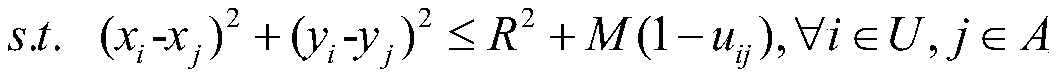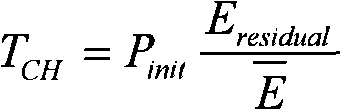Patents
Literature
1014 results about "Network deployment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Deployment, in the context of network administration, refers to the process of setting up a new computer or system to the point where it is ready for productive work in a live environment.
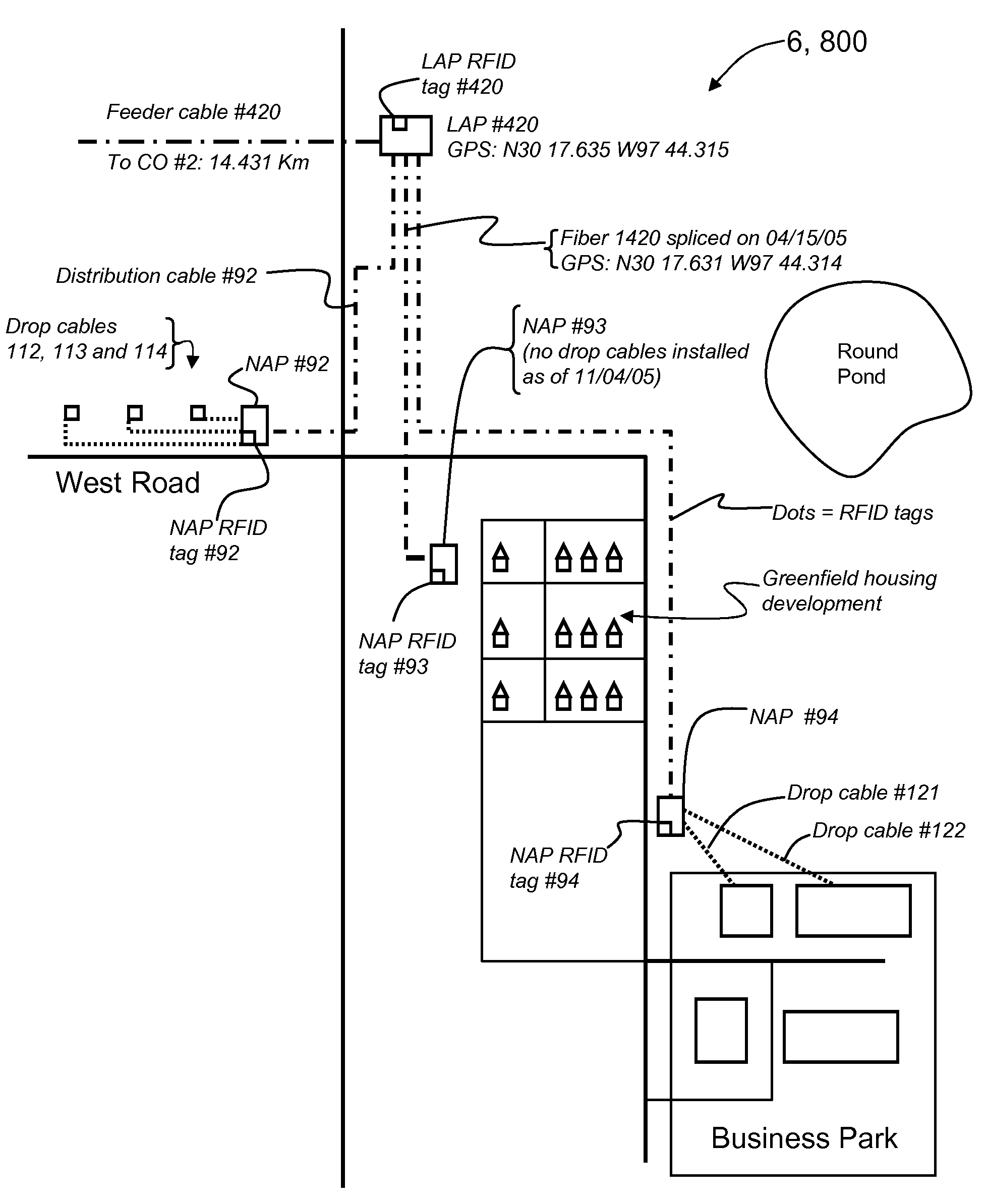
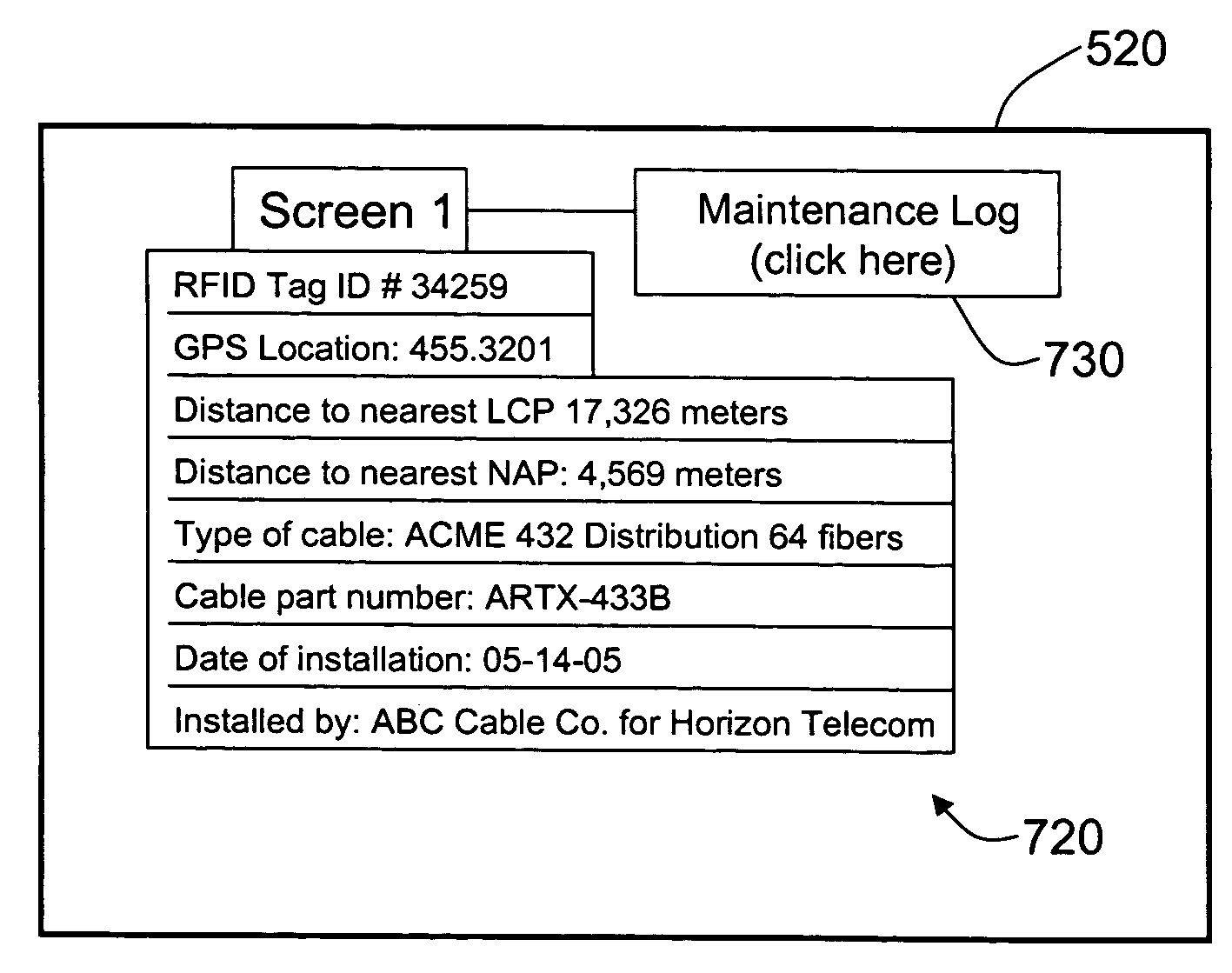
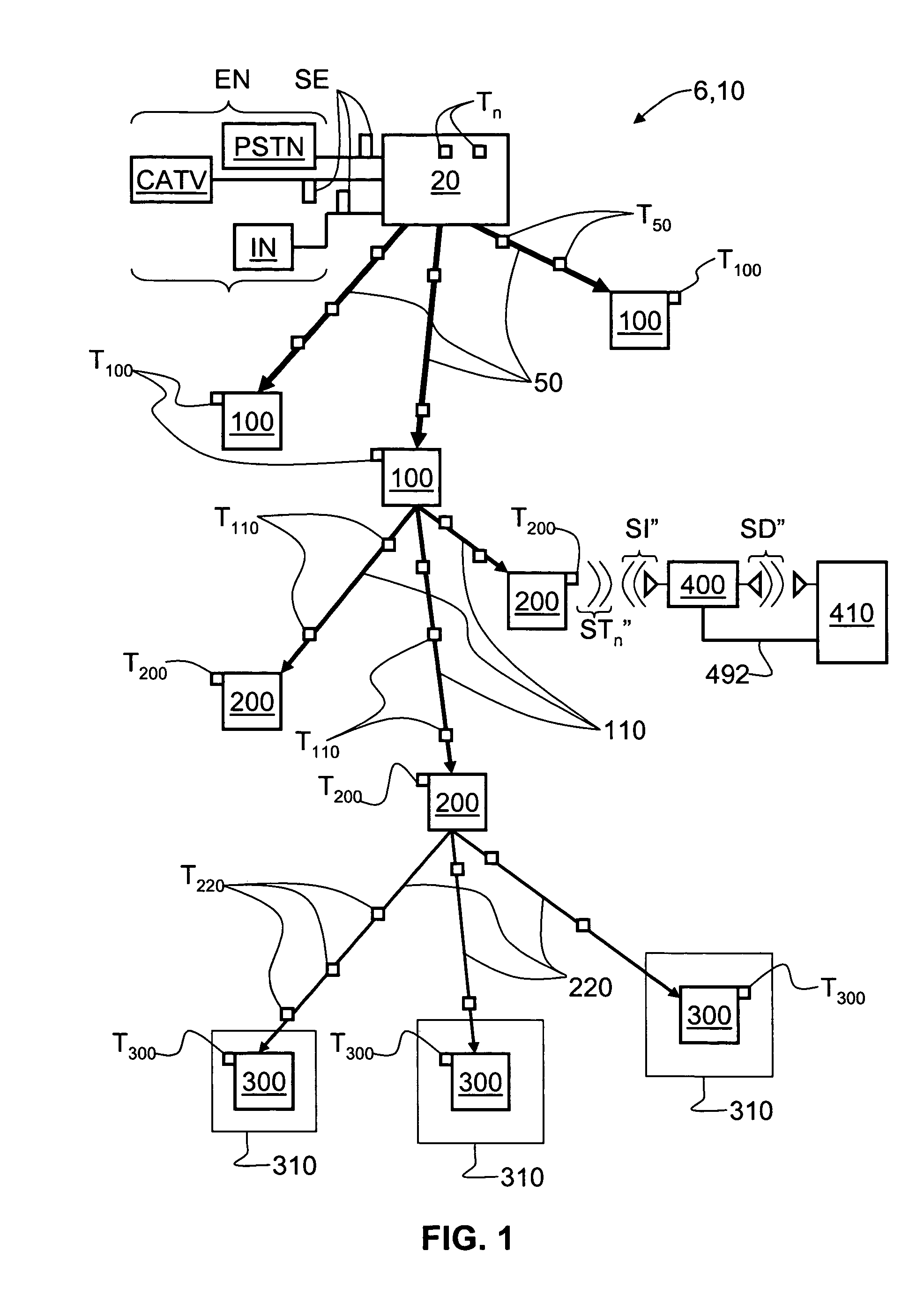
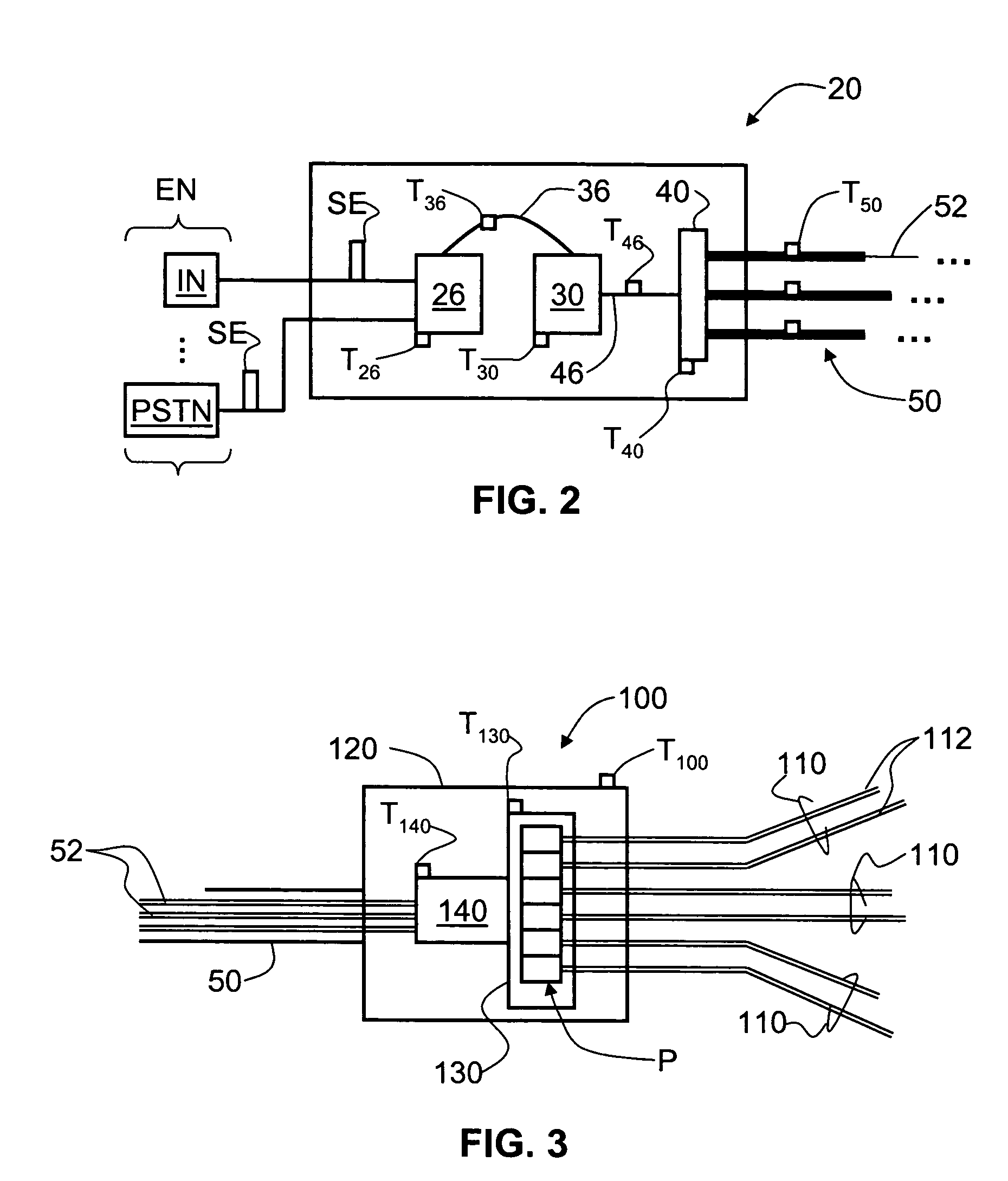
RFID Systems and Methods for Optical Fiber Network Deployment and Maintenance
InactiveUS20090097846A1Multiplex system selection arrangementsElectromagnetic network arrangementsNetwork deploymentService personnel
An optical-fiber-network (OFN) radio-frequency identification (RFID) system for deploying and / or maintaining and / or provisioning service and / or locating faults in an OFN. The system includes a plurality of OFN components, and at least one RFID tag that includes RFID tag data that has at least one property of the OFN component associated with the RFID tag. The RFID tag data is written to and read from the RFID tags using one or more mobile RFID readers either prior to, during or after deploying the OFN components. An OFN-component-data database unit is used to store and process the RFID tag data and is automatically updated by the one or more mobile RFID readers. This allows for different maps of the OFN to be made, such as an inventory map and a maintenance map, and for the maps to be automatically updated. The OFN-RFID system allows for mobile automated operations and management of OFN components by service personnel, and provides for faster and more accurate OFN system deployment and maintenance.
Owner:CORNING CABLE SYST LLC
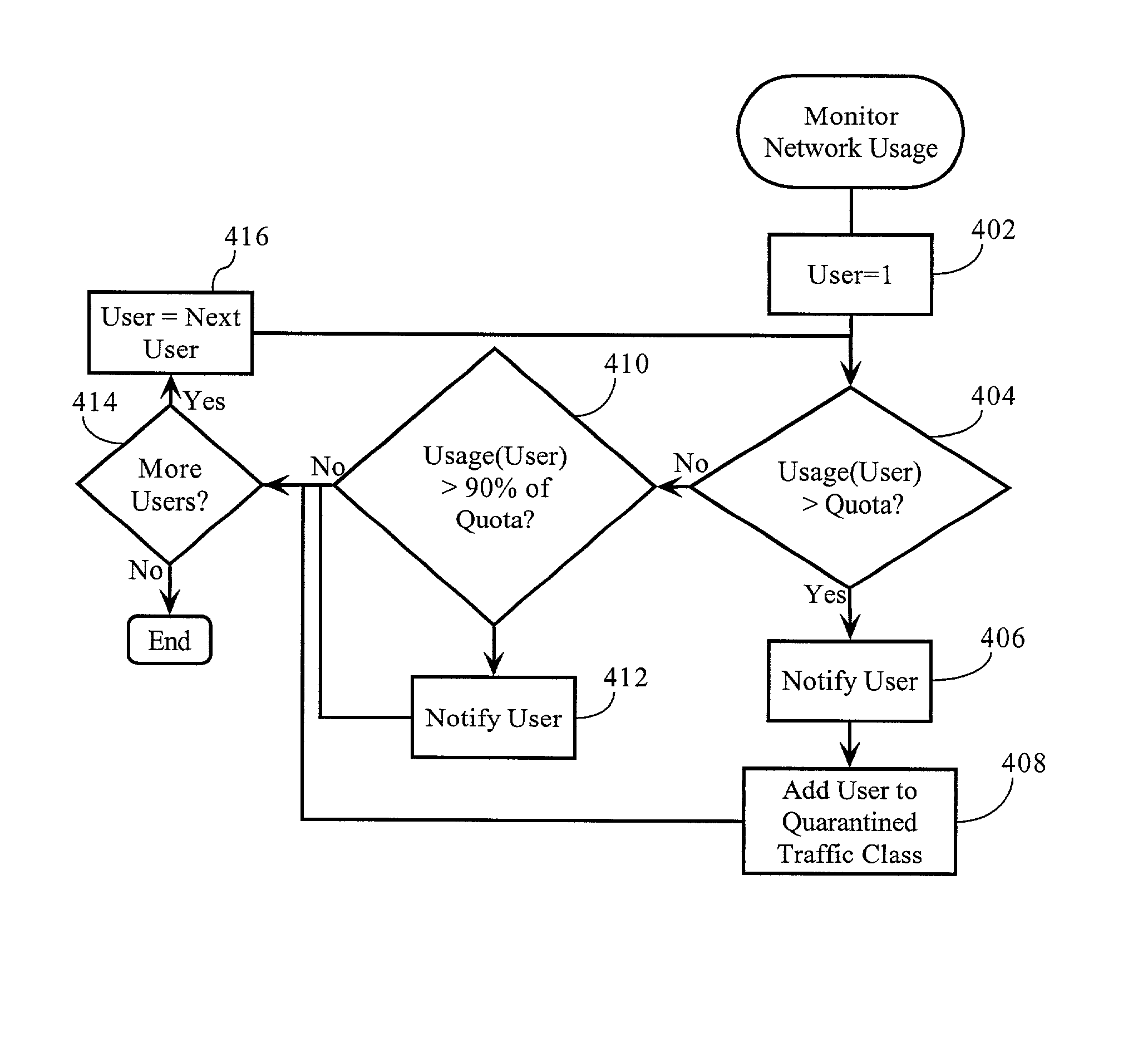
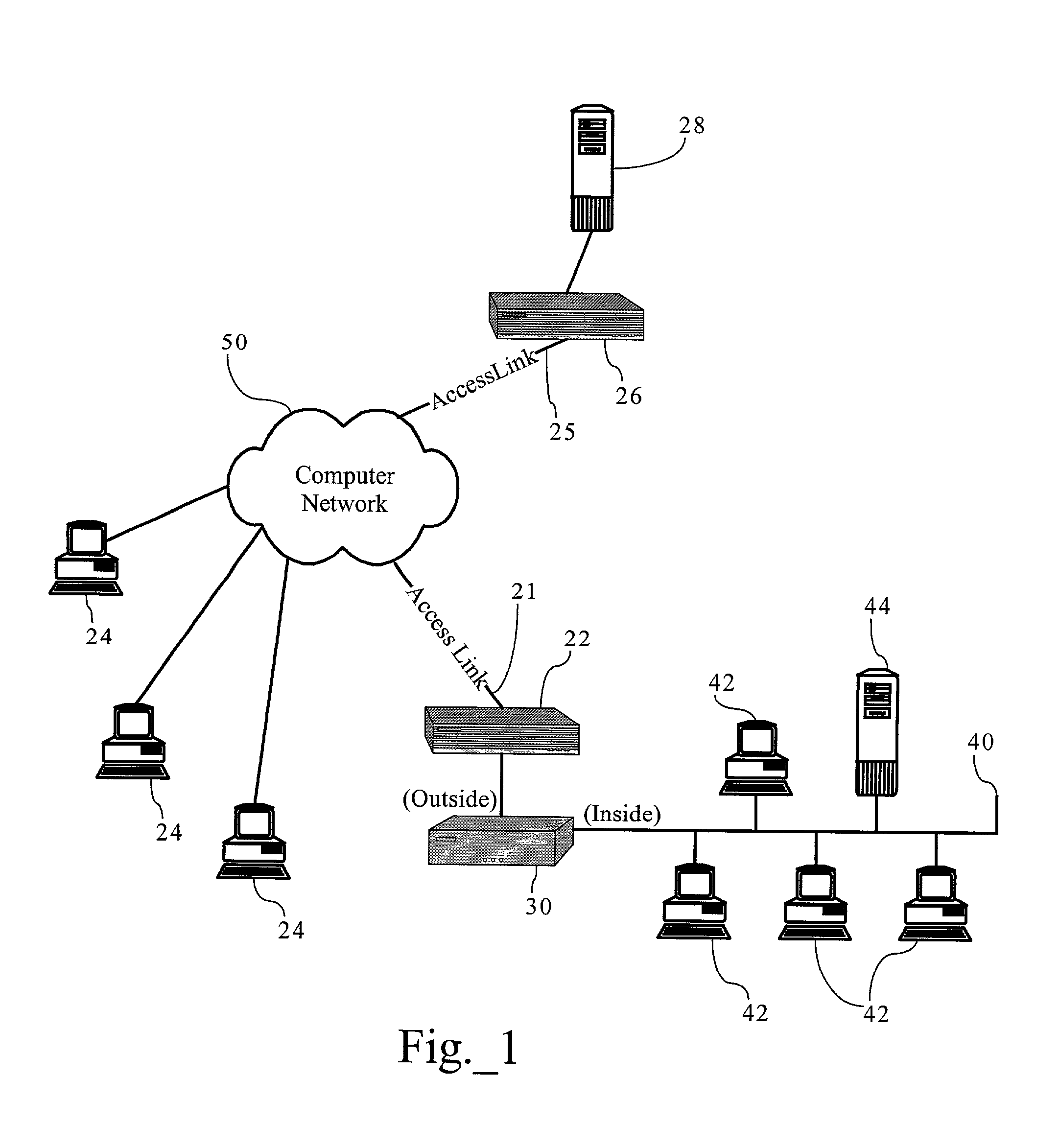
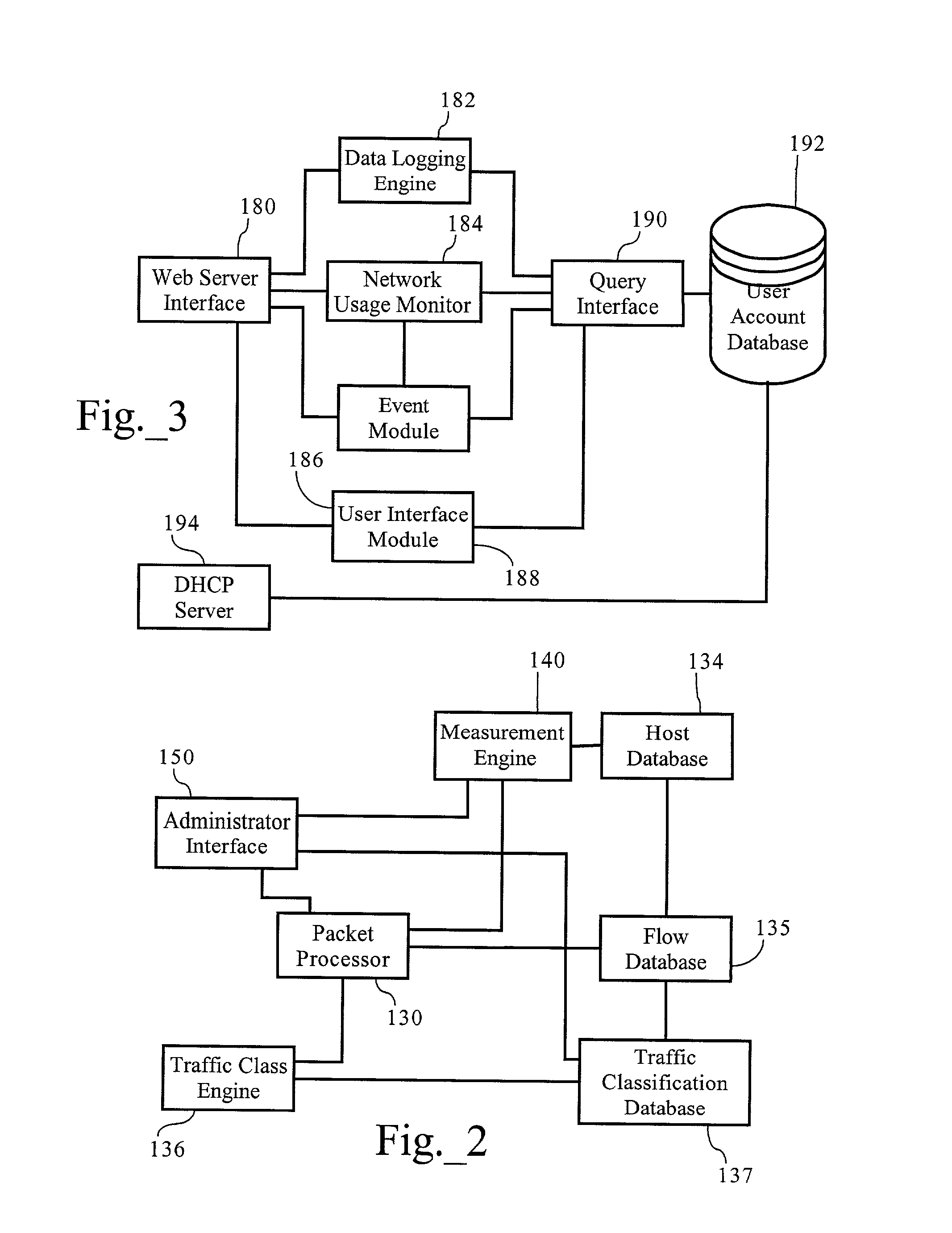
Volume-based network management scheme
Methods, apparatuses and systems allowing for deployment of volume-based network policies across a computer network. In one embodiment, the present invention monitors network utilization of a plurality of users and detects the occurrence of network utilization milestones or other events for individual users, such as exceeding a data transfer allotment or threshold. To enforce the allotment or threshold, the present invention is operative to deny, degrade, or otherwise affect a characteristic associated with network access provided to such users.
