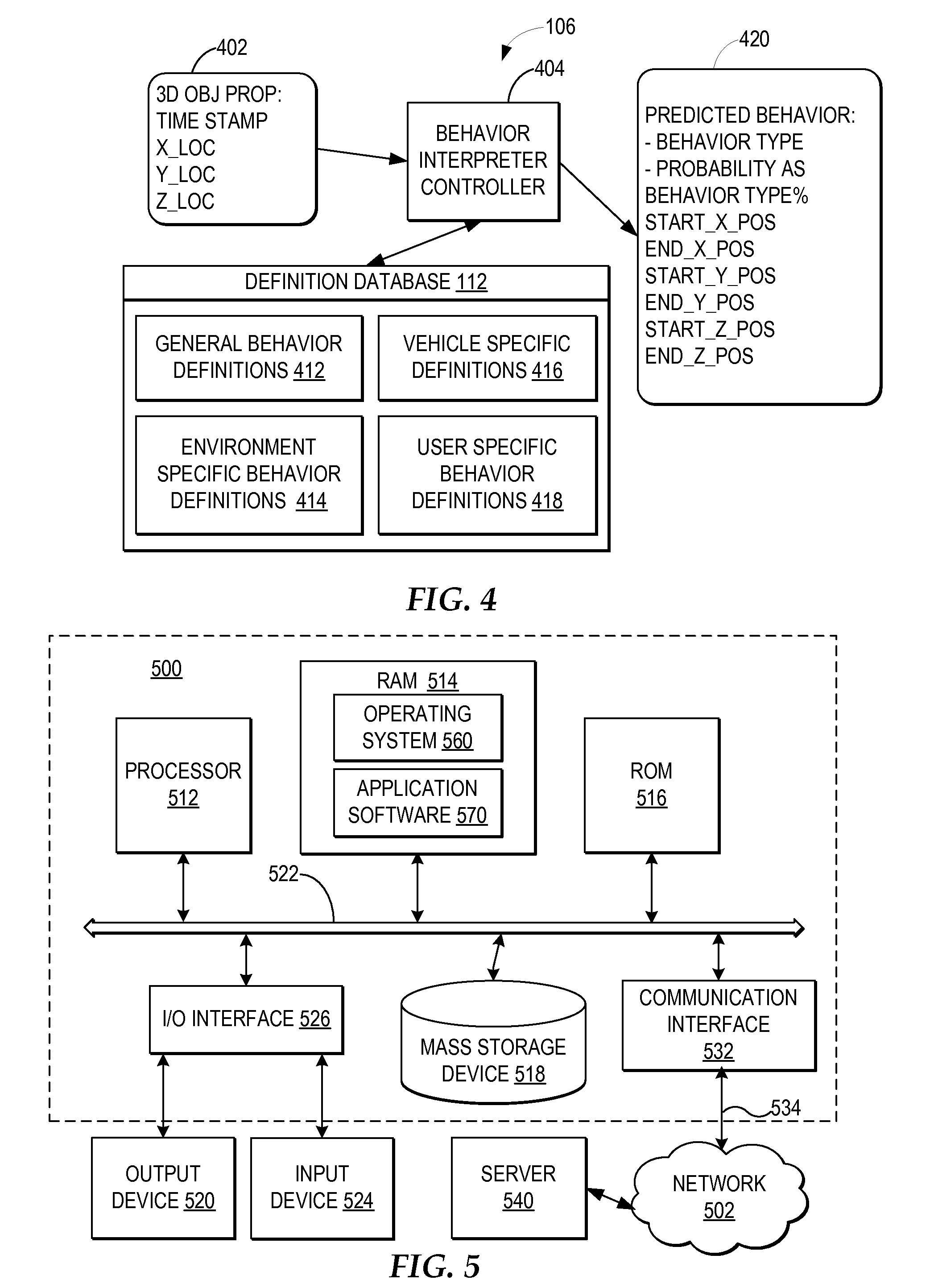
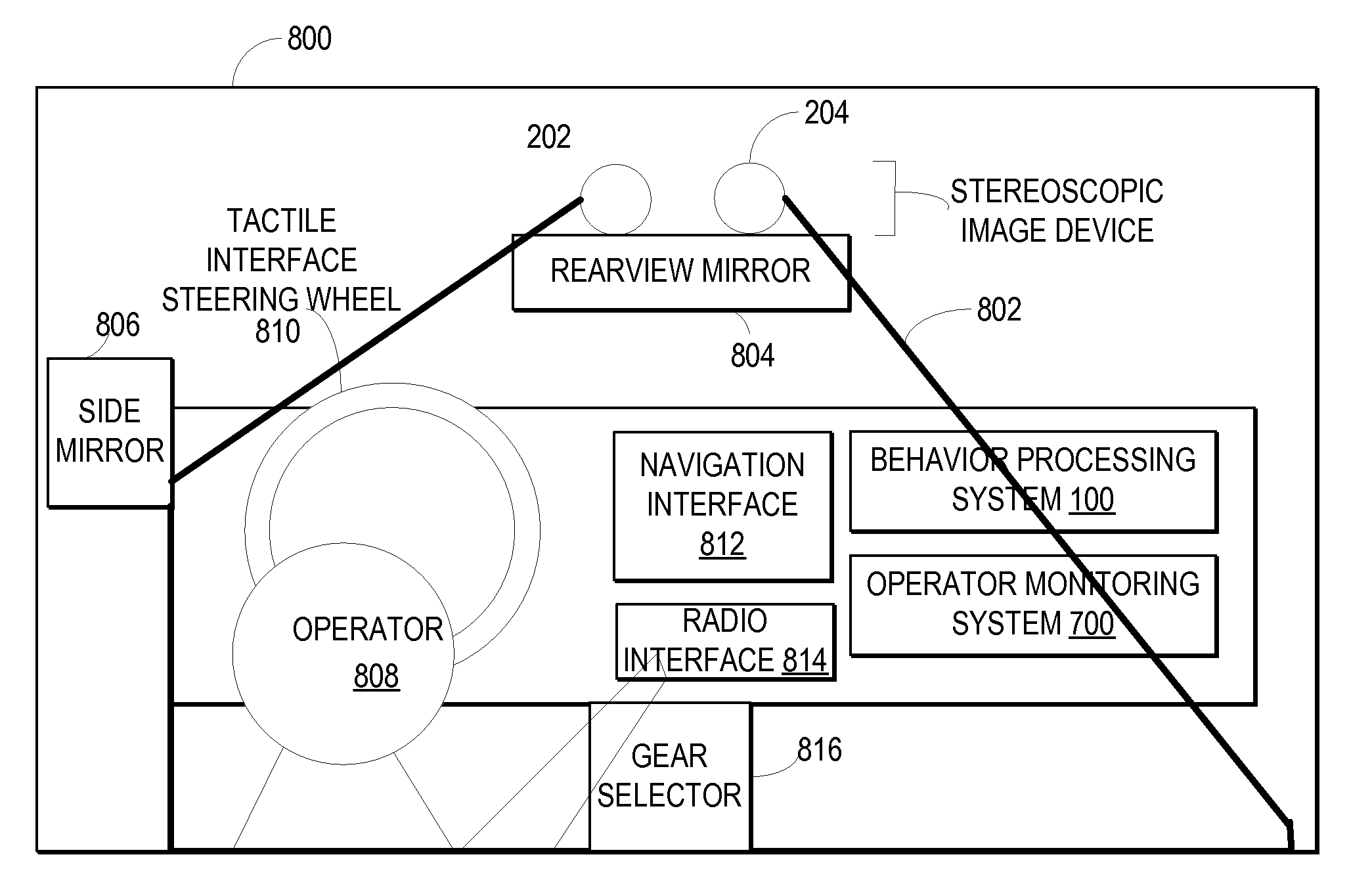
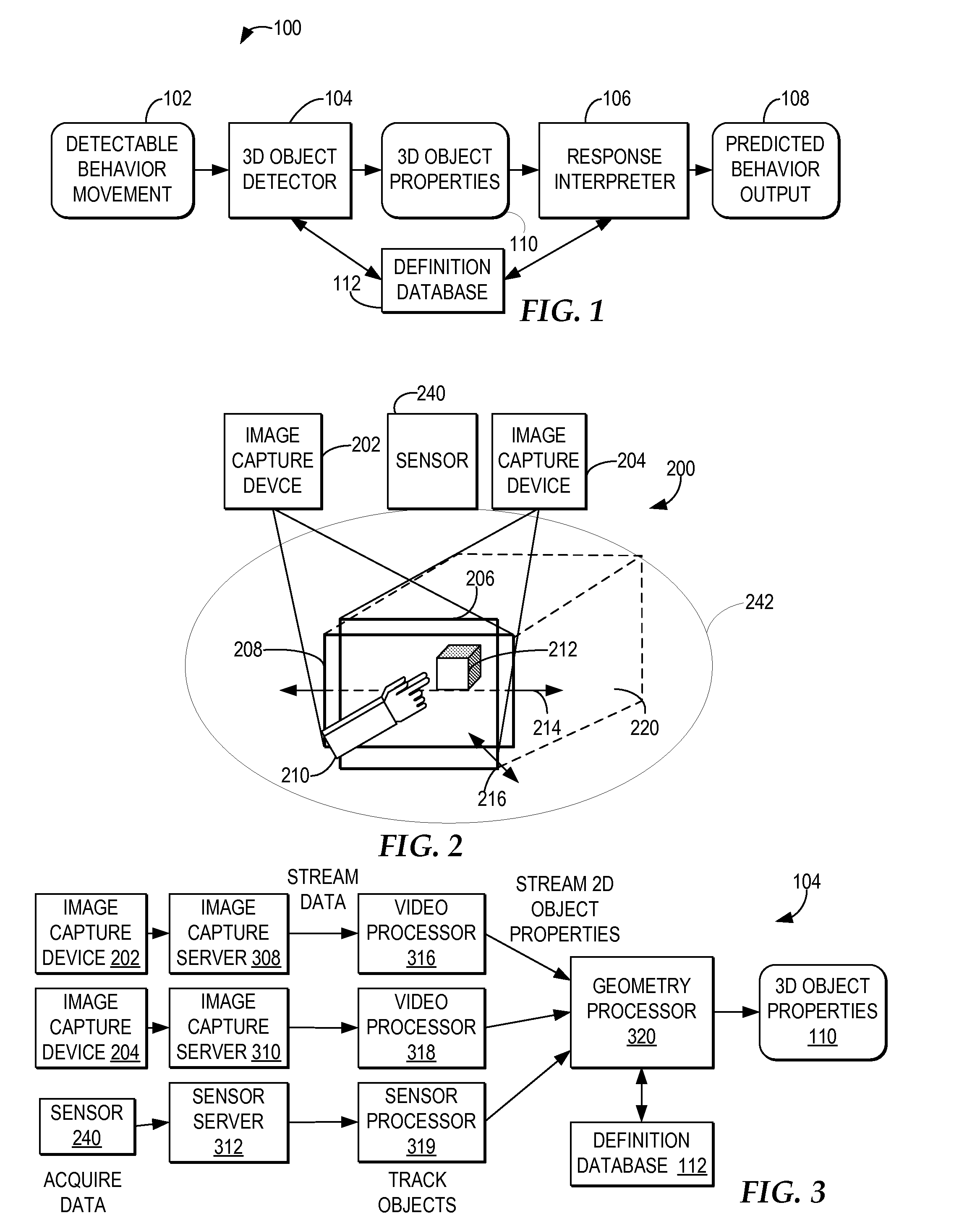
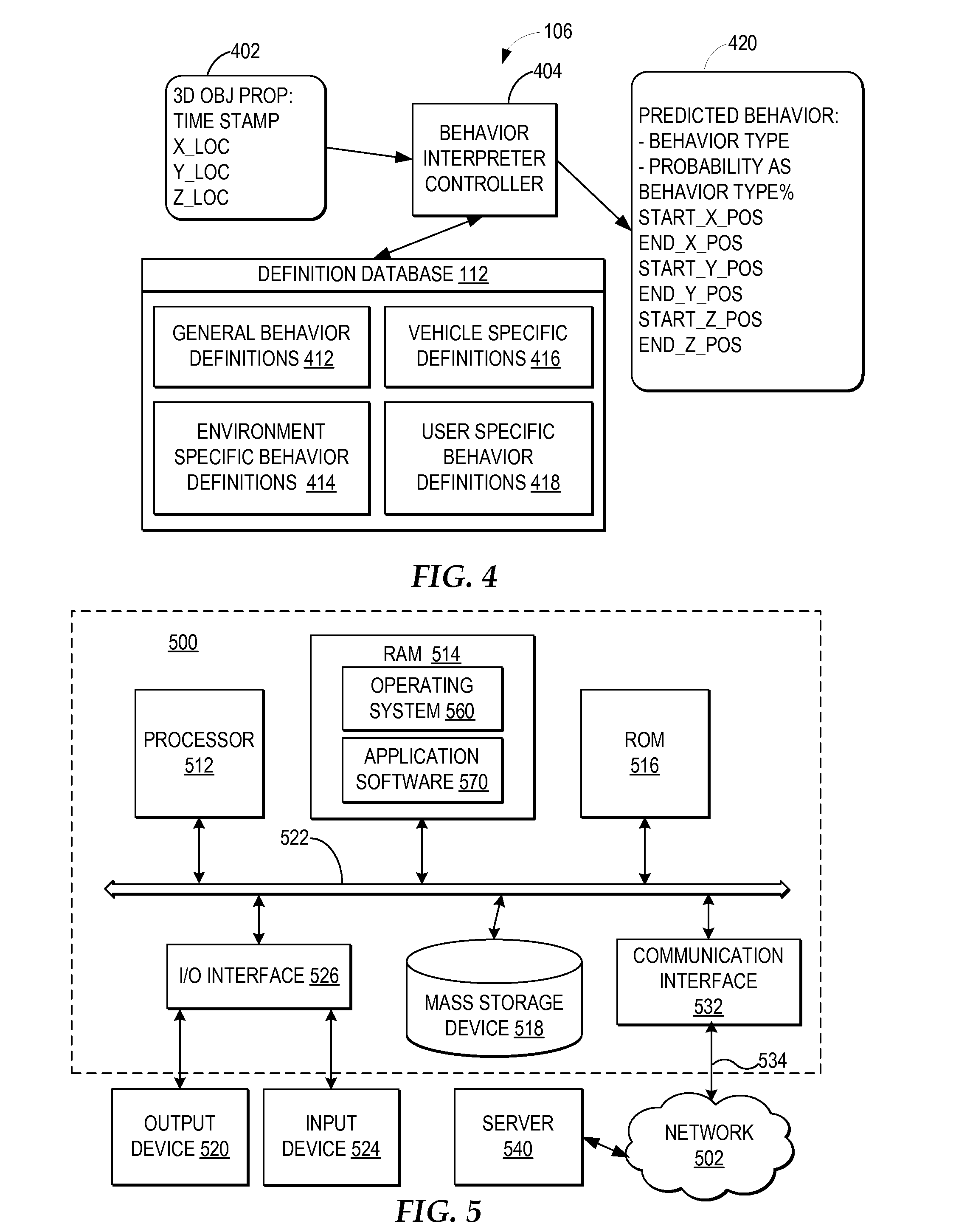
Warning a vehicle operator of unsafe operation behavior based on a 3D captured image stream
InactiveUS7792328B2Digital data processing detailsCharacter and pattern recognitionSimulationMonitoring system
A computer-implemented method, system, and program product includes a behavior processing system for capturing a three-dimensional movement of an operator of a vehicle, wherein the three-dimensional movement is determined by using at least one image capture device aimed at the operator, and identifying at least one behavior of the operator from the captured three-dimensional movement. An operator monitoring system for a vehicle determines whether the predicted behavior and the current operational state of the vehicle indicate unsafe operation of the vehicle and the operator monitoring system notifies the operator when unsafe operator of the vehicle is indicated by the operator's behavior for the current operational state of the vehicle.
Owner:LINKEDIN
Warning a vehicle operator of unsafe operation behavior based on a 3D captured image stream
InactiveUS20080169914A1Digital data processing detailsCharacter and pattern recognitionSimulationMonitoring system
A computer-implemented method, system, and program product includes a behavior processing system for capturing a three-dimensional movement of an operator of a vehicle, wherein the three-dimensional movement is determined by using at least one image capture device aimed at the operator, and identifying at least one behavior of the operator from the captured three-dimensional movement. An operator monitoring system for a vehicle determines whether the predicted behavior and the current operational state of the vehicle indicate unsafe operation of the vehicle and the operator monitoring system notifies the operator when unsafe operator of the vehicle is indicated by the operator's behavior for the current operational state of the vehicle.
Owner:LINKEDIN
Monitoring system for determining and communicating a cost of insurance
InactiveUS20120158436A1FinanceRegistering/indicating working of vehiclesMonitoring systemOperational behavior
Means are provided for recording, storing, calculating, communicating and reviewing one or more operational aspects of a machine. Insurance costs are based, in part, on activities of the machine operator. A discount may be provided in exchange for recording the operational aspects and providing the recorded information to the insurer. The party may review information and decide whether to provide it to the insurer. The means for reviewing may present comparative information. Information that causes insurance costs to vary may be highlighted. Provided data may be used to verify insurance application information, generate actuarial information or determine insurance rates. Operating data may be reviewed on display medium so a party can observe how his operating behavior compares to that of other operators of similar machines and may be manipulated so a party can understand how changes in operating behavior can affect his insurance rates.
Owner:PROGRESSIVE CASUALTY INSURANCE
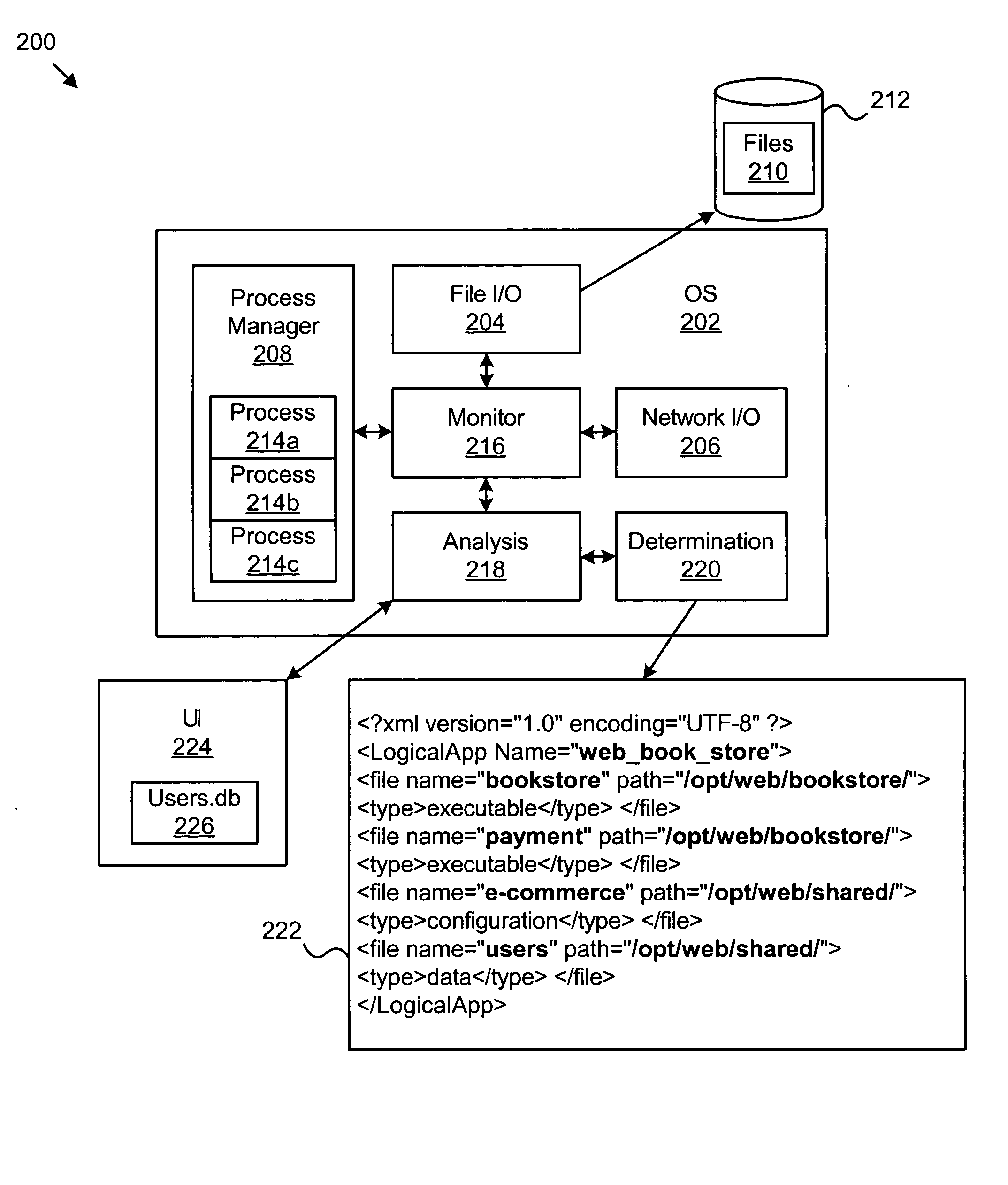
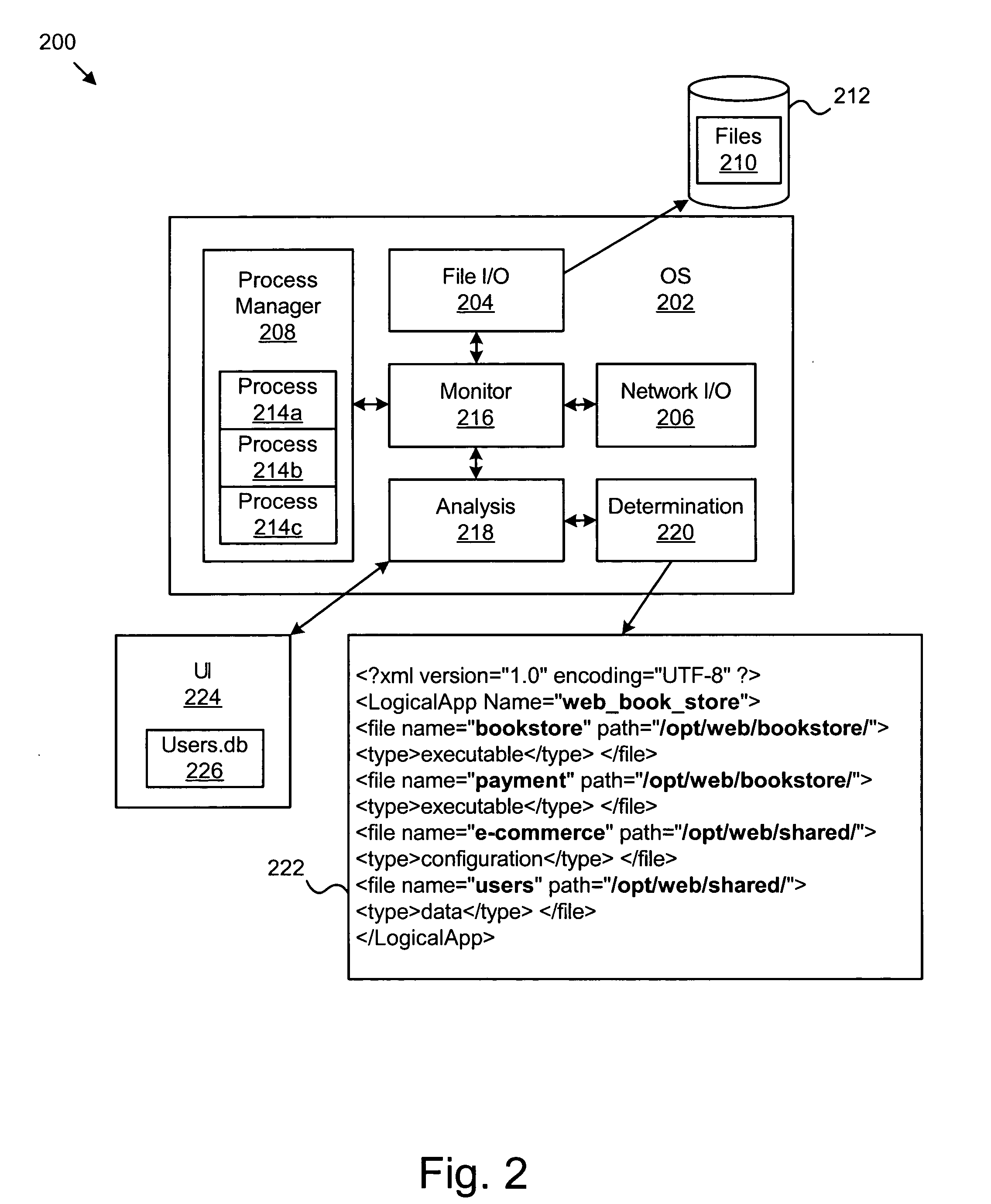
Apparatus, system, and method for automatically discovering and grouping resources used by a business process
InactiveUS20060037022A1Program control using stored programsResource allocationOperational behaviorBusiness process
An apparatus, system, and method are provided for automatically discovering and grouping files and other resources used by a business process. The present invention includes a monitoring module that collects trace data representative of operational behavior of software applications. An analysis module analyzes the trace data to discover resources affiliated with the business process. A determination module defines a logical application corresponding to the business process and includes the resources discovered by the analysis module. The logical application is automatically defined such that business policies may be readily implemented on the logical application as a whole. Manual identification of resources for a business process is eliminated or substantially reduced.
