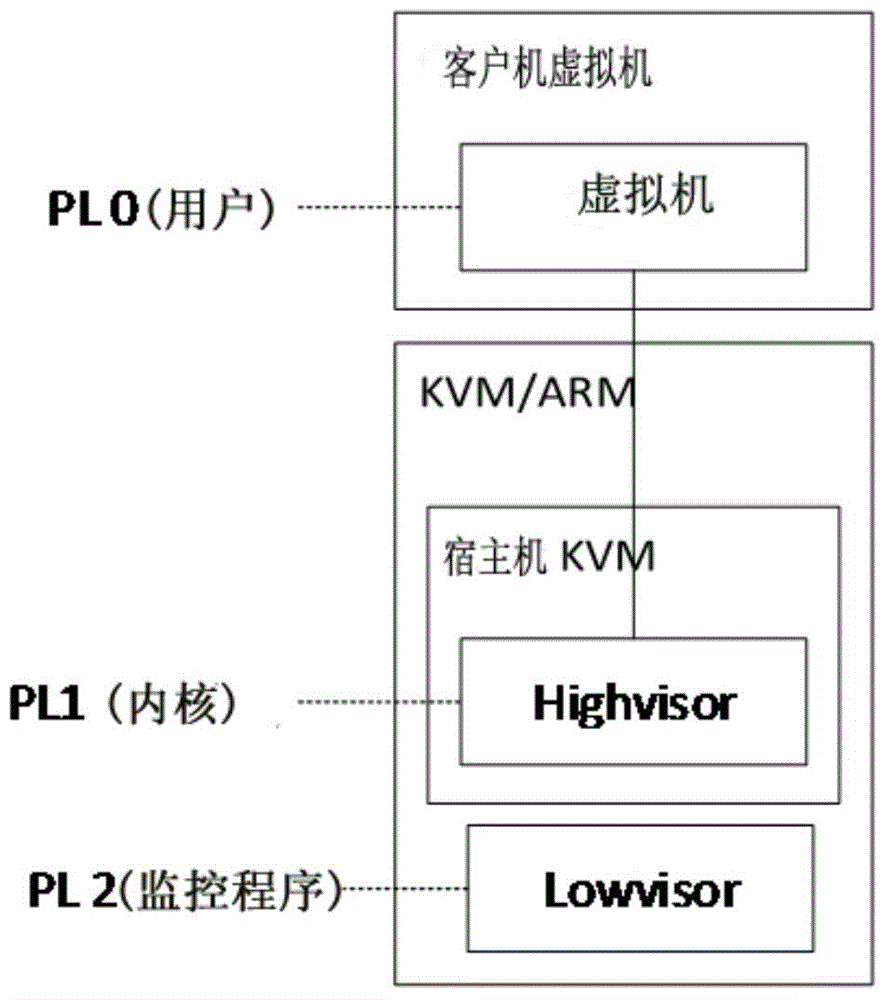
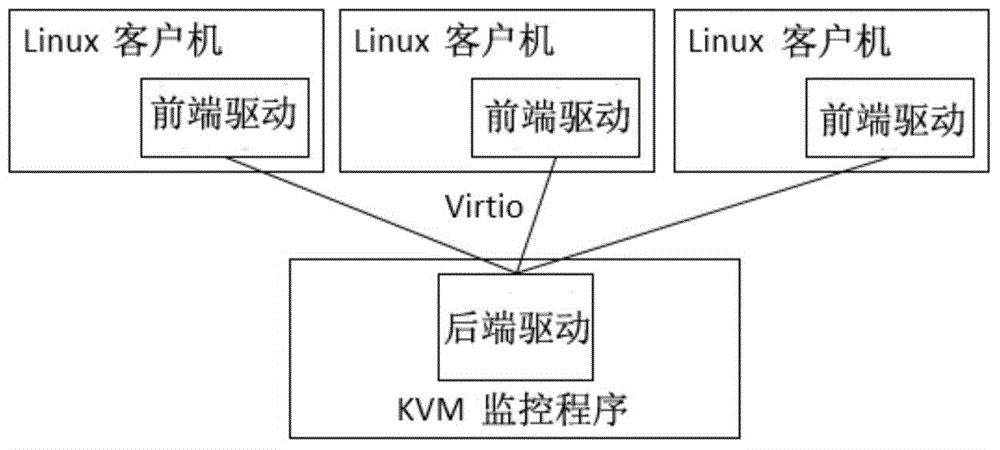
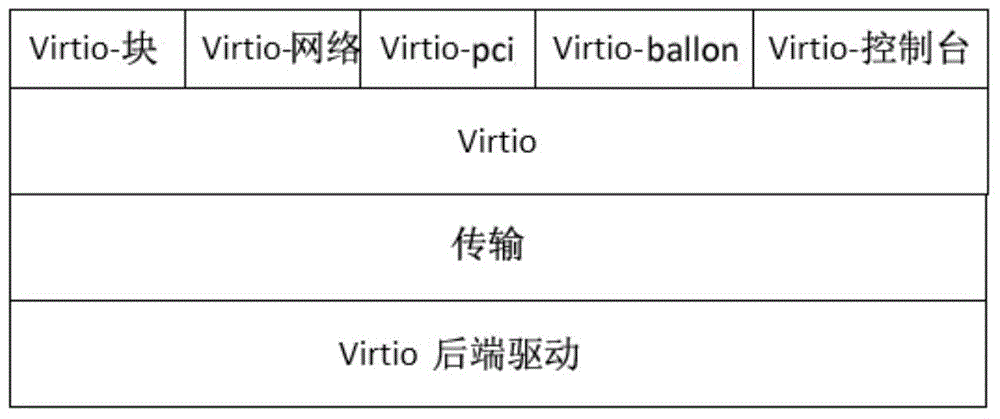
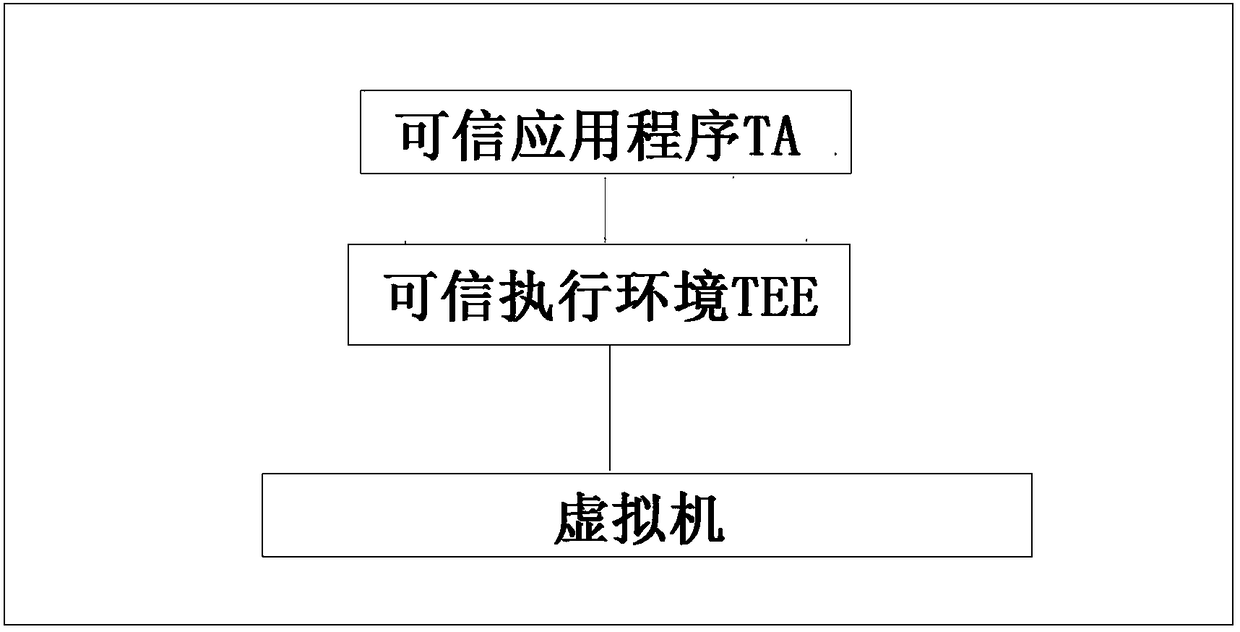
Patents
Literature
69 results about "Nested virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
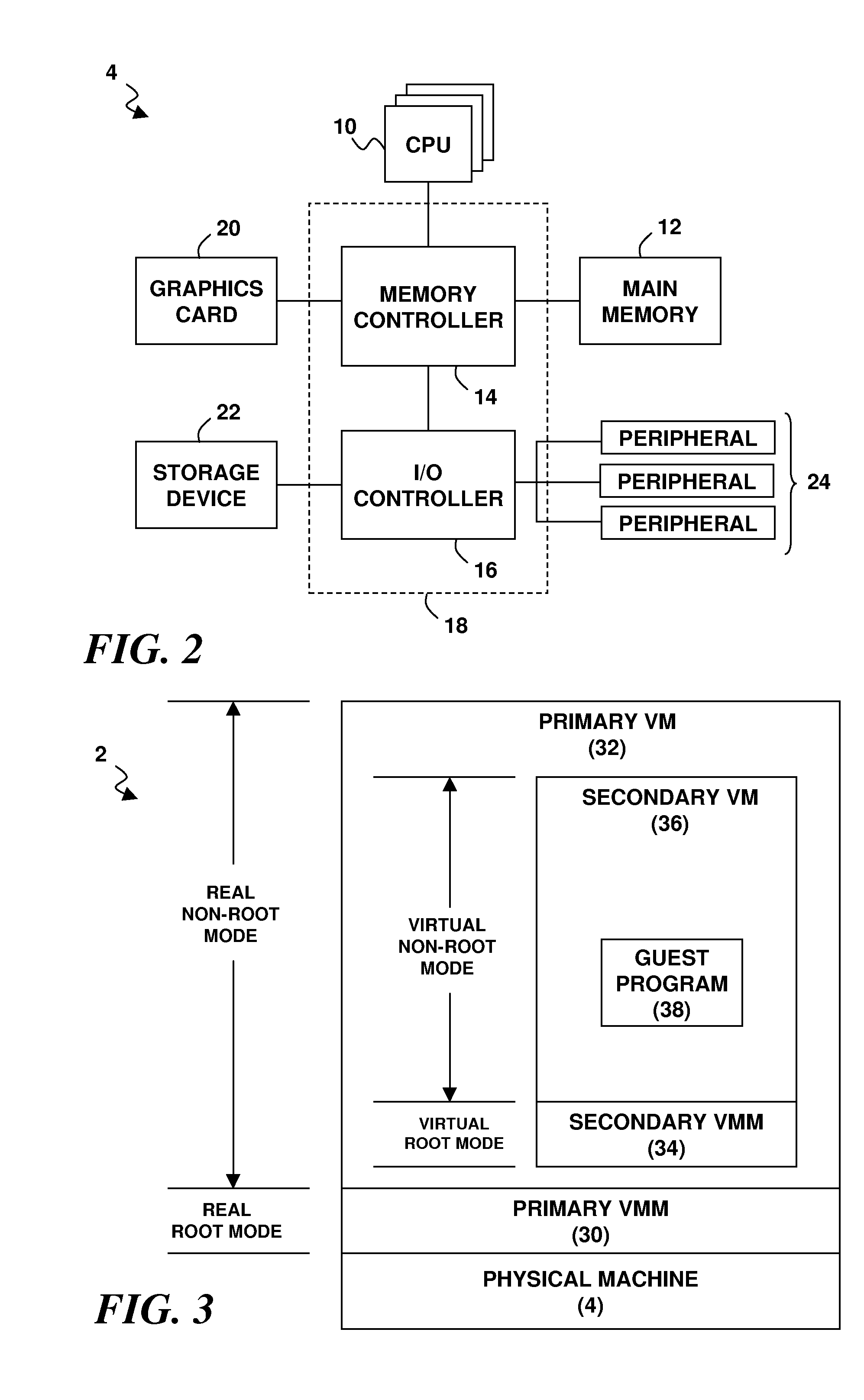
Virtualization, in computing, refers to the act of creating a virtual version of something, including but not limited to a virtual computer hardware platform, operating system, storage device, or computer network resources. A hypervisor is a software layer that creates the virtualization by abstracting away the underlying physical infrastructure and presenting virtual resources to the system. The term virtual machine typically refers to an encapsulated entity which includes the operating system, the applications running inside it as well as meta data that define it. It is treated as a "guest" which runs on top of a physical server which serves as the "host". Virtualization is often considered the key enabling technology in delivering infrastructure as a service solutions. Nested virtualization refers to the act of creating an additional layer of abstraction and encapsulation in a pre-existing virtualized environment.
Storage virtualization system and methods
InactiveUS6857059B2Reduce consumptionWithout impactInput/output to record carriersMemory adressing/allocation/relocationStorage area networkNetwork virtualization
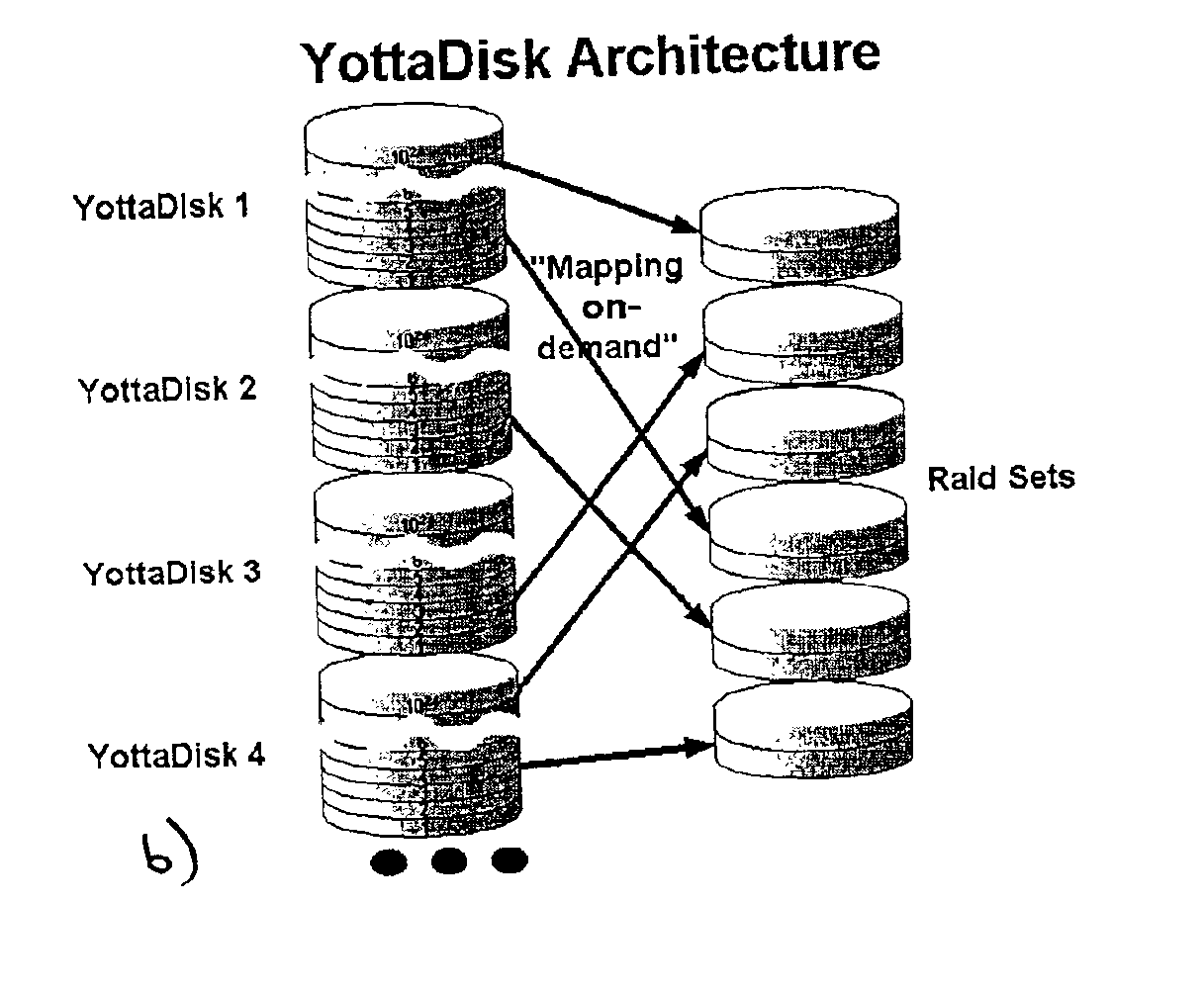
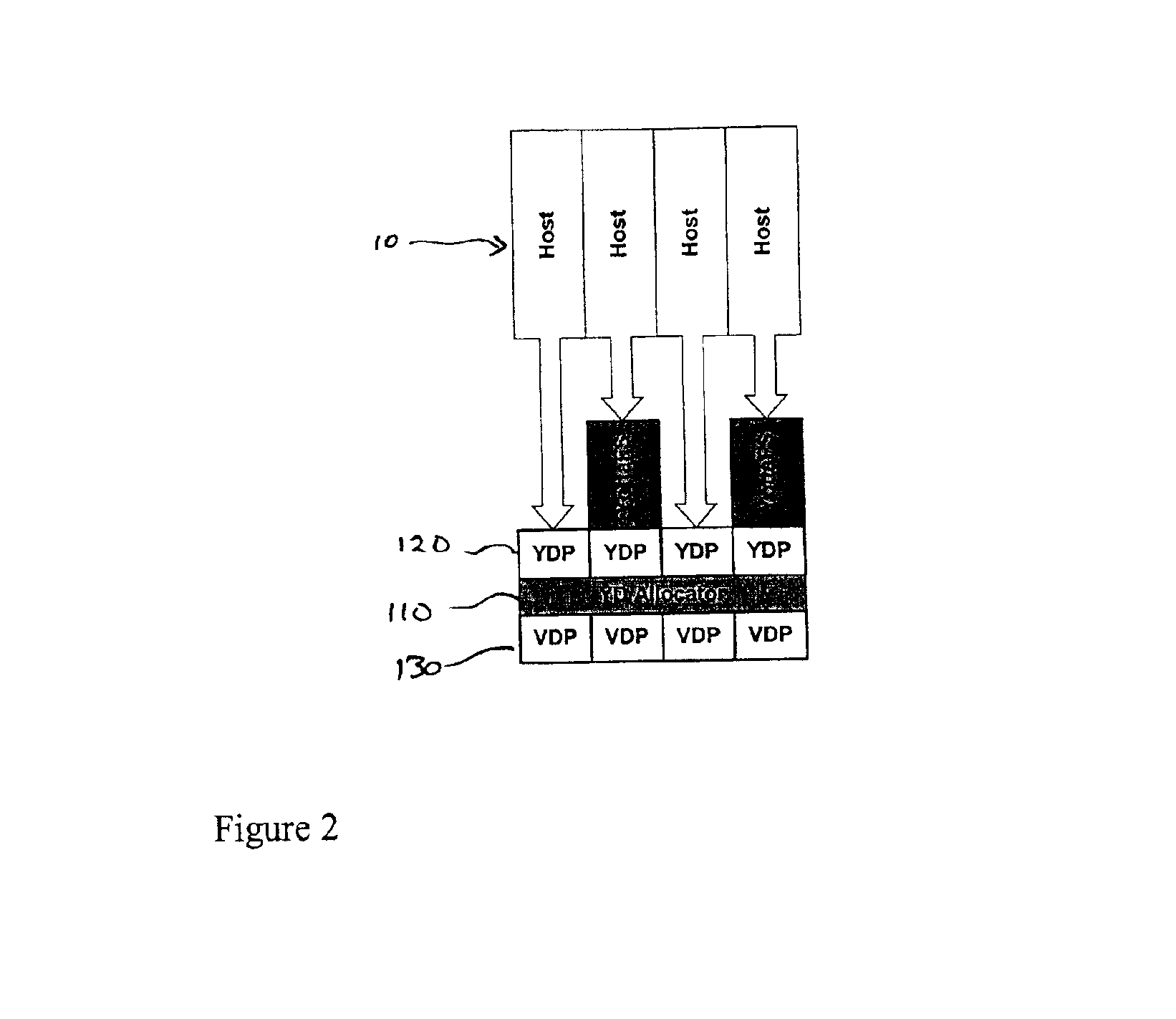
Storage virtualization systems and methods that allow customers to manage storage as a utility rather than as islands of storage which are independent of each other. A demand mapped virtual disk image of up to an arbitrarily large size is presented to a host system. The virtualization system allocates physical storage from a storage pool dynamically in response to host I / O requests, e.g., SCSI I / O requests, allowing for the amortization of storage resources through a disk subsystem while maintaining coherency amongst I / O RAID traffic. In one embodiment, the virtualization functionality is implemented in a controller device, such as a controller card residing in a switch device or other network device, coupled to a storage system on a storage area network (SAN). The resulting virtual disk image that is observed by the host computer is larger than the amount of physical storage actually consumed.