Owner:CA TECH INC
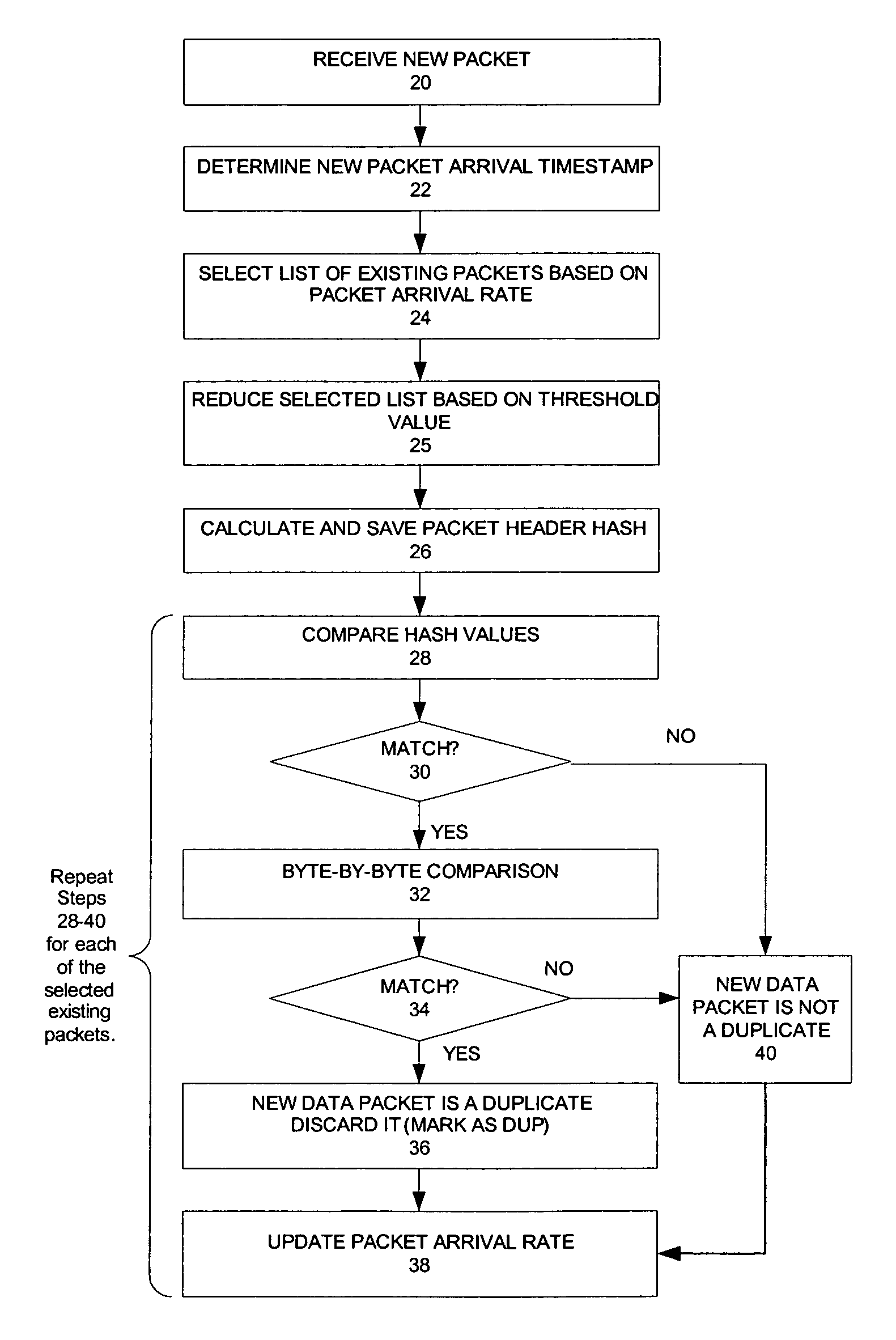
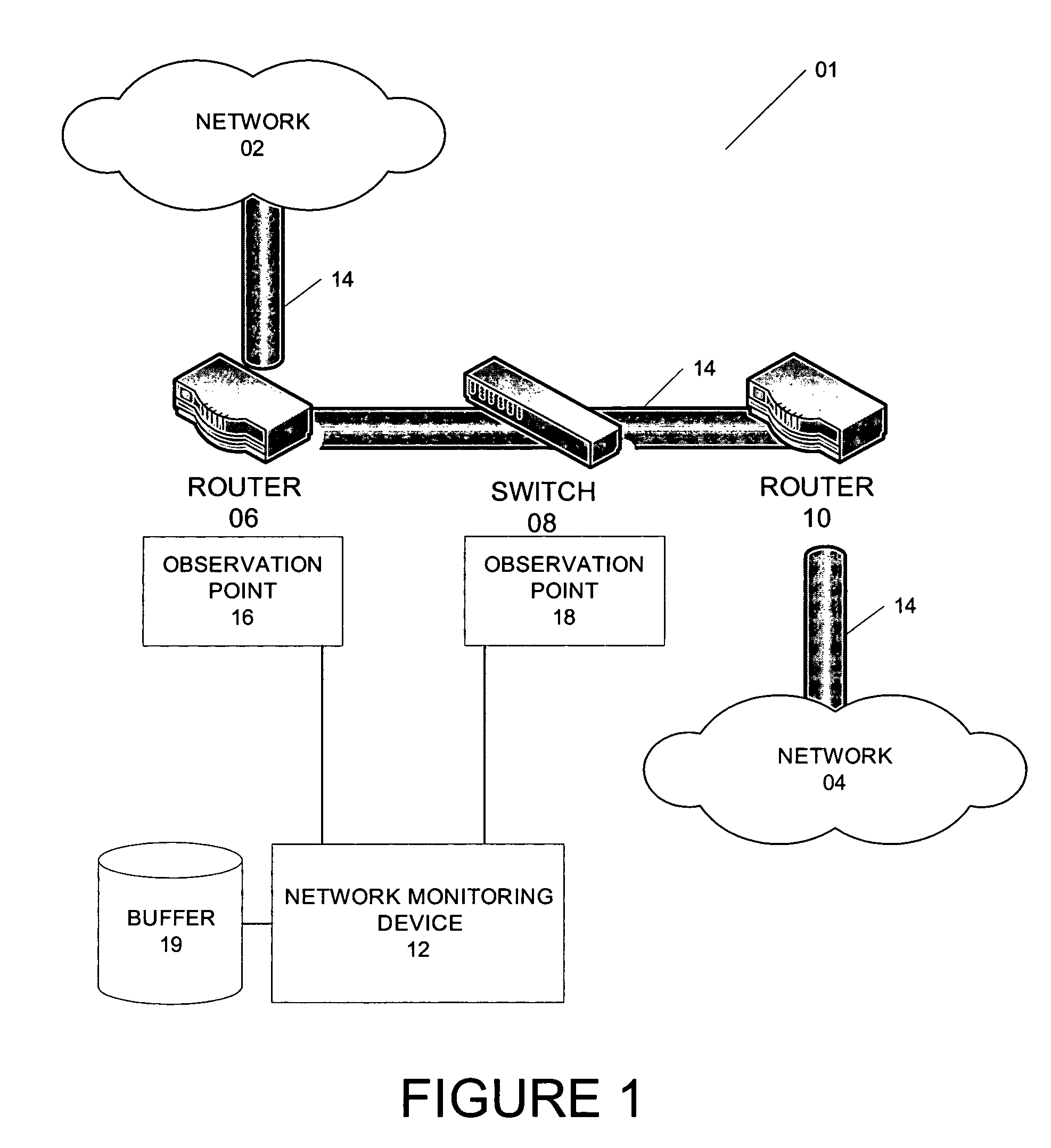
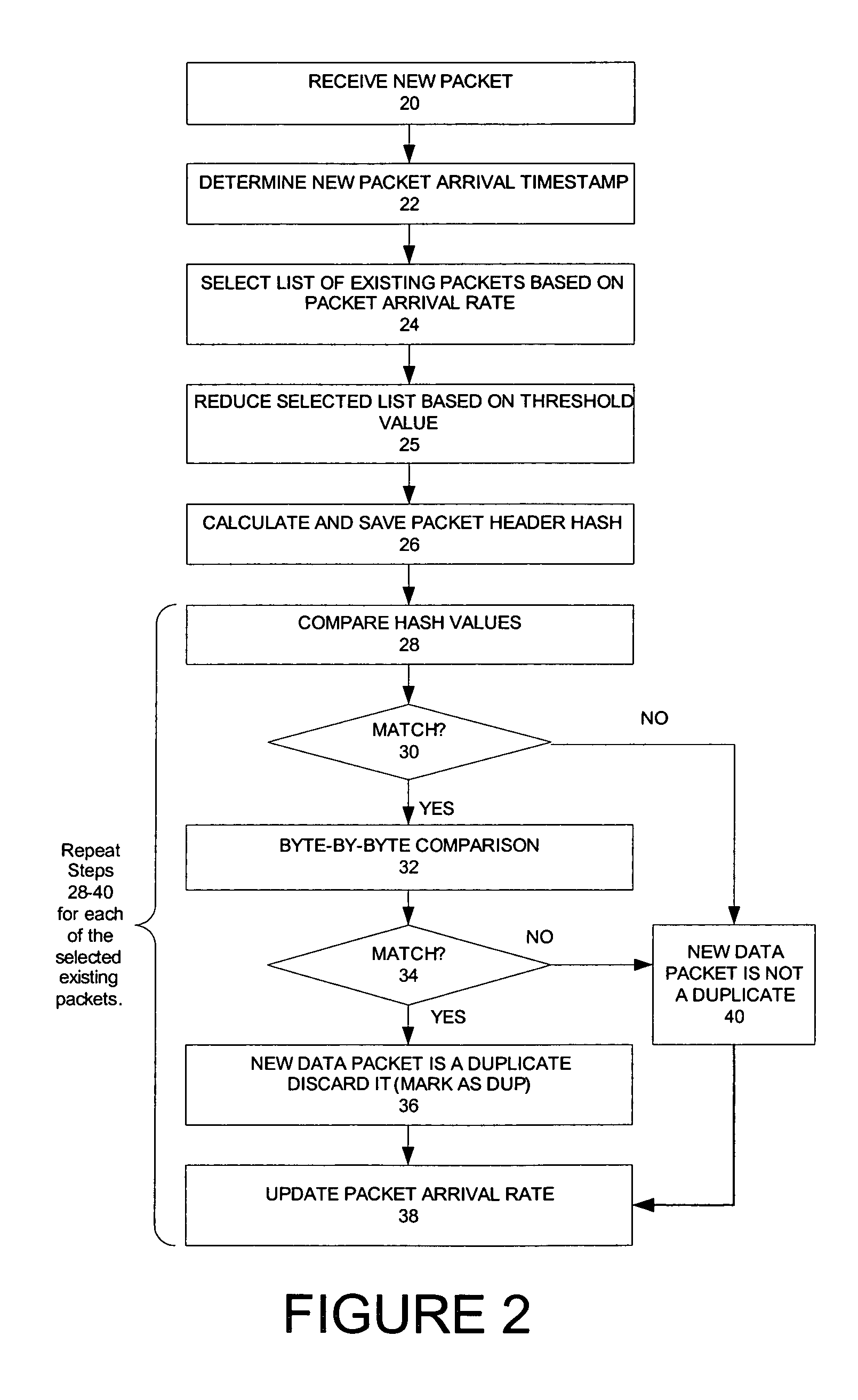
Method and system for identifying duplicate packets in flow-based network monitoring system
A network monitoring device configured to collect a new packet from one or more observation points of a network and to compare the new packet with a list of a number of received packets based on a packet arrival rate and to identify a duplicate packet. In particular, the number of received packets in the list is equivalent to a number of packets received within a time period, i.e. the packet arrival rate. Stated differently, the network monitoring device is to compare the new packets with received packets stored in a queue of a buffer and wherein the queue has a size based on a packet arrival rate collected at one or more observation points. In addition, the time period is further adjusted according to a threshold value. The threshold value is a variable parameter that can be adjusted to compensate for different network deployment. In one embodiment, the threshold value is a time value that is not more than a transmission time of a TCP retransmitted packet.
Owner:RIVERBED TECH LLC
System and Method for Optical Layer Management in Optical Modules and Remote Control of Optical Modules
ActiveUS20120275784A1Low costMultiplex system selection arrangementsTime-division optical multiplex systemsTransceiverNetwork connection
A system and method for managing the optical layer network data communications of an optical fiber data network by an optical transceiver module is disclosed. The management of the optical layer network data communications comprising data link layer functions or layer 2 functions in an OSI model. Benefits include reduction in reduced cost of network deployments from consolidation of network equipment, such as switches, and reduction in power consumed as well as enabling point-to-multipoint network connections from previously only point-to-point network connection.
Owner:SOTO ALEXANDER I +1
Distributed software defined networking
ActiveUS9843624B1Software maintainance/managementDigital data authenticationNetwork deploymentDistributed computing
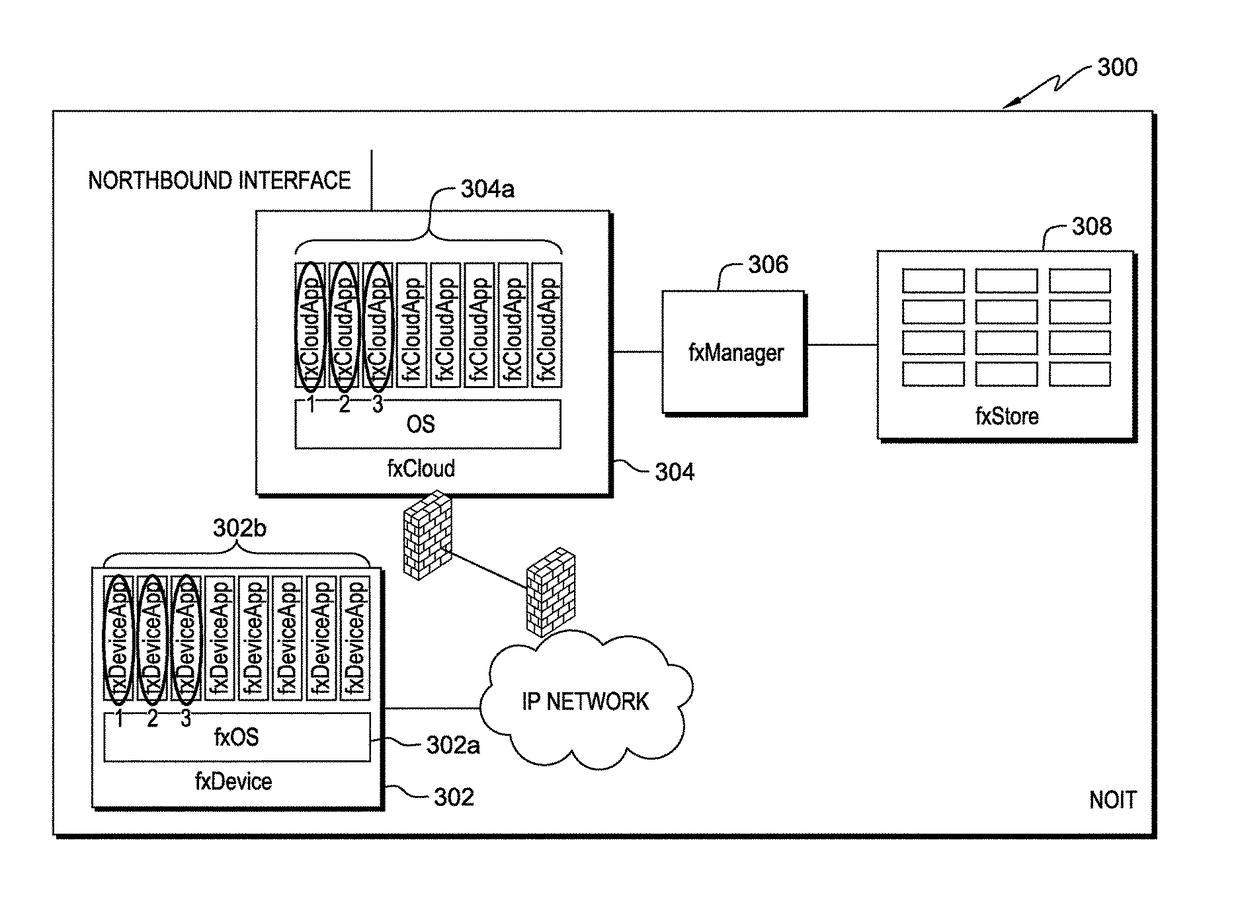
The Distributed Software Defined Network (dSDN) disclosed herein is an end-to-end architecture that enables secure and flexible programmability across a network with full lifecycle management of services and infrastructure applications (fxDeviceApp). The dSDN also harmonizes application deployment across the network independent of the hardware vendor. As a result, the dSDN simplifies the network deployment lifecycle from concept to design to implementation to decommissioning.
Owner:EDGE NETWORKING SYST LLC
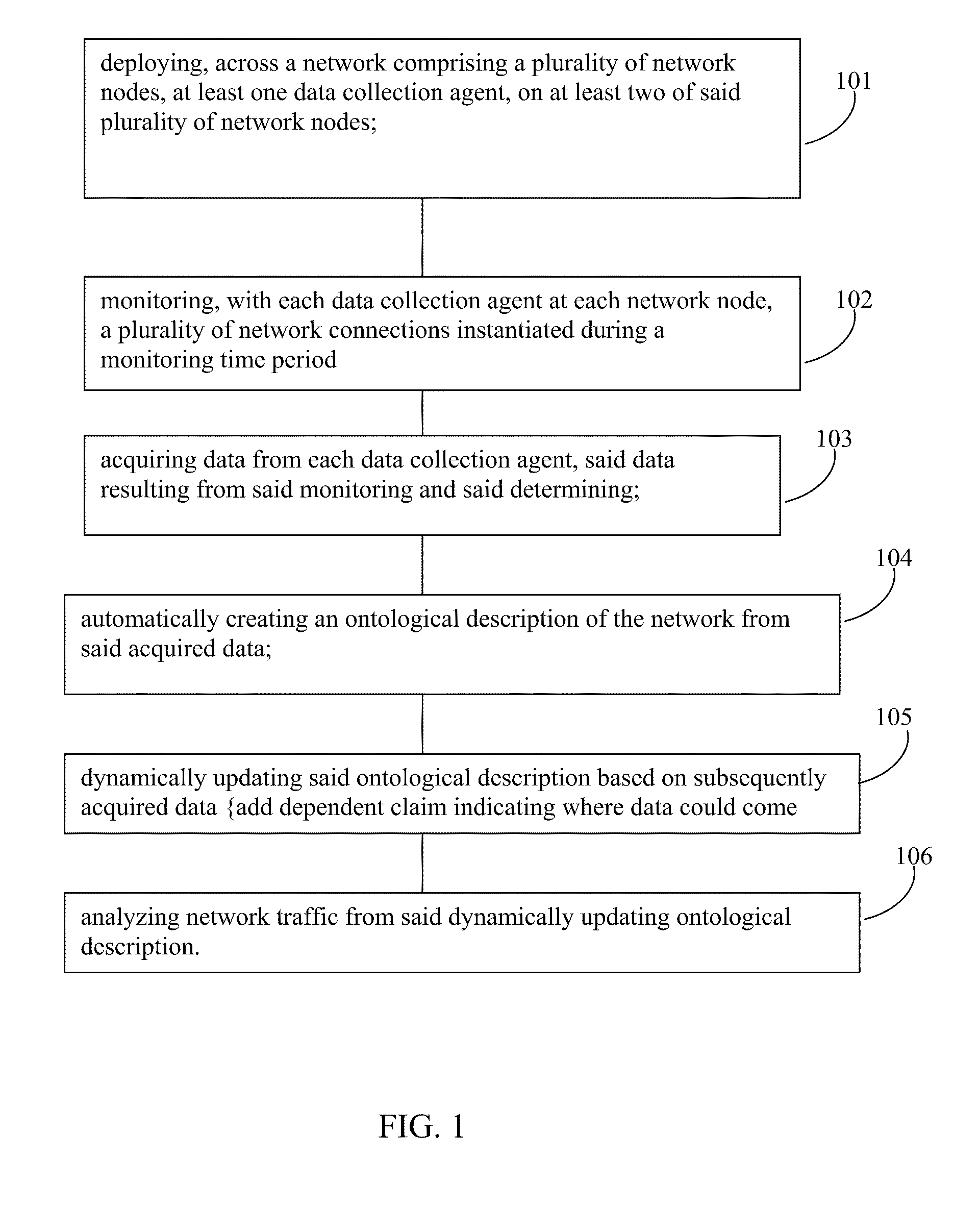
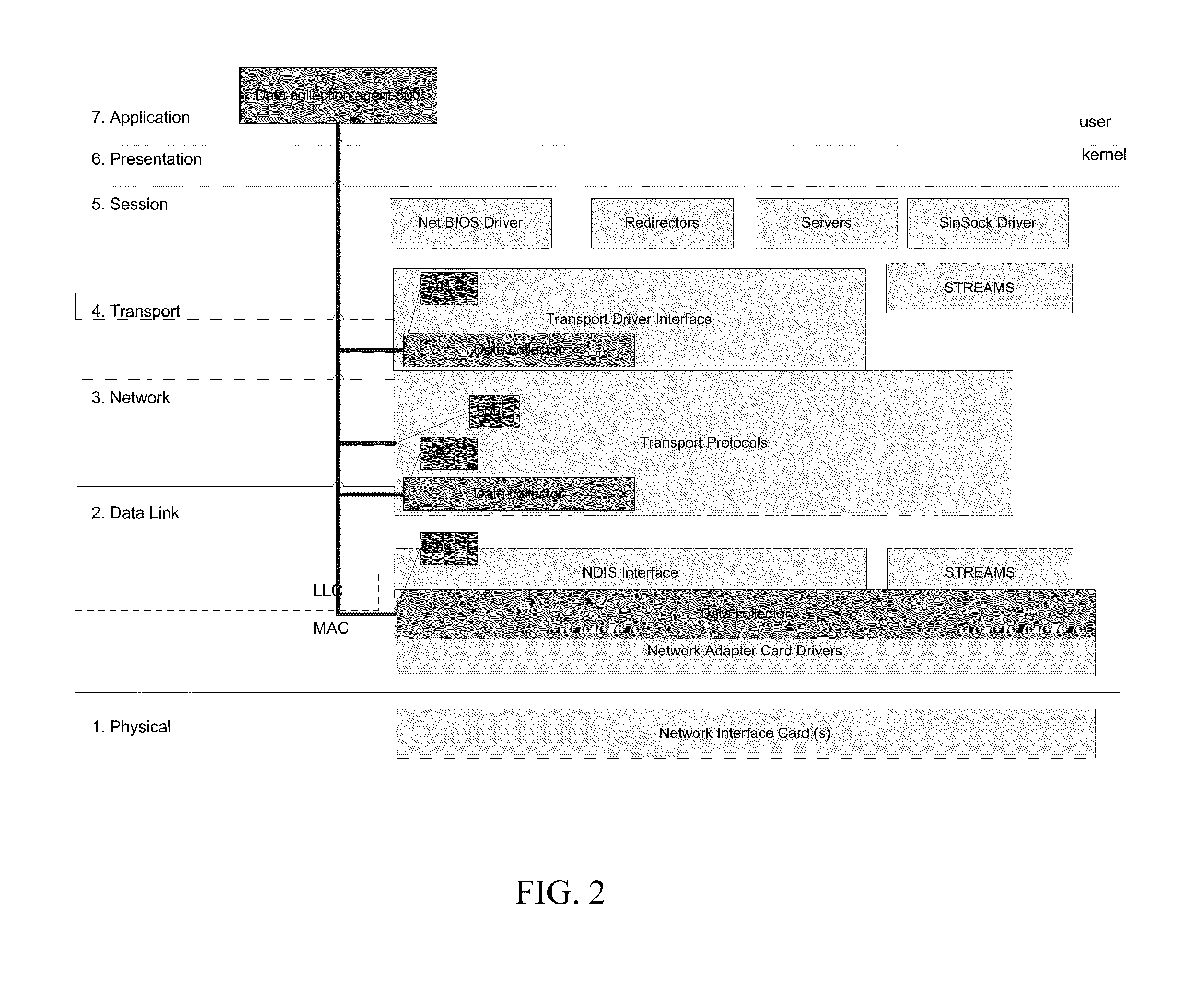
Network traffic analysis using a dynamically updating ontological network description
ActiveUS20100077078A1Improved ability to analyze network trafficDescribe wellDigital data processing detailsAnalogue secracy/subscription systemsTraffic capacityNetwork deployment
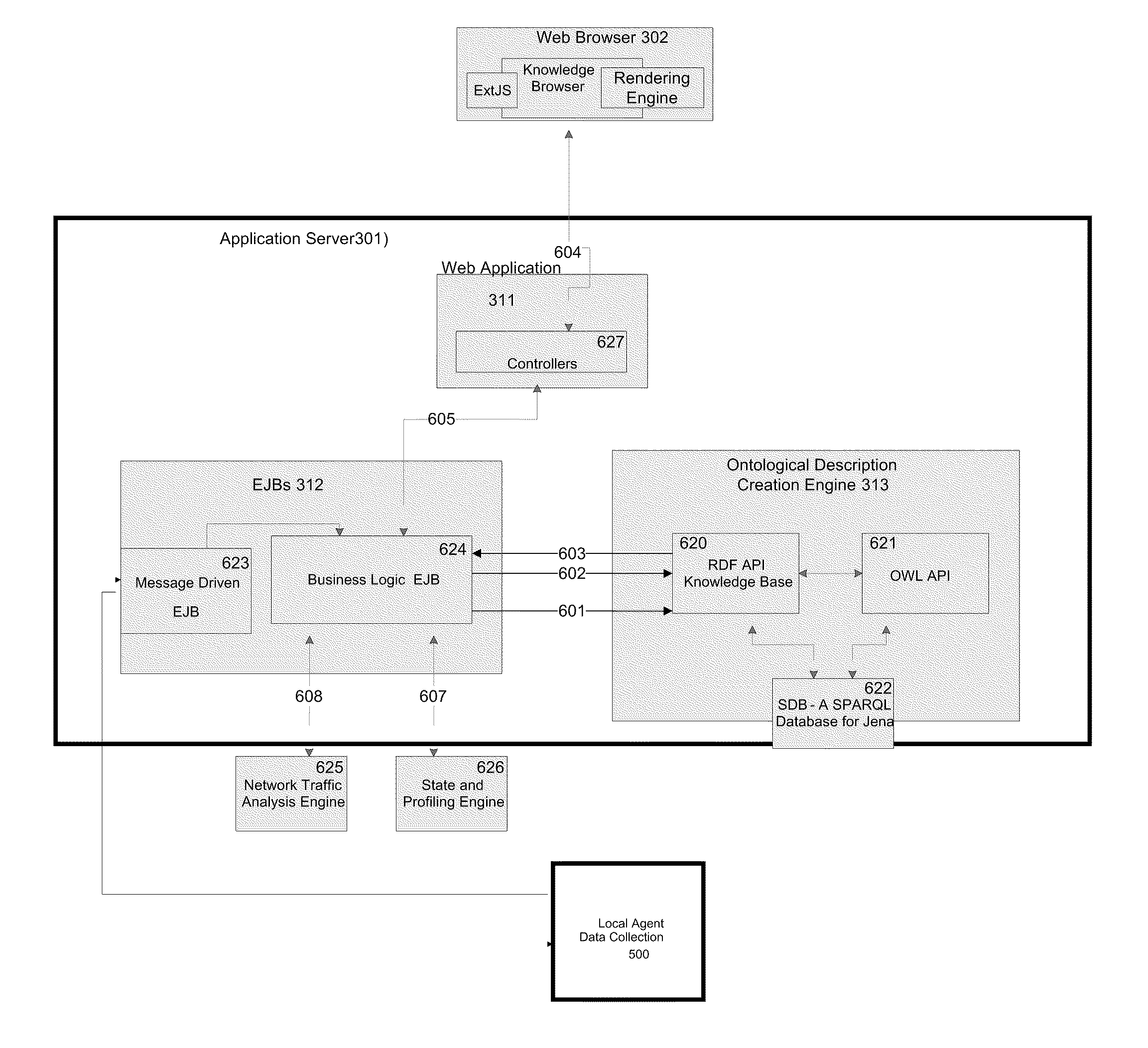
Network traffic analysis is performed by deploying, across a network having a plurality of network nodes, at least one data collection agent, on at least two of the plurality of network nodes. Each data collection agent may monitor at each network node, a plurality of network connections instantiated during a monitoring time period. Data resulting from the monitoring is acquired from the data collection agents and an ontological description of the network is automatically created from the acquired data. The ontological description is dynamically updated and network traffic analysis is performed using the dynamically updating ontological description.
