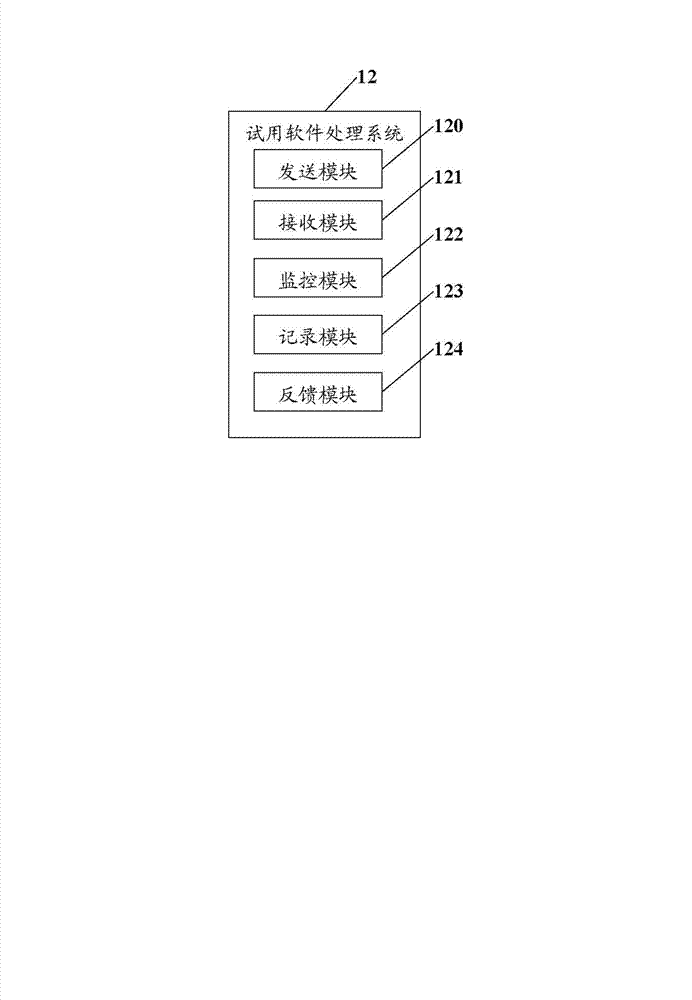
Patents
Literature
286 results about "Authorization Mode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
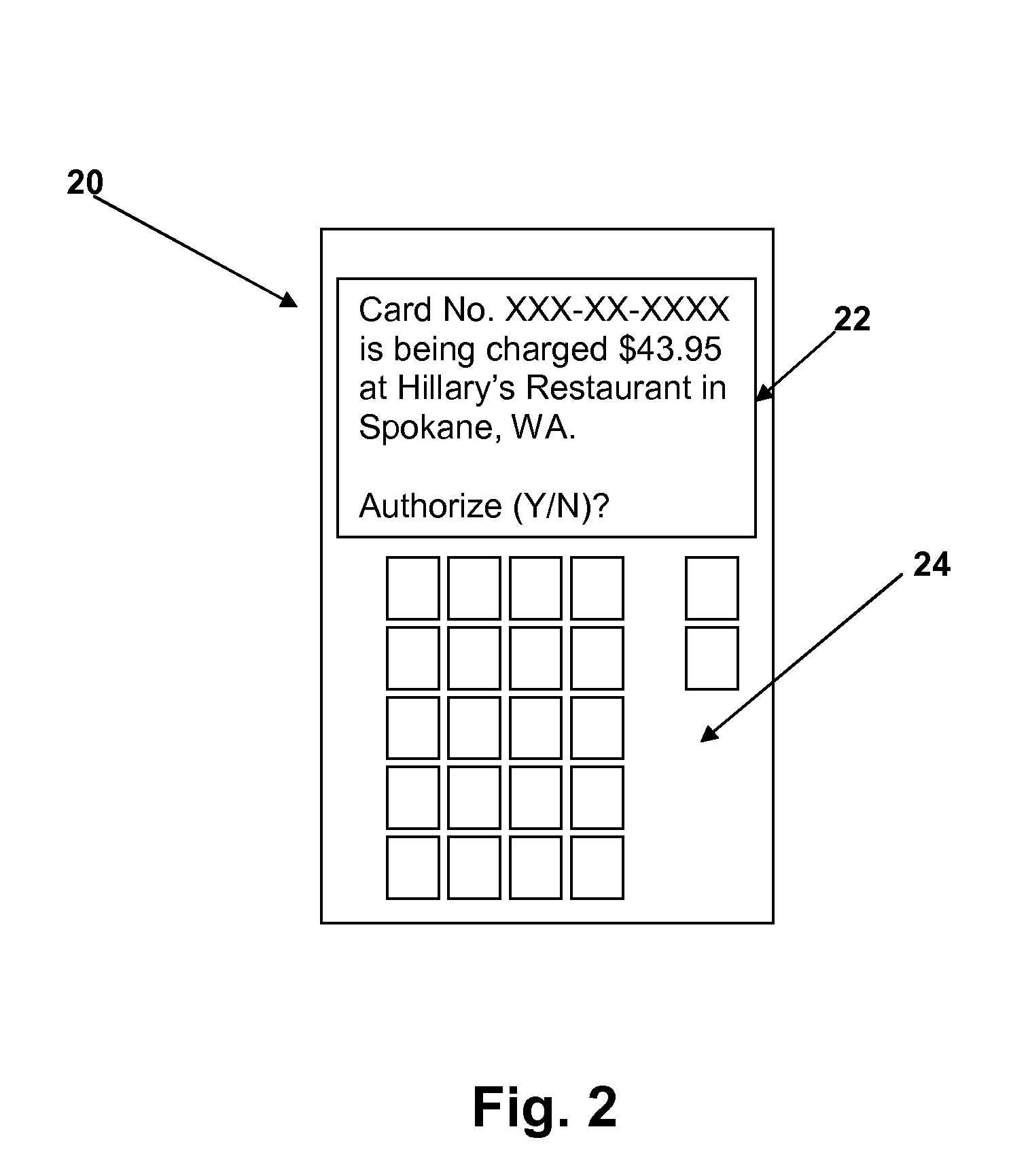
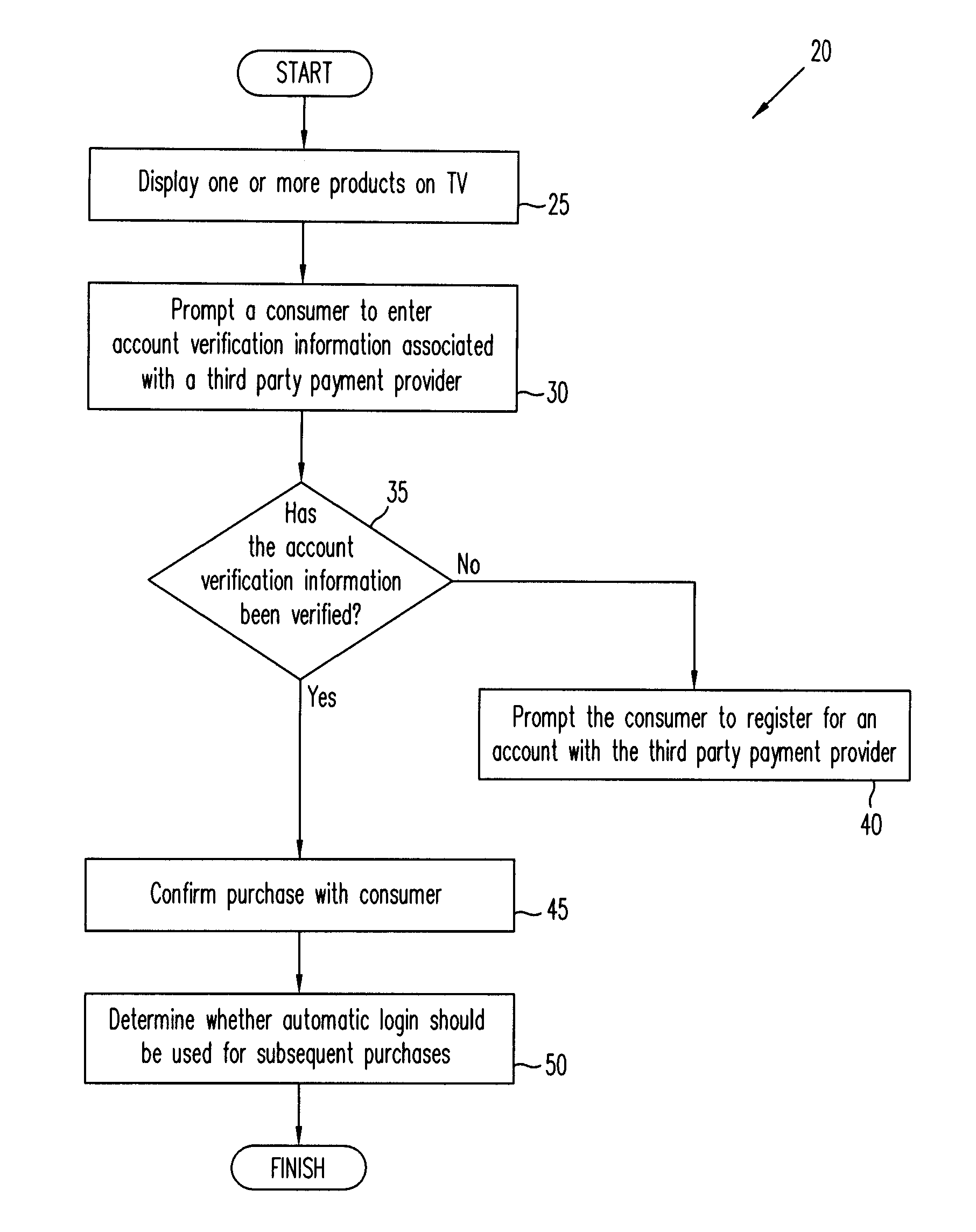
Change the authentication mode to Windows. Windows Authentication mode provides the developer to authenticate a user based on Windows user accounts. This is the default authentication mode provided by ASP.Net. You can easily get the Identity of the user by using User.Identity.Name.
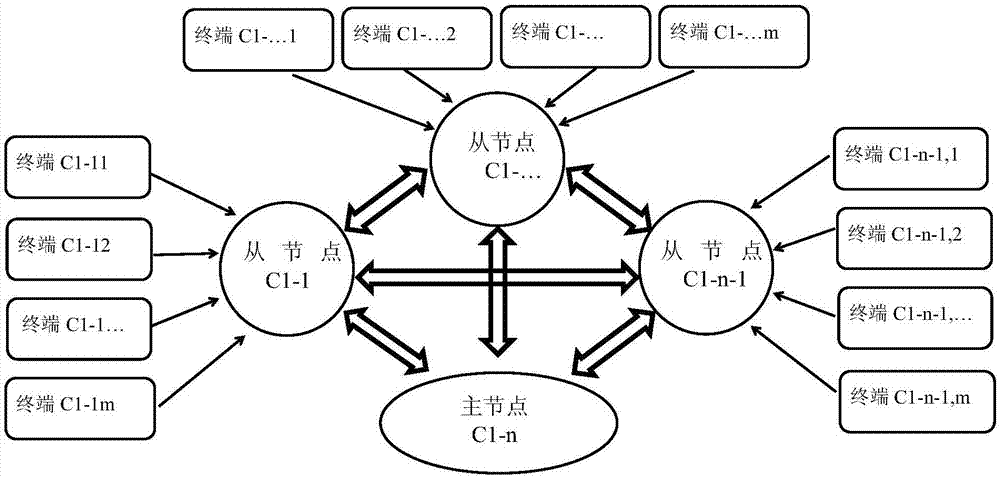
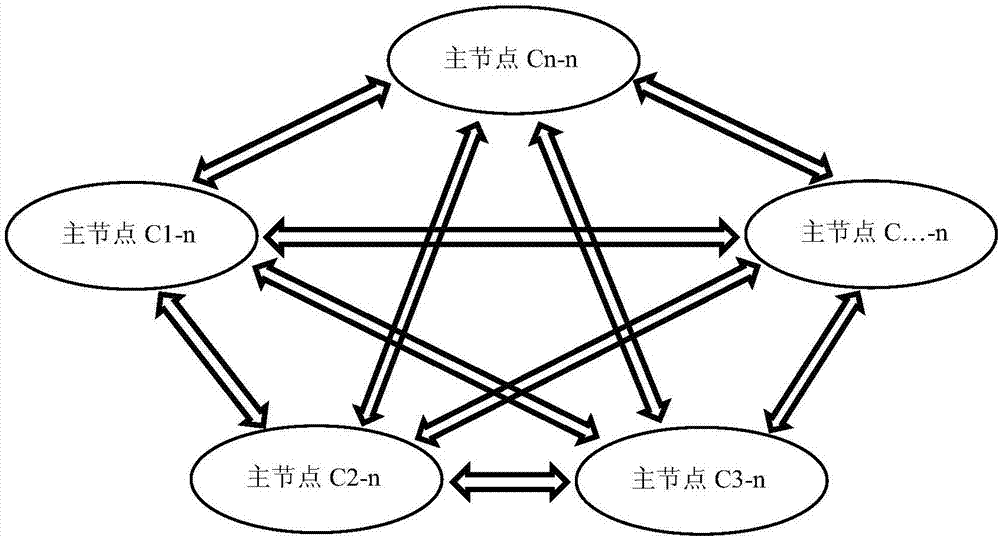
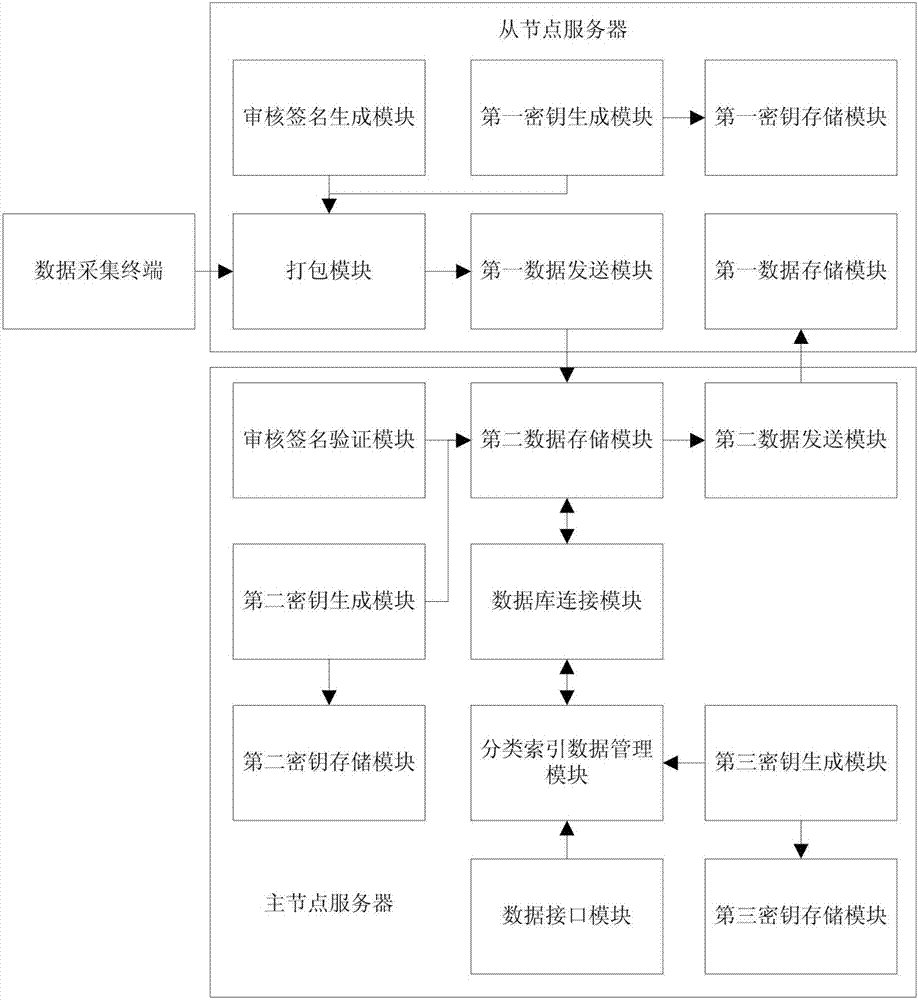
Data management system and method based on composite blockchain network
InactiveCN107222482AIntegrity guaranteedGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationAuthorization ModeStructure of Management Information
The invention relates to a data management system and method based on a composite blockchain network, wherein the system comprises a first-level blockchain network and at least one second-level blockchain network; the second-level blockchain network comprises multiple mutually connected slave node servers; the second-level blockchain network sets a master node server in all the slave node servers; and the master node servers in all the second-level blockchain networks are mutually connected, so that the first-level blockchain network is formed. By means of the data management system and method disclosed by the invention, the integrity, the authenticity and the standardization of data can be ensured through audit signature verification of the composite multi-level blockchain network; the security of the data is ensured in a hierarchical encryption and multiple authorization mode; structural design of hierarchical storage of detailed data and classified index data is carried out through a blockchain technology and the composite multi-level network; therefore, the data is relatively smooth to interconnect, intercommunicate and exchange; furthermore, audit tracing can be realized; and the data retrieving, applying and sharing efficiency can be increased.
Owner:黑龙江卓亚科技有限公司
Method of authorizing an operation to be performed on a targeted computing device
ActiveUS20150074764A1Digital data processing detailsComputer security arrangementsAuthorization ModeAuthentication server
A method of authorizing an operation to be performed on a targeted computing device is provided. The method includes generating a request to perform an operation on the targeted computing device, signing the request with a private key of a first private, public key pair, transmitting the request to an authentication server, receiving an authorization response from the authentication server that includes the request and an authorization token, and transmitting the authorization response to the targeted computing device.
Owner:THE BOEING CO
Access control method and system based on block chain technology
ActiveCN108123936AResistance to failureResist being attackedFinancePayment protocolsAuthorization ModeData privacy protection
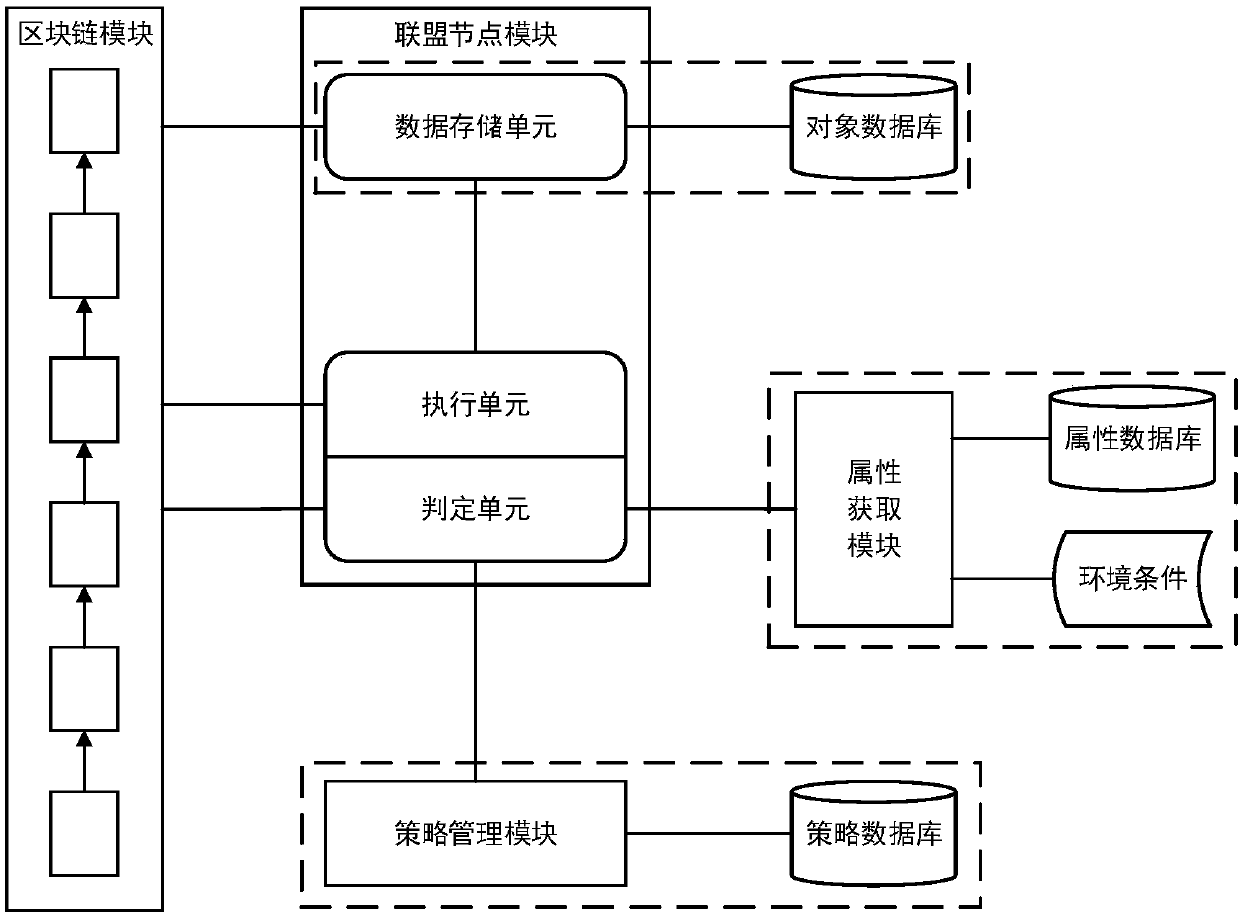
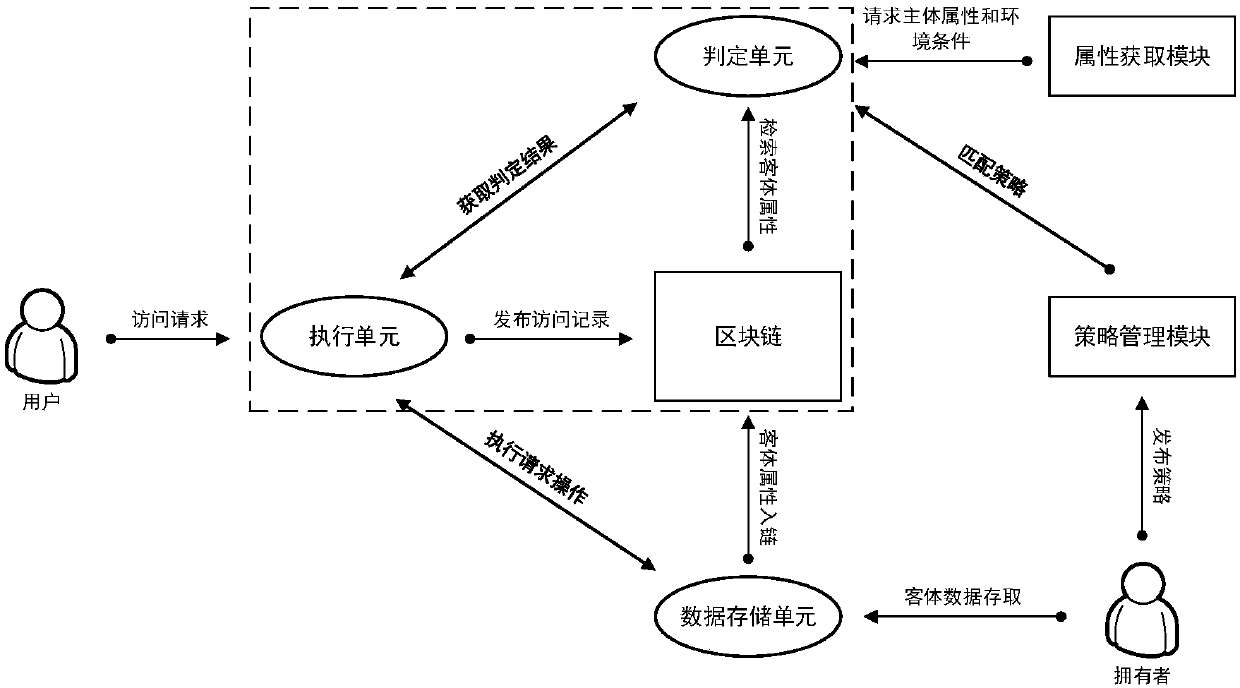
The invention provides an access control method and system based on block chain technology. The block chain technology is combined with attribute-based access control in the method, and the method comprises the following steps: adding an object in a chain, binding a judgment process of attribute and strategy on all block chain nodes with reference to the strategy. The access authorization is converted from a centralized manner into a distributed manner, the consistency check of the judgment results in the whole network is achieved by using a consensus mechanism of the block chain, and the authorized operations for accessing the recorded transactions are permanently recorded on the block chain. The method has the advantages of anti-single point failure, flexible authorization mode, accurateaccess boundary, and record auditability. The access control method and system provided by the invention are applicable to operating environments such as enterprises and governments that have the need of data privacy protection and realize multi-branch cooperation work based on a block chain platform, the access permissions of users in the system can be dynamically and scalably managed, fine-grained permission management is achieved for the strategy and the attribute, and the access control method and system are of important practical significance for protecting the security of information systems in a distributed network environment.
