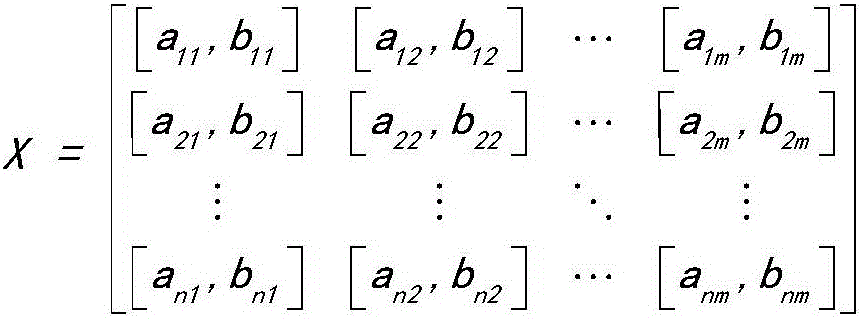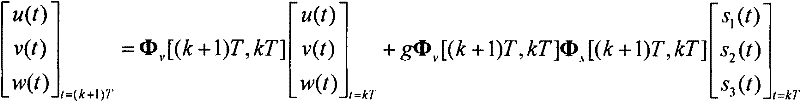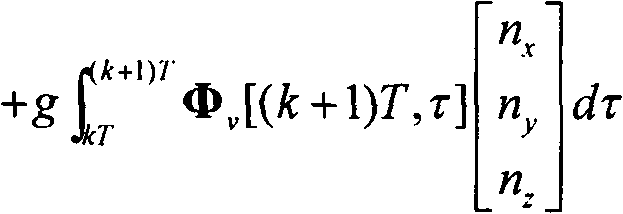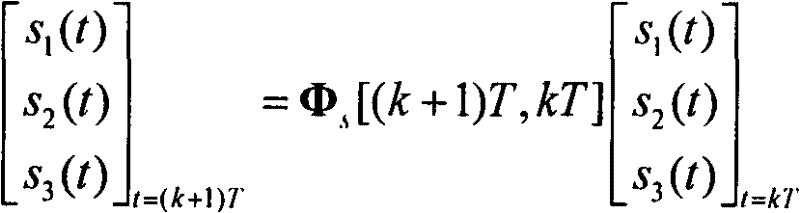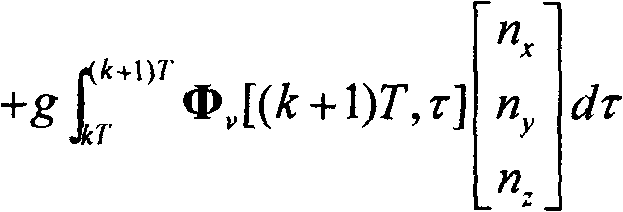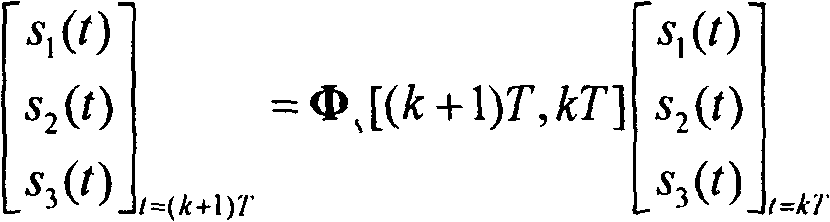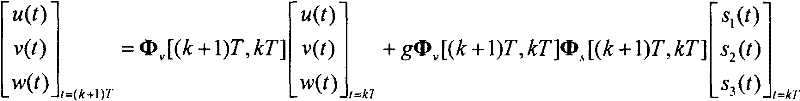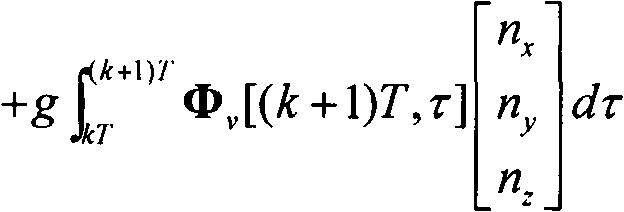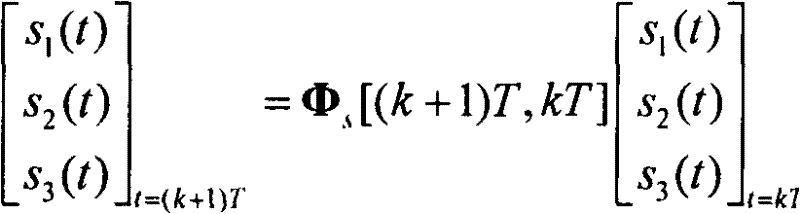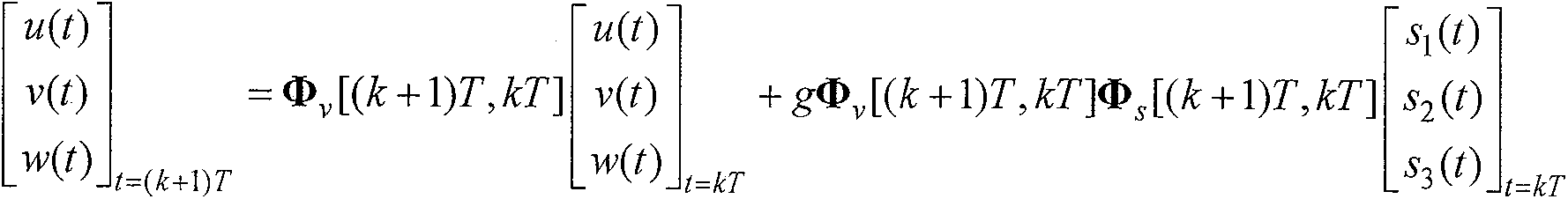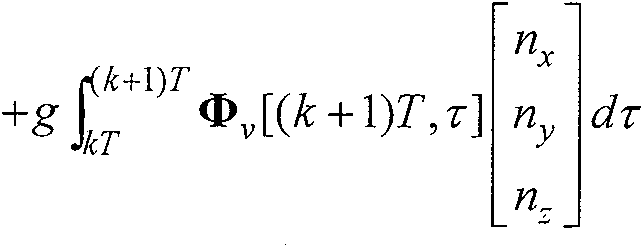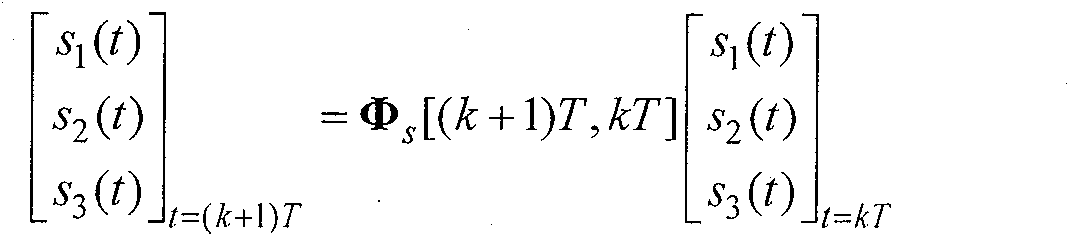Patents
Literature
45 results about "Number form" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A number form is a mental map of numbers, which automatically and involuntarily appears whenever someone who experiences number-forms thinks of numbers. Numbers are mapped into distinct spatial locations and the mapping may be different across individuals. Number forms were first documented and named by Sir Francis Galton in his The Visions of Sane Persons (Galton 1881a). Later research has identified them as a type of synesthesia (Seron, Pesenti & Noël 1992; Sagiv et al. 2006).
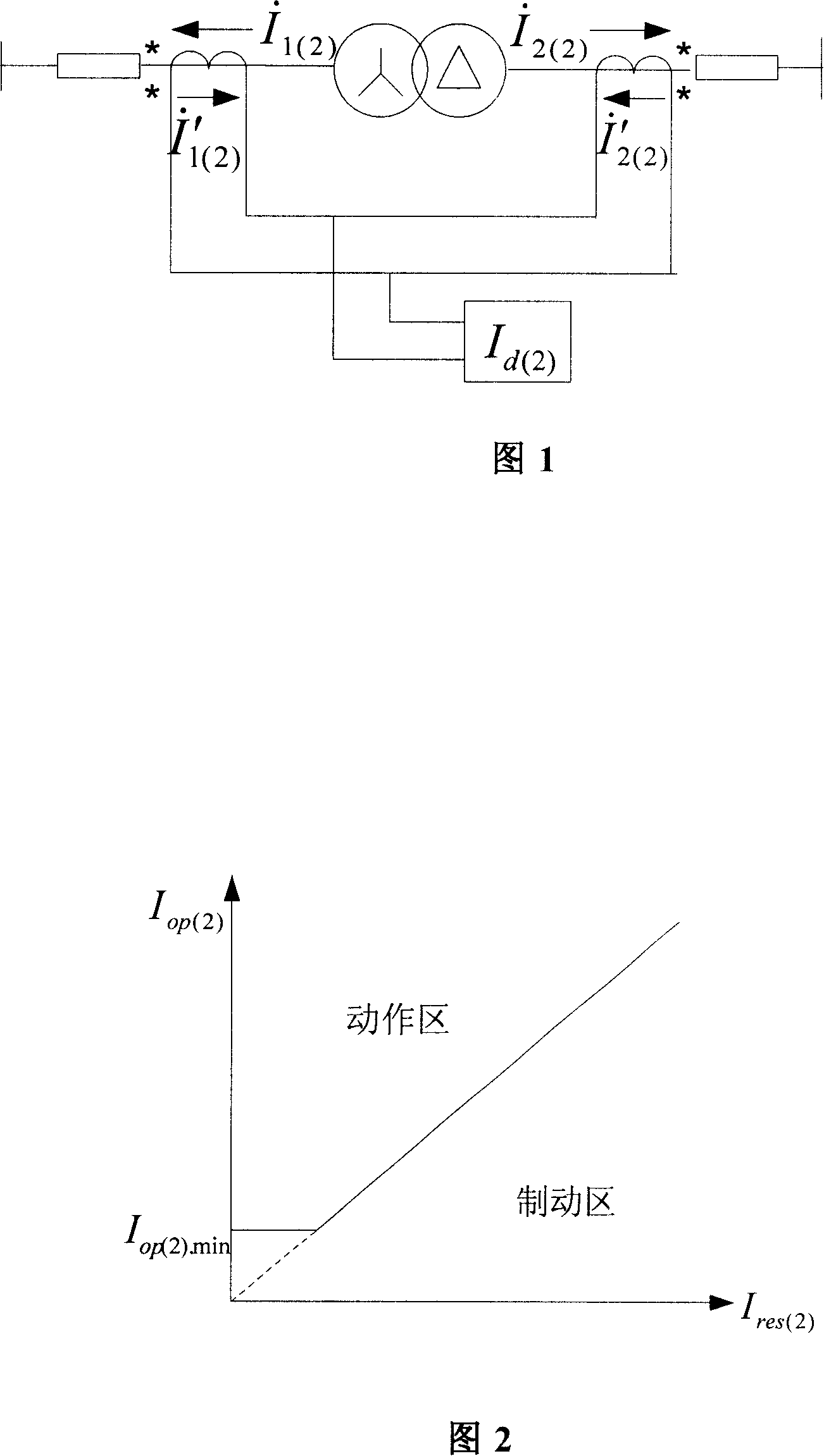
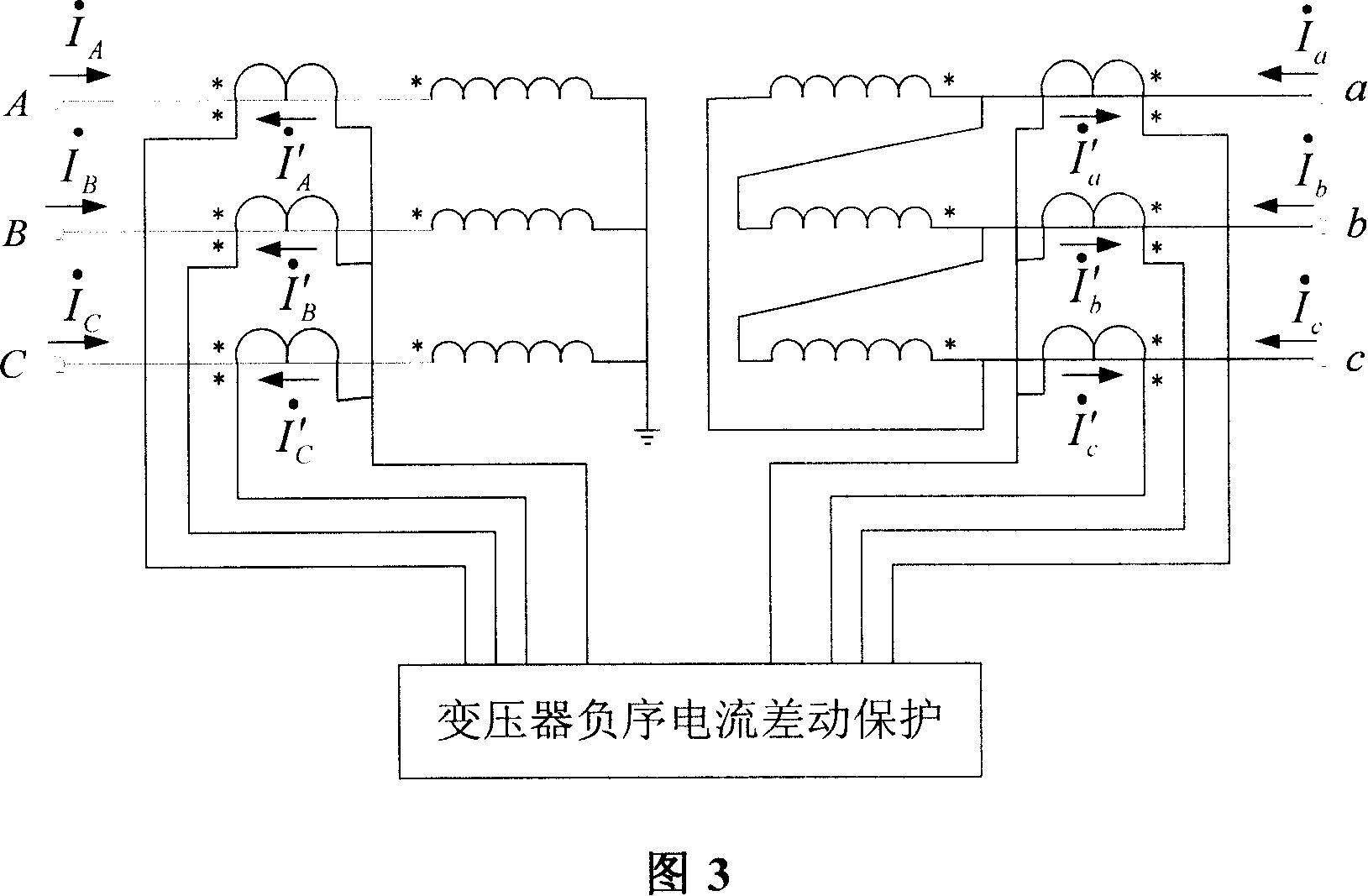
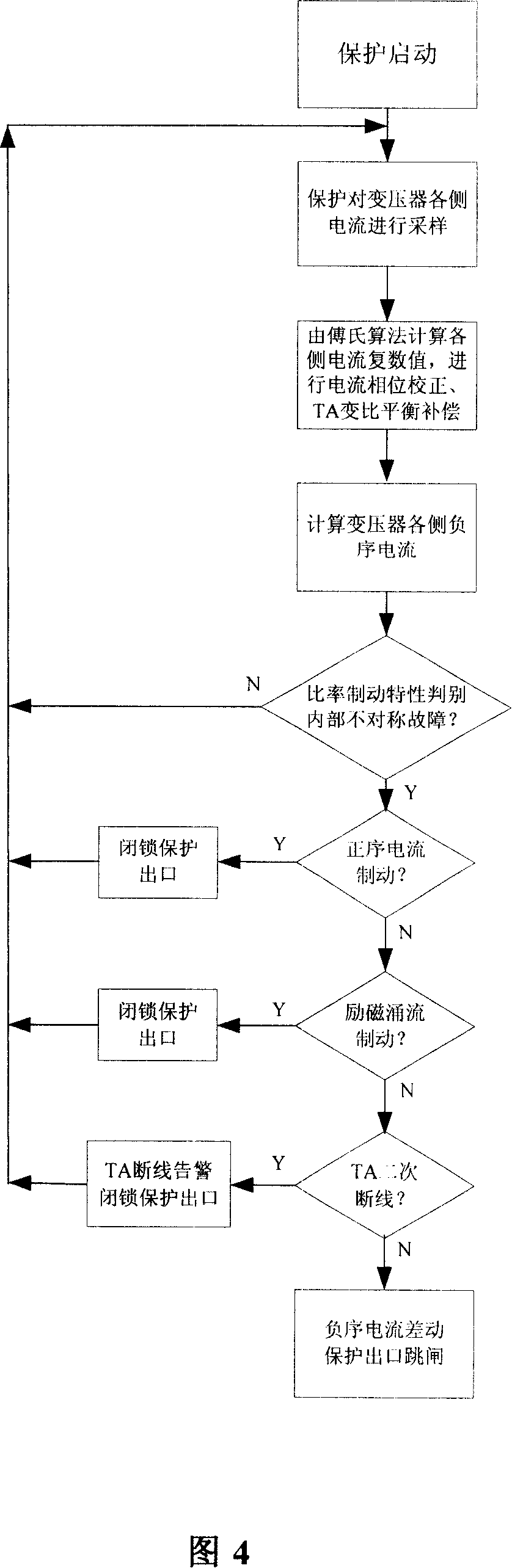
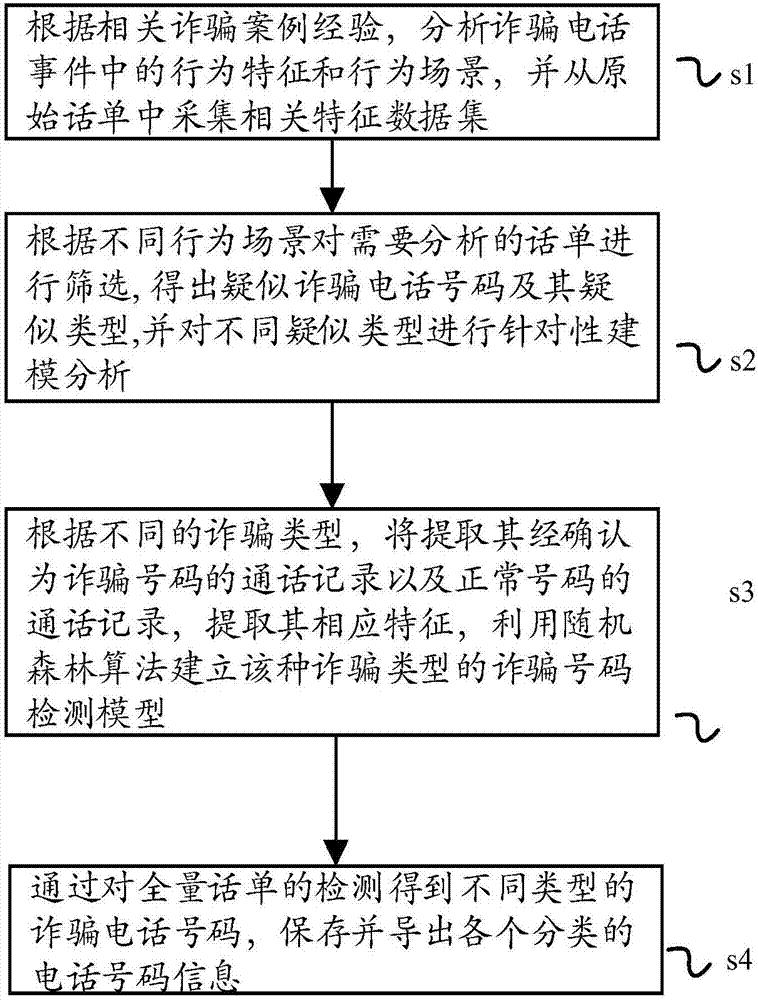
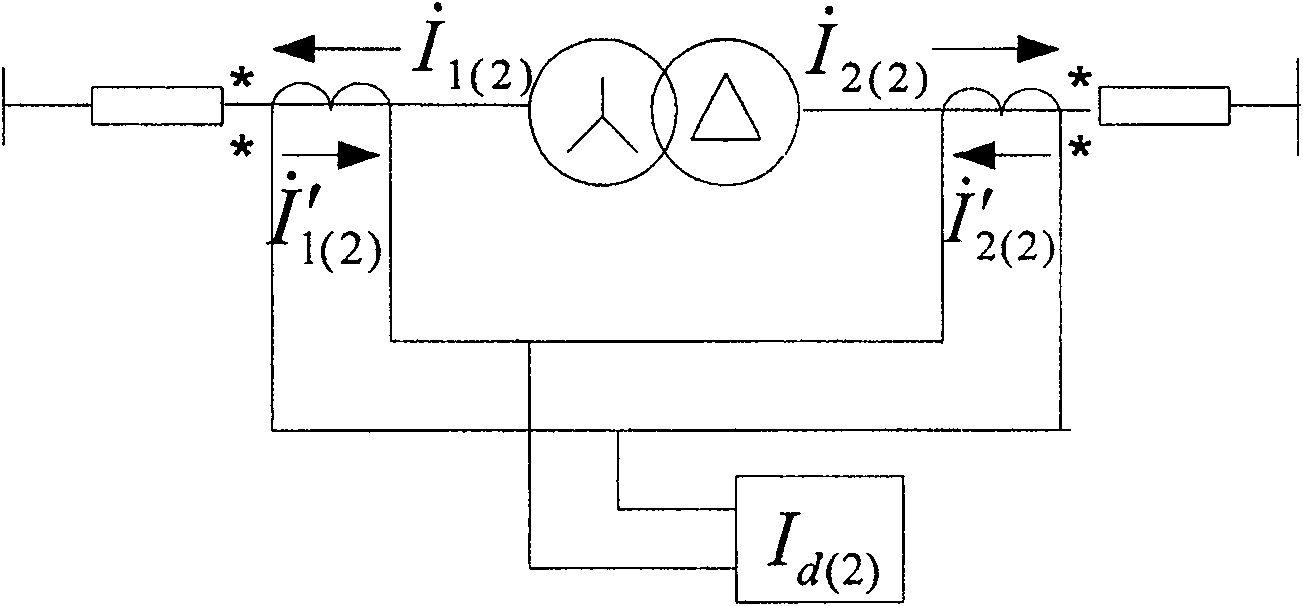
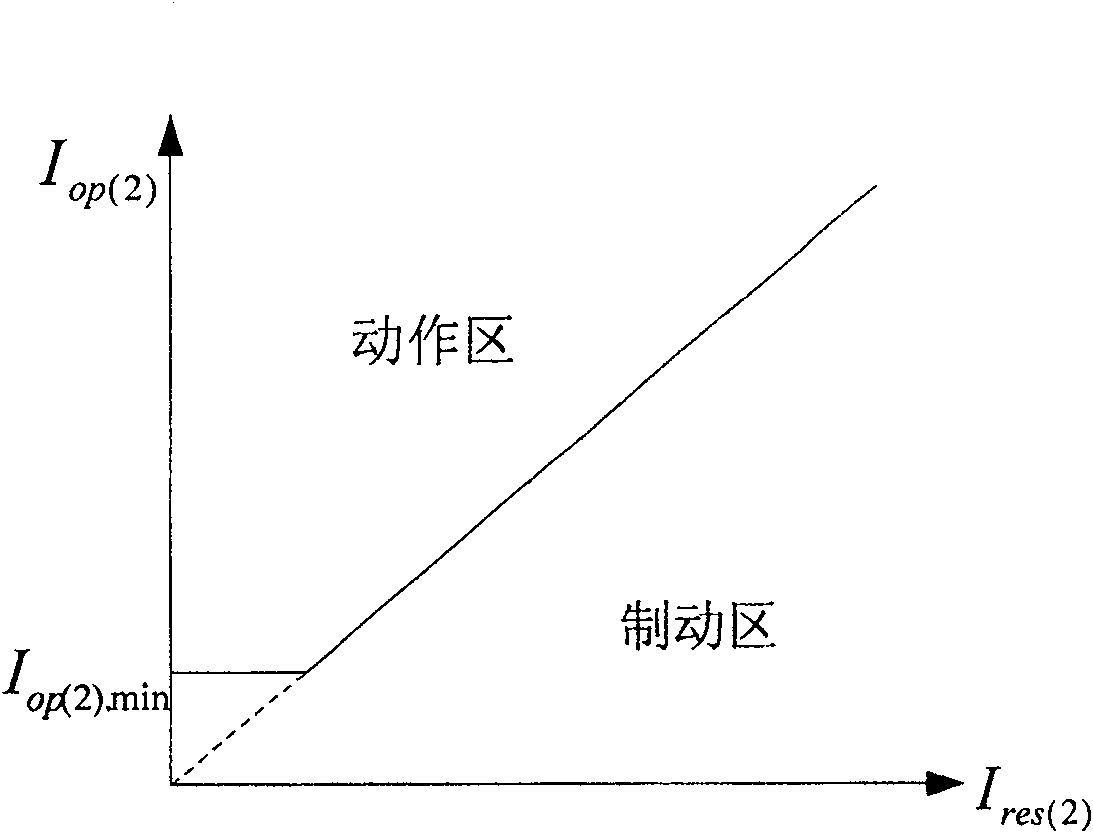
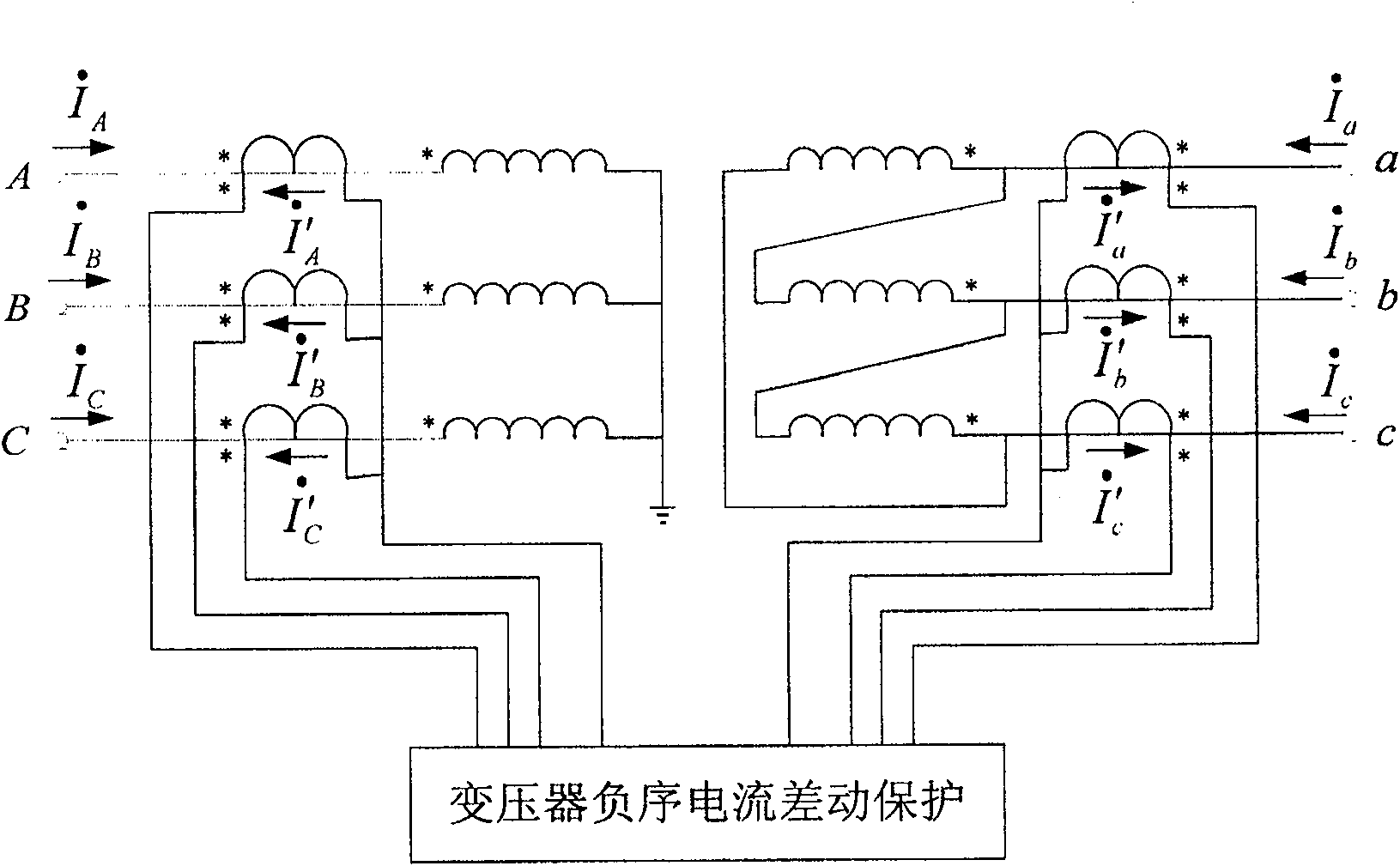
A differential protection method for negative sequence current of large power transformer
ActiveCN1964149AHigh protection sensitivityClearly distinguish internal and external asymmetrical faultsEmergency protective circuit arrangementsPhase correctionSecondary loop
The disclosed protection method for internal fault of large power transformer comprises: the protector samples the secondary current of current transformers on power transformer sides to obtain current instantaneous value and calculate complex number form of electric values by Fourier algorithm, corrects phase of connection form, and balances amplitude of transformation ratio; then, it calculates the complex number form of negative sequence current according to three-phase ac complex form, and computes negative sequence differential current and break current as the negative sequence differential protection principle to decide asymmetric inside and outside fault and drop out all breakers. This invention also contains exactly the negative sequence differential rate breaking feature and protection criterion, the adjusting means for protection values, the positive sequence current breaking criterion, and the block function for error action protection.
Owner:BEIJING SIFANG JIBAO AUTOMATION +1
Method for analyzing fraudulent phone number
InactiveCN107506776ACharacter and pattern recognitionSubstation equipmentTelecommunications networkFeature set
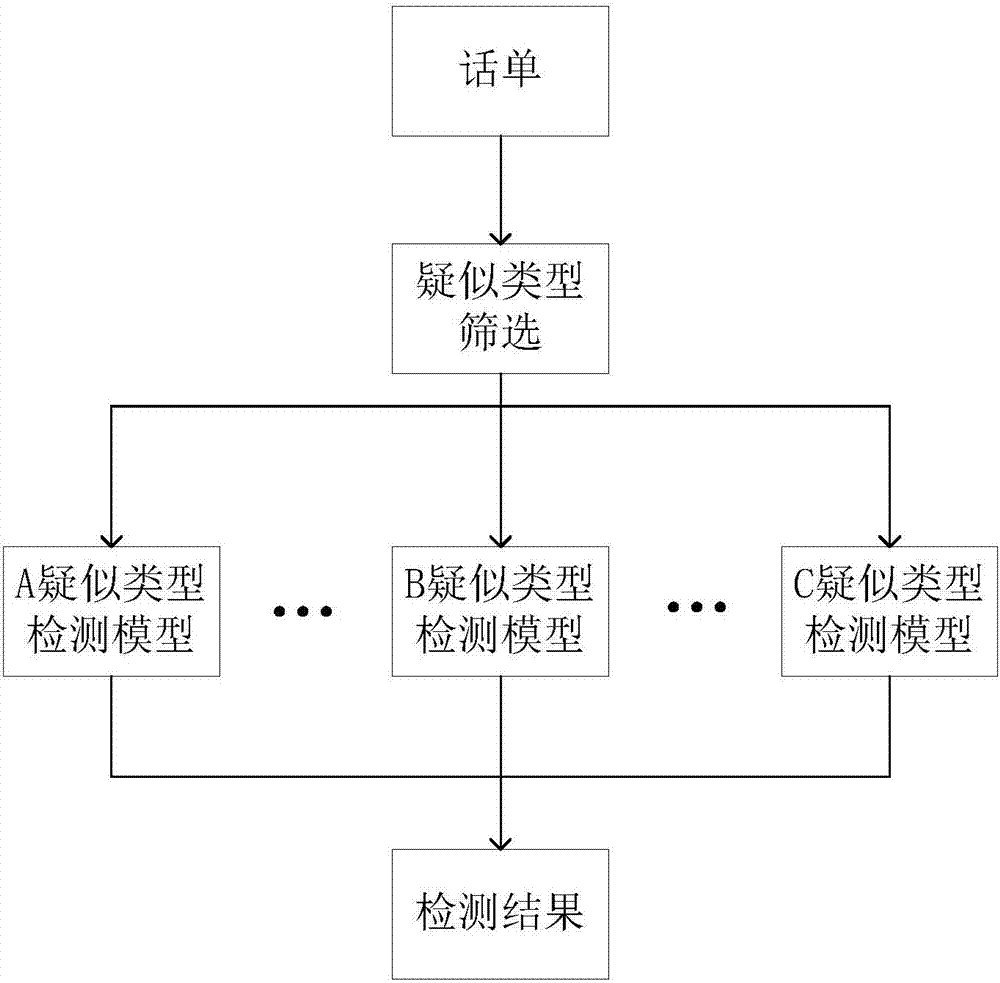