Owner:RED HAT
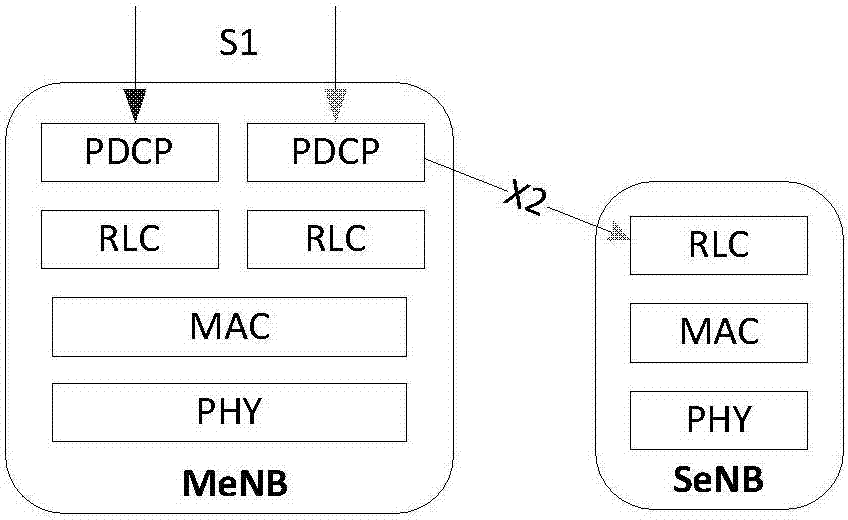
Method for switching base stations for user equipment (UE), base stations and UE
InactiveCN104301955AImprove efficiencyImprove data transfer performanceSignal allocationConnection managementNetwork deploymentHeterogeneous network
The invention discloses a method for switching base stations for user equipment (UE), the base stations and the UE, and relates to a mobile communication system deployed in a heterogeneous network. The method for switching the base stations for the UE includes the steps that when the main base station of the double-link UE is switched, and the target base station determines that the UE keeps connection with the secondary base station and configuration; the target base station builds connection with the UE while the UE keeps connection with the secondary base station and configuration. The invention further discloses other three methods for switching the base stations for the UE and the corresponding base stations and UE. According to the technical scheme, when the UE transmits data and / or moves, the user interface of the UE and the connected secondary base station will not be interrupted when the main base station connected to the UE is changed, and namely data transmission can continue. Thus, the performance and handing capacity of data transmission of the UE are improved, and the use efficiency of wireless resources is improved.
Owner:ZTE CORP
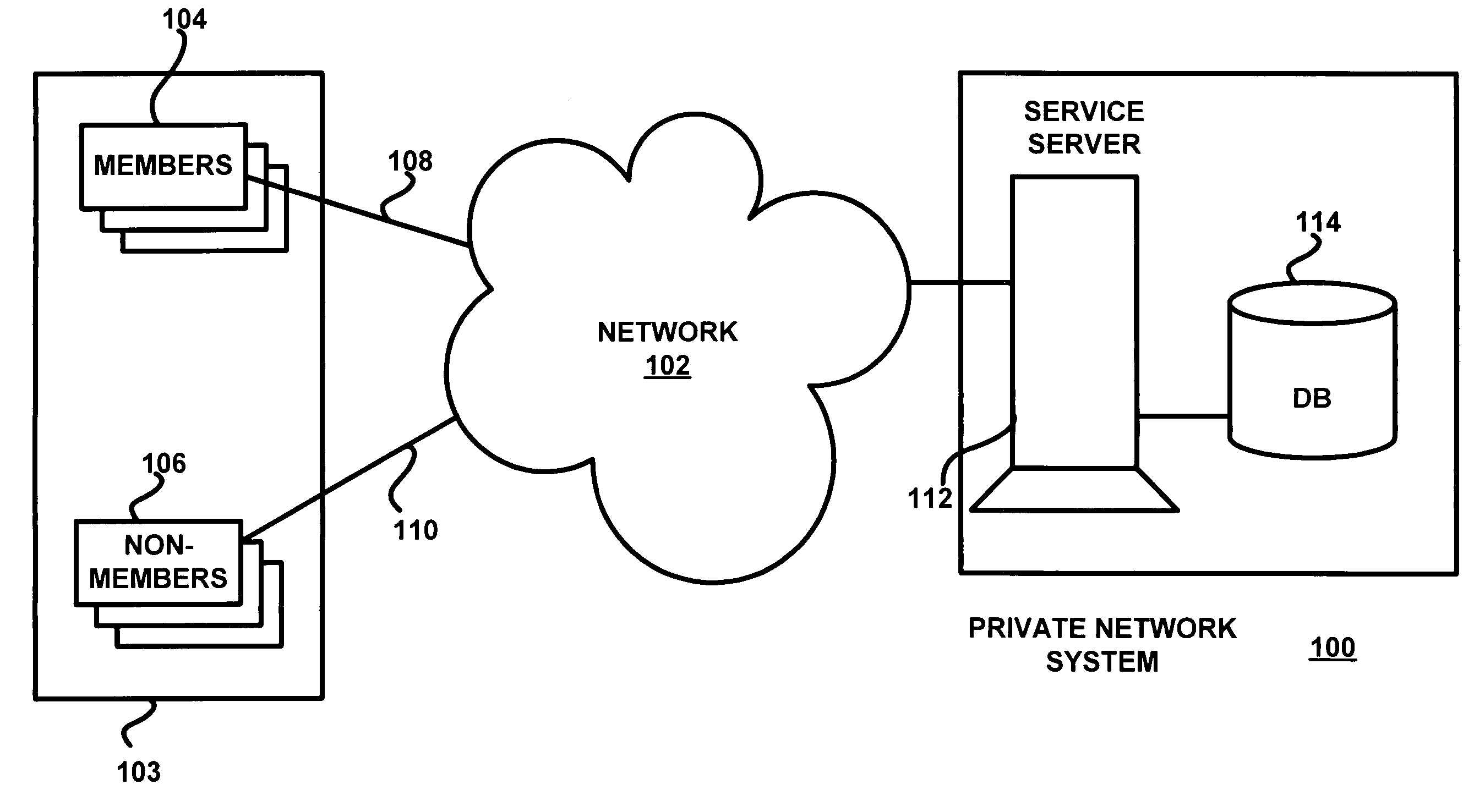
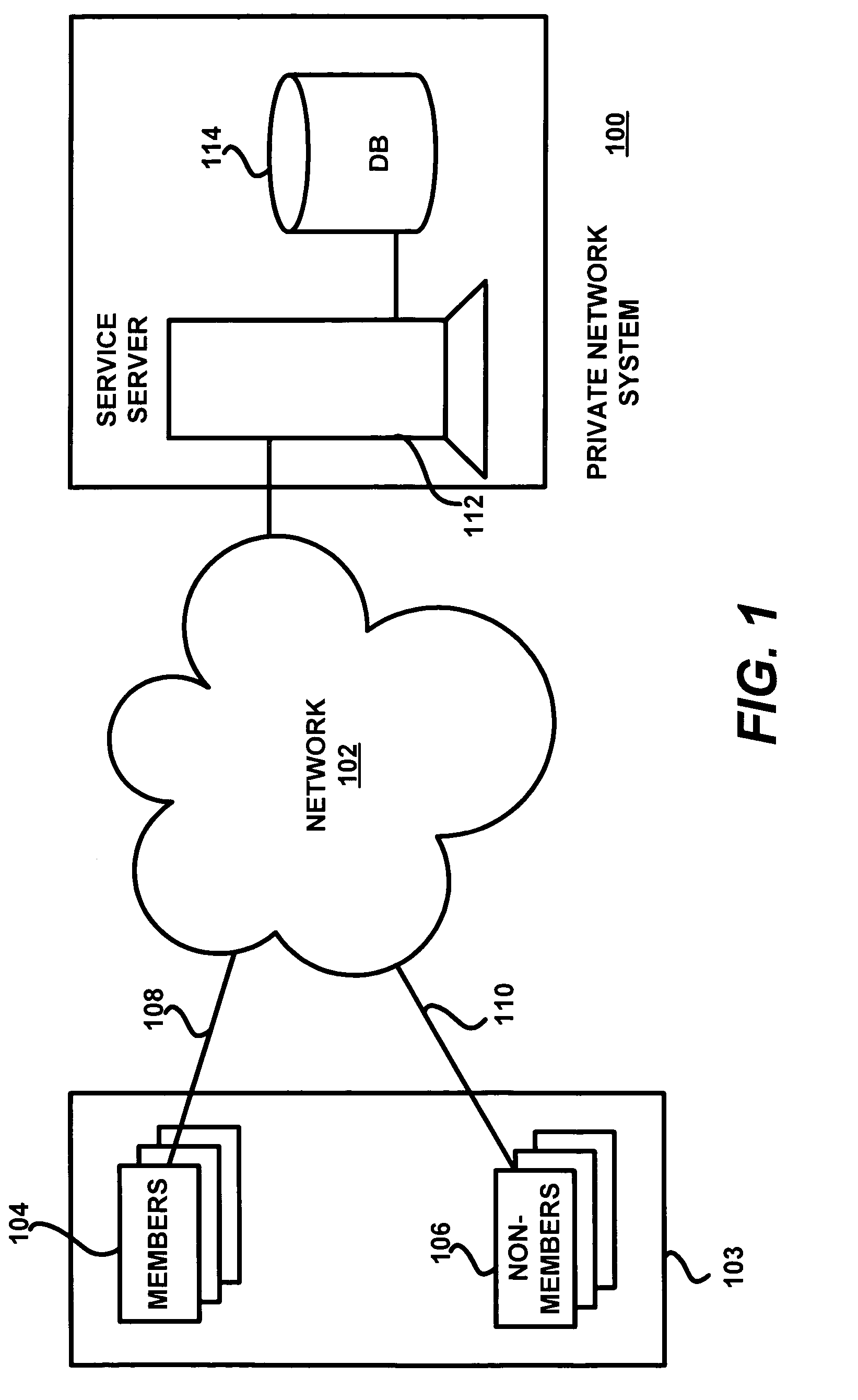
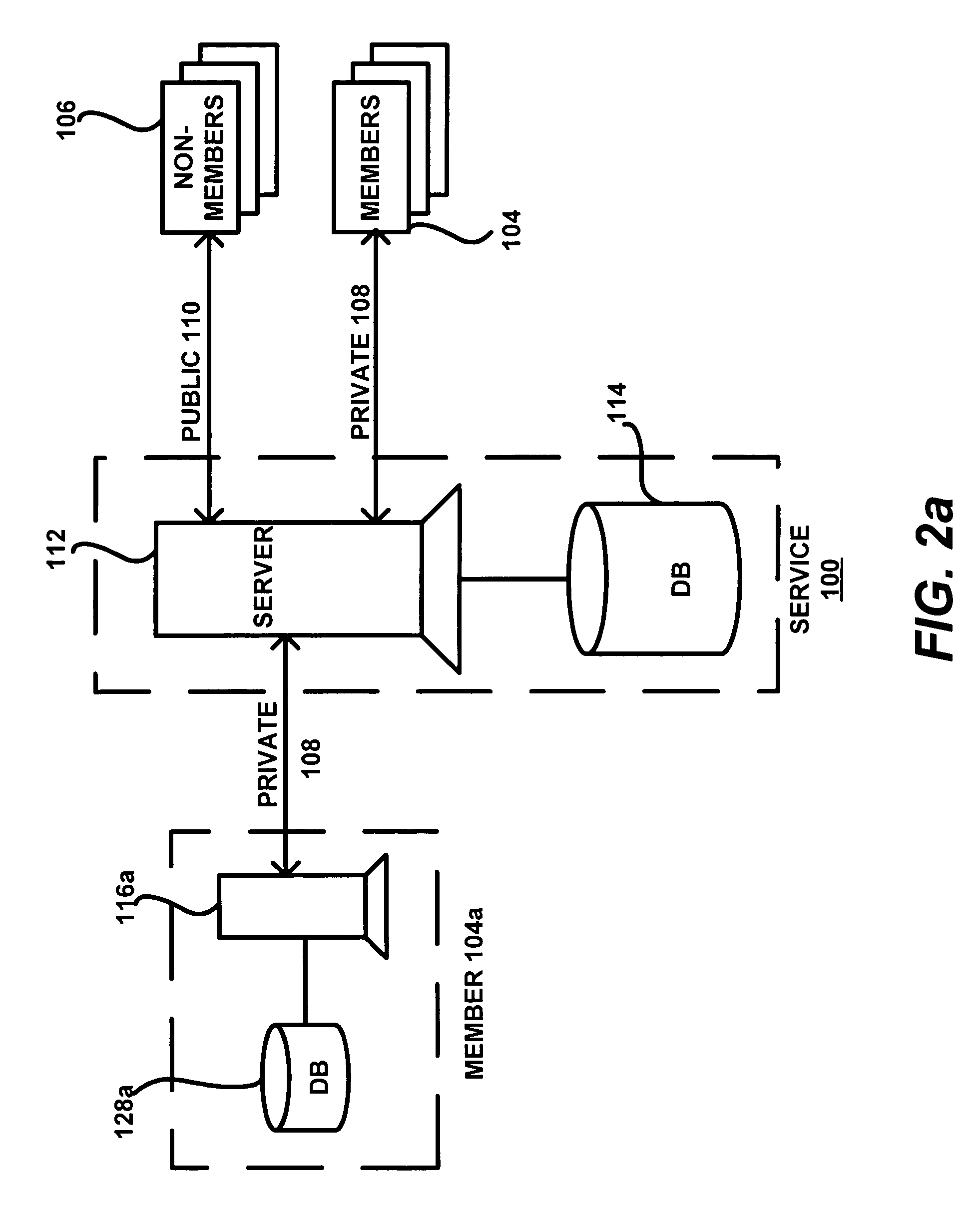
Viral engine for network deployment
ActiveUS7389324B2Data processing applicationsDigital data processing detailsPersonalizationNetwork deployment
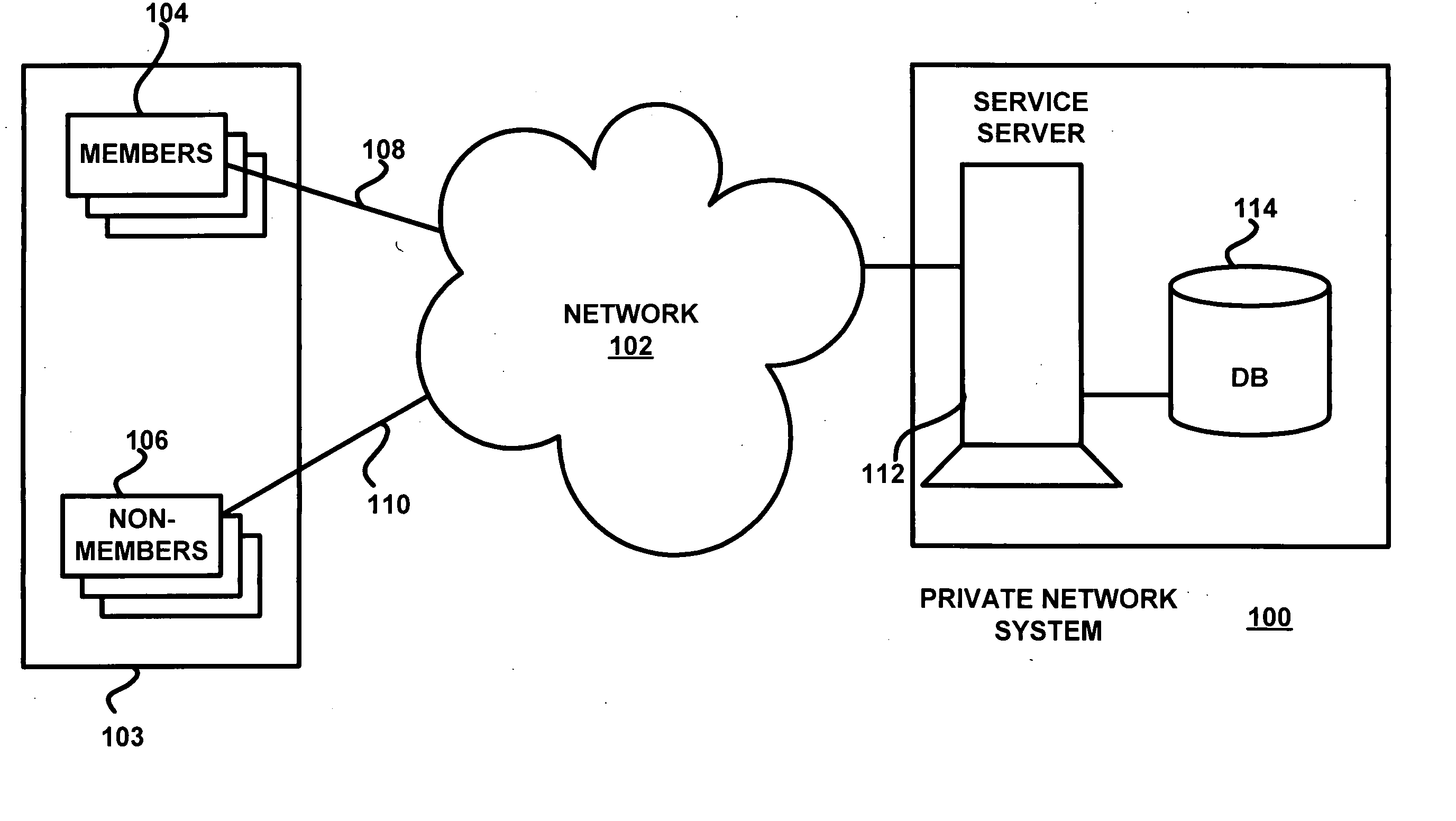
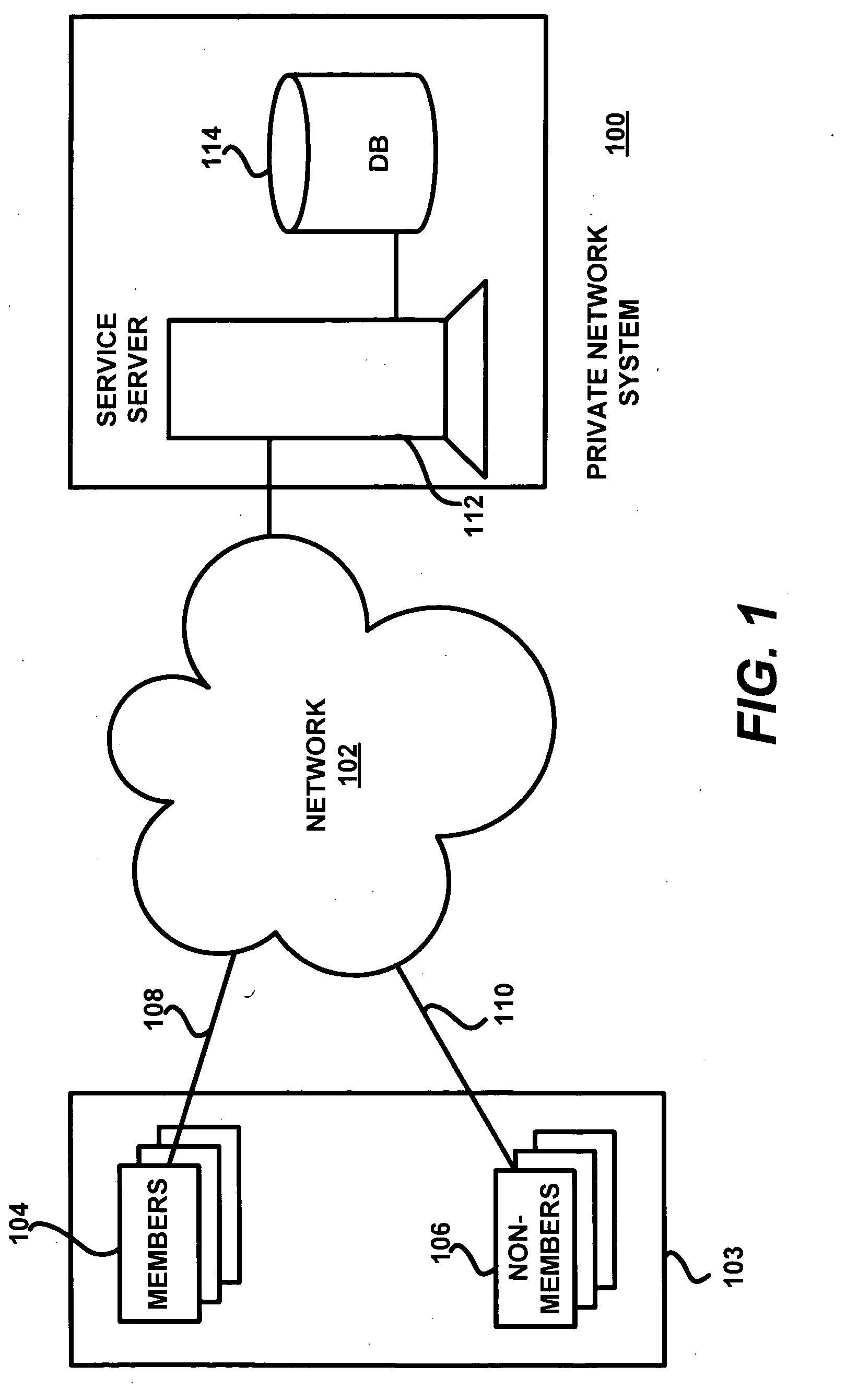
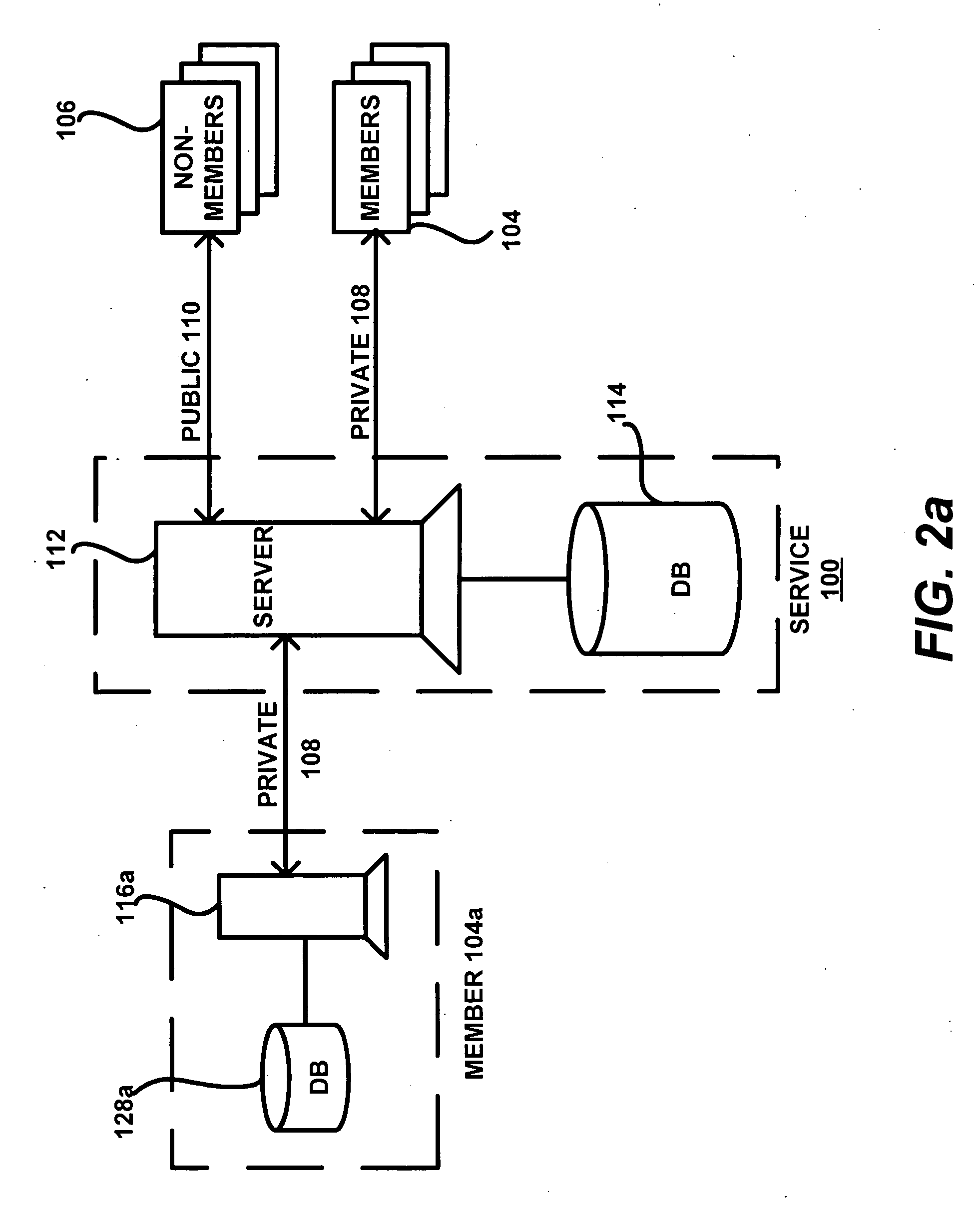
A private network system operates over a public network to provide an asymmetric service to members with information from other members and non-members. The system includes central servers and databases connected via the public network to client systems of public network users. The users may be members who communicate with a private protocol or non-members who communicate with the public protocol. A process for the private service includes communication of information between users via the private service servers. The private service server implements the private service, which includes a viral engine for network deployment. Features of the viral engine include genetic algorithms, data mining, personalization, frictionless service setup, user maximization, and member-controlled privacy. A sample setup process and contact update wizard that include several viral engine features are described.