Owner:IBM CORP
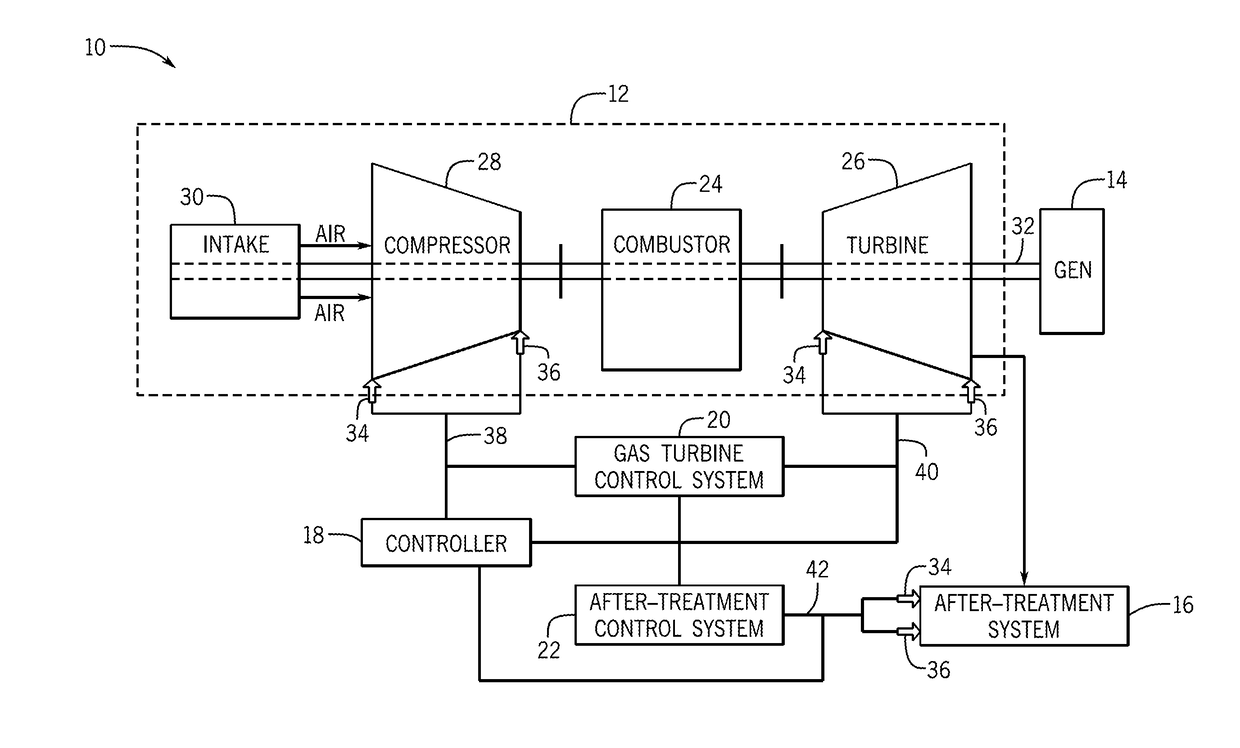
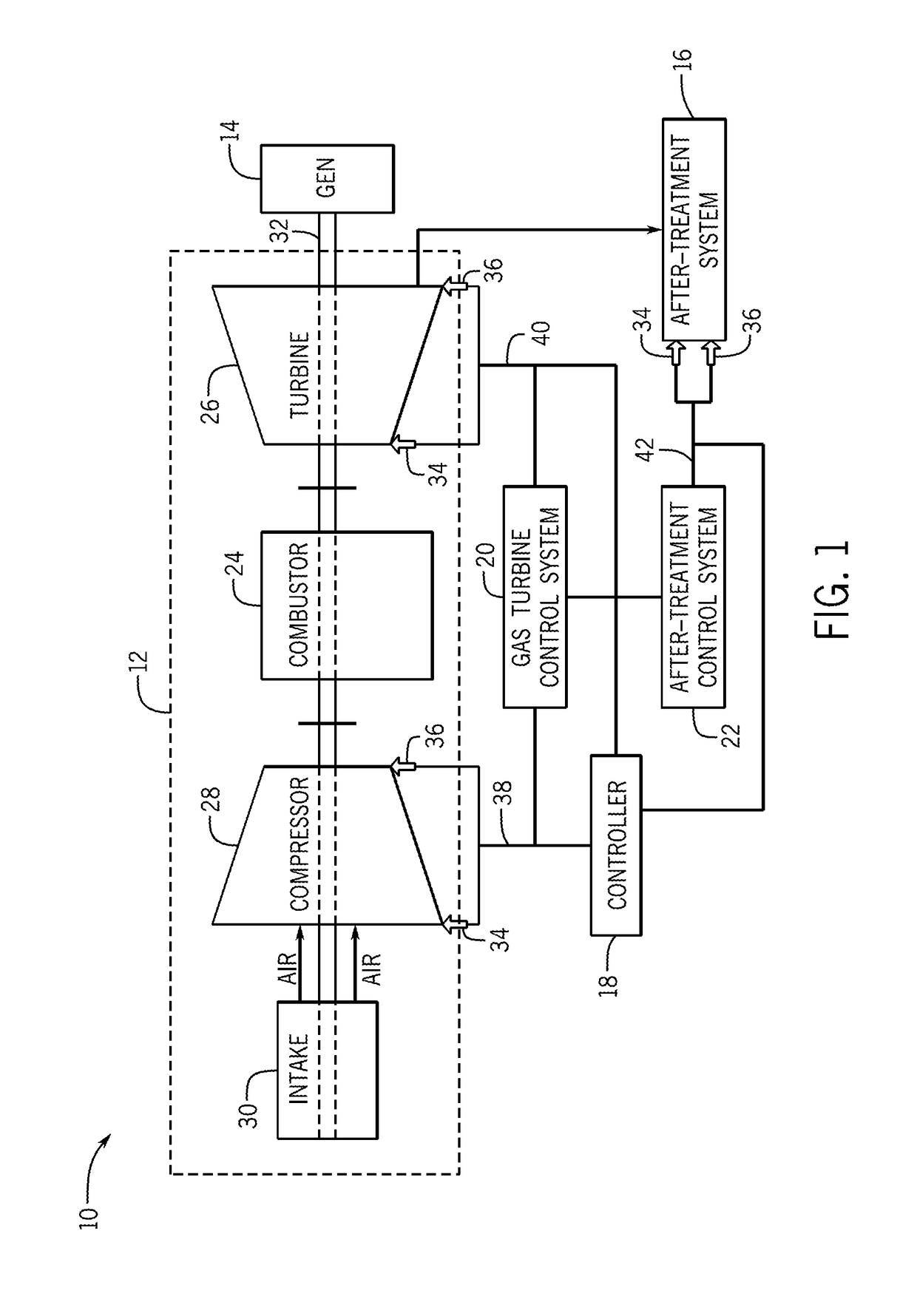
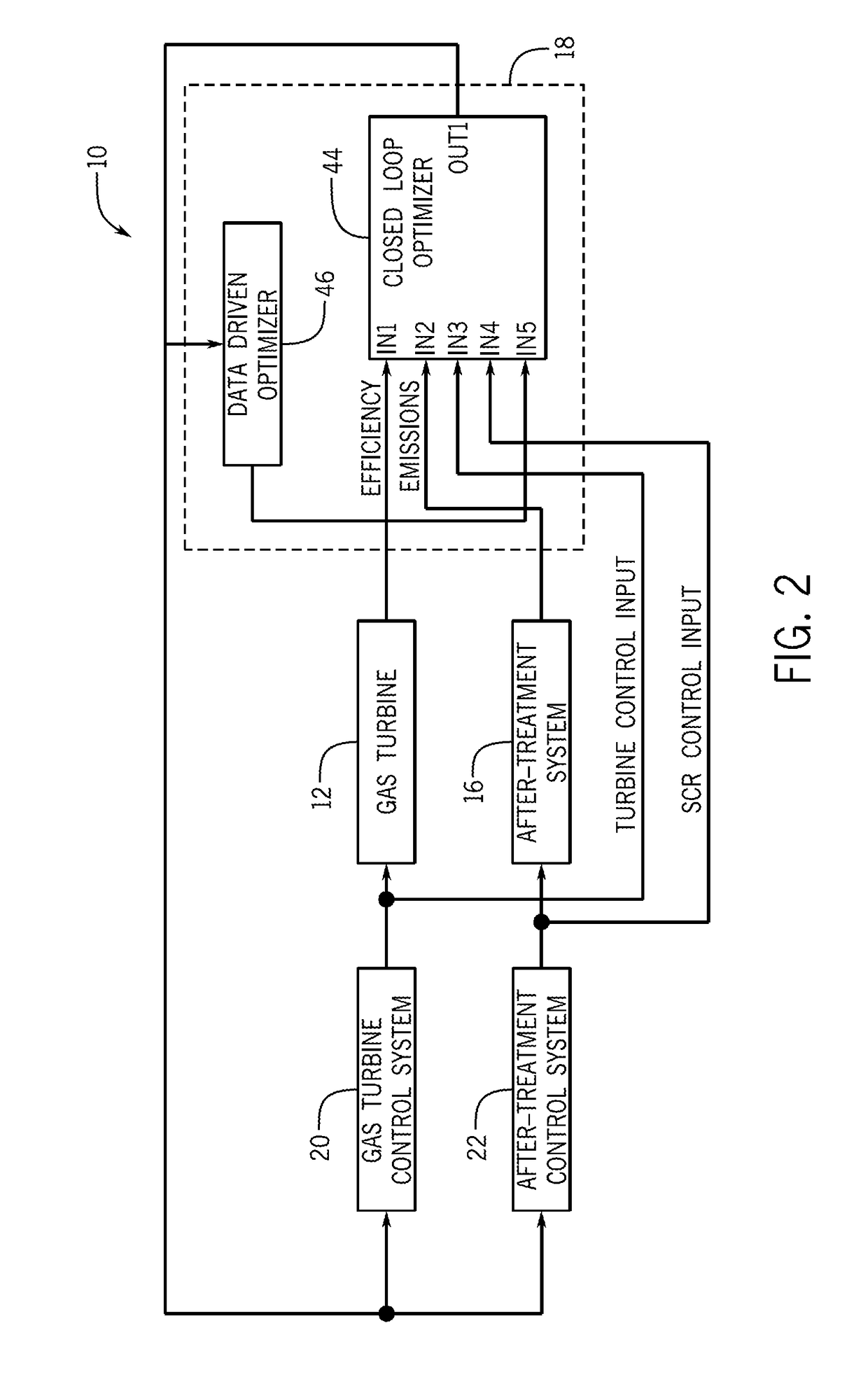
Enhanced performance of a gas turbine
ActiveUS20170175645A1Reduce outputMinimizes outputExhaust apparatusEngine fuctionsAfter treatmentOperational behavior
In one embodiment, a system may include a gas turbine system. the gas turbine system includes a gas turbine, an after-treatment system that may receive exhaust gases from the gas turbine system, and a controller that may receive inputs and model operational behavior of an industrial plant based on the inputs. The industrial plant may include the gas turbine and the after-treatment system. The controller may also determine one or more operational parameter setpoints for the industrial plant, select the one or more operational parameter setpoints that reduce an output of a cost function, and apply the one or more operational parameter setpoints to control the industrial plant.
Owner:GENERAL ELECTRIC CO
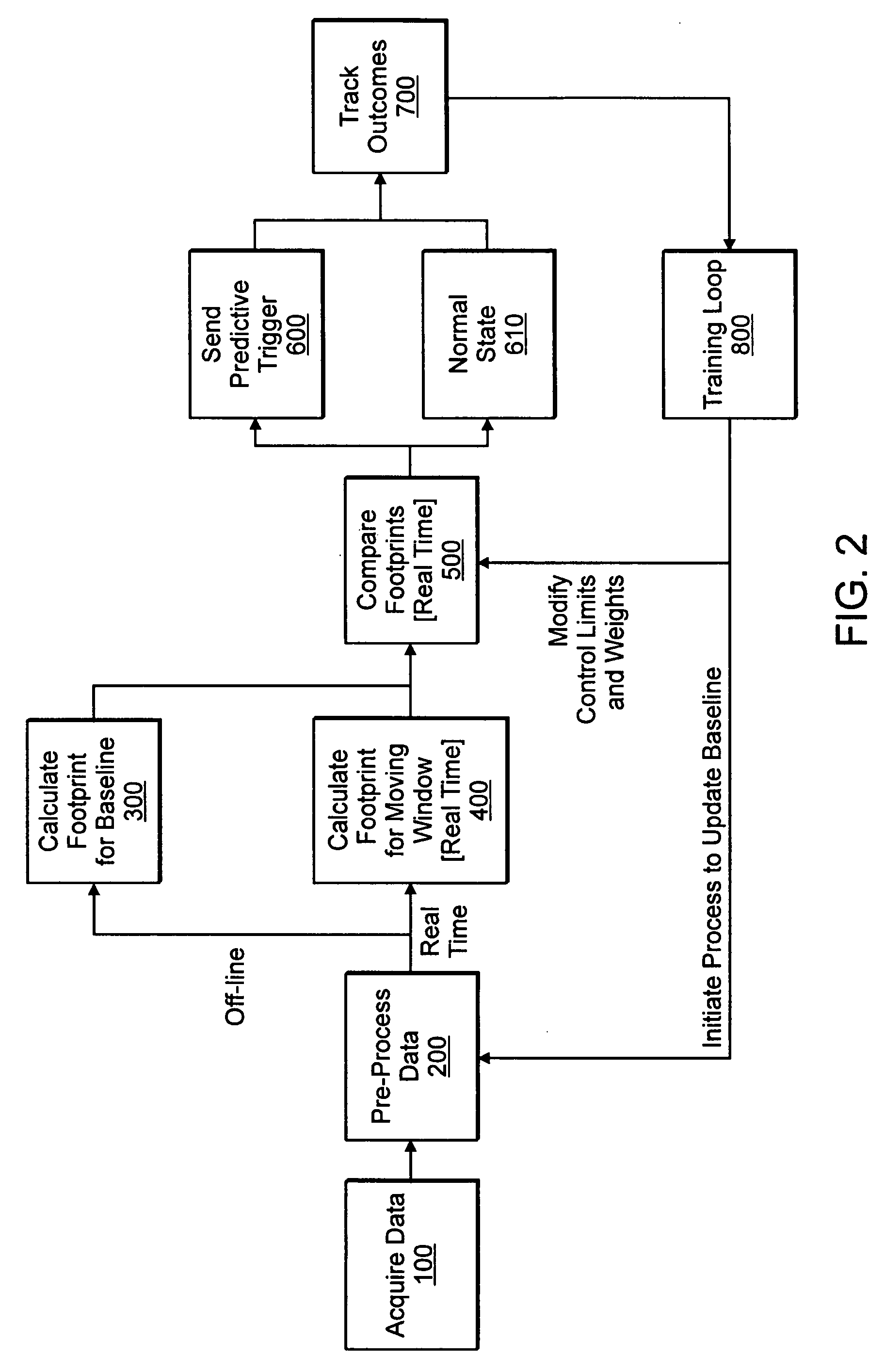
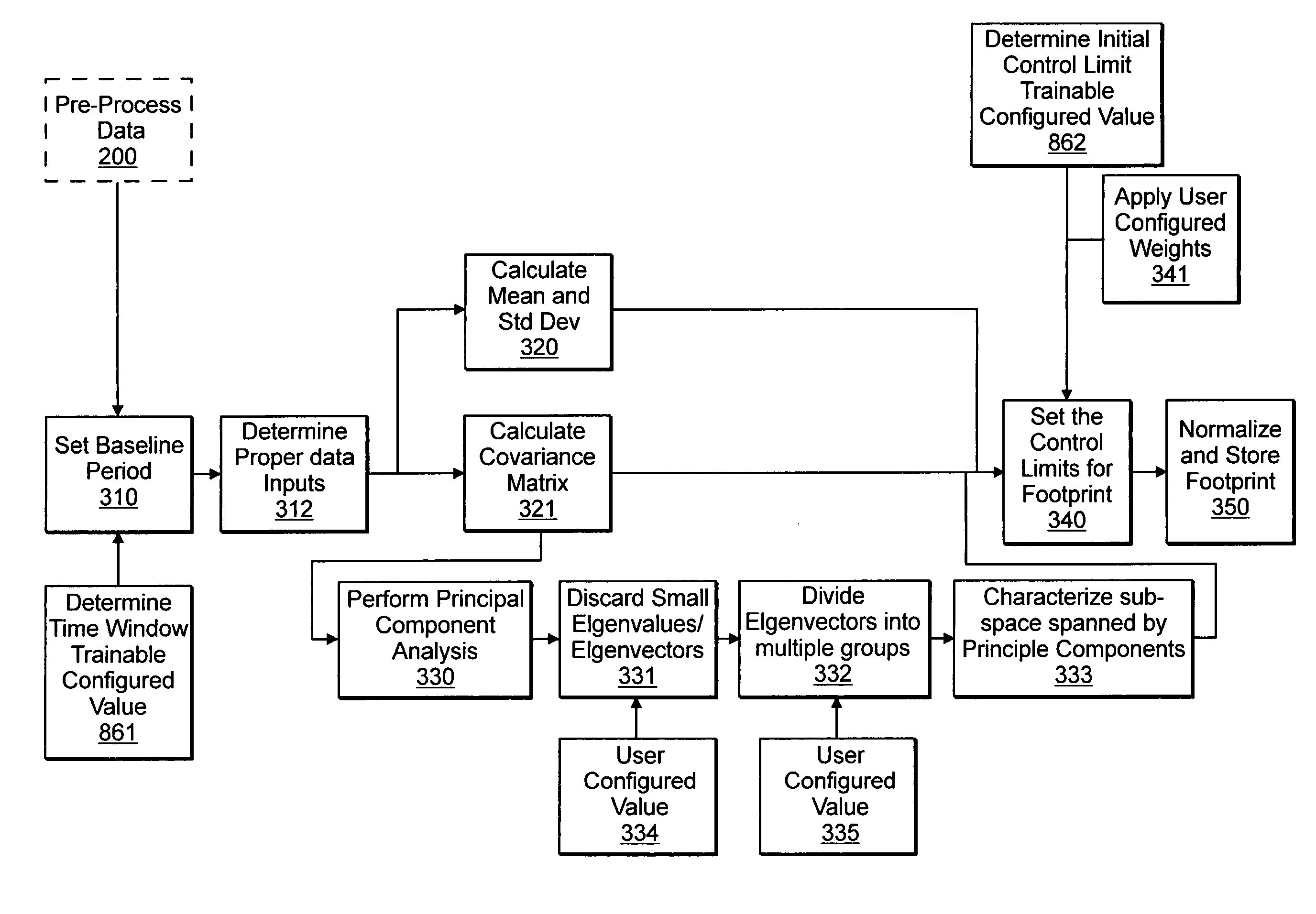
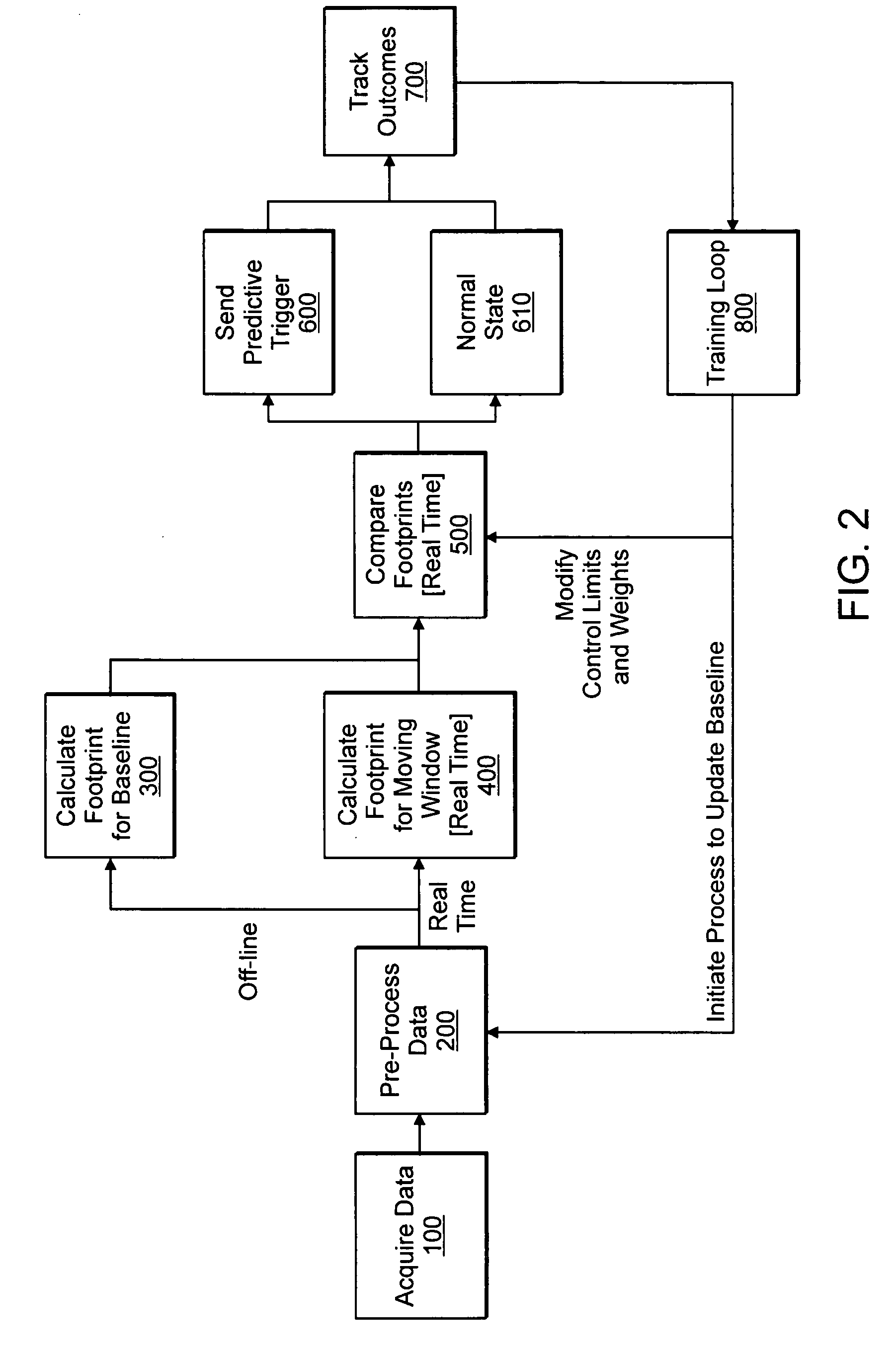
System and method for monitoring performance of groupings of network infrastructure and applications using statistical analysis
InactiveUS20060020924A1Non-redundant fault processingProgram loading/initiatingOperational behaviorUnit group
Systems, methods and computer program products for monitoring performance of groupings of network infrastructure and applications using statistical analysis. A method, system and computer program monitors managed unit groupings of executing software applications and execution infrastructure to detect deviations in performance. Logic acquires time-series data from at least one managed unit grouping of executing software applications and execution infrastructure. Other logic derives a statistical description of expected behavior from an initial set of acquired data. Logic derives a statistical description of operating behavior from acquired data corresponding to a defined moving window of time slots. Logic compares the statistical description of expected behavior with the statistical description of operating behavior; and logic reports predictive triggers, said logic to report being responsive to said logic to compare and said logic to report identifying instances where the statistical description of operating behavior deviates from statistical description of operating behavior to indicates a statistically significant probability that an operating anomaly exists within the at least managed unit grouping corresponding to the acquired time-series data.