The invention, which belongs to the field of communication network security and machine learning, discloses a method for analyzing a fraudulent phone number. The method includes: analyzing a behavioral characteristic and a behavior scene in a phone fraud event according to relevant fraud case experience and original call bill information of various telecommunication fraud events, and carrying out screening on original call bills for different behavior scenes; extracting and establishing multi-dimensional feature sets for different fraud types; establishing different types of fraud phone detection models by using a random forest algorithm, carrying out offline training on fraud phone number classification models periodically; carrying out quasi real-time detection and determination in an actual network; identifying a fraud phone event and a fraud phone number form lots of call bill information; and then carrying out reporting and processing on the fraud phone event and the fraud phone number by taking a corresponding way to maintain security of the telecommunications network. Therefore, a fraud phone number in communication can be identified effectively and accurately.
Owner:EVERSEC BEIJING TECH
Compression and uncompression method of integral data and device thereof
ActiveCN101008890AHigh costReduce consumptionCode conversionHandling data according to predetermined rulesData compressionNumber form
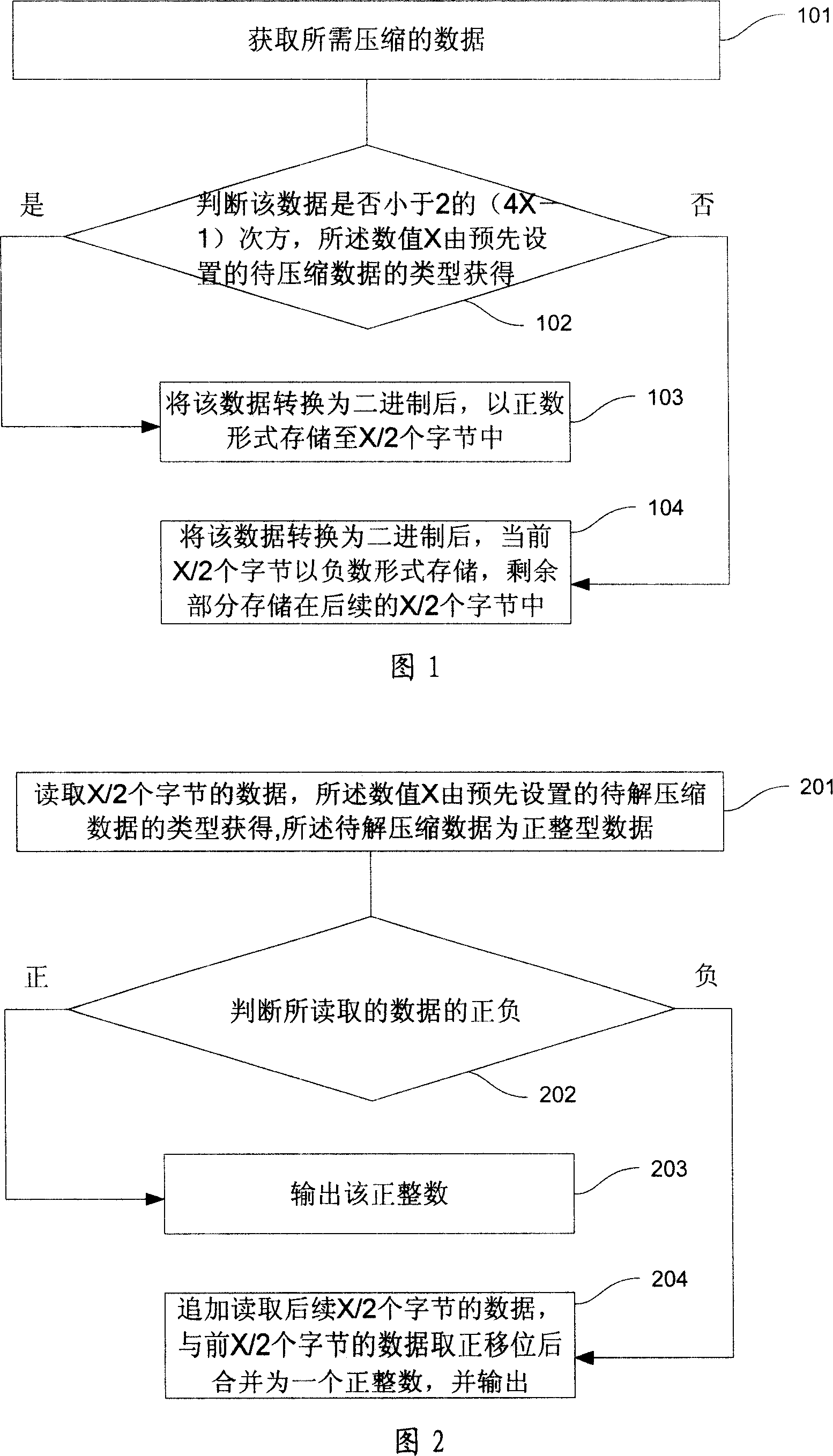
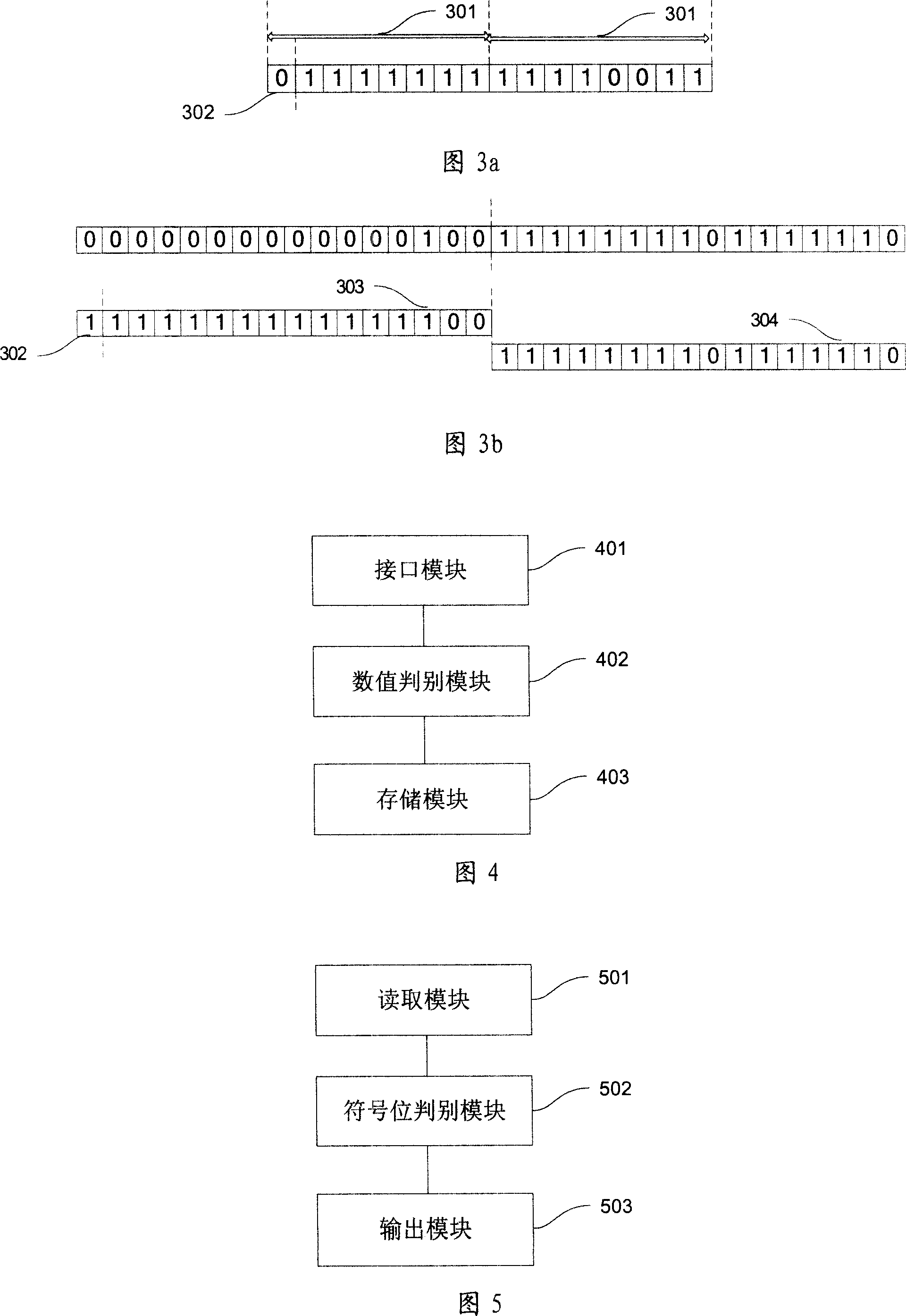
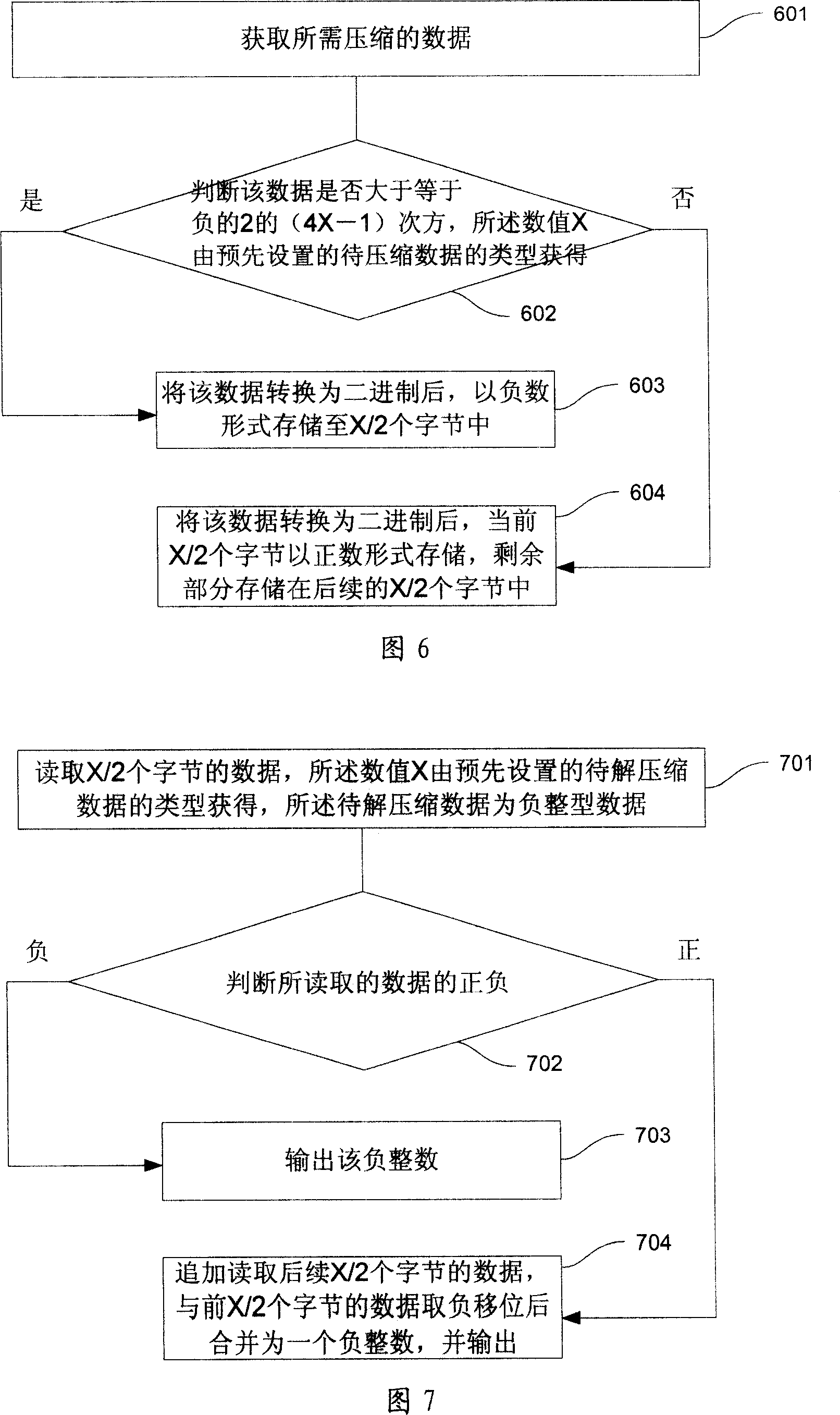
This invention provides one integral data compression method and device, which comprises the following steps: getting needed compressed data; judging whether data is less than 2 4X-1, if the data X is got by preset compressed data; if yes, converting the data into two bit and storing the number form into X / 2 bit; if not, converting the data into two bit and storing the bit by negative form; remaining part is stored in back bit.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Huffman decoding method suitable for JPEG code stream
InactiveCN101017574AShorten the timeReduce occupancyImage codingTelevision systemsDecoding methodsProcessor register
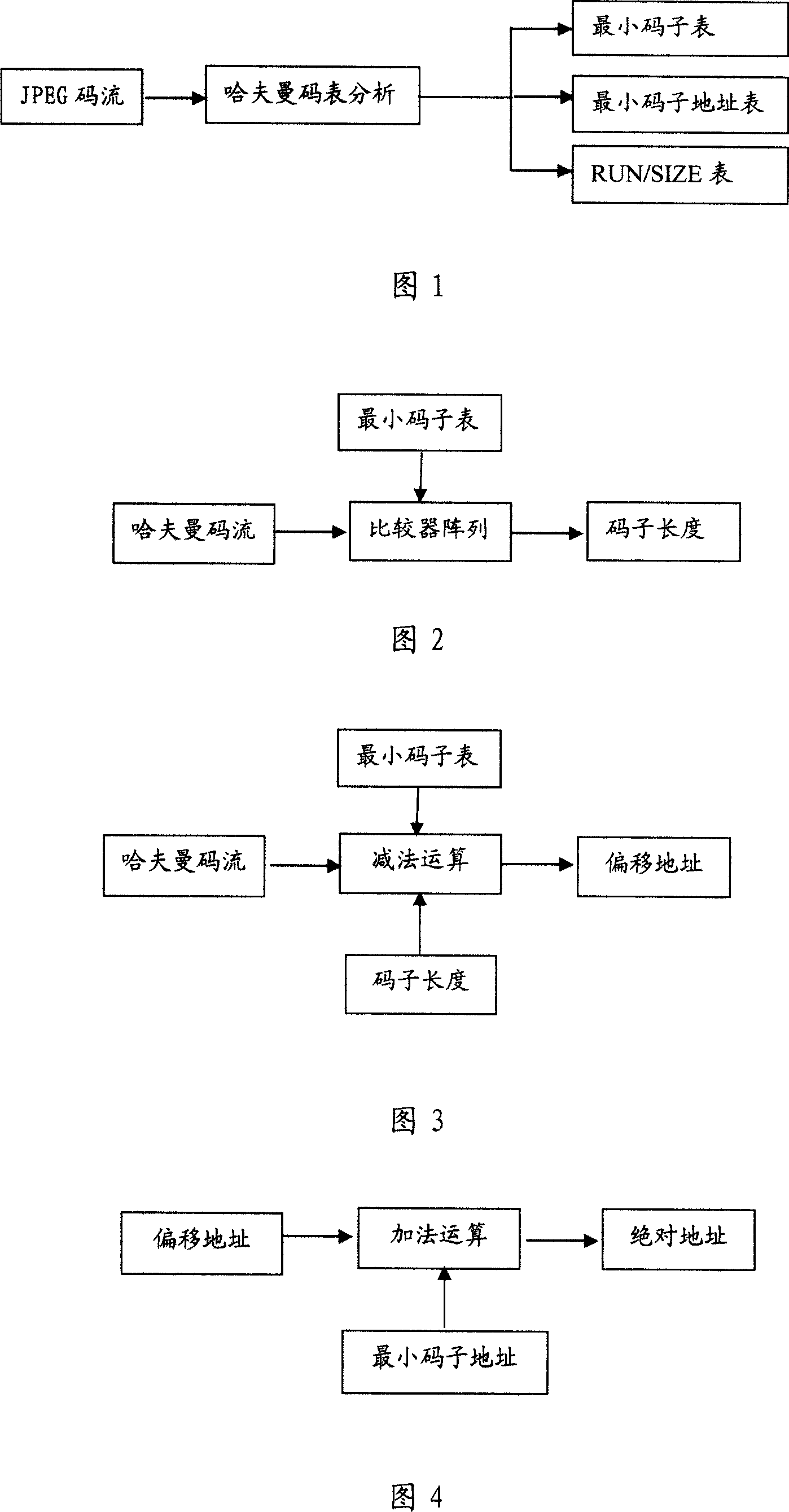
This invention provides one Holman decoding method for JPEG codes flow, which comprises the following steps: a, according to the flow number list to establish minimum code sub list; b, according to the code number forming minimum code address list; c, adopting 0 to 16 bit comparer to get the Holman code relative RUN / SIZE list; d, according to SIZE value to restore codes front data. Comparing with current technique, this method forms different codes length minimum codes list and address list to lower the register array materials occupancy.
