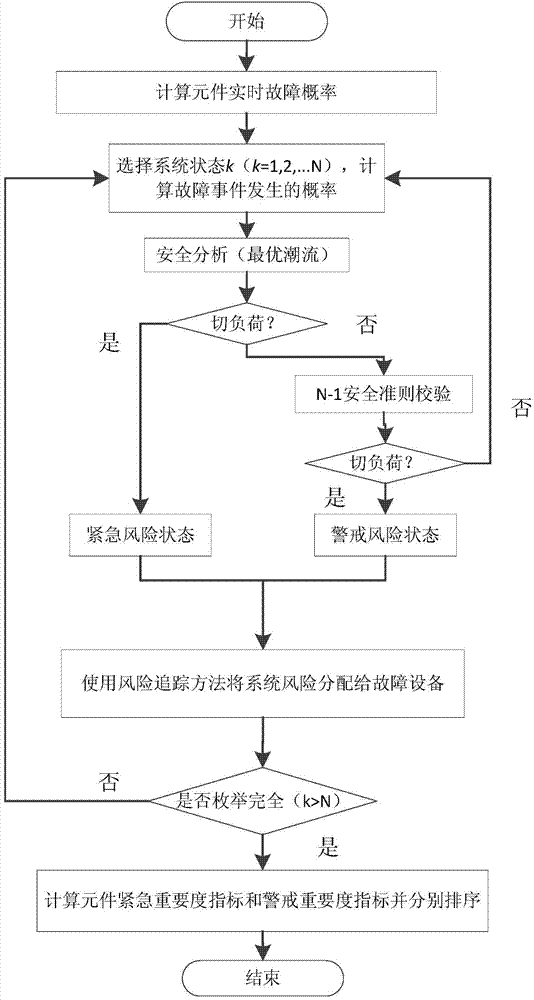
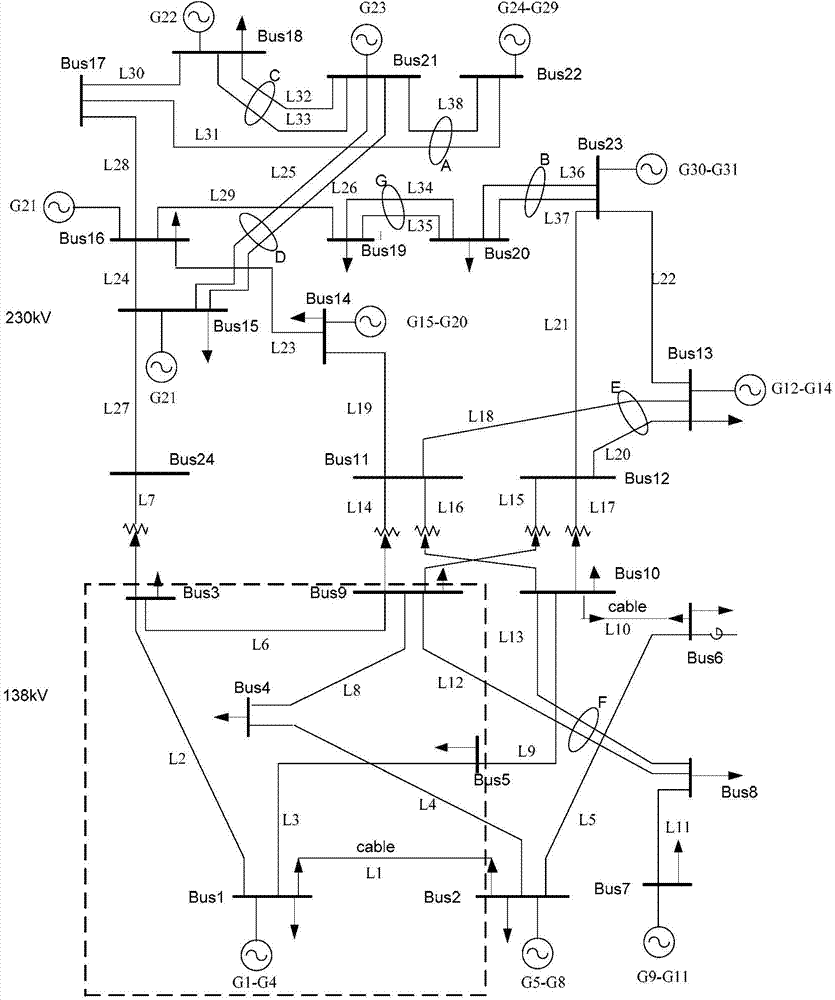
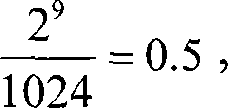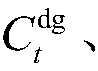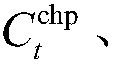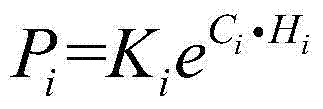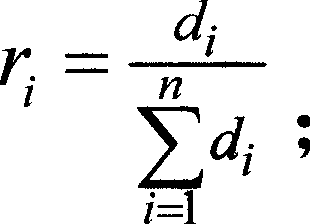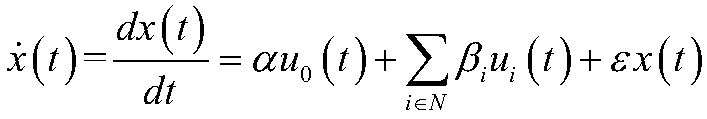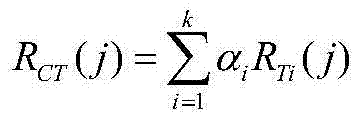Patents
Literature
280 results about "System risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System risk is a danger caused by an occurrence at the local or company level that is substantive enough to impact the broader financial system.
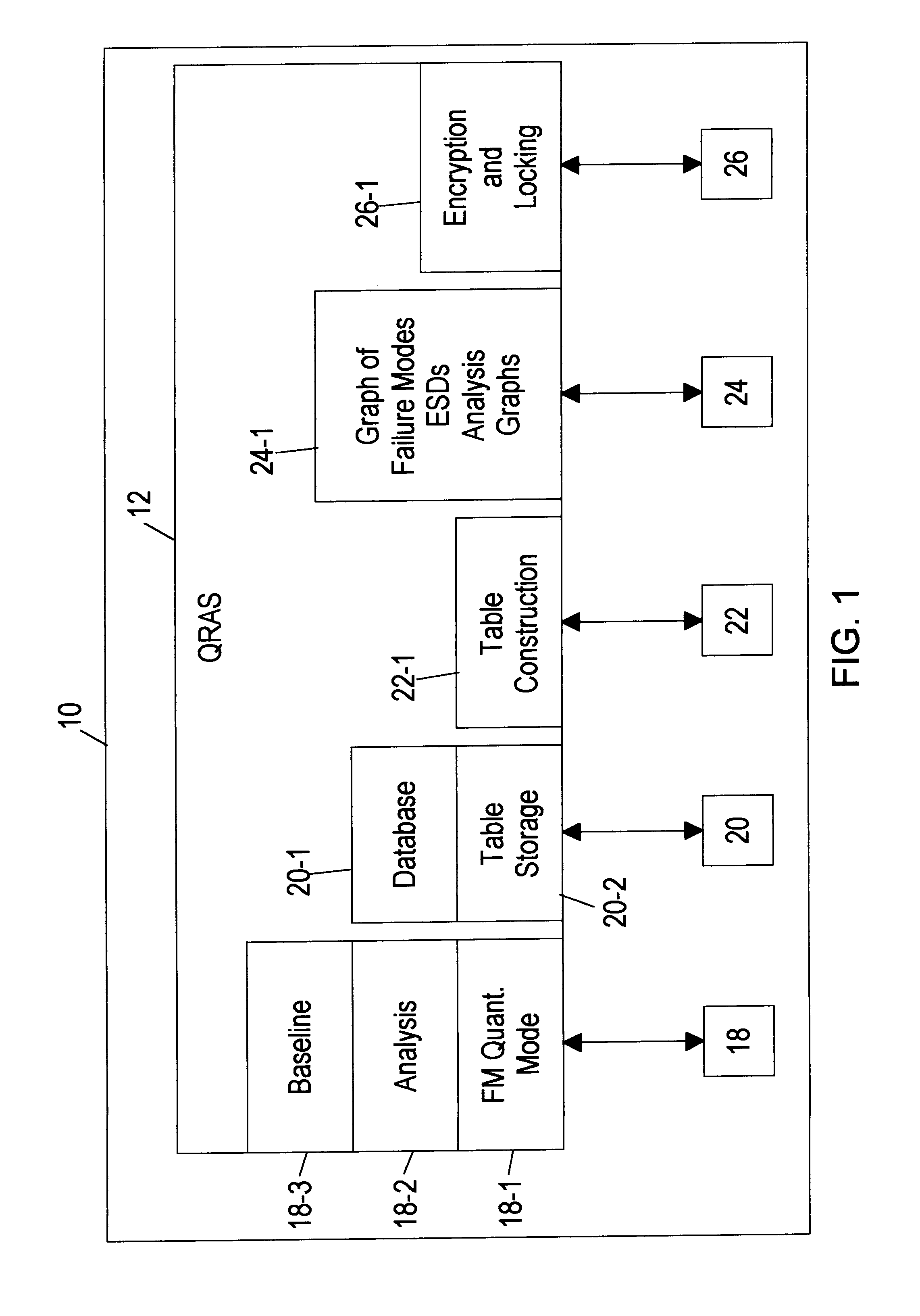
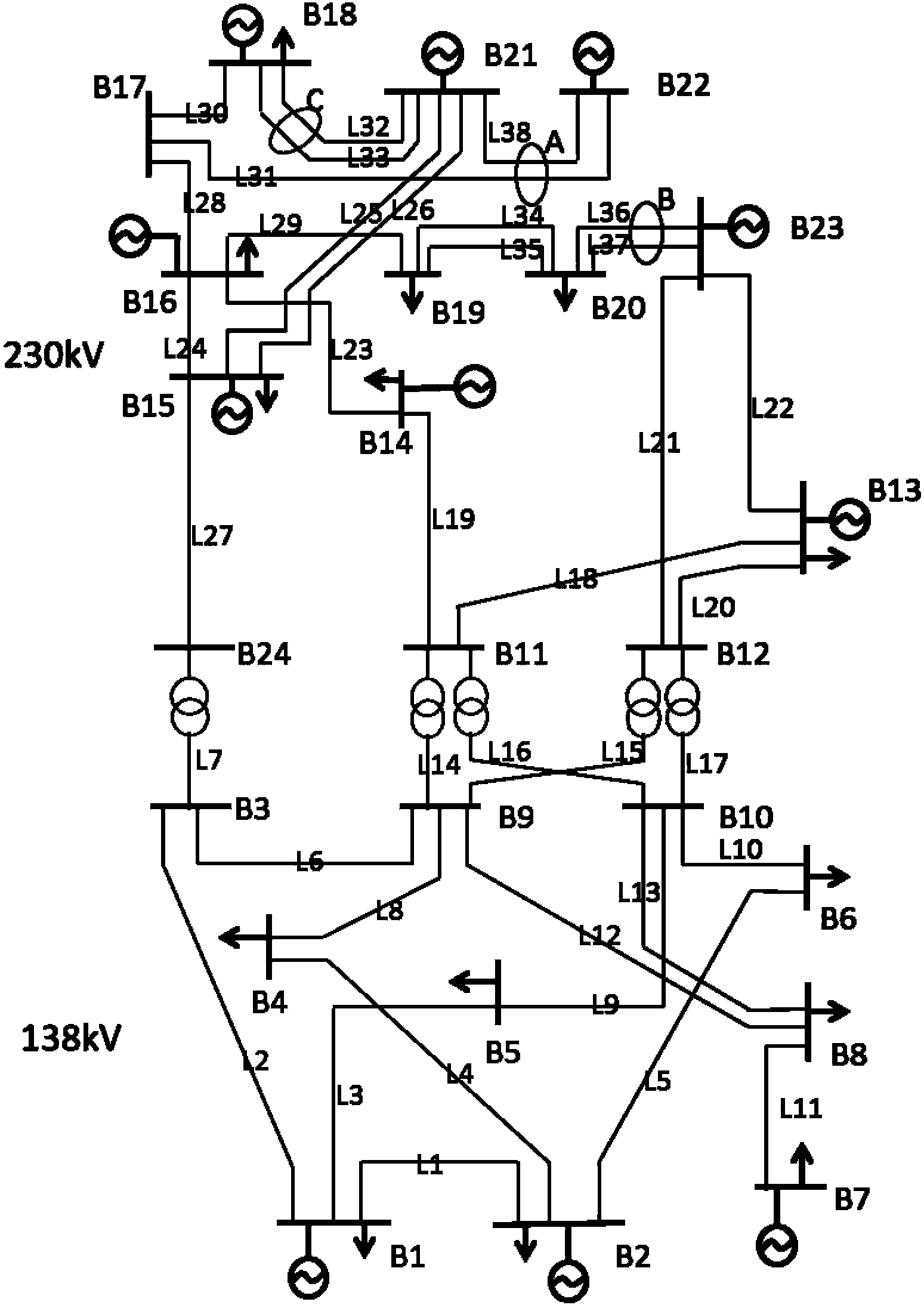
Quantitative risk assessment system (QRAS)
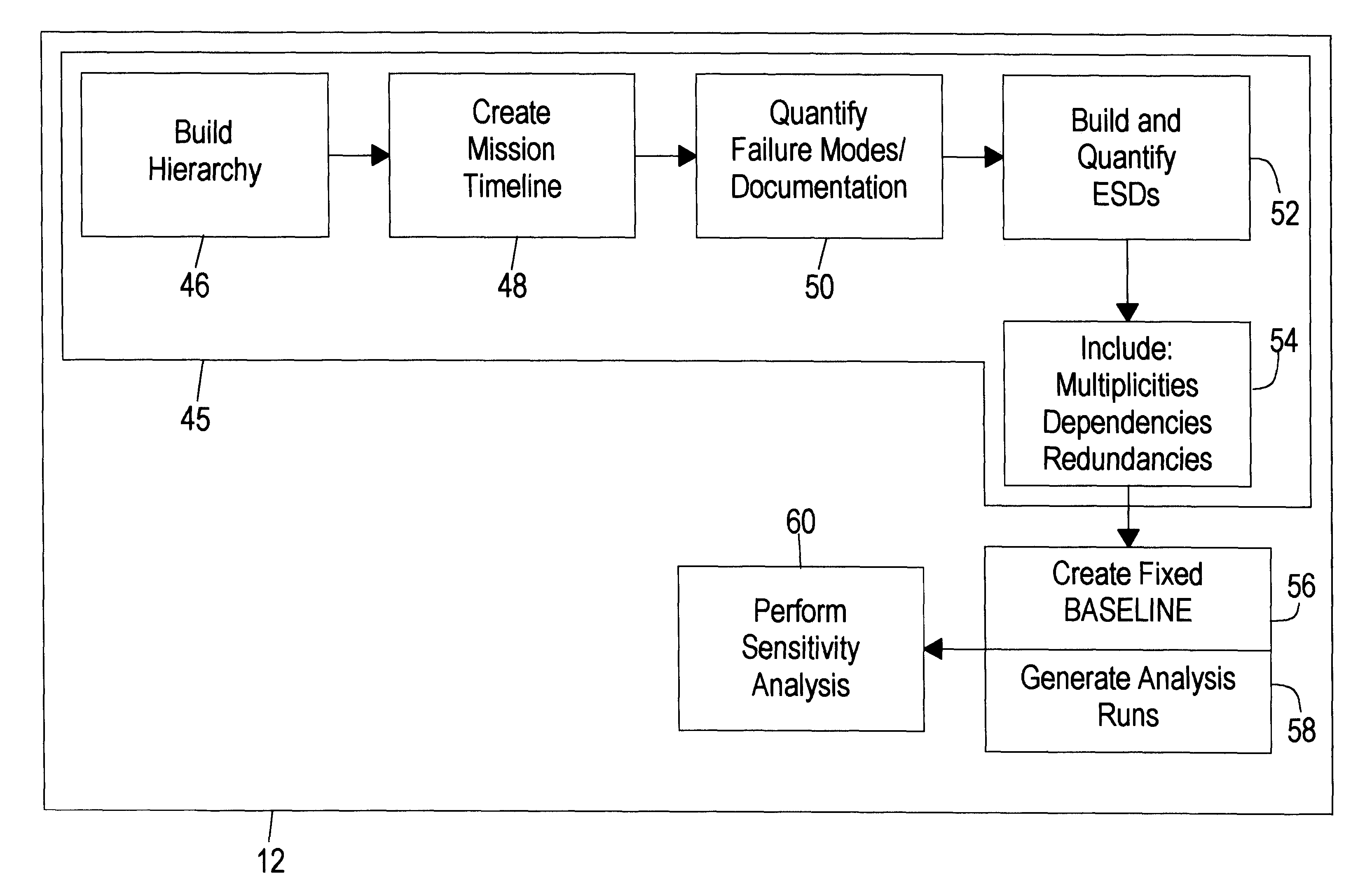
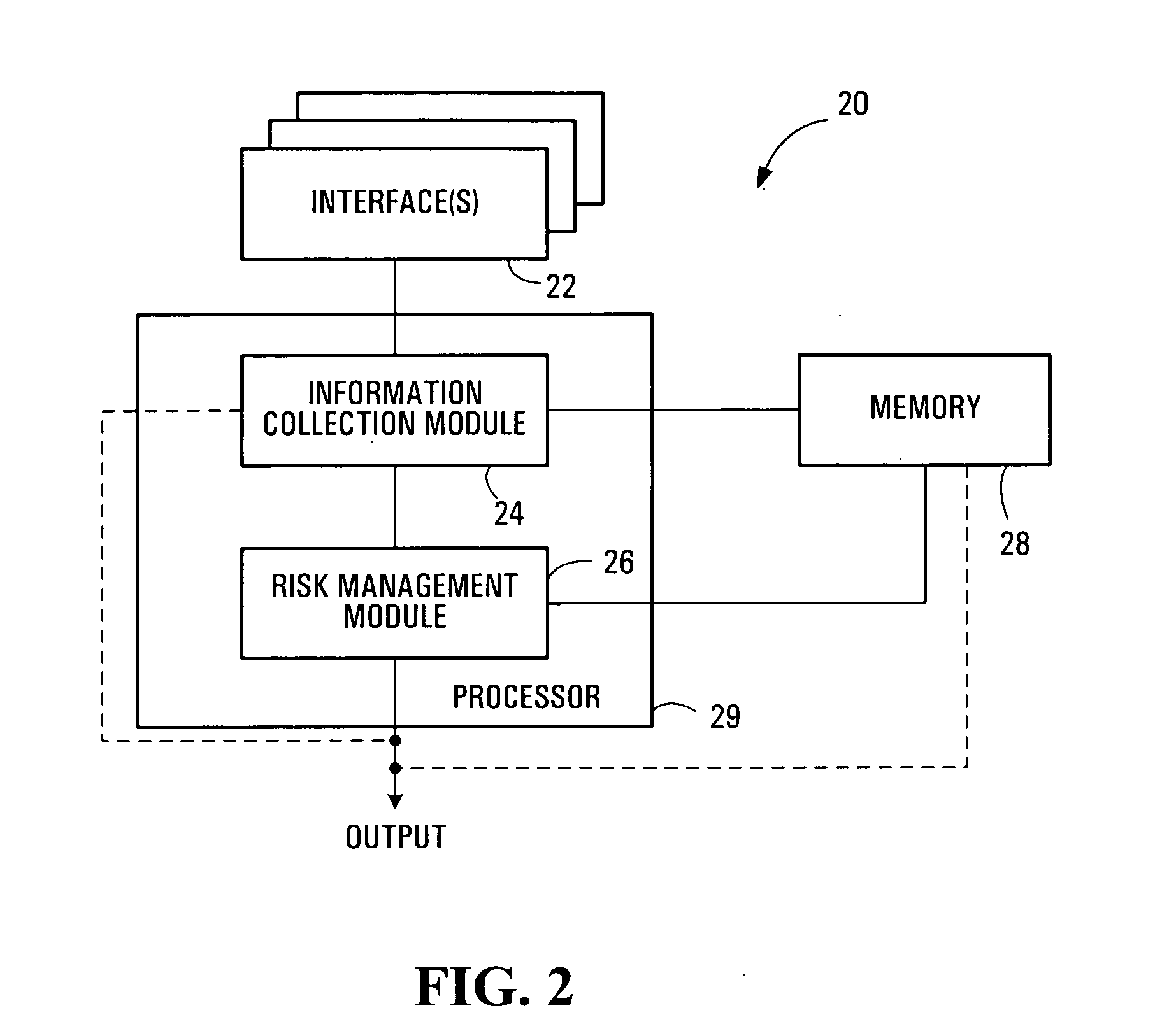
A quantitative risk assessment system (QRAS) builds a risk model of a system for which risk of failure is being assessed, then analyzes the risk of the system corresponding to the risk model. The QRAS performs sensitivity analysis of the risk model by altering fundamental components and quantifications built into the risk model, then re-analyzes the risk of the system using the modifications. More particularly, the risk model is built by building a hierarchy, creating a mission timeline, quantifying failure modes, and building / editing event sequence diagrams. Multiplicities, dependencies, and redundancies of the system are included in the risk model. For analysis runs, a fixed baseline is first constructed and stored. This baseline contains the lowest level scenarios, preserved in event tree structure. The analysis runs, at any level of the hierarchy and below, access this baseline for risk quantitative computation as well as ranking of particular risks. A standalone Tool Box capability exists, allowing the user to store application programs within QRAS.
Owner:NAT AERONAUTICS & SPACE ADMINISTATION U S GOVERNMENT AS REPRESENTED BY THE ADMINISTATOR +1
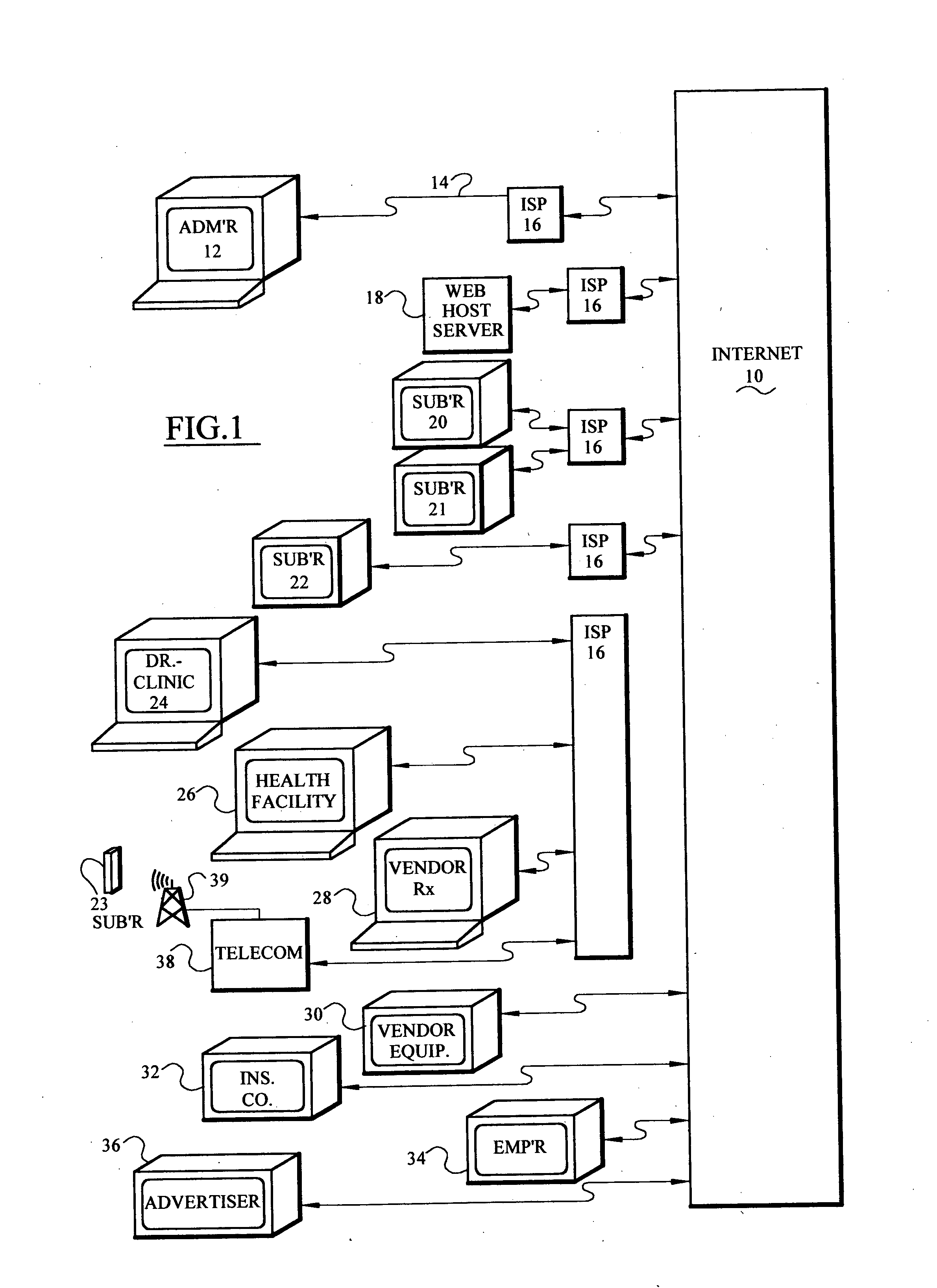
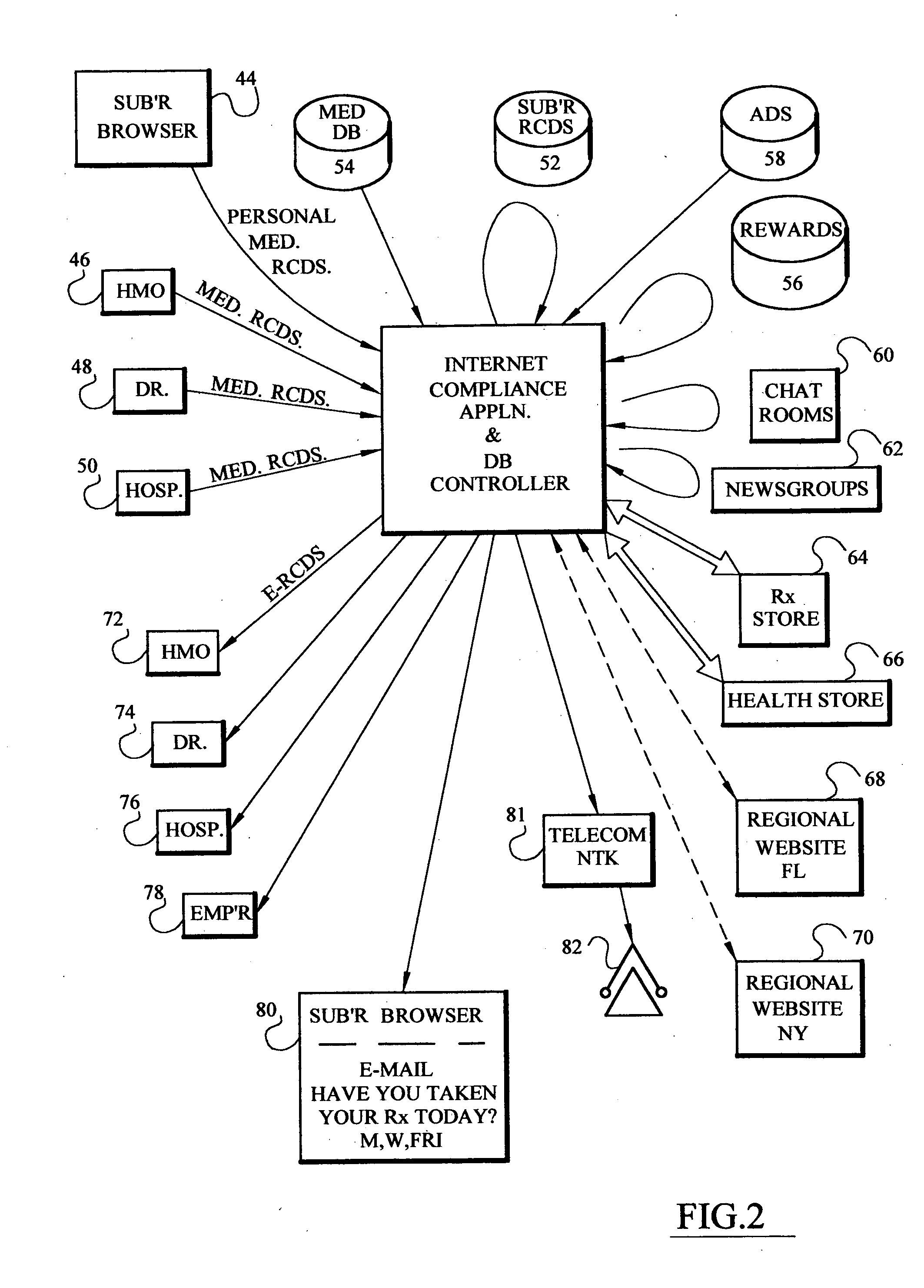
Computer based risk level monitor and patient compliance method and system
InactiveUS20050102159A1Improve compliance rateVAR reductionData processing applicationsHealth-index calculationRisk levelTotal risk
The risk monitor, as a computer-based method, program or system, monitors medical compliance by a plurality of patients having a corresponding plurality of medical compliance plans. The plans for each patient are displayed and the system accepts input from the patient indicative and / or heathcare providers of the patient's compliance with the plan. The system then assesses or analyzes the input and assigns a corresponding risk value based upon a range of risk values for various degrees of compliance. In addition, the patient's lifestyle inputs can be added to determine the risk value. The assessment continues for a plurality of patients thereby providing an indication of the risk value (a total risk value) for a patient, doctor, group of healthcare providers, a clinic or a hospital. By implementing various communication episodes (telephone calls, e-mails, letters), the system seeks to reduce the risk value for a particular patient and for the plurality of patients by altering the communication episodes and monitoring the resulting risk values both individually and as a group.
