Privilege management system and method
A permission management and permission technology, applied in the field of information security, can solve problems such as waste of manpower and material resources, modify or cancel permissions, increase system risks, etc., achieve low difficulty and complexity, ensure timeliness, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
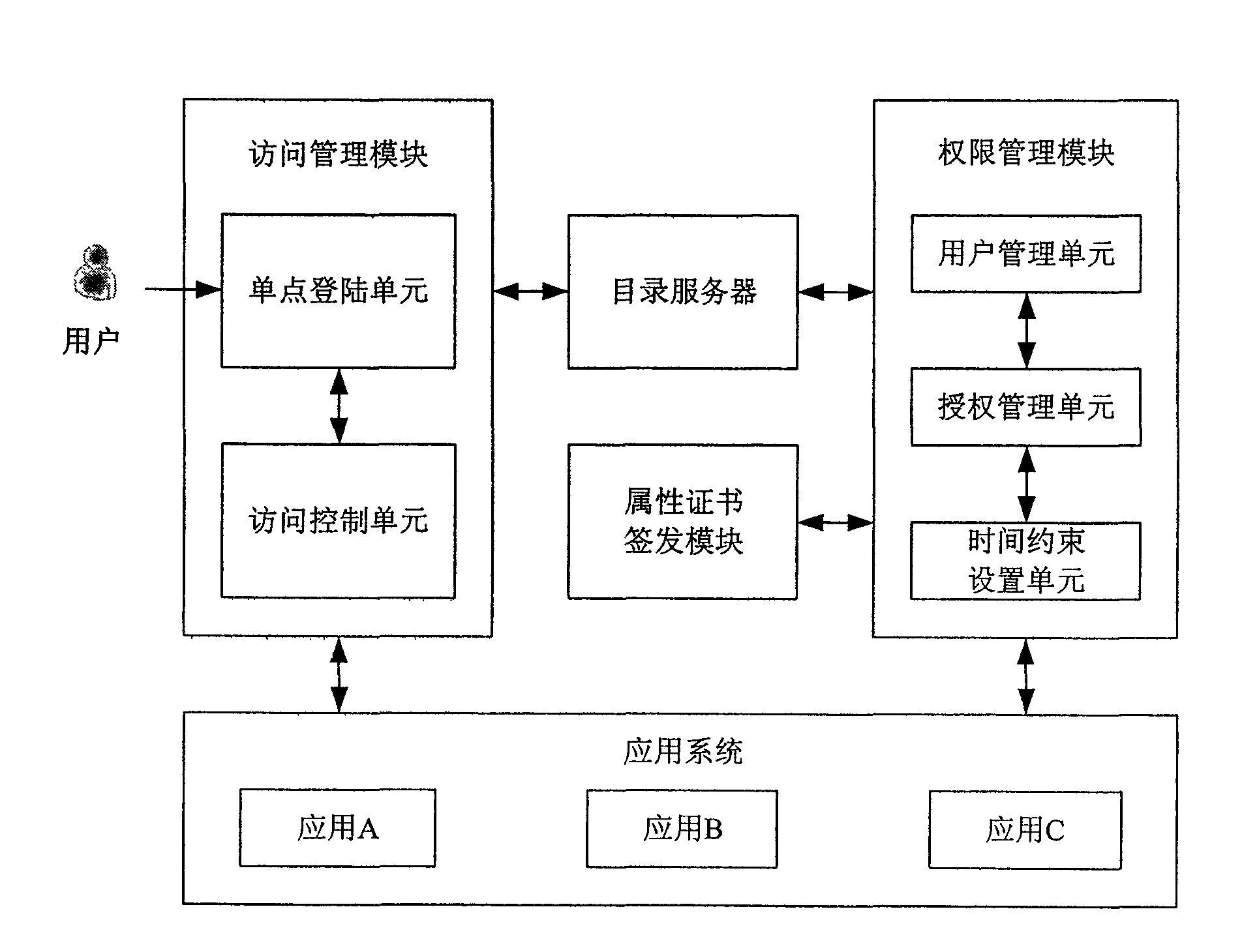
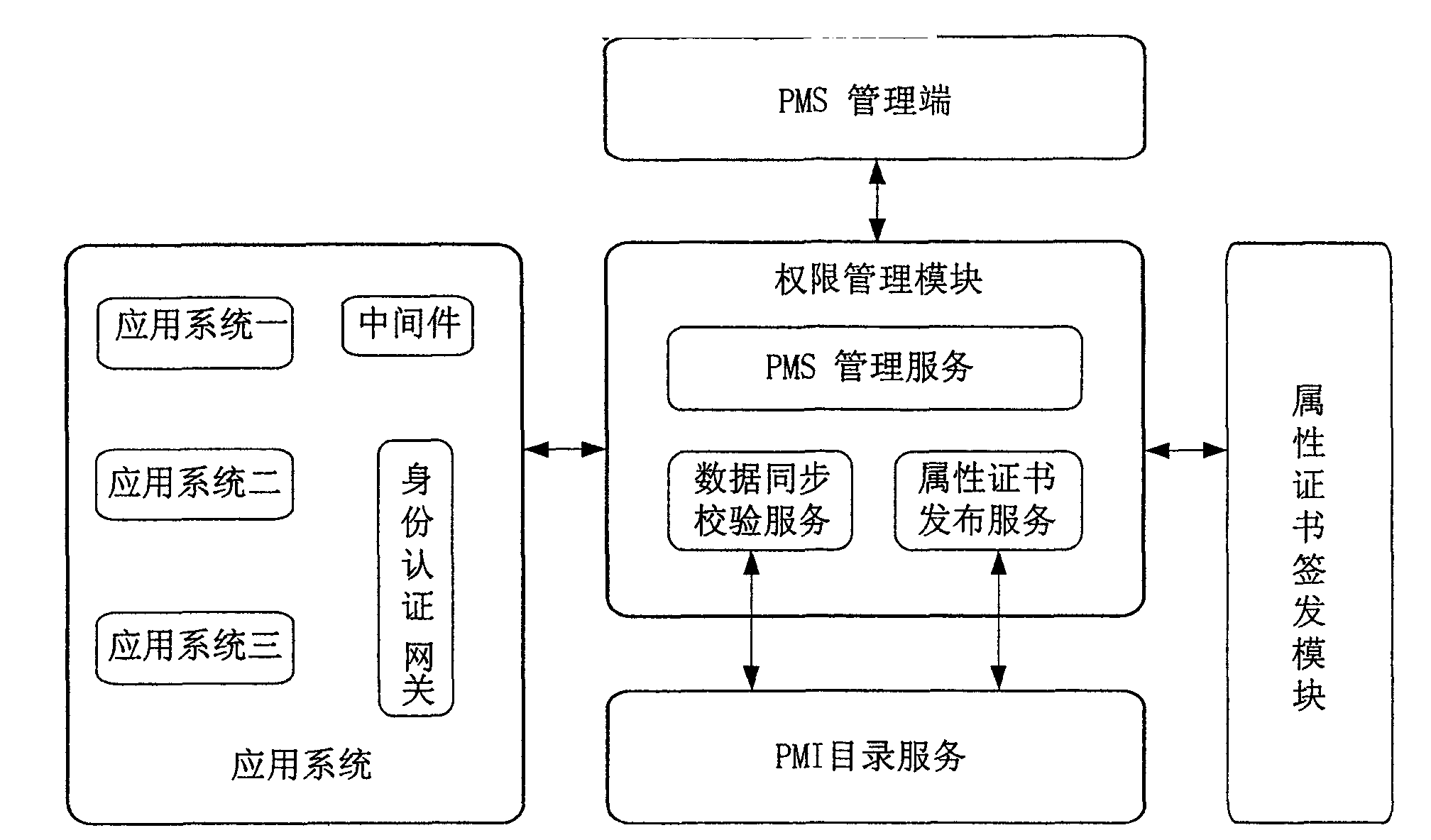
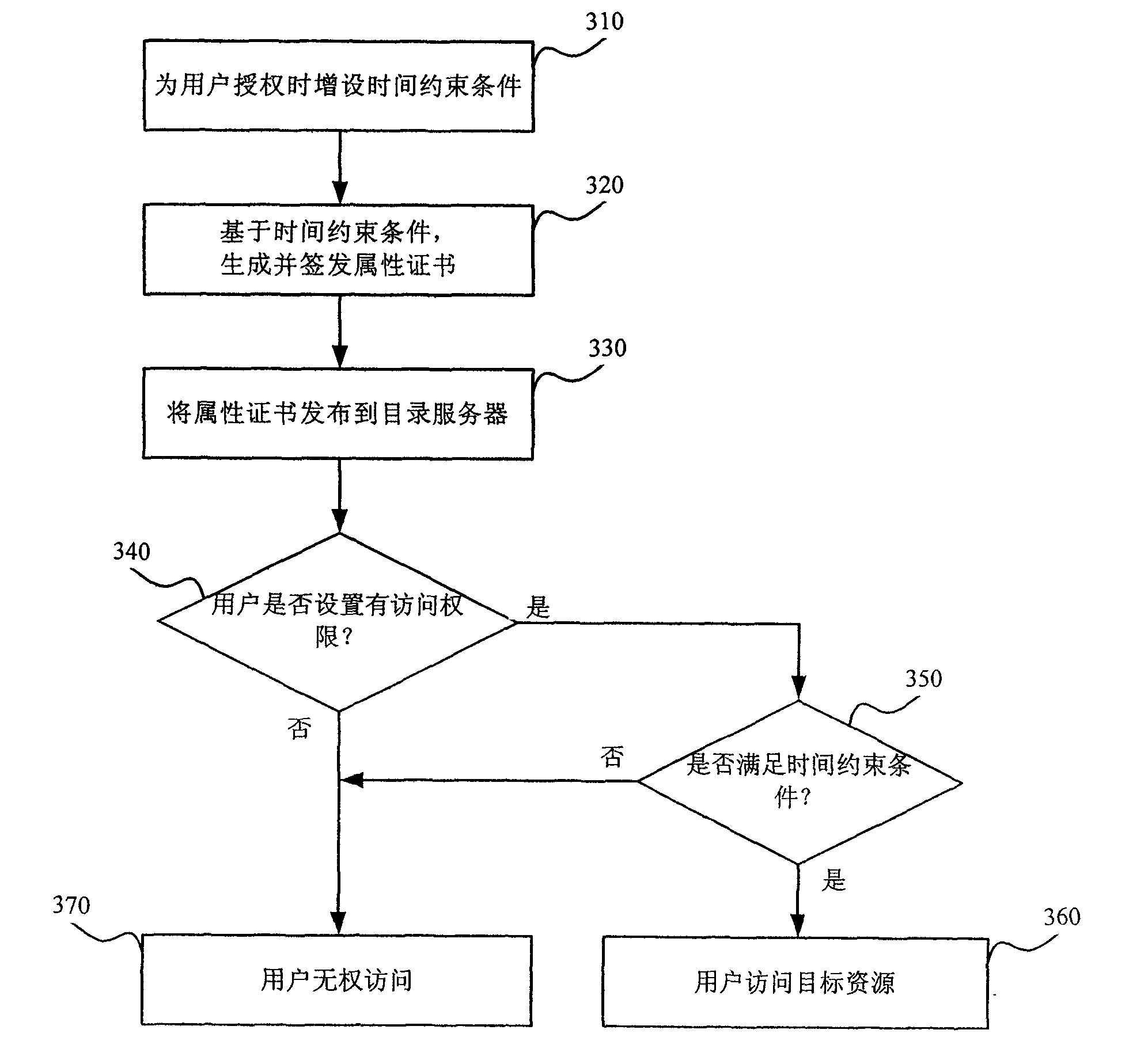
[0026]The technical core of the present invention is: adding time-constrained authorization on the basis of the existing authorization method, that is, when authorizing the user, while granting the user's authority, it also adds a time-constrained condition to the authority, and includes the time-constrained The authorization results of the conditions are published to the directory server. In this way, when the access control module provides access control services for the business, it not only needs to retrieve whether there is a binding relationship between the user identity and the corresponding resource, but also needs to judge the time constraints contained in it. If the current access time satisfies Only when the time constraints are met, the access control is allowed, and the business system can display the corresponding resource information for the user; on the contrary, if the current access time does not meet the time constraints, even if the binding relationship betw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com