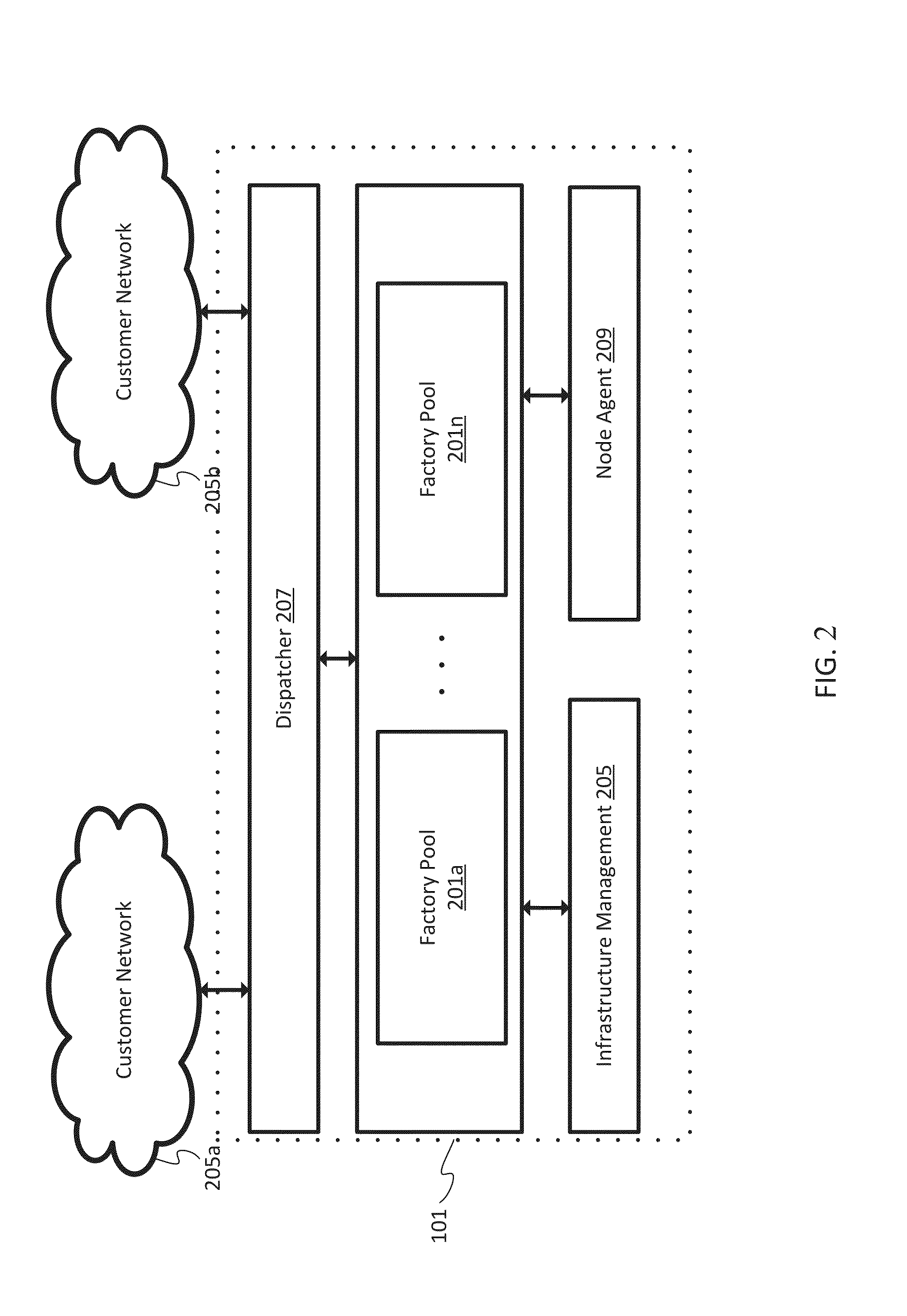
Patents
Literature
61 results about "Service virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
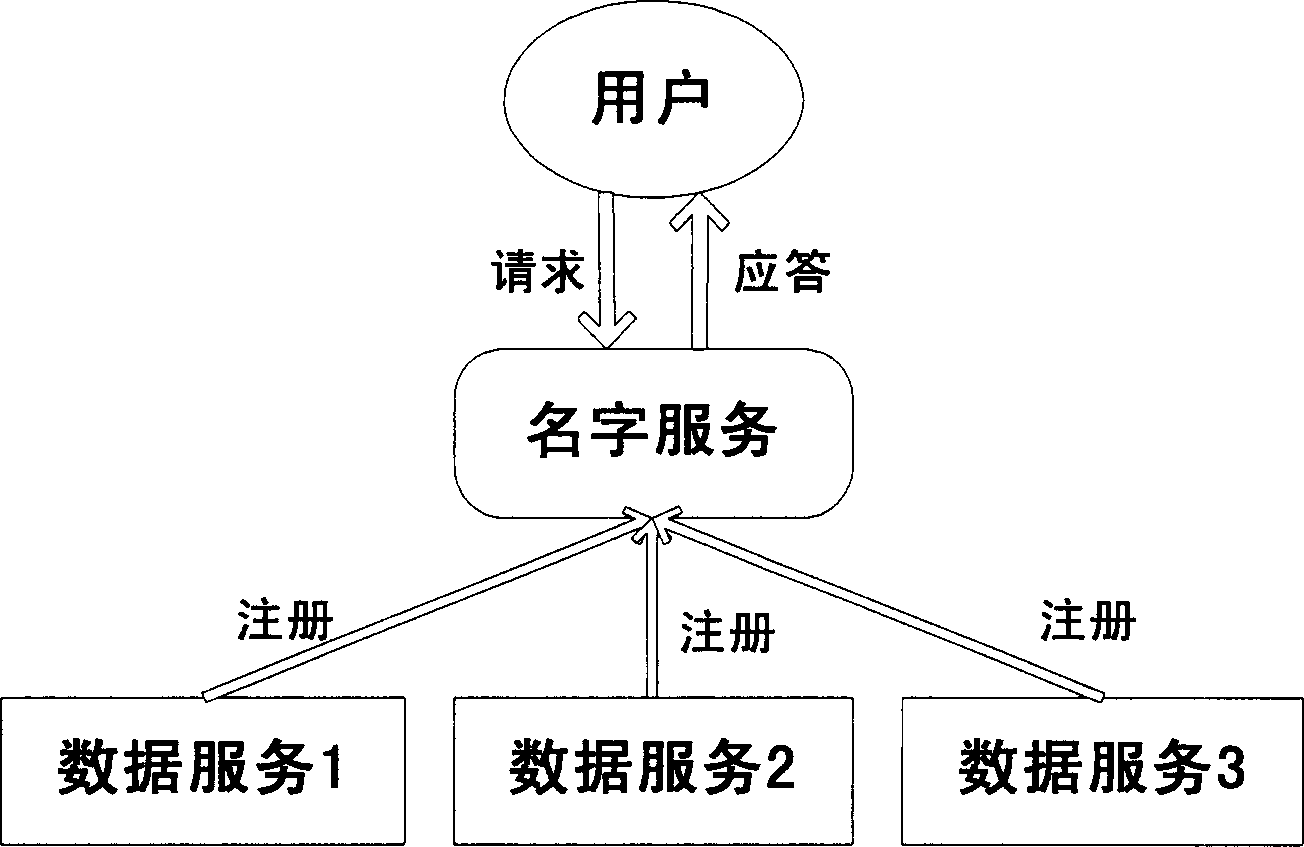
In software engineering, service virtualization or service virtualisation is a method to emulate the behavior of specific components in heterogeneous component-based applications such as API-driven applications, cloud-based applications and service-oriented architectures. It is used to provide software development and QA/testing teams access to dependent system components that are needed to exercise an application under test (AUT), but are unavailable or difficult-to-access for development and testing purposes. With the behavior of the dependent components "virtualized", testing and development can proceed without accessing the actual live components. Service virtualization is recognized by vendors, industry analysts, and industry publications as being different than mocking.
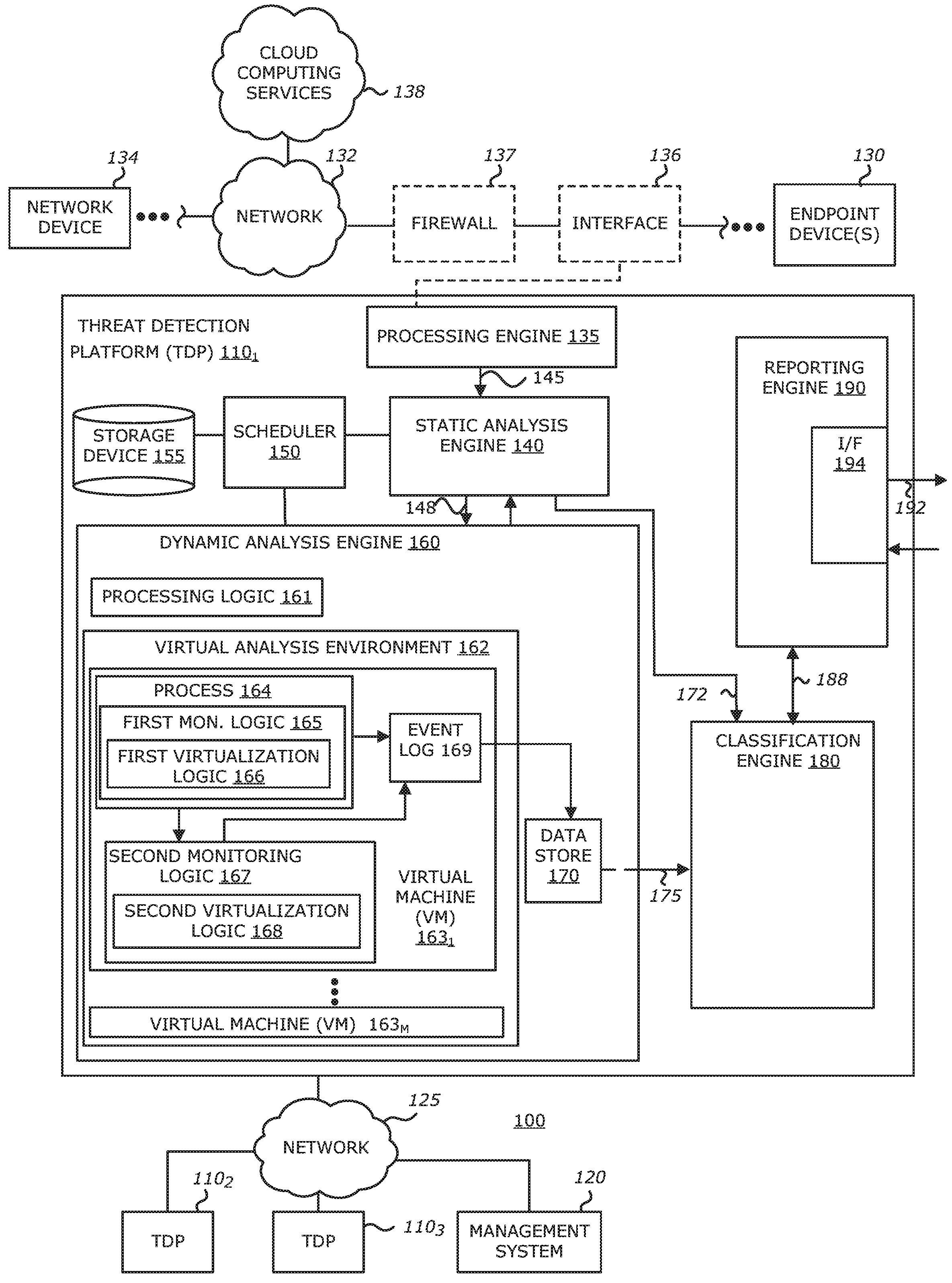
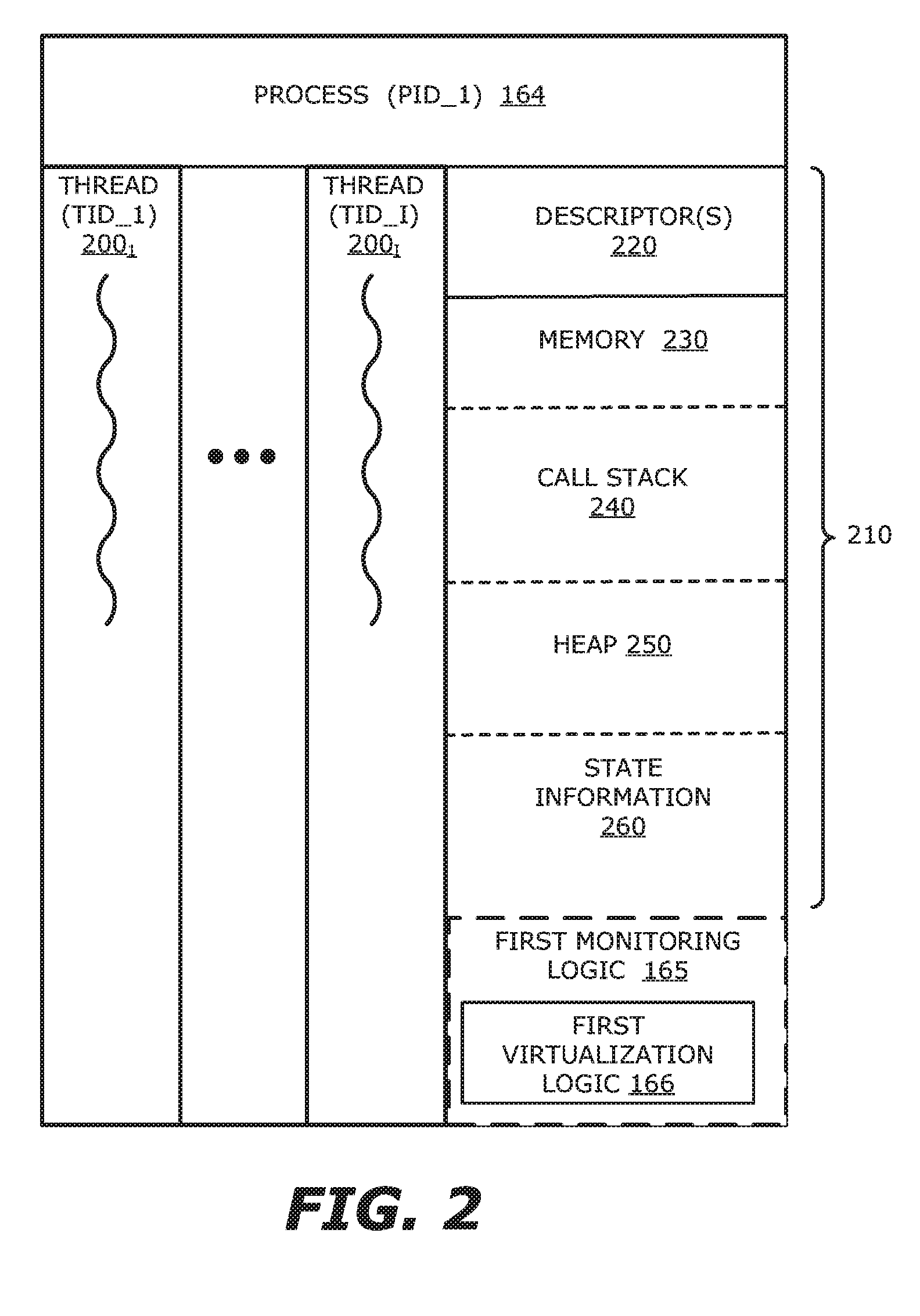
Selective virtualization for security threat detection
ActiveUS20160335110A1Platform integrity maintainanceTransmissionVirtualizationService virtualization
Selective virtualization of resources is provided, where the resources may be intercepted and services or the resources may be intercepted and redirected. Virtualization logic monitors for a first plurality of requests that are initiated during processing of an object within the virtual machine. Each of the first plurality of requests, such as system calls for example, is associated with an activity to be performed in connection with one or more resources. The virtualization logic selectively virtualizes resources associated with a second plurality of requests that are initiated during the processing of the object within the virtual machine, where the second plurality of requests is lesser in number than the first plurality of requests.
Owner:FIREEYE SECURITY HLDG US LLC
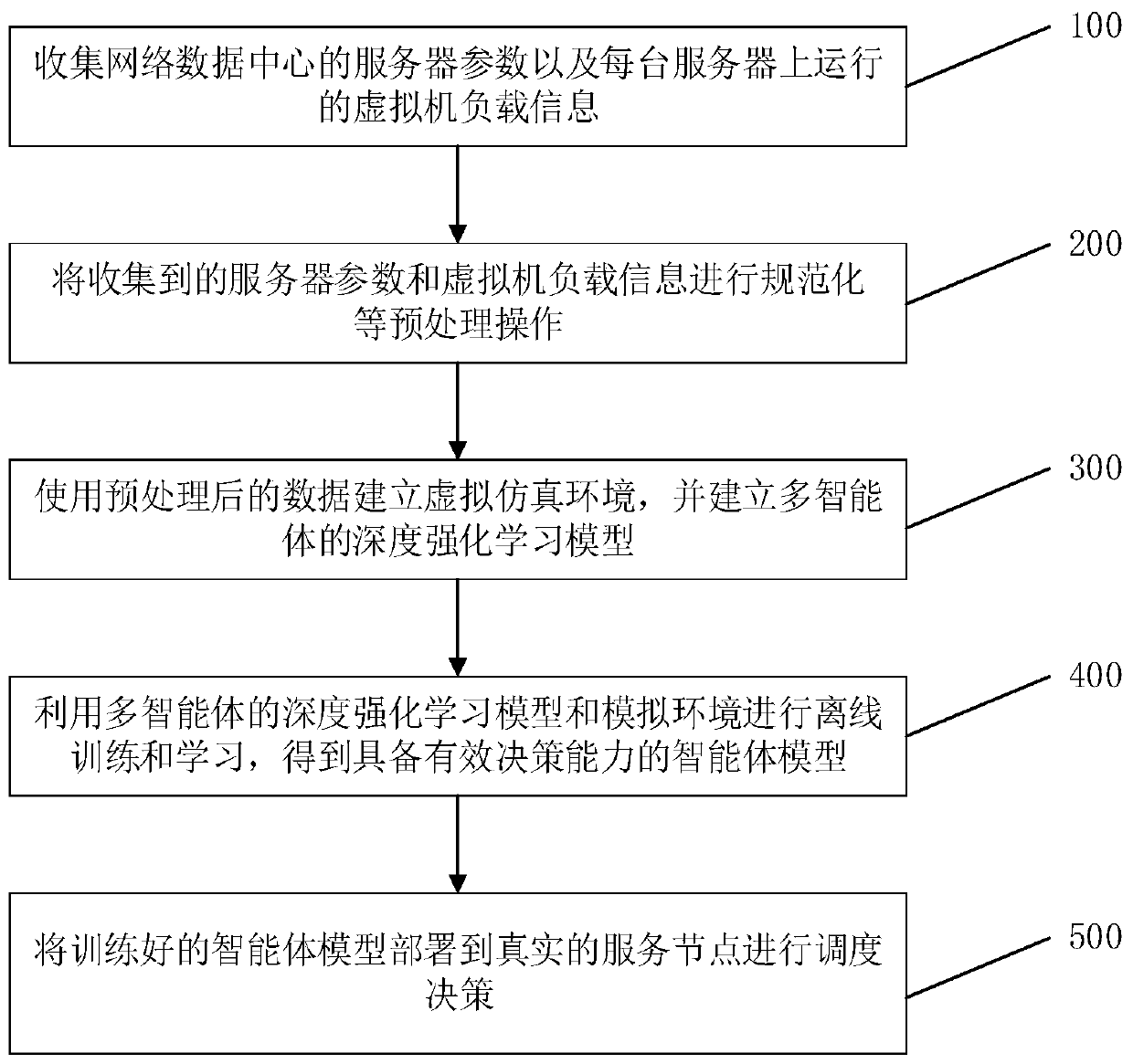
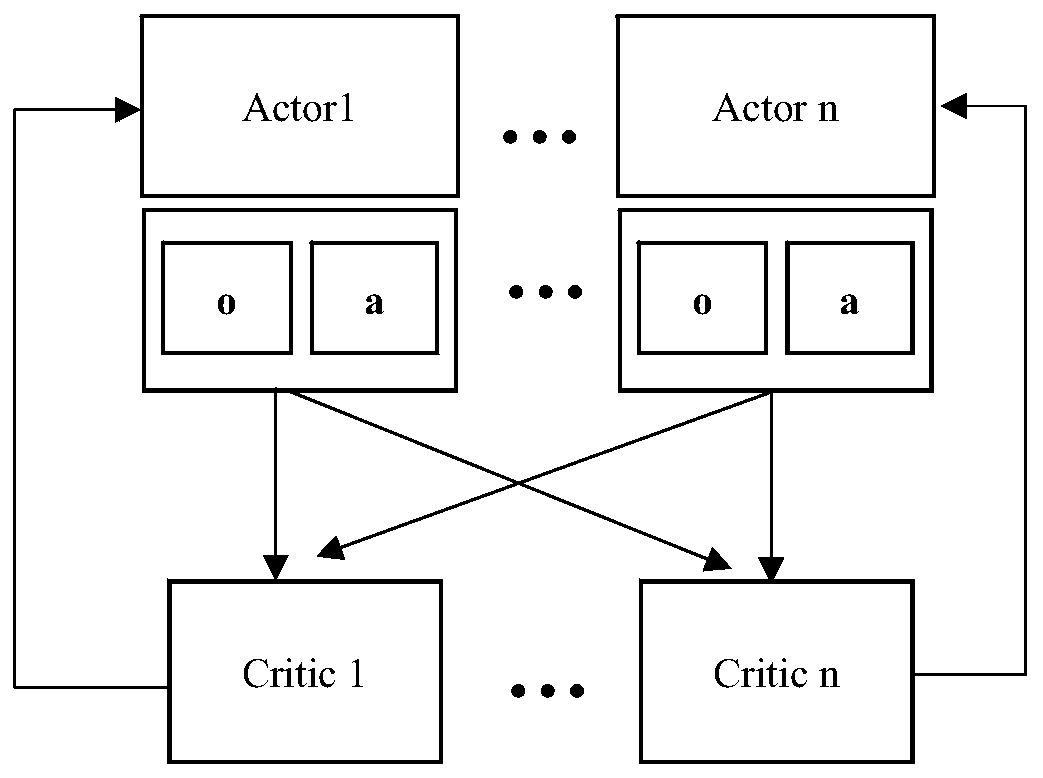
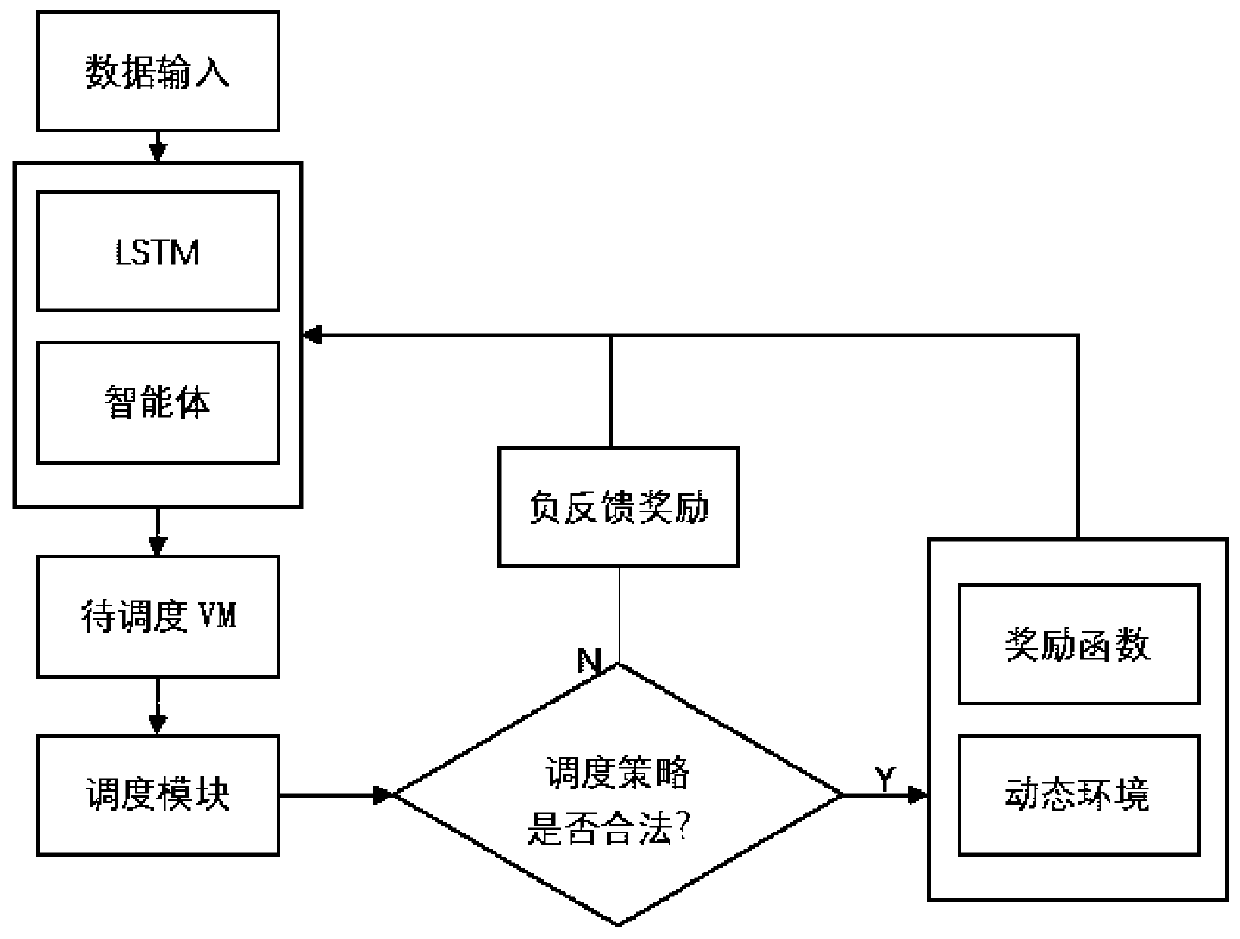
Multi-agent reinforcement learning scheduling method and system, and electronic device
ActiveCN109947567ALoad balancingEnhanced informationProgram initiation/switchingResource allocationData centerNetwork data
The invention relates to a multi-agent reinforcement learning scheduling method, a multi-agent reinforcement learning scheduling system and electronic equipment. The method comprises the following steps: step a, collecting server parameters of a network data center and virtual machine load information running on each server; b, establishing a virtual simulation environment by using the parametersof the server and the load information of the virtual machine, and establishing a deep reinforcement learning model of multiple agents; c, performing offline training and learning by utilizing the deep reinforcement learning model of the multiple agents and a simulation environment, and training an agent model for each server; and d, deploying the agent model to a real service node, and schedulingaccording to the load condition of each service node. The service running on the server is virtualized through the virtualization technology, load balancing is carried out in a virtual machine scheduling mode, resource distribution is more macroscopic, and a strategy that multiple agents generate cooperation in a complex dynamic environment can be achieved.
