Virtual network isolation system established on virtual machine and implementation method thereof
A virtual network and isolation system technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as software VPN server configuration troubles, hardware VPN equipment costs are high, data security cannot be verified, and achieve low cost , security improvement, the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
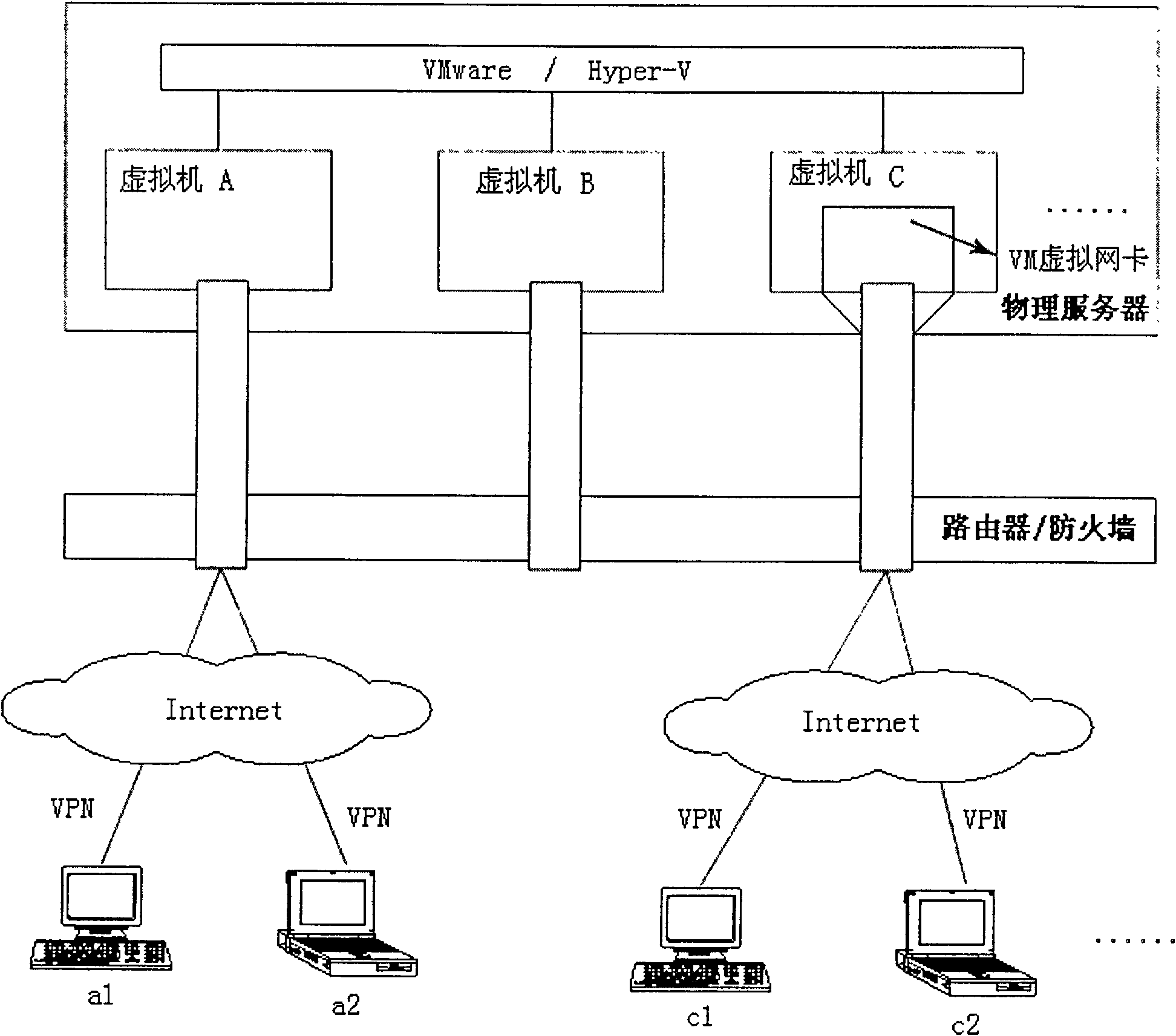
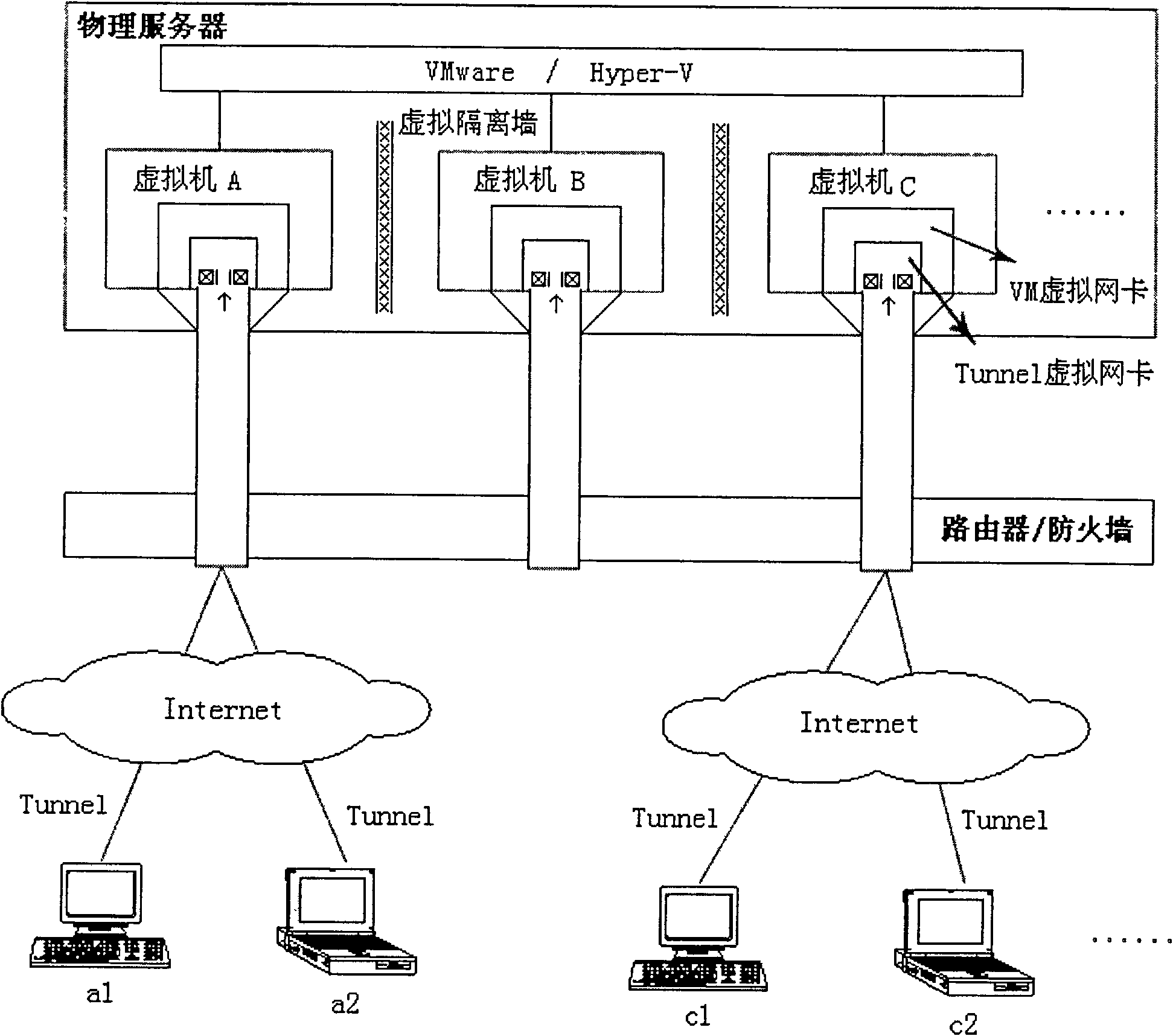
