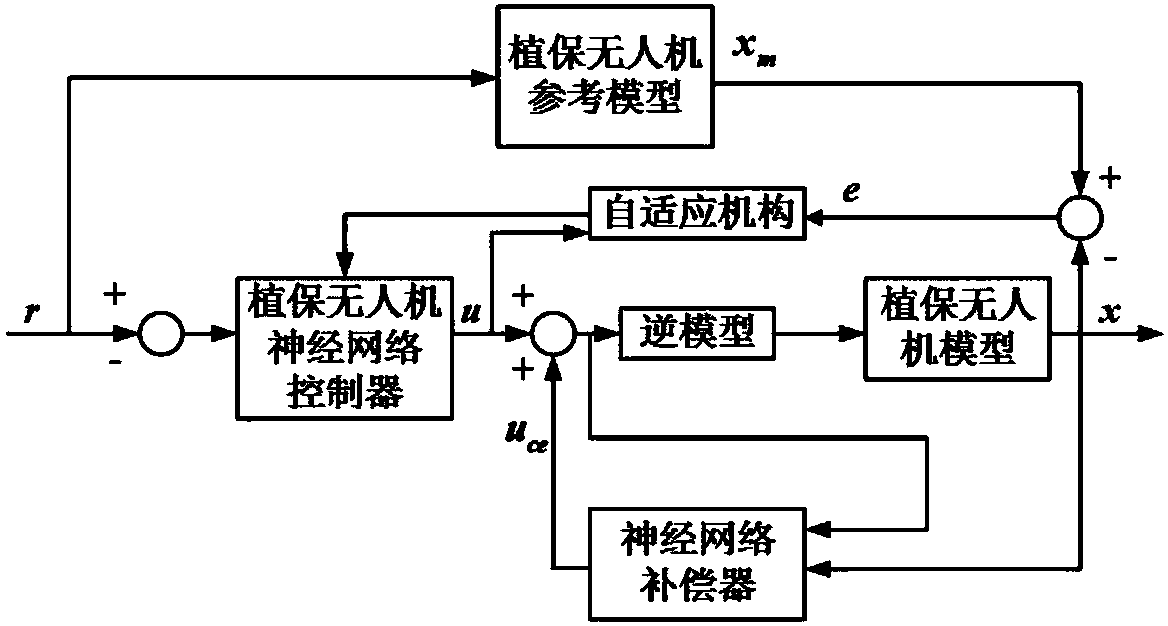
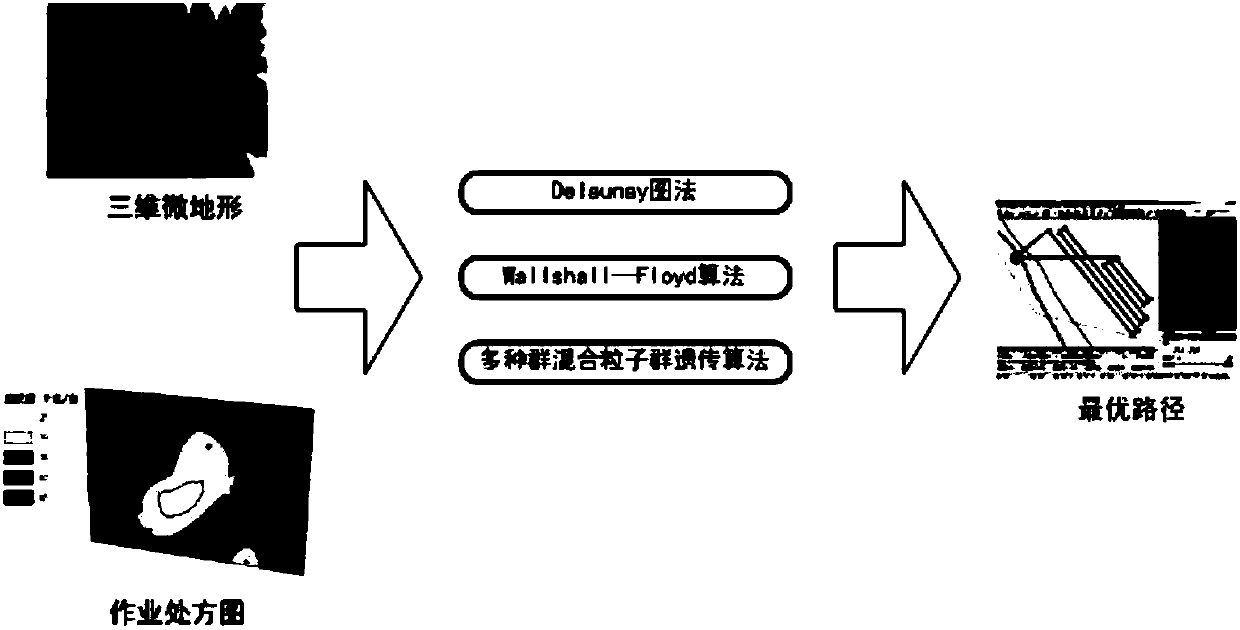
Patents
Literature
2671results about How to "Achieve isolation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
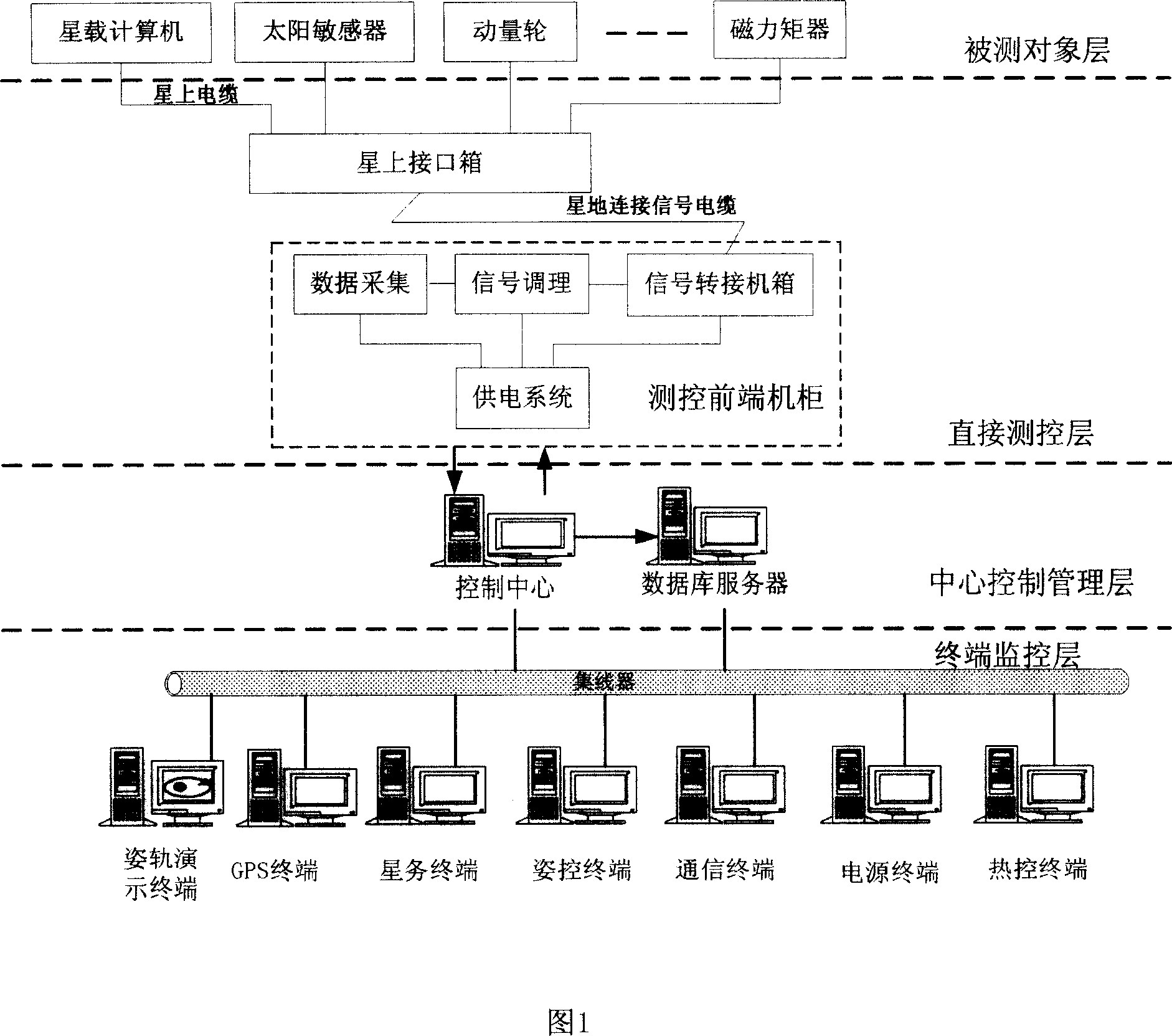
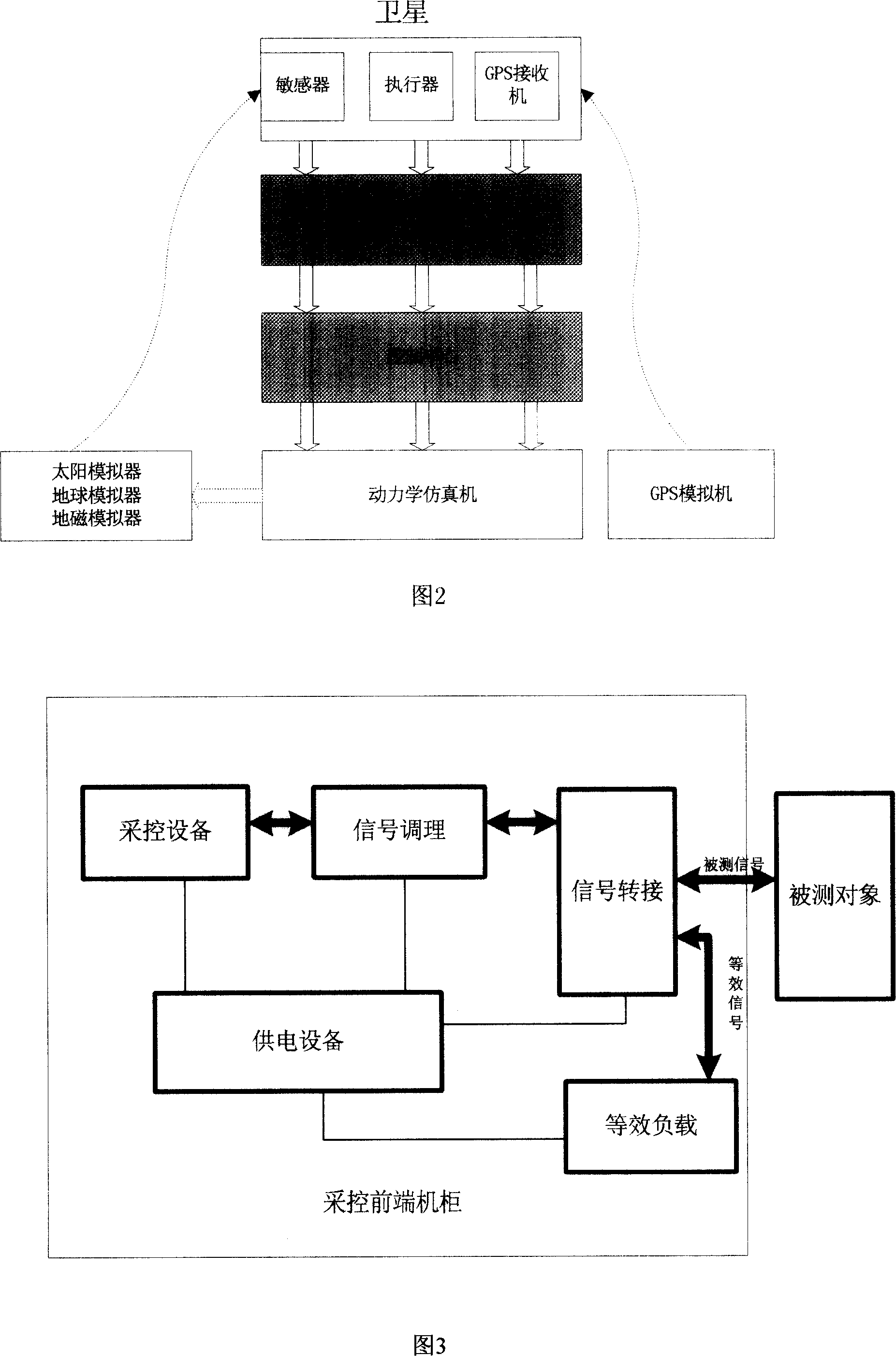
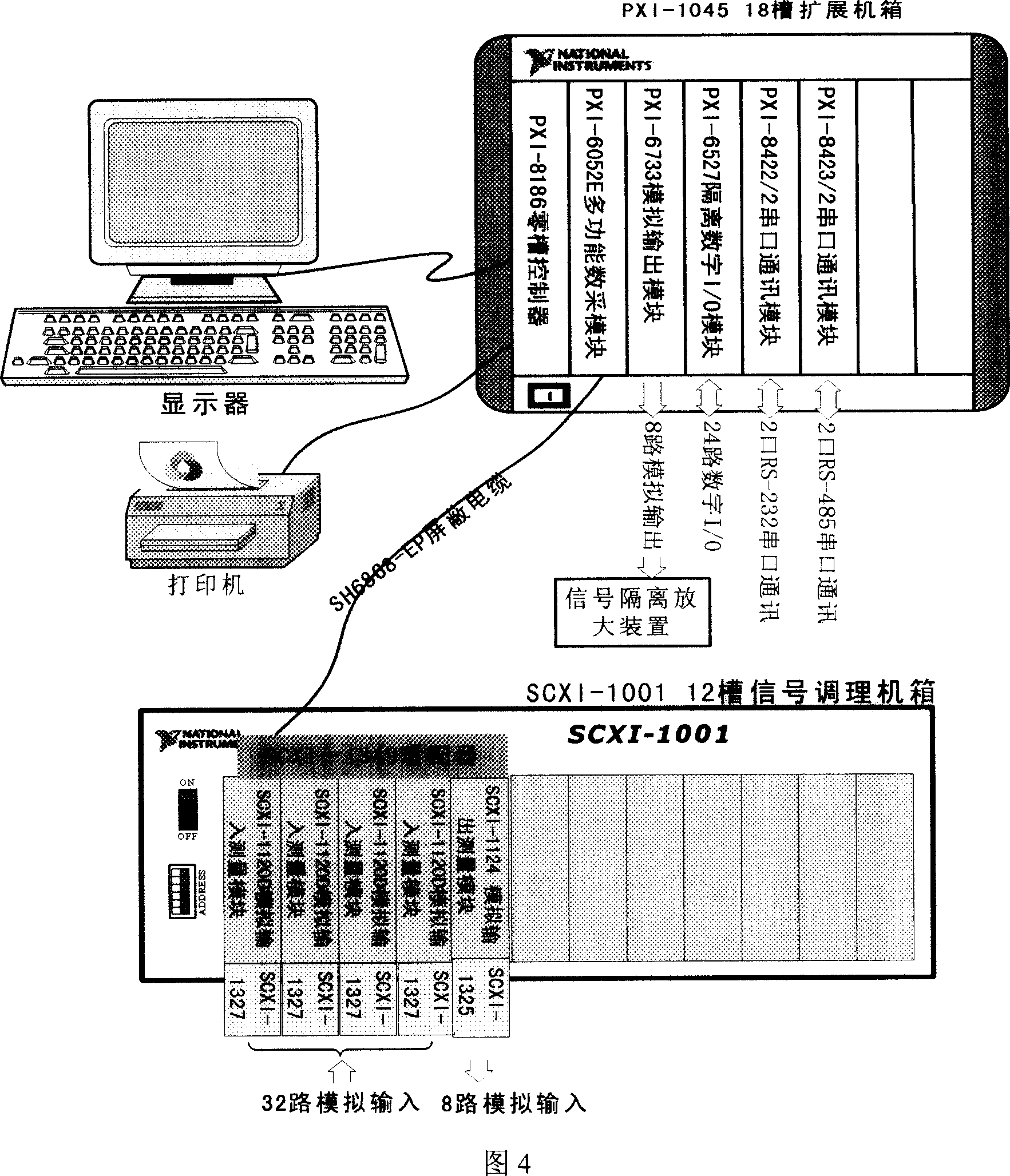
Universal micro-satellite comprehensive testing platform based on PXI system
InactiveCN1982863AReliability advantageFacilitate fault diagnosisStructural/machines measurementCosmonautic vehicle trackingControl layerComputer terminal
A universal micro-satellite integrated test platform based on PXI system is formed by interconnecting tested object, direct measurement-control layer, central control management layer and terminal monitoring layer to each other.
Owner:SHANGHAI ENG CENT FOR MICROSATELLITES
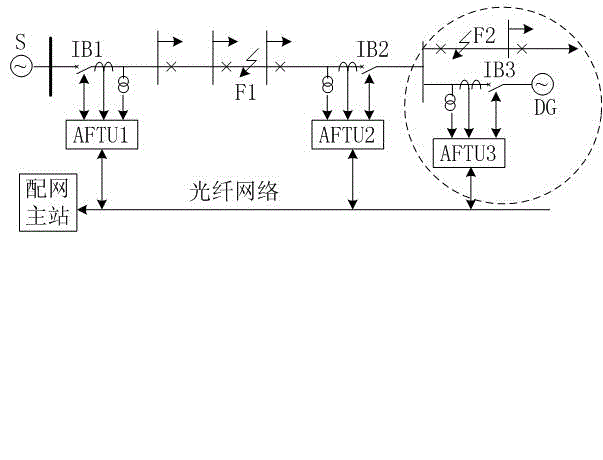
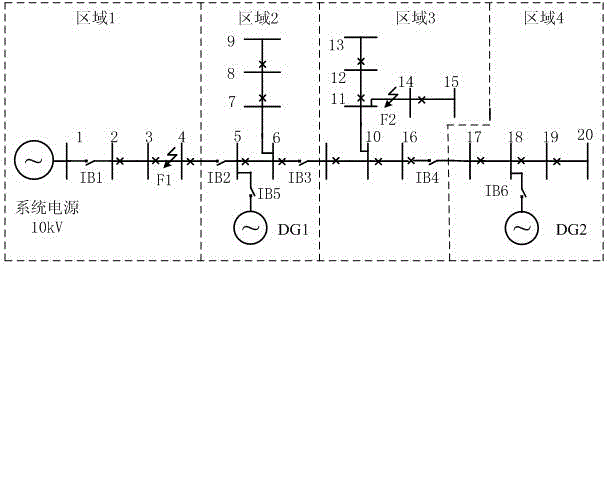
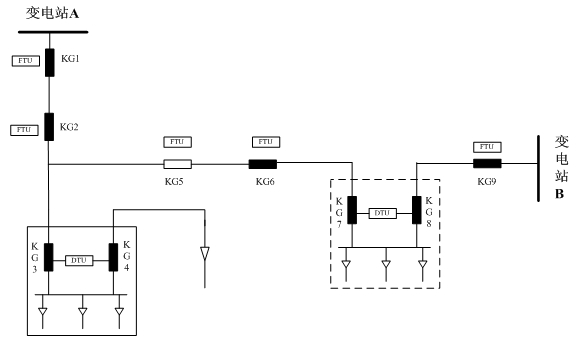
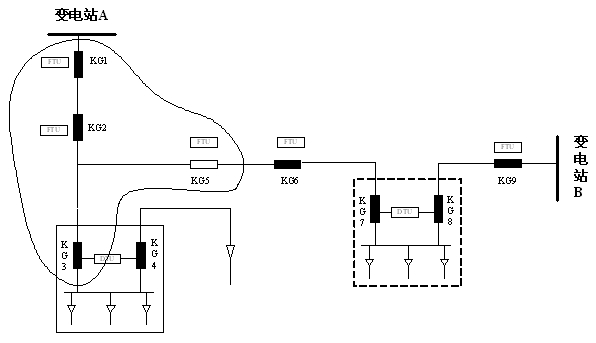
DG (distributed generation)-containing power distribution network distributed protection and control method
InactiveCN102882197ARapid positioningAchieve isolationEmergency protective circuit arrangementsIslandingComputer terminal
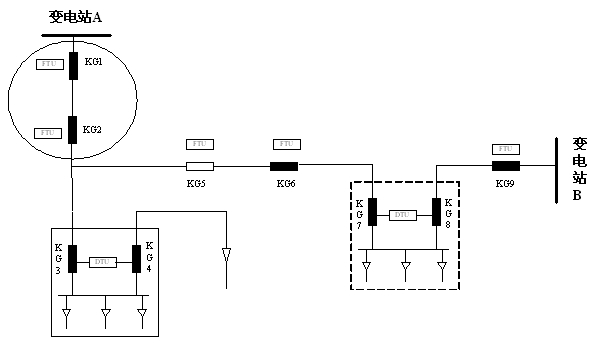
The invention discloses a DG (distributed generation)-containing power distribution network distributed protection and control method, and provides a protection and control technical method based on an AFTU (advanced feeder terminal unit) for the phenomenon that the high-permeability distributed power access power distribution network causes great difficulties in traditional power distribution protection and control. The method disclosed by the invention divides the DG-containing power distribution network into multiple areas capable of running as islands in advance according to the DG capacity and load. Circuit breakers and AFTUs are arranged at the feeder outlet, the DG access position and the area boundary, and the AFTUs are connected through an optical network. Each AFTU detects local electric quantity information in real time and performs information interaction with other AFTUs. The method disclosed by the invention quickly positions the fault section according to the local and neighbor electric quantity information, and realizes the fault isolation and island running. A reclosing and island network re-connection control strategy is designed by use of the related AFTU information.