Owner:K5 SYST
System and method for monitoring performance of network infrastructure and applications by automatically identifying system variables or components constructed from such variables that dominate variance of performance
InactiveUS20060020866A1Electronic circuit testingNon-redundant fault processingStatistical analysisParallel computing
Systems, methods and computer program products for monitoring performance of network infrastructure and applications by automatically identifying system variables or combinations constructed from such variables that dominate variance of system performance. A method, system and computer program monitors performance of executing software applications and execution infrastructure components to detect deviations in performance. Logic acquires data from executing software applications and execution infrastructure, said data including descriptive data variables and outcomes data variables. Other logic statistically analyzes said acquired data to identify instances where the statistical description of operating behavior deviates from expected operating behavior and to indicate with a statistically significant probability that an operating anomaly exists within said executing software applications and execution infrastructure; and logic, cooperating with the logic to statistically analyze, filters out non-essential variables in the acquired data from being utilized by the logic to statistically analyze, such that remaining variables and combinations thereof account for a substantial contribution in the variance of performance of the executing software applications and execution infrastructure.
Owner:K5 SYST
User intention recognition method and device
ActiveCN104951428AImprove accuracyImprove recallSpecial data processing applicationsOperational behaviorTarget text
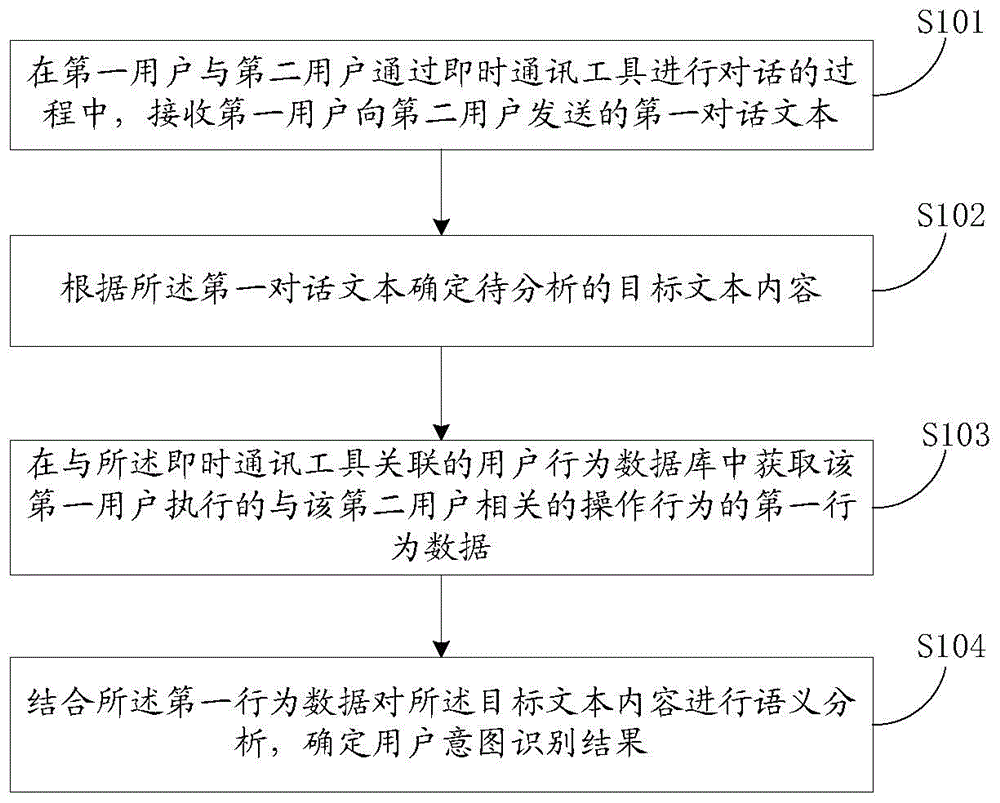
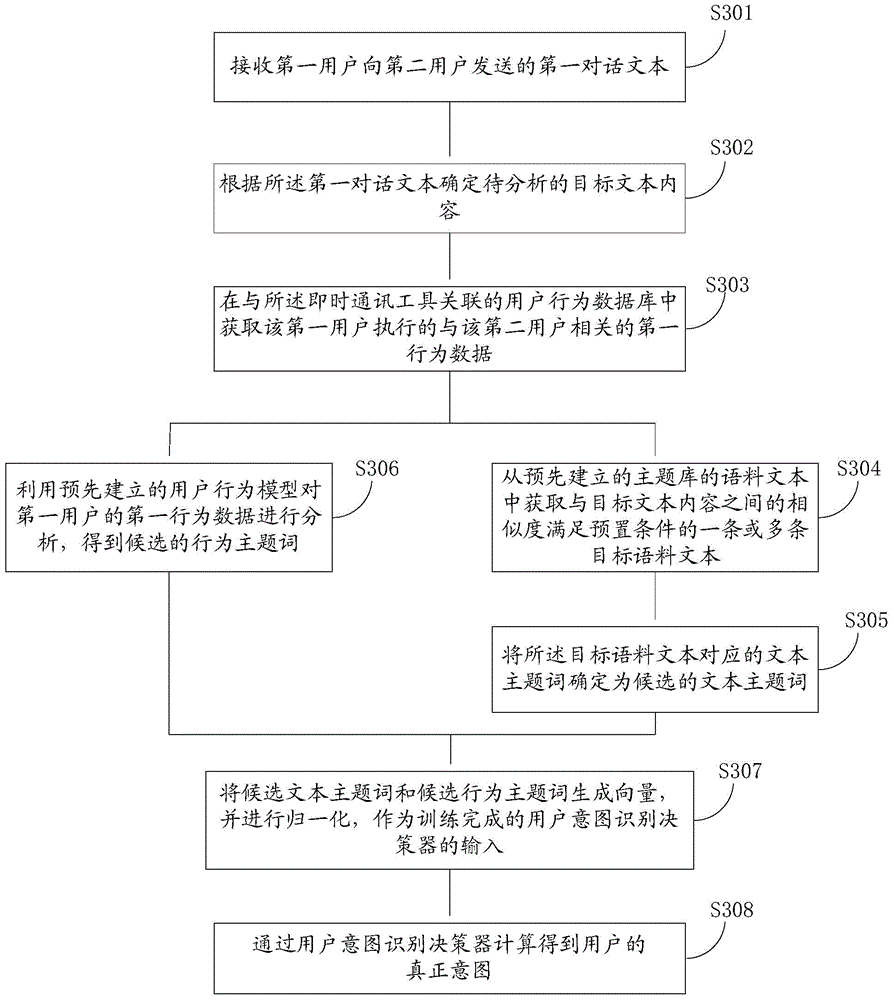
The invention discloses a user intention recognition method and device. The method includes the steps that in the process that a first user and a second user conduct conversation through an instant messaging tool, a first conversation text sent to the second user by the first user is received; the target text content to be analyzed is determined according to the first conversation text; first behavior data of the operation behavior executed by the first user and related to the second user are obtained in a user behavior database associated with the instant messaging tool; semantic analysis is conducted on the target text content in combination with the first behavior data, and the user intention recognition result is determined. By means of the user intention recognition method and device, the real intension of users can be recognized more accurately.
Owner:ZHEJIANG TMALL TECH CO LTD
Method for monitoring plants with mechanical components
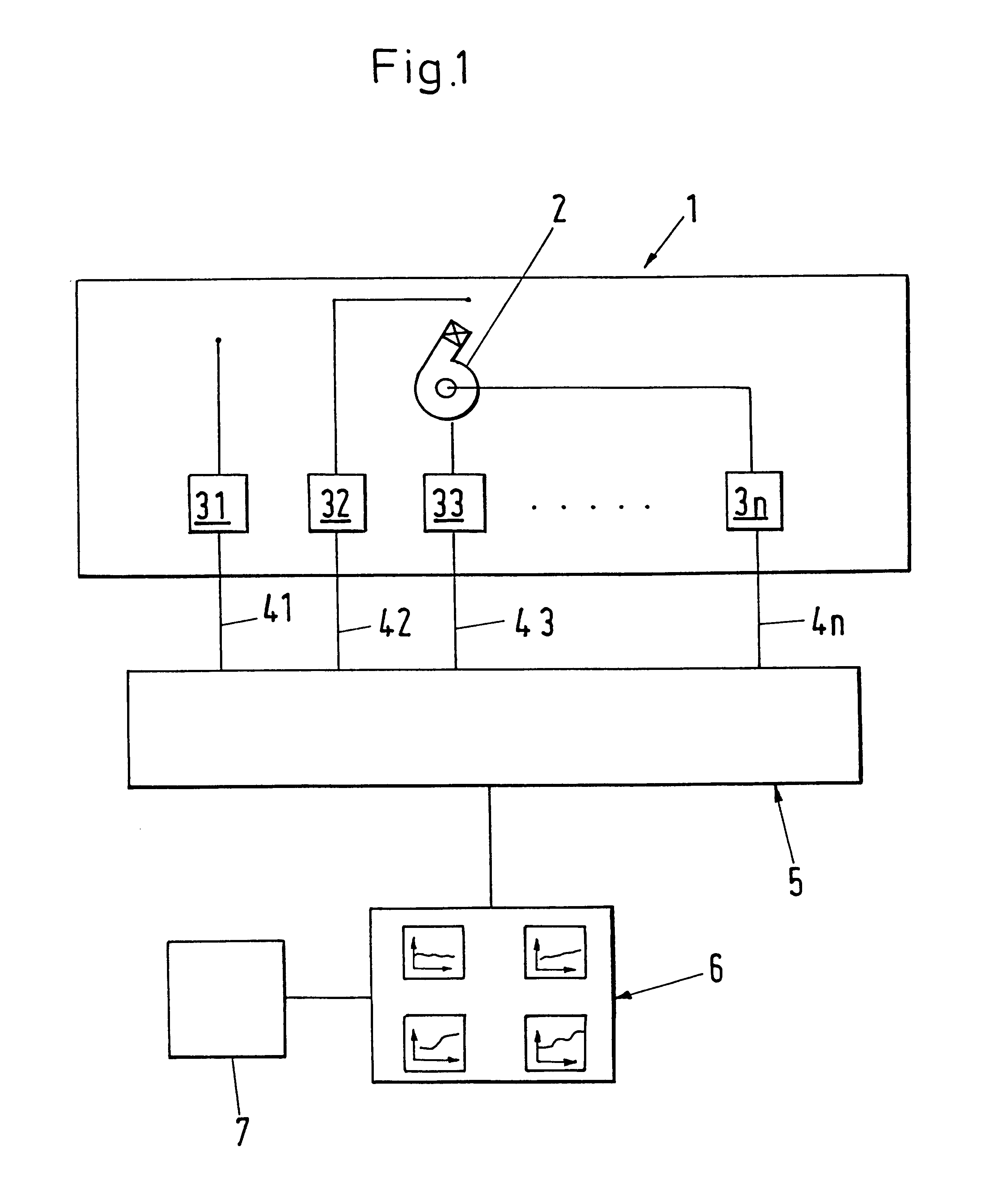
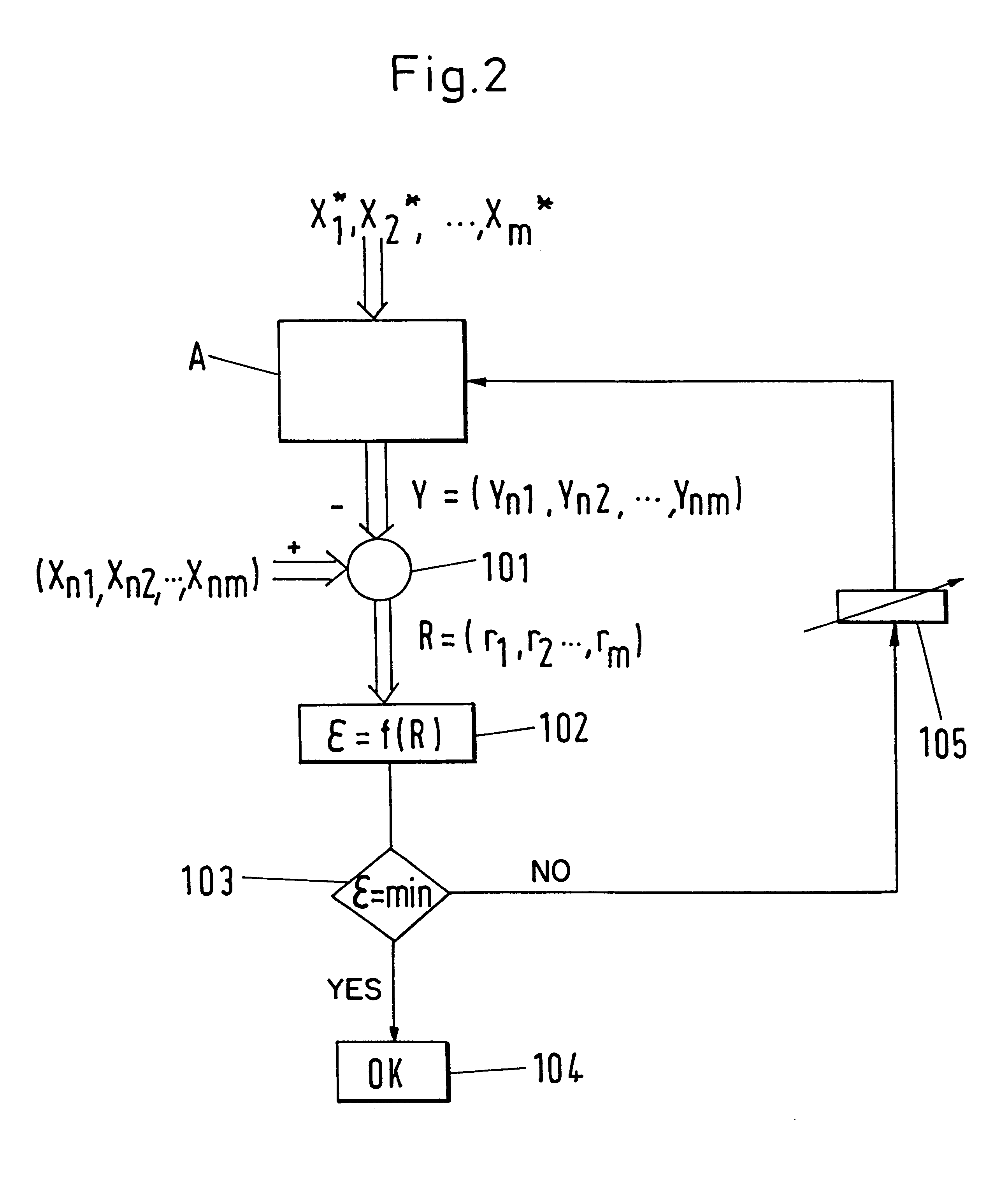
InactiveUS6208953B1Unnecessary standstill timeReduce maintenance costsPlug gaugesRegistering/indicating working of machinesMechanical componentsOperational behavior
In a method for monitoring plants with mechanical components, measured values (xiT; xiu) are determined at predeterminable time intervals for a fixed set of parameters (xi). The measured values (xiT) which are determined for various working points during a modelling phase are used for the generation of a model for the operating behavior of the components. With the help of the model for the operating behavior at least one monitoring value (r; snu) is derived at predeterminable time intervals which is independent of the respective current working point. The temporal behavior of the monitoring value (r; snu) is used for estimating the wear in the components and / or for the detection of operating disturbances.
Owner:SULZER INNOTEC
Multi-policy commercial product recommending system based on context information
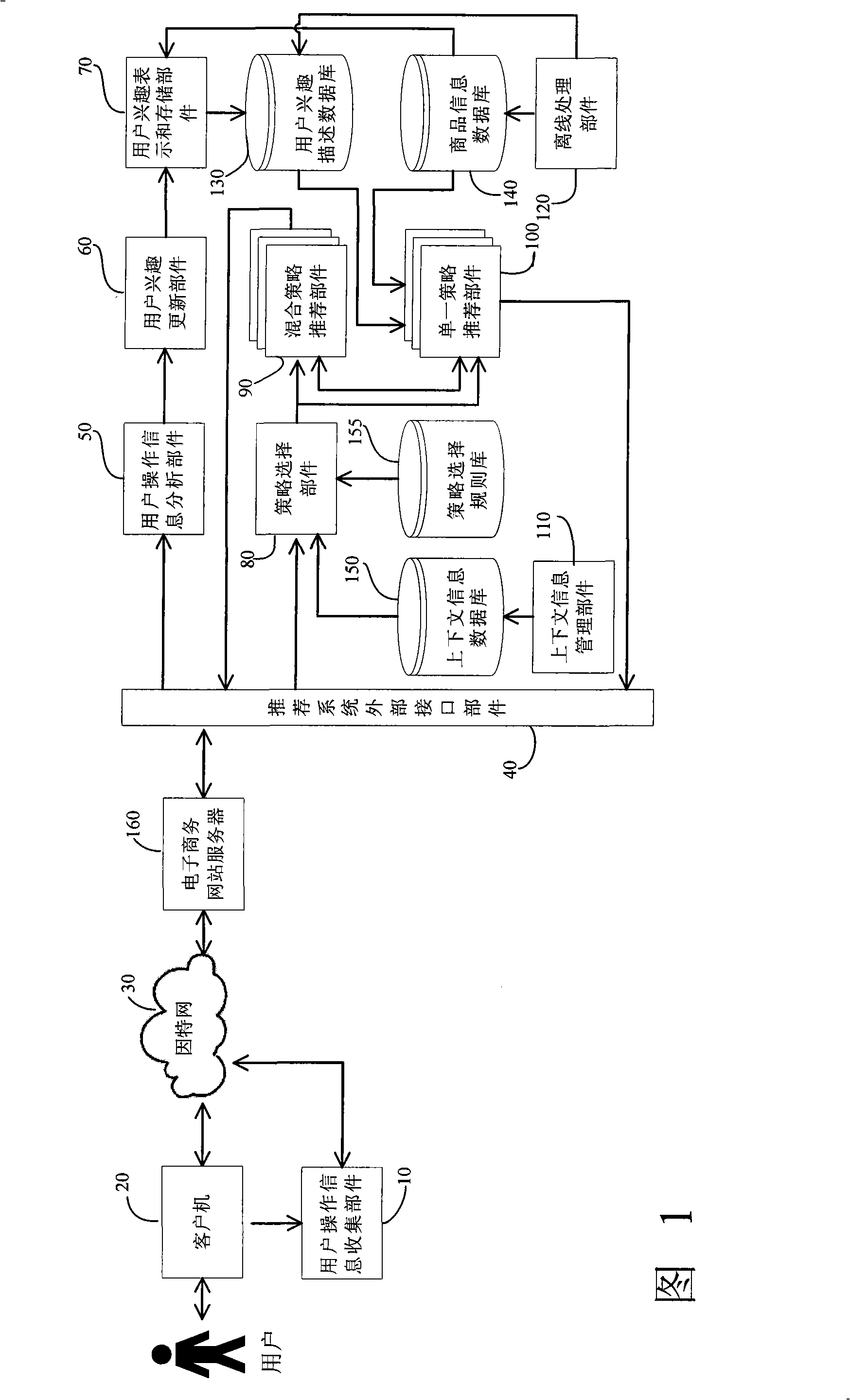
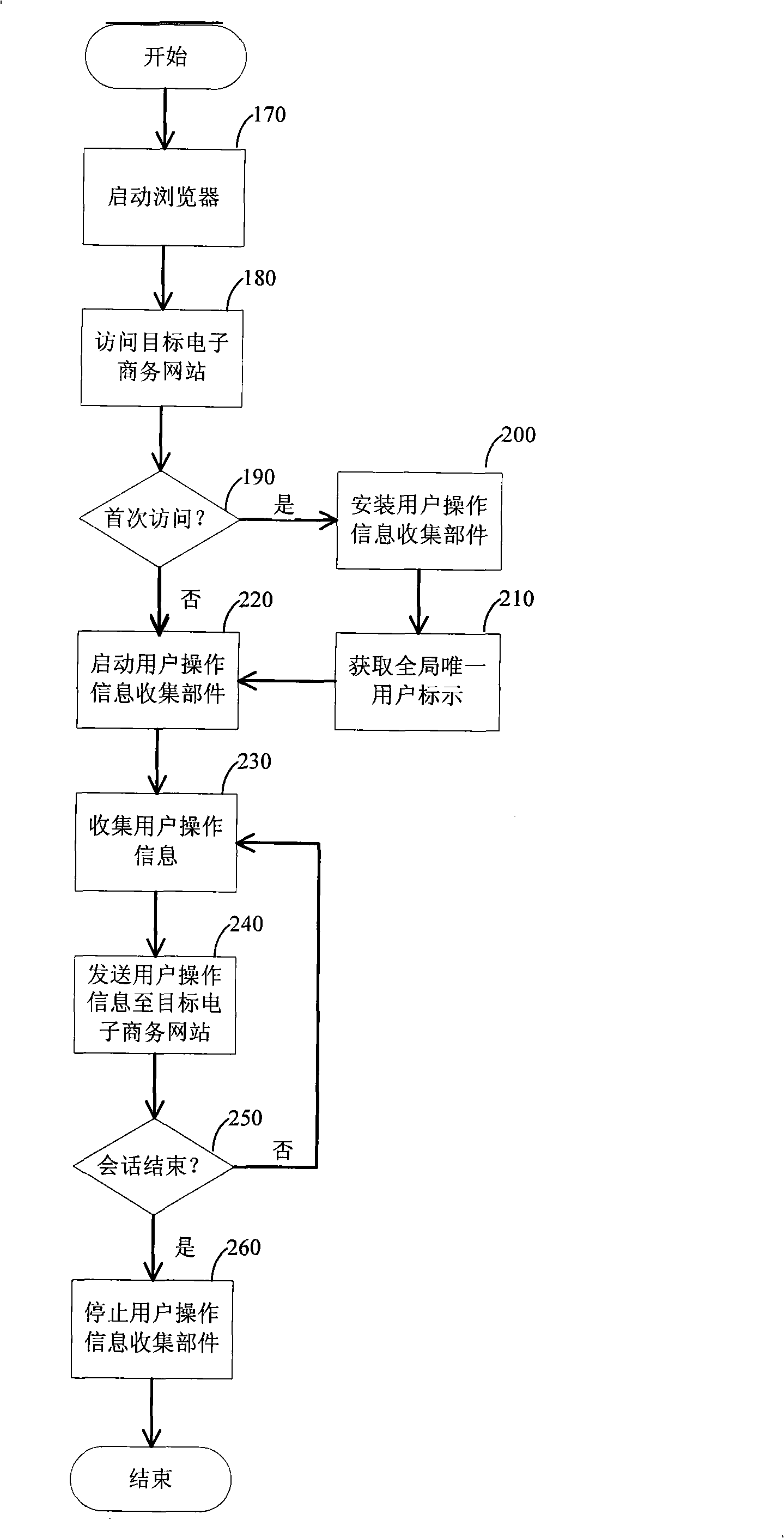
InactiveCN101271558AHigh degree of personalizationImprove recommendation qualityCommerceSpecial data processing applicationsPersonalizationRecommendation quality
The invention discloses a multi-strategy commodity recommendation system basing on context information. The recommendation system acquires the operation information of a user through an information acquisition part which is operated by the user, analyzes the operation action of the user and establishes the interest description model of the user. During the interaction process between the user and an electronic commerce website, a recommendation strategy fitting the present user and the context information of the system is dynamically selected according to a strategy selection rule. The recommendation strategy describes and generates a personalized commodity recommendation list according with the interest and the requirement of the user according to the interest of the user. Through the selection of the recommendation strategy, the multi-strategy commodity recommendation system basing on context information improves the adaptability of the system to various applications and system dynamic changes. And compared with the existing recommendation system, the multi-strategy commodity recommendation system basing on context information is improved in the recommendation quality, the recommendation scale and the recommendation performance.
