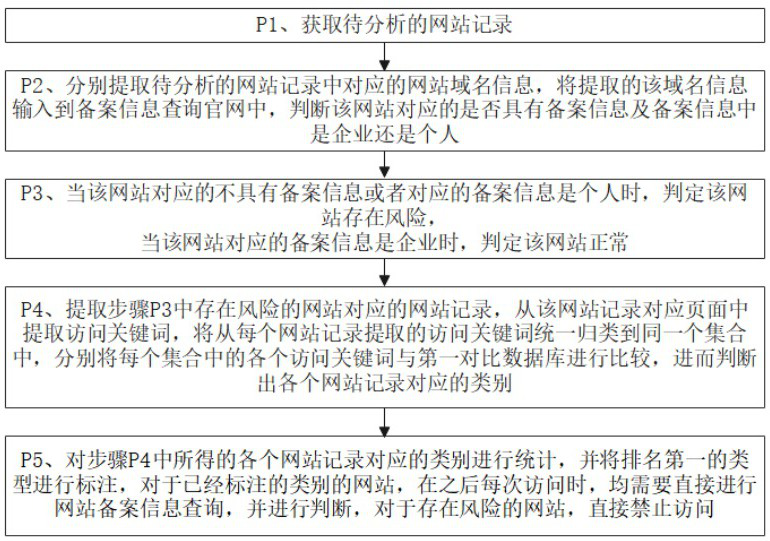
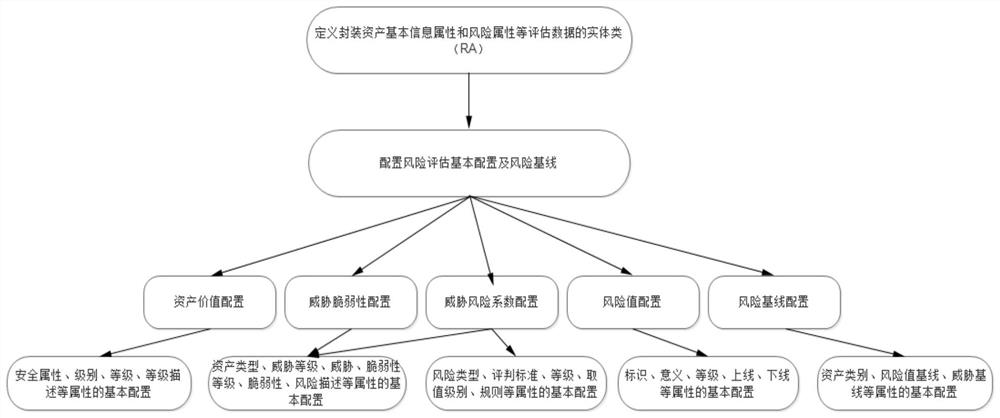
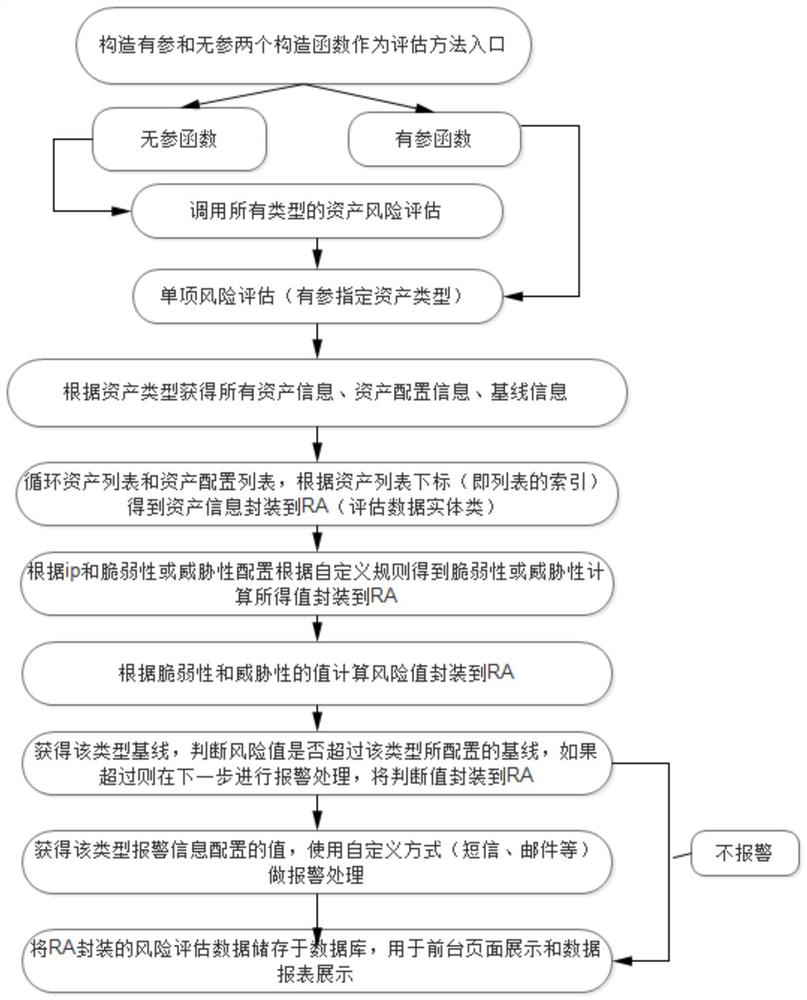
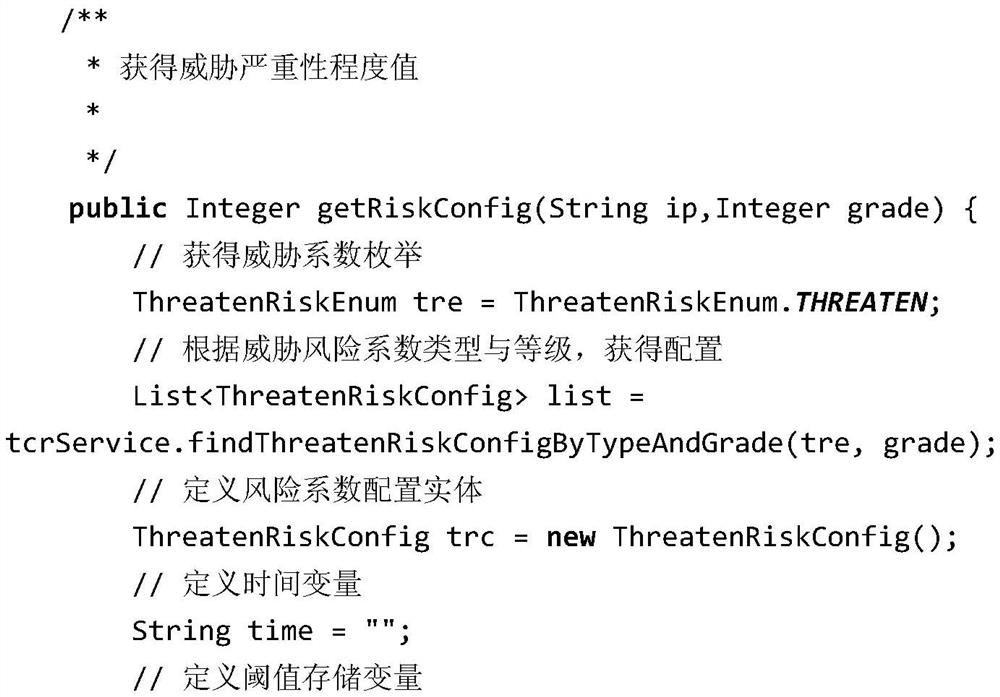
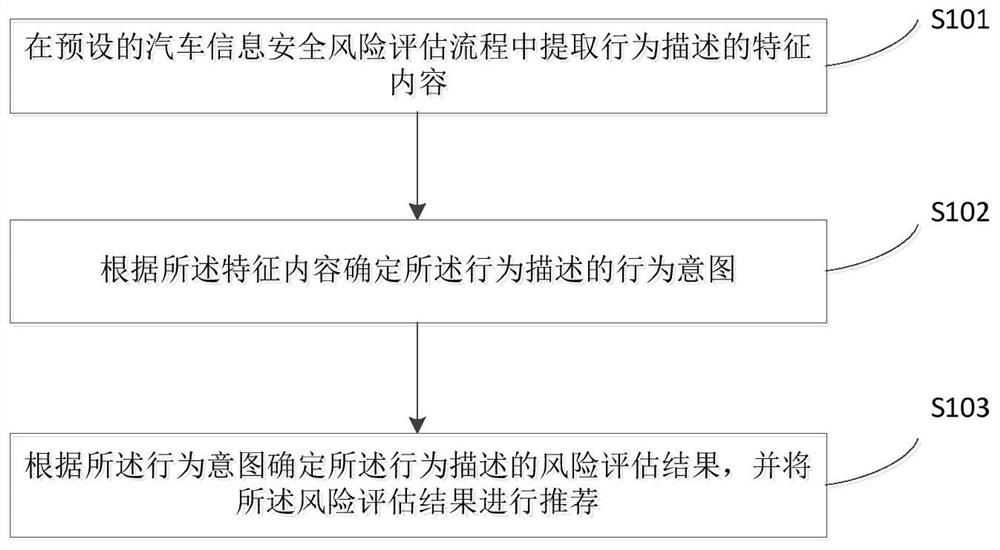
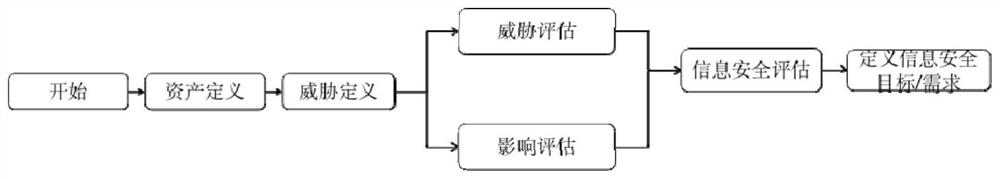
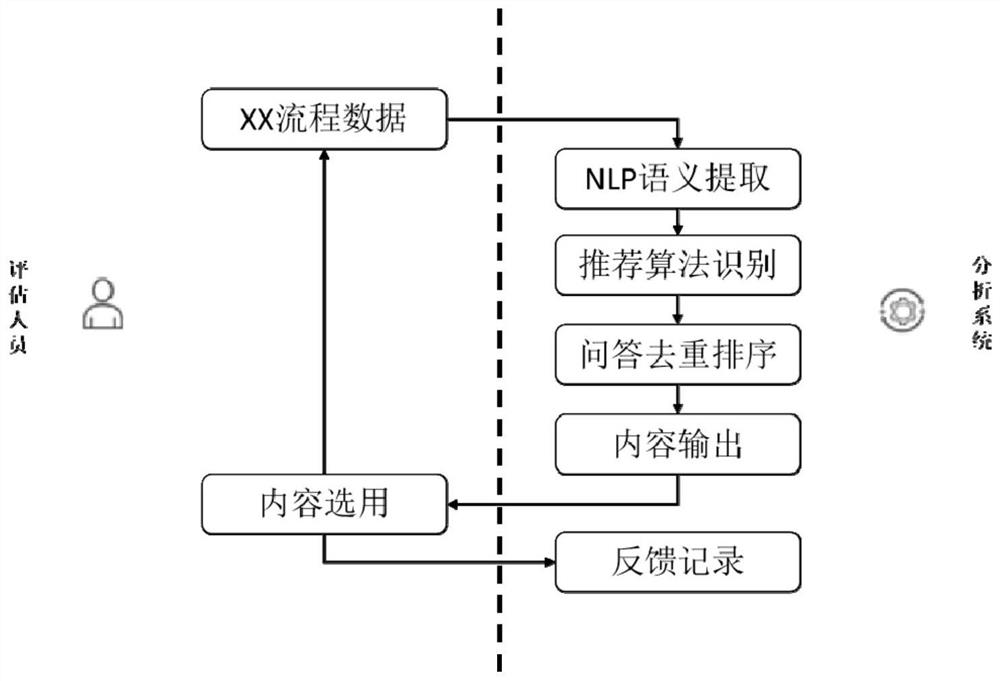
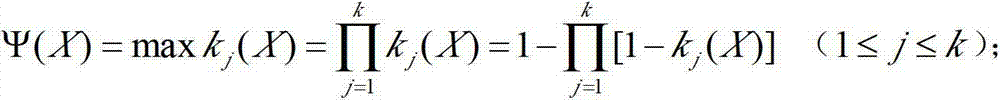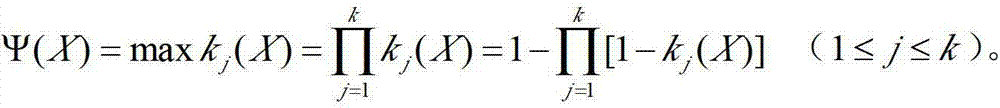Patents
Literature
38 results about "Information security risk assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Asset dependence relation-based information security risk evaluation method and system
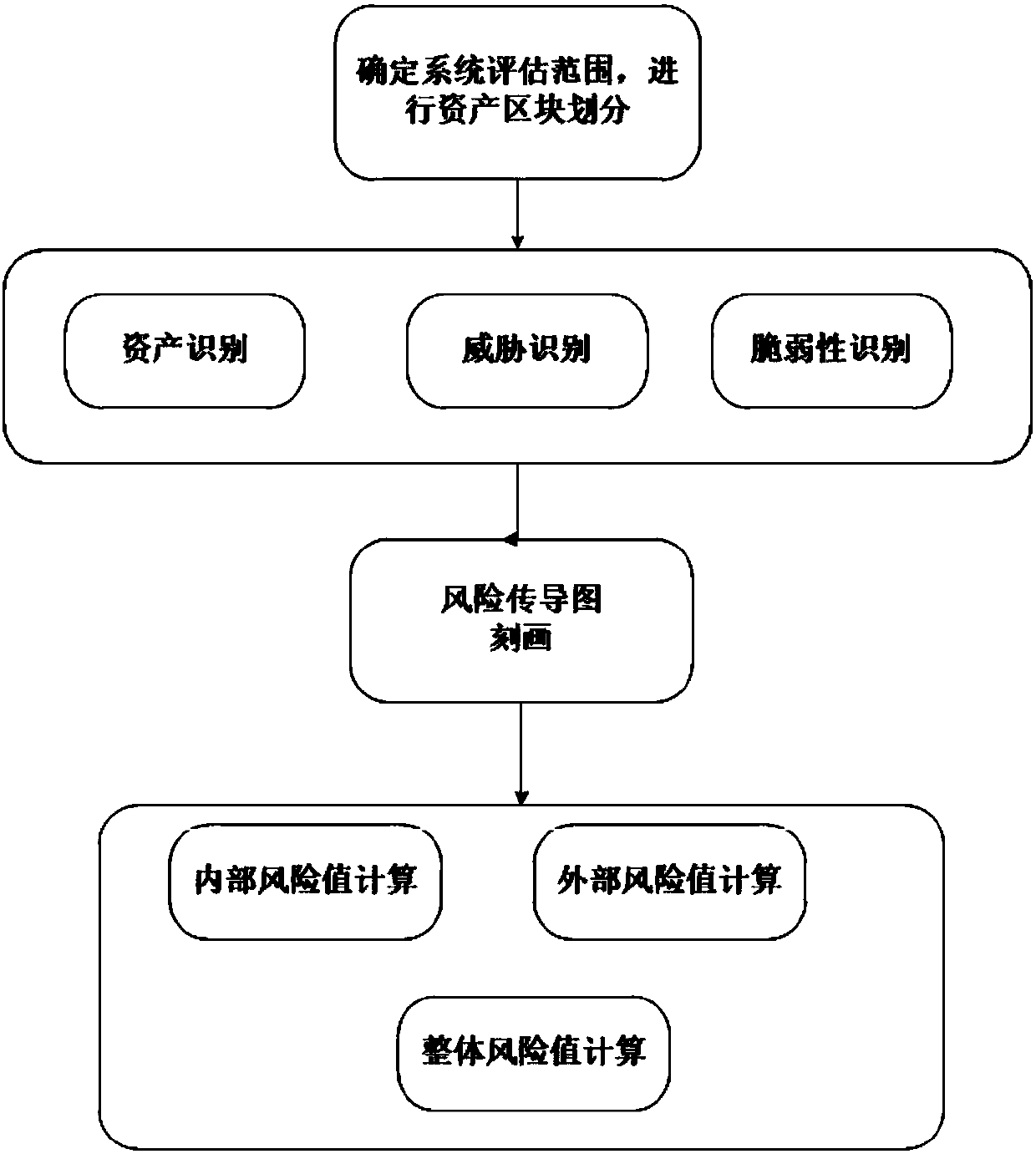
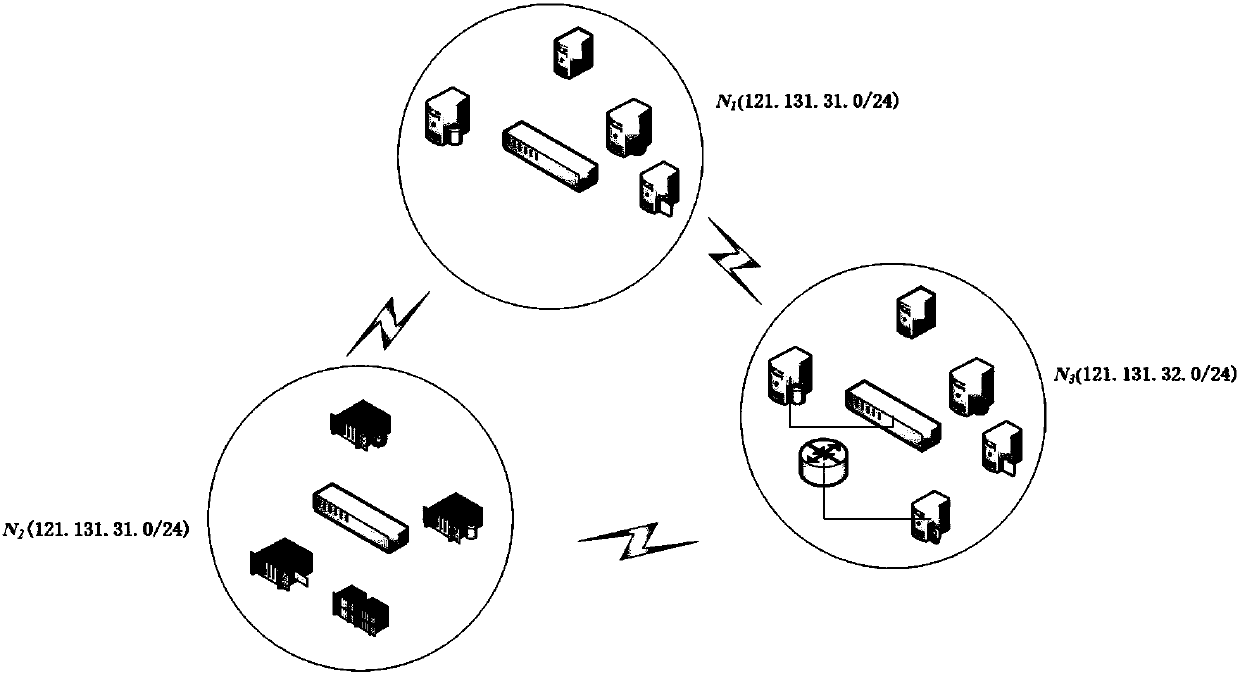
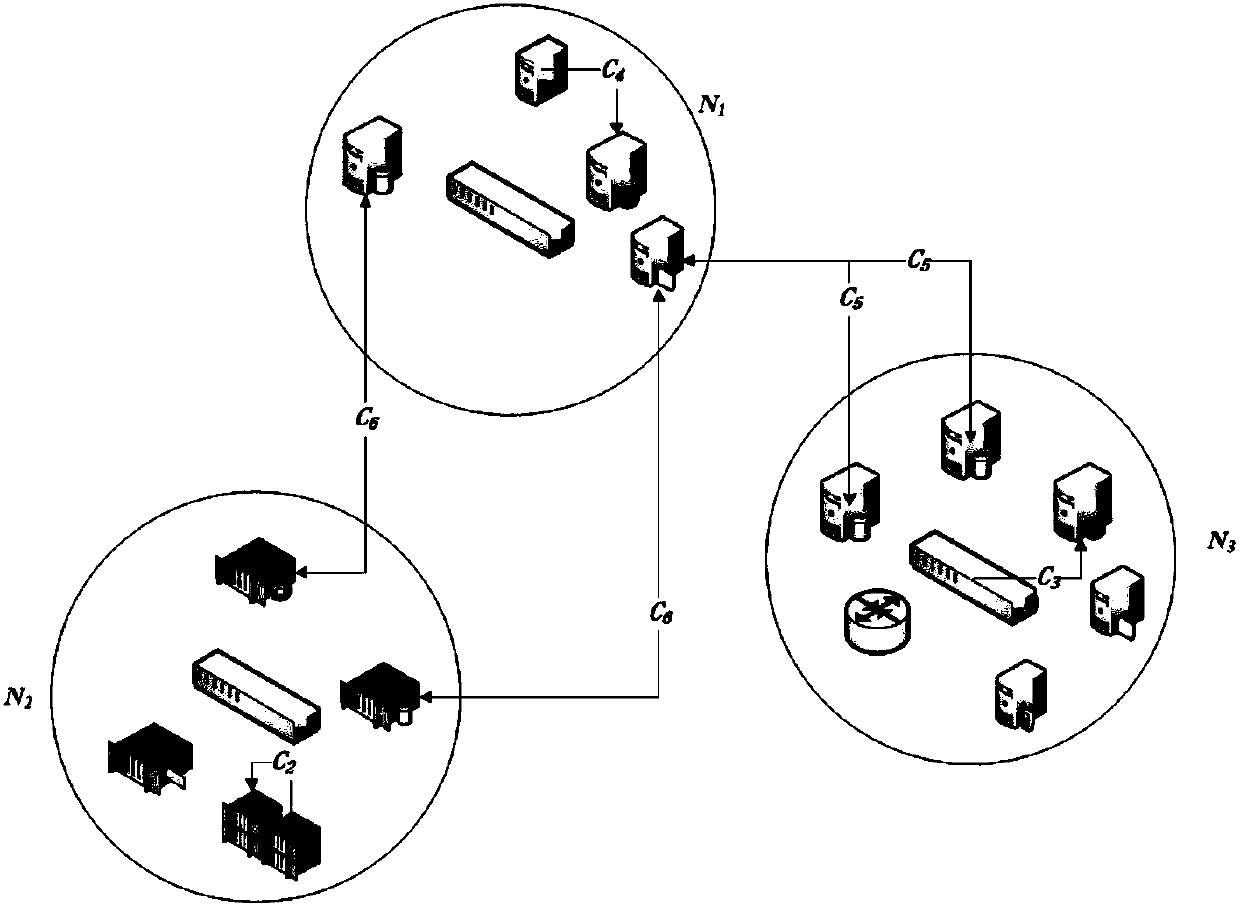
The invention discloses an asset dependence relation-based information security risk evaluation method and system. The method comprises the following steps of acquiring an asset range in a to-be-evaluated information system, and dividing the asset into blocks; identifying threats, vulnerability and asset significance of the to-be-evaluated information system, and acquiring significance value of the asset, threat value of the threat, and a vulnerability value of the vulnerability; calculating to build a security dependence relation matrix of assets by using a dependence structure matrix, determining a risk conduction coefficient of the assets by using a Delphi method and building a risk conduction relation; and calculating interior risk value and an exterior risk value of each block and overall risk value of the to-be-evaluated information system according to the risk conduction relation and asset significance, threat value and vulnerability value. The method can acquire a weak link ofthe system more accurately, and acquire more reliable information security risk evaluation results.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
Safety integrated management platform based on electric system quality system, risk assessment and safety testing and evaluation
InactiveCN103927631AImprove development efficiencyImprove performanceResourcesStatistical analysisElectric power system
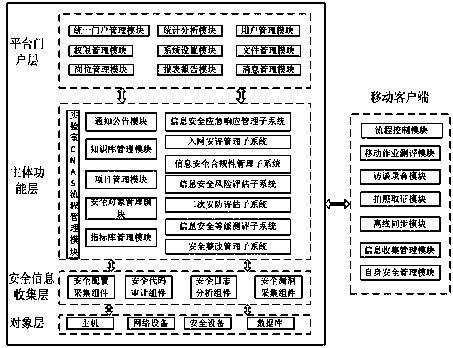
The invention discloses a safety integrated management platform based on an electric system quality system, risk assessment and safety testing and evaluation. The safety integrated management platform comprises a platform portal layer, a main function layer, a safety information collecting layer, an object layer and a mobile client side; the platform portal layer comprises a unified portal management module, a statistic analysis module, an authority management module, a user management module and a system setting module; the main function layer comprises a lab CNAS process management module, a project management module, a safety object management module, an index base management module, an information safety risk assessment subsystem, an information safety level testing and evaluation subsystem, a secondary safety and protection assessment subsystem and a safety rectification and management subsystem. A testing and evaluation tool library based on an electric power enterprise can be formed, and an assessment, testing and evaluation system and method and a management model of an electrical generation system can be set up.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