Owner:UNIV OF SCI & TECH BEIJING
Data delivery system, server apparatus, reproducing apparatus, data delivery method, data playback method, storage medium, control, signal, and transmission data signal
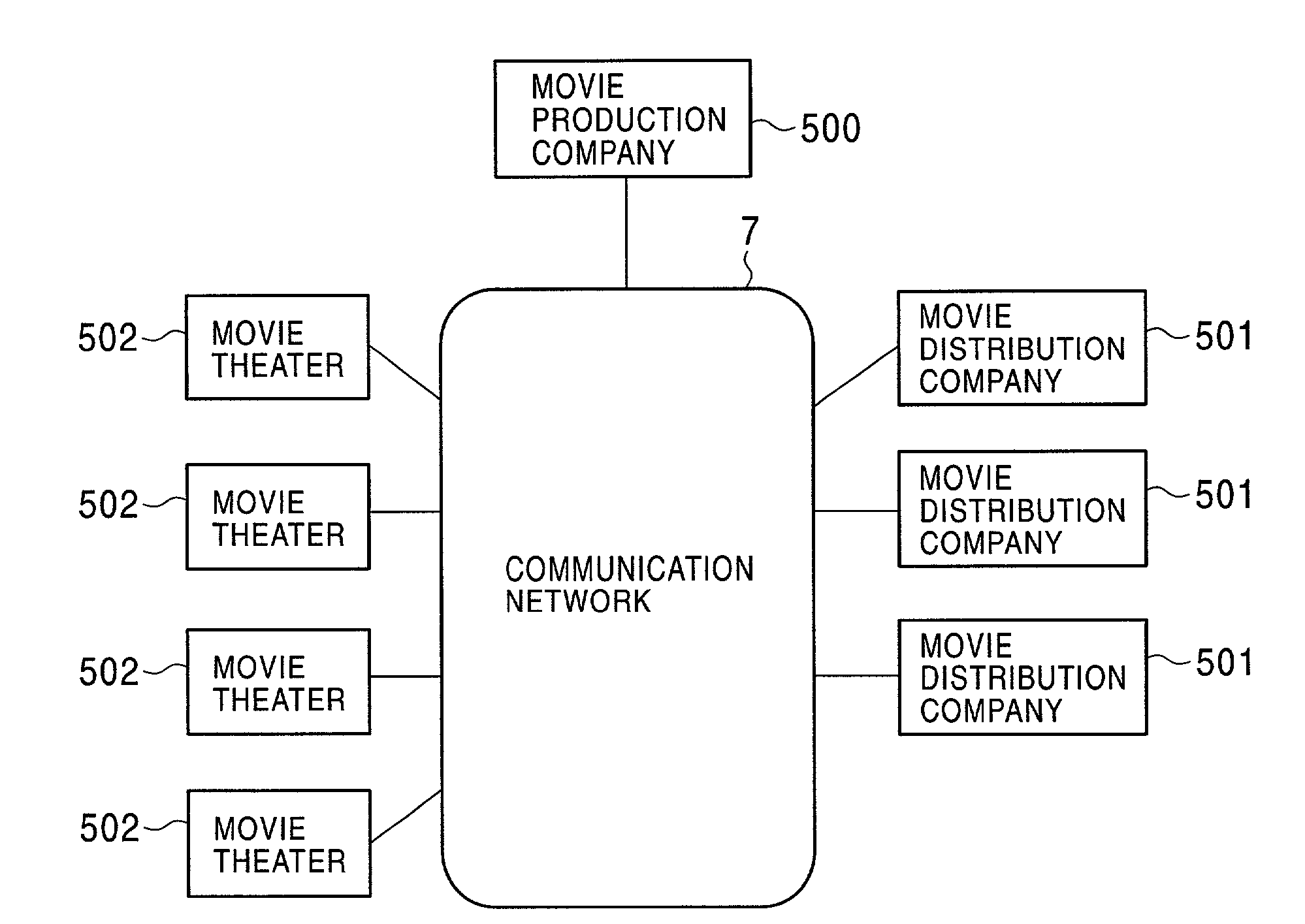
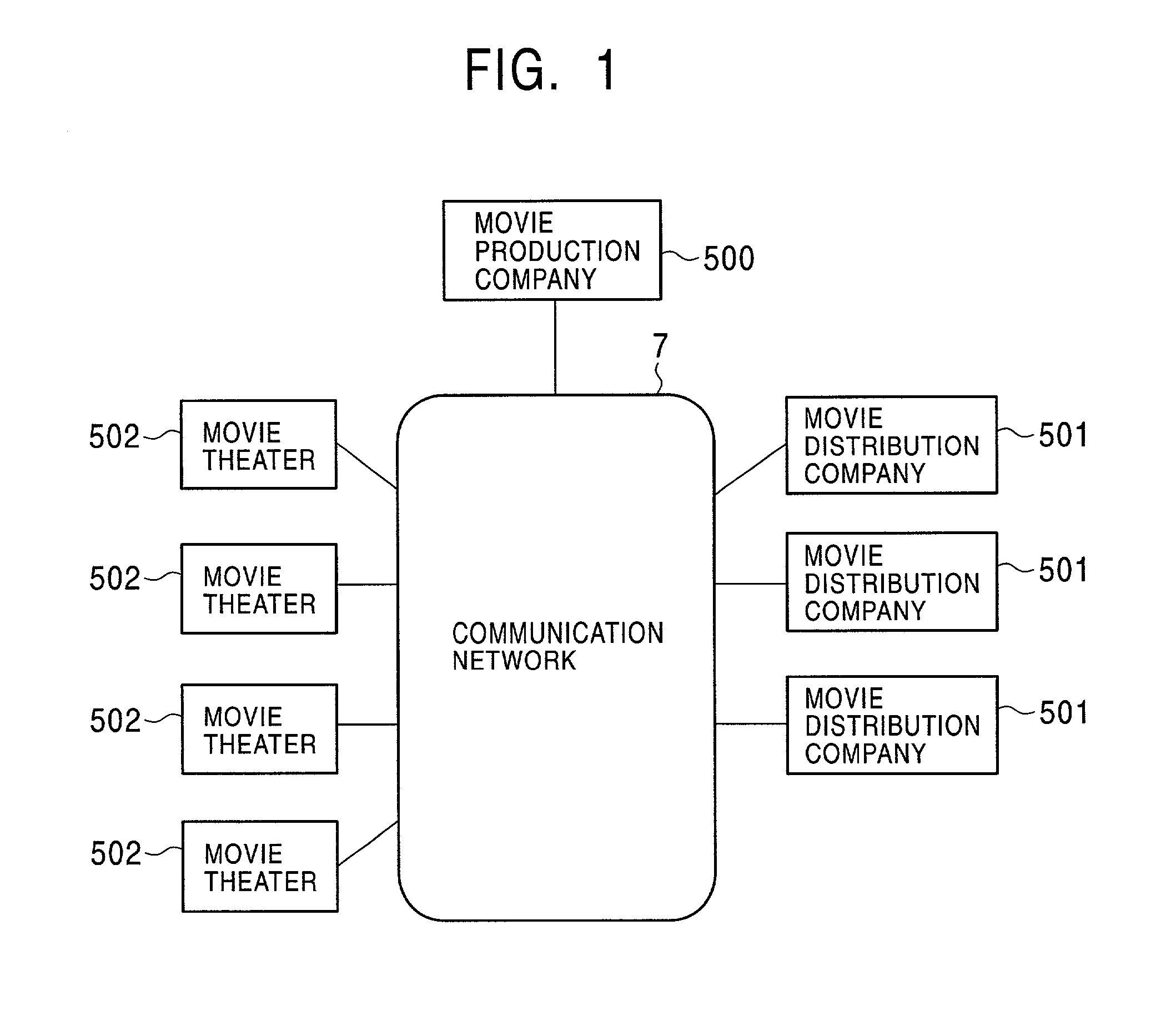
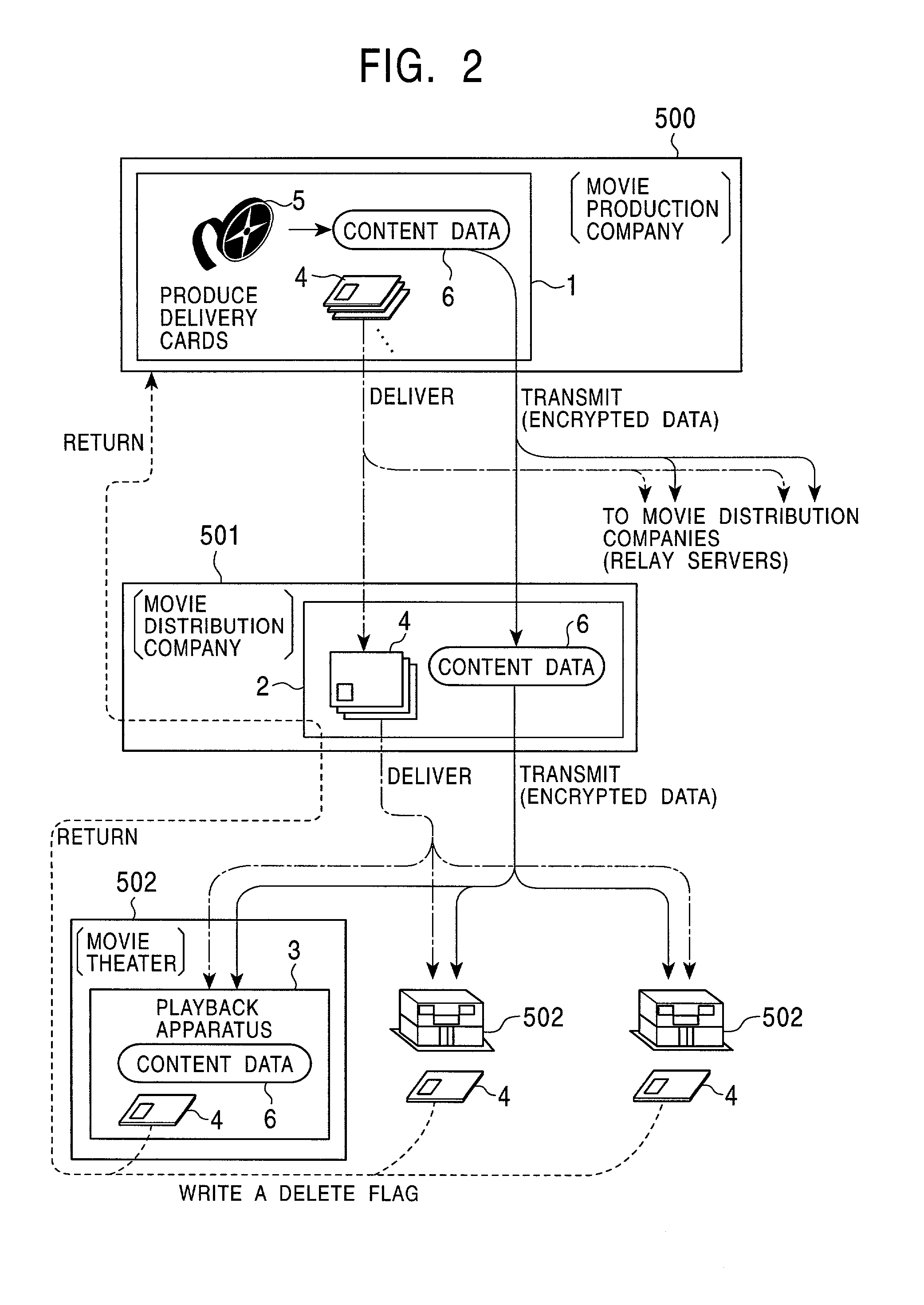
InactiveUS7263188B2Precise managementKey distribution for secure communicationData taking preventionAuthorization ModeData signal
A data delivery system has a capability of effectively and reliably protecting copyright of the data. A video source of a movie or the like is delivered in the form of encrypted data from a server apparatus to a playback apparatus. A decryption key used to decrypt the encrypted data is stored on a storage medium such as a memory card, and the storage medium is sent from the server apparatus to the playback apparatus in parallel with the delivery of the encrypted data. After completion of the playing of the movie by the playback apparatus in a movie theater, the storage medium is returned to the server apparatus. The server apparatus examines information stored on the storage medium to check whether the video source delivered in the form of data has been properly used in an authorized manner.
Owner:SONY CORP
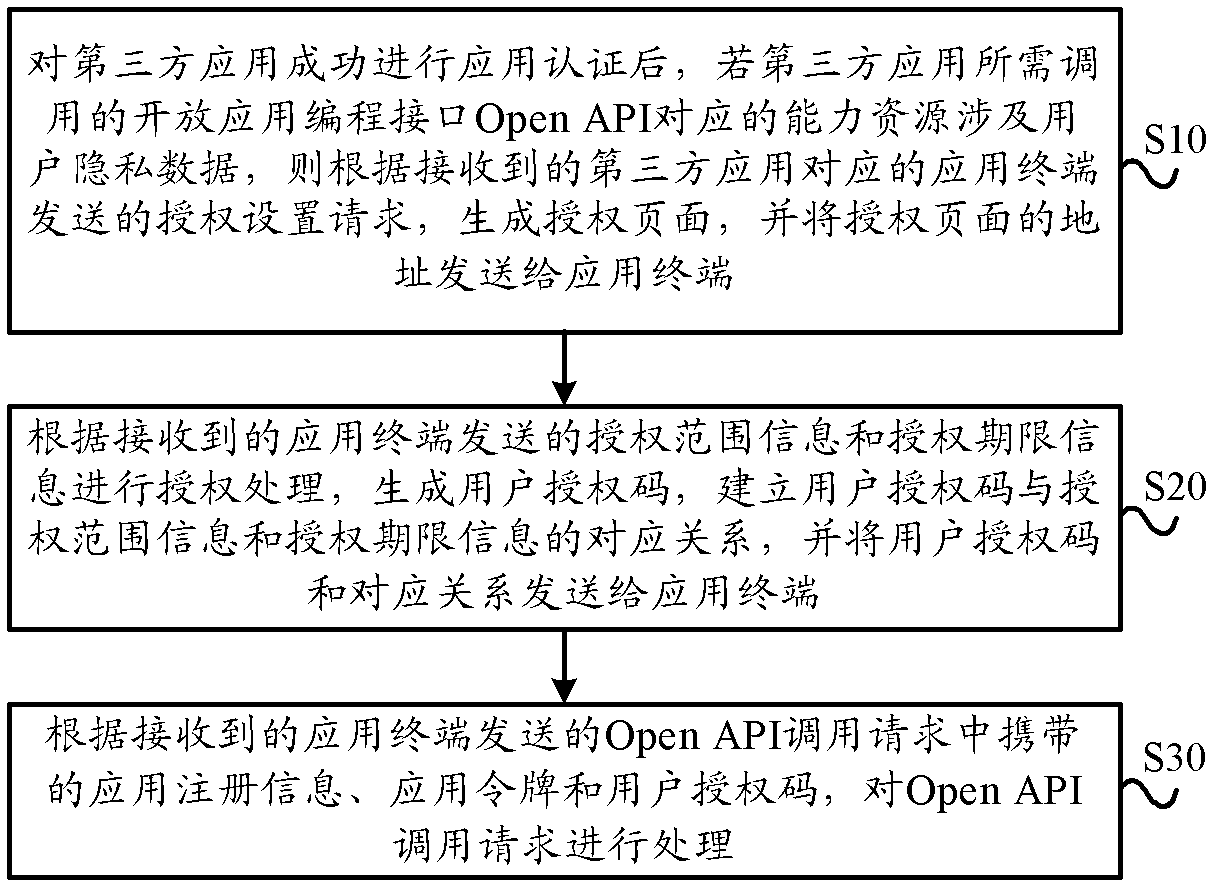
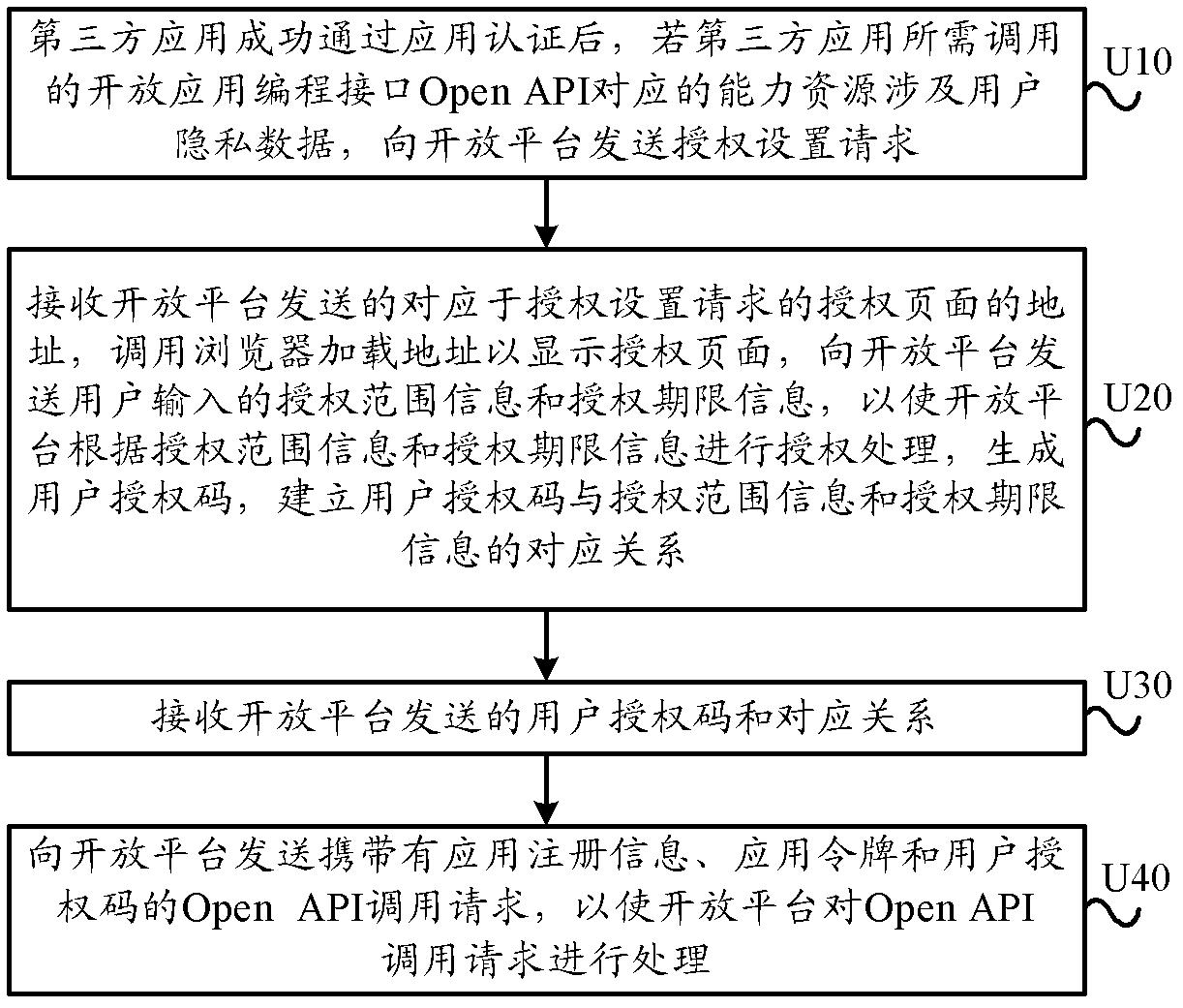
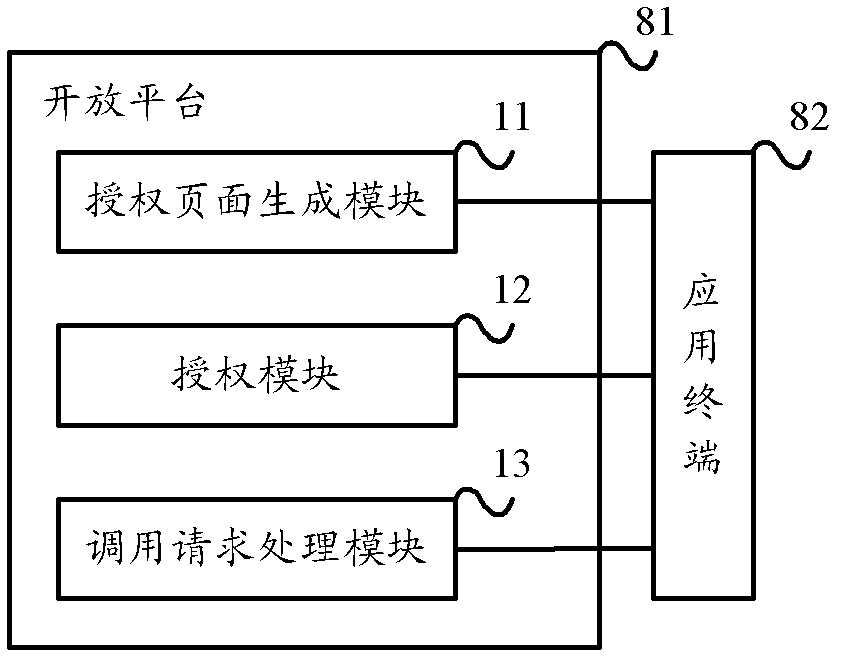
User authorization method, application terminal, open platform and system
The invention provides a user authorization method, an application terminal, an open platform and a system. The method includes: if capacity resources corresponding to Open API (application programming interface) needed to be called by a third party application relates to user privacy data, generating an authorization page according to a received authorization setup request and sending the authorization page to an application terminal; performing authorization processing according to received authorization range information and authorization deadline information sent by the application terminal to generate a user authorization code, setting up a corresponding relation between the user authorization code and each of the authorization range information and authorization deadline information, and sending the user authorization code and the corresponding relations to the application terminal; and processing the Open API calling request according to the received Open API calling request. By the aid of the user authorization method, the application terminal, the open platform and the system, users can modify the authorization range and authorization deadline of capacity resources according to own wills, so that flexibility in user authorization is greatly improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Software authorization system based on public key cryptosystem
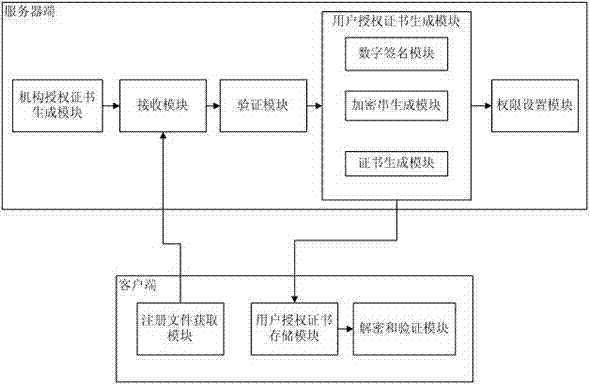
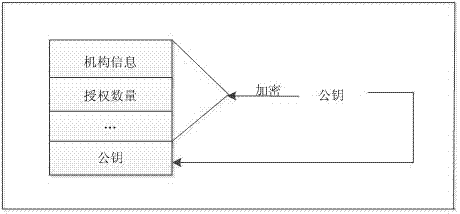
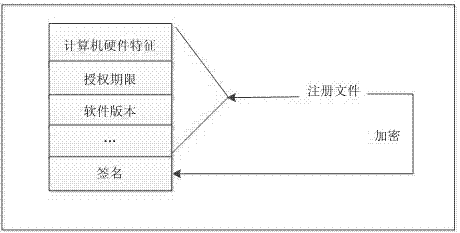
ActiveCN103491097APrevent illegal copyingEasy to upgradeVersion controlUser identity/authority verificationAuthorization certificateAuthorization Mode
The invention discloses a software authorization system based on public key cryptosystem. The software authorization system comprises a server end and a client end, wherein the server end comprises an institution authorization certification generation module, a receiving module, a verification module and a user authorization certificate generation module. The user authorization certificate generation module comprises a digital signing module used for carrying out digital signing on computer hardware characteristics h0 in a user registration file with an RSA private key to generate S0, an encryption string generation module used for carrying out preset hybrid operations on obtained software version information v, user information u, an authorization term ex, current time cur and s0 to generate an encryption string signB64 and a certificate generation module used for generating a user authorization certificate with the encryption string signB64 and the RSA public key. The method can prevent software from being illegally copied, meanwhile, the software can be managed by a software issuer in a concentrated mode, and upgrading and tracking of the software, pushing personalized services for users and other after-sale management are facilitated.
Owner:HUAZHONG NORMAL UNIV
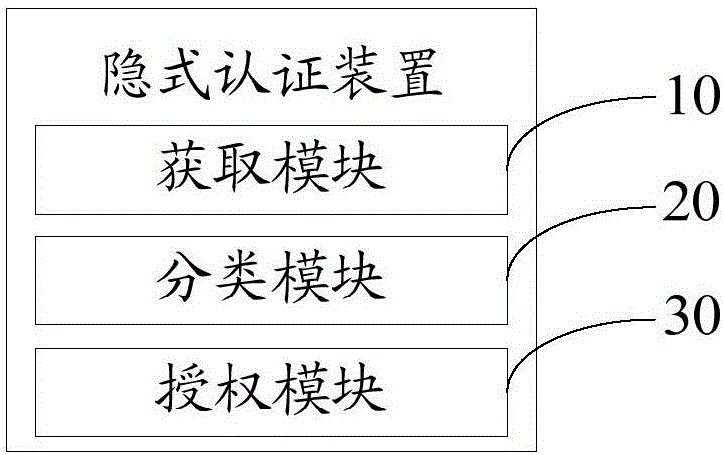
Hidden type authentication device and method
InactiveCN106156566ASimplify Authentication PolicyEnsure safetyDigital data authenticationSubstation equipmentAuthorization ModeComputer terminal
The invention discloses a hidden type authentication device. The device comprises an acquiring module, a classifying module and an authorization module, wherein the acquiring module is used for acquiring user behaviors in a process of inputting a control instruction if the control instruction for opening a pre-set user interface of a mobile terminal is received; the classifying module is used for classifying the user behaviors based on a pre-configured classifying device and acquiring a Boolean value returned back by the classifying device; and the authorization module is used for judging that the mobile terminal enters an authorization mode if the Boolean value is real, and opening the user interface. The invention further discloses a hidden type authentication method. With the adoption of the hidden type authentication device and method, an authentication strategy of the mobile terminal is simplified and the authentication of user authorities can be realized through collecting the user behaviors; and a user does not need to be forced to repeatedly input decrypting information and user experience is improved.