Owner:SHENZHEN INST OF ADVANCED TECH
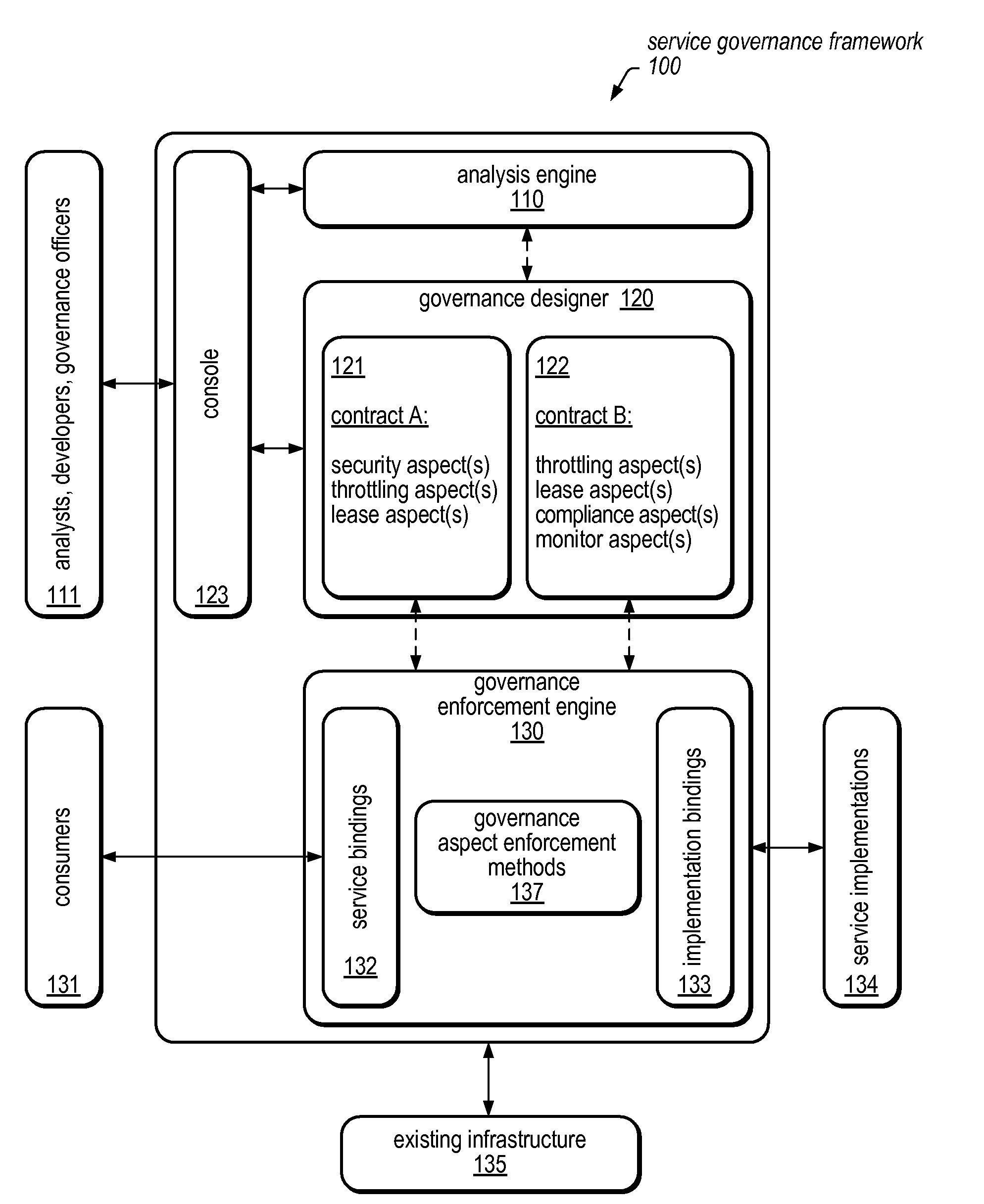
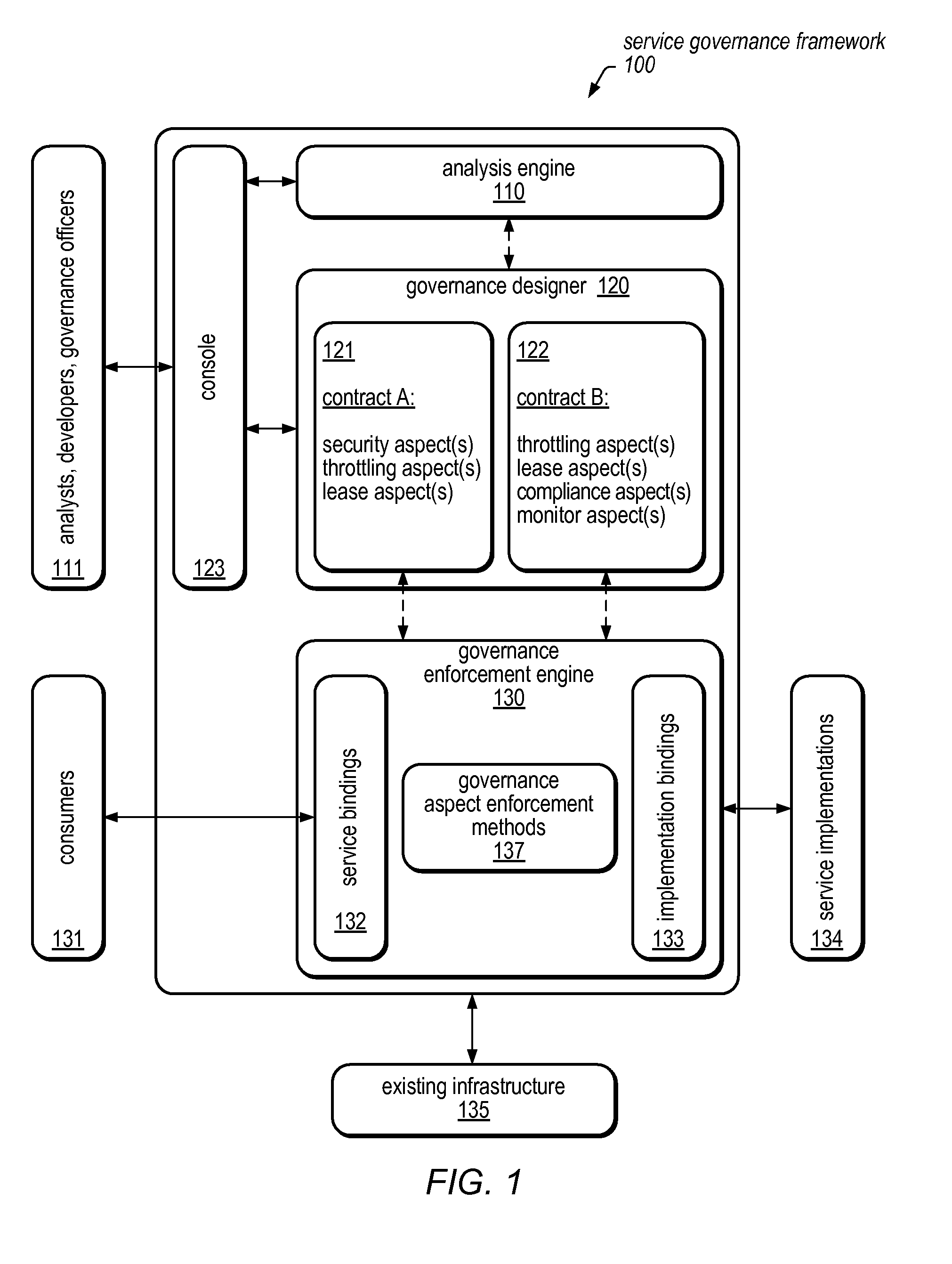
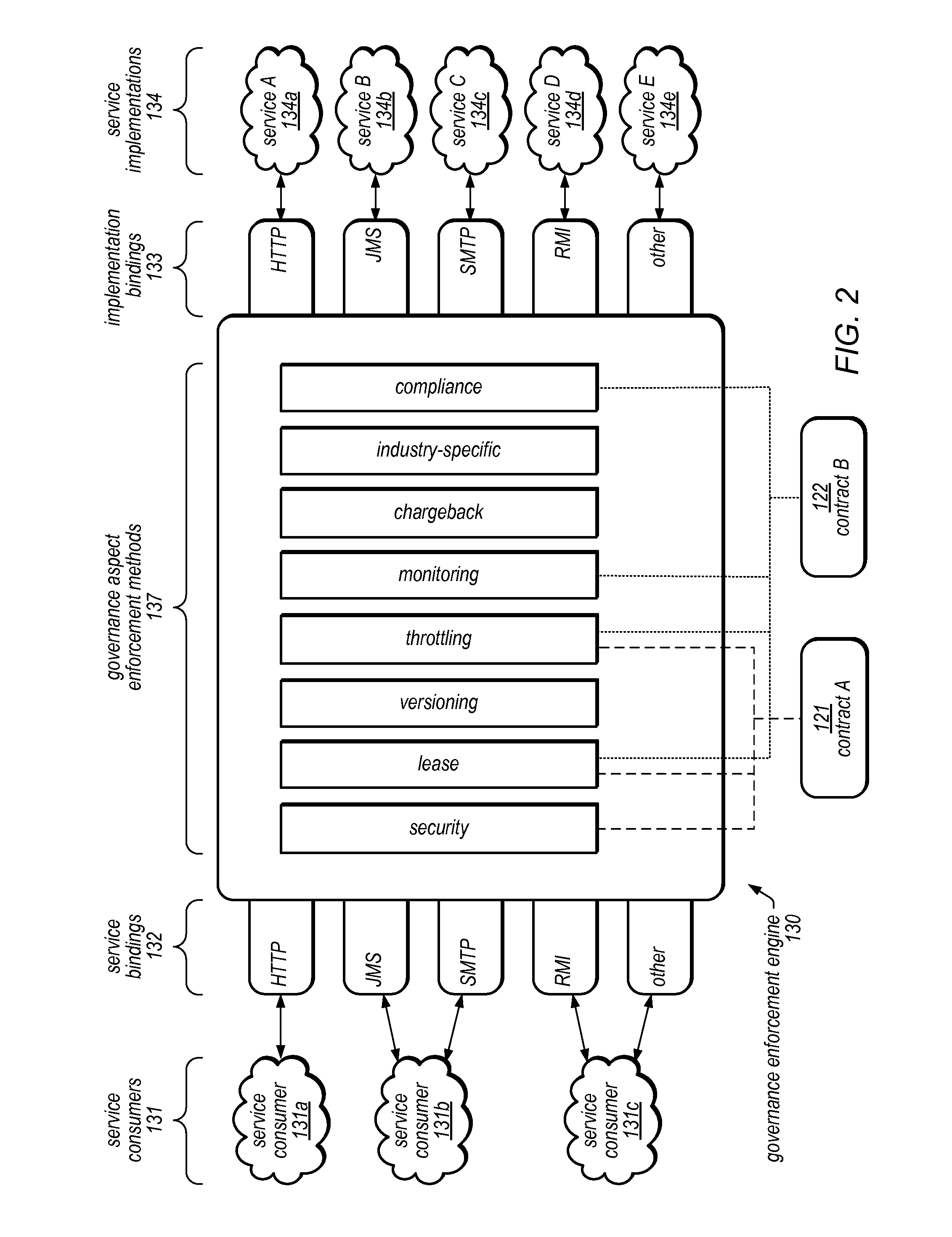
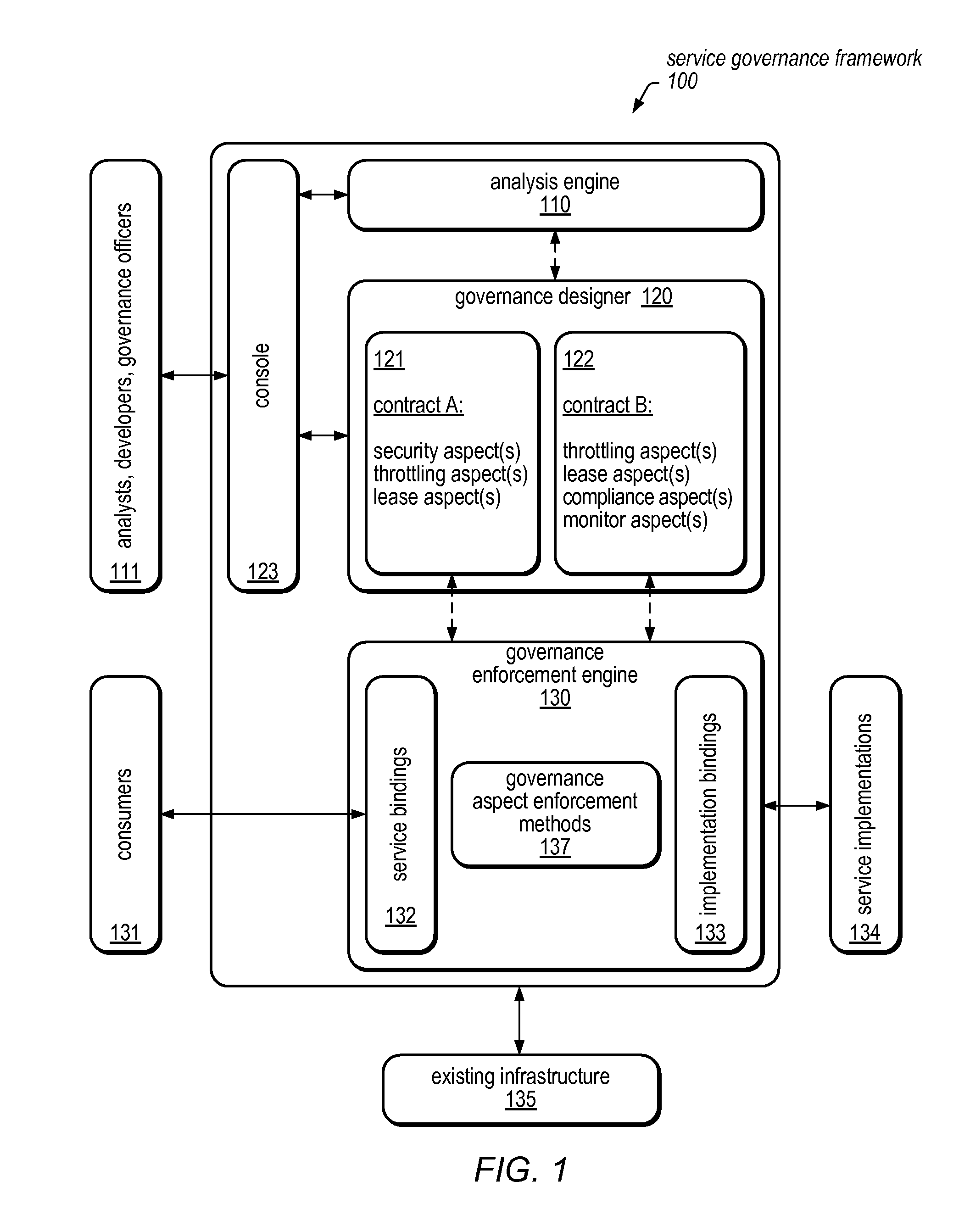
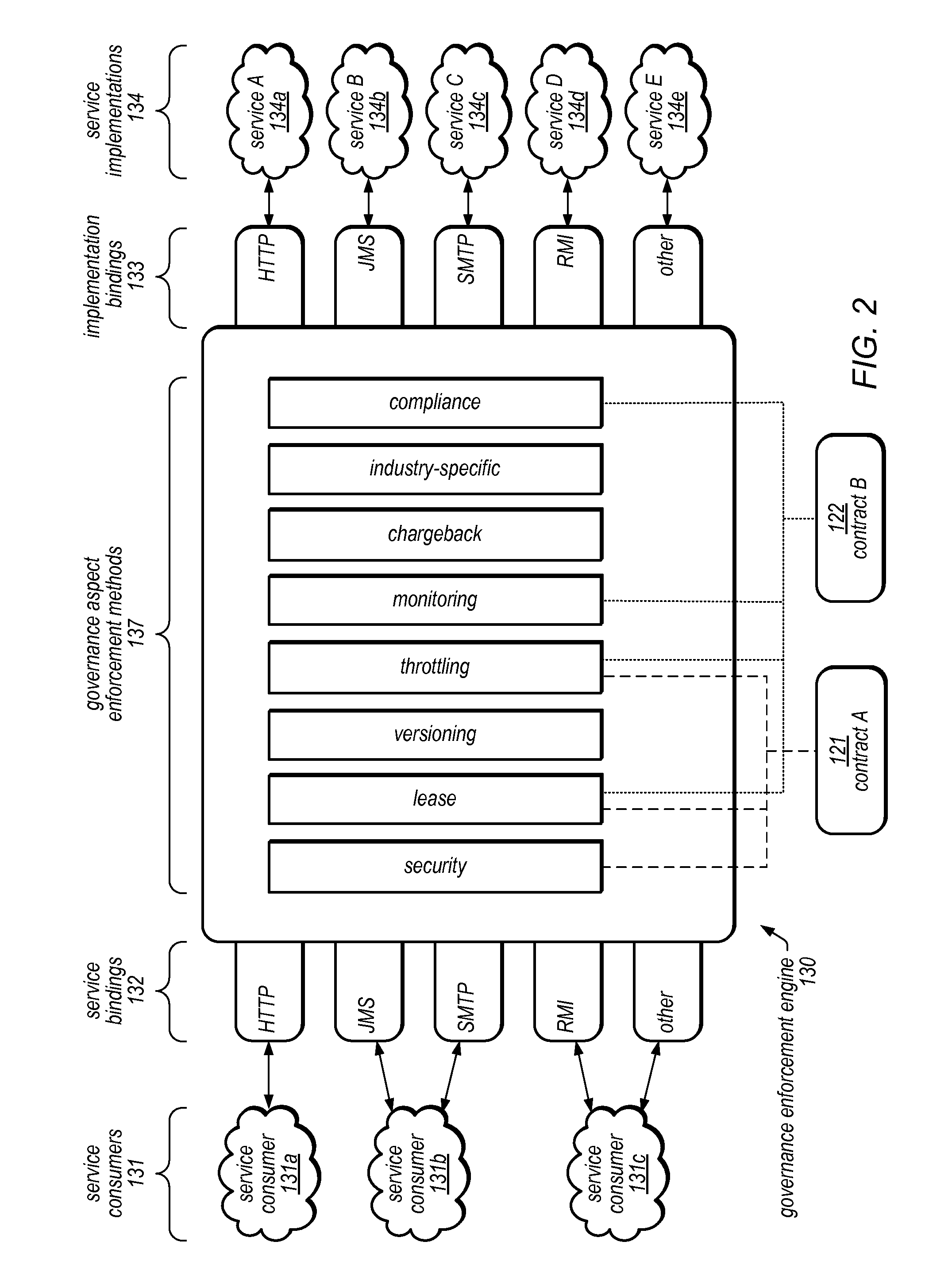
System and Method for Service Virtualization in a Service Governance Framework
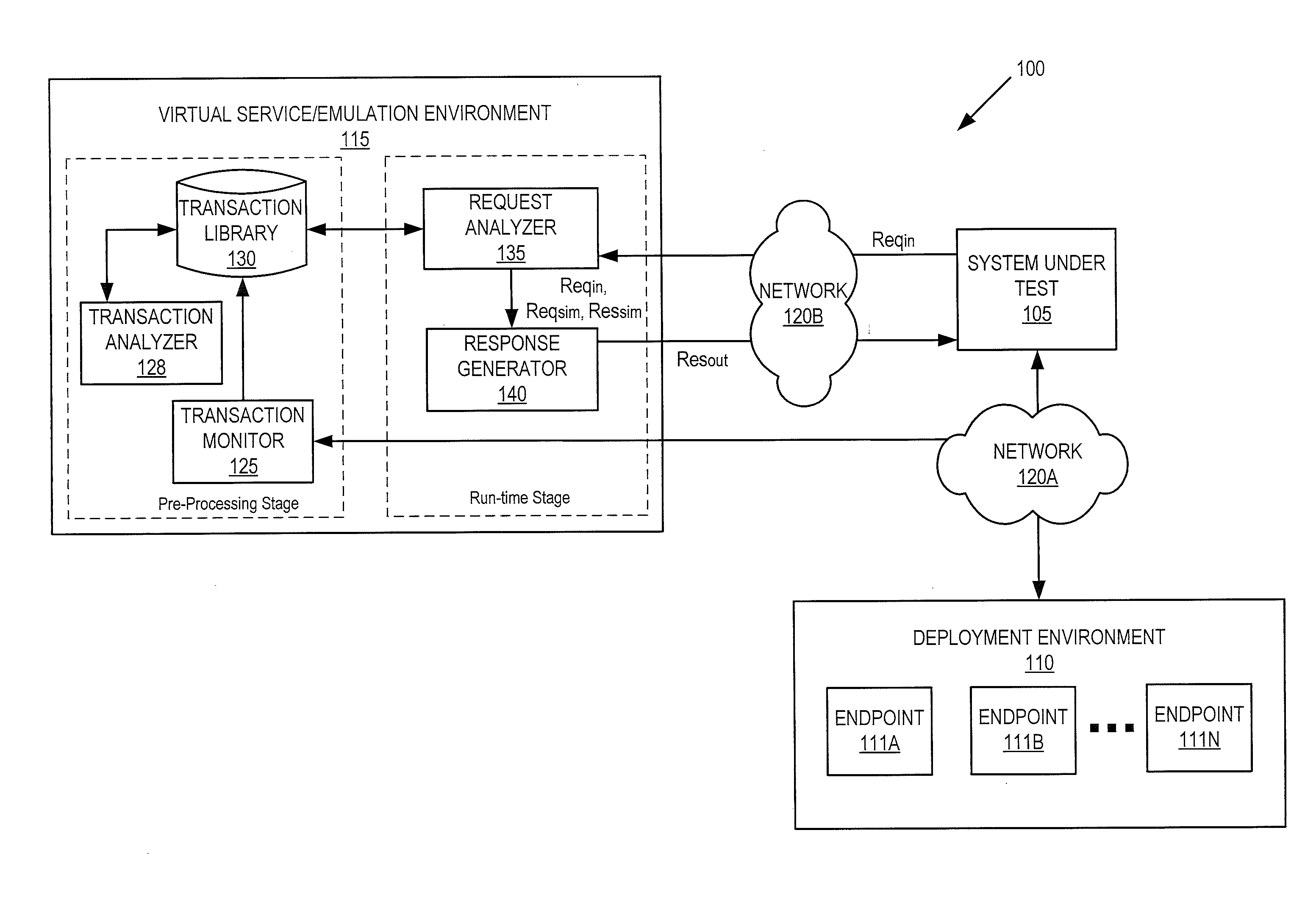
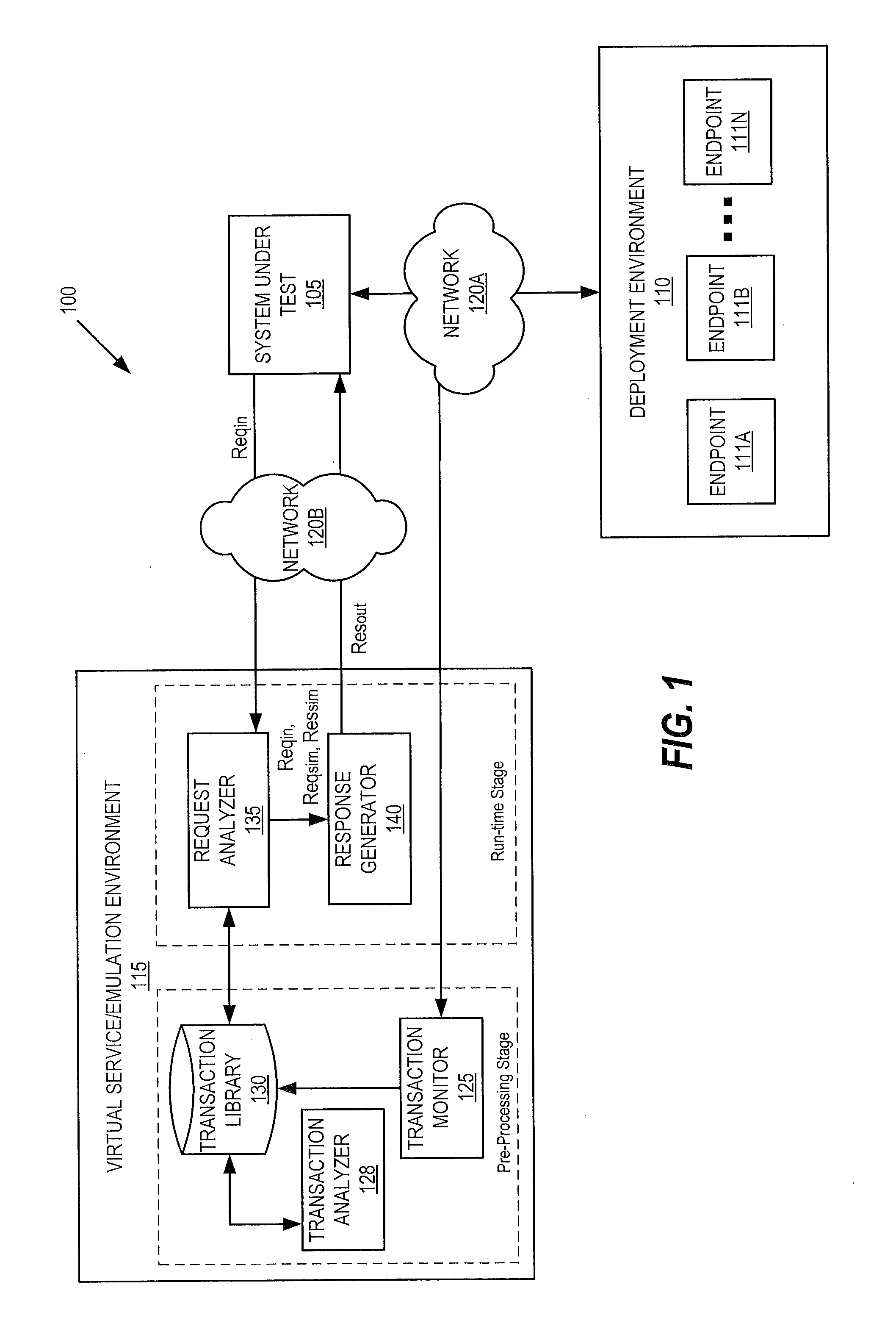
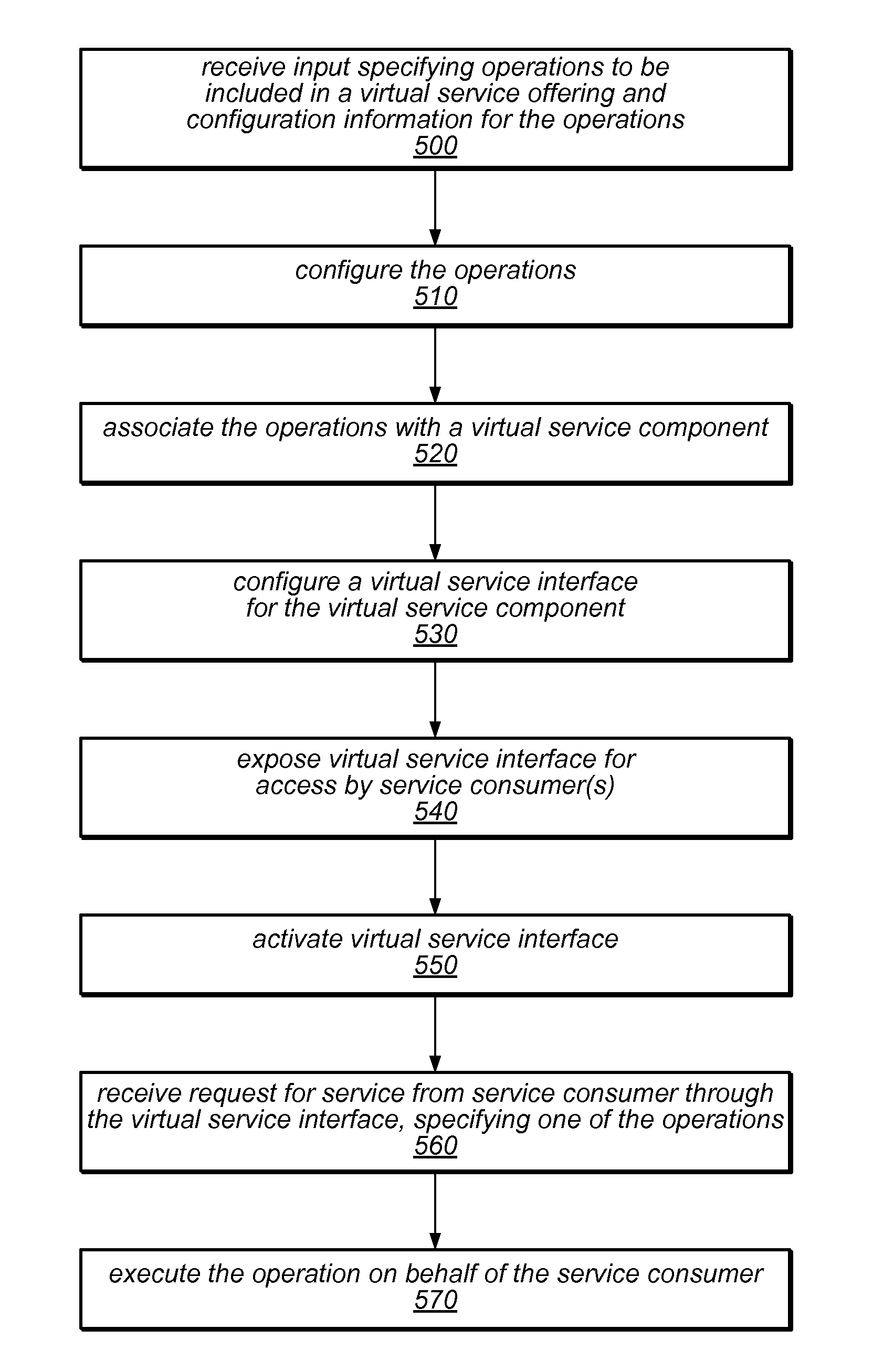
A service governance framework may provide a platform for development and hosting of virtual service offerings and generation of interfaces to operations thereof, dependent on configurable functional parameters and / or non-functional aspects associated therewith. Virtualization techniques may be applied at an endpoint level, binding level, message level, operation level, and / or service level at design time, and supported with corresponding changes at runtime. Users having various roles may access the framework to specify operations of services provided by computing service sources to include in a virtual service offering, specify configuration parameter values associated with them, and / or specify a contract of non-functional aspect clauses for the virtual service offering. The framework may produce the interface by modifying an interface provided by the computing service sources (e.g., a WSDL). The framework may include aspect enforcement methods and an underlying common information model, and may support versioning and life cycles of service offerings and / or components.
Owner:SUN MICROSYSTEMS INC
Undifferentiated service domains
ActiveUS20140330948A1Easy to operateMinimize time to bootDigital computer detailsProgram controlVirtualizationService domain
Guest domains (virtual machines) may execute at a virtualization server. During execution, the guest domains may request various services to facilitate their operation. The virtualization server may disaggregate the services requested by the guest domains among various service domains. A service domain may be configured to provide one the services. The virtualization server may also maintain a pool of partially initialized service domains. When a guest domain requests a particular service, one of the partially initialized service domains may be selected from the pool, and the partially initialized service domain may complete initialization to become an initialized service domain. The initialized service domain may thus be configured to provide the service requested by a guest domain. The virtualization server may periodically replenish the pool of partially initialized service domains to ensure that a partially initialized service domain is available upon demand from one of the guest domains.
Owner:CITRIX SYST INC
Online backup method based on data block redundancy and virtualized storage
InactiveCN1633086AImprove data securityImprove reliabilityFault responseData switching networksVirtualizationCombined use
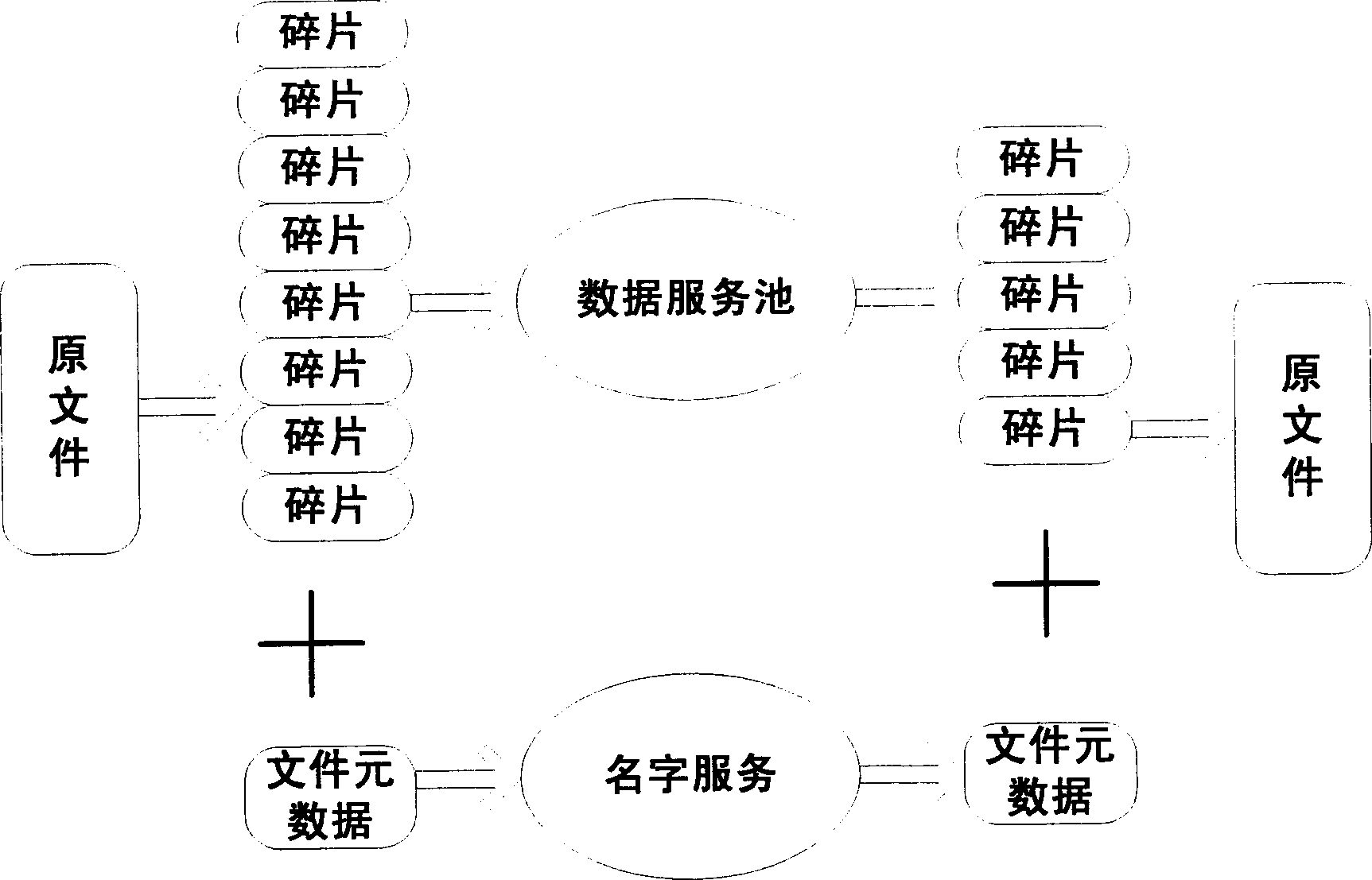
This invention provides an on-line backup method based on data unblock redundancy and virtual storage, which divides a message to fragments to realize data unblock redundancy and virtual data service to get high data safety, reliability to extend the system with cheap hardware.