Information security risk assessment method oriented to typical metallurgy process control system
InactiveCN104331072AGuaranteed safe operationLow costElectric testing/monitoringProbabilistic methodRisk indicator
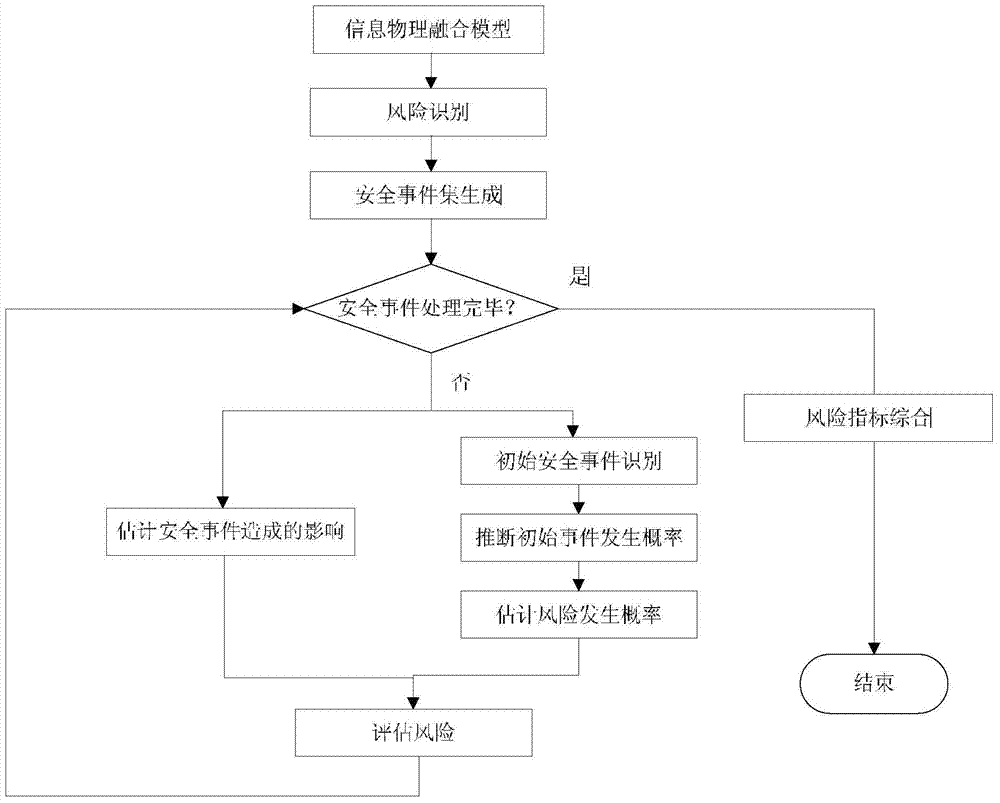
The invention provides an information security risk assessment method oriented to a typical metallurgy process control system and belongs to the technical field of industrial control system information security. The system robustness under different attack modes and policies is analyzed by establishing an attack model under the typical scenes of the metallurgy process, and therefore, the security risk assessment on the typical metallurgy process control system in different attack modes and a failure mode can be realized. Based on the risk theory, the method is used for performing the security risk assessment by use of a random probability algorithm by defining the metallurgy process control system as a physical information fusion system; from the two aspects of the occurrence probability and the influence of attack sources or failure sources, a security assessment method based on risk indexes is developed. Quantitative estimation is performed based on risk indexes; a security incident set is created based on the established physical information fusion model and attack model, and then the security incident set is combined with the calculated robustness assessment indexes for the quantitative estimation, and therefore, the weak security links in the control system can be located conveniently.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
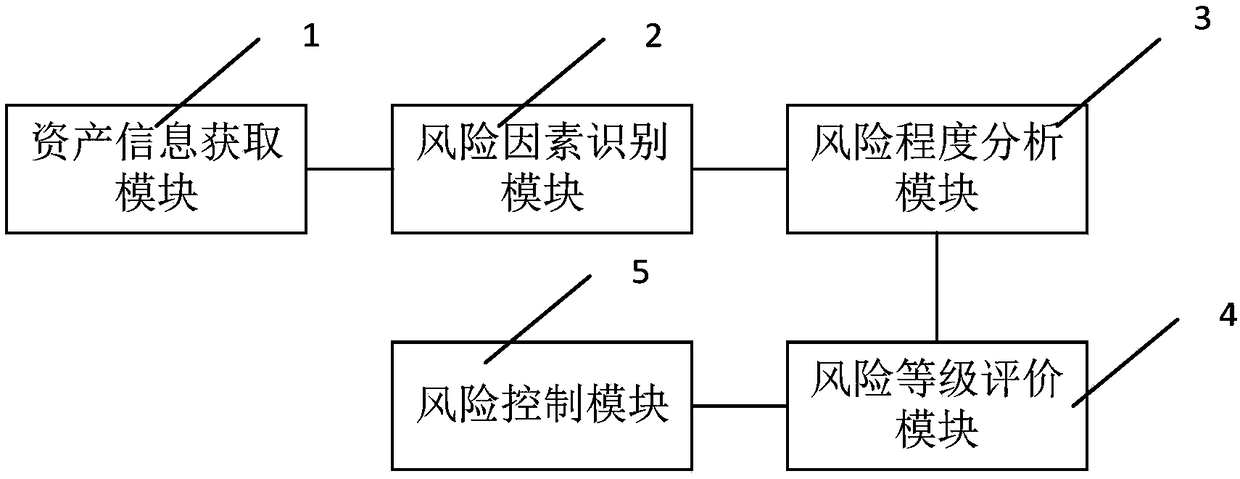
Information security risk assessment system and method
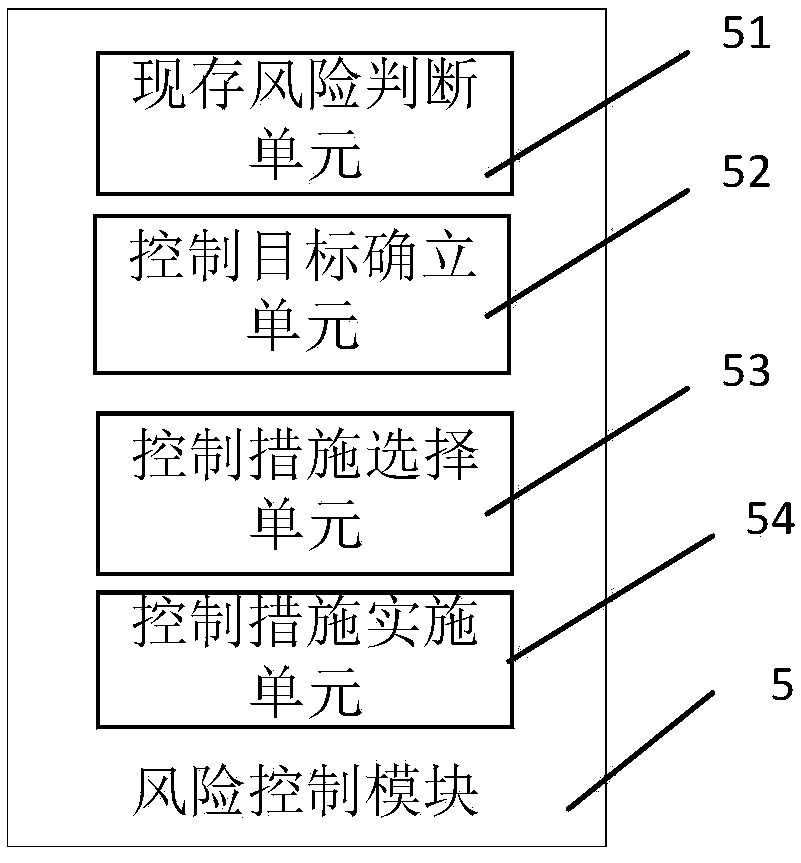
The information security risk assessment system disclosed by the invention comprises an asset information acquisition module, a risk factor identification module, a risk degree analysis module, a riskgrade evaluation module and a risk control module. The risk factor identification module is used for identifying risk factors. The risk degree analysis module is used for synthesizing the analysis results according to the existing security measures analysis information, threat source analysis information, threat behavior analysis information, vulnerability analysis information, asset value analysis information and impact degree analysis information. The risk grade evaluation module is used for obtaining the risk evaluation report according to the comprehensive evaluation risk grade of the risk evaluation algorithm library. The risk control module is used to make corresponding risk control measures according to the risk assessment report. By combining the frequency of threat sources, the severity of vulnerability utilization and asset value to calculate the risk rating, comprehensive assessment, assessment of a wider range, can be based on the assessment data to make corresponding riskcontrol measures.