Owner:NUBIA TECHNOLOGY CO LTD
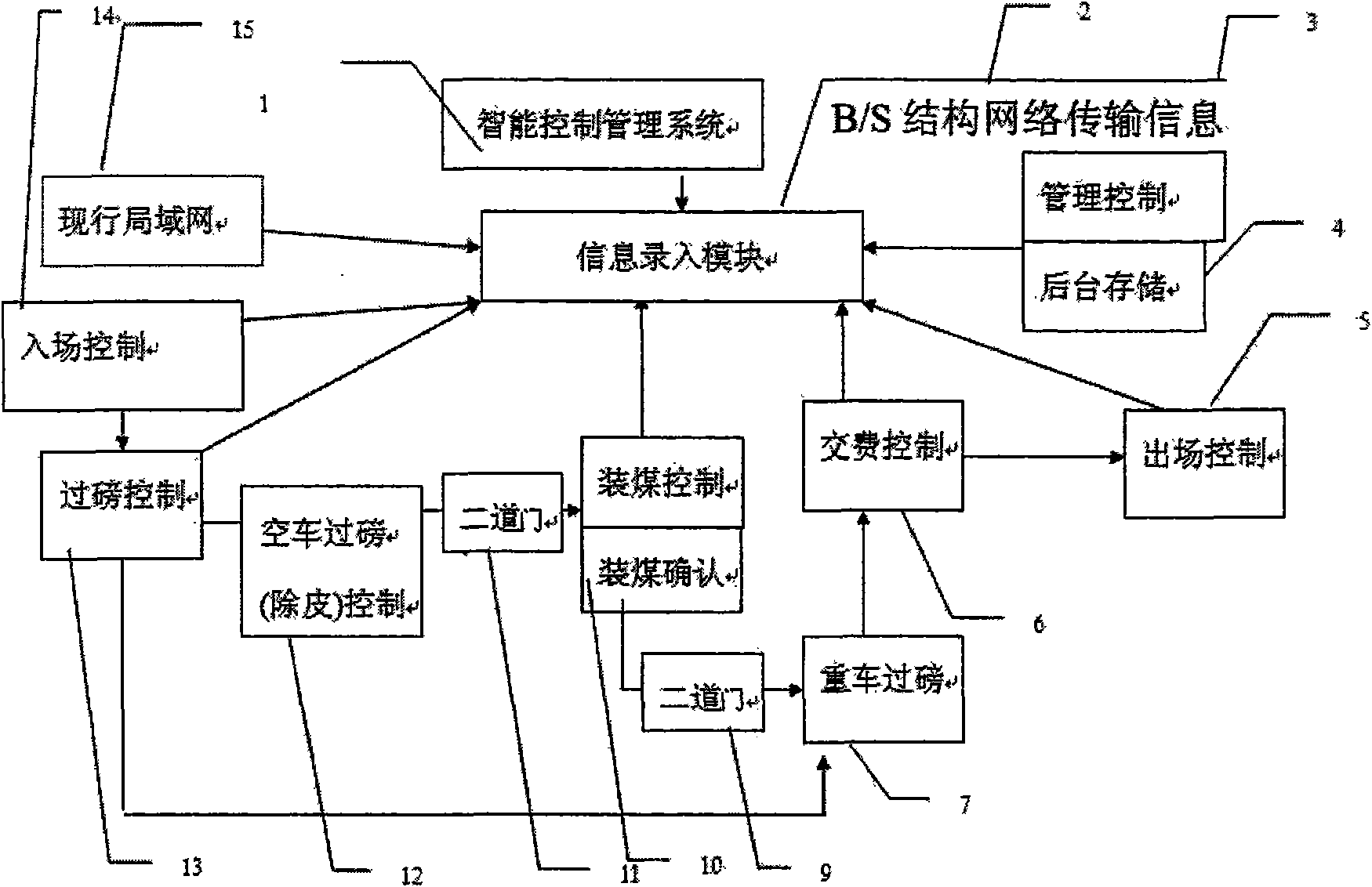
Intelligent control device system for mineral material transportation and sale flow and system application method
InactiveCN101587333AQuantity is easy to controlAuthorization managementTicket-issuing apparatusData processing applicationsPaymentAuthorization Mode
The invention discloses a combined control device system for material storage goods yard transportation and sale and a system application method. The system comprises an information inputting module, a loading control module, a weighing control module, a payment control module, an exit control module, a background storage module, a management control module and an information inquiry module which are mutually connected; and the system consists of hardware and software. The method comprises asking for a goods card during empty vehicle entrance, weighing an empty vehicle and excluding tare, swiping the card at a goods yard, weighing and determining a heavy vehicle, paying and determining, and swiping the card / shooting pictures / comparing / determining / releasing during exit; and the method can thoroughly avoid the illegal actions such as man-made weighing cheat, loading cheat, variety switch, vehicle change, and the like. The system is authorized to different departments with different level authorities through an authorization mode of different levels, has the functions of video, positioning and locking of identity cards, and avoids the illegal actions of switching license plates and vehicles. The system and the method automatically identify, determine and balance, improve the working efficiency, and are widely applicable to storage and transportation goods yards and storehouses in various industries such as coal, metallurgy, oil products, and the like.
Owner:XIAN ZHONGTAI ELECTRONICS TECH
A system and method for authorizing access request
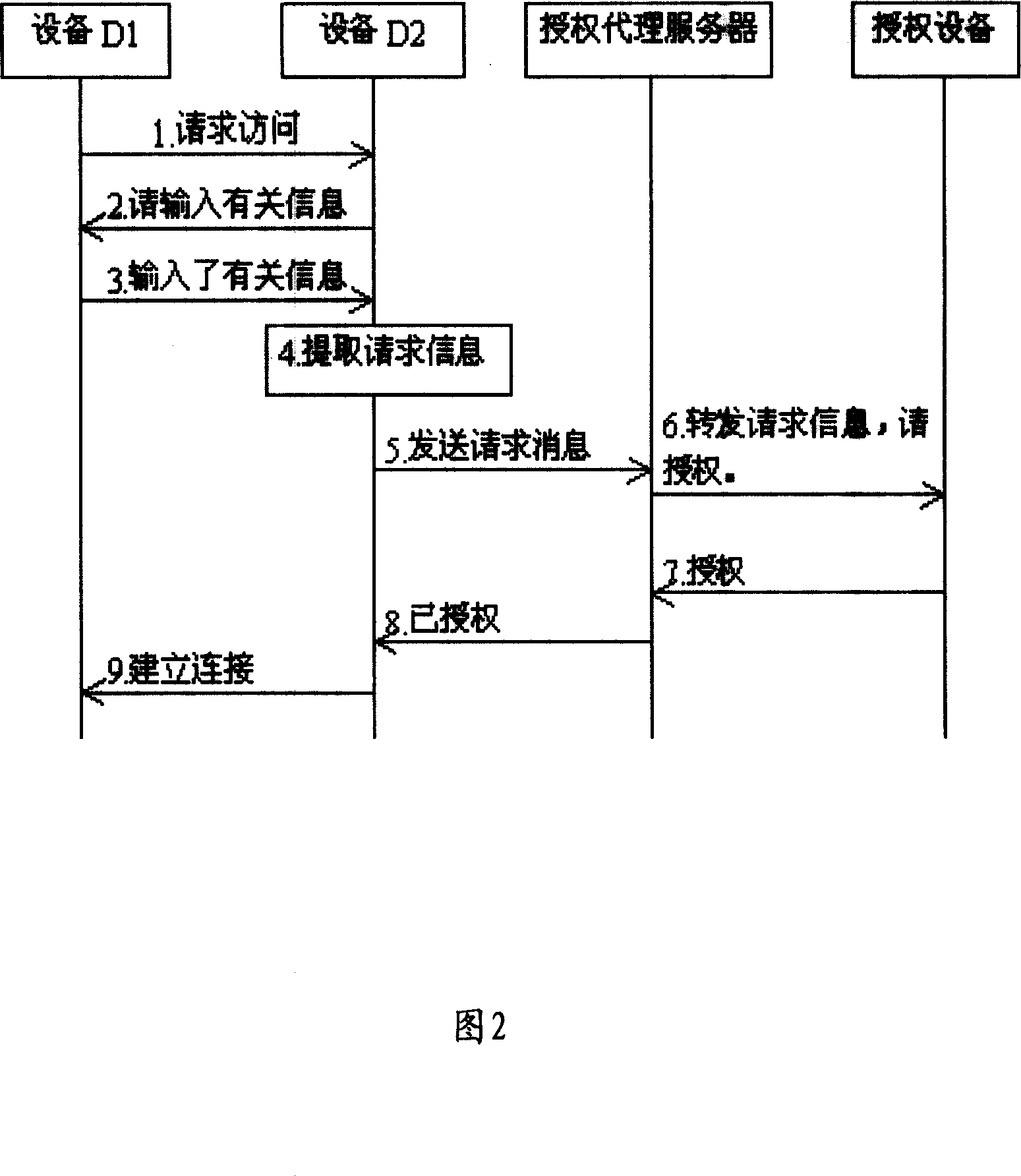
ActiveCN101127625ATo achieve the purpose of one-time authorizationFlexible operationData taking preventionAuthorization ModeProxy server
The utility model relates to a system and a method which authorize for visiting request, which adopts the technical proposal that: the system comprises at least a visited equipment, at least an authorizing equipment and at least an authorized agent server; wherein, the visited equipment is provided with a manage module of connecting the request; the authorized agency server comprises a transfer module of the visiting solicited information, a transfer module of the authorized information and a management module of the authorized mode. The method of the utility model is that: the visited equipment gets the visiting solicited information of the visiting equipment and sends to the authorized agency server; the visiting solicited information is transferred by the authorized agency server to the authorizing equipment and is fed back to the visited equipment that the authorization is made after the authorizing of the authorizing equipment is received. For the technical proposal, one-time authorizing can be realized for the visiting request using the utility model and the authorizing process becomes simple, flexible and safe.
Owner:HUAWEI TECH CO LTD
Digital copyright protection method and system for media network application
InactiveCN1937495AIn line with psychological characteristicsGreat authorityPublic key for secure communicationProgram/content distribution protectionAuthorization ModeThe Internet
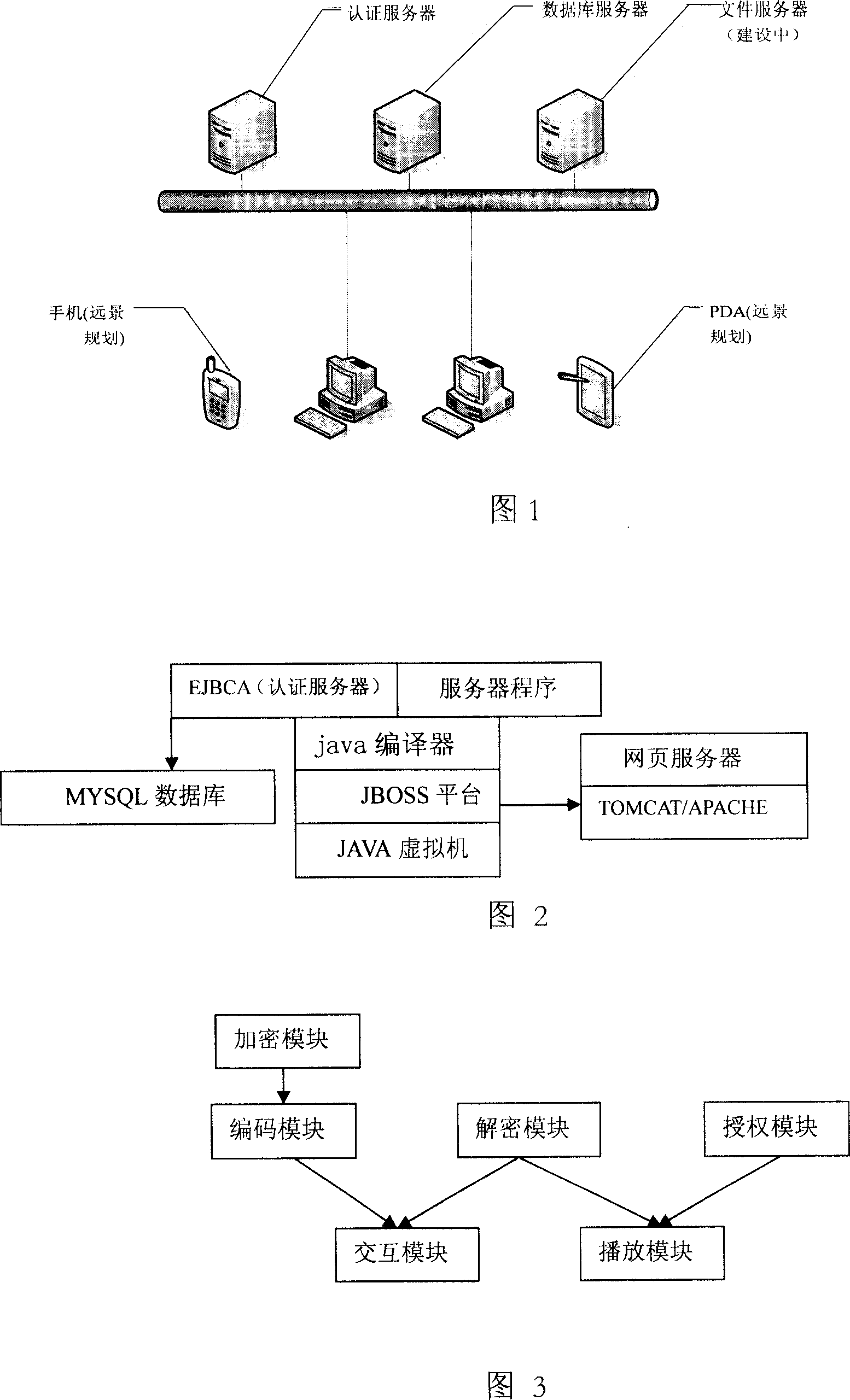
The media document owner encrypts his media documents via a encrypt module on the user end, and then uploads the encrypted documents to the data server via network. The owner manages the use right of these encrypted document by himself. This system includes the authentication server connected to the Internet, the data server and several user ends. Every user end has encryption module, authorization module, decoder module and playback module. The media document owner encrypts and authorizes their documents at the user end. It decreases the load of system server, increases the encryption efficiency. It is easy to renew the algorithm and is flexible and easy to use. The user will feel more confident by possessing the power of authorization.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Data authentication
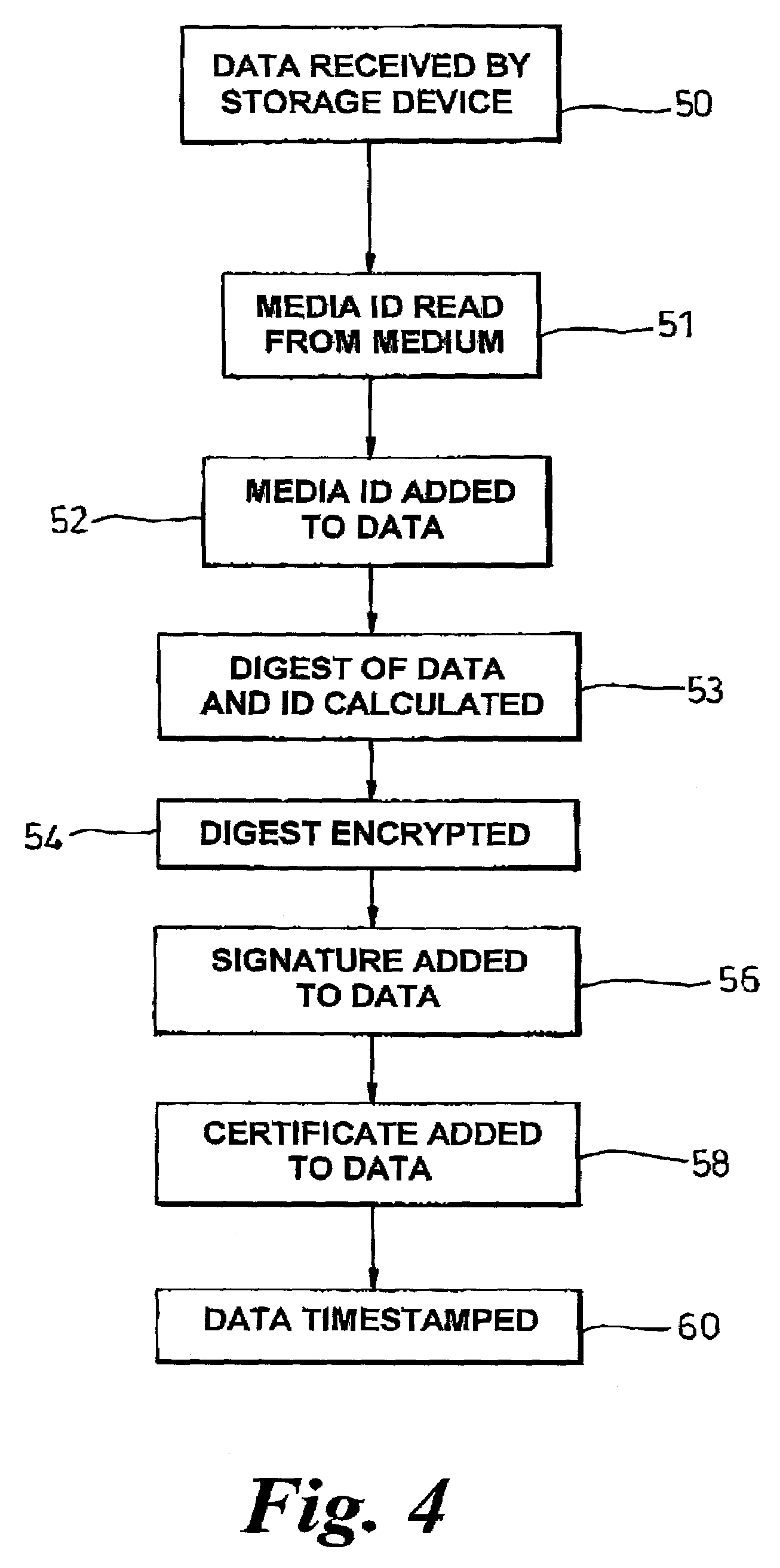
ActiveUS7194636B2Digital data processing detailsUser identity/authority verificationDigital signatureData content
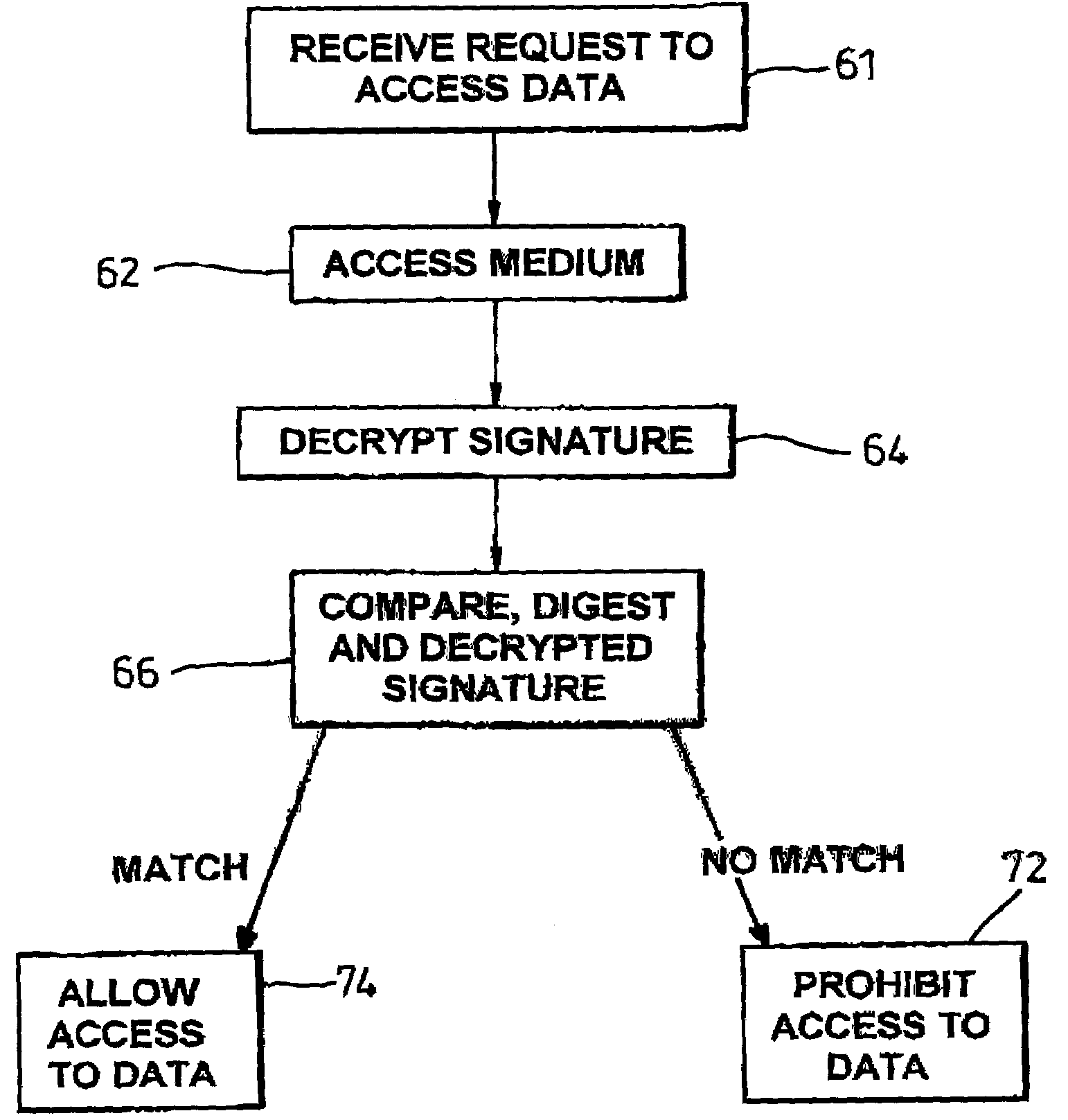
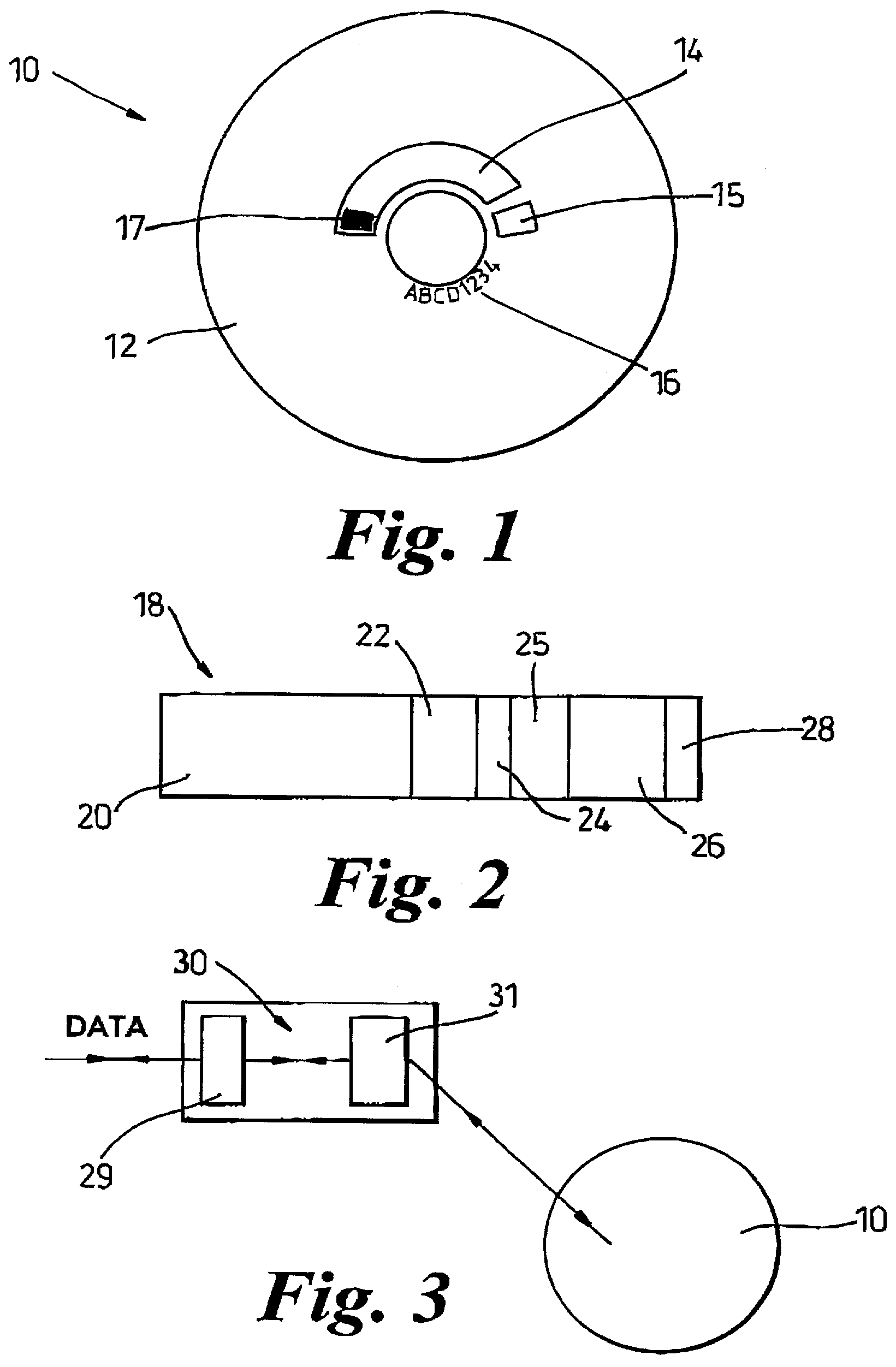
A storage medium carrying data content has an electronically readable modification-resistant identifier for distinguishing that medium from other storage media. The medium stores a digital signature associated with a data content portion carried by the storage medium. The identifier read from the storage medium generates the digital signature. The identifier and digital signature enable verification of storage of the data content on an authorised storage medium in an authorised manner.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
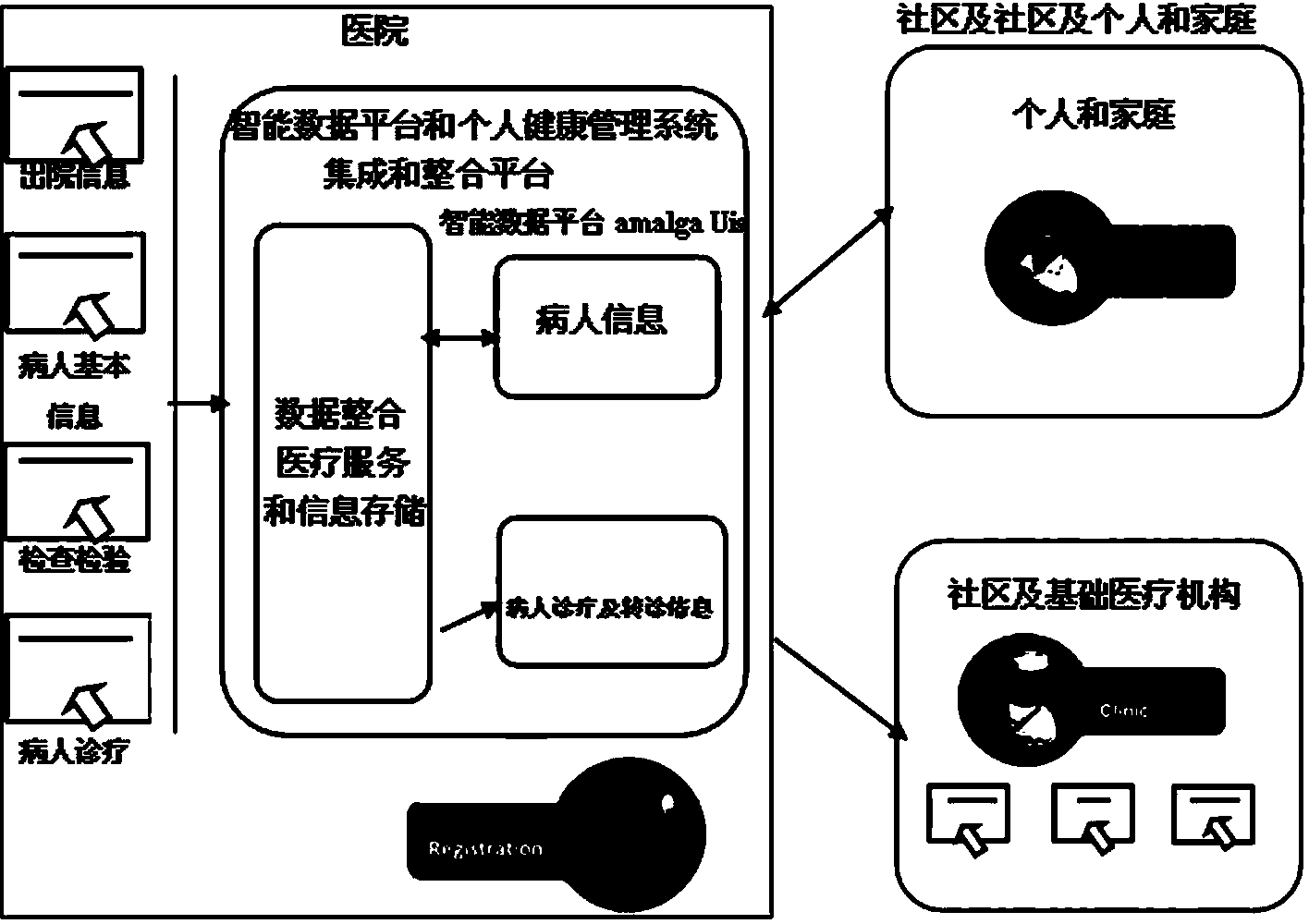
Medical information intelligent data platform, use method and application thereof
InactiveCN103530524AFlexible receptionEnable unified accessSpecial data processing applicationsAuthorization ModeData information
The invention discloses a medical information intelligent data platform, a use method and the application of the medical information intelligent data platform, and relates to the technology of medical information. The medical information intelligent data platform is a unified information resource center which can integrate the medical information, achieves medical data unified management, information sharing, early warning and monitoring, and is suitable for tertiary medical institutions in the whole country. The platform comprises an application server, a data server and a client terminal, wherein the application server, the data server and the client terminal are communicated in a wireless or wire mode, the data server is used for storing data information, the data server and a service system are interconnected in an authorization mode, and the data server obtains the data information from the service system. A system server sends out a command to the data server, and the data information of the service system is collected to the data server in a regular or real-time mode, and stored in the data server. A data calling and showing platform and a calling center are installed on the application server. The calling center is used for conducting content transferring between the client terminal and the application server.