Owner:EMC IP HLDG CO LLC
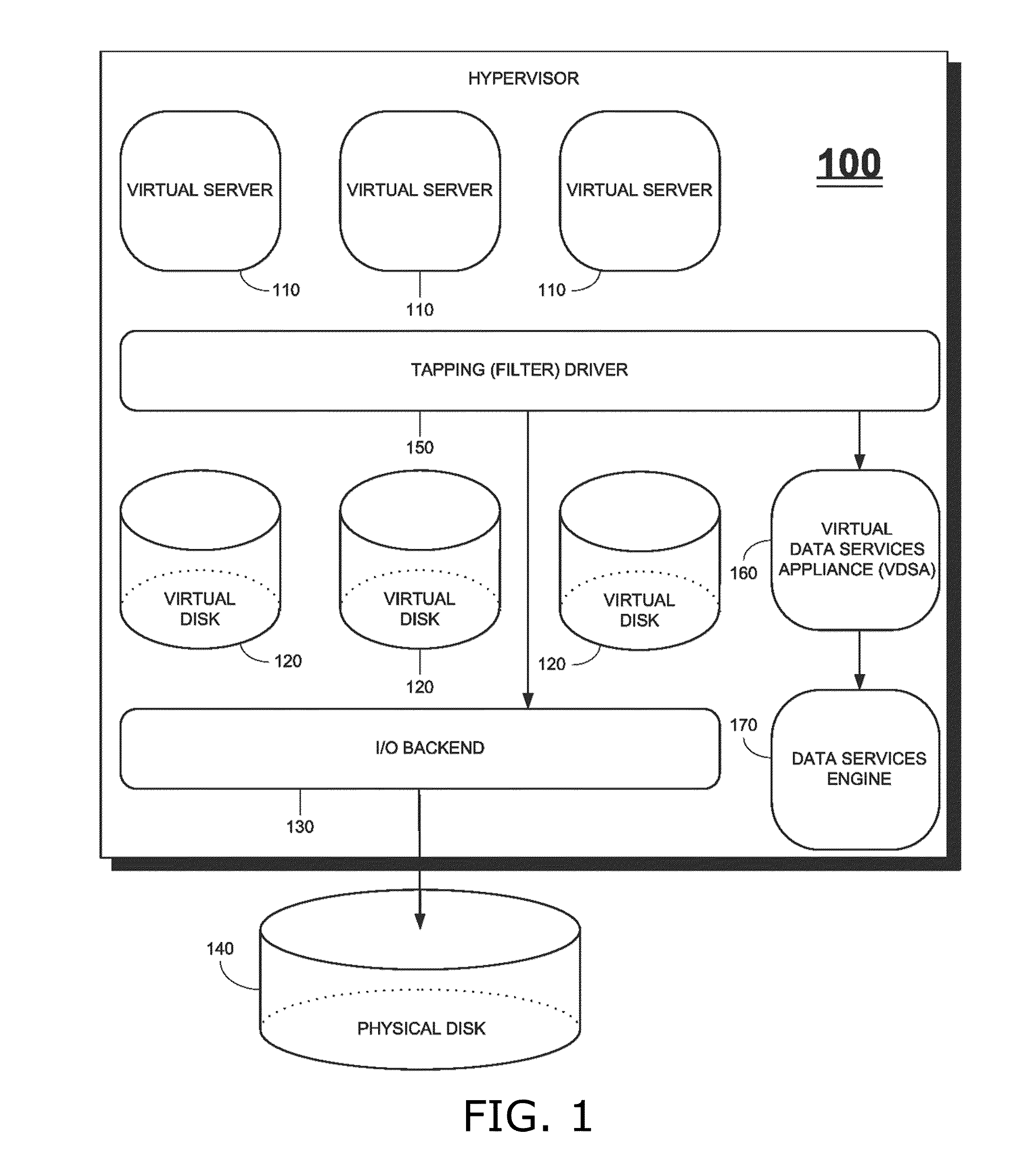
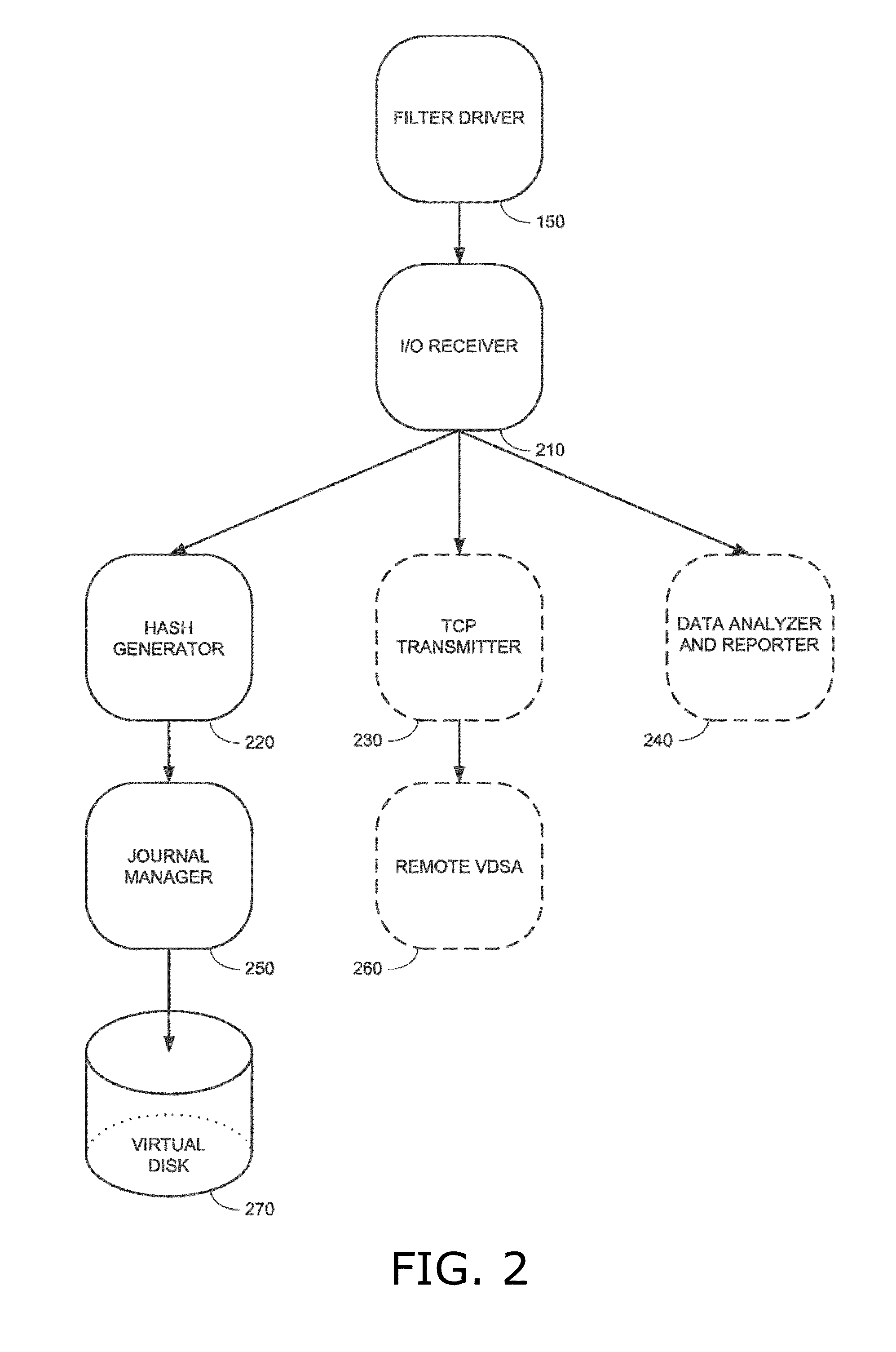
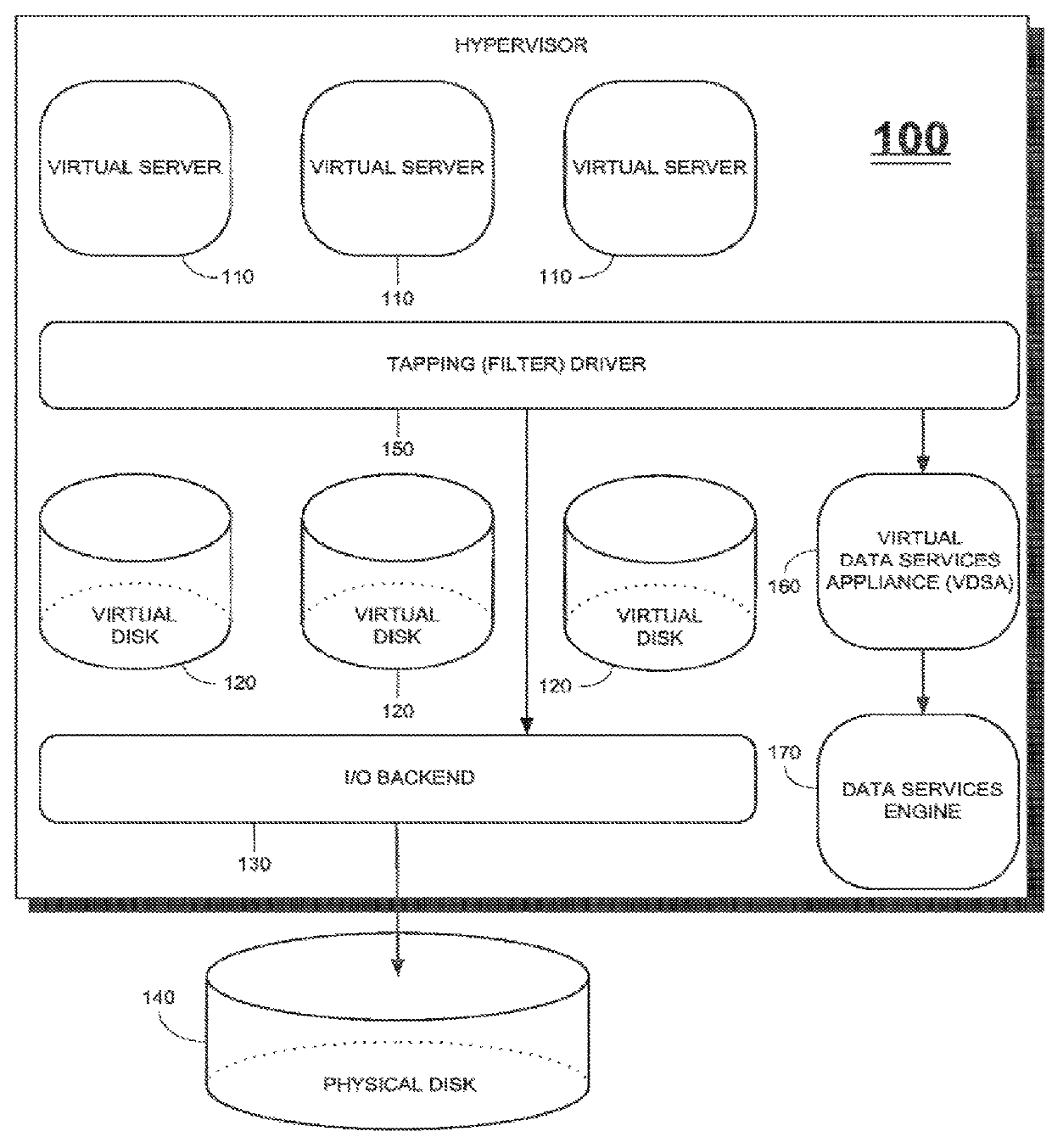
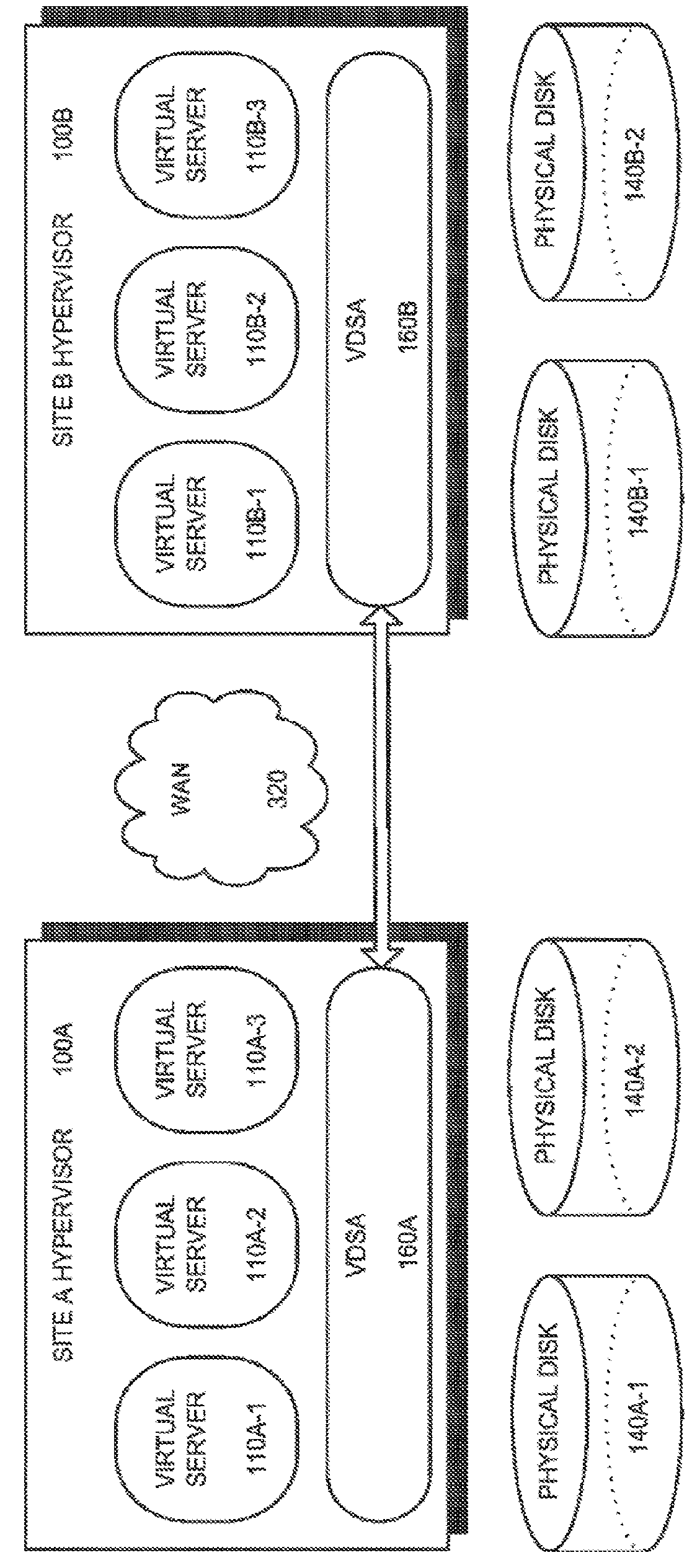
Methods and apparatus for providing hypervisor level data services for server virtualization
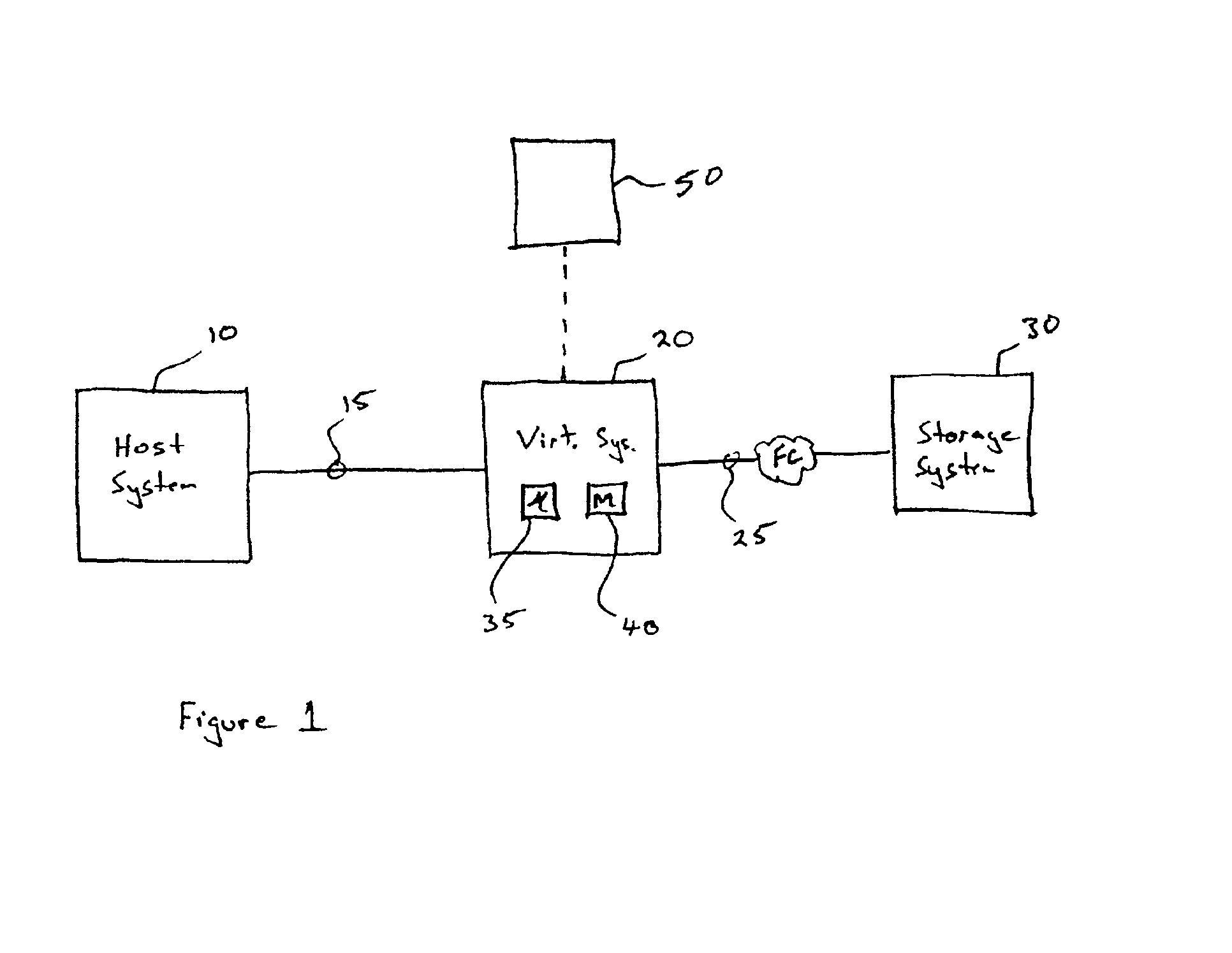
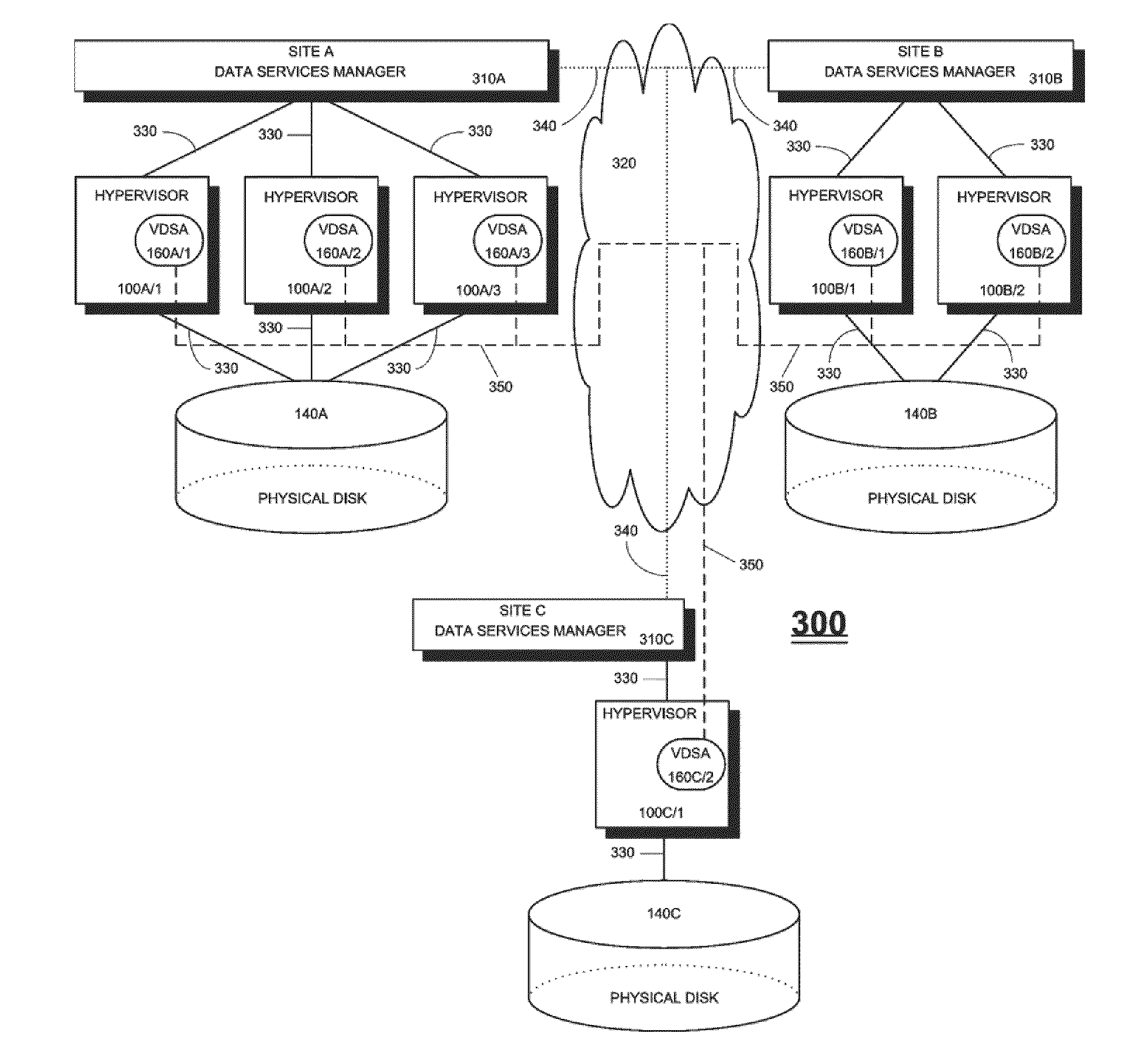
A system for cloud-based data services for multiple enterprises, including a plurality of cloud hypervisors that cooperatively provide cloud-based services to multiple enterprises, each hypervisor including a plurality of cloud virtual servers, each cloud virtual server being associated with an enterprise, at least one cloud virtual disk that is read from and written to by the at least one virtual server, each cloud virtual disk being associated with an enterprise, and a virtual data services appliance, which provides cloud-based data services, and multiple data services managers, one data services manager per respective enterprise, each of which coordinates the respective virtual data services appliances for those cloud hypervisors that service its corresponding enterprise.
Owner:ZERTO
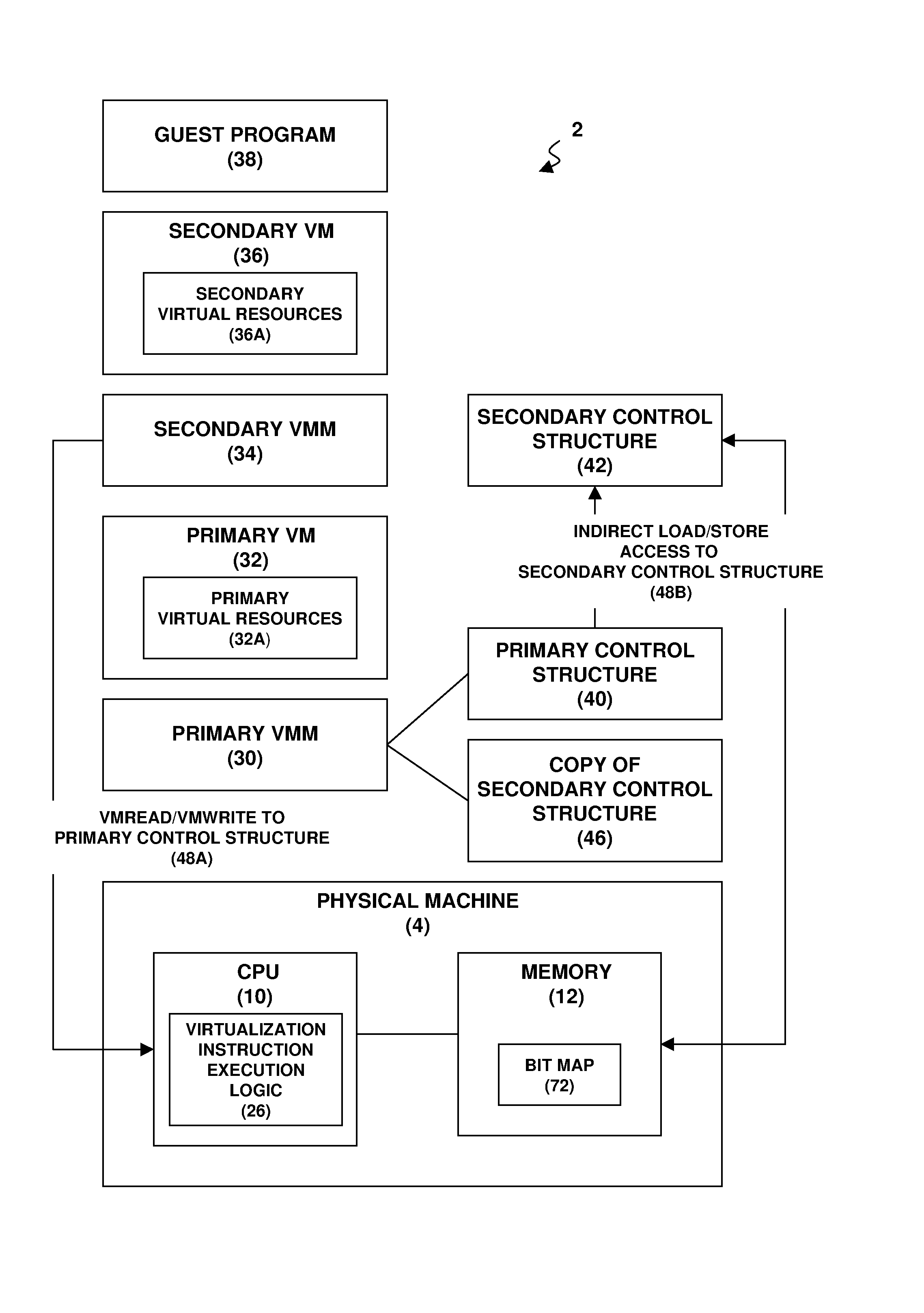
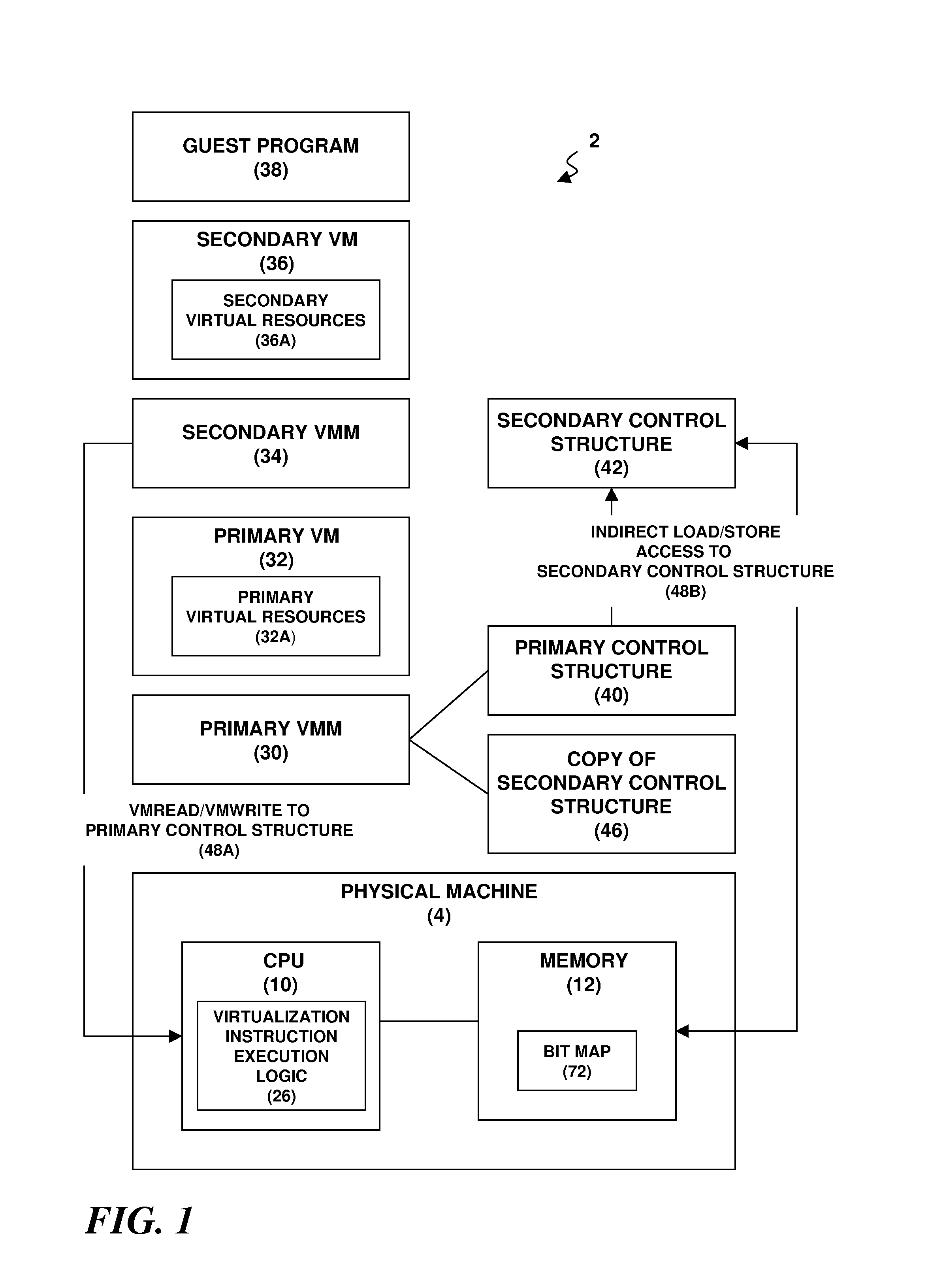
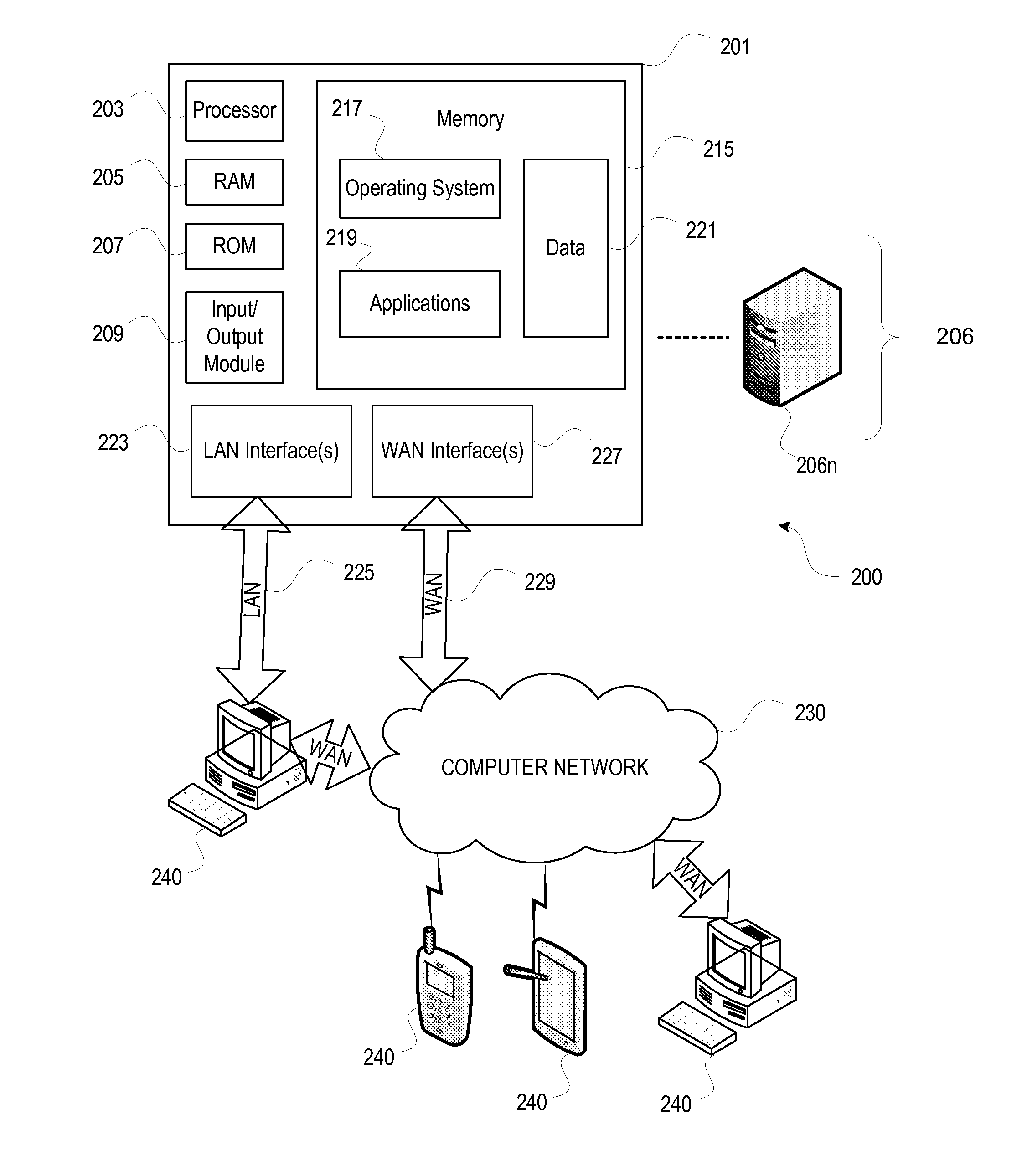
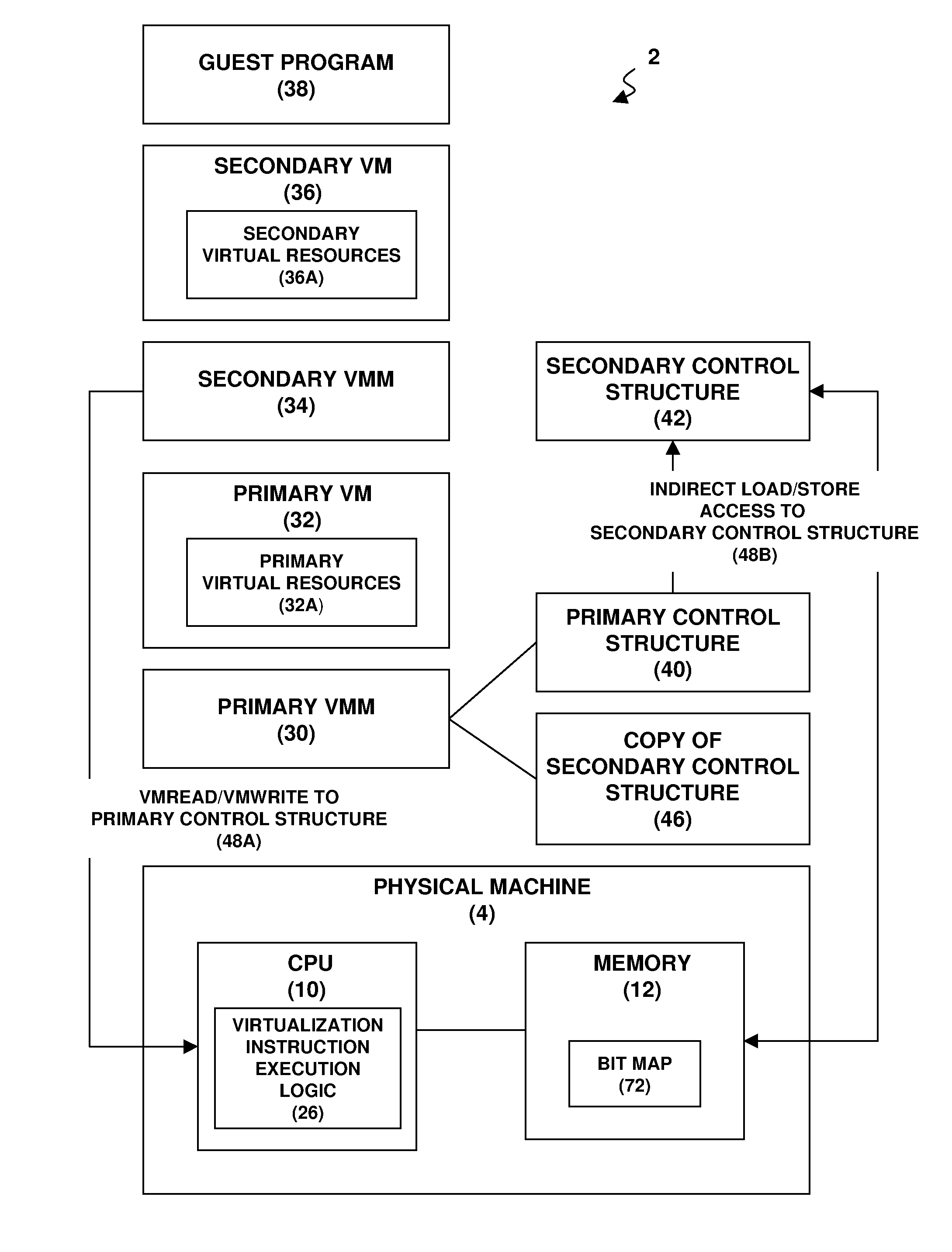
Nested Virtualization Performance In A Computer System
InactiveUS20110072428A1Improve performanceSoftware simulation/interpretation/emulationMemory systemsVirtualizationData access
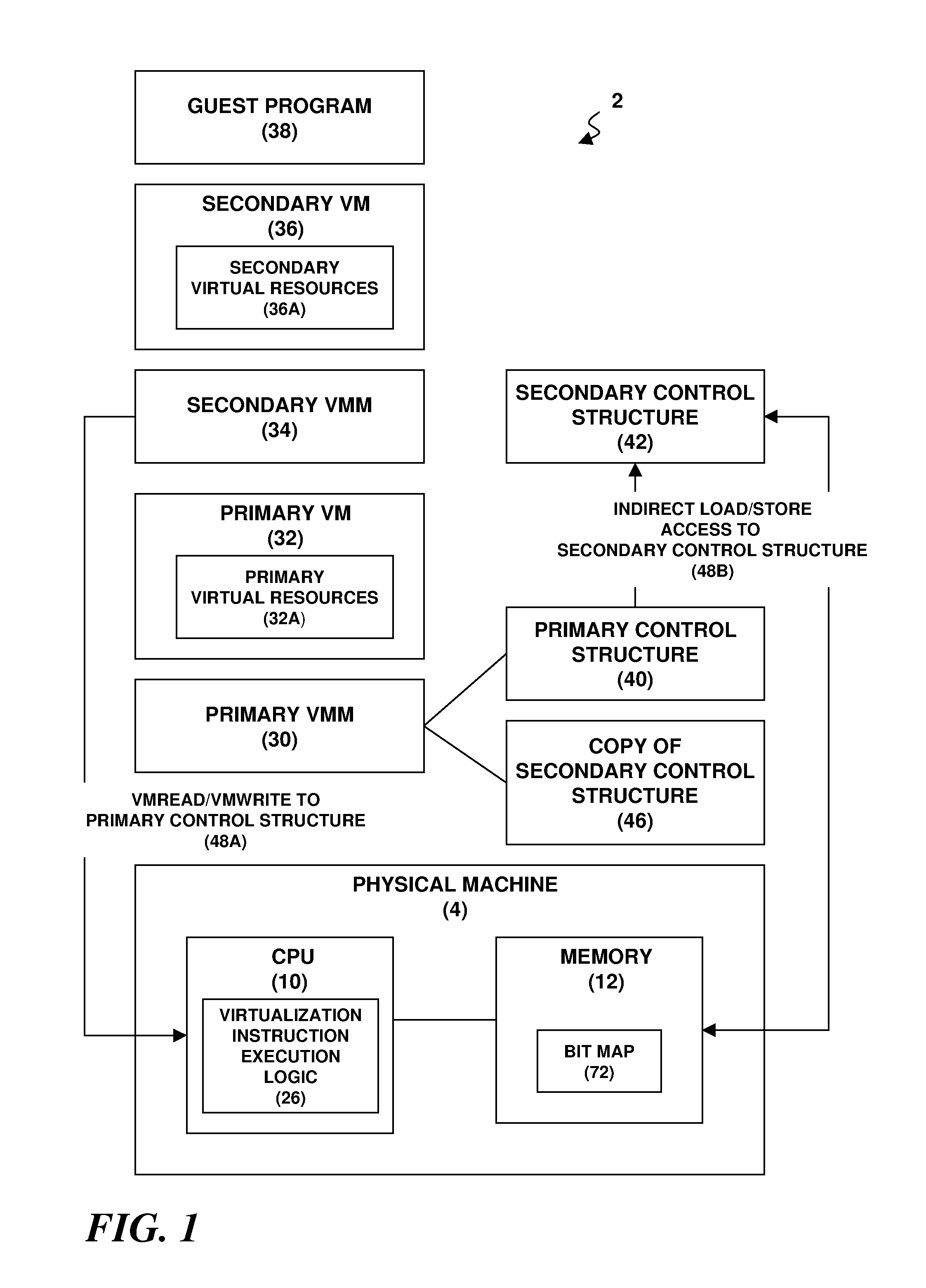
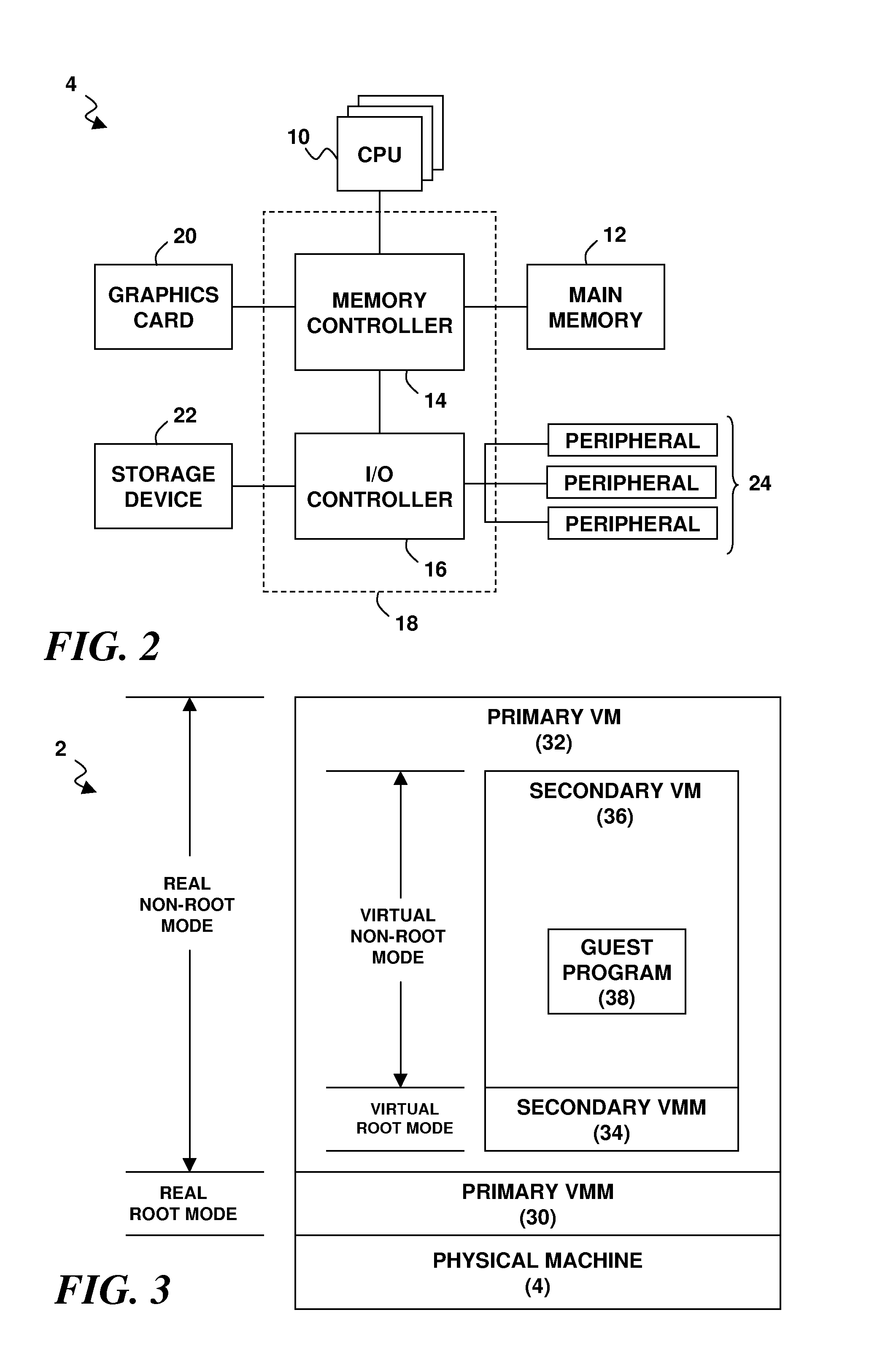
A virtualization architecture for improving the performance of nested virtualization in a computer system. A virtualization instruction reads or writes data in a control structure used by a virtual machine monitor (VMM) to maintain state on a virtual machine (VM) to support transitions between a root mode of operation of a CPU in which the VMM executes and a non-root mode of operation of the CPU in which the VM executes. A privileged data access is made to a primary control structure according to the virtualization instruction if the CPU is in the root mode. A non-privileged data access is made to a secondary control structure according to the virtualization instruction if the CPU is in the non-root mode and a secondary control structure field in the primary control structure is enabled.