Owner:PEKING UNIV
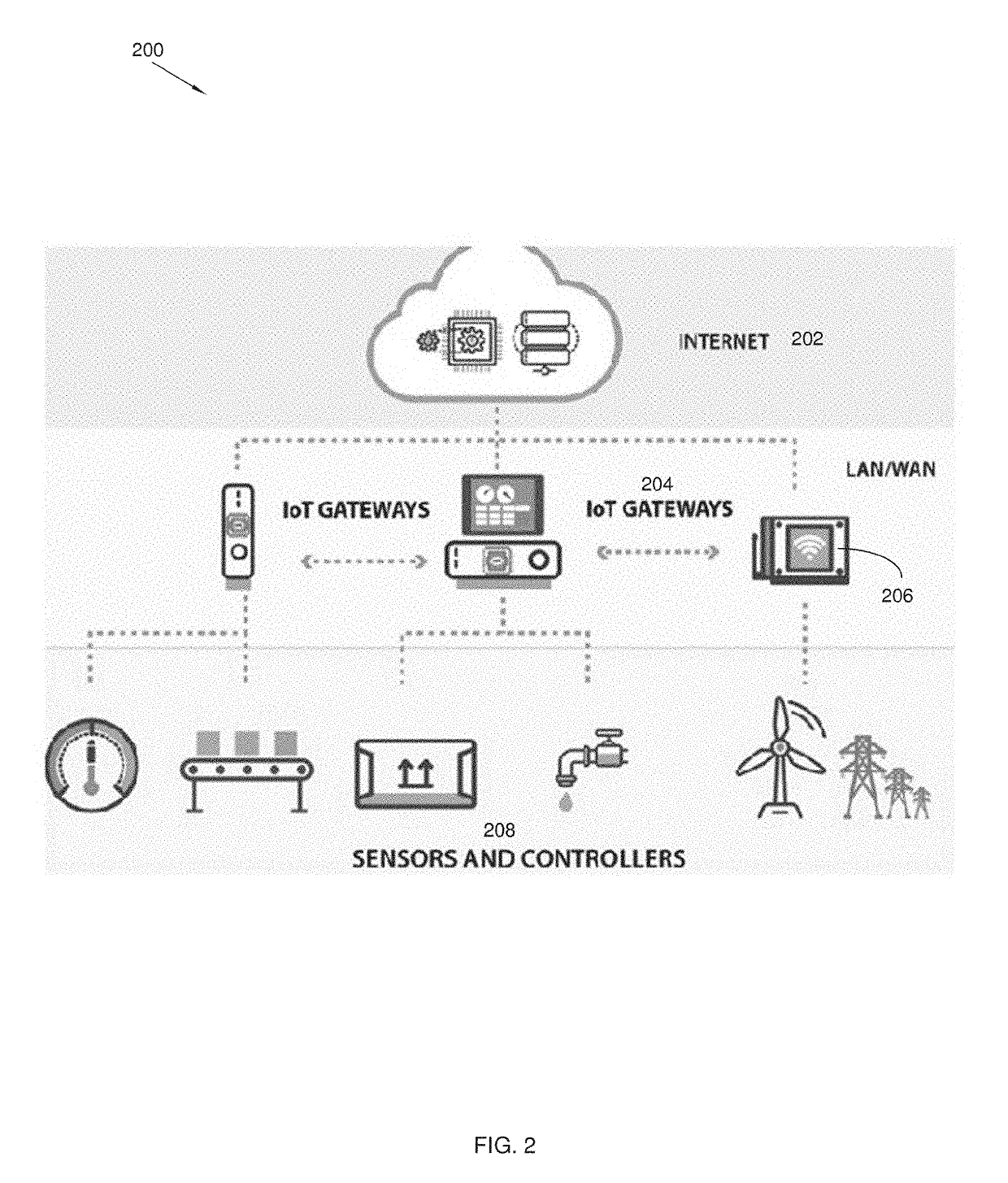
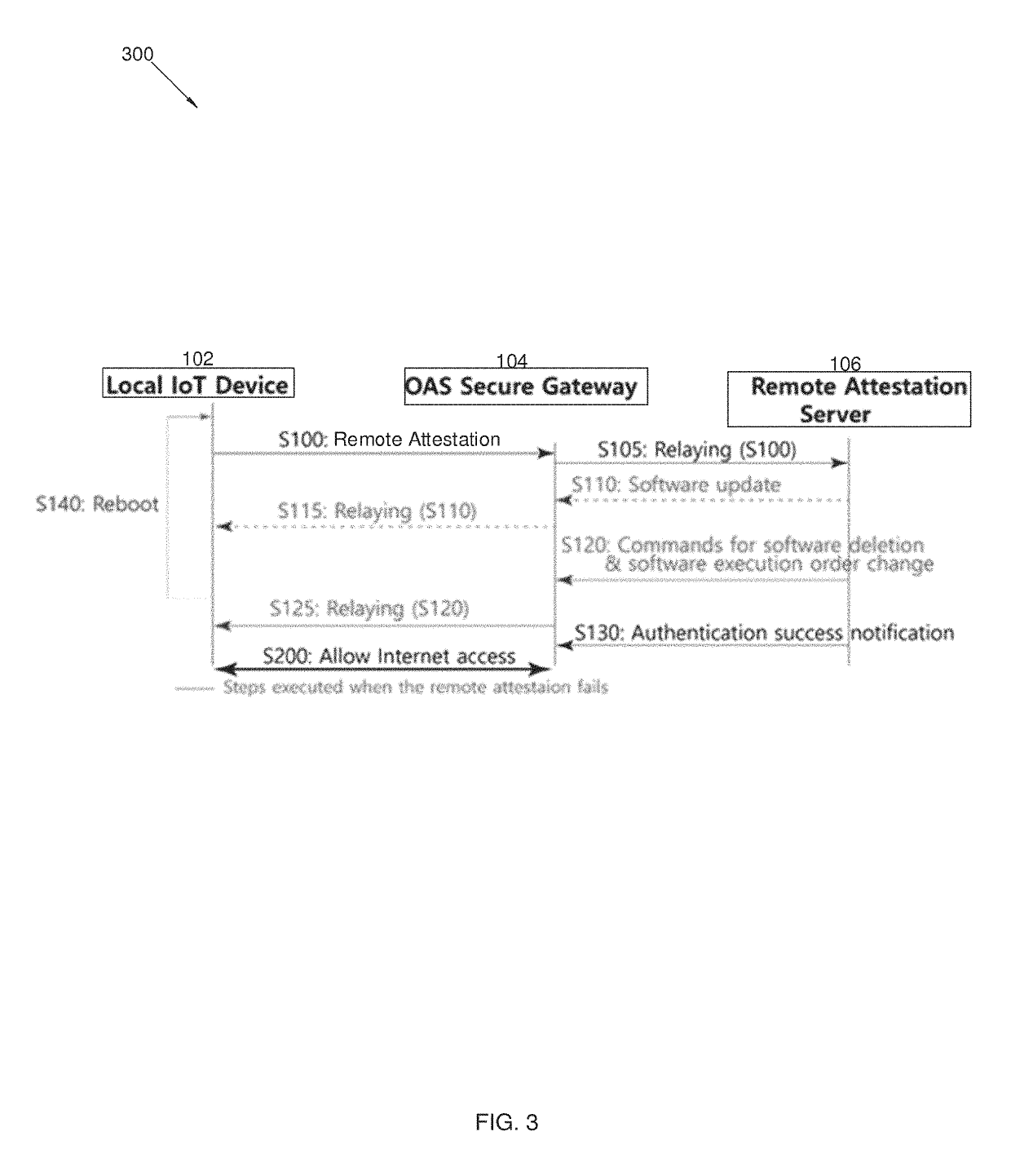
Security system and method for internet of things
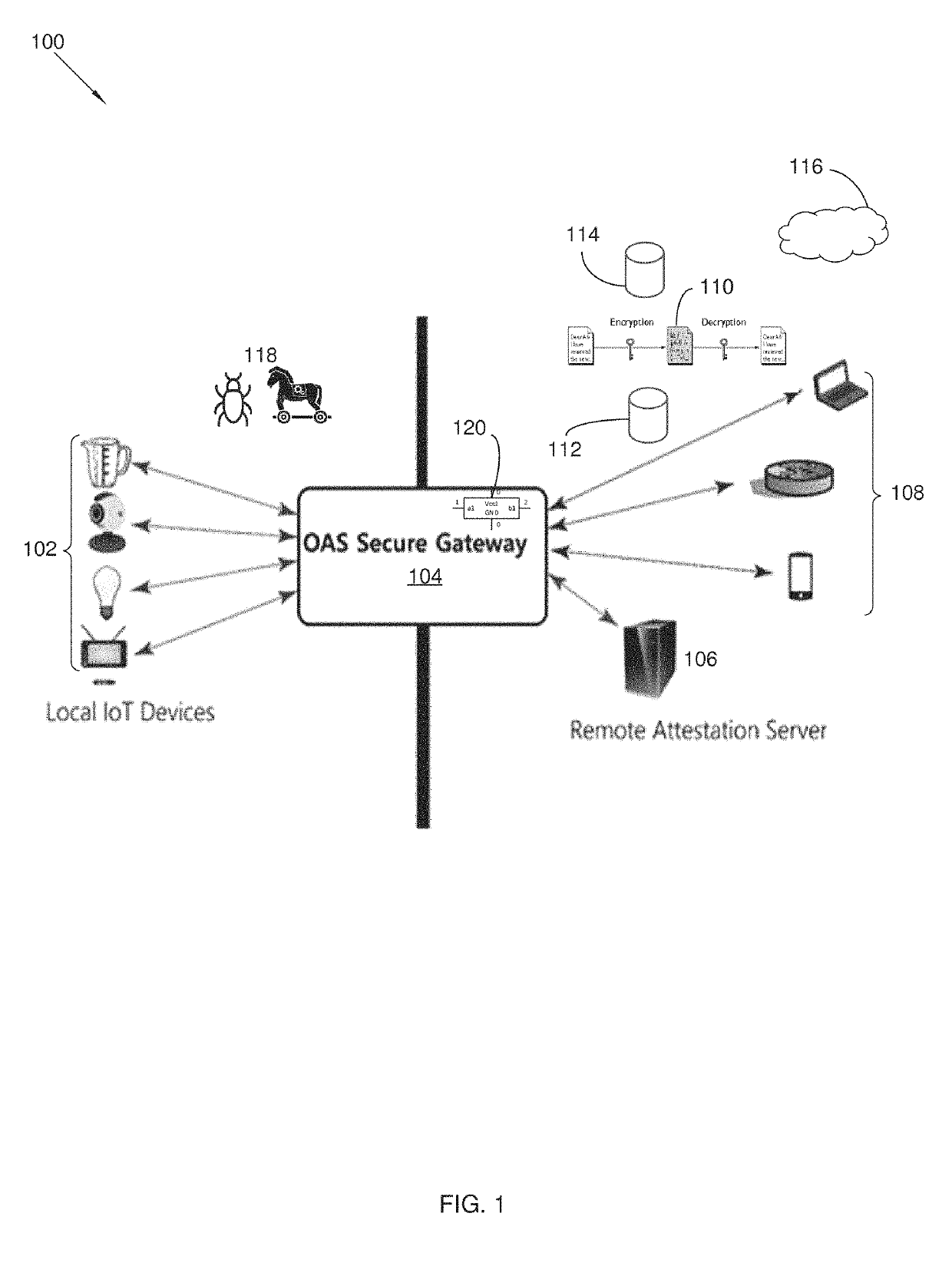
ActiveUS10346614B1Protect connectionQuickly detect potential problemEncryption apparatus with shift registers/memoriesPlatform integrity maintainancePacket communicationTraffic capacity
A security system and method for the Internet of Things integrates a multitude of devices and protocols. The security system includes an OAS security gateway that protects the local IoT devices from external network-based attacks through remote attestation requests to a remote attestation server. The remote attestation message is used by the remote attestation server to analyze the software execution history of the local IoT device, so as to detect malware or insecure software. A cryptographic chip operatively integrates in the security gateway. The security system also performs data packet encryption and decryption of communications between the local IoT devices and remote user devices with an encryption engine. A service virtualization engine converts incompatible communication protocols between the IoT device and the remote user device. A network traffic sanitization engine filters data packet communications between the local IoT device and the remote attestation server.
Owner:LEE SANGSOO
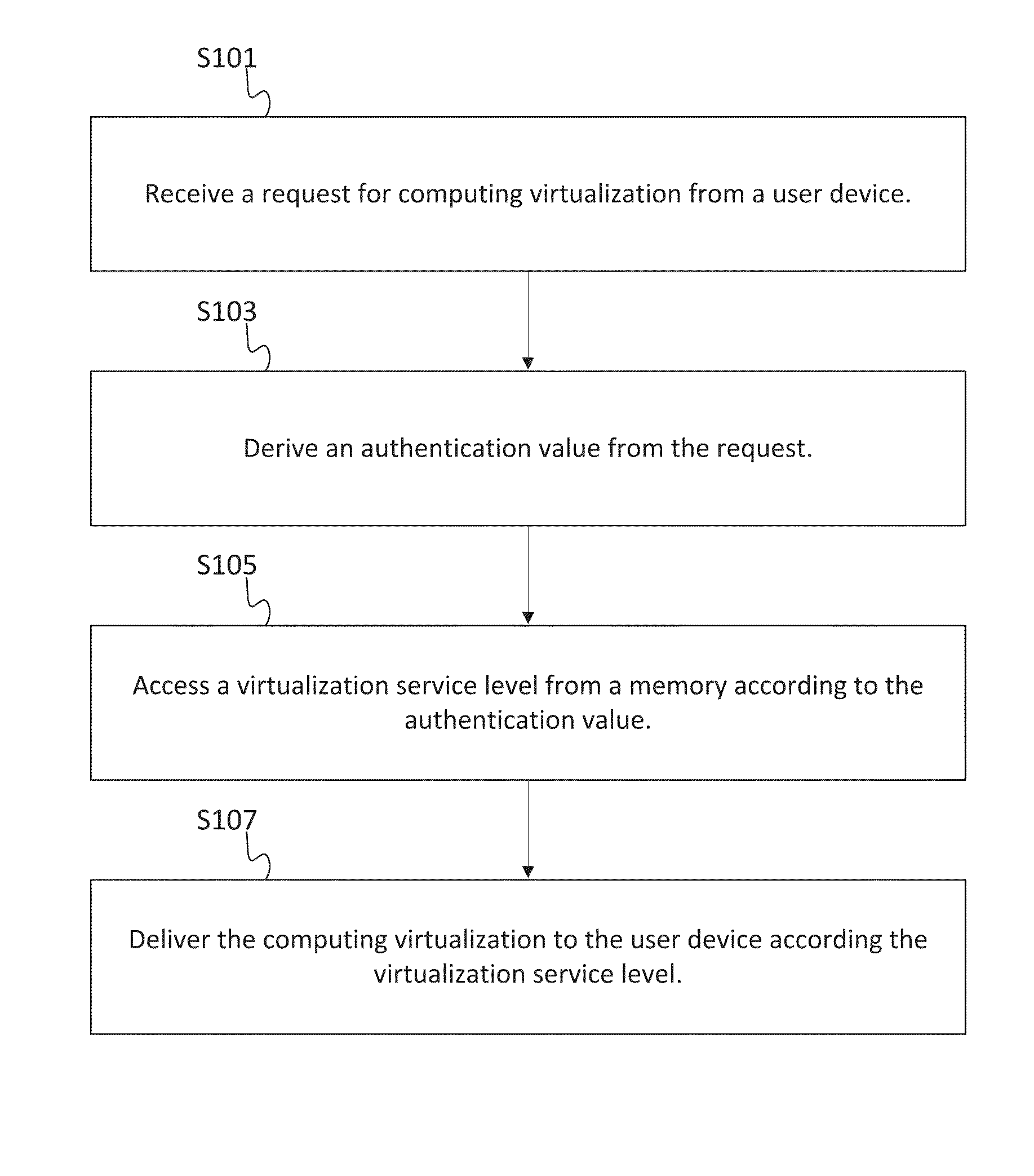
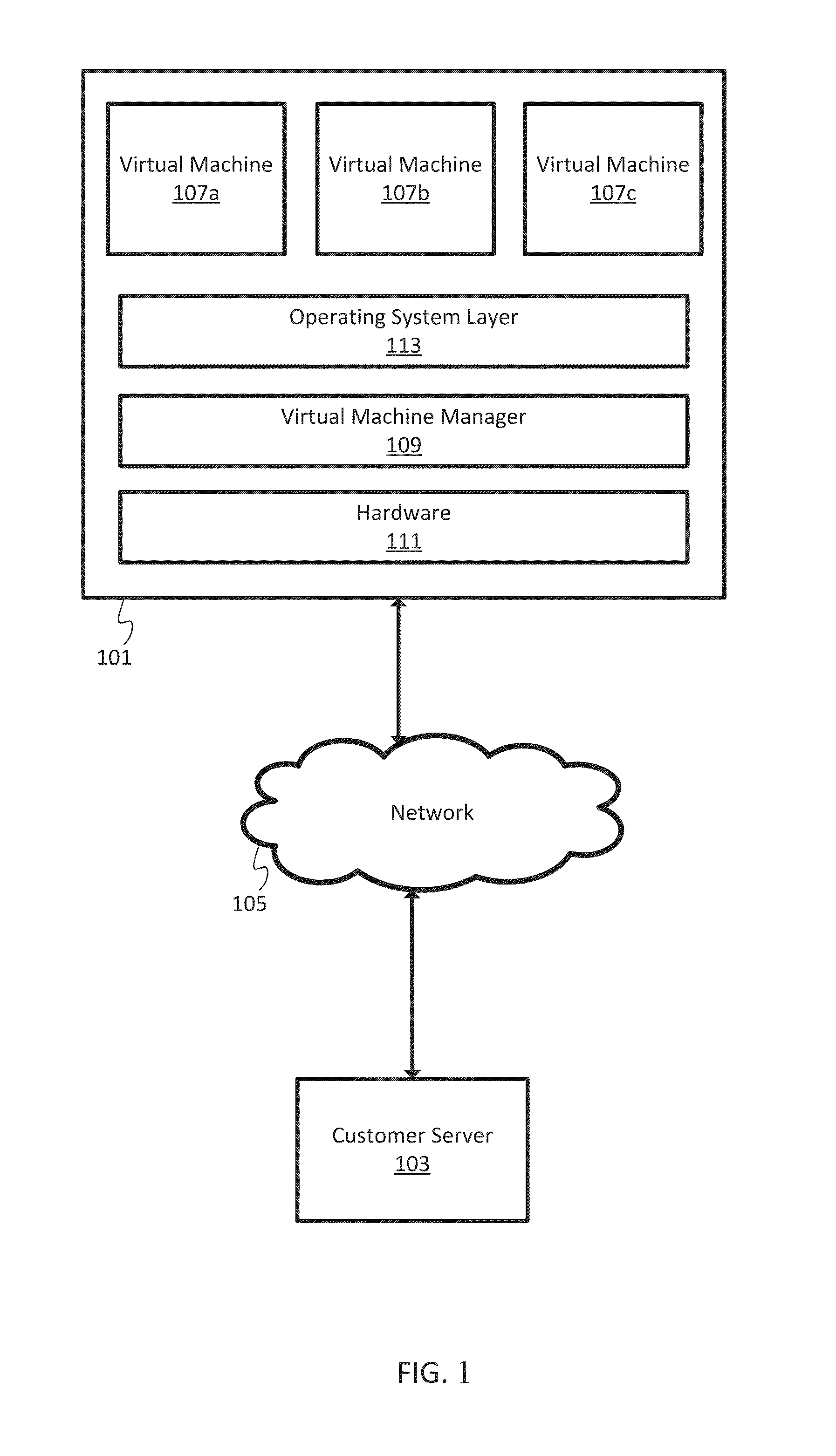
Differentiated service levels in virtualized computing
InactiveUS20140173591A1Software simulation/interpretation/emulationMemory systemsDifferentiated servicesVirtualization
In one implementation, a host provides virtualized computing to one or more customer networks. The virtualized computing may include hardware virtualization quantified in the resources of the virtual machines, services virtualization quantified in the quantity or types of services performed on host, or processing virtualization quantified by process occurrences. When the host receives a request for computing virtualization from a user device, the host derives an authentication value and accesses a virtualization service level from a memory. The host is configured to deliver the computing virtualization to the user device according the virtualization service level.
Owner:CISCO TECH INC
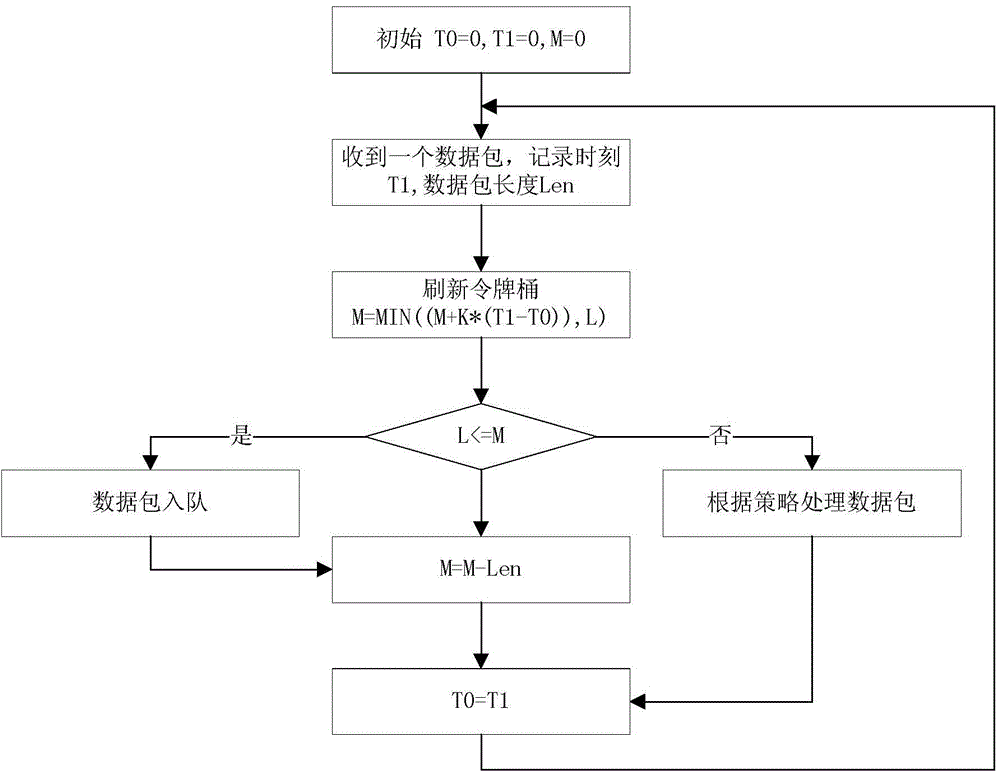
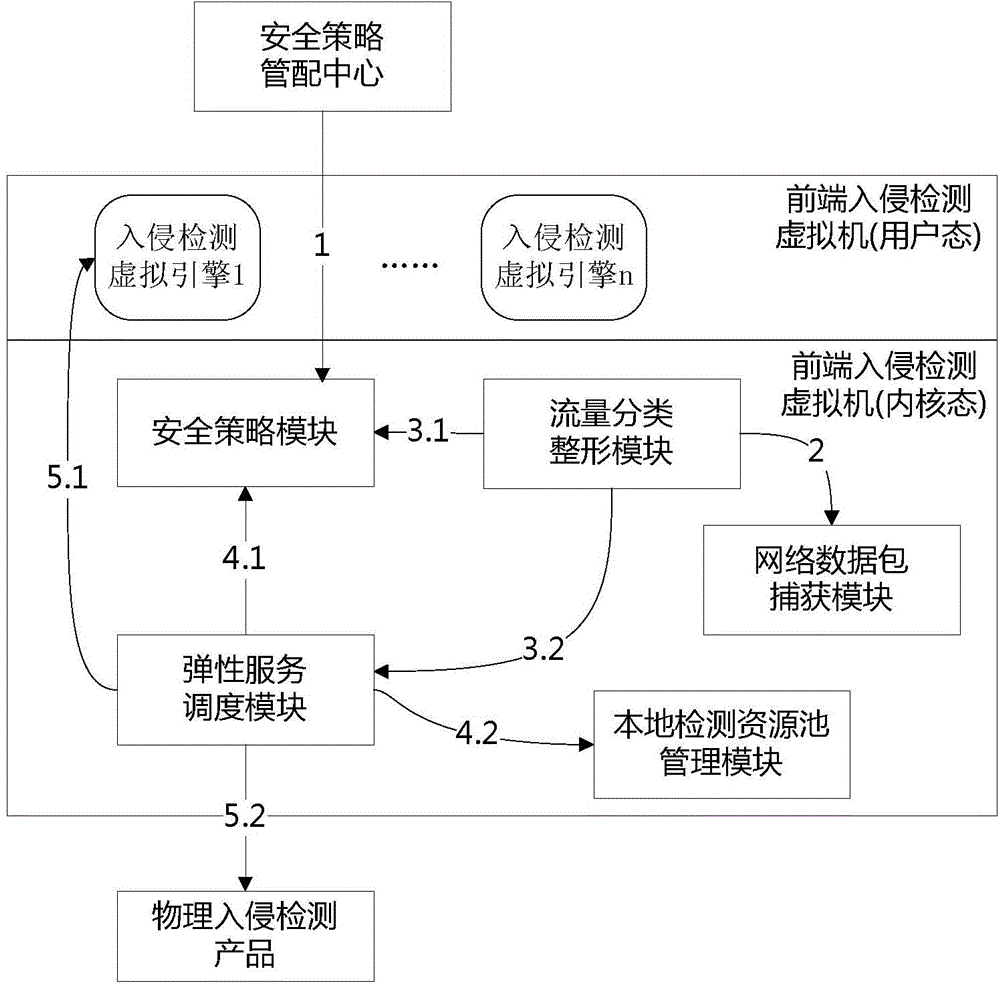
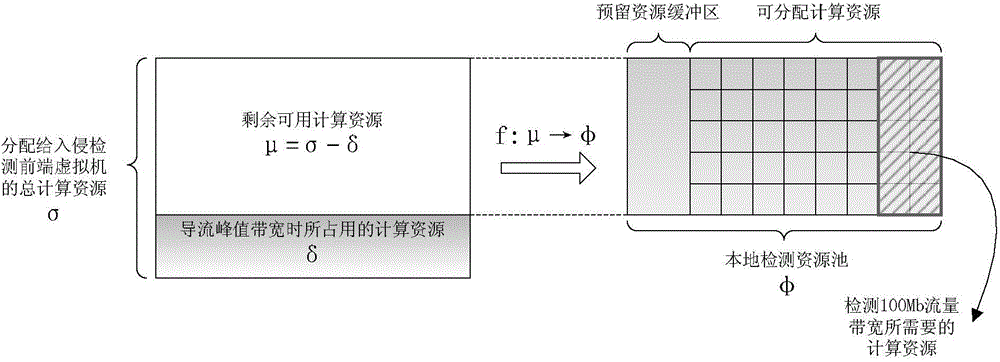
On-demand-service virtualization network intrusion detection method and device
InactiveCN104580120ASolve security issuesIncrease flexibilityTransmissionResource poolVirtualization
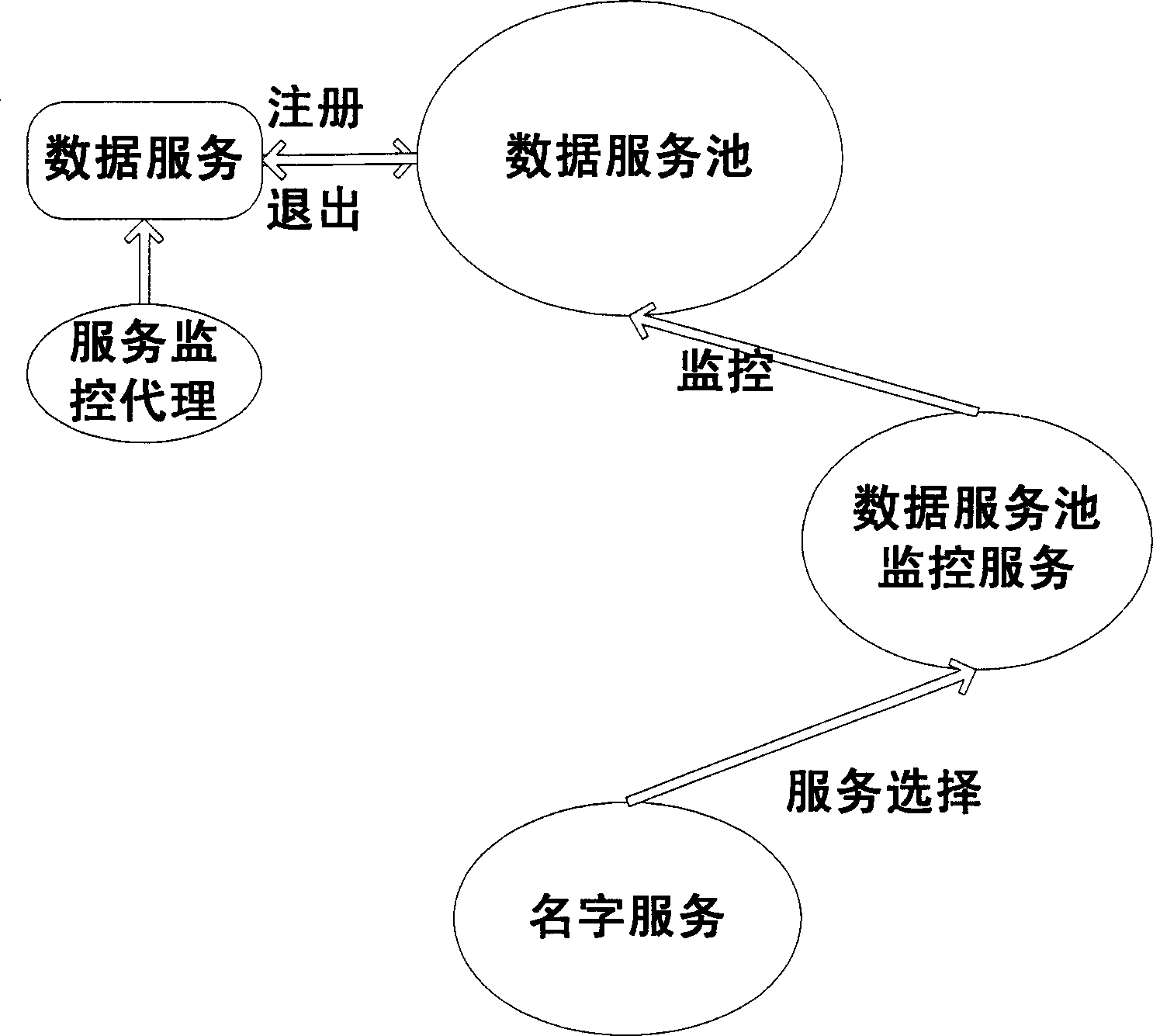
The invention discloses an on-demand-service virtualization network intrusion detection method and device, and relates to the technical field of information security. The virtualization network intrusion detection device comprises an elastic service scheduling module, and a local detection resource pool management module, wherein the elastic service scheduling module is used for evaluating whether the residual resource in a local detection resource pool can provide a local detection service or not, sending a local detection resource regulation command to the local detection resource pool management module if the residual resource can provide the local detection service, and exporting flow to be detected to an external hardware network intrusion detection product if the residual resource cannot provide the local detection service; the local detection resource pool management module allocates corresponding resources to the local detection resource from the residual resource of the local detection resource pool when receiving the local detection resource regulation command. The invention further discloses an on-demand-service virtualization network intrusion detection method. According to the technical scheme provided by the invention, the safety protection problem of a server virtualization application scene under a virtualization network environment is effectively solved.