[0045] A virtual network isolation system built on a virtual machine, such as figure 2 As shown, it includes a router\firewall, a physical server, and a plurality of clients. The physical server includes a plurality of virtual machines, and each virtual machine serves some clients. The virtual machine is provided with a VM virtual network card, so The physical server is also provided with
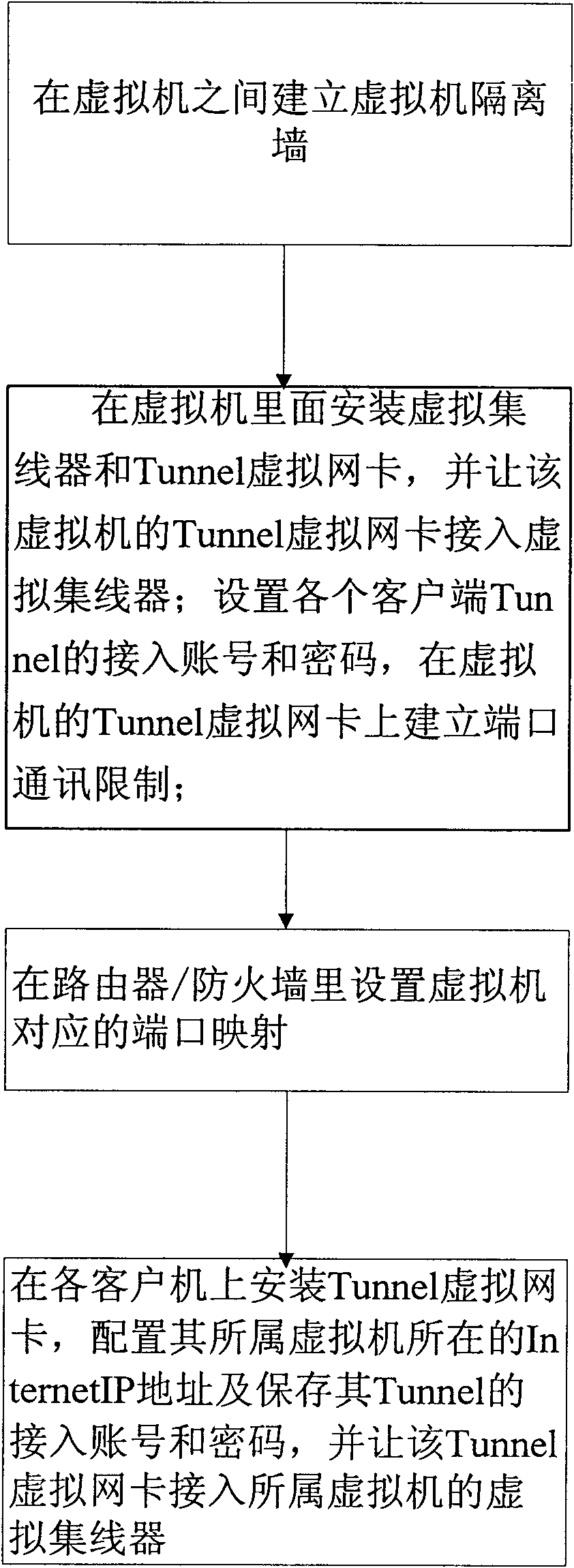
[0046] Located between virtual machines, it is used to isolate virtual machines and prevent information between virtual machines from being sent and received by each other;
[0047] The client is connected to the virtual machine through the router / firewall, specifically to the virtual machine to which it belongs in the physical server.
[0048] Preferably, the virtual network isolation system established on the virtual machine further includes a port communication restriction module, and the port communication restriction module is used to restrict port communication between each client m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com