Owner:IBM CORP
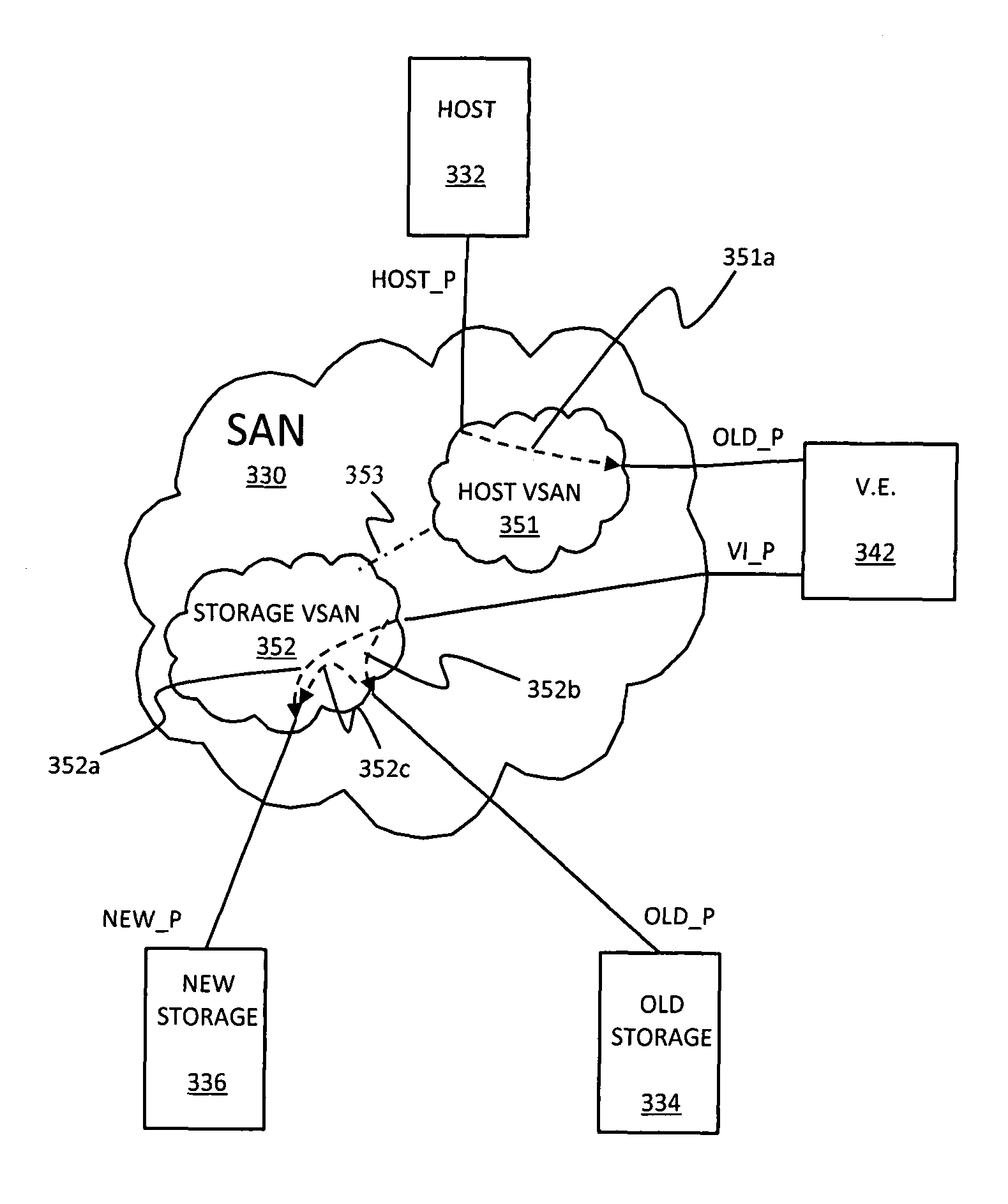
Non-disruptive data mobility using virtual storage area networks with split-path virtualization
ActiveUS8028062B1Computer security arrangementsMultiple digital computer combinationsArea networkName server
A system creates a storage area network (SAN) centric storage virtualization layer in front of storage devices. The system allows data mobility and migration without disruption to the one or more host servers attached to the SAN. Specifically, the host servers are not disrupted when switching I / Os between physical and virtual storage, for example, by taking advantage of WWPN spoofing and Fibre Channel VSAN technology. The use of VSANs effectively allow multiple virtual directors and / or switches to be created within a physical director and / or switches, each with their own separate name server, thereby providing complete isolation from one another. The host-storage pathing information is unchanged as the original physical storage port's WWPNs are spoofed by the virtual storage port. The result is two identical WWPNs within the SAN which is normally disallowed; however, by separating the physical port WWPN into one VSAN and the virtual port WWPN into another, the restriction may be circumvented.
Owner:EMC IP HLDG CO LLC
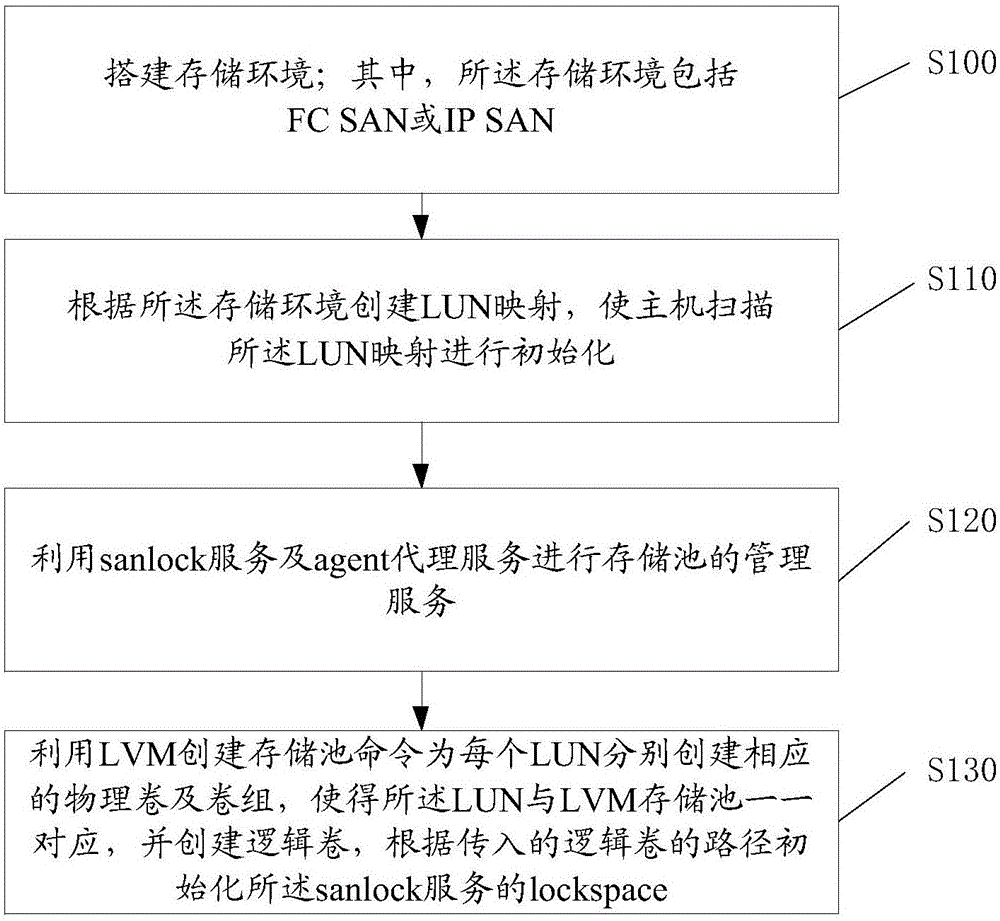
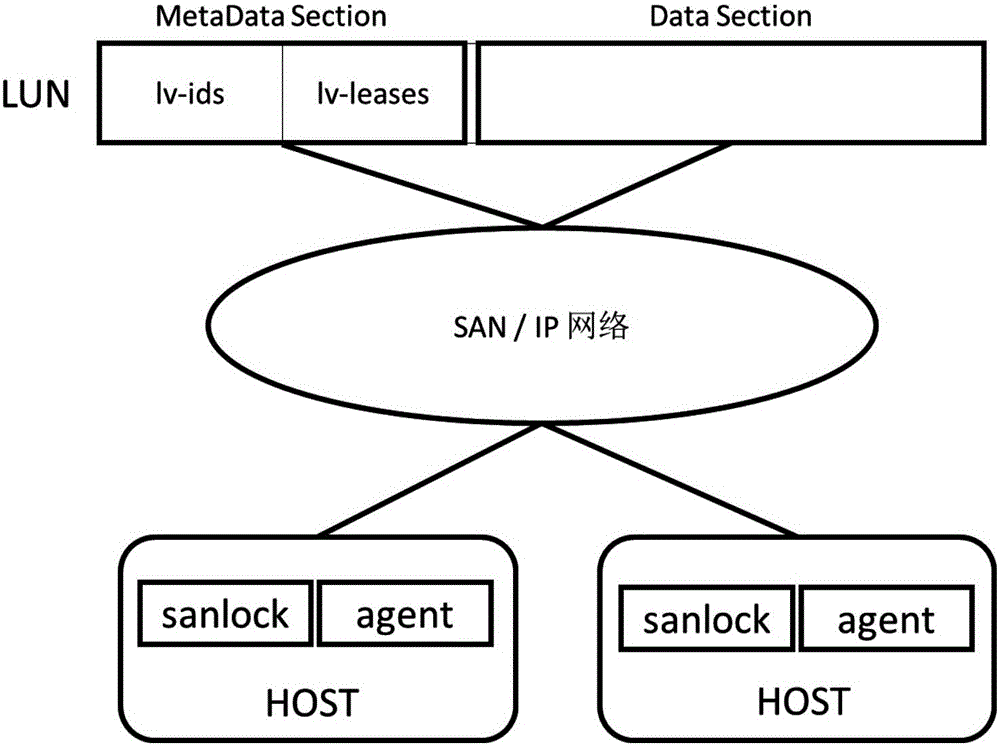
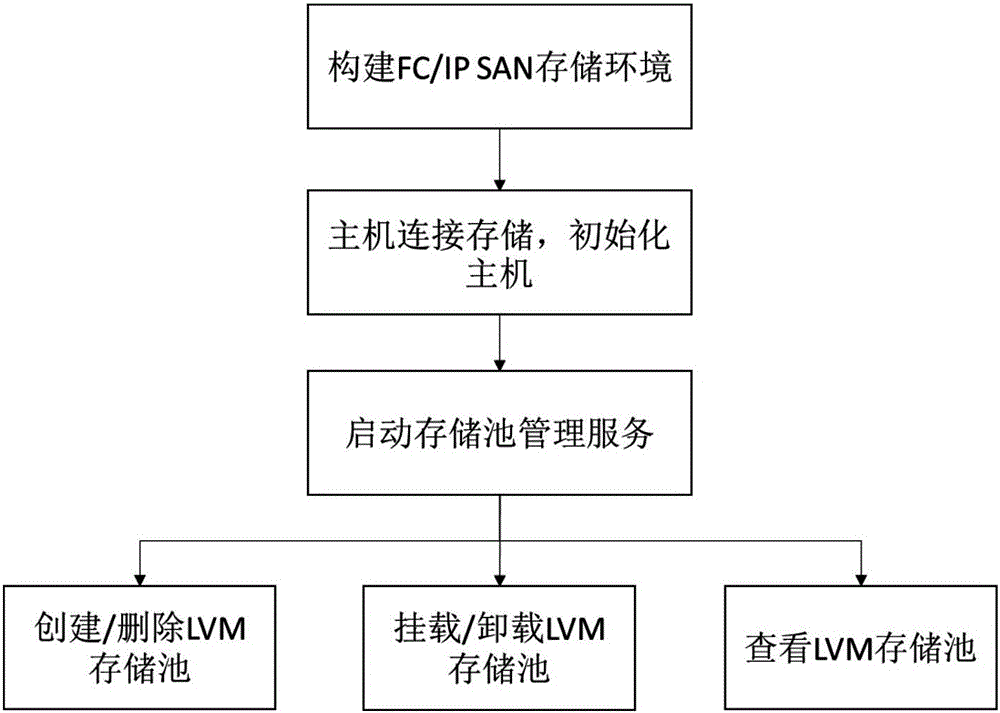
Storage pool building method and system
InactiveCN106201357AImplement the buildMeet performance needsInput/output to record carriersSpatial integrationData virtualization
The invention discloses a storage pool building method and system. The method comprises the steps that a storage environment is set up; LUN mapping is created, and a host scans LUN mapping to conduct initialization; management service of a storage pool is conducted by means of sanlock service and agent service; a storage pool command is created by means of LVM, a corresponding physical volume and volume group are created for each LUN separately, the LUNs are in one-to-one correspondence with the LVM storage pools, a logical volume is created, and lockspace of the sanlock service is initialized according to an incoming path of the logical volume; a lightweight storage pool building method is achieved; for storage virtualization, hardware resource storing is shown in an abstraction mode, scattered storage spaces are integrated, and partition and distribution are conducted again to meet the requirements of different applications on performance and capacity. Meanwhile, data security of backup of stored data, failure recovery and the like can be planed uniformly.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Multi-hypervisor virtual machines
ActiveUS20160147556A1Improve performanceNegatively impacts the I/O performance of the benchmarked systemSoftware simulation/interpretation/emulationMemory systemsMemory footprintNested virtualization
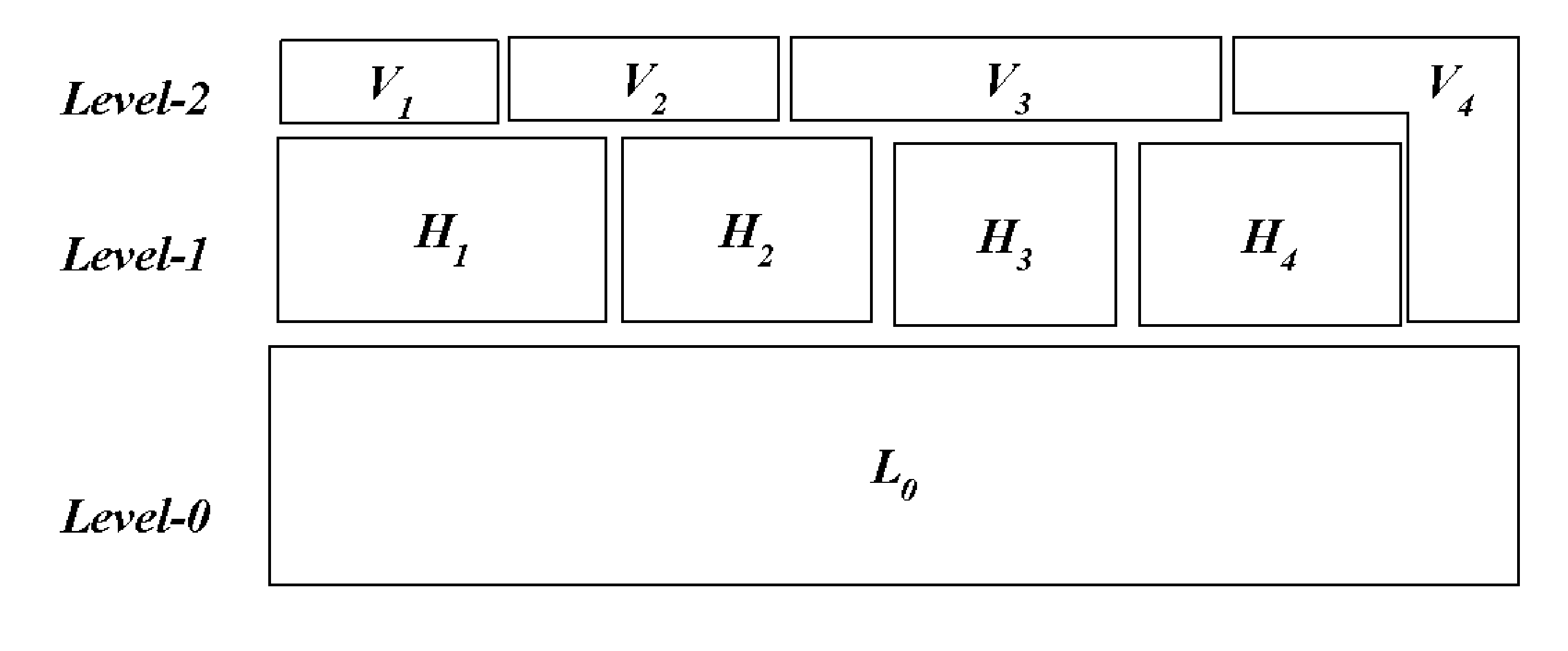
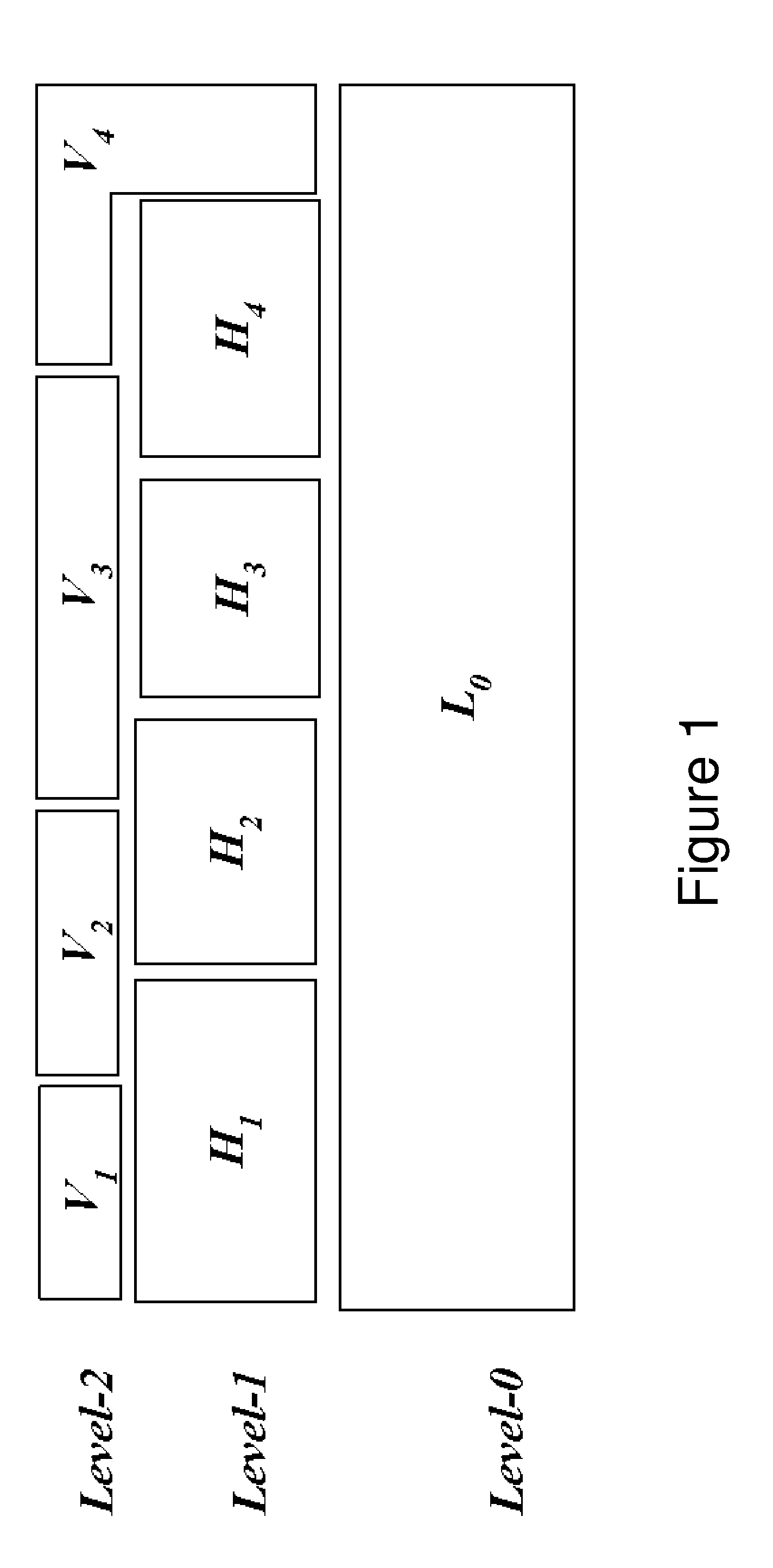
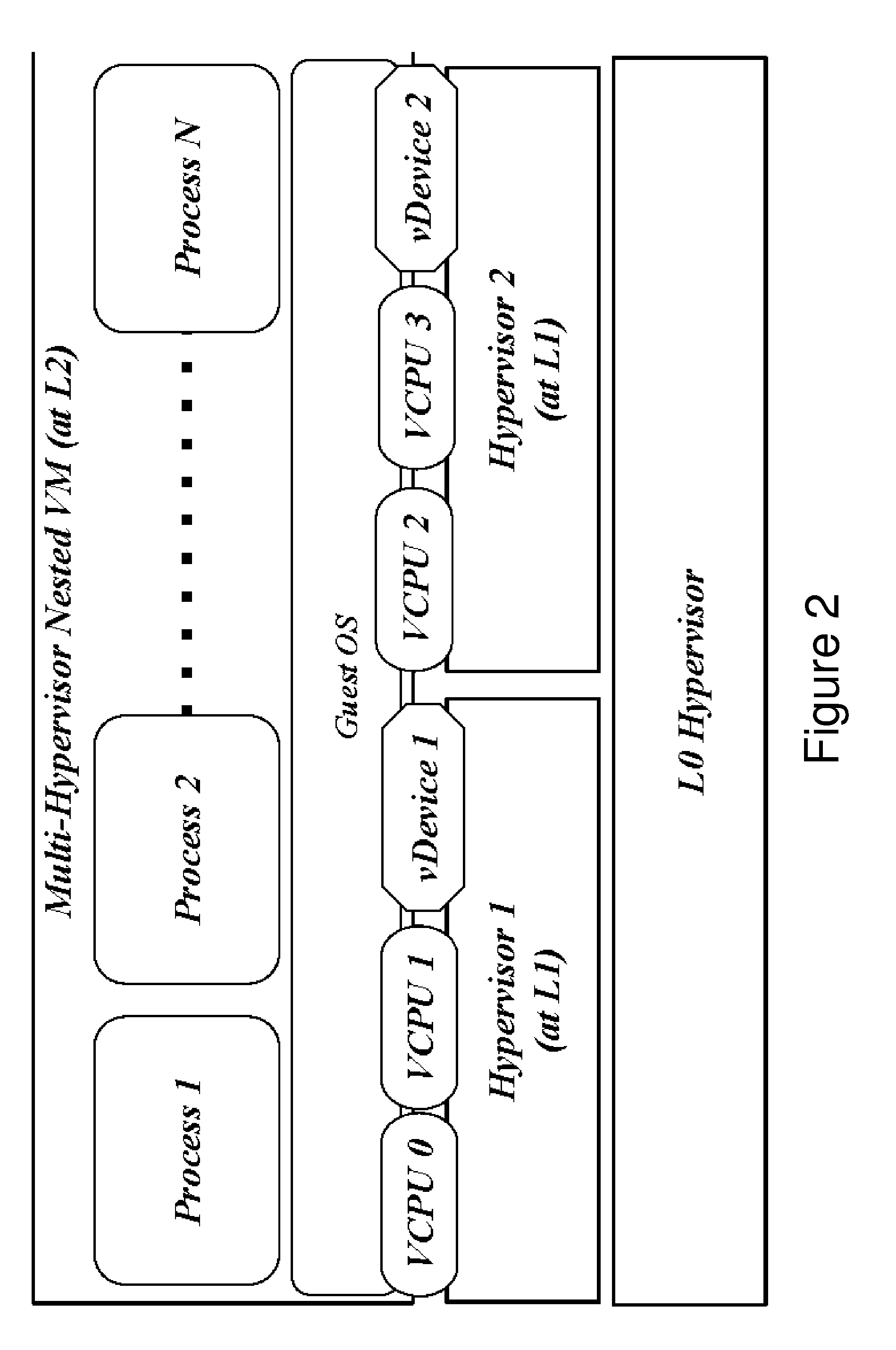
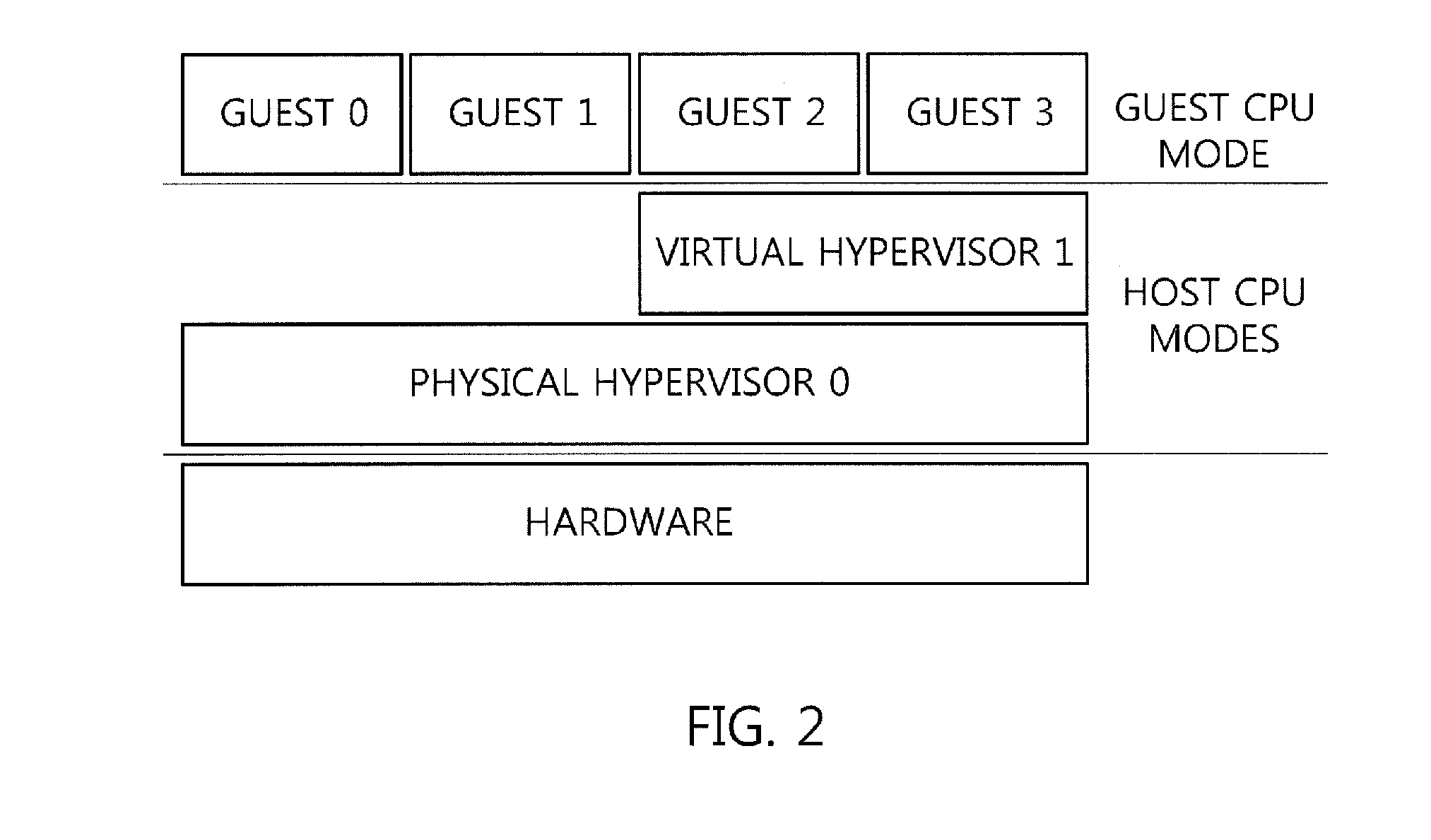
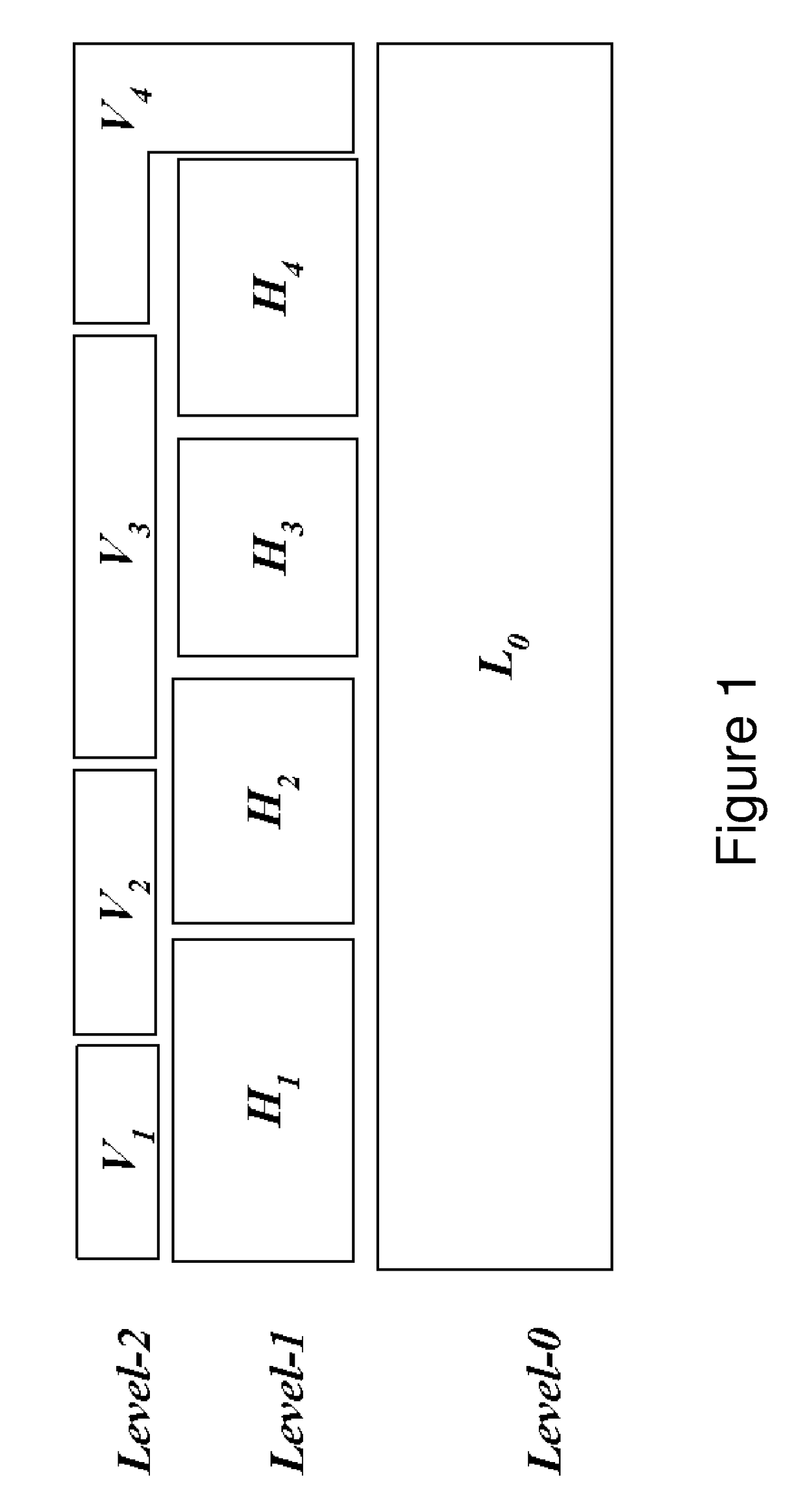
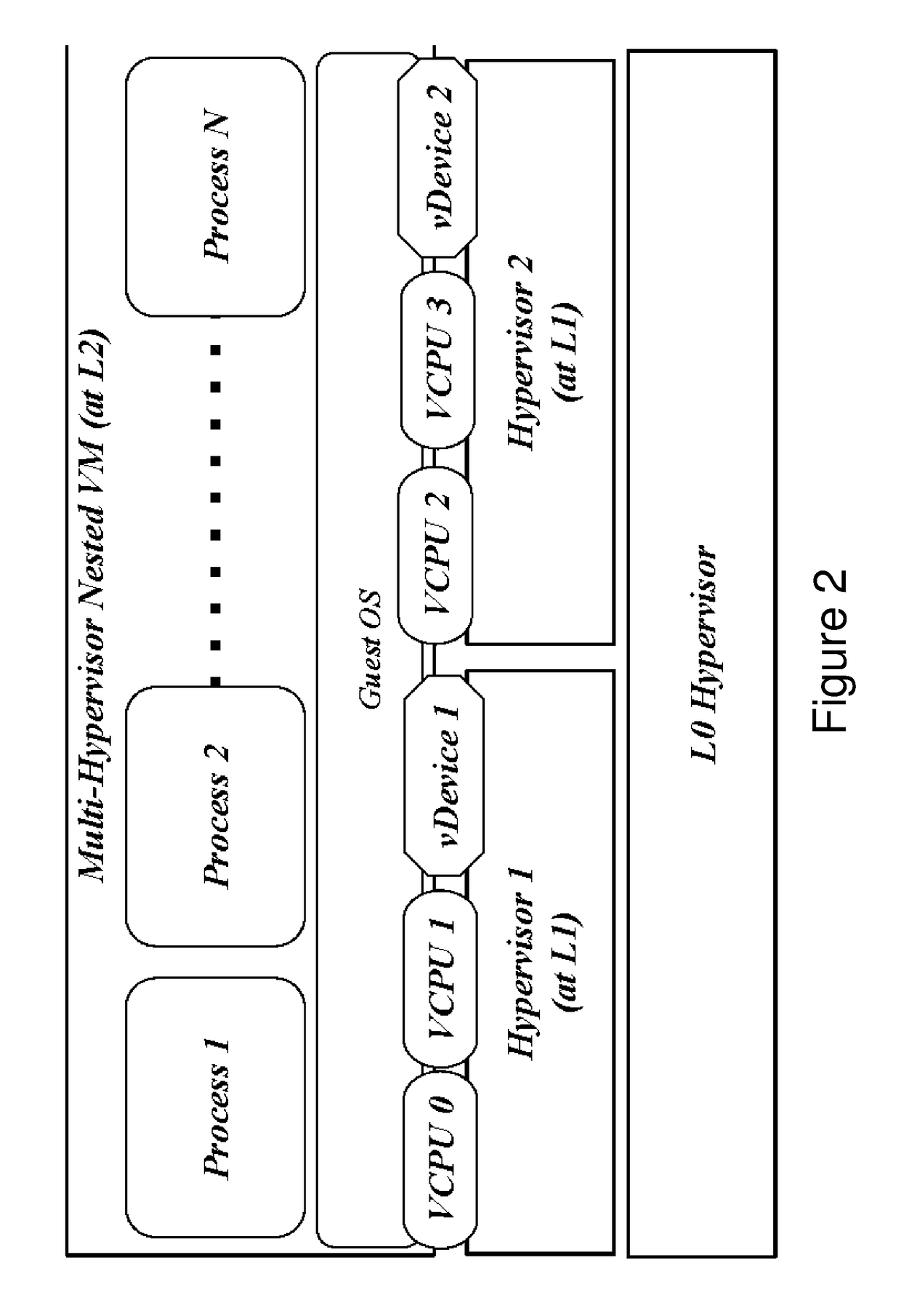
Standard nested virtualization allows a hypervisor to run other hypervisors as guests, i.e. a level-0 (L0) hypervisor can run multiple level-1 (L1) hypervisors, each of which can run multiple level-2 (L2) virtual machines (VMs), with each L2 VM is restricted to run on only one L1 hypervisor. Span provides a Multi-hypervisor VM in which a single VM can simultaneously run on multiple hypervisors, which permits a VM to benefit from different services provided by multiple hypervisors that co-exist on a single physical machine. Span allows (a) the memory footprint of the VM to be shared across two hypervisors, and (b) the responsibility for CPU and I / O scheduling to be distributed among the two hypervisors. Span VMs can achieve performance comparable to traditional (single-hypervisor) nested VMs for common benchmarks.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Virtual gateway protection method, virtual security gateway and system for server virtualization
InactiveCN102244622AAvoid influenceNetworks interconnectionNetwork connectionsTraffic capacitySecurity policy
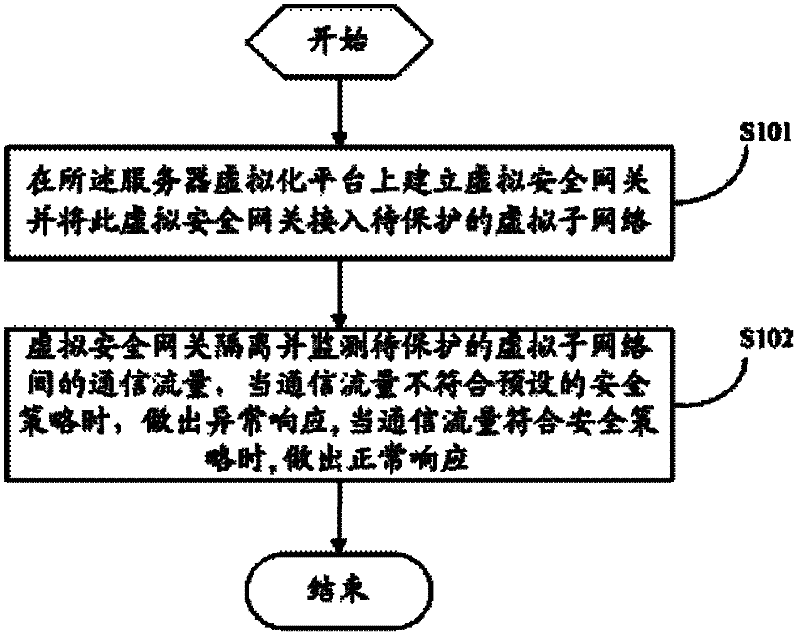
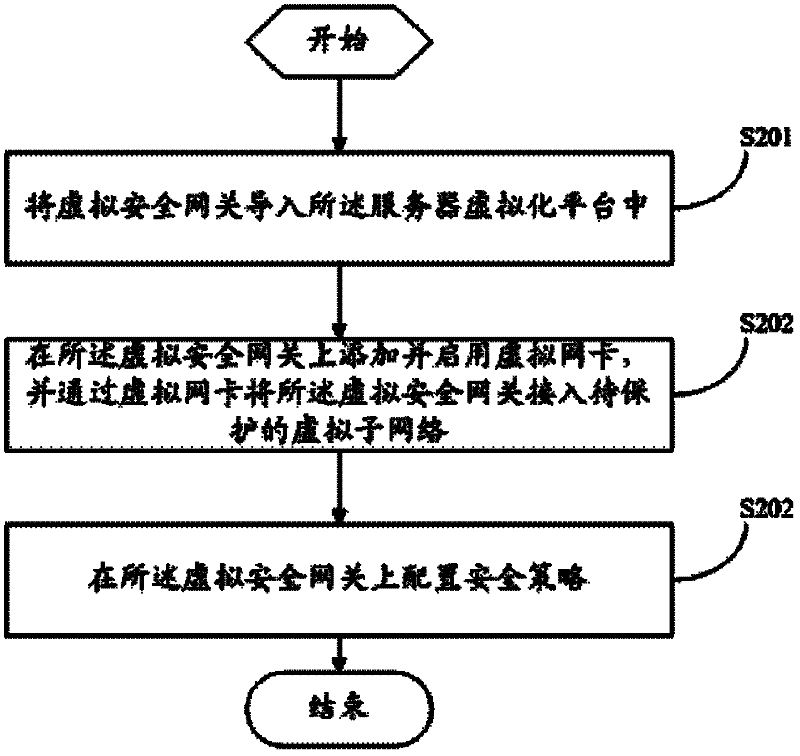
