Patents
Literature
53results about How to "Prevent leaks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
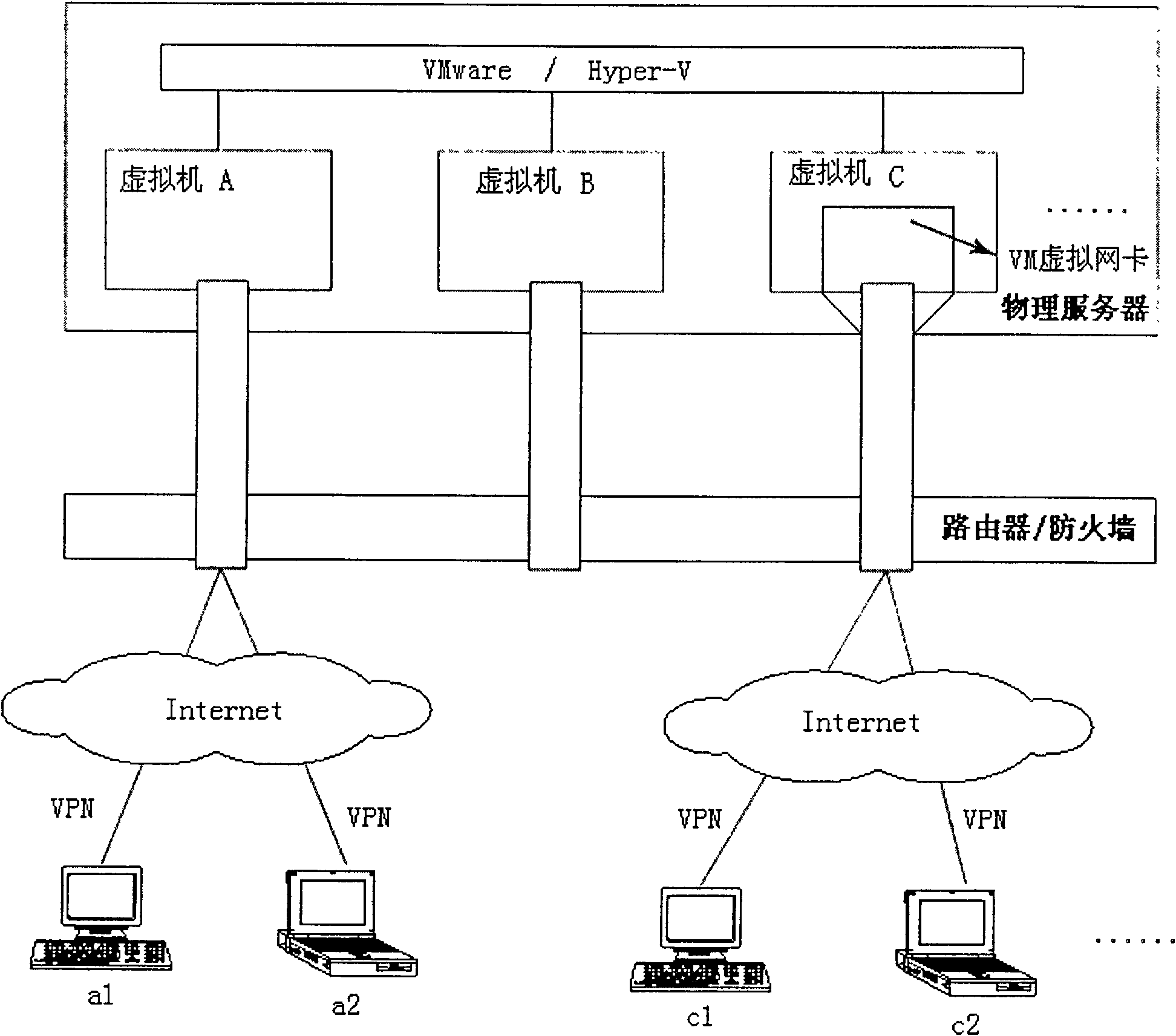
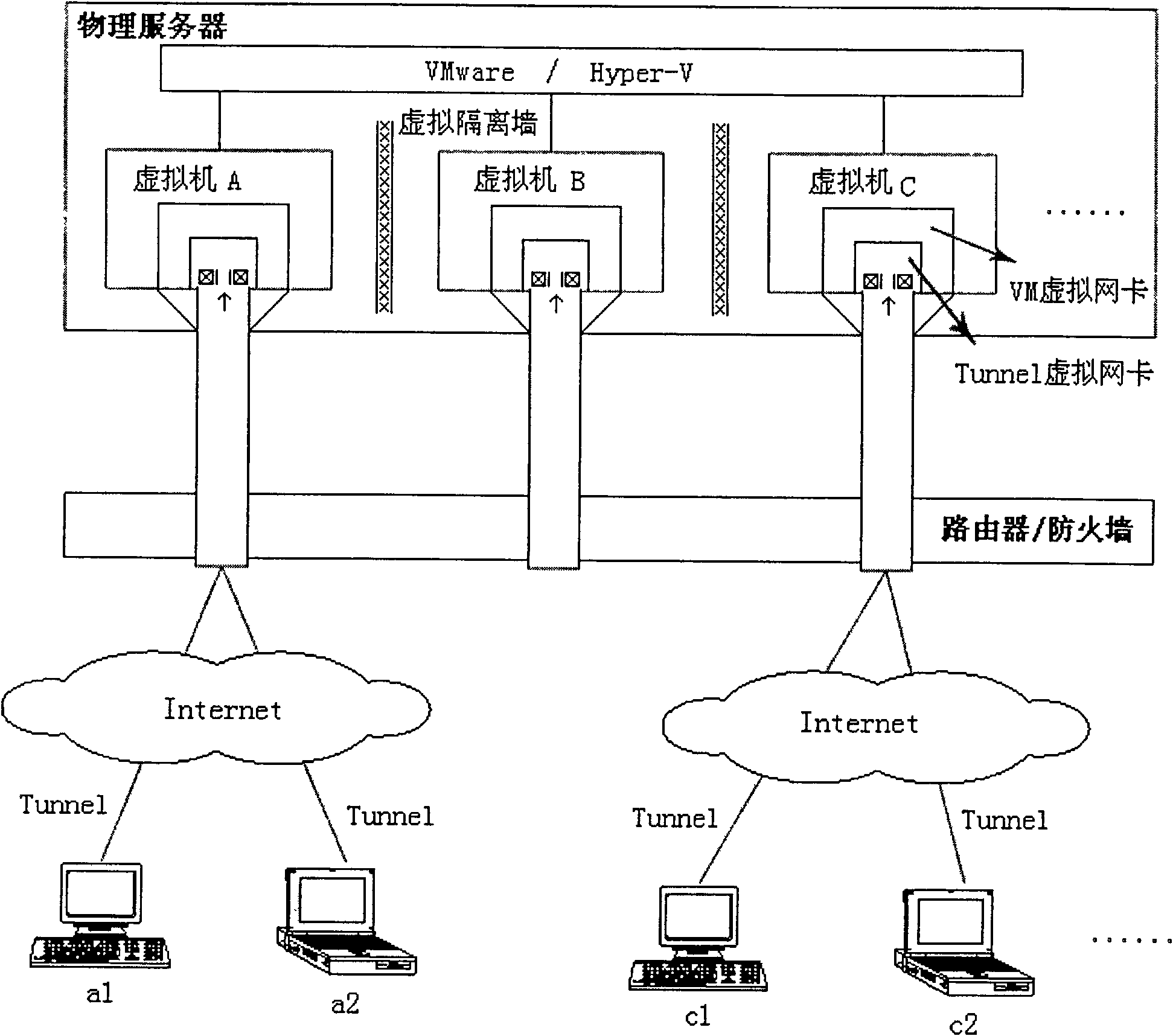
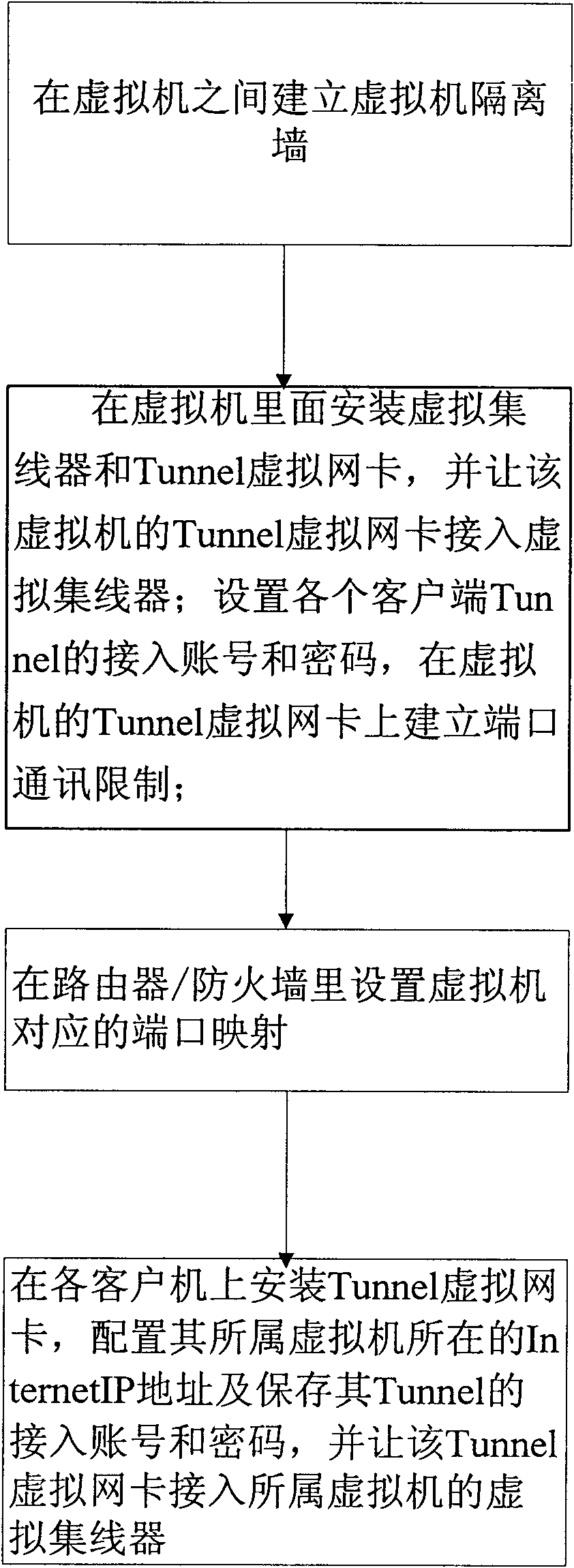
Virtual network isolation system established on virtual machine and implementation method thereof
The invention discloses a virtual network isolation system established on a virtual machine, which comprises a router / a firewall, a physical server and a plurality of clients, wherein the physical server comprises a plurality of virtual machines and is also provided with an isolation wall, and the virtual machine is internally provided with a port communication limitation module. The invention further discloses a virtual network isolation method established on the virtual machine, which comprises the following steps: (1) establishing the isolation wall between virtual machines firstly; (2) arranging a virtual hub and a Tunnel virtual network card in the virtual machine, accessing the Tunnel virtual card of the virtual machine into the virtual hub, and establishing port communication limitation; (3) setting port mapping corresponding to the virtual machine; and (4) arranging the Tunnel virtual network card on each client, configuring Internet IP address and accessing to the virtual hub.The invention provides a safe, low-cost, rapid and conveniently-maintained network environment.
Owner:广州爱迅信息技术有限公司
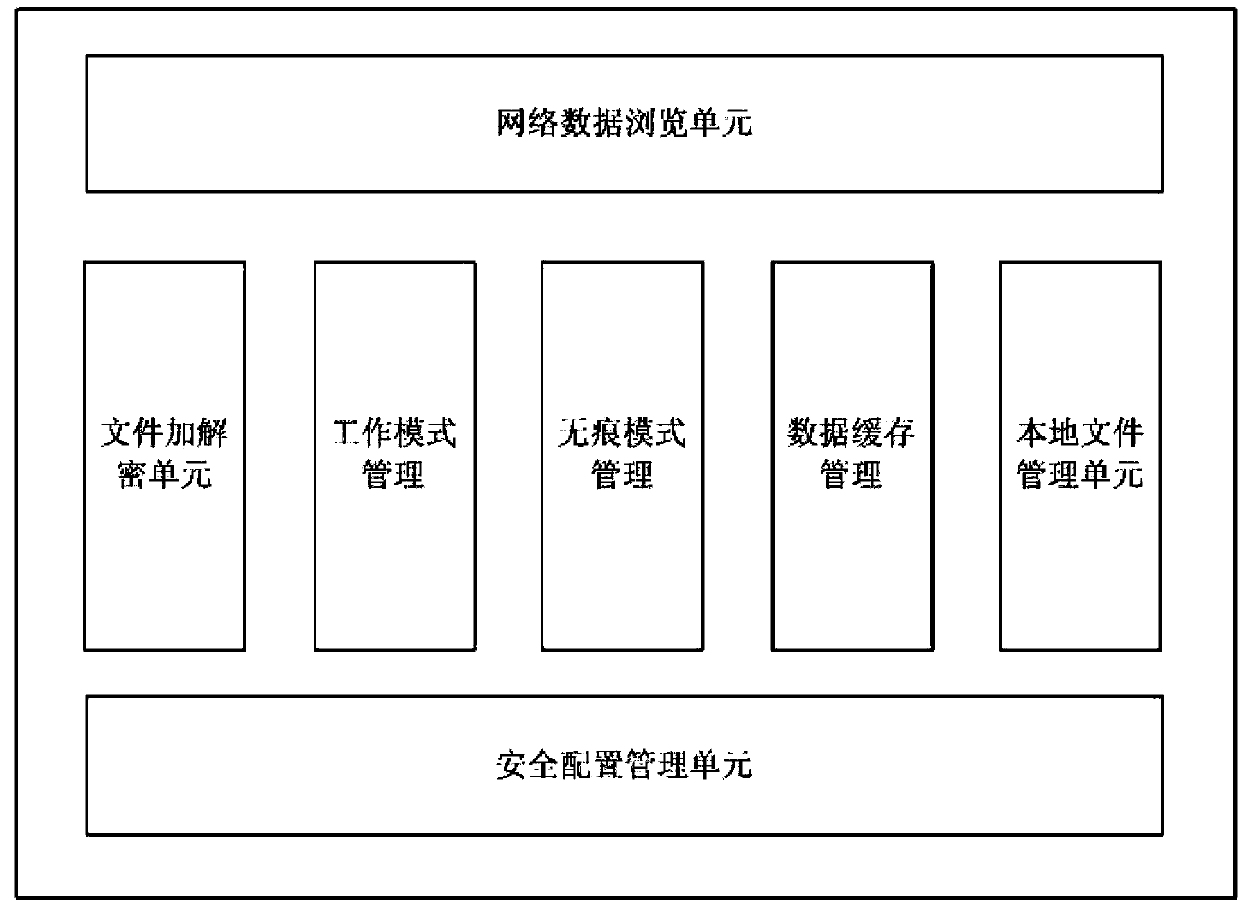
Mobile intelligent terminal security browser and working method thereof
ActiveCN103390026APrevent Information LeakagePrevent leaksDigital data protectionInternal/peripheral component protectionMetadataEngineering
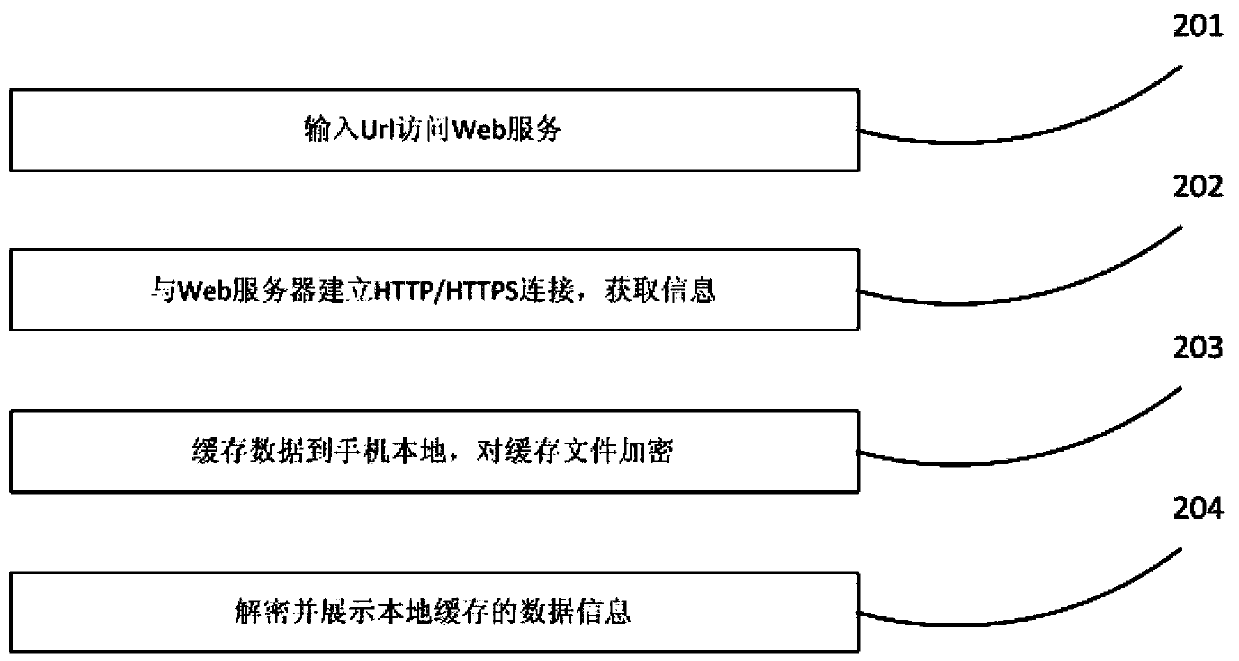
The invention relates to a mobile intelligent terminal security browser and a working method thereof. The mobile intelligent terminal security browser comprises a network data browse unit, a local file management unit, a data cache management unit, a security configuration management unit, a working mode management unit, a file encryption and decryption unit and a traceless security management unit. The working method of the mobile intelligent terminal security browser comprises the steps that 1, a user configures the working mode of the browser at the mobile intelligent terminal; 2, the user switches the working mode of the browser into a security mode when downloading and / or caching data; and 3, the user opens a local encryption file under the security mode. The working method has the advantages that the corresponding file can be decrypted only at the mobile intelligent terminal bound with the file, and personal information and enterprise information are mutually isolated, so that different levels of security protection means of individuals and enterprises are realized; and meanwhile, mobile phone virus and Trojan are effectively prevented from stealing data, and the risk caused by losing of mobile intelligent terminal equipment is also greatly reduced.