Owner:BEIJING VENUS INFORMATION TECH +1
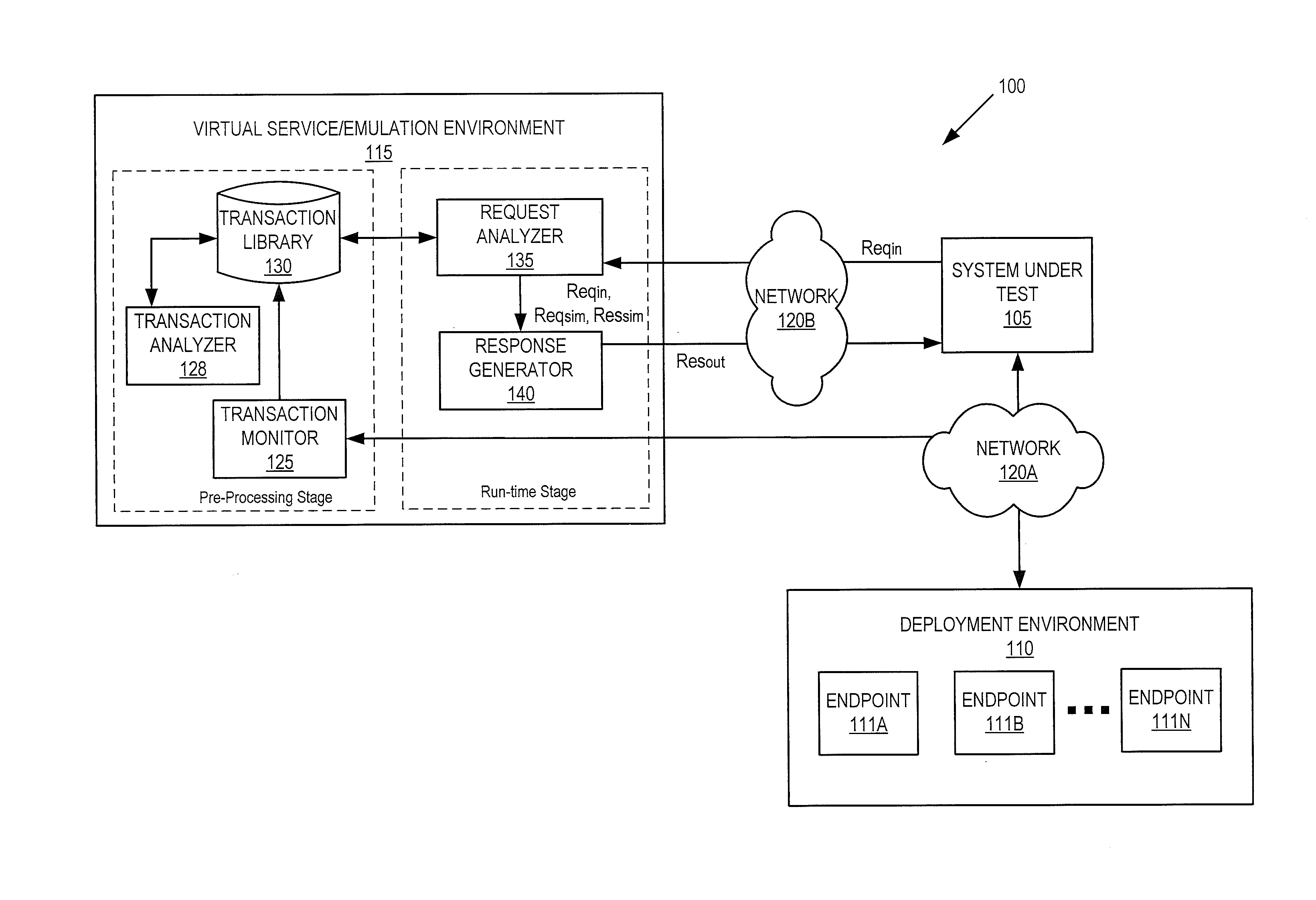
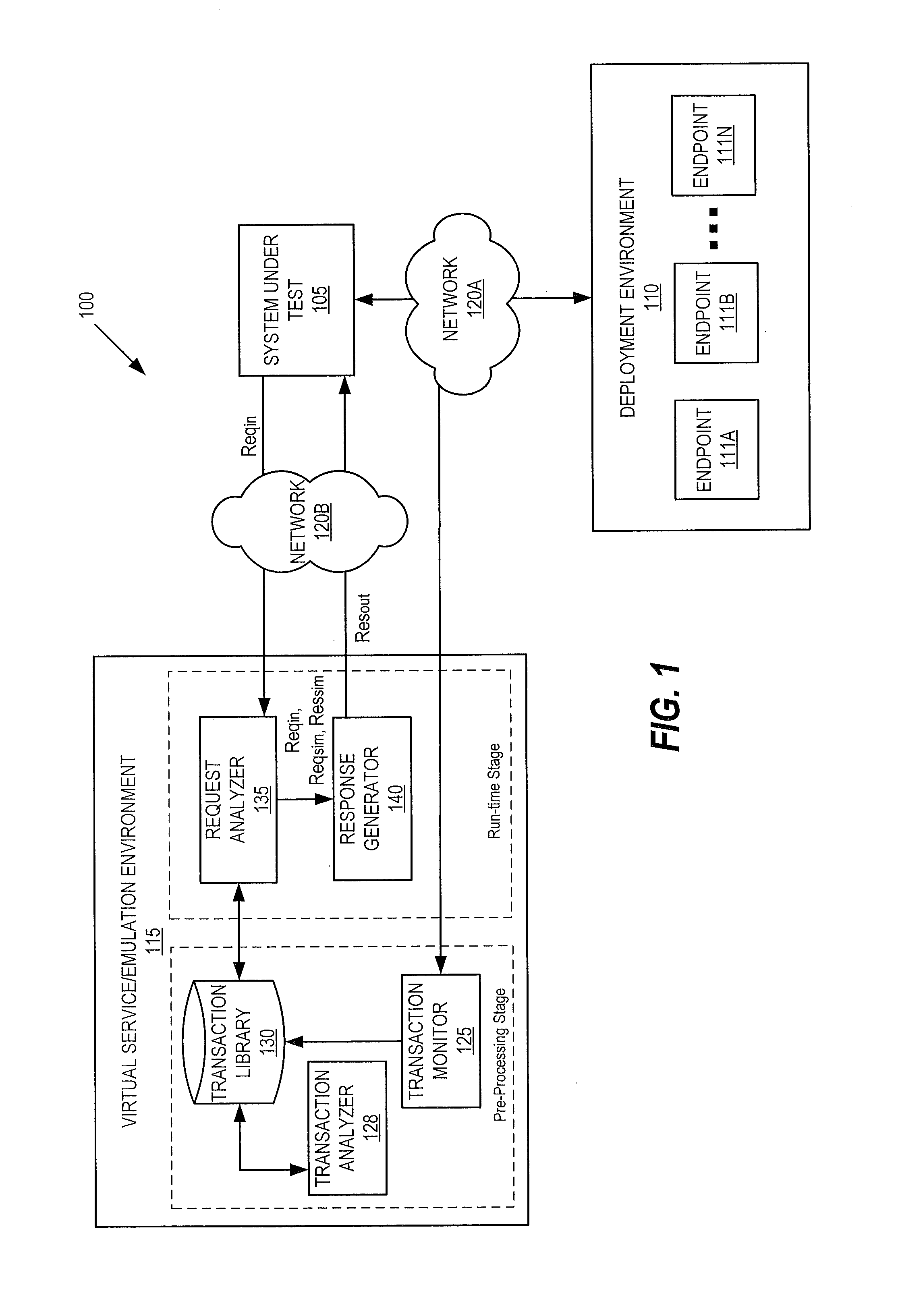
Message matching for opaque service virtualization
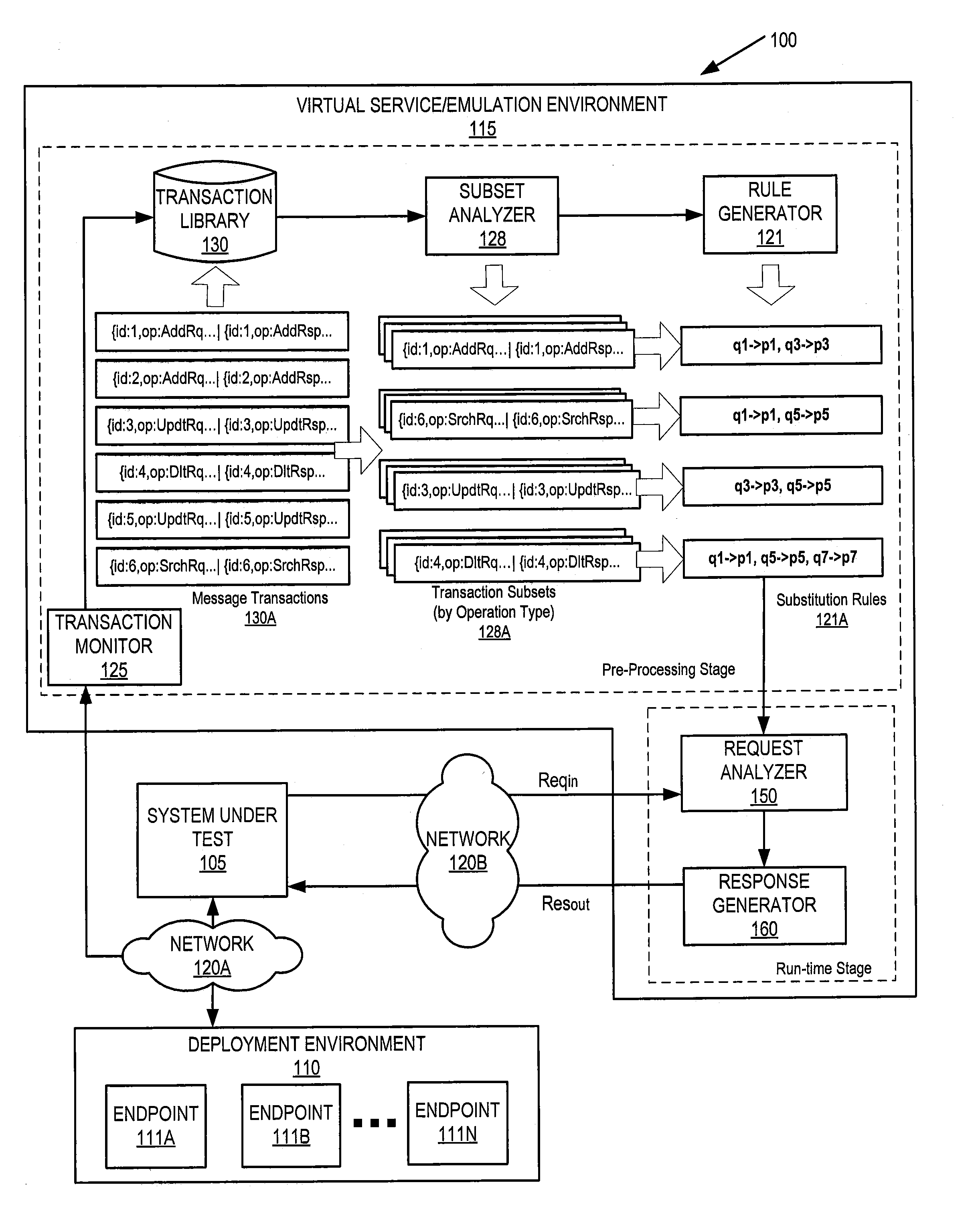
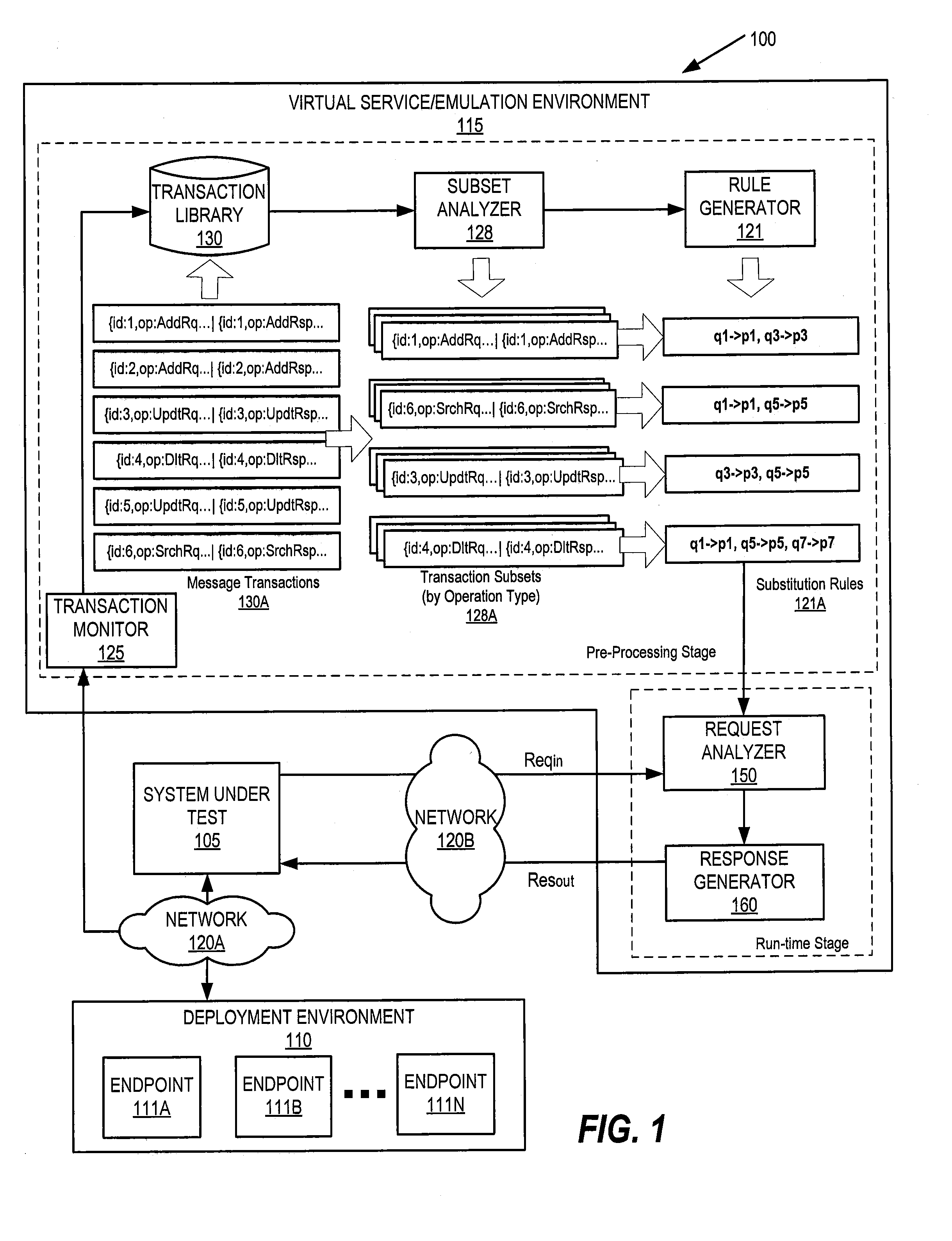
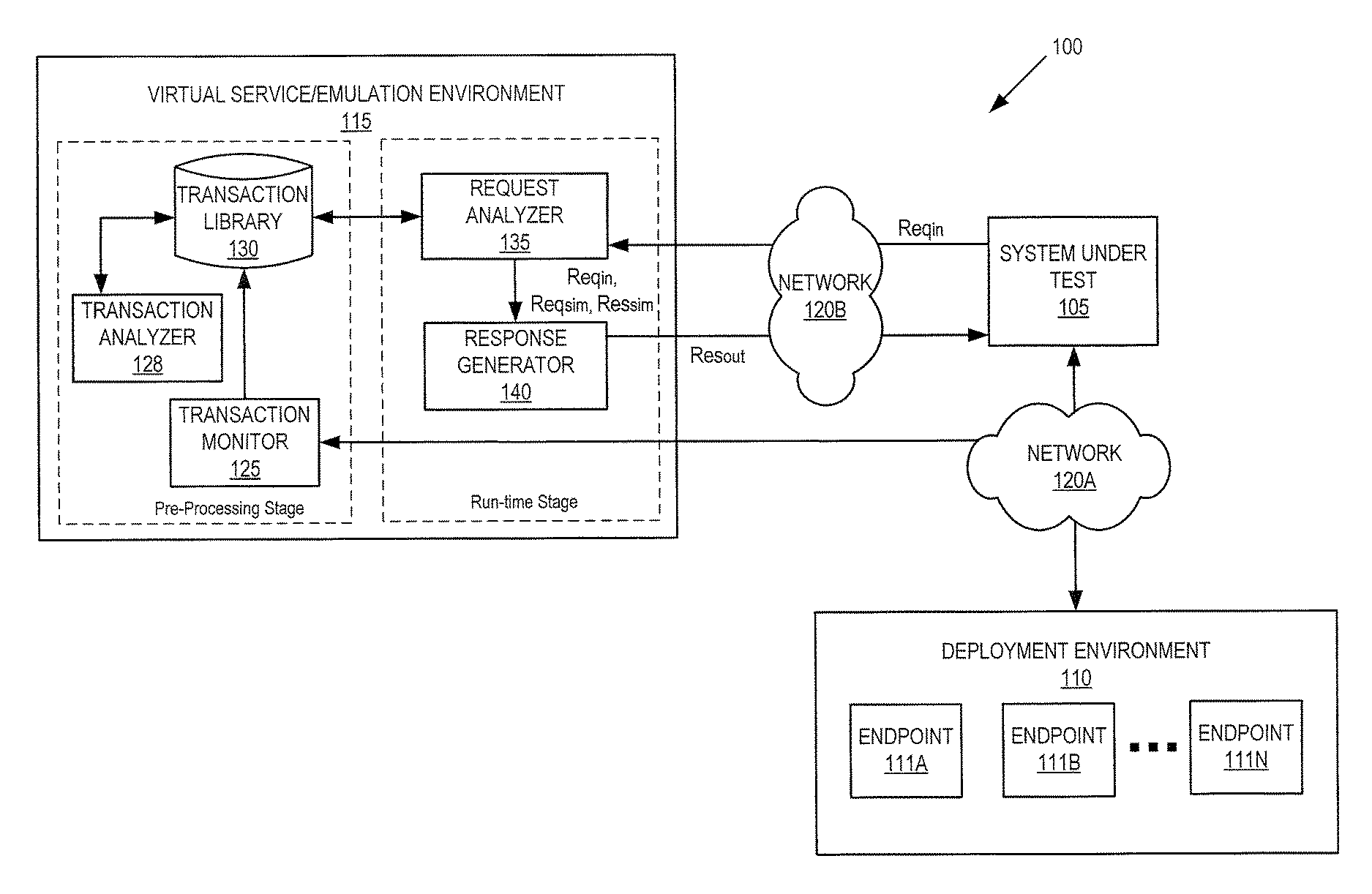
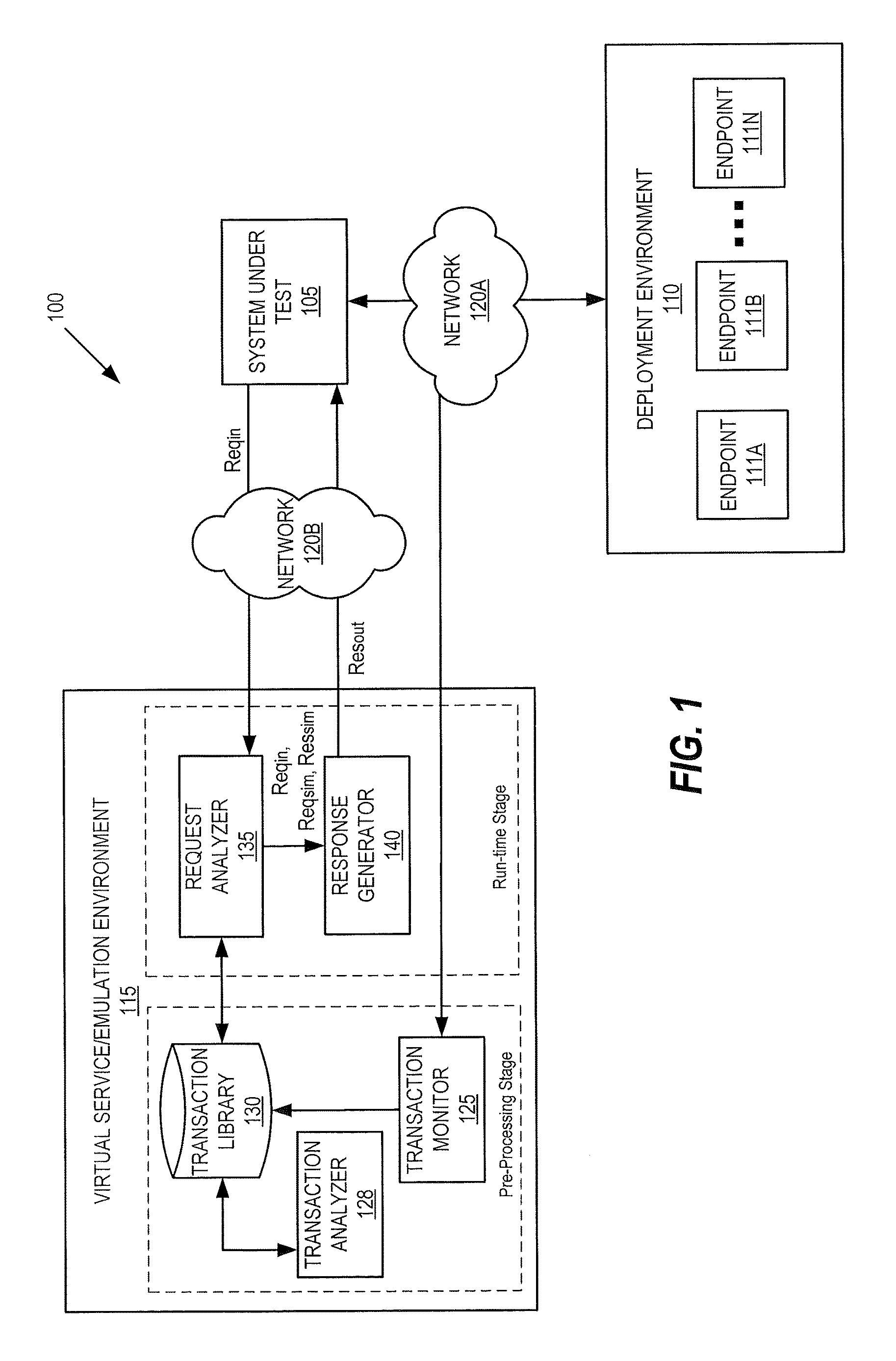
ActiveUS20150268975A1Error detection/correctionSoftware simulation/interpretation/emulationVirtualizationSystem under test
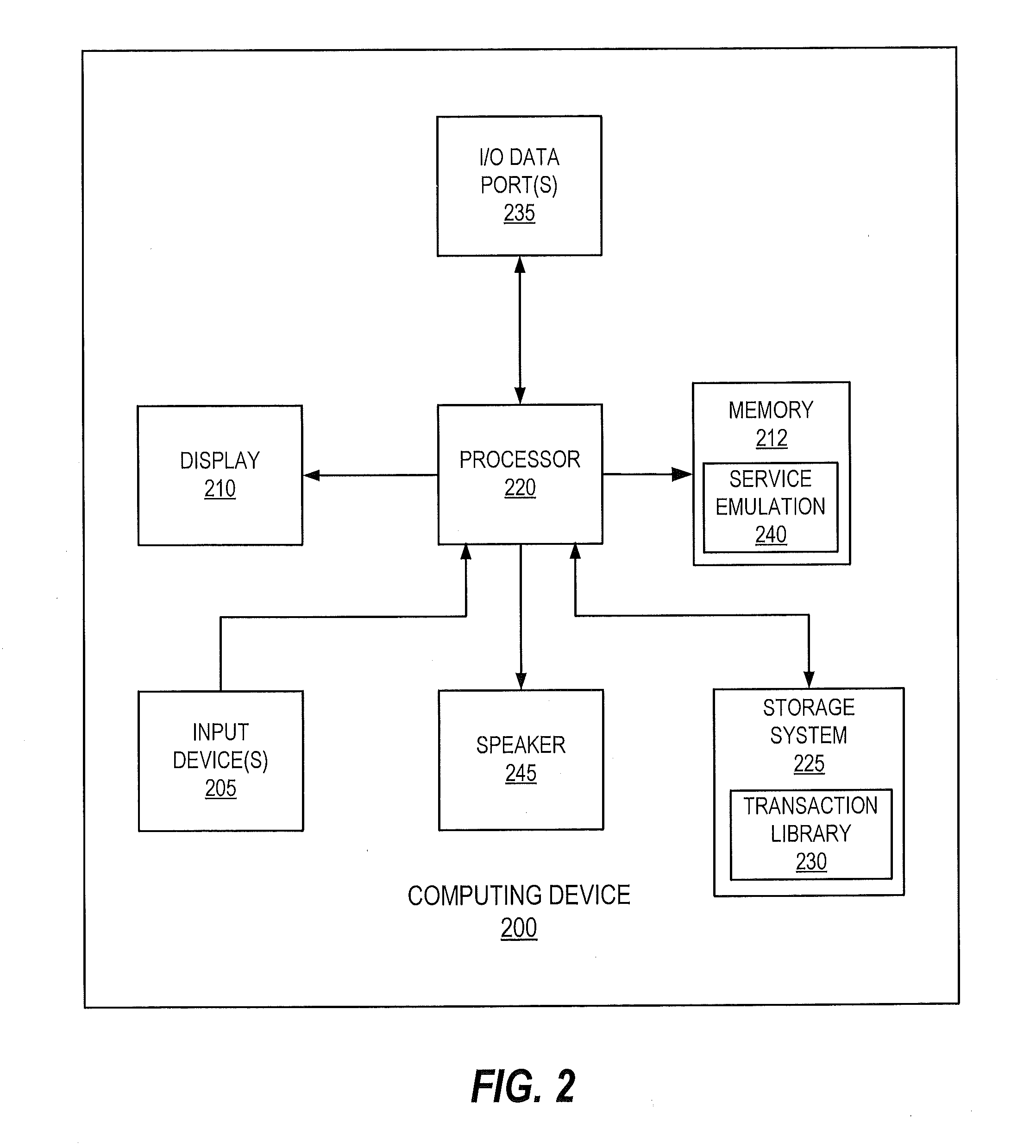
In a service emulation method, a transaction library storing a plurality of messages communicated between a system under test and a target system upon which the system under test depends is accessed responsive to receiving a request from the system under test. One of the messages stored in the transaction library is identified as corresponding to the received request based on a distance measure therebetween, and a response to the received request is generated using the one of the messages that was identified. Related systems and computer program products are also discussed.
Owner:CA TECH INC
System and method for service virtualization in a service governance framework
ActiveUS8886571B2Ticket-issuing apparatusMultiprogramming arrangementsInformation modelSupport services
A service governance framework may provide a platform for development and hosting of virtual service offerings and generation of interfaces to operations thereof, dependent on configurable functional parameters and / or non-functional aspects associated therewith. Virtualization techniques may be applied at an endpoint level, binding level, message level, operation level, and / or service level at design time, and supported with corresponding changes at runtime. Users having various roles may access the framework to specify operations of services provided by computing service sources to include in a virtual service offering, specify configuration parameter values associated with them, and / or specify a contract of non-functional aspect clauses for the virtual service offering. The framework may produce the interface by modifying an interface provided by the computing service sources (e.g., a WSDL). The framework may include aspect enforcement methods and an underlying common information model, and may support versioning and life cycles of service offerings and / or components.
Owner:SUN MICROSYSTEMS INC
Entropy weighted message matching for opaque service virtualization
In a service emulation method, a transaction library storing a plurality of messages communicated between a system under test and a target system upon which the system under test depends is accessed responsive to receiving a request from the system under test. One of the messages stored in the transaction library is identified as corresponding to the received request based on different weightings assigned to respective sections of the messages, and a response to the received request is generated using the one of the messages that was identified. Related systems and computer program products are also discussed.
Owner:CA TECH INC
Secure virtualization system suitable for use in trusted execution environment (TEE)
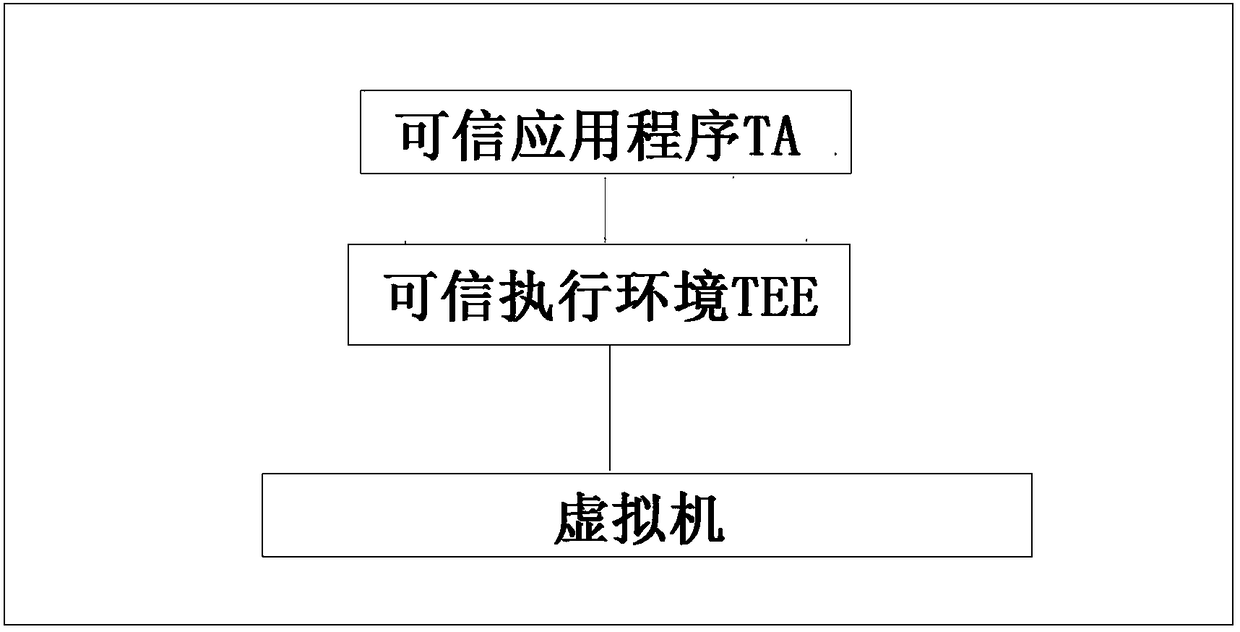
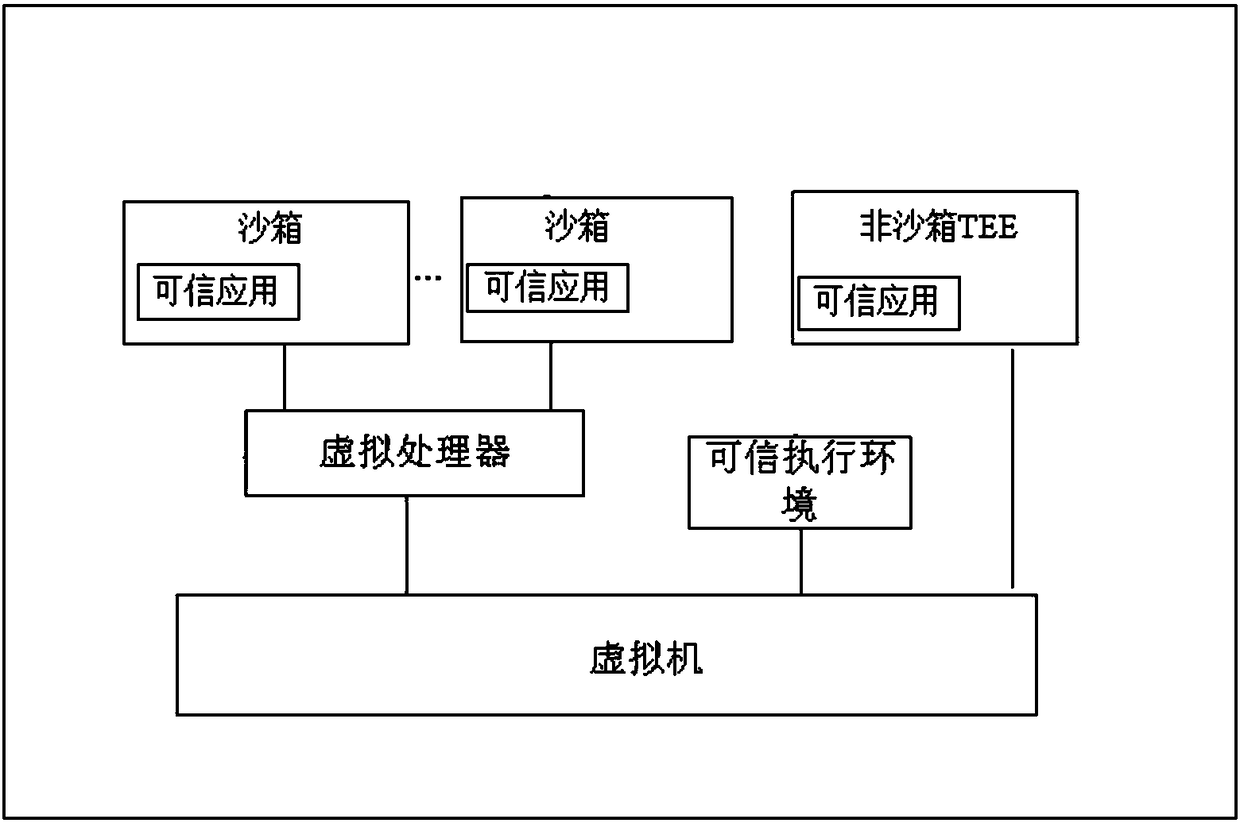
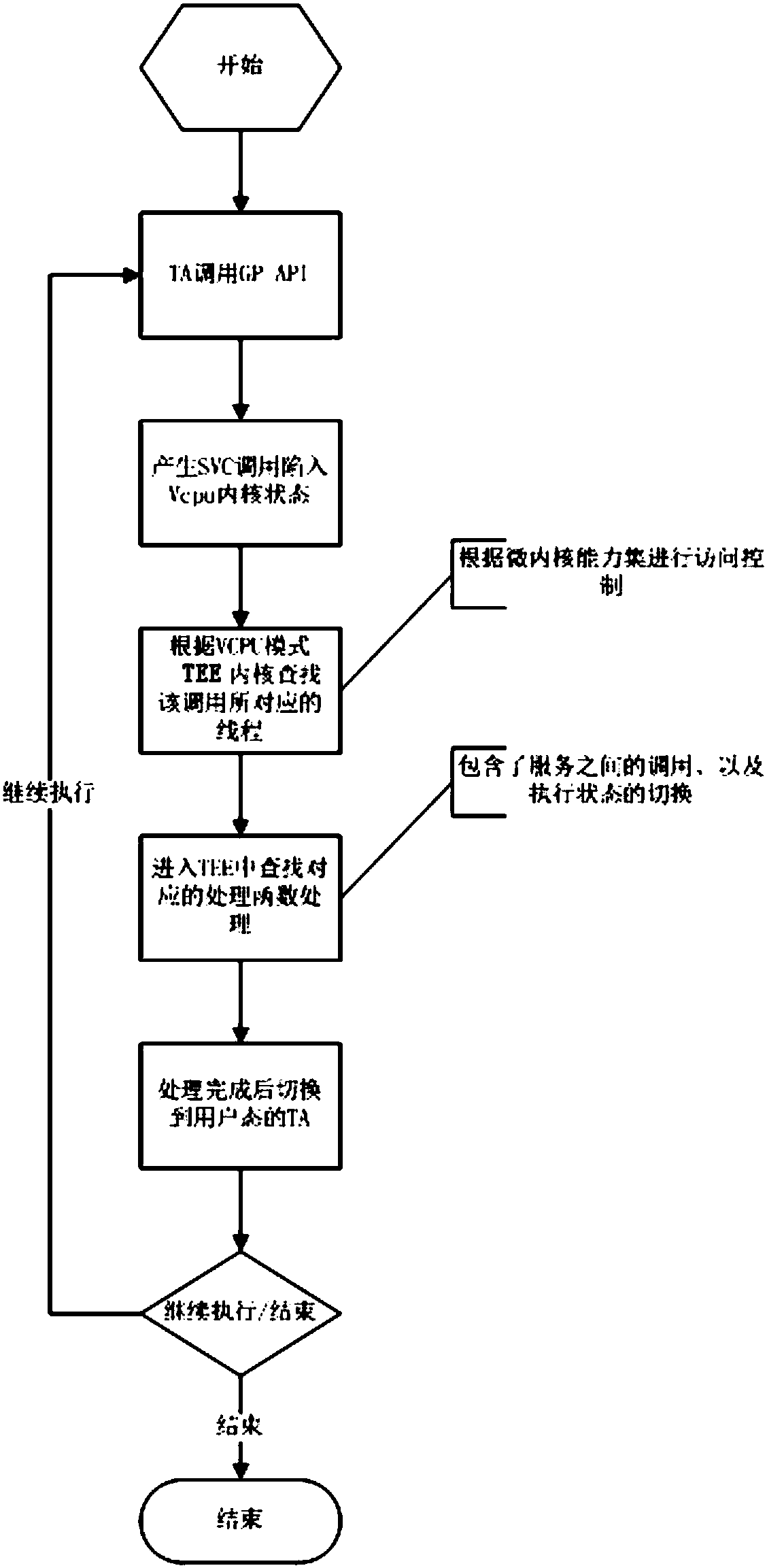
ActiveCN108509251AAchieve isolationImprove securityInternal/peripheral component protectionPlatform integrity maintainanceMemory virtualizationApplication software
The invention discloses a secure virtualization system suitable for use in a trusted execution environment (TEE). The system includes at least one virtual machine, at least one trusted application (TA) and the at least one trusted execution environment. The virtual machine is built through Micro Hypervisor. The trusted execution environment is run on the virtual machine. The trusted application isrun in the trusted execution environment of the virtual machine. The trusted execution environment is configured to access the virtual machine in a first mode to realize calling of resources. Under the first mode, the virtual machine allows accessing of the trusted execution environment to the resources after it is determined that the trusted execution environment has access authority. The systemhas the advantages of: on the basis of trusted virtualization technology, building the virtual machine through the Micro Hypervisor, and running the GP (Global Platform) TEE and the corresponding TAon the virtual machine. Both the TEE and the TA are run on the respective virtual machine, thus complete isolation is realized, and security is greatly improved.