Owner:YANTAI POWER SUPPLY COMPANY OF STATE GRID SHANDONG ELECTRIC POWER +2
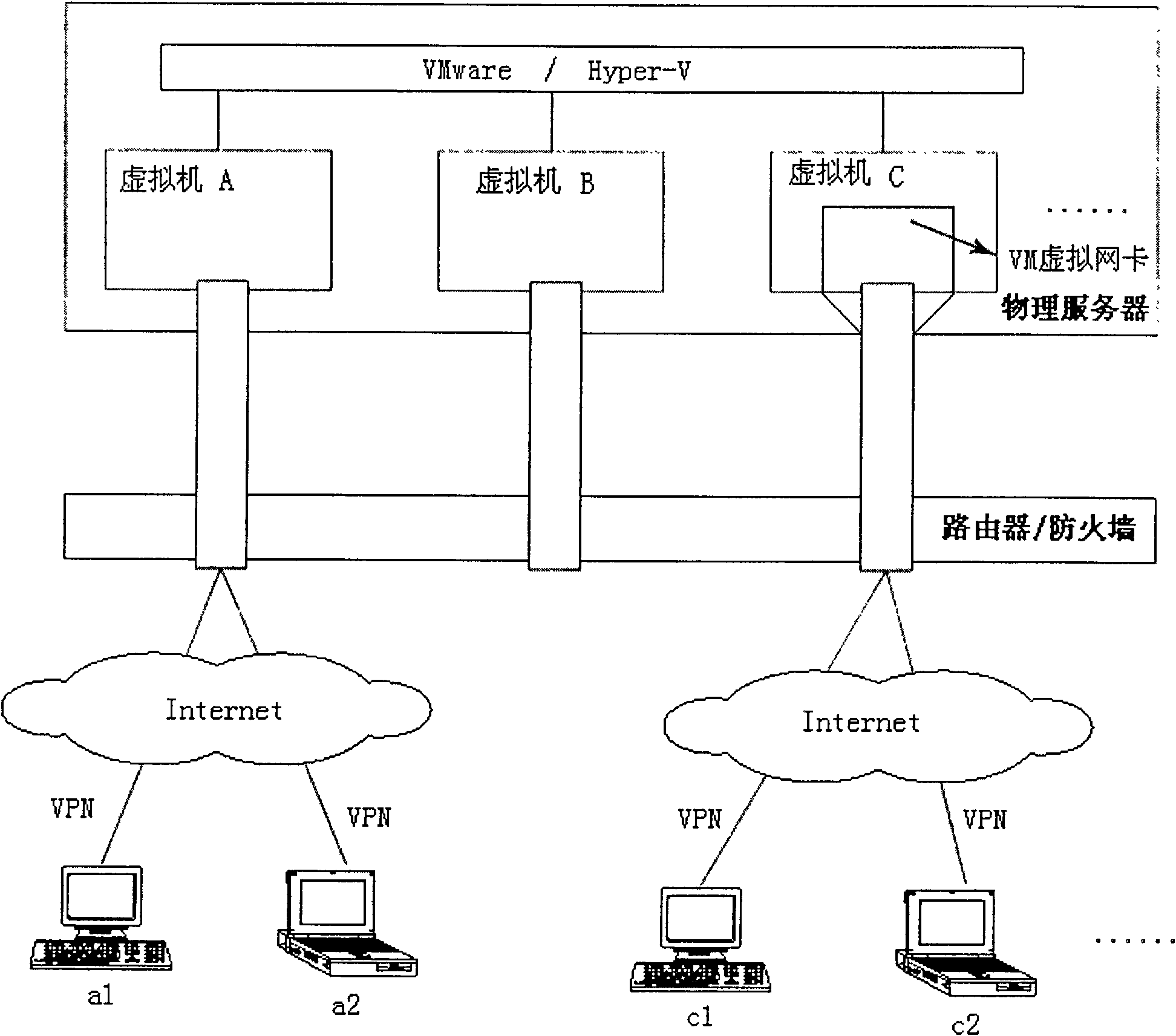
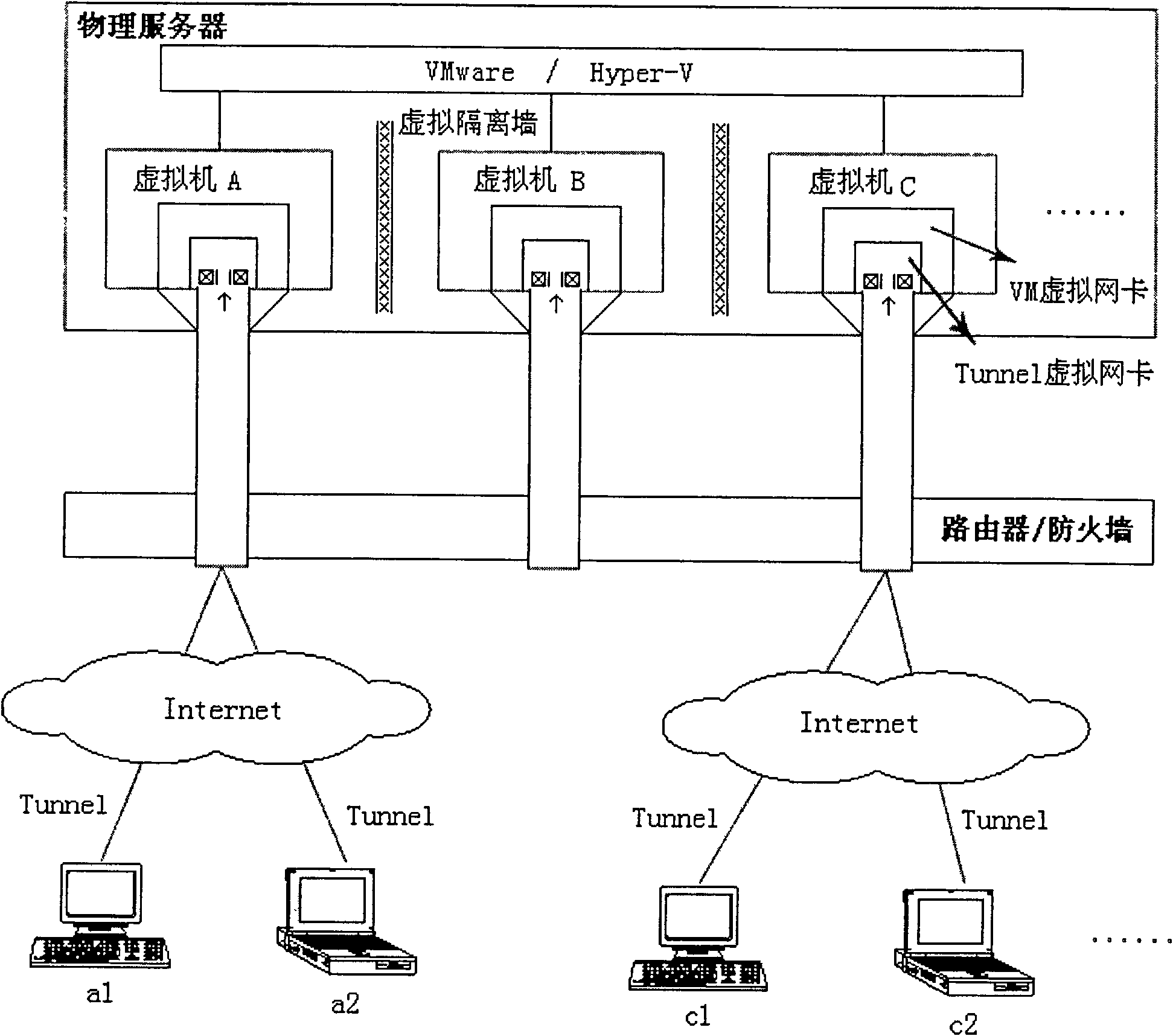
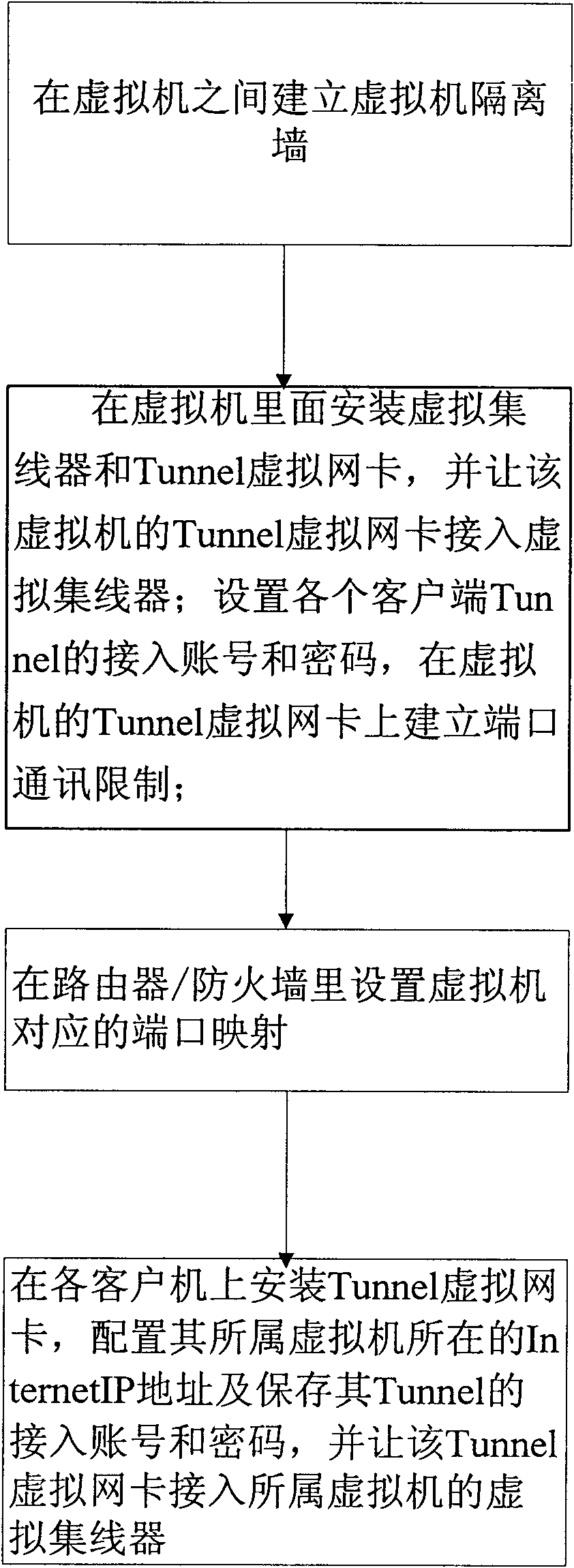
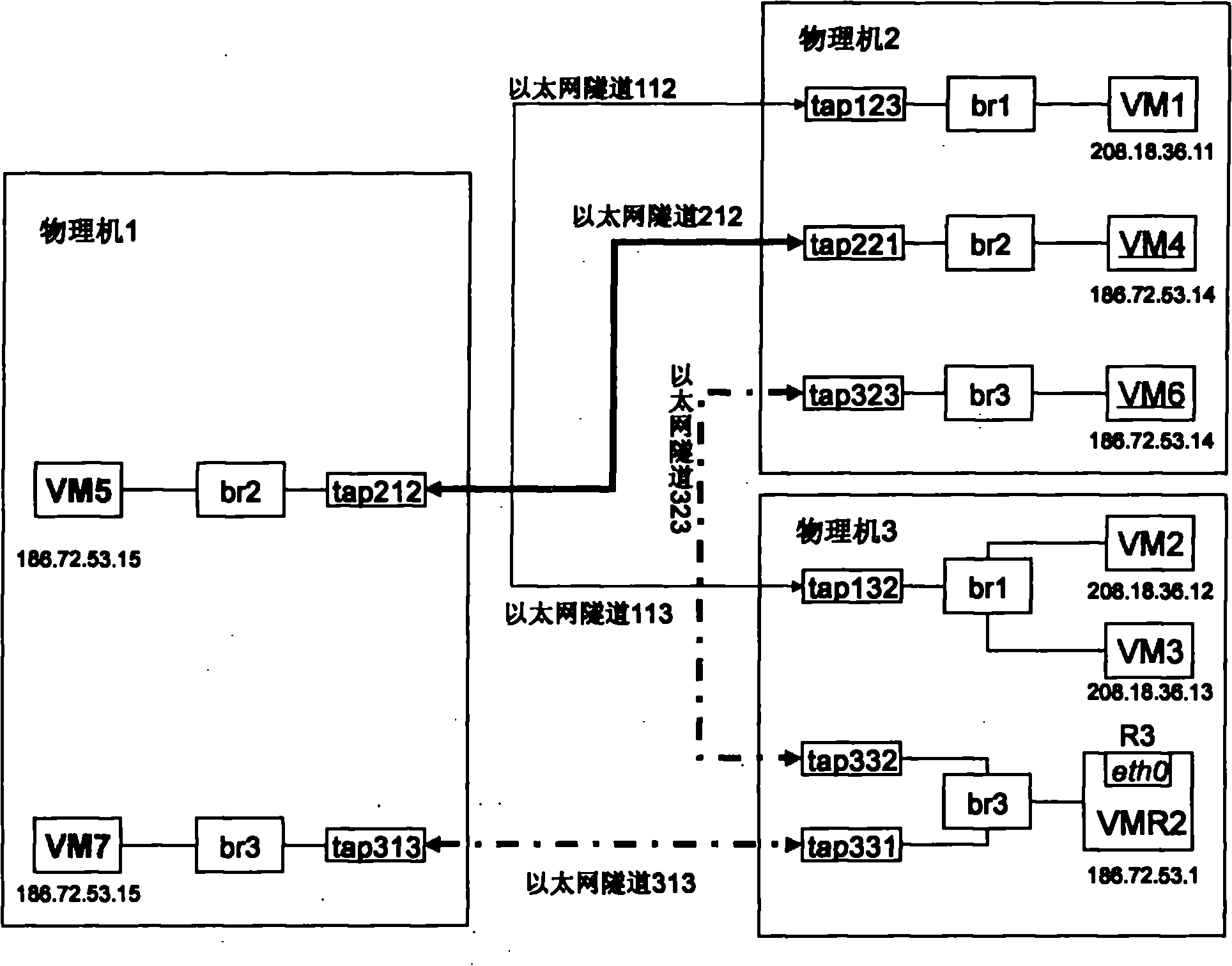
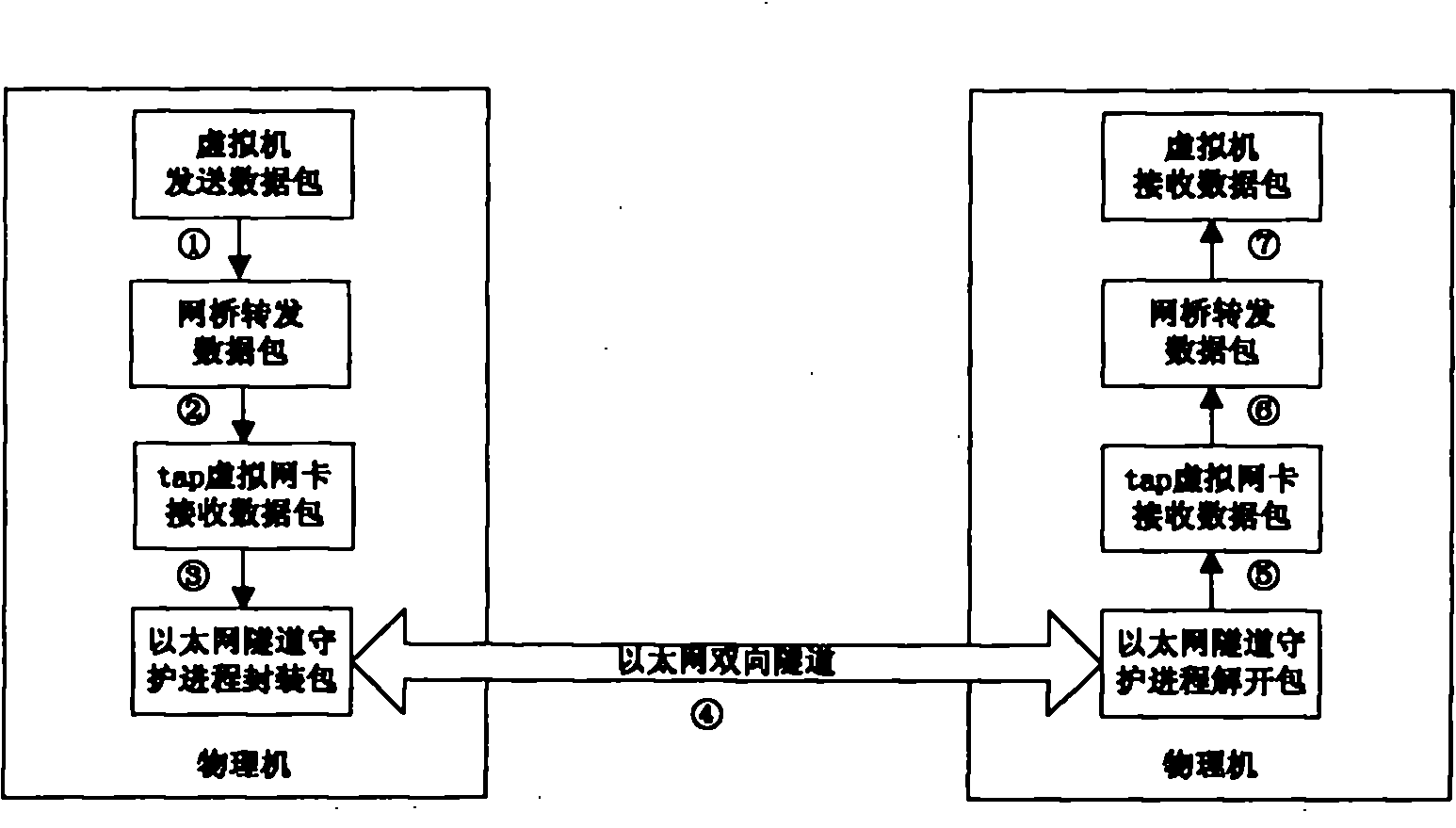
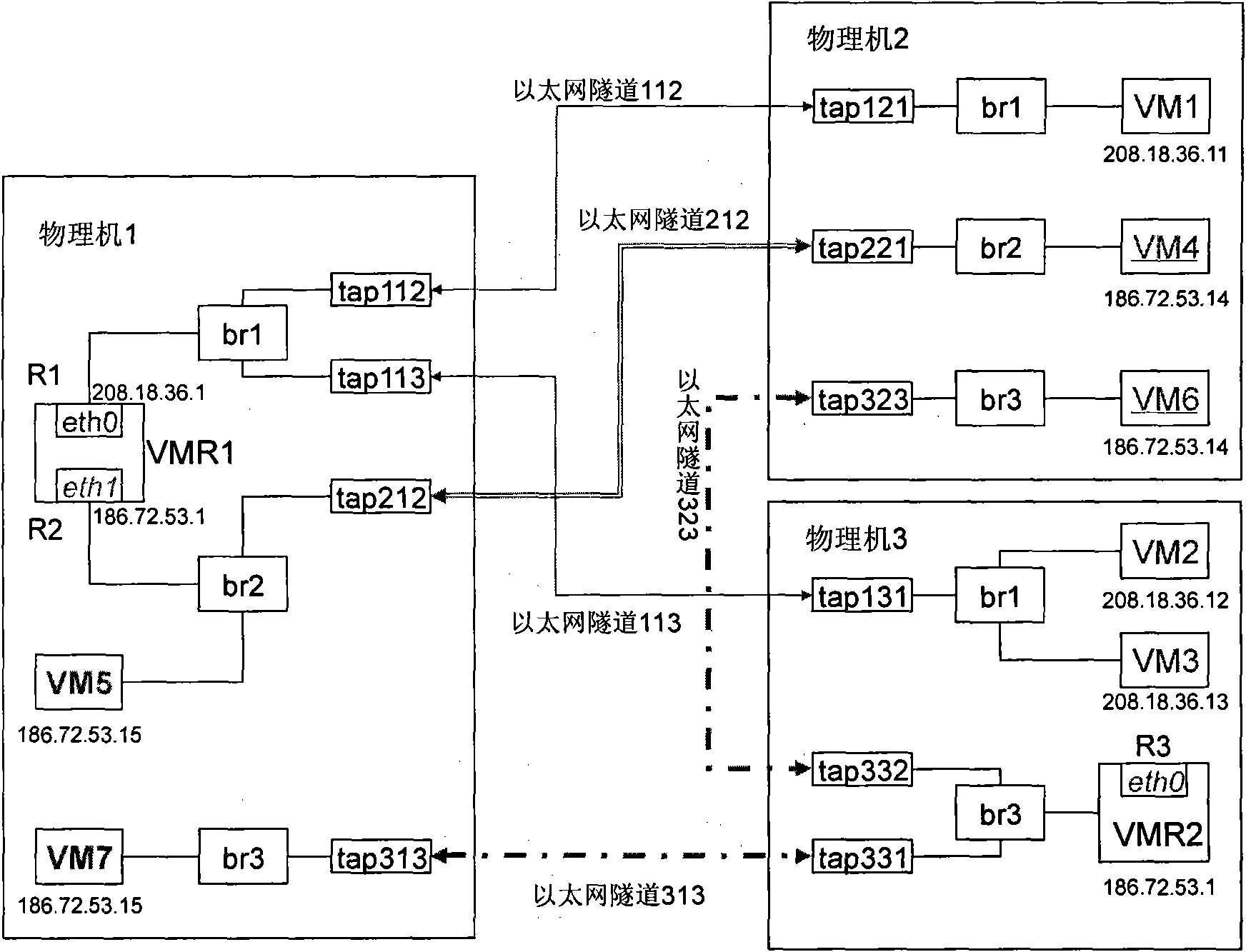
Virtual network isolation system established on virtual machine and implementation method thereof
The invention discloses a virtual network isolation system established on a virtual machine, which comprises a router / a firewall, a physical server and a plurality of clients, wherein the physical server comprises a plurality of virtual machines and is also provided with an isolation wall, and the virtual machine is internally provided with a port communication limitation module. The invention further discloses a virtual network isolation method established on the virtual machine, which comprises the following steps: (1) establishing the isolation wall between virtual machines firstly; (2) arranging a virtual hub and a Tunnel virtual network card in the virtual machine, accessing the Tunnel virtual card of the virtual machine into the virtual hub, and establishing port communication limitation; (3) setting port mapping corresponding to the virtual machine; and (4) arranging the Tunnel virtual network card on each client, configuring Internet IP address and accessing to the virtual hub.The invention provides a safe, low-cost, rapid and conveniently-maintained network environment.