Owner:CHINA NAT SOFTWARE & SERVICE
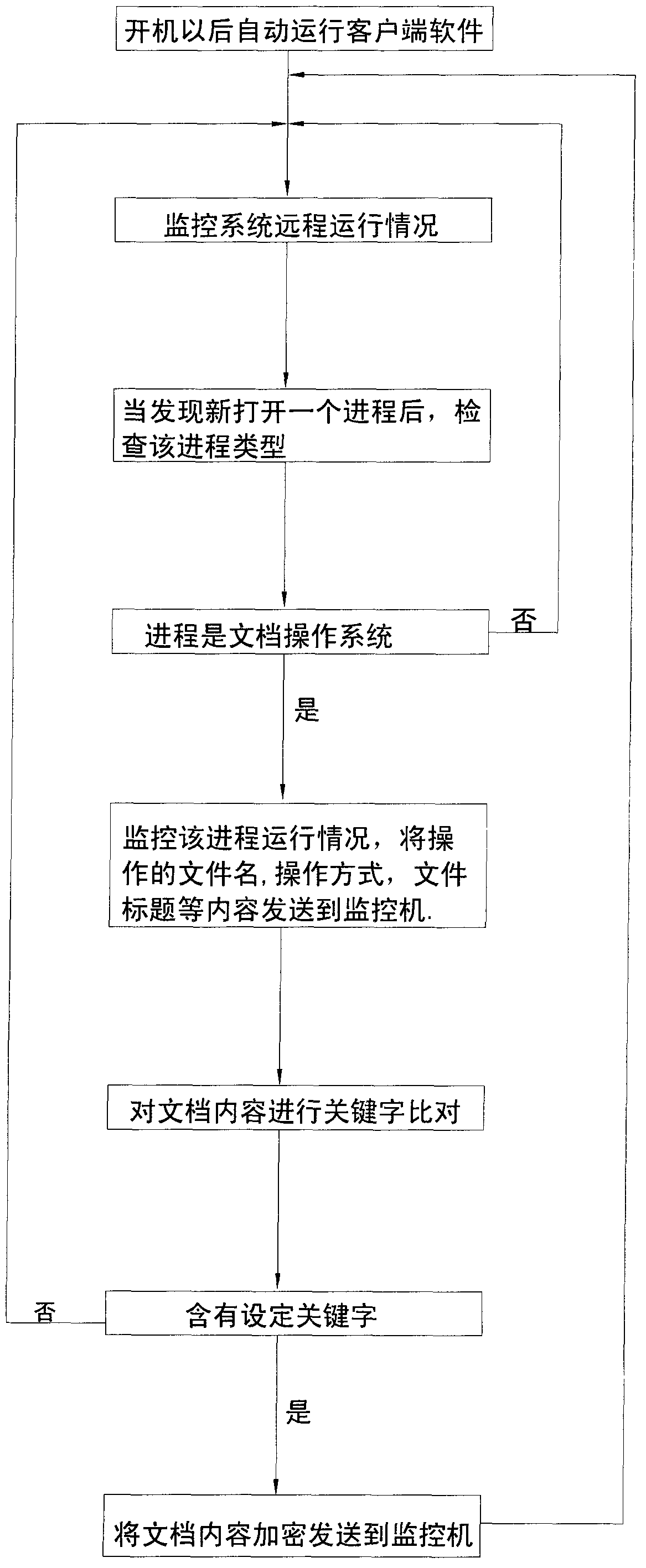
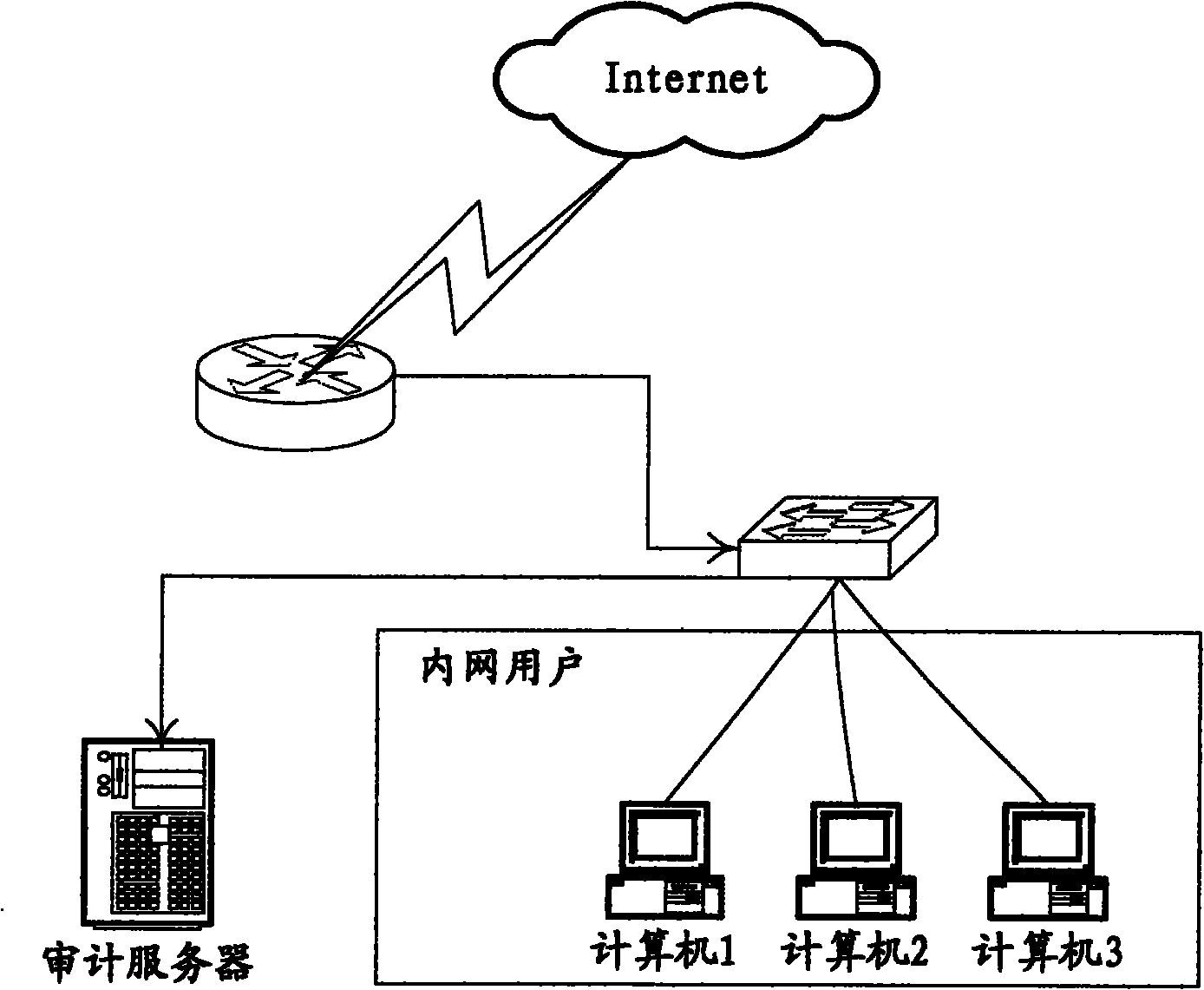
Computer document operational safety audit system
ActiveCN103413088AEnsure safetyIntegrity guaranteedPlatform integrity maintainanceClient-sideDocument preparation
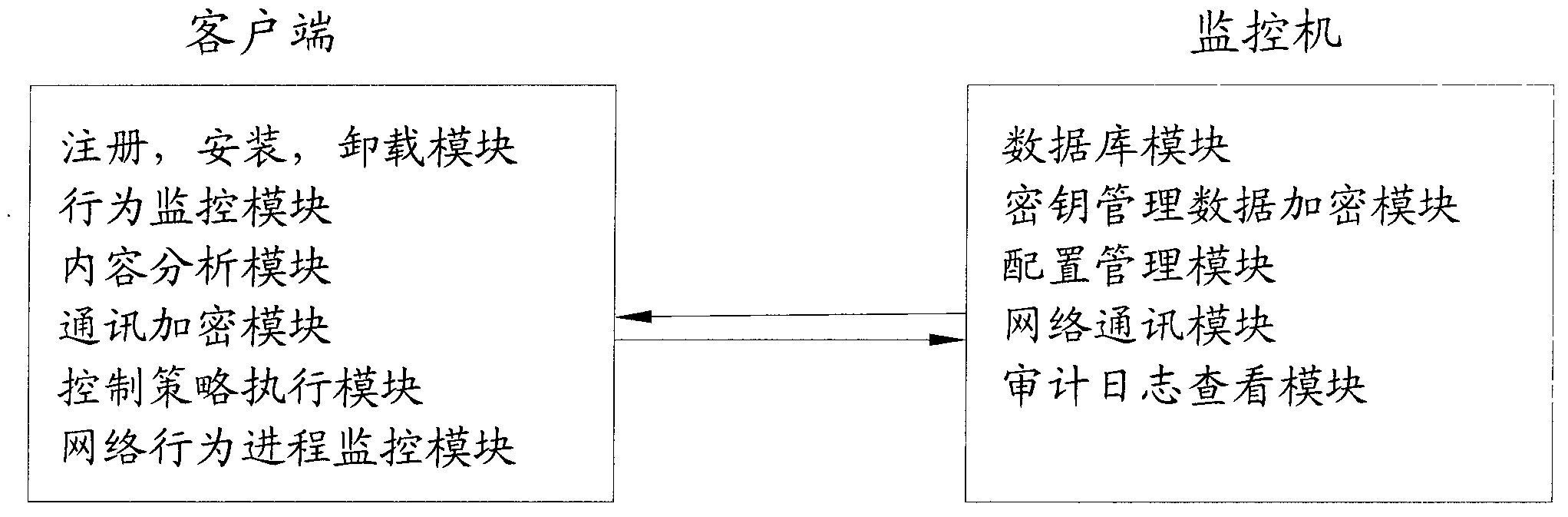
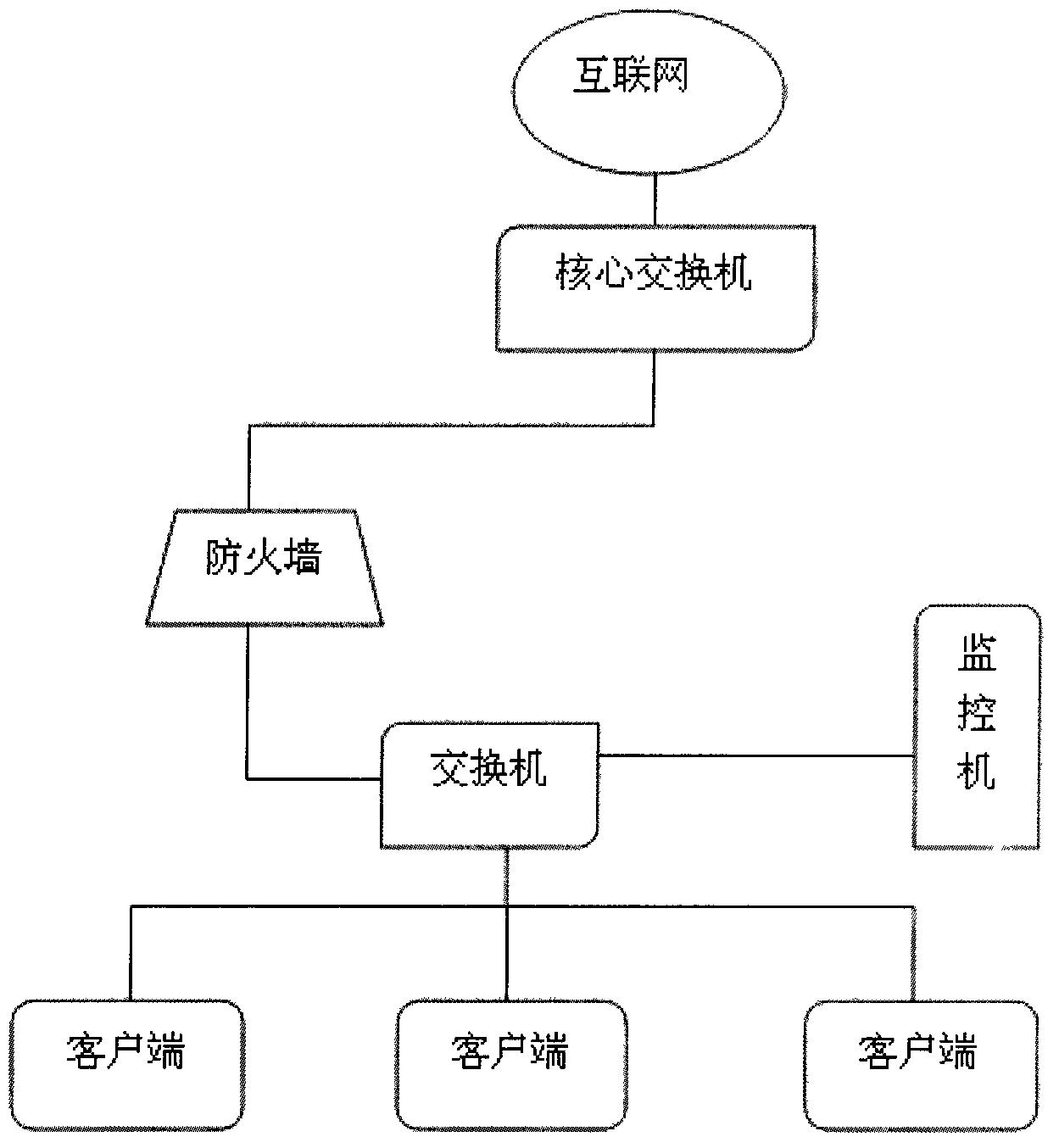
The invention discloses a computer document operational safety audit system which is characterized by comprising a monitor and client side software. According to the computer document operational safety audit system, editing work of a monitored terminal document is monitored, according to a predefined strategy, the secret related performance of the document is automatically analyzed, a title of the edited document is recorded to be a log to be sent to a secrecy competent department, the network function of a computer is immediately shielded when the condition that the edited document is possibly related to secrets is discovered, secret divulging behaviors are prevented, meanwhile, an alarm is given to the secrecy competent department and related leaders for check in the future, besides the monitoring on the document edited by users, secret related performance analysis will be automatically carried out on the document when operations such as copying, shearing and printing are carried out on the document, once the secret related function is discovered, the alarm is given to an alarm server, and the copy of the document is saved on the alarm server for check in the future.
Owner:深圳市利谱信息技术有限公司
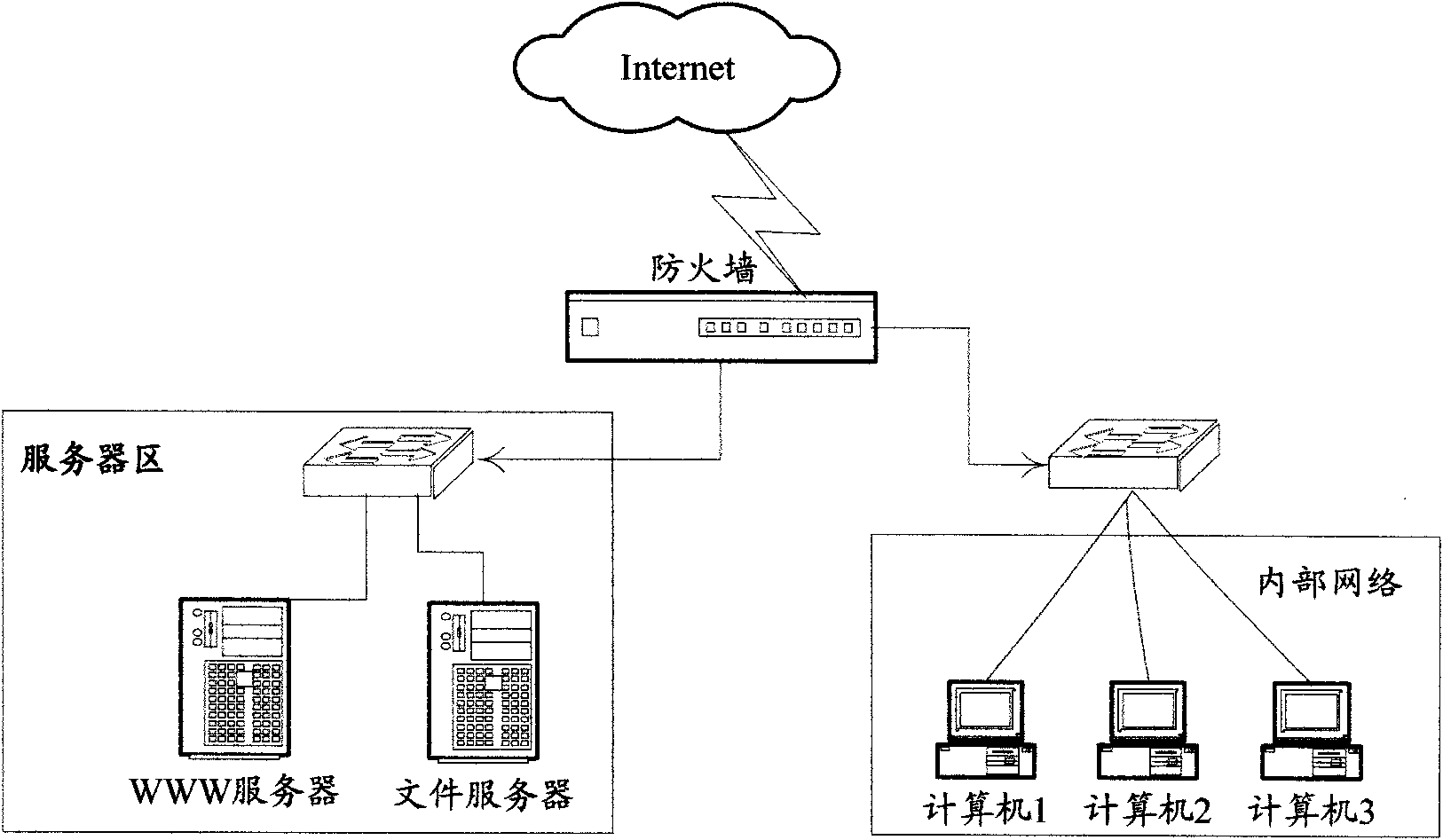
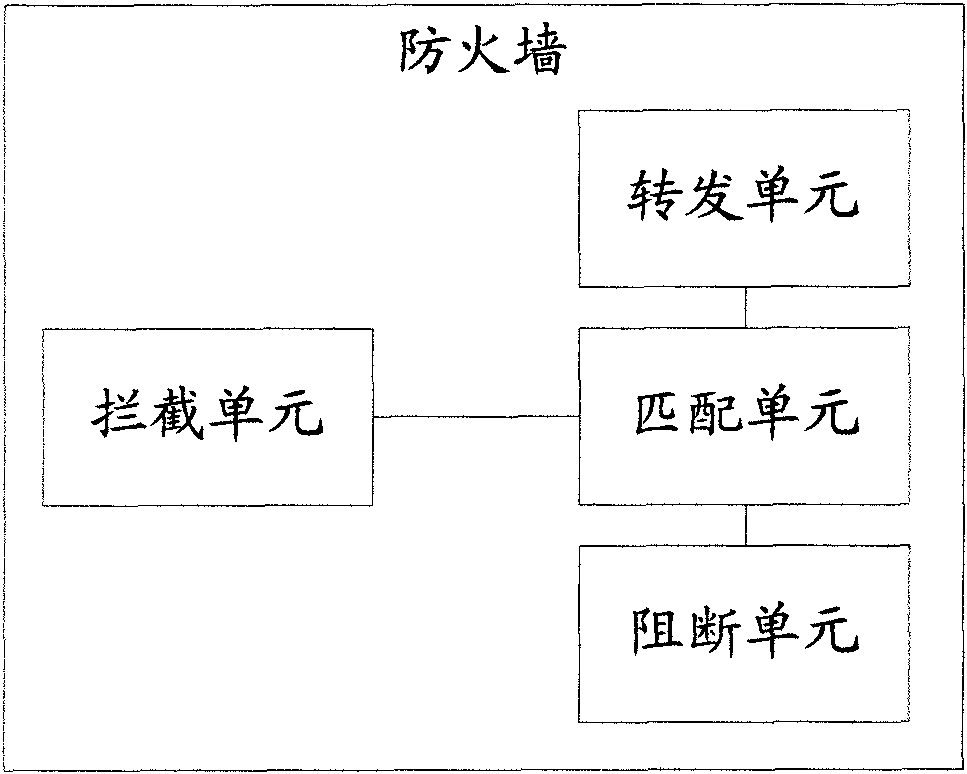
Method for preventing sensitive data from betraying confidential matters and device thereof
The invention discloses a method for preventing sensitive data from betraying confidential matters and a device thereof, and relates to the field of network security, aiming at solving the problem that the existing technology for preventing sensitive data from betraying confidential matters can not effectively prevent the sensitive data from betraying confidential matters. The method comprises the steps that a firewall intercepts connecting request sent by an access source; sensitive data access policy matching is carried out on the connecting request by the firewall; if the matching result is allowed, the connecting request is transmitted, and target data is allowed to be accessed; and if the matching result is not allowed, the connecting request is blocked. The firewall comprises an intercepting unit used for intercepting the connecting request sent by an access source, a matching unit used for carrying out sensitive data access policy matching on the intercepted connecting request, a transmitting unit used for transmitting the connecting request and allowing the target data to be accessed when the matching result is allowed to be triggered, and a blocking unit used for blocking the connecting request when the matching result is not allowed to be triggered.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
Substrate storage container
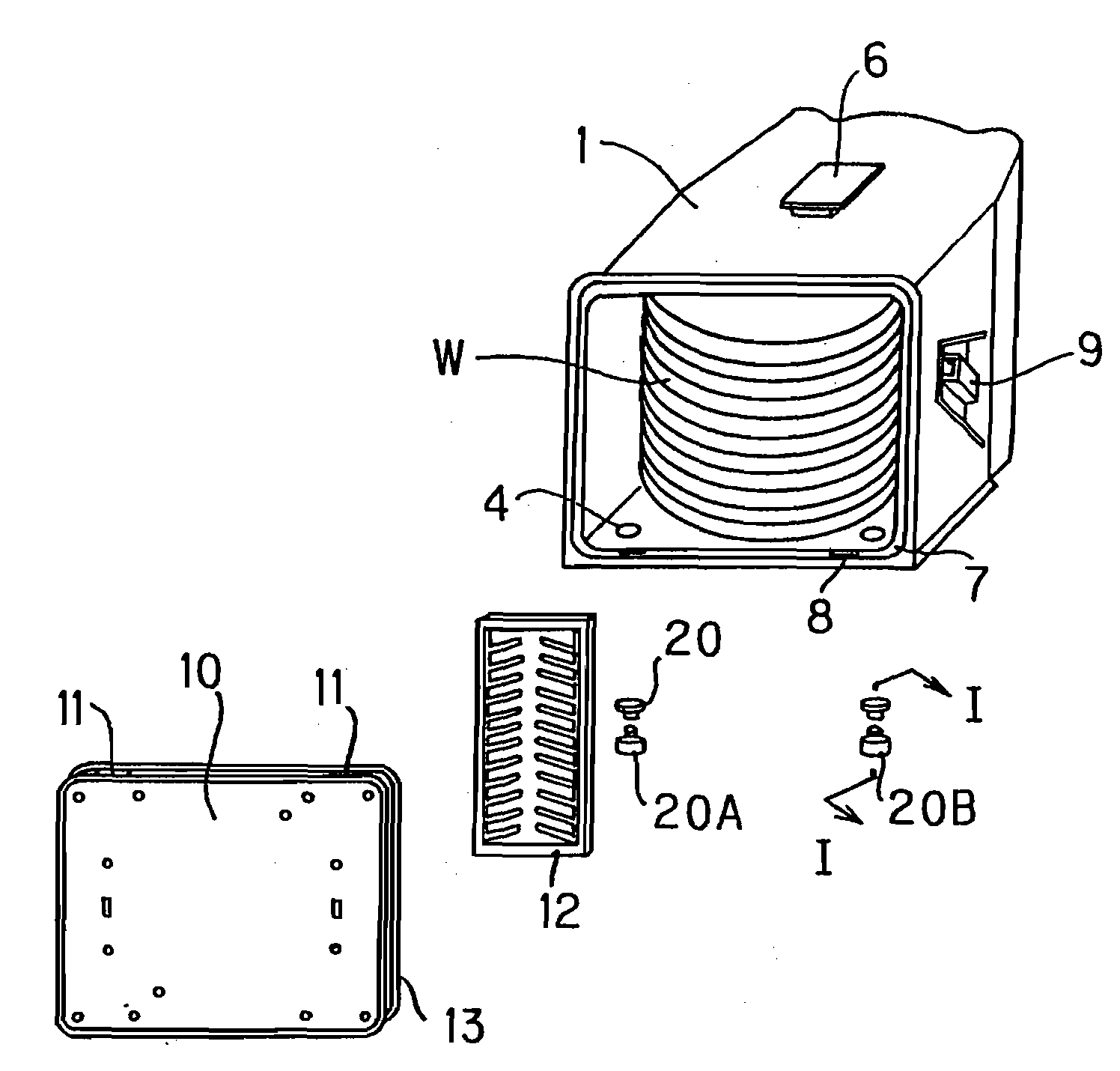
InactiveUS20080149528A1Avoid displacementPrevent leaksOperating means/releasing devices for valvesCheck valvesEngineeringCheck valve
Owner:SHIN-ETSU POLYMER CO LTD
Method for auditing TIM chat contents
ActiveCN108965105APrevent leaksImprove the safety of useProgram loading/initiatingData switching networksSystem administratorApplication software
A method for auditing TIM chat contents comprises the following steps: a) installing a windows message hook function; b) loading the DLL dynamic library of the windows system into a TIM application program through the windows message hook function; c) storing the real address as an original address; d) completing a hook operation of an export function of the message sending and receiving in the TIM program; e) the windows message hook function judging whether the sent message and the file contains secret-related key words set by a system administrator; f) the windows message hook function blocking a sent message or a file; g ) the windows system storing the message or the file sent by the TIM application program to a local sqlite database of the system. The message sending and receiving export functions of a TIM chat tool are obtained, and the chat information is analyzed and blocked, so that the audit on the chat information by the TIM software is improved, and secret divulging is prevented.
Owner:山东华软金盾软件股份有限公司
Robot transmission with pressure compensation device
ActiveCN103429396APrevent leaksDouble leak resistanceProgramme-controlled manipulatorGearing detailsPaint robotHand held
The invention relates to a robot transmission (1) for a multi-axis robot, in particular for a painting robot or a hand-held robot of a painting system for painting motor vehicle body components. Said transmission comprises a transmission housing (6) which is filled, when in operation, at least partially with a lubricant according to an operationally-dependent lubricant pressure, in order to lubricate the robot transmission (1), and has a construction-defined maximum pressure for the lubrication pressure. The transmission housing (6) is not air-tight if the lubrication pressure in the transmission housing (6) exceeds the maximum pressure. According to the invention, the robot transmission also comprises a pressure compensation device (7) which compensates the pressure in the transmission housing (6) and thus prevents the lubrication pressure in the transmission housing (6) from exceeding the maximum pressure.