Owner:XUZHOU TONGRUAN COMP SYST INTEGRATION
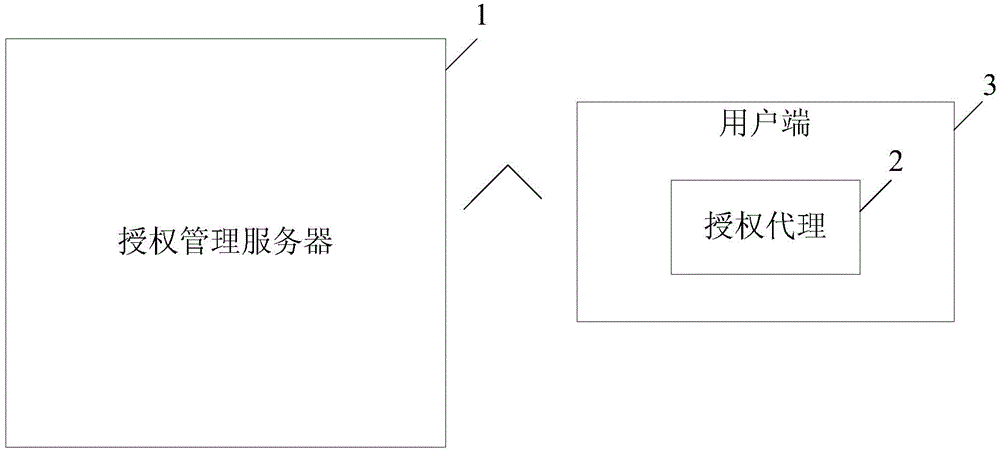
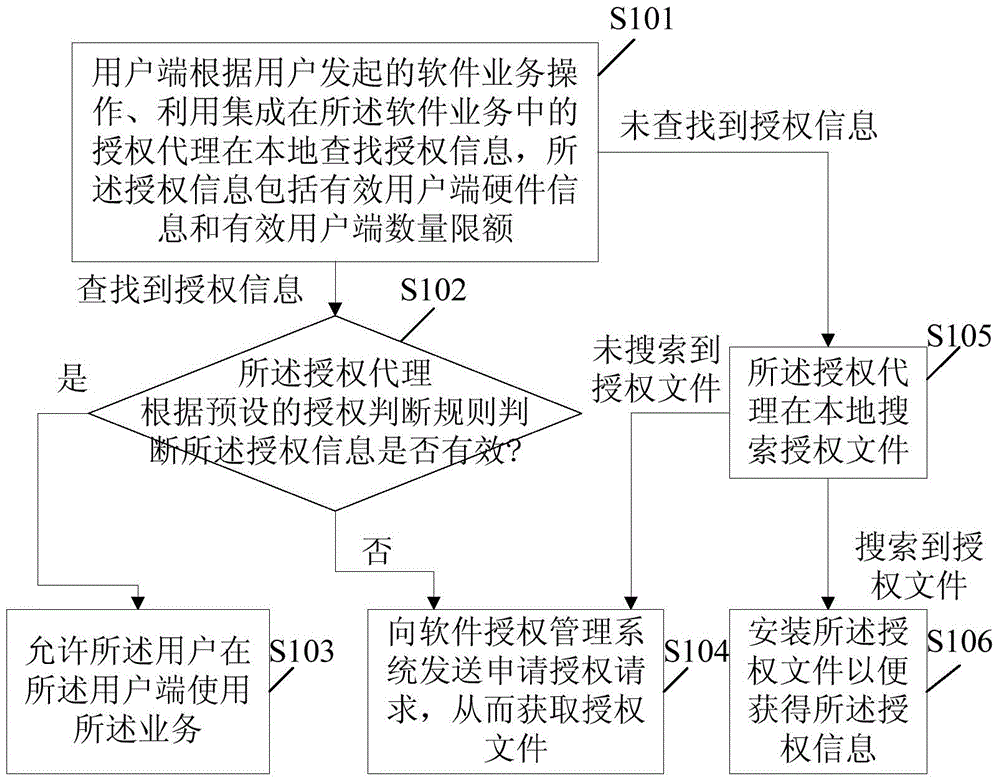
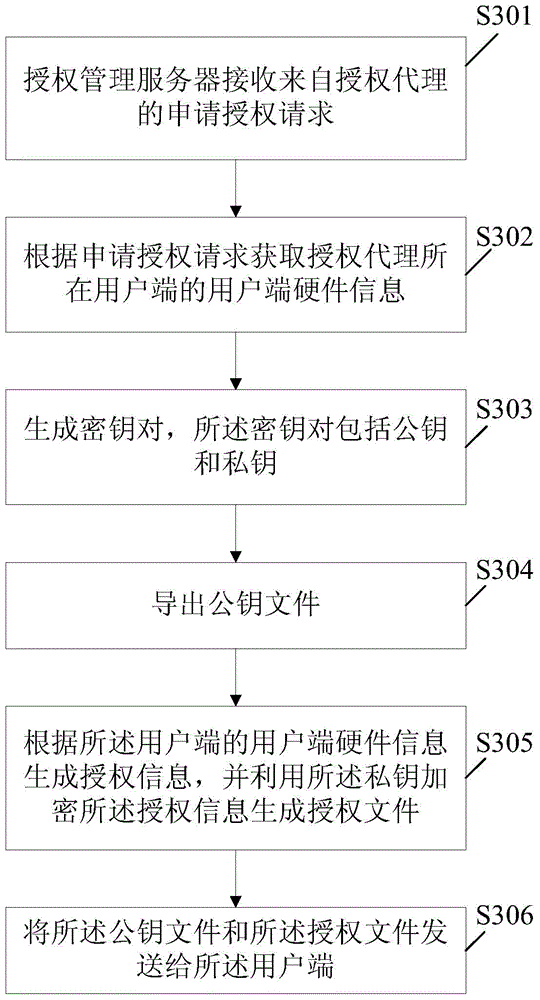
Software authorization management method and software authorization management system
ActiveCN104580316AQuality improvementMeet different needsUser identity/authority verificationProgram/content distribution protectionAuthorization ModeSoftware engineering
The embodiment of the invention discloses a software authorization management method and a software authorization management system. The software authorization management method comprises the following steps: a user side searching authorization information locally by utilizing an authorized agency integrated in software business according to the operation of the software business initiated by a user, wherein the authorization information comprises effective user side hardware information and effective user side quantitative restriction; if the authorization information is searched, the authorized agency judging whether the authorization information is effective or not according to a preset authorization judgment rule, if the authorization information is effective, permitting the user to use the business on the user side; if the authorization information is ineffective, sending an application authorization request to an authorization management server, and thus obtaining an authorization file; if the authorization information is not searched, the authorization agency searching the authorization file locally, and if the authorization file is searched, installing the authorization file so as to obtain the authorization information; if the authorization file is not searched, sending the application authorization request to the authorization management server, and thus obtaining the authorization file.
Owner:深圳市国信互联科技有限公司
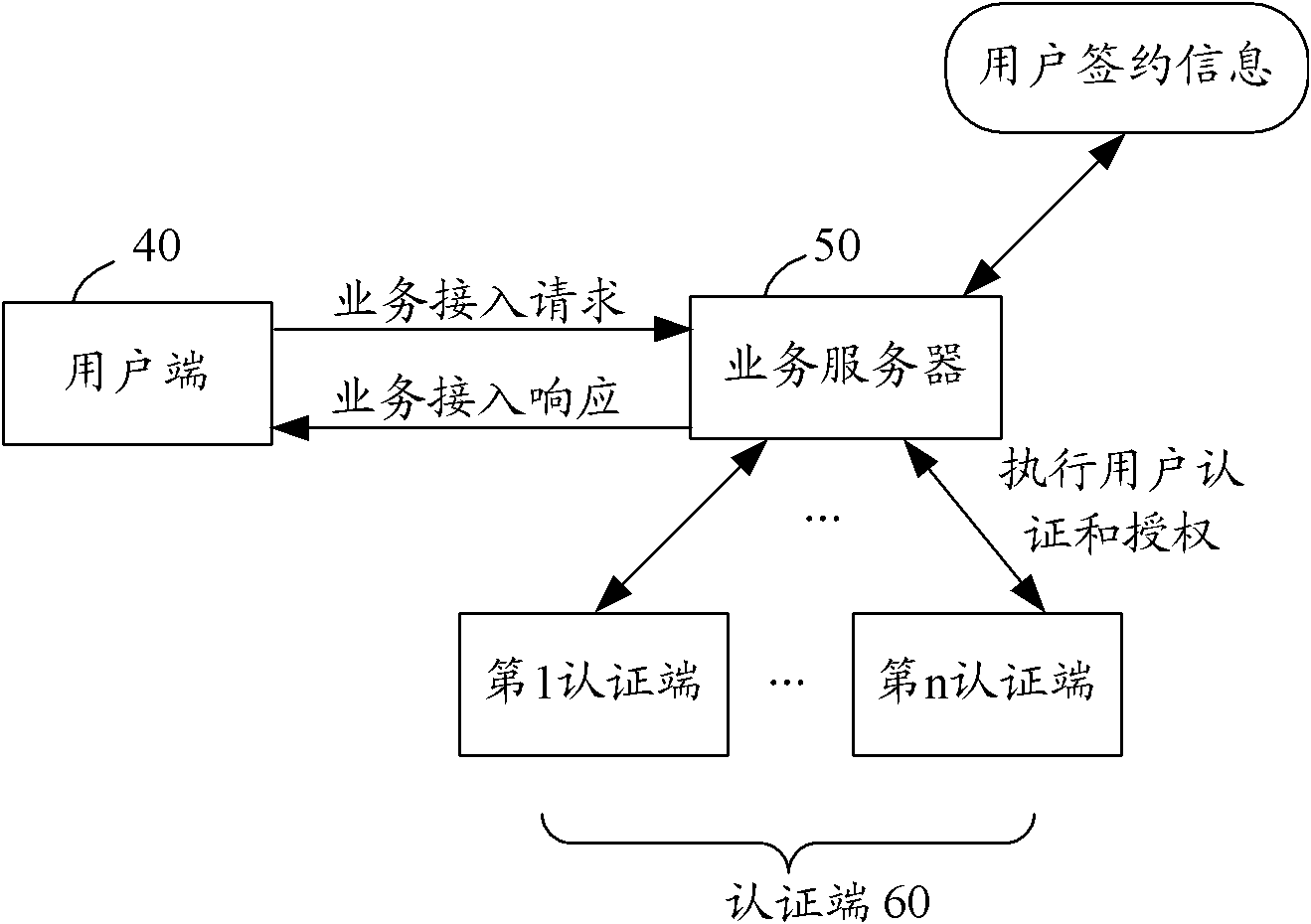
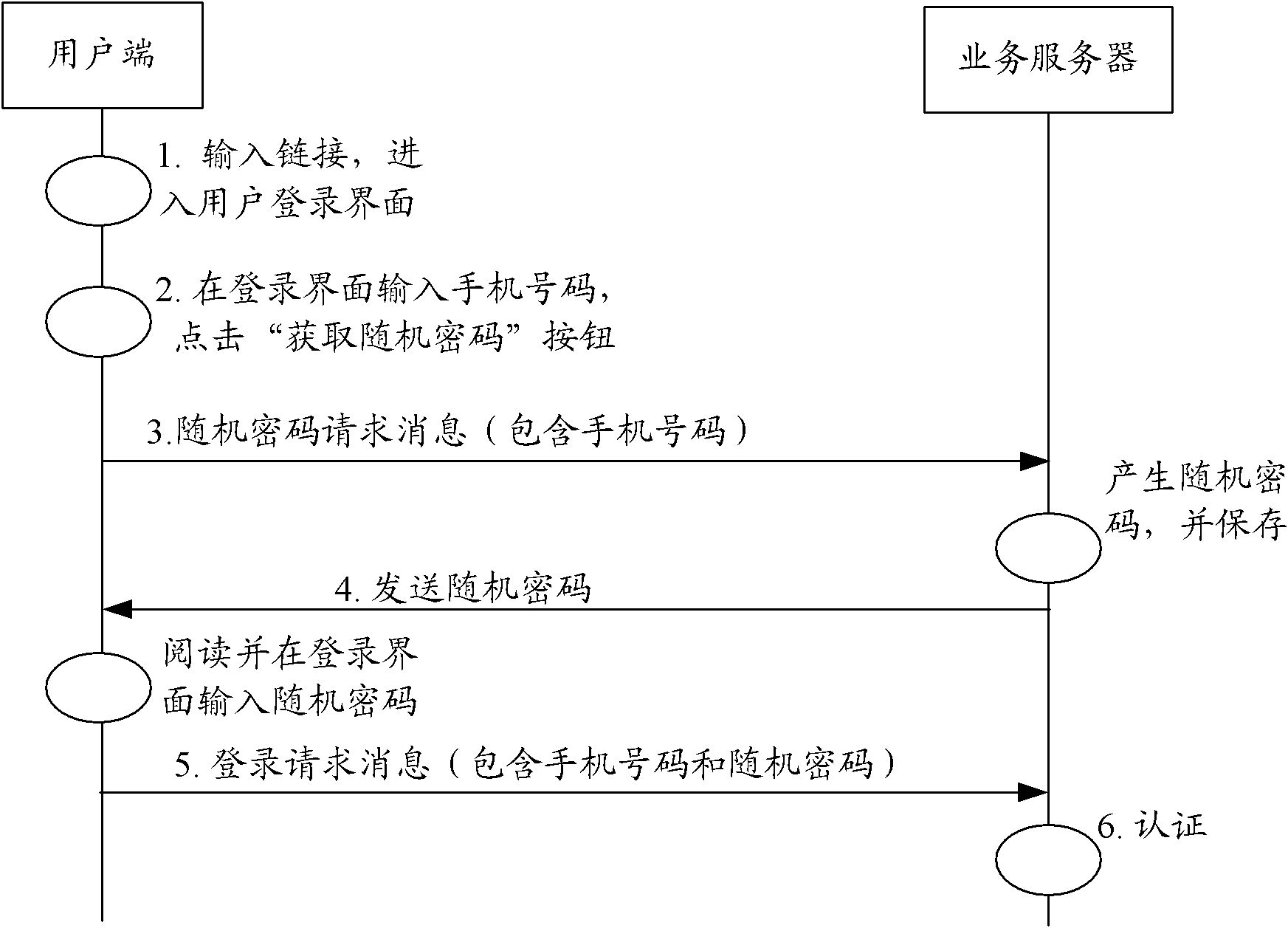
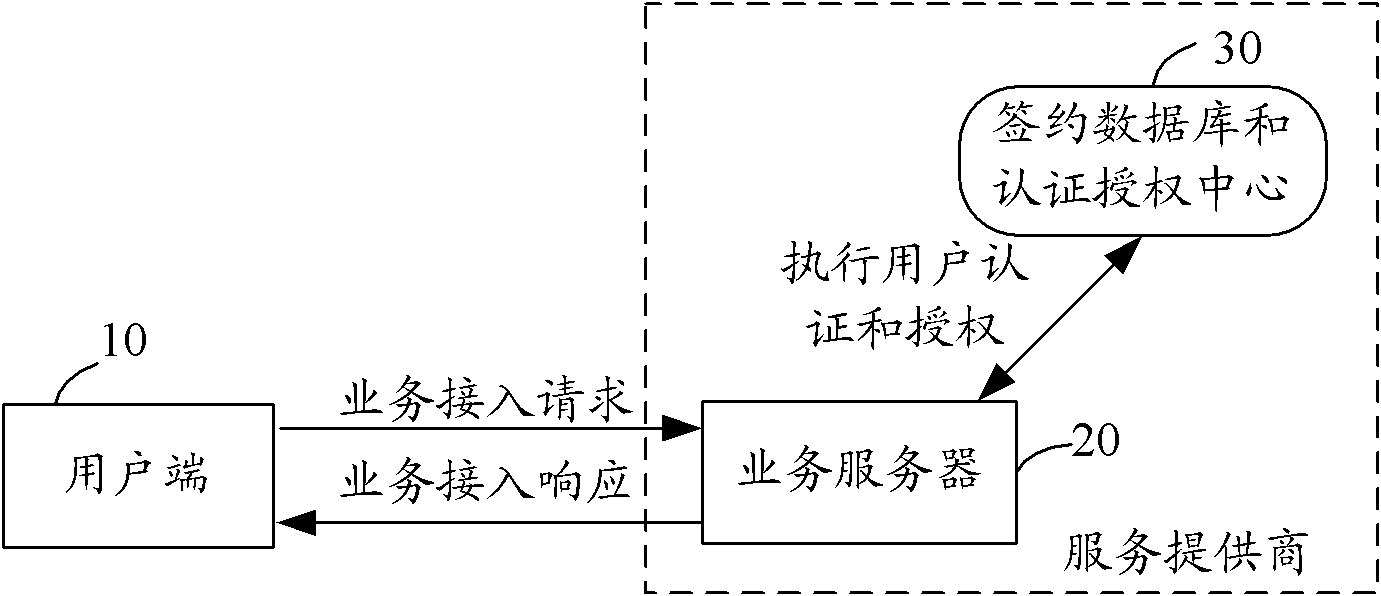
User authentication and authorization method and system for implementing user authentication and authorization method
ActiveCN102111275AEnsure safetyUser identity/authority verificationAuthorization ModeInternet privacy
The invention provides a user authentication and authorization method and a system for implementing the user authentication and authorization method. When a user end launches a business access request, a business server checks whether the user is a contracted user in accordance with identity information of the user; if the user is the contracted user based on the user identity information, the communication mode of at least one social relation user is selected from the user contracted information as an authentication end; the business server judges the validity of the user identity in accordance with information provided by the authentication end; and if the user identity is valid, the business server authorizes a user end and carries out corresponding business access responses. The method and the system for implementing the method provided by the invention are used to overcome the defects in a background technology and effectively ensure the security of user information and network services by using a mode that the communication mode of at least one social relation user is selected from the contracted information which is kept at the time of signing a business service by the user as the authentication end, and the business server judges the validity of the user end identity in accordance with the information provided by the authentication end and authorizes the user end.
Owner:王冬梅
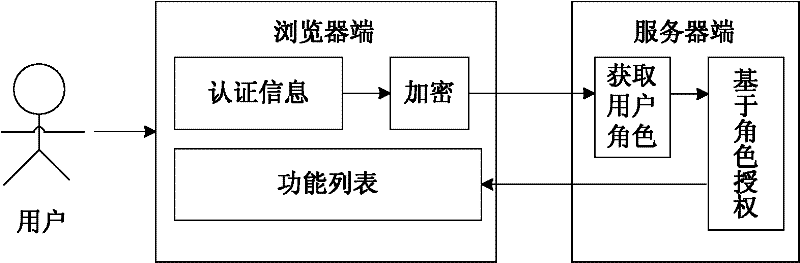
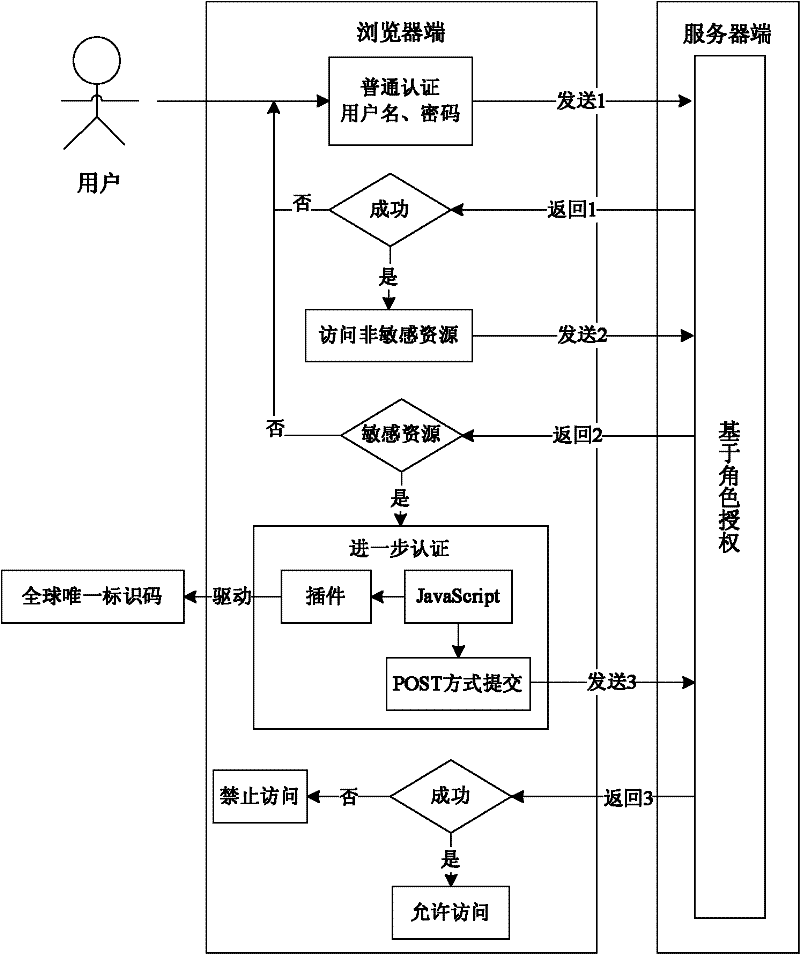
Role-based web remote authentication and authorization method and system thereof
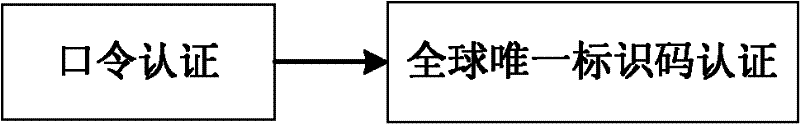
The invention relates to a role-based web remote authentication and authorization method and a system thereof. According to the authentication and authorization method, user authority is defined according to a user role; when the user requests remote access to resources of different levels, a mode in which the user needs to be authenticated is selected; when the user requests access to resources at a low level in the system, wherein the resources are non-sensitive ones, password authentication is only needed to be carried out; and when the user requests access to resources at a high level in the system, wherein the resources are sensitive one, a global unique identification code is used to carry out authentication. During the authentication process with utilization of the global unique identification code, collection on the global unique identification code is realized on a Web browser terminal by using a loading plug-in unit or control technology. According to the invention, because a grading authentication and authorization mode is employed, complexity of authentication and authorization of a user can be reduced and thus security of the authentication and authorization is enhanced; and cross-platform and cross-browser utilization can be realized, so that better user experience can be realized.
Owner:CHINA STANDARD SOFTWARE
Unified certification method for users
InactiveCN107786571ALogin securityKey distribution for secure communicationAuthorization ModeThird platform
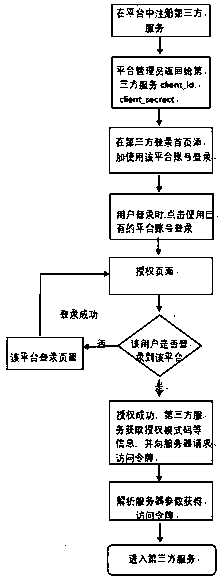
The invention relates to a unified certification method for users. The method comprises the steps that a third platform or a website is accessed to a platform, and register and accessing application are conducted on the platform; the platform which is registered by the users or a logging button of the website is accessed to the third platform or the website; the users carry unique identification,a unique secret key and a call-back address in logging, and the users are positioned to an authorization page of an authorization server; the authorization page is started, the users click authorization, and the third platform or the website acquires logging information of the current users; after authorization succeeds, the authorization server can generate an authorization mode code; the third platform or the website acquires the authorization mode code, corresponding parameters are set, and the authorization mode code is used for requesting an access token from the authorization server; thethird party website parses data which is returned by the authorization server, the access token is obtained, and user information is acquired. According to the unified certification method for users,the users can log in and have access to different platforms or websites at one time, and the users log in the website more safely and quickly.