Owner:PLAXO INC
Rack level pre-installed interconnect for enabling cableless server/storage/networking deployment
ActiveUS20150280827A1Multiplex system selection arrangementsNear-field transmissionNetwork deploymentTelecommunications link
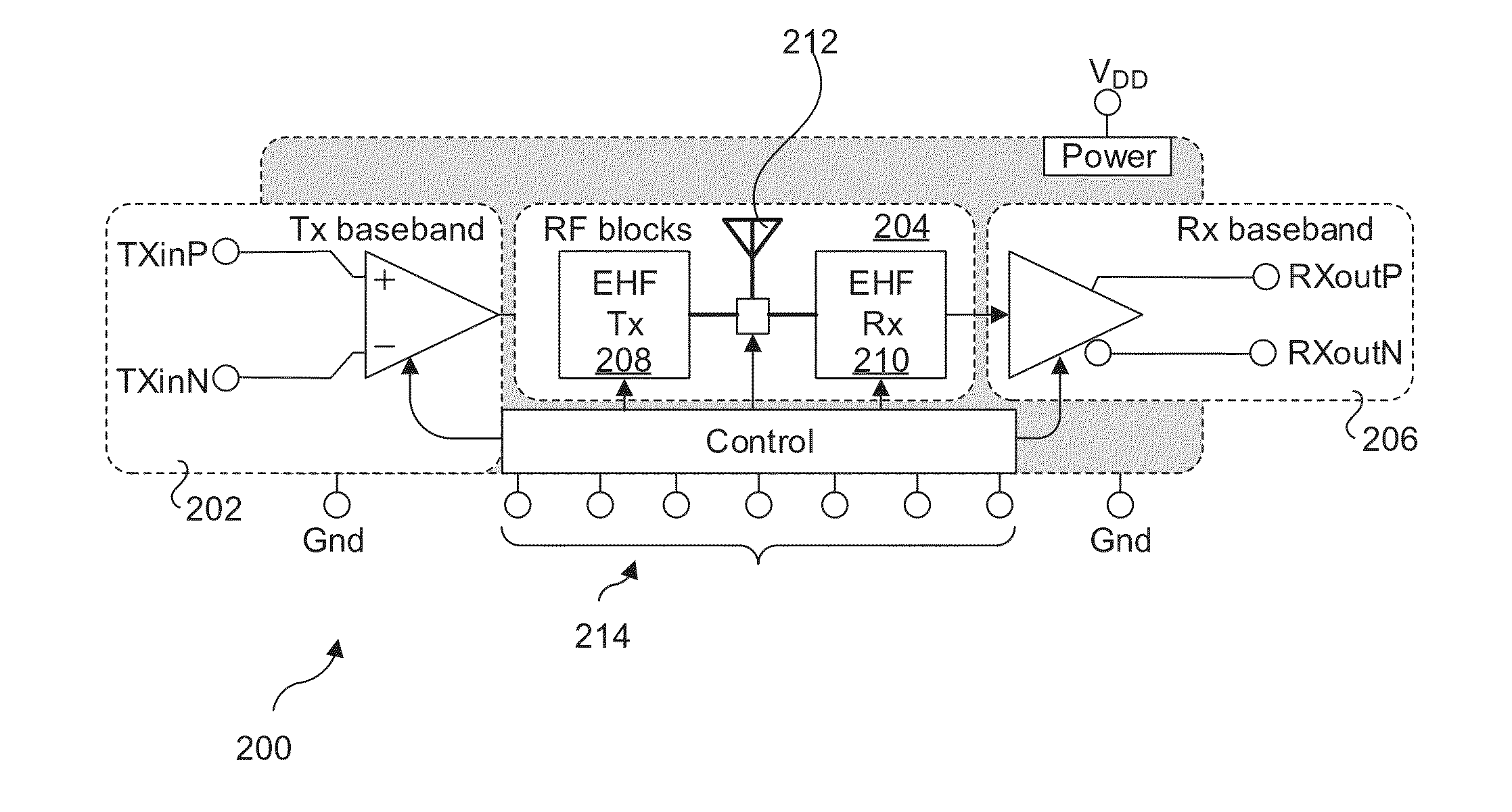
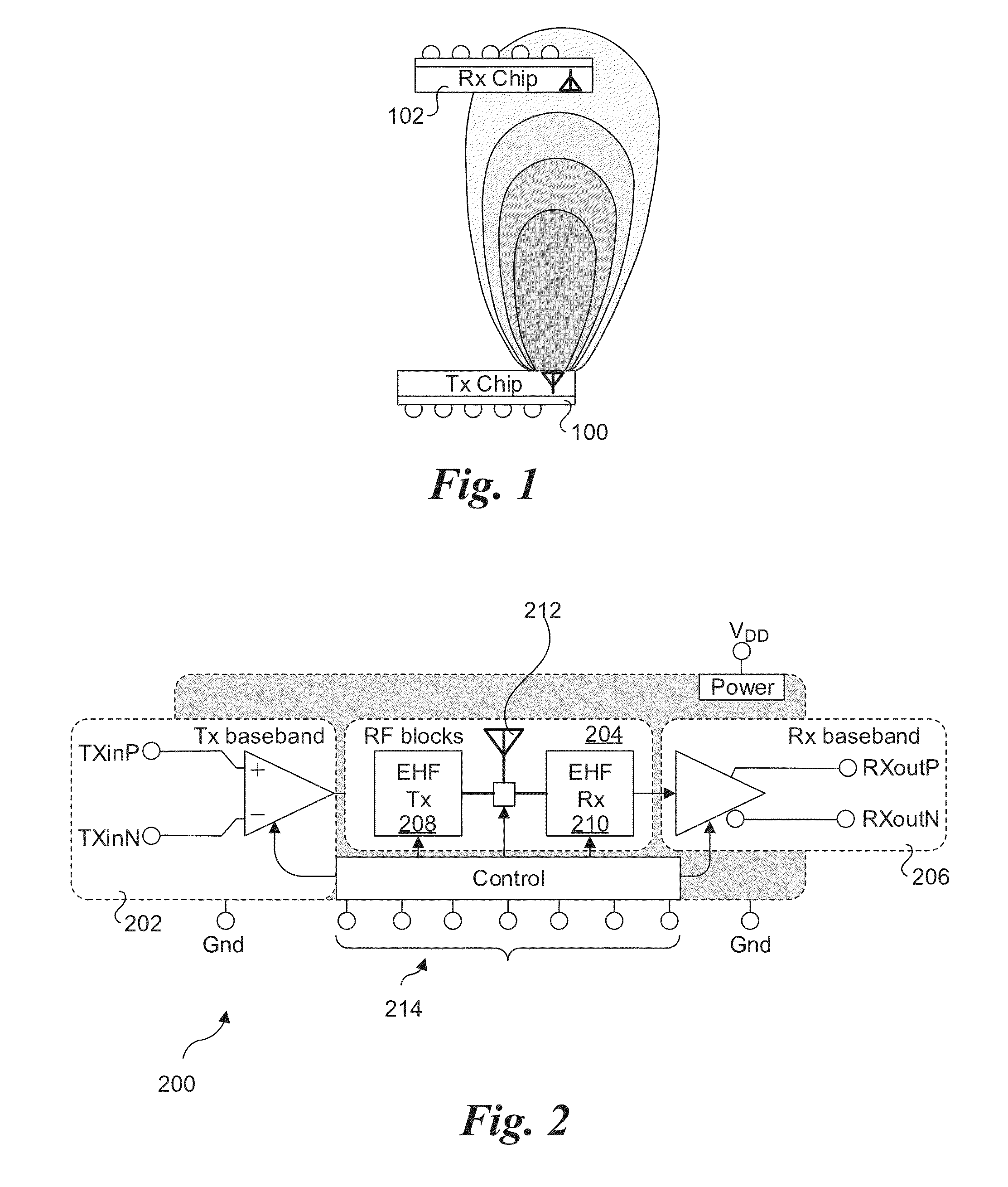
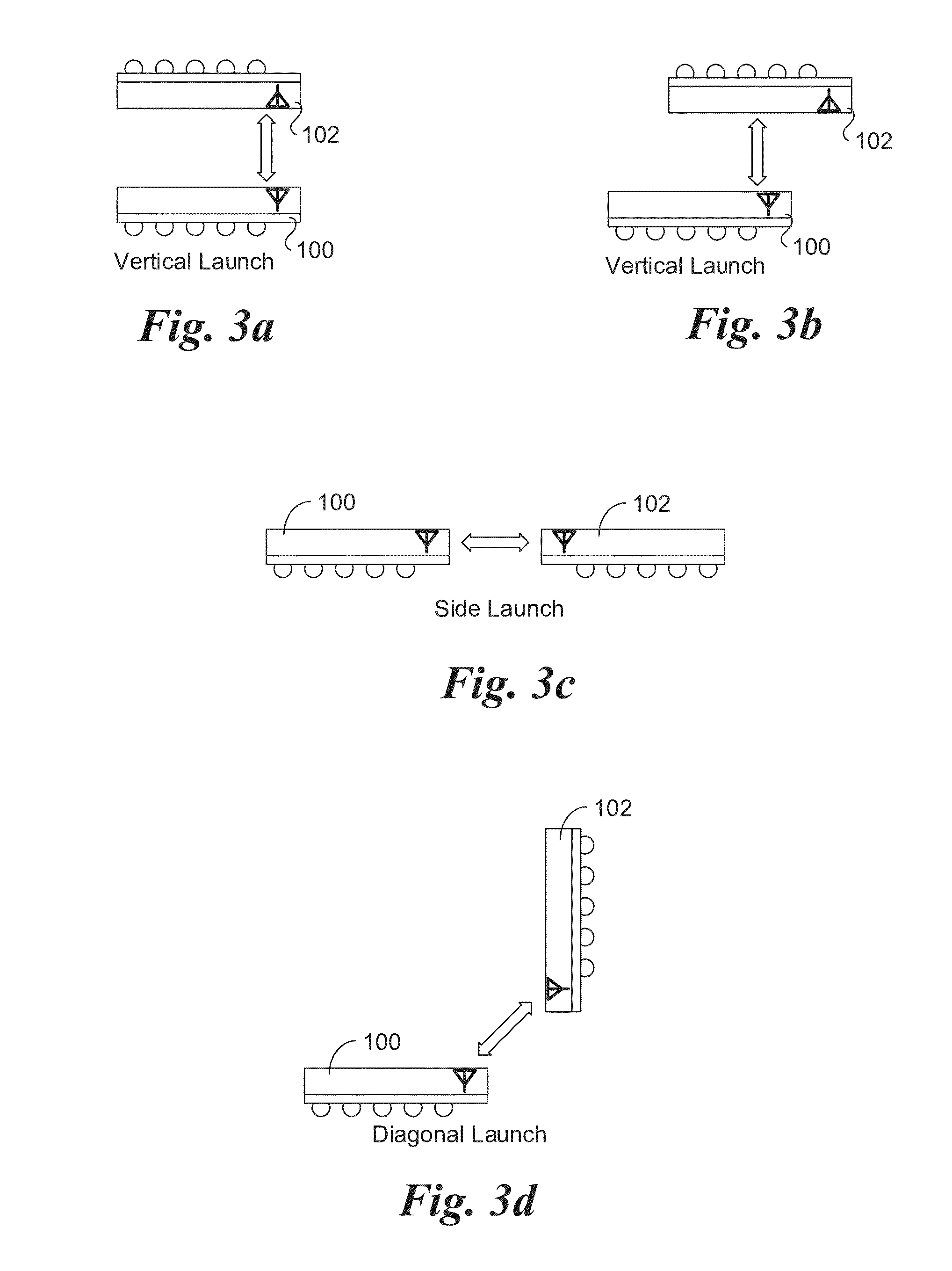
Apparatus and methods for rack level pre-installed interconnect for enabling cableless server, storage, and networking deployment. Plastic cable waveguides are configured to couple millimeter-wave radio frequency (RF) signals between two or more Extremely High Frequency (EHF) transceiver chips, thus supporting millimeter-wave wireless communication links enabling components in the separate chassis to communicate without requiring wire or optical cables between the chassis. Various configurations are disclosed, including multiple configurations for server chassis, storage chassis and arrays, and network / switch chassis. A plurality of plastic cable waveguide may be coupled to applicable support / mounting members, which in turn are mounted to a rack and / or top-of-rack switches. This enables the plastic cable waveguides to be pre-installed at the rack level, and further enables racks to be installed and replaced without requiring further cabling for the supported communication links. The communication links support link bandwidths of up to 6 gigabits per second, and may be aggregated to facilitate multi-lane links.
Owner:INTEL CORP
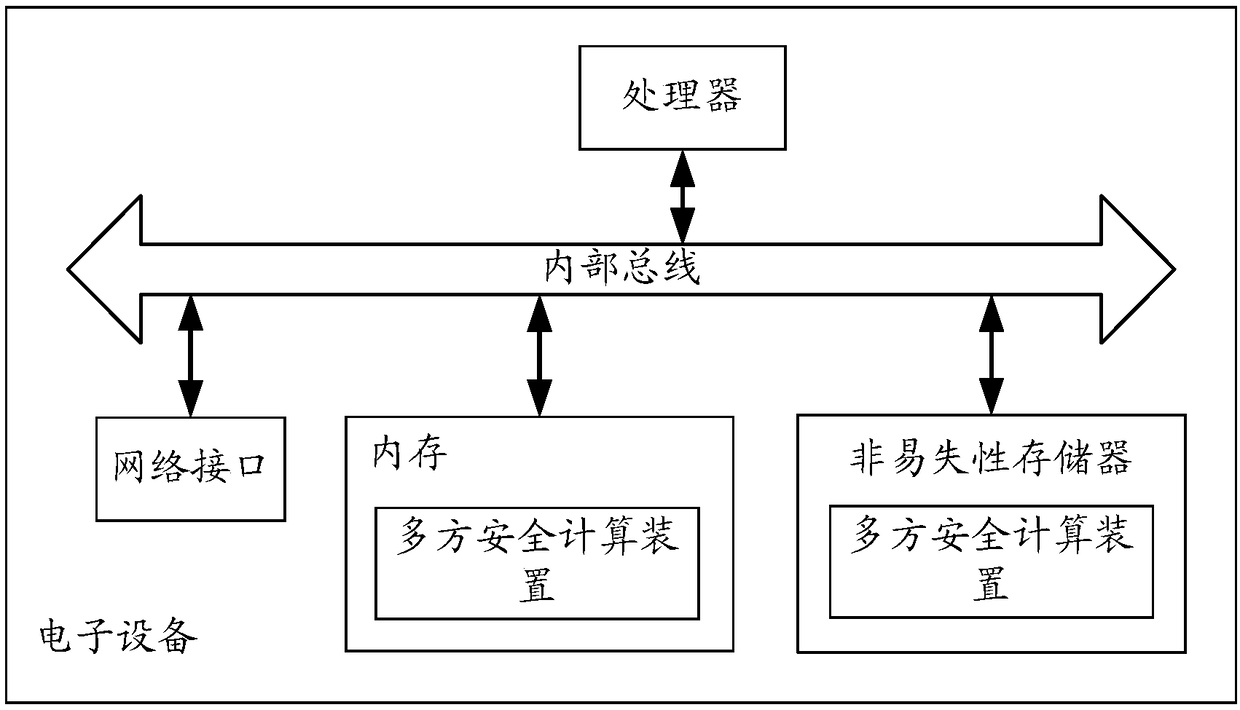
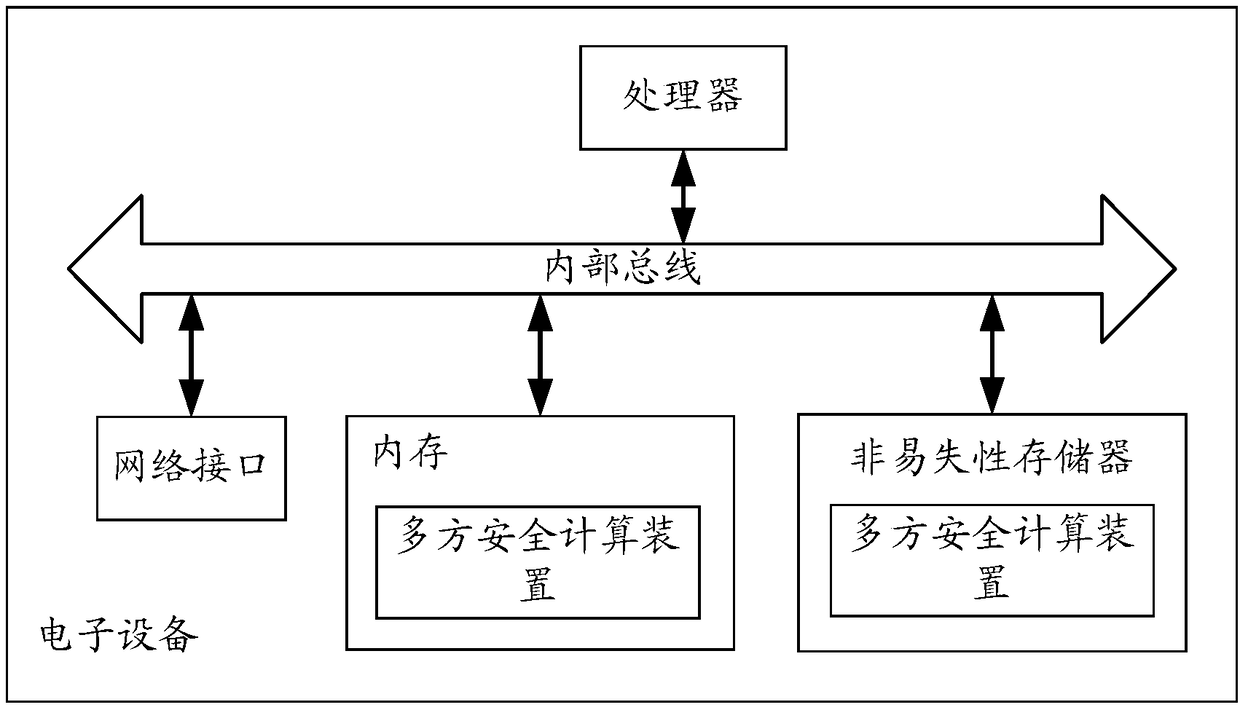
Multi-party safety calculation method and device, and electronic equipment
ActiveCN109255247AAvoid the Risk of Privacy LeakageDigital data processing detailsDigital data protectionInternet privacyElectric equipment
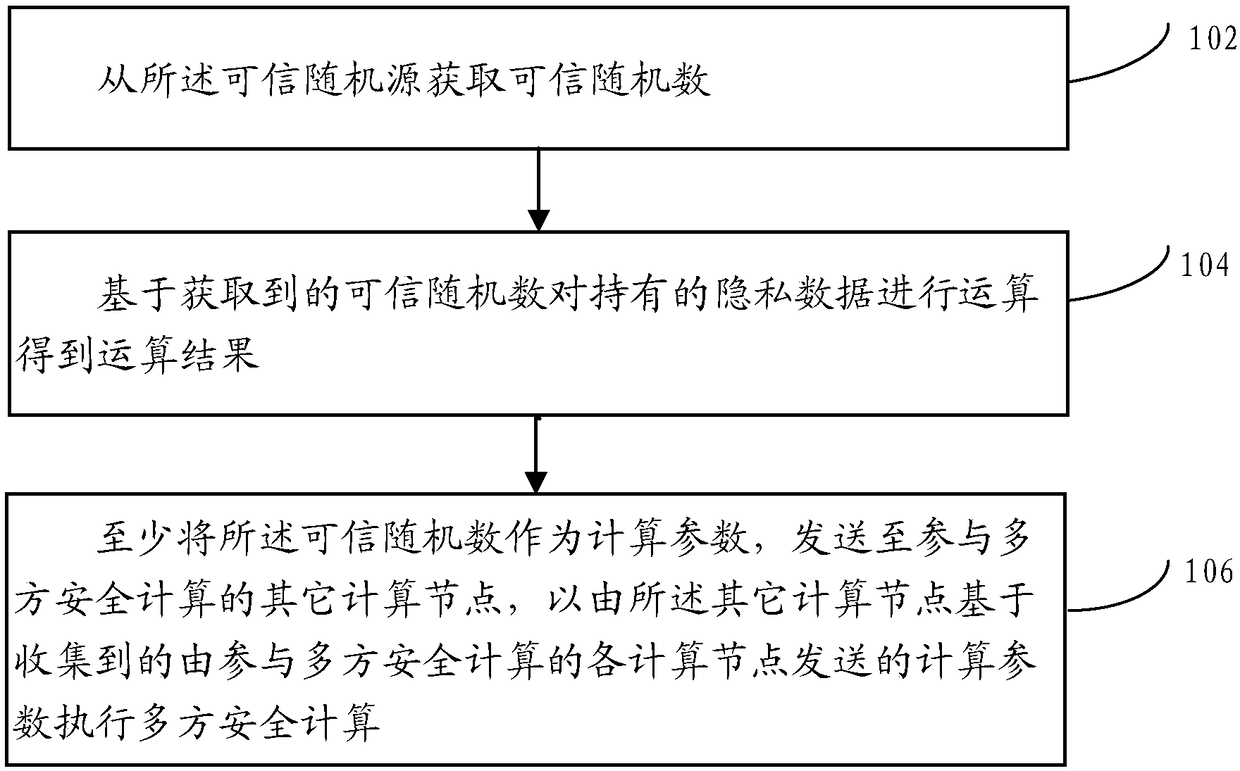
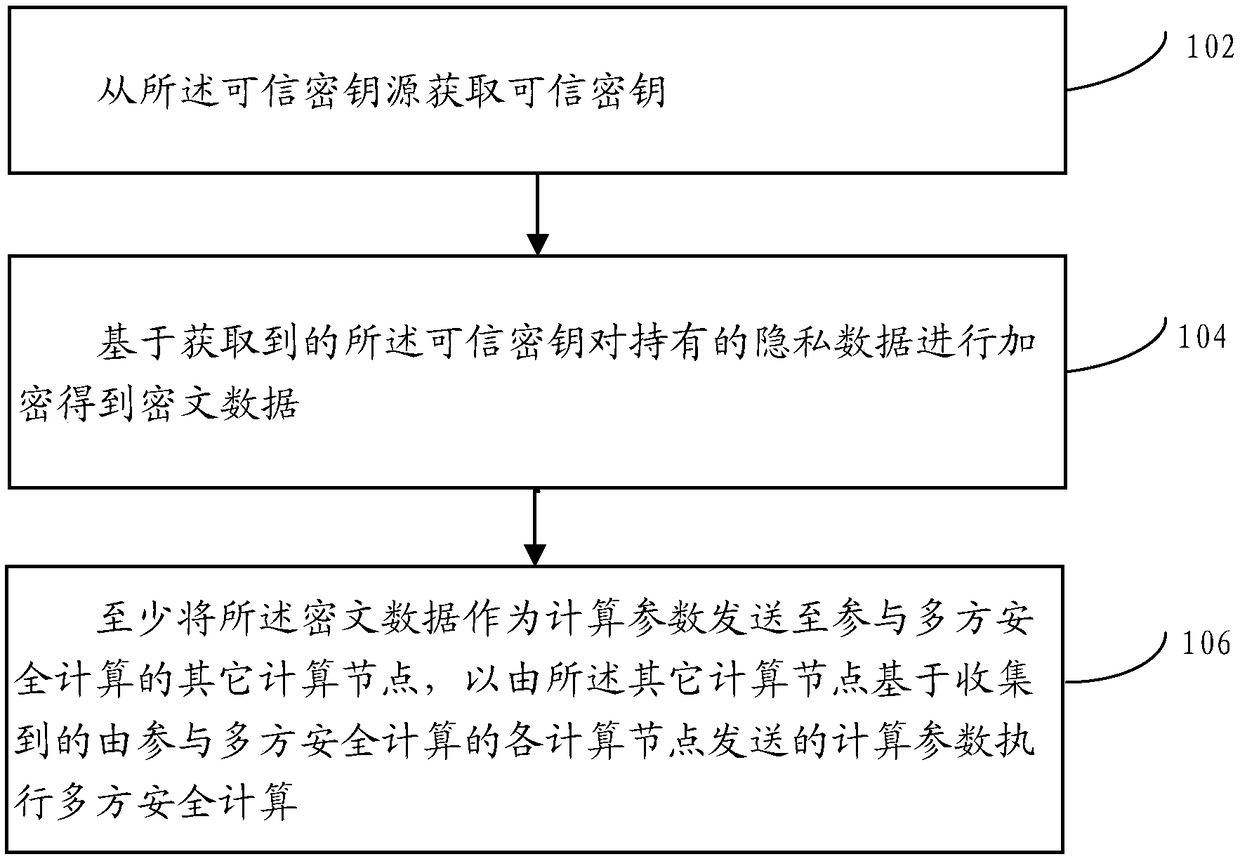
A multi-party secure computing method is applied to any computing node deployed in a distributed network. A plurality of computing nodes are deployed in the distributed network, and the plurality of computing nodes participate in the multi-party secure computing together based on the privacy data held by the plurality of computing nodes respectively; Wherein the computing node is docked with a trusted random source. The method comprises: obtaining a trusted random number from the trusted random source; Calculating the held privacy data based on the obtained trusted random number to obtain an operation result; sending at least the trusted random number as a computational parameter to other computational nodes participating in the multi-party security computation to perform the multi-party security computation by the other computational nodes based on the collected computational parameters sent by each computational node participating in the multi-party security computation.
