An information security risk assessment method
A technology for risk assessment and information security, applied in the field of information security, it can solve the problems of ignoring potential threats, single assessment items, and small assessment scope, and achieves the effect of clear description and processing plan, high risk visualization, and wide assessment scope.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
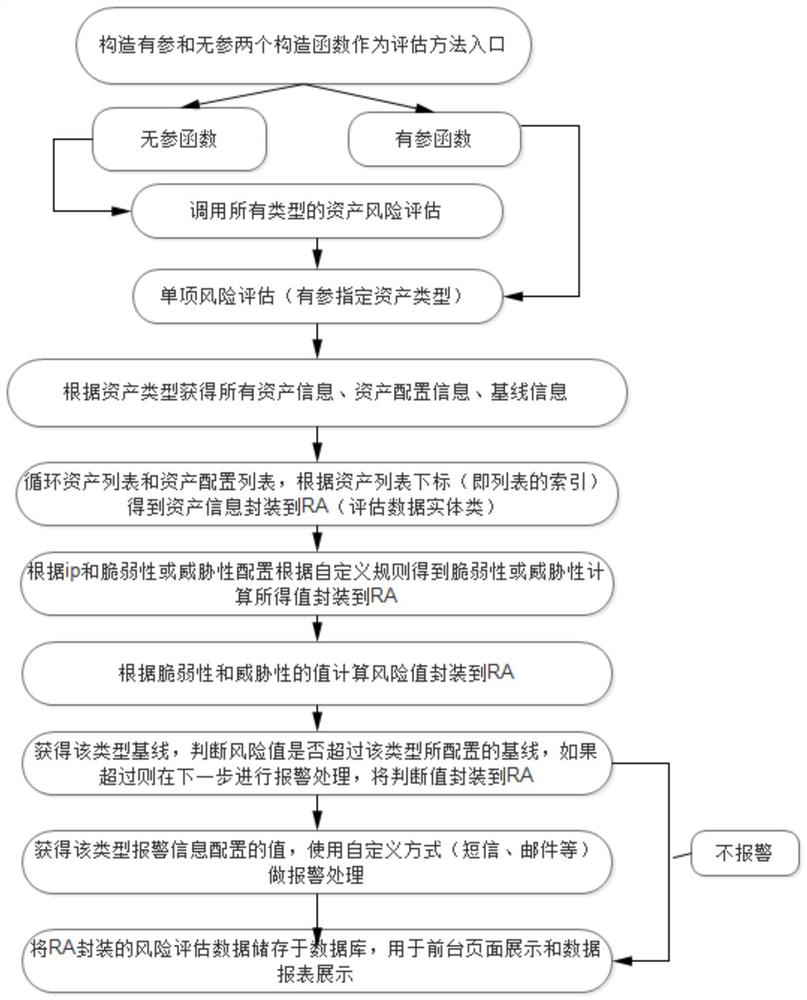
[0038] The first step is to define the risk assessment data entity class:
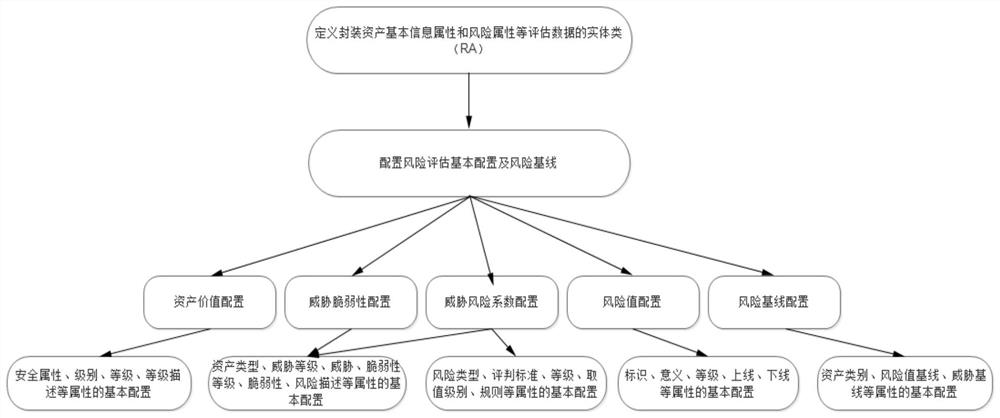
[0039] Define entity class attributes, basic asset information attributes, such as asset number, name, asset value, etc., risk attributes, such as threat, vulnerability, risk value, risk level and other attributes are used as package evaluation data.
[0040] The second step is to configure risk assessment rules and risk baselines. The specific process can be as follows figure 1 Shown:
[0041] 1. Configure the security attribute level and level description of asset value. Security attributes include availability, integrity, and confidentiality, which are used to calculate the value of assets.
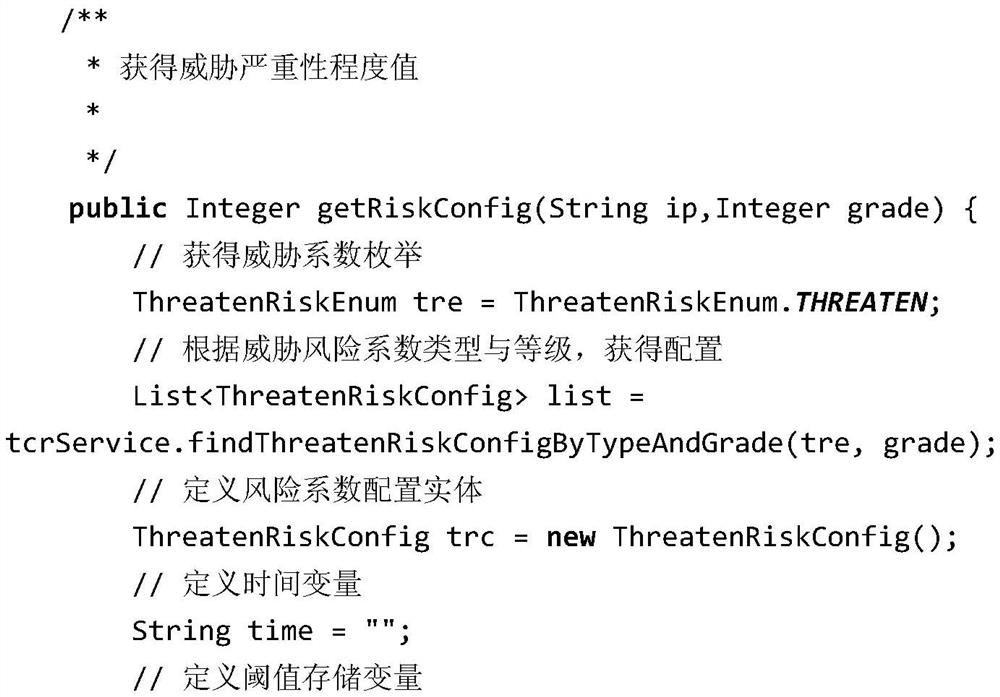
[0042] 2. Configure the risk type, judgment standard, level and value level of the threat risk coefficient and define the rules of this level. The risk type includes vulnerability and threat, which is used to evaluate the risk according to the rules and judgment standards.
[0043] 3. Configure the type of as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com