Owner:向心力信息技术股份有限公司
Information security risk assessment method and system based on situation awareness learning
InactiveCN110401649AEase of evaluationReduce sizeMathematical modelsPlatform integrity maintainanceInformation security risk managementData set
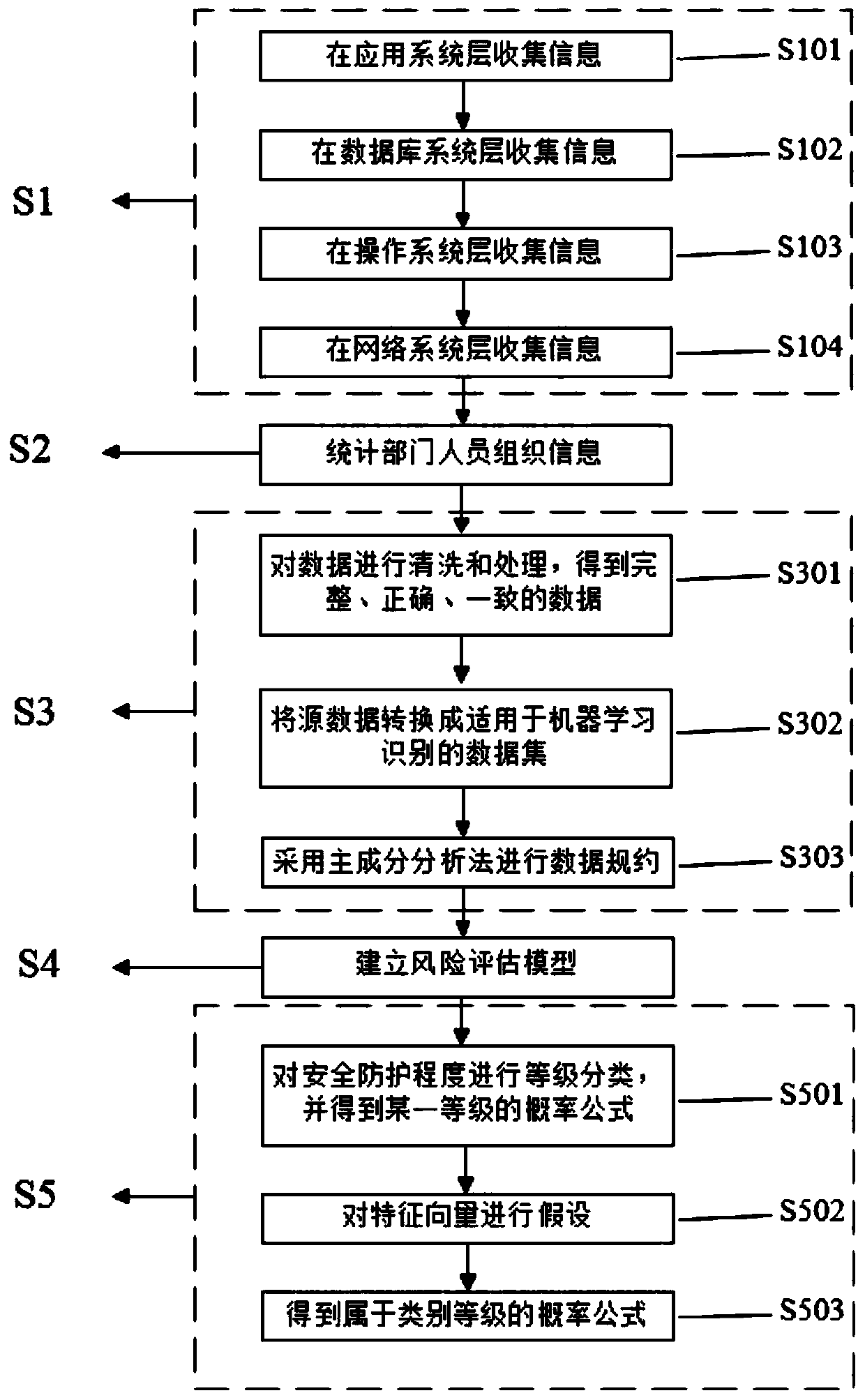
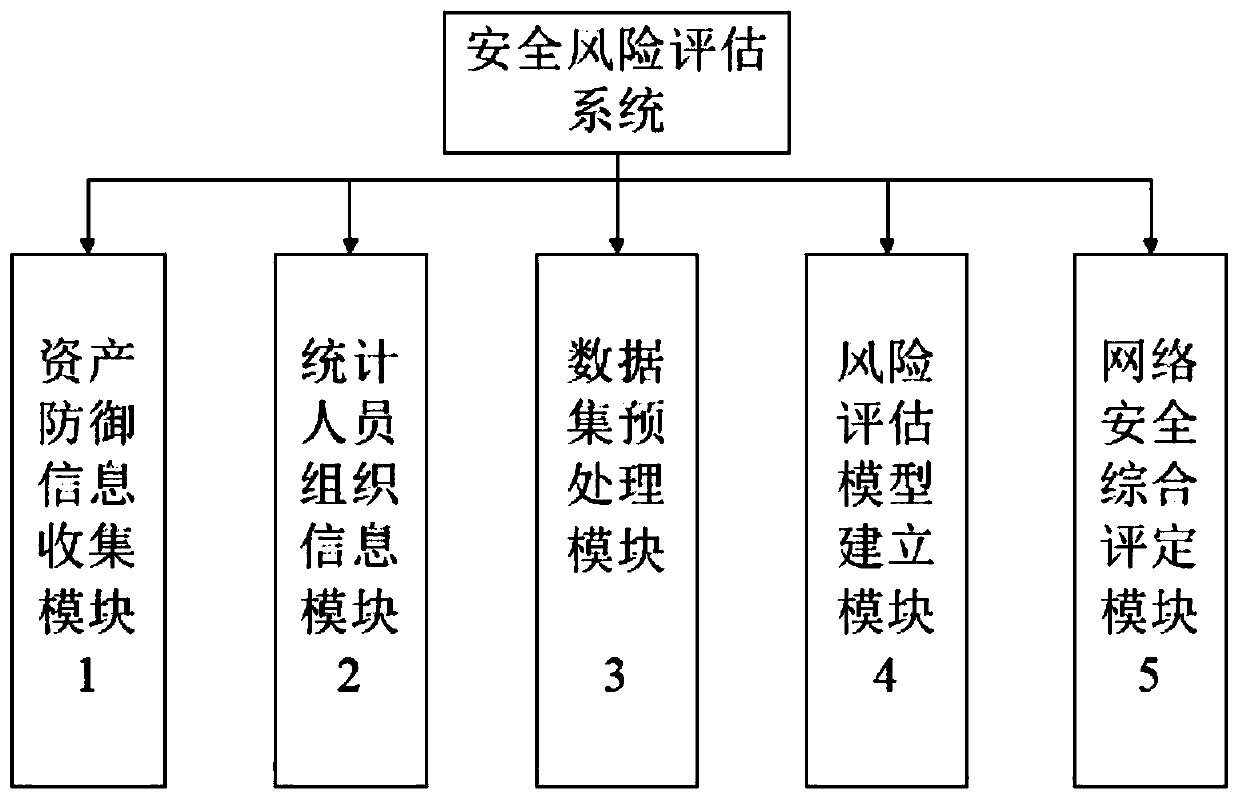
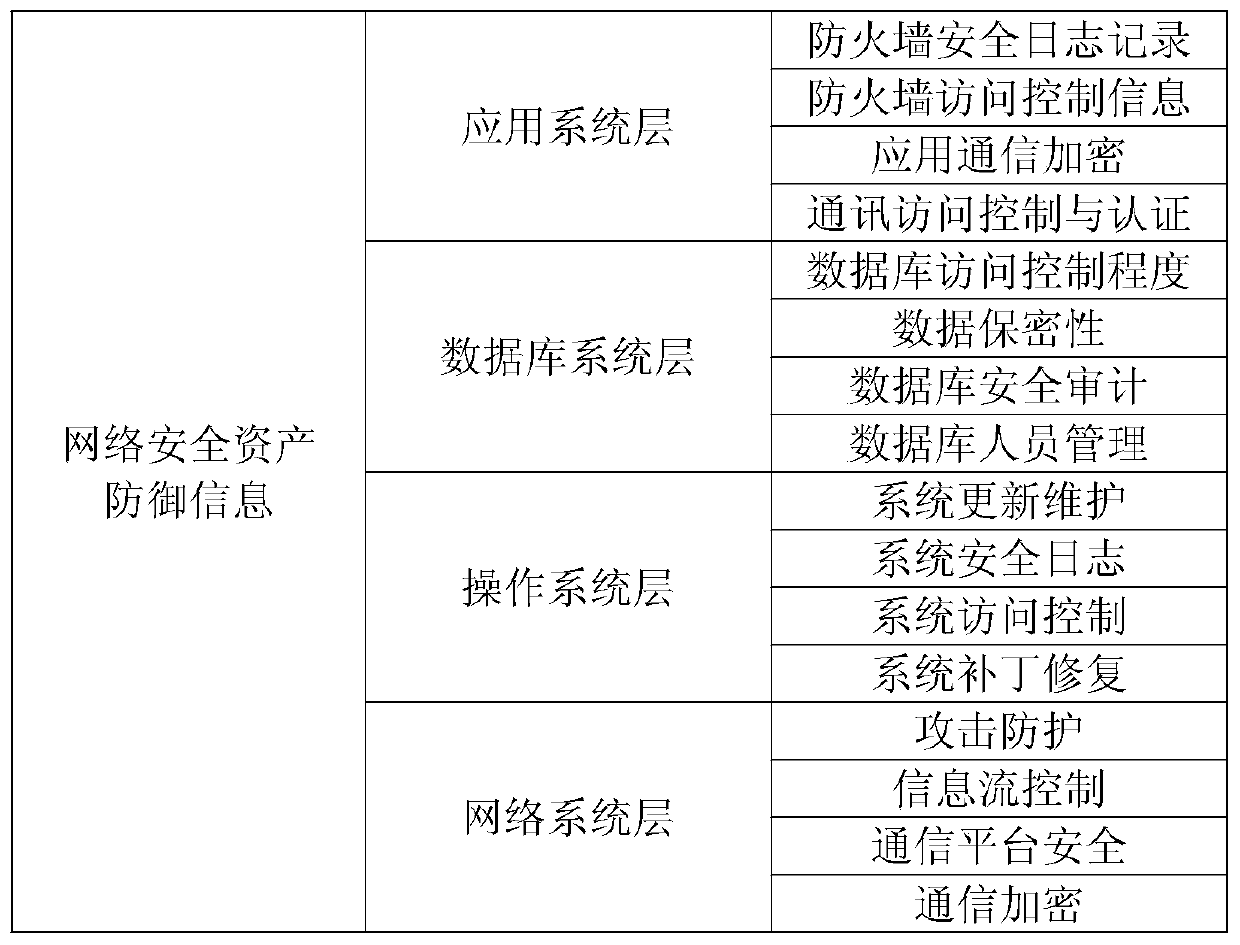
The invention discloses an information security risk assessment method and system based on situation awareness learning. The method comprises the following steps: firstly, collecting network securityasset defense information and department personnel organization information; then, preprocessing the collected information; performing format unification, useless data filtering, repeated data mergingand the like on the data; then, in combination with an existing information security risk assessment standard and an existing information security risk assessment model, systematically establishing entry information of the risk assessment model, and finally, grading network security according to the collected information by utilizing a Bayesian network machine learning algorithm. The system comprises an asset defense information collection module, a statistical personnel organization information module, a data set preprocessing module, a risk assessment model establishment module and a network security comprehensive assessment module. According to the invention, a set of more complete risk assessment system is constructed in multiple aspects and multiple ways, and security assessment grading is carried out, so that risk measures are selected in a targeted manner to reduce and control risks.
Owner:湖北央中巨石信息技术有限公司
Security policy level joint modeling method based on consultative objective risk analysis system (CORAS)-Petri
InactiveCN103095712AImprove accuracyHigh precisionData switching networksUnified Modeling LanguageSecurity policy
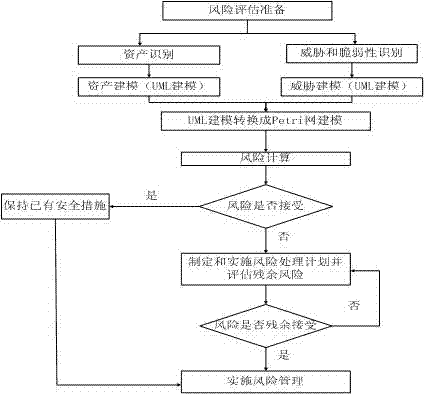
The invention relates to the field of network information security risk assessment and discloses a security policy level joint modeling method based on a consultative objective risk analysis system (CORAS)-Petri. Aimed at a vulnerable spot and defect of a CORAS framework and improving of the CORAS framework, and based on unified modeling language modeling, a Petri net describing network or information system dynamic behavior is introduced, a risk assessment method based on an analytic hierarchy process (AHP) and fuzzy comprehensive evaluation risk assessment method is introduced in a risk computing method of the CORAS framework to compute the risk, and the security policy level joint modeling method can not only reduce working amount of estimation and improves estimation efficiency, but also can refer to previous estimation conclusion, strengthens accuracy and effectiveness of estimation, and therefore improves acquaintance of information system security risk. People can take effectively security protection measures to ensure security of an information system.
Owner:WUXI NANLIGONG TECH DEV
Information safety risk assessment method
ActiveCN106656996AComprehensive assessment itemsWide range of assessmentsPlatform integrity maintainanceTransmissionAssessment dataData content
The invention discloses an information safety risk assessment method and relates to the technical field of information safety. The method is complete in assessment item and wide in assessment range, supports custom rule assessment, can find threats and potential threats in time and can carry out early warning processing better; and meanwhile, assessment data is comprehensive in data content, risk visualization is high, and embodiment of the potential threats and description of risk conditions and processing schemes are clear.
