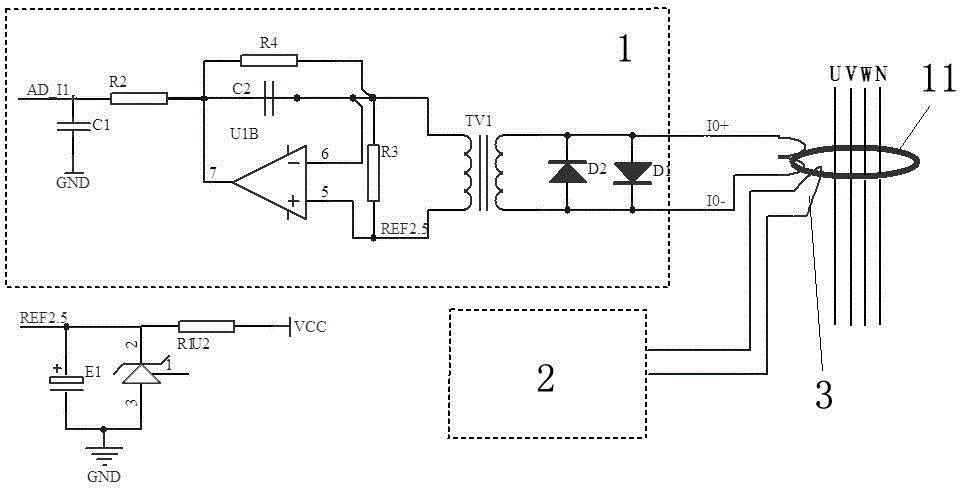
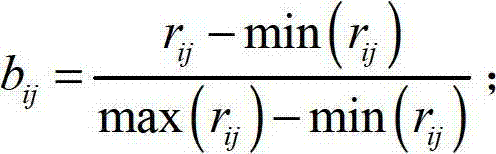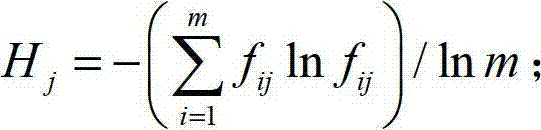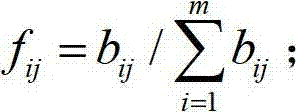Patents
Literature
143 results about "Information systems security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information systems security, more commonly referred to as INFOSEC, refers to the processes and methodologies involved with keeping information confidential, available, and assuring its integrity. It also refers to: Access controls, which prevent unauthorized personnel from entering or accessing a system.
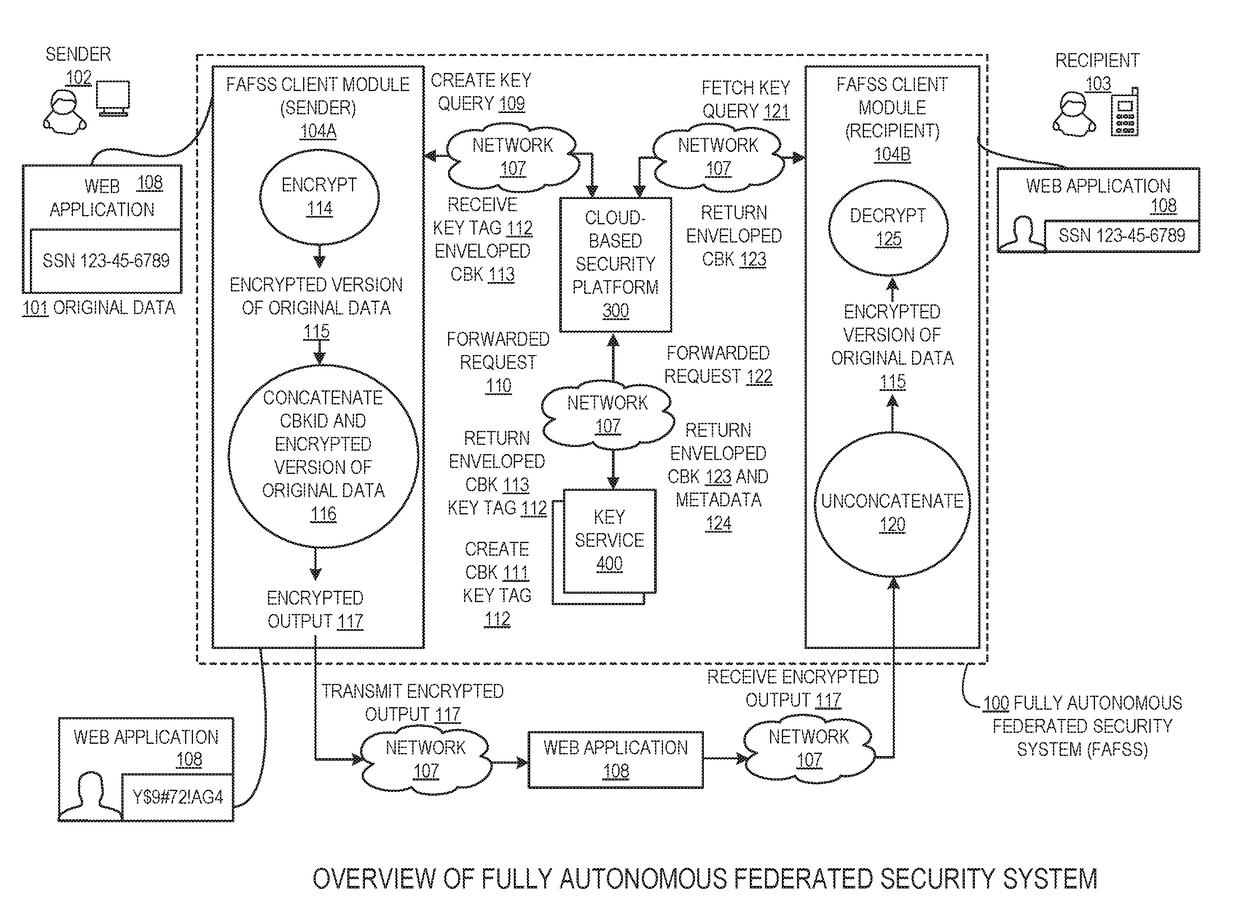
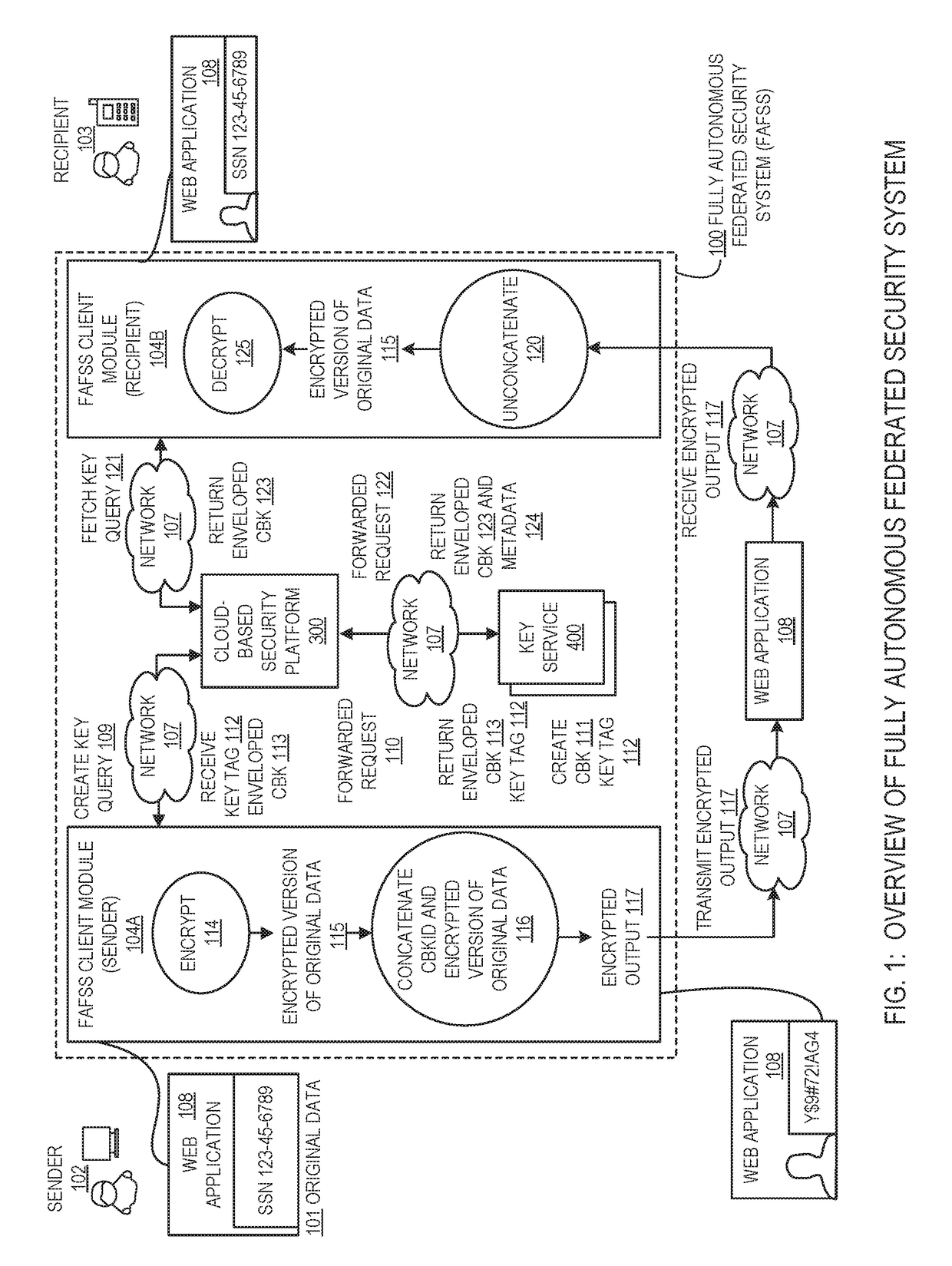
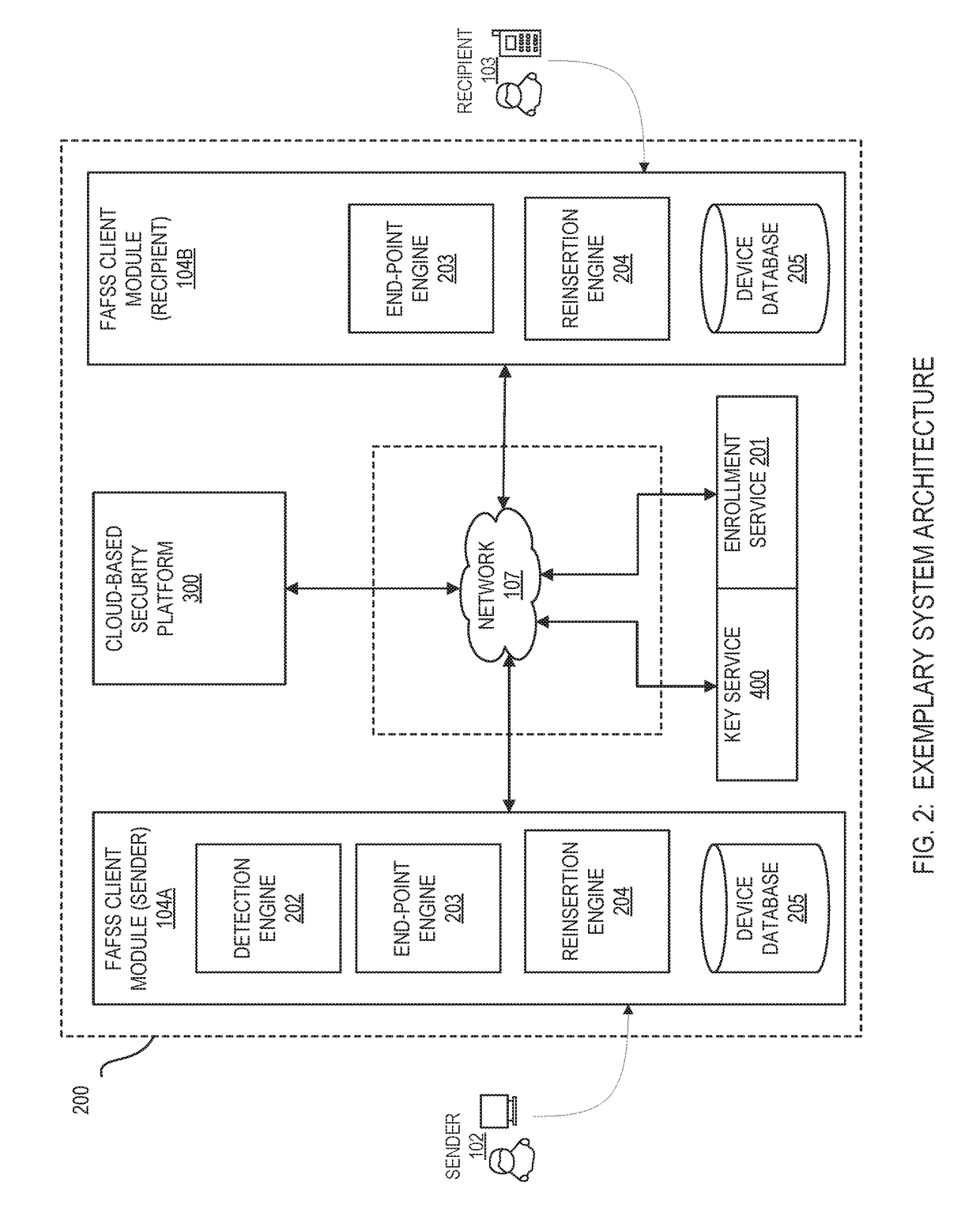
Systems and methods for encryption and provision of information security using platform services
ActiveUS9608809B1Enhanced interactionOptimizationKey distribution for secure communicationDigital data protectionCiphertextOriginal data
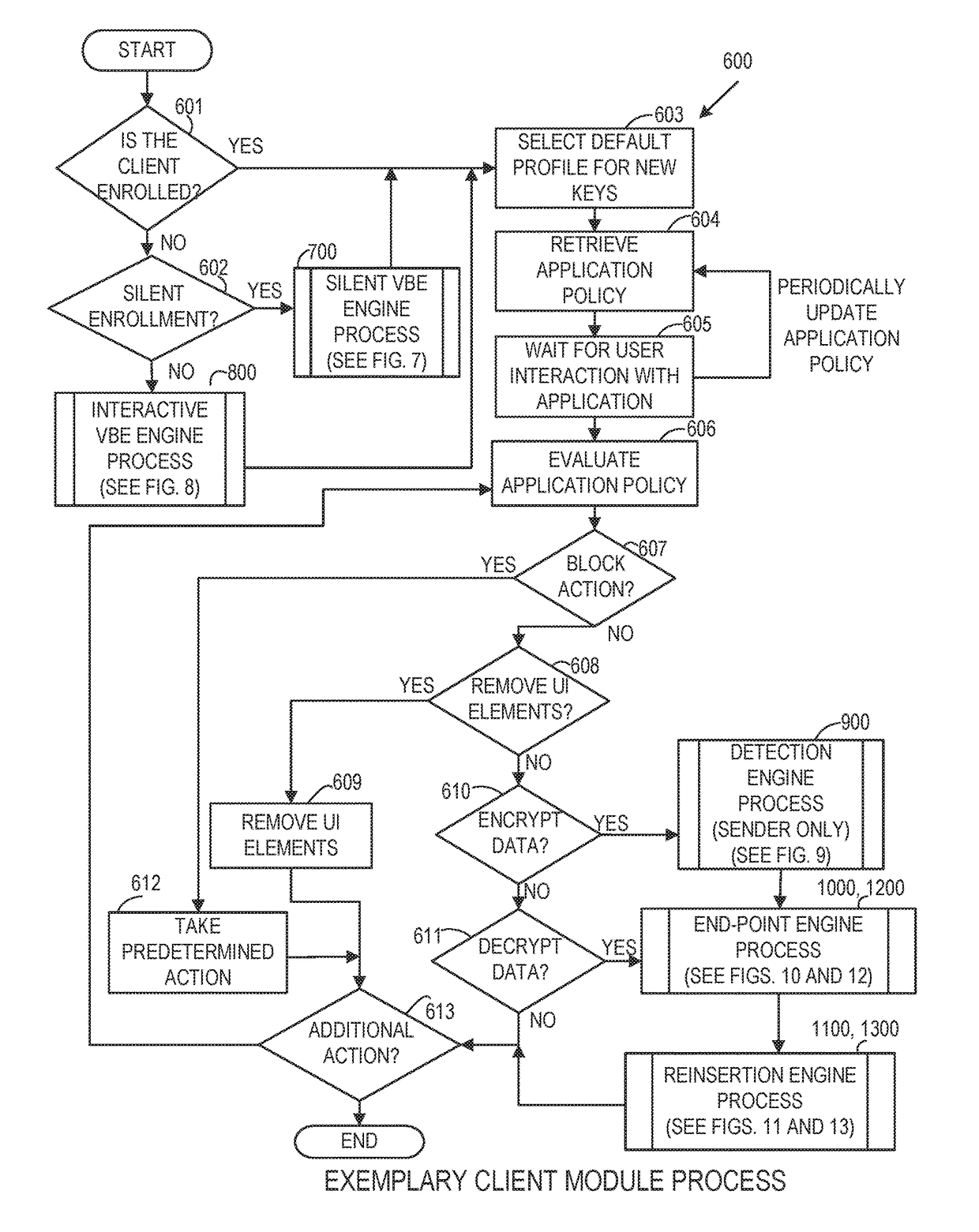
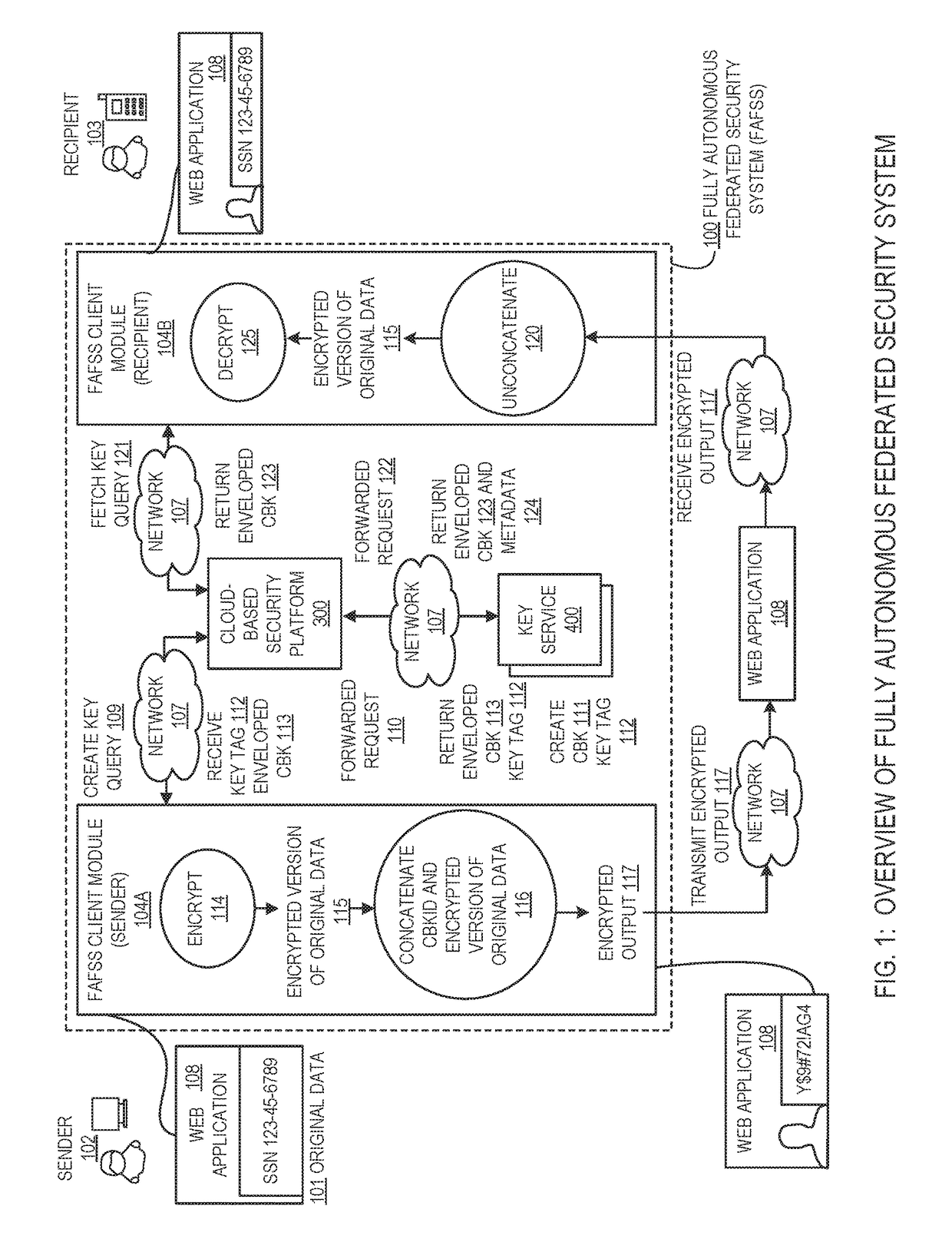
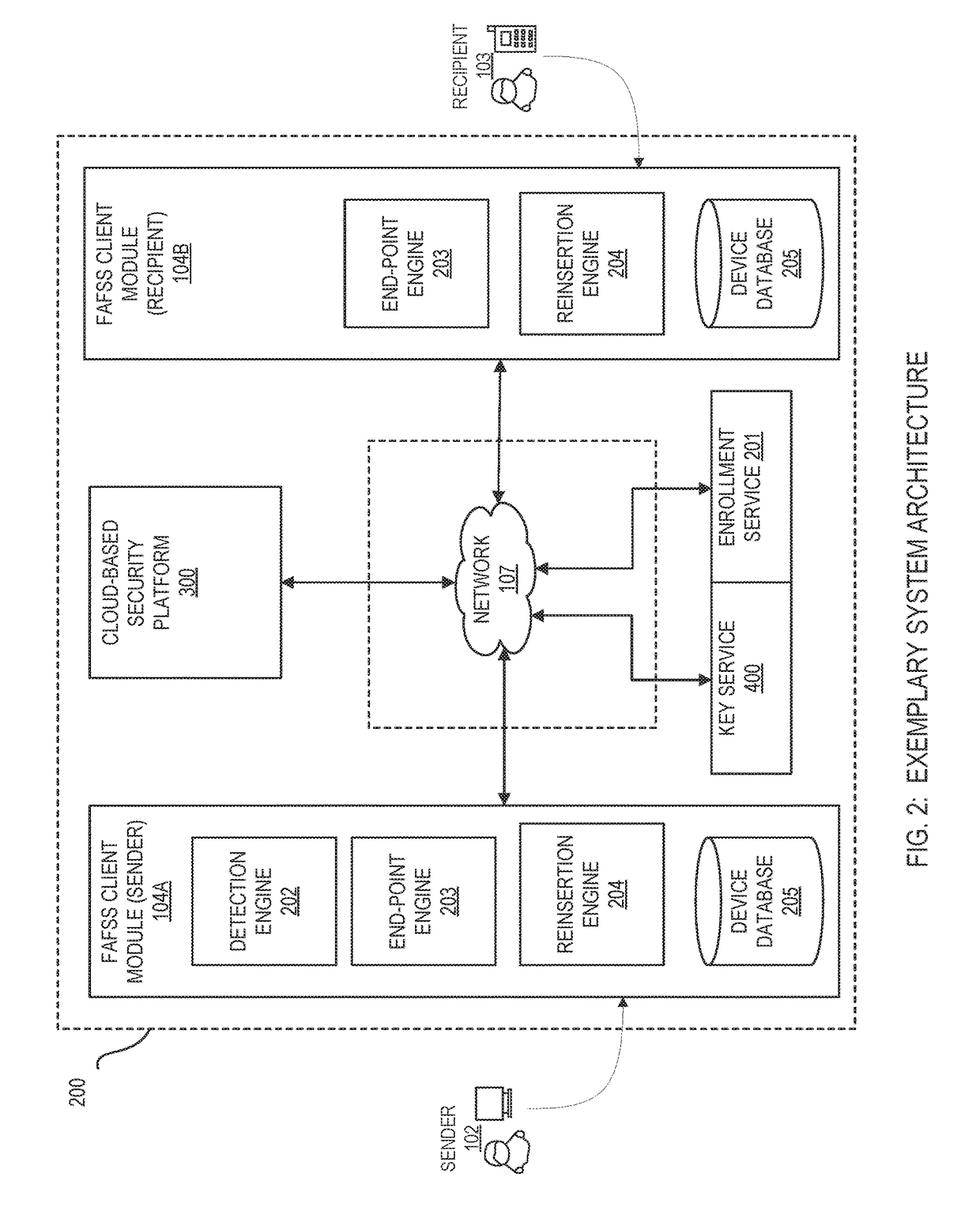
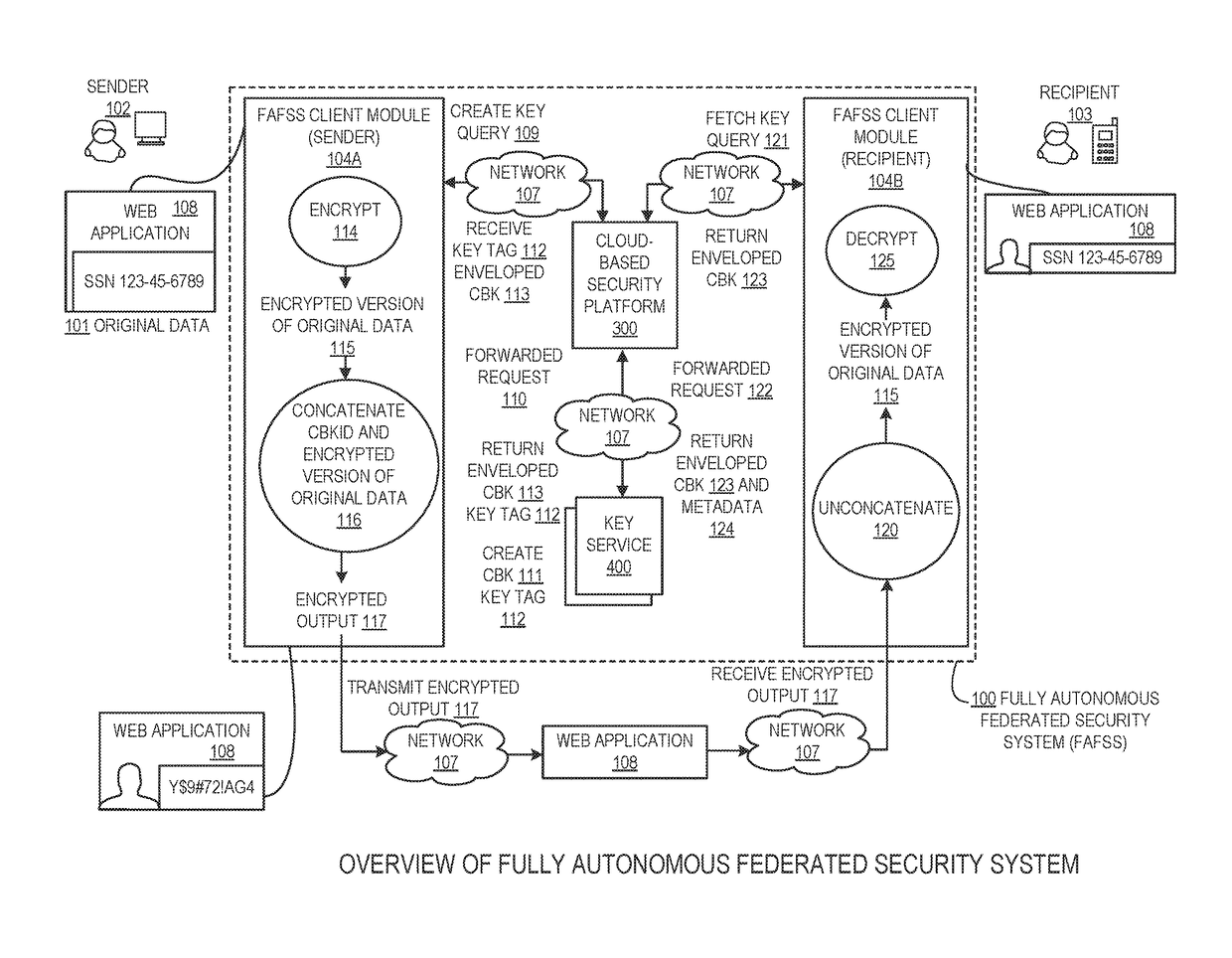
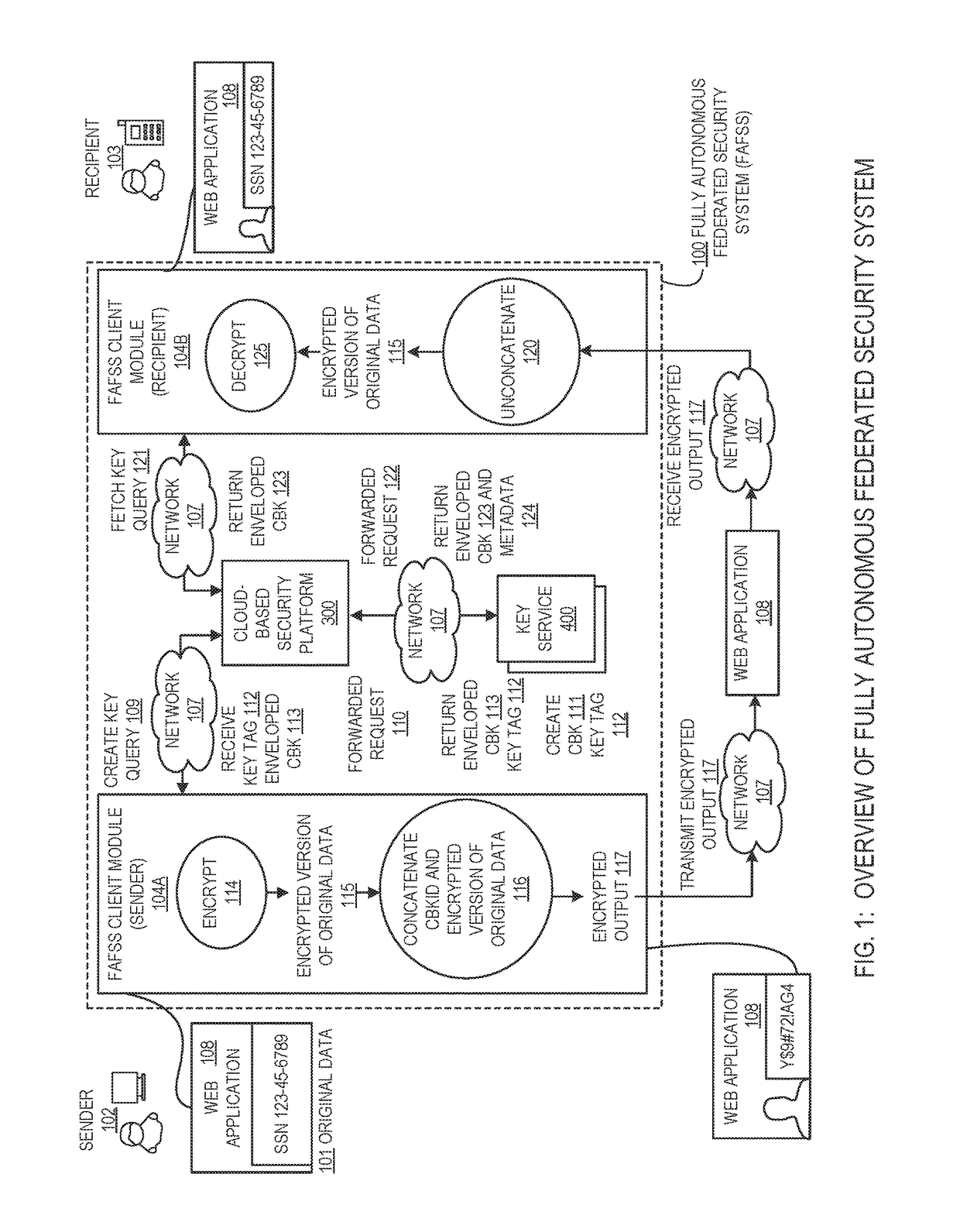
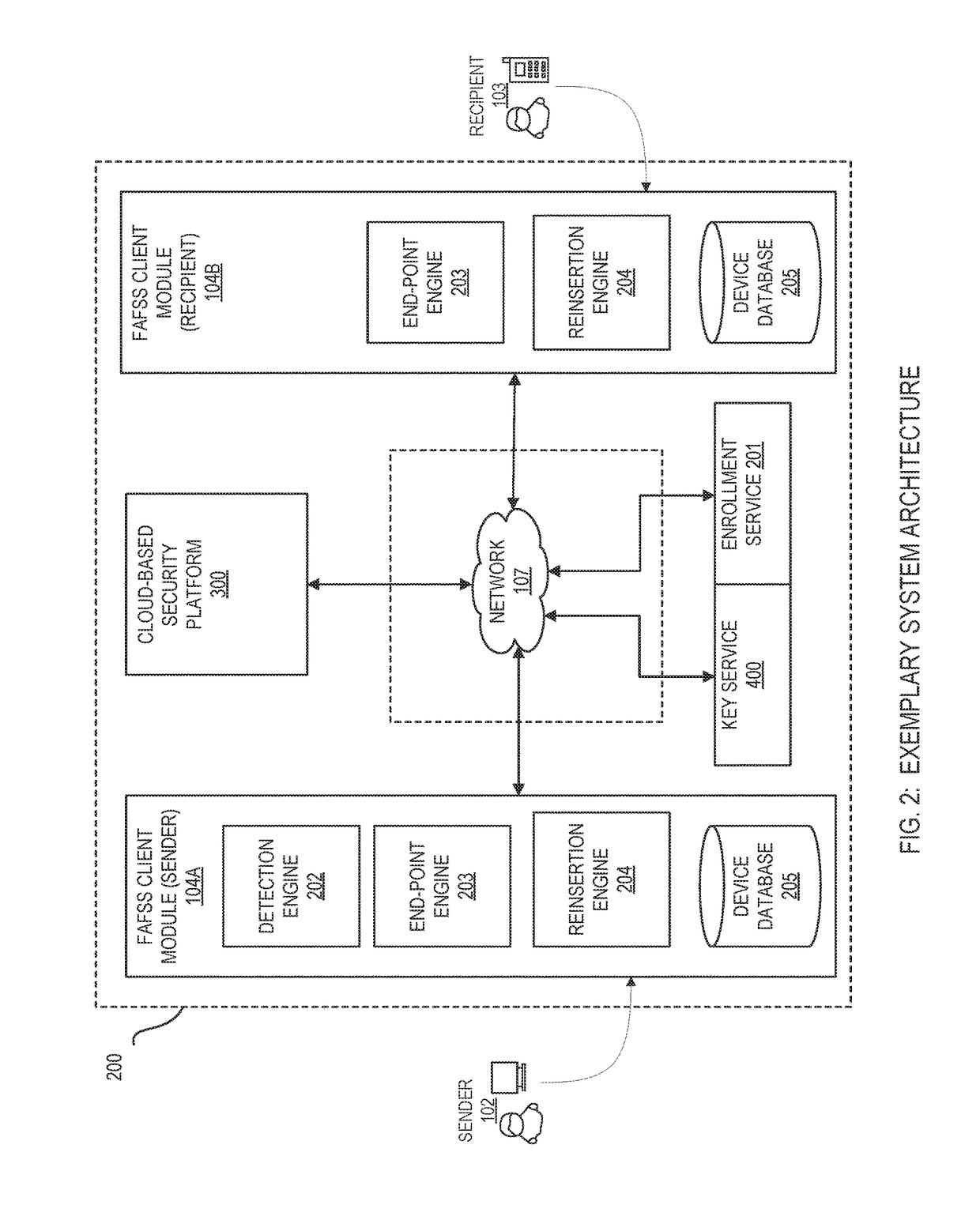
Systems and methods for securing or encrypting data or other information arising from a user's interaction with software and / or hardware, resulting in transformation of original data into ciphertext. Generally, the ciphertext is generated using context-based keys that depend on the environment in which the original data originated and / or was accessed. The ciphertext can be stored in a user's storage device or in an enterprise database (e.g., at-rest encryption) or shared with other users (e.g., cryptographic communication). The system generally allows for secure federation across organizations, including mechanisms to ensure that the system itself and any other actor with pervasive access to the network cannot compromise the confidentially of the protected data.