Owner:MONDSHINE ROBERT B
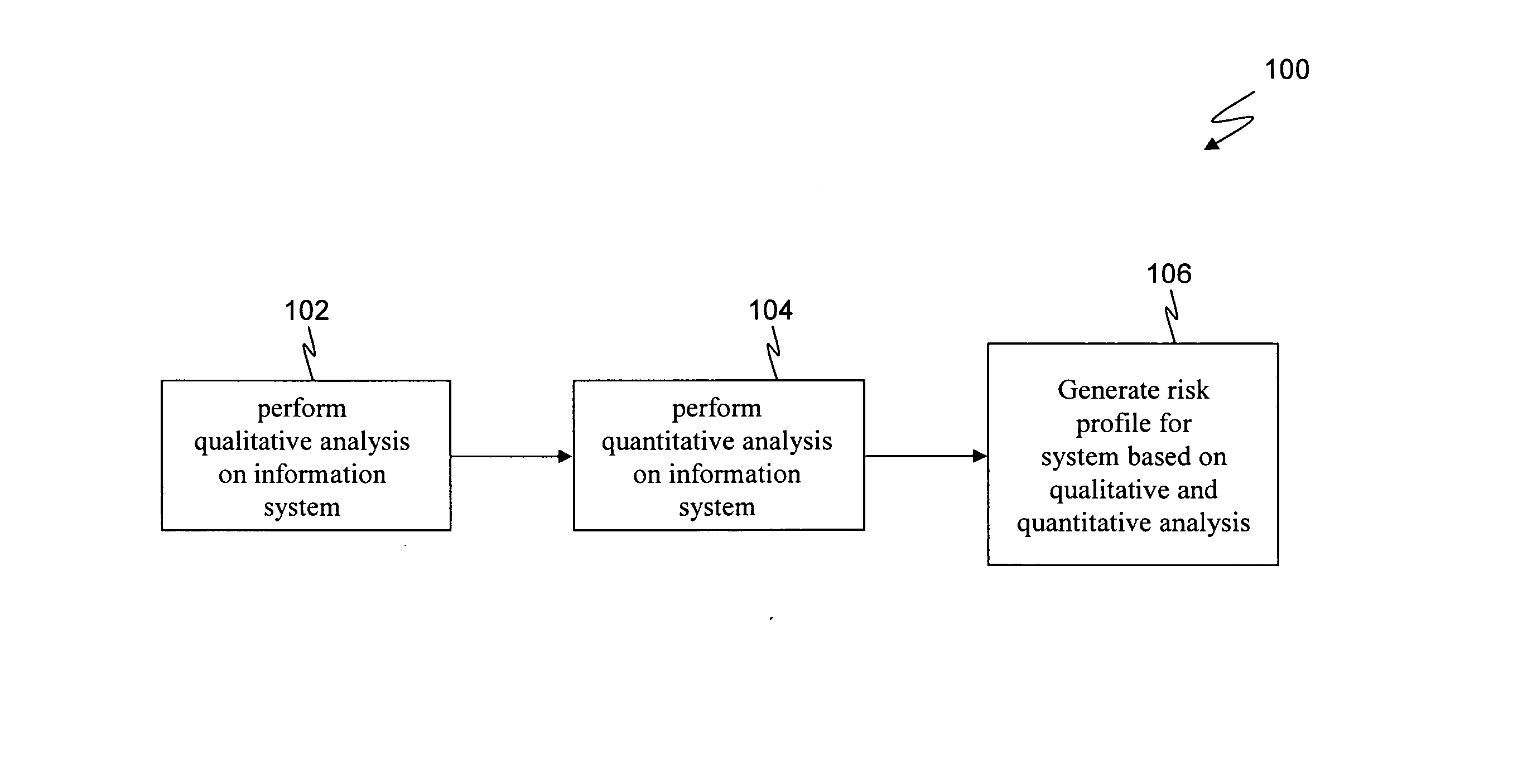
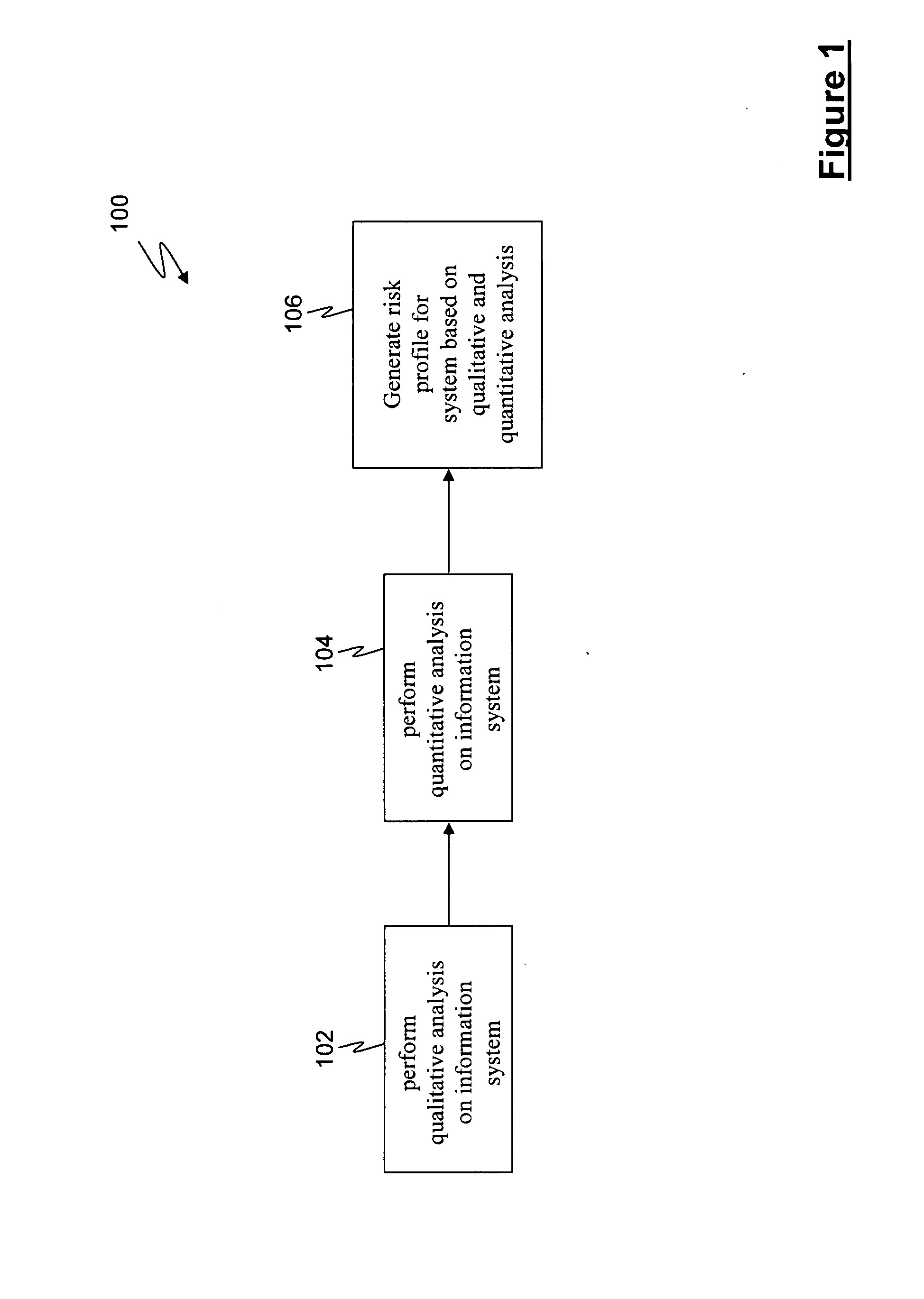
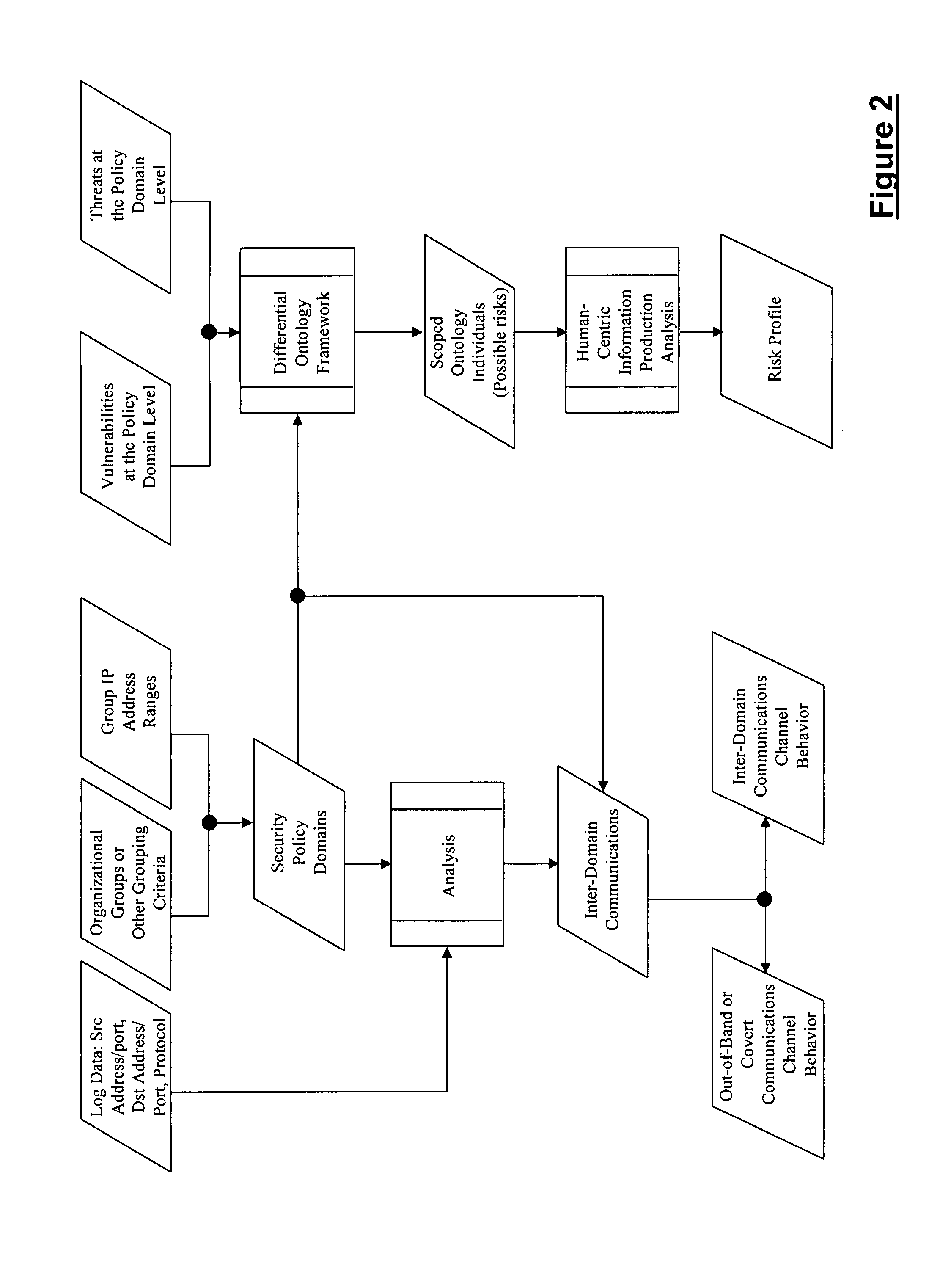
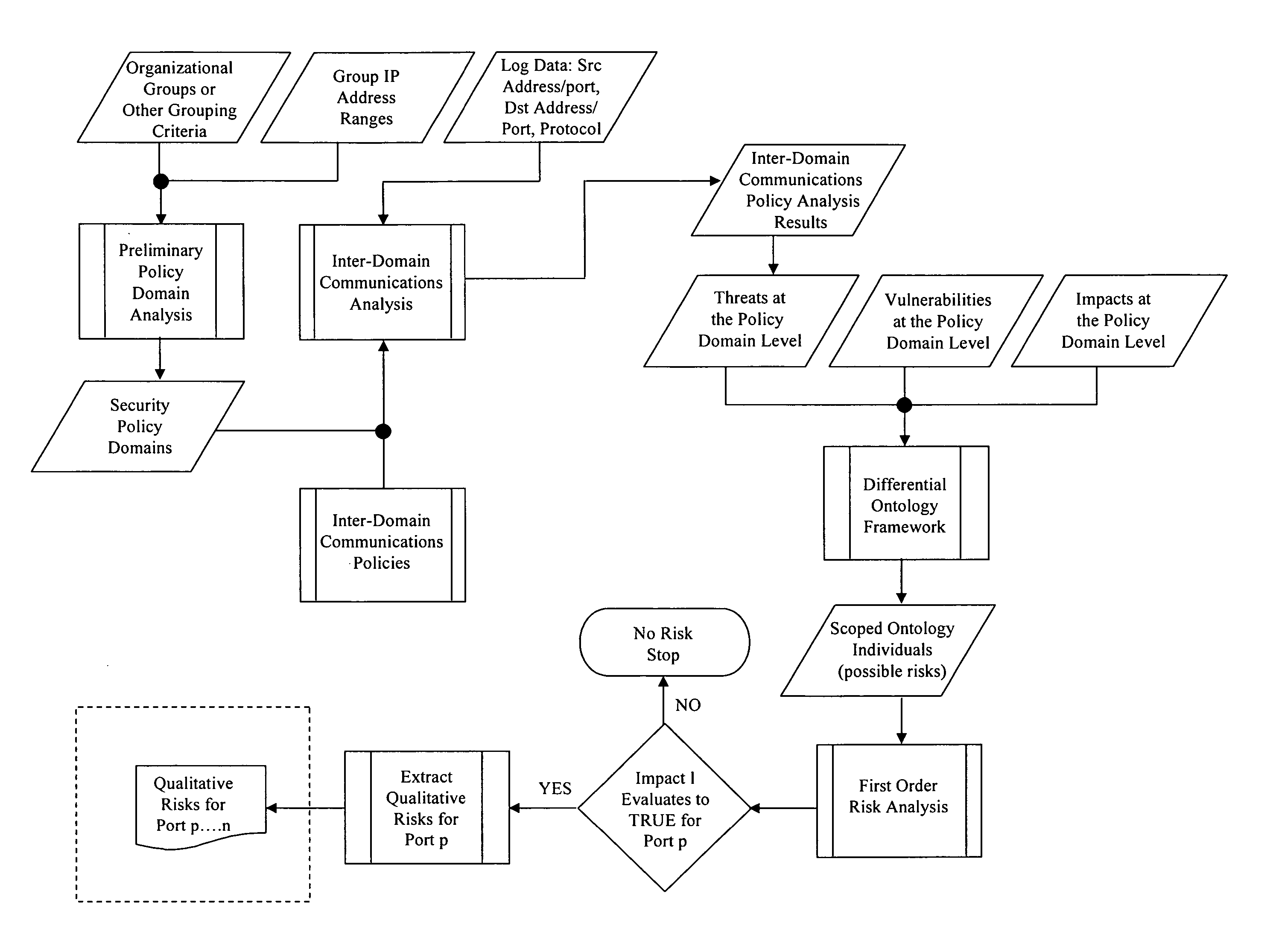
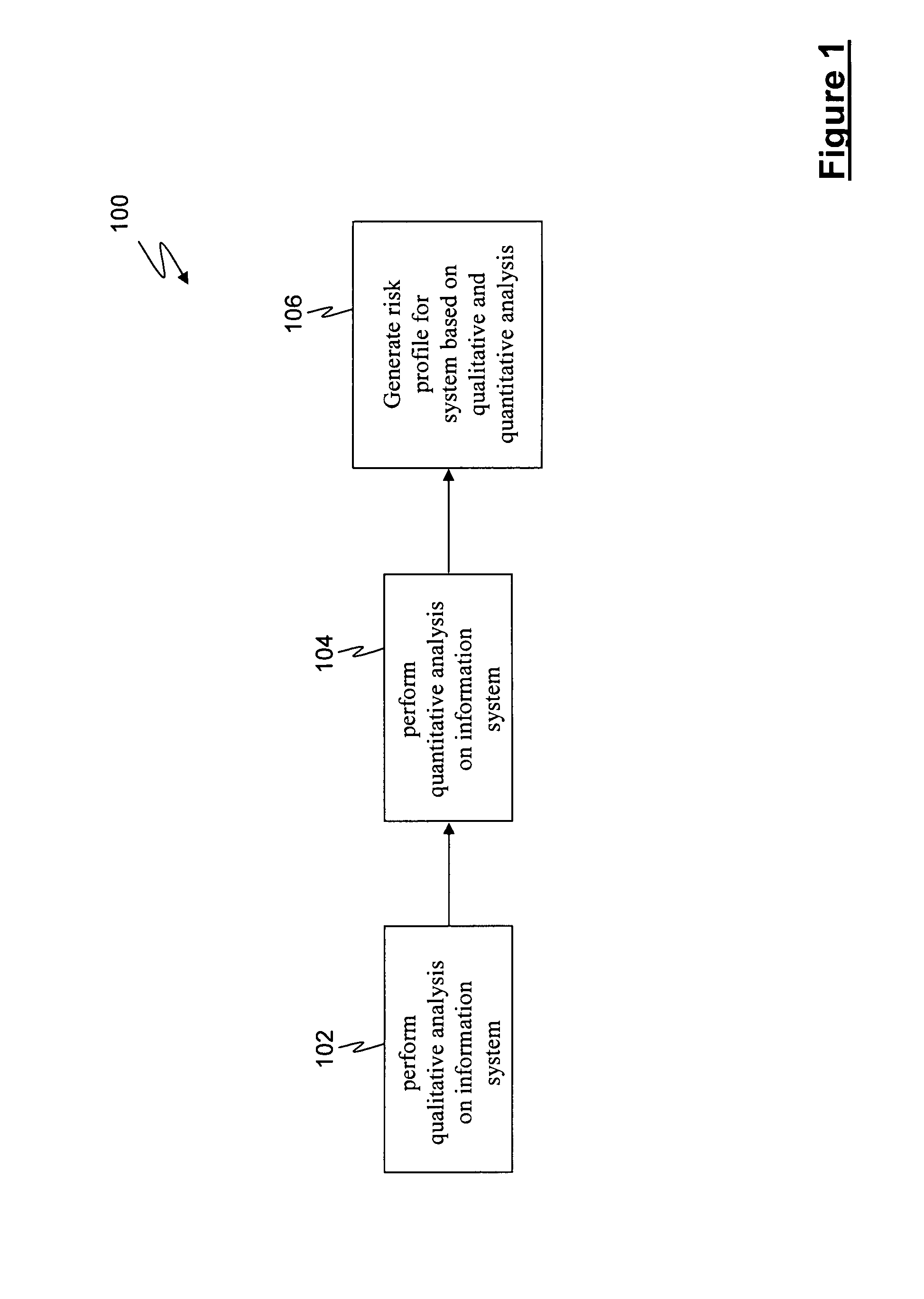
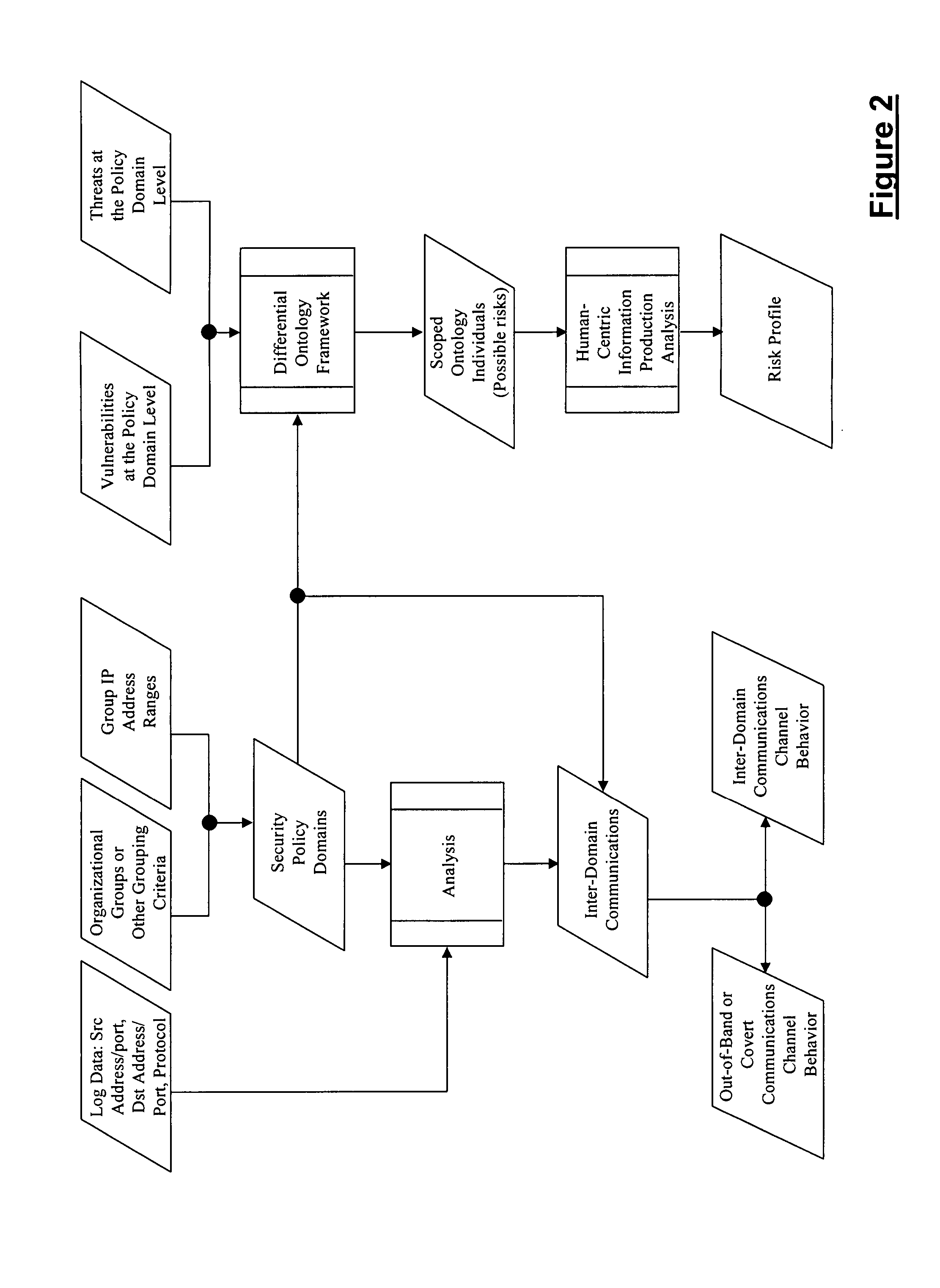
Method for evaluating system risk
A method for evaluating a system having at least one portal is provided, wherein the method includes examining the at least one portal to identify at least one accessible portal, performing a qualitative analysis responsive to the at least one accessible portal, performing a quantitative analysis responsive to the qualitative analysis and generating a risk profile responsive to the performing a qualitative analysis and the performing a quantitative analysis.