Owner:上海广电集成电路有限公司
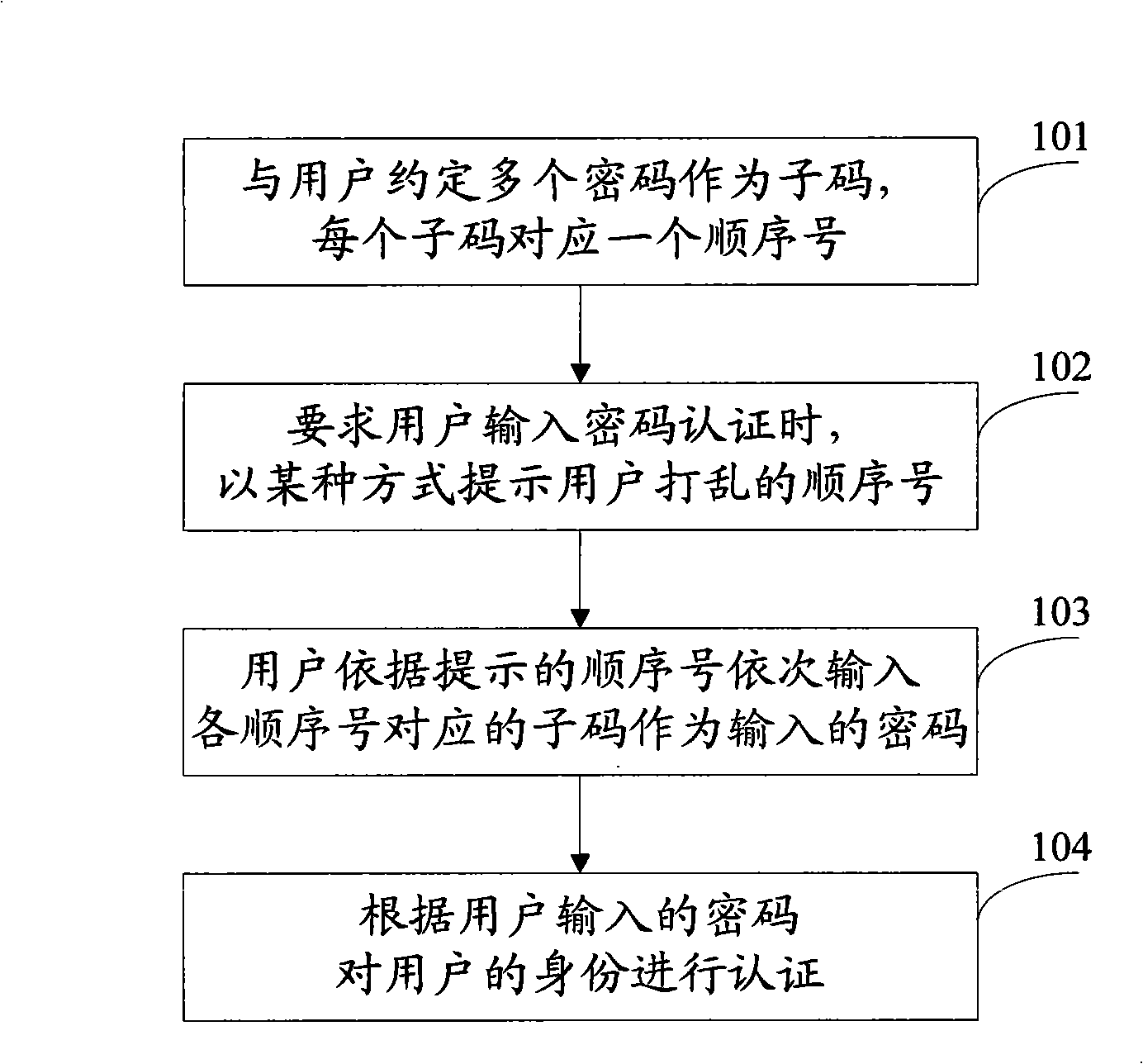
Authentication method adopting complex cryptographic technique
InactiveCN101291225AImprove securityEasy to operateKey distribution for secure communicationUser identity/authority verificationUser inputPassword
The invention provides a method for utilizing the duplex type cryptographic technique to authenticate. The method comprises the following steps that: a plurality of subcodes are appointed for a user using a password, different subcodes correspond to different sequence numbers, and all the subcodes and the sequence numbers form a duplex type password; when the authentication process is performed, the sequence of all the sequence numbers is disrupted, the disrupted sequence numbers are indicated to the user; according to the indicated sequence numbers, the user inputs the subcodes corresponding to the sequence numbers in sequence to finish the input of the password; according to the passwords inputted by the user, the identity of the user is authenticated. In the process of authenticating the password of the user, the method can realize simple operation of the user and high security.
Owner:丁洪涛
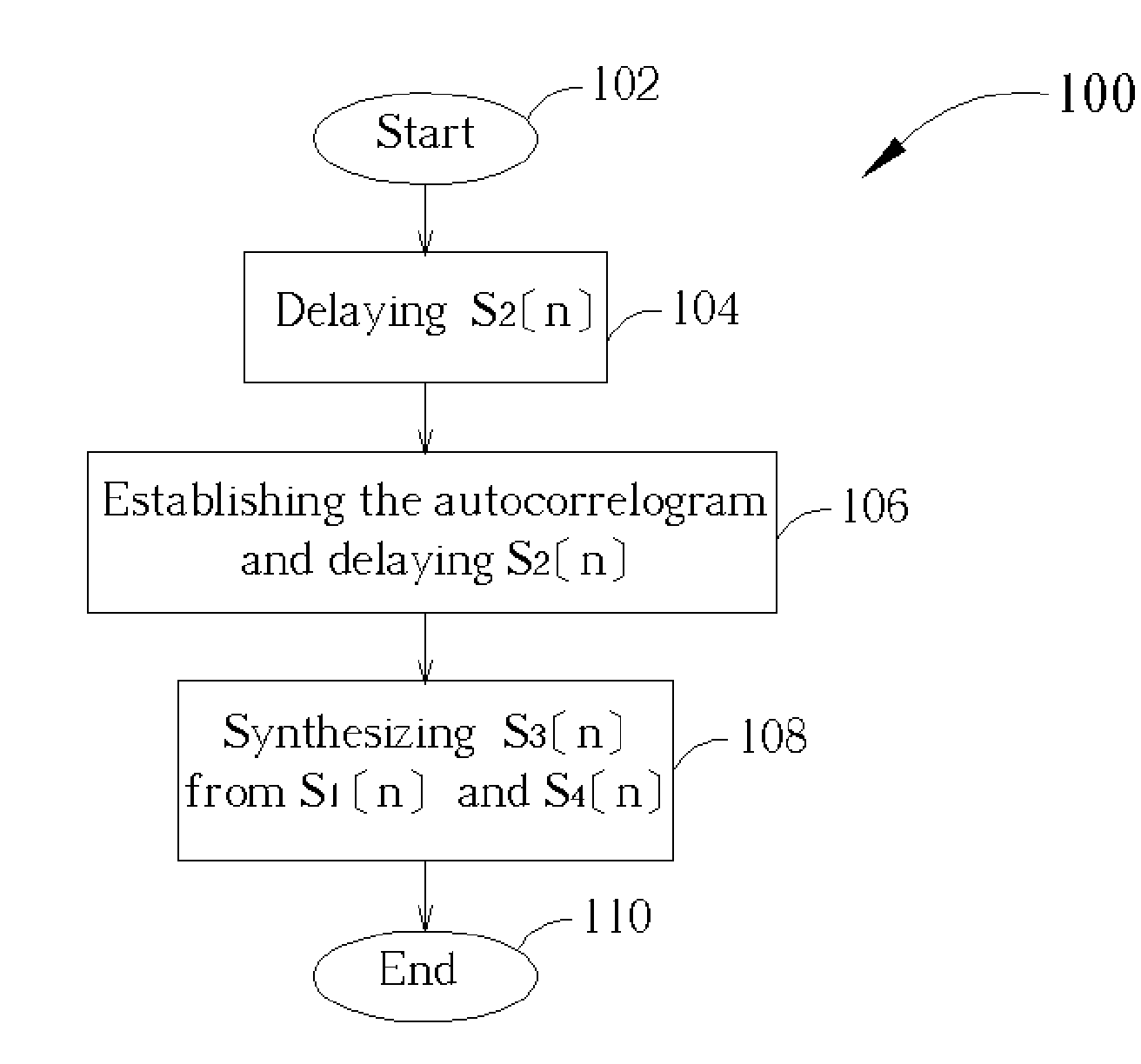
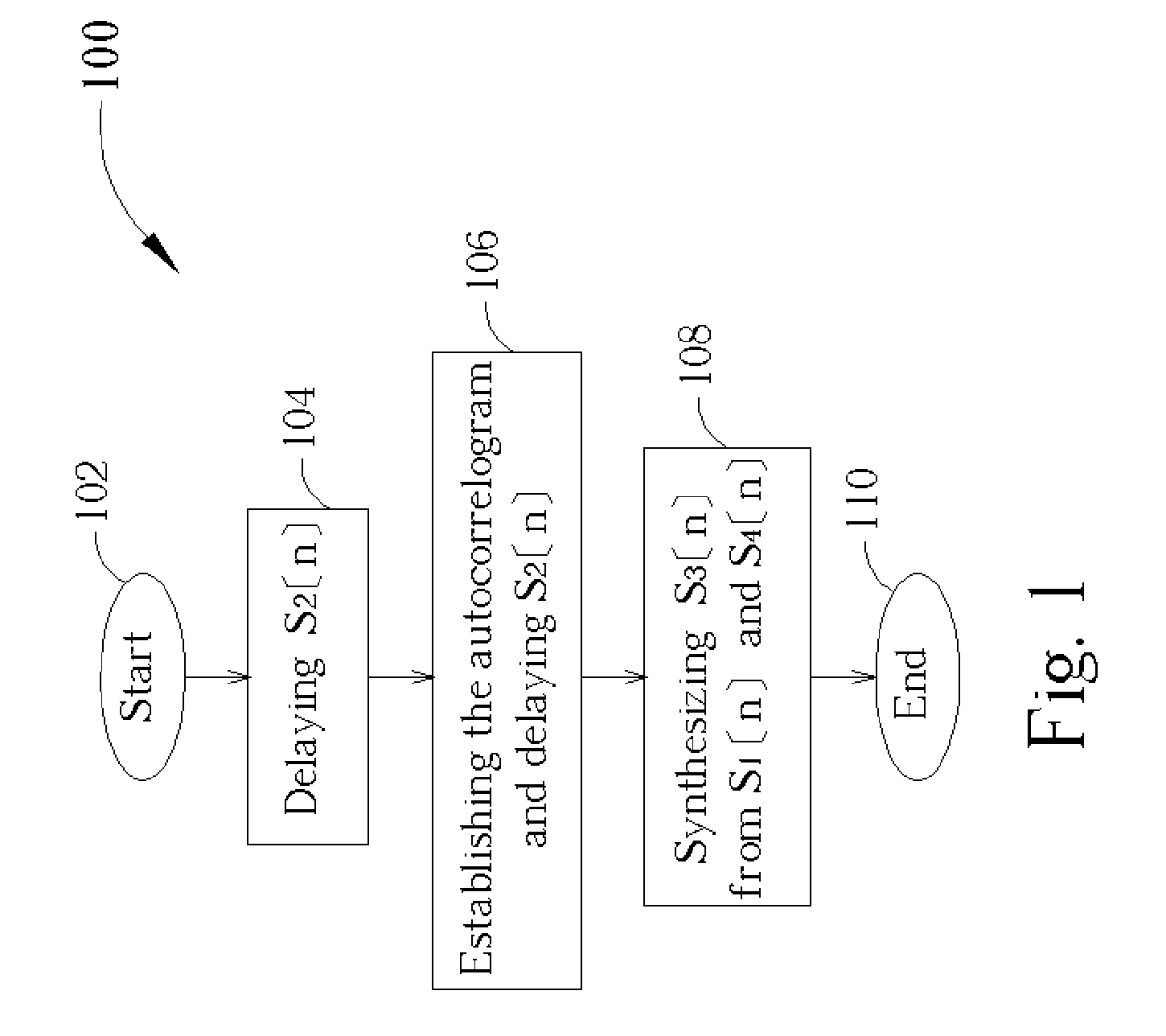
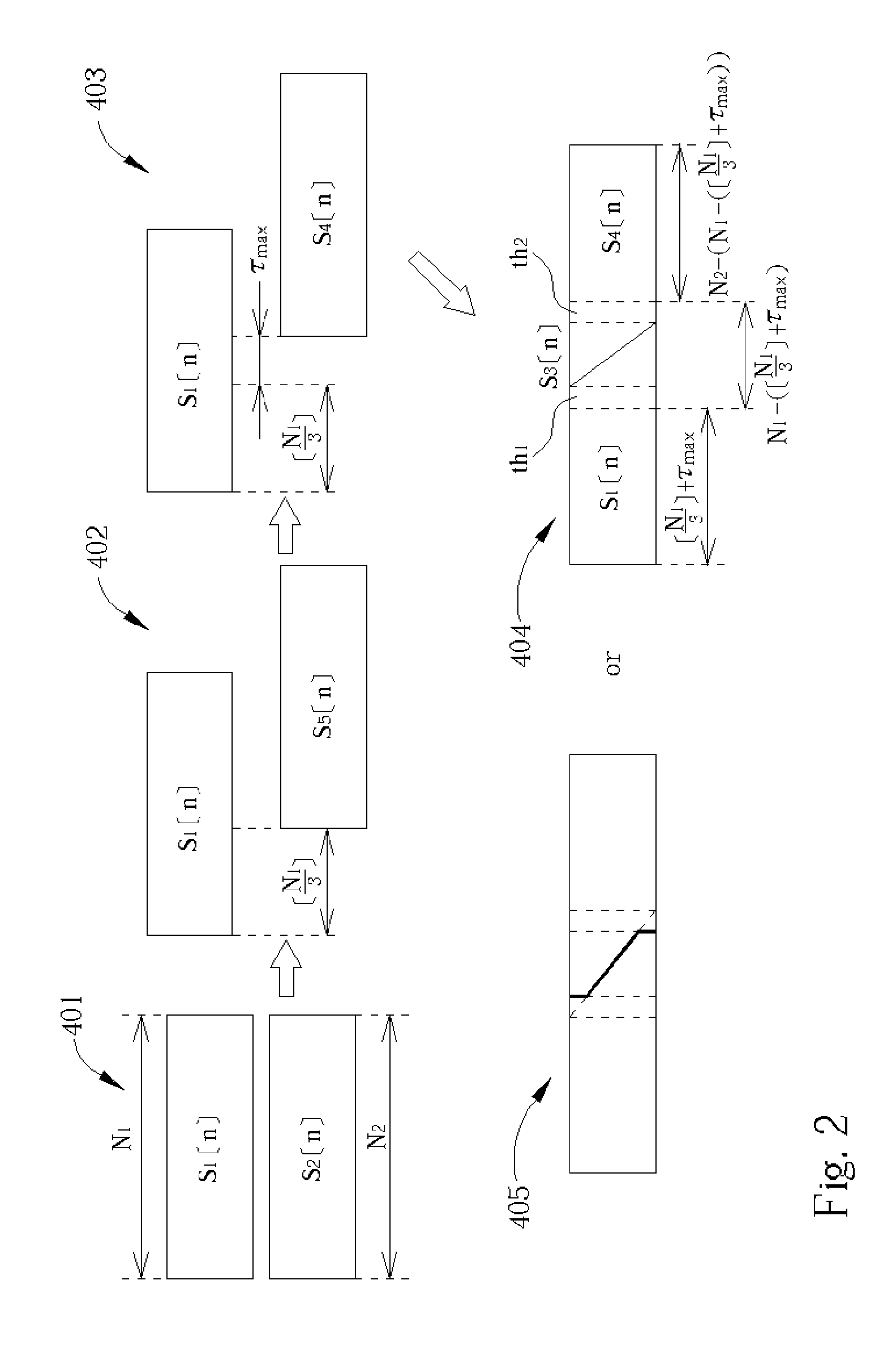
Nonlinear overlap method for time scaling
InactiveUS7173986B2Efficient synthesisQuality improvementAmplitude-modulated carrier systemsAmplitude demodulationCorrelation functionNumber form
A nonlinear overlap method for time scaling to synthesize an S1[n] and an S2[n] into an S3[n] is disclosed. The S1[n] and the S2[n] having N1 and N2 signals respectively. The nonlinear overlap method includes the following steps: (a) delaying the S2[n] by a predetermined number and forming an S5[n], (b) establishing a correlogram of a cross-correlation function of the S1[n] and S5[n], and (c) setting S3[n] as a number of S1[n] when 0<=n<; as a number formed by overlap-adding the S1[n] and an S4[n] in a weighting manner when (the predetermined number+the maximum index+the first threshold)<=n<(N1−a second threshold); and as a number of S4 wherein the first and second thresholds are not equal to zero at the same time, and the S4[n] is formed by delaying the S5[n] by the maximum index.