Owner:IONIC SECURITY
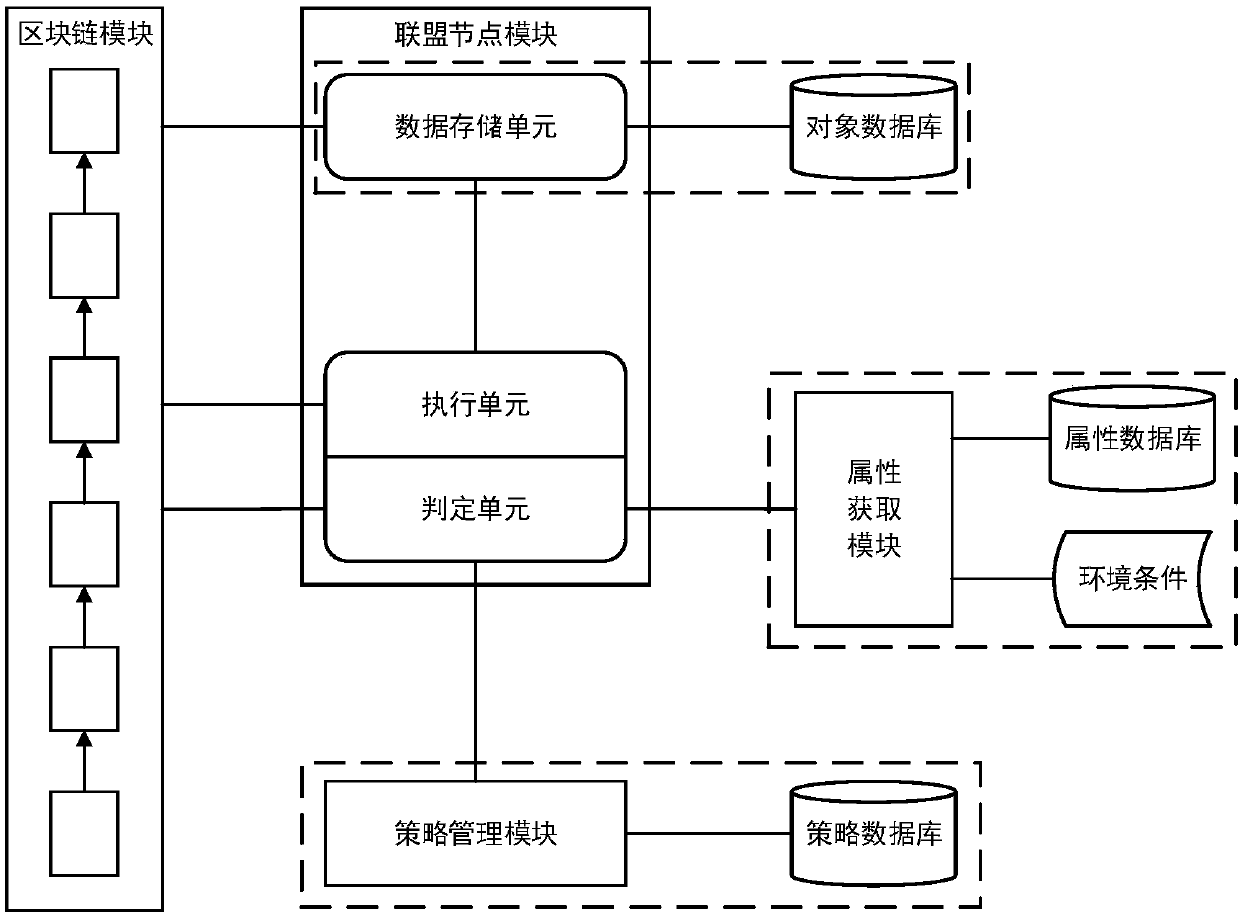
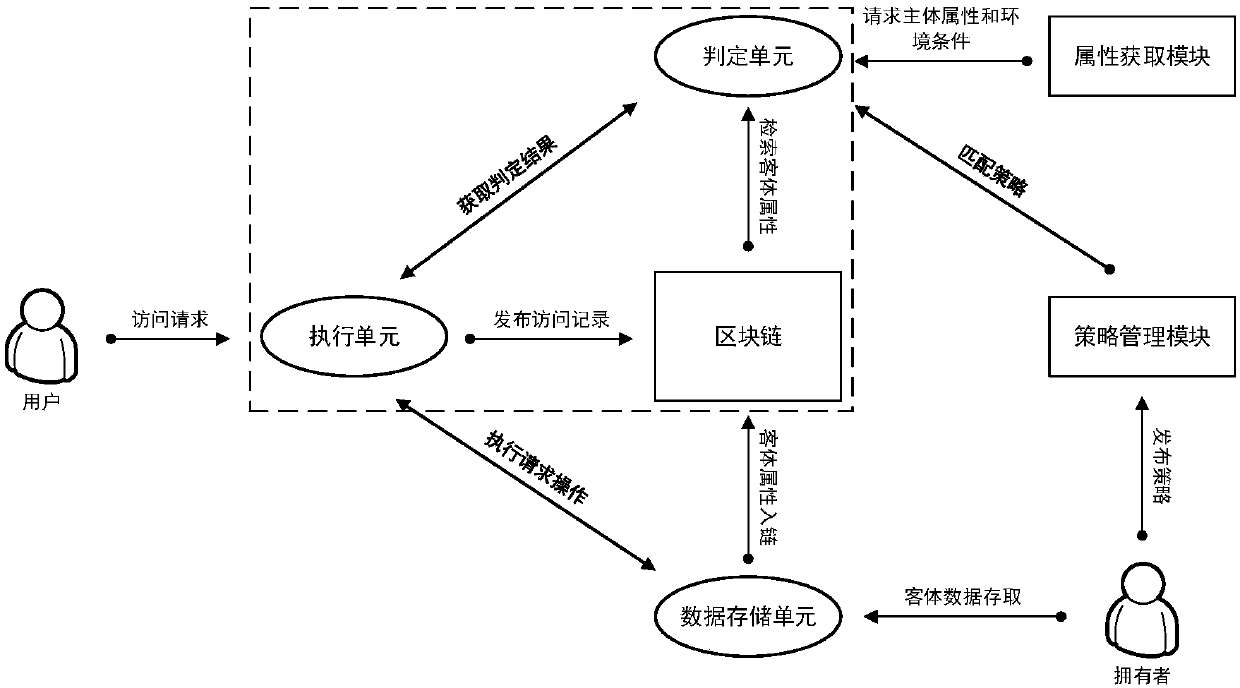
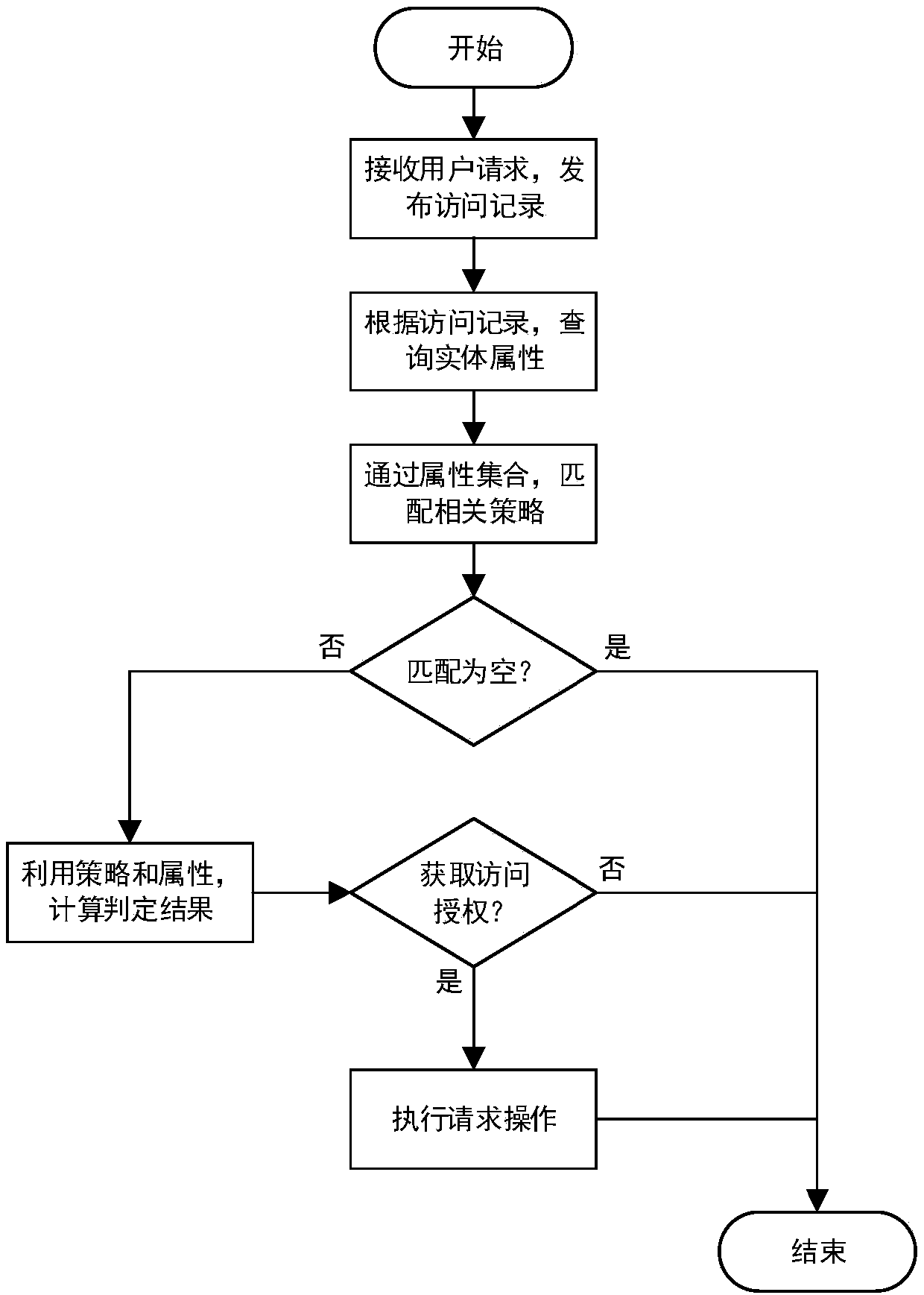
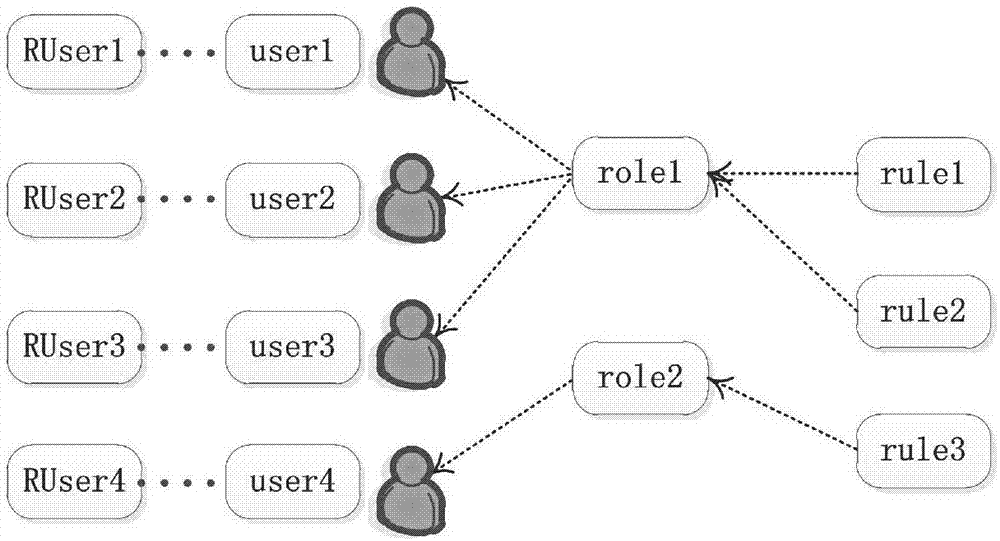
Access control method and system based on block chain technology
ActiveCN108123936AResistance to failureResist being attackedFinancePayment protocolsAuthorization ModeData privacy protection
The invention provides an access control method and system based on block chain technology. The block chain technology is combined with attribute-based access control in the method, and the method comprises the following steps: adding an object in a chain, binding a judgment process of attribute and strategy on all block chain nodes with reference to the strategy. The access authorization is converted from a centralized manner into a distributed manner, the consistency check of the judgment results in the whole network is achieved by using a consensus mechanism of the block chain, and the authorized operations for accessing the recorded transactions are permanently recorded on the block chain. The method has the advantages of anti-single point failure, flexible authorization mode, accurateaccess boundary, and record auditability. The access control method and system provided by the invention are applicable to operating environments such as enterprises and governments that have the need of data privacy protection and realize multi-branch cooperation work based on a block chain platform, the access permissions of users in the system can be dynamically and scalably managed, fine-grained permission management is achieved for the strategy and the attribute, and the access control method and system are of important practical significance for protecting the security of information systems in a distributed network environment.