Owner:EAST CHINA NORMAL UNIV
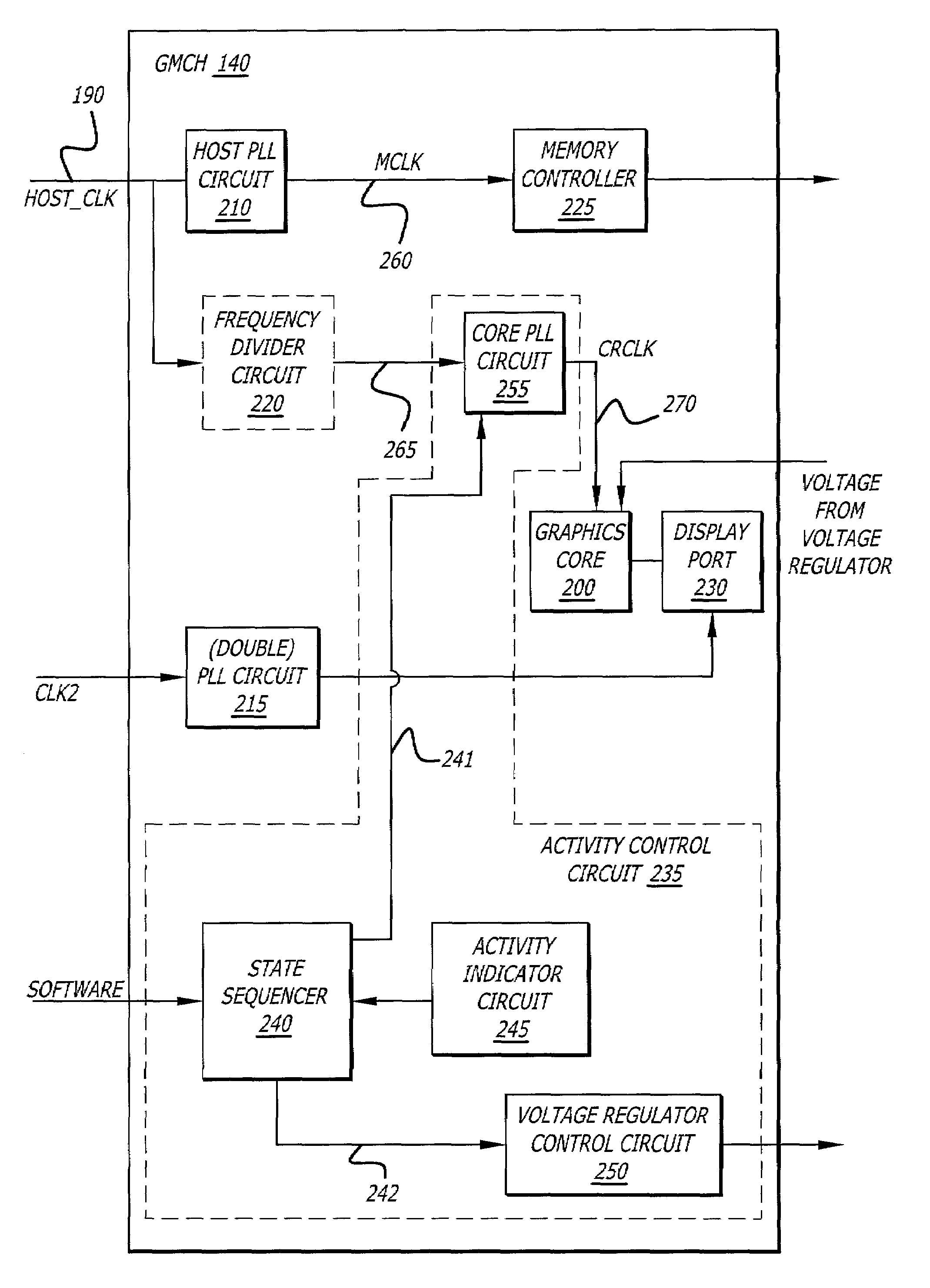
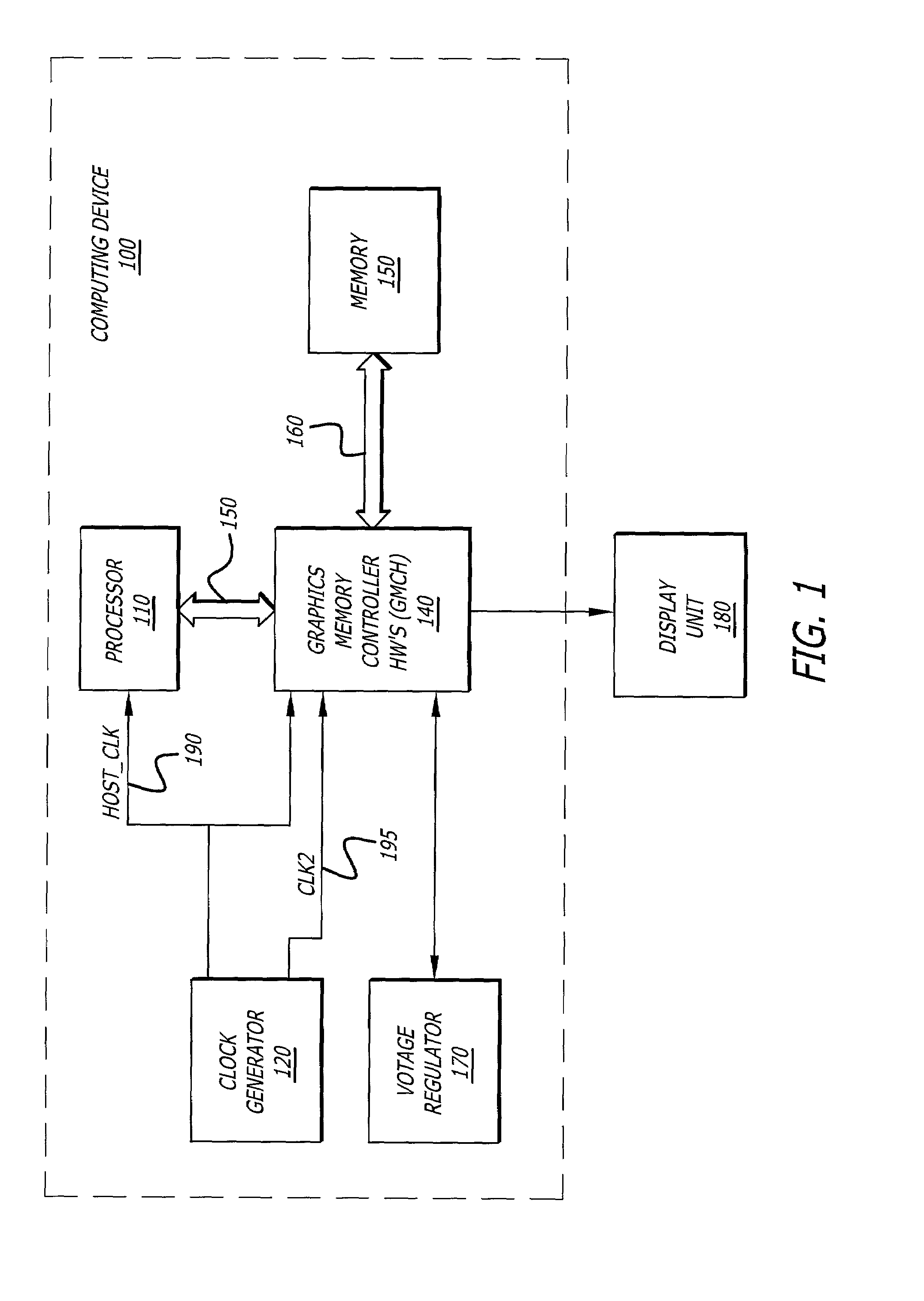
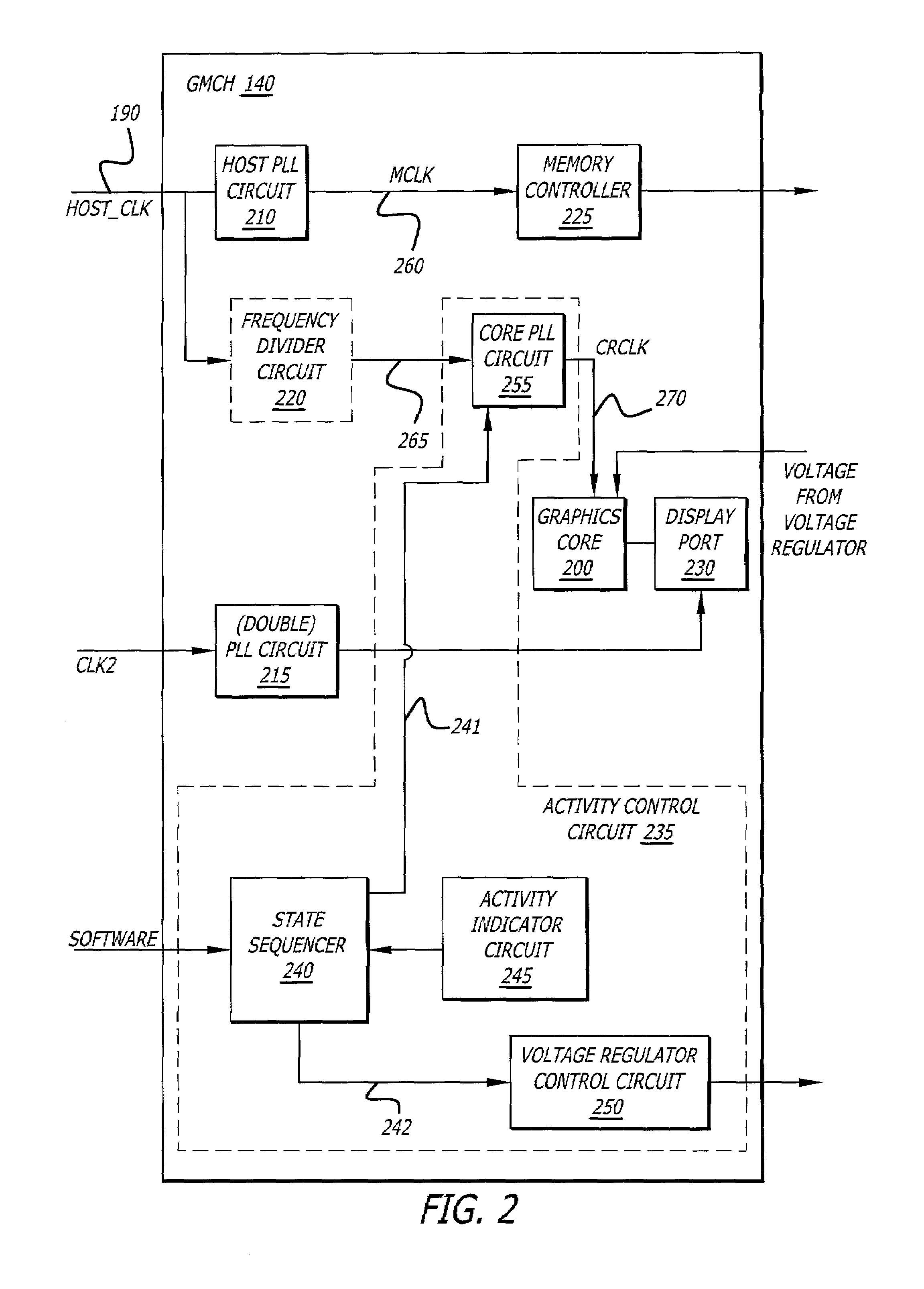
Power management for an integrated graphics device
In one embodiment of the invention, an integrated device is described that employs a mechanism to control power consumption of a graphics memory controller hub (GMCH) through both voltage and frequency adjustment of clock signal received from a clock generator. The GMCH comprises a graphics core and a circuit to alter operational behavior, such as the frequency of a render clock signal supplied to the graphics core. The circuit is adapted to monitor idleness of the graphics core and reduce a frequency level of the render clock signal if the idleness exceeds a determined percentage of time.
Owner:INTEL CORP
Methods, systems, and computer program products for summarizing operational behavior of a computer program
InactiveUS20050273757A1Simple processSmall artifacts (whichError detection/correctionReverse engineeringCall stackOperational behavior
Methods, systems, and computer program products for summarizing operational behavior of a computer program are disclosed. A method for summarizing the operational behavior of a computer program may include executing a computer program in a mode that allows control over execution of the computer program. Execution of the program is paused at predetermined locations corresponding to each instruction in the computer program. For each location, contents of a call stack containing function calls made by the program that have not yet returned are recorded. For each function call in the call stack, information regarding conditions under which the function was called are recorded. Execution of the program is resumed until the next pause location is encountered.
Owner:ANDERSON CRAIG D
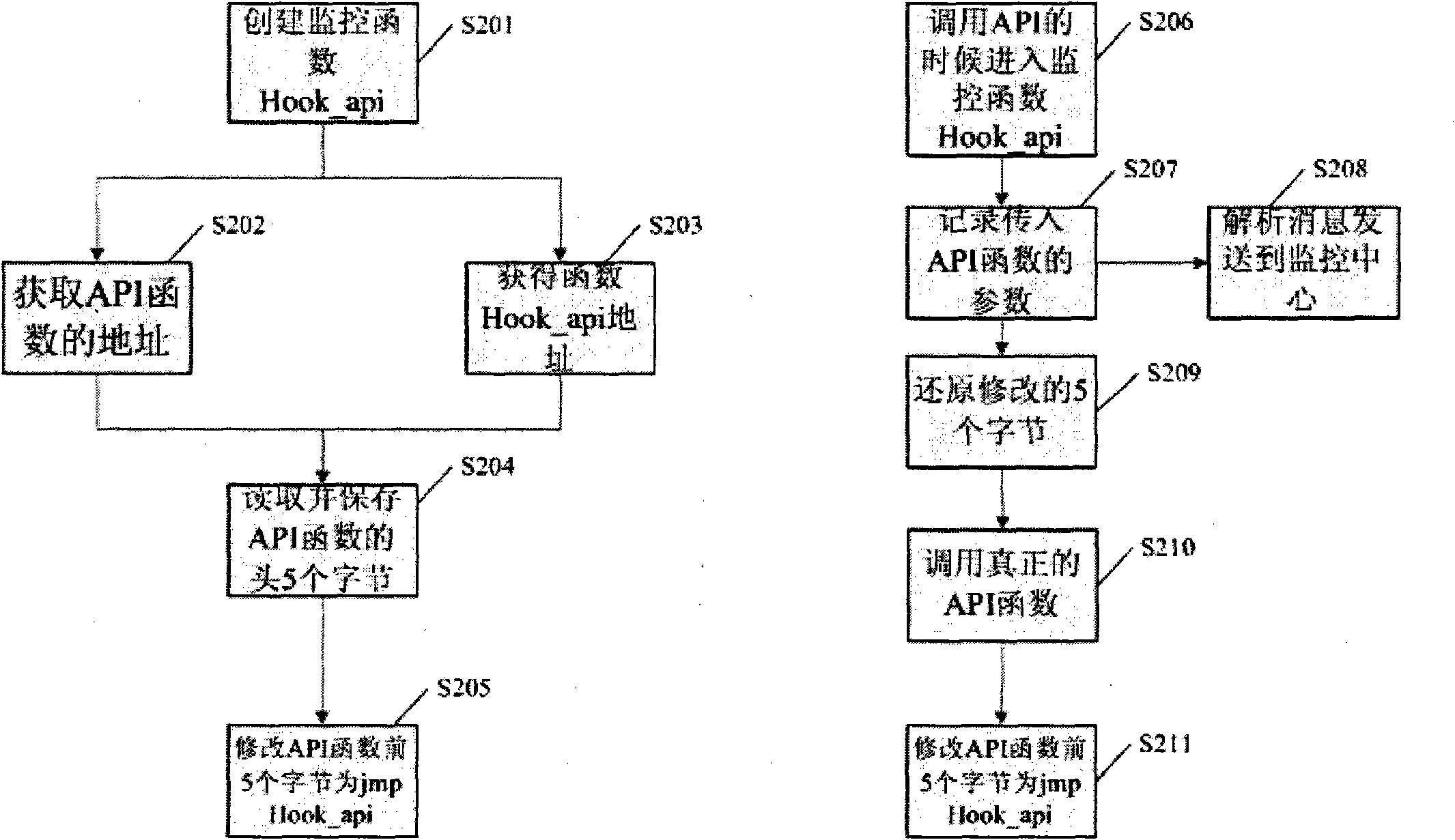
Automatic analysis method and system of malicious codes based on API (application program interface) HOOK
InactiveCN102314561APlatform integrity maintainanceData switching networksOperational systemApplication programming interface
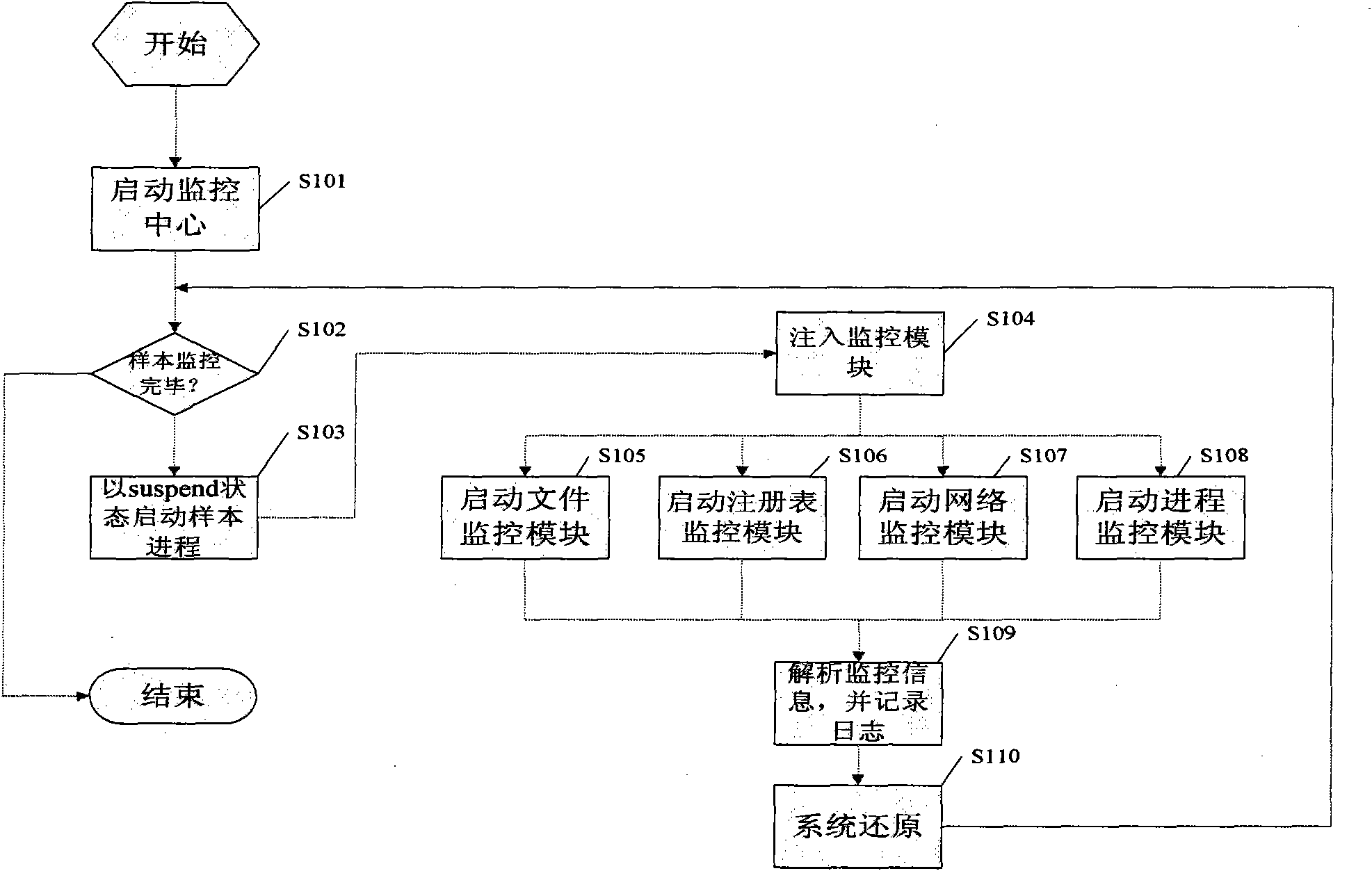
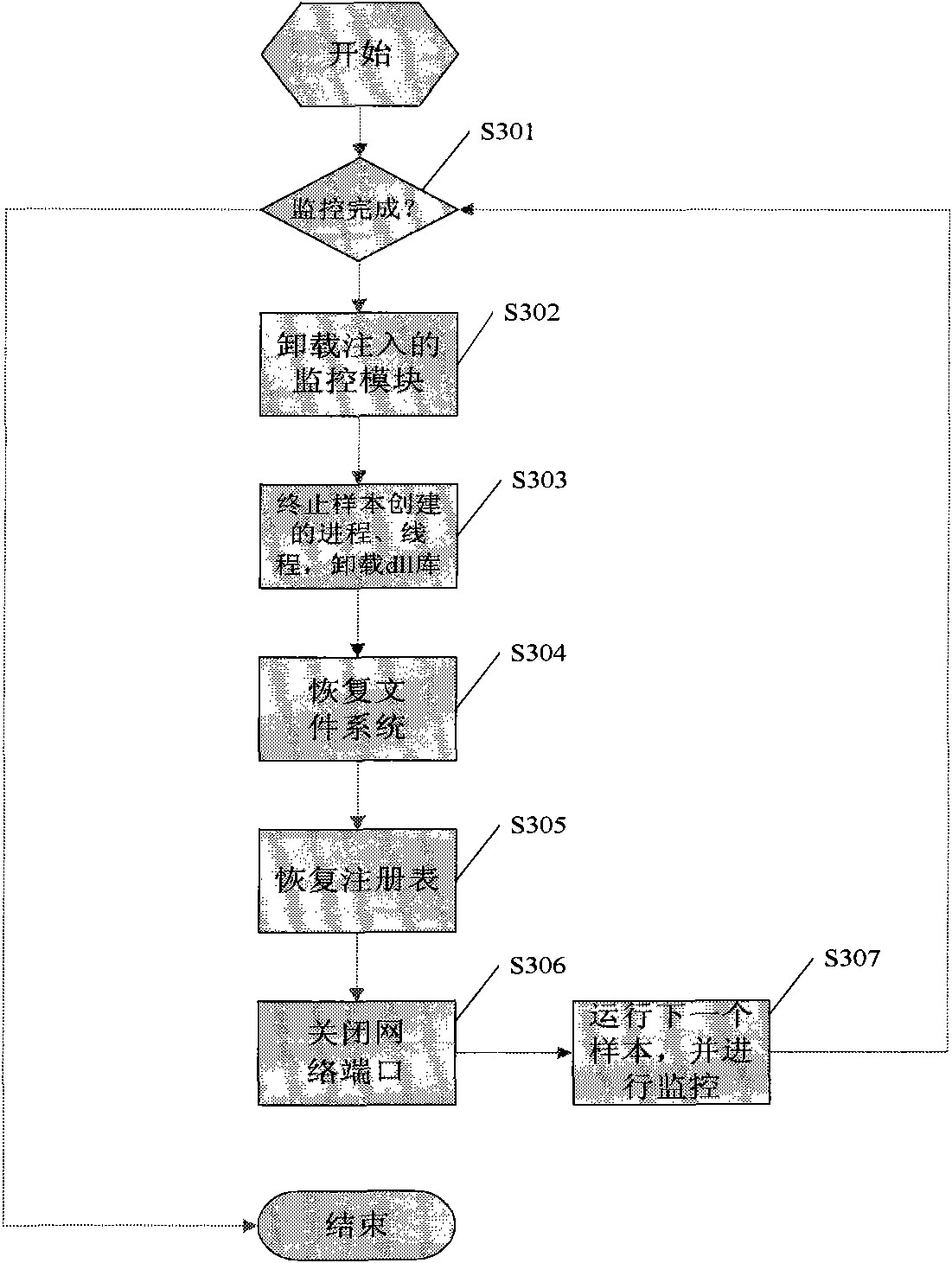
The invention provides an automatic analysis method and system of malicious codes based on an API (application program interface) HOOK. An API HOOK technology and a remote thread implantation technology are utilized to monitor samples; influences of the malicious codes on the whole system in an operation process are recorded, and a dynamic analysis report is automatically generated; influences of malicious code samples on a file, a network, and a registry and a key process are recorded, and when the operation of the samples ends, the system recovers the state before the samples are executed; the whole monitoring, recording and reduction process ends automatically without manual intervention; monitoring software can only run a sample each time, the monitoring software is used for monitoring the host process of the samples and process threads created by the host process of the samples, and when the monitoring software finishes the monitoring, the system recovers the state before the samples are operated; behaviors such as creation, deletion, modification and the like of the malicious code samples on the file are detected, operation behaviors of the malicious code samples on the network are detected, behaviors such as addition, deletion, modification and the like of the malicious code samples on the registry are detected, and operation behaviors of the malicious code samples on the create process are detected; and finally the dynamic monitoring report on the malicious code samples is submitted, and when the monitoring is finished, the monitoring software carries out inversion operation to restore the system to the state before the samples are operated according to the operations and influences of the samples on an operating system. The intelligent analysis technology of the malicious codes is suitable for analyzing a great deal of samples without the manual intervention, and is quicker in analysis speed and less in garbage in the analysis report.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Scanner having connected and unconnected operational behaviors
InactiveUS20110075228A1Buying/selling/leasing transactionsSpecial data processing applicationsOperational behaviorWorld Wide Web
Owner:GOOGLE LLC
Method and device for detecting abnormal account number
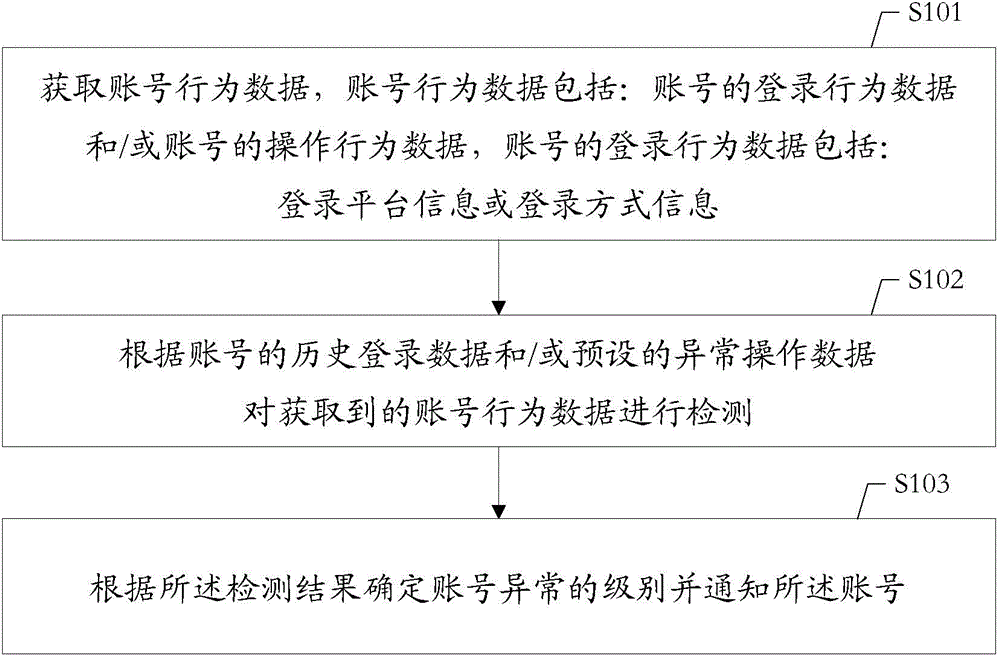
ActiveCN104468249AReduce the risk of exceptionsImprove securityData switching networksInternet privacyOperational behavior
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Personalized recommendation method and system based on probability model and user behavior analysis
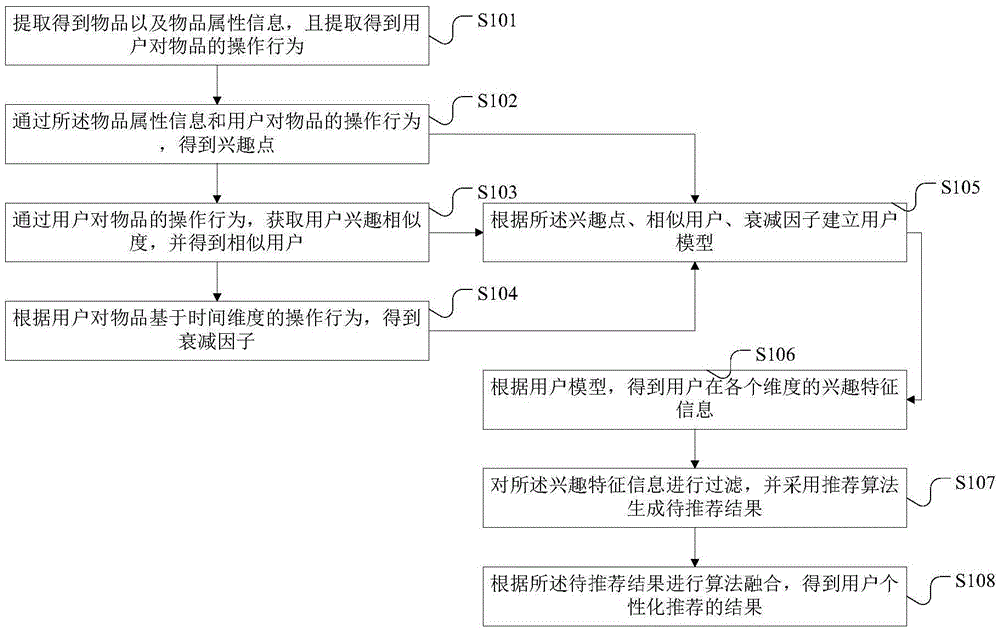
InactiveCN105574216AAccurately characterize acquisition needsSolve overloadSpecial data processing applicationsPersonalizationOriginal data
The invention discloses a personalized recommendation method and system based on a probability model and user behavior analysis. The method includes the steps that article information and article attribute information are extracted, and operation behaviors of users on articles are extracted; interest points are obtained according to the article attribute information and the operation behaviors of the users on the articles; user interest similarity is obtained according to the operation behaviors of the users on the articles, and similar users are obtained; a decay factor is obtained according to the operation behaviors of the users on the articles based on the time dimension, and a user model is set up; interest characteristic information, at all dimensions, of the users is obtained according to the user model; after filtering, a recommendation algorithm is adopted to generate results to be recommended, and algorithm fusion is conducted to obtain personalized recommendation results of the users. After original data is preprocessed, the user model is set up, the interest points of the users and essential information acquisition requirements are depicted accurately to provide accurate personalized recommendation, and therefore the problems of information overload and long-tail articles in the network are solved.