Owner:DUERR SYST GMBH
Wireless authentication secretive mobile storage apparatus and encryption authenticating method
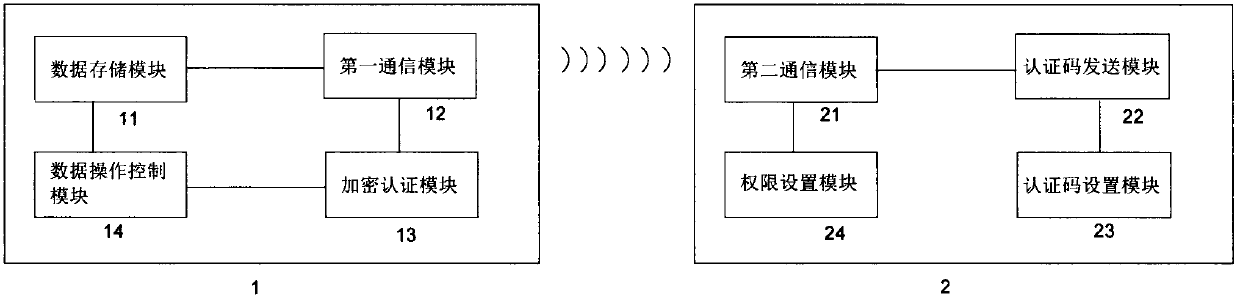
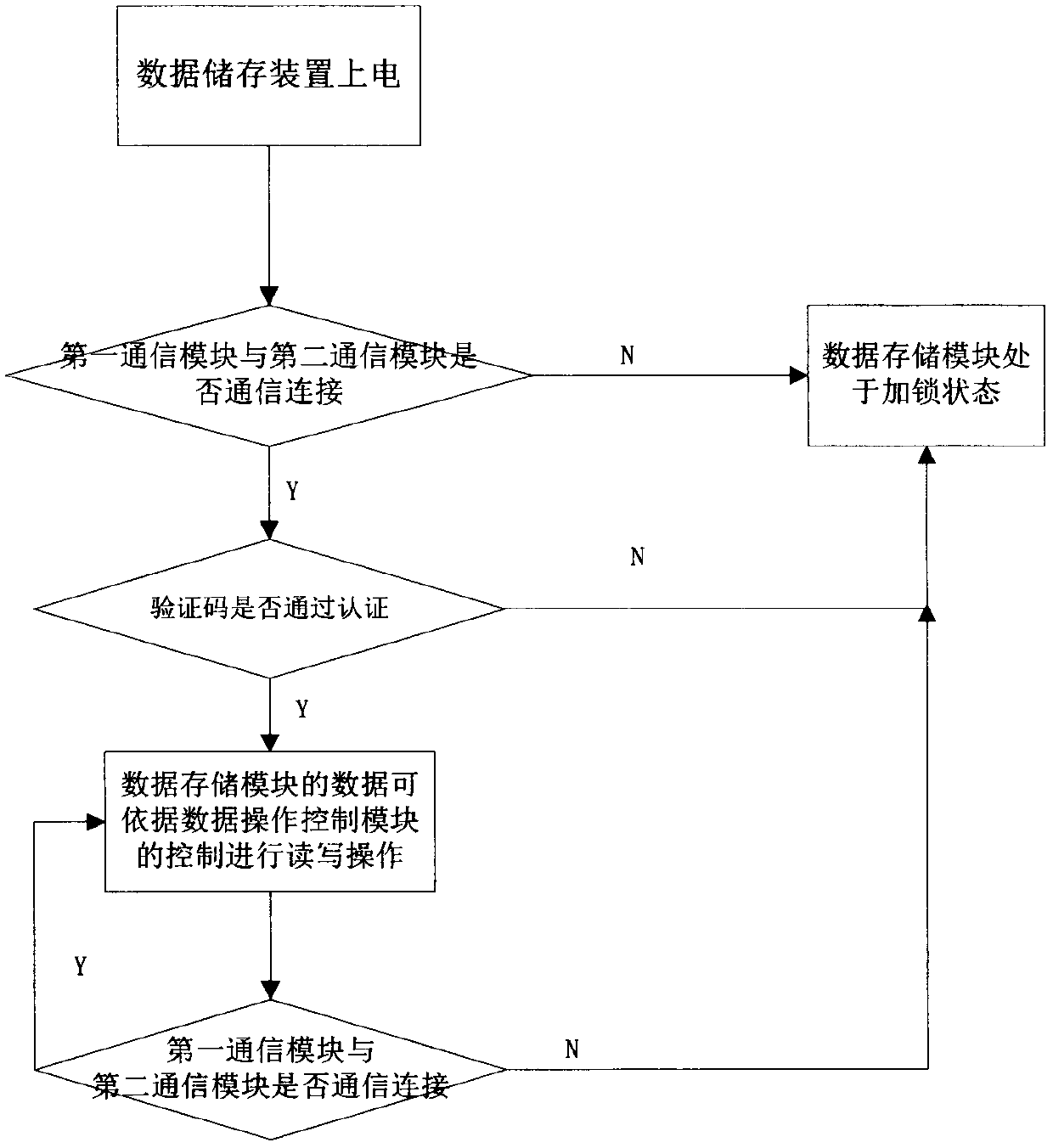
InactiveCN107864133AEnsure safetyPrevent leaksDigital data protectionInternal/peripheral component protectionRemovable mediaEncryption
The invention provides a wireless authentication secretive mobile storage apparatus. The wireless authentication secretive mobile storage apparatus comprises a data storage apparatus and an encryptionauthenticating apparatus; the data storage apparatus includes a data storage module, a first communication module, an encryption authenticating module and a data operation control module; the encryption authenticating apparatus includes a second communication module and an authentication code sending module; and when the first communication module is in a communication connection with the secondcommunication module, the authentication code sending module is used for sending an authentication code to the encryption authenticating module, the encryption authenticating module is used for performing authentication on the authentication code and sending authentication information to the data operation control module, and the data operation control module is used for controlling a read / write operation of the data storage module. The wireless authentication secretive mobile storage apparatus is provided with the special encryption authenticating apparatus, so only after being encrypted by the encryption authenticating apparatus, the data can be transmitted; and in this way, the security of the data in the mobile storage apparatus can be effectively guaranteed, the leakage is avoided, and the privacy of a user is protected better.
Owner:卢冠熊
Sensor component housing
InactiveCN103547914APrevent leaksLow costThermometer detailsTemperature measurement in motorsEngineering
Owner:SCHOTT AG
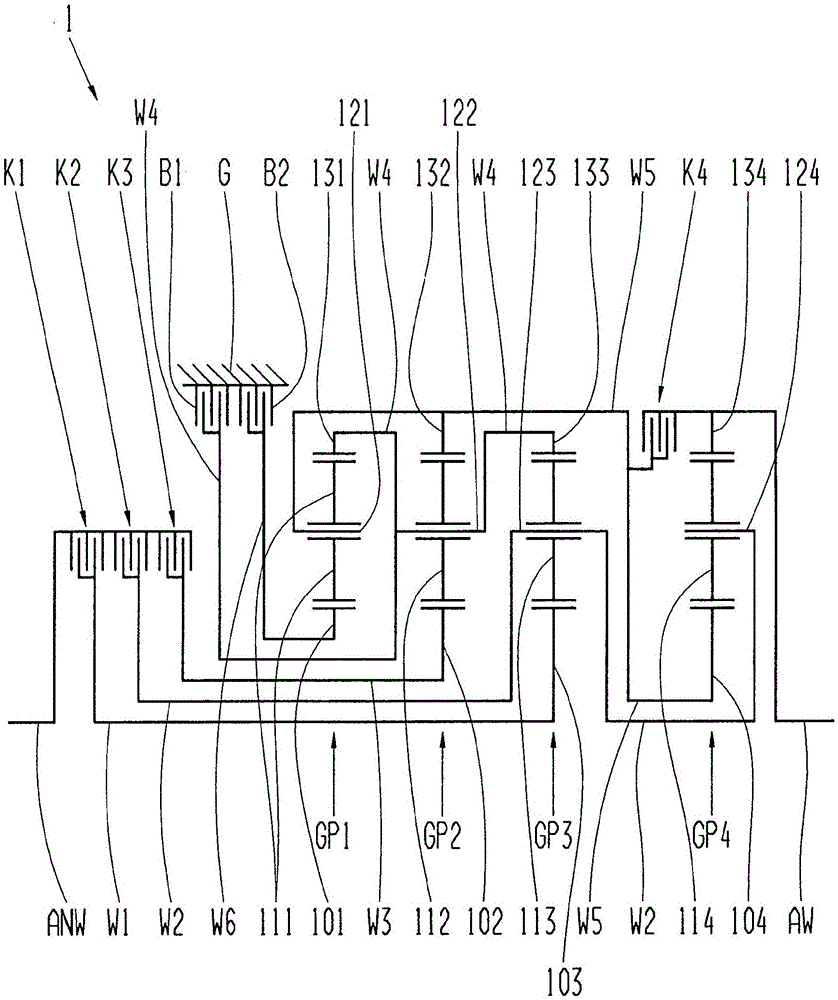
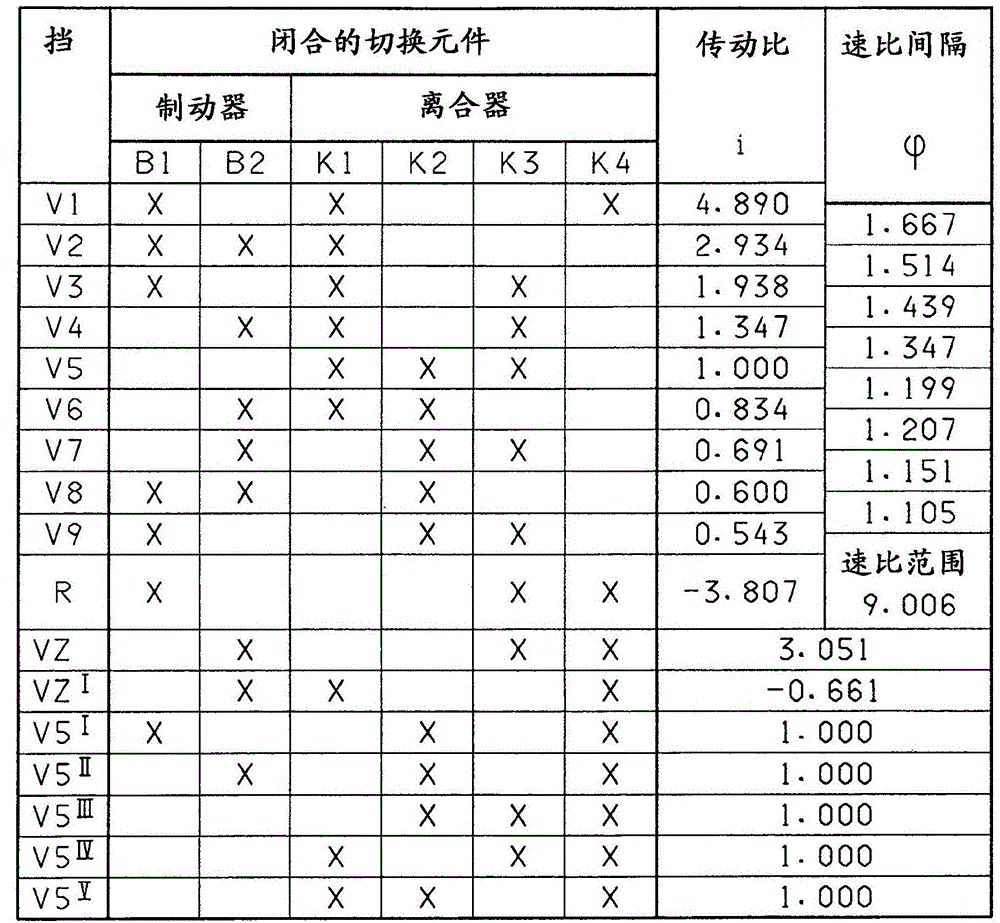
Transmission for a motor vehicle
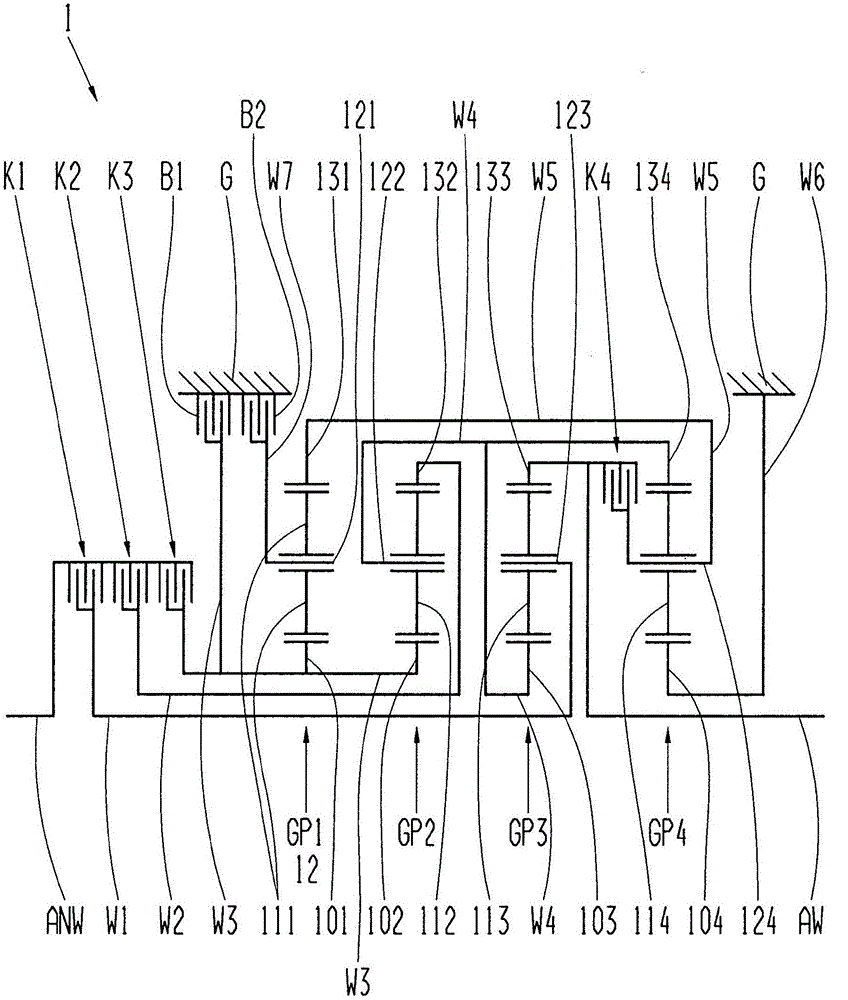
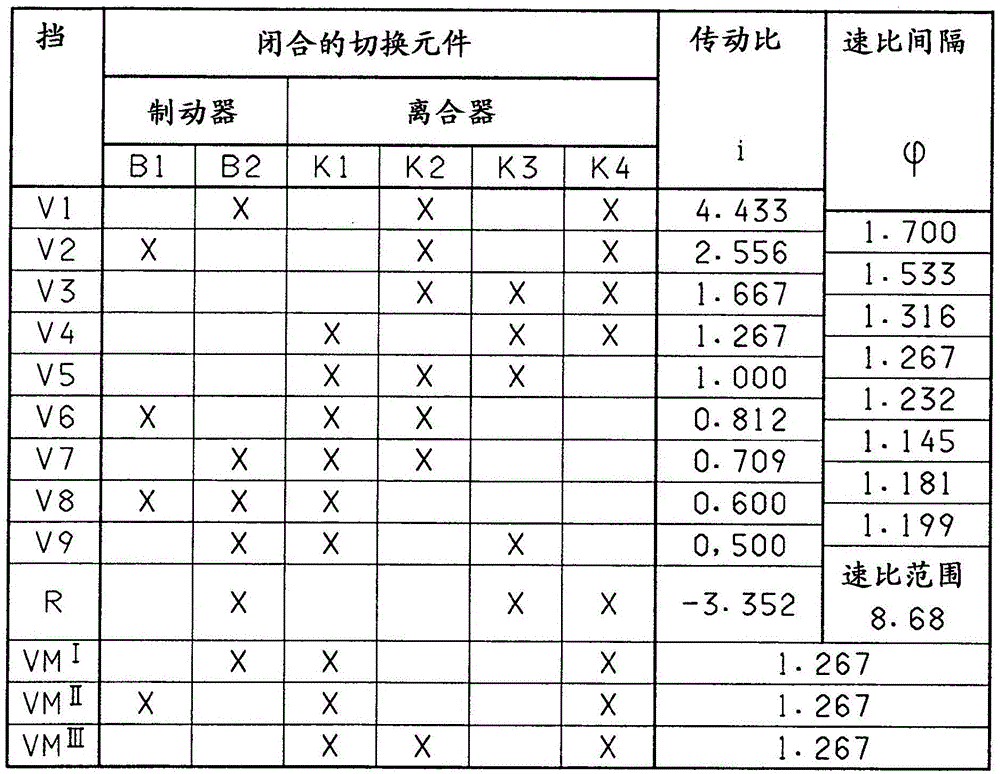
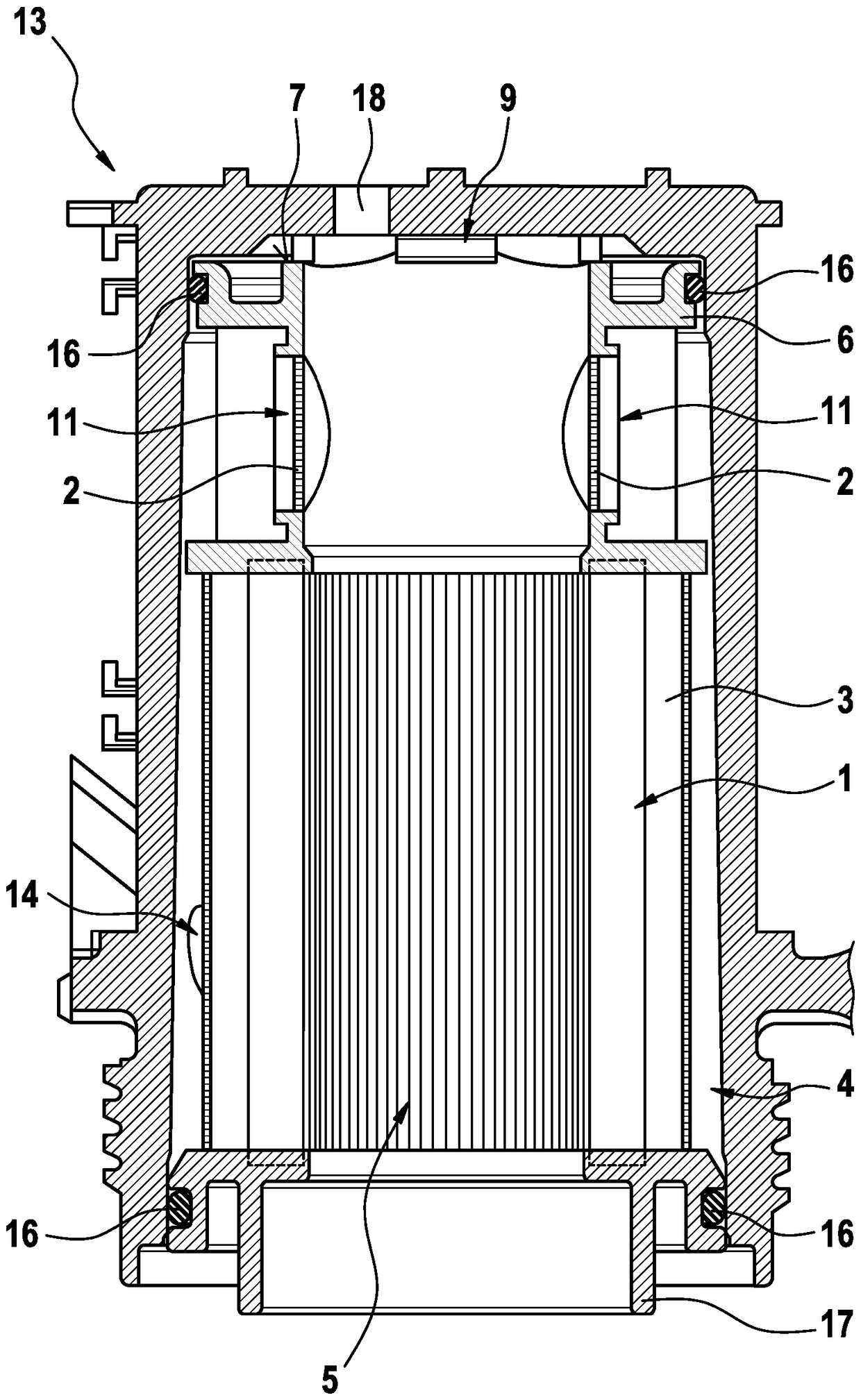
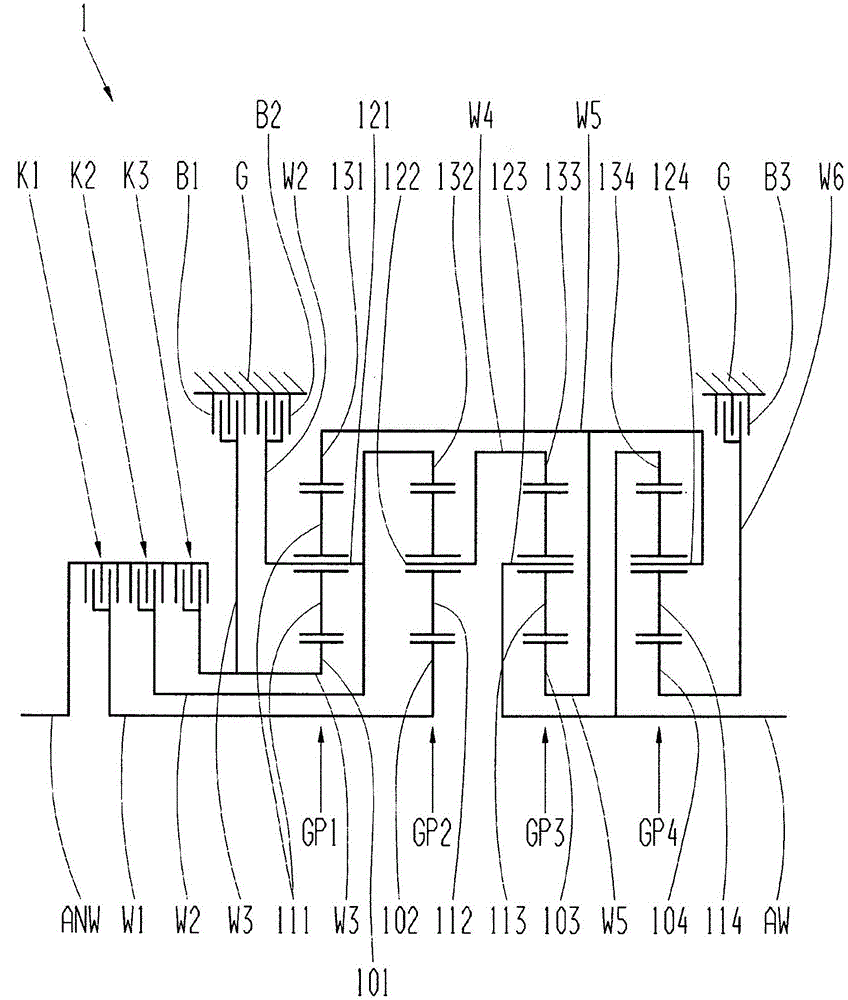
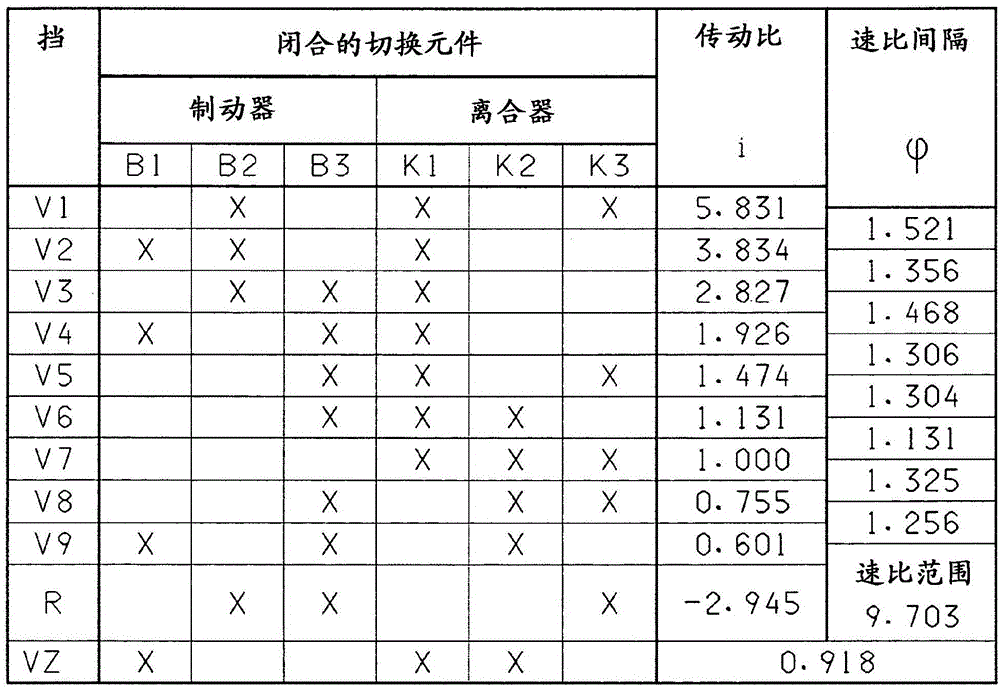
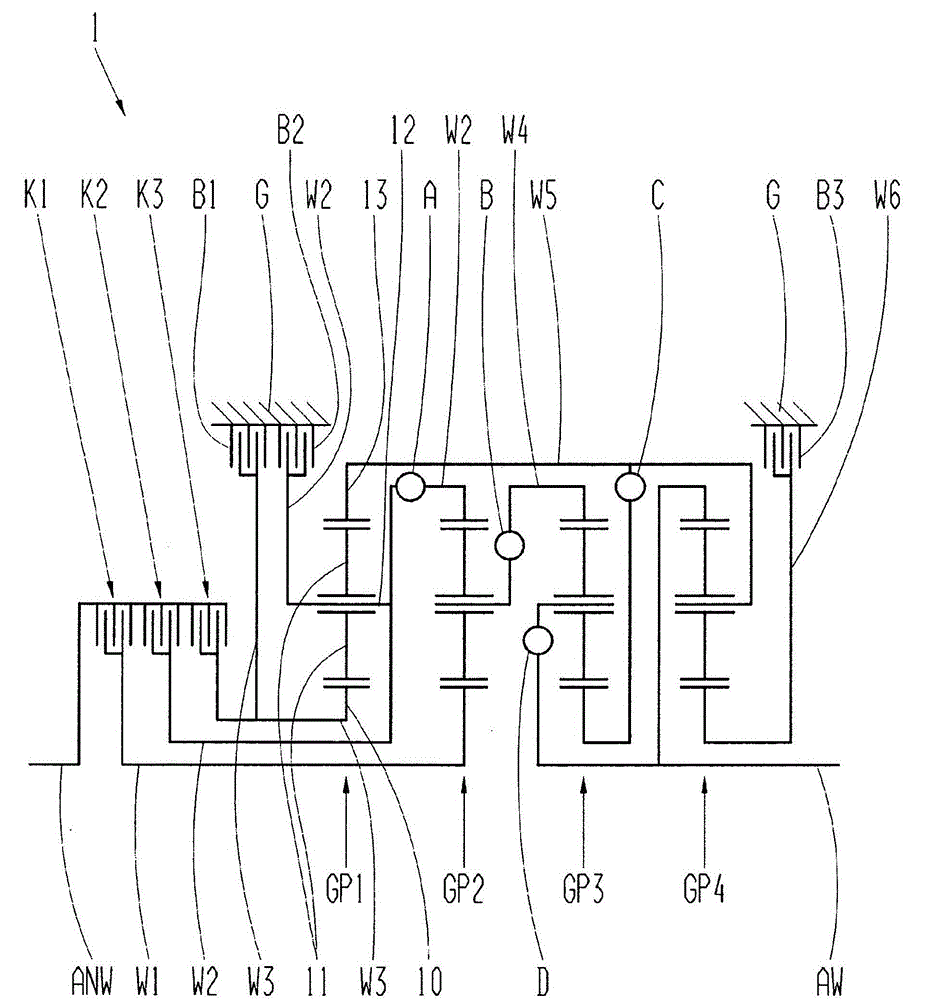
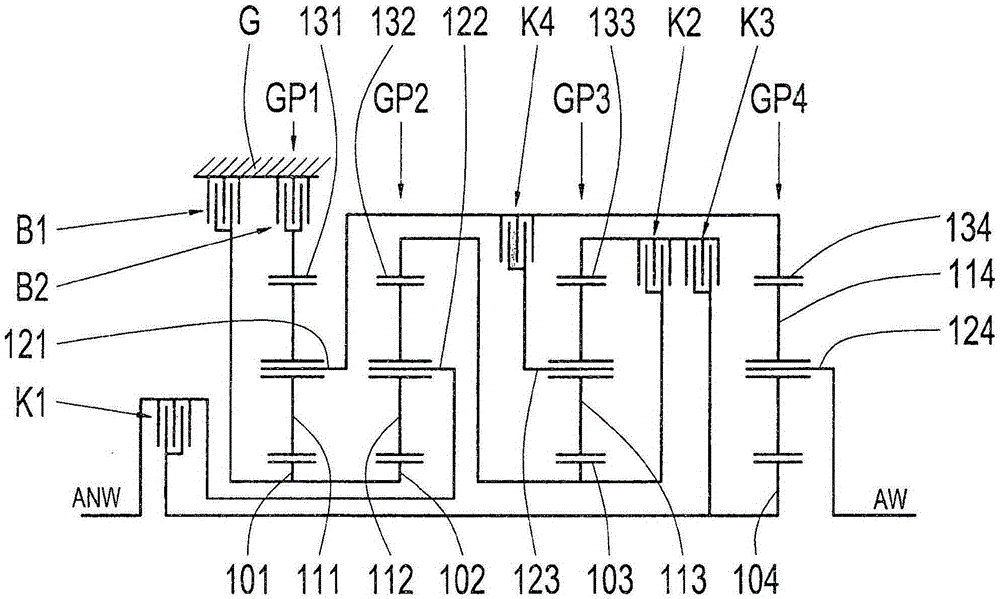
InactiveCN105051419AImprove efficiencyPrevent leaksToothed gearingsTransmission elementsEngineeringSpur gear
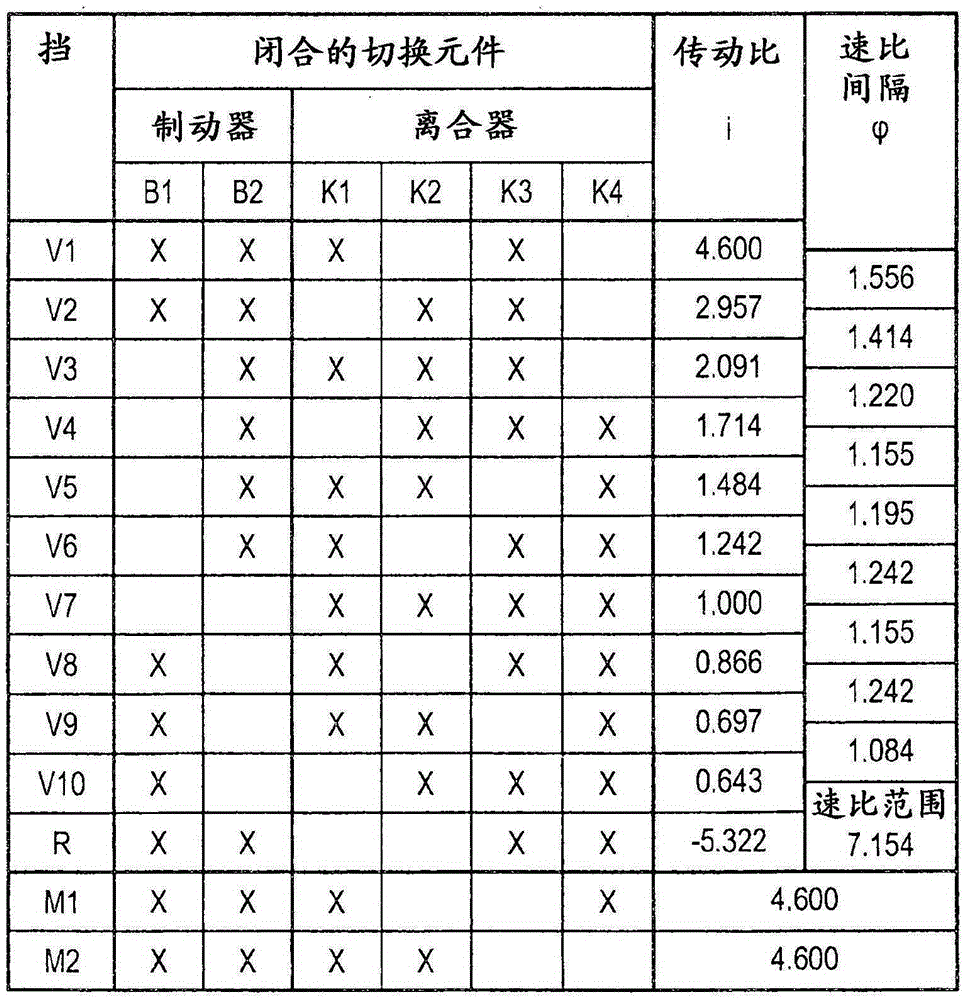
The invention relates to a transmission, in particular multi-stage transmission, for a motor vehicle, comprising a housing, a drive input shaft, a drive output shaft, at least four planetary gear sets and multiple shift elements in the form of at least four clutches and at least two brakes, the planetary gear sets each comprising a sun gear, at least one planet gear, a planet gear carrier and an internal gear, wherein the drive input shaft can be connected by means of the third clutch to the first brake and to the sun gear of the first planetary gear set and to the sun gear of the second planetary gear set, and wherein the internal gear of the first planetary gear set is connected to the planet gear carrier of the fourth planetary gear set, and wherein the planet gear carrier of the fourth planetary gear set can be connected by means of the fourth clutch to the drive output shaft, and wherein the sun gear of the fourth planetary gear set is connected to the housing, and wherein the second brake is connected to the planet gear carrier of the first planetary gear set.
