Security policy level joint modeling method based on consultative objective risk analysis system (CORAS)-Petri
A modeling method and security policy technology, applied in the field of network information security risk assessment, to achieve the effect of improving accuracy and precision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
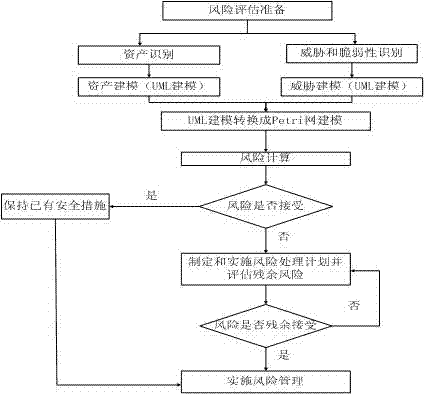
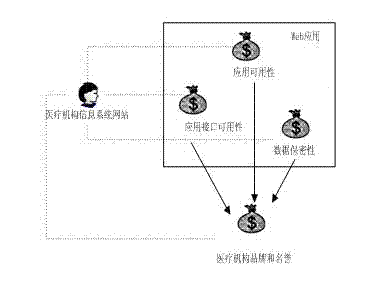
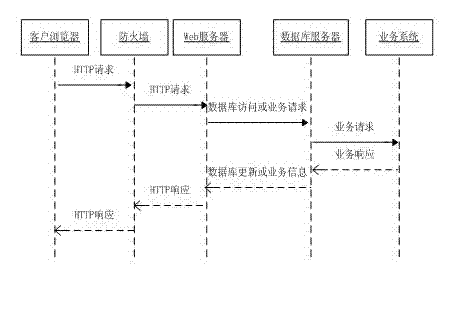
[0034] The information system of a medical institution is analyzed and researched by using the security policy hierarchical joint modeling method based on CORAS-Petri, and the steps are as follows:
[0035] The first step is to assess preparation. The main work of assessment preparation is to establish a project leadership team and project implementation team, collect system information of assessment objects, start assessment project management, and conduct training on basic knowledge and skills of risk assessment for relevant participants in the assessment, so as to facilitate the smooth implementation of the project. The use of the CORAS-Petri tool in the evaluation preparation stage is to input the evaluation team organization information, evaluation plan and plan into the CORAS-Petri system after the evaluation team members and evaluation projects are established, and through the project management function of CORAS-Petri, establish a comprehensive evaluation system. Archi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com