Owner:DATAGRAND TECH INC
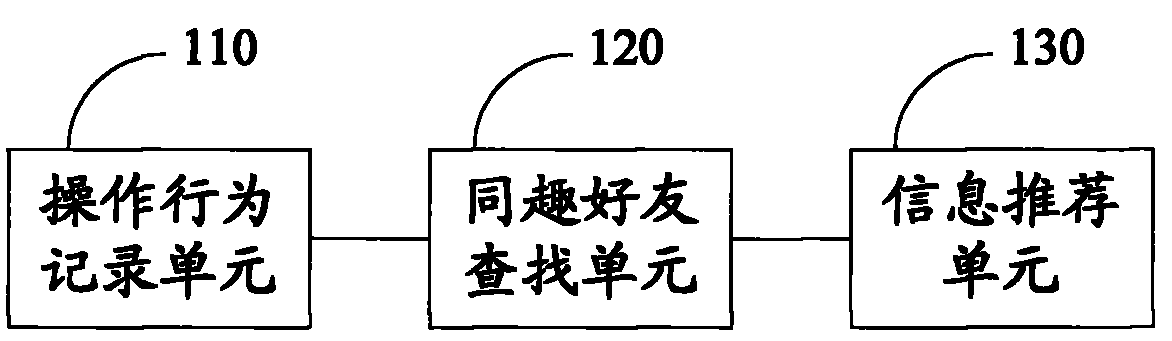
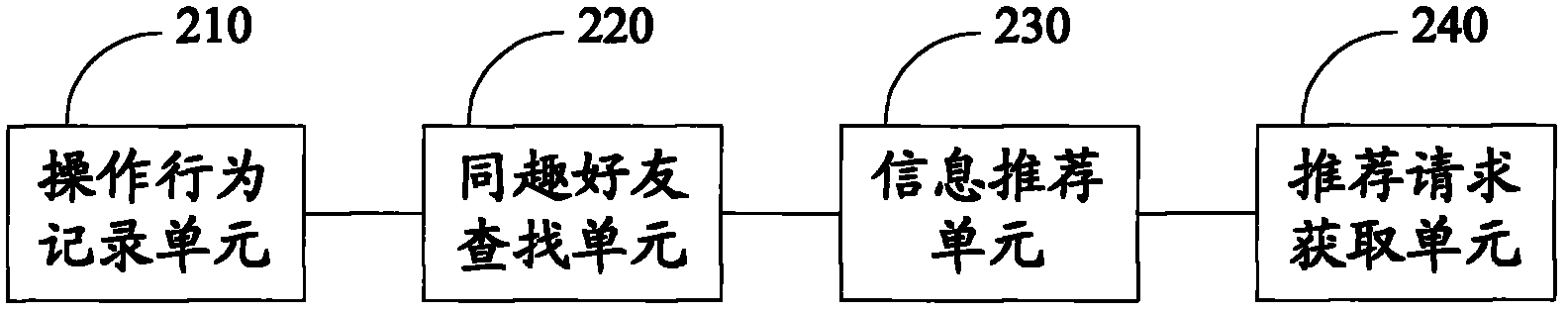
Information recommendation method and system
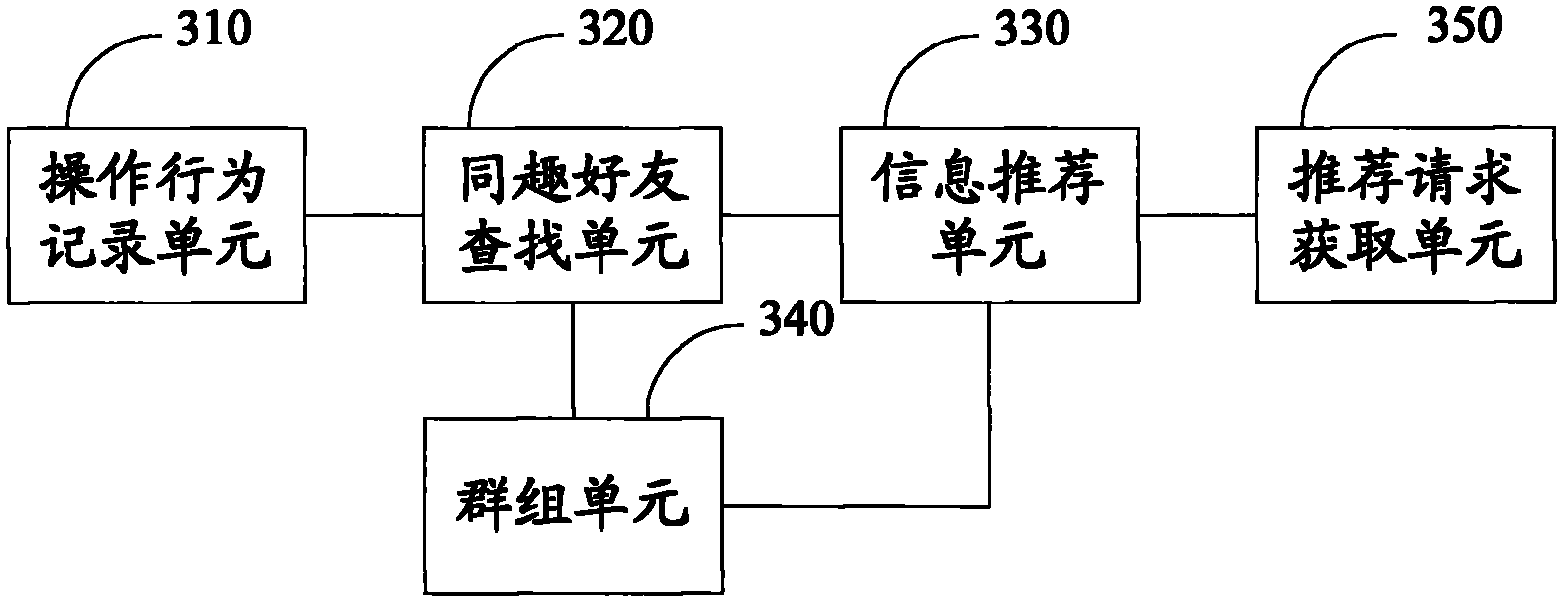
InactiveCN101916286AAchieve recommendationImprove efficiencyTransmissionSpecial data processing applicationsOperational behaviorRecommender system
The embodiment of the invention discloses an information recommendation method. The information recommendation method comprises the following steps of: recording an operation behavior of a user; recording, searching and acquiring identical taste friends of the user according to the operation behavior of the user; and sending user identification information and / or operation behavior record of the identical taste friends of the user to the user. The embodiment of the invention also discloses an information recommendation system. The method and the system can fulfill the purpose of recommending possibly more interesting information to the user, and improve the efficiency and accuracy of recommending the information to the user.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Randomization-based encryption apparatus and method
InactiveUS20050002531A1Reduce computational complexityIncrease variabilityDigital data protectionDigital storageObfuscationTheoretical computer science
A method for encryption data subdivided into segments of random lengths. A data source having a state corresponding to initialization parameters and the number of patterns output therefrom provides for a reversible encryption process. Decryption is accomplished by repeating encryption using a data source having an identical initial state. The data source consists random pattern generation machines (RPGMs). A portion of RPGMs may each contain patterns of a different length. Randomly selecting an RPGM and outputting a pattern therefrom effectively provides a pattern of random length. The data source may output patterns interpreted to govern the behavior of obfuscation operations. Patterns output from the data source may be interpreted as instructions as to what obfuscation to perform and what parameters shall define the obfuscation.
Owner:MICHAELSEN DAVID L
Detection and analysis method for abnormal behaviors of user in big data environment
ActiveCN106789885AAbnormal Behavioral IntelligenceAbnormal behavior intelligent detection intelligenceTransmissionSpecial data processing applicationsGranularityAnomalous behavior
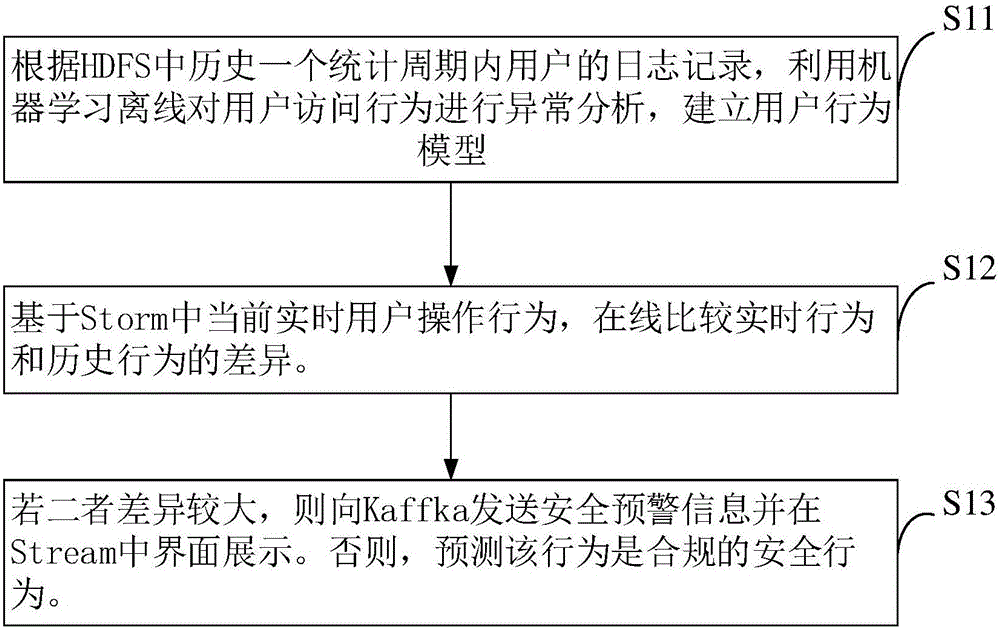
The invention relates to a detection and analysis method for the abnormal behaviors of a user in a big data environment. The method is characterized in that the method comprises the following steps: enabling a user abnormal behavior detection system to carry out the abnormality analysis of user access behaviors in an offline mode through machine learning according to the log record of the user in HDFS in one historical statistical period, and building a user behavior model; enabling the user abnormal behavior detection system to carry out the online comparison of real-time behaviors and historical behaviors based on the current real-time user's operation behavior in Storm; transmitting safety early-warning information to Kaffka and displaying the safety early-warning information at a Stream interface if the difference between real-time behaviors and historical behaviors is big, or else judging that the behavior is a legal safe behavior. Compared with the prior art, the method supports the definition of a behavior mode or a user portrait according to the historical use behavior habit of the user at a Hadoop platform through a machine learning algorithm. A training system updates a model each month in a default manner, and the granularity of the model is one minute.
Owner:STATE GRID CORP OF CHINA +2
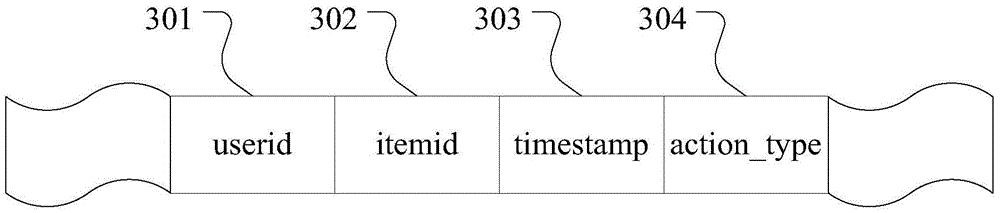
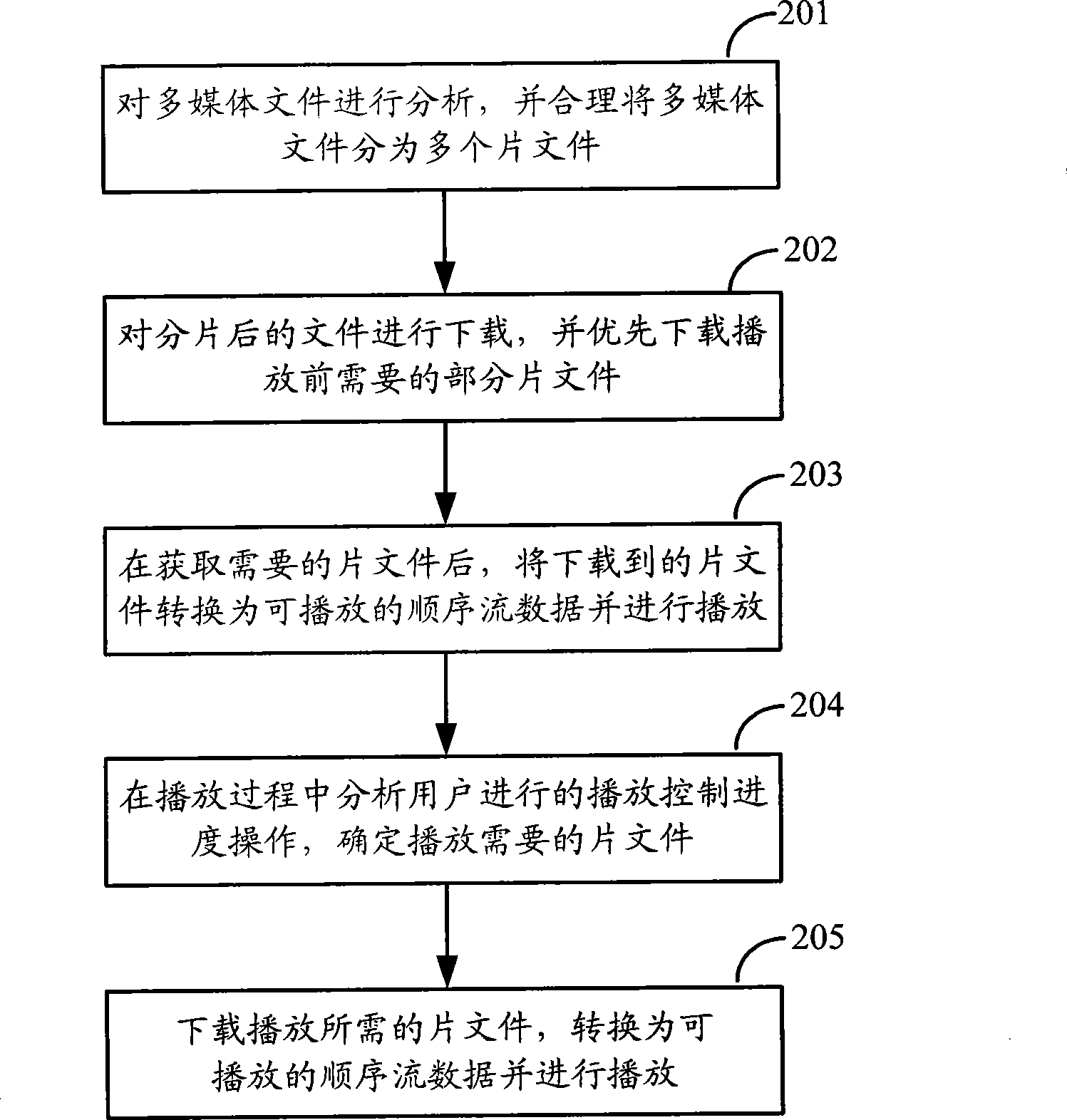
Method for downloading and playing multimedia file and equipment thereof
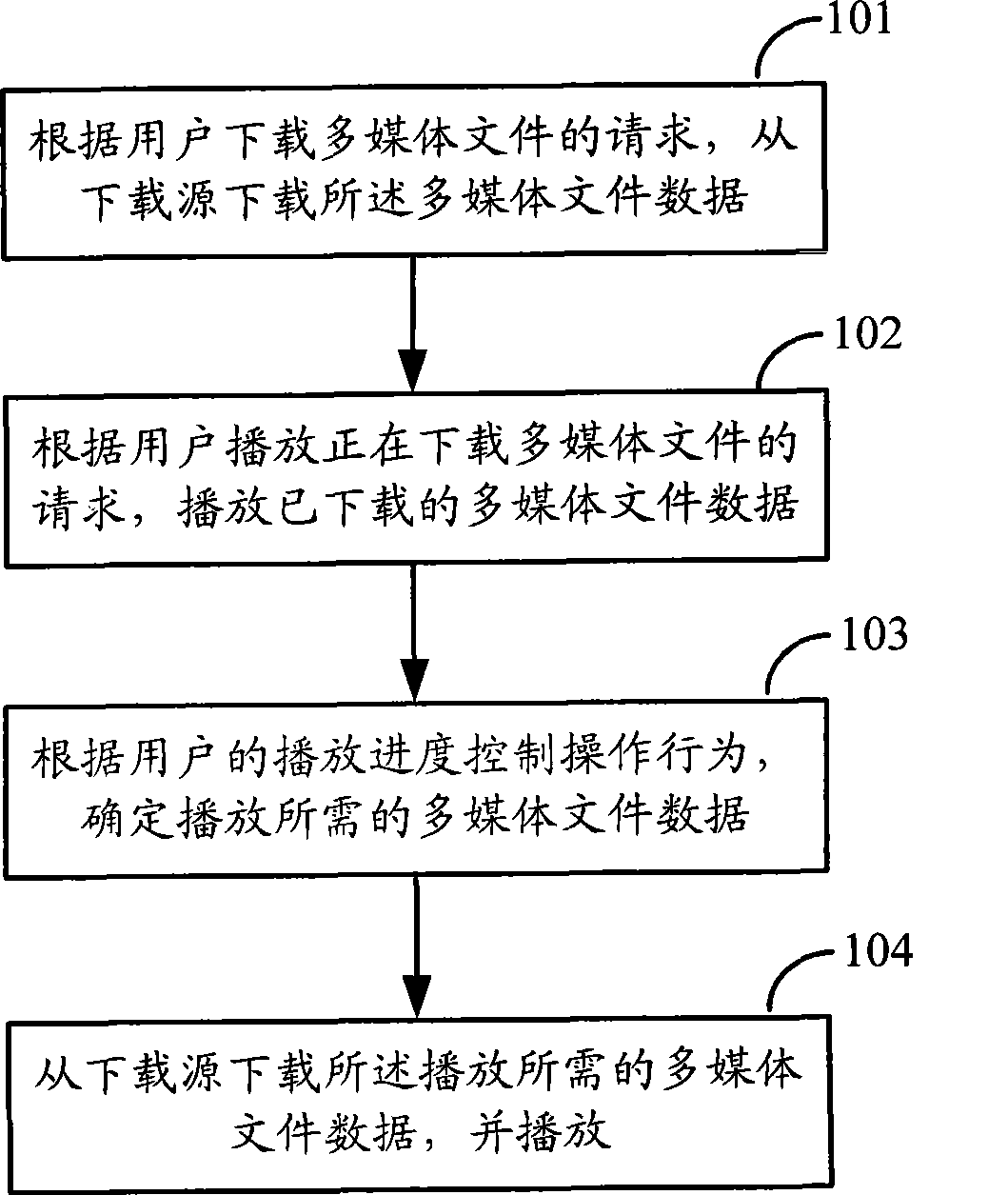
ActiveCN101447994ARecord information storageCarrier indexing/addressing/timing/synchronisingOperational behaviorMultimedia
The invention discloses a method for downloading and playing a multimedia file. The method comprises the following steps: dividing the multimedia file into a plurality of subfiles and downloading a plurality of the subfiles from a download resource according to a request of downloading the multimedia file from a user; playing the downloaded subfiles according to a request of playing the multimedia file which is being downloaded from the user; determining the subfiles required for playing according to the play progress control operation behavior of the user; and downloading and playing the subfiles required for the playing from the download resource.