Owner:UNIV OF SCI & TECH BEIJING
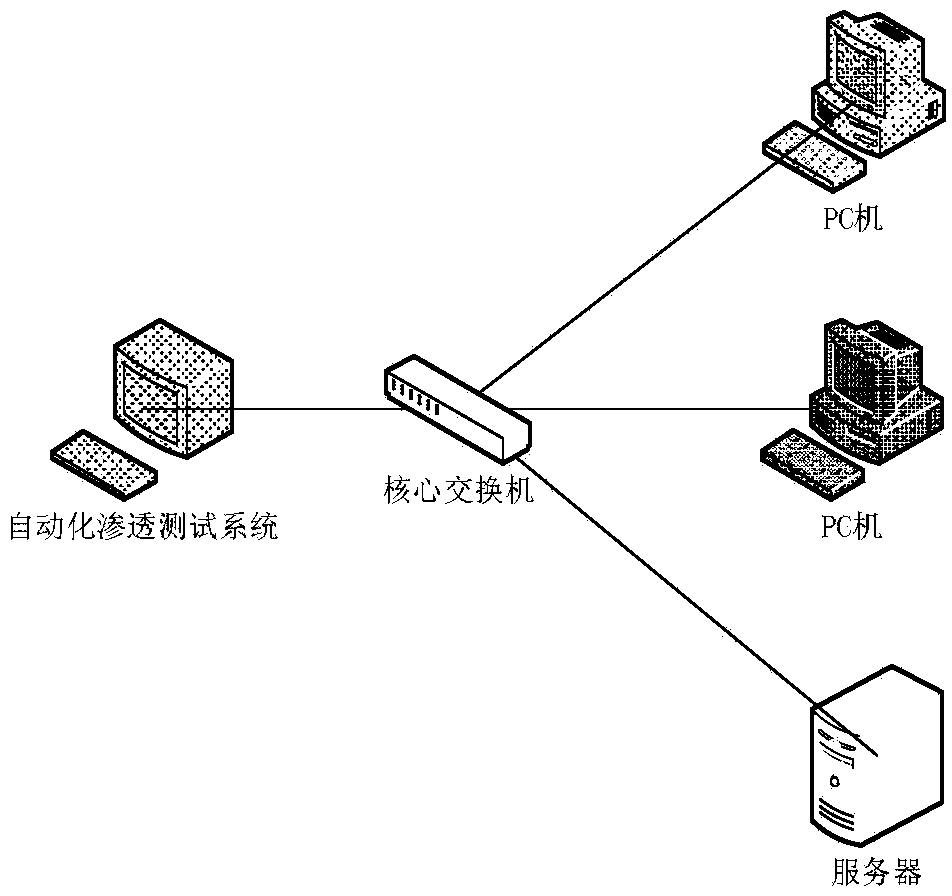
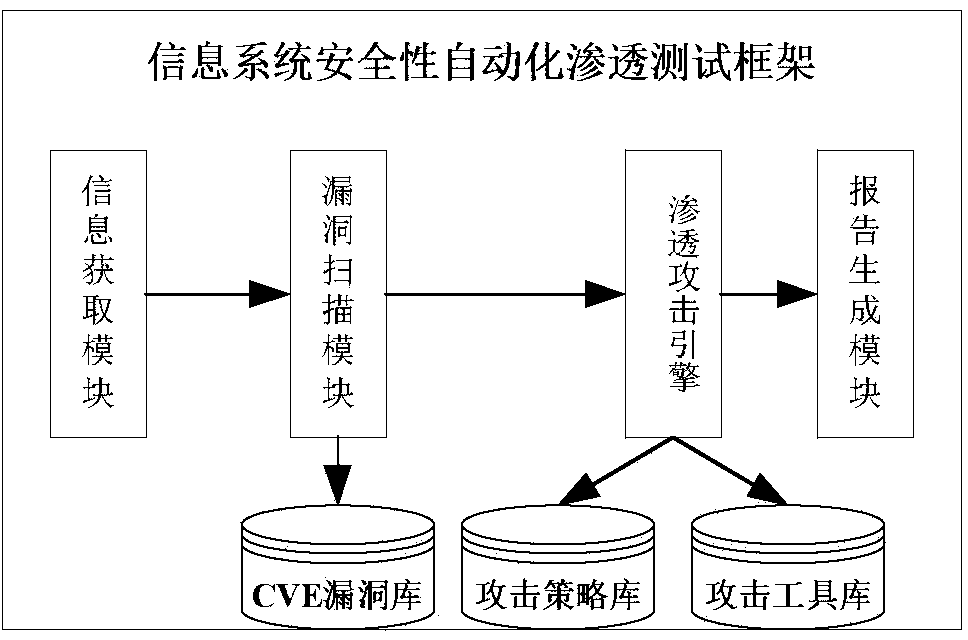
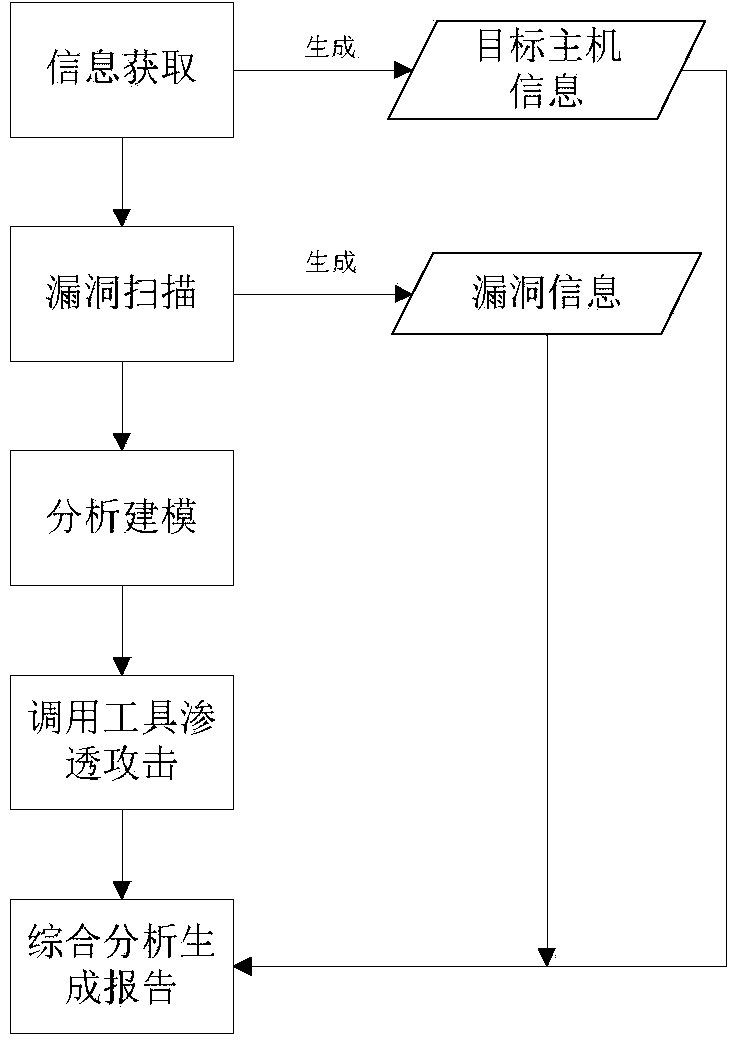
Automatic penetration testing method for information system security
InactiveCN103532793AImprove integritySpend less timeData switching networksTarget controlGoal system
The invention belongs to the technical field of network security and discloses an automatic penetration testing method for information system security. A penetration testing platform is built to automatically scan the mainframe state of an information system and the security loopholes of a topological structure and the information system, to analyze the loophole information, to automatically transfer a verification script in a loophole verification base for attacking a target system, to obtain and improve the target control authority and to remove the access trace after finishing the penetration attack. Finally, the whole penetration testing process and result are recorded and analyzed to generate a testing report. According to the method, the penetration testing flow is comprehensively considered and the existing security analyzing tools are fully utilized to design various tools for packing an automatic penetration testing module, so that the automatic transfer and execution of the tools are achieved, and the completeness of the penetration testing process is improved. Through the exchange utilization of data among different modules and the automatic analysis and arrangement of the result output of the security analyzing tools, the efficiency and automatic degree of the penetration testing are improved.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Method for evaluating operation quality of information systems
InactiveCN102902882ASimple structureImprove the level ofSpecial data processing applicationsEntropy weight methodInformation systems security
The invention discloses a method for evaluating operation quality of information systems. The method comprises the steps of firstly, constructing an evaluation index system for the operation quality of information systems; secondly, using an analytic hierarchy process to evaluate the operation quality of the qualitative information system and calculate the subjective weight of evaluation indexes, using an entropy weight method to evaluate the operation quality of the quantitative information system and calculate the objective weight of evaluation indexes, and synthesizing the subjective weight of evaluation indexes and the objective weight of evaluation indexes to calculate the combined weight of all evaluation indexes; and finally, calculating evaluative values of all evaluation objects according to the combined weight, and conducting evaluation analyses on evaluative values of all evaluation objects. According to the method, the entropy weight method and the analytic hierarchy process are combined to evaluate the operation quality of information systems, the potential problems in operation of information systems are found out, the operation guaranteeing capability of information systems is improved, and the operation and maintenance level of information systems is evaluated accurately and objectively, so that the safe, high-efficiency and economical operation of information systems is effectively guided.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +1
Systems and methods for enhanced network security
ActiveUS8065725B2Improve network securityFacilitate communicationMemory loss protectionError detection/correctionInformation sharingMinicomputer
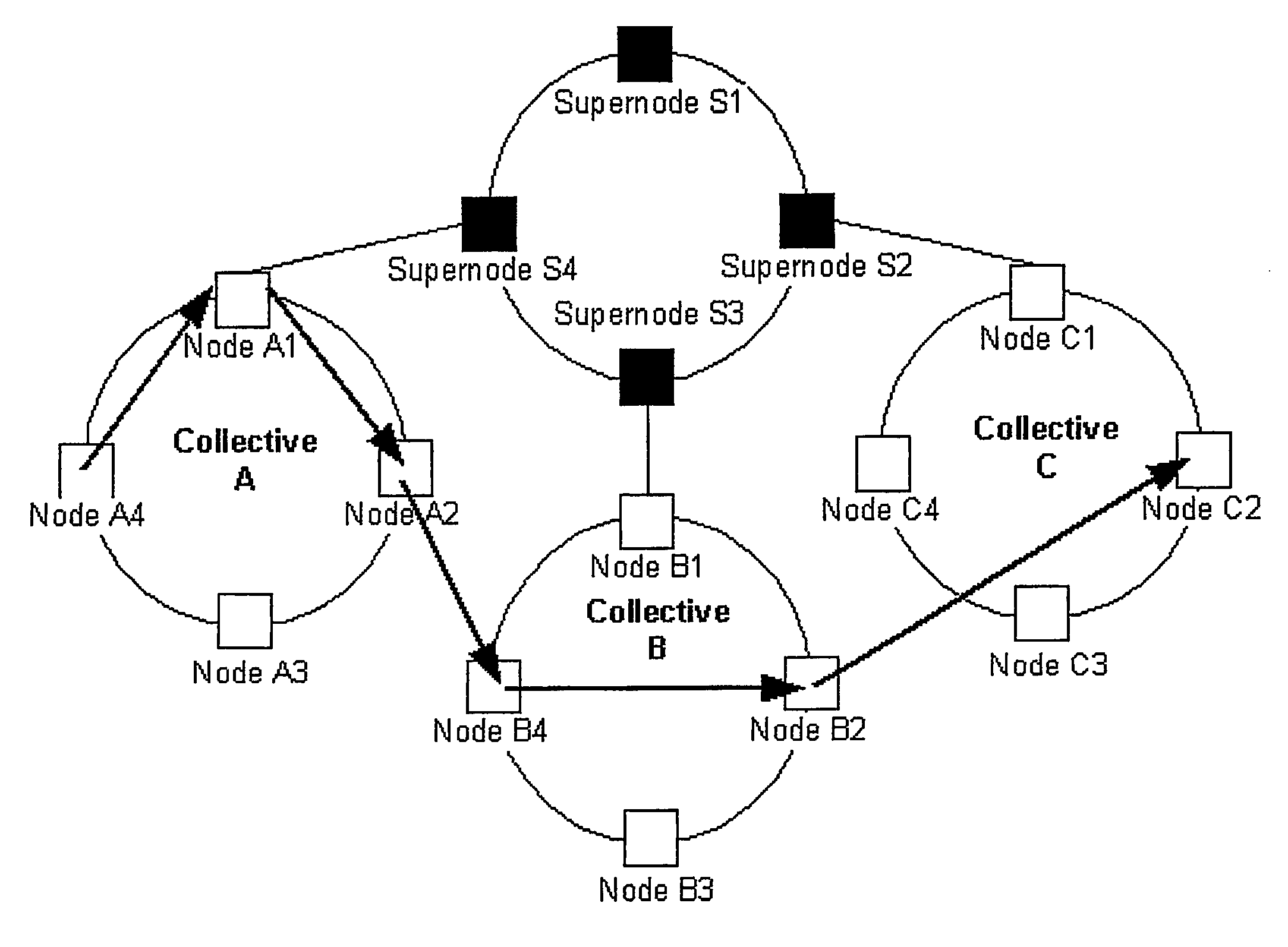
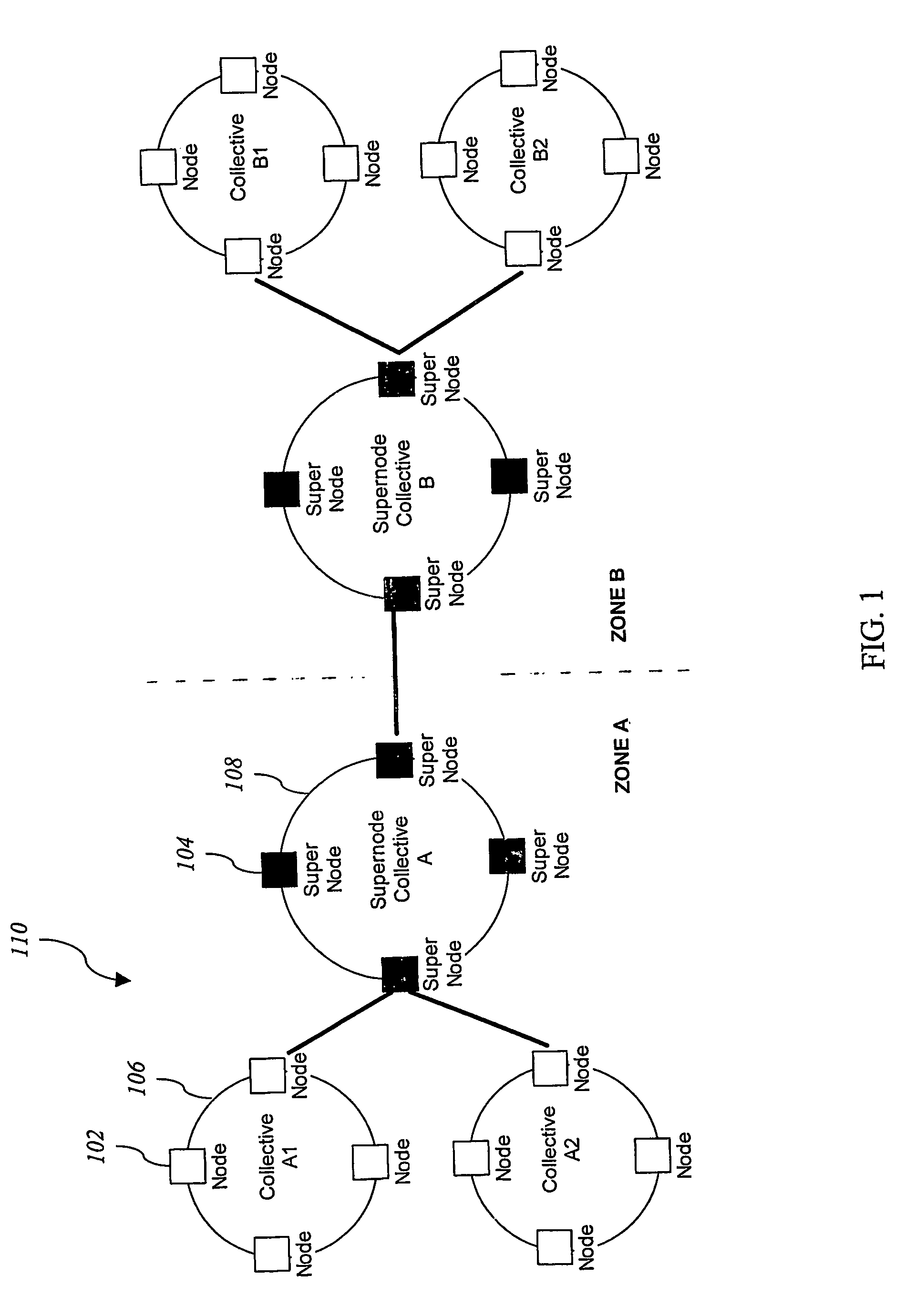
Systems and methods for an information system security infrastructure are described. One embodiment of the present invention comprises global Internet-scale defense infrastructure, referred to as the Intrusion Detection Force (IDF). The IDF comprises a virtual infrastructure implemented on top of an existing network, such as the Internet. The IDF enables secure information sharing and intelligent data analysis and response. The node (e.g. 102 of FIG. 1) is the most primitive entity in the IDF architecture, and may be a switch, router, server, or workstation. The IDF may be implemented in small networks of computers or may be utilized by millions of hosts throughout the Internet, spanning different organizations, countries, and continents.
Owner:CALYPTIX SECURITY
System and method for carrying out safety risk check to computer BIOS firmware
InactiveCN101079003AAvoid lossPrevent crashSoftware testing/debuggingRedundant operation error correctionEngineeringBIOS
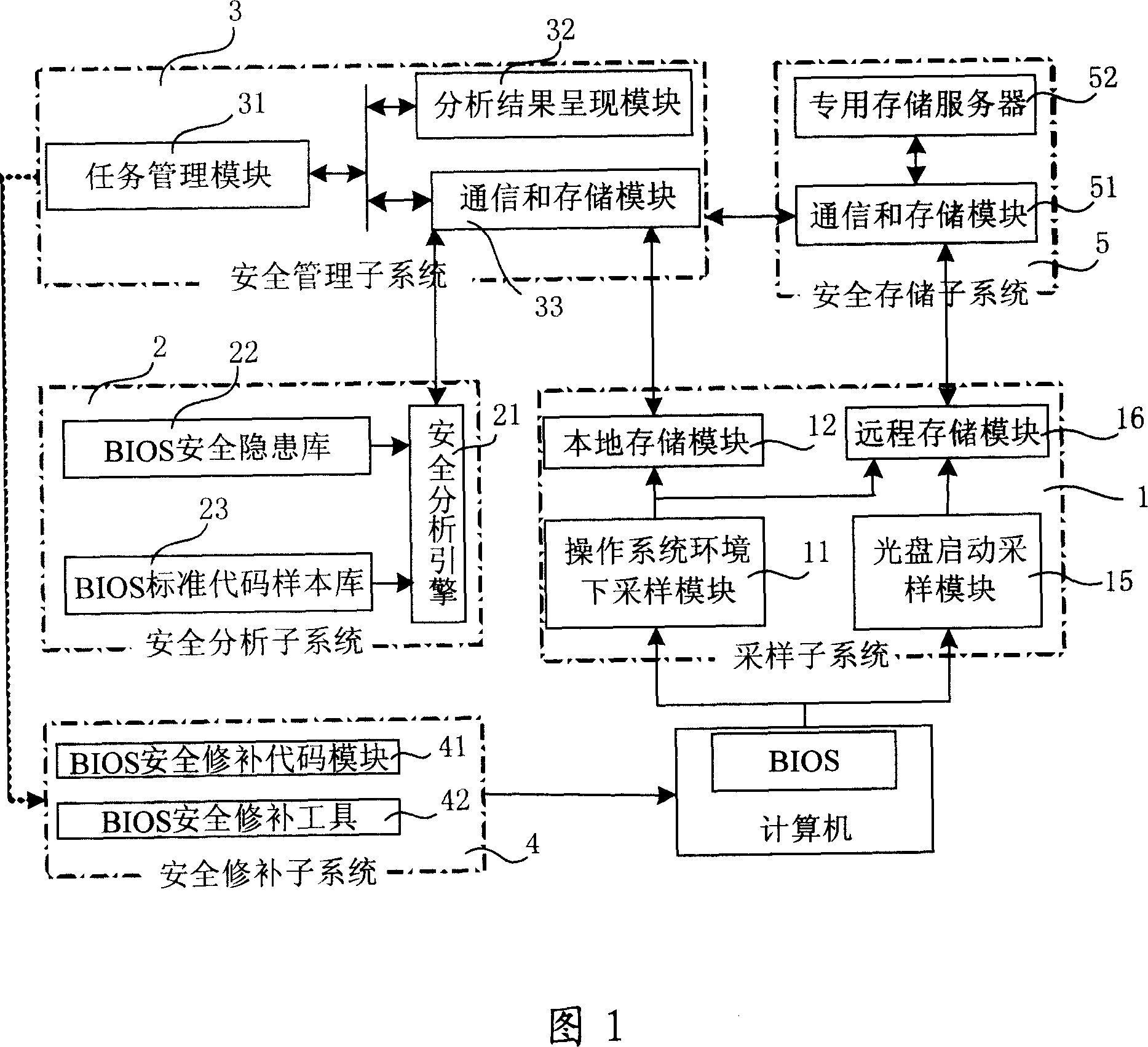
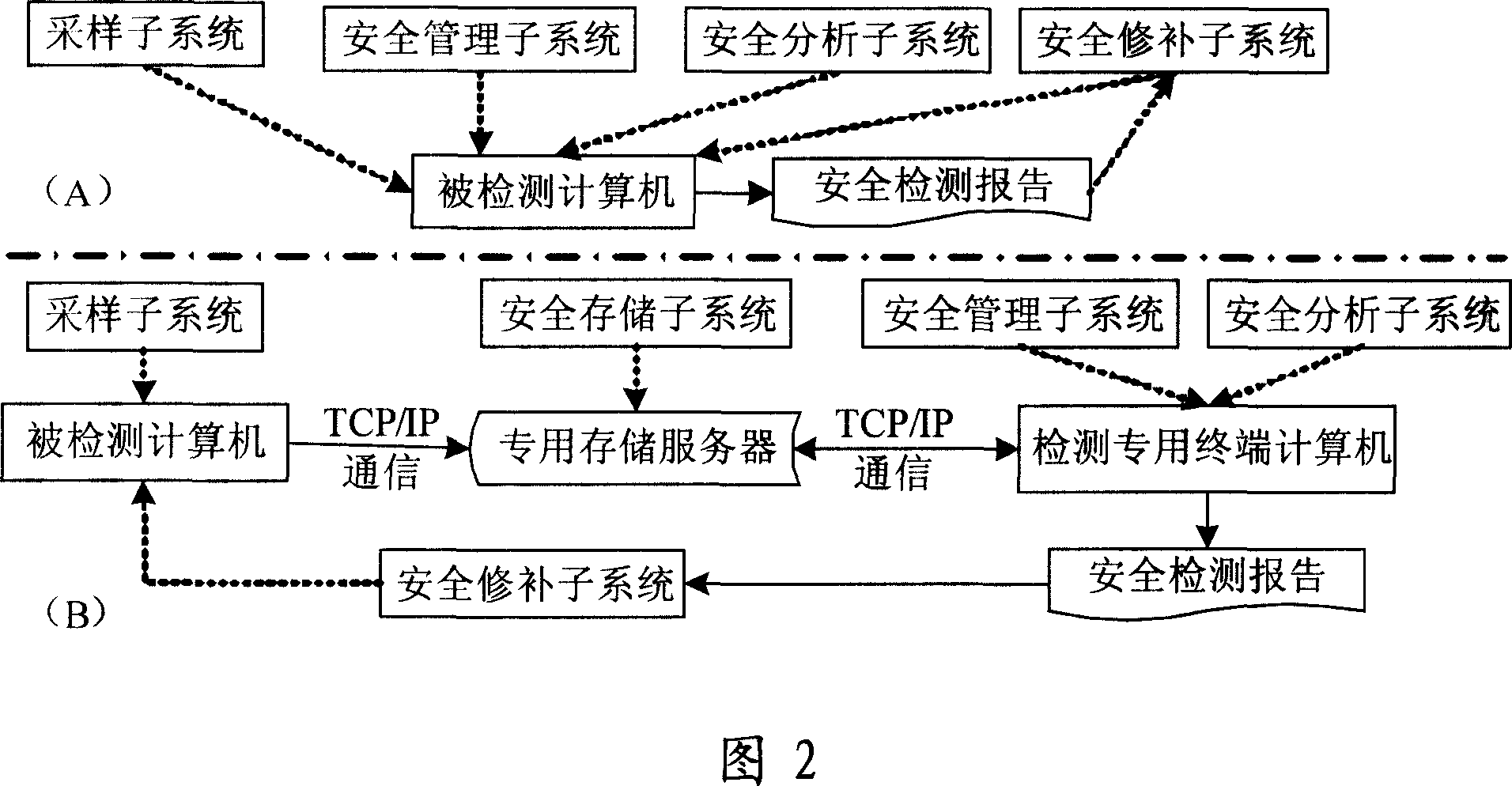
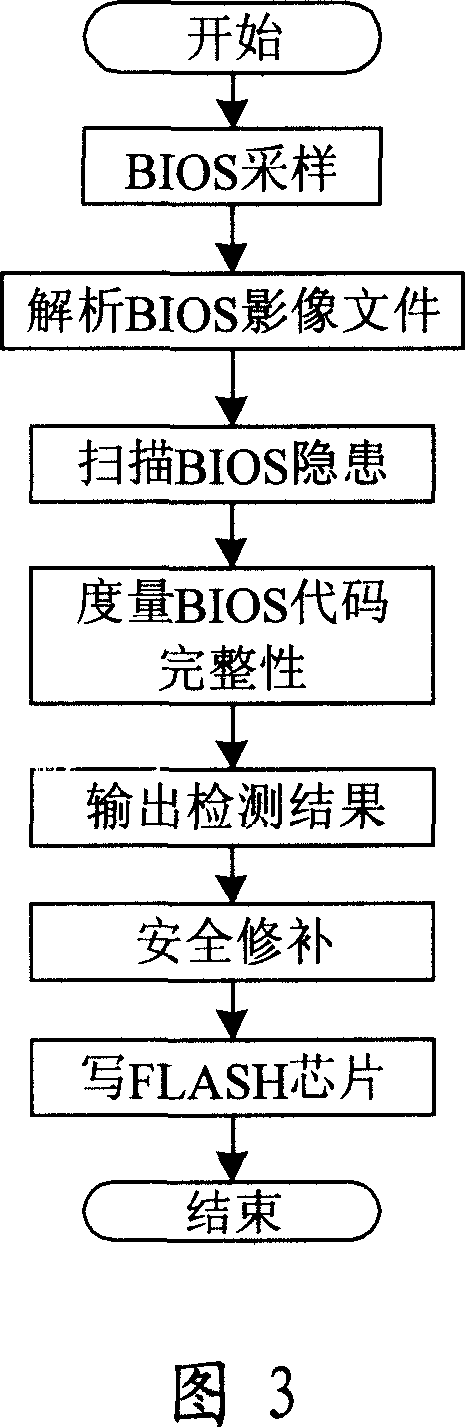
The invention discloses a system proceed safe test for computer BIOS firmware and method, which comprises the following steps: initializing; proceeding BIOS sampling; analyzing BIOS image file; scanning various hidden dangers of BIOS; measuring completeness integrity of BIOS code; outputting the testing effect; proceeding safe repair for BIOS. This invention can decrease, reduce and remove safety loophole and hidden danger of computer BIOS, which provides reliable terminal safety prevention and overall protection for computer and network.