Owner:ADVANCED NEW TECH CO LTD
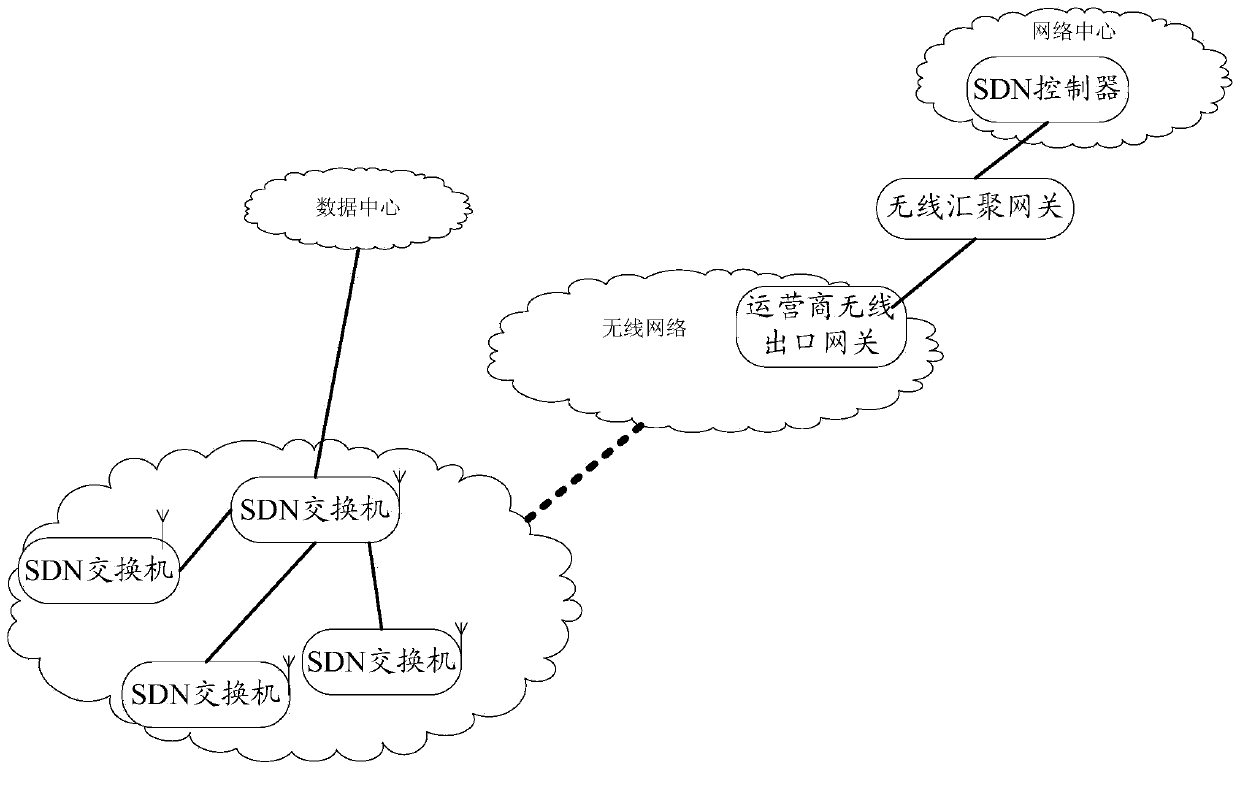
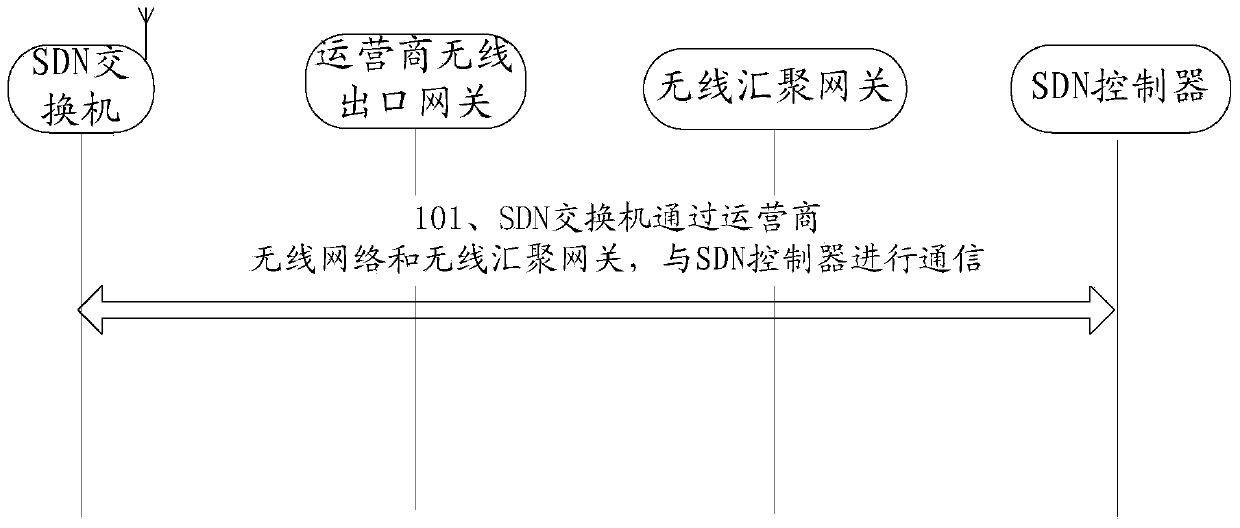
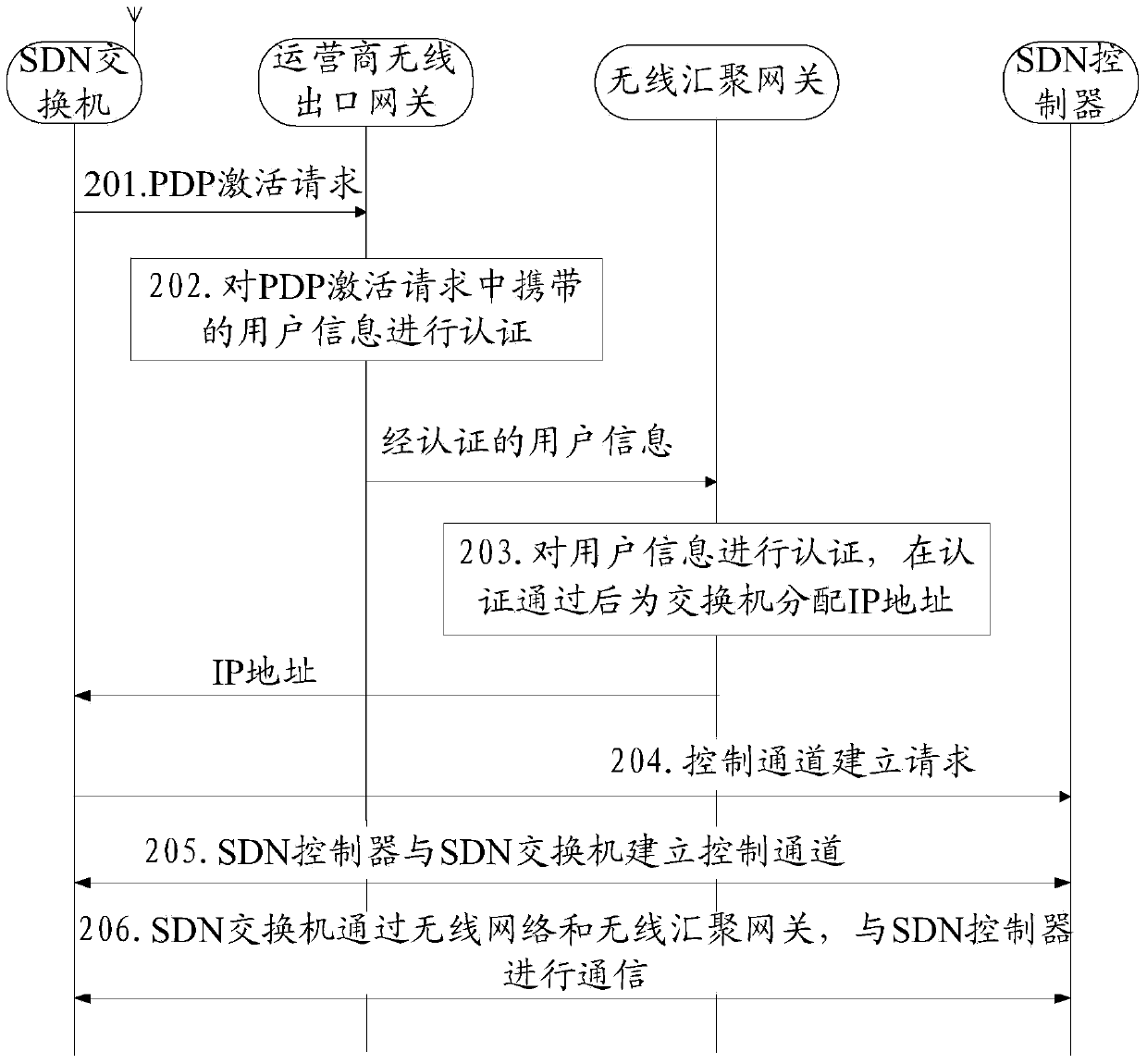
Communication method, software defined network SDN switch and communication system
ActiveCN103428771ALower deployment costsDeployment pushNetwork traffic/resource managementConnection managementWide area networkControl network
The invention discloses a communication method, a software defined network SDN switch and a communication system, and relates to the field of communication. The control system deployment cost of SDN equipment based on OpenFlow in the wide area network environment deployment process can be lowered. The communication method is applied to an SDN based on the OpenFlow, an SDN control network comprises the SDN switch, an operator wireless exit gateway, a wireless convergence gateway and an SDN controller, the SDN switch is connected to an operator wireless network served by the operator wireless exit gateway through a wireless communication module, and the wireless convergence gateway is respectively connected to the wireless exit gateway of the operator wireless network and the SDN controller through a wired network. The communication method comprises the step that the SDN switch is in communication with the SDN controller through the operator wireless network and the operator wireless exit gateway. The communication method is mainly used for the achievement process of the SDN control network based on the OpenFlow.
Owner:MAIPU COMM TECH CO LTD
Multi-party safety calculation method and device, and electronic equipment
ActiveCN109241016AAvoid the Risk of Privacy LeakageKey distribution for secure communicationData stream serial/continuous modificationCiphertextCalculation methods
A multi-party secure computing method is applied to any computing node deployed in a distributed network. A plurality of computing nodes are deployed in the distributed network, and the plurality of computing nodes participate in the multi-party secure computing together based on the privacy data held by the plurality of computing nodes respectively; Wherein the computing node is corresponding toa trusted key source; The method includes obtaining a trusted key from the trusted key source; Encrypting the held privacy data based on the obtained trusted key to obtain ciphertext data; sending atleast the ciphertext data as computational parameters to other computational nodes participating in the multi-party security computation to perform the multi-party security computation by the other computational nodes based on the collected computational parameters sent by each computational node participating in the multi-party security computation.
Owner:ADVANCED NEW TECH CO LTD
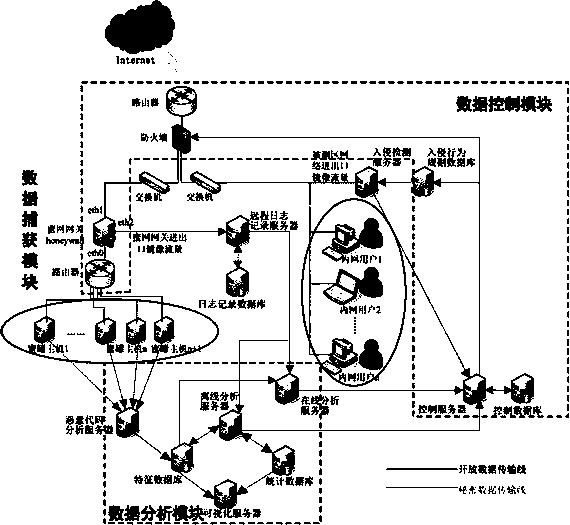
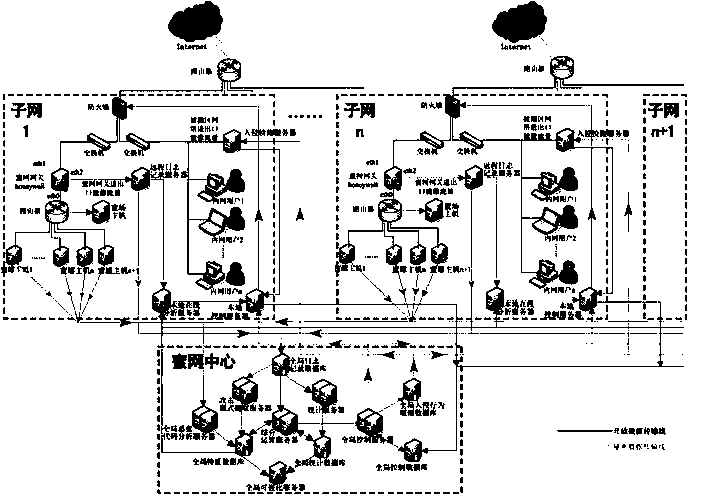
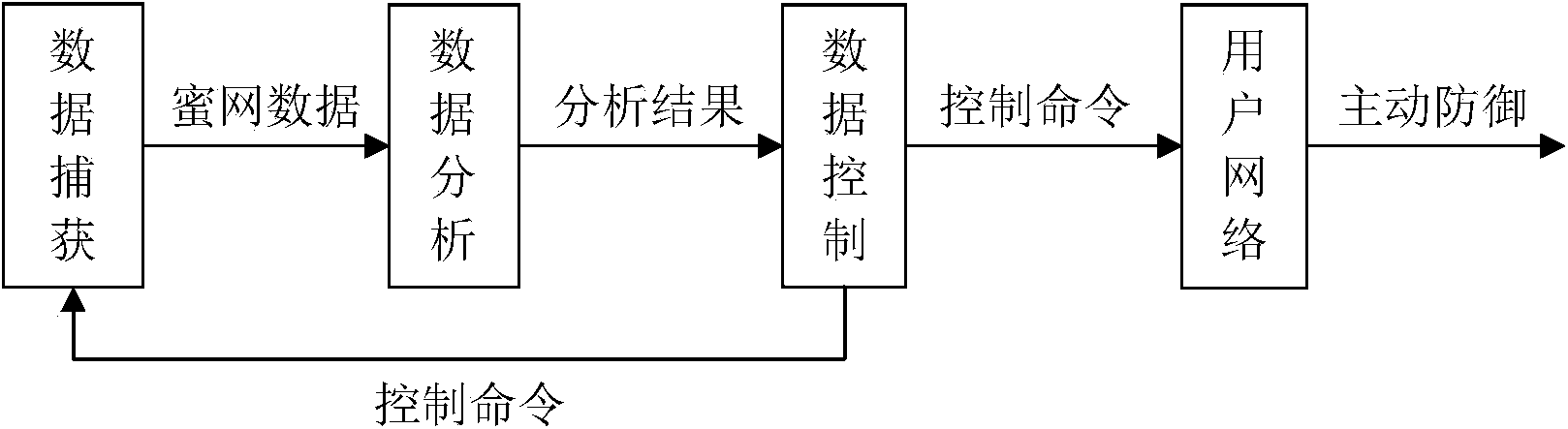
Cooperative type active defense system based on honey nets
The invention provides a cooperative type active defense system based on honey nets. The cooperative type active defense system comprises a data capture module, a data analysis module and a data control module and is characterized in that the data capture module, the data analysis module and the data control module are arranged at the center of one honey net and a plurality of sub nets in a distributed mode. The cooperative type active defense system depends on a honey net technology, a cooperative type active defense thought is adopted, attacker information captured by the different honey nets is shared in real time, active defensiveness of a network layer is achieved, defensive initiative and real-time performance are improved, and the cooperative type active defense system is suitable for large-scale enterprise networks. The cooperative type active defense system built through the method is high in defense rate, hit rate and robustness, and time delay from the time that attackers are firstly found to the time that all network deployment and control is achieved is greatly reduced.
Owner:XI AN JIAOTONG UNIV
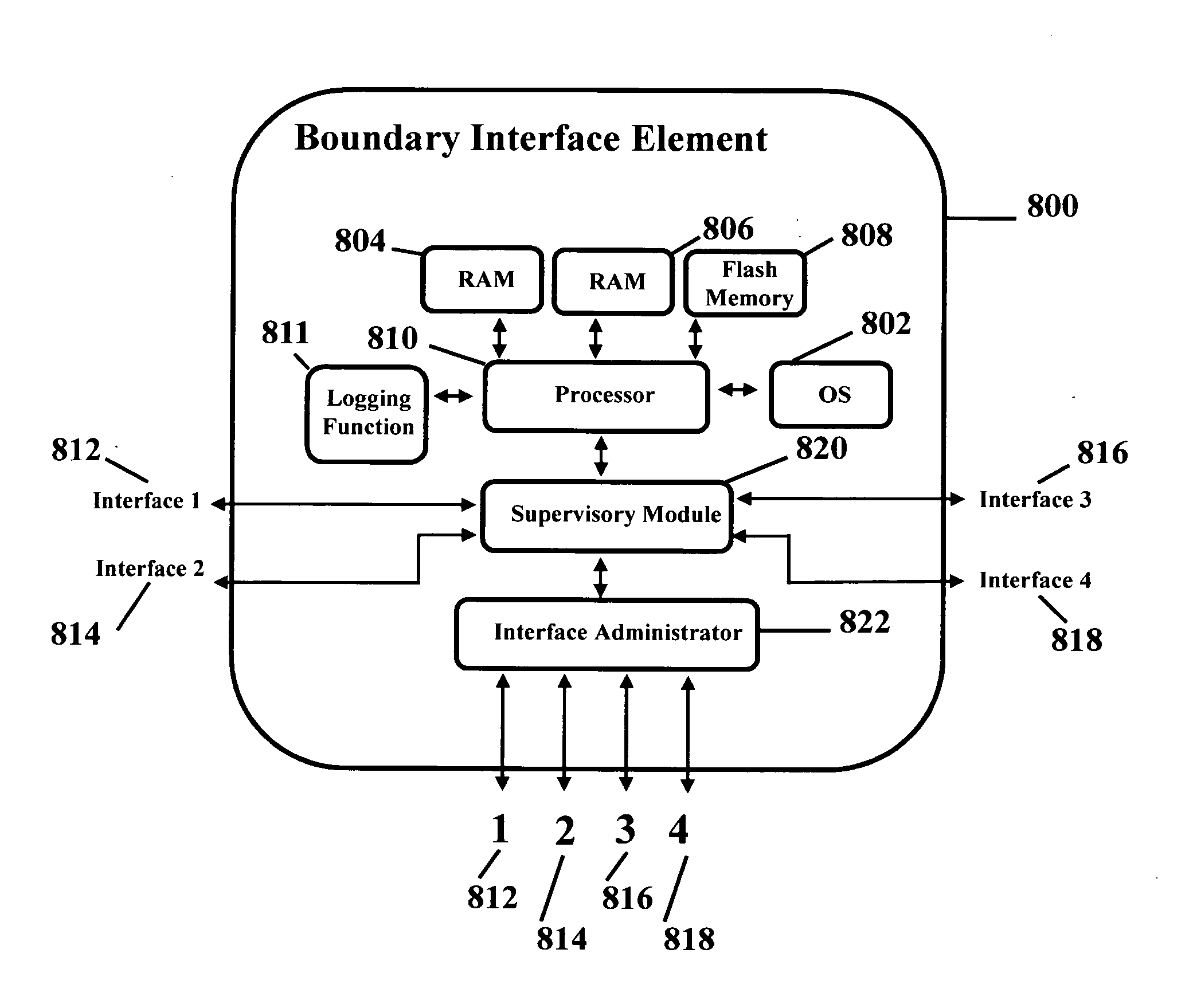
Independent role based authorization in boundary interface elements
ActiveUS20100132027A1Multiple digital computer combinationsProgram controlNetwork deploymentAuthorization
A boundary interface element for communications networks is disclosed. The boundary interface element is adapted for enabling a network administrator for a first network coupled to a first network interface of the boundary interface element to configure a policy for the first network interface independently of the other administrators of the other interfaces, while restricting access to a second network interface of the boundary interface element. Similarly, the boundary interface element enables a network administrator for a second network coupled to the second network interface of the boundary interface element to configure a policy for the second network interface while restricting access to the first network interface. The network administrator for the first network is permitted to view the policy configured for the second network interface, and the network administrator for the second network is permitted to view the policy configured for the first network interface. The boundary interface element may be employed in a variety of network deployment scenarios.
Owner:AT&T INTPROP I L P
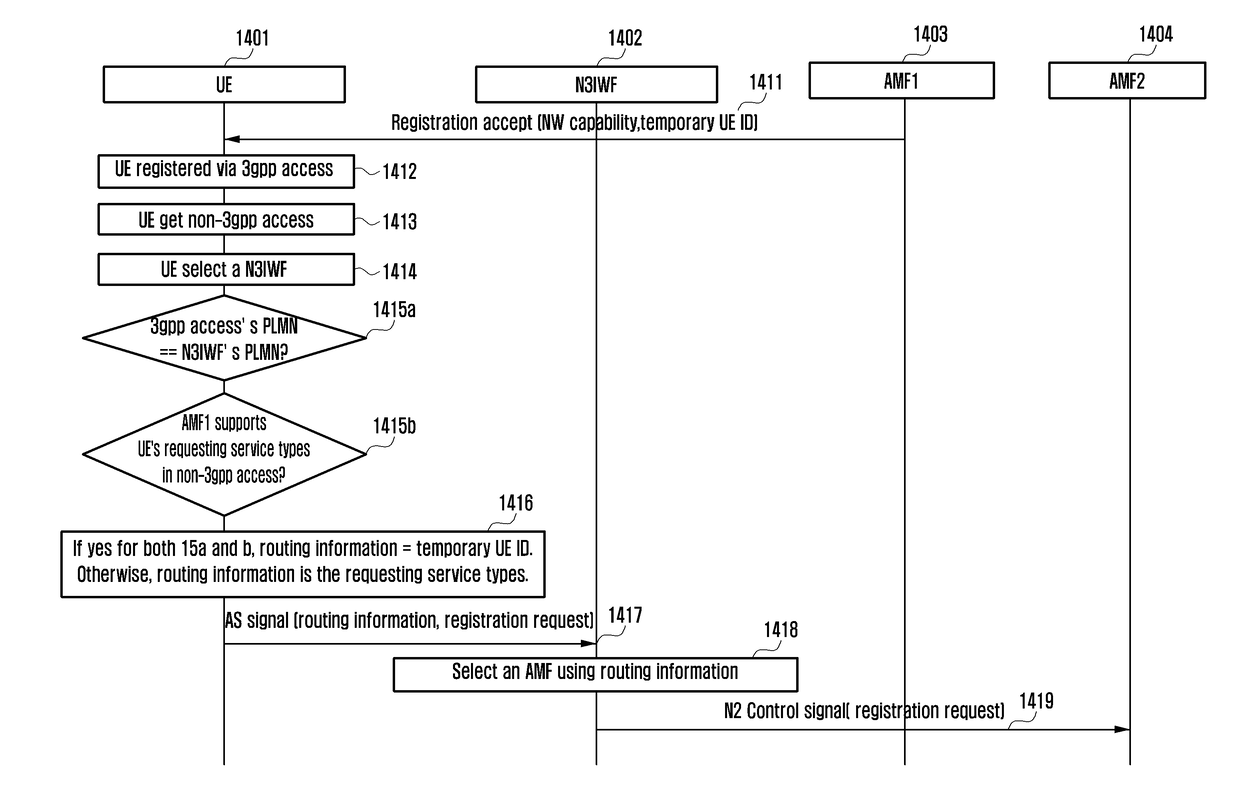
Method and apparatus for selecting an access and mobility management function in a mobile communication system
ActiveUS20180199279A1Increase stickiness and persistenceReducing stickiness and persistenceNetwork traffic/resource managementAssess restrictionNetwork deploymentCommunications system
The present disclosure relates to a communication technique of fusing a 5G communication system for supporting higher data transmission rate beyond a 4G system with an IoT technology and a system thereof, and provides an intelligent service (for example, smart home, smart building, smart city, smart car or connected car, health care, digital education, retail business, security and safety related service, or the like) based on the 5G communication technology and the IoT related technology. A method for appropriately finding a network node providing services that user equipment (UE) wants in a 5G mobile communication system when a user initially accesses a G network includes a method for managing network deployment information and a method for transmitting an initial access request message with a detailed proposal technology. In addition, even when the service provided to the user equipment is modified after the initial access, a network node providing the corresponding service may be found in a similar manner.
Owner:SAMSUNG ELECTRONICS CO LTD
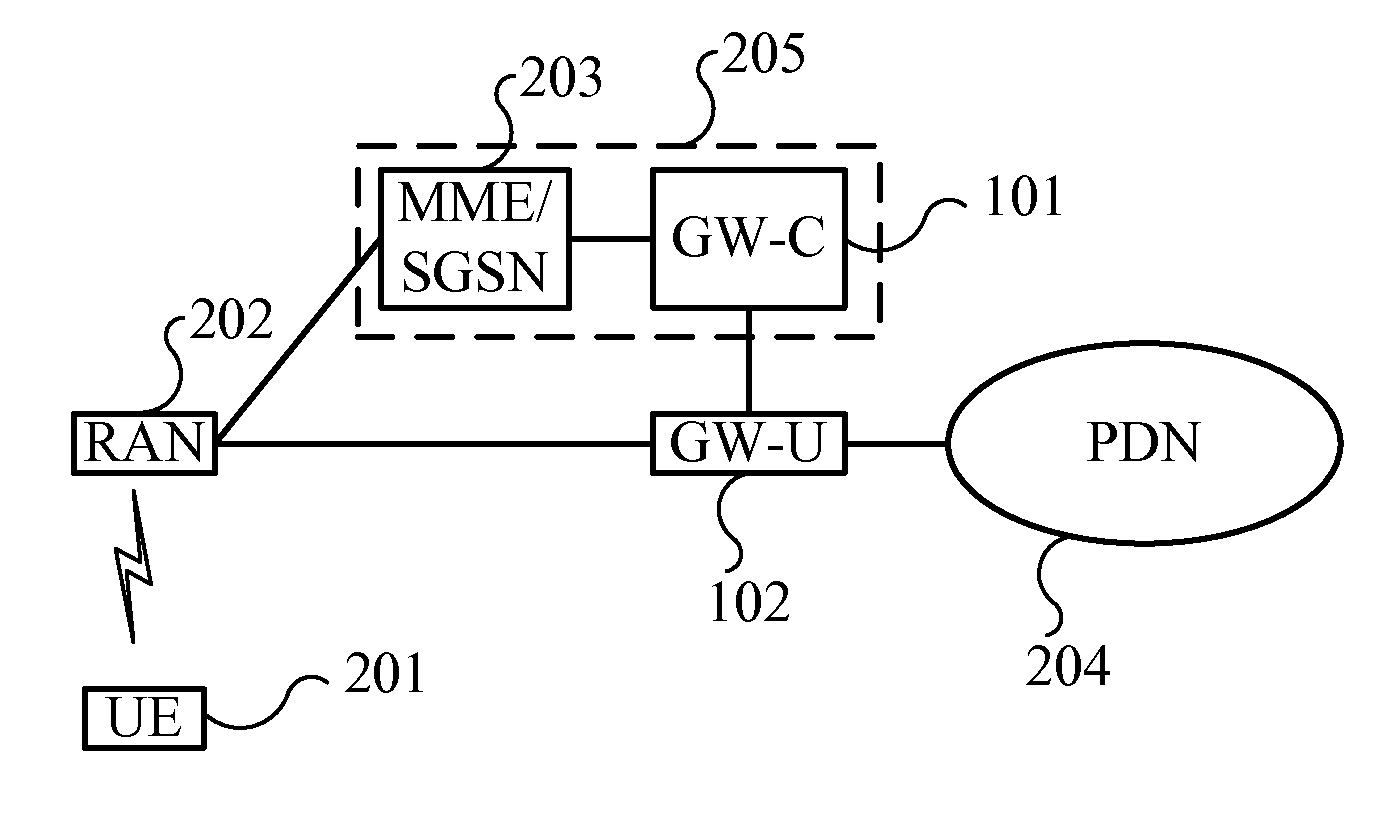
Gateway system, device and communication method
ActiveUS20150110095A1Network is convenientLow costWireless commuication servicesTransmissionNetwork deploymentIp address
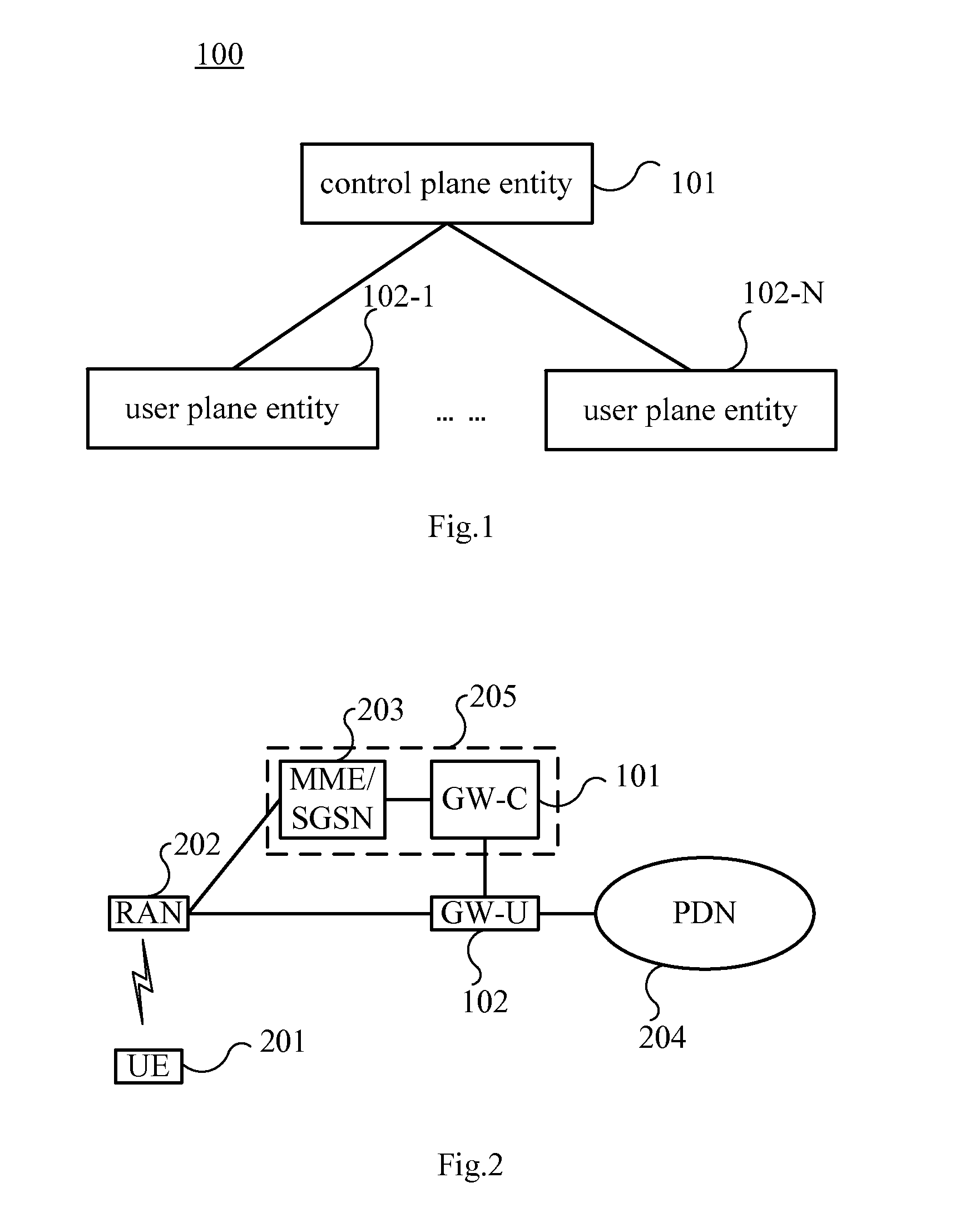
Embodiments of the present invention provide a gateway system and a communication method. The gateway system includes: a control plane entity, connected or integrated with a mobility management network element, and configured to allocate an IP address to UE and configure a data path for connecting a user plane entity with an RAN, a PDN or another gateway; one or more user plane entities, located between the PDN and the RAN, independent of the control plane entity, configured to forward data on the data path configured by the control plane entity. The gateway system is composed of the control plane entity and the user plane entity which are independent of each other, the number of the user plane entities may be independently changed to adapt to the change of network traffic without replacing all gateway entities, the network deployment is more convenient and the cost is lower.