Owner:广州爱迅信息技术有限公司
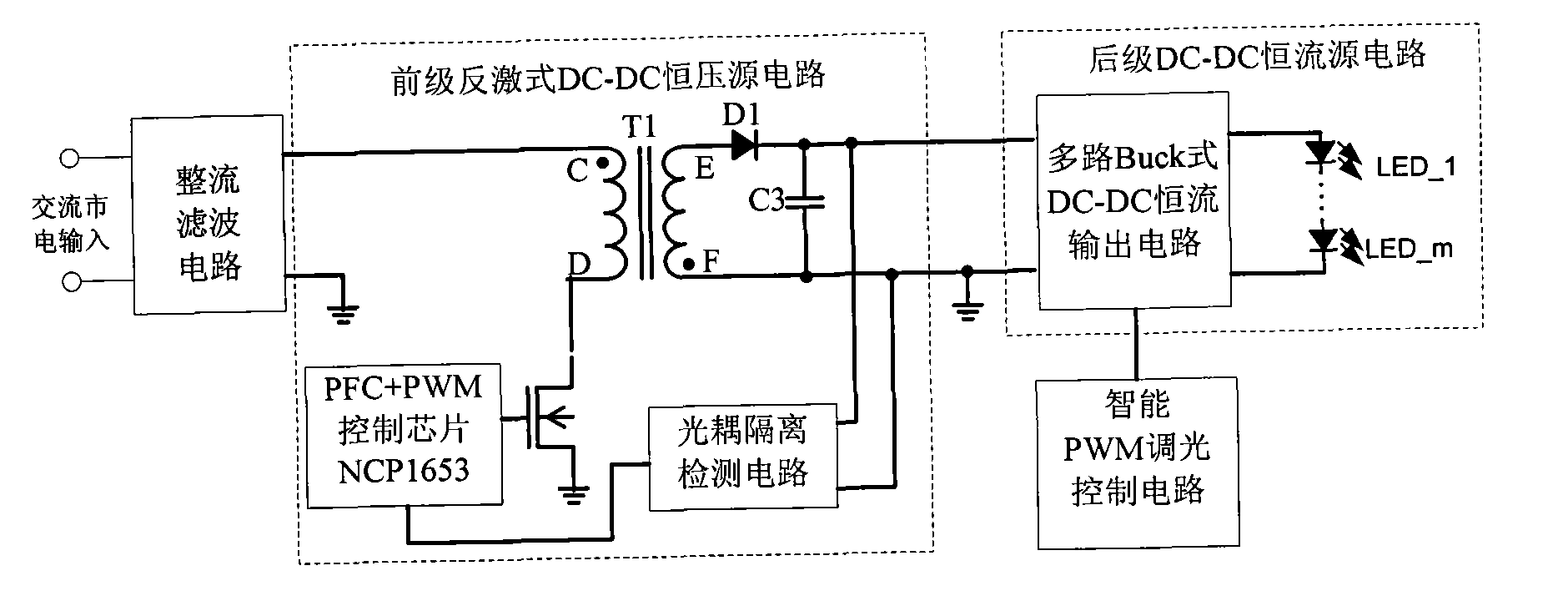
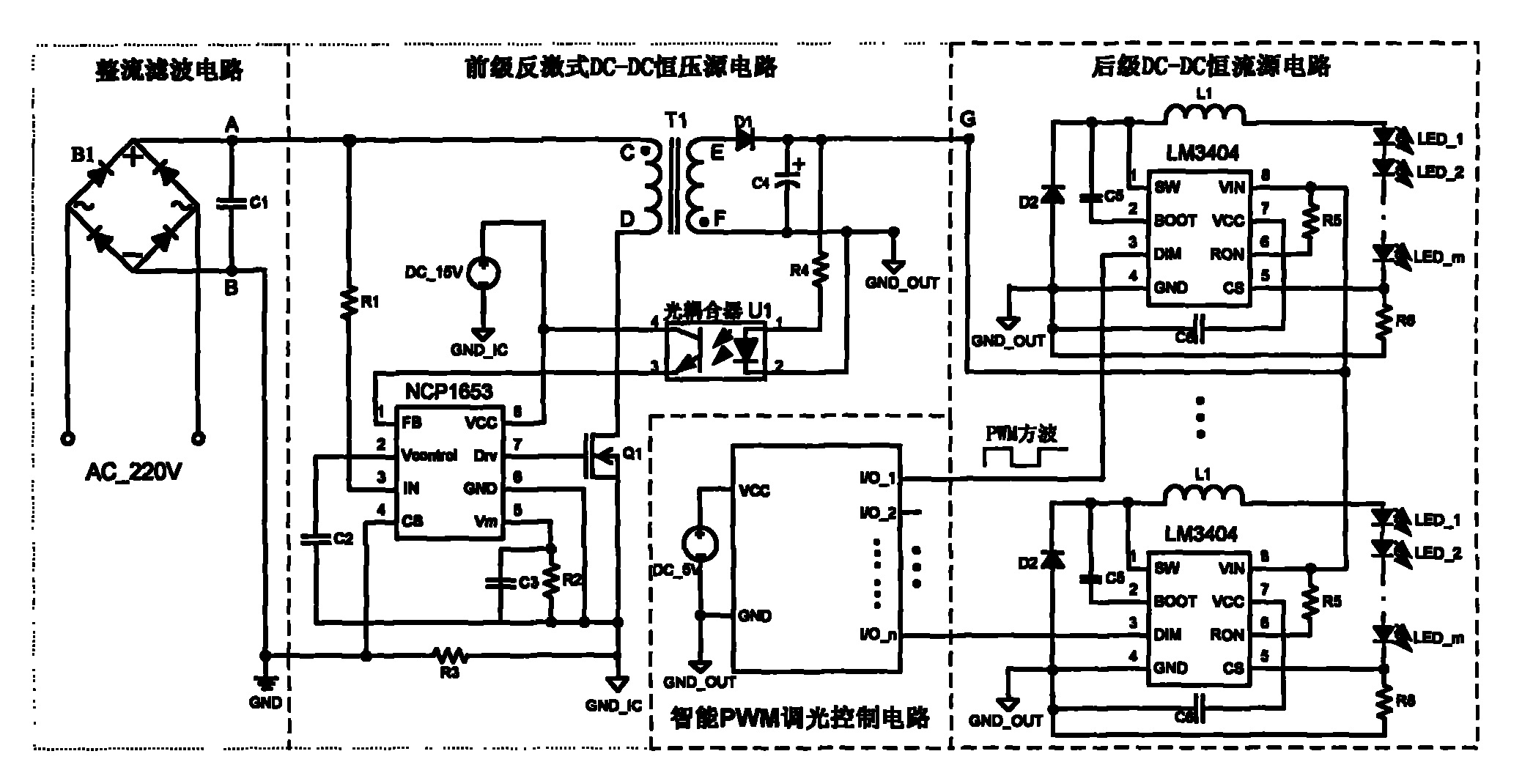
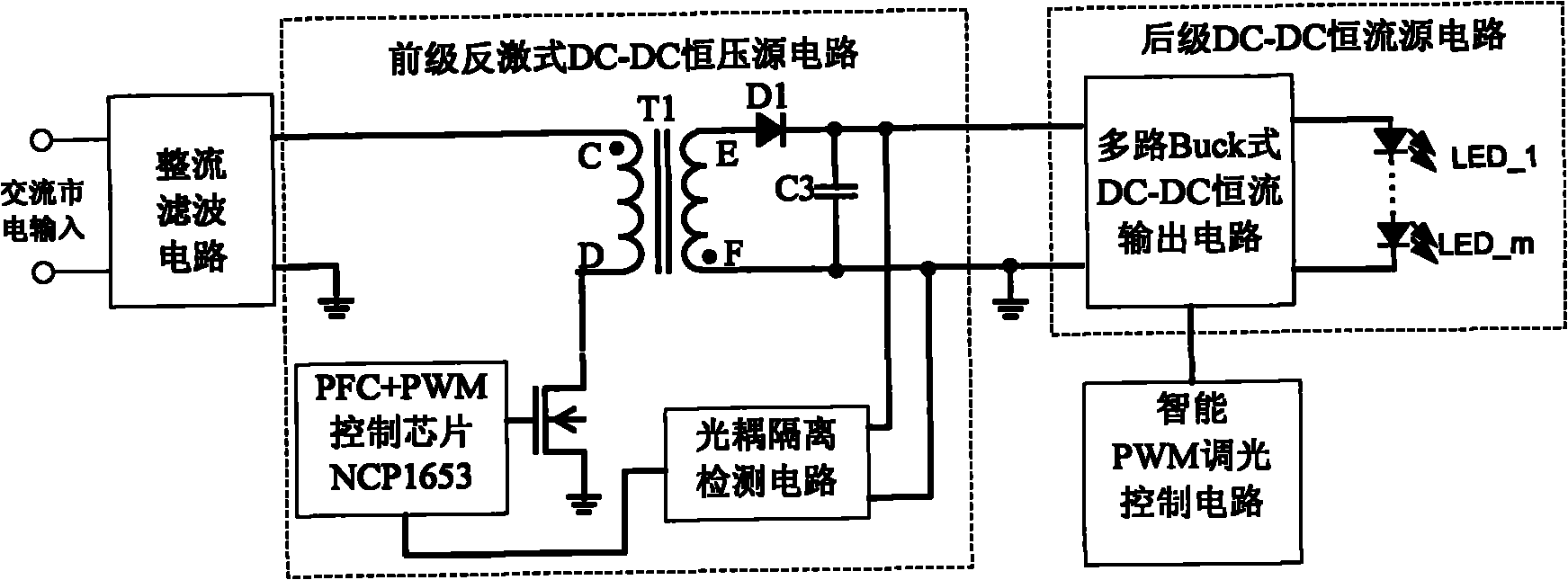
Fly-back street lamp illumination LED constant-current driving power supply with intelligent dimming function
InactiveCN101835317AIncrease profitImprove power factorElectric light circuit arrangementEnergy saving control techniquesDc dc converterTransformer
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
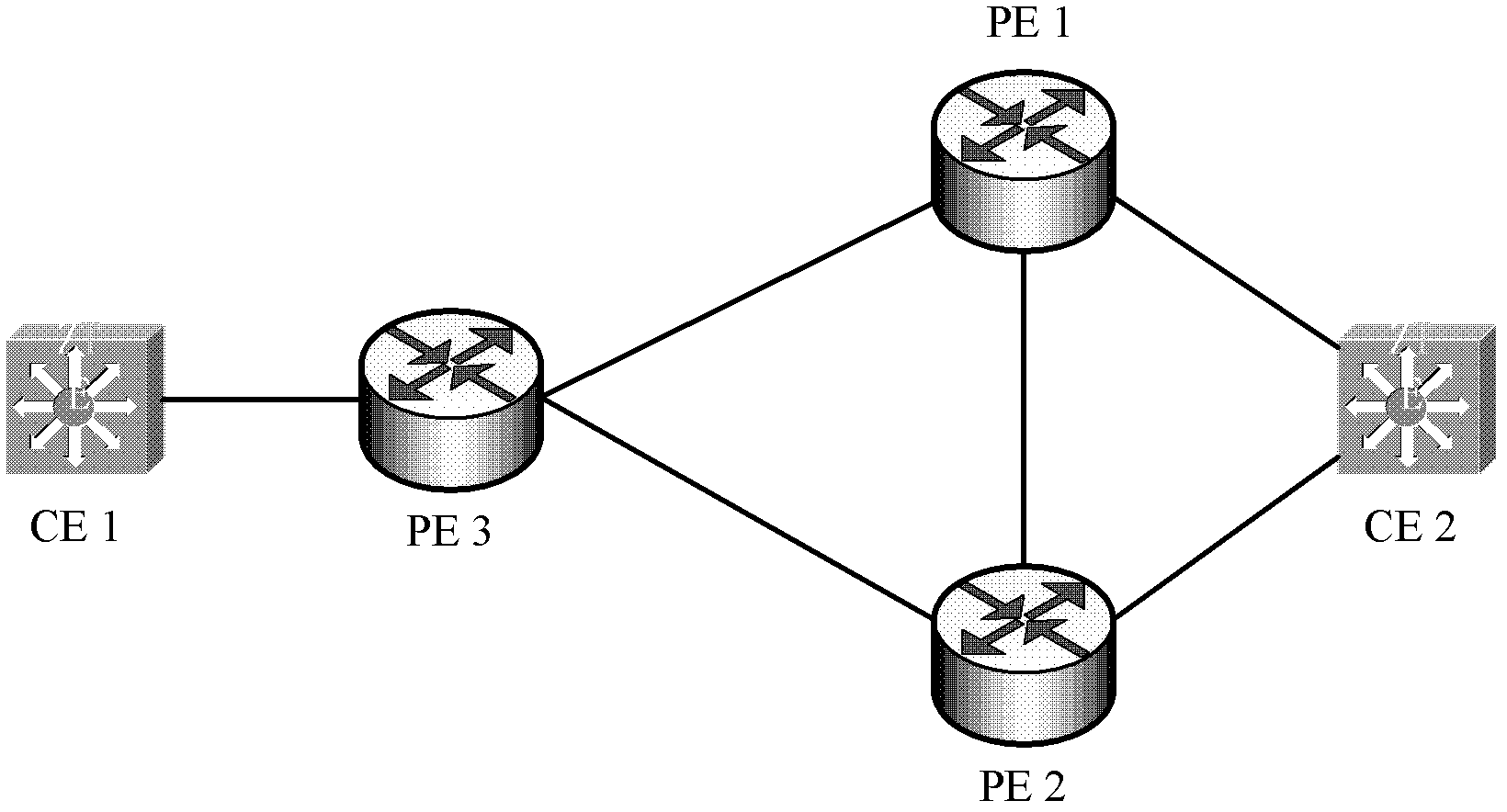
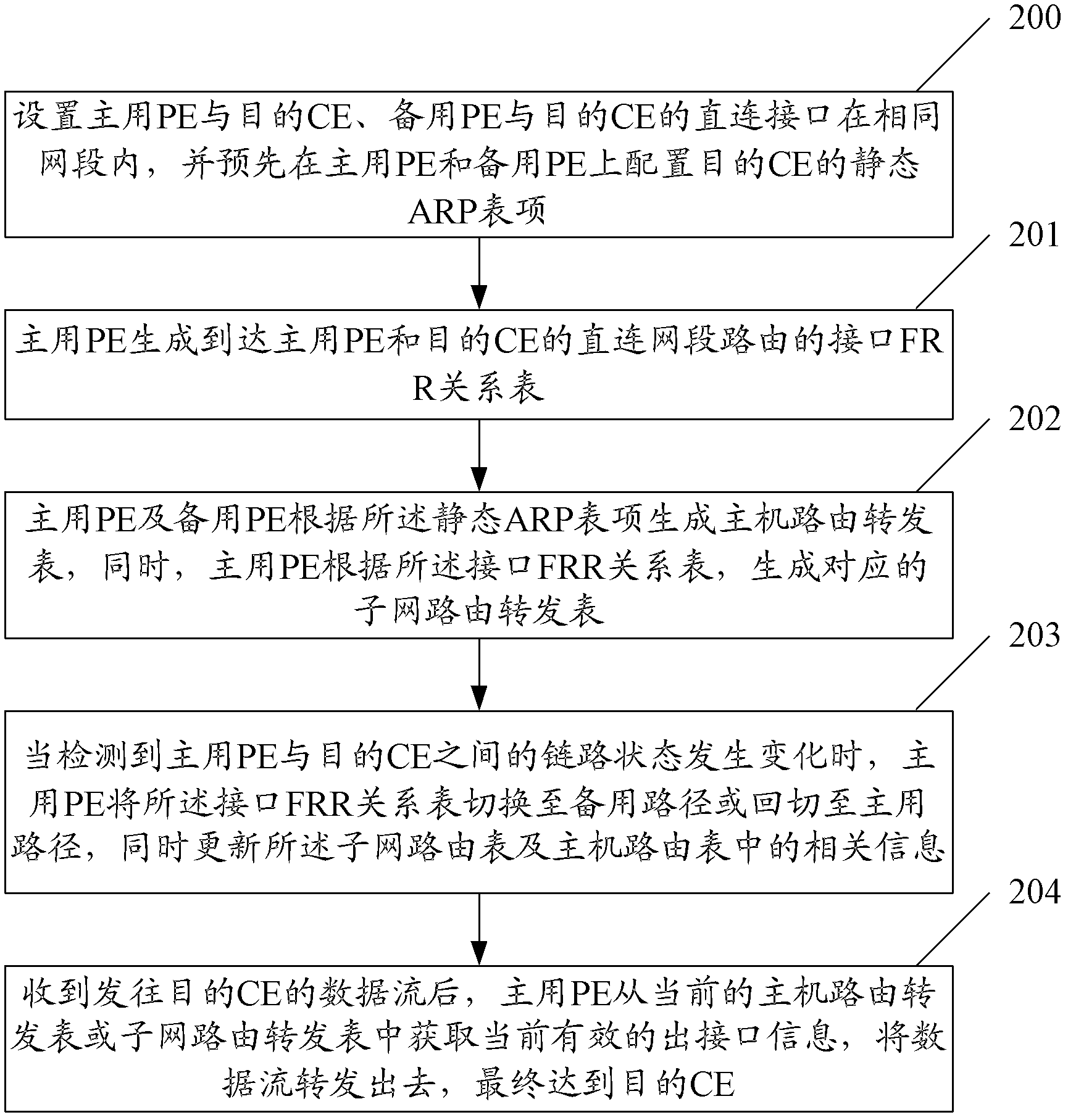
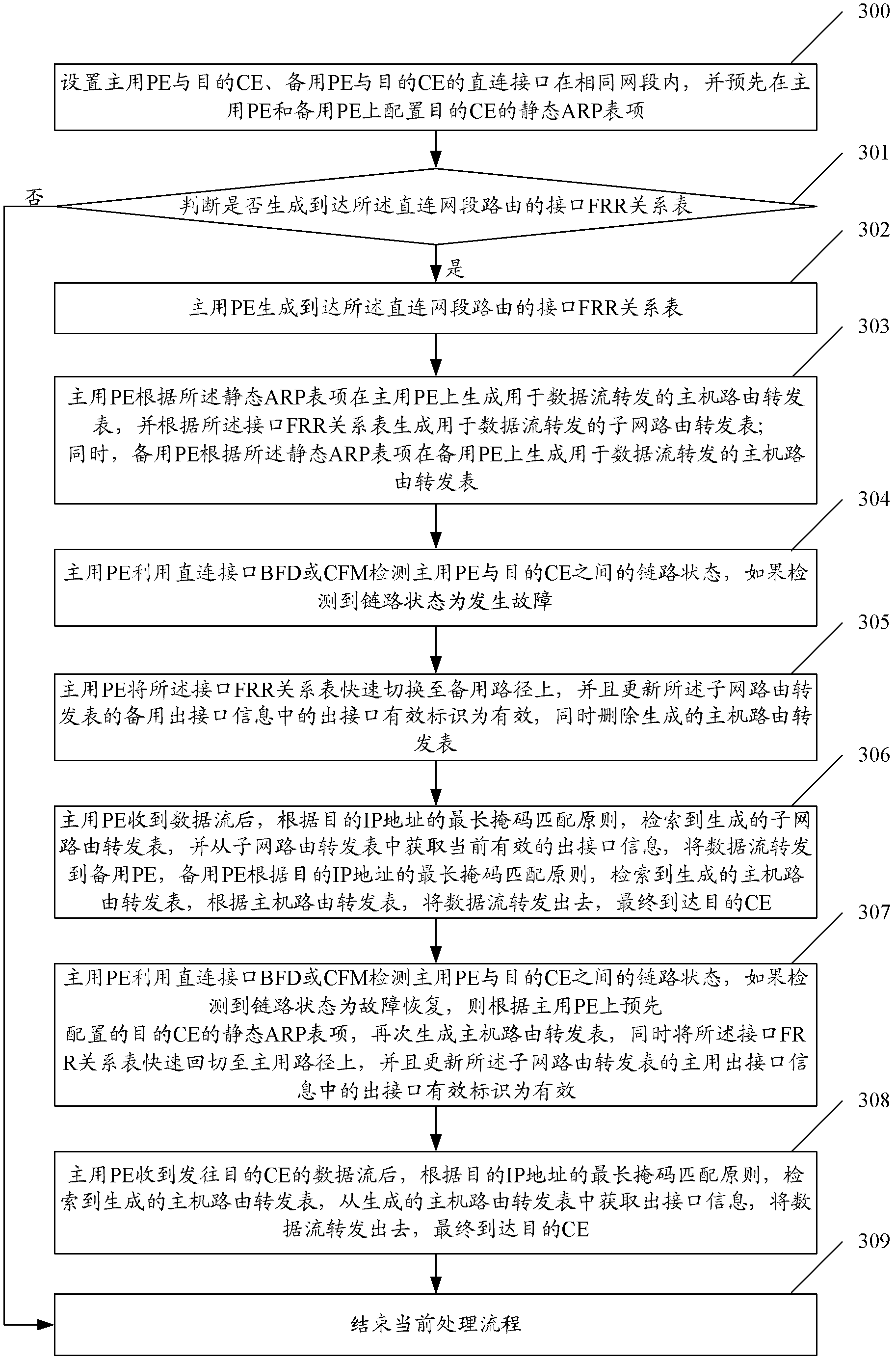
CE dual-homed link protection method in MPLS L3VPN and system thereof
The invention discloses a CE dual-homed link protection method in MPLS L3VPN and a system thereof. The method comprises the following steps: ARP items of a target CE are configured on a main PE and a standby PE; the main PE generates an interface FRR relation table of a direct connecting network segment route which reaches the main PE and the target CE; simultaneously, the main PE and the standby PE generate a host route forwarding table according to static ARP items, and the main PE generates a corresponding subnet route forwarding table according to the interface FRR relation table; after detecting that a link state between the main PE and the target CE changes, the main PE switches the interface FRR relation table into a standby path or switches the interface FRR relation table back into a main path, and updates related information in a subnet routing table and a host routing table; after receiving a data flow, the main PE obtains present effective out interface information from the present host route forwarding table or subnet route forwarding table, and forwards the data flow to reach the target CE. By employing the method and the system of the invention, the rapid switching of the data flow can be effectively realized.
Owner:ZTE CORP
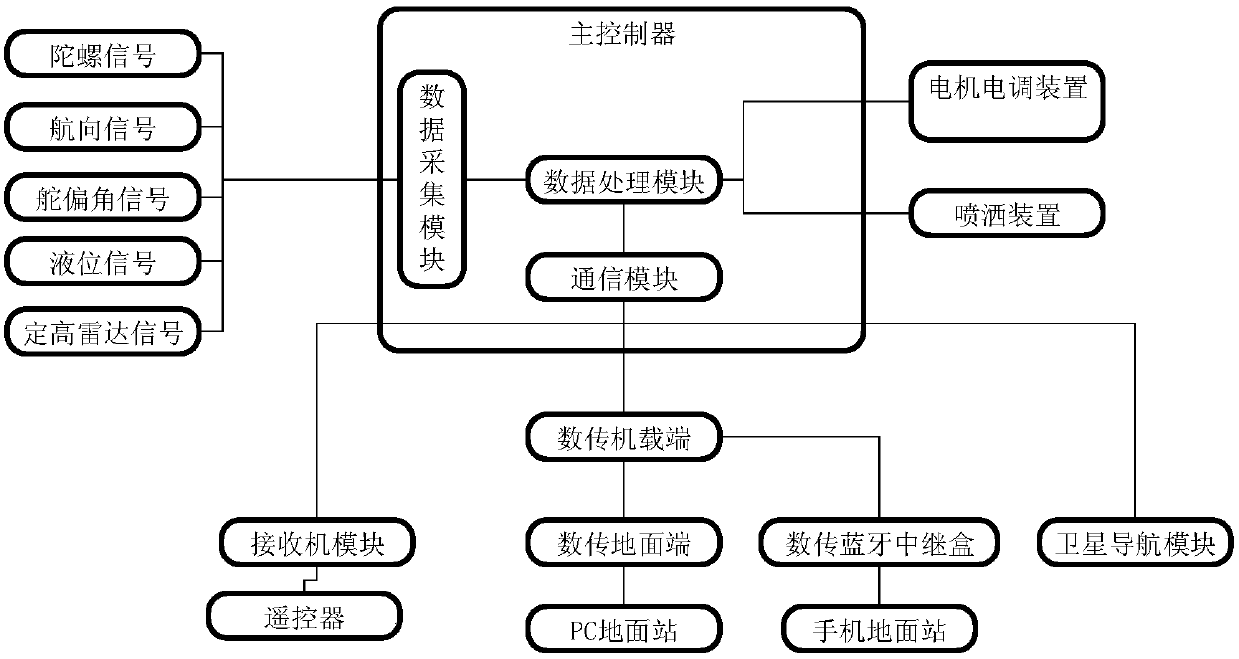
Unmanned plane flight control system and method thereof
ActiveCN107728642ARealize functionImprove work efficiencyPosition/course control in three dimensionsTerrainControl system
The invention discloses an unmanned plane flight control system. The unmanned plane flight control system comprises a main controller, an execution mechanism, a communication device and a ground station device. The master control system comprises a data collection module, a data processing module and a communication module. The data collection module is used for collecting measurement signals of various sensors and uploading the measurement signals to the data processing module. The data processing module can perform management and control on various flight modes and on an execution mechanismin the unmanned plane flight. The execution mechanism comprises a motor electric regulation device and a spraying device. The ground station device can perform track programming and can perform formation on multiple unmanned planes to carry out cooperated programming of multiple unmanned planes. The master controller realizes unmanned plane terrain simulation flight control, highly reliable faulttolerance control and autonomous obstacle avoidance control.