Owner:STEPHENSON PETER R
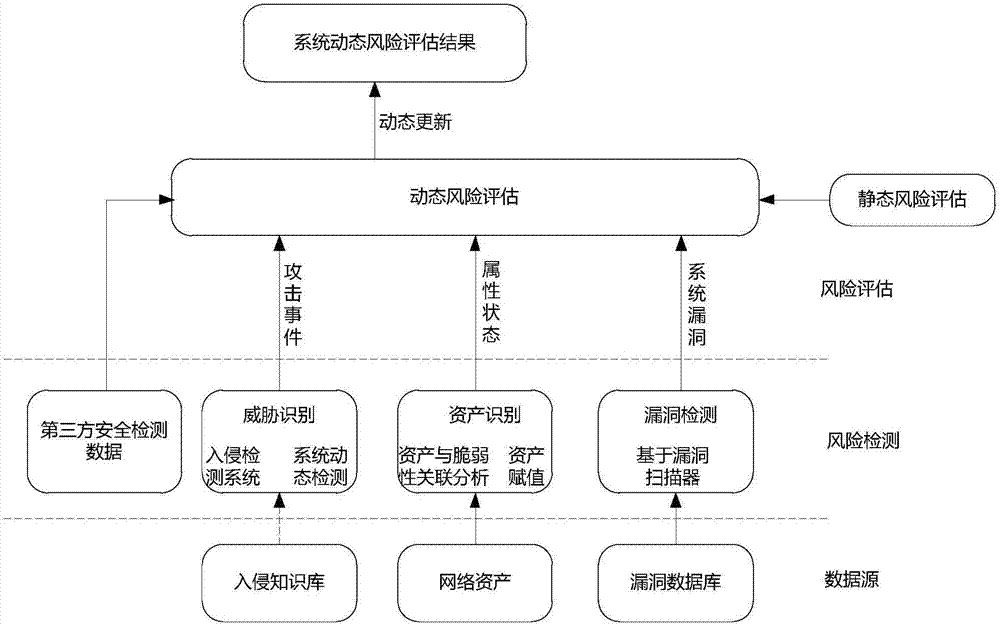
Network security risk assessment method
InactiveCN107204876AImprove real-time performanceImprove accuracyData switching networksThird partyMonitoring system
The invention discloses a network security risk assessment method. The security of a target network is assessed dynamically by combining an intrusion detection system, vulnerability detection and real-time attack events obtained by a third party on the basis of static risk assessment. With regard to risk assessment, the asset value is usually defined by specialists or managers during static assessment and no great change occurs in a certain period; dynamic changes of threatening and vulnerable information can be assessed by aid of corresponding tools; the intrusion detection system and a firewall are taken as monitoring systems and can warn of anomalous events at any time, and warning information is possible threats to a system and is also an important basis for assessment of a system risk condition. With the adoption of the network security risk assessment method, the accuracy and instantaneity of network risk assessment can be improved effectively, security defense measures can be carried out according to risk assessment results, and risks can be controlled effectively in time.
Owner:成都网络空间安全技术有限公司
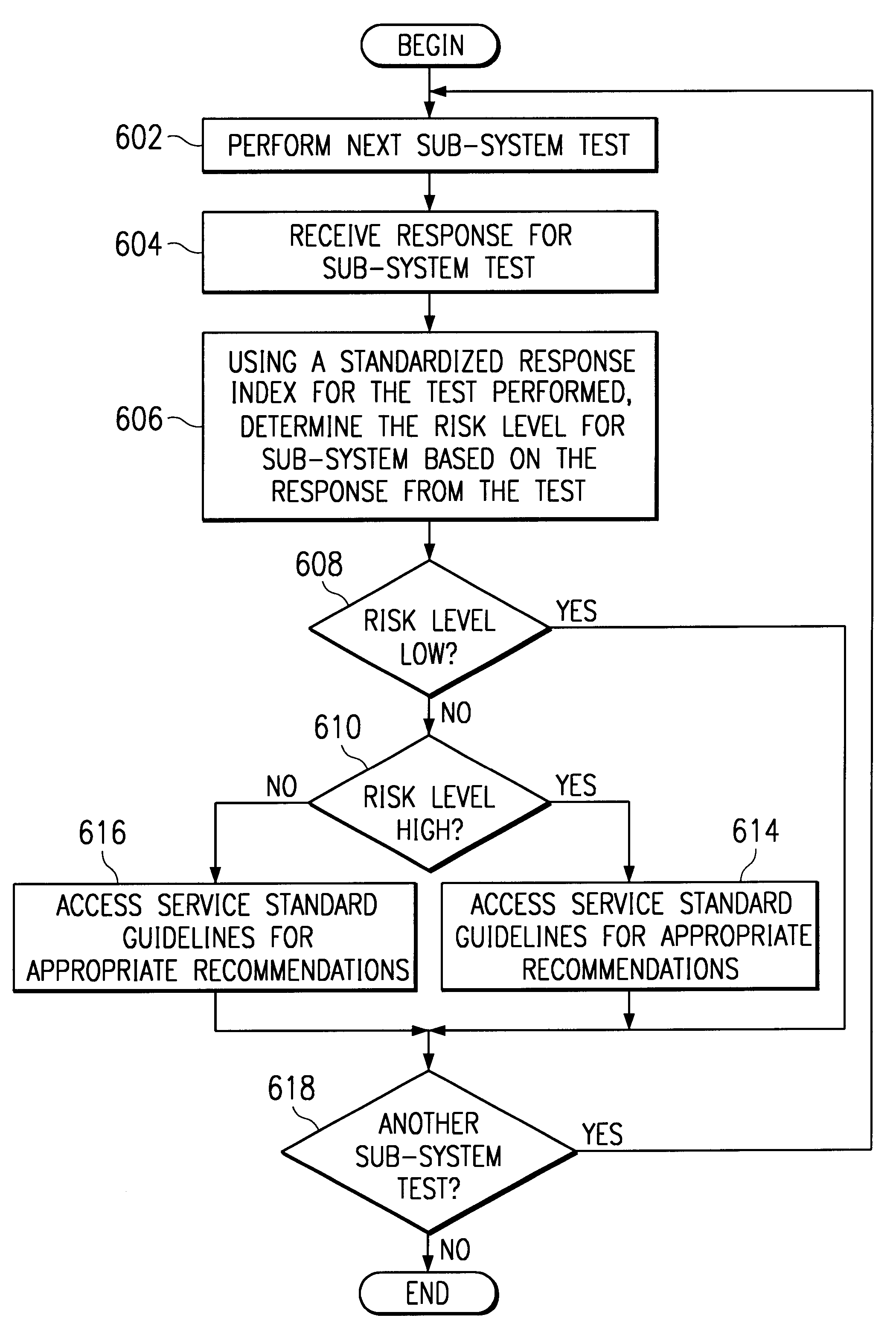
Automated risk assessment tool for AIX-based computer systems
A system administrator or service provider executes the risk assessment script that automatically performs a series of hardware, software, and firmware tests on the system. Each test provides the administrator / service provider with a determination output that is standardized into risk assessment levels. Depending on the type of test and the risk level assigned to the determination from the test, the administrator / service provider can recommend various courses of action to reduce the risk to the system.
Owner:IBM CORP
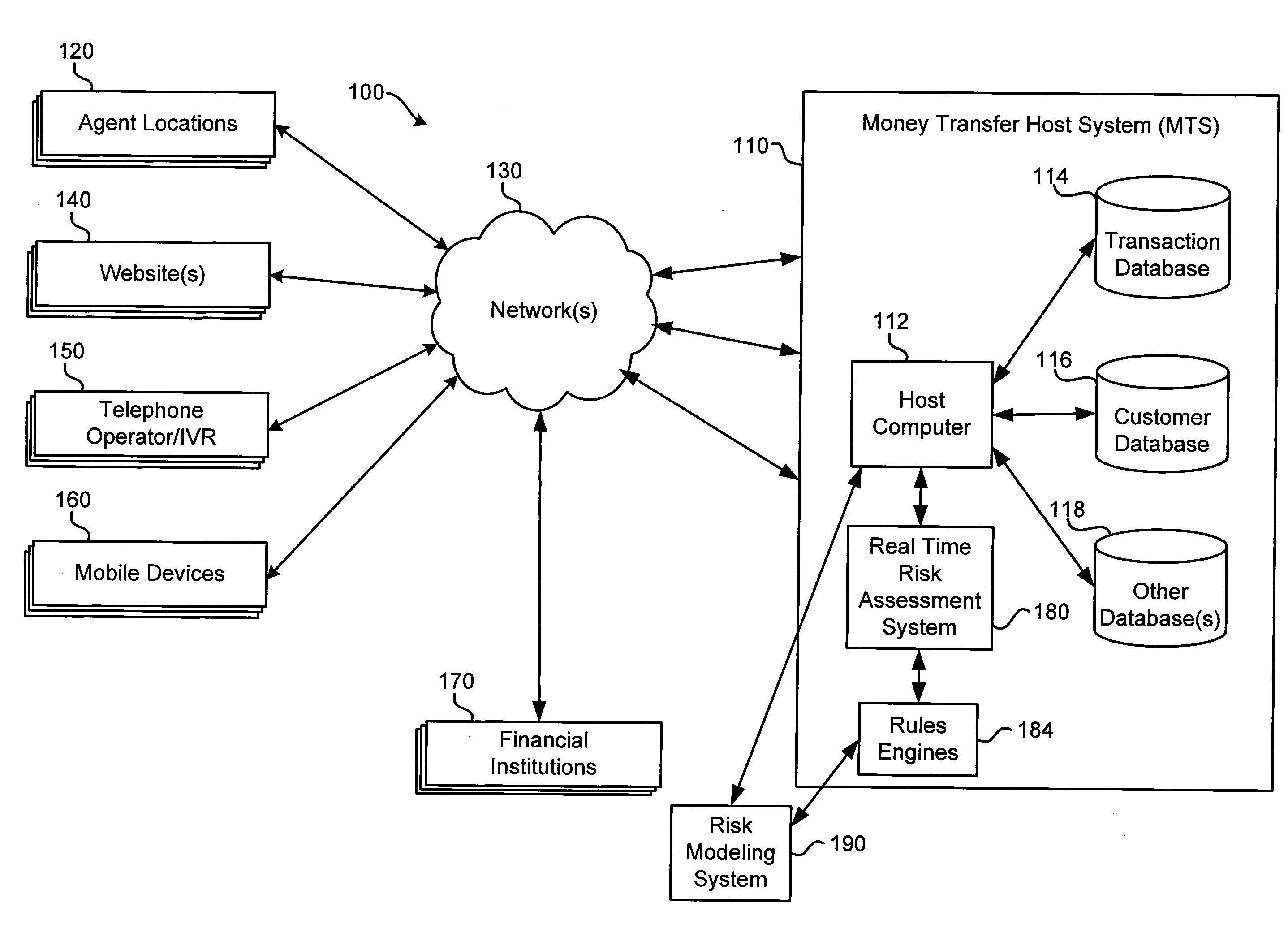
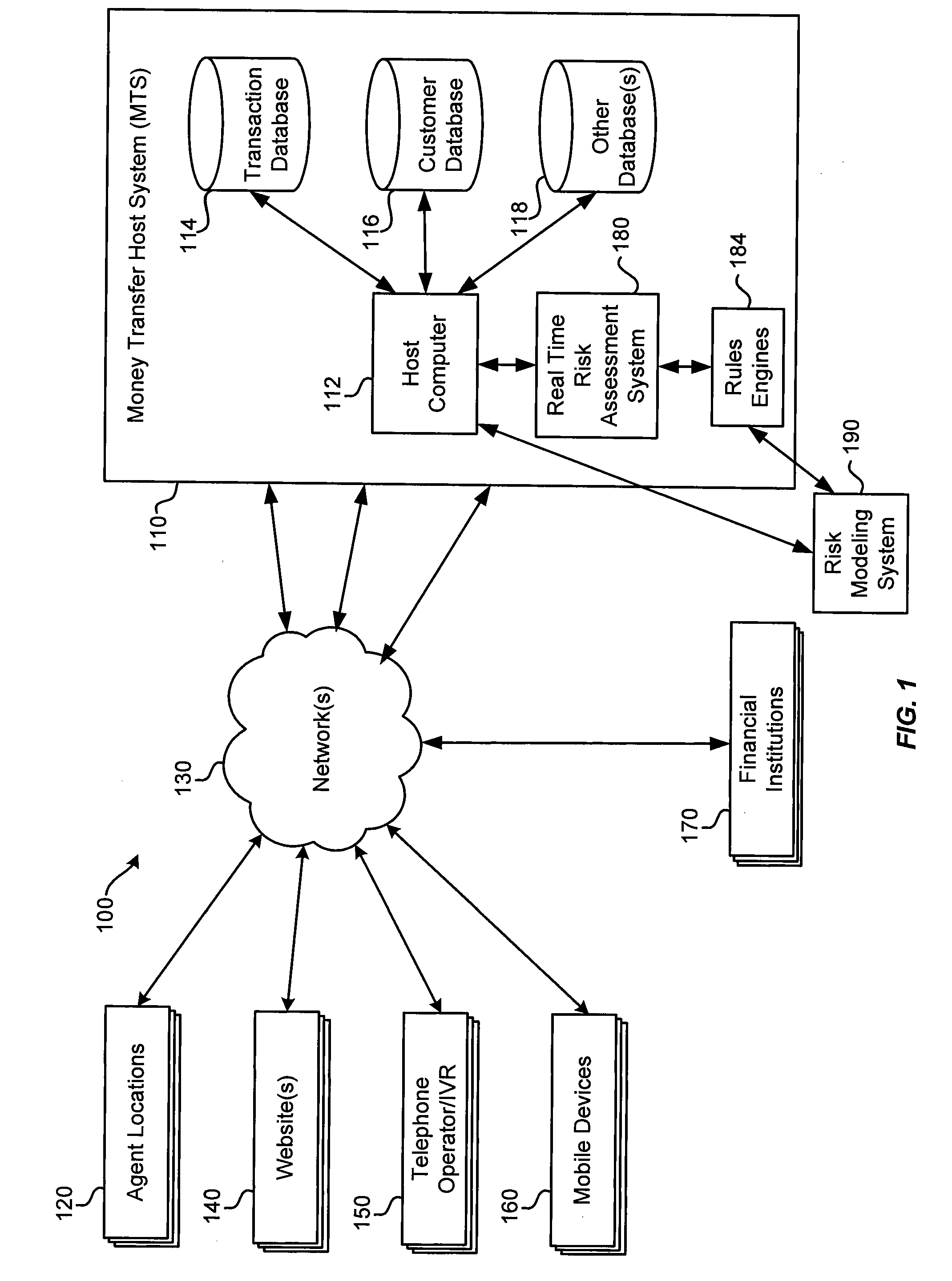
Risk analysis of money transfer transactions
A money transfer system includes a risk assessment system and a risk modeling system. The risk assessment system uses rules engines and Z scores to assess, on a real time basis, risk factors associated with money transfers. The risk modeling system develops risk scores based on historical transaction data in order to create a risk model. The risk model may be analyzed over time to refine the rules engines and take other actions to understand and reduce the risk of improper activity in connection with money transfers.
Owner:THE WESTERN UNION CO
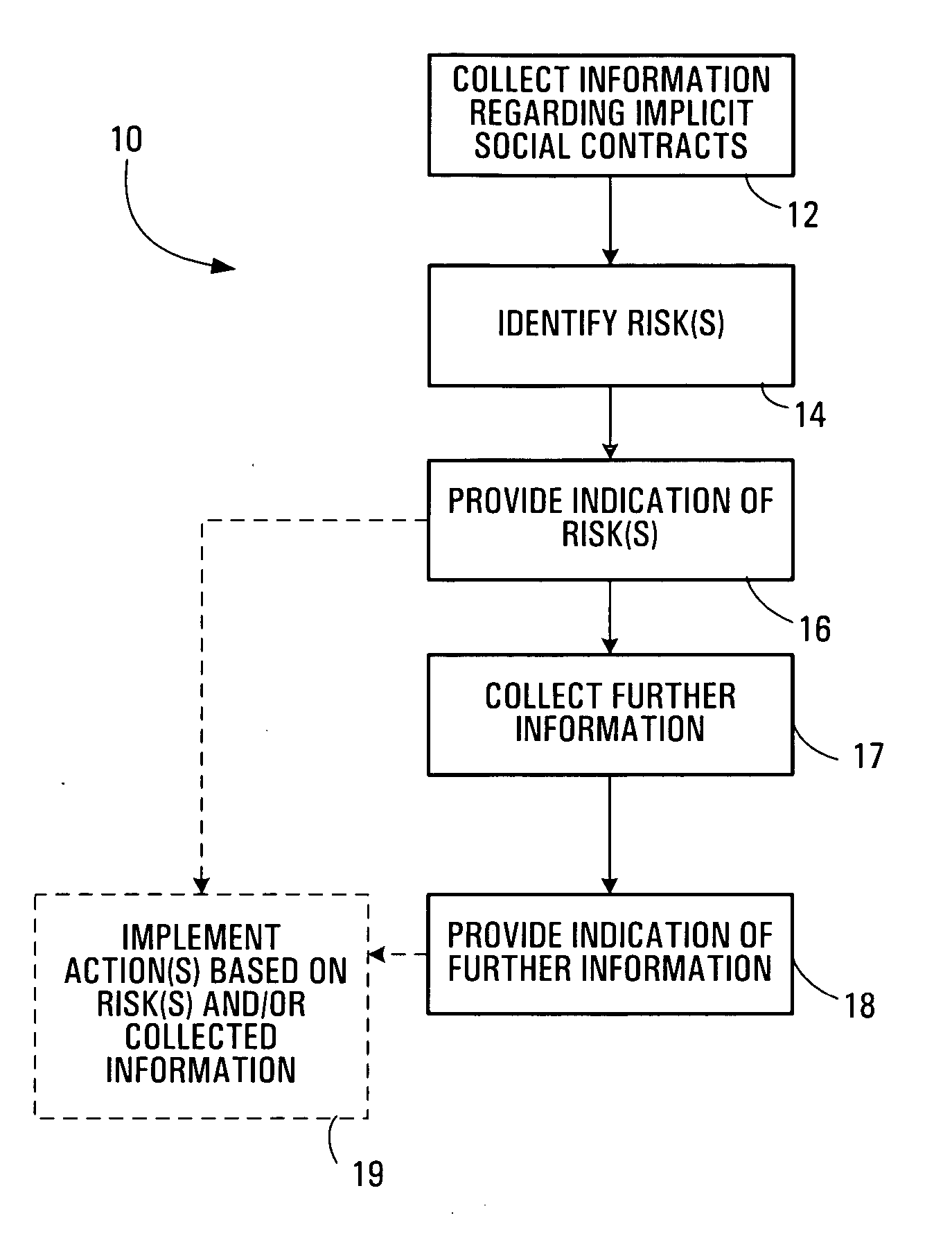
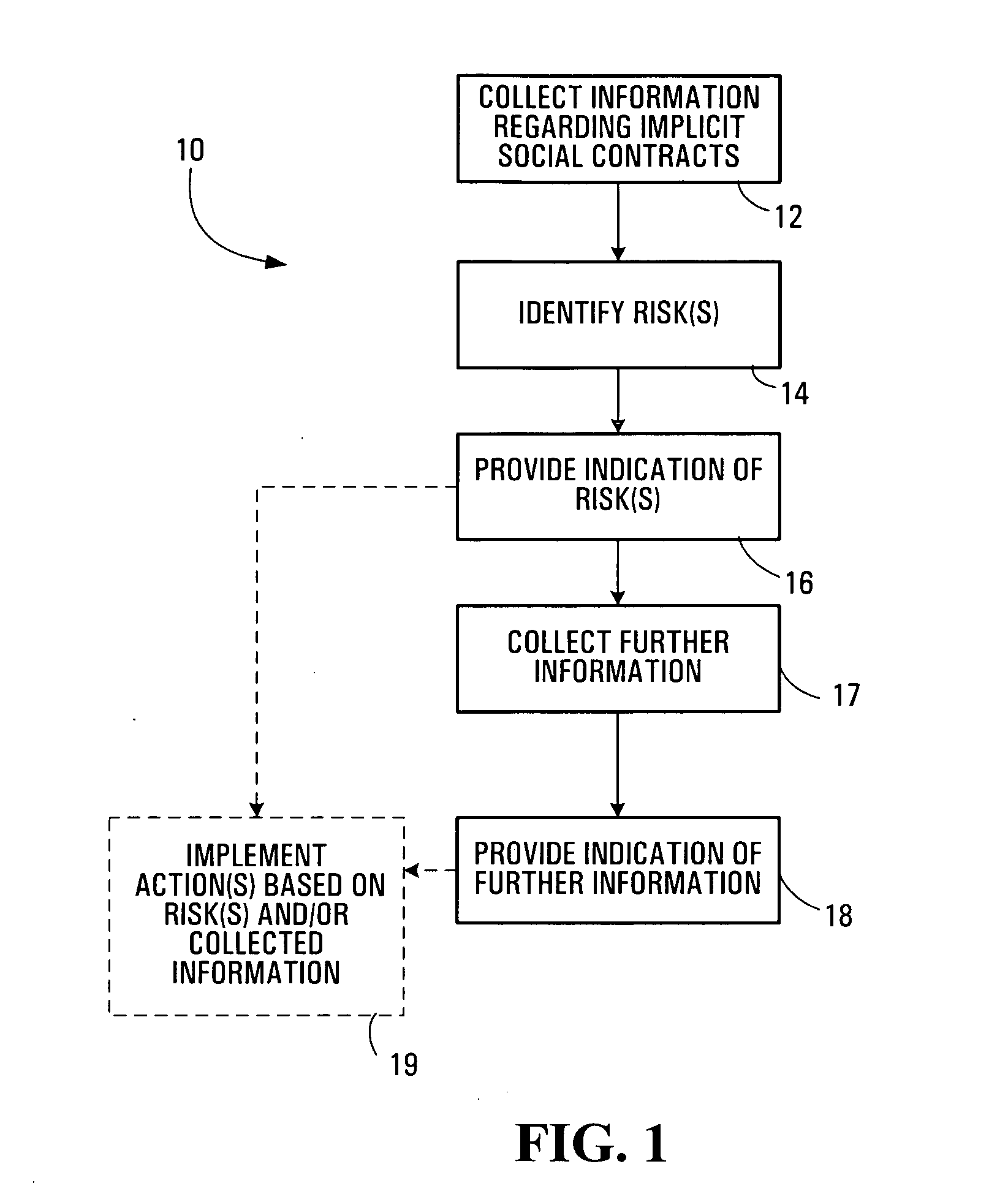
Risk management methods and systems
InactiveUS20060155553A1Technique is also at riskFinanceMultiprogramming arrangementsProgram planningRemedial action
Risk management methods and systems are disclosed. Information regarding implicit social contracts affecting an organization is collected from one or more sources which are external to the organization. A reputation risk to the organization is then identified based on the collected information, and an indication of the identified reputation risk is provided to the organization. If multiple reputation risks are identified, then the risks may be ranked according to one or more ranking priority criteria. Once identified, reputation risks may be used, for example, in determining a valuation associated with the organization, implementing a remedial action plan for the organization to mitigate the reputation risks, and implementing a training program to disseminate the implicit social contracts, the reputation risks, or both. Reviews of activities of other organizations or legal proceedings relating to the implicit social contracts or any identified risks may be useful in assessing the magnitude of a risk.