Owner:ALI CORP
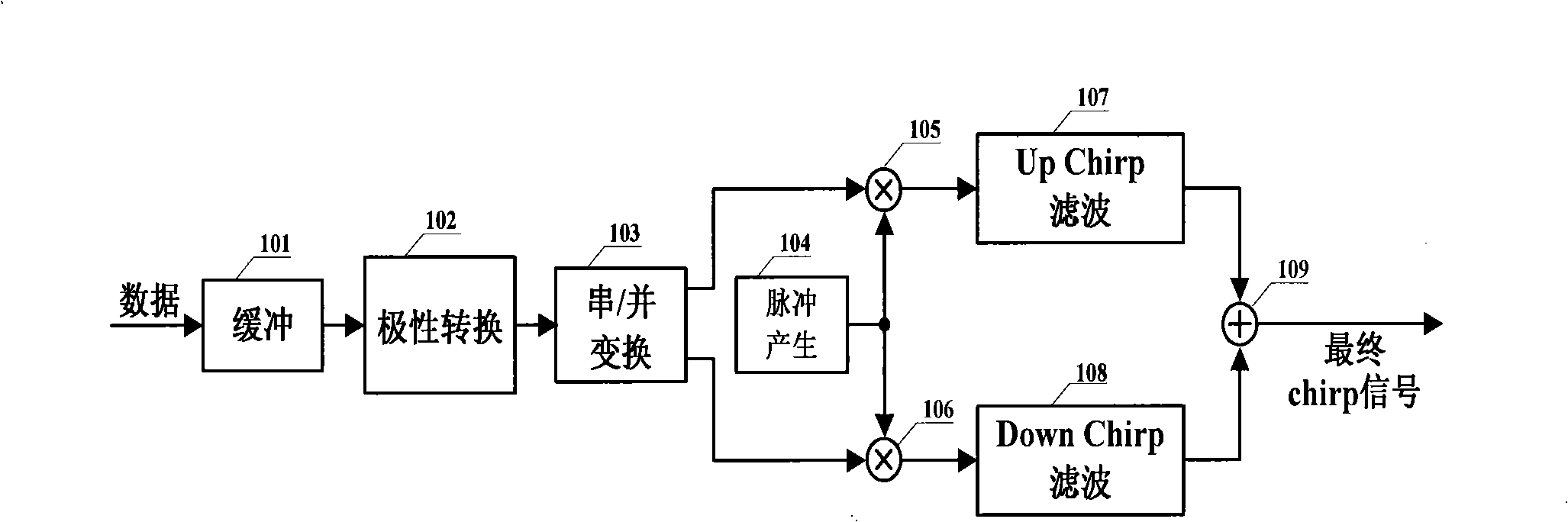
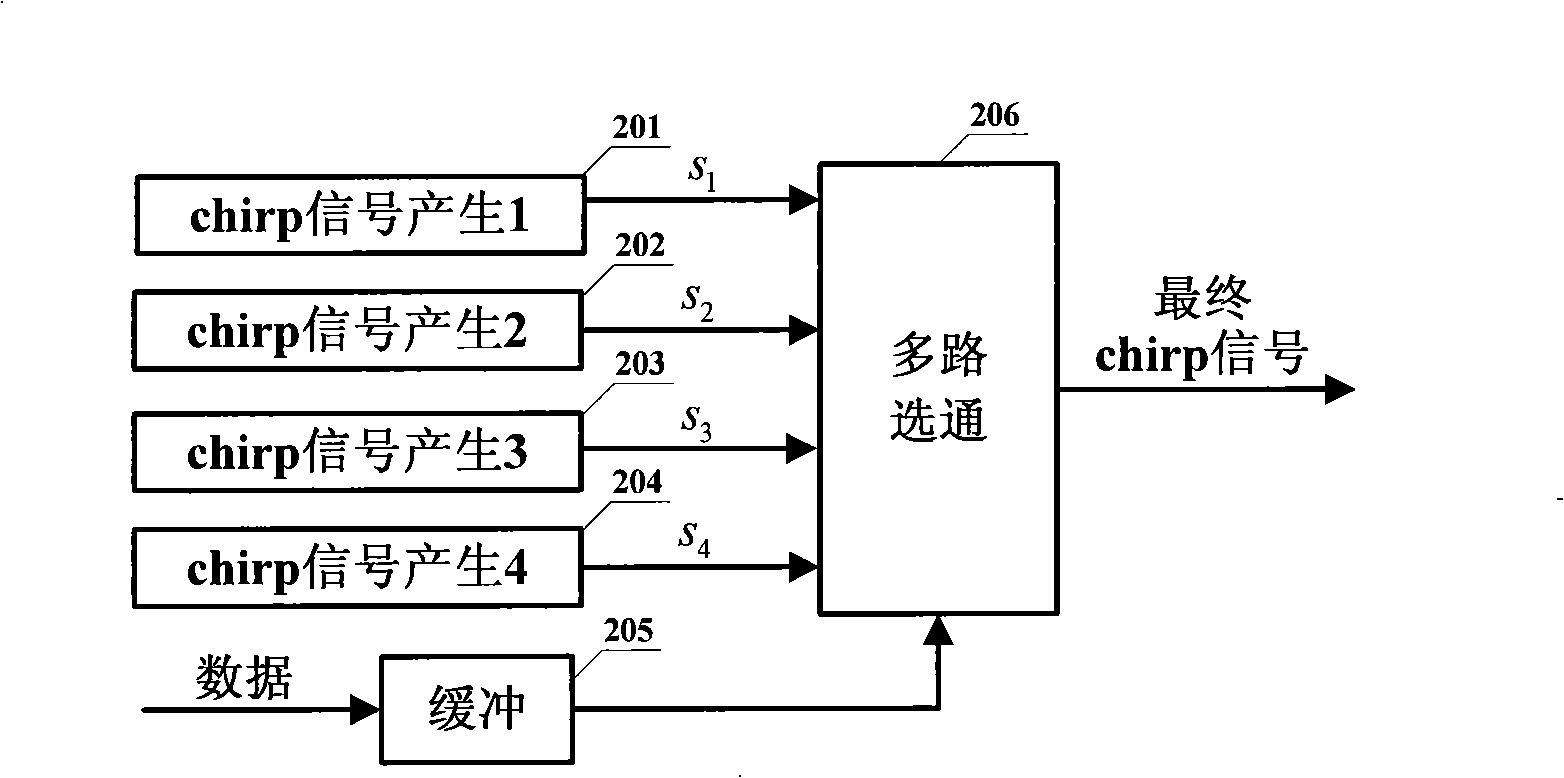
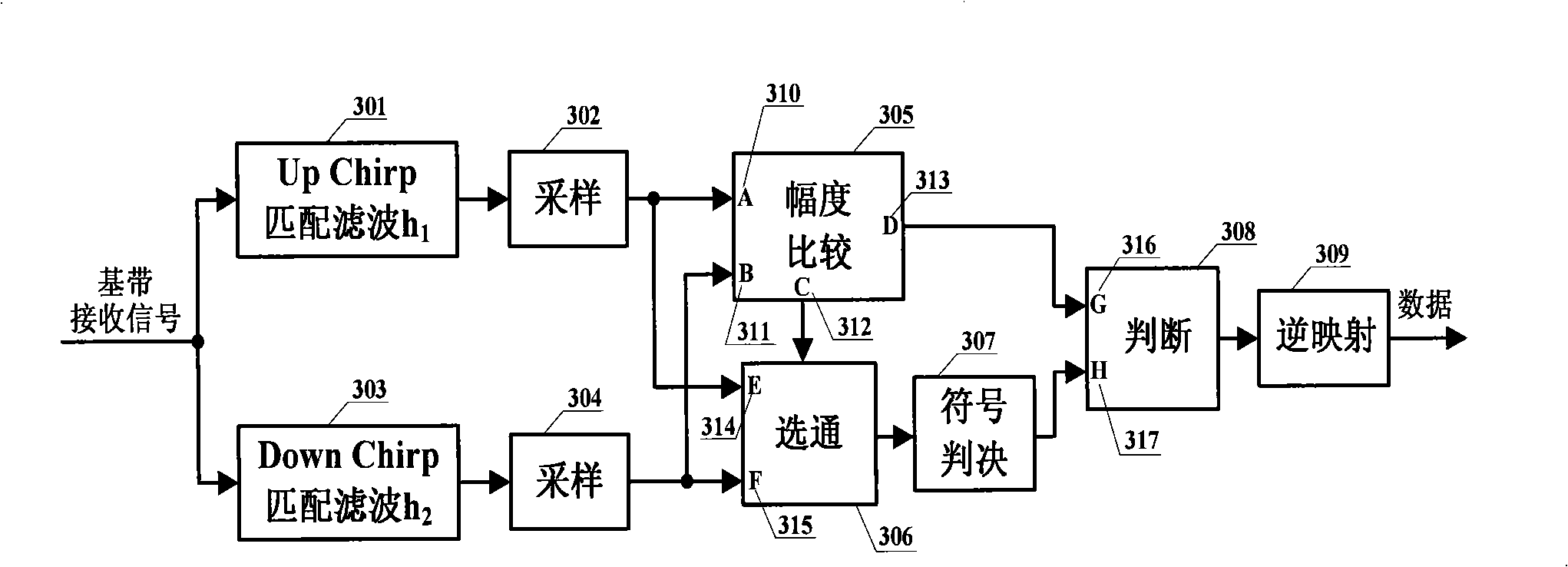
Modulating method for Chirp ultra wide band communication system
InactiveCN101312357AImprove transmission efficiencyMultiple carrier systemsCommunications systemData stream
The invention provides a modulator approach with 4-ary bi-orthogonal keying (4BOK), which aims at increasing data transmission efficiency and guaranteeing simple realization simultaneously. The modulator approach groups binary data streams to be modulated according to the form that one group comprises two bits (namely, a quaternary number expressed by a binary number), the value collection of each quaternary number is D=[11,10,01,00], and then each signal which is in quaternary number form can be converted to a collection S=[s<1>, s<2>,s<3>,s<4>] by a conversion circuit according to one-to-one correspondence. The modulator approach can provide much higher rate of data transmission capacity and reduces complexity simultaneously.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
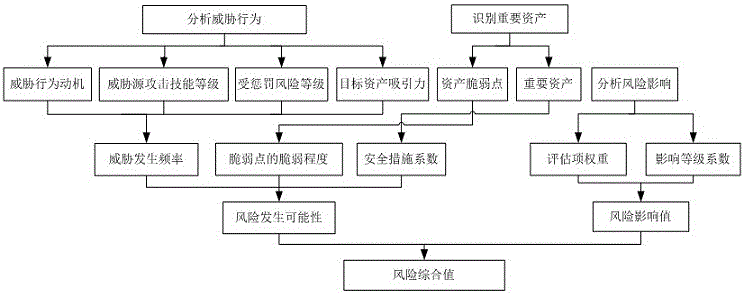
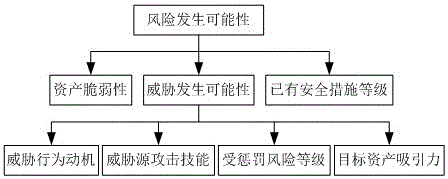
Method for evaluating information safety risk based on interval number and ideal solution
InactiveCN106295332AReduce the impactAvoid pitfalls of losing expert informationPlatform integrity maintainanceInference methodsEngineeringNumber form
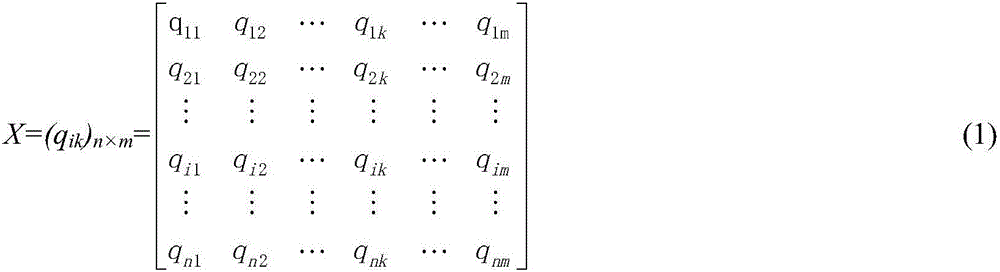
The invention provides a method for evaluating information safety risk based on interval number and ideal solution. The method comprises the following steps of establishing a new evaluation matrix form, wherein the rows and lines of the evaluation matrix are used for respectively expressing an expert set and a factor set; presenting the expert evaluation comments in the interval number form, and filling the matrix; in addition, introducing the index of correlation degree with the ideal solution, and sequencing the authority of the expert comments by technique for order preference by similarity to ideal solution; finally, performing compound operation on the factor evaluation computed by the comprehensive expert comments and the factor weight computed by the analytic hierarchy process, so as to obtain the integral comprehensive evaluation. The method has the advantages that a model for fuzzy comprehensive evaluation based on interval number is studied, the new single factor evaluation matrix form containing more information is proposed, the information involved in the evaluation process is furthest remained by the matrix, and the defect of losing of expert information of the existing model is overcome.
Owner:HUBEI UNIV OF TECH
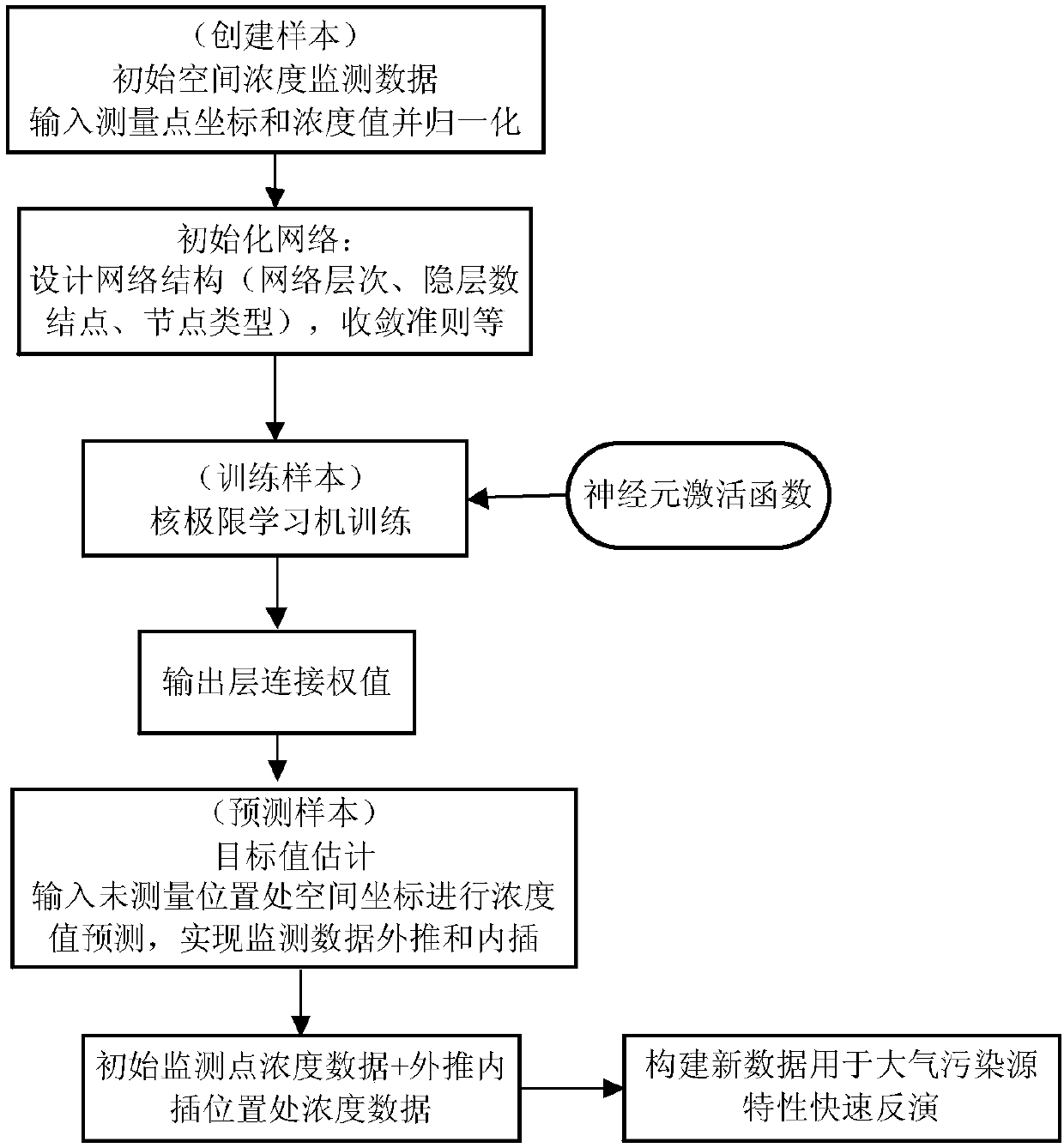
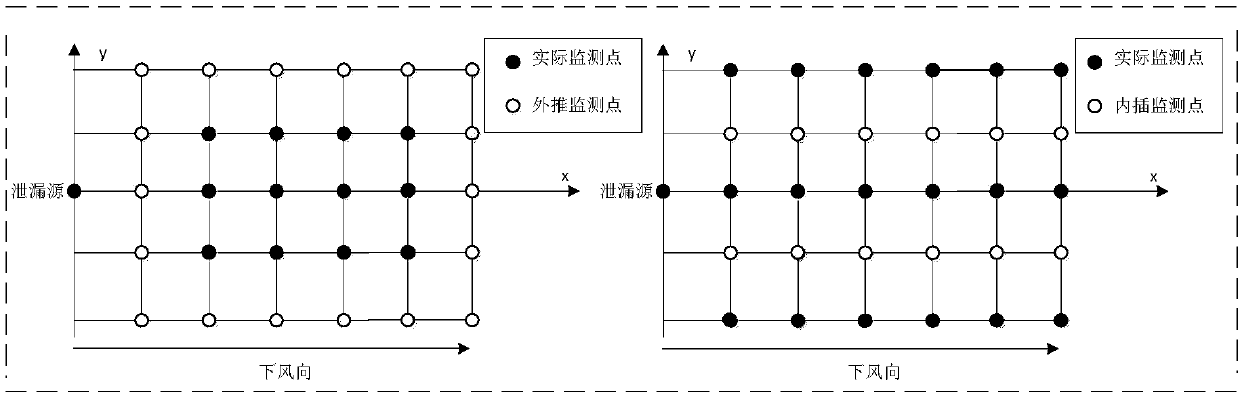
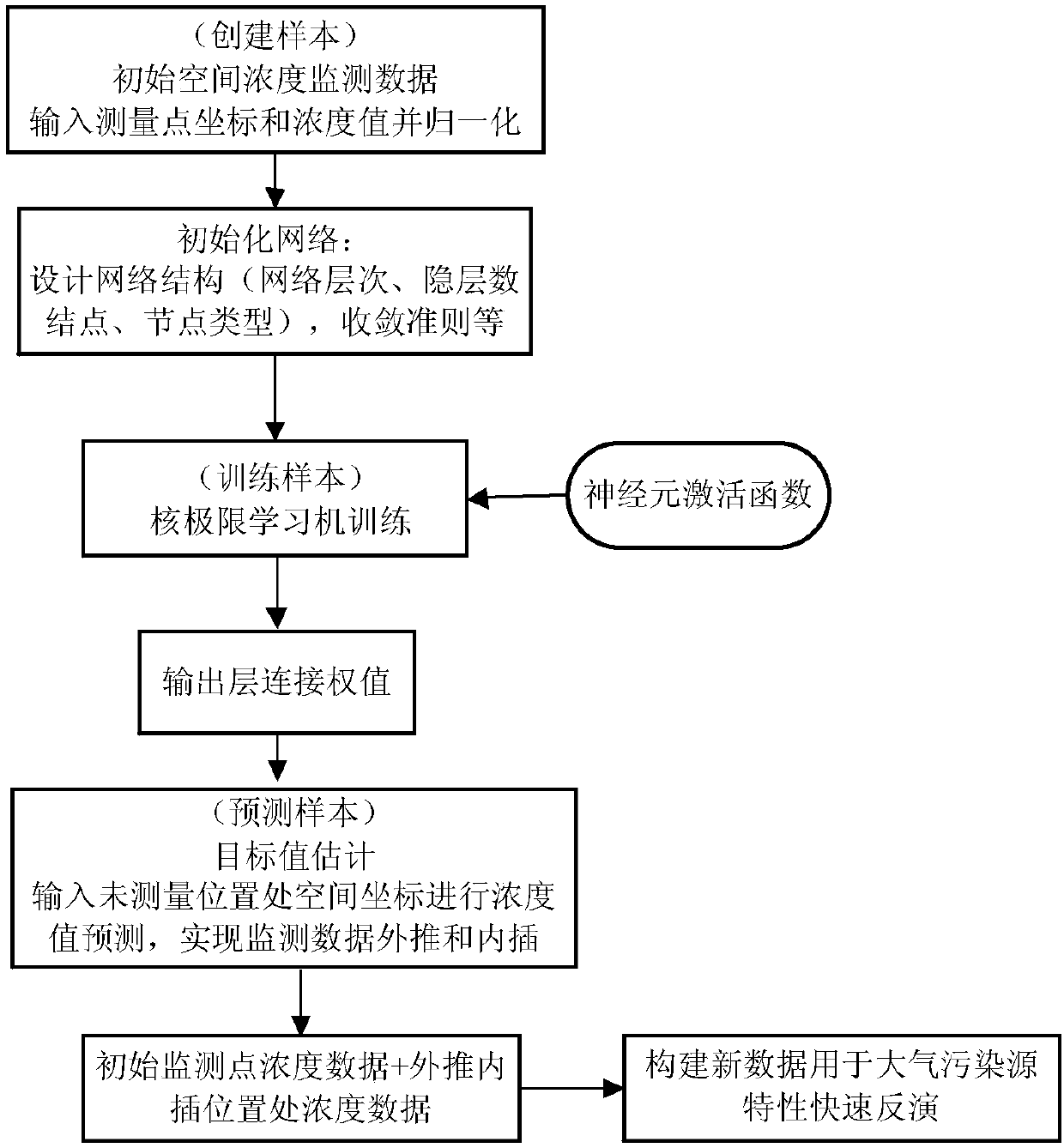
Kernel extreme learning machine-based virtual extension method for leaked gas monitoring concentration data
InactiveCN107067080AIncrease the number ofExpand the monitoring areaAnalysing gaseous mixturesNeural architecturesLearning machineNumber form
The invention discloses a kernel extreme learning machine-based virtual extension method for leaked gas monitoring concentration data, and relates to the technical field of dangerous chemicals. The extension method comprises the steps of firstly selecting position point coordinates Xs and Ys and concentration data of a monitored space region S1 as a training sample set, wherein coordinate values are input values of a network, and the concentration data serves as an output value of the network, so that the network is constructed and trained; and secondly determining coordinates (XPn, YPn) according to space positions S2-S1 of virtual monitoring points needed to be extrapolated or interpolated, wherein n is a predicted point number, the predicted point number forms input values in a predicted sample set together with the coordinates in the training sample set and is input to the trained network, the output value of the network is a to-be-predicted target value, namely, gas concentration data of all monitoring points of a virtually extended space S2, and data on an initial monitoring surface S1 is kept unchanged. According to the method, the source characteristic inverse computation precision is effectively improved without adding the monitoring points; and moreover, the workload is reduced and the working efficiency is improved.