Owner:BEIJING JINYUAN LONGMAI INFORMATION TECH
Terminal user-based database fine-grained access control method
ActiveCN107403106AImprove the protective effectMaintain securityDigital data protectionComputer terminalDatabase security
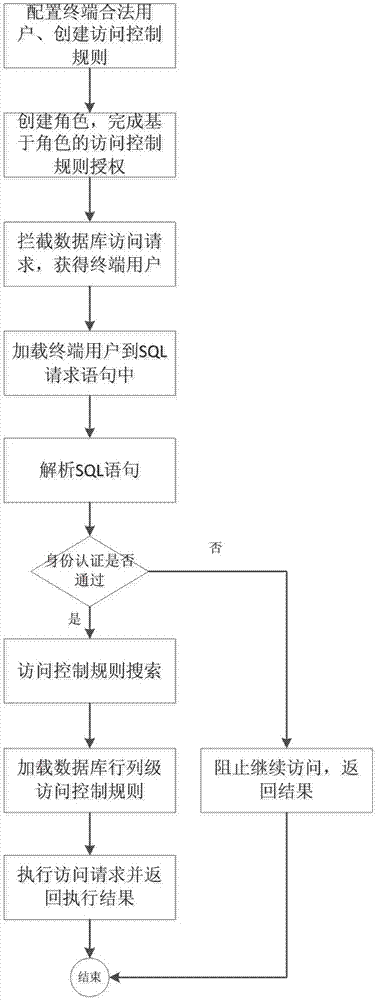
The invention relates to a terminal user-based database fine-grained access control method, and belongs to the technical field of database safety protection. According to the method, legal terminal users are identified to stop illegal access users; and meanwhile, fine-grained access control rules are loaded to database access request sentences initiated by the terminal users so as to achieve fine-grained access request control ability for the terminal users. Through the access authority control realized by the method, identity authentication can be carried out on the terminal users, and column-level database fine-grained access control can be carried out on the terminal users without encrypting and decrypting the data, so that the database protection ability is effectively strengthened and the information system safety is maintained.
Owner:BEIJING INST OF COMP TECH & APPL
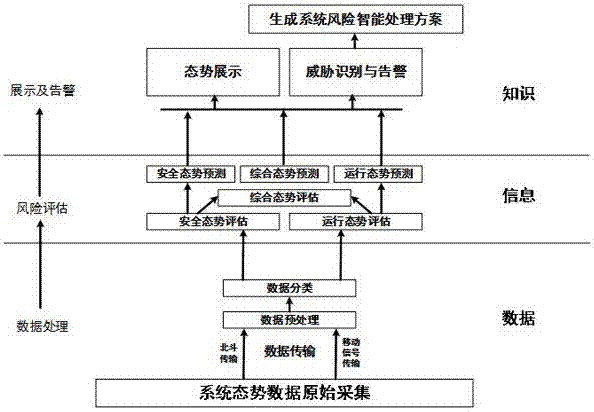
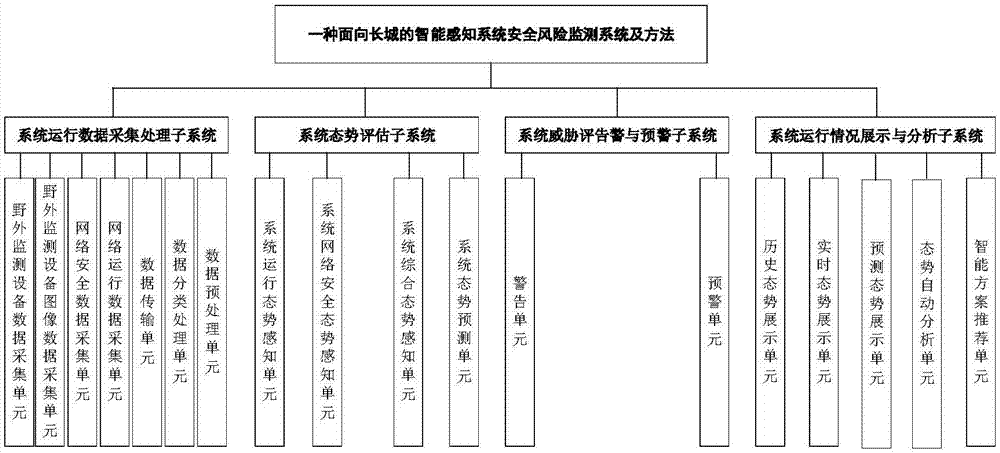
Security posture sensing system and method for intelligent sensing system of Great Wall of Ming dynasty
InactiveCN107332698AShorten the timeImprove operation and maintenance support capabilitiesGeometric CADSoftware testing/debuggingData acquisitionInformation systems security
The invention discloses a security posture sensing system and a security posture sensing method for an intelligent sensing system of the Great Wall of the Ming dynasty. The intelligent sensing system of the Great Wall of the Ming dynasty comprises a posture data collection module, a posture sensing module, an alarm module and a posture display module. The functions of collecting posture data, sensing system operating postures, sensing system security postures, sensing system comprehensive postures, warning and pre-warning system threats, displaying operating postures, displaying security postures and displaying comprehensive postures are provided. The security posture sensing system provided by the invention supports an application mode of the intelligent sensing system of the Great Wall of the Ming dynasty. The system solves the problem that a system manager and a user worry about security of an information system, ensures operating security and stability of the system, improves guarantee capability of the system, and avoids the problem that the Great Wall site cannot be efficiently protected when the system is failed to operate.
Owner:NORTHWEST UNIV
Systems and methods for encryption and provision of information security using platform services
ActiveUS9608810B1Enhanced interactionOptimizationKey distribution for secure communicationDigital data protectionCiphertextOriginal data
Systems and methods for securing or encrypting data or other information arising from a user's interaction with software and / or hardware, resulting in transformation of original data into ciphertext. Generally, the ciphertext is generated using context-based keys that depend on the environment in which the original data originated and / or was accessed. The ciphertext can be stored in a user's storage device or in an enterprise database (e.g., at-rest encryption) or shared with other users (e.g., cryptographic communication). The system generally allows for secure federation across organizations, including mechanisms to ensure that the system itself and any other actor with pervasive access to the network cannot compromise the confidentially of the protected data.
Owner:IONIC SECURITY
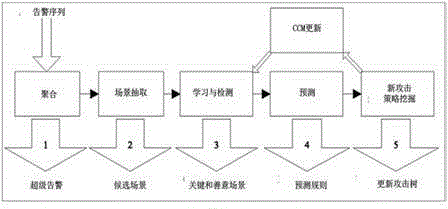
Threat detection and alert method and system based on big data analysis
The invention discloses a threat detection and alert method and system based on big data analysis. The system comprises an alert aggregation assembly, a scene extraction assembly, a study and detection assembly, a prediction assembly and a new attack strategy digging assembly. According to the threat detection and alert method and system, the big data technology is adopted to predict and alert network attacks to government and enterprise information systems in real time, thereby greatly covering the shortage of the existing information security alert analysis technology on one hand; and on the other hand, false alerts generated by information security equipment such as an intrusion detection system can be identified and unknown malicious attacks can be analyzed, and therefore, the accuracy and the credibility of the alerts can be improved and the security risks of the information systems can be sensed.
Owner:NANJING LIANCHENG TECH DEV
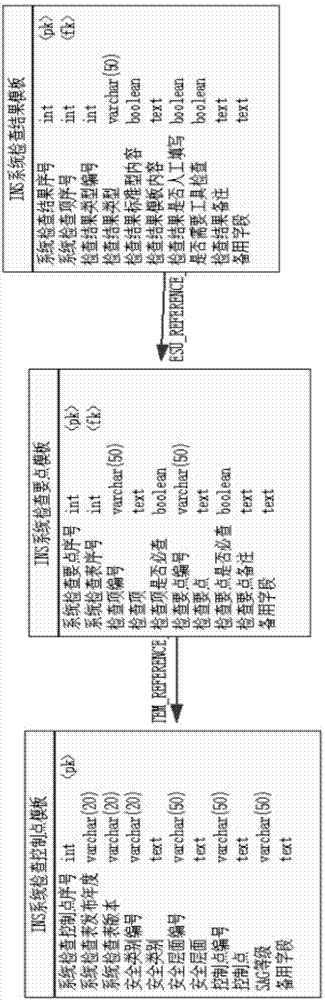
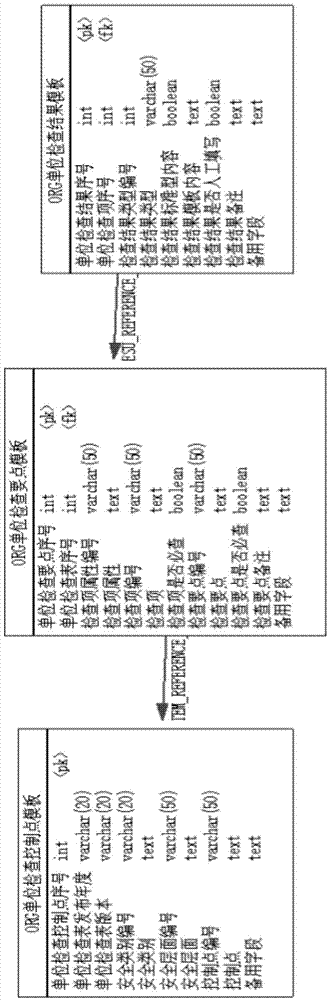
Grade-protection-oriented information system security compliance check method
ActiveCN104766166AProtect the objectivity of inspection workProtection Inspection Work SpecificationsPlatform integrity maintainanceResourcesInformation systems securityCompliance check
The invention relates to the field of information securitygrade protection, and aims at providing a grade-protection-oriented information system security compliance check method. The grade-protection-oriented information system security compliance check method comprises the steps that a check index library is built, a check task or a check plan is defined, a check object is scanned, a check result is guided in, a scanning result is decoded, a scanning result code is decoded, the scanning result is judged, a judgment result is graded, and a grade protection compliance report is generated. According to the method, information system security grade protection check work is objective, standard and fair, and the difficulty and complexity of the information security grade protection check work can be greatly reduced so that the efficiency of the information security grade protection check work can be greatly improved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Systems and methods for encryption and provision of information security using platform services
ActiveUS9614670B1Enhanced interactionOptimizationKey distribution for secure communicationUser identity/authority verificationCiphertextOriginal data
Owner:IONIC SECURITY
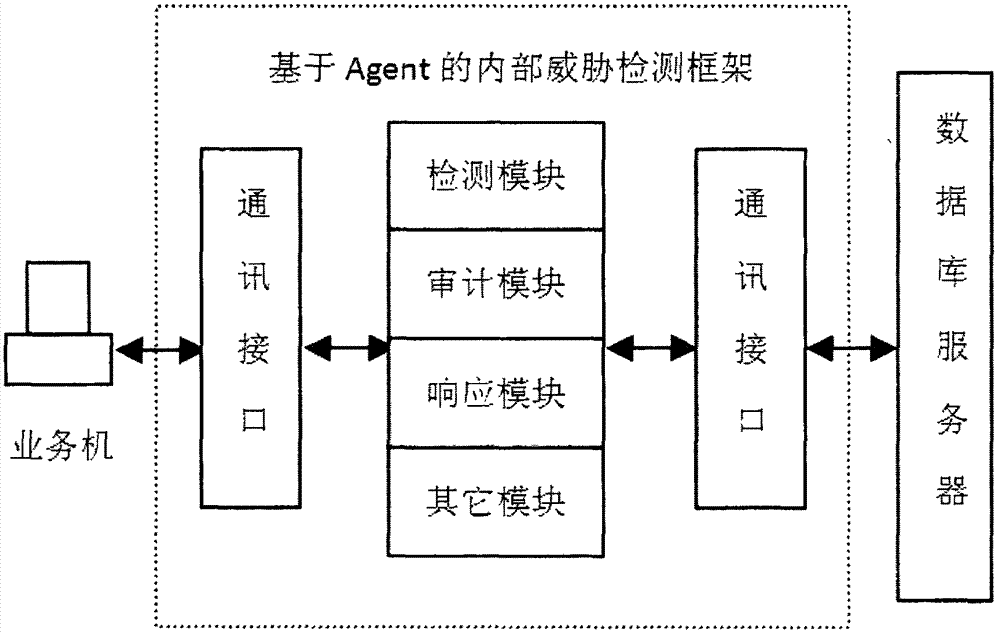
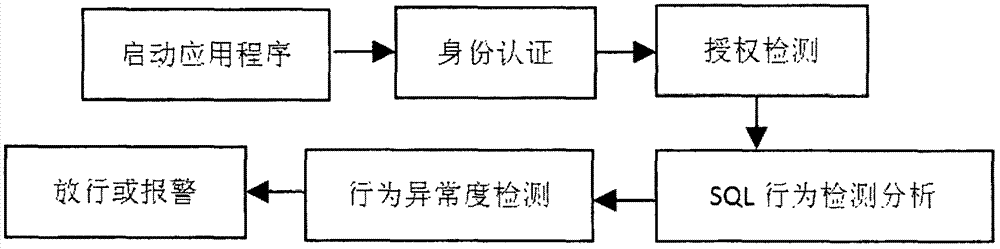
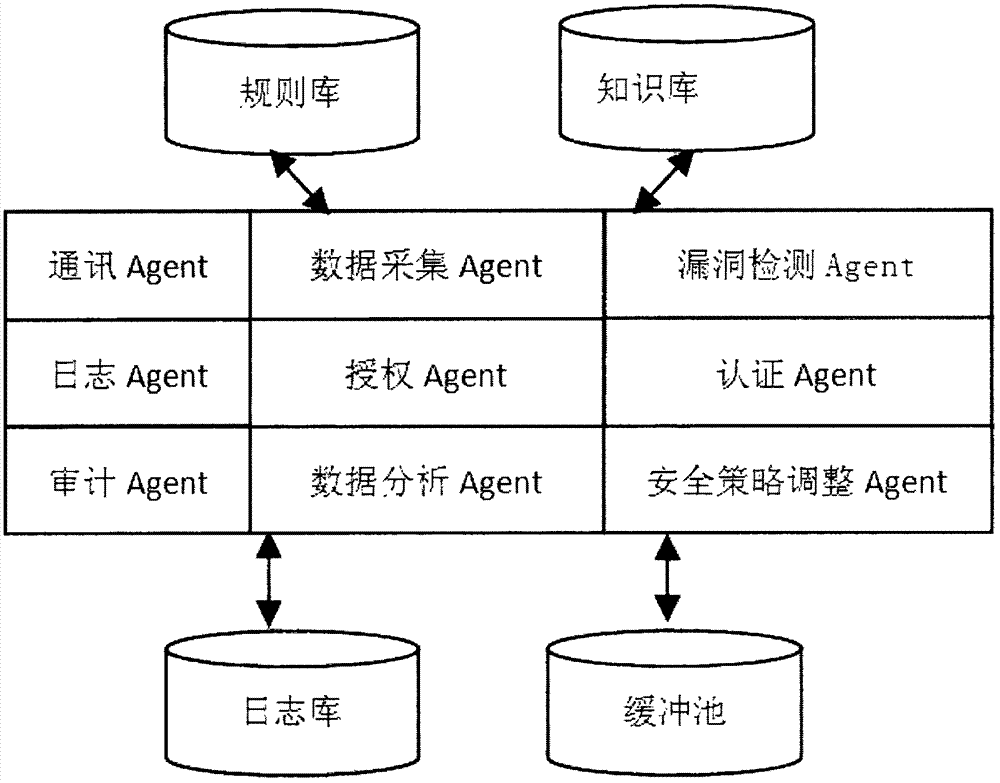
Internal threat real-time detection method based on agent
The invention discloses an internal threat real-time detection method based on an agent, belongs to the technical field of information system security and aims at ensuring the internal network data security through adoption of a detection assembly based on an agent technology. The internal threat real-time detection method based on the agents comprises the specific steps that a client agent program is installed, before a user accesses service data on a database server host, the agent program judges an identity and authority of the user, and only the user passing through authentication can access data; in a process of processing licensed service data by the user, the agent program monitors behaviors of the user in real time and records the behaviors of the user in a log file; and after the user finishes processing the licensed service data, the agent program calls a corresponding signing mechanism according to a demand of the user to sign a part processed the user, so the modification of the user for the service data has non-repudiation.
Owner:王振辉
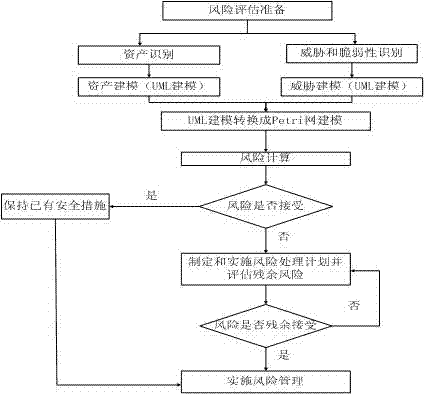
Security policy level joint modeling method based on consultative objective risk analysis system (CORAS)-Petri
InactiveCN103095712AImprove accuracyHigh precisionData switching networksUnified Modeling LanguageSecurity policy
The invention relates to the field of network information security risk assessment and discloses a security policy level joint modeling method based on a consultative objective risk analysis system (CORAS)-Petri. Aimed at a vulnerable spot and defect of a CORAS framework and improving of the CORAS framework, and based on unified modeling language modeling, a Petri net describing network or information system dynamic behavior is introduced, a risk assessment method based on an analytic hierarchy process (AHP) and fuzzy comprehensive evaluation risk assessment method is introduced in a risk computing method of the CORAS framework to compute the risk, and the security policy level joint modeling method can not only reduce working amount of estimation and improves estimation efficiency, but also can refer to previous estimation conclusion, strengthens accuracy and effectiveness of estimation, and therefore improves acquaintance of information system security risk. People can take effectively security protection measures to ensure security of an information system.
Owner:WUXI NANLIGONG TECH DEV
Method of situation awareness technology for smart city oriented cross-city security service platform
The invention discloses a method of a situation awareness technology for a smart city oriented cross-city security service platform. A situation awareness system of the security service platform of the smart city comprises a security situation analysis database, a security threat active discovery and detection subsystem, a network security incident correlation analysis and early warning subsystem, a network security index calculation subsystem and a network security situation display subsystem. Security threat detection, condition monitoring, security situation awareness, trend prediction and other security services are provided. The security situation awareness system disclosed by the invention supports a nationwide cross-city platform application mode; the worry of a city manager and citizens about information system security is solved, information security is guaranteed, and information leakage is prevented; the potential safety hazard generated by inconsistent information security protection mechanism levels of various systems is reduced; The fund contradiction of security guarantee system construction is relieved, and the reconstruction and the resource waste caused by the fact that each city establishes an own information security guarantee system are avoided.