Owner:BROHMAN CAROLE GLORIA +1
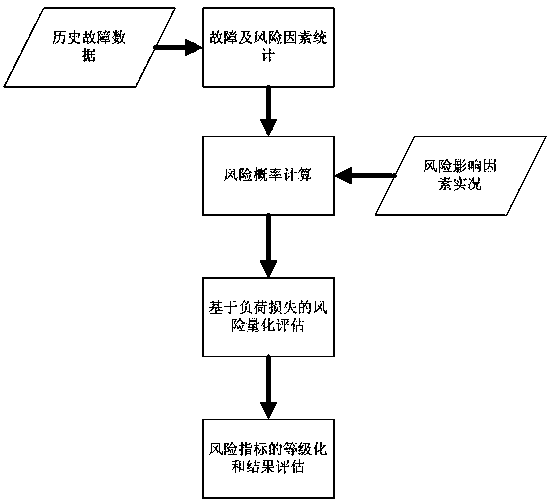
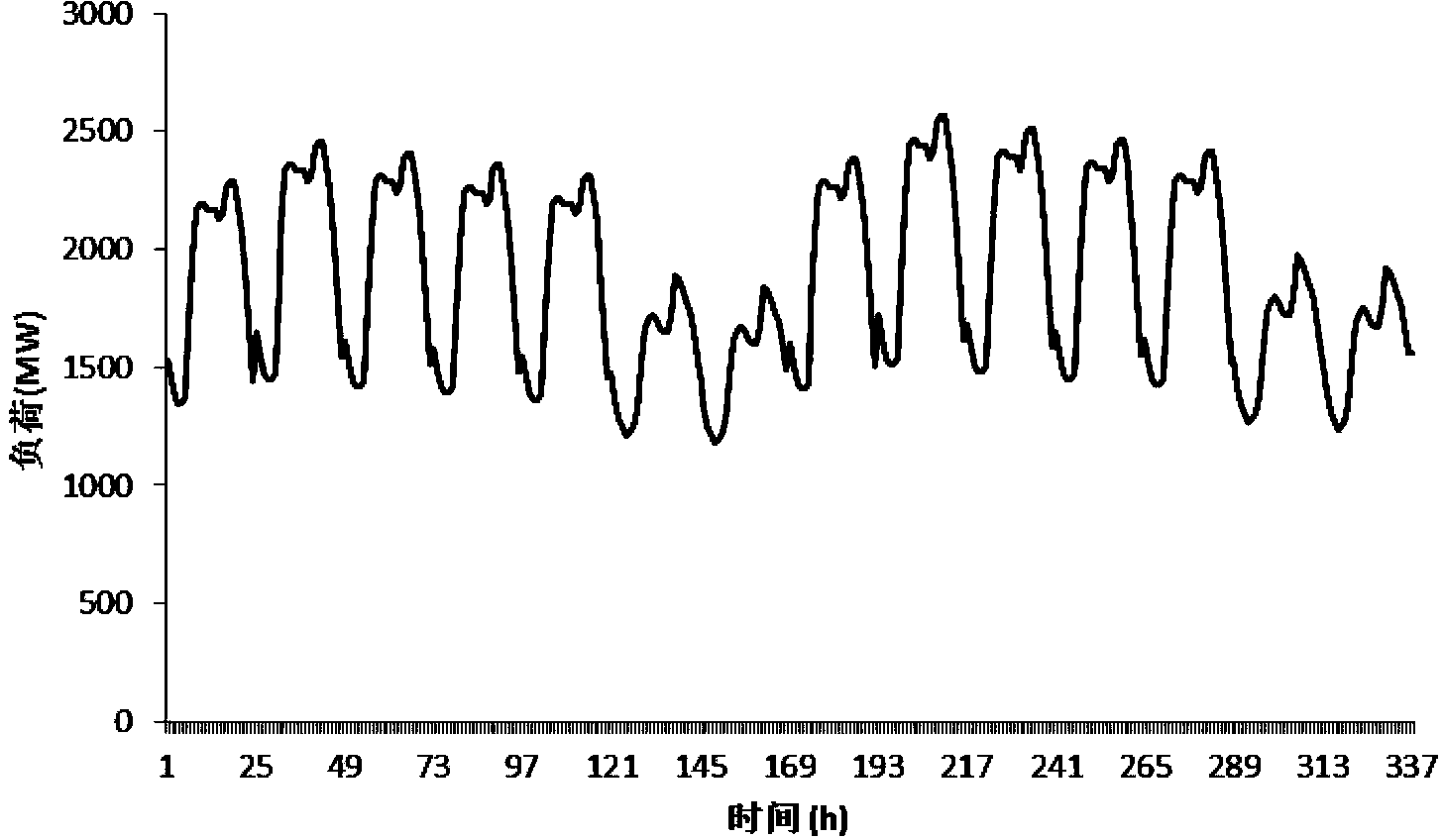
Risk evaluation method for operation of large power grid
InactiveCN103632310AReal-timeRealization riskData processing applicationsLoad lossLoad following power plant
The invention belongs to a risk evaluation method for the operation of a large power grid. The method comprises the following steps of (1) statistics of fault and risk factors; (2) computation of risk probability; (3) risk quantitative evaluation based on the load loss; (4) classification and result evaluation on risk index. According to the risk evaluation method for the operation of the large power grid, the occurring probability of power system accidents and the number of load loss of the system are combined to form a new quantitative index, so a scheduling person can be helped to perform real-time risk evaluation and analysis, can further comprehensively master the safe operation condition of the power grid, and controls the risk level of the system within a reasonable range by adopting necessary measures, and the occurrence of the disaster fault is avoided. The real-time evaluation and management and control on the risk are realized by a power gird scheduling center and the method belongs to a load loss-based risk evaluation method for the operation of the large power grid.
Owner:CHINA SOUTHERN POWER GRID COMPANY
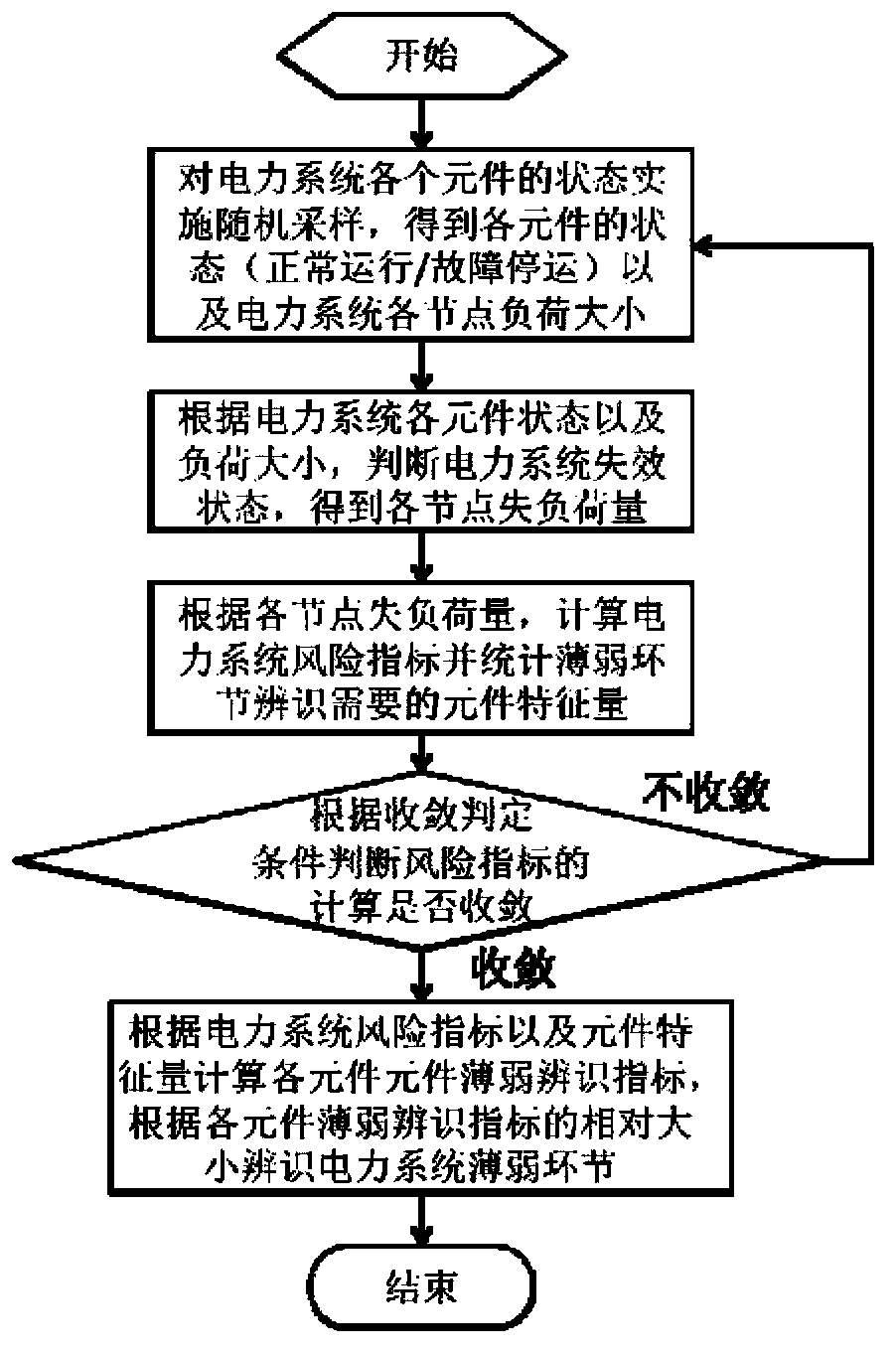
Power system weak link identification method based on risk evaluation
ActiveCN103426056AImprove weak linksRealize precise identificationResourcesSystem failureRisk evaluation
The invention relates to a power system weak link identification method based on risk evaluation and belongs to the field of power system analysis. The method includes acquiring fault probability of elements of a power system, a future load curve of the power system, states of the elements and load of nodes of the power system; utilizing a minimum load shedding loss optimization model to judge the failure state of the power system and determining the optimum load shedding quantity of each node under each element sampling state; finishing calculation of risk indicators of the power system through repeated sampling and power system failure state judgment; conducting statistics on the weak link characteristic quantity corresponding to faults of generators and an electric transmission and transformation device, calculating five element weakness recognition indicators of the elements according to the risk indicators and the weak link characteristic quantity and finally sorting the recognition indicator values to recognize the weak link of a generator set and the electric transmission and transformation device. By means of the method, the weak link of the power system is improved, large-area power failure of the power system is prevented, and operation safety of the power system is improved.
Owner:TSINGHUA UNIV
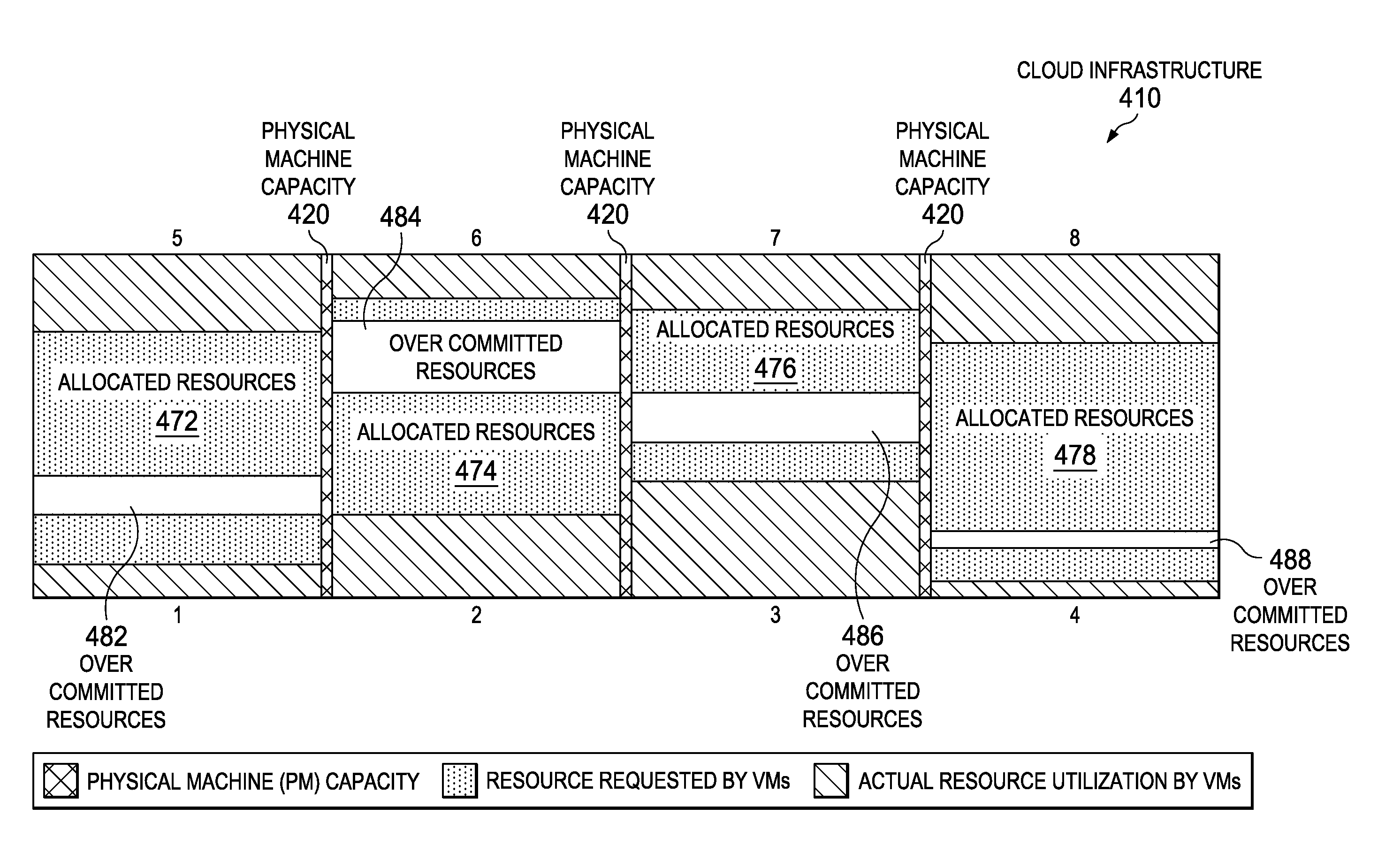
Managing risk in resource over-committed systems
InactiveUS20130238780A1Digital computer detailsSoftware simulation/interpretation/emulationWorkloadShared resource
Risk associated with over-committing shared resources is determined. In response to receiving a request to provision a new workload, a candidate mix of virtual machines is selected from plurality of virtual machines already running on a cloud infrastructure. A utilization profile is then created for an aggregate behavior of the candidate mix of virtual machines and a new virtual machine running the new workload. A risk inherent in over-commitment if the new workload is grouped with the candidate mix of virtual machines is determined, and whether that risk is acceptable. If the risk is acceptable, the new workload is provisioned by over-committing the candidate mix of virtual machines with the new virtual machine running on the cloud infrastructure.
Owner:IBM CORP
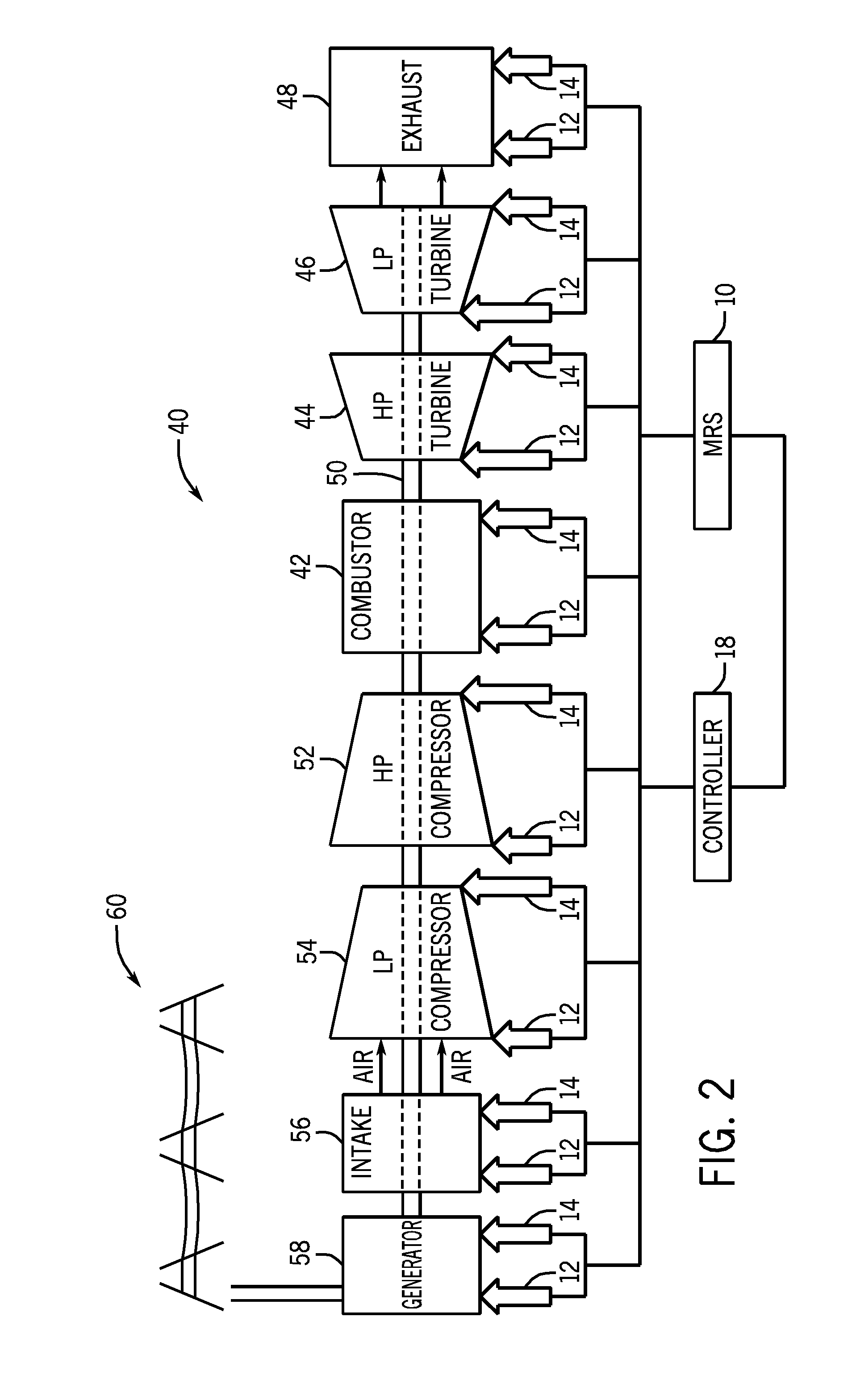
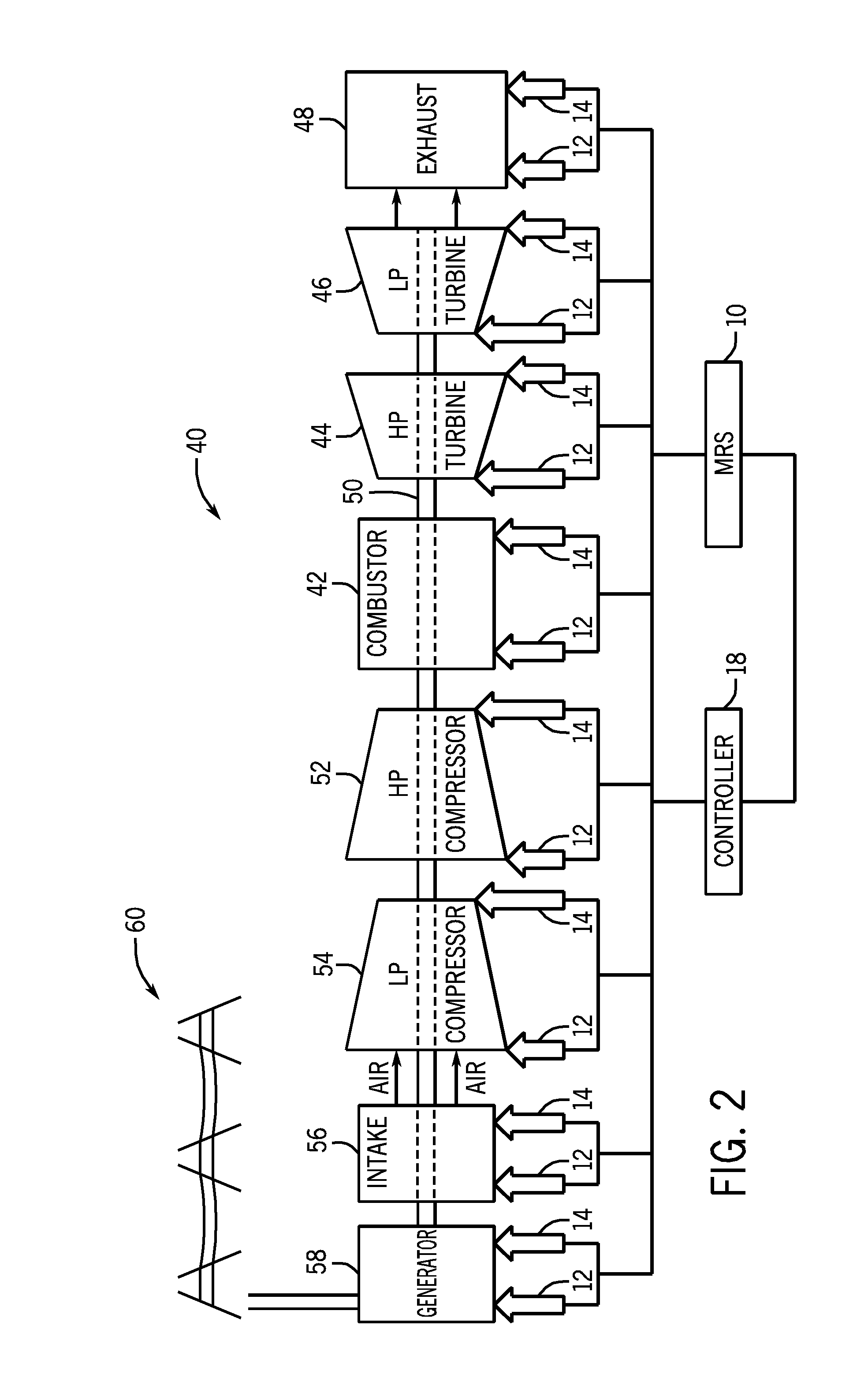
Systems and methods for improved reliability operations
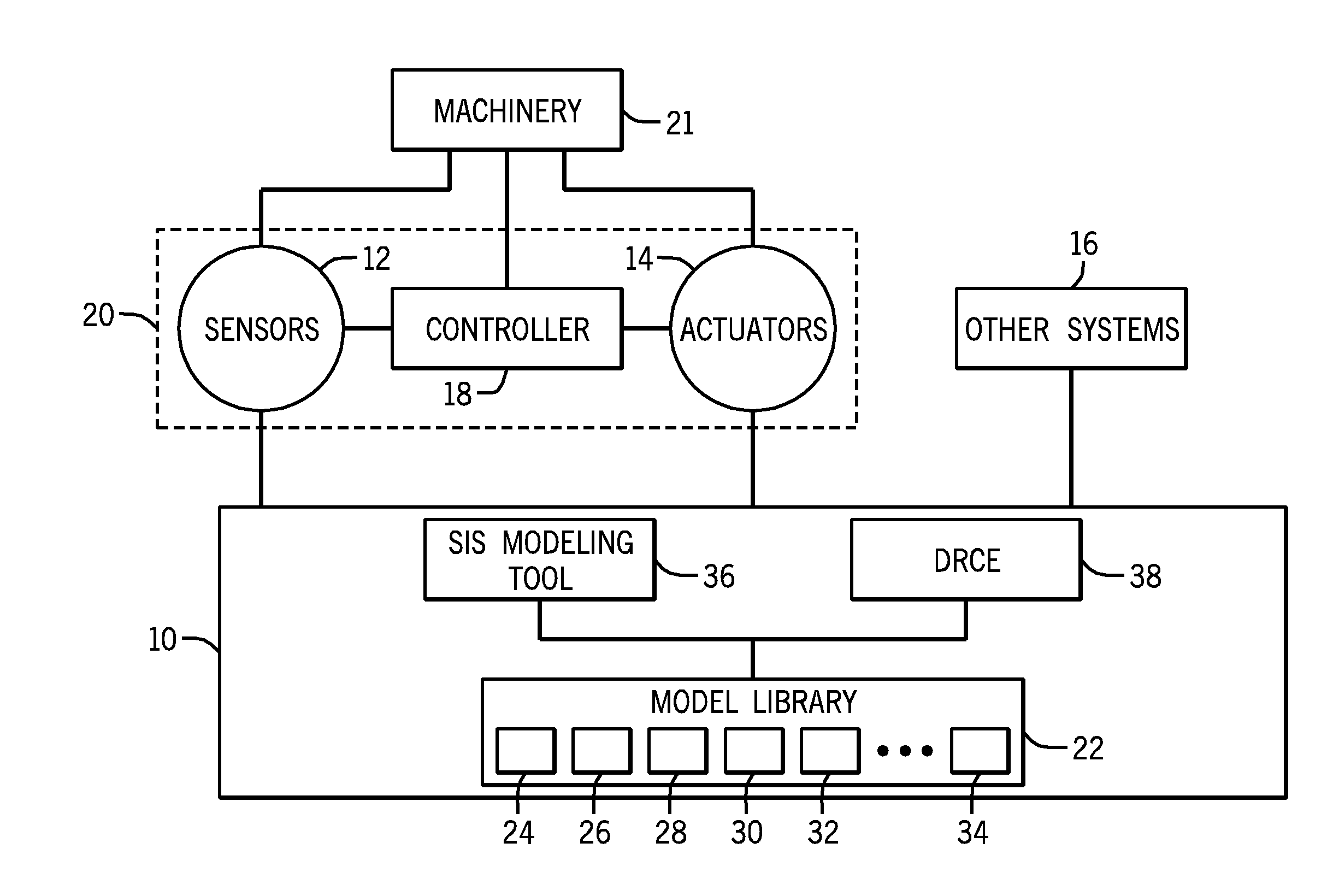
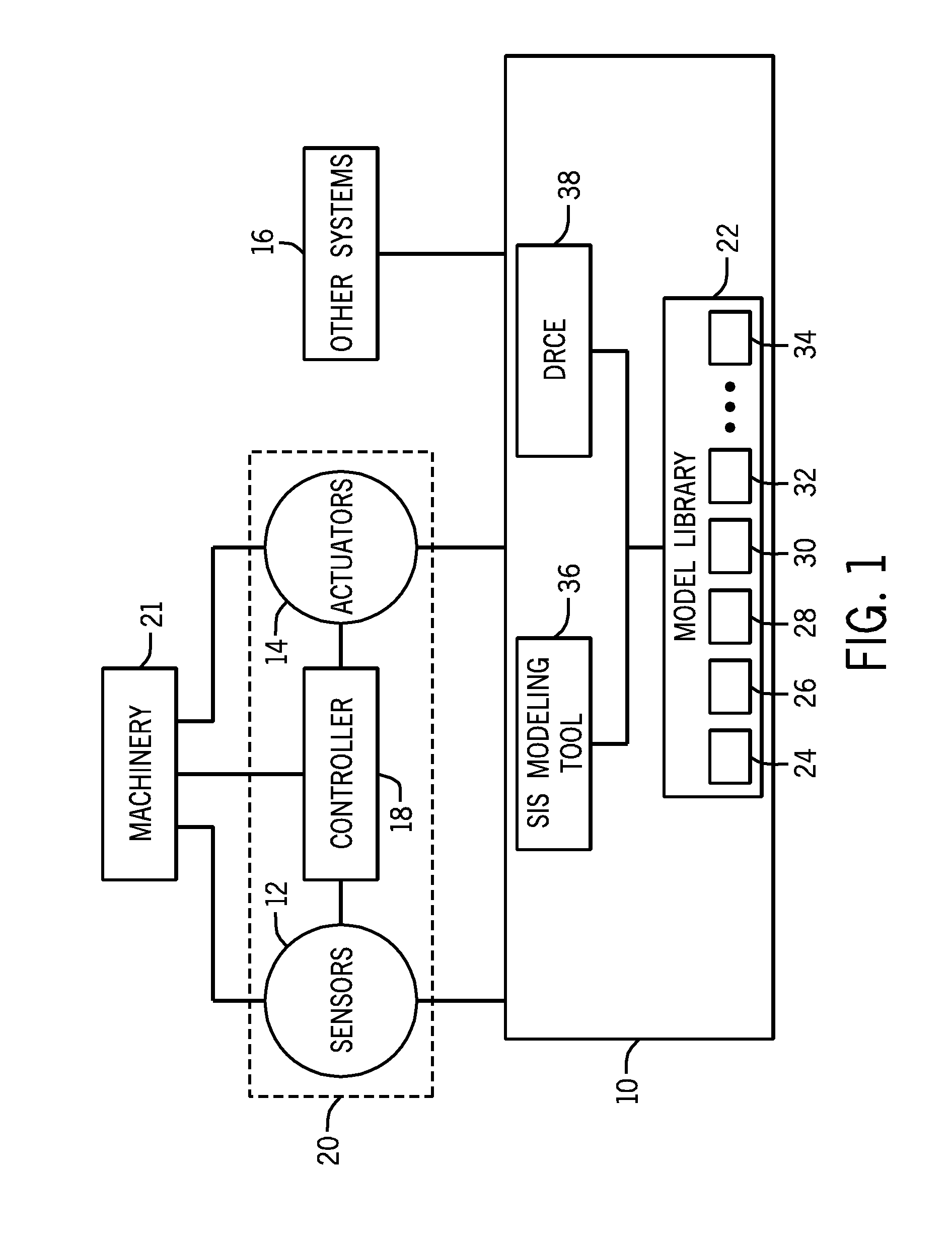
ActiveUS20130262064A1Testing/monitoring control systemsAnalogue processes for specific applicationsFault toleranceEngineering
A system may include a model library configured to model a safety system, wherein the model library comprises a plurality of subsystem models, and each of the plurality of subsystem models is configured to derive a reliability measure. The system further includes a fault tolerance input and a maintenance policy input. The system further includes a dynamic risk calculation engine (DRCE) configured to use a user-defined set of the plurality of subsystem models, the fault tolerance input and the maintenance policy input, to derive a system risk for an apparatus.
