Credible platform and method for controlling hardware equipment by using same
A hardware device and platform control technology, applied in the field of information security, can solve problems such as not giving a chip credibility evaluation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0135] The invention provides a trusted platform control module and a method for controlling trusted hardware devices. The following is the specific implementation method.
[0136] 1. Implementation of the trusted platform control module:
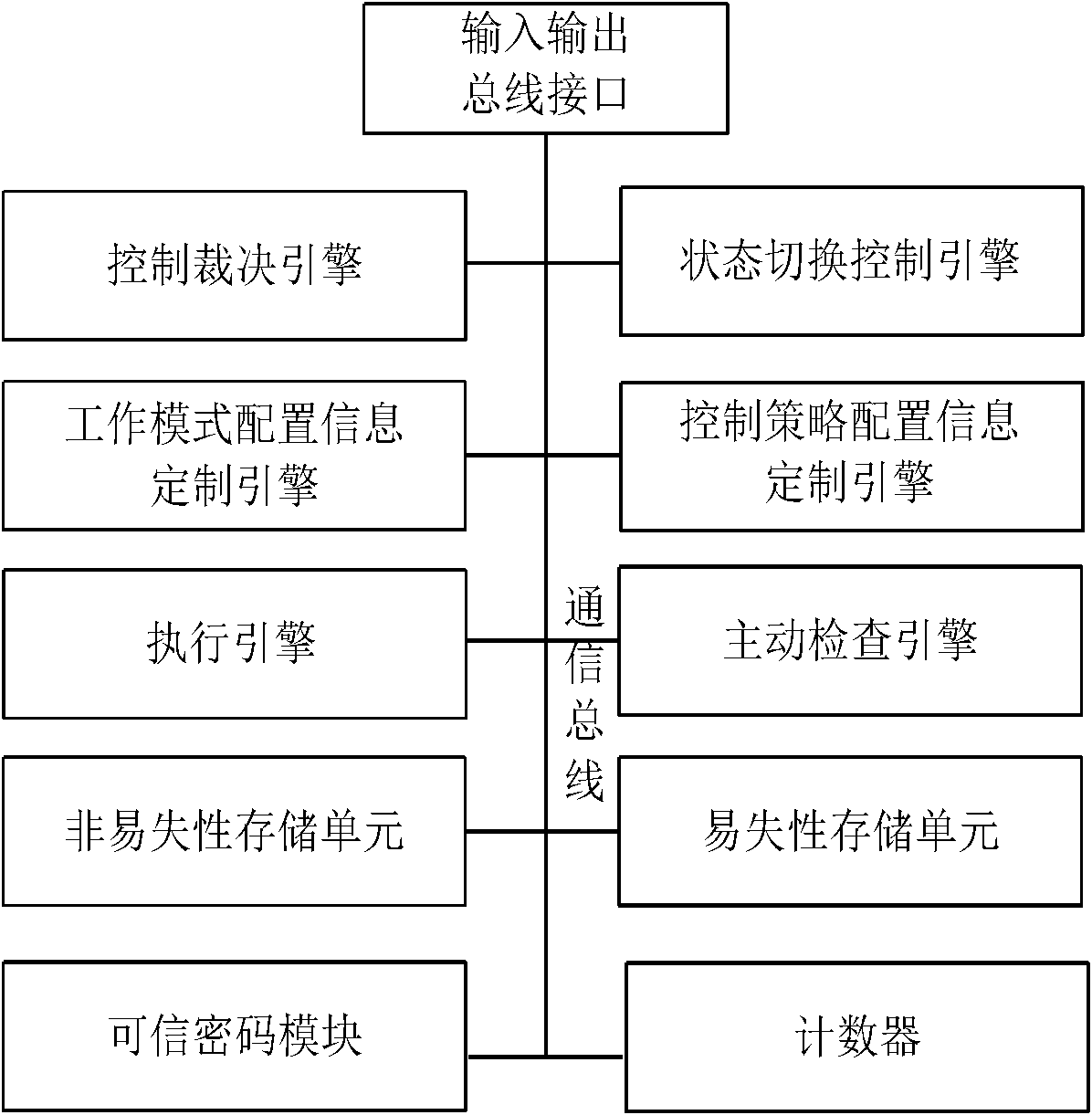
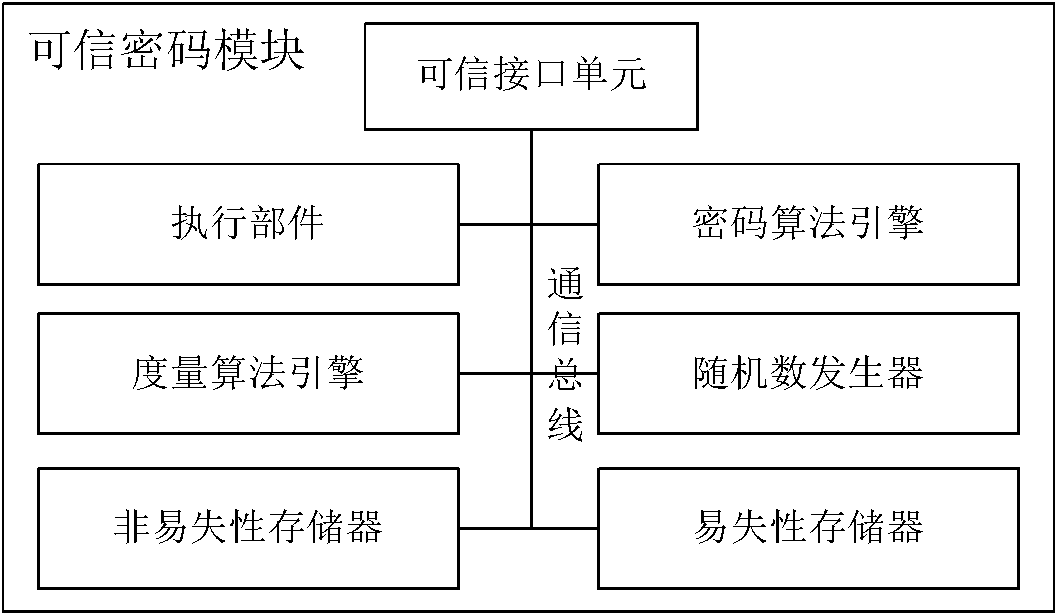
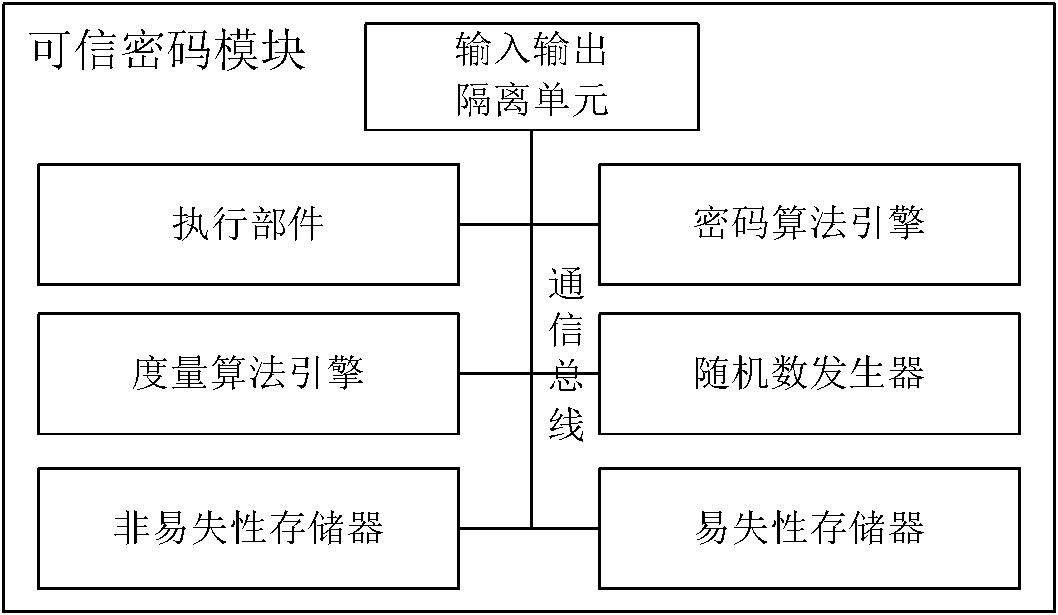
[0137] A trusted platform control module is divided into two parts: functional composition and hardware structure. The hardware includes input and output bus interfaces, execution engines, volatile storage units, non-volatile storage units, trusted password modules, control and ruling engines, working mode configuration information customization engines, control strategy configuration information customization engines, and active inspection engines and state switching controls the engine. Functions include trusted cryptographic module management function, trusted measurement function, trusted storage function, trusted reporting function, trusted device control function, trusted hardware device control policy generation function, trusted h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com