Multi-party safety calculation method and device, and electronic equipment
A secure, multi-party technology, applied in the field of distributed computing, which can solve the problems of leaking private data, incorrect, malicious algorithm implementation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
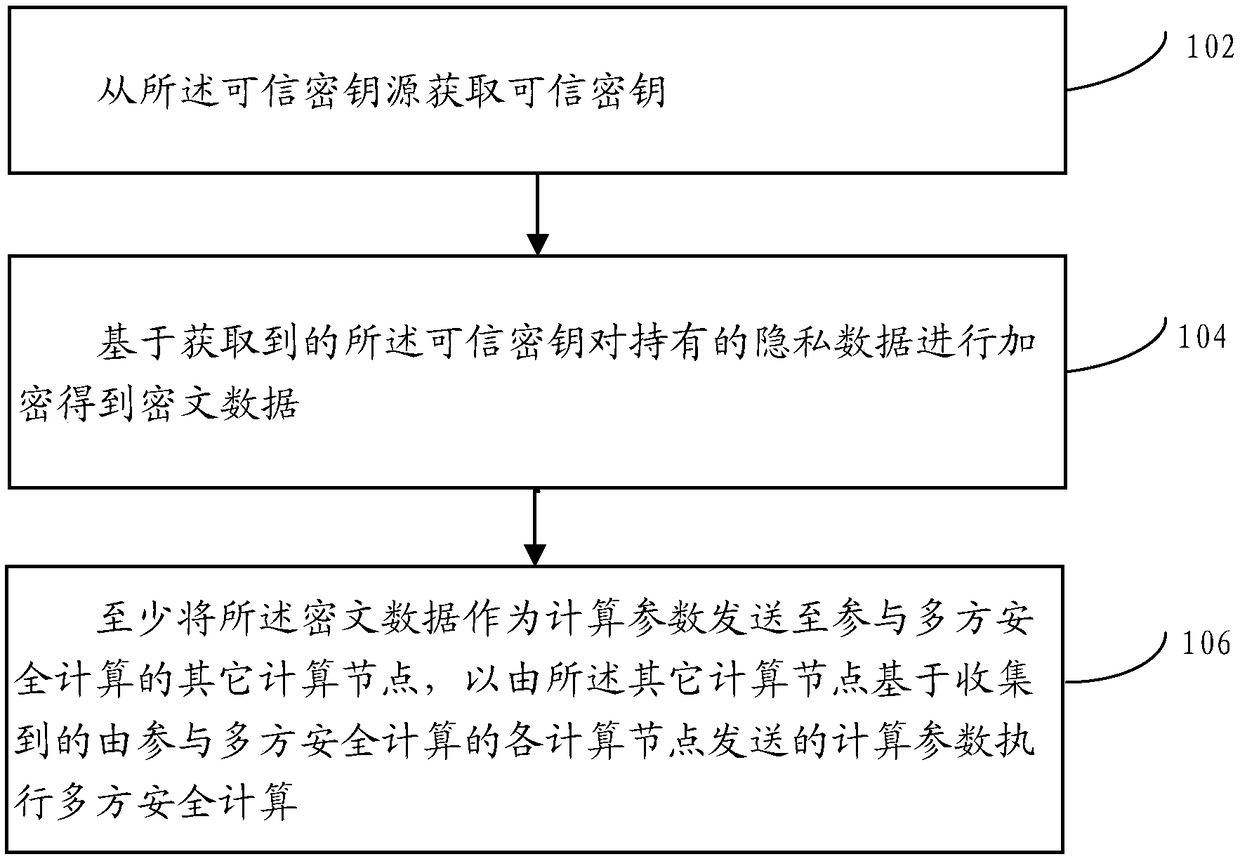
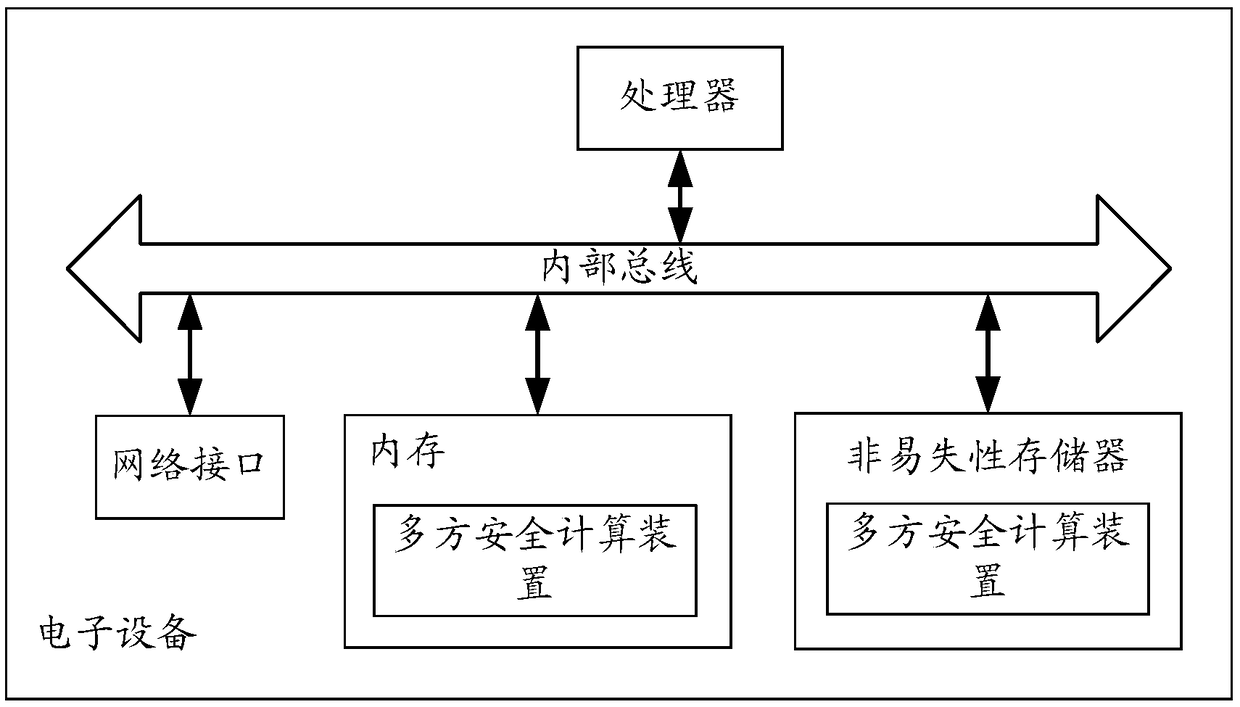
[0075] For computing nodes equipped with multi-party secure computing algorithms such as homomorphic encryption and obfuscated circuits, one or more random numbers are usually generated based on the carried random algorithm as a random key, and the generated random key is used to hold the The private data is encrypted and calculated to obtain ciphertext data, and then the calculated ciphertext data is used as calculation parameters and transmitted to other computing nodes participating in multi-party security calculations.
[0076] In practical applications, malicious multi-party security algorithms may use known keys held by other computing nodes participating in multi-party security calculations to encrypt private data held; further, in this way, the ciphertext When the data is sent to other computing nodes participating in multi-party secure computing, other computing nodes can decrypt the ciphertext data based on the known keys they hold, and obtain the private data held by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com