Owner:昆山云景商务服务有限公司
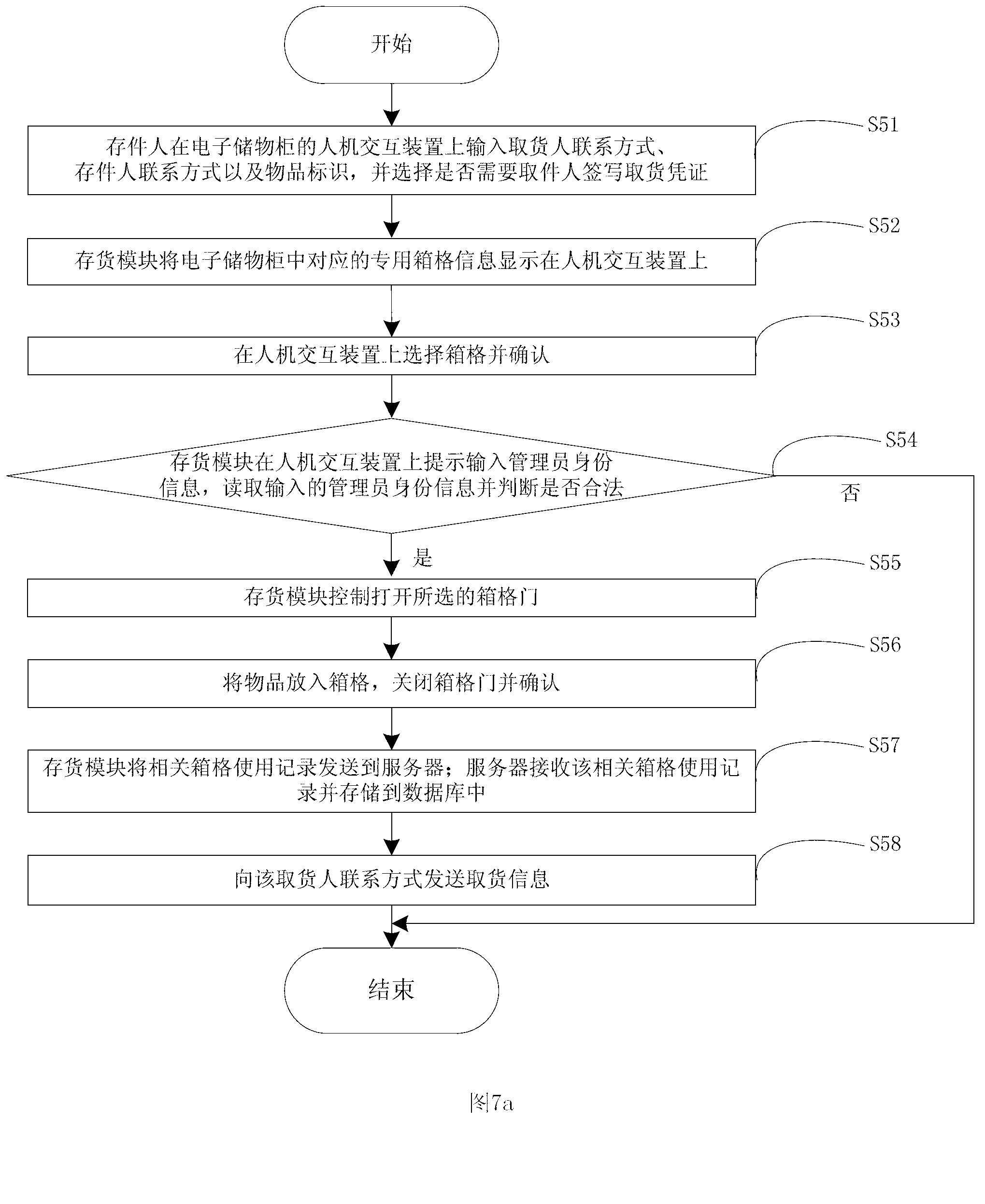
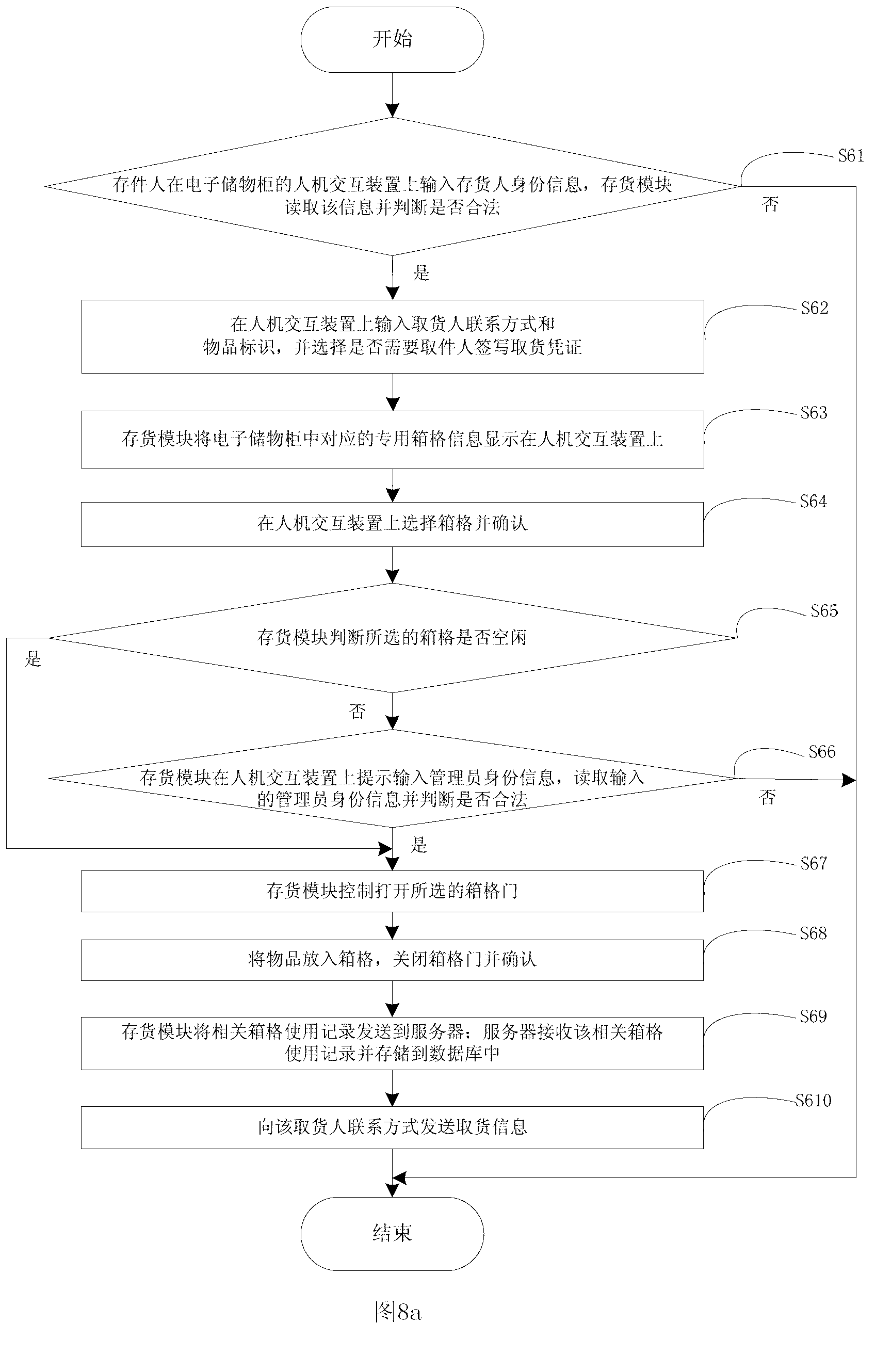
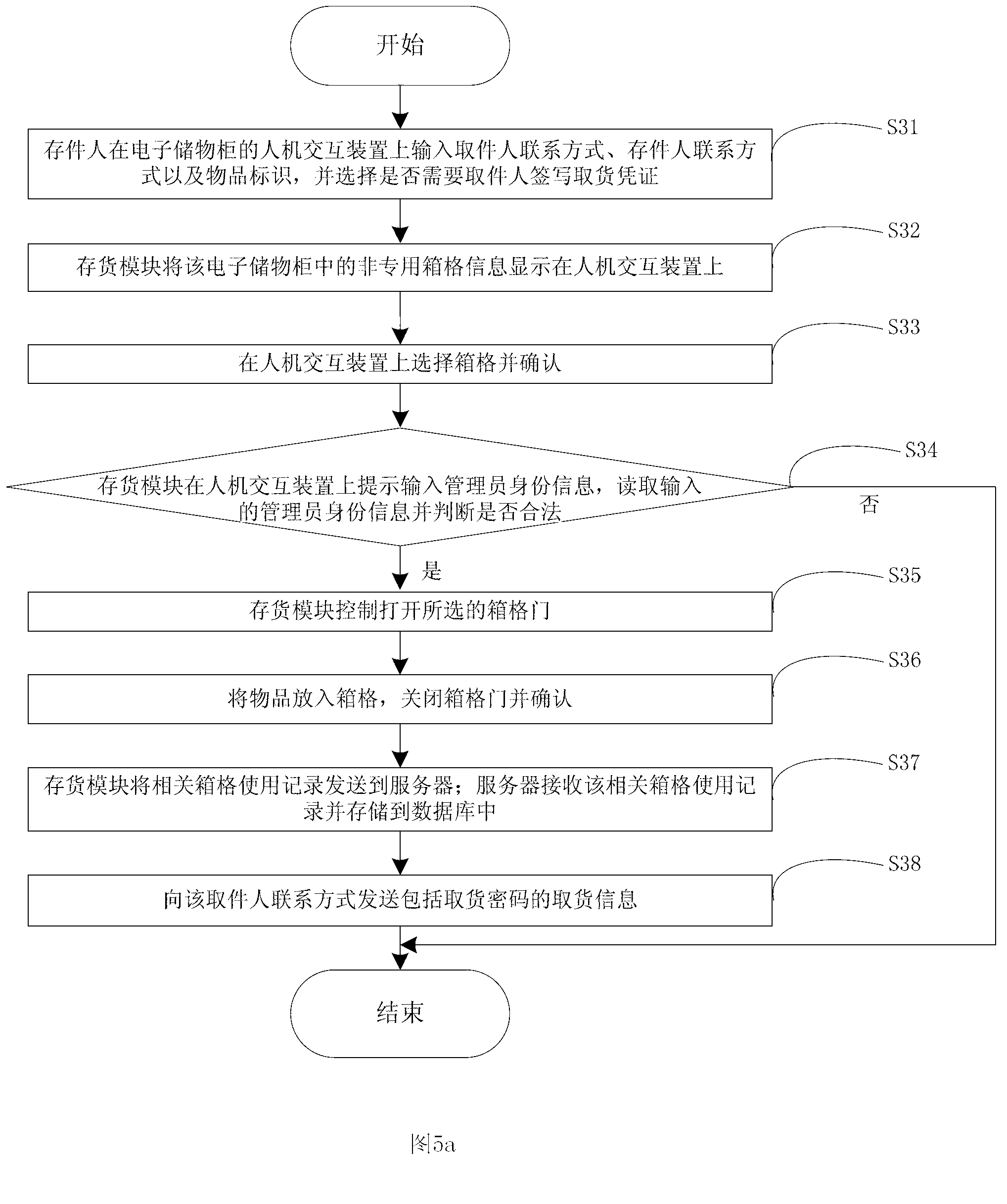
System for depositing in or withdrawing from electronic cabinet cells and delivering method
ActiveCN103236116AImprove space utilizationRealize dedicatedApparatus for meter-controlled dispensingAuthorization ModeControl unit
The invention discloses a system for depositing in or withdrawing from electronic cabinet cells and a delivering method. The system comprises a server and a plurality of electronic cabinets, wherein the server comprises a database; the electronic cabinet comprises a central control unit, a monitoring device and a plurality of cells. The invention provides the delivering method aiming to non-dedicated cells. The delivering method has the advantages that articles of users can be deposited in the same cell, so that the space utilization efficiency of the cells is improved. The delivering method aiming to dedicated cells causes the users to specially use the cells, and ensures that users can use the cells at any moment. Through the way of cabinet administrator authorization, the safety hand-over of the articles is achieved, the cells are prevented from being malevolently used by unregistered delivery, the functions that the users sign the delivery credentials and the delivery personnel withdraw the delivery credentials are achieved, and registered user and the registered delivery personnel can operate correspondingly, without random ciphers generated by the system.
Owner:CHENGDU WOLAILA GRID INFORMATION TECH
Authenticating a limited input device via an authenticated application
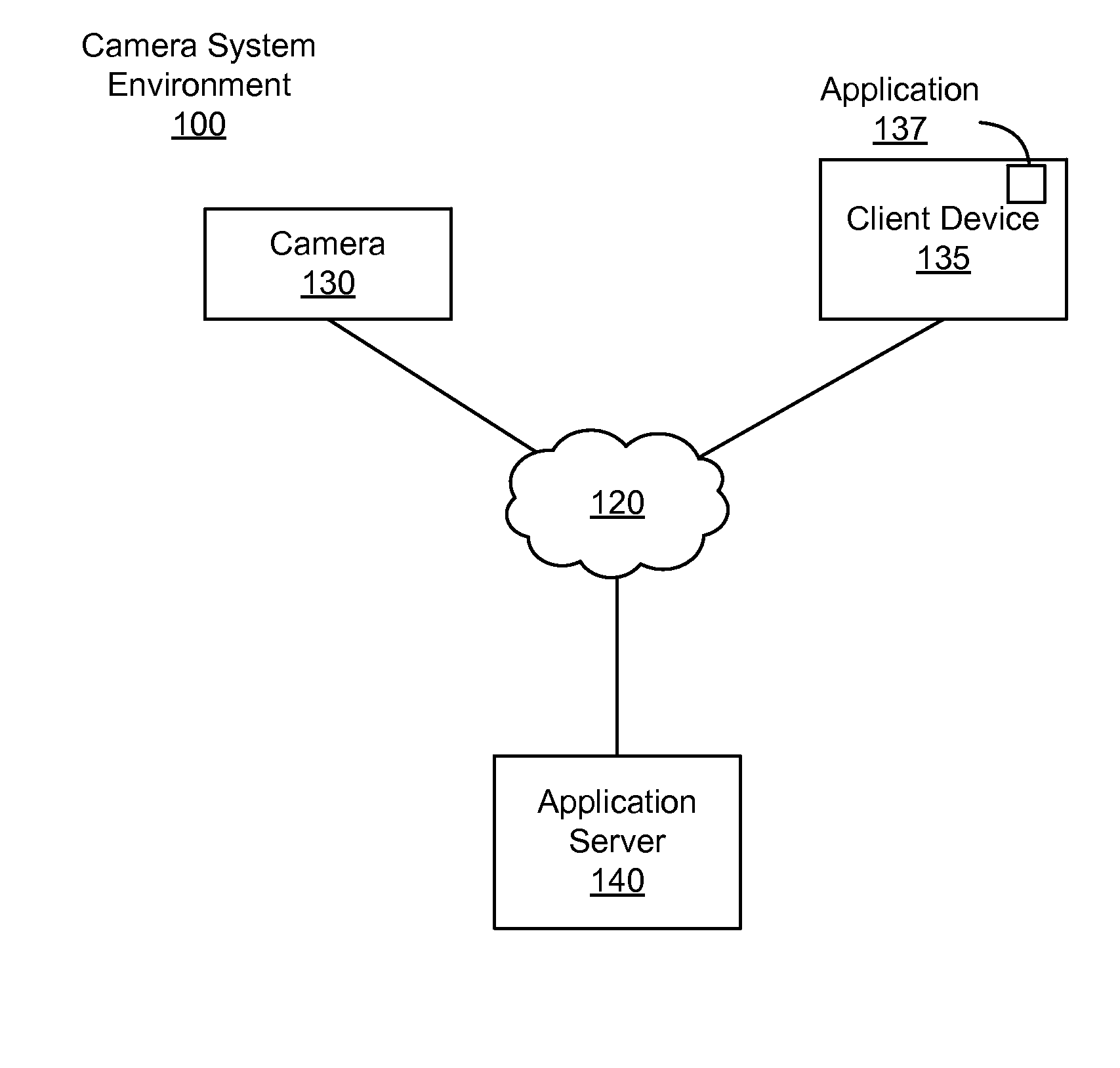
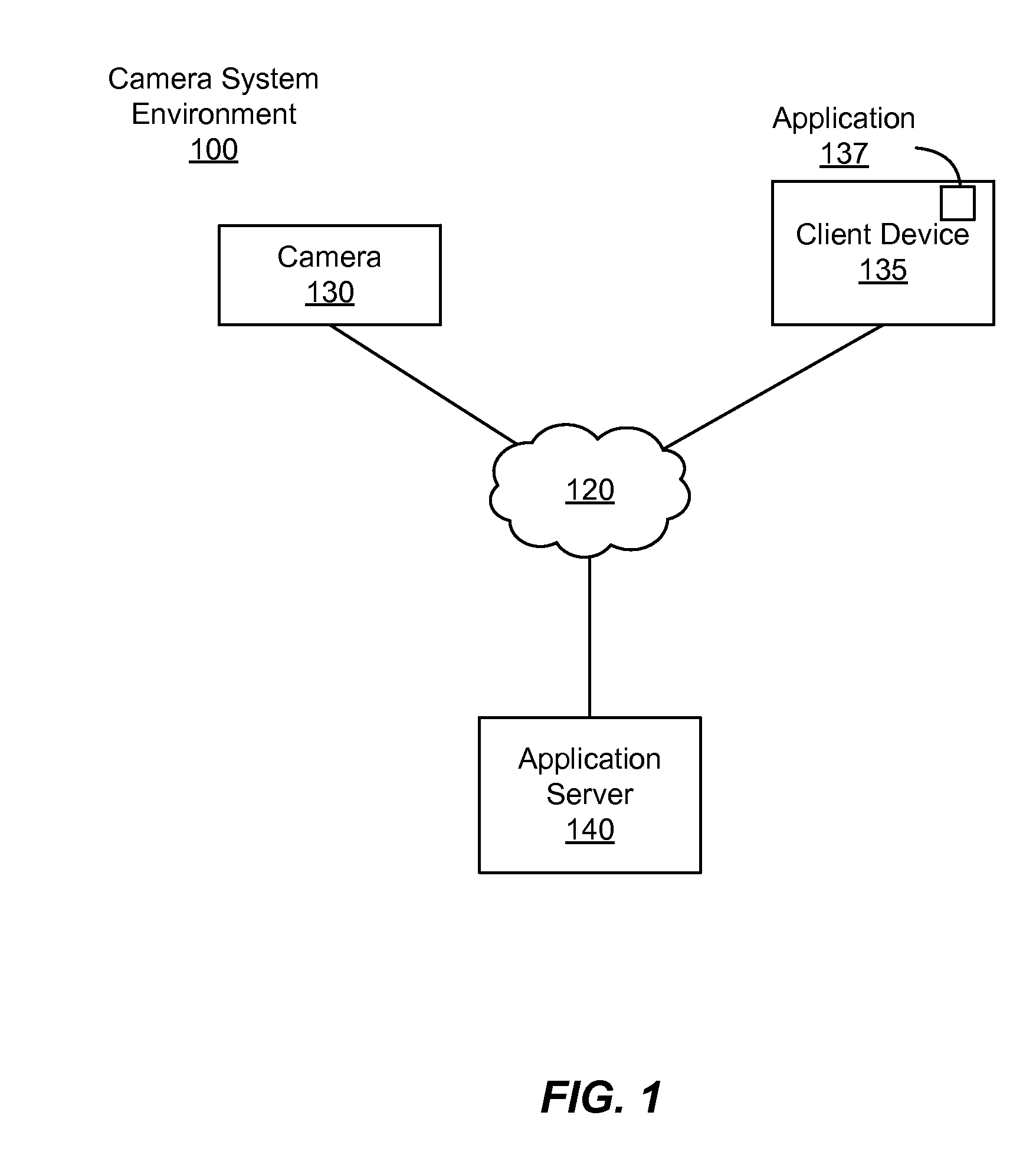
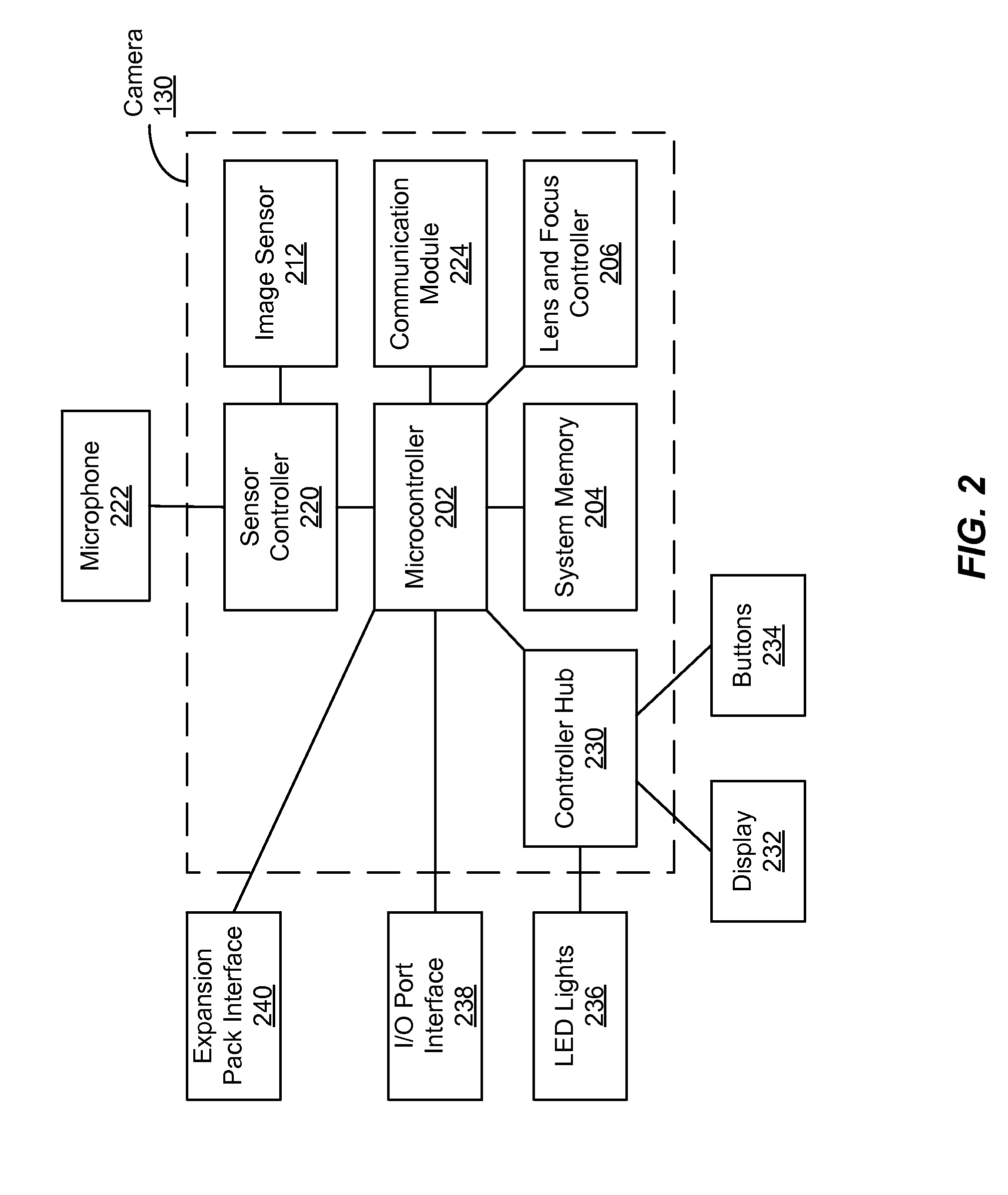
ActiveUS20160099941A1Television system detailsDigital data processing detailsAuthorization ModeApplication server
A limited input device, such as a camera, is authenticated based on a request received from an authenticated application. The application can request an application server to provide the application with a one-time authorization code. The request includes the device identifier associated with the camera. The server stores an association between the one-time authorization code and the device identifier of the camera, and provides the application with the one-time authorization code. The application provides the camera with the one-time authorization code. The camera transmits a request for an access token to the server, the request for the access token including the one-time authorization code and the device identifier associated with the camera. The server verifies the device identifier associated with the camera with that associated with the one-time authorization code, and upon a positive verification authenticates the camera by providing the camera with the access token.
Owner:GOPRO
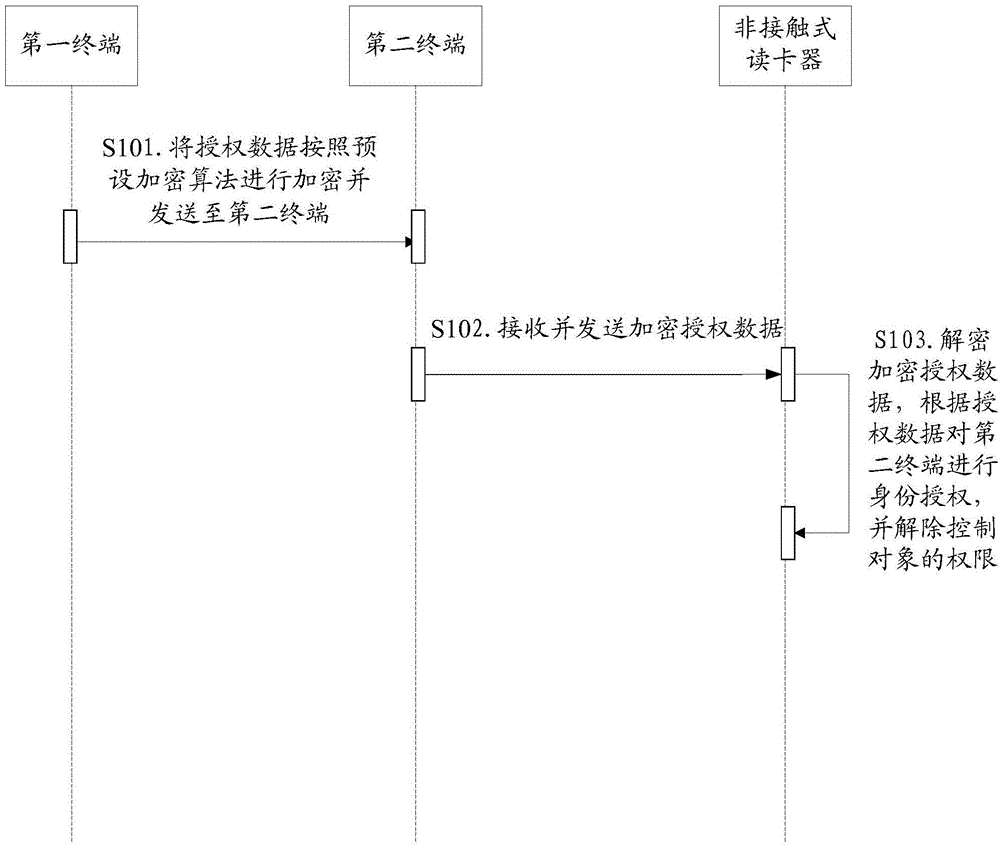
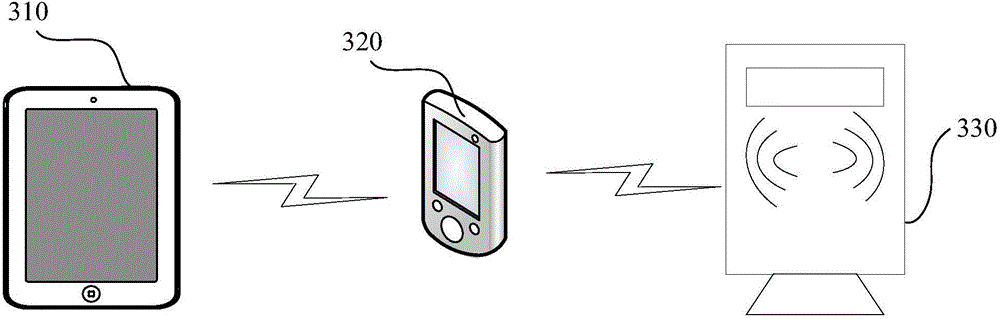
Identity authorization controlling method and system
InactiveCN104392165AImprove the efficiency of identity authorizationImprove efficiencyDigital data authenticationAuthorization ModeControl system
The invention discloses an identity authorization controlling method and an identity authorization controlling system. The method comprises the following steps that a first terminal encrypts authorization data according to a preset encryption algorithm, acquires encryption authorization data and transmits the encryption authorization data to a second terminal; the second terminal receives the encryption authorization data and transmits the encryption authorization data to a non-contact card reader in a near-distance wireless communication way; when sensing the second terminal in the near-distance wireless communication way, the non-contact card reader acquires the encryption authorization data, decrypts the encryption authorization data according to a decryption algorithm corresponding to the encryption algorithm to acquire the authorization data, performs identity authorization for the second terminal according to the authorization data, and releases the limits of authority of a controlled target. By the scheme, the identity authorization efficiency of the second terminal is greatly improved, the efficiency of releasing the limits of authority of the controlled target is improved, meanwhile, the cost caused by manufacturing an IC (integrated circuit) card is avoided, and the cost is saved.