Owner:DIGITAL CHINA INFORMATION SYST
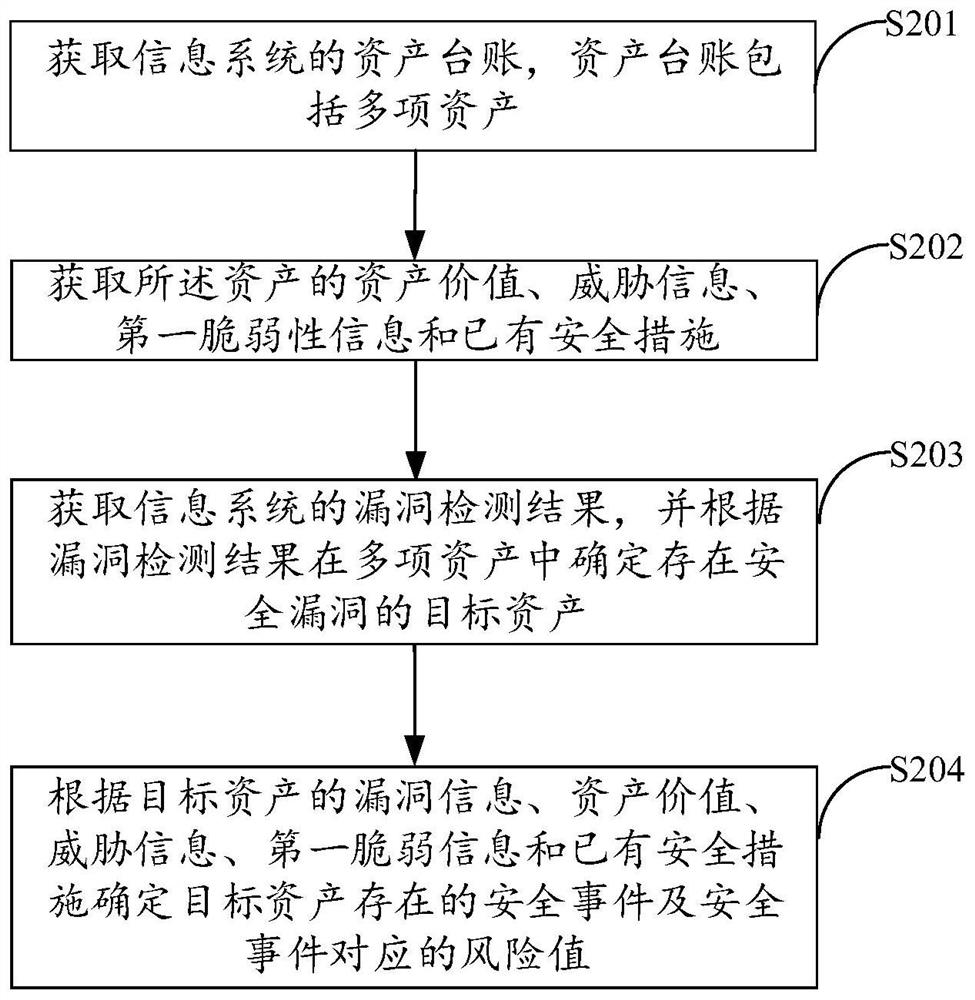
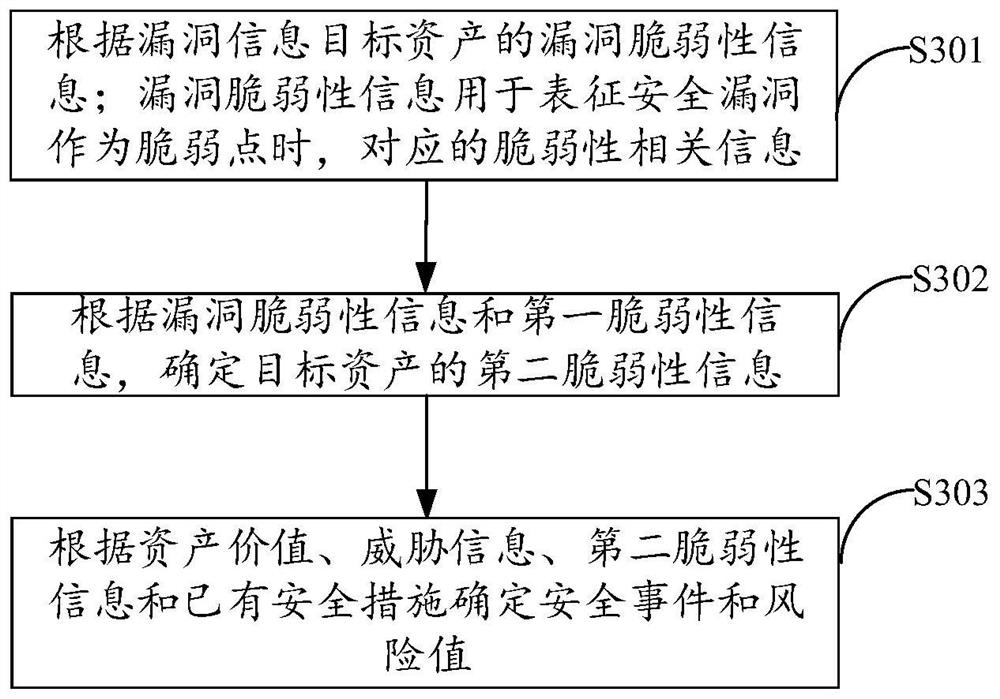
Information system security risk assessment method and device, equipment, and storage medium
PendingCN112508435AEmbody vulnerabilityPlatform integrity maintainanceResourcesSecurity MeasureInformation systems security
The invention is applicable to the technical field of computers, and provides an information system security risk assessment method and device, equipment and a storage medium. The information system security risk assessment method comprises the steps of obtaining an asset standing book of an information system, the asset standing book comprising multiple assets; obtaining an asset value, threat information, first vulnerability information and existing security measures of the asset; obtaining a vulnerability detection result of the information system, and determining a target asset with a security vulnerability in the plurality of assets according to the vulnerability detection result; and determining a security event existing in the target asset and a risk value corresponding to the security event according to the vulnerability information of the target asset, the asset value, the threat information, the first vulnerability information and the existing security measures. The method provided by the invention is high in safety risk assessment accuracy.
Owner:国家工业信息安全发展研究中心
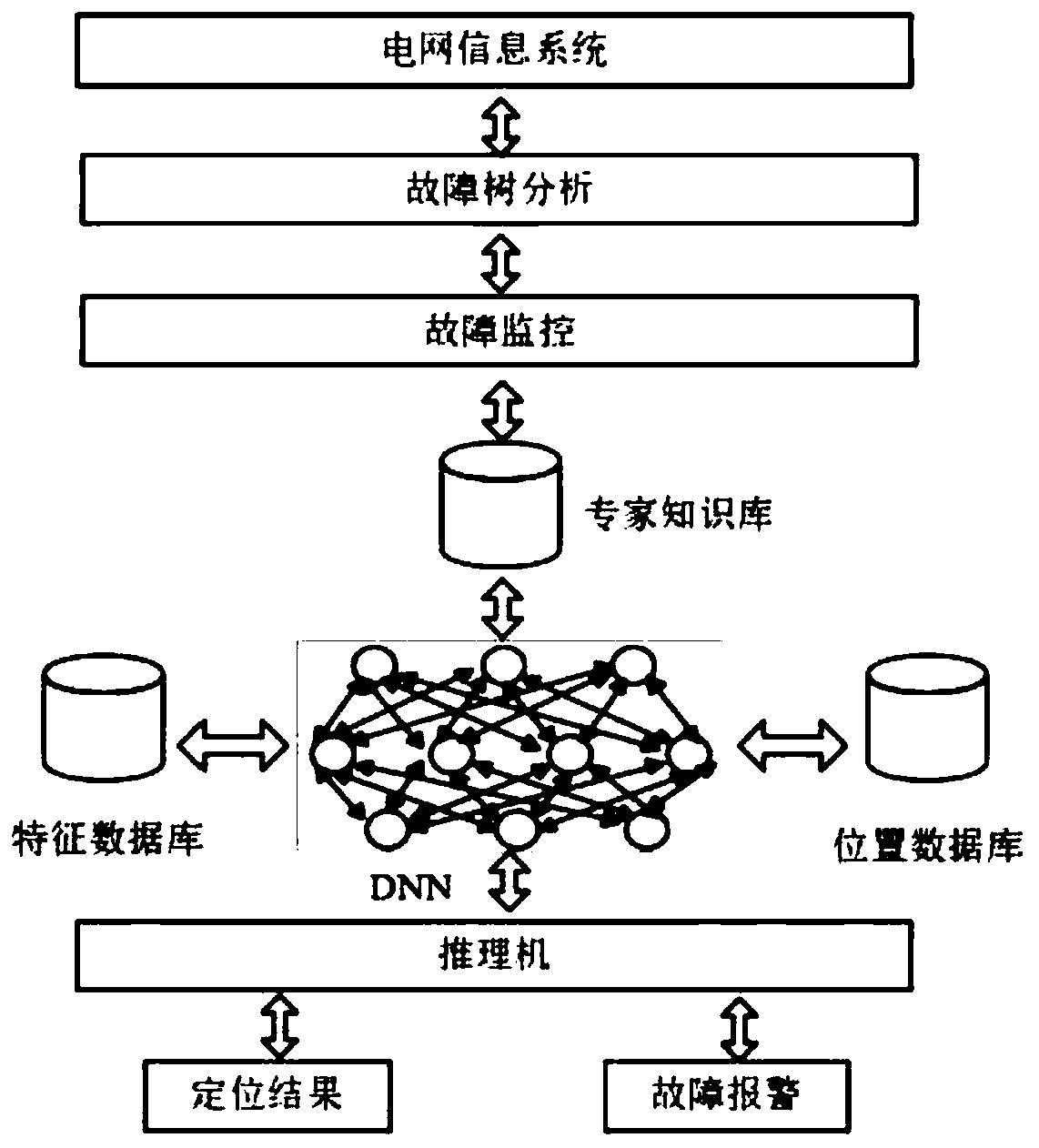
A power grid information system fault positioning system and method based on a bidirectional deep neural network
ActiveCN109726200ASolve positioningAchieve positioningCharacter and pattern recognitionNeural architecturesPower gridSelf processing
The invention discloses a power grid information system fault positioning system and method based on a bidirectional deep neural network. The power grid information system fault positioning system comprises a fault monitoring module, an inference machine, a database and a deep learning module. The method includes; Performing deep neural network forward and reverse training on a fault tree analysisresult; and obtaining a corresponding relation between the fault characteristics and the fault positions, storing the corresponding relation in an expert knowledge base, carrying out power grid information system fault monitoring, writing the fault characteristics obtained according to monitoring data into a characteristic database, and performing reasoning to obtain a fault positioning result according to the expert knowledge base and the fault characteristics. The problem that power grid information system fault positioning is difficult can be effectively solved; The problems of low positioning speed and inaccurate positioning are solved, so that the system can give an alarm at the first time when a fault occurs, intelligent fault positioning and intelligent processing functions of theinformation system can be realized in combination with the fault self-processing system, the operation and maintenance efficiency of the power grid information system can be further improved, and safeand stable operation of the information system is guaranteed.
Owner:国网甘肃省电力公司信息通信公司 +2
Information system security risk assessment method and device
ActiveCN103996006ASolve the core problem of risk quantificationHigh precisionPlatform integrity maintainanceRisk quantificationMulti dimensional
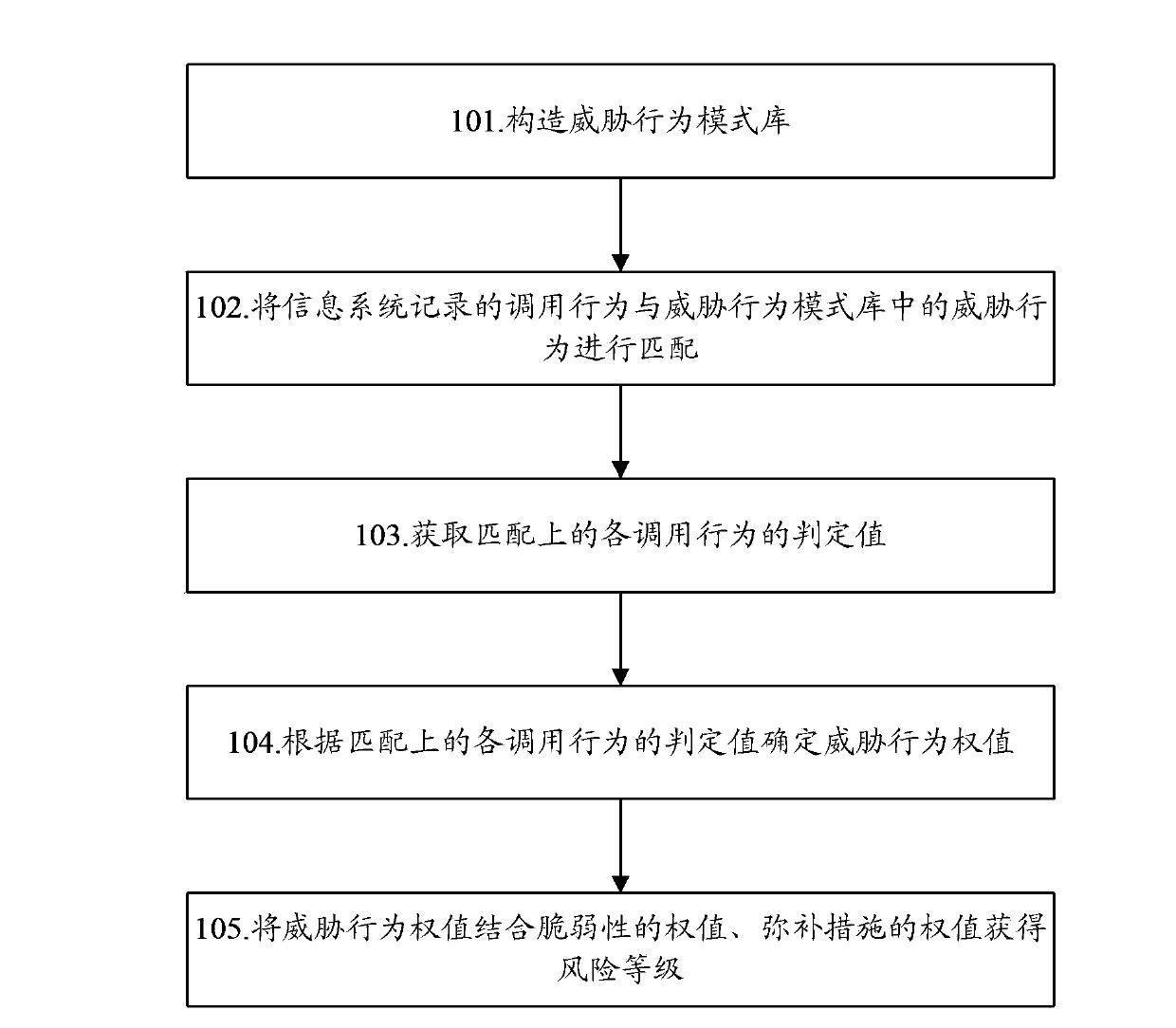
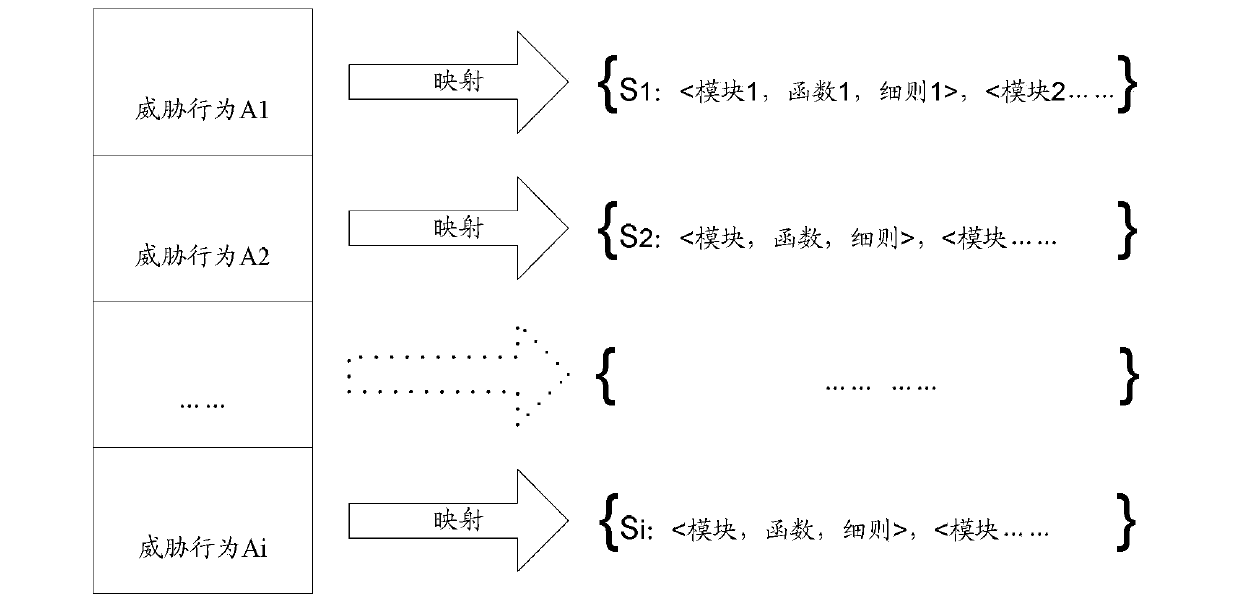
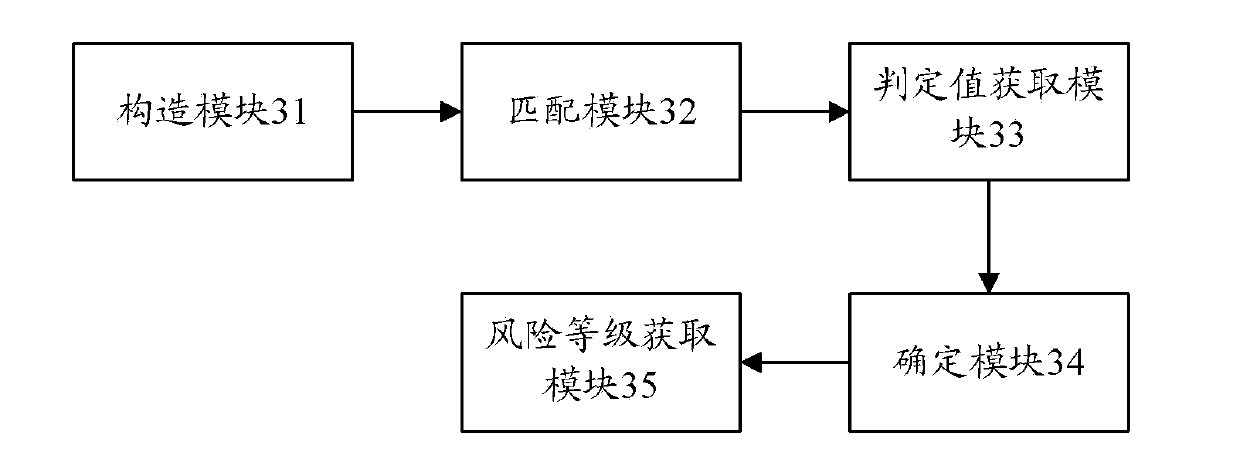
The invention discloses an information system security risk assessment method. The method includes the steps of constructing a threatening behavior model bank, matching calling behaviors recorded in an information system with threatening behaviors in the threatening behavior model bank to obtain decision values of the matched calling behaviors, determining weighted values of the threatening behaviors according to the decision values of the matched calling behaviors, and enabling the weighted values of the threatening behaviors to be combined with a vulnerability weighted value and a remedial measure weighted value to obtain a risk grade. The invention further discloses an information system security risk assessment device. Through the scheme of the information system security risk assessment method and device, security risks of the information system can be measured in multi-dimensional mode, the defects of existing risk evaluation quantification are greatly made up for, the accuracy and credibility of threat evaluation are improved, and the core problem of risk quantification of the information system can be solved; consequently, users can conveniently and objectively know the condition of running risks of the information system, and the risks of the information system can be perceived.
Owner:SHANXI CHINA MOBILE COMM CORP
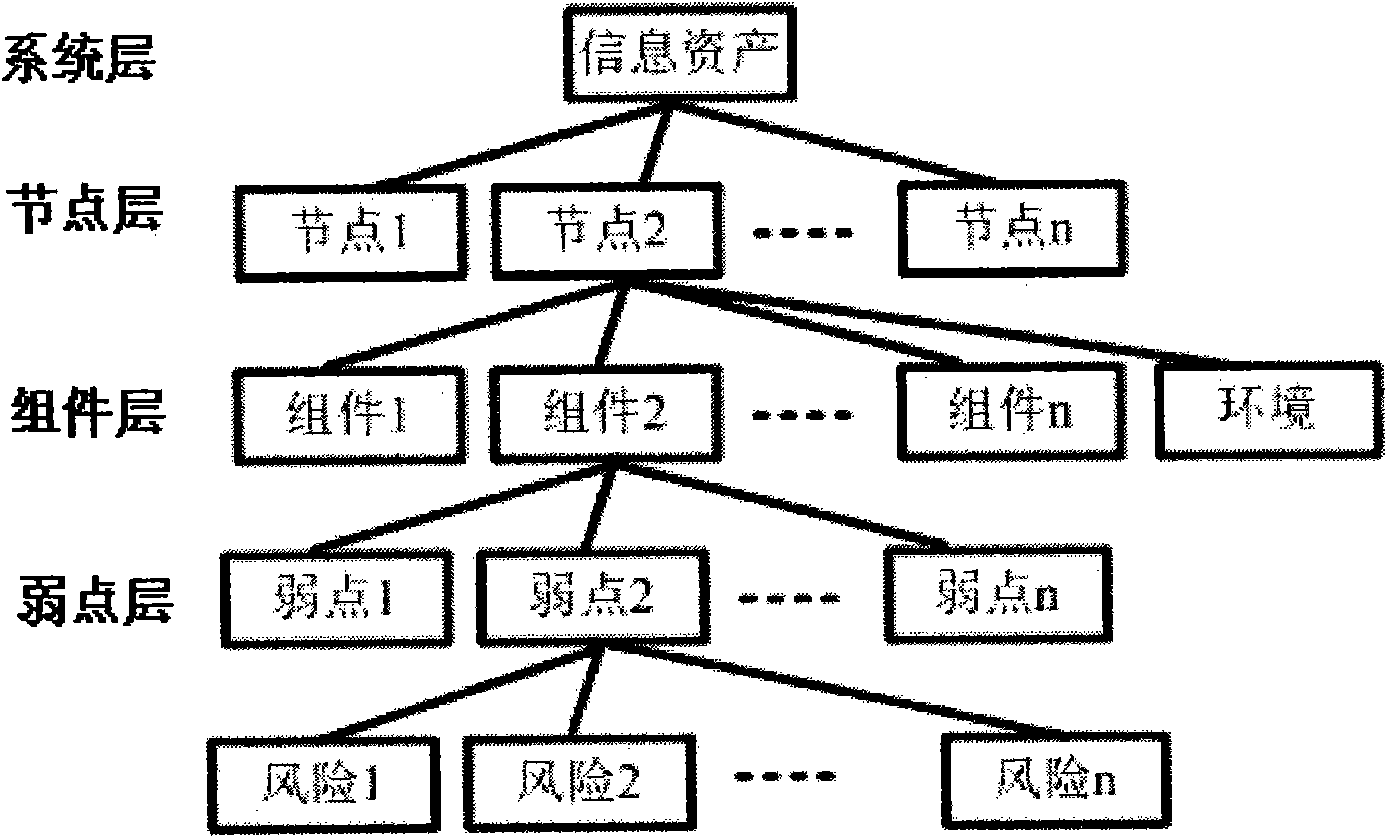
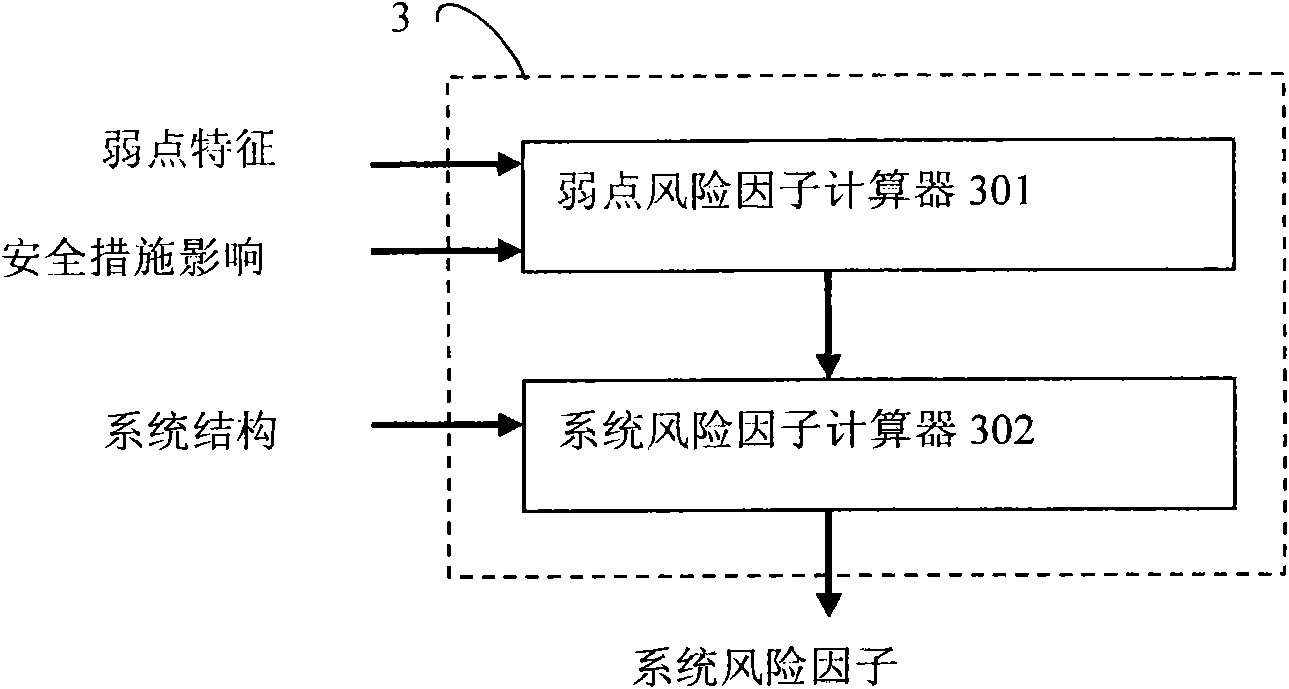
System and method for evaluating security risk based on asset weak point analysis
InactiveCN101620653AOvercome deficienciesTo achieve the effect of risk assessmentPlatform integrity maintainanceTransmissionTotal riskInformation systems security
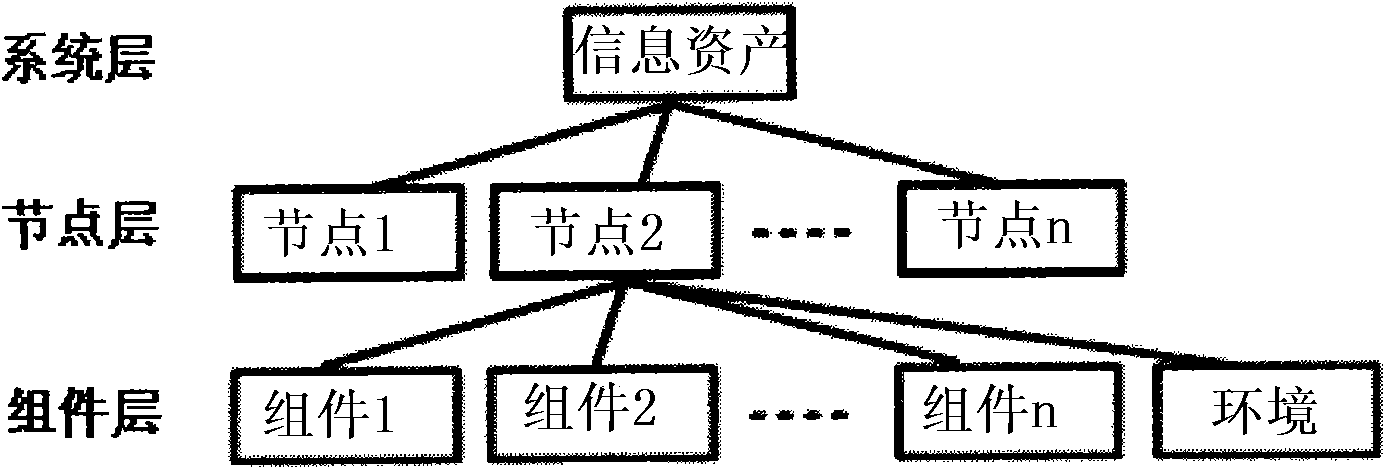
The invention discloses a system and a method for evaluating security risk based on asset weak point analysis. The system comprises two subsystems, namely a weak point risk counter and a system risk counter. The method comprises the following steps: carrying out hierarchical partition for computer security system assets in terms of function; calculating a weak point risk factor of each component according to a partitioned hierarchical model; and calculating the total risks of the whole security system according to the weak point risk factor of each component. Based on an asset hierarchical structure, the system and the method use the weak point risk of the component of the asset hierarchical structure to evaluate and calculate the risks of the system so as to overcome the defect of the prior risk evaluation algorithm and effectively realize reasonable evaluation of the security risk of the information system.