Owner:HUAWEI TECH CO LTD
Viral engine for network deployment
ActiveUS20060080284A1Overcome problemsData processing applicationsComputer security arrangementsPersonalizationNetwork deployment
A private network system operates over a public network to provide an asymmetric service to members with information from other members and non-members. The system includes central servers and databases connected via the public network to client systems of public network users. The users may be members who communicate with a private protocol or non-members who communicate with the public protocol. A process for the private service includes communication of information between users via the private service servers. The private service server implements the private service, which includes a viral engine for network deployment. Features of the viral engine include genetic algorithms, data mining, personalization, frictionless service setup, user maximization, and member-controlled privacy. A sample setup process and contact update wizard that include several viral engine features are described.
Owner:PLAXO INC
Load managing method, device and system
The invention discloses a load managing method, device and system and relates to the communication technology. When a macro base station determines that user plane load of a user needs to be switched to a small base station, the macro base station transmits a user plane load transfer request carrying the information of the user plane load requiring transfer and the bottom configuration information of the user in the macro base station, the macro base station and the small base station can partially transfer the user plane load according to the user plane load transfer request, and accordingly load switching under the network deployment with the user plane being separated from a control plane.
Owner:DATANG MOBILE COMM EQUIP CO LTD
RFID systems and methods for optical fiber network deployment and maintenance
InactiveUS7760094B1Reduce riskFaster and accurate installationMultiplex system selection arrangementsFibre mechanical structuresNetwork deploymentComputer hardware
Owner:CORNING CABLE SYST LLC
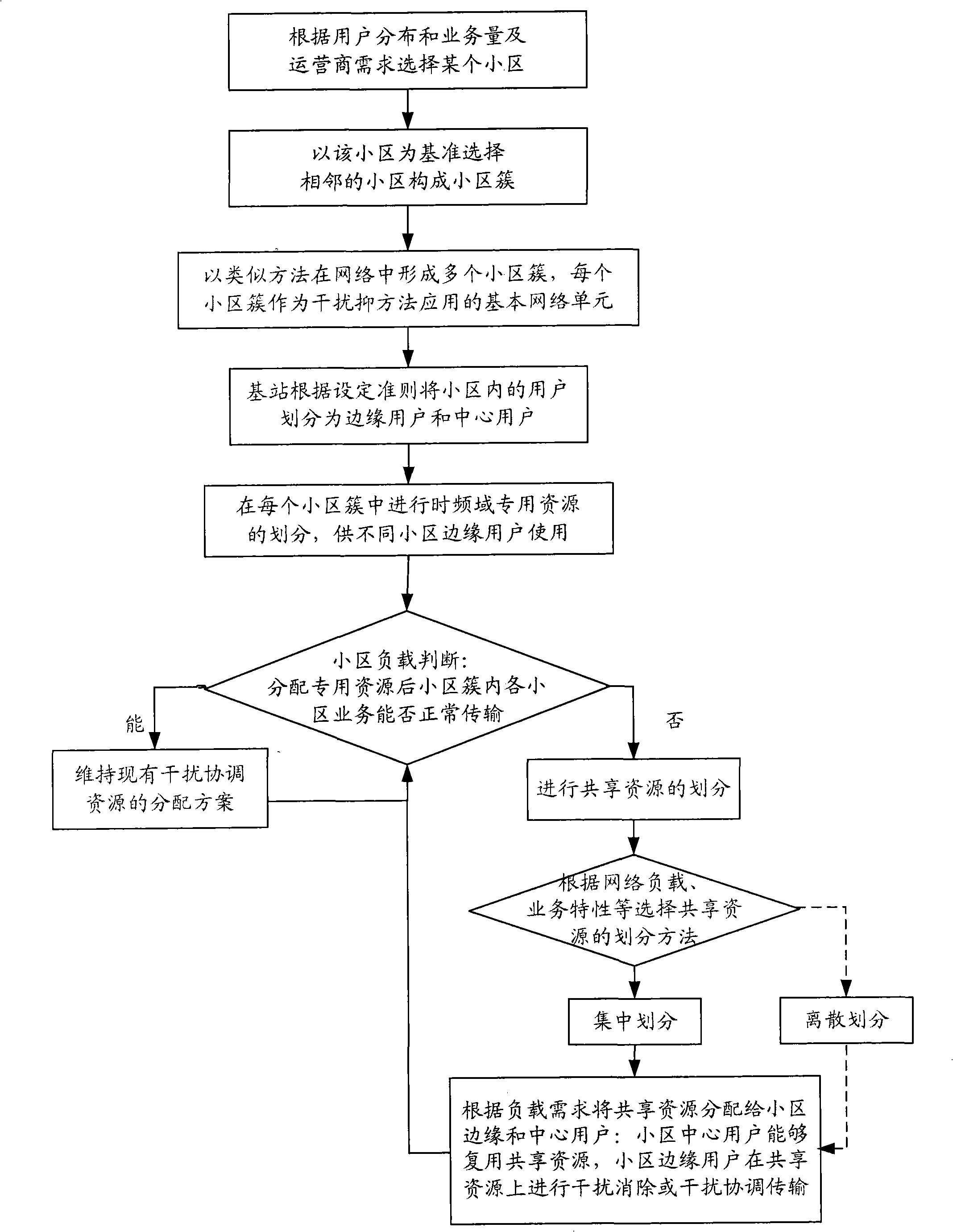
Interference suppressing method in wireless communication system
ActiveCN101291515AImprove quality and efficiencyImprove system efficiencyRadio/inductive link selection arrangementsNetwork deploymentCommunications system
The invention provides a method for restraining the interference in a wireless communication system. According to the business and the user characteristic, a plurality of cells in the system are divided into a plurality of cell clusters; each cell cluster utilizes the same time-frequency resource distributing method, different cell clusters utilize different time-frequency resource distributing methods; and the interference suppression between different cells and different cell clusters is realized by flexibly dividing and adjusting the time-frequency two-dimension resource in order to respond to the change in the load in the cell, thereby effectively avoiding the interference between cells. On the basis of dividing the special resource for coordinating the interference for an edge user of the cell, the method utilizes an intensified or discrete dividing method to divide the shared resource in order to realize the flexible response to the change in the load of the cell and the interference suppression between cells, improves the flexibility of the system to respond to the change in the load of the cell and the system efficiency, saves the network investment and improves the flexibility of the network design.
Owner:COMBA TELECOM SYST CHINA LTD
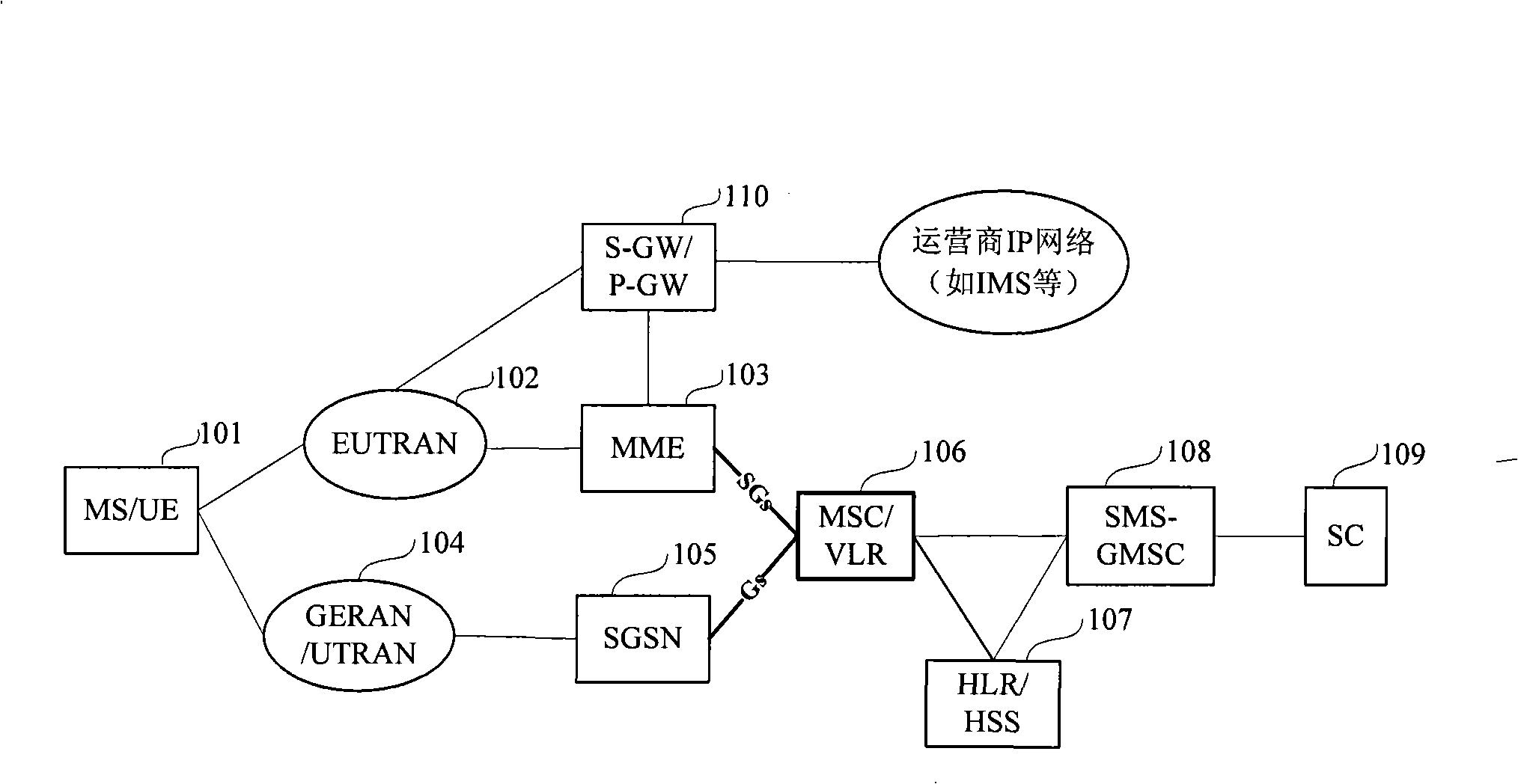
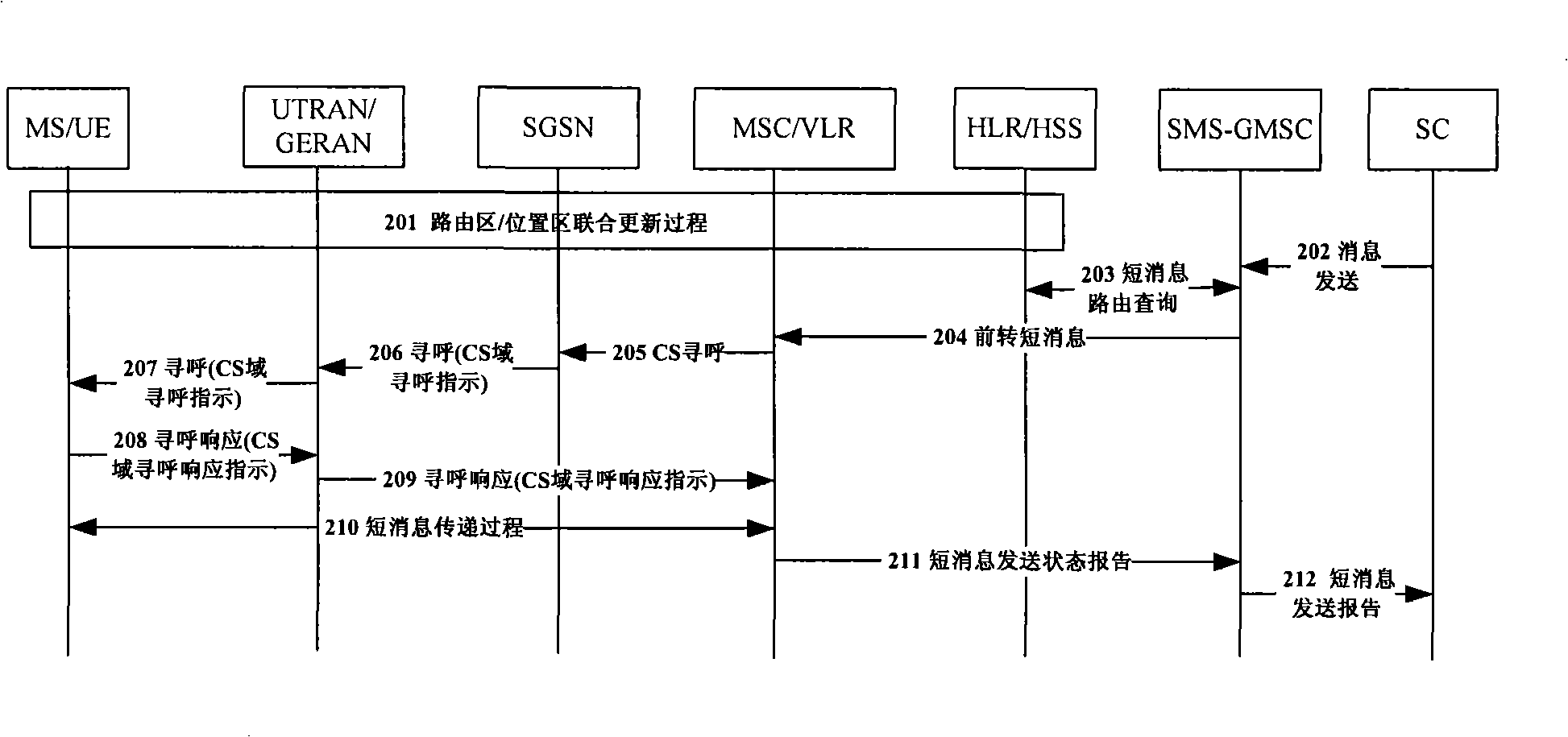
Short message end call method and system
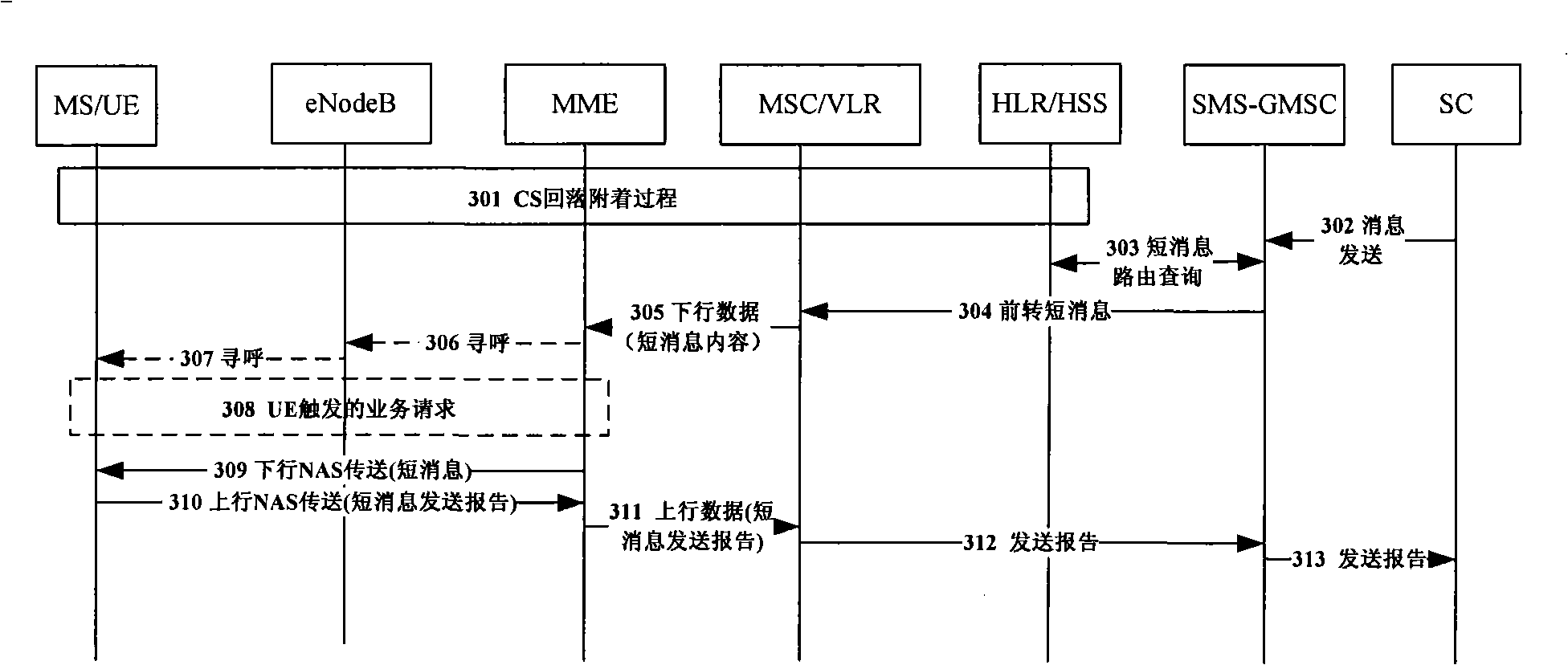
InactiveCN101291461AReduce processing loadReduce occupancyRadio/inductive link selection arrangementsNetwork deploymentProcessor register
The invention discloses a method and a system for finally calling short message. The method comprises the steps of: receiving the short message; sending circuit domain paging request message to a packet domain network element which is recorded in incidence relation by a mobile switching center or a visitor location register; carrying short message service indicating information in the circuit domain paging request message; receiving the circuit domain paging request message by the packet domain network element; obtaining the short message service indicating information in the circuit domain paging request message; and carrying out corresponding short message final calling flow. By the aid of the technical proposal of the invention, the short passage final calling flow can be accurately carried out under various conditions; the problem of finally calling the short message under ISR in the prior art is solved, processing load of a network, occupation of internal storage resource and signaling load are reduced; processing of MSC / VLR to the received short message can be kept consistent; and the method and the system are favorable for development, maintenance and network distribution of relevant products.
Owner:ZTE CORP
Cost optimization unmanned aerial vehicle base station deployment method based on an improved genetic algorithm
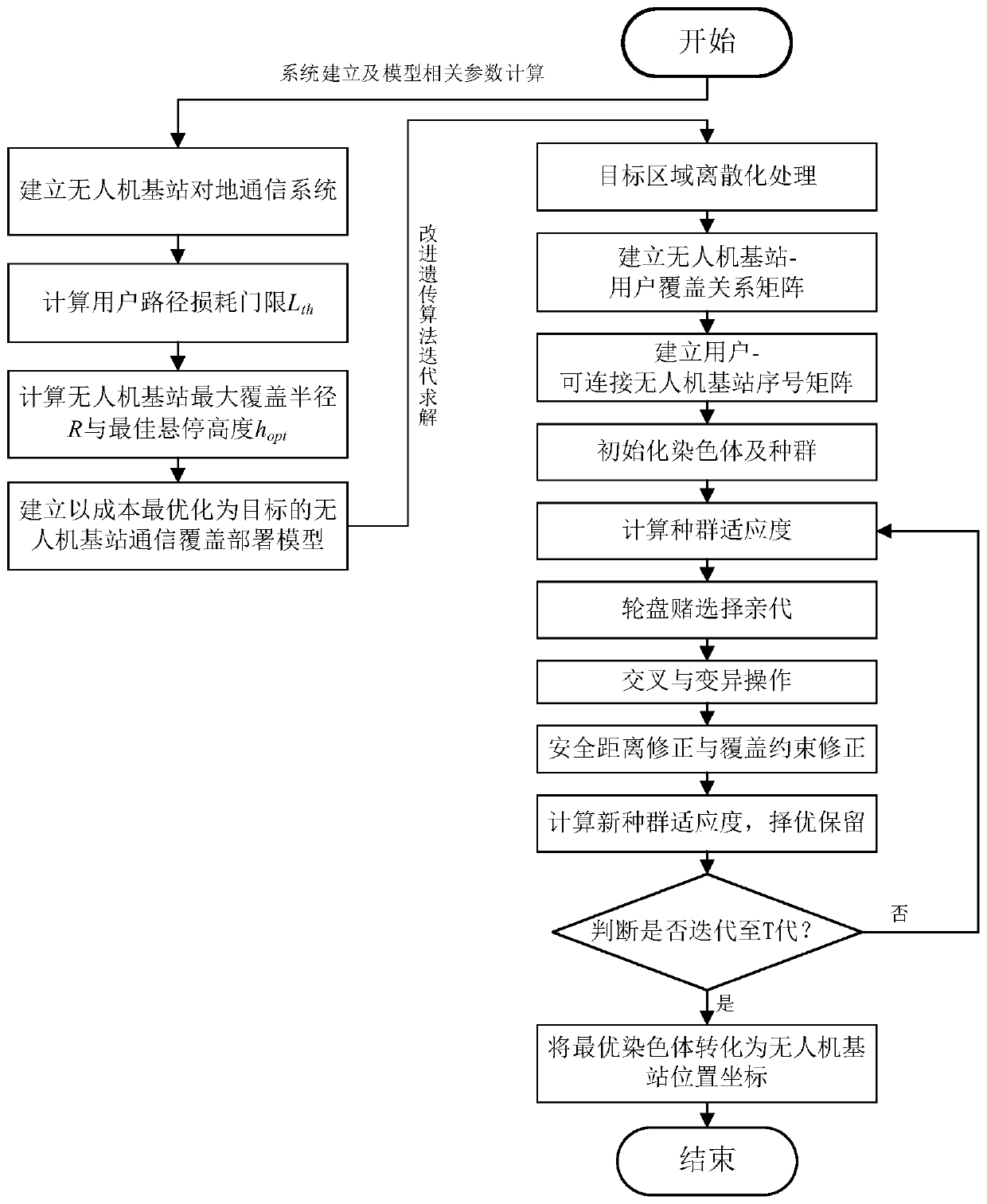
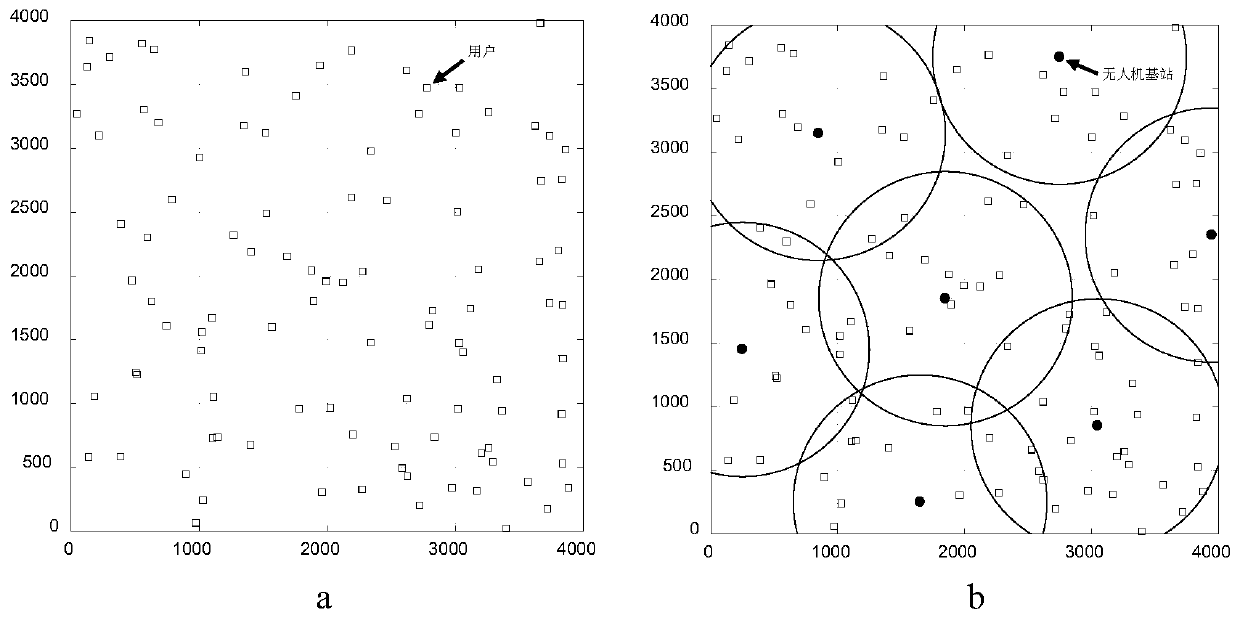
ActiveCN109819453AMaximize coverageReduce complexityTransmission monitoringNetwork planningNetwork deploymentDisaster area
The invention discloses a cost optimization unmanned aerial vehicle base station deployment method based on an improved genetic algorithm, and mainly solves the problem that the unmanned aerial vehicle base station deployment cost is difficult to optimize in the prior art. The realization method comprises the following steps: 1) establishing a ground wireless communication coverage model of the unmanned aerial vehicle base station; 2) calculating the maximum coverage radius and the optimal hovering height of the unmanned aerial vehicle base station in the unmanned aerial vehicle base station ground wireless communication coverage model scene; 3) deploying the unmanned aerial vehicle base stations at the optimal hovering height, enabling the deployment problem to be reduced from three-dimensional dimensionality to a two-dimensional plane, establishing an unmanned aerial vehicle base station deployment optimization model taking unmanned aerial vehicle base station deployment number optimization as a target, and solving the model to obtain an optimal chromosome; 4) converting the optimal chromosome into a corresponding unmanned aerial vehicle base station coordinate set to obtain an optimal unmanned aerial vehicle base station deployment scheme, reducing the complexity of the deployment problem, improving the solution accuracy, and being applicable to communication network deployment planning, temporary communication network construction and disaster area emergency communication.