Owner:HITACHI BUILDING TECH GUANGZHOU CO LTD
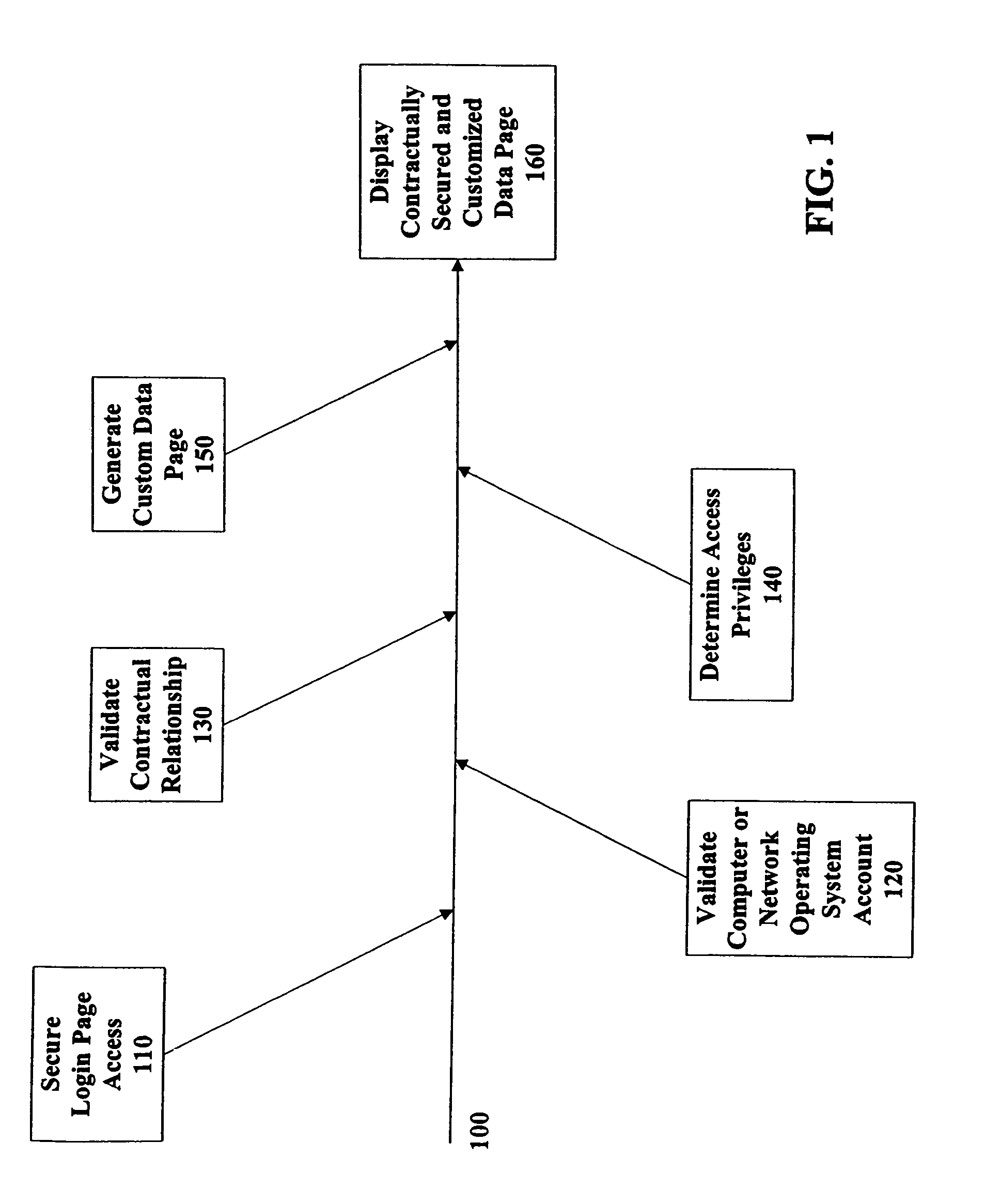
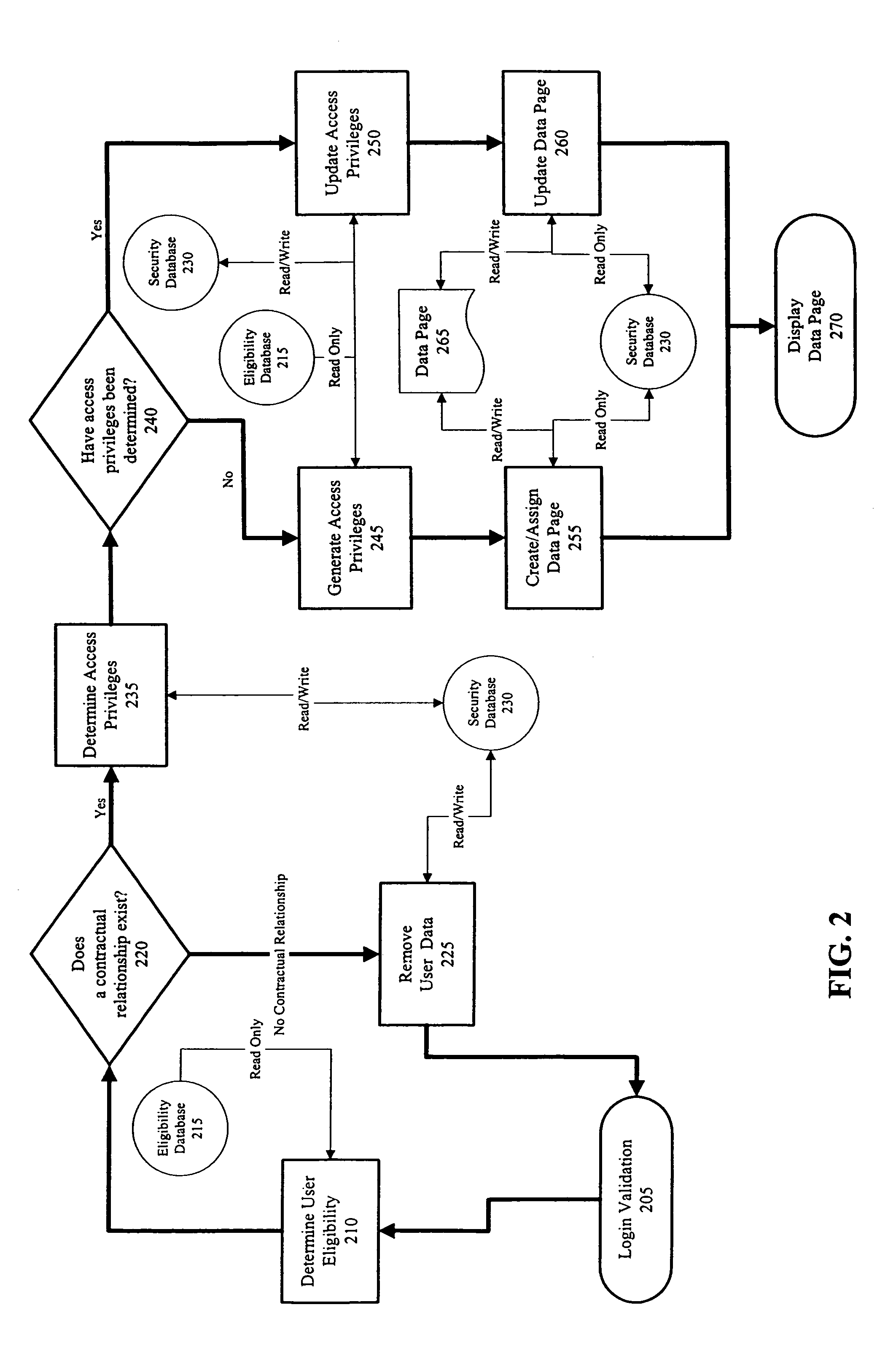
Method and system for user authentication and authorization of services
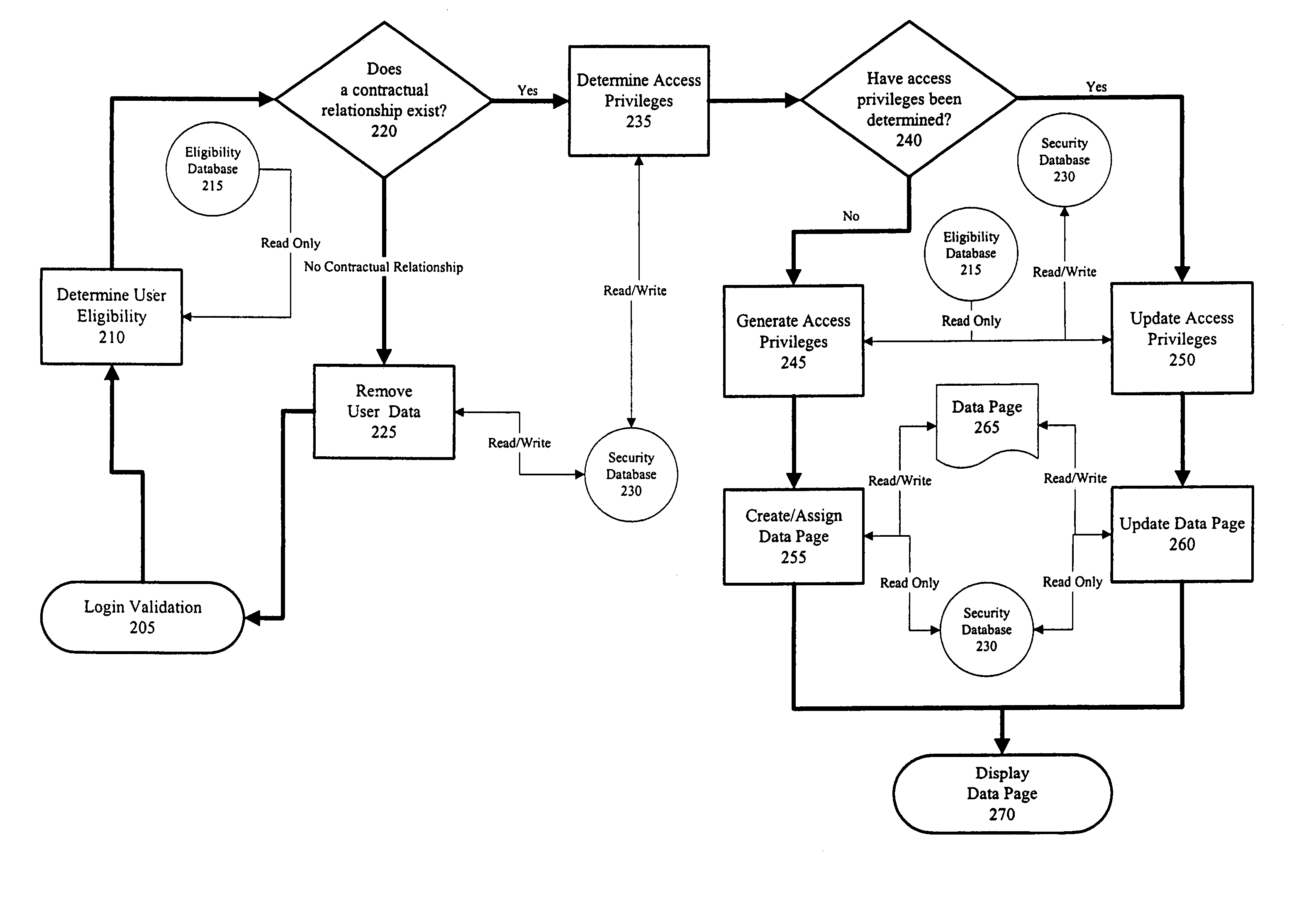
InactiveUS7210163B2Increase flexibilityImprove securityFinanceDigital data processing detailsAuthorization ModePassword
An extended authorization system and method implementing a second layer of access authorization. The first layer of access authorization corresponds to conventional access authorization processing such as, for example, validating an entered user identifier and password. The second layer of access authorization determines if the user has a valid contractual or other business relationship with an information system provider. The status and type of contractual or other business relationship may determine user access privileges which allow the user to access services provided by an information system. When a user has a valid contractual or other business relationship with an information system provider, first layer authorization login data such as, for example, a user identifier and password may be generated for the user.
Owner:FUJITSU LTD
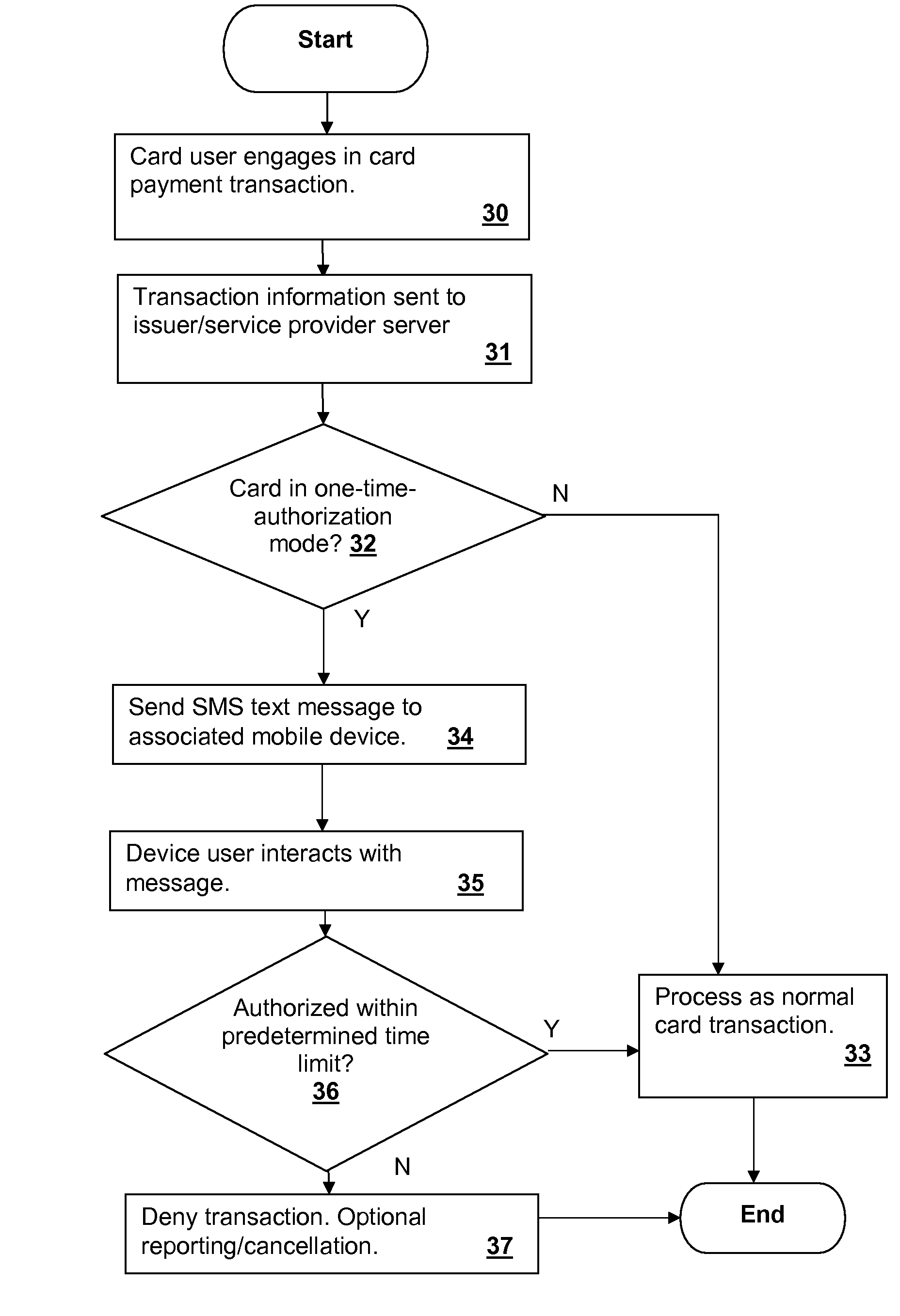
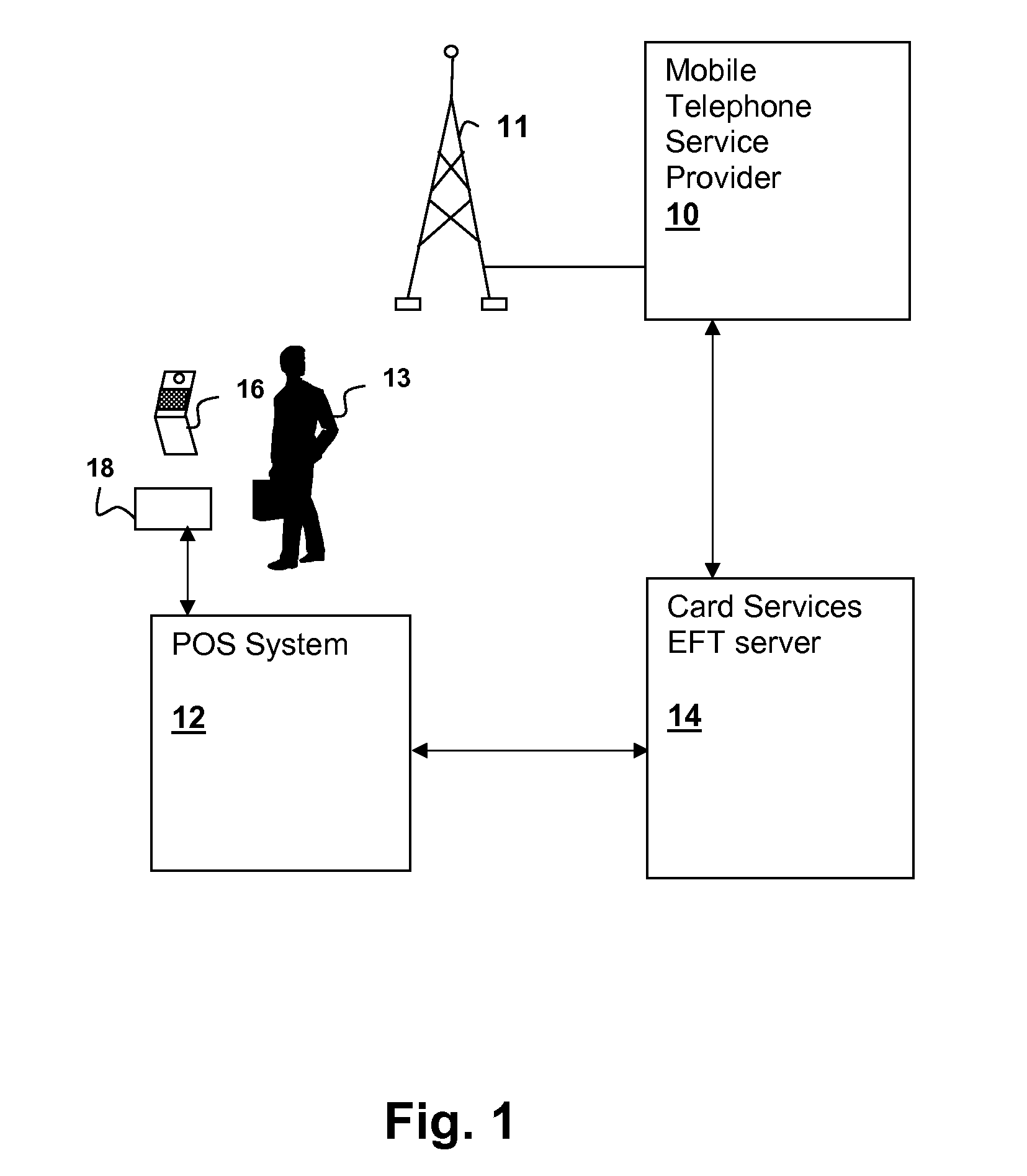
System for securing card payment transactions using a mobile communication device
InactiveUS20090083160A1FinanceBuying/selling/leasing transactionsComputer hardwareAuthorization Mode
An authorization system and computer program for provision and process of a personal identification number (PIN) via a short-message-service (SMS) text message to a mobile communication device. The authorization system and computer program receive a communication from the user indicating a one-time-authorization mode. The authorization system and computer program retrieve information from a point-of-sales location and process a unique identifier for the mobile communication device. A text message is sent to the identified mobile device. The message communicates a one-time-use PIN with required PIN return via the point-of-sales system. The confirmation is processed, which authorization only occurring after confirmation. The PIN response period is voided after a short time, further improving security of the transaction.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
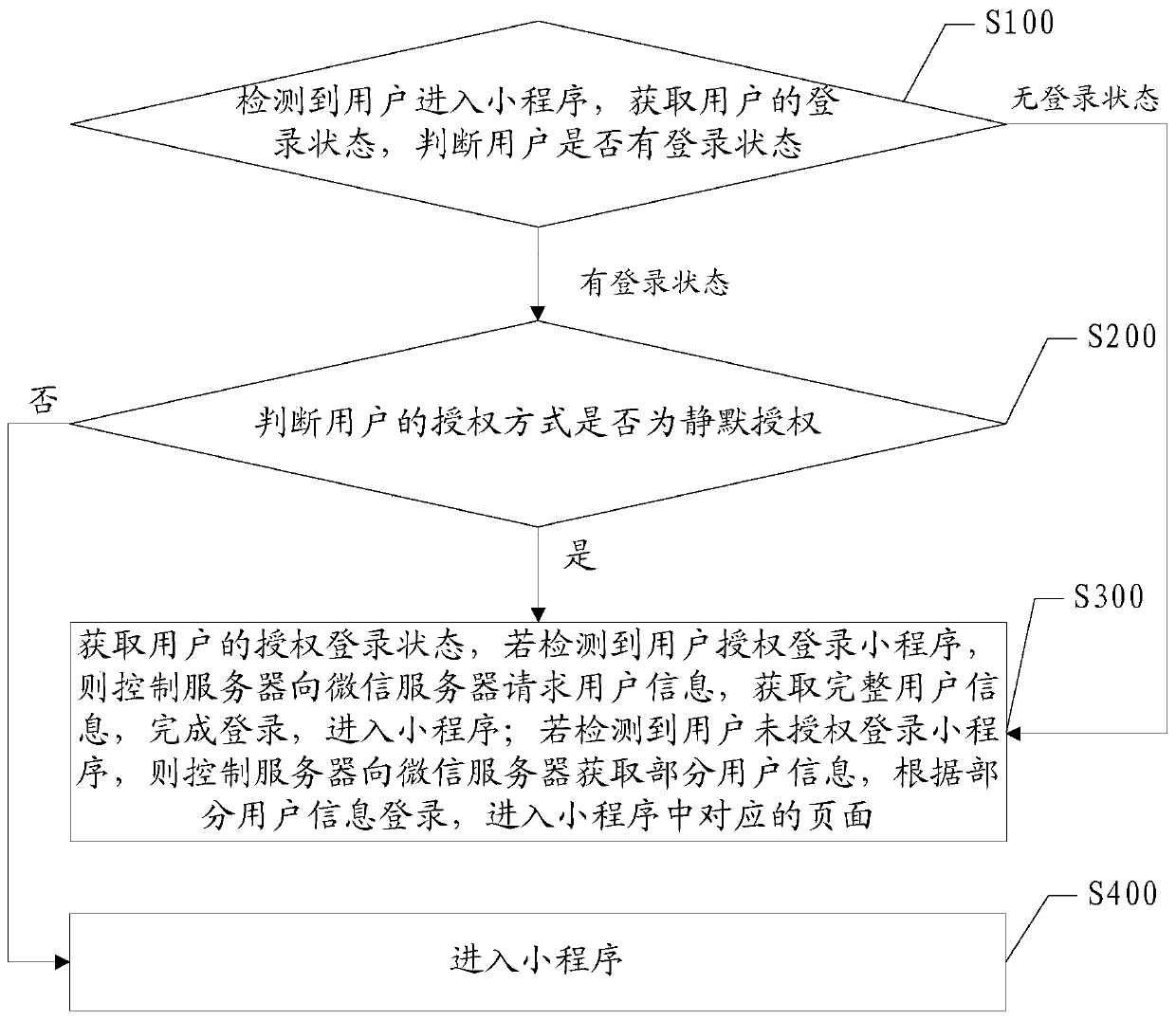
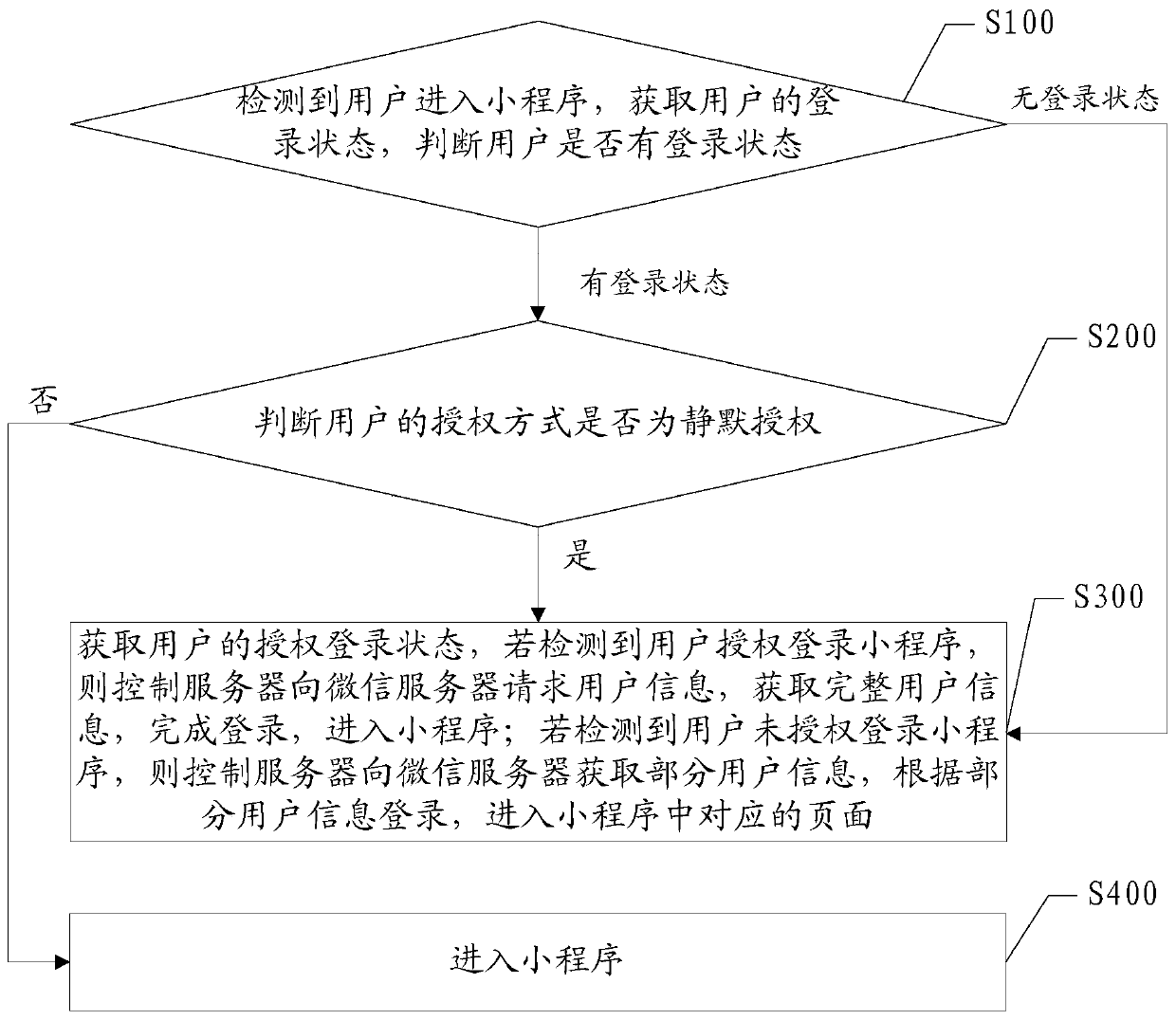
Method and device for controlling login state based on mini-program architecture
ActiveCN109995755AReduce churnReduce request timeUser identity/authority verificationAuthorization ModeClient-side
The invention discloses a method and device for controlling login state based on mini-program architecture, and the method comprises the steps: detecting that a user enters a small program, and obtaining the login state of the user; if the user has the login state and the authorization mode is not silent authorization, entering the applet; if the user has the login state and the authorization modeis silent authorization, obtaining the authorization login state of the user, and if it is detected that the user authorizes to log in the applet, enabling the control server to request user information from the WeChat server, obtain complete user information, complete login and enter the applet; and if it is detected that the user does not authorize to log in the applet, controlling the server to obtain a part of user information from the WeChat server, logging in according to the part of user information, and entering a corresponding page in the applet. According to the embodiment of the invention, when the small program is logged in, the server side stores the authorization login information of the user, and the authorization login information is improved from the client side to the WeChat side to the server side to the client side to the server side, so that the request time is greatly reduced, and the user loss is reduced.