Owner:沈阳微可信科技有限公司
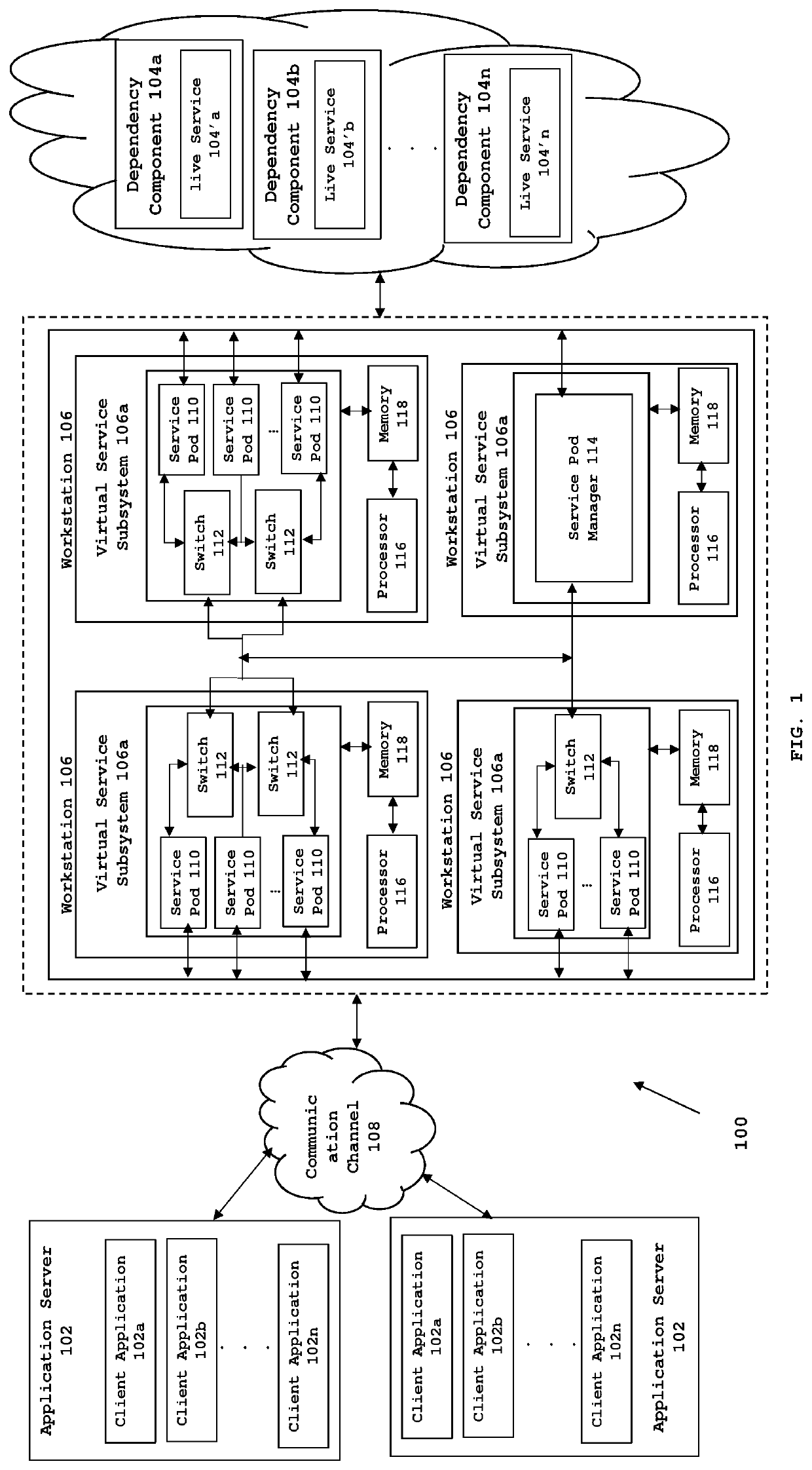
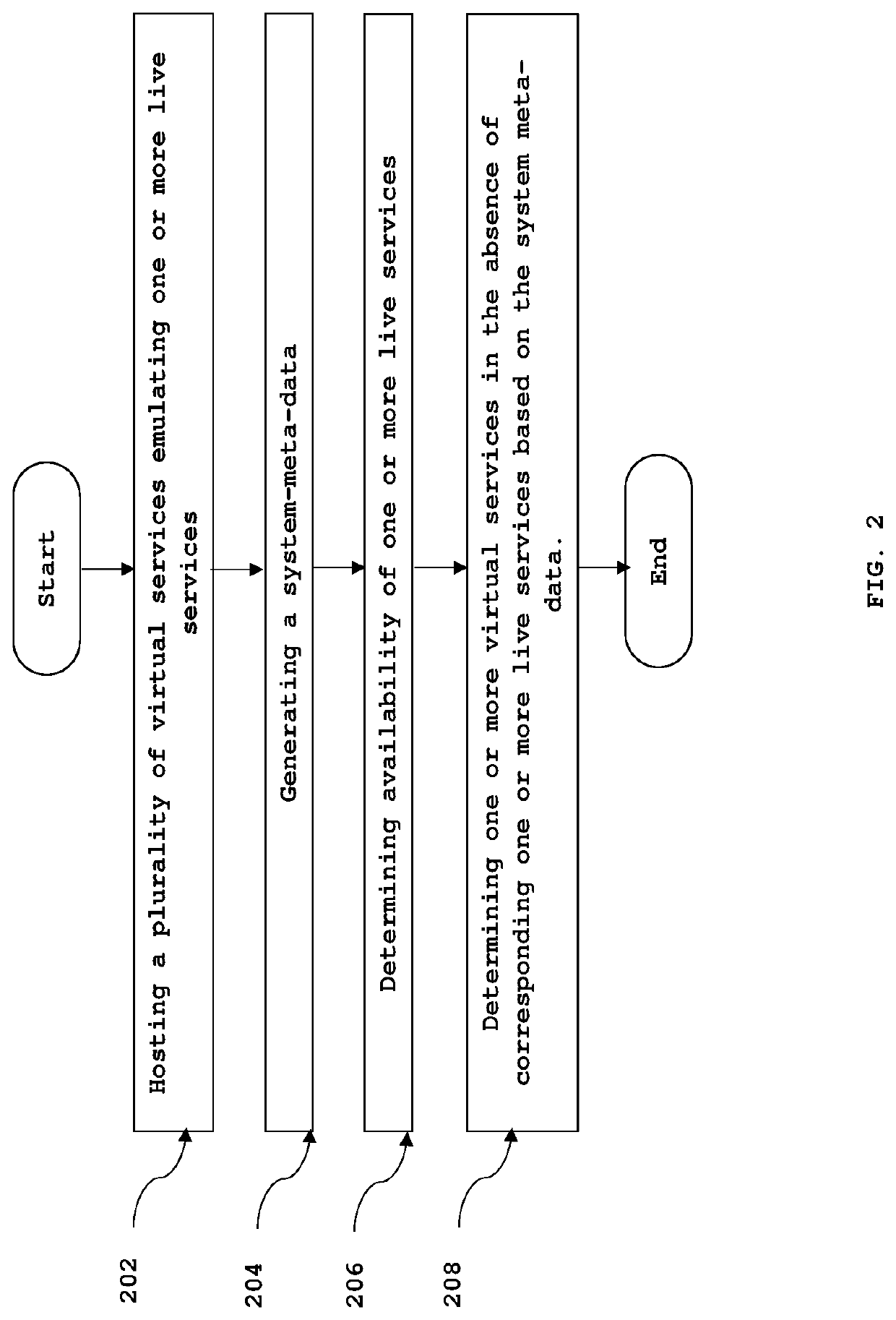
System and a method for optimized server-less service virtualization
A system and a method for providing service virtualization in a distributed computing architecture without a central server is disclosed. The present invention provides one or more service pods implementable on one or more workstations. Each of the one or more service pods is configured to host one or more virtual services. Each of the one or more service pods interface with one or more live services to generate virtual service data to emulate said live services. The one or more service pods interface with each other via a network fabric technique and interact with one or more client applications to be tested. Each of the one or more service pods are configured to receive and process requests from one or more client applications using various modes of service pods. The present invention provides complete abstraction of the one or more workstations from the one or more service pods.
Owner:COGNIZANT TECH SOLUTIONS INDIA PVT
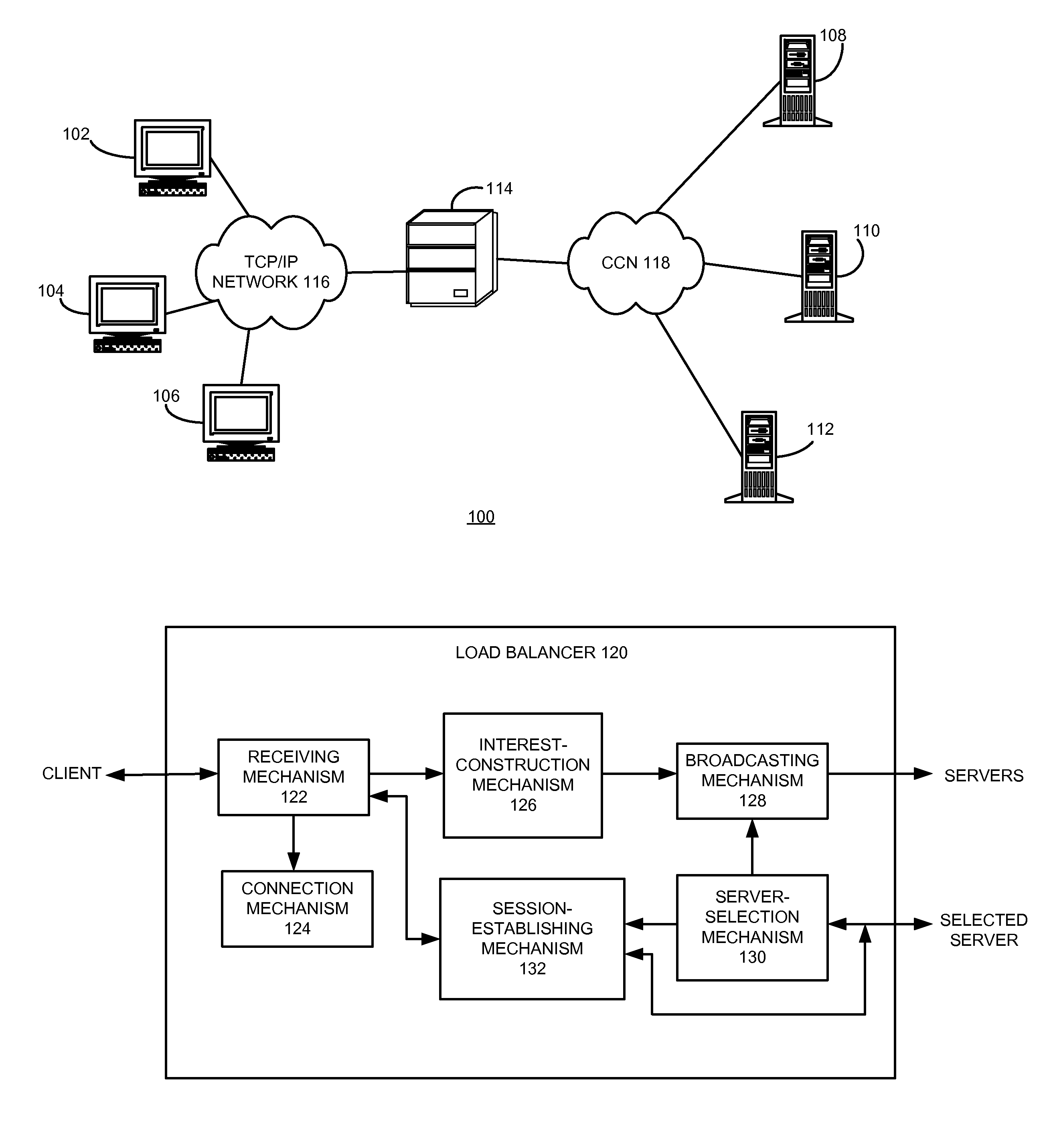
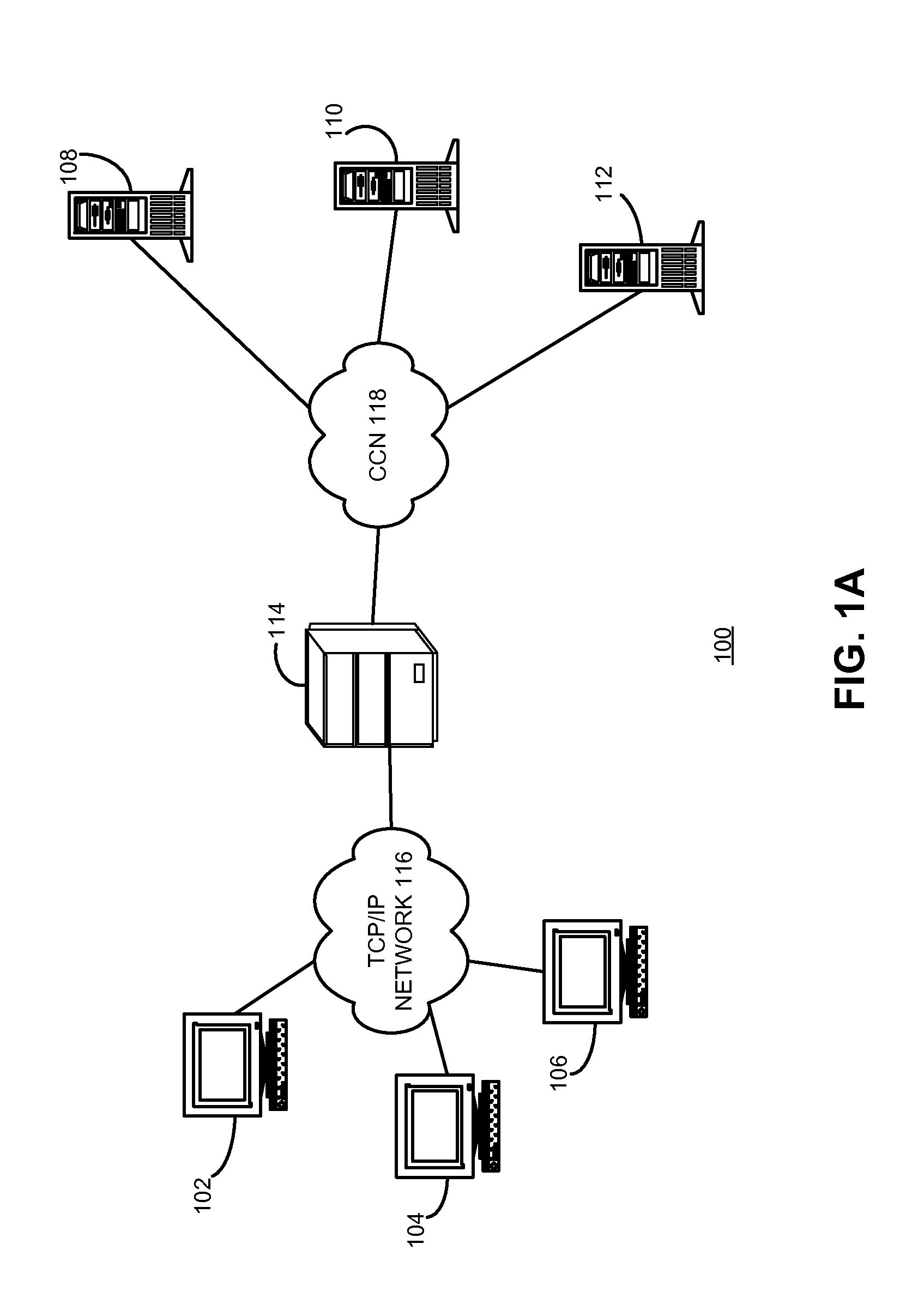
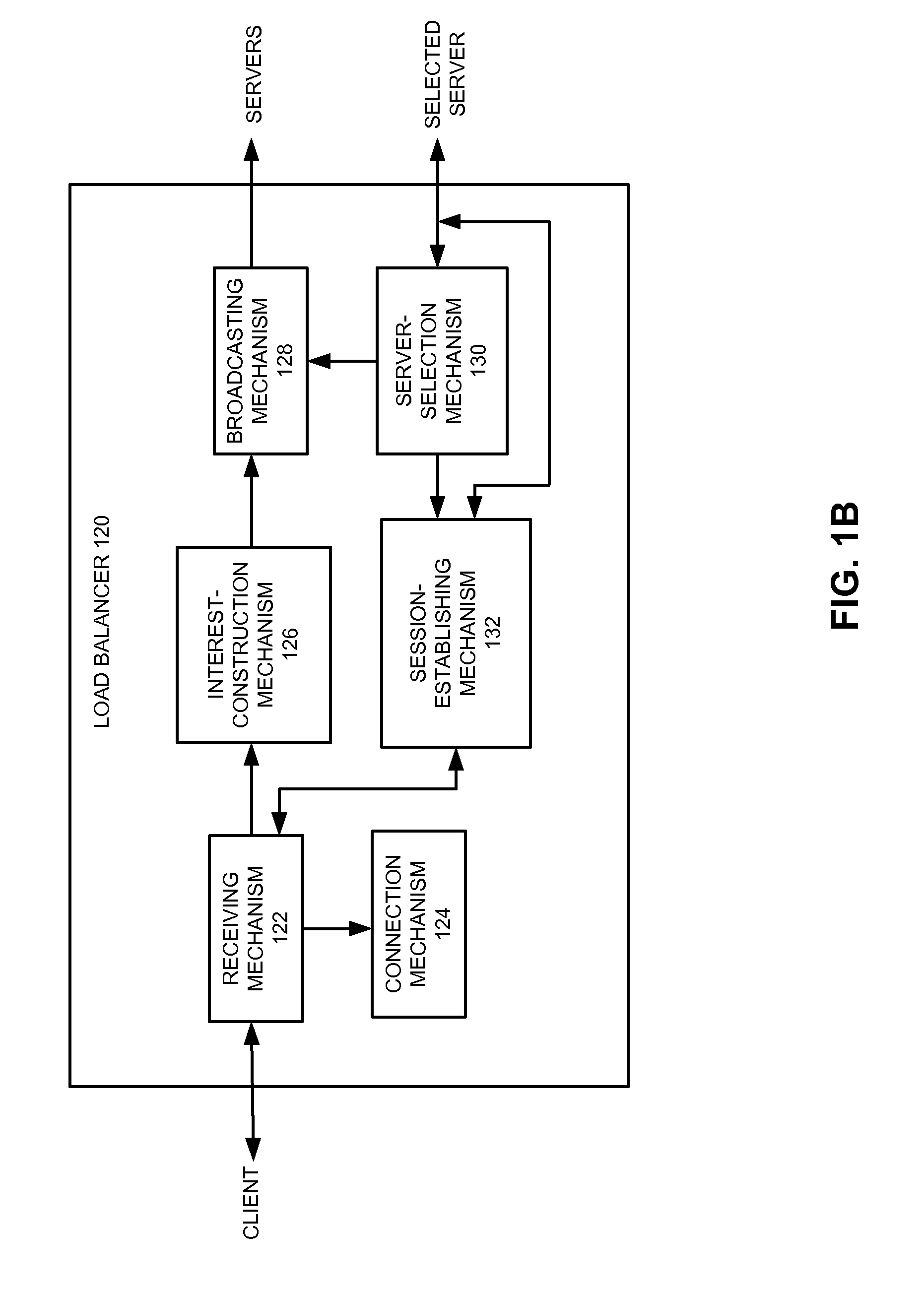
Service virtualization over content-centric networks
ActiveUS8244881B2Facilitate virtualizationData processing applicationsMultiple digital computer combinationsContent centricClient data
One embodiment of the present invention provides a system for facilitating network service virtualization. During operation, the system receives a service request from a client, and initializes a communication session with the client. The system constructs an interest using session state information that can identify the client and / or a previous communication session. The interest comprises a hierarchically structured variable-length name. The system then broadcasts the interest to a number of servers. The system subsequently forwards to the client data received from a server which responds first to the interest.
Owner:CISCO TECH INC
Response prototypes with robust substitution rules for service virtualization
In a method of service emulation, a transaction subset including ones of a plurality of message transactions previously communicated between a system under test and a target system for emulation is defined. The message transactions include requests and responses thereto that are stored in a computer-readable memory. Variable sections of the requests and variable sections of the responses of the transaction subset are identified, for example, based on respective message structures thereof. Substitution rules, which indicate a correspondence between respective ones of the variable sections of the requests and respective ones of the variable sections of the responses, are determined for the transaction subset based on commonalities therebetween. Responsive to receiving an incoming request from the system under test, a response to the incoming request is generated according to the substitution rules. Related computer systems and computer program products are also discussed.