Owner:XIDIAN UNIV
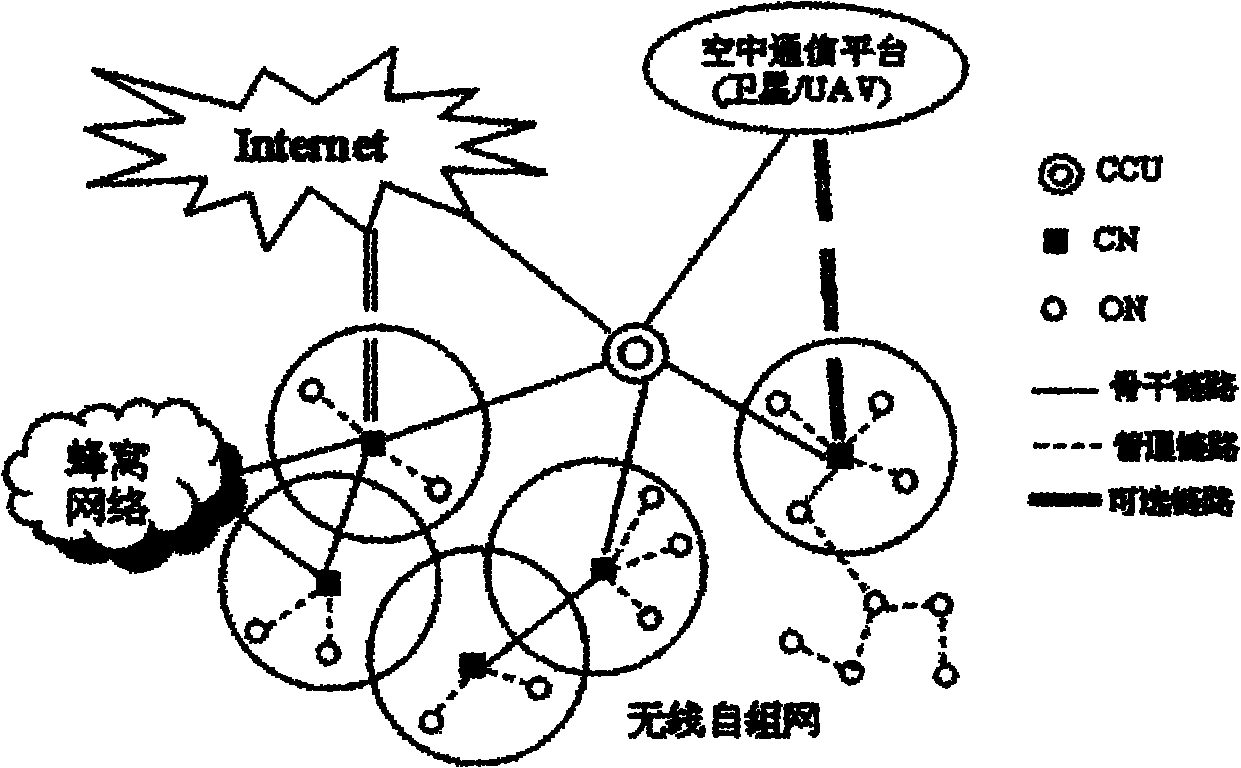
Wireless self-organized network-based integrated heterogeneous emergency communication network
InactiveCN102006574AAchieving Network InvulnerabilityAchieve reliabilityNetwork topologiesWireless commuication servicesStructure of Management InformationEmergency situations
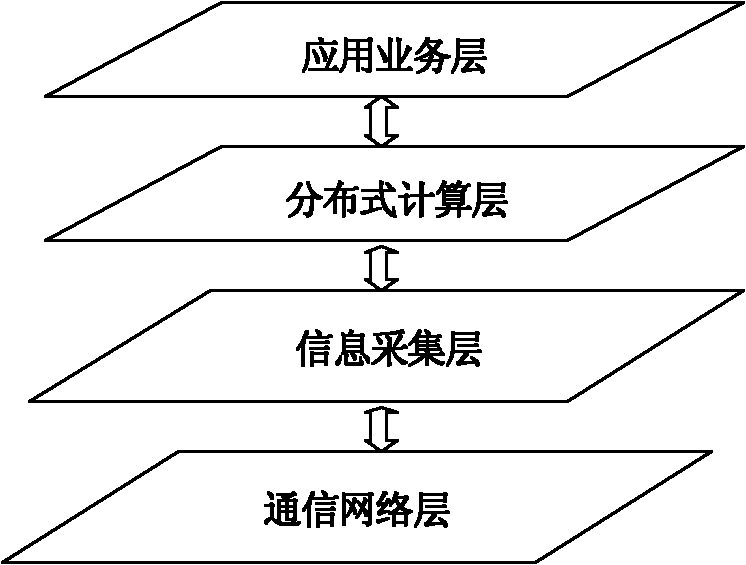
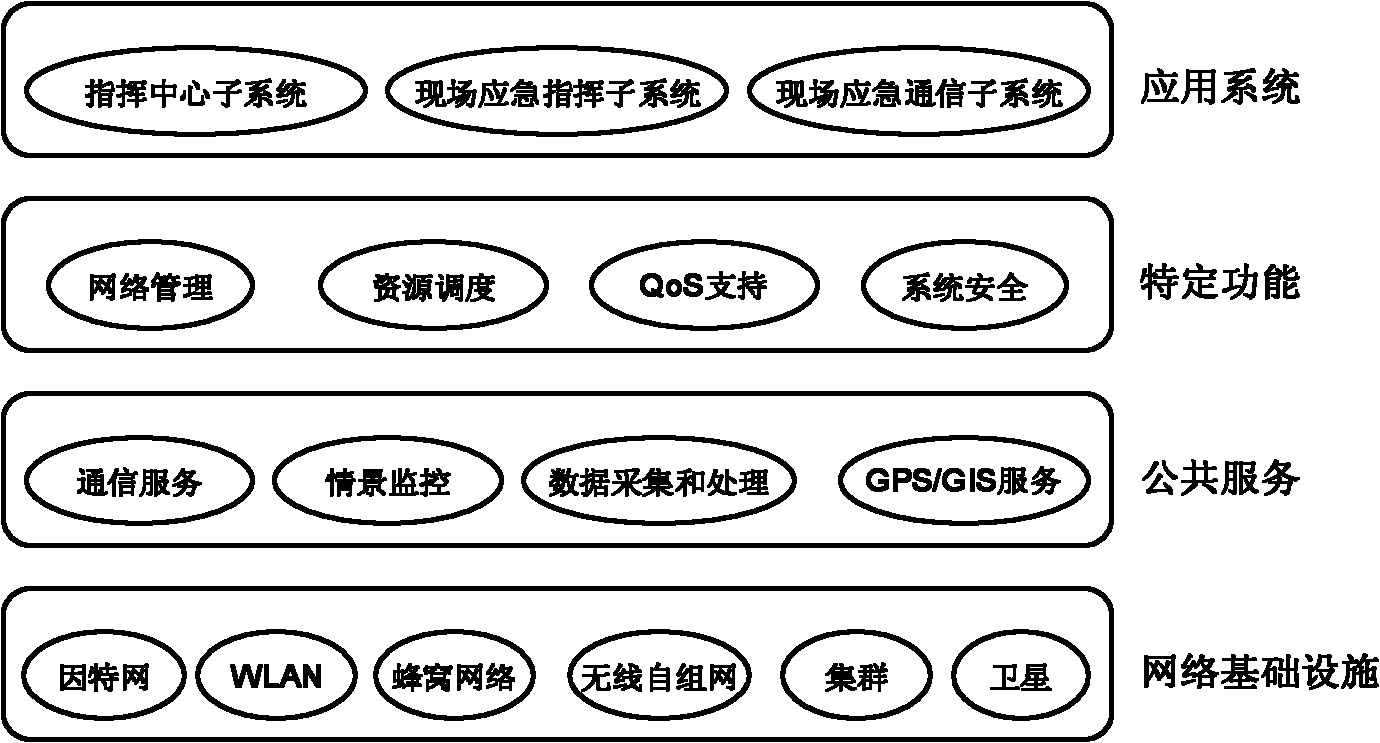
The invention discloses a wireless self-organized network-based integrated heterogeneous emergency communication network. The emergency communication network comprises a layered framework, a layered framework-based system structure and a layered framework-based network structure, wherein the layered framework consists of a communication network layer, an information acquisition layer, a distributed computation layer and an application service layer sequentially from bottom to top; the system structure consists of a network infrastructure layer, a public service layer, a specific functional layer and an application system layer sequentially from bottom to top; and the network structure is a layered three-dimensional communication network structure. The emergency communication network provided by the invention can adapt to various emergency network deployment situations, can provide network capacity and a coverage area at any given time or place as required, can be conveniently expandedto a network of a required scale, enhances situational perception capability of an emergency occasion by comprehensively utilizing various communication measures, shortens transmission time delay andcall establishment time, can support the requirement on the performance of various services and expands the communication ranges and service support capabilities of various user groups on different emergency occasions.
Owner:PLA UNIV OF SCI & TECH
Multi-party safety calculation method and device, and electronic equipment
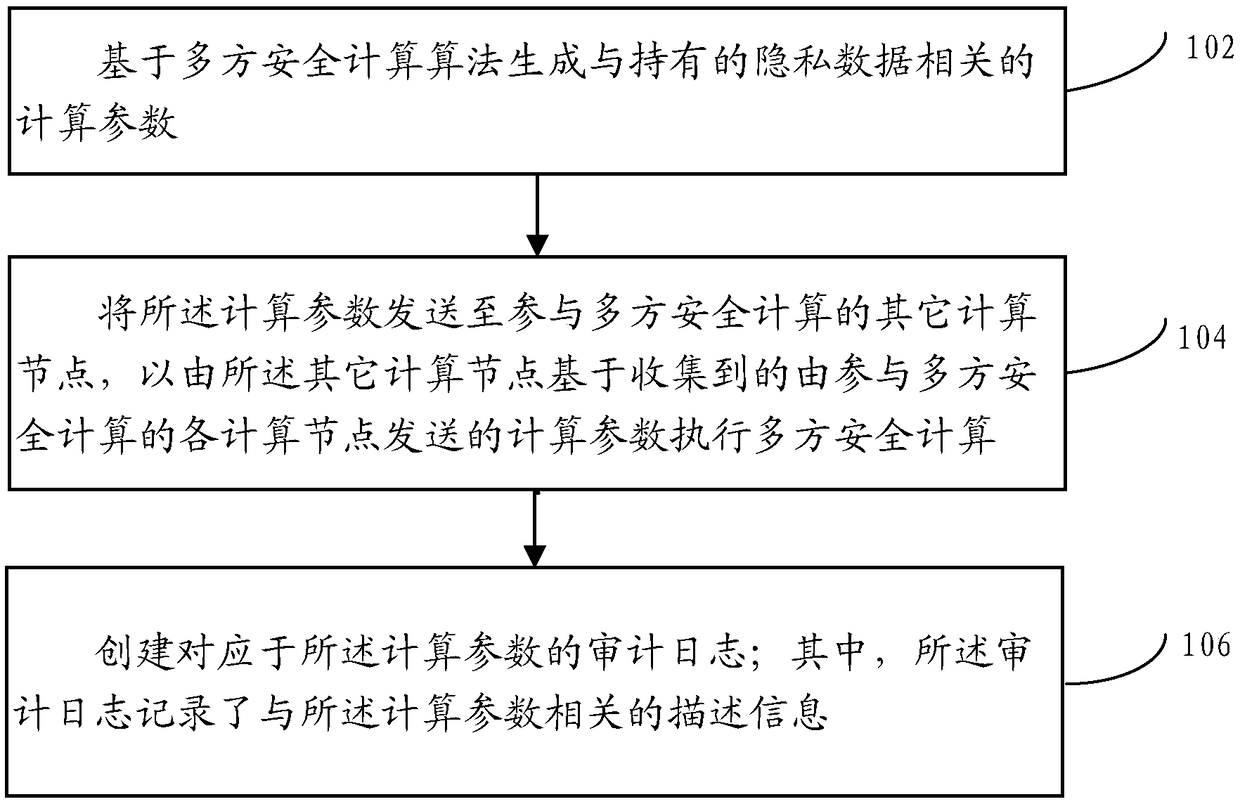
ActiveCN109359470AEasy to auditDigital data protectionInternal/peripheral component protectionNetwork deploymentInternet privacy
A multi-party secure computing method is applied to any computing node deployed in a distributed network. Wherein a plurality of computing nodes are deployed in the distributed network, and the plurality of computing nodes jointly participate in multi-party secure computing based on the privacy data held by the plurality of computing nodes, wherein the method comprises the following steps of: generating computing parameters related to the held privacy data based on a multi-party secure computing algorithm; Sending the computing parameters to other computing nodes participating in the multi-party security computing to perform the multi-party security computing by the other computing nodes based on the collected computing parameters sent by each computing node participating in the multi-party security computing; And creating an audit log corresponding to the calculation parameter; Wherein the audit log records description information related to the calculation parameter.
Owner:ADVANCED NEW TECH CO LTD
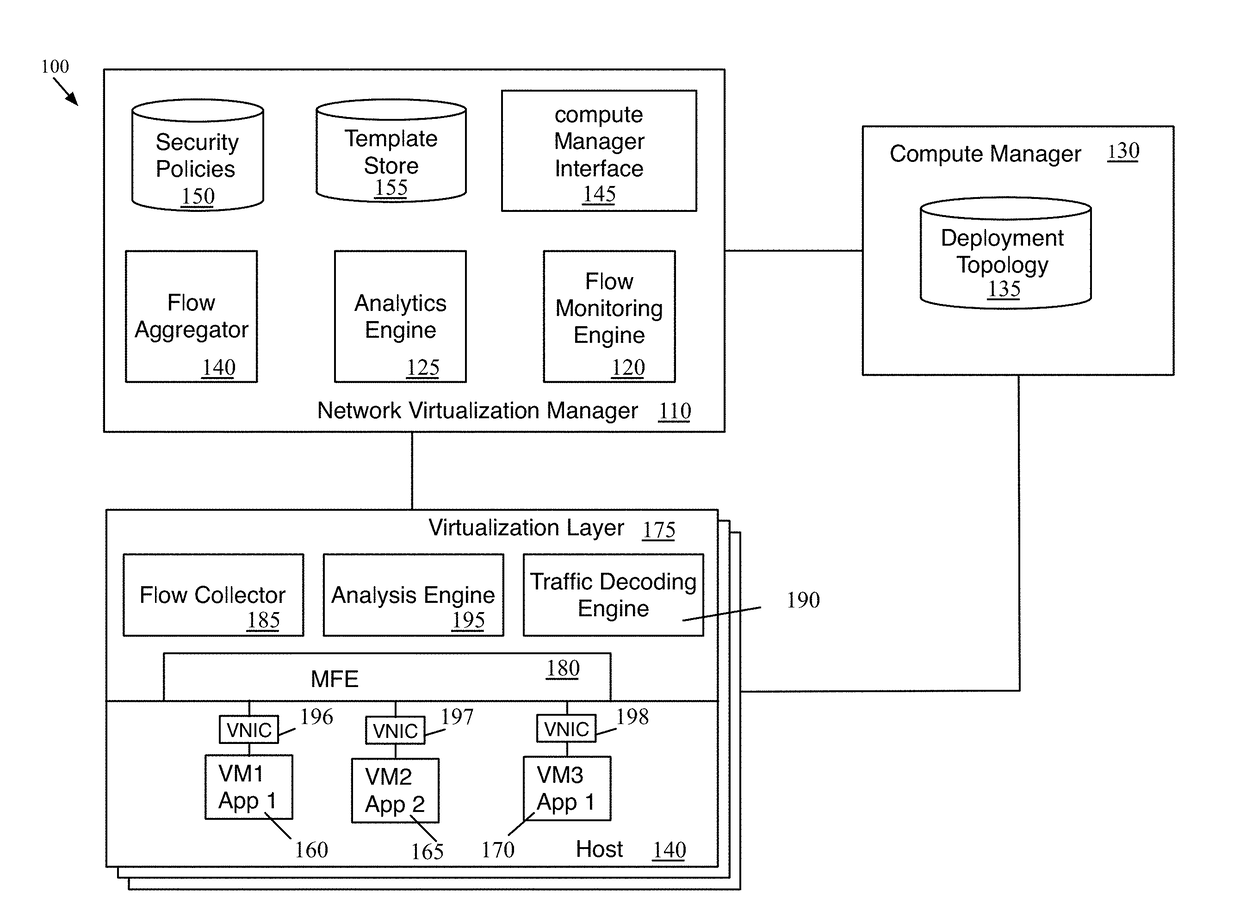
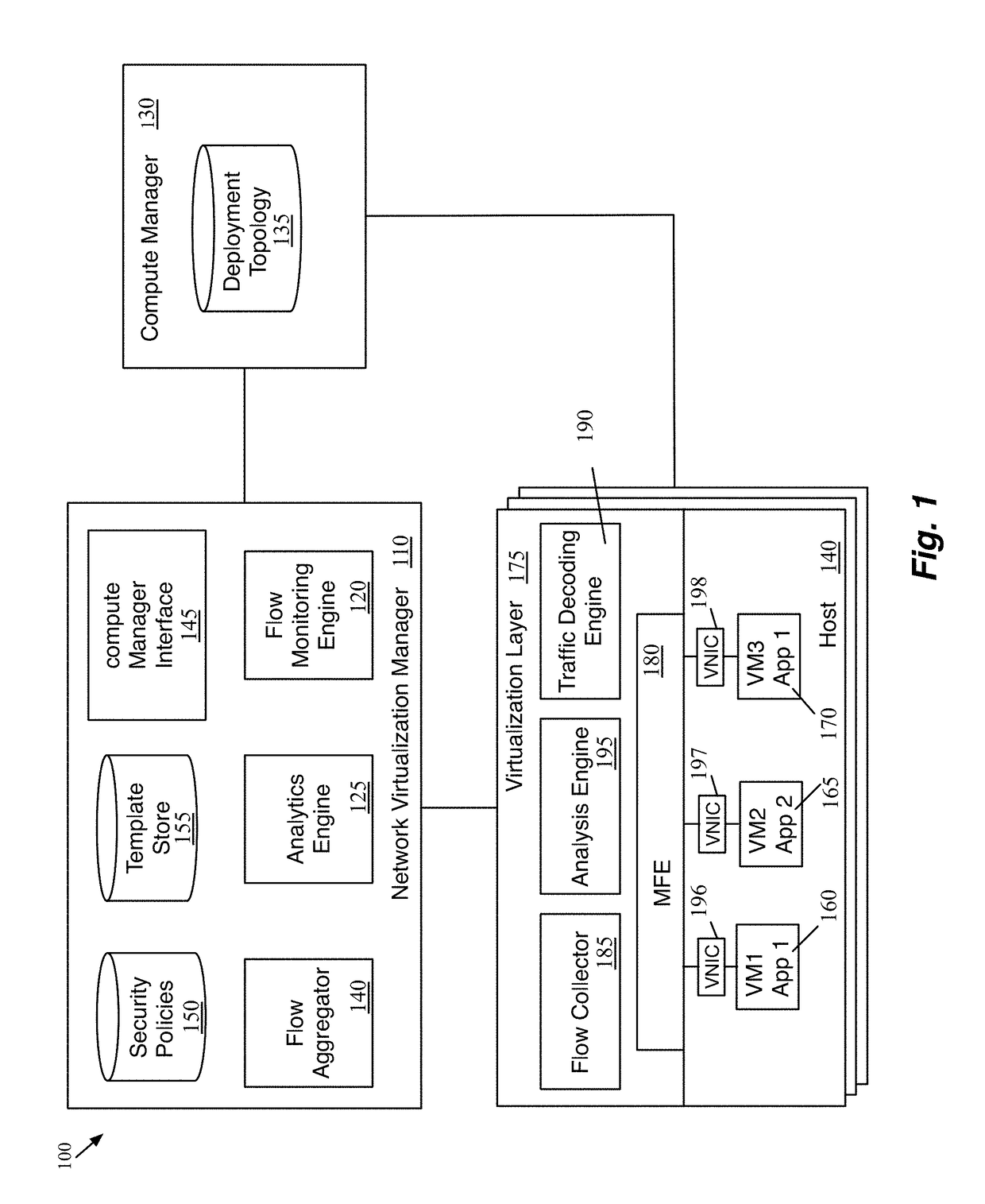
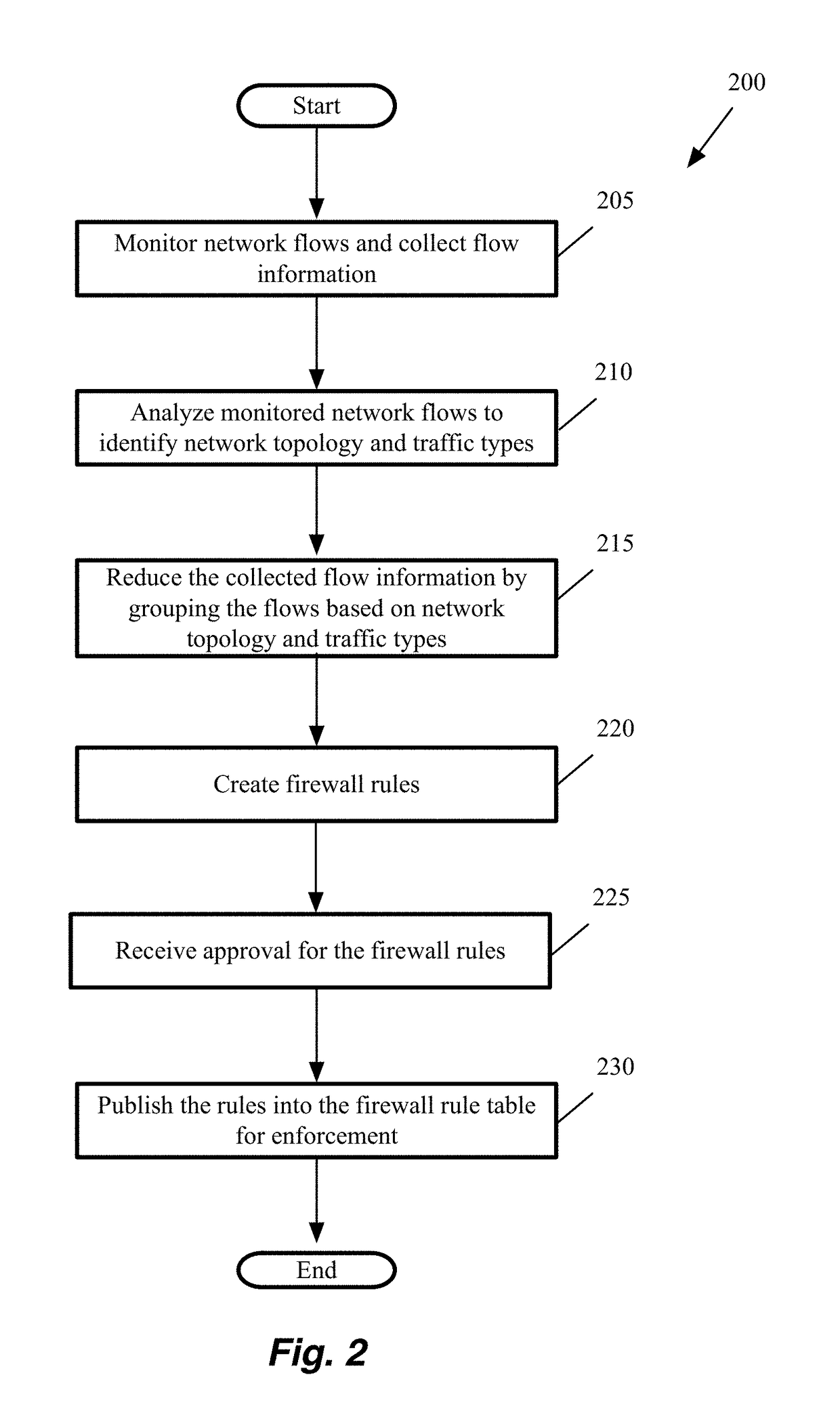
Providing application visibility for micro-segmentation of a network deployment
A method of creating micro-segmentation policies for a network is provided. The method identifies a set of network nodes as seed nodes. The method monitors network packet traffic flows for the seed nodes to collect traffic flow information. The method identifies a set of related nodes for the set of seed nodes based on the collected network flow information. The method analyzes the collected network flow information to identify micro-segmentation policies for the network.
Owner:NICIRA
Energy priority node clustering method for wireless sensor network
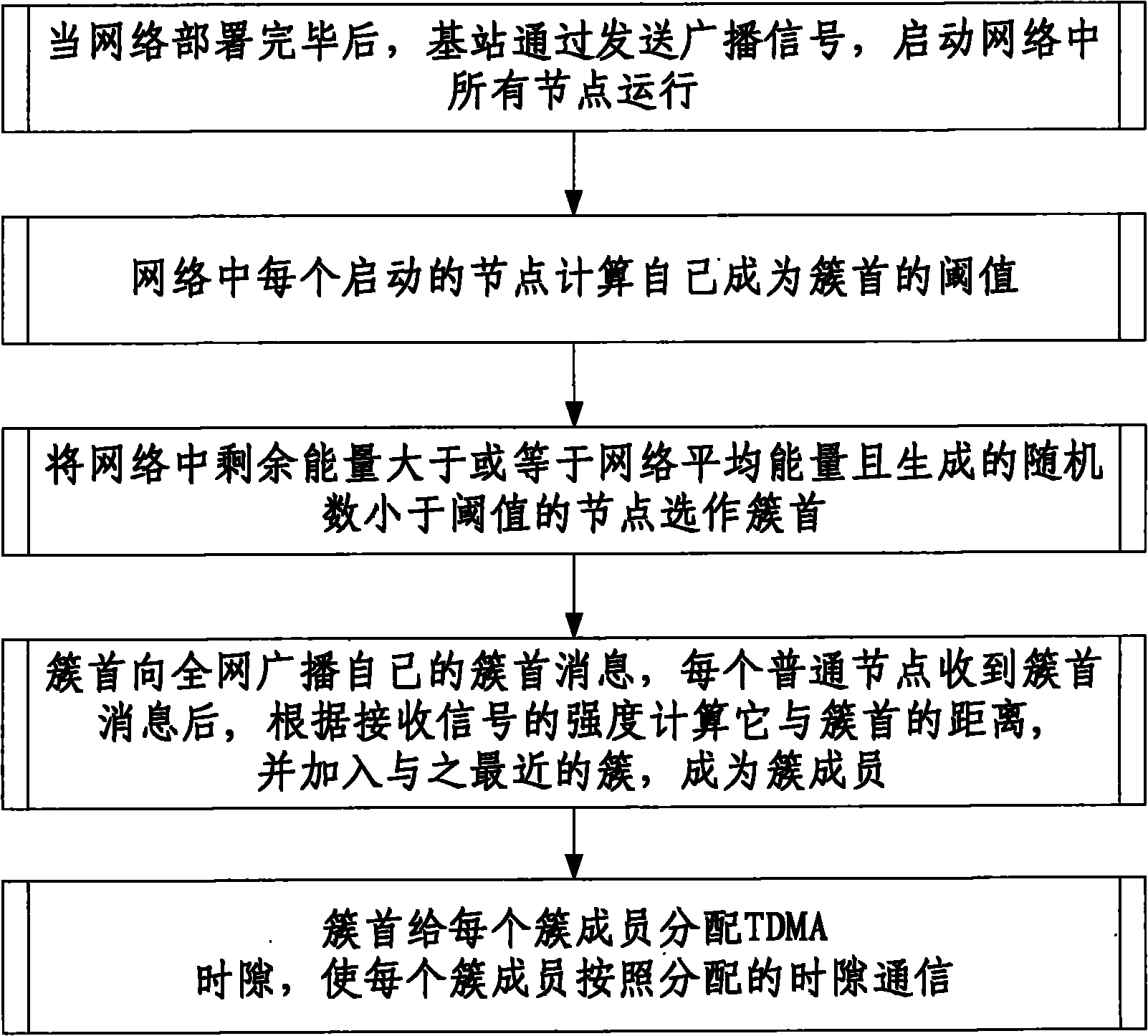
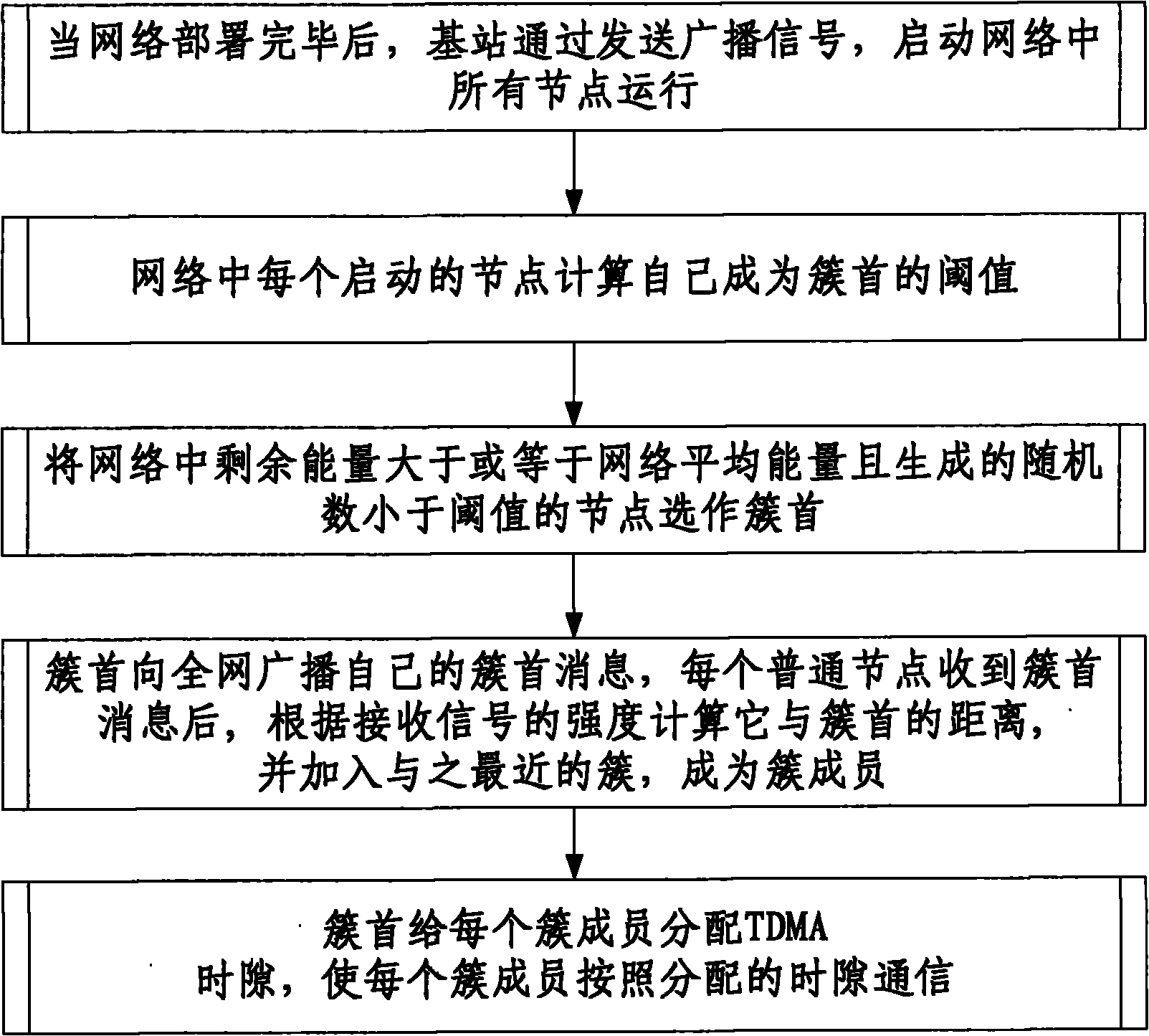
ActiveCN102256267AProlong survival timeImprove performancePower managementNetwork topologiesNode clusteringRest energy
The invention discloses an energy priority node clustering method for a wireless sensor network. The method comprises the following steps that: after network deployment is finished, a base station starts running all nodes in a network by transmitting a broadcast signal; each started node in the network computes own threshold value for becoming a cluster head; the nodes of which rest energy is more than or equal to the average energy of the network and which generate random numbers lower than the threshold values in the network are selected to be the cluster heads; the cluster heads broadcast own cluster head messages to the whole network, and each ordinary node computes own distances away from the cluster heads according to received signal strength after receiving the cluster head messages, and is added into the closest cluster as a cluster member; and the cluster heads allocate time division multiple access (TDMA) timeslots to each cluster member, so that each cluster member performs communication according to the allocated timeslots. By the method provided by the invention, the time to live of the network can be remarkably prolonged, and performance remarkably higher than that of a low energy adaptive clustering hierarchy (LEACH) protocol is ensured.