Owner:BEIJING BOYING TONGHANG TECH CO LTD
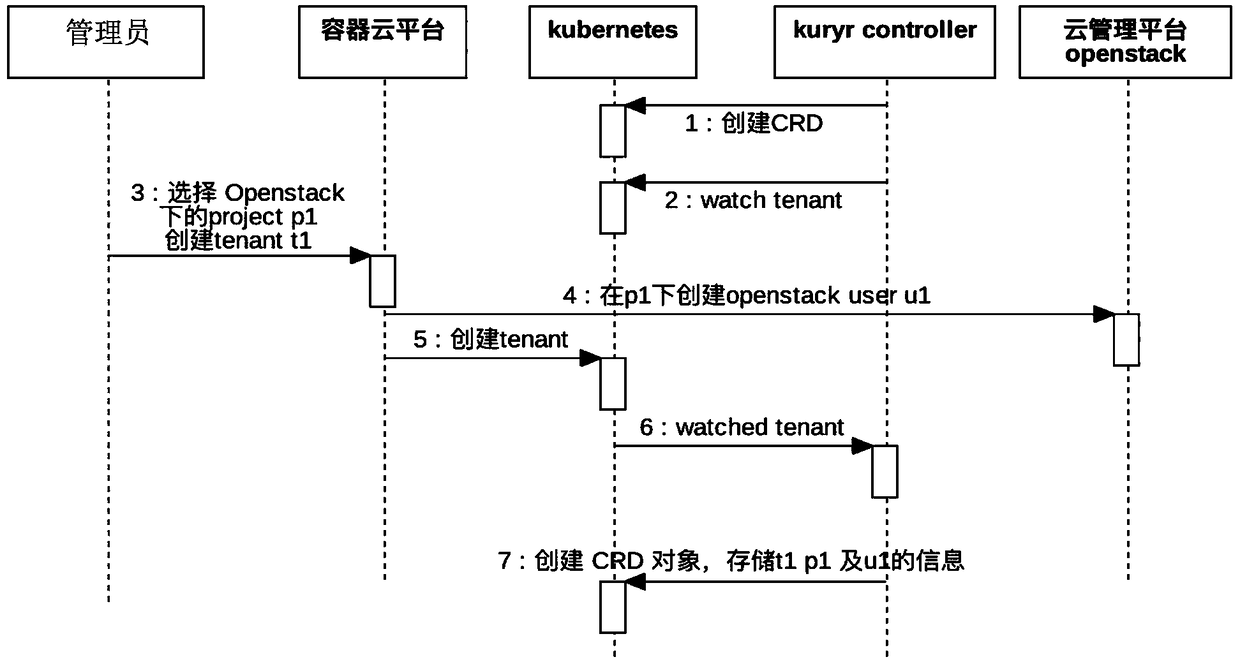
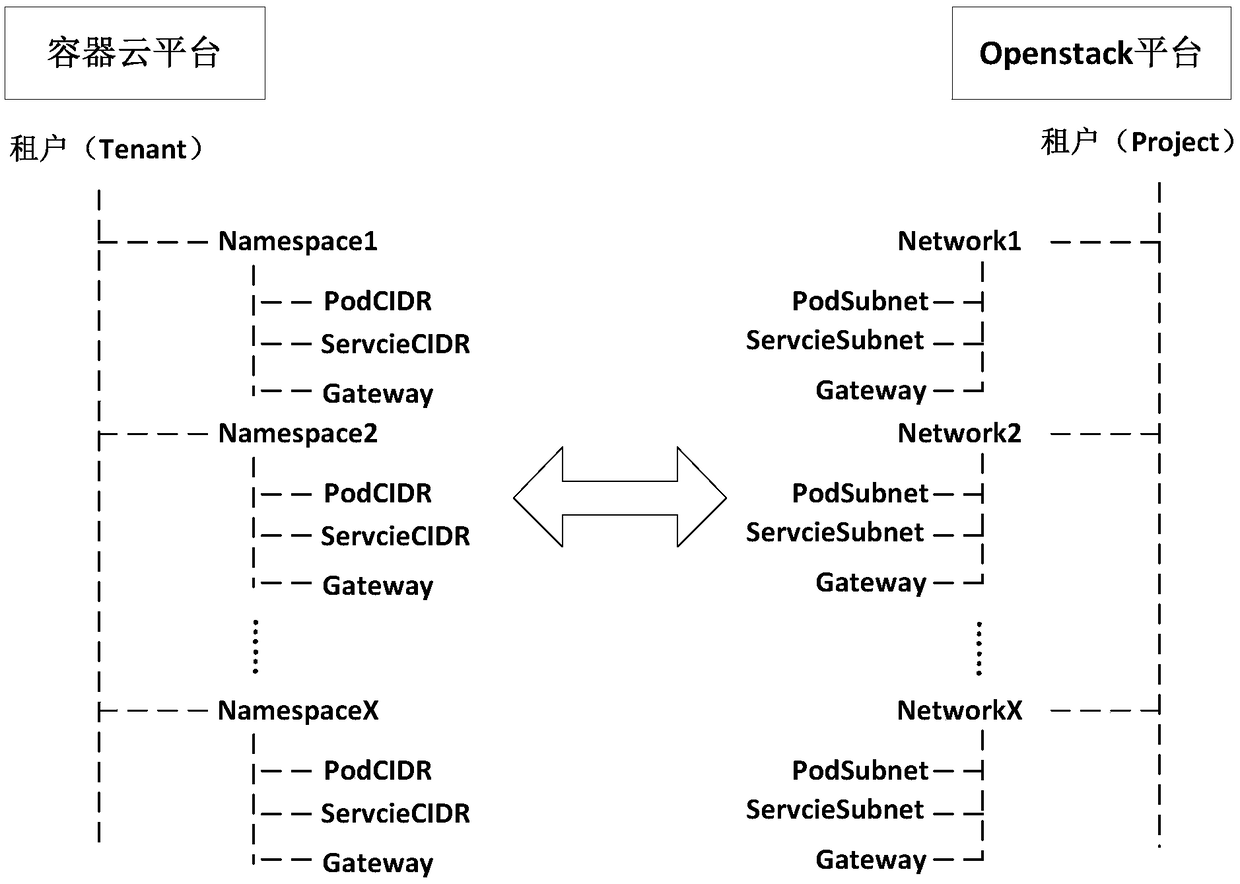
Tenant network isolation method based on kubernetes network, storage medium, and electronic device
ActiveCN108989091AAchieve isolationAchieve mutual accessData switching networksNetwork modelNetwork isolation
The invention provides a tenant network isolation method based on a Kubernetes network, comprising the following steps: selecting an Openstack tenant and creates a corresponding container tenant in aKubernetes cluster by a container cloud platform administrator; monitoring events that create container tenants in the cluster and sends requests to create privileged users; creating CRD object; translating Kubernetes network model into Openstack Neutron network model to generate Neutron information, and sending Neutron information to CNI Driver for pod binding. By interfacing with an Openstack tenant, container tenants in Kubernetes cluster implement complete network isolation among tenants, and each container tenant makes use of Openstack Neutron's powerful SDN network function to plan and configure the network, so as to realize mutual access between tenant's inner container service and virtual machine service.
Owner:杭州才云科技有限公司
Automatic rapid protection control method of novel feeder
ActiveCN102790383ARapid positioningAchieve isolationEmergency protective circuit arrangementsInformation technology support systemPrimary stationPower flow
The invention particularly discloses an automatic rapid protection control method of a novel feeder. The automatic rapid protection control method comprises the following steps of: 1, mounting an STU (smart terminal unit) on each circuit switch and each interconnection switch in a network distribution structure, configuring a protective element into each STU, connecting the adjacent STUs, forming an annular network, and finally, connecting the annular network to an automatic main station of the feeder; 2, configuring each element in network distribution; 3, rapidly identifying a fault by the STUs according to local and adjacent current information and switch position information; 4, transmitting the fault identifying result to the adjacent STUs and the automatic main station of the feeder through a communication network by the STUs, and 5, carrying out isolation and power supply restoration on the fault. The automatic rapid protection control method has the beneficial effects that: an FTU (feeder terminal unit) in an original feeder is upgraded into the STU with intelligent judgment ability; and the fault section can be rapidly located by the local and adjacent current information and switch position information, so that isolation of a fault area and the power supply restoration of a non-fault area are achieved.
Owner:SHANDONG UNIV
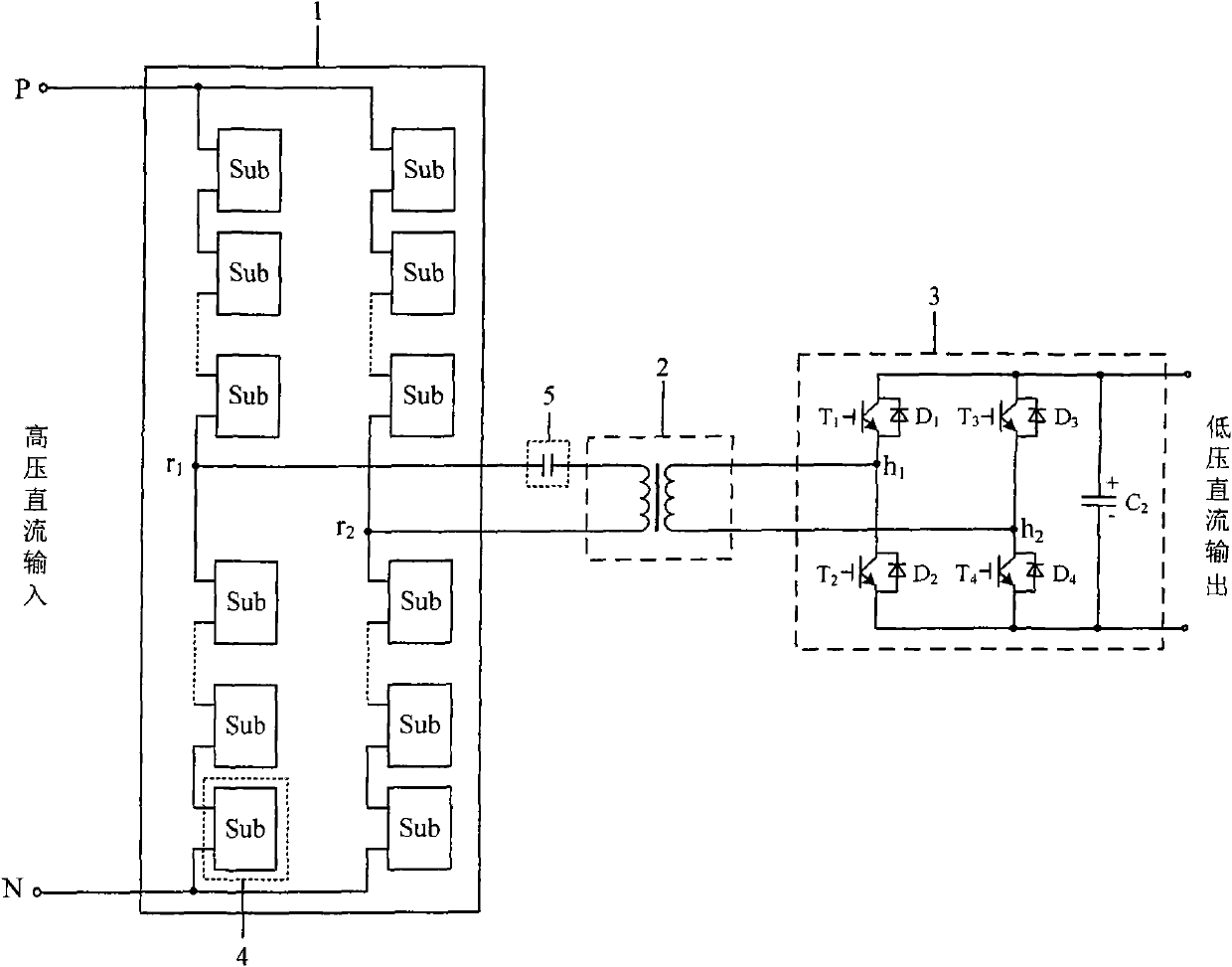
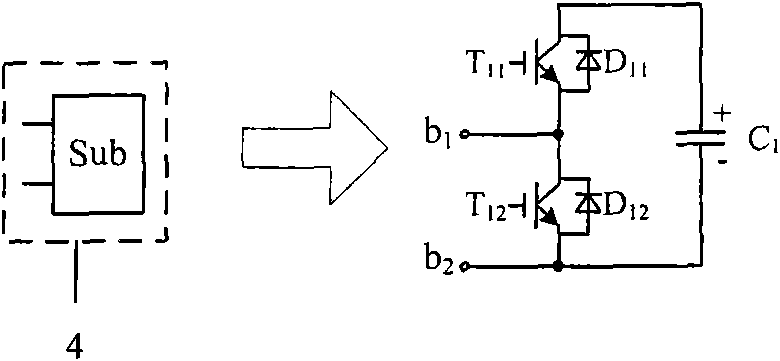
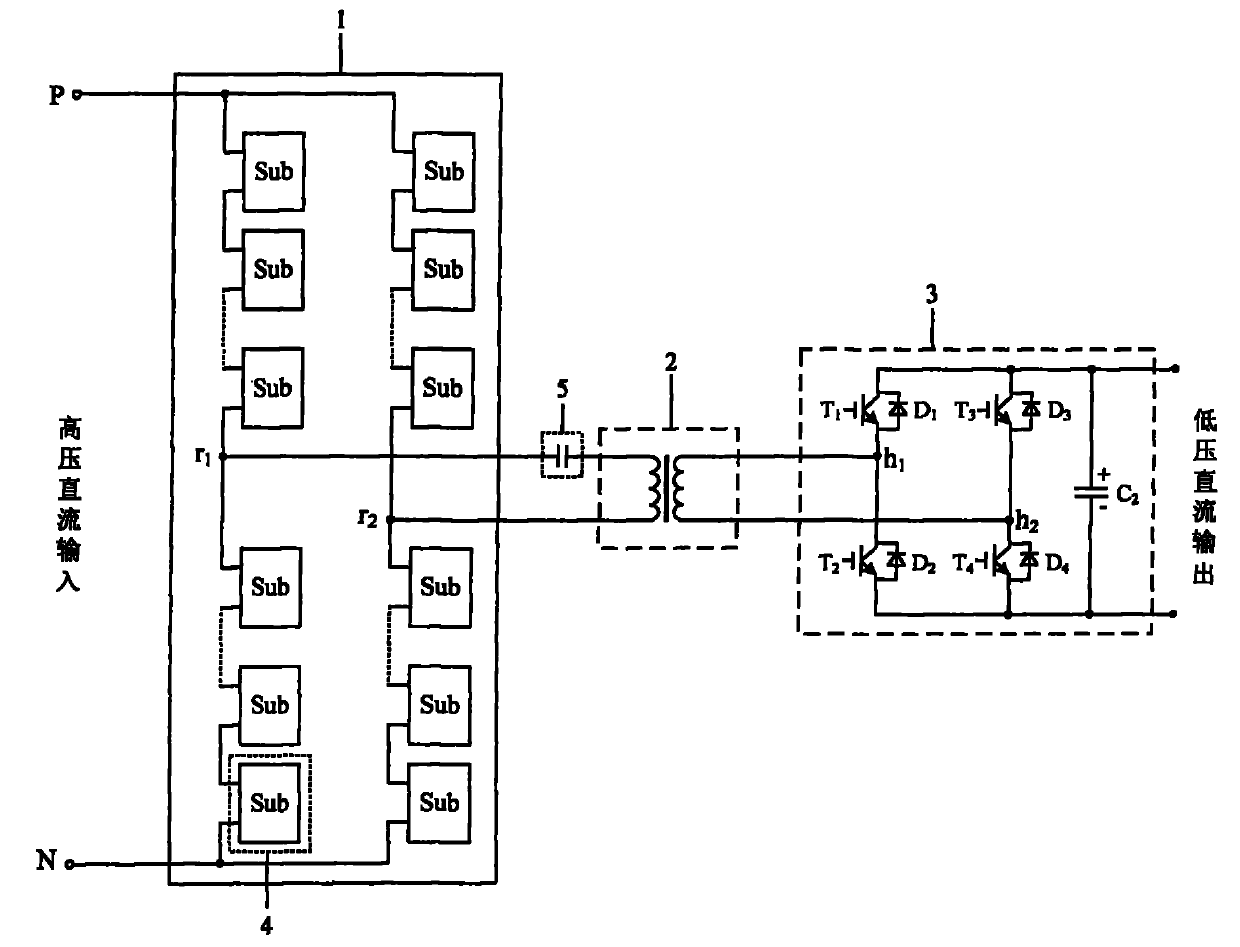
High-voltage direct-current direct-current (HVDC-DC) power electronic converter transformer
InactiveCN101795072AAchieve isolationNo need to change configurationAc-dc conversionDc-dc conversionCapacitanceLow voltage
The invention relates to a high-voltage direct-current direct-current (HVDC-DC) power electronic converter transformer comprising a cascade modular converter (1), a double-winding medium or high-frequency transformer (2) and a fully-controlled H bridge (3). The cascade modular converter (1) consists of two same bridge arms, and the two bridge arms are formed by connecting the same number of sub-modules end to end in a cascading way; the middle points of both the two bridge arms are respectively connected with two leads of the primary side of the double-winding medium or high-frequency transformer (2); and the secondary side of the double-winding medium or high-frequency transformer (2) is directly connected with the fully-controlled H bridge (3) or is connected in series with a resonant capacitor (5) between the double-winding medium or high-frequency transformer (2) and the fully-controlled H bridge (3). The HVDC-DC power electronic converter transformer can realize the conversion of the high-voltage DC voltage and the low-voltage DC voltage and has the electrical isolation function. Compared with the prior HVDC-DC converting device, the HVDC-DC power electronic converter transformer has the advantages of small volume and light weight.
Owner:INST OF ELECTRICAL ENG CHINESE ACAD OF SCI
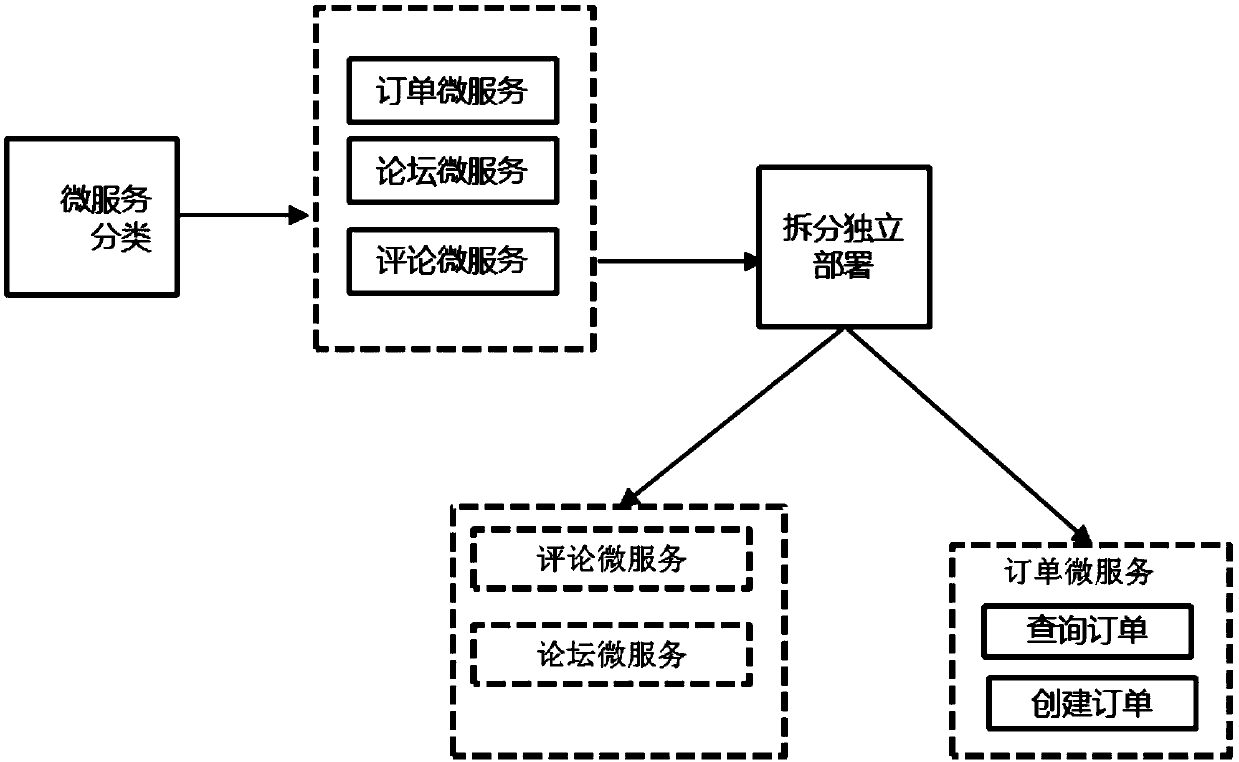
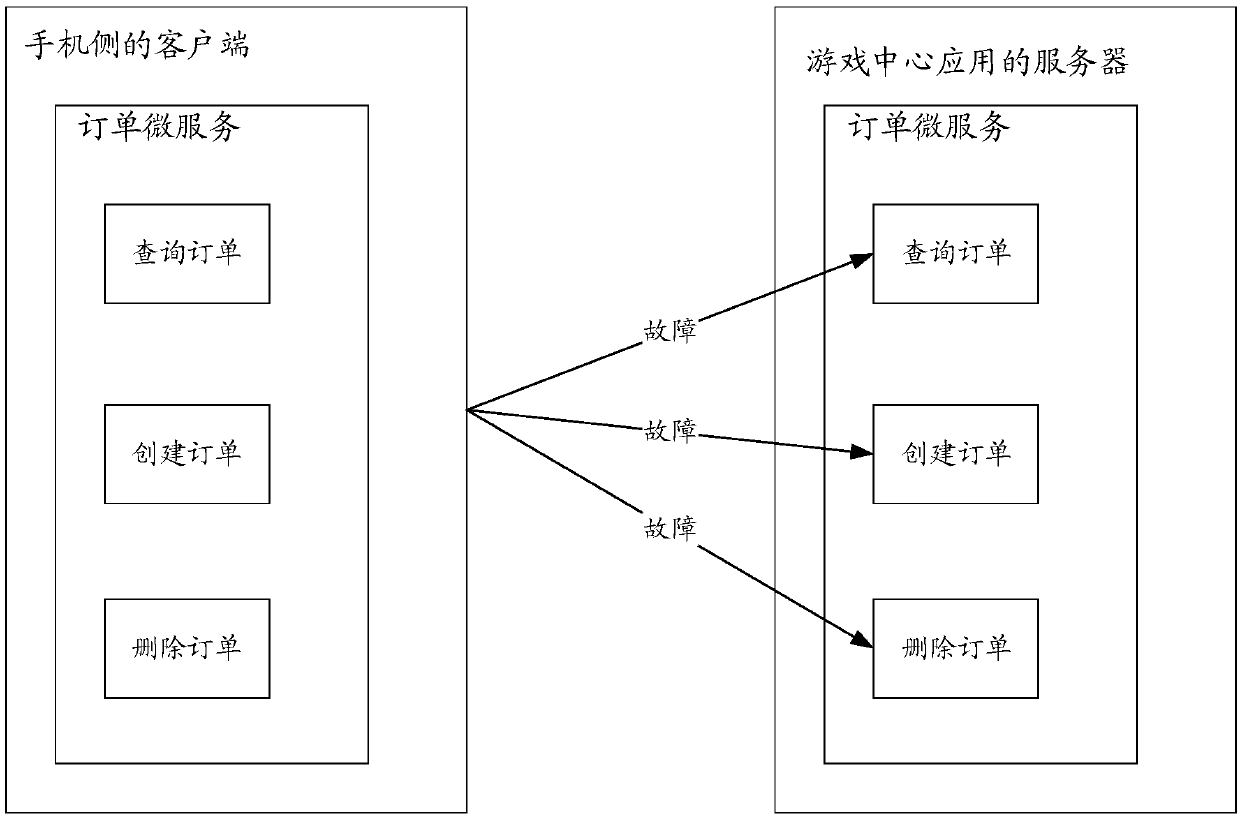
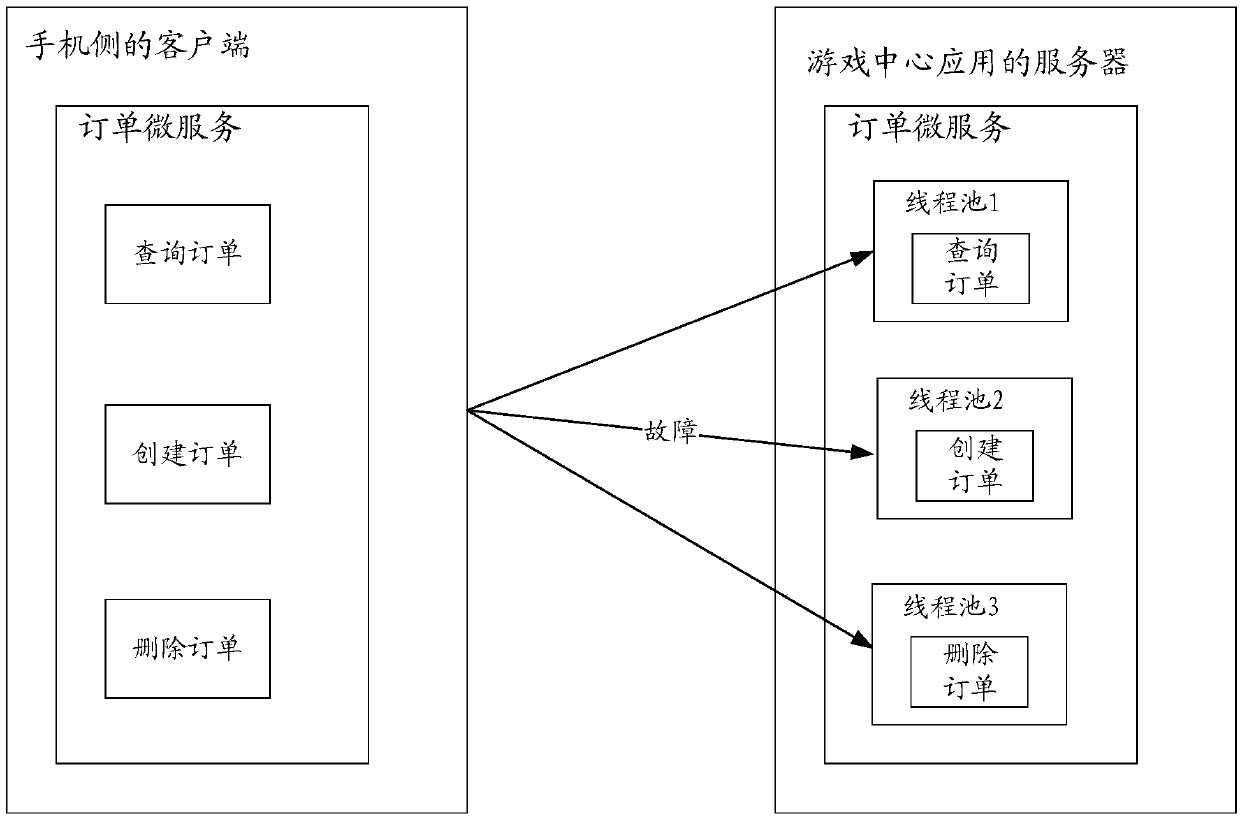
Micro-service processing method and micro-service processing equipment
ActiveCN109582472APrevent proliferationReduce hardware costsInterprogram communicationVideo gamesComputer terminalComputer science
The invention provides a micro-service processing method and micro-service processing equipment, which are applied to a server for providing a micro-service, and the method comprises the following steps that: the server receives a message for calling the micro-service from a terminal for consuming the micro-service, and the message comprises a service identifier and an interface identifier of a target micro-service; And then the server determines a corresponding target thread pool according to the service identifier and the interface identifier of the target micro-service, and finally calls the working thread in the target thread pool to execute the message, and the method can limit the fault influence range in the thread pool, prevents the fault influence range from diffusing into the whole micro-service process, and is low in hardware and operation and maintenance cost.