Owner:SHENZHEN THUNDER NETWORK TECH
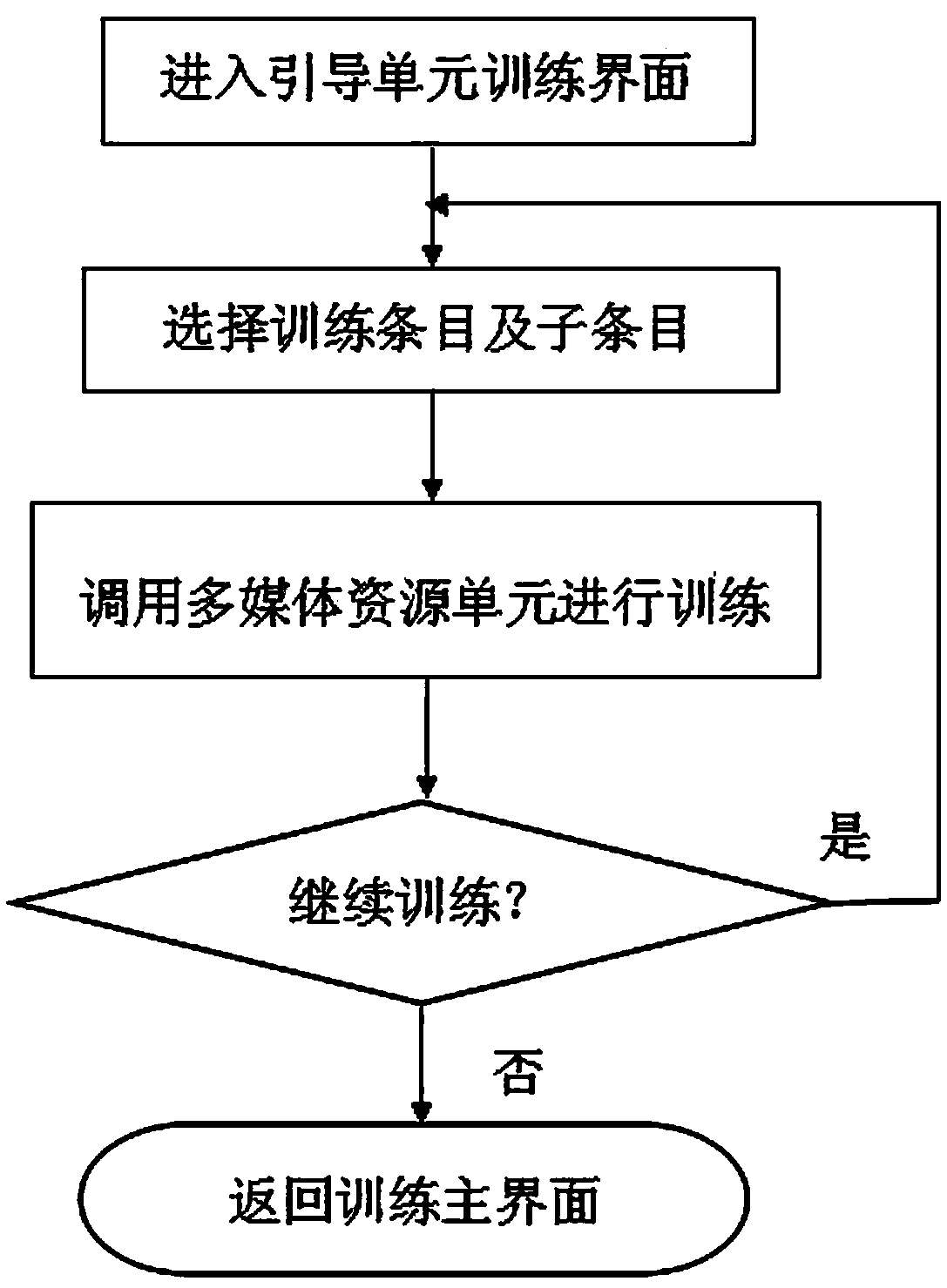
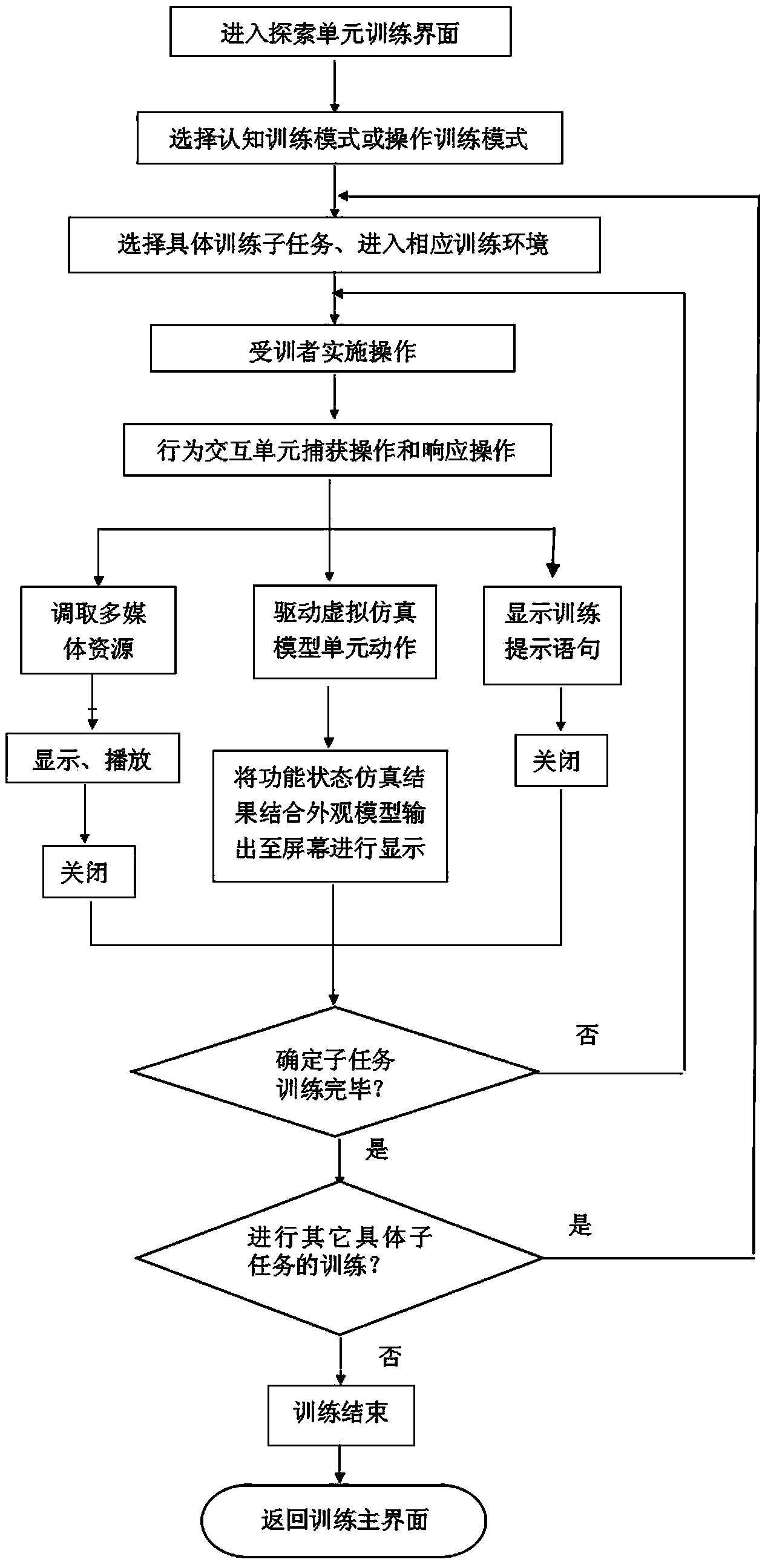
Unmanned aerial vehicle simulation training system and control method thereof
InactiveCN104111861ACultivate self-learning abilityLess mitigation equipmentData processing applicationsSoftware simulation/interpretation/emulationThree dimensional simulationSimulation
The invention discloses an unmanned aerial vehicle simulation training system and a control method of the unmanned aerial vehicle simulation training system, and relates to the technical field of simulation training. The unmanned aerial vehicle simulation training system comprises human-computer interaction unit, a training unit, a behavior interaction unit, a virtual simulation model unit, a training evaluation data unit and a multimedia source unit. The human-computer interaction unit provides a visual window of a virtual unmanned aerial vehicle three-dimensional simulation model. The training unit provides a system operation manual, and represents a guide unit, an exploration unit and an assessment unit. The behavior interaction unit converts instructions of the human-computer interaction unit into control instructions on the virtual unmanned aerial vehicle three-dimensional simulation model, and drives the corresponding virtual simulation model unit to act. The virtual simulation model unit provides appearance and function states of the virtual unmanned aerial vehicle three-dimensional simulation model. The training evaluation data unit records operation behavior in the evaluation process, judges operation correctness and displays and stores the evaluation result. The multimedia source unit provides multimedia sources of equipment. The unmanned aerial vehicle simulation training system and the control method of the unmanned aerial vehicle simulation training system are high in interactivity and autonomous learning capacity, and training missions are carried out conveniently.
Owner:PEOPLES LIBERATION ARMY ORDNANCE ENG COLLEGE
Method and system for conducting parental control over mobile equipment
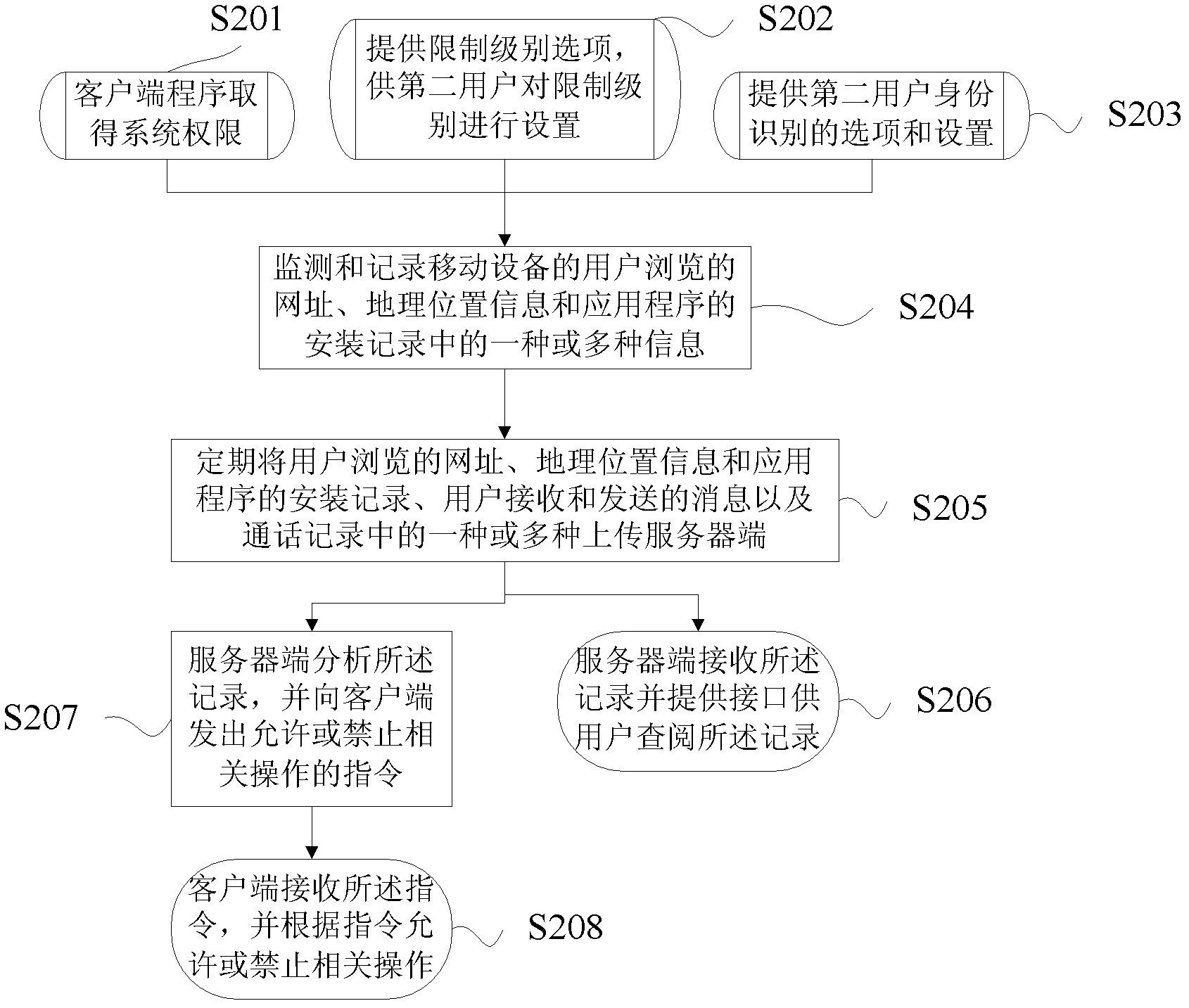
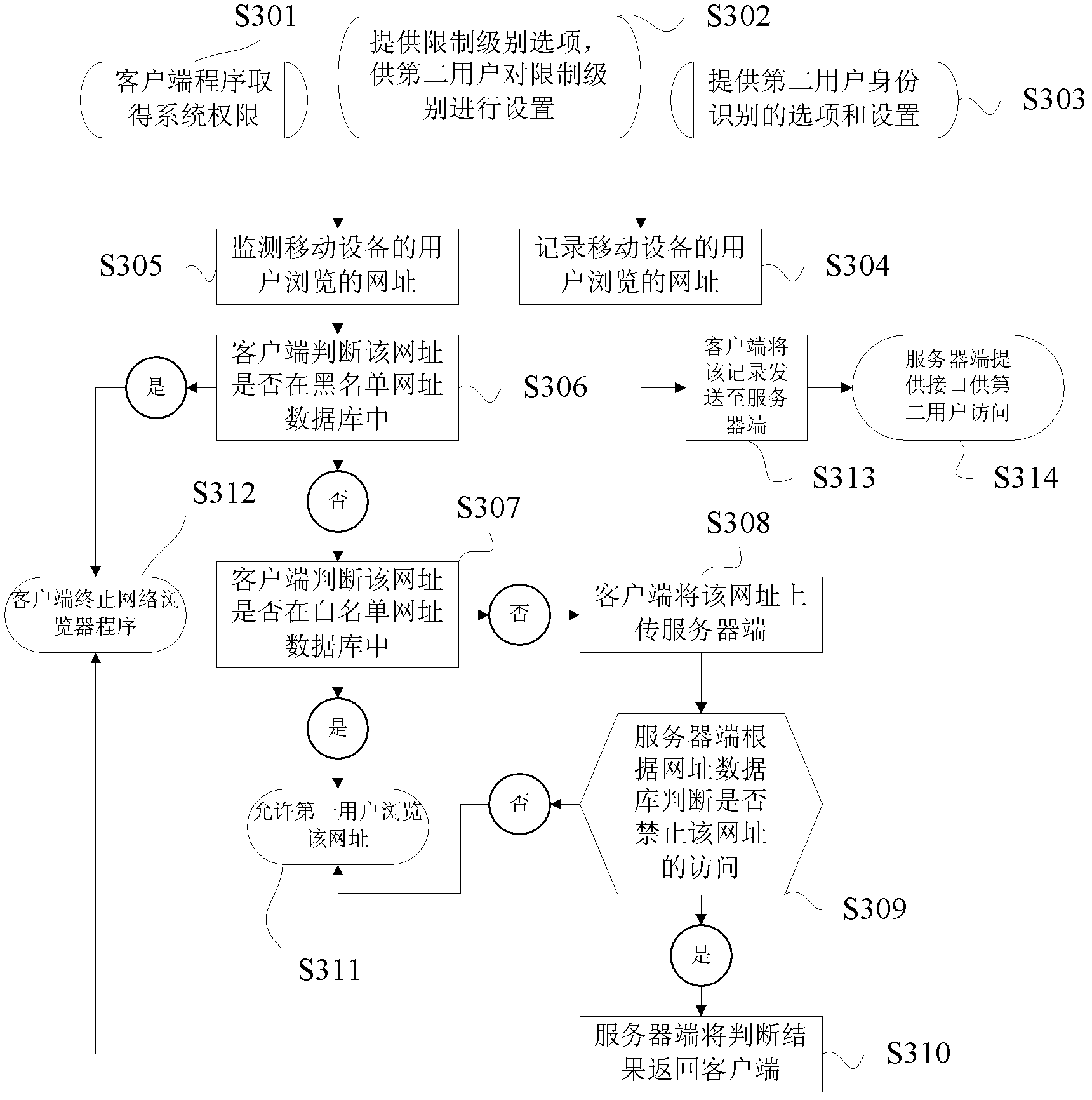
InactiveCN103188227AOperation monitoringReal-time analysis receivedTransmissionLocation information based serviceGeolocationOperational behavior
The invention provides a method and system for conducting parental control over mobile equipment. The method for conducting the parental control over the mobile equipment includes the following steps of monitoring and recording one or more kinds of information, including web addresses browsed by a user, geographical location information, installation events of application programs, and starting events of the application programs, of the mobile equipment, and uploading one or more kinds of information, including the web addresses browsed by the user of the mobile equipment, the geographical location information, the installation events of the application programs, messages received and sent by the user and call records, to a server, wherein the server receives records and provides an interface which enables a user to look up the records. The method and system for conducting the parental control over the mobile equipment has the advantages of monitoring operations of the user of the mobile equipment in real time and enabling a parent to monitor the operations of the user of the mobile equipment through access to data of the server.