Owner:BEIJING VENUS INFORMATION TECH +1
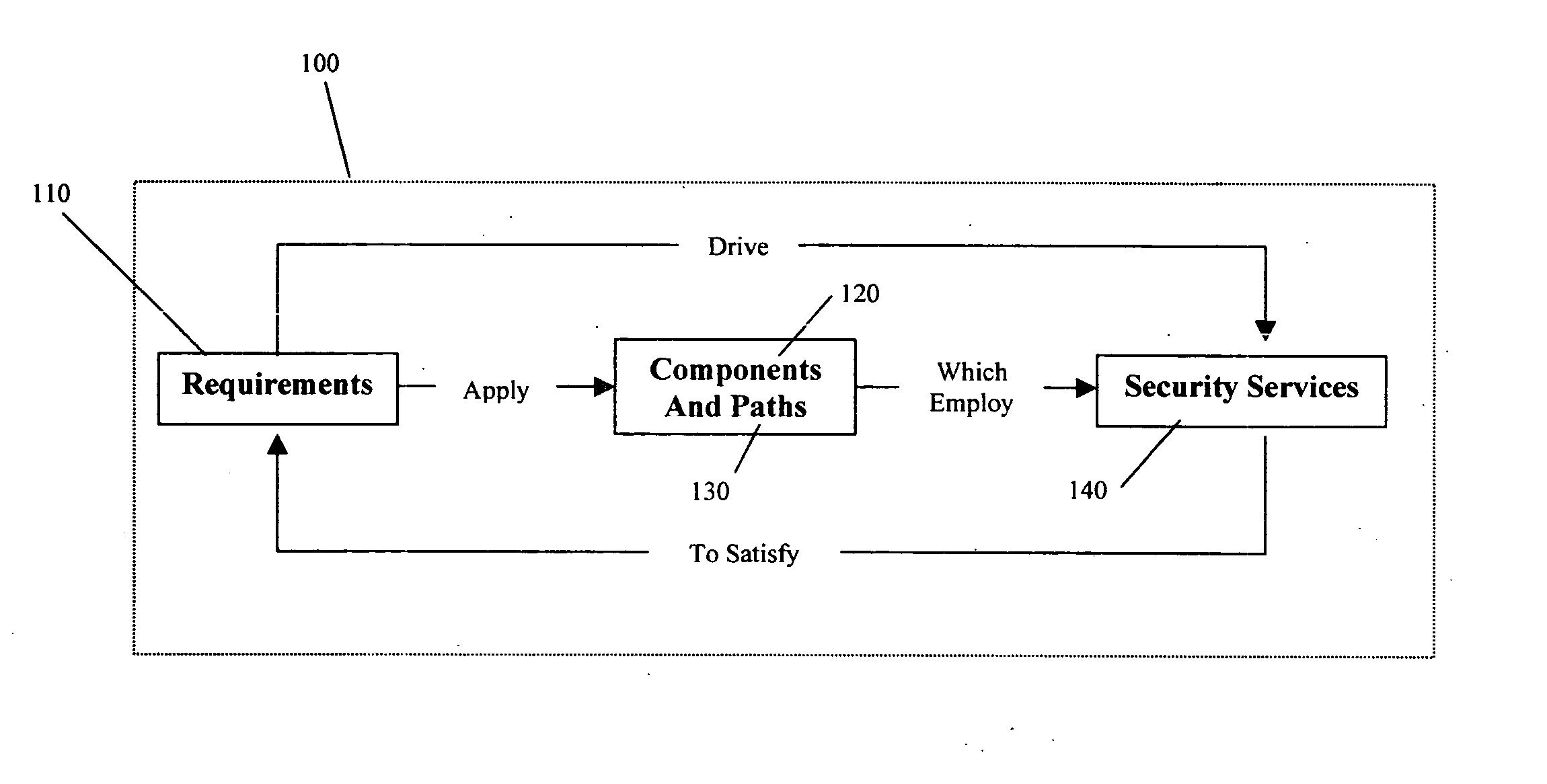
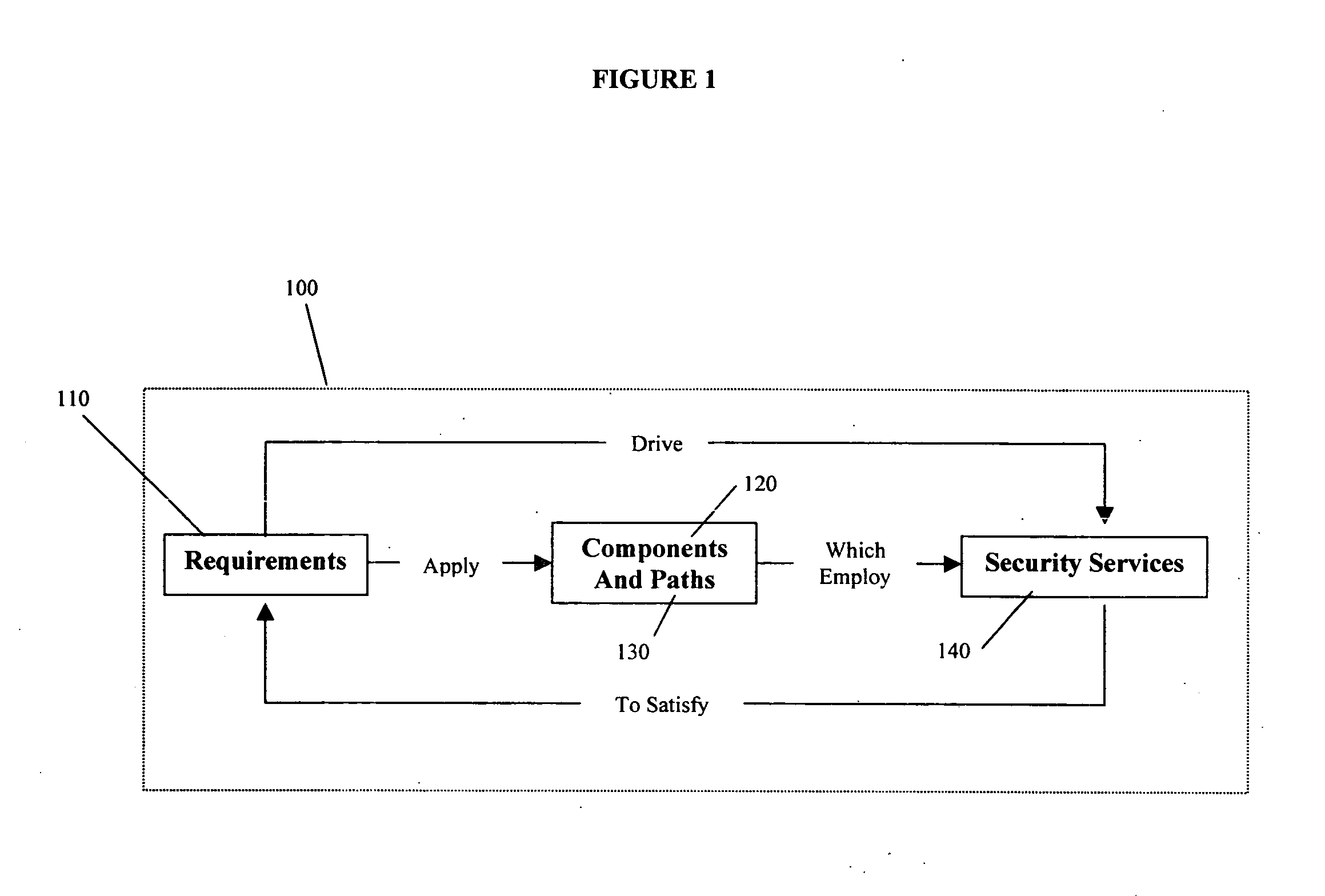
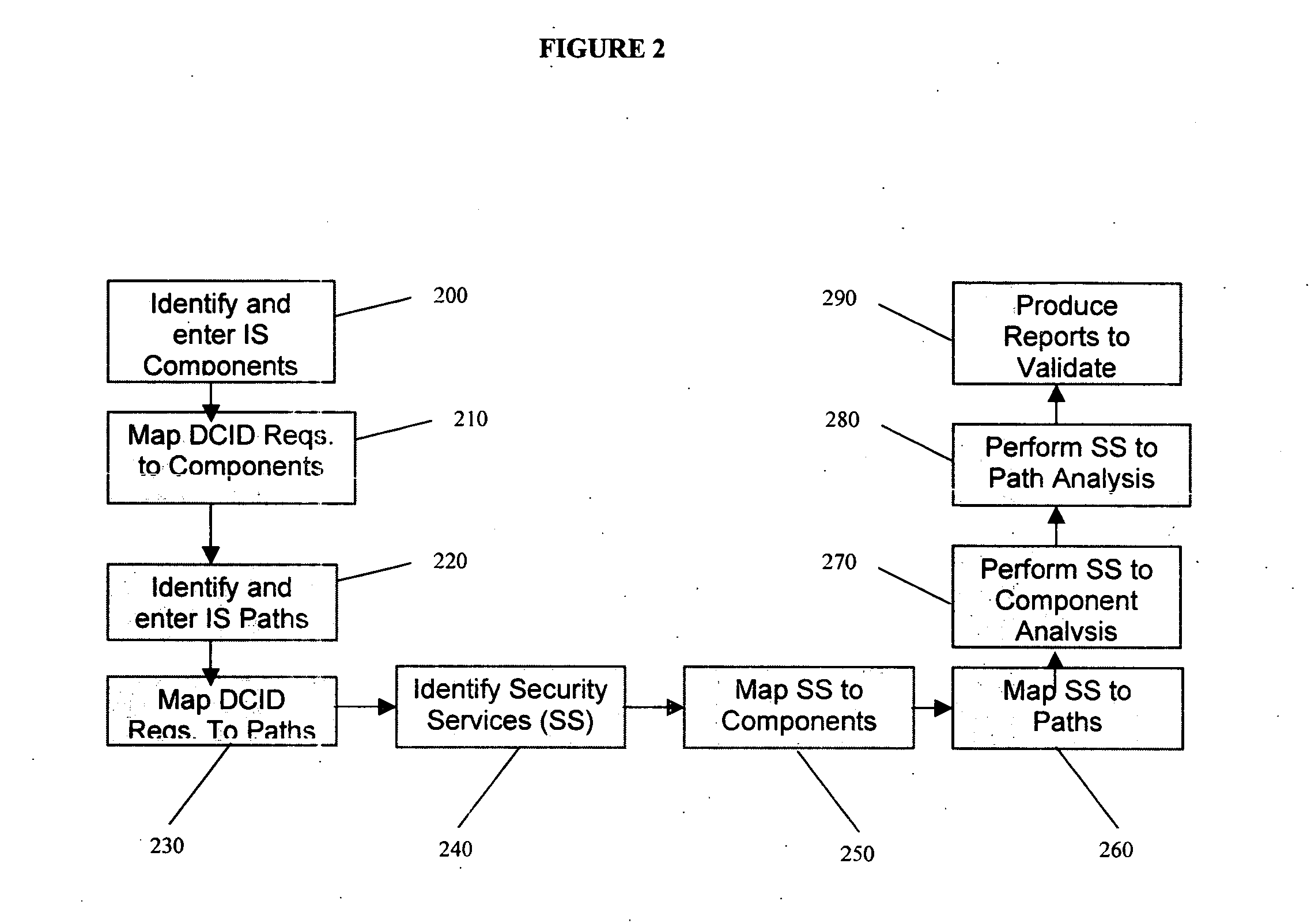
Method, system, and medium for the analysis of information system security
InactiveUS20060107313A1Digital data processing detailsUser identity/authority verificationSecurity analysisInformation systems security
A method, system, and medium for performing a security analysis of a system, which is comprised of components and paths wherein a user identifies the components and paths of a system, associates a set of predetermined requirements to the components and paths of a system, and wherein the user selects security services to satisfy the requirements of the paths and components of the system. In at least some embodiments of the invention, the method comprises the publication of reports detailing the components, paths, requirements, and security services of a system as well as the rationale that a security service satisfies the requirements mapped to the components and paths of the system.
Owner:DOWLESS & ASSOCS
Systems and methods for encryption and provision of information security using platform services
ActiveUS10020936B1Enhanced interactionOptimizationKey distribution for secure communicationUser identity/authority verificationCiphertextOriginal data
Systems and methods for securing or encrypting data or other information arising from a user's interaction with software and / or hardware, resulting in transformation of original data into ciphertext. Generally, the ciphertext is generated using context-based keys that depend on the environment in which the original data originated and / or was accessed. The ciphertext can be stored in a user's storage device or in an enterprise database (e.g., at-rest encryption) or shared with other users (e.g., cryptographic communication). The system generally allows for secure federation across organizations, including mechanisms to ensure that the system itself and any other actor with pervasive access to the network cannot compromise the confidentially of the protected data.
Owner:IONIC SECURITY
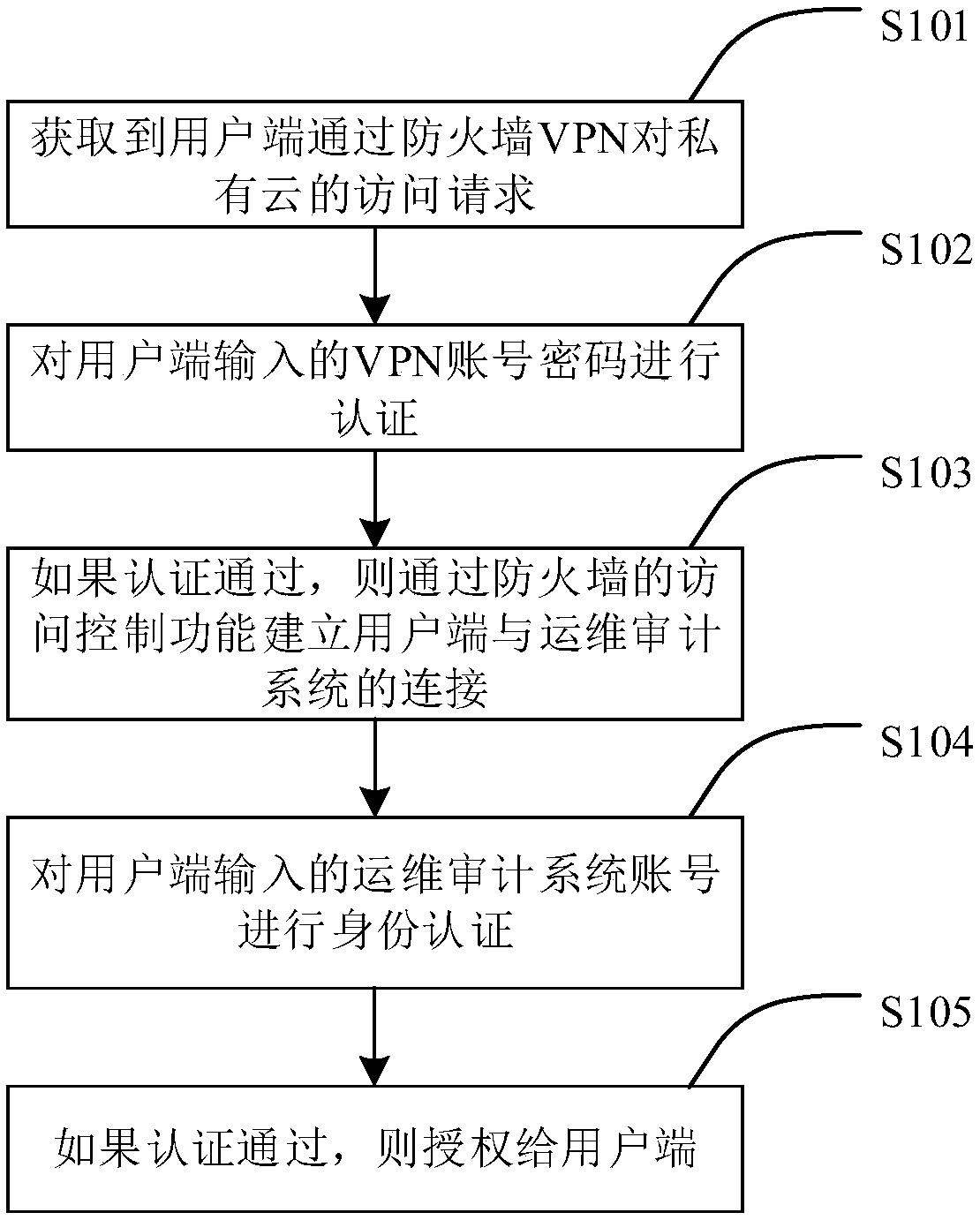
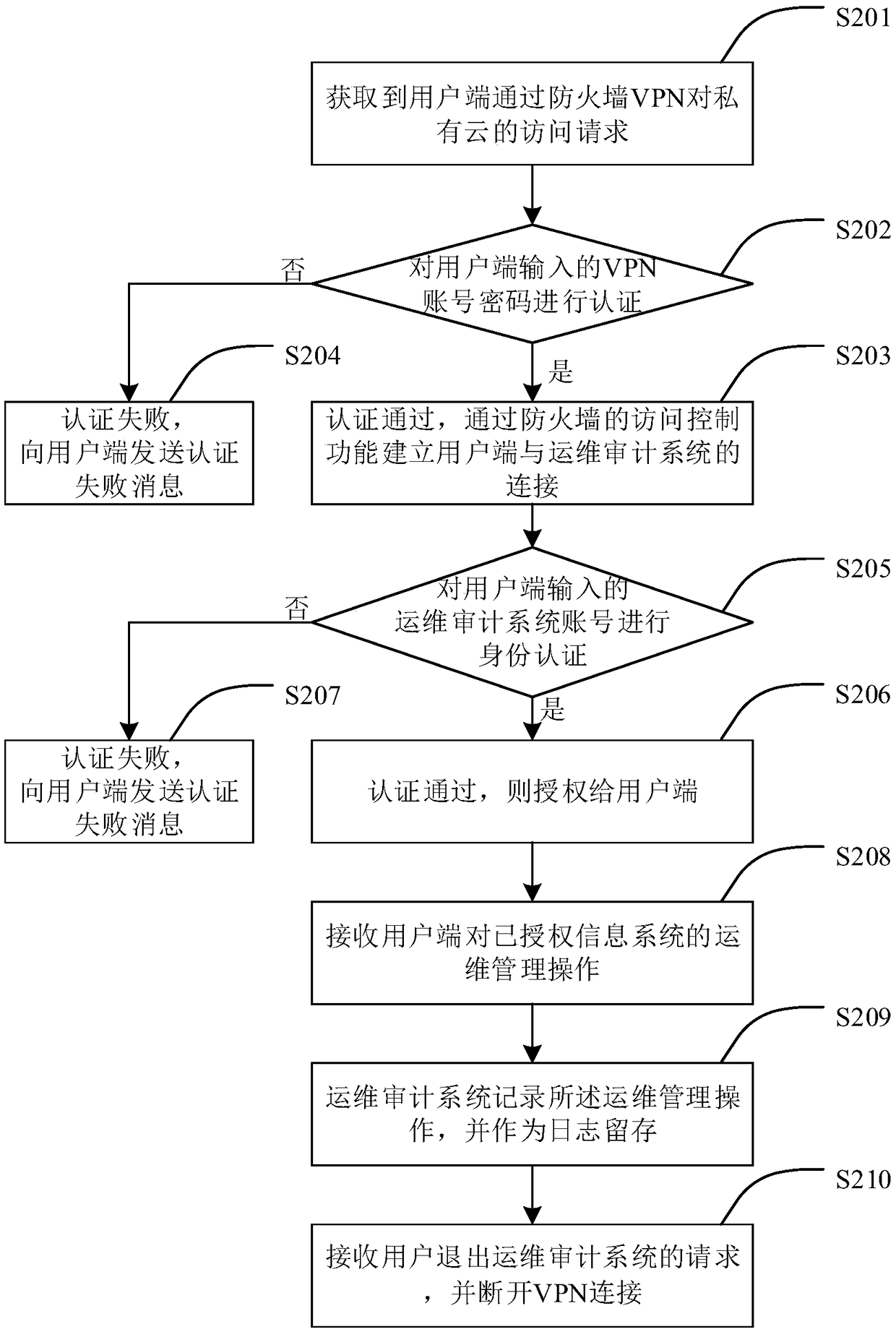
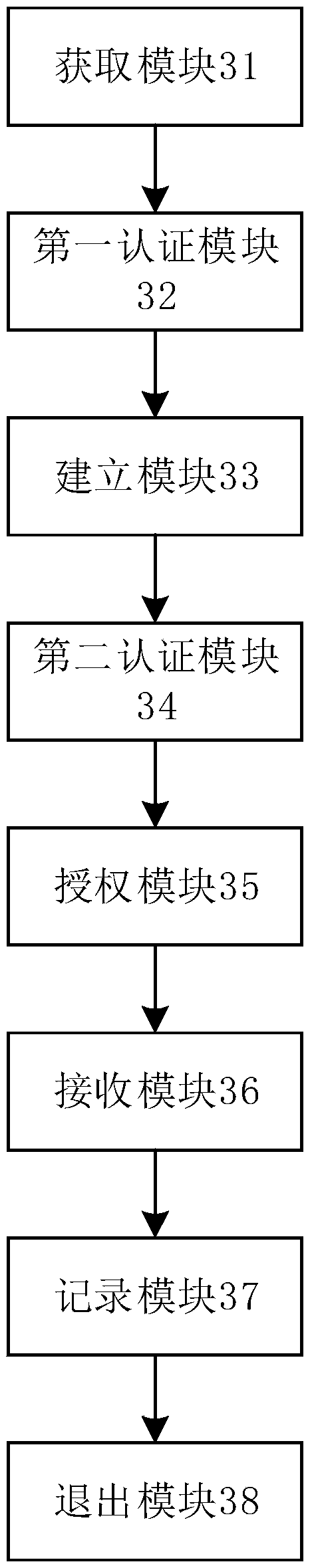
Security operation and maintenance method and apparatus of private cloud platform information system
InactiveCN108881299AReduce stepsAchieve authenticationNetworks interconnectionPasswordPrivate network
The invention, which belongs to the technical field of private cloud maintenance, provides a security operation and maintenance method and apparatus of a private cloud platform information system. Themethod comprises: an access request to a private cloud by a user terminal through a firewall virtual private network (VPN) is obtained; a VPN account password inputted by the user terminal is authenticated; if authentication is done successfully, connection between the user terminal and an operation and maintenance audit system is established by using the access control function of the firewall;identity authentication is carried out on an account number, inputted by the user terminal, of the operation and maintenance audit system; and if authentication is done successfully, the user terminalis authorized. Therefore, the authentication, authorization, and auditing functions of the operation and maintenance operation of the user are realized; and a safety problem that the information system is likely to be exposed in a public network is solved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
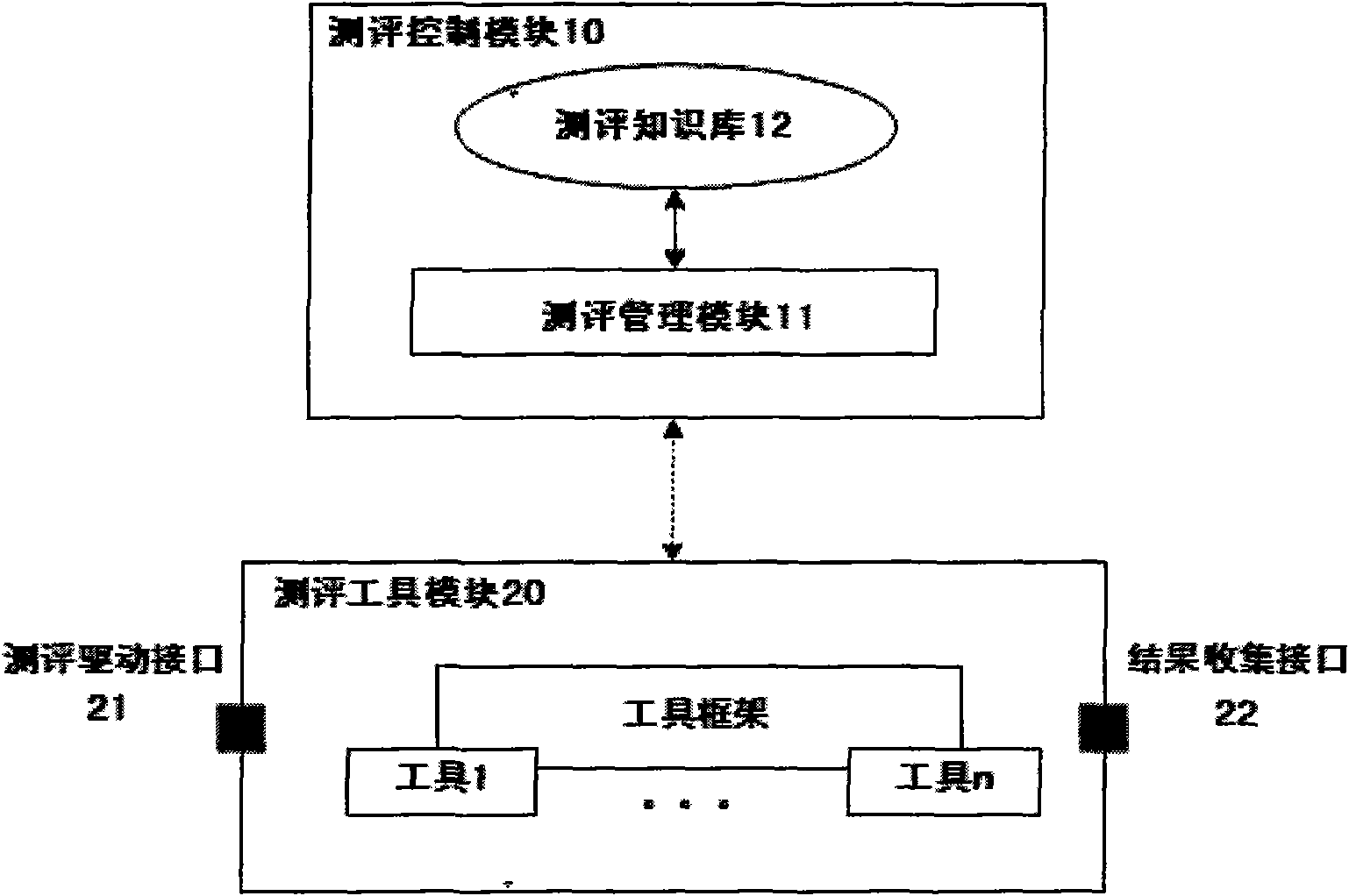
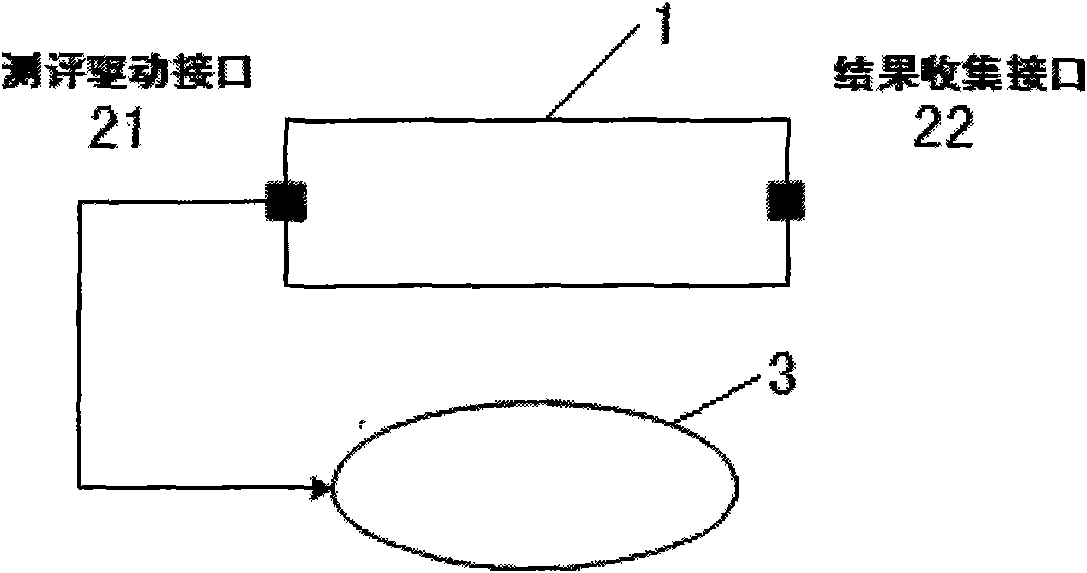
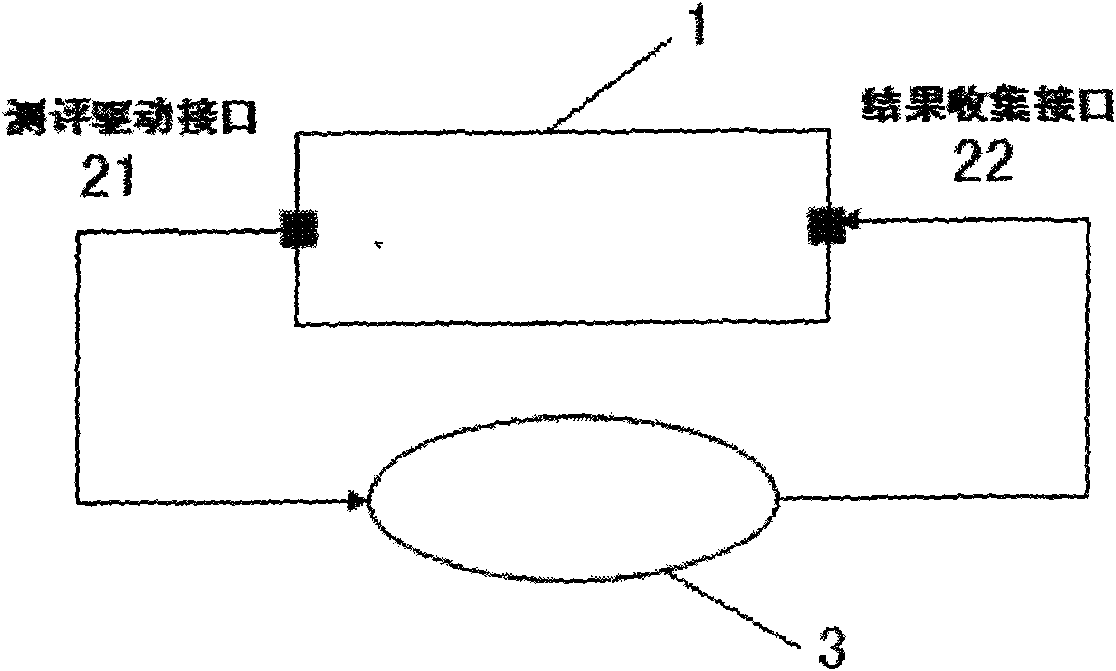
Closed loop type information system security class assessment tool
InactiveCN101562535AImprove automationImprove standardizationData switching networksInterface designClosed loop