Owner:ZF FRIEDRICHSHAFEN AG
Reducible relief opening
InactiveCN102245904ASmall flow cross-sectional areaAvoid adverse consequencesPump componentsPump controlEngineeringCentrifugal pump
The invention relates to a reducible relief opening. A single or multi-stage centrifugal pump has a driven impeller (1) or impellers disposed in the pump housing and a shaft seal. The impeller has one or more adjustable relief openings (4) in at least one cover disc (3). One or more sleeve-like inserts (12, 13) are disposed in one or more relief openings (4).
Owner:KSB AG
Substrate storage container
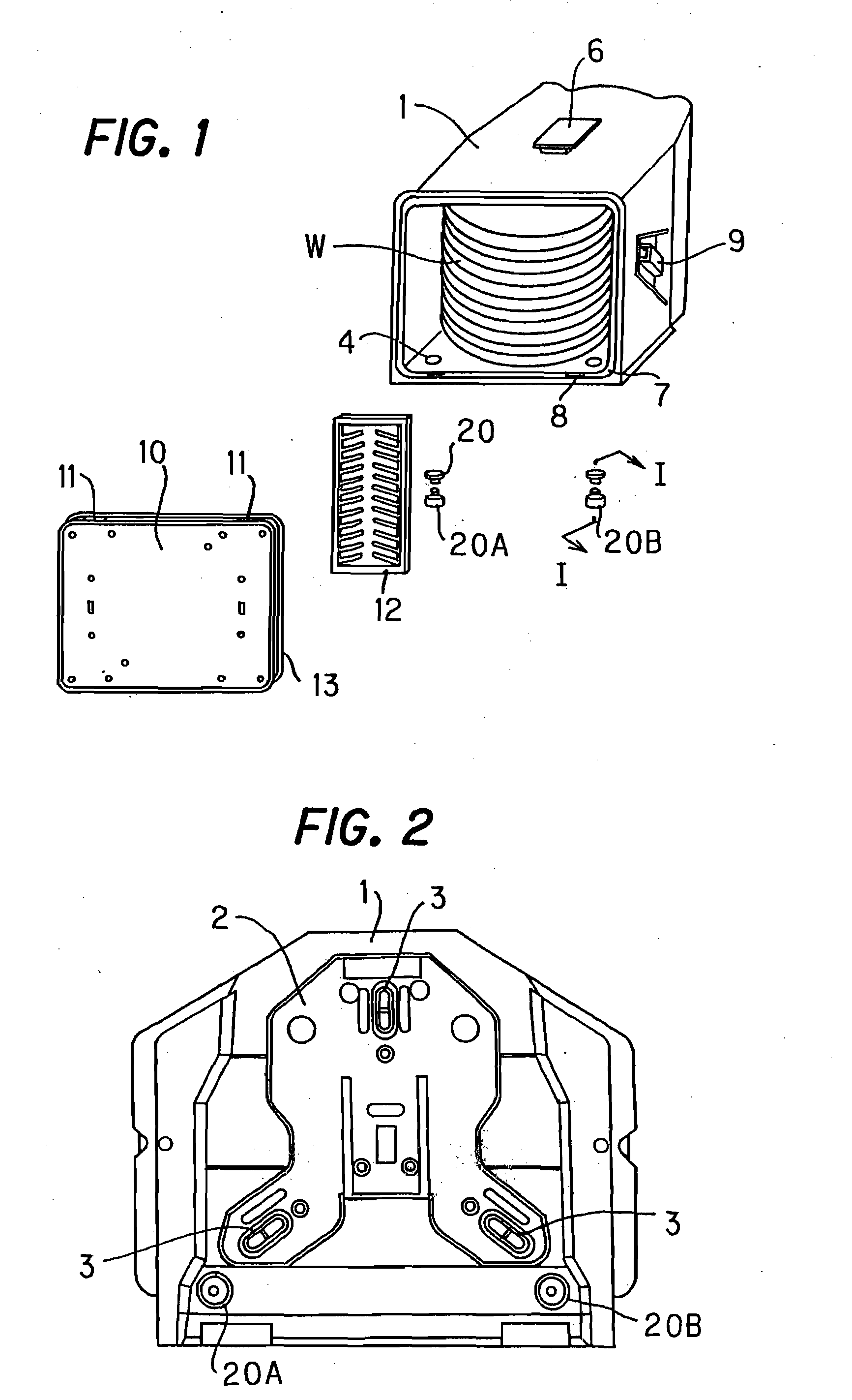
InactiveUS20080149527A1Avoid displacementPrevent leaksOperating means/releasing devices for valvesCheck valvesEngineeringCheck valve
A substrate storage container includes a container body for accomodating and aligning semiconductor wafers, a door which opens and closes the front of the container body and a pair of valve units disposed at the bottom of the container body for controlling gas flow. Each valve unit includes a fixed sleeve for gas flow, fitted in a rib of a through-hole of the container body, a holding sleeve fitted in the through-hole of the container body with an o-ring interposed therebetween and mated and threaded with the fixed sleeve, a check valve built between the fixed sleeve and the holding sleeve, leaving a clearance, an elastically deformable element for opening and closing the check valve, an interior lid sleeve for gas flow, opposing the check valve and supporting the elastically deformable element, and a filter interposed between the holding sleeve and the interior lid sleeve.
Owner:SHIN-ETSU POLYMER CO LTD
Suppression method of offshore ground clutter and azimuth ambiguity thereof of SAR images
ActiveCN110261855ANo loss of azimuth resolutionPrevent leaksRadio wave reradiation/reflectionImage resolutionRadar
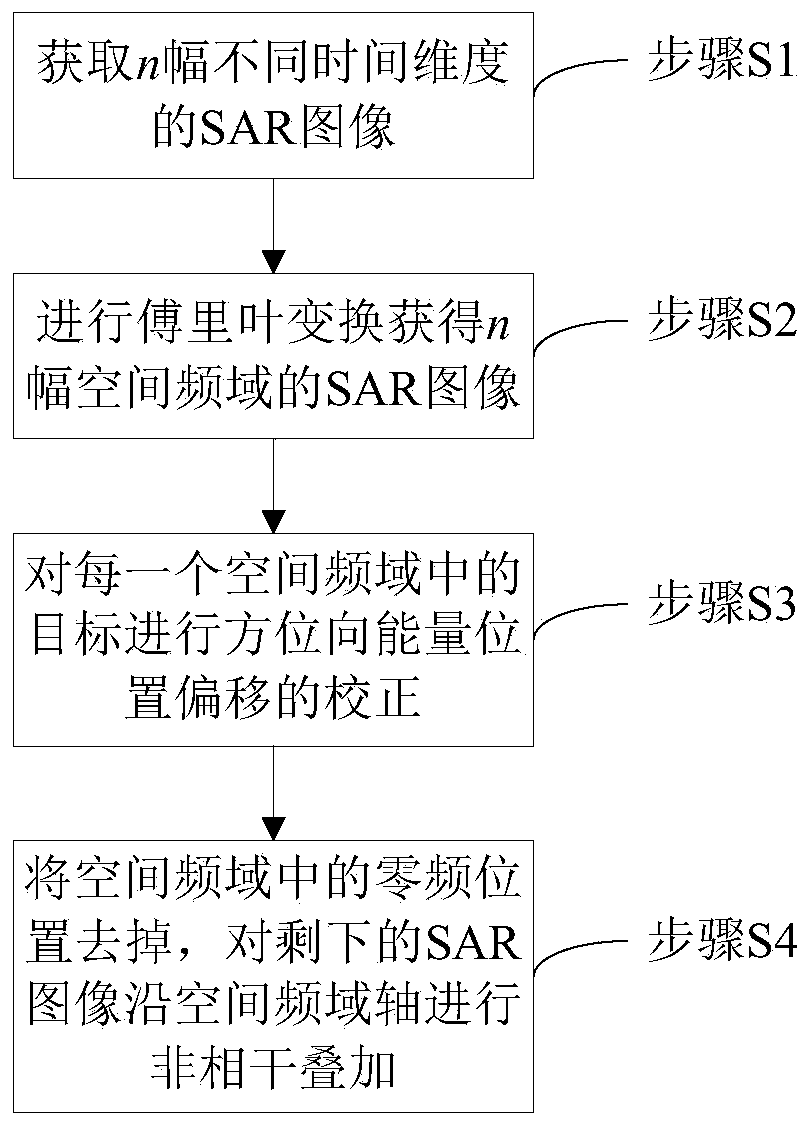
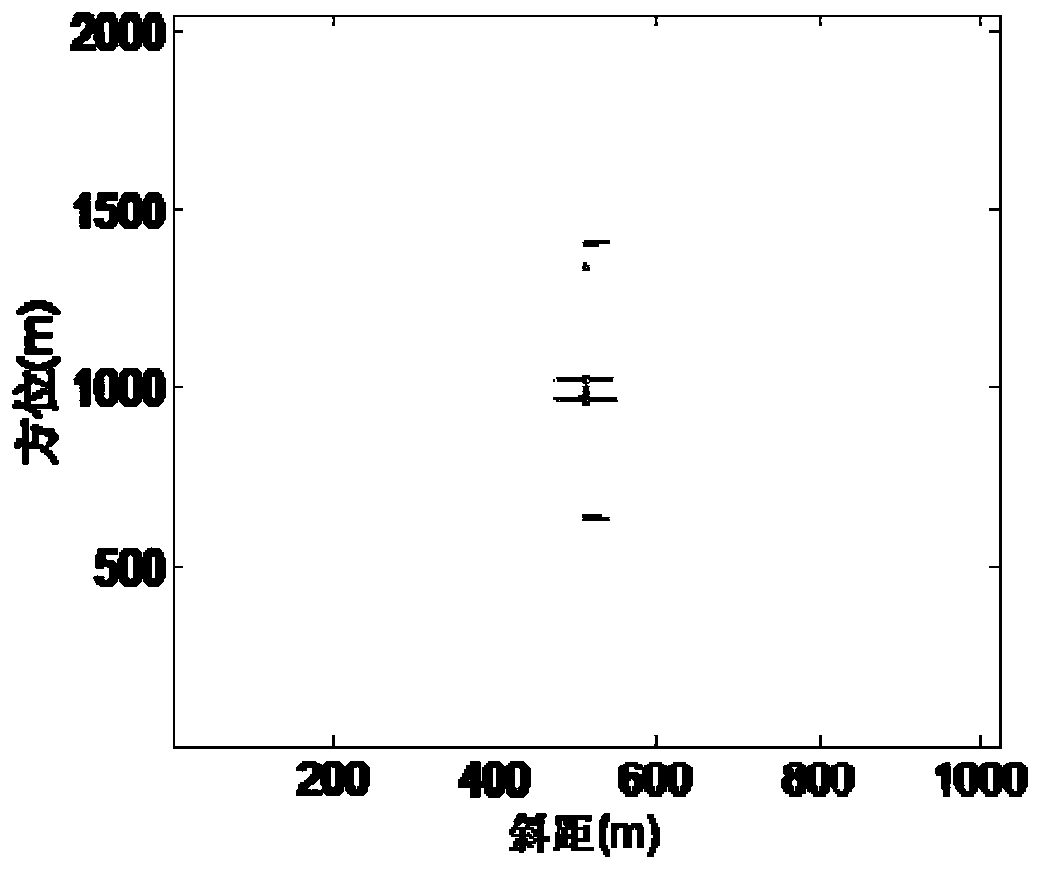
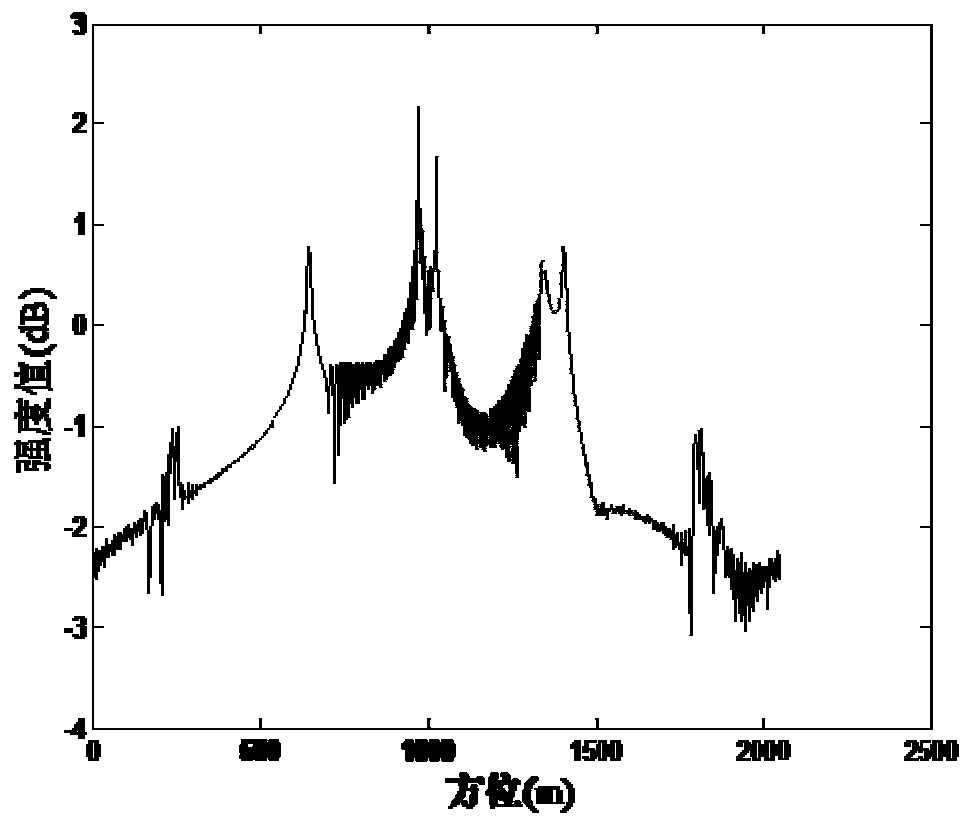
The invention relates to a suppression method of offshore ground clutter and azimuth ambiguity thereof of SAR images. The method comprises the following steps of: acquiring SAR images of the same scene region at different moments through radar to obtain n SAR images with different time dimensions, performing Fourier transform on the obtained n SAR images with different time dimensions along the time dimensions to obtain n SAR images in a space frequency domain, accumulating a stationary target and distance and azimuth ambiguity energy thereof in the n SAR images in the space frequency domain at a zero frequency position in the space frequency domain, removing the zero frequency position in the space frequency domain, and performing incoherent superposition on the rest SAR images along a space frequency domain axis to obtain a pure ocean SAR image from which the stationary ground clutter and the azimuth ambiguity thereof are removed. According to the method, the static ground clutter is filtered through the multi-temporal SAR images, the azimuth resolution is not lost while azimuth ambiguity is suppressed, the static ground clutter and azimuth ambiguity energy thereof are completely removed while ocean moving target information is not lost, and the phenomenon of alarm missing is prevented.
