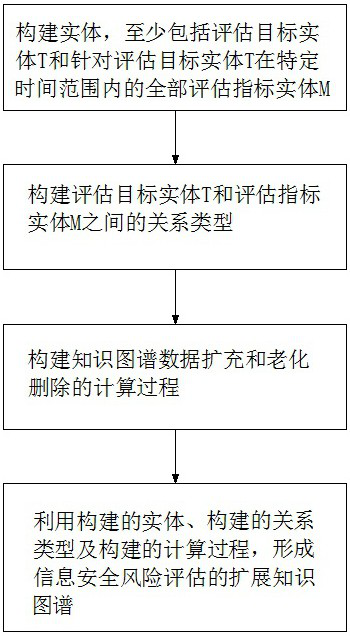
An extended knowledge map and construction method and system for information security risk assessment
A knowledge map and risk assessment technology, applied in the fields of artificial intelligence, database, and information security, can solve the problems of ignoring the map of the index system, inconvenient information security risks, and low query efficiency, and achieve the goal of improving query efficiency and maintainability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
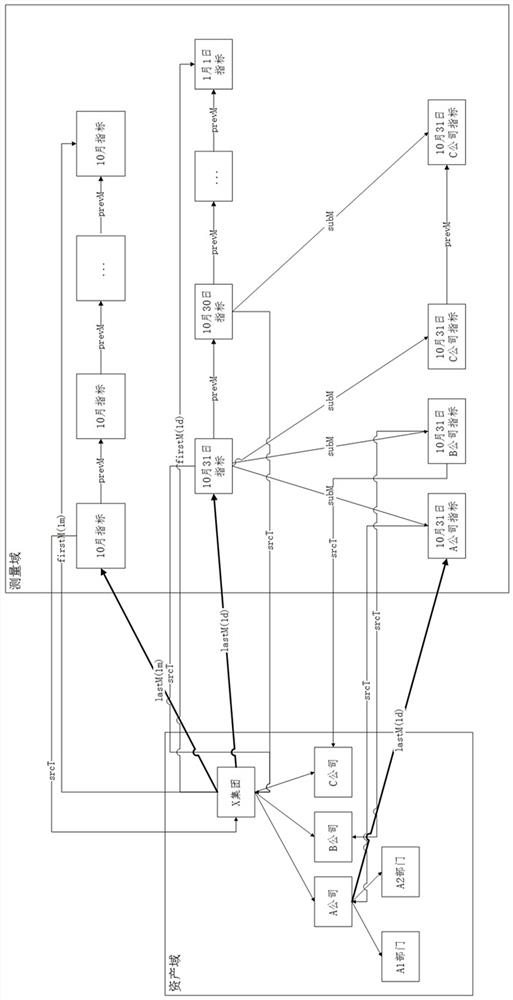
[0223] refer to figure 2 , if an enterprise X group is used as the evaluation target entity, the evaluation is carried out on a daily basis. A variety of quantitative characteristics were measured daily from January 1, and a comprehensive score was calculated. Assume that the most recent evaluation occurred on October 31st. Then, the institution itself is a T-type entity, and the index systems of each date constitute an M-type entity. T points to the M entity on January 1 with a firstM relationship, and points to the M entity on October 31 with a lastM relationship. At the same time, the M entity on October 31 points to the M entity on October 30 with a prevM relationship, and so on until it points to the M entity on January 1.
[0224] X Group has three companies under its jurisdiction, A, B, and C, which are also used as evaluation targets, corresponding to the corresponding T entities. These T entities and related relationships exist in the asset domain knowledge graph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com