Owner:航天科工智慧产业发展有限公司
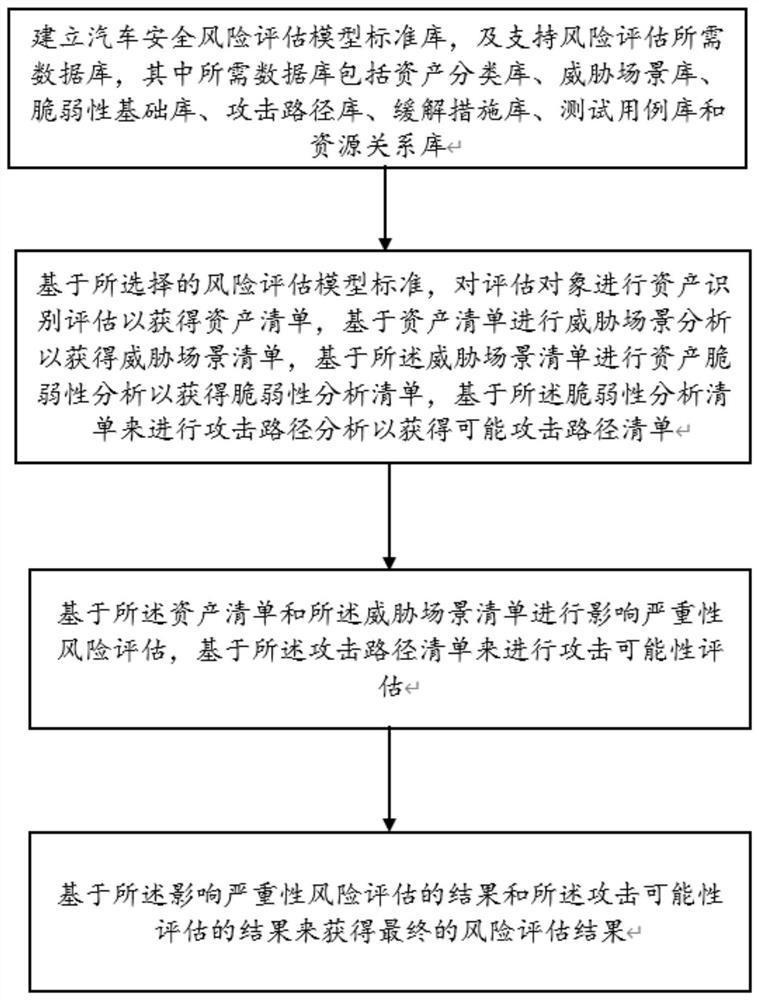
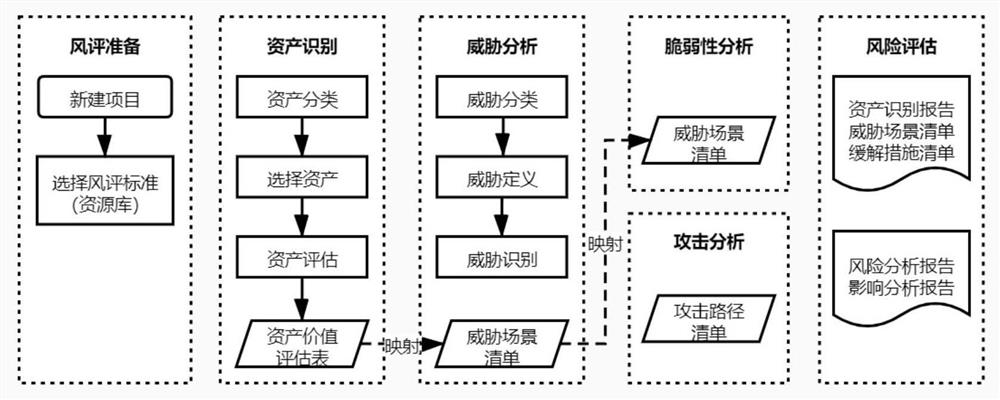
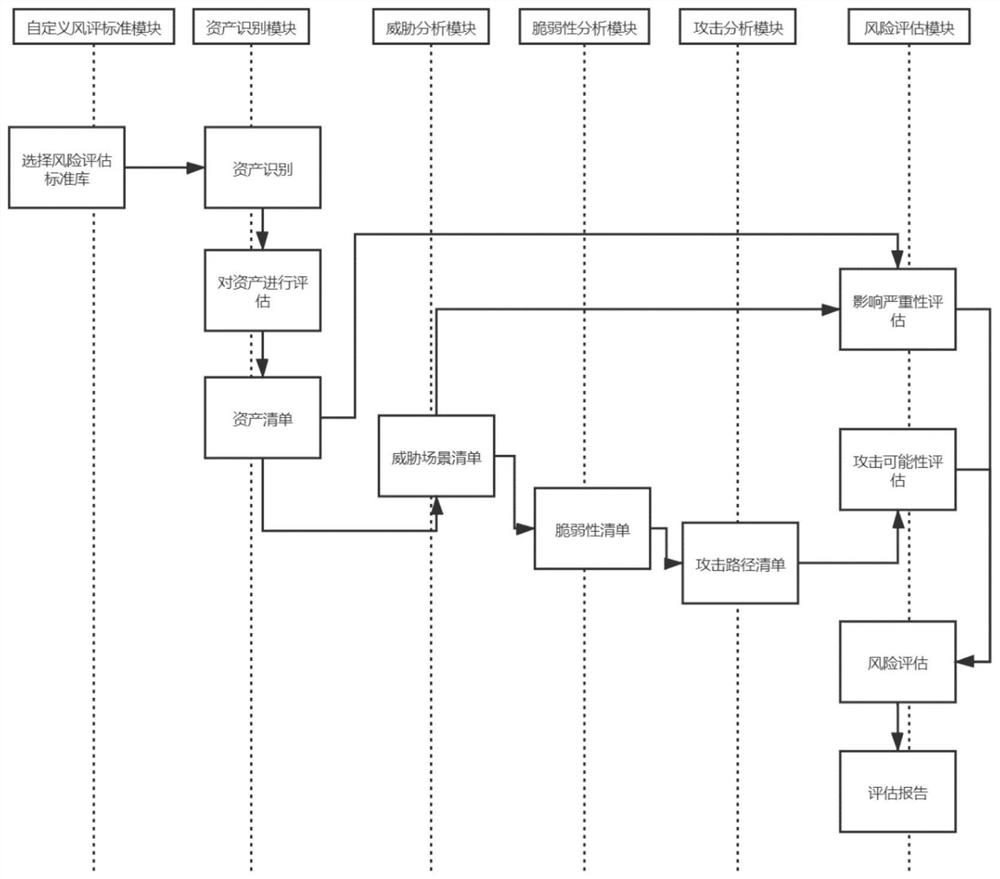
Intelligent network automobile information security risk assessment method and system
PendingCN112329022AFacilitate the automation processQuality assurancePlatform integrity maintainanceTransmissionIntelligent NetworkInformation security management
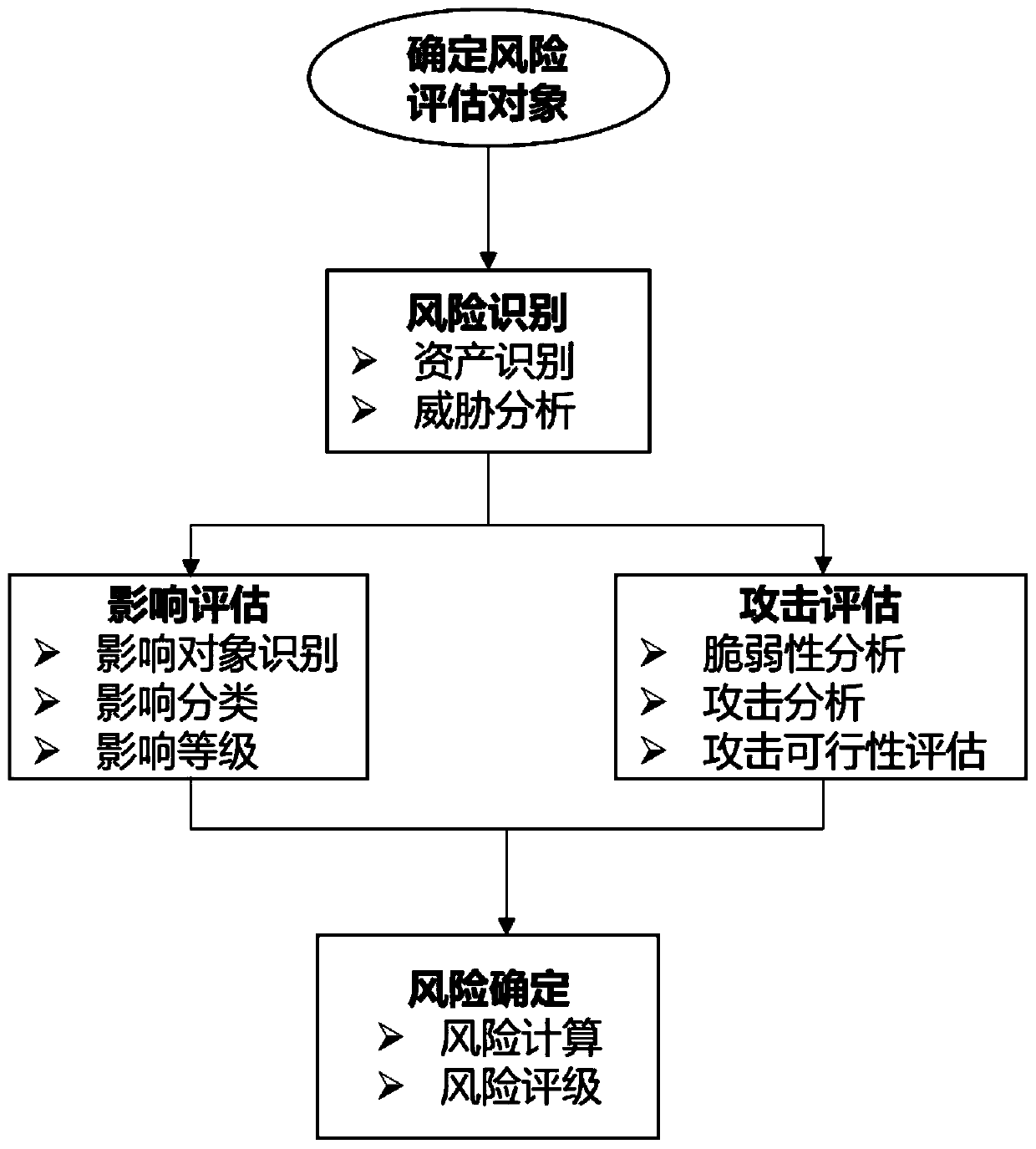
The invention discloses an intelligent network automobile information security risk automatic evaluation method and system. The method comprises steps of sequentially carrying out the risk evaluationaccording to steps, asset recognition, threat analysis, vulnerability analysis and attack path analysis after an evaluation object is selected; after preliminary risk assessment, a threat severity andinfluence severity analysis report being generated, the threat severity of an assessment object being subjected to grade assessment, and the influence caused by the threat severity being assessed; then, risk disposal and mitigation measures being implemented, and threats and influences brought by the threats of the evaluation object being reduced; and finally, generating a risk assessment report.The method is advantaged in that the range of the method covers automobile information safety management, including automobile information safety comprehensive management, product development periodinformation safety management and information safety management after product mass production, and information safety risk assessment automation of software and hardware related to network communication (including an automobile internal network) of an intelligent networked automobile in the automobile design, research, development and manufacturing process is achieved; and efficiency is improved.
Owner:浙江长三角车联网安全技术有限公司
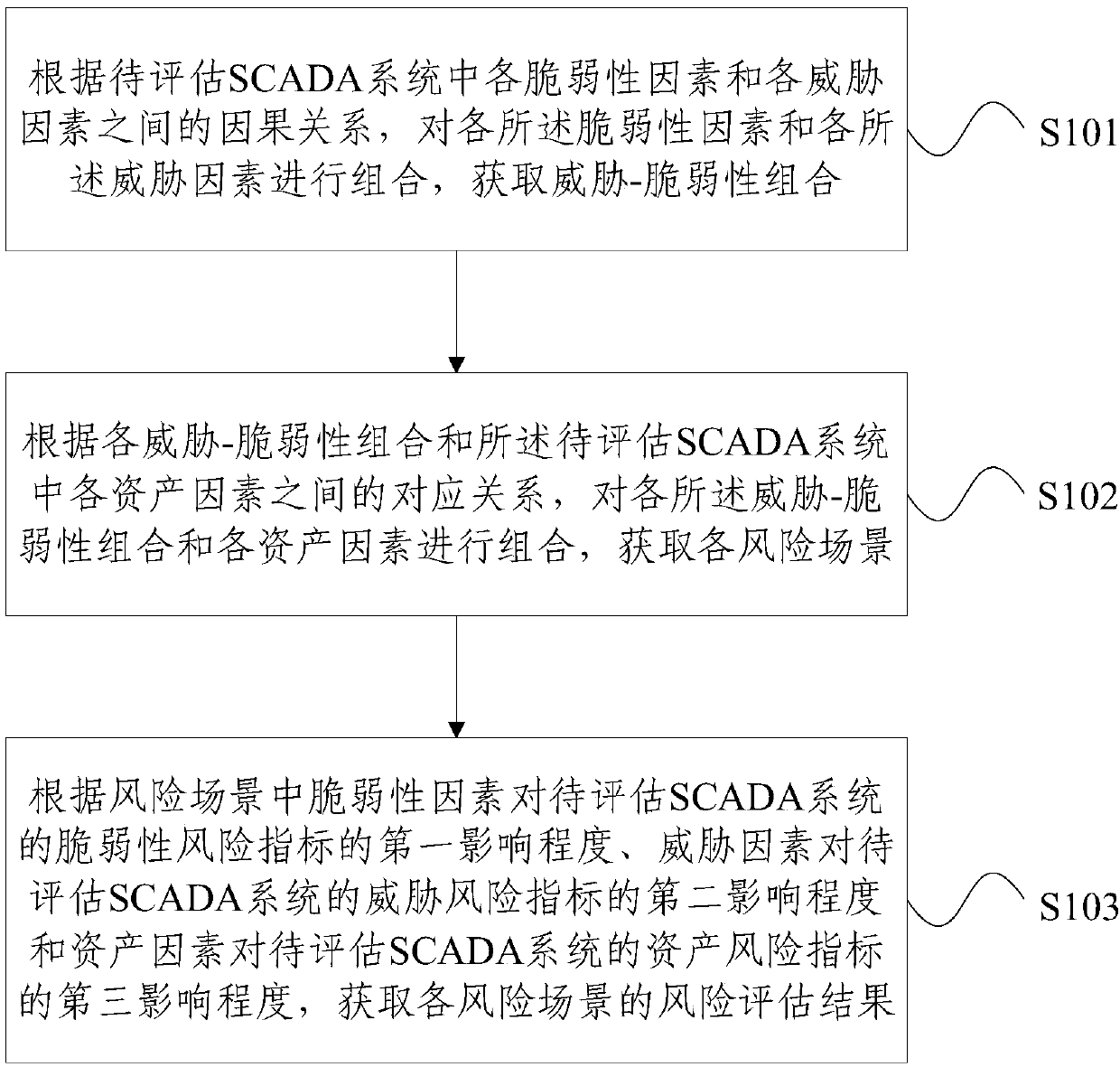
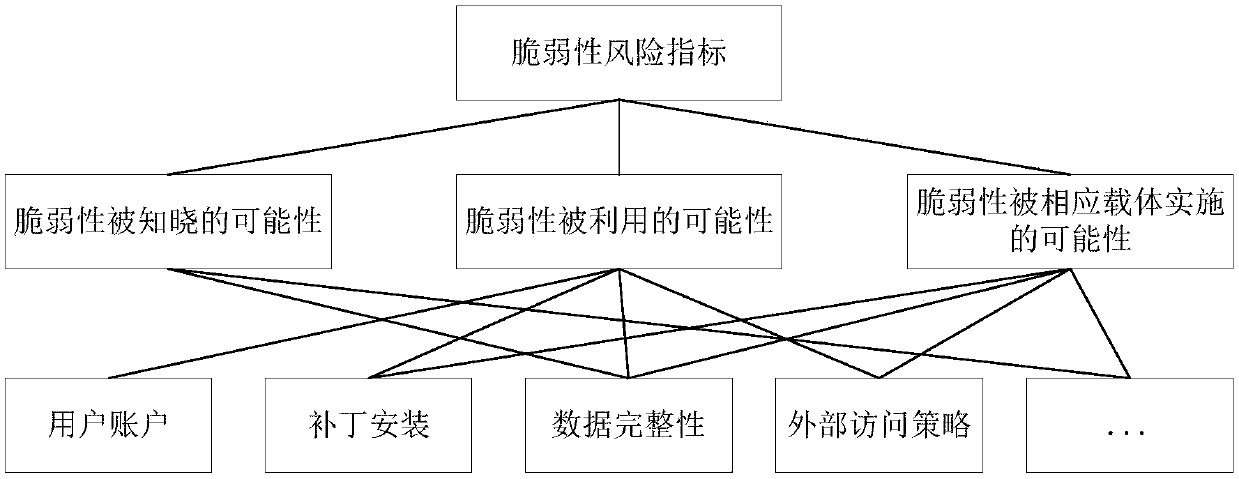
SCADA system information security risk assessment method and system
ActiveCN108833416AAccurate risk assessment resultsResourcesData switching networksSCADAVulnerability factor
The invention provides an SCADA system information security risk assessment method and system. The method includes the following steps: according to a causal relationship between each vulnerability factor and each threat factor in an SCADA system to be assessed, combining each vulnerability factor and each threat factor to obtain threat-vulnerability combinations; according to a corresponding relationship between each threat-vulnerability combination and each asset factor in the SCADA system to be evaluated, combining each threat-vulnerability combination and each asset factor to obtain each risk scenario; and according to the first influence degree of the vulnerability factors on a vulnerability risk indicator of the SCADA system to be assessed in each risk scenario, the second influencedegree of the threat factors on a threat risk indicator, and the third influence degree of the asset factors on an asset risk indicator, obtaining risk assessment results of the risk scenarios. According to the scheme of the invention, the risk assessment results can be quantitatively obtained, and thus the risk assessment results can be more accurate.
