Wireless authentication secretive mobile storage apparatus and encryption authenticating method
A mobile storage device, encryption authentication technology, applied in security devices, wireless communications, computer security devices, etc., can solve the problems of confidentiality loopholes, complicated operations, easy to leak, etc., to prevent leakage, protect privacy, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
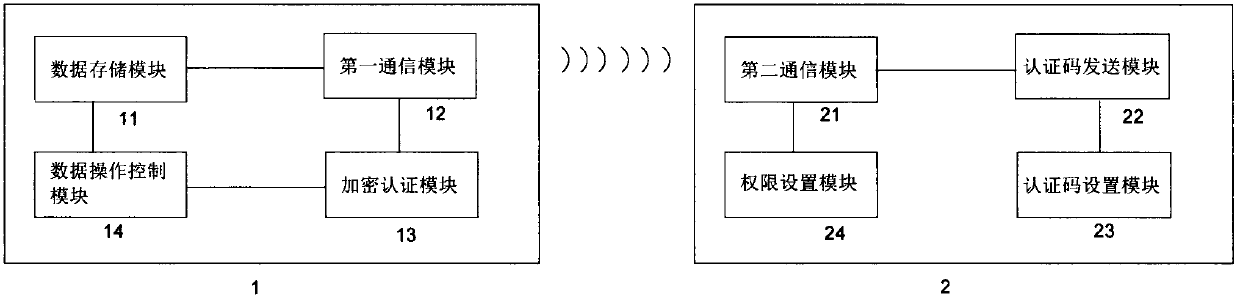
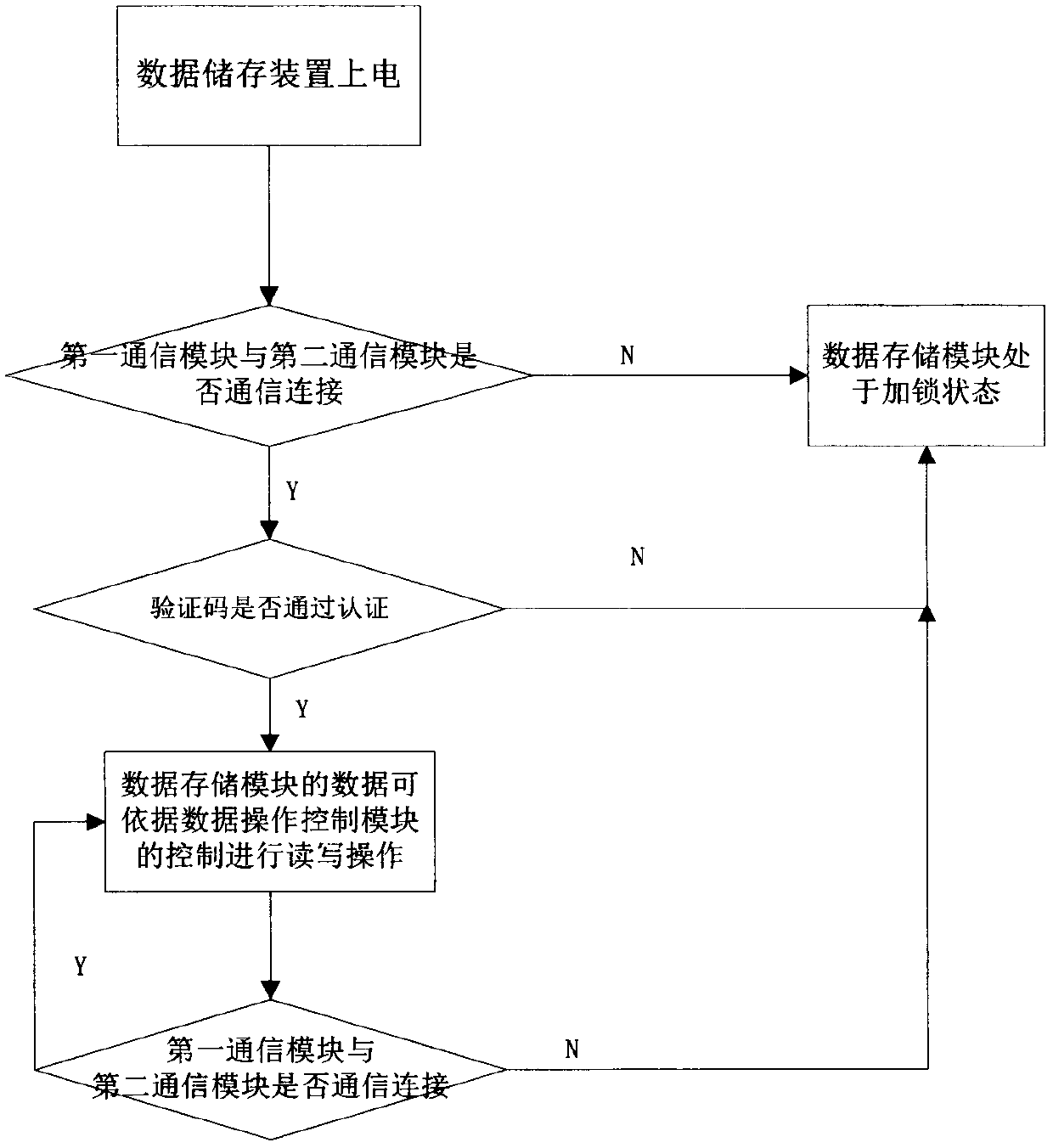
[0023] The implementation of the present invention will be illustrated by specific specific examples below, and those skilled in the art can easily understand other advantages and effects of the present invention from the contents disclosed in this specification.
[0024] see figure 1 , 2 . It should be noted that the structures, proportions, sizes, etc. shown in the drawings attached to this specification are only used to match the content disclosed in the specification, for those who are familiar with this technology to understand and read, and are not used to limit the implementation of the present invention. Limiting conditions, so there is no technical substantive meaning, any modification of structure, change of proportional relationship or adjustment of size, without affecting the effect and purpose of the present invention, should still fall within the scope of the present invention. The disclosed technical content must be within the scope covered.
[0025] Such as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com