The invention provides a virtual gateway protection method, a virtual security gateway and a system for server virtualization. The method comprises the following steps that: the virtual security gateway is established on a server virtualization platform and accessed to virtual sub-networks to be protected; the virtual security gateway isolates and monitors the communication traffic between the virtual sub-networks, when the communication traffic is against a preset security strategy, the virtual security gateway makes an unexpected response, and when the communication traffic conforms to the security strategy, the virtual security gateway makes a normal response. The method disclosed by the invention establishes the virtual security gateway on the server virtualization platform so as to isolate and monitor the communication traffic between virtual machines, so that the virtual security gateway can make a response in time when the security of the protected virtual machines is threatened, and the virtual machines in a whole virtual network are protected from being influenced.
Owner:BEIJING LEADSEC TECH
Continuous integration method based on container virtualization
InactiveCN105653449ALow costGuaranteed uptimeSoftware testing/debuggingSoftware simulation/interpretation/emulationVirtualizationContinuous integration
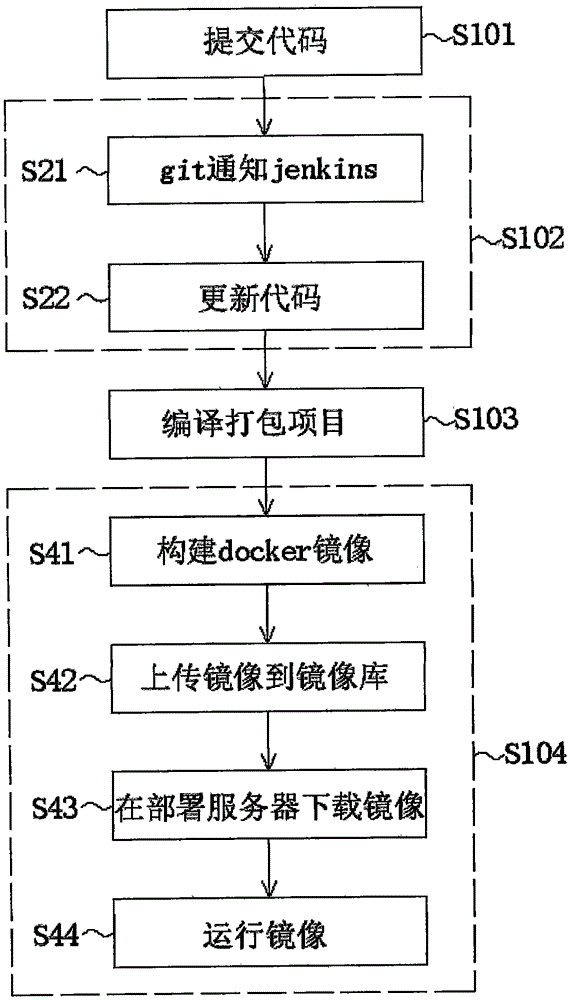
The invention relates to the technical field of software development, in particular to a continuous integration method based on container virtualization. The continuous integration method comprises the following steps: S101: submitting a code; S102: code update: updating the submitted code; S103: compiling and packaging items; and S104: carrying out container virtualization, and operating a mirror image through a virtualized container. After the method is adopted, a container virtualization technology is selected, difference in a practical environment is shielded through docker, and an application operation environment is uniformly specified through a dockerfile. Compared with a virtual machine, the docker is low in cost and simple in operation and can adapt to frequent deployment in the test environment. In addition, on the basis of a container virtualization technology, the continuous integration method can carry out interference-free deployment in a single machine environment, can conveniently carry out lateral expansion, can automatically carry out continuous integration after the code is automatically submitted on the basis of a git trigger mechanism, and reduces an artificial workload.
Owner:HUNAN ANTVISION SOFTWARE
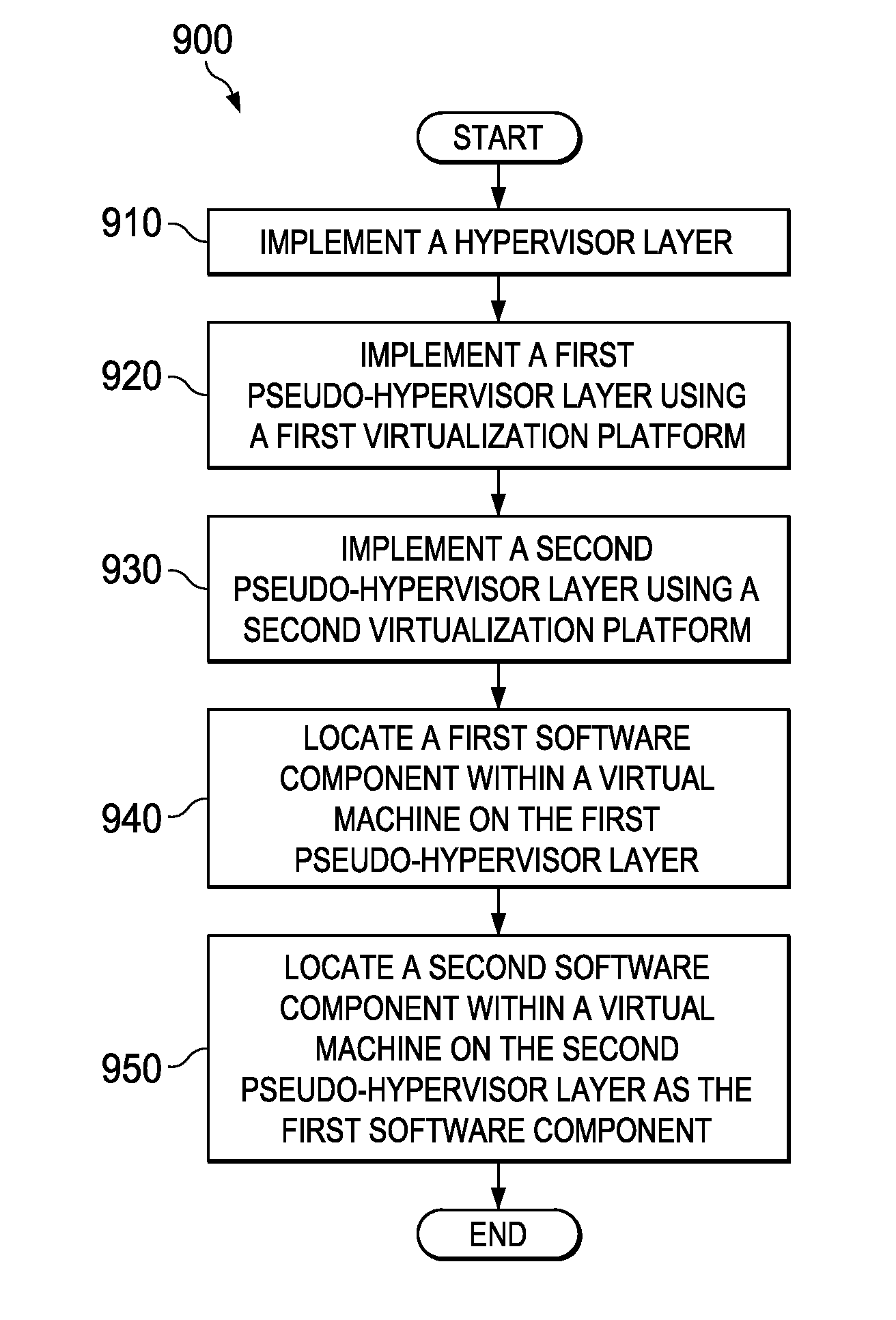
Fine-Grained Cloud Management Control Using Nested Virtualization
InactiveUS20120260247A1Digital computer detailsSoftware simulation/interpretation/emulationData processing systemGranularity
A computer implemented method, a computer program product and a data processing system allocate resources within a computing organization. A hypervisor layer is implemented on an underlying hardware. The hypervisor layer comprises a set of virtual machines. A first pseudo-hypervisor layer is then implemented within a first one of the set of virtual machines of the hypervisor layer. The first pseudo-hypervisor layer comprises a second set of virtual machines. A first software component is located within a first virtual machine of the second set of virtual machines of the first pseudo-hypervisor layer. A second software component is collocated within a second virtual machine of the second set of virtual machines of the first pseudo-hypervisor layer.
Owner:IBM CORP
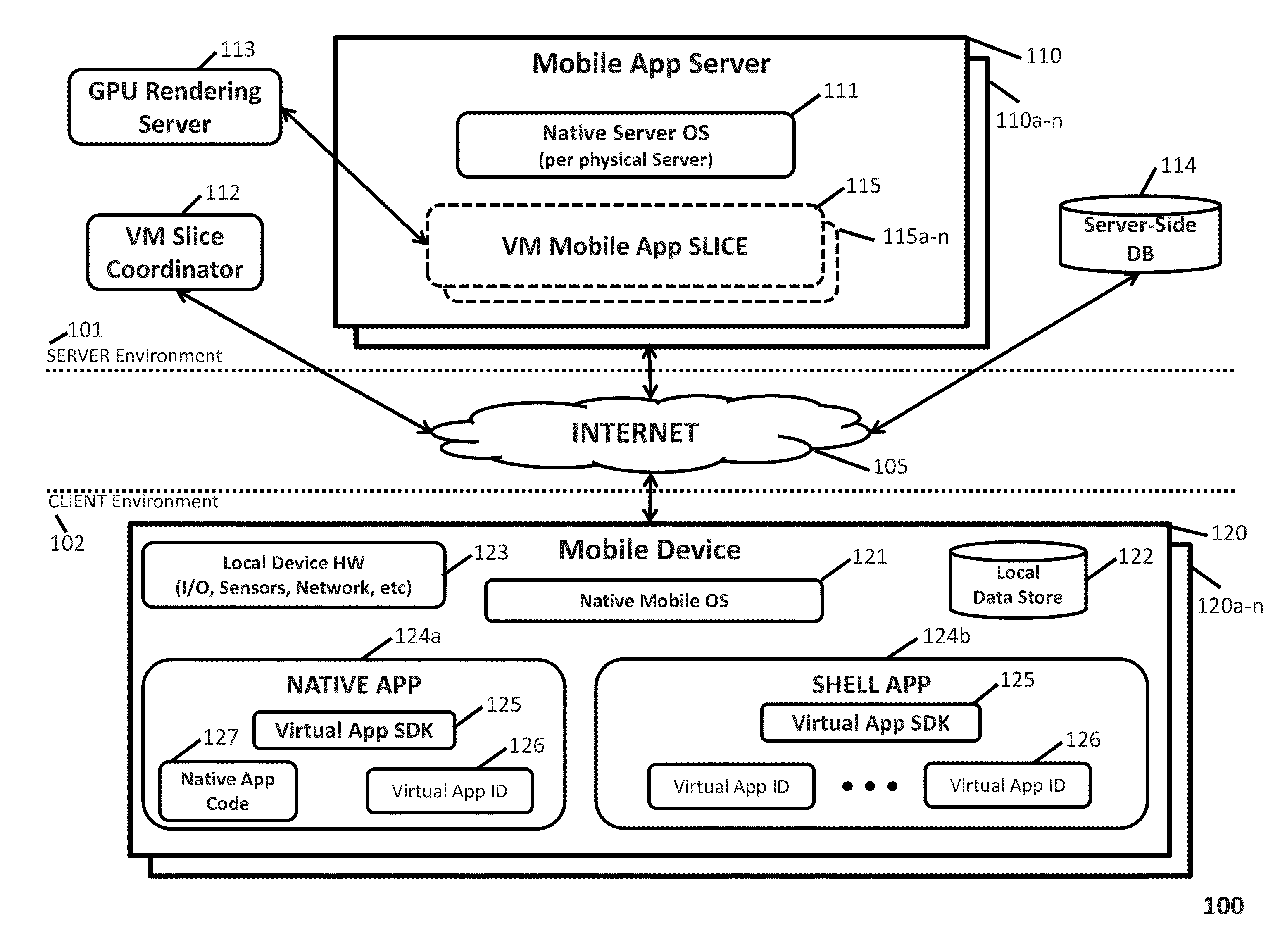
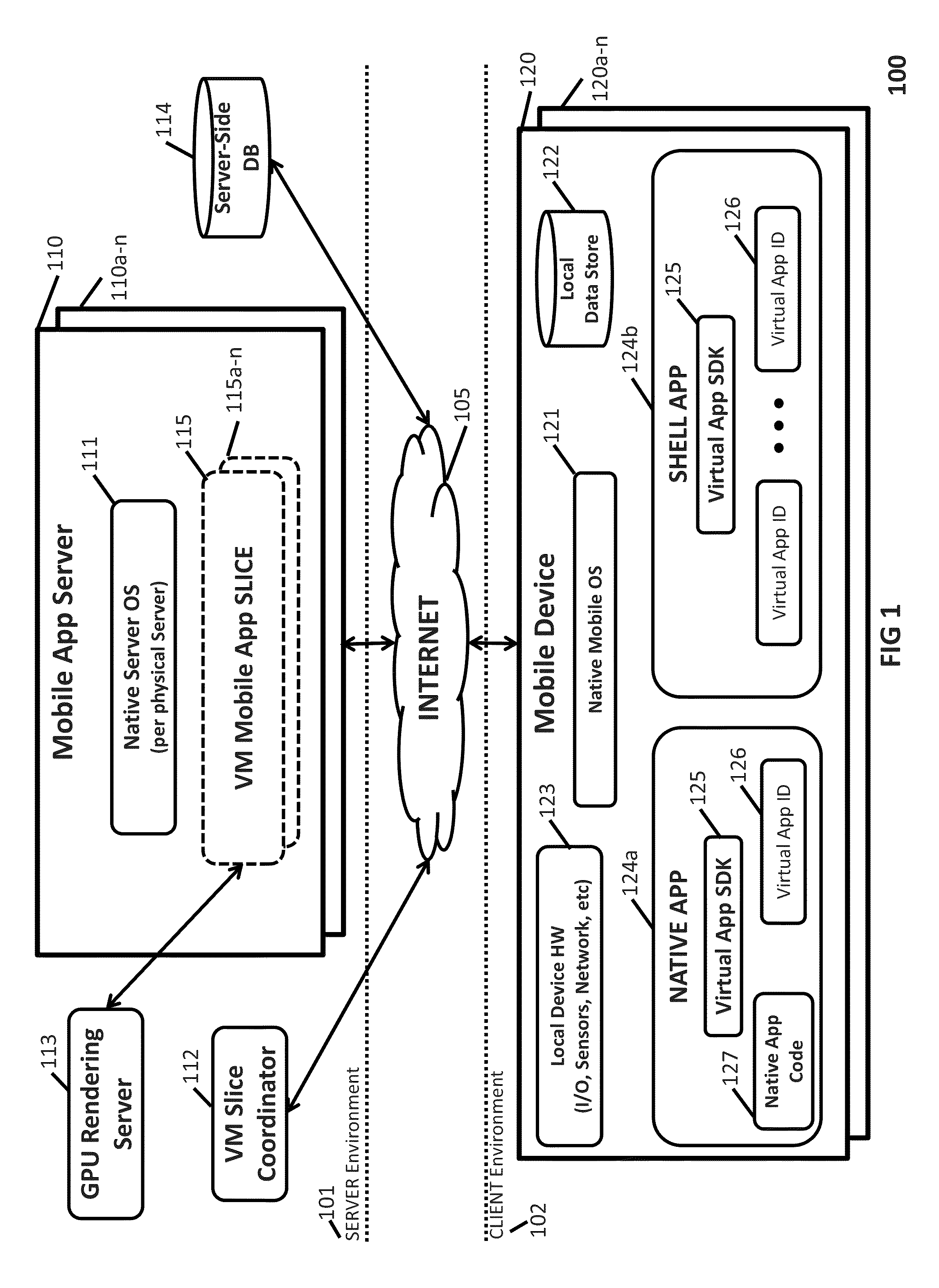
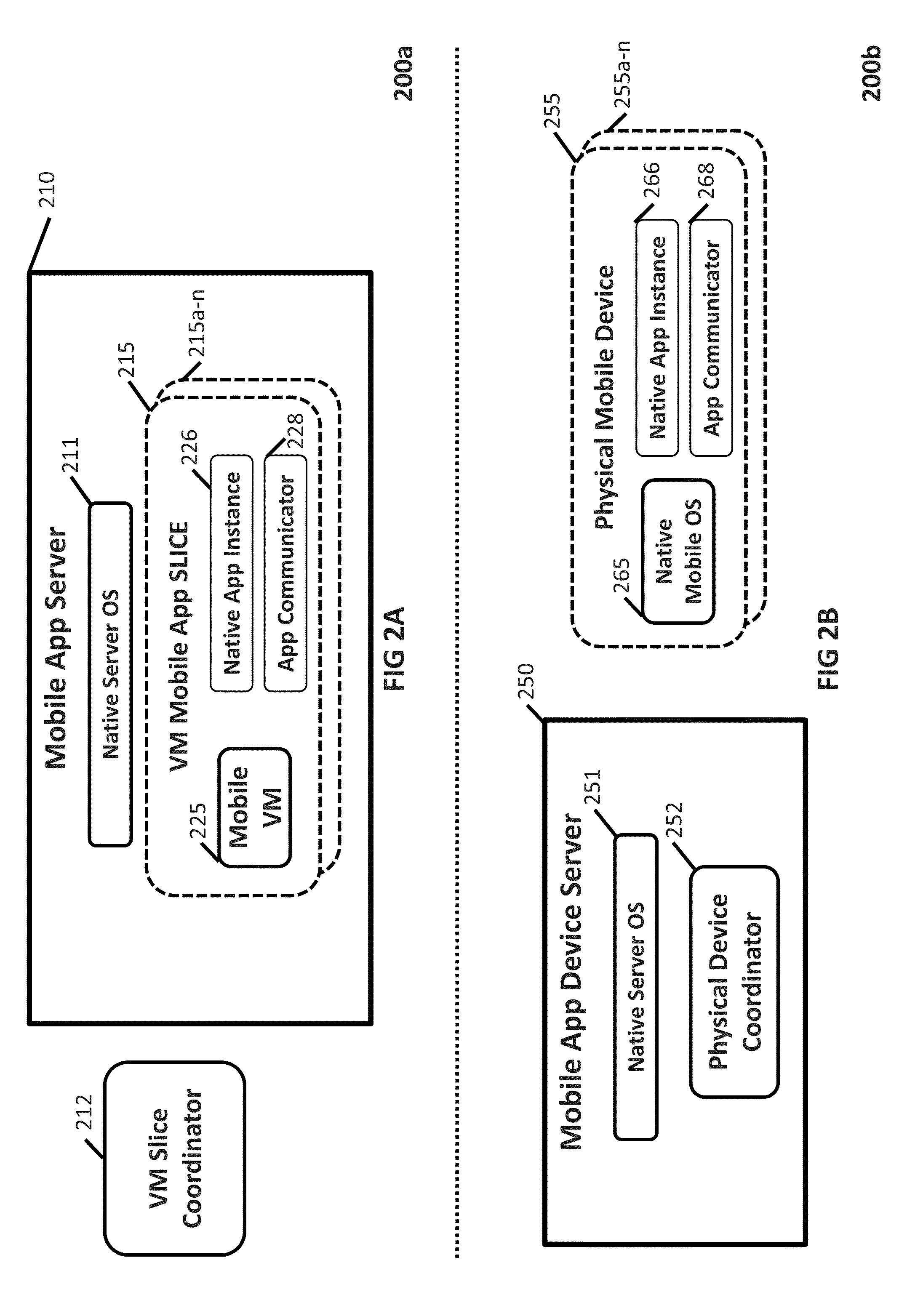
Remote virtualization of mobile apps
InactiveUS9451043B2Minimize artifactEffectively run “ trial ” versionInterprogram communicationMultiple digital computer combinationsMobile appsNative client
The present invention includes various embodiments of a mobile app remote virtualization system and process that enables users of remote client devices to control mobile apps running in a host server environment. The resulting user experience is practically equivalent to running native mobile apps, even when such mobile apps require access to local client device resources, as well as when native versions of such mobile apps do not exist for the user's client device. The functionality afforded by the mobile app remote virtualization system and process of the present invention enables a variety of novel scenarios and “use cases” that have not previously been available to mobile device users.