Owner:GENERAL ELECTRIC CO
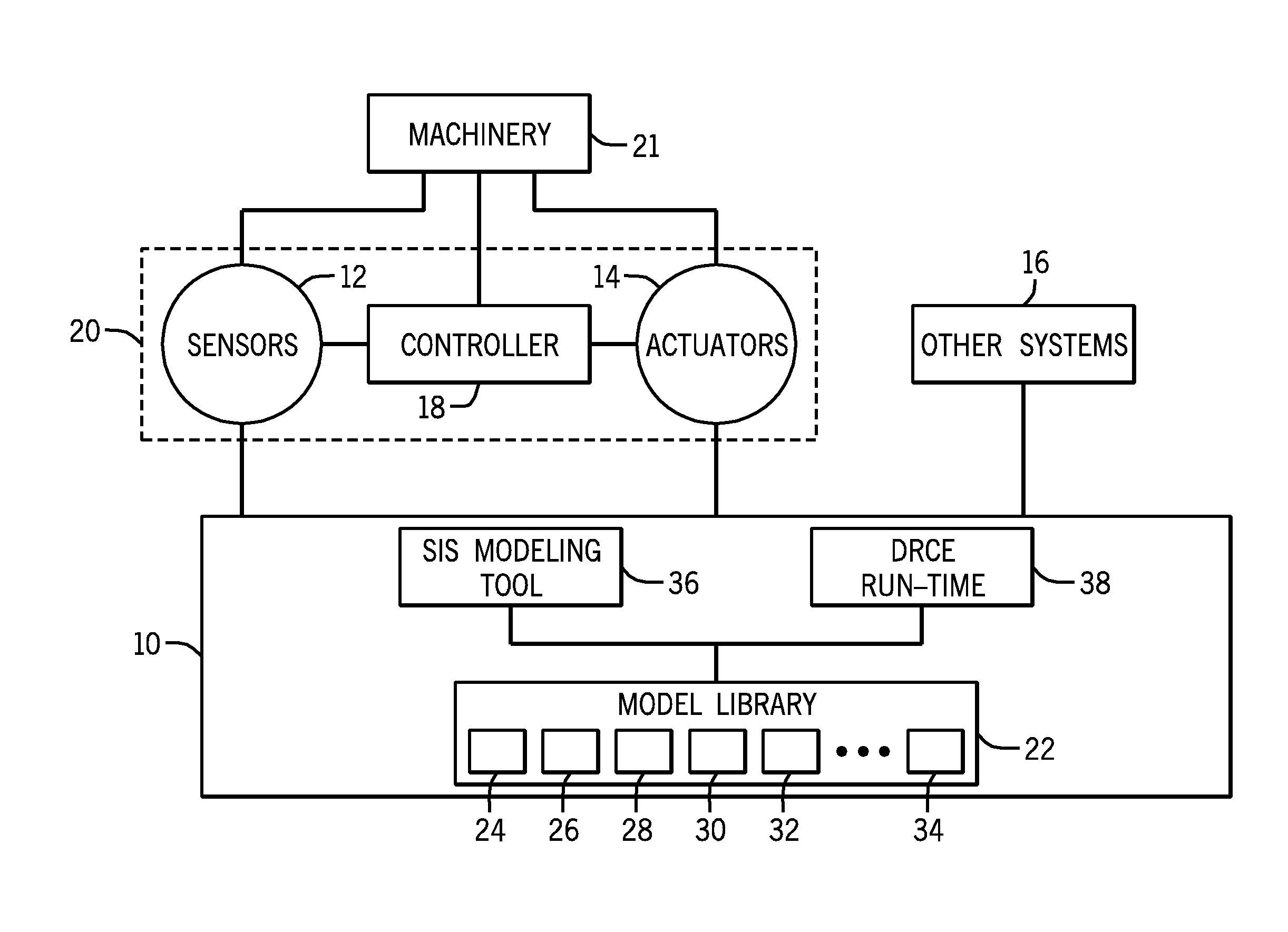
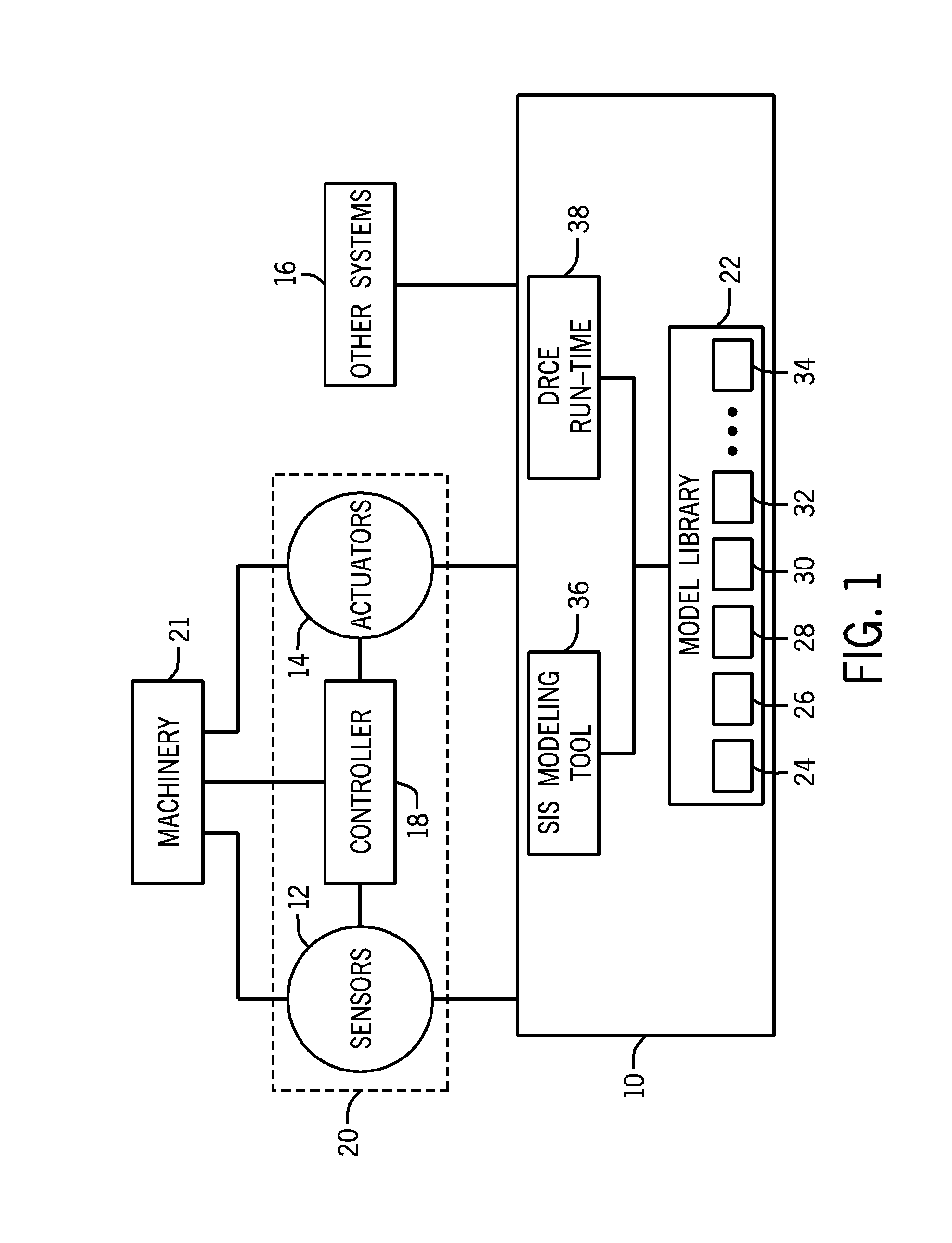
Systems and Methods For Dynamic Risk Derivation
A system may include a dynamic risk calculation engine (DRCE) system. The DRCE includes a model library configured to model a system, wherein the model library comprises a plurality of subsystem models, and each of the plurality of subsystem models is configured to derive a reliability measure. The DRCE further includes a fault tolerance input and a maintenance policy input. The DRCE additionally includes a run-time risk calculation engine configured to use a user-defined set of the plurality of subsystem models, the fault tolerance input, and the maintenance policy input, to derive a system risk for an apparatus.
Owner:GENERAL ELECTRIC CO
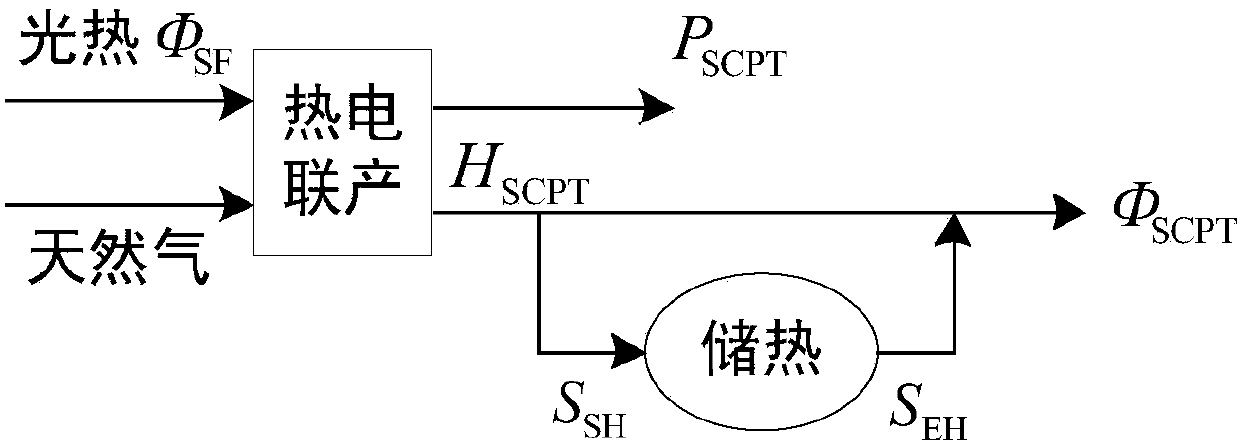
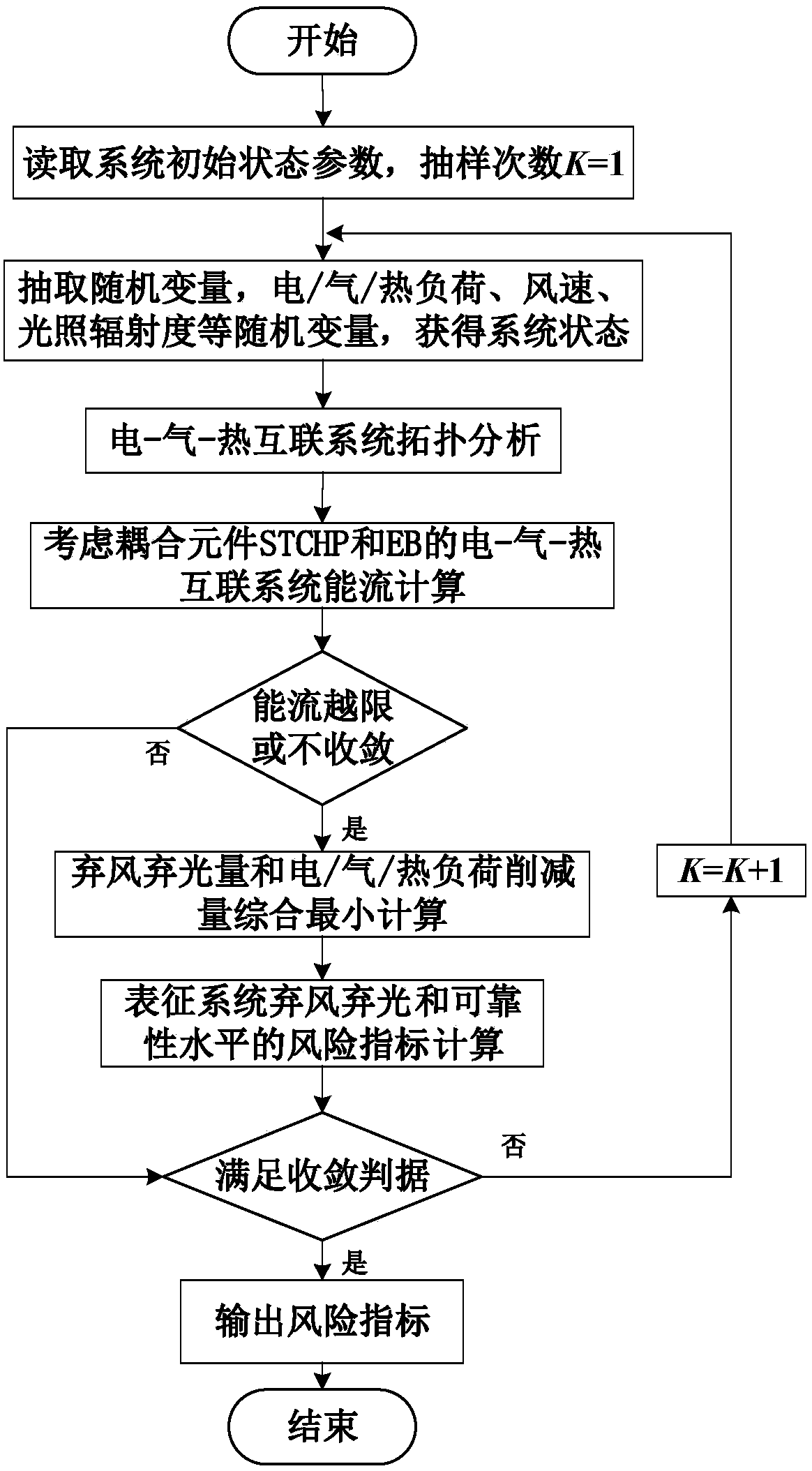
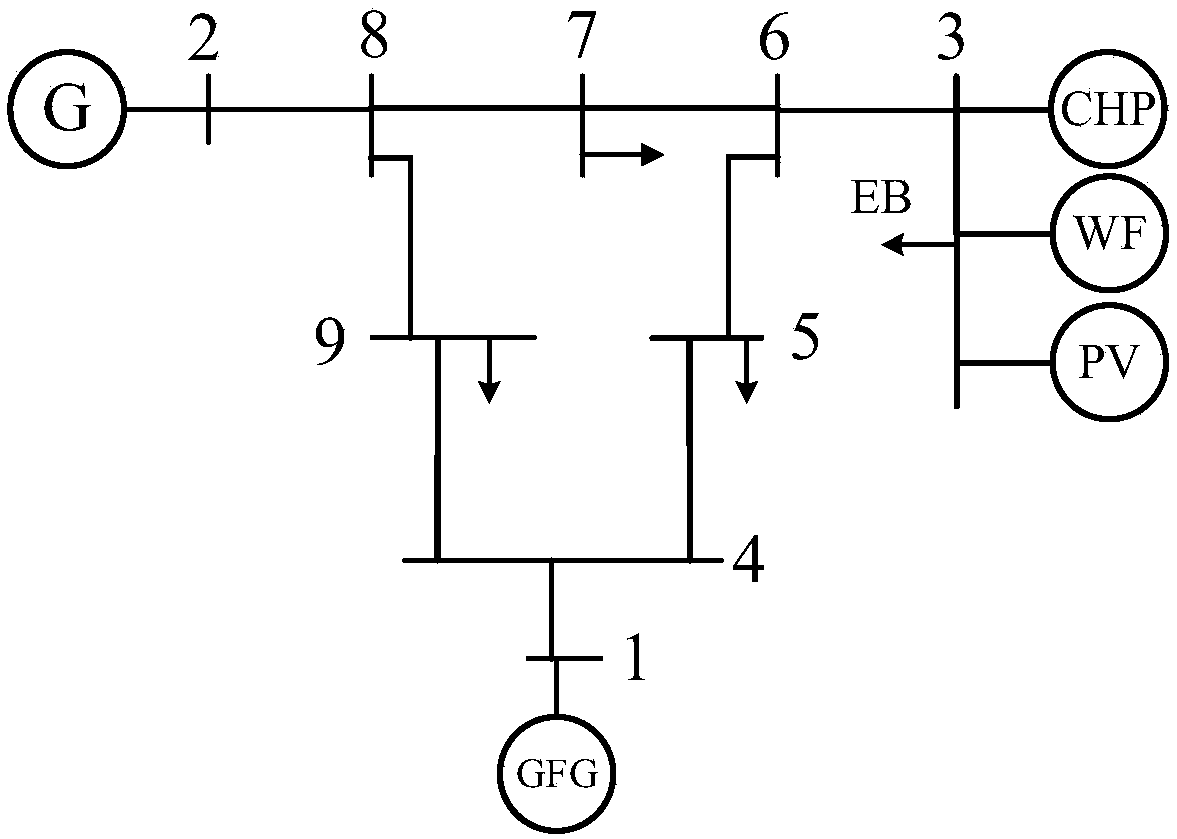
Electric-gas-heat interconnection system risk evaluation method for considering solar thermal CHP plants and electric boiler
ActiveCN107730129APreserve actual operating characteristicsReasonable quantification of the severity of wind and solar curtailmentDesign optimisation/simulationResourcesCogenerationEngineering
The invention discloses an electric-gas-heat interconnection system risk evaluation method for considering solar thermal CHP plants (STCHP) and an electric boiler (EB). The method comprises steps of establishing an energy flow model based on a coupling element STCHP and EB, and a wind and light abandoning and electric / gas / heat load reduction composite minimal optimization model; establishing a system level risk index of electric power / gas quantity / heating power insufficient expectations and wind abandoning / light abandoning expectations of the electric-gas-heat interconnection system; based onthe established energy flow model, the established load reduction model and the evaluation index, further considering various random factors of element faults, electric / gas / heat load, wind electricitypower and photoelectric power and providing a step and schedule graph about electric-gas-heat interconnection system risk evaluation for considering the STCHP and the EB; and finally, achieving calculation and analysis work of the electric-gas-heat interconnection system risk evaluation for considering the STCHP and the EB on an MATLAB platform through programs.
Owner:CHONGQING UNIV
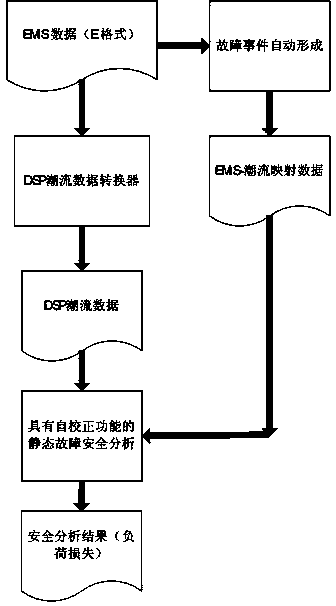
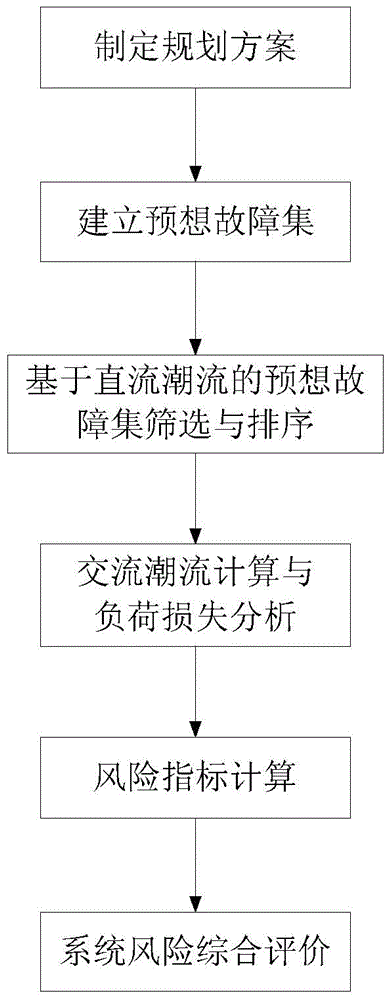
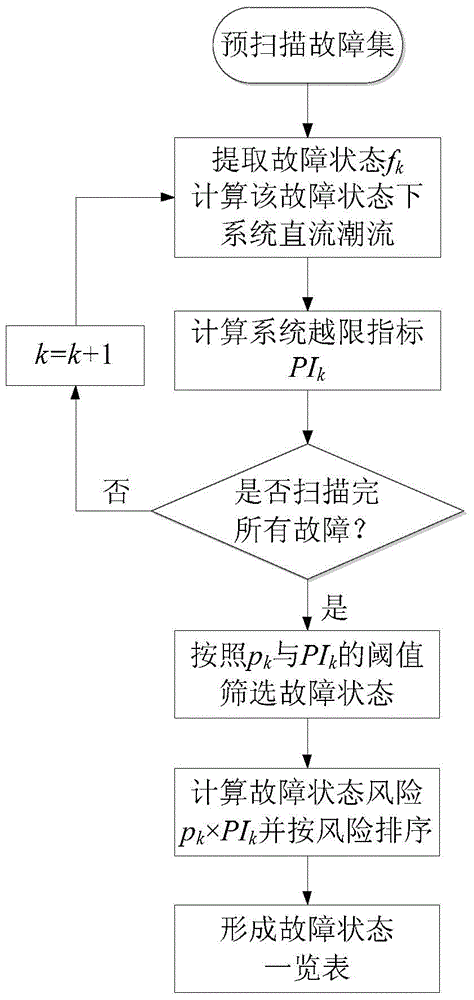
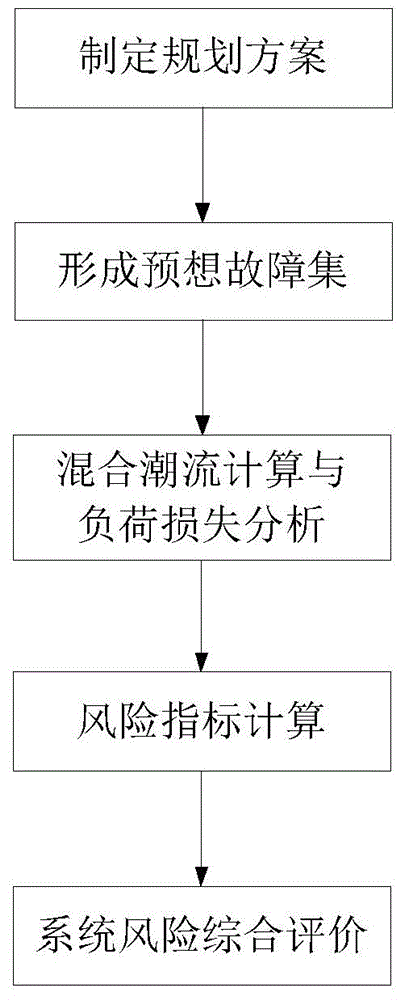
Method for evaluating electric power system risk based on fault pre-scanning
The invention discloses a method for evaluating the electric power system risk based on fault pre-scanning. The method comprises the steps that firstly, according to the current structure of an electric power system and a planning scheme, a corresponding planning scheme model is established; secondly, based on device data and a power grid structure, predicted faults and the possibility of the predicated faults of a power grid are analyzed, and then a pre-scanning fault set is formed; thirdly, through the risk state based on direct-current power flow, screening and ordering are conducted on the predicated fault set, so that a fault state list is formed; fourthly, all power flow corresponding to the faults in the list is worked out, and for the fault with the power flow out of range, the consequence of the fault is load loss; fifthly, according to the load loss of the fault states and the possibility of the fault states, the system risk indicator is worked out; sixthly, according to the system risk indicator, the system weak link is found out. By the adoption of the method for the evaluating electric power system risk based on fault pre-scanning, analysis of all the fault sates in the fault set through alternating-current power flow is avoided, so that the calculation amount of follow-up alternating-current power flow analysis and risk indicator processing is greatly reduced, and a large mount of calculation time is saved.