Owner:CA TECH INC
Authenticated service virtualization
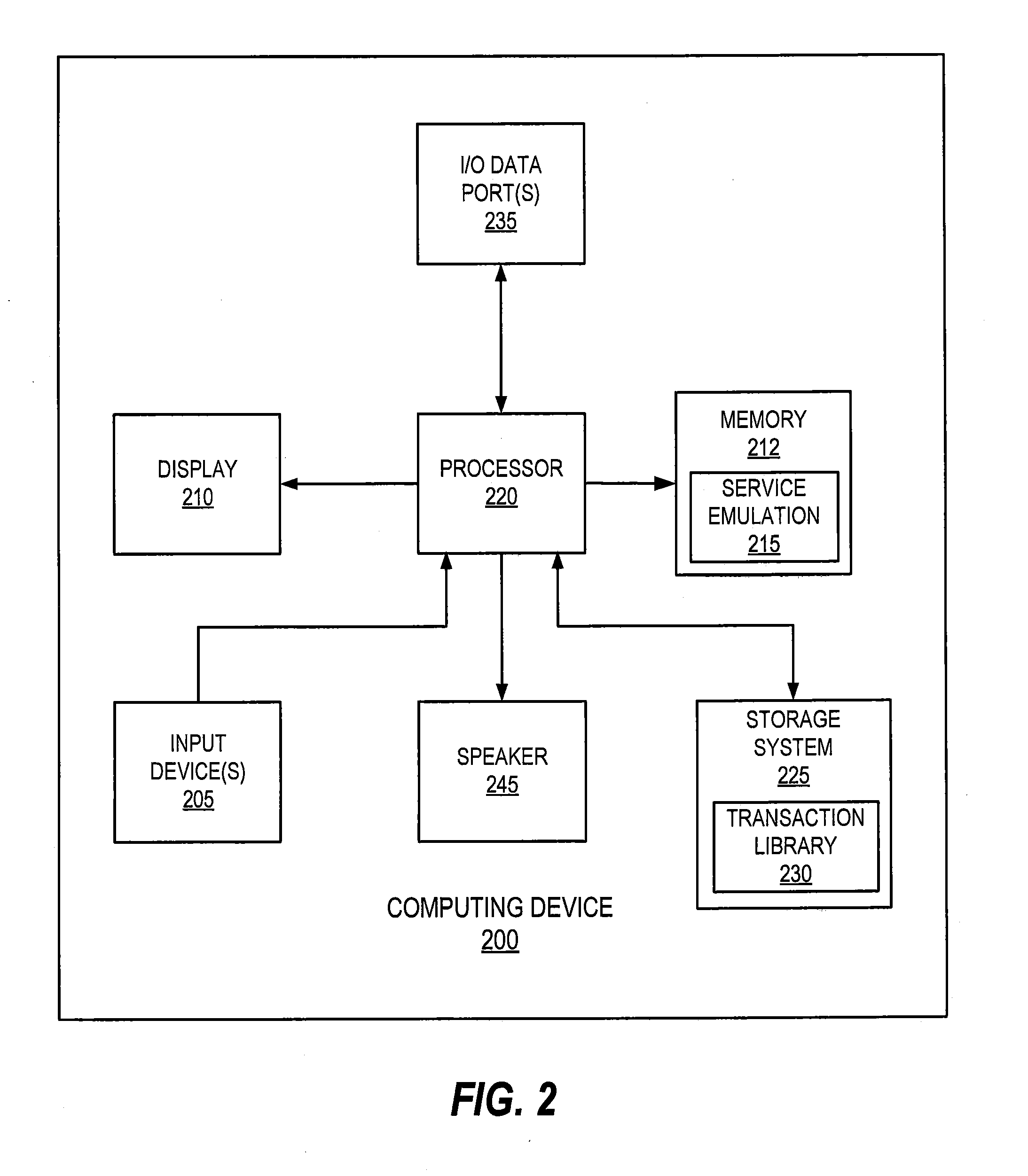
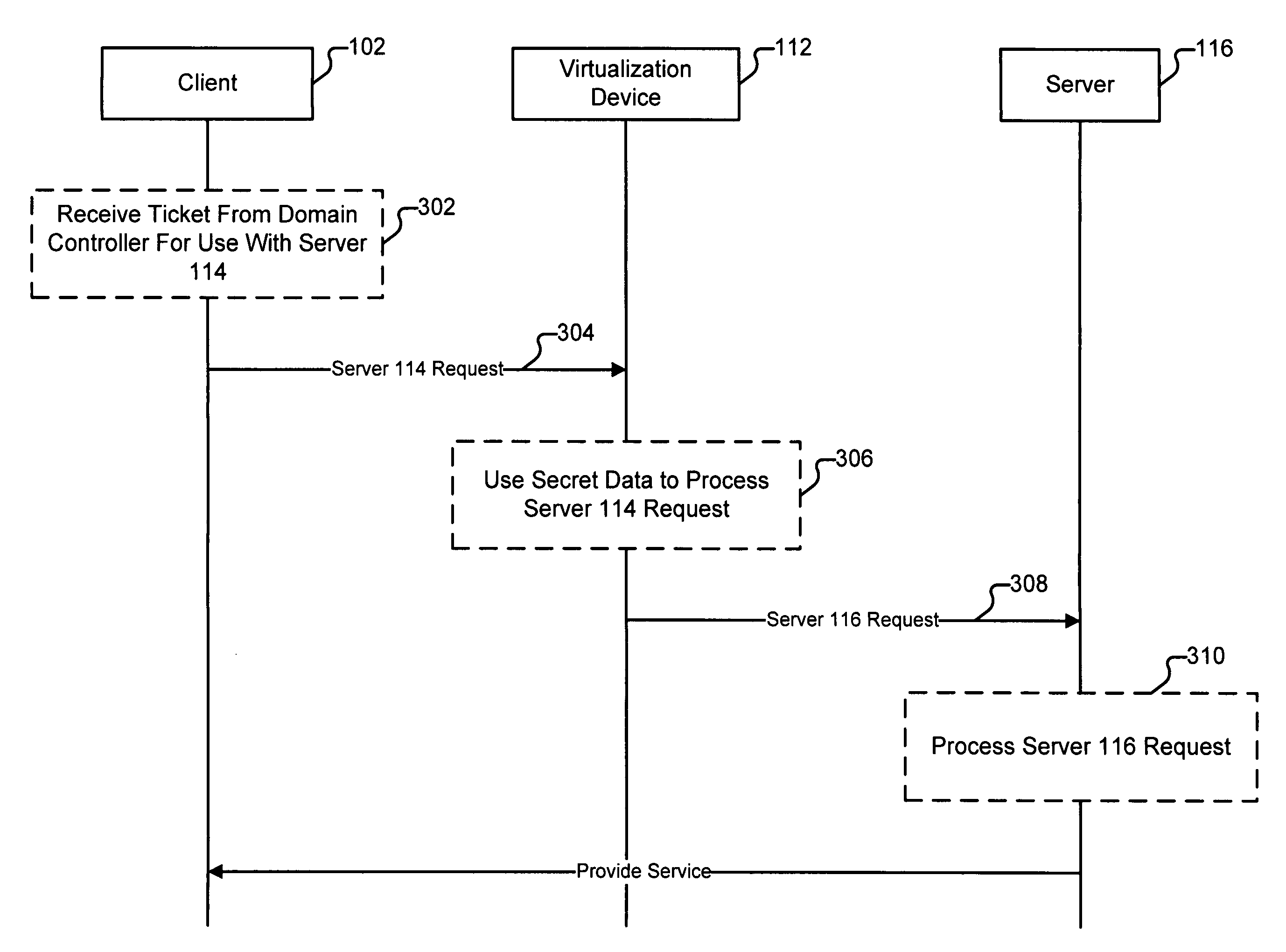
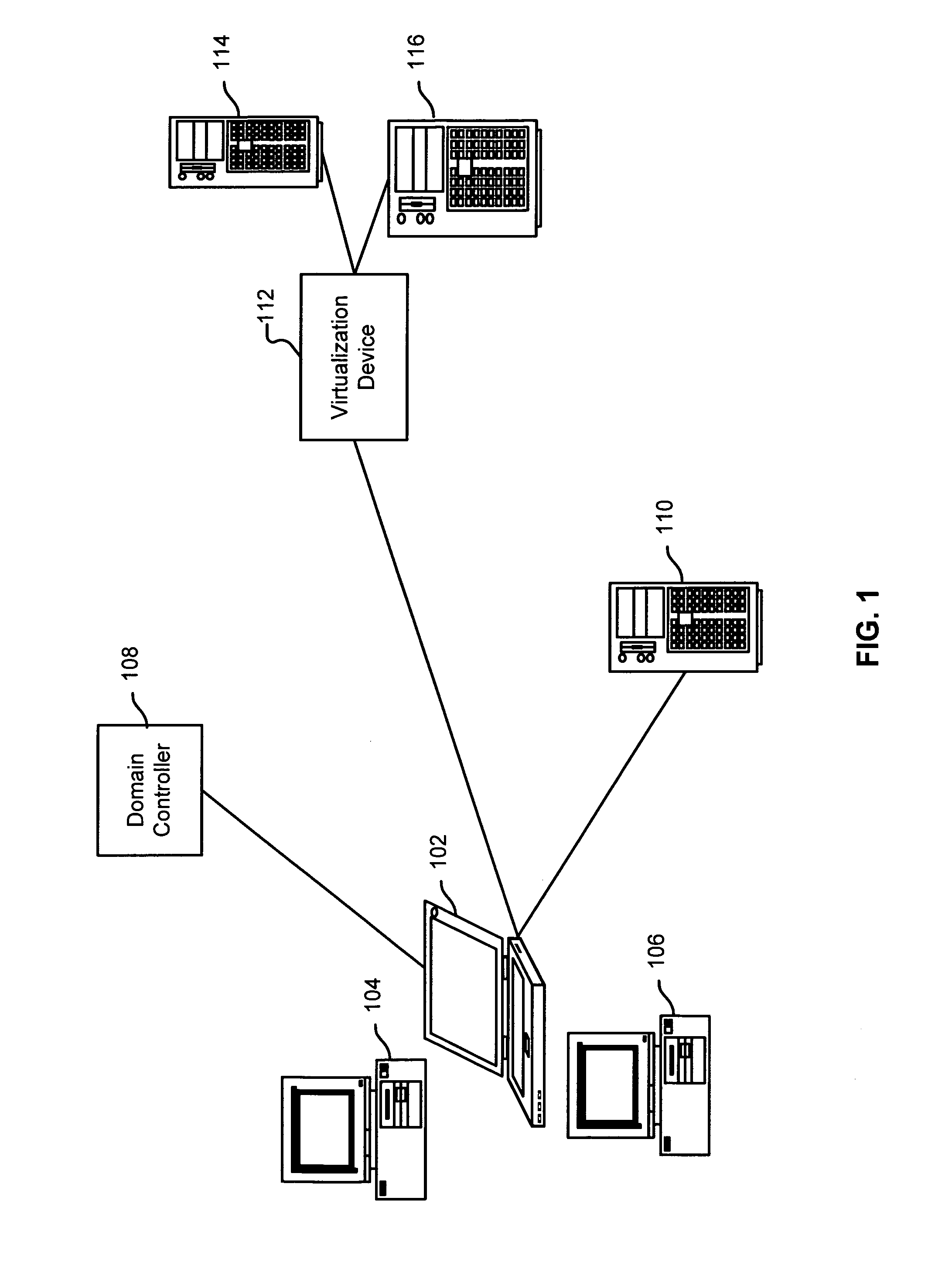
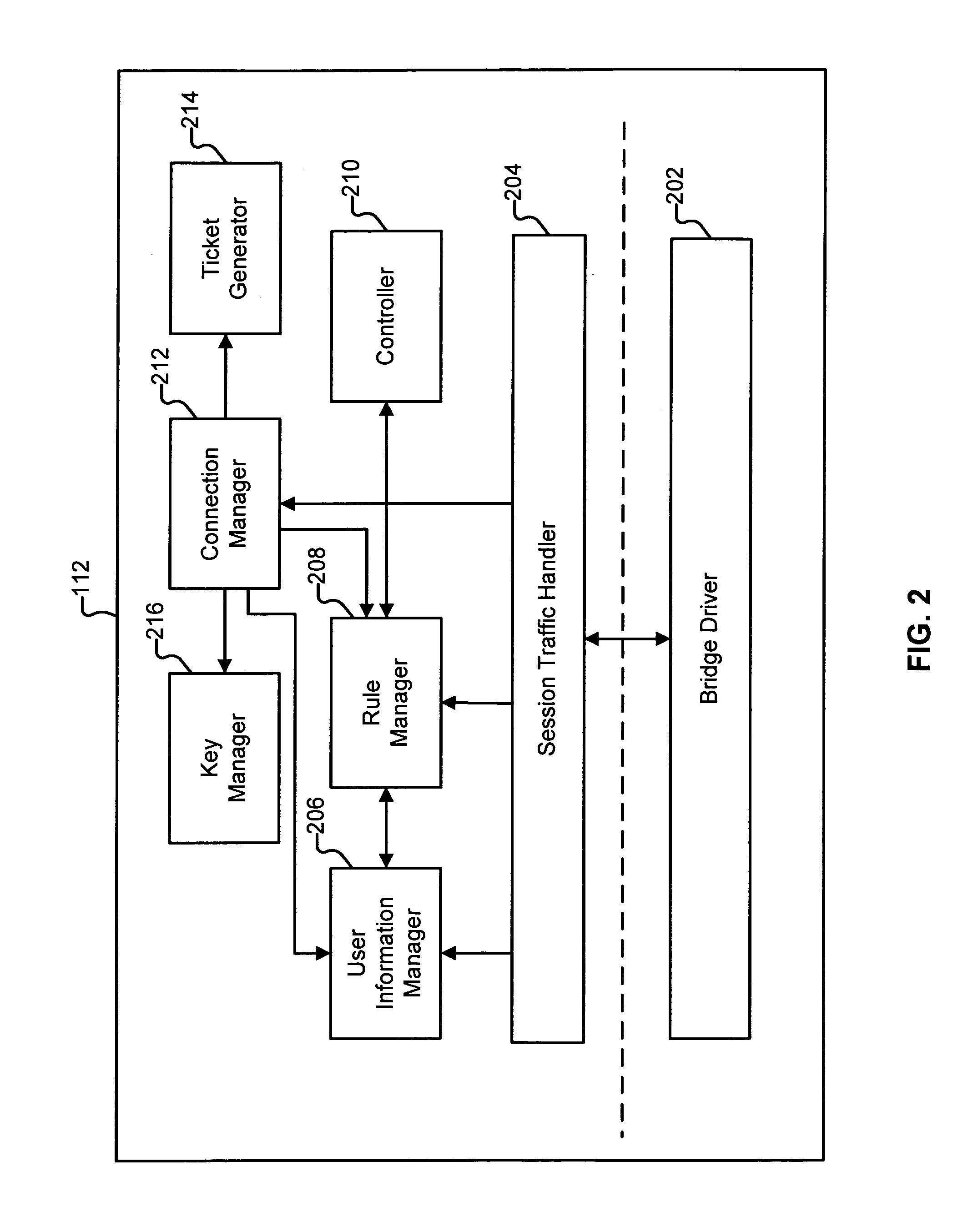
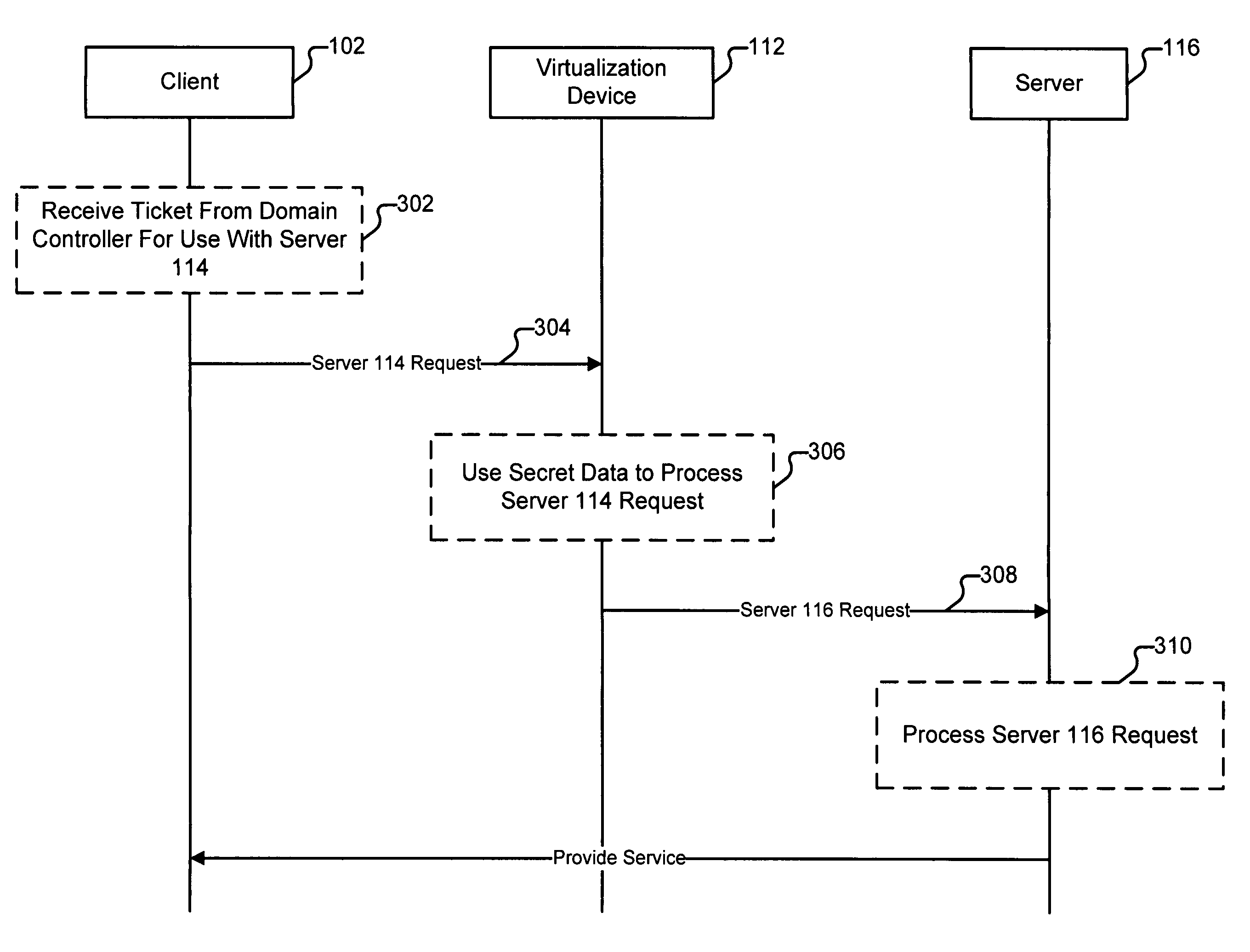
ActiveUS20090150988A1Digital data processing detailsUser identity/authority verificationVirtualizationClient-side
Virtualizing a service is disclosed. A request to access a service from a first server is received from a client. A secret data associated with the first server is used to process the received request. The processed request is sent to a second server. The first and second servers are associated with a virtualization; and wherein the processed request can be used by the second server to authenticate the client.
Owner:EMC IP HLDG CO LLC
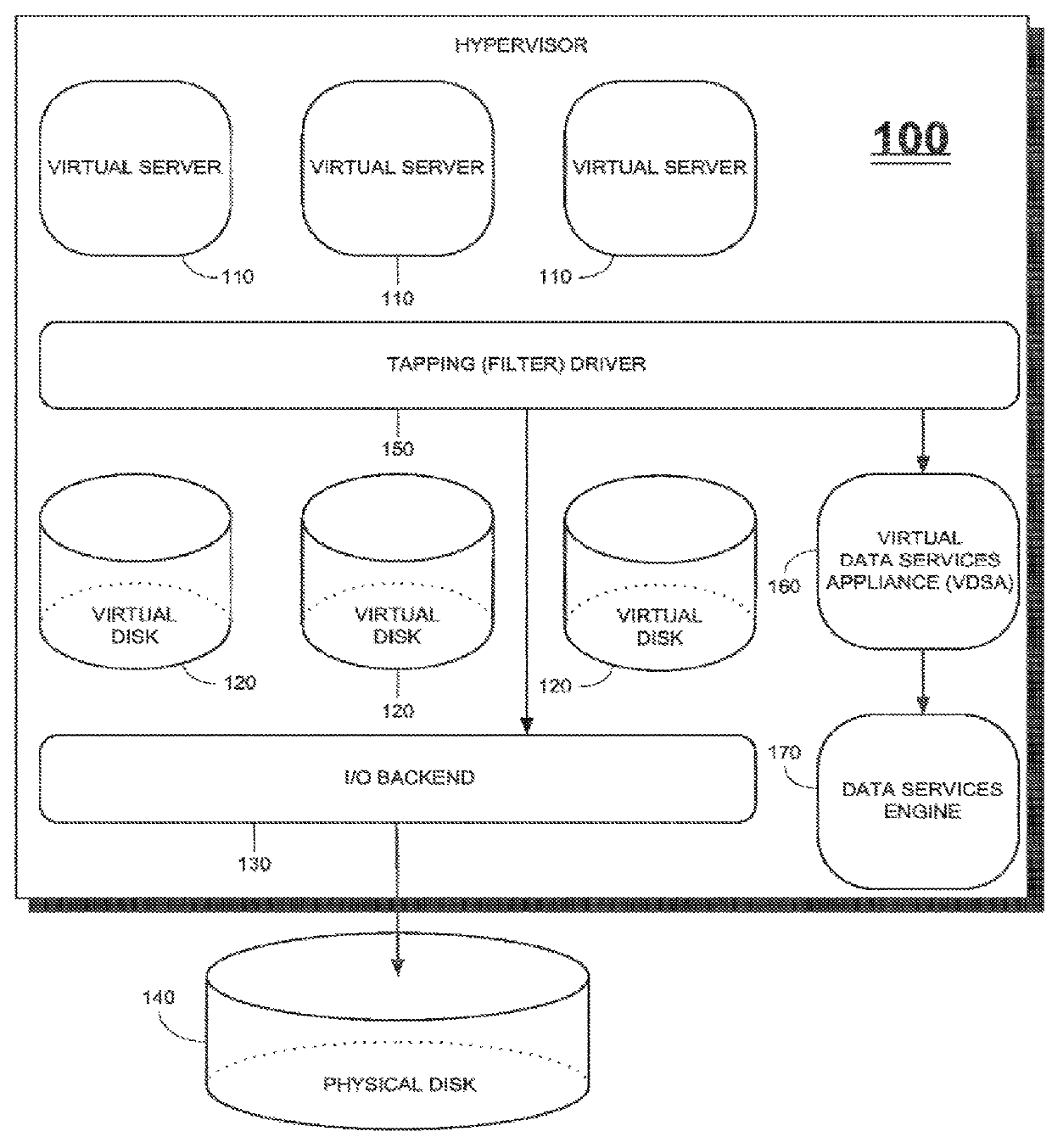
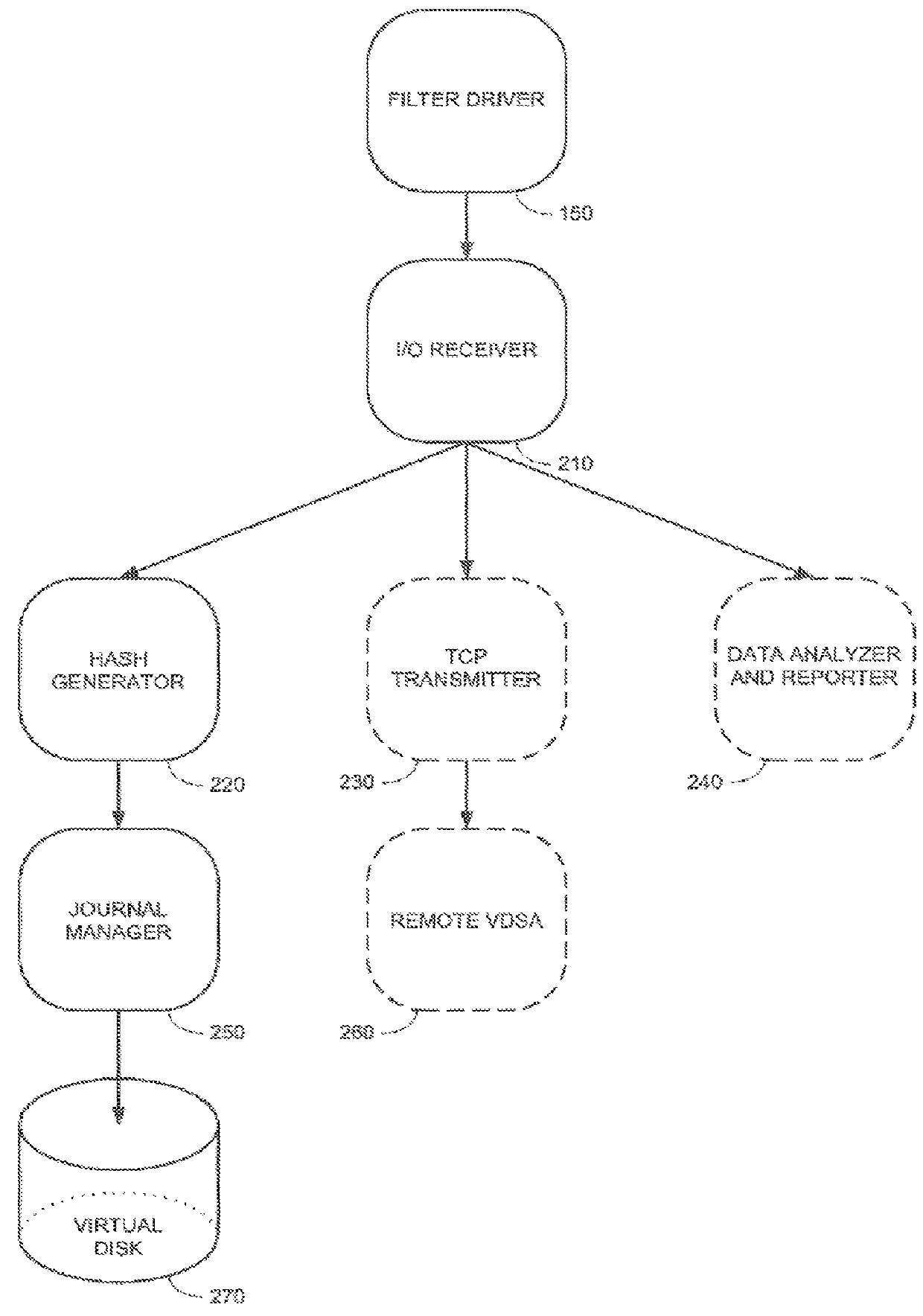
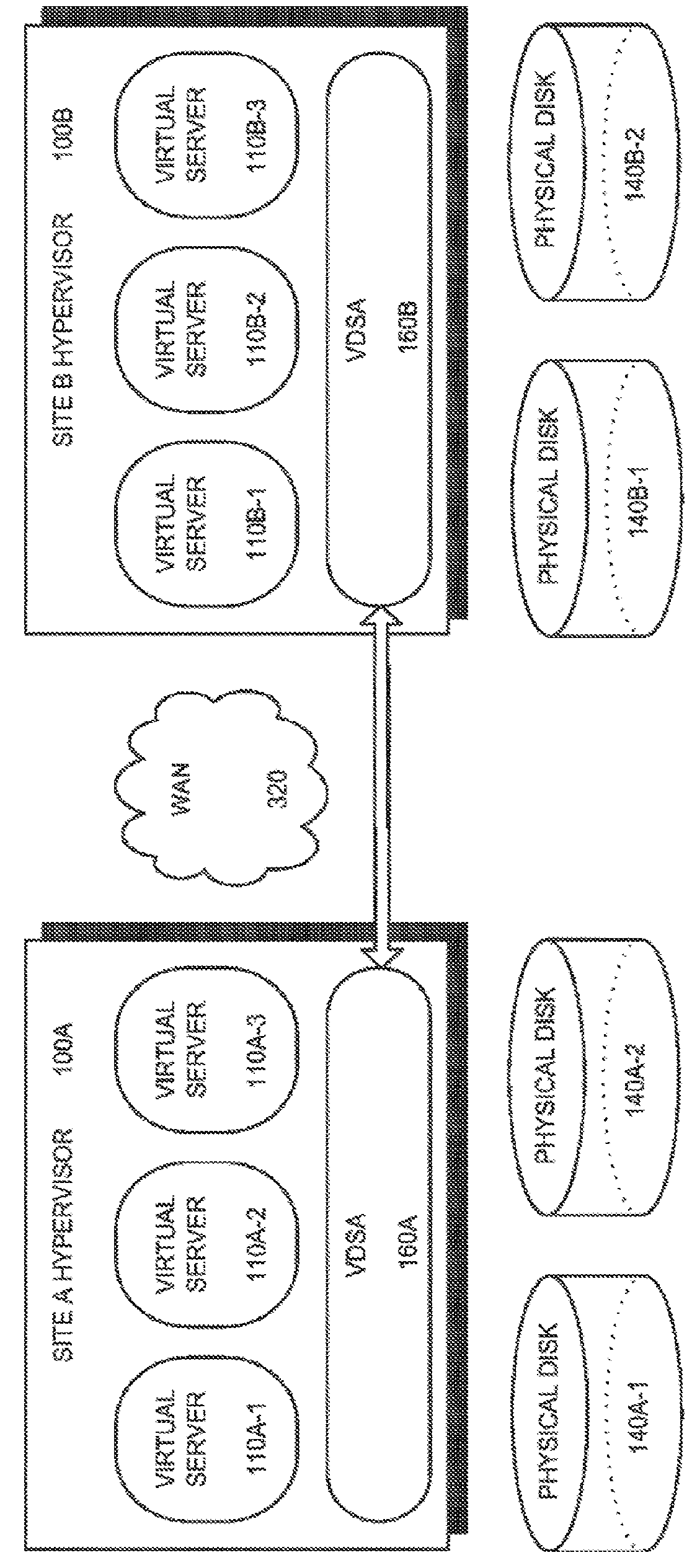
Methods and apparatus for providing hypervisor level data services for server virtualization
ActiveUS20160034296A1Data switching networksSoftware simulation/interpretation/emulationMemory virtualizationLevel data
A system for cloud-based data services for multiple enterprises, including a plurality of cloud hypervisors that cooperatively provide cloud-based services to multiple enterprises, each hypervisor including a plurality of cloud virtual servers, each cloud virtual server being associated with an enterprise, at least one cloud virtual disk that is read from and written to by the at least one virtual server, each cloud virtual disk being associated with an enterprise, and a virtual data services appliance, which provides cloud-based data services, and multiple data services managers, one data services manager per respective enterprise, each of which coordinates the respective virtual data services appliances for those cloud hypervisors that service its corresponding enterprise.
Owner:ZERTO
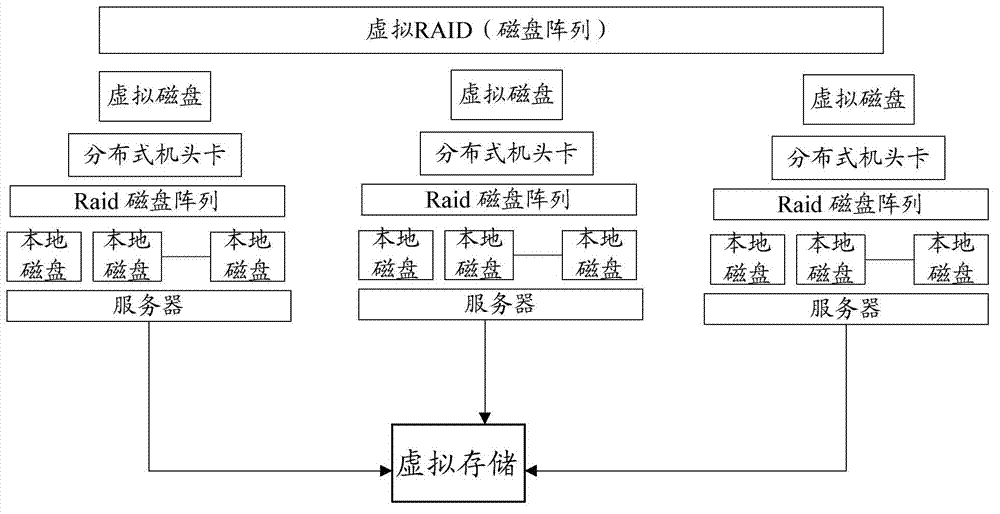
Storage virtualization system
ActiveCN103207762AAchieve stabilityAchieve reliabilityInput/output to record carriersNetwork virtualizationSystem virtualization
The invention provides a storage virtualization system. The storage virtualization system comprises servers, local disks, a Raid card, Raid disk arrays, virtual disks and distributed head cards, wherein the servers are used for providing software operating environments and a virtual machine control platform for a virtual machine and are provided with all-in-one machine managing units; a virtual Raid array is formed by local disks of all the servers through the Raid card by the all-in-one machine managing units; and a Raid disk array is formed by the local disks through an ISCSI (Internet Small Computer System Interface) channel by the Raid card, and a virtual memory is formed by the plurality of virtual Raid arrays through a network. According to the storage virtualization system provided by the invention, the problem of the shared storage in the conventional low-cost desktop virtualization scheme is solved, the high-reliability functions of the virtual HR (Human Resource) are realized, the shared storage is disaffiliated, and the stability and the reliability of a desktop are achieved; and meanwhile, the installation and maintenance cost of the system is lowered as well.
Owner:ISOFTSTONE INFORMATION TECHNOLOGY (GROUP) CO LTD
Entropy weighted message matching for opaque service virtualization
In a service emulation method, a transaction library storing a plurality of messages communicated between a system under test and a target system upon which the system under test depends is accessed responsive to receiving a request from the system under test. One of the messages stored in the transaction library is identified as corresponding to the received request based on different weightings assigned to respective sections of the messages, and a response to the received request is generated using the one of the messages that was identified. Related systems and computer program products are also discussed.
Owner:CA TECH INC
Authenticated service virtualization
ActiveUS8387130B2Digital data processing detailsUser identity/authority verificationVirtualizationClient-side
Virtualizing a service is disclosed. A request to access a service from a first server is received from a client. A secret data associated with the first server is used to process the received request. The processed request is sent to a second server. The first and second servers are associated with a virtualization; and wherein the processed request can be used by the second server to authenticate the client.