Owner:SHENZHEN DIANMAO TECH CO LTD
Authentication and authorization processing method and device
InactiveCN103685139ASolve the processing efficiency is not highImprove processing efficiencyUser identity/authority verificationThird partyApplication server
The invention provides an authentication and authorization processing method and device. The method comprises the following steps: sending authorization information to a user agent by a third-party application server or an authorization server, wherein the user agent generates first authentication and authorization data according to user information and the authorization information, and the first authentication and authorization data is used for authorizing the third-party application server to visit data resources stored in other service providers except for the third-party application server; receiving the first authentication and authorization data from the user agent by the third-party application server. Through the method, the problem of low authentication and authorization processing efficiency caused by complex authentication and authorization process in the prior art is solved, the authentication and authorization process is simple, and the authentication and authorization processing efficiency is improved.
Owner:ZTE CORP
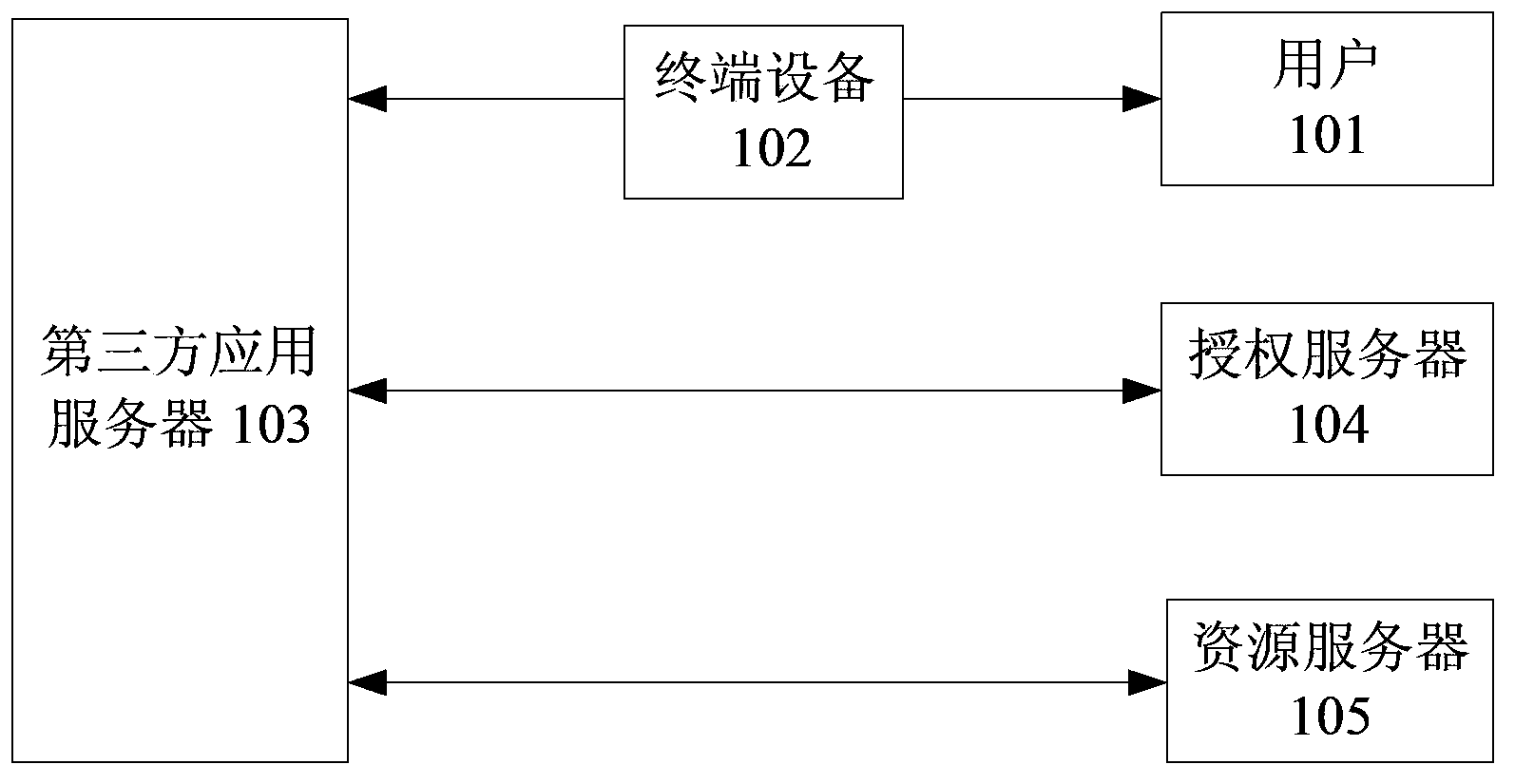
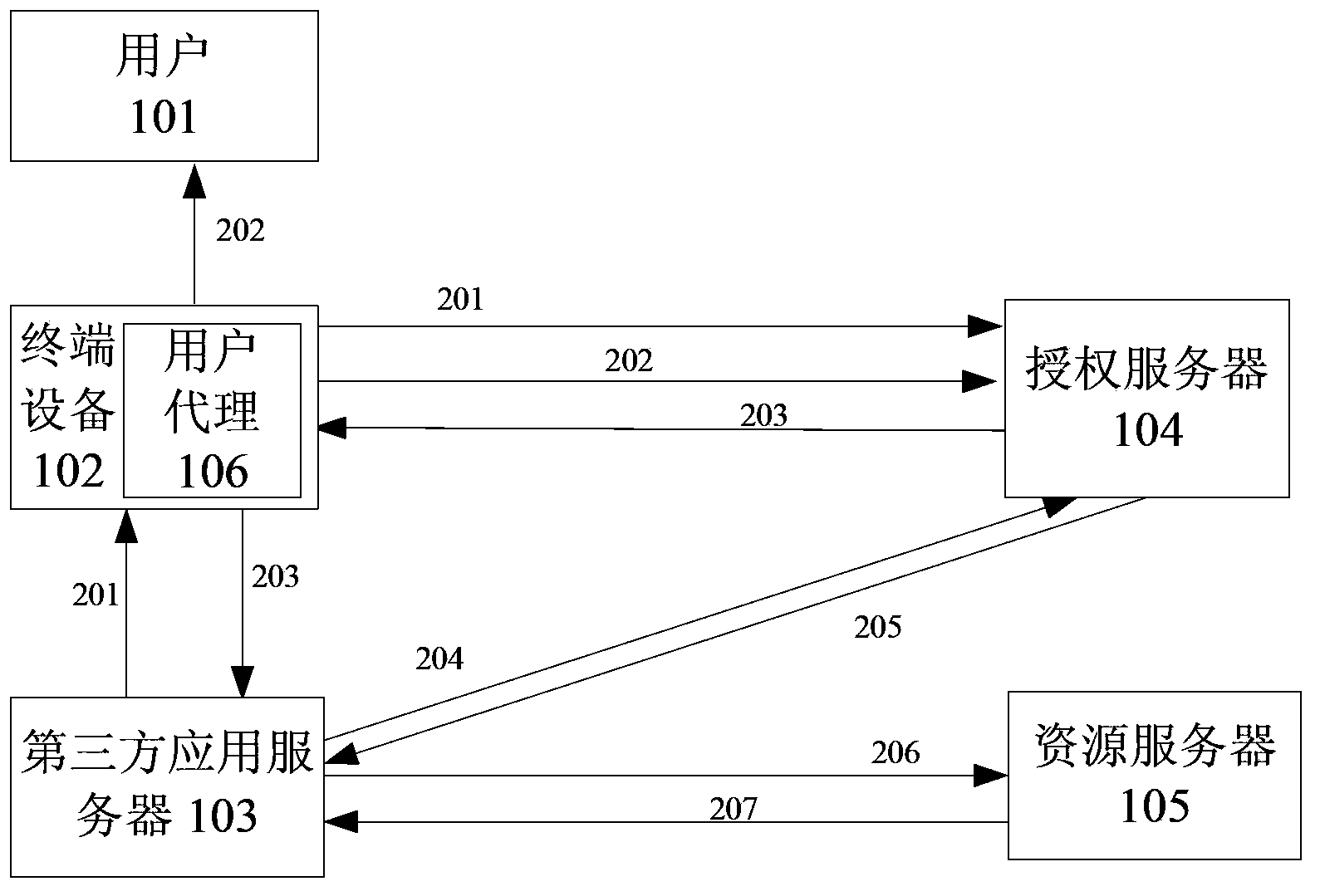
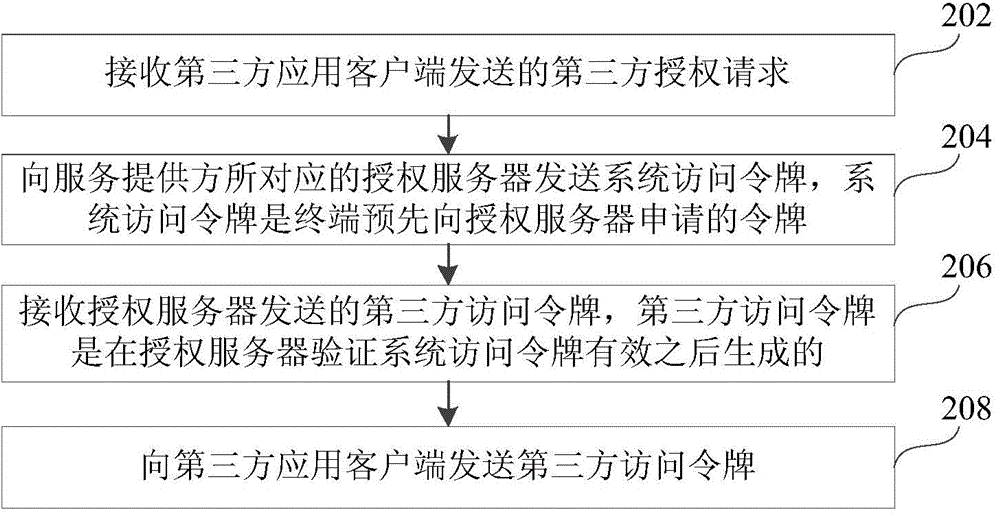
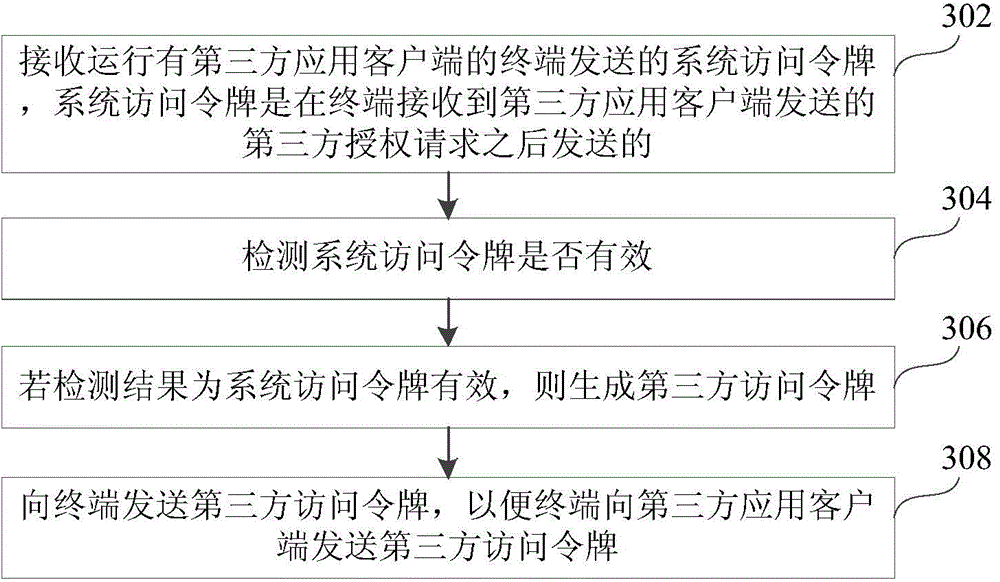
Authorization method, apparatus and system based on oAuth protocol
The invention discloses an authorization method, apparatus and system based on an oAuth protocol, and belongs to the technical field of a computer. The method comprises the following steps: receiving a third-party authorization request sent by a third-party application client; sending a system access token to an authorization server corresponding to a service provider, wherein the system access token is a token applied for by a terminal in advance from the authorization server; receiving a third-party access token sent by the authorization server, wherein the third-party access token is generated after the authorization server verifies that the system access token is valid; and sending the third-party access token to the third-party application client. According to the invention, the problem of severely affected smoothness and convenience of an authorization process, caused by enormous repeated operation during realization of authorization of multiple third-party applications by use of a conventional authorization method related to in the prior art is solved; and the enormous repeated operation is avoided, the smoothness and convenience of the authorization process are improved, and the security of a whole authorization process is improved.
Owner:TENCENT TECH (BEIJING) CO LTD
Intelligent electronic seal system and authorization control method thereof
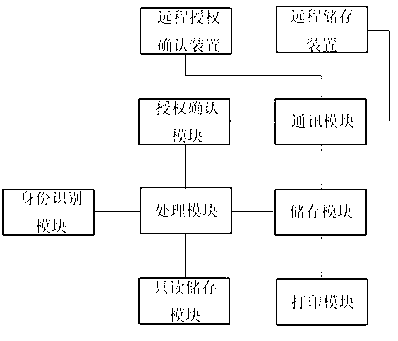
InactiveCN103186846AEasy transferEasy to identify by computerDigital data authenticationOffice automationElectronic documentAuthorization Mode
The invention discloses an intelligent electronic seal system comprising an identity recognition module, a processing module, a storage module, a read-only storage module and a printing module. The processing module is respectively connected with the identify recognition module, the storage module and the read-only storage module. The printing module is connected with the storage module. The real-only storage module is provided with a space to store an impression patterning, wherein the impression patterning is stored in the space storing the impression patterning. The intelligent electronic seal system has the advantages that a convenient and quick electronic seal authorization mode is provided, the mode of an electronic seal can be conveniently recognized by a computer, transferring of electronic documents and development of electronic commerce are benefited, a requirement of a traditional seal habit is met, and certain flexibility is achieved. Identity recognition information of a user, seal utilization information and a safety mechanism used for inquiring and checking utilization conditions of the seal are added, and the seal is prevented from being misappropriated.
Owner:张殿礼
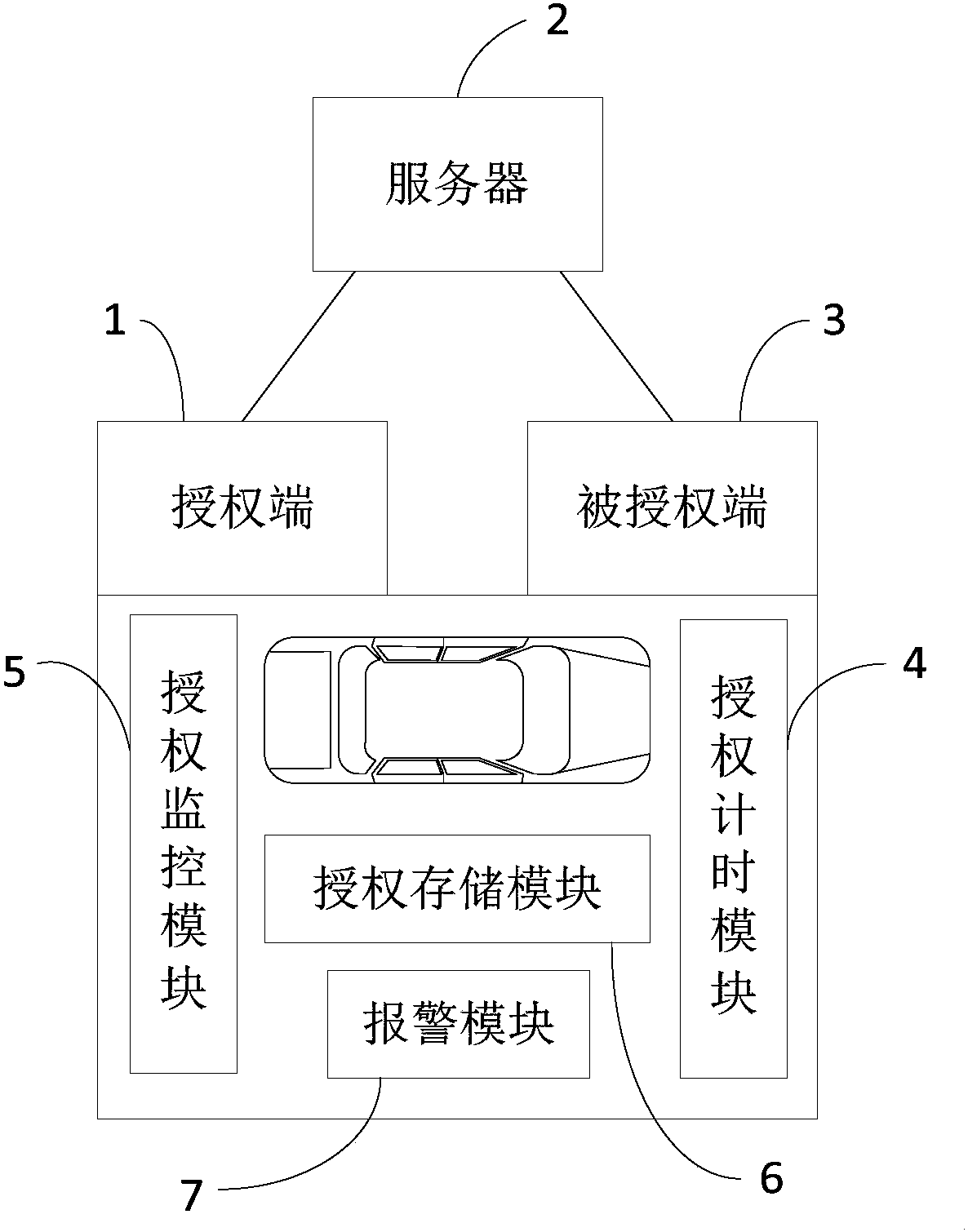
Vehicle authorization management method and system
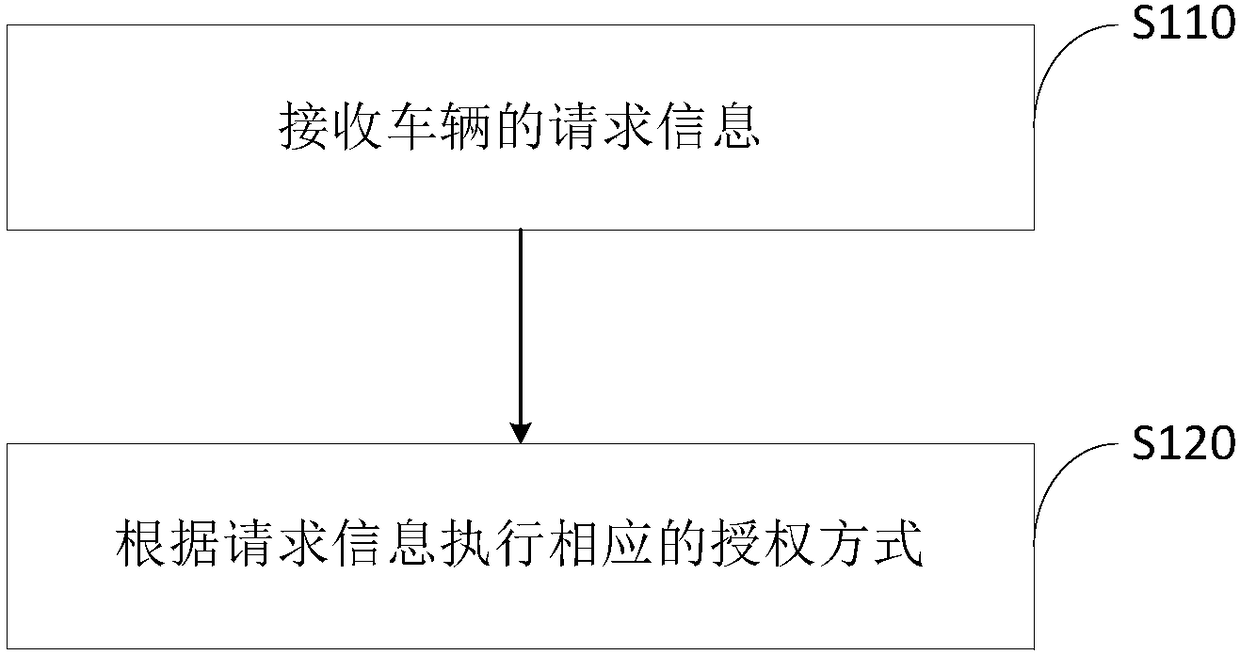
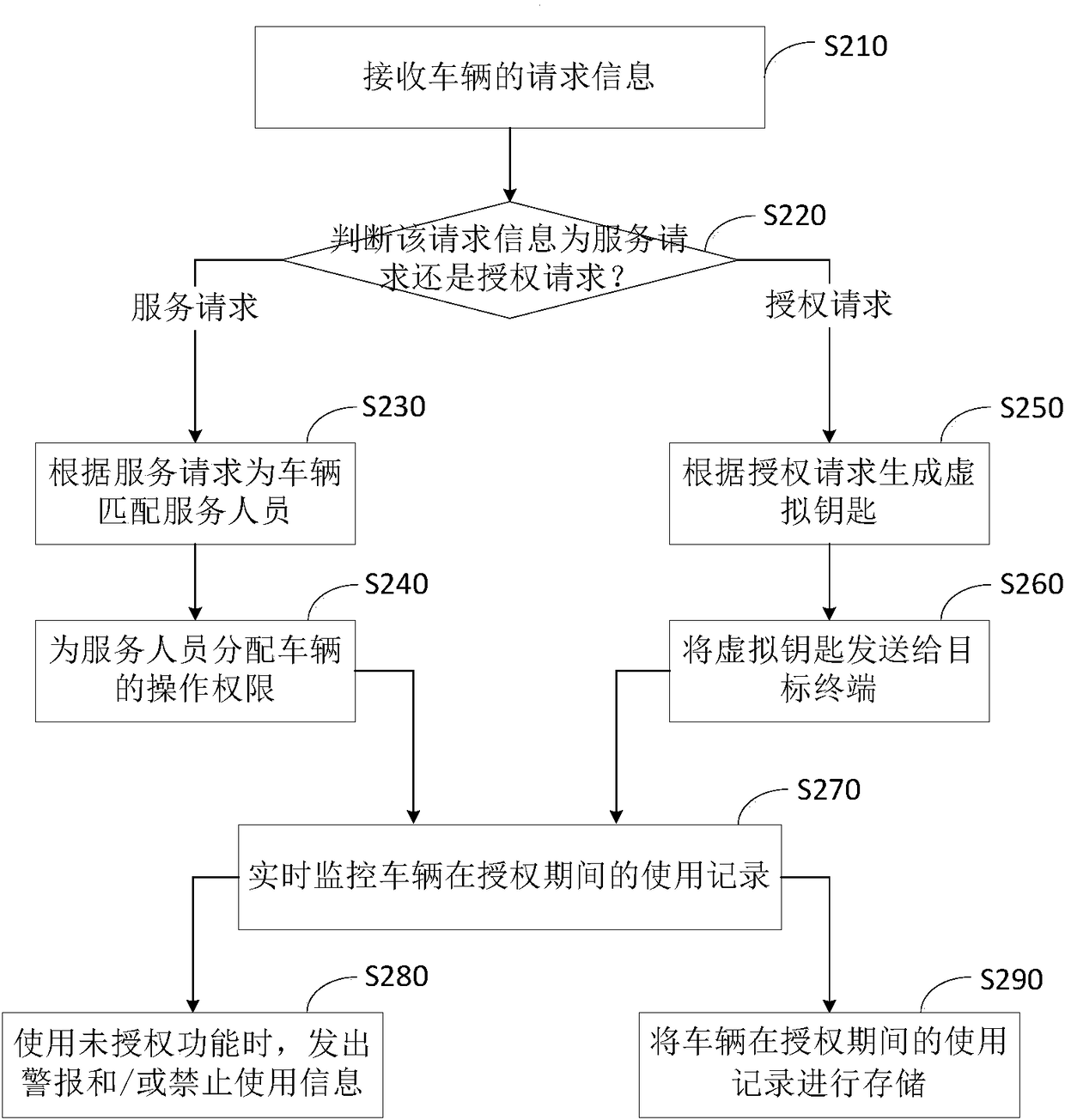
InactiveCN108108598ATicket-issuing apparatusParticular environment based servicesAuthorization ModeElectronic communication technology
The invention belongs to the field of automobile electronic-communication technology, and particularly relates to a vehicle authorization management method and system. For better satisfying differentuse requirements of vehicles, the vehicle authorization management method provided by the invention includes the following steps: receiving request information of a vehicle; and executing a corresponding authorization manner according to the request information, wherein authorization manners include a service authorization manner and an active authorization manner. The authorization management method also includes: monitoring use records of the vehicle in an authorized period in real time; and storing the use records. According to the method, use authority of the vehicle can be flexibly and conveniently allocated and managed through the service authorization manner or the active authorization manner without the need for transferring vehicle use right through a manner of transferring a key,and vehicle use experience of a vehicle owner is improved; and in addition, the use records of the vehicle in the authorized period can also be stored to facilitate viewing of the vehicle owner on driving mileage of the vehicle in the authorized period, and thus authorized use behaviors of the vehicle of the vehicle owner are effectively managed.