Owner:SHANGHAI RADIO EQUIP RES INST
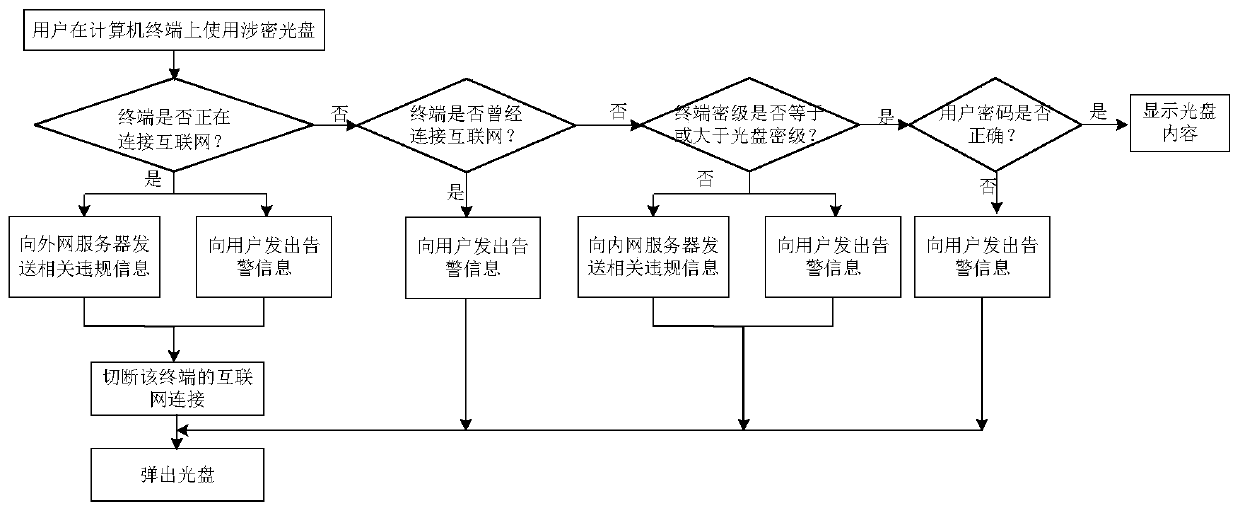
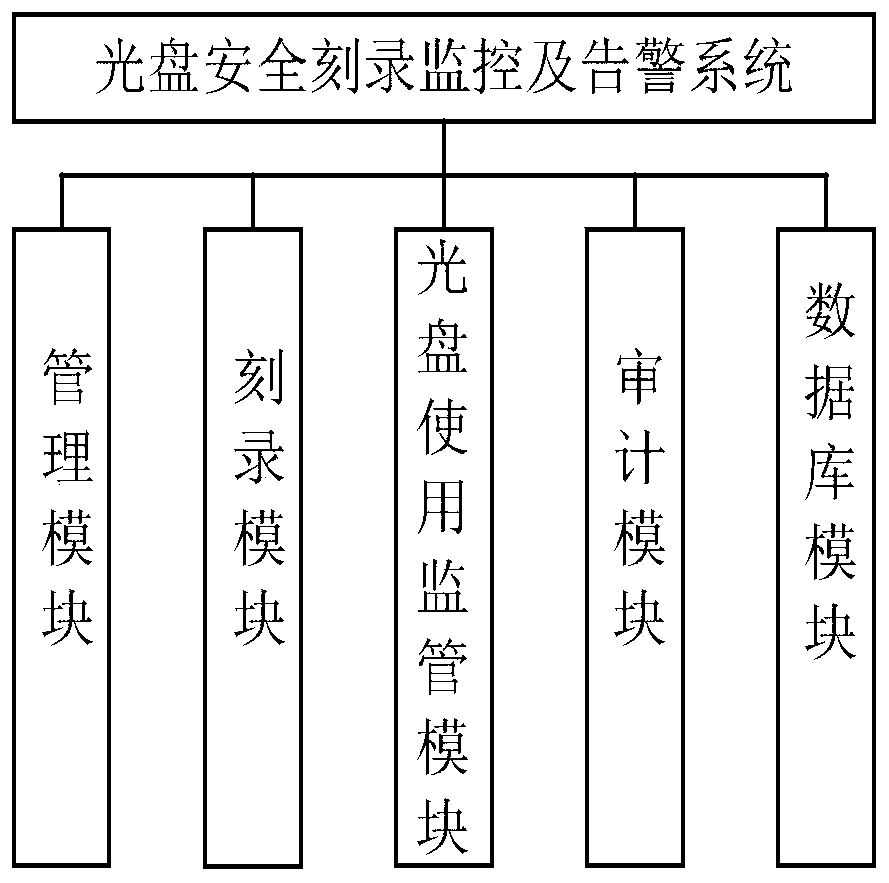
Optical disc safety recording monitoring and alarming method
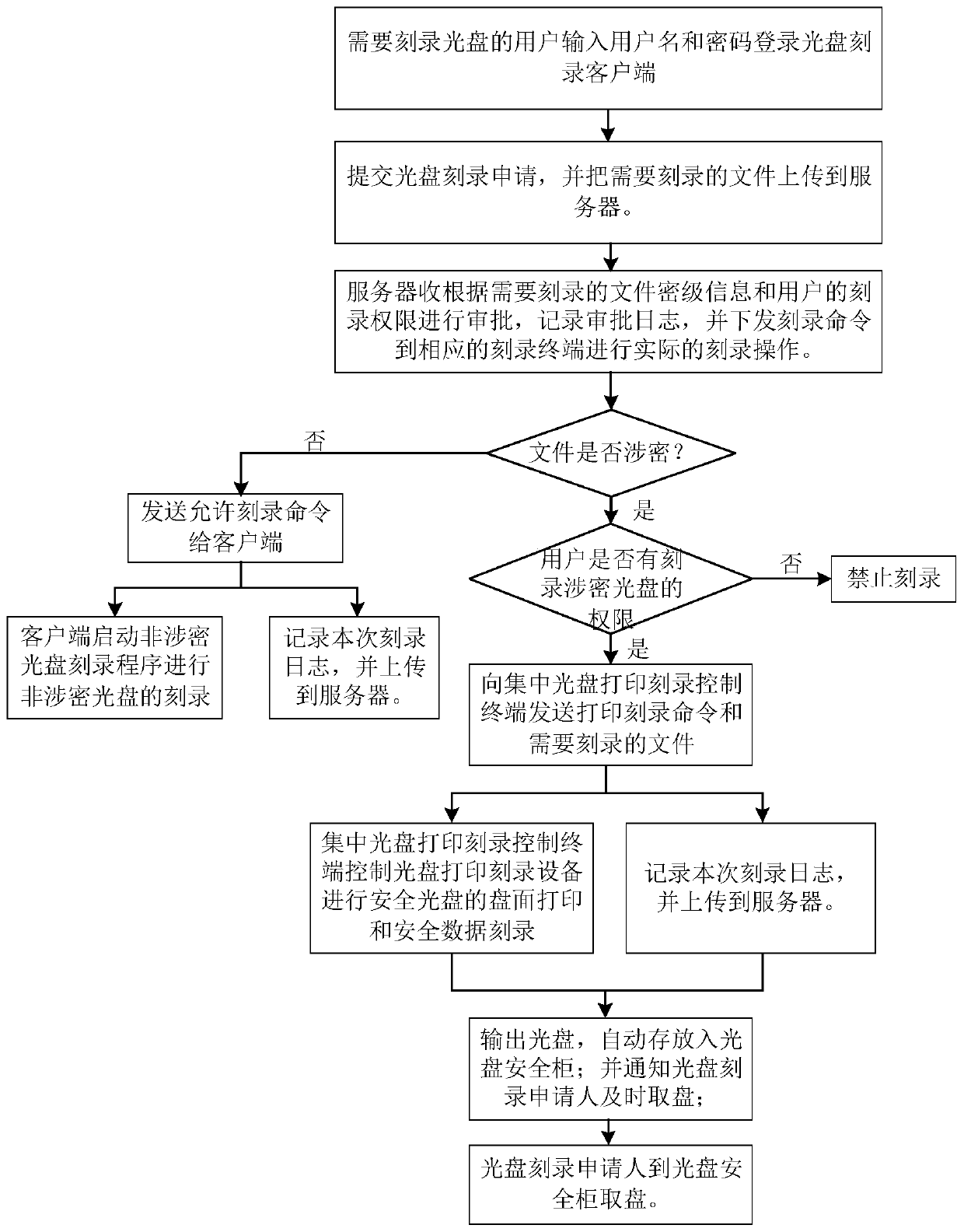
ActiveCN110674538AEnsure safetyPrevent leaksDigital data protectionInternal/peripheral component protectionEngineeringIntranet
The invention discloses an optical disc safety recording monitoring and alarming method. The method comprises the following steps that: firstly, an applicant logs in an optical disk burning client, submits an optical disk burning application, and uploads a file to be burnt to an intranet server for approval; after examination and approval, the recording device carries out actual compact disc recording; after burning is completed, the optical discs are automatically stored in the optical disc safety cabinet; and when the applicant passes identity information authentication, the optical disc canbe taken away, and when a user uses the secret-related optical disc on other computer terminals, a special optical disc monitoring and browsing tool must be operated firstly to check whether the useenvironment is safe or not, prevent illegal use of the optical disc and insert the optical disc into an optical disc recycling box for recycling after the optical disc is used up. According to the invention, the behavior of burning the optical disc is better controlled, the security of secret-related files is ensured, the use of the optical disc is effectively supervised, the illegal use of the optical disc is prevented in time, and the secret leakage of the optical disc in the use process is prevented.
Owner:HANGZHOU DIANZI UNIV
Transmission for motor vehicle
InactiveCN105051417AImprove accessibilityLow costToothed gearingsTransmission elementsDrive shaftEngineering
Transmission, in particular multi-step transmission, for a motor vehicle, comprising a housing, a drive shaft, an output shaft, at least four planetary gear sets, wherein the planetary gear sets in each case comprise a sun gear, a planet, a planetary carrier and an internal gear, and a plurality of shifting elements in the form of at least four clutches and at least two brakes, wherein the drive shaft can be connected via the second clutch to the planetary carrier of the third planetary gear set and the planetary carrier of the fourth planetary gear set, wherein the first brake is connected to the internal gear of the first planetary gear set and to the planetary carrier of the second planetary gear set, wherein the second brake is connected to the sun gear of the first planetary gear set, and wherein the planetary carrier of the first planetary gear set is connected to the sun gear of the fourth planetary gear set.
Owner:ZF FRIEDRICHSHAFEN AG
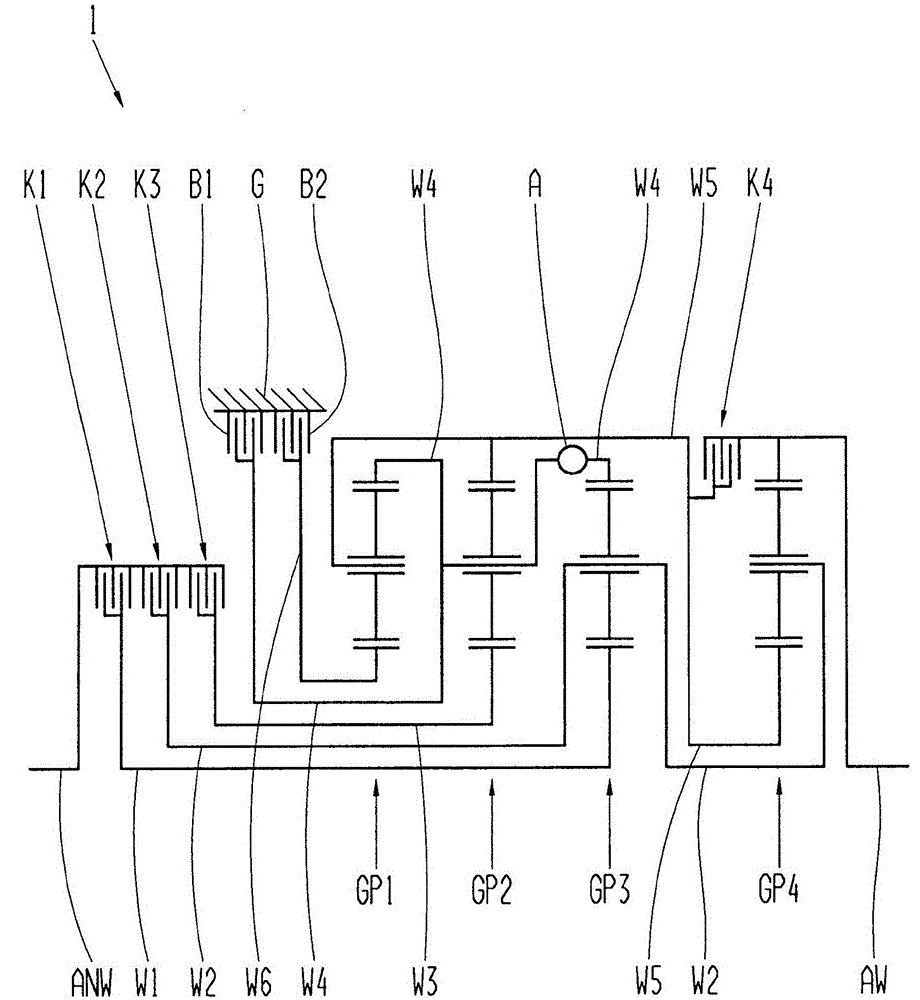
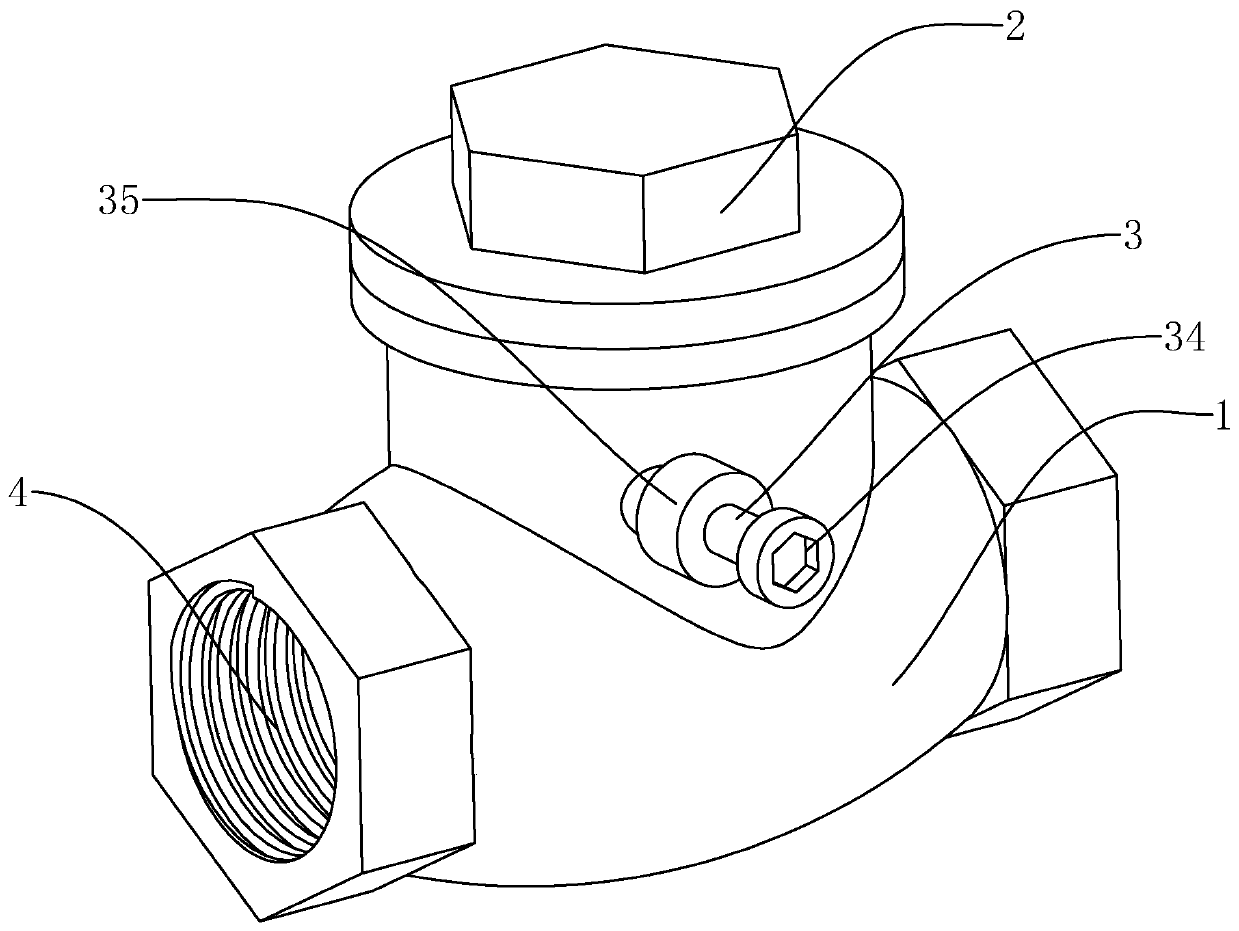
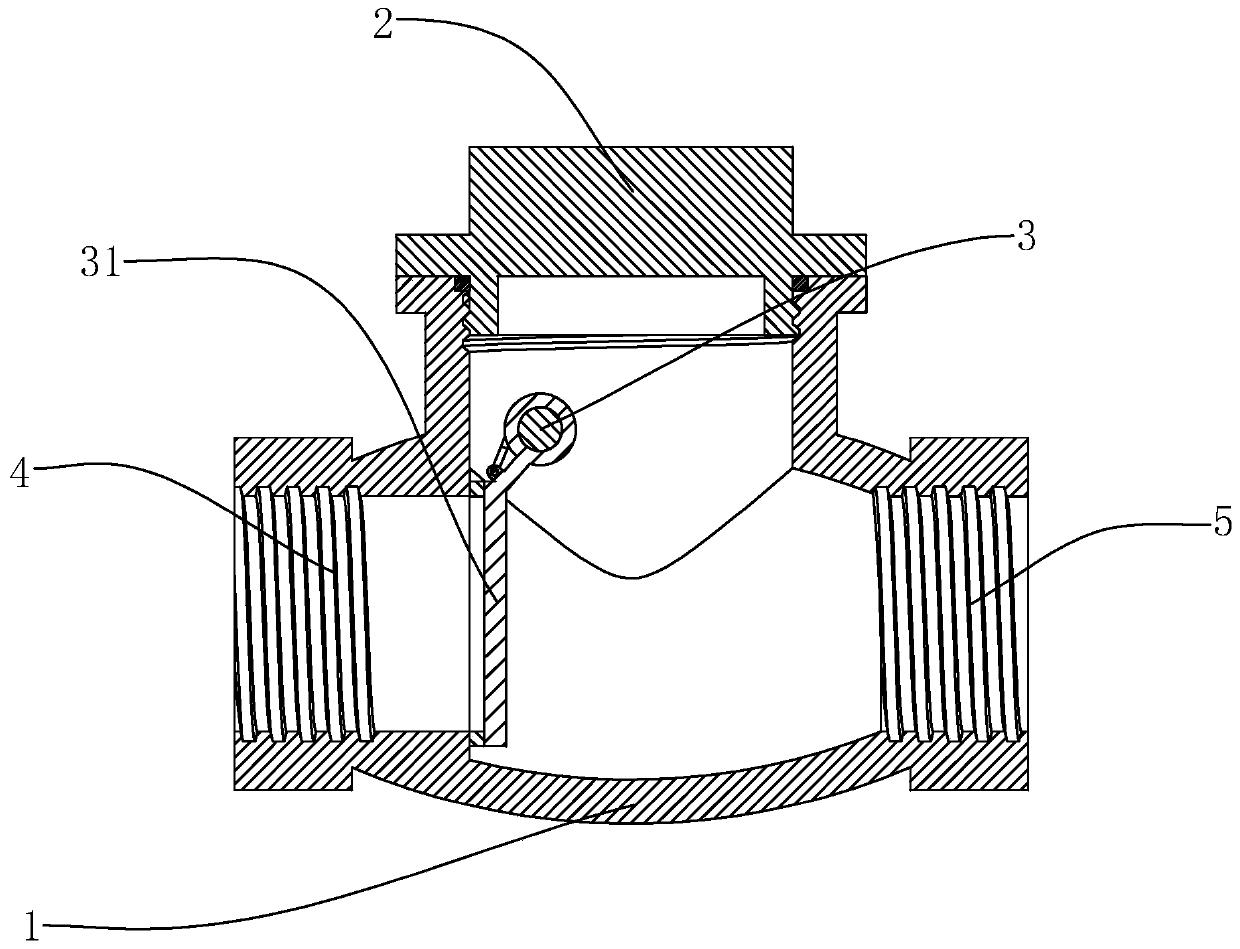
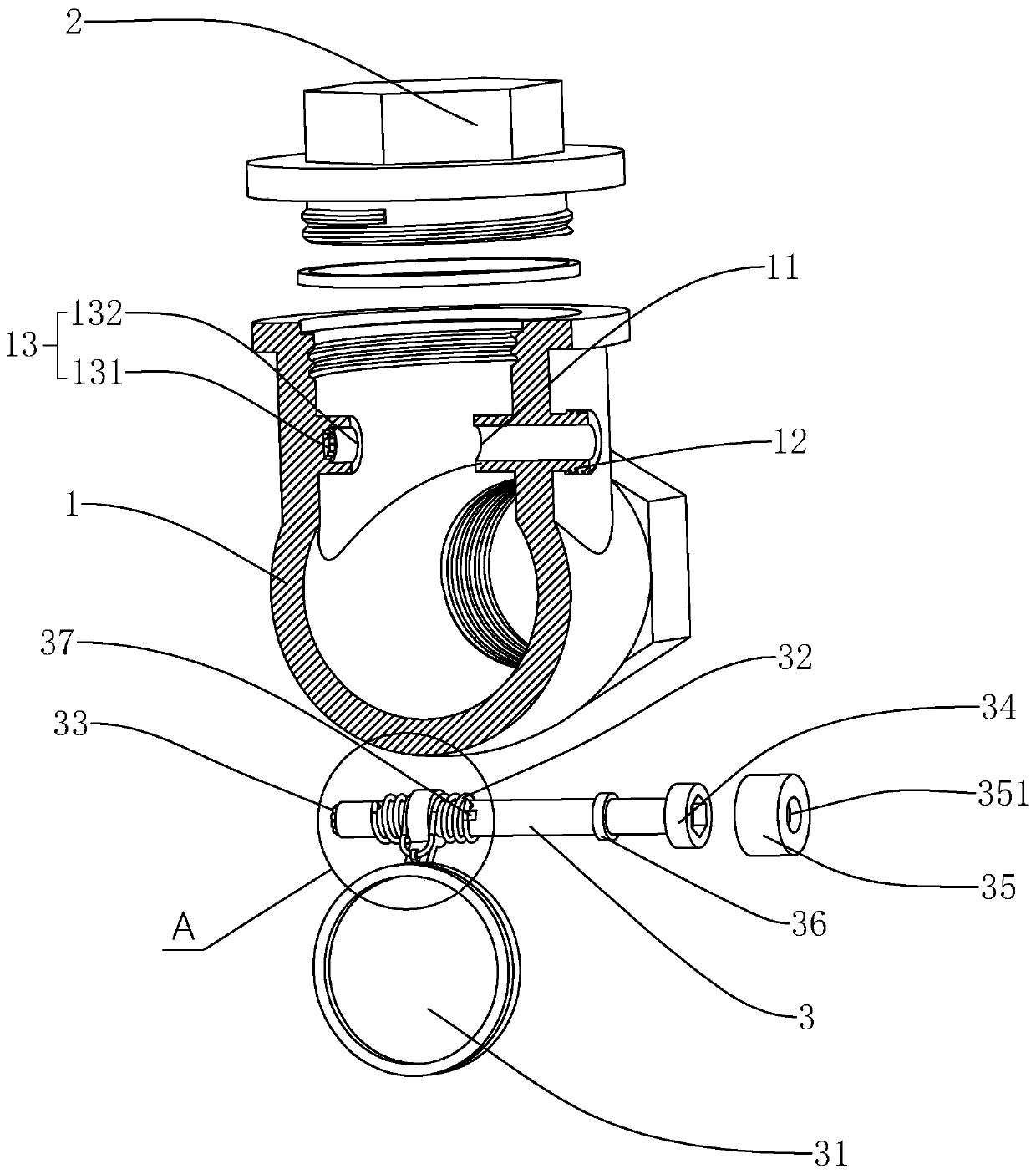
Adjustable swing check valve
The invention relates to the technical field of one-way valves and aims at providing a swing check valve. The swing check valve comprises a valve body, a valve cover, a rotating shaft and a valve clack, wherein the rotating shaft is sleeved with a torsion spring capable of relatively twisting and generating a torsion force; one extending end of the torsion spring is a rotating end, and the other extending end is a working end; the working end is fixedly connected with the valve clack; the rotating end is fixedly connected with the rotating shaft; and the rotating end can rotate in the rotatingdirection of the valve clack so that the working end can twist to generate the torsion force; one end of the rotating shaft is provided with a spline shaft extending in the axial direction; a flower-type groove matched with the valve body is formed in the valve body; and the rotating shaft can move in the shaft axis direction of the rotating shaft, and the movable distance is greater than the length of the spline shaft. The swing check valve solves the problem that when the swing check valve is installed in a non horizontal pipeline and mediums flow from top to bottom, the valve clack cannotcompletely seal a medium outlet due to the influence of self weight, so that the check valve loses the function of preventing the medium backflow.