Owner:EMC IP HLDG CO LLC
Emergency command cloud service implementation method and system based on microkernel cluster
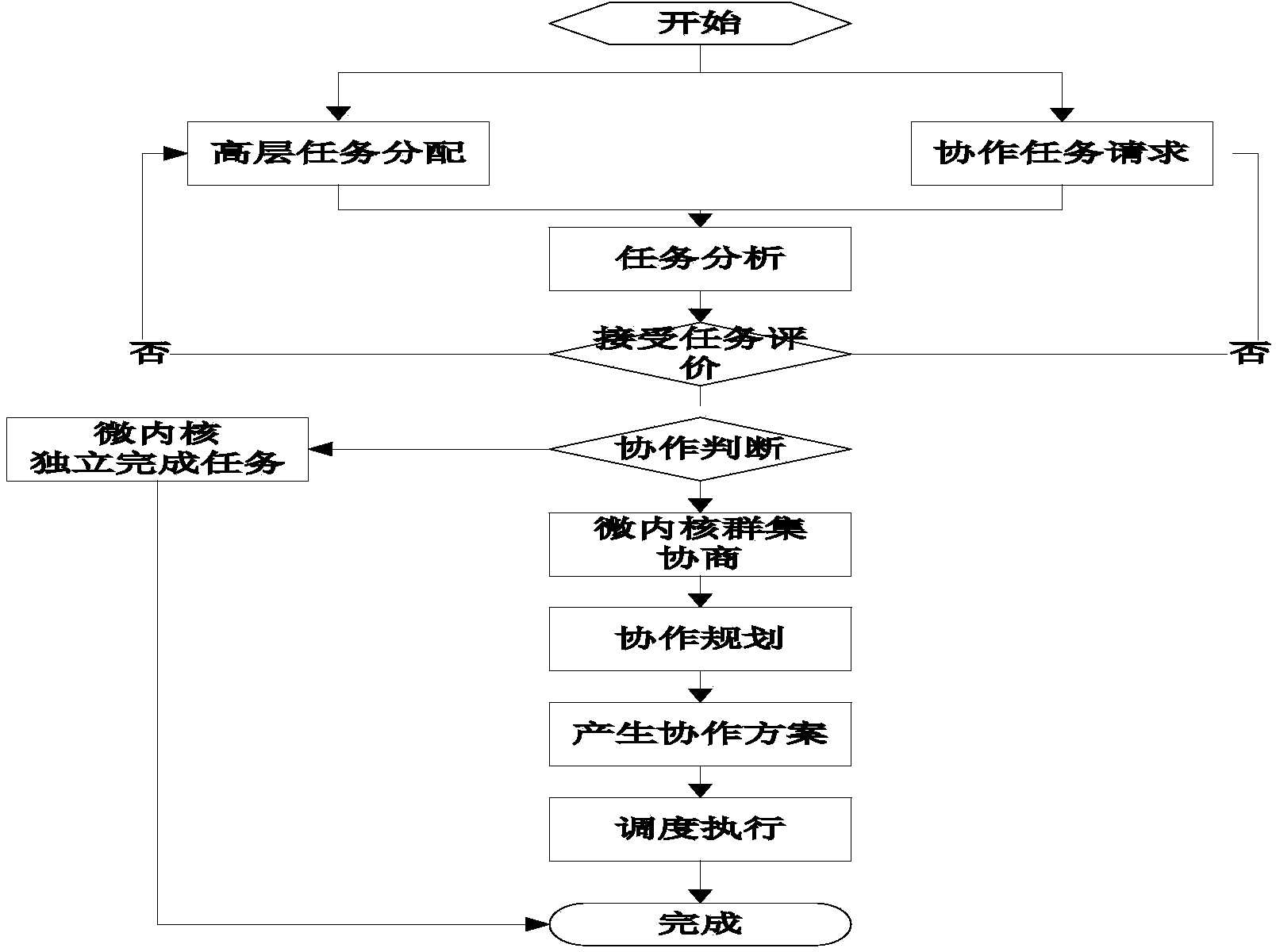
ActiveCN103617084AAssisted Synthetic ReasoningAuxiliary emergency decision-makingResource allocationTransmissionUnexpected eventsCommand system
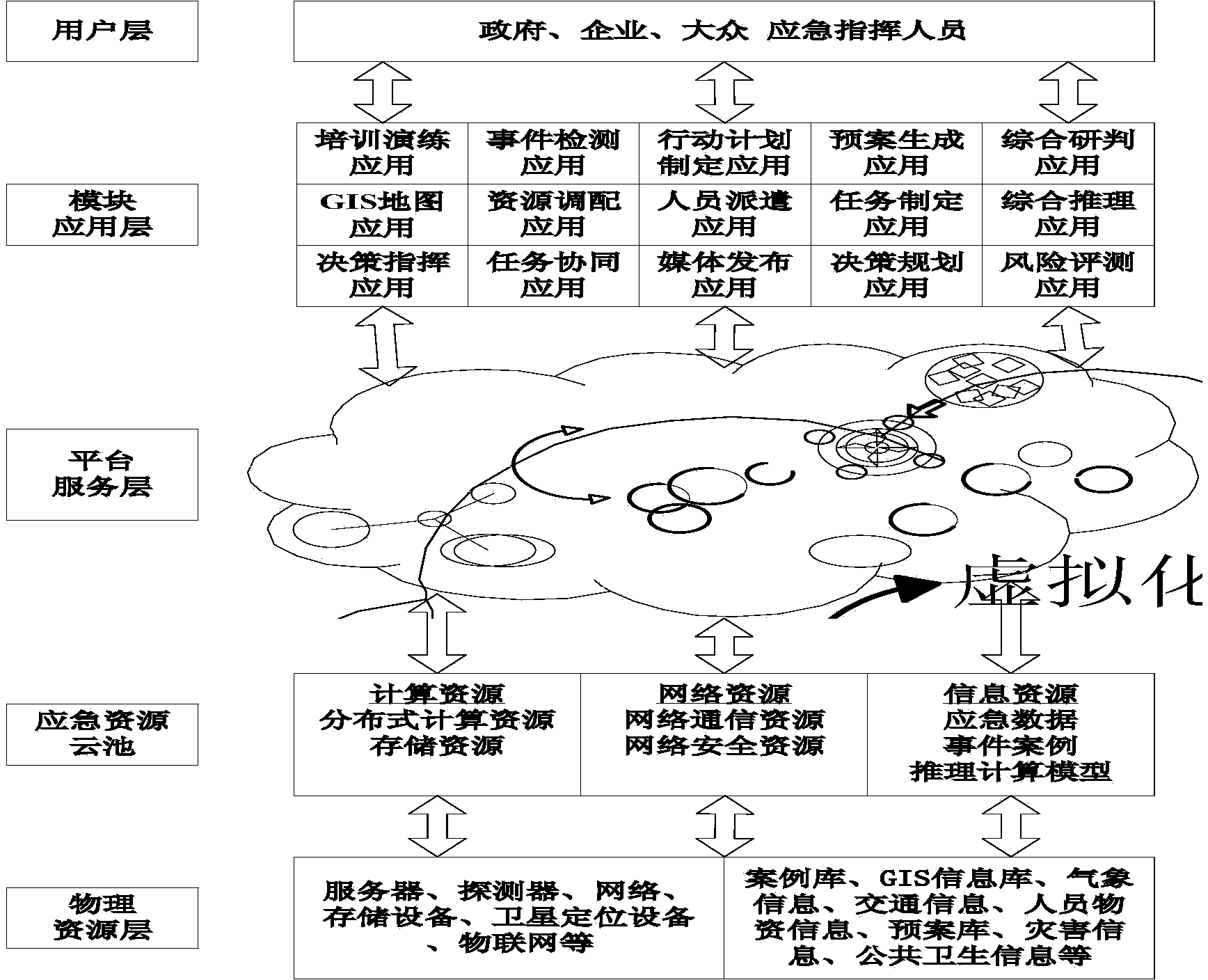
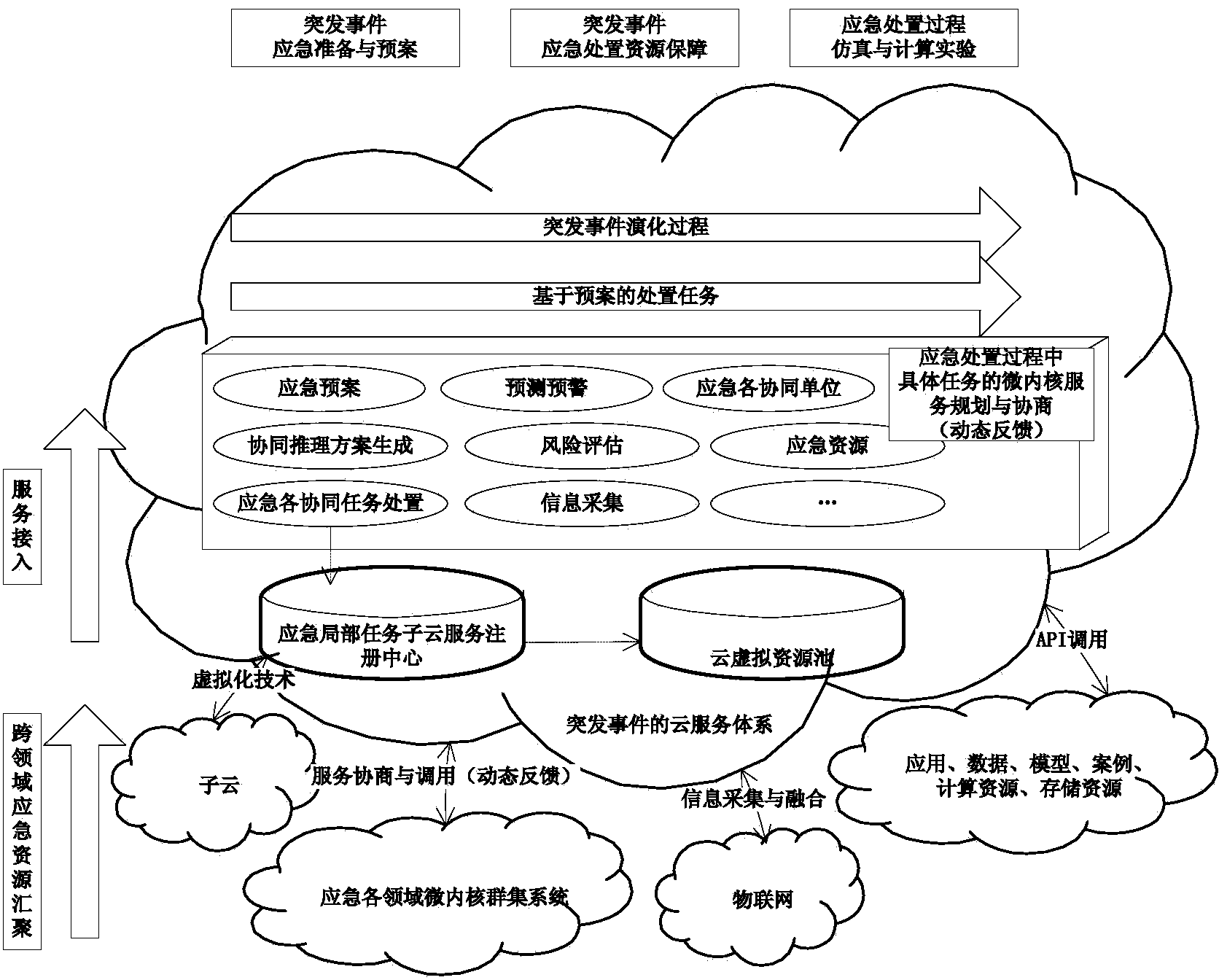
The invention provides an emergency command cloud service implementation method and system based on a microkernel cluster. Various kinds of services with specific business processing capacity is virtually encapsulated into the microkernel cluster, mutual synergy is performed according to the service plans generated according to upper module application, and the microcosmic services provided each member in the cluster are combined and encapsulated to convert into macroscopic service manners capable of realizing emergency treatment task planning. The system comprises a physical resource layer, an emergency resource cloud pool, a platform service layer, a module application layer and a user layer. By the emergency command system built by the service method, dynamic searching of valuable emergency service resources in various fields can be achieved, the system capabilities of massive dynamic information and knowledge reasoning, complex function and process recombination calculation, storage and service are improved, and diversified emergency tasks such as emergency cross-department and cross-field real-time information processing, large-range public opinion analysis, complex module deduction, dynamic disaster situation prediction and remote monitoring can be achieved.
Owner:STATE GRID CORP OF CHINA +2
A method and a device for realizing dual-live disaster recovery for a server virtualization system
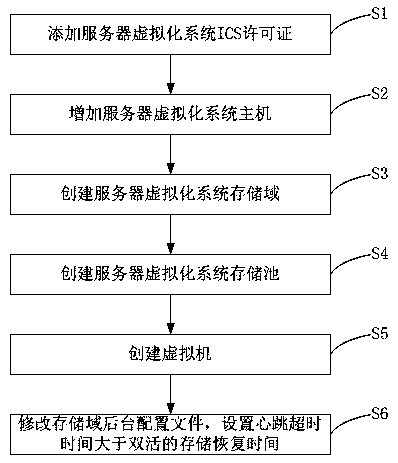
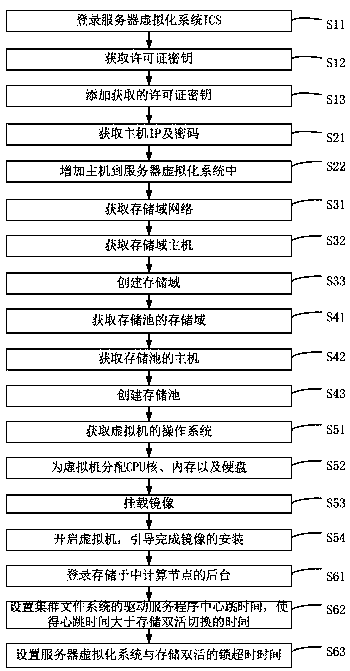
ActiveCN109240855AImprove securityAdapt to needsSoftware simulation/interpretation/emulationRedundant operation error correctionData accessComputer module
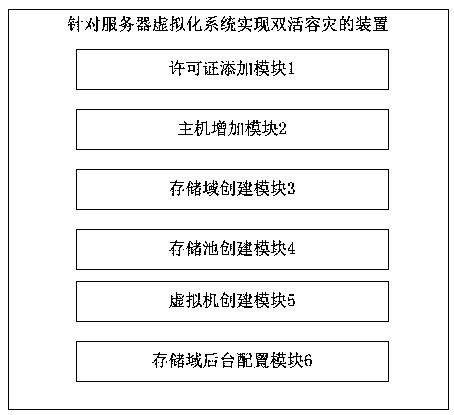
The invention provides a method and a device for realizing dual-live disaster recovery for a server virtualization system. The method includes: configuring a server virtualization system ICS, and creating a CFS storage domain and a shared storage pool; Modifying the storage domain profile to set the heartbeat timeout to be greater than the dual live storage recovery time. The device comprises a license adding module, which is used for adding an ICS license of a server virtualization system; A host adding module, configured to add a server virtualization system host; A storage domain creation module for creating a server virtualized system storage domain; A storage pool creation module for creating a server virtualization system storage pool; A virtual machine creation module for creating avirtual machine; The storage domain background configuration module used for modifying the storage domain background configuration file and setting the heartbeat timeout time to be greater than the dual-live storage recovery time. The invention enhances the safety of data access, more adapts to the needs of enterprise-level customers, and promotes the perfection of the functions of the company'svirtualized products.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
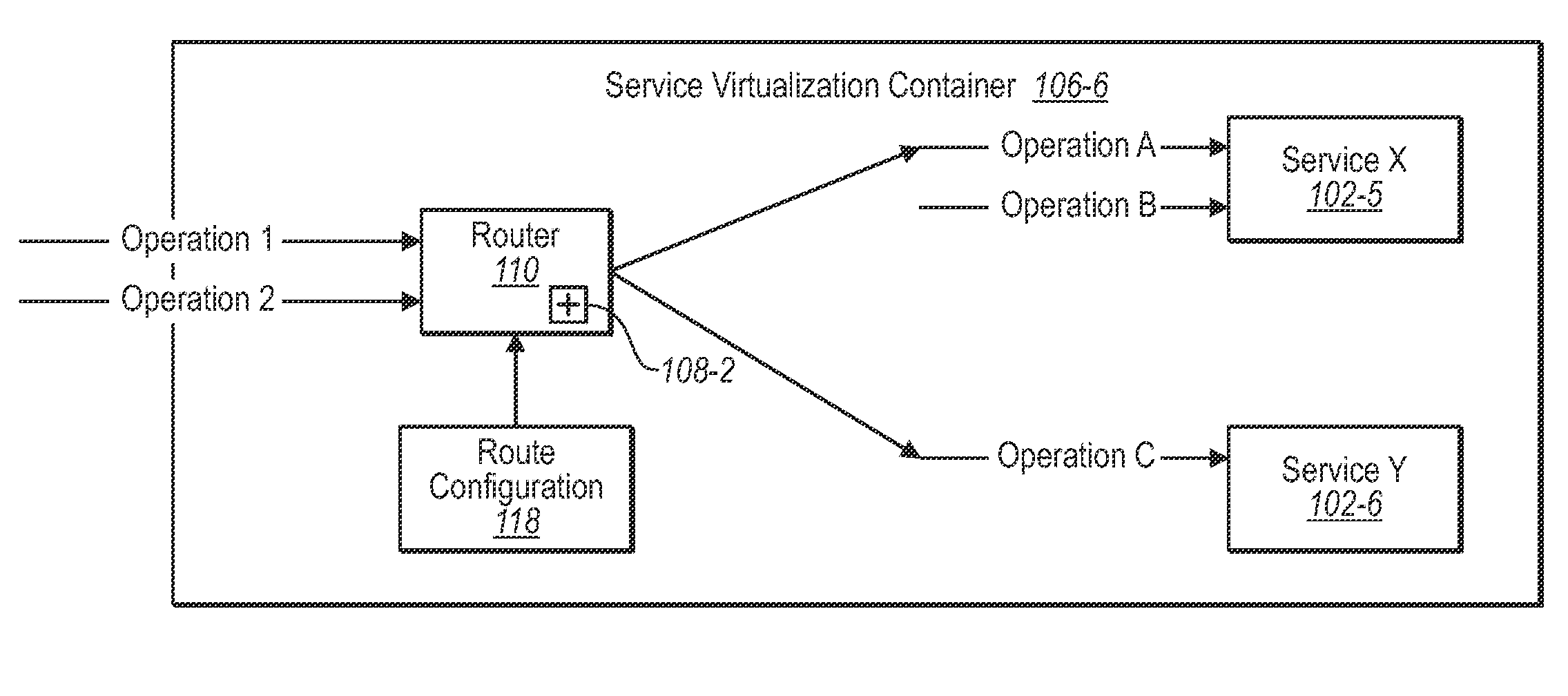
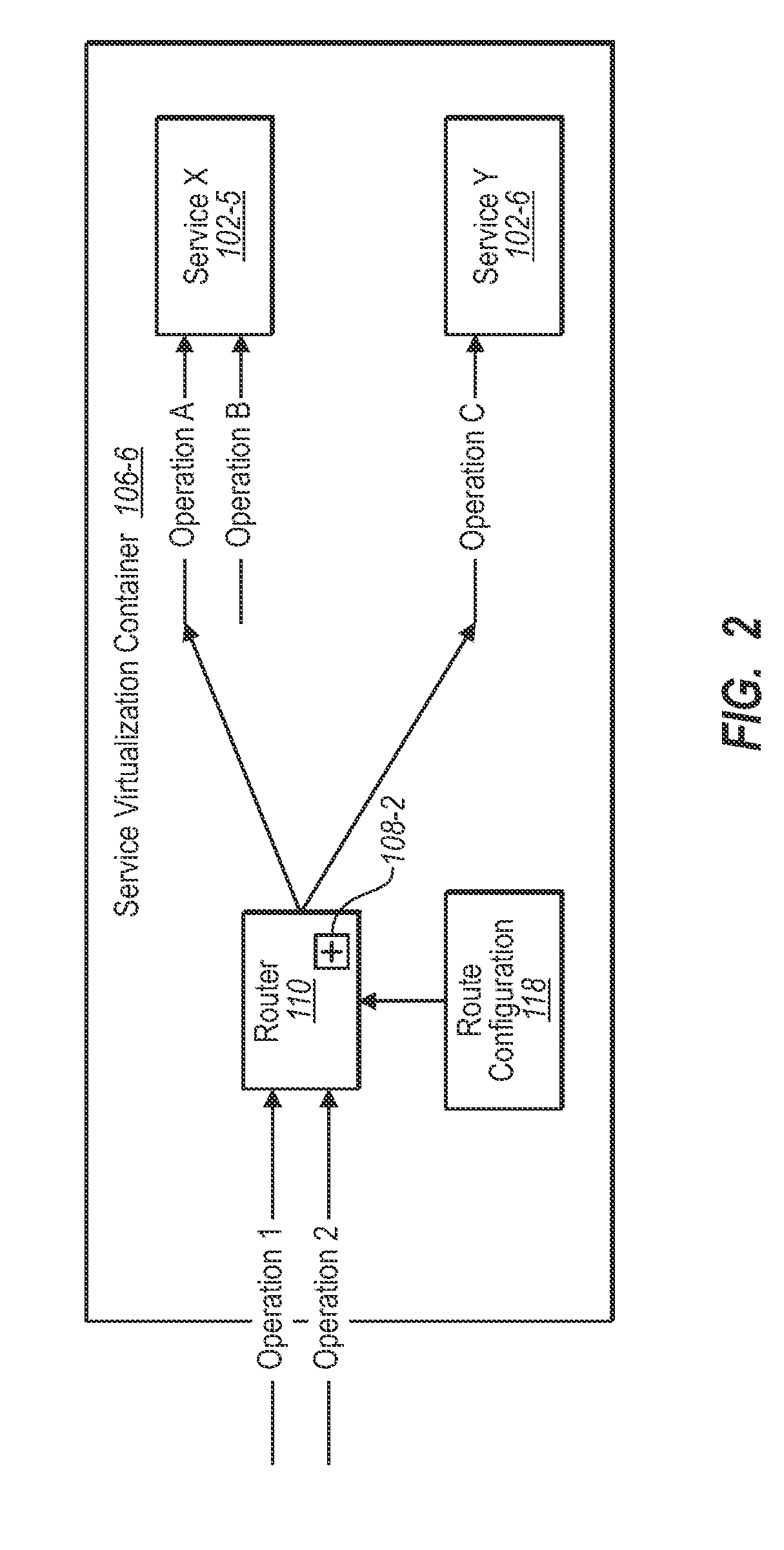
Service virtualization container
Service virtualization containers to aggregate service functionality from a plurality of services into an apparent service exhibiting the aggregated functionality. A plurality of service implementations is assigned to a service virtualization container. The container selects some of the service operations from the service implementations. One or more message characteristics are assigned to the service operations in one or more routing tables. A message is received at a service endpoint different from the service endpoints of any of the service implementations. A determination is made of one or more message characteristics. The one or more routing tables are consulted to select a determined service operation based on the message characteristics. The message is routed to the selected service implementation. Embodiments may also include functionality for aggregating metadata from service implementations and providing metadata based on the aggregated metadata to clients requesting metadata from a service virtualization container.
Owner:MICROSOFT TECH LICENSING LLC
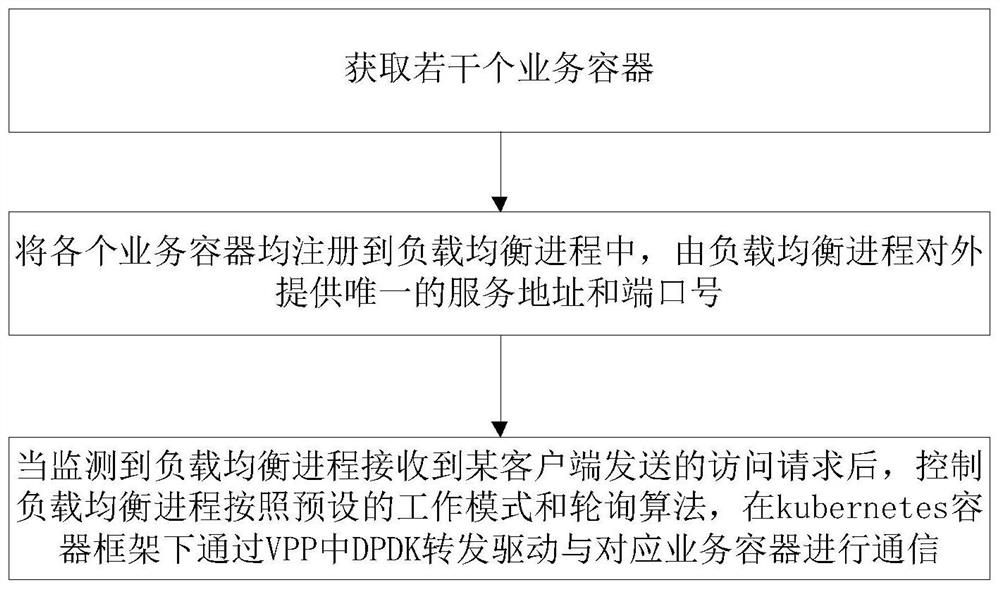
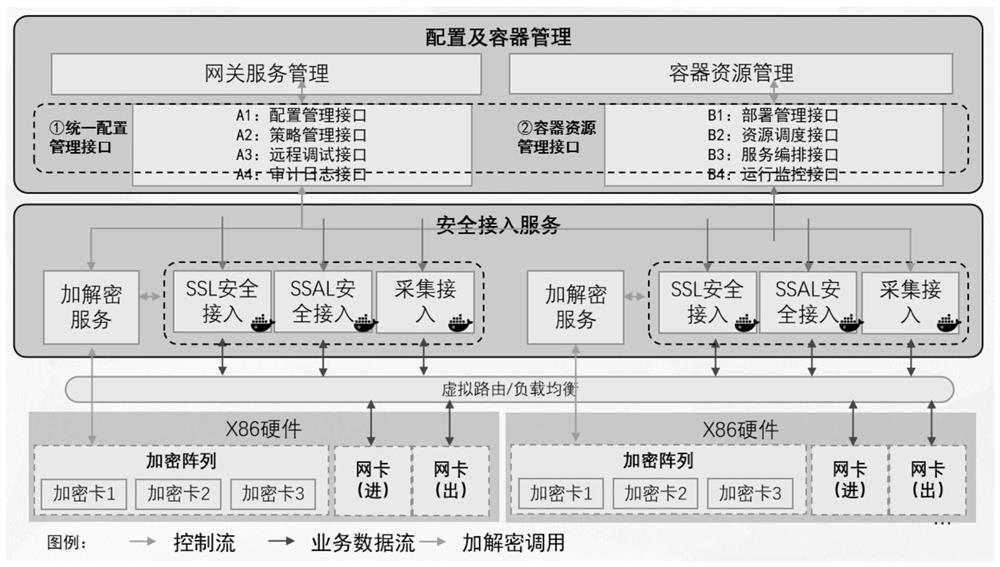
Cluster type virtualization data forwarding method, device and system based on VPP
ActiveCN112905305AImprove distribution performanceRealize dynamic scalingSoftware simulation/interpretation/emulationVirtualizationComputer network
The invention discloses a cluster virtualization data forwarding method, device and system based on VPP, and the method comprises the steps: obtaining a plurality of service containers, forming a containerized cluster, wherein the service containers are obtained through the virtualization of a safety access service; registering all the service containers in a load balancing process, and enabling the load balancing process to provide a unique service address and a unique port number for the outside; when it is monitored that the load balancing process receives an access request sent by a certain client, controlling the load balancing process to communicate with a corresponding service container through a DPDK forwarding driver in the VPP under a kubernetes container framework according to a preset working mode and a polling algorithm, and completing data forwarding. In the invention, the receiving and sending packet drive of all data is based on the DPDK, and the message copy from the user mode to the kernel mode is not involved, so that the performance of the traditional gateway access service based on the DPDK forwarding drive is not influenced.
Owner:STATE GRID ELECTRIC POWER RES INST +3
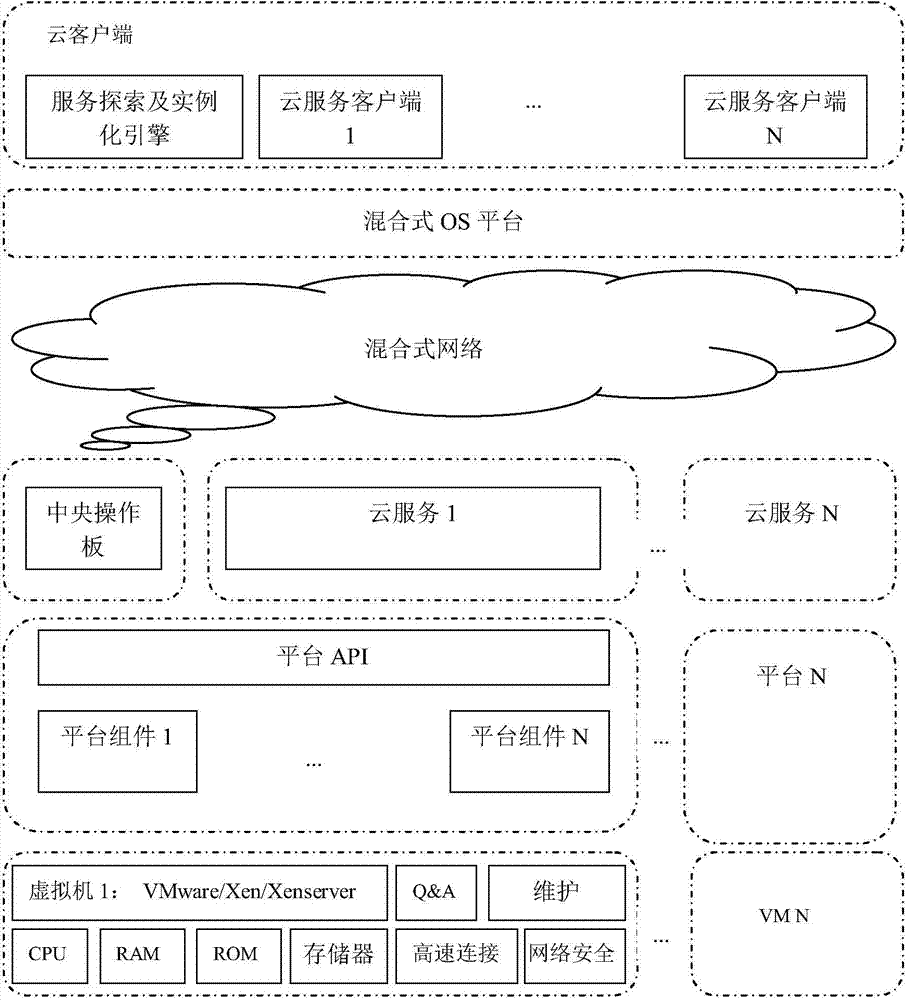
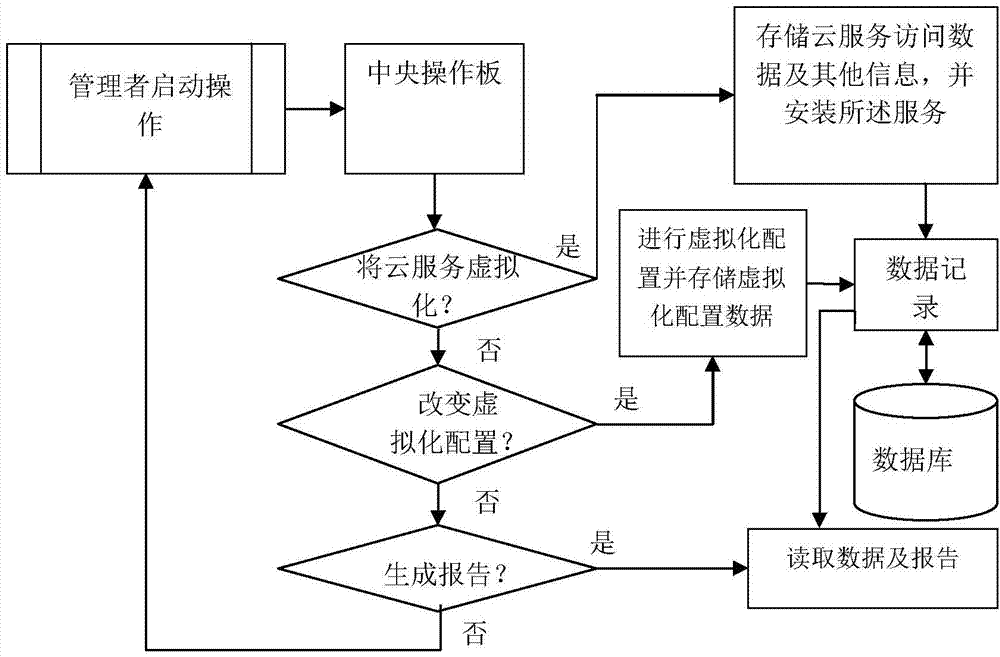
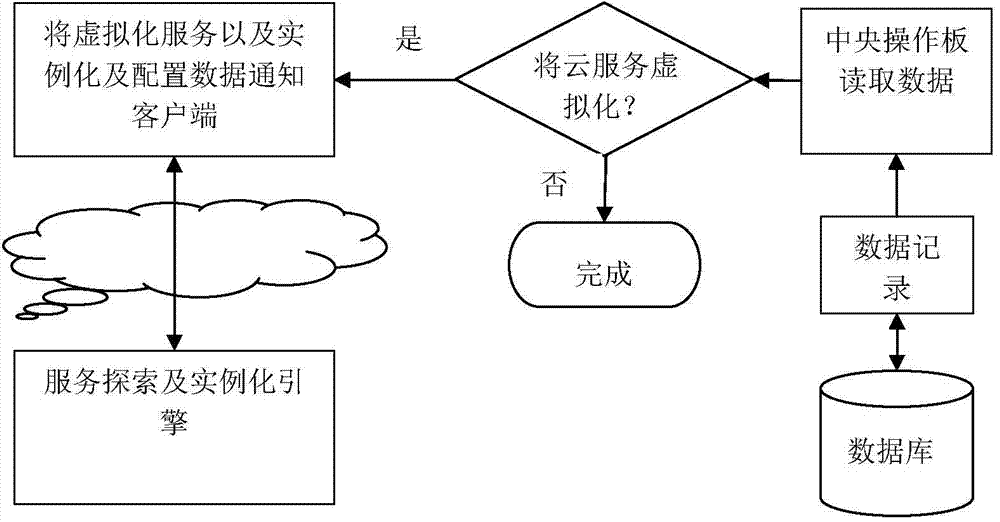
A system used for end-to-end cloud service virtualization
A system used for end-to-end cloud service virtualization is disclosed. The system comprises a central operation panel. The central operation panel is outside an individual virtual machine or in an individual virtual machine, and is used for establishing, updating, deleting, monitoring and regulating all virtual cloud service activities. By the scheme, the system can virtualize a plurality of cloud services through the central operation panel, and one client can visit a plurality of cloud services without the need of establishing and using a plurality of clients.
Owner:深圳市汇洋信息技术有限公司
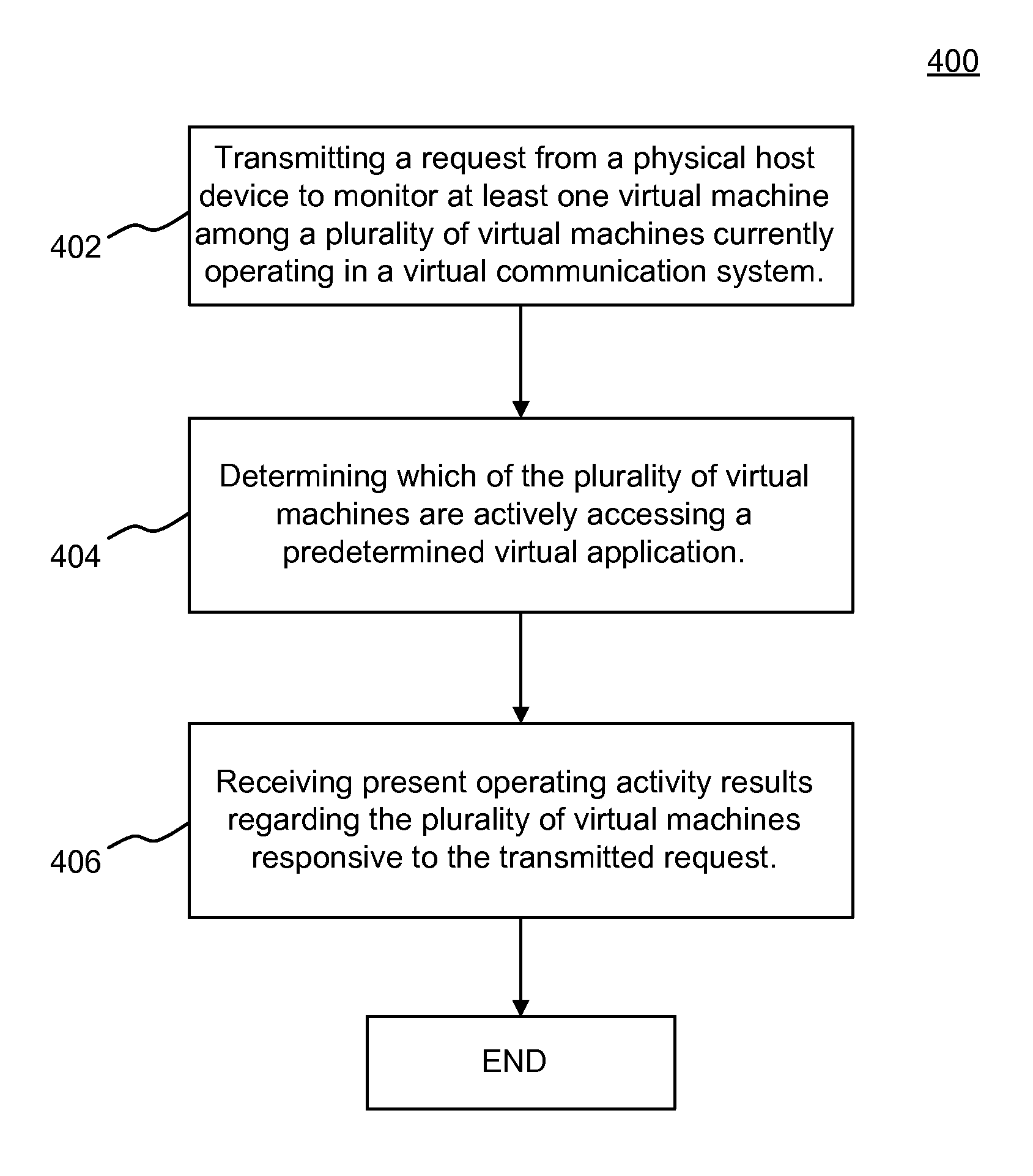
Automatic determination of a virtual machine's dependencies on storage virtualization
Disclosed are examples of observing and measuring virtual machine (VM) activity in a VM communication system environment. According to one example embodiment, an example operation may include transmitting a request from a physical host device to monitor at least one virtual machine among various virtual machines currently operating in a virtual communication system. Additional operations may include determining which of the virtual machines are actively accessing a predetermined virtual application, such as a virtual storage application. The operations may also include receiving present operating activity results regarding the virtual machines responsive to the transmitted request.