Owner:EVIE LABS INC
Migration tool for implementing desktop virtualization
At least a method and a system for migrating a plurality of endpoint computing devices of an organization are described herein. User applications, data, and settings are migrated from a plurality of endpoint computing devices of the organization into a client server operating environment employing a thin client implementation. A server may execute software for deploying the thin client implementation. By way of creating a personalized virtualization disk for each endpoint computing device, migration to a thin client virtualized desktop implementation may be easily performed by the organization without modification, change, or loss of user installed applications, personalized settings, and user data.
Owner:CITRIX SYST INC
Nested Virtualization Performance In A Computer System
InactiveUS20120191948A1Improve performanceDigital computer detailsSoftware simulation/interpretation/emulationVirtualizationData access
A virtualization architecture for improving the performance of nested virtualization in a computer system. A virtualization instruction reads or writes data in a control structure used by a virtual machine monitor (VMM) to maintain state on a virtual machine (VM) to support transitions between a root mode of operation of a CPU in which the VMM executes and a non-root mode of operation of the CPU in which the VM executes. A privileged data access is made to a primary control structure according to the virtualization instruction if the CPU is in the root mode. A non-privileged data access is made to a secondary control structure according to the virtualization instruction if the CPU is in the non-root mode and a secondary control structure field in the primary control structure is enabled.
Owner:INT BUSINESS MASCH CORP
Lightweight nested virtualization implementation method based on physical resource penetration mechanism
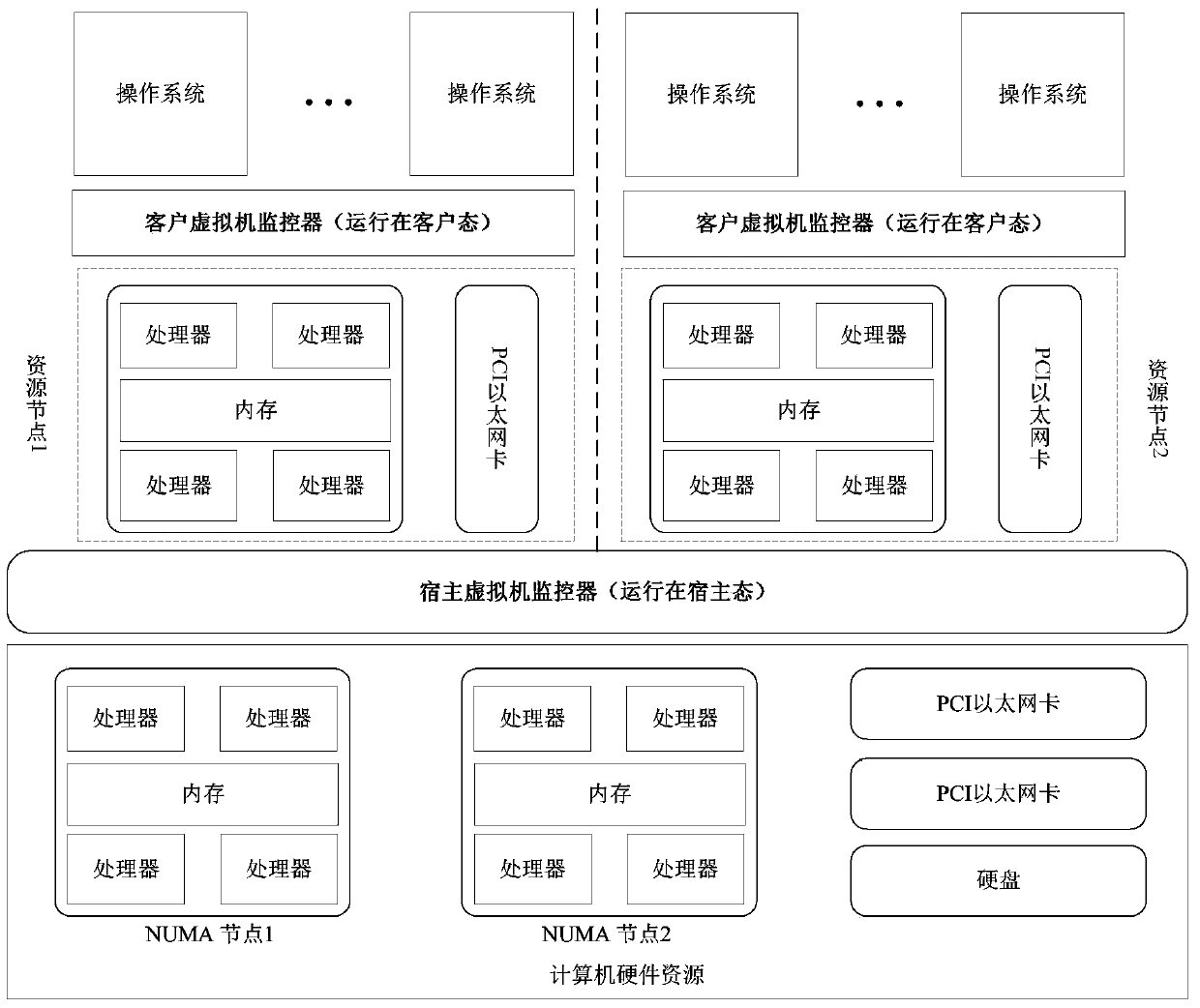
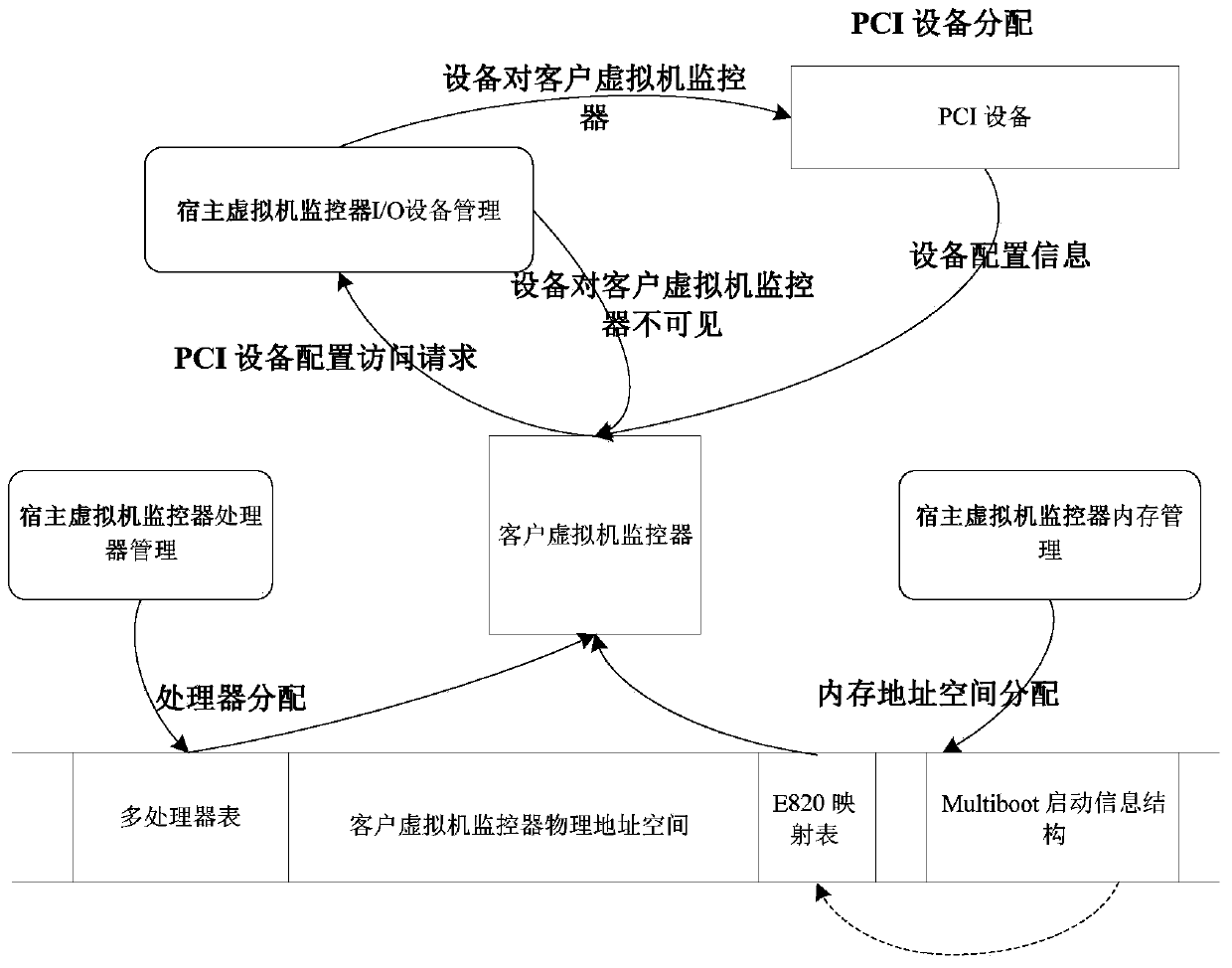
ActiveCN103995733AAvoid Performance Isolation ProblemsPerformance Isolation GuaranteeProgram loading/initiatingSoftware simulation/interpretation/emulationComputer hardwareResource virtualization
The invention discloses a lightweight nested virtualization implementation method based on a physical resource penetration mechanism. The lightweight nested virtualization implementation method is different from physical resource virtualization through a traditional nested virtualization technology, the method mainly emphasizes management and monitoring on physical resources, and extra performance expenditure caused by virtualization on the physical resources is avoided. Besides, through resource management and control based on NUMA codes, the performance isolation of the traditional virtualization technology on NUMA architecture is avoided. Due to the method, physical equipment is grouped by a host hypervisor, guest hypervisors directly run on different resource groups, and therefore not only can performance loads caused by resource scheduling and sharing be avoided, but also the MUNA characteristic can be fully used for improving the system performance and guaranteeing the performance isolation between different guest hypervisors.
Owner:XI AN JIAOTONG UNIV
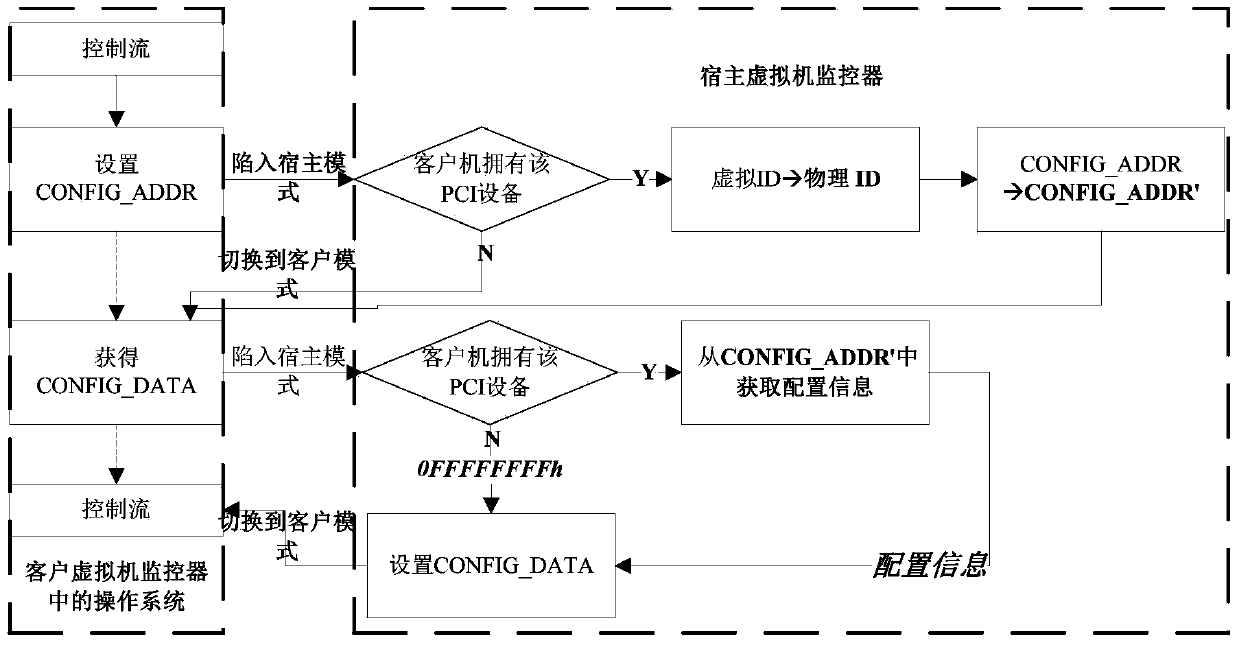
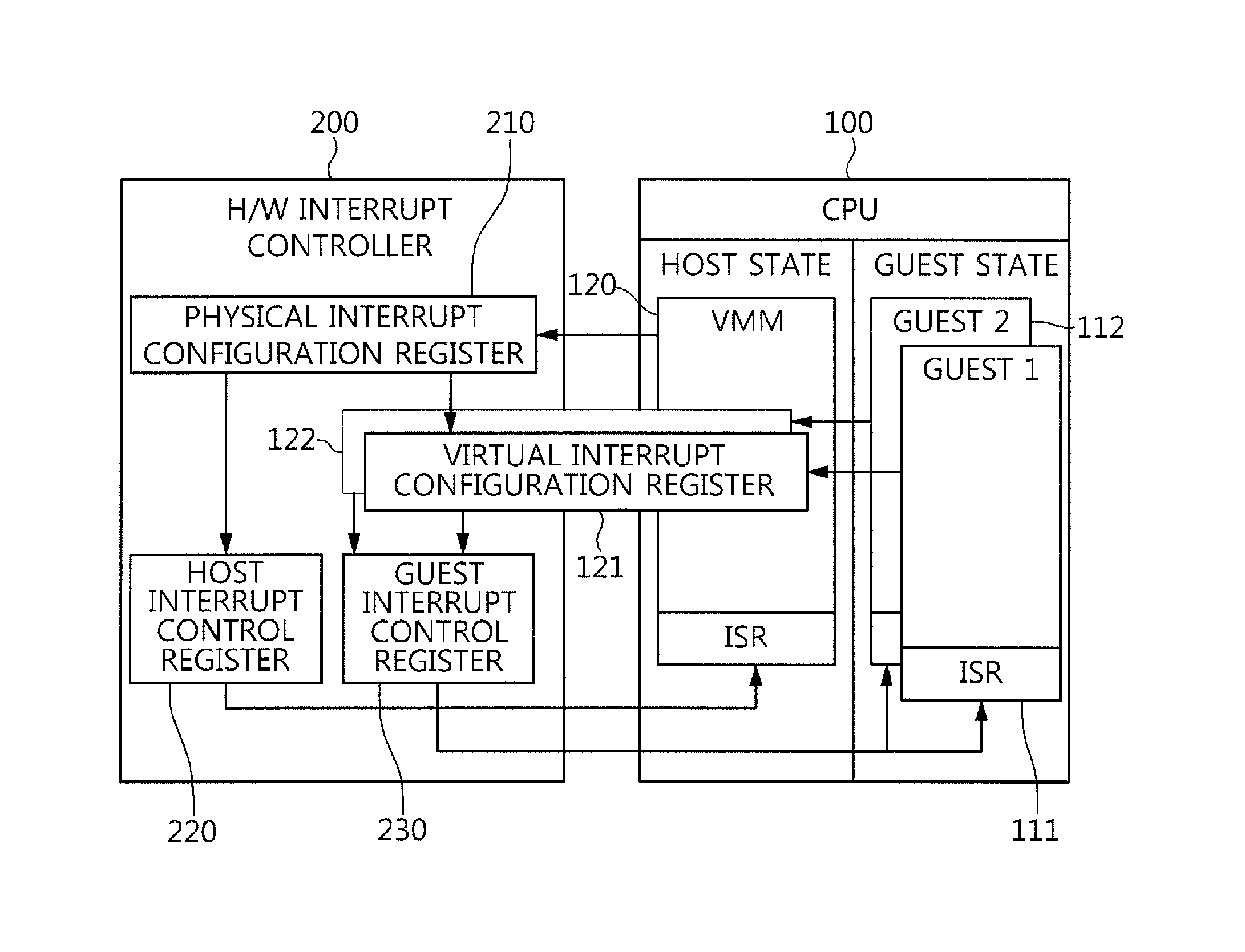
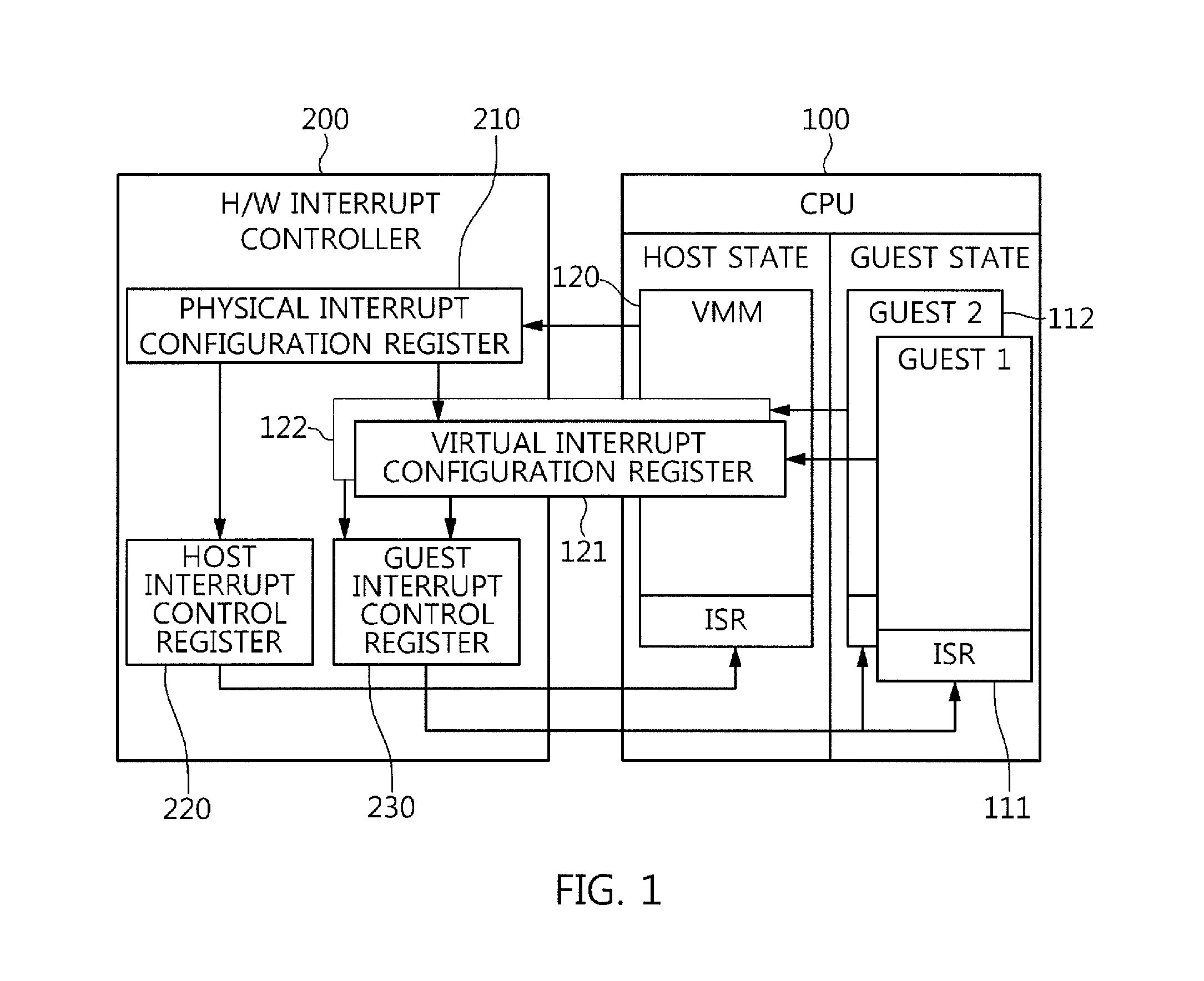
Hybrid virtualization method for interrupt controller in nested virtualization environment
InactiveUS20160085568A1Reduce Interrupt LatencyProgram initiation/switchingSoftware simulation/interpretation/emulationNested virtualizationVirtual machine
Disclosed is a hybrid virtualization method for an interrupt controller in nested virtualized environment, which can reduce guest interrupt latency. A hybrid virtualization method includes operating a Virtual Machine Manager (VMM) which enables a program executed on a host and a program executed on a guest to be simultaneously used, providing, by the VMM, a virtual interrupt configuration register to the guest, and selectively utilizing full virtualization and partial virtualization. Full virtualization is used when guests which are running simultaneously request the same interrupt. In this case, the interrupt is trapped by the VMM before being injected to the different guests. Partial virtualization allows a guest to directly handle incoming interrupt and avoids expensive traps to the hypervisor to reduce the latency. This virtualization technique can be used by any kind of VMM which is physical hypervisor or virtual hypervisor for processing interrupts of their respective guests.
Owner:ELECTRONICS & TELECOMM RES INST
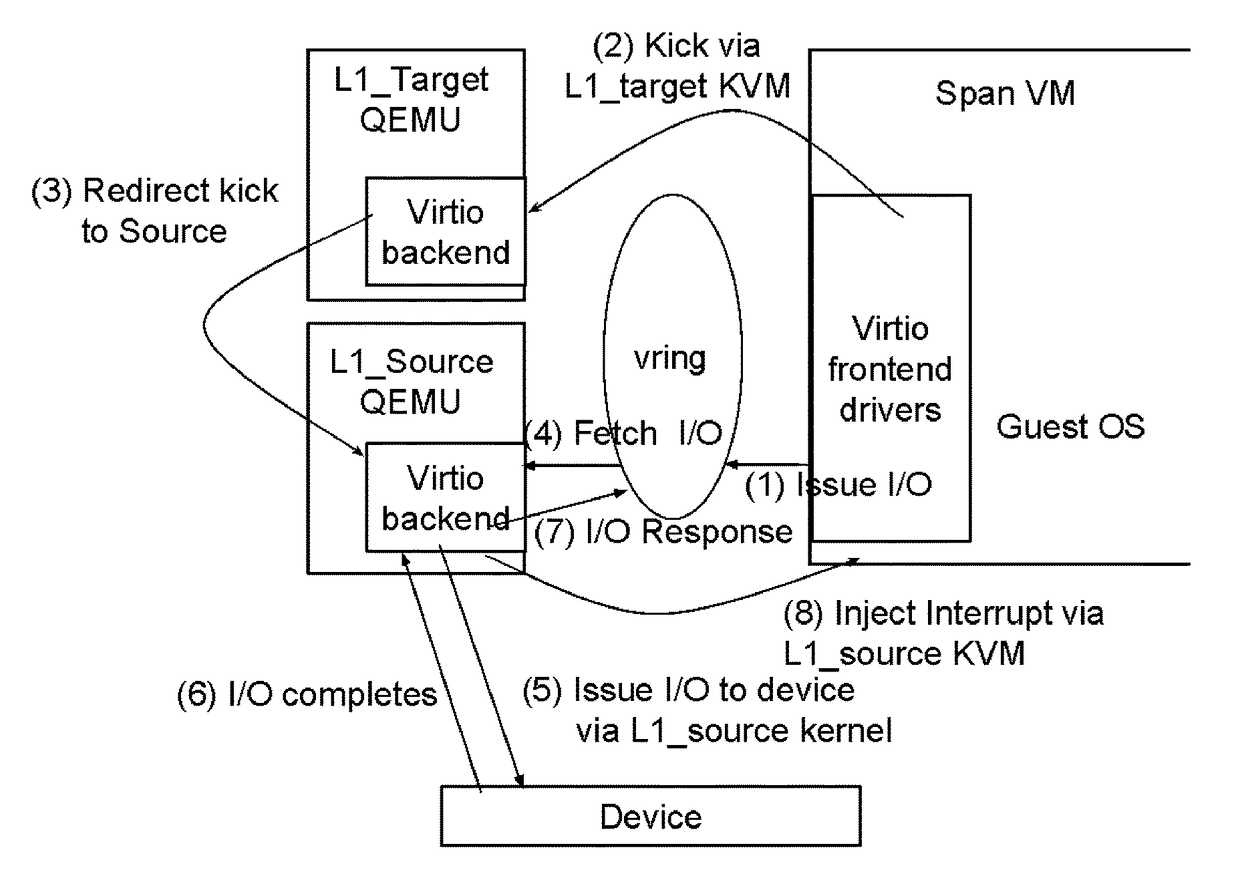
Embedded network virtualization environment VirtIO (virtual input and output) network virtualization working method
ActiveCN104618158AReduce the number of context switchesSave CPU resourcesData switching networksSoftware simulation/interpretation/emulationTime delaysNetwork virtualization
The invention provides an embedded network virtualization environment VirtIO virtualization working method. The embedded network virtualization environment VirtIO virtualization working method comprises, for a VirtIO front drive program, introducing a delay mechanism to a VirtIO network so that a client does not immediately transfer the control right to a host when performing network data I / O (input / output) but caching the data into a queue, and after a certain time, performs context switching to inform the host to obtain the data from the cache queue. The embedded network virtualization environment VirtIO virtualization working method can obviously reduce the number of times of context switching between the client and the host, save a large number of CPU (central processing unit) resources to process more network I / O. Experiments show that, within a set time delay, network throughput can be increased by more than three times.