Owner:TIANJIN UNIV +1
Method for evaluating power system static risk based on hybrid power flow
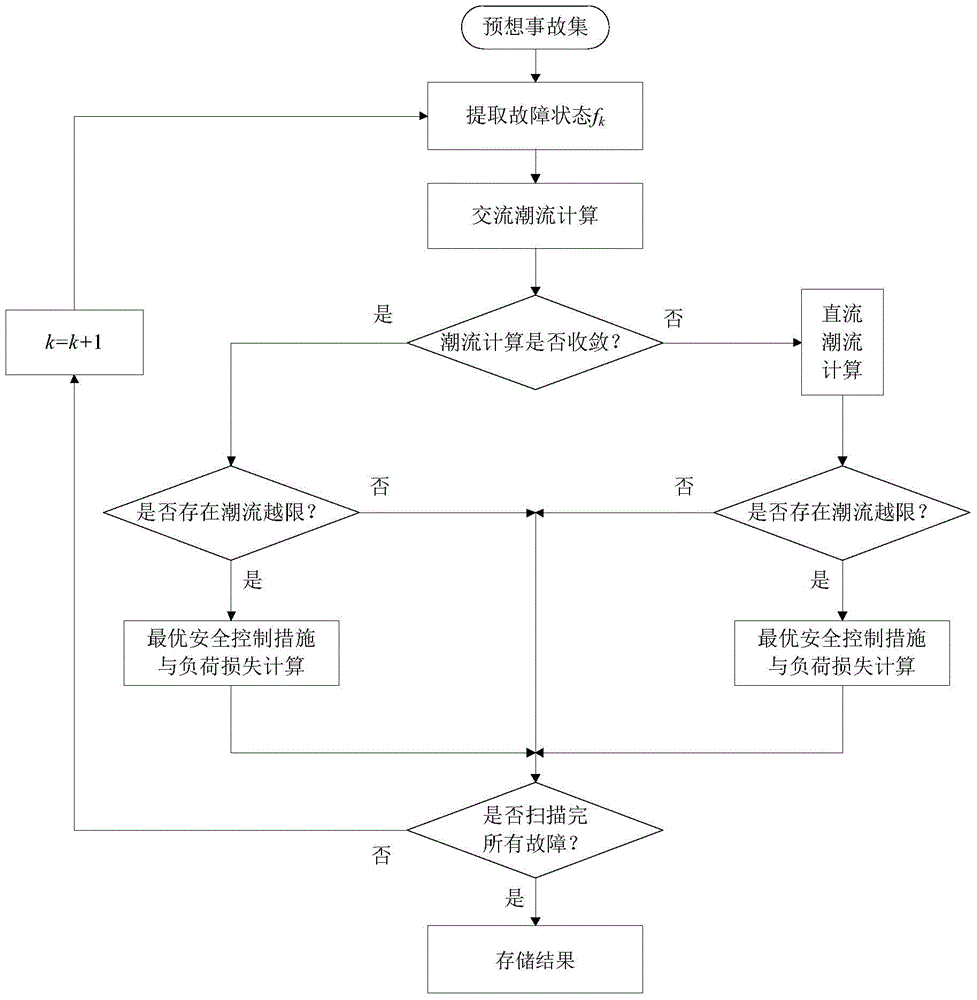
ActiveCN103985066AAvoid Pessimistic EvaluationsAvoid the problem of non-convergence of resultsData processing applicationsElectric power systemPower grid
The invention discloses a method for evaluating the power system static risk based on hybrid power flow. The method comprises the steps that (1) according to the current structure of a power system and a planning scheme, a corresponding planning scheme model is established; (2) according to equipment data and the structure of a power grid, predicated faults of the power grid and the possibility of the predicated faults are analyzed, and then a predicated fault set is established; (3) the power flow corresponding to all the faults in the predicated fault set is worked out through the risk state based on the hybrid power flow, and for the fault with power flow out of range, load loss is used as a fault consequence; (4) according to the load loss of the fault states and the possibility of the fault, the system risk indicator is worked out; (5) according to the system risk indicator, the weak link of the system is found. According to the method for evaluating the power system static risk based on the hybrid power flow, the problem that when high-order fault occurs in a large complicated power grid, misconvergence of power flow is caused due to the fact that only alternating-current power flow is applied during risk evaluation is solved through the hybrid power flow.
Owner:TIANJIN UNIV +1
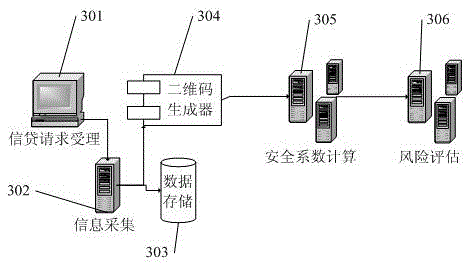
Bank credit system risk assessment method and device
The invention discloses a bank credit system risk assessment method and device. When enterprise credit risk assessment is performed, enterprise profit capability and assets and other traditional indexes are examined, and business contact activity between enterprises and the cash flow situation are also comprehensively considered. Mass data are utilized, potential useful new evaluation indexes are mined, and the current new technologies, such as data mining and social networks, are integrated in the assessment process so that accuracy of the assessment result can be enhanced. Therefore, the new indexes are combined with the conventional indexes, and a new enterprise credit risk assessment system is given and applied to a BP algorithm of machine learning so that a concrete and feasible support model is provided for formulation of the risk avoiding scheme of the financial system, and the problems in the prior art that accuracy is low and overall performance is poor due to the fact that only the conventional risk indexes or part of financial phenomena act as the risk assessment method can be solved.
Owner:JILIN UNIV
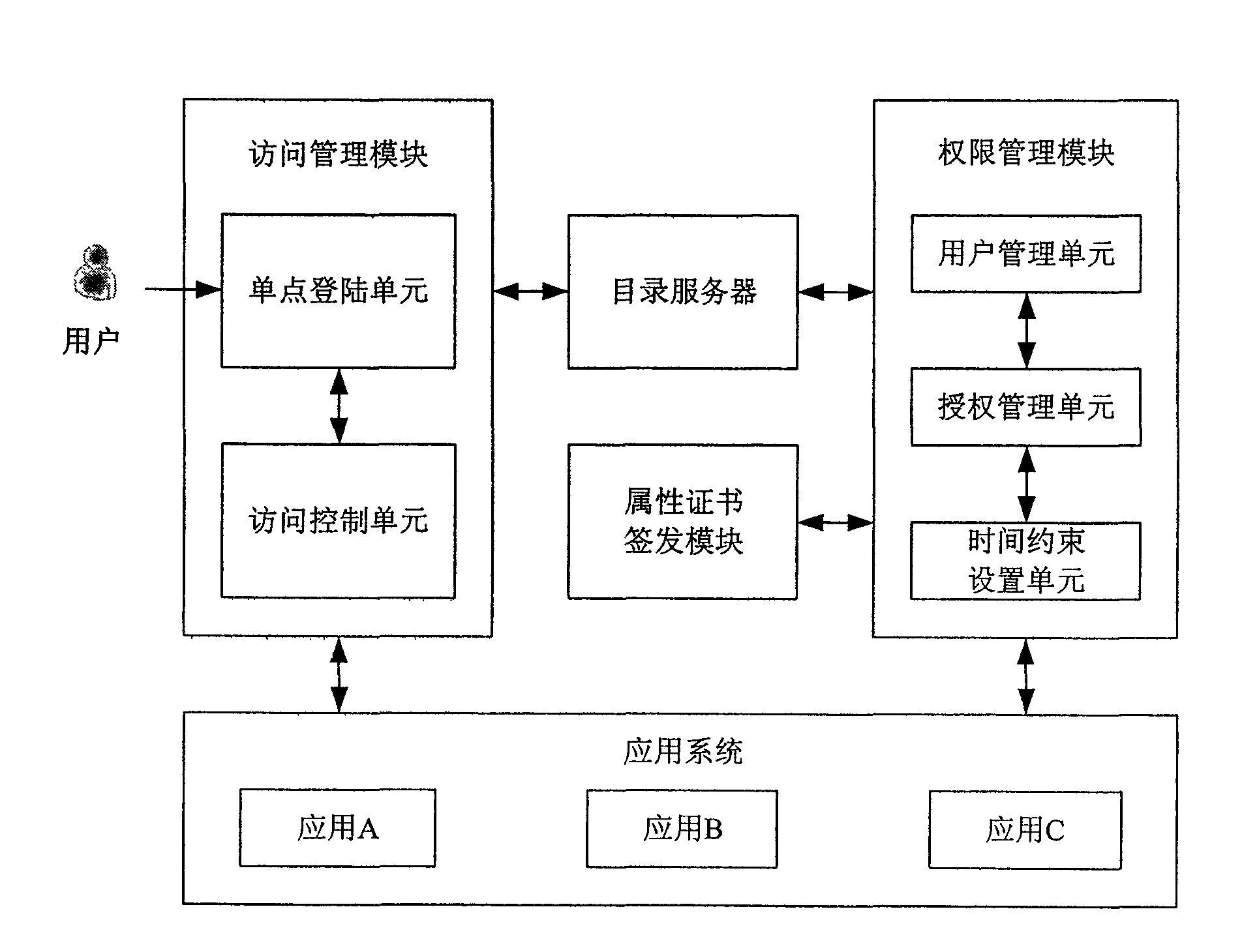
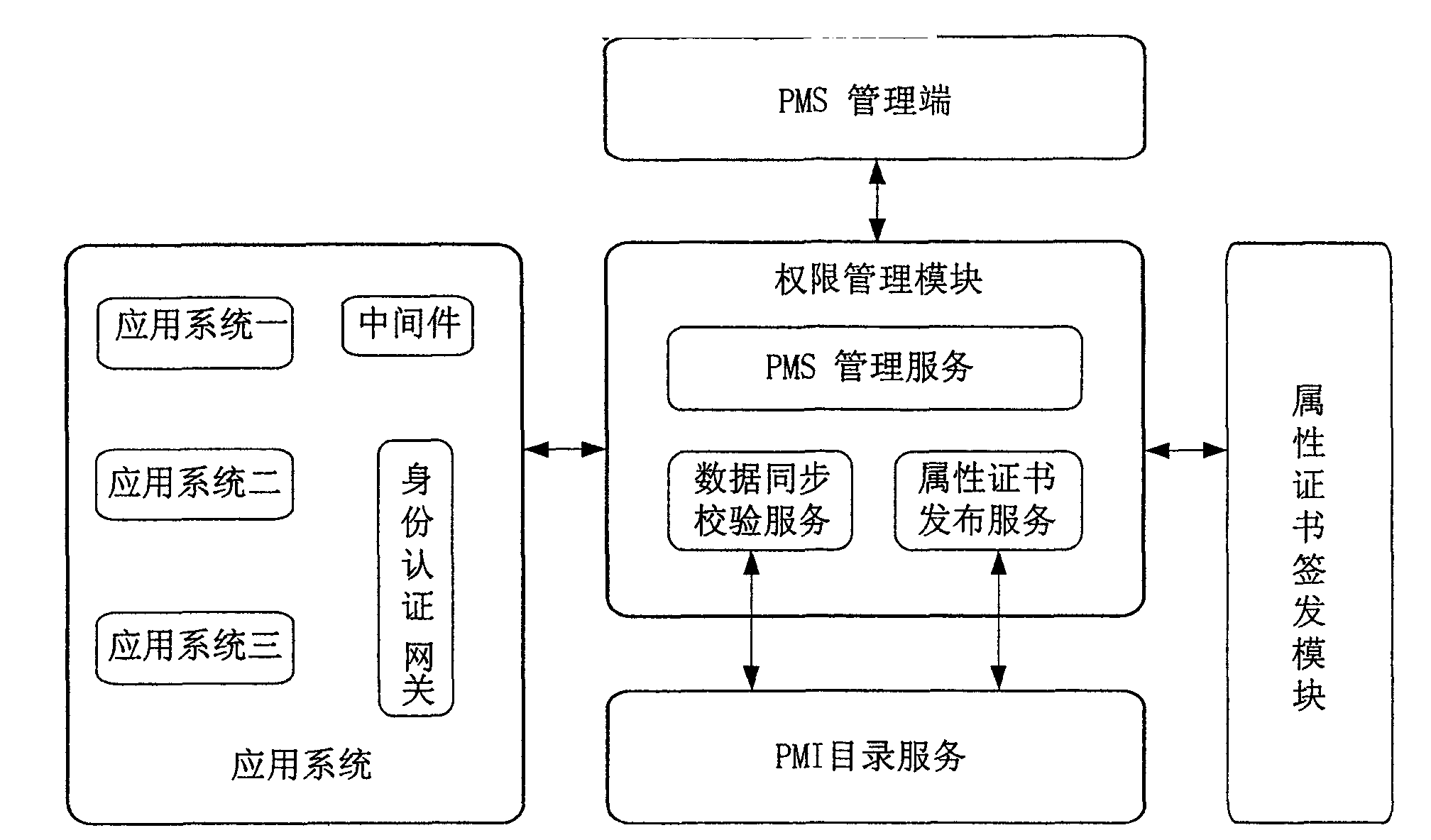
Privilege management system and method
InactiveCN101640687AStrong timelinessGuaranteed timelinessUser identity/authority verificationRights managementAccess management
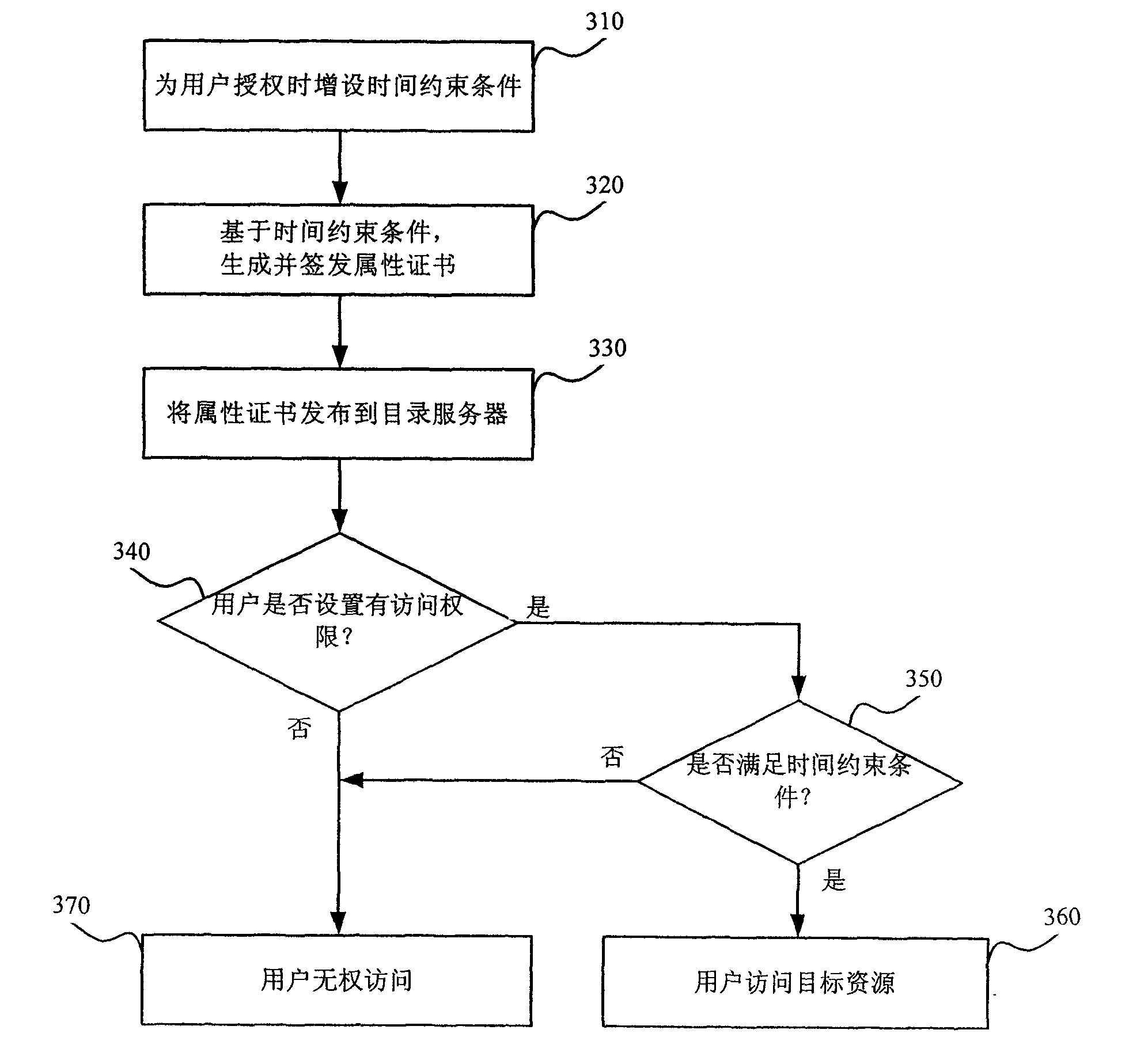
The invention discloses a privilege management system, wherein a privilege management module is used for managing establishment of authorization strategy and distribution of privilege and setting a time constraint condition for relative privilege during authorization according to actual needs; an attribute certificate signing module signs an attribute certificate according to a binding relationship and the time constraint condition between a user and the privilege; a catalogue server stores the attribute certificate and user information; and an access management module establishes a safety mechanism between the user and a target resource, carries out privilege authentication according to the attribute certificate and the user information when the user tries to access the target resource todetermine whether the user is allowed to access the target resource or not, thereby protecting the safety of the target resource. In addition, the invention discloses a privilege management method. The privilege management system and method can conveniently carry out setting and automatic cancel on the privilege in time, thereby lowering the difficulty and the complexity of the privilege management and also the system risk.
Owner:国家信息中心
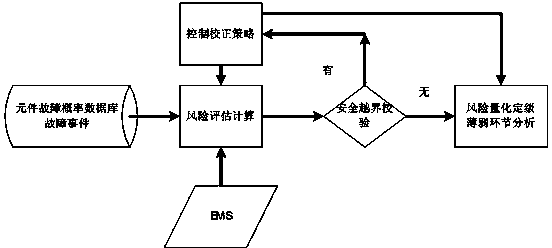
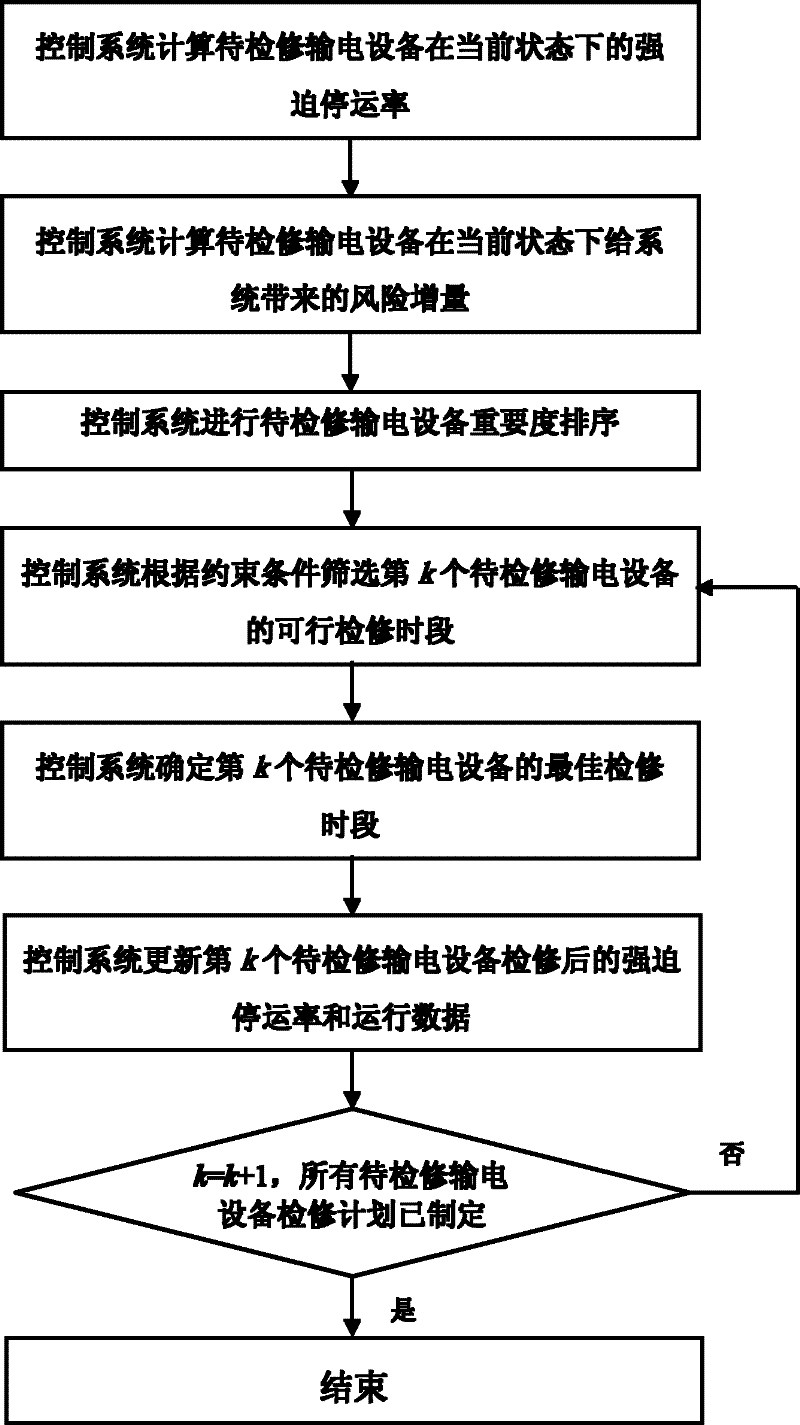
A condition-based maintenance method for power transmission equipment based on system risk
The invention discloses a method for maintaining the state of power transmission equipment based on a system risk. The method comprises the following steps that: a control system calculates the forced stoppage rate of the power transmission equipment to be maintained under the current state; the control system calculates a risk increment which is brought to the system by the power transmission equipment to be maintained under the current state; the control system sequences the importance of the power transmission equipment to be maintained; the control system screens feasible maintenance timeintervals of the kth power transmission equipment to be maintained according to restraint conditions; the control system determines the optimum maintenance time interval of the kth power transmissionequipment to be maintained; the control system updates the forced stoppage rate and operating data of the kth power transmission equipment to be maintained after maintenance, wherein k is equal to k+1; and if maintenance schedules of all pieces of power transmission equipment to be maintained are made, the system ends operation, otherwise, the system repeatedly executes the operation. By the method, a new equipment importance evaluation index is provided and can reflect the current state of the equipment and influence size of the system risk. On the premise of an operating mode of a power system and the time sequence change of the state of the equipment, the total risk of the system in investigation time is minimized.
Owner:XI AN JIAOTONG UNIV
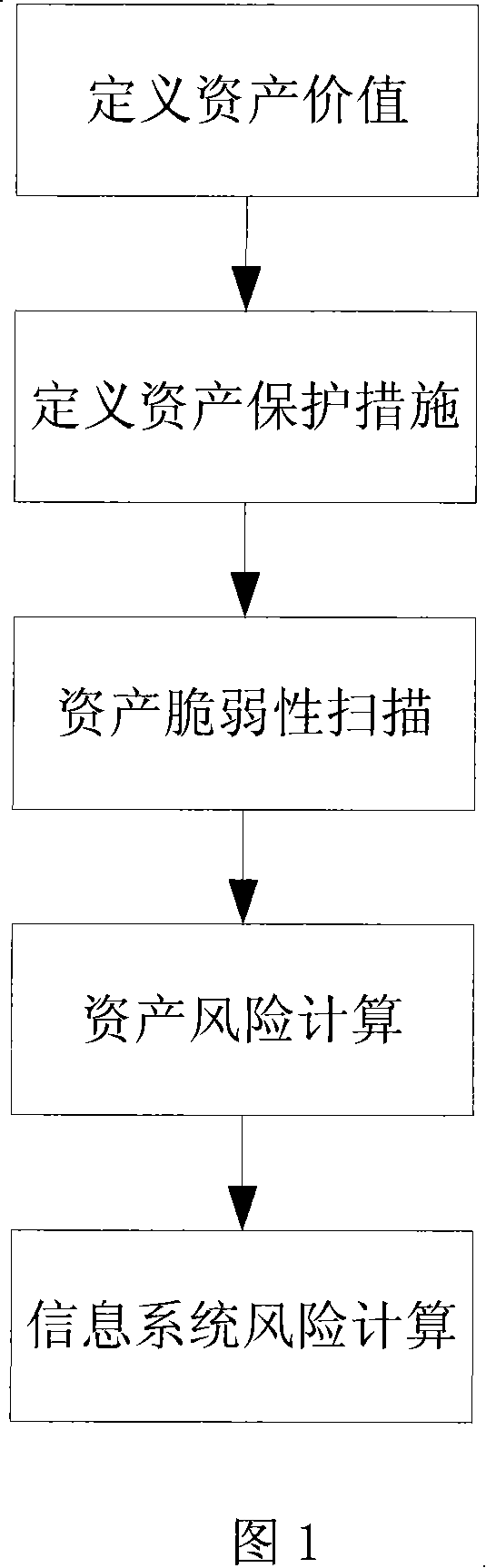
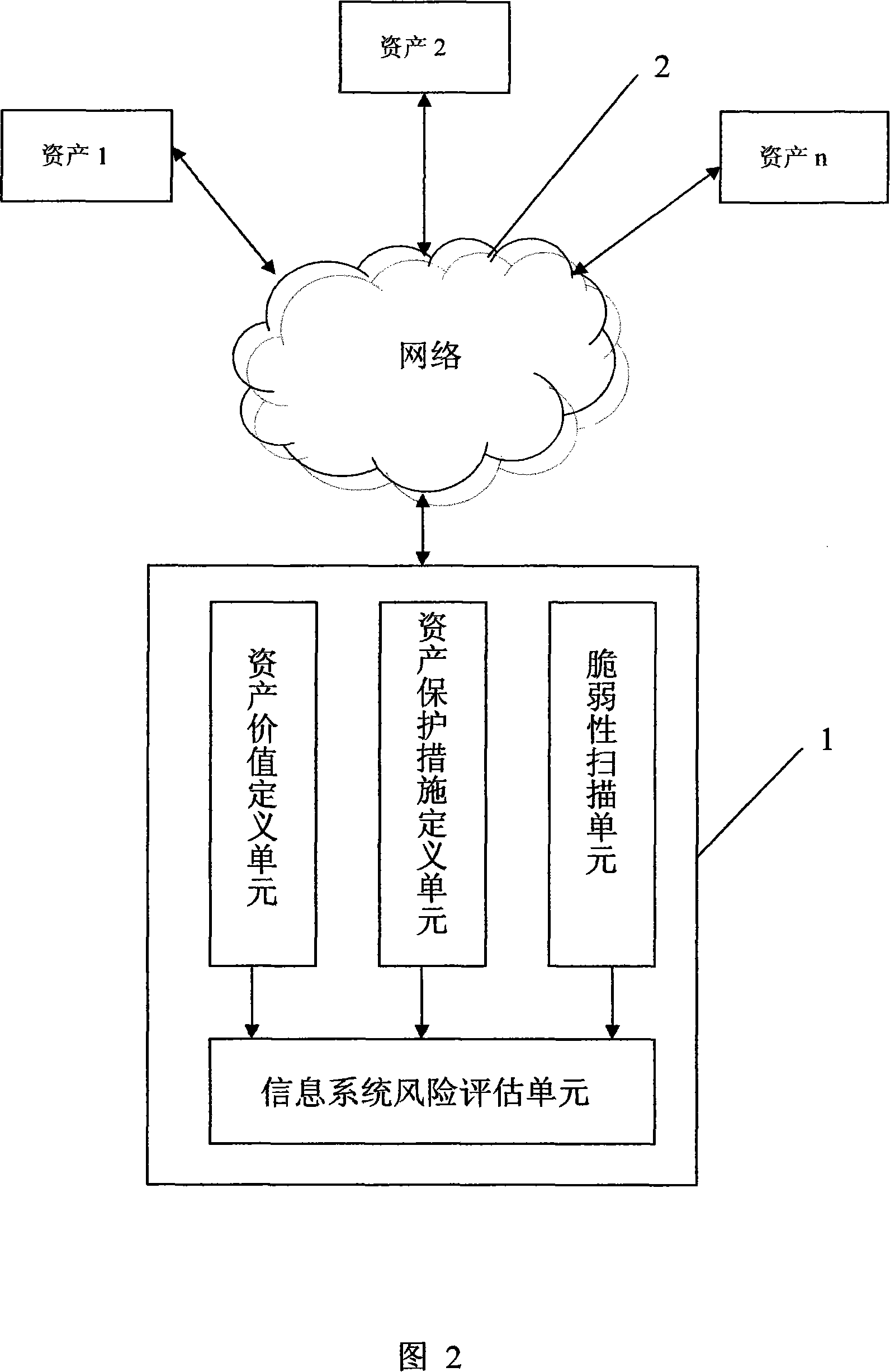
An information system risk evaluation method and system
InactiveCN101150432AThe impact of vulnerability is highlightedEasy to compare the relative value of vulnerabilityComputer security arrangementsData switching networksProbit modelThe Internet
This invention discloses a method and a system for risk evaluation of an information system, in which, the method includes: computing the risk value of each asset in the information system and computing the risk value of the information system according to the risk values of the assets, and the computation is based on a probability model. A risk evaluation system is installed on the UE of the internet containing a vulnerability scan unit, an asset value defining unit, an asset safeguard defining unit and a risk evaluation unit of the information system, which can quantize the risk values of assests and the information system together in an appointed fixed space and the quantized result shows the degree of vulnerability of assests or the information system.