Owner:兴科迪科技(泰州)有限公司
Device for monitoring states and diagnosing faults of coal mine underground working surface conveyer
InactiveCN101727085AEasy to expand monitoring volumeSimple structureComputer controlSimulator controlEngineeringCrusher
The invention discloses a device for monitoring conditions and diagnosing faults of a coal mine underground working surface conveyer, which consists of a state monitoring and fault diagnosis central station and a substation, uses PLC for control, adopts a modularization design, and supports multi-bus data transmission. The device realizes the real-time monitoring and display of the following parameters: the bearing temperature, the oil temperature and the oil level of a speed reducer matched with the devices of a working surface conveyer namely a slat conveyer, a reversed loader, a crusher and the like; the stator temperature and the rotor bearing temperature of a motor; and the flow and the pressure of cooling water, and the distance between a coal mining machine and the slat conveyer, and the like. The device diagnoses the running states of the conveyer and makes an early warning or an alarm. The device can meet different requirements underground a coal mine, has the advantages of simple structure, convenient maintenance and expansion, convenient and fast network deployment and the like, reaches the aims of performing long-distance and on-site real-time monitoring and fault diagnosis on the working surface conveyer, and realizes the production target of safe, stable and reliable operations in a coal mine.
Owner:TAIYUAN UNIV OF TECH
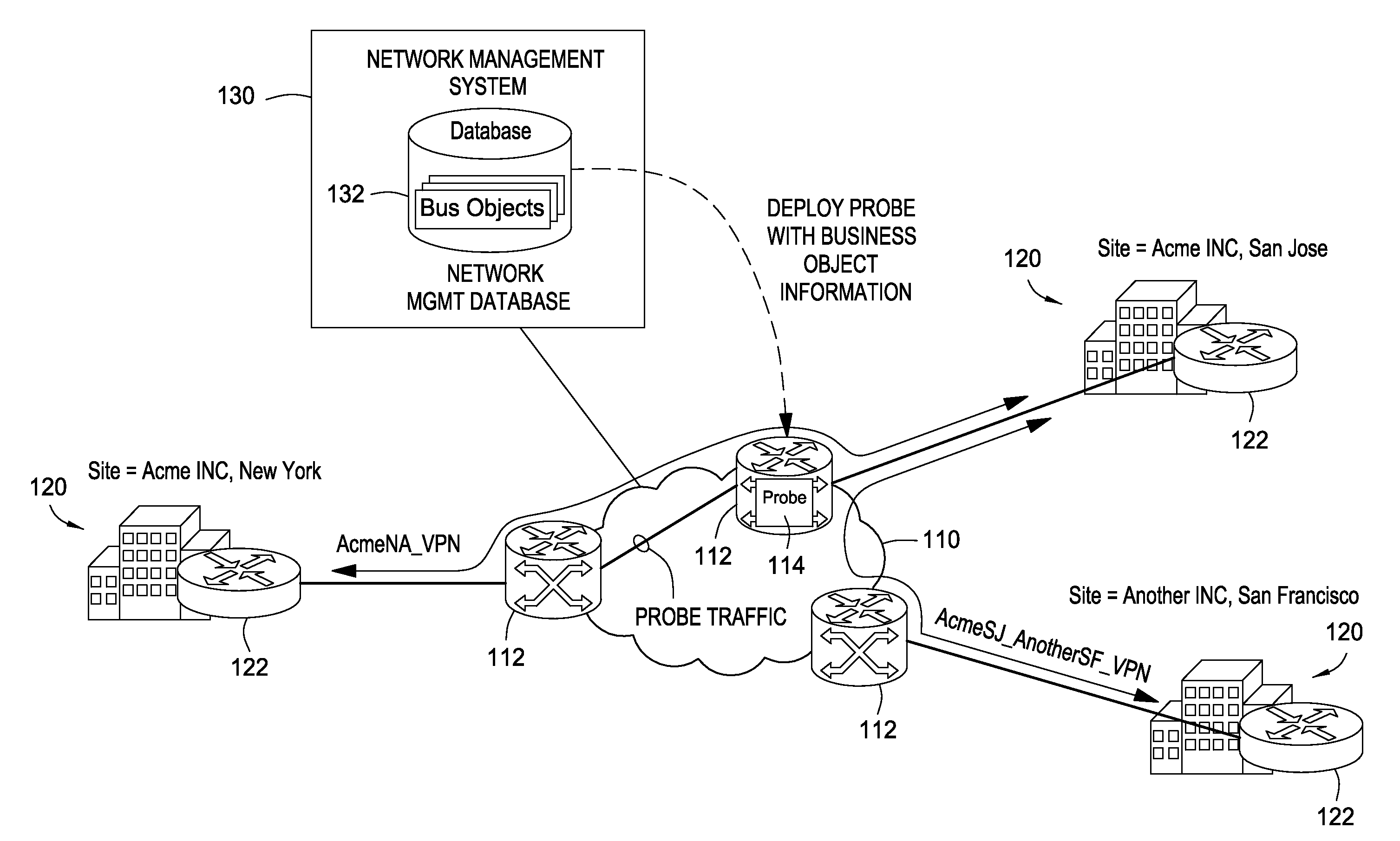
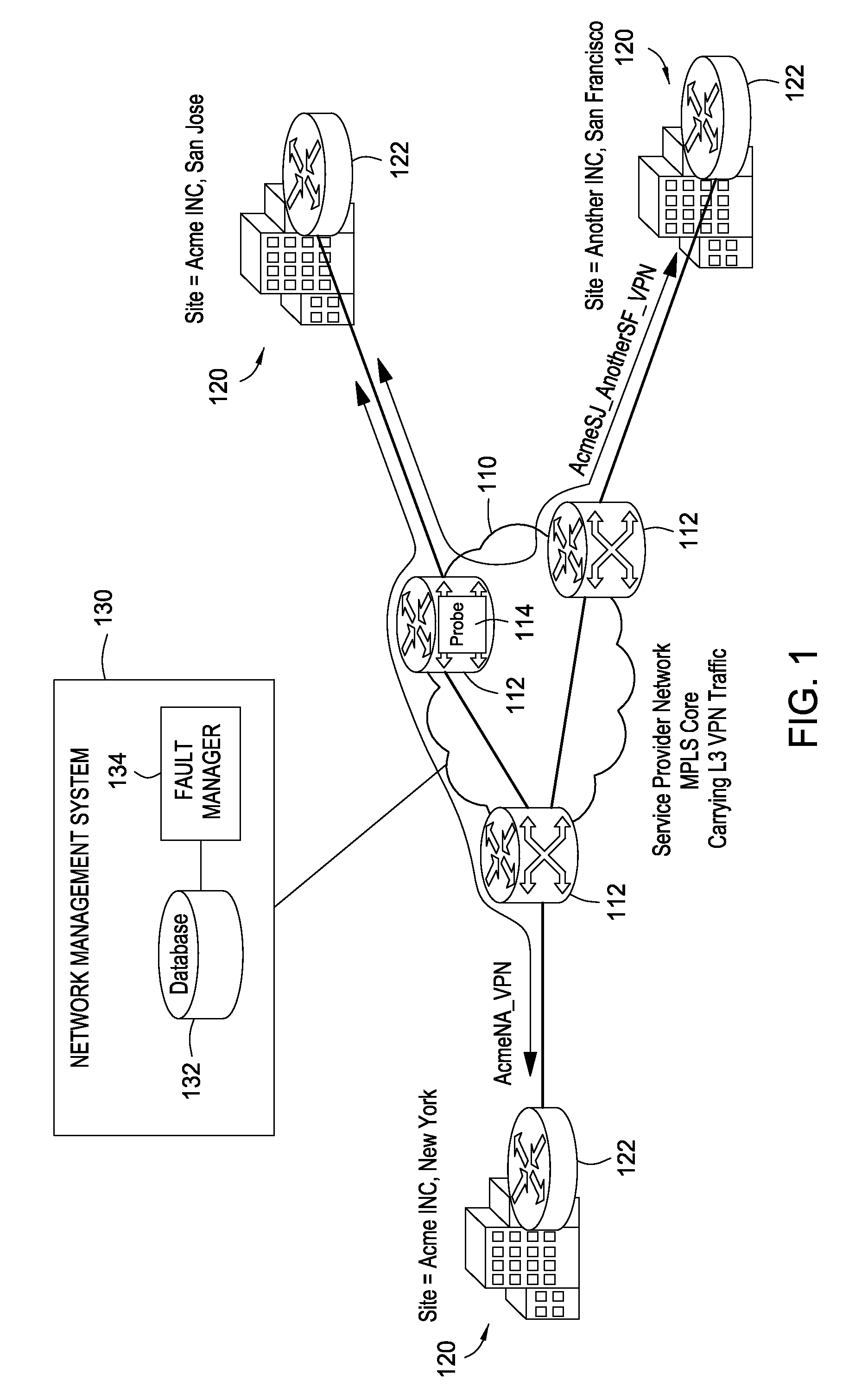
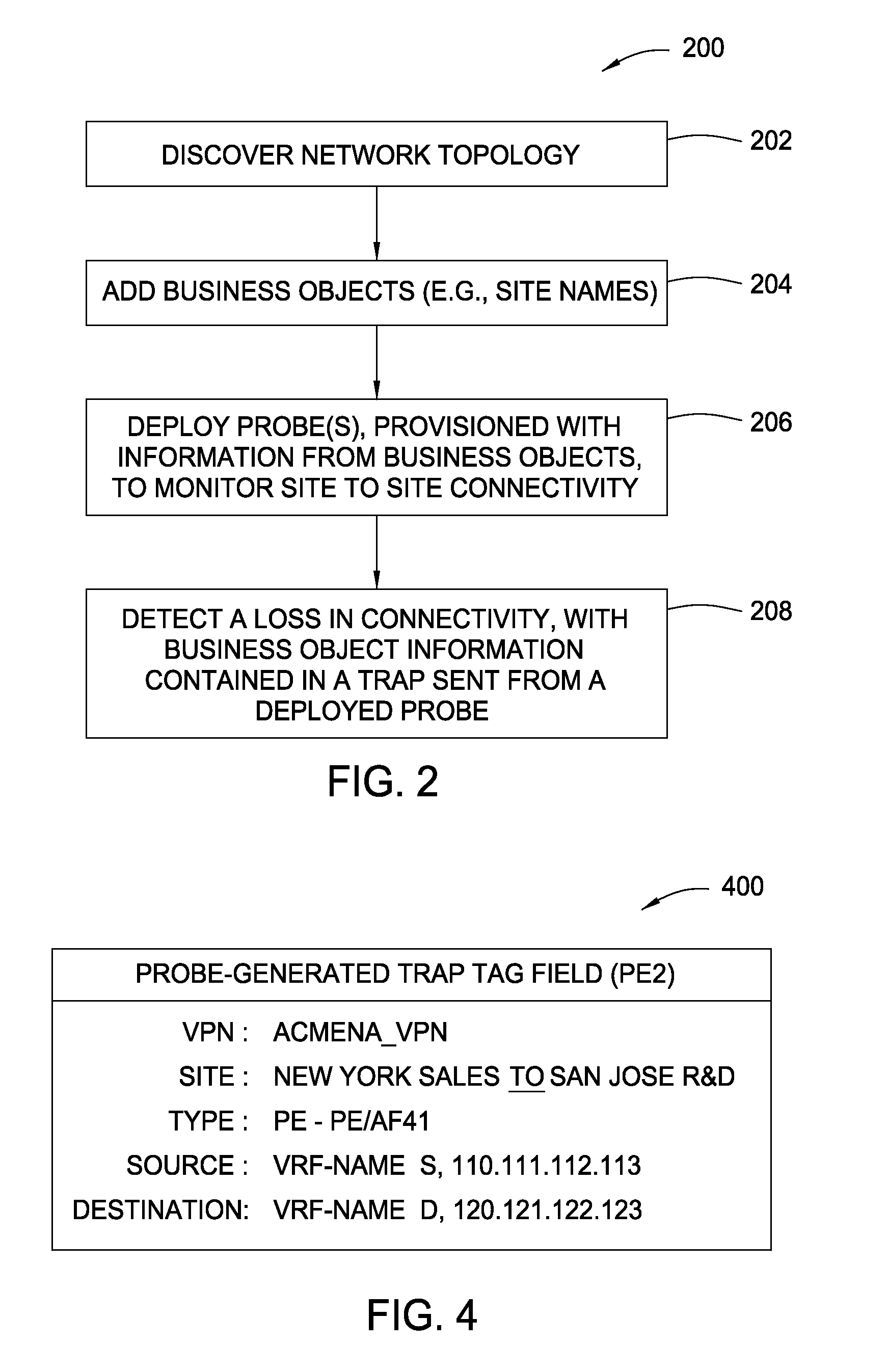
Connectivity outage detection: network/ip sla probes reporting business impact information
InactiveUS20080091822A1Digital computer detailsNetwork connectionsNetwork deploymentOutage detection
Techniques for accurate determination of service impact are provided by provisioning network deployed probes with actual business object information related to business entities, such as VPN sites. Such probes are capable of sending a network trap (or alarm) containing actual business information in response to detecting a loss of connectivity. As a result, service impact caused by the loss of connectivity may be determined accurately by simply parsing the contents of a network trap, thus avoiding the complication and inaccuracy of conventional impact analysis.
Owner:CISCO TECH INC
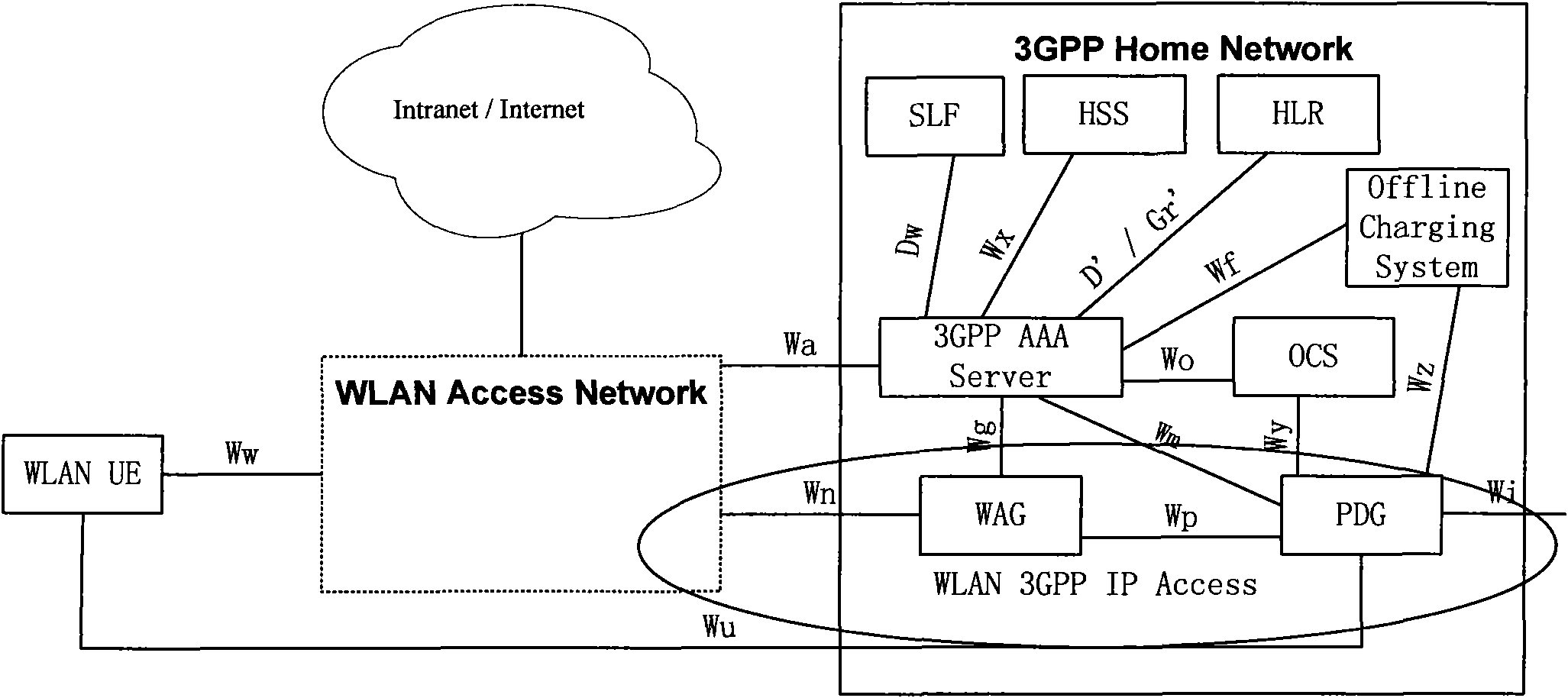
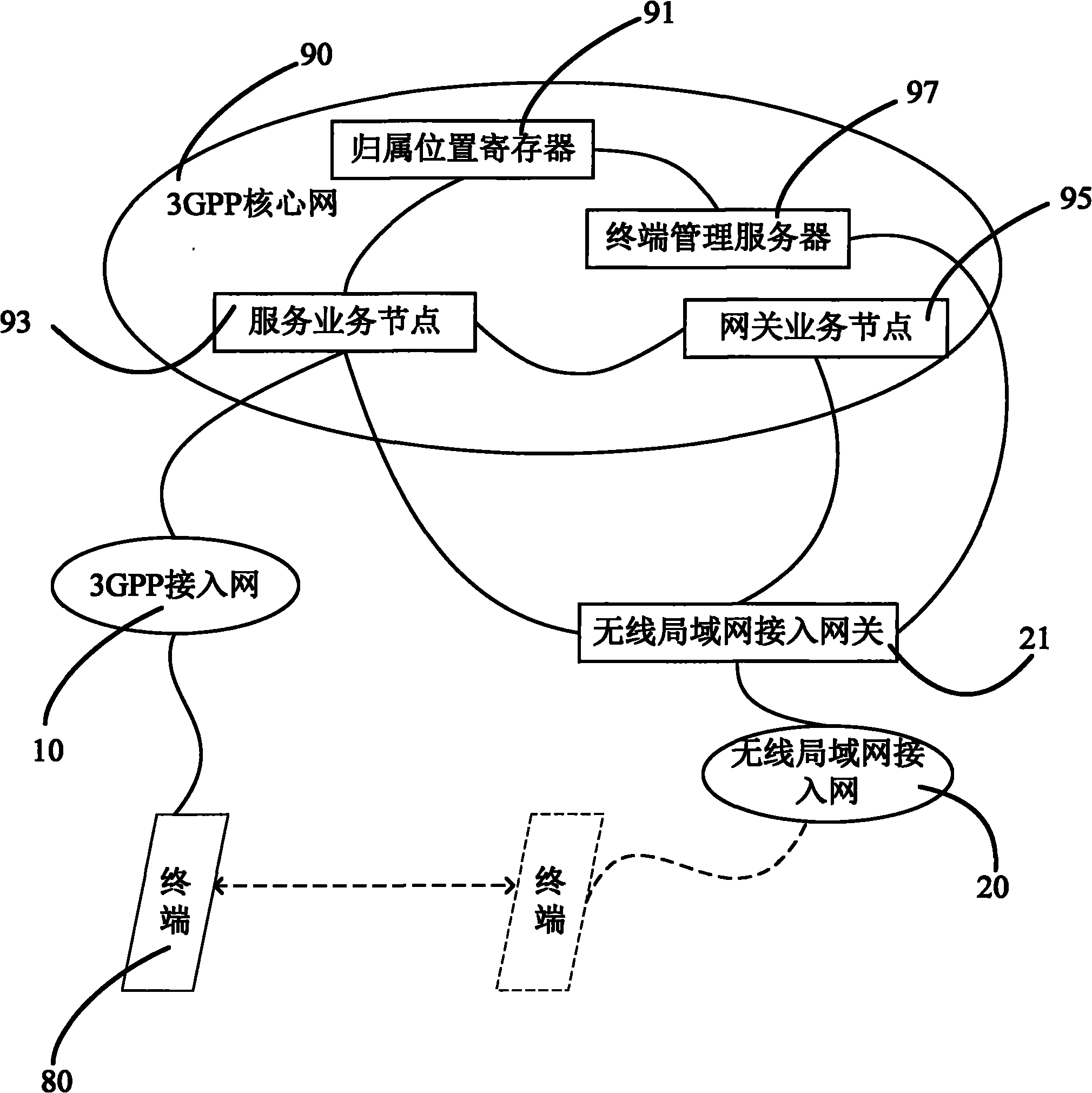
Network capable of switching terminal from 3GPP to WLAN and switching method
InactiveCN101867987ALow technical requirementsSeamless roamingData switching networksWireless communicationAccess networkNetwork deployment
The invention relates to a network capable of switching a terminal from 3GPP to a wireless local area network (WLAN). The network comprises a 3GPP access network, a WLAN access network and a 3GPP core network, wherein a home location register, a service node, a gateway service node and a terminal management server is also arranged in the 3GPP core network; and a WLAN access gateway is arranged between the WLAN access network and the 3GPP core network. The network has the advantages of realizing seamless switching of services without mobile IP technology, supporting superposed mobile IP technology application, meeting the requirement of EPC network evolution in the future, not changing original equipment of the conventional core network, quickly pushing WLAN and 3GPP fused services, promoting the development of fixed mobile convergence (FMC) services, along with low network design and realization cost and simple realization of terminal equipment.
Owner:SHANGHAI DINGZHU COMM TECH
Distributed gateway, message processing method and message processing device based on distributed gateway
ActiveCN104702476AReduce implementation complexityIncrease flexibilityNetworks interconnectionExtensibilityIp address
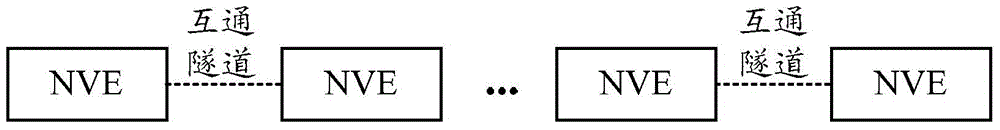
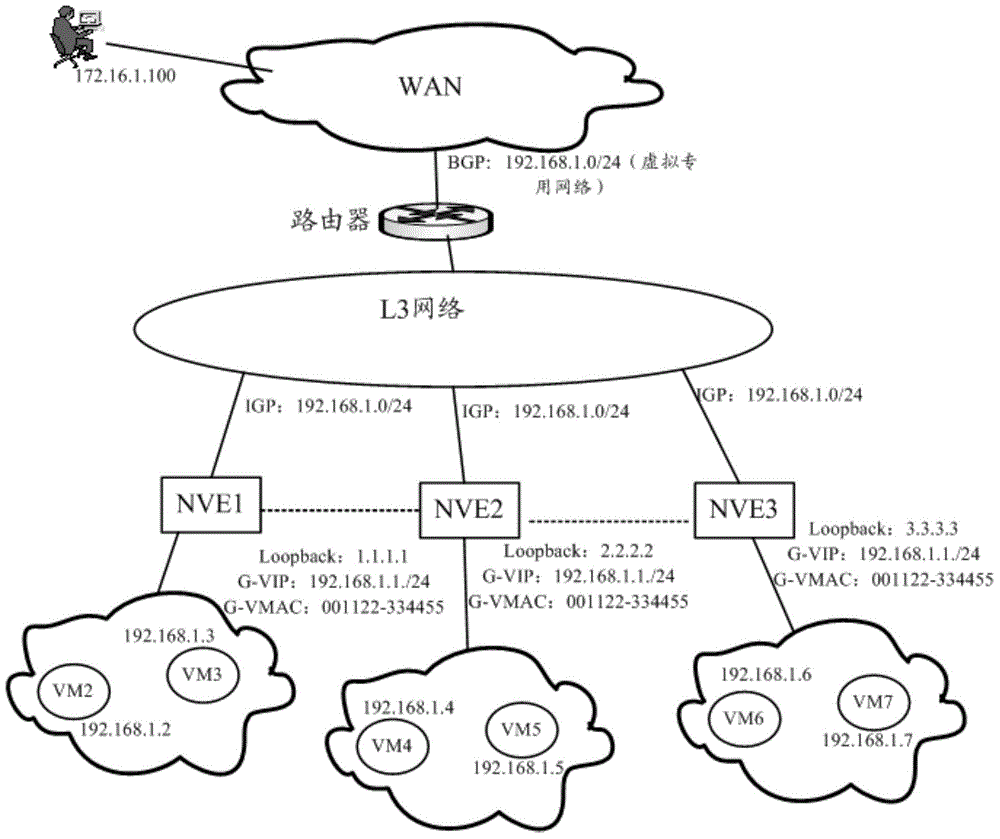
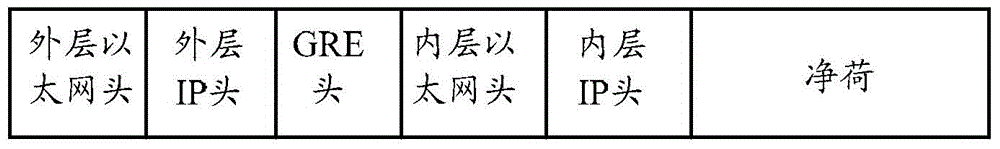
The invention discloses a distributed gateway, a message processing method and a message processing device based on the distributed gateway, which aim at improving the flexibility and expandability of network deployment, realizing load sharing and traffic optimization, and improving efficiency. The distributed gateway comprises a plurality of network virtualization endpoints (NVE). Each NVE has the same virtual internet protocol (VIP) address and the same virtual media access control (VMAC) address. Each NVE establishes interconnecting tunnels with other NVEs through the IP address of an outer layer tunnel. Each NVE is configured with a routing protocol for releasing a network segment route of a corresponding subnet.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com