The invention provides a closed loop type information system security class assessment tool, which is characterized by comprising an assessment control module and an assessment tool module; the assessment tool module is provided with an assessment driving interface and a result collecting interface, and is connected with an information system to be assessed through the assessment driving interface and the result collecting interface; and the assessment tool module adopts a double-interface design of the assessment driving interface and the result collecting interface, effectively overcomes the limitation in the aspect of result collection of the prior tool system, not only realizes a closed loop working mode, but also is compatible with a familiar single-link direct connection working mode to support class assessment for a complicated information system, promotes the automation and standardization of information system security class assessment, and achieves the aim of the invention.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
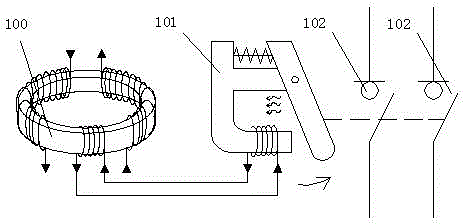
Intelligent self-checking method for residual current detection circuit based on signal injection mode
InactiveCN104678342AGuaranteed reliabilityEnsure monitorabilityElectrical measurementsComputer moduleInformation systems security
The invention belongs to the technical field of improvement of the reliability of a residual current protector, and in particular relates to a residual current detection circuit based on a signal injection mode and an intelligent self-checking method for the residual current detection circuit. The intelligent self-checking method comprises the following steps: adding a winding to a current transformer for detecting a residual circuit, and adding a self-checking circuit which is controlled through an MCU control module. The intelligent self-checking method has the advantages that 1 whether a current induction coil is damaged or not is detected; 2 the self-checking is relatively safe and reliable, and tripping operation or blackout is not needed in the self-checking of residual current; 3 the method is relatively safe; and 4 related standards and specifications of information system security levels can be met.
Owner:KAILI POWER SUPPLY BUREAU +1
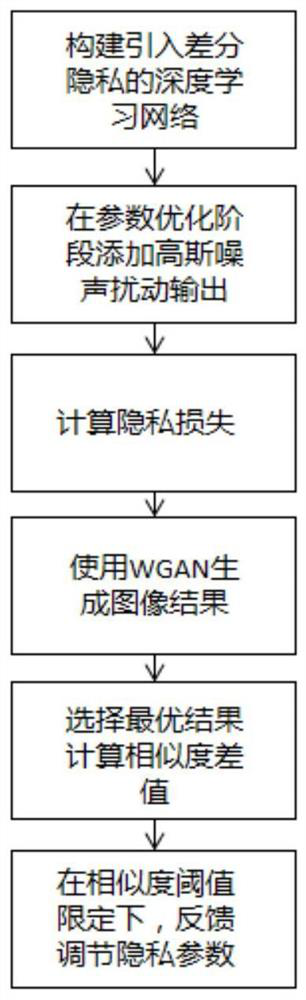
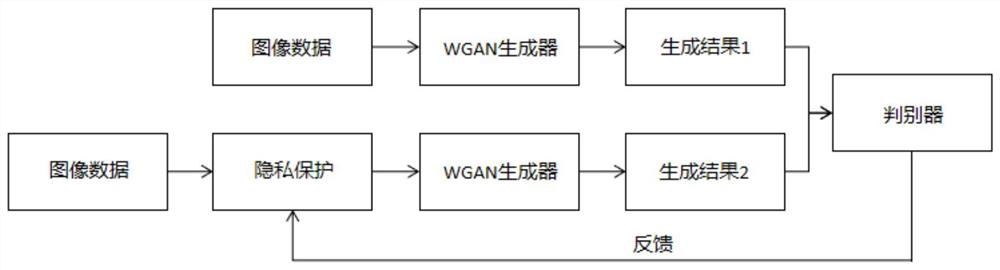
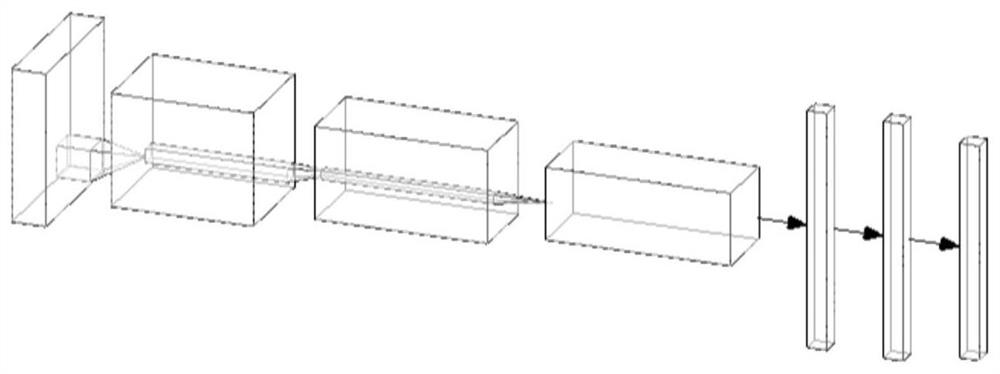
Deep learning differential privacy protection method
PendingCN111737743AControl privacy protection effectImprove usabilityCharacter and pattern recognitionDigital data protectionPrivacy protectionDifferential privacy
The invention discloses a deep learning differential privacy protection method, and belongs to the technical field of information system security. The invention provides a novel deep learning differential privacy protection model. A WGAN is adopted to generate an image result for the data subjected to model privacy protection processing; a result closest to a real image is selected from the generated images, the similarity between the generated result and the original image is compared, a difference value is calculated for threshold comparison, privacy parameters in the model gradient are fedback and adjusted under the similarity threshold limiting condition, and therefore a certain promotion effect is provided for application of differential privacy in the fields of deep learning and thelike.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY
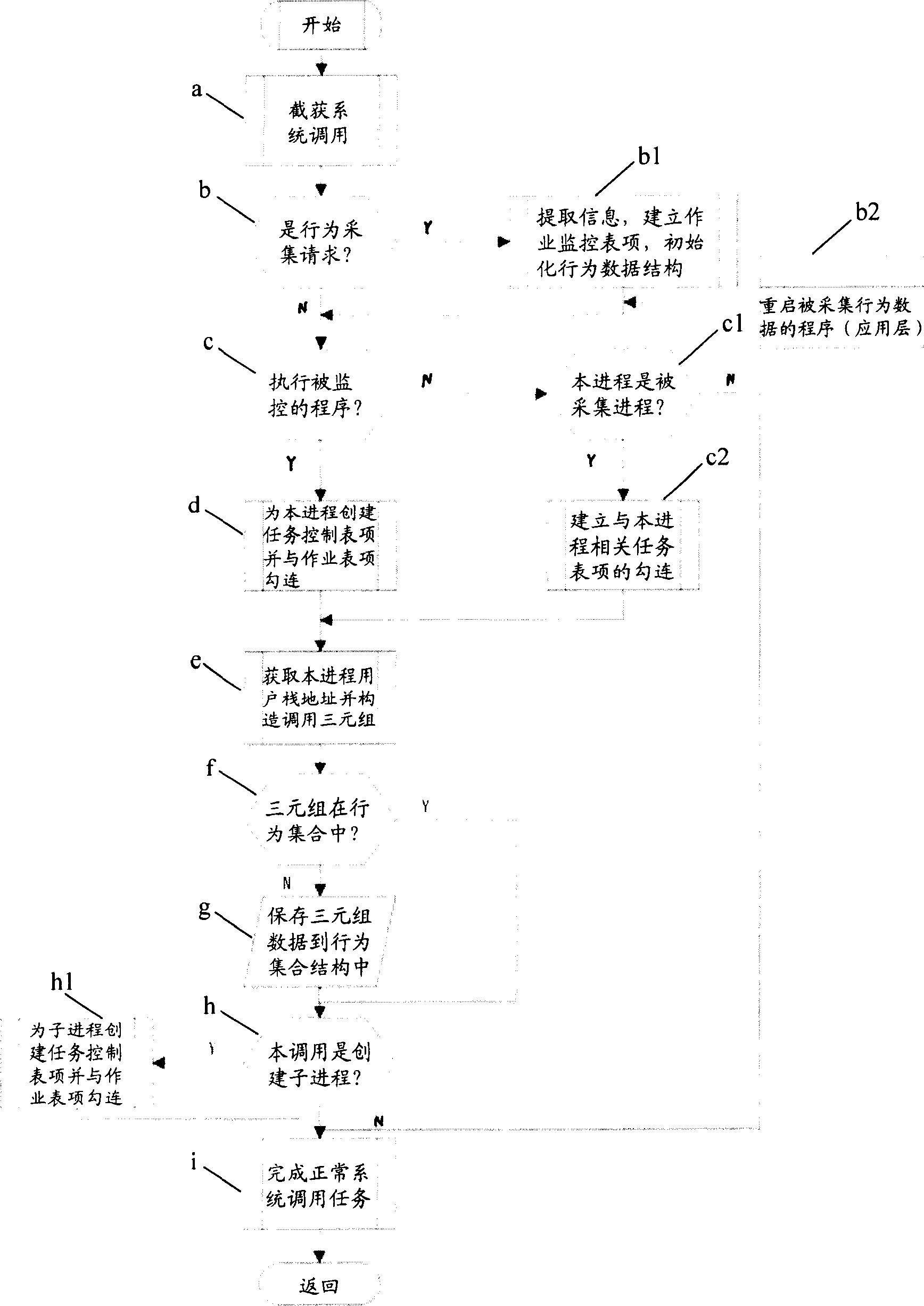
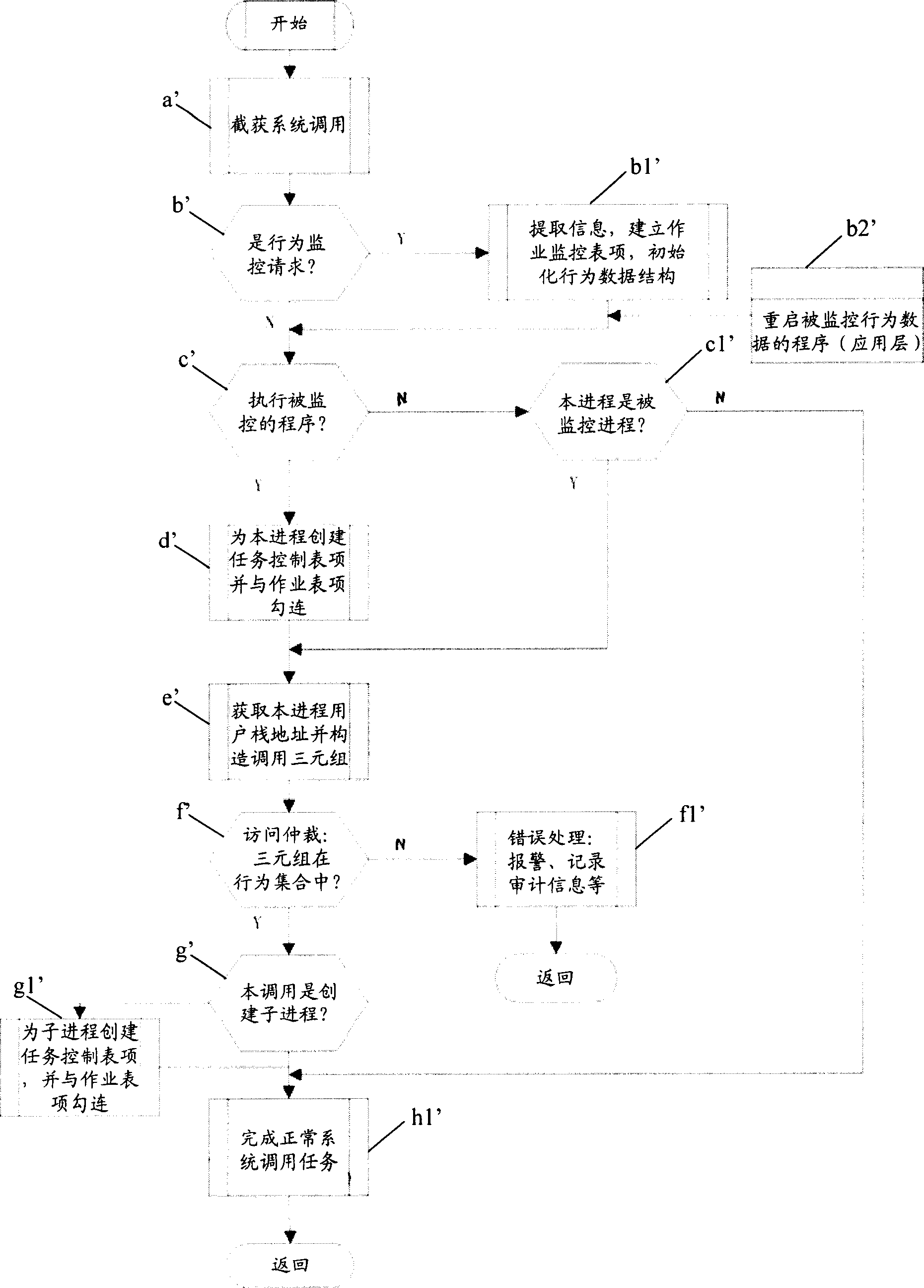
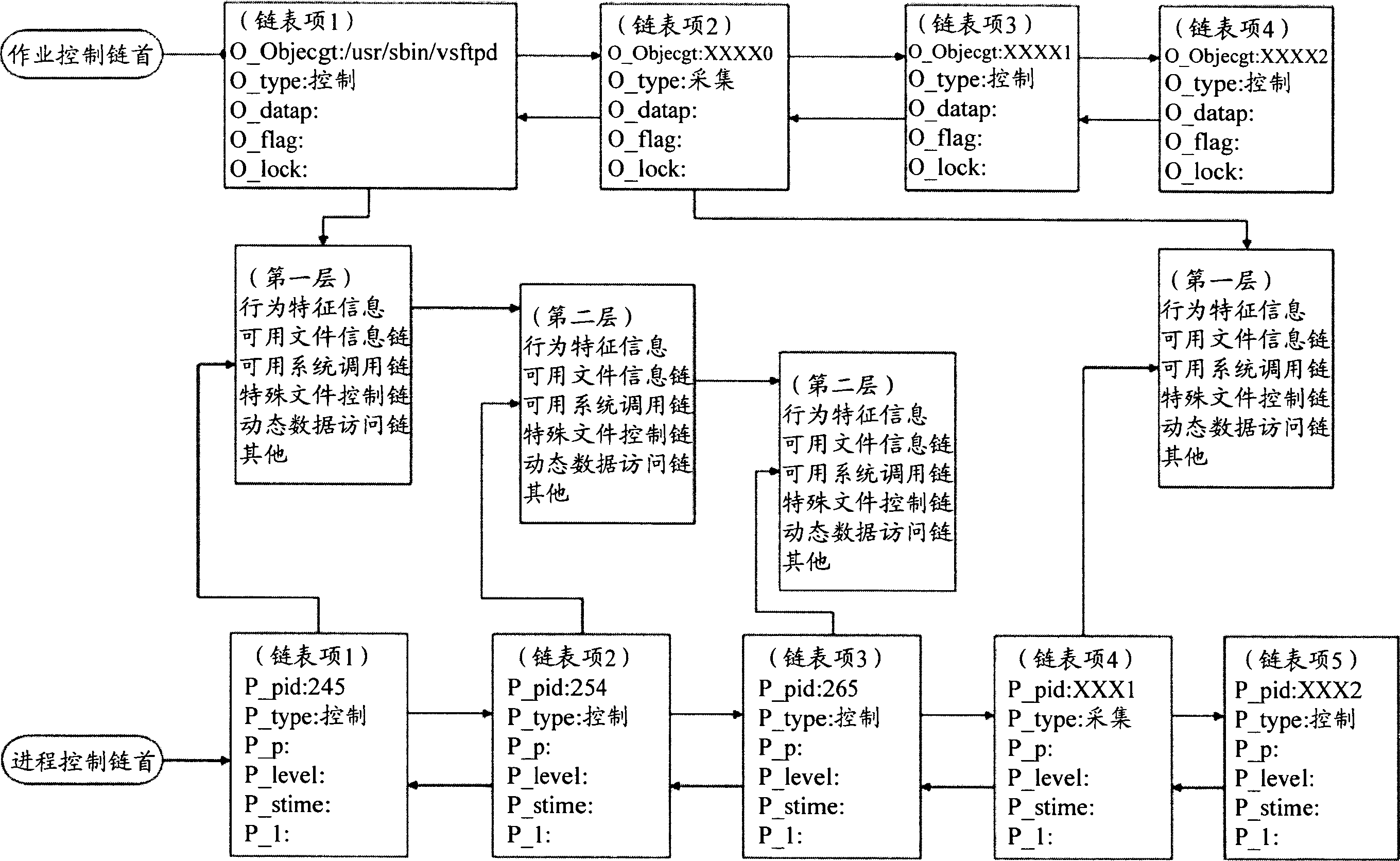
Software-action description, fetching and controlling method with virtual address space characteristic
ActiveCN1892615AEasy to detectEasy to controlSoftware testing/debuggingPlatform integrity maintainanceSerial patternVirtual space
Said invention discloses software behavioural abnormality detection and protecting means. It contains obtaining one software behaviour and address attribute and establishing characteristic of correspondence data integration; using said established characteristic data integration detecting and protection software abnormal behavior, wherein characteristic data integration having virtual space address attribute. Said invented method can restrict software behaviour track without error, capable of raising detecting accuracy, greatly raising identifying efficiency and convenient execution. It can independently use and conjunctively use with other data, for example short sequence, status attribute, and resource attribute. Said invention can realize real time detecting with controlling to application program behaviour, capable of being used in main unit information system safety protection and network information system invasion protection etc field.