Owner:HUAWEI TECH CO LTD
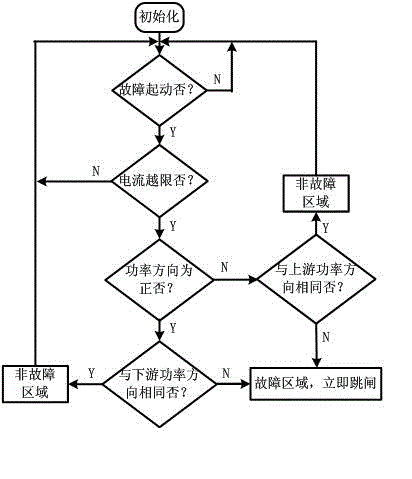
Method based on topology protection of distributing network
InactiveCN102005746ARealize judgmentAchieve isolationEmergency protective circuit arrangementsInformation technology support systemTransformerStructure of Management Information
The invention discloses a method based on the topology protection of a distributing network, which comprises the following steps: (1) all distributing automation terminals respectively form a distributing network topology structure, and each distributing automation terminal is linked with adjacent nodes in a lateral communication mode; and (2) whether each switch is an adjacent node is judged based on a line failure criterion; if yes, the network topology protection corresponding to the switch is activated to trip the switch of the node; and otherwise, the network topology protection is not activated, wherein the line failure criterion is as follows: if the switch is not a transformer substation outlet switch and a line overcurrent failure is detected in one and only one of N adjacent nodes, the fact that the switch is a failed adjacent node is judged; and if the switch is a transformer substation outlet switch and a line overcurrent failure is detected in one and only one of N nodes including the transformer substation outlet switch, the fact that the transformer substation outlet switch is a failed adjacent node is judged. The method can rapidly, accurately and selectively position the failure and isolate the failure.
Owner:NR ELECTRIC CO LTD +1
Ball joint locking method and device
ActiveCN103610555AAchieve instant multi-point lockAchieve isolationJointsOperating tablesEngineeringSacroiliac joint
The invention provides a ball joint locking method and a locking device designed according to the method. A ball head of a ball joint is sleeved with a connecting sleeve which can be movably locked with the ball head or be in a release state with the ball head. An abutting assembly connected with a hydraulic system is arranged in a position corresponding to a matching position of the ball head and the connecting sleeve at locking time. Under the action of pressure oil provided by the hydraulic system, the abutting assembly is forced to instantly press the outer surface of the ball head and enables the ball head to abut against the position matched with the connecting sleeve at the same time, so that the abutting assembly and the connecting sleeve lock the ball head in a multipoint mode. When pressure is released, the abutting assembly and the connecting sleeve can restore to original positions automatically, so that the locking state and the release state of the ball joint can be switched quickly. According to the ball joint locking method and the locking device, the characteristics that the hydraulic system is small in inertia and quick in response are fully utilized, so that that the device have the advantages of being simple in structure, reliable in locking, and good in effect, and can ensure rigid connection and bear certain load moment at the same time. Moreover, locking devices can be connected in series through the same oil path for utilization in one product.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
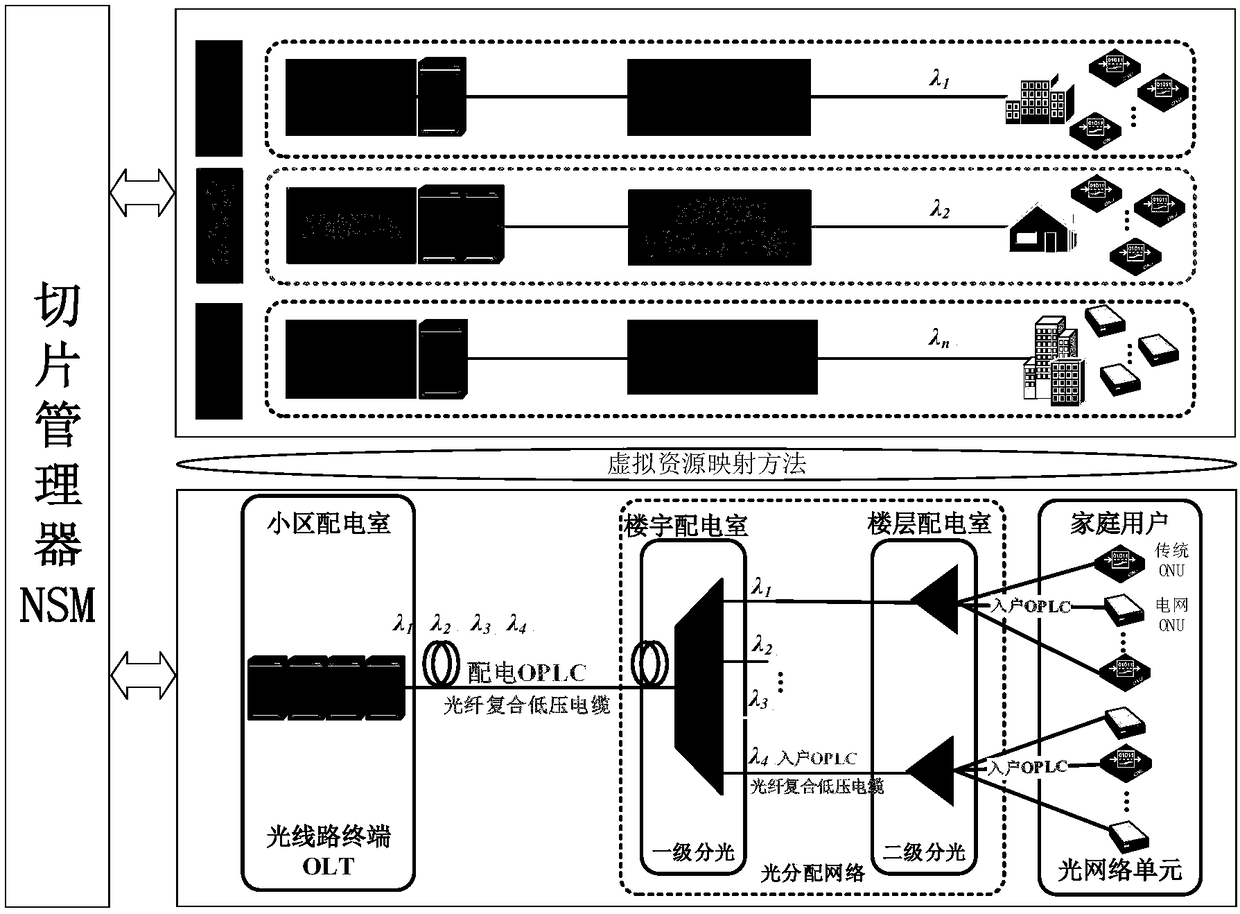
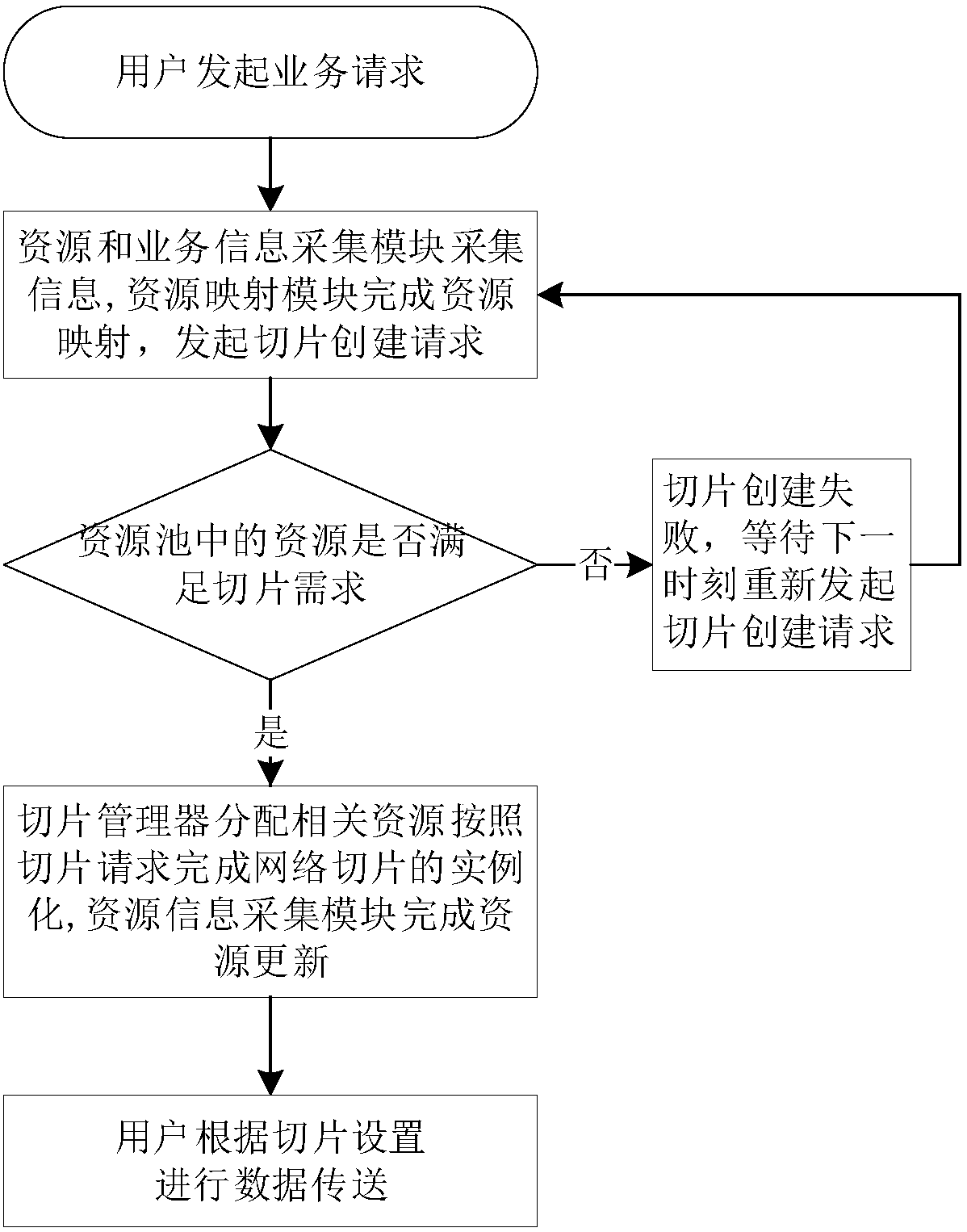
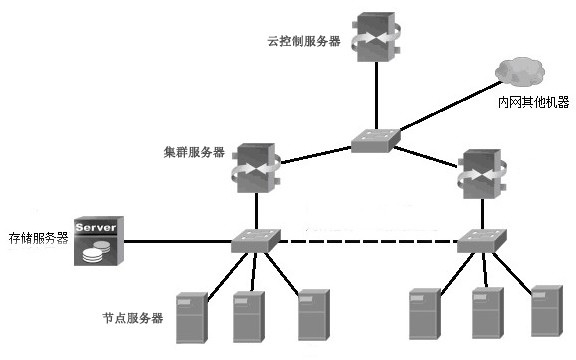
Virtual resource slice management method and apparatus of power optical fiber access network
InactiveCN108111931AAchieve isolationRealize on-demand distributionMultiplex system selection arrangementsUser needsAccess network
The invention provides a virtual resource slice management method and apparatus of a power optical fiber access network. The method includes: receiving slice requests generated for users according tobusiness requests of different users by an optical network unit ONU; dividing an optical line terminal OLT of the power optical fiber access network into a plurality of virtual OLTs based on resourceinformation of the slice requests and the business requests of the users, and performing slice resource configuration according to the plurality of virtual OLTs to obtain a plurality of slice resources; and respectively distributing the plurality of slice resources to the users and / or businesses corresponding to the business requests of the different users. According to the method and apparatus, the physical OLT is divided into the plurality of virtual OLTs to realize slice configuration, different users or different businesses are divided into different network slices according to user requirements to satisfy differentiated network requirements of the users, business isolation is realized, the network reliability is improved, and the maximization of the utilization rate of the resources of the electric power optical fiber access network is realized.
Owner:STATE GRID LIAONING ELECTRIC POWER RES INST +2
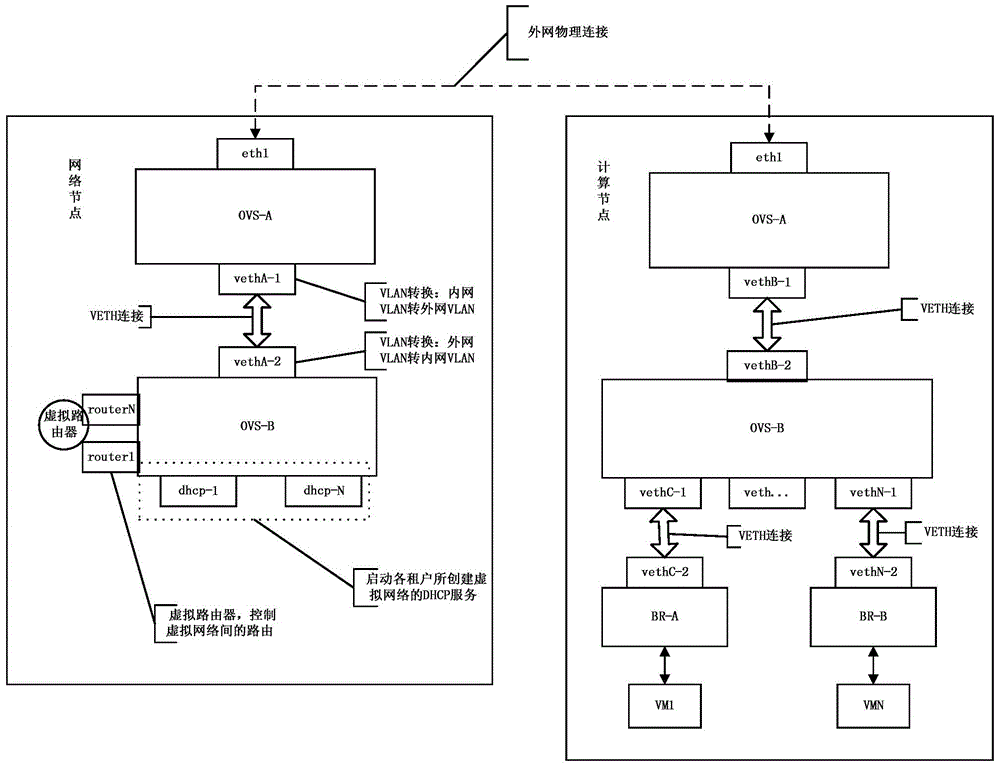
A multi-tenant virtual network isolating method
ActiveCN104394130AAvoid single point of failure problemsImprove reliabilityTransmissionCloud computingPhysical interface
The invention relates to the technical field of cloud computing and particularly to a highly-flexible multi-tenant virtual network isolating method. In the invention, the method comprises: firstly creating two virtual switches OVS-A and OVS-B in an initialized process; then adding a physical interface eth1 connecting to an external network to the OVS-A; and then creating a VETH device to connect the OVS-A with the OVS-B. A process of creating a private network and starting a virtual machine comprises: (1) adding an internal port dhcp-N and setting an internal network VLAN-N; (2) creating private network space netns-N; (3) accessing the dhcp-N port to the netns-N; (4) setting an internal and external network VLAN converting rule at both ends of the VETH device connected to OVS-A and OVS-B of the network node and the computing node; (5) creating a linux network bridge at the computing node; (6) creating a VETH device to connect to the BR-N with the OVS-B; and (7) the virtual machine bridging to BR-N to be started and obtaining an IP through the dhcp service started at the step (3). The invention provides the highly flexible multi-tenant virtual network isolating method.
Owner:G CLOUD TECH
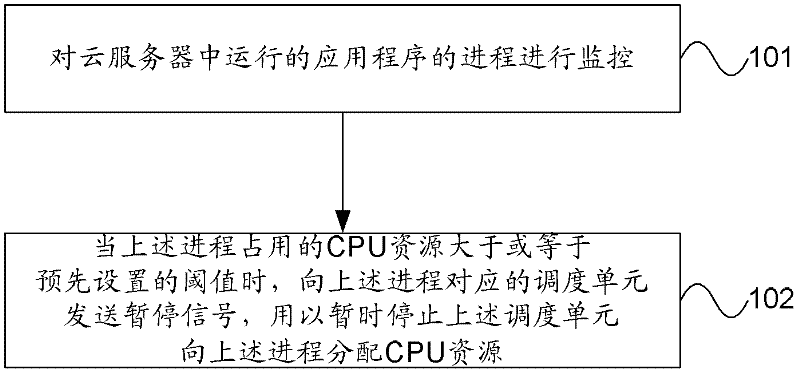
Method and device for realizing service isolation in cloud computing system, and cloud server
InactiveCN102307224AAvoid problems with a limited numberImprove resource utilizationResource allocationTransmissionResource utilizationApplication software
The embodiment of the invention provides a method and a device for realizing isolated services in a cloud computing system, and a cloud server. The method comprises the following steps of: monitoring a progress of an application program running in the cloud server; and when centre process unit (CPU) resources occupied by the progress are greater than or equal to a preset threshold value, sending a pause signal to a scheduling unit corresponding to the progress so as to temporarily stop the scheduling unit from distributing the CPU resources to the progress. By the embodiment of the invention, the problem of a finite number of services isolated by a virtual machine due to a large quantity of system resources, occupied by a mapping of a virtual machine monitor (VMM) from the virtual machine to a physical machine, in the cloud computing system in the prior art can be solved, so that isolation of more services can be realized; therefore, the resource utilization rate of the cloud computing system can be increased.
Owner:HUAWEI SOFTWARE TECH
Shield tunneling machine for tunnel connecting passageway and connecting passageway tunneling method of shield tunneling machine
ActiveCN106437735AReaction support enoughCompact and reasonable structure designTunnelsShield tunnelingUltimate tensile strength
The invention belongs to the technical field of tunnel construction equipment, and relates to a shield tunneling machine for a tunnel connecting passageway and a connecting passageway tunneling method of the shield tunneling machine. The shield tunneling machine comprises a start end supporting walking platform and a receiving end supporting walking platform which are respectively arranged on material transportation rails in two main tunnels, a shield tunneling machine main unit, a counterforce supporting frame and a main tunnel supporting assembly which are respectively arranged on the start end supporting walking platform and a corresponding main tunnel duct piece, and a start end socket sealing assembly and a receiving end socket sealing assembly which are respectively arranged at the start end and the receiving end of the connecting passageway, wherein a duct piece hanging assembly is arranged on the start end supporting walking platform; a jacking tunneling assembly is arranged between the counterforce supporting frame and the shield tunneling machine main unit. The shield tunneling machine can realize automatically mechanical excavation; the labor intensity is greatly reduced, the energy consumption is reduced, and the cost is reduced; meanwhile, equipment construction is stable, and the efficiency is high; settling of the ground is effectively controlled, and the construction risk is reduced.