Owner:ZHONGCHI VALVE IND GRP CO LTD
Turbine housing with wall cladding
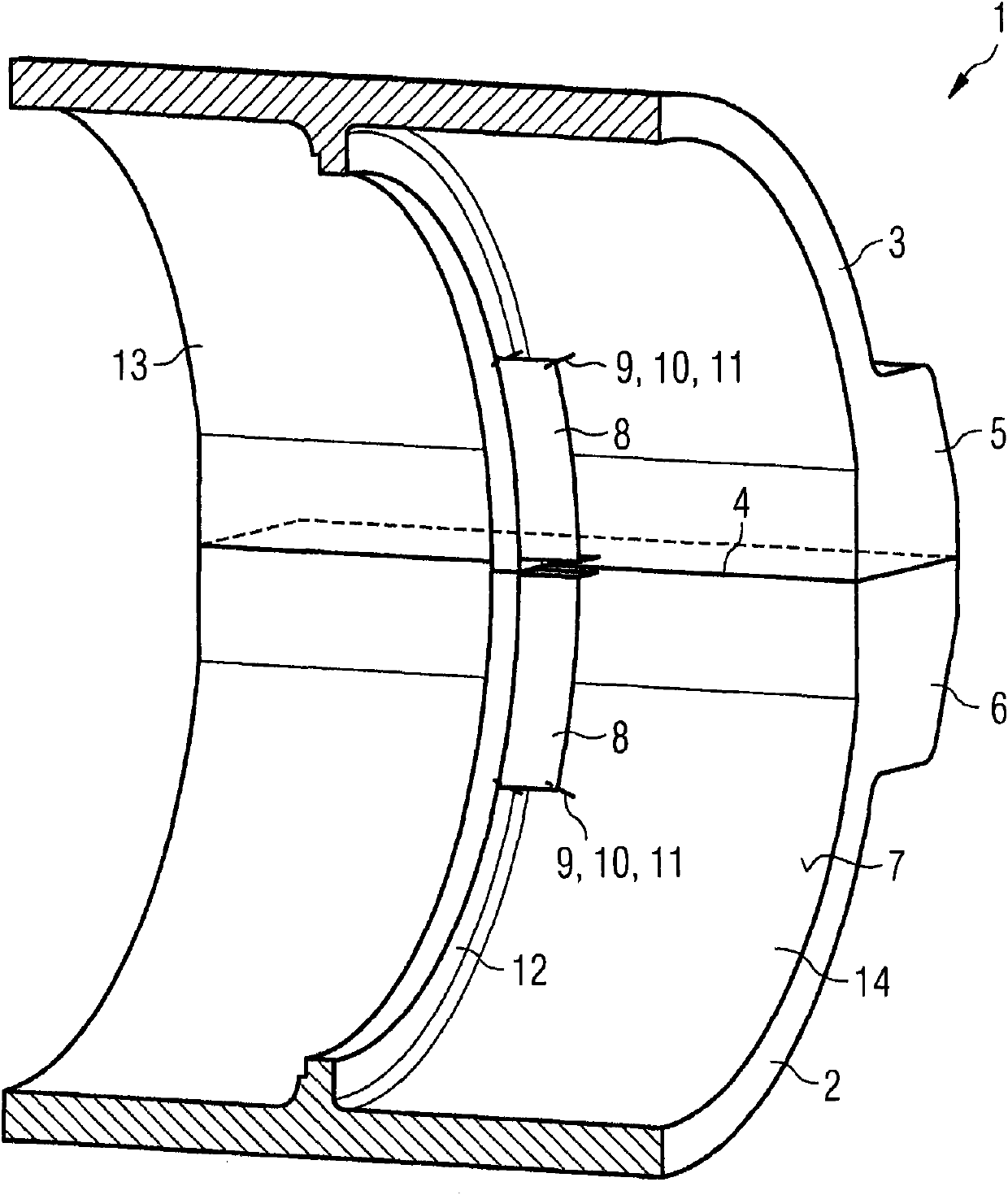
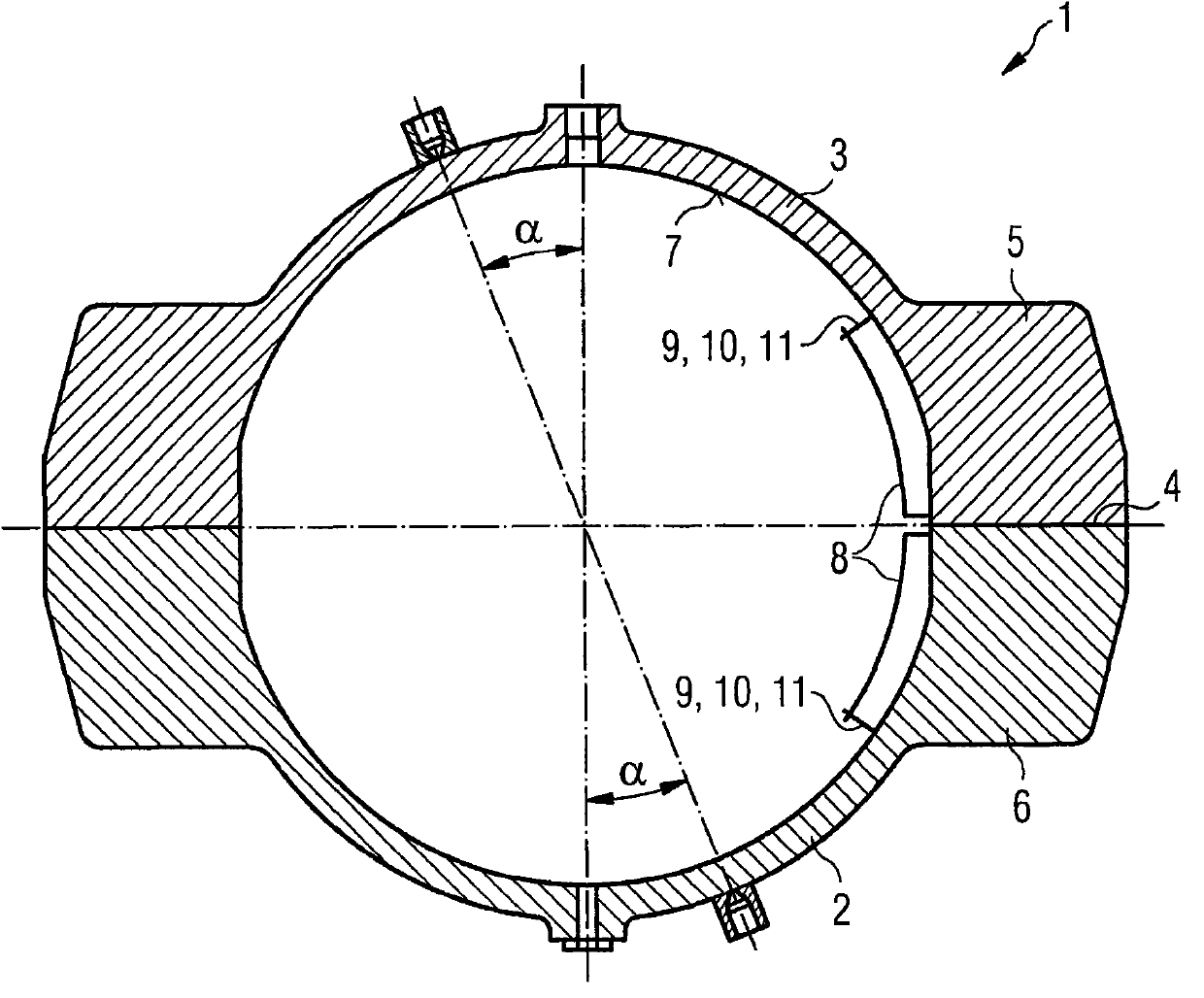
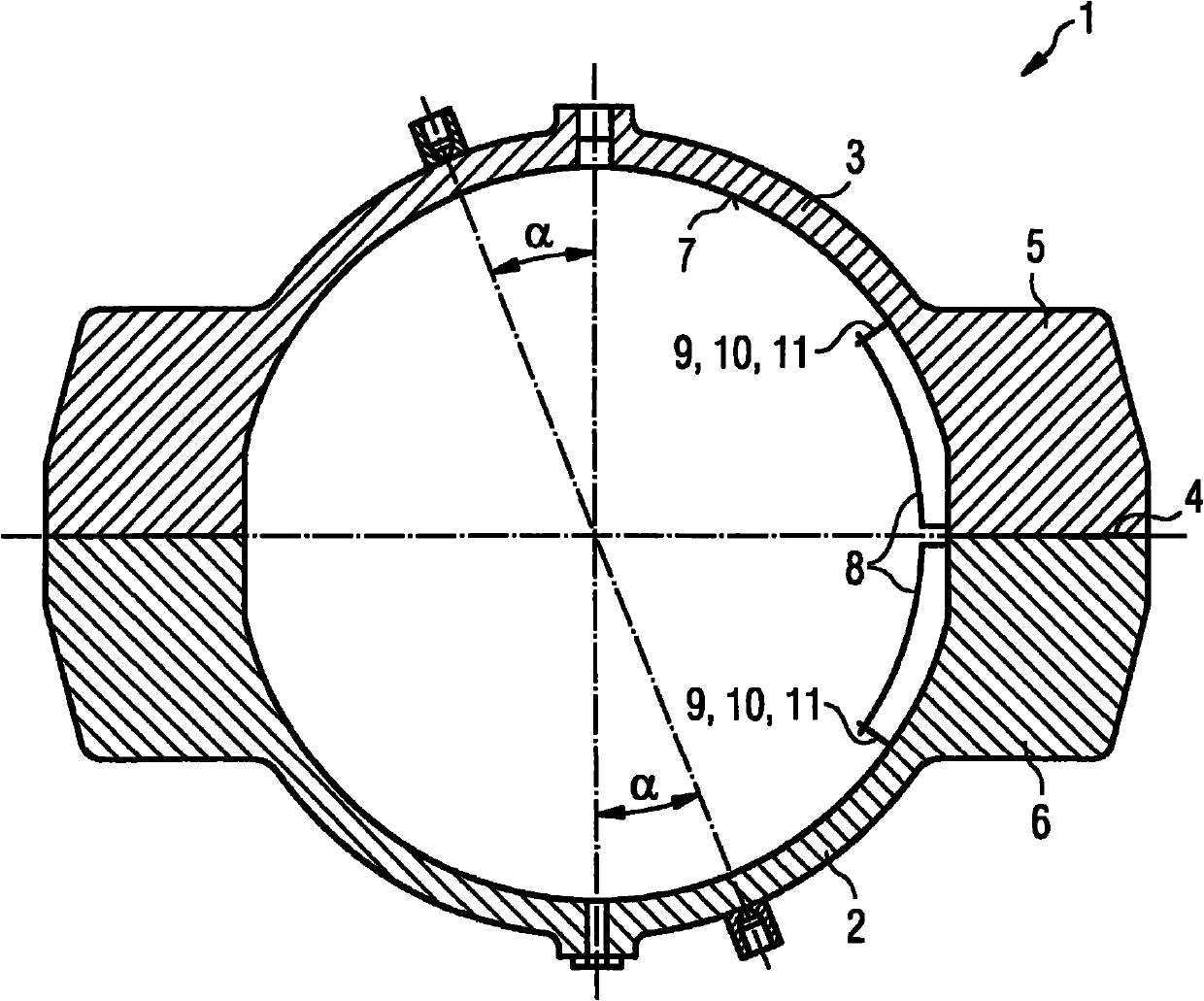
InactiveCN101994530AImprove sealingReduce heat transferMachines/enginesEngine componentsThermal radiationTurbine
A turbine housing (1) for a turbine is provided. The turbine housing (1) includes a wall cladding (8) on an inner wall (7) of the turbine housing. In a region of joint flanges (5, 6), the wall cladding (8) is arranged and embodied such that the wall cladding reduces convective heat transfer and thermal radiation in a region of the joint flanges (5, 6).
Owner:SIEMENS AG
Method for producing a valve device and corresponding valve device
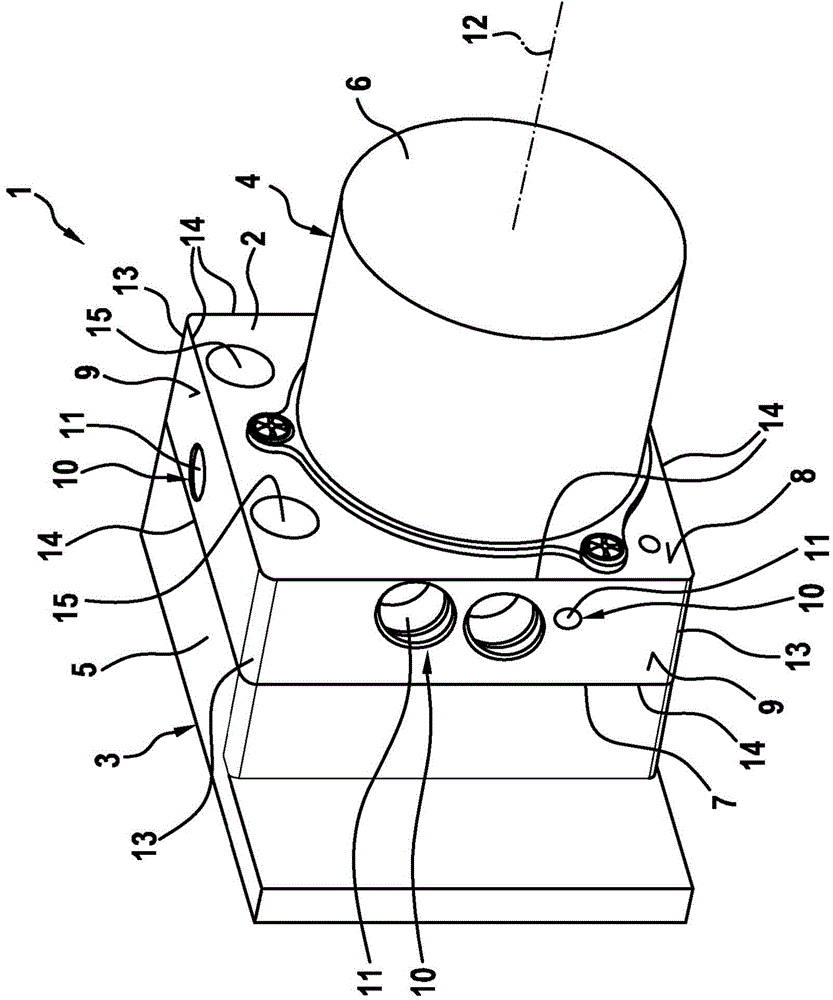
InactiveCN104797376ASave materialImprove surface qualityBraking action transmissionServomotor componentsBiomedical engineeringExtrusion
The invention relates to a method for producing a valve device (1) having a valve block (2) and at least one attachment part (3, 4) contacting a contact surface (7, 8) of the valve block (2), wherein the valve block (2) is produced by means of extrusion molding in an extrusion direction (12) and subsequent separation perpendicular to the extrusion device (12). According to the invention, the contact surface (7, 8) is formed for the attachment part (3, 4) by the separation. The invention further relates to a valve device (1).