Owner:BEIJING MUNICIPAL INST OF LABOUR PROTECTION
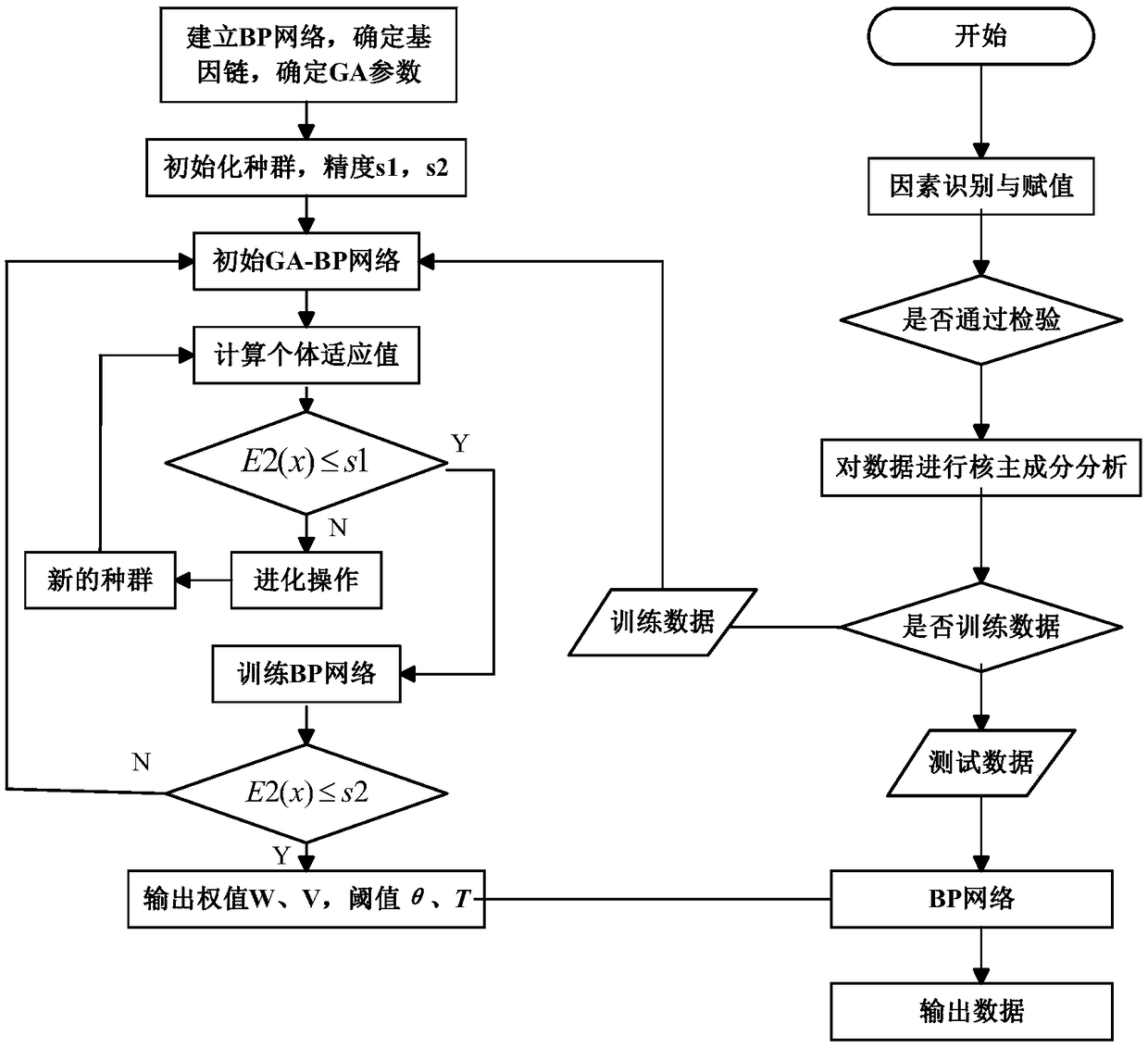
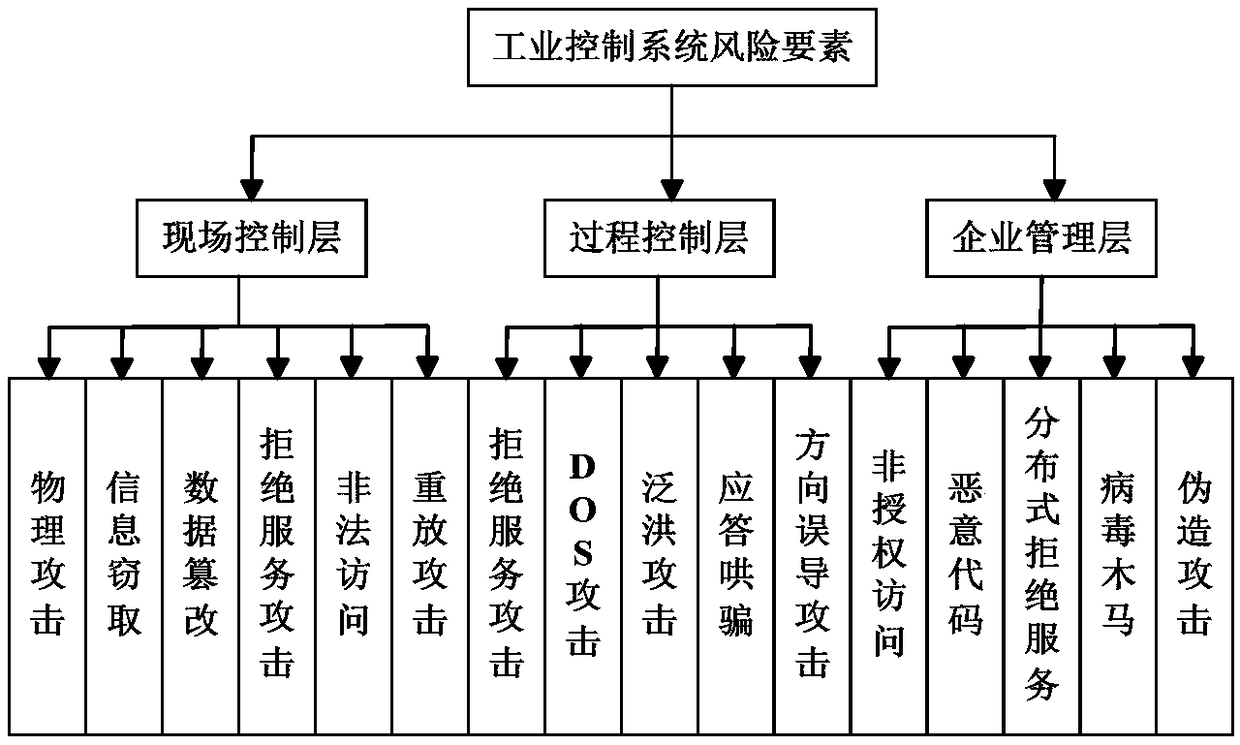
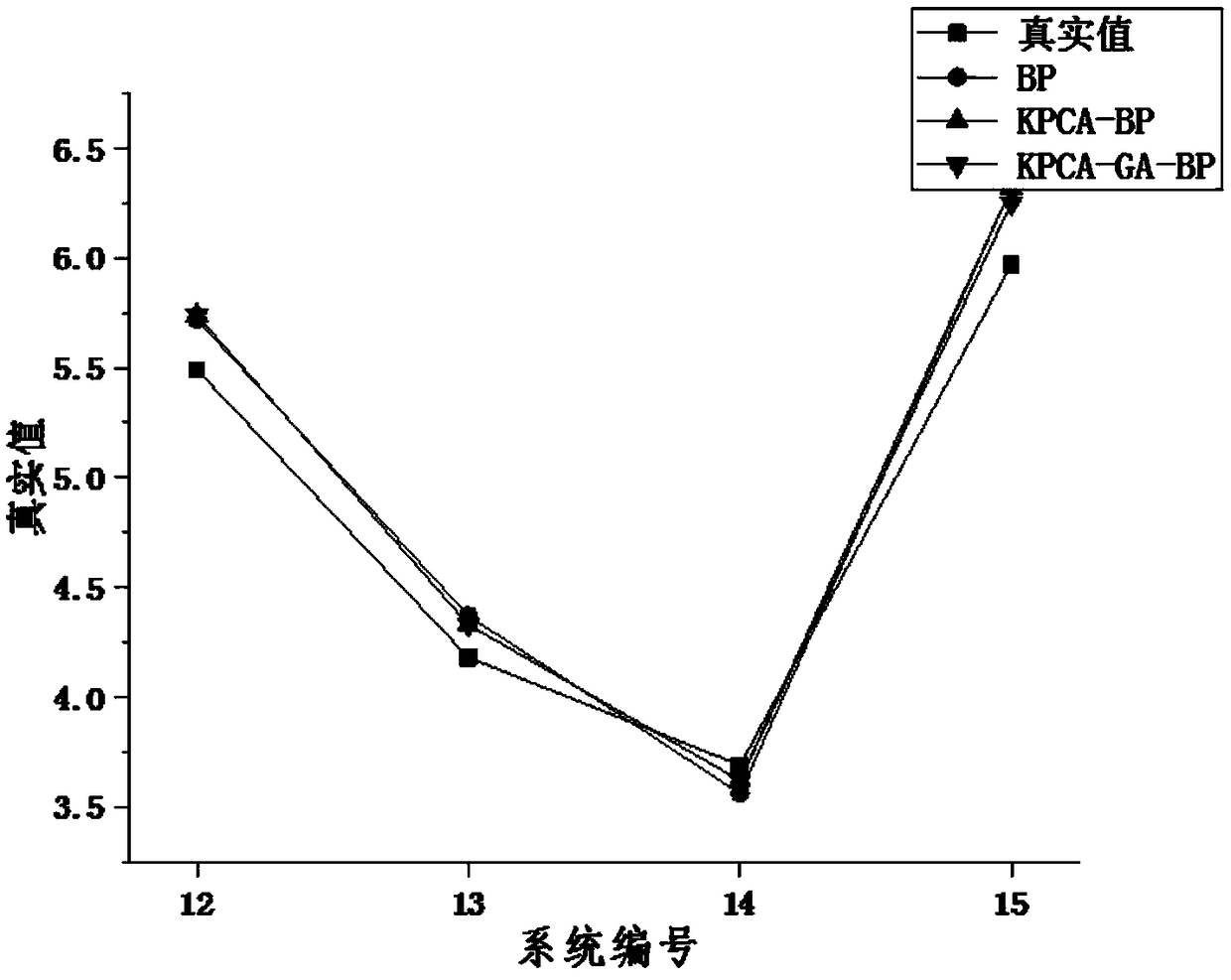
An information security risk assessment method for an industrial control system
InactiveCN109359469AImprove evaluation accuracyGood precisionPlatform integrity maintainanceNeural learning methodsData setDimensionality reduction
The invention relates to an information security risk assessment method of an industrial control system, comprising the following steps: S1, obtaining a risk assessment value and a plurality of sets of assessment scores corresponding to a plurality of risk assessment elements as an initial sample data set; S2, the initial sample data is processed by KPCA, and the principal component is selected according to the cumulative contribution rate to obtain the reduced-dimension sample data set; S3, training the BP neural network optimized by the genetic algorithm to obtain a prediction model by taking the reduced-dimension sample data set as a training sample; S4, inputting evaluation scores of a plurality of risk evaluation elements into a prediction model to obtain a prediction value of a riskevaluation value. Compared with the prior art, the invention not only improves the problem of parameter selection in the neural network, but also effectively improves the evaluation precision of the risk evaluation model, which is the combination of conventional modeling and intelligent method, and has important significance for the industrial control system.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER +1
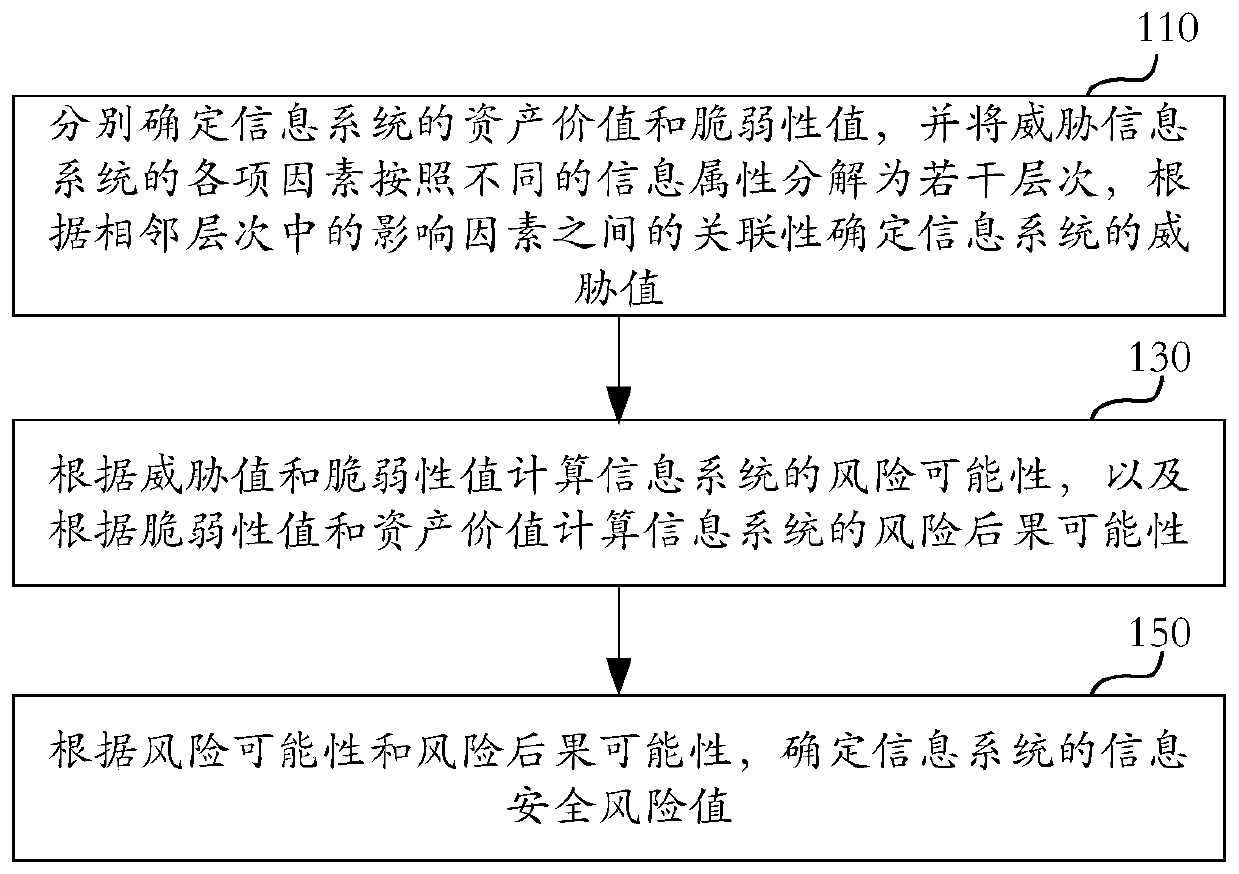
Information security risk assessment method and device, equipment and storage medium
ActiveCN111444514AReflects the threat intensity of the entire networkAccurate assessmentPlatform integrity maintainanceInformation systemReliability engineering
The embodiment of the invention discloses an information security risk assessment method and device, equipment and a storage medium. The method comprises the following steps that: 1, the asset value and the vulnerability value of an information system are determined respectively; each influence factor threatening the information system is decomposed into a plurality of hierarchies according to different information attributes, a threat value of the information system is determined according to the relevance between the influence factors in the adjacent hierarchies, and the vulnerability valueis used for describing the weakness degree of the assets in the aspect of security; the risk possibility of the information system is calculated according to the threat value and the vulnerability value, and the risk consequence possibility of the information system is calculated according to the vulnerability value and the asset value; and an information security risk value of the information system is determined according to the risk possibility and the risk consequence possibility. According to the technical scheme of the embodiment of the invention, the security risk state of the information system can be accurately evaluated.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for evaluating information safety risk based on interval number and ideal solution
InactiveCN106295332AReduce the impactAvoid pitfalls of losing expert informationPlatform integrity maintainanceInference methodsEngineeringNumber form
The invention provides a method for evaluating information safety risk based on interval number and ideal solution. The method comprises the following steps of establishing a new evaluation matrix form, wherein the rows and lines of the evaluation matrix are used for respectively expressing an expert set and a factor set; presenting the expert evaluation comments in the interval number form, and filling the matrix; in addition, introducing the index of correlation degree with the ideal solution, and sequencing the authority of the expert comments by technique for order preference by similarity to ideal solution; finally, performing compound operation on the factor evaluation computed by the comprehensive expert comments and the factor weight computed by the analytic hierarchy process, so as to obtain the integral comprehensive evaluation. The method has the advantages that a model for fuzzy comprehensive evaluation based on interval number is studied, the new single factor evaluation matrix form containing more information is proposed, the information involved in the evaluation process is furthest remained by the matrix, and the defect of losing of expert information of the existing model is overcome.
Owner:HUBEI UNIV OF TECH
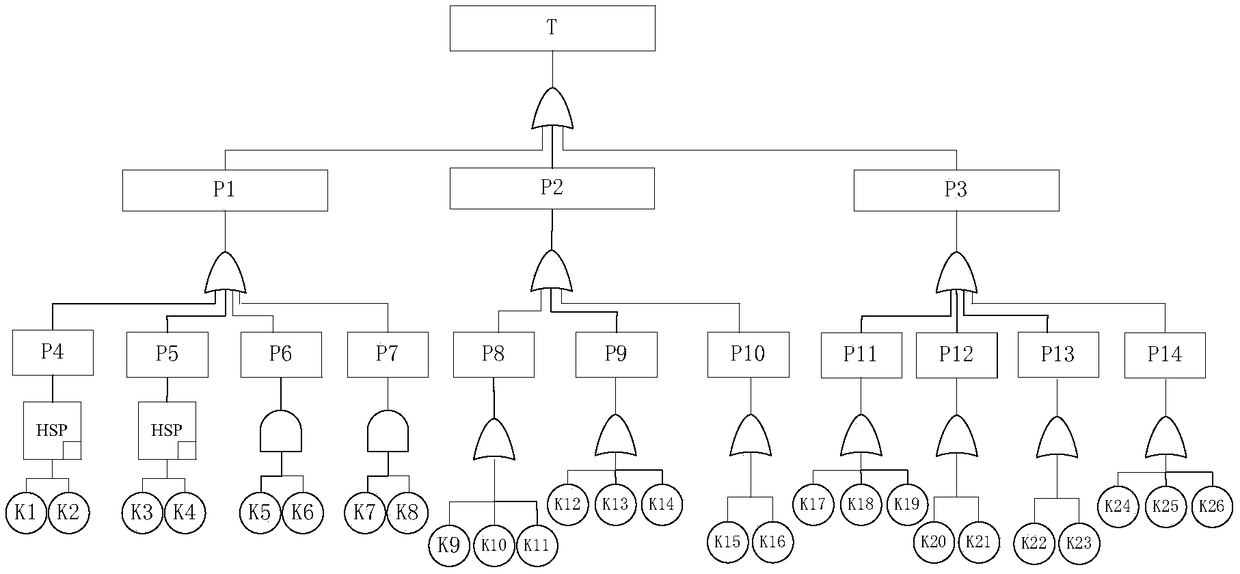
Information security risk assessment method based on fault tree and system thereof
InactiveCN103095730AEffective Corrective MeasuresEasy and safe maintenanceData switching networksQualitative analysisComputer science
The invention discloses an information security risk assessment method based on a fault tree and a system of the information security risk assessment method. According to the information security risk assessment method, a fault tree analysis method is adopted to achieve system risk calculation for a network device, non-intersecting minimum cutest is adopted to carry out risk qualitative analysis and top event probability analysis, location of the weakest link of the system is conducted quickly and occurrence probability of the weakest link of the system is calculated, through the method, system safety grading is carried out, and corresponding rectification measures are put forward. Due to the fact that the information security risk assessment method is adopted, the information security risk assessment method based on the fault tree and the system of the information security risk assessment method are suitable for safety assessment of an application system constructed on a network security hardware device in a frame mode.