Owner:SHANGHAI JIAO TONG UNIV
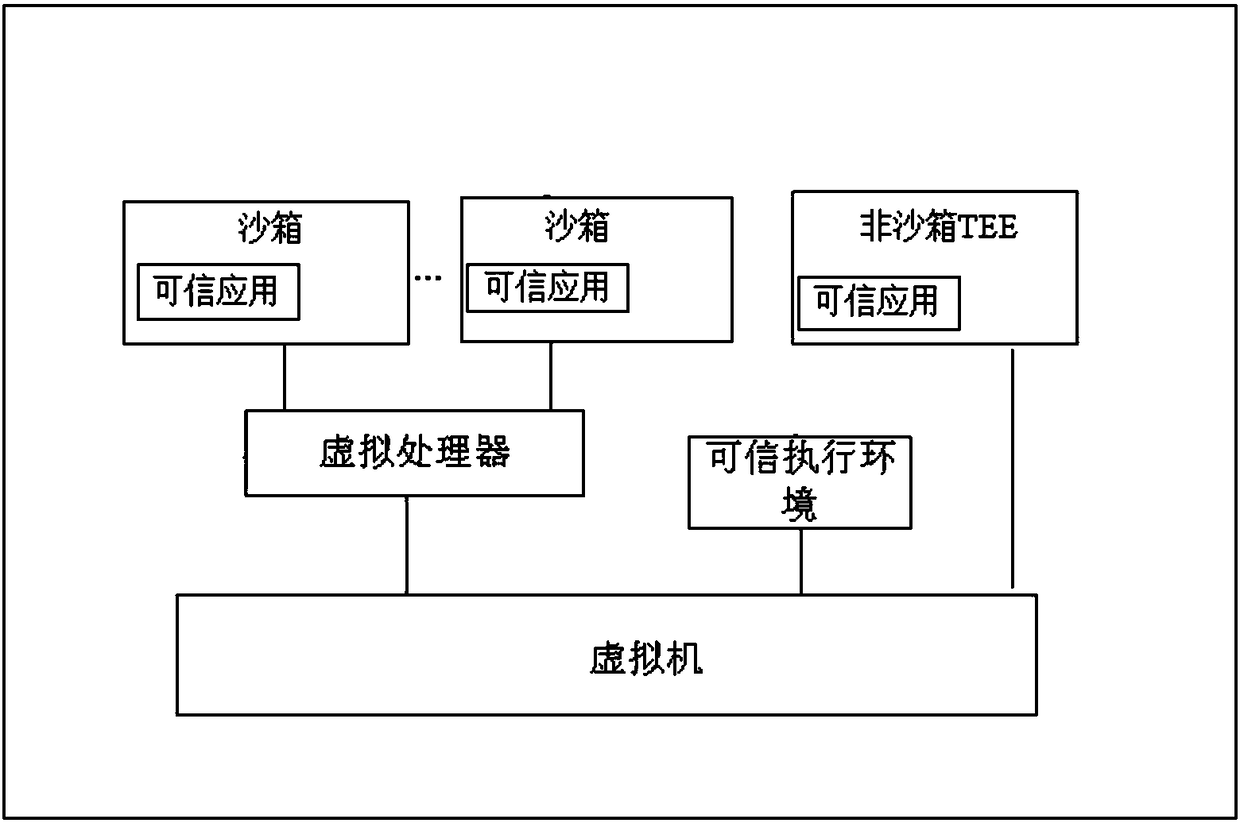
Secure virtualization system suitable for use in trusted execution environment (TEE)
ActiveCN108509251AAchieve isolationImprove securityInternal/peripheral component protectionPlatform integrity maintainanceMemory virtualizationApplication software
The invention discloses a secure virtualization system suitable for use in a trusted execution environment (TEE). The system includes at least one virtual machine, at least one trusted application (TA) and the at least one trusted execution environment. The virtual machine is built through Micro Hypervisor. The trusted execution environment is run on the virtual machine. The trusted application isrun in the trusted execution environment of the virtual machine. The trusted execution environment is configured to access the virtual machine in a first mode to realize calling of resources. Under the first mode, the virtual machine allows accessing of the trusted execution environment to the resources after it is determined that the trusted execution environment has access authority. The systemhas the advantages of: on the basis of trusted virtualization technology, building the virtual machine through the Micro Hypervisor, and running the GP (Global Platform) TEE and the corresponding TAon the virtual machine. Both the TEE and the TA are run on the respective virtual machine, thus complete isolation is realized, and security is greatly improved.
Owner:沈阳微可信科技有限公司
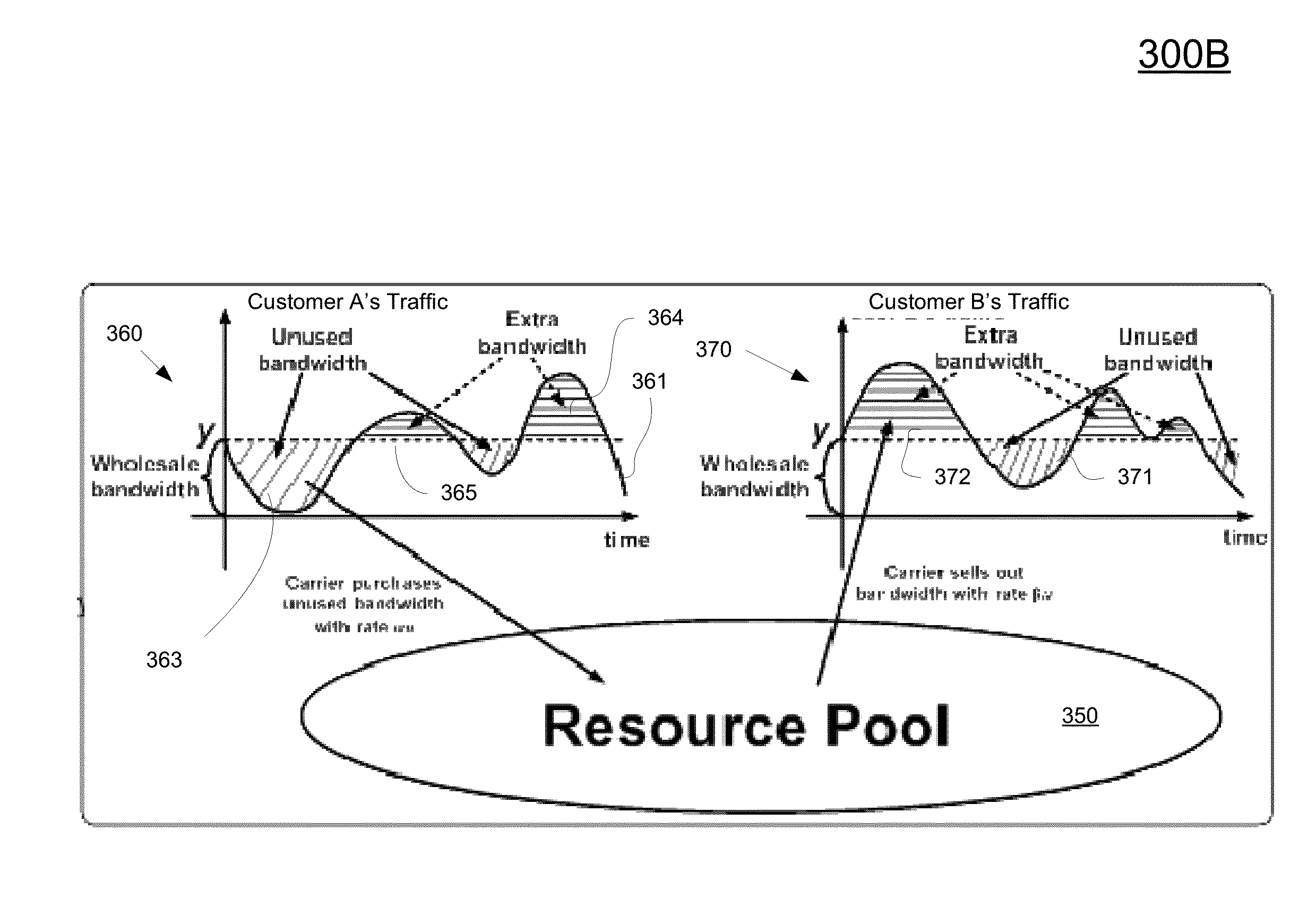
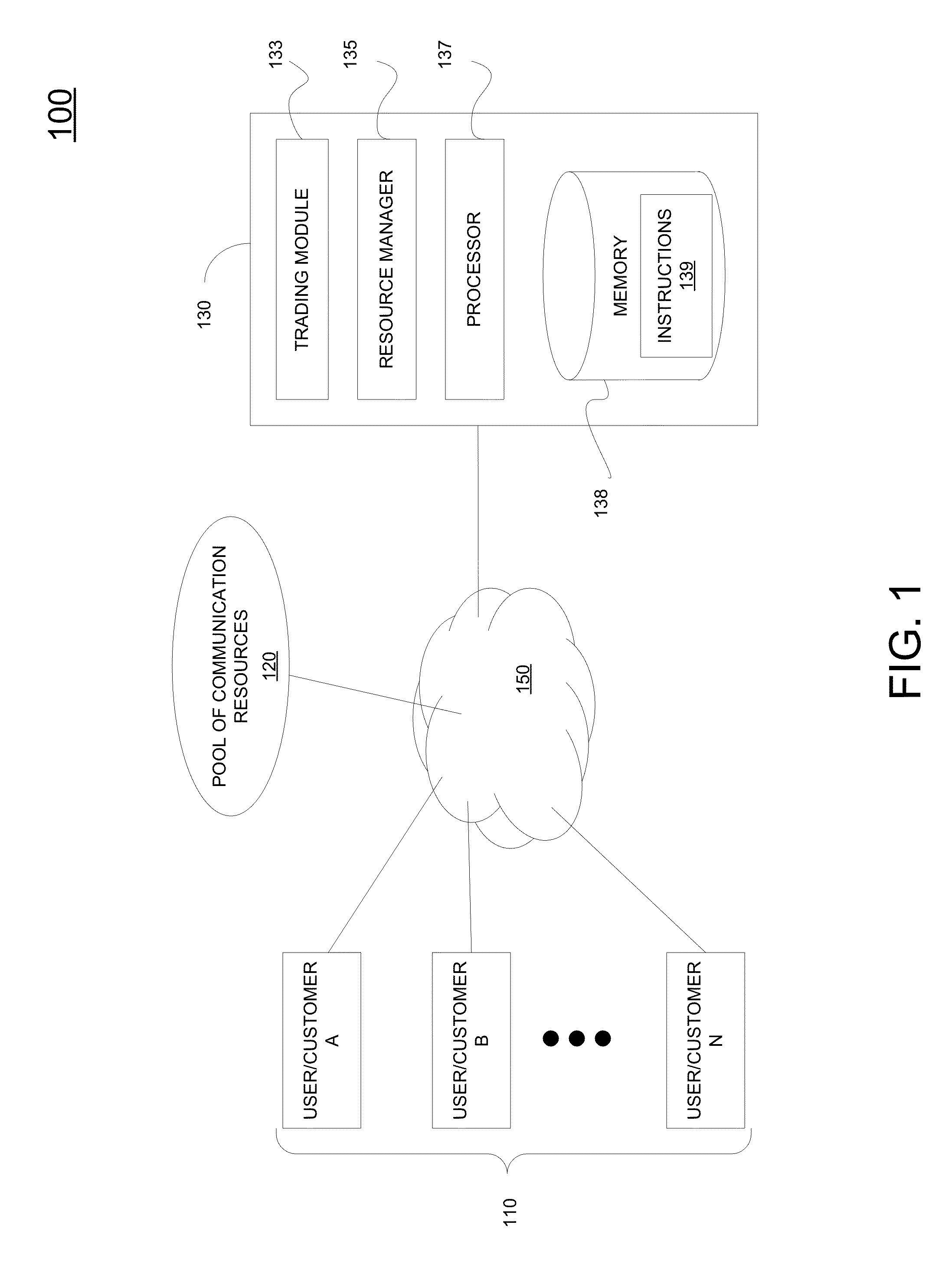
Dynamic resource pooling and trading mechanism in network virtualization
InactiveUS20150146521A1Metering/charging/biilling arrangementsError preventionDynamic resourceNetwork virtualization
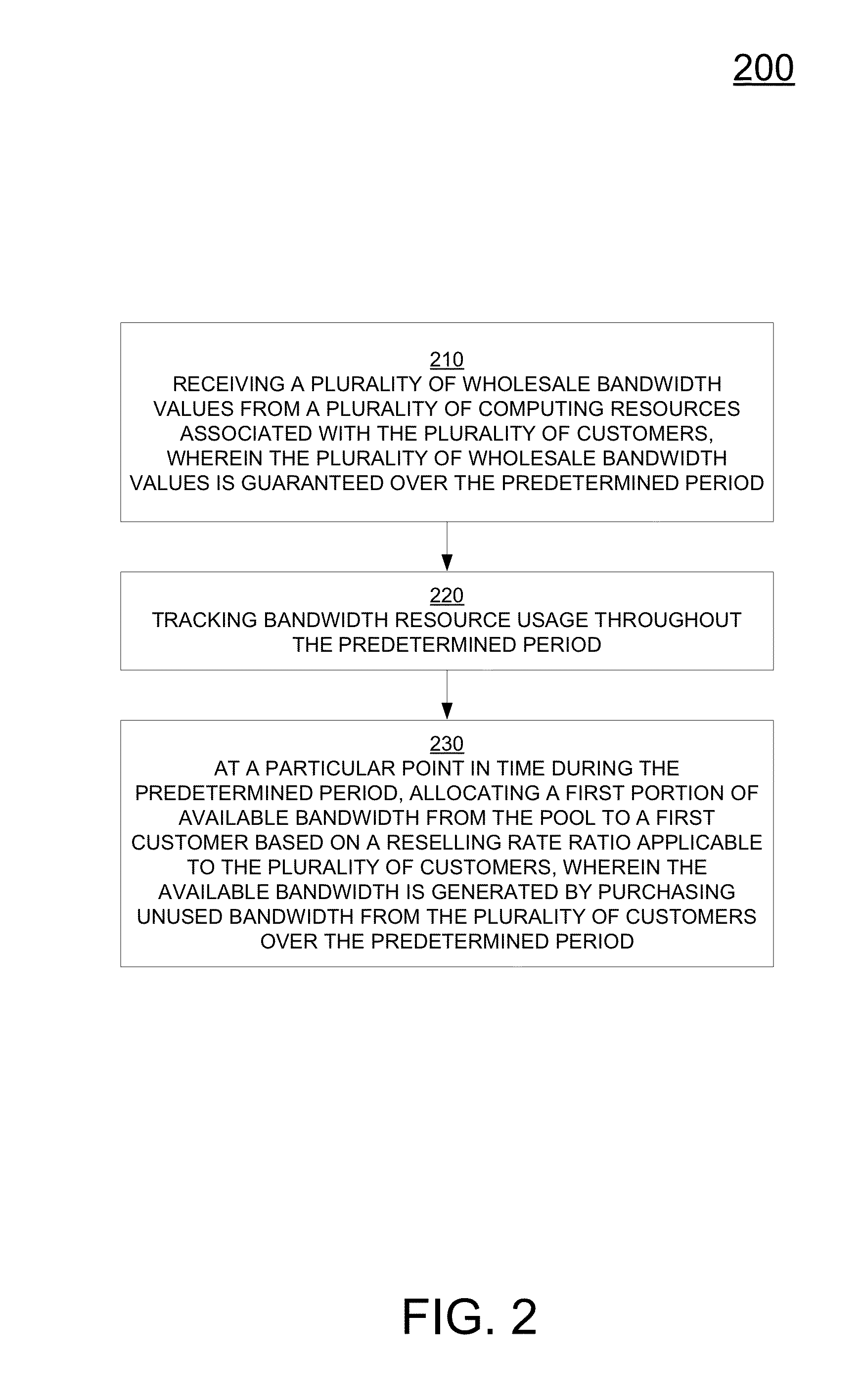
A method for managing a pool of bandwidth resources available over a communication network as executed by a processor. The method includes receiving a plurality of wholesale bandwidth values requesting bandwidth from the pool of bandwidth resources from a plurality of computing resources associated with the plurality of customers, wherein the wholesale bandwidth values are guaranteed over a predetermined period, and wherein the pool has a maximum capacity. The method includes tracking bandwidth resource usage throughout the predetermined period. The method includes allocating a first portion of available bandwidth from the pool to a first customer based on a reselling rate ratio applicable to the plurality of customers at a particular point in time during the predetermined period. Available bandwidth is generated by purchasing unused bandwidth from the plurality of customers over the predetermined period.
Owner:FUTUREWEI TECH INC
Network and system for network virtualization
InactiveUS20130272216A1Level of flexibilityGuaranteed resourcesNetwork traffic/resource managementWireless commuication servicesNetwork virtualizationNested virtualization
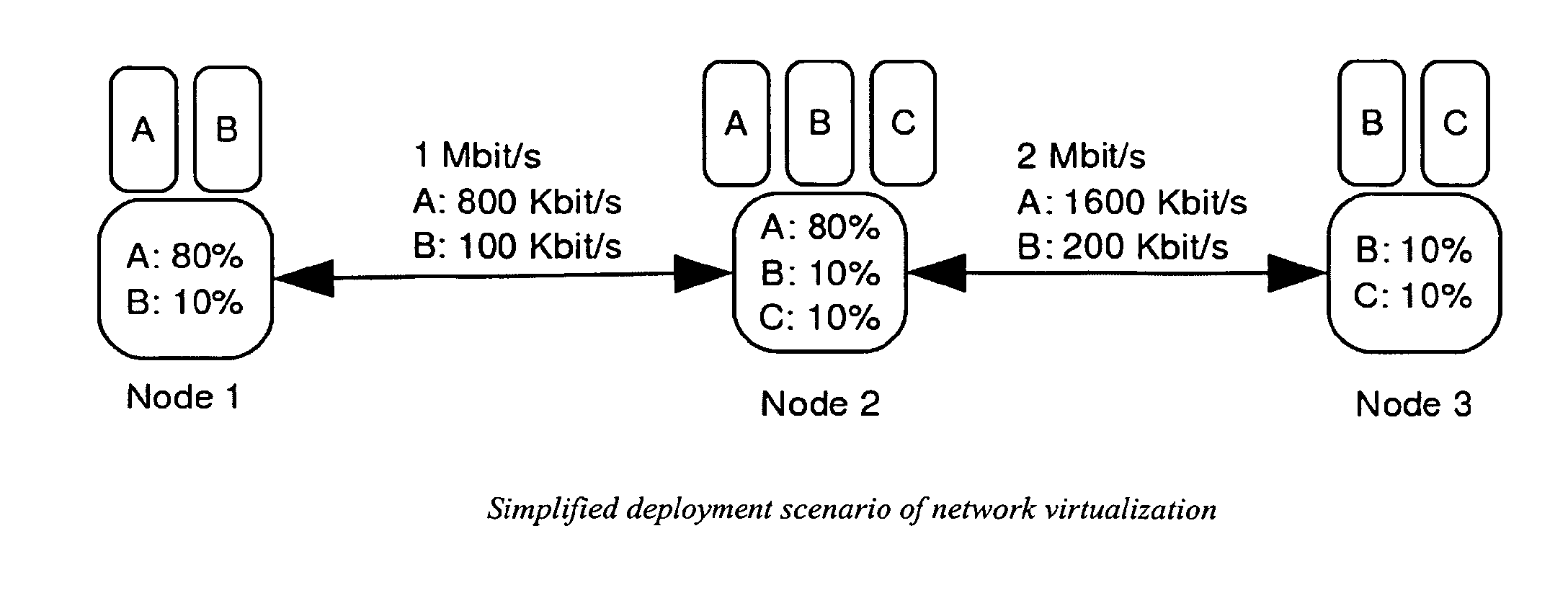
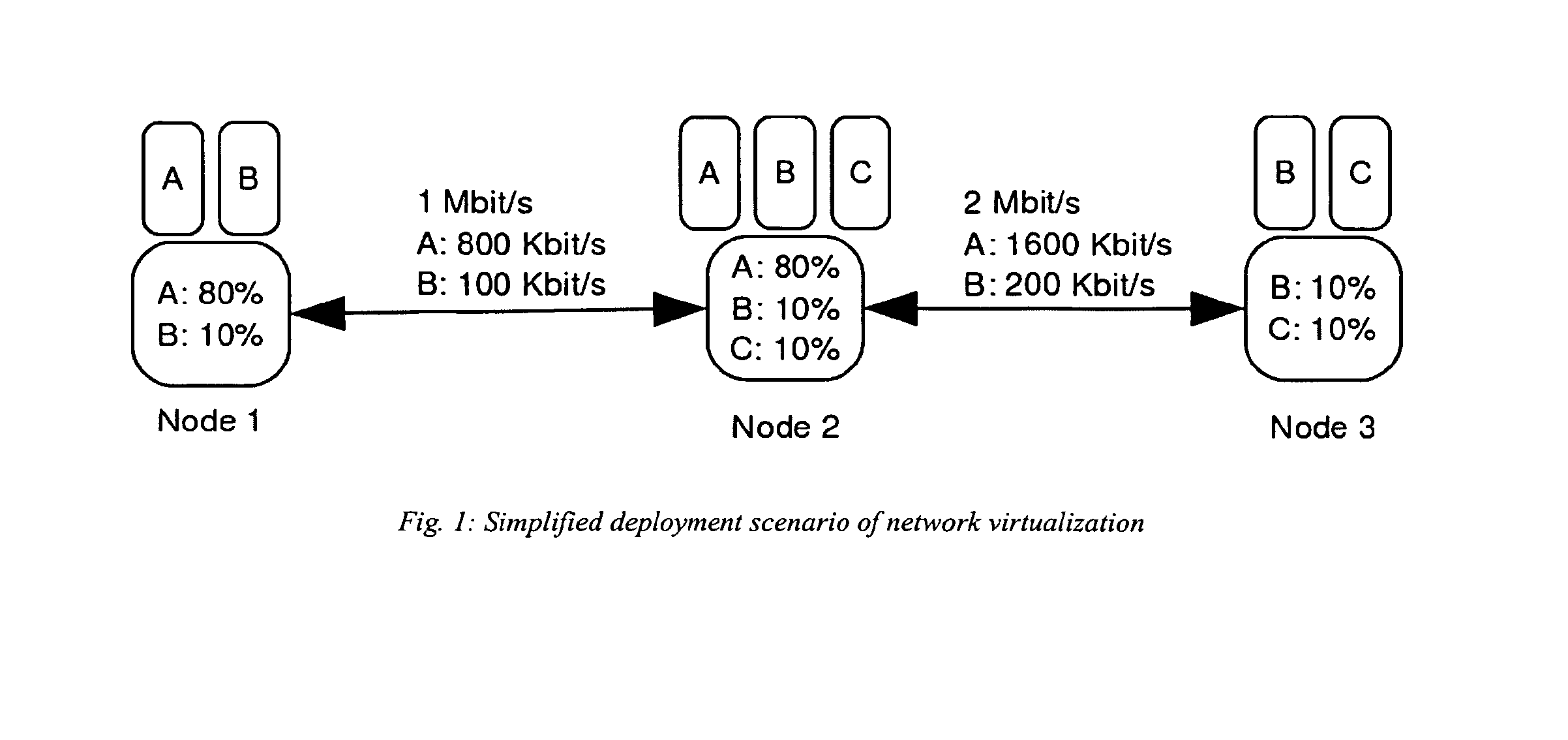
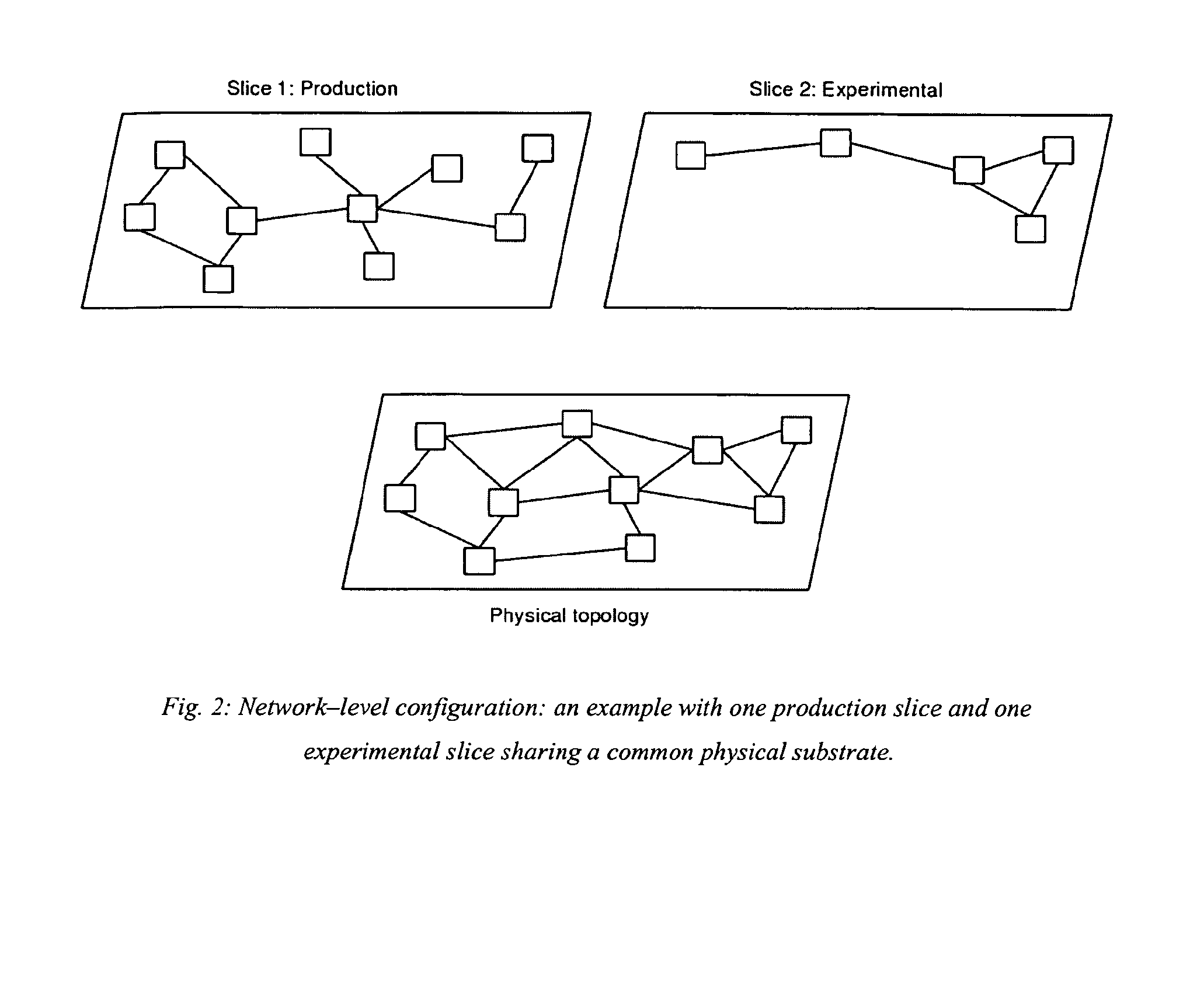
Currently available network virtualization solutions are either specifically tailored for wired networks composed of nodes with very large processing power and storage space. The present invention relates to a novel virtualization framework specifically tailored to wireless networks. Such framework provides Wireless Internet Service Providers (WISP) with an effective virtualization solution, allowing production traffic to share part of the available network resources with a variable number of network slices where novel solutions, such as new routing protocols, services or network operation tools, can be experimentally tested in a severely controlled yet realistic environment.