Owner:NIO ANHUI HLDG CO LTD
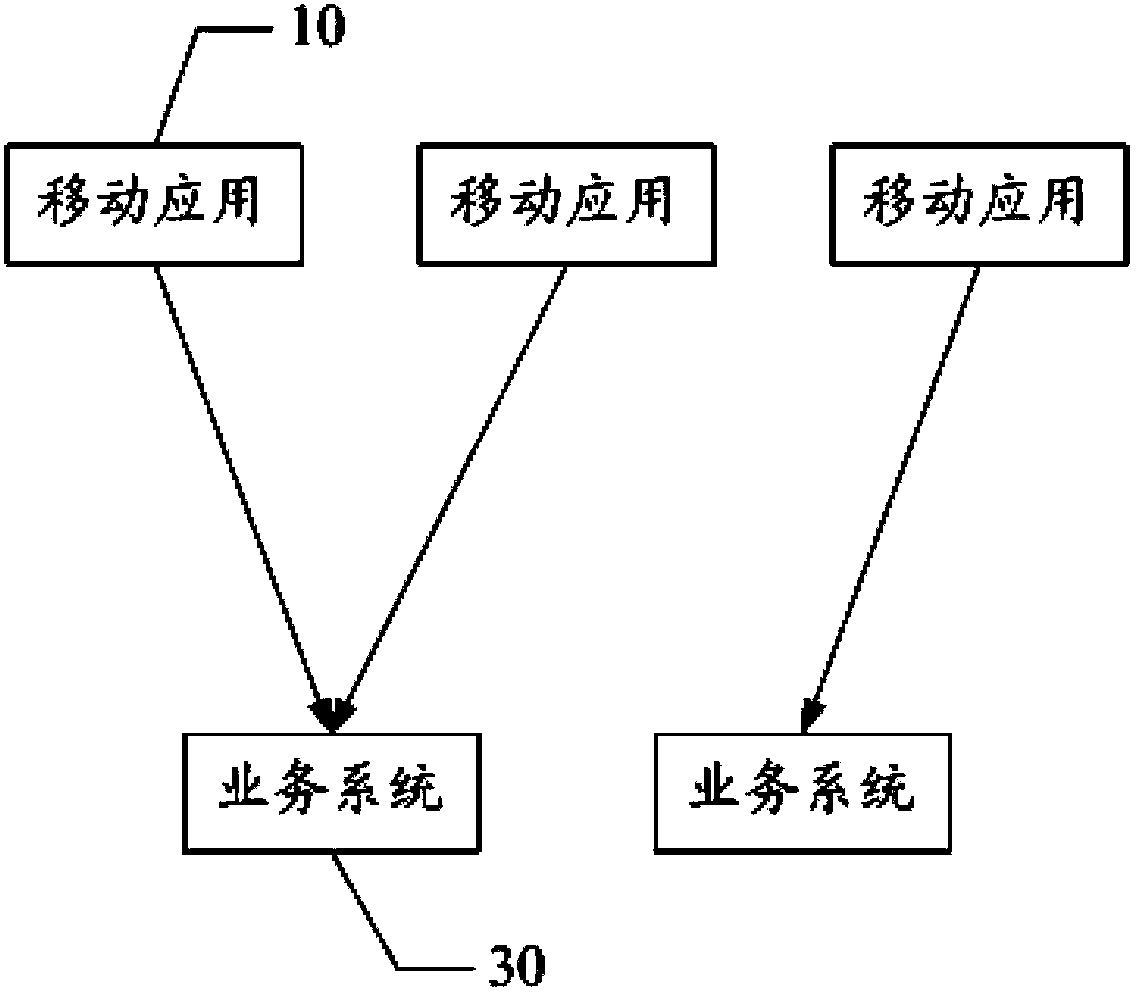
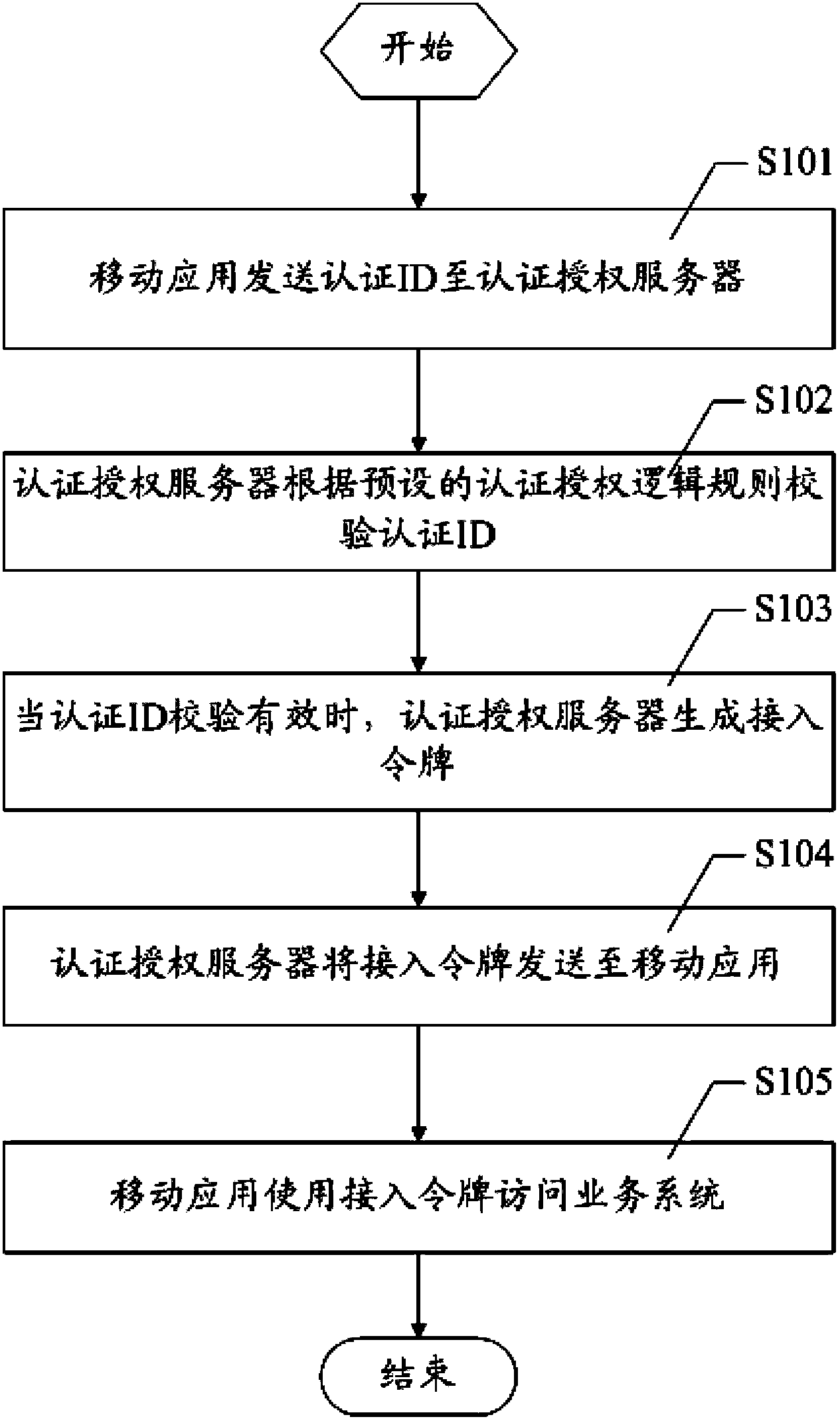
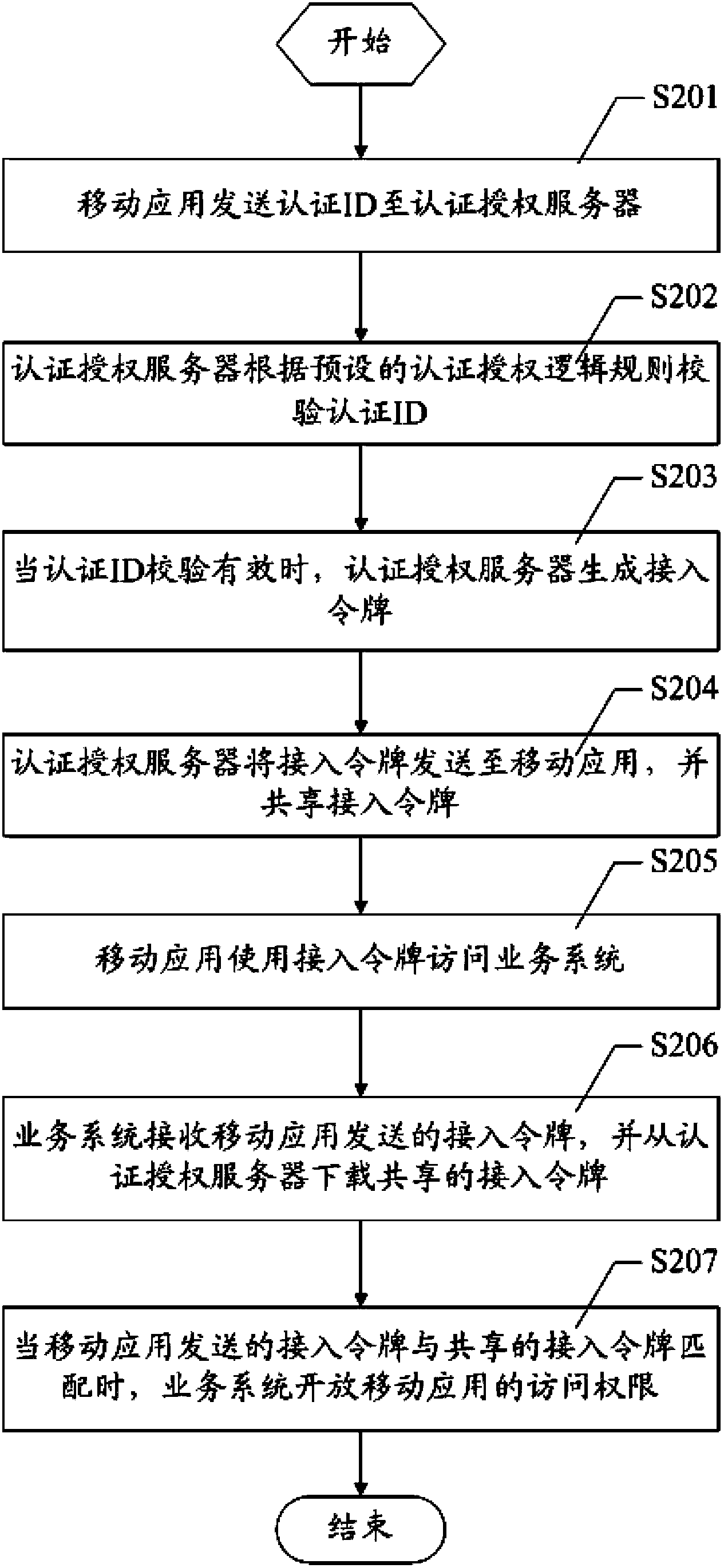
A mobile application access authentication and authorization method and system
ActiveCN103686724AAffect normal workFacilitates secure access controlSecurity arrangementAuthorization ModeAuthorization logic
The invention discloses a mobile application access authentication and authorization method and system. The method comprises that mobile application transmits an authentication ID to an authentication and authorization server; that the authentication and authorization server verifies the authentication ID according to a preset authentication and authorization logic rule, that the authentication and authorization server generates an access token and transmits the access token to the mobile application when the authentication ID is valid; and that the mobile application has access to a service system with the access token. The method separates the authentication and authorization logic rule from the service system, performs unified management on mobile application access authority with the authentication and authorization server, prevents the normal operation of the service system from being influenced when the authentication and authorization logic rule is modified or redeployed, and dynamically transmits the access token to the mobile application with the authentication and authorization server so as to be beneficial to secure access control of the service system access.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
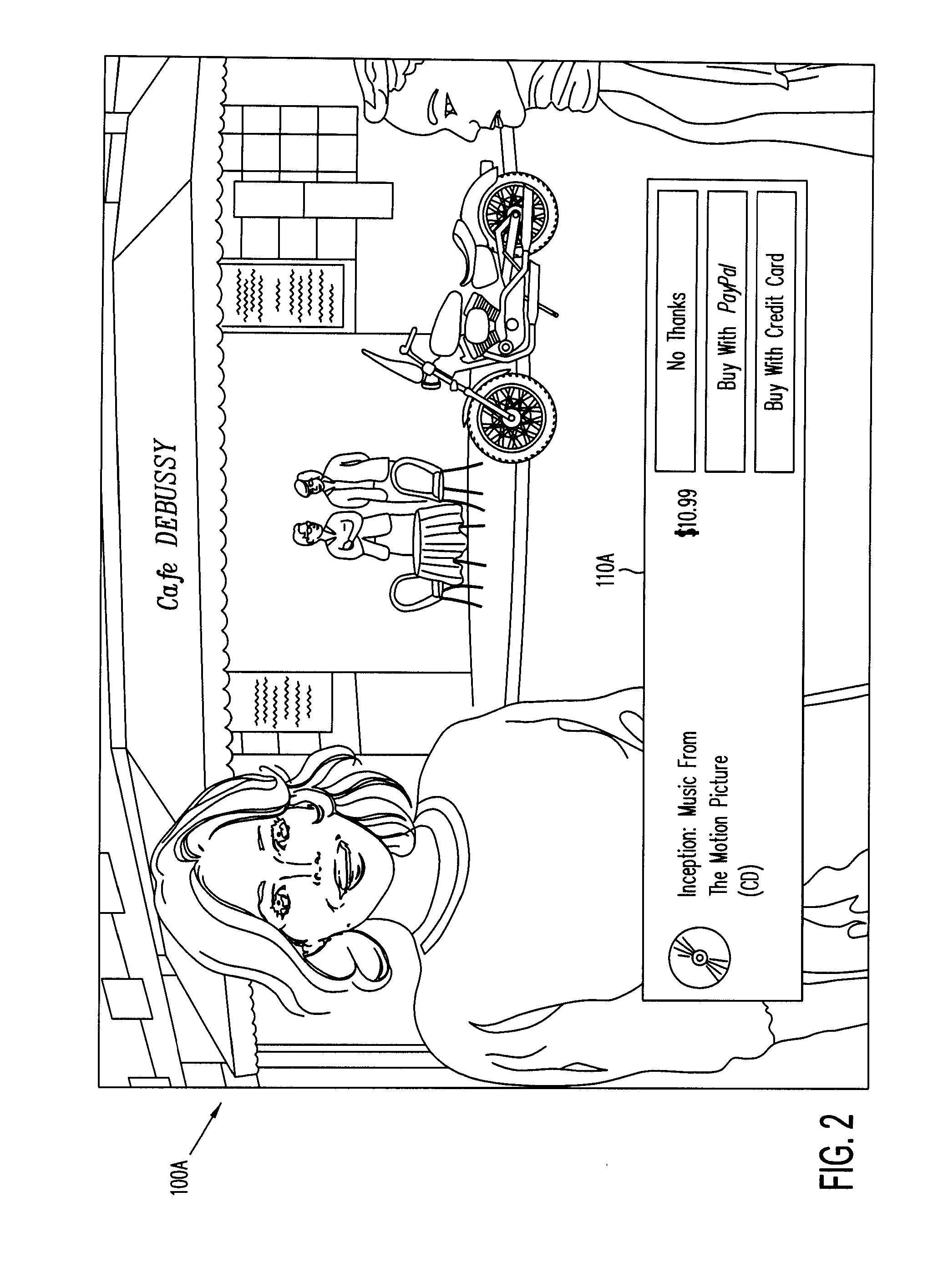
Payment Authentication and Authorization Non-Web Devices
ActiveUS20120240150A1Buying/selling/leasing transactionsElectrical cable transmission adaptationPaymentAuthorization Mode
The present disclosure involves a method of conducting a transaction. In one aspect, the method includes: displaying a media program on a media display device; indicating, while the media program is being displayed, an item associated with the media program is available for purchase; receiving authentication information of a prospective purchaser of the item; and completing a purchase of the item in response to the authentication information. In another aspect, the method includes: receiving, from a media display device, a user authentication request that contains user login credentials; granting the user authentication request in response to the user login credentials; and sending an authentication permission to the media display device; wherein the receiving and the sending are each performed such that the user login credentials and the authentication permission are sent through one or more intermediate hops without being inspected by any of the intermediate hops.
Owner:PAYPAL INC
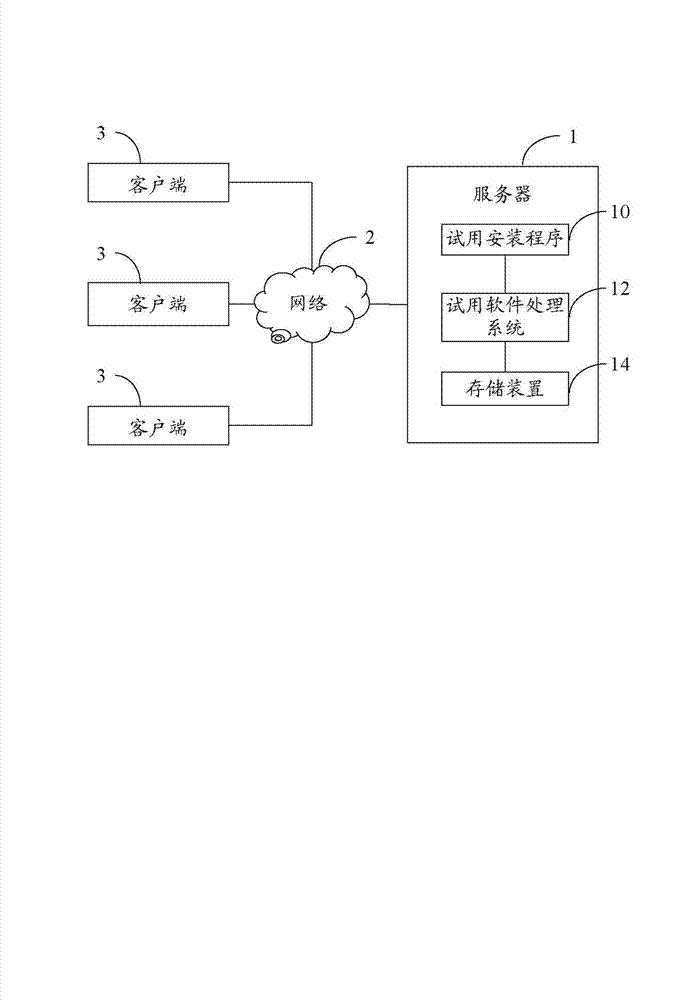
Demoware processing system and method
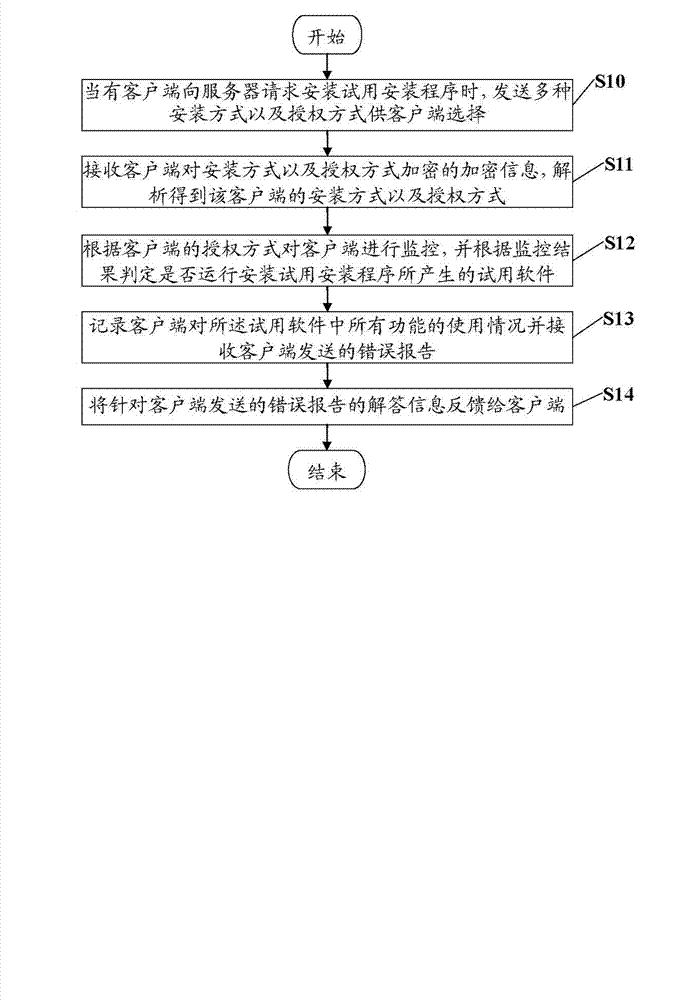
InactiveCN103365675AReal-time monitoring of function usagePlatform integrity maintainanceProgram loading/initiatingComputer hardwareAuthorization Mode
In a method for processing shareware using a host computer, a plurality of installation modes and authorization modes are sent to a client computer if the client computer requests the host computer for a shareware installation file of the shareware in the host computer. A selected installation mode and a selected authorization mode of the client computer are determined by decrypting encrypted data from the client computer using a preset decryption formula. The method further monitors the client computer according to the selected authorization mode to determining whether the client computer is allowed to run the shareware. When the client computer runs the shareware, the method records usage status of all functions of the shareware in the client computer and receiving error reports from the client computer. The method further sends solutions to the client computer in response to the error reports.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
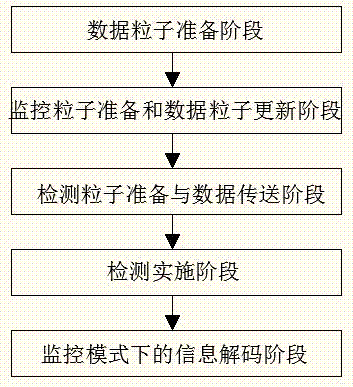
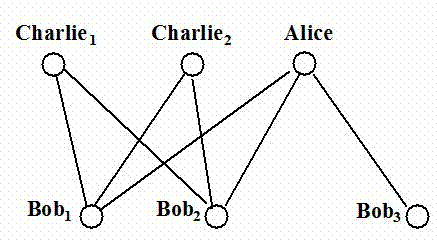
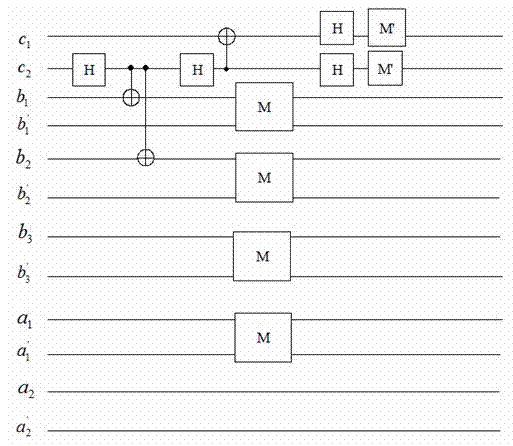
Combined quantum broadcast communication monitoring method based on partially entangled GHZ channel
InactiveCN103763114ARealize the flowAvoid demandSpecial service provision for substationPhotonic quantum communicationAuthorization ModeBroadcast data
The invention discloses a combined quantum broadcast communication monitoring method based on a partially entangled GHZ channel. The method includes the steps that a multi-particle partially entangled GHZ state is prepared through a sender on the basis of an information transfer mode, a corresponding number of auxiliary particles are led in according to the number of supervisors to be used as control particles, a part of particles in the GHZ state are selected to be used as monitored particles, CNOT operation is performed on the auxiliary particles and the selected monitored particles, then the particles are sent to the supervisors and receiving users, the sender performs Bell measurement, check bits are published, the supervisors perform single-particle measurement, measuring results are used as authorization information to be released to the corresponding legal authorization limited users, and the authorization limited users obtain real broadcast data of the sender according to Bell measuring results, checking information and the authorization information. According to the method, the effect that the flow directions of the broadcast data are monitored by the supervisors in a combined mode under the authorization mode is achieved, the requirement for the maximum entangled channel and complicated entanglement concentration operation can be avoided, and the method has good practicability and feasibility.
Owner:SUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com