Owner:BEIJING NETQIN TECH
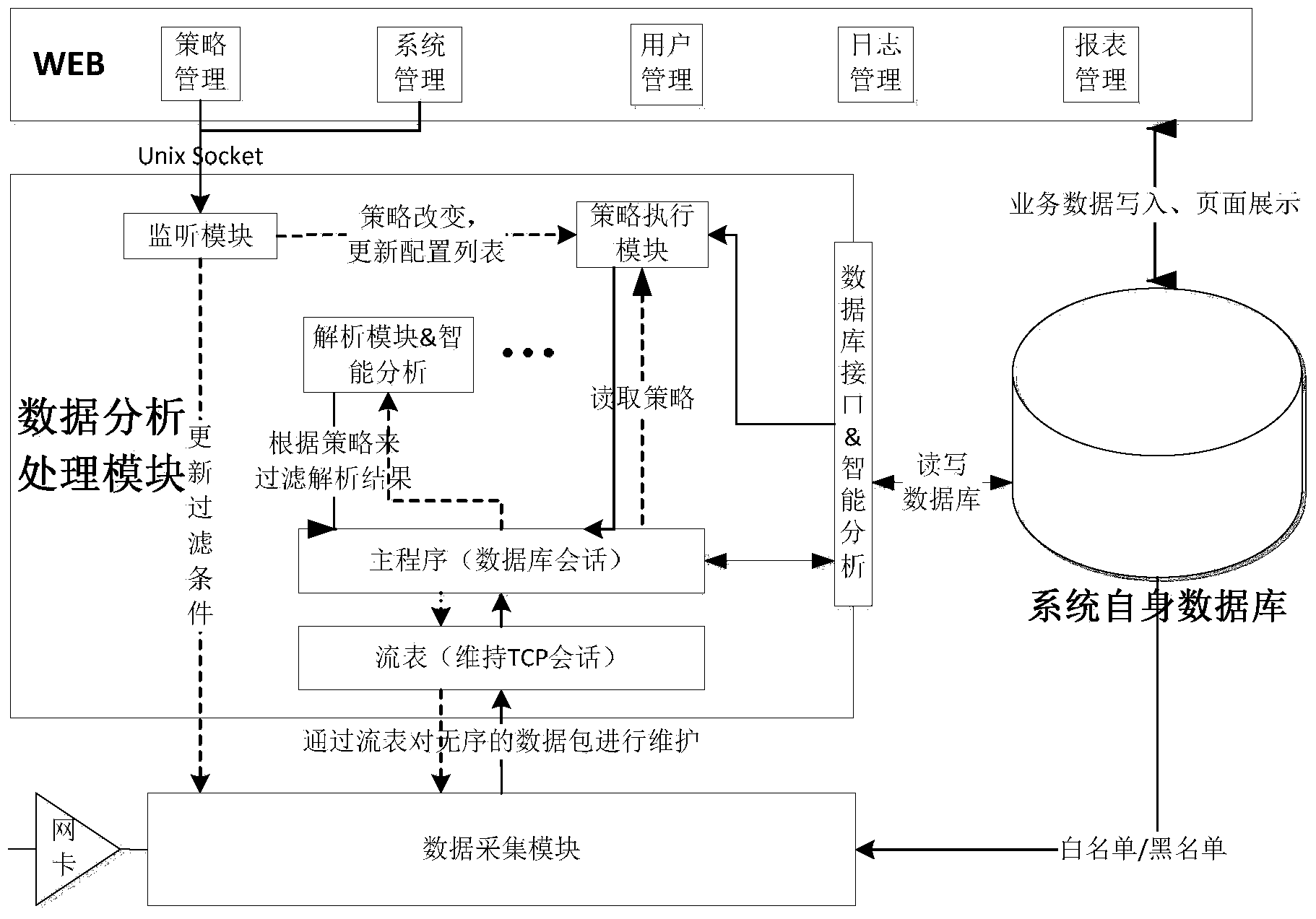
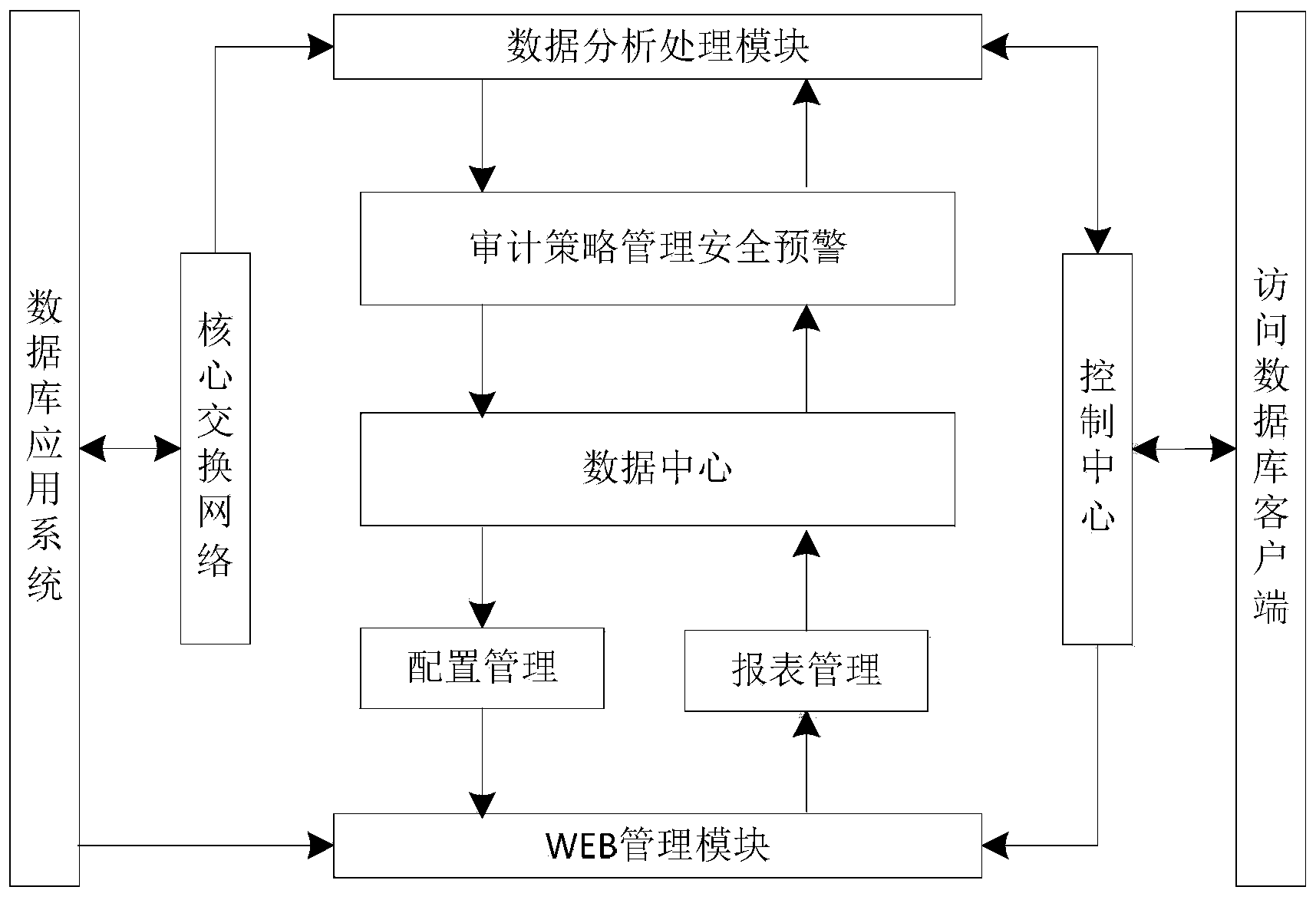
Database auditing monitoring system and database auditing monitoring method
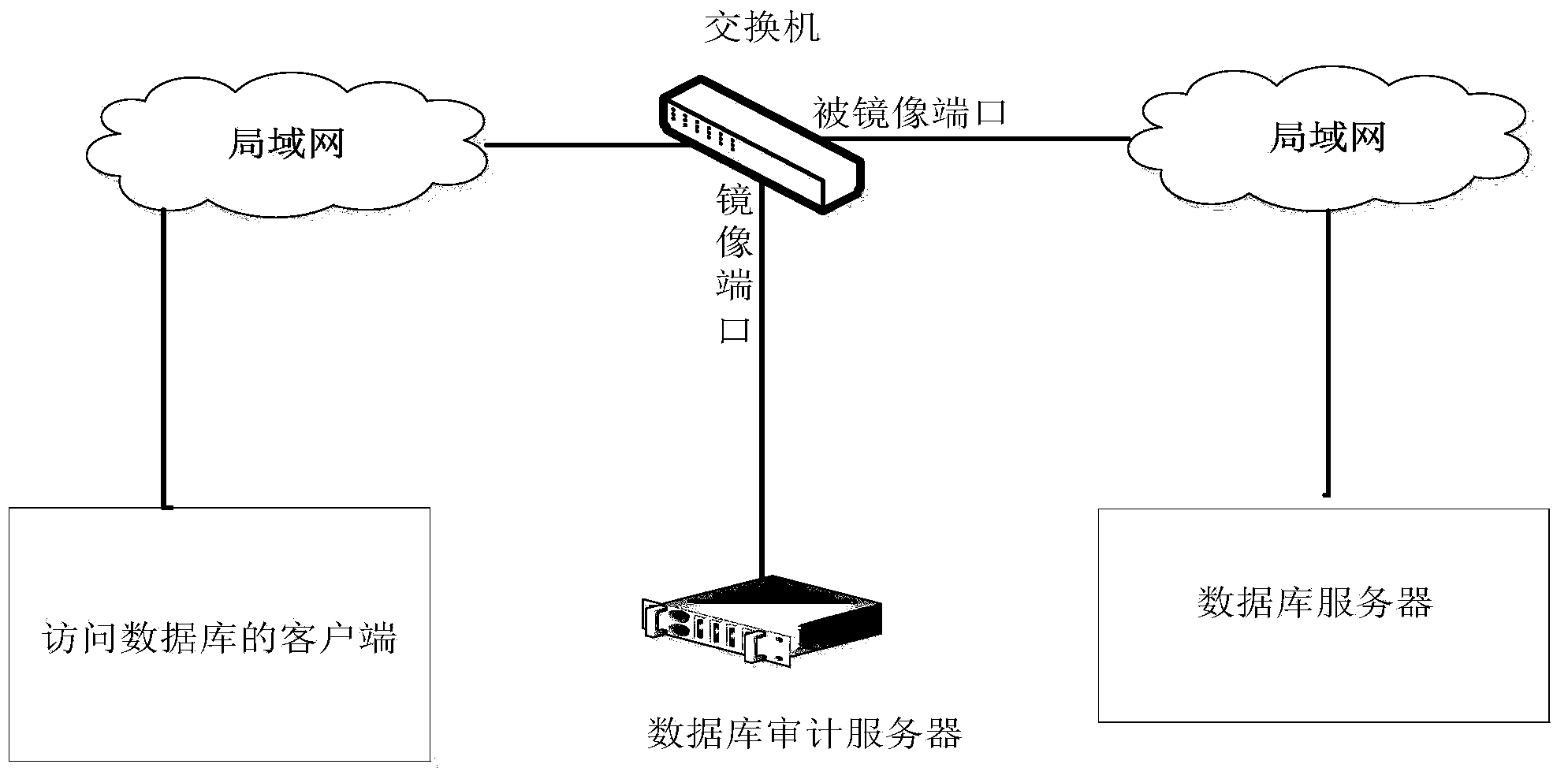
InactiveCN104063473ANo burden on resourcesSimple formatComputer security arrangementsSpecial data processing applicationsDatabase serverMonitoring system
The invention discloses a database auditing monitoring system and a database auditing monitoring method. The database auditing monitoring system comprises a hardware part and a module part, wherein the hardware part comprises a switchboard, a local area network and a database auditing server, the switchboard is respectively connected into the local area network at the two ends through a duplicated port, and is connected with the database auditing server through a mirror port, the local area network at the two ends is respectively communicated with a database accessing client and a database server, and the module part comprises a WEB management module, a local database module, a data collecting module and a data analysis and processing module. The database auditing monitoring system and the database auditing monitoring method have the advantages that various kinds of operation behaviors on the database server are monitored and recorded through a monitoring module arranged in the data analysis and processing module, through the analysis on network data, various kinds of operation and hostile attack event information on the database server can be analyzed intelligently in real time and is recorded into an auditing database so that inquiry and analysis can be realized in future, and the monitoring and the auditing on the operation of a target database system are realized.
Owner:北京华电天益信息科技有限公司
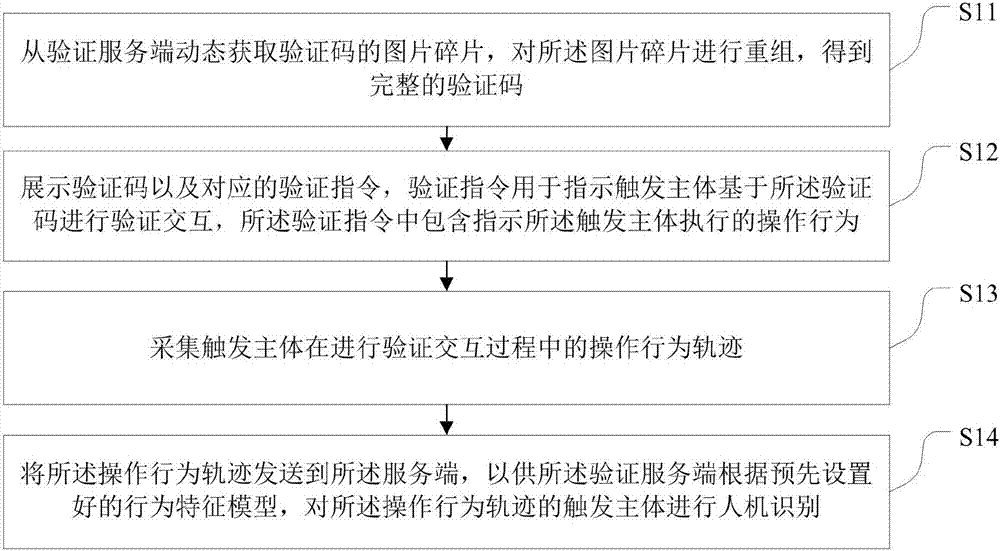
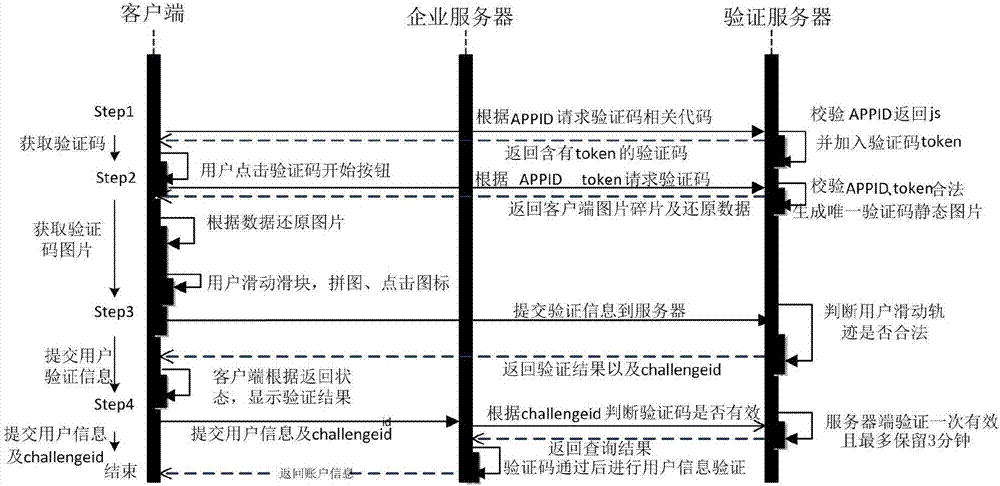
Man-machine recognition method and system, terminal equipment and readable storage medium
InactiveCN107153786AImprove experienceImprove accuracyDigital data authenticationTerminal equipmentOperational behavior
The invention provides a man-machine recognition method and system, terminal equipment and a readable storage medium. The method comprises the following steps: dynamically acquiring image fragments of a verification code from a verification server, and recombining the image fragments so as to obtain a complete verification code; displaying the verification code and a corresponding verification instruction, wherein the verification instruction is used for indicating a trigger body to perform verification interaction based on the verification code and comprises an operation behavior indicating the trigger body to execute; acquiring an operation behavior trace of the trigger body in the process of performing verification interaction; transmitting the operation behavior trace to the server, so that the server performs man-machine recognition on the trigger body of the operation behavior trace according to a preset behavior characteristic model. According to the man-machine recognition method disclosed by the invention, whether a current operation user is a normal user or an abnormal user can be accurately recognized, the man-machine recognition accuracy is improved, and the user experience is improved.
Owner:北京奇点数聚科技有限公司
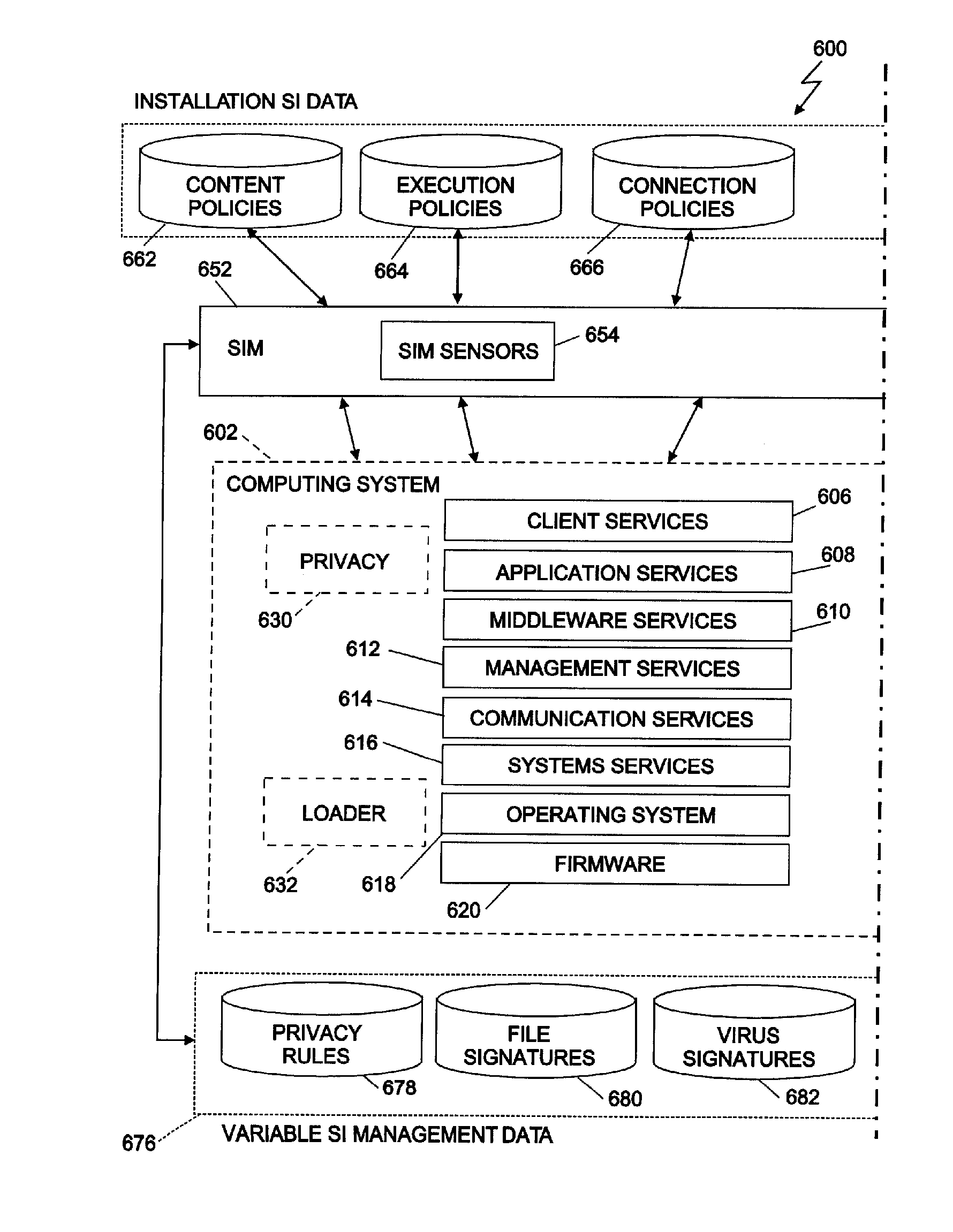
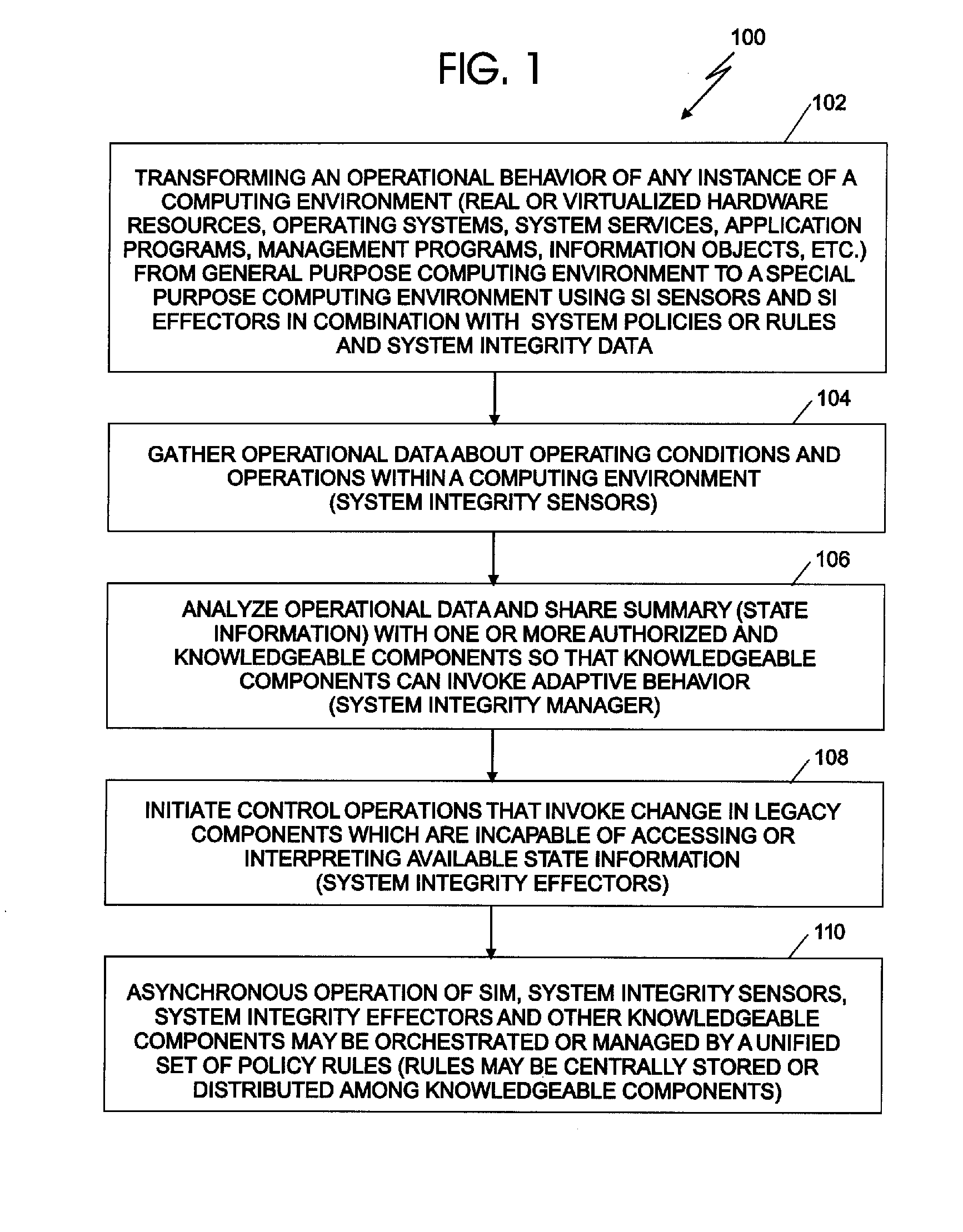
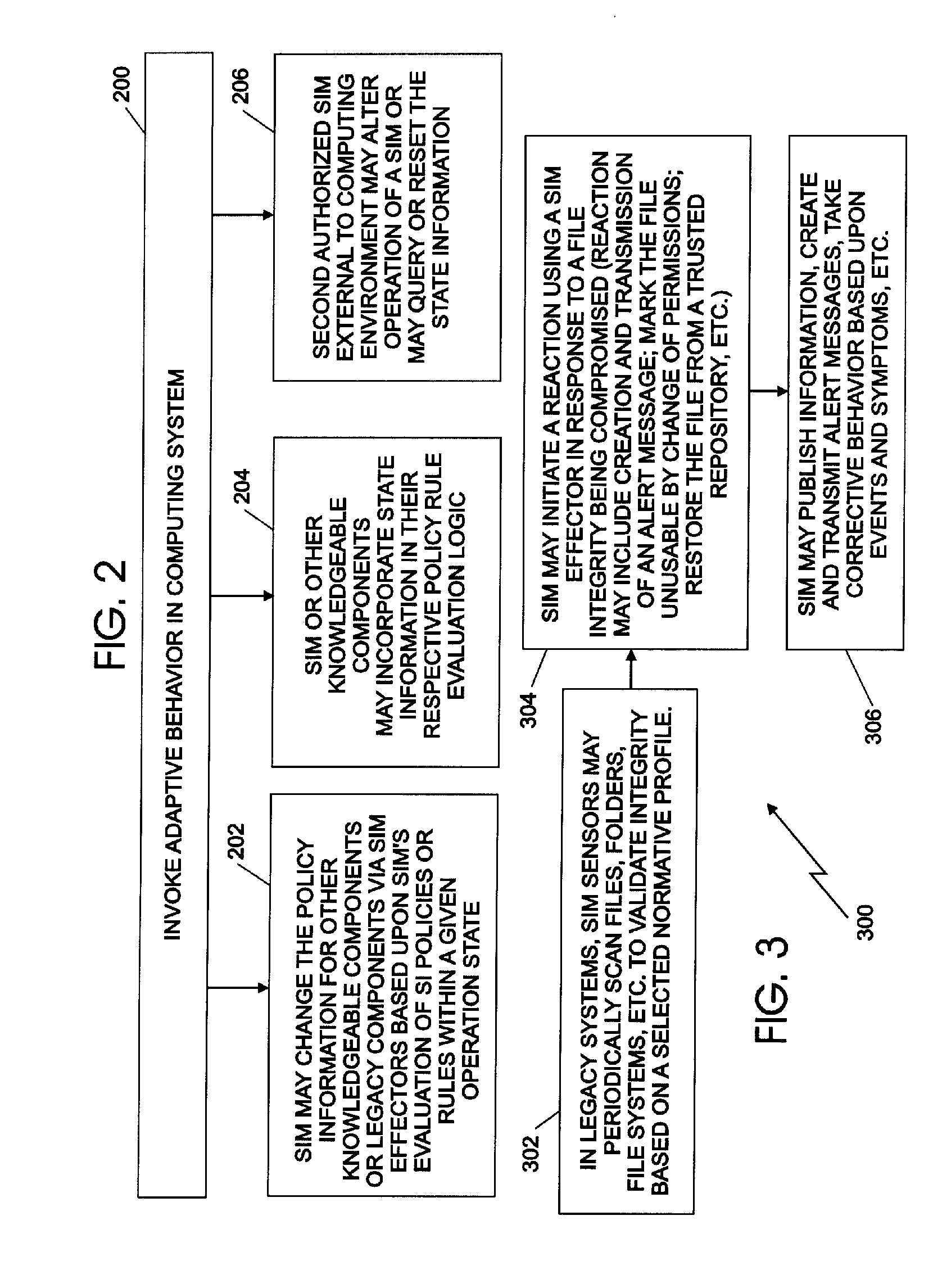
System integrity manager
InactiveUS20070044151A1Provide securityMemory loss protectionError detection/correctionComputer hardwareGeneral purpose
A system integrity manager, system, computer program product and method for providing security may include transforming an operational behavior of an instance of a computing system from a general purpose computing system to a special purpose computing system. The operational behavior may be transformed by using at least one of a system integrity sensor and a system integrity effector and a set of system integrity policies and system integrity data.