Owner:HARBIN UNIV OF SCI & TECH
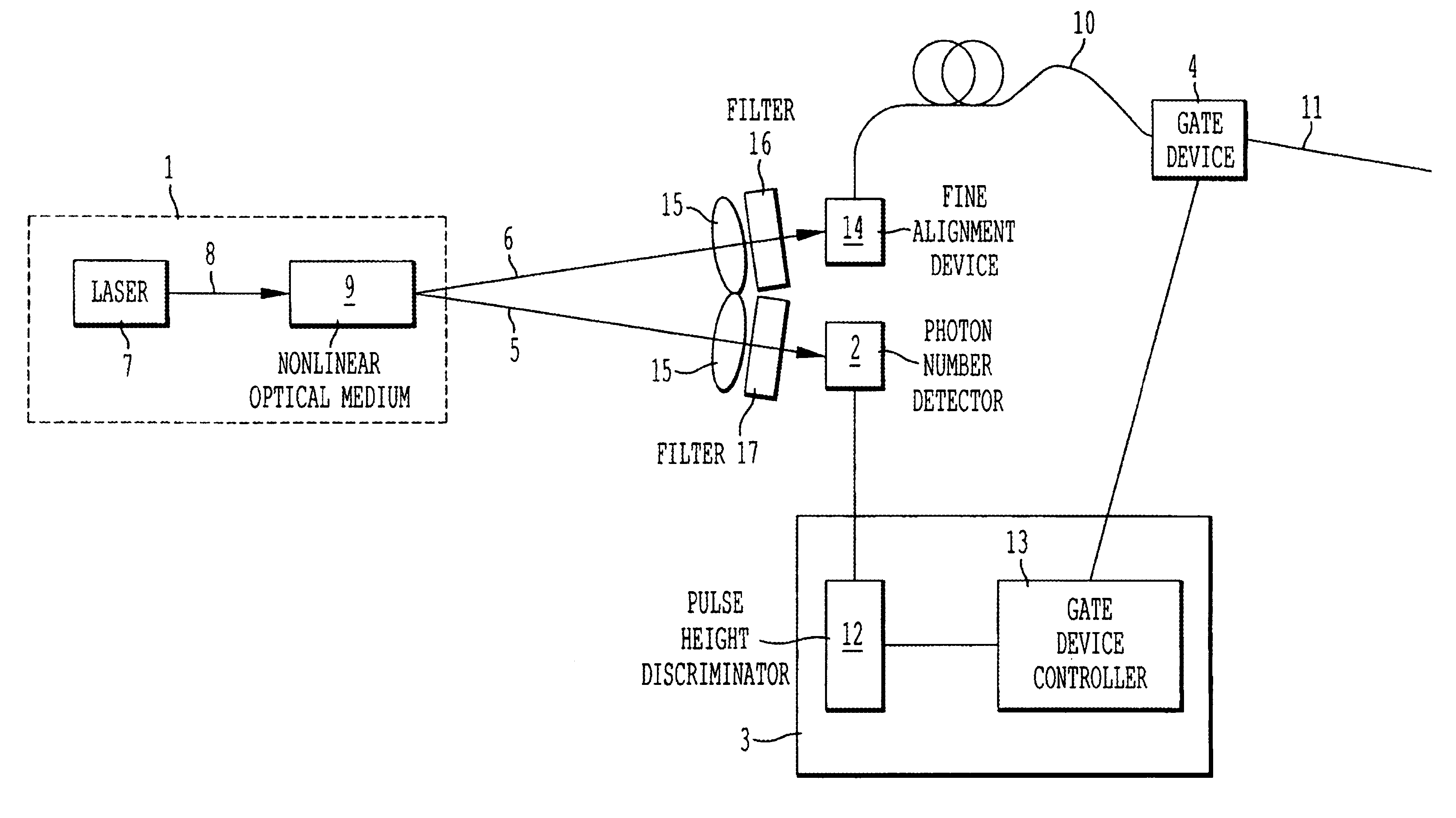
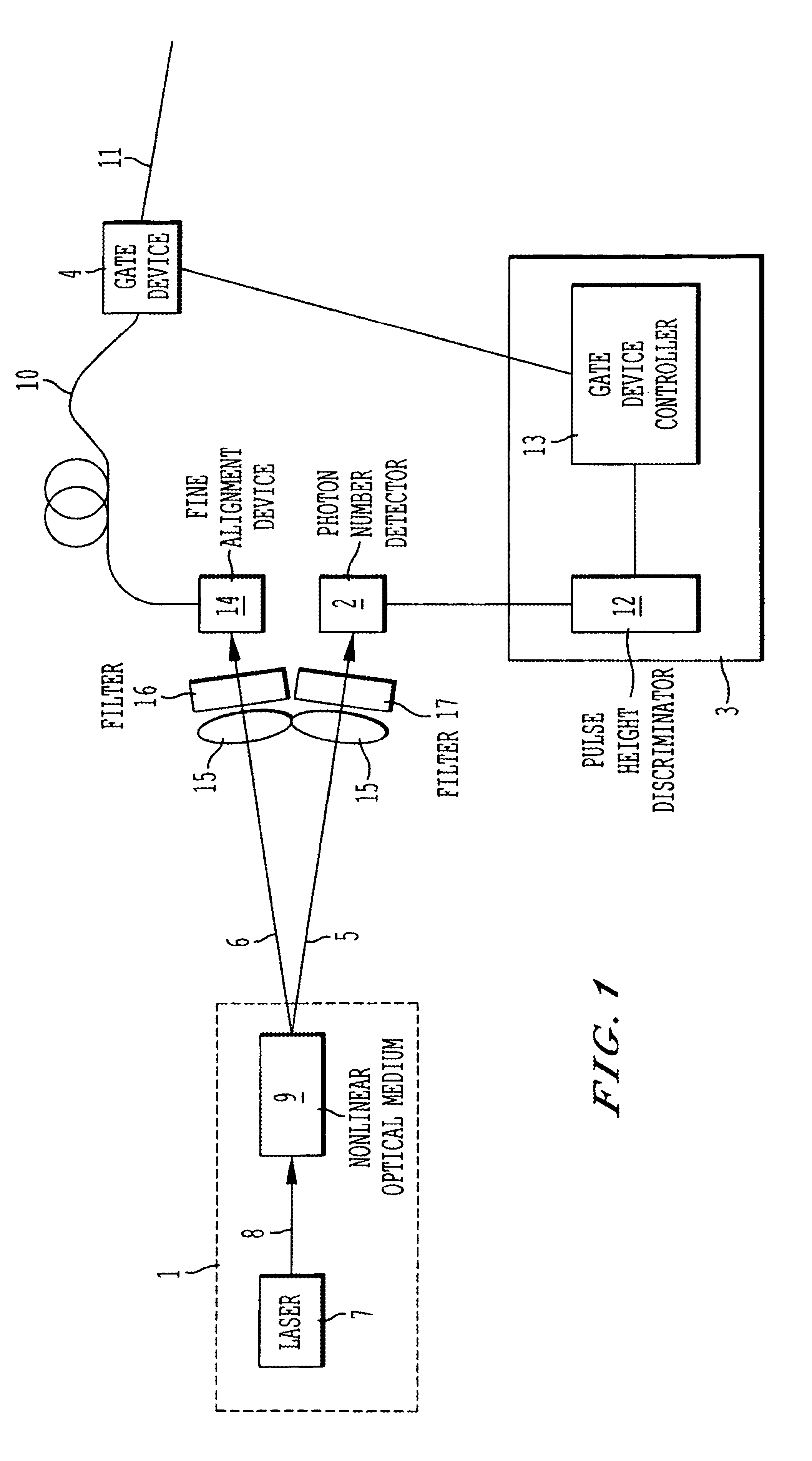
Generator for producing photon number state
InactiveUS7049574B1Generate accuratelyTimely controlKey distribution for secure communicationMaterial analysis by optical meansControl signalNumber form
An apparatus for generating a specified number of photons whose generating time is known, and further an apparatus for generating a specified number of photons in the known schedule are provided. The particularly important specified number is 1 and it is able to be applied to quantum cryptographic communication. The apparatus comprises a photon pair source for generating a photon pair that comprises a signal photon and an idler photon and correlates with the generating time, photon number detectors for detecting the photon number of idler photons, a controller for controlling the gate device in conformity with the information on the photon number form the photon number detector, and a gate device for controlling the emission of the signal photon.
Owner:MITSUBISHI ELECTRIC CORP
System for obtaining electronic map inquiry address via network number plate
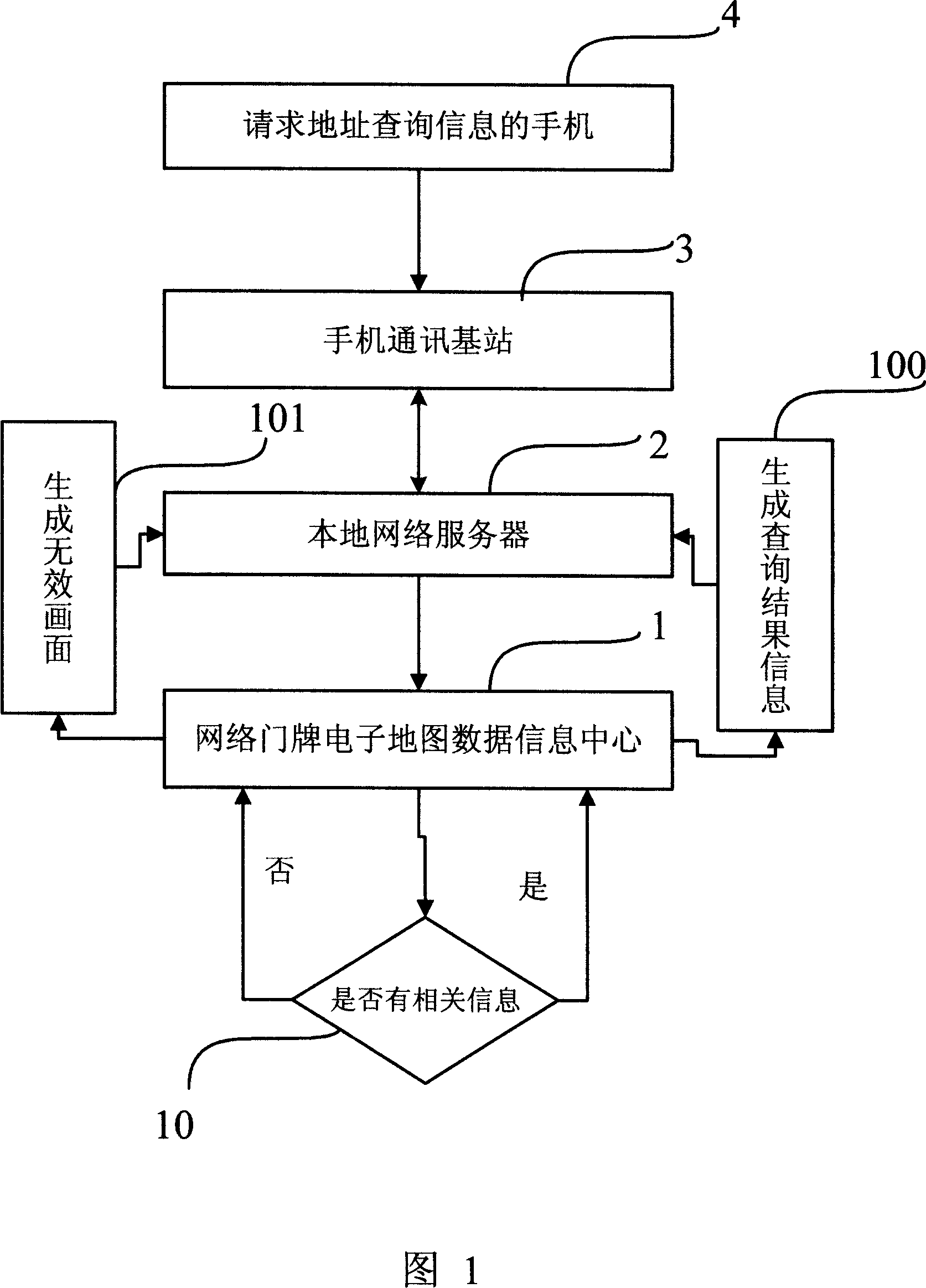
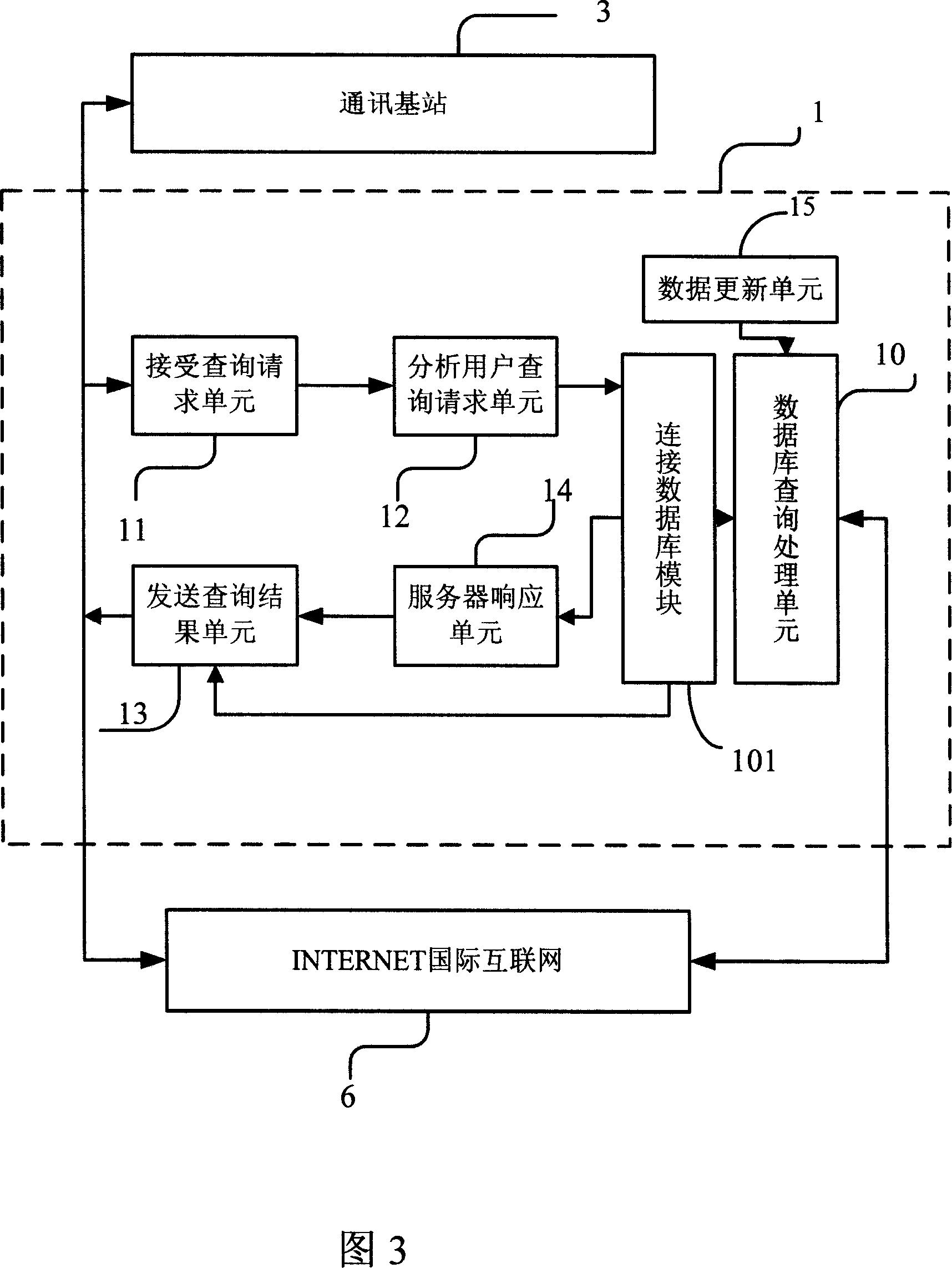
InactiveCN1933518AAvoid duplicationAvoid number skippingInstruments for road network navigationRadio/inductive link selection arrangementsInternet networkData information
A system utilizing network gate number to obtain query address of electronic map applies mobile phone and international Internet as operation platform of local network server and mobile phone communication base station based on data information center of electronic map in network gate number form to obtain query address of electronic map then sends electronic map information obtained from databank to mobile phone of inquirer by said system in short-image mode.
Owner:王益群
Cloud service trust evaluation method based on multi-parameter interval number multi-attribute decision-making
InactiveCN106656603AGuarantee authenticityEnsure objectivityData switching networksTime complexityConnection number
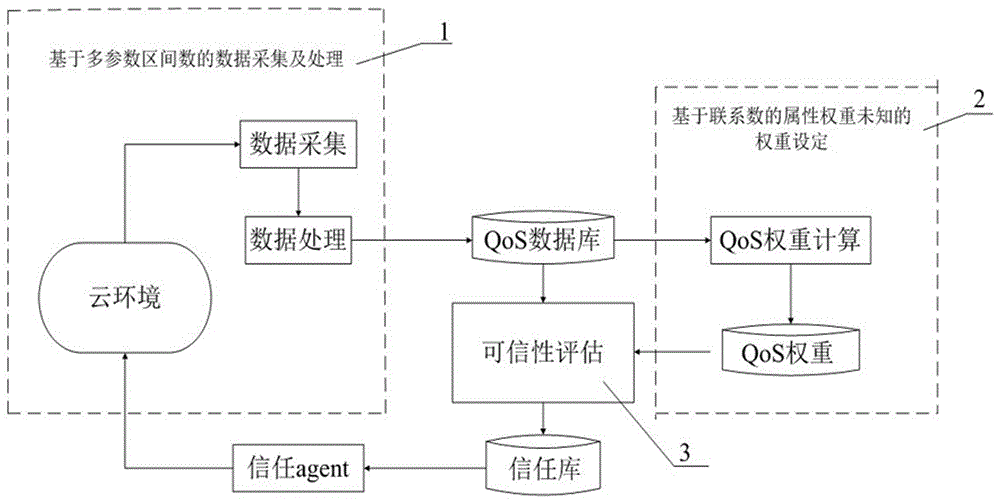
The invention discloses a cloud service trust evaluation method based on multi-parameter interval number multi-attribute decision-making. The method comprises the following steps: first collecting QoS index data in a multi-parameter interval number form, and listing a decision-making matrix, converting an index value in the multi-parameter interval number form into a binary connection number, and then normalizing the decision-making matrix according to the cost type and the benefit type to obtain a normalized decision-making matrix; secondly, determining the QoS index weight based on the unknown weight setting of the attribute weight of the connection number; and finally performing the cloud service trust evaluation by use of a principle value model based on the normalized decision-making matrix and the QoS index weight. By use of the evaluation method disclosed by the invention, the QoS index data is collected in the multi-parameter interval number form and then normalized so as to guarantee the reality and the objectivity of the data; the index weight is determined based on the unknown interval number multi-attribute decision-making method of the attribute weight of the connection number, thereby improving the objectivity of the decision-making; the cloud service trust evaluation is performed according to the principle value model, the time complexity of the evaluation method is lowered. The evaluation method disclosed by the invention has strong objectivity and practicability.