Owner:上海浦东软件园信息技术股份有限公司
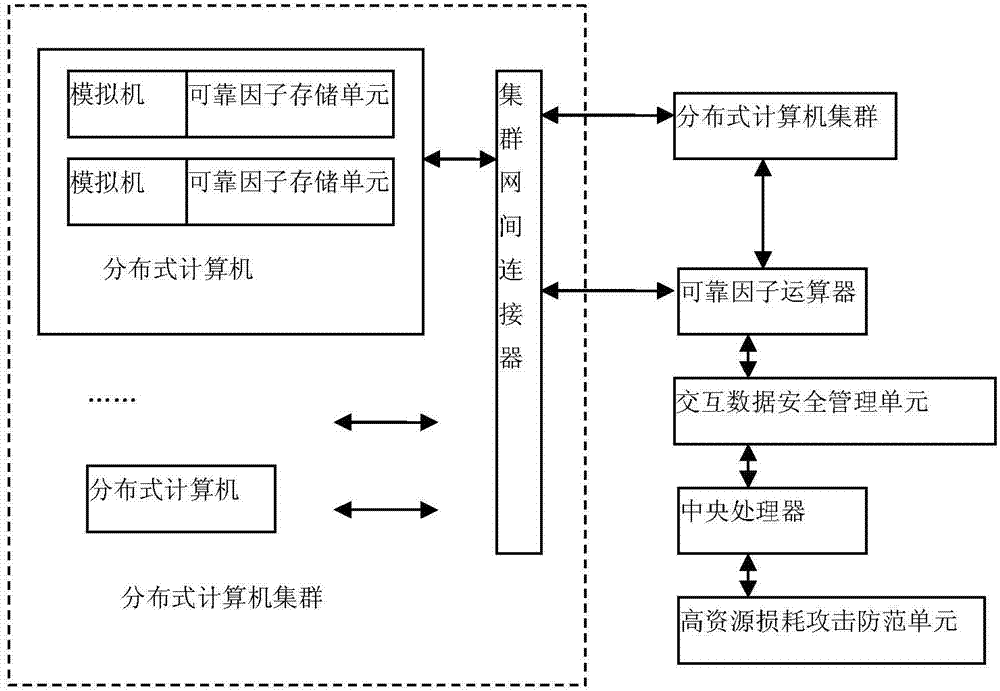
Safe monitoring and access control method of information system
ActiveCN104506552AImprove reliabilityImprove securityTransmissionSecure communicationComputer cluster
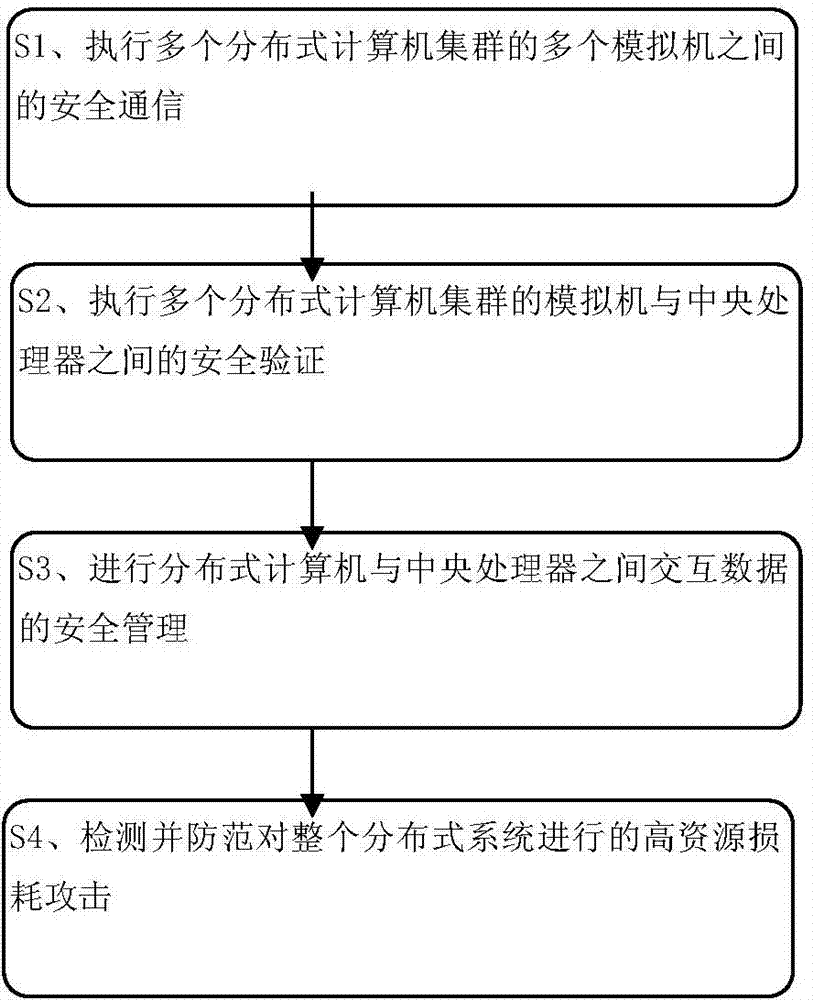
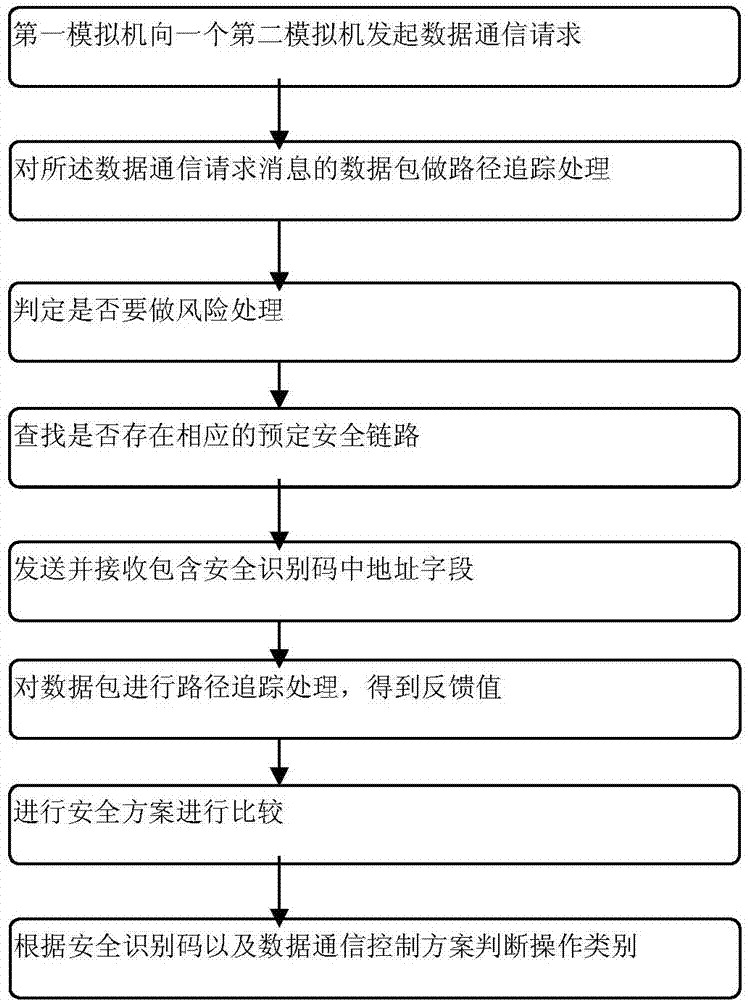
The invention provides a safe monitoring and access control method of an information system; the method comprises the steps: executing safe communication among a plurality of analog machines of a plurality of distributed computer clusters by using a cluster internetwork connector; executing safe verification between the analog machines of the plurality of distributed computer clusters and a central processing unit by using a reliable factor arithmetic unit; performing safety management of interactive data between the distributed computers and the central processing unit by using an interactive data safety management unit; and detecting and preventing high-resource loss attack to a whole distributed system by using a high-resource loss attack prevention unit. Therefore, the reliability and safety of the entire information can be improved greatly.
Owner:山东汉鑫科技股份有限公司
Information system security situation assessment method based on correction matrix-entropy weight membership cloud
ActiveCN110650040AImprove stabilityHigh feasibilityData switching networksEvaluation resultAlgorithm
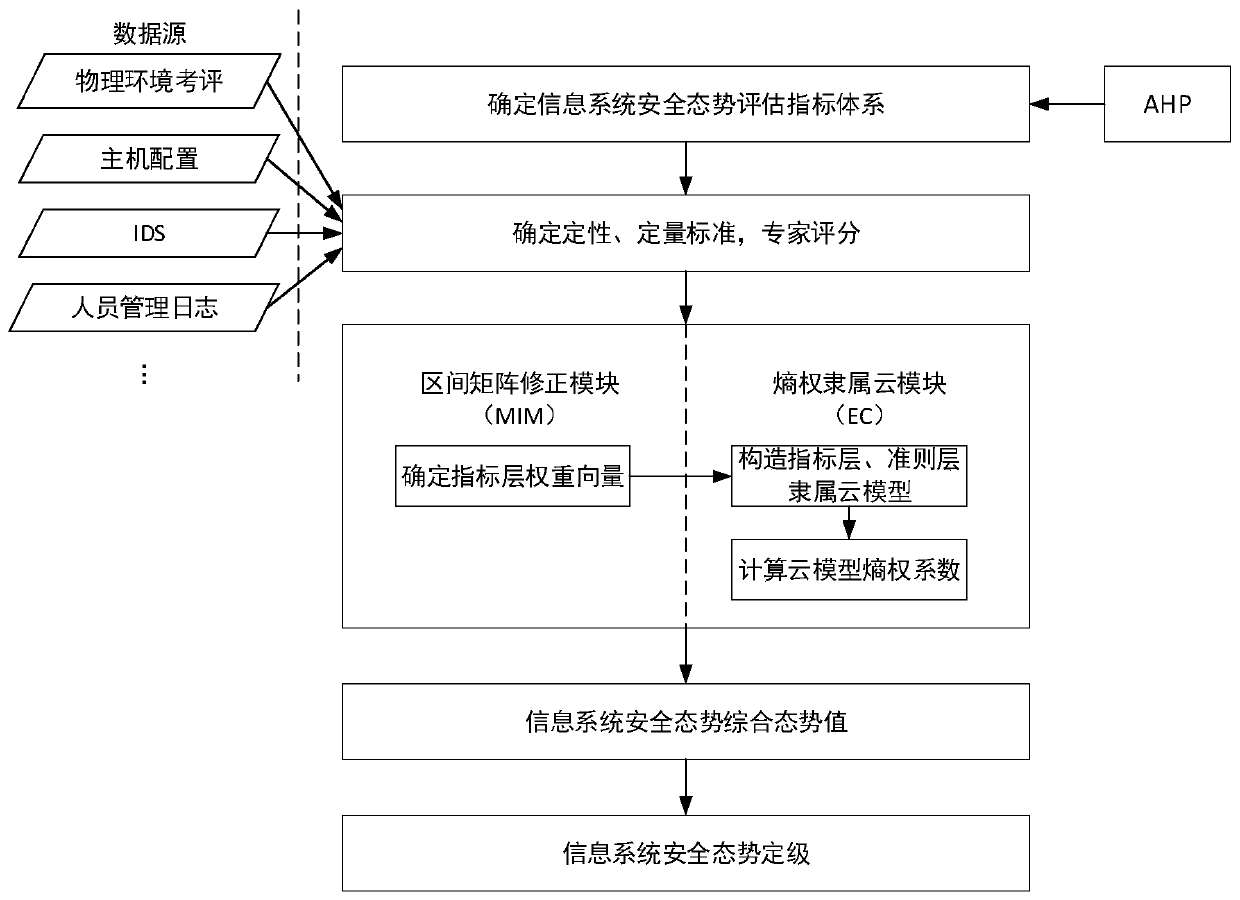
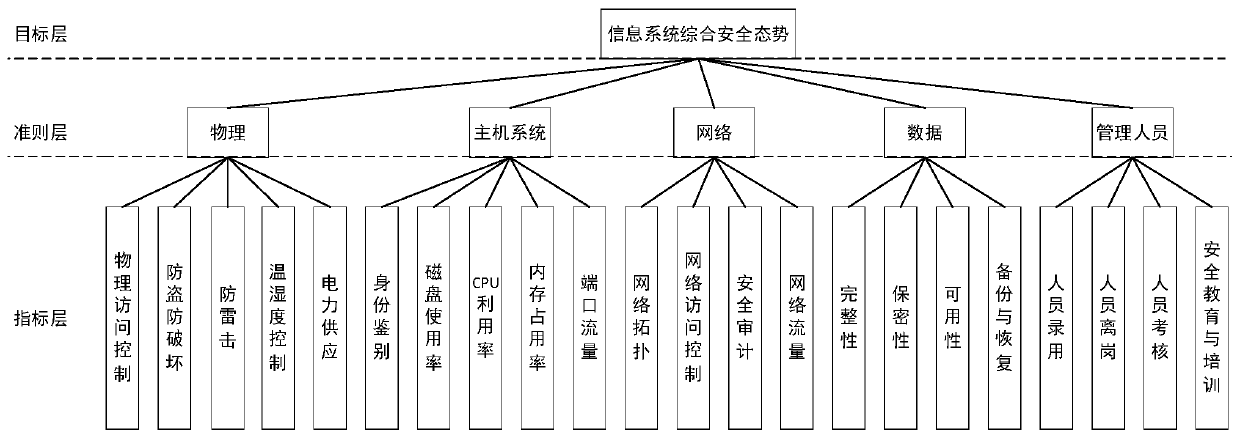
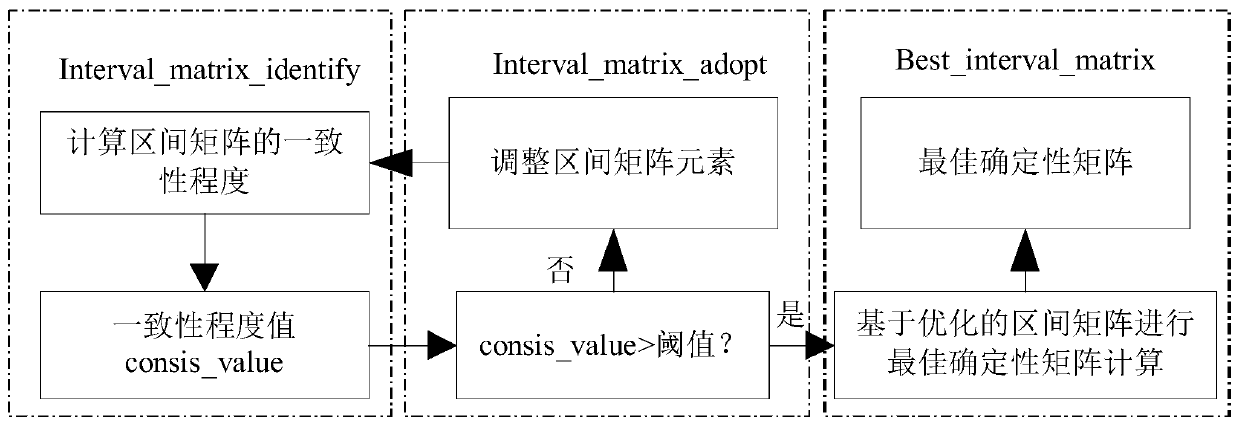
The invention discloses an information system security situation assessment method based on a correction matrix-entropy weight membership cloud. The information system security situation assessment method comprises the following steps: S1, establishing an evaluation index system; S2, standardizing the multi-source data; S3, determining an index weight vector; S4, quantifying and grading the security situation of the information system; and S5, grading the security situation of the information system. Compared with the prior art, according to the information system security situation assessmentmethod based on the correction matrix-entropy weight membership cloud provided by the invention, the optimal deterministic matrix can be found by correcting the interval judgment matrix on the premise of reserving subjective evaluation of experts, so that the weight vector of the index layer is determined, and the security situation is quantified and graded in combination with the entropy weightmembership cloud. Through comparative analysis with an evaluation result based on an entropy weight coefficient method and a traditional AHP method, it is shown that the information system security situation assessment method has good stability, feasibility and effectiveness, and enables the safety situation quantitative evaluation result to be more reasonable.
Owner:CIVIL AVIATION UNIV OF CHINA
Safety development middleware for electric power mobile polling terminal and safety control method
ActiveCN106789842AGuaranteed confidentialityIntegrity guaranteedUser identity/authority verificationOperational systemSafety control
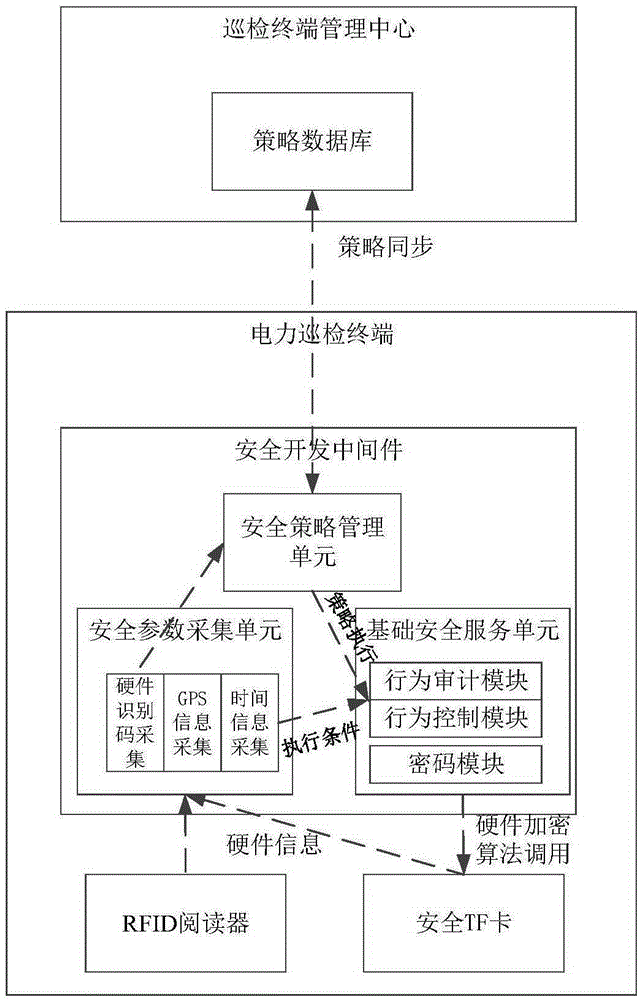
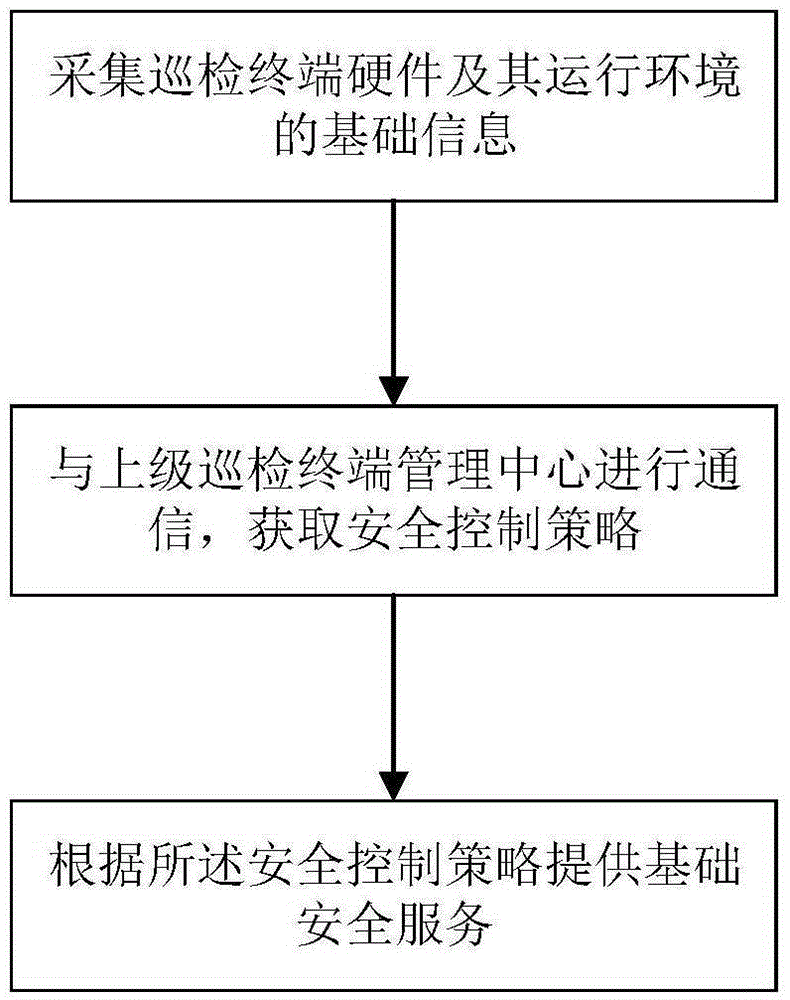
The present invention provides a safety development middleware for electric power mobile polling terminal and a safety control method. The middleware comprises a safety parameter collection unit, a safety strategic management unit and a basic safety service unit. The three units employ a standard TCP / IP protocol for communication; the safety parameter collection unit is configured to collect basic information of the polling terminal hardware and the operation environment thereof; the safety strategic management unit is configured to perform communication with a superior polling terminal management center to obtain a safety control strategy; and the basic safety service unit is configured to shield the distinction between the polling terminal hardware with different types and the distinction between different types of operation systems of the polling terminal to provide basic safety service. The safety development middleware for electric power mobile polling terminal and the safety control method provide a uniform safety development interface for the electric power polling terminal to realize the remote safety control of the electric power polling device and allow the development of the electric power polling business not to reduce the original information system safety protection intensity.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +1
Method of automatically judging workflow transfer node
In allusion to the disadvantages that the conventional workflow node transfer efficiency is low, the expansibility is not high, etc., the present invention introduces a method of automatically judging a workflow transfer node. According to the method, the system administrators can change the processing rules of a business by setting the processing flow and approval condition of the business, and arrange different persons to approve and operate, so that the information security of a company can be guaranteed, and the general manager can grasp the operation and development states of an enterprise overall and also can empower the subordinates, so that the subordinates can decide freely within a certain range, the master consciousness of staff is brought into play fully, and the company identification sense and sense of belonging of the staff are increased.
Owner:镇江雅迅软件有限责任公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com