On-demand-service virtualization network intrusion detection method and device
A virtualized network and intrusion detection technology, applied in the field of virtualized network intrusion detection, can solve problems such as inability to allocate and use hardware resources on demand, data congestion on packet capture ports, etc., achieve good platform adaptability, reduce consumption and impact, Guaranteed detection performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
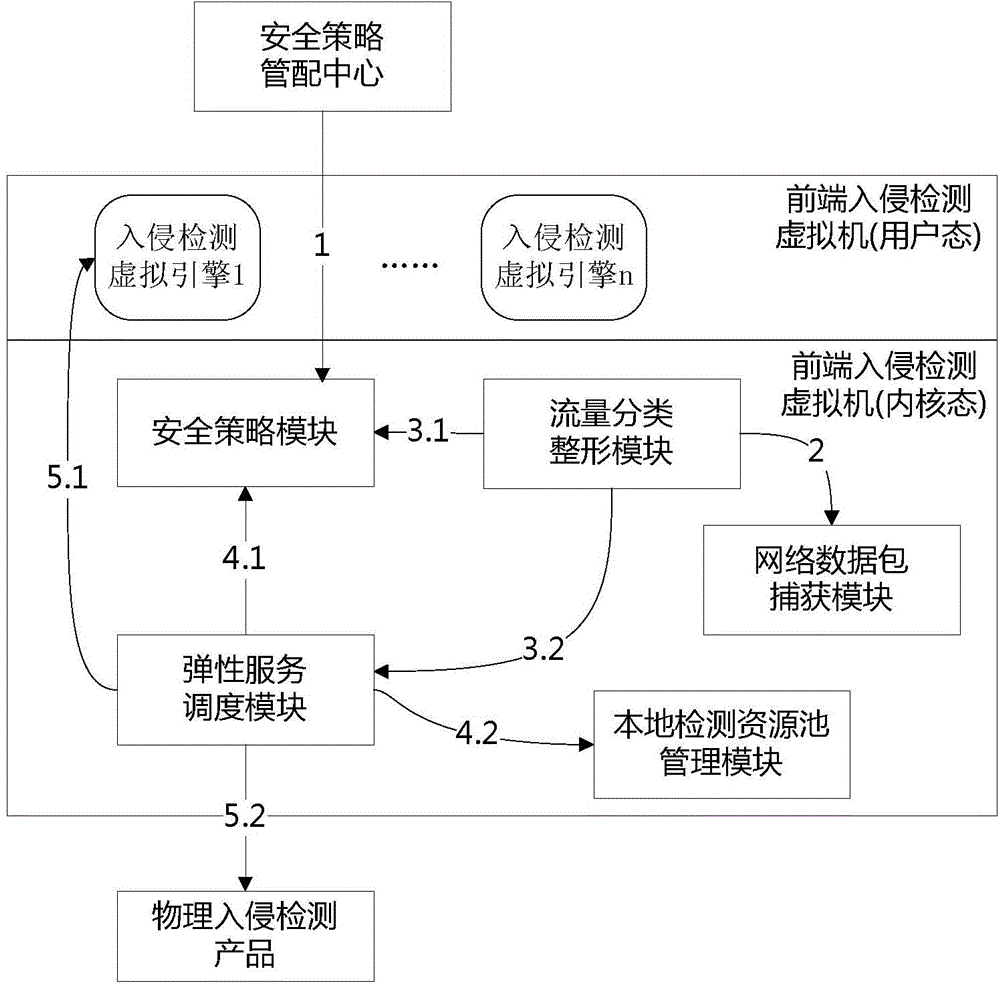
[0030] The invention discloses a network intrusion detection device capable of on-demand service in a virtualized network, which at least includes a network data packet capture module, a flow classification shaping module, an elastic service scheduling module, a local detection resource pool management module, and a network intrusion detection engine module and the security policy module, where:
[0031]The network data packet capture module runs in the kernel state of the network intrusion detection front-end virtual machine, monitors the network data flow on the virtual switch, and captures the data packets of the network interface specified by the security policy. Among them, the network interface specified by the security policy refers to the network interface on the virtual switch corresponding to the virtual machine or virtual network that needs to be monitored given by the security policy (such as the network flow specified by the IP address of the virtual machine or by ...