Owner:CHINA RAILWAY ENGINEERING EQUIPMENT GROUP CO LTD
Virtual machine network system and creation method thereof
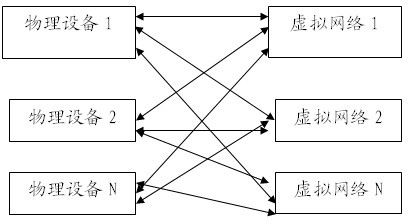
InactiveCN102469004ADistribution no longer has special requirementsThere will be no problem of IP conflictNetworks interconnectionNetwork interface controllerNetwork segment
The invention provides a virtual machine network system that comprises at least one virtual machine network. The virtual machine network includes a specific network bridge; first virtual network cards on all virtual machines in the virtual machine network are connected with the specific network bridge; and network bridges in different virtual machine networks are isolated from each other. Besides, the virtual machine network also comprises connection channels that are used for connecting virtual machines on different physical machines, wherein the virtual machines belong to one same virtual machine network; and the specific network bridge in the virtual machine network is connected to the connection channels by a second virtual network card. According to the invention, it is allowed that there are repeated network segments between different virtual machine networks, so that no IP conflict will occur. In addition, restriction that virtual machines with a same network segment should be distributed on a same physical machine according to a current technical scheme can be broken; and there is no more special requirement on distribution of virtual machines.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
System of virtual machine based on virtualizing technique of processor, and implementation method
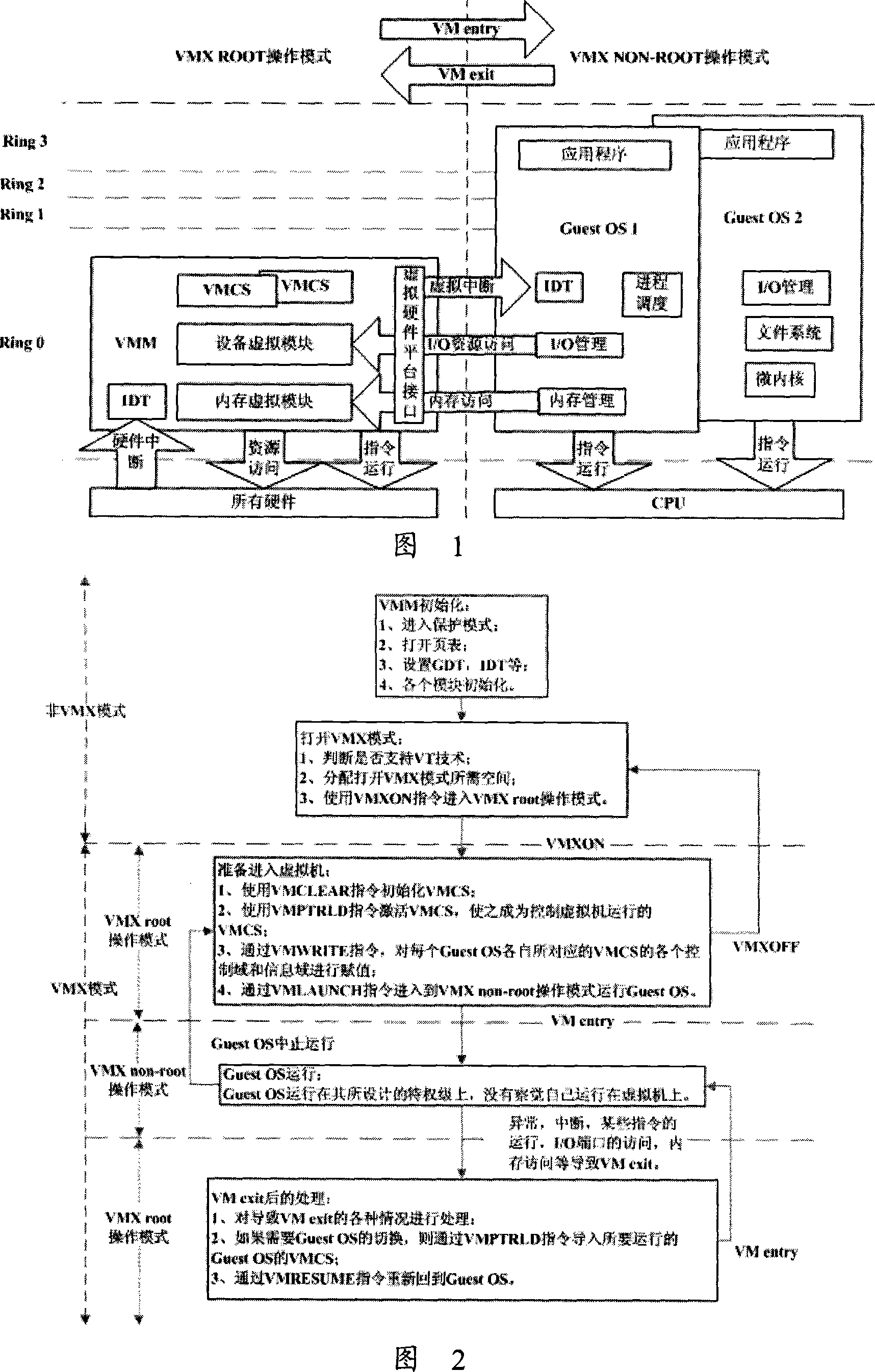
InactiveCN101093449ASimple structureEasy to useSoftware simulation/interpretation/emulationOperational systemOperation mode
A virtualizer system based on processor virtualization technology consists of processor with virtualization technique, bottom layer hardware, virtualizer monitor and a numbers of virtual operation system. It is featured as switching in one end of virtualizer monitor to various virtual operation systems through virtual hardware platform interface and another end to said bottom layer hardware device except processor and connecting various operation systems directly to processor.
Owner:ZHEJIANG UNIV
Full automatic unpacking unloader
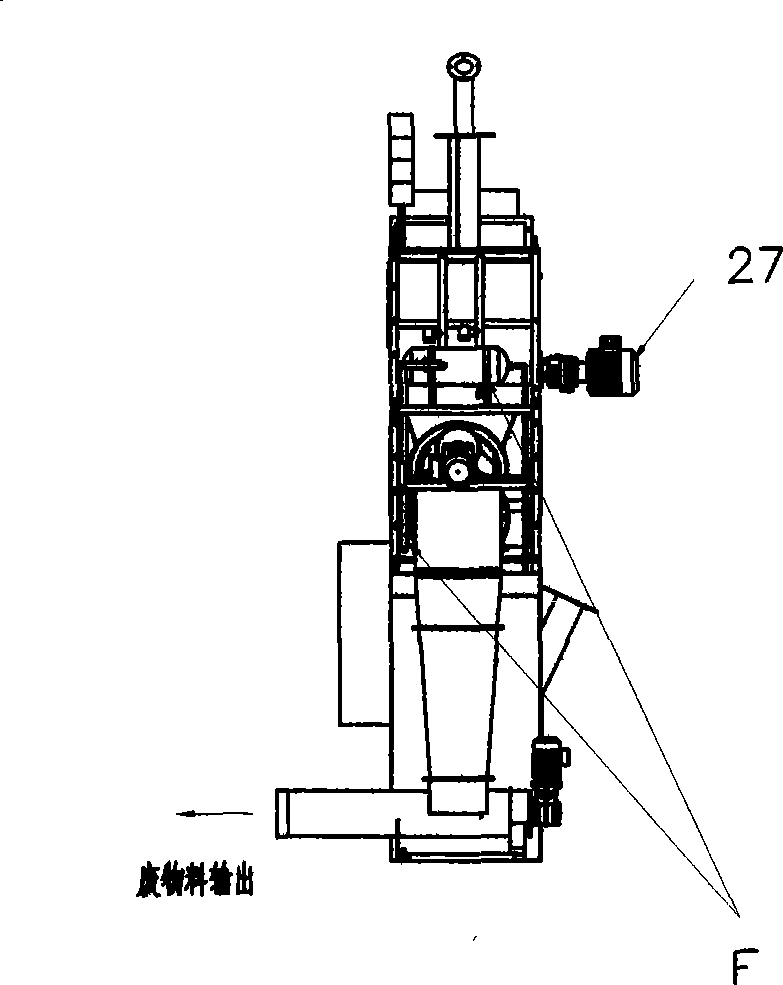
The invention relates to a solid material unpacking machine, in particular to a full automatic unpacking and unloading machine, which is characterized in that: all stages of mechanisms are connected through flanges; a bag breaking mechanism, a screening mechanism and a material output mechanism are arranged on a main body frame; the outer surface of the main body frame is connected with a surface panel in a splicing mode; the surface panel on the top of the main body frame is provided with a main dust removal outlet; and a channel formed from the feeding inlet end of a feeding mechanism to the outlet end of the material output mechanism and the outlet end of a waste bag output mechanism is a one-way communication channel. The full automatic unpacking and unloading machine has the advantages that the machine has high work efficiency, energy conservation, environmental protection, small volume, light weight and the like, can safely and stably separate solid materials from packages in automatic high-speed running, and convey the materials to downstream equipment, while the waste packages enter a waste bag recovery device for recovery, and the machine can particularly meet the requirements of unloading, separating and collecting toxic and corrosive powder, and particle materials.
Owner:HANRUI PUZER BULK HANDLING TECH SHANGHAI
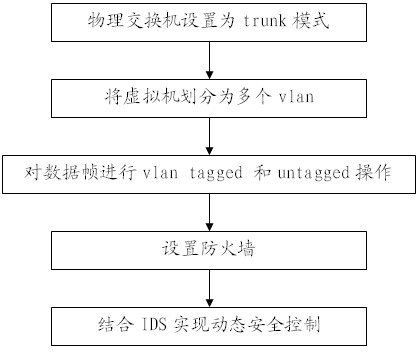
Safety isolation method for virtual network and physical network of cloud computing
InactiveCN102255903AImplement security controlsControl accessTransmissionSafety controlNetwork isolation
The invention provides a safety isolation method for a virtual network and a physical network of cloud computing, wherein the isolation between the both layers of networks is realized by carrying out VLAN (Virtual Local Area Network) tagged and untagged operations on data frames, the access control of three layers is realized by a fire wall, the dynamic safety control is realized with the addition of IDS (Intrusion Detection System) software, so that not only can the communication between different VLANs be controlled, but also the access of other machines in the inner network to the cloud inner network can be controlled. Simultaneously, the network isolation can be performed between virtual machines or between virtual machines and physical machines by employing the VLAN, so that the physical machines and the virtual machines are divided in the different VLANs, namely, the isolation between the physical network and the virtual network can be realized.
Owner:GCI SCI & TECH
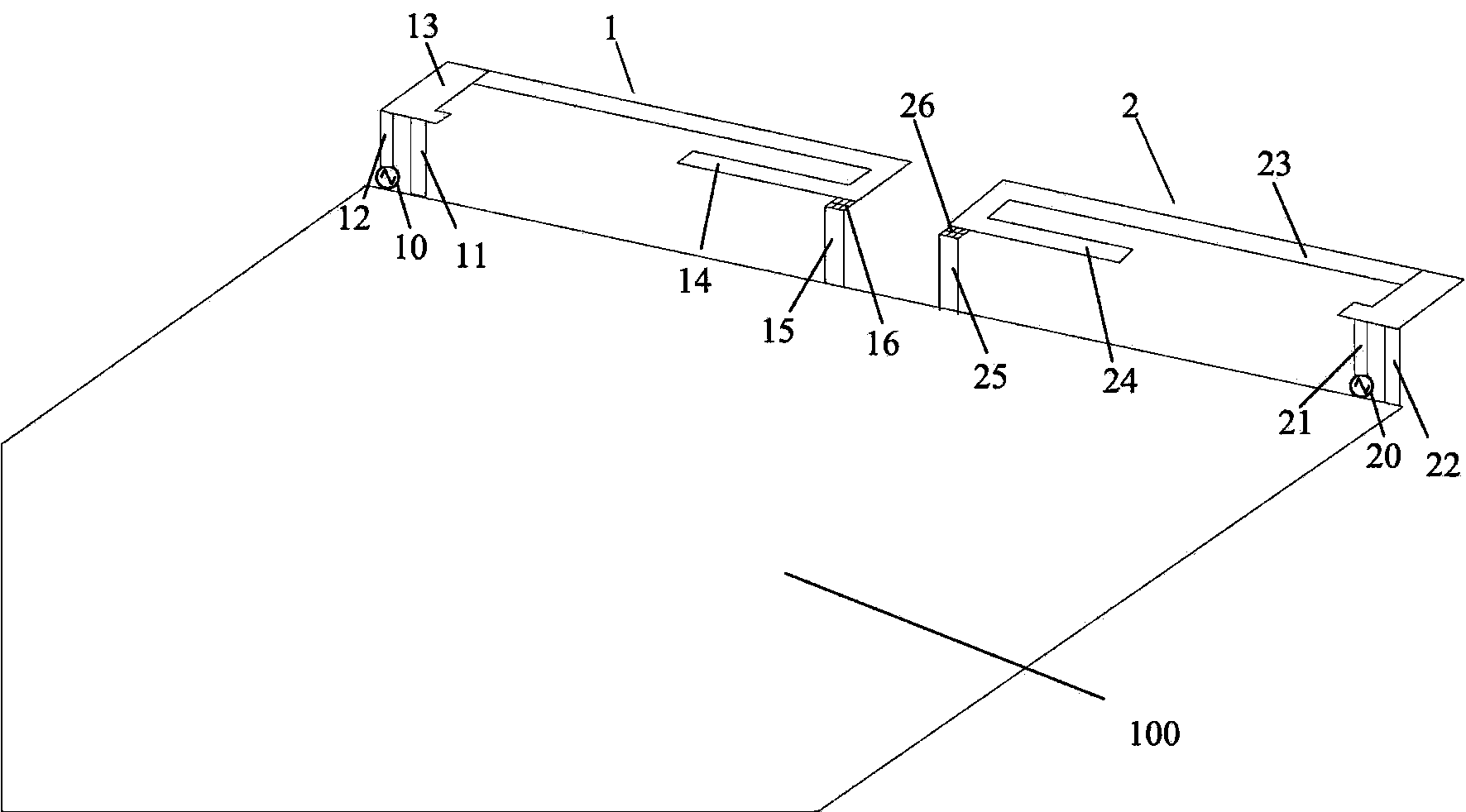
Narrow-spacing low-SAR high-isolation MIMO antenna
InactiveCN104022354AImprove isolationExcite symmetrical currentAntenna arraysAntenna couplingsNon symmetricResonance
The invention discloses a narrow-spacing low-SAR high-isolation MIMO antenna. The narrow-spacing low-SAR high-isolation MIMO antenna comprises a PCB and two antenna bodies used for supporting different service signals, wherein the two antenna bodies are distributed on the two sides of the top end of the PCB and respectively provided with feeding points, the antenna bodies are connected to the PCB through the feeding points respectively, and the feeding points of the two antenna bodies are asymmetrically distributed. According to the antenna, the feeding positions are arranged in the asymmetrical positions on the same side of the PCB, it is avoided that the feeding positions of the antenna are located in the symmetrical current resonance positions, and the isolation degree between the antennas is improved.
Owner:GUANGDONG UNIV OF TECH
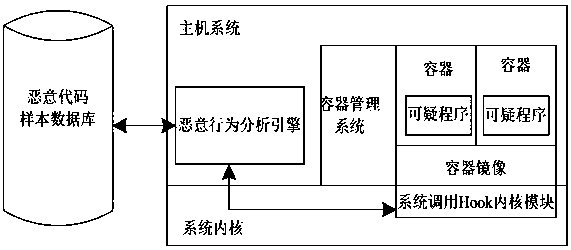
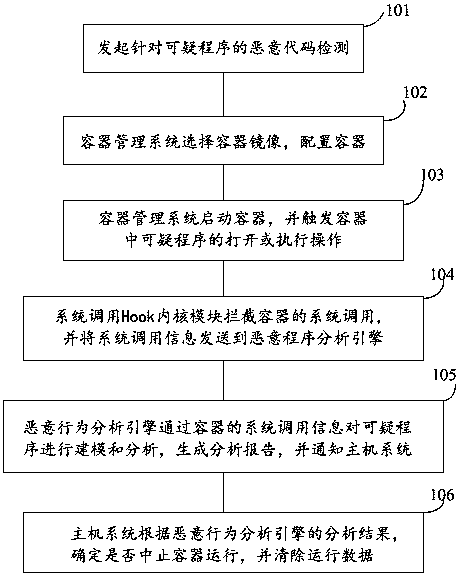
Container-based malicious code detection sandbox system and detection method
InactiveCN107679399AGood isolation and securityReduce system resource consumptionPlatform integrity maintainanceSoftware simulation/interpretation/emulationComputer securityManagement system
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
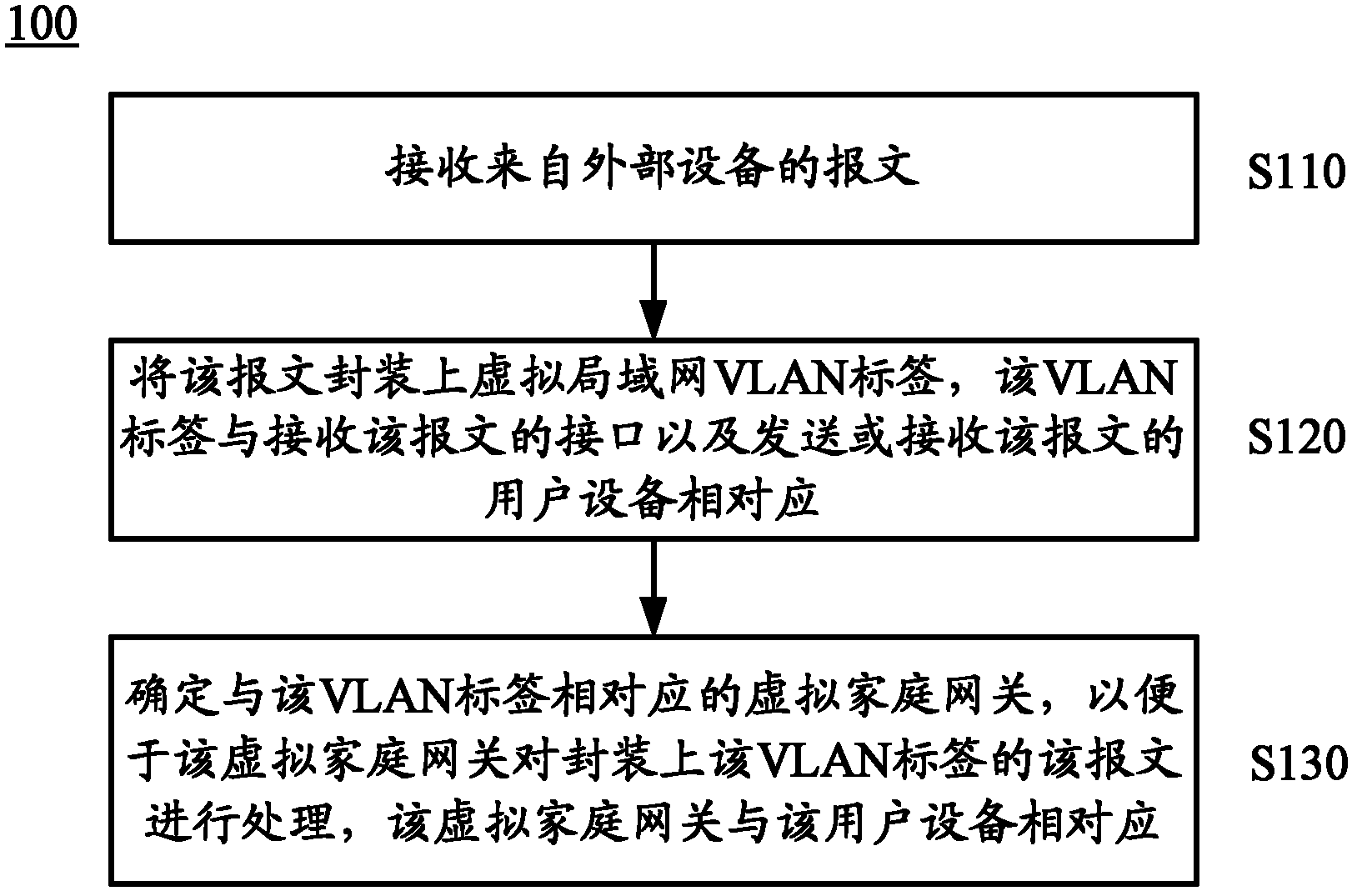
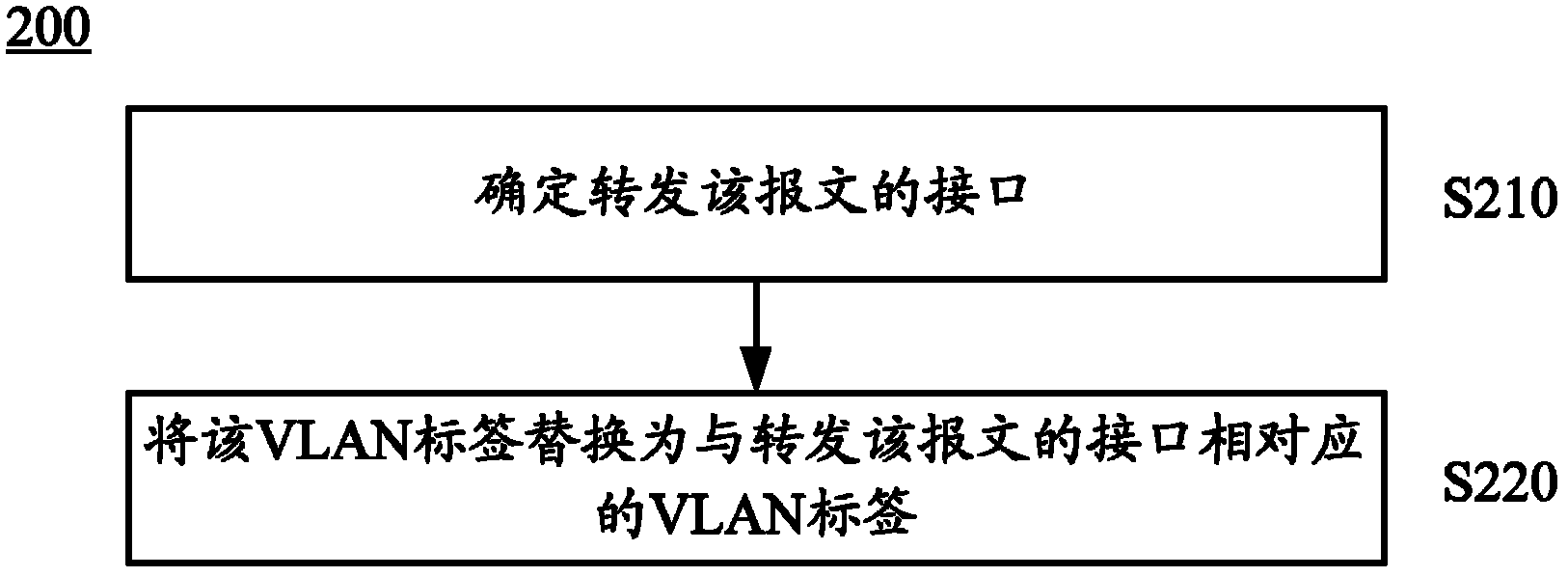
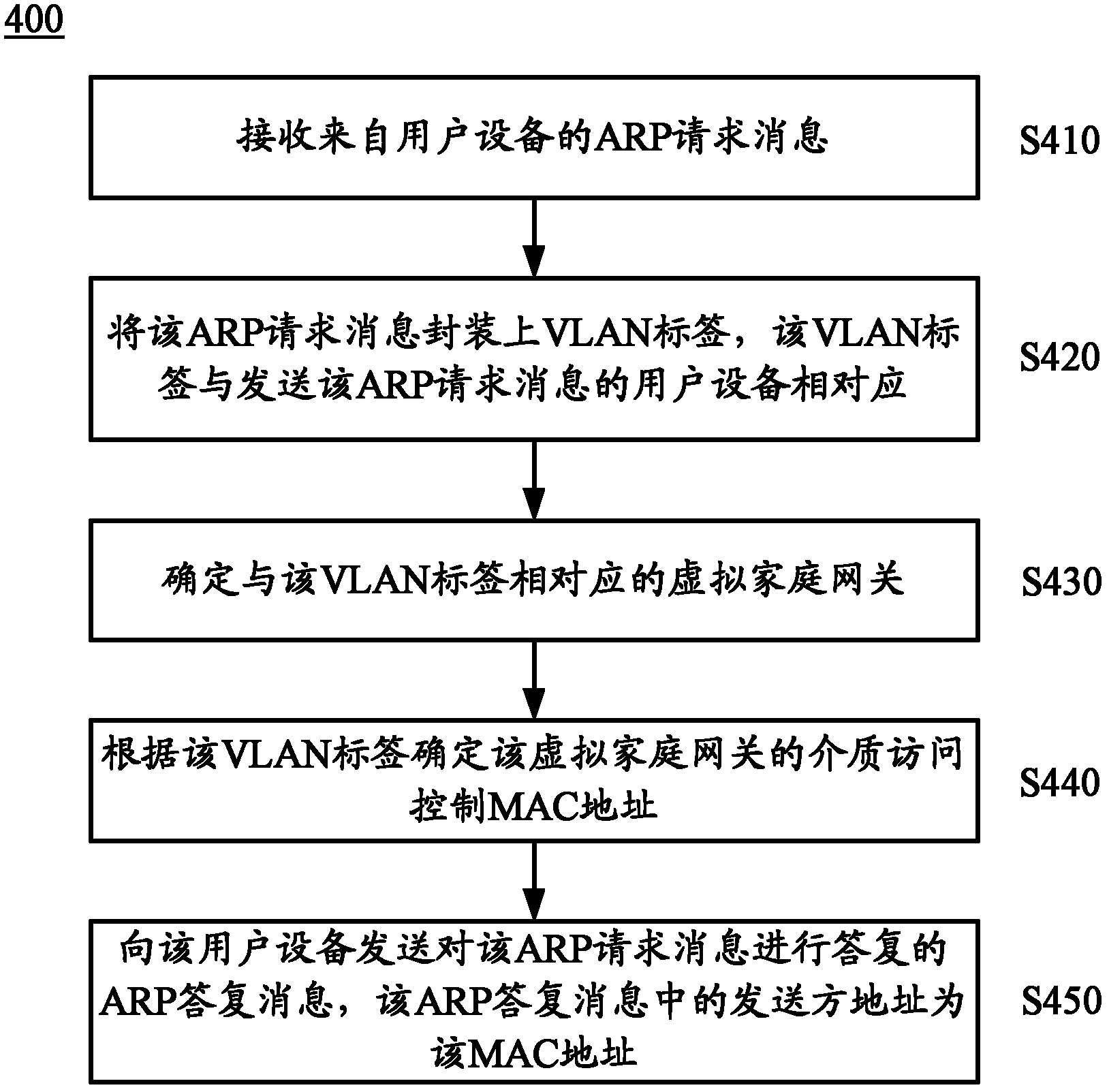
A method for processing message and a device thereof
ActiveCN102217245ARealize IDAchieve isolationNetworks interconnectionComputer hardwareUser equipment
The invention provides a method for processing message and a device thereof. The method includes receiving a message from an external equipment; packaging the message with a VLAN (Virtual Local Area Network)mark which is corresponding to the user equipment sending or receiving the message; determining a virtual family gateway corresponding to the VLAN mark to make convenience for processing the message packaged with the VLAN mark by the virtual family gateway which is corresponding to the user equipment. The device includes an interface board and a service board. In the invention, by packaging the VLAN mark which is corresponding to the user equipment and the virtual family gateway onto the received message, i.e. the identification and isolation of the virtual family gateway can be realized by the VLAN mark, thus, large amount of virtual family gateways which are capable of providing family gateway function can be virturalized with limited resouce, and the requirement of high performance, small volume and low consumption is satisfied.
