Distributed type big data system risk recognition method based on LSA-GCC
A risk identification, big data technology, applied in the field of cloud computing, can solve problems such as unsatisfactory WebService effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0088] The present invention will be further described in conjunction with the accompanying drawings and specific embodiments.
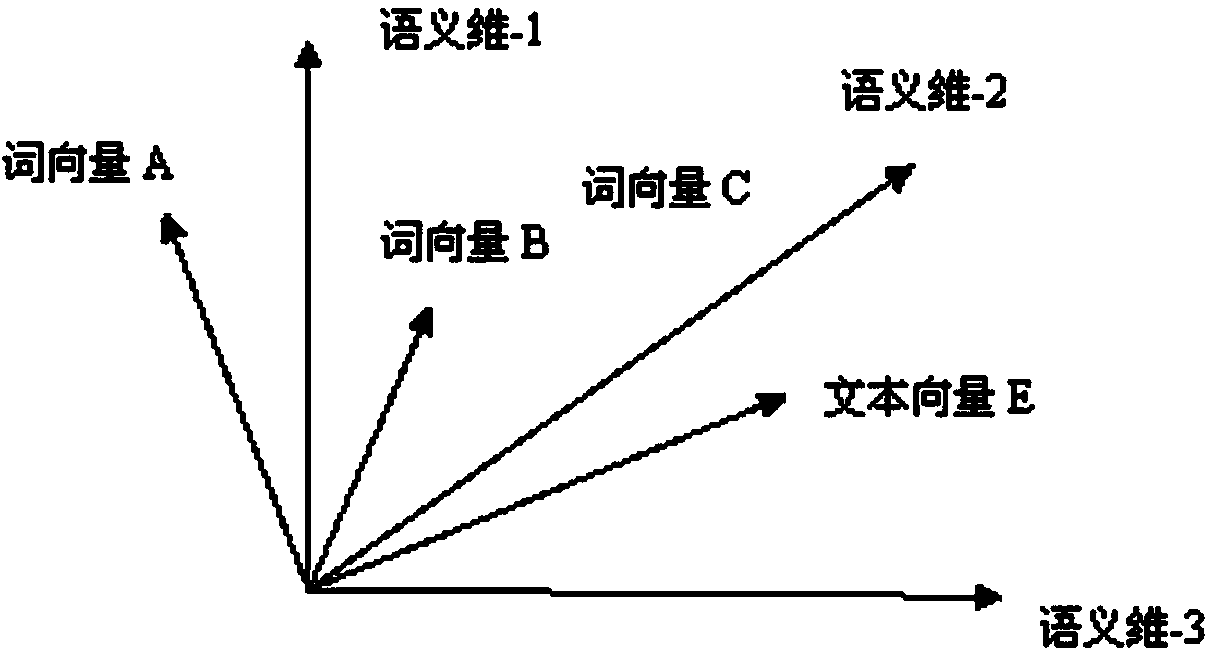
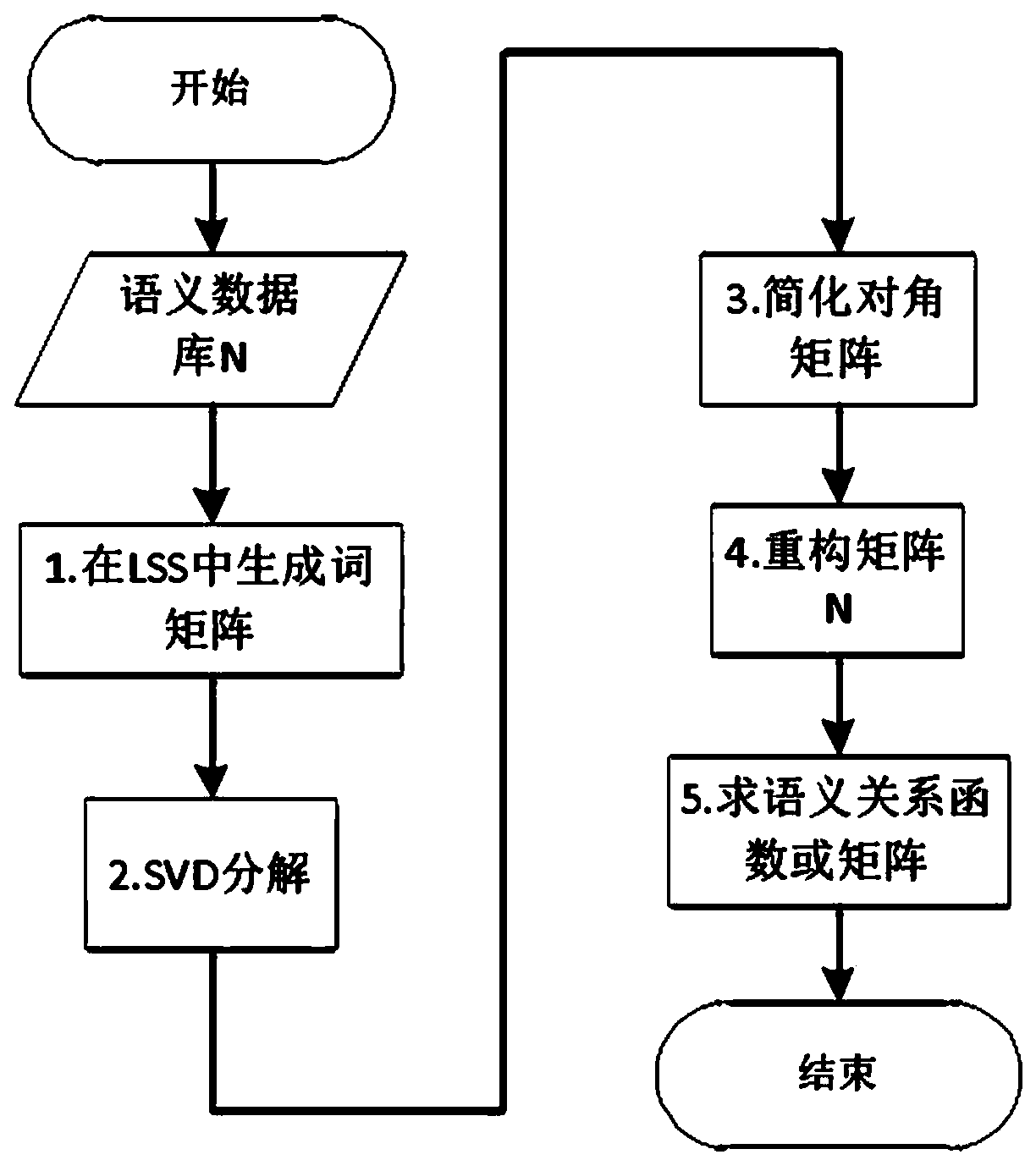
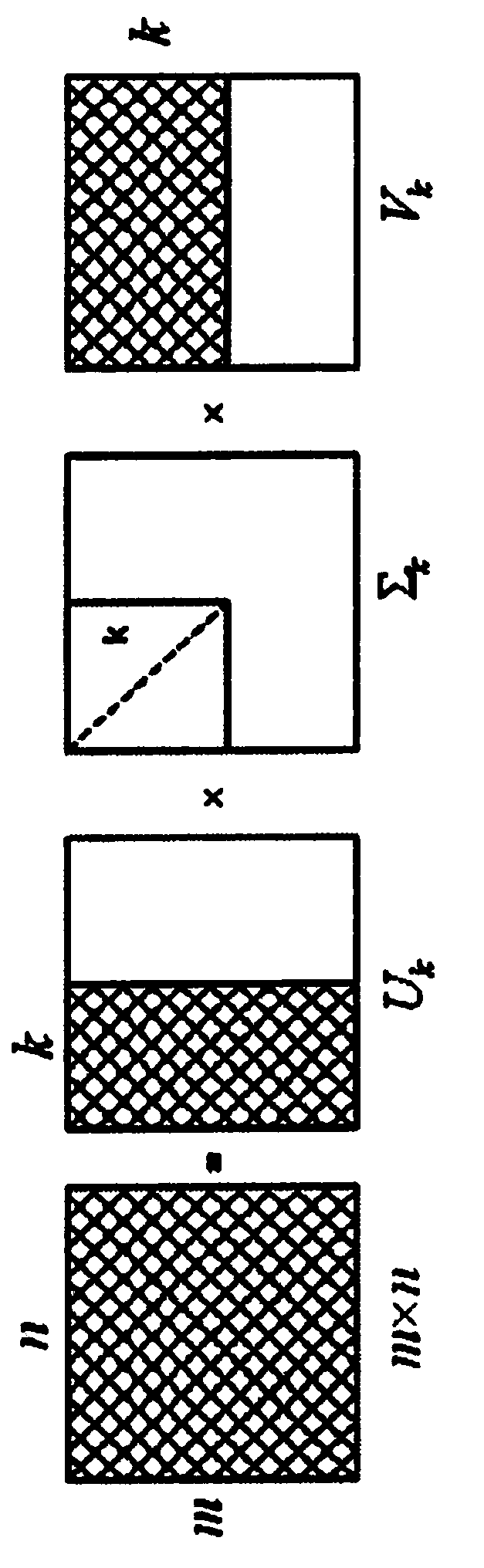
[0089] Cloud computing is a new generation product of cluster computing, parallel computing, and grid computing, which integrates various concepts and technologies of distributed computing. The cloud computing environment typically presents the characteristics of large-scale distribution, complex structure, diversified architecture, dynamic computing and service virtualization, among which virtualization technology is one of the key technologies of cloud computing. Virtualization puts forward higher security and quality requirements for service-oriented (WebService) cloud computing system suppliers, while traditional research mostly focuses on information system risk assessment and network intrusion detection, lacking in-depth research on cloud computing. Therefore, it is necessary to conduct risk assessment research on service-oriented cloud computi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com