Owner:ROBERT BOSCH GMBH
Filter element having two filter media
ActiveCN108472565AStable designNo airtightnessInternal combustion piston enginesDispersed particle filtrationFilter mediaMechanical engineering
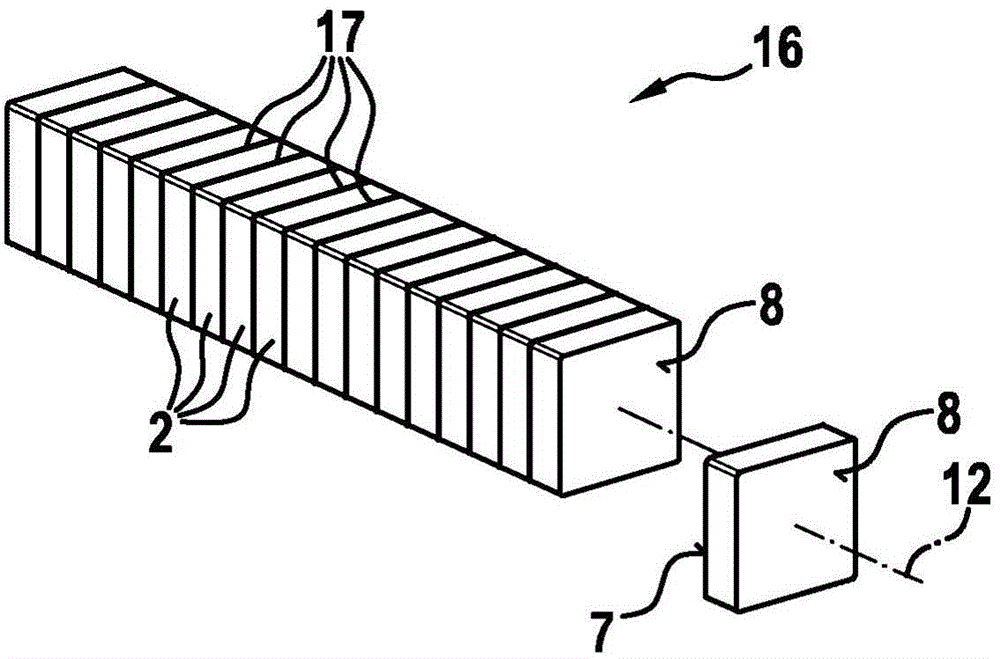
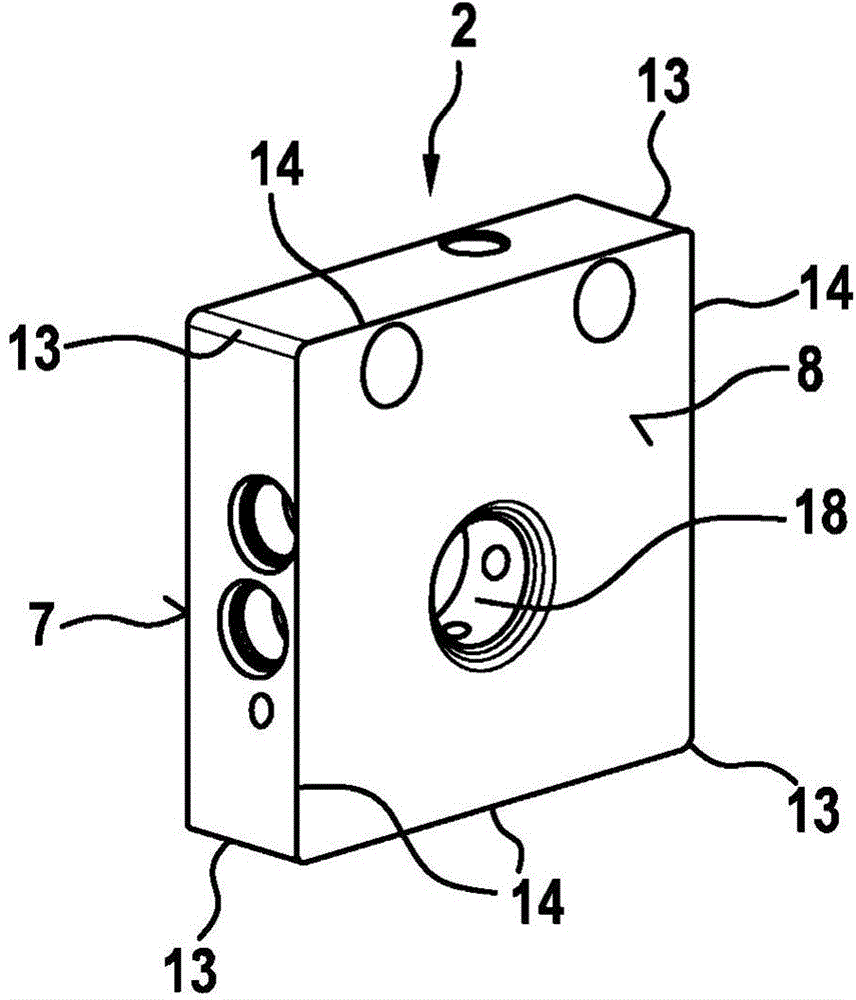
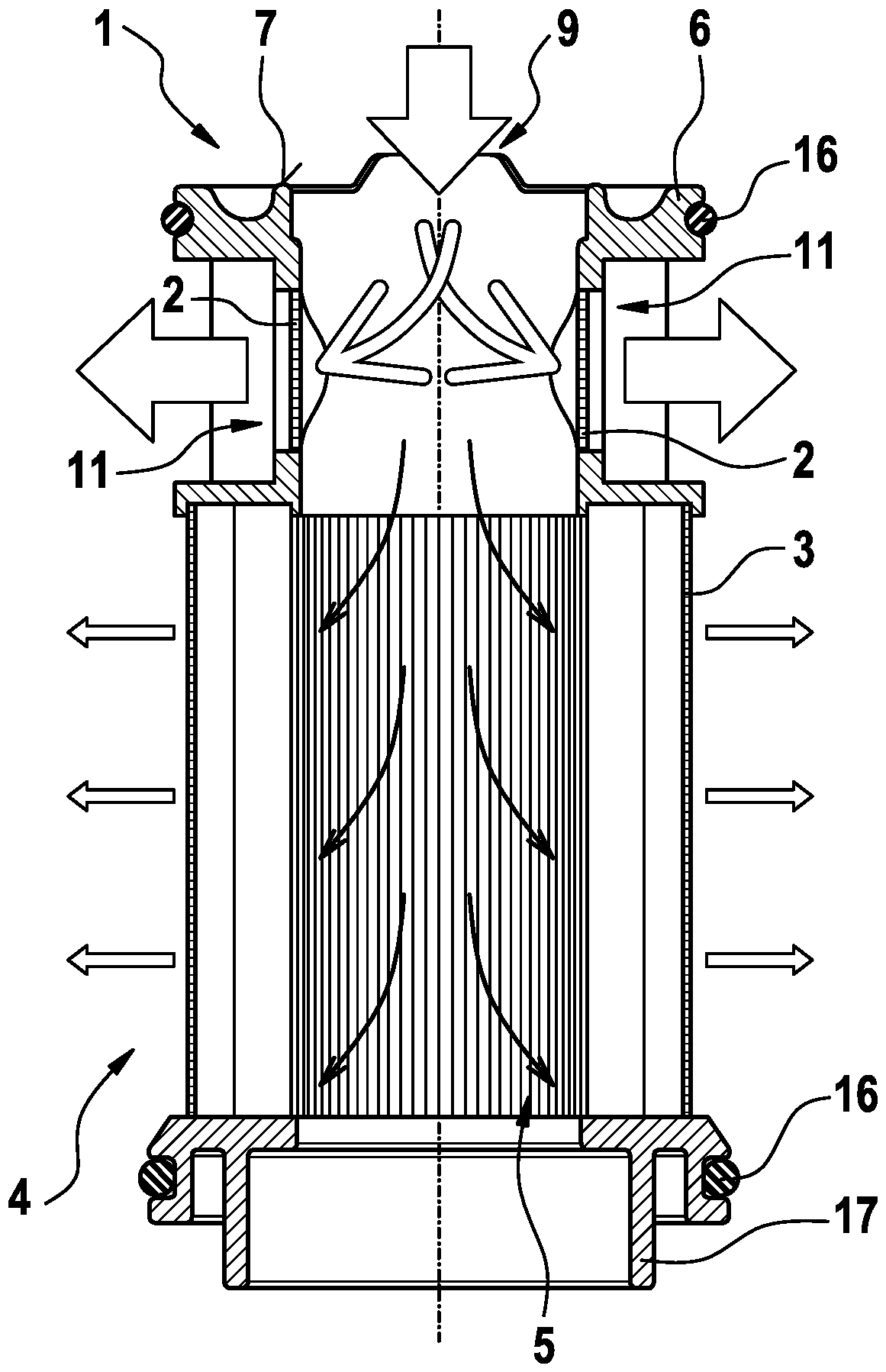
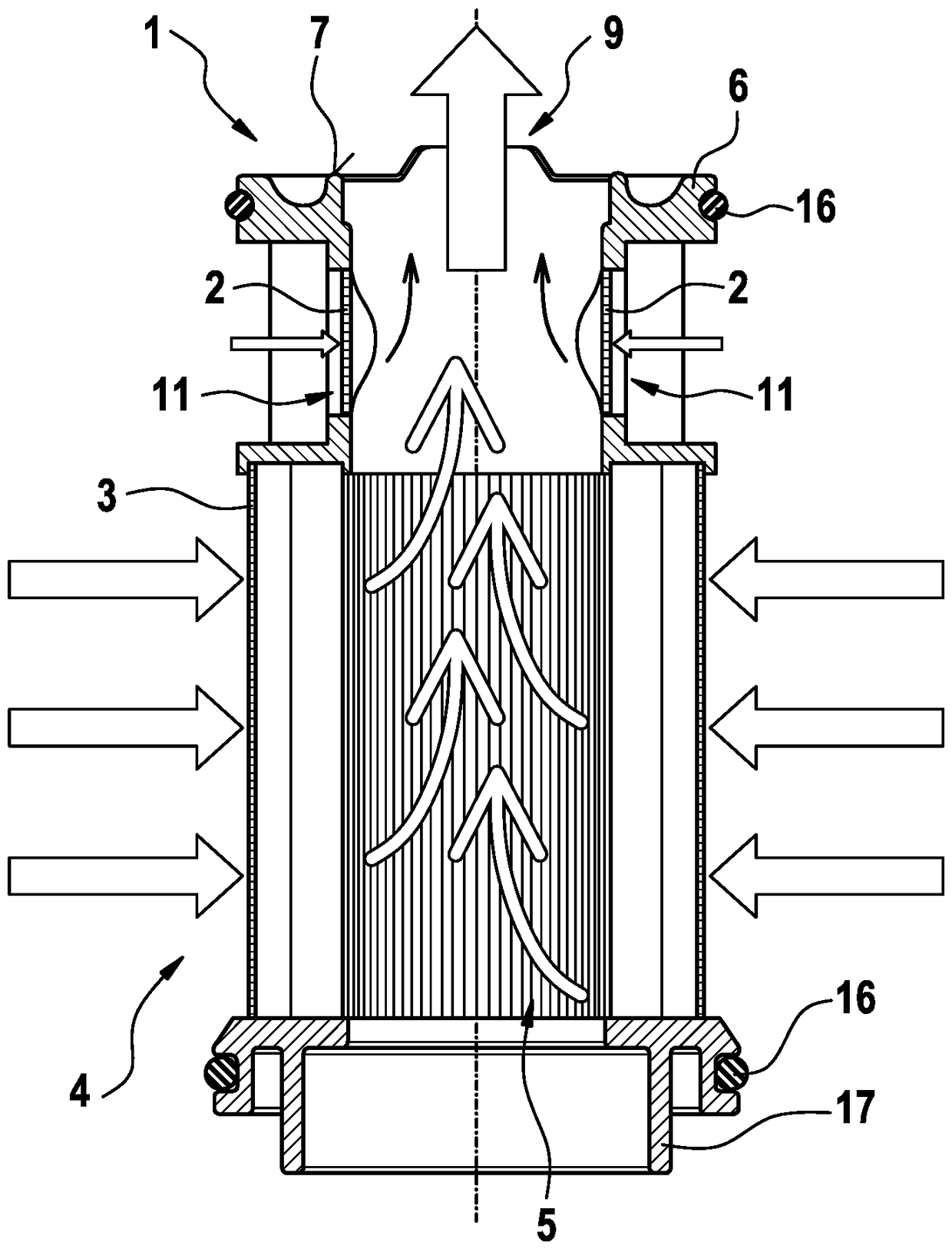
The invention relates to a filter element (1), comprising a first filter medium (2) and a second filter medium (3), wherein the filter element (1) has an non-filtering side (4), via which a fluid canbe input, and a filtering side (5), via which the fluid can be output, wherein the first filter medium (2) and the second filter medium (3) are arranged between the non-filtering side (4) and the filtering side (5), and wherein the first filter medium (2) has a lower relative pressure drop than the second filter medium (3) in a fluid flow direction from the filtering side (5) to the non-filteringside (4).
Owner:ROBERT BOSCH GMBH
Transmission for a motor vehicle
InactiveCN105051420AImprove accessibilityLow costToothed gearingsTransmission elementsMotor vehicle crashClutch
The invention relates to a transmission, in particular multi-stage transmission, for a motor vehicle, comprising a housing, a drive input shaft, a drive output shaft, at least four planetary gear sets and six shift elements in the form of at least three clutches and at least two brakes, the planetary gear sets each comprising a sun gear, at least one planet gear, a planet gear carrier and an internal gear, wherein the drive input shaft can be connected by means of the second clutch to the planet gear carrier of the first planetary gear set, and the planet gear carrier of the first planetary gear set can be connected to the second brake, and the drive input shaft can be connected by means of the third clutch to the first brake, and the drive input shaft can be connected by means of the third clutch to the sun gear of the first planetary gear set.
Owner:ZF FRIEDRICHSHAFEN AG
Transmission for a motor vehicle
InactiveCN105393021AImprove efficiencyReduce noise emissionsToothed gearingsTransmission elementsCouplingEngineering
The invention relates to a transmission, in particular a multi-step transmission for a motor vehicle, comprising a housing, an input shaft, an output shaft and at least four planetary wheel sets. Said planetary wheel sets comprise a sun gear, at least one planetary gear, a planetary wheel support and a ring gear, in addition to several switching elements in the form of at last four couplings and at least two brakes. Said sun gear, at least two planetary gear sets, in particular sun gears of the first and the second planetary gear set can be connected by means of the first brake to the housing.
Owner:ZF FRIEDRICHSHAFEN AG
Tamper-proof encryption implementation method and device in batch data uploading process
InactiveCN108965310AImprove securityPrevent leaksMultiple keys/algorithms usageUser identity/authority verificationData transmissionTamper resistance
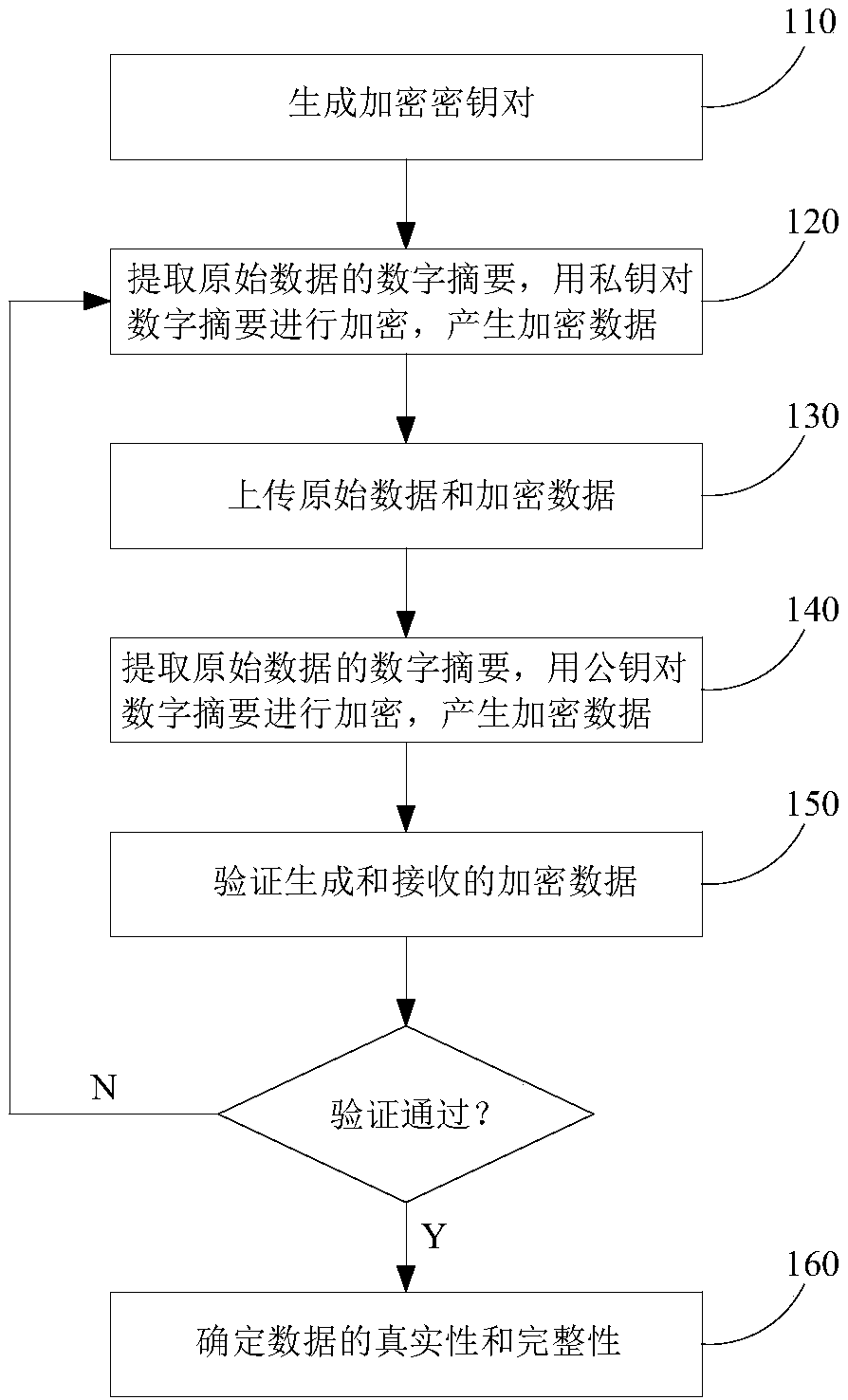
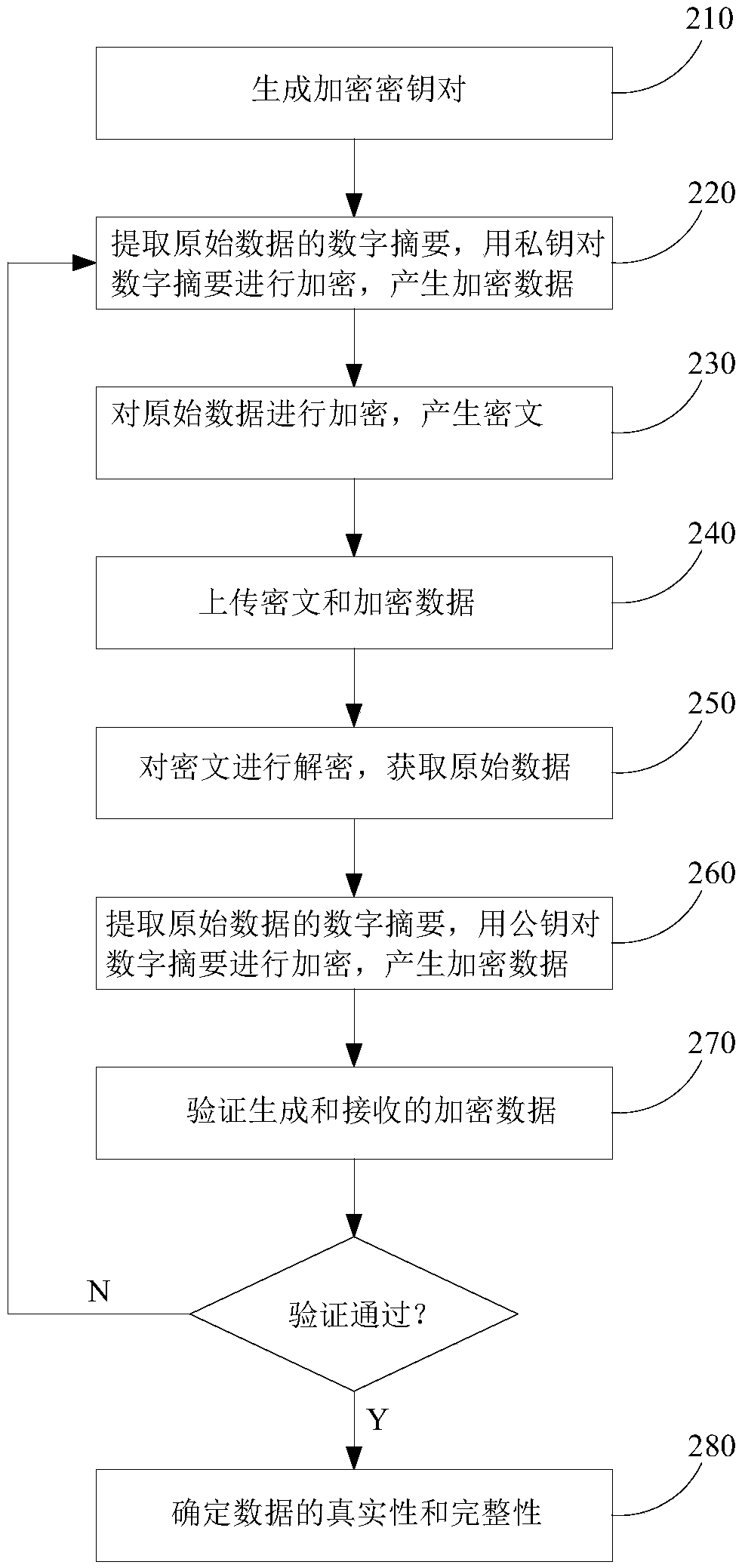
The invention discloses a tamper-proof encryption implementation method and device in the batch data uploading process. The implementation method comprises the following steps of: generating a key pair by using a 3DES algorithm; by a sending terminal, extracting a first digital digest for to-be-sent original data by using a SHA256 algorithm, and then carrying out RSA algorithm encryption on the first digital digest by using a private key to generate first encrypted data; by the sending terminal, uploading the original data and the first encrypted data, so that the original data and the first encrypted data are received by a receiving terminal; by the receiving terminal, extracting a second digital digest for the original data by using the SHA256 algorithm, and then carrying out RSA algorithm encryption on the second digital digest by using a public key to generate second encrypted data; by the receiving terminal, carrying out consistency verification on the second encrypted data and the first encrypted data; and if the consistency verification is passed, determining authenticity and integrity of the data received by the receiving terminal. According to the invention, authenticity and non-repudiation of the data are ensured, and benefits of both data transmission parties are effectively ensured.
Owner:GUANGDONG QIMING TECHNOLOGY DEVELOPMENT CO LTD
Blood vessel segmentation method based on geodesic distance map and process function equation
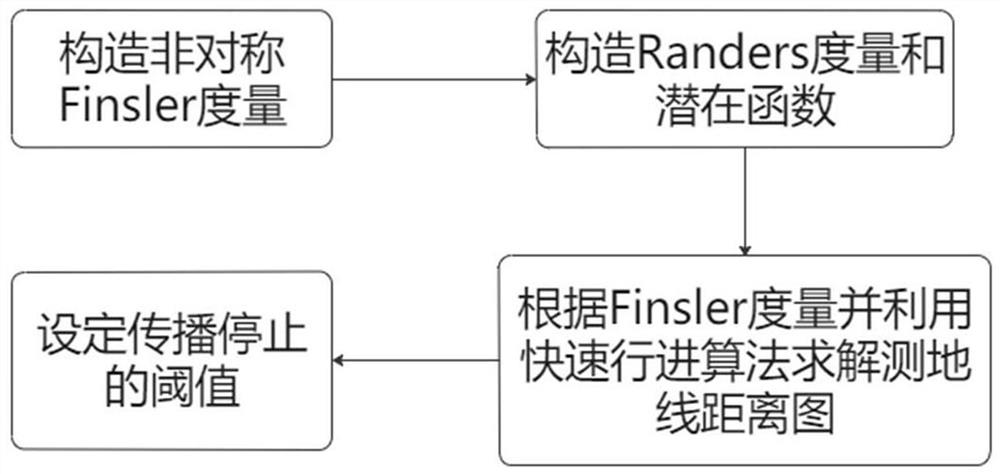
ActiveCN112651933APrevent leaksAccurate segmentationImage enhancementImage analysisPhysicsComputer vision
The invention discloses a blood vessel segmentation method based on a geodesic distance map and a process function equation, and the method comprises the steps: enabling the front propagation based on the geodesic distance map to be expanded to the application of an asymmetric Finsler measurement condition, considering the anisotropy and asymmetry of a boundary, strengthening the description of a measurement function, and setting a freezing criterion of the front propagation; the situation of leakage in the anterior propagation process is effectively prevented, smooth anterior propagation is guaranteed, the target object can be found more accurately and quickly, and accurate segmentation of the blood vessel is achieved.