Storage battery internal resistance measuring method and circuit, health status detection method and system
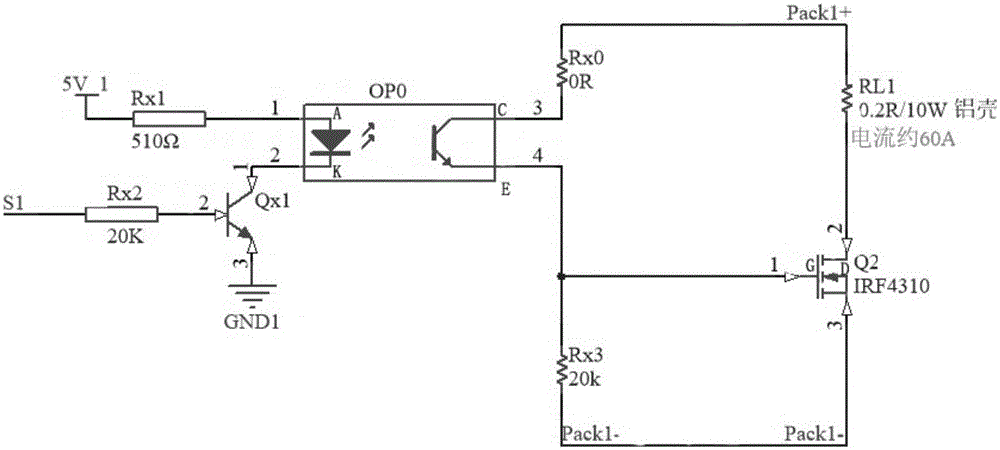
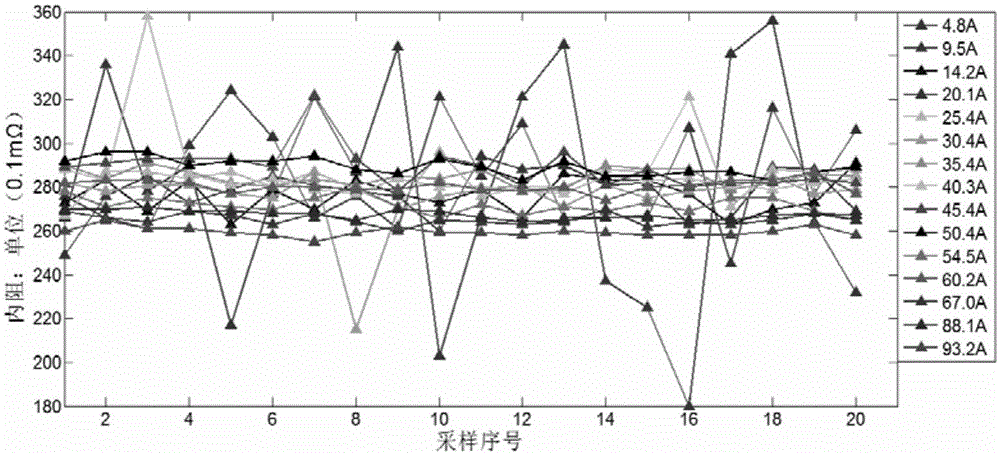
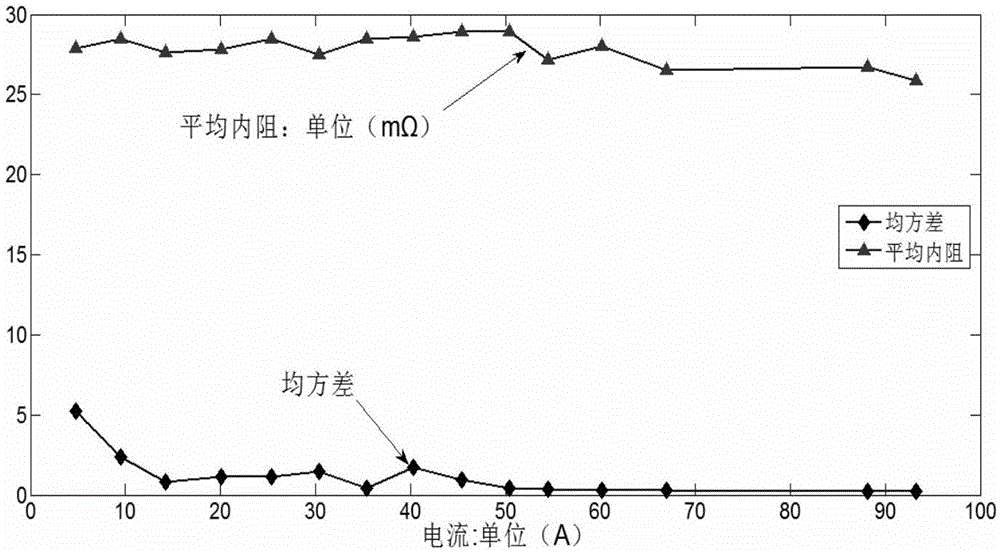
ActiveCN105092977ANo damageReduce lossResistance/reactance/impedenceElectrical testingInternal resistanceTerminal voltage
The invention discloses a storage battery internal resistance measuring method. According to the invention, the storage battery internal resistance measuring method is based on heavy current millisecond pulsed discharge and includes the following steps: the storage batter generating a discharge loop which matches the capacity of the storage battery of discharge current via a design, performing a heavy current millisecond pulsed discharge, detecting in the pulsed discharge process the variation process of a terminal voltage and the discharge current of the storage battery, and based on the Ohm law, calculating the internal resistance of the storage battery. The method can accurately measure the internal resistance of the storage battery on-line.
Owner:郑贵林
Backplane connector with improved pin header
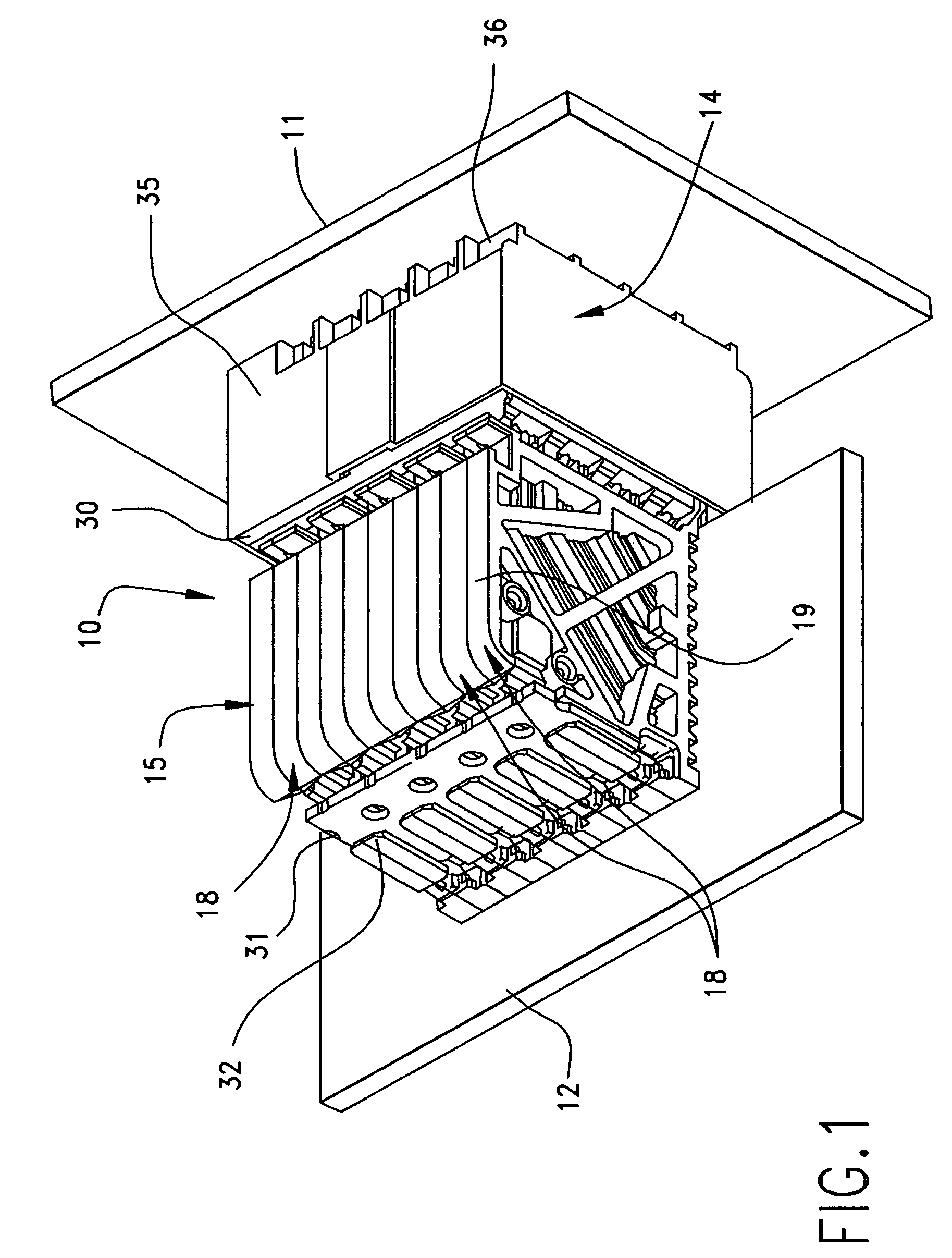
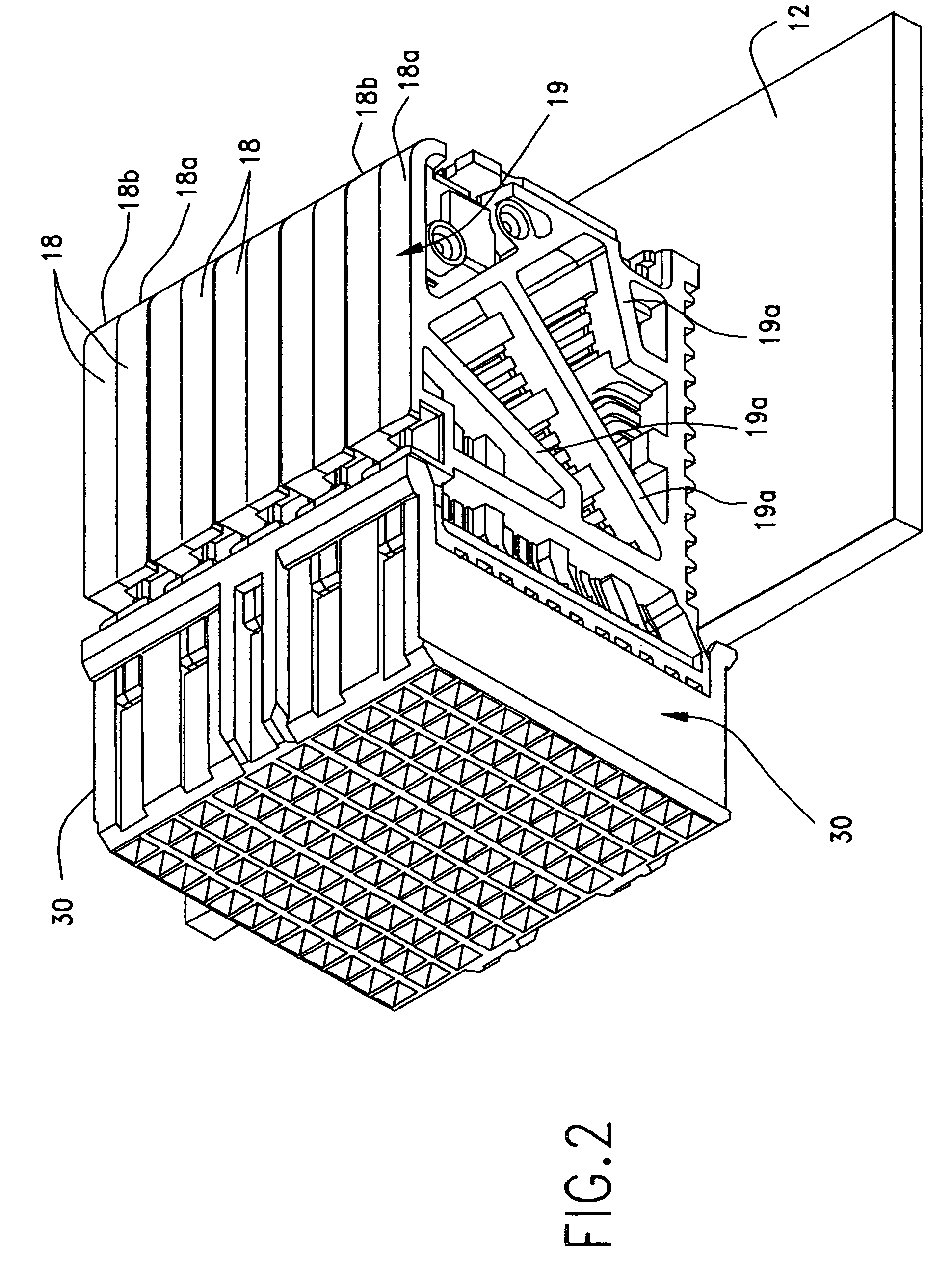
ActiveUS7914305B2Simple designEffective isolationTwo-part coupling devicesCoupling protective earth/shielding arrangementsDielectricGround contact
A backplane electrical connector having a pin header that includes a one-piece housing supporting a plurality of columns of edge coupled differential signal pairs of contacts each separated by a ground contact. The pin header housing base is formed with a plurality of air passageways extending through the base, including an air passageway disposed between each signal contact in one column and an immediately adjacent signal contact in an adjacent column for electrically isolating the adjacent signal contacts from each other by an air dielectric medium. Core-outs which extend only partially through the housing base are provided between each signal contact and an adjacent ground contact in an adjacent column for further isolating differential signal pairs.
Owner:MOLEX INC
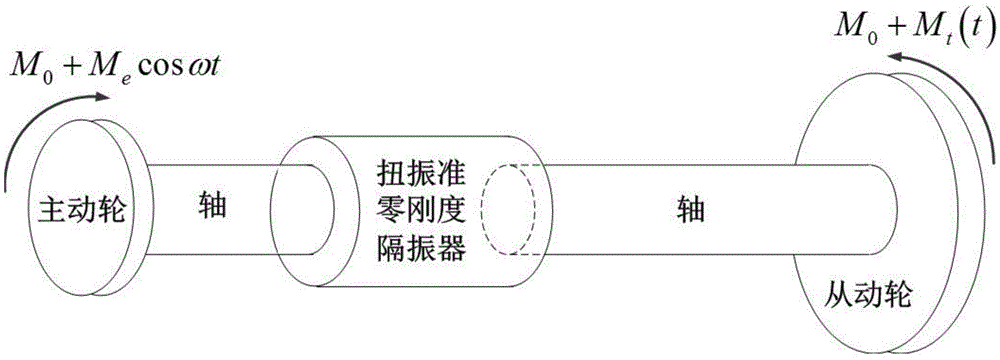
Torsion quasi-zero stiffness vibration isolator
ActiveCN104455199AImprove static stiffnessPositive torsional stiffnessVibration suppression adjustmentsDynamic stiffnessCoupling
The invention discloses a torsion quasi-zero stiffness vibration isolator. The torsion quasi-zero stiffness vibration isolator is mainly composed of a negative-stiffness cam-roller-radial spring mechanism and a positive-stiffness rubber spring vulcanized on a first coupling and a second coupling, and is further provided with a radial spring supporting component used for supporting a radial spring and guaranteeing that the radial spring only deforms in the radial direction. When the first coupling and the second coupling rotate relative to each other, the cam-roller-radial spring mechanism generates negative torsion stiffness, the rubber spring has positive torsion stiffness; under the parallel combination of the positive-stiffness element and the negative-stiffness element, the vibration isolator has the high static stiffness and low dynamic stiffness characteristic that the vibration isolator can bear large static loads, namely, the vibration isolator can transmit large static torque. The stiffness is zero at the static balance position, and the micro stiffness characteristic is shown near the static balance position. Thus, the vibration isolator can isolate ultralow-frequency torsion vibration of a shaft system.
Owner:HUNAN UNIV
Network slice management method and apparatus
PendingCN107889155AAchieve isolationAvoid mutual interferenceNetwork traffic/resource managementTransmissionAccess networkNetwork element
The invention discloses a network slice management method and apparatus. The method comprises the following steps: a first network element receives slice configuration information sent by a second network element; and the first network element performs scheduling management on slices on an access network side according to the slice configuration information.