Owner:GUILIN UNIV OF ELECTRONIC TECH
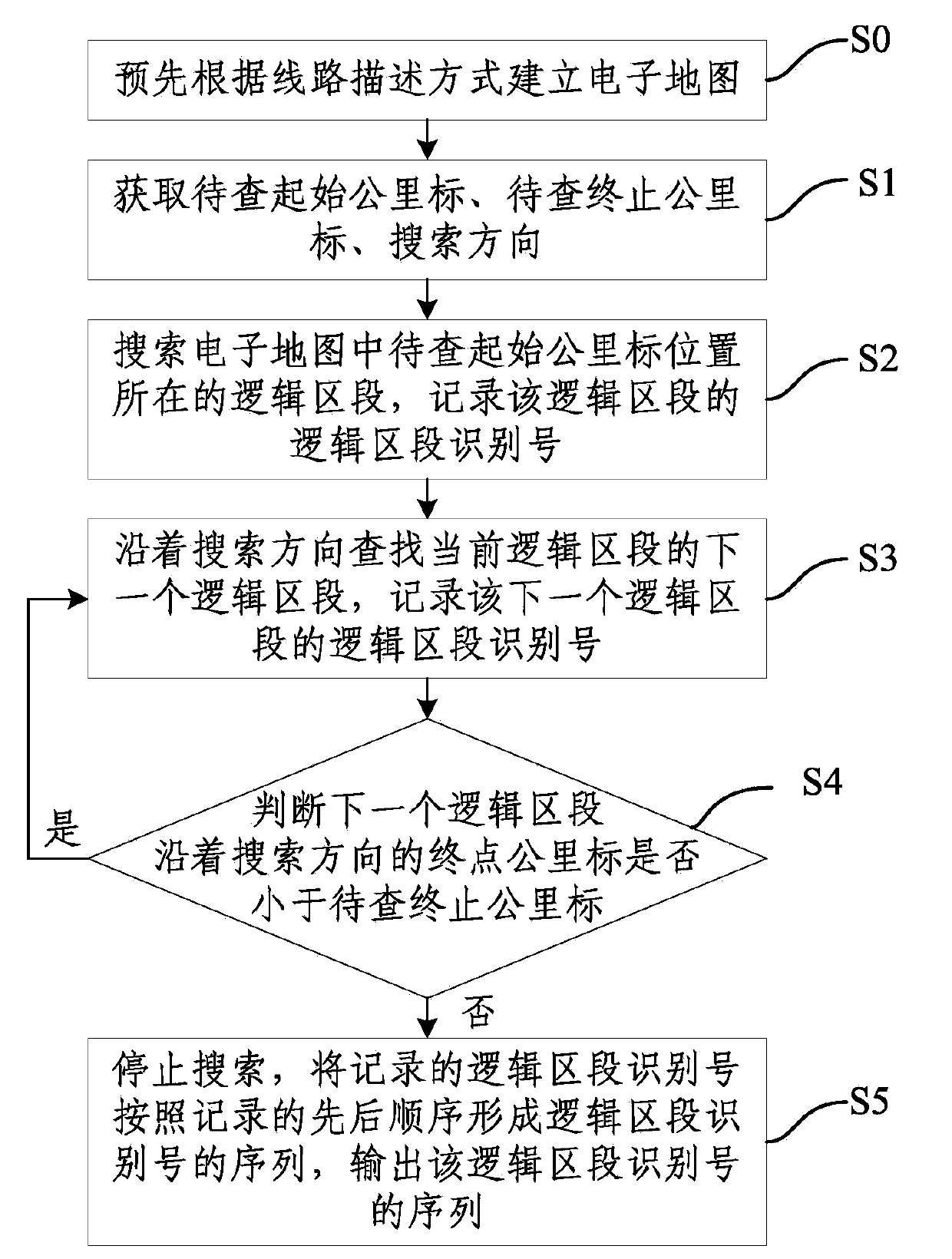
Zone searching method and system
ActiveCN103738364AReduce security risksReasonable and effective operationSignalling indicators on vehicleNumber formElectronic map
The invention provides a zone searching method and system. The zone searching method comprises the steps that S0, an electronic map is built according to a line description mode in advance; S1, a starting kilometer post to be searched, a terminating kilometer post to be searched and a searching direction are obtained; S2, a logical zone, where the starting kilometer post to be searched is located, in the electronic map is searched, and the logical zone identify number of the logical zone is recorded; S3, a next logical zone of the current logical zone is searched in the searching direction, and the logical zone identify number of the next logical zone is recorded; S4, whether a terminating kilometer post of the next logical zone in the searching direction is smaller than the terminating kilometer post to be searched or not is judged, if yes, the S3 is carried out, and if not, the S5 is carried out; S5, searching is ended, the recorded logical zone identify numbers form a sequence of the logical zone identify numbers according to the sequence of recording, and the sequence of the logical zone identify numbers is output. By means of the zone searching method and system, potential safety hazard caused when a train passes through a corresponding track line can be reduced.
Owner:TRAFFIC CONTROL TECH CO LTD
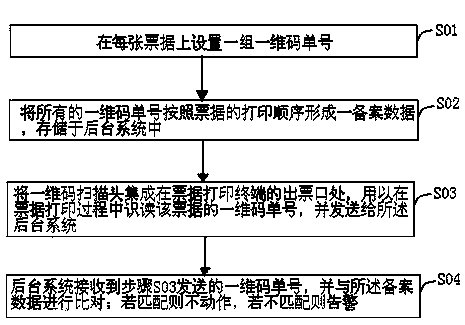
Method for automatically identifying code numbers of industry bills in process of printing
InactiveCN103839030AAvoid non-correspondenceSimple methodTypewritersSensing by electromagnetic radiationNumber formComputer terminal
The invention relates to a method for automatically identifying code numbers of industry bills in the process of printing. The method is characterized by comprising the following steps that 1, a set of one-dimensional code number is set on each bill; 2, all one-dimensional code numbers form reference data according to the printing sequence of the bills to be stored in a background system; 3, a one-dimensional scanning head is integrated at a bill outlet of a bill printing terminal and used for identifying and reading the one-dimensional code number of each bill in the process of printing of the bill, and sending the one-dimensional code numbers to the background system; 4, the background system receives the one-dimensional code numbers sent by the step 3, the one-dimensional code numbers are compared with the reference data, if the one-dimensional code numbers and the reference data are matched, no action is carried out, and if the one-dimensional code numbers and the reference data are not matched, an alarm is given. The method achieves monitoring of the bill printing, and avoids the problem that the bills do not correspond to the actual reference code numbers.
Owner:FUJIAN SHIDA COMP EQUIP
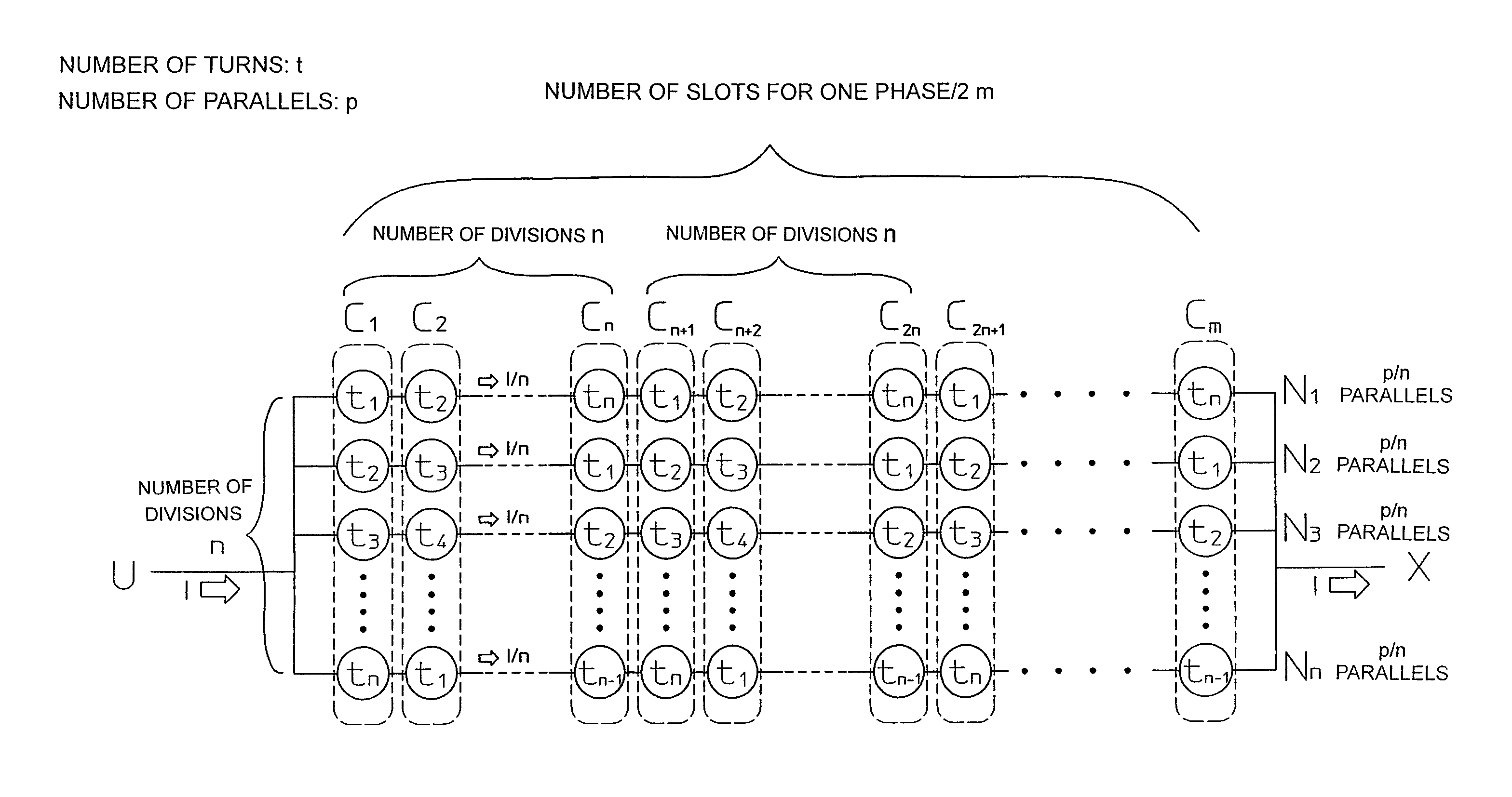
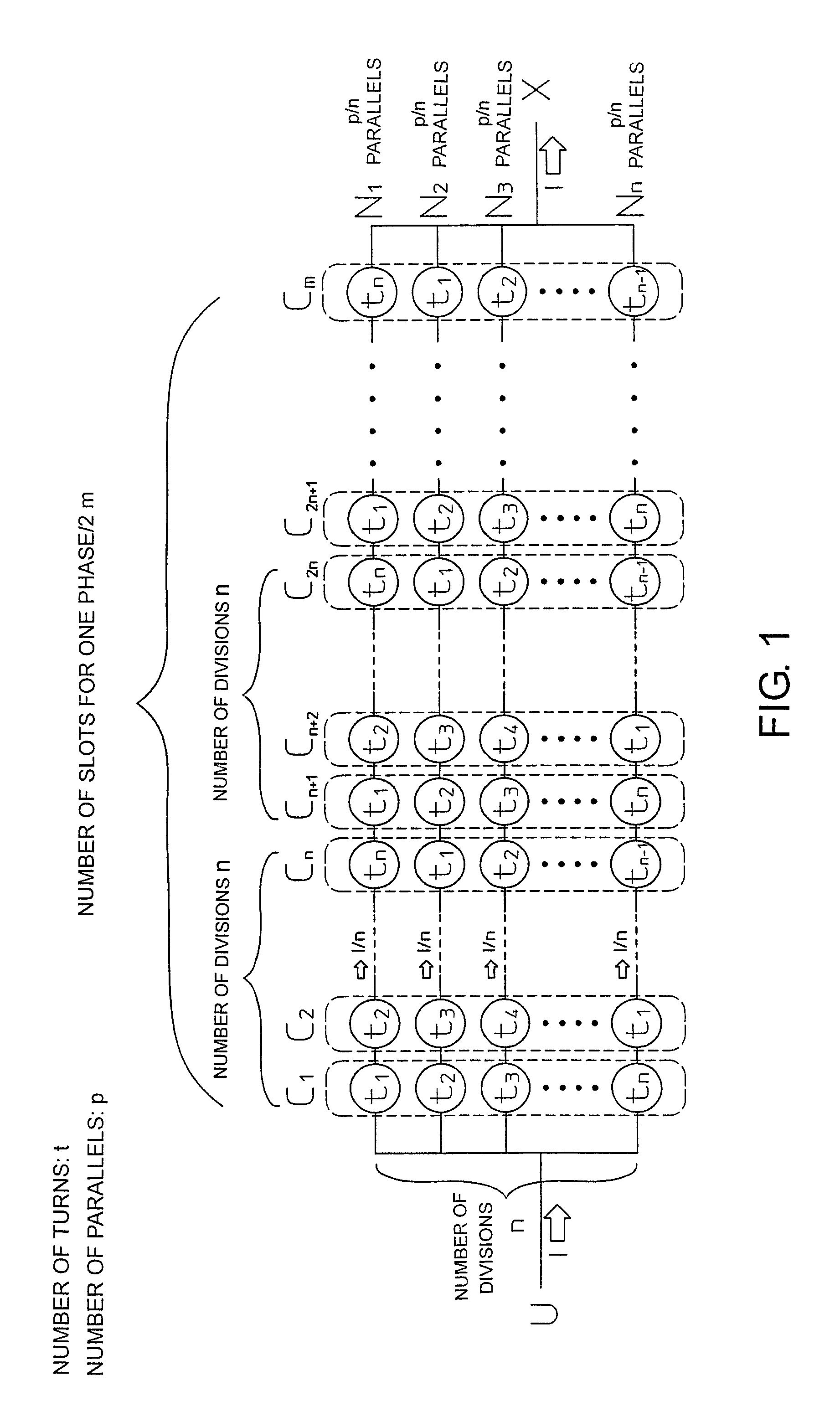
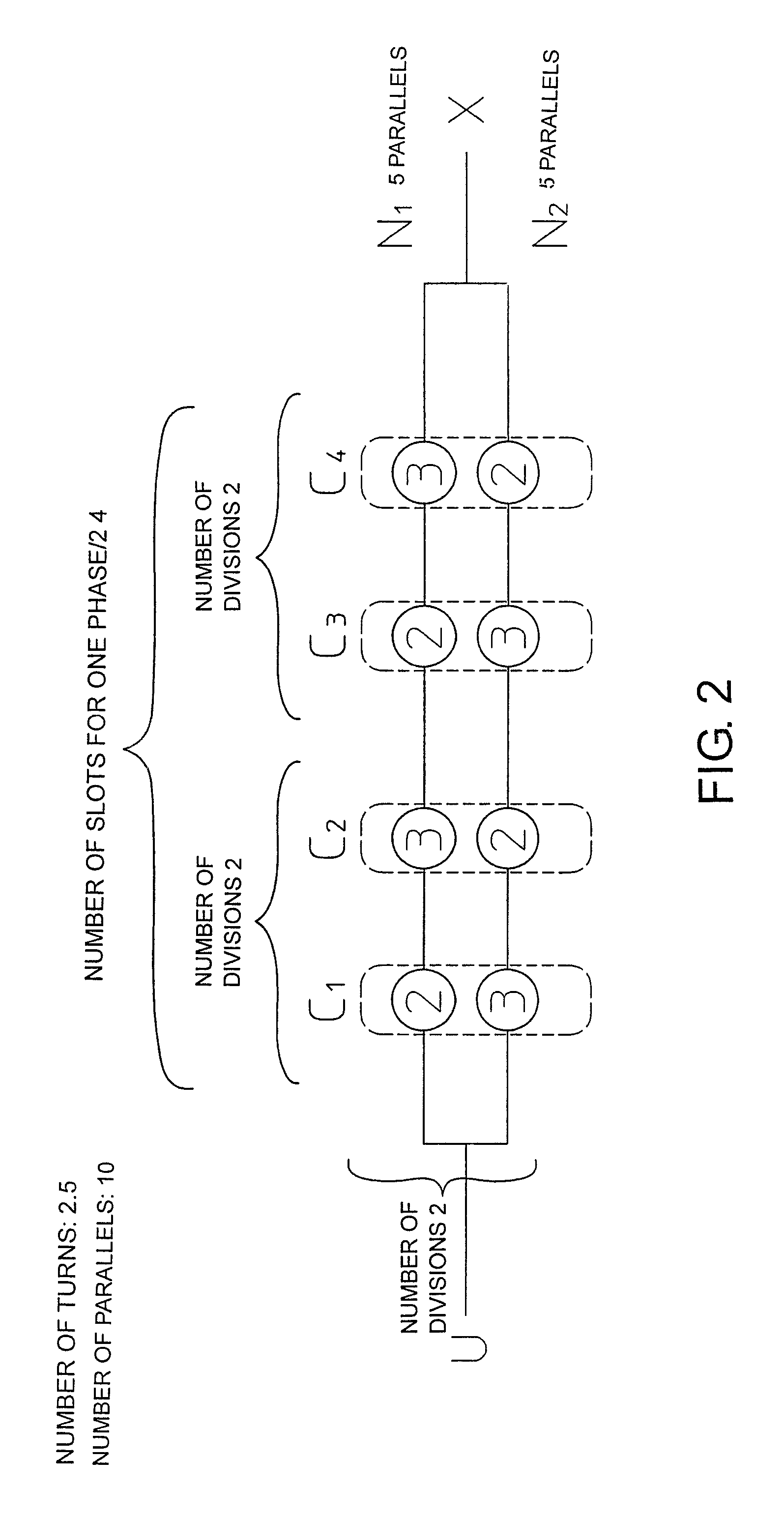
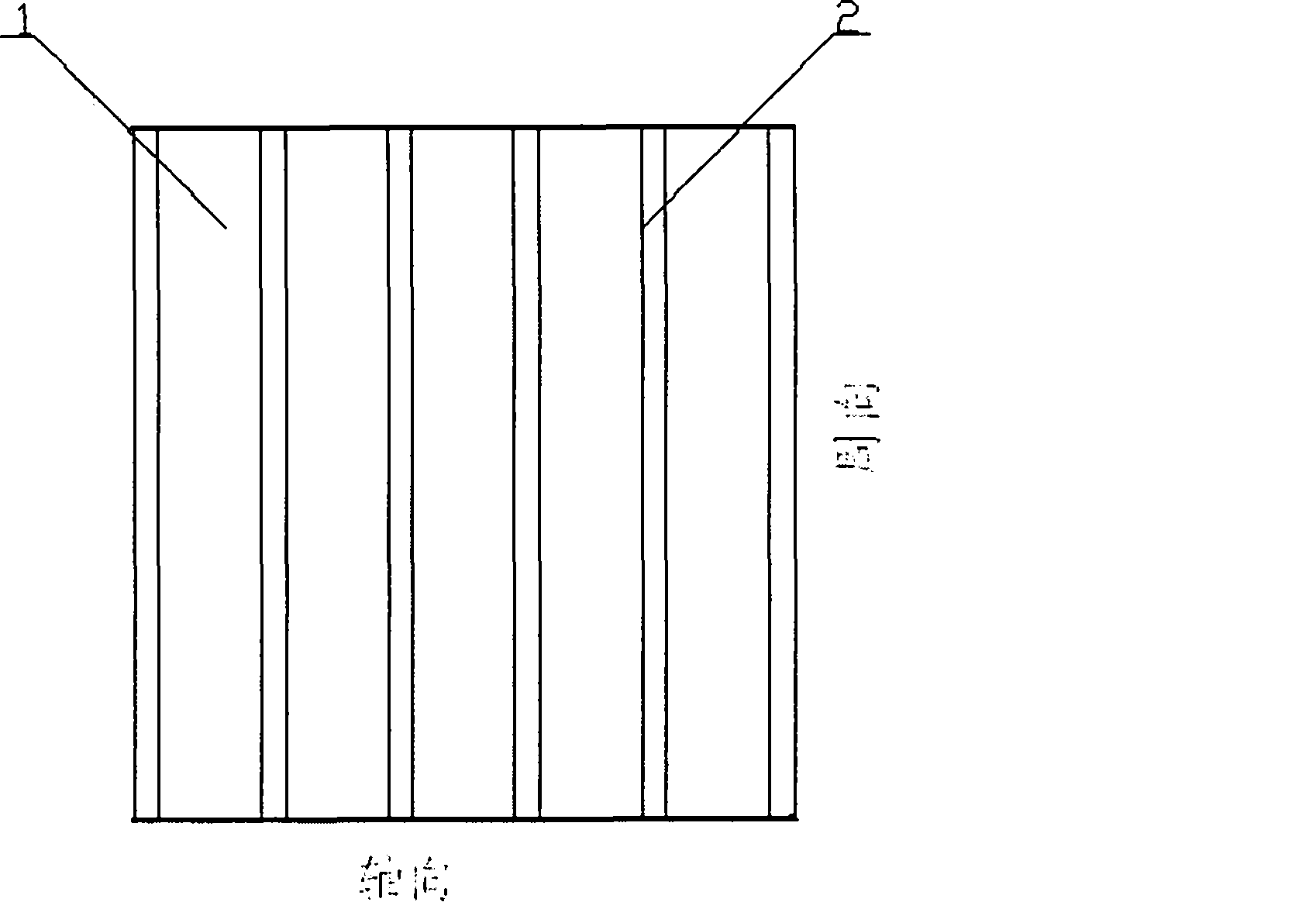
Three-phase electric-motor winding with differing turn numbers forming fractional effective turns
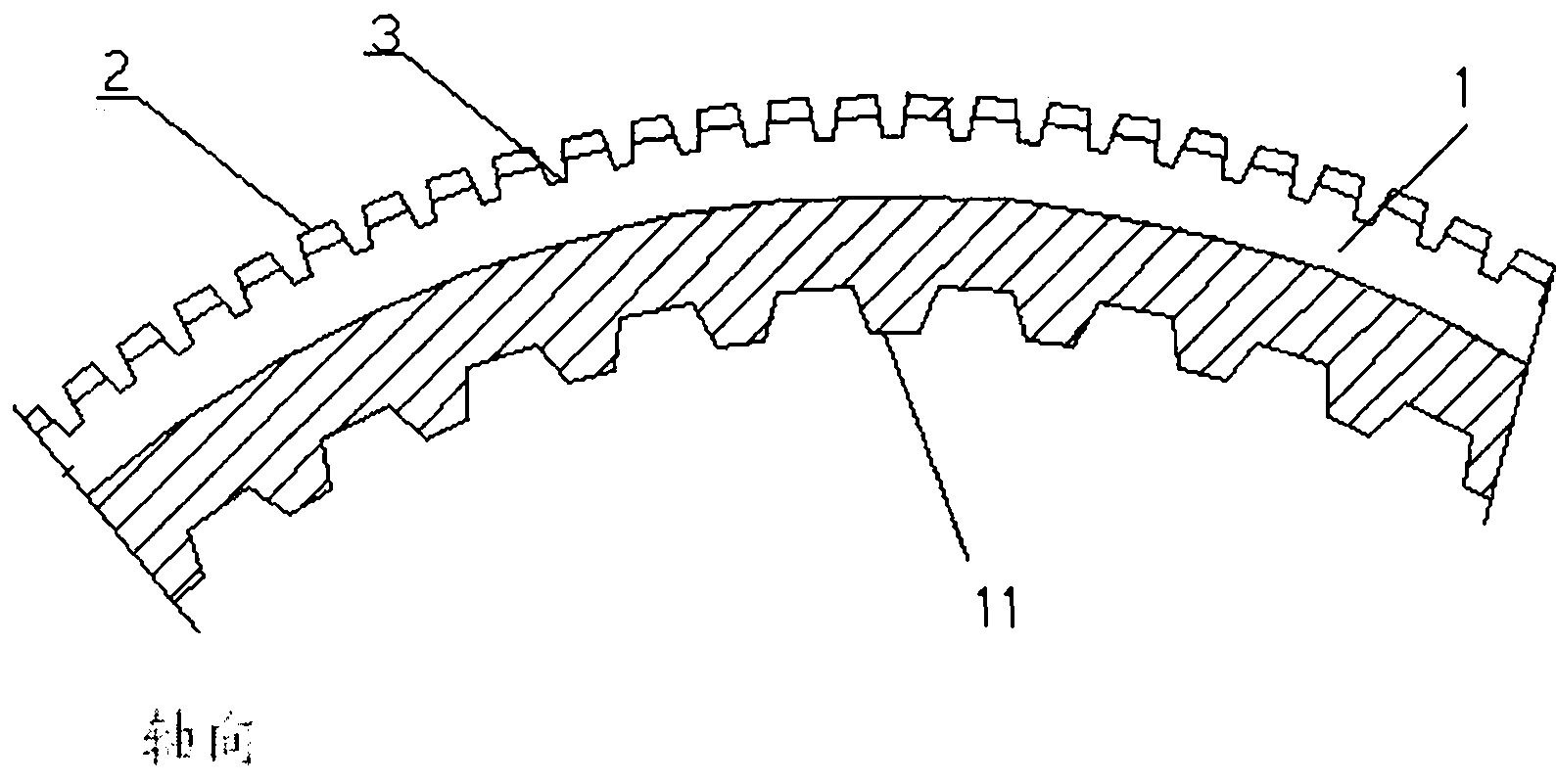
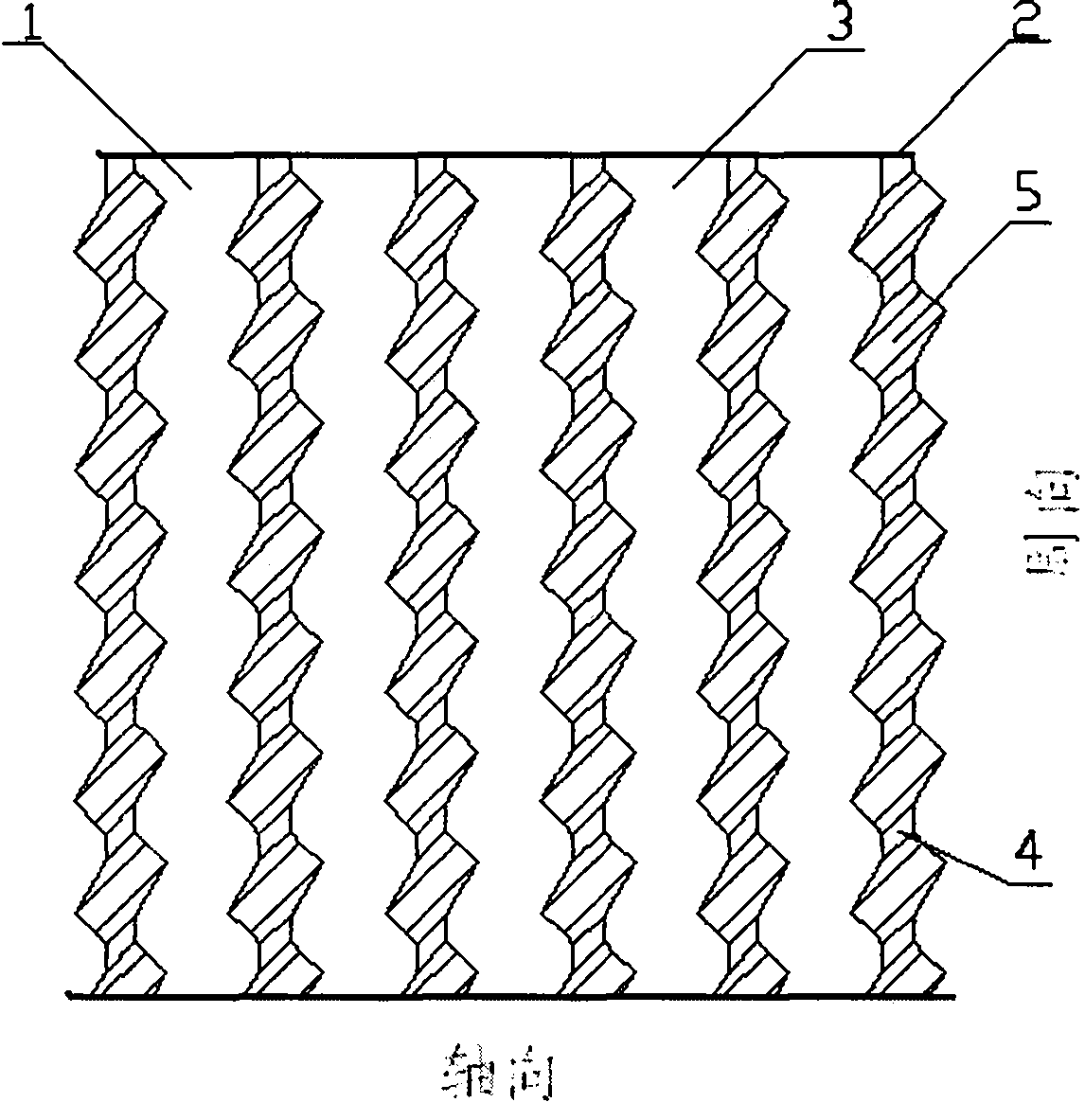
A motor is provided. When m is half of a number of slots of one phase and n is a divisor of m, the overall parallel winding of a total number of parallels p is equally divided n-fold into partial parallel windings Ni, having a number of parallels p / n, each partial parallel winding Ni comprises m sub-coils, the m sub-coils including n types of m / n sub-coils having a number of turns tj, at least one of the sub-coils differing in number of turns from the other sub-coils, and, for each pair of the slots in the stator, one sub-coil of each partial parallel winding Ni is wound around the pair of slots, and n sub-coils wound around the pair of the slots include every one of the n types of the sub-coils of the numbers of tj.