Owner:OPEN INVENTION NEWTORK LLC
A method and apparatus for mixed orchestration of services
ActiveCN109039686AAchieve the purpose of interactionRealize logical associationData switching networksVirtualizationService virtualization
A method and apparatus for mix orchestration of services are provided in embodiments of that present invention. The method includes: logically associating one or more components of service virtualization components corresponding to the first virtual platform and / or logically associating one or more components of service containerization components corresponding to the second virtual platform according to the services received by the first virtual platform and / or the second virtual platform; logically associating one or more components of a common component with one or more components of a business virtualization component and / or one or more components of a business containment component; based on logical associations of components in a business virtualization component and / or logical associations of components in a business containment component, and logical associations of the common component with the service virtualization component and / or logical associations with the service containerization component, deploying the service, thus solving the problem of mixed orchestration of the service of the first virtual platform and the second virtual platform.
Owner:ZTE CORP
Labeling gateway for compartmented multi-operator network elements over heterogeneous network
The present invention provides adequate service virtualization and compartmentalization in Network Management Systems for heterogeneous Network Elements to provide interoperability. It introduces a generic mediation layer that can be added to each Network Element that does not provide a network compartmentalization model that is compatible with the one used by the Network Management System. The mediation layer acts as a reverse proxy for the Network Management System to provide an operator with transparent access to an appropriate Management Service. The present invention is also instrumental in providing a high level of security in such hybrid networks.
Owner:ALCATEL LUCENT SAS
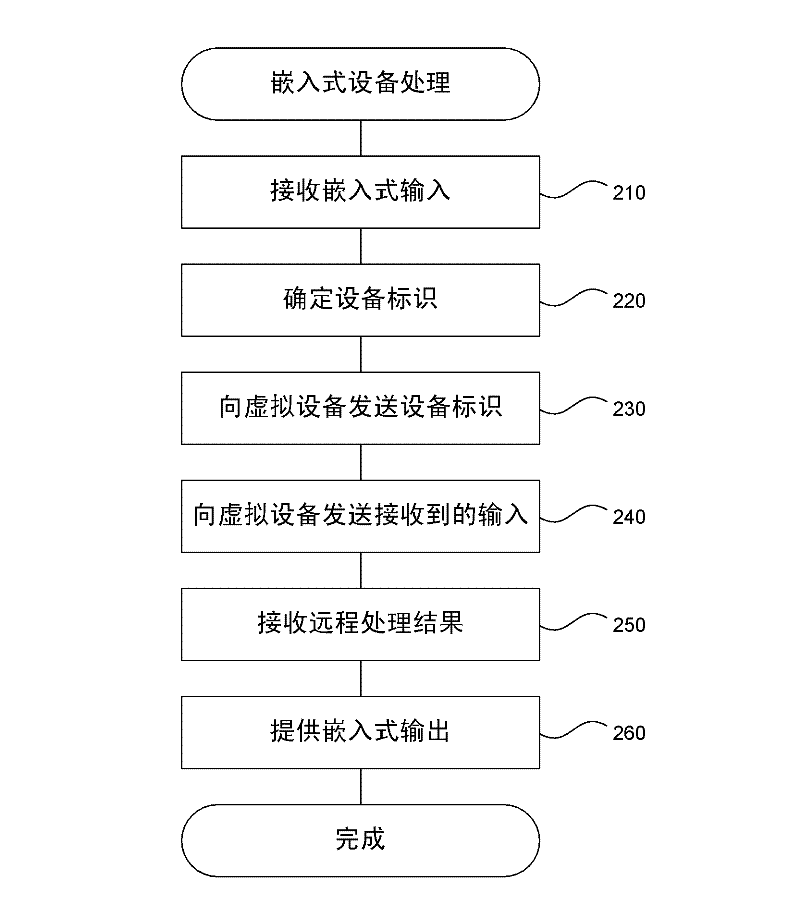
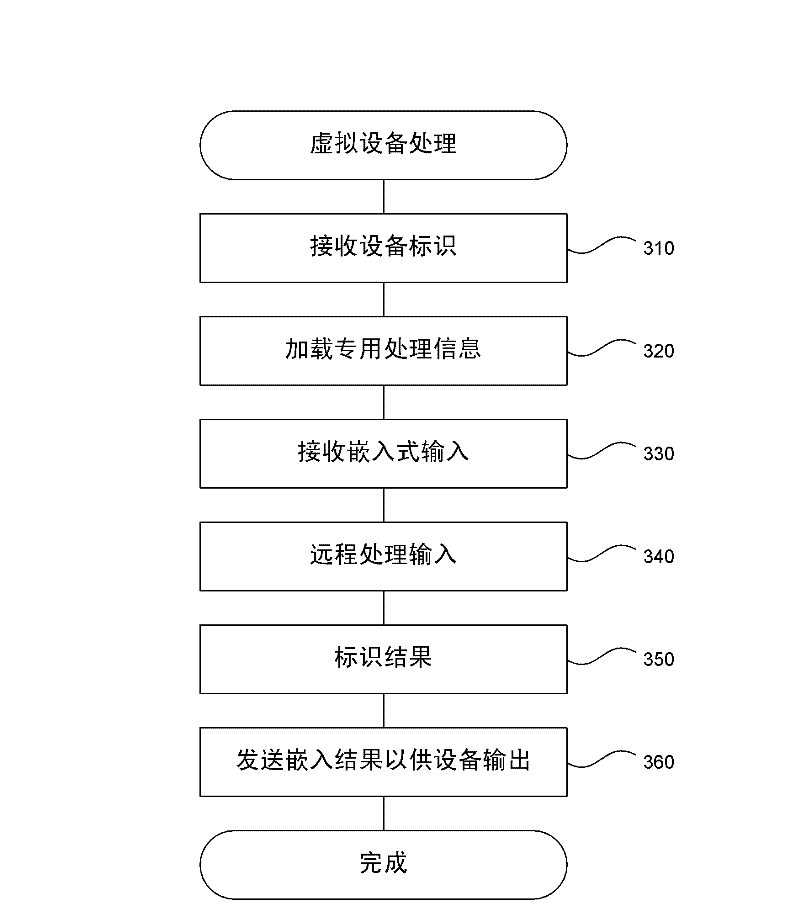
Virtualizing embedded devices
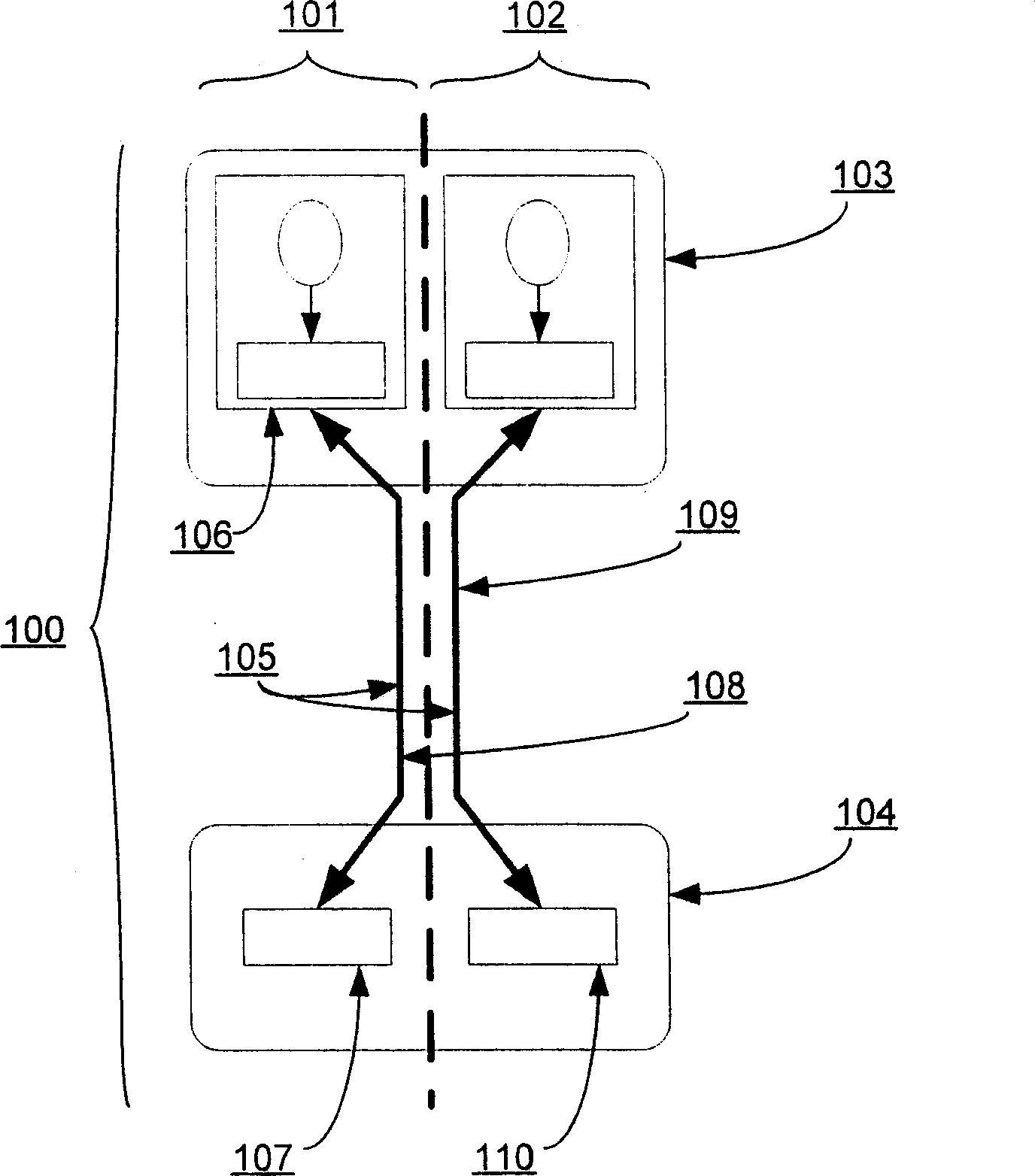
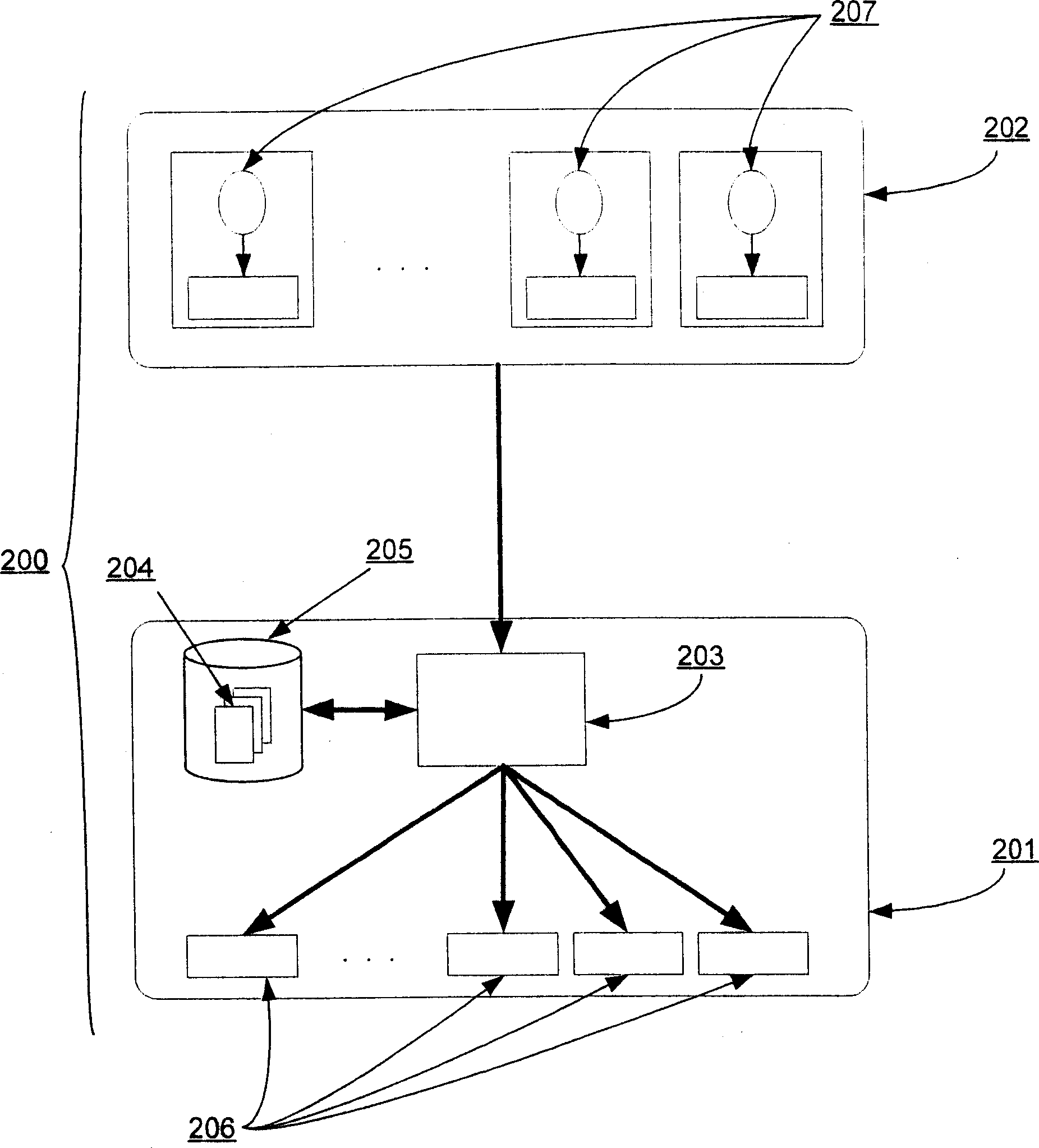
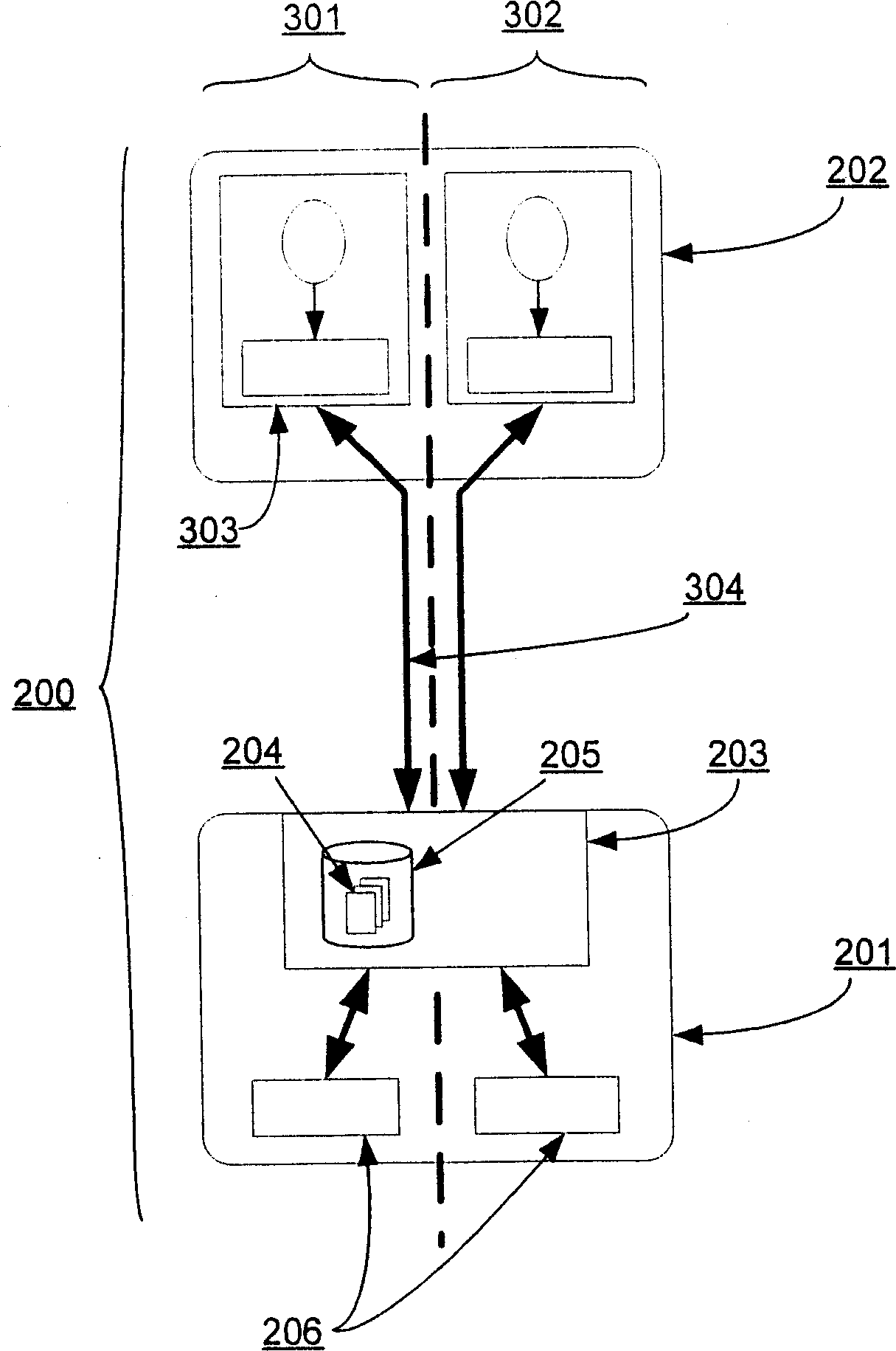
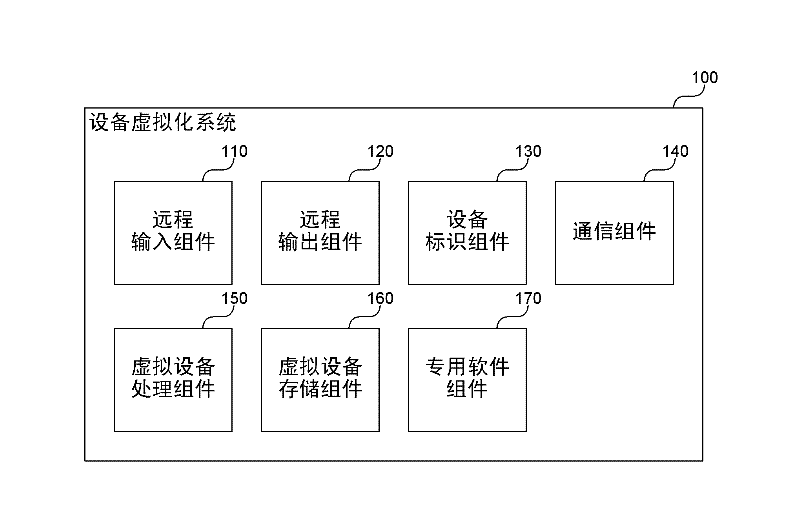
ActiveCN102609297AHigh usefulnessThe testing process is simpleMultiple digital computer combinationsBootstrappingApplication specificEmbedded system
A device virtualization system is described herein that separates common computer processing tasks of an embedded device from the application-specific peripherals of the embedded device to allow at least some functions of the device to be offloaded to servers or other computing devices. The device virtualization system greatly simplifies management, configuration, and control of virtual embedded devices. Because much of the software of the device runs on the virtualization server, information technology (IT) personnel can be assigned to manage the virtualization server and to apply any updates and diagnose any problems that occur. Moreover, a single server or group of servers can be used to provide virtualization services for a wide variety of virtualized embedded devices for a wide variety of users. Thus, the system enhances the usefulness of embedded devices and allows a longer lifetime and wider variety of uses than embedded devices today.
Owner:MICROSOFT TECH LICENSING LLC
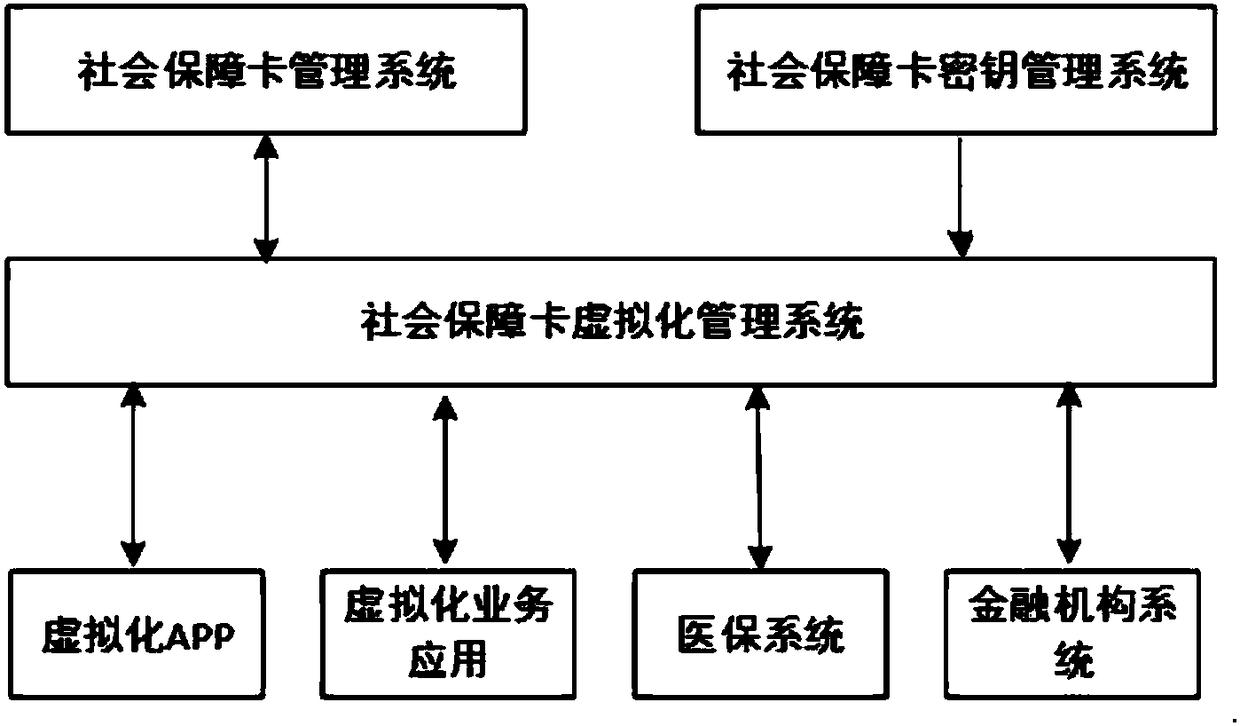
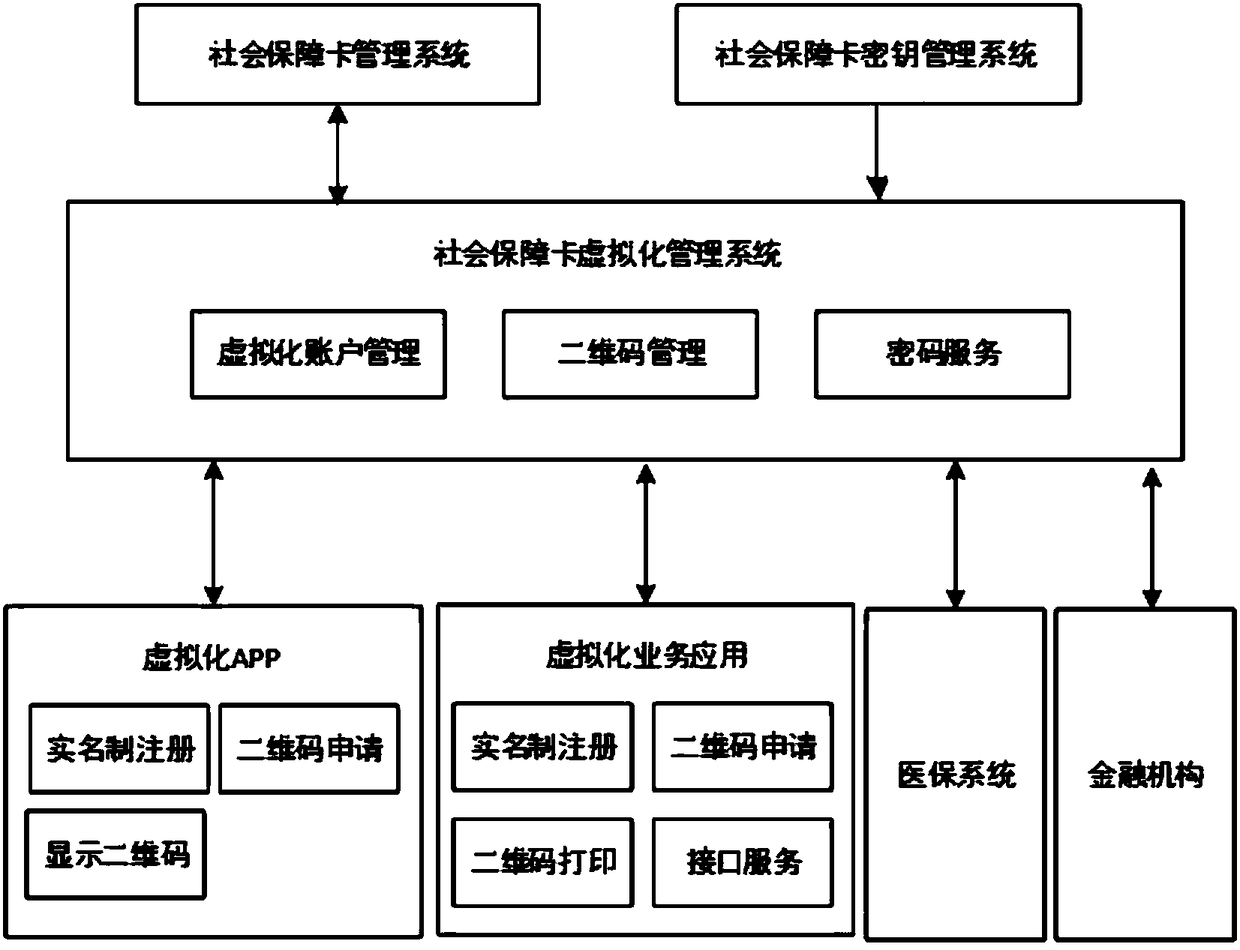
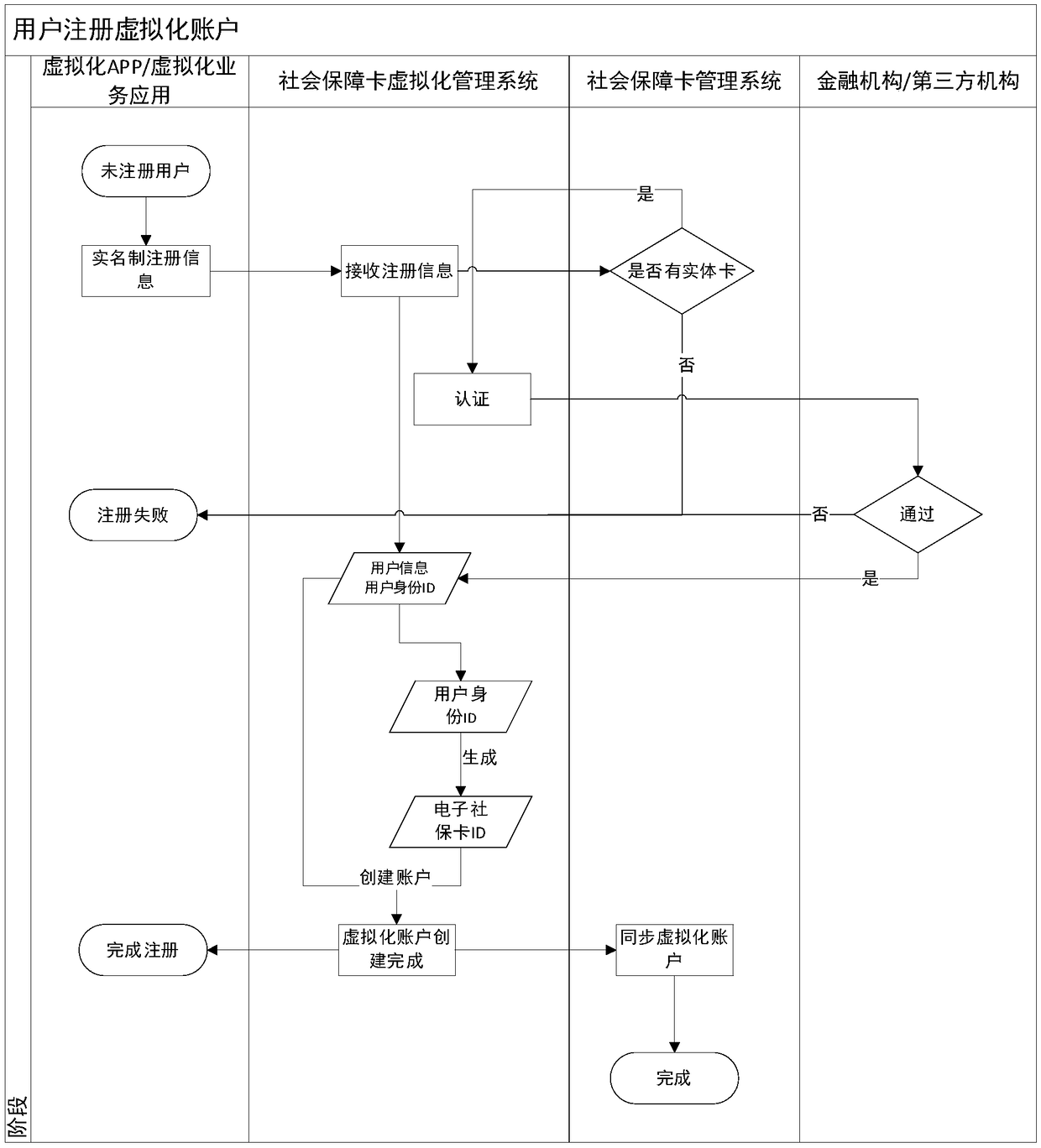
Social security card virtualization system and implementation method
InactiveCN108108985AOptimize service processEasy to useFinanceCo-operative working arrangementsService flowVirtualization
The invention discloses a social security card virtualization system and a method. The social security card virtualization system includes a social security card management system, a social security card key management system, a social security card virtualization management system, a virtualized APP, a virtualized business application, a medical insurance system and a financial institution system; the social security card management system manages social security physical cards, and the management of the social security physical cards involves the card production and card issuance of the physical cards; the social security card key management system provides keys for the encryption of social security virtual cards; the social security virtual card management system performs management soas to provide services of applying for and generating virtual cards for insured people who have the physical cards; the virtualized APP provides mobile services of the social security virtual cards; the virtualized business application provides computer-side social security virtual card services; and the medical insurance system and the financial institution system provide settlement services. With the social security card virtualization system and the method of the invention adopted, online and offline integrated social security card services can be provided; the optimization of a service flow can be promoted; the use of two-dimensional codes is safer. The social security card virtualization system and the method can replace physical cards to perform online services. The social security card virtualization system and the method have the advantages of high efficiency and low cost.
Owner:DAREWAY SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com