Owner:IBM CORP
Method and device for collecting user behavior data
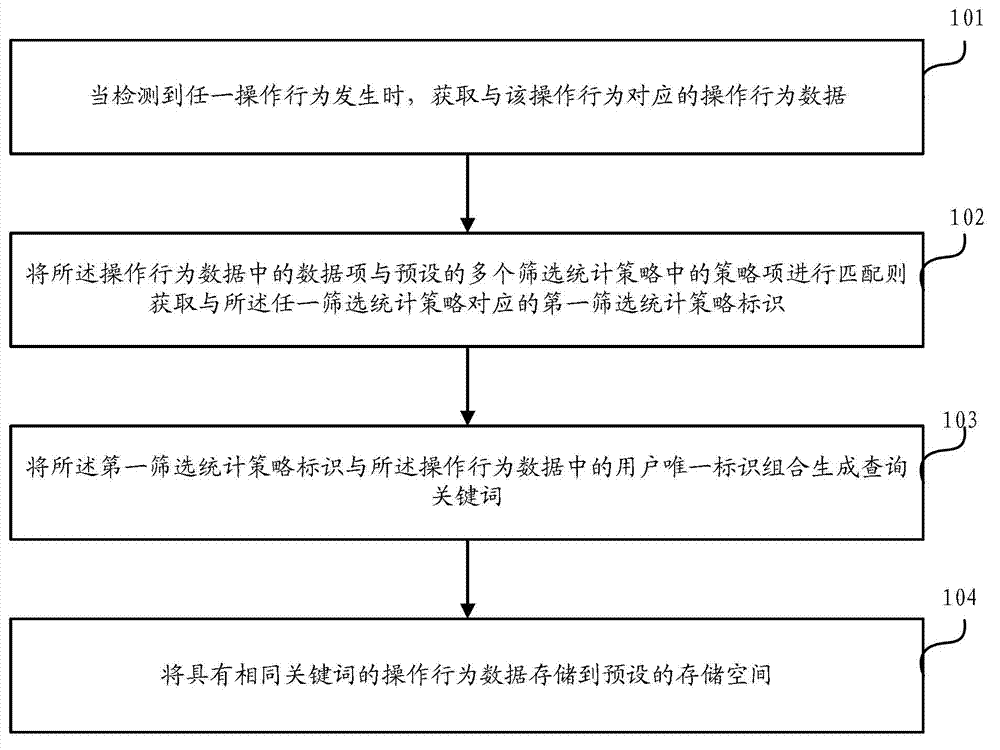
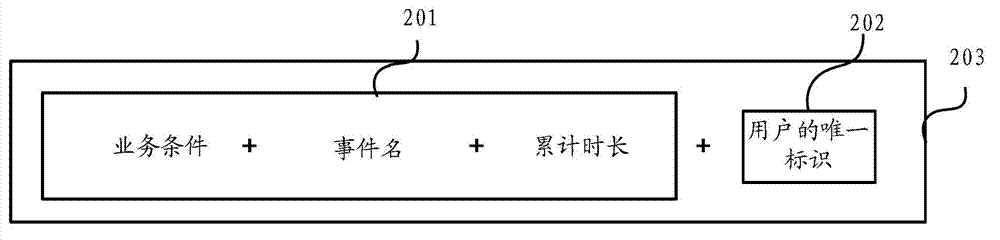
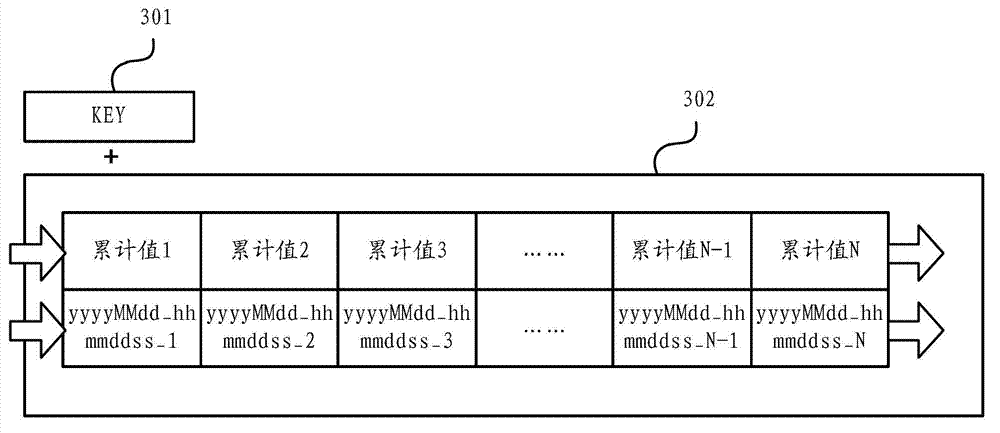
ActiveCN103593376ATroubleshoot snapshot issuesHigh precisionWeb data indexingWebsite content managementMultiple criteriaOperational behavior
The invention discloses a method and a device for collecting user behavior data. The method includes when occurrence of any operation behavior is detected, generating operation behavior data corresponding to the operation behavior; matching a data item in the operation behavior data with strategy items in multiple preset screening statistical strategies, and if the data item is matched with any screening statistical strategy successfully, acquiring a first screening statistical strategy identity corresponding to the screening statistical strategy; combining the first screening statistical strategy identity with a unique user identity in the operation behavior data to generate a keyword; storing the operation behavior data with same keyword into a preset storage space. By the method and the device, through real-time pre-computation processing, when any operation behavior occurs, the operation behavior data are subjected to classified storage according to multiple conditions, so that description of the user operation behavior data is enabled to be richer, and analysis accuracy of the user behavior data is improved.
Owner:ADVANCED NEW TECH CO LTD
Voice control method and apparatus for application program
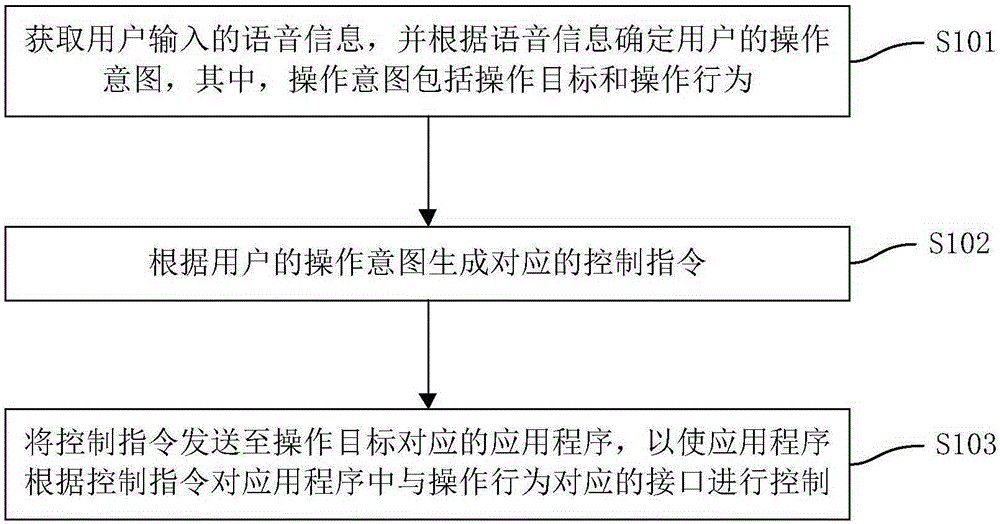
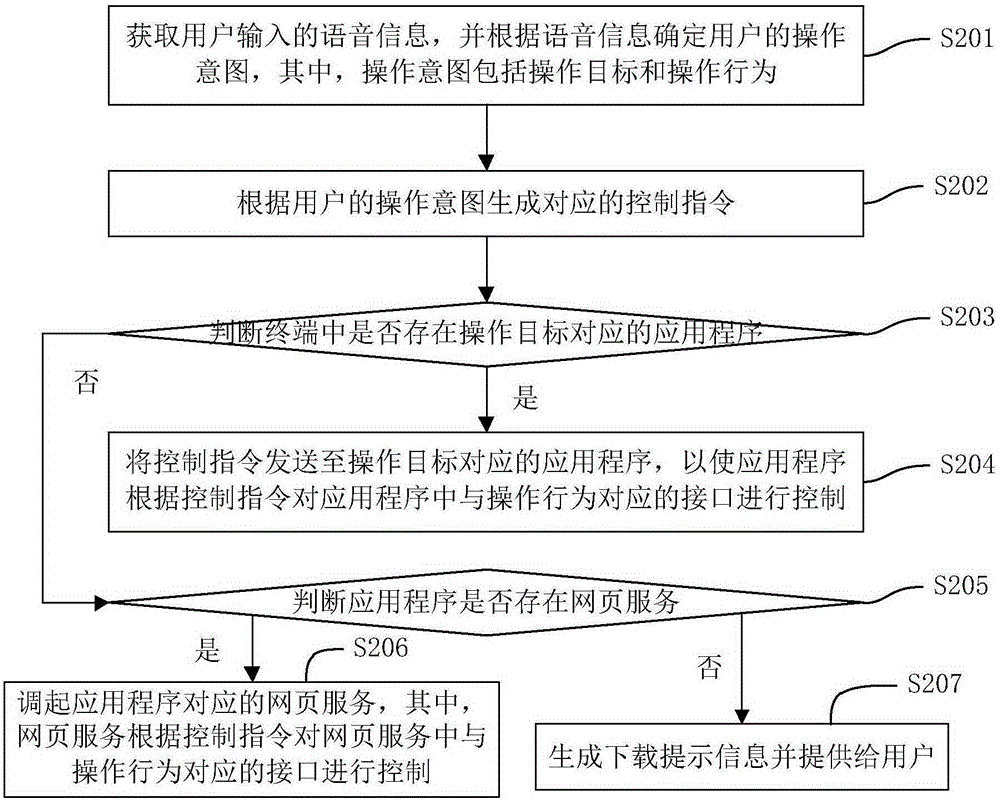
ActiveCN105183422AShorten the path of operationSave operating timeProgram loading/initiatingSound input/outputUser inputApplication software
The invention discloses a voice control method and apparatus for an application program. The method comprises: obtaining voice information input by a user, and determining an operation intention of the user according to the voice information, wherein the operation intention comprises an operation target and an operation behavior; generating a corresponding control instruction according to the operation intention of the user; and sending the control instruction to an application program corresponding to the operation target, so that the application program controls an interface corresponding to the operation behavior in the application program according to the control instruction. According to the method, the voice of the user is automatically identified, so that the operation intention of the user is analyzed more accurately and the operation target and the operation behavior are analyzed; and the operation behavior is finished in one step directly for the user according to the operation target and the operation behavior, so that the operation path of the user is shortened, the operation time of the user is saved, the demand satisfaction of the user is improved, and the user experience is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
A garbage mail processing system and garbage mail sorting method
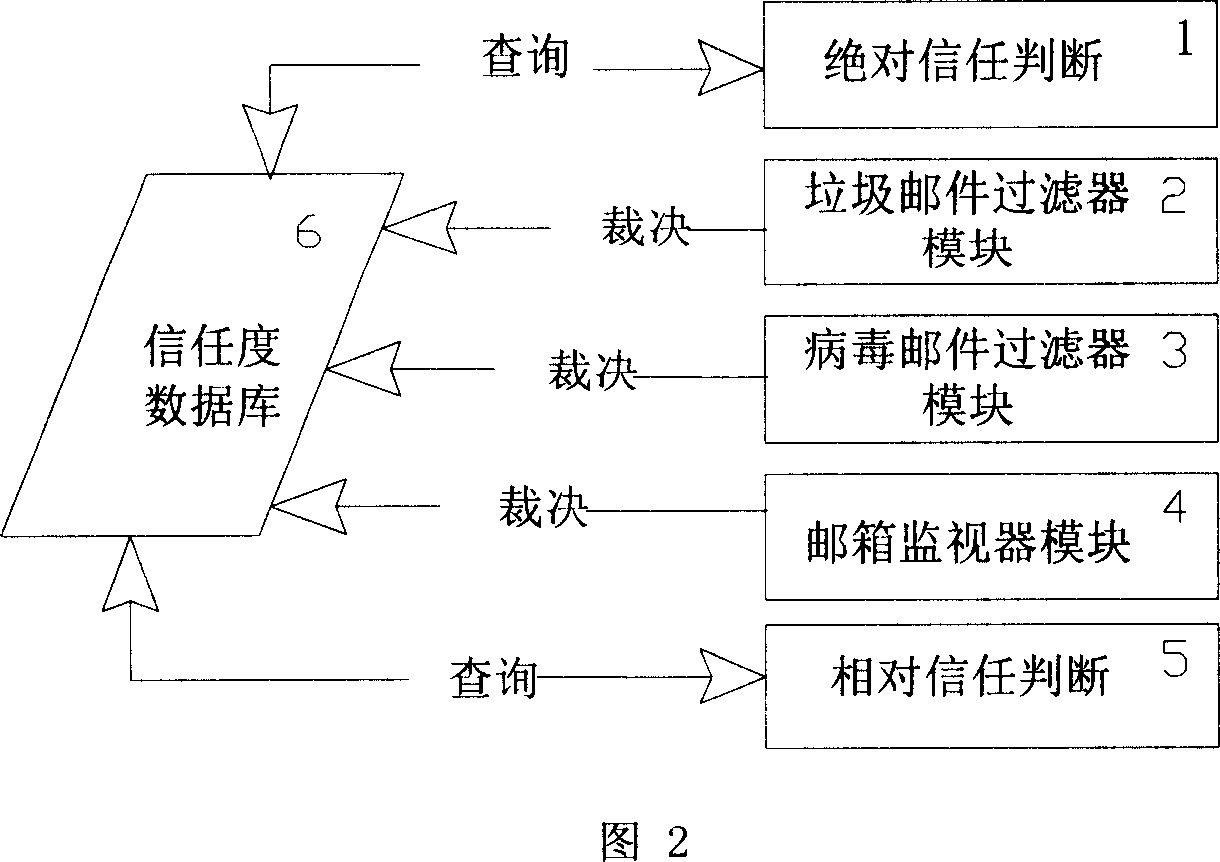
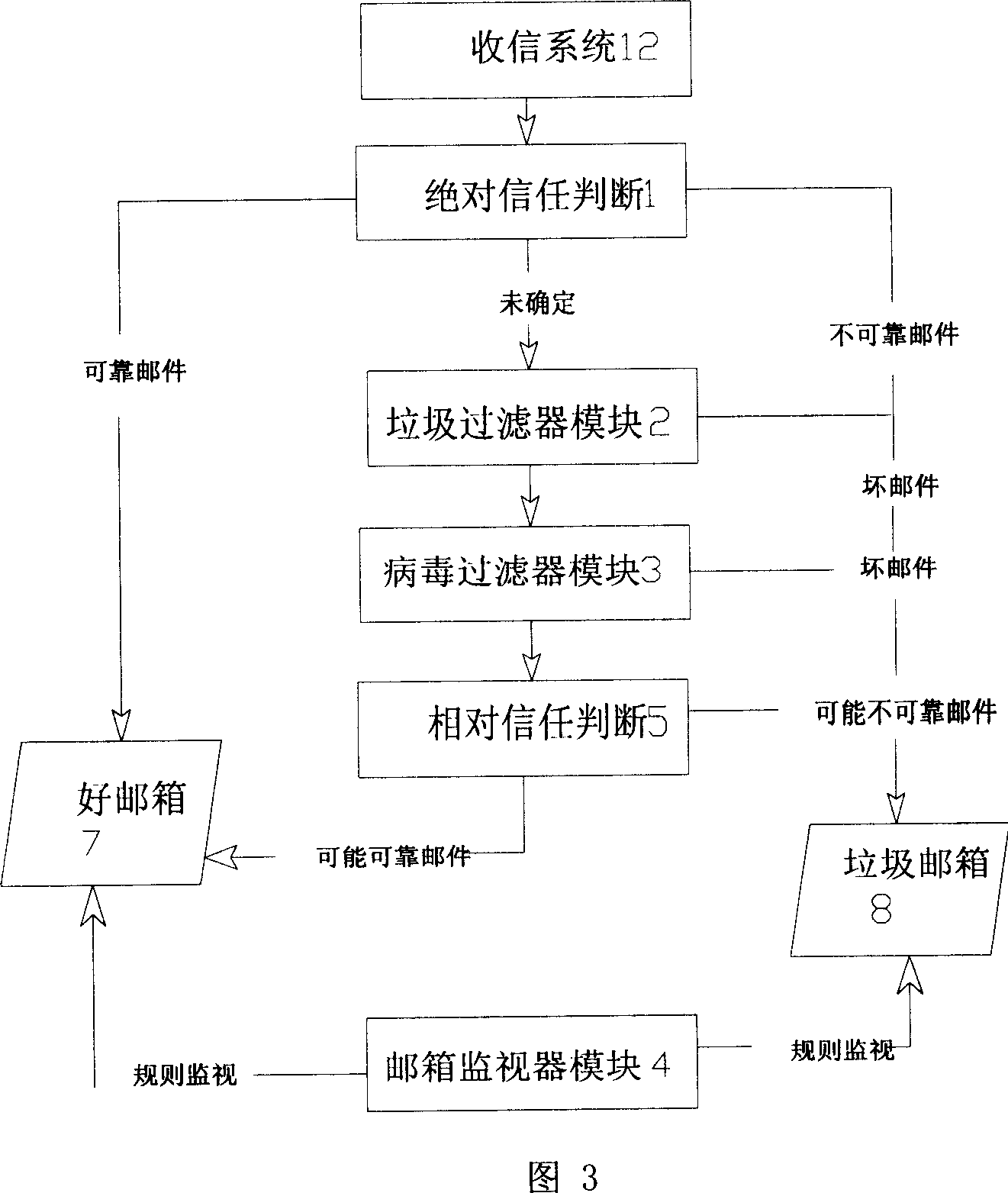
ActiveCN101060421ASolve generation difficultiesImprove filter interception rateOffice automationData switching networksProcess systemsHandling system
The related garbage mail process system compromises: a garbage mail filter module in SMTP, a virus analysis module, a mail-box monitor 1, a trust database 2, and a trustness level judgment module 3 for calling the trustness value and comparing with the reference value, wherein the filter module modifies the mail trustness value according to all other process results. This invention improves system process capacity, and enhances protection on illegal access.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data synchronization method and device
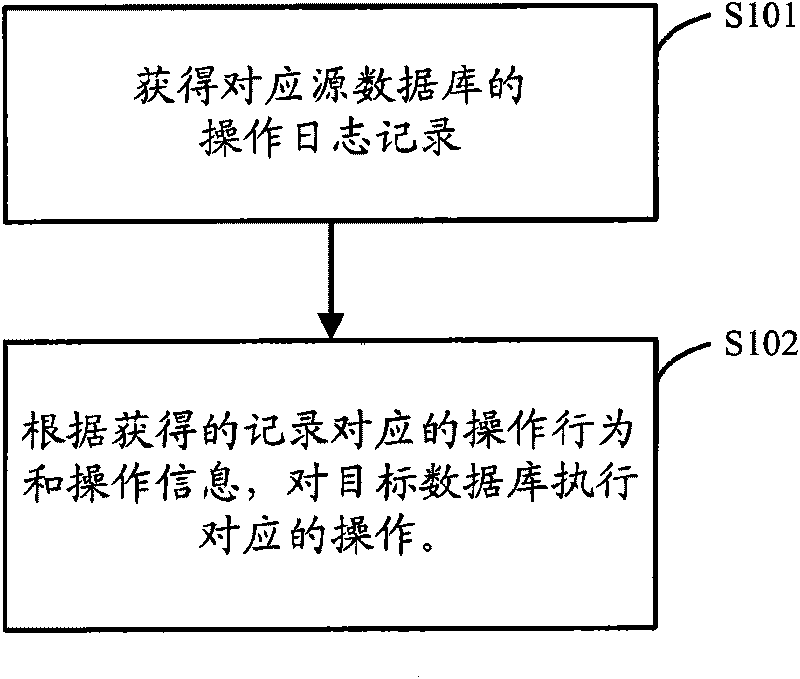
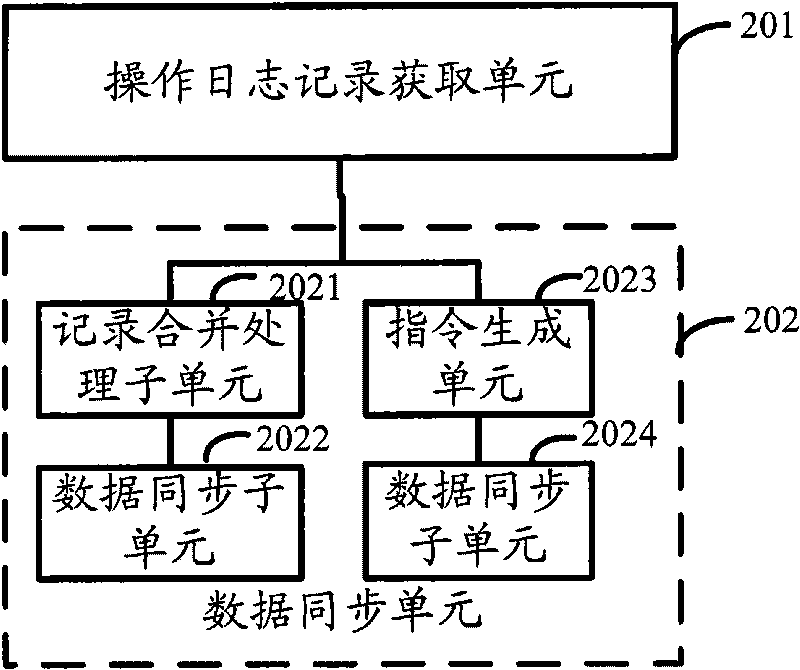
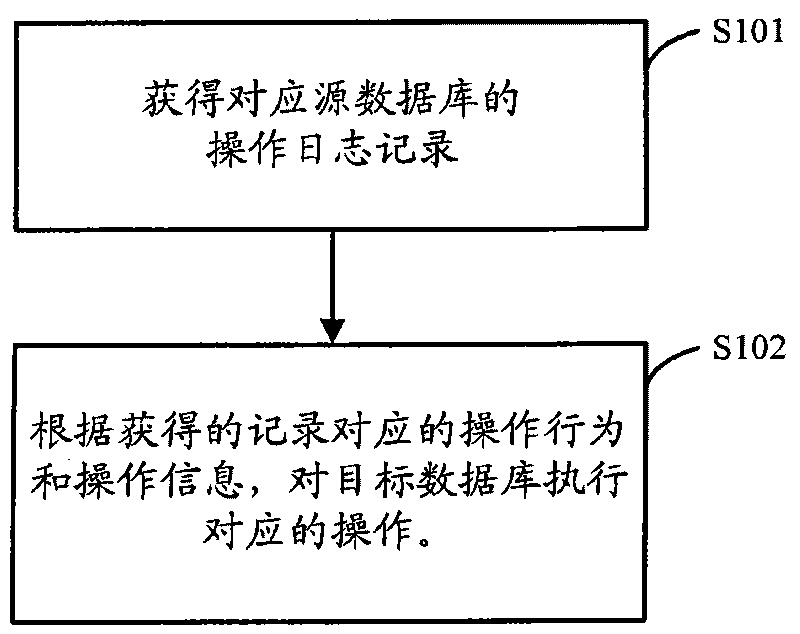
ActiveCN101719149AAchieve synchronizationImprove real-time performanceSpecial data processing applicationsData synchronizationData operations
The embodiment of the invention provides a data synchronization method which comprises the following steps: acquiring operation log records corresponding to a source database, wherein the operation log records are used for recording various operation behaviors and operation information of the source database in the specified duration before the current time; and executing corresponding operations on a target database according to the operation behaviors and the operation information corresponding to each of the acquired operation log records. The data synchronization method provided by the embodiment of the invention analyzes the data operation aiming at the source database by reading the logs of the source database, and executes the same data operation on the target database to realize the data synchronization between the databases. The data synchronization method provided by the embodiment of the invention and the device thereof reduce the system cost in the data synchronization method and improve the real-time property and accuracy of data synchronization.
Owner:UNION MOBILE PAY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com