Owner:OKUMA CORP
Laguerre output method for rigid body space motion state
ActiveCN102445202ASimplified Computational ComplexityEasy to use in engineeringInstruments for comonautical navigationComputation complexityAngular velocity
The present invention discloses a Laguerre output method for a rigid body space motion state. According to the method, three velocity components of a machine shaft system and a three-ary number form linear differential equations by defining the three-ary number; a Laguerre orthogonal polynomial is adopted to proximately and closely depict a rolling angle p, a pitching angle q, and a yawing angular velocity r; a state transition matrix of the system can be solved according to a manner of an arbitrary order keeper so as to acquire an expression of a rigid body motion discrete state equation, such that the singularity problem of the attitude equation is avoided so as to acquire the main motion state of the rigid body. According to the present invention, the three-ary number is introduced, such that the state transition matrix is the block upper triangular manner, and can be solved by reducing the order so as to substantially simplify the calculation complexity, and be easily used by the engineering.
Owner:XIAN FEISIDA AUTOMATION ENG
Devices and methods for playing electronic bingo game
ActiveUS20090017895A1Board gamesApparatus for meter-controlled dispensingNumber formNumber generator
An electronic bingo game and method for playing the same is disclosed. A bingo card having a plurality of numbered spaces is presented to a player, in which at least one of the numbered spaces is hidden to the player's view, thereby forming covered and uncovered portions of the bingo card. A random number generator draws bingo numbers until the occurrence of a game ending event, which numbers are compared to the numbered spaces on both the covered and uncovered portions of the bingo card. If the pattern of numbers formed on the uncovered portion of the bingo card forms one or more of a set of designated winning bingo patterns, a first award is paid to the player. The player is then presented with the opportunity to reveal one or more of the covered spaces on the bingo card whereupon a second prize is paid if the pattern of numbers formed on the uncovered spaces forms one or more of a set of designated winning bingo patterns.
Owner:AGS CORP
Chinese character digital coding input method
InactiveCN101446862ASmall amount of memoryHigh input rateInput/output processes for data processingChinese charactersArabic numerals
The invention discloses a Chinese character digital coding input method. Five basic starting strokes, that is, horizontal stroke, vertical stroke, left falling stroke, dot stroke and turning stroke are normalized into four strokes, that is, the horizontal stroke, the vertical stroke, the left falling stroke and the right falling stroke (dot stroke), and two of the four basic stroke codes are combined to form 16 starting two-stroke combined stroke codes which are represented by English letters, number of ones places of the 'horizontal stroke' of the four strokes of the Chinese characters is represented by Arabic numerals 0-9, and tens place is represented by W; number of the ones place of the 'vertical stroke' is represented by the Arabic numerals 0-9, and the tens place is represented by E; number of the ones place of the 'left falling stroke' is represented by the Arabic numerals 0-9, and the tens place is represented by I; number of the ones place of the 'right falling stroke' is represented by the Arabic numerals 0-9, and the tens place is represented by 0; the numbers of the stroke number form a group of Arabic numerals codes in the order of the horizontal stroke, the vertical stroke, the left falling stroke and the right falling stroke from the right to the left, when the Chinese characters are inputted through a computer, the memory is small, the method is easy to be learned and used, the input rate is high, and the coincident code rate is low. The method is also applicable to Chinese character computer input all over the world, and also applicable to computer input of traditional Chinese characters.
Owner:欧诗淼
Method for generating mutual random graphic group among communication equipment and application system
InactiveCN102316100AReduce transfer volumeSave resourcesUser identity/authority verificationGraphicsConfidentiality
The invention relates to a method for generating mutual random graphic groups among communication equipment and an application system. Graphics are coded into word groups, ninety thousand of word groups are formed through indexing, one byte and one byte index are required only to translate the word groups into character groups and a database with ninety thousand of groups of characters can be circulated. Firstly, numbers formed by 0 to 9 are downloaded, then three hundred of graphics corresponding to graphic codes are formed and finally ninety thousand of word groups are formed through graphic coding. Therefore, only numbers are downloaded and the downloading operation is rapid and convenient. Then, the numbers are translated into three hundred of graphic codes and the like. Finally, characters, programs and the like are formed through indexing. The method can be used for realizing the triple guarantees of security data such as programs, article confidentiality, passwords and the like, wherein the triple guarantees comprise that: 1) original numbers can guarantee that no original graphic code groups are imported incorrectly and cannot be translated; 2) the list of ninety thousand of word groups cannot be converted into the character groups when indexes do not exist; and 3) each character group consists of two characters, every two character groups are different combinations, the decoding of one graphic code is insignificant and the decoding is enabled to be more difficult by introducing multiple indexes. Since a graphic code group decoder is installed, in combination with original code bars and indexes, the downloading efficiency and the character translation efficiency are improved.
Owner:徐文呈
Method for mapping and de-mapping of non-binary symbols in data communication systems
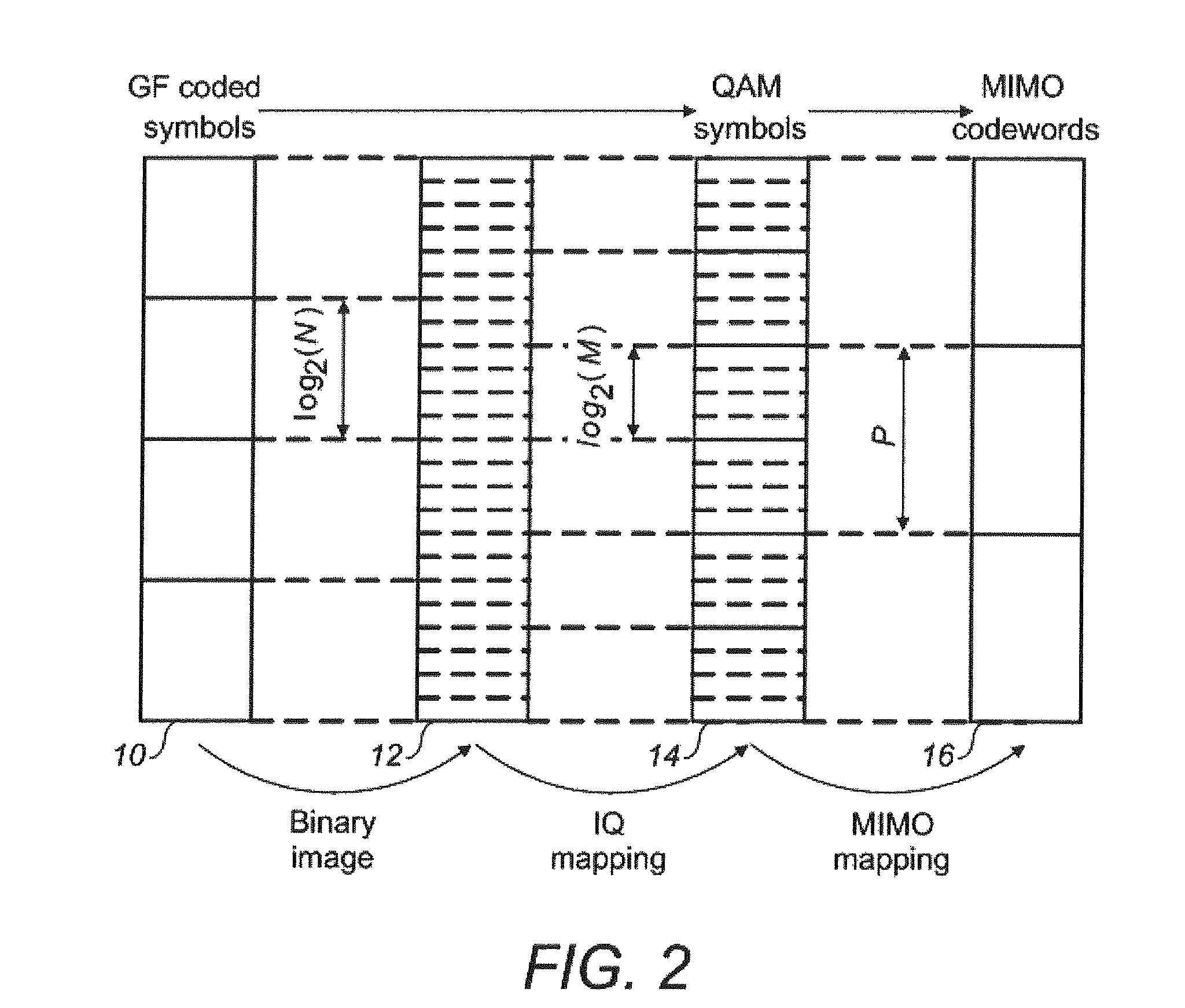
ActiveUS8732563B2Less computationally intensiveLower performance requirementsSite diversityError detection/correctionCommunications systemPhysical layer
Owner:SAMSUNG ELECTRONICS CO LTD
Number association implementation method and system
InactiveCN102868986ARealize associationSimplify the optimization processCommmunication supplementary servicesData switching networksSession Initiation ProtocolSession control
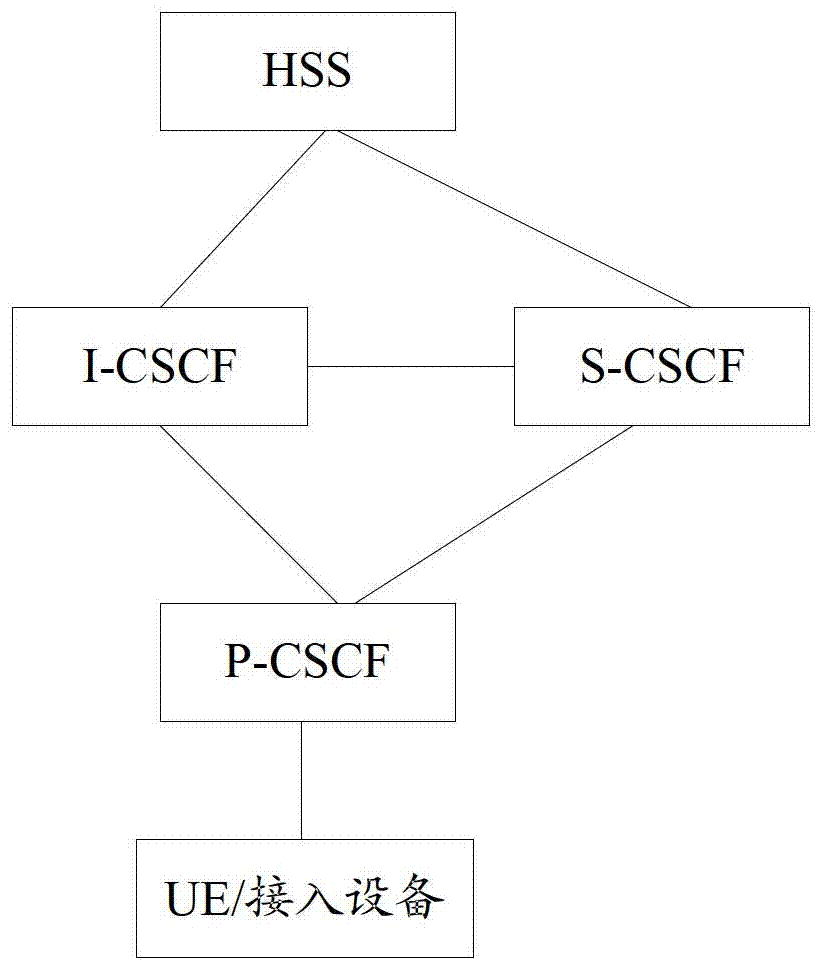
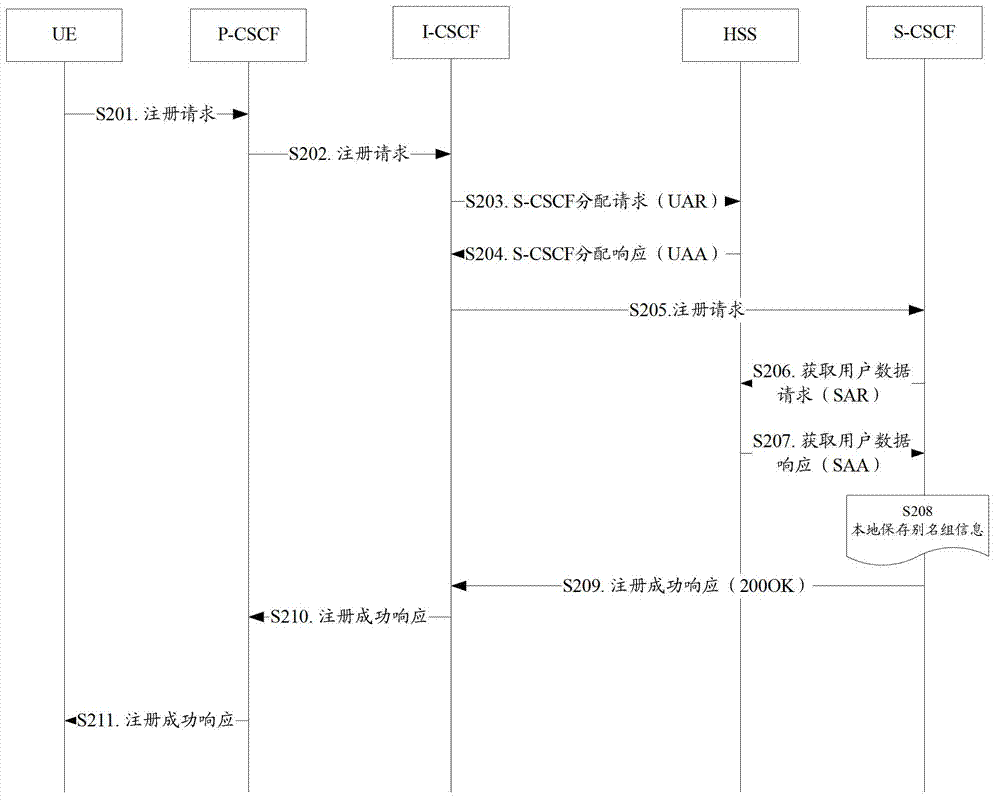
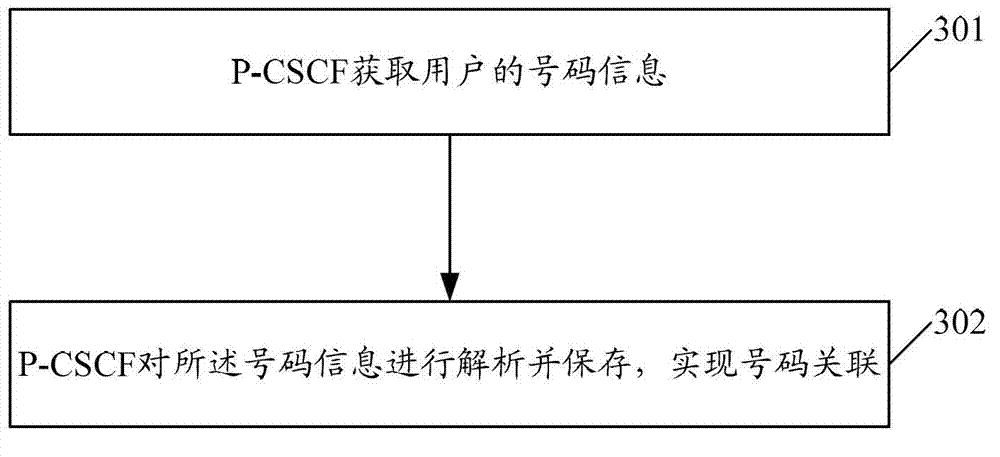
The invention provides a number association implementation method and system. The method comprises the following steps of: acquiring number information of a user through a P-CSCF (proxy-call session control function); and analyzing and saving the number information through the P-CSCF to realize number association. According to the method provided by the invention, the number information of the user is acquired through the P-CSCF, and the number information is analyzed and saved for realizing number association, wherein the number form can be of SIP (session initiation protocol) format or TEL (telephone) format, thus the processing of optimizing business can be simplified, the efficiency can be improved and the implementation cost can be reduced.
