Authentication method adopting complex cryptographic technique
A cryptographic technology and cryptographic technology, applied in the field of authentication using double-entry cryptography, can solve the problems of user leakage, low security, and inability to determine the identity of the password user, and achieve the effect of improved security and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
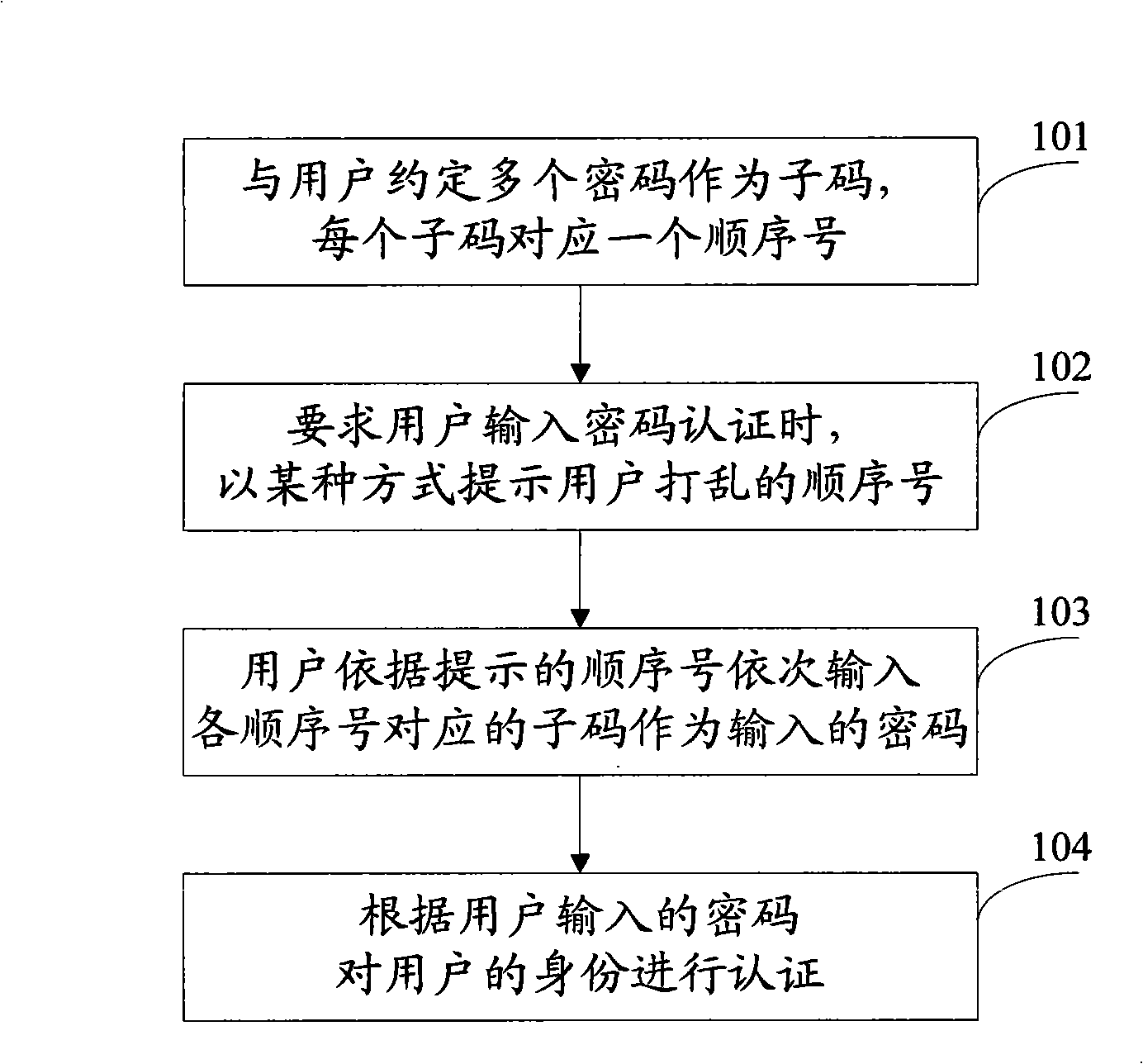
[0030] Refer below figure 1 The shown flow chart of the present invention adopting the interactive multiple password technique for authentication is described in detail for the present invention. Include the following steps:
[0031] Step 101: First, the user of the password and the service organization agree on multiple relatively simple passwords, which we call subcodes in this article. At the same time, each subcode also agrees on a corresponding sequence number. All subcodes and their corresponding sequence numbers together form a compound password.
[0032] The subcodes and subcodes are independent of each other, and the sequence numbers corresponding to different subcodes are also independent and different from each other. That is to say, the double-entry password is composed of several subcodes with sequential numbers. It can also be said that the double-entry password is divided into several parts according to the agreed rules, and each part is a subcode. It can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com