Method for preventing sensitive data from betraying confidential matters and device thereof
A technology for sensitive data and data, applied in the field of network security, can solve the problem that anti-sensitive data cannot effectively prevent the leakage of sensitive data, and achieve the effect of preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
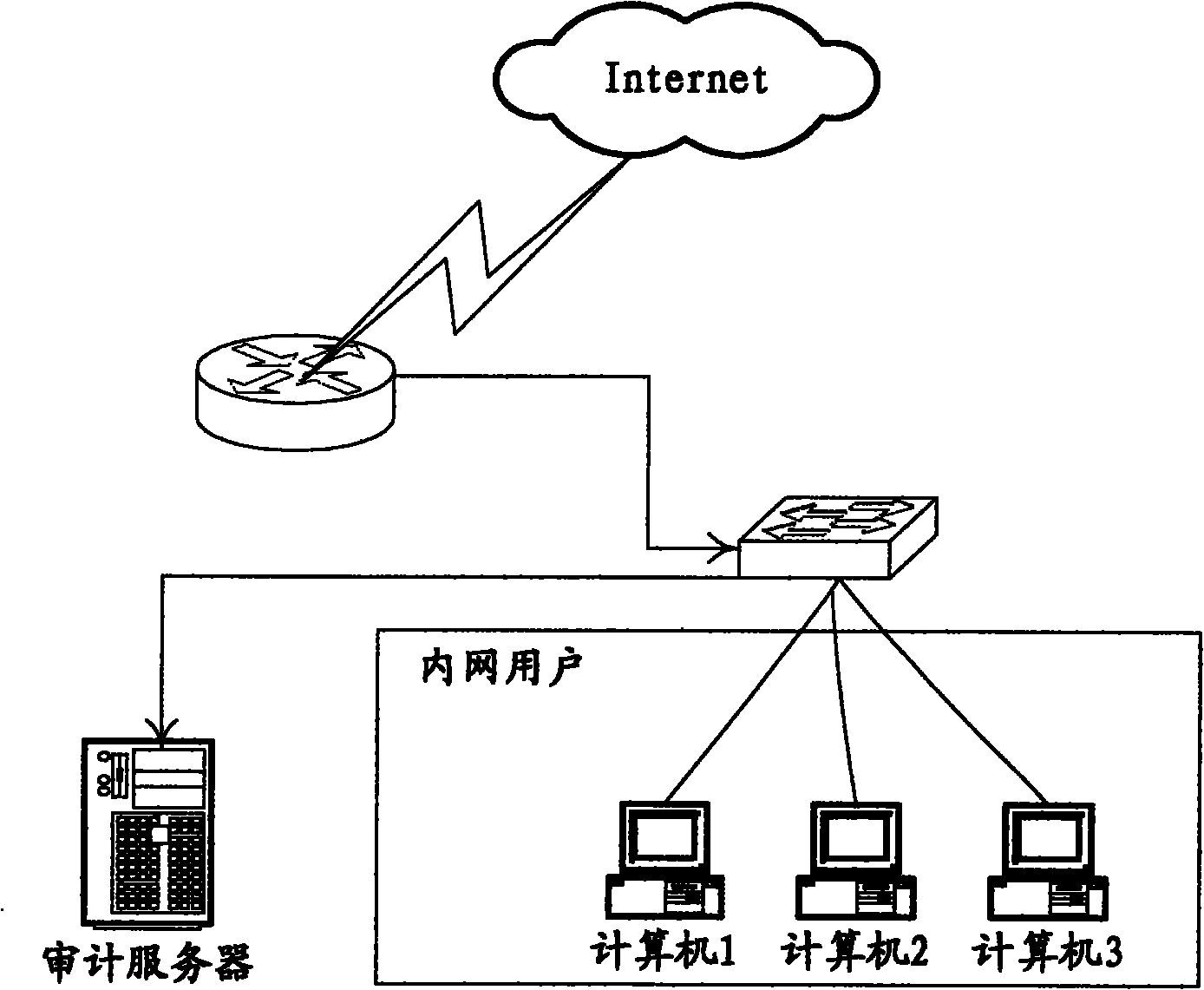
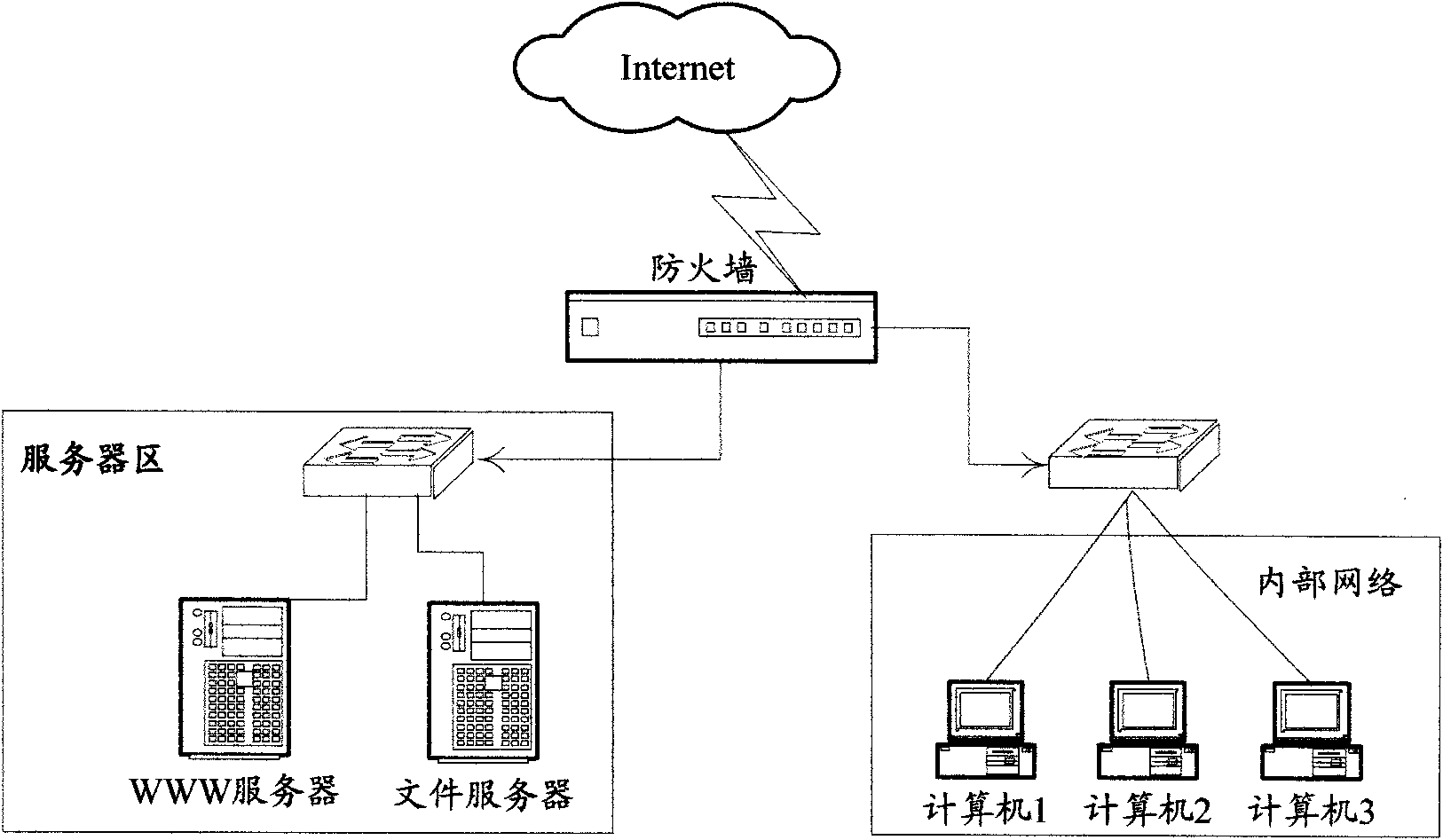
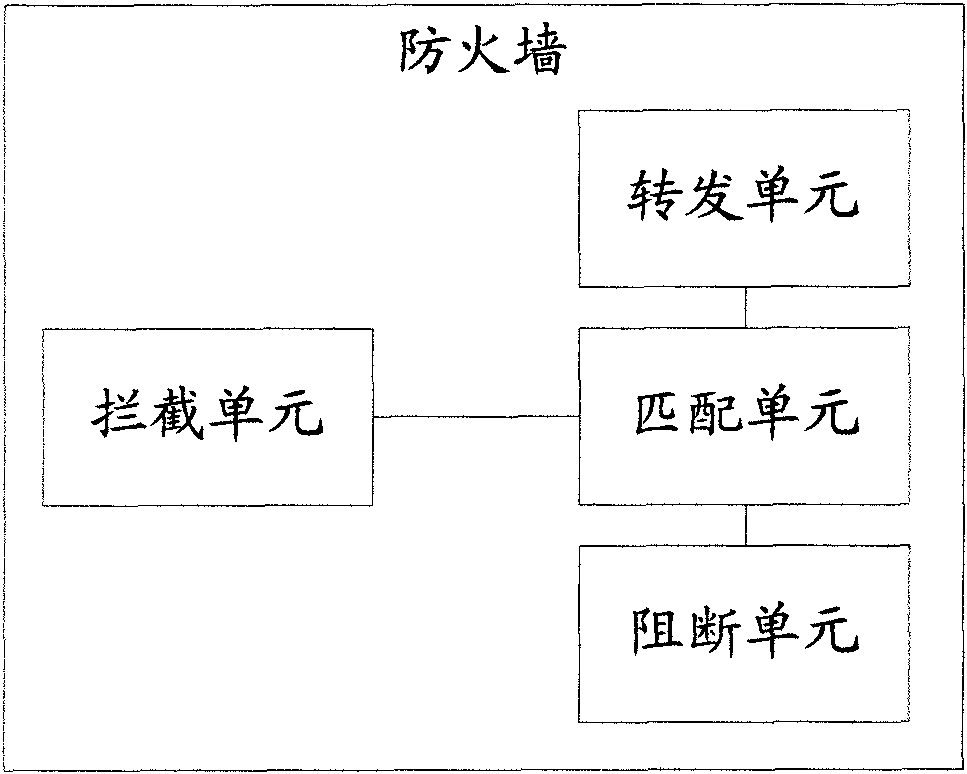
[0014] Due to the inherent characteristics of the Internet, it is very weak in network security, so a large number of related network security products have emerged, such as firewalls, intrusion detection, vulnerability scanning, and security auditing. The characteristics of these security products are to protect private networks or Resources are not accessed and modified without authorization, or audit logs are recorded for future evidence collection, etc. The main idea of the invention is to prevent the sensitive data of the enterprise from being published on the Internet on the firewall. see figure 2 As shown, the firewall network deployment in the embodiment of the present invention is as follows: the deployment location of the firewall is usually between the Internet and the server area or / and the internal network, and the deployment location of the firewall determines that it is the first security guarantee for network security, and it is also The most important secu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com