Embodiment 2
[0057] The invention also discloses a virtualized network intrusion detection method that can provide flexible services on demand, the detailed flow of the method is as follows Figure 4 shown, including the following operations:
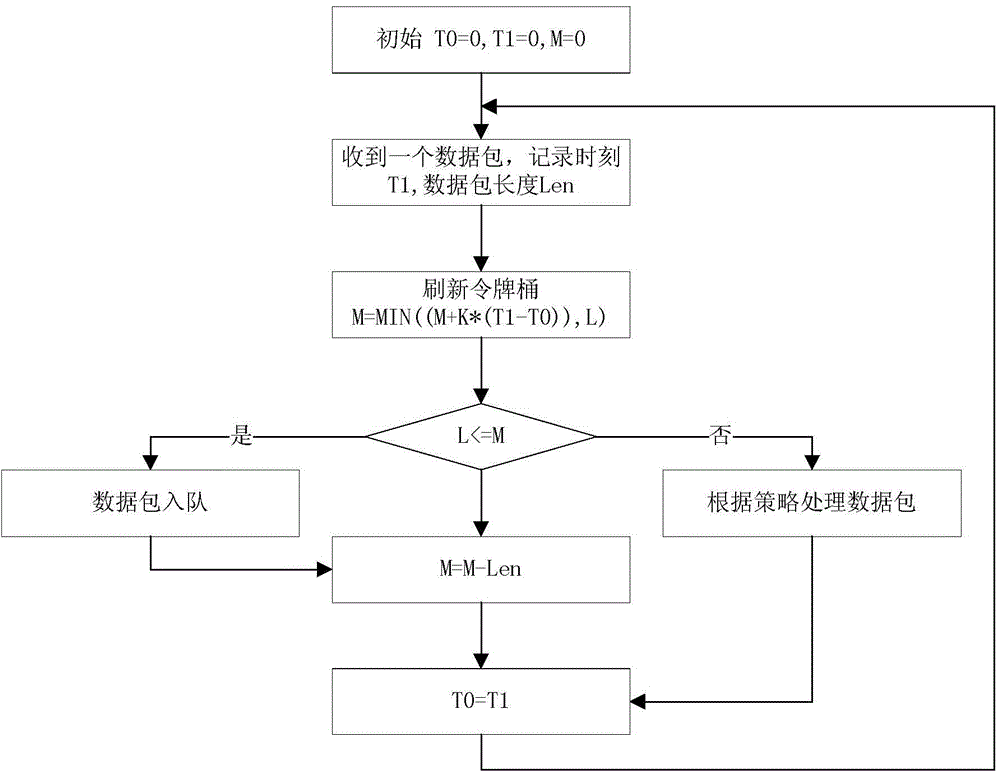
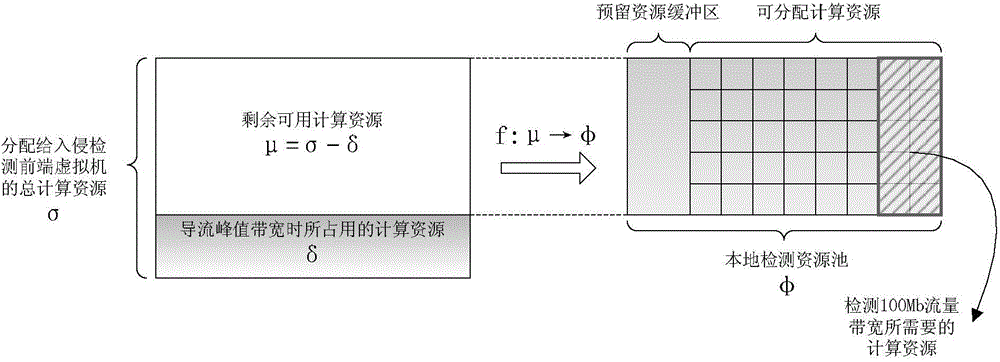
[0058] When a data packet of a network service flow is captured, first judge whether the data packet needs to be monitored according to the virtual network security domain boundary policy in the security policy, and discard it if not; otherwise, find the detection source corresponding to the network flow If the upper limit of the traffic bandwidth is -1, it will be directly exported to the hardware network intrusion detection product through the elastic service scheduling module; otherwise, it will be classified according to the security policy, and the corresponding detection source corresponding to the local detection source to which the data packet belongs will be found. Queue, and calculate whether the data packet is allowed to enter the queue t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com