Owner:SUZHOU CHIEN SHIUNG INST OF TECH
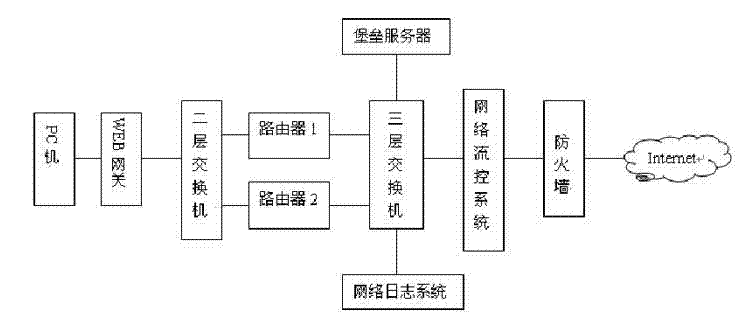
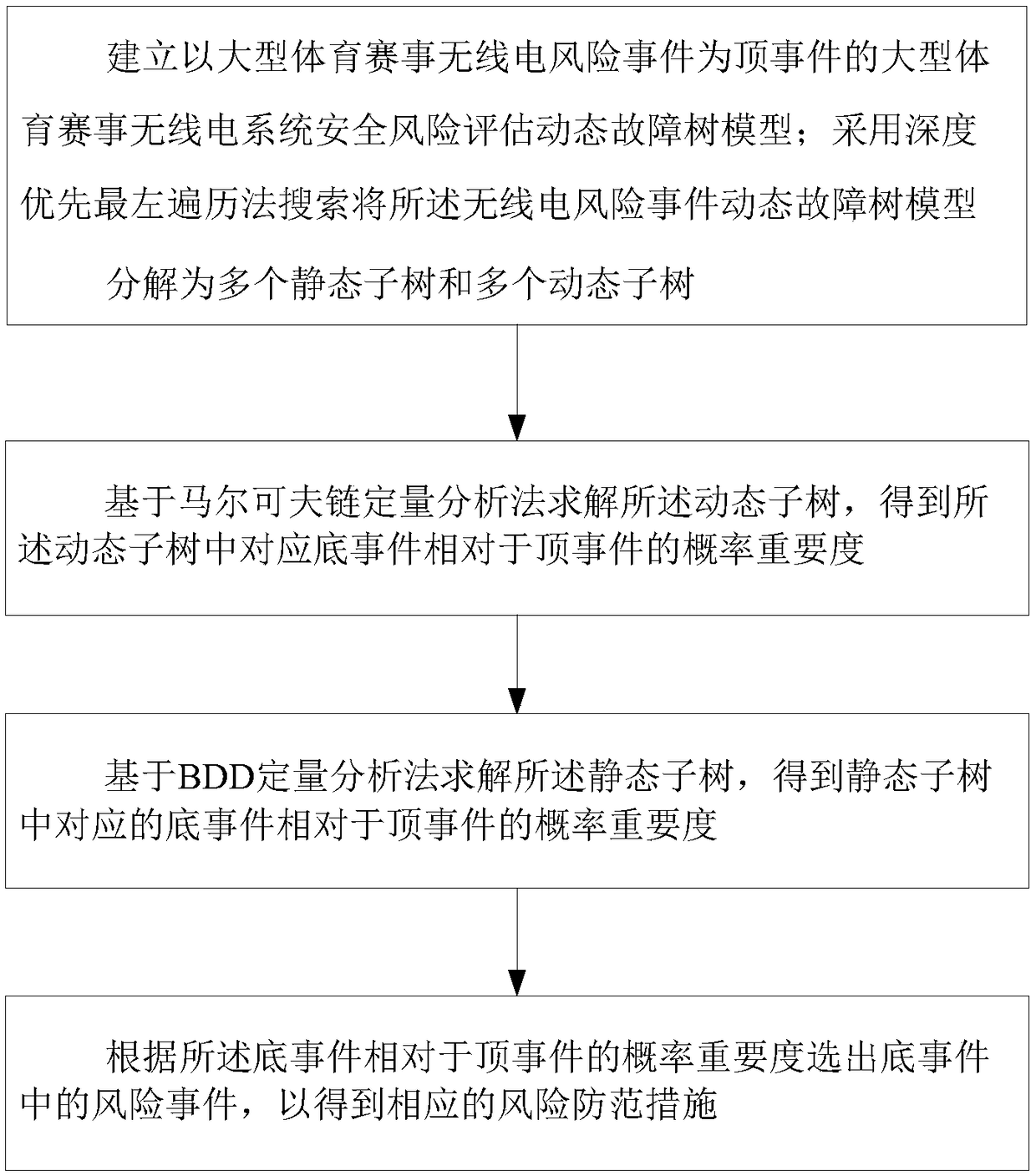
A large-scale sports event radio system information security risk assessment method
The invention discloses a large-scale sports event radio system information security risk assessment method, which comprises the following steps: taking a large-scale sports event radio risk event asa top event to establish a large-scale sports event radio system security risk assessment dynamic fault tree model; The dynamic fault tree model is decomposed into a plurality of static sub-trees anda plurality of dynamic sub-trees by using a depth-first leftmost traversal search method; The dynamic subtree is solved based on the Markov chain quantitative analysis method, and the probability importance degree of the corresponding bottom event relative to the top event is obtained. the static sub-tree is sloved based on the BDD quantitative analysis method to obtain the probability importancedegree of the corresponding bottom event relative to the top event; According to the probability importance degree of the bottom event, the risk event is selected to obtain the corresponding risk prevention measures. The invention introduces the quantitative analysis theory of the dynamic fault tree, can analyze the safety risk of the radio system of the large-scale sports events, and provides a reference for developing the safety risk assessment of the radio system of the large-scale sports events.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
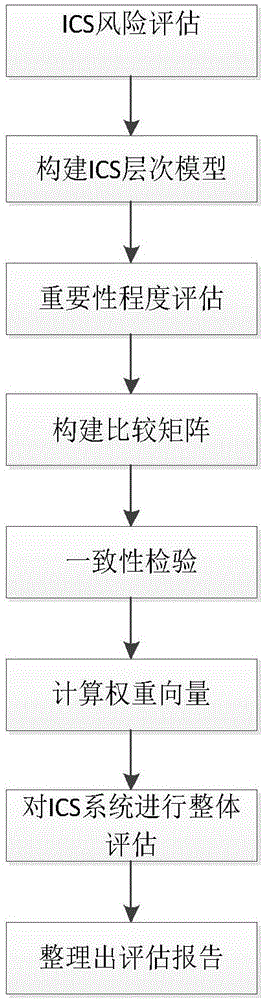
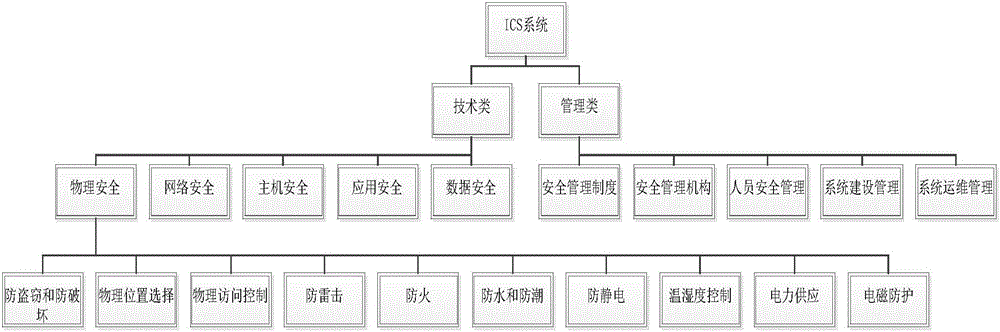
ICS information safety assessment method based on analytic hierarchy method
InactiveCN106384193AEnsure safetyThe assessment results are accurateResourcesRisk ControlComputer science
The present invention discloses an ICS information safety assessment method based on an analytic hierarchy method. The method comprises: performing ICS risk assessment and constructing an ICS hierarchical model of a project control system to be assessed; constructing a comparison matrix for the importance degree assessment; performing the consistency check of the comparison matrix; performing integral assessment of the ICS system to be assessed; and arranging the assessment report. The ICS information safety assessment method takes the analytic hierarchy method as the basis and performs improvement of the ICS information safety assessment, and preferably selects a weight ratio through comparison compared to the current assessment method so as to allow the assessment result to be more accurate, allow the information in the assessment report to be more reasonable and comprehensive and allow the whole assessment process thinking to be clearer; and moreover, the ICS information safety assessment method based on the analytic hierarchy method is scientific and rigorous and employs scientific method and means for the information safety risk assessment to provide the scientific basis for avoiding and defusing the industry information safety risk, or controlling the risk into an acceptable level and maximally ensuring the network and information safety.
Owner:CHINA ELECTRONICS STANDARDIZATION INST
Information safety risk evaluation system accurate in evaluation
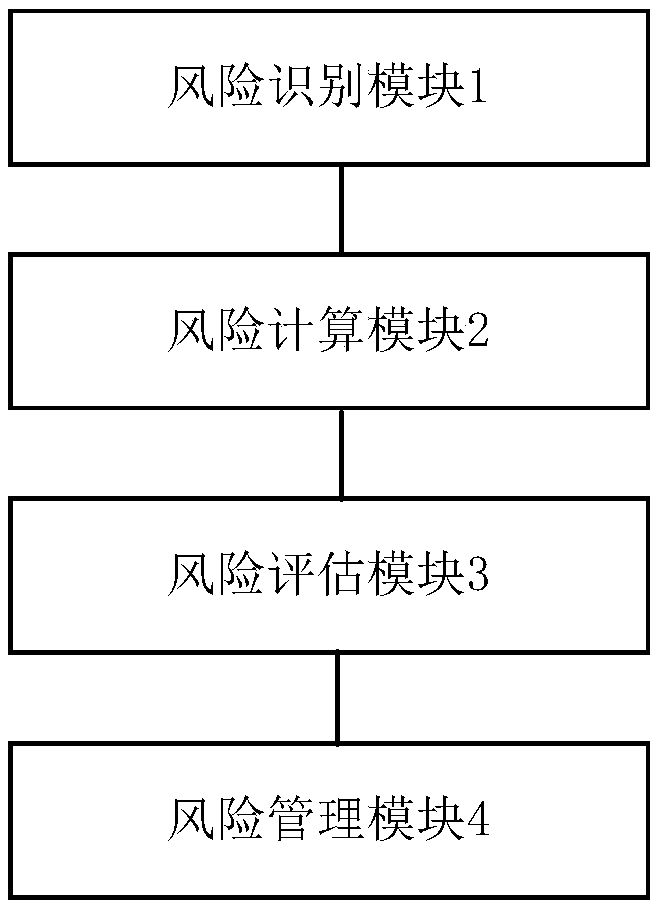
InactiveCN107862205AReduce security risksImprove securityPlatform integrity maintainanceRisk identificationEngineering
The invention provides an information safety risk evaluation system accurate in evaluation. The information safety risk evaluation system includes a risk identification module, a risk calculation module, a risk evaluation module and a risk management module, wherein the risk identification module is used for identifying information safety risks, the risk calculation module is used for calculatinginformation safety risk values according to identification results, the risk evaluation module is used for evaluating the information safety risks according to the information safety risk values, andthe risk management module is used for processing and controlling the information safety risks according to evaluation results; the risk identification module includes a first risk identification unit, a second risk identification unit and a third risk identification unit, wherein the first risk identification unit is used for identifying property, the second risk identification unit is used for identifying threats which an information system faces, and the third risk identification unit is used for identifying risk-resistant capabilities of the information system. The information safety riskevaluation system accurate in evaluation has the advantage of achieving accurate information safety risk evaluation.
Owner:龚土婷
Power plant control system information security risk assessment system
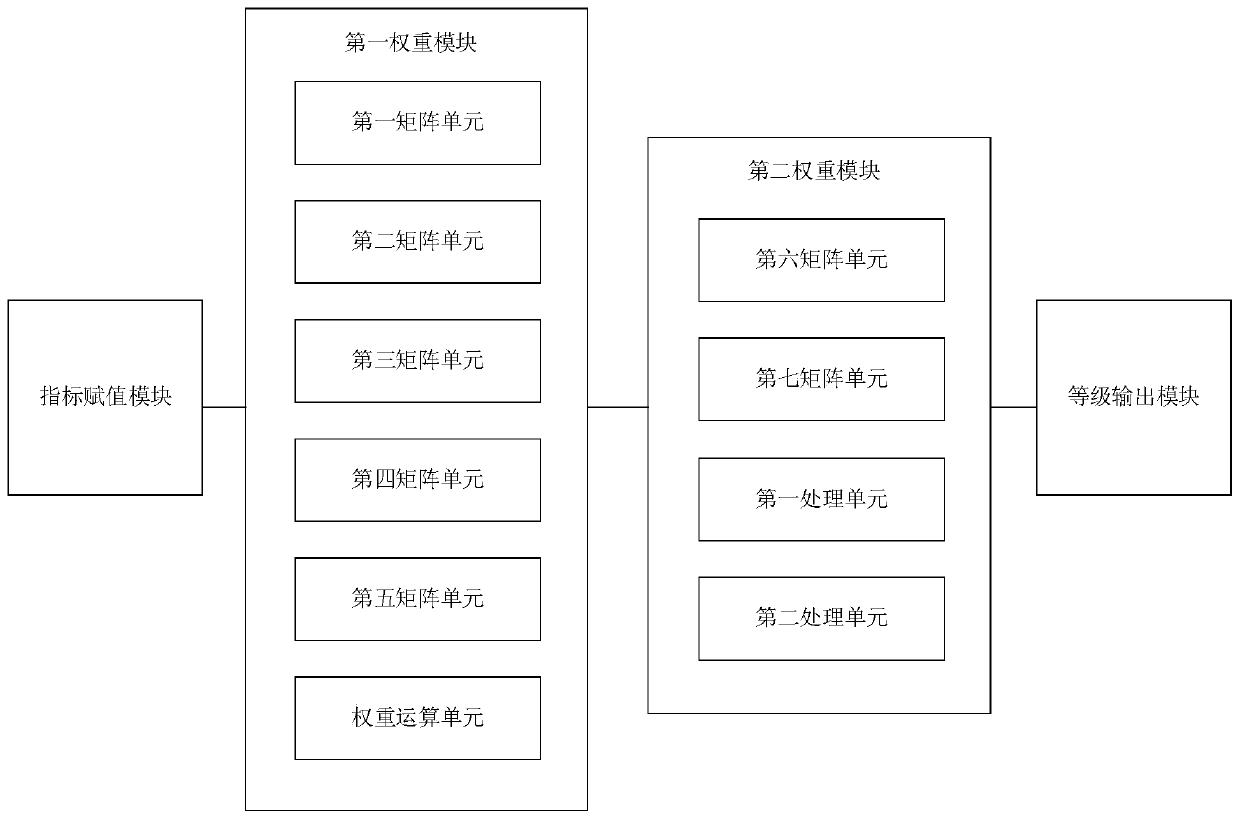
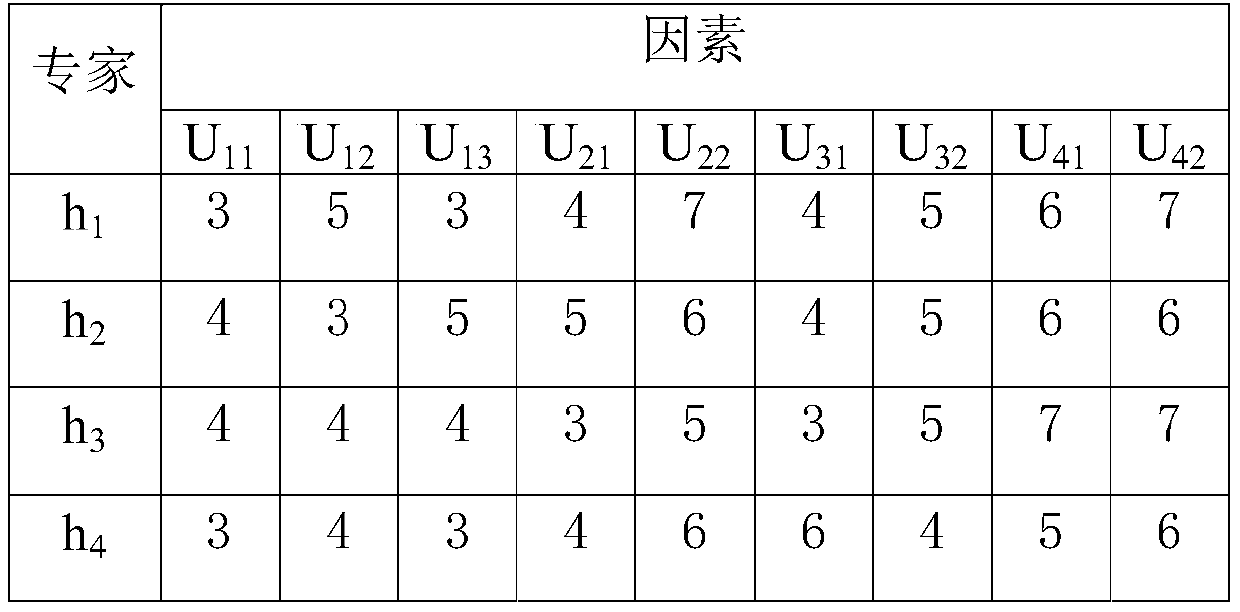
PendingCN110276528AOvercome the subjectivity and imprecise problemReasonable handlingResourcesComplex mathematical operationsControl systemTOPSIS
The invention relates to a power plant control system information security risk assessment system. The system comprises an index assignment module used for performing data input for a preset risk assessment index system model to obtain an index assignment sample; a first weight module used for solving an index influence weight vector of the index assignment sample through a D-AHP method; a second weight module used for solving an accuracy weight vector of the index assignment sample through a TOPSIS method; and a grade output module used for integrating the index influence weight vector, the accuracy weight vector and the index assignment sample to obtain the information security risk grade of the evaluation object. Compared with the prior art, risk assessment can be accurately and effectively carried out through a few sample values, a large amount of manpower and material resources are saved, meanwhile, the problem that a few samples are high in subjectivity and inaccurate is solved, uncertain sample data can be reasonably processed, and the accuracy of an assessment result is improved.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER
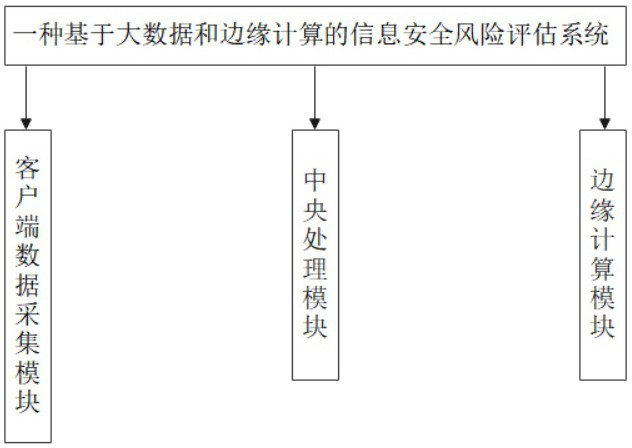
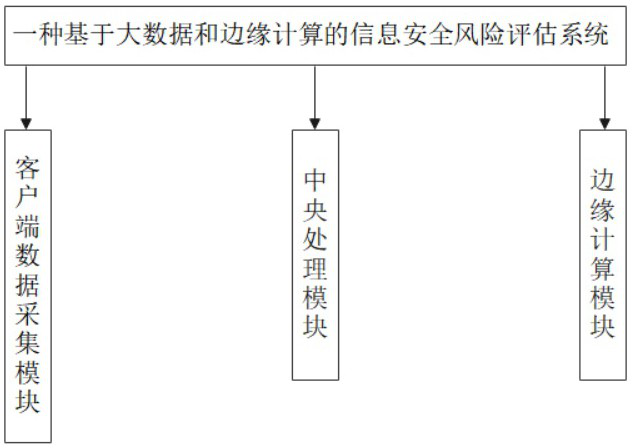
Information security risk assessment system and method based on big data and edge computing
ActiveCN113467314AGet rid of dependenceGet it in timeProgramme controlComputer controlWeb siteAttack
The invention discloses an information security risk assessment method based on big data and edge computing, and the method is characterized in that the method comprises the following steps: S1, a client device carries out the statistics of the number of attacks per unit time, the time of attacking each time, and the records of websites recently visited by a user on the device through a defense system of a network; according to the system and method, technologies such as big data and edge computing are applied, so that the system is more accurate in information security risk assessment feedback, and when the to-be-managed equipment does not receive a control instruction sent by the management equipment for a long time, the edge computing technology is applied to analyze data on the equipment under the condition that the operation of the current equipment is not influenced, and the self equipment is controlled according to an analysis result, so that the time of alternating current feedback between the equipment is saved, and equipment paralysis caused by an emergency situation is also avoided.