Owner:山东省人工智能研究院
Power grid monitoring abnormal information processing method and system
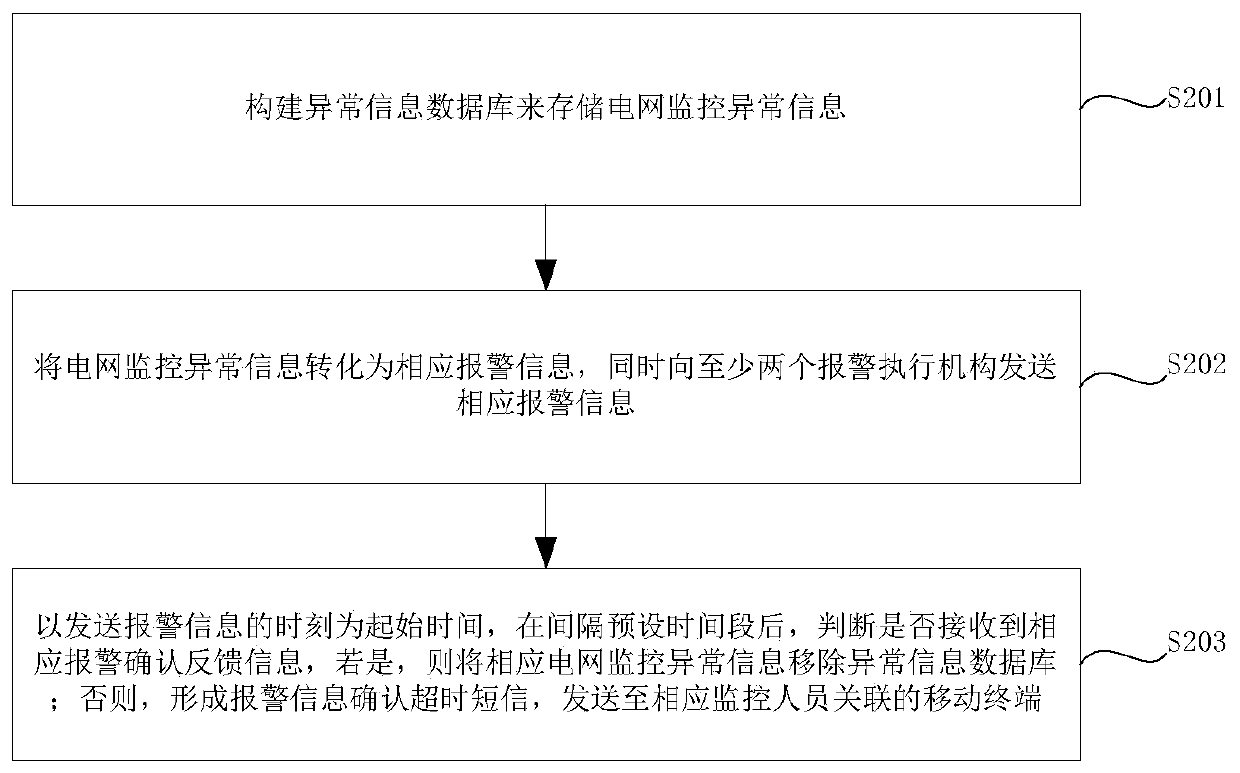
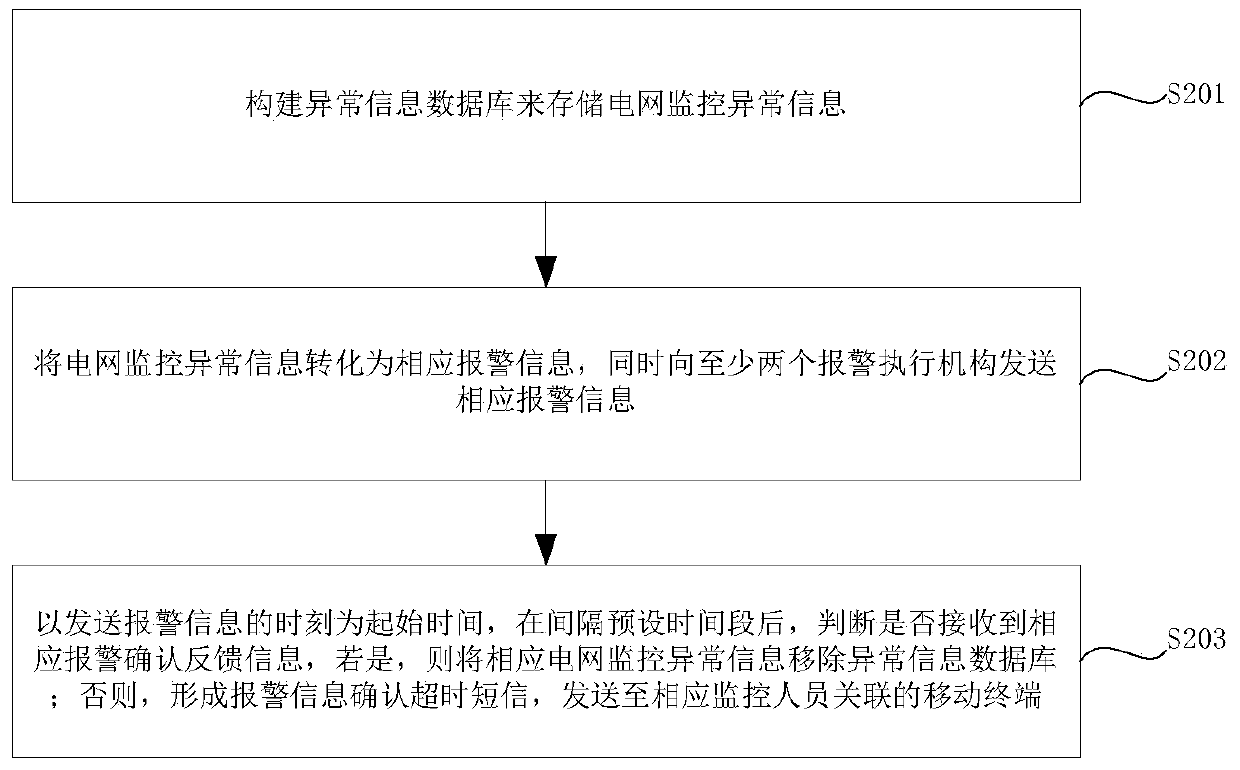
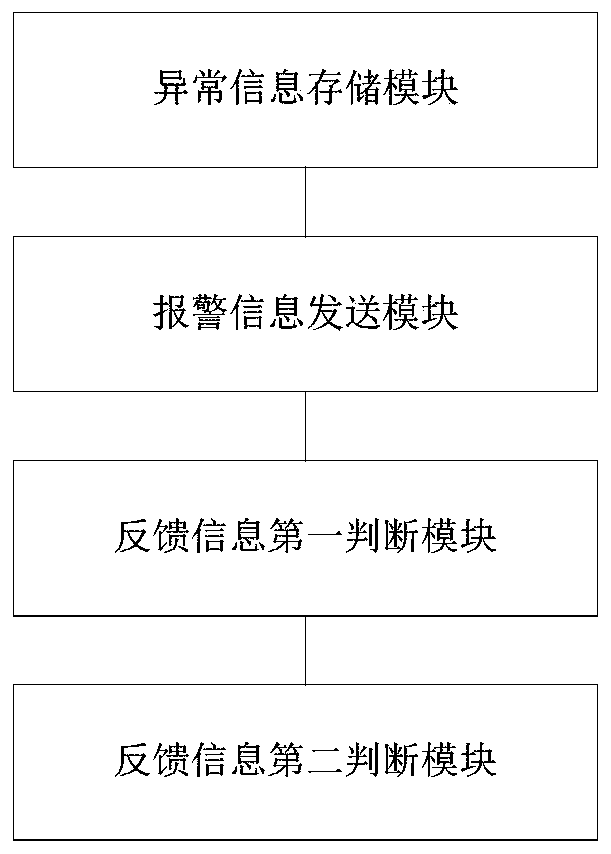
InactiveCN110135594APrevent leak monitoringPrevent the situationData processing applicationsInformation processingPower grid
The invention provides a power grid monitoring abnormal information processing method and system. The power grid monitoring abnormal information processing method comprises the following steps: constructing an abnormal information database to store power grid monitoring abnormal information; converting the power grid monitoring abnormity information into corresponding alarm information and sendingthe alarm information to a first alarm execution mechanism; judging whether corresponding alarm confirmation feedback information is received or not at an interval of a first preset time period by taking the moment of sending the alarm information to the first alarm execution mechanism as the starting time, and if so, removing the corresponding power grid monitoring abnormality information from the abnormality information database; otherwise, sending corresponding alarm information to a second alarm execution mechanism; judging whether corresponding alarm confirmation feedback information isreceived or not at an interval of a second preset time period by taking the moment of sending the alarm information to the second alarm execution mechanism as the starting time, and if so, removing the power grid monitoring abnormality information from the abnormality information database; otherwise, forming and sending an alarm information confirmation timeout short message to the mobile terminal associated with the monitoring personnel.
Owner:JINING POWER SUPPLY CO OF STATE GRID SHANDONG ELECTRIC POWER CO +1
Device and method based on pixel encryption
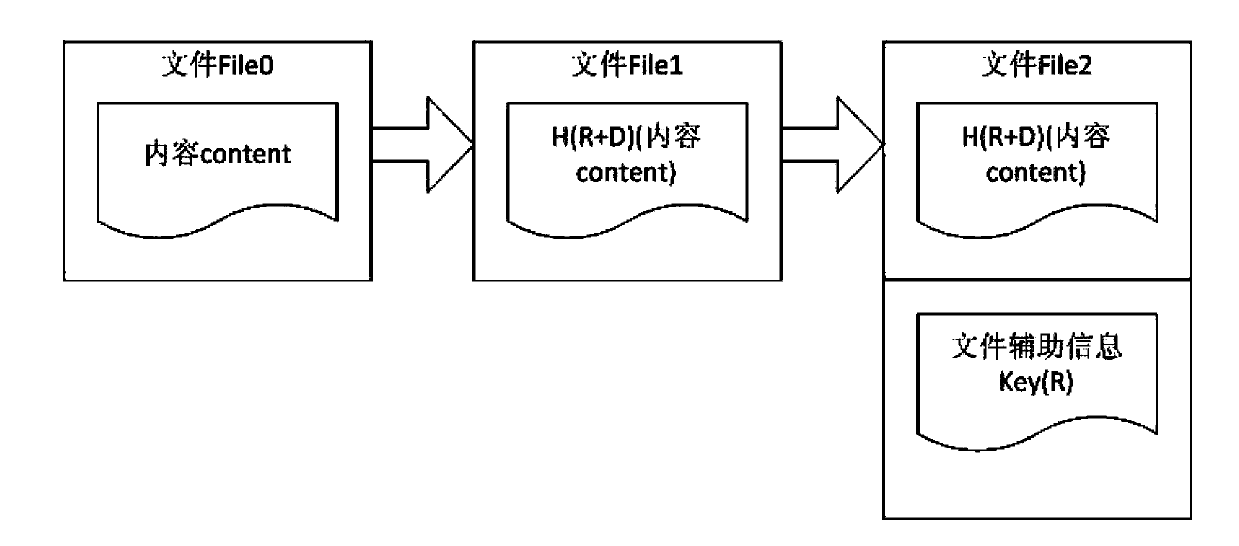
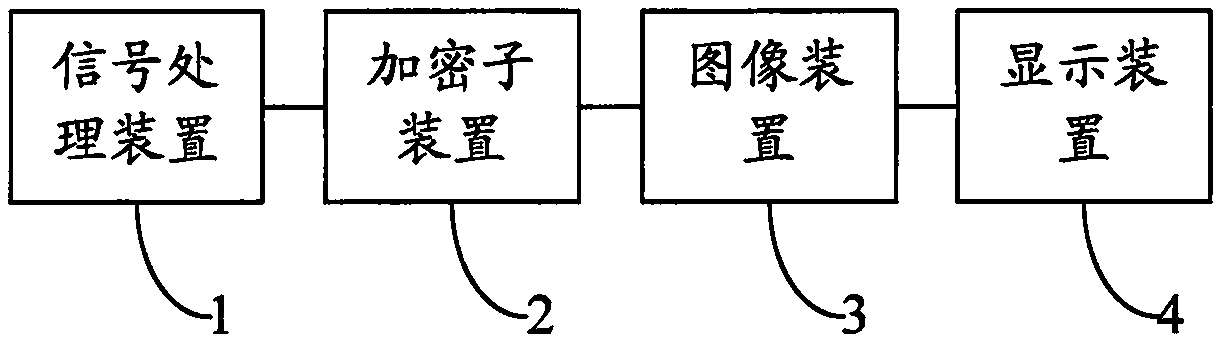
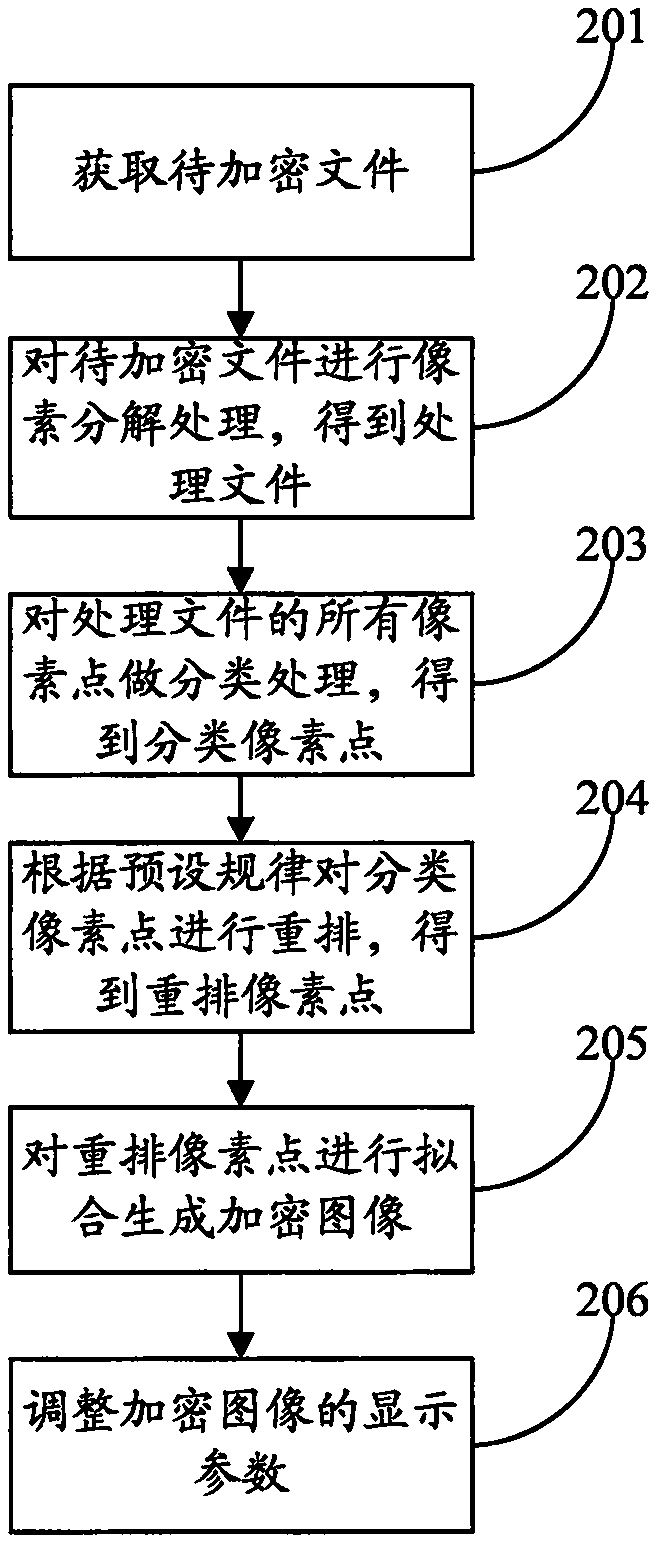
PendingCN110087079APrevent leaksImprove confidentialityDigital video signal modificationTransmissionComputer hardwareDecomposition
The invention discloses a device and method based on pixel encryption in the technical field of information security. The device based on pixel encryption comprises a signal processing device, an encryption sub-device, an image device and a display device. The signal processing device is used for carrying out pixel decomposition on the to-be-encrypted file to obtain a processed file. The encryption subdevice is used for encrypting the processing file to obtain an encrypted file. The image device is used for fitting the encrypted file to generate an encrypted image; the display device is used for displaying the encrypted image. According to the device based on pixel encryption, a to-be-encrypted file is processed through a signal processing device, and an encryption sub-device encrypts theprocessed file. A new picture is generated through the image device, an original picture is changed, and the situation that information of a to-be-encrypted file is leaked through a shooting means isfundamentally eradicated.
Owner:沈阳圣狩软件科技有限公司
Outdoor fire hydrant capable of preventing water leakage
InactiveCN112854372AEasy maintenanceEasy to installFire rescueDrawing-off water installationsWater leakageWater flow
The invention relates to the field of fire fighting equipment, and discloses an outdoor fire hydrant capable of preventing water leakage. The outdoor fire hydrant comprises a leakage preventing pipeline, the leakage preventing pipeline is fixedly connected to an underground water conveying pipeline, a leakage preventing cavity is formed between the end faces of the two sides of the leakage preventing pipeline in a communicating mode, a leakage preventing valve element is arranged at the upper end of the leakage preventing cavity, and when the leakage preventing valve element moves upwards, the leakage preventing cavity can be closed. According to the outdoor fire hydrant, the leakage preventing pipeline is installed between the underground water conveying pipeline and a fire hydrant main body, leakage of high-pressure water flow inside the underground water conveying pipeline is effectively blocked through the leakage preventing valve element inside the leakage preventing pipeline, when the ground surface fire hydrant is damaged, the water flow leakage condition is prevented in time, normal operation of traffic is conveniently maintained, meanwhile, the maintenance and installation of the fire hydrant is conducted conveniently, the state of a drainage hole can be controlled according to the opening and closing conditions of a rubber valve element, accumulated water inside the fire hydrant can be drained in time, and the service life of the fire hydrant can be prolonged conveniently.
Owner:杭州衣拾感商贸有限公司
Transmission for a motor vehicle
InactiveCN105051414ARun economyImprove driving comfort performanceToothed gearingsTransmission elementsGear wheelEngineering
The invention relates to a transmission, in particular multi-stage transmission, for a motor vehicle, comprising a housing, a drive input shaft, a drive output shaft, at least four planetary gear sets and multiple shift elements in the form of at least three clutches and at least three brakes, the planetary gear sets each comprising a sun gear, at least one planet gear, a planet gear carrier and an internal gear, wherein the drive input shaft can be connected by means of the second clutch to the planet gear carrier of the first planetary gear set, and the planet gear carrier of the first planetary gear set is connected to the second brake, and the internal gear of the first planetary gear set is connected to the planet gear carrier of the fourth planetary gear set, and the planet gear carrier of the fourth planetary gear set is connected to the sun gear of the third planetary gear set, and the sun gear of the fourth planetary gear set is connected to the third brake, and the planet gear carrier of the third planetary gear set is connected to the drive output shaft, and the internal gear of the third planetary gear set is connected to the internal gear of the fourth planetary gear set, and the third clutch is connected to the first brake, and the third clutch is connected to the sun gear of the first planetary gear set.
Owner:ZF FRIEDRICHSHAFEN AG
Fuel rod storage device
ActiveCN105355243APrevent closureImprove sturdinessNuclear energy generationReactor fuel elementsDevice formAutomotive engineering
The present invention relates to a fuel rod storage device, particularly to a fuel rod storage device for fuel rods, preferably damaged fuel rods. The fuel rod storage device forms an integrated, preferably forged fuel rod storage device, and is provided with an inner cavity enclosed by a storage device bottom, a storage device housing and a storage device cover, wherein the storage device cover is provided with a storage device cover opening capable of being sealed by a sealed member, at least an accommodation pipe for the fuel rod is arranged inside the inner cavity, and is sealed on the end portion of the storage device bottom side in a fluid sealing manner, and the sealed member can be loaded, preferably screwed into the storage device opening.
Owner:GNS核能服务有限公司
Novel vacuum suction plate structure
The invention relates to the technical field of mechanical structures, and particularly relates to a novel vacuum suction plate structure. A suction plate body, a left side cover and a right side cover are designed in an embedded mode; a side cover sealing gasket is embedded into a sealing gasket positioning groove in the bottom face of the groove firstly, and then the suction plate body is embedded into a side cover groove and fastened to the suction plate body through fixing screws on the end faces of the side cover. The positions of stainless steel balls in stepped holes are adjusted in a self-adaptive mode according to the vacuum suction force, and a suction cup assembly is in threaded connection with internal threads of through holes of suction cup pressing strips through external threads of suction cup fixing nuts and is sealed through an annular sealing ring; a filter screen is arranged between the suction cup fixing nuts and a throttling valve and positioned on an air channel of the suction cup fixing nuts and the throttling valve, and the effects of filtering air and preventing dust impurities in air from being sucked into a suction plate through the air channel and affecting vacuum control elements after blockage to cause damage and action failure are achieved.
Owner:福州派可吉贸易有限公司
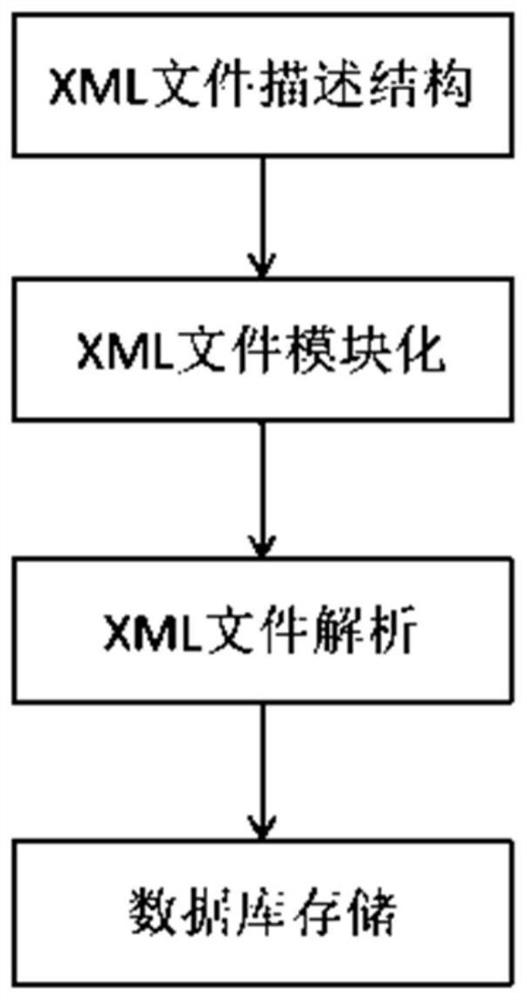
Storage method for FPGA structure description
PendingCN114282062AQuickly learn about internal architecture detailsPrevent leaksDigital data protectionSemi-structured data indexingSoftware engineeringModularity
The invention relates to a storage method for FPGA structure description, and belongs to the technical field of data processing. The method comprises the following steps of: 1) describing the structure information of the FPGA by using a plurality of label files based on XML (Extensible Markup Language); 2) modularizing the XML file; 3) analyzing the XML file, and processing data in the XML file to enable the data to accord with rule constraints of the SQLite database; according to the method, the XML file content is subjected to encryption protection, the plaintext leakage condition is effectively eradicated, meanwhile, developers can rapidly know the internal architecture details of the FPGA, later architecture maintenance and upgrading are facilitated, and the development efficiency is improved.
Owner:山东芯慧微电子科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com