Owner:BEIJING VENUS INFORMATION TECH
Risk assessment for relief pressure system
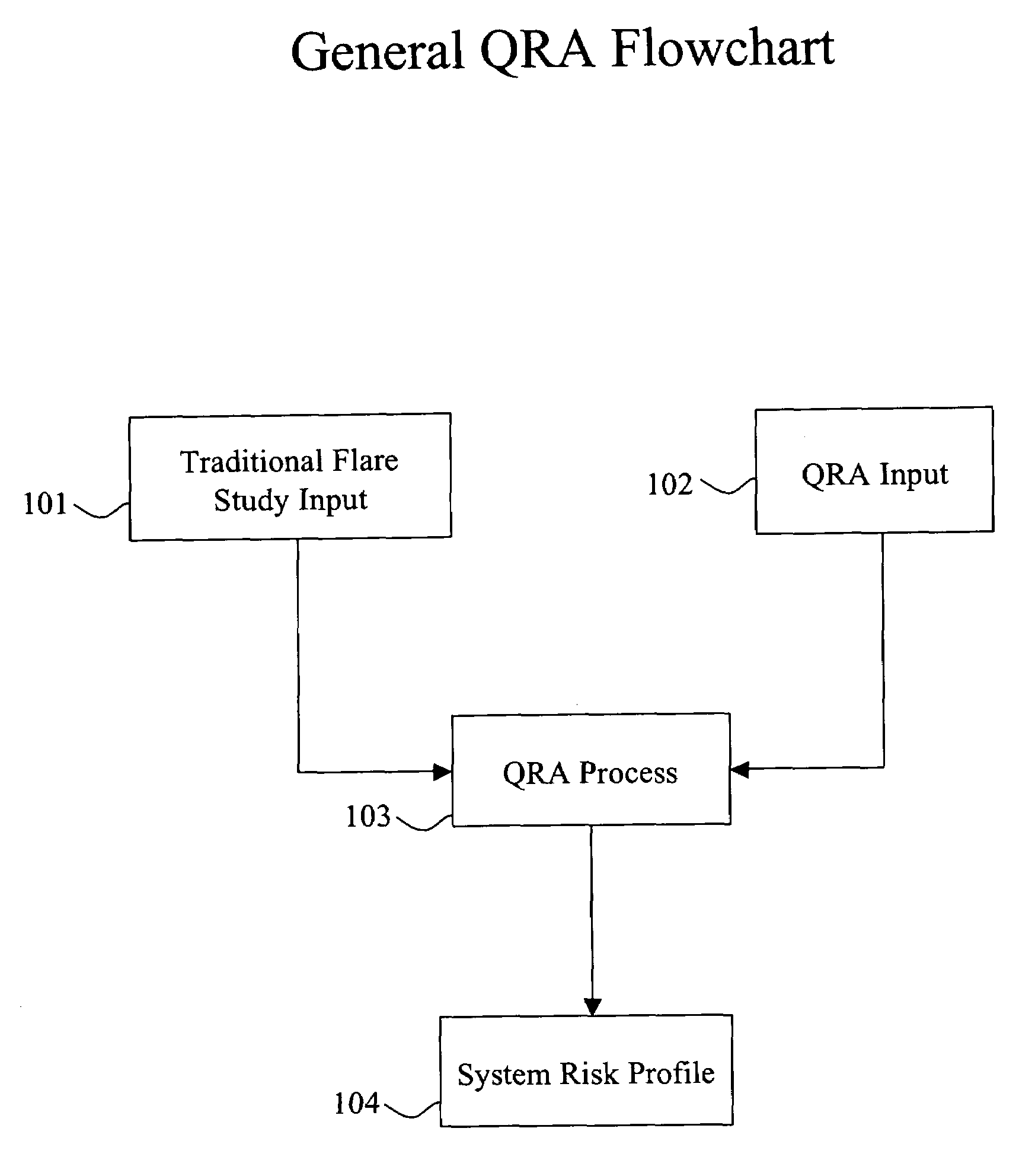
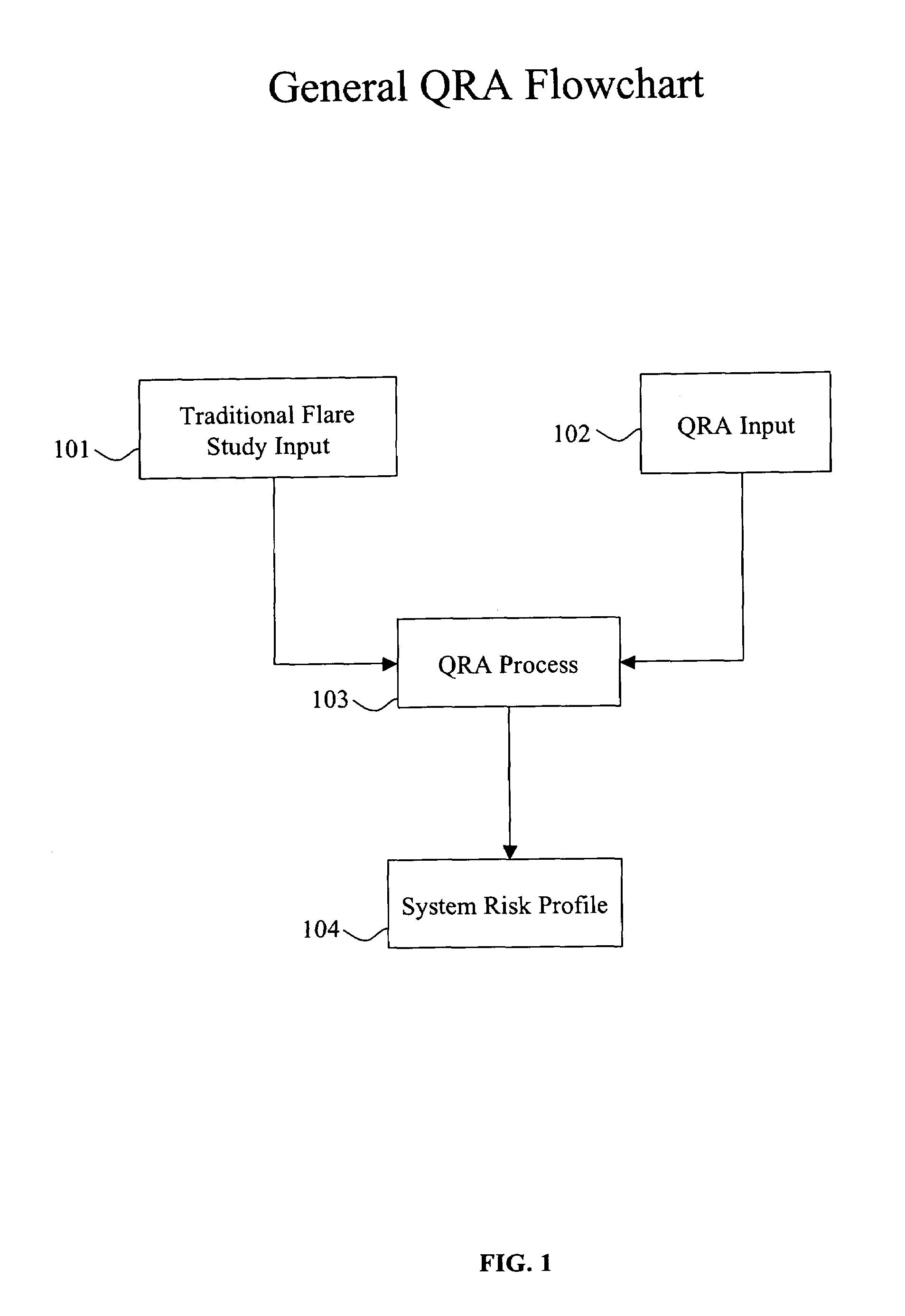
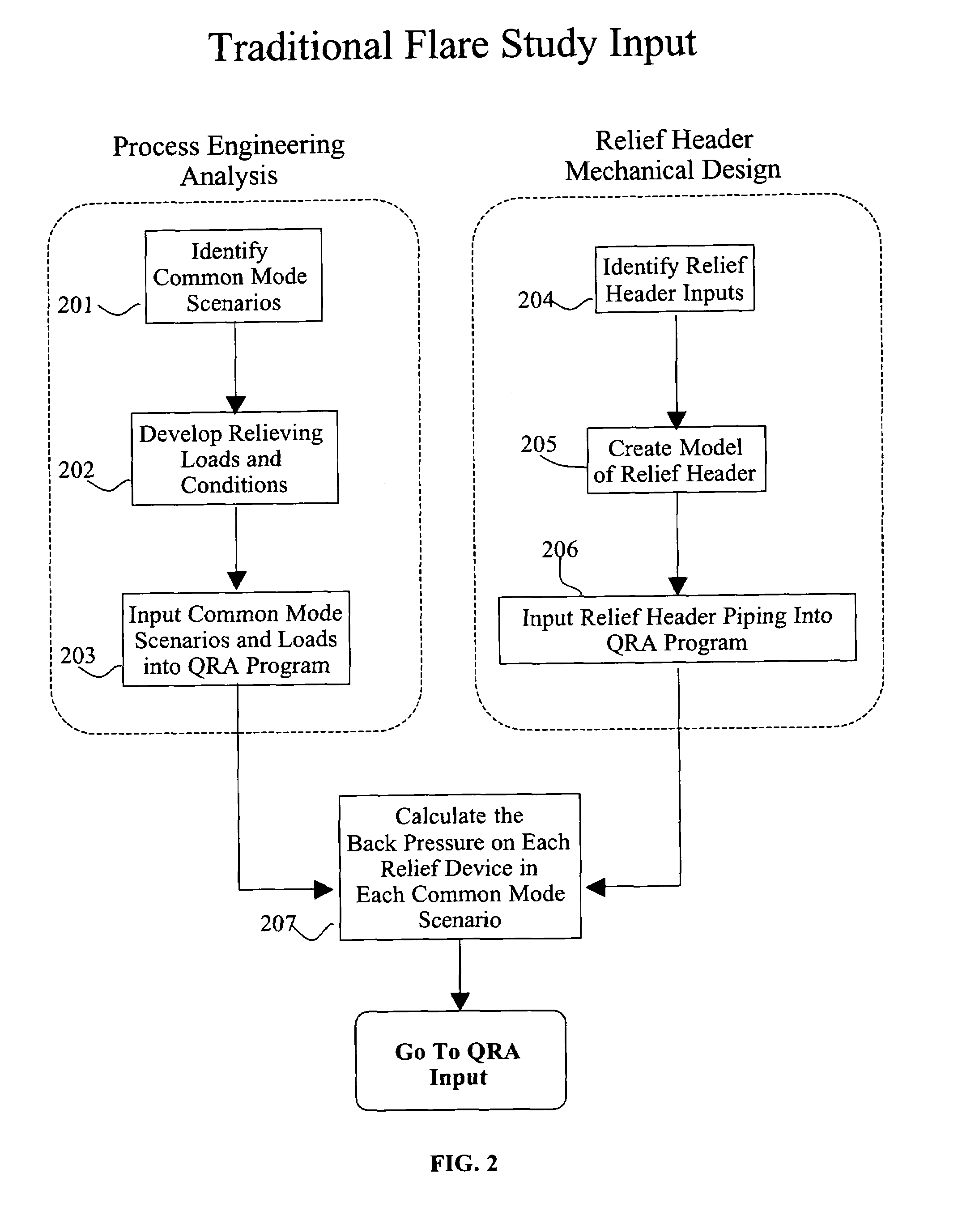
Quantitative Risk Analysis (QRA) can be applied to provide a more realistic assessment of the risk associated with vessel accumulation due to common mode scenarios. The QRA process takes the results of a traditional flare study and QRA inputs such as the frequencies of the common mode scenarios and the layers of protection that will tend to reduce the severity of the common mode scenario, and generates an system risk profile, such as an accumulation versus frequency relationship for each vessel discharging to the relief header. This relationship provides an estimate of the overall risk associated with the relief header system. The QRA program makes the above analysis process possible by automating the generation, execution, and interpretation of the many possible permutations that are required to characterize the system.
Owner:SIEMENS ENERGY INC
Virtual power plant combined heat and power scheduling robust optimization model
InactiveCN106127389ASolve modeling problemsReduce riskEnergy industryResourcesRobustificationDistributed generator
The invention provides a virtual power plant combined heat and power scheduling robust optimization model. A model aggregation unit comprises a distributed generating set, a wind turbine generator set, a photovoltaic set, a combined heat and power (CHP) set, a boiler, electric energy storage, heat energy storage, an electric load and a heat load. Participation of the CHP set in the SRM (Spinning Reserve Market) situation is considered. Aiming at the facing uncertain problem of a virtual power plant (VPP) and resulting risks, robust optimization (RO) is utilized to process uncertainty of the EM electricity price, the SRM electricity price, the wind power capacity, the photovoltaic capacity, the electric load and the heat load, and risk quantification indexes are established, and thus robustness and economical efficiency of a RO model are balanced. The model provided by the invention well solves the existing combined heat and power scheduling optimization model establishment problem of the VPP when participating EM and SRM at the same time, and improves flexibility of decision making, and thus the profit of the VPP is increased. Meanwhile, the introduction of the RO model effectively reduces system risks, and thus the effective reference is provided for a decision maker to select a proper robust factor.
Owner:HOHAI UNIV
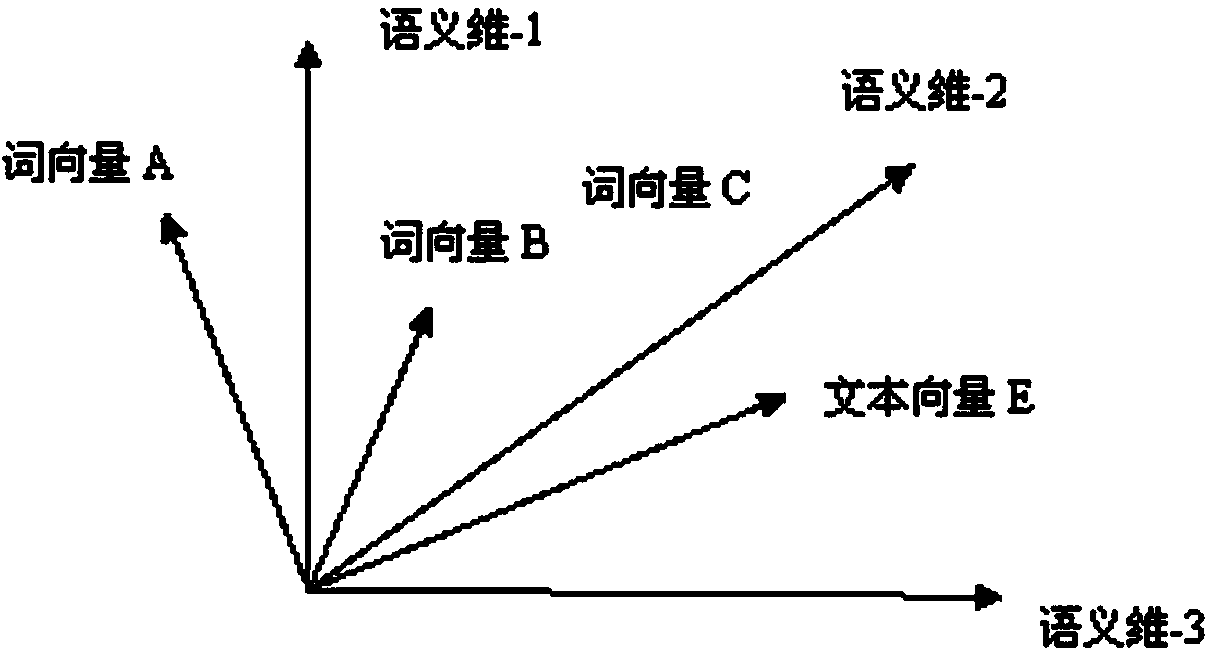
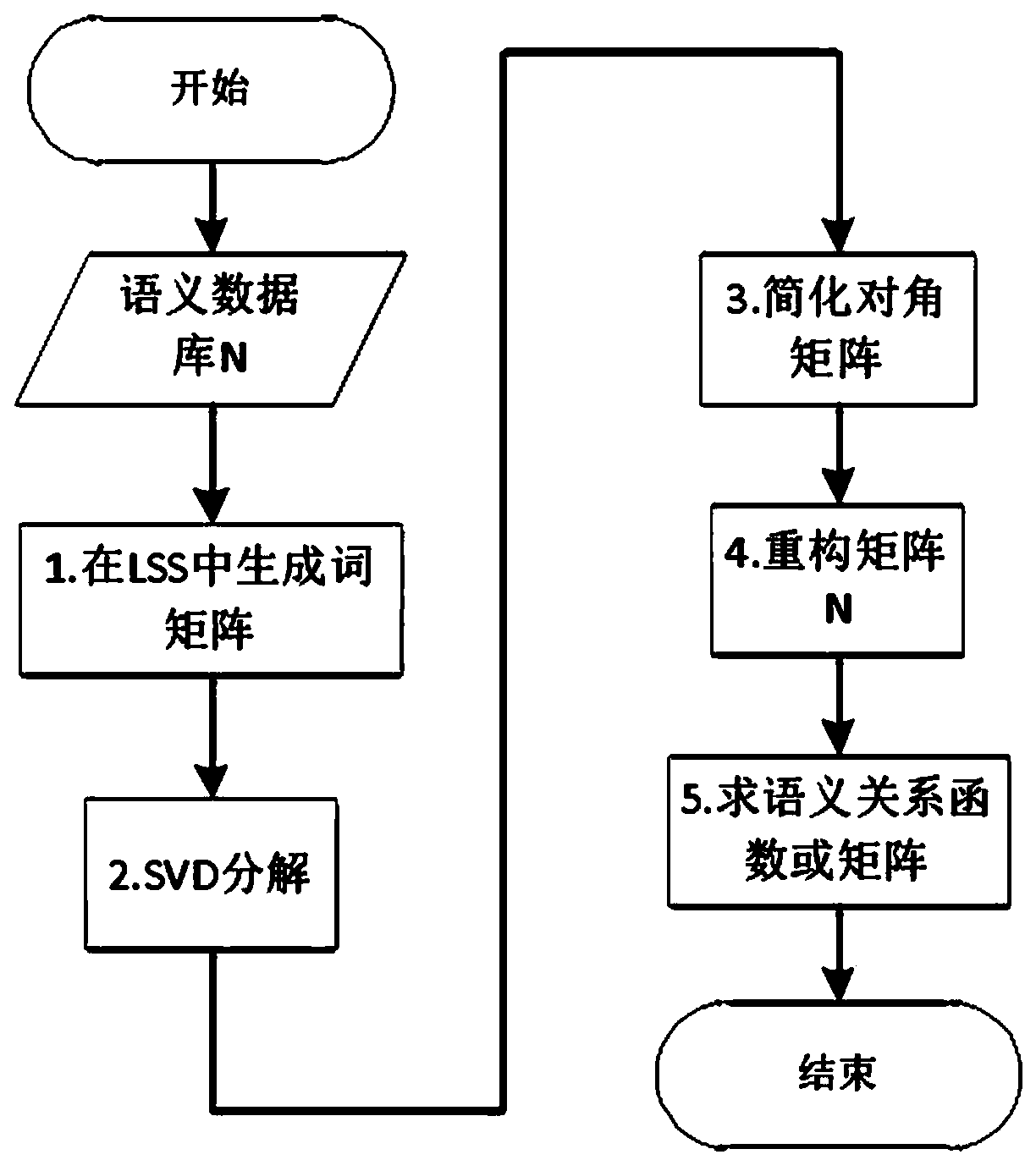
Distributed type big data system risk recognition method based on LSA-GCC
InactiveCN104636449AEasy to identifyAccurate judgmentTransmissionSpecial data processing applicationsPattern recognitionCluster algorithm
The invention discloses a distributed type big data system risk recognition method based on LSA-GCC which comprises the first step of establishing an LSA-GCC model, the LSA-GCC model is used for mapping a data set to a semantic space, and classifying the data set by a clustering algorithm, extracting a specifically classified prototype vector from clustering results, giving a certain weight to each classification, and establishing an initial prototype vector model; the second step of conducting feedforward recognition to a risk through an LSA-SAM safety recognition model, the LSA-SAM safety recognition model conducts information system risk evaluation based on the LSA-GCC model, after data to be evaluated are mapped to the same semantic space, calculating the prototype vector of the each classification and obtaining similarity belonging to the classification, obtaining a cumulative sum of the similarity and the weight of the corresponding classification, finally obtaining risk value of the data to be evaluated by averaging, namely obtaining the risk value at an arrival moment of the data.
Owner:XIAMEN UNIV +1
Power system equipment importance assessing and sorting method based on risk analysis
InactiveCN103700025AImprove risk management and control response capabilitiesPracticalForecastingDirect effectsElectric power system
The invention discloses a power system equipment importance assessing and sorting method based on risk analysis. Based on risk assessment of a power system, the importance of power grid equipment for the overall operational risk of the power system under different operating conditions can be shown truly and comprehensively; during assessment of the equipment importance, the commonly-used certainty security standard of power enterprises is also taken into account while comprehensively considering uncertainties of power grid operation, so that the defects that by the conventional importance assessing method, uncertainties of the grid operation cannot be comprehensively considered, the evaluation angle is single, the practicality is not high and the like are effectively overcome, and more comprehensive risk assessment information than that provided by the conventional assessing method can be provided. In the power system equipment importance assessing and sorting method, the equipment importance assessment is carried out by dividing system risk levels, so that both direct influence and indirect influence of the equipment on the safe operation of the power system can be reflected and references can be provided for a local control and optimization scheme of risk management and control of the power system so as to improve responsiveness to the risk management and control of the power system.