Owner:广州赛度检测服务有限公司
Information Security Risk Evaluation System
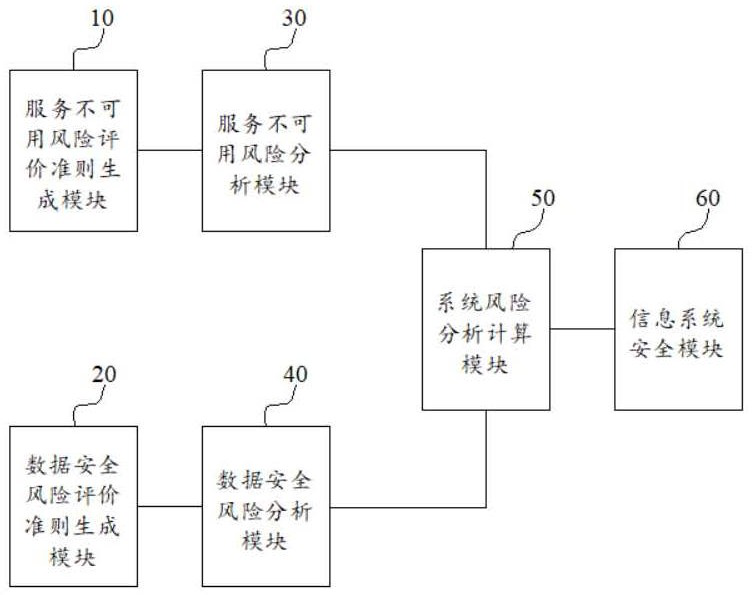
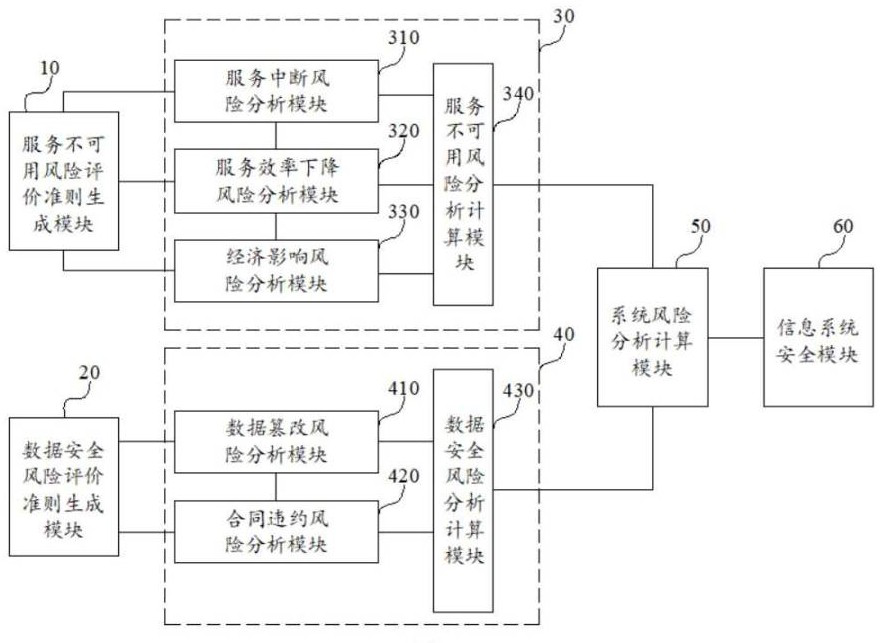
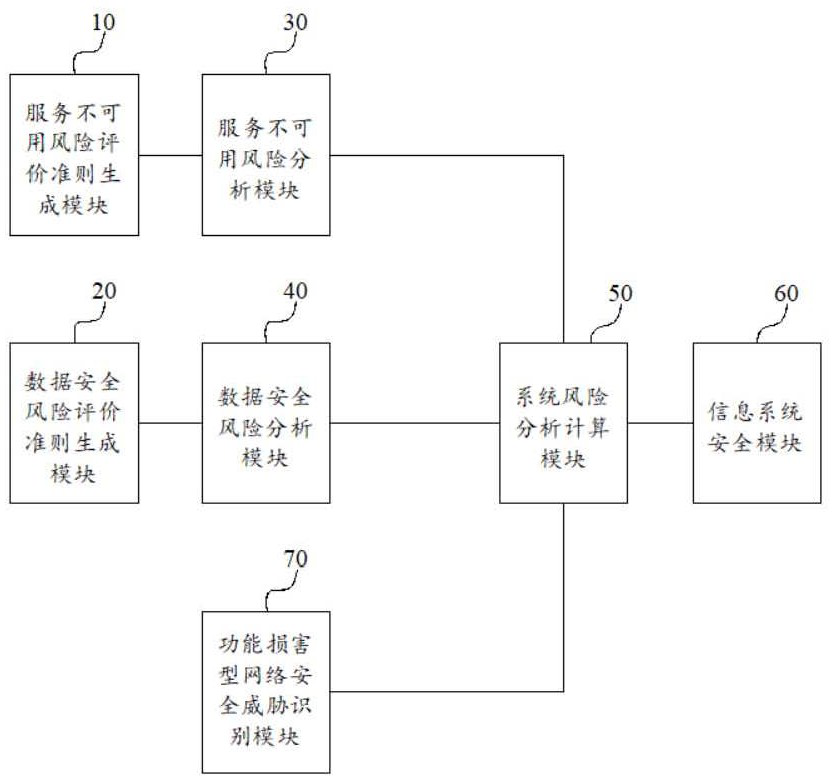
ActiveCN112800437BReduce the difficulty of evaluationImprove accuracyDigital data protectionPlatform integrity maintainanceInformation systems securitySystem risk
The present invention provides an information security risk assessment system, including: a service unavailability risk assessment criterion generation module, a data security risk assessment criterion generation module, a service unavailability risk analysis and calculation module, a data security risk analysis module, and a system risk analysis and calculation module and information system security modules. The information security risk assessment system provided by the present invention can accurately analyze and calculate the business network security risk, so that the information security risk assessment system provided by the present invention can accurately adopt different levels of risk protection for different levels of business network security risks measures to improve its security performance.
Owner:国家信息中心
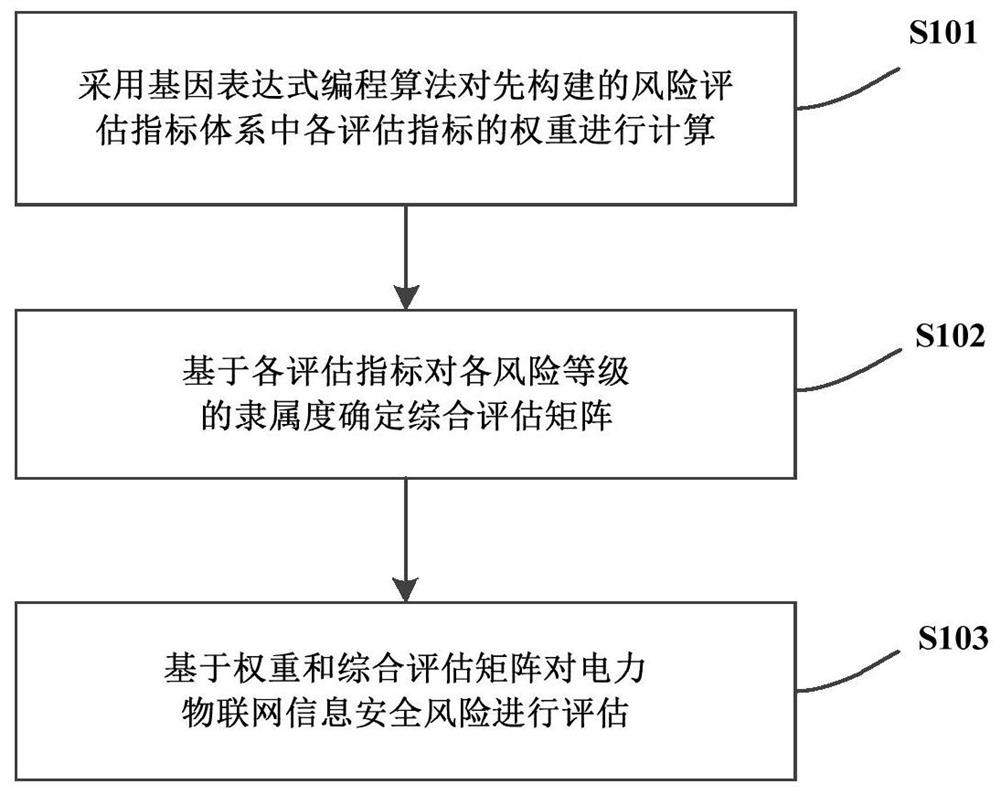
Electric power Internet-of-things information security risk assessment method and device
PendingCN111695754AImprove accuracyEasy assessment processResourcesTransmissionIndex systemRisk rating
The invention provides an electric power Internet of Things information security risk assessment method and device. The method comprises the steps of utilizing a gene expression programming algorithmto calculate the weight of each assessment index in a pre-constructed risk assessment index system; determining a comprehensive evaluation matrix based on the membership degree of each evaluation index to each risk level; and evaluating the information security risk of the power Internet-of-things based on the weight and the comprehensive evaluation matrix. The evaluation process is simplified, the weight is calculated by adopting a gene expression programming algorithm, the determination of the weight is objective and accurate, the information security risk of the electric power Internet-of-things is evaluated based on the weight and the comprehensive evaluation matrix, the relationship of each evaluation index in the risk evaluation index system is considered, and the accuracy of the evaluation result is greatly improved; in consideration of a large number of factors influencing safe and stable operation of the electric power Internet-of-things, relatively high correlation between the factors and non-additivity between the influence factors, the reliability and stability of safe operation of the electric power Internet-of-things are improved.
Owner:CHINA ELECTRIC POWER RES INST +4
Industrial control information security risk assessment model based on distributed inspection
PendingCN110794795AIncrease the identification and analysis engineImprove accuracyTotal factory controlProgramme total factory controlCollection systemIndustrial control system
The invention relates to the field of information security of an industrial control system, in particular to an industrial control information security risk assessment model based on distributed inspection. An inspection assessment model is constructed by combining industrial control network characteristics; system asset information is collected automatically to form an industrial control asset inspection list; and an asset object inspection model is formed automatically. According to the invention, industrial data are collected and automatic analysis is carried out on the data, and reductionanalysis is carried out on various industrial communication protocols, so that the asset information attributes of the industrial control system are fully and accurately identified; because of combination of the automatically and intelligently generated asset inspection object model with the distributed inspection evaluation implementation mode, the workload of inspection personnel is reduced andmanual and artificial misoperation and misjudgment are reduced, so that high-efficiency risk evaluation system architecture based on industrial control network characteristics is constructed.
Owner:上海三零卫士信息安全有限公司
Information security risk assessment method for full life cycle of intelligent networked automobile
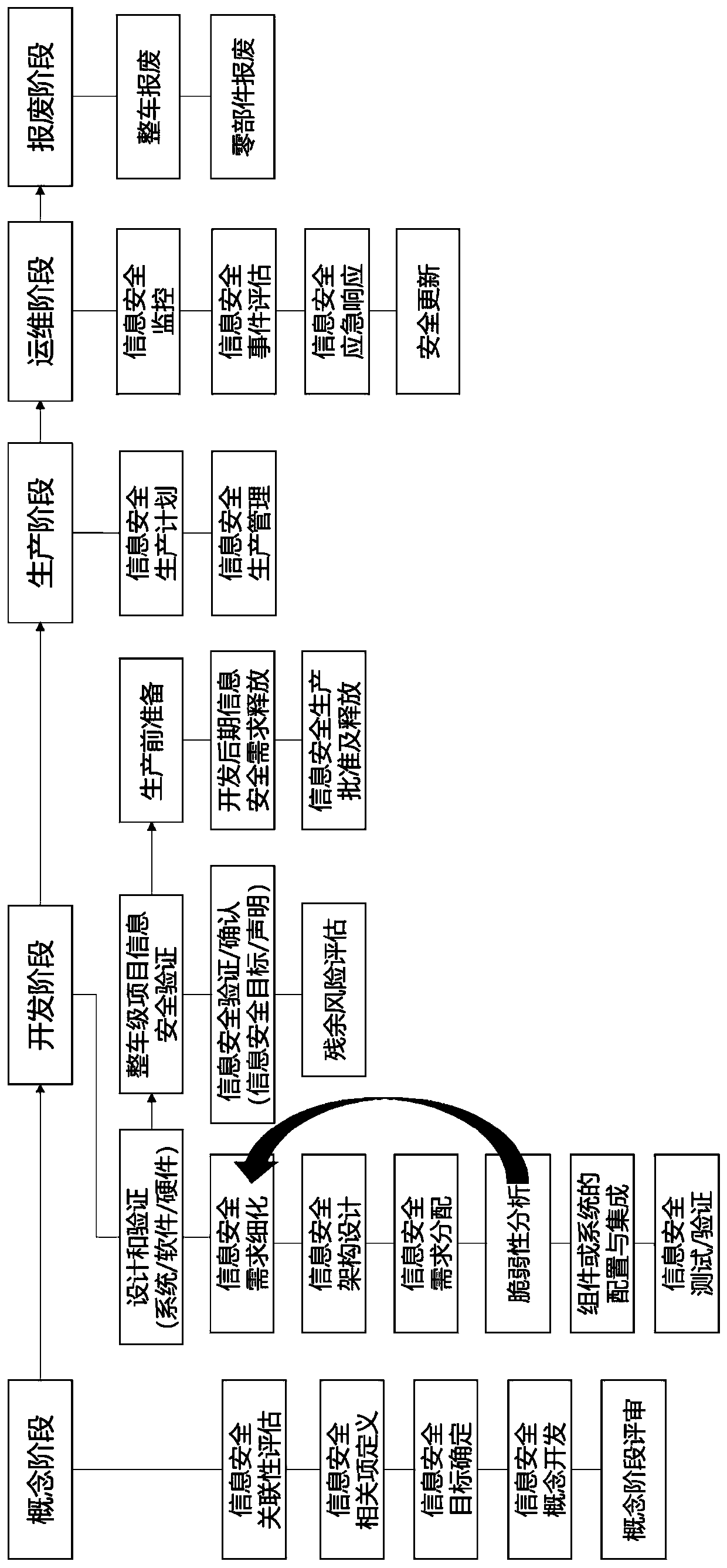
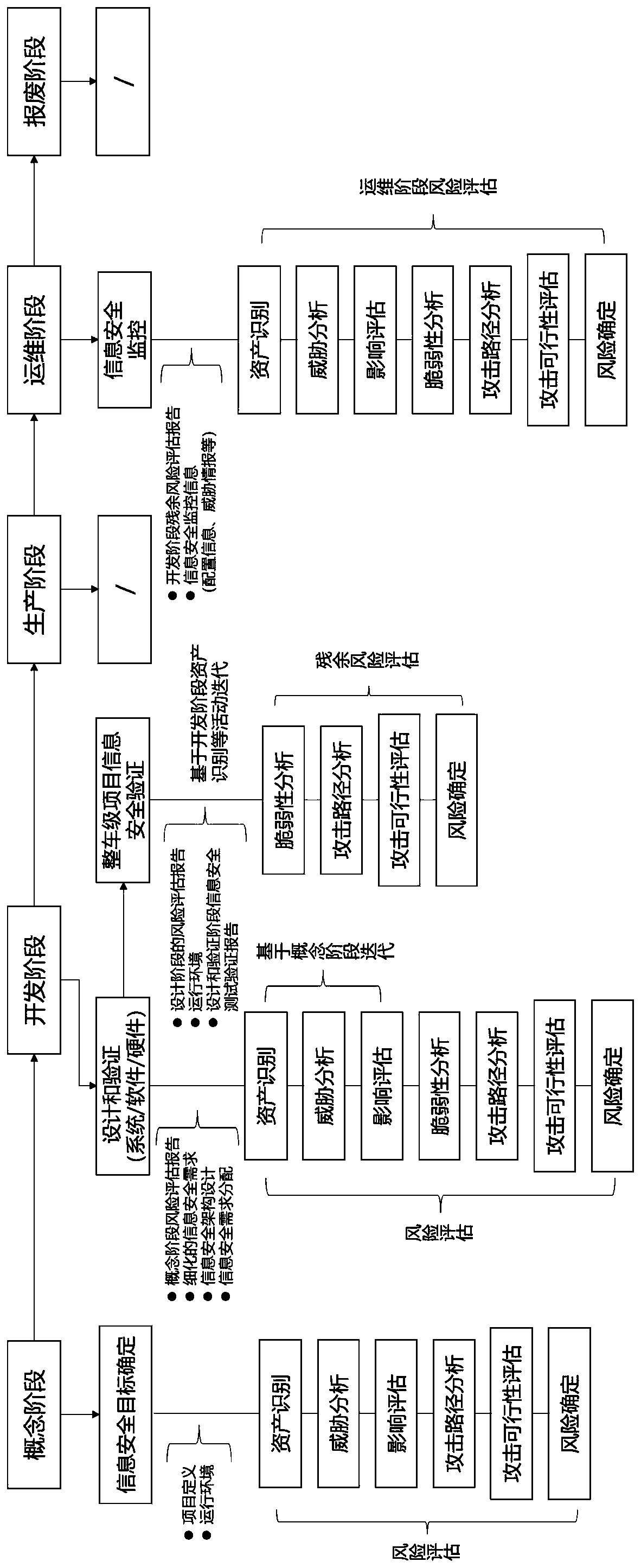
PendingCN110826906AClear implementation nodesClear requirementsResourcesIntelligent NetworkFull life cycle
The invention discloses an information security risk assessment method for the full life cycle of an intelligent networked automobile, and the method comprises the following steps: 1, dividing the intelligent networked automobile into five life cycles: a concept stage, a development stage, a production stage, an operation and maintenance stage and a scrapping stage; and 2, for the five life cyclesdivided in the step 1, carrying out risk assessment on the automobile in each life cycle, and not carrying out risk assessment on the automobile in the production stage and the scrap stage. Accordingto the information security risk assessment method for the full life cycle of the intelligent networked automobile, through the arrangement of the step 1 and the step 2, the life cycle of the automobile can be effectively divided, and then staged assessment is carried out on the automobile according to the divided life cycle.