Owner:ZTE CORP
Credible platform and method for controlling hardware equipment by using same
InactiveCN102063592AEnsure safetyImprove security assurancePlatform integrity maintainanceEngineeringWork Performances
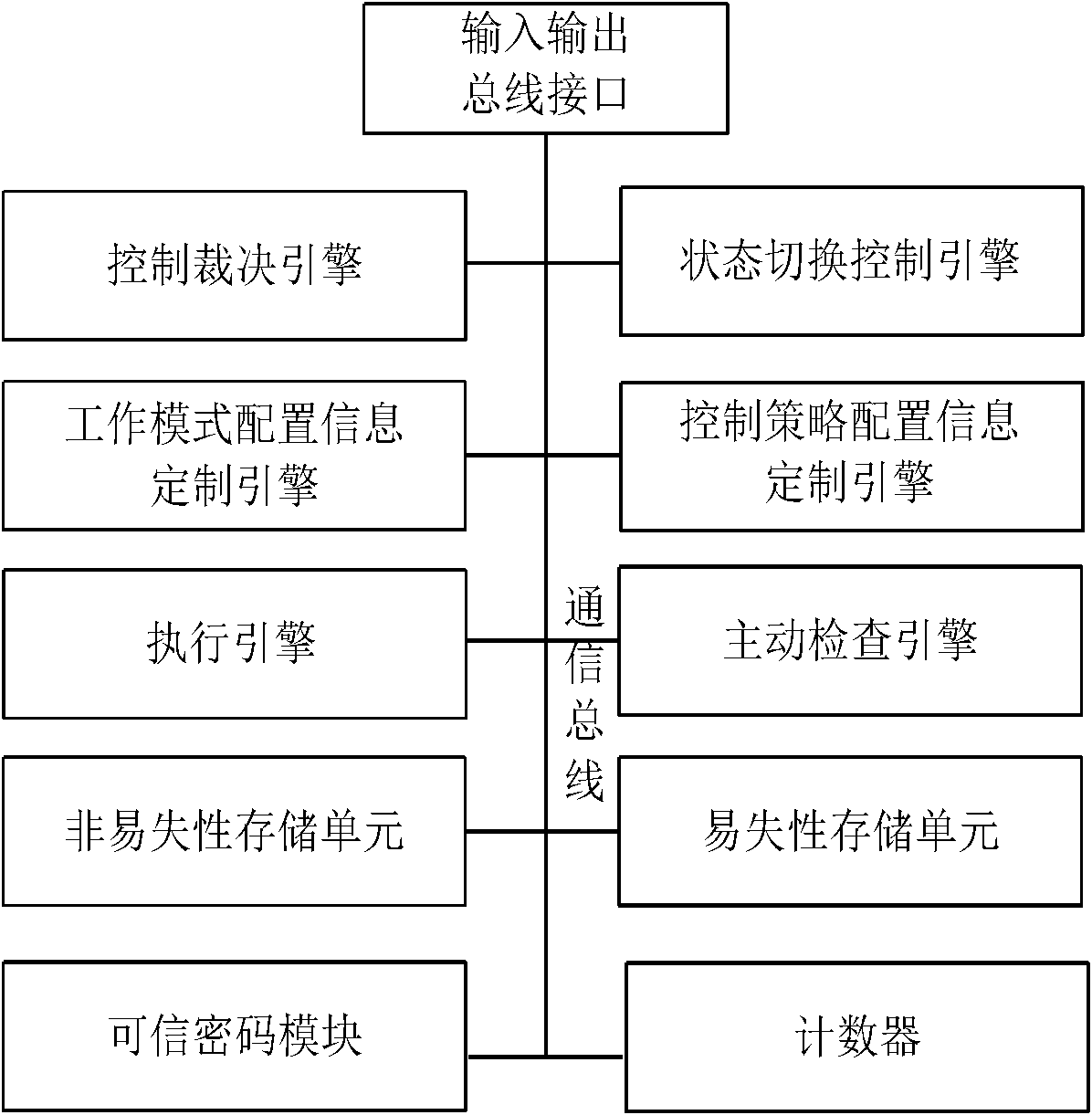
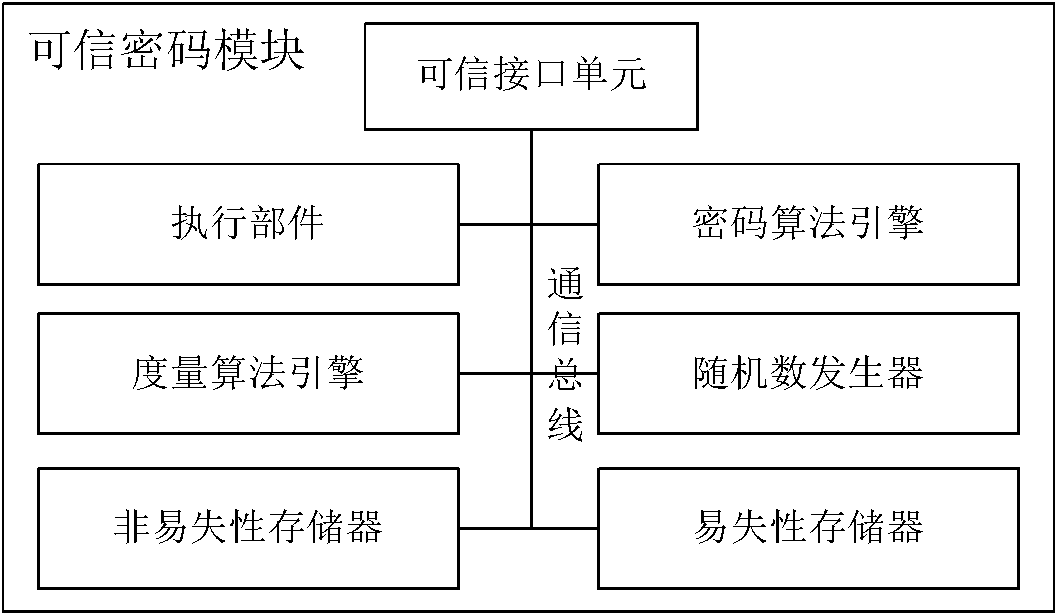
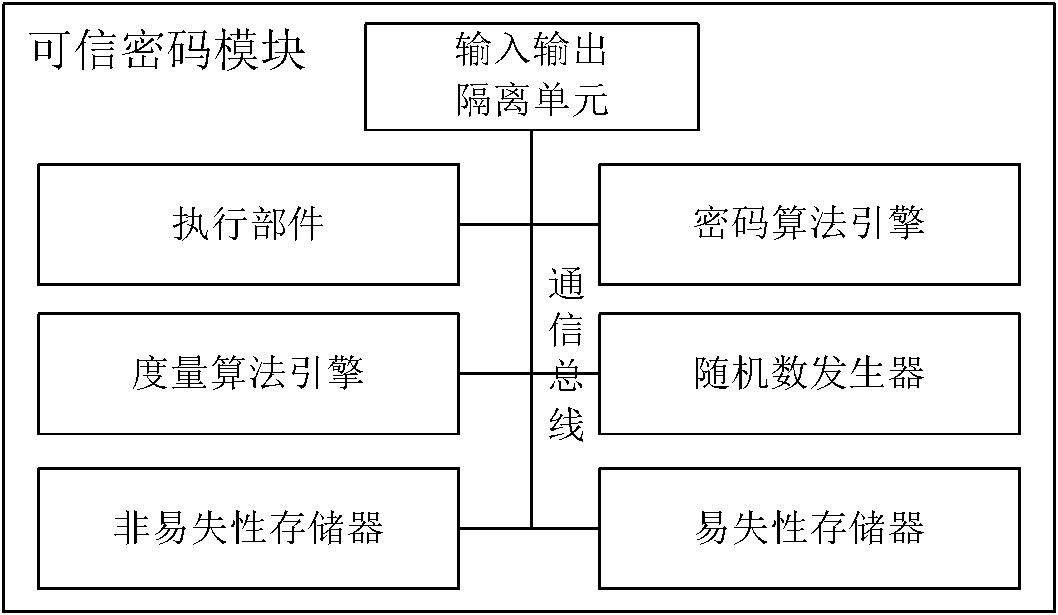
The invention relates to a credible platform and a method for controlling hardware equipment by using the same, belonging to the field of a computer. The credible platform comprises the hardware equipment and a credible platform control module with the function of active control, wherein hardware units, such as an active measure engine, a control ruling engine, a working mode custom engine, a credible control strategy configuration engine, and on the like, are arranged in the credible platform control module so as to realize the control functions of actively checking working mode configuration information, control strategy configuration information, firmware codes and circuit working states, and on the like for the hardware equipment. Through the identity legitimacy authentication and theactive control of the credible hardware equipment, which are realized by the credible pipeline technology, the active control and active check function, the security control system of credible hardware equipment which can not be bypassed by the upper layer can be stilled provided for the accessor of credible platform in incredible or lower-credibility computing environment without modifying the computing platform system structure and obviously reducing the system working performance.
Owner:BEIJING UNIV OF TECH
Secure access mode for intranet and extranet
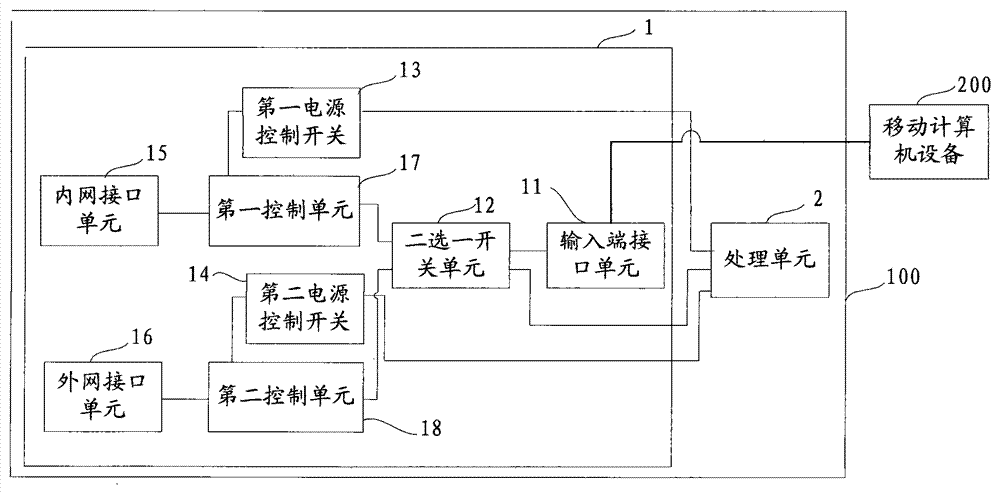
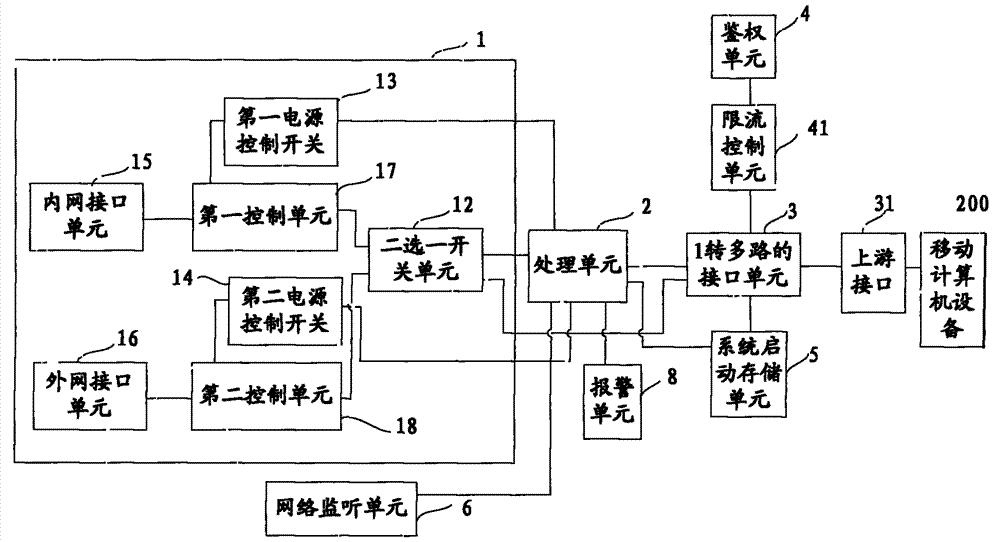
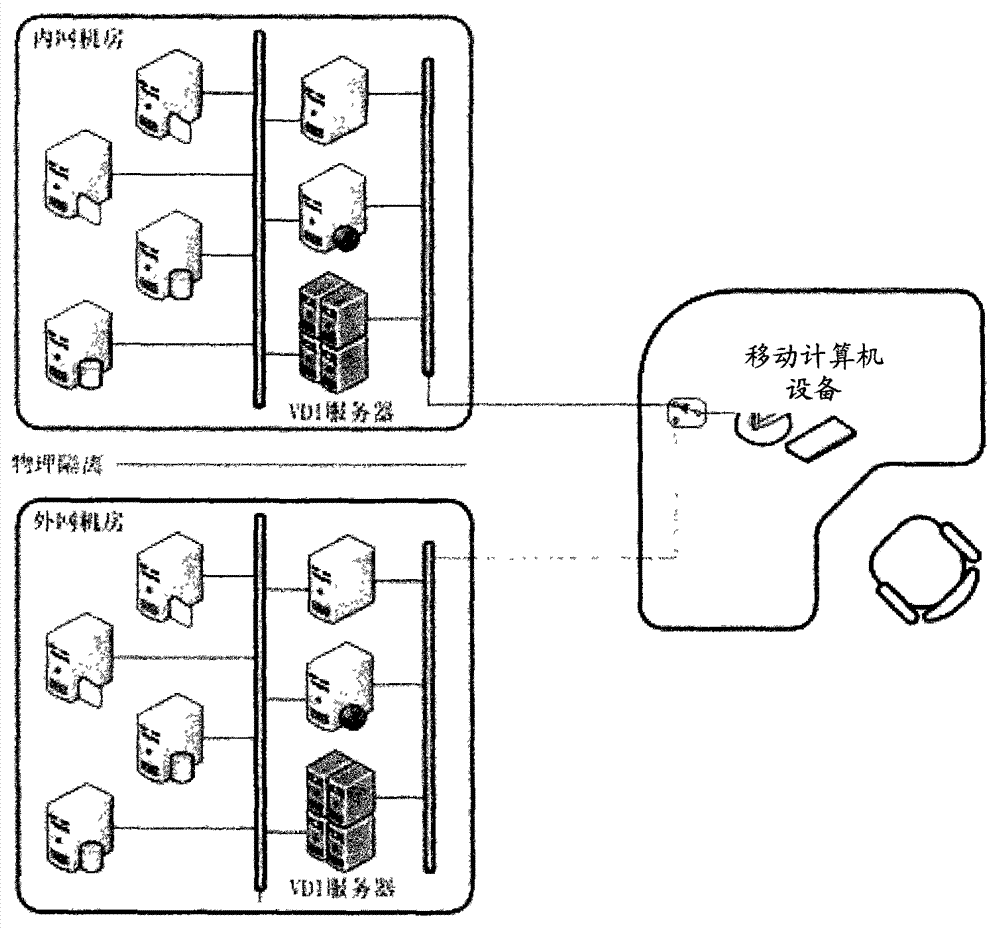
InactiveCN103532978AProtect information securityImprove information securityData switching current supplyPower controlComputer equipment
The invention provides a secure access mode for an intranet and an extranet. An input-end interface unit of intranet and extranet safety equipment is connected with a first control unit and a second control unit respectively through a two-channel switch unit; when mobile computer equipment selects an extranet mode, a processing unit controls the two-channel switch unit to gate the second control unit, switches on a second power control switch to enter an extranet system and switches off a first power control switch to cut off connection with an intranet system at the moment; and when the mobile computer equipment selects an intranet mode, the processing unit controls the two-channel switch unit to gate the first control unit, switches on the first power control switch to enter the intranet system and switches off the second power control switch to cut off connection with the extranet system at the moment. The secure access mode for the intranet and the extranet is used for realizing isolation and safety protection of the intranet and extranet systems, and information security of the intranet system can be protected effectively.
Owner:BEIJING AISIMENG TECH
Critical temperature testing system of gunpowder and explosive thermal explosion
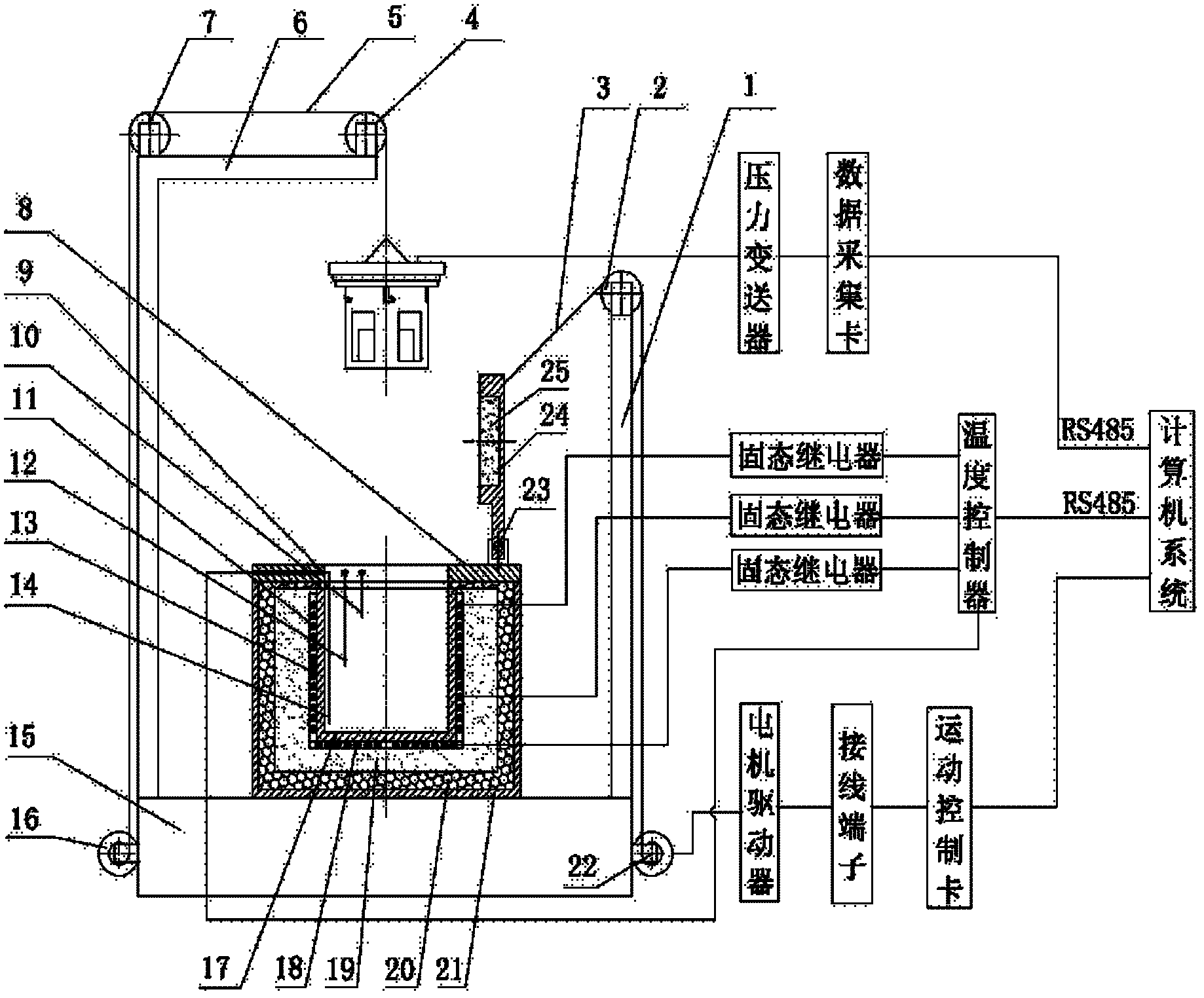
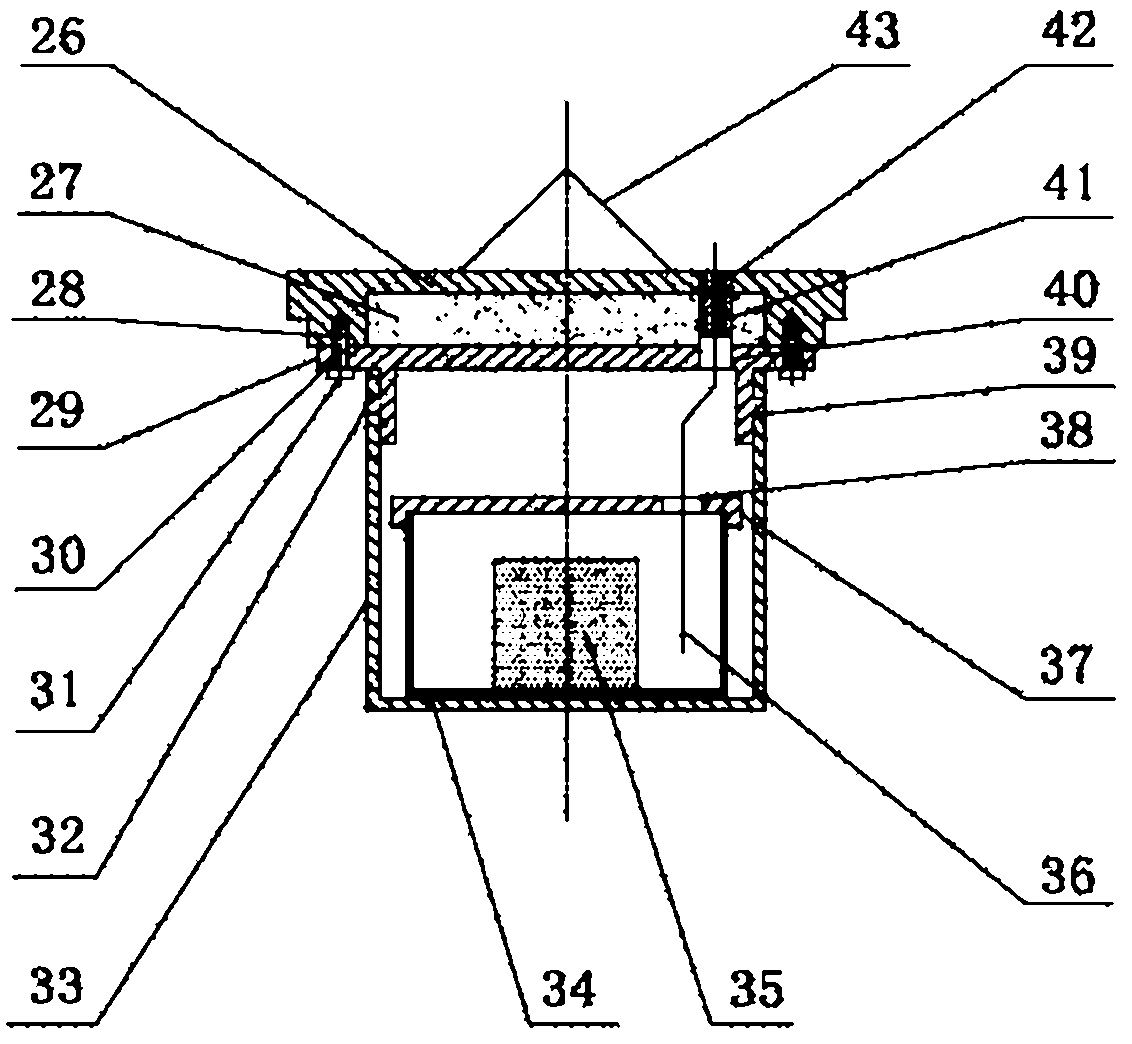
InactiveCN102608158ADifficult to collectChange the ambient temperatureMaterial heat developmentHeat conductingData acquisition
The invention discloses a critical temperature testing system of gunpowder and explosive thermal explosion, comprising a temperature-rising heating unit, a reactor unit, an automatic sample feeding unit, a pressure detection unit and a computer, wherein the temperature-rising heating unit comprises a heat-conducting layer, a heat preservation layer, and a single-cavity heating furnace body containing three groups of heating layers and ceramic heat-isolating layers; and the temperature and the temperature-rising speed of the heating furnace body are controlled by the computer. The reactor unit comprises a testing furnace cover, a lifting basket, a sample tank and a pre-heating furnace cover; the automatic sample feeding unit comprises a furnace body bracket, two stepping motors, a pulley wheel and a steel wire rope; the air pressure detection unit comprises a pressure sensor; the pressure sensor is mounted in the sample tank through the testing furnace cover and is connected with the computer; and the computer is provided with a data acquisition card, an image display control piece and a data processing unit. When the critical temperature testing system is used, a gunpowder or explosive sample with the certain size is placed into a special explosion-proof furnace and the sample is heated at the equal temperature or temperature-rising condition, so as to detect the thermal explosion critical temperature when the sample is combusted or exploded.
Owner:XIAN MODERN CHEM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com