Owner:ZTE CORP
Medical image segmentation algorithm used in CT room
InactiveCN105701803AConvenient clinical diagnosisSolve the over-segmentation problemImage enhancementImage analysisImage segmentation algorithmCharacteristic space
The present invention discloses a medical image segmentation algorithm used in a CT room. The segmentation steps of the algorithm are that: firstly, a CT image is segmented into different small areas via a watershed algorithm, then an average gray value of the small areas is mapped to a high dimension characteristic space according to a KFCM algorithm and by utilizing a Mercer kernel, so that the original characteristics which are not displayed in a watershed algorithm segmentation image are displayed. The algorithm comprises the following steps of (1) pre-processing an image, and carrying out the median filtering; (2) carrying out the watershed segmentation on the pre-processed image, and storing the label k of each small area; (3) calculating the average gray value x<k> of each area, wherein the average gray value x<k> represents a sample set of an input space, k =1, 2, ..., n, n is the area number formed after the image watershed segmentation; (4) selecting a classification number C, a threshold value epsilon and a fuzzy exponent m; (5) calculating a clustering center and a weighting matrix. The medical image segmentation algorithm used in the CT room utilizes the advantages of the watershed algorithm and the weighted kernel clustering, also greatly overcomes the disadvantages of the two algorithms.
Owner:孙燕新
A differential protection method for negative sequence current of large power transformer
ActiveCN100550557CHigh protection sensitivityClearly distinguish internal and external asymmetrical faultsEmergency protective circuit arrangementsPhase correctionSecondary loop
The disclosed protection method for internal fault of large power transformer comprises: the protector samples the secondary current of current transformers on power transformer sides to obtain current instantaneous value and calculate complex number form of electric values by Fourier algorithm, corrects phase of connection form, and balances amplitude of transformation ratio; then, it calculates the complex number form of negative sequence current according to three-phase ac complex form, and computes negative sequence differential current and break current as the negative sequence differential protection principle to decide asymmetric inside and outside fault and drop out all breakers. This invention also contains exactly the negative sequence differential rate breaking feature and protection criterion, the adjusting means for protection values, the positive sequence current breaking criterion, and the block function for error action protection.
Owner:BEIJING SIFANG JIBAO AUTOMATION +1
Arbitrary order output method for rigid body space motion state
ActiveCN102359789ASimplified Computational ComplexityEasy to use in engineeringInstruments for comonautical navigationMatrix differential equationComputation complexity
The present invention discloses an arbitrary order output method for a rigid body space motion state. According to the method, three velocity components of a machine shaft system and a three-ary number form a linear differential equation by defining the three-ary number; a state transition matrix can be solved according to a manner of an arbitrary order keeper so as to acquire an expression of a rigid body motion discrete state equation, such that the singularity problem of the attitude equation is avoided so as to acquire the main motion state of the rigid body. According to the present invention, the three-ary number is introduced, such that the state transition matrix is the block upper triangular manner, and can be solved by reducing the order so as to substantially simplify the calculation complexity, and be easily used by the engineering.
Owner:XIAN FEISIDA AUTOMATION ENG
Intelligent visitor system based on two-dimensional code reservation
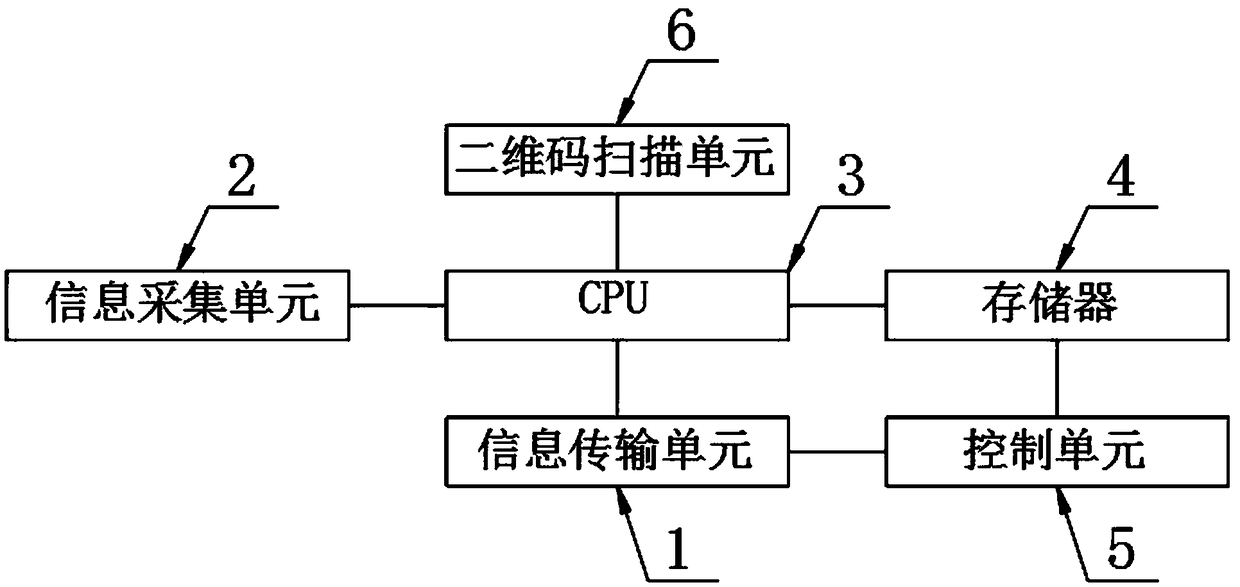
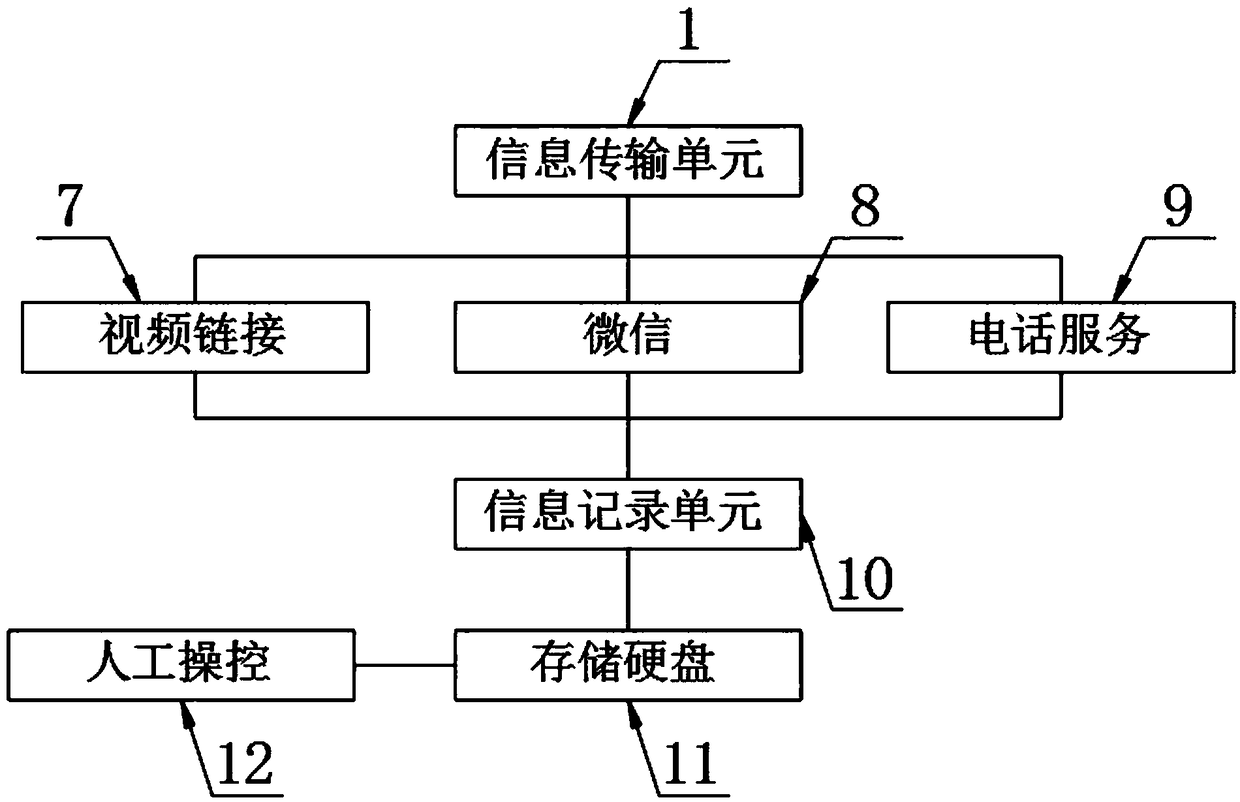
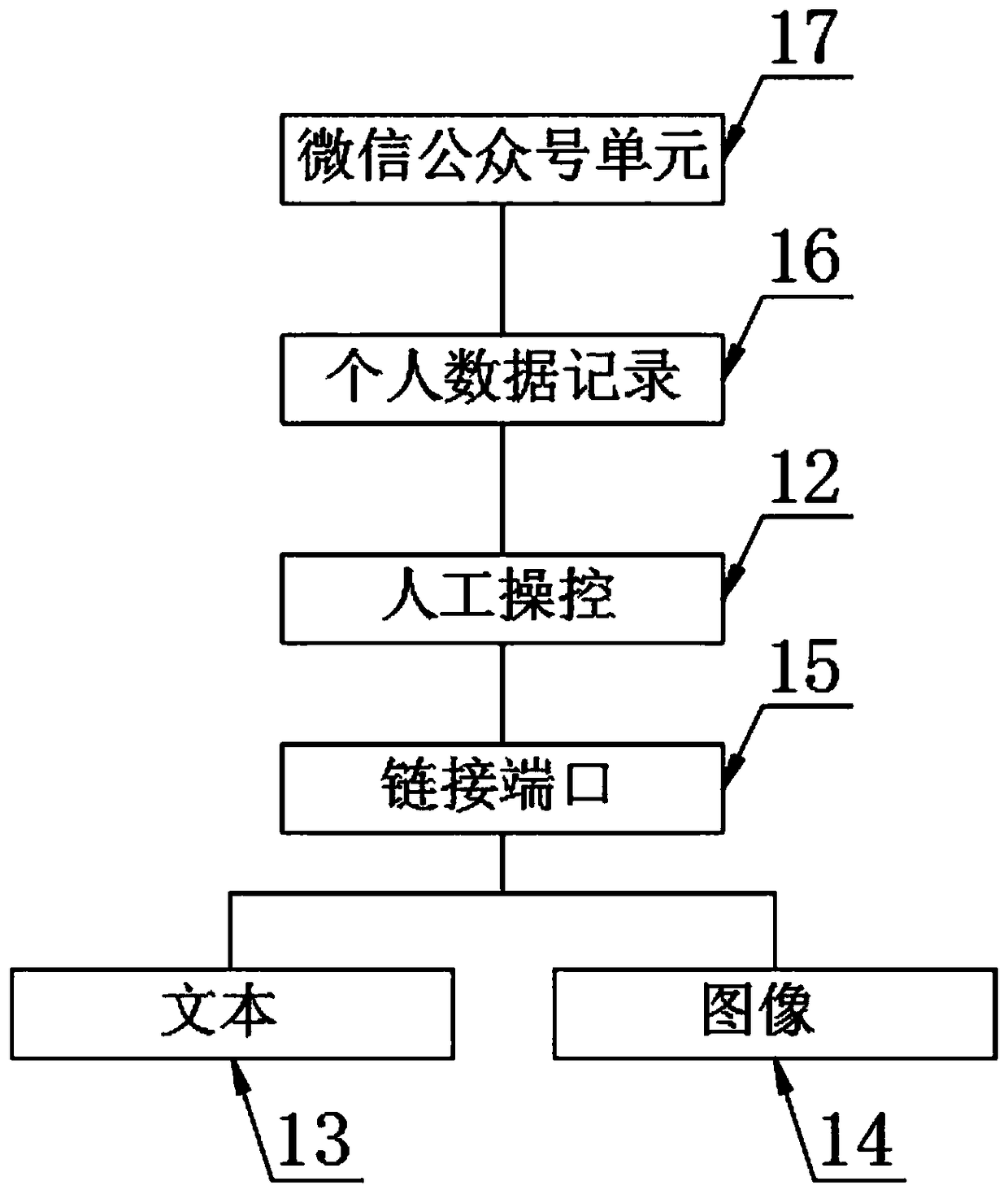
PendingCN109034439AConvenient inspectionEasy to classifyReservationsCo-operative working arrangementsComputer hardwareInformation transmission
The invention discloses an intelligent visitor system based on two-dimensional code reservation, includes an information transmission unit and an information acquisition unit, a CPU is arranged at theoutput end of the information transmission unit, the CPU output end is provided with a memory, the memory output end is provided with a control unit, the CPU input end is provided with a two-dimensional code scanning unit, the information transmission unit comprises a video link, a micro-message and a telephone service, the telephone service output end is provided with an information recording unit, and the information recording unit output end is provided with a storage hard disk. The invention utilizes the storage hard disk to store the specific information of the internal staff of the company, including looks, the timbre, fingerprint and the specific data information of the ID card number form a separate personal data record to form a separate two-dimensional code. The staff member approaches the required two-dimensional code to the entrance guard. After the CPU checks the information with the internal information of the memory, and after the manual operation checks the contrasteddata with the internal data of the memory, the entrance guard is opened after confirming that the contrasted data is correct.
Owner:珠海数图信息技术有限公司
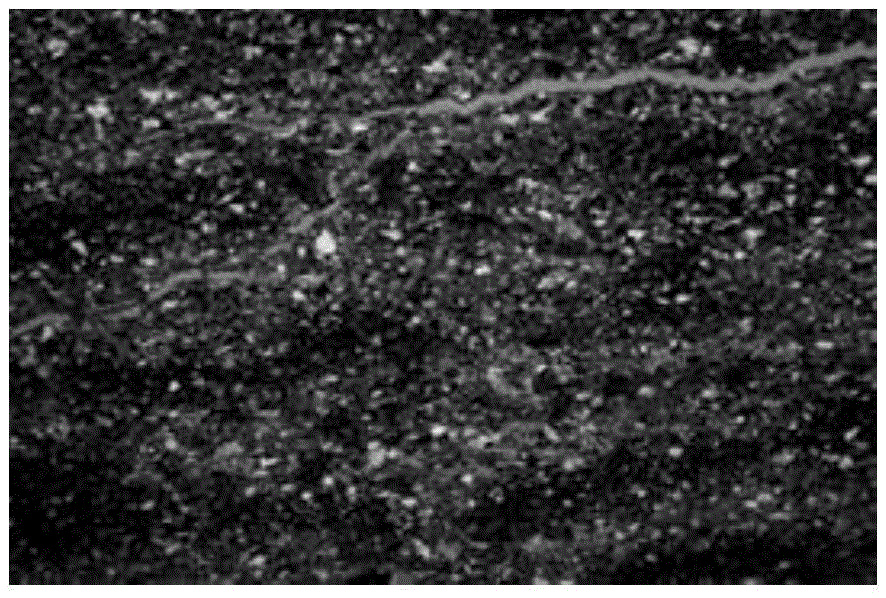
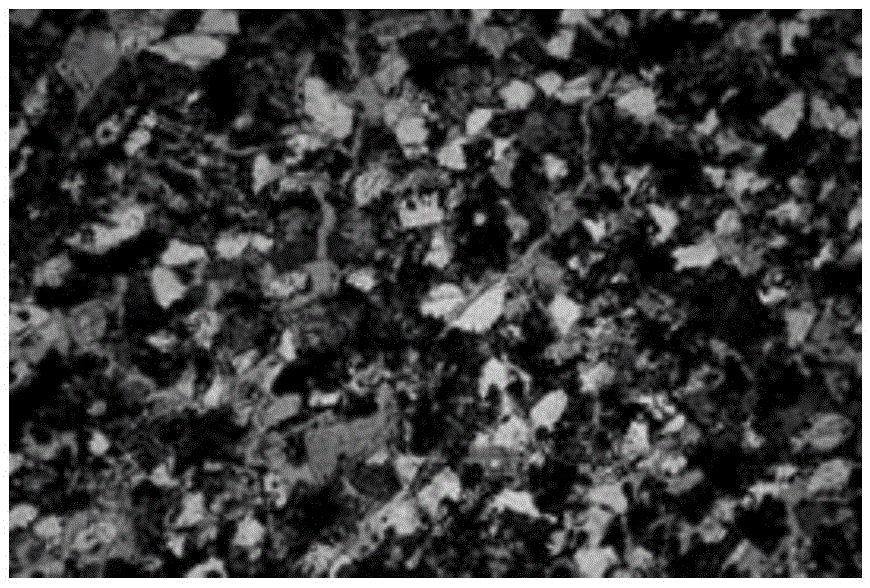
High-definition scanning observation method for ultra-heavy oil sandstone reservoirs
ActiveCN103743742BHigh precisionImprove integrityMaterial analysis by optical meansPermeability/surface area analysisNumber formMicroscopic scale
The invention discloses a high-definition scanning observation technology for a super-heavy oil sandstone storage layer, relates to the field of super-heavy oil sandstone storage layer observation, and aims at providing a super-heavy oil sandstone storage layer high-definition scanning observation technology which is capable of visually expressing the heterogeneity of the storage layer, improving the precision and the integrity of description and improving the observation efficiency. The technology comprises the following steps: a, choosing a super-heavy oil sandstone storage-layer casting thin sheet; b, flat putting the super-heavy oil sandstone storage-layer casting thin sheet on a scanner and adjusting the scanner; c, previewing and scanning the target thin sheet, numbering formed photographs and saving; and d, observing and describing the microscopic characteristics of the super-heavy oil sandstone storage layer on a computer screen. The technology is effective supplement of restrictiveness of conventional microscope observation technology, helps to enrich description means of the super-heavy oil sandstone storage layer and improve the description technology of the super-heavy oil sandstone storage layer.
Owner:PETROCHINA CO LTD
Heat transfer pipe for condensation
InactiveCN101338987BPlay the role of condensation heat transfer enhancementImproved heat transfer performance on the condensing sideHeat transfer modificationTubular elementsCondensation heat transferNumber form
The invention provides a heat transfer pipe used for condensation. Fins which can increase the heat exchange area are pressed on the external surface of the heat transfer pipe. The heat transfer pipe is characterized in that two or more than two layers of fin platforms in composite structure are pressed on the fins; fin slots are arranged between the fin platforms; the fin platforms can be L-shaped, three-step-shaped, V-shaped, Y-shaped or in the shape with one square above and in the middle of the two squares. As the steps on the side walls of the fin platforms or the turning points multipled in number formed based on the slots on the top of the fin platforms through processing play a role in condensation and reinforcement of heat transfer, the heat exchange performance of the condensation side of the heat transfer pipe is improved by 6.5 to 15.0 percent compared with the prior art according to the test results by adopting R134a for condensation.
Owner:WOLVERINE TUBE (SHANGHAI) CO LTD
Emmett output method for rigid body space motion state
ActiveCN102445203ASimplified Computational ComplexityEasy to use in engineeringInstruments for comonautical navigationComputation complexityNumber form
The invention discloses an Emmett output method for rigid body space motion state, wherein the method comprises the following steps of: defining ternary number, so that three speed components of a machine body shaft system and the ternary number form simultaneous differential equations; using an Emmett orthogonal polynomial to carry out approximation description to rolling, pitching and yaw ratesp, q and r; solving a state transition matrix of the system according to the manner of an any-order retainer to acquire an expression of a movement discrete state equation of the rigid body, avoidingan attitude equation singularity problem to acquire the main motion state of the rigid body. The method is introduced with the ternary number, so that the state transition matrix is in the form of a blocked upper triangle, can be solved in an order-reducing manner, thus the calculating complexity is greatly simplified for the convenience of engineering use.
Owner:XIAN FEISIDA AUTOMATION ENG
Chinese character digital coding input method
InactiveCN101446862BSmall amount of memoryHigh input rateInput/output processes for data processingArabic numeralsChinese characters
The invention discloses a Chinese character digital coding input method. Five basic starting strokes, that is, horizontal stroke, vertical stroke, left falling stroke, dot stroke and turning stroke are normalized into four strokes, that is, the horizontal stroke, the vertical stroke, the left falling stroke and the right falling stroke (dot stroke), and two of the four basic stroke codes are combined to form 16 starting two-stroke combined stroke codes which are represented by English letters, number of ones places of the 'horizontal stroke' of the four strokes of the Chinese characters is represented by Arabic numerals 0-9, and tens place is represented by W; number of the ones place of the 'vertical stroke' is represented by the Arabic numerals 0-9, and the tens place is represented by E; number of the ones place of the 'left falling stroke' is represented by the Arabic numerals 0-9, and the tens place is represented by I; number of the ones place of the 'right falling stroke' is represented by the Arabic numerals 0-9, and the tens place is represented by 0; the numbers of the stroke number form a group of Arabic numerals codes in the order of the horizontal stroke, the verticalstroke, the left falling stroke and the right falling stroke from the right to the left, when the Chinese characters are inputted through a computer, the memory is small, the method is easy to be learned and used, the input rate is high, and the coincident code rate is low. The method is also applicable to Chinese character computer input all over the world, and also applicable to computer input of traditional Chinese characters.
Owner:欧诗淼
Laguerre output method for rigid body space motion state
ActiveCN102445202BSimplified Computational ComplexityEasy to use in engineeringInstruments for comonautical navigationComputation complexityAngular velocity
The present invention discloses a Laguerre output method for a rigid body space motion state. According to the method, three velocity components of a machine shaft system and a three-ary number form linear differential equations by defining the three-ary number; a Laguerre orthogonal polynomial is adopted to proximately and closely depict a rolling angle p, a pitching angle q, and a yawing angular velocity r; a state transition matrix of the system can be solved according to a manner of an arbitrary order keeper so as to acquire an expression of a rigid body motion discrete state equation, such that the singularity problem of the attitude equation is avoided so as to acquire the main motion state of the rigid body. According to the present invention, the three-ary number is introduced, such that the state transition matrix is the block upper triangular manner, and can be solved by reducing the order so as to substantially simplify the calculation complexity, and be easily used by the engineering.
Owner:XIAN FEISIDA AUTOMATION ENG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com