Owner:BEIHANG UNIV +1
Factory hazard source identification method based on BIM
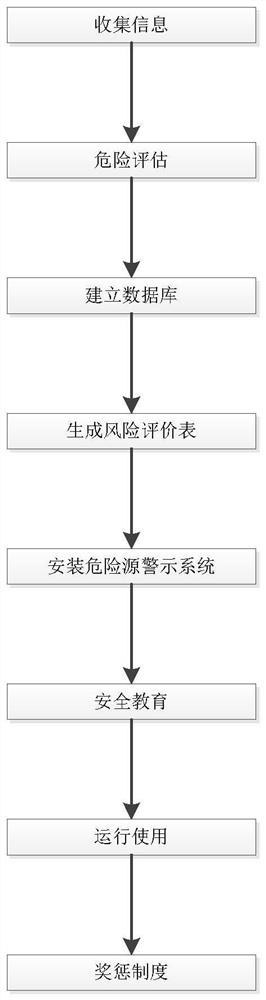
InactiveCN114331068ARaise security awarenessIncrease motivationGeometric CADDigital data information retrievalRisk identificationHazard
The invention relates to the technical field of hazard source identification, and discloses a BIM-based factory hazard source identification method, which comprises the steps of A, information collection, B, safety risk assessment, C, database establishment, D, modeling based on BIM, E, hazard source warning system installation, F, safety education, G, operation and use, and H, reward and punishment system. Safety education is conducted on workers regularly, the workers have risk identification consciousness thought, a reward and punishment system is set, the workers are encouraged to check by themselves and others, the workers are rewarded, the safety consciousness of the workers and the enthusiasm of the workers can be enhanced, risks are reduced, meanwhile, the production of factories can be improved, and the production efficiency is improved. The system arranges on-site supervisors, timely corrects the non-standard operation of the on-site workers, eliminates the danger, and is provided with a danger source warning system, so that the on-site operation condition can be observed from the central control at any time, the workers are reminded to pay attention to rest, and the danger caused by fatigue operation is prevented.
Owner:中国检验认证集团浙江有限公司
An information security risk assessment system and method based on big data and edge computing
ActiveCN113467314BGet rid of dependenceSave time communicating feedbackProgramme controlSecuring communicationWeb siteAttack
Owner:广州赛度检测服务有限公司
An information security risk assessment method
ActiveCN106656996BComprehensive assessment itemsWide range of assessmentsPlatform integrity maintainanceTransmissionData contentEvaluation data
Owner:航天科工智慧产业发展有限公司
Industrial control information security risk assessment model based on distributed inspection
InactiveCN112116227AAvoid data falsificationAvoid covering up situationsResourcesInformation security risk assessmentReal-time computing
The invention relates to the technical field of industrial control system information security, and discloses an industrial control information security risk assessment model based on distributed inspection, which comprises the following steps: S1, formulating an information security risk list according to a target to be assessed; S2, selecting a risk assessment method, wherein the risk assessmentmethod comprises a qualitative risk assessment method and a quantitative risk assessment method; and S3, on the basis of the information security risk list, obtaining an industrial control system communication data packet, analyzing the industrial control system communication data packet, obtaining system asset related elements, storing the system asset related elements to form an asset sample list, and collecting system asset information in a field random spot check and retrieval mode. The industrial control information security risk assessment model based on distributed inspection can solvethe problems that the inspection efficiency is reduced and the inspection accuracy is poor due to the fact that a large number of manual operation parts need to be carried out by workers in the inspection process at present.
Owner:恩善(厦门)信息科技有限公司
Automobile information security risk assessment method and device, electronic equipment and storage medium
PendingCN112597500AImprove efficiencyImprove accuracyPlatform integrity maintainanceResourcesComputer scienceIndustrial engineering
Owner:CHINA INTELLIGENT & CONNECTED VEHICLES (BEIJING) RES INST CO LTD
Network information security risk assessment model
PendingCN112422509AAchieving the effect of risk visualizationHold up steadilyEnergy saving control techniquesTransmissionDisplay boardComputer science
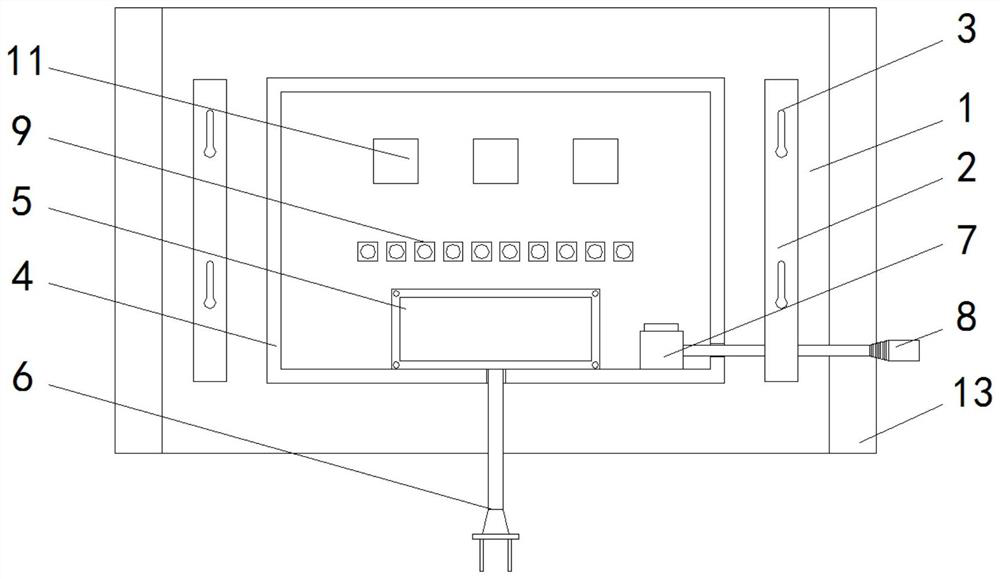
The invention relates to the technical field of network security, and discloses a network information security risk assessment model, which comprises a display board, hanging boards are fixedly arranged on the left side and the right side of the front side of the display board, a power line is connected to a power supply and a data line is connected to a computer system by arranging color light beads and white light beads, and when the system has a risk, the power line is transmitted to a main control chip by a data line, the main control chip sends the signal to the relay, the relay turns onand turns off the color light lamp bead and the white light lamp bead after signal conversion, the color light lamp bead has three colors of red, yellow and green which represent high risk, easy riskand safety respectively, and the current safety condition is represented by which lamp is turned on while the white light lamp bead only emits white light. The number of the white-light lamp beads isten, and the white-light lamp beads represent different levels of the current safety condition, so that a user can judge and evaluate the current risk in real time according to the color and the number of the lighted lamps so as to make a response strategy in time, and the risk visualization effect is achieved.
Owner:江苏正信信息安全测试有限公司
An extended knowledge map and construction method and system for information security risk assessment
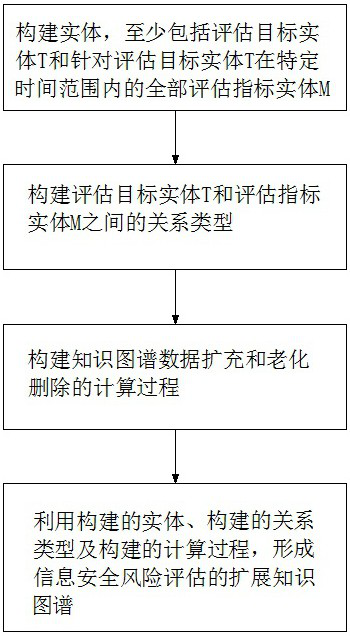
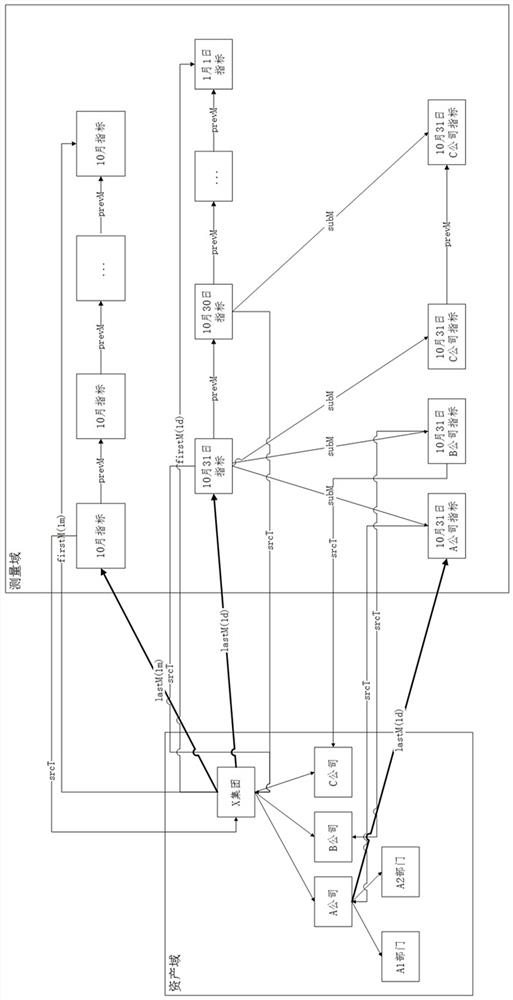
ActiveCN112559774BImprove query efficiencyImprove maintainabilityRelational databasesSpecial data processing applicationsData expansionComputation process
The present invention belongs to the technical field of information security, artificial intelligence and database, and specifically relates to an extended knowledge map and construction method and system for information security risk assessment, including the following steps: constructing an entity, including at least the evaluation target entity T and the evaluation target entity T All evaluation index entities M within a specific time range; construct the relationship type between the evaluation target entity T and the evaluation index entity M; construct the calculation process of knowledge map data expansion, aging, prediction and aggregation; use the constructed entity, the constructed The relationship type and the calculation process of construction form an extended knowledge graph of information security risk assessment. In the present invention, the evaluation index data is also graph-based modeling, so that the evaluation index information is also included in the traditional information security knowledge map, and a sufficient association is established with the evaluation object, thereby bringing convenience to risk evaluation, improving query efficiency and maintainability sex.
Owner:北京金睛云华科技有限公司 +1
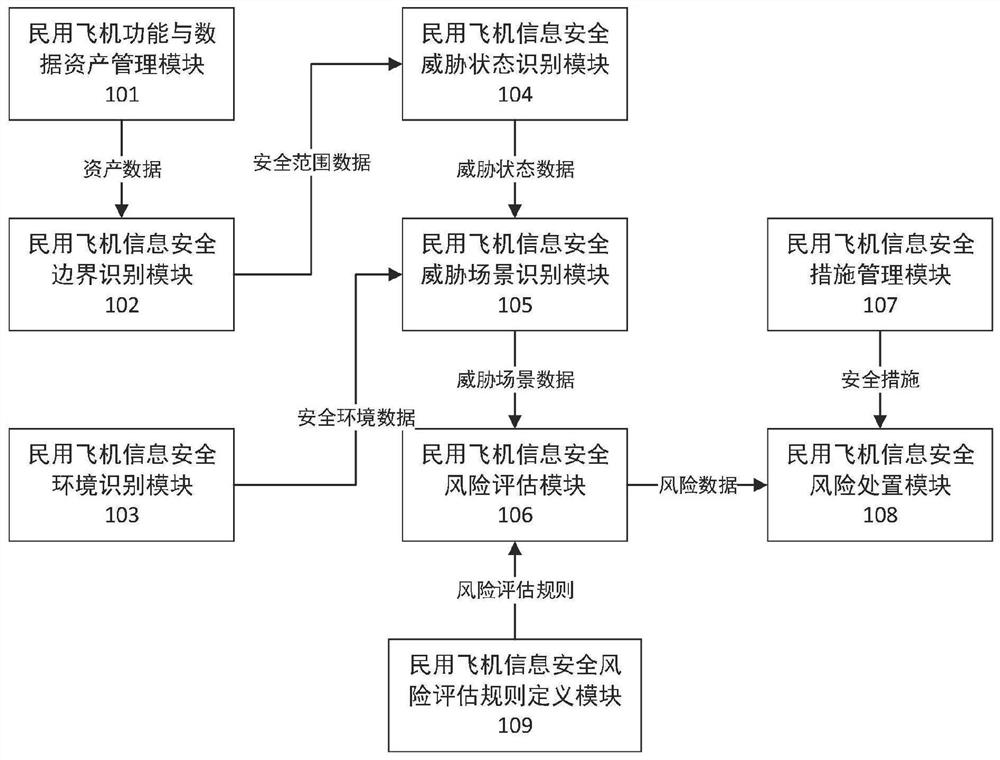
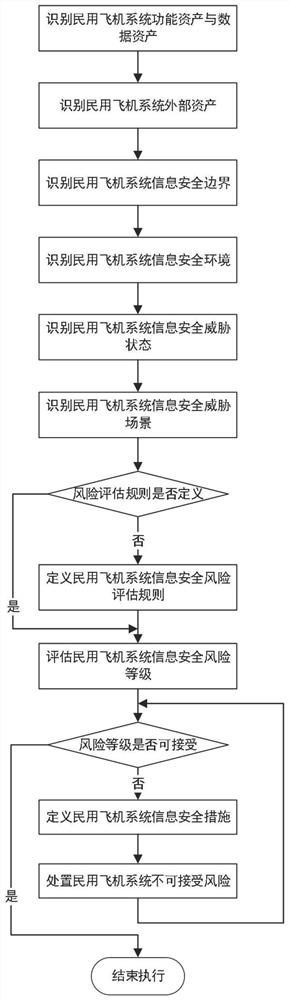
Civil aircraft information safety risk analysis system
The invention discloses a civil aircraft information safety risk analysis system. The system comprises a civil aircraft function and data asset management module, a civil aircraft information security boundary identification module, a civil aircraft information security environment identification module, a civil aircraft information security threat state identification module, a civil aircraft information security threat scene identification module, a civil aircraft information security risk assessment rule definition module, a civil aircraft information safety risk assessment module, a civil aircraft information safety measure management module and a civil aircraft information safety risk disposal module. The invention belongs to the technical field of aircraft safety risk analysis, and particularly provides a civil aircraft information safety risk analysis system which is used for prospective analysis and demand evaluation of flight safety so as to provide important support for reducing human errors and improving flight safety.
Owner:中航机载系统共性技术有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com