Owner:ASSOCIAZIONE CREATE NET
Apparatus and method for preemptively protecting against malicious code by selective virtualization
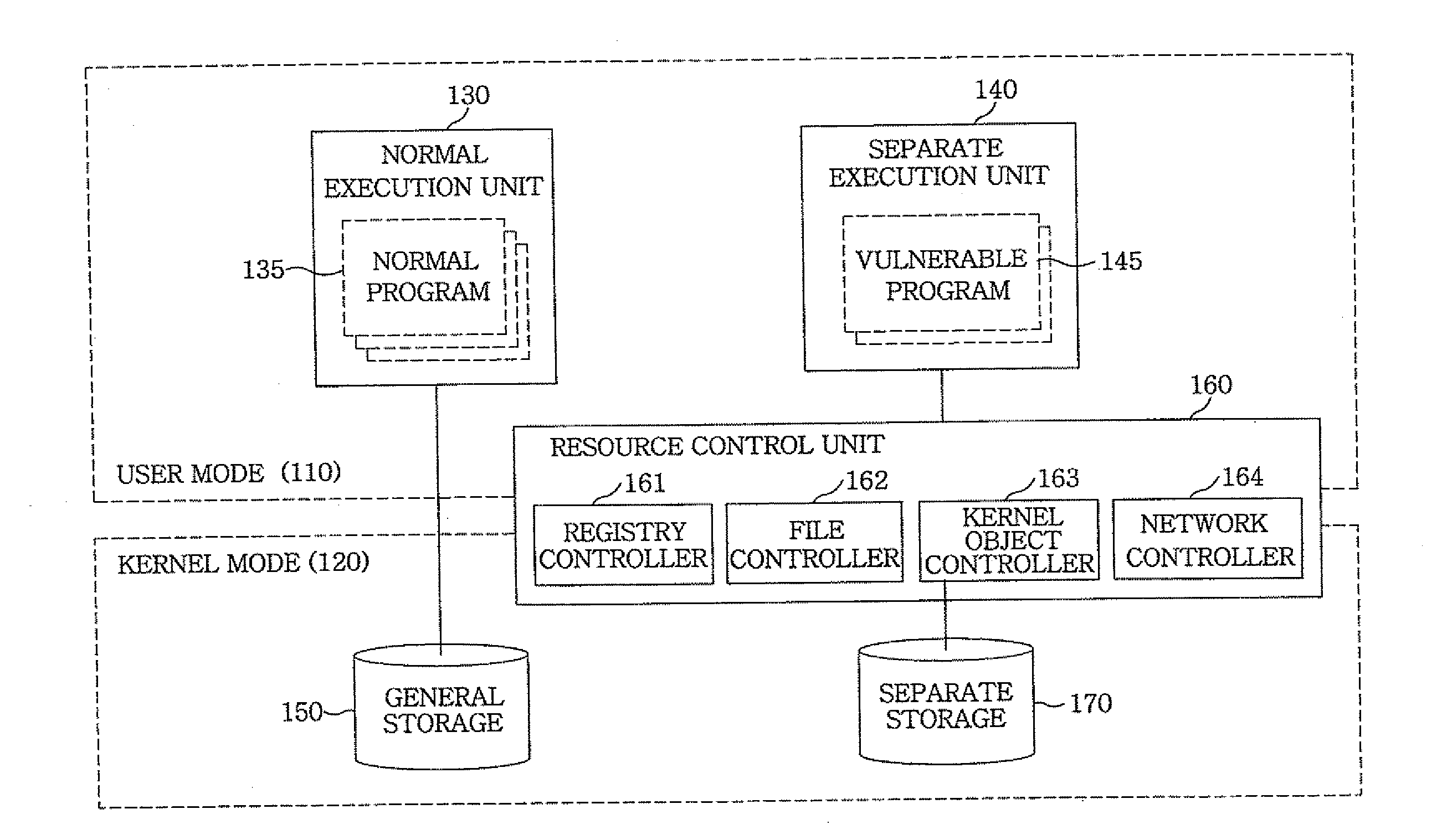
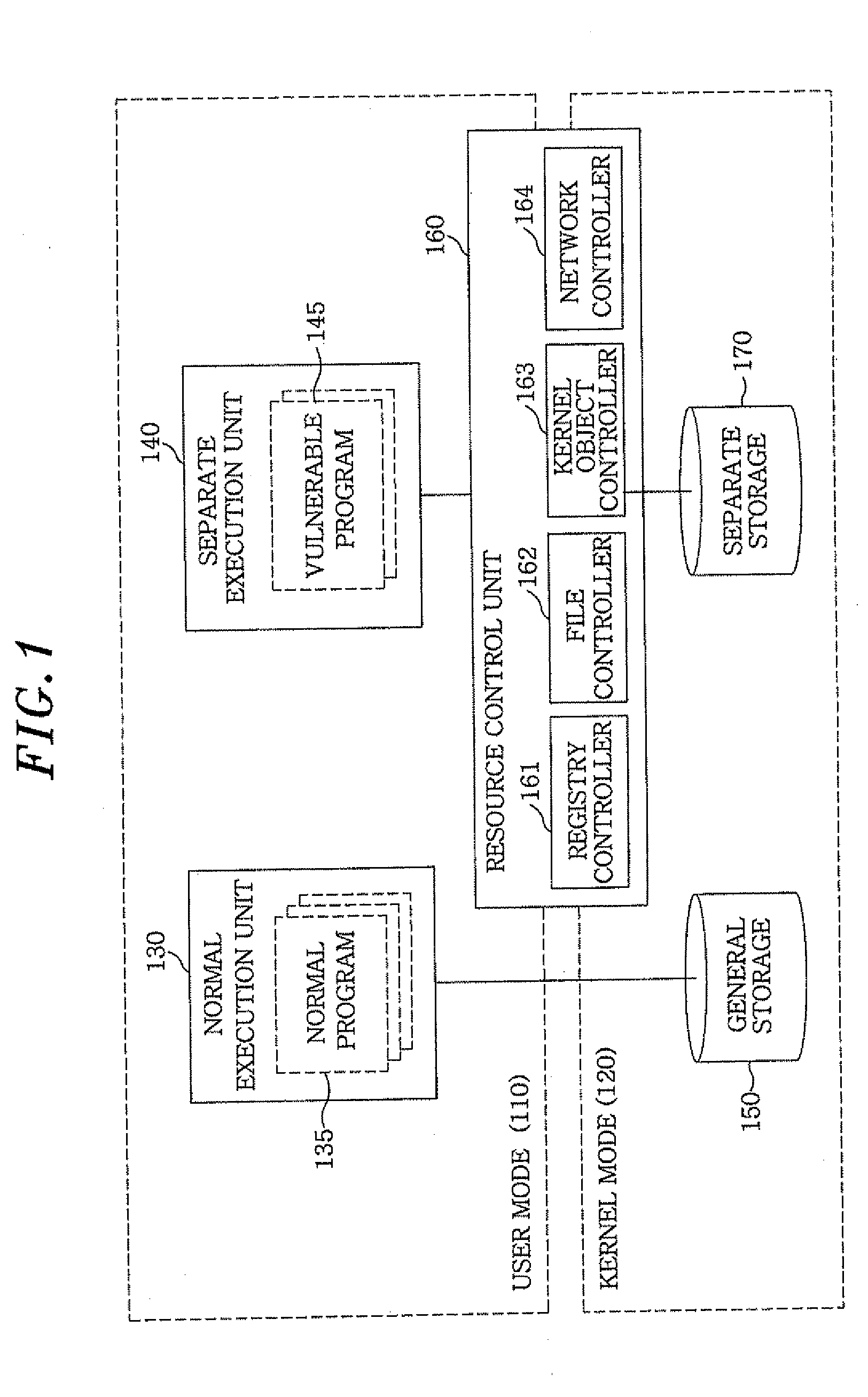
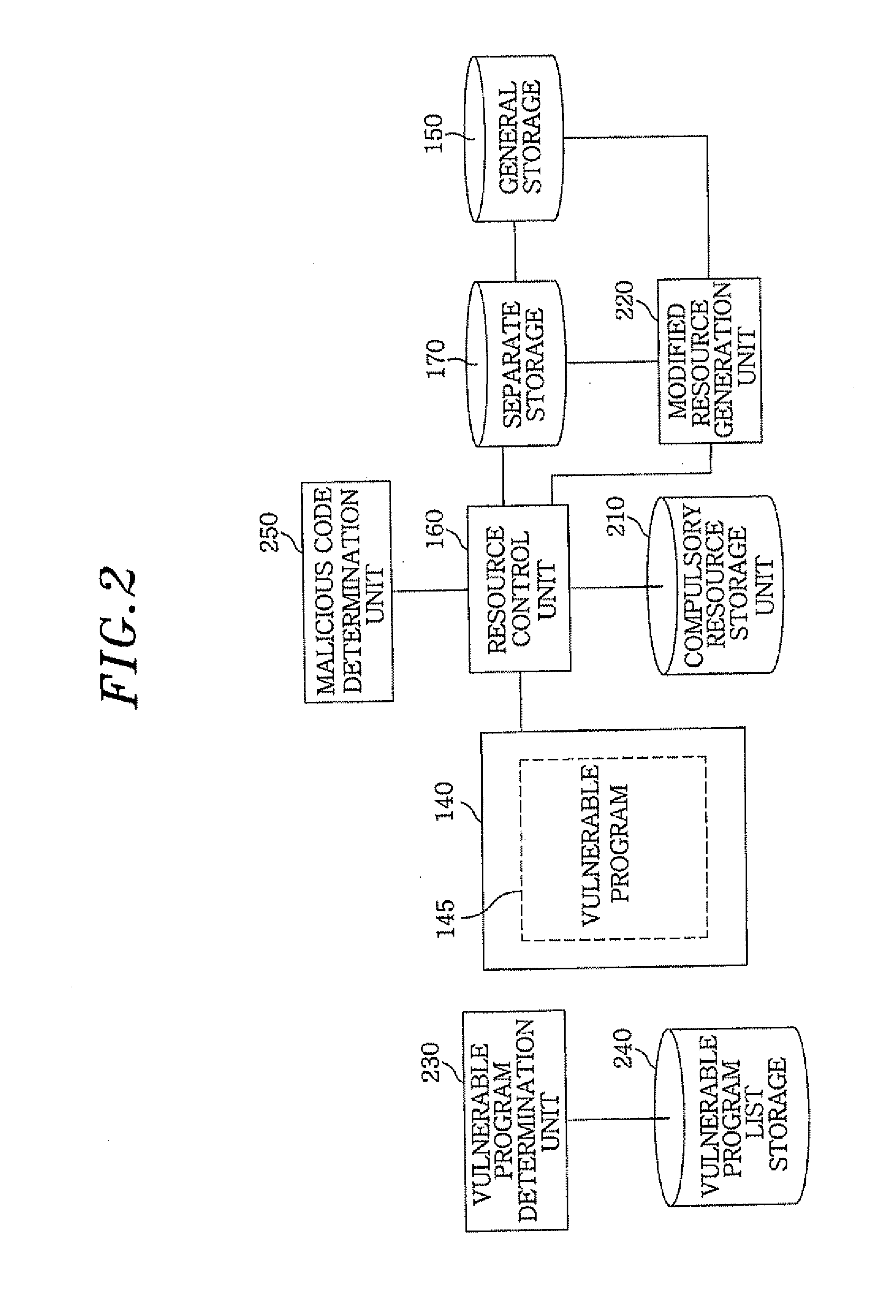
ActiveUS20110296526A1Accurate acquisitionMinimize impactMemory loss protectionDigital computer detailsVirtualizationOperational system
An apparatus for preemptively protecting against malicious code by selective virtualization comprises: a compulsory resource storage unit which selects and stores compulsory resources required for executing a vulnerable program having an interface with an external source in a separated space; a modified resource-generating unit which generates a new resource by modifying the content of a resource accessed by the vulnerable program in the event the vulnerable program accesses a resource other than said compulsory resources; and a resource control unit which performs an operating system-level virtualization when the vulnerable program accesses the compulsory resource, and permits the vulnerable program to access the modified resource when the vulnerable program accesses a resource other than the compulsory resource.
Owner:AHNLAB INC
Fine-grained cloud management control using nested virtualization
InactiveUS8484639B2Multiple digital computer combinationsSoftware simulation/interpretation/emulationData processing systemData treatment
A computer implemented method, a computer program product and a data processing system allocate resources within a computing organization. A hypervisor layer is implemented on an underlying hardware. The hypervisor layer comprises a set of virtual machines. A first pseudo-hypervisor layer is then implemented within a first one of the set of virtual machines of the hypervisor layer. The first pseudo-hypervisor layer comprises a second set of virtual machines. A first software component is located within a first virtual machine of the second set of virtual machines of the first pseudo-hypervisor layer. A second software component is collocated within a second virtual machine of the second set of virtual machines of the first pseudo-hypervisor layer.
Owner:INT BUSINESS MASCH CORP
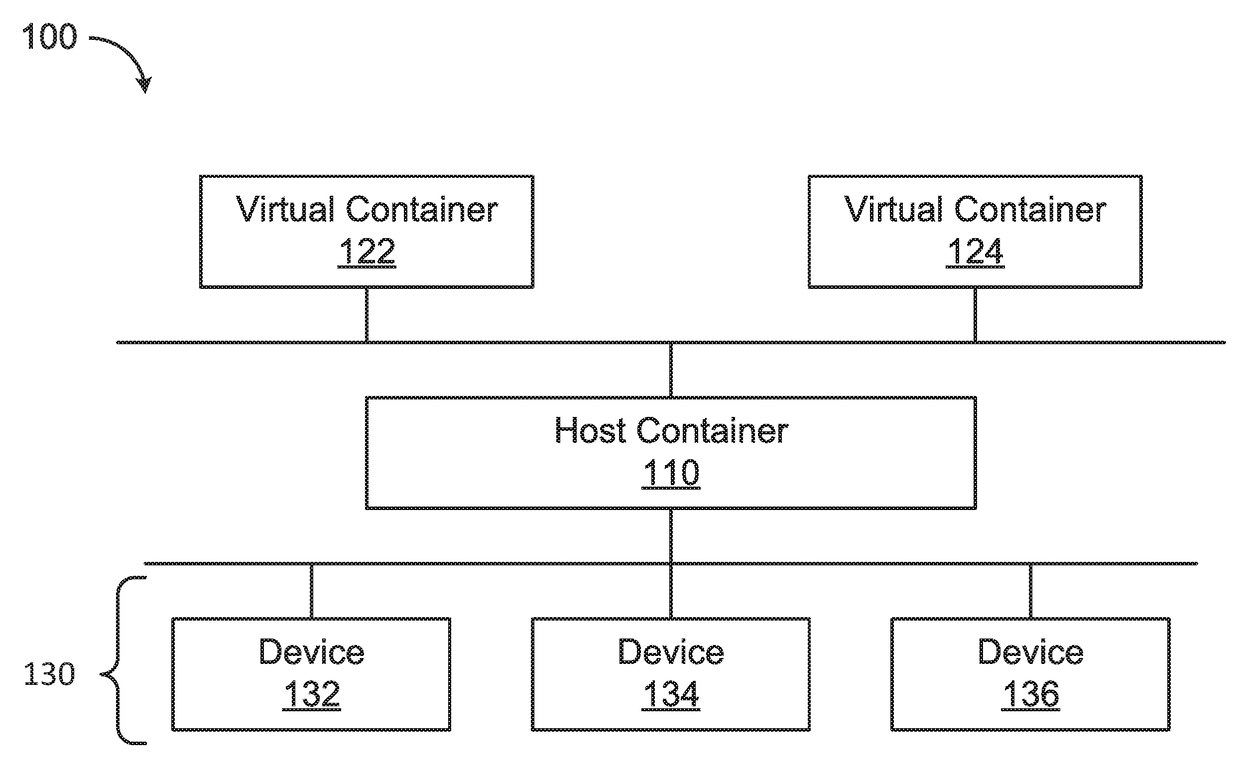
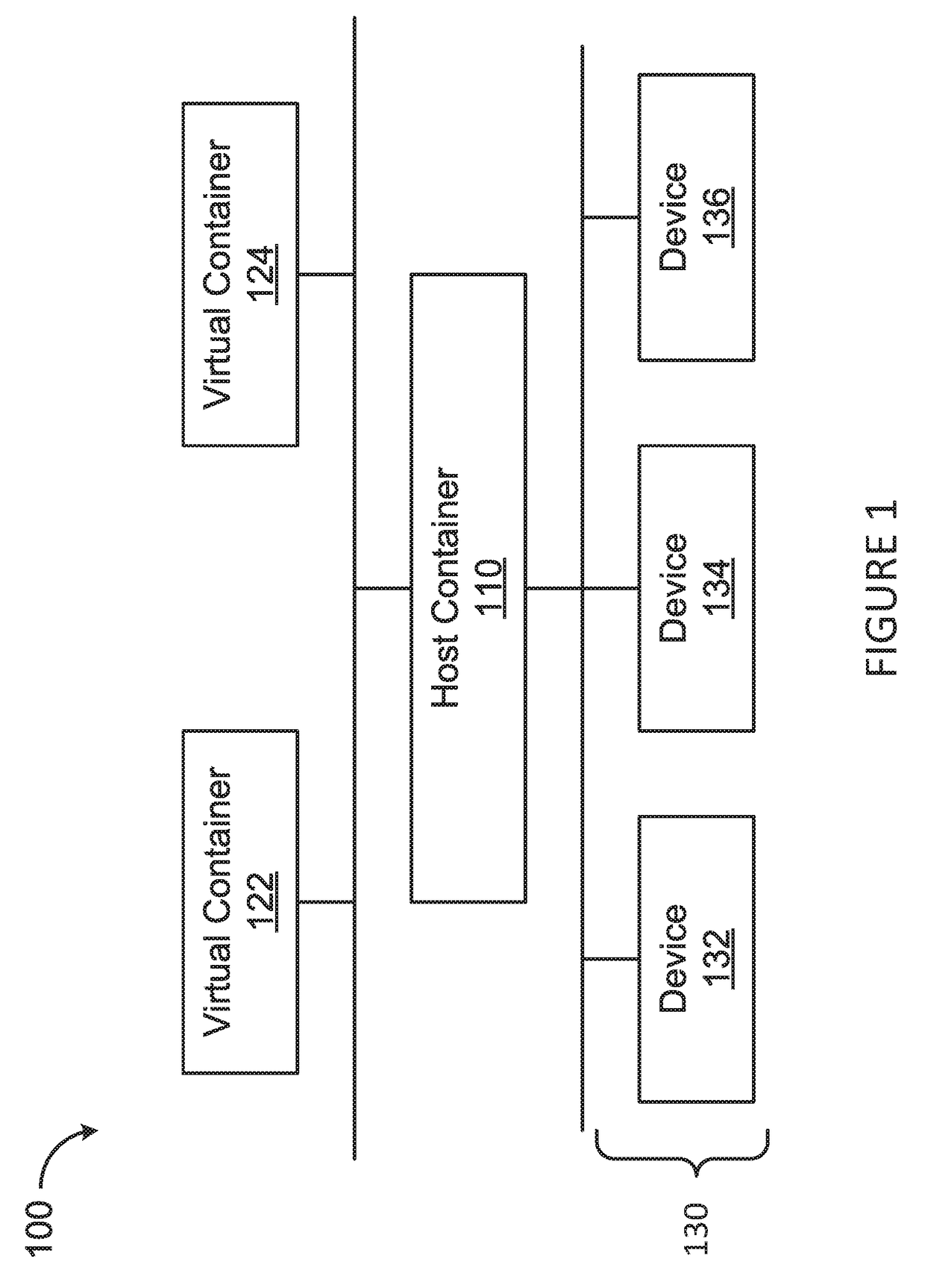
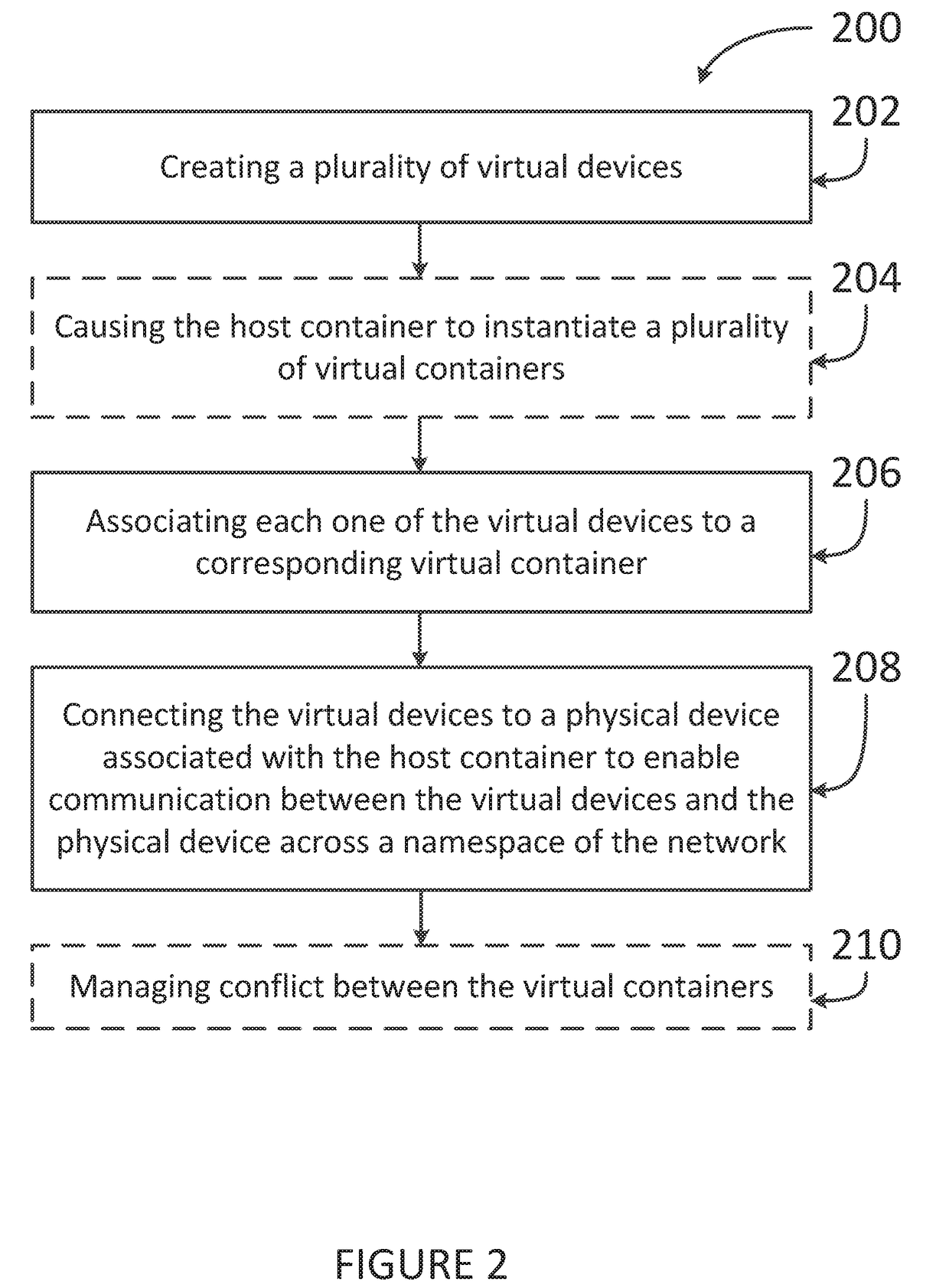
Device virtualization for containers
The present disclosure provides systems, methods, and computer-readable media for setting up a network. A plurality of virtual devices are created. Each one of the virtual devices is associated to a corresponding virtual container. Then, the virtual devices are connected to a real device, which is associated with a host container, in order to enable communication between the virtual devices and the real device across a namespace of the network.
Owner:HUAWEI TECH CO LTD
Methods and apparatus for providing hypervisor level data services for server virtualization
ActiveUS20160034296A1Data switching networksSoftware simulation/interpretation/emulationMemory virtualizationLevel data
A system for cloud-based data services for multiple enterprises, including a plurality of cloud hypervisors that cooperatively provide cloud-based services to multiple enterprises, each hypervisor including a plurality of cloud virtual servers, each cloud virtual server being associated with an enterprise, at least one cloud virtual disk that is read from and written to by the at least one virtual server, each cloud virtual disk being associated with an enterprise, and a virtual data services appliance, which provides cloud-based data services, and multiple data services managers, one data services manager per respective enterprise, each of which coordinates the respective virtual data services appliances for those cloud hypervisors that service its corresponding enterprise.
Owner:ZERTO
Apparatus for performing storage virtualization
ActiveUS9032164B2Increase overheadImprove throughputInput/output to record carriersData switching networksVirtual targetData management
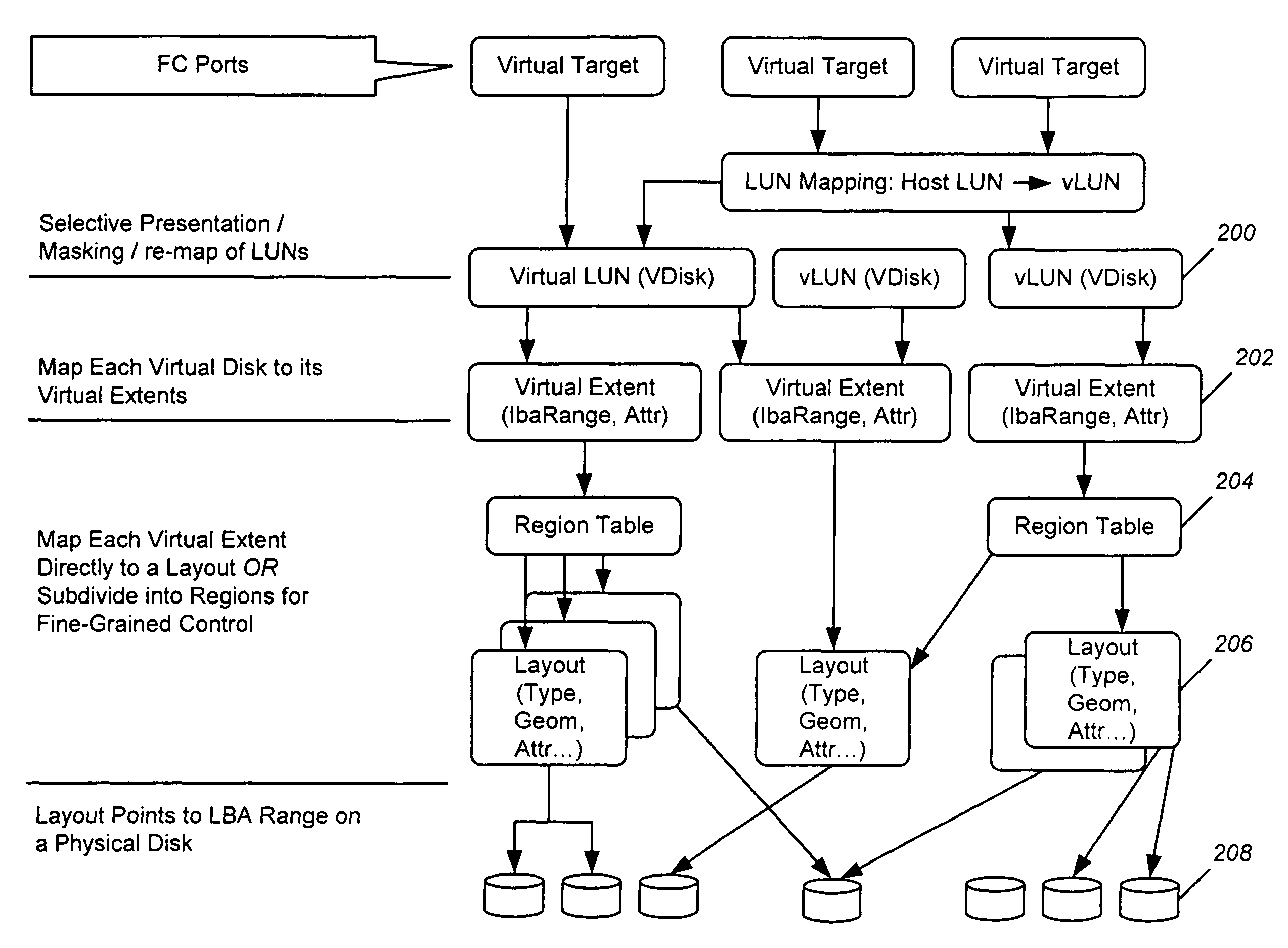
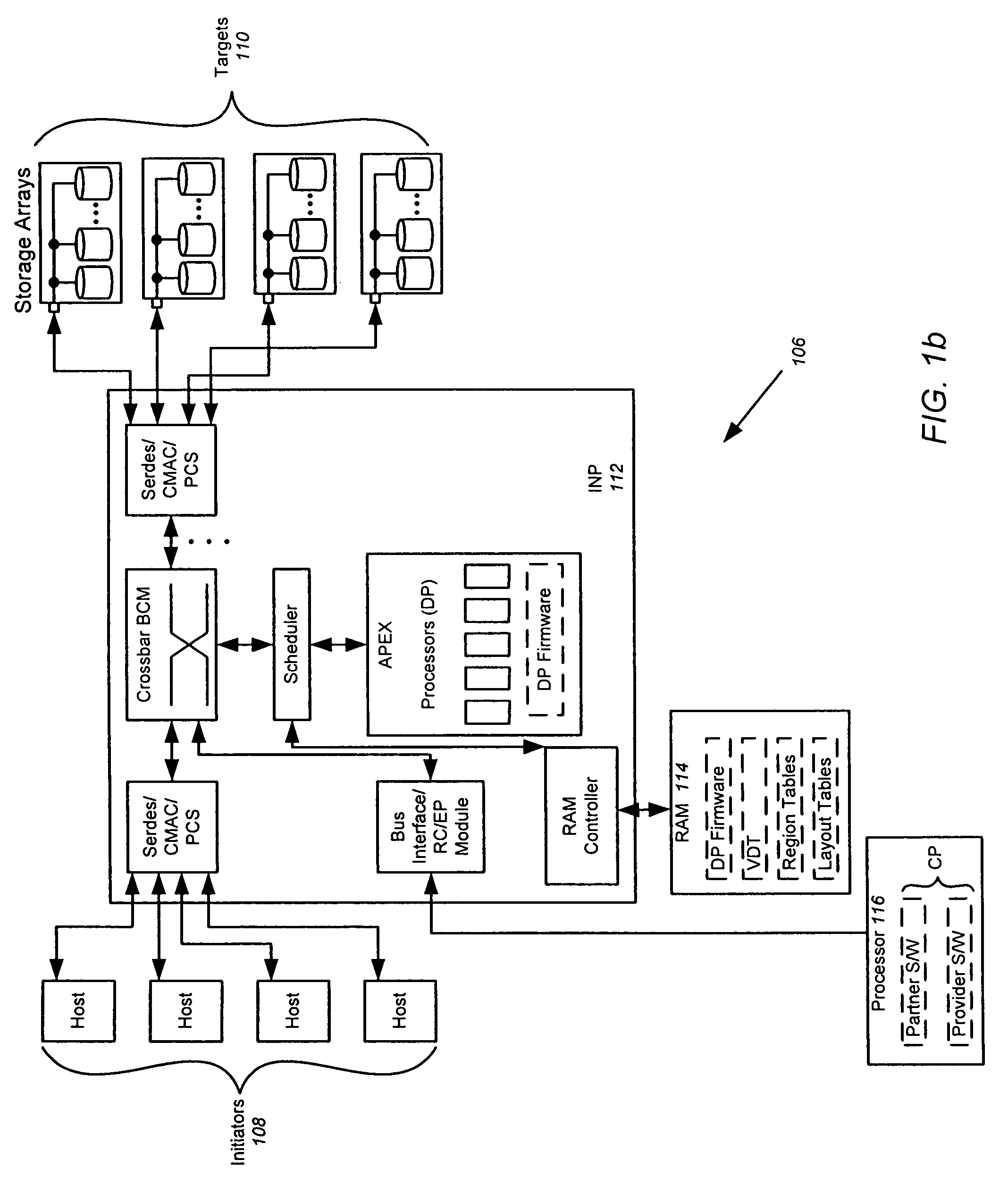
The splitting of storage applications and functions into a control path (CP) component and a data path (DP) component is disclosed. Reads and writes may be handled primarily in the DP. The CP may be responsible for discovery, configuration, and exception handling. The CP can also be enabled for orchestrating complex data management operations such as snapshots and migration. Storage virtualization maps a virtual I / O to one or more physical I / O. A virtual target (vTarget) in the virtual domain is associated with one physical port in the physical domain. Each vTarget may be associated with one or more virtual LUNs (vLUNs). Each vLUN includes one or more vExtents. Each vExtent may point to a region table, and each entry in the region table may contain a pointer to a region representing a portion of a pExtent, and attributes (e.g. read / write, read only, no access) for that region.