Owner:ZHEJIANG UNIV +2
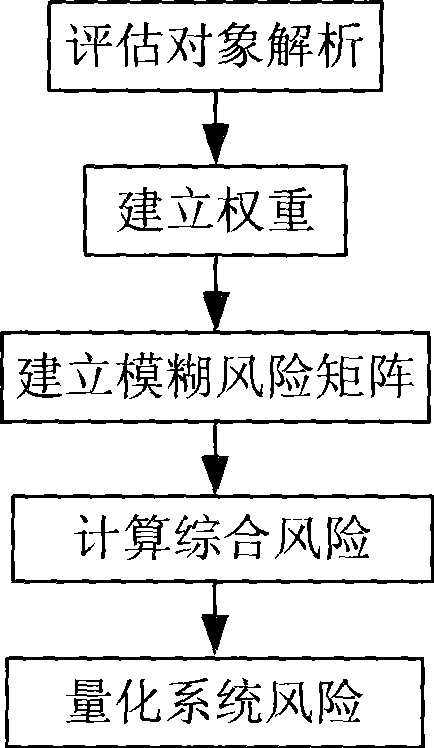
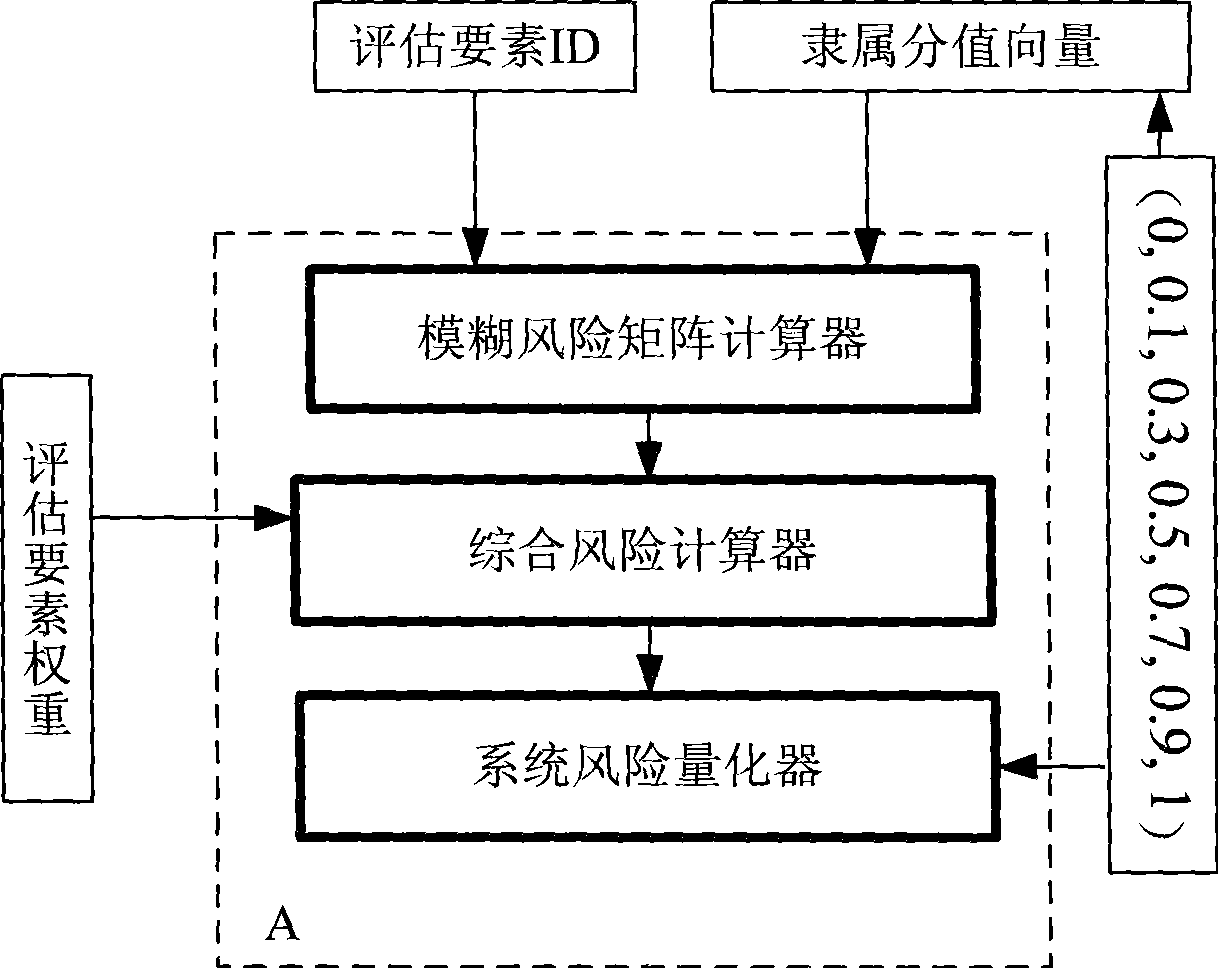
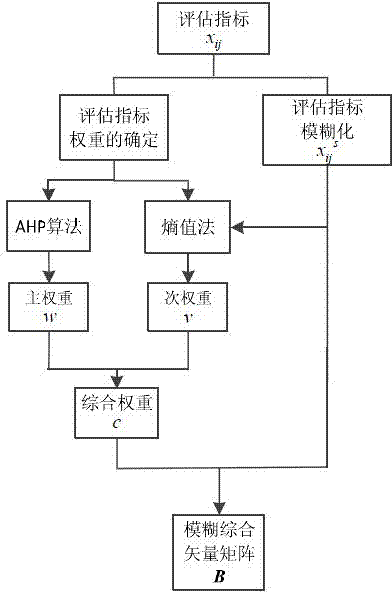
Fuzzy risk evaluation system and method for computer information security
InactiveCN101470779AImprove objectivity and fairnessReduce subjective factorsPlatform integrity maintainanceFuzzy logic based systemsRisk levelFuzzy computing
The invention relates to a fuzzy risk evaluation system and a method of a computer message system, wherein the method comprises calculating out the fuzzy grade subjection degree of evaluation factors according to the risk judgment to the evaluation factors by users, combing the subjection procedure vectors of all the evaluation factors to be a fuzzy risk matrix calculator of a fuzzy risk matrix, calculating out a comprehensive risk counter of fuzzy risks of an integral system according to the fuzzy risk matrix of all the evaluation factors and weight vectors of the evaluation factors, and calculating out a system risk quantizer of risk deterministic vector values of the integral system according to the comprehensive fuzzy risk and risk level standard of the system. The invention has the advantages that fully considering the relationship among the evaluation factors, a subjection relationship table and a weight table of each factor are established through introducing a fuzzy calculating technique, thereby reducing subjective factors, and improving objective fairness of evaluation results.
Owner:BEIJING VENUS INFORMATION TECH
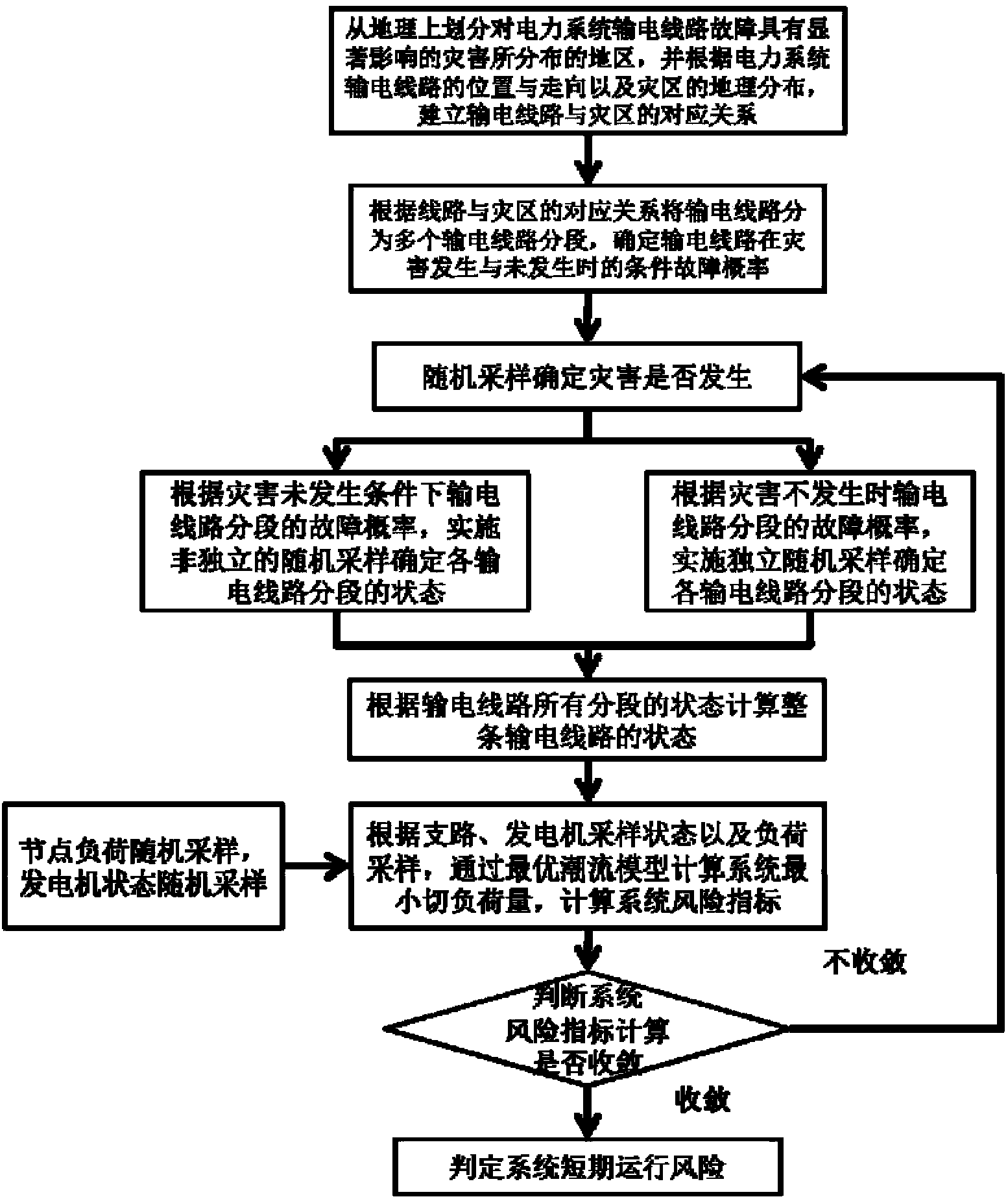
Power system short-term risk determination method taking disaster factors into account
ActiveCN103440400AImprove the level of operational safety and reliabilitySignificant safety benefitsData processing applicationsSpecial data processing applicationsFailure rateElectric power system
The invention relates to a power system short-term risk determination method taking disaster factors into account and belongs to the field of power system reliability and risk analysis. The method comprises the steps: geographically dividing regions where disasters causing power system transmission line failure are distributed (disaster regions for short, e.g. regions of lightning strokes, ice disasters, bird hazards and the like); establishing a corresponding relationship between power transmission devices and the disaster regions according to positions of the power transmission devices of a power system and the geographical distribution of the disaster regions; calculating the conditional failure rate of the power transmission devices located in the disaster regions when the disasters occur through carrying out statistics on historical failure of the power transmission devices of the power system and reasons for the historical failure; determining the power outage risk of the power system in a future short term by using power system risk assessment techniques according to weather forecast information and the conditional failure rate of the power transmission devices. By using the method, potential power outage accidents of the power system under disaster weather are warned, and maintenance plans and operating modes for the power system are arranged reasonably, so that large-scale power outage accidents of the power system are prevented.
Owner:TSINGHUA UNIV
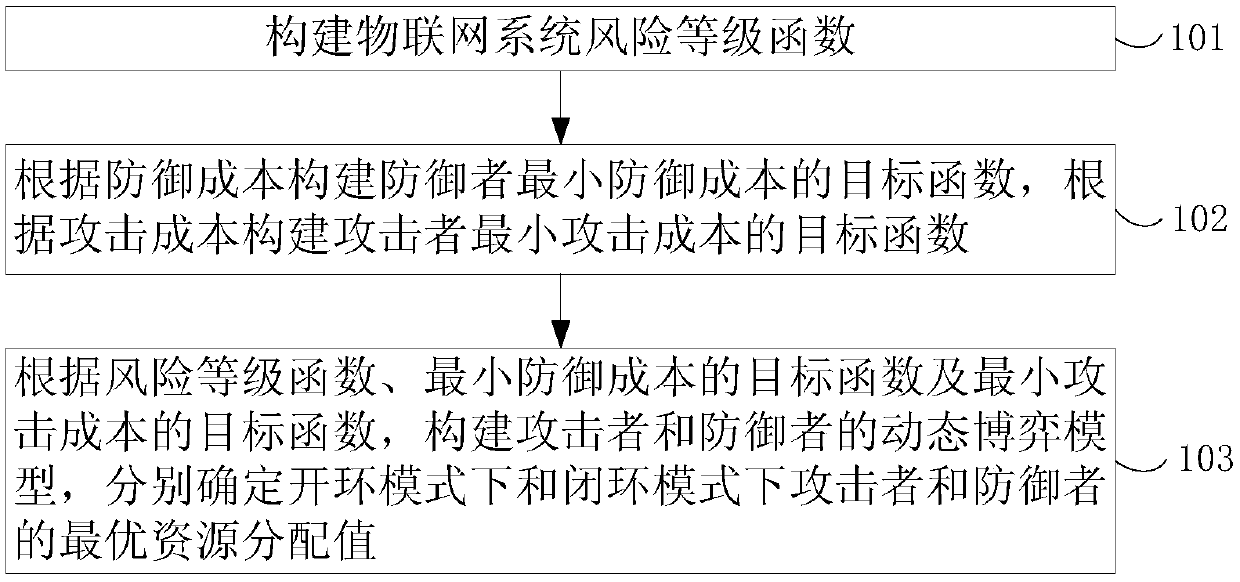
Dynamic game method and device oriented to internet of things threat-defense resource allocation
InactiveCN109639729AEfficient allocationEfficient resource allocationData switching networksRisk levelThe Internet
The invention provides a dynamic game method and device oriented to internet of things threat-defense resource allocation. The optimal allocation of the resources in the internet of things threat-defense can be realized. The method comprises the following steps: constructing an internet of things system risk level function; constructing a target function of minimum defense cost of a defender according to the defense cost, and constructing a target function of the minimum attack cost of an attacker according to the attack cost; and constructing a dynamic game model of the attacker and the defender according to the risk level function, the target function of the minimum defense cost and the target function of the maximum attack cost, and respectively determining the optimal resource allocation values of the attacker and the defender under an opened-loop mode and a closed-loop mode, wherein the opened-loop mode is used for representing a state that the attacker and the defender abide by unchanged established policy at the beginning of the game, and the closed-loop mode is used for representing the dynamic change states of the defender and the attacker after the game is started. The dynamic game method disclosed by the invention relates to the field of internet of things network security.
Owner:UNIV OF SCI & TECH BEIJING
Method for evaluating system risk
Owner:STEPHENSON PETER R
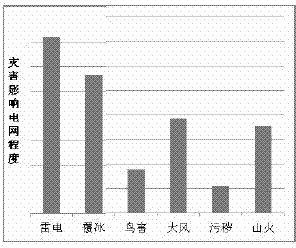
Multi-index fuzzy evaluation method for grid faults caused by disasters
InactiveCN103678943AObjective reflectionComprehensive objective influence abilitySpecial data processing applicationsGrid faultNatural disaster
The invention belongs to the technical field of electrical power system risk evaluation, and particularly relates to a multi-index fuzzy evaluation method for grid faults caused by disasters. The evaluation method comprises the following steps of providing four indexes for evaluating a grid affected by the disasters according to an operational aspect of an electric transmission line; fuzzifying the indexes by utilizing a fuzzy mathematic theory; respectively carrying out weight analysis on the evaluated indexes through an analytic hierarchy process and an entropy evaluation method to obtain a primary weight and a secondary weight of each evaluated index; and synthesizing the weights obtained by the two methods, and combining a method of weighted mean obtain a comprehensive evaluation result of the grid faults caused by the disasters, and form a fuzzy synthetic evaluation method. The evaluation method takes multiple influence factors of natural disasters on the grid into account, can be used for carrying out comprehensive comparison and analysis on influence of various natural disasters on the grid, and has stronger comprehensive and objectivity.
Owner:STATE GRID CORP OF CHINA +2
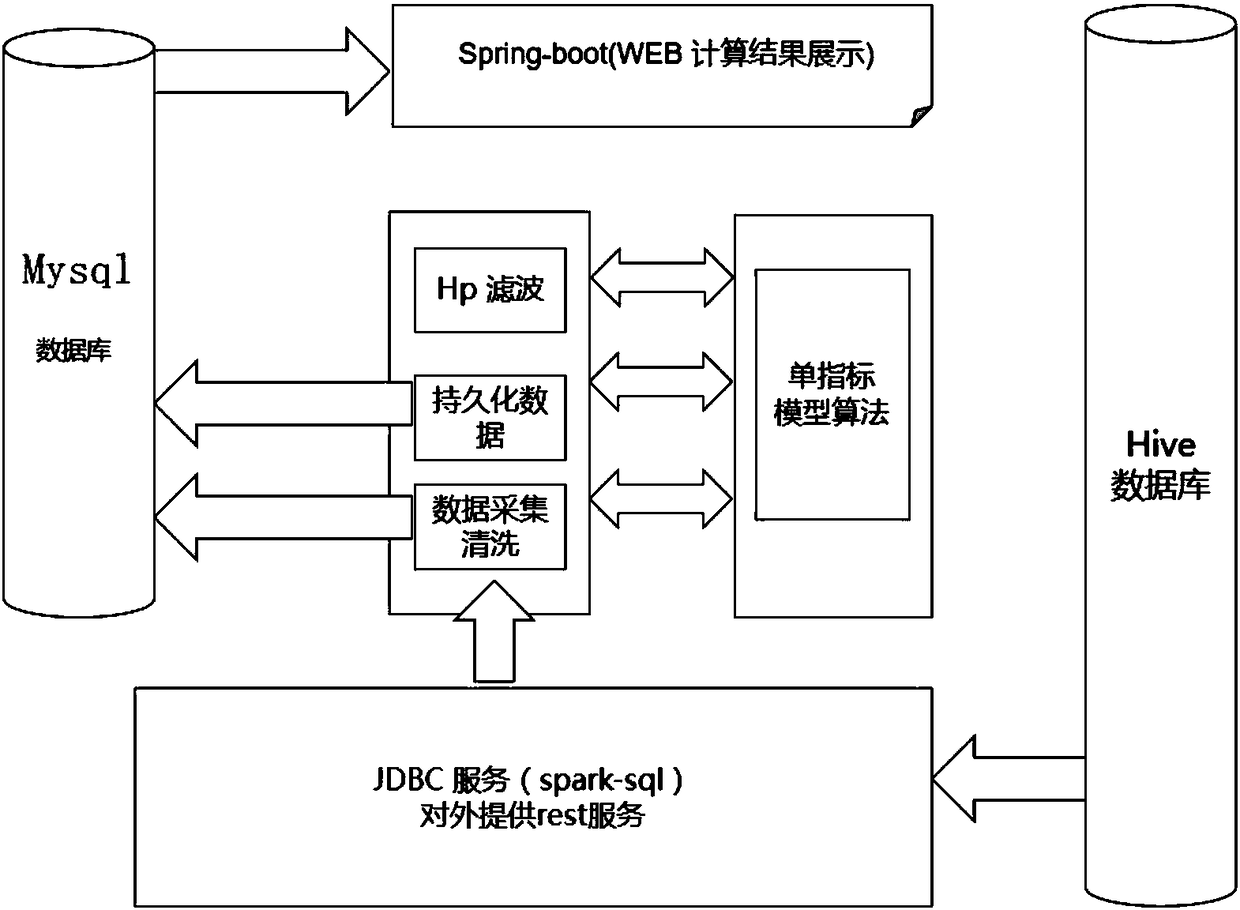
Single-index prediction and early warning method based on artificial intelligent big data platform
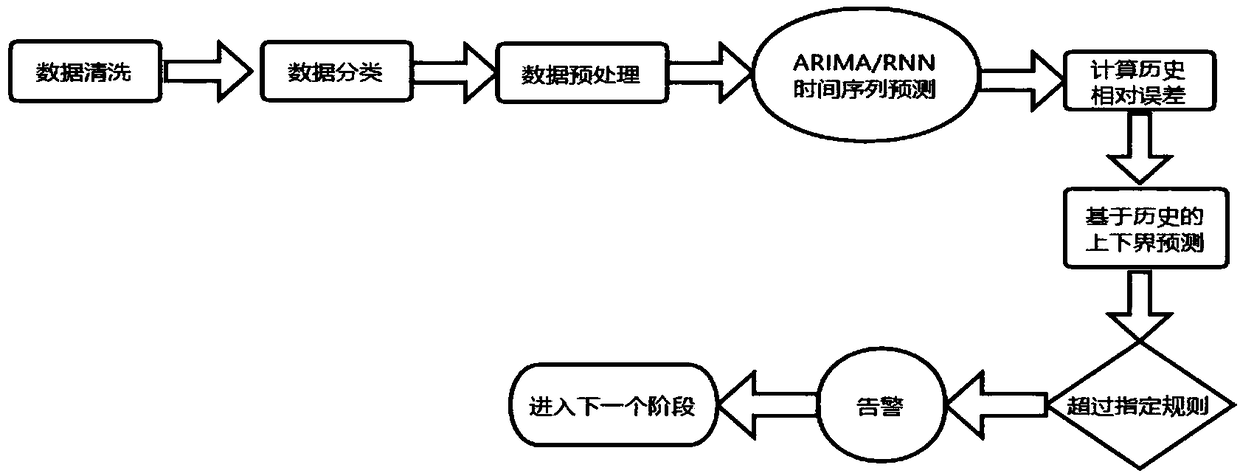
InactiveCN108197011AInhibit deteriorationPotential risk fast and efficientHardware monitoringSufficient timeData platform
The invention discloses a single-index prediction and early warning method based on an artificial intelligent big data platform. The method includes the steps: (1) single-index prediction based on theartificial intelligent big data platform; (2) single-index warning based on the artificial intelligent big data platform. Based on the range interval of historical upper and lower bound predictive index values, warning is performed once historical upper and lower bound threshold ranges are continuously and repeatedly broken through within a period of time, namely, abnormity exists within the period of time. Intelligent analysis is performed based on historical index data, index abnormity trend can be judged in real time according to corresponding early warning strategies by the aid of index data of indexes monitored by the artificial intelligent big data platform in real time, potential risks are discovered before a monitoring system, early warning for a production system is realized, enough time is reserved for operation and maintenance experts to remove system faults, and production system risks are avoided as far as possible.
Owner:上海洞识信息科技有限公司
Online risk evaluation method for power distribution network
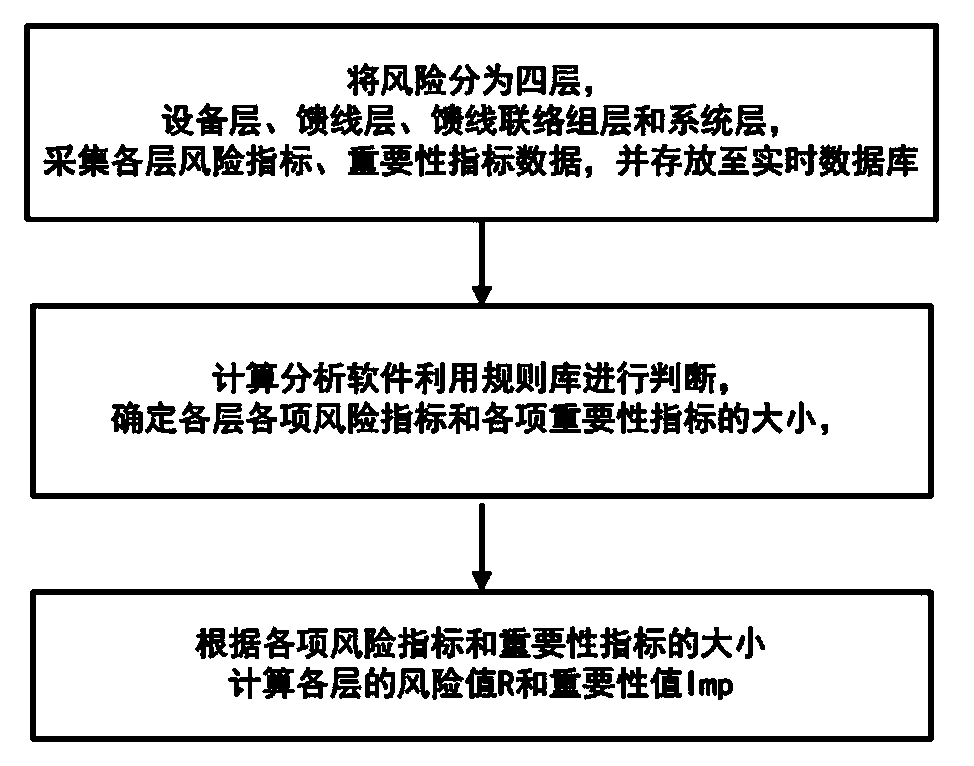
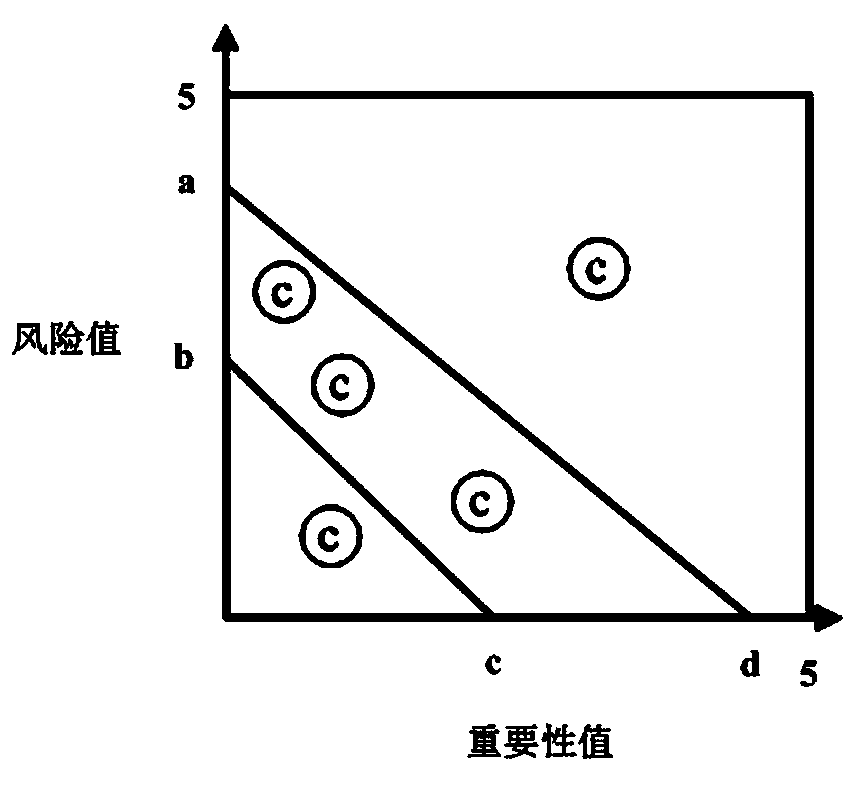
InactiveCN103985068AComprehensive considerationReduce riskData processing applicationsElectric power systemRisk indicator
The invention relates to an online risk evaluation method for a power distribution network, and belongs to the field of electric power system risk evaluation. Risks are divided into a device layer, a feeder layer, a feeder contact group layer and a system layer through the online risk evaluation method. The method comprises the steps of firstly, respectively collecting data of risk indexes and importance indexes of each layer, and storing the data into a real-time database; then, judging numerical values of the risk indexes and numerical values of the importance indexes of each layer by the combination of judgment criteria defined by a rule base, wherein the risk indexes and the importance indexes are divided into five levels in the rule base; finally, respectively calculating the risk value R and the importance value Imp of each layer. According to the online risk evaluation method, the risks of the power distribution network are divided into the four layers and five levels, so that the influence of the risks of components in the power distribution network on the risks of the power distribution network is considered, the system risks can be known, the device risks can also be known, importance of each component in the power distribution network is provided, and clearer guidance is provided for reducing the risks.
Owner:HUNAN UNIV +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com