Owner:AVAGO TECH INT SALES PTE LTD
Storage virtualization system
ActiveCN103207762AAchieve stabilityAchieve reliabilityInput/output to record carriersNetwork virtualizationSystem virtualization
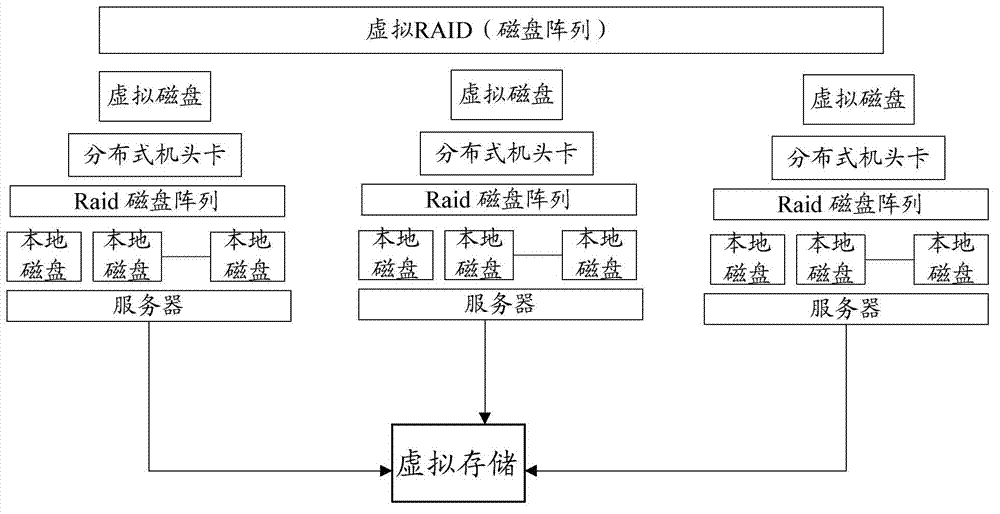
The invention provides a storage virtualization system. The storage virtualization system comprises servers, local disks, a Raid card, Raid disk arrays, virtual disks and distributed head cards, wherein the servers are used for providing software operating environments and a virtual machine control platform for a virtual machine and are provided with all-in-one machine managing units; a virtual Raid array is formed by local disks of all the servers through the Raid card by the all-in-one machine managing units; and a Raid disk array is formed by the local disks through an ISCSI (Internet Small Computer System Interface) channel by the Raid card, and a virtual memory is formed by the plurality of virtual Raid arrays through a network. According to the storage virtualization system provided by the invention, the problem of the shared storage in the conventional low-cost desktop virtualization scheme is solved, the high-reliability functions of the virtual HR (Human Resource) are realized, the shared storage is disaffiliated, and the stability and the reliability of a desktop are achieved; and meanwhile, the installation and maintenance cost of the system is lowered as well.
Owner:ISOFTSTONE INFORMATION TECHNOLOGY (GROUP) CO LTD
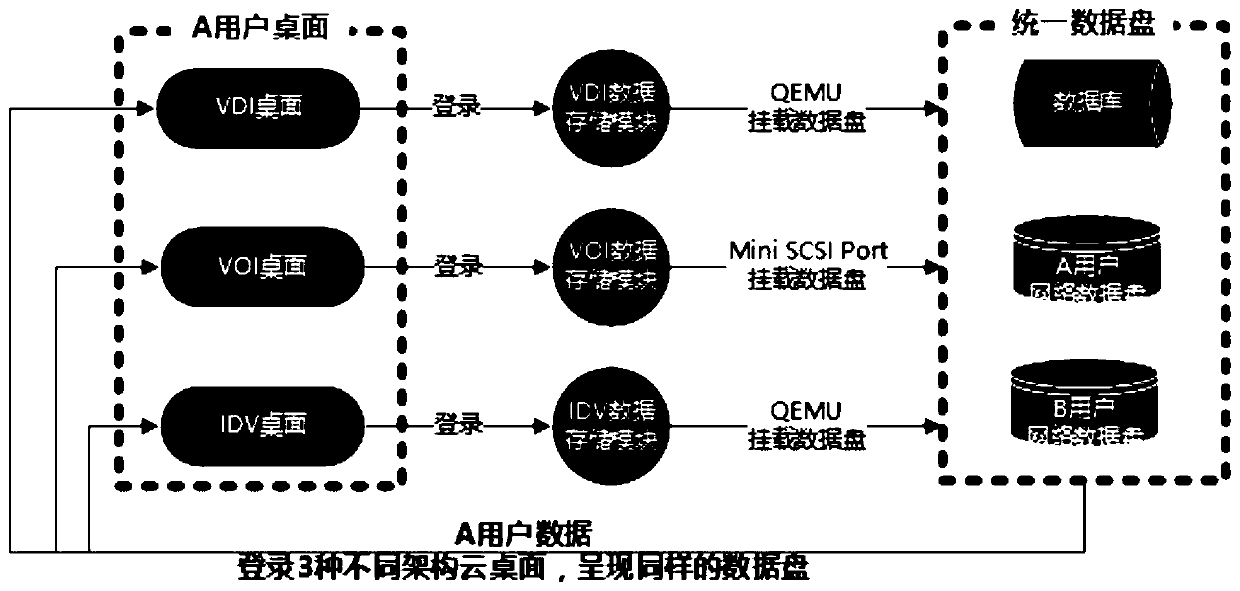
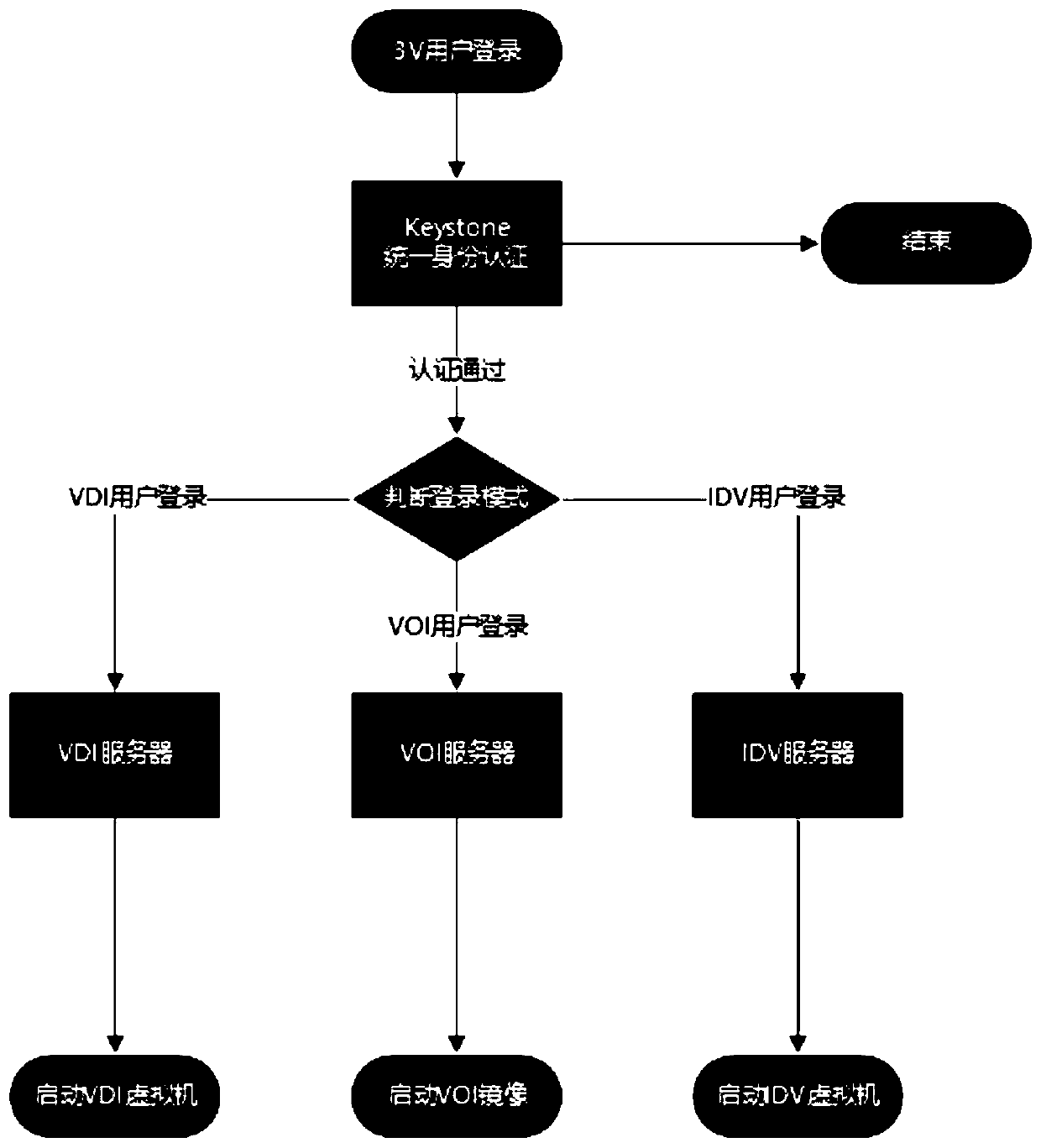
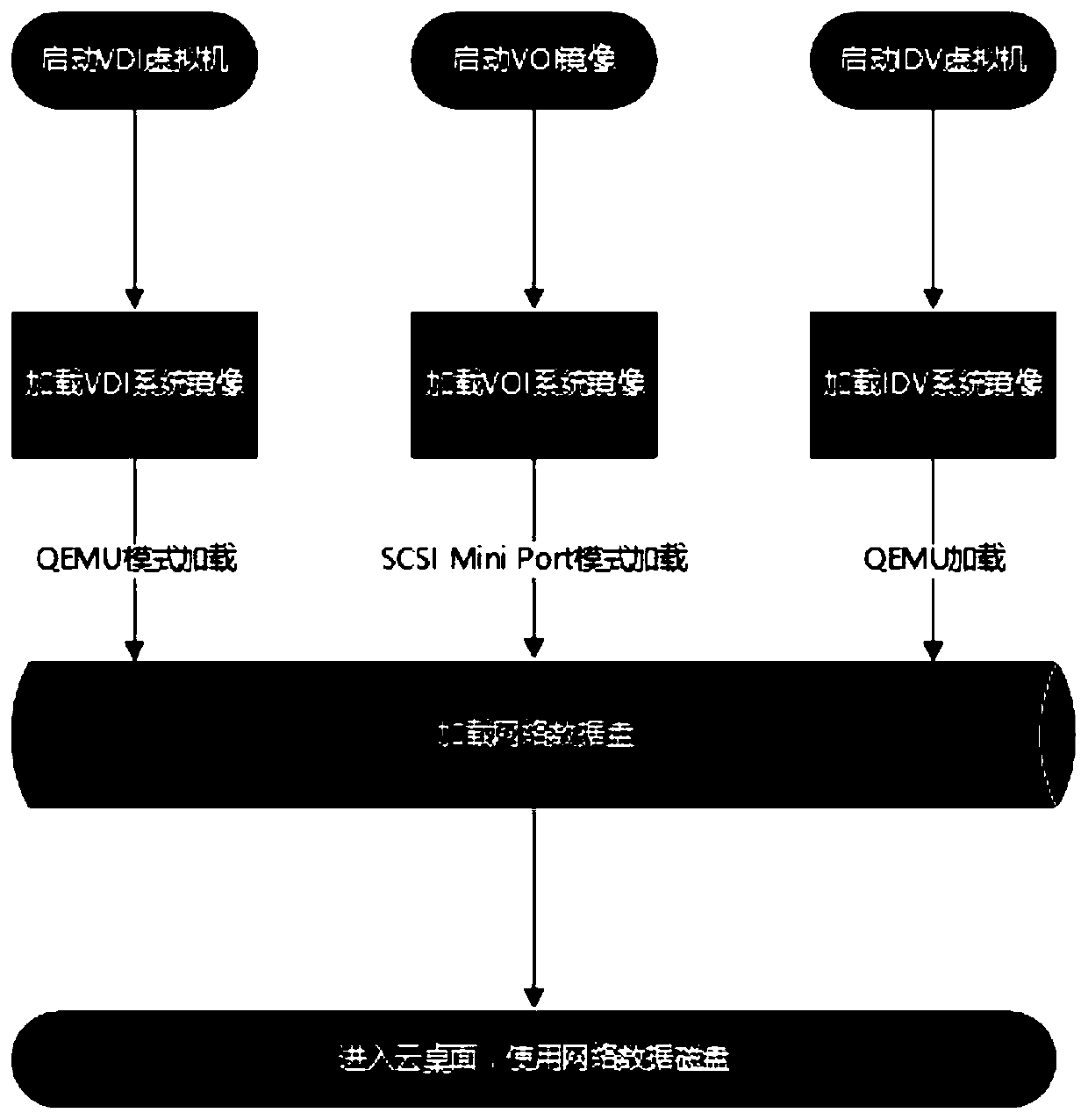
Data disk technology simultaneously supporting 3V desktop virtualization architecture
PendingCN110347337AMeet the need to access the same dataInput/output to record carriersExecution for user interfacesData synchronizationData virtualization
The invention discloses a data disk technology simultaneously supporting a 3V desktop virtualization architecture. The invention relates to the technical field of desktop virtualization, in particularto a desktop virtualization system which comprises three user login clients including a VDI client, a VOI client and an IDV client, and a user registers in a Keystone and is bound with a system mirror image, a network data disk and an MAC address. Data disks of three desktop virtualization architectures of VDI, VOI and IDV are connected. A user uses any desktop virtualization; the data of the user can be accessed; a universal network disk technology irrelevant to a virtualization architecture is used; the identity authentication of the cloud desktop is passed; the same part of data belongingto the user can be directly accessed; according to the method, the processes of network disk login, different cloud desktop data synchronization and the like do not need to be executed again, the technology is suitable for a scene of simultaneously reading and writing data on various desktop virtualization architectures, and the requirement of a user for accessing the same data on different desktops, different physical devices, different networks and different positions can be met.
Owner:北京和信创天科技股份有限公司
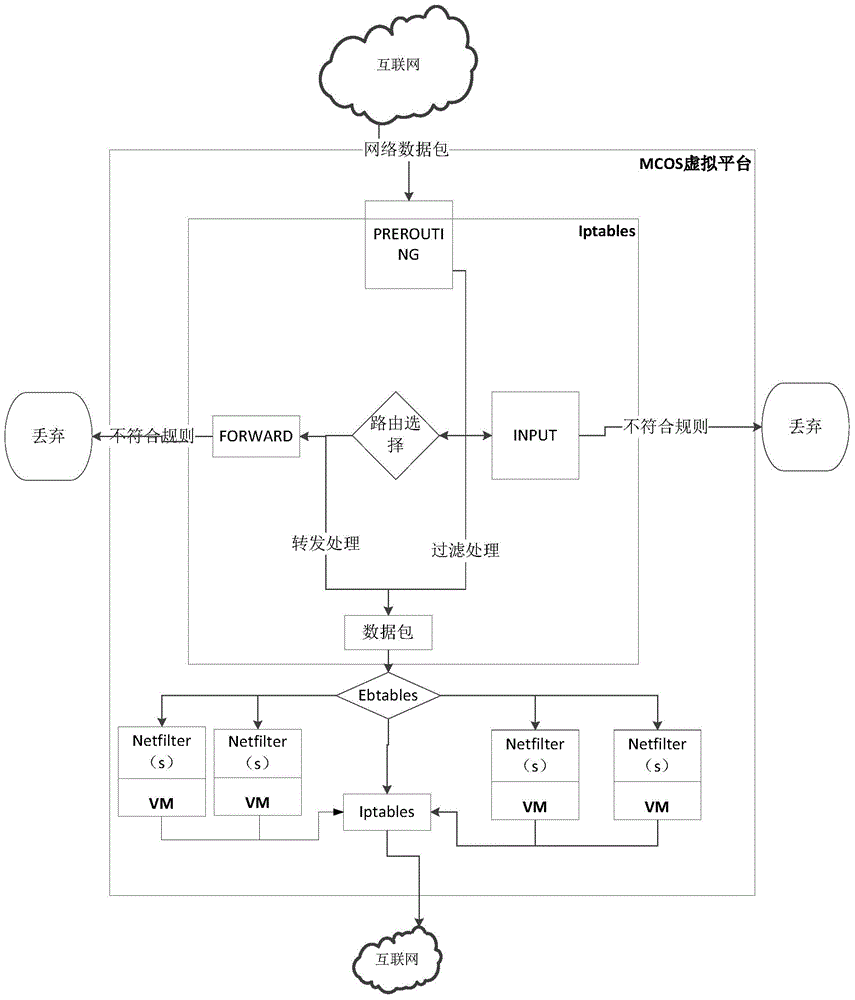
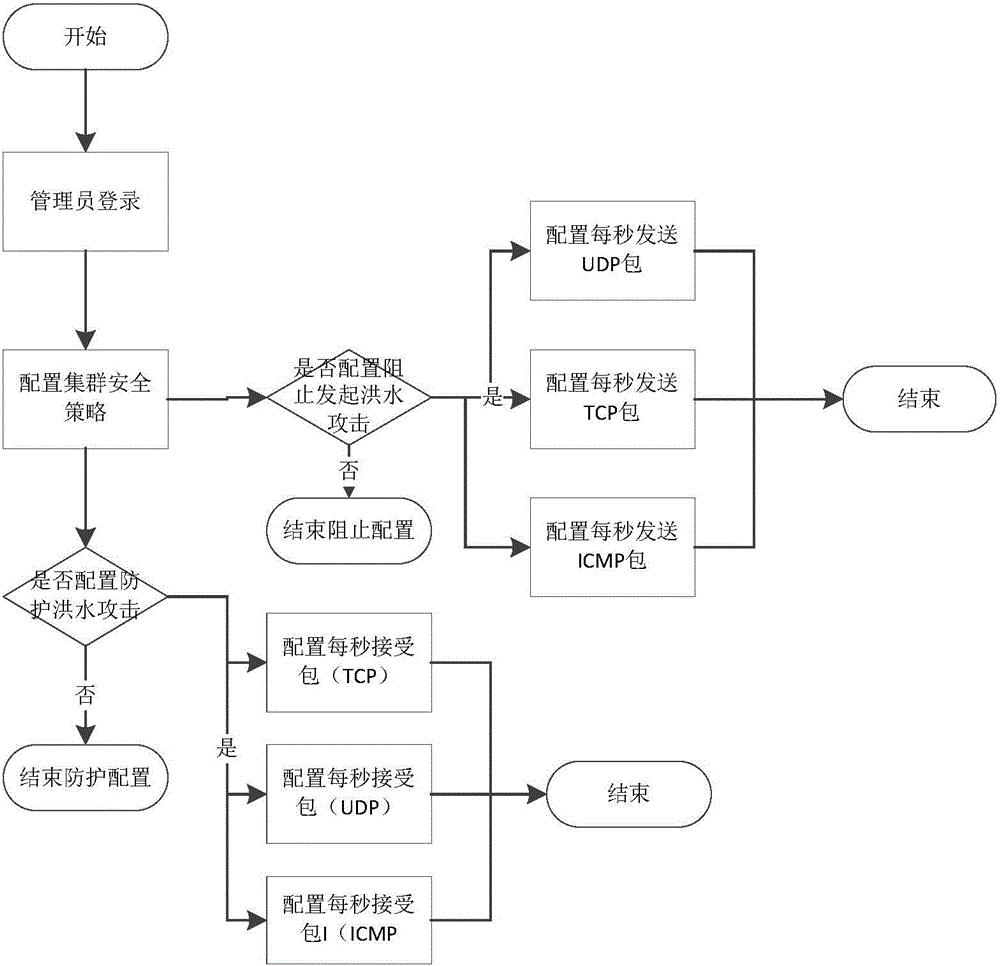
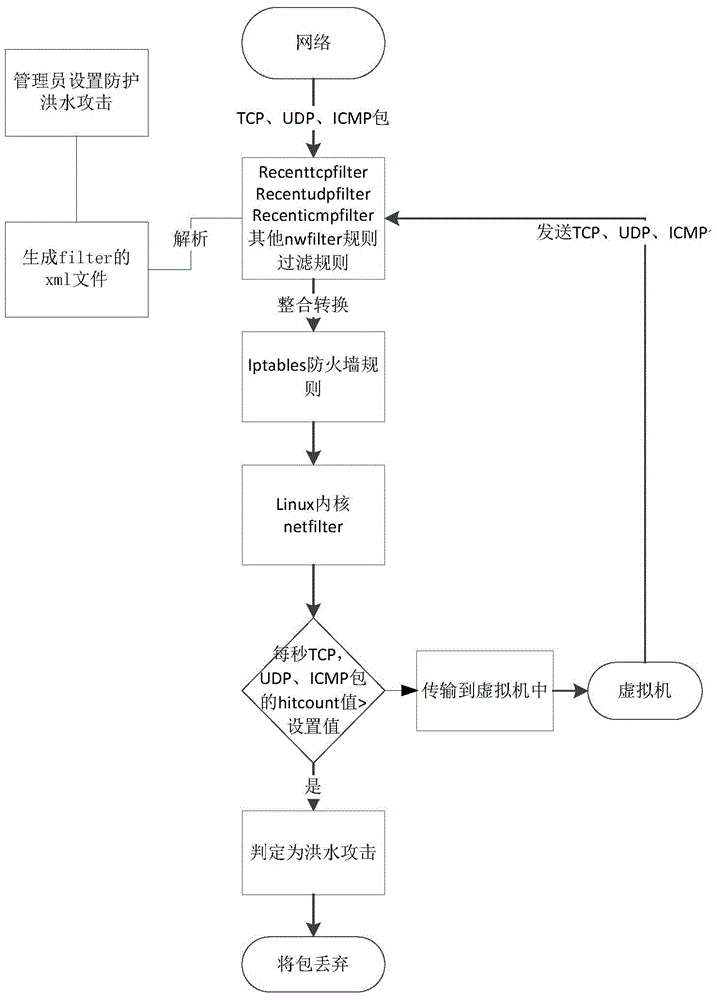
Method for preventing flood attacks in desktop virtualization
The invention discloses a method for preventing flood attacks in desktop virtualization. The method comprises the steps that a system configures a cluster safety strategy and a strategy for preventing or stopping initiation of the flood attacks; when network data packets enter a server, a system fire wall analyzes the network data packets and judges whether the data packets are input or forwarded; filtering is carried out again through an Ethernet fire wall Ebtables; if virtual machines are adopted as receiving ends of the network data packets, the data packets are filtered by netfilters of the virtual machines and enter the virtual machines, and if local systems are adopted as the receiving ends of the data packets, the data packets enter local programs to be processed or used. The method has the advantages that through the setting of a desktop virtualization platform and the virtual machines, the flood attacks of TCPs, UDPs and ICPMs can be effectively prevented, the virtual machines can share one filter rule, and if the filter rule is changed, all the virtual machines can be modified in an unified mode.
Owner:MASSCLOUDS
A method and a device for realizing dual-live disaster recovery for a server virtualization system
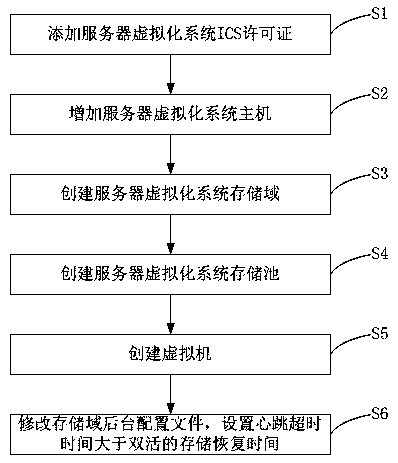
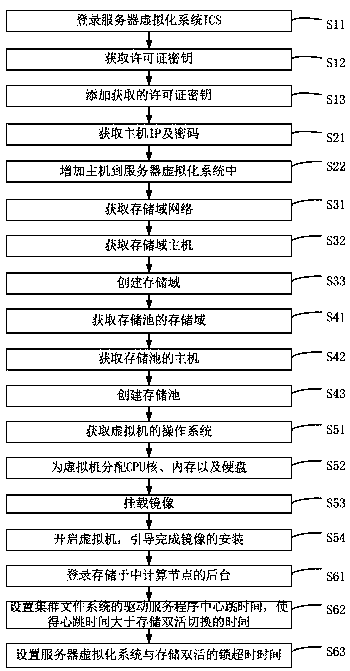
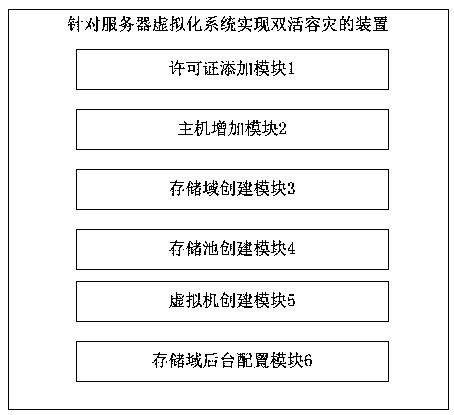
ActiveCN109240855AImprove securityAdapt to needsSoftware simulation/interpretation/emulationRedundant operation error correctionData accessComputer module
The invention provides a method and a device for realizing dual-live disaster recovery for a server virtualization system. The method includes: configuring a server virtualization system ICS, and creating a CFS storage domain and a shared storage pool; Modifying the storage domain profile to set the heartbeat timeout to be greater than the dual live storage recovery time. The device comprises a license adding module, which is used for adding an ICS license of a server virtualization system; A host adding module, configured to add a server virtualization system host; A storage domain creation module for creating a server virtualized system storage domain; A storage pool creation module for creating a server virtualization system storage pool; A virtual machine creation module for creating avirtual machine; The storage domain background configuration module used for modifying the storage domain background configuration file and setting the heartbeat timeout time to be greater than the dual-live storage recovery time. The invention enhances the safety of data access, more adapts to the needs of enterprise-level customers, and promotes the perfection of the functions of the company'svirtualized products.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Multi-hypervisor virtual machines
Standard nested virtualization allows a hypervisor to run other hypervisors as guests, i.e. a level-0 (L0) hypervisor can run multiple level-1 (L1) hypervisors, each of which can run multiple level-2 (L2) virtual machines (VMs), with each L2 VM is restricted to run on only one L1 hypervisor. Span provides a Multi-hypervisor VM in which a single VM can simultaneously run on multiple hypervisors, which permits a VM to benefit from different services provided by multiple hypervisors that co-exist on a single physical machine. Span allows (a) the memory footprint of the VM to be shared across two hypervisors, and (b) the responsibility for CPU and I / O scheduling to be distributed among the two hypervisors. Span VMs can achieve performance comparable to traditional (single-hypervisor) nested VMs for common benchmarks.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
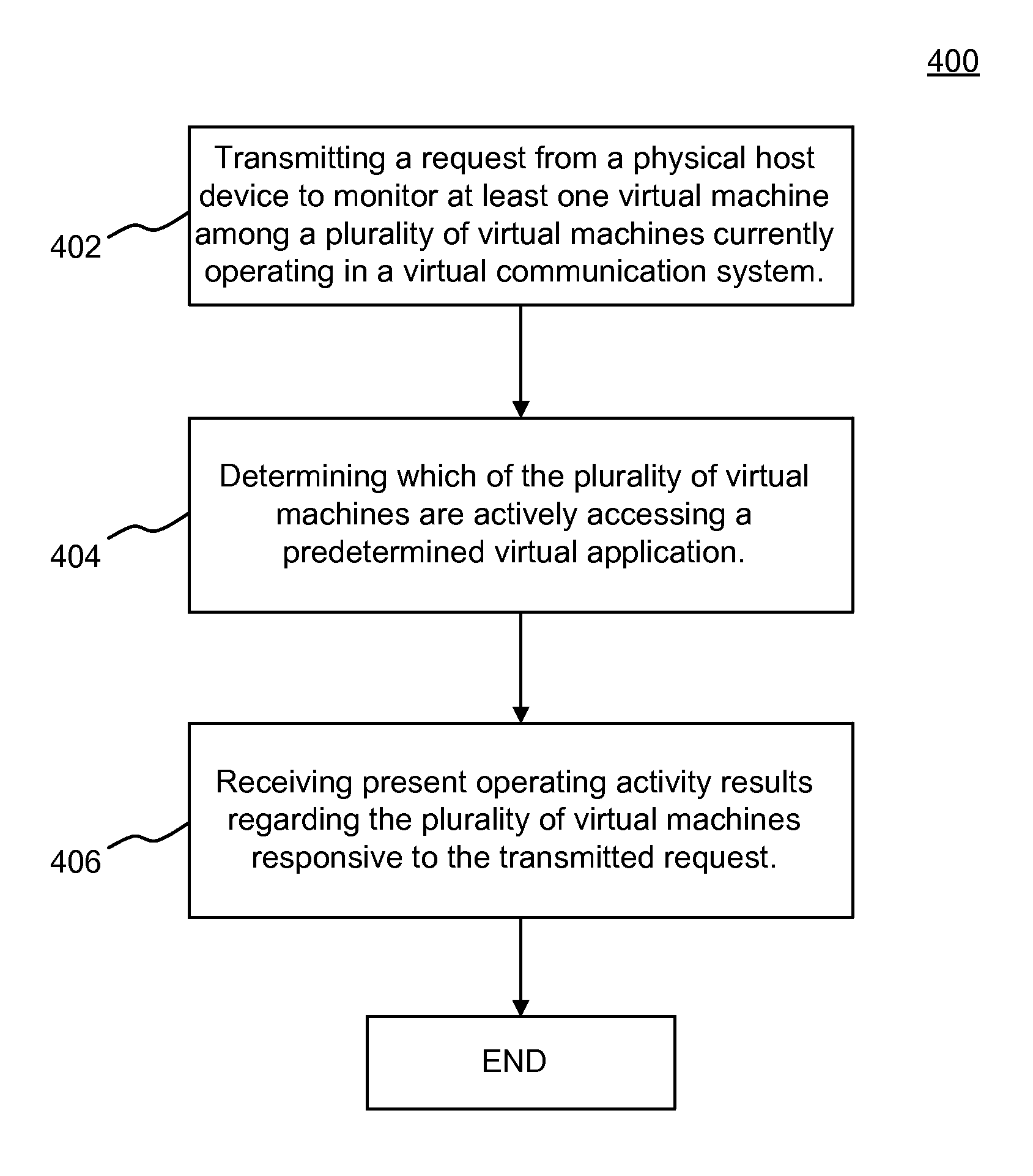
Automatic determination of a virtual machine's dependencies on storage virtualization
Disclosed are examples of observing and measuring virtual machine (VM) activity in a VM communication system environment. According to one example embodiment, an example operation may include transmitting a request from a physical host device to monitor at least one virtual machine among various virtual machines currently operating in a virtual communication system. Additional operations may include determining which of the virtual machines are actively accessing a predetermined virtual application, such as a virtual storage application. The operations may also include receiving present operating activity results regarding the virtual machines responsive to the transmitted request.
Owner:OPEN INVENTION NEWTORK LLC
Method for achieving central management of desktop virtualization off-line desktop
InactiveCN103793264AImprove operation and maintenance efficiencyImprove work efficiencySoftware simulation/interpretation/emulationOperational systemApplication software
The invention provides a method for achieving central management of a desktop virtualization off-line desktop and belongs to the field of cloud computing and desktop virtualization. According to the method, an operation system, an application program and user files of the desktop are layered and are synchronous with a backstage server within a fixed time interval so as to achieve the aim of unified management of physical desktops in an enterprise. After a Mirage client terminal is installed on an operation system of a newly-bought client terminal, a manager just needs to deploy standardized mirror images and application software of a user through a guide and the whole deploying is quietly carried out backstage. The Mirage carries out locking of a threshold value on data transmission and system performances and deploying can be carried out through a wide-area network. In the time of updating, the user can not feel lowering of any performance at all, and the user continues operation of the system. After deploying is finished, the operation system just needs to be rebooted and the whole mirror images and the